-
 @ 2b24a1fa:17750f64
2025-04-03 10:11:13
@ 2b24a1fa:17750f64
2025-04-03 10:11:13Ist es wirklich so, dass Gendern für mehr Gleichberechtigung sorgt, für ein friedlicheres Miteinander? Abgesehen von den grammatikalischen Verirrungen, die sich dabei in die Sprache schleichen, darf die Frage erlaubt sein, warum ein Gemeinschaftsgefühl, das „Wir“ in immer kleinere Einheiten, auch sprachlich geteilt werden soll. Muss ich tatsächlich alle benennen?
https://soundcloud.com/radiomuenchen/gendern-die-sakralsprache-des?
Dann wäre das eine Liste von Namen. Verlese ich die nicht, sondern gendere mit Glottisschlag und allem was dazu gehört, unterteile ich ja doch in Gruppen. Und Gruppen haben zur Eigenart, dass es Zugehörigkeiten gibt und ausgeschlossen sein. So beginnt der Kampf. Zunächst war die Frau minderwertig, jetzt ist der Mann toxisch. Und was, wann zu wem, wie gesagt werden darf wird zum Spießrutenlauf. „Misgendern“ ist beispielsweise eine Wortneuschöpfungen, die eine Incorrectness der Sprache bezeichnet, die bis in die Strafbarkeit reichen will.
Einer, der von dieser rigide anmutenden Sprach-Religion getriggert wird, ist Gerald Ehegartner. Er ist Lehrer, Musiker, Theater- und Wildnispädagoge und Autor und nimmt sich immer wieder dem Gemeingut Sprache an. Heute mit einem Text, den er mit: „Gendern, die Sakralsprache des Wokeismus“ betitelt hat.
Sprecherin: Sabrina Khalil
-
 @ 2b24a1fa:17750f64
2025-04-03 10:05:21
@ 2b24a1fa:17750f64
2025-04-03 10:05:21Der Deutsche Bundestag wurde neu gewählt. Für einige Abgeordnete und Regierungsmitglieder heißt es Time to Say Goodbye. Abschied ist ein scharfes Schwert. Auch bei Radio München werden Trennungs- und Verlassenheitsgefühle getriggert. Umso mehr, wenn es sich nicht nur um duselige Allerweltsliebe handelt, sondern um den Abgang großer Helden.
https://soundcloud.com/radiomuenchen/nachruf-3-christian-der-wachstumliche
Sie bezahlten ihren todesmutigen und fast ehrenamtlichen Einsatz nicht mit dem Leben, jedoch mit der einen oder anderen Falte in Hemd oder Bluse, manchmal sogar im Gesicht. Was bleibt? Eine bescheidene Pension? Ein lausig bezahlter Manager-Job in einem Konzern? Wir wollen jedenfalls nicht, dass diese Volkshelden vom Zahn der Zeit abgenagt, vergessen werden und setzen ihnen deshalb ein bescheidenes akustisches, aber nachhaltiges Denkmal. Hören Sie die kleine satirische Reihe „Nachrufe“ von unserem Autor Jonny Rieder.
Folge 3: Christian der Wachstümliche
Sprecher: Karsten Troyke
Bild: Markus Mitterer für Radio München
Radio München
-
 @ 2b24a1fa:17750f64
2025-04-03 10:03:24
@ 2b24a1fa:17750f64
2025-04-03 10:03:24Der Deutsche Bundestag wurde neu gewählt. Für einige Abgeordnete und Regierungsmitglieder heißt es Time to Say Goodbye. Abschied ist ein scharfes Schwert. Auch bei Radio München werden Trennungs- und Verlassenheitsgefühle getriggert. Umso mehr, wenn es sich nicht nur um duselige Allerweltsliebe handelt, sondern um den Abgang großer Helden.
Sie bezahlten ihren todesmutigen und fast ehrenamtlichen Einsatz nicht mit dem Leben, jedoch mit der einen oder anderen Falte in Hemd oder Bluse, manchmal sogar im Gesicht. Was bleibt? Eine bescheidene Pension? Ein lausig bezahlter Manager-Job in einem Konzern? Wir wollen jedenfalls nicht, dass diese Volkshelden vom Zahn der Zeit abgenagt, vergessen werden und setzen ihnen deshalb ein bescheidenes akustisches, aber nachhaltiges Denkmal. Hören Sie die kleine satirische Reihe „Nachrufe“ von unserem Autor Jonny Rieder.
