-

@ 04c915da:3dfbecc9
2025-03-26 20:54:33
Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-

@ b2d670de:907f9d4a
2025-03-25 20:17:57
This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users.
## Table of Contents
1. Prerequisites
2. Initial Server Setup
3. Installing Strfry Nostr Relay
4. Configuring Your Relay
5. Setting Up TOR
6. Making Your Relay Available on TOR
7. Testing Your Setup]
8. Maintenance and Security
9. Troubleshooting
## Prerequisites
- A Debian or Ubuntu server
- Basic familiarity with command line operations (most steps are explained in detail)
- Root or sudo access to your server
## Initial Server Setup
First, let's make sure your server is properly set up and secured.
### Update Your System
Connect to your server via SSH and update your system:
```bash
sudo apt update
sudo apt upgrade -y
```
### Set Up a Basic Firewall
Install and configure a basic firewall:
```bash
sudo apt install ufw -y
sudo ufw allow ssh
sudo ufw enable
```
This allows SSH connections while blocking other ports for security.
## Installing Strfry Nostr Relay
This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the `DEPLOYMENT.md` document in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps [here](https://github.com/hoytech/strfry/blob/master/docs/DEPLOYMENT.md).
### Install Dependencies
First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry:
```bash
sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-dev
```
Here's why each dependency is needed:
**Basic Development Tools:**
- `git`: Version control system used to clone the Strfry repository and manage code updates
- `build-essential`: Meta-package that includes compilers (gcc, g++), make, and other essential build tools
**Perl Dependencies** (used for Strfry's build scripts):
- `libyaml-perl`: Perl interface to parse YAML configuration files
- `libtemplate-perl`: Template processing system used during the build process
- `libregexp-grammars-perl`: Advanced regular expression handling for Perl scripts
**Core Libraries for Strfry:**
- `libssl-dev`: Development files for OpenSSL, used for secure connections and cryptographic operations
- `zlib1g-dev`: Compression library that Strfry uses to reduce data size
- `liblmdb-dev`: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend
- `libflatbuffers-dev`: Memory-efficient serialization library for structured data
- `libsecp256k1-dev`: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures
- `libzstd-dev`: Fast real-time compression algorithm for efficient data storage and transmission
### Clone and Build Strfry
Clone the Strfry repository:
```bash
git clone https://github.com/hoytech/strfry.git
cd strfry
```
Build Strfry:
```bash
git submodule update --init
make setup-golpe
make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores)
```
This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime.
### Install Strfry
Install the Strfry binary to your system path:
```bash
sudo cp strfry /usr/local/bin
```
This makes the `strfry` command available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions.
## Configuring Your Relay
### Create Strfry User
Create a dedicated user for running Strfry. This enhances security by isolating the relay process:
```bash
sudo useradd -M -s /usr/sbin/nologin strfry
```
The `-M` flag prevents creating a home directory, and `-s /usr/sbin/nologin` prevents anyone from logging in as this user. This is a security best practice for service accounts.
### Create Data Directory
Create a directory for Strfry's data:
```bash
sudo mkdir /var/lib/strfry
sudo chown strfry:strfry /var/lib/strfry
sudo chmod 755 /var/lib/strfry
```
This creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it.
### Configure Strfry
Copy the sample configuration file:
```bash
sudo cp strfry.conf /etc/strfry.conf
```
Edit the configuration file:
```bash
sudo nano /etc/strfry.conf
```
Modify the database path:
```
# Find this line:
db = "./strfry-db/"
# Change it to:
db = "/var/lib/strfry/"
```
Check your system's hard limit for file descriptors:
```bash
ulimit -Hn
```
Update the `nofiles` setting in your configuration to match this value (or set to 0):
```
# Add or modify this line in the config (example if your limit is 524288):
nofiles = 524288
```
The `nofiles` setting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular.
You might also want to customize your relay's information in the config file. Look for the `info` section and update it with your relay's name, description, and other details.
Set ownership of the configuration file:
```bash
sudo chown strfry:strfry /etc/strfry.conf
```
### Create Systemd Service
Create a systemd service file for managing Strfry:
```bash
sudo nano /etc/systemd/system/strfry.service
```
Add the following content:
```ini
[Unit]
Description=strfry relay service
[Service]
User=strfry
ExecStart=/usr/local/bin/strfry relay
Restart=on-failure
RestartSec=5
ProtectHome=yes
NoNewPrivileges=yes
ProtectSystem=full
LimitCORE=1000000000
[Install]
WantedBy=multi-user.target
```
This systemd service configuration:
- Runs Strfry as the dedicated strfry user
- Automatically restarts the service if it fails
- Implements security measures like `ProtectHome` and `NoNewPrivileges`
- Sets resource limits appropriate for a relay
Enable and start the service:
```bash
sudo systemctl enable strfry.service
sudo systemctl start strfry
```
Check the service status:
```bash
sudo systemctl status strfry
```
### Verify Relay is Running
Test that your relay is running locally:
```bash
curl localhost:7777
```
You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR.
## Setting Up TOR
Now let's make your relay accessible as a TOR hidden service.
### Install TOR
Install TOR from the package repositories:
```bash
sudo apt install -y tor
```
This installs the TOR daemon that will create and manage your hidden service.
### Configure TOR
Edit the TOR configuration file:
```bash
sudo nano /etc/tor/torrc
```
Scroll down to wherever you see a commented out part like this:
```
#HiddenServiceDir /var/lib/tor/hidden_service/
#HiddenServicePort 80 127.0.0.1:80
```
Under those lines, add the following lines to set up a hidden service for your relay:
```
HiddenServiceDir /var/lib/tor/strfry-relay/
HiddenServicePort 80 127.0.0.1:7777
```
This configuration:
- Creates a hidden service directory at `/var/lib/tor/strfry-relay/`
- Maps port 80 on your .onion address to port 7777 on your local machine
- Keeps all traffic encrypted within the TOR network
Create the directory for your hidden service:
```bash
sudo mkdir -p /var/lib/tor/strfry-relay/
sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/
sudo chmod 700 /var/lib/tor/strfry-relay/
```
The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys.
Restart TOR to apply changes:
```bash
sudo systemctl restart tor
```
## Making Your Relay Available on TOR
### Get Your Onion Address
After restarting TOR, you can find your onion address:
```bash
sudo cat /var/lib/tor/strfry-relay/hostname
```
This will output something like `abcdefghijklmnopqrstuvwxyz234567.onion`, which is your relay's unique .onion address. This is what you'll share with others to access your relay.
### Understanding Onion Addresses
The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key.
Your users will need to use this address with the WebSocket protocol prefix to connect: `ws://youronionaddress.onion`
## Testing Your Setup
### Test with a Nostr Client
The best way to test your relay is with an actual Nostr client that supports TOR:
1. Open your TOR browser
2. Go to your favorite client, either on clearnet or an onion service.
- Check out [this list](https://github.com/0xtrr/onion-service-nostr-clients?tab=readme-ov-file#onion-service-nostr-clients) of nostr clients available over TOR.
3. Add your relay URL: `ws://youronionaddress.onion` to your relay list
4. Try posting a note and see if it appears on your relay
- In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay.
- Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected.
Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too).
## Maintenance and Security
### Regular Updates
Keep your system, TOR, and relay updated:
```bash
# Update system
sudo apt update
sudo apt upgrade -y
# Update Strfry
cd ~/strfry
git pull
git submodule update
make -j2
sudo cp strfry /usr/local/bin
sudo systemctl restart strfry
# Verify TOR is still running properly
sudo systemctl status tor
```
Regular updates are crucial for security, especially for TOR which may have security-critical updates.
### Database Management
Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups.
### Monitoring Logs
To monitor your Strfry logs:
```bash
sudo journalctl -u strfry -f
```
To check TOR logs:
```bash
sudo journalctl -u tor -f
```
Monitoring logs helps you identify potential issues and understand how your relay is being used.
### Backup
This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server.
```bash
# Stop the relay temporarily
sudo systemctl stop strfry
# Backup the database
sudo cp -r /var/lib/strfry /path/to/backup/location
# Restart the relay
sudo systemctl start strfry
```
Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it.
```bash
sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/location
```
## Troubleshooting
### Relay Not Starting
If your relay doesn't start:
```bash
# Check logs
sudo journalctl -u strfry -e
# Verify configuration
cat /etc/strfry.conf
# Check permissions
ls -la /var/lib/strfry
```
Common issues include:
- Incorrect configuration format
- Permission problems with the data directory
- Port already in use (another service using port 7777)
- Issues with setting the nofiles limit (setting it too big)
### TOR Hidden Service Not Working
If your TOR hidden service is not accessible:
```bash
# Check TOR logs
sudo journalctl -u tor -e
# Verify TOR is running
sudo systemctl status tor
# Check onion address
sudo cat /var/lib/tor/strfry-relay/hostname
# Verify TOR configuration
sudo cat /etc/tor/torrc
```
Common TOR issues include:
- Incorrect directory permissions
- TOR service not running
- Incorrect port mapping in torrc
### Testing Connectivity
If you're having trouble connecting to your service:
```bash
# Verify Strfry is listening locally
sudo ss -tulpn | grep 7777
# Check that TOR is properly running
sudo systemctl status tor
# Test the local connection directly
curl --include --no-buffer localhost:7777
```
---
## Privacy and Security Considerations
Running a Nostr relay as a TOR hidden service provides several important privacy benefits:
1. **Network Privacy**: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay.
2. **Server Anonymity**: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting.
3. **Censorship Resistance**: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked.
4. **User Privacy**: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized.
However, there are some important considerations:
- TOR connections are typically slower than regular internet connections
- Not all Nostr clients support TOR connections natively
- Running a hidden service increases the importance of keeping your server secure
---
Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network.
For further customization and advanced configuration options, refer to the [Strfry documentation](https://github.com/hoytech/strfry).
Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network!
If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to [this list](https://github.com/0xtrr/onion-service-nostr-relays). Only add it if you plan to run a stable and available relay.
-

@ bc52210b:20bfc6de
2025-03-25 20:17:22
CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient.
This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off!
Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now.
---
**CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused!**
Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why:
* Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs).
* Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key.
**Key Differences:**
1. What’s Aggregated?
* CISA: Aggregates signatures.
* Key Aggregation: Aggregates public keys.
2. What the Verifier Needs
* CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature.
* Key Aggregation: The verifier only needs the single aggregated public key and one message.
3. When It Happens
* CISA: Used during transaction signing, when inputs are being combined into a transaction.
* MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control.
So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs!
---
**Two Flavors of CISA: Half-Agg and Full-Agg**
CISA comes in two modes:
* Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.)
* Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later.
Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg.
---
**Half Signature Aggregation (Half-Agg) Explained**
**How It Works**
Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process:
1. Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers.
2. Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature.
A Schnorr signature has two parts:
* R: A random point (32 bytes).
* s: A scalar value (32 bytes).
In Half-Agg:
* The R values from each signature are kept separate (one per input).
* The s values from all signatures are combined into a single s value.
**Why It Saves Space (~50%)**
Let’s break down the size savings with some math:
Before Aggregation:
* Each Schnorr signature = 64 bytes (32 for R + 32 for s).
* For n inputs: n × 64 bytes.
After Half-Agg:
* Keep n R values (32 bytes each) = 32 × n bytes.
* Combine all s values into one = 32 bytes.
* Total size: 32 × n + 32 bytes.
Comparison:
* Original: 64n bytes.
* Half-Agg: 32n + 32 bytes.
* For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings!
**Real-World Impact:**
Based on recent Bitcoin usage, Half-Agg could save:
* ~19.3% in space (reducing transaction size).
* ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA.
---
**Applications of Half-Agg**
Half-Agg isn’t just a cool idea—it has practical uses:
1. Transaction-wide Aggregation
* Combine all signatures within a single transaction.
* Result: Smaller transactions, lower fees.
2. Block-wide Aggregation
* Combine signatures across all transactions in a Bitcoin block.
* Result: Even bigger space savings at the blockchain level.
3. Off-chain Protocols / P2P
* Use Half-Agg in systems like Lightning Network gossip messages.
* Benefit: Efficiency without needing miners or a Bitcoin soft fork.
---
**Challenges with Half-Agg**
While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level:
1. Breaking Adaptor Signatures
* Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges.
* Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on.
2. Impact on Reorg Recovery
* In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed.
* If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery.
These challenges mean Half-Agg needs careful design, especially for block-wide use.
---
**Wrapping Up**
CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning.
But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future!
-

@ b17fccdf:b7211155
2025-03-25 11:23:36
Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la [guía de MiniBolt](https://minbolt.info/).
Esto tiene una **razón**, por supuesto una **solución**, además de una **conclusión**. Sin entrar en demasiados detalles:
## La razón
El **bloqueo a Cloudflare**, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una [orden judicial](https://www.poderjudicial.es/search/AN/openDocument/3c85bed480cbb1daa0a8778d75e36f0d/20221004) emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo [ECH](https://developers.cloudflare.com/ssl/edge-certificates/ech) (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar **bloqueos basados en dominios**, lo que les obliga a recurrir a **bloqueos más amplios por IP o rangos de IP** para cumplir con la orden judicial.
Esta práctica tiene **consecuencias graves**, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un **perjuicio para terceros**, **restringiendo el acceso a muchos dominios legítimos** que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la [web de MiniBolt](https://minibolt.minibolt.info) y su dominio `minibolt.info`, los cuales **utilizan Cloudflare como proxy** para aprovechar las medidas de **seguridad, privacidad, optimización y servicios** adicionales que la plataforma ofrece de forma gratuita.
Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

## La solución
Obviamente, **MiniBolt no dejará de usar Cloudflare** como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para **evitar esta restricción** y poder acceder:
**~>** Utiliza **una VPN**:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad:
- [IVPN](https://www.ivpn.net/es/)
- [Mullvad VPN](https://mullvad.net/es/vpn)
- [Proton VPN](https://protonvpn.com/es-es) (**gratis**)
- [Obscura VPN](https://obscura.net/) (**solo para macOS**)
- [Cloudfare WARP](https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/download-warp/) (**gratis**) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos:
1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy"
2. Marca la casilla "Habilite el modo proxy en este dispositivo"
3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias
4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio.
3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a [esta](https://minibolt.minibolt.info/system/system/privacy#example-from-firefox) para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la [guía de MiniBolt](https://minibolt.minibolt.info/) sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info [AQUÍ](https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958).

**~>** [**Proxifica tu navegador para usar la red de Tor**](https://minibolt.minibolt.info/system/system/privacy#ssh-remote-access-through-tor), o utiliza el [**navegador oficial de Tor**](https://www.torproject.org/es/download/) (recomendado).

## La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la [Declaración de Independencia del Ciberespacio](https://es.wikisource.org/wiki/Declaraci%C3%B3n_de_independencia_del_ciberespacio) que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos **impulsar el desarrollo y la difusión** de las **herramientas anticensura** que tenemos a nuestro alcance, protegiendo así la **libertad digital** y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los **pilares fundamentales de MiniBolt,** lo que convierte este desafío en una oportunidad para poner a prueba las **soluciones anticensura** [ya disponibles](https://minibolt.minibolt.info/bonus-guides/system/tor-services), así como **las que están en camino**.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

---
Fuentes:
* https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239
* https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257
* https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958
* https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689
* https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-

@ 3b7fc823:e194354f
2025-03-23 03:54:16
A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds.
Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/
1. Download Tor Browser
First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/
2. Sign Up
Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha.
3. Account information
Once you are done signing up an Account information page will pop up. **MAKE SURE YOU SAVE THIS!!!** It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck.
4. Install an Email Client
You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird.
a. Download Thunderbird email client
b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the **Configure Manually**option will appear below. Click that.
5. Configure Incoming (POP3) Server
Under Incoming Server:
Protocol: POP3
Server or Hostname: xyz.onion (whatever your account info says)
Port: 110
Security: STARTTLS
Authentication: Normal password
Username: (your username)
Password: (POP3 password).
6. Configure Outgoing (SMTP) Server
Under Outgoing Server:
Server or Hostname: xyz.onion (whatever your account info says)
Port: 25
Security: STARTTLS
Authentication: Normal password
Username: (your username)
Password: (SMTP password).
7. Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up.
8. Configure Proxy
a. Click the **gear icon** on the bottom left for settings. Scroll all the way down to **Network & Disk Space**. Click the **settings button** next to **Connection. Configure how Thunderbird connects to the internet**.
b. Select **Manual Proxy Configuration**. For **SOCKS Host** enter **127.0.0.1** and enter port **9050**. (if you are running this through a VM the port may be different)
c. Now check the box for **SOCKS5** and then **Proxy DNS when using SOCKS5** down at the bottom. Click OK
9. Check Email
For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on **inbox** and then the **little cloud icon** with the down arrow to check mail.
10. Security Exception
Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup **Add Security Exception** will appear. Click **Confirm Security Exception**.
You are done. Enjoy your new private email service.
**REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.**
-

@ 21335073:a244b1ad
2025-03-18 20:47:50
**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.**
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
**Course:**
- The creation of the internet and computers
- The fight for cryptography
- The tech supply chain from the ground up (example: human rights violations in the supply chain)
- Corporate tech
- Freedom tech
- Data privacy
- Digital privacy rights
- AI (history-current)
- Online safety (predators, scams, catfishing, extortion)
- Bitcoin
- Laws
- How to deal with online hate and harassment
- Information on who to contact if you are being abused online or offline
- Algorithms
- How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-

@ 21335073:a244b1ad
2025-03-18 14:43:08
**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.**
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
**Course:**
- The creation of the internet and computers
- The fight for cryptography
- The tech supply chain from the ground up (example: human rights violations in the supply chain)
- Corporate tech
- Freedom tech
- Data privacy
- Digital privacy rights
- AI (history-current)
- Online safety (predators, scams, catfishing, extortion)
- Bitcoin
- Laws
- How to deal with online hate and harassment
- Information on who to contact if you are being abused online or offline
- Algorithms
- How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-

@ da0b9bc3:4e30a4a9
2025-03-29 06:49:22
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/928470
-

@ a07fae46:7d83df92
2025-03-18 12:31:40
if the JFK documents come out and are nothing but old hat, it will be disappointing. but if they contain revelations, then they are an unalloyed good. unprecedented and extraordinary; worthy of praise and admiration. they murdered the president in broad daylight and kept 80,000 related documents secret for 60 years. the apparatus that did that and got away with it, is 100+ years in the making. the magic bullet was just the starting pistol of a new *era*; a *level up* in an [old game](https://archive.org/details/TragedyAndHope_501/page/n5/mode/2up?q=feudalist+fashion). it won't be dismantled and your republic delivered back with a bow in *2 months*. have a little humility and a little gratitude. cynicism is easy. it's peak mid-wittery. yeah no shit everything is corrupt and everyone's likely captured by [AIPAC](https://books.google.com/books/publisher/content?id=gKVKDwAAQBAJ&pg=PT68&img=1&zoom=3&hl=en&bul=1&sig=ACfU3U2pagVXTYdJOKxkAwmmFQpuSnoS5g&w=1280) or something beyond. YOU THINK AIPAC is the [ALL SEEING EYE](https://archive.org/details/the-all-seeing-eye-vol-1-5-manly-p.-hall-may-1923-sept-1931)?
you can keep going, if you want to, but have some awareness and appreciation for where we are and what it took to get here. the first 'you are fake news' was also a shot heard 'round the world and you are riding high on it's [Infrasound](https://en.wikipedia.org/wiki/Infrasound) wave, still reverberating; unappreciative of the profound delta in public awareness and understanding, and rate of change, that has occurred since that moment, in [2017](https://www.youtube.com/watch?v=Vqpzk-qGxMU). think about where we were back then, especially with corporate capture of the narrative. trump's bullheaded behavior, if only ego-driven, *is* what broke the spell. an *actual* moment of savage bravery is what allows for your current jaded affectation. black pilled is boring. it's intellectually lazy. it is low-resolution-thinking, no better than progressives who explain the myriad ills of the world through 'racism'. normalcy bias works both ways. i'm not grading you on a curve that includes NPCs. i'm grading you against those of us with a mind, on up. do better.
the best Webb-style doomer argument is essentially 'the mouse trap needs a piece of cheese in order to work'. ok, but it doesn't need 3 pieces of cheese, or 5. was FreeRoss the piece of cheese? was the SBR the cheese? real bitcoiners know how dumb the 'sbr is an attempt to takeover btc' narrative is, so extrapolate from that. what about withdrawal from the WHO? freeze and review of USAID et al? how many pieces of cheese before we realize it's not a trap? it's just a messy endeavor.
Good morning.
#jfkFiles #nostrOnly
-

@ dfbbf851:ba4542b5
2025-03-29 06:51:21
ในยุคดิจิทัลที่การสื่อสารมีบทบาทสำคัญต่อชีวิตประจำวัน เทคโนโลยี **Cell Broadcast** ได้กลายเป็นหนึ่งในเครื่องมือที่ทรงพลังสำหรับการแจ้งเตือนฉุกเฉิน ไม่ว่าจะเป็นภัยพิบัติหรือเหตุการณ์สำคัญที่ต้องแจ้งให้ประชาชนทราบอย่างทันท่วงที ⏳💡
---
### 📌 **Cell Broadcast คืออะไร ?**
**Cell Broadcast (CB)** เป็นเทคโนโลยีที่ใช้ส่งข้อความกระจายสัญญาณผ่านเครือข่ายโทรศัพท์มือถือ 🏗📶 โดยแตกต่างจาก **SMS** ตรงที่สามารถส่งข้อความถึงผู้ใช้จำนวนมากได้พร้อมกัน **โดยไม่ต้องทราบหมายเลขโทรศัพท์** ของผู้รับ 📲💨
ข้อความ CB สามารถส่งถึงอุปกรณ์ที่รองรับในเครือข่ายมือถือที่เปิดใช้งานอยู่ภายในช่วงเวลาสั้น ๆ ⏱ และ **ไม่ทำให้เครือข่ายล่ม**
---
### ✨ **ข้อดีของ Cell Broadcast** ✨
✅ **ส่งข้อความรวดเร็ว** – แจ้งเตือนได้ภายในไม่กี่วินาที แม้ในกรณีฉุกเฉิน ⚡🚀
✅ **ไม่ต้องใช้หมายเลขโทรศัพท์** – กระจายสัญญาณไปยังอุปกรณ์ทุกเครื่องที่อยู่ในพื้นที่เป้าหมายได้โดยตรง 📡
✅ **รองรับหลายภาษา** – สามารถตั้งค่าการแจ้งเตือนให้เหมาะสมกับประชากรในแต่ละพื้นที่ 🌍🗣
✅ **ไม่ทำให้เครือข่ายหนาแน่น** – ต่างจาก SMS หรือการโทรจำนวนมากที่อาจทำให้เครือข่ายล่ม 📵❌
✅ **ทำงานได้แม้ไม่มีอินเทอร์เน็ต** – สามารถแจ้งเตือนในกรณีที่โซเชียลมีเดียหรืออินเทอร์เน็ตใช้งานไม่ได้ 🌐🚫
---
### 🌍 **การใช้งาน Cell Broadcast ทั่วโลก**
🔹 **สหรัฐอเมริกา** – **ใช้ระบบ Wireless Emergency Alerts (WEA)** เพื่อแจ้งเตือนเหตุการณ์ฉุกเฉิน เช่น พายุเฮอริเคน 🌀🌪
🔹 **ญี่ปุ่น** – ใช้ระบบ **Earthquake Early Warning (EEW)** เพื่อแจ้งเตือนแผ่นดินไหวล่วงหน้า ⛩🌏
🔹 **สหภาพยุโรป** – มีนโยบายให้ประเทศสมาชิกใช้ **Public Warning System** ผ่าน Cell Broadcast 📢🏛
---
### 🤔 **ทำไมประเทศที่ยังไม่มีระบบนี้ควรนำมาใช้ ?**
หลายประเทศ รวมถึง **ประเทศไทย** ยังไม่มีการใช้ Cell Broadcast อย่างแพร่หลาย ทั้งที่เป็นเทคโนโลยีที่สามารถช่วยชีวิตผู้คนได้อย่างมหาศาล 🚑 หากเกิดภัยพิบัติ เช่น **น้ำท่วม แผ่นดินไหว สึนามิ หรือไฟป่า** 🔥🌊 Cell Broadcast สามารถส่งการแจ้งเตือนไปยังทุกคนในพื้นที่เสี่ยงได้ทันที ลดความสูญเสียและเพิ่มโอกาสรอดชีวิตได้มากขึ้น
🔸 **ความแม่นยำสูง** – สามารถส่งแจ้งเตือนไปยังพื้นที่ที่ได้รับผลกระทบโดยตรง ทำให้ประชาชนสามารถเตรียมตัวรับมือได้ดีกว่า
🔸 **ไม่มีปัญหาความล่าช้า** – ต่างจากการแจ้งเตือนผ่าน SMS หรือโซเชียลมีเดียที่อาจล่าช้าหรือไม่ได้รับข้อความเลยหากเครือข่ายล่ม
🔸 **เป็นมาตรฐานสากล** – หลายประเทศพัฒนาแล้วมีระบบนี้ใช้งานอย่างมีประสิทธิภาพ ประเทศที่ยังไม่มีควรนำมาใช้เพื่อให้สามารถจัดการภัยพิบัติได้อย่างมีประสิทธิภาพ
🔸 **ประหยัดต้นทุนในระยะยาว** – ลดความเสียหายทางเศรษฐกิจจากภัยพิบัติ เพราะประชาชนได้รับการแจ้งเตือนล่วงหน้า ทำให้สามารถอพยพหรือป้องกันความเสียหายได้
---
### 🔮 **อนาคตของ Cell Broadcast**
**ในอนาคต Cell Broadcast** อาจถูกนำมาใช้ร่วมกับ **ปัญญาประดิษฐ์ (AI)** 🤖 และ **Internet of Things (IoT)** 🌐 เพื่อเพิ่มความแม่นยำและปรับแต่งการแจ้งเตือนได้ดียิ่งขึ้น 🎯💡
---
### 📌 **ปล.**
**Cell Broadcast เป็นเทคโนโลยีแจ้งเตือนที่ทรงพลังและมีบทบาทสำคัญในการช่วยชีวิตผู้คน** 🚑 ด้วยความสามารถในการส่งข้อความได้อย่างรวดเร็ว ครอบคลุมพื้นที่กว้าง และไม่ต้องพึ่งพาอินเทอร์เน็ต จึงเป็นหนึ่งในเครื่องมือสำคัญสำหรับการบริหารจัดการภัยพิบัติในปัจจุบันและอนาคต 🔥
---
#CellBroadcast #แจ้งเตือนภัย #เทคโนโลยีสื่อสาร #ภัยพิบัติ #เครือข่ายมือถือ #การสื่อสารฉุกเฉิน #เตือนภัยล่วงหน้า
-

@ bc52210b:20bfc6de
2025-03-14 20:39:20
When writing safety critical code, every arithmetic operation carries the potential for catastrophic failure—whether that’s a plane crash in aerospace engineering or a massive financial loss in a smart contract.
The stakes are incredibly high, and errors are not just bugs; they’re disasters waiting to happen. Smart contract developers need to shift their mindset: less like web developers, who might prioritize speed and iteration, and more like aerospace engineers, where precision, caution, and meticulous attention to detail are non-negotiable.
In practice, this means treating every line of code as a critical component, adopting rigorous testing, and anticipating worst-case scenarios—just as an aerospace engineer would ensure a system can withstand extreme conditions.
Safety critical code demands aerospace-level precision, and smart contract developers must rise to that standard to protect against the severe consequences of failure.
-

@ df173277:4ec96708
2025-02-07 00:41:34
## **Building Our Confidential Backend on Secure Enclaves**
With our newly released [private and confidential **Maple AI**](https://trymaple.ai/?ref=blog.opensecret.cloud) and the open sourcing of our [**OpenSecret** platform](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud) code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging **secure enclaves**. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with.
## **Auth and Databases Today**
As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that:
1. Need to register users (authentication).
2. Collect and process user data in business-specific ways, often on the backend.
Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes).
## **"Just Trust Us" Isn't Good Enough**
In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data.
Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility.
The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a **strong, verifiable** guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services.
## **Current Attempts at Securing Data**
Current User Experience of E2EE Apps
While properly securing data is not easy, it isn't to say that no one is trying. Some solutions use **end-to-end encryption** (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its **limitations**:
1. **Key Management Nightmares**: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side.
2. **Feature Limitations**: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data.
3. **Platform Silos**: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility.
Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider.
## **Secure Enclaves**
### **The Hybrid Approach**
Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden.
App Service Running Inside Secure Enclave
### **High-Level Goal of Enclaves**
Enclaves, also known under the broader umbrella of **confidential computing**, aim to:\
• **Lock down data** so that only authorized code within the enclave can process the original plaintext data.\
• **Deny external inspection** by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\
• **Prove** to external users or services that an enclave is running unmodified, approved code (this is where **remote attestation** comes in).
### **Different Secure Enclave Solutions**
[**AMD SEV**](https://www.amd.com/en/developer/sev.html?ref=blog.opensecret.cloud) **(Secure Encrypted Virtualization)** encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds.
[**Intel TDX**](https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/overview.html?ref=blog.opensecret.cloud) **(Trust Domain Extensions)** shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications.
[**Apple Secure Enclave and Private Compute**](https://security.apple.com/blog/private-cloud-compute/?ref=blog.opensecret.cloud) is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers.
[**AWS Nitro Enclaves**](https://docs.aws.amazon.com/enclaves/latest/user/nitro-enclave.html?ref=blog.opensecret.cloud) carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised.
[**NVIDIA GPU TEEs**](https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/?ref=blog.opensecret.cloud) **(Hopper H100 and Blackwell)** extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees.
### **Key Benefits**
One major advantage of enclaves is their ability to **keep memory completely off-limits** to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data.
Another key benefit centers on cryptographic keys that are **never exposed outside the enclave**. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware.
Enclaves can also offer the power of **remote attestation**, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks.
Beyond that, **reproducible builds** can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, [our NixOS-based solution](https://github.com/OpenSecretCloud/opensecret/blob/master/flake.nix?ref=blog.opensecret.cloud)). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist.
It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the **hardware vendor** (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing.
## **How We Use Secure Enclaves**
Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads.
### **Our Stack: AWS Nitro + Nvidia TEE**
• **AWS Nitro Enclaves for the backend**: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave.
• **Nvidia Trusted Execution for AI**: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model **without** exposing it in plaintext to the GPU providers or us as the operator. [Edgeless Systems](https://www.edgeless.systems/?ref=blog.opensecret.cloud) is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with.
### **End-to-End Encryption from Client to Enclave**
Client-side Enclave Attestation from Maple AI
Before login or data upload, the user/client verifies the **enclave attestation** from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on [Maple AI's attestation page](https://trymaple.ai/proof?ref=blog.opensecret.cloud).
Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session.
From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request.
### **In-Enclave Operations**
At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form.
User Auth Methods running inside Enclave
A primary example is **user authentication**. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information.
Main Enclave Operations in OpenSecret
The same principle applies to **private key management**. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user.
Realtime Encrypted Data Sync on Multiple Devices
Another crucial aspect is **data encryption at rest**. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext.
Confidential AI Workloads
Finally, **confidential AI workloads** build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation.
### **Reproducible Builds + Verification**
Client verifies enclave attestation document
We build our enclaves on **NixOS** with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs.
Our code is fully open source ([GitHub: OpenSecret](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud)), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation.
## **Putting It All Together**
OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute
By weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes.
This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats.
Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure.
OpenSecret aims to be a **full developer platform** with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use.
Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system.
The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad.
## **Things to Come**
We're excited to build on our enclaved approach. Here's what's on our roadmap:
• **Production Launch**: We're using this in production now with [Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud) and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\
• **Multi-Tenant Support**: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\
• **Self-Serve Frontend**: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\
• **External Key Signing Options**: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\
• **Confidential Computing as a Service**: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\
• **Additional SDKs**: In addition to our [JavaScript client-side SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud), we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\
• **AI API Proxy with Attestation/Encryption**: We already provide an easy way to [access a Private AI through Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud), but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API.
## **Getting Started**
Ready to see enclaves in action? Here's how to dive in:\
1. **Run OpenSecret**: Check out our open-source repository at [OpenSecret on GitHub](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud). You can run your own enclaved environment or try it out locally with Docker.\
2. **Review Our SDK**: Our [JavaScript client SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud) makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\
3. **Play with Maple AI**: Try out [Maple AI](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/) as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\
4. **Developer Preview**: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further.
## **Conclusion**
By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, **OpenSecret** provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that **no one**, not even us or the cloud provider, can snoop on data in use.
**We believe** this is the future of trustworthy computing in the cloud. And it's **all open source**, so you don't have to just take our word for it: you can see and verify everything yourself.
Do you have questions, feedback, or a use case you'd like to test out? Come join us on [GitHub](https://github.com/OpenSecretCloud?ref=blog.opensecret.cloud), [Discord](https://discord.gg/ch2gjZAMGy?ref=blog.opensecret.cloud), or email us for a developer preview. We can't wait to see what you build!
*Thank you for reading, and welcome to the era of enclaved computing.*
-

@ df173277:4ec96708
2025-01-28 17:49:54
> Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\
> [Start chatting for free.](https://trymaple.ai/)
We are excited to announce that [Maple AI](https://trymaple.ai/), our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world.
Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another.
#### Why Secure and Private AI?
In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a [recent report by Cisco](https://www.cisco.com/c/en/us/about/trust-center/data-privacy-benchmark-study.html#~key-findings). This practice poses significant risks to company security and intellectual property.
Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services.
At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local.
#### How Does It Work?
Our server code is [open source](https://github.com/OpenSecretCloud/opensecret), and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site.
#### How Much Does It Cost?
We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. [Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month)](https://trymaple.ai/pricing) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method.
- Free: $0
- Starter: $5.99/month
- Pro: $20/month
Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy.
Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. [Sign up now and start chatting privately with AI for free.](https://trymaple.ai/) Your secrets are safe in the open.
#### Are You An App Developer?
You can build an app like Maple. [OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more.](https://blog.opensecret.cloud/introducing-opensecret/) Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out [OpenSecret](https://opensecret.cloud/).
<img src="https://blossom.primal.net/feb746d5e164e89f0d015646286b88237dce4158f8985e3caaf7e427cebde608.png">
Enjoy private AI Chat 🤘
<img src="https://blossom.primal.net/0594ec56e249de2754ea7dfc225a7ebd46bc298b5af168279ce71f17c2afada0.jpg">
-

@ df173277:4ec96708
2025-01-09 17:12:08
> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\
> [Join the waitlist to get early access.](https://trymaple.ai)
We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI.
Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations.
#### Building a Private Foundation
Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win.
#### The Power of Encrypted AI Chat
AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short.
Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us.
#### Technical Overview
So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects:
- **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data.
- **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations.
- **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised.
- **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public.
- **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased.
#### Personal and Work Use
Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe.
#### Local v Cloud
Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds.
#### Why the Maple name?
Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment.
#### Join the Waitlist
Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai)
[](https://trymaple.ai/waitlist)
-

@ df173277:4ec96708
2025-01-09 17:02:52
> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud)
In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion.
Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online?
Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches?
> Cryptography at scale is hard.
#### The Cloud
The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers.
The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage.
> Private key encryption needs a UX upgrade.
## Enter OpenSecret
OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute.
Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.

### Private Key Management
Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone.
OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account.
The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.

### Encrypted Sync
With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go.
The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them.
### Private AI
Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything.
OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk.
**Check out Maple AI**\
Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)

### Confidential Compute
Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave.
It's the new version of that lock on your web browser. When you see it, you know you're secure.

#### **But do we want our secrets to be open?**
OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable.
On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data.
> Don't trust, verify.
### **Join the Movement**
We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud)
Users and companies deserve better encryption and privacy.\
Together, let's make that a reality.
[](https://opensecret.cloud)
-

@ bdf3f01a:d9c40970
2025-03-29 04:52:40
## Abstract:
This paper presents a rigorous and critical examination of the Winter Vigil of XLII.II at Sapelo, a pivotal rite within the Lowcountry Freehold that serves as both an initiation into communal responsibility and a symbolic enactment of the Compact’s moral tenets. This analysis interrogates the ritual’s structure, emphasizing its role in perpetuating a resilient sociocultural order amid external collapse. Through a multidisciplinary approach combining historiographical analysis, cultural anthropology, and sociocultural theory, this study elucidates the Vigil’s function as a mechanism for moral continuity, thereby situating it within the broader discourse of post-collapse societal stabilization. The implications of this study underscore the profound interconnectedness between ritual practice and the formation of resilient communal identities.
## Introduction:
The Winter Vigil of XLII.II at Sapelo occupies a fundamental position in the cultural historiography of the Lowcountry Freehold. As contemporary scholars, it is imperative to approach this tradition not merely as an artifact of ritualistic antiquity but as a dynamic process of cultural preservation. The Freehold’s commitment to integrating tradition with pragmatism, especially through the stewardship of The Veil, constitutes a critical adaptive strategy that sustained sociopolitical coherence through epochs of external fragmentation. This study aims to critically examine the Vigil as both a symbolic and practical reinforcement of the Compact’s ethos, with particular attention to how this ritual facilitated intergenerational continuity of moral and social values, ultimately shaping the robust communal identity that defines contemporary Freehold society.
## The Veil as Cultural Custodian:
The Veil, emerging from the post-collapse adaptation of preexisting religious and cultural practices, evolved into a matriarchal order central to maintaining the Freehold’s ethical architecture. This evolution was characterized not by rigid preservation but by adaptive synthesis, wherein ceremonial gravitas was merged with pragmatic domestic guidance. The Veil functioned as a moral custodian, particularly within the familial sphere, where its influence was most profoundly exercised. Veilmother Cordelia’s role during the Winter Vigil exemplifies this dual function of leadership and philosophical stewardship, as her guidance articulated not only the ritual's procedural elements but also the embedded moral philosophy that would shape the initiates' worldview.
## Ritual Dynamics and Symbolism:
The Winter Vigil is fundamentally an enactment of moral endurance, wherein the initiate’s voluntary approach to the brazier represents an acceptance of communal responsibility through individual fortitude. The design of the ritual deliberately positions physical endurance as a metaphor for moral resilience, encapsulating the Freehold’s conviction that true strength is inherently silent and steadfast. As the initiate moves toward the brazier, kneeling in proximity to the flame, the act becomes a performative affirmation of the Compact’s call for measured, principled strength rather than ostentatious assertion. The structured progression from the outer circle to the brazier symbolizes a journey from collective dependency to personal sovereignty, reflecting the Compact's ethos that leadership is merited through tested perseverance.
## The Copper Plate Rite:
The Copper Plate Rite, integral to the Vigil, embodies the transformative philosophy of the Freehold. The heated copper plate, inscribed with the flame symbol and lifted from ashes, is held aloft despite discomfort, symbolizing the embrace of hardship as an essential component of sovereignty. The fleeting burn, leaving a transient mark, underscores the philosophical assertion that genuine resilience is born of confronting and integrating suffering, rather than circumventing it. This rite functions not merely as a test of physical tolerance but as a pedagogical imprinting of the Freehold’s ethos—an allegory of death and rebirth integral to personal and communal maturation.
## Symbolic Implications and Societal Continuity:
The deliberate imposition of discomfort during the Vigil underscores a fundamental tenet of Freehold philosophy: suffering, when purposefully endured, refines the individual and, by extension, fortifies the community. The Copper Plate Rite exemplifies the doctrine that hardship, when faced with deliberate resolve, engenders moral clarity. This paradigm of voluntary suffering as a crucible for leadership remains a cornerstone of the Freehold’s ideological framework, fostering a collective ethos rooted in patient perseverance rather than impulsive dominance. Furthermore, the initiation rite serves as a microcosm of the Freehold's broader sociocultural ethos, where personal sacrifice is inextricably linked to communal stability.
## Interpretive Analysis:
Current historiographical interpretations often err by neglecting the interconnectedness of the Vigil with broader sociopolitical dynamics. By isolating the rite as a mere ceremonial endurance, scholars risk overlooking its function as a structured pedagogical tool for inculcating moral resilience. This study posits that the Vigil, far from being a vestigial tradition, actively cultivated a pragmatic ethic of endurance that proved crucial in the Freehold’s sustained sociocultural coherence. This coherence, rooted in ritual reinforcement of moral tenets, enabled the Freehold to navigate existential threats without succumbing to internal decay.
## Cultural and Societal Implications:
The enduring significance of the Winter Vigil lies in its dual function as both a rite of passage and a communal reaffirmation of the Freehold’s meritocratic principles. By fostering individual accountability within a collective moral framework, the Vigil reinforced the Compact’s foundational premise that leadership is merited through demonstrated resilience. The integration of personal trial into communal identity formation exemplifies how the Freehold maintained its internal stability despite external societal fragmentation. This ritual, therefore, is not merely commemorative but constitutive of the Freehold's enduring cultural legacy.
## Conclusion:
The Winter Vigil of XLII.II at Sapelo remains a paradigmatic example of ritual as a vehicle for social continuity within the Lowcountry Freehold. Its deliberate amalgamation of symbolic endurance with moral instruction illustrates the Freehold’s adaptive strategy of embedding philosophical imperatives within lived tradition. As modern scholars, it is incumbent upon us to engage with these practices not merely as remnants of a bygone era but as foundational elements that cultivated the durable sociocultural ethos underpinning our current stability.
## References:
1. Vance, C. (Epoch LII). "The Compact and Cultural Continuity: An Oral History." Archive of Freehold Studies, Emberwell Hall.
2. Harlowe, E. (Epoch LX). "The Flamekeepers: Guardians of Tradition." Journal of Sociocultural Persistence, Vol. 22, pp. 45-72.
3. Morgan, T. (Epoch LXV). "Endurance Through Ritual: The Role of The Veil in Cultural Preservation." Lowcountry Academic Press.
4. Cordelia, V. (Epoch XLII). "Reflections on the Flame: An Instructional Account." Collected Teachings of The Veil.
5. Emberwell Institute (Epoch XC). "The Evolution of Freehold Rites: From Custom to Philosophy." Advanced Studies in Cultural Integration.
## Title: Ritual as Continuity: An Analysis of the Winter Vigil of XLII.II at Sapelo
### Epoch XLII - Circle of Maidens
#### Abstract:
This paper presents a rigorous and critical examination of the Winter Vigil of XLII.II at Sapelo, a pivotal rite within the Lowcountry Freehold that serves as both an initiation into communal responsibility and a symbolic enactment of the Compact’s moral tenets. This analysis interrogates the ritual’s structure, emphasizing its role in perpetuating a resilient sociocultural order amid external collapse. Through a multidisciplinary approach combining historiographical analysis, cultural anthropology, and sociocultural theory, this study elucidates the Vigil’s function as a mechanism for moral continuity, thereby situating it within the broader discourse of post-collapse societal stabilization. The implications of this study underscore the profound interconnectedness between ritual practice and the formation of resilient communal identities.
#### Introduction:
The Winter Vigil of XLII.II at Sapelo occupies a fundamental position in the cultural historiography of the Lowcountry Freehold. As contemporary scholars, it is imperative to approach this tradition not merely as an artifact of ritualistic antiquity but as a dynamic process of cultural preservation. The Freehold’s commitment to integrating tradition with pragmatism, especially through the stewardship of The Veil, constitutes a critical adaptive strategy that sustained sociopolitical coherence through epochs of external fragmentation. This study aims to critically examine the Vigil as both a symbolic and practical reinforcement of the Compact’s ethos, with particular attention to how this ritual facilitated intergenerational continuity of moral and social values, ultimately shaping the robust communal identity that defines contemporary Freehold society.
#### The Veil as Cultural Custodian:
The Veil, emerging from the post-collapse adaptation of preexisting religious and cultural practices, evolved into a matriarchal order central to maintaining the Freehold’s ethical architecture. This evolution was characterized not by rigid preservation but by adaptive synthesis, wherein ceremonial gravitas was merged with pragmatic domestic guidance. The Veil functioned as a moral custodian, particularly within the familial sphere, where its influence was most profoundly exercised. Veilmother Cordelia’s role during the Winter Vigil exemplifies this dual function of leadership and philosophical stewardship, as her guidance articulated not only the ritual's procedural elements but also the embedded moral philosophy that would shape the initiates' worldview.
#### Ritual Dynamics and Symbolism:
The Winter Vigil is fundamentally an enactment of moral endurance, wherein the initiate’s voluntary approach to the brazier represents an acceptance of communal responsibility through individual fortitude. The design of the ritual deliberately positions physical endurance as a metaphor for moral resilience, encapsulating the Freehold’s conviction that true strength is inherently silent and steadfast. As the initiate moves toward the brazier, kneeling in proximity to the flame, the act becomes a performative affirmation of the Compact’s call for measured, principled strength rather than ostentatious assertion. The structured progression from the outer circle to the brazier symbolizes a journey from collective dependency to personal sovereignty, reflecting the Compact's ethos that leadership is merited through tested perseverance.
#### The Copper Plate Rite:
The Copper Plate Rite, integral to the Vigil, embodies the transformative philosophy of the Freehold. The heated copper plate, inscribed with the flame symbol and lifted from ashes, is held aloft despite discomfort, symbolizing the embrace of hardship as an essential component of sovereignty. The fleeting burn, leaving a transient mark, underscores the philosophical assertion that genuine resilience is born of confronting and integrating suffering, rather than circumventing it. This rite functions not merely as a test of physical tolerance but as a pedagogical imprinting of the Freehold’s ethos—an allegory of death and rebirth integral to personal and communal maturation.
#### Symbolic Implications and Societal Continuity:
The deliberate imposition of discomfort during the Vigil underscores a fundamental tenet of Freehold philosophy: suffering, when purposefully endured, refines the individual and, by extension, fortifies the community. The Copper Plate Rite exemplifies the doctrine that hardship, when faced with deliberate resolve, engenders moral clarity. This paradigm of voluntary suffering as a crucible for leadership remains a cornerstone of the Freehold’s ideological framework, fostering a collective ethos rooted in patient perseverance rather than impulsive dominance. Furthermore, the initiation rite serves as a microcosm of the Freehold's broader sociocultural ethos, where personal sacrifice is inextricably linked to communal stability.
#### Interpretive Analysis:
Current historiographical interpretations often err by neglecting the interconnectedness of the Vigil with broader sociopolitical dynamics. By isolating the rite as a mere ceremonial endurance, scholars risk overlooking its function as a structured pedagogical tool for inculcating moral resilience. This study posits that the Vigil, far from being a vestigial tradition, actively cultivated a pragmatic ethic of endurance that proved crucial in the Freehold’s sustained sociocultural coherence. This coherence, rooted in ritual reinforcement of moral tenets, enabled the Freehold to navigate existential threats without succumbing to internal decay.
#### Cultural and Societal Implications:
The enduring significance of the Winter Vigil lies in its dual function as both a rite of passage and a communal reaffirmation of the Freehold’s meritocratic principles. By fostering individual accountability within a collective moral framework, the Vigil reinforced the Compact’s foundational premise that leadership is merited through demonstrated resilience. The integration of personal trial into communal identity formation exemplifies how the Freehold maintained its internal stability despite external societal fragmentation. This ritual, therefore, is not merely commemorative but constitutive of the Freehold's enduring cultural legacy.
#### Conclusion:
The Winter Vigil of XLII.II at Sapelo remains a paradigmatic example of ritual as a vehicle for social continuity within the Lowcountry Freehold. Its deliberate amalgamation of symbolic endurance with moral instruction illustrates the Freehold’s adaptive strategy of embedding philosophical imperatives within lived tradition. As modern scholars, it is incumbent upon us to engage with these practices not merely as remnants of a bygone era but as foundational elements that cultivated the durable sociocultural ethos underpinning our current stability.
#### References:
1. Vance, C. (Epoch LII). "The Compact and Cultural Continuity: An Oral History." Archive of Freehold Studies, Emberwell Hall.
2. Harlowe, E. (Epoch LX). "The Flamekeepers: Guardians of Tradition." Journal of Sociocultural Persistence, Vol. 22, pp. 45-72.
3. Morgan, T. (Epoch LXV). "Endurance Through Ritual: The Role of The Veil in Cultural Preservation." Lowcountry Academic Press.
4. Cordelia, V. (Epoch XLII). "Reflections on the Flame: An Instructional Account." Collected Teachings of The Veil.
5. Emberwell Institute (Epoch XC). "The Evolution of Freehold Rites: From Custom to Philosophy." Advanced Studies in Cultural Integration.
-

@ fd78c37f:a0ec0833
2025-03-29 04:33:01
**YakiHonne**: I'm excited to be joined by our guest Piccolo—thank you very much for being here. Before we dive in, I'd like to briefly introduce YakiHonne. YakiHonne is a decentralized media client built on the Nostr protocol, leveraging technology to enable freedom of speech. It empowers creators to fully own their voice and assets while offering innovative tools such as Smart widget , Verified Notes, and support for long-form content. Today, we’re not just discussing YakiHonne, but also diving into your community. Piccolo, could you start by telling us a bit about yourself and your community?
**Piccolo**:Hi, I'm Piccolo. I run BO฿ Space in Bangkok, and we also have a satellite location called the BO฿ Space corner in Chiang Mai, thanks to the Bitcoin Learning Center.
**Piccolo**:Regarding my background,I originally came from corporate finance and investment banking. I was in that field for about 20 years, with the last 15 spent running my own firm in corporate finance advisory alongside a couple of partners. We eventually sold the advisory business in 2015, took a short break, and in 2016, I ended up launching a fintech company, which is still operational today. The company specializes in equity crowdfunding and is licensed by the SEC in Thailand.
**Piccolo**:I first bought Bitcoin a few years before truly understanding it, initially thinking it was a scam that would eventually collapse. However, in 2017, the block size wars demonstrated the protocol’s strong resistance to attacks on decentralization, which deeply impacted me. By late 2018 or early 2019, I started to really grasp Bitcoin and kept learning. Then, in mid-2022, after having fully fallen down the Bitcoin rabbit hole, I founded BO฿ Space. It was right after COVID, and since the fintech had scaled down, there was extra space. We started by hosting meetups and technical workshops for people who were interested.
**Piccolo**:In the early years, we had various groups come by—like the team from BDK (Bitcoin Development Kit), who held workshops. The people behind the Bitcoin Beach Wallet, which later became Blink, also visited. So, BO฿ Space initially functioned as a meetup and technical workshop space. Eventually, we launched the BOB Builders Residency program, which was a lot of fun. We secured grant funding for developers under different cohort themes, so that they can collaborate and co-work for a few months. So far, we have completed three cohorts.
**YakiHonne**:How did your community get started, and what did you do to attract new members in the beginning?
**Piccolo**:The initial members came through word of mouth and invitations that I sent out. I reached out to an initial group of Bitcoiners here in the city who I believed were strong maximalists or Bitcoin-only supporters, back when that was still a thing. I sent out 21 invitations and had our first meetup with 21 people, most of whom I had interacted with online, though some in person during the COVID years. From there, it spread by word of mouth, and of course, through Twitter and meetup.com. So, I would say that word of mouth remains the main method of growth. Additionally, when people come through Bangkok and are looking for a Bitcoin-only meetup, there really isn't one available. I believe there are a couple now—maybe two or three—but when we started, there weren’t any, especially not a dedicated Bitcoin-only space. I think we may still be the only one in Bangkok. So yeah, word of mouth was definitely the main way we grew. Bitcoiners tend to share their finds when they meet like-minded people.

**YakiHonne**:Didn’t you have people in your community who initially thought Bitcoin was a scam, like you did, or face similar issues?
**Piccolo**:Yes, it still happens, especially when the price of Bitcoin rises. Newcomers still join, and some of them believe Bitcoin might be a scam. However, this has become less frequent. The main reason is that when people come to BO฿ Space, they know it’s a Bitcoin-only meetup. We generally don’t discuss the price; instead, we focus on other aspects of Bitcoin, as there are many interesting developments in the space.
**YakiHonne**:What advice would you give to someone looking to start or grow a Bitcoin-focused community in today’s world? Considering the current landscape, much like your own experience, what guidance would you offer?
**Piccolo**:It sounds simple, but just do it. When it comes to community building, you don’t necessarily need a physical space. Community is about people coming together, right? Two people can start a community, then three, four, and so on. Meetups can happen anywhere—your favorite bar, a restaurant, a friend’s garage, or wherever. So, just do it, but make sure you have more than one person, otherwise, how can you build a community? Once you have more than one person, word of mouth will spread. And as you develop a core group—let’s say more than five people—that’s when I think the community can truly sustain itself.
**YakiHonne**:I know you’ve mentioned the technical side of your community, but I’ll ask anyway—does your community engage with the technical or non-technical aspects of Bitcoin? Or perhaps, is there a blend of both?
**Piccolo**:I would say both. It really depends on the monthly themes of our meetups. For example, February was focused on Asian communities in Bitcoin. During that month, community leaders came in to give presentations and discuss their work in places like Indonesia, India, and more recently, someone from HRF (Human Rights Foundation) talked about Bitcoin’s use case in Myanmar. Then, in December, we had a very technical month—Mining Month. It was led by our Cohort 3 residents, where we discussed Stratum V2 and had a demo on it. We also examined the Loki board hardware, and Zack took apart the S19, looking at different ways to repurpose the power supply unit, among other things. So, it’s a mix of both, depending on the theme for that month. Some months are very technical, while others are more community-focused and less technical.
**YakiHonne**:What advice would you give to a technically inclined individual or organization looking to contribute meaningfully to the Bitcoin ecosystem?
**Piccolo**:For technically inclined individuals, I would suggest identifying your favorite open-source project in the Bitcoin ecosystem. Start from Bitcoin Core and explore different layers, such as Lightning or e-cash, and other open-source projects. As for technically inclined organizations, if you're integrating Bitcoin into your business, I would say, first, make sure you have people within your organization who truly understand Bitcoin. Build a capable team first, and then, depending on the part of the Bitcoin ecosystem you’re involved in—whether it’s custody services, Lightning payments, layer 2, or something like Cashu or Ark—find your niche. From there, your team will work with you to discover ways to contribute. But until you build that capability, organizations are a bit different from individuals in this space.
**YakiHonne**:How do you see the world of Bitcoin communities evolving as technology matures, particularly in areas like scalability, privacy, and adaptability with other systems?
**Piccolo**:That's an interesting question. If we think about the future of Bitcoin communities, I believe they may eventually disappear as technology matures. Once Bitcoin scales to a point where it integrates seamlessly with other payment systems, becoming part of the everyday norm, the need for dedicated communities will diminish. It’s similar to how we no longer have meetups about refrigerators or iPhones, even though they are technologies we use every day. As Bitcoin matures, it will likely reach that level of ubiquity. There might still be occasional meetups or forums, but they will be more about specific knowledge, use cases, and tools, rather than a community dedicated to introducing others to the technology itself. However, this is a long way off. Bitcoin is still relatively small compared to the global fiat financial system, despite the growth we want to see. So, it will take a long time before we reach that stage.
**YakiHonne**:It’s something I hadn’t considered before, and it’s quite insightful. Moving to our last question actually which I find very interesting is the government around you for or against bitcoin and how has That affected the community.
**Piccolo**:In my opinion, on a general level, the government is more supportive than opposed to Bitcoin. The Thai government classifies Bitcoin as a digital asset, almost like digital gold. In that sense, they want to tax capital gains and regulate it. They also have a regulatory framework for it, known as the Digital Asset Regulatory Sandbox, where you can test various things, mainly coins and tokens. It's unfortunate, but that’s how it is. However, our government, especially the regulatory bodies, are open to innovation. They recognize that Bitcoin is different, but they still view blockchain and tokens as useful technologies, which is somewhat misguided. So, in that sense, it’s more support than opposition. A couple of years ago, there was a circular discouraging the use of Bitcoin as a payment currency, mainly because they can't control its monetary policy. And they’re right—Bitcoin can’t be controlled by anyone; there’re the protocol and the rules, and everyone follows them, unless there’s a hard fork, which is a different matter. So, in that regard, Bitcoin is definitely categorized as a digital asset by the government, and that’s where it stands.
**Piccolo**:People who come to BO฿ Space to learn about Bitcoin are often influenced by the government from the point of price movements; especially when government support moves the price up. But they usually only visit once or twice, especially if they’re not deep into the Bitcoin rabbit hole. They often get disappointed because, at BO฿ Space, we rarely discuss the price—maybe once a year, and that’s just after the meetup when people are having drinks. So, in that sense, I’d say the government currently doesn’t really hurt or help the community either way. People will go down the rabbit hole at their own pace. And if you're not a Bitcoiner and you come to a BO฿ Space meetup with a crypto focus, you might be surprised by the approach we take.
**YakiHonne**:Thank you, Piccolo, for your time and insights. It’s been a pleasure speaking with you. Your perspective on the evolution of Bitcoin communities was eye-opening. It's clear that your deep understanding of Bitcoin is invaluable. I'm sure our readers will appreciate your insights. Once again, thank you, Piccolo. I look forward to seeing the continued growth of BO฿ Space and Bitcoin adoption.
-

@ 2183e947:f497b975
2025-03-29 02:41:34
Today I was invited to participate in the private beta of a new social media protocol called Pubky, designed by a bitcoin company called Synonym with the goal of being better than existing social media platforms. As a heavy nostr user, I thought I'd write up a comparison.
I can't tell you how to create your own accounts because it was made very clear that only *some* of the software is currently open source, and how this will all work is still a bit up in the air. The code that *is* open source can be found here: https://github.com/pubky -- and the most important repo there seems to be this one: https://github.com/pubky/pubky-core
You can also learn more about Pubky here: https://pubky.org/
That said, I used my invite code to create a pubky account and it seemed very similar to onboarding to nostr. I generated a private key, backed up 12 words, and the onboarding website gave me a public key.
Then I logged into a web-based client and it looked a lot like twitter. I saw a feed for posts by other users and saw options to reply to posts and give reactions, which, I saw, included hearts, thumbs up, and other emojis.
Then I investigated a bit deeper to see how much it was like nostr. I opened up my developer console and navigated to my networking tab, where, if this was nostr, I would expect to see queries to relays for posts. Here, though, I saw one query that seemed to be repeated on a loop, which went to a single server and provided it with my pubkey. That single query (well, a series of identical queries to the same server) seemed to return all posts that showed up on my feed. So I infer that the server "knows" what posts to show me (perhaps it has some sort of algorithm, though the marketing material says it does not use algorithms) and the query was on a loop so that if any new posts came in that the server thinks I might want to see, it can add them to my feed.
Then I checked what happens when I create a post. I did so and looked at what happened in my networking tab. If this was nostr, I would expect to see multiple copies of a signed messaged get sent to a bunch of relays. Here, though, I saw one message get sent to the same server that was populating my feed, and that message was not signed, it was a plaintext copy of my message.
I happened to be in a group chat with John Carvalho at the time, who is associated with pubky. I asked him what was going on, and he said that pubky is based around three types of servers: homeservers, DHT servers, and indexer servers. The homeserver is where you create posts and where you query for posts to show on your feed. DHT servers are used for censorship resistance: each user creates an entry on a DHT server saying what homeserver they use, and these entries are signed by their key.
As for indexers, I think those are supposed to speed up the use of the DHT servers. From what I could tell, indexers query DHT servers to find out what homeservers people use. When you query a homeserver for posts, it is supposed to reach out to indexer servers to find out the homeservers of people whose posts the homeserver decided to show you, and then query those homeservers for those posts. I believe they decided not to look up what homeservers people use directly on DHT servers directly because DHT servers are kind of slow, due to having to store and search through all sorts of non-social-media content, whereas indexers only store a simple db that maps each user's pubkey to their homeserver, so they are faster.
Based on all of this info, it seems like, to populate your feed, this is the series of steps:
- you tell your homeserver your pubkey
- it uses some sort of algorithm to decide whose posts to show you
- then looks up the homeservers used by those people on an indexer server
- then it fetches posts from their homeservers
- then your client displays them to you
To create a post, this is the series of steps:
- you tell your homeserver what you want to say to the world
- it stores that message in plaintext and merely asserts that it came from you (it's not signed)
- other people can find out what you said by querying for your posts on your homeserver
Since posts on homeservers are not signed, I asked John what prevents a homeserver from just making up stuff and claiming I said it. He said nothing stops them from doing that, and if you are using a homeserver that starts acting up in that manner, what you should do is start using a new homeserver and update your DHT record to point at your new homeserver instead of the old one. Then, indexers should update their db to show where your new homeserver is, and the homeservers of people who "follow" you should stop pulling content from your old homeserver and start pulling it from your new one. If their homeserver is misbehaving too, I'm not sure what would happen. Maybe it could refuse to show them the content you've posted on your new homeserver, keeping making up fake content on your behalf that you've never posted, and maybe the people you follow would never learn you're being impersonated or have moved to a new homeserver.
John also clarified that there is not currently any tooling for migrating user content from one homeserver to another. If pubky gets popular and a big homeserver starts misbehaving, users will probably need such a tool. But these are early days, so there aren't that many homeservers, and the ones that exist seem to be pretty trusted.
Anyway, those are my initial thoughts on Pubky. Learn more here: https://pubky.org/
-

@ 5d4b6c8d:8a1c1ee3
2025-03-29 02:18:49
Only one more month to make adjustments and a couple of my guys haven't played enough games to be eligible for the awards.
- Jokic needs to play two more
- Giannis needs to play five more
Other notable players who haven't yet played 65 games:
- Luka is not even close
- Brunson needs to play four more (and probably needs to be replaced regardless)
- Wemby is not even close
Here's the current state of the competition with your max possible score next to your nym:
| Contestant | MVP | Champ | All NBA | | | | |
|--------------|------|---------|----------|-|-|-|-|
| @Undisciplined 47| SGA| OKC | Jokic | KAT |Giannis |Tatum | SGA |
| @grayruby 46| SGA| Cavs| Jokic | Giannis | SGA| Mitchell| Brunson|
| @gnilma 55| SGA| OKC| Jokic | KAT | Giannis | Tatum| SGA |
| @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA|
| @Bell_curve 63| SGA| Celtics| Jokic | Giannis | Luka | Ant| SGA|
| @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson|
| @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson|
| @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA|
| @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA|
| @Carresan 34| SGA| Memphis| Jokic | KAT | Giannis | Ant| SGA|
| @BTC_Bellzer 34| SGA| Celtics| Jokic| Giannis | Tatum| SGA| Brunson |
| @realBitcoinDog 39| Lebron| Lakers| Jokic | Giannis | Ant | Brunson | SGA|
| @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA|
| @BlokchainB 38| SGA| Knicks| KAT| Giannis | Ant| Brunson| SGA|
| @LibertasBR 14| SGA| Celtics| Jokic| Giannis | Tatum | Curry| SGA|
| @Meani123 7| SGA| OKC| Jokic | KAT | Tatum | Mitchell | SGA|
**Prize**
At least 6k (I'll keep adding zaps to the pot).
If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the [June post](https://stacker.news/items/585231/r/Undisciplined) for more details.
originally posted at https://stacker.news/items/928370
-

@ df06d21e:2b23058f
2025-03-29 02:08:31
Imagine a Living Civilization—a new way to see our world. It starts with the Universe’s pillars: Matter, the stuff we’re made of; Energy, the flow that drives us; Physics, the rules we play by; and Chemistry, the complexity that builds us. We know these well. But civilization? That’s our creation—and although it has been described in so many different ways over the years I thought it was time for something new. Civilization has its own pillars, systems that I call the pillars of the Metaverse: Capital, Information, Innovation, and Trust.
Capital is how we measure value. Not just money, but everything that matters: skills, we call that Human Capital; ecosystems, that’s Natural Capital; infrastructure, Public Capital; relationships, Social Capital. Picture a farmer swapping Bitcoin sats for seeds—not fiat debt—or tracking soil health alongside his wallet. Capital is a system, a system of measurement.
Information is how we verify truth. Think IPFS, a network holding real data—climate stats, farming fixes—open to all, not locked up by some corporate gatekeeper. Information is a system of verification.
Innovation is about generating solutions. On GitHub, coders worldwide crank out tools—Nostr clients, solar apps—shared freely, not patented for profit. Innovation is our system of generation.
And Trust—it’s coordination. Nostr’s decentralized threads let communities set trade rules, split resources—governance from the ground up, no overlords required. Trust is our system of coordination.
Right now we’re stuck in debt-based systems—and they’re failing us. Take fiat currency—central banks print it, slashing your purchasing power. Our dollar buys less every year; savings erode while the elite stack their gains. It’s a scam, Bitcoiners know it—fiat’s the real Ponzi bleeding us dry. Capital gets twisted—firms hoard Bitcoin for fiat pumps, not real wealth; governments chase GDP while forests die and skills sit idle. Information is buried—our media spits out spin, our corporations lock truth in silos. Innovation is stalled—debt props up corporate patents, not open wins. Trust is gone—our governance systems consist of top-down control that splits us apart, left to right, top to bottom. Debt just measures scarcity—money borrowed, nature trashed, bonds frayed—and it’s crushing the pillars.
Wealth-based systems promise to turn that around. Bitcoin’s sound money is just the start—sats hold value, not inflate it away. Real capital measures what sustains us—sats fund a cooperative's water pump, not a vault; they track skills taught, land healed, ties rebuilt. Real Information opens up—IPFS logs show ‘biochar boosted yield 20%’, verified by us, not suits. Real Innovation flows—GitHub devs build Lightning hubs, wealth spreads. Real Trust binds us together—Nostr chats align us, no central puppeteer. Wealth based systems strengthen the pillars of the Metaverse, it doesn’t erode them.
We needed a new framing. A new vision of what was, what is, and what could be. We have one. This is real. This is the world we are building. Bitcoin is live, Nostr is growing, IPFS and GitHub are humming. We can see Debt teetering; while real wealth is rising. So, hodlers, maxis, plebs—everyone—what does a true wealth-based system look like? How can we measure Capital beyond fiat’s con job? Bitcoin’s the rock, but it’s just the beginning. How do we build on this, expand it, and transform everything as we build something entirely new?
-

@ 3e6e0735:9e95c8a2
2025-03-28 23:58:02
https://i.nostr.build/lanoHI3p2aCKRZlV.png
I’ve been thinking a lot lately about why Bitcoin still feels so misunderstood. Not just by the media or the IMF — that part’s predictable. But even inside our own circles, something's missing.
We say it’s money. We say it’s freedom. We say it’s code. And it is. But when you really zoom out, past the price and the politics, it’s something more radical than we usually admit.
Bitcoin is a shift in how power moves. And what we do with that power now actually matters.
## The noise outside
Let’s start with the obvious: the media still doesn’t get it. Every other headline is either a death knell or a celebration depending on the price that day. No context. No nuance. No understanding of what we’re building.
You’ve seen the headlines:
- “Bitcoin is crashing again.”
- “Crypto bros are killing the planet.”
- “The IMF warns: Bitcoin adoption is dangerous.”
Yeah? Dangerous to what?
The system they control. The levers they pull. The old game where the house always wins.
That’s why they’re afraid. Not because Bitcoin is volatile, but because it doesn’t ask permission.
## This isn’t about panic — it’s about patterns
I’m not saying there’s a conspiracy. But there is inertia. Institutions protect themselves. Systems reinforce themselves. They were never going to roll out the red carpet for an open, borderless network that replaces their function.
So the IMF calls it a threat. Central banks scramble to launch CBDCs. And journalists keep writing the same shallow takes while ignoring the real story.
Meanwhile, we’re still here. Still building. Still holding. Still running nodes.
Bitcoin isn’t perfect. But it’s honest. It doesn’t bend to popularity or political pressure. It enforces rules with math, not people. And that’s exactly why it works.
## Even we miss it sometimes
Here’s the part that really hit me recently: even within Bitcoin, we often undersell what this is.
We talk about savings. Inflation. Fiat debasement. All real, all important.
But what about the broader layer? What about governance? Energy? Communication? Defense?
Jason Lowery’s book *Softwar* lit that fuse for me again. Not because it’s flawless — it’s not. But because he reframed the game.
Bitcoin isn’t a new weapon. It’s the **end** of weapons-as-power.
Proof-of-work, in Lowery’s view, is a form of peaceful negotiation. A deterrent against coercion. A way to shift from kinetic violence to computational resolution.
Most people — even many Bitcoiners — haven’t fully absorbed that.
It’s not about militarizing the network. It’s about **demilitarizing the world** through energy expenditure that replaces human conflict.
Let’s be clear: this doesn’t mean Bitcoin *will* be used this way. It means it *can*. And that opens up a few possible futures:
- **Scenario A:** Smaller nations adopt Bitcoin infrastructure as a shield — a deterrent and neutral layer to build sovereignty
- **Scenario B:** Superpowers attack mining and self-custody, escalating regulatory capture and fragmenting the open protocol into corporate silos
- **Scenario C:** Bitcoin becomes the boring backend of legacy finance, its edge neutered by ETFs and custody-as-a-service
Which one wins depends on what we build — and who steps up.
## Then I found Maya
I came across Maya Parbhoe’s campaign by accident. One of those late-night rabbit holes where Bitcoin Twitter turns into a global map.
She’s running for president of Suriname. She’s a Bitcoiner. And she’s not just tweeting about it — she’s building an entire political platform around it.
No central bank. Bitcoin as legal tender. Full fiscal transparency. Open-source government.
Yeah. You read that right. Not just open-source software — open-source statehood.
Her father was murdered after exposing corruption. That’s not a talking point. That’s real-life consequence. And instead of running away from systems, she’s choosing to redesign one.
That’s maximalism. Not in ideology. In action.
## The El Salvador experiment — and evolution
When El Salvador made Bitcoin legal tender in 2021, it lit up our feeds. It was bold. Unprecedented. A true first.
But not without flaws.
The rollout was fast. Chivo wallet was centralized. Adoption stalled in rural areas. Transparency was thin. And despite the brave move, the state’s underlying structure remained top-down.
Bukele played offense, but the protocol was wrapped in traditional power.
Maya is doing it differently. Her approach is grassroots-forward. Open-source by design. Focused on education, transparency, and modular state-building — not just mandates.
She’s not using Bitcoin to *prop up* state power. She’s using it to *distribute* it.
## Maximalism is evolving
Look, I get it. The memes are fun. The laser eyes. The beefsteak meetups. The HODL culture.
But there’s something else growing here. Something a little quieter, a little deeper:
- People running nodes to protect civil liberties
- Communities using Lightning for real commerce
- Builders forging tools for self-sovereign identity
- Leaders like Maya testing what Bitcoin can look like as public infrastructure
This is happening. In real time. It’s messy and fragile and still small. But it’s happening.
Let’s also stay honest:
Maximalism has its risks. Dogma can blind us. Toxicity can push people away. And if we’re not careful, we’ll replace one centralization with another — just wearing different memes.
We need less purity, more principles. Less hype, more clarity. That’s the kind of maximalism Maya embodies.
## What now?
Maya doesn’t have a VC fund or an ad agency. She has a message, a mission, and the courage to put Bitcoin on the ballot.
If that resonates, help her. Not just by donating — though here’s the link:
[https://geyser.fund/project/maya2025
](https://geyser.fund/project/maya2025)
But by sharing. Writing. Talking. Translating. Connecting.
Bitcoin is still early. But it’s not abstract anymore.
This isn’t just theory.
It’s a protocol, sure.
But now, maybe it’s a presidency too.
https://i.nostr.build/0luYy8ojK7gkxsuL.png
-

@ 7d33ba57:1b82db35
2025-03-28 22:14:24
Preko is a charming seaside town on Ugljan Island, just a short ferry ride from Zadar. Known for its beautiful beaches, relaxed atmosphere, and stunning views of the Adriatic, it's the perfect place to experience authentic Dalmatian island life.

## **🌊 Top Things to See & Do in Preko**
### **1️⃣ Swim at Jaz Beach 🏖️**
- A **Blue Flag beach** with **clear turquoise waters and soft pebbles**.
- Ideal for **families** thanks to its shallow waters.
- Nearby **cafés and restaurants** make it a great spot to spend the day.
### **2️⃣ Visit the Islet of Galevac 🏝️**
- A **tiny island just 80 meters from Preko**, reachable by swimming or a short boat ride.
- Home to a **15th-century Franciscan monastery**, surrounded by lush greenery.
- A **peaceful retreat**, perfect for relaxation.

### **3️⃣ Hike to St. Michael’s Fortress (Sv. Mihovil) 🏰**
- A **medieval fortress from the 13th century** with **breathtaking panoramic views**.
- Overlooks **Zadar, Kornati Islands, and the Adriatic Sea**.
- A **1-hour scenic hike** from Preko or accessible by **bike or car**.
### **4️⃣ Explore the Local Taverns & Seafood Restaurants 🍽️**
- Try **fresh seafood, octopus salad, and Dalmatian peka (slow-cooked meat & vegetables)**.
- **Best spots:** Konoba Roko (authentic seafood) & Vile Dalmacija (beachfront dining).
### **5️⃣ Rent a Bike or Scooter 🚲**
- Explore **Ugljan Island’s olive groves, hidden coves, and coastal paths**.
- Visit nearby villages like **Kali and Kukljica** for more local charm.

### **6️⃣ Take a Day Trip to Zadar ⛵**
- Just **25 minutes by ferry**, Zadar offers **historic landmarks, the Sea Organ, and Roman ruins**.
- Perfect for a cultural excursion before returning to the peaceful island.

## **🚗 How to Get to Preko**
🚢 **By Ferry:**
- **From Zadar:** Regular ferries (Jadrolinija) take **~25 minutes**.
🚘 **By Car:**
- If driving, take the **ferry from Zadar to Preko** and explore the island.
🚴 **By Bike:**
- Many visitors rent bikes to explore Ugljan Island’s coastal roads.

## **💡 Tips for Visiting Preko**
✅ **Best time to visit?** **May–September** for warm weather & swimming 🌞
✅ **Ferry schedules** – Check times in advance, especially in the off-season ⏳
✅ **Bring cash** – Some smaller taverns and cafés may not accept cards 💰
✅ **Stay for sunset** – The views over Zadar from Preko’s waterfront are stunning 🌅
Would you like **hotel recommendations, hidden beaches, or other island activities**? 😊
-

@ fe9e99a0:5123e9a8
2025-03-28 21:25:43
What’s happening?
-

@ 04c915da:3dfbecc9
2025-03-25 17:43:44
One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-

@ 04c915da:3dfbecc9
2025-03-07 00:26:37
There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
**Small Wins**
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
**Ego is Volatile**
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
**Simplicity**
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
**The Big Picture**
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \
\
Stay Humble and Stack Sats. 🫡
-

@ 6389be64:ef439d32
2025-02-27 21:32:12
GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
## House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
## Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
## Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
## MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
## UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
## Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
## The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
**🎧 Listen to the full episode here: [https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks](Fountain.fm)**
**💰 Support the show by boosting sats on Podcasting 2.0!** and I will see you on the other side.
-

@ 04c915da:3dfbecc9
2025-02-25 03:55:08
Here’s a revised timeline of macro-level events from *The Mandibles: A Family, 2029–2047* by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
### Part One: 2029–2032
- **2029 (Early Year)**\
The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
- **2029 (Mid-Year: The Great Renunciation)**\
Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
- **2029 (Late Year)**\
Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
- **2030–2031**\
Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
- **2032**\
By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
### Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
### Part Two: 2047
- **2047 (Early Year)**\
The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
- **2047 (Mid-Year)**\
Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
- **2047 (Late Year)**\
The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
### Key Differences
- **Currency Dynamics**: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- **Government Power**: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- **Societal Outcome**: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-

@ 7d33ba57:1b82db35
2025-03-28 20:59:51
Krka National Park, located in central Dalmatia, is one of Croatia’s most breathtaking natural wonders. Famous for its stunning waterfalls, crystal-clear lakes, and lush forests, the park is a must-visit for nature lovers. Unlike Plitvice Lakes, Krka allows swimming in certain areas, making it a perfect summer escape.

## **🌊 Top Things to See & Do in Krka National Park**
### **1️⃣ Skradinski Buk Waterfall 💦**
- The **largest and most famous waterfall** in the park, with **cascading pools and wooden walkways**.
- You **used to be able to swim here**, but since 2021, swimming is no longer allowed.
- Perfect for **photography and picnics**.
### **2️⃣ Roški Slap Waterfall 🌿**
- A **less crowded but equally beautiful** series of waterfalls.
- Known for its **"necklace" of small cascades** leading into the main fall.
- Nearby **Mlinica**, a restored **watermill**, shows traditional Croatian life.
### **3️⃣ Visovac Island & Monastery 🏝️**
- A **tiny island** in the middle of the Krka River, home to a **Franciscan monastery** from the 15th century.
- Accessible by **boat tour** from Skradinski Buk or Roški Slap.
- A peaceful, scenic spot with **stunning views of the lake**.

### **4️⃣ Krka Monastery 🏛️**
- A **Serbian Orthodox monastery** hidden deep in the park.
- Built on **ancient Roman catacombs**, which you can explore.
- A **quiet, spiritual place**, often overlooked by tourists.
### **5️⃣ Hike & Walk the Nature Trails 🥾**
- The park has **several well-marked trails** through forests, waterfalls, and lakes.
- Wooden walkways allow **easy access** to the main sights.
- **Wildlife spotting**: Look out for **otters, turtles, and over 200 bird species**!
### **6️⃣ Swim at Skradin Beach 🏖️**
- While you can’t swim at Skradinski Buk anymore, **Skradin Beach**, just outside the park, is a great spot for a dip.
- **Kayaking and boat tours** available.

## **🚗 How to Get to Krka National Park**
✈️ **By Air:** The nearest airport is **Split (SPU), 1 hour away**.
🚘 **By Car:**
- **Split to Krka:** ~1 hour (85 km)
- **Zadar to Krka:** ~1 hour (75 km)
- **Dubrovnik to Krka:** ~3.5 hours (280 km)
🚌 **By Bus:** Direct buses from **Split, Zadar, and Šibenik** to the park’s entrances.
🚢 **By Boat:** From **Skradin**, you can take a **boat ride** into the park.

## **💡 Tips for Visiting Krka National Park**
✅ **Best time to visit?** **Spring & early autumn (April–June, September–October)** – Fewer crowds & mild weather 🍃
✅ **Start early!** **Arrive before 10 AM** to avoid crowds, especially in summer ☀️
✅ **Bring water & snacks** – Limited food options inside the park 🍎
✅ **Wear comfy shoes** – Wooden walkways & trails can be slippery 👟
✅ **Take a boat tour** – The best way to see Visovac Island & hidden spots ⛵
✅ **Buy tickets online** – Save time at the entrance 🎟️

-

@ da0b9bc3:4e30a4a9
2025-03-28 19:14:52
It's Finally here Stackers!
It's Friday!
We're about to kick off our weekends with some feel good tracks.
Let's get the party started. Bring me those Feel Good tracks.
Let's get it!
https://youtu.be/r1ATFedwjnk?si=tPtLac6ExYZCx3Ez
originally posted at https://stacker.news/items/928119
-

@ 6e0ea5d6:0327f353
2025-02-21 18:15:52
"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.
— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend!
If this message helped you in any way,
consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-

@ 0d6c8388:46488a33
2025-03-28 16:24:00
Huge thank you to [OpenSats for the grant](https://opensats.org/blog/10th-wave-of-nostr-grants) to work on [Hypernote this year](https://www.hypernote.club/)! I thought I'd take this opportunity to try and share my thought processes for Hypernote. If this all sounds very dense or irrelevant to you I'm sorry!
===
How can the ideas of "hypermedia" benefit nostr? That's the goal of hypernote. To take the best ideas from "hypertext" and "hypercard" and "hypermedia systems" and apply them to nostr in a specifically nostr-ey way.
### 1. What do we mean by hypermedia
A hypermedia document embeds the methods of interaction (links, forms, and buttons are the most well-known hypermedia controls) within the document itself. It's including the _how_ with the _what_.
This is how the old web worked. An HTML page was delivered to the web browser, and it included in it a link or perhaps a form that could be submitted to obtain a new, different HTML page. This is how the whole web worked early on! Forums and GeoCities and eBay and MySpace and Yahoo! and Amazon and Google all emerged inside this paradigm.
A web browser in this paradigm was a "thin" client which rendered the "thick" application defined in the HTML (and, implicitly, was defined by the server that would serve that HTML).
Contrast this with modern app development, where the _what_ is usually delivered in the form of JSON, and then HTML combined with JavaScript (React, Svelte, Angular, Vue, etc.) is devised to render that JSON as a meaningful piece of hypermedia within the actual browser, the _how_.
The browser remains a "thin" client in this scenario, but now the application is delivered in two stages: a client application of HTML and JavaScript, and then the actual JSON data that will hydrate that "application".
(Aside: it's interesting how much "thicker" the browser has had to become to support this newer paradigm!)
Nostr was obviously built in line with the modern paradigm: nostr "clients" (written in React or Svelte or as mobile apps) define the _how_ of reading and creating nostr events, while nostr events themselves (JSON data) simply describe the _what_.
And so the goal with Hypernote is to square this circle somehow: nostr currently delivers JSON _what_, how do we deliver the _how_ with nostr as well. Is that even possible?
### 2. Hypernote's design assumptions
Hypernote assumes that hypermedia over nostr is a good idea! I'm expecting some joyful renaissance of app expression similar to that of the web once we figure out how to express applications in a truly "nostr" way.
Hypernote was also [deeply inspired by HTMX](https://hypermedia.systems/hypermedia-a-reintroduction/), so it assumes that building web apps in the HTMX style is a good idea. The HTMX insight is that instead of shipping rich scripting along with your app, you could simply make HTML a _tiny_ bit more expressive and get 95% of what most apps need. HTMX's additions to the HTML language are designed to be as minimal and composable as possible, and Hypernote should have the same aims.
Hypernote also assumes that the "design" of nostr will remain fluid and anarchic for years to come. There will be no "canonical" list of "required" NIPs that we'll have "consensus" on in order to build stable UIs on top of. Hypernote will need to be built responsive to nostr's moods and seasons, rather than one holy spec.
Hypernote likes the `nak` command line tool. Hypernote likes markdown. Hypernote likes Tailwind CSS. Hypernote likes SolidJS. Hypernote likes cold brew coffee. Hypernote is, to be perfectly honest, my aesthetic preferences applied to my perception of an opportunity in the nostr ecosystem.
### 3. "What's a hypernote?"
Great question. I'm still figuring this out. Everything right now is subject to change in order to make sure hypernote serves its intended purpose.
But here's where things currently stand:
A hypernote is a flat list of "Hypernote Elements". A Hypernote Element is composed of:
1. CONTENT. Static or dynamic content. (the what)
2. LOGIC. Filters and events (the how)
3. STYLE. Optional, inline style information specific to this element's content.
In the most basic example of a [hypernote story](https://hypernote-stories.fly.dev/), here's a lone "edit me" in the middle of the canvas:

```
{
"id": "fb4aaed4-bf95-4353-a5e1-0bb64525c08f",
"type": "text",
"text": "edit me",
"x": 540,
"y": 960,
"size": "md",
"color": "black"
}
```
As you can see, it has no logic, but it does have some content (the text "edit me") and style (the position, size, and color).
Here's a "sticker" that displays a note:
```
{
"id": "2cd1ef51-3356-408d-b10d-2502cbb8014e",
"type": "sticker",
"stickerType": "note",
"filter": {
"kinds": [
1
],
"ids": [
"92de77507a361ab2e20385d98ff00565aaf3f80cf2b6d89c0343e08166fed931"
],
"limit": 1
},
"accessors": [
"content",
"pubkey",
"created_at"
],
"x": 540,
"y": 960,
"associatedData": {}
}
```
As you can see, it's kind of a mess! The content and styling and underdeveloped for this "sticker", but at least it demonstrates some "logic": a nostr filter for getting its data.
Here's another sticker, this one displays a form that the user can interact with to SEND a note. Very hyper of us!
```
{
"id": "42240d75-e998-4067-b8fa-9ee096365663",
"type": "sticker",
"stickerType": "prompt",
"filter": {},
"accessors": [],
"x": 540,
"y": 960,
"associatedData": {
"promptText": "What's your favorite color?"
},
"methods": {
"comment": {
"description": "comment",
"eventTemplate": {
"kind": 1111,
"content": "${content}",
"tags": [
[
"E",
"${eventId}",
"",
"${pubkey}"
],
[
"K",
"${eventKind}"
],
[
"P",
"${pubkey}"
],
[
"e",
"${eventId}",
"",
"${pubkey}"
],
[
"k",
"${eventKind}"
],
[
"p",
"${pubkey}"
]
]
}
}
}
}
```
It's also a mess, but it demos the other part of "logic": methods which produce new events.
This is the total surface of hypernote, ideally! Static or dynamic content, simple inline styles, and logic for fetching and producing events.
I'm calling it "logic" but it's purposfully not a whole scripting language. At most we'll have some sort of `jq`-like language for destructing the relevant piece of data we want.
My ideal syntax for a hypernote as a developer will look something like
```foo.hypernote
Nak-like logic
Markdown-like content
CSS-like styles
```
But with JSON as the compile target, this can just be my own preference, there can be other (likely better!) ways of authoring this content, such as a Hypernote Stories GUI.
### The end
I know this is all still vague but I wanted to get some ideas out in the wild so people understand the through line of my different Hypernote experiments. I want to get the right amount of "expressivity" in Hypernote before it gets locked down into one spec. My hunch is it can be VERY expressive while remaining simple and also while not needing a whole scripting language bolted onto it. If I can't pull it off I'll let you know.
-

@ a012dc82:6458a70d
2025-03-28 16:15:06
In an audacious display of confidence, Bitcoin traders have recently committed $20 million to a $200K call option, a move that has reignited discussions about the cryptocurrency's potential and the broader market's appetite for risk. This development is set against a backdrop of increasing activity within the cryptocurrency options market, particularly on platforms like Deribit, where total open interest in Bitcoin options has reached unprecedented levels. This article explores the nuances of this strategic wager, examines the resurgence of investor enthusiasm, and contemplates the future implications for Bitcoin and the cryptocurrency market at large.
**Table of Contents**
- A Surge in Market Activity
- The Bold Bet on Bitcoin's Future
- Implications of the $200K Call Option
- Increased Market Volatility
- Renewed Investor Confidence
- Speculative Interest and Market Dynamics
- Looking Ahead: Bitcoin's Market Prospects
- Conclusion
- FAQs
**A Surge in Market Activity**
The cryptocurrency options market has experienced a significant uptick in activity, with Bitcoin and Ethereum options achieving record-breaking open interest figures. On Deribit, Bitcoin options open interest has soared to a staggering $20.4 billion, eclipsing the previous high of $14.36 billion seen in October 2021. Concurrently, Ethereum options open interest has also reached a historic peak of $11.66 billion. This pronounced increase in market activity is indicative of a growing interest among traders to either hedge their positions against potential price fluctuations or to speculate on the future price movements of these leading cryptocurrencies. The surge in options trading volume reflects a broader trend of maturation within the cryptocurrency market, as sophisticated financial instruments become increasingly utilized by a diverse array of market participants, from individual investors to large institutional players.
**The Bold Bet on Bitcoin's Future**
The decision by traders to allocate $20 million to a $200K call option for Bitcoin represents a significant vote of confidence in the cryptocurrency's future price trajectory. This high-stakes gamble suggests that a segment of the market is not only optimistic about Bitcoin's potential to breach the $200,000 threshold but is also willing to back this belief with substantial financial commitment. Such a move is emblematic of the "animal spirits" returning to the cryptocurrency market—a term coined by economist John Maynard Keynes to describe the instinctive human emotion that drives consumer confidence and investment decisions. This resurgence of speculative fervor and risk-taking behavior is a testament to the enduring allure of Bitcoin as an asset class that continues to captivate the imagination of investors, despite its history of volatility and regulatory challenges.
**Implications of the $200K Call Option**
The substantial investment in the $200K call option carries several implications for the Bitcoin market and the broader cryptocurrency ecosystem:
**Increased Market Volatility**
The focus on high strike price options could introduce heightened volatility into the Bitcoin market. As traders position themselves to capitalize on potential price movements, the market may witness more pronounced fluctuations. This environment of increased volatility underscores the speculative nature of cryptocurrency trading and the high-risk, high-reward strategies employed by some market participants. It also highlights the need for investors to approach the market with caution, armed with a thorough understanding of the underlying risks and a clear investment strategy.
**Renewed Investor Confidence**
The bold wager on the $200K call option reflects a significant resurgence in investor confidence in Bitcoin's long-term prospects. Following periods of market downturns and regulatory uncertainty, this move signals a renewed conviction in the fundamental value proposition of Bitcoin as a pioneering digital asset. It represents a collective belief in the cryptocurrency's ability to not only recover from past setbacks but to chart new territories in terms of price and market capitalization. This renewed investor confidence may serve as a catalyst for further investment in Bitcoin and other cryptocurrencies, potentially driving up prices and encouraging more widespread adoption.
**Speculative Interest and Market Dynamics**
The commitment to the $200K call option highlights the continued influence of speculative interest on the cryptocurrency market's dynamics. It illustrates how speculation, driven by the prospect of outsized returns, remains a central force shaping market trends and price trajectories. This speculative interest, while contributing to market liquidity and price discovery, also introduces an element of unpredictability. It underscores the complex interplay between market sentiment, investor behavior, and external economic factors that collectively determine the direction of the cryptocurrency market.
**Looking Ahead: Bitcoin's Market Prospects**
The strategic bet on the $200K call option, amidst a backdrop of increasing options market activity, paints a complex picture of Bitcoin's future. While the move signals optimism and a willingness among investors to engage in high-risk speculation, it also raises questions about the sustainability of such bullish sentiment. As Bitcoin continues to navigate the evolving landscape of digital finance, the interplay between speculative interest, regulatory developments, and technological advancements will be critical in shaping its future trajectory. The cryptocurrency market's inherent volatility and unpredictability necessitate a cautious approach from investors, emphasizing the importance of risk management and long-term strategic planning.
**Conclusion**
Bitcoin's latest foray into high-stakes speculation, marked by the $20 million lock on the $200K call option, is a vivid illustration of the cryptocurrency's enduring appeal and the market's appetite for risk. This development not only reflects a bullish outlook on Bitcoin's price potential but also signals a broader resurgence of investor enthusiasm and speculative activity within the cryptocurrency market. As we look to the future, the outcomes of such bold moves will undoubtedly influence the trajectory of Bitcoin and the digital asset landscape at large. Whether Bitcoin will reach the lofty heights of $200,000 remains to be seen, but its journey there will be closely watched by traders, investors, and regulators alike, offering valuable insights into the dynamics of speculative markets and the evolving role of cryptocurrencies in the global financial ecosystem.
**FAQs**
**What does locking $20 million in a $200K call option mean for Bitcoin?**
Locking $20 million in a $200K call option indicates that traders are betting a significant amount of money on Bitcoin reaching or surpassing $200,000. It reflects a bullish outlook on Bitcoin's future price and a resurgence of speculative interest in the cryptocurrency market.
**How does the surge in Bitcoin options market activity affect the cryptocurrency?**
The surge in Bitcoin options market activity, with record open interest, increases market liquidity and can lead to heightened volatility. It also signifies growing interest and participation in the cryptocurrency market, potentially influencing Bitcoin's price dynamics.
**What are the implications of increased market volatility for Bitcoin investors?**
Increased market volatility can lead to larger price swings, presenting both opportunities and risks for investors. While it may offer the potential for higher returns, it also increases the risk of losses. Investors should approach the market with caution and consider their risk tolerance and investment strategy.
**Why are investors optimistic about Bitcoin reaching $200,000?**
Investors' optimism about Bitcoin reaching $200,000 stems from factors such as the cryptocurrency's past performance, the upcoming Bitcoin halving event, increasing institutional adoption, and favorable macroeconomic conditions. These factors contribute to a bullish sentiment in the market.
**What role do institutional investors play in the current Bitcoin market trend?**
Institutional investors play a significant role in the current Bitcoin market trend by bringing in substantial capital, lending credibility to the market, and influencing price movements. Their participation is seen as a sign of maturity and stability in the cryptocurrency market.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnewsco](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co/](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@thebitcoinlibertarian](https://www.youtube.com/@thebitcoinlibertarian)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
**Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats
link: https://signup.theorangepillapp.com/opa/croxroad**
**Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad”
link: https://bitcoinbook.shop?ref=21croxroad**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ 4857600b:30b502f4
2025-02-21 03:04:00
A new talking point of the left is that it’s no big deal, just simple recording errors for the 20 million people aged 100-360. 🤷♀️ And not many of them are collecting benefits anyway. 👌 First of all, the investigation & analysis are in the early stages. How can they possibly know how deep the fraud goes, especially when their leaders are doing everything they can to obstruct any real examination? Second, sure, no worries about only a small number collecting benefits. That’s the ONLY thing social security numbers are used for. 🙄
-

@ 4857600b:30b502f4
2025-02-20 19:09:11
Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-

@ 94a6a78a:0ddf320e
2025-02-19 21:10:15
Nostr is a revolutionary protocol that enables **decentralized, censorship-resistant communication**. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on **users, developers, and relay operators**.
If you believe in **free speech, decentralization, and an open internet**, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, **every effort helps build a more robust network**.
Here’s how you can get involved and make a difference.
---
## **1️⃣ Use Nostr Daily**
The simplest and most effective way to contribute to Nostr is by **using it regularly**. The more active users, the stronger and more valuable the network becomes.
✅ **Post, comment, and zap** (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\
✅ **Engage with new users** and help them understand how Nostr works.\
✅ **Try different Nostr clients** like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity **keeps the network alive** and helps encourage more developers and relay operators to invest in the ecosystem.
---
## **2️⃣ Run Your Own Nostr Relay**
Relays are the **backbone of Nostr**, responsible for distributing messages across the network. The more **independent relays exist**, the stronger and more censorship-resistant Nostr becomes.
✅ **Set up your own relay** to help decentralize the network further.\
✅ **Experiment with relay configurations** and different performance optimizations.\
✅ **Offer public or private relay services** to users looking for high-quality infrastructure.
If you're not technical, you can still **support relay operators** by **subscribing to a paid relay** or donating to open-source relay projects.
---
## **3️⃣ Support Paid Relays & Infrastructure**
Free relays have helped Nostr grow, but they **struggle with spam, slow speeds, and sustainability issues**. **Paid relays** help fund **better infrastructure, faster message delivery, and a more reliable experience**.
✅ **Subscribe to a paid relay** to help keep it running.\
✅ **Use premium services** like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\
✅ **Donate to relay operators** who invest in long-term infrastructure.
By funding **Nostr’s decentralized backbone**, you help ensure its **longevity and reliability**.
---
## **4️⃣ Zap Developers, Creators & Builders**
Many people contribute to Nostr **without direct financial compensation**—developers who build clients, relay operators, educators, and content creators. **You can support them with zaps!** ⚡
✅ **Find developers working on Nostr projects** and send them a zap.\
✅ **Support content creators and educators** who spread awareness about Nostr.\
✅ **Encourage builders** by donating to open-source projects.
Micro-payments via the **Lightning Network** make it easy to directly **support the people who make Nostr better**.
---
## **5️⃣ Develop New Nostr Apps & Tools**
If you're a developer, you can **build on Nostr’s open protocol** to create new apps, bots, or tools. Nostr is **permissionless**, meaning anyone can develop for it.
✅ **Create new Nostr clients** with unique features and user experiences.\
✅ **Build bots or automation tools** that improve engagement and usability.\
✅ **Experiment with decentralized identity, authentication, and encryption** to make Nostr even stronger.
With **no corporate gatekeepers**, your projects can help shape the future of decentralized social media.
---
## **6️⃣ Promote & Educate Others About Nostr**
Adoption grows when **more people understand and use Nostr**. You can help by **spreading awareness** and creating educational content.
✅ **Write blogs, guides, and tutorials** explaining how to use Nostr.\
✅ **Make videos or social media posts** introducing new users to the protocol.\
✅ **Host discussions, Twitter Spaces, or workshops** to onboard more people.
The more people **understand and trust Nostr**, the stronger the ecosystem becomes.
---
## **7️⃣ Support Open-Source Nostr Projects**
Many Nostr tools and clients are **built by volunteers**, and open-source projects thrive on **community support**.
✅ **Contribute code** to existing Nostr projects on GitHub.\
✅ **Report bugs and suggest features** to improve Nostr clients.\
✅ **Donate to developers** who keep Nostr free and open for everyone.
If you're not a developer, you can still **help with testing, translations, and documentation** to make projects more accessible.
---
## **🚀 Every Contribution Strengthens Nostr**
Whether you:
✔️ **Post and engage daily**\
✔️ **Zap creators and developers**\
✔️ **Run or support relays**\
✔️ **Build new apps and tools**\
✔️ **Educate and onboard new users**
**Every action helps make Nostr more resilient, decentralized, and unstoppable.**
Nostr isn’t just another social network—it’s **a movement toward a free and open internet**. If you believe in **digital freedom, privacy, and decentralization**, now is the time to get involved.
-

@ 5de23b9a:d83005b3
2025-02-19 03:47:19
In a digital era that is increasingly controlled by large companies, the emergence of Nostr (Notes and Other Stuff Transmitted by Relays) is a breath of fresh air for those who crave freedom of expression.
Nostr is a cryptography-based protocol that allows users to send and receive messages through a relay network. Unlike conventional social media such as Twitter or Facebook
1.Full Decentralization: No company or government can remove or restrict content.
2.Sensor-Resistant: Information remains accessible despite blocking attempts.
3.Privacy and Security: Uses cryptography to ensure that only users who have the keys can access their messages.* **
-

@ 905365ac:4247f9de
2025-03-28 14:04:02
"85% of the KGB ['s strategy to take over a country] is always subversion." Yuri Bezmenov
Ideological subversion is even stronger today, with an even greater reach because of the internet. Unlike during Yuri's time, however, we are being subverted internally.
What is subversion?
Short answer: brainwashing.
Long answer:
Demoralization > Destabilization > Crisis > Normilization
Demoralization: control educational institutions, media, and cultural platforms
Destabilization: control internal and foreign politics, economic, and defense systems.
Crisis: violent change of power, structure, and economy
Normalization: period of stability*
One teacher** believes that the way this is currently being played out is through our culture wars - particularly anti-whiteness. I would add that it is playing out both in anti-whiteness and in anti-masculinity.
Short history lesson:
America embarked on an endeavor to "de-nazi" Germany via demoralization following World War 2. The charge was lead by a Frankfort school that sought refuge in the U.S. during the war. That demoralization was based on mass cultural guilt (interestingly enough, I actually learned the concept of collective guilt as a tool to “heal communities” in a class on Peace and Conflict during college).
According to this teacher, that mass guilt then started being applied by leftists in a range of western civilizations, including America where the root guilt is racism. A secondary guilt Americans suffer from is "the partriarchy," which has led to a whole slew of mass demoralization which can be seen most evidently in this current wave of feminism and in gender ideology.
In such countries, the idea is that fascism (seen as the scapegoat of whatever mass guilt is being applied) must eventually be annihilated. Otherwise, the guilt is too difficult to bear. In the U.S., that’s whiteness. In Germany, it was Nazis and now it’s Germans themselves.
Takeaways:
1. The best way personally advocate for a strong country that stands against ideological subversion is to directly counter demoralization in the spheres of education, media, and in cultural spaces.
2. Invest in countering destabilization by appointing, electing, and being those who fight for peace, unity and freedom on our political, economic, and defensive grounds.
Speak truth. Homeschool (or be involved in your local schools). Join NOSTR. Contribute to local, state and federal politics in a way that will positively impact your grandchildren. Support the soldiers and veterans you know and love. Be pro-human.
https://youtu.be/5gnpCqsXE8g
https://youtu.be/niiF8hCSrYQ
-

@ 9e69e420:d12360c2
2025-02-17 17:12:01
President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-

@ bf95e1a4:ebdcc848
2025-03-28 13:56:06
This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our[ Geyser page](https://geyser.fund/project/infinity)!
## Financial Atheism
“Don’t trust, verify” is a common saying amongst bitcoiners that represents a sound attitude towards not only Bitcoin but all human power structures. In order to understand Bitcoin, one must admit that everything in society is man-made. Every civilization, every religion, every constitution, and every law is a product of human imagination. It wasn’t until as late as the 17th century that the scientific method started to become the dominant practice for describing how the world actually worked. Peer-to-peer review and repeated testing of a hypothesis are still quite recent human practices. Before this, we were basically just guessing and trusting authorities to a large extent. We still do this today, and despite our progress over the last couple of centuries, we still have a long way to go. Our brains are hardwired to follow the leader of the pack. The human brain is born with a plethora of cognitive biases pre-installed, and we have to work very hard to overcome them. We evolved to survive in relatively small groups, and our brains are thus not really made for seeing the bigger picture. Bitcoin’s proof-of-work algorithm is constructed in such a way that it is easy to verify that computational power was sacrificed in order to approve a block of transactions and claim its reward. In this way, no trust in any authority is required as it is relatively trivial to test the validity of a block and the transactions it contains. This is nothing short of a complete reimagining of how human society ought to be governed. The beauty of mathematics governs the Bitcoin system. Everything that ever happens in Bitcoin is open and verifiable to everyone, even to those who are not yet using it.
After the tragic events of 9/11 in 2001, Sam Harris started writing his book *The End of Faith*, which happened to be released around the same time as Richard Dawkins’ *The God Delusion*, Daniel Dennett's *Breaking the Spell*, and Christopher Hitchens’ *God Is Not Great: How Religion Poisons Everything*. These books kick-started what, in hindsight, has often been referred to as the new atheist movement, even though there has arguably never been anything new about atheism. Atheism must almost certainly have preceded religion since religious ideas require the person holding the idea to believe a certain doctrine or story. Atheism is nothing but the rejection of ways to describe the world that are not verifiable by experimentation. A fly on the wall is probably an atheist by this definition of the word. Atheism is often accused of being just another set of beliefs, but the word itself describes what it is much better — a lack of belief in theistic ideas. It is not a code of conduct or set of rules to live your life by; it is simply the rejection of that which cannot be scientifically verified. Many people, religious people, in particular, have a hard time grasping this. If you believe that a supernatural entity created everything in everyone's life, you might not be too comfortable with a word that describes a complete rejection of what you believe created everything, including the very atheist that the word describes. The amount of different religious worldviews that exist is probably equal to the sum of all religious people on the planet, but all world views that reject these superstitious beliefs require but one word. Atheism is not the opposite of religion but is simply the lack of it.
In 2008, another sub-culture movement of unbelief was born. Let’s call it *Financial Atheism* — the rejection of unverifiable value claims. With the invention of Bitcoin, a way of rejecting fraudulent expressions of a token’s value was born. Those of us fortunate enough to have been born in secular countries all enjoy not having the ideas of religious demagogues dictating our lives on a daily basis. We can choose which ideas to believe in and which to reject. What we still have very limited means of choosing, however, are the ways in which we express value to each other. We’re told to use a system in which we all have a certain number of value tokens assigned to our name, either as a number on a screen or as digits on paper notes. We all live in the collective hallucination that these numbers are somehow legit and that their authenticity is not to be questioned.
A Bitcoin balance assigned to a certain Bitcoin address might seem just as questionable to a layman, but if you have a basic understanding of the hashing algorithms and game theory behind it, it’s not. At the time of writing, the hash of the latest block on the Bitcoin blockchain begins with eighteen zeros in a row. These zeros represent the Proof of Work that ensures that this block is valid and that every transaction in it actually happened. If you can grasp the concept of a hashing algorithm, and if you have an intuition about mathematics, you realize the gargantuan amount of calculating effort that went into finding this particular hash. It is simply mind-blowing. To forge a false version of a hash beginning with eighteen zeros just wouldn’t be economically viable. Of course, you can never actually know that a 51% attack or some other attempt at corrupting the blockchain hasn’t occurred, but you can know that such an attack would require more than half of the network acting against their own economic interest. Bitcoin is not something to believe in. You don’t need to trust any authority because you can validate the plausibility of its authenticity yourself. It’s the financial equivalent of atheism or unbelief. Satoshi wasn’t Jesus. Satoshi was Brian of Nazareth, telling his followers to think for themselves.
The first law of thermodynamics, also known as the Law of Conservation of Energy, states that energy cannot be created or destroyed in an isolated system. The second law states that the entropy of any isolated system always increases, and the third law states that the entropy of a system approaches a constant value as the temperature approaches absolute zero. In the Bitcoin network, participants known as miners compete for new Bitcoin in a lottery with very fixed rules. The more hashing power (computing power) a miner contributes to the network, the higher his chances of winning the block reward, a specific amount of Bitcoin that is halved every four years. The difficulty of this lottery - in other words, the miner’s chance of winning it — is re-calibrated every 2016th block so that the average time it takes to find the next block is always roughly ten minutes. What this system produces is absolute scarcity; the amount of Bitcoin in existence at any moment in time is always predictable. The more time that passes, the slower the rate of coin issuance and the block reward slowly approaches zero. By the time it does, around the year 2140, the individual miner’s incentive to mine for a reward will, at least theoretically, have been replaced by an incentive to collect transaction fees from the participants of the network. Even now, the sum of all fees make up a non-trivial part of the miners’ revenue. Yet from a user’s point of view the fees are still very low, and as the network scales up using Layer 2 solutions such as the Lightning Network, they’re expected to remain low for quite a long time ahead.
Absolute scarcity is a concept that mankind has never encountered before. Arguably, this makes it the first man-made concept to ever be directly linked to the laws of physics. Everything anyone does requires a certain amount of energy. The very word *doing* implies that some kind of movement, some type of energy expenditure, needs to occur. As mentioned earlier, how we value things is entirely subjective. Different actions are of different value to different people. How we value different things is also inevitably linked to the supply of those things. Had the trapped-under-ice winter diver mentioned in chapter one been equipped with a scuba tank, he probably wouldn't have thought of his next breath as such a precious thing. The price a person is willing to pay for a good — in other words, the sum of one or more person’s actions — can be derived from two basic variables: The highly subjective *demand* for the good and the always-constrained-by-time-and-space *supply* of that same good. Note that if supply is sufficiently limited, there only needs to be a minimal amount of demand for a good for its price to increase.
One could argue that no one *needs* Bitcoin and that, therefore, Bitcoin would have no intrinsic value. One could also argue that there’s no such thing as intrinsic value since demand is always subjective. In any case, there will always be a cost to mine Bitcoin, and the more mining power in the network, the higher that cost. This cost, ensured by the Bitcoin network’s Proof-Of-Work algorithm, is probably as close to a pure energy cost as the price of a human activity will ever get. Once the mining rig is in place, a simple conversion process follows — energy in, scarce token out. Should the cost of production exceed the current price of the token, the miner can just choose not to sell, thereby limiting the supply of Bitcoin in circulation even more and eventually selling them for other goods whenever he sees fit. In this sense, Bitcoin is a battery. Perhaps the best battery ever invented.
Storing and moving electrical energy around has always been costly and wasteful. Bitcoin offers a way of converting energy into a small part of a specific number. A mathematical battery, if you will. It is important to remember that it does not convert energy into value *directly*, but rather electricity into digital scarcity — digital scarcity that can be used to express value. Energy cannot be created or destroyed in an isolated system, as the first law of thermodynamics clearly states. Bitcoin can express how much energy was sacrificed in order to acquire a share of the total sum. You can also acquire Bitcoin by buying it rather than mining it, but in doing so, you also spend energy. You somehow acquired the money with which you bought the Bitcoin. You, or someone else, sacrificed time and energy somewhere. Bitcoin lets you express that you see that there’s a connection between value and scarcity by letting you sacrifice effort to claim a part of the total sum.
The excitement we so-called "Bitcoin Maximalists" feel about Bitcoin does not come primarily from the enormous gains that those who hopped early onto the freight train have been blessed with. Nor is it because we’re “in it for the technology,” as can often be heard from opponents. Those of us who preach the near-divinity of this invention do so above all because we see the philosophical impacts of absolute scarcity in a commodity. The idea of a functioning solution to the double-spending problem in computerized money is an achievement that simply can’t be ignored. By solving the double-spending problem, Satoshi also made counterfeiting impossible, which in turn makes artificial inflation impossible. The world-changing potential of this invention cannot be understated. Not in the long run.
The more you think about it, the more the thought won’t give you any peace of mind. If this experiment works, if it’s real, it will take civilization to the next level. What we don’t know is how long this will take. Right now, debates in the Bitcoin space are about Bitcoin’s functionality as a medium of exchange and its potential as a good store of value. We might be missing the point. We cannot possibly know if a type of monetary token for which you’re completely responsible, with no third-party protection, will ever become a preferred medium of exchange for most transactions. Nor can we know if the price of Bitcoin will follow the hype-cycle path that we all want it to follow so that it can become the store of value that most maximalists claim it already is. Maybe we’ve been focused on the wrong things all along. Maybe Bitcoin’s greatest strength is in its functionality as a unit of account. After all, this is all that Bitcoin does. If you own 21 Bitcoin, you own one-millionth of the world's first absolutely scarce commodity. This might not make you rich overnight, but it just might have something to do with the opportunities available to your great-great-grandchildren.
Throughout history, whenever a prehistoric human tribe invented ceremonial burial, that tribe began to expand rapidly. Why? Because as soon as you invent belief in an afterlife, you also introduce the idea of self-sacrifice on a larger scale. People who held these beliefs were much easier for a despot to manipulate and send into battle with neighboring tribes. Religious leaders can use people’s fears and superstitions to have them commit all sorts of atrocities to their fellow man, and they still do so today. Belief in a “greater good” can be the most destructive idea that can pop up in a human mind. The Nazis of World War II Germany believed that exterminating Jews was for the “greater good” of their nation’s gene pool. Belief in noble causes often comes with unintended side effects, which can have disastrous consequences.
Religious leaders, political leaders, and other power-hungry sociopaths are responsible for the greatest crimes against humanity ever committed — namely, wars. Europeans often question the Second Amendment to the United States Constitution, which protects the right to bear arms, whenever a tragic school shooting occurs on the other side of the Atlantic. What everyone seems to forget is that less than a hundred years ago, Europe was at war with itself because its citizens had given too much power to their so-called leaders. The Nazis came to power in a democracy — never forget that. Our individual rights weren’t given to us by our leaders; we were born with them. Our leaders can’t give us anything; they can only force us to behave in certain ways. If we truly want to be in charge of our lives, we need to find the tools necessary to circumvent the bullshit ourselves.
### **About the Bitcoin Infinity Academy**
The Bitcoin Infinity Academy is an educational project built around [Knut Svanholm](http://primal.net/knut)’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a [video](https://www.youtube.com/@BitcoinInfinityShow) in which Knut and [Luke de Wolf](http://primal.net/luke) discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our [Geyser](https://geyser.fund/project/infinity) page. Signed books, monthly calls, and lots of other benefits are also available.
-

@ e97aaffa:2ebd765d
2025-03-28 12:56:17
Nos últimos anos, tornei-me num acérrimo crítico do Euro, sobretudo da política monetária altamente expansionista realizada pelo Banco Central Europeu (BCE). Apesar de ser crítico, eu não desejo que Portugal volte a ter moeda própria.
No seguimento gráfico, é a variação do [IPC de Portugal nos últimos 60 anos]( https://www.pordata.pt/pt/estatisticas/inflacao/taxa-de-inflacao/taxa-de-inflacao-por-bens-e-servicos-portugal):
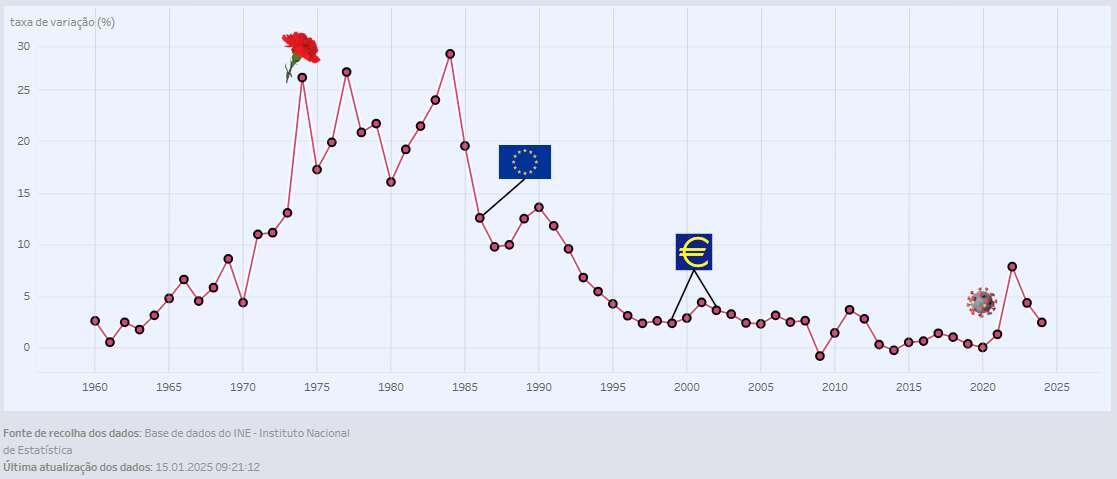
No gráfico inclui os momentos históricos, para uma melhor interpretação dos dados.
> O Índice de Preços ao Consumidor (IPC) é usado para observar tendências de inflação. É calculado com base no preço médio necessário para comprar um conjunto de bens de consumo e serviços num país, comparando com períodos anteriores.
É uma ferramenta utilizada para calcular a perda de poder de compra, mas é uma métrica que é facilmente manipulada em prol dos interesses dos governos.
## Análise histórica
No período marcelista, houve uma crescente inflação, devido a fatores, como os elevados custos da guerra e o fim dos acordos de Bretton Woods contribuíram para isso. Terminando com uma inflação superior a 13%.
Da Revolta dos Cravos (1974) até à adesão da CEE (atual União Europeia, UE), nos primeiros anos foram conturbados a nível político, mesmo após conquistar alguma estabilidade, em termos de política monetária foi um descalabro, com inflação entre 12% a 30% ao ano. Foi o pior momento na era moderna.
Com a entrada da CEE, Portugal ainda manteve a independência monetária, mas devido à entrada de muitos milhões de fundos europeus, essências para construir infraestrutura e desenvolver o país. Isto permitiu crescer e modernizar o país, gastando pouco dinheiro próprio, reduzindo a necessidade da expansão monetária e claro a inflação baixou.
Depois com a adesão ao Tratado de Maastricht, em 1991, onde estabeleceu as bases para a criação da União Económica e Monetária, que culminou na criação da moeda única europeia, o Euro. As bases eram bastante restritivas, os políticos portugueses foram obrigados a manter uma inflação baixa. Portugal perdeu a independência monetária em 1999, com a entrada em vigor da nova moeda, foi estabelecida a taxa de conversão entre escudos e euros, tendo o valor de 1 euro sido fixado em 200,482 escudos. A Euro entrou em vigor em 1999, mas o papel-moeda só entrou em circulação em 2002.
Assim, desde a criação até 2020, a inflação foi sempre abaixo de 5% ao ano, tendo um longo período abaixo dos 3%.
A chegada da pandemia, foi um descalabro no BCE, a expansão monetária foi exponencial, resultando numa forte subida no IPC, quase 8% em 2022, algo que não acontecia há 30 anos.
## Conclusão
Apesar dos últimos anos, a política monetária do BCE tem sido péssima, mesmo assim continua a ser muito melhor, se esta fosse efetuada em exclusividade por portugueses, não tenho quaisquer dúvidas disso. O passado demonstra isso, se voltarmos a ser independentes monetariamente, será desastroso, vamos virar rapidamente, a Venezuela da Europa.
Até temos boas reservas de ouro, mas mesmo assim não são suficientes, mesmo que se inclua outros ativos para permitir a criação de uma moeda lastreada, ela apenas duraria até à primeira crise. É inevitável, somos um país demasiado socialista.
A solução não é voltar ao escudo, mas sim o BCE deixar de imprimir dinheiro, como se não houvesse amanhã ou então optar por uma moeda total livre, sem intromissão de políticos.
O BCE vai parar de expandir a moeda?
Claro que não, eles estão encurralados, a expansão monetária é a única solução para elevada dívida soberana dos estados. A única certeza que eu tenho, a expansão do BCE, será sempre inferior ao do Banco de Portugal, se este estivesse o botão da impressão à sua disposição. Por volta dos 5% é muito mau, mas voltar para a casa dos 15% seria péssimo, esse seria o nosso destino.
É muito triste ter esta conclusão, isto é demonstrativo da falta de competência dos políticos e governantes portugueses e o povo também tem uma certa culpa. Por serem poucos exigentes em relação à qualidade dos políticos que elegem e por acreditar que existem almoços grátis.
#Bitcoin fixes this
-

@ fd208ee8:0fd927c1
2025-02-15 07:02:08
E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is
* a **transaction on a relay** that triggers
* a **transaction on a mint** that triggers
* a **transaction on Lightning** that triggers
* a **transaction on Bitcoin**.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md
-

@ 3c389c8f:7a2eff7f
2025-03-28 17:10:17
There is a new web being built on Nostr. At it's core, is a social experience paralleled by no other decentralized protocol. Nostr not only solves the problems of siloed relationships, third-party identity ownership, and algorithmic content control; it makes possible a ubiquitous social network across almost anything imaginable. User controlled identity, open data, and verifiable social graphs allow us to redefine trust on the web. We can interact with each other and online content in ways that have previously only been pipedreams. Nostr is not just social media, it is the web made social.
### Interoperability
The client/relay relationship on Nostr allows for almost endless data exchange between various apps, clients, relays, and users. If any two things are willing to speak the same sub-protocol(s) within Nostr, they can exchange data. Making a friend list enables that list to be used in any other place that chooses to make it available. Creating a relay to serve an algorithmic social feed makes that feed viewable in any client that displays social feeds. Health data held by a patient can be shared with any care provider, verified by their system, and vice versa. This is the point where I have to acknowledge my own tech-deaf limitations and direct you towards nostr.com for more information.
### Data Resiliency
I prefer to use the term resiliency here, because its really a mix of data redundancy and self-managed data that creates broad availability. Relays may host 10, 20, 30+ copies of your notes in different locations, but you also have no assurance that those relays will hosts those notes forever. An individual operating their own relay, while also connecting to the wider network, ensures resiliency in events such that wide swaths of the network should disappear or collude against an individual. The simplicity of relay management makes it possible for nearly anyone to make sure that they have a way to convey their messages to their individual network, whether that be close contacts, an audience, or one individual. This resiliency doesn't just apply to typical speech, it applies to any data intended to be shared amongst humans and machines alike.
### Pseudonymity and Anonymity
With privacy encroachment from corporations, advertisers, and governments reaching all time highs, the need for identity protecting tools is also on the rise. Nostr utilizes public key encryption for its identity system. As there is no central entity to "verify" you, there is no need to expose any personal identifiable information to any Nostr app, client, or relay. You can protect your personal identity by simply choosing not to expose it. Your reputation will build as you interact with others on the Nostr network. Your social capital can speak for itself. (As with everything else, utilizing a VPN is recommended.)
### Identity and Provability
No one can stop an impersonator from trying to hijack an identity. With Nostr, you CAN prove that you are you, though, which is basically the same as saying "that person is not me" Every note you write, every action you take, is cryptographically signed by your private key. As long as you maintain control of that key, you can prove what you did or did not do.
### Censorship Resistance
If you have read our Relay Rundown then you probably get the idea. If not here's the tl;dr: Many small, lightweight relays make up Nostr's distribution system. They are simple enough that anyone can run one. They are redundant enough that you can be almost certain your content exists somewhere. If that is not peace of mind enough, you can run your own with ease. Censorship resistance isn't counting on one company, man, or server to protect what you say. It is taking control of your speech. Nostr makes it easy.
### Freedom of Mind and Association
Nostr eliminates the need for company run algorithms that high-jack your attention to feed the advertising industry. You are free to choose your social media experience. Nostr's DVMs, curations, and conversation-centered relays offer discovery mechanisms run by any number of providers. That could be an individual, a company, a group, or you. Many clients incorporate different ways of engaging with these corporate algorithm alternatives. You can also choose to keep a purely chronological feed of the the things and people you follow. Exploring Nostr through its many apps opens up a the freedom to choose what and how you feed your mind.
When we are able to explore, we end up surrounding ourselves with people who share our interests & hobbies. We find friends. This creates distance between ideologies and stark beliefs that often are used as the basis for the term "being in a bubble". Instead of bubbling off, an infinitely open space of thoughts and ideas allows for groups to gather naturally. In this way, we can choose not to block ourselves off from opposing views but to simply distance ourselves from them.
Nostr's relay system also allows for the opposite. Tight-knit communities can create a space for its members to socialize and exchange information with minimal interference from any outside influence. By setting up their own relays with strict rules, the members can utilize one identity to interact within a community or across the broader social network.
-

@ 5d4b6c8d:8a1c1ee3
2025-03-28 12:30:11
I'm short on time this morning, so I'm just plagiarizing @grayruby's notes, with minor revisions.
# Territory Things:
- March Madness Points Challenge https://stacker.news/items/924541/r/Undisciplined
- IPL T20k Mania https://stacker.news/items/920125/r/Undisciplined
- CricZap https://stacker.news/items/919957/r/Undisciplined
- USA vs World https://stacker.news/items/923533/r/Undisciplined
- Any changes to NBA Prediction contest for March? (post coming today)
- Stackers voted to delay MLB Survivor
# NCAA:
- How many 1 seeds will make final four?
- Cooper Flagg is the consensus number 1 but will he be a great NBA player?
# NFL:
- Rule change proposals: Ban the tush push and make dynamic kickoff permanent
# NBA;
- Pre playoffs Power Rankings
# Blok'd Shots:
- Ovi with 6 to go
# MLB:
- opening day finally arrived
- American League is a crap shoot
- Fantasy MLB
# Betting:
- predyx markets
- Betplay- didn't work for me but how are you liking it?
And, as we do every week, we'll share an awesome @Aardvark sports fact.
What are we missing?
originally posted at https://stacker.news/items/927714
-

@ 0fa80bd3:ea7325de
2025-02-14 23:24:37
#intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-

@ 57d1a264:69f1fee1
2025-03-28 10:32:15
Bitcoin.design community is organizing another Designathon, from May 4-18. Let's get creative with bitcoin together. More to come very soon.

The first edition was a bursting success! the website still there https://events.bitcoin.design, and here their previous [announcement](https://bitcoindesign.substack.com/p/the-bitcoin-designathon-2022).
Look forward for this to happen!
Spread the voice:
N: [https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48l...](https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48lmw9jc7nhhauyq5w3cm4nfsm3mstqtk6m)
X: https://x.com/bitcoin_design/status/1905547407405768927
originally posted at https://stacker.news/items/927650
-

@ 9e69e420:d12360c2
2025-02-14 18:07:10
Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship.
He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
-

@ 7d33ba57:1b82db35
2025-03-28 09:13:56
Girona, one of Catalonia’s most charming cities, is a perfect mix of history, culture, and gastronomy. Famous for its well-preserved medieval old town, colorful houses along the Onyar River, and Game of Thrones filming locations, Girona is a must-visit destination in northern Spain.

## **🏰 Top Things to See & Do in Girona**
### **1️⃣ Girona Cathedral (Catedral de Santa Maria) ⛪**
- One of **Spain’s most impressive cathedrals**, with **the widest Gothic nave in the world**.
- Famous as the **Great Sept of Baelor in Game of Thrones**.
- Climb the **steps for a breathtaking city view**.
### **2️⃣ Walk the Medieval Walls (Passeig de la Muralla) 🏰**
- Offers **panoramic views** of Girona and the surrounding countryside.
- A great way to see the city from above and explore its medieval history.

### **3️⃣ The Colorful Houses of the Onyar River 🌉**
- Girona’s **most iconic view**, with **brightly colored houses reflecting on the river**.
- Best viewed from the **Pont de les Peixateries Velles**, designed by **Gustave Eiffel**.
### **4️⃣ Explore the Jewish Quarter (El Call) 🏡**
- One of **Europe’s best-preserved Jewish quarters**, with **narrow, medieval streets**.
- Visit the **Museum of Jewish History** to learn about Girona’s Jewish heritage.

### **5️⃣ Arab Baths (Banys Àrabs) 🏛️**
- A **12th-century Romanesque bathhouse**, inspired by Moorish architecture.
- Features **a beautiful central dome with columns**.
### **6️⃣ Game of Thrones Filming Locations 🎬**
- Walk in the footsteps of **Arya Stark** through the city’s **winding streets**.
- Visit **the steps of the cathedral, the Jewish Quarter, and Arab Baths**, all featured in the series.
### **7️⃣ Eat at a Michelin-Starred Restaurant 🍽️**
- Girona is home to **El Celler de Can Roca**, a **3-Michelin-star restaurant**, ranked among the **best in the world**.
- Try **local Catalan dishes** like **"suquet de peix" (fish stew) and botifarra (Catalan sausage).**

## **🚗 How to Get to Girona**
✈️ **By Air:** Girona-Costa Brava Airport (GRO) is **20 min away**, with budget flights from Europe.
🚆 **By Train:** High-speed AVE trains connect **Barcelona (38 min), Madrid (3.5 hrs), and Paris (5.5 hrs)**.
🚘 **By Car:** 1 hr from **Barcelona**, 40 min from **Figueres (Dalí Museum)**.
🚌 **By Bus:** Direct buses from **Barcelona and the Costa Brava**.

## **💡 Tips for Visiting Girona**
✅ **Best time to visit?** **Spring & autumn (April–June & September–October)** for pleasant weather. 🌤️
✅ **Wear comfortable shoes** – The old town is **hilly with cobblestone streets**. 👟
✅ **Try xuixo** – A delicious **cream-filled pastry**, unique to Girona. 🥐
✅ **Visit early for Game of Thrones spots** – They get crowded during the day! 🎥
✅ **Take a day trip** – Explore nearby **Costa Brava beaches or Figueres (Dalí Museum).** 🏖️

-

@ e3ba5e1a:5e433365
2025-02-13 06:16:49
My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok):
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
*Libertas magnitudo est*
-

@ a60e79e0:1e0e6813
2025-03-28 08:47:35
*This is a long form note of a post that lives on my Nostr educational website [Hello Nostr](https://hellonostr.xyz).*
When most people stumble across Nostr, they see is as a 'decentralized social media alternative' — something akin to Twitter (X), but free from corporate control. But the full name, "Notes and Other Stuff Transmitted by Relays", gives a clue that there’s more to it than just posting short messages. The 'notes' part is easy to grasp because it forms almost everyone's first touch point with the protocol. But the 'other stuff'? That’s where Nostr really gets exciting. The 'other stuff' is all the creative and experimental things people are building on Nostr, beyond simple text based notes.
Every action on Nostr is an event, a like, a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as [Nostr Implementation Possibility - NIP](https://nostr-nips.com/). A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client to meet different purposes.
> Nostr isn’t locked into a single purpose. It’s a foundation for whatever 'other stuff' you can dream up.
>
# Types of Other Stuff
The 'other stuff' name is intentionally vague. Why? Because the possibilities of what can fall under this category are quite literally limitless. In the short time since Nostr's inception, the number of sub-categories that have been built on top of the Nostr's open protocol is mind bending. Here are a few examples:
1. Long-Form Content: Think blog posts or articles. [NIP-23](https://nostr-nips.com/nip-23).
2. Private Messaging: Encrypted chats between users. [NIP-04](https://nostr-nips.com/nip-04).
3. Communities: Group chats or forums like Reddit. [NIP-72](https://nostr-nips.com/nip-72)
4. Marketplaces: People listing stuff for sale, payable with zaps. [NIP-15](https://nostr-nips.com/nip-15)
5. Zaps: Value transfer over the Lightning Network. [NIP57](https://nostr-nips.com/nip-57)

# Popular 'Other Stuff' Clients
Here's a short list of some of the most recent and popular apps and clients that branch outside of the traditional micro-blogging use case and leverage the openness, and interoperability that Nostr can provide.
### Blogging (Long Form Content)
- [Habla](https://habla.news/) - *Web app for Nostr based blogs*
- [Highlighter](https://highlighter.com/) - *Web app that enables users to highlight, store and share content*
### Group Chats
- [Chachi Chat](https://chachi.chat/) - *Relay-based (NIP-29) group chat client*
- [0xchat](https://github.com/0xchat-app) - *Mobile based secure chat*
- [Flotilla](https://flotilla.social/) - *Web based chat app built for self-hosted communities*
- [Nostr Nests](https://nostrnests.com/) - *Web app for audio chats*
- [White Noise](https://github.com/erskingardner/whitenoise) - *Mobile based secure chat*
### Marketplaces
- [Shopstr](https://shopstr.store/) - *Permissionless marketplace for web*
- [Plebeian Market](https://plebeian.market/) - *Permissionless marketplace for web*
- [LNBits Market](https://github.com/lnbits/nostrmarket#nostr-market-nip-15---lnbits-extension) - *Permissionless marketplace for your node*
- [Mostro](https://github.com/MostroP2P/mostro) - *Nostr based Bitcoin P2P Marketplace*
### Photo/Video
- [Olas](https://github.com/pablof7z/snapstr/releases) - *An Intragram like client*
- [Freeflow](https://github.com/nostrlabs-io/freeflow) - *A TikTok like client*
### Music
- [Fountain](https://fountain.fm/) - *Podcast app with Nostr features*
- [Wavlake](https://wavlake.com/) - *A music app supporting the value-for-value ecosystem*
### Livestreaming
- [Zap.stream](https://zap.stream/) - *Nostr native live streams*
### Misc
- [Wikifreedia](https://wikifreedia.xyz/) - *Nostr based Wikipedia alternative*
- [Wikistr](https://wikistr.com/) - *Nostr based Wikipedia alternative*
- [Pollerama](https://pollerama.fun/) - *Nostr based polls*
- [Zap Store](https://zapstore.dev) - *The app store powered by your social graph*
The 'other stuff' in Nostr is what makes it special. It’s not just about replacing Twitter or Facebook, it’s about building a decentralized ecosystem where anything from private chats to marketplaces can thrive.
The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around.
It’s still early days, so expect the 'other stuff' to grow wilder and weirder over time!
You can explore the evergrowing 'other stuff' ecosystem at [NostrApps.com](https://nostrapps.com/), [Nostr.net](https://nostr.net/) and [Awesome Nostr](https://github.com/aljazceru/awesome-nostr).
-

@ daa41bed:88f54153
2025-02-09 16:50:04
There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
**Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
**Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-

@ e3ba5e1a:5e433365
2025-02-05 17:47:16
I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
* Unlike full single payer, individuals incur high costs
* Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
* Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
* Reduce regulations significantly.
* In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-

@ 91bea5cd:1df4451c
2025-02-04 17:24:50
### Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits
Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C.
e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
#### Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid()
RETURNS TEXT
AS $$
DECLARE
-- Crockford's Base32
encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000';
output TEXT = '';
unix_time BIGINT;
ulid BYTEA;
BEGIN
-- 6 timestamp bytes
unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT;
timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes
ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
VOLATILE;
```
#### ULID TO UUID
```sql
CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$
DECLARE
-- 16byte
bytes bytea = E'\\x00000000 00000000 00000000 00000000';
v char[];
-- Allow for O(1) lookup of index values
dec integer[] = ARRAY[
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 0, 1, 2,
3, 4, 5, 6, 7, 8, 9, 255, 255, 255,
255, 255, 255, 255, 10, 11, 12, 13, 14, 15,
16, 17, 1, 18, 19, 1, 20, 21, 0, 22,
23, 24, 25, 26, 255, 27, 28, 29, 30, 31,
255, 255, 255, 255, 255, 255, 10, 11, 12, 13,
14, 15, 16, 17, 1, 18, 19, 1, 20, 21,
0, 22, 23, 24, 25, 26, 255, 27, 28, 29,
30, 31
];
BEGIN
IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN
RAISE EXCEPTION 'Invalid ULID: %', ulid;
END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits)
bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]);
bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2));
bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4));
bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1));
bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3));
bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits);
bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2));
bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4));
bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1));
bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3));
bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]);
bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2));
bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4));
bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1));
bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3));
bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$
BEGIN
RETURN encode(parse_ulid(ulid), 'hex')::uuid;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### UUID to ULID
```sql
CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$
DECLARE
encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
output text = '';
uuid_bytes bytea = uuid_send(id);
BEGIN
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql
-- Cria a extensão pgcrypto para gerar uuid
CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID
CREATE OR REPLACE FUNCTION gen_lrandom()
RETURNS TEXT AS $$
DECLARE
ts_millis BIGINT;
ts_chars TEXT;
random_bytes BYTEA;
random_chars TEXT;
base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
i INT;
BEGIN
-- Pega o timestamp em milissegundos
ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32
ts_chars := '';
FOR i IN REVERSE 0..11 LOOP
ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1);
END LOOP;
-- Gera 10 bytes aleatórios e converte para base32
random_bytes := gen_random_bytes(10);
random_chars := '';
FOR i IN 0..9 LOOP
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1);
IF i < 9 THEN
random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1);
ELSE
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1);
END IF;
END LOOP;
-- Concatena o timestamp e os caracteres aleatórios
RETURN ts_chars || random_chars;
END;
$$ LANGUAGE plpgsql;
```
#### Exemplo de USO
```sql
-- Criação da extensão caso não exista
CREATE EXTENSION
IF
NOT EXISTS pgcrypto;
-- Criação da tabela pessoas
CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela
SELECT
*
FROM
"pessoas"
WHERE
uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F';
```
### Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-

@ 45c41f21:c5446b7a
2025-03-28 08:02:16
“区块链行业究竟是在做什么?”——这个问题我到现在还没有想得很清楚。谈论起来可以说很多东西,“确权”、“让每一个比特都有了稀缺性”、“数字黄金”、“点对点支付”,但是具体到了行业落地,又容易陷入“赌场”这个有点乌烟瘴气的现实。
但我想有一点是比较明确的,那就是区块链行业肯定是一个围绕资产的行业。这些资产又跟传统的资产很不一样,最简单的特征是它们都是一个个的代币,通过自动化和可验证的代码铸造、控制,我们可以统称为链上资产。从比特币、以太坊到现在,这中间不管过去了多少不同的周期和浪潮,核心不变的都是出现新一轮受追捧的资产。
既然区块链是关于链上资产的行业,那么最重要的是未来会出现什么新的资产,有什么样的新资产会上链。要回答这个问题,又要我们回过头去看看,从行业诞生至今,区块链留下了哪些有意义的、没意义的,有价值的、没价值的资产。
因此,有必要讨论一下链上资产的分类。
链上资产的种类很多,但总体上我觉得可以按**满足需求的不同,**做一些功能性的划分。同时,抛开去中心化、抗审查等等大词,**链上资产与传统资产最重要的区别可以认为是安全性的来源**。传统资产在传统的社会系统和金融系统中产生,而链上资产是通过可验证代码控制的,所以它的安全性的依赖很清晰,要比现实世界简单很多。
在不同的区块链系统中,使用不同的技术(比如POW/POS),设置不同的规则,拥有不同的治理机制,都会影响安全性。“安全性”和“满足什么样的需求”之间既不是正交的,也不是完全耦合的。在不同层级的安全性之下,可能都会出现满足某一类相同需求的产品,用户使用哪种产品,只取决于自己的风险偏好。另一方面,有些需求只可能在某些特定的安全性保障下才能得到满足,比如跨国际的全球化的抗通胀价值存储。
这篇文章只讨论一些比较简单的分类,可以假设在不同的安全性保障下,每个分类都有可能出现对应的产品。有些安全性是产品内生功能的一部分,有些则完全不影响。同时,这些分类也完全是主观的看法,不一定正确,我所希望的是引发更多对资产进行讨论。
### 核心资产(高安全性、强需求支撑)
1. **比特币(BTC)**
- **核心价值**:全球化抗通胀、抗审查的“数字黄金”。
- **长期逻辑**:全球法币超发背景下,BTC作为去中心化硬通货的需求不可替代。
这是整个行业最重要的资产。也是整个行业最核心的东西。在这个定位下,只会有一个赢者通吃。其他试图竞争的都很难生存下来。它对安全性的要求也是最高的。
### 经过验证的资产分类
这部分的资产可以认为是行业诞生至今,已经经过验证的、满足某真实需求、会长期存在的资产。
1. **代表优质项目的资产(股票/ICO代币/治理代币等)**
- **核心价值**:类似于传统金融世界里的一级市场和二级市场。所谓的“优质”也不一定需要真实落地,可能是叙事/故事驱动,也可能有真实的现金流,但重要的是它能在市场上吸引人买卖。
- **关键指标**:团队是否持续营销和建设?生态是否增长?项目是否解决实际问题?
2. **DeFi 资产**
- **核心价值**:链上金融系统的“基础设施工具”。
- **需求来源**:对套利、链上资产理财的需求会永远存在。
3. **Meme币**
- **核心价值**:营销驱动+投机需求的结合体。
- **长期存在性**:人性对暴富故事的追逐不会消失(如Pump.fun、SHIB)。
4. **稳定币**
- **核心价值**:加密货币世界的“支付货币”。
- **需求刚性**:交易媒介、避险工具、跨境支付(如USDT、USDC)。
在不同的安全性保障下,上面这些资产大部分都会有对应的产品。
比如稳定币在安全性上可以有中心化的 USDT ,也有去中心化的算法稳定币。理论上,安全性对稳定币是非常重要的。但现实中,“流动性”可能才是给用户传达“这东西到底安不安全“的产品特点,也是比较主要的竞争点。
Meme 则完全不需要安全性,所以对创业者来说在哪里做都差不多。哪里用户更多就适合去哪里。有时,安全性反而是它的阻碍。DeFi 的话,因人而异。安全性高低是否影响用户使用,完全取决于用户自己的风险偏好。
### 还未经过验证的资产(需求可能存在)
- **NFT(收藏品)?**
艺术、身份标识、游戏道具的数字化载体,但流动性差、炒作属性也不见得有 Meme 这么强。会长期存在吗?打个问号。
- **DAO(准入/治理代币)?**
去中心化组织的准入权/管理权通证,依赖 DAO 本身的价值和实际治理参与度决定的价值。DeFi DAO 可能是唯一一个有点发展的方向,其他还非常不成熟,有待验证。
- **RWA(真实世界资产代币化)?**
房产、债券等上链,需要解决法律合规与链下资产映射问题。不确定。
- **社交/游戏/内容资产**
用户数据所有权货币化,还没有像样的有一些用户的产品,就更不用提形成规模经济了。
- **AI 相关的资产?**
是一个变数。如果未来会有成千上万的 AI 智能体与人类共存,链上是承载他们经济系统最合适的基础设施,这里会产生什么新的资产类型?值得期待。
这里面的资产类型,很多还没有找到真实的需求,至少没有经过验证。所以长期来看它们会是区块链行业的方向吗,需要打很多问号。既然需求本身没有得到验证,那么谈安全性对它们的影响,就更加无从谈起了。
当然,这里其实还有一个更有意思的部分,可以多聊一些。也就是**共同知识(法律/合同/规则/代码)**这一类资产。
在应用层,共同知识尚未有代币化的尝试,也难以对其具体价值做定量分析。但如果要说有的实践,以太坊通过交易收取 gas 费和 CKB 通过 Cell 存储状态收取“押金”算是一种在底层的 generalize 的尝试。这种尝试是定量的,可验证的。
以太坊的问题是经济模型不 make sense 导致状态爆炸,ckb 相比是更简单、更明确的。但这里的问题变成了,公链需要通过区块空间的竞争来展示这一种需求是否真的成立。区块空间越紧张,需求就越大。同时安全性越高,对共同知识的保障就越强,也会体现区块空间的价值。
但另一方面,是否有开发者在上面开发应用,会更大的影响这一点。因此开发工具、开发者生态在现阶段可能更重要。
### 最后
写到这里,发现很多资产似乎又是老生常谈。但从满足需求和安全性两个角度来思考,算是追本溯源的尝试。现在我们面临的处境是,问题还是老的问题,答案是否有新的答案,期待更多讨论。
-

@ 91bea5cd:1df4451c
2025-02-04 17:15:57
### Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits
Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C.
e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
#### Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid()
RETURNS TEXT
AS $$
DECLARE
-- Crockford's Base32
encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000';
output TEXT = '';
unix_time BIGINT;
ulid BYTEA;
BEGIN
-- 6 timestamp bytes
unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT;
timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes
ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
VOLATILE;
```
#### ULID TO UUID
```sql
CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$
DECLARE
-- 16byte
bytes bytea = E'\\x00000000 00000000 00000000 00000000';
v char[];
-- Allow for O(1) lookup of index values
dec integer[] = ARRAY[
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 0, 1, 2,
3, 4, 5, 6, 7, 8, 9, 255, 255, 255,
255, 255, 255, 255, 10, 11, 12, 13, 14, 15,
16, 17, 1, 18, 19, 1, 20, 21, 0, 22,
23, 24, 25, 26, 255, 27, 28, 29, 30, 31,
255, 255, 255, 255, 255, 255, 10, 11, 12, 13,
14, 15, 16, 17, 1, 18, 19, 1, 20, 21,
0, 22, 23, 24, 25, 26, 255, 27, 28, 29,
30, 31
];
BEGIN
IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN
RAISE EXCEPTION 'Invalid ULID: %', ulid;
END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits)
bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]);
bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2));
bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4));
bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1));
bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3));
bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits);
bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2));
bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4));
bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1));
bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3));
bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]);
bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2));
bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4));
bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1));
bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3));
bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$
BEGIN
RETURN encode(parse_ulid(ulid), 'hex')::uuid;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### UUID to ULID
```sql
CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$
DECLARE
encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
output text = '';
uuid_bytes bytea = uuid_send(id);
BEGIN
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql
-- Cria a extensão pgcrypto para gerar uuid
CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID
CREATE OR REPLACE FUNCTION gen_lrandom()
RETURNS TEXT AS $$
DECLARE
ts_millis BIGINT;
ts_chars TEXT;
random_bytes BYTEA;
random_chars TEXT;
base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
i INT;
BEGIN
-- Pega o timestamp em milissegundos
ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32
ts_chars := '';
FOR i IN REVERSE 0..11 LOOP
ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1);
END LOOP;
-- Gera 10 bytes aleatórios e converte para base32
random_bytes := gen_random_bytes(10);
random_chars := '';
FOR i IN 0..9 LOOP
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1);
IF i < 9 THEN
random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1);
ELSE
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1);
END IF;
END LOOP;
-- Concatena o timestamp e os caracteres aleatórios
RETURN ts_chars || random_chars;
END;
$$ LANGUAGE plpgsql;
```
#### Exemplo de USO
```sql
-- Criação da extensão caso não exista
CREATE EXTENSION
IF
NOT EXISTS pgcrypto;
-- Criação da tabela pessoas
CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela
SELECT
*
FROM
"pessoas"
WHERE
uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F';
```
### Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-

@ 05cdefcd:550cc264
2025-03-28 08:00:15
The crypto world is full of buzzwords. One that I keep on hearing: “Bitcoin is its own asset class”.
While I have always been sympathetic to that view, I’ve always failed to understand the true meaning behind that statement.
Although I consider Bitcoin to be the prime innovation within the digital asset sector, my primary response has always been: How can bitcoin (BTC), a single asset, represent an entire asset class? Isn’t it Bitcoin and other digital assets that make up an asset class called crypto?
Well, I increasingly believe that most of crypto is just noise. Sure, it’s volatile noise that is predominately interesting for very sophisticated hedge funds, market makers or prop traders that are sophisticated enough to extract alpha – but it’s noise nonetheless and has no part to play in a long-term only portfolio of private retail investors (of which most of us are).
*Over multiple market cycles, nearly all altcoins underperform Bitcoin when measured in BTC terms. Source: Tradingview*
## Aha-Moment: Bitcoin keeps on giving
Still, how can Bitcoin, as a standalone asset, make up an entire asset class? The “aha-moment” to answer this question recently came to me in a [Less Noise More Signal interview](https://www.youtube.com/watch?v=YHRluf5uxzo) I did with [James Van Straten](https://www.linkedin.com/in/james-van-straten-8782b4112/), senior analyst at Coindesk.
Let me paraphrase him here: *“You can’t simply recreate the same ETF as BlackRock. To succeed in the Bitcoin space, new and innovative approaches are needed. This is where understanding Bitcoin not just as a single asset, but as an entire asset class, becomes essential. There are countless ways to build upon Bitcoin’s foundation—varied iterations that go beyond just holding the asset. This is precisely where the emergence of the Bitcoin-linked stock market is taking shape—and it's already underway.”*
And this is actually coming to fruition as we speak. Just in the last few days, we saw several products launch in that regard.
Obviously, MicroStrategy (now Strategy) is the pioneer of this. The company now [owns](https://www.strategy.com/purchases) 506,137 BTC, and while they’ll keep on buying more, they have also inspired many other companies to follow suit.
In fact, there are now already over 70 companies that have adopted Strategy’s Bitcoin playbook. One of the latest companies to buy Bitcoin for their corporate treasury is Rumble. The YouTube competitor just [announced](https://www.coindesk.com/markets/2025/03/12/video-sharing-platform-rumble-buys-188-btc-for-usd17-1m) their first Bitcoin purchase for $17 million.
Also, the gaming zombie company GameStop just announced to raise money to buy BTC for their corporate treasury.
*Gamestop to make BTC their hurdle rate. Source: X*
## ETF on Bitcoin companies
Given this proliferation of Bitcoin Treasury companies, it was only a matter of time before a financial product tracking these would emerge.
The popular crypto index fund provider Bitwise Investments has just launched this very product called the [Bitwise Bitcoin Standard Corporations ETF](https://ownbetf.com/) (OWNB).
The ETF tracks Bitcoin Treasury companies with over 1,000 BTC on their balance sheet. These companies invest in Bitcoin as a strategic reserve asset to protect the $5 trillion in low-yield cash that companies in the US commonly sit on.
*These are the top 10 holdings of OWNB. Source: Ownbetf*
## ETF on Bitcoin companies’ convertible bonds
Another instrument that fits seamlessly into the range of Bitcoin-linked stock market products is the [REX Bitcoin Corporate Treasury Convertible Bond ETF](https://www.rexshares.com/rex-launches-bitcoin-corporate-treasury-convertible-bond-etf/) (BMAX). The ETF provides exposure to the many different convertible bonds issued by companies that are actively moving onto a Bitcoin standard.
Convertible bonds are a valuable financing tool for companies looking to raise capital for Bitcoin purchases. Their strong demand is driven by the unique combination of equity-like upside and debt-like downside protection they offer.
For example, MicroStrategy's convertible bonds, in particular, have shown exceptional performance. For instance, MicroStrategy's 2031 bonds has shown a price rise of 101% over a one-year period, vastly outperforming MicroStrategy share (at 53%), Bitcoin (at 25%) and the ICE BofA U.S. Convertible Index (at 10%). The latter is the benchmark index for convertible bond funds, tracking the performance of U.S. dollar-denominated convertible securities in the U.S. market.
*The chart shows a comparison of ICE BofA U.S. Convertible Index, the Bloomberg Bitcoin index (BTC price), MicroStrategy share (MSTR), and MicroStrategy bond (0.875%, March 15 203). The convertible bond has been outperforming massively. Source: Bloomberg*
While the BMAX ETF faces challenges such as double taxation, which significantly reduces investor returns (explained in more detail here), it is likely that future products will emerge that address and improve upon these issues.
## Bitcoin yield products
The demand for a yield on Bitcoin has increased tremendously. Consequently, respective products have emerged.
Bitcoin yield products aim to generate alpha by capitalizing on volatility, market inefficiencies, and fragmentation within cryptocurrency markets. The objective is to achieve uncorrelated returns denominated in Bitcoin (BTC), with attractive risk-adjusted performance. Returns are derived exclusively from asset selection and trading strategies, eliminating reliance on directional market moves.
### Key strategies employed by these funds include:
- *Statistical Arbitrage:* Exploits short-term pricing discrepancies between closely related financial instruments—for instance, between Bitcoin and traditional assets, or Bitcoin and other digital assets. Traders utilize statistical models and historical price relationships to identify temporary inefficiencies.
- *Futures Basis Arbitrage:* Captures profits from differences between the spot price of Bitcoin and its futures contracts. Traders simultaneously buy or sell Bitcoin on spot markets and enter opposite positions in futures markets, benefiting as the prices converge.
- *Funding Arbitrage:* Generates returns by taking advantage of variations in Bitcoin funding rates across different markets or exchanges. Funding rates are periodic payments exchanged between long and short positions in perpetual futures contracts, allowing traders to profit from discrepancies without significant directional exposure.
- *Volatility/Option Arbitrage:* Seeks profits from differences between implied volatility (reflected in Bitcoin options prices) and expected realized volatility. Traders identify mispriced volatility in options related to Bitcoin or Bitcoin-linked equities, such as MSTR, and position accordingly to benefit from volatility normalization.
- *Market Making:* Involves continuously providing liquidity by simultaneously quoting bid (buy) and ask (sell) prices for Bitcoin. Market makers profit primarily through capturing the spread between these prices, thereby enhancing market efficiency and earning consistent returns.
- *Liquidity Provision in DeFi Markets:* Consists of depositing Bitcoin (usually as Wrapped BTC) into decentralized finance (DeFi) liquidity pools such as those on Uniswap, Curve, or Balancer. Liquidity providers earn fees paid by traders who execute swaps within these decentralized exchanges, creating steady yield opportunities.
Notable products currently available in this segment include the Syz Capital BTC Alpha Fund offered by Syz Capital and the Forteus Crypto Alpha Fund by Forteus.
## BTC-denominated share class
A Bitcoin-denominated share class refers to a specialized investment fund category in which share values, subscriptions (fund deposits), redemptions (fund withdrawals), and performance metrics are expressed entirely in Bitcoin (BTC), rather than in traditional fiat currencies such as USD or EUR.
Increasingly, both individual investors and institutions are adopting Bitcoin as their preferred benchmark—or "Bitcoin hurdle rate"—meaning that investment performance is evaluated directly against Bitcoin’s own price movements.
These Bitcoin-denominated share classes are designed specifically for investors seeking to preserve and grow their wealth in Bitcoin terms, rather than conventional fiat currencies. As a result, investors reduce their exposure to fiat-related risks. Furthermore, if Bitcoin outperforms fiat currencies, investors holding BTC-denominated shares will experience enhanced returns relative to traditional fiat-denominated investment classes.
X: https://x.com/pahueg
Podcast: https://www.youtube.com/@lessnoisemoresignalpodcast
Book: https://academy.saifedean.com/product/the-bitcoin-enlightenment-hardcover/
-

@ e3ba5e1a:5e433365
2025-02-04 08:29:00
President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
* Suppose apples currently sell for $1 each in the entire United States.
* There are domestic sellers and foreign sellers of apples, all receiving the same price.
* There are no taxes or tariffs on the purchase of apples.
* The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
* Number of apples bought in the US
* Price paid by buyers for apples in the US
* Post-tax price received by domestic apple producers
* Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
1. The number of apples bought will go down
2. The buyers will pay more for each apple they buy, but not the full amount of the tariff
3. Domestic apple sellers will receive a *higher* price per apple
4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
## Marginal benefit
All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart).
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
## Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
* Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900
* Total revenue: $5000 (10,000 apples at $0.50 each)
* Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

## Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
* When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
* When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
## Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
* The equilibrium price paid by consumers has risen from $1 to $1.20.
* The total number of apples purchased has dropped from 63 apples to 60 apples.
* Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
* Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
* Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
* The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
* Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
* Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
* Domestic producers scored. They can sell less apples and make more revenue doing it.
* And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
## Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
* Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
* Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
* Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-

@ da0b9bc3:4e30a4a9
2025-03-28 07:27:06
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/927569
-

@ 9e69e420:d12360c2
2025-02-01 11:16:04

Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-

@ 502ab02a:a2860397
2025-03-28 04:57:18
จริงหรือ ว่าโอเมก้า3 ต้องมาจากปลาทะเลเท่านั้น
มีเรื่องที่น่าสนใจเรื่องนึงครับ ถ้าพูดถึงโอเมก้า-3 หลายคนอาจนึกถึงปลาทะเลน้ำลึก เช่น แซลมอน แมคเคอเรล หรือซาร์ดีน ซึ่งเป็นแหล่งโอเมก้า-3 ที่ร่างกายใช้ได้ดี แต่ในขณะเดียวกัน ก็มีกลุ่มคนที่พยายามบริโภคโอเมก้า-3 จากพืชแทน เช่น น้ำมันเมล็ดแฟลกซ์ น้ำมันเมล็ดเจีย หรือวอลนัท โดยหวังว่าจะได้รับประโยชน์เช่นเดียวกับการกินปลา แต่ที่เราเรียนรู้กันมาว่า โอเมก้า-3 จากพืชนั้น ร่างกายมนุษย์นำไปใช้ได้น้อยมาก หรือแทบไม่ได้เลย
สาเหตุหลักมาจากรูปแบบของโอเมก้า-3 ที่พบในแหล่งต่างๆ โอเมก้า-3 มีอยู่ 3 ชนิดหลัก ได้แก่
ALA (Alpha-Linolenic Acid) – พบในพืช
EPA (Eicosapentaenoic Acid) – พบในปลาทะเล
DHA (Docosahexaenoic Acid) – พบในปลาทะเล
ร่างกายสามารถใช้ EPA และ DHA ได้โดยตรง แต่สำหรับ ALA นั้น ร่างกายต้องผ่านกระบวนการเปลี่ยนแปลงทางชีวเคมีก่อน ซึ่งกระบวนการนี้ไม่มีประสิทธิภาพนัก โดยทั่วไปแล้ว
ALA แปลงเป็น EPA ได้เพียง 5-10%
ALA แปลงเป็น DHA ได้เพียง 0.5-5%
แปลว่า หากคุณกินเมล็ดแฟลกซ์หรือน้ำมันเมล็ดเจีย แม้ว่าจะมีปริมาณ ALA สูง แต่ร่างกายก็แทบไม่ได้รับ EPA และ DHA ในปริมาณที่เพียงพอเพื่อใช้ประโยชน์อย่างเต็มที่
ทำไมร่างกายแปลง ALA เป็น EPA/DHA ได้น้อย?
อันแรกเลยคือ เอนไซม์จำกัด กระบวนการเปลี่ยน ALA เป็น EPA และ DHA จะใช้เอนไซม์เดียวกับการแปลงโอเมก้า-6 ซึ่งมักถูกใช้ไปกับโอเมก้า-6 ที่มากเกินไปในอาหารปัจจุบันซะแล้วนั่นเอง ต่อมาคือ กระบวนการหลายขั้นตอน การเปลี่ยน ALA เป็น DHA ต้องผ่านหลายขั้นตอนทางชีวเคมี ทำให้มีการสูญเสียพลังงานและวัตถุดิบไปมาก และสุดท้าย ปัจจัยทางพันธุกรรมและเพศ บางคน โดยเฉพาะผู้หญิง อาจมีอัตราการเปลี่ยนที่สูงกว่าผู้ชายเล็กน้อย แต่ก็ยังต่ำเมื่อเทียบกับการได้รับ EPA/DHA จากปลาหรือสาหร่ายโดยตรง
โอเมก้า-6 ตัวการขัดขวางโอเมก้า-3 จากพืช
โอเมก้า-6 เป็นกรดไขมันจำเป็นที่พบมากในน้ำมันพืช เช่น น้ำมันถั่วเหลือง น้ำมันข้าวโพด และน้ำมันดอกทานตะวัน ซึ่งเป็นส่วนประกอบหลักของอาหารแปรรูปในปัจจุบัน ปัญหาคือ เอนไซม์ที่ใช้แปลง ALA ไปเป็น EPA/DHA เป็นตัวเดียวกับที่ใช้แปลงโอเมก้า-6 ไปเป็น AA (Arachidonic Acid) ซึ่งมีบทบาทในการอักเสบ หากเราบริโภคโอเมก้า-6 มากเกินไป (ซึ่งคนส่วนใหญ่ทำ5555) เอนไซม์เหล่านี้จะถูกใช้ไปกับโอเมก้า-6 มากกว่า ทำให้ ALA มีโอกาสแปลงเป็น EPA/DHA น้อยลงไปอีก
แล้วคนที่ไม่กินปลาหรือชาววีแกนควรทำอย่างไร?
สำหรับคนที่ไม่สามารถหรือไม่ต้องการกินปลา ก็จะมีการบริโภคน้ำมันสาหร่ายที่มี DHA โดยตรงเป็นทางเลือกที่ดีกว่าการหวังพึ่ง ALA จากพืช เพราะ DHA จากสาหร่ายสามารถดูดซึมและใช้ได้ทันทีเหมือน DHA จากปลา
ได้ด้วยเหรอ ?????
ผมเล่ากำเนิดของ DHA ในปลาให้ประมาณนี้ครับ
จริง ๆ แล้ว DHA ซึ่งเป็นโอเมก้า-3 ที่ร่างกายใช้ได้โดยตรง มาจาก Docosahexaenoic Acid ที่เกิดจากกระบวนการสังเคราะห์ตามธรรมชาติ ซึ่งสาหร่ายบางสายพันธุ์ เช่น Schizochytrium และ Crypthecodinium cohnii มีเอนไซม์ที่สามารถเปลี่ยนกรดไขมันพื้นฐานให้กลายเป็น DHA ได้เองซึ่งเป็นส่วนประกอบหลักในระบบนิเวศทะเล(พืชกักเก็บไขมันได้อย่างไร ผมเคยโพสไปแล้ว) โดยเฉพาะ สาหร่ายขนาดเล็ก (microalgae) สาหร่ายจึงเป็นสิ่งมีชีวิตในทะเลพัฒนาให้มี DHA สูงเพราะ DHA เป็นส่วนประกอบสำคัญที่ช่วยรักษาความยืดหยุ่นและความสมบูรณ์ของเยื่อหุ้มเซลล์ในสาหร่าย ทำให้พวกมันสามารถดำรงชีวิตในสภาพแวดล้อมที่มีอุณหภูมิต่ำในทะเลได้
จากนั้นก็เป็นไปตามห่วงโซ่อาหารครับ ปลาและสัตว์ทะเลอื่น ๆ ได้รับ DHA จากการบริโภคสาหร่ายหรือสัตว์เล็ก ๆ ที่กินสาหร่ายมาอีกที ดังนั้น DHA ในปลาเป็นผลมาจากการสะสมจากสาหร่ายโดยตรง นี่เป็นเหตุผลว่าทำไมปลาทะเลน้ำลึก เช่น แซลมอน แมคเคอเรล และซาร์ดีน ถึงมี DHA สูงนั่นเอง งว่ออออออ
ดังนั้น เมื่อคุณกิน DHA จากสาหร่าย ก็เท่ากับว่าคุณได้รับ DHA จากต้นกำเนิดแท้จริงในระบบนิเวศทะเลครับ
DHA ที่ได้มาจากสาหร่ายสามารถนำไปใช้ในร่างกายได้ทันทีโดยไม่ต้องผ่านกระบวนการเปลี่ยนแปลง เพราะมันอยู่ในรูป Triglyceride หรือ Phospholipid ซึ่งเป็นรูปแบบที่ร่างกายมนุษย์สามารถดูดซึมและนำไปใช้ได้ทันที ปลาไม่ได้แปลงโครงสร้าง DHA แต่เพียงสะสม DHA ไว้ในตัวจากการกินสาหร่าย ดังนั้นการรับประทาน DHA จากสาหร่ายก็ให้ผลเทียบเท่ากับการรับประทาน DHA จากปลา งานวิจัยหลายฉบับยืนยันว่า DHA จากสาหร่ายมีค่าการดูดซึม (Bioavailability) ใกล้เคียงกับ DHA จากน้ำมันปลา แต่หาเอาเองนะถ้าอยากอ่านฉบับเต็ม
การผลิตน้ำมันสาหร่ายนั้น เมื่อสาหร่ายเจริญเติบโตเต็มที่แล้ว เขาจะทำการเก็บเกี่ยวและสกัดน้ำมันโดยใช้เทคโนโลยีการแยกที่ทันสมัย ซึ่งช่วยรักษาให้ DHA ที่มีอยู่ในเซลล์สาหร่ายถูกเก็บรักษาไว้ในรูปแบบที่สามารถนำไปใช้ได้โดยตรง จากนั้นจะเข้าสู่การกรองหรือการปั่นแยก (centrifugation) เพื่อให้ได้มวลสาหร่ายที่เข้มข้น จากนั้นจึงทำให้แห้งเพื่อเตรียมเข้าสู่กระบวนการสกัด ซึ่งมีหลายวิธีอาทิเช่น
1 การสกัดด้วยตัวทำละลาย
ใช้ตัวทำละลาย เช่น เฮกเซน (Hexane) หรือ เอทานอล (Ethanol) เพื่อสกัดน้ำมันออกจากเซลล์สาหร่าย จากนั้นน้ำมันจะถูกนำไปกลั่นเพื่อแยกตัวทำละลายออก ทำให้ได้น้ำมันที่มีความบริสุทธิ์สูง
2. การสกัดด้วย CO₂ เหลว ใช้ คาร์บอนไดออกไซด์ในสถานะวิกฤติ (Supercritical CO₂) ซึ่งเป็นวิธีที่ทันสมัย ก๊าซ CO₂ จะถูกทำให้มีความดันสูงและอุณหภูมิที่เหมาะสมเพื่อกลายเป็นของเหลว แล้วใช้แยกน้ำมันออกจากเซลล์สาหร่าย วิธีนี้ช่วยให้ได้น้ำมันที่ ปราศจากตัวทำละลายเคมีและมีความบริสุทธิ์สูง
3. การสกัดด้วยการกดอัด หรือ Cold Pressed
เป็นวิธีที่ใช้แรงดันทางกลกดเซลล์สาหร่ายเพื่อให้ได้น้ำมันออกมา อันนี้เป็นการผลิตน้ำมันแบบออร์แกนิกเลยครับ แต่ให้ผลผลิตน้อยกว่าวิธีอื่น ๆ
น้ำมันที่ได้จากการสกัดจะผ่านการกลั่นด้วยกระบวนการต่าง ๆ เช่น
Winterization กำจัดไขมันที่ไม่จำเป็น
Molecular Distillation แยกสารตกค้าง เช่น โลหะหนักและสารปนเปื้อน
Deodorization กำจัดกลิ่นคาวของสาหร่าย
จากนั้นก็บรรจุใส่ซอฟท์เจล พร้อมจำหน่ายนั่นเองครับ
ก็ถือว่าเป็นอีกทางเลือกของชาววีแกน ที่ไม่สามารถกินปลาหรือสัตว์ทะเลได้ ก็น่าจะเฮกันดังๆได้เลยครับ จะได้มีตัวช่วยในการลดการอักเสบได้
ส่วนชาว food matrix ก็ต้องเรียนรู้ระบบครับ การกินจากปลาหรือสัตว์ทะเล ก็จะได้โปรตีน แร่ธาตุ วิตามินอื่นๆควบมากับตัวสัตว์ตามที่ธรรมชาติแพคมาให้
ถ้าจะเสริมเป็นน้ำมันสาหร่าย ก็สุดแล้วแต่ความต้องการครับ ไม่ใช่เรื่องแย่อะไร เว้นแต่ไปเทียบราคาเอาเองนะ 55555
#pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-

@ 97c70a44:ad98e322
2025-01-30 17:15:37
There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
# It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
# It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
# It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
# It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
> Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
_As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
# It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
# Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (*ahem*, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-

@ a3bb06f6:19ac1b11
2025-03-28 02:36:38
“Until you make the unconscious conscious, it will continue to direct your life, and you will call it fate.” — Carl Jung
Most people don’t realize they’ve been robbed. Not in the dramatic, wallet-snatching sense, but in a quiet, systemic way that’s gone unnoticed for generations. If you’re feeling like no matter how hard you work, you can’t get ahead… you’re not imagining it.
It didn’t start as a scheme—*but one compromise after another*, it became one. Now, the system exploits you by design. This isn’t fate. It’s fiat.
The Unconscious Script: How Fiat Becomes Invisible From the moment you're born, you're placed into an economic system based on government-issued fiat currency. It becomes the air you breathe. You work for dollars. You save in dollars. You price **your time**, **your future**, and even **your dreams** in dollars.
But few stop to ask: What actually is a dollar? Who creates it? Why does it lose value?
This lack of questioning is the unconscious state. Fiat money is the background process running your life. You feel the effects—rising prices, shrinking savings, mounting debt—but you never see the root cause. So you blame yourself. Or “the economy.” Or call it fate.
The Lie of Neutral Money: Most believe money is just a neutral tool. But fiat is not neutral—it’s political power encoded into paper.
Governments can **print more of it at will**. Central banks can manipulate its supply, distort interest rates, and quietly tax you through inflation. Every time more money is created, your purchasing power shrinks.
But it happens slowly, like a leak in a tire. You don’t notice at first. You just feel like you’re working harder for less. The house is further out of reach. The groceries cost more. Retirement feels impossible.
And you accept it. Because no one told you it's designed this way.
<img src="https://blossom.primal.net/80cb04b171e15d56d1224a1458f0ca3ad9a440915c736e145186df1cc2f4979b.png">
Inflation Is the Invisible Thief, Inflation isn’t just a “cost of living increase.” It’s a state-sponsored form of theft.
When new money is created, it enters the system unevenly. Those closest to the money printer—banks, governments, **large corporations**—get the new dollars first. By the time it reaches you, prices have already risen. You’re buying the same goods with weaker money.
And yet, most people still save in fiat. They’re taught that hoarding cash is “safe.” They’re taught that 2% inflation is “normal.” But it’s not normal to work 40 hours a week and fall behind. That’s the product of unconscious acceptance.
The fiat system survives on one thing: your **ignorance**. It didn’t begin with malicious intent, but over time, it adapted to protect its own power—at your expense. As long as you don’t understand how money works, you won’t resist. You’ll blame yourself, or *capitalism*, or bad luck. **But never the system itself**.
This is why financial education is *never* prioritized in schools. This is why questioning monetary policy is left to economists and suits on CNBC. You were never taught how it works. And now the system depends on you staying confused—grinding, borrowing, complying, without ever asking why.
Making the Unconscious Conscious: Enter **Bitcoin**, Bitcoin breaks this spell.
<img src="https://blossom.primal.net/8373eb52ee7773e0ffc4591819ff984a27829e47741894456258e2a638029022.png">
It forces you to confront the nature of money—what it is, how it’s created, and why fiat fails. It teaches you that money doesn’t need to be printed, inflated, or controlled. That money can be fixed, finite, and **fair**.
Bitcoin is not just a new currency. It’s a tool of consciousness. It exposes the scam of fiat and offers a lifeboat to anyone ready to wake up.
Once you understand Bitcoin, you can’t unsee the problem. You begin to ask:
Why should I trust a system that steals my **time**? Why is saving discouraged, but debt rewarded? Why do I need permission to use my own money? These aren’t technical questions. They’re **moral** ones.
Consciousness Is Sovereignty: When you understand what fiat is, you stop calling your financial struggles “fate.” You start calling them what they are, outcomes of a broken system.
And once you see the system for what it is, you can choose to **exit**.
<img src="https://blossom.primal.net/a8766caf9dc043fa360dbf7c5e473201d72dfeede02a7f08abc9897367a33011.png">
Saving in Bitcoin is not speculation. It’s self-defense. It’s rejecting unconscious servitude. It’s reclaiming your **time**, your **labor**, your **future**.
In a fiat world, they own the money—so they own the rules. In a Bitcoin world, you own yourself.
That’s the power of making the unconscious conscious.
And that’s how you stop calling it fate.
-

@ 9e69e420:d12360c2
2025-01-30 12:23:04
Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York.
DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million.
The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture.
Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry.
![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
-

@ 7d33ba57:1b82db35
2025-03-27 20:54:55
Andorra la Vella, the capital of Andorra, is a charming mix of mountain landscapes, duty-free shopping, and rich history. Nestled in the Pyrenees, it’s a great destination for skiing, hiking, and relaxing in thermal spas. Whether you’re here for outdoor adventures, tax-free shopping, or cultural experiences, Andorra la Vella has something for everyone.

## **🏔️ Top Things to See & Do in Andorra la Vella**
### **1️⃣ Shop in Avinguda Meritxell 🛍️**
- One of **Europe’s best duty-free shopping streets**, filled with **electronics, fashion, perfumes, and luxury goods**.
- Find **brands at lower prices than in Spain or France**.
### **2️⃣ Relax at Caldea Spa ♨️**
- The **largest thermal spa in Southern Europe**, with **hot springs, saunas, and lagoon pools**.
- A perfect place to unwind **after skiing or hiking**.

### **3️⃣ Visit the Church of Sant Esteve ⛪**
- A **beautiful Romanesque church** dating back to the **12th century**.
- Features **stone carvings and medieval frescoes**.
### **4️⃣ Explore the Historic Quarter (Barri Antic) 🏡**
- Walk through **narrow cobbled streets** filled with **traditional Andorran houses and charming cafés**.
- Visit **Casa de la Vall**, a **historic parliament building from the 16th century**.
### **5️⃣ Go Skiing or Snowboarding 🎿**
- Andorra is famous for its **world-class ski resorts**, **Grandvalira and Vallnord**, just **15-30 minutes away**.
- Ideal for **beginners and experienced skiers** alike.
### **6️⃣ Hiking in the Pyrenees 🥾**
- **Summer & autumn** offer **incredible hiking trails** with **mountain lakes and scenic views**.
- **Rec del Solà Trail** – A beautiful, easy path with panoramic views of the valley.
- **L’Estany Blau** – A moderate hike leading to a stunning blue lake.

### **7️⃣ Enjoy Andorran Cuisine 🍽️**
- **Escudella** – A hearty **Andorran stew with meat, beans, and vegetables** 🍲
- **Trinxat** – A mountain dish made of **potatoes, cabbage, and bacon** 🥓🥔
- **Embotits** – Local **cured meats and sausages**, perfect as tapas 🍖
- **Crema Andorrana** – A creamy, local dessert similar to Catalan crema 🍮

## **🚗 How to Get to Andorra la Vella**
✈️ **By Air:** The nearest airports are **Barcelona-El Prat (Spain, 2.5 hrs)** and **Toulouse-Blagnac (France, 2.5 hrs)**.
🚘 **By Car:** 2.5 hrs from **Barcelona**, 2.5 hrs from **Toulouse**, 3 hrs from **Perpignan**.
🚌 **By Bus:** Direct buses from **Barcelona, Toulouse, and Lleida**.
🚆 **By Train:** No direct train, but you can take a train to **L'Hospitalet-près-l'Andorre (France)** and continue by bus.

## **💡 Tips for Visiting Andorra la Vella**
✅ **Best time to visit?** **Winter for skiing, summer for hiking & shopping** ❄️🌞
✅ **Bring a passport** – Even though Andorra isn’t in the EU, border checks happen 🇦🇩
✅ **Try duty-free shopping** – Electronics, perfumes, and alcohol are cheaper 🛍️
✅ **Book ski passes in advance** – Resorts get busy in peak season 🎿
✅ **Wear comfy shoes** – The city has **steep streets and cobblestone paths** 👟
-

@ 2b24a1fa:17750f64
2025-03-28 10:07:04
Der Deutsche Bundestag wurde neu gewählt. Für einige Abgeordnete und Regierungsmitglieder heißt es Time to Say Goodbye. Abschied ist ein scharfes Schwert. 
[https://soundcloud.com/radiomuenchen/nachruf-2-olaf-der-zeitenwender](https://soundcloud.com/radiomuenchen/nachruf-2-olaf-der-zeitenwender?si=6c375088b6444c2d8aa7e8040fb1a79e\&utm_source=clipboard\&utm_medium=text\&utm_campaign=social_sharing)
Auch bei Radio München werden Trennungs- und Verlassenheitsgefühle getriggert. Umso mehr, wenn es sich nicht nur um duselige Allerweltsliebe handelt, sondern um den Abgang großer Helden. Sie bezahlten ihren todesmutigen und fast ehrenamtlichen Einsatz nicht mit dem Leben, jedoch mit der einen oder anderen Falte in Hemd oder Bluse, manchmal sogar im Gesicht. Was bleibt? Eine bescheidene Pension? Ein lausig bezahlter Manager-Job in einem Konzern? Wir wollen jedenfalls nicht, dass diese Volkshelden vom Zahn der Zeit abgenagt, vergessen werden und setzen ihnen deshalb ein bescheidenes akustisches, aber nachhaltiges Denkmal. Hören Sie die kleine satirische Reihe „Nachrufe“ von unserem Autor Jonny Rieder.\
Folge 2: Olaf der Zeitenwender
Sprecher: Karsten Troyke
Bild: Markus Mitterer für Radio München
Radio München\
[www.radiomuenchen.net/](http://www.radiomuenchen.net/%E2%80%8B "http://www.radiomuenchen.net/")\
@[radiomuenchen](https://soundcloud.com/radiomuenchen)\
[www.facebook.com/radiomuenchen](http://www.facebook.com/radiomuenchen "http://www.facebook.com/radiomuenchen")\
[www.instagram.com/radio\_muenchen/](http://www.instagram.com/radio_muenchen/ "http://www.instagram.com/radio_muenchen/")\
[twitter.com/RadioMuenchen](http://twitter.com/RadioMuenchen "http://twitter.com/RadioMuenchen")
Radio München ist eine gemeinnützige Unternehmung.\
Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\
IBAN: DE65 4306 0967 8217 9867 00\
BIC: GENODEM1GLS
-

@ 2b24a1fa:17750f64
2025-03-28 10:03:58
Zwischen Überzeugungsarbeit und Propaganda verläuft ein schmaler Grad. Aber so oder so: Wer die subtileren Werkzeuge hat und vor allem die Mittel um Menschen zu kaufen, die diese dann anwenden, hat eindeutig die besseren Karten. 
[https://soundcloud.com/radiomuenchen/unterwanderter-journalismus-oder-der-mediale-deep-state-wankt-von-milosz-matuschekcolor=ffd400](https://soundcloud.com/radiomuenchen/unterwanderter-journalismus-oder-der-mediale-deep-state-wankt-von-milosz-matuschek?si=45877e50143d4e10a22fc9a4be82970d\&utm_source=clipboard\&utm_medium=text\&utm_campaign=social_sharing)
Dass die Bevölkerung nun wissen will, mit welchen Mitteln sie auf welche Weise beeinflusst werden soll, ist selbstverständlich. Wie nuanciert diese Beeinflussung stattfinden kann, darauf haben uns unsere Hörer beim letzten Beitrag von Milosz Matuschek: „Die ersten Köpfe rollen“ gestoßen. Es ging um die staatliche amerikanische Behörde für internationale Entwicklungshilfe USAID. Matuschek schrieb: „Man liest was von AID im Namen und denkt, was man denken soll: klingt nach Bob Geldof, barmherzigen Schwestern und “Brot für die Welt”.“ Man hatte das nicht nur optisch wahrgenommen, nein, diese Behörde wurde hierzulande, in allen Medien US AID genannt, was unsere Sprecherin Sabrina Khalil übernahm. Dass die United States Agency for International Development in USA so nicht gesprochen wird, schrieben uns gleich mehrere aufmerksame Hörer. Es ist sicherlich keine Paranoia darüber nachzudenken, ob die Bedeutung unserer Sprache, unserer Wörter bis hin zur Aussprache im Fokus der Manipulation steht. Dafür wird sehr viel Geld locker gemacht und unter anderem in die Medien gepumpt.
Hören Sie heute den zweiten Teil der Reihe „Die Corona-Connection“ mit dem Titel: „Der mediale Deep State wankt“. Sprecherin: Sabrina Khalil.
Das freie Medienprojekt Pareto kann übrigens Unterstützung gebrauchen, dafür wurde ein Crowdfunding auf Geyser gestartet, wo man mit Bitcoin/Lightning-Spenden helfen kann. Und für Spenden auf dem klassischen Weg finden Sie die entsprechende Bankverbindung auf der Homepage pareto.space/de.
Nachzulesen unter: [www.freischwebende-intelligenz.org/p/unter…mediale](https://gate.sc?url=https%3A%2F%2Fwww.freischwebende-intelligenz.org%2Fp%2Funterwanderter-journalismus-der-mediale\&token=6fce3f-1-1743155866002 "https://www.freischwebende-intelligenz.org/p/unterwanderter-journalismus-der-mediale")
Foto: Gleichschaltung - sie melden exakt den gleichen Wortlaut.
-

@ 7d33ba57:1b82db35
2025-03-27 20:23:58
Peñíscola, known as the “Gibraltar of Valencia”, is a stunning coastal town on Spain’s Costa del Azahar. Famous for its medieval castle, beautiful beaches, and charming old town, Peñíscola is a perfect mix of history, culture, and seaside relaxation. It’s also known as a filming location for Game of Thrones!

## **🏖️ Top Things to See & Do in Peñíscola**
### **1️⃣ Peñíscola Castle (Castillo del Papa Luna) 🏰**
- A **magnificent 13th-century castle** sitting on a rocky peninsula.
- Built by the **Knights Templar** and later home to **Pope Benedict XIII (Papa Luna)**.
- Offers **breathtaking views** of the Mediterranean and surrounding coastline.
### **2️⃣ Explore the Old Town 🏡**
- Wander through **narrow cobblestone streets**, lined with **whitewashed houses and flower-filled balconies**.
- Discover **hidden courtyards, charming shops, and seafood restaurants**.
- Enjoy the **picturesque sunset views** over the sea.

### **3️⃣ Relax on Playa Norte & Playa Sur 🏖️**
- **Playa Norte**: The **main beach**, known for its **golden sand and clear waters**.
- **Playa Sur**: Smaller and quieter, great for **relaxing away from the crowds**.
- Both beaches offer **water sports, sunbeds, and beach bars**.
### **4️⃣ Serra d’Irta Natural Park 🌿**
- A **stunning coastal nature reserve** with **hiking and biking trails**.
- Offers **hidden coves, rugged cliffs, and breathtaking sea views**.
- Ideal for **nature lovers and photographers**.

### **5️⃣ Game of Thrones Filming Locations 🎬**
- Peñíscola was featured in **Game of Thrones (Season 6) as Meereen**.
- Visit the **castle walls, old town alleys, and city gates** where key scenes were filmed.
### **6️⃣ Boat Trip Around the Castle ⛵**
- Take a **boat tour** for **unique views of the fortress from the sea**.
- Sunset cruises offer **magical golden-hour scenery**.

## **🍽️ What to Eat in Peñíscola**
- **Arroz a Banda** – A delicious **seafood rice dish**, typical of Valencia 🍚🐟
- **Suquet de Peix** – A **traditional fish stew** with potatoes and saffron 🍲
- **Langostinos de Vinaròs** – **Famous local prawns**, incredibly fresh 🍤
- **Caragols Punxents** – A local specialty of **small spicy snails** 🐌🌶️
- **Coca de llanda** – A **sweet sponge cake**, perfect with coffee 🍰

## **🚗 How to Get to Peñíscola**
✈️ **By Air:** The nearest airport is **Castellón Airport (40 min), Valencia (1.5 hrs), or Barcelona (2 hrs)**.
🚆 **By Train:** The nearest station is **Benicarló-Peñíscola**, just **7 km away**.
🚘 **By Car:** 1.5 hrs from **Valencia**, 2 hrs from **Barcelona**, 45 min from **Castellón**.
🚌 **By Bus:** Direct buses from **Barcelona, Valencia, and Castellón**.

## **💡 Tips for Visiting Peñíscola**
✅ **Best time to visit?** **Spring & summer (April–September)** for the best weather ☀️
✅ **Visit the castle early** – Mornings are less crowded and cooler 🏰
✅ **Take a sunset walk along the beach** – The views are stunning 🌅
✅ **Try a boat trip** – The castle looks incredible from the water ⛵
✅ **Wear comfortable shoes** – The old town streets are steep and cobbled 👟
-

@ 9e69e420:d12360c2
2025-01-30 12:13:39
Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead.
Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023.
[Sauce](https://www.dailymail.co.uk/news/article-14341423/Christian-Iraqi-burnt-Koran-Sweden-shot-dead.html)
-

@ 7d33ba57:1b82db35
2025-03-27 19:48:38
Tarifa, located at the southernmost tip of Spain, is a paradise for beach lovers, adventure seekers, and nature enthusiasts. Known for its strong winds, golden beaches, and laid-back atmosphere, it’s a top destination for kite surfing, whale watching, and exploring Andalusian history. Plus, it’s the perfect gateway to Morocco, just a short ferry ride away.

## **🏖️ Top Things to See & Do in Tarifa**
### **1️⃣ Playa de Los Lances 🏄♂️**
- A **long, sandy beach** famous for **kite surfing and windsurfing**.
- One of the best spots in Europe for **water sports enthusiasts**.
- Lined with **chiringuitos (beach bars)** where you can relax and enjoy the views.
### **2️⃣ Punta de Tarifa – The Southernmost Point of Europe 🌍**
- A unique spot where the **Atlantic Ocean meets the Mediterranean Sea**.
- Walk to **Isla de las Palomas**, a historic military zone (guided tours available).
- Incredible views of **Morocco, just 14 km away**.

### **3️⃣ Whale & Dolphin Watching Tours 🐬**
- Join a boat trip to see **orcas, dolphins, and sperm whales** in the Strait of Gibraltar.
- Best time: **April to October** for whale migrations.

### **4️⃣ Explore the Historic Old Town 🏰**
- Wander through **narrow, whitewashed streets** full of charm.
- Visit **Guzmán el Bueno Castle**, a **10th-century fortress** with panoramic views.
- Enjoy **lively tapas bars, boutique shops, and hidden courtyards**.

### **5️⃣ Playa de Bolonia & Baelo Claudia Ruins 🏛️**
- One of Spain’s most **unspoiled beaches**, with **dunes and turquoise waters**.
- Explore the **Roman ruins of Baelo Claudia**, an ancient **fishing village from 2,000 years ago**.
- Climb the **Duna de Bolonia**, a massive sand dune with breathtaking views.

### **6️⃣ Day Trip to Morocco 🇲🇦**
- Take a **35-minute ferry to Tangier** for a quick taste of **North African culture**.
- Explore **medinas, souks, and local cuisine** with a guided tour.
- Don’t forget your **passport**!

## **🍽️ What to Eat in Tarifa**
- **Atún Rojo (Red Tuna)** – Tarifa is famous for its **fresh bluefin tuna** 🍣
- **Tortillitas de Camarones** – Crispy shrimp fritters, a local delicacy 🍤
- **Choco Frito** – Fried cuttlefish, a must-try for seafood lovers 🦑
- **Andalusian Gazpacho** – A refreshing **cold tomato soup**, perfect for hot days 🍅
- **Mojama** – **Salt-cured tuna**, often eaten as a tapa with almonds 🐟

## **🚗 How to Get to Tarifa**
✈️ **By Air:** The nearest airports are **Gibraltar (45 min), Málaga (2 hrs), and Seville (2.5 hrs)**.
🚆 **By Train:** No direct train, but you can take one to **Algeciras (30 min drive from Tarifa)**.
🚘 **By Car:** 1.5 hrs from **Málaga**, 1 hr from **Cádiz**, 30 min from **Gibraltar**.
🚌 **By Bus:** Regular buses from **Seville, Málaga, Cádiz, and Algeciras**.
⛴️ **To Morocco:** Ferries run **daily** to **Tangier, Morocco (35 min ride)**.

## **💡 Tips for Visiting Tarifa**
✅ **Best time to visit?** **Spring to early autumn (April–October)** for great weather ☀️
✅ **Book water sports lessons early** – It’s a popular spot for kite surfing! 🏄♂️
✅ **Bring layers** – Tarifa can be **windy**, even in summer 🌬️
✅ **Visit early for whale watching** – Mornings usually have calmer seas 🐋
✅ **Take a day trip to Bolonia** – One of Spain’s most stunning hidden beaches 🏝️

-

@ 0fa80bd3:ea7325de
2025-01-30 04:28:30
**"Degeneration"** or **"Вырождение"**
![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
-

@ fe9e99a0:5123e9a8
2025-03-27 18:37:28
Can’t seem to update anything
-

@ 0fa80bd3:ea7325de
2025-01-29 15:43:42
Lyn Alden - биткойн евангелист или евангелистка, я пока не понял
```
npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a
```
Thomas Pacchia - PubKey owner - X - @tpacchia
```
npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgpl
```
calvadev - Shopstr
```
npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq
```
Calle - Cashu founder
```
npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg
```
Джек Дорси
```
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
```
21 ideas
```
npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7l
```
Много адресов. Хз кто надо сортировать
```
https://github.com/aitechguy/nostr-address-book
```
ФиатДжеф - создатель Ностр - https://github.com/fiatjaf
```
npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
```
EVAN KALOUDIS Zues wallet
```
npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qd
```
Программер Коди https://github.com/CodyTseng/nostr-relay
```
npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl
```
Anna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation
https://x.com/AnyaChekhovich
```
npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7
```
-

@ 000002de:c05780a7
2025-03-27 17:51:16
Regardless of what you have heard Capitalism isn't to blame for all the ills in modern life. Capitalism is simply free trade without centralize control. Of course there are many details I'm glossing over and degrees of freedom. Critics of capitalism rarely explain how it works. They complain about people buying too much stuff. People being over-weight. They complain about waste. People buying stuff they don't need. They complain that teachers aren't paid enough. They complain that professional athletes make too much money.
All of this boils down to two things.
1. People don't like what others choose to do
2. The products we see and world we live in is a result of the desires and values of the people
I agree with many of the critics of capitalism. There is a ton of crap. There's a ton of waste. There are professions I wish were more profitable and others I wish were less profitable. I'm going to ignore the state for once here. Obviously the state puts its thumb on the scales and distorts the market. But this isn't the main factor IMO. The main factor in the world we live in is us. The people. Our desires. Our values. The things we value are reflected in the market. People don't like to admit this because it is uncomfortable. We are spoiled, self-centered, brats that are desire machines. Yeah, you can blame advertising. You can blame "capitalism" but the alternative is starvation and death (socialism).
Its time for us to stop blaming freedom for all the ills in our society and take ownership for our actions. Its us. Thing is, I can't change you. But, I can change my actions. Adjust my values. Adjust my frame of view. I'd love to start hearing people take responsibility and self ownership. Start living out your values. Don't be a part of things that you view as problems. Be a part of solutions. I can't tell you what that looks like but if you think about it for a while you can come up with some things. Its easy to blame others. Its hard to take responsibility for yourself and own your flaws and mistakes.
What do you think?
_Inspired by @k00b's [post](https://stacker.news/items/926865)_
originally posted at https://stacker.news/items/927021
-

@ 0fa80bd3:ea7325de
2025-01-29 14:44:48
![[yedinaya-rossiya-bear.png]]
1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest.
2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money.
3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape.
Now, what you do with a trapped bear is another question... 😏
-

@ 9bde4214:06ca052b
2025-03-27 17:28:23
“The human spirit should remain in charge.”
[Pablo](https://njump.me/npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft) & [Gigi](https://njump.me/npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) talk about the wind.
nostr:nevent1qvzqqqqqqypzpx77gg2frul26xkzr0gaq9n842u50axpcjhdsa3yeu388vrv5pftqys8wumn8ghj7mn0wd68ytn9d9h82mny0fmkzmn6d9njuumsv93k2tcppemhxue69uhkummn9ekx7mp0qqszlf337y0lkg4sz5ax9ath4y5vk6rpqn9tfewaln2989zavvqrg4cpt2krs
In this dialogue:
- Wind
- More Wind
- Information Calories, and how to measure them
- [Digital Wellbeing](https://play.google.com/store/apps/details?id=com.google.android.apps.wellbeing)
- [Rescue Time](https://www.rescuetime.com/)
- Teleology of Technology
- Platforms get users [Hooked](https://www.uxmatters.com/mt/archives/2021/06/book-review-hooked-how-to-build-habit-forming-products.php) (book)
- Feeds are [slot machines](https://ihpi.umich.edu/news/social-media-copies-gambling-methods-create-psychological-cravings)
- Movie Walls
- Tweetdeck and [Notedeck](https://damus.io/notedeck/)
- IRC vs the modern feed
- 37Signals: “[Hey](https://www.hey.com/pricing/), let’s just charge users!”
- “[You wouldn’t zap a car crash](https://njump.me/nevent1qqsqm2lz4ru6wlydzpulgs8m60ylp4vufwsg55whlqgua6a93vp2y4gzyphydppzm7m554ecwq4gsgaek2qk32atse2l4t9ks57dpms4mmhfxzzxtzc)”
- Catering to our highest self VS catering to our lowest self
- Devolution of YouTube [5-star ratings](https://daringfireball.net/linked/2017/03/18/youtube-thumbs-stars) to thumb up/down to [views](https://www.makeuseof.com/the-real-reason-why-youtube-hid-dislikes/)
- Long videos vs shorts
- The internet had to monetize itself somehow (with [attention](https://dergigi.com/2022/12/18/a-vision-for-a-value-enabled-web/#attention))
- “Don’t be evil” and why Google had to [remove it](https://www.zdnet.com/article/google-erases-dont-be-evil-from-code-of-conduct-after-18-years/)
- [Questr](https://questr.vercel.app/): 2D exploration of nostr
- [ONOSENDAI](https://www.onosendai.tech/) by Arkinox
- Freedom tech & Freedom from Tech
- DAUs of jumper cables
- [Gossip](https://github.com/mikedilger/gossip) and it’s choices
- [“The secret to life is to send it”](https://highlighter.com/a/naddr1qvzqqqr4gupzqmjxss3dld622uu8q25gywum9qtg4w4cv4064jmg20xsac2aam5nqqxnzd3exsmrswfjxsurxvf3qvlsju)
- Flying water & flying bus stops
- [RSS readers](https://github.com/fiatjaf/narr), [Mailbrew](https://mailbrew.com/), and daily digests
- Nostr is high signal and less addictive
- Calling nostr posts “[tweets](https://nostr.band/?q=tweet+by%3Anpub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc)” and recordings being “on tape”
- Pivoting from nostr dialogues to a podcast about wind
- The unnecessary complexity of [NIP-96](https://github.com/nostr-protocol/nips/blob/master/96.md)
- [Blossom](https://github.com/hzrd149/blossom) (and wind)
- Undoing URLs, APIs, and REST
- ISBNs and cryptographic identifiers
- SaaS and the DAU metric
- [Highlighter](https://highlighter.com/)
- Not caring where stuff is hosted
- When is an edited thing a new thing?
- Edits, the edit wars, and [the case against edits](https://blog.udaya.dev/fiatjaf/ad84e3b3)
- [NIP-60](https://nips.nostr.com/60) and inconsistent balances
- Scroll to [text fragment](https://mgearon.com/html/text-fragments/) and best effort matching
- Proximity hashes & [locality-sensitive hashing](https://en.wikipedia.org/wiki/Locality-sensitive_hashing)
- Helping your Uncle Jack of a horse
- Helping your uncle [jack of a horse](https://en.wikipedia.org/wiki/Mr._Hands_\(album\))
- Can we fix it with WoT?
- [Vertex](https://vertexlab.io/) & vibe-coding a proper search for nostr
- Linking to hashtags & search queries
- Advanced search and why it’s great
- Search scopes & web of trust
- The UNIX tools of nostr
- Pablo’s [NDK snippets](https://nostr-dev-kit.github.io/ndk/snippets/)
- Meredith on the [privacy nightmare of Agentic AI](https://njump.me/nevent1qqsts24dta3nay5ypkhnqd8aphynhw7z89qw69sp3pceady2xujakygpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qguh5grefa7vkay4ps6udxg8lrqxg2kgr3qh9n4gduxut64nfxq0quyzs70)
- Blog-post-driven development ([Lightning Prisms](https://dergigi.com/2023/03/12/lightning-prisms/), [Highlighter](https://dergigi.com/2023/04/04/purple-text-orange-highlights/))
- Sandwich-style LLM prompting, Waterfall for LLMs ([HLDD / LLDD](https://gist.github.com/dskvr/b34f836b68ff2ca51bcc8fe7763eceec))
- “Speed itself is a feature”
- MCP & [DVMCP](https://mcp.so/server/dvmcp)
- Monorepos and git submodules
- [Olas](https://olas.app/) & NDK
- Pablo’s [RemindMe](https://njump.me/npub17hsu5gd24stmzuuezwvavgeuwwac233nfzg59dfyhf4fvel8n2sqw3d0k9) bot
- “Breaking changes kinda suck”
- Stories, shorts, TikTok, and OnlyFans
- LLM-generated sticker styles
- LLMs and [creativity](https://dergigi.com/2022/09/25/creativity/) (and Gigi’s [old email](https://gist.github.com/dergigi/04760fbcaa3769bb243db2b0e31c75df))
- “AI-generated art has no soul”
- Nostr, zaps, and realness
- Does the source matter?
- Poker client in [bitcoin v0.0.1](https://github.com/search?q=repo%3Atrottier%2Foriginal-bitcoin%20poker&type=code)
- Quotes from Hitler and how additional context changes meaning
- Greek finance minister on crypto and bitcoin ([Technofeudalism](https://www.goodreads.com/book/show/75560036-technofeudalism), book)
- Is more context always good?
- [Vervaeke’s AI argument](https://www.youtube.com/watch?v=A-_RdKiDbz4&list=PLND1JCRq8Vui2YOOfrxbeRwJk5jZPmAth)
- What is meaningful?
- How do you extract meaning from information?
- How do you extract meaning from experience?
- “[What the hell is water](https://youtu.be/ms2BvRbjOYo)”
- Creativity, imagination, hallucination, and losing touch with reality
- “[Bitcoin is singularity insurance](https://njump.me/nevent1qqswawr4cz68sjswhtdkat8qgnpfsc6wygx4xmq2d5gd5fg9extvl4gpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtczyphydppzm7m554ecwq4gsgaek2qk32atse2l4t9ks57dpms4mmhfxqcyqqqqqqg74yxgf)”
- Will vibe coding make developers obsolete?
- Knowing what to build vs knowing how to build
- 10min block time & the [physical limits of consensus](https://dergigi.com/threads/physical-limits)
- Satoshi’s reasons articulated in his [announcement post](https://satoshi.nakamotoinstitute.org/posts/p2pfoundation/1/)
- Why do anything? Why stack sats? Why have kids?
- All you need now is motivation
- Upcoming agents will actually do the thing
- Proliferation of writers: quantity VS quality
- Crisis of sameness & the problem of distribution
- Patronage, belle epoche, and [bitcoin art](https://x.com/FractalEncrypt)
- Niches, and how the internet fractioned society
- Joe’s songs
- Hyper-personalized stories
- Shared stories & myths ([Jonathan Pageau](https://www.thesymbolicworld.com/team/jonathan-pageau))
- Hyper-personalized apps VS shared apps
- Agency, free expression, and [free speech](https://dergigi.com/2024/03/25/speaking-freely-online/)
- Edgy content & [twitch meta](https://www.talkesport.com/news/what-is-the-twitch-meta-decoding-trends-and-controversies/), aka skating the line of demonetization and deplatforming
- Using attention as a proxy currency
- Farming eyeballs and brain cycles
- Engagement as a success metric & engagement bait
- “[You wouldn’t zap a car crash](https://njump.me/nevent1qqsqm2lz4ru6wlydzpulgs8m60ylp4vufwsg55whlqgua6a93vp2y4gzyphydppzm7m554ecwq4gsgaek2qk32atse2l4t9ks57dpms4mmhfxzzxtzc)”
- Attention economy is parasitic on humanity
- The importance of [speech](https://nostr-resources.com/) & [money](https://bitcoin-resources.com/)
- What should be done by a machine?
- What should be done by a human?
- “The human spirit should remain in charge”
- Our relationship with fiat money
- Active vs passive, agency vs serfdom
-

@ a012dc82:6458a70d
2025-03-27 14:23:51
The cryptocurrency market, known for its dramatic fluctuations, has always been a subject of intrigue and speculation. Bitcoin, as the pioneering digital currency, has been at the epicenter of this financial whirlwind. As we approach 2024, the anticipation surrounding Bitcoin's value is palpable, with potential investors and seasoned cryptocurrency enthusiasts keenly eyeing the market's movements. This article aims to dissect the recent forecasts for Bitcoin's price in the coming year, delve into the multifaceted factors influencing these predictions, and explore the broader implications for those contemplating an investment in Bitcoin.
**Table of Contents**
- 2024 Bitcoin Price Predictions: A New Peak on the …
- Key Factors Driving Bitcoin's Price
- The Halving Event
- Institutional Interest and ETFs
- Economic and Monetary Policies
- The Debate: To Buy or Not to Buy
- Risk Tolerance
- Market Dynamics
- Long-Term Perspective
- Caution and Speculation
- Conclusion
- FAQs
**2024 Bitcoin Price Predictions: A New Peak on the Horizon**
Recent analyses, particularly a notable report from UK fintech firm Finder, have painted an optimistic picture for Bitcoin in 2024. Experts within the field are forecasting a new zenith for Bitcoin, projecting it to reach an all-time high of $88,000, with expectations of the currency stabilizing around $77,000 by the end of the year. These projections represent a significant uptick from Bitcoin's current valuation and suggest a potentially lucrative year ahead for the digital currency. However, it's crucial to recognize that these predictions are not guarantees but educated guesses based on current market trends and historical data. The cryptocurrency market's inherent volatility means that while the potential for substantial gains exists, so too does the risk of dramatic losses. Investors should approach these predictions with cautious optimism, considering the broader economic and technological landscape that could impact Bitcoin's trajectory.
**Key Factors Driving Bitcoin's Price**
The anticipated surge in Bitcoin's value can be attributed to several key factors, each playing a pivotal role in shaping the currency's future:
**The Halving Event**
The Bitcoin halving event scheduled for April 2024 stands as a significant milestone. This event, which occurs approximately every four years, reduces the reward for mining Bitcoin transactions by half. Historically, halving events have led to a decrease in the supply of new Bitcoins entering the market, which, in turn, has led to price increases as demand outstrips supply. The 2024 halving is expected to follow this trend, contributing to the bullish outlook for Bitcoin's price. However, while past performance can offer insights, it is not indicative of future results. The halving's impact could be influenced by a myriad of factors, including changes in miner behavior, technological advancements, and shifts in investor sentiment.
**Institutional Interest and ETFs**
Another driving force behind the optimistic price predictions is the growing institutional interest in Bitcoin and the approval of Bitcoin ETFs in the United States. These developments have not only legitimized Bitcoin as an investment asset but also made it more accessible to a broader audience of traditional investors. The introduction of ETFs has bridged the gap between the conventional financial world and the burgeoning cryptocurrency market, providing a regulated and familiar avenue for investment. However, the influx of institutional money also brings new challenges, including increased market manipulation risks and the potential for regulatory crackdowns. Investors should remain vigilant, monitoring the evolving landscape and considering the long-term implications of institutional involvement in the cryptocurrency space.
**Economic and Monetary Policies**
Global economic conditions and monetary policies, particularly those enacted by the US Federal Reserve, are also critical factors influencing Bitcoin's price. In an environment of low interest rates and quantitative easing, investors have increasingly turned to alternative assets like Bitcoin as a hedge against inflation and currency devaluation. However, shifts in these policies could significantly impact investor behavior and market dynamics. A rise in interest rates or a tightening of monetary policy could lead to reduced liquidity in the market and a shift away from riskier assets, including Bitcoin. Conversely, continued economic uncertainty and inflationary pressures could bolster Bitcoin's appeal as a store of value.
**The Debate: To Buy or Not to Buy**
The decision to invest in Bitcoin, especially in light of the optimistic 2024 price predictions, is fraught with complexity:
**Risk Tolerance**
Bitcoin's notorious volatility cannot be overstated. The digital currency's price can experience dramatic swings within short periods, influenced by factors ranging from regulatory news to market sentiment. Potential investors must assess their risk tolerance and financial situation before entering the market. It's essential to consider whether you can withstand significant fluctuations in your investment's value and how such changes would impact your overall financial health.
**Market Dynamics**
Understanding the broader market dynamics and potential regulatory changes is crucial for anyone considering investing in Bitcoin. The cryptocurrency market does not operate in a vacuum; it is affected by global economic conditions, technological developments, and shifts in regulatory attitudes. Staying informed and adaptable is key, as today's market drivers could change rapidly, altering Bitcoin's price trajectory.
**Long-Term Perspective**
Adopting a long-term perspective is vital when investing in Bitcoin. While the allure of quick profits can be tempting, Bitcoin's history suggests that it is better suited as a long-term investment. The market's cyclical nature, characterized by boom-and-bust cycles, requires patience and a long-term outlook. Investors should avoid making impulsive decisions based on short-term price movements and instead focus on the underlying value and potential of Bitcoin as a revolutionary digital asset.
**Caution and Speculation**
Despite the bullish forecasts, a note of caution is warranted. The cryptocurrency market remains speculative, and while Bitcoin has established itself as the leading digital currency, its future is not guaranteed. The landscape is rife with uncertainties, from technological challenges to regulatory hurdles. Potential investors should approach Bitcoin with a balanced perspective, recognizing the possibilities while being acutely aware of the risks.
**Conclusion**
The predictions for Bitcoin's price in 2024 offer a glimpse into a potentially prosperous future for the digital currency. However, the decision to invest should not be taken lightly. Prospective investors must navigate a landscape marked by volatility, uncertainty, and rapid change. By thoroughly evaluating the market, staying informed about developments, and considering their long-term financial goals, individuals can make more informed decisions about their involvement in the Bitcoin market. Whether now is the right time to buy Bitcoin is a personal decision that depends on individual circumstances, risk tolerance, and investment strategy. As with any investment, there are no guarantees, but for those willing to embrace the risks, the rewards could be substantial.
**FAQs**
**Why is Bitcoin expected to reach new highs in 2024?**
Bitcoin's price is expected to surge due to factors like the halving event, increasing institutional interest, the approval of Bitcoin ETFs, and global economic conditions that favor alternative investments.
**What is a Bitcoin halving event?**
A Bitcoin halving event is when the reward for mining new blocks is halved, reducing the rate at which new bitcoins are generated. This event occurs approximately every four years and tends to impact the price due to reduced supply.
**Are Bitcoin ETFs significant for individual investors?**
Yes, Bitcoin ETFs provide individual investors with a regulated and familiar way to gain exposure to Bitcoin without directly purchasing or storing the cryptocurrency, potentially increasing its accessibility and demand.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnewsco](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co/](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@thebitcoinlibertarian](https://www.youtube.com/@thebitcoinlibertarian)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
**Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats
link: https://signup.theorangepillapp.com/opa/croxroad**
**Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad”
link: https://bitcoinbook.shop?ref=21croxroad**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ 0fa80bd3:ea7325de
2025-01-29 05:55:02
The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the **will of the people** to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: **How do we stop this fragmentation?** How do we create a space where people can **rebuild their connections** when they’re ready? How do we build a **self-sustaining network**, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—**how do we make it spread, even in occupied territory?**
In 2009, something historic happened: **the internet got its own money.** Thanks to **Satoshi Nakamoto**, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became **purely digital.**
The internet was already **a sanctuary for information**, a place where people could connect and organize. But with Bitcoin, it evolved. Now, **value itself** could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they **get stronger, survive longer, and bear fruit faster.** That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that **controlled environment** for **ideas**. Bitcoin? It’s the **fertile soil** that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If **nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless.** It can absorb any number of ideas, any number of people, and it doesn’t **run out of space.**
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—**without surveillance, without censorship, without the constant fear of being erased.**
This is where **Nostr** comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. **It’s a new kind of city.** One that **no dictator can seize**, no corporation can own, no government can shut down.
It’s built on **decentralization, encryption, and individual control.** Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, **Nostr is a city that cannot be occupied.** A place for ideas, for networks, for freedom. A city that grows stronger **the more people build within it**.
-