Folge 4: Annalena die Völkerballerina
Sprecher: Karsten Troyke
Bild: Markus Mitterer für Radio München
-
 @ 2b24a1fa:17750f64
2025-04-03 09:57:35
@ 2b24a1fa:17750f64
2025-04-03 09:57:35Es sind immer die gleichen Mechanismen: Die Faktoren Zeitdruck und Angst machen enorm viele Menschen gefügig. 500 Milliarden Euro für Infrastruktur und den sogenannten Klimaschutz, 400 Milliarden für die Bundeswehr – also fast eine Billion Euro Schulden, innerhalb von weniger als vier Wochen nach der Wahl mit Winkelzügen den Bundesbürgern auferlegt.
https://soundcloud.com/radiomuenchen/es-lebe-die-freiheit-verdammt?
Wahlversprechen oder Parteiprogramme, das auf keinen Fall zu tun, sind Makulatur. Keine Diskussion über einen Haushalt, keine Diskussion über die Notwendigkeiten und schon sind Fragen anhängig, ob die Aufträge, die nun vergeben werden, nach den rechtmäßigen Ausschreibungskriterien vonstatten gehen, oder ob auch bei diesen unvorstellbaren Summen die Spezlwirtschaft im Land fortgeführt wird.
Wo ist der Wille des Volkes geblieben? Wo die Freiheit, tatsächlich über unser Leben und Wirtschaften zu entscheiden?
Der Autor, Wirtschafts- und Finanzexperte Andreas Geltinger schaut auf die einstigen Ideen wirtschaftlichen Handelns und analysiert, womit wir es jetzt zu tun haben.
Sprecher: Karsten Troyke.
-
 @ 2b24a1fa:17750f64
2025-04-03 09:34:29
@ 2b24a1fa:17750f64
2025-04-03 09:34:29Kartografiert, aufgekauft, betoniert, beschildert. Wo ist die Freiheit? Wo ist Platz zum Erforschen im Nicht-Definierten? Also wo sind die Erfahrungsräume, die sich von Generation zu Generation üblicherweise immer wieder die Jugend erobert, um darin zu wachsen und zu reifen?
https://soundcloud.com/radiomuenchen/abwartend-skeptisch-von-kenneth-anders
Perspektivwechsel: Wo sind eigentlich die Jugendlichen abgeblieben, die nach diesen Räumen Ausschau halten? Sie bewegen sich in „Spaces“. Seit Corona staatlich verordnet, suchen sie auf flachen Bildschirmen, in einer artifiziellen Welt, ihren Horizont zu erweitern.
Der Kulturwissenschaftler Kenneth Anders hat sich auf Spurensuche bei Jugendlichen auf dem Land gemacht. Hören Sie sein Resumée mit dem Titel „Abwartend skeptisch“.
Nachzulesen ist der Beitrag auf der Webseite: oderamazonas.de
Sprecherin: Sabrina Khalil
Bild: KI
www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
-
 @ 2b24a1fa:17750f64
2025-04-03 09:28:52
@ 2b24a1fa:17750f64
2025-04-03 09:28:5221 Monate, also fast zwei Jahre verbringt Johanna Findeisen bereits in Untersuchungshaft. Trägt sie reichsbürgerliche Ideen mit sich? Oder hat sie Straftaten geplant? Es ist ein Fall im sogenannten „Reichsbürgerprozess“. Mit diesem beschäftigt sich einer ihrer Anwälte Prof. Martin Schwab. Bei den Prozessen, so der Jurist, gehe es eher um Gesinnungsfragen.
Fakten zu Straftaten, auch geplanten, seien nicht aufzufinden. Und eine Untersuchungshaft für die Aufdeckung einer möglicherweise falschen Gesinnung – die Johanna Findeisen vehement bestreitet - ist in unserem Rechtssystem nicht vorgesehen. Dennoch sind die Termine für diese Untersuchungen bereits bis 2026 anberaumt.