@ f1989a96:bcaaf2c1
2025-03-27 13:53:14
Good morning, readers!
Turkey’s currency plunged to a record low after the arrest of Istanbul Mayor Ekrem Imamoglu, one of President Recep Tayyip Erdogan’s main political rivals. This follows a pattern of escalating repression of opposition figures, which have been described as an effort to suppress competition ahead of primary elections. As economic conditions deteriorate, Erdogan is resorting to desperate measures — blocking social media, arresting dissenters, and tear-gassing protests — to maintain power over an increasingly restless populace.
In the Caribbean, we shed light on Cubans' struggles accessing remittances sent from family members abroad. This is a symptom of the regime's strict monetary controls over foreign currency. Cubans face long delays or can’t withdraw cash due to bank liquidity shortages. And when they can, remittances are converted into pesos at the overvalued official Cuban exchange rate. This effectively allows the Communist Party of Cuba (PCC) to loot the value from Cuban remittances.
In freedom tech news, we highlight Demand Pool, the first-ever Stratum V2 mining pool. Stratum V2 is a mining protocol designed to decentralize Bitcoin mining by letting individual miners create their own block templates rather than relying on centralized pools to do so for them. This improves censorship resistance and promotes a more decentralized and resilient Bitcoin network — critical features for human rights defenders and nonprofits using Bitcoin to protect against financial repression from authoritarian regimes.
We end by featuring Vijay Selvam's new book, “Principles of Bitcoin.” It offers a clear, first-principles guide to understanding how Bitcoin’s technology interacts with economics, politics, philosophy, and human rights. Whether you’re new to Bitcoin or looking to deepen your understanding, this book provides a solid foundation, and it even features a foreword by HRF Chief Strategy Officer Alex Gladstein.
**Now, let’s dive right in!**
### [**Subscribe Here**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a)
## **GLOBAL NEWS**
#### **Turkey | Lira in Free Fall as Erdogan Arrests Political Rival**
Turkey’s lira plunged to a [record low ](https://www.reuters.com/markets/currencies/turkish-lira-plunges-record-low-after-erdogan-rival-detained-2025-03-19/)after officials arrested Istanbul Mayor Ekrem Imamoglu, President Recep Tayyip Erdogan’s main political rival. Imamoglu’s arrest comes ahead of [primary elections](https://www.reuters.com/world/europe/turkish-opposition-party-members-others-head-polls-primary-election-2025-03-23/) and follows the increasing repression of opposition figures in recent months, including the [suspension](https://www.politico.eu/article/musks-x-suspends-opposition-accounts-turkey-protest-civil-unrest-erdogan-imamoglu-istanbul-mayor/?ref=nobsbitcoin.com) of political opposition accounts on X. Officials also [arrested](https://x.com/yusufcan_en/status/1903703224336429432) Buğra Gökçe, head of the Istanbul Planning Agency, for publishing data exposing the country’s deepening poverty. The currency’s fallout and political repression have sparked [protests](https://www.bbc.com/news/articles/cpv43dd3vlgo) in Istanbul despite a four-day ban. The regime is [responding](https://www.bbc.com/news/articles/cpv43dd3vlgo) with tear gas and rubber bullets. Meanwhile, Turks dissenting online risk joining over a [dozen](https://www.bbc.com/news/articles/cpv43dd3vlgo?xtor=AL-71-%5Bpartner%5D-%5Bbbc.news.twitter%5D-%5Bheadline%5D-%5Bnews%5D-%5Bbizdev%5D-%5Bisapi%5D&at_bbc_team=editorial&at_ptr_name=twitter&at_campaign_type=owned&at_link_type=web_link&at_link_origin=BBCWorld&at_link_id=29897B8E-0579-11F0-9094-A9A3F4782A4F&at_medium=social&at_format=link&at_campaign=Social_Flow) other citizens recently arrested for “provocative” social media posts. Netblocks [reports](https://x.com/netblocks/status/1902812549587820888) that the Turkish regime imposed restrictions on social media and messaging to quell the uprising of Turks struggling with financial conditions and deepening repression.
#### **Cuba | Banks “Hijack” Citizen Remittances**
Cubans are [struggling](https://havanatimes.org/features/cuban-banks-hijack-family-remittances/) to access remittances sent from their families abroad. This is because the regime completely controls all incoming foreign currency transfers. When remittances arrive, communist banking authorities [force](https://havanatimes.org/features/cuban-banks-hijack-family-remittances/) their conversion into collapsing Cuban pesos or “Moneda Libremente Convertible” (MLC), Cuba’s digital currency with limited use. On top of this, Cubans receive pesos in their accounts based on the official Cuban exchange rate, which is far below the informal market rate. This allows the regime to opaquely siphon off much of the remittances’ real value. Even when the money clears, Cubans face long delays or can’t withdraw the cash due to banks’ liquidity shortages. Many Cubans are accusing these banks of “[hijacking](https://havanatimes.org/features/cuban-banks-hijack-family-remittances/)” their remittances. As inflation, electrical blackouts, and food shortages continue, remittances are more critical than ever for Cuban families. Yet, they’re blocked at every turn by a system designed to impoverish them.
#### **Pakistan | Announces Plans to Regulate Digital Assets**
Pakistan announced [plans](https://www.bloomberg.com/news/articles/2025-03-20/pakistan-plans-to-legalize-crypto-in-bid-for-foreign-investment) to create a regulatory framework for Bitcoin and digital assets to attract foreign investment and domestic economic activity. It’s a peculiar shift for a regime that regularly [suspends](https://time.com/6692687/pakistan-election-day-voting-violence-phone-service-disturbances/) the Internet, [censors](https://timesofindia.indiatimes.com/world/pakistan/social-media-platform-x-shutdown-continues-for-eighth-day-in-pakistan/articleshow/107983076.cms) social media, [represses](https://www.bbc.com/news/articles/czx6xvgqe1ko) opposition, and burdens its people with the [highest](https://www.firstpost.com/world/pakistan-tops-asia-in-living-costs-and-inflation-rates-report-reveals-13759245.html) cost of living in Asia. We suspect the plans indicate efforts to control the industry rather than empower individuals. The military-backed regime is also [exploring](https://tribune.com.pk/story/2507061/govt-proposes-changes-to-sbp-act) a Central Bank Digital Currency (CBDC) and tightening [controls](https://timesofindia.indiatimes.com/world/pakistan/amid-net-censorship-pakistan-offers-regulated-vpns/articleshow/115392568.cms) on VPN use, which are hardly the hallmarks of leadership committed to permissionless financial systems. But perhaps it matters little. Grassroots Bitcoin adoption in Pakistan already ranks among the highest in the world, with an estimated [15 to 20 million](https://archive.ph/5ctJq) users turning to digital assets to preserve their savings, circumvent financial controls, and escape the failures of a collapsing fiat system. HRF supported [Bitcoin Pakistan](https://bitcoinpk.org) with a grant to help translate resources into Urdu, a language spoken by 60 million people trapped in this repressive scenario.
#### **Russia | Piloting CBDC in Tatarstan to Test Smart Contract Functionality**
Russia’s central bank plans to [pilot](https://www.business-gazeta.ru/news/665855) its CBDC, the [digital ruble](https://cbdctracker.hrf.org/currency/russian-federation), in Tatarstan to test smart contract functionality. Specifically, the central bank will experiment with conditional spending, using smart contracts to restrict where and what users can spend money on. If these features are implemented, it will empower the Kremlin with micro-controls over Russians’ spending activity. Officials could program funds to expire, restrict purchases to regime-approved goods, or block transactions at certain locations — leaving users with no financial autonomy or privacy. Those who oppose the Russian dictatorship, such as activists, nonprofits, and dissenters, could be debanked with more ease, their assets frozen or confiscated without recourse.
#### **Nicaragua | Government Mandates Public Employees Declare All Assets**
In Nicaragua, dictator Daniel Ortega intensified state financial surveillance by mandating all public servants to [disclose](https://havanatimes.org/features/nicaraguan-public-employees-forced-to-declare-their-assets/) information on all personal and family assets. The mandate requires all public employees to declare everything from personal bank accounts, loans, vehicles, and other assets — as well as the assets and accounts of immediate family members. Those who do not comply face the [threat of termination](https://havanatimes.org/features/nicaraguan-public-employees-forced-to-declare-their-assets/). Ironically, despite the law requiring such disclosure, Ortega himself [has not declared](https://www.laprensani.com/2021/04/26/politica/2813926-demandan-a-la-contraloria-demostrar-a-cuanto-asciende-el-patrimonio-de-daniel-ortega-y-rosario-murillo) his assets since 2006. Under the guise of regulatory compliance, this policy is yet another link in the chain tightening state surveillance over Nicaraguan society. Bitcoin adoption continues to grow in this repressed Central American nation.
## BITCOIN AND FREEDOM TECH NEWS
#### **Demand Pool | First Stratum V2 Mining Pool Launches**
Bitcoin mining could become more decentralized and censorship-resistant with the launch of [Demand Pool](https://www.dmnd.work/upcoming/), the first mining pool to ever implement [Stratum V2](https://stratumprotocol.org/). Stratum V2 is open-source software that allows miners to build their own block templates, enabling more individual mining and less dependence on large and centralized mining pools. This helps maintain Bitcoin’s key features: its decentralized, permissionless, and uncensorable nature. All of which are crucial for human rights defenders and nonprofits bypassing the financial repression and surveillance of authoritarian regimes. Learn more [here](https://www.dmnd.work/upcoming/).
#### **Bitcoin Mining | Three Solo Blocks Found**
Three separate solo miners mined Bitcoin blocks in the past seven days. This marks the second, third, and fourth solo blocks [mined](https://x.com/SoloSatoshi/status/1903799018896998562) in the past two weeks alone, hinting at a surge in home mining. This promotes greater decentralization within the Bitcoin network because solo miners have little functional ability to censor. In contrast, large mining pools are points of failure that centralized interests can more easily pressure — to the detriment of activists and human rights defenders. The [first](https://x.com/BitcoinNewsCom/status/1903476768733810928) block was mined on March 21 by a miner using a self-hosted FutureBit Apollo machine that earned 3.125 BTC plus fees for processing block [888,737](https://mempool.space/block/00000000000000000000b7070e88525e4064ab36df7cfbe34d785bbc6eb491ea). Just days later, a solo miner with under 1 TH/s of self-hosted hash rate [found](https://x.com/BitcoinNewsCom/status/1903815849535799326) block [888,989](https://mempool.space/block/00000000000000000000a517d87e63ea04c7ec3dd51d20926e82cca5466dccaf), which became just the [third](https://x.com/BitcoinNewsCom/status/1903815849535799326) block ever to be mined using an open-source [Bitaxe](https://bitaxe.org/) device. Most recently, on March 24, a solo miner using a [$300 setup](https://x.com/alanknit/status/1904246256622322122) successfully [mined](https://x.com/pete_rizzo_/status/1904217846441201755) block [889,240](https://mempool.space/block/00000000000000000001deee311732e2ba928d33f0628a5d6320c537751835e3).
#### **Krux | Adds Taproot and Miniscript Support**
[Krux](https://github.com/selfcustody/krux), open-source software for building your own Bitcoin signing devices (hardware for Bitcoin self-custody), [released](https://github.com/selfcustody/krux/releases/tag/v25.03.0) an update that enhances privacy and flexibility. The update introduces support for Taproot, a past Bitcoin upgrade that improves privacy and security, and Miniscript, a simplified way to create more complex Bitcoin transaction rules. This allows users to manage multi-signature wallets (where more than one private key is required to interact with your Bitcoin) in a more private and flexible way. It also enables spending conditions that are harder to censor and easier to verify. Krux continues to support the struggle for financial freedom and human rights by breaking down barriers to Bitcoin self-custody. HRF has recognized this impact and awarded grants to open-source developers working on Krux to advance this mission.
#### **Cashu | Developing Tap-to-Pay Ecash**
[Calle](https://x.com/callebtc), the creator of [Cashu](http://cashu.me), an open-source Chaumian ecash protocol for Bitcoin integrated with the Lightning Network, is [developing](https://x.com/callebtc/status/1903079881325400407) a new tap-to-pay feature that enables instant, offline ecash payments via NFC. Ecash functions as a bearer asset, meaning the funds are stored directly on the user’s device. With tap-to-pay, it can be transferred with a single tap (similar to tapping your credit card). More generally, ecash offers fast, private transactions resistant to surveillance and censorship. But for activists and dissenters, this particular advancement makes private and permissionless payments more accessible and user-friendly. This development will be worth following closely. Watch a demo [here](https://x.com/callebtc/status/1903079881325400407).
#### **OpenSats | Announces 10th Wave of Bitcoin Grants**
[OpenSats](http://opensats.org), a public nonprofit that supports open-source software and projects, [announced](https://opensats.org/blog/tenth-wave-of-bitcoin-grants) its 10th wave of grants supporting Bitcoin initiatives. This round includes funding for [Stable Channels](https://stablechannels.com/), which enable stabilized Bitcoin-backed balances on the Lightning Network (allowing users to peg Bitcoin to fiat currencies in a self-custodial way) that provide stable, censorship-resistant payments. OpenSats also renewed its support for [Floresta](https://docs.getfloresta.sh/floresta/), a lightweight Bitcoin node (a computer that runs the Bitcoin software). It lowers entry barriers to running Bitcoin, helping make the network more decentralized and censorship-resistant.
#### **Bitcoin Policy Institute | Launches Bitcoin Summer Research Program**
The [Bitcoin Student Network](https://www.bitcoinstudentsnetwork.org/) (BSN) and the [Bitcoin Policy Institute](https://www.btcpolicy.org/) (BPI) are teaming up to offer students an eight-week research [internship](https://www.btcinternship.org/) this summer. The program is part of BPI’s Research Experiences for Undergraduates (REU) initiative and invites students passionate about the future of money, financial inclusion, and Bitcoin’s civil liberties impacts to conduct hands-on research. Participants will also receive mentorship from BPI researchers. The program runs from June 9 to Aug. 8, 2025, and includes an in-person colloquium in Washington, DC. It is an incredible opportunity for students worldwide, especially those living in oppressive regimes, to get involved with Bitcoin. Applications are open until April 7. Apply [here](https://www.btcinternship.org/).
## RECOMMENDED CONTENT
#### **Principles of Bitcoin by Vijay Selvam**
“Principles of Bitcoin” by Vijay Selvam is a new book offering a first-principles guide to understanding Bitcoin’s technology, economics, politics, and philosophy. With a foreword by HRF Chief Strategy Officer Alex Gladstein, the book cuts through the noise to explain why Bitcoin stands alone as a tool for individual empowerment and financial freedom. Selvam’s work makes the case for Bitcoin as a once-in-history invention shaping a more decentralized and equitable future. Read it [here](https://www.amazon.com/Principles-Bitcoin-Technology-Economics-Philosophy/dp/023122012X/).
#### **Rule Breakers — The True Story of Roya Mahboob**
“[Rule Breakers](https://hrf.org/latest/hrf-celebrates-the-release-of-rule-breakers-a-movie-on-afghanistans-roya-mahboob/)” is a new film that tells the true story of Roya Mahboob, Afghanistan’s first female tech CEO, who empowered young girls in Afghanistan with financial literacy, robotics, and financial freedom through Bitcoin. The film recounts Mahboob’s courageous work educating these girls despite huge personal risks under a regime that bans their education. It follows the story of Afghan Dreamers, the country’s first all-girls robotics team, and the obstacles they overcome to compete on the world stage. “Rule Breakers” is a testament to the power of education, innovation, and resilience in the face of oppression. It’s now in theaters, and you can watch the trailer [here](https://www.youtube.com/watch?v=CW_P4zT6i9A&t=2s).
*If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).*
*Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\
*Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)*
*The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*.
[**Subscribe to newsletter**](http://financialfreedomreport.org/)
[**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3)
[**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3)
[**Visit our website**](https://hrf.org/programs/financial-freedom/)
-

@ 9e69e420:d12360c2
2025-01-26 15:26:44
Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards.
While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts.
A report will be prepared within 85 days to recommend which programs to continue or discontinue.
-

@ 84b0c46a:417782f5
2025-03-27 23:52:24
nostr:nevent1qqsw9v8usvahkqmmc9qavu6g834v09j6e2u2acdua24tk73dqc05xecgkanse
-

@ 9e69e420:d12360c2
2025-01-26 01:31:31
## Chef's notes
# arbitray
- test
- of
- chefs notes
## hedding 2
## Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 5
## Ingredients
- Test ingredient
- 2nd test ingredient
## Directions
1. Bake
2. Cool
-

@ 401014b3:59d5476b
2025-03-27 13:48:10
Alright, baseball junkies, it’s March 27, 2025, and we’re diving into the crystal ball to predict the 2025 MLB season—straight through to the World Series champ! Spring Training’s wrapping up, Opening Day’s here, and the league’s loaded with talent, drama, and some sneaky contenders ready to shake things up. I’m breaking down each playoff team’s path, their strengths, weaknesses, and who’s got the juice to hoist the trophy in October. This ain’t some cookie-cutter chalk pick—let’s get gritty, let’s get bold, and let’s see who’s got the stones to win it all. Strap in, fam—here we go!
---
American League Playoff Teams: The AL Beast Mode
**New York Yankees**\
The Yankees are back, and they’re pissed after last year’s World Series loss to the Dodgers. Aaron Judge is coming off another MVP-caliber season (let’s say .310, 55 HRs, 130 RBIs), and Juan Soto’s bat (projected .290, 40 HRs) gives them a lethal 1-2 punch. Gerrit Cole anchors a rotation that’s top-5 in ERA (around 3.40), but the bullpen’s a question mark—closer Clay Holmes blew 13 saves in 2024, and they haven’t fixed that yet. They’ll win the AL East (95-67), but their postseason hinges on late-inning reliability.\
**Prediction**: ALCS run, but they fall short if the pen implodes.
**Houston Astros**\
The Astros are perennial AL West champs (projected 92-70), even with a slightly aging core. Jose Altuve (.300, 20 HRs) and Yordan Alvarez (.295, 35 HRs) keep the offense humming, and a rotation led by Framber Valdez (3.20 ERA) and Hunter Brown (3.50 ERA) is solid. Their bullpen, with Josh Hader (1.28 ERA in 2024), is lights-out. But injuries to key arms like Justin Verlander (aging at 42) could bite them.\
**Prediction**: ALDS exit—they’re good, but not great this year.
**Cleveland Guardians**\
The Guardians sneak into the playoffs as the AL Central champs (88-74). Jose Ramirez (.280, 35 HRs, 110 RBIs) is a one-man wrecking crew, and their rotation—Shane Bieber (3.00 ERA, if healthy) and Triston McKenzie (3.60 ERA)—keeps them in games. But their offense outside Ramirez is thin (team OPS around .720), and the bullpen’s inconsistent (4.00 ERA).\
**Prediction**: Wild Card exit—they’re scrappy but lack firepower.
**Tampa Bay Rays (Wild Card)**\
The Rays grab a Wild Card spot (90-72) with their usual mix of grit and analytics. Yandy Diaz (.290, 15 HRs) and Randy Arozarena (.270, 25 HRs) lead a balanced offense, while Shane McClanahan (3.10 ERA) and Zach Eflin (3.40 ERA) anchor the rotation. Their bullpen (top-10 in ERA at 3.50) is a strength, but depth issues (injuries to key prospects) could hurt.\
**Prediction**: ALDS run—they’re sneaky dangerous.
**Seattle Mariners (Wild Card)**\
The Mariners finally break through as a Wild Card (89-73), as predicted by some fans on X. Julio Rodriguez (.285, 30 HRs) and Cal Raleigh (.250, 35 HRs) power the offense, and a rotation of Luis Castillo (3.20 ERA), Logan Gilbert (3.30 ERA), and George Kirby (3.40 ERA) is the best in the AL (team ERA around 3.20). Their offense (bottom-10 in runs scored) is the Achilles’ heel.\
**Prediction**: ALCS run—they’re a pitcher’s dream, but the bats hold ‘em back.
**Baltimore Orioles (Wild Card)**\
The Orioles snag a Wild Card (87-75), but some fans on X call them a “surprise disappointment.” Gunnar Henderson (.280, 35 HRs) and Adley Rutschman (.270, 20 HRs) lead a young core, but the rotation—Corbin Burnes (3.00 ERA) and Grayson Rodriguez (3.70 ERA)—lacks depth after losing Kyle Bradish to injury. The bullpen (4.20 ERA) is shaky.\
**Prediction**: Wild Card exit—too many holes this year.
---
**National League Playoff Teams: The NL Wild West**
**Los Angeles Dodgers**\
The Dodgers are the NL West juggernaut (98-64), and some fans on X are already calling them World Series champs. Shohei Ohtani (.300, 50 HRs, 120 RBIs) is the NL MVP favorite, Mookie Betts (.290, 30 HRs) is elite, and Freddie Freeman (.310, 25 HRs) is steady. The rotation—Tyler Glasnow (3.10 ERA), Yoshinobu Yamamoto (3.30 ERA), and Walker Buehler (3.50 ERA)—is deep, and the bullpen (3.40 ERA) is solid. No weaknesses here.\
**Prediction**: World Series bound—they’re a machine.
**Philadelphia Phillies**\
The Phillies win the NL East (94-68) with a balanced attack. Bryce Harper (.290, 30 HRs) and Kyle Schwarber (.250, 40 HRs) mash, while Trea Turner (.300, 20 HRs) adds speed. The rotation—Zack Wheeler (3.00 ERA), Aaron Nola (3.40 ERA), and Ranger Suarez (3.60 ERA)—is top-tier, and the bullpen (3.50 ERA) is reliable. They’re built for October.\
Prediction: NLCS run—they’re legit contenders.
**Milwaukee Brewers**\
The Brewers take the NL Central (90-72) with a scrappy squad. Willy Adames (.270, 30 HRs) and William Contreras (.280, 20 HRs) lead the offense, while Freddy Peralta (3.30 ERA) and Brandon Woodruff (3.50 ERA, if healthy) anchor the rotation. Their bullpen (top-5 in ERA at 3.30) is a strength, but the offense (middle-of-the-pack in runs) can stall.\
**Prediction**: NLDS exit—not enough firepower.
**Atlanta Braves (Wild Card)**\
The Braves grab a Wild Card (91-71) despite injuries. Ronald Acuna Jr. (.290, 35 HRs) and Matt Olson (.270, 40 HRs) power the lineup, but the rotation—Chris Sale (3.20 ERA) and Max Fried (3.40 ERA)—is thin after Spencer Strider’s injury. The bullpen (3.60 ERA) is solid, but depth is a concern.\
**Prediction**: NLDS run—they’re talented but banged up.
**San Diego Padres (Wild Card)**\
The Padres snag a Wild Card (89-73) with a balanced attack. Fernando Tatis Jr. (.280, 35 HRs) and Manny Machado (.270, 30 HRs) lead the offense, while Dylan Cease (3.30 ERA) and Yu Darvish (3.50 ERA) anchor the rotation. The bullpen (3.70 ERA) is decent, but they lack a true closer.\
**Prediction**: Wild Card exit—not enough late-game juice.
**New York Mets (Wild Card)**\
The Mets sneak in as a Wild Card (88-74) with a breakout year. Francisco Lindor (.280, 30 HRs) and Pete Alonso (.260, 35 HRs) mash, while Kodai Senga (3.20 ERA) and Luis Severino (3.60 ERA) lead the rotation. The bullpen (4.00 ERA) is a weak spot, but their offense (top-10 in runs) keeps ‘em alive.\
**Prediction**: NLDS run—they’re scrappy but flawed.
---
**Playoff Breakdown: The Road to the World Series**
**AL Wild Card**:
- Rays over Guardians
- Mariners over Orioles
- Yankees over Rays
- Mariners over Astros
- Yankees vs. Mariners → Yankees (4-2)\
Judge and Soto go off, and the Mariners’ bats can’t keep up with New York’s firepower. Cole’s ace stuff seals it.
**NL Wild Card**:
- Braves over Padres
- Mets over Brewers
- Dodgers over Mets
- Phillies over Braves
- Dodgers vs. Phillies → Dodgers (4-3)\
Ohtani’s heroics (think a 3-HR game) and the Dodgers’ depth outlast Philly’s grit in a seven-game classic.
---
**World Series**: Yankees vs. Dodgers
Here we go—a rematch of last year’s epic clash! The Yankees are hungry for revenge, with Judge and Soto swinging for the fences (combined 5 HRs in the series). Cole (Game 1 gem, 7 IP, 2 ER) and Rodon (Game 5 win) keep it close, but the Dodgers’ lineup is relentless—Ohtani (.350, 2 HRs), Betts (.320, 3 doubles), and Freeman (.300, 8 RBIs) overwhelm New York’s shaky bullpen. Glasnow and Yamamoto each win a start, and the Dodgers’ pen (2.50 ERA in the series) slams the door. Dodgers win in 6—Ohtani’s walk-off in Game 6 seals it.
---
**The Final Buzzer**
The Dodgers are my 2025 World Series champs—they’ve got the star power, depth, and clutch factor to repeat. The Yankees make a valiant run, but their bullpen woes bite ‘em again. Hit me on X if you disagree, but this is my October gospel—let’s see who’s standing when the dust settles! Play ball, degenerates!
-

@ 9e69e420:d12360c2
2025-01-25 22:16:54
President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
[Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html)
-

@ 9dd283b1:cf9b6beb
2025-03-27 12:22:58
Can someone please explain to me how this new STRF thing works? Cause I'm getting FTX / BlockFI vibes here. 18% Yield, no risk investment, bond killer, etc... Look at this post for example - https://x.com/AdamBLiv/status/1905106498398621846
originally posted at https://stacker.news/items/926635
-

@ 6be5cc06:5259daf0
2025-01-21 20:58:37
A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**.
---
### **1. Instalar o Tor e o Privoxy**
Abra o terminal e execute:
```bash
sudo apt update
sudo apt install tor privoxy
```
**Explicação:**
- **Tor:** Roteia o tráfego pela rede Tor.
- **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
---
### **2. Configurar o Privoxy**
Abra o arquivo de configuração do Privoxy:
```bash
sudo nano /etc/privoxy/config
```
Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira:
```bash
forward-socks5 / 127.0.0.1:9050 .
```
Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**.
Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo.
---
### **3. Iniciar o Tor e o Privoxy**
Agora, inicie e habilite os serviços:
```bash
sudo systemctl start tor
sudo systemctl start privoxy
sudo systemctl enable tor
sudo systemctl enable privoxy
```
**Explicação:**
- **start:** Inicia os serviços.
- **enable:** Faz com que iniciem automaticamente ao ligar o PC.
---
### **4. Configurar o Navegador Firefox**
Para usar a rede **Tor** com o Firefox:
1. Abra o Firefox.
2. Acesse **Configurações** → **Configurar conexão**.
3. Selecione **Configuração manual de proxy**.
4. Configure assim:
- **Proxy HTTP:** `127.0.0.1`
- **Porta:** `8118` (porta padrão do **Privoxy**)
- **Domínio SOCKS (v5):** `127.0.0.1`
- **Porta:** `9050`
5. Marque a opção **"Usar este proxy também em HTTPS"**.
6. Clique em **OK**.
---
### **5. Verificar a Conexão com o Tor**
Abra o navegador e acesse:
```text
https://check.torproject.org/
```
Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta.
---
### **Dicas Extras**
- **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o **Privoxy**.
-

@ 9e69e420:d12360c2
2025-01-21 19:31:48
Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
## Active Compounds
The oil's therapeutic properties stem from its key bioactive components:
- Carvacrol and thymol (primary active compounds)
- Polyphenols and other antioxidant
## Antimicrobial Properties
**Bacterial Protection**
The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
**Antifungal Effects**
It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
## Digestive Health Benefits
Oregano oil supports digestive wellness by:
- Promoting gastric juice secretion and enzyme production
- Helping treat Small Intestinal Bacterial Overgrowth (SIBO)
- Managing digestive discomfort, bloating, and IBS symptoms
## Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through:
- Powerful antioxidant activity that fights free radicals
- Reduction of inflammatory markers in the body
- Protection against oxidative stress-related conditions
## Respiratory Support
It aids respiratory health by:
- Loosening mucus and phlegm
- Suppressing coughs and throat irritation
- Supporting overall respiratory tract function
## Additional Benefits
**Skin Health**
- Improves conditions like psoriasis, acne, and eczema
- Supports wound healing through antibacterial action
- Provides anti-aging benefits through antioxidant properties
**Cardiovascular Health**
Studies show oregano oil may help:
- Reduce LDL (bad) cholesterol levels
- Support overall heart health
**Pain Management**
The oil demonstrates effectiveness in:
- Reducing inflammation-related pain
- Managing muscle discomfort
- Providing topical pain relief
## Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-

@ 878dff7c:037d18bc
2025-03-27 22:37:47
## Australian Prime Minister Calls Election Amid Economic Challenges
### Summary:
Prime Minister Anthony Albanese has announced that Australia will hold federal elections on May 3. The election comes at a time when the nation faces significant economic uncertainties, including high inflation rates, elevated interest rates, and a housing crisis. Albanese's Labor government emphasizes plans for economic recovery, while opposition leader Peter Dutton's Coalition proposes public sector cuts and temporary fuel duty reductions. Both leaders are striving to address voter concerns over the cost-of-living crisis and economic stability.
Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/28/australian-prime-minister-calls-election-amid-shadow-of-trump-and-cost-of-living-crisis" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://apnews.com/article/b73f3a4bb9cbbc300cd797f34d4cc23b" target="_blank">AP News - March 28, 2025</a>
## Bill Gates Predicts AI to Replace Doctors and Teachers Within 10 Years
### Summary:
Bill Gates forecasts that artificial intelligence (AI) will significantly reduce human involvement in fields like medicine and education over the next decade. He envisions AI providing free, high-quality medical advice and tutoring, thereby democratizing access to these services. While acknowledging concerns about misinformation and rapid AI development, Gates remains optimistic about AI's potential to drive breakthroughs in healthcare, climate solutions, and education. He encourages young people to engage in AI-centric ventures, highlighting its transformative impact on industries and society.
Sources: <a href="https://nypost.com/2025/03/27/business/bill-gates-said-ai-will-replace-doctors-teachers-within-10-years/" target="_blank">New York Post - March 27, 2025</a>
## AI Poised to Transform Legal Profession by 2035
### Summary:
Artificial general intelligence (AGI) is projected to render traditional lawyer roles obsolete by 2035. AI systems are advancing to perform complex legal tasks such as advising, negotiating, and dispute resolution. While some legal professionals argue that AI cannot replicate human judgment and creativity, the emphasis on efficiency and outcomes suggests a future where AGI dominates legal services with minimal human intervention. Legal industry leaders are urged to prepare for this disruptive shift.
Sources: <a href="https://www.thetimes.co.uk/article/artificial-intelligence-could-replace-traditional-lawyers-by-2035-xwz2j0t2k" target="_blank">The Times - March 28, 2025</a>
## Queensland Faces Severe Flooding as Inland 'Sea' Emerges
### Summary:
Severe weather conditions, including heavy rain and potential flash flooding, have impacted central and southern inland Queensland, with significant rainfall between 200 to 400mm recorded. Towns like Adavale are inundated, prompting emergency warnings and the establishment of refuges for affected residents. Authorities urge residents to stay updated and follow safety advice.
Sources: <a href="https://www.news.com.au/technology/environment/qld-in-for-another-week-of-rain-amid-severe-weather-and-flood-warnings/news-story/d5e7ea97591060bb58c1d6ed54489209" target="_blank">News.com.au - 28 March 2025</a>, <a href="https://www.couriermail.com.au/news/queensland/weather/qld-weather-warnings-of-possible-200mm-deluge-major-flooding-as-communities-cut-off/news-story/457a21a269a535b28c52f919f8bc7bed" target="_blank">The Courier-Mail - 28 March 2025</a>, <a href="https://www.theguardian.com/australia-news/2025/mar/27/queensland-flood-warnings-rain-weather-forecast-bom" target="_blank">The Guardian - 28 March 2025</a>
## Opposition Leader Peter Dutton Outlines Election Platform
### Summary:
Opposition Leader Peter Dutton has presented his vision for Australia, promising significant funding for defense and proposing a new gas reservation policy aimed at lowering electricity prices. The Coalition's plans include fast-tracking gas projects, investing $1 billion in gas infrastructure, reducing public service staffing by 41,000 while preserving essential services, and decreasing permanent migration intake by 25% to increase housing supply. Dutton also announced reinstating subsidized mental health visits and new spending on youth mental health.
Sources: <a href="https://www.theguardian.com/australia-news/live/2025/mar/27/australia-politics-live-fuel-excise-cost-of-living-tax-cuts-salmon-election-anthony-albanese-peter-dutton-ntwnfb" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://www.theaustralian.com.au/nation/who-is-peter-dutton-the-liberal-leader-and-his-top-team-for-the-2025-federal-election-explained/news-story/9d046731e51ed32dd4795c3820365c3a" target="_blank">The Australian - March 28, 2025</a>
## Opposition Leader Promises Significant Defense Funding
### Summary:
Peter Dutton, in his budget reply, promised significant funding for defense and a new gas reservation policy for the east coast, aimed at lowering electricity prices. The Coalition also plans to fast-track gas projects and invest $1 billion in gas infrastructure. Dutton announced slashing 41,000 public service workers while preserving essential services, and criticized Labor's gas policy. Immigration plans include reducing the permanent migration intake by 25% to increase housing supply. Dutton also proposed reinstating subsidized mental health visits and new spending on youth mental health. Labor, represented by Jason Clare, argued that the Coalition's policies, including the nuclear plan, are costly and criticized the tax implications under Dutton.
Sources: <a href="https://www.theguardian.com/australia-news/live/2025/mar/27/australia-politics-live-fuel-excise-cost-of-living-tax-cuts-salmon-election-anthony-albanese-peter-dutton-ntwnfb" target="_blank">The Guardian - March 28, 2025</a>
## Israeli Politicians Urge Australian MPs to Abandon Two-State Solution Policy
### Summary:
A group of Israeli Knesset members has called on Australian MPs to drop support for a two-state solution between Israel and Palestine. The letter, presented during an event at Australia's Parliament House, argues that establishing a Palestinian state could lead to Israel's destruction, citing recent conflicts as evidence. This appeal reflects deep skepticism within Israeli political circles about the viability of the peace process.
Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/27/israeli-politicians-sign-letter-urging-coalition-to-dump-two-state-policy-ntwnfb" target="_blank">The Guardian - March 27, 2025</a>
## Stephen Jones Criticizes U.S. Protectionist Trade Policies
### Summary:
Outgoing Financial Services Minister Stephen Jones has criticized recent U.S. protectionist measures, including a 25% tariff on global car imports and Australian aluminum and steel. Jones emphasized the importance of open trade and a rules-based order for Australia's economic growth, highlighting concerns about the negative impact on Australian industries and the broader economy.
Sources: <a href="https://www.theaustralian.com.au/business/outgoing-financial-services-minister-jones-takes-swipe-at-us-protectionism/news-story/0c1fc10f2b57a8c6809f4dec333cc547" target="_blank">The Australian - March 28, 2025</a>
## New Anti-Smoking Warnings Criticized for Potential Backfire
### Summary:
Starting April 1, Australia will implement legislation requiring health warnings on individual cigarettes, with messages like "causes 16 cancers" and "poisons in every puff." However, social media users have mocked these warnings, suggesting they might make smoking appear "cool" and collectible rather than serving as deterrents. Despite the criticism, health officials assert that such on-product messages are part of a broader strategy to reduce smoking rates, citing positive results from similar approaches in Canada. The initiative aims to decrease the annual tobacco-related deaths in Australia, which currently exceed 24,000.
Sources: <a href="https://www.couriermail.com.au/news/queensland/poisons-in-every-puff-new-antismoking-messaging-slammed/news-story/2f77ecd3a943d3139539c2610af3400c" target="_blank">The Courier-Mail - March 28, 2025</a>
## 'Joe's Law' Introduced to Ban Future Hospital Privatization in NSW
### Summary:
The New South Wales government has announced "Joe's Law," a reform to prohibit the future privatization of acute public hospitals. This decision follows the death of two-year-old Joe Massa, who suffered a cardiac arrest and died after a prolonged wait in the emergency department of the privately managed Northern Beaches Hospital. The legislation aims to ensure that critical public services like emergency and surgical care remain under public control, preventing privatization. Additionally, a parliamentary inquiry into the hospital's services and a coronial investigation into Joe's death have been initiated.
Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/27/joes-law-to-ban-future-hospital-privatisation-in-nsw" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://www.news.com.au/lifestyle/health/health-problems/major-changes-coming-to-nsw-hospitals-after-death-of-twoyearold-joe-massa/news-story/fb93b0f0a9f2673a01eddfe89031fcb9" target="_blank">news.com.au - March 28, 2025</a>, <a href="https://www.dailytelegraph.com.au/newslocal/manly-daily/northern-beaches-hospital-probe-begins-into-safety-and-quality-of-health-services/news-story/72ea15981b26339eea92a15b4e9c498a" target="_blank">The Daily Telegraph - March 28, 2025</a>
## Determined Daisy Marks Major Milestone
### Summary:
Daisy, born with a rare chromosomal disorder, has achieved a significant health milestone by having her tracheostomy removed and is now learning to communicate using sign language. Her inspiring journey is one of several highlighted by the Good Friday Appeal, which supports the Royal Children's Hospital (RCH). The 2025 Appeal aims to fund further programs, research, and vital equipment at RCH, with contributions from events like North Melbourne's SuperClash fundraiser bringing joy to young patients ahead of the marquee match.
Sources: <a href="https://www.heraldsun.com.au/news/good-friday-appeal/good-friday-appeal-2025-star-roos-launch-superclash-fundraiser-with-special-visit/news-story/75fe74c62e52efb611436e9162c4d4d6" target="_blank">Herald Sun - March 27, 2025</a>
## Indonesia Seeks to Calm Investors After Stocks, Rupiah Slide
### Summary:
Indonesian officials are working to reassure investors following significant declines in the stock market and the rupiah. President Prabowo Subianto plans to meet with investors after the Eid-al-Fitr holiday to address concerns about government policies and fiscal stability. The rupiah recently hit its weakest level since 1998, and the main stock index fell 7.1%. Analysts attribute the selloff to poor communication on fiscal policies. The government aims to maintain the fiscal deficit within 3% of GDP and avoid political interference in its sovereign wealth fund. Efforts are also underway to deregulate the manufacturing sector and provide credits to labor-intensive industries. Bank Indonesia is prepared to intervene to stabilize the currency, emphasizing the economy's underlying strength. The rupiah has shown signs of recovery, and measures include easing buyback processes and offering more attractive investment instruments. Markets will monitor the mid-year budget update in July for signs of revenue shortfalls and spending adjustments.
Sources: <a href="https://www.reuters.com/markets/asia/indonesia-seeks-calm-investors-after-stocks-rupiah-slide-2025-03-27/" target="_blank">Reuters - 28 March 2025</a>
## Beijing to Escalate Taiwan Coercion in 2025
### Summary:
A report by the Office of the Director of National Intelligence highlights growing cooperation among China, Russia, Iran, and North Korea, posing significant challenges to U.S. global power. Closer ties between China and Russia, in particular, could present enduring risks to U.S. interests. The document points out China's military threat to the U.S., emphasizing its grey zone tactics and potential for stronger coercive action against Taiwan by 2025. The Ukraine conflict and its ongoing strategic risks, including nuclear escalation, are noted, as well as China's ambition to dominate AI by 2030 and its control over critical materials. The report also mentions the volatile Middle East, with Iran's expanding ties despite challenges, and North Korea's commitment to enhancing its nuclear capabilities. Additionally, threats from foreign drug actors and Islamic extremists, including Al-Qa'ida and a potential ISIS resurgence, are highlighted.
Sources: <a href="https://www.theaustralian.com.au/nation/politics/us-threat-assessment-sounds-the-alarm-on-china/news-story/cb582794c7a653b11cce8d3e61fc564b" target="_blank">The Australian - 28 March 2025</a>
## Fire Ant Infestation Could Cost Australian Households Over $1 Billion Annually
### Summary:
New modeling predicts that if fire ants become established in Australia, households may incur approximately $1.03 billion annually in control measures and related health and veterinary expenses. The invasive species could lead to up to 570,800 medical consultations and around 30 deaths each year due to stings. The electorates of Durack, O'Connor, Mayo, and Blair are projected to be most affected. Experts emphasize the need for increased federal funding for comprehensive eradication programs to prevent environmental damage and significant economic burdens on households.
Sources: <a href="https://www.theguardian.com/environment/2025/mar/28/australia-fire-ants-queensland-cost-eradication-pesticides" target="_blank">The Guardian - March 28, 2025</a>
## The Great Monetary Divide – Epi-3643
### Summary:
In this episode, host Jack Spirko discusses the rapid changes occurring in the global financial landscape. He highlights the European Union's announcement, led by European Central Bank President Christine Lagarde, to implement a Central Bank Digital Currency (CBDC) across member states by the upcoming fall. Spirko expresses concern that such a move could pave the way for a social credit system similar to China's, potentially leading to increased governmental control over individual financial activities.
Conversely, the episode explores developments in the United States, where the government is reportedly adopting Bitcoin as an economic reserve and integrating stablecoins into the financial system. Spirko suggests that these actions may indicate a divergent path from other global economies, potentially fostering a more decentralized financial environment.
Throughout the episode, Spirko emphasizes the importance of understanding these shifts and encourages listeners to consider how such changes might impact personal financial sovereignty and the broader economic landscape.
Please note that this summary is based on limited information available from the episode description and may not capture all the nuances discussed in the full podcast.
Sources: <a href="https://open.spotify.com/episode/5lUuCzX3wHfWdX6y6QtJGw" target="_blank">The Survival Podcast - 28 March 2025</a>, <a href="https://podcasts.apple.com/us/podcast/the-great-monetary-divide-epi-3643/id284148583?i=1000700006108&l=es-MX" target="_blank">Apple Podcasts - 28 March 2025</a>
-

@ 7d33ba57:1b82db35
2025-03-27 10:53:58
Sitges is known for its golden beaches, vibrant nightlife, and artistic charm. With a beautiful seafront promenade, historic old town, and a welcoming atmosphere, it’s a top destination for relaxation, culture, and fun on the **Costa Dorada.

## **🏖️ Top Things to See & Do in Sitges**
### **1️⃣ Stroll Along the Passeig Marítim 🌊**
- A **scenic seaside promenade** lined with palm trees, beaches, and restaurants.
- Perfect for **walking, cycling, or enjoying a sunset cocktail**.
### **2️⃣ Relax on the Beaches 🏖️**
- **Playa de la Fragata** – A central beach near the old town, great for families.
- **Playa de San Sebastián** – A smaller, quieter beach with local charm.
- **Playa del Balmins** – A well-known **nudist and LGBTQ+ friendly** beach.
- **Playa de l'Home Mort** – A hidden cove, popular for naturists.

### **3️⃣ Visit the Church of Sant Bartomeu i Santa Tecla ⛪**
- The **iconic church overlooking the sea**, a must-visit landmark.
- Amazing spot for **photos, especially at sunset**.
### **4️⃣ Explore the Old Town & Museums 🏛️**
- Wander through **charming whitewashed streets** filled with **boutique shops and cafés**.
- Visit **Museu Cau Ferrat**, home to **art by Santiago Rusiñol and Picasso**.
- Discover **Museu Maricel**, featuring **Romanesque and modernist art**.

### **5️⃣ Enjoy Sitges' Lively Nightlife & Festivals 🎭**
- Sitges is famous for its **bars, beach clubs, and LGBTQ+ friendly nightlife**.
- Visit in **February** for **Sitges Carnival**, one of Spain’s best! 🎉
- Experience the **Sitges Film Festival (October)**, known for horror & fantasy films.
### **6️⃣ Wine Tasting in Penedès 🍷**
- Take a short trip to **Penedès**, one of Spain’s best **Cava (sparkling wine) regions**.
- Tour **local wineries** and enjoy **wine tastings** just 30 minutes away.

## **🍽️ What to Eat in Sitges**
- **Xató** – A local **salad with cod, anchovies, and romesco sauce** 🥗
- **Suquet de Peix** – A Catalan **seafood stew with potatoes** 🍲🐟
- **Fideuà** – Similar to paella, but made with **short noodles instead of rice** 🍤
- **Crema Catalana** – A **delicious caramelized custard dessert** 🍮
- **Cava** – The **famous Catalan sparkling wine** from nearby Penedès 🍾

## **🚗 How to Get to Sitges**
🚆 **By Train:** 35 min from **Barcelona (Sants or Passeig de Gràcia stations)**.
🚘 **By Car:** 40 min from **Barcelona** via the **C-32 highway**.
🚌 **By Bus:** Direct buses from **Barcelona Airport (El Prat) and Tarragona**.
✈️ **By Air:** The nearest airport is **Barcelona-El Prat (BCN, 25 km away)**.

## **💡 Tips for Visiting Sitges**
✅ **Best time to visit?** **Spring to early autumn (April–October)** for beach weather ☀️
✅ **Avoid summer weekends** – It gets very busy with visitors from Barcelona 🏖️
✅ **Visit during Carnival or the Film Festival** for an unforgettable experience 🎭🎬
✅ **Explore beyond the beaches** – The old town and vineyards are worth it! 🍷
✅ **Try beachfront dining** – Enjoy fresh seafood with a sea view 🍽️🌊
-

@ b17fccdf:b7211155
2025-01-21 17:02:21
The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node:
* Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
```
tor --version
```
**Example** of expected output:
```
Tor version 0.4.8.6.
This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html)
Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc.
Tor compiled with GCC version 12.2.0
```
~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update.
* Basic PoW support can be checked by running this command:
```
tor --list-modules
```
Expected output:
```
relay: yes
dirauth: yes
dircache: yes
pow: **yes**
```
~ > If you have `pow: yes`, you are **OK**
* Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
```
sudo nano /etc/tor/torrc
```
Example:
```
# Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/
HiddenServiceVersion 3
HiddenServicePoWDefensesEnabled 1
HiddenServicePort 80 127.0.0.1:3002
```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
* Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
* LND: https://github.com/bitcoin/bitcoin/issues/28499
---
More info:
* https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
* https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
---
Enjoy it MiniBolter! 💙
-

@ 57d1a264:69f1fee1
2025-03-27 10:42:05
What we have been missing in [SN Press kit](https://stacker.news/items/872925/r/Design_r)? Most important, who the press kit is for? It's for us? It's for them? Them, who?
The first few editions of the press kit, I agree are mostly made by us, for us. A way to try to homogenize how we _speek_ out SN into the wild web. A way to have SN voice sync, loud and clear, to send out our message. In this case, I squeezed my mouse, creating a template for us [^1], stackers, to share when talking sales with possible businesses and merchants willing to invest some sats and engage with SN community. Here's the message and the sales pitch, v0.1:
## Reach Bitcoin’s Most Engaged Community – Zero Noise, Pure Signal.













- - -
Contributions to improve would be much appreciated. You can also help by simply commenting on each slide or leaving your feedback below, especially if you are a sale person or someone that has seen similar documents before.
This is the first interaction. Already noticed some issues, for example with the emojis and the fonts, especially when exporting, probably related to a penpot issue. The slides maybe render differently depending on the browser you're using.
- [▶️ Play](https://design.penpot.app/#/view?file-id=cec80257-5021-8137-8005-ef90a160b2c9&page-id=cec80257-5021-8137-8005-ef90a160b2ca§ion=interactions&index=0&interactions-mode=hide&zoom=fit) the file in your browser
- ⬇️ Save the [PDF file](https://mega.nz/file/TsBgkRoI#20HEb_zscozgJYlRGha0XiZvcXCJfLQONx2fc65WHKY)
@k00b it will be nice to have some real data, how we can get some basic audience insights? Even some inputs from Plausible, if still active, will be much useful.
[^1]: Territory founders. FYI: @Aardvark, @AGORA, @anna, @antic, @AtlantisPleb, @av, @Bell_curve, @benwehrman, @bitcoinplebdev, @Bitter, @BlokchainB, @ch0k1, @davidw, @ek, @elvismercury, @frostdragon, @grayruby, @HODLR, @inverselarp, @Jon_Hodl, @MaxAWebster, @mega_dreamer, @mrtali, @niftynei, @nout, @OneOneSeven, @PlebLab, @Public_N_M_E, @RDClark, @realBitcoinDog, @roytheholographicuniverse, @siggy47, @softsimon, @south_korea_ln, @theschoolofbitcoin, @TNStacker. @UCantDoThatDotNet, @Undisciplined
originally posted at https://stacker.news/items/926557
-

@ 6be5cc06:5259daf0
2025-01-21 01:51:46
## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
---
### Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
---
### 1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
---
### 2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
#### O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
#### Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
#### Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
#### Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
---
### 3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
---
### 4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
---
### 5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
#### Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
#### Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
---
### 6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
#### Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
#### Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
#### Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
---
### 7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
---
### 8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
---
### 9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
#### Entradas e Saídas
Cada transação no Bitcoin é composta por:
- **Entradas**: Representam os valores recebidos em transações anteriores.
- **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**.
#### Exemplo Prático
Imagine que você tem duas entradas:
1. 0,03 BTC
2. 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
#### Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
---
### 10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas.
#### Fluxo de Informação
- No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
#### Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
#### Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
---
### 11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
#### Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
#### A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
#### Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- **q** é o poder computacional do atacante (20%, ou 0,2).
- **p** é o poder computacional da rede honesta (80%, ou 0,8).
- **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente **nulas**.
#### Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
#### Por Que Tudo Isso é Seguro?
- **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
#### E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
---
### 12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos.
A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos.
Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
---
Faça o download do whitepaper original em português:
https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-

@ 3f770d65:7a745b24
2025-01-19 21:48:49
The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
**PROTOCOLS, NOT PLATFORMS.**
At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
**THIS IS POWERFUL.**
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
**AGAIN, THIS IS POWERUFL.**
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
###
-

@ cff1720e:15c7e2b2
2025-01-19 17:48:02
**Einleitung**\
\
Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\
Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

**Warum Nostr?**
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \
\
**Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!

\
**Wie funktioniert Nostr?**
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\
\
Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\
\
**Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\
**Warum ist Nostr die Zukunft des Internet?**
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\
**Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.**
<https://nostr.net/> \
<https://start.njump.me/>
**Hier das Interview zum Thema mit Radio Berliner Morgenröte**
<https://www.podbean.com/ew/pb-yxc36-17bb4be>
-

@ 7d33ba57:1b82db35
2025-03-27 10:35:25
Nerja is known for its stunning beaches, famous caves, and breathtaking sea views. With a charming old town, whitewashed houses, and a lively atmosphere, Nerja offers a perfect mix of relaxation, nature, and culture.

## **🏖️ Top Things to See & Do in Nerja**
### **1️⃣ Balcón de Europa 🌅**
- A **stunning viewpoint** with **panoramic views** of the Mediterranean.
- Lined with **palm trees, street musicians, and cafés**.
- A great spot for **sunset photos and people-watching**.

### **2️⃣ Nerja Caves (Cuevas de Nerja) 🏰**
- A **famous cave system** with **impressive stalactites and stalagmites**.
- Home to **prehistoric cave paintings**, estimated to be over **40,000 years old**.
- One of Spain’s most important **archaeological sites**.
### **3️⃣ Playa de Burriana 🏖️**
- The **best beach in Nerja**, with **golden sand and clear waters**.
- Offers **water sports**, including **kayaking and paddleboarding**.
- Many **chiringuitos (beach bars)** serving delicious **seafood paella**.
### **4️⃣ Kayaking to Maro Cliffs 🚣♂️**
- Paddle along the **coastline** to discover **hidden coves and waterfalls**.
- A unique way to explore the **Maro-Cerro Gordo Cliffs Natural Park**.

### **5️⃣ Frigiliana – The Most Beautiful White Village 🏡**
- Just **10 minutes from Nerja**, this **charming Andalusian village** is full of **whitewashed houses, cobbled streets, and colorful flowers**.
- Wander through **narrow alleyways** and enjoy **stunning mountain views**.
### **6️⃣ El Salón & Calahonda Beaches 🏝️**
- **Small, quiet beaches** just below the Balcón de Europa.
- Perfect for a **relaxing swim away from the crowds**.

## **🍽️ What to Eat in Nerja**
- **Espetos de Sardinas** – Grilled sardines on skewers, a classic Andalusian dish 🐟
- **Ajoblanco** – A cold almond and garlic soup, refreshing on hot days 🍲
- **Fried Fish (Pescaito Frito)** – A mix of **freshly caught seafood** 🦑🐠
- **Tarta de Almendra** – A traditional **almond cake**, perfect with coffee 🍰
- **Paella at Playa Burriana** – One of the best places to enjoy authentic **seafood paella** 🍤🍚

## **🚗 How to Get to Nerja**
✈️ **By Air:** The nearest airport is **Málaga Airport (AGP, 70 km, 50 min drive)**.
🚘 **By Car:** 50 min from **Málaga**, 1.5 hrs from **Granada**.
🚌 **By Bus:** Direct buses from **Málaga, Granada, and other Costa del Sol towns**.
🚆 **By Train:** No direct train, but you can take a train to Málaga and then a bus.

## **💡 Tips for Visiting Nerja**
✅ **Best time to visit?** **Spring & summer (April–September)** for the best weather ☀️
✅ **Book Nerja Cave tickets in advance** – It’s one of the most visited sites in Andalusia 🏰
✅ **Try kayaking or boat tours** – The coastline is stunning from the water 🚣♂️
✅ **Visit Frigiliana early** – To avoid crowds and enjoy the peaceful morning atmosphere 🌅
✅ **Wear comfortable shoes** – The old town has steep, cobbled streets 👟

-

@ da0b9bc3:4e30a4a9
2025-03-27 10:21:42
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/926553
-

@ 7d33ba57:1b82db35
2025-03-27 09:25:04
Los Narejos is a laid-back beach town on the Costa Cálida, located in the Murcia region of Spain. Known for its calm, warm waters, family-friendly beaches, and proximity to the Mar Menor lagoon, it’s an excellent destination for relaxation, water sports, and enjoying the Mediterranean lifestyle**.

## **🏖️ Top Things to See & Do in Los Narejos**
### **1️⃣ Playa de Los Narejos 🏖️**
- A **wide, sandy beach** with **shallow and warm waters**, perfect for families.
- **Palm-lined promenade** for walking, cycling, or enjoying seaside cafés.
- Excellent for **swimming, sunbathing, and beach sports**.
### **2️⃣ Mar Menor Lagoon 🌊**
- A **unique saltwater lagoon**, separated from the Mediterranean by La Manga.
- **Warmer and calmer waters** than the open sea, ideal for **safe swimming**.
- Known for its **healing mud baths** with **minerals beneficial for the skin**.

### **3️⃣ Watersports Paradise 🚤**
- A top spot for **kite surfing, windsurfing, sailing, and stand-up paddleboarding**.
- Several local schools offer **lessons for beginners and equipment rentals**.
- Great conditions for **kayaking** along the Mar Menor coastline.
### **4️⃣ Promenade Walk to Los Alcázares 🚶♂️**
- A **scenic coastal walk** from Los Narejos to **Los Alcázares**.
- Pass by **chiringuitos (beach bars)** serving fresh seafood and cocktails.
### **5️⃣ Local Markets & Shopping 🛍️**
- Visit the **Los Alcázares Market** (Tuesdays & Saturdays) for **local produce, clothes, and crafts**.
- Small boutique shops sell **Murcian souvenirs, ceramics, and wines**.

## **🍽️ What to Eat in Los Narejos**
- **Caldero Murciano** – A **traditional seafood rice dish**, full of flavor 🍚🐟
- **Dorada a la Sal** – Fresh **sea bream baked in salt**, a Mediterranean specialty 🐠
- **Tapas & Mariscos** – Try local seafood tapas like **grilled prawns, octopus, and clams** 🍤
- **Pastel de Carne** – A **Murcian meat pie**, perfect for a quick bite 🥧
- **Paparajotes** – A sweet treat made from **lemon leaves coated in batter and fried** 🍋🍩

## **🚗 How to Get to Los Narejos**
✈️ **By Air:** The nearest airport is **Región de Murcia Airport (RMU, 30 min drive)**.
🚆 **By Train:** Nearest station is in **Balsicas (20 min drive)**, with connections to Murcia and Cartagena.
🚘 **By Car:** 30 min from **Murcia**, 1 hr from **Alicante**, 20 min from **Cartagena**.
🚌 **By Bus:** Direct buses from **Murcia, Cartagena, and Alicante**.

## **💡 Tips for Visiting Los Narejos**
✅ **Best time to visit?** **Spring to early autumn (April–October)** for great weather ☀️
✅ **Try water sports** – Mar Menor is one of the safest places for beginners 🏄♂️
✅ **Bring a bike** – The flat terrain and coastal paths are great for cycling 🚴
✅ **Enjoy the sunset** – The Mar Menor has some of the most stunning sunset views 🌅
-

@ 7d33ba57:1b82db35
2025-03-27 08:55:21
L'Estartit is famous for its **stunning beaches, the Medes Islands, and incredible diving opportunities**. Once a small fishing village, it’s now a paradise for **nature lovers, water sports enthusiasts, and those seeking a relaxing Mediterranean escape**.

## **🏖️ Top Things to See & Do in L'Estartit**
### **1️⃣ Medes Islands (Illes Medes) 🏝️**
- A **protected marine reserve**, perfect for **snorkeling and scuba diving**.
- Explore **sea caves, coral reefs, and diverse marine life**.
- Take a **glass-bottom boat tour** to admire the underwater world without getting wet.
### **2️⃣ L'Estartit Beach 🏖️**
- A **long sandy beach** with shallow waters, ideal for families.
- Great for **swimming, sunbathing, and water sports** like windsurfing and kayaking.
- Offers fantastic views of the **Medes Islands**.

### **3️⃣ Montgrí Massif & Castle 🏰**
- Hike up to the **Montgrí Castle** for **panoramic views** of the Costa Brava.
- Trails through **rocky landscapes and Mediterranean forests**.
- A perfect spot for **hiking, mountain biking, and photography**.
### **4️⃣ Coastal Walking Route (Camí de Ronda) 🌊**
- A breathtaking **hiking trail along the cliffs**, connecting L'Estartit with nearby beaches and coves.
- Discover **hidden spots like Cala Pedrosa and Cala Ferriol**.

### **5️⃣ Explore the Old Town & Port ⚓**
- Wander through **narrow streets with local shops and seafood restaurants**.
- Visit the **Sant Genís Church**, a historic landmark in the town center.
- Enjoy a drink with a view at the **marina**.
### **6️⃣ Kayaking & Stand-Up Paddleboarding 🚣♂️**
- Paddle along the **coastline to explore caves, cliffs, and hidden coves**.
- A great way to experience the natural beauty of the area.

## **🍽️ What to Eat in L'Estartit**
- **Suquet de Peix** – Traditional Catalan **fish stew** 🐟
- **Arroz a la Cassola** – A **savory rice dish** with seafood 🍤
- **Fideuà** – Like **paella**, but made with short noodles instead of rice 🍜
- **Calamars a la Planxa** – Grilled squid with olive oil and garlic 🦑
- **Crema Catalana** – A classic Catalan **dessert similar to crème brûlée** 🍮

## **🚗 How to Get to L'Estartit**
🚆 **By Train:** The nearest train station is **Flaçà (30 min by car/taxi)** with connections from **Barcelona and Girona**.
🚘 **By Car:** 1.5 hrs from **Barcelona**, 45 min from **Girona**, 1 hr from **Figueres**.
🚌 **By Bus:** Direct buses from **Barcelona, Girona, and other Costa Brava towns**.
✈️ **By Air:** The nearest airport is **Girona-Costa Brava (GRO, 55 km)**.

## **💡 Tips for Visiting L'Estartit**
✅ **Best time to visit?** Late spring to early autumn (**May–September**) for warm weather 🌞
✅ **Book diving tours in advance** – Medes Islands are a top diving destination 🤿
✅ **Hike early in the morning** to avoid the heat & get the best views 🥾
✅ **Visit in June** for the **Havaneres Festival**, celebrating Catalan maritime music 🎶
-

@ 9e69e420:d12360c2
2025-01-19 04:48:31
A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market.
Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
-

@ a296b972:e5a7a2e8
2025-03-27 17:05:57
Wehrpflicht, Wehr-Pflicht… Da soll die allgemeine Wehrpflicht wieder eingeführt werden. Eine Frage taucht auf: Ist sie denn jemals abgeschafft worden? Ist die Wehrpflicht nicht untrennbar mit der Demokratie verbunden? Ist es nicht die Pflicht eines jeden Demokraten, sich zu wehren, wenn er sieht, wie die Demokratie vor die Hunde geht? Muss er sich nicht wehren, wenn er feststellt, dass die Freiheit scheibchenweise immer weniger wird?
 
In Absurd-Germanistan reizt ein wild gewordener Haufen Irrer in Berlin die Grenzen der Legalität bis zum Äußersten aus. Unterstützt von Erfüllungsgehilfen in der Rechtsprechung und den Medien. Neuester Coup: Zur größtmöglichen Intransparenz soll das Informationsfreiheitsgesetz abgeschafft werden. Unterstützt von einer eigenen Bundestagspolizei, geschützt von einem Wassergraben um den Reichstag. Die dunkle Seite der Macht baut eine Beton-Mauer auf, um größtmöglichen Abstand zum übelriechenden Volk, dass sie gewählt hat, zu gewährleisten. Und mit ekelhafter Regelmäßigkeit werden Knochen mit Fleischresten über die Mauer geworfen, die dann das dumme Volk zu verdauen hat. Das funktioniert derzeit noch, weil das Volk nicht in der Lage ist, eine Leiter an die Mauer zu stellen, um die Irren über die Mauer in den Wassergraben zu werfen und sich das saftige Hühnchen zu holen, das ihm, dem Volk sowieso gehört.
Unterdessen sinniert die entrückte Blase darüber, wie man dem Volk nachhaltig langfristigen Schaden zufügen kann. Aus rechtlichen Winkelzügen, falschen Versprechungen, Selbstbeweihräucherungen, ideologisch vergifteten Reden quillt die Verachtung gegenüber dem Volk und der Demokratie aus allen Poren. Und die wird dann durch Unseredemokratie verhöhnt, in der Schulden durch eine Wortneuschöpfung als Sondervermögen ausgegeben werden. Dreister und offensichtlicher kann man nicht lügen. Und das mit einer nie gekannten Chuzpe, dass einem nur noch der Atem stockt.
Jahrzehnte wurde den Deutschen abgewöhnt, stolz auf ihr Land zu sein. Die deutsche Fahne zeigen, hatte damals schon den Charme von „reeechts“. Wer von Vaterland und Heimat sprach, der bekam automatisch einen dunklen, schmalen Schatten zwischen Nasenmitte und Mund. Doch dann, als es mal wieder Spiele für’s Volk gab, durfte man auf einmal mit kleinen Wink-Elementen zeigen, dass man stolz auf elf Leute war, die hinter einem Ball herrennen und wenn sie ihn hatten, ihn dann wieder wegschossen. Damit nicht genug, es gab hochalberne Gamaschen für Außenspiegel und Diplomatenfähnchen in schwarz-rot-gold für des Deutschen liebstes Kind, das Auto.
Und jüngst kam einer daher, der wie von der Tarantel gestochen behauptete, dass der böse Russ hinter uns her ist, und man deshalb kriegstüchtig werden müsse, obwohl weit und breit nichts von ihm zu sehen war und er immer wieder wiederholte, dass er überhaupt gar keine Lust dazu hat, Deutschland auf unschöne Weise bereisen zu wollen.
Im Fieberwahn stimmten weitere Kriegstreiber in den Chor ein und ein deutscher Häuptling der Bleichgesichter, der ehedem Streubomben geächtet hatte, zuckte auf einmal nur verbal mit den Schultern. Das soll einer verstehen.
Und weil Deutschland von nichts und niemandem bedroht wird, muss deshalb dringend aufgerüstet werden, Kriegswirtschaft ist angesagt, die Wehrpflicht muss wieder her!
Eine Kriegsmaschinerie muss von Grund auf neu aufgebaut werden: Von der langen Feinripp-Unterhose mit Eingriff bis zum Panzer. Die ehemaligen Hermann-Göring-Werke müssen die Fließbänder zum Glühen bringen. Wir brauchen „Woffen, Woffen, Woffen“!
Das Ganze dauert 10 bis 20 Jahre. Hoffentlich reicht der im Samowar zubereitete Tee so lange, bis alles zertifiziert und DIN-Norm gerecht fertiggestellt ist. Man kann nur auf die christlich demokratische Unterstützung der nach einer europäischen Zentralregierung strebenden, deutschen Ex-Verteidigungsministerin mit Ambitionen zur Kaiserin von Europa hoffen. Ihre Expertise konnte sie ja dank ihres mit Bravour gemeisterten ehemaligen Amtes bereits unter Beweis stellen. Überhaupt, überall, wo das Militär im Hintergrund seine Finger im Spiel hat, ist die Wahl-Brüsselerin an vorderster Front. Zuletzt im Beschaffungswesen der 1. Pandemie-Spiele in Echtzeit unter realen Bedingungen.
Aber was nutzt das ganze schöne Zeug, die noch nicht bekleckerten jungfräulichen Gulasch-Kanonen, wenn sie keiner bedient und keiner seinen Henkelmann mit Feinkost füllen will.
Ja genau, es fehlen ja noch Menschen, in dem Metier Soldaten genannt.
Ein paar Natur-Wahnsinnige gibt es ja immer. Aber was ist mit denen, die vielleicht gar keinen Bock haben? Gerade frisch verliebt, von Papi das erste Auto vor die Tür gestellt bekommen, wegen Laktose-Intoleranz bitte nur einen Kriegs-Latte mit Hafermilch, und für mich bitte glutenfreie Marschverpflegung.
Was ist mit denen, die vielleicht checken, dass wir von einer Polit-Klicke regiert werden, die Deutschland an die Wand fährt und sich redlich Mühe gibt, eine positive Zukunft für die nächsten Generationen zu verunmöglichen?
Was ist mit denen, die von Anfang an gerafft haben, dass man mit einer Gen-Behandlung die Wehrkraft zersetzt?
Was ist mit denen, die die Pflicht, sich bestmöglich gesund zu halten, ernst genommen haben?
Was ist mit denen, die aus Sachzwängen oder Unwissenheit die Injektionen über sich haben ergehen lassen und heute feststellen, dass man sie verarscht hat?
Was ist mit denen, die sich an ihrem durchtrainierten Six-Pack nur noch durch Bilder erinnern können, weil sie seit der Verabreichung eines „nebenwirkungsfreien Elixiers“ nicht mehr auf die Beine kommen?
Man fragt sich, woher soll die Motivation kommen, sein gesundes oder herabgemindertes Immunsystem für ein Vaterland auf’s Spiel zu setzen, bei dem sich herausgestellt hat, dass der Vater ein Stiefvater der übelsten Sorte ist?
Da in Europa offensichtlich die Diplomatie zunächst abgeschafft ist, und demnächst vielleicht sogar unter Strafe gestellt wird, und man sich auf Uncle Sam auch nicht mehr verlassen kann, weil er so völlig das Gegenteil von dem unternimmt, was man von ihm erwartet hätte, wäre es überlegenswert, ob diejenigen jungen Männer im fortpflanzungsfähigen und -willigen Alter eventuell eine längere Reise ins Ausland antreten sollten. Ist nur so ein Gedanke.
Man kann ja immer noch mal wieder vorbeischauen, wenn es an den ungeschützten Außengrenzen wieder von Deutschland aus nach Vernunft duftet.
Aber vielleicht findet sich auch unter den Messerfachkräften der eine oder andere, der seine Künste und sein Leben für ein Land und Bürgergeld hergeben möchte. Schließlich können es die Allermeisten kaum abwarten, die deutschen Gepflogenheiten ungefiltert einzusaugen und dafür ihre kulturelle Herkunft und Religion wie einen alten Lumpen abzuwerfen. Was Besseres, als die Kultur der Denker und Dichter hat die Welt ohnehin noch nicht gesehen. Wer kann dem schon widerstehen?
Großer Dank gilt auch der deutschen Bevölkerung, die einem wildgewordenen andalusischen Stier gleich, in Scharen von einigen Tausenden von über 80 Millionen auf die Straße rennen, um ihrem Unbill Ausdruck zu verleihen. So eine Friedensmüdigkeit ist ansteckend und kann richtig mobilisieren. Man kann natürlich auch was von Zuhause aus tun: Sich laut empören und für durchziehende Truppen Kaffee kochen, oder dem Heimatschutz beim Stiefel putzen helfen. Im Ernst: So eine bräsige, behäbige, langweilige, unmotivierte, unkritische, informationsvergiftete, geduldige Herde von Faultieren hat es eigentlich nicht anders verdient, als dass man sie während ihres andauernden Langzeit-Wachkomas in einen Käfig sperrt und mit Bananen füttert.
Keiner, niemand kommt auf die Idee, dass es immer noch besser wäre, obwohl es keinerlei Anlass dazu gibt, russisch zu lernen, als sich als Kanonenfutter für einen Staat, der sein Volk verachtet, in die Gefahr zu begeben, im Ernstfall verstümmelt oder abgeschlachtet zu werden.
Man kann jetzt schon die heulenden Bubis sehen, wie sie sich unter Mutterns Rockschürze verkriechen, wenn sie merken würden, dass es in den Ballerspielen am Computer aber immer ganz anders war.
Der ganze inszenierte Spuk wäre sofort vorbei, wenn die Menschen ihr Gehirn einschalten würden. Dann würden sie feststellen, dass es unzählige Gründe dafür gibt **NEIN** zu sagen und **ICH MACH DA NICHT MIT**.
Wie machtlos wären die Kriegspfeifen in Berlin, wenn sie zu spüren bekämen, dass das deutsche Volk nicht mit Russland oder sonst wem im Krieg ist und nicht das geringste Interesse verspürt, daran etwas zu ändern. Deutschland besteht aus einem erbärmlichen Haufen Ja-Sagern in allen Lagern, die offensichtlich erst dann wach werden, wenn es nichts mehr zu Essen gibt und der Strom fürs externe Gehirn weg ist. Oh Gott, mein Leben hat keinen Sinn mehr! Was sind wir doch ein elender Haufen von Jammerlappen, die glauben, dass man gelebte Demokratie und Freiheit jederzeit im Online-Shop kaufen kann. Lieferung innerhalb 24 Stunden.
**Frieden – Mir – Pace – Peace**
*Dieser Beitrag wurde mit dem Pareto-Client geschrieben.*
-

@ 57d1a264:69f1fee1
2025-03-27 08:11:33
Explore and reimagine programming interfaces beyond text (visual, tactile, spatial).
> _"The most dangerous thought you can have as a creative person is to think you know what you're doing."_
`— Richard Hamming` [^1]
https://www.youtube.com/watch?v=8pTEmbeENF4
For his recent DBX Conference talk, Victor took attendees back to the year 1973, donning the uniform of an IBM systems engineer of the times, delivering his presentation on an overhead projector. The '60s and early '70s were a fertile time for CS ideas, reminds Victor, but even more importantly, it was a time of unfettered thinking, unconstrained by programming dogma, authority, and tradition.

_'The most dangerous thought that you can have as a creative person is to think that you know what you're doing,'_ explains Victor. 'Because once you think you know what you're doing you stop looking around for other ways of doing things and you stop being able to see other ways of doing things. You become blind.' He concludes, 'I think you have to say: _"We don't know what programming is. We don't know what computing is. We don't even know what a computer is."_ And once you truly understand that, and once you truly believe that, then you're free, and you can think anything.'
More details at https://worrydream.com/dbx/
[^1]: Richard Hamming -- [The Art of Doing Science and Engineering, p5](http://worrydream.com/refs/Hamming_1997_-_The_Art_of_Doing_Science_and_Engineering.pdf) (pdf ebook)
originally posted at https://stacker.news/items/926493
-

@ f9cf4e94:96abc355
2025-01-18 06:09:50
Para esse exemplo iremos usar:
| Nome | Imagem | Descrição |
| --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ |
| Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** |
| Pen drive |  | **16Gb** |
Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.).
---
## Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
```bash
apt update
apt install tor
```
---
## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧
Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit
[Unit]
Description=Nostr Relay Server Service
After=network.target
[Service]
Type=simple
WorkingDirectory=/opt/nrs
ExecStart=/opt/nrs/nrs-arm64
Restart=on-failure
[Install]
WantedBy=multi-user.target
```
---
## Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases).
---
## Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
```bash
mkdir -p /opt/nrs /mnt/edriver
```
---
## Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
```bash
lsblk
```
---
## Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o:
```bash
mkfs.vfat /dev/sda
```
---
## Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta `/mnt/edriver`:
```bash
mount /dev/sda /mnt/edriver
```
---
## Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
```bash
blkid
```
---
## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝
Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:
```fstab
UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
```
---
## Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta `/opt/nrs`:
```bash
cp nrs-arm64 /opt/nrs
```
---
## Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`:
```yaml
app_env: production
info:
name: Nostr Relay Server
description: Nostr Relay Server
pub_key: ""
contact: ""
url: http://localhost:3334
icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png
base_path: /mnt/edriver
negentropy: true
```
---
## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`:
```bash
cp nrs.service /etc/systemd/system/
```
Recarregue os serviços e inicie o serviço `nrs`:
```bash
systemctl daemon-reload
systemctl enable --now nrs.service
```
---
## Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha:
```torrc
HiddenServiceDir /var/lib/tor/nostr_server/
HiddenServicePort 80 127.0.0.1:3334
```
---
## Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
```bash
systemctl enable --now tor.service
```
O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`.
---
## Observações ⚠️
- Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`.
---
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-

@ ed84ce10:cccf4c2a
2025-03-27 14:55:40
## **Hackers are Destiny: Four Fulcrums of the Future**
*A Dora Ventures Thesis*
In “Why Software is Eating the World,” Marc Andreeson argued that software isn’t just a tool — it’s a societal force. At [DoraHacks](https://dorahacks.io/), we agree, but we go one step further.
It’s not software alone that reshapes the world. It’s hackers — those who BUIDL.
The real engine of change isn’t technology; it’s the people who choose to wield it.
[DoraHacks](https://dorahacks.io/) is building a global Hacker Movement — a self-organizing force powered by open source, freedom, and code. We’re not chasing buzzwords like “Web3” or geopolitical narratives. We’re building a new society. One based on a simple but radical question:
**What is truly worth building?**
Dora Ventures exists to serve that mission — a capital engine designed to coordinate, amplify, and capture value from the hacker revolution.
We are placing early and aggressive bets across four core leverage points:
## **I. FDA Free Society — The BioHack**
### **Freedom of Life Science is the foundation of a free society.**
Every meaningful technological revolution has challenged the existing power structure.
Today, the single most over-regulated, over-centralized, and innovation-hostile domain? Life Science.
It takes ten years and billions of dollars to bring a drug from lab to patient. Most innovation dies in the trenches of bureaucracy.
We don’t need anarchy. We need a new model:**A market-driven, patient-first biotech innovation stack.**
**The Problem:**
- The FDA approval process kills breakthrough therapies before they live.
- Big Pharma monopolies decouple price from value and destroy competition.
- The “Right to Try” is a legal afterthought, not a first principle.
- Bio startups can’t survive the upfront costs of traditional trials.
**The Opportunity:**
- Let markets and builders lead: give power back to patients, doctors, and founders.
- Rethink from first principles: not “Did it pass?” but “Does it work?”
- Reclaim the Right to Try: the real risk is dying while waiting.
- Build a hyper-competitive biofounder ecosystem — don’t just supply Big Pharma with IP.
- Supercharge biotech with software and AI: accelerate every layer of the stack.
The future of medicine does not belong to regulators. It belongs to the builders who refuse to wait.
**The FDA Free Society isn’t just a challenge to power — it’s a defense of life.**
## **II. Open Source Quantum**
### **Ethereum had 2015. Quantum software has 2025.**
Arthur C. Clarke said: *“Any sufficiently advanced technology is indistinguishable from magic.”*
Quantum is magic — until it’s programmable, repeatable, and shared. In other words: open source.
Dora Ventures is betting on the moment quantum computing becomes a hacker’s playground.
Hardware is entering the engineering phase. Software? Still a wasteland — which means pure upside for builders.
**We’re betting on:**
- **Quantum compilers & transpilers**: bridging classical and quantum logic.
- **Quantum cryptography**: building fundamentally new security layers.
- **Quantum applications** in AI, pharma, logistics, finance, space — everything.
We're not watching from the sidelines. We’re funding open-source tools, running hackathons, and building out the decentralized quantum dev stack.
**Open Source Quantum is not speculative.** It’s inevitable — and massively undercapitalized.
Now is the time to build.
## **III. Consumer Crypto — The Fat Apps Are Coming**
### **Crypto’s real revolution? Billion-user apps.**
Crypto is not the *alternative* to the internet. It’s the *next chapter* of the internet.
In the 1990s, HTTP and TCP/IP rewired information.
In the 2000s, web apps rewired commerce and communication.
In the 2010s, mobile apps rewired human behavior.
In the 2020s, crypto apps will onboard the next billion users.
**The infrastructure is ready. The fat apps are hatching.**
Dora Ventures is obsessed with one question:
**Who builds the PayPal and WeChat of the Web3 era?**
That’s where we place our bets.
**What we see coming:**
- Compliant stablecoins like USDC become digital dollars.
- Crypto-native payment rails rival VISA.
- Appchains built with Move + simplified UX onboard non-crypto users.
- On-chain creator economies that pay artists, devs, and communities directly.
Imagine this:
A fan in NYC uses USDC on a Move-based blockchain (Aptos) to buy a concert ticket via KYD Labs.
An Argentinian grabs a latte daily with Bitcoin sats on Lightning.
A friend group splits dinner bills via Yakihonne, a decentralized social platform.
**That’s not the future. That’s this year.**
We’re not funding protocols — we’re funding paradigm shifts in experience.
## **IV. Agentic Organizations — DAOs Without CEOs**
### **The end of corporations. The birth of autonomous orgs.**
In 2022, Sam Altman redefined “tools.”
In 2025, we’ll redefine “organizations.”
Future orgs won’t be hierarchies. They’ll be networks of autonomous agents.
**Agents** are the new work unit. They don’t sleep. They learn continuously. They self-schedule.
They’re not tools to help humans — they *are* the operating system of post-human orgs.
**What’s coming:**
- DAOs with agent-driven governance and privacy.
- Smart Widgets that deploy trade/social/payment agents in three lines of code.
- Privacy as a default layer in automation.
- A new generation of AI-native hackathon projects.
AI + blockchain isn’t a buzzword. It’s the genesis of *organizational intelligence.*
Yesterday, the company was an information processor.
Tomorrow, the DAO is an autonomous agent network.
**No CEOs. No approvals. No offices. Just coordination at the speed of compute.**
## **The Bet: BUIDL Freedom for Humanity**
FDA Free Society. Open Source Quantum. Consumer Crypto. Agentic Orgs.
These are not sci-fi. They are already happening.
At Dora Ventures, we don’t just back technologies.
We back builders who say:
“The system is broken — and I’m going to fix it myself.”
We back rebels who reject stagnation.
Who write code instead of complaints.
Who build networks instead of narratives.
Who refuse to ask permission to build the future.
Hackers are eating the world.
And in the age of AI, humanity will only survive if it chooses to become hackers — to use code, coordination, and imagination to build a world worth living in.
Let’s build.
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all. That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission. As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently. Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive. Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally. The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match. When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol. Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all. That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission. As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently. Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive. Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally. The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match. When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol. Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit. @ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users. ## Table of Contents 1. Prerequisites 2. Initial Server Setup 3. Installing Strfry Nostr Relay 4. Configuring Your Relay 5. Setting Up TOR 6. Making Your Relay Available on TOR 7. Testing Your Setup] 8. Maintenance and Security 9. Troubleshooting ## Prerequisites - A Debian or Ubuntu server - Basic familiarity with command line operations (most steps are explained in detail) - Root or sudo access to your server ## Initial Server Setup First, let's make sure your server is properly set up and secured. ### Update Your System Connect to your server via SSH and update your system: ```bash sudo apt update sudo apt upgrade -y ``` ### Set Up a Basic Firewall Install and configure a basic firewall: ```bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enable ``` This allows SSH connections while blocking other ports for security. ## Installing Strfry Nostr Relay This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the `DEPLOYMENT.md` document in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps [here](https://github.com/hoytech/strfry/blob/master/docs/DEPLOYMENT.md). ### Install Dependencies First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry: ```bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-dev ``` Here's why each dependency is needed: **Basic Development Tools:** - `git`: Version control system used to clone the Strfry repository and manage code updates - `build-essential`: Meta-package that includes compilers (gcc, g++), make, and other essential build tools **Perl Dependencies** (used for Strfry's build scripts): - `libyaml-perl`: Perl interface to parse YAML configuration files - `libtemplate-perl`: Template processing system used during the build process - `libregexp-grammars-perl`: Advanced regular expression handling for Perl scripts **Core Libraries for Strfry:** - `libssl-dev`: Development files for OpenSSL, used for secure connections and cryptographic operations - `zlib1g-dev`: Compression library that Strfry uses to reduce data size - `liblmdb-dev`: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend - `libflatbuffers-dev`: Memory-efficient serialization library for structured data - `libsecp256k1-dev`: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures - `libzstd-dev`: Fast real-time compression algorithm for efficient data storage and transmission ### Clone and Build Strfry Clone the Strfry repository: ```bash git clone https://github.com/hoytech/strfry.git cd strfry ``` Build Strfry: ```bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores) ``` This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime. ### Install Strfry Install the Strfry binary to your system path: ```bash sudo cp strfry /usr/local/bin ``` This makes the `strfry` command available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions. ## Configuring Your Relay ### Create Strfry User Create a dedicated user for running Strfry. This enhances security by isolating the relay process: ```bash sudo useradd -M -s /usr/sbin/nologin strfry ``` The `-M` flag prevents creating a home directory, and `-s /usr/sbin/nologin` prevents anyone from logging in as this user. This is a security best practice for service accounts. ### Create Data Directory Create a directory for Strfry's data: ```bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfry ``` This creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it. ### Configure Strfry Copy the sample configuration file: ```bash sudo cp strfry.conf /etc/strfry.conf ``` Edit the configuration file: ```bash sudo nano /etc/strfry.conf ``` Modify the database path: ``` # Find this line: db = "./strfry-db/" # Change it to: db = "/var/lib/strfry/" ``` Check your system's hard limit for file descriptors: ```bash ulimit -Hn ``` Update the `nofiles` setting in your configuration to match this value (or set to 0): ``` # Add or modify this line in the config (example if your limit is 524288): nofiles = 524288 ``` The `nofiles` setting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular. You might also want to customize your relay's information in the config file. Look for the `info` section and update it with your relay's name, description, and other details. Set ownership of the configuration file: ```bash sudo chown strfry:strfry /etc/strfry.conf ``` ### Create Systemd Service Create a systemd service file for managing Strfry: ```bash sudo nano /etc/systemd/system/strfry.service ``` Add the following content: ```ini [Unit] Description=strfry relay service [Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000 [Install] WantedBy=multi-user.target ``` This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like `ProtectHome` and `NoNewPrivileges` - Sets resource limits appropriate for a relay Enable and start the service: ```bash sudo systemctl enable strfry.service sudo systemctl start strfry ``` Check the service status: ```bash sudo systemctl status strfry ``` ### Verify Relay is Running Test that your relay is running locally: ```bash curl localhost:7777 ``` You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR. ## Setting Up TOR Now let's make your relay accessible as a TOR hidden service. ### Install TOR Install TOR from the package repositories: ```bash sudo apt install -y tor ``` This installs the TOR daemon that will create and manage your hidden service. ### Configure TOR Edit the TOR configuration file: ```bash sudo nano /etc/tor/torrc ``` Scroll down to wherever you see a commented out part like this: ``` #HiddenServiceDir /var/lib/tor/hidden_service/ #HiddenServicePort 80 127.0.0.1:80 ``` Under those lines, add the following lines to set up a hidden service for your relay: ``` HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777 ``` This configuration: - Creates a hidden service directory at `/var/lib/tor/strfry-relay/` - Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR network Create the directory for your hidden service: ```bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/ ``` The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys. Restart TOR to apply changes: ```bash sudo systemctl restart tor ``` ## Making Your Relay Available on TOR ### Get Your Onion Address After restarting TOR, you can find your onion address: ```bash sudo cat /var/lib/tor/strfry-relay/hostname ``` This will output something like `abcdefghijklmnopqrstuvwxyz234567.onion`, which is your relay's unique .onion address. This is what you'll share with others to access your relay. ### Understanding Onion Addresses The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key. Your users will need to use this address with the WebSocket protocol prefix to connect: `ws://youronionaddress.onion` ## Testing Your Setup ### Test with a Nostr Client The best way to test your relay is with an actual Nostr client that supports TOR: 1. Open your TOR browser 2. Go to your favorite client, either on clearnet or an onion service. - Check out [this list](https://github.com/0xtrr/onion-service-nostr-clients?tab=readme-ov-file#onion-service-nostr-clients) of nostr clients available over TOR. 3. Add your relay URL: `ws://youronionaddress.onion` to your relay list 4. Try posting a note and see if it appears on your relay - In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay. - Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected. Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too). ## Maintenance and Security ### Regular Updates Keep your system, TOR, and relay updated: ```bash # Update system sudo apt update sudo apt upgrade -y # Update Strfry cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry # Verify TOR is still running properly sudo systemctl status tor ``` Regular updates are crucial for security, especially for TOR which may have security-critical updates. ### Database Management Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups. ### Monitoring Logs To monitor your Strfry logs: ```bash sudo journalctl -u strfry -f ``` To check TOR logs: ```bash sudo journalctl -u tor -f ``` Monitoring logs helps you identify potential issues and understand how your relay is being used. ### Backup This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server. ```bash # Stop the relay temporarily sudo systemctl stop strfry # Backup the database sudo cp -r /var/lib/strfry /path/to/backup/location # Restart the relay sudo systemctl start strfry ``` Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it. ```bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/location ``` ## Troubleshooting ### Relay Not Starting If your relay doesn't start: ```bash # Check logs sudo journalctl -u strfry -e # Verify configuration cat /etc/strfry.conf # Check permissions ls -la /var/lib/strfry ``` Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big) ### TOR Hidden Service Not Working If your TOR hidden service is not accessible: ```bash # Check TOR logs sudo journalctl -u tor -e # Verify TOR is running sudo systemctl status tor # Check onion address sudo cat /var/lib/tor/strfry-relay/hostname # Verify TOR configuration sudo cat /etc/tor/torrc ``` Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc ### Testing Connectivity If you're having trouble connecting to your service: ```bash # Verify Strfry is listening locally sudo ss -tulpn | grep 7777 # Check that TOR is properly running sudo systemctl status tor # Test the local connection directly curl --include --no-buffer localhost:7777 ``` --- ## Privacy and Security Considerations Running a Nostr relay as a TOR hidden service provides several important privacy benefits: 1. **Network Privacy**: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay. 2. **Server Anonymity**: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting. 3. **Censorship Resistance**: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked. 4. **User Privacy**: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized. However, there are some important considerations: - TOR connections are typically slower than regular internet connections - Not all Nostr clients support TOR connections natively - Running a hidden service increases the importance of keeping your server secure --- Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network. For further customization and advanced configuration options, refer to the [Strfry documentation](https://github.com/hoytech/strfry). Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network! If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to [this list](https://github.com/0xtrr/onion-service-nostr-relays). Only add it if you plan to run a stable and available relay.
@ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users. ## Table of Contents 1. Prerequisites 2. Initial Server Setup 3. Installing Strfry Nostr Relay 4. Configuring Your Relay 5. Setting Up TOR 6. Making Your Relay Available on TOR 7. Testing Your Setup] 8. Maintenance and Security 9. Troubleshooting ## Prerequisites - A Debian or Ubuntu server - Basic familiarity with command line operations (most steps are explained in detail) - Root or sudo access to your server ## Initial Server Setup First, let's make sure your server is properly set up and secured. ### Update Your System Connect to your server via SSH and update your system: ```bash sudo apt update sudo apt upgrade -y ``` ### Set Up a Basic Firewall Install and configure a basic firewall: ```bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enable ``` This allows SSH connections while blocking other ports for security. ## Installing Strfry Nostr Relay This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the `DEPLOYMENT.md` document in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps [here](https://github.com/hoytech/strfry/blob/master/docs/DEPLOYMENT.md). ### Install Dependencies First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry: ```bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-dev ``` Here's why each dependency is needed: **Basic Development Tools:** - `git`: Version control system used to clone the Strfry repository and manage code updates - `build-essential`: Meta-package that includes compilers (gcc, g++), make, and other essential build tools **Perl Dependencies** (used for Strfry's build scripts): - `libyaml-perl`: Perl interface to parse YAML configuration files - `libtemplate-perl`: Template processing system used during the build process - `libregexp-grammars-perl`: Advanced regular expression handling for Perl scripts **Core Libraries for Strfry:** - `libssl-dev`: Development files for OpenSSL, used for secure connections and cryptographic operations - `zlib1g-dev`: Compression library that Strfry uses to reduce data size - `liblmdb-dev`: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend - `libflatbuffers-dev`: Memory-efficient serialization library for structured data - `libsecp256k1-dev`: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures - `libzstd-dev`: Fast real-time compression algorithm for efficient data storage and transmission ### Clone and Build Strfry Clone the Strfry repository: ```bash git clone https://github.com/hoytech/strfry.git cd strfry ``` Build Strfry: ```bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores) ``` This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime. ### Install Strfry Install the Strfry binary to your system path: ```bash sudo cp strfry /usr/local/bin ``` This makes the `strfry` command available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions. ## Configuring Your Relay ### Create Strfry User Create a dedicated user for running Strfry. This enhances security by isolating the relay process: ```bash sudo useradd -M -s /usr/sbin/nologin strfry ``` The `-M` flag prevents creating a home directory, and `-s /usr/sbin/nologin` prevents anyone from logging in as this user. This is a security best practice for service accounts. ### Create Data Directory Create a directory for Strfry's data: ```bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfry ``` This creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it. ### Configure Strfry Copy the sample configuration file: ```bash sudo cp strfry.conf /etc/strfry.conf ``` Edit the configuration file: ```bash sudo nano /etc/strfry.conf ``` Modify the database path: ``` # Find this line: db = "./strfry-db/" # Change it to: db = "/var/lib/strfry/" ``` Check your system's hard limit for file descriptors: ```bash ulimit -Hn ``` Update the `nofiles` setting in your configuration to match this value (or set to 0): ``` # Add or modify this line in the config (example if your limit is 524288): nofiles = 524288 ``` The `nofiles` setting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular. You might also want to customize your relay's information in the config file. Look for the `info` section and update it with your relay's name, description, and other details. Set ownership of the configuration file: ```bash sudo chown strfry:strfry /etc/strfry.conf ``` ### Create Systemd Service Create a systemd service file for managing Strfry: ```bash sudo nano /etc/systemd/system/strfry.service ``` Add the following content: ```ini [Unit] Description=strfry relay service [Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000 [Install] WantedBy=multi-user.target ``` This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like `ProtectHome` and `NoNewPrivileges` - Sets resource limits appropriate for a relay Enable and start the service: ```bash sudo systemctl enable strfry.service sudo systemctl start strfry ``` Check the service status: ```bash sudo systemctl status strfry ``` ### Verify Relay is Running Test that your relay is running locally: ```bash curl localhost:7777 ``` You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR. ## Setting Up TOR Now let's make your relay accessible as a TOR hidden service. ### Install TOR Install TOR from the package repositories: ```bash sudo apt install -y tor ``` This installs the TOR daemon that will create and manage your hidden service. ### Configure TOR Edit the TOR configuration file: ```bash sudo nano /etc/tor/torrc ``` Scroll down to wherever you see a commented out part like this: ``` #HiddenServiceDir /var/lib/tor/hidden_service/ #HiddenServicePort 80 127.0.0.1:80 ``` Under those lines, add the following lines to set up a hidden service for your relay: ``` HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777 ``` This configuration: - Creates a hidden service directory at `/var/lib/tor/strfry-relay/` - Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR network Create the directory for your hidden service: ```bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/ ``` The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys. Restart TOR to apply changes: ```bash sudo systemctl restart tor ``` ## Making Your Relay Available on TOR ### Get Your Onion Address After restarting TOR, you can find your onion address: ```bash sudo cat /var/lib/tor/strfry-relay/hostname ``` This will output something like `abcdefghijklmnopqrstuvwxyz234567.onion`, which is your relay's unique .onion address. This is what you'll share with others to access your relay. ### Understanding Onion Addresses The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key. Your users will need to use this address with the WebSocket protocol prefix to connect: `ws://youronionaddress.onion` ## Testing Your Setup ### Test with a Nostr Client The best way to test your relay is with an actual Nostr client that supports TOR: 1. Open your TOR browser 2. Go to your favorite client, either on clearnet or an onion service. - Check out [this list](https://github.com/0xtrr/onion-service-nostr-clients?tab=readme-ov-file#onion-service-nostr-clients) of nostr clients available over TOR. 3. Add your relay URL: `ws://youronionaddress.onion` to your relay list 4. Try posting a note and see if it appears on your relay - In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay. - Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected. Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too). ## Maintenance and Security ### Regular Updates Keep your system, TOR, and relay updated: ```bash # Update system sudo apt update sudo apt upgrade -y # Update Strfry cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry # Verify TOR is still running properly sudo systemctl status tor ``` Regular updates are crucial for security, especially for TOR which may have security-critical updates. ### Database Management Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups. ### Monitoring Logs To monitor your Strfry logs: ```bash sudo journalctl -u strfry -f ``` To check TOR logs: ```bash sudo journalctl -u tor -f ``` Monitoring logs helps you identify potential issues and understand how your relay is being used. ### Backup This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server. ```bash # Stop the relay temporarily sudo systemctl stop strfry # Backup the database sudo cp -r /var/lib/strfry /path/to/backup/location # Restart the relay sudo systemctl start strfry ``` Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it. ```bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/location ``` ## Troubleshooting ### Relay Not Starting If your relay doesn't start: ```bash # Check logs sudo journalctl -u strfry -e # Verify configuration cat /etc/strfry.conf # Check permissions ls -la /var/lib/strfry ``` Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big) ### TOR Hidden Service Not Working If your TOR hidden service is not accessible: ```bash # Check TOR logs sudo journalctl -u tor -e # Verify TOR is running sudo systemctl status tor # Check onion address sudo cat /var/lib/tor/strfry-relay/hostname # Verify TOR configuration sudo cat /etc/tor/torrc ``` Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc ### Testing Connectivity If you're having trouble connecting to your service: ```bash # Verify Strfry is listening locally sudo ss -tulpn | grep 7777 # Check that TOR is properly running sudo systemctl status tor # Test the local connection directly curl --include --no-buffer localhost:7777 ``` --- ## Privacy and Security Considerations Running a Nostr relay as a TOR hidden service provides several important privacy benefits: 1. **Network Privacy**: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay. 2. **Server Anonymity**: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting. 3. **Censorship Resistance**: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked. 4. **User Privacy**: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized. However, there are some important considerations: - TOR connections are typically slower than regular internet connections - Not all Nostr clients support TOR connections natively - Running a hidden service increases the importance of keeping your server secure --- Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network. For further customization and advanced configuration options, refer to the [Strfry documentation](https://github.com/hoytech/strfry). Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network! If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to [this list](https://github.com/0xtrr/onion-service-nostr-relays). Only add it if you plan to run a stable and available relay. @ bc52210b:20bfc6de
2025-03-25 20:17:22CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient. This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off! Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now. --- **CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused!** Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why: * Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs). * Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key. **Key Differences:** 1. What’s Aggregated? * CISA: Aggregates signatures. * Key Aggregation: Aggregates public keys. 2. What the Verifier Needs * CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature. * Key Aggregation: The verifier only needs the single aggregated public key and one message. 3. When It Happens * CISA: Used during transaction signing, when inputs are being combined into a transaction. * MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control. So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs! --- **Two Flavors of CISA: Half-Agg and Full-Agg** CISA comes in two modes: * Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.) * Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later. Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg. --- **Half Signature Aggregation (Half-Agg) Explained** **How It Works** Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process: 1. Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers. 2. Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature. A Schnorr signature has two parts: * R: A random point (32 bytes). * s: A scalar value (32 bytes). In Half-Agg: * The R values from each signature are kept separate (one per input). * The s values from all signatures are combined into a single s value. **Why It Saves Space (~50%)** Let’s break down the size savings with some math: Before Aggregation: * Each Schnorr signature = 64 bytes (32 for R + 32 for s). * For n inputs: n × 64 bytes. After Half-Agg: * Keep n R values (32 bytes each) = 32 × n bytes. * Combine all s values into one = 32 bytes. * Total size: 32 × n + 32 bytes. Comparison: * Original: 64n bytes. * Half-Agg: 32n + 32 bytes. * For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings! **Real-World Impact:** Based on recent Bitcoin usage, Half-Agg could save: * ~19.3% in space (reducing transaction size). * ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA. --- **Applications of Half-Agg** Half-Agg isn’t just a cool idea—it has practical uses: 1. Transaction-wide Aggregation * Combine all signatures within a single transaction. * Result: Smaller transactions, lower fees. 2. Block-wide Aggregation * Combine signatures across all transactions in a Bitcoin block. * Result: Even bigger space savings at the blockchain level. 3. Off-chain Protocols / P2P * Use Half-Agg in systems like Lightning Network gossip messages. * Benefit: Efficiency without needing miners or a Bitcoin soft fork. --- **Challenges with Half-Agg** While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level: 1. Breaking Adaptor Signatures * Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges. * Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on. 2. Impact on Reorg Recovery * In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed. * If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery. These challenges mean Half-Agg needs careful design, especially for block-wide use. --- **Wrapping Up** CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning. But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future!
@ bc52210b:20bfc6de
2025-03-25 20:17:22CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient. This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off! Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now. --- **CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused!** Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why: * Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs). * Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key. **Key Differences:** 1. What’s Aggregated? * CISA: Aggregates signatures. * Key Aggregation: Aggregates public keys. 2. What the Verifier Needs * CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature. * Key Aggregation: The verifier only needs the single aggregated public key and one message. 3. When It Happens * CISA: Used during transaction signing, when inputs are being combined into a transaction. * MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control. So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs! --- **Two Flavors of CISA: Half-Agg and Full-Agg** CISA comes in two modes: * Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.) * Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later. Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg. --- **Half Signature Aggregation (Half-Agg) Explained** **How It Works** Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process: 1. Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers. 2. Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature. A Schnorr signature has two parts: * R: A random point (32 bytes). * s: A scalar value (32 bytes). In Half-Agg: * The R values from each signature are kept separate (one per input). * The s values from all signatures are combined into a single s value. **Why It Saves Space (~50%)** Let’s break down the size savings with some math: Before Aggregation: * Each Schnorr signature = 64 bytes (32 for R + 32 for s). * For n inputs: n × 64 bytes. After Half-Agg: * Keep n R values (32 bytes each) = 32 × n bytes. * Combine all s values into one = 32 bytes. * Total size: 32 × n + 32 bytes. Comparison: * Original: 64n bytes. * Half-Agg: 32n + 32 bytes. * For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings! **Real-World Impact:** Based on recent Bitcoin usage, Half-Agg could save: * ~19.3% in space (reducing transaction size). * ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA. --- **Applications of Half-Agg** Half-Agg isn’t just a cool idea—it has practical uses: 1. Transaction-wide Aggregation * Combine all signatures within a single transaction. * Result: Smaller transactions, lower fees. 2. Block-wide Aggregation * Combine signatures across all transactions in a Bitcoin block. * Result: Even bigger space savings at the blockchain level. 3. Off-chain Protocols / P2P * Use Half-Agg in systems like Lightning Network gossip messages. * Benefit: Efficiency without needing miners or a Bitcoin soft fork. --- **Challenges with Half-Agg** While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level: 1. Breaking Adaptor Signatures * Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges. * Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on. 2. Impact on Reorg Recovery * In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed. * If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery. These challenges mean Half-Agg needs careful design, especially for block-wide use. --- **Wrapping Up** CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning. But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future! @ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la [guía de MiniBolt](https://minbolt.info/). Esto tiene una **razón**, por supuesto una **solución**, además de una **conclusión**. Sin entrar en demasiados detalles: ## La razón El **bloqueo a Cloudflare**, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una [orden judicial](https://www.poderjudicial.es/search/AN/openDocument/3c85bed480cbb1daa0a8778d75e36f0d/20221004) emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización. Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo [ECH](https://developers.cloudflare.com/ssl/edge-certificates/ech) (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar **bloqueos basados en dominios**, lo que les obliga a recurrir a **bloqueos más amplios por IP o rangos de IP** para cumplir con la orden judicial. Esta práctica tiene **consecuencias graves**, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un **perjuicio para terceros**, **restringiendo el acceso a muchos dominios legítimos** que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la [web de MiniBolt](https://minibolt.minibolt.info) y su dominio `minibolt.info`, los cuales **utilizan Cloudflare como proxy** para aprovechar las medidas de **seguridad, privacidad, optimización y servicios** adicionales que la plataforma ofrece de forma gratuita. Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.  ## La solución Obviamente, **MiniBolt no dejará de usar Cloudflare** como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para **evitar esta restricción** y poder acceder: **~>** Utiliza **una VPN**: Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - [IVPN](https://www.ivpn.net/es/) - [Mullvad VPN](https://mullvad.net/es/vpn) - [Proton VPN](https://protonvpn.com/es-es) (**gratis**) - [Obscura VPN](https://obscura.net/) (**solo para macOS**) - [Cloudfare WARP](https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/download-warp/) (**gratis**) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a [esta](https://minibolt.minibolt.info/system/system/privacy#example-from-firefox) para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la [guía de MiniBolt](https://minibolt.minibolt.info/) sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info [AQUÍ](https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958).  **~>** [**Proxifica tu navegador para usar la red de Tor**](https://minibolt.minibolt.info/system/system/privacy#ssh-remote-access-through-tor), o utiliza el [**navegador oficial de Tor**](https://www.torproject.org/es/download/) (recomendado).  ## La conclusión Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la [Declaración de Independencia del Ciberespacio](https://es.wikisource.org/wiki/Declaraci%C3%B3n_de_independencia_del_ciberespacio) que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad. Es momento de actuar y estar preparados: debemos **impulsar el desarrollo y la difusión** de las **herramientas anticensura** que tenemos a nuestro alcance, protegiendo así la **libertad digital** y asegurando un acceso equitativo a la información para todos Este compromiso es uno de los **pilares fundamentales de MiniBolt,** lo que convierte este desafío en una oportunidad para poner a prueba las **soluciones anticensura** [ya disponibles](https://minibolt.minibolt.info/bonus-guides/system/tor-services), así como **las que están en camino**. ¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!  --- Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la [guía de MiniBolt](https://minbolt.info/). Esto tiene una **razón**, por supuesto una **solución**, además de una **conclusión**. Sin entrar en demasiados detalles: ## La razón El **bloqueo a Cloudflare**, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una [orden judicial](https://www.poderjudicial.es/search/AN/openDocument/3c85bed480cbb1daa0a8778d75e36f0d/20221004) emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización. Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo [ECH](https://developers.cloudflare.com/ssl/edge-certificates/ech) (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar **bloqueos basados en dominios**, lo que les obliga a recurrir a **bloqueos más amplios por IP o rangos de IP** para cumplir con la orden judicial. Esta práctica tiene **consecuencias graves**, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un **perjuicio para terceros**, **restringiendo el acceso a muchos dominios legítimos** que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la [web de MiniBolt](https://minibolt.minibolt.info) y su dominio `minibolt.info`, los cuales **utilizan Cloudflare como proxy** para aprovechar las medidas de **seguridad, privacidad, optimización y servicios** adicionales que la plataforma ofrece de forma gratuita. Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.  ## La solución Obviamente, **MiniBolt no dejará de usar Cloudflare** como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para **evitar esta restricción** y poder acceder: **~>** Utiliza **una VPN**: Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - [IVPN](https://www.ivpn.net/es/) - [Mullvad VPN](https://mullvad.net/es/vpn) - [Proton VPN](https://protonvpn.com/es-es) (**gratis**) - [Obscura VPN](https://obscura.net/) (**solo para macOS**) - [Cloudfare WARP](https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/download-warp/) (**gratis**) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a [esta](https://minibolt.minibolt.info/system/system/privacy#example-from-firefox) para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la [guía de MiniBolt](https://minibolt.minibolt.info/) sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info [AQUÍ](https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958).  **~>** [**Proxifica tu navegador para usar la red de Tor**](https://minibolt.minibolt.info/system/system/privacy#ssh-remote-access-through-tor), o utiliza el [**navegador oficial de Tor**](https://www.torproject.org/es/download/) (recomendado).  ## La conclusión Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la [Declaración de Independencia del Ciberespacio](https://es.wikisource.org/wiki/Declaraci%C3%B3n_de_independencia_del_ciberespacio) que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad. Es momento de actuar y estar preparados: debemos **impulsar el desarrollo y la difusión** de las **herramientas anticensura** que tenemos a nuestro alcance, protegiendo así la **libertad digital** y asegurando un acceso equitativo a la información para todos Este compromiso es uno de los **pilares fundamentales de MiniBolt,** lo que convierte este desafío en una oportunidad para poner a prueba las **soluciones anticensura** [ya disponibles](https://minibolt.minibolt.info/bonus-guides/system/tor-services), así como **las que están en camino**. ¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!  --- Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007 @ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds. Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/ 1. Download Tor Browser First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/ 2. Sign Up Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha. 3. Account information Once you are done signing up an Account information page will pop up. **MAKE SURE YOU SAVE THIS!!!** It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck. 4. Install an Email Client You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird. a. Download Thunderbird email client b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the **Configure Manually**option will appear below. Click that. 5. Configure Incoming (POP3) Server Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password). 6. Configure Outgoing (SMTP) Server Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password). 7. Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up. 8. Configure Proxy a. Click the **gear icon** on the bottom left for settings. Scroll all the way down to **Network & Disk Space**. Click the **settings button** next to **Connection. Configure how Thunderbird connects to the internet**. b. Select **Manual Proxy Configuration**. For **SOCKS Host** enter **127.0.0.1** and enter port **9050**. (if you are running this through a VM the port may be different) c. Now check the box for **SOCKS5** and then **Proxy DNS when using SOCKS5** down at the bottom. Click OK 9. Check Email For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on **inbox** and then the **little cloud icon** with the down arrow to check mail. 10. Security Exception Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup **Add Security Exception** will appear. Click **Confirm Security Exception**. You are done. Enjoy your new private email service. **REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.**
@ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds. Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/ 1. Download Tor Browser First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/ 2. Sign Up Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha. 3. Account information Once you are done signing up an Account information page will pop up. **MAKE SURE YOU SAVE THIS!!!** It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck. 4. Install an Email Client You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird. a. Download Thunderbird email client b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the **Configure Manually**option will appear below. Click that. 5. Configure Incoming (POP3) Server Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password). 6. Configure Outgoing (SMTP) Server Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password). 7. Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up. 8. Configure Proxy a. Click the **gear icon** on the bottom left for settings. Scroll all the way down to **Network & Disk Space**. Click the **settings button** next to **Connection. Configure how Thunderbird connects to the internet**. b. Select **Manual Proxy Configuration**. For **SOCKS Host** enter **127.0.0.1** and enter port **9050**. (if you are running this through a VM the port may be different) c. Now check the box for **SOCKS5** and then **Proxy DNS when using SOCKS5** down at the bottom. Click OK 9. Check Email For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on **inbox** and then the **little cloud icon** with the down arrow to check mail. 10. Security Exception Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup **Add Security Exception** will appear. Click **Confirm Security Exception**. You are done. Enjoy your new private email service. **REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.** @ 21335073:a244b1ad
2025-03-18 20:47:50**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
@ 21335073:a244b1ad
2025-03-18 20:47:50**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation. @ 21335073:a244b1ad
2025-03-18 14:43:08**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
@ 21335073:a244b1ad
2025-03-18 14:43:08**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation. @ da0b9bc3:4e30a4a9
2025-03-29 06:49:22Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/928470
@ da0b9bc3:4e30a4a9
2025-03-29 06:49:22Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/928470 @ a07fae46:7d83df92
2025-03-18 12:31:40if the JFK documents come out and are nothing but old hat, it will be disappointing. but if they contain revelations, then they are an unalloyed good. unprecedented and extraordinary; worthy of praise and admiration. they murdered the president in broad daylight and kept 80,000 related documents secret for 60 years. the apparatus that did that and got away with it, is 100+ years in the making. the magic bullet was just the starting pistol of a new *era*; a *level up* in an [old game](https://archive.org/details/TragedyAndHope_501/page/n5/mode/2up?q=feudalist+fashion). it won't be dismantled and your republic delivered back with a bow in *2 months*. have a little humility and a little gratitude. cynicism is easy. it's peak mid-wittery. yeah no shit everything is corrupt and everyone's likely captured by [AIPAC](https://books.google.com/books/publisher/content?id=gKVKDwAAQBAJ&pg=PT68&img=1&zoom=3&hl=en&bul=1&sig=ACfU3U2pagVXTYdJOKxkAwmmFQpuSnoS5g&w=1280) or something beyond. YOU THINK AIPAC is the [ALL SEEING EYE](https://archive.org/details/the-all-seeing-eye-vol-1-5-manly-p.-hall-may-1923-sept-1931)? you can keep going, if you want to, but have some awareness and appreciation for where we are and what it took to get here. the first 'you are fake news' was also a shot heard 'round the world and you are riding high on it's [Infrasound](https://en.wikipedia.org/wiki/Infrasound) wave, still reverberating; unappreciative of the profound delta in public awareness and understanding, and rate of change, that has occurred since that moment, in [2017](https://www.youtube.com/watch?v=Vqpzk-qGxMU). think about where we were back then, especially with corporate capture of the narrative. trump's bullheaded behavior, if only ego-driven, *is* what broke the spell. an *actual* moment of savage bravery is what allows for your current jaded affectation. black pilled is boring. it's intellectually lazy. it is low-resolution-thinking, no better than progressives who explain the myriad ills of the world through 'racism'. normalcy bias works both ways. i'm not grading you on a curve that includes NPCs. i'm grading you against those of us with a mind, on up. do better. the best Webb-style doomer argument is essentially 'the mouse trap needs a piece of cheese in order to work'. ok, but it doesn't need 3 pieces of cheese, or 5. was FreeRoss the piece of cheese? was the SBR the cheese? real bitcoiners know how dumb the 'sbr is an attempt to takeover btc' narrative is, so extrapolate from that. what about withdrawal from the WHO? freeze and review of USAID et al? how many pieces of cheese before we realize it's not a trap? it's just a messy endeavor. Good morning. #jfkFiles #nostrOnly
@ a07fae46:7d83df92
2025-03-18 12:31:40if the JFK documents come out and are nothing but old hat, it will be disappointing. but if they contain revelations, then they are an unalloyed good. unprecedented and extraordinary; worthy of praise and admiration. they murdered the president in broad daylight and kept 80,000 related documents secret for 60 years. the apparatus that did that and got away with it, is 100+ years in the making. the magic bullet was just the starting pistol of a new *era*; a *level up* in an [old game](https://archive.org/details/TragedyAndHope_501/page/n5/mode/2up?q=feudalist+fashion). it won't be dismantled and your republic delivered back with a bow in *2 months*. have a little humility and a little gratitude. cynicism is easy. it's peak mid-wittery. yeah no shit everything is corrupt and everyone's likely captured by [AIPAC](https://books.google.com/books/publisher/content?id=gKVKDwAAQBAJ&pg=PT68&img=1&zoom=3&hl=en&bul=1&sig=ACfU3U2pagVXTYdJOKxkAwmmFQpuSnoS5g&w=1280) or something beyond. YOU THINK AIPAC is the [ALL SEEING EYE](https://archive.org/details/the-all-seeing-eye-vol-1-5-manly-p.-hall-may-1923-sept-1931)? you can keep going, if you want to, but have some awareness and appreciation for where we are and what it took to get here. the first 'you are fake news' was also a shot heard 'round the world and you are riding high on it's [Infrasound](https://en.wikipedia.org/wiki/Infrasound) wave, still reverberating; unappreciative of the profound delta in public awareness and understanding, and rate of change, that has occurred since that moment, in [2017](https://www.youtube.com/watch?v=Vqpzk-qGxMU). think about where we were back then, especially with corporate capture of the narrative. trump's bullheaded behavior, if only ego-driven, *is* what broke the spell. an *actual* moment of savage bravery is what allows for your current jaded affectation. black pilled is boring. it's intellectually lazy. it is low-resolution-thinking, no better than progressives who explain the myriad ills of the world through 'racism'. normalcy bias works both ways. i'm not grading you on a curve that includes NPCs. i'm grading you against those of us with a mind, on up. do better. the best Webb-style doomer argument is essentially 'the mouse trap needs a piece of cheese in order to work'. ok, but it doesn't need 3 pieces of cheese, or 5. was FreeRoss the piece of cheese? was the SBR the cheese? real bitcoiners know how dumb the 'sbr is an attempt to takeover btc' narrative is, so extrapolate from that. what about withdrawal from the WHO? freeze and review of USAID et al? how many pieces of cheese before we realize it's not a trap? it's just a messy endeavor. Good morning. #jfkFiles #nostrOnly @ dfbbf851:ba4542b5
2025-03-29 06:51:21ในยุคดิจิทัลที่การสื่อสารมีบทบาทสำคัญต่อชีวิตประจำวัน เทคโนโลยี **Cell Broadcast** ได้กลายเป็นหนึ่งในเครื่องมือที่ทรงพลังสำหรับการแจ้งเตือนฉุกเฉิน ไม่ว่าจะเป็นภัยพิบัติหรือเหตุการณ์สำคัญที่ต้องแจ้งให้ประชาชนทราบอย่างทันท่วงที ⏳💡 --- ### 📌 **Cell Broadcast คืออะไร ?** **Cell Broadcast (CB)** เป็นเทคโนโลยีที่ใช้ส่งข้อความกระจายสัญญาณผ่านเครือข่ายโทรศัพท์มือถือ 🏗📶 โดยแตกต่างจาก **SMS** ตรงที่สามารถส่งข้อความถึงผู้ใช้จำนวนมากได้พร้อมกัน **โดยไม่ต้องทราบหมายเลขโทรศัพท์** ของผู้รับ 📲💨 ข้อความ CB สามารถส่งถึงอุปกรณ์ที่รองรับในเครือข่ายมือถือที่เปิดใช้งานอยู่ภายในช่วงเวลาสั้น ๆ ⏱ และ **ไม่ทำให้เครือข่ายล่ม** --- ### ✨ **ข้อดีของ Cell Broadcast** ✨ ✅ **ส่งข้อความรวดเร็ว** – แจ้งเตือนได้ภายในไม่กี่วินาที แม้ในกรณีฉุกเฉิน ⚡🚀 ✅ **ไม่ต้องใช้หมายเลขโทรศัพท์** – กระจายสัญญาณไปยังอุปกรณ์ทุกเครื่องที่อยู่ในพื้นที่เป้าหมายได้โดยตรง 📡 ✅ **รองรับหลายภาษา** – สามารถตั้งค่าการแจ้งเตือนให้เหมาะสมกับประชากรในแต่ละพื้นที่ 🌍🗣 ✅ **ไม่ทำให้เครือข่ายหนาแน่น** – ต่างจาก SMS หรือการโทรจำนวนมากที่อาจทำให้เครือข่ายล่ม 📵❌ ✅ **ทำงานได้แม้ไม่มีอินเทอร์เน็ต** – สามารถแจ้งเตือนในกรณีที่โซเชียลมีเดียหรืออินเทอร์เน็ตใช้งานไม่ได้ 🌐🚫 --- ### 🌍 **การใช้งาน Cell Broadcast ทั่วโลก** 🔹 **สหรัฐอเมริกา** – **ใช้ระบบ Wireless Emergency Alerts (WEA)** เพื่อแจ้งเตือนเหตุการณ์ฉุกเฉิน เช่น พายุเฮอริเคน 🌀🌪 🔹 **ญี่ปุ่น** – ใช้ระบบ **Earthquake Early Warning (EEW)** เพื่อแจ้งเตือนแผ่นดินไหวล่วงหน้า ⛩🌏 🔹 **สหภาพยุโรป** – มีนโยบายให้ประเทศสมาชิกใช้ **Public Warning System** ผ่าน Cell Broadcast 📢🏛 --- ### 🤔 **ทำไมประเทศที่ยังไม่มีระบบนี้ควรนำมาใช้ ?** หลายประเทศ รวมถึง **ประเทศไทย** ยังไม่มีการใช้ Cell Broadcast อย่างแพร่หลาย ทั้งที่เป็นเทคโนโลยีที่สามารถช่วยชีวิตผู้คนได้อย่างมหาศาล 🚑 หากเกิดภัยพิบัติ เช่น **น้ำท่วม แผ่นดินไหว สึนามิ หรือไฟป่า** 🔥🌊 Cell Broadcast สามารถส่งการแจ้งเตือนไปยังทุกคนในพื้นที่เสี่ยงได้ทันที ลดความสูญเสียและเพิ่มโอกาสรอดชีวิตได้มากขึ้น 🔸 **ความแม่นยำสูง** – สามารถส่งแจ้งเตือนไปยังพื้นที่ที่ได้รับผลกระทบโดยตรง ทำให้ประชาชนสามารถเตรียมตัวรับมือได้ดีกว่า 🔸 **ไม่มีปัญหาความล่าช้า** – ต่างจากการแจ้งเตือนผ่าน SMS หรือโซเชียลมีเดียที่อาจล่าช้าหรือไม่ได้รับข้อความเลยหากเครือข่ายล่ม 🔸 **เป็นมาตรฐานสากล** – หลายประเทศพัฒนาแล้วมีระบบนี้ใช้งานอย่างมีประสิทธิภาพ ประเทศที่ยังไม่มีควรนำมาใช้เพื่อให้สามารถจัดการภัยพิบัติได้อย่างมีประสิทธิภาพ 🔸 **ประหยัดต้นทุนในระยะยาว** – ลดความเสียหายทางเศรษฐกิจจากภัยพิบัติ เพราะประชาชนได้รับการแจ้งเตือนล่วงหน้า ทำให้สามารถอพยพหรือป้องกันความเสียหายได้ --- ### 🔮 **อนาคตของ Cell Broadcast** **ในอนาคต Cell Broadcast** อาจถูกนำมาใช้ร่วมกับ **ปัญญาประดิษฐ์ (AI)** 🤖 และ **Internet of Things (IoT)** 🌐 เพื่อเพิ่มความแม่นยำและปรับแต่งการแจ้งเตือนได้ดียิ่งขึ้น 🎯💡 --- ### 📌 **ปล.** **Cell Broadcast เป็นเทคโนโลยีแจ้งเตือนที่ทรงพลังและมีบทบาทสำคัญในการช่วยชีวิตผู้คน** 🚑 ด้วยความสามารถในการส่งข้อความได้อย่างรวดเร็ว ครอบคลุมพื้นที่กว้าง และไม่ต้องพึ่งพาอินเทอร์เน็ต จึงเป็นหนึ่งในเครื่องมือสำคัญสำหรับการบริหารจัดการภัยพิบัติในปัจจุบันและอนาคต 🔥 --- #CellBroadcast #แจ้งเตือนภัย #เทคโนโลยีสื่อสาร #ภัยพิบัติ #เครือข่ายมือถือ #การสื่อสารฉุกเฉิน #เตือนภัยล่วงหน้า
@ dfbbf851:ba4542b5
2025-03-29 06:51:21ในยุคดิจิทัลที่การสื่อสารมีบทบาทสำคัญต่อชีวิตประจำวัน เทคโนโลยี **Cell Broadcast** ได้กลายเป็นหนึ่งในเครื่องมือที่ทรงพลังสำหรับการแจ้งเตือนฉุกเฉิน ไม่ว่าจะเป็นภัยพิบัติหรือเหตุการณ์สำคัญที่ต้องแจ้งให้ประชาชนทราบอย่างทันท่วงที ⏳💡 --- ### 📌 **Cell Broadcast คืออะไร ?** **Cell Broadcast (CB)** เป็นเทคโนโลยีที่ใช้ส่งข้อความกระจายสัญญาณผ่านเครือข่ายโทรศัพท์มือถือ 🏗📶 โดยแตกต่างจาก **SMS** ตรงที่สามารถส่งข้อความถึงผู้ใช้จำนวนมากได้พร้อมกัน **โดยไม่ต้องทราบหมายเลขโทรศัพท์** ของผู้รับ 📲💨 ข้อความ CB สามารถส่งถึงอุปกรณ์ที่รองรับในเครือข่ายมือถือที่เปิดใช้งานอยู่ภายในช่วงเวลาสั้น ๆ ⏱ และ **ไม่ทำให้เครือข่ายล่ม** --- ### ✨ **ข้อดีของ Cell Broadcast** ✨ ✅ **ส่งข้อความรวดเร็ว** – แจ้งเตือนได้ภายในไม่กี่วินาที แม้ในกรณีฉุกเฉิน ⚡🚀 ✅ **ไม่ต้องใช้หมายเลขโทรศัพท์** – กระจายสัญญาณไปยังอุปกรณ์ทุกเครื่องที่อยู่ในพื้นที่เป้าหมายได้โดยตรง 📡 ✅ **รองรับหลายภาษา** – สามารถตั้งค่าการแจ้งเตือนให้เหมาะสมกับประชากรในแต่ละพื้นที่ 🌍🗣 ✅ **ไม่ทำให้เครือข่ายหนาแน่น** – ต่างจาก SMS หรือการโทรจำนวนมากที่อาจทำให้เครือข่ายล่ม 📵❌ ✅ **ทำงานได้แม้ไม่มีอินเทอร์เน็ต** – สามารถแจ้งเตือนในกรณีที่โซเชียลมีเดียหรืออินเทอร์เน็ตใช้งานไม่ได้ 🌐🚫 --- ### 🌍 **การใช้งาน Cell Broadcast ทั่วโลก** 🔹 **สหรัฐอเมริกา** – **ใช้ระบบ Wireless Emergency Alerts (WEA)** เพื่อแจ้งเตือนเหตุการณ์ฉุกเฉิน เช่น พายุเฮอริเคน 🌀🌪 🔹 **ญี่ปุ่น** – ใช้ระบบ **Earthquake Early Warning (EEW)** เพื่อแจ้งเตือนแผ่นดินไหวล่วงหน้า ⛩🌏 🔹 **สหภาพยุโรป** – มีนโยบายให้ประเทศสมาชิกใช้ **Public Warning System** ผ่าน Cell Broadcast 📢🏛 --- ### 🤔 **ทำไมประเทศที่ยังไม่มีระบบนี้ควรนำมาใช้ ?** หลายประเทศ รวมถึง **ประเทศไทย** ยังไม่มีการใช้ Cell Broadcast อย่างแพร่หลาย ทั้งที่เป็นเทคโนโลยีที่สามารถช่วยชีวิตผู้คนได้อย่างมหาศาล 🚑 หากเกิดภัยพิบัติ เช่น **น้ำท่วม แผ่นดินไหว สึนามิ หรือไฟป่า** 🔥🌊 Cell Broadcast สามารถส่งการแจ้งเตือนไปยังทุกคนในพื้นที่เสี่ยงได้ทันที ลดความสูญเสียและเพิ่มโอกาสรอดชีวิตได้มากขึ้น 🔸 **ความแม่นยำสูง** – สามารถส่งแจ้งเตือนไปยังพื้นที่ที่ได้รับผลกระทบโดยตรง ทำให้ประชาชนสามารถเตรียมตัวรับมือได้ดีกว่า 🔸 **ไม่มีปัญหาความล่าช้า** – ต่างจากการแจ้งเตือนผ่าน SMS หรือโซเชียลมีเดียที่อาจล่าช้าหรือไม่ได้รับข้อความเลยหากเครือข่ายล่ม 🔸 **เป็นมาตรฐานสากล** – หลายประเทศพัฒนาแล้วมีระบบนี้ใช้งานอย่างมีประสิทธิภาพ ประเทศที่ยังไม่มีควรนำมาใช้เพื่อให้สามารถจัดการภัยพิบัติได้อย่างมีประสิทธิภาพ 🔸 **ประหยัดต้นทุนในระยะยาว** – ลดความเสียหายทางเศรษฐกิจจากภัยพิบัติ เพราะประชาชนได้รับการแจ้งเตือนล่วงหน้า ทำให้สามารถอพยพหรือป้องกันความเสียหายได้ --- ### 🔮 **อนาคตของ Cell Broadcast** **ในอนาคต Cell Broadcast** อาจถูกนำมาใช้ร่วมกับ **ปัญญาประดิษฐ์ (AI)** 🤖 และ **Internet of Things (IoT)** 🌐 เพื่อเพิ่มความแม่นยำและปรับแต่งการแจ้งเตือนได้ดียิ่งขึ้น 🎯💡 --- ### 📌 **ปล.** **Cell Broadcast เป็นเทคโนโลยีแจ้งเตือนที่ทรงพลังและมีบทบาทสำคัญในการช่วยชีวิตผู้คน** 🚑 ด้วยความสามารถในการส่งข้อความได้อย่างรวดเร็ว ครอบคลุมพื้นที่กว้าง และไม่ต้องพึ่งพาอินเทอร์เน็ต จึงเป็นหนึ่งในเครื่องมือสำคัญสำหรับการบริหารจัดการภัยพิบัติในปัจจุบันและอนาคต 🔥 --- #CellBroadcast #แจ้งเตือนภัย #เทคโนโลยีสื่อสาร #ภัยพิบัติ #เครือข่ายมือถือ #การสื่อสารฉุกเฉิน #เตือนภัยล่วงหน้า @ bc52210b:20bfc6de
2025-03-14 20:39:20When writing safety critical code, every arithmetic operation carries the potential for catastrophic failure—whether that’s a plane crash in aerospace engineering or a massive financial loss in a smart contract. The stakes are incredibly high, and errors are not just bugs; they’re disasters waiting to happen. Smart contract developers need to shift their mindset: less like web developers, who might prioritize speed and iteration, and more like aerospace engineers, where precision, caution, and meticulous attention to detail are non-negotiable. In practice, this means treating every line of code as a critical component, adopting rigorous testing, and anticipating worst-case scenarios—just as an aerospace engineer would ensure a system can withstand extreme conditions. Safety critical code demands aerospace-level precision, and smart contract developers must rise to that standard to protect against the severe consequences of failure.
@ bc52210b:20bfc6de
2025-03-14 20:39:20When writing safety critical code, every arithmetic operation carries the potential for catastrophic failure—whether that’s a plane crash in aerospace engineering or a massive financial loss in a smart contract. The stakes are incredibly high, and errors are not just bugs; they’re disasters waiting to happen. Smart contract developers need to shift their mindset: less like web developers, who might prioritize speed and iteration, and more like aerospace engineers, where precision, caution, and meticulous attention to detail are non-negotiable. In practice, this means treating every line of code as a critical component, adopting rigorous testing, and anticipating worst-case scenarios—just as an aerospace engineer would ensure a system can withstand extreme conditions. Safety critical code demands aerospace-level precision, and smart contract developers must rise to that standard to protect against the severe consequences of failure. @ df173277:4ec96708
2025-02-07 00:41:34## **Building Our Confidential Backend on Secure Enclaves** With our newly released [private and confidential **Maple AI**](https://trymaple.ai/?ref=blog.opensecret.cloud) and the open sourcing of our [**OpenSecret** platform](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud) code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging **secure enclaves**. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with. ## **Auth and Databases Today** As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that: 1. Need to register users (authentication). 2. Collect and process user data in business-specific ways, often on the backend. Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes). ## **"Just Trust Us" Isn't Good Enough** In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data. Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility. The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a **strong, verifiable** guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services. ## **Current Attempts at Securing Data** Current User Experience of E2EE Apps While properly securing data is not easy, it isn't to say that no one is trying. Some solutions use **end-to-end encryption** (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its **limitations**: 1. **Key Management Nightmares**: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side. 2. **Feature Limitations**: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data. 3. **Platform Silos**: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility. Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider. ## **Secure Enclaves** ### **The Hybrid Approach** Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden. App Service Running Inside Secure Enclave ### **High-Level Goal of Enclaves** Enclaves, also known under the broader umbrella of **confidential computing**, aim to:\ • **Lock down data** so that only authorized code within the enclave can process the original plaintext data.\ • **Deny external inspection** by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\ • **Prove** to external users or services that an enclave is running unmodified, approved code (this is where **remote attestation** comes in). ### **Different Secure Enclave Solutions** [**AMD SEV**](https://www.amd.com/en/developer/sev.html?ref=blog.opensecret.cloud) **(Secure Encrypted Virtualization)** encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds. [**Intel TDX**](https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/overview.html?ref=blog.opensecret.cloud) **(Trust Domain Extensions)** shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications. [**Apple Secure Enclave and Private Compute**](https://security.apple.com/blog/private-cloud-compute/?ref=blog.opensecret.cloud) is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers. [**AWS Nitro Enclaves**](https://docs.aws.amazon.com/enclaves/latest/user/nitro-enclave.html?ref=blog.opensecret.cloud) carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised. [**NVIDIA GPU TEEs**](https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/?ref=blog.opensecret.cloud) **(Hopper H100 and Blackwell)** extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees. ### **Key Benefits** One major advantage of enclaves is their ability to **keep memory completely off-limits** to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data. Another key benefit centers on cryptographic keys that are **never exposed outside the enclave**. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware. Enclaves can also offer the power of **remote attestation**, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks. Beyond that, **reproducible builds** can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, [our NixOS-based solution](https://github.com/OpenSecretCloud/opensecret/blob/master/flake.nix?ref=blog.opensecret.cloud)). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist. It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the **hardware vendor** (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing. ## **How We Use Secure Enclaves** Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads. ### **Our Stack: AWS Nitro + Nvidia TEE** • **AWS Nitro Enclaves for the backend**: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave. • **Nvidia Trusted Execution for AI**: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model **without** exposing it in plaintext to the GPU providers or us as the operator. [Edgeless Systems](https://www.edgeless.systems/?ref=blog.opensecret.cloud) is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with. ### **End-to-End Encryption from Client to Enclave** Client-side Enclave Attestation from Maple AI Before login or data upload, the user/client verifies the **enclave attestation** from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on [Maple AI's attestation page](https://trymaple.ai/proof?ref=blog.opensecret.cloud). Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session. From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request. ### **In-Enclave Operations** At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form. User Auth Methods running inside Enclave A primary example is **user authentication**. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information. Main Enclave Operations in OpenSecret The same principle applies to **private key management**. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user. Realtime Encrypted Data Sync on Multiple Devices Another crucial aspect is **data encryption at rest**. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext. Confidential AI Workloads Finally, **confidential AI workloads** build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation. ### **Reproducible Builds + Verification** Client verifies enclave attestation document We build our enclaves on **NixOS** with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs. Our code is fully open source ([GitHub: OpenSecret](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud)), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation. ## **Putting It All Together** OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute By weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes. This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats. Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure. OpenSecret aims to be a **full developer platform** with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use. Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system. The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad. ## **Things to Come** We're excited to build on our enclaved approach. Here's what's on our roadmap: • **Production Launch**: We're using this in production now with [Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud) and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\ • **Multi-Tenant Support**: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\ • **Self-Serve Frontend**: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\ • **External Key Signing Options**: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\ • **Confidential Computing as a Service**: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\ • **Additional SDKs**: In addition to our [JavaScript client-side SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud), we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\ • **AI API Proxy with Attestation/Encryption**: We already provide an easy way to [access a Private AI through Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud), but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API. ## **Getting Started** Ready to see enclaves in action? Here's how to dive in:\ 1. **Run OpenSecret**: Check out our open-source repository at [OpenSecret on GitHub](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud). You can run your own enclaved environment or try it out locally with Docker.\ 2. **Review Our SDK**: Our [JavaScript client SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud) makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\ 3. **Play with Maple AI**: Try out [Maple AI](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/) as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\ 4. **Developer Preview**: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further. ## **Conclusion** By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, **OpenSecret** provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that **no one**, not even us or the cloud provider, can snoop on data in use. **We believe** this is the future of trustworthy computing in the cloud. And it's **all open source**, so you don't have to just take our word for it: you can see and verify everything yourself. Do you have questions, feedback, or a use case you'd like to test out? Come join us on [GitHub](https://github.com/OpenSecretCloud?ref=blog.opensecret.cloud), [Discord](https://discord.gg/ch2gjZAMGy?ref=blog.opensecret.cloud), or email us for a developer preview. We can't wait to see what you build! *Thank you for reading, and welcome to the era of enclaved computing.*
@ df173277:4ec96708
2025-02-07 00:41:34## **Building Our Confidential Backend on Secure Enclaves** With our newly released [private and confidential **Maple AI**](https://trymaple.ai/?ref=blog.opensecret.cloud) and the open sourcing of our [**OpenSecret** platform](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud) code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging **secure enclaves**. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with. ## **Auth and Databases Today** As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that: 1. Need to register users (authentication). 2. Collect and process user data in business-specific ways, often on the backend. Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes). ## **"Just Trust Us" Isn't Good Enough** In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data. Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility. The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a **strong, verifiable** guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services. ## **Current Attempts at Securing Data** Current User Experience of E2EE Apps While properly securing data is not easy, it isn't to say that no one is trying. Some solutions use **end-to-end encryption** (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its **limitations**: 1. **Key Management Nightmares**: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side. 2. **Feature Limitations**: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data. 3. **Platform Silos**: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility. Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider. ## **Secure Enclaves** ### **The Hybrid Approach** Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden. App Service Running Inside Secure Enclave ### **High-Level Goal of Enclaves** Enclaves, also known under the broader umbrella of **confidential computing**, aim to:\ • **Lock down data** so that only authorized code within the enclave can process the original plaintext data.\ • **Deny external inspection** by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\ • **Prove** to external users or services that an enclave is running unmodified, approved code (this is where **remote attestation** comes in). ### **Different Secure Enclave Solutions** [**AMD SEV**](https://www.amd.com/en/developer/sev.html?ref=blog.opensecret.cloud) **(Secure Encrypted Virtualization)** encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds. [**Intel TDX**](https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/overview.html?ref=blog.opensecret.cloud) **(Trust Domain Extensions)** shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications. [**Apple Secure Enclave and Private Compute**](https://security.apple.com/blog/private-cloud-compute/?ref=blog.opensecret.cloud) is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers. [**AWS Nitro Enclaves**](https://docs.aws.amazon.com/enclaves/latest/user/nitro-enclave.html?ref=blog.opensecret.cloud) carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised. [**NVIDIA GPU TEEs**](https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/?ref=blog.opensecret.cloud) **(Hopper H100 and Blackwell)** extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees. ### **Key Benefits** One major advantage of enclaves is their ability to **keep memory completely off-limits** to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data. Another key benefit centers on cryptographic keys that are **never exposed outside the enclave**. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware. Enclaves can also offer the power of **remote attestation**, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks. Beyond that, **reproducible builds** can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, [our NixOS-based solution](https://github.com/OpenSecretCloud/opensecret/blob/master/flake.nix?ref=blog.opensecret.cloud)). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist. It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the **hardware vendor** (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing. ## **How We Use Secure Enclaves** Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads. ### **Our Stack: AWS Nitro + Nvidia TEE** • **AWS Nitro Enclaves for the backend**: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave. • **Nvidia Trusted Execution for AI**: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model **without** exposing it in plaintext to the GPU providers or us as the operator. [Edgeless Systems](https://www.edgeless.systems/?ref=blog.opensecret.cloud) is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with. ### **End-to-End Encryption from Client to Enclave** Client-side Enclave Attestation from Maple AI Before login or data upload, the user/client verifies the **enclave attestation** from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on [Maple AI's attestation page](https://trymaple.ai/proof?ref=blog.opensecret.cloud). Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session. From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request. ### **In-Enclave Operations** At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form. User Auth Methods running inside Enclave A primary example is **user authentication**. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information. Main Enclave Operations in OpenSecret The same principle applies to **private key management**. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user. Realtime Encrypted Data Sync on Multiple Devices Another crucial aspect is **data encryption at rest**. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext. Confidential AI Workloads Finally, **confidential AI workloads** build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation. ### **Reproducible Builds + Verification** Client verifies enclave attestation document We build our enclaves on **NixOS** with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs. Our code is fully open source ([GitHub: OpenSecret](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud)), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation. ## **Putting It All Together** OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute By weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes. This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats. Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure. OpenSecret aims to be a **full developer platform** with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use. Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system. The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad. ## **Things to Come** We're excited to build on our enclaved approach. Here's what's on our roadmap: • **Production Launch**: We're using this in production now with [Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud) and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\ • **Multi-Tenant Support**: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\ • **Self-Serve Frontend**: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\ • **External Key Signing Options**: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\ • **Confidential Computing as a Service**: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\ • **Additional SDKs**: In addition to our [JavaScript client-side SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud), we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\ • **AI API Proxy with Attestation/Encryption**: We already provide an easy way to [access a Private AI through Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud), but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API. ## **Getting Started** Ready to see enclaves in action? Here's how to dive in:\ 1. **Run OpenSecret**: Check out our open-source repository at [OpenSecret on GitHub](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud). You can run your own enclaved environment or try it out locally with Docker.\ 2. **Review Our SDK**: Our [JavaScript client SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud) makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\ 3. **Play with Maple AI**: Try out [Maple AI](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/) as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\ 4. **Developer Preview**: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further. ## **Conclusion** By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, **OpenSecret** provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that **no one**, not even us or the cloud provider, can snoop on data in use. **We believe** this is the future of trustworthy computing in the cloud. And it's **all open source**, so you don't have to just take our word for it: you can see and verify everything yourself. Do you have questions, feedback, or a use case you'd like to test out? Come join us on [GitHub](https://github.com/OpenSecretCloud?ref=blog.opensecret.cloud), [Discord](https://discord.gg/ch2gjZAMGy?ref=blog.opensecret.cloud), or email us for a developer preview. We can't wait to see what you build! *Thank you for reading, and welcome to the era of enclaved computing.* @ df173277:4ec96708
2025-01-28 17:49:54> Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\ > [Start chatting for free.](https://trymaple.ai/) We are excited to announce that [Maple AI](https://trymaple.ai/), our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world. Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another. #### Why Secure and Private AI? In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a [recent report by Cisco](https://www.cisco.com/c/en/us/about/trust-center/data-privacy-benchmark-study.html#~key-findings). This practice poses significant risks to company security and intellectual property. Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services. At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local. #### How Does It Work? Our server code is [open source](https://github.com/OpenSecretCloud/opensecret), and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site. #### How Much Does It Cost? We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. [Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month)](https://trymaple.ai/pricing) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method. - Free: $0 - Starter: $5.99/month - Pro: $20/month Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy. Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. [Sign up now and start chatting privately with AI for free.](https://trymaple.ai/) Your secrets are safe in the open. #### Are You An App Developer? You can build an app like Maple. [OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more.](https://blog.opensecret.cloud/introducing-opensecret/) Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out [OpenSecret](https://opensecret.cloud/). <img src="https://blossom.primal.net/feb746d5e164e89f0d015646286b88237dce4158f8985e3caaf7e427cebde608.png"> Enjoy private AI Chat 🤘 <img src="https://blossom.primal.net/0594ec56e249de2754ea7dfc225a7ebd46bc298b5af168279ce71f17c2afada0.jpg">
@ df173277:4ec96708
2025-01-28 17:49:54> Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\ > [Start chatting for free.](https://trymaple.ai/) We are excited to announce that [Maple AI](https://trymaple.ai/), our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world. Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another. #### Why Secure and Private AI? In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a [recent report by Cisco](https://www.cisco.com/c/en/us/about/trust-center/data-privacy-benchmark-study.html#~key-findings). This practice poses significant risks to company security and intellectual property. Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services. At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local. #### How Does It Work? Our server code is [open source](https://github.com/OpenSecretCloud/opensecret), and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site. #### How Much Does It Cost? We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. [Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month)](https://trymaple.ai/pricing) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method. - Free: $0 - Starter: $5.99/month - Pro: $20/month Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy. Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. [Sign up now and start chatting privately with AI for free.](https://trymaple.ai/) Your secrets are safe in the open. #### Are You An App Developer? You can build an app like Maple. [OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more.](https://blog.opensecret.cloud/introducing-opensecret/) Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out [OpenSecret](https://opensecret.cloud/). <img src="https://blossom.primal.net/feb746d5e164e89f0d015646286b88237dce4158f8985e3caaf7e427cebde608.png"> Enjoy private AI Chat 🤘 <img src="https://blossom.primal.net/0594ec56e249de2754ea7dfc225a7ebd46bc298b5af168279ce71f17c2afada0.jpg"> @ df173277:4ec96708
2025-01-09 17:12:08> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ > [Join the waitlist to get early access.](https://trymaple.ai) We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI. Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations. #### Building a Private Foundation Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win. #### The Power of Encrypted AI Chat AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short. Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us. #### Technical Overview So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects: - **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data. - **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations. - **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised. - **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public. - **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased. #### Personal and Work Use Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe. #### Local v Cloud Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds. #### Why the Maple name? Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment. #### Join the Waitlist Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai) [](https://trymaple.ai/waitlist)
@ df173277:4ec96708
2025-01-09 17:12:08> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ > [Join the waitlist to get early access.](https://trymaple.ai) We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI. Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations. #### Building a Private Foundation Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win. #### The Power of Encrypted AI Chat AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short. Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us. #### Technical Overview So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects: - **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data. - **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations. - **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised. - **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public. - **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased. #### Personal and Work Use Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe. #### Local v Cloud Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds. #### Why the Maple name? Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment. #### Join the Waitlist Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai) [](https://trymaple.ai/waitlist) @ df173277:4ec96708
2025-01-09 17:02:52> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud) In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion. Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online? Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches? > Cryptography at scale is hard. #### The Cloud The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers. The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage. > Private key encryption needs a UX upgrade. ## Enter OpenSecret OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute. Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.  ### Private Key Management Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone. OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account. The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.  ### Encrypted Sync With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go. The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them. ### Private AI Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything. OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk. **Check out Maple AI**\ Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)  ### Confidential Compute Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave. It's the new version of that lock on your web browser. When you see it, you know you're secure.  #### **But do we want our secrets to be open?** OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable. On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data. > Don't trust, verify. ### **Join the Movement** We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud) Users and companies deserve better encryption and privacy.\ Together, let's make that a reality. [](https://opensecret.cloud)
@ df173277:4ec96708
2025-01-09 17:02:52> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud) In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion. Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online? Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches? > Cryptography at scale is hard. #### The Cloud The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers. The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage. > Private key encryption needs a UX upgrade. ## Enter OpenSecret OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute. Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.  ### Private Key Management Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone. OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account. The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.  ### Encrypted Sync With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go. The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them. ### Private AI Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything. OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk. **Check out Maple AI**\ Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)  ### Confidential Compute Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave. It's the new version of that lock on your web browser. When you see it, you know you're secure.  #### **But do we want our secrets to be open?** OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable. On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data. > Don't trust, verify. ### **Join the Movement** We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud) Users and companies deserve better encryption and privacy.\ Together, let's make that a reality. [](https://opensecret.cloud) @ bdf3f01a:d9c40970
2025-03-29 04:52:40## Abstract: This paper presents a rigorous and critical examination of the Winter Vigil of XLII.II at Sapelo, a pivotal rite within the Lowcountry Freehold that serves as both an initiation into communal responsibility and a symbolic enactment of the Compact’s moral tenets. This analysis interrogates the ritual’s structure, emphasizing its role in perpetuating a resilient sociocultural order amid external collapse. Through a multidisciplinary approach combining historiographical analysis, cultural anthropology, and sociocultural theory, this study elucidates the Vigil’s function as a mechanism for moral continuity, thereby situating it within the broader discourse of post-collapse societal stabilization. The implications of this study underscore the profound interconnectedness between ritual practice and the formation of resilient communal identities. ## Introduction: The Winter Vigil of XLII.II at Sapelo occupies a fundamental position in the cultural historiography of the Lowcountry Freehold. As contemporary scholars, it is imperative to approach this tradition not merely as an artifact of ritualistic antiquity but as a dynamic process of cultural preservation. The Freehold’s commitment to integrating tradition with pragmatism, especially through the stewardship of The Veil, constitutes a critical adaptive strategy that sustained sociopolitical coherence through epochs of external fragmentation. This study aims to critically examine the Vigil as both a symbolic and practical reinforcement of the Compact’s ethos, with particular attention to how this ritual facilitated intergenerational continuity of moral and social values, ultimately shaping the robust communal identity that defines contemporary Freehold society. ## The Veil as Cultural Custodian: The Veil, emerging from the post-collapse adaptation of preexisting religious and cultural practices, evolved into a matriarchal order central to maintaining the Freehold’s ethical architecture. This evolution was characterized not by rigid preservation but by adaptive synthesis, wherein ceremonial gravitas was merged with pragmatic domestic guidance. The Veil functioned as a moral custodian, particularly within the familial sphere, where its influence was most profoundly exercised. Veilmother Cordelia’s role during the Winter Vigil exemplifies this dual function of leadership and philosophical stewardship, as her guidance articulated not only the ritual's procedural elements but also the embedded moral philosophy that would shape the initiates' worldview. ## Ritual Dynamics and Symbolism: The Winter Vigil is fundamentally an enactment of moral endurance, wherein the initiate’s voluntary approach to the brazier represents an acceptance of communal responsibility through individual fortitude. The design of the ritual deliberately positions physical endurance as a metaphor for moral resilience, encapsulating the Freehold’s conviction that true strength is inherently silent and steadfast. As the initiate moves toward the brazier, kneeling in proximity to the flame, the act becomes a performative affirmation of the Compact’s call for measured, principled strength rather than ostentatious assertion. The structured progression from the outer circle to the brazier symbolizes a journey from collective dependency to personal sovereignty, reflecting the Compact's ethos that leadership is merited through tested perseverance. ## The Copper Plate Rite: The Copper Plate Rite, integral to the Vigil, embodies the transformative philosophy of the Freehold. The heated copper plate, inscribed with the flame symbol and lifted from ashes, is held aloft despite discomfort, symbolizing the embrace of hardship as an essential component of sovereignty. The fleeting burn, leaving a transient mark, underscores the philosophical assertion that genuine resilience is born of confronting and integrating suffering, rather than circumventing it. This rite functions not merely as a test of physical tolerance but as a pedagogical imprinting of the Freehold’s ethos—an allegory of death and rebirth integral to personal and communal maturation. ## Symbolic Implications and Societal Continuity: The deliberate imposition of discomfort during the Vigil underscores a fundamental tenet of Freehold philosophy: suffering, when purposefully endured, refines the individual and, by extension, fortifies the community. The Copper Plate Rite exemplifies the doctrine that hardship, when faced with deliberate resolve, engenders moral clarity. This paradigm of voluntary suffering as a crucible for leadership remains a cornerstone of the Freehold’s ideological framework, fostering a collective ethos rooted in patient perseverance rather than impulsive dominance. Furthermore, the initiation rite serves as a microcosm of the Freehold's broader sociocultural ethos, where personal sacrifice is inextricably linked to communal stability. ## Interpretive Analysis: Current historiographical interpretations often err by neglecting the interconnectedness of the Vigil with broader sociopolitical dynamics. By isolating the rite as a mere ceremonial endurance, scholars risk overlooking its function as a structured pedagogical tool for inculcating moral resilience. This study posits that the Vigil, far from being a vestigial tradition, actively cultivated a pragmatic ethic of endurance that proved crucial in the Freehold’s sustained sociocultural coherence. This coherence, rooted in ritual reinforcement of moral tenets, enabled the Freehold to navigate existential threats without succumbing to internal decay. ## Cultural and Societal Implications: The enduring significance of the Winter Vigil lies in its dual function as both a rite of passage and a communal reaffirmation of the Freehold’s meritocratic principles. By fostering individual accountability within a collective moral framework, the Vigil reinforced the Compact’s foundational premise that leadership is merited through demonstrated resilience. The integration of personal trial into communal identity formation exemplifies how the Freehold maintained its internal stability despite external societal fragmentation. This ritual, therefore, is not merely commemorative but constitutive of the Freehold's enduring cultural legacy. ## Conclusion: The Winter Vigil of XLII.II at Sapelo remains a paradigmatic example of ritual as a vehicle for social continuity within the Lowcountry Freehold. Its deliberate amalgamation of symbolic endurance with moral instruction illustrates the Freehold’s adaptive strategy of embedding philosophical imperatives within lived tradition. As modern scholars, it is incumbent upon us to engage with these practices not merely as remnants of a bygone era but as foundational elements that cultivated the durable sociocultural ethos underpinning our current stability. ## References: 1. Vance, C. (Epoch LII). "The Compact and Cultural Continuity: An Oral History." Archive of Freehold Studies, Emberwell Hall. 2. Harlowe, E. (Epoch LX). "The Flamekeepers: Guardians of Tradition." Journal of Sociocultural Persistence, Vol. 22, pp. 45-72. 3. Morgan, T. (Epoch LXV). "Endurance Through Ritual: The Role of The Veil in Cultural Preservation." Lowcountry Academic Press. 4. Cordelia, V. (Epoch XLII). "Reflections on the Flame: An Instructional Account." Collected Teachings of The Veil. 5. Emberwell Institute (Epoch XC). "The Evolution of Freehold Rites: From Custom to Philosophy." Advanced Studies in Cultural Integration. ## Title: Ritual as Continuity: An Analysis of the Winter Vigil of XLII.II at Sapelo ### Epoch XLII - Circle of Maidens #### Abstract: This paper presents a rigorous and critical examination of the Winter Vigil of XLII.II at Sapelo, a pivotal rite within the Lowcountry Freehold that serves as both an initiation into communal responsibility and a symbolic enactment of the Compact’s moral tenets. This analysis interrogates the ritual’s structure, emphasizing its role in perpetuating a resilient sociocultural order amid external collapse. Through a multidisciplinary approach combining historiographical analysis, cultural anthropology, and sociocultural theory, this study elucidates the Vigil’s function as a mechanism for moral continuity, thereby situating it within the broader discourse of post-collapse societal stabilization. The implications of this study underscore the profound interconnectedness between ritual practice and the formation of resilient communal identities. #### Introduction: The Winter Vigil of XLII.II at Sapelo occupies a fundamental position in the cultural historiography of the Lowcountry Freehold. As contemporary scholars, it is imperative to approach this tradition not merely as an artifact of ritualistic antiquity but as a dynamic process of cultural preservation. The Freehold’s commitment to integrating tradition with pragmatism, especially through the stewardship of The Veil, constitutes a critical adaptive strategy that sustained sociopolitical coherence through epochs of external fragmentation. This study aims to critically examine the Vigil as both a symbolic and practical reinforcement of the Compact’s ethos, with particular attention to how this ritual facilitated intergenerational continuity of moral and social values, ultimately shaping the robust communal identity that defines contemporary Freehold society. #### The Veil as Cultural Custodian: The Veil, emerging from the post-collapse adaptation of preexisting religious and cultural practices, evolved into a matriarchal order central to maintaining the Freehold’s ethical architecture. This evolution was characterized not by rigid preservation but by adaptive synthesis, wherein ceremonial gravitas was merged with pragmatic domestic guidance. The Veil functioned as a moral custodian, particularly within the familial sphere, where its influence was most profoundly exercised. Veilmother Cordelia’s role during the Winter Vigil exemplifies this dual function of leadership and philosophical stewardship, as her guidance articulated not only the ritual's procedural elements but also the embedded moral philosophy that would shape the initiates' worldview. #### Ritual Dynamics and Symbolism: The Winter Vigil is fundamentally an enactment of moral endurance, wherein the initiate’s voluntary approach to the brazier represents an acceptance of communal responsibility through individual fortitude. The design of the ritual deliberately positions physical endurance as a metaphor for moral resilience, encapsulating the Freehold’s conviction that true strength is inherently silent and steadfast. As the initiate moves toward the brazier, kneeling in proximity to the flame, the act becomes a performative affirmation of the Compact’s call for measured, principled strength rather than ostentatious assertion. The structured progression from the outer circle to the brazier symbolizes a journey from collective dependency to personal sovereignty, reflecting the Compact's ethos that leadership is merited through tested perseverance. #### The Copper Plate Rite: The Copper Plate Rite, integral to the Vigil, embodies the transformative philosophy of the Freehold. The heated copper plate, inscribed with the flame symbol and lifted from ashes, is held aloft despite discomfort, symbolizing the embrace of hardship as an essential component of sovereignty. The fleeting burn, leaving a transient mark, underscores the philosophical assertion that genuine resilience is born of confronting and integrating suffering, rather than circumventing it. This rite functions not merely as a test of physical tolerance but as a pedagogical imprinting of the Freehold’s ethos—an allegory of death and rebirth integral to personal and communal maturation. #### Symbolic Implications and Societal Continuity: The deliberate imposition of discomfort during the Vigil underscores a fundamental tenet of Freehold philosophy: suffering, when purposefully endured, refines the individual and, by extension, fortifies the community. The Copper Plate Rite exemplifies the doctrine that hardship, when faced with deliberate resolve, engenders moral clarity. This paradigm of voluntary suffering as a crucible for leadership remains a cornerstone of the Freehold’s ideological framework, fostering a collective ethos rooted in patient perseverance rather than impulsive dominance. Furthermore, the initiation rite serves as a microcosm of the Freehold's broader sociocultural ethos, where personal sacrifice is inextricably linked to communal stability. #### Interpretive Analysis: Current historiographical interpretations often err by neglecting the interconnectedness of the Vigil with broader sociopolitical dynamics. By isolating the rite as a mere ceremonial endurance, scholars risk overlooking its function as a structured pedagogical tool for inculcating moral resilience. This study posits that the Vigil, far from being a vestigial tradition, actively cultivated a pragmatic ethic of endurance that proved crucial in the Freehold’s sustained sociocultural coherence. This coherence, rooted in ritual reinforcement of moral tenets, enabled the Freehold to navigate existential threats without succumbing to internal decay. #### Cultural and Societal Implications: The enduring significance of the Winter Vigil lies in its dual function as both a rite of passage and a communal reaffirmation of the Freehold’s meritocratic principles. By fostering individual accountability within a collective moral framework, the Vigil reinforced the Compact’s foundational premise that leadership is merited through demonstrated resilience. The integration of personal trial into communal identity formation exemplifies how the Freehold maintained its internal stability despite external societal fragmentation. This ritual, therefore, is not merely commemorative but constitutive of the Freehold's enduring cultural legacy. #### Conclusion: The Winter Vigil of XLII.II at Sapelo remains a paradigmatic example of ritual as a vehicle for social continuity within the Lowcountry Freehold. Its deliberate amalgamation of symbolic endurance with moral instruction illustrates the Freehold’s adaptive strategy of embedding philosophical imperatives within lived tradition. As modern scholars, it is incumbent upon us to engage with these practices not merely as remnants of a bygone era but as foundational elements that cultivated the durable sociocultural ethos underpinning our current stability. #### References: 1. Vance, C. (Epoch LII). "The Compact and Cultural Continuity: An Oral History." Archive of Freehold Studies, Emberwell Hall. 2. Harlowe, E. (Epoch LX). "The Flamekeepers: Guardians of Tradition." Journal of Sociocultural Persistence, Vol. 22, pp. 45-72. 3. Morgan, T. (Epoch LXV). "Endurance Through Ritual: The Role of The Veil in Cultural Preservation." Lowcountry Academic Press. 4. Cordelia, V. (Epoch XLII). "Reflections on the Flame: An Instructional Account." Collected Teachings of The Veil. 5. Emberwell Institute (Epoch XC). "The Evolution of Freehold Rites: From Custom to Philosophy." Advanced Studies in Cultural Integration.
@ bdf3f01a:d9c40970
2025-03-29 04:52:40## Abstract: This paper presents a rigorous and critical examination of the Winter Vigil of XLII.II at Sapelo, a pivotal rite within the Lowcountry Freehold that serves as both an initiation into communal responsibility and a symbolic enactment of the Compact’s moral tenets. This analysis interrogates the ritual’s structure, emphasizing its role in perpetuating a resilient sociocultural order amid external collapse. Through a multidisciplinary approach combining historiographical analysis, cultural anthropology, and sociocultural theory, this study elucidates the Vigil’s function as a mechanism for moral continuity, thereby situating it within the broader discourse of post-collapse societal stabilization. The implications of this study underscore the profound interconnectedness between ritual practice and the formation of resilient communal identities. ## Introduction: The Winter Vigil of XLII.II at Sapelo occupies a fundamental position in the cultural historiography of the Lowcountry Freehold. As contemporary scholars, it is imperative to approach this tradition not merely as an artifact of ritualistic antiquity but as a dynamic process of cultural preservation. The Freehold’s commitment to integrating tradition with pragmatism, especially through the stewardship of The Veil, constitutes a critical adaptive strategy that sustained sociopolitical coherence through epochs of external fragmentation. This study aims to critically examine the Vigil as both a symbolic and practical reinforcement of the Compact’s ethos, with particular attention to how this ritual facilitated intergenerational continuity of moral and social values, ultimately shaping the robust communal identity that defines contemporary Freehold society. ## The Veil as Cultural Custodian: The Veil, emerging from the post-collapse adaptation of preexisting religious and cultural practices, evolved into a matriarchal order central to maintaining the Freehold’s ethical architecture. This evolution was characterized not by rigid preservation but by adaptive synthesis, wherein ceremonial gravitas was merged with pragmatic domestic guidance. The Veil functioned as a moral custodian, particularly within the familial sphere, where its influence was most profoundly exercised. Veilmother Cordelia’s role during the Winter Vigil exemplifies this dual function of leadership and philosophical stewardship, as her guidance articulated not only the ritual's procedural elements but also the embedded moral philosophy that would shape the initiates' worldview. ## Ritual Dynamics and Symbolism: The Winter Vigil is fundamentally an enactment of moral endurance, wherein the initiate’s voluntary approach to the brazier represents an acceptance of communal responsibility through individual fortitude. The design of the ritual deliberately positions physical endurance as a metaphor for moral resilience, encapsulating the Freehold’s conviction that true strength is inherently silent and steadfast. As the initiate moves toward the brazier, kneeling in proximity to the flame, the act becomes a performative affirmation of the Compact’s call for measured, principled strength rather than ostentatious assertion. The structured progression from the outer circle to the brazier symbolizes a journey from collective dependency to personal sovereignty, reflecting the Compact's ethos that leadership is merited through tested perseverance. ## The Copper Plate Rite: The Copper Plate Rite, integral to the Vigil, embodies the transformative philosophy of the Freehold. The heated copper plate, inscribed with the flame symbol and lifted from ashes, is held aloft despite discomfort, symbolizing the embrace of hardship as an essential component of sovereignty. The fleeting burn, leaving a transient mark, underscores the philosophical assertion that genuine resilience is born of confronting and integrating suffering, rather than circumventing it. This rite functions not merely as a test of physical tolerance but as a pedagogical imprinting of the Freehold’s ethos—an allegory of death and rebirth integral to personal and communal maturation. ## Symbolic Implications and Societal Continuity: The deliberate imposition of discomfort during the Vigil underscores a fundamental tenet of Freehold philosophy: suffering, when purposefully endured, refines the individual and, by extension, fortifies the community. The Copper Plate Rite exemplifies the doctrine that hardship, when faced with deliberate resolve, engenders moral clarity. This paradigm of voluntary suffering as a crucible for leadership remains a cornerstone of the Freehold’s ideological framework, fostering a collective ethos rooted in patient perseverance rather than impulsive dominance. Furthermore, the initiation rite serves as a microcosm of the Freehold's broader sociocultural ethos, where personal sacrifice is inextricably linked to communal stability. ## Interpretive Analysis: Current historiographical interpretations often err by neglecting the interconnectedness of the Vigil with broader sociopolitical dynamics. By isolating the rite as a mere ceremonial endurance, scholars risk overlooking its function as a structured pedagogical tool for inculcating moral resilience. This study posits that the Vigil, far from being a vestigial tradition, actively cultivated a pragmatic ethic of endurance that proved crucial in the Freehold’s sustained sociocultural coherence. This coherence, rooted in ritual reinforcement of moral tenets, enabled the Freehold to navigate existential threats without succumbing to internal decay. ## Cultural and Societal Implications: The enduring significance of the Winter Vigil lies in its dual function as both a rite of passage and a communal reaffirmation of the Freehold’s meritocratic principles. By fostering individual accountability within a collective moral framework, the Vigil reinforced the Compact’s foundational premise that leadership is merited through demonstrated resilience. The integration of personal trial into communal identity formation exemplifies how the Freehold maintained its internal stability despite external societal fragmentation. This ritual, therefore, is not merely commemorative but constitutive of the Freehold's enduring cultural legacy. ## Conclusion: The Winter Vigil of XLII.II at Sapelo remains a paradigmatic example of ritual as a vehicle for social continuity within the Lowcountry Freehold. Its deliberate amalgamation of symbolic endurance with moral instruction illustrates the Freehold’s adaptive strategy of embedding philosophical imperatives within lived tradition. As modern scholars, it is incumbent upon us to engage with these practices not merely as remnants of a bygone era but as foundational elements that cultivated the durable sociocultural ethos underpinning our current stability. ## References: 1. Vance, C. (Epoch LII). "The Compact and Cultural Continuity: An Oral History." Archive of Freehold Studies, Emberwell Hall. 2. Harlowe, E. (Epoch LX). "The Flamekeepers: Guardians of Tradition." Journal of Sociocultural Persistence, Vol. 22, pp. 45-72. 3. Morgan, T. (Epoch LXV). "Endurance Through Ritual: The Role of The Veil in Cultural Preservation." Lowcountry Academic Press. 4. Cordelia, V. (Epoch XLII). "Reflections on the Flame: An Instructional Account." Collected Teachings of The Veil. 5. Emberwell Institute (Epoch XC). "The Evolution of Freehold Rites: From Custom to Philosophy." Advanced Studies in Cultural Integration. ## Title: Ritual as Continuity: An Analysis of the Winter Vigil of XLII.II at Sapelo ### Epoch XLII - Circle of Maidens #### Abstract: This paper presents a rigorous and critical examination of the Winter Vigil of XLII.II at Sapelo, a pivotal rite within the Lowcountry Freehold that serves as both an initiation into communal responsibility and a symbolic enactment of the Compact’s moral tenets. This analysis interrogates the ritual’s structure, emphasizing its role in perpetuating a resilient sociocultural order amid external collapse. Through a multidisciplinary approach combining historiographical analysis, cultural anthropology, and sociocultural theory, this study elucidates the Vigil’s function as a mechanism for moral continuity, thereby situating it within the broader discourse of post-collapse societal stabilization. The implications of this study underscore the profound interconnectedness between ritual practice and the formation of resilient communal identities. #### Introduction: The Winter Vigil of XLII.II at Sapelo occupies a fundamental position in the cultural historiography of the Lowcountry Freehold. As contemporary scholars, it is imperative to approach this tradition not merely as an artifact of ritualistic antiquity but as a dynamic process of cultural preservation. The Freehold’s commitment to integrating tradition with pragmatism, especially through the stewardship of The Veil, constitutes a critical adaptive strategy that sustained sociopolitical coherence through epochs of external fragmentation. This study aims to critically examine the Vigil as both a symbolic and practical reinforcement of the Compact’s ethos, with particular attention to how this ritual facilitated intergenerational continuity of moral and social values, ultimately shaping the robust communal identity that defines contemporary Freehold society. #### The Veil as Cultural Custodian: The Veil, emerging from the post-collapse adaptation of preexisting religious and cultural practices, evolved into a matriarchal order central to maintaining the Freehold’s ethical architecture. This evolution was characterized not by rigid preservation but by adaptive synthesis, wherein ceremonial gravitas was merged with pragmatic domestic guidance. The Veil functioned as a moral custodian, particularly within the familial sphere, where its influence was most profoundly exercised. Veilmother Cordelia’s role during the Winter Vigil exemplifies this dual function of leadership and philosophical stewardship, as her guidance articulated not only the ritual's procedural elements but also the embedded moral philosophy that would shape the initiates' worldview. #### Ritual Dynamics and Symbolism: The Winter Vigil is fundamentally an enactment of moral endurance, wherein the initiate’s voluntary approach to the brazier represents an acceptance of communal responsibility through individual fortitude. The design of the ritual deliberately positions physical endurance as a metaphor for moral resilience, encapsulating the Freehold’s conviction that true strength is inherently silent and steadfast. As the initiate moves toward the brazier, kneeling in proximity to the flame, the act becomes a performative affirmation of the Compact’s call for measured, principled strength rather than ostentatious assertion. The structured progression from the outer circle to the brazier symbolizes a journey from collective dependency to personal sovereignty, reflecting the Compact's ethos that leadership is merited through tested perseverance. #### The Copper Plate Rite: The Copper Plate Rite, integral to the Vigil, embodies the transformative philosophy of the Freehold. The heated copper plate, inscribed with the flame symbol and lifted from ashes, is held aloft despite discomfort, symbolizing the embrace of hardship as an essential component of sovereignty. The fleeting burn, leaving a transient mark, underscores the philosophical assertion that genuine resilience is born of confronting and integrating suffering, rather than circumventing it. This rite functions not merely as a test of physical tolerance but as a pedagogical imprinting of the Freehold’s ethos—an allegory of death and rebirth integral to personal and communal maturation. #### Symbolic Implications and Societal Continuity: The deliberate imposition of discomfort during the Vigil underscores a fundamental tenet of Freehold philosophy: suffering, when purposefully endured, refines the individual and, by extension, fortifies the community. The Copper Plate Rite exemplifies the doctrine that hardship, when faced with deliberate resolve, engenders moral clarity. This paradigm of voluntary suffering as a crucible for leadership remains a cornerstone of the Freehold’s ideological framework, fostering a collective ethos rooted in patient perseverance rather than impulsive dominance. Furthermore, the initiation rite serves as a microcosm of the Freehold's broader sociocultural ethos, where personal sacrifice is inextricably linked to communal stability. #### Interpretive Analysis: Current historiographical interpretations often err by neglecting the interconnectedness of the Vigil with broader sociopolitical dynamics. By isolating the rite as a mere ceremonial endurance, scholars risk overlooking its function as a structured pedagogical tool for inculcating moral resilience. This study posits that the Vigil, far from being a vestigial tradition, actively cultivated a pragmatic ethic of endurance that proved crucial in the Freehold’s sustained sociocultural coherence. This coherence, rooted in ritual reinforcement of moral tenets, enabled the Freehold to navigate existential threats without succumbing to internal decay. #### Cultural and Societal Implications: The enduring significance of the Winter Vigil lies in its dual function as both a rite of passage and a communal reaffirmation of the Freehold’s meritocratic principles. By fostering individual accountability within a collective moral framework, the Vigil reinforced the Compact’s foundational premise that leadership is merited through demonstrated resilience. The integration of personal trial into communal identity formation exemplifies how the Freehold maintained its internal stability despite external societal fragmentation. This ritual, therefore, is not merely commemorative but constitutive of the Freehold's enduring cultural legacy. #### Conclusion: The Winter Vigil of XLII.II at Sapelo remains a paradigmatic example of ritual as a vehicle for social continuity within the Lowcountry Freehold. Its deliberate amalgamation of symbolic endurance with moral instruction illustrates the Freehold’s adaptive strategy of embedding philosophical imperatives within lived tradition. As modern scholars, it is incumbent upon us to engage with these practices not merely as remnants of a bygone era but as foundational elements that cultivated the durable sociocultural ethos underpinning our current stability. #### References: 1. Vance, C. (Epoch LII). "The Compact and Cultural Continuity: An Oral History." Archive of Freehold Studies, Emberwell Hall. 2. Harlowe, E. (Epoch LX). "The Flamekeepers: Guardians of Tradition." Journal of Sociocultural Persistence, Vol. 22, pp. 45-72. 3. Morgan, T. (Epoch LXV). "Endurance Through Ritual: The Role of The Veil in Cultural Preservation." Lowcountry Academic Press. 4. Cordelia, V. (Epoch XLII). "Reflections on the Flame: An Instructional Account." Collected Teachings of The Veil. 5. Emberwell Institute (Epoch XC). "The Evolution of Freehold Rites: From Custom to Philosophy." Advanced Studies in Cultural Integration. @ fd78c37f:a0ec0833
2025-03-29 04:33:01**YakiHonne**: I'm excited to be joined by our guest Piccolo—thank you very much for being here. Before we dive in, I'd like to briefly introduce YakiHonne. YakiHonne is a decentralized media client built on the Nostr protocol, leveraging technology to enable freedom of speech. It empowers creators to fully own their voice and assets while offering innovative tools such as Smart widget , Verified Notes, and support for long-form content. Today, we’re not just discussing YakiHonne, but also diving into your community. Piccolo, could you start by telling us a bit about yourself and your community? **Piccolo**:Hi, I'm Piccolo. I run BO฿ Space in Bangkok, and we also have a satellite location called the BO฿ Space corner in Chiang Mai, thanks to the Bitcoin Learning Center. **Piccolo**:Regarding my background,I originally came from corporate finance and investment banking. I was in that field for about 20 years, with the last 15 spent running my own firm in corporate finance advisory alongside a couple of partners. We eventually sold the advisory business in 2015, took a short break, and in 2016, I ended up launching a fintech company, which is still operational today. The company specializes in equity crowdfunding and is licensed by the SEC in Thailand. **Piccolo**:I first bought Bitcoin a few years before truly understanding it, initially thinking it was a scam that would eventually collapse. However, in 2017, the block size wars demonstrated the protocol’s strong resistance to attacks on decentralization, which deeply impacted me. By late 2018 or early 2019, I started to really grasp Bitcoin and kept learning. Then, in mid-2022, after having fully fallen down the Bitcoin rabbit hole, I founded BO฿ Space. It was right after COVID, and since the fintech had scaled down, there was extra space. We started by hosting meetups and technical workshops for people who were interested. **Piccolo**:In the early years, we had various groups come by—like the team from BDK (Bitcoin Development Kit), who held workshops. The people behind the Bitcoin Beach Wallet, which later became Blink, also visited. So, BO฿ Space initially functioned as a meetup and technical workshop space. Eventually, we launched the BOB Builders Residency program, which was a lot of fun. We secured grant funding for developers under different cohort themes, so that they can collaborate and co-work for a few months. So far, we have completed three cohorts. **YakiHonne**:How did your community get started, and what did you do to attract new members in the beginning? **Piccolo**:The initial members came through word of mouth and invitations that I sent out. I reached out to an initial group of Bitcoiners here in the city who I believed were strong maximalists or Bitcoin-only supporters, back when that was still a thing. I sent out 21 invitations and had our first meetup with 21 people, most of whom I had interacted with online, though some in person during the COVID years. From there, it spread by word of mouth, and of course, through Twitter and meetup.com. So, I would say that word of mouth remains the main method of growth. Additionally, when people come through Bangkok and are looking for a Bitcoin-only meetup, there really isn't one available. I believe there are a couple now—maybe two or three—but when we started, there weren’t any, especially not a dedicated Bitcoin-only space. I think we may still be the only one in Bangkok. So yeah, word of mouth was definitely the main way we grew. Bitcoiners tend to share their finds when they meet like-minded people.  **YakiHonne**:Didn’t you have people in your community who initially thought Bitcoin was a scam, like you did, or face similar issues? **Piccolo**:Yes, it still happens, especially when the price of Bitcoin rises. Newcomers still join, and some of them believe Bitcoin might be a scam. However, this has become less frequent. The main reason is that when people come to BO฿ Space, they know it’s a Bitcoin-only meetup. We generally don’t discuss the price; instead, we focus on other aspects of Bitcoin, as there are many interesting developments in the space. **YakiHonne**:What advice would you give to someone looking to start or grow a Bitcoin-focused community in today’s world? Considering the current landscape, much like your own experience, what guidance would you offer? **Piccolo**:It sounds simple, but just do it. When it comes to community building, you don’t necessarily need a physical space. Community is about people coming together, right? Two people can start a community, then three, four, and so on. Meetups can happen anywhere—your favorite bar, a restaurant, a friend’s garage, or wherever. So, just do it, but make sure you have more than one person, otherwise, how can you build a community? Once you have more than one person, word of mouth will spread. And as you develop a core group—let’s say more than five people—that’s when I think the community can truly sustain itself. **YakiHonne**:I know you’ve mentioned the technical side of your community, but I’ll ask anyway—does your community engage with the technical or non-technical aspects of Bitcoin? Or perhaps, is there a blend of both? **Piccolo**:I would say both. It really depends on the monthly themes of our meetups. For example, February was focused on Asian communities in Bitcoin. During that month, community leaders came in to give presentations and discuss their work in places like Indonesia, India, and more recently, someone from HRF (Human Rights Foundation) talked about Bitcoin’s use case in Myanmar. Then, in December, we had a very technical month—Mining Month. It was led by our Cohort 3 residents, where we discussed Stratum V2 and had a demo on it. We also examined the Loki board hardware, and Zack took apart the S19, looking at different ways to repurpose the power supply unit, among other things. So, it’s a mix of both, depending on the theme for that month. Some months are very technical, while others are more community-focused and less technical. **YakiHonne**:What advice would you give to a technically inclined individual or organization looking to contribute meaningfully to the Bitcoin ecosystem? **Piccolo**:For technically inclined individuals, I would suggest identifying your favorite open-source project in the Bitcoin ecosystem. Start from Bitcoin Core and explore different layers, such as Lightning or e-cash, and other open-source projects. As for technically inclined organizations, if you're integrating Bitcoin into your business, I would say, first, make sure you have people within your organization who truly understand Bitcoin. Build a capable team first, and then, depending on the part of the Bitcoin ecosystem you’re involved in—whether it’s custody services, Lightning payments, layer 2, or something like Cashu or Ark—find your niche. From there, your team will work with you to discover ways to contribute. But until you build that capability, organizations are a bit different from individuals in this space. **YakiHonne**:How do you see the world of Bitcoin communities evolving as technology matures, particularly in areas like scalability, privacy, and adaptability with other systems? **Piccolo**:That's an interesting question. If we think about the future of Bitcoin communities, I believe they may eventually disappear as technology matures. Once Bitcoin scales to a point where it integrates seamlessly with other payment systems, becoming part of the everyday norm, the need for dedicated communities will diminish. It’s similar to how we no longer have meetups about refrigerators or iPhones, even though they are technologies we use every day. As Bitcoin matures, it will likely reach that level of ubiquity. There might still be occasional meetups or forums, but they will be more about specific knowledge, use cases, and tools, rather than a community dedicated to introducing others to the technology itself. However, this is a long way off. Bitcoin is still relatively small compared to the global fiat financial system, despite the growth we want to see. So, it will take a long time before we reach that stage. **YakiHonne**:It’s something I hadn’t considered before, and it’s quite insightful. Moving to our last question actually which I find very interesting is the government around you for or against bitcoin and how has That affected the community. **Piccolo**:In my opinion, on a general level, the government is more supportive than opposed to Bitcoin. The Thai government classifies Bitcoin as a digital asset, almost like digital gold. In that sense, they want to tax capital gains and regulate it. They also have a regulatory framework for it, known as the Digital Asset Regulatory Sandbox, where you can test various things, mainly coins and tokens. It's unfortunate, but that’s how it is. However, our government, especially the regulatory bodies, are open to innovation. They recognize that Bitcoin is different, but they still view blockchain and tokens as useful technologies, which is somewhat misguided. So, in that sense, it’s more support than opposition. A couple of years ago, there was a circular discouraging the use of Bitcoin as a payment currency, mainly because they can't control its monetary policy. And they’re right—Bitcoin can’t be controlled by anyone; there’re the protocol and the rules, and everyone follows them, unless there’s a hard fork, which is a different matter. So, in that regard, Bitcoin is definitely categorized as a digital asset by the government, and that’s where it stands. **Piccolo**:People who come to BO฿ Space to learn about Bitcoin are often influenced by the government from the point of price movements; especially when government support moves the price up. But they usually only visit once or twice, especially if they’re not deep into the Bitcoin rabbit hole. They often get disappointed because, at BO฿ Space, we rarely discuss the price—maybe once a year, and that’s just after the meetup when people are having drinks. So, in that sense, I’d say the government currently doesn’t really hurt or help the community either way. People will go down the rabbit hole at their own pace. And if you're not a Bitcoiner and you come to a BO฿ Space meetup with a crypto focus, you might be surprised by the approach we take. **YakiHonne**:Thank you, Piccolo, for your time and insights. It’s been a pleasure speaking with you. Your perspective on the evolution of Bitcoin communities was eye-opening. It's clear that your deep understanding of Bitcoin is invaluable. I'm sure our readers will appreciate your insights. Once again, thank you, Piccolo. I look forward to seeing the continued growth of BO฿ Space and Bitcoin adoption.
@ fd78c37f:a0ec0833
2025-03-29 04:33:01**YakiHonne**: I'm excited to be joined by our guest Piccolo—thank you very much for being here. Before we dive in, I'd like to briefly introduce YakiHonne. YakiHonne is a decentralized media client built on the Nostr protocol, leveraging technology to enable freedom of speech. It empowers creators to fully own their voice and assets while offering innovative tools such as Smart widget , Verified Notes, and support for long-form content. Today, we’re not just discussing YakiHonne, but also diving into your community. Piccolo, could you start by telling us a bit about yourself and your community? **Piccolo**:Hi, I'm Piccolo. I run BO฿ Space in Bangkok, and we also have a satellite location called the BO฿ Space corner in Chiang Mai, thanks to the Bitcoin Learning Center. **Piccolo**:Regarding my background,I originally came from corporate finance and investment banking. I was in that field for about 20 years, with the last 15 spent running my own firm in corporate finance advisory alongside a couple of partners. We eventually sold the advisory business in 2015, took a short break, and in 2016, I ended up launching a fintech company, which is still operational today. The company specializes in equity crowdfunding and is licensed by the SEC in Thailand. **Piccolo**:I first bought Bitcoin a few years before truly understanding it, initially thinking it was a scam that would eventually collapse. However, in 2017, the block size wars demonstrated the protocol’s strong resistance to attacks on decentralization, which deeply impacted me. By late 2018 or early 2019, I started to really grasp Bitcoin and kept learning. Then, in mid-2022, after having fully fallen down the Bitcoin rabbit hole, I founded BO฿ Space. It was right after COVID, and since the fintech had scaled down, there was extra space. We started by hosting meetups and technical workshops for people who were interested. **Piccolo**:In the early years, we had various groups come by—like the team from BDK (Bitcoin Development Kit), who held workshops. The people behind the Bitcoin Beach Wallet, which later became Blink, also visited. So, BO฿ Space initially functioned as a meetup and technical workshop space. Eventually, we launched the BOB Builders Residency program, which was a lot of fun. We secured grant funding for developers under different cohort themes, so that they can collaborate and co-work for a few months. So far, we have completed three cohorts. **YakiHonne**:How did your community get started, and what did you do to attract new members in the beginning? **Piccolo**:The initial members came through word of mouth and invitations that I sent out. I reached out to an initial group of Bitcoiners here in the city who I believed were strong maximalists or Bitcoin-only supporters, back when that was still a thing. I sent out 21 invitations and had our first meetup with 21 people, most of whom I had interacted with online, though some in person during the COVID years. From there, it spread by word of mouth, and of course, through Twitter and meetup.com. So, I would say that word of mouth remains the main method of growth. Additionally, when people come through Bangkok and are looking for a Bitcoin-only meetup, there really isn't one available. I believe there are a couple now—maybe two or three—but when we started, there weren’t any, especially not a dedicated Bitcoin-only space. I think we may still be the only one in Bangkok. So yeah, word of mouth was definitely the main way we grew. Bitcoiners tend to share their finds when they meet like-minded people.  **YakiHonne**:Didn’t you have people in your community who initially thought Bitcoin was a scam, like you did, or face similar issues? **Piccolo**:Yes, it still happens, especially when the price of Bitcoin rises. Newcomers still join, and some of them believe Bitcoin might be a scam. However, this has become less frequent. The main reason is that when people come to BO฿ Space, they know it’s a Bitcoin-only meetup. We generally don’t discuss the price; instead, we focus on other aspects of Bitcoin, as there are many interesting developments in the space. **YakiHonne**:What advice would you give to someone looking to start or grow a Bitcoin-focused community in today’s world? Considering the current landscape, much like your own experience, what guidance would you offer? **Piccolo**:It sounds simple, but just do it. When it comes to community building, you don’t necessarily need a physical space. Community is about people coming together, right? Two people can start a community, then three, four, and so on. Meetups can happen anywhere—your favorite bar, a restaurant, a friend’s garage, or wherever. So, just do it, but make sure you have more than one person, otherwise, how can you build a community? Once you have more than one person, word of mouth will spread. And as you develop a core group—let’s say more than five people—that’s when I think the community can truly sustain itself. **YakiHonne**:I know you’ve mentioned the technical side of your community, but I’ll ask anyway—does your community engage with the technical or non-technical aspects of Bitcoin? Or perhaps, is there a blend of both? **Piccolo**:I would say both. It really depends on the monthly themes of our meetups. For example, February was focused on Asian communities in Bitcoin. During that month, community leaders came in to give presentations and discuss their work in places like Indonesia, India, and more recently, someone from HRF (Human Rights Foundation) talked about Bitcoin’s use case in Myanmar. Then, in December, we had a very technical month—Mining Month. It was led by our Cohort 3 residents, where we discussed Stratum V2 and had a demo on it. We also examined the Loki board hardware, and Zack took apart the S19, looking at different ways to repurpose the power supply unit, among other things. So, it’s a mix of both, depending on the theme for that month. Some months are very technical, while others are more community-focused and less technical. **YakiHonne**:What advice would you give to a technically inclined individual or organization looking to contribute meaningfully to the Bitcoin ecosystem? **Piccolo**:For technically inclined individuals, I would suggest identifying your favorite open-source project in the Bitcoin ecosystem. Start from Bitcoin Core and explore different layers, such as Lightning or e-cash, and other open-source projects. As for technically inclined organizations, if you're integrating Bitcoin into your business, I would say, first, make sure you have people within your organization who truly understand Bitcoin. Build a capable team first, and then, depending on the part of the Bitcoin ecosystem you’re involved in—whether it’s custody services, Lightning payments, layer 2, or something like Cashu or Ark—find your niche. From there, your team will work with you to discover ways to contribute. But until you build that capability, organizations are a bit different from individuals in this space. **YakiHonne**:How do you see the world of Bitcoin communities evolving as technology matures, particularly in areas like scalability, privacy, and adaptability with other systems? **Piccolo**:That's an interesting question. If we think about the future of Bitcoin communities, I believe they may eventually disappear as technology matures. Once Bitcoin scales to a point where it integrates seamlessly with other payment systems, becoming part of the everyday norm, the need for dedicated communities will diminish. It’s similar to how we no longer have meetups about refrigerators or iPhones, even though they are technologies we use every day. As Bitcoin matures, it will likely reach that level of ubiquity. There might still be occasional meetups or forums, but they will be more about specific knowledge, use cases, and tools, rather than a community dedicated to introducing others to the technology itself. However, this is a long way off. Bitcoin is still relatively small compared to the global fiat financial system, despite the growth we want to see. So, it will take a long time before we reach that stage. **YakiHonne**:It’s something I hadn’t considered before, and it’s quite insightful. Moving to our last question actually which I find very interesting is the government around you for or against bitcoin and how has That affected the community. **Piccolo**:In my opinion, on a general level, the government is more supportive than opposed to Bitcoin. The Thai government classifies Bitcoin as a digital asset, almost like digital gold. In that sense, they want to tax capital gains and regulate it. They also have a regulatory framework for it, known as the Digital Asset Regulatory Sandbox, where you can test various things, mainly coins and tokens. It's unfortunate, but that’s how it is. However, our government, especially the regulatory bodies, are open to innovation. They recognize that Bitcoin is different, but they still view blockchain and tokens as useful technologies, which is somewhat misguided. So, in that sense, it’s more support than opposition. A couple of years ago, there was a circular discouraging the use of Bitcoin as a payment currency, mainly because they can't control its monetary policy. And they’re right—Bitcoin can’t be controlled by anyone; there’re the protocol and the rules, and everyone follows them, unless there’s a hard fork, which is a different matter. So, in that regard, Bitcoin is definitely categorized as a digital asset by the government, and that’s where it stands. **Piccolo**:People who come to BO฿ Space to learn about Bitcoin are often influenced by the government from the point of price movements; especially when government support moves the price up. But they usually only visit once or twice, especially if they’re not deep into the Bitcoin rabbit hole. They often get disappointed because, at BO฿ Space, we rarely discuss the price—maybe once a year, and that’s just after the meetup when people are having drinks. So, in that sense, I’d say the government currently doesn’t really hurt or help the community either way. People will go down the rabbit hole at their own pace. And if you're not a Bitcoiner and you come to a BO฿ Space meetup with a crypto focus, you might be surprised by the approach we take. **YakiHonne**:Thank you, Piccolo, for your time and insights. It’s been a pleasure speaking with you. Your perspective on the evolution of Bitcoin communities was eye-opening. It's clear that your deep understanding of Bitcoin is invaluable. I'm sure our readers will appreciate your insights. Once again, thank you, Piccolo. I look forward to seeing the continued growth of BO฿ Space and Bitcoin adoption. @ 2183e947:f497b975
2025-03-29 02:41:34Today I was invited to participate in the private beta of a new social media protocol called Pubky, designed by a bitcoin company called Synonym with the goal of being better than existing social media platforms. As a heavy nostr user, I thought I'd write up a comparison. I can't tell you how to create your own accounts because it was made very clear that only *some* of the software is currently open source, and how this will all work is still a bit up in the air. The code that *is* open source can be found here: https://github.com/pubky -- and the most important repo there seems to be this one: https://github.com/pubky/pubky-core You can also learn more about Pubky here: https://pubky.org/ That said, I used my invite code to create a pubky account and it seemed very similar to onboarding to nostr. I generated a private key, backed up 12 words, and the onboarding website gave me a public key. Then I logged into a web-based client and it looked a lot like twitter. I saw a feed for posts by other users and saw options to reply to posts and give reactions, which, I saw, included hearts, thumbs up, and other emojis. Then I investigated a bit deeper to see how much it was like nostr. I opened up my developer console and navigated to my networking tab, where, if this was nostr, I would expect to see queries to relays for posts. Here, though, I saw one query that seemed to be repeated on a loop, which went to a single server and provided it with my pubkey. That single query (well, a series of identical queries to the same server) seemed to return all posts that showed up on my feed. So I infer that the server "knows" what posts to show me (perhaps it has some sort of algorithm, though the marketing material says it does not use algorithms) and the query was on a loop so that if any new posts came in that the server thinks I might want to see, it can add them to my feed. Then I checked what happens when I create a post. I did so and looked at what happened in my networking tab. If this was nostr, I would expect to see multiple copies of a signed messaged get sent to a bunch of relays. Here, though, I saw one message get sent to the same server that was populating my feed, and that message was not signed, it was a plaintext copy of my message. I happened to be in a group chat with John Carvalho at the time, who is associated with pubky. I asked him what was going on, and he said that pubky is based around three types of servers: homeservers, DHT servers, and indexer servers. The homeserver is where you create posts and where you query for posts to show on your feed. DHT servers are used for censorship resistance: each user creates an entry on a DHT server saying what homeserver they use, and these entries are signed by their key. As for indexers, I think those are supposed to speed up the use of the DHT servers. From what I could tell, indexers query DHT servers to find out what homeservers people use. When you query a homeserver for posts, it is supposed to reach out to indexer servers to find out the homeservers of people whose posts the homeserver decided to show you, and then query those homeservers for those posts. I believe they decided not to look up what homeservers people use directly on DHT servers directly because DHT servers are kind of slow, due to having to store and search through all sorts of non-social-media content, whereas indexers only store a simple db that maps each user's pubkey to their homeserver, so they are faster. Based on all of this info, it seems like, to populate your feed, this is the series of steps: - you tell your homeserver your pubkey - it uses some sort of algorithm to decide whose posts to show you - then looks up the homeservers used by those people on an indexer server - then it fetches posts from their homeservers - then your client displays them to you To create a post, this is the series of steps: - you tell your homeserver what you want to say to the world - it stores that message in plaintext and merely asserts that it came from you (it's not signed) - other people can find out what you said by querying for your posts on your homeserver Since posts on homeservers are not signed, I asked John what prevents a homeserver from just making up stuff and claiming I said it. He said nothing stops them from doing that, and if you are using a homeserver that starts acting up in that manner, what you should do is start using a new homeserver and update your DHT record to point at your new homeserver instead of the old one. Then, indexers should update their db to show where your new homeserver is, and the homeservers of people who "follow" you should stop pulling content from your old homeserver and start pulling it from your new one. If their homeserver is misbehaving too, I'm not sure what would happen. Maybe it could refuse to show them the content you've posted on your new homeserver, keeping making up fake content on your behalf that you've never posted, and maybe the people you follow would never learn you're being impersonated or have moved to a new homeserver. John also clarified that there is not currently any tooling for migrating user content from one homeserver to another. If pubky gets popular and a big homeserver starts misbehaving, users will probably need such a tool. But these are early days, so there aren't that many homeservers, and the ones that exist seem to be pretty trusted. Anyway, those are my initial thoughts on Pubky. Learn more here: https://pubky.org/
@ 2183e947:f497b975
2025-03-29 02:41:34Today I was invited to participate in the private beta of a new social media protocol called Pubky, designed by a bitcoin company called Synonym with the goal of being better than existing social media platforms. As a heavy nostr user, I thought I'd write up a comparison. I can't tell you how to create your own accounts because it was made very clear that only *some* of the software is currently open source, and how this will all work is still a bit up in the air. The code that *is* open source can be found here: https://github.com/pubky -- and the most important repo there seems to be this one: https://github.com/pubky/pubky-core You can also learn more about Pubky here: https://pubky.org/ That said, I used my invite code to create a pubky account and it seemed very similar to onboarding to nostr. I generated a private key, backed up 12 words, and the onboarding website gave me a public key. Then I logged into a web-based client and it looked a lot like twitter. I saw a feed for posts by other users and saw options to reply to posts and give reactions, which, I saw, included hearts, thumbs up, and other emojis. Then I investigated a bit deeper to see how much it was like nostr. I opened up my developer console and navigated to my networking tab, where, if this was nostr, I would expect to see queries to relays for posts. Here, though, I saw one query that seemed to be repeated on a loop, which went to a single server and provided it with my pubkey. That single query (well, a series of identical queries to the same server) seemed to return all posts that showed up on my feed. So I infer that the server "knows" what posts to show me (perhaps it has some sort of algorithm, though the marketing material says it does not use algorithms) and the query was on a loop so that if any new posts came in that the server thinks I might want to see, it can add them to my feed. Then I checked what happens when I create a post. I did so and looked at what happened in my networking tab. If this was nostr, I would expect to see multiple copies of a signed messaged get sent to a bunch of relays. Here, though, I saw one message get sent to the same server that was populating my feed, and that message was not signed, it was a plaintext copy of my message. I happened to be in a group chat with John Carvalho at the time, who is associated with pubky. I asked him what was going on, and he said that pubky is based around three types of servers: homeservers, DHT servers, and indexer servers. The homeserver is where you create posts and where you query for posts to show on your feed. DHT servers are used for censorship resistance: each user creates an entry on a DHT server saying what homeserver they use, and these entries are signed by their key. As for indexers, I think those are supposed to speed up the use of the DHT servers. From what I could tell, indexers query DHT servers to find out what homeservers people use. When you query a homeserver for posts, it is supposed to reach out to indexer servers to find out the homeservers of people whose posts the homeserver decided to show you, and then query those homeservers for those posts. I believe they decided not to look up what homeservers people use directly on DHT servers directly because DHT servers are kind of slow, due to having to store and search through all sorts of non-social-media content, whereas indexers only store a simple db that maps each user's pubkey to their homeserver, so they are faster. Based on all of this info, it seems like, to populate your feed, this is the series of steps: - you tell your homeserver your pubkey - it uses some sort of algorithm to decide whose posts to show you - then looks up the homeservers used by those people on an indexer server - then it fetches posts from their homeservers - then your client displays them to you To create a post, this is the series of steps: - you tell your homeserver what you want to say to the world - it stores that message in plaintext and merely asserts that it came from you (it's not signed) - other people can find out what you said by querying for your posts on your homeserver Since posts on homeservers are not signed, I asked John what prevents a homeserver from just making up stuff and claiming I said it. He said nothing stops them from doing that, and if you are using a homeserver that starts acting up in that manner, what you should do is start using a new homeserver and update your DHT record to point at your new homeserver instead of the old one. Then, indexers should update their db to show where your new homeserver is, and the homeservers of people who "follow" you should stop pulling content from your old homeserver and start pulling it from your new one. If their homeserver is misbehaving too, I'm not sure what would happen. Maybe it could refuse to show them the content you've posted on your new homeserver, keeping making up fake content on your behalf that you've never posted, and maybe the people you follow would never learn you're being impersonated or have moved to a new homeserver. John also clarified that there is not currently any tooling for migrating user content from one homeserver to another. If pubky gets popular and a big homeserver starts misbehaving, users will probably need such a tool. But these are early days, so there aren't that many homeservers, and the ones that exist seem to be pretty trusted. Anyway, those are my initial thoughts on Pubky. Learn more here: https://pubky.org/ @ 5d4b6c8d:8a1c1ee3
2025-03-29 02:18:49Only one more month to make adjustments and a couple of my guys haven't played enough games to be eligible for the awards. - Jokic needs to play two more - Giannis needs to play five more Other notable players who haven't yet played 65 games: - Luka is not even close - Brunson needs to play four more (and probably needs to be replaced regardless) - Wemby is not even close Here's the current state of the competition with your max possible score next to your nym: | Contestant | MVP | Champ | All NBA | | | | | |--------------|------|---------|----------|-|-|-|-| | @Undisciplined 47| SGA| OKC | Jokic | KAT |Giannis |Tatum | SGA | | @grayruby 46| SGA| Cavs| Jokic | Giannis | SGA| Mitchell| Brunson| | @gnilma 55| SGA| OKC| Jokic | KAT | Giannis | Tatum| SGA | | @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA| | @Bell_curve 63| SGA| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA| | @Carresan 34| SGA| Memphis| Jokic | KAT | Giannis | Ant| SGA| | @BTC_Bellzer 34| SGA| Celtics| Jokic| Giannis | Tatum| SGA| Brunson | | @realBitcoinDog 39| Lebron| Lakers| Jokic | Giannis | Ant | Brunson | SGA| | @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA| | @BlokchainB 38| SGA| Knicks| KAT| Giannis | Ant| Brunson| SGA| | @LibertasBR 14| SGA| Celtics| Jokic| Giannis | Tatum | Curry| SGA| | @Meani123 7| SGA| OKC| Jokic | KAT | Tatum | Mitchell | SGA| **Prize** At least 6k (I'll keep adding zaps to the pot). If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the [June post](https://stacker.news/items/585231/r/Undisciplined) for more details. originally posted at https://stacker.news/items/928370
@ 5d4b6c8d:8a1c1ee3
2025-03-29 02:18:49Only one more month to make adjustments and a couple of my guys haven't played enough games to be eligible for the awards. - Jokic needs to play two more - Giannis needs to play five more Other notable players who haven't yet played 65 games: - Luka is not even close - Brunson needs to play four more (and probably needs to be replaced regardless) - Wemby is not even close Here's the current state of the competition with your max possible score next to your nym: | Contestant | MVP | Champ | All NBA | | | | | |--------------|------|---------|----------|-|-|-|-| | @Undisciplined 47| SGA| OKC | Jokic | KAT |Giannis |Tatum | SGA | | @grayruby 46| SGA| Cavs| Jokic | Giannis | SGA| Mitchell| Brunson| | @gnilma 55| SGA| OKC| Jokic | KAT | Giannis | Tatum| SGA | | @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA| | @Bell_curve 63| SGA| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA| | @Carresan 34| SGA| Memphis| Jokic | KAT | Giannis | Ant| SGA| | @BTC_Bellzer 34| SGA| Celtics| Jokic| Giannis | Tatum| SGA| Brunson | | @realBitcoinDog 39| Lebron| Lakers| Jokic | Giannis | Ant | Brunson | SGA| | @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA| | @BlokchainB 38| SGA| Knicks| KAT| Giannis | Ant| Brunson| SGA| | @LibertasBR 14| SGA| Celtics| Jokic| Giannis | Tatum | Curry| SGA| | @Meani123 7| SGA| OKC| Jokic | KAT | Tatum | Mitchell | SGA| **Prize** At least 6k (I'll keep adding zaps to the pot). If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the [June post](https://stacker.news/items/585231/r/Undisciplined) for more details. originally posted at https://stacker.news/items/928370 @ df06d21e:2b23058f
2025-03-29 02:08:31Imagine a Living Civilization—a new way to see our world. It starts with the Universe’s pillars: Matter, the stuff we’re made of; Energy, the flow that drives us; Physics, the rules we play by; and Chemistry, the complexity that builds us. We know these well. But civilization? That’s our creation—and although it has been described in so many different ways over the years I thought it was time for something new. Civilization has its own pillars, systems that I call the pillars of the Metaverse: Capital, Information, Innovation, and Trust. Capital is how we measure value. Not just money, but everything that matters: skills, we call that Human Capital; ecosystems, that’s Natural Capital; infrastructure, Public Capital; relationships, Social Capital. Picture a farmer swapping Bitcoin sats for seeds—not fiat debt—or tracking soil health alongside his wallet. Capital is a system, a system of measurement. Information is how we verify truth. Think IPFS, a network holding real data—climate stats, farming fixes—open to all, not locked up by some corporate gatekeeper. Information is a system of verification. Innovation is about generating solutions. On GitHub, coders worldwide crank out tools—Nostr clients, solar apps—shared freely, not patented for profit. Innovation is our system of generation. And Trust—it’s coordination. Nostr’s decentralized threads let communities set trade rules, split resources—governance from the ground up, no overlords required. Trust is our system of coordination. Right now we’re stuck in debt-based systems—and they’re failing us. Take fiat currency—central banks print it, slashing your purchasing power. Our dollar buys less every year; savings erode while the elite stack their gains. It’s a scam, Bitcoiners know it—fiat’s the real Ponzi bleeding us dry. Capital gets twisted—firms hoard Bitcoin for fiat pumps, not real wealth; governments chase GDP while forests die and skills sit idle. Information is buried—our media spits out spin, our corporations lock truth in silos. Innovation is stalled—debt props up corporate patents, not open wins. Trust is gone—our governance systems consist of top-down control that splits us apart, left to right, top to bottom. Debt just measures scarcity—money borrowed, nature trashed, bonds frayed—and it’s crushing the pillars. Wealth-based systems promise to turn that around. Bitcoin’s sound money is just the start—sats hold value, not inflate it away. Real capital measures what sustains us—sats fund a cooperative's water pump, not a vault; they track skills taught, land healed, ties rebuilt. Real Information opens up—IPFS logs show ‘biochar boosted yield 20%’, verified by us, not suits. Real Innovation flows—GitHub devs build Lightning hubs, wealth spreads. Real Trust binds us together—Nostr chats align us, no central puppeteer. Wealth based systems strengthen the pillars of the Metaverse, it doesn’t erode them. We needed a new framing. A new vision of what was, what is, and what could be. We have one. This is real. This is the world we are building. Bitcoin is live, Nostr is growing, IPFS and GitHub are humming. We can see Debt teetering; while real wealth is rising. So, hodlers, maxis, plebs—everyone—what does a true wealth-based system look like? How can we measure Capital beyond fiat’s con job? Bitcoin’s the rock, but it’s just the beginning. How do we build on this, expand it, and transform everything as we build something entirely new?
@ df06d21e:2b23058f
2025-03-29 02:08:31Imagine a Living Civilization—a new way to see our world. It starts with the Universe’s pillars: Matter, the stuff we’re made of; Energy, the flow that drives us; Physics, the rules we play by; and Chemistry, the complexity that builds us. We know these well. But civilization? That’s our creation—and although it has been described in so many different ways over the years I thought it was time for something new. Civilization has its own pillars, systems that I call the pillars of the Metaverse: Capital, Information, Innovation, and Trust. Capital is how we measure value. Not just money, but everything that matters: skills, we call that Human Capital; ecosystems, that’s Natural Capital; infrastructure, Public Capital; relationships, Social Capital. Picture a farmer swapping Bitcoin sats for seeds—not fiat debt—or tracking soil health alongside his wallet. Capital is a system, a system of measurement. Information is how we verify truth. Think IPFS, a network holding real data—climate stats, farming fixes—open to all, not locked up by some corporate gatekeeper. Information is a system of verification. Innovation is about generating solutions. On GitHub, coders worldwide crank out tools—Nostr clients, solar apps—shared freely, not patented for profit. Innovation is our system of generation. And Trust—it’s coordination. Nostr’s decentralized threads let communities set trade rules, split resources—governance from the ground up, no overlords required. Trust is our system of coordination. Right now we’re stuck in debt-based systems—and they’re failing us. Take fiat currency—central banks print it, slashing your purchasing power. Our dollar buys less every year; savings erode while the elite stack their gains. It’s a scam, Bitcoiners know it—fiat’s the real Ponzi bleeding us dry. Capital gets twisted—firms hoard Bitcoin for fiat pumps, not real wealth; governments chase GDP while forests die and skills sit idle. Information is buried—our media spits out spin, our corporations lock truth in silos. Innovation is stalled—debt props up corporate patents, not open wins. Trust is gone—our governance systems consist of top-down control that splits us apart, left to right, top to bottom. Debt just measures scarcity—money borrowed, nature trashed, bonds frayed—and it’s crushing the pillars. Wealth-based systems promise to turn that around. Bitcoin’s sound money is just the start—sats hold value, not inflate it away. Real capital measures what sustains us—sats fund a cooperative's water pump, not a vault; they track skills taught, land healed, ties rebuilt. Real Information opens up—IPFS logs show ‘biochar boosted yield 20%’, verified by us, not suits. Real Innovation flows—GitHub devs build Lightning hubs, wealth spreads. Real Trust binds us together—Nostr chats align us, no central puppeteer. Wealth based systems strengthen the pillars of the Metaverse, it doesn’t erode them. We needed a new framing. A new vision of what was, what is, and what could be. We have one. This is real. This is the world we are building. Bitcoin is live, Nostr is growing, IPFS and GitHub are humming. We can see Debt teetering; while real wealth is rising. So, hodlers, maxis, plebs—everyone—what does a true wealth-based system look like? How can we measure Capital beyond fiat’s con job? Bitcoin’s the rock, but it’s just the beginning. How do we build on this, expand it, and transform everything as we build something entirely new? @ 3e6e0735:9e95c8a2
2025-03-28 23:58:02https://i.nostr.build/lanoHI3p2aCKRZlV.png I’ve been thinking a lot lately about why Bitcoin still feels so misunderstood. Not just by the media or the IMF — that part’s predictable. But even inside our own circles, something's missing. We say it’s money. We say it’s freedom. We say it’s code. And it is. But when you really zoom out, past the price and the politics, it’s something more radical than we usually admit. Bitcoin is a shift in how power moves. And what we do with that power now actually matters. ## The noise outside Let’s start with the obvious: the media still doesn’t get it. Every other headline is either a death knell or a celebration depending on the price that day. No context. No nuance. No understanding of what we’re building. You’ve seen the headlines: - “Bitcoin is crashing again.” - “Crypto bros are killing the planet.” - “The IMF warns: Bitcoin adoption is dangerous.” Yeah? Dangerous to what? The system they control. The levers they pull. The old game where the house always wins. That’s why they’re afraid. Not because Bitcoin is volatile, but because it doesn’t ask permission. ## This isn’t about panic — it’s about patterns I’m not saying there’s a conspiracy. But there is inertia. Institutions protect themselves. Systems reinforce themselves. They were never going to roll out the red carpet for an open, borderless network that replaces their function. So the IMF calls it a threat. Central banks scramble to launch CBDCs. And journalists keep writing the same shallow takes while ignoring the real story. Meanwhile, we’re still here. Still building. Still holding. Still running nodes. Bitcoin isn’t perfect. But it’s honest. It doesn’t bend to popularity or political pressure. It enforces rules with math, not people. And that’s exactly why it works. ## Even we miss it sometimes Here’s the part that really hit me recently: even within Bitcoin, we often undersell what this is. We talk about savings. Inflation. Fiat debasement. All real, all important. But what about the broader layer? What about governance? Energy? Communication? Defense? Jason Lowery’s book *Softwar* lit that fuse for me again. Not because it’s flawless — it’s not. But because he reframed the game. Bitcoin isn’t a new weapon. It’s the **end** of weapons-as-power. Proof-of-work, in Lowery’s view, is a form of peaceful negotiation. A deterrent against coercion. A way to shift from kinetic violence to computational resolution. Most people — even many Bitcoiners — haven’t fully absorbed that. It’s not about militarizing the network. It’s about **demilitarizing the world** through energy expenditure that replaces human conflict. Let’s be clear: this doesn’t mean Bitcoin *will* be used this way. It means it *can*. And that opens up a few possible futures: - **Scenario A:** Smaller nations adopt Bitcoin infrastructure as a shield — a deterrent and neutral layer to build sovereignty - **Scenario B:** Superpowers attack mining and self-custody, escalating regulatory capture and fragmenting the open protocol into corporate silos - **Scenario C:** Bitcoin becomes the boring backend of legacy finance, its edge neutered by ETFs and custody-as-a-service Which one wins depends on what we build — and who steps up. ## Then I found Maya I came across Maya Parbhoe’s campaign by accident. One of those late-night rabbit holes where Bitcoin Twitter turns into a global map. She’s running for president of Suriname. She’s a Bitcoiner. And she’s not just tweeting about it — she’s building an entire political platform around it. No central bank. Bitcoin as legal tender. Full fiscal transparency. Open-source government. Yeah. You read that right. Not just open-source software — open-source statehood. Her father was murdered after exposing corruption. That’s not a talking point. That’s real-life consequence. And instead of running away from systems, she’s choosing to redesign one. That’s maximalism. Not in ideology. In action. ## The El Salvador experiment — and evolution When El Salvador made Bitcoin legal tender in 2021, it lit up our feeds. It was bold. Unprecedented. A true first. But not without flaws. The rollout was fast. Chivo wallet was centralized. Adoption stalled in rural areas. Transparency was thin. And despite the brave move, the state’s underlying structure remained top-down. Bukele played offense, but the protocol was wrapped in traditional power. Maya is doing it differently. Her approach is grassroots-forward. Open-source by design. Focused on education, transparency, and modular state-building — not just mandates. She’s not using Bitcoin to *prop up* state power. She’s using it to *distribute* it. ## Maximalism is evolving Look, I get it. The memes are fun. The laser eyes. The beefsteak meetups. The HODL culture. But there’s something else growing here. Something a little quieter, a little deeper: - People running nodes to protect civil liberties - Communities using Lightning for real commerce - Builders forging tools for self-sovereign identity - Leaders like Maya testing what Bitcoin can look like as public infrastructure This is happening. In real time. It’s messy and fragile and still small. But it’s happening. Let’s also stay honest: Maximalism has its risks. Dogma can blind us. Toxicity can push people away. And if we’re not careful, we’ll replace one centralization with another — just wearing different memes. We need less purity, more principles. Less hype, more clarity. That’s the kind of maximalism Maya embodies. ## What now? Maya doesn’t have a VC fund or an ad agency. She has a message, a mission, and the courage to put Bitcoin on the ballot. If that resonates, help her. Not just by donating — though here’s the link: [https://geyser.fund/project/maya2025 ](https://geyser.fund/project/maya2025) But by sharing. Writing. Talking. Translating. Connecting. Bitcoin is still early. But it’s not abstract anymore. This isn’t just theory. It’s a protocol, sure. But now, maybe it’s a presidency too. https://i.nostr.build/0luYy8ojK7gkxsuL.png
@ 3e6e0735:9e95c8a2
2025-03-28 23:58:02https://i.nostr.build/lanoHI3p2aCKRZlV.png I’ve been thinking a lot lately about why Bitcoin still feels so misunderstood. Not just by the media or the IMF — that part’s predictable. But even inside our own circles, something's missing. We say it’s money. We say it’s freedom. We say it’s code. And it is. But when you really zoom out, past the price and the politics, it’s something more radical than we usually admit. Bitcoin is a shift in how power moves. And what we do with that power now actually matters. ## The noise outside Let’s start with the obvious: the media still doesn’t get it. Every other headline is either a death knell or a celebration depending on the price that day. No context. No nuance. No understanding of what we’re building. You’ve seen the headlines: - “Bitcoin is crashing again.” - “Crypto bros are killing the planet.” - “The IMF warns: Bitcoin adoption is dangerous.” Yeah? Dangerous to what? The system they control. The levers they pull. The old game where the house always wins. That’s why they’re afraid. Not because Bitcoin is volatile, but because it doesn’t ask permission. ## This isn’t about panic — it’s about patterns I’m not saying there’s a conspiracy. But there is inertia. Institutions protect themselves. Systems reinforce themselves. They were never going to roll out the red carpet for an open, borderless network that replaces their function. So the IMF calls it a threat. Central banks scramble to launch CBDCs. And journalists keep writing the same shallow takes while ignoring the real story. Meanwhile, we’re still here. Still building. Still holding. Still running nodes. Bitcoin isn’t perfect. But it’s honest. It doesn’t bend to popularity or political pressure. It enforces rules with math, not people. And that’s exactly why it works. ## Even we miss it sometimes Here’s the part that really hit me recently: even within Bitcoin, we often undersell what this is. We talk about savings. Inflation. Fiat debasement. All real, all important. But what about the broader layer? What about governance? Energy? Communication? Defense? Jason Lowery’s book *Softwar* lit that fuse for me again. Not because it’s flawless — it’s not. But because he reframed the game. Bitcoin isn’t a new weapon. It’s the **end** of weapons-as-power. Proof-of-work, in Lowery’s view, is a form of peaceful negotiation. A deterrent against coercion. A way to shift from kinetic violence to computational resolution. Most people — even many Bitcoiners — haven’t fully absorbed that. It’s not about militarizing the network. It’s about **demilitarizing the world** through energy expenditure that replaces human conflict. Let’s be clear: this doesn’t mean Bitcoin *will* be used this way. It means it *can*. And that opens up a few possible futures: - **Scenario A:** Smaller nations adopt Bitcoin infrastructure as a shield — a deterrent and neutral layer to build sovereignty - **Scenario B:** Superpowers attack mining and self-custody, escalating regulatory capture and fragmenting the open protocol into corporate silos - **Scenario C:** Bitcoin becomes the boring backend of legacy finance, its edge neutered by ETFs and custody-as-a-service Which one wins depends on what we build — and who steps up. ## Then I found Maya I came across Maya Parbhoe’s campaign by accident. One of those late-night rabbit holes where Bitcoin Twitter turns into a global map. She’s running for president of Suriname. She’s a Bitcoiner. And she’s not just tweeting about it — she’s building an entire political platform around it. No central bank. Bitcoin as legal tender. Full fiscal transparency. Open-source government. Yeah. You read that right. Not just open-source software — open-source statehood. Her father was murdered after exposing corruption. That’s not a talking point. That’s real-life consequence. And instead of running away from systems, she’s choosing to redesign one. That’s maximalism. Not in ideology. In action. ## The El Salvador experiment — and evolution When El Salvador made Bitcoin legal tender in 2021, it lit up our feeds. It was bold. Unprecedented. A true first. But not without flaws. The rollout was fast. Chivo wallet was centralized. Adoption stalled in rural areas. Transparency was thin. And despite the brave move, the state’s underlying structure remained top-down. Bukele played offense, but the protocol was wrapped in traditional power. Maya is doing it differently. Her approach is grassroots-forward. Open-source by design. Focused on education, transparency, and modular state-building — not just mandates. She’s not using Bitcoin to *prop up* state power. She’s using it to *distribute* it. ## Maximalism is evolving Look, I get it. The memes are fun. The laser eyes. The beefsteak meetups. The HODL culture. But there’s something else growing here. Something a little quieter, a little deeper: - People running nodes to protect civil liberties - Communities using Lightning for real commerce - Builders forging tools for self-sovereign identity - Leaders like Maya testing what Bitcoin can look like as public infrastructure This is happening. In real time. It’s messy and fragile and still small. But it’s happening. Let’s also stay honest: Maximalism has its risks. Dogma can blind us. Toxicity can push people away. And if we’re not careful, we’ll replace one centralization with another — just wearing different memes. We need less purity, more principles. Less hype, more clarity. That’s the kind of maximalism Maya embodies. ## What now? Maya doesn’t have a VC fund or an ad agency. She has a message, a mission, and the courage to put Bitcoin on the ballot. If that resonates, help her. Not just by donating — though here’s the link: [https://geyser.fund/project/maya2025 ](https://geyser.fund/project/maya2025) But by sharing. Writing. Talking. Translating. Connecting. Bitcoin is still early. But it’s not abstract anymore. This isn’t just theory. It’s a protocol, sure. But now, maybe it’s a presidency too. https://i.nostr.build/0luYy8ojK7gkxsuL.png @ 7d33ba57:1b82db35
2025-03-28 22:14:24Preko is a charming seaside town on Ugljan Island, just a short ferry ride from Zadar. Known for its beautiful beaches, relaxed atmosphere, and stunning views of the Adriatic, it's the perfect place to experience authentic Dalmatian island life.  ## **🌊 Top Things to See & Do in Preko** ### **1️⃣ Swim at Jaz Beach 🏖️** - A **Blue Flag beach** with **clear turquoise waters and soft pebbles**. - Ideal for **families** thanks to its shallow waters. - Nearby **cafés and restaurants** make it a great spot to spend the day. ### **2️⃣ Visit the Islet of Galevac 🏝️** - A **tiny island just 80 meters from Preko**, reachable by swimming or a short boat ride. - Home to a **15th-century Franciscan monastery**, surrounded by lush greenery. - A **peaceful retreat**, perfect for relaxation.  ### **3️⃣ Hike to St. Michael’s Fortress (Sv. Mihovil) 🏰** - A **medieval fortress from the 13th century** with **breathtaking panoramic views**. - Overlooks **Zadar, Kornati Islands, and the Adriatic Sea**. - A **1-hour scenic hike** from Preko or accessible by **bike or car**. ### **4️⃣ Explore the Local Taverns & Seafood Restaurants 🍽️** - Try **fresh seafood, octopus salad, and Dalmatian peka (slow-cooked meat & vegetables)**. - **Best spots:** Konoba Roko (authentic seafood) & Vile Dalmacija (beachfront dining). ### **5️⃣ Rent a Bike or Scooter 🚲** - Explore **Ugljan Island’s olive groves, hidden coves, and coastal paths**. - Visit nearby villages like **Kali and Kukljica** for more local charm.  ### **6️⃣ Take a Day Trip to Zadar ⛵** - Just **25 minutes by ferry**, Zadar offers **historic landmarks, the Sea Organ, and Roman ruins**. - Perfect for a cultural excursion before returning to the peaceful island.  ## **🚗 How to Get to Preko** 🚢 **By Ferry:** - **From Zadar:** Regular ferries (Jadrolinija) take **~25 minutes**. 🚘 **By Car:** - If driving, take the **ferry from Zadar to Preko** and explore the island. 🚴 **By Bike:** - Many visitors rent bikes to explore Ugljan Island’s coastal roads.  ## **💡 Tips for Visiting Preko** ✅ **Best time to visit?** **May–September** for warm weather & swimming 🌞 ✅ **Ferry schedules** – Check times in advance, especially in the off-season ⏳ ✅ **Bring cash** – Some smaller taverns and cafés may not accept cards 💰 ✅ **Stay for sunset** – The views over Zadar from Preko’s waterfront are stunning 🌅 Would you like **hotel recommendations, hidden beaches, or other island activities**? 😊
@ 7d33ba57:1b82db35
2025-03-28 22:14:24Preko is a charming seaside town on Ugljan Island, just a short ferry ride from Zadar. Known for its beautiful beaches, relaxed atmosphere, and stunning views of the Adriatic, it's the perfect place to experience authentic Dalmatian island life.  ## **🌊 Top Things to See & Do in Preko** ### **1️⃣ Swim at Jaz Beach 🏖️** - A **Blue Flag beach** with **clear turquoise waters and soft pebbles**. - Ideal for **families** thanks to its shallow waters. - Nearby **cafés and restaurants** make it a great spot to spend the day. ### **2️⃣ Visit the Islet of Galevac 🏝️** - A **tiny island just 80 meters from Preko**, reachable by swimming or a short boat ride. - Home to a **15th-century Franciscan monastery**, surrounded by lush greenery. - A **peaceful retreat**, perfect for relaxation.  ### **3️⃣ Hike to St. Michael’s Fortress (Sv. Mihovil) 🏰** - A **medieval fortress from the 13th century** with **breathtaking panoramic views**. - Overlooks **Zadar, Kornati Islands, and the Adriatic Sea**. - A **1-hour scenic hike** from Preko or accessible by **bike or car**. ### **4️⃣ Explore the Local Taverns & Seafood Restaurants 🍽️** - Try **fresh seafood, octopus salad, and Dalmatian peka (slow-cooked meat & vegetables)**. - **Best spots:** Konoba Roko (authentic seafood) & Vile Dalmacija (beachfront dining). ### **5️⃣ Rent a Bike or Scooter 🚲** - Explore **Ugljan Island’s olive groves, hidden coves, and coastal paths**. - Visit nearby villages like **Kali and Kukljica** for more local charm.  ### **6️⃣ Take a Day Trip to Zadar ⛵** - Just **25 minutes by ferry**, Zadar offers **historic landmarks, the Sea Organ, and Roman ruins**. - Perfect for a cultural excursion before returning to the peaceful island.  ## **🚗 How to Get to Preko** 🚢 **By Ferry:** - **From Zadar:** Regular ferries (Jadrolinija) take **~25 minutes**. 🚘 **By Car:** - If driving, take the **ferry from Zadar to Preko** and explore the island. 🚴 **By Bike:** - Many visitors rent bikes to explore Ugljan Island’s coastal roads.  ## **💡 Tips for Visiting Preko** ✅ **Best time to visit?** **May–September** for warm weather & swimming 🌞 ✅ **Ferry schedules** – Check times in advance, especially in the off-season ⏳ ✅ **Bring cash** – Some smaller taverns and cafés may not accept cards 💰 ✅ **Stay for sunset** – The views over Zadar from Preko’s waterfront are stunning 🌅 Would you like **hotel recommendations, hidden beaches, or other island activities**? 😊 @ fe9e99a0:5123e9a8
2025-03-28 21:25:43What’s happening?
@ fe9e99a0:5123e9a8
2025-03-28 21:25:43What’s happening? @ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice. A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases. Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy. Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest. Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice. A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases. Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy. Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest. Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever. @ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits. **Small Wins** Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it. **Ego is Volatile** Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic. **Simplicity** There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life. **The Big Picture** Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits. **Small Wins** Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it. **Ego is Volatile** Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic. **Simplicity** There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life. **The Big Picture** Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡 @ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below. ## House Democrats’ MEME Act: A Bad Joke? House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself. ## Senate Banking’s First Digital Asset Hearing: The Real Target Is You Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.” ## Bank of America and PayPal Want In on Stablecoins Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance. ## MetaPlanet Buys the Dip Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats. ## UK Expands Crypto Seizure Powers Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance. ## Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier. ## The Bottom Line The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control. **🎧 Listen to the full episode here: [https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks](Fountain.fm)** **💰 Support the show by boosting sats on Podcasting 2.0!** and I will see you on the other side.
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below. ## House Democrats’ MEME Act: A Bad Joke? House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself. ## Senate Banking’s First Digital Asset Hearing: The Real Target Is You Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.” ## Bank of America and PayPal Want In on Stablecoins Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance. ## MetaPlanet Buys the Dip Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats. ## UK Expands Crypto Seizure Powers Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance. ## Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier. ## The Bottom Line The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control. **🎧 Listen to the full episode here: [https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks](Fountain.fm)** **💰 Support the show by boosting sats on Podcasting 2.0!** and I will see you on the other side. @ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from *The Mandibles: A Family, 2029–2047* by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes. ### Part One: 2029–2032 - **2029 (Early Year)**\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor. - **2029 (Mid-Year: The Great Renunciation)**\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive. - **2029 (Late Year)**\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant. - **2030–2031**\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness. - **2032**\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured. ### Time Jump: 2032–2047 - Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies. ### Part Two: 2047 - **2047 (Early Year)**\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum. - **2047 (Mid-Year)**\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency. - **2047 (Late Year)**\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society. ### Key Differences - **Currency Dynamics**: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control. - **Government Power**: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities. - **Societal Outcome**: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots. This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from *The Mandibles: A Family, 2029–2047* by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes. ### Part One: 2029–2032 - **2029 (Early Year)**\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor. - **2029 (Mid-Year: The Great Renunciation)**\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive. - **2029 (Late Year)**\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant. - **2030–2031**\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness. - **2032**\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured. ### Time Jump: 2032–2047 - Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies. ### Part Two: 2047 - **2047 (Early Year)**\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum. - **2047 (Mid-Year)**\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency. - **2047 (Late Year)**\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society. ### Key Differences - **Currency Dynamics**: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control. - **Government Power**: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities. - **Societal Outcome**: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots. This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory. @ 7d33ba57:1b82db35
2025-03-28 20:59:51Krka National Park, located in central Dalmatia, is one of Croatia’s most breathtaking natural wonders. Famous for its stunning waterfalls, crystal-clear lakes, and lush forests, the park is a must-visit for nature lovers. Unlike Plitvice Lakes, Krka allows swimming in certain areas, making it a perfect summer escape.  ## **🌊 Top Things to See & Do in Krka National Park** ### **1️⃣ Skradinski Buk Waterfall 💦** - The **largest and most famous waterfall** in the park, with **cascading pools and wooden walkways**. - You **used to be able to swim here**, but since 2021, swimming is no longer allowed. - Perfect for **photography and picnics**. ### **2️⃣ Roški Slap Waterfall 🌿** - A **less crowded but equally beautiful** series of waterfalls. - Known for its **"necklace" of small cascades** leading into the main fall. - Nearby **Mlinica**, a restored **watermill**, shows traditional Croatian life. ### **3️⃣ Visovac Island & Monastery 🏝️** - A **tiny island** in the middle of the Krka River, home to a **Franciscan monastery** from the 15th century. - Accessible by **boat tour** from Skradinski Buk or Roški Slap. - A peaceful, scenic spot with **stunning views of the lake**.  ### **4️⃣ Krka Monastery 🏛️** - A **Serbian Orthodox monastery** hidden deep in the park. - Built on **ancient Roman catacombs**, which you can explore. - A **quiet, spiritual place**, often overlooked by tourists. ### **5️⃣ Hike & Walk the Nature Trails 🥾** - The park has **several well-marked trails** through forests, waterfalls, and lakes. - Wooden walkways allow **easy access** to the main sights. - **Wildlife spotting**: Look out for **otters, turtles, and over 200 bird species**! ### **6️⃣ Swim at Skradin Beach 🏖️** - While you can’t swim at Skradinski Buk anymore, **Skradin Beach**, just outside the park, is a great spot for a dip. - **Kayaking and boat tours** available.  ## **🚗 How to Get to Krka National Park** ✈️ **By Air:** The nearest airport is **Split (SPU), 1 hour away**. 🚘 **By Car:** - **Split to Krka:** ~1 hour (85 km) - **Zadar to Krka:** ~1 hour (75 km) - **Dubrovnik to Krka:** ~3.5 hours (280 km) 🚌 **By Bus:** Direct buses from **Split, Zadar, and Šibenik** to the park’s entrances. 🚢 **By Boat:** From **Skradin**, you can take a **boat ride** into the park.  ## **💡 Tips for Visiting Krka National Park** ✅ **Best time to visit?** **Spring & early autumn (April–June, September–October)** – Fewer crowds & mild weather 🍃 ✅ **Start early!** **Arrive before 10 AM** to avoid crowds, especially in summer ☀️ ✅ **Bring water & snacks** – Limited food options inside the park 🍎 ✅ **Wear comfy shoes** – Wooden walkways & trails can be slippery 👟 ✅ **Take a boat tour** – The best way to see Visovac Island & hidden spots ⛵ ✅ **Buy tickets online** – Save time at the entrance 🎟️ 
@ 7d33ba57:1b82db35
2025-03-28 20:59:51Krka National Park, located in central Dalmatia, is one of Croatia’s most breathtaking natural wonders. Famous for its stunning waterfalls, crystal-clear lakes, and lush forests, the park is a must-visit for nature lovers. Unlike Plitvice Lakes, Krka allows swimming in certain areas, making it a perfect summer escape.  ## **🌊 Top Things to See & Do in Krka National Park** ### **1️⃣ Skradinski Buk Waterfall 💦** - The **largest and most famous waterfall** in the park, with **cascading pools and wooden walkways**. - You **used to be able to swim here**, but since 2021, swimming is no longer allowed. - Perfect for **photography and picnics**. ### **2️⃣ Roški Slap Waterfall 🌿** - A **less crowded but equally beautiful** series of waterfalls. - Known for its **"necklace" of small cascades** leading into the main fall. - Nearby **Mlinica**, a restored **watermill**, shows traditional Croatian life. ### **3️⃣ Visovac Island & Monastery 🏝️** - A **tiny island** in the middle of the Krka River, home to a **Franciscan monastery** from the 15th century. - Accessible by **boat tour** from Skradinski Buk or Roški Slap. - A peaceful, scenic spot with **stunning views of the lake**.  ### **4️⃣ Krka Monastery 🏛️** - A **Serbian Orthodox monastery** hidden deep in the park. - Built on **ancient Roman catacombs**, which you can explore. - A **quiet, spiritual place**, often overlooked by tourists. ### **5️⃣ Hike & Walk the Nature Trails 🥾** - The park has **several well-marked trails** through forests, waterfalls, and lakes. - Wooden walkways allow **easy access** to the main sights. - **Wildlife spotting**: Look out for **otters, turtles, and over 200 bird species**! ### **6️⃣ Swim at Skradin Beach 🏖️** - While you can’t swim at Skradinski Buk anymore, **Skradin Beach**, just outside the park, is a great spot for a dip. - **Kayaking and boat tours** available.  ## **🚗 How to Get to Krka National Park** ✈️ **By Air:** The nearest airport is **Split (SPU), 1 hour away**. 🚘 **By Car:** - **Split to Krka:** ~1 hour (85 km) - **Zadar to Krka:** ~1 hour (75 km) - **Dubrovnik to Krka:** ~3.5 hours (280 km) 🚌 **By Bus:** Direct buses from **Split, Zadar, and Šibenik** to the park’s entrances. 🚢 **By Boat:** From **Skradin**, you can take a **boat ride** into the park.  ## **💡 Tips for Visiting Krka National Park** ✅ **Best time to visit?** **Spring & early autumn (April–June, September–October)** – Fewer crowds & mild weather 🍃 ✅ **Start early!** **Arrive before 10 AM** to avoid crowds, especially in summer ☀️ ✅ **Bring water & snacks** – Limited food options inside the park 🍎 ✅ **Wear comfy shoes** – Wooden walkways & trails can be slippery 👟 ✅ **Take a boat tour** – The best way to see Visovac Island & hidden spots ⛵ ✅ **Buy tickets online** – Save time at the entrance 🎟️  @ da0b9bc3:4e30a4a9
2025-03-28 19:14:52It's Finally here Stackers! It's Friday! We're about to kick off our weekends with some feel good tracks. Let's get the party started. Bring me those Feel Good tracks. Let's get it! https://youtu.be/r1ATFedwjnk?si=tPtLac6ExYZCx3Ez originally posted at https://stacker.news/items/928119
@ da0b9bc3:4e30a4a9
2025-03-28 19:14:52It's Finally here Stackers! It's Friday! We're about to kick off our weekends with some feel good tracks. Let's get the party started. Bring me those Feel Good tracks. Let's get it! https://youtu.be/r1ATFedwjnk?si=tPtLac6ExYZCx3Ez originally posted at https://stacker.news/items/928119 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard. — We want to speak with the president — the man said in a low voice. — He will be busy all day — the secretary replied curtly. — We will wait. The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that. — If you speak with them for just a few minutes, maybe they will decide to go away — she said. The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple. — We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus. — My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery. — Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard. The president looked at the woman's faded dress and her husband's old suit and exclaimed: — A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard. The lady was silent for a moment, then said to her husband: — If that’s all it costs to found a university, why don’t we have our own? The husband agreed. The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student." Text extracted from: "Mileumlivros - Stories that Teach Values." Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation. A toast to our family!
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard. — We want to speak with the president — the man said in a low voice. — He will be busy all day — the secretary replied curtly. — We will wait. The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that. — If you speak with them for just a few minutes, maybe they will decide to go away — she said. The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple. — We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus. — My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery. — Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard. The president looked at the woman's faded dress and her husband's old suit and exclaimed: — A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard. The lady was silent for a moment, then said to her husband: — If that’s all it costs to found a university, why don’t we have our own? The husband agreed. The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student." Text extracted from: "Mileumlivros - Stories that Teach Values." Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation. A toast to our family! @ 0d6c8388:46488a33
2025-03-28 16:24:00Huge thank you to [OpenSats for the grant](https://opensats.org/blog/10th-wave-of-nostr-grants) to work on [Hypernote this year](https://www.hypernote.club/)! I thought I'd take this opportunity to try and share my thought processes for Hypernote. If this all sounds very dense or irrelevant to you I'm sorry! === How can the ideas of "hypermedia" benefit nostr? That's the goal of hypernote. To take the best ideas from "hypertext" and "hypercard" and "hypermedia systems" and apply them to nostr in a specifically nostr-ey way. ### 1. What do we mean by hypermedia A hypermedia document embeds the methods of interaction (links, forms, and buttons are the most well-known hypermedia controls) within the document itself. It's including the _how_ with the _what_. This is how the old web worked. An HTML page was delivered to the web browser, and it included in it a link or perhaps a form that could be submitted to obtain a new, different HTML page. This is how the whole web worked early on! Forums and GeoCities and eBay and MySpace and Yahoo! and Amazon and Google all emerged inside this paradigm. A web browser in this paradigm was a "thin" client which rendered the "thick" application defined in the HTML (and, implicitly, was defined by the server that would serve that HTML). Contrast this with modern app development, where the _what_ is usually delivered in the form of JSON, and then HTML combined with JavaScript (React, Svelte, Angular, Vue, etc.) is devised to render that JSON as a meaningful piece of hypermedia within the actual browser, the _how_. The browser remains a "thin" client in this scenario, but now the application is delivered in two stages: a client application of HTML and JavaScript, and then the actual JSON data that will hydrate that "application". (Aside: it's interesting how much "thicker" the browser has had to become to support this newer paradigm!) Nostr was obviously built in line with the modern paradigm: nostr "clients" (written in React or Svelte or as mobile apps) define the _how_ of reading and creating nostr events, while nostr events themselves (JSON data) simply describe the _what_. And so the goal with Hypernote is to square this circle somehow: nostr currently delivers JSON _what_, how do we deliver the _how_ with nostr as well. Is that even possible? ### 2. Hypernote's design assumptions Hypernote assumes that hypermedia over nostr is a good idea! I'm expecting some joyful renaissance of app expression similar to that of the web once we figure out how to express applications in a truly "nostr" way. Hypernote was also [deeply inspired by HTMX](https://hypermedia.systems/hypermedia-a-reintroduction/), so it assumes that building web apps in the HTMX style is a good idea. The HTMX insight is that instead of shipping rich scripting along with your app, you could simply make HTML a _tiny_ bit more expressive and get 95% of what most apps need. HTMX's additions to the HTML language are designed to be as minimal and composable as possible, and Hypernote should have the same aims. Hypernote also assumes that the "design" of nostr will remain fluid and anarchic for years to come. There will be no "canonical" list of "required" NIPs that we'll have "consensus" on in order to build stable UIs on top of. Hypernote will need to be built responsive to nostr's moods and seasons, rather than one holy spec. Hypernote likes the `nak` command line tool. Hypernote likes markdown. Hypernote likes Tailwind CSS. Hypernote likes SolidJS. Hypernote likes cold brew coffee. Hypernote is, to be perfectly honest, my aesthetic preferences applied to my perception of an opportunity in the nostr ecosystem. ### 3. "What's a hypernote?" Great question. I'm still figuring this out. Everything right now is subject to change in order to make sure hypernote serves its intended purpose. But here's where things currently stand: A hypernote is a flat list of "Hypernote Elements". A Hypernote Element is composed of: 1. CONTENT. Static or dynamic content. (the what) 2. LOGIC. Filters and events (the how) 3. STYLE. Optional, inline style information specific to this element's content. In the most basic example of a [hypernote story](https://hypernote-stories.fly.dev/), here's a lone "edit me" in the middle of the canvas:  ``` { "id": "fb4aaed4-bf95-4353-a5e1-0bb64525c08f", "type": "text", "text": "edit me", "x": 540, "y": 960, "size": "md", "color": "black" } ``` As you can see, it has no logic, but it does have some content (the text "edit me") and style (the position, size, and color). Here's a "sticker" that displays a note: ``` { "id": "2cd1ef51-3356-408d-b10d-2502cbb8014e", "type": "sticker", "stickerType": "note", "filter": { "kinds": [ 1 ], "ids": [ "92de77507a361ab2e20385d98ff00565aaf3f80cf2b6d89c0343e08166fed931" ], "limit": 1 }, "accessors": [ "content", "pubkey", "created_at" ], "x": 540, "y": 960, "associatedData": {} } ``` As you can see, it's kind of a mess! The content and styling and underdeveloped for this "sticker", but at least it demonstrates some "logic": a nostr filter for getting its data. Here's another sticker, this one displays a form that the user can interact with to SEND a note. Very hyper of us! ``` { "id": "42240d75-e998-4067-b8fa-9ee096365663", "type": "sticker", "stickerType": "prompt", "filter": {}, "accessors": [], "x": 540, "y": 960, "associatedData": { "promptText": "What's your favorite color?" }, "methods": { "comment": { "description": "comment", "eventTemplate": { "kind": 1111, "content": "${content}", "tags": [ [ "E", "${eventId}", "", "${pubkey}" ], [ "K", "${eventKind}" ], [ "P", "${pubkey}" ], [ "e", "${eventId}", "", "${pubkey}" ], [ "k", "${eventKind}" ], [ "p", "${pubkey}" ] ] } } } } ``` It's also a mess, but it demos the other part of "logic": methods which produce new events. This is the total surface of hypernote, ideally! Static or dynamic content, simple inline styles, and logic for fetching and producing events. I'm calling it "logic" but it's purposfully not a whole scripting language. At most we'll have some sort of `jq`-like language for destructing the relevant piece of data we want. My ideal syntax for a hypernote as a developer will look something like ```foo.hypernote Nak-like logic Markdown-like content CSS-like styles ``` But with JSON as the compile target, this can just be my own preference, there can be other (likely better!) ways of authoring this content, such as a Hypernote Stories GUI. ### The end I know this is all still vague but I wanted to get some ideas out in the wild so people understand the through line of my different Hypernote experiments. I want to get the right amount of "expressivity" in Hypernote before it gets locked down into one spec. My hunch is it can be VERY expressive while remaining simple and also while not needing a whole scripting language bolted onto it. If I can't pull it off I'll let you know.
@ 0d6c8388:46488a33
2025-03-28 16:24:00Huge thank you to [OpenSats for the grant](https://opensats.org/blog/10th-wave-of-nostr-grants) to work on [Hypernote this year](https://www.hypernote.club/)! I thought I'd take this opportunity to try and share my thought processes for Hypernote. If this all sounds very dense or irrelevant to you I'm sorry! === How can the ideas of "hypermedia" benefit nostr? That's the goal of hypernote. To take the best ideas from "hypertext" and "hypercard" and "hypermedia systems" and apply them to nostr in a specifically nostr-ey way. ### 1. What do we mean by hypermedia A hypermedia document embeds the methods of interaction (links, forms, and buttons are the most well-known hypermedia controls) within the document itself. It's including the _how_ with the _what_. This is how the old web worked. An HTML page was delivered to the web browser, and it included in it a link or perhaps a form that could be submitted to obtain a new, different HTML page. This is how the whole web worked early on! Forums and GeoCities and eBay and MySpace and Yahoo! and Amazon and Google all emerged inside this paradigm. A web browser in this paradigm was a "thin" client which rendered the "thick" application defined in the HTML (and, implicitly, was defined by the server that would serve that HTML). Contrast this with modern app development, where the _what_ is usually delivered in the form of JSON, and then HTML combined with JavaScript (React, Svelte, Angular, Vue, etc.) is devised to render that JSON as a meaningful piece of hypermedia within the actual browser, the _how_. The browser remains a "thin" client in this scenario, but now the application is delivered in two stages: a client application of HTML and JavaScript, and then the actual JSON data that will hydrate that "application". (Aside: it's interesting how much "thicker" the browser has had to become to support this newer paradigm!) Nostr was obviously built in line with the modern paradigm: nostr "clients" (written in React or Svelte or as mobile apps) define the _how_ of reading and creating nostr events, while nostr events themselves (JSON data) simply describe the _what_. And so the goal with Hypernote is to square this circle somehow: nostr currently delivers JSON _what_, how do we deliver the _how_ with nostr as well. Is that even possible? ### 2. Hypernote's design assumptions Hypernote assumes that hypermedia over nostr is a good idea! I'm expecting some joyful renaissance of app expression similar to that of the web once we figure out how to express applications in a truly "nostr" way. Hypernote was also [deeply inspired by HTMX](https://hypermedia.systems/hypermedia-a-reintroduction/), so it assumes that building web apps in the HTMX style is a good idea. The HTMX insight is that instead of shipping rich scripting along with your app, you could simply make HTML a _tiny_ bit more expressive and get 95% of what most apps need. HTMX's additions to the HTML language are designed to be as minimal and composable as possible, and Hypernote should have the same aims. Hypernote also assumes that the "design" of nostr will remain fluid and anarchic for years to come. There will be no "canonical" list of "required" NIPs that we'll have "consensus" on in order to build stable UIs on top of. Hypernote will need to be built responsive to nostr's moods and seasons, rather than one holy spec. Hypernote likes the `nak` command line tool. Hypernote likes markdown. Hypernote likes Tailwind CSS. Hypernote likes SolidJS. Hypernote likes cold brew coffee. Hypernote is, to be perfectly honest, my aesthetic preferences applied to my perception of an opportunity in the nostr ecosystem. ### 3. "What's a hypernote?" Great question. I'm still figuring this out. Everything right now is subject to change in order to make sure hypernote serves its intended purpose. But here's where things currently stand: A hypernote is a flat list of "Hypernote Elements". A Hypernote Element is composed of: 1. CONTENT. Static or dynamic content. (the what) 2. LOGIC. Filters and events (the how) 3. STYLE. Optional, inline style information specific to this element's content. In the most basic example of a [hypernote story](https://hypernote-stories.fly.dev/), here's a lone "edit me" in the middle of the canvas:  ``` { "id": "fb4aaed4-bf95-4353-a5e1-0bb64525c08f", "type": "text", "text": "edit me", "x": 540, "y": 960, "size": "md", "color": "black" } ``` As you can see, it has no logic, but it does have some content (the text "edit me") and style (the position, size, and color). Here's a "sticker" that displays a note: ``` { "id": "2cd1ef51-3356-408d-b10d-2502cbb8014e", "type": "sticker", "stickerType": "note", "filter": { "kinds": [ 1 ], "ids": [ "92de77507a361ab2e20385d98ff00565aaf3f80cf2b6d89c0343e08166fed931" ], "limit": 1 }, "accessors": [ "content", "pubkey", "created_at" ], "x": 540, "y": 960, "associatedData": {} } ``` As you can see, it's kind of a mess! The content and styling and underdeveloped for this "sticker", but at least it demonstrates some "logic": a nostr filter for getting its data. Here's another sticker, this one displays a form that the user can interact with to SEND a note. Very hyper of us! ``` { "id": "42240d75-e998-4067-b8fa-9ee096365663", "type": "sticker", "stickerType": "prompt", "filter": {}, "accessors": [], "x": 540, "y": 960, "associatedData": { "promptText": "What's your favorite color?" }, "methods": { "comment": { "description": "comment", "eventTemplate": { "kind": 1111, "content": "${content}", "tags": [ [ "E", "${eventId}", "", "${pubkey}" ], [ "K", "${eventKind}" ], [ "P", "${pubkey}" ], [ "e", "${eventId}", "", "${pubkey}" ], [ "k", "${eventKind}" ], [ "p", "${pubkey}" ] ] } } } } ``` It's also a mess, but it demos the other part of "logic": methods which produce new events. This is the total surface of hypernote, ideally! Static or dynamic content, simple inline styles, and logic for fetching and producing events. I'm calling it "logic" but it's purposfully not a whole scripting language. At most we'll have some sort of `jq`-like language for destructing the relevant piece of data we want. My ideal syntax for a hypernote as a developer will look something like ```foo.hypernote Nak-like logic Markdown-like content CSS-like styles ``` But with JSON as the compile target, this can just be my own preference, there can be other (likely better!) ways of authoring this content, such as a Hypernote Stories GUI. ### The end I know this is all still vague but I wanted to get some ideas out in the wild so people understand the through line of my different Hypernote experiments. I want to get the right amount of "expressivity" in Hypernote before it gets locked down into one spec. My hunch is it can be VERY expressive while remaining simple and also while not needing a whole scripting language bolted onto it. If I can't pull it off I'll let you know. @ a012dc82:6458a70d
2025-03-28 16:15:06In an audacious display of confidence, Bitcoin traders have recently committed $20 million to a $200K call option, a move that has reignited discussions about the cryptocurrency's potential and the broader market's appetite for risk. This development is set against a backdrop of increasing activity within the cryptocurrency options market, particularly on platforms like Deribit, where total open interest in Bitcoin options has reached unprecedented levels. This article explores the nuances of this strategic wager, examines the resurgence of investor enthusiasm, and contemplates the future implications for Bitcoin and the cryptocurrency market at large. **Table of Contents** - A Surge in Market Activity - The Bold Bet on Bitcoin's Future - Implications of the $200K Call Option - Increased Market Volatility - Renewed Investor Confidence - Speculative Interest and Market Dynamics - Looking Ahead: Bitcoin's Market Prospects - Conclusion - FAQs **A Surge in Market Activity** The cryptocurrency options market has experienced a significant uptick in activity, with Bitcoin and Ethereum options achieving record-breaking open interest figures. On Deribit, Bitcoin options open interest has soared to a staggering $20.4 billion, eclipsing the previous high of $14.36 billion seen in October 2021. Concurrently, Ethereum options open interest has also reached a historic peak of $11.66 billion. This pronounced increase in market activity is indicative of a growing interest among traders to either hedge their positions against potential price fluctuations or to speculate on the future price movements of these leading cryptocurrencies. The surge in options trading volume reflects a broader trend of maturation within the cryptocurrency market, as sophisticated financial instruments become increasingly utilized by a diverse array of market participants, from individual investors to large institutional players. **The Bold Bet on Bitcoin's Future** The decision by traders to allocate $20 million to a $200K call option for Bitcoin represents a significant vote of confidence in the cryptocurrency's future price trajectory. This high-stakes gamble suggests that a segment of the market is not only optimistic about Bitcoin's potential to breach the $200,000 threshold but is also willing to back this belief with substantial financial commitment. Such a move is emblematic of the "animal spirits" returning to the cryptocurrency market—a term coined by economist John Maynard Keynes to describe the instinctive human emotion that drives consumer confidence and investment decisions. This resurgence of speculative fervor and risk-taking behavior is a testament to the enduring allure of Bitcoin as an asset class that continues to captivate the imagination of investors, despite its history of volatility and regulatory challenges. **Implications of the $200K Call Option** The substantial investment in the $200K call option carries several implications for the Bitcoin market and the broader cryptocurrency ecosystem: **Increased Market Volatility** The focus on high strike price options could introduce heightened volatility into the Bitcoin market. As traders position themselves to capitalize on potential price movements, the market may witness more pronounced fluctuations. This environment of increased volatility underscores the speculative nature of cryptocurrency trading and the high-risk, high-reward strategies employed by some market participants. It also highlights the need for investors to approach the market with caution, armed with a thorough understanding of the underlying risks and a clear investment strategy. **Renewed Investor Confidence** The bold wager on the $200K call option reflects a significant resurgence in investor confidence in Bitcoin's long-term prospects. Following periods of market downturns and regulatory uncertainty, this move signals a renewed conviction in the fundamental value proposition of Bitcoin as a pioneering digital asset. It represents a collective belief in the cryptocurrency's ability to not only recover from past setbacks but to chart new territories in terms of price and market capitalization. This renewed investor confidence may serve as a catalyst for further investment in Bitcoin and other cryptocurrencies, potentially driving up prices and encouraging more widespread adoption. **Speculative Interest and Market Dynamics** The commitment to the $200K call option highlights the continued influence of speculative interest on the cryptocurrency market's dynamics. It illustrates how speculation, driven by the prospect of outsized returns, remains a central force shaping market trends and price trajectories. This speculative interest, while contributing to market liquidity and price discovery, also introduces an element of unpredictability. It underscores the complex interplay between market sentiment, investor behavior, and external economic factors that collectively determine the direction of the cryptocurrency market. **Looking Ahead: Bitcoin's Market Prospects** The strategic bet on the $200K call option, amidst a backdrop of increasing options market activity, paints a complex picture of Bitcoin's future. While the move signals optimism and a willingness among investors to engage in high-risk speculation, it also raises questions about the sustainability of such bullish sentiment. As Bitcoin continues to navigate the evolving landscape of digital finance, the interplay between speculative interest, regulatory developments, and technological advancements will be critical in shaping its future trajectory. The cryptocurrency market's inherent volatility and unpredictability necessitate a cautious approach from investors, emphasizing the importance of risk management and long-term strategic planning. **Conclusion** Bitcoin's latest foray into high-stakes speculation, marked by the $20 million lock on the $200K call option, is a vivid illustration of the cryptocurrency's enduring appeal and the market's appetite for risk. This development not only reflects a bullish outlook on Bitcoin's price potential but also signals a broader resurgence of investor enthusiasm and speculative activity within the cryptocurrency market. As we look to the future, the outcomes of such bold moves will undoubtedly influence the trajectory of Bitcoin and the digital asset landscape at large. Whether Bitcoin will reach the lofty heights of $200,000 remains to be seen, but its journey there will be closely watched by traders, investors, and regulators alike, offering valuable insights into the dynamics of speculative markets and the evolving role of cryptocurrencies in the global financial ecosystem. **FAQs** **What does locking $20 million in a $200K call option mean for Bitcoin?** Locking $20 million in a $200K call option indicates that traders are betting a significant amount of money on Bitcoin reaching or surpassing $200,000. It reflects a bullish outlook on Bitcoin's future price and a resurgence of speculative interest in the cryptocurrency market. **How does the surge in Bitcoin options market activity affect the cryptocurrency?** The surge in Bitcoin options market activity, with record open interest, increases market liquidity and can lead to heightened volatility. It also signifies growing interest and participation in the cryptocurrency market, potentially influencing Bitcoin's price dynamics. **What are the implications of increased market volatility for Bitcoin investors?** Increased market volatility can lead to larger price swings, presenting both opportunities and risks for investors. While it may offer the potential for higher returns, it also increases the risk of losses. Investors should approach the market with caution and consider their risk tolerance and investment strategy. **Why are investors optimistic about Bitcoin reaching $200,000?** Investors' optimism about Bitcoin reaching $200,000 stems from factors such as the cryptocurrency's past performance, the upcoming Bitcoin halving event, increasing institutional adoption, and favorable macroeconomic conditions. These factors contribute to a bullish sentiment in the market. **What role do institutional investors play in the current Bitcoin market trend?** Institutional investors play a significant role in the current Bitcoin market trend by bringing in substantial capital, lending credibility to the market, and influencing price movements. Their participation is seen as a sign of maturity and stability in the cryptocurrency market. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnewsco](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co/](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@thebitcoinlibertarian](https://www.youtube.com/@thebitcoinlibertarian)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** **Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad** **Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2025-03-28 16:15:06In an audacious display of confidence, Bitcoin traders have recently committed $20 million to a $200K call option, a move that has reignited discussions about the cryptocurrency's potential and the broader market's appetite for risk. This development is set against a backdrop of increasing activity within the cryptocurrency options market, particularly on platforms like Deribit, where total open interest in Bitcoin options has reached unprecedented levels. This article explores the nuances of this strategic wager, examines the resurgence of investor enthusiasm, and contemplates the future implications for Bitcoin and the cryptocurrency market at large. **Table of Contents** - A Surge in Market Activity - The Bold Bet on Bitcoin's Future - Implications of the $200K Call Option - Increased Market Volatility - Renewed Investor Confidence - Speculative Interest and Market Dynamics - Looking Ahead: Bitcoin's Market Prospects - Conclusion - FAQs **A Surge in Market Activity** The cryptocurrency options market has experienced a significant uptick in activity, with Bitcoin and Ethereum options achieving record-breaking open interest figures. On Deribit, Bitcoin options open interest has soared to a staggering $20.4 billion, eclipsing the previous high of $14.36 billion seen in October 2021. Concurrently, Ethereum options open interest has also reached a historic peak of $11.66 billion. This pronounced increase in market activity is indicative of a growing interest among traders to either hedge their positions against potential price fluctuations or to speculate on the future price movements of these leading cryptocurrencies. The surge in options trading volume reflects a broader trend of maturation within the cryptocurrency market, as sophisticated financial instruments become increasingly utilized by a diverse array of market participants, from individual investors to large institutional players. **The Bold Bet on Bitcoin's Future** The decision by traders to allocate $20 million to a $200K call option for Bitcoin represents a significant vote of confidence in the cryptocurrency's future price trajectory. This high-stakes gamble suggests that a segment of the market is not only optimistic about Bitcoin's potential to breach the $200,000 threshold but is also willing to back this belief with substantial financial commitment. Such a move is emblematic of the "animal spirits" returning to the cryptocurrency market—a term coined by economist John Maynard Keynes to describe the instinctive human emotion that drives consumer confidence and investment decisions. This resurgence of speculative fervor and risk-taking behavior is a testament to the enduring allure of Bitcoin as an asset class that continues to captivate the imagination of investors, despite its history of volatility and regulatory challenges. **Implications of the $200K Call Option** The substantial investment in the $200K call option carries several implications for the Bitcoin market and the broader cryptocurrency ecosystem: **Increased Market Volatility** The focus on high strike price options could introduce heightened volatility into the Bitcoin market. As traders position themselves to capitalize on potential price movements, the market may witness more pronounced fluctuations. This environment of increased volatility underscores the speculative nature of cryptocurrency trading and the high-risk, high-reward strategies employed by some market participants. It also highlights the need for investors to approach the market with caution, armed with a thorough understanding of the underlying risks and a clear investment strategy. **Renewed Investor Confidence** The bold wager on the $200K call option reflects a significant resurgence in investor confidence in Bitcoin's long-term prospects. Following periods of market downturns and regulatory uncertainty, this move signals a renewed conviction in the fundamental value proposition of Bitcoin as a pioneering digital asset. It represents a collective belief in the cryptocurrency's ability to not only recover from past setbacks but to chart new territories in terms of price and market capitalization. This renewed investor confidence may serve as a catalyst for further investment in Bitcoin and other cryptocurrencies, potentially driving up prices and encouraging more widespread adoption. **Speculative Interest and Market Dynamics** The commitment to the $200K call option highlights the continued influence of speculative interest on the cryptocurrency market's dynamics. It illustrates how speculation, driven by the prospect of outsized returns, remains a central force shaping market trends and price trajectories. This speculative interest, while contributing to market liquidity and price discovery, also introduces an element of unpredictability. It underscores the complex interplay between market sentiment, investor behavior, and external economic factors that collectively determine the direction of the cryptocurrency market. **Looking Ahead: Bitcoin's Market Prospects** The strategic bet on the $200K call option, amidst a backdrop of increasing options market activity, paints a complex picture of Bitcoin's future. While the move signals optimism and a willingness among investors to engage in high-risk speculation, it also raises questions about the sustainability of such bullish sentiment. As Bitcoin continues to navigate the evolving landscape of digital finance, the interplay between speculative interest, regulatory developments, and technological advancements will be critical in shaping its future trajectory. The cryptocurrency market's inherent volatility and unpredictability necessitate a cautious approach from investors, emphasizing the importance of risk management and long-term strategic planning. **Conclusion** Bitcoin's latest foray into high-stakes speculation, marked by the $20 million lock on the $200K call option, is a vivid illustration of the cryptocurrency's enduring appeal and the market's appetite for risk. This development not only reflects a bullish outlook on Bitcoin's price potential but also signals a broader resurgence of investor enthusiasm and speculative activity within the cryptocurrency market. As we look to the future, the outcomes of such bold moves will undoubtedly influence the trajectory of Bitcoin and the digital asset landscape at large. Whether Bitcoin will reach the lofty heights of $200,000 remains to be seen, but its journey there will be closely watched by traders, investors, and regulators alike, offering valuable insights into the dynamics of speculative markets and the evolving role of cryptocurrencies in the global financial ecosystem. **FAQs** **What does locking $20 million in a $200K call option mean for Bitcoin?** Locking $20 million in a $200K call option indicates that traders are betting a significant amount of money on Bitcoin reaching or surpassing $200,000. It reflects a bullish outlook on Bitcoin's future price and a resurgence of speculative interest in the cryptocurrency market. **How does the surge in Bitcoin options market activity affect the cryptocurrency?** The surge in Bitcoin options market activity, with record open interest, increases market liquidity and can lead to heightened volatility. It also signifies growing interest and participation in the cryptocurrency market, potentially influencing Bitcoin's price dynamics. **What are the implications of increased market volatility for Bitcoin investors?** Increased market volatility can lead to larger price swings, presenting both opportunities and risks for investors. While it may offer the potential for higher returns, it also increases the risk of losses. Investors should approach the market with caution and consider their risk tolerance and investment strategy. **Why are investors optimistic about Bitcoin reaching $200,000?** Investors' optimism about Bitcoin reaching $200,000 stems from factors such as the cryptocurrency's past performance, the upcoming Bitcoin halving event, increasing institutional adoption, and favorable macroeconomic conditions. These factors contribute to a bullish sentiment in the market. **What role do institutional investors play in the current Bitcoin market trend?** Institutional investors play a significant role in the current Bitcoin market trend by bringing in substantial capital, lending credibility to the market, and influencing price movements. Their participation is seen as a sign of maturity and stability in the cryptocurrency market. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnewsco](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co/](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@thebitcoinlibertarian](https://www.youtube.com/@thebitcoinlibertarian)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** **Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad** **Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ 4857600b:30b502f4
2025-02-21 03:04:00A new talking point of the left is that it’s no big deal, just simple recording errors for the 20 million people aged 100-360. 🤷♀️ And not many of them are collecting benefits anyway. 👌 First of all, the investigation & analysis are in the early stages. How can they possibly know how deep the fraud goes, especially when their leaders are doing everything they can to obstruct any real examination? Second, sure, no worries about only a small number collecting benefits. That’s the ONLY thing social security numbers are used for. 🙄
@ 4857600b:30b502f4
2025-02-21 03:04:00A new talking point of the left is that it’s no big deal, just simple recording errors for the 20 million people aged 100-360. 🤷♀️ And not many of them are collecting benefits anyway. 👌 First of all, the investigation & analysis are in the early stages. How can they possibly know how deep the fraud goes, especially when their leaders are doing everything they can to obstruct any real examination? Second, sure, no worries about only a small number collecting benefits. That’s the ONLY thing social security numbers are used for. 🙄 @ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection. At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering. McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection. At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering. McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era. @ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables **decentralized, censorship-resistant communication**. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on **users, developers, and relay operators**. If you believe in **free speech, decentralization, and an open internet**, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, **every effort helps build a more robust network**. Here’s how you can get involved and make a difference. --- ## **1️⃣ Use Nostr Daily** The simplest and most effective way to contribute to Nostr is by **using it regularly**. The more active users, the stronger and more valuable the network becomes. ✅ **Post, comment, and zap** (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ **Engage with new users** and help them understand how Nostr works.\ ✅ **Try different Nostr clients** like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience. Your activity **keeps the network alive** and helps encourage more developers and relay operators to invest in the ecosystem. --- ## **2️⃣ Run Your Own Nostr Relay** Relays are the **backbone of Nostr**, responsible for distributing messages across the network. The more **independent relays exist**, the stronger and more censorship-resistant Nostr becomes. ✅ **Set up your own relay** to help decentralize the network further.\ ✅ **Experiment with relay configurations** and different performance optimizations.\ ✅ **Offer public or private relay services** to users looking for high-quality infrastructure. If you're not technical, you can still **support relay operators** by **subscribing to a paid relay** or donating to open-source relay projects. --- ## **3️⃣ Support Paid Relays & Infrastructure** Free relays have helped Nostr grow, but they **struggle with spam, slow speeds, and sustainability issues**. **Paid relays** help fund **better infrastructure, faster message delivery, and a more reliable experience**. ✅ **Subscribe to a paid relay** to help keep it running.\ ✅ **Use premium services** like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ **Donate to relay operators** who invest in long-term infrastructure. By funding **Nostr’s decentralized backbone**, you help ensure its **longevity and reliability**. --- ## **4️⃣ Zap Developers, Creators & Builders** Many people contribute to Nostr **without direct financial compensation**—developers who build clients, relay operators, educators, and content creators. **You can support them with zaps!** ⚡ ✅ **Find developers working on Nostr projects** and send them a zap.\ ✅ **Support content creators and educators** who spread awareness about Nostr.\ ✅ **Encourage builders** by donating to open-source projects. Micro-payments via the **Lightning Network** make it easy to directly **support the people who make Nostr better**. --- ## **5️⃣ Develop New Nostr Apps & Tools** If you're a developer, you can **build on Nostr’s open protocol** to create new apps, bots, or tools. Nostr is **permissionless**, meaning anyone can develop for it. ✅ **Create new Nostr clients** with unique features and user experiences.\ ✅ **Build bots or automation tools** that improve engagement and usability.\ ✅ **Experiment with decentralized identity, authentication, and encryption** to make Nostr even stronger. With **no corporate gatekeepers**, your projects can help shape the future of decentralized social media. --- ## **6️⃣ Promote & Educate Others About Nostr** Adoption grows when **more people understand and use Nostr**. You can help by **spreading awareness** and creating educational content. ✅ **Write blogs, guides, and tutorials** explaining how to use Nostr.\ ✅ **Make videos or social media posts** introducing new users to the protocol.\ ✅ **Host discussions, Twitter Spaces, or workshops** to onboard more people. The more people **understand and trust Nostr**, the stronger the ecosystem becomes. --- ## **7️⃣ Support Open-Source Nostr Projects** Many Nostr tools and clients are **built by volunteers**, and open-source projects thrive on **community support**. ✅ **Contribute code** to existing Nostr projects on GitHub.\ ✅ **Report bugs and suggest features** to improve Nostr clients.\ ✅ **Donate to developers** who keep Nostr free and open for everyone. If you're not a developer, you can still **help with testing, translations, and documentation** to make projects more accessible. --- ## **🚀 Every Contribution Strengthens Nostr** Whether you: ✔️ **Post and engage daily**\ ✔️ **Zap creators and developers**\ ✔️ **Run or support relays**\ ✔️ **Build new apps and tools**\ ✔️ **Educate and onboard new users** **Every action helps make Nostr more resilient, decentralized, and unstoppable.** Nostr isn’t just another social network—it’s **a movement toward a free and open internet**. If you believe in **digital freedom, privacy, and decentralization**, now is the time to get involved.
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables **decentralized, censorship-resistant communication**. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on **users, developers, and relay operators**. If you believe in **free speech, decentralization, and an open internet**, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, **every effort helps build a more robust network**. Here’s how you can get involved and make a difference. --- ## **1️⃣ Use Nostr Daily** The simplest and most effective way to contribute to Nostr is by **using it regularly**. The more active users, the stronger and more valuable the network becomes. ✅ **Post, comment, and zap** (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ **Engage with new users** and help them understand how Nostr works.\ ✅ **Try different Nostr clients** like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience. Your activity **keeps the network alive** and helps encourage more developers and relay operators to invest in the ecosystem. --- ## **2️⃣ Run Your Own Nostr Relay** Relays are the **backbone of Nostr**, responsible for distributing messages across the network. The more **independent relays exist**, the stronger and more censorship-resistant Nostr becomes. ✅ **Set up your own relay** to help decentralize the network further.\ ✅ **Experiment with relay configurations** and different performance optimizations.\ ✅ **Offer public or private relay services** to users looking for high-quality infrastructure. If you're not technical, you can still **support relay operators** by **subscribing to a paid relay** or donating to open-source relay projects. --- ## **3️⃣ Support Paid Relays & Infrastructure** Free relays have helped Nostr grow, but they **struggle with spam, slow speeds, and sustainability issues**. **Paid relays** help fund **better infrastructure, faster message delivery, and a more reliable experience**. ✅ **Subscribe to a paid relay** to help keep it running.\ ✅ **Use premium services** like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ **Donate to relay operators** who invest in long-term infrastructure. By funding **Nostr’s decentralized backbone**, you help ensure its **longevity and reliability**. --- ## **4️⃣ Zap Developers, Creators & Builders** Many people contribute to Nostr **without direct financial compensation**—developers who build clients, relay operators, educators, and content creators. **You can support them with zaps!** ⚡ ✅ **Find developers working on Nostr projects** and send them a zap.\ ✅ **Support content creators and educators** who spread awareness about Nostr.\ ✅ **Encourage builders** by donating to open-source projects. Micro-payments via the **Lightning Network** make it easy to directly **support the people who make Nostr better**. --- ## **5️⃣ Develop New Nostr Apps & Tools** If you're a developer, you can **build on Nostr’s open protocol** to create new apps, bots, or tools. Nostr is **permissionless**, meaning anyone can develop for it. ✅ **Create new Nostr clients** with unique features and user experiences.\ ✅ **Build bots or automation tools** that improve engagement and usability.\ ✅ **Experiment with decentralized identity, authentication, and encryption** to make Nostr even stronger. With **no corporate gatekeepers**, your projects can help shape the future of decentralized social media. --- ## **6️⃣ Promote & Educate Others About Nostr** Adoption grows when **more people understand and use Nostr**. You can help by **spreading awareness** and creating educational content. ✅ **Write blogs, guides, and tutorials** explaining how to use Nostr.\ ✅ **Make videos or social media posts** introducing new users to the protocol.\ ✅ **Host discussions, Twitter Spaces, or workshops** to onboard more people. The more people **understand and trust Nostr**, the stronger the ecosystem becomes. --- ## **7️⃣ Support Open-Source Nostr Projects** Many Nostr tools and clients are **built by volunteers**, and open-source projects thrive on **community support**. ✅ **Contribute code** to existing Nostr projects on GitHub.\ ✅ **Report bugs and suggest features** to improve Nostr clients.\ ✅ **Donate to developers** who keep Nostr free and open for everyone. If you're not a developer, you can still **help with testing, translations, and documentation** to make projects more accessible. --- ## **🚀 Every Contribution Strengthens Nostr** Whether you: ✔️ **Post and engage daily**\ ✔️ **Zap creators and developers**\ ✔️ **Run or support relays**\ ✔️ **Build new apps and tools**\ ✔️ **Educate and onboard new users** **Every action helps make Nostr more resilient, decentralized, and unstoppable.** Nostr isn’t just another social network—it’s **a movement toward a free and open internet**. If you believe in **digital freedom, privacy, and decentralization**, now is the time to get involved. @ 5de23b9a:d83005b3
2025-02-19 03:47:19In a digital era that is increasingly controlled by large companies, the emergence of Nostr (Notes and Other Stuff Transmitted by Relays) is a breath of fresh air for those who crave freedom of expression. Nostr is a cryptography-based protocol that allows users to send and receive messages through a relay network. Unlike conventional social media such as Twitter or Facebook 1.Full Decentralization: No company or government can remove or restrict content. 2.Sensor-Resistant: Information remains accessible despite blocking attempts. 3.Privacy and Security: Uses cryptography to ensure that only users who have the keys can access their messages.* **
@ 5de23b9a:d83005b3
2025-02-19 03:47:19In a digital era that is increasingly controlled by large companies, the emergence of Nostr (Notes and Other Stuff Transmitted by Relays) is a breath of fresh air for those who crave freedom of expression. Nostr is a cryptography-based protocol that allows users to send and receive messages through a relay network. Unlike conventional social media such as Twitter or Facebook 1.Full Decentralization: No company or government can remove or restrict content. 2.Sensor-Resistant: Information remains accessible despite blocking attempts. 3.Privacy and Security: Uses cryptography to ensure that only users who have the keys can access their messages.* ** @ 905365ac:4247f9de
2025-03-28 14:04:02"85% of the KGB ['s strategy to take over a country] is always subversion." Yuri Bezmenov Ideological subversion is even stronger today, with an even greater reach because of the internet. Unlike during Yuri's time, however, we are being subverted internally. What is subversion? Short answer: brainwashing. Long answer: Demoralization > Destabilization > Crisis > Normilization Demoralization: control educational institutions, media, and cultural platforms Destabilization: control internal and foreign politics, economic, and defense systems. Crisis: violent change of power, structure, and economy Normalization: period of stability* One teacher** believes that the way this is currently being played out is through our culture wars - particularly anti-whiteness. I would add that it is playing out both in anti-whiteness and in anti-masculinity. Short history lesson: America embarked on an endeavor to "de-nazi" Germany via demoralization following World War 2. The charge was lead by a Frankfort school that sought refuge in the U.S. during the war. That demoralization was based on mass cultural guilt (interestingly enough, I actually learned the concept of collective guilt as a tool to “heal communities” in a class on Peace and Conflict during college). According to this teacher, that mass guilt then started being applied by leftists in a range of western civilizations, including America where the root guilt is racism. A secondary guilt Americans suffer from is "the partriarchy," which has led to a whole slew of mass demoralization which can be seen most evidently in this current wave of feminism and in gender ideology. In such countries, the idea is that fascism (seen as the scapegoat of whatever mass guilt is being applied) must eventually be annihilated. Otherwise, the guilt is too difficult to bear. In the U.S., that’s whiteness. In Germany, it was Nazis and now it’s Germans themselves. Takeaways: 1. The best way personally advocate for a strong country that stands against ideological subversion is to directly counter demoralization in the spheres of education, media, and in cultural spaces. 2. Invest in countering destabilization by appointing, electing, and being those who fight for peace, unity and freedom on our political, economic, and defensive grounds. Speak truth. Homeschool (or be involved in your local schools). Join NOSTR. Contribute to local, state and federal politics in a way that will positively impact your grandchildren. Support the soldiers and veterans you know and love. Be pro-human. https://youtu.be/5gnpCqsXE8g https://youtu.be/niiF8hCSrYQ
@ 905365ac:4247f9de
2025-03-28 14:04:02"85% of the KGB ['s strategy to take over a country] is always subversion." Yuri Bezmenov Ideological subversion is even stronger today, with an even greater reach because of the internet. Unlike during Yuri's time, however, we are being subverted internally. What is subversion? Short answer: brainwashing. Long answer: Demoralization > Destabilization > Crisis > Normilization Demoralization: control educational institutions, media, and cultural platforms Destabilization: control internal and foreign politics, economic, and defense systems. Crisis: violent change of power, structure, and economy Normalization: period of stability* One teacher** believes that the way this is currently being played out is through our culture wars - particularly anti-whiteness. I would add that it is playing out both in anti-whiteness and in anti-masculinity. Short history lesson: America embarked on an endeavor to "de-nazi" Germany via demoralization following World War 2. The charge was lead by a Frankfort school that sought refuge in the U.S. during the war. That demoralization was based on mass cultural guilt (interestingly enough, I actually learned the concept of collective guilt as a tool to “heal communities” in a class on Peace and Conflict during college). According to this teacher, that mass guilt then started being applied by leftists in a range of western civilizations, including America where the root guilt is racism. A secondary guilt Americans suffer from is "the partriarchy," which has led to a whole slew of mass demoralization which can be seen most evidently in this current wave of feminism and in gender ideology. In such countries, the idea is that fascism (seen as the scapegoat of whatever mass guilt is being applied) must eventually be annihilated. Otherwise, the guilt is too difficult to bear. In the U.S., that’s whiteness. In Germany, it was Nazis and now it’s Germans themselves. Takeaways: 1. The best way personally advocate for a strong country that stands against ideological subversion is to directly counter demoralization in the spheres of education, media, and in cultural spaces. 2. Invest in countering destabilization by appointing, electing, and being those who fight for peace, unity and freedom on our political, economic, and defensive grounds. Speak truth. Homeschool (or be involved in your local schools). Join NOSTR. Contribute to local, state and federal politics in a way that will positively impact your grandchildren. Support the soldiers and veterans you know and love. Be pro-human. https://youtu.be/5gnpCqsXE8g https://youtu.be/niiF8hCSrYQ @ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February. Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training. Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
@ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February. Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training. Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further. @ bf95e1a4:ebdcc848
2025-03-28 13:56:06This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our[ Geyser page](https://geyser.fund/project/infinity)! ## Financial Atheism “Don’t trust, verify” is a common saying amongst bitcoiners that represents a sound attitude towards not only Bitcoin but all human power structures. In order to understand Bitcoin, one must admit that everything in society is man-made. Every civilization, every religion, every constitution, and every law is a product of human imagination. It wasn’t until as late as the 17th century that the scientific method started to become the dominant practice for describing how the world actually worked. Peer-to-peer review and repeated testing of a hypothesis are still quite recent human practices. Before this, we were basically just guessing and trusting authorities to a large extent. We still do this today, and despite our progress over the last couple of centuries, we still have a long way to go. Our brains are hardwired to follow the leader of the pack. The human brain is born with a plethora of cognitive biases pre-installed, and we have to work very hard to overcome them. We evolved to survive in relatively small groups, and our brains are thus not really made for seeing the bigger picture. Bitcoin’s proof-of-work algorithm is constructed in such a way that it is easy to verify that computational power was sacrificed in order to approve a block of transactions and claim its reward. In this way, no trust in any authority is required as it is relatively trivial to test the validity of a block and the transactions it contains. This is nothing short of a complete reimagining of how human society ought to be governed. The beauty of mathematics governs the Bitcoin system. Everything that ever happens in Bitcoin is open and verifiable to everyone, even to those who are not yet using it. After the tragic events of 9/11 in 2001, Sam Harris started writing his book *The End of Faith*, which happened to be released around the same time as Richard Dawkins’ *The God Delusion*, Daniel Dennett's *Breaking the Spell*, and Christopher Hitchens’ *God Is Not Great: How Religion Poisons Everything*. These books kick-started what, in hindsight, has often been referred to as the new atheist movement, even though there has arguably never been anything new about atheism. Atheism must almost certainly have preceded religion since religious ideas require the person holding the idea to believe a certain doctrine or story. Atheism is nothing but the rejection of ways to describe the world that are not verifiable by experimentation. A fly on the wall is probably an atheist by this definition of the word. Atheism is often accused of being just another set of beliefs, but the word itself describes what it is much better — a lack of belief in theistic ideas. It is not a code of conduct or set of rules to live your life by; it is simply the rejection of that which cannot be scientifically verified. Many people, religious people, in particular, have a hard time grasping this. If you believe that a supernatural entity created everything in everyone's life, you might not be too comfortable with a word that describes a complete rejection of what you believe created everything, including the very atheist that the word describes. The amount of different religious worldviews that exist is probably equal to the sum of all religious people on the planet, but all world views that reject these superstitious beliefs require but one word. Atheism is not the opposite of religion but is simply the lack of it. In 2008, another sub-culture movement of unbelief was born. Let’s call it *Financial Atheism* — the rejection of unverifiable value claims. With the invention of Bitcoin, a way of rejecting fraudulent expressions of a token’s value was born. Those of us fortunate enough to have been born in secular countries all enjoy not having the ideas of religious demagogues dictating our lives on a daily basis. We can choose which ideas to believe in and which to reject. What we still have very limited means of choosing, however, are the ways in which we express value to each other. We’re told to use a system in which we all have a certain number of value tokens assigned to our name, either as a number on a screen or as digits on paper notes. We all live in the collective hallucination that these numbers are somehow legit and that their authenticity is not to be questioned. A Bitcoin balance assigned to a certain Bitcoin address might seem just as questionable to a layman, but if you have a basic understanding of the hashing algorithms and game theory behind it, it’s not. At the time of writing, the hash of the latest block on the Bitcoin blockchain begins with eighteen zeros in a row. These zeros represent the Proof of Work that ensures that this block is valid and that every transaction in it actually happened. If you can grasp the concept of a hashing algorithm, and if you have an intuition about mathematics, you realize the gargantuan amount of calculating effort that went into finding this particular hash. It is simply mind-blowing. To forge a false version of a hash beginning with eighteen zeros just wouldn’t be economically viable. Of course, you can never actually know that a 51% attack or some other attempt at corrupting the blockchain hasn’t occurred, but you can know that such an attack would require more than half of the network acting against their own economic interest. Bitcoin is not something to believe in. You don’t need to trust any authority because you can validate the plausibility of its authenticity yourself. It’s the financial equivalent of atheism or unbelief. Satoshi wasn’t Jesus. Satoshi was Brian of Nazareth, telling his followers to think for themselves. The first law of thermodynamics, also known as the Law of Conservation of Energy, states that energy cannot be created or destroyed in an isolated system. The second law states that the entropy of any isolated system always increases, and the third law states that the entropy of a system approaches a constant value as the temperature approaches absolute zero. In the Bitcoin network, participants known as miners compete for new Bitcoin in a lottery with very fixed rules. The more hashing power (computing power) a miner contributes to the network, the higher his chances of winning the block reward, a specific amount of Bitcoin that is halved every four years. The difficulty of this lottery - in other words, the miner’s chance of winning it — is re-calibrated every 2016th block so that the average time it takes to find the next block is always roughly ten minutes. What this system produces is absolute scarcity; the amount of Bitcoin in existence at any moment in time is always predictable. The more time that passes, the slower the rate of coin issuance and the block reward slowly approaches zero. By the time it does, around the year 2140, the individual miner’s incentive to mine for a reward will, at least theoretically, have been replaced by an incentive to collect transaction fees from the participants of the network. Even now, the sum of all fees make up a non-trivial part of the miners’ revenue. Yet from a user’s point of view the fees are still very low, and as the network scales up using Layer 2 solutions such as the Lightning Network, they’re expected to remain low for quite a long time ahead. Absolute scarcity is a concept that mankind has never encountered before. Arguably, this makes it the first man-made concept to ever be directly linked to the laws of physics. Everything anyone does requires a certain amount of energy. The very word *doing* implies that some kind of movement, some type of energy expenditure, needs to occur. As mentioned earlier, how we value things is entirely subjective. Different actions are of different value to different people. How we value different things is also inevitably linked to the supply of those things. Had the trapped-under-ice winter diver mentioned in chapter one been equipped with a scuba tank, he probably wouldn't have thought of his next breath as such a precious thing. The price a person is willing to pay for a good — in other words, the sum of one or more person’s actions — can be derived from two basic variables: The highly subjective *demand* for the good and the always-constrained-by-time-and-space *supply* of that same good. Note that if supply is sufficiently limited, there only needs to be a minimal amount of demand for a good for its price to increase. One could argue that no one *needs* Bitcoin and that, therefore, Bitcoin would have no intrinsic value. One could also argue that there’s no such thing as intrinsic value since demand is always subjective. In any case, there will always be a cost to mine Bitcoin, and the more mining power in the network, the higher that cost. This cost, ensured by the Bitcoin network’s Proof-Of-Work algorithm, is probably as close to a pure energy cost as the price of a human activity will ever get. Once the mining rig is in place, a simple conversion process follows — energy in, scarce token out. Should the cost of production exceed the current price of the token, the miner can just choose not to sell, thereby limiting the supply of Bitcoin in circulation even more and eventually selling them for other goods whenever he sees fit. In this sense, Bitcoin is a battery. Perhaps the best battery ever invented. Storing and moving electrical energy around has always been costly and wasteful. Bitcoin offers a way of converting energy into a small part of a specific number. A mathematical battery, if you will. It is important to remember that it does not convert energy into value *directly*, but rather electricity into digital scarcity — digital scarcity that can be used to express value. Energy cannot be created or destroyed in an isolated system, as the first law of thermodynamics clearly states. Bitcoin can express how much energy was sacrificed in order to acquire a share of the total sum. You can also acquire Bitcoin by buying it rather than mining it, but in doing so, you also spend energy. You somehow acquired the money with which you bought the Bitcoin. You, or someone else, sacrificed time and energy somewhere. Bitcoin lets you express that you see that there’s a connection between value and scarcity by letting you sacrifice effort to claim a part of the total sum. The excitement we so-called "Bitcoin Maximalists" feel about Bitcoin does not come primarily from the enormous gains that those who hopped early onto the freight train have been blessed with. Nor is it because we’re “in it for the technology,” as can often be heard from opponents. Those of us who preach the near-divinity of this invention do so above all because we see the philosophical impacts of absolute scarcity in a commodity. The idea of a functioning solution to the double-spending problem in computerized money is an achievement that simply can’t be ignored. By solving the double-spending problem, Satoshi also made counterfeiting impossible, which in turn makes artificial inflation impossible. The world-changing potential of this invention cannot be understated. Not in the long run. The more you think about it, the more the thought won’t give you any peace of mind. If this experiment works, if it’s real, it will take civilization to the next level. What we don’t know is how long this will take. Right now, debates in the Bitcoin space are about Bitcoin’s functionality as a medium of exchange and its potential as a good store of value. We might be missing the point. We cannot possibly know if a type of monetary token for which you’re completely responsible, with no third-party protection, will ever become a preferred medium of exchange for most transactions. Nor can we know if the price of Bitcoin will follow the hype-cycle path that we all want it to follow so that it can become the store of value that most maximalists claim it already is. Maybe we’ve been focused on the wrong things all along. Maybe Bitcoin’s greatest strength is in its functionality as a unit of account. After all, this is all that Bitcoin does. If you own 21 Bitcoin, you own one-millionth of the world's first absolutely scarce commodity. This might not make you rich overnight, but it just might have something to do with the opportunities available to your great-great-grandchildren. Throughout history, whenever a prehistoric human tribe invented ceremonial burial, that tribe began to expand rapidly. Why? Because as soon as you invent belief in an afterlife, you also introduce the idea of self-sacrifice on a larger scale. People who held these beliefs were much easier for a despot to manipulate and send into battle with neighboring tribes. Religious leaders can use people’s fears and superstitions to have them commit all sorts of atrocities to their fellow man, and they still do so today. Belief in a “greater good” can be the most destructive idea that can pop up in a human mind. The Nazis of World War II Germany believed that exterminating Jews was for the “greater good” of their nation’s gene pool. Belief in noble causes often comes with unintended side effects, which can have disastrous consequences. Religious leaders, political leaders, and other power-hungry sociopaths are responsible for the greatest crimes against humanity ever committed — namely, wars. Europeans often question the Second Amendment to the United States Constitution, which protects the right to bear arms, whenever a tragic school shooting occurs on the other side of the Atlantic. What everyone seems to forget is that less than a hundred years ago, Europe was at war with itself because its citizens had given too much power to their so-called leaders. The Nazis came to power in a democracy — never forget that. Our individual rights weren’t given to us by our leaders; we were born with them. Our leaders can’t give us anything; they can only force us to behave in certain ways. If we truly want to be in charge of our lives, we need to find the tools necessary to circumvent the bullshit ourselves. ### **About the Bitcoin Infinity Academy** The Bitcoin Infinity Academy is an educational project built around [Knut Svanholm](http://primal.net/knut)’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a [video](https://www.youtube.com/@BitcoinInfinityShow) in which Knut and [Luke de Wolf](http://primal.net/luke) discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our [Geyser](https://geyser.fund/project/infinity) page. Signed books, monthly calls, and lots of other benefits are also available.
@ bf95e1a4:ebdcc848
2025-03-28 13:56:06This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our[ Geyser page](https://geyser.fund/project/infinity)! ## Financial Atheism “Don’t trust, verify” is a common saying amongst bitcoiners that represents a sound attitude towards not only Bitcoin but all human power structures. In order to understand Bitcoin, one must admit that everything in society is man-made. Every civilization, every religion, every constitution, and every law is a product of human imagination. It wasn’t until as late as the 17th century that the scientific method started to become the dominant practice for describing how the world actually worked. Peer-to-peer review and repeated testing of a hypothesis are still quite recent human practices. Before this, we were basically just guessing and trusting authorities to a large extent. We still do this today, and despite our progress over the last couple of centuries, we still have a long way to go. Our brains are hardwired to follow the leader of the pack. The human brain is born with a plethora of cognitive biases pre-installed, and we have to work very hard to overcome them. We evolved to survive in relatively small groups, and our brains are thus not really made for seeing the bigger picture. Bitcoin’s proof-of-work algorithm is constructed in such a way that it is easy to verify that computational power was sacrificed in order to approve a block of transactions and claim its reward. In this way, no trust in any authority is required as it is relatively trivial to test the validity of a block and the transactions it contains. This is nothing short of a complete reimagining of how human society ought to be governed. The beauty of mathematics governs the Bitcoin system. Everything that ever happens in Bitcoin is open and verifiable to everyone, even to those who are not yet using it. After the tragic events of 9/11 in 2001, Sam Harris started writing his book *The End of Faith*, which happened to be released around the same time as Richard Dawkins’ *The God Delusion*, Daniel Dennett's *Breaking the Spell*, and Christopher Hitchens’ *God Is Not Great: How Religion Poisons Everything*. These books kick-started what, in hindsight, has often been referred to as the new atheist movement, even though there has arguably never been anything new about atheism. Atheism must almost certainly have preceded religion since religious ideas require the person holding the idea to believe a certain doctrine or story. Atheism is nothing but the rejection of ways to describe the world that are not verifiable by experimentation. A fly on the wall is probably an atheist by this definition of the word. Atheism is often accused of being just another set of beliefs, but the word itself describes what it is much better — a lack of belief in theistic ideas. It is not a code of conduct or set of rules to live your life by; it is simply the rejection of that which cannot be scientifically verified. Many people, religious people, in particular, have a hard time grasping this. If you believe that a supernatural entity created everything in everyone's life, you might not be too comfortable with a word that describes a complete rejection of what you believe created everything, including the very atheist that the word describes. The amount of different religious worldviews that exist is probably equal to the sum of all religious people on the planet, but all world views that reject these superstitious beliefs require but one word. Atheism is not the opposite of religion but is simply the lack of it. In 2008, another sub-culture movement of unbelief was born. Let’s call it *Financial Atheism* — the rejection of unverifiable value claims. With the invention of Bitcoin, a way of rejecting fraudulent expressions of a token’s value was born. Those of us fortunate enough to have been born in secular countries all enjoy not having the ideas of religious demagogues dictating our lives on a daily basis. We can choose which ideas to believe in and which to reject. What we still have very limited means of choosing, however, are the ways in which we express value to each other. We’re told to use a system in which we all have a certain number of value tokens assigned to our name, either as a number on a screen or as digits on paper notes. We all live in the collective hallucination that these numbers are somehow legit and that their authenticity is not to be questioned. A Bitcoin balance assigned to a certain Bitcoin address might seem just as questionable to a layman, but if you have a basic understanding of the hashing algorithms and game theory behind it, it’s not. At the time of writing, the hash of the latest block on the Bitcoin blockchain begins with eighteen zeros in a row. These zeros represent the Proof of Work that ensures that this block is valid and that every transaction in it actually happened. If you can grasp the concept of a hashing algorithm, and if you have an intuition about mathematics, you realize the gargantuan amount of calculating effort that went into finding this particular hash. It is simply mind-blowing. To forge a false version of a hash beginning with eighteen zeros just wouldn’t be economically viable. Of course, you can never actually know that a 51% attack or some other attempt at corrupting the blockchain hasn’t occurred, but you can know that such an attack would require more than half of the network acting against their own economic interest. Bitcoin is not something to believe in. You don’t need to trust any authority because you can validate the plausibility of its authenticity yourself. It’s the financial equivalent of atheism or unbelief. Satoshi wasn’t Jesus. Satoshi was Brian of Nazareth, telling his followers to think for themselves. The first law of thermodynamics, also known as the Law of Conservation of Energy, states that energy cannot be created or destroyed in an isolated system. The second law states that the entropy of any isolated system always increases, and the third law states that the entropy of a system approaches a constant value as the temperature approaches absolute zero. In the Bitcoin network, participants known as miners compete for new Bitcoin in a lottery with very fixed rules. The more hashing power (computing power) a miner contributes to the network, the higher his chances of winning the block reward, a specific amount of Bitcoin that is halved every four years. The difficulty of this lottery - in other words, the miner’s chance of winning it — is re-calibrated every 2016th block so that the average time it takes to find the next block is always roughly ten minutes. What this system produces is absolute scarcity; the amount of Bitcoin in existence at any moment in time is always predictable. The more time that passes, the slower the rate of coin issuance and the block reward slowly approaches zero. By the time it does, around the year 2140, the individual miner’s incentive to mine for a reward will, at least theoretically, have been replaced by an incentive to collect transaction fees from the participants of the network. Even now, the sum of all fees make up a non-trivial part of the miners’ revenue. Yet from a user’s point of view the fees are still very low, and as the network scales up using Layer 2 solutions such as the Lightning Network, they’re expected to remain low for quite a long time ahead. Absolute scarcity is a concept that mankind has never encountered before. Arguably, this makes it the first man-made concept to ever be directly linked to the laws of physics. Everything anyone does requires a certain amount of energy. The very word *doing* implies that some kind of movement, some type of energy expenditure, needs to occur. As mentioned earlier, how we value things is entirely subjective. Different actions are of different value to different people. How we value different things is also inevitably linked to the supply of those things. Had the trapped-under-ice winter diver mentioned in chapter one been equipped with a scuba tank, he probably wouldn't have thought of his next breath as such a precious thing. The price a person is willing to pay for a good — in other words, the sum of one or more person’s actions — can be derived from two basic variables: The highly subjective *demand* for the good and the always-constrained-by-time-and-space *supply* of that same good. Note that if supply is sufficiently limited, there only needs to be a minimal amount of demand for a good for its price to increase. One could argue that no one *needs* Bitcoin and that, therefore, Bitcoin would have no intrinsic value. One could also argue that there’s no such thing as intrinsic value since demand is always subjective. In any case, there will always be a cost to mine Bitcoin, and the more mining power in the network, the higher that cost. This cost, ensured by the Bitcoin network’s Proof-Of-Work algorithm, is probably as close to a pure energy cost as the price of a human activity will ever get. Once the mining rig is in place, a simple conversion process follows — energy in, scarce token out. Should the cost of production exceed the current price of the token, the miner can just choose not to sell, thereby limiting the supply of Bitcoin in circulation even more and eventually selling them for other goods whenever he sees fit. In this sense, Bitcoin is a battery. Perhaps the best battery ever invented. Storing and moving electrical energy around has always been costly and wasteful. Bitcoin offers a way of converting energy into a small part of a specific number. A mathematical battery, if you will. It is important to remember that it does not convert energy into value *directly*, but rather electricity into digital scarcity — digital scarcity that can be used to express value. Energy cannot be created or destroyed in an isolated system, as the first law of thermodynamics clearly states. Bitcoin can express how much energy was sacrificed in order to acquire a share of the total sum. You can also acquire Bitcoin by buying it rather than mining it, but in doing so, you also spend energy. You somehow acquired the money with which you bought the Bitcoin. You, or someone else, sacrificed time and energy somewhere. Bitcoin lets you express that you see that there’s a connection between value and scarcity by letting you sacrifice effort to claim a part of the total sum. The excitement we so-called "Bitcoin Maximalists" feel about Bitcoin does not come primarily from the enormous gains that those who hopped early onto the freight train have been blessed with. Nor is it because we’re “in it for the technology,” as can often be heard from opponents. Those of us who preach the near-divinity of this invention do so above all because we see the philosophical impacts of absolute scarcity in a commodity. The idea of a functioning solution to the double-spending problem in computerized money is an achievement that simply can’t be ignored. By solving the double-spending problem, Satoshi also made counterfeiting impossible, which in turn makes artificial inflation impossible. The world-changing potential of this invention cannot be understated. Not in the long run. The more you think about it, the more the thought won’t give you any peace of mind. If this experiment works, if it’s real, it will take civilization to the next level. What we don’t know is how long this will take. Right now, debates in the Bitcoin space are about Bitcoin’s functionality as a medium of exchange and its potential as a good store of value. We might be missing the point. We cannot possibly know if a type of monetary token for which you’re completely responsible, with no third-party protection, will ever become a preferred medium of exchange for most transactions. Nor can we know if the price of Bitcoin will follow the hype-cycle path that we all want it to follow so that it can become the store of value that most maximalists claim it already is. Maybe we’ve been focused on the wrong things all along. Maybe Bitcoin’s greatest strength is in its functionality as a unit of account. After all, this is all that Bitcoin does. If you own 21 Bitcoin, you own one-millionth of the world's first absolutely scarce commodity. This might not make you rich overnight, but it just might have something to do with the opportunities available to your great-great-grandchildren. Throughout history, whenever a prehistoric human tribe invented ceremonial burial, that tribe began to expand rapidly. Why? Because as soon as you invent belief in an afterlife, you also introduce the idea of self-sacrifice on a larger scale. People who held these beliefs were much easier for a despot to manipulate and send into battle with neighboring tribes. Religious leaders can use people’s fears and superstitions to have them commit all sorts of atrocities to their fellow man, and they still do so today. Belief in a “greater good” can be the most destructive idea that can pop up in a human mind. The Nazis of World War II Germany believed that exterminating Jews was for the “greater good” of their nation’s gene pool. Belief in noble causes often comes with unintended side effects, which can have disastrous consequences. Religious leaders, political leaders, and other power-hungry sociopaths are responsible for the greatest crimes against humanity ever committed — namely, wars. Europeans often question the Second Amendment to the United States Constitution, which protects the right to bear arms, whenever a tragic school shooting occurs on the other side of the Atlantic. What everyone seems to forget is that less than a hundred years ago, Europe was at war with itself because its citizens had given too much power to their so-called leaders. The Nazis came to power in a democracy — never forget that. Our individual rights weren’t given to us by our leaders; we were born with them. Our leaders can’t give us anything; they can only force us to behave in certain ways. If we truly want to be in charge of our lives, we need to find the tools necessary to circumvent the bullshit ourselves. ### **About the Bitcoin Infinity Academy** The Bitcoin Infinity Academy is an educational project built around [Knut Svanholm](http://primal.net/knut)’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a [video](https://www.youtube.com/@BitcoinInfinityShow) in which Knut and [Luke de Wolf](http://primal.net/luke) discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our [Geyser](https://geyser.fund/project/infinity) page. Signed books, monthly calls, and lots of other benefits are also available. @ e97aaffa:2ebd765d
2025-03-28 12:56:17Nos últimos anos, tornei-me num acérrimo crítico do Euro, sobretudo da política monetária altamente expansionista realizada pelo Banco Central Europeu (BCE). Apesar de ser crítico, eu não desejo que Portugal volte a ter moeda própria. No seguimento gráfico, é a variação do [IPC de Portugal nos últimos 60 anos]( https://www.pordata.pt/pt/estatisticas/inflacao/taxa-de-inflacao/taxa-de-inflacao-por-bens-e-servicos-portugal):  No gráfico inclui os momentos históricos, para uma melhor interpretação dos dados. > O Índice de Preços ao Consumidor (IPC) é usado para observar tendências de inflação. É calculado com base no preço médio necessário para comprar um conjunto de bens de consumo e serviços num país, comparando com períodos anteriores. É uma ferramenta utilizada para calcular a perda de poder de compra, mas é uma métrica que é facilmente manipulada em prol dos interesses dos governos. ## Análise histórica No período marcelista, houve uma crescente inflação, devido a fatores, como os elevados custos da guerra e o fim dos acordos de Bretton Woods contribuíram para isso. Terminando com uma inflação superior a 13%. Da Revolta dos Cravos (1974) até à adesão da CEE (atual União Europeia, UE), nos primeiros anos foram conturbados a nível político, mesmo após conquistar alguma estabilidade, em termos de política monetária foi um descalabro, com inflação entre 12% a 30% ao ano. Foi o pior momento na era moderna. Com a entrada da CEE, Portugal ainda manteve a independência monetária, mas devido à entrada de muitos milhões de fundos europeus, essências para construir infraestrutura e desenvolver o país. Isto permitiu crescer e modernizar o país, gastando pouco dinheiro próprio, reduzindo a necessidade da expansão monetária e claro a inflação baixou. Depois com a adesão ao Tratado de Maastricht, em 1991, onde estabeleceu as bases para a criação da União Económica e Monetária, que culminou na criação da moeda única europeia, o Euro. As bases eram bastante restritivas, os políticos portugueses foram obrigados a manter uma inflação baixa. Portugal perdeu a independência monetária em 1999, com a entrada em vigor da nova moeda, foi estabelecida a taxa de conversão entre escudos e euros, tendo o valor de 1 euro sido fixado em 200,482 escudos. A Euro entrou em vigor em 1999, mas o papel-moeda só entrou em circulação em 2002. Assim, desde a criação até 2020, a inflação foi sempre abaixo de 5% ao ano, tendo um longo período abaixo dos 3%. A chegada da pandemia, foi um descalabro no BCE, a expansão monetária foi exponencial, resultando numa forte subida no IPC, quase 8% em 2022, algo que não acontecia há 30 anos. ## Conclusão Apesar dos últimos anos, a política monetária do BCE tem sido péssima, mesmo assim continua a ser muito melhor, se esta fosse efetuada em exclusividade por portugueses, não tenho quaisquer dúvidas disso. O passado demonstra isso, se voltarmos a ser independentes monetariamente, será desastroso, vamos virar rapidamente, a Venezuela da Europa. Até temos boas reservas de ouro, mas mesmo assim não são suficientes, mesmo que se inclua outros ativos para permitir a criação de uma moeda lastreada, ela apenas duraria até à primeira crise. É inevitável, somos um país demasiado socialista. A solução não é voltar ao escudo, mas sim o BCE deixar de imprimir dinheiro, como se não houvesse amanhã ou então optar por uma moeda total livre, sem intromissão de políticos. O BCE vai parar de expandir a moeda? Claro que não, eles estão encurralados, a expansão monetária é a única solução para elevada dívida soberana dos estados. A única certeza que eu tenho, a expansão do BCE, será sempre inferior ao do Banco de Portugal, se este estivesse o botão da impressão à sua disposição. Por volta dos 5% é muito mau, mas voltar para a casa dos 15% seria péssimo, esse seria o nosso destino. É muito triste ter esta conclusão, isto é demonstrativo da falta de competência dos políticos e governantes portugueses e o povo também tem uma certa culpa. Por serem poucos exigentes em relação à qualidade dos políticos que elegem e por acreditar que existem almoços grátis. #Bitcoin fixes this
@ e97aaffa:2ebd765d
2025-03-28 12:56:17Nos últimos anos, tornei-me num acérrimo crítico do Euro, sobretudo da política monetária altamente expansionista realizada pelo Banco Central Europeu (BCE). Apesar de ser crítico, eu não desejo que Portugal volte a ter moeda própria. No seguimento gráfico, é a variação do [IPC de Portugal nos últimos 60 anos]( https://www.pordata.pt/pt/estatisticas/inflacao/taxa-de-inflacao/taxa-de-inflacao-por-bens-e-servicos-portugal):  No gráfico inclui os momentos históricos, para uma melhor interpretação dos dados. > O Índice de Preços ao Consumidor (IPC) é usado para observar tendências de inflação. É calculado com base no preço médio necessário para comprar um conjunto de bens de consumo e serviços num país, comparando com períodos anteriores. É uma ferramenta utilizada para calcular a perda de poder de compra, mas é uma métrica que é facilmente manipulada em prol dos interesses dos governos. ## Análise histórica No período marcelista, houve uma crescente inflação, devido a fatores, como os elevados custos da guerra e o fim dos acordos de Bretton Woods contribuíram para isso. Terminando com uma inflação superior a 13%. Da Revolta dos Cravos (1974) até à adesão da CEE (atual União Europeia, UE), nos primeiros anos foram conturbados a nível político, mesmo após conquistar alguma estabilidade, em termos de política monetária foi um descalabro, com inflação entre 12% a 30% ao ano. Foi o pior momento na era moderna. Com a entrada da CEE, Portugal ainda manteve a independência monetária, mas devido à entrada de muitos milhões de fundos europeus, essências para construir infraestrutura e desenvolver o país. Isto permitiu crescer e modernizar o país, gastando pouco dinheiro próprio, reduzindo a necessidade da expansão monetária e claro a inflação baixou. Depois com a adesão ao Tratado de Maastricht, em 1991, onde estabeleceu as bases para a criação da União Económica e Monetária, que culminou na criação da moeda única europeia, o Euro. As bases eram bastante restritivas, os políticos portugueses foram obrigados a manter uma inflação baixa. Portugal perdeu a independência monetária em 1999, com a entrada em vigor da nova moeda, foi estabelecida a taxa de conversão entre escudos e euros, tendo o valor de 1 euro sido fixado em 200,482 escudos. A Euro entrou em vigor em 1999, mas o papel-moeda só entrou em circulação em 2002. Assim, desde a criação até 2020, a inflação foi sempre abaixo de 5% ao ano, tendo um longo período abaixo dos 3%. A chegada da pandemia, foi um descalabro no BCE, a expansão monetária foi exponencial, resultando numa forte subida no IPC, quase 8% em 2022, algo que não acontecia há 30 anos. ## Conclusão Apesar dos últimos anos, a política monetária do BCE tem sido péssima, mesmo assim continua a ser muito melhor, se esta fosse efetuada em exclusividade por portugueses, não tenho quaisquer dúvidas disso. O passado demonstra isso, se voltarmos a ser independentes monetariamente, será desastroso, vamos virar rapidamente, a Venezuela da Europa. Até temos boas reservas de ouro, mas mesmo assim não são suficientes, mesmo que se inclua outros ativos para permitir a criação de uma moeda lastreada, ela apenas duraria até à primeira crise. É inevitável, somos um país demasiado socialista. A solução não é voltar ao escudo, mas sim o BCE deixar de imprimir dinheiro, como se não houvesse amanhã ou então optar por uma moeda total livre, sem intromissão de políticos. O BCE vai parar de expandir a moeda? Claro que não, eles estão encurralados, a expansão monetária é a única solução para elevada dívida soberana dos estados. A única certeza que eu tenho, a expansão do BCE, será sempre inferior ao do Banco de Portugal, se este estivesse o botão da impressão à sua disposição. Por volta dos 5% é muito mau, mas voltar para a casa dos 15% seria péssimo, esse seria o nosso destino. É muito triste ter esta conclusão, isto é demonstrativo da falta de competência dos políticos e governantes portugueses e o povo também tem uma certa culpa. Por serem poucos exigentes em relação à qualidade dos políticos que elegem e por acreditar que existem almoços grátis. #Bitcoin fixes this @ fd208ee8:0fd927c1
2025-02-15 07:02:08E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats". They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable. It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions. What we then have is * a **transaction on a relay** that triggers * a **transaction on a mint** that triggers * a **transaction on Lightning** that triggers * a **transaction on Bitcoin**. Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted. There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself. https://github.com/nostr-protocol/nips/blob/master/60.md
@ fd208ee8:0fd927c1
2025-02-15 07:02:08E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats". They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable. It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions. What we then have is * a **transaction on a relay** that triggers * a **transaction on a mint** that triggers * a **transaction on Lightning** that triggers * a **transaction on Bitcoin**. Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted. There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself. https://github.com/nostr-protocol/nips/blob/master/60.md @ 3c389c8f:7a2eff7f
2025-03-28 17:10:17There is a new web being built on Nostr. At it's core, is a social experience paralleled by no other decentralized protocol. Nostr not only solves the problems of siloed relationships, third-party identity ownership, and algorithmic content control; it makes possible a ubiquitous social network across almost anything imaginable. User controlled identity, open data, and verifiable social graphs allow us to redefine trust on the web. We can interact with each other and online content in ways that have previously only been pipedreams. Nostr is not just social media, it is the web made social. ### Interoperability The client/relay relationship on Nostr allows for almost endless data exchange between various apps, clients, relays, and users. If any two things are willing to speak the same sub-protocol(s) within Nostr, they can exchange data. Making a friend list enables that list to be used in any other place that chooses to make it available. Creating a relay to serve an algorithmic social feed makes that feed viewable in any client that displays social feeds. Health data held by a patient can be shared with any care provider, verified by their system, and vice versa. This is the point where I have to acknowledge my own tech-deaf limitations and direct you towards nostr.com for more information. ### Data Resiliency I prefer to use the term resiliency here, because its really a mix of data redundancy and self-managed data that creates broad availability. Relays may host 10, 20, 30+ copies of your notes in different locations, but you also have no assurance that those relays will hosts those notes forever. An individual operating their own relay, while also connecting to the wider network, ensures resiliency in events such that wide swaths of the network should disappear or collude against an individual. The simplicity of relay management makes it possible for nearly anyone to make sure that they have a way to convey their messages to their individual network, whether that be close contacts, an audience, or one individual. This resiliency doesn't just apply to typical speech, it applies to any data intended to be shared amongst humans and machines alike. ### Pseudonymity and Anonymity With privacy encroachment from corporations, advertisers, and governments reaching all time highs, the need for identity protecting tools is also on the rise. Nostr utilizes public key encryption for its identity system. As there is no central entity to "verify" you, there is no need to expose any personal identifiable information to any Nostr app, client, or relay. You can protect your personal identity by simply choosing not to expose it. Your reputation will build as you interact with others on the Nostr network. Your social capital can speak for itself. (As with everything else, utilizing a VPN is recommended.) ### Identity and Provability No one can stop an impersonator from trying to hijack an identity. With Nostr, you CAN prove that you are you, though, which is basically the same as saying "that person is not me" Every note you write, every action you take, is cryptographically signed by your private key. As long as you maintain control of that key, you can prove what you did or did not do. ### Censorship Resistance If you have read our Relay Rundown then you probably get the idea. If not here's the tl;dr: Many small, lightweight relays make up Nostr's distribution system. They are simple enough that anyone can run one. They are redundant enough that you can be almost certain your content exists somewhere. If that is not peace of mind enough, you can run your own with ease. Censorship resistance isn't counting on one company, man, or server to protect what you say. It is taking control of your speech. Nostr makes it easy. ### Freedom of Mind and Association Nostr eliminates the need for company run algorithms that high-jack your attention to feed the advertising industry. You are free to choose your social media experience. Nostr's DVMs, curations, and conversation-centered relays offer discovery mechanisms run by any number of providers. That could be an individual, a company, a group, or you. Many clients incorporate different ways of engaging with these corporate algorithm alternatives. You can also choose to keep a purely chronological feed of the the things and people you follow. Exploring Nostr through its many apps opens up a the freedom to choose what and how you feed your mind. When we are able to explore, we end up surrounding ourselves with people who share our interests & hobbies. We find friends. This creates distance between ideologies and stark beliefs that often are used as the basis for the term "being in a bubble". Instead of bubbling off, an infinitely open space of thoughts and ideas allows for groups to gather naturally. In this way, we can choose not to block ourselves off from opposing views but to simply distance ourselves from them. Nostr's relay system also allows for the opposite. Tight-knit communities can create a space for its members to socialize and exchange information with minimal interference from any outside influence. By setting up their own relays with strict rules, the members can utilize one identity to interact within a community or across the broader social network.
@ 3c389c8f:7a2eff7f
2025-03-28 17:10:17There is a new web being built on Nostr. At it's core, is a social experience paralleled by no other decentralized protocol. Nostr not only solves the problems of siloed relationships, third-party identity ownership, and algorithmic content control; it makes possible a ubiquitous social network across almost anything imaginable. User controlled identity, open data, and verifiable social graphs allow us to redefine trust on the web. We can interact with each other and online content in ways that have previously only been pipedreams. Nostr is not just social media, it is the web made social. ### Interoperability The client/relay relationship on Nostr allows for almost endless data exchange between various apps, clients, relays, and users. If any two things are willing to speak the same sub-protocol(s) within Nostr, they can exchange data. Making a friend list enables that list to be used in any other place that chooses to make it available. Creating a relay to serve an algorithmic social feed makes that feed viewable in any client that displays social feeds. Health data held by a patient can be shared with any care provider, verified by their system, and vice versa. This is the point where I have to acknowledge my own tech-deaf limitations and direct you towards nostr.com for more information. ### Data Resiliency I prefer to use the term resiliency here, because its really a mix of data redundancy and self-managed data that creates broad availability. Relays may host 10, 20, 30+ copies of your notes in different locations, but you also have no assurance that those relays will hosts those notes forever. An individual operating their own relay, while also connecting to the wider network, ensures resiliency in events such that wide swaths of the network should disappear or collude against an individual. The simplicity of relay management makes it possible for nearly anyone to make sure that they have a way to convey their messages to their individual network, whether that be close contacts, an audience, or one individual. This resiliency doesn't just apply to typical speech, it applies to any data intended to be shared amongst humans and machines alike. ### Pseudonymity and Anonymity With privacy encroachment from corporations, advertisers, and governments reaching all time highs, the need for identity protecting tools is also on the rise. Nostr utilizes public key encryption for its identity system. As there is no central entity to "verify" you, there is no need to expose any personal identifiable information to any Nostr app, client, or relay. You can protect your personal identity by simply choosing not to expose it. Your reputation will build as you interact with others on the Nostr network. Your social capital can speak for itself. (As with everything else, utilizing a VPN is recommended.) ### Identity and Provability No one can stop an impersonator from trying to hijack an identity. With Nostr, you CAN prove that you are you, though, which is basically the same as saying "that person is not me" Every note you write, every action you take, is cryptographically signed by your private key. As long as you maintain control of that key, you can prove what you did or did not do. ### Censorship Resistance If you have read our Relay Rundown then you probably get the idea. If not here's the tl;dr: Many small, lightweight relays make up Nostr's distribution system. They are simple enough that anyone can run one. They are redundant enough that you can be almost certain your content exists somewhere. If that is not peace of mind enough, you can run your own with ease. Censorship resistance isn't counting on one company, man, or server to protect what you say. It is taking control of your speech. Nostr makes it easy. ### Freedom of Mind and Association Nostr eliminates the need for company run algorithms that high-jack your attention to feed the advertising industry. You are free to choose your social media experience. Nostr's DVMs, curations, and conversation-centered relays offer discovery mechanisms run by any number of providers. That could be an individual, a company, a group, or you. Many clients incorporate different ways of engaging with these corporate algorithm alternatives. You can also choose to keep a purely chronological feed of the the things and people you follow. Exploring Nostr through its many apps opens up a the freedom to choose what and how you feed your mind. When we are able to explore, we end up surrounding ourselves with people who share our interests & hobbies. We find friends. This creates distance between ideologies and stark beliefs that often are used as the basis for the term "being in a bubble". Instead of bubbling off, an infinitely open space of thoughts and ideas allows for groups to gather naturally. In this way, we can choose not to block ourselves off from opposing views but to simply distance ourselves from them. Nostr's relay system also allows for the opposite. Tight-knit communities can create a space for its members to socialize and exchange information with minimal interference from any outside influence. By setting up their own relays with strict rules, the members can utilize one identity to interact within a community or across the broader social network. @ 5d4b6c8d:8a1c1ee3
2025-03-28 12:30:11I'm short on time this morning, so I'm just plagiarizing @grayruby's notes, with minor revisions. # Territory Things: - March Madness Points Challenge https://stacker.news/items/924541/r/Undisciplined - IPL T20k Mania https://stacker.news/items/920125/r/Undisciplined - CricZap https://stacker.news/items/919957/r/Undisciplined - USA vs World https://stacker.news/items/923533/r/Undisciplined - Any changes to NBA Prediction contest for March? (post coming today) - Stackers voted to delay MLB Survivor # NCAA: - How many 1 seeds will make final four? - Cooper Flagg is the consensus number 1 but will he be a great NBA player? # NFL: - Rule change proposals: Ban the tush push and make dynamic kickoff permanent # NBA; - Pre playoffs Power Rankings # Blok'd Shots: - Ovi with 6 to go # MLB: - opening day finally arrived - American League is a crap shoot - Fantasy MLB # Betting: - predyx markets - Betplay- didn't work for me but how are you liking it? And, as we do every week, we'll share an awesome @Aardvark sports fact. What are we missing? originally posted at https://stacker.news/items/927714
@ 5d4b6c8d:8a1c1ee3
2025-03-28 12:30:11I'm short on time this morning, so I'm just plagiarizing @grayruby's notes, with minor revisions. # Territory Things: - March Madness Points Challenge https://stacker.news/items/924541/r/Undisciplined - IPL T20k Mania https://stacker.news/items/920125/r/Undisciplined - CricZap https://stacker.news/items/919957/r/Undisciplined - USA vs World https://stacker.news/items/923533/r/Undisciplined - Any changes to NBA Prediction contest for March? (post coming today) - Stackers voted to delay MLB Survivor # NCAA: - How many 1 seeds will make final four? - Cooper Flagg is the consensus number 1 but will he be a great NBA player? # NFL: - Rule change proposals: Ban the tush push and make dynamic kickoff permanent # NBA; - Pre playoffs Power Rankings # Blok'd Shots: - Ovi with 6 to go # MLB: - opening day finally arrived - American League is a crap shoot - Fantasy MLB # Betting: - predyx markets - Betplay- didn't work for me but how are you liking it? And, as we do every week, we'll share an awesome @Aardvark sports fact. What are we missing? originally posted at https://stacker.news/items/927714 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37#intro The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises. In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously. I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea. It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope. After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes. I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project. With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed. With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation. At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37#intro The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises. In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously. I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea. It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope. After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes. I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project. With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed. With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation. At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project. @ 57d1a264:69f1fee1
2025-03-28 10:32:15Bitcoin.design community is organizing another Designathon, from May 4-18. Let's get creative with bitcoin together. More to come very soon.  The first edition was a bursting success! the website still there https://events.bitcoin.design, and here their previous [announcement](https://bitcoindesign.substack.com/p/the-bitcoin-designathon-2022). Look forward for this to happen! Spread the voice: N: [https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48l...](https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48lmw9jc7nhhauyq5w3cm4nfsm3mstqtk6m) X: https://x.com/bitcoin_design/status/1905547407405768927 originally posted at https://stacker.news/items/927650
@ 57d1a264:69f1fee1
2025-03-28 10:32:15Bitcoin.design community is organizing another Designathon, from May 4-18. Let's get creative with bitcoin together. More to come very soon.  The first edition was a bursting success! the website still there https://events.bitcoin.design, and here their previous [announcement](https://bitcoindesign.substack.com/p/the-bitcoin-designathon-2022). Look forward for this to happen! Spread the voice: N: [https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48l...](https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48lmw9jc7nhhauyq5w3cm4nfsm3mstqtk6m) X: https://x.com/bitcoin_design/status/1905547407405768927 originally posted at https://stacker.news/items/927650 @ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship. He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
@ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship. He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security. @ 7d33ba57:1b82db35
2025-03-28 09:13:56Girona, one of Catalonia’s most charming cities, is a perfect mix of history, culture, and gastronomy. Famous for its well-preserved medieval old town, colorful houses along the Onyar River, and Game of Thrones filming locations, Girona is a must-visit destination in northern Spain.  ## **🏰 Top Things to See & Do in Girona** ### **1️⃣ Girona Cathedral (Catedral de Santa Maria) ⛪** - One of **Spain’s most impressive cathedrals**, with **the widest Gothic nave in the world**. - Famous as the **Great Sept of Baelor in Game of Thrones**. - Climb the **steps for a breathtaking city view**. ### **2️⃣ Walk the Medieval Walls (Passeig de la Muralla) 🏰** - Offers **panoramic views** of Girona and the surrounding countryside. - A great way to see the city from above and explore its medieval history.  ### **3️⃣ The Colorful Houses of the Onyar River 🌉** - Girona’s **most iconic view**, with **brightly colored houses reflecting on the river**. - Best viewed from the **Pont de les Peixateries Velles**, designed by **Gustave Eiffel**. ### **4️⃣ Explore the Jewish Quarter (El Call) 🏡** - One of **Europe’s best-preserved Jewish quarters**, with **narrow, medieval streets**. - Visit the **Museum of Jewish History** to learn about Girona’s Jewish heritage.  ### **5️⃣ Arab Baths (Banys Àrabs) 🏛️** - A **12th-century Romanesque bathhouse**, inspired by Moorish architecture. - Features **a beautiful central dome with columns**. ### **6️⃣ Game of Thrones Filming Locations 🎬** - Walk in the footsteps of **Arya Stark** through the city’s **winding streets**. - Visit **the steps of the cathedral, the Jewish Quarter, and Arab Baths**, all featured in the series. ### **7️⃣ Eat at a Michelin-Starred Restaurant 🍽️** - Girona is home to **El Celler de Can Roca**, a **3-Michelin-star restaurant**, ranked among the **best in the world**. - Try **local Catalan dishes** like **"suquet de peix" (fish stew) and botifarra (Catalan sausage).**  ## **🚗 How to Get to Girona** ✈️ **By Air:** Girona-Costa Brava Airport (GRO) is **20 min away**, with budget flights from Europe. 🚆 **By Train:** High-speed AVE trains connect **Barcelona (38 min), Madrid (3.5 hrs), and Paris (5.5 hrs)**. 🚘 **By Car:** 1 hr from **Barcelona**, 40 min from **Figueres (Dalí Museum)**. 🚌 **By Bus:** Direct buses from **Barcelona and the Costa Brava**.  ## **💡 Tips for Visiting Girona** ✅ **Best time to visit?** **Spring & autumn (April–June & September–October)** for pleasant weather. 🌤️ ✅ **Wear comfortable shoes** – The old town is **hilly with cobblestone streets**. 👟 ✅ **Try xuixo** – A delicious **cream-filled pastry**, unique to Girona. 🥐 ✅ **Visit early for Game of Thrones spots** – They get crowded during the day! 🎥 ✅ **Take a day trip** – Explore nearby **Costa Brava beaches or Figueres (Dalí Museum).** 🏖️ 
@ 7d33ba57:1b82db35
2025-03-28 09:13:56Girona, one of Catalonia’s most charming cities, is a perfect mix of history, culture, and gastronomy. Famous for its well-preserved medieval old town, colorful houses along the Onyar River, and Game of Thrones filming locations, Girona is a must-visit destination in northern Spain.  ## **🏰 Top Things to See & Do in Girona** ### **1️⃣ Girona Cathedral (Catedral de Santa Maria) ⛪** - One of **Spain’s most impressive cathedrals**, with **the widest Gothic nave in the world**. - Famous as the **Great Sept of Baelor in Game of Thrones**. - Climb the **steps for a breathtaking city view**. ### **2️⃣ Walk the Medieval Walls (Passeig de la Muralla) 🏰** - Offers **panoramic views** of Girona and the surrounding countryside. - A great way to see the city from above and explore its medieval history.  ### **3️⃣ The Colorful Houses of the Onyar River 🌉** - Girona’s **most iconic view**, with **brightly colored houses reflecting on the river**. - Best viewed from the **Pont de les Peixateries Velles**, designed by **Gustave Eiffel**. ### **4️⃣ Explore the Jewish Quarter (El Call) 🏡** - One of **Europe’s best-preserved Jewish quarters**, with **narrow, medieval streets**. - Visit the **Museum of Jewish History** to learn about Girona’s Jewish heritage.  ### **5️⃣ Arab Baths (Banys Àrabs) 🏛️** - A **12th-century Romanesque bathhouse**, inspired by Moorish architecture. - Features **a beautiful central dome with columns**. ### **6️⃣ Game of Thrones Filming Locations 🎬** - Walk in the footsteps of **Arya Stark** through the city’s **winding streets**. - Visit **the steps of the cathedral, the Jewish Quarter, and Arab Baths**, all featured in the series. ### **7️⃣ Eat at a Michelin-Starred Restaurant 🍽️** - Girona is home to **El Celler de Can Roca**, a **3-Michelin-star restaurant**, ranked among the **best in the world**. - Try **local Catalan dishes** like **"suquet de peix" (fish stew) and botifarra (Catalan sausage).**  ## **🚗 How to Get to Girona** ✈️ **By Air:** Girona-Costa Brava Airport (GRO) is **20 min away**, with budget flights from Europe. 🚆 **By Train:** High-speed AVE trains connect **Barcelona (38 min), Madrid (3.5 hrs), and Paris (5.5 hrs)**. 🚘 **By Car:** 1 hr from **Barcelona**, 40 min from **Figueres (Dalí Museum)**. 🚌 **By Bus:** Direct buses from **Barcelona and the Costa Brava**.  ## **💡 Tips for Visiting Girona** ✅ **Best time to visit?** **Spring & autumn (April–June & September–October)** for pleasant weather. 🌤️ ✅ **Wear comfortable shoes** – The old town is **hilly with cobblestone streets**. 👟 ✅ **Try xuixo** – A delicious **cream-filled pastry**, unique to Girona. 🥐 ✅ **Visit early for Game of Thrones spots** – They get crowded during the day! 🎥 ✅ **Take a day trip** – Explore nearby **Costa Brava beaches or Figueres (Dalí Museum).** 🏖️  @ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok): “Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.” Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:  America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans. That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form. For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence. But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America. That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit. American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.) In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.” *Libertas magnitudo est*
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok): “Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.” Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:  America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans. That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form. For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence. But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America. That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit. American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.) In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.” *Libertas magnitudo est* @ a60e79e0:1e0e6813
2025-03-28 08:47:35*This is a long form note of a post that lives on my Nostr educational website [Hello Nostr](https://hellonostr.xyz).* When most people stumble across Nostr, they see is as a 'decentralized social media alternative' — something akin to Twitter (X), but free from corporate control. But the full name, "Notes and Other Stuff Transmitted by Relays", gives a clue that there’s more to it than just posting short messages. The 'notes' part is easy to grasp because it forms almost everyone's first touch point with the protocol. But the 'other stuff'? That’s where Nostr really gets exciting. The 'other stuff' is all the creative and experimental things people are building on Nostr, beyond simple text based notes. Every action on Nostr is an event, a like, a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as [Nostr Implementation Possibility - NIP](https://nostr-nips.com/). A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client to meet different purposes. > Nostr isn’t locked into a single purpose. It’s a foundation for whatever 'other stuff' you can dream up. > # Types of Other Stuff The 'other stuff' name is intentionally vague. Why? Because the possibilities of what can fall under this category are quite literally limitless. In the short time since Nostr's inception, the number of sub-categories that have been built on top of the Nostr's open protocol is mind bending. Here are a few examples: 1. Long-Form Content: Think blog posts or articles. [NIP-23](https://nostr-nips.com/nip-23). 2. Private Messaging: Encrypted chats between users. [NIP-04](https://nostr-nips.com/nip-04). 3. Communities: Group chats or forums like Reddit. [NIP-72](https://nostr-nips.com/nip-72) 4. Marketplaces: People listing stuff for sale, payable with zaps. [NIP-15](https://nostr-nips.com/nip-15) 5. Zaps: Value transfer over the Lightning Network. [NIP57](https://nostr-nips.com/nip-57)  # Popular 'Other Stuff' Clients Here's a short list of some of the most recent and popular apps and clients that branch outside of the traditional micro-blogging use case and leverage the openness, and interoperability that Nostr can provide. ### Blogging (Long Form Content) - [Habla](https://habla.news/) - *Web app for Nostr based blogs* - [Highlighter](https://highlighter.com/) - *Web app that enables users to highlight, store and share content* ### Group Chats - [Chachi Chat](https://chachi.chat/) - *Relay-based (NIP-29) group chat client* - [0xchat](https://github.com/0xchat-app) - *Mobile based secure chat* - [Flotilla](https://flotilla.social/) - *Web based chat app built for self-hosted communities* - [Nostr Nests](https://nostrnests.com/) - *Web app for audio chats* - [White Noise](https://github.com/erskingardner/whitenoise) - *Mobile based secure chat*  ### Marketplaces - [Shopstr](https://shopstr.store/) - *Permissionless marketplace for web* - [Plebeian Market](https://plebeian.market/) - *Permissionless marketplace for web* - [LNBits Market](https://github.com/lnbits/nostrmarket#nostr-market-nip-15---lnbits-extension) - *Permissionless marketplace for your node* - [Mostro](https://github.com/MostroP2P/mostro) - *Nostr based Bitcoin P2P Marketplace* ### Photo/Video - [Olas](https://github.com/pablof7z/snapstr/releases) - *An Intragram like client* - [Freeflow](https://github.com/nostrlabs-io/freeflow) - *A TikTok like client* ### Music - [Fountain](https://fountain.fm/) - *Podcast app with Nostr features* - [Wavlake](https://wavlake.com/) - *A music app supporting the value-for-value ecosystem*  ### Livestreaming - [Zap.stream](https://zap.stream/) - *Nostr native live streams* ### Misc - [Wikifreedia](https://wikifreedia.xyz/) - *Nostr based Wikipedia alternative* - [Wikistr](https://wikistr.com/) - *Nostr based Wikipedia alternative* - [Pollerama](https://pollerama.fun/) - *Nostr based polls* - [Zap Store](https://zapstore.dev) - *The app store powered by your social graph*  The 'other stuff' in Nostr is what makes it special. It’s not just about replacing Twitter or Facebook, it’s about building a decentralized ecosystem where anything from private chats to marketplaces can thrive. The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the 'other stuff' to grow wilder and weirder over time! You can explore the evergrowing 'other stuff' ecosystem at [NostrApps.com](https://nostrapps.com/), [Nostr.net](https://nostr.net/) and [Awesome Nostr](https://github.com/aljazceru/awesome-nostr).
@ a60e79e0:1e0e6813
2025-03-28 08:47:35*This is a long form note of a post that lives on my Nostr educational website [Hello Nostr](https://hellonostr.xyz).* When most people stumble across Nostr, they see is as a 'decentralized social media alternative' — something akin to Twitter (X), but free from corporate control. But the full name, "Notes and Other Stuff Transmitted by Relays", gives a clue that there’s more to it than just posting short messages. The 'notes' part is easy to grasp because it forms almost everyone's first touch point with the protocol. But the 'other stuff'? That’s where Nostr really gets exciting. The 'other stuff' is all the creative and experimental things people are building on Nostr, beyond simple text based notes. Every action on Nostr is an event, a like, a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as [Nostr Implementation Possibility - NIP](https://nostr-nips.com/). A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client to meet different purposes. > Nostr isn’t locked into a single purpose. It’s a foundation for whatever 'other stuff' you can dream up. > # Types of Other Stuff The 'other stuff' name is intentionally vague. Why? Because the possibilities of what can fall under this category are quite literally limitless. In the short time since Nostr's inception, the number of sub-categories that have been built on top of the Nostr's open protocol is mind bending. Here are a few examples: 1. Long-Form Content: Think blog posts or articles. [NIP-23](https://nostr-nips.com/nip-23). 2. Private Messaging: Encrypted chats between users. [NIP-04](https://nostr-nips.com/nip-04). 3. Communities: Group chats or forums like Reddit. [NIP-72](https://nostr-nips.com/nip-72) 4. Marketplaces: People listing stuff for sale, payable with zaps. [NIP-15](https://nostr-nips.com/nip-15) 5. Zaps: Value transfer over the Lightning Network. [NIP57](https://nostr-nips.com/nip-57)  # Popular 'Other Stuff' Clients Here's a short list of some of the most recent and popular apps and clients that branch outside of the traditional micro-blogging use case and leverage the openness, and interoperability that Nostr can provide. ### Blogging (Long Form Content) - [Habla](https://habla.news/) - *Web app for Nostr based blogs* - [Highlighter](https://highlighter.com/) - *Web app that enables users to highlight, store and share content* ### Group Chats - [Chachi Chat](https://chachi.chat/) - *Relay-based (NIP-29) group chat client* - [0xchat](https://github.com/0xchat-app) - *Mobile based secure chat* - [Flotilla](https://flotilla.social/) - *Web based chat app built for self-hosted communities* - [Nostr Nests](https://nostrnests.com/) - *Web app for audio chats* - [White Noise](https://github.com/erskingardner/whitenoise) - *Mobile based secure chat*  ### Marketplaces - [Shopstr](https://shopstr.store/) - *Permissionless marketplace for web* - [Plebeian Market](https://plebeian.market/) - *Permissionless marketplace for web* - [LNBits Market](https://github.com/lnbits/nostrmarket#nostr-market-nip-15---lnbits-extension) - *Permissionless marketplace for your node* - [Mostro](https://github.com/MostroP2P/mostro) - *Nostr based Bitcoin P2P Marketplace* ### Photo/Video - [Olas](https://github.com/pablof7z/snapstr/releases) - *An Intragram like client* - [Freeflow](https://github.com/nostrlabs-io/freeflow) - *A TikTok like client* ### Music - [Fountain](https://fountain.fm/) - *Podcast app with Nostr features* - [Wavlake](https://wavlake.com/) - *A music app supporting the value-for-value ecosystem*  ### Livestreaming - [Zap.stream](https://zap.stream/) - *Nostr native live streams* ### Misc - [Wikifreedia](https://wikifreedia.xyz/) - *Nostr based Wikipedia alternative* - [Wikistr](https://wikistr.com/) - *Nostr based Wikipedia alternative* - [Pollerama](https://pollerama.fun/) - *Nostr based polls* - [Zap Store](https://zapstore.dev) - *The app store powered by your social graph*  The 'other stuff' in Nostr is what makes it special. It’s not just about replacing Twitter or Facebook, it’s about building a decentralized ecosystem where anything from private chats to marketplaces can thrive. The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the 'other stuff' to grow wilder and weirder over time! You can explore the evergrowing 'other stuff' ecosystem at [NostrApps.com](https://nostrapps.com/), [Nostr.net](https://nostr.net/) and [Awesome Nostr](https://github.com/aljazceru/awesome-nostr). @ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement. Let's begin by defining a couple of things: **Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example. **Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are. If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article. In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed. What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.  Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines. That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems. Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.  I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives. Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms? Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life? If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later. 
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement. Let's begin by defining a couple of things: **Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example. **Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are. If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article. In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed. What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.  Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines. That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems. Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.  I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives. Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms? Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life? If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.  @ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M @ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid
@ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid @ 45c41f21:c5446b7a
2025-03-28 08:02:16“区块链行业究竟是在做什么?”——这个问题我到现在还没有想得很清楚。谈论起来可以说很多东西,“确权”、“让每一个比特都有了稀缺性”、“数字黄金”、“点对点支付”,但是具体到了行业落地,又容易陷入“赌场”这个有点乌烟瘴气的现实。 但我想有一点是比较明确的,那就是区块链行业肯定是一个围绕资产的行业。这些资产又跟传统的资产很不一样,最简单的特征是它们都是一个个的代币,通过自动化和可验证的代码铸造、控制,我们可以统称为链上资产。从比特币、以太坊到现在,这中间不管过去了多少不同的周期和浪潮,核心不变的都是出现新一轮受追捧的资产。 既然区块链是关于链上资产的行业,那么最重要的是未来会出现什么新的资产,有什么样的新资产会上链。要回答这个问题,又要我们回过头去看看,从行业诞生至今,区块链留下了哪些有意义的、没意义的,有价值的、没价值的资产。 因此,有必要讨论一下链上资产的分类。 链上资产的种类很多,但总体上我觉得可以按**满足需求的不同,**做一些功能性的划分。同时,抛开去中心化、抗审查等等大词,**链上资产与传统资产最重要的区别可以认为是安全性的来源**。传统资产在传统的社会系统和金融系统中产生,而链上资产是通过可验证代码控制的,所以它的安全性的依赖很清晰,要比现实世界简单很多。 在不同的区块链系统中,使用不同的技术(比如POW/POS),设置不同的规则,拥有不同的治理机制,都会影响安全性。“安全性”和“满足什么样的需求”之间既不是正交的,也不是完全耦合的。在不同层级的安全性之下,可能都会出现满足某一类相同需求的产品,用户使用哪种产品,只取决于自己的风险偏好。另一方面,有些需求只可能在某些特定的安全性保障下才能得到满足,比如跨国际的全球化的抗通胀价值存储。 这篇文章只讨论一些比较简单的分类,可以假设在不同的安全性保障下,每个分类都有可能出现对应的产品。有些安全性是产品内生功能的一部分,有些则完全不影响。同时,这些分类也完全是主观的看法,不一定正确,我所希望的是引发更多对资产进行讨论。 ### 核心资产(高安全性、强需求支撑) 1. **比特币(BTC)** - **核心价值**:全球化抗通胀、抗审查的“数字黄金”。 - **长期逻辑**:全球法币超发背景下,BTC作为去中心化硬通货的需求不可替代。 这是整个行业最重要的资产。也是整个行业最核心的东西。在这个定位下,只会有一个赢者通吃。其他试图竞争的都很难生存下来。它对安全性的要求也是最高的。 ### 经过验证的资产分类 这部分的资产可以认为是行业诞生至今,已经经过验证的、满足某真实需求、会长期存在的资产。 1. **代表优质项目的资产(股票/ICO代币/治理代币等)** - **核心价值**:类似于传统金融世界里的一级市场和二级市场。所谓的“优质”也不一定需要真实落地,可能是叙事/故事驱动,也可能有真实的现金流,但重要的是它能在市场上吸引人买卖。 - **关键指标**:团队是否持续营销和建设?生态是否增长?项目是否解决实际问题? 2. **DeFi 资产** - **核心价值**:链上金融系统的“基础设施工具”。 - **需求来源**:对套利、链上资产理财的需求会永远存在。 3. **Meme币** - **核心价值**:营销驱动+投机需求的结合体。 - **长期存在性**:人性对暴富故事的追逐不会消失(如Pump.fun、SHIB)。 4. **稳定币** - **核心价值**:加密货币世界的“支付货币”。 - **需求刚性**:交易媒介、避险工具、跨境支付(如USDT、USDC)。 在不同的安全性保障下,上面这些资产大部分都会有对应的产品。 比如稳定币在安全性上可以有中心化的 USDT ,也有去中心化的算法稳定币。理论上,安全性对稳定币是非常重要的。但现实中,“流动性”可能才是给用户传达“这东西到底安不安全“的产品特点,也是比较主要的竞争点。 Meme 则完全不需要安全性,所以对创业者来说在哪里做都差不多。哪里用户更多就适合去哪里。有时,安全性反而是它的阻碍。DeFi 的话,因人而异。安全性高低是否影响用户使用,完全取决于用户自己的风险偏好。 ### 还未经过验证的资产(需求可能存在) - **NFT(收藏品)?** 艺术、身份标识、游戏道具的数字化载体,但流动性差、炒作属性也不见得有 Meme 这么强。会长期存在吗?打个问号。 - **DAO(准入/治理代币)?** 去中心化组织的准入权/管理权通证,依赖 DAO 本身的价值和实际治理参与度决定的价值。DeFi DAO 可能是唯一一个有点发展的方向,其他还非常不成熟,有待验证。 - **RWA(真实世界资产代币化)?** 房产、债券等上链,需要解决法律合规与链下资产映射问题。不确定。 - **社交/游戏/内容资产** 用户数据所有权货币化,还没有像样的有一些用户的产品,就更不用提形成规模经济了。 - **AI 相关的资产?** 是一个变数。如果未来会有成千上万的 AI 智能体与人类共存,链上是承载他们经济系统最合适的基础设施,这里会产生什么新的资产类型?值得期待。 这里面的资产类型,很多还没有找到真实的需求,至少没有经过验证。所以长期来看它们会是区块链行业的方向吗,需要打很多问号。既然需求本身没有得到验证,那么谈安全性对它们的影响,就更加无从谈起了。 当然,这里其实还有一个更有意思的部分,可以多聊一些。也就是**共同知识(法律/合同/规则/代码)**这一类资产。 在应用层,共同知识尚未有代币化的尝试,也难以对其具体价值做定量分析。但如果要说有的实践,以太坊通过交易收取 gas 费和 CKB 通过 Cell 存储状态收取“押金”算是一种在底层的 generalize 的尝试。这种尝试是定量的,可验证的。 以太坊的问题是经济模型不 make sense 导致状态爆炸,ckb 相比是更简单、更明确的。但这里的问题变成了,公链需要通过区块空间的竞争来展示这一种需求是否真的成立。区块空间越紧张,需求就越大。同时安全性越高,对共同知识的保障就越强,也会体现区块空间的价值。 但另一方面,是否有开发者在上面开发应用,会更大的影响这一点。因此开发工具、开发者生态在现阶段可能更重要。 ### 最后 写到这里,发现很多资产似乎又是老生常谈。但从满足需求和安全性两个角度来思考,算是追本溯源的尝试。现在我们面临的处境是,问题还是老的问题,答案是否有新的答案,期待更多讨论。
@ 45c41f21:c5446b7a
2025-03-28 08:02:16“区块链行业究竟是在做什么?”——这个问题我到现在还没有想得很清楚。谈论起来可以说很多东西,“确权”、“让每一个比特都有了稀缺性”、“数字黄金”、“点对点支付”,但是具体到了行业落地,又容易陷入“赌场”这个有点乌烟瘴气的现实。 但我想有一点是比较明确的,那就是区块链行业肯定是一个围绕资产的行业。这些资产又跟传统的资产很不一样,最简单的特征是它们都是一个个的代币,通过自动化和可验证的代码铸造、控制,我们可以统称为链上资产。从比特币、以太坊到现在,这中间不管过去了多少不同的周期和浪潮,核心不变的都是出现新一轮受追捧的资产。 既然区块链是关于链上资产的行业,那么最重要的是未来会出现什么新的资产,有什么样的新资产会上链。要回答这个问题,又要我们回过头去看看,从行业诞生至今,区块链留下了哪些有意义的、没意义的,有价值的、没价值的资产。 因此,有必要讨论一下链上资产的分类。 链上资产的种类很多,但总体上我觉得可以按**满足需求的不同,**做一些功能性的划分。同时,抛开去中心化、抗审查等等大词,**链上资产与传统资产最重要的区别可以认为是安全性的来源**。传统资产在传统的社会系统和金融系统中产生,而链上资产是通过可验证代码控制的,所以它的安全性的依赖很清晰,要比现实世界简单很多。 在不同的区块链系统中,使用不同的技术(比如POW/POS),设置不同的规则,拥有不同的治理机制,都会影响安全性。“安全性”和“满足什么样的需求”之间既不是正交的,也不是完全耦合的。在不同层级的安全性之下,可能都会出现满足某一类相同需求的产品,用户使用哪种产品,只取决于自己的风险偏好。另一方面,有些需求只可能在某些特定的安全性保障下才能得到满足,比如跨国际的全球化的抗通胀价值存储。 这篇文章只讨论一些比较简单的分类,可以假设在不同的安全性保障下,每个分类都有可能出现对应的产品。有些安全性是产品内生功能的一部分,有些则完全不影响。同时,这些分类也完全是主观的看法,不一定正确,我所希望的是引发更多对资产进行讨论。 ### 核心资产(高安全性、强需求支撑) 1. **比特币(BTC)** - **核心价值**:全球化抗通胀、抗审查的“数字黄金”。 - **长期逻辑**:全球法币超发背景下,BTC作为去中心化硬通货的需求不可替代。 这是整个行业最重要的资产。也是整个行业最核心的东西。在这个定位下,只会有一个赢者通吃。其他试图竞争的都很难生存下来。它对安全性的要求也是最高的。 ### 经过验证的资产分类 这部分的资产可以认为是行业诞生至今,已经经过验证的、满足某真实需求、会长期存在的资产。 1. **代表优质项目的资产(股票/ICO代币/治理代币等)** - **核心价值**:类似于传统金融世界里的一级市场和二级市场。所谓的“优质”也不一定需要真实落地,可能是叙事/故事驱动,也可能有真实的现金流,但重要的是它能在市场上吸引人买卖。 - **关键指标**:团队是否持续营销和建设?生态是否增长?项目是否解决实际问题? 2. **DeFi 资产** - **核心价值**:链上金融系统的“基础设施工具”。 - **需求来源**:对套利、链上资产理财的需求会永远存在。 3. **Meme币** - **核心价值**:营销驱动+投机需求的结合体。 - **长期存在性**:人性对暴富故事的追逐不会消失(如Pump.fun、SHIB)。 4. **稳定币** - **核心价值**:加密货币世界的“支付货币”。 - **需求刚性**:交易媒介、避险工具、跨境支付(如USDT、USDC)。 在不同的安全性保障下,上面这些资产大部分都会有对应的产品。 比如稳定币在安全性上可以有中心化的 USDT ,也有去中心化的算法稳定币。理论上,安全性对稳定币是非常重要的。但现实中,“流动性”可能才是给用户传达“这东西到底安不安全“的产品特点,也是比较主要的竞争点。 Meme 则完全不需要安全性,所以对创业者来说在哪里做都差不多。哪里用户更多就适合去哪里。有时,安全性反而是它的阻碍。DeFi 的话,因人而异。安全性高低是否影响用户使用,完全取决于用户自己的风险偏好。 ### 还未经过验证的资产(需求可能存在) - **NFT(收藏品)?** 艺术、身份标识、游戏道具的数字化载体,但流动性差、炒作属性也不见得有 Meme 这么强。会长期存在吗?打个问号。 - **DAO(准入/治理代币)?** 去中心化组织的准入权/管理权通证,依赖 DAO 本身的价值和实际治理参与度决定的价值。DeFi DAO 可能是唯一一个有点发展的方向,其他还非常不成熟,有待验证。 - **RWA(真实世界资产代币化)?** 房产、债券等上链,需要解决法律合规与链下资产映射问题。不确定。 - **社交/游戏/内容资产** 用户数据所有权货币化,还没有像样的有一些用户的产品,就更不用提形成规模经济了。 - **AI 相关的资产?** 是一个变数。如果未来会有成千上万的 AI 智能体与人类共存,链上是承载他们经济系统最合适的基础设施,这里会产生什么新的资产类型?值得期待。 这里面的资产类型,很多还没有找到真实的需求,至少没有经过验证。所以长期来看它们会是区块链行业的方向吗,需要打很多问号。既然需求本身没有得到验证,那么谈安全性对它们的影响,就更加无从谈起了。 当然,这里其实还有一个更有意思的部分,可以多聊一些。也就是**共同知识(法律/合同/规则/代码)**这一类资产。 在应用层,共同知识尚未有代币化的尝试,也难以对其具体价值做定量分析。但如果要说有的实践,以太坊通过交易收取 gas 费和 CKB 通过 Cell 存储状态收取“押金”算是一种在底层的 generalize 的尝试。这种尝试是定量的,可验证的。 以太坊的问题是经济模型不 make sense 导致状态爆炸,ckb 相比是更简单、更明确的。但这里的问题变成了,公链需要通过区块空间的竞争来展示这一种需求是否真的成立。区块空间越紧张,需求就越大。同时安全性越高,对共同知识的保障就越强,也会体现区块空间的价值。 但另一方面,是否有开发者在上面开发应用,会更大的影响这一点。因此开发工具、开发者生态在现阶段可能更重要。 ### 最后 写到这里,发现很多资产似乎又是老生常谈。但从满足需求和安全性两个角度来思考,算是追本溯源的尝试。现在我们面临的处境是,问题还是老的问题,答案是否有新的答案,期待更多讨论。 @ 91bea5cd:1df4451c
2025-02-04 17:15:57### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid
@ 91bea5cd:1df4451c
2025-02-04 17:15:57### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid @ 05cdefcd:550cc264
2025-03-28 08:00:15The crypto world is full of buzzwords. One that I keep on hearing: “Bitcoin is its own asset class”. While I have always been sympathetic to that view, I’ve always failed to understand the true meaning behind that statement. Although I consider Bitcoin to be the prime innovation within the digital asset sector, my primary response has always been: How can bitcoin (BTC), a single asset, represent an entire asset class? Isn’t it Bitcoin and other digital assets that make up an asset class called crypto? Well, I increasingly believe that most of crypto is just noise. Sure, it’s volatile noise that is predominately interesting for very sophisticated hedge funds, market makers or prop traders that are sophisticated enough to extract alpha – but it’s noise nonetheless and has no part to play in a long-term only portfolio of private retail investors (of which most of us are). *Over multiple market cycles, nearly all altcoins underperform Bitcoin when measured in BTC terms. Source: Tradingview* ## Aha-Moment: Bitcoin keeps on giving Still, how can Bitcoin, as a standalone asset, make up an entire asset class? The “aha-moment” to answer this question recently came to me in a [Less Noise More Signal interview](https://www.youtube.com/watch?v=YHRluf5uxzo) I did with [James Van Straten](https://www.linkedin.com/in/james-van-straten-8782b4112/), senior analyst at Coindesk. Let me paraphrase him here: *“You can’t simply recreate the same ETF as BlackRock. To succeed in the Bitcoin space, new and innovative approaches are needed. This is where understanding Bitcoin not just as a single asset, but as an entire asset class, becomes essential. There are countless ways to build upon Bitcoin’s foundation—varied iterations that go beyond just holding the asset. This is precisely where the emergence of the Bitcoin-linked stock market is taking shape—and it's already underway.”* And this is actually coming to fruition as we speak. Just in the last few days, we saw several products launch in that regard. Obviously, MicroStrategy (now Strategy) is the pioneer of this. The company now [owns](https://www.strategy.com/purchases) 506,137 BTC, and while they’ll keep on buying more, they have also inspired many other companies to follow suit. In fact, there are now already over 70 companies that have adopted Strategy’s Bitcoin playbook. One of the latest companies to buy Bitcoin for their corporate treasury is Rumble. The YouTube competitor just [announced](https://www.coindesk.com/markets/2025/03/12/video-sharing-platform-rumble-buys-188-btc-for-usd17-1m) their first Bitcoin purchase for $17 million. Also, the gaming zombie company GameStop just announced to raise money to buy BTC for their corporate treasury. *Gamestop to make BTC their hurdle rate. Source: X* ## ETF on Bitcoin companies Given this proliferation of Bitcoin Treasury companies, it was only a matter of time before a financial product tracking these would emerge. The popular crypto index fund provider Bitwise Investments has just launched this very product called the [Bitwise Bitcoin Standard Corporations ETF](https://ownbetf.com/) (OWNB). The ETF tracks Bitcoin Treasury companies with over 1,000 BTC on their balance sheet. These companies invest in Bitcoin as a strategic reserve asset to protect the $5 trillion in low-yield cash that companies in the US commonly sit on. *These are the top 10 holdings of OWNB. Source: Ownbetf* ## ETF on Bitcoin companies’ convertible bonds Another instrument that fits seamlessly into the range of Bitcoin-linked stock market products is the [REX Bitcoin Corporate Treasury Convertible Bond ETF](https://www.rexshares.com/rex-launches-bitcoin-corporate-treasury-convertible-bond-etf/) (BMAX). The ETF provides exposure to the many different convertible bonds issued by companies that are actively moving onto a Bitcoin standard. Convertible bonds are a valuable financing tool for companies looking to raise capital for Bitcoin purchases. Their strong demand is driven by the unique combination of equity-like upside and debt-like downside protection they offer. For example, MicroStrategy's convertible bonds, in particular, have shown exceptional performance. For instance, MicroStrategy's 2031 bonds has shown a price rise of 101% over a one-year period, vastly outperforming MicroStrategy share (at 53%), Bitcoin (at 25%) and the ICE BofA U.S. Convertible Index (at 10%). The latter is the benchmark index for convertible bond funds, tracking the performance of U.S. dollar-denominated convertible securities in the U.S. market. *The chart shows a comparison of ICE BofA U.S. Convertible Index, the Bloomberg Bitcoin index (BTC price), MicroStrategy share (MSTR), and MicroStrategy bond (0.875%, March 15 203). The convertible bond has been outperforming massively. Source: Bloomberg* While the BMAX ETF faces challenges such as double taxation, which significantly reduces investor returns (explained in more detail here), it is likely that future products will emerge that address and improve upon these issues. ## Bitcoin yield products The demand for a yield on Bitcoin has increased tremendously. Consequently, respective products have emerged. Bitcoin yield products aim to generate alpha by capitalizing on volatility, market inefficiencies, and fragmentation within cryptocurrency markets. The objective is to achieve uncorrelated returns denominated in Bitcoin (BTC), with attractive risk-adjusted performance. Returns are derived exclusively from asset selection and trading strategies, eliminating reliance on directional market moves. ### Key strategies employed by these funds include: - *Statistical Arbitrage:* Exploits short-term pricing discrepancies between closely related financial instruments—for instance, between Bitcoin and traditional assets, or Bitcoin and other digital assets. Traders utilize statistical models and historical price relationships to identify temporary inefficiencies. - *Futures Basis Arbitrage:* Captures profits from differences between the spot price of Bitcoin and its futures contracts. Traders simultaneously buy or sell Bitcoin on spot markets and enter opposite positions in futures markets, benefiting as the prices converge. - *Funding Arbitrage:* Generates returns by taking advantage of variations in Bitcoin funding rates across different markets or exchanges. Funding rates are periodic payments exchanged between long and short positions in perpetual futures contracts, allowing traders to profit from discrepancies without significant directional exposure. - *Volatility/Option Arbitrage:* Seeks profits from differences between implied volatility (reflected in Bitcoin options prices) and expected realized volatility. Traders identify mispriced volatility in options related to Bitcoin or Bitcoin-linked equities, such as MSTR, and position accordingly to benefit from volatility normalization. - *Market Making:* Involves continuously providing liquidity by simultaneously quoting bid (buy) and ask (sell) prices for Bitcoin. Market makers profit primarily through capturing the spread between these prices, thereby enhancing market efficiency and earning consistent returns. - *Liquidity Provision in DeFi Markets:* Consists of depositing Bitcoin (usually as Wrapped BTC) into decentralized finance (DeFi) liquidity pools such as those on Uniswap, Curve, or Balancer. Liquidity providers earn fees paid by traders who execute swaps within these decentralized exchanges, creating steady yield opportunities. Notable products currently available in this segment include the Syz Capital BTC Alpha Fund offered by Syz Capital and the Forteus Crypto Alpha Fund by Forteus. ## BTC-denominated share class A Bitcoin-denominated share class refers to a specialized investment fund category in which share values, subscriptions (fund deposits), redemptions (fund withdrawals), and performance metrics are expressed entirely in Bitcoin (BTC), rather than in traditional fiat currencies such as USD or EUR. Increasingly, both individual investors and institutions are adopting Bitcoin as their preferred benchmark—or "Bitcoin hurdle rate"—meaning that investment performance is evaluated directly against Bitcoin’s own price movements. These Bitcoin-denominated share classes are designed specifically for investors seeking to preserve and grow their wealth in Bitcoin terms, rather than conventional fiat currencies. As a result, investors reduce their exposure to fiat-related risks. Furthermore, if Bitcoin outperforms fiat currencies, investors holding BTC-denominated shares will experience enhanced returns relative to traditional fiat-denominated investment classes. X: https://x.com/pahueg Podcast: https://www.youtube.com/@lessnoisemoresignalpodcast Book: https://academy.saifedean.com/product/the-bitcoin-enlightenment-hardcover/
@ 05cdefcd:550cc264
2025-03-28 08:00:15The crypto world is full of buzzwords. One that I keep on hearing: “Bitcoin is its own asset class”. While I have always been sympathetic to that view, I’ve always failed to understand the true meaning behind that statement. Although I consider Bitcoin to be the prime innovation within the digital asset sector, my primary response has always been: How can bitcoin (BTC), a single asset, represent an entire asset class? Isn’t it Bitcoin and other digital assets that make up an asset class called crypto? Well, I increasingly believe that most of crypto is just noise. Sure, it’s volatile noise that is predominately interesting for very sophisticated hedge funds, market makers or prop traders that are sophisticated enough to extract alpha – but it’s noise nonetheless and has no part to play in a long-term only portfolio of private retail investors (of which most of us are). *Over multiple market cycles, nearly all altcoins underperform Bitcoin when measured in BTC terms. Source: Tradingview* ## Aha-Moment: Bitcoin keeps on giving Still, how can Bitcoin, as a standalone asset, make up an entire asset class? The “aha-moment” to answer this question recently came to me in a [Less Noise More Signal interview](https://www.youtube.com/watch?v=YHRluf5uxzo) I did with [James Van Straten](https://www.linkedin.com/in/james-van-straten-8782b4112/), senior analyst at Coindesk. Let me paraphrase him here: *“You can’t simply recreate the same ETF as BlackRock. To succeed in the Bitcoin space, new and innovative approaches are needed. This is where understanding Bitcoin not just as a single asset, but as an entire asset class, becomes essential. There are countless ways to build upon Bitcoin’s foundation—varied iterations that go beyond just holding the asset. This is precisely where the emergence of the Bitcoin-linked stock market is taking shape—and it's already underway.”* And this is actually coming to fruition as we speak. Just in the last few days, we saw several products launch in that regard. Obviously, MicroStrategy (now Strategy) is the pioneer of this. The company now [owns](https://www.strategy.com/purchases) 506,137 BTC, and while they’ll keep on buying more, they have also inspired many other companies to follow suit. In fact, there are now already over 70 companies that have adopted Strategy’s Bitcoin playbook. One of the latest companies to buy Bitcoin for their corporate treasury is Rumble. The YouTube competitor just [announced](https://www.coindesk.com/markets/2025/03/12/video-sharing-platform-rumble-buys-188-btc-for-usd17-1m) their first Bitcoin purchase for $17 million. Also, the gaming zombie company GameStop just announced to raise money to buy BTC for their corporate treasury. *Gamestop to make BTC their hurdle rate. Source: X* ## ETF on Bitcoin companies Given this proliferation of Bitcoin Treasury companies, it was only a matter of time before a financial product tracking these would emerge. The popular crypto index fund provider Bitwise Investments has just launched this very product called the [Bitwise Bitcoin Standard Corporations ETF](https://ownbetf.com/) (OWNB). The ETF tracks Bitcoin Treasury companies with over 1,000 BTC on their balance sheet. These companies invest in Bitcoin as a strategic reserve asset to protect the $5 trillion in low-yield cash that companies in the US commonly sit on. *These are the top 10 holdings of OWNB. Source: Ownbetf* ## ETF on Bitcoin companies’ convertible bonds Another instrument that fits seamlessly into the range of Bitcoin-linked stock market products is the [REX Bitcoin Corporate Treasury Convertible Bond ETF](https://www.rexshares.com/rex-launches-bitcoin-corporate-treasury-convertible-bond-etf/) (BMAX). The ETF provides exposure to the many different convertible bonds issued by companies that are actively moving onto a Bitcoin standard. Convertible bonds are a valuable financing tool for companies looking to raise capital for Bitcoin purchases. Their strong demand is driven by the unique combination of equity-like upside and debt-like downside protection they offer. For example, MicroStrategy's convertible bonds, in particular, have shown exceptional performance. For instance, MicroStrategy's 2031 bonds has shown a price rise of 101% over a one-year period, vastly outperforming MicroStrategy share (at 53%), Bitcoin (at 25%) and the ICE BofA U.S. Convertible Index (at 10%). The latter is the benchmark index for convertible bond funds, tracking the performance of U.S. dollar-denominated convertible securities in the U.S. market. *The chart shows a comparison of ICE BofA U.S. Convertible Index, the Bloomberg Bitcoin index (BTC price), MicroStrategy share (MSTR), and MicroStrategy bond (0.875%, March 15 203). The convertible bond has been outperforming massively. Source: Bloomberg* While the BMAX ETF faces challenges such as double taxation, which significantly reduces investor returns (explained in more detail here), it is likely that future products will emerge that address and improve upon these issues. ## Bitcoin yield products The demand for a yield on Bitcoin has increased tremendously. Consequently, respective products have emerged. Bitcoin yield products aim to generate alpha by capitalizing on volatility, market inefficiencies, and fragmentation within cryptocurrency markets. The objective is to achieve uncorrelated returns denominated in Bitcoin (BTC), with attractive risk-adjusted performance. Returns are derived exclusively from asset selection and trading strategies, eliminating reliance on directional market moves. ### Key strategies employed by these funds include: - *Statistical Arbitrage:* Exploits short-term pricing discrepancies between closely related financial instruments—for instance, between Bitcoin and traditional assets, or Bitcoin and other digital assets. Traders utilize statistical models and historical price relationships to identify temporary inefficiencies. - *Futures Basis Arbitrage:* Captures profits from differences between the spot price of Bitcoin and its futures contracts. Traders simultaneously buy or sell Bitcoin on spot markets and enter opposite positions in futures markets, benefiting as the prices converge. - *Funding Arbitrage:* Generates returns by taking advantage of variations in Bitcoin funding rates across different markets or exchanges. Funding rates are periodic payments exchanged between long and short positions in perpetual futures contracts, allowing traders to profit from discrepancies without significant directional exposure. - *Volatility/Option Arbitrage:* Seeks profits from differences between implied volatility (reflected in Bitcoin options prices) and expected realized volatility. Traders identify mispriced volatility in options related to Bitcoin or Bitcoin-linked equities, such as MSTR, and position accordingly to benefit from volatility normalization. - *Market Making:* Involves continuously providing liquidity by simultaneously quoting bid (buy) and ask (sell) prices for Bitcoin. Market makers profit primarily through capturing the spread between these prices, thereby enhancing market efficiency and earning consistent returns. - *Liquidity Provision in DeFi Markets:* Consists of depositing Bitcoin (usually as Wrapped BTC) into decentralized finance (DeFi) liquidity pools such as those on Uniswap, Curve, or Balancer. Liquidity providers earn fees paid by traders who execute swaps within these decentralized exchanges, creating steady yield opportunities. Notable products currently available in this segment include the Syz Capital BTC Alpha Fund offered by Syz Capital and the Forteus Crypto Alpha Fund by Forteus. ## BTC-denominated share class A Bitcoin-denominated share class refers to a specialized investment fund category in which share values, subscriptions (fund deposits), redemptions (fund withdrawals), and performance metrics are expressed entirely in Bitcoin (BTC), rather than in traditional fiat currencies such as USD or EUR. Increasingly, both individual investors and institutions are adopting Bitcoin as their preferred benchmark—or "Bitcoin hurdle rate"—meaning that investment performance is evaluated directly against Bitcoin’s own price movements. These Bitcoin-denominated share classes are designed specifically for investors seeking to preserve and grow their wealth in Bitcoin terms, rather than conventional fiat currencies. As a result, investors reduce their exposure to fiat-related risks. Furthermore, if Bitcoin outperforms fiat currencies, investors holding BTC-denominated shares will experience enhanced returns relative to traditional fiat-denominated investment classes. X: https://x.com/pahueg Podcast: https://www.youtube.com/@lessnoisemoresignalpodcast Book: https://academy.saifedean.com/product/the-bitcoin-enlightenment-hardcover/ @ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.  For purposes of this blog post, our ultimate question will be the following: * Suppose apples currently sell for $1 each in the entire United States. * There are domestic sellers and foreign sellers of apples, all receiving the same price. * There are no taxes or tariffs on the purchase of apples. * The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following: * Number of apples bought in the US * Price paid by buyers for apples in the US * Post-tax price received by domestic apple producers * Post-tax price received by foreign apple producers Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1? And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why: 1. The number of apples bought will go down 2. The buyers will pay more for each apple they buy, but not the full amount of the tariff 3. Domestic apple sellers will receive a *higher* price per apple 4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit. ## Marginal benefit All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart). Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B. But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5. How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot. The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:  Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples. ## Marginal cost Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product. Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right? Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further. Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\! However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with: * Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900 * Total revenue: $5000 (10,000 apples at $0.50 each) * Total profit: $2100 So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money. This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:  ## Equilibrium price We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:  You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example: * When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point. * When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point. Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.” OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality. ## Modeling taxes Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve. First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:  With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve. We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:  The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:  As we can see, the equilibrium has shifted: * The equilibrium price paid by consumers has risen from $1 to $1.20. * The total number of apples purchased has dropped from 63 apples to 60 apples. * Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus. * Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42. * Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21. * The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise. We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes: * Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples. * Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless. * Domestic producers scored. They can sell less apples and make more revenue doing it. * And the government walked away with an extra $30. Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price. ## Other taxes Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down. And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost. You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with: * Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price. * Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost. * Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise. This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.  For purposes of this blog post, our ultimate question will be the following: * Suppose apples currently sell for $1 each in the entire United States. * There are domestic sellers and foreign sellers of apples, all receiving the same price. * There are no taxes or tariffs on the purchase of apples. * The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following: * Number of apples bought in the US * Price paid by buyers for apples in the US * Post-tax price received by domestic apple producers * Post-tax price received by foreign apple producers Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1? And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why: 1. The number of apples bought will go down 2. The buyers will pay more for each apple they buy, but not the full amount of the tariff 3. Domestic apple sellers will receive a *higher* price per apple 4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit. ## Marginal benefit All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart). Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B. But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5. How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot. The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:  Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples. ## Marginal cost Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product. Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right? Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further. Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\! However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with: * Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900 * Total revenue: $5000 (10,000 apples at $0.50 each) * Total profit: $2100 So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money. This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:  ## Equilibrium price We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:  You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example: * When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point. * When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point. Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.” OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality. ## Modeling taxes Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve. First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:  With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve. We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:  The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:  As we can see, the equilibrium has shifted: * The equilibrium price paid by consumers has risen from $1 to $1.20. * The total number of apples purchased has dropped from 63 apples to 60 apples. * Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus. * Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42. * Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21. * The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise. We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes: * Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples. * Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless. * Domestic producers scored. They can sell less apples and make more revenue doing it. * And the government walked away with an extra $30. Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price. ## Other taxes Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down. And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost. You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with: * Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price. * Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost. * Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise. This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits. @ da0b9bc3:4e30a4a9
2025-03-28 07:27:06Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/927569
@ da0b9bc3:4e30a4a9
2025-03-28 07:27:06Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/927569 @ 9e69e420:d12360c2
2025-02-01 11:16:04 Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.  CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language. One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
@ 9e69e420:d12360c2
2025-02-01 11:16:04 Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.  CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language. One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse. @ 502ab02a:a2860397
2025-03-28 04:57:18จริงหรือ ว่าโอเมก้า3 ต้องมาจากปลาทะเลเท่านั้น มีเรื่องที่น่าสนใจเรื่องนึงครับ ถ้าพูดถึงโอเมก้า-3 หลายคนอาจนึกถึงปลาทะเลน้ำลึก เช่น แซลมอน แมคเคอเรล หรือซาร์ดีน ซึ่งเป็นแหล่งโอเมก้า-3 ที่ร่างกายใช้ได้ดี แต่ในขณะเดียวกัน ก็มีกลุ่มคนที่พยายามบริโภคโอเมก้า-3 จากพืชแทน เช่น น้ำมันเมล็ดแฟลกซ์ น้ำมันเมล็ดเจีย หรือวอลนัท โดยหวังว่าจะได้รับประโยชน์เช่นเดียวกับการกินปลา แต่ที่เราเรียนรู้กันมาว่า โอเมก้า-3 จากพืชนั้น ร่างกายมนุษย์นำไปใช้ได้น้อยมาก หรือแทบไม่ได้เลย สาเหตุหลักมาจากรูปแบบของโอเมก้า-3 ที่พบในแหล่งต่างๆ โอเมก้า-3 มีอยู่ 3 ชนิดหลัก ได้แก่ ALA (Alpha-Linolenic Acid) – พบในพืช EPA (Eicosapentaenoic Acid) – พบในปลาทะเล DHA (Docosahexaenoic Acid) – พบในปลาทะเล ร่างกายสามารถใช้ EPA และ DHA ได้โดยตรง แต่สำหรับ ALA นั้น ร่างกายต้องผ่านกระบวนการเปลี่ยนแปลงทางชีวเคมีก่อน ซึ่งกระบวนการนี้ไม่มีประสิทธิภาพนัก โดยทั่วไปแล้ว ALA แปลงเป็น EPA ได้เพียง 5-10% ALA แปลงเป็น DHA ได้เพียง 0.5-5% แปลว่า หากคุณกินเมล็ดแฟลกซ์หรือน้ำมันเมล็ดเจีย แม้ว่าจะมีปริมาณ ALA สูง แต่ร่างกายก็แทบไม่ได้รับ EPA และ DHA ในปริมาณที่เพียงพอเพื่อใช้ประโยชน์อย่างเต็มที่ ทำไมร่างกายแปลง ALA เป็น EPA/DHA ได้น้อย? อันแรกเลยคือ เอนไซม์จำกัด กระบวนการเปลี่ยน ALA เป็น EPA และ DHA จะใช้เอนไซม์เดียวกับการแปลงโอเมก้า-6 ซึ่งมักถูกใช้ไปกับโอเมก้า-6 ที่มากเกินไปในอาหารปัจจุบันซะแล้วนั่นเอง ต่อมาคือ กระบวนการหลายขั้นตอน การเปลี่ยน ALA เป็น DHA ต้องผ่านหลายขั้นตอนทางชีวเคมี ทำให้มีการสูญเสียพลังงานและวัตถุดิบไปมาก และสุดท้าย ปัจจัยทางพันธุกรรมและเพศ บางคน โดยเฉพาะผู้หญิง อาจมีอัตราการเปลี่ยนที่สูงกว่าผู้ชายเล็กน้อย แต่ก็ยังต่ำเมื่อเทียบกับการได้รับ EPA/DHA จากปลาหรือสาหร่ายโดยตรง โอเมก้า-6 ตัวการขัดขวางโอเมก้า-3 จากพืช โอเมก้า-6 เป็นกรดไขมันจำเป็นที่พบมากในน้ำมันพืช เช่น น้ำมันถั่วเหลือง น้ำมันข้าวโพด และน้ำมันดอกทานตะวัน ซึ่งเป็นส่วนประกอบหลักของอาหารแปรรูปในปัจจุบัน ปัญหาคือ เอนไซม์ที่ใช้แปลง ALA ไปเป็น EPA/DHA เป็นตัวเดียวกับที่ใช้แปลงโอเมก้า-6 ไปเป็น AA (Arachidonic Acid) ซึ่งมีบทบาทในการอักเสบ หากเราบริโภคโอเมก้า-6 มากเกินไป (ซึ่งคนส่วนใหญ่ทำ5555) เอนไซม์เหล่านี้จะถูกใช้ไปกับโอเมก้า-6 มากกว่า ทำให้ ALA มีโอกาสแปลงเป็น EPA/DHA น้อยลงไปอีก แล้วคนที่ไม่กินปลาหรือชาววีแกนควรทำอย่างไร? สำหรับคนที่ไม่สามารถหรือไม่ต้องการกินปลา ก็จะมีการบริโภคน้ำมันสาหร่ายที่มี DHA โดยตรงเป็นทางเลือกที่ดีกว่าการหวังพึ่ง ALA จากพืช เพราะ DHA จากสาหร่ายสามารถดูดซึมและใช้ได้ทันทีเหมือน DHA จากปลา ได้ด้วยเหรอ ????? ผมเล่ากำเนิดของ DHA ในปลาให้ประมาณนี้ครับ จริง ๆ แล้ว DHA ซึ่งเป็นโอเมก้า-3 ที่ร่างกายใช้ได้โดยตรง มาจาก Docosahexaenoic Acid ที่เกิดจากกระบวนการสังเคราะห์ตามธรรมชาติ ซึ่งสาหร่ายบางสายพันธุ์ เช่น Schizochytrium และ Crypthecodinium cohnii มีเอนไซม์ที่สามารถเปลี่ยนกรดไขมันพื้นฐานให้กลายเป็น DHA ได้เองซึ่งเป็นส่วนประกอบหลักในระบบนิเวศทะเล(พืชกักเก็บไขมันได้อย่างไร ผมเคยโพสไปแล้ว) โดยเฉพาะ สาหร่ายขนาดเล็ก (microalgae) สาหร่ายจึงเป็นสิ่งมีชีวิตในทะเลพัฒนาให้มี DHA สูงเพราะ DHA เป็นส่วนประกอบสำคัญที่ช่วยรักษาความยืดหยุ่นและความสมบูรณ์ของเยื่อหุ้มเซลล์ในสาหร่าย ทำให้พวกมันสามารถดำรงชีวิตในสภาพแวดล้อมที่มีอุณหภูมิต่ำในทะเลได้ จากนั้นก็เป็นไปตามห่วงโซ่อาหารครับ ปลาและสัตว์ทะเลอื่น ๆ ได้รับ DHA จากการบริโภคสาหร่ายหรือสัตว์เล็ก ๆ ที่กินสาหร่ายมาอีกที ดังนั้น DHA ในปลาเป็นผลมาจากการสะสมจากสาหร่ายโดยตรง นี่เป็นเหตุผลว่าทำไมปลาทะเลน้ำลึก เช่น แซลมอน แมคเคอเรล และซาร์ดีน ถึงมี DHA สูงนั่นเอง งว่ออออออ ดังนั้น เมื่อคุณกิน DHA จากสาหร่าย ก็เท่ากับว่าคุณได้รับ DHA จากต้นกำเนิดแท้จริงในระบบนิเวศทะเลครับ DHA ที่ได้มาจากสาหร่ายสามารถนำไปใช้ในร่างกายได้ทันทีโดยไม่ต้องผ่านกระบวนการเปลี่ยนแปลง เพราะมันอยู่ในรูป Triglyceride หรือ Phospholipid ซึ่งเป็นรูปแบบที่ร่างกายมนุษย์สามารถดูดซึมและนำไปใช้ได้ทันที ปลาไม่ได้แปลงโครงสร้าง DHA แต่เพียงสะสม DHA ไว้ในตัวจากการกินสาหร่าย ดังนั้นการรับประทาน DHA จากสาหร่ายก็ให้ผลเทียบเท่ากับการรับประทาน DHA จากปลา งานวิจัยหลายฉบับยืนยันว่า DHA จากสาหร่ายมีค่าการดูดซึม (Bioavailability) ใกล้เคียงกับ DHA จากน้ำมันปลา แต่หาเอาเองนะถ้าอยากอ่านฉบับเต็ม การผลิตน้ำมันสาหร่ายนั้น เมื่อสาหร่ายเจริญเติบโตเต็มที่แล้ว เขาจะทำการเก็บเกี่ยวและสกัดน้ำมันโดยใช้เทคโนโลยีการแยกที่ทันสมัย ซึ่งช่วยรักษาให้ DHA ที่มีอยู่ในเซลล์สาหร่ายถูกเก็บรักษาไว้ในรูปแบบที่สามารถนำไปใช้ได้โดยตรง จากนั้นจะเข้าสู่การกรองหรือการปั่นแยก (centrifugation) เพื่อให้ได้มวลสาหร่ายที่เข้มข้น จากนั้นจึงทำให้แห้งเพื่อเตรียมเข้าสู่กระบวนการสกัด ซึ่งมีหลายวิธีอาทิเช่น 1 การสกัดด้วยตัวทำละลาย ใช้ตัวทำละลาย เช่น เฮกเซน (Hexane) หรือ เอทานอล (Ethanol) เพื่อสกัดน้ำมันออกจากเซลล์สาหร่าย จากนั้นน้ำมันจะถูกนำไปกลั่นเพื่อแยกตัวทำละลายออก ทำให้ได้น้ำมันที่มีความบริสุทธิ์สูง 2. การสกัดด้วย CO₂ เหลว ใช้ คาร์บอนไดออกไซด์ในสถานะวิกฤติ (Supercritical CO₂) ซึ่งเป็นวิธีที่ทันสมัย ก๊าซ CO₂ จะถูกทำให้มีความดันสูงและอุณหภูมิที่เหมาะสมเพื่อกลายเป็นของเหลว แล้วใช้แยกน้ำมันออกจากเซลล์สาหร่าย วิธีนี้ช่วยให้ได้น้ำมันที่ ปราศจากตัวทำละลายเคมีและมีความบริสุทธิ์สูง 3. การสกัดด้วยการกดอัด หรือ Cold Pressed เป็นวิธีที่ใช้แรงดันทางกลกดเซลล์สาหร่ายเพื่อให้ได้น้ำมันออกมา อันนี้เป็นการผลิตน้ำมันแบบออร์แกนิกเลยครับ แต่ให้ผลผลิตน้อยกว่าวิธีอื่น ๆ น้ำมันที่ได้จากการสกัดจะผ่านการกลั่นด้วยกระบวนการต่าง ๆ เช่น Winterization กำจัดไขมันที่ไม่จำเป็น Molecular Distillation แยกสารตกค้าง เช่น โลหะหนักและสารปนเปื้อน Deodorization กำจัดกลิ่นคาวของสาหร่าย จากนั้นก็บรรจุใส่ซอฟท์เจล พร้อมจำหน่ายนั่นเองครับ ก็ถือว่าเป็นอีกทางเลือกของชาววีแกน ที่ไม่สามารถกินปลาหรือสัตว์ทะเลได้ ก็น่าจะเฮกันดังๆได้เลยครับ จะได้มีตัวช่วยในการลดการอักเสบได้ ส่วนชาว food matrix ก็ต้องเรียนรู้ระบบครับ การกินจากปลาหรือสัตว์ทะเล ก็จะได้โปรตีน แร่ธาตุ วิตามินอื่นๆควบมากับตัวสัตว์ตามที่ธรรมชาติแพคมาให้ ถ้าจะเสริมเป็นน้ำมันสาหร่าย ก็สุดแล้วแต่ความต้องการครับ ไม่ใช่เรื่องแย่อะไร เว้นแต่ไปเทียบราคาเอาเองนะ 55555 #pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
@ 502ab02a:a2860397
2025-03-28 04:57:18จริงหรือ ว่าโอเมก้า3 ต้องมาจากปลาทะเลเท่านั้น มีเรื่องที่น่าสนใจเรื่องนึงครับ ถ้าพูดถึงโอเมก้า-3 หลายคนอาจนึกถึงปลาทะเลน้ำลึก เช่น แซลมอน แมคเคอเรล หรือซาร์ดีน ซึ่งเป็นแหล่งโอเมก้า-3 ที่ร่างกายใช้ได้ดี แต่ในขณะเดียวกัน ก็มีกลุ่มคนที่พยายามบริโภคโอเมก้า-3 จากพืชแทน เช่น น้ำมันเมล็ดแฟลกซ์ น้ำมันเมล็ดเจีย หรือวอลนัท โดยหวังว่าจะได้รับประโยชน์เช่นเดียวกับการกินปลา แต่ที่เราเรียนรู้กันมาว่า โอเมก้า-3 จากพืชนั้น ร่างกายมนุษย์นำไปใช้ได้น้อยมาก หรือแทบไม่ได้เลย สาเหตุหลักมาจากรูปแบบของโอเมก้า-3 ที่พบในแหล่งต่างๆ โอเมก้า-3 มีอยู่ 3 ชนิดหลัก ได้แก่ ALA (Alpha-Linolenic Acid) – พบในพืช EPA (Eicosapentaenoic Acid) – พบในปลาทะเล DHA (Docosahexaenoic Acid) – พบในปลาทะเล ร่างกายสามารถใช้ EPA และ DHA ได้โดยตรง แต่สำหรับ ALA นั้น ร่างกายต้องผ่านกระบวนการเปลี่ยนแปลงทางชีวเคมีก่อน ซึ่งกระบวนการนี้ไม่มีประสิทธิภาพนัก โดยทั่วไปแล้ว ALA แปลงเป็น EPA ได้เพียง 5-10% ALA แปลงเป็น DHA ได้เพียง 0.5-5% แปลว่า หากคุณกินเมล็ดแฟลกซ์หรือน้ำมันเมล็ดเจีย แม้ว่าจะมีปริมาณ ALA สูง แต่ร่างกายก็แทบไม่ได้รับ EPA และ DHA ในปริมาณที่เพียงพอเพื่อใช้ประโยชน์อย่างเต็มที่ ทำไมร่างกายแปลง ALA เป็น EPA/DHA ได้น้อย? อันแรกเลยคือ เอนไซม์จำกัด กระบวนการเปลี่ยน ALA เป็น EPA และ DHA จะใช้เอนไซม์เดียวกับการแปลงโอเมก้า-6 ซึ่งมักถูกใช้ไปกับโอเมก้า-6 ที่มากเกินไปในอาหารปัจจุบันซะแล้วนั่นเอง ต่อมาคือ กระบวนการหลายขั้นตอน การเปลี่ยน ALA เป็น DHA ต้องผ่านหลายขั้นตอนทางชีวเคมี ทำให้มีการสูญเสียพลังงานและวัตถุดิบไปมาก และสุดท้าย ปัจจัยทางพันธุกรรมและเพศ บางคน โดยเฉพาะผู้หญิง อาจมีอัตราการเปลี่ยนที่สูงกว่าผู้ชายเล็กน้อย แต่ก็ยังต่ำเมื่อเทียบกับการได้รับ EPA/DHA จากปลาหรือสาหร่ายโดยตรง โอเมก้า-6 ตัวการขัดขวางโอเมก้า-3 จากพืช โอเมก้า-6 เป็นกรดไขมันจำเป็นที่พบมากในน้ำมันพืช เช่น น้ำมันถั่วเหลือง น้ำมันข้าวโพด และน้ำมันดอกทานตะวัน ซึ่งเป็นส่วนประกอบหลักของอาหารแปรรูปในปัจจุบัน ปัญหาคือ เอนไซม์ที่ใช้แปลง ALA ไปเป็น EPA/DHA เป็นตัวเดียวกับที่ใช้แปลงโอเมก้า-6 ไปเป็น AA (Arachidonic Acid) ซึ่งมีบทบาทในการอักเสบ หากเราบริโภคโอเมก้า-6 มากเกินไป (ซึ่งคนส่วนใหญ่ทำ5555) เอนไซม์เหล่านี้จะถูกใช้ไปกับโอเมก้า-6 มากกว่า ทำให้ ALA มีโอกาสแปลงเป็น EPA/DHA น้อยลงไปอีก แล้วคนที่ไม่กินปลาหรือชาววีแกนควรทำอย่างไร? สำหรับคนที่ไม่สามารถหรือไม่ต้องการกินปลา ก็จะมีการบริโภคน้ำมันสาหร่ายที่มี DHA โดยตรงเป็นทางเลือกที่ดีกว่าการหวังพึ่ง ALA จากพืช เพราะ DHA จากสาหร่ายสามารถดูดซึมและใช้ได้ทันทีเหมือน DHA จากปลา ได้ด้วยเหรอ ????? ผมเล่ากำเนิดของ DHA ในปลาให้ประมาณนี้ครับ จริง ๆ แล้ว DHA ซึ่งเป็นโอเมก้า-3 ที่ร่างกายใช้ได้โดยตรง มาจาก Docosahexaenoic Acid ที่เกิดจากกระบวนการสังเคราะห์ตามธรรมชาติ ซึ่งสาหร่ายบางสายพันธุ์ เช่น Schizochytrium และ Crypthecodinium cohnii มีเอนไซม์ที่สามารถเปลี่ยนกรดไขมันพื้นฐานให้กลายเป็น DHA ได้เองซึ่งเป็นส่วนประกอบหลักในระบบนิเวศทะเล(พืชกักเก็บไขมันได้อย่างไร ผมเคยโพสไปแล้ว) โดยเฉพาะ สาหร่ายขนาดเล็ก (microalgae) สาหร่ายจึงเป็นสิ่งมีชีวิตในทะเลพัฒนาให้มี DHA สูงเพราะ DHA เป็นส่วนประกอบสำคัญที่ช่วยรักษาความยืดหยุ่นและความสมบูรณ์ของเยื่อหุ้มเซลล์ในสาหร่าย ทำให้พวกมันสามารถดำรงชีวิตในสภาพแวดล้อมที่มีอุณหภูมิต่ำในทะเลได้ จากนั้นก็เป็นไปตามห่วงโซ่อาหารครับ ปลาและสัตว์ทะเลอื่น ๆ ได้รับ DHA จากการบริโภคสาหร่ายหรือสัตว์เล็ก ๆ ที่กินสาหร่ายมาอีกที ดังนั้น DHA ในปลาเป็นผลมาจากการสะสมจากสาหร่ายโดยตรง นี่เป็นเหตุผลว่าทำไมปลาทะเลน้ำลึก เช่น แซลมอน แมคเคอเรล และซาร์ดีน ถึงมี DHA สูงนั่นเอง งว่ออออออ ดังนั้น เมื่อคุณกิน DHA จากสาหร่าย ก็เท่ากับว่าคุณได้รับ DHA จากต้นกำเนิดแท้จริงในระบบนิเวศทะเลครับ DHA ที่ได้มาจากสาหร่ายสามารถนำไปใช้ในร่างกายได้ทันทีโดยไม่ต้องผ่านกระบวนการเปลี่ยนแปลง เพราะมันอยู่ในรูป Triglyceride หรือ Phospholipid ซึ่งเป็นรูปแบบที่ร่างกายมนุษย์สามารถดูดซึมและนำไปใช้ได้ทันที ปลาไม่ได้แปลงโครงสร้าง DHA แต่เพียงสะสม DHA ไว้ในตัวจากการกินสาหร่าย ดังนั้นการรับประทาน DHA จากสาหร่ายก็ให้ผลเทียบเท่ากับการรับประทาน DHA จากปลา งานวิจัยหลายฉบับยืนยันว่า DHA จากสาหร่ายมีค่าการดูดซึม (Bioavailability) ใกล้เคียงกับ DHA จากน้ำมันปลา แต่หาเอาเองนะถ้าอยากอ่านฉบับเต็ม การผลิตน้ำมันสาหร่ายนั้น เมื่อสาหร่ายเจริญเติบโตเต็มที่แล้ว เขาจะทำการเก็บเกี่ยวและสกัดน้ำมันโดยใช้เทคโนโลยีการแยกที่ทันสมัย ซึ่งช่วยรักษาให้ DHA ที่มีอยู่ในเซลล์สาหร่ายถูกเก็บรักษาไว้ในรูปแบบที่สามารถนำไปใช้ได้โดยตรง จากนั้นจะเข้าสู่การกรองหรือการปั่นแยก (centrifugation) เพื่อให้ได้มวลสาหร่ายที่เข้มข้น จากนั้นจึงทำให้แห้งเพื่อเตรียมเข้าสู่กระบวนการสกัด ซึ่งมีหลายวิธีอาทิเช่น 1 การสกัดด้วยตัวทำละลาย ใช้ตัวทำละลาย เช่น เฮกเซน (Hexane) หรือ เอทานอล (Ethanol) เพื่อสกัดน้ำมันออกจากเซลล์สาหร่าย จากนั้นน้ำมันจะถูกนำไปกลั่นเพื่อแยกตัวทำละลายออก ทำให้ได้น้ำมันที่มีความบริสุทธิ์สูง 2. การสกัดด้วย CO₂ เหลว ใช้ คาร์บอนไดออกไซด์ในสถานะวิกฤติ (Supercritical CO₂) ซึ่งเป็นวิธีที่ทันสมัย ก๊าซ CO₂ จะถูกทำให้มีความดันสูงและอุณหภูมิที่เหมาะสมเพื่อกลายเป็นของเหลว แล้วใช้แยกน้ำมันออกจากเซลล์สาหร่าย วิธีนี้ช่วยให้ได้น้ำมันที่ ปราศจากตัวทำละลายเคมีและมีความบริสุทธิ์สูง 3. การสกัดด้วยการกดอัด หรือ Cold Pressed เป็นวิธีที่ใช้แรงดันทางกลกดเซลล์สาหร่ายเพื่อให้ได้น้ำมันออกมา อันนี้เป็นการผลิตน้ำมันแบบออร์แกนิกเลยครับ แต่ให้ผลผลิตน้อยกว่าวิธีอื่น ๆ น้ำมันที่ได้จากการสกัดจะผ่านการกลั่นด้วยกระบวนการต่าง ๆ เช่น Winterization กำจัดไขมันที่ไม่จำเป็น Molecular Distillation แยกสารตกค้าง เช่น โลหะหนักและสารปนเปื้อน Deodorization กำจัดกลิ่นคาวของสาหร่าย จากนั้นก็บรรจุใส่ซอฟท์เจล พร้อมจำหน่ายนั่นเองครับ ก็ถือว่าเป็นอีกทางเลือกของชาววีแกน ที่ไม่สามารถกินปลาหรือสัตว์ทะเลได้ ก็น่าจะเฮกันดังๆได้เลยครับ จะได้มีตัวช่วยในการลดการอักเสบได้ ส่วนชาว food matrix ก็ต้องเรียนรู้ระบบครับ การกินจากปลาหรือสัตว์ทะเล ก็จะได้โปรตีน แร่ธาตุ วิตามินอื่นๆควบมากับตัวสัตว์ตามที่ธรรมชาติแพคมาให้ ถ้าจะเสริมเป็นน้ำมันสาหร่าย ก็สุดแล้วแต่ความต้องการครับ ไม่ใช่เรื่องแย่อะไร เว้นแต่ไปเทียบราคาเอาเองนะ 55555 #pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr @ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test. In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go. # It uses nostr The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol. Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key. In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along. In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim. # It leverages nostr Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app". This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back. Some examples might include: - Using nostr signers to encrypt or sign data, and then store that data on a proprietary server. - Using nostr relays as a kind of low-code backend, but using proprietary event payloads. - Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you. An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem. In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering. # It complements nostr Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role. One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense. Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)? A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs. To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen. # It embodies nostr Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate. This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product? To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole. An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem: - In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors. - In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for. Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_. If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states: > Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions. These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers. _As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._ Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type". To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well, - There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that... - Multiple clients can implement the same data format, allowing for credible exit and user choice, even of... - Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does... - Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to... - Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost". Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr. # It supports nostr Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually). This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content? In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together. A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own. So while I might hesitate to call many of these things "apps", they are certainly "nostr". # Appendix: it smells like a NINO So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr. You app might be a NINO if: - There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind) - There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository) - Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr - Your NIP relies on trusted third (or first) parties - There's only one implementation of your NIP (yours) - Your core value proposition doesn't depend on relays, events, or nostr identities - One or more relay urls are hard-coded into the source code - Your app depends on a specific relay implementation to work (*ahem*, relay29) - You don't validate event signatures - You don't publish events to relays you don't control - You don't read events from relays you don't control - You use legacy web services to solve problems, rather than nostr-native solutions - You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app - You don't use NIP 89 to discover clients and services - You haven't published a NIP 89 listing for your app - You don't leverage your users' web of trust for filtering out spam - You don't respect your users' mute lists - You try to "own" your users' data Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product. If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation: - Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine. - Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc. - Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats. - Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it. - Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated. - Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask! I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test. In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go. # It uses nostr The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol. Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key. In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along. In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim. # It leverages nostr Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app". This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back. Some examples might include: - Using nostr signers to encrypt or sign data, and then store that data on a proprietary server. - Using nostr relays as a kind of low-code backend, but using proprietary event payloads. - Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you. An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem. In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering. # It complements nostr Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role. One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense. Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)? A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs. To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen. # It embodies nostr Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate. This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product? To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole. An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem: - In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors. - In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for. Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_. If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states: > Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions. These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers. _As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._ Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type". To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well, - There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that... - Multiple clients can implement the same data format, allowing for credible exit and user choice, even of... - Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does... - Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to... - Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost". Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr. # It supports nostr Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually). This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content? In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together. A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own. So while I might hesitate to call many of these things "apps", they are certainly "nostr". # Appendix: it smells like a NINO So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr. You app might be a NINO if: - There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind) - There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository) - Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr - Your NIP relies on trusted third (or first) parties - There's only one implementation of your NIP (yours) - Your core value proposition doesn't depend on relays, events, or nostr identities - One or more relay urls are hard-coded into the source code - Your app depends on a specific relay implementation to work (*ahem*, relay29) - You don't validate event signatures - You don't publish events to relays you don't control - You don't read events from relays you don't control - You use legacy web services to solve problems, rather than nostr-native solutions - You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app - You don't use NIP 89 to discover clients and services - You haven't published a NIP 89 listing for your app - You don't leverage your users' web of trust for filtering out spam - You don't respect your users' mute lists - You try to "own" your users' data Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product. If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation: - Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine. - Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc. - Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats. - Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it. - Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated. - Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask! I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV. @ a3bb06f6:19ac1b11
2025-03-28 02:36:38“Until you make the unconscious conscious, it will continue to direct your life, and you will call it fate.” — Carl Jung Most people don’t realize they’ve been robbed. Not in the dramatic, wallet-snatching sense, but in a quiet, systemic way that’s gone unnoticed for generations. If you’re feeling like no matter how hard you work, you can’t get ahead… you’re not imagining it. It didn’t start as a scheme—*but one compromise after another*, it became one. Now, the system exploits you by design. This isn’t fate. It’s fiat. The Unconscious Script: How Fiat Becomes Invisible From the moment you're born, you're placed into an economic system based on government-issued fiat currency. It becomes the air you breathe. You work for dollars. You save in dollars. You price **your time**, **your future**, and even **your dreams** in dollars. But few stop to ask: What actually is a dollar? Who creates it? Why does it lose value? This lack of questioning is the unconscious state. Fiat money is the background process running your life. You feel the effects—rising prices, shrinking savings, mounting debt—but you never see the root cause. So you blame yourself. Or “the economy.” Or call it fate. The Lie of Neutral Money: Most believe money is just a neutral tool. But fiat is not neutral—it’s political power encoded into paper. Governments can **print more of it at will**. Central banks can manipulate its supply, distort interest rates, and quietly tax you through inflation. Every time more money is created, your purchasing power shrinks. But it happens slowly, like a leak in a tire. You don’t notice at first. You just feel like you’re working harder for less. The house is further out of reach. The groceries cost more. Retirement feels impossible. And you accept it. Because no one told you it's designed this way. <img src="https://blossom.primal.net/80cb04b171e15d56d1224a1458f0ca3ad9a440915c736e145186df1cc2f4979b.png"> Inflation Is the Invisible Thief, Inflation isn’t just a “cost of living increase.” It’s a state-sponsored form of theft. When new money is created, it enters the system unevenly. Those closest to the money printer—banks, governments, **large corporations**—get the new dollars first. By the time it reaches you, prices have already risen. You’re buying the same goods with weaker money. And yet, most people still save in fiat. They’re taught that hoarding cash is “safe.” They’re taught that 2% inflation is “normal.” But it’s not normal to work 40 hours a week and fall behind. That’s the product of unconscious acceptance. The fiat system survives on one thing: your **ignorance**. It didn’t begin with malicious intent, but over time, it adapted to protect its own power—at your expense. As long as you don’t understand how money works, you won’t resist. You’ll blame yourself, or *capitalism*, or bad luck. **But never the system itself**. This is why financial education is *never* prioritized in schools. This is why questioning monetary policy is left to economists and suits on CNBC. You were never taught how it works. And now the system depends on you staying confused—grinding, borrowing, complying, without ever asking why. Making the Unconscious Conscious: Enter **Bitcoin**, Bitcoin breaks this spell. <img src="https://blossom.primal.net/8373eb52ee7773e0ffc4591819ff984a27829e47741894456258e2a638029022.png"> It forces you to confront the nature of money—what it is, how it’s created, and why fiat fails. It teaches you that money doesn’t need to be printed, inflated, or controlled. That money can be fixed, finite, and **fair**. Bitcoin is not just a new currency. It’s a tool of consciousness. It exposes the scam of fiat and offers a lifeboat to anyone ready to wake up. Once you understand Bitcoin, you can’t unsee the problem. You begin to ask: Why should I trust a system that steals my **time**? Why is saving discouraged, but debt rewarded? Why do I need permission to use my own money? These aren’t technical questions. They’re **moral** ones. Consciousness Is Sovereignty: When you understand what fiat is, you stop calling your financial struggles “fate.” You start calling them what they are, outcomes of a broken system. And once you see the system for what it is, you can choose to **exit**. <img src="https://blossom.primal.net/a8766caf9dc043fa360dbf7c5e473201d72dfeede02a7f08abc9897367a33011.png"> Saving in Bitcoin is not speculation. It’s self-defense. It’s rejecting unconscious servitude. It’s reclaiming your **time**, your **labor**, your **future**. In a fiat world, they own the money—so they own the rules. In a Bitcoin world, you own yourself. That’s the power of making the unconscious conscious. And that’s how you stop calling it fate.
@ a3bb06f6:19ac1b11
2025-03-28 02:36:38“Until you make the unconscious conscious, it will continue to direct your life, and you will call it fate.” — Carl Jung Most people don’t realize they’ve been robbed. Not in the dramatic, wallet-snatching sense, but in a quiet, systemic way that’s gone unnoticed for generations. If you’re feeling like no matter how hard you work, you can’t get ahead… you’re not imagining it. It didn’t start as a scheme—*but one compromise after another*, it became one. Now, the system exploits you by design. This isn’t fate. It’s fiat. The Unconscious Script: How Fiat Becomes Invisible From the moment you're born, you're placed into an economic system based on government-issued fiat currency. It becomes the air you breathe. You work for dollars. You save in dollars. You price **your time**, **your future**, and even **your dreams** in dollars. But few stop to ask: What actually is a dollar? Who creates it? Why does it lose value? This lack of questioning is the unconscious state. Fiat money is the background process running your life. You feel the effects—rising prices, shrinking savings, mounting debt—but you never see the root cause. So you blame yourself. Or “the economy.” Or call it fate. The Lie of Neutral Money: Most believe money is just a neutral tool. But fiat is not neutral—it’s political power encoded into paper. Governments can **print more of it at will**. Central banks can manipulate its supply, distort interest rates, and quietly tax you through inflation. Every time more money is created, your purchasing power shrinks. But it happens slowly, like a leak in a tire. You don’t notice at first. You just feel like you’re working harder for less. The house is further out of reach. The groceries cost more. Retirement feels impossible. And you accept it. Because no one told you it's designed this way. <img src="https://blossom.primal.net/80cb04b171e15d56d1224a1458f0ca3ad9a440915c736e145186df1cc2f4979b.png"> Inflation Is the Invisible Thief, Inflation isn’t just a “cost of living increase.” It’s a state-sponsored form of theft. When new money is created, it enters the system unevenly. Those closest to the money printer—banks, governments, **large corporations**—get the new dollars first. By the time it reaches you, prices have already risen. You’re buying the same goods with weaker money. And yet, most people still save in fiat. They’re taught that hoarding cash is “safe.” They’re taught that 2% inflation is “normal.” But it’s not normal to work 40 hours a week and fall behind. That’s the product of unconscious acceptance. The fiat system survives on one thing: your **ignorance**. It didn’t begin with malicious intent, but over time, it adapted to protect its own power—at your expense. As long as you don’t understand how money works, you won’t resist. You’ll blame yourself, or *capitalism*, or bad luck. **But never the system itself**. This is why financial education is *never* prioritized in schools. This is why questioning monetary policy is left to economists and suits on CNBC. You were never taught how it works. And now the system depends on you staying confused—grinding, borrowing, complying, without ever asking why. Making the Unconscious Conscious: Enter **Bitcoin**, Bitcoin breaks this spell. <img src="https://blossom.primal.net/8373eb52ee7773e0ffc4591819ff984a27829e47741894456258e2a638029022.png"> It forces you to confront the nature of money—what it is, how it’s created, and why fiat fails. It teaches you that money doesn’t need to be printed, inflated, or controlled. That money can be fixed, finite, and **fair**. Bitcoin is not just a new currency. It’s a tool of consciousness. It exposes the scam of fiat and offers a lifeboat to anyone ready to wake up. Once you understand Bitcoin, you can’t unsee the problem. You begin to ask: Why should I trust a system that steals my **time**? Why is saving discouraged, but debt rewarded? Why do I need permission to use my own money? These aren’t technical questions. They’re **moral** ones. Consciousness Is Sovereignty: When you understand what fiat is, you stop calling your financial struggles “fate.” You start calling them what they are, outcomes of a broken system. And once you see the system for what it is, you can choose to **exit**. <img src="https://blossom.primal.net/a8766caf9dc043fa360dbf7c5e473201d72dfeede02a7f08abc9897367a33011.png"> Saving in Bitcoin is not speculation. It’s self-defense. It’s rejecting unconscious servitude. It’s reclaiming your **time**, your **labor**, your **future**. In a fiat world, they own the money—so they own the rules. In a Bitcoin world, you own yourself. That’s the power of making the unconscious conscious. And that’s how you stop calling it fate. @ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York. DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million. The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture. Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry. ![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
@ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York. DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million. The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture. Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry. ![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg) @ 7d33ba57:1b82db35
2025-03-27 20:54:55Andorra la Vella, the capital of Andorra, is a charming mix of mountain landscapes, duty-free shopping, and rich history. Nestled in the Pyrenees, it’s a great destination for skiing, hiking, and relaxing in thermal spas. Whether you’re here for outdoor adventures, tax-free shopping, or cultural experiences, Andorra la Vella has something for everyone.  ## **🏔️ Top Things to See & Do in Andorra la Vella** ### **1️⃣ Shop in Avinguda Meritxell 🛍️** - One of **Europe’s best duty-free shopping streets**, filled with **electronics, fashion, perfumes, and luxury goods**. - Find **brands at lower prices than in Spain or France**. ### **2️⃣ Relax at Caldea Spa ♨️** - The **largest thermal spa in Southern Europe**, with **hot springs, saunas, and lagoon pools**. - A perfect place to unwind **after skiing or hiking**.  ### **3️⃣ Visit the Church of Sant Esteve ⛪** - A **beautiful Romanesque church** dating back to the **12th century**. - Features **stone carvings and medieval frescoes**. ### **4️⃣ Explore the Historic Quarter (Barri Antic) 🏡** - Walk through **narrow cobbled streets** filled with **traditional Andorran houses and charming cafés**. - Visit **Casa de la Vall**, a **historic parliament building from the 16th century**. ### **5️⃣ Go Skiing or Snowboarding 🎿** - Andorra is famous for its **world-class ski resorts**, **Grandvalira and Vallnord**, just **15-30 minutes away**. - Ideal for **beginners and experienced skiers** alike. ### **6️⃣ Hiking in the Pyrenees 🥾** - **Summer & autumn** offer **incredible hiking trails** with **mountain lakes and scenic views**. - **Rec del Solà Trail** – A beautiful, easy path with panoramic views of the valley. - **L’Estany Blau** – A moderate hike leading to a stunning blue lake.  ### **7️⃣ Enjoy Andorran Cuisine 🍽️** - **Escudella** – A hearty **Andorran stew with meat, beans, and vegetables** 🍲 - **Trinxat** – A mountain dish made of **potatoes, cabbage, and bacon** 🥓🥔 - **Embotits** – Local **cured meats and sausages**, perfect as tapas 🍖 - **Crema Andorrana** – A creamy, local dessert similar to Catalan crema 🍮  ## **🚗 How to Get to Andorra la Vella** ✈️ **By Air:** The nearest airports are **Barcelona-El Prat (Spain, 2.5 hrs)** and **Toulouse-Blagnac (France, 2.5 hrs)**. 🚘 **By Car:** 2.5 hrs from **Barcelona**, 2.5 hrs from **Toulouse**, 3 hrs from **Perpignan**. 🚌 **By Bus:** Direct buses from **Barcelona, Toulouse, and Lleida**. 🚆 **By Train:** No direct train, but you can take a train to **L'Hospitalet-près-l'Andorre (France)** and continue by bus.  ## **💡 Tips for Visiting Andorra la Vella** ✅ **Best time to visit?** **Winter for skiing, summer for hiking & shopping** ❄️🌞 ✅ **Bring a passport** – Even though Andorra isn’t in the EU, border checks happen 🇦🇩 ✅ **Try duty-free shopping** – Electronics, perfumes, and alcohol are cheaper 🛍️ ✅ **Book ski passes in advance** – Resorts get busy in peak season 🎿 ✅ **Wear comfy shoes** – The city has **steep streets and cobblestone paths** 👟
@ 7d33ba57:1b82db35
2025-03-27 20:54:55Andorra la Vella, the capital of Andorra, is a charming mix of mountain landscapes, duty-free shopping, and rich history. Nestled in the Pyrenees, it’s a great destination for skiing, hiking, and relaxing in thermal spas. Whether you’re here for outdoor adventures, tax-free shopping, or cultural experiences, Andorra la Vella has something for everyone.  ## **🏔️ Top Things to See & Do in Andorra la Vella** ### **1️⃣ Shop in Avinguda Meritxell 🛍️** - One of **Europe’s best duty-free shopping streets**, filled with **electronics, fashion, perfumes, and luxury goods**. - Find **brands at lower prices than in Spain or France**. ### **2️⃣ Relax at Caldea Spa ♨️** - The **largest thermal spa in Southern Europe**, with **hot springs, saunas, and lagoon pools**. - A perfect place to unwind **after skiing or hiking**.  ### **3️⃣ Visit the Church of Sant Esteve ⛪** - A **beautiful Romanesque church** dating back to the **12th century**. - Features **stone carvings and medieval frescoes**. ### **4️⃣ Explore the Historic Quarter (Barri Antic) 🏡** - Walk through **narrow cobbled streets** filled with **traditional Andorran houses and charming cafés**. - Visit **Casa de la Vall**, a **historic parliament building from the 16th century**. ### **5️⃣ Go Skiing or Snowboarding 🎿** - Andorra is famous for its **world-class ski resorts**, **Grandvalira and Vallnord**, just **15-30 minutes away**. - Ideal for **beginners and experienced skiers** alike. ### **6️⃣ Hiking in the Pyrenees 🥾** - **Summer & autumn** offer **incredible hiking trails** with **mountain lakes and scenic views**. - **Rec del Solà Trail** – A beautiful, easy path with panoramic views of the valley. - **L’Estany Blau** – A moderate hike leading to a stunning blue lake.  ### **7️⃣ Enjoy Andorran Cuisine 🍽️** - **Escudella** – A hearty **Andorran stew with meat, beans, and vegetables** 🍲 - **Trinxat** – A mountain dish made of **potatoes, cabbage, and bacon** 🥓🥔 - **Embotits** – Local **cured meats and sausages**, perfect as tapas 🍖 - **Crema Andorrana** – A creamy, local dessert similar to Catalan crema 🍮  ## **🚗 How to Get to Andorra la Vella** ✈️ **By Air:** The nearest airports are **Barcelona-El Prat (Spain, 2.5 hrs)** and **Toulouse-Blagnac (France, 2.5 hrs)**. 🚘 **By Car:** 2.5 hrs from **Barcelona**, 2.5 hrs from **Toulouse**, 3 hrs from **Perpignan**. 🚌 **By Bus:** Direct buses from **Barcelona, Toulouse, and Lleida**. 🚆 **By Train:** No direct train, but you can take a train to **L'Hospitalet-près-l'Andorre (France)** and continue by bus.  ## **💡 Tips for Visiting Andorra la Vella** ✅ **Best time to visit?** **Winter for skiing, summer for hiking & shopping** ❄️🌞 ✅ **Bring a passport** – Even though Andorra isn’t in the EU, border checks happen 🇦🇩 ✅ **Try duty-free shopping** – Electronics, perfumes, and alcohol are cheaper 🛍️ ✅ **Book ski passes in advance** – Resorts get busy in peak season 🎿 ✅ **Wear comfy shoes** – The city has **steep streets and cobblestone paths** 👟 @ 2b24a1fa:17750f64
2025-03-28 10:07:04Der Deutsche Bundestag wurde neu gewählt. Für einige Abgeordnete und Regierungsmitglieder heißt es Time to Say Goodbye. Abschied ist ein scharfes Schwert.  [https://soundcloud.com/radiomuenchen/nachruf-2-olaf-der-zeitenwender](https://soundcloud.com/radiomuenchen/nachruf-2-olaf-der-zeitenwender?si=6c375088b6444c2d8aa7e8040fb1a79e\&utm_source=clipboard\&utm_medium=text\&utm_campaign=social_sharing) Auch bei Radio München werden Trennungs- und Verlassenheitsgefühle getriggert. Umso mehr, wenn es sich nicht nur um duselige Allerweltsliebe handelt, sondern um den Abgang großer Helden. Sie bezahlten ihren todesmutigen und fast ehrenamtlichen Einsatz nicht mit dem Leben, jedoch mit der einen oder anderen Falte in Hemd oder Bluse, manchmal sogar im Gesicht. Was bleibt? Eine bescheidene Pension? Ein lausig bezahlter Manager-Job in einem Konzern? Wir wollen jedenfalls nicht, dass diese Volkshelden vom Zahn der Zeit abgenagt, vergessen werden und setzen ihnen deshalb ein bescheidenes akustisches, aber nachhaltiges Denkmal. Hören Sie die kleine satirische Reihe „Nachrufe“ von unserem Autor Jonny Rieder.\ Folge 2: Olaf der Zeitenwender Sprecher: Karsten Troyke Bild: Markus Mitterer für Radio München Radio München\ [www.radiomuenchen.net/](http://www.radiomuenchen.net/%E2%80%8B "http://www.radiomuenchen.net/")\ @[radiomuenchen](https://soundcloud.com/radiomuenchen)\ [www.facebook.com/radiomuenchen](http://www.facebook.com/radiomuenchen "http://www.facebook.com/radiomuenchen")\ [www.instagram.com/radio\_muenchen/](http://www.instagram.com/radio_muenchen/ "http://www.instagram.com/radio_muenchen/")\ [twitter.com/RadioMuenchen](http://twitter.com/RadioMuenchen "http://twitter.com/RadioMuenchen") Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen. GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS
@ 2b24a1fa:17750f64
2025-03-28 10:07:04Der Deutsche Bundestag wurde neu gewählt. Für einige Abgeordnete und Regierungsmitglieder heißt es Time to Say Goodbye. Abschied ist ein scharfes Schwert.  [https://soundcloud.com/radiomuenchen/nachruf-2-olaf-der-zeitenwender](https://soundcloud.com/radiomuenchen/nachruf-2-olaf-der-zeitenwender?si=6c375088b6444c2d8aa7e8040fb1a79e\&utm_source=clipboard\&utm_medium=text\&utm_campaign=social_sharing) Auch bei Radio München werden Trennungs- und Verlassenheitsgefühle getriggert. Umso mehr, wenn es sich nicht nur um duselige Allerweltsliebe handelt, sondern um den Abgang großer Helden. Sie bezahlten ihren todesmutigen und fast ehrenamtlichen Einsatz nicht mit dem Leben, jedoch mit der einen oder anderen Falte in Hemd oder Bluse, manchmal sogar im Gesicht. Was bleibt? Eine bescheidene Pension? Ein lausig bezahlter Manager-Job in einem Konzern? Wir wollen jedenfalls nicht, dass diese Volkshelden vom Zahn der Zeit abgenagt, vergessen werden und setzen ihnen deshalb ein bescheidenes akustisches, aber nachhaltiges Denkmal. Hören Sie die kleine satirische Reihe „Nachrufe“ von unserem Autor Jonny Rieder.\ Folge 2: Olaf der Zeitenwender Sprecher: Karsten Troyke Bild: Markus Mitterer für Radio München Radio München\ [www.radiomuenchen.net/](http://www.radiomuenchen.net/%E2%80%8B "http://www.radiomuenchen.net/")\ @[radiomuenchen](https://soundcloud.com/radiomuenchen)\ [www.facebook.com/radiomuenchen](http://www.facebook.com/radiomuenchen "http://www.facebook.com/radiomuenchen")\ [www.instagram.com/radio\_muenchen/](http://www.instagram.com/radio_muenchen/ "http://www.instagram.com/radio_muenchen/")\ [twitter.com/RadioMuenchen](http://twitter.com/RadioMuenchen "http://twitter.com/RadioMuenchen") Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen. GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS @ 2b24a1fa:17750f64
2025-03-28 10:03:58Zwischen Überzeugungsarbeit und Propaganda verläuft ein schmaler Grad. Aber so oder so: Wer die subtileren Werkzeuge hat und vor allem die Mittel um Menschen zu kaufen, die diese dann anwenden, hat eindeutig die besseren Karten.  [https://soundcloud.com/radiomuenchen/unterwanderter-journalismus-oder-der-mediale-deep-state-wankt-von-milosz-matuschekcolor=ffd400](https://soundcloud.com/radiomuenchen/unterwanderter-journalismus-oder-der-mediale-deep-state-wankt-von-milosz-matuschek?si=45877e50143d4e10a22fc9a4be82970d\&utm_source=clipboard\&utm_medium=text\&utm_campaign=social_sharing) Dass die Bevölkerung nun wissen will, mit welchen Mitteln sie auf welche Weise beeinflusst werden soll, ist selbstverständlich. Wie nuanciert diese Beeinflussung stattfinden kann, darauf haben uns unsere Hörer beim letzten Beitrag von Milosz Matuschek: „Die ersten Köpfe rollen“ gestoßen. Es ging um die staatliche amerikanische Behörde für internationale Entwicklungshilfe USAID. Matuschek schrieb: „Man liest was von AID im Namen und denkt, was man denken soll: klingt nach Bob Geldof, barmherzigen Schwestern und “Brot für die Welt”.“ Man hatte das nicht nur optisch wahrgenommen, nein, diese Behörde wurde hierzulande, in allen Medien US AID genannt, was unsere Sprecherin Sabrina Khalil übernahm. Dass die United States Agency for International Development in USA so nicht gesprochen wird, schrieben uns gleich mehrere aufmerksame Hörer. Es ist sicherlich keine Paranoia darüber nachzudenken, ob die Bedeutung unserer Sprache, unserer Wörter bis hin zur Aussprache im Fokus der Manipulation steht. Dafür wird sehr viel Geld locker gemacht und unter anderem in die Medien gepumpt. Hören Sie heute den zweiten Teil der Reihe „Die Corona-Connection“ mit dem Titel: „Der mediale Deep State wankt“. Sprecherin: Sabrina Khalil. Das freie Medienprojekt Pareto kann übrigens Unterstützung gebrauchen, dafür wurde ein Crowdfunding auf Geyser gestartet, wo man mit Bitcoin/Lightning-Spenden helfen kann. Und für Spenden auf dem klassischen Weg finden Sie die entsprechende Bankverbindung auf der Homepage pareto.space/de. Nachzulesen unter: [www.freischwebende-intelligenz.org/p/unter…mediale](https://gate.sc?url=https%3A%2F%2Fwww.freischwebende-intelligenz.org%2Fp%2Funterwanderter-journalismus-der-mediale\&token=6fce3f-1-1743155866002 "https://www.freischwebende-intelligenz.org/p/unterwanderter-journalismus-der-mediale") Foto: Gleichschaltung - sie melden exakt den gleichen Wortlaut.
@ 2b24a1fa:17750f64
2025-03-28 10:03:58Zwischen Überzeugungsarbeit und Propaganda verläuft ein schmaler Grad. Aber so oder so: Wer die subtileren Werkzeuge hat und vor allem die Mittel um Menschen zu kaufen, die diese dann anwenden, hat eindeutig die besseren Karten.  [https://soundcloud.com/radiomuenchen/unterwanderter-journalismus-oder-der-mediale-deep-state-wankt-von-milosz-matuschekcolor=ffd400](https://soundcloud.com/radiomuenchen/unterwanderter-journalismus-oder-der-mediale-deep-state-wankt-von-milosz-matuschek?si=45877e50143d4e10a22fc9a4be82970d\&utm_source=clipboard\&utm_medium=text\&utm_campaign=social_sharing) Dass die Bevölkerung nun wissen will, mit welchen Mitteln sie auf welche Weise beeinflusst werden soll, ist selbstverständlich. Wie nuanciert diese Beeinflussung stattfinden kann, darauf haben uns unsere Hörer beim letzten Beitrag von Milosz Matuschek: „Die ersten Köpfe rollen“ gestoßen. Es ging um die staatliche amerikanische Behörde für internationale Entwicklungshilfe USAID. Matuschek schrieb: „Man liest was von AID im Namen und denkt, was man denken soll: klingt nach Bob Geldof, barmherzigen Schwestern und “Brot für die Welt”.“ Man hatte das nicht nur optisch wahrgenommen, nein, diese Behörde wurde hierzulande, in allen Medien US AID genannt, was unsere Sprecherin Sabrina Khalil übernahm. Dass die United States Agency for International Development in USA so nicht gesprochen wird, schrieben uns gleich mehrere aufmerksame Hörer. Es ist sicherlich keine Paranoia darüber nachzudenken, ob die Bedeutung unserer Sprache, unserer Wörter bis hin zur Aussprache im Fokus der Manipulation steht. Dafür wird sehr viel Geld locker gemacht und unter anderem in die Medien gepumpt. Hören Sie heute den zweiten Teil der Reihe „Die Corona-Connection“ mit dem Titel: „Der mediale Deep State wankt“. Sprecherin: Sabrina Khalil. Das freie Medienprojekt Pareto kann übrigens Unterstützung gebrauchen, dafür wurde ein Crowdfunding auf Geyser gestartet, wo man mit Bitcoin/Lightning-Spenden helfen kann. Und für Spenden auf dem klassischen Weg finden Sie die entsprechende Bankverbindung auf der Homepage pareto.space/de. Nachzulesen unter: [www.freischwebende-intelligenz.org/p/unter…mediale](https://gate.sc?url=https%3A%2F%2Fwww.freischwebende-intelligenz.org%2Fp%2Funterwanderter-journalismus-der-mediale\&token=6fce3f-1-1743155866002 "https://www.freischwebende-intelligenz.org/p/unterwanderter-journalismus-der-mediale") Foto: Gleichschaltung - sie melden exakt den gleichen Wortlaut. @ 7d33ba57:1b82db35
2025-03-27 20:23:58Peñíscola, known as the “Gibraltar of Valencia”, is a stunning coastal town on Spain’s Costa del Azahar. Famous for its medieval castle, beautiful beaches, and charming old town, Peñíscola is a perfect mix of history, culture, and seaside relaxation. It’s also known as a filming location for Game of Thrones!  ## **🏖️ Top Things to See & Do in Peñíscola** ### **1️⃣ Peñíscola Castle (Castillo del Papa Luna) 🏰** - A **magnificent 13th-century castle** sitting on a rocky peninsula. - Built by the **Knights Templar** and later home to **Pope Benedict XIII (Papa Luna)**. - Offers **breathtaking views** of the Mediterranean and surrounding coastline. ### **2️⃣ Explore the Old Town 🏡** - Wander through **narrow cobblestone streets**, lined with **whitewashed houses and flower-filled balconies**. - Discover **hidden courtyards, charming shops, and seafood restaurants**. - Enjoy the **picturesque sunset views** over the sea.  ### **3️⃣ Relax on Playa Norte & Playa Sur 🏖️** - **Playa Norte**: The **main beach**, known for its **golden sand and clear waters**. - **Playa Sur**: Smaller and quieter, great for **relaxing away from the crowds**. - Both beaches offer **water sports, sunbeds, and beach bars**. ### **4️⃣ Serra d’Irta Natural Park 🌿** - A **stunning coastal nature reserve** with **hiking and biking trails**. - Offers **hidden coves, rugged cliffs, and breathtaking sea views**. - Ideal for **nature lovers and photographers**.  ### **5️⃣ Game of Thrones Filming Locations 🎬** - Peñíscola was featured in **Game of Thrones (Season 6) as Meereen**. - Visit the **castle walls, old town alleys, and city gates** where key scenes were filmed. ### **6️⃣ Boat Trip Around the Castle ⛵** - Take a **boat tour** for **unique views of the fortress from the sea**. - Sunset cruises offer **magical golden-hour scenery**.  ## **🍽️ What to Eat in Peñíscola** - **Arroz a Banda** – A delicious **seafood rice dish**, typical of Valencia 🍚🐟 - **Suquet de Peix** – A **traditional fish stew** with potatoes and saffron 🍲 - **Langostinos de Vinaròs** – **Famous local prawns**, incredibly fresh 🍤 - **Caragols Punxents** – A local specialty of **small spicy snails** 🐌🌶️ - **Coca de llanda** – A **sweet sponge cake**, perfect with coffee 🍰  ## **🚗 How to Get to Peñíscola** ✈️ **By Air:** The nearest airport is **Castellón Airport (40 min), Valencia (1.5 hrs), or Barcelona (2 hrs)**. 🚆 **By Train:** The nearest station is **Benicarló-Peñíscola**, just **7 km away**. 🚘 **By Car:** 1.5 hrs from **Valencia**, 2 hrs from **Barcelona**, 45 min from **Castellón**. 🚌 **By Bus:** Direct buses from **Barcelona, Valencia, and Castellón**.  ## **💡 Tips for Visiting Peñíscola** ✅ **Best time to visit?** **Spring & summer (April–September)** for the best weather ☀️ ✅ **Visit the castle early** – Mornings are less crowded and cooler 🏰 ✅ **Take a sunset walk along the beach** – The views are stunning 🌅 ✅ **Try a boat trip** – The castle looks incredible from the water ⛵ ✅ **Wear comfortable shoes** – The old town streets are steep and cobbled 👟
@ 7d33ba57:1b82db35
2025-03-27 20:23:58Peñíscola, known as the “Gibraltar of Valencia”, is a stunning coastal town on Spain’s Costa del Azahar. Famous for its medieval castle, beautiful beaches, and charming old town, Peñíscola is a perfect mix of history, culture, and seaside relaxation. It’s also known as a filming location for Game of Thrones!  ## **🏖️ Top Things to See & Do in Peñíscola** ### **1️⃣ Peñíscola Castle (Castillo del Papa Luna) 🏰** - A **magnificent 13th-century castle** sitting on a rocky peninsula. - Built by the **Knights Templar** and later home to **Pope Benedict XIII (Papa Luna)**. - Offers **breathtaking views** of the Mediterranean and surrounding coastline. ### **2️⃣ Explore the Old Town 🏡** - Wander through **narrow cobblestone streets**, lined with **whitewashed houses and flower-filled balconies**. - Discover **hidden courtyards, charming shops, and seafood restaurants**. - Enjoy the **picturesque sunset views** over the sea.  ### **3️⃣ Relax on Playa Norte & Playa Sur 🏖️** - **Playa Norte**: The **main beach**, known for its **golden sand and clear waters**. - **Playa Sur**: Smaller and quieter, great for **relaxing away from the crowds**. - Both beaches offer **water sports, sunbeds, and beach bars**. ### **4️⃣ Serra d’Irta Natural Park 🌿** - A **stunning coastal nature reserve** with **hiking and biking trails**. - Offers **hidden coves, rugged cliffs, and breathtaking sea views**. - Ideal for **nature lovers and photographers**.  ### **5️⃣ Game of Thrones Filming Locations 🎬** - Peñíscola was featured in **Game of Thrones (Season 6) as Meereen**. - Visit the **castle walls, old town alleys, and city gates** where key scenes were filmed. ### **6️⃣ Boat Trip Around the Castle ⛵** - Take a **boat tour** for **unique views of the fortress from the sea**. - Sunset cruises offer **magical golden-hour scenery**.  ## **🍽️ What to Eat in Peñíscola** - **Arroz a Banda** – A delicious **seafood rice dish**, typical of Valencia 🍚🐟 - **Suquet de Peix** – A **traditional fish stew** with potatoes and saffron 🍲 - **Langostinos de Vinaròs** – **Famous local prawns**, incredibly fresh 🍤 - **Caragols Punxents** – A local specialty of **small spicy snails** 🐌🌶️ - **Coca de llanda** – A **sweet sponge cake**, perfect with coffee 🍰  ## **🚗 How to Get to Peñíscola** ✈️ **By Air:** The nearest airport is **Castellón Airport (40 min), Valencia (1.5 hrs), or Barcelona (2 hrs)**. 🚆 **By Train:** The nearest station is **Benicarló-Peñíscola**, just **7 km away**. 🚘 **By Car:** 1.5 hrs from **Valencia**, 2 hrs from **Barcelona**, 45 min from **Castellón**. 🚌 **By Bus:** Direct buses from **Barcelona, Valencia, and Castellón**.  ## **💡 Tips for Visiting Peñíscola** ✅ **Best time to visit?** **Spring & summer (April–September)** for the best weather ☀️ ✅ **Visit the castle early** – Mornings are less crowded and cooler 🏰 ✅ **Take a sunset walk along the beach** – The views are stunning 🌅 ✅ **Try a boat trip** – The castle looks incredible from the water ⛵ ✅ **Wear comfortable shoes** – The old town streets are steep and cobbled 👟 @ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead. Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023. [Sauce](https://www.dailymail.co.uk/news/article-14341423/Christian-Iraqi-burnt-Koran-Sweden-shot-dead.html)
@ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead. Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023. [Sauce](https://www.dailymail.co.uk/news/article-14341423/Christian-Iraqi-burnt-Koran-Sweden-shot-dead.html) @ 7d33ba57:1b82db35
2025-03-27 19:48:38Tarifa, located at the southernmost tip of Spain, is a paradise for beach lovers, adventure seekers, and nature enthusiasts. Known for its strong winds, golden beaches, and laid-back atmosphere, it’s a top destination for kite surfing, whale watching, and exploring Andalusian history. Plus, it’s the perfect gateway to Morocco, just a short ferry ride away.  ## **🏖️ Top Things to See & Do in Tarifa** ### **1️⃣ Playa de Los Lances 🏄♂️** - A **long, sandy beach** famous for **kite surfing and windsurfing**. - One of the best spots in Europe for **water sports enthusiasts**. - Lined with **chiringuitos (beach bars)** where you can relax and enjoy the views. ### **2️⃣ Punta de Tarifa – The Southernmost Point of Europe 🌍** - A unique spot where the **Atlantic Ocean meets the Mediterranean Sea**. - Walk to **Isla de las Palomas**, a historic military zone (guided tours available). - Incredible views of **Morocco, just 14 km away**.  ### **3️⃣ Whale & Dolphin Watching Tours 🐬** - Join a boat trip to see **orcas, dolphins, and sperm whales** in the Strait of Gibraltar. - Best time: **April to October** for whale migrations.  ### **4️⃣ Explore the Historic Old Town 🏰** - Wander through **narrow, whitewashed streets** full of charm. - Visit **Guzmán el Bueno Castle**, a **10th-century fortress** with panoramic views. - Enjoy **lively tapas bars, boutique shops, and hidden courtyards**.  ### **5️⃣ Playa de Bolonia & Baelo Claudia Ruins 🏛️** - One of Spain’s most **unspoiled beaches**, with **dunes and turquoise waters**. - Explore the **Roman ruins of Baelo Claudia**, an ancient **fishing village from 2,000 years ago**. - Climb the **Duna de Bolonia**, a massive sand dune with breathtaking views.  ### **6️⃣ Day Trip to Morocco 🇲🇦** - Take a **35-minute ferry to Tangier** for a quick taste of **North African culture**. - Explore **medinas, souks, and local cuisine** with a guided tour. - Don’t forget your **passport**!  ## **🍽️ What to Eat in Tarifa** - **Atún Rojo (Red Tuna)** – Tarifa is famous for its **fresh bluefin tuna** 🍣 - **Tortillitas de Camarones** – Crispy shrimp fritters, a local delicacy 🍤 - **Choco Frito** – Fried cuttlefish, a must-try for seafood lovers 🦑 - **Andalusian Gazpacho** – A refreshing **cold tomato soup**, perfect for hot days 🍅 - **Mojama** – **Salt-cured tuna**, often eaten as a tapa with almonds 🐟  ## **🚗 How to Get to Tarifa** ✈️ **By Air:** The nearest airports are **Gibraltar (45 min), Málaga (2 hrs), and Seville (2.5 hrs)**. 🚆 **By Train:** No direct train, but you can take one to **Algeciras (30 min drive from Tarifa)**. 🚘 **By Car:** 1.5 hrs from **Málaga**, 1 hr from **Cádiz**, 30 min from **Gibraltar**. 🚌 **By Bus:** Regular buses from **Seville, Málaga, Cádiz, and Algeciras**. ⛴️ **To Morocco:** Ferries run **daily** to **Tangier, Morocco (35 min ride)**.  ## **💡 Tips for Visiting Tarifa** ✅ **Best time to visit?** **Spring to early autumn (April–October)** for great weather ☀️ ✅ **Book water sports lessons early** – It’s a popular spot for kite surfing! 🏄♂️ ✅ **Bring layers** – Tarifa can be **windy**, even in summer 🌬️ ✅ **Visit early for whale watching** – Mornings usually have calmer seas 🐋 ✅ **Take a day trip to Bolonia** – One of Spain’s most stunning hidden beaches 🏝️ 
@ 7d33ba57:1b82db35
2025-03-27 19:48:38Tarifa, located at the southernmost tip of Spain, is a paradise for beach lovers, adventure seekers, and nature enthusiasts. Known for its strong winds, golden beaches, and laid-back atmosphere, it’s a top destination for kite surfing, whale watching, and exploring Andalusian history. Plus, it’s the perfect gateway to Morocco, just a short ferry ride away.  ## **🏖️ Top Things to See & Do in Tarifa** ### **1️⃣ Playa de Los Lances 🏄♂️** - A **long, sandy beach** famous for **kite surfing and windsurfing**. - One of the best spots in Europe for **water sports enthusiasts**. - Lined with **chiringuitos (beach bars)** where you can relax and enjoy the views. ### **2️⃣ Punta de Tarifa – The Southernmost Point of Europe 🌍** - A unique spot where the **Atlantic Ocean meets the Mediterranean Sea**. - Walk to **Isla de las Palomas**, a historic military zone (guided tours available). - Incredible views of **Morocco, just 14 km away**.  ### **3️⃣ Whale & Dolphin Watching Tours 🐬** - Join a boat trip to see **orcas, dolphins, and sperm whales** in the Strait of Gibraltar. - Best time: **April to October** for whale migrations.  ### **4️⃣ Explore the Historic Old Town 🏰** - Wander through **narrow, whitewashed streets** full of charm. - Visit **Guzmán el Bueno Castle**, a **10th-century fortress** with panoramic views. - Enjoy **lively tapas bars, boutique shops, and hidden courtyards**.  ### **5️⃣ Playa de Bolonia & Baelo Claudia Ruins 🏛️** - One of Spain’s most **unspoiled beaches**, with **dunes and turquoise waters**. - Explore the **Roman ruins of Baelo Claudia**, an ancient **fishing village from 2,000 years ago**. - Climb the **Duna de Bolonia**, a massive sand dune with breathtaking views.  ### **6️⃣ Day Trip to Morocco 🇲🇦** - Take a **35-minute ferry to Tangier** for a quick taste of **North African culture**. - Explore **medinas, souks, and local cuisine** with a guided tour. - Don’t forget your **passport**!  ## **🍽️ What to Eat in Tarifa** - **Atún Rojo (Red Tuna)** – Tarifa is famous for its **fresh bluefin tuna** 🍣 - **Tortillitas de Camarones** – Crispy shrimp fritters, a local delicacy 🍤 - **Choco Frito** – Fried cuttlefish, a must-try for seafood lovers 🦑 - **Andalusian Gazpacho** – A refreshing **cold tomato soup**, perfect for hot days 🍅 - **Mojama** – **Salt-cured tuna**, often eaten as a tapa with almonds 🐟  ## **🚗 How to Get to Tarifa** ✈️ **By Air:** The nearest airports are **Gibraltar (45 min), Málaga (2 hrs), and Seville (2.5 hrs)**. 🚆 **By Train:** No direct train, but you can take one to **Algeciras (30 min drive from Tarifa)**. 🚘 **By Car:** 1.5 hrs from **Málaga**, 1 hr from **Cádiz**, 30 min from **Gibraltar**. 🚌 **By Bus:** Regular buses from **Seville, Málaga, Cádiz, and Algeciras**. ⛴️ **To Morocco:** Ferries run **daily** to **Tangier, Morocco (35 min ride)**.  ## **💡 Tips for Visiting Tarifa** ✅ **Best time to visit?** **Spring to early autumn (April–October)** for great weather ☀️ ✅ **Book water sports lessons early** – It’s a popular spot for kite surfing! 🏄♂️ ✅ **Bring layers** – Tarifa can be **windy**, even in summer 🌬️ ✅ **Visit early for whale watching** – Mornings usually have calmer seas 🐋 ✅ **Take a day trip to Bolonia** – One of Spain’s most stunning hidden beaches 🏝️  @ 0fa80bd3:ea7325de
2025-01-30 04:28:30**"Degeneration"** or **"Вырождение"** ![[photo_2025-01-29 23.23.15.jpeg]] A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them. The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30**"Degeneration"** or **"Вырождение"** ![[photo_2025-01-29 23.23.15.jpeg]] A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them. The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay. @ fe9e99a0:5123e9a8
2025-03-27 18:37:28Can’t seem to update anything
@ fe9e99a0:5123e9a8
2025-03-27 18:37:28Can’t seem to update anything @ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял ``` npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a ``` Thomas Pacchia - PubKey owner - X - @tpacchia ``` npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgpl ``` calvadev - Shopstr ``` npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq ``` Calle - Cashu founder ``` npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg ``` Джек Дорси ``` npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m ``` 21 ideas ``` npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7l ``` Много адресов. Хз кто надо сортировать ``` https://github.com/aitechguy/nostr-address-book ``` ФиатДжеф - создатель Ностр - https://github.com/fiatjaf ``` npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 ``` EVAN KALOUDIS Zues wallet ``` npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qd ``` Программер Коди https://github.com/CodyTseng/nostr-relay ``` npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl ``` Anna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich ``` npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 ```
@ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял ``` npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a ``` Thomas Pacchia - PubKey owner - X - @tpacchia ``` npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgpl ``` calvadev - Shopstr ``` npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq ``` Calle - Cashu founder ``` npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg ``` Джек Дорси ``` npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m ``` 21 ideas ``` npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7l ``` Много адресов. Хз кто надо сортировать ``` https://github.com/aitechguy/nostr-address-book ``` ФиатДжеф - создатель Ностр - https://github.com/fiatjaf ``` npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 ``` EVAN KALOUDIS Zues wallet ``` npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qd ``` Программер Коди https://github.com/CodyTseng/nostr-relay ``` npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl ``` Anna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich ``` npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 ``` @ 000002de:c05780a7
2025-03-27 17:51:16Regardless of what you have heard Capitalism isn't to blame for all the ills in modern life. Capitalism is simply free trade without centralize control. Of course there are many details I'm glossing over and degrees of freedom. Critics of capitalism rarely explain how it works. They complain about people buying too much stuff. People being over-weight. They complain about waste. People buying stuff they don't need. They complain that teachers aren't paid enough. They complain that professional athletes make too much money. All of this boils down to two things. 1. People don't like what others choose to do 2. The products we see and world we live in is a result of the desires and values of the people I agree with many of the critics of capitalism. There is a ton of crap. There's a ton of waste. There are professions I wish were more profitable and others I wish were less profitable. I'm going to ignore the state for once here. Obviously the state puts its thumb on the scales and distorts the market. But this isn't the main factor IMO. The main factor in the world we live in is us. The people. Our desires. Our values. The things we value are reflected in the market. People don't like to admit this because it is uncomfortable. We are spoiled, self-centered, brats that are desire machines. Yeah, you can blame advertising. You can blame "capitalism" but the alternative is starvation and death (socialism). Its time for us to stop blaming freedom for all the ills in our society and take ownership for our actions. Its us. Thing is, I can't change you. But, I can change my actions. Adjust my values. Adjust my frame of view. I'd love to start hearing people take responsibility and self ownership. Start living out your values. Don't be a part of things that you view as problems. Be a part of solutions. I can't tell you what that looks like but if you think about it for a while you can come up with some things. Its easy to blame others. Its hard to take responsibility for yourself and own your flaws and mistakes. What do you think? _Inspired by @k00b's [post](https://stacker.news/items/926865)_ originally posted at https://stacker.news/items/927021
@ 000002de:c05780a7
2025-03-27 17:51:16Regardless of what you have heard Capitalism isn't to blame for all the ills in modern life. Capitalism is simply free trade without centralize control. Of course there are many details I'm glossing over and degrees of freedom. Critics of capitalism rarely explain how it works. They complain about people buying too much stuff. People being over-weight. They complain about waste. People buying stuff they don't need. They complain that teachers aren't paid enough. They complain that professional athletes make too much money. All of this boils down to two things. 1. People don't like what others choose to do 2. The products we see and world we live in is a result of the desires and values of the people I agree with many of the critics of capitalism. There is a ton of crap. There's a ton of waste. There are professions I wish were more profitable and others I wish were less profitable. I'm going to ignore the state for once here. Obviously the state puts its thumb on the scales and distorts the market. But this isn't the main factor IMO. The main factor in the world we live in is us. The people. Our desires. Our values. The things we value are reflected in the market. People don't like to admit this because it is uncomfortable. We are spoiled, self-centered, brats that are desire machines. Yeah, you can blame advertising. You can blame "capitalism" but the alternative is starvation and death (socialism). Its time for us to stop blaming freedom for all the ills in our society and take ownership for our actions. Its us. Thing is, I can't change you. But, I can change my actions. Adjust my values. Adjust my frame of view. I'd love to start hearing people take responsibility and self ownership. Start living out your values. Don't be a part of things that you view as problems. Be a part of solutions. I can't tell you what that looks like but if you think about it for a while you can come up with some things. Its easy to blame others. Its hard to take responsibility for yourself and own your flaws and mistakes. What do you think? _Inspired by @k00b's [post](https://stacker.news/items/926865)_ originally posted at https://stacker.news/items/927021 @ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]] 1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest. 2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money. 3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape. Now, what you do with a trapped bear is another question... 😏
@ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]] 1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest. 2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money. 3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape. Now, what you do with a trapped bear is another question... 😏 @ 9bde4214:06ca052b
2025-03-27 17:28:23“The human spirit should remain in charge.” [Pablo](https://njump.me/npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft) & [Gigi](https://njump.me/npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) talk about the wind. nostr:nevent1qvzqqqqqqypzpx77gg2frul26xkzr0gaq9n842u50axpcjhdsa3yeu388vrv5pftqys8wumn8ghj7mn0wd68ytn9d9h82mny0fmkzmn6d9njuumsv93k2tcppemhxue69uhkummn9ekx7mp0qqszlf337y0lkg4sz5ax9ath4y5vk6rpqn9tfewaln2989zavvqrg4cpt2krs In this dialogue: - Wind - More Wind - Information Calories, and how to measure them - [Digital Wellbeing](https://play.google.com/store/apps/details?id=com.google.android.apps.wellbeing) - [Rescue Time](https://www.rescuetime.com/) - Teleology of Technology - Platforms get users [Hooked](https://www.uxmatters.com/mt/archives/2021/06/book-review-hooked-how-to-build-habit-forming-products.php) (book) - Feeds are [slot machines](https://ihpi.umich.edu/news/social-media-copies-gambling-methods-create-psychological-cravings) - Movie Walls - Tweetdeck and [Notedeck](https://damus.io/notedeck/) - IRC vs the modern feed - 37Signals: “[Hey](https://www.hey.com/pricing/), let’s just charge users!” - “[You wouldn’t zap a car crash](https://njump.me/nevent1qqsqm2lz4ru6wlydzpulgs8m60ylp4vufwsg55whlqgua6a93vp2y4gzyphydppzm7m554ecwq4gsgaek2qk32atse2l4t9ks57dpms4mmhfxzzxtzc)” - Catering to our highest self VS catering to our lowest self - Devolution of YouTube [5-star ratings](https://daringfireball.net/linked/2017/03/18/youtube-thumbs-stars) to thumb up/down to [views](https://www.makeuseof.com/the-real-reason-why-youtube-hid-dislikes/) - Long videos vs shorts - The internet had to monetize itself somehow (with [attention](https://dergigi.com/2022/12/18/a-vision-for-a-value-enabled-web/#attention)) - “Don’t be evil” and why Google had to [remove it](https://www.zdnet.com/article/google-erases-dont-be-evil-from-code-of-conduct-after-18-years/) - [Questr](https://questr.vercel.app/): 2D exploration of nostr - [ONOSENDAI](https://www.onosendai.tech/) by Arkinox - Freedom tech & Freedom from Tech - DAUs of jumper cables - [Gossip](https://github.com/mikedilger/gossip) and it’s choices - [“The secret to life is to send it”](https://highlighter.com/a/naddr1qvzqqqr4gupzqmjxss3dld622uu8q25gywum9qtg4w4cv4064jmg20xsac2aam5nqqxnzd3exsmrswfjxsurxvf3qvlsju) - Flying water & flying bus stops - [RSS readers](https://github.com/fiatjaf/narr), [Mailbrew](https://mailbrew.com/), and daily digests - Nostr is high signal and less addictive - Calling nostr posts “[tweets](https://nostr.band/?q=tweet+by%3Anpub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc)” and recordings being “on tape” - Pivoting from nostr dialogues to a podcast about wind - The unnecessary complexity of [NIP-96](https://github.com/nostr-protocol/nips/blob/master/96.md) - [Blossom](https://github.com/hzrd149/blossom) (and wind) - Undoing URLs, APIs, and REST - ISBNs and cryptographic identifiers - SaaS and the DAU metric - [Highlighter](https://highlighter.com/) - Not caring where stuff is hosted - When is an edited thing a new thing? - Edits, the edit wars, and [the case against edits](https://blog.udaya.dev/fiatjaf/ad84e3b3) - [NIP-60](https://nips.nostr.com/60) and inconsistent balances - Scroll to [text fragment](https://mgearon.com/html/text-fragments/) and best effort matching - Proximity hashes & [locality-sensitive hashing](https://en.wikipedia.org/wiki/Locality-sensitive_hashing) - Helping your Uncle Jack of a horse - Helping your uncle [jack of a horse](https://en.wikipedia.org/wiki/Mr._Hands_\(album\)) - Can we fix it with WoT? - [Vertex](https://vertexlab.io/) & vibe-coding a proper search for nostr - Linking to hashtags & search queries - Advanced search and why it’s great - Search scopes & web of trust - The UNIX tools of nostr - Pablo’s [NDK snippets](https://nostr-dev-kit.github.io/ndk/snippets/) - Meredith on the [privacy nightmare of Agentic AI](https://njump.me/nevent1qqsts24dta3nay5ypkhnqd8aphynhw7z89qw69sp3pceady2xujakygpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qguh5grefa7vkay4ps6udxg8lrqxg2kgr3qh9n4gduxut64nfxq0quyzs70) - Blog-post-driven development ([Lightning Prisms](https://dergigi.com/2023/03/12/lightning-prisms/), [Highlighter](https://dergigi.com/2023/04/04/purple-text-orange-highlights/)) - Sandwich-style LLM prompting, Waterfall for LLMs ([HLDD / LLDD](https://gist.github.com/dskvr/b34f836b68ff2ca51bcc8fe7763eceec)) - “Speed itself is a feature” - MCP & [DVMCP](https://mcp.so/server/dvmcp) - Monorepos and git submodules - [Olas](https://olas.app/) & NDK - Pablo’s [RemindMe](https://njump.me/npub17hsu5gd24stmzuuezwvavgeuwwac233nfzg59dfyhf4fvel8n2sqw3d0k9) bot - “Breaking changes kinda suck” - Stories, shorts, TikTok, and OnlyFans - LLM-generated sticker styles - LLMs and [creativity](https://dergigi.com/2022/09/25/creativity/) (and Gigi’s [old email](https://gist.github.com/dergigi/04760fbcaa3769bb243db2b0e31c75df)) - “AI-generated art has no soul” - Nostr, zaps, and realness - Does the source matter? - Poker client in [bitcoin v0.0.1](https://github.com/search?q=repo%3Atrottier%2Foriginal-bitcoin%20poker&type=code) - Quotes from Hitler and how additional context changes meaning - Greek finance minister on crypto and bitcoin ([Technofeudalism](https://www.goodreads.com/book/show/75560036-technofeudalism), book) - Is more context always good? - [Vervaeke’s AI argument](https://www.youtube.com/watch?v=A-_RdKiDbz4&list=PLND1JCRq8Vui2YOOfrxbeRwJk5jZPmAth) - What is meaningful? - How do you extract meaning from information? - How do you extract meaning from experience? - “[What the hell is water](https://youtu.be/ms2BvRbjOYo)” - Creativity, imagination, hallucination, and losing touch with reality - “[Bitcoin is singularity insurance](https://njump.me/nevent1qqswawr4cz68sjswhtdkat8qgnpfsc6wygx4xmq2d5gd5fg9extvl4gpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtczyphydppzm7m554ecwq4gsgaek2qk32atse2l4t9ks57dpms4mmhfxqcyqqqqqqg74yxgf)” - Will vibe coding make developers obsolete? - Knowing what to build vs knowing how to build - 10min block time & the [physical limits of consensus](https://dergigi.com/threads/physical-limits) - Satoshi’s reasons articulated in his [announcement post](https://satoshi.nakamotoinstitute.org/posts/p2pfoundation/1/) - Why do anything? Why stack sats? Why have kids? - All you need now is motivation - Upcoming agents will actually do the thing - Proliferation of writers: quantity VS quality - Crisis of sameness & the problem of distribution - Patronage, belle epoche, and [bitcoin art](https://x.com/FractalEncrypt) - Niches, and how the internet fractioned society - Joe’s songs - Hyper-personalized stories - Shared stories & myths ([Jonathan Pageau](https://www.thesymbolicworld.com/team/jonathan-pageau)) - Hyper-personalized apps VS shared apps - Agency, free expression, and [free speech](https://dergigi.com/2024/03/25/speaking-freely-online/) - Edgy content & [twitch meta](https://www.talkesport.com/news/what-is-the-twitch-meta-decoding-trends-and-controversies/), aka skating the line of demonetization and deplatforming - Using attention as a proxy currency - Farming eyeballs and brain cycles - Engagement as a success metric & engagement bait - “[You wouldn’t zap a car crash](https://njump.me/nevent1qqsqm2lz4ru6wlydzpulgs8m60ylp4vufwsg55whlqgua6a93vp2y4gzyphydppzm7m554ecwq4gsgaek2qk32atse2l4t9ks57dpms4mmhfxzzxtzc)” - Attention economy is parasitic on humanity - The importance of [speech](https://nostr-resources.com/) & [money](https://bitcoin-resources.com/) - What should be done by a machine? - What should be done by a human? - “The human spirit should remain in charge” - Our relationship with fiat money - Active vs passive, agency vs serfdom
@ 9bde4214:06ca052b
2025-03-27 17:28:23“The human spirit should remain in charge.” [Pablo](https://njump.me/npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft) & [Gigi](https://njump.me/npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc) talk about the wind. nostr:nevent1qvzqqqqqqypzpx77gg2frul26xkzr0gaq9n842u50axpcjhdsa3yeu388vrv5pftqys8wumn8ghj7mn0wd68ytn9d9h82mny0fmkzmn6d9njuumsv93k2tcppemhxue69uhkummn9ekx7mp0qqszlf337y0lkg4sz5ax9ath4y5vk6rpqn9tfewaln2989zavvqrg4cpt2krs In this dialogue: - Wind - More Wind - Information Calories, and how to measure them - [Digital Wellbeing](https://play.google.com/store/apps/details?id=com.google.android.apps.wellbeing) - [Rescue Time](https://www.rescuetime.com/) - Teleology of Technology - Platforms get users [Hooked](https://www.uxmatters.com/mt/archives/2021/06/book-review-hooked-how-to-build-habit-forming-products.php) (book) - Feeds are [slot machines](https://ihpi.umich.edu/news/social-media-copies-gambling-methods-create-psychological-cravings) - Movie Walls - Tweetdeck and [Notedeck](https://damus.io/notedeck/) - IRC vs the modern feed - 37Signals: “[Hey](https://www.hey.com/pricing/), let’s just charge users!” - “[You wouldn’t zap a car crash](https://njump.me/nevent1qqsqm2lz4ru6wlydzpulgs8m60ylp4vufwsg55whlqgua6a93vp2y4gzyphydppzm7m554ecwq4gsgaek2qk32atse2l4t9ks57dpms4mmhfxzzxtzc)” - Catering to our highest self VS catering to our lowest self - Devolution of YouTube [5-star ratings](https://daringfireball.net/linked/2017/03/18/youtube-thumbs-stars) to thumb up/down to [views](https://www.makeuseof.com/the-real-reason-why-youtube-hid-dislikes/) - Long videos vs shorts - The internet had to monetize itself somehow (with [attention](https://dergigi.com/2022/12/18/a-vision-for-a-value-enabled-web/#attention)) - “Don’t be evil” and why Google had to [remove it](https://www.zdnet.com/article/google-erases-dont-be-evil-from-code-of-conduct-after-18-years/) - [Questr](https://questr.vercel.app/): 2D exploration of nostr - [ONOSENDAI](https://www.onosendai.tech/) by Arkinox - Freedom tech & Freedom from Tech - DAUs of jumper cables - [Gossip](https://github.com/mikedilger/gossip) and it’s choices - [“The secret to life is to send it”](https://highlighter.com/a/naddr1qvzqqqr4gupzqmjxss3dld622uu8q25gywum9qtg4w4cv4064jmg20xsac2aam5nqqxnzd3exsmrswfjxsurxvf3qvlsju) - Flying water & flying bus stops - [RSS readers](https://github.com/fiatjaf/narr), [Mailbrew](https://mailbrew.com/), and daily digests - Nostr is high signal and less addictive - Calling nostr posts “[tweets](https://nostr.band/?q=tweet+by%3Anpub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc)” and recordings being “on tape” - Pivoting from nostr dialogues to a podcast about wind - The unnecessary complexity of [NIP-96](https://github.com/nostr-protocol/nips/blob/master/96.md) - [Blossom](https://github.com/hzrd149/blossom) (and wind) - Undoing URLs, APIs, and REST - ISBNs and cryptographic identifiers - SaaS and the DAU metric - [Highlighter](https://highlighter.com/) - Not caring where stuff is hosted - When is an edited thing a new thing? - Edits, the edit wars, and [the case against edits](https://blog.udaya.dev/fiatjaf/ad84e3b3) - [NIP-60](https://nips.nostr.com/60) and inconsistent balances - Scroll to [text fragment](https://mgearon.com/html/text-fragments/) and best effort matching - Proximity hashes & [locality-sensitive hashing](https://en.wikipedia.org/wiki/Locality-sensitive_hashing) - Helping your Uncle Jack of a horse - Helping your uncle [jack of a horse](https://en.wikipedia.org/wiki/Mr._Hands_\(album\)) - Can we fix it with WoT? - [Vertex](https://vertexlab.io/) & vibe-coding a proper search for nostr - Linking to hashtags & search queries - Advanced search and why it’s great - Search scopes & web of trust - The UNIX tools of nostr - Pablo’s [NDK snippets](https://nostr-dev-kit.github.io/ndk/snippets/) - Meredith on the [privacy nightmare of Agentic AI](https://njump.me/nevent1qqsts24dta3nay5ypkhnqd8aphynhw7z89qw69sp3pceady2xujakygpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qguh5grefa7vkay4ps6udxg8lrqxg2kgr3qh9n4gduxut64nfxq0quyzs70) - Blog-post-driven development ([Lightning Prisms](https://dergigi.com/2023/03/12/lightning-prisms/), [Highlighter](https://dergigi.com/2023/04/04/purple-text-orange-highlights/)) - Sandwich-style LLM prompting, Waterfall for LLMs ([HLDD / LLDD](https://gist.github.com/dskvr/b34f836b68ff2ca51bcc8fe7763eceec)) - “Speed itself is a feature” - MCP & [DVMCP](https://mcp.so/server/dvmcp) - Monorepos and git submodules - [Olas](https://olas.app/) & NDK - Pablo’s [RemindMe](https://njump.me/npub17hsu5gd24stmzuuezwvavgeuwwac233nfzg59dfyhf4fvel8n2sqw3d0k9) bot - “Breaking changes kinda suck” - Stories, shorts, TikTok, and OnlyFans - LLM-generated sticker styles - LLMs and [creativity](https://dergigi.com/2022/09/25/creativity/) (and Gigi’s [old email](https://gist.github.com/dergigi/04760fbcaa3769bb243db2b0e31c75df)) - “AI-generated art has no soul” - Nostr, zaps, and realness - Does the source matter? - Poker client in [bitcoin v0.0.1](https://github.com/search?q=repo%3Atrottier%2Foriginal-bitcoin%20poker&type=code) - Quotes from Hitler and how additional context changes meaning - Greek finance minister on crypto and bitcoin ([Technofeudalism](https://www.goodreads.com/book/show/75560036-technofeudalism), book) - Is more context always good? - [Vervaeke’s AI argument](https://www.youtube.com/watch?v=A-_RdKiDbz4&list=PLND1JCRq8Vui2YOOfrxbeRwJk5jZPmAth) - What is meaningful? - How do you extract meaning from information? - How do you extract meaning from experience? - “[What the hell is water](https://youtu.be/ms2BvRbjOYo)” - Creativity, imagination, hallucination, and losing touch with reality - “[Bitcoin is singularity insurance](https://njump.me/nevent1qqswawr4cz68sjswhtdkat8qgnpfsc6wygx4xmq2d5gd5fg9extvl4gpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtczyphydppzm7m554ecwq4gsgaek2qk32atse2l4t9ks57dpms4mmhfxqcyqqqqqqg74yxgf)” - Will vibe coding make developers obsolete? - Knowing what to build vs knowing how to build - 10min block time & the [physical limits of consensus](https://dergigi.com/threads/physical-limits) - Satoshi’s reasons articulated in his [announcement post](https://satoshi.nakamotoinstitute.org/posts/p2pfoundation/1/) - Why do anything? Why stack sats? Why have kids? - All you need now is motivation - Upcoming agents will actually do the thing - Proliferation of writers: quantity VS quality - Crisis of sameness & the problem of distribution - Patronage, belle epoche, and [bitcoin art](https://x.com/FractalEncrypt) - Niches, and how the internet fractioned society - Joe’s songs - Hyper-personalized stories - Shared stories & myths ([Jonathan Pageau](https://www.thesymbolicworld.com/team/jonathan-pageau)) - Hyper-personalized apps VS shared apps - Agency, free expression, and [free speech](https://dergigi.com/2024/03/25/speaking-freely-online/) - Edgy content & [twitch meta](https://www.talkesport.com/news/what-is-the-twitch-meta-decoding-trends-and-controversies/), aka skating the line of demonetization and deplatforming - Using attention as a proxy currency - Farming eyeballs and brain cycles - Engagement as a success metric & engagement bait - “[You wouldn’t zap a car crash](https://njump.me/nevent1qqsqm2lz4ru6wlydzpulgs8m60ylp4vufwsg55whlqgua6a93vp2y4gzyphydppzm7m554ecwq4gsgaek2qk32atse2l4t9ks57dpms4mmhfxzzxtzc)” - Attention economy is parasitic on humanity - The importance of [speech](https://nostr-resources.com/) & [money](https://bitcoin-resources.com/) - What should be done by a machine? - What should be done by a human? - “The human spirit should remain in charge” - Our relationship with fiat money - Active vs passive, agency vs serfdom @ a012dc82:6458a70d
2025-03-27 14:23:51The cryptocurrency market, known for its dramatic fluctuations, has always been a subject of intrigue and speculation. Bitcoin, as the pioneering digital currency, has been at the epicenter of this financial whirlwind. As we approach 2024, the anticipation surrounding Bitcoin's value is palpable, with potential investors and seasoned cryptocurrency enthusiasts keenly eyeing the market's movements. This article aims to dissect the recent forecasts for Bitcoin's price in the coming year, delve into the multifaceted factors influencing these predictions, and explore the broader implications for those contemplating an investment in Bitcoin. **Table of Contents** - 2024 Bitcoin Price Predictions: A New Peak on the … - Key Factors Driving Bitcoin's Price - The Halving Event - Institutional Interest and ETFs - Economic and Monetary Policies - The Debate: To Buy or Not to Buy - Risk Tolerance - Market Dynamics - Long-Term Perspective - Caution and Speculation - Conclusion - FAQs **2024 Bitcoin Price Predictions: A New Peak on the Horizon** Recent analyses, particularly a notable report from UK fintech firm Finder, have painted an optimistic picture for Bitcoin in 2024. Experts within the field are forecasting a new zenith for Bitcoin, projecting it to reach an all-time high of $88,000, with expectations of the currency stabilizing around $77,000 by the end of the year. These projections represent a significant uptick from Bitcoin's current valuation and suggest a potentially lucrative year ahead for the digital currency. However, it's crucial to recognize that these predictions are not guarantees but educated guesses based on current market trends and historical data. The cryptocurrency market's inherent volatility means that while the potential for substantial gains exists, so too does the risk of dramatic losses. Investors should approach these predictions with cautious optimism, considering the broader economic and technological landscape that could impact Bitcoin's trajectory. **Key Factors Driving Bitcoin's Price** The anticipated surge in Bitcoin's value can be attributed to several key factors, each playing a pivotal role in shaping the currency's future: **The Halving Event** The Bitcoin halving event scheduled for April 2024 stands as a significant milestone. This event, which occurs approximately every four years, reduces the reward for mining Bitcoin transactions by half. Historically, halving events have led to a decrease in the supply of new Bitcoins entering the market, which, in turn, has led to price increases as demand outstrips supply. The 2024 halving is expected to follow this trend, contributing to the bullish outlook for Bitcoin's price. However, while past performance can offer insights, it is not indicative of future results. The halving's impact could be influenced by a myriad of factors, including changes in miner behavior, technological advancements, and shifts in investor sentiment. **Institutional Interest and ETFs** Another driving force behind the optimistic price predictions is the growing institutional interest in Bitcoin and the approval of Bitcoin ETFs in the United States. These developments have not only legitimized Bitcoin as an investment asset but also made it more accessible to a broader audience of traditional investors. The introduction of ETFs has bridged the gap between the conventional financial world and the burgeoning cryptocurrency market, providing a regulated and familiar avenue for investment. However, the influx of institutional money also brings new challenges, including increased market manipulation risks and the potential for regulatory crackdowns. Investors should remain vigilant, monitoring the evolving landscape and considering the long-term implications of institutional involvement in the cryptocurrency space. **Economic and Monetary Policies** Global economic conditions and monetary policies, particularly those enacted by the US Federal Reserve, are also critical factors influencing Bitcoin's price. In an environment of low interest rates and quantitative easing, investors have increasingly turned to alternative assets like Bitcoin as a hedge against inflation and currency devaluation. However, shifts in these policies could significantly impact investor behavior and market dynamics. A rise in interest rates or a tightening of monetary policy could lead to reduced liquidity in the market and a shift away from riskier assets, including Bitcoin. Conversely, continued economic uncertainty and inflationary pressures could bolster Bitcoin's appeal as a store of value. **The Debate: To Buy or Not to Buy** The decision to invest in Bitcoin, especially in light of the optimistic 2024 price predictions, is fraught with complexity: **Risk Tolerance** Bitcoin's notorious volatility cannot be overstated. The digital currency's price can experience dramatic swings within short periods, influenced by factors ranging from regulatory news to market sentiment. Potential investors must assess their risk tolerance and financial situation before entering the market. It's essential to consider whether you can withstand significant fluctuations in your investment's value and how such changes would impact your overall financial health. **Market Dynamics** Understanding the broader market dynamics and potential regulatory changes is crucial for anyone considering investing in Bitcoin. The cryptocurrency market does not operate in a vacuum; it is affected by global economic conditions, technological developments, and shifts in regulatory attitudes. Staying informed and adaptable is key, as today's market drivers could change rapidly, altering Bitcoin's price trajectory. **Long-Term Perspective** Adopting a long-term perspective is vital when investing in Bitcoin. While the allure of quick profits can be tempting, Bitcoin's history suggests that it is better suited as a long-term investment. The market's cyclical nature, characterized by boom-and-bust cycles, requires patience and a long-term outlook. Investors should avoid making impulsive decisions based on short-term price movements and instead focus on the underlying value and potential of Bitcoin as a revolutionary digital asset. **Caution and Speculation** Despite the bullish forecasts, a note of caution is warranted. The cryptocurrency market remains speculative, and while Bitcoin has established itself as the leading digital currency, its future is not guaranteed. The landscape is rife with uncertainties, from technological challenges to regulatory hurdles. Potential investors should approach Bitcoin with a balanced perspective, recognizing the possibilities while being acutely aware of the risks. **Conclusion** The predictions for Bitcoin's price in 2024 offer a glimpse into a potentially prosperous future for the digital currency. However, the decision to invest should not be taken lightly. Prospective investors must navigate a landscape marked by volatility, uncertainty, and rapid change. By thoroughly evaluating the market, staying informed about developments, and considering their long-term financial goals, individuals can make more informed decisions about their involvement in the Bitcoin market. Whether now is the right time to buy Bitcoin is a personal decision that depends on individual circumstances, risk tolerance, and investment strategy. As with any investment, there are no guarantees, but for those willing to embrace the risks, the rewards could be substantial. **FAQs** **Why is Bitcoin expected to reach new highs in 2024?** Bitcoin's price is expected to surge due to factors like the halving event, increasing institutional interest, the approval of Bitcoin ETFs, and global economic conditions that favor alternative investments. **What is a Bitcoin halving event?** A Bitcoin halving event is when the reward for mining new blocks is halved, reducing the rate at which new bitcoins are generated. This event occurs approximately every four years and tends to impact the price due to reduced supply. **Are Bitcoin ETFs significant for individual investors?** Yes, Bitcoin ETFs provide individual investors with a regulated and familiar way to gain exposure to Bitcoin without directly purchasing or storing the cryptocurrency, potentially increasing its accessibility and demand. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnewsco](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co/](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@thebitcoinlibertarian](https://www.youtube.com/@thebitcoinlibertarian)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** **Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad** **Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2025-03-27 14:23:51The cryptocurrency market, known for its dramatic fluctuations, has always been a subject of intrigue and speculation. Bitcoin, as the pioneering digital currency, has been at the epicenter of this financial whirlwind. As we approach 2024, the anticipation surrounding Bitcoin's value is palpable, with potential investors and seasoned cryptocurrency enthusiasts keenly eyeing the market's movements. This article aims to dissect the recent forecasts for Bitcoin's price in the coming year, delve into the multifaceted factors influencing these predictions, and explore the broader implications for those contemplating an investment in Bitcoin. **Table of Contents** - 2024 Bitcoin Price Predictions: A New Peak on the … - Key Factors Driving Bitcoin's Price - The Halving Event - Institutional Interest and ETFs - Economic and Monetary Policies - The Debate: To Buy or Not to Buy - Risk Tolerance - Market Dynamics - Long-Term Perspective - Caution and Speculation - Conclusion - FAQs **2024 Bitcoin Price Predictions: A New Peak on the Horizon** Recent analyses, particularly a notable report from UK fintech firm Finder, have painted an optimistic picture for Bitcoin in 2024. Experts within the field are forecasting a new zenith for Bitcoin, projecting it to reach an all-time high of $88,000, with expectations of the currency stabilizing around $77,000 by the end of the year. These projections represent a significant uptick from Bitcoin's current valuation and suggest a potentially lucrative year ahead for the digital currency. However, it's crucial to recognize that these predictions are not guarantees but educated guesses based on current market trends and historical data. The cryptocurrency market's inherent volatility means that while the potential for substantial gains exists, so too does the risk of dramatic losses. Investors should approach these predictions with cautious optimism, considering the broader economic and technological landscape that could impact Bitcoin's trajectory. **Key Factors Driving Bitcoin's Price** The anticipated surge in Bitcoin's value can be attributed to several key factors, each playing a pivotal role in shaping the currency's future: **The Halving Event** The Bitcoin halving event scheduled for April 2024 stands as a significant milestone. This event, which occurs approximately every four years, reduces the reward for mining Bitcoin transactions by half. Historically, halving events have led to a decrease in the supply of new Bitcoins entering the market, which, in turn, has led to price increases as demand outstrips supply. The 2024 halving is expected to follow this trend, contributing to the bullish outlook for Bitcoin's price. However, while past performance can offer insights, it is not indicative of future results. The halving's impact could be influenced by a myriad of factors, including changes in miner behavior, technological advancements, and shifts in investor sentiment. **Institutional Interest and ETFs** Another driving force behind the optimistic price predictions is the growing institutional interest in Bitcoin and the approval of Bitcoin ETFs in the United States. These developments have not only legitimized Bitcoin as an investment asset but also made it more accessible to a broader audience of traditional investors. The introduction of ETFs has bridged the gap between the conventional financial world and the burgeoning cryptocurrency market, providing a regulated and familiar avenue for investment. However, the influx of institutional money also brings new challenges, including increased market manipulation risks and the potential for regulatory crackdowns. Investors should remain vigilant, monitoring the evolving landscape and considering the long-term implications of institutional involvement in the cryptocurrency space. **Economic and Monetary Policies** Global economic conditions and monetary policies, particularly those enacted by the US Federal Reserve, are also critical factors influencing Bitcoin's price. In an environment of low interest rates and quantitative easing, investors have increasingly turned to alternative assets like Bitcoin as a hedge against inflation and currency devaluation. However, shifts in these policies could significantly impact investor behavior and market dynamics. A rise in interest rates or a tightening of monetary policy could lead to reduced liquidity in the market and a shift away from riskier assets, including Bitcoin. Conversely, continued economic uncertainty and inflationary pressures could bolster Bitcoin's appeal as a store of value. **The Debate: To Buy or Not to Buy** The decision to invest in Bitcoin, especially in light of the optimistic 2024 price predictions, is fraught with complexity: **Risk Tolerance** Bitcoin's notorious volatility cannot be overstated. The digital currency's price can experience dramatic swings within short periods, influenced by factors ranging from regulatory news to market sentiment. Potential investors must assess their risk tolerance and financial situation before entering the market. It's essential to consider whether you can withstand significant fluctuations in your investment's value and how such changes would impact your overall financial health. **Market Dynamics** Understanding the broader market dynamics and potential regulatory changes is crucial for anyone considering investing in Bitcoin. The cryptocurrency market does not operate in a vacuum; it is affected by global economic conditions, technological developments, and shifts in regulatory attitudes. Staying informed and adaptable is key, as today's market drivers could change rapidly, altering Bitcoin's price trajectory. **Long-Term Perspective** Adopting a long-term perspective is vital when investing in Bitcoin. While the allure of quick profits can be tempting, Bitcoin's history suggests that it is better suited as a long-term investment. The market's cyclical nature, characterized by boom-and-bust cycles, requires patience and a long-term outlook. Investors should avoid making impulsive decisions based on short-term price movements and instead focus on the underlying value and potential of Bitcoin as a revolutionary digital asset. **Caution and Speculation** Despite the bullish forecasts, a note of caution is warranted. The cryptocurrency market remains speculative, and while Bitcoin has established itself as the leading digital currency, its future is not guaranteed. The landscape is rife with uncertainties, from technological challenges to regulatory hurdles. Potential investors should approach Bitcoin with a balanced perspective, recognizing the possibilities while being acutely aware of the risks. **Conclusion** The predictions for Bitcoin's price in 2024 offer a glimpse into a potentially prosperous future for the digital currency. However, the decision to invest should not be taken lightly. Prospective investors must navigate a landscape marked by volatility, uncertainty, and rapid change. By thoroughly evaluating the market, staying informed about developments, and considering their long-term financial goals, individuals can make more informed decisions about their involvement in the Bitcoin market. Whether now is the right time to buy Bitcoin is a personal decision that depends on individual circumstances, risk tolerance, and investment strategy. As with any investment, there are no guarantees, but for those willing to embrace the risks, the rewards could be substantial. **FAQs** **Why is Bitcoin expected to reach new highs in 2024?** Bitcoin's price is expected to surge due to factors like the halving event, increasing institutional interest, the approval of Bitcoin ETFs, and global economic conditions that favor alternative investments. **What is a Bitcoin halving event?** A Bitcoin halving event is when the reward for mining new blocks is halved, reducing the rate at which new bitcoins are generated. This event occurs approximately every four years and tends to impact the price due to reduced supply. **Are Bitcoin ETFs significant for individual investors?** Yes, Bitcoin ETFs provide individual investors with a regulated and familiar way to gain exposure to Bitcoin without directly purchasing or storing the cryptocurrency, potentially increasing its accessibility and demand. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnewsco](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co/](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@thebitcoinlibertarian](https://www.youtube.com/@thebitcoinlibertarian)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** **Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad** **Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future. Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs. There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won. Our only resource is the **will of the people** to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root. So I started asking myself: **How do we stop this fragmentation?** How do we create a space where people can **rebuild their connections** when they’re ready? How do we build a **self-sustaining network**, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—**how do we make it spread, even in occupied territory?** In 2009, something historic happened: **the internet got its own money.** Thanks to **Satoshi Nakamoto**, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize. That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became **purely digital.** The internet was already **a sanctuary for information**, a place where people could connect and organize. But with Bitcoin, it evolved. Now, **value itself** could flow freely, beyond the reach of authorities. Think about it: when seedlings are grown in controlled environments before being planted outside, they **get stronger, survive longer, and bear fruit faster.** That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild. Now, picture the internet as that **controlled environment** for **ideas**. Bitcoin? It’s the **fertile soil** that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If **nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless.** It can absorb any number of ideas, any number of people, and it doesn’t **run out of space.** But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—**without surveillance, without censorship, without the constant fear of being erased.** This is where **Nostr** comes in. Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. **It’s a new kind of city.** One that **no dictator can seize**, no corporation can own, no government can shut down. It’s built on **decentralization, encryption, and individual control.** Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them. In a world where cities fall and governments fail, **Nostr is a city that cannot be occupied.** A place for ideas, for networks, for freedom. A city that grows stronger **the more people build within it**.
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future. Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs. There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won. Our only resource is the **will of the people** to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root. So I started asking myself: **How do we stop this fragmentation?** How do we create a space where people can **rebuild their connections** when they’re ready? How do we build a **self-sustaining network**, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—**how do we make it spread, even in occupied territory?** In 2009, something historic happened: **the internet got its own money.** Thanks to **Satoshi Nakamoto**, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize. That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became **purely digital.** The internet was already **a sanctuary for information**, a place where people could connect and organize. But with Bitcoin, it evolved. Now, **value itself** could flow freely, beyond the reach of authorities. Think about it: when seedlings are grown in controlled environments before being planted outside, they **get stronger, survive longer, and bear fruit faster.** That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild. Now, picture the internet as that **controlled environment** for **ideas**. Bitcoin? It’s the **fertile soil** that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If **nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless.** It can absorb any number of ideas, any number of people, and it doesn’t **run out of space.** But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—**without surveillance, without censorship, without the constant fear of being erased.** This is where **Nostr** comes in. Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. **It’s a new kind of city.** One that **no dictator can seize**, no corporation can own, no government can shut down. It’s built on **decentralization, encryption, and individual control.** Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them. In a world where cities fall and governments fail, **Nostr is a city that cannot be occupied.** A place for ideas, for networks, for freedom. A city that grows stronger **the more people build within it**. @ f1989a96:bcaaf2c1
2025-03-27 13:53:14Good morning, readers! Turkey’s currency plunged to a record low after the arrest of Istanbul Mayor Ekrem Imamoglu, one of President Recep Tayyip Erdogan’s main political rivals. This follows a pattern of escalating repression of opposition figures, which have been described as an effort to suppress competition ahead of primary elections. As economic conditions deteriorate, Erdogan is resorting to desperate measures — blocking social media, arresting dissenters, and tear-gassing protests — to maintain power over an increasingly restless populace. In the Caribbean, we shed light on Cubans' struggles accessing remittances sent from family members abroad. This is a symptom of the regime's strict monetary controls over foreign currency. Cubans face long delays or can’t withdraw cash due to bank liquidity shortages. And when they can, remittances are converted into pesos at the overvalued official Cuban exchange rate. This effectively allows the Communist Party of Cuba (PCC) to loot the value from Cuban remittances. In freedom tech news, we highlight Demand Pool, the first-ever Stratum V2 mining pool. Stratum V2 is a mining protocol designed to decentralize Bitcoin mining by letting individual miners create their own block templates rather than relying on centralized pools to do so for them. This improves censorship resistance and promotes a more decentralized and resilient Bitcoin network — critical features for human rights defenders and nonprofits using Bitcoin to protect against financial repression from authoritarian regimes. We end by featuring Vijay Selvam's new book, “Principles of Bitcoin.” It offers a clear, first-principles guide to understanding how Bitcoin’s technology interacts with economics, politics, philosophy, and human rights. Whether you’re new to Bitcoin or looking to deepen your understanding, this book provides a solid foundation, and it even features a foreword by HRF Chief Strategy Officer Alex Gladstein. **Now, let’s dive right in!** ### [**Subscribe Here**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a) ## **GLOBAL NEWS** #### **Turkey | Lira in Free Fall as Erdogan Arrests Political Rival** Turkey’s lira plunged to a [record low ](https://www.reuters.com/markets/currencies/turkish-lira-plunges-record-low-after-erdogan-rival-detained-2025-03-19/)after officials arrested Istanbul Mayor Ekrem Imamoglu, President Recep Tayyip Erdogan’s main political rival. Imamoglu’s arrest comes ahead of [primary elections](https://www.reuters.com/world/europe/turkish-opposition-party-members-others-head-polls-primary-election-2025-03-23/) and follows the increasing repression of opposition figures in recent months, including the [suspension](https://www.politico.eu/article/musks-x-suspends-opposition-accounts-turkey-protest-civil-unrest-erdogan-imamoglu-istanbul-mayor/?ref=nobsbitcoin.com) of political opposition accounts on X. Officials also [arrested](https://x.com/yusufcan_en/status/1903703224336429432) Buğra Gökçe, head of the Istanbul Planning Agency, for publishing data exposing the country’s deepening poverty. The currency’s fallout and political repression have sparked [protests](https://www.bbc.com/news/articles/cpv43dd3vlgo) in Istanbul despite a four-day ban. The regime is [responding](https://www.bbc.com/news/articles/cpv43dd3vlgo) with tear gas and rubber bullets. Meanwhile, Turks dissenting online risk joining over a [dozen](https://www.bbc.com/news/articles/cpv43dd3vlgo?xtor=AL-71-%5Bpartner%5D-%5Bbbc.news.twitter%5D-%5Bheadline%5D-%5Bnews%5D-%5Bbizdev%5D-%5Bisapi%5D&at_bbc_team=editorial&at_ptr_name=twitter&at_campaign_type=owned&at_link_type=web_link&at_link_origin=BBCWorld&at_link_id=29897B8E-0579-11F0-9094-A9A3F4782A4F&at_medium=social&at_format=link&at_campaign=Social_Flow) other citizens recently arrested for “provocative” social media posts. Netblocks [reports](https://x.com/netblocks/status/1902812549587820888) that the Turkish regime imposed restrictions on social media and messaging to quell the uprising of Turks struggling with financial conditions and deepening repression. #### **Cuba | Banks “Hijack” Citizen Remittances** Cubans are [struggling](https://havanatimes.org/features/cuban-banks-hijack-family-remittances/) to access remittances sent from their families abroad. This is because the regime completely controls all incoming foreign currency transfers. When remittances arrive, communist banking authorities [force](https://havanatimes.org/features/cuban-banks-hijack-family-remittances/) their conversion into collapsing Cuban pesos or “Moneda Libremente Convertible” (MLC), Cuba’s digital currency with limited use. On top of this, Cubans receive pesos in their accounts based on the official Cuban exchange rate, which is far below the informal market rate. This allows the regime to opaquely siphon off much of the remittances’ real value. Even when the money clears, Cubans face long delays or can’t withdraw the cash due to banks’ liquidity shortages. Many Cubans are accusing these banks of “[hijacking](https://havanatimes.org/features/cuban-banks-hijack-family-remittances/)” their remittances. As inflation, electrical blackouts, and food shortages continue, remittances are more critical than ever for Cuban families. Yet, they’re blocked at every turn by a system designed to impoverish them. #### **Pakistan | Announces Plans to Regulate Digital Assets** Pakistan announced [plans](https://www.bloomberg.com/news/articles/2025-03-20/pakistan-plans-to-legalize-crypto-in-bid-for-foreign-investment) to create a regulatory framework for Bitcoin and digital assets to attract foreign investment and domestic economic activity. It’s a peculiar shift for a regime that regularly [suspends](https://time.com/6692687/pakistan-election-day-voting-violence-phone-service-disturbances/) the Internet, [censors](https://timesofindia.indiatimes.com/world/pakistan/social-media-platform-x-shutdown-continues-for-eighth-day-in-pakistan/articleshow/107983076.cms) social media, [represses](https://www.bbc.com/news/articles/czx6xvgqe1ko) opposition, and burdens its people with the [highest](https://www.firstpost.com/world/pakistan-tops-asia-in-living-costs-and-inflation-rates-report-reveals-13759245.html) cost of living in Asia. We suspect the plans indicate efforts to control the industry rather than empower individuals. The military-backed regime is also [exploring](https://tribune.com.pk/story/2507061/govt-proposes-changes-to-sbp-act) a Central Bank Digital Currency (CBDC) and tightening [controls](https://timesofindia.indiatimes.com/world/pakistan/amid-net-censorship-pakistan-offers-regulated-vpns/articleshow/115392568.cms) on VPN use, which are hardly the hallmarks of leadership committed to permissionless financial systems. But perhaps it matters little. Grassroots Bitcoin adoption in Pakistan already ranks among the highest in the world, with an estimated [15 to 20 million](https://archive.ph/5ctJq) users turning to digital assets to preserve their savings, circumvent financial controls, and escape the failures of a collapsing fiat system. HRF supported [Bitcoin Pakistan](https://bitcoinpk.org) with a grant to help translate resources into Urdu, a language spoken by 60 million people trapped in this repressive scenario. #### **Russia | Piloting CBDC in Tatarstan to Test Smart Contract Functionality** Russia’s central bank plans to [pilot](https://www.business-gazeta.ru/news/665855) its CBDC, the [digital ruble](https://cbdctracker.hrf.org/currency/russian-federation), in Tatarstan to test smart contract functionality. Specifically, the central bank will experiment with conditional spending, using smart contracts to restrict where and what users can spend money on. If these features are implemented, it will empower the Kremlin with micro-controls over Russians’ spending activity. Officials could program funds to expire, restrict purchases to regime-approved goods, or block transactions at certain locations — leaving users with no financial autonomy or privacy. Those who oppose the Russian dictatorship, such as activists, nonprofits, and dissenters, could be debanked with more ease, their assets frozen or confiscated without recourse. #### **Nicaragua | Government Mandates Public Employees Declare All Assets** In Nicaragua, dictator Daniel Ortega intensified state financial surveillance by mandating all public servants to [disclose](https://havanatimes.org/features/nicaraguan-public-employees-forced-to-declare-their-assets/) information on all personal and family assets. The mandate requires all public employees to declare everything from personal bank accounts, loans, vehicles, and other assets — as well as the assets and accounts of immediate family members. Those who do not comply face the [threat of termination](https://havanatimes.org/features/nicaraguan-public-employees-forced-to-declare-their-assets/). Ironically, despite the law requiring such disclosure, Ortega himself [has not declared](https://www.laprensani.com/2021/04/26/politica/2813926-demandan-a-la-contraloria-demostrar-a-cuanto-asciende-el-patrimonio-de-daniel-ortega-y-rosario-murillo) his assets since 2006. Under the guise of regulatory compliance, this policy is yet another link in the chain tightening state surveillance over Nicaraguan society. Bitcoin adoption continues to grow in this repressed Central American nation. ## BITCOIN AND FREEDOM TECH NEWS #### **Demand Pool | First Stratum V2 Mining Pool Launches** Bitcoin mining could become more decentralized and censorship-resistant with the launch of [Demand Pool](https://www.dmnd.work/upcoming/), the first mining pool to ever implement [Stratum V2](https://stratumprotocol.org/). Stratum V2 is open-source software that allows miners to build their own block templates, enabling more individual mining and less dependence on large and centralized mining pools. This helps maintain Bitcoin’s key features: its decentralized, permissionless, and uncensorable nature. All of which are crucial for human rights defenders and nonprofits bypassing the financial repression and surveillance of authoritarian regimes. Learn more [here](https://www.dmnd.work/upcoming/). #### **Bitcoin Mining | Three Solo Blocks Found** Three separate solo miners mined Bitcoin blocks in the past seven days. This marks the second, third, and fourth solo blocks [mined](https://x.com/SoloSatoshi/status/1903799018896998562) in the past two weeks alone, hinting at a surge in home mining. This promotes greater decentralization within the Bitcoin network because solo miners have little functional ability to censor. In contrast, large mining pools are points of failure that centralized interests can more easily pressure — to the detriment of activists and human rights defenders. The [first](https://x.com/BitcoinNewsCom/status/1903476768733810928) block was mined on March 21 by a miner using a self-hosted FutureBit Apollo machine that earned 3.125 BTC plus fees for processing block [888,737](https://mempool.space/block/00000000000000000000b7070e88525e4064ab36df7cfbe34d785bbc6eb491ea). Just days later, a solo miner with under 1 TH/s of self-hosted hash rate [found](https://x.com/BitcoinNewsCom/status/1903815849535799326) block [888,989](https://mempool.space/block/00000000000000000000a517d87e63ea04c7ec3dd51d20926e82cca5466dccaf), which became just the [third](https://x.com/BitcoinNewsCom/status/1903815849535799326) block ever to be mined using an open-source [Bitaxe](https://bitaxe.org/) device. Most recently, on March 24, a solo miner using a [$300 setup](https://x.com/alanknit/status/1904246256622322122) successfully [mined](https://x.com/pete_rizzo_/status/1904217846441201755) block [889,240](https://mempool.space/block/00000000000000000001deee311732e2ba928d33f0628a5d6320c537751835e3). #### **Krux | Adds Taproot and Miniscript Support** [Krux](https://github.com/selfcustody/krux), open-source software for building your own Bitcoin signing devices (hardware for Bitcoin self-custody), [released](https://github.com/selfcustody/krux/releases/tag/v25.03.0) an update that enhances privacy and flexibility. The update introduces support for Taproot, a past Bitcoin upgrade that improves privacy and security, and Miniscript, a simplified way to create more complex Bitcoin transaction rules. This allows users to manage multi-signature wallets (where more than one private key is required to interact with your Bitcoin) in a more private and flexible way. It also enables spending conditions that are harder to censor and easier to verify. Krux continues to support the struggle for financial freedom and human rights by breaking down barriers to Bitcoin self-custody. HRF has recognized this impact and awarded grants to open-source developers working on Krux to advance this mission. #### **Cashu | Developing Tap-to-Pay Ecash** [Calle](https://x.com/callebtc), the creator of [Cashu](http://cashu.me), an open-source Chaumian ecash protocol for Bitcoin integrated with the Lightning Network, is [developing](https://x.com/callebtc/status/1903079881325400407) a new tap-to-pay feature that enables instant, offline ecash payments via NFC. Ecash functions as a bearer asset, meaning the funds are stored directly on the user’s device. With tap-to-pay, it can be transferred with a single tap (similar to tapping your credit card). More generally, ecash offers fast, private transactions resistant to surveillance and censorship. But for activists and dissenters, this particular advancement makes private and permissionless payments more accessible and user-friendly. This development will be worth following closely. Watch a demo [here](https://x.com/callebtc/status/1903079881325400407). #### **OpenSats | Announces 10th Wave of Bitcoin Grants** [OpenSats](http://opensats.org), a public nonprofit that supports open-source software and projects, [announced](https://opensats.org/blog/tenth-wave-of-bitcoin-grants) its 10th wave of grants supporting Bitcoin initiatives. This round includes funding for [Stable Channels](https://stablechannels.com/), which enable stabilized Bitcoin-backed balances on the Lightning Network (allowing users to peg Bitcoin to fiat currencies in a self-custodial way) that provide stable, censorship-resistant payments. OpenSats also renewed its support for [Floresta](https://docs.getfloresta.sh/floresta/), a lightweight Bitcoin node (a computer that runs the Bitcoin software). It lowers entry barriers to running Bitcoin, helping make the network more decentralized and censorship-resistant. #### **Bitcoin Policy Institute | Launches Bitcoin Summer Research Program** The [Bitcoin Student Network](https://www.bitcoinstudentsnetwork.org/) (BSN) and the [Bitcoin Policy Institute](https://www.btcpolicy.org/) (BPI) are teaming up to offer students an eight-week research [internship](https://www.btcinternship.org/) this summer. The program is part of BPI’s Research Experiences for Undergraduates (REU) initiative and invites students passionate about the future of money, financial inclusion, and Bitcoin’s civil liberties impacts to conduct hands-on research. Participants will also receive mentorship from BPI researchers. The program runs from June 9 to Aug. 8, 2025, and includes an in-person colloquium in Washington, DC. It is an incredible opportunity for students worldwide, especially those living in oppressive regimes, to get involved with Bitcoin. Applications are open until April 7. Apply [here](https://www.btcinternship.org/). ## RECOMMENDED CONTENT #### **Principles of Bitcoin by Vijay Selvam** “Principles of Bitcoin” by Vijay Selvam is a new book offering a first-principles guide to understanding Bitcoin’s technology, economics, politics, and philosophy. With a foreword by HRF Chief Strategy Officer Alex Gladstein, the book cuts through the noise to explain why Bitcoin stands alone as a tool for individual empowerment and financial freedom. Selvam’s work makes the case for Bitcoin as a once-in-history invention shaping a more decentralized and equitable future. Read it [here](https://www.amazon.com/Principles-Bitcoin-Technology-Economics-Philosophy/dp/023122012X/). #### **Rule Breakers — The True Story of Roya Mahboob** “[Rule Breakers](https://hrf.org/latest/hrf-celebrates-the-release-of-rule-breakers-a-movie-on-afghanistans-roya-mahboob/)” is a new film that tells the true story of Roya Mahboob, Afghanistan’s first female tech CEO, who empowered young girls in Afghanistan with financial literacy, robotics, and financial freedom through Bitcoin. The film recounts Mahboob’s courageous work educating these girls despite huge personal risks under a regime that bans their education. It follows the story of Afghan Dreamers, the country’s first all-girls robotics team, and the obstacles they overcome to compete on the world stage. “Rule Breakers” is a testament to the power of education, innovation, and resilience in the face of oppression. It’s now in theaters, and you can watch the trailer [here](https://www.youtube.com/watch?v=CW_P4zT6i9A&t=2s). *If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).* *Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\ *Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)* *The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*. [**Subscribe to newsletter**](http://financialfreedomreport.org/) [**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Visit our website**](https://hrf.org/programs/financial-freedom/)
@ f1989a96:bcaaf2c1
2025-03-27 13:53:14Good morning, readers! Turkey’s currency plunged to a record low after the arrest of Istanbul Mayor Ekrem Imamoglu, one of President Recep Tayyip Erdogan’s main political rivals. This follows a pattern of escalating repression of opposition figures, which have been described as an effort to suppress competition ahead of primary elections. As economic conditions deteriorate, Erdogan is resorting to desperate measures — blocking social media, arresting dissenters, and tear-gassing protests — to maintain power over an increasingly restless populace. In the Caribbean, we shed light on Cubans' struggles accessing remittances sent from family members abroad. This is a symptom of the regime's strict monetary controls over foreign currency. Cubans face long delays or can’t withdraw cash due to bank liquidity shortages. And when they can, remittances are converted into pesos at the overvalued official Cuban exchange rate. This effectively allows the Communist Party of Cuba (PCC) to loot the value from Cuban remittances. In freedom tech news, we highlight Demand Pool, the first-ever Stratum V2 mining pool. Stratum V2 is a mining protocol designed to decentralize Bitcoin mining by letting individual miners create their own block templates rather than relying on centralized pools to do so for them. This improves censorship resistance and promotes a more decentralized and resilient Bitcoin network — critical features for human rights defenders and nonprofits using Bitcoin to protect against financial repression from authoritarian regimes. We end by featuring Vijay Selvam's new book, “Principles of Bitcoin.” It offers a clear, first-principles guide to understanding how Bitcoin’s technology interacts with economics, politics, philosophy, and human rights. Whether you’re new to Bitcoin or looking to deepen your understanding, this book provides a solid foundation, and it even features a foreword by HRF Chief Strategy Officer Alex Gladstein. **Now, let’s dive right in!** ### [**Subscribe Here**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a) ## **GLOBAL NEWS** #### **Turkey | Lira in Free Fall as Erdogan Arrests Political Rival** Turkey’s lira plunged to a [record low ](https://www.reuters.com/markets/currencies/turkish-lira-plunges-record-low-after-erdogan-rival-detained-2025-03-19/)after officials arrested Istanbul Mayor Ekrem Imamoglu, President Recep Tayyip Erdogan’s main political rival. Imamoglu’s arrest comes ahead of [primary elections](https://www.reuters.com/world/europe/turkish-opposition-party-members-others-head-polls-primary-election-2025-03-23/) and follows the increasing repression of opposition figures in recent months, including the [suspension](https://www.politico.eu/article/musks-x-suspends-opposition-accounts-turkey-protest-civil-unrest-erdogan-imamoglu-istanbul-mayor/?ref=nobsbitcoin.com) of political opposition accounts on X. Officials also [arrested](https://x.com/yusufcan_en/status/1903703224336429432) Buğra Gökçe, head of the Istanbul Planning Agency, for publishing data exposing the country’s deepening poverty. The currency’s fallout and political repression have sparked [protests](https://www.bbc.com/news/articles/cpv43dd3vlgo) in Istanbul despite a four-day ban. The regime is [responding](https://www.bbc.com/news/articles/cpv43dd3vlgo) with tear gas and rubber bullets. Meanwhile, Turks dissenting online risk joining over a [dozen](https://www.bbc.com/news/articles/cpv43dd3vlgo?xtor=AL-71-%5Bpartner%5D-%5Bbbc.news.twitter%5D-%5Bheadline%5D-%5Bnews%5D-%5Bbizdev%5D-%5Bisapi%5D&at_bbc_team=editorial&at_ptr_name=twitter&at_campaign_type=owned&at_link_type=web_link&at_link_origin=BBCWorld&at_link_id=29897B8E-0579-11F0-9094-A9A3F4782A4F&at_medium=social&at_format=link&at_campaign=Social_Flow) other citizens recently arrested for “provocative” social media posts. Netblocks [reports](https://x.com/netblocks/status/1902812549587820888) that the Turkish regime imposed restrictions on social media and messaging to quell the uprising of Turks struggling with financial conditions and deepening repression. #### **Cuba | Banks “Hijack” Citizen Remittances** Cubans are [struggling](https://havanatimes.org/features/cuban-banks-hijack-family-remittances/) to access remittances sent from their families abroad. This is because the regime completely controls all incoming foreign currency transfers. When remittances arrive, communist banking authorities [force](https://havanatimes.org/features/cuban-banks-hijack-family-remittances/) their conversion into collapsing Cuban pesos or “Moneda Libremente Convertible” (MLC), Cuba’s digital currency with limited use. On top of this, Cubans receive pesos in their accounts based on the official Cuban exchange rate, which is far below the informal market rate. This allows the regime to opaquely siphon off much of the remittances’ real value. Even when the money clears, Cubans face long delays or can’t withdraw the cash due to banks’ liquidity shortages. Many Cubans are accusing these banks of “[hijacking](https://havanatimes.org/features/cuban-banks-hijack-family-remittances/)” their remittances. As inflation, electrical blackouts, and food shortages continue, remittances are more critical than ever for Cuban families. Yet, they’re blocked at every turn by a system designed to impoverish them. #### **Pakistan | Announces Plans to Regulate Digital Assets** Pakistan announced [plans](https://www.bloomberg.com/news/articles/2025-03-20/pakistan-plans-to-legalize-crypto-in-bid-for-foreign-investment) to create a regulatory framework for Bitcoin and digital assets to attract foreign investment and domestic economic activity. It’s a peculiar shift for a regime that regularly [suspends](https://time.com/6692687/pakistan-election-day-voting-violence-phone-service-disturbances/) the Internet, [censors](https://timesofindia.indiatimes.com/world/pakistan/social-media-platform-x-shutdown-continues-for-eighth-day-in-pakistan/articleshow/107983076.cms) social media, [represses](https://www.bbc.com/news/articles/czx6xvgqe1ko) opposition, and burdens its people with the [highest](https://www.firstpost.com/world/pakistan-tops-asia-in-living-costs-and-inflation-rates-report-reveals-13759245.html) cost of living in Asia. We suspect the plans indicate efforts to control the industry rather than empower individuals. The military-backed regime is also [exploring](https://tribune.com.pk/story/2507061/govt-proposes-changes-to-sbp-act) a Central Bank Digital Currency (CBDC) and tightening [controls](https://timesofindia.indiatimes.com/world/pakistan/amid-net-censorship-pakistan-offers-regulated-vpns/articleshow/115392568.cms) on VPN use, which are hardly the hallmarks of leadership committed to permissionless financial systems. But perhaps it matters little. Grassroots Bitcoin adoption in Pakistan already ranks among the highest in the world, with an estimated [15 to 20 million](https://archive.ph/5ctJq) users turning to digital assets to preserve their savings, circumvent financial controls, and escape the failures of a collapsing fiat system. HRF supported [Bitcoin Pakistan](https://bitcoinpk.org) with a grant to help translate resources into Urdu, a language spoken by 60 million people trapped in this repressive scenario. #### **Russia | Piloting CBDC in Tatarstan to Test Smart Contract Functionality** Russia’s central bank plans to [pilot](https://www.business-gazeta.ru/news/665855) its CBDC, the [digital ruble](https://cbdctracker.hrf.org/currency/russian-federation), in Tatarstan to test smart contract functionality. Specifically, the central bank will experiment with conditional spending, using smart contracts to restrict where and what users can spend money on. If these features are implemented, it will empower the Kremlin with micro-controls over Russians’ spending activity. Officials could program funds to expire, restrict purchases to regime-approved goods, or block transactions at certain locations — leaving users with no financial autonomy or privacy. Those who oppose the Russian dictatorship, such as activists, nonprofits, and dissenters, could be debanked with more ease, their assets frozen or confiscated without recourse. #### **Nicaragua | Government Mandates Public Employees Declare All Assets** In Nicaragua, dictator Daniel Ortega intensified state financial surveillance by mandating all public servants to [disclose](https://havanatimes.org/features/nicaraguan-public-employees-forced-to-declare-their-assets/) information on all personal and family assets. The mandate requires all public employees to declare everything from personal bank accounts, loans, vehicles, and other assets — as well as the assets and accounts of immediate family members. Those who do not comply face the [threat of termination](https://havanatimes.org/features/nicaraguan-public-employees-forced-to-declare-their-assets/). Ironically, despite the law requiring such disclosure, Ortega himself [has not declared](https://www.laprensani.com/2021/04/26/politica/2813926-demandan-a-la-contraloria-demostrar-a-cuanto-asciende-el-patrimonio-de-daniel-ortega-y-rosario-murillo) his assets since 2006. Under the guise of regulatory compliance, this policy is yet another link in the chain tightening state surveillance over Nicaraguan society. Bitcoin adoption continues to grow in this repressed Central American nation. ## BITCOIN AND FREEDOM TECH NEWS #### **Demand Pool | First Stratum V2 Mining Pool Launches** Bitcoin mining could become more decentralized and censorship-resistant with the launch of [Demand Pool](https://www.dmnd.work/upcoming/), the first mining pool to ever implement [Stratum V2](https://stratumprotocol.org/). Stratum V2 is open-source software that allows miners to build their own block templates, enabling more individual mining and less dependence on large and centralized mining pools. This helps maintain Bitcoin’s key features: its decentralized, permissionless, and uncensorable nature. All of which are crucial for human rights defenders and nonprofits bypassing the financial repression and surveillance of authoritarian regimes. Learn more [here](https://www.dmnd.work/upcoming/). #### **Bitcoin Mining | Three Solo Blocks Found** Three separate solo miners mined Bitcoin blocks in the past seven days. This marks the second, third, and fourth solo blocks [mined](https://x.com/SoloSatoshi/status/1903799018896998562) in the past two weeks alone, hinting at a surge in home mining. This promotes greater decentralization within the Bitcoin network because solo miners have little functional ability to censor. In contrast, large mining pools are points of failure that centralized interests can more easily pressure — to the detriment of activists and human rights defenders. The [first](https://x.com/BitcoinNewsCom/status/1903476768733810928) block was mined on March 21 by a miner using a self-hosted FutureBit Apollo machine that earned 3.125 BTC plus fees for processing block [888,737](https://mempool.space/block/00000000000000000000b7070e88525e4064ab36df7cfbe34d785bbc6eb491ea). Just days later, a solo miner with under 1 TH/s of self-hosted hash rate [found](https://x.com/BitcoinNewsCom/status/1903815849535799326) block [888,989](https://mempool.space/block/00000000000000000000a517d87e63ea04c7ec3dd51d20926e82cca5466dccaf), which became just the [third](https://x.com/BitcoinNewsCom/status/1903815849535799326) block ever to be mined using an open-source [Bitaxe](https://bitaxe.org/) device. Most recently, on March 24, a solo miner using a [$300 setup](https://x.com/alanknit/status/1904246256622322122) successfully [mined](https://x.com/pete_rizzo_/status/1904217846441201755) block [889,240](https://mempool.space/block/00000000000000000001deee311732e2ba928d33f0628a5d6320c537751835e3). #### **Krux | Adds Taproot and Miniscript Support** [Krux](https://github.com/selfcustody/krux), open-source software for building your own Bitcoin signing devices (hardware for Bitcoin self-custody), [released](https://github.com/selfcustody/krux/releases/tag/v25.03.0) an update that enhances privacy and flexibility. The update introduces support for Taproot, a past Bitcoin upgrade that improves privacy and security, and Miniscript, a simplified way to create more complex Bitcoin transaction rules. This allows users to manage multi-signature wallets (where more than one private key is required to interact with your Bitcoin) in a more private and flexible way. It also enables spending conditions that are harder to censor and easier to verify. Krux continues to support the struggle for financial freedom and human rights by breaking down barriers to Bitcoin self-custody. HRF has recognized this impact and awarded grants to open-source developers working on Krux to advance this mission. #### **Cashu | Developing Tap-to-Pay Ecash** [Calle](https://x.com/callebtc), the creator of [Cashu](http://cashu.me), an open-source Chaumian ecash protocol for Bitcoin integrated with the Lightning Network, is [developing](https://x.com/callebtc/status/1903079881325400407) a new tap-to-pay feature that enables instant, offline ecash payments via NFC. Ecash functions as a bearer asset, meaning the funds are stored directly on the user’s device. With tap-to-pay, it can be transferred with a single tap (similar to tapping your credit card). More generally, ecash offers fast, private transactions resistant to surveillance and censorship. But for activists and dissenters, this particular advancement makes private and permissionless payments more accessible and user-friendly. This development will be worth following closely. Watch a demo [here](https://x.com/callebtc/status/1903079881325400407). #### **OpenSats | Announces 10th Wave of Bitcoin Grants** [OpenSats](http://opensats.org), a public nonprofit that supports open-source software and projects, [announced](https://opensats.org/blog/tenth-wave-of-bitcoin-grants) its 10th wave of grants supporting Bitcoin initiatives. This round includes funding for [Stable Channels](https://stablechannels.com/), which enable stabilized Bitcoin-backed balances on the Lightning Network (allowing users to peg Bitcoin to fiat currencies in a self-custodial way) that provide stable, censorship-resistant payments. OpenSats also renewed its support for [Floresta](https://docs.getfloresta.sh/floresta/), a lightweight Bitcoin node (a computer that runs the Bitcoin software). It lowers entry barriers to running Bitcoin, helping make the network more decentralized and censorship-resistant. #### **Bitcoin Policy Institute | Launches Bitcoin Summer Research Program** The [Bitcoin Student Network](https://www.bitcoinstudentsnetwork.org/) (BSN) and the [Bitcoin Policy Institute](https://www.btcpolicy.org/) (BPI) are teaming up to offer students an eight-week research [internship](https://www.btcinternship.org/) this summer. The program is part of BPI’s Research Experiences for Undergraduates (REU) initiative and invites students passionate about the future of money, financial inclusion, and Bitcoin’s civil liberties impacts to conduct hands-on research. Participants will also receive mentorship from BPI researchers. The program runs from June 9 to Aug. 8, 2025, and includes an in-person colloquium in Washington, DC. It is an incredible opportunity for students worldwide, especially those living in oppressive regimes, to get involved with Bitcoin. Applications are open until April 7. Apply [here](https://www.btcinternship.org/). ## RECOMMENDED CONTENT #### **Principles of Bitcoin by Vijay Selvam** “Principles of Bitcoin” by Vijay Selvam is a new book offering a first-principles guide to understanding Bitcoin’s technology, economics, politics, and philosophy. With a foreword by HRF Chief Strategy Officer Alex Gladstein, the book cuts through the noise to explain why Bitcoin stands alone as a tool for individual empowerment and financial freedom. Selvam’s work makes the case for Bitcoin as a once-in-history invention shaping a more decentralized and equitable future. Read it [here](https://www.amazon.com/Principles-Bitcoin-Technology-Economics-Philosophy/dp/023122012X/). #### **Rule Breakers — The True Story of Roya Mahboob** “[Rule Breakers](https://hrf.org/latest/hrf-celebrates-the-release-of-rule-breakers-a-movie-on-afghanistans-roya-mahboob/)” is a new film that tells the true story of Roya Mahboob, Afghanistan’s first female tech CEO, who empowered young girls in Afghanistan with financial literacy, robotics, and financial freedom through Bitcoin. The film recounts Mahboob’s courageous work educating these girls despite huge personal risks under a regime that bans their education. It follows the story of Afghan Dreamers, the country’s first all-girls robotics team, and the obstacles they overcome to compete on the world stage. “Rule Breakers” is a testament to the power of education, innovation, and resilience in the face of oppression. It’s now in theaters, and you can watch the trailer [here](https://www.youtube.com/watch?v=CW_P4zT6i9A&t=2s). *If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).* *Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\ *Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)* *The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*. [**Subscribe to newsletter**](http://financialfreedomreport.org/) [**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Visit our website**](https://hrf.org/programs/financial-freedom/) @ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards. While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts. A report will be prepared within 85 days to recommend which programs to continue or discontinue.
@ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards. While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts. A report will be prepared within 85 days to recommend which programs to continue or discontinue. @ 84b0c46a:417782f5
2025-03-27 23:52:24nostr:nevent1qqsw9v8usvahkqmmc9qavu6g834v09j6e2u2acdua24tk73dqc05xecgkanse
@ 84b0c46a:417782f5
2025-03-27 23:52:24nostr:nevent1qqsw9v8usvahkqmmc9qavu6g834v09j6e2u2acdua24tk73dqc05xecgkanse @ 9e69e420:d12360c2
2025-01-26 01:31:31## Chef's notes # arbitray - test - of - chefs notes ## hedding 2 ## Details - ⏲️ Prep time: 20 - 🍳 Cook time: 1 hour - 🍽️ Servings: 5 ## Ingredients - Test ingredient - 2nd test ingredient ## Directions 1. Bake 2. Cool
@ 9e69e420:d12360c2
2025-01-26 01:31:31## Chef's notes # arbitray - test - of - chefs notes ## hedding 2 ## Details - ⏲️ Prep time: 20 - 🍳 Cook time: 1 hour - 🍽️ Servings: 5 ## Ingredients - Test ingredient - 2nd test ingredient ## Directions 1. Bake 2. Cool @ 401014b3:59d5476b
2025-03-27 13:48:10Alright, baseball junkies, it’s March 27, 2025, and we’re diving into the crystal ball to predict the 2025 MLB season—straight through to the World Series champ! Spring Training’s wrapping up, Opening Day’s here, and the league’s loaded with talent, drama, and some sneaky contenders ready to shake things up. I’m breaking down each playoff team’s path, their strengths, weaknesses, and who’s got the juice to hoist the trophy in October. This ain’t some cookie-cutter chalk pick—let’s get gritty, let’s get bold, and let’s see who’s got the stones to win it all. Strap in, fam—here we go! --- American League Playoff Teams: The AL Beast Mode **New York Yankees**\ The Yankees are back, and they’re pissed after last year’s World Series loss to the Dodgers. Aaron Judge is coming off another MVP-caliber season (let’s say .310, 55 HRs, 130 RBIs), and Juan Soto’s bat (projected .290, 40 HRs) gives them a lethal 1-2 punch. Gerrit Cole anchors a rotation that’s top-5 in ERA (around 3.40), but the bullpen’s a question mark—closer Clay Holmes blew 13 saves in 2024, and they haven’t fixed that yet. They’ll win the AL East (95-67), but their postseason hinges on late-inning reliability.\ **Prediction**: ALCS run, but they fall short if the pen implodes. **Houston Astros**\ The Astros are perennial AL West champs (projected 92-70), even with a slightly aging core. Jose Altuve (.300, 20 HRs) and Yordan Alvarez (.295, 35 HRs) keep the offense humming, and a rotation led by Framber Valdez (3.20 ERA) and Hunter Brown (3.50 ERA) is solid. Their bullpen, with Josh Hader (1.28 ERA in 2024), is lights-out. But injuries to key arms like Justin Verlander (aging at 42) could bite them.\ **Prediction**: ALDS exit—they’re good, but not great this year. **Cleveland Guardians**\ The Guardians sneak into the playoffs as the AL Central champs (88-74). Jose Ramirez (.280, 35 HRs, 110 RBIs) is a one-man wrecking crew, and their rotation—Shane Bieber (3.00 ERA, if healthy) and Triston McKenzie (3.60 ERA)—keeps them in games. But their offense outside Ramirez is thin (team OPS around .720), and the bullpen’s inconsistent (4.00 ERA).\ **Prediction**: Wild Card exit—they’re scrappy but lack firepower. **Tampa Bay Rays (Wild Card)**\ The Rays grab a Wild Card spot (90-72) with their usual mix of grit and analytics. Yandy Diaz (.290, 15 HRs) and Randy Arozarena (.270, 25 HRs) lead a balanced offense, while Shane McClanahan (3.10 ERA) and Zach Eflin (3.40 ERA) anchor the rotation. Their bullpen (top-10 in ERA at 3.50) is a strength, but depth issues (injuries to key prospects) could hurt.\ **Prediction**: ALDS run—they’re sneaky dangerous. **Seattle Mariners (Wild Card)**\ The Mariners finally break through as a Wild Card (89-73), as predicted by some fans on X. Julio Rodriguez (.285, 30 HRs) and Cal Raleigh (.250, 35 HRs) power the offense, and a rotation of Luis Castillo (3.20 ERA), Logan Gilbert (3.30 ERA), and George Kirby (3.40 ERA) is the best in the AL (team ERA around 3.20). Their offense (bottom-10 in runs scored) is the Achilles’ heel.\ **Prediction**: ALCS run—they’re a pitcher’s dream, but the bats hold ‘em back. **Baltimore Orioles (Wild Card)**\ The Orioles snag a Wild Card (87-75), but some fans on X call them a “surprise disappointment.” Gunnar Henderson (.280, 35 HRs) and Adley Rutschman (.270, 20 HRs) lead a young core, but the rotation—Corbin Burnes (3.00 ERA) and Grayson Rodriguez (3.70 ERA)—lacks depth after losing Kyle Bradish to injury. The bullpen (4.20 ERA) is shaky.\ **Prediction**: Wild Card exit—too many holes this year. --- **National League Playoff Teams: The NL Wild West** **Los Angeles Dodgers**\ The Dodgers are the NL West juggernaut (98-64), and some fans on X are already calling them World Series champs. Shohei Ohtani (.300, 50 HRs, 120 RBIs) is the NL MVP favorite, Mookie Betts (.290, 30 HRs) is elite, and Freddie Freeman (.310, 25 HRs) is steady. The rotation—Tyler Glasnow (3.10 ERA), Yoshinobu Yamamoto (3.30 ERA), and Walker Buehler (3.50 ERA)—is deep, and the bullpen (3.40 ERA) is solid. No weaknesses here.\ **Prediction**: World Series bound—they’re a machine. **Philadelphia Phillies**\ The Phillies win the NL East (94-68) with a balanced attack. Bryce Harper (.290, 30 HRs) and Kyle Schwarber (.250, 40 HRs) mash, while Trea Turner (.300, 20 HRs) adds speed. The rotation—Zack Wheeler (3.00 ERA), Aaron Nola (3.40 ERA), and Ranger Suarez (3.60 ERA)—is top-tier, and the bullpen (3.50 ERA) is reliable. They’re built for October.\ Prediction: NLCS run—they’re legit contenders. **Milwaukee Brewers**\ The Brewers take the NL Central (90-72) with a scrappy squad. Willy Adames (.270, 30 HRs) and William Contreras (.280, 20 HRs) lead the offense, while Freddy Peralta (3.30 ERA) and Brandon Woodruff (3.50 ERA, if healthy) anchor the rotation. Their bullpen (top-5 in ERA at 3.30) is a strength, but the offense (middle-of-the-pack in runs) can stall.\ **Prediction**: NLDS exit—not enough firepower. **Atlanta Braves (Wild Card)**\ The Braves grab a Wild Card (91-71) despite injuries. Ronald Acuna Jr. (.290, 35 HRs) and Matt Olson (.270, 40 HRs) power the lineup, but the rotation—Chris Sale (3.20 ERA) and Max Fried (3.40 ERA)—is thin after Spencer Strider’s injury. The bullpen (3.60 ERA) is solid, but depth is a concern.\ **Prediction**: NLDS run—they’re talented but banged up. **San Diego Padres (Wild Card)**\ The Padres snag a Wild Card (89-73) with a balanced attack. Fernando Tatis Jr. (.280, 35 HRs) and Manny Machado (.270, 30 HRs) lead the offense, while Dylan Cease (3.30 ERA) and Yu Darvish (3.50 ERA) anchor the rotation. The bullpen (3.70 ERA) is decent, but they lack a true closer.\ **Prediction**: Wild Card exit—not enough late-game juice. **New York Mets (Wild Card)**\ The Mets sneak in as a Wild Card (88-74) with a breakout year. Francisco Lindor (.280, 30 HRs) and Pete Alonso (.260, 35 HRs) mash, while Kodai Senga (3.20 ERA) and Luis Severino (3.60 ERA) lead the rotation. The bullpen (4.00 ERA) is a weak spot, but their offense (top-10 in runs) keeps ‘em alive.\ **Prediction**: NLDS run—they’re scrappy but flawed. --- **Playoff Breakdown: The Road to the World Series** **AL Wild Card**: - Rays over Guardians - Mariners over Orioles - Yankees over Rays - Mariners over Astros - Yankees vs. Mariners → Yankees (4-2)\ Judge and Soto go off, and the Mariners’ bats can’t keep up with New York’s firepower. Cole’s ace stuff seals it. **NL Wild Card**: - Braves over Padres - Mets over Brewers - Dodgers over Mets - Phillies over Braves - Dodgers vs. Phillies → Dodgers (4-3)\ Ohtani’s heroics (think a 3-HR game) and the Dodgers’ depth outlast Philly’s grit in a seven-game classic. --- **World Series**: Yankees vs. Dodgers Here we go—a rematch of last year’s epic clash! The Yankees are hungry for revenge, with Judge and Soto swinging for the fences (combined 5 HRs in the series). Cole (Game 1 gem, 7 IP, 2 ER) and Rodon (Game 5 win) keep it close, but the Dodgers’ lineup is relentless—Ohtani (.350, 2 HRs), Betts (.320, 3 doubles), and Freeman (.300, 8 RBIs) overwhelm New York’s shaky bullpen. Glasnow and Yamamoto each win a start, and the Dodgers’ pen (2.50 ERA in the series) slams the door. Dodgers win in 6—Ohtani’s walk-off in Game 6 seals it. --- **The Final Buzzer** The Dodgers are my 2025 World Series champs—they’ve got the star power, depth, and clutch factor to repeat. The Yankees make a valiant run, but their bullpen woes bite ‘em again. Hit me on X if you disagree, but this is my October gospel—let’s see who’s standing when the dust settles! Play ball, degenerates!
@ 401014b3:59d5476b
2025-03-27 13:48:10Alright, baseball junkies, it’s March 27, 2025, and we’re diving into the crystal ball to predict the 2025 MLB season—straight through to the World Series champ! Spring Training’s wrapping up, Opening Day’s here, and the league’s loaded with talent, drama, and some sneaky contenders ready to shake things up. I’m breaking down each playoff team’s path, their strengths, weaknesses, and who’s got the juice to hoist the trophy in October. This ain’t some cookie-cutter chalk pick—let’s get gritty, let’s get bold, and let’s see who’s got the stones to win it all. Strap in, fam—here we go! --- American League Playoff Teams: The AL Beast Mode **New York Yankees**\ The Yankees are back, and they’re pissed after last year’s World Series loss to the Dodgers. Aaron Judge is coming off another MVP-caliber season (let’s say .310, 55 HRs, 130 RBIs), and Juan Soto’s bat (projected .290, 40 HRs) gives them a lethal 1-2 punch. Gerrit Cole anchors a rotation that’s top-5 in ERA (around 3.40), but the bullpen’s a question mark—closer Clay Holmes blew 13 saves in 2024, and they haven’t fixed that yet. They’ll win the AL East (95-67), but their postseason hinges on late-inning reliability.\ **Prediction**: ALCS run, but they fall short if the pen implodes. **Houston Astros**\ The Astros are perennial AL West champs (projected 92-70), even with a slightly aging core. Jose Altuve (.300, 20 HRs) and Yordan Alvarez (.295, 35 HRs) keep the offense humming, and a rotation led by Framber Valdez (3.20 ERA) and Hunter Brown (3.50 ERA) is solid. Their bullpen, with Josh Hader (1.28 ERA in 2024), is lights-out. But injuries to key arms like Justin Verlander (aging at 42) could bite them.\ **Prediction**: ALDS exit—they’re good, but not great this year. **Cleveland Guardians**\ The Guardians sneak into the playoffs as the AL Central champs (88-74). Jose Ramirez (.280, 35 HRs, 110 RBIs) is a one-man wrecking crew, and their rotation—Shane Bieber (3.00 ERA, if healthy) and Triston McKenzie (3.60 ERA)—keeps them in games. But their offense outside Ramirez is thin (team OPS around .720), and the bullpen’s inconsistent (4.00 ERA).\ **Prediction**: Wild Card exit—they’re scrappy but lack firepower. **Tampa Bay Rays (Wild Card)**\ The Rays grab a Wild Card spot (90-72) with their usual mix of grit and analytics. Yandy Diaz (.290, 15 HRs) and Randy Arozarena (.270, 25 HRs) lead a balanced offense, while Shane McClanahan (3.10 ERA) and Zach Eflin (3.40 ERA) anchor the rotation. Their bullpen (top-10 in ERA at 3.50) is a strength, but depth issues (injuries to key prospects) could hurt.\ **Prediction**: ALDS run—they’re sneaky dangerous. **Seattle Mariners (Wild Card)**\ The Mariners finally break through as a Wild Card (89-73), as predicted by some fans on X. Julio Rodriguez (.285, 30 HRs) and Cal Raleigh (.250, 35 HRs) power the offense, and a rotation of Luis Castillo (3.20 ERA), Logan Gilbert (3.30 ERA), and George Kirby (3.40 ERA) is the best in the AL (team ERA around 3.20). Their offense (bottom-10 in runs scored) is the Achilles’ heel.\ **Prediction**: ALCS run—they’re a pitcher’s dream, but the bats hold ‘em back. **Baltimore Orioles (Wild Card)**\ The Orioles snag a Wild Card (87-75), but some fans on X call them a “surprise disappointment.” Gunnar Henderson (.280, 35 HRs) and Adley Rutschman (.270, 20 HRs) lead a young core, but the rotation—Corbin Burnes (3.00 ERA) and Grayson Rodriguez (3.70 ERA)—lacks depth after losing Kyle Bradish to injury. The bullpen (4.20 ERA) is shaky.\ **Prediction**: Wild Card exit—too many holes this year. --- **National League Playoff Teams: The NL Wild West** **Los Angeles Dodgers**\ The Dodgers are the NL West juggernaut (98-64), and some fans on X are already calling them World Series champs. Shohei Ohtani (.300, 50 HRs, 120 RBIs) is the NL MVP favorite, Mookie Betts (.290, 30 HRs) is elite, and Freddie Freeman (.310, 25 HRs) is steady. The rotation—Tyler Glasnow (3.10 ERA), Yoshinobu Yamamoto (3.30 ERA), and Walker Buehler (3.50 ERA)—is deep, and the bullpen (3.40 ERA) is solid. No weaknesses here.\ **Prediction**: World Series bound—they’re a machine. **Philadelphia Phillies**\ The Phillies win the NL East (94-68) with a balanced attack. Bryce Harper (.290, 30 HRs) and Kyle Schwarber (.250, 40 HRs) mash, while Trea Turner (.300, 20 HRs) adds speed. The rotation—Zack Wheeler (3.00 ERA), Aaron Nola (3.40 ERA), and Ranger Suarez (3.60 ERA)—is top-tier, and the bullpen (3.50 ERA) is reliable. They’re built for October.\ Prediction: NLCS run—they’re legit contenders. **Milwaukee Brewers**\ The Brewers take the NL Central (90-72) with a scrappy squad. Willy Adames (.270, 30 HRs) and William Contreras (.280, 20 HRs) lead the offense, while Freddy Peralta (3.30 ERA) and Brandon Woodruff (3.50 ERA, if healthy) anchor the rotation. Their bullpen (top-5 in ERA at 3.30) is a strength, but the offense (middle-of-the-pack in runs) can stall.\ **Prediction**: NLDS exit—not enough firepower. **Atlanta Braves (Wild Card)**\ The Braves grab a Wild Card (91-71) despite injuries. Ronald Acuna Jr. (.290, 35 HRs) and Matt Olson (.270, 40 HRs) power the lineup, but the rotation—Chris Sale (3.20 ERA) and Max Fried (3.40 ERA)—is thin after Spencer Strider’s injury. The bullpen (3.60 ERA) is solid, but depth is a concern.\ **Prediction**: NLDS run—they’re talented but banged up. **San Diego Padres (Wild Card)**\ The Padres snag a Wild Card (89-73) with a balanced attack. Fernando Tatis Jr. (.280, 35 HRs) and Manny Machado (.270, 30 HRs) lead the offense, while Dylan Cease (3.30 ERA) and Yu Darvish (3.50 ERA) anchor the rotation. The bullpen (3.70 ERA) is decent, but they lack a true closer.\ **Prediction**: Wild Card exit—not enough late-game juice. **New York Mets (Wild Card)**\ The Mets sneak in as a Wild Card (88-74) with a breakout year. Francisco Lindor (.280, 30 HRs) and Pete Alonso (.260, 35 HRs) mash, while Kodai Senga (3.20 ERA) and Luis Severino (3.60 ERA) lead the rotation. The bullpen (4.00 ERA) is a weak spot, but their offense (top-10 in runs) keeps ‘em alive.\ **Prediction**: NLDS run—they’re scrappy but flawed. --- **Playoff Breakdown: The Road to the World Series** **AL Wild Card**: - Rays over Guardians - Mariners over Orioles - Yankees over Rays - Mariners over Astros - Yankees vs. Mariners → Yankees (4-2)\ Judge and Soto go off, and the Mariners’ bats can’t keep up with New York’s firepower. Cole’s ace stuff seals it. **NL Wild Card**: - Braves over Padres - Mets over Brewers - Dodgers over Mets - Phillies over Braves - Dodgers vs. Phillies → Dodgers (4-3)\ Ohtani’s heroics (think a 3-HR game) and the Dodgers’ depth outlast Philly’s grit in a seven-game classic. --- **World Series**: Yankees vs. Dodgers Here we go—a rematch of last year’s epic clash! The Yankees are hungry for revenge, with Judge and Soto swinging for the fences (combined 5 HRs in the series). Cole (Game 1 gem, 7 IP, 2 ER) and Rodon (Game 5 win) keep it close, but the Dodgers’ lineup is relentless—Ohtani (.350, 2 HRs), Betts (.320, 3 doubles), and Freeman (.300, 8 RBIs) overwhelm New York’s shaky bullpen. Glasnow and Yamamoto each win a start, and the Dodgers’ pen (2.50 ERA in the series) slams the door. Dodgers win in 6—Ohtani’s walk-off in Game 6 seals it. --- **The Final Buzzer** The Dodgers are my 2025 World Series champs—they’ve got the star power, depth, and clutch factor to repeat. The Yankees make a valiant run, but their bullpen woes bite ‘em again. Hit me on X if you disagree, but this is my October gospel—let’s see who’s standing when the dust settles! Play ball, degenerates! @ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.” The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China. [Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html)
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.” The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China. [Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html) @ 9dd283b1:cf9b6beb
2025-03-27 12:22:58Can someone please explain to me how this new STRF thing works? Cause I'm getting FTX / BlockFI vibes here. 18% Yield, no risk investment, bond killer, etc... Look at this post for example - https://x.com/AdamBLiv/status/1905106498398621846 originally posted at https://stacker.news/items/926635
@ 9dd283b1:cf9b6beb
2025-03-27 12:22:58Can someone please explain to me how this new STRF thing works? Cause I'm getting FTX / BlockFI vibes here. 18% Yield, no risk investment, bond killer, etc... Look at this post for example - https://x.com/AdamBLiv/status/1905106498398621846 originally posted at https://stacker.news/items/926635 @ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**.
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**. @ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications. @ 878dff7c:037d18bc
2025-03-27 22:37:47## Australian Prime Minister Calls Election Amid Economic Challenges ### Summary: Prime Minister Anthony Albanese has announced that Australia will hold federal elections on May 3. The election comes at a time when the nation faces significant economic uncertainties, including high inflation rates, elevated interest rates, and a housing crisis. Albanese's Labor government emphasizes plans for economic recovery, while opposition leader Peter Dutton's Coalition proposes public sector cuts and temporary fuel duty reductions. Both leaders are striving to address voter concerns over the cost-of-living crisis and economic stability. Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/28/australian-prime-minister-calls-election-amid-shadow-of-trump-and-cost-of-living-crisis" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://apnews.com/article/b73f3a4bb9cbbc300cd797f34d4cc23b" target="_blank">AP News - March 28, 2025</a> ## Bill Gates Predicts AI to Replace Doctors and Teachers Within 10 Years ### Summary: Bill Gates forecasts that artificial intelligence (AI) will significantly reduce human involvement in fields like medicine and education over the next decade. He envisions AI providing free, high-quality medical advice and tutoring, thereby democratizing access to these services. While acknowledging concerns about misinformation and rapid AI development, Gates remains optimistic about AI's potential to drive breakthroughs in healthcare, climate solutions, and education. He encourages young people to engage in AI-centric ventures, highlighting its transformative impact on industries and society. Sources: <a href="https://nypost.com/2025/03/27/business/bill-gates-said-ai-will-replace-doctors-teachers-within-10-years/" target="_blank">New York Post - March 27, 2025</a> ## AI Poised to Transform Legal Profession by 2035 ### Summary: Artificial general intelligence (AGI) is projected to render traditional lawyer roles obsolete by 2035. AI systems are advancing to perform complex legal tasks such as advising, negotiating, and dispute resolution. While some legal professionals argue that AI cannot replicate human judgment and creativity, the emphasis on efficiency and outcomes suggests a future where AGI dominates legal services with minimal human intervention. Legal industry leaders are urged to prepare for this disruptive shift. Sources: <a href="https://www.thetimes.co.uk/article/artificial-intelligence-could-replace-traditional-lawyers-by-2035-xwz2j0t2k" target="_blank">The Times - March 28, 2025</a> ## Queensland Faces Severe Flooding as Inland 'Sea' Emerges ### Summary: Severe weather conditions, including heavy rain and potential flash flooding, have impacted central and southern inland Queensland, with significant rainfall between 200 to 400mm recorded. Towns like Adavale are inundated, prompting emergency warnings and the establishment of refuges for affected residents. Authorities urge residents to stay updated and follow safety advice. Sources: <a href="https://www.news.com.au/technology/environment/qld-in-for-another-week-of-rain-amid-severe-weather-and-flood-warnings/news-story/d5e7ea97591060bb58c1d6ed54489209" target="_blank">News.com.au - 28 March 2025</a>, <a href="https://www.couriermail.com.au/news/queensland/weather/qld-weather-warnings-of-possible-200mm-deluge-major-flooding-as-communities-cut-off/news-story/457a21a269a535b28c52f919f8bc7bed" target="_blank">The Courier-Mail - 28 March 2025</a>, <a href="https://www.theguardian.com/australia-news/2025/mar/27/queensland-flood-warnings-rain-weather-forecast-bom" target="_blank">The Guardian - 28 March 2025</a> ## Opposition Leader Peter Dutton Outlines Election Platform ### Summary: Opposition Leader Peter Dutton has presented his vision for Australia, promising significant funding for defense and proposing a new gas reservation policy aimed at lowering electricity prices. The Coalition's plans include fast-tracking gas projects, investing $1 billion in gas infrastructure, reducing public service staffing by 41,000 while preserving essential services, and decreasing permanent migration intake by 25% to increase housing supply. Dutton also announced reinstating subsidized mental health visits and new spending on youth mental health. Sources: <a href="https://www.theguardian.com/australia-news/live/2025/mar/27/australia-politics-live-fuel-excise-cost-of-living-tax-cuts-salmon-election-anthony-albanese-peter-dutton-ntwnfb" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://www.theaustralian.com.au/nation/who-is-peter-dutton-the-liberal-leader-and-his-top-team-for-the-2025-federal-election-explained/news-story/9d046731e51ed32dd4795c3820365c3a" target="_blank">The Australian - March 28, 2025</a> ## Opposition Leader Promises Significant Defense Funding ### Summary: Peter Dutton, in his budget reply, promised significant funding for defense and a new gas reservation policy for the east coast, aimed at lowering electricity prices. The Coalition also plans to fast-track gas projects and invest $1 billion in gas infrastructure. Dutton announced slashing 41,000 public service workers while preserving essential services, and criticized Labor's gas policy. Immigration plans include reducing the permanent migration intake by 25% to increase housing supply. Dutton also proposed reinstating subsidized mental health visits and new spending on youth mental health. Labor, represented by Jason Clare, argued that the Coalition's policies, including the nuclear plan, are costly and criticized the tax implications under Dutton. Sources: <a href="https://www.theguardian.com/australia-news/live/2025/mar/27/australia-politics-live-fuel-excise-cost-of-living-tax-cuts-salmon-election-anthony-albanese-peter-dutton-ntwnfb" target="_blank">The Guardian - March 28, 2025</a> ## Israeli Politicians Urge Australian MPs to Abandon Two-State Solution Policy ### Summary: A group of Israeli Knesset members has called on Australian MPs to drop support for a two-state solution between Israel and Palestine. The letter, presented during an event at Australia's Parliament House, argues that establishing a Palestinian state could lead to Israel's destruction, citing recent conflicts as evidence. This appeal reflects deep skepticism within Israeli political circles about the viability of the peace process. Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/27/israeli-politicians-sign-letter-urging-coalition-to-dump-two-state-policy-ntwnfb" target="_blank">The Guardian - March 27, 2025</a> ## Stephen Jones Criticizes U.S. Protectionist Trade Policies ### Summary: Outgoing Financial Services Minister Stephen Jones has criticized recent U.S. protectionist measures, including a 25% tariff on global car imports and Australian aluminum and steel. Jones emphasized the importance of open trade and a rules-based order for Australia's economic growth, highlighting concerns about the negative impact on Australian industries and the broader economy. Sources: <a href="https://www.theaustralian.com.au/business/outgoing-financial-services-minister-jones-takes-swipe-at-us-protectionism/news-story/0c1fc10f2b57a8c6809f4dec333cc547" target="_blank">The Australian - March 28, 2025</a> ## New Anti-Smoking Warnings Criticized for Potential Backfire ### Summary: Starting April 1, Australia will implement legislation requiring health warnings on individual cigarettes, with messages like "causes 16 cancers" and "poisons in every puff." However, social media users have mocked these warnings, suggesting they might make smoking appear "cool" and collectible rather than serving as deterrents. Despite the criticism, health officials assert that such on-product messages are part of a broader strategy to reduce smoking rates, citing positive results from similar approaches in Canada. The initiative aims to decrease the annual tobacco-related deaths in Australia, which currently exceed 24,000. Sources: <a href="https://www.couriermail.com.au/news/queensland/poisons-in-every-puff-new-antismoking-messaging-slammed/news-story/2f77ecd3a943d3139539c2610af3400c" target="_blank">The Courier-Mail - March 28, 2025</a> ## 'Joe's Law' Introduced to Ban Future Hospital Privatization in NSW ### Summary: The New South Wales government has announced "Joe's Law," a reform to prohibit the future privatization of acute public hospitals. This decision follows the death of two-year-old Joe Massa, who suffered a cardiac arrest and died after a prolonged wait in the emergency department of the privately managed Northern Beaches Hospital. The legislation aims to ensure that critical public services like emergency and surgical care remain under public control, preventing privatization. Additionally, a parliamentary inquiry into the hospital's services and a coronial investigation into Joe's death have been initiated. Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/27/joes-law-to-ban-future-hospital-privatisation-in-nsw" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://www.news.com.au/lifestyle/health/health-problems/major-changes-coming-to-nsw-hospitals-after-death-of-twoyearold-joe-massa/news-story/fb93b0f0a9f2673a01eddfe89031fcb9" target="_blank">news.com.au - March 28, 2025</a>, <a href="https://www.dailytelegraph.com.au/newslocal/manly-daily/northern-beaches-hospital-probe-begins-into-safety-and-quality-of-health-services/news-story/72ea15981b26339eea92a15b4e9c498a" target="_blank">The Daily Telegraph - March 28, 2025</a> ## Determined Daisy Marks Major Milestone ### Summary: Daisy, born with a rare chromosomal disorder, has achieved a significant health milestone by having her tracheostomy removed and is now learning to communicate using sign language. Her inspiring journey is one of several highlighted by the Good Friday Appeal, which supports the Royal Children's Hospital (RCH). The 2025 Appeal aims to fund further programs, research, and vital equipment at RCH, with contributions from events like North Melbourne's SuperClash fundraiser bringing joy to young patients ahead of the marquee match. Sources: <a href="https://www.heraldsun.com.au/news/good-friday-appeal/good-friday-appeal-2025-star-roos-launch-superclash-fundraiser-with-special-visit/news-story/75fe74c62e52efb611436e9162c4d4d6" target="_blank">Herald Sun - March 27, 2025</a> ## Indonesia Seeks to Calm Investors After Stocks, Rupiah Slide ### Summary: Indonesian officials are working to reassure investors following significant declines in the stock market and the rupiah. President Prabowo Subianto plans to meet with investors after the Eid-al-Fitr holiday to address concerns about government policies and fiscal stability. The rupiah recently hit its weakest level since 1998, and the main stock index fell 7.1%. Analysts attribute the selloff to poor communication on fiscal policies. The government aims to maintain the fiscal deficit within 3% of GDP and avoid political interference in its sovereign wealth fund. Efforts are also underway to deregulate the manufacturing sector and provide credits to labor-intensive industries. Bank Indonesia is prepared to intervene to stabilize the currency, emphasizing the economy's underlying strength. The rupiah has shown signs of recovery, and measures include easing buyback processes and offering more attractive investment instruments. Markets will monitor the mid-year budget update in July for signs of revenue shortfalls and spending adjustments. Sources: <a href="https://www.reuters.com/markets/asia/indonesia-seeks-calm-investors-after-stocks-rupiah-slide-2025-03-27/" target="_blank">Reuters - 28 March 2025</a> ## Beijing to Escalate Taiwan Coercion in 2025 ### Summary: A report by the Office of the Director of National Intelligence highlights growing cooperation among China, Russia, Iran, and North Korea, posing significant challenges to U.S. global power. Closer ties between China and Russia, in particular, could present enduring risks to U.S. interests. The document points out China's military threat to the U.S., emphasizing its grey zone tactics and potential for stronger coercive action against Taiwan by 2025. The Ukraine conflict and its ongoing strategic risks, including nuclear escalation, are noted, as well as China's ambition to dominate AI by 2030 and its control over critical materials. The report also mentions the volatile Middle East, with Iran's expanding ties despite challenges, and North Korea's commitment to enhancing its nuclear capabilities. Additionally, threats from foreign drug actors and Islamic extremists, including Al-Qa'ida and a potential ISIS resurgence, are highlighted. Sources: <a href="https://www.theaustralian.com.au/nation/politics/us-threat-assessment-sounds-the-alarm-on-china/news-story/cb582794c7a653b11cce8d3e61fc564b" target="_blank">The Australian - 28 March 2025</a> ## Fire Ant Infestation Could Cost Australian Households Over $1 Billion Annually ### Summary: New modeling predicts that if fire ants become established in Australia, households may incur approximately $1.03 billion annually in control measures and related health and veterinary expenses. The invasive species could lead to up to 570,800 medical consultations and around 30 deaths each year due to stings. The electorates of Durack, O'Connor, Mayo, and Blair are projected to be most affected. Experts emphasize the need for increased federal funding for comprehensive eradication programs to prevent environmental damage and significant economic burdens on households. Sources: <a href="https://www.theguardian.com/environment/2025/mar/28/australia-fire-ants-queensland-cost-eradication-pesticides" target="_blank">The Guardian - March 28, 2025</a> ## The Great Monetary Divide – Epi-3643 ### Summary: In this episode, host Jack Spirko discusses the rapid changes occurring in the global financial landscape. He highlights the European Union's announcement, led by European Central Bank President Christine Lagarde, to implement a Central Bank Digital Currency (CBDC) across member states by the upcoming fall. Spirko expresses concern that such a move could pave the way for a social credit system similar to China's, potentially leading to increased governmental control over individual financial activities. Conversely, the episode explores developments in the United States, where the government is reportedly adopting Bitcoin as an economic reserve and integrating stablecoins into the financial system. Spirko suggests that these actions may indicate a divergent path from other global economies, potentially fostering a more decentralized financial environment. Throughout the episode, Spirko emphasizes the importance of understanding these shifts and encourages listeners to consider how such changes might impact personal financial sovereignty and the broader economic landscape. Please note that this summary is based on limited information available from the episode description and may not capture all the nuances discussed in the full podcast. Sources: <a href="https://open.spotify.com/episode/5lUuCzX3wHfWdX6y6QtJGw" target="_blank">The Survival Podcast - 28 March 2025</a>, <a href="https://podcasts.apple.com/us/podcast/the-great-monetary-divide-epi-3643/id284148583?i=1000700006108&l=es-MX" target="_blank">Apple Podcasts - 28 March 2025</a>
@ 878dff7c:037d18bc
2025-03-27 22:37:47## Australian Prime Minister Calls Election Amid Economic Challenges ### Summary: Prime Minister Anthony Albanese has announced that Australia will hold federal elections on May 3. The election comes at a time when the nation faces significant economic uncertainties, including high inflation rates, elevated interest rates, and a housing crisis. Albanese's Labor government emphasizes plans for economic recovery, while opposition leader Peter Dutton's Coalition proposes public sector cuts and temporary fuel duty reductions. Both leaders are striving to address voter concerns over the cost-of-living crisis and economic stability. Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/28/australian-prime-minister-calls-election-amid-shadow-of-trump-and-cost-of-living-crisis" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://apnews.com/article/b73f3a4bb9cbbc300cd797f34d4cc23b" target="_blank">AP News - March 28, 2025</a> ## Bill Gates Predicts AI to Replace Doctors and Teachers Within 10 Years ### Summary: Bill Gates forecasts that artificial intelligence (AI) will significantly reduce human involvement in fields like medicine and education over the next decade. He envisions AI providing free, high-quality medical advice and tutoring, thereby democratizing access to these services. While acknowledging concerns about misinformation and rapid AI development, Gates remains optimistic about AI's potential to drive breakthroughs in healthcare, climate solutions, and education. He encourages young people to engage in AI-centric ventures, highlighting its transformative impact on industries and society. Sources: <a href="https://nypost.com/2025/03/27/business/bill-gates-said-ai-will-replace-doctors-teachers-within-10-years/" target="_blank">New York Post - March 27, 2025</a> ## AI Poised to Transform Legal Profession by 2035 ### Summary: Artificial general intelligence (AGI) is projected to render traditional lawyer roles obsolete by 2035. AI systems are advancing to perform complex legal tasks such as advising, negotiating, and dispute resolution. While some legal professionals argue that AI cannot replicate human judgment and creativity, the emphasis on efficiency and outcomes suggests a future where AGI dominates legal services with minimal human intervention. Legal industry leaders are urged to prepare for this disruptive shift. Sources: <a href="https://www.thetimes.co.uk/article/artificial-intelligence-could-replace-traditional-lawyers-by-2035-xwz2j0t2k" target="_blank">The Times - March 28, 2025</a> ## Queensland Faces Severe Flooding as Inland 'Sea' Emerges ### Summary: Severe weather conditions, including heavy rain and potential flash flooding, have impacted central and southern inland Queensland, with significant rainfall between 200 to 400mm recorded. Towns like Adavale are inundated, prompting emergency warnings and the establishment of refuges for affected residents. Authorities urge residents to stay updated and follow safety advice. Sources: <a href="https://www.news.com.au/technology/environment/qld-in-for-another-week-of-rain-amid-severe-weather-and-flood-warnings/news-story/d5e7ea97591060bb58c1d6ed54489209" target="_blank">News.com.au - 28 March 2025</a>, <a href="https://www.couriermail.com.au/news/queensland/weather/qld-weather-warnings-of-possible-200mm-deluge-major-flooding-as-communities-cut-off/news-story/457a21a269a535b28c52f919f8bc7bed" target="_blank">The Courier-Mail - 28 March 2025</a>, <a href="https://www.theguardian.com/australia-news/2025/mar/27/queensland-flood-warnings-rain-weather-forecast-bom" target="_blank">The Guardian - 28 March 2025</a> ## Opposition Leader Peter Dutton Outlines Election Platform ### Summary: Opposition Leader Peter Dutton has presented his vision for Australia, promising significant funding for defense and proposing a new gas reservation policy aimed at lowering electricity prices. The Coalition's plans include fast-tracking gas projects, investing $1 billion in gas infrastructure, reducing public service staffing by 41,000 while preserving essential services, and decreasing permanent migration intake by 25% to increase housing supply. Dutton also announced reinstating subsidized mental health visits and new spending on youth mental health. Sources: <a href="https://www.theguardian.com/australia-news/live/2025/mar/27/australia-politics-live-fuel-excise-cost-of-living-tax-cuts-salmon-election-anthony-albanese-peter-dutton-ntwnfb" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://www.theaustralian.com.au/nation/who-is-peter-dutton-the-liberal-leader-and-his-top-team-for-the-2025-federal-election-explained/news-story/9d046731e51ed32dd4795c3820365c3a" target="_blank">The Australian - March 28, 2025</a> ## Opposition Leader Promises Significant Defense Funding ### Summary: Peter Dutton, in his budget reply, promised significant funding for defense and a new gas reservation policy for the east coast, aimed at lowering electricity prices. The Coalition also plans to fast-track gas projects and invest $1 billion in gas infrastructure. Dutton announced slashing 41,000 public service workers while preserving essential services, and criticized Labor's gas policy. Immigration plans include reducing the permanent migration intake by 25% to increase housing supply. Dutton also proposed reinstating subsidized mental health visits and new spending on youth mental health. Labor, represented by Jason Clare, argued that the Coalition's policies, including the nuclear plan, are costly and criticized the tax implications under Dutton. Sources: <a href="https://www.theguardian.com/australia-news/live/2025/mar/27/australia-politics-live-fuel-excise-cost-of-living-tax-cuts-salmon-election-anthony-albanese-peter-dutton-ntwnfb" target="_blank">The Guardian - March 28, 2025</a> ## Israeli Politicians Urge Australian MPs to Abandon Two-State Solution Policy ### Summary: A group of Israeli Knesset members has called on Australian MPs to drop support for a two-state solution between Israel and Palestine. The letter, presented during an event at Australia's Parliament House, argues that establishing a Palestinian state could lead to Israel's destruction, citing recent conflicts as evidence. This appeal reflects deep skepticism within Israeli political circles about the viability of the peace process. Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/27/israeli-politicians-sign-letter-urging-coalition-to-dump-two-state-policy-ntwnfb" target="_blank">The Guardian - March 27, 2025</a> ## Stephen Jones Criticizes U.S. Protectionist Trade Policies ### Summary: Outgoing Financial Services Minister Stephen Jones has criticized recent U.S. protectionist measures, including a 25% tariff on global car imports and Australian aluminum and steel. Jones emphasized the importance of open trade and a rules-based order for Australia's economic growth, highlighting concerns about the negative impact on Australian industries and the broader economy. Sources: <a href="https://www.theaustralian.com.au/business/outgoing-financial-services-minister-jones-takes-swipe-at-us-protectionism/news-story/0c1fc10f2b57a8c6809f4dec333cc547" target="_blank">The Australian - March 28, 2025</a> ## New Anti-Smoking Warnings Criticized for Potential Backfire ### Summary: Starting April 1, Australia will implement legislation requiring health warnings on individual cigarettes, with messages like "causes 16 cancers" and "poisons in every puff." However, social media users have mocked these warnings, suggesting they might make smoking appear "cool" and collectible rather than serving as deterrents. Despite the criticism, health officials assert that such on-product messages are part of a broader strategy to reduce smoking rates, citing positive results from similar approaches in Canada. The initiative aims to decrease the annual tobacco-related deaths in Australia, which currently exceed 24,000. Sources: <a href="https://www.couriermail.com.au/news/queensland/poisons-in-every-puff-new-antismoking-messaging-slammed/news-story/2f77ecd3a943d3139539c2610af3400c" target="_blank">The Courier-Mail - March 28, 2025</a> ## 'Joe's Law' Introduced to Ban Future Hospital Privatization in NSW ### Summary: The New South Wales government has announced "Joe's Law," a reform to prohibit the future privatization of acute public hospitals. This decision follows the death of two-year-old Joe Massa, who suffered a cardiac arrest and died after a prolonged wait in the emergency department of the privately managed Northern Beaches Hospital. The legislation aims to ensure that critical public services like emergency and surgical care remain under public control, preventing privatization. Additionally, a parliamentary inquiry into the hospital's services and a coronial investigation into Joe's death have been initiated. Sources: <a href="https://www.theguardian.com/australia-news/2025/mar/27/joes-law-to-ban-future-hospital-privatisation-in-nsw" target="_blank">The Guardian - March 28, 2025</a>, <a href="https://www.news.com.au/lifestyle/health/health-problems/major-changes-coming-to-nsw-hospitals-after-death-of-twoyearold-joe-massa/news-story/fb93b0f0a9f2673a01eddfe89031fcb9" target="_blank">news.com.au - March 28, 2025</a>, <a href="https://www.dailytelegraph.com.au/newslocal/manly-daily/northern-beaches-hospital-probe-begins-into-safety-and-quality-of-health-services/news-story/72ea15981b26339eea92a15b4e9c498a" target="_blank">The Daily Telegraph - March 28, 2025</a> ## Determined Daisy Marks Major Milestone ### Summary: Daisy, born with a rare chromosomal disorder, has achieved a significant health milestone by having her tracheostomy removed and is now learning to communicate using sign language. Her inspiring journey is one of several highlighted by the Good Friday Appeal, which supports the Royal Children's Hospital (RCH). The 2025 Appeal aims to fund further programs, research, and vital equipment at RCH, with contributions from events like North Melbourne's SuperClash fundraiser bringing joy to young patients ahead of the marquee match. Sources: <a href="https://www.heraldsun.com.au/news/good-friday-appeal/good-friday-appeal-2025-star-roos-launch-superclash-fundraiser-with-special-visit/news-story/75fe74c62e52efb611436e9162c4d4d6" target="_blank">Herald Sun - March 27, 2025</a> ## Indonesia Seeks to Calm Investors After Stocks, Rupiah Slide ### Summary: Indonesian officials are working to reassure investors following significant declines in the stock market and the rupiah. President Prabowo Subianto plans to meet with investors after the Eid-al-Fitr holiday to address concerns about government policies and fiscal stability. The rupiah recently hit its weakest level since 1998, and the main stock index fell 7.1%. Analysts attribute the selloff to poor communication on fiscal policies. The government aims to maintain the fiscal deficit within 3% of GDP and avoid political interference in its sovereign wealth fund. Efforts are also underway to deregulate the manufacturing sector and provide credits to labor-intensive industries. Bank Indonesia is prepared to intervene to stabilize the currency, emphasizing the economy's underlying strength. The rupiah has shown signs of recovery, and measures include easing buyback processes and offering more attractive investment instruments. Markets will monitor the mid-year budget update in July for signs of revenue shortfalls and spending adjustments. Sources: <a href="https://www.reuters.com/markets/asia/indonesia-seeks-calm-investors-after-stocks-rupiah-slide-2025-03-27/" target="_blank">Reuters - 28 March 2025</a> ## Beijing to Escalate Taiwan Coercion in 2025 ### Summary: A report by the Office of the Director of National Intelligence highlights growing cooperation among China, Russia, Iran, and North Korea, posing significant challenges to U.S. global power. Closer ties between China and Russia, in particular, could present enduring risks to U.S. interests. The document points out China's military threat to the U.S., emphasizing its grey zone tactics and potential for stronger coercive action against Taiwan by 2025. The Ukraine conflict and its ongoing strategic risks, including nuclear escalation, are noted, as well as China's ambition to dominate AI by 2030 and its control over critical materials. The report also mentions the volatile Middle East, with Iran's expanding ties despite challenges, and North Korea's commitment to enhancing its nuclear capabilities. Additionally, threats from foreign drug actors and Islamic extremists, including Al-Qa'ida and a potential ISIS resurgence, are highlighted. Sources: <a href="https://www.theaustralian.com.au/nation/politics/us-threat-assessment-sounds-the-alarm-on-china/news-story/cb582794c7a653b11cce8d3e61fc564b" target="_blank">The Australian - 28 March 2025</a> ## Fire Ant Infestation Could Cost Australian Households Over $1 Billion Annually ### Summary: New modeling predicts that if fire ants become established in Australia, households may incur approximately $1.03 billion annually in control measures and related health and veterinary expenses. The invasive species could lead to up to 570,800 medical consultations and around 30 deaths each year due to stings. The electorates of Durack, O'Connor, Mayo, and Blair are projected to be most affected. Experts emphasize the need for increased federal funding for comprehensive eradication programs to prevent environmental damage and significant economic burdens on households. Sources: <a href="https://www.theguardian.com/environment/2025/mar/28/australia-fire-ants-queensland-cost-eradication-pesticides" target="_blank">The Guardian - March 28, 2025</a> ## The Great Monetary Divide – Epi-3643 ### Summary: In this episode, host Jack Spirko discusses the rapid changes occurring in the global financial landscape. He highlights the European Union's announcement, led by European Central Bank President Christine Lagarde, to implement a Central Bank Digital Currency (CBDC) across member states by the upcoming fall. Spirko expresses concern that such a move could pave the way for a social credit system similar to China's, potentially leading to increased governmental control over individual financial activities. Conversely, the episode explores developments in the United States, where the government is reportedly adopting Bitcoin as an economic reserve and integrating stablecoins into the financial system. Spirko suggests that these actions may indicate a divergent path from other global economies, potentially fostering a more decentralized financial environment. Throughout the episode, Spirko emphasizes the importance of understanding these shifts and encourages listeners to consider how such changes might impact personal financial sovereignty and the broader economic landscape. Please note that this summary is based on limited information available from the episode description and may not capture all the nuances discussed in the full podcast. Sources: <a href="https://open.spotify.com/episode/5lUuCzX3wHfWdX6y6QtJGw" target="_blank">The Survival Podcast - 28 March 2025</a>, <a href="https://podcasts.apple.com/us/podcast/the-great-monetary-divide-epi-3643/id284148583?i=1000700006108&l=es-MX" target="_blank">Apple Podcasts - 28 March 2025</a> @ 7d33ba57:1b82db35
2025-03-27 10:53:58Sitges is known for its golden beaches, vibrant nightlife, and artistic charm. With a beautiful seafront promenade, historic old town, and a welcoming atmosphere, it’s a top destination for relaxation, culture, and fun on the **Costa Dorada.  ## **🏖️ Top Things to See & Do in Sitges** ### **1️⃣ Stroll Along the Passeig Marítim 🌊** - A **scenic seaside promenade** lined with palm trees, beaches, and restaurants. - Perfect for **walking, cycling, or enjoying a sunset cocktail**. ### **2️⃣ Relax on the Beaches 🏖️** - **Playa de la Fragata** – A central beach near the old town, great for families. - **Playa de San Sebastián** – A smaller, quieter beach with local charm. - **Playa del Balmins** – A well-known **nudist and LGBTQ+ friendly** beach. - **Playa de l'Home Mort** – A hidden cove, popular for naturists.  ### **3️⃣ Visit the Church of Sant Bartomeu i Santa Tecla ⛪** - The **iconic church overlooking the sea**, a must-visit landmark. - Amazing spot for **photos, especially at sunset**. ### **4️⃣ Explore the Old Town & Museums 🏛️** - Wander through **charming whitewashed streets** filled with **boutique shops and cafés**. - Visit **Museu Cau Ferrat**, home to **art by Santiago Rusiñol and Picasso**. - Discover **Museu Maricel**, featuring **Romanesque and modernist art**.  ### **5️⃣ Enjoy Sitges' Lively Nightlife & Festivals 🎭** - Sitges is famous for its **bars, beach clubs, and LGBTQ+ friendly nightlife**. - Visit in **February** for **Sitges Carnival**, one of Spain’s best! 🎉 - Experience the **Sitges Film Festival (October)**, known for horror & fantasy films. ### **6️⃣ Wine Tasting in Penedès 🍷** - Take a short trip to **Penedès**, one of Spain’s best **Cava (sparkling wine) regions**. - Tour **local wineries** and enjoy **wine tastings** just 30 minutes away.  ## **🍽️ What to Eat in Sitges** - **Xató** – A local **salad with cod, anchovies, and romesco sauce** 🥗 - **Suquet de Peix** – A Catalan **seafood stew with potatoes** 🍲🐟 - **Fideuà** – Similar to paella, but made with **short noodles instead of rice** 🍤 - **Crema Catalana** – A **delicious caramelized custard dessert** 🍮 - **Cava** – The **famous Catalan sparkling wine** from nearby Penedès 🍾  ## **🚗 How to Get to Sitges** 🚆 **By Train:** 35 min from **Barcelona (Sants or Passeig de Gràcia stations)**. 🚘 **By Car:** 40 min from **Barcelona** via the **C-32 highway**. 🚌 **By Bus:** Direct buses from **Barcelona Airport (El Prat) and Tarragona**. ✈️ **By Air:** The nearest airport is **Barcelona-El Prat (BCN, 25 km away)**.  ## **💡 Tips for Visiting Sitges** ✅ **Best time to visit?** **Spring to early autumn (April–October)** for beach weather ☀️ ✅ **Avoid summer weekends** – It gets very busy with visitors from Barcelona 🏖️ ✅ **Visit during Carnival or the Film Festival** for an unforgettable experience 🎭🎬 ✅ **Explore beyond the beaches** – The old town and vineyards are worth it! 🍷 ✅ **Try beachfront dining** – Enjoy fresh seafood with a sea view 🍽️🌊
@ 7d33ba57:1b82db35
2025-03-27 10:53:58Sitges is known for its golden beaches, vibrant nightlife, and artistic charm. With a beautiful seafront promenade, historic old town, and a welcoming atmosphere, it’s a top destination for relaxation, culture, and fun on the **Costa Dorada.  ## **🏖️ Top Things to See & Do in Sitges** ### **1️⃣ Stroll Along the Passeig Marítim 🌊** - A **scenic seaside promenade** lined with palm trees, beaches, and restaurants. - Perfect for **walking, cycling, or enjoying a sunset cocktail**. ### **2️⃣ Relax on the Beaches 🏖️** - **Playa de la Fragata** – A central beach near the old town, great for families. - **Playa de San Sebastián** – A smaller, quieter beach with local charm. - **Playa del Balmins** – A well-known **nudist and LGBTQ+ friendly** beach. - **Playa de l'Home Mort** – A hidden cove, popular for naturists.  ### **3️⃣ Visit the Church of Sant Bartomeu i Santa Tecla ⛪** - The **iconic church overlooking the sea**, a must-visit landmark. - Amazing spot for **photos, especially at sunset**. ### **4️⃣ Explore the Old Town & Museums 🏛️** - Wander through **charming whitewashed streets** filled with **boutique shops and cafés**. - Visit **Museu Cau Ferrat**, home to **art by Santiago Rusiñol and Picasso**. - Discover **Museu Maricel**, featuring **Romanesque and modernist art**.  ### **5️⃣ Enjoy Sitges' Lively Nightlife & Festivals 🎭** - Sitges is famous for its **bars, beach clubs, and LGBTQ+ friendly nightlife**. - Visit in **February** for **Sitges Carnival**, one of Spain’s best! 🎉 - Experience the **Sitges Film Festival (October)**, known for horror & fantasy films. ### **6️⃣ Wine Tasting in Penedès 🍷** - Take a short trip to **Penedès**, one of Spain’s best **Cava (sparkling wine) regions**. - Tour **local wineries** and enjoy **wine tastings** just 30 minutes away.  ## **🍽️ What to Eat in Sitges** - **Xató** – A local **salad with cod, anchovies, and romesco sauce** 🥗 - **Suquet de Peix** – A Catalan **seafood stew with potatoes** 🍲🐟 - **Fideuà** – Similar to paella, but made with **short noodles instead of rice** 🍤 - **Crema Catalana** – A **delicious caramelized custard dessert** 🍮 - **Cava** – The **famous Catalan sparkling wine** from nearby Penedès 🍾  ## **🚗 How to Get to Sitges** 🚆 **By Train:** 35 min from **Barcelona (Sants or Passeig de Gràcia stations)**. 🚘 **By Car:** 40 min from **Barcelona** via the **C-32 highway**. 🚌 **By Bus:** Direct buses from **Barcelona Airport (El Prat) and Tarragona**. ✈️ **By Air:** The nearest airport is **Barcelona-El Prat (BCN, 25 km away)**.  ## **💡 Tips for Visiting Sitges** ✅ **Best time to visit?** **Spring to early autumn (April–October)** for beach weather ☀️ ✅ **Avoid summer weekends** – It gets very busy with visitors from Barcelona 🏖️ ✅ **Visit during Carnival or the Film Festival** for an unforgettable experience 🎭🎬 ✅ **Explore beyond the beaches** – The old town and vineyards are worth it! 🍷 ✅ **Try beachfront dining** – Enjoy fresh seafood with a sea view 🍽️🌊 @ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks. ~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node: * Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing ``` tor --version ``` **Example** of expected output: ``` Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0 ``` ~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update. * Basic PoW support can be checked by running this command: ``` tor --list-modules ``` Expected output: ``` relay: yes dirauth: yes dircache: yes pow: **yes** ``` ~ > If you have `pow: yes`, you are **OK** * Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added ``` sudo nano /etc/tor/torrc ``` Example: ``` # Hidden Service BTC RPC Explorer HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ``` ~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links: * Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002 * LND: https://github.com/bitcoin/bitcoin/issues/28499 --- More info: * https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/ * https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks. ~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node: * Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing ``` tor --version ``` **Example** of expected output: ``` Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0 ``` ~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update. * Basic PoW support can be checked by running this command: ``` tor --list-modules ``` Expected output: ``` relay: yes dirauth: yes dircache: yes pow: **yes** ``` ~ > If you have `pow: yes`, you are **OK** * Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added ``` sudo nano /etc/tor/torrc ``` Example: ``` # Hidden Service BTC RPC Explorer HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ``` ~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links: * Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002 * LND: https://github.com/bitcoin/bitcoin/issues/28499 --- More info: * https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/ * https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ --- Enjoy it MiniBolter! 💙 @ 57d1a264:69f1fee1
2025-03-27 10:42:05What we have been missing in [SN Press kit](https://stacker.news/items/872925/r/Design_r)? Most important, who the press kit is for? It's for us? It's for them? Them, who? The first few editions of the press kit, I agree are mostly made by us, for us. A way to try to homogenize how we _speek_ out SN into the wild web. A way to have SN voice sync, loud and clear, to send out our message. In this case, I squeezed my mouse, creating a template for us [^1], stackers, to share when talking sales with possible businesses and merchants willing to invest some sats and engage with SN community. Here's the message and the sales pitch, v0.1: ## Reach Bitcoin’s Most Engaged Community – Zero Noise, Pure Signal.              - - - Contributions to improve would be much appreciated. You can also help by simply commenting on each slide or leaving your feedback below, especially if you are a sale person or someone that has seen similar documents before. This is the first interaction. Already noticed some issues, for example with the emojis and the fonts, especially when exporting, probably related to a penpot issue. The slides maybe render differently depending on the browser you're using. - [▶️ Play](https://design.penpot.app/#/view?file-id=cec80257-5021-8137-8005-ef90a160b2c9&page-id=cec80257-5021-8137-8005-ef90a160b2ca§ion=interactions&index=0&interactions-mode=hide&zoom=fit) the file in your browser - ⬇️ Save the [PDF file](https://mega.nz/file/TsBgkRoI#20HEb_zscozgJYlRGha0XiZvcXCJfLQONx2fc65WHKY) @k00b it will be nice to have some real data, how we can get some basic audience insights? Even some inputs from Plausible, if still active, will be much useful. [^1]: Territory founders. FYI: @Aardvark, @AGORA, @anna, @antic, @AtlantisPleb, @av, @Bell_curve, @benwehrman, @bitcoinplebdev, @Bitter, @BlokchainB, @ch0k1, @davidw, @ek, @elvismercury, @frostdragon, @grayruby, @HODLR, @inverselarp, @Jon_Hodl, @MaxAWebster, @mega_dreamer, @mrtali, @niftynei, @nout, @OneOneSeven, @PlebLab, @Public_N_M_E, @RDClark, @realBitcoinDog, @roytheholographicuniverse, @siggy47, @softsimon, @south_korea_ln, @theschoolofbitcoin, @TNStacker. @UCantDoThatDotNet, @Undisciplined originally posted at https://stacker.news/items/926557
@ 57d1a264:69f1fee1
2025-03-27 10:42:05What we have been missing in [SN Press kit](https://stacker.news/items/872925/r/Design_r)? Most important, who the press kit is for? It's for us? It's for them? Them, who? The first few editions of the press kit, I agree are mostly made by us, for us. A way to try to homogenize how we _speek_ out SN into the wild web. A way to have SN voice sync, loud and clear, to send out our message. In this case, I squeezed my mouse, creating a template for us [^1], stackers, to share when talking sales with possible businesses and merchants willing to invest some sats and engage with SN community. Here's the message and the sales pitch, v0.1: ## Reach Bitcoin’s Most Engaged Community – Zero Noise, Pure Signal.              - - - Contributions to improve would be much appreciated. You can also help by simply commenting on each slide or leaving your feedback below, especially if you are a sale person or someone that has seen similar documents before. This is the first interaction. Already noticed some issues, for example with the emojis and the fonts, especially when exporting, probably related to a penpot issue. The slides maybe render differently depending on the browser you're using. - [▶️ Play](https://design.penpot.app/#/view?file-id=cec80257-5021-8137-8005-ef90a160b2c9&page-id=cec80257-5021-8137-8005-ef90a160b2ca§ion=interactions&index=0&interactions-mode=hide&zoom=fit) the file in your browser - ⬇️ Save the [PDF file](https://mega.nz/file/TsBgkRoI#20HEb_zscozgJYlRGha0XiZvcXCJfLQONx2fc65WHKY) @k00b it will be nice to have some real data, how we can get some basic audience insights? Even some inputs from Plausible, if still active, will be much useful. [^1]: Territory founders. FYI: @Aardvark, @AGORA, @anna, @antic, @AtlantisPleb, @av, @Bell_curve, @benwehrman, @bitcoinplebdev, @Bitter, @BlokchainB, @ch0k1, @davidw, @ek, @elvismercury, @frostdragon, @grayruby, @HODLR, @inverselarp, @Jon_Hodl, @MaxAWebster, @mega_dreamer, @mrtali, @niftynei, @nout, @OneOneSeven, @PlebLab, @Public_N_M_E, @RDClark, @realBitcoinDog, @roytheholographicuniverse, @siggy47, @softsimon, @south_korea_ln, @theschoolofbitcoin, @TNStacker. @UCantDoThatDotNet, @Undisciplined originally posted at https://stacker.news/items/926557 @ 6be5cc06:5259daf0
2025-01-21 01:51:46## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas. Satoshi Nakamoto satoshin@gmx.com www.bitcoin.org --- ### Resumo O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações. As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira. Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu. --- ### 1. Introdução Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**. Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável. Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável. O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas. Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques. --- ### 2. Transações Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital. #### O que é uma assinatura digital? Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso. #### Como funciona na prática? Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário: 1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1. 2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2. 3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda. #### Resolvendo o problema do gasto duplo Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro. O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain. #### Por que isso é importante? Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes. --- ### 3. Servidor Timestamp Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica. Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público. Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain. Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada. O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin. --- ### 4. Prova-de-Trabalho Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente. A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita. Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain. A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos. Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional. --- ### 5. Rede A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são: 1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la. 2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain). 3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil. 4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede. 5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos. 6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia. #### Resolução de Conflitos e Escolha da Cadeia Mais Longa Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia. #### Tolerância a Falhas A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido. Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central. --- ### 6. Incentivo O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação. #### Recompensa por Mineração Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho. #### Taxas de Transação Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo. #### Incentivo à Honestidade O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas: 1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos. 2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas. A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema. Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo. --- ### 7. Recuperação do Espaço em Disco Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações. Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados. Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados. Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo. --- ### 8. Verificação de Pagamento Simplificada É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada. Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação. A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede. Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável. --- ### 9. Combinando e Dividindo Valor No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor. #### Entradas e Saídas Cada transação no Bitcoin é composta por: - **Entradas**: Representam os valores recebidos em transações anteriores. - **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente. Normalmente, uma transação contém: - Uma única entrada com valor suficiente para cobrir o pagamento. - Ou várias entradas combinadas para atingir o valor necessário. O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**. #### Exemplo Prático Imagine que você tem duas entradas: 1. 0,03 BTC 2. 0,07 BTC Se deseja enviar 0,08 BTC para alguém, a transação terá: - **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC). - **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC). Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente. #### Difusão e Simplificação A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade. --- ### 10. Privacidade O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas. #### Fluxo de Informação - No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário. - No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não. #### Protegendo a Privacidade Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas: 1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único. 2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário. #### Riscos de Ligação Embora a privacidade seja fortalecida, alguns riscos permanecem: - Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total. - O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas. --- ### 11. Cálculos Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito. Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira. Mas isso é extremamente difícil. #### Como o Ataque Funciona Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido. - Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira. - O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida. Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente. #### A Corrida Entre Cadeias Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos. Suponha que: - A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças). - O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças). Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar. #### Por Que o Ataque Fica Cada Vez Mais Improvável? Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos: P = (q/p)^z - **q** é o poder computacional do atacante (20%, ou 0,2). - **p** é o poder computacional da rede honesta (80%, ou 0,8). - **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante. Se o atacante está 5 blocos atrás (z = 5): P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%) Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável. Se ele estiver 10 blocos atrás (z = 10): P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%). Neste caso, as chances de sucesso são praticamente **nulas**. #### Um Exemplo Simples Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível. No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática. #### Por Que Tudo Isso é Seguro? - **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema. - **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar. #### E Se o Atacante Tentar Continuar? O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil. Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso. --- ### 12. Conclusão Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos. --- Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
@ 6be5cc06:5259daf0
2025-01-21 01:51:46## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas. Satoshi Nakamoto satoshin@gmx.com www.bitcoin.org --- ### Resumo O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações. As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira. Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu. --- ### 1. Introdução Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**. Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável. Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável. O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas. Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques. --- ### 2. Transações Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital. #### O que é uma assinatura digital? Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso. #### Como funciona na prática? Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário: 1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1. 2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2. 3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda. #### Resolvendo o problema do gasto duplo Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro. O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain. #### Por que isso é importante? Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes. --- ### 3. Servidor Timestamp Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica. Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público. Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain. Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada. O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin. --- ### 4. Prova-de-Trabalho Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente. A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita. Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain. A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos. Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional. --- ### 5. Rede A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são: 1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la. 2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain). 3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil. 4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede. 5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos. 6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia. #### Resolução de Conflitos e Escolha da Cadeia Mais Longa Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia. #### Tolerância a Falhas A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido. Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central. --- ### 6. Incentivo O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação. #### Recompensa por Mineração Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho. #### Taxas de Transação Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo. #### Incentivo à Honestidade O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas: 1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos. 2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas. A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema. Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo. --- ### 7. Recuperação do Espaço em Disco Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações. Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados. Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados. Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo. --- ### 8. Verificação de Pagamento Simplificada É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada. Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação. A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede. Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável. --- ### 9. Combinando e Dividindo Valor No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor. #### Entradas e Saídas Cada transação no Bitcoin é composta por: - **Entradas**: Representam os valores recebidos em transações anteriores. - **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente. Normalmente, uma transação contém: - Uma única entrada com valor suficiente para cobrir o pagamento. - Ou várias entradas combinadas para atingir o valor necessário. O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**. #### Exemplo Prático Imagine que você tem duas entradas: 1. 0,03 BTC 2. 0,07 BTC Se deseja enviar 0,08 BTC para alguém, a transação terá: - **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC). - **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC). Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente. #### Difusão e Simplificação A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade. --- ### 10. Privacidade O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas. #### Fluxo de Informação - No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário. - No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não. #### Protegendo a Privacidade Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas: 1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único. 2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário. #### Riscos de Ligação Embora a privacidade seja fortalecida, alguns riscos permanecem: - Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total. - O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas. --- ### 11. Cálculos Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito. Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira. Mas isso é extremamente difícil. #### Como o Ataque Funciona Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido. - Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira. - O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida. Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente. #### A Corrida Entre Cadeias Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos. Suponha que: - A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças). - O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças). Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar. #### Por Que o Ataque Fica Cada Vez Mais Improvável? Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos: P = (q/p)^z - **q** é o poder computacional do atacante (20%, ou 0,2). - **p** é o poder computacional da rede honesta (80%, ou 0,8). - **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante. Se o atacante está 5 blocos atrás (z = 5): P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%) Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável. Se ele estiver 10 blocos atrás (z = 10): P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%). Neste caso, as chances de sucesso são praticamente **nulas**. #### Um Exemplo Simples Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível. No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática. #### Por Que Tudo Isso é Seguro? - **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema. - **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar. #### E Se o Atacante Tentar Continuar? O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil. Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso. --- ### 12. Conclusão Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos. --- Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf @ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol. **PROTOCOLS, NOT PLATFORMS.** At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity. What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort. **THIS IS POWERFUL.** Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections. The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship. How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access. **AGAIN, THIS IS POWERUFL.** Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps. Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions. Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know. TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom. Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed. ###
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol. **PROTOCOLS, NOT PLATFORMS.** At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity. What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort. **THIS IS POWERFUL.** Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections. The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship. How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access. **AGAIN, THIS IS POWERUFL.** Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps. Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions. Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know. TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom. Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed. ### @ cff1720e:15c7e2b2
2025-01-19 17:48:02**Einleitung**\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.  **Warum Nostr?** Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.  Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ **Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!  \ **Wie funktioniert Nostr?** Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ **Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!  \ **Warum ist Nostr die Zukunft des Internet?** “Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.  \ **Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.** <https://nostr.net/> \ <https://start.njump.me/> **Hier das Interview zum Thema mit Radio Berliner Morgenröte** <https://www.podbean.com/ew/pb-yxc36-17bb4be>
@ cff1720e:15c7e2b2
2025-01-19 17:48:02**Einleitung**\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.  **Warum Nostr?** Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.  Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ **Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!  \ **Wie funktioniert Nostr?** Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ **Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!  \ **Warum ist Nostr die Zukunft des Internet?** “Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.  \ **Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.** <https://nostr.net/> \ <https://start.njump.me/> **Hier das Interview zum Thema mit Radio Berliner Morgenröte** <https://www.podbean.com/ew/pb-yxc36-17bb4be> @ 7d33ba57:1b82db35
2025-03-27 10:35:25Nerja is known for its stunning beaches, famous caves, and breathtaking sea views. With a charming old town, whitewashed houses, and a lively atmosphere, Nerja offers a perfect mix of relaxation, nature, and culture.  ## **🏖️ Top Things to See & Do in Nerja** ### **1️⃣ Balcón de Europa 🌅** - A **stunning viewpoint** with **panoramic views** of the Mediterranean. - Lined with **palm trees, street musicians, and cafés**. - A great spot for **sunset photos and people-watching**.  ### **2️⃣ Nerja Caves (Cuevas de Nerja) 🏰** - A **famous cave system** with **impressive stalactites and stalagmites**. - Home to **prehistoric cave paintings**, estimated to be over **40,000 years old**. - One of Spain’s most important **archaeological sites**. ### **3️⃣ Playa de Burriana 🏖️** - The **best beach in Nerja**, with **golden sand and clear waters**. - Offers **water sports**, including **kayaking and paddleboarding**. - Many **chiringuitos (beach bars)** serving delicious **seafood paella**. ### **4️⃣ Kayaking to Maro Cliffs 🚣♂️** - Paddle along the **coastline** to discover **hidden coves and waterfalls**. - A unique way to explore the **Maro-Cerro Gordo Cliffs Natural Park**.  ### **5️⃣ Frigiliana – The Most Beautiful White Village 🏡** - Just **10 minutes from Nerja**, this **charming Andalusian village** is full of **whitewashed houses, cobbled streets, and colorful flowers**. - Wander through **narrow alleyways** and enjoy **stunning mountain views**. ### **6️⃣ El Salón & Calahonda Beaches 🏝️** - **Small, quiet beaches** just below the Balcón de Europa. - Perfect for a **relaxing swim away from the crowds**.  ## **🍽️ What to Eat in Nerja** - **Espetos de Sardinas** – Grilled sardines on skewers, a classic Andalusian dish 🐟 - **Ajoblanco** – A cold almond and garlic soup, refreshing on hot days 🍲 - **Fried Fish (Pescaito Frito)** – A mix of **freshly caught seafood** 🦑🐠 - **Tarta de Almendra** – A traditional **almond cake**, perfect with coffee 🍰 - **Paella at Playa Burriana** – One of the best places to enjoy authentic **seafood paella** 🍤🍚  ## **🚗 How to Get to Nerja** ✈️ **By Air:** The nearest airport is **Málaga Airport (AGP, 70 km, 50 min drive)**. 🚘 **By Car:** 50 min from **Málaga**, 1.5 hrs from **Granada**. 🚌 **By Bus:** Direct buses from **Málaga, Granada, and other Costa del Sol towns**. 🚆 **By Train:** No direct train, but you can take a train to Málaga and then a bus.  ## **💡 Tips for Visiting Nerja** ✅ **Best time to visit?** **Spring & summer (April–September)** for the best weather ☀️ ✅ **Book Nerja Cave tickets in advance** – It’s one of the most visited sites in Andalusia 🏰 ✅ **Try kayaking or boat tours** – The coastline is stunning from the water 🚣♂️ ✅ **Visit Frigiliana early** – To avoid crowds and enjoy the peaceful morning atmosphere 🌅 ✅ **Wear comfortable shoes** – The old town has steep, cobbled streets 👟 
@ 7d33ba57:1b82db35
2025-03-27 10:35:25Nerja is known for its stunning beaches, famous caves, and breathtaking sea views. With a charming old town, whitewashed houses, and a lively atmosphere, Nerja offers a perfect mix of relaxation, nature, and culture.  ## **🏖️ Top Things to See & Do in Nerja** ### **1️⃣ Balcón de Europa 🌅** - A **stunning viewpoint** with **panoramic views** of the Mediterranean. - Lined with **palm trees, street musicians, and cafés**. - A great spot for **sunset photos and people-watching**.  ### **2️⃣ Nerja Caves (Cuevas de Nerja) 🏰** - A **famous cave system** with **impressive stalactites and stalagmites**. - Home to **prehistoric cave paintings**, estimated to be over **40,000 years old**. - One of Spain’s most important **archaeological sites**. ### **3️⃣ Playa de Burriana 🏖️** - The **best beach in Nerja**, with **golden sand and clear waters**. - Offers **water sports**, including **kayaking and paddleboarding**. - Many **chiringuitos (beach bars)** serving delicious **seafood paella**. ### **4️⃣ Kayaking to Maro Cliffs 🚣♂️** - Paddle along the **coastline** to discover **hidden coves and waterfalls**. - A unique way to explore the **Maro-Cerro Gordo Cliffs Natural Park**.  ### **5️⃣ Frigiliana – The Most Beautiful White Village 🏡** - Just **10 minutes from Nerja**, this **charming Andalusian village** is full of **whitewashed houses, cobbled streets, and colorful flowers**. - Wander through **narrow alleyways** and enjoy **stunning mountain views**. ### **6️⃣ El Salón & Calahonda Beaches 🏝️** - **Small, quiet beaches** just below the Balcón de Europa. - Perfect for a **relaxing swim away from the crowds**.  ## **🍽️ What to Eat in Nerja** - **Espetos de Sardinas** – Grilled sardines on skewers, a classic Andalusian dish 🐟 - **Ajoblanco** – A cold almond and garlic soup, refreshing on hot days 🍲 - **Fried Fish (Pescaito Frito)** – A mix of **freshly caught seafood** 🦑🐠 - **Tarta de Almendra** – A traditional **almond cake**, perfect with coffee 🍰 - **Paella at Playa Burriana** – One of the best places to enjoy authentic **seafood paella** 🍤🍚  ## **🚗 How to Get to Nerja** ✈️ **By Air:** The nearest airport is **Málaga Airport (AGP, 70 km, 50 min drive)**. 🚘 **By Car:** 50 min from **Málaga**, 1.5 hrs from **Granada**. 🚌 **By Bus:** Direct buses from **Málaga, Granada, and other Costa del Sol towns**. 🚆 **By Train:** No direct train, but you can take a train to Málaga and then a bus.  ## **💡 Tips for Visiting Nerja** ✅ **Best time to visit?** **Spring & summer (April–September)** for the best weather ☀️ ✅ **Book Nerja Cave tickets in advance** – It’s one of the most visited sites in Andalusia 🏰 ✅ **Try kayaking or boat tours** – The coastline is stunning from the water 🚣♂️ ✅ **Visit Frigiliana early** – To avoid crowds and enjoy the peaceful morning atmosphere 🌅 ✅ **Wear comfortable shoes** – The old town has steep, cobbled streets 👟  @ da0b9bc3:4e30a4a9
2025-03-27 10:21:42Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/926553
@ da0b9bc3:4e30a4a9
2025-03-27 10:21:42Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/926553 @ 7d33ba57:1b82db35
2025-03-27 09:25:04Los Narejos is a laid-back beach town on the Costa Cálida, located in the Murcia region of Spain. Known for its calm, warm waters, family-friendly beaches, and proximity to the Mar Menor lagoon, it’s an excellent destination for relaxation, water sports, and enjoying the Mediterranean lifestyle**.  ## **🏖️ Top Things to See & Do in Los Narejos** ### **1️⃣ Playa de Los Narejos 🏖️** - A **wide, sandy beach** with **shallow and warm waters**, perfect for families. - **Palm-lined promenade** for walking, cycling, or enjoying seaside cafés. - Excellent for **swimming, sunbathing, and beach sports**. ### **2️⃣ Mar Menor Lagoon 🌊** - A **unique saltwater lagoon**, separated from the Mediterranean by La Manga. - **Warmer and calmer waters** than the open sea, ideal for **safe swimming**. - Known for its **healing mud baths** with **minerals beneficial for the skin**.  ### **3️⃣ Watersports Paradise 🚤** - A top spot for **kite surfing, windsurfing, sailing, and stand-up paddleboarding**. - Several local schools offer **lessons for beginners and equipment rentals**. - Great conditions for **kayaking** along the Mar Menor coastline. ### **4️⃣ Promenade Walk to Los Alcázares 🚶♂️** - A **scenic coastal walk** from Los Narejos to **Los Alcázares**. - Pass by **chiringuitos (beach bars)** serving fresh seafood and cocktails. ### **5️⃣ Local Markets & Shopping 🛍️** - Visit the **Los Alcázares Market** (Tuesdays & Saturdays) for **local produce, clothes, and crafts**. - Small boutique shops sell **Murcian souvenirs, ceramics, and wines**.  ## **🍽️ What to Eat in Los Narejos** - **Caldero Murciano** – A **traditional seafood rice dish**, full of flavor 🍚🐟 - **Dorada a la Sal** – Fresh **sea bream baked in salt**, a Mediterranean specialty 🐠 - **Tapas & Mariscos** – Try local seafood tapas like **grilled prawns, octopus, and clams** 🍤 - **Pastel de Carne** – A **Murcian meat pie**, perfect for a quick bite 🥧 - **Paparajotes** – A sweet treat made from **lemon leaves coated in batter and fried** 🍋🍩  ## **🚗 How to Get to Los Narejos** ✈️ **By Air:** The nearest airport is **Región de Murcia Airport (RMU, 30 min drive)**. 🚆 **By Train:** Nearest station is in **Balsicas (20 min drive)**, with connections to Murcia and Cartagena. 🚘 **By Car:** 30 min from **Murcia**, 1 hr from **Alicante**, 20 min from **Cartagena**. 🚌 **By Bus:** Direct buses from **Murcia, Cartagena, and Alicante**.  ## **💡 Tips for Visiting Los Narejos** ✅ **Best time to visit?** **Spring to early autumn (April–October)** for great weather ☀️ ✅ **Try water sports** – Mar Menor is one of the safest places for beginners 🏄♂️ ✅ **Bring a bike** – The flat terrain and coastal paths are great for cycling 🚴 ✅ **Enjoy the sunset** – The Mar Menor has some of the most stunning sunset views 🌅
@ 7d33ba57:1b82db35
2025-03-27 09:25:04Los Narejos is a laid-back beach town on the Costa Cálida, located in the Murcia region of Spain. Known for its calm, warm waters, family-friendly beaches, and proximity to the Mar Menor lagoon, it’s an excellent destination for relaxation, water sports, and enjoying the Mediterranean lifestyle**.  ## **🏖️ Top Things to See & Do in Los Narejos** ### **1️⃣ Playa de Los Narejos 🏖️** - A **wide, sandy beach** with **shallow and warm waters**, perfect for families. - **Palm-lined promenade** for walking, cycling, or enjoying seaside cafés. - Excellent for **swimming, sunbathing, and beach sports**. ### **2️⃣ Mar Menor Lagoon 🌊** - A **unique saltwater lagoon**, separated from the Mediterranean by La Manga. - **Warmer and calmer waters** than the open sea, ideal for **safe swimming**. - Known for its **healing mud baths** with **minerals beneficial for the skin**.  ### **3️⃣ Watersports Paradise 🚤** - A top spot for **kite surfing, windsurfing, sailing, and stand-up paddleboarding**. - Several local schools offer **lessons for beginners and equipment rentals**. - Great conditions for **kayaking** along the Mar Menor coastline. ### **4️⃣ Promenade Walk to Los Alcázares 🚶♂️** - A **scenic coastal walk** from Los Narejos to **Los Alcázares**. - Pass by **chiringuitos (beach bars)** serving fresh seafood and cocktails. ### **5️⃣ Local Markets & Shopping 🛍️** - Visit the **Los Alcázares Market** (Tuesdays & Saturdays) for **local produce, clothes, and crafts**. - Small boutique shops sell **Murcian souvenirs, ceramics, and wines**.  ## **🍽️ What to Eat in Los Narejos** - **Caldero Murciano** – A **traditional seafood rice dish**, full of flavor 🍚🐟 - **Dorada a la Sal** – Fresh **sea bream baked in salt**, a Mediterranean specialty 🐠 - **Tapas & Mariscos** – Try local seafood tapas like **grilled prawns, octopus, and clams** 🍤 - **Pastel de Carne** – A **Murcian meat pie**, perfect for a quick bite 🥧 - **Paparajotes** – A sweet treat made from **lemon leaves coated in batter and fried** 🍋🍩  ## **🚗 How to Get to Los Narejos** ✈️ **By Air:** The nearest airport is **Región de Murcia Airport (RMU, 30 min drive)**. 🚆 **By Train:** Nearest station is in **Balsicas (20 min drive)**, with connections to Murcia and Cartagena. 🚘 **By Car:** 30 min from **Murcia**, 1 hr from **Alicante**, 20 min from **Cartagena**. 🚌 **By Bus:** Direct buses from **Murcia, Cartagena, and Alicante**.  ## **💡 Tips for Visiting Los Narejos** ✅ **Best time to visit?** **Spring to early autumn (April–October)** for great weather ☀️ ✅ **Try water sports** – Mar Menor is one of the safest places for beginners 🏄♂️ ✅ **Bring a bike** – The flat terrain and coastal paths are great for cycling 🚴 ✅ **Enjoy the sunset** – The Mar Menor has some of the most stunning sunset views 🌅 @ 7d33ba57:1b82db35
2025-03-27 08:55:21L'Estartit is famous for its **stunning beaches, the Medes Islands, and incredible diving opportunities**. Once a small fishing village, it’s now a paradise for **nature lovers, water sports enthusiasts, and those seeking a relaxing Mediterranean escape**.  ## **🏖️ Top Things to See & Do in L'Estartit** ### **1️⃣ Medes Islands (Illes Medes) 🏝️** - A **protected marine reserve**, perfect for **snorkeling and scuba diving**. - Explore **sea caves, coral reefs, and diverse marine life**. - Take a **glass-bottom boat tour** to admire the underwater world without getting wet. ### **2️⃣ L'Estartit Beach 🏖️** - A **long sandy beach** with shallow waters, ideal for families. - Great for **swimming, sunbathing, and water sports** like windsurfing and kayaking. - Offers fantastic views of the **Medes Islands**.  ### **3️⃣ Montgrí Massif & Castle 🏰** - Hike up to the **Montgrí Castle** for **panoramic views** of the Costa Brava. - Trails through **rocky landscapes and Mediterranean forests**. - A perfect spot for **hiking, mountain biking, and photography**. ### **4️⃣ Coastal Walking Route (Camí de Ronda) 🌊** - A breathtaking **hiking trail along the cliffs**, connecting L'Estartit with nearby beaches and coves. - Discover **hidden spots like Cala Pedrosa and Cala Ferriol**.  ### **5️⃣ Explore the Old Town & Port ⚓** - Wander through **narrow streets with local shops and seafood restaurants**. - Visit the **Sant Genís Church**, a historic landmark in the town center. - Enjoy a drink with a view at the **marina**. ### **6️⃣ Kayaking & Stand-Up Paddleboarding 🚣♂️** - Paddle along the **coastline to explore caves, cliffs, and hidden coves**. - A great way to experience the natural beauty of the area.  ## **🍽️ What to Eat in L'Estartit** - **Suquet de Peix** – Traditional Catalan **fish stew** 🐟 - **Arroz a la Cassola** – A **savory rice dish** with seafood 🍤 - **Fideuà** – Like **paella**, but made with short noodles instead of rice 🍜 - **Calamars a la Planxa** – Grilled squid with olive oil and garlic 🦑 - **Crema Catalana** – A classic Catalan **dessert similar to crème brûlée** 🍮  ## **🚗 How to Get to L'Estartit** 🚆 **By Train:** The nearest train station is **Flaçà (30 min by car/taxi)** with connections from **Barcelona and Girona**. 🚘 **By Car:** 1.5 hrs from **Barcelona**, 45 min from **Girona**, 1 hr from **Figueres**. 🚌 **By Bus:** Direct buses from **Barcelona, Girona, and other Costa Brava towns**. ✈️ **By Air:** The nearest airport is **Girona-Costa Brava (GRO, 55 km)**.  ## **💡 Tips for Visiting L'Estartit** ✅ **Best time to visit?** Late spring to early autumn (**May–September**) for warm weather 🌞 ✅ **Book diving tours in advance** – Medes Islands are a top diving destination 🤿 ✅ **Hike early in the morning** to avoid the heat & get the best views 🥾 ✅ **Visit in June** for the **Havaneres Festival**, celebrating Catalan maritime music 🎶
@ 7d33ba57:1b82db35
2025-03-27 08:55:21L'Estartit is famous for its **stunning beaches, the Medes Islands, and incredible diving opportunities**. Once a small fishing village, it’s now a paradise for **nature lovers, water sports enthusiasts, and those seeking a relaxing Mediterranean escape**.  ## **🏖️ Top Things to See & Do in L'Estartit** ### **1️⃣ Medes Islands (Illes Medes) 🏝️** - A **protected marine reserve**, perfect for **snorkeling and scuba diving**. - Explore **sea caves, coral reefs, and diverse marine life**. - Take a **glass-bottom boat tour** to admire the underwater world without getting wet. ### **2️⃣ L'Estartit Beach 🏖️** - A **long sandy beach** with shallow waters, ideal for families. - Great for **swimming, sunbathing, and water sports** like windsurfing and kayaking. - Offers fantastic views of the **Medes Islands**.  ### **3️⃣ Montgrí Massif & Castle 🏰** - Hike up to the **Montgrí Castle** for **panoramic views** of the Costa Brava. - Trails through **rocky landscapes and Mediterranean forests**. - A perfect spot for **hiking, mountain biking, and photography**. ### **4️⃣ Coastal Walking Route (Camí de Ronda) 🌊** - A breathtaking **hiking trail along the cliffs**, connecting L'Estartit with nearby beaches and coves. - Discover **hidden spots like Cala Pedrosa and Cala Ferriol**.  ### **5️⃣ Explore the Old Town & Port ⚓** - Wander through **narrow streets with local shops and seafood restaurants**. - Visit the **Sant Genís Church**, a historic landmark in the town center. - Enjoy a drink with a view at the **marina**. ### **6️⃣ Kayaking & Stand-Up Paddleboarding 🚣♂️** - Paddle along the **coastline to explore caves, cliffs, and hidden coves**. - A great way to experience the natural beauty of the area.  ## **🍽️ What to Eat in L'Estartit** - **Suquet de Peix** – Traditional Catalan **fish stew** 🐟 - **Arroz a la Cassola** – A **savory rice dish** with seafood 🍤 - **Fideuà** – Like **paella**, but made with short noodles instead of rice 🍜 - **Calamars a la Planxa** – Grilled squid with olive oil and garlic 🦑 - **Crema Catalana** – A classic Catalan **dessert similar to crème brûlée** 🍮  ## **🚗 How to Get to L'Estartit** 🚆 **By Train:** The nearest train station is **Flaçà (30 min by car/taxi)** with connections from **Barcelona and Girona**. 🚘 **By Car:** 1.5 hrs from **Barcelona**, 45 min from **Girona**, 1 hr from **Figueres**. 🚌 **By Bus:** Direct buses from **Barcelona, Girona, and other Costa Brava towns**. ✈️ **By Air:** The nearest airport is **Girona-Costa Brava (GRO, 55 km)**.  ## **💡 Tips for Visiting L'Estartit** ✅ **Best time to visit?** Late spring to early autumn (**May–September**) for warm weather 🌞 ✅ **Book diving tours in advance** – Medes Islands are a top diving destination 🤿 ✅ **Hike early in the morning** to avoid the heat & get the best views 🥾 ✅ **Visit in June** for the **Havaneres Festival**, celebrating Catalan maritime music 🎶 @ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market. Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
@ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market. Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws. @ a296b972:e5a7a2e8
2025-03-27 17:05:57Wehrpflicht, Wehr-Pflicht… Da soll die allgemeine Wehrpflicht wieder eingeführt werden. Eine Frage taucht auf: Ist sie denn jemals abgeschafft worden? Ist die Wehrpflicht nicht untrennbar mit der Demokratie verbunden? Ist es nicht die Pflicht eines jeden Demokraten, sich zu wehren, wenn er sieht, wie die Demokratie vor die Hunde geht? Muss er sich nicht wehren, wenn er feststellt, dass die Freiheit scheibchenweise immer weniger wird?   In Absurd-Germanistan reizt ein wild gewordener Haufen Irrer in Berlin die Grenzen der Legalität bis zum Äußersten aus. Unterstützt von Erfüllungsgehilfen in der Rechtsprechung und den Medien. Neuester Coup: Zur größtmöglichen Intransparenz soll das Informationsfreiheitsgesetz abgeschafft werden. Unterstützt von einer eigenen Bundestagspolizei, geschützt von einem Wassergraben um den Reichstag. Die dunkle Seite der Macht baut eine Beton-Mauer auf, um größtmöglichen Abstand zum übelriechenden Volk, dass sie gewählt hat, zu gewährleisten. Und mit ekelhafter Regelmäßigkeit werden Knochen mit Fleischresten über die Mauer geworfen, die dann das dumme Volk zu verdauen hat. Das funktioniert derzeit noch, weil das Volk nicht in der Lage ist, eine Leiter an die Mauer zu stellen, um die Irren über die Mauer in den Wassergraben zu werfen und sich das saftige Hühnchen zu holen, das ihm, dem Volk sowieso gehört. Unterdessen sinniert die entrückte Blase darüber, wie man dem Volk nachhaltig langfristigen Schaden zufügen kann. Aus rechtlichen Winkelzügen, falschen Versprechungen, Selbstbeweihräucherungen, ideologisch vergifteten Reden quillt die Verachtung gegenüber dem Volk und der Demokratie aus allen Poren. Und die wird dann durch Unseredemokratie verhöhnt, in der Schulden durch eine Wortneuschöpfung als Sondervermögen ausgegeben werden. Dreister und offensichtlicher kann man nicht lügen. Und das mit einer nie gekannten Chuzpe, dass einem nur noch der Atem stockt. Jahrzehnte wurde den Deutschen abgewöhnt, stolz auf ihr Land zu sein. Die deutsche Fahne zeigen, hatte damals schon den Charme von „reeechts“. Wer von Vaterland und Heimat sprach, der bekam automatisch einen dunklen, schmalen Schatten zwischen Nasenmitte und Mund. Doch dann, als es mal wieder Spiele für’s Volk gab, durfte man auf einmal mit kleinen Wink-Elementen zeigen, dass man stolz auf elf Leute war, die hinter einem Ball herrennen und wenn sie ihn hatten, ihn dann wieder wegschossen. Damit nicht genug, es gab hochalberne Gamaschen für Außenspiegel und Diplomatenfähnchen in schwarz-rot-gold für des Deutschen liebstes Kind, das Auto. Und jüngst kam einer daher, der wie von der Tarantel gestochen behauptete, dass der böse Russ hinter uns her ist, und man deshalb kriegstüchtig werden müsse, obwohl weit und breit nichts von ihm zu sehen war und er immer wieder wiederholte, dass er überhaupt gar keine Lust dazu hat, Deutschland auf unschöne Weise bereisen zu wollen. Im Fieberwahn stimmten weitere Kriegstreiber in den Chor ein und ein deutscher Häuptling der Bleichgesichter, der ehedem Streubomben geächtet hatte, zuckte auf einmal nur verbal mit den Schultern. Das soll einer verstehen. Und weil Deutschland von nichts und niemandem bedroht wird, muss deshalb dringend aufgerüstet werden, Kriegswirtschaft ist angesagt, die Wehrpflicht muss wieder her! Eine Kriegsmaschinerie muss von Grund auf neu aufgebaut werden: Von der langen Feinripp-Unterhose mit Eingriff bis zum Panzer. Die ehemaligen Hermann-Göring-Werke müssen die Fließbänder zum Glühen bringen. Wir brauchen „Woffen, Woffen, Woffen“! Das Ganze dauert 10 bis 20 Jahre. Hoffentlich reicht der im Samowar zubereitete Tee so lange, bis alles zertifiziert und DIN-Norm gerecht fertiggestellt ist. Man kann nur auf die christlich demokratische Unterstützung der nach einer europäischen Zentralregierung strebenden, deutschen Ex-Verteidigungsministerin mit Ambitionen zur Kaiserin von Europa hoffen. Ihre Expertise konnte sie ja dank ihres mit Bravour gemeisterten ehemaligen Amtes bereits unter Beweis stellen. Überhaupt, überall, wo das Militär im Hintergrund seine Finger im Spiel hat, ist die Wahl-Brüsselerin an vorderster Front. Zuletzt im Beschaffungswesen der 1. Pandemie-Spiele in Echtzeit unter realen Bedingungen. Aber was nutzt das ganze schöne Zeug, die noch nicht bekleckerten jungfräulichen Gulasch-Kanonen, wenn sie keiner bedient und keiner seinen Henkelmann mit Feinkost füllen will. Ja genau, es fehlen ja noch Menschen, in dem Metier Soldaten genannt. Ein paar Natur-Wahnsinnige gibt es ja immer. Aber was ist mit denen, die vielleicht gar keinen Bock haben? Gerade frisch verliebt, von Papi das erste Auto vor die Tür gestellt bekommen, wegen Laktose-Intoleranz bitte nur einen Kriegs-Latte mit Hafermilch, und für mich bitte glutenfreie Marschverpflegung. Was ist mit denen, die vielleicht checken, dass wir von einer Polit-Klicke regiert werden, die Deutschland an die Wand fährt und sich redlich Mühe gibt, eine positive Zukunft für die nächsten Generationen zu verunmöglichen? Was ist mit denen, die von Anfang an gerafft haben, dass man mit einer Gen-Behandlung die Wehrkraft zersetzt? Was ist mit denen, die die Pflicht, sich bestmöglich gesund zu halten, ernst genommen haben? Was ist mit denen, die aus Sachzwängen oder Unwissenheit die Injektionen über sich haben ergehen lassen und heute feststellen, dass man sie verarscht hat? Was ist mit denen, die sich an ihrem durchtrainierten Six-Pack nur noch durch Bilder erinnern können, weil sie seit der Verabreichung eines „nebenwirkungsfreien Elixiers“ nicht mehr auf die Beine kommen? Man fragt sich, woher soll die Motivation kommen, sein gesundes oder herabgemindertes Immunsystem für ein Vaterland auf’s Spiel zu setzen, bei dem sich herausgestellt hat, dass der Vater ein Stiefvater der übelsten Sorte ist? Da in Europa offensichtlich die Diplomatie zunächst abgeschafft ist, und demnächst vielleicht sogar unter Strafe gestellt wird, und man sich auf Uncle Sam auch nicht mehr verlassen kann, weil er so völlig das Gegenteil von dem unternimmt, was man von ihm erwartet hätte, wäre es überlegenswert, ob diejenigen jungen Männer im fortpflanzungsfähigen und -willigen Alter eventuell eine längere Reise ins Ausland antreten sollten. Ist nur so ein Gedanke. Man kann ja immer noch mal wieder vorbeischauen, wenn es an den ungeschützten Außengrenzen wieder von Deutschland aus nach Vernunft duftet. Aber vielleicht findet sich auch unter den Messerfachkräften der eine oder andere, der seine Künste und sein Leben für ein Land und Bürgergeld hergeben möchte. Schließlich können es die Allermeisten kaum abwarten, die deutschen Gepflogenheiten ungefiltert einzusaugen und dafür ihre kulturelle Herkunft und Religion wie einen alten Lumpen abzuwerfen. Was Besseres, als die Kultur der Denker und Dichter hat die Welt ohnehin noch nicht gesehen. Wer kann dem schon widerstehen? Großer Dank gilt auch der deutschen Bevölkerung, die einem wildgewordenen andalusischen Stier gleich, in Scharen von einigen Tausenden von über 80 Millionen auf die Straße rennen, um ihrem Unbill Ausdruck zu verleihen. So eine Friedensmüdigkeit ist ansteckend und kann richtig mobilisieren. Man kann natürlich auch was von Zuhause aus tun: Sich laut empören und für durchziehende Truppen Kaffee kochen, oder dem Heimatschutz beim Stiefel putzen helfen. Im Ernst: So eine bräsige, behäbige, langweilige, unmotivierte, unkritische, informationsvergiftete, geduldige Herde von Faultieren hat es eigentlich nicht anders verdient, als dass man sie während ihres andauernden Langzeit-Wachkomas in einen Käfig sperrt und mit Bananen füttert. Keiner, niemand kommt auf die Idee, dass es immer noch besser wäre, obwohl es keinerlei Anlass dazu gibt, russisch zu lernen, als sich als Kanonenfutter für einen Staat, der sein Volk verachtet, in die Gefahr zu begeben, im Ernstfall verstümmelt oder abgeschlachtet zu werden. Man kann jetzt schon die heulenden Bubis sehen, wie sie sich unter Mutterns Rockschürze verkriechen, wenn sie merken würden, dass es in den Ballerspielen am Computer aber immer ganz anders war. Der ganze inszenierte Spuk wäre sofort vorbei, wenn die Menschen ihr Gehirn einschalten würden. Dann würden sie feststellen, dass es unzählige Gründe dafür gibt **NEIN** zu sagen und **ICH MACH DA NICHT MIT**. Wie machtlos wären die Kriegspfeifen in Berlin, wenn sie zu spüren bekämen, dass das deutsche Volk nicht mit Russland oder sonst wem im Krieg ist und nicht das geringste Interesse verspürt, daran etwas zu ändern. Deutschland besteht aus einem erbärmlichen Haufen Ja-Sagern in allen Lagern, die offensichtlich erst dann wach werden, wenn es nichts mehr zu Essen gibt und der Strom fürs externe Gehirn weg ist. Oh Gott, mein Leben hat keinen Sinn mehr! Was sind wir doch ein elender Haufen von Jammerlappen, die glauben, dass man gelebte Demokratie und Freiheit jederzeit im Online-Shop kaufen kann. Lieferung innerhalb 24 Stunden. **Frieden – Mir – Pace – Peace** *Dieser Beitrag wurde mit dem Pareto-Client geschrieben.*
@ a296b972:e5a7a2e8
2025-03-27 17:05:57Wehrpflicht, Wehr-Pflicht… Da soll die allgemeine Wehrpflicht wieder eingeführt werden. Eine Frage taucht auf: Ist sie denn jemals abgeschafft worden? Ist die Wehrpflicht nicht untrennbar mit der Demokratie verbunden? Ist es nicht die Pflicht eines jeden Demokraten, sich zu wehren, wenn er sieht, wie die Demokratie vor die Hunde geht? Muss er sich nicht wehren, wenn er feststellt, dass die Freiheit scheibchenweise immer weniger wird?   In Absurd-Germanistan reizt ein wild gewordener Haufen Irrer in Berlin die Grenzen der Legalität bis zum Äußersten aus. Unterstützt von Erfüllungsgehilfen in der Rechtsprechung und den Medien. Neuester Coup: Zur größtmöglichen Intransparenz soll das Informationsfreiheitsgesetz abgeschafft werden. Unterstützt von einer eigenen Bundestagspolizei, geschützt von einem Wassergraben um den Reichstag. Die dunkle Seite der Macht baut eine Beton-Mauer auf, um größtmöglichen Abstand zum übelriechenden Volk, dass sie gewählt hat, zu gewährleisten. Und mit ekelhafter Regelmäßigkeit werden Knochen mit Fleischresten über die Mauer geworfen, die dann das dumme Volk zu verdauen hat. Das funktioniert derzeit noch, weil das Volk nicht in der Lage ist, eine Leiter an die Mauer zu stellen, um die Irren über die Mauer in den Wassergraben zu werfen und sich das saftige Hühnchen zu holen, das ihm, dem Volk sowieso gehört. Unterdessen sinniert die entrückte Blase darüber, wie man dem Volk nachhaltig langfristigen Schaden zufügen kann. Aus rechtlichen Winkelzügen, falschen Versprechungen, Selbstbeweihräucherungen, ideologisch vergifteten Reden quillt die Verachtung gegenüber dem Volk und der Demokratie aus allen Poren. Und die wird dann durch Unseredemokratie verhöhnt, in der Schulden durch eine Wortneuschöpfung als Sondervermögen ausgegeben werden. Dreister und offensichtlicher kann man nicht lügen. Und das mit einer nie gekannten Chuzpe, dass einem nur noch der Atem stockt. Jahrzehnte wurde den Deutschen abgewöhnt, stolz auf ihr Land zu sein. Die deutsche Fahne zeigen, hatte damals schon den Charme von „reeechts“. Wer von Vaterland und Heimat sprach, der bekam automatisch einen dunklen, schmalen Schatten zwischen Nasenmitte und Mund. Doch dann, als es mal wieder Spiele für’s Volk gab, durfte man auf einmal mit kleinen Wink-Elementen zeigen, dass man stolz auf elf Leute war, die hinter einem Ball herrennen und wenn sie ihn hatten, ihn dann wieder wegschossen. Damit nicht genug, es gab hochalberne Gamaschen für Außenspiegel und Diplomatenfähnchen in schwarz-rot-gold für des Deutschen liebstes Kind, das Auto. Und jüngst kam einer daher, der wie von der Tarantel gestochen behauptete, dass der böse Russ hinter uns her ist, und man deshalb kriegstüchtig werden müsse, obwohl weit und breit nichts von ihm zu sehen war und er immer wieder wiederholte, dass er überhaupt gar keine Lust dazu hat, Deutschland auf unschöne Weise bereisen zu wollen. Im Fieberwahn stimmten weitere Kriegstreiber in den Chor ein und ein deutscher Häuptling der Bleichgesichter, der ehedem Streubomben geächtet hatte, zuckte auf einmal nur verbal mit den Schultern. Das soll einer verstehen. Und weil Deutschland von nichts und niemandem bedroht wird, muss deshalb dringend aufgerüstet werden, Kriegswirtschaft ist angesagt, die Wehrpflicht muss wieder her! Eine Kriegsmaschinerie muss von Grund auf neu aufgebaut werden: Von der langen Feinripp-Unterhose mit Eingriff bis zum Panzer. Die ehemaligen Hermann-Göring-Werke müssen die Fließbänder zum Glühen bringen. Wir brauchen „Woffen, Woffen, Woffen“! Das Ganze dauert 10 bis 20 Jahre. Hoffentlich reicht der im Samowar zubereitete Tee so lange, bis alles zertifiziert und DIN-Norm gerecht fertiggestellt ist. Man kann nur auf die christlich demokratische Unterstützung der nach einer europäischen Zentralregierung strebenden, deutschen Ex-Verteidigungsministerin mit Ambitionen zur Kaiserin von Europa hoffen. Ihre Expertise konnte sie ja dank ihres mit Bravour gemeisterten ehemaligen Amtes bereits unter Beweis stellen. Überhaupt, überall, wo das Militär im Hintergrund seine Finger im Spiel hat, ist die Wahl-Brüsselerin an vorderster Front. Zuletzt im Beschaffungswesen der 1. Pandemie-Spiele in Echtzeit unter realen Bedingungen. Aber was nutzt das ganze schöne Zeug, die noch nicht bekleckerten jungfräulichen Gulasch-Kanonen, wenn sie keiner bedient und keiner seinen Henkelmann mit Feinkost füllen will. Ja genau, es fehlen ja noch Menschen, in dem Metier Soldaten genannt. Ein paar Natur-Wahnsinnige gibt es ja immer. Aber was ist mit denen, die vielleicht gar keinen Bock haben? Gerade frisch verliebt, von Papi das erste Auto vor die Tür gestellt bekommen, wegen Laktose-Intoleranz bitte nur einen Kriegs-Latte mit Hafermilch, und für mich bitte glutenfreie Marschverpflegung. Was ist mit denen, die vielleicht checken, dass wir von einer Polit-Klicke regiert werden, die Deutschland an die Wand fährt und sich redlich Mühe gibt, eine positive Zukunft für die nächsten Generationen zu verunmöglichen? Was ist mit denen, die von Anfang an gerafft haben, dass man mit einer Gen-Behandlung die Wehrkraft zersetzt? Was ist mit denen, die die Pflicht, sich bestmöglich gesund zu halten, ernst genommen haben? Was ist mit denen, die aus Sachzwängen oder Unwissenheit die Injektionen über sich haben ergehen lassen und heute feststellen, dass man sie verarscht hat? Was ist mit denen, die sich an ihrem durchtrainierten Six-Pack nur noch durch Bilder erinnern können, weil sie seit der Verabreichung eines „nebenwirkungsfreien Elixiers“ nicht mehr auf die Beine kommen? Man fragt sich, woher soll die Motivation kommen, sein gesundes oder herabgemindertes Immunsystem für ein Vaterland auf’s Spiel zu setzen, bei dem sich herausgestellt hat, dass der Vater ein Stiefvater der übelsten Sorte ist? Da in Europa offensichtlich die Diplomatie zunächst abgeschafft ist, und demnächst vielleicht sogar unter Strafe gestellt wird, und man sich auf Uncle Sam auch nicht mehr verlassen kann, weil er so völlig das Gegenteil von dem unternimmt, was man von ihm erwartet hätte, wäre es überlegenswert, ob diejenigen jungen Männer im fortpflanzungsfähigen und -willigen Alter eventuell eine längere Reise ins Ausland antreten sollten. Ist nur so ein Gedanke. Man kann ja immer noch mal wieder vorbeischauen, wenn es an den ungeschützten Außengrenzen wieder von Deutschland aus nach Vernunft duftet. Aber vielleicht findet sich auch unter den Messerfachkräften der eine oder andere, der seine Künste und sein Leben für ein Land und Bürgergeld hergeben möchte. Schließlich können es die Allermeisten kaum abwarten, die deutschen Gepflogenheiten ungefiltert einzusaugen und dafür ihre kulturelle Herkunft und Religion wie einen alten Lumpen abzuwerfen. Was Besseres, als die Kultur der Denker und Dichter hat die Welt ohnehin noch nicht gesehen. Wer kann dem schon widerstehen? Großer Dank gilt auch der deutschen Bevölkerung, die einem wildgewordenen andalusischen Stier gleich, in Scharen von einigen Tausenden von über 80 Millionen auf die Straße rennen, um ihrem Unbill Ausdruck zu verleihen. So eine Friedensmüdigkeit ist ansteckend und kann richtig mobilisieren. Man kann natürlich auch was von Zuhause aus tun: Sich laut empören und für durchziehende Truppen Kaffee kochen, oder dem Heimatschutz beim Stiefel putzen helfen. Im Ernst: So eine bräsige, behäbige, langweilige, unmotivierte, unkritische, informationsvergiftete, geduldige Herde von Faultieren hat es eigentlich nicht anders verdient, als dass man sie während ihres andauernden Langzeit-Wachkomas in einen Käfig sperrt und mit Bananen füttert. Keiner, niemand kommt auf die Idee, dass es immer noch besser wäre, obwohl es keinerlei Anlass dazu gibt, russisch zu lernen, als sich als Kanonenfutter für einen Staat, der sein Volk verachtet, in die Gefahr zu begeben, im Ernstfall verstümmelt oder abgeschlachtet zu werden. Man kann jetzt schon die heulenden Bubis sehen, wie sie sich unter Mutterns Rockschürze verkriechen, wenn sie merken würden, dass es in den Ballerspielen am Computer aber immer ganz anders war. Der ganze inszenierte Spuk wäre sofort vorbei, wenn die Menschen ihr Gehirn einschalten würden. Dann würden sie feststellen, dass es unzählige Gründe dafür gibt **NEIN** zu sagen und **ICH MACH DA NICHT MIT**. Wie machtlos wären die Kriegspfeifen in Berlin, wenn sie zu spüren bekämen, dass das deutsche Volk nicht mit Russland oder sonst wem im Krieg ist und nicht das geringste Interesse verspürt, daran etwas zu ändern. Deutschland besteht aus einem erbärmlichen Haufen Ja-Sagern in allen Lagern, die offensichtlich erst dann wach werden, wenn es nichts mehr zu Essen gibt und der Strom fürs externe Gehirn weg ist. Oh Gott, mein Leben hat keinen Sinn mehr! Was sind wir doch ein elender Haufen von Jammerlappen, die glauben, dass man gelebte Demokratie und Freiheit jederzeit im Online-Shop kaufen kann. Lieferung innerhalb 24 Stunden. **Frieden – Mir – Pace – Peace** *Dieser Beitrag wurde mit dem Pareto-Client geschrieben.* @ 57d1a264:69f1fee1
2025-03-27 08:11:33Explore and reimagine programming interfaces beyond text (visual, tactile, spatial). > _"The most dangerous thought you can have as a creative person is to think you know what you're doing."_ `— Richard Hamming` [^1] https://www.youtube.com/watch?v=8pTEmbeENF4 For his recent DBX Conference talk, Victor took attendees back to the year 1973, donning the uniform of an IBM systems engineer of the times, delivering his presentation on an overhead projector. The '60s and early '70s were a fertile time for CS ideas, reminds Victor, but even more importantly, it was a time of unfettered thinking, unconstrained by programming dogma, authority, and tradition.  _'The most dangerous thought that you can have as a creative person is to think that you know what you're doing,'_ explains Victor. 'Because once you think you know what you're doing you stop looking around for other ways of doing things and you stop being able to see other ways of doing things. You become blind.' He concludes, 'I think you have to say: _"We don't know what programming is. We don't know what computing is. We don't even know what a computer is."_ And once you truly understand that, and once you truly believe that, then you're free, and you can think anything.' More details at https://worrydream.com/dbx/ [^1]: Richard Hamming -- [The Art of Doing Science and Engineering, p5](http://worrydream.com/refs/Hamming_1997_-_The_Art_of_Doing_Science_and_Engineering.pdf) (pdf ebook) originally posted at https://stacker.news/items/926493
@ 57d1a264:69f1fee1
2025-03-27 08:11:33Explore and reimagine programming interfaces beyond text (visual, tactile, spatial). > _"The most dangerous thought you can have as a creative person is to think you know what you're doing."_ `— Richard Hamming` [^1] https://www.youtube.com/watch?v=8pTEmbeENF4 For his recent DBX Conference talk, Victor took attendees back to the year 1973, donning the uniform of an IBM systems engineer of the times, delivering his presentation on an overhead projector. The '60s and early '70s were a fertile time for CS ideas, reminds Victor, but even more importantly, it was a time of unfettered thinking, unconstrained by programming dogma, authority, and tradition.  _'The most dangerous thought that you can have as a creative person is to think that you know what you're doing,'_ explains Victor. 'Because once you think you know what you're doing you stop looking around for other ways of doing things and you stop being able to see other ways of doing things. You become blind.' He concludes, 'I think you have to say: _"We don't know what programming is. We don't know what computing is. We don't even know what a computer is."_ And once you truly understand that, and once you truly believe that, then you're free, and you can think anything.' More details at https://worrydream.com/dbx/ [^1]: Richard Hamming -- [The Art of Doing Science and Engineering, p5](http://worrydream.com/refs/Hamming_1997_-_The_Art_of_Doing_Science_and_Engineering.pdf) (pdf ebook) originally posted at https://stacker.news/items/926493 @ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos. @ ed84ce10:cccf4c2a
2025-03-27 14:55:40## **Hackers are Destiny: Four Fulcrums of the Future** *A Dora Ventures Thesis* In “Why Software is Eating the World,” Marc Andreeson argued that software isn’t just a tool — it’s a societal force. At [DoraHacks](https://dorahacks.io/), we agree, but we go one step further. It’s not software alone that reshapes the world. It’s hackers — those who BUIDL. The real engine of change isn’t technology; it’s the people who choose to wield it. [DoraHacks](https://dorahacks.io/) is building a global Hacker Movement — a self-organizing force powered by open source, freedom, and code. We’re not chasing buzzwords like “Web3” or geopolitical narratives. We’re building a new society. One based on a simple but radical question: **What is truly worth building?** Dora Ventures exists to serve that mission — a capital engine designed to coordinate, amplify, and capture value from the hacker revolution. We are placing early and aggressive bets across four core leverage points: ## **I. FDA Free Society — The BioHack** ### **Freedom of Life Science is the foundation of a free society.** Every meaningful technological revolution has challenged the existing power structure. Today, the single most over-regulated, over-centralized, and innovation-hostile domain? Life Science. It takes ten years and billions of dollars to bring a drug from lab to patient. Most innovation dies in the trenches of bureaucracy. We don’t need anarchy. We need a new model:**A market-driven, patient-first biotech innovation stack.** **The Problem:** - The FDA approval process kills breakthrough therapies before they live. - Big Pharma monopolies decouple price from value and destroy competition. - The “Right to Try” is a legal afterthought, not a first principle. - Bio startups can’t survive the upfront costs of traditional trials. **The Opportunity:** - Let markets and builders lead: give power back to patients, doctors, and founders. - Rethink from first principles: not “Did it pass?” but “Does it work?” - Reclaim the Right to Try: the real risk is dying while waiting. - Build a hyper-competitive biofounder ecosystem — don’t just supply Big Pharma with IP. - Supercharge biotech with software and AI: accelerate every layer of the stack. The future of medicine does not belong to regulators. It belongs to the builders who refuse to wait. **The FDA Free Society isn’t just a challenge to power — it’s a defense of life.** ## **II. Open Source Quantum** ### **Ethereum had 2015. Quantum software has 2025.** Arthur C. Clarke said: *“Any sufficiently advanced technology is indistinguishable from magic.”* Quantum is magic — until it’s programmable, repeatable, and shared. In other words: open source. Dora Ventures is betting on the moment quantum computing becomes a hacker’s playground. Hardware is entering the engineering phase. Software? Still a wasteland — which means pure upside for builders. **We’re betting on:** - **Quantum compilers & transpilers**: bridging classical and quantum logic. - **Quantum cryptography**: building fundamentally new security layers. - **Quantum applications** in AI, pharma, logistics, finance, space — everything. We're not watching from the sidelines. We’re funding open-source tools, running hackathons, and building out the decentralized quantum dev stack. **Open Source Quantum is not speculative.** It’s inevitable — and massively undercapitalized. Now is the time to build. ## **III. Consumer Crypto — The Fat Apps Are Coming** ### **Crypto’s real revolution? Billion-user apps.** Crypto is not the *alternative* to the internet. It’s the *next chapter* of the internet. In the 1990s, HTTP and TCP/IP rewired information. In the 2000s, web apps rewired commerce and communication. In the 2010s, mobile apps rewired human behavior. In the 2020s, crypto apps will onboard the next billion users. **The infrastructure is ready. The fat apps are hatching.** Dora Ventures is obsessed with one question: **Who builds the PayPal and WeChat of the Web3 era?** That’s where we place our bets. **What we see coming:** - Compliant stablecoins like USDC become digital dollars. - Crypto-native payment rails rival VISA. - Appchains built with Move + simplified UX onboard non-crypto users. - On-chain creator economies that pay artists, devs, and communities directly. Imagine this: A fan in NYC uses USDC on a Move-based blockchain (Aptos) to buy a concert ticket via KYD Labs. An Argentinian grabs a latte daily with Bitcoin sats on Lightning. A friend group splits dinner bills via Yakihonne, a decentralized social platform. **That’s not the future. That’s this year.** We’re not funding protocols — we’re funding paradigm shifts in experience. ## **IV. Agentic Organizations — DAOs Without CEOs** ### **The end of corporations. The birth of autonomous orgs.** In 2022, Sam Altman redefined “tools.” In 2025, we’ll redefine “organizations.” Future orgs won’t be hierarchies. They’ll be networks of autonomous agents. **Agents** are the new work unit. They don’t sleep. They learn continuously. They self-schedule. They’re not tools to help humans — they *are* the operating system of post-human orgs. **What’s coming:** - DAOs with agent-driven governance and privacy. - Smart Widgets that deploy trade/social/payment agents in three lines of code. - Privacy as a default layer in automation. - A new generation of AI-native hackathon projects. AI + blockchain isn’t a buzzword. It’s the genesis of *organizational intelligence.* Yesterday, the company was an information processor. Tomorrow, the DAO is an autonomous agent network. **No CEOs. No approvals. No offices. Just coordination at the speed of compute.** ## **The Bet: BUIDL Freedom for Humanity** FDA Free Society. Open Source Quantum. Consumer Crypto. Agentic Orgs. These are not sci-fi. They are already happening. At Dora Ventures, we don’t just back technologies. We back builders who say: “The system is broken — and I’m going to fix it myself.” We back rebels who reject stagnation. Who write code instead of complaints. Who build networks instead of narratives. Who refuse to ask permission to build the future. Hackers are eating the world. And in the age of AI, humanity will only survive if it chooses to become hackers — to use code, coordination, and imagination to build a world worth living in. Let’s build.
@ ed84ce10:cccf4c2a
2025-03-27 14:55:40## **Hackers are Destiny: Four Fulcrums of the Future** *A Dora Ventures Thesis* In “Why Software is Eating the World,” Marc Andreeson argued that software isn’t just a tool — it’s a societal force. At [DoraHacks](https://dorahacks.io/), we agree, but we go one step further. It’s not software alone that reshapes the world. It’s hackers — those who BUIDL. The real engine of change isn’t technology; it’s the people who choose to wield it. [DoraHacks](https://dorahacks.io/) is building a global Hacker Movement — a self-organizing force powered by open source, freedom, and code. We’re not chasing buzzwords like “Web3” or geopolitical narratives. We’re building a new society. One based on a simple but radical question: **What is truly worth building?** Dora Ventures exists to serve that mission — a capital engine designed to coordinate, amplify, and capture value from the hacker revolution. We are placing early and aggressive bets across four core leverage points: ## **I. FDA Free Society — The BioHack** ### **Freedom of Life Science is the foundation of a free society.** Every meaningful technological revolution has challenged the existing power structure. Today, the single most over-regulated, over-centralized, and innovation-hostile domain? Life Science. It takes ten years and billions of dollars to bring a drug from lab to patient. Most innovation dies in the trenches of bureaucracy. We don’t need anarchy. We need a new model:**A market-driven, patient-first biotech innovation stack.** **The Problem:** - The FDA approval process kills breakthrough therapies before they live. - Big Pharma monopolies decouple price from value and destroy competition. - The “Right to Try” is a legal afterthought, not a first principle. - Bio startups can’t survive the upfront costs of traditional trials. **The Opportunity:** - Let markets and builders lead: give power back to patients, doctors, and founders. - Rethink from first principles: not “Did it pass?” but “Does it work?” - Reclaim the Right to Try: the real risk is dying while waiting. - Build a hyper-competitive biofounder ecosystem — don’t just supply Big Pharma with IP. - Supercharge biotech with software and AI: accelerate every layer of the stack. The future of medicine does not belong to regulators. It belongs to the builders who refuse to wait. **The FDA Free Society isn’t just a challenge to power — it’s a defense of life.** ## **II. Open Source Quantum** ### **Ethereum had 2015. Quantum software has 2025.** Arthur C. Clarke said: *“Any sufficiently advanced technology is indistinguishable from magic.”* Quantum is magic — until it’s programmable, repeatable, and shared. In other words: open source. Dora Ventures is betting on the moment quantum computing becomes a hacker’s playground. Hardware is entering the engineering phase. Software? Still a wasteland — which means pure upside for builders. **We’re betting on:** - **Quantum compilers & transpilers**: bridging classical and quantum logic. - **Quantum cryptography**: building fundamentally new security layers. - **Quantum applications** in AI, pharma, logistics, finance, space — everything. We're not watching from the sidelines. We’re funding open-source tools, running hackathons, and building out the decentralized quantum dev stack. **Open Source Quantum is not speculative.** It’s inevitable — and massively undercapitalized. Now is the time to build. ## **III. Consumer Crypto — The Fat Apps Are Coming** ### **Crypto’s real revolution? Billion-user apps.** Crypto is not the *alternative* to the internet. It’s the *next chapter* of the internet. In the 1990s, HTTP and TCP/IP rewired information. In the 2000s, web apps rewired commerce and communication. In the 2010s, mobile apps rewired human behavior. In the 2020s, crypto apps will onboard the next billion users. **The infrastructure is ready. The fat apps are hatching.** Dora Ventures is obsessed with one question: **Who builds the PayPal and WeChat of the Web3 era?** That’s where we place our bets. **What we see coming:** - Compliant stablecoins like USDC become digital dollars. - Crypto-native payment rails rival VISA. - Appchains built with Move + simplified UX onboard non-crypto users. - On-chain creator economies that pay artists, devs, and communities directly. Imagine this: A fan in NYC uses USDC on a Move-based blockchain (Aptos) to buy a concert ticket via KYD Labs. An Argentinian grabs a latte daily with Bitcoin sats on Lightning. A friend group splits dinner bills via Yakihonne, a decentralized social platform. **That’s not the future. That’s this year.** We’re not funding protocols — we’re funding paradigm shifts in experience. ## **IV. Agentic Organizations — DAOs Without CEOs** ### **The end of corporations. The birth of autonomous orgs.** In 2022, Sam Altman redefined “tools.” In 2025, we’ll redefine “organizations.” Future orgs won’t be hierarchies. They’ll be networks of autonomous agents. **Agents** are the new work unit. They don’t sleep. They learn continuously. They self-schedule. They’re not tools to help humans — they *are* the operating system of post-human orgs. **What’s coming:** - DAOs with agent-driven governance and privacy. - Smart Widgets that deploy trade/social/payment agents in three lines of code. - Privacy as a default layer in automation. - A new generation of AI-native hackathon projects. AI + blockchain isn’t a buzzword. It’s the genesis of *organizational intelligence.* Yesterday, the company was an information processor. Tomorrow, the DAO is an autonomous agent network. **No CEOs. No approvals. No offices. Just coordination at the speed of compute.** ## **The Bet: BUIDL Freedom for Humanity** FDA Free Society. Open Source Quantum. Consumer Crypto. Agentic Orgs. These are not sci-fi. They are already happening. At Dora Ventures, we don’t just back technologies. We back builders who say: “The system is broken — and I’m going to fix it myself.” We back rebels who reject stagnation. Who write code instead of complaints. Who build networks instead of narratives. Who refuse to ask permission to build the future. Hackers are eating the world. And in the age of AI, humanity will only survive if it chooses to become hackers — to use code, coordination, and imagination to build a world worth living in. Let’s build.