Das soll aber heute nicht unser Thema sein. Es geht um die Untersuchungshaft selbst. Prof. Martin Schwab ist in regelmäßigem, telefonischen Kontakt mit Johanna Findeisen und stellt dort Verhältnisse fest, die den Tatbestand der Folter erfüllen. Kein Mensch, selbst der Verurteilte, darf in seiner Menschenwürde herabgesetzt werden. Nun wird der Fall Johanna Findeisen bislang lediglich untersucht. Wie kann also sein, dass sie im Transport zum Gericht gefesselt wird? Warum wurde sie bei ihrer Rückkehr körperinvasiv untersucht? Was übrigens nach einem öffentlichkeitswirksamen Antrag ans Oberlandesgericht erfolgreich unterbunden wurde. Warum wird ihre Post zurückgehalten? Warum durfte sie, bei zwei Stunden Besuchszeit im Monat, ihren Angehörigen nur hinter einer Scheibe begegnen? Warum wird sie, ohne Morgentoilette, abgeholt und in eine fensterlose Zelle ins Gericht gebracht, wo sie zwei Stunden bis zum Gerichtstermin ausharren muss? Und warum wird die fiebernde Johanna, bei Minusgraden und offener Türe gezwungen, sich nackt auszuziehen, sich zur Wand zu drehen und sich einer erniedrigenden Leibesvisitation zu stellen?
Auch dem Pfarrer und Autor Jürgen Fliege geht dieser Fall nah und fragte sich, was Johanna Findeisen, neben einer guten Verteidigung gebrauchen könnte und er ihr geben: Beistand! Hören Sie seinen offenen Brief an die Inhaftierte.
Sprecherin: Sabrina Khalil.
Wer sich gegen die – in einzelnen Haftanstalten – untragbaren Zustände, gegen die dortigen Menschenrechtsverletzungen engagieren möchte, kann das beispielsweise auf der Webseite www.folter-nein-danke.eu tun.
-
 @ 8dac122d:0fc98d37
2025-04-03 16:08:55
@ 8dac122d:0fc98d37
2025-04-03 16:08:55Satoshi Nakamoto 50th ₿DAY Commemorative Poster
As per pictures, auctioning this unique print of Satoshi's 50th birthday on the 5th of April 1975. A commemorative anniversary of “obscure but brilliant reference”, and as “extremely political reminder” of the signing of Gold Executive Order 6102 the same day in 1933, which prohibited the ownership of gold coins in the United States.
Item details: - Size of the piece is 20″ x 30″. - Vertical matte paper. - One piece ONLY. - Frame not included. - National and international shipping available.
Starting bid:
21,000 satsBid increments:1,000 satsEnds at:April 5, 23:59UTC timeRules: - The bidding will increase by increments of1,000 satsonly (or multiples) - The auction is listed on multiple sites, blogs, forums and platforms, I will continue to manage and update this price across all sites for transparency, especially in the last 12hrs of the auction. I will have multiple parties in the same room / location managing the countdown to ensure accuracy and transparency across domains. - Any bids lodged in the last 10 minutes will extend the auction deadline by 10 minutes - Winner to contact auctioneer within 24 hours via nostr DM:AGORA@stacker.newsornpub13kkpytvjcxsqka9pdshw3094urgh8fxwx7ru258lved9wr7f35mspal584. - Payment methods accepted: Bitcoin ONLY via a Lightning addressAGORA@coinos.io. Happy to provide a LN invoice when easier. -AGORA_@tuta.iois the contact email for this auctioneer for all additional details and private discussions. - Shipping is to be organized via the auctioneers email above at conclusion of sale at the buyers request, via the auctioneer preferred service provider, paid for by the buyer to eliminate any confusion or losses.originally posted at https://stacker.news/items/933454
-
 @ 2b24a1fa:17750f64
2025-04-03 09:28:32
@ 2b24a1fa:17750f64
2025-04-03 09:28:32„Das ist ein netter alter Onkel, der sich bemüht, der Welt Gutes zu tun“, antwortete Anfang 2021 der Sohn einer Freundin auf ihre Frage, was Bill Gates mit der Pandemie zu tun haben könnte. Ich erinnere mich, damals wurde man als Verschwörungstheoretiker tituliert, und zwar maximal abwertend, wenn man allein den Namen ins Spiel brachte. Es ist wirklich Zeit, sich wieder für das Ansehen der Verschwörungstheorie einzusetzen, denn ohne sie wird kein einziger Kriminalfall aufgedeckt, der von mehr als einer Person durchgeführt wurde.
Kommen wir zum dritten Teil der Reihe „Corona-Connection“ von Milosz Matuschek in dem er sich in deren Epizentrum begibt. Bill Gates, der undemokratisch zu Macht gekommene, selbsternannte Philanthrop, gehört zu den Hauptfiguren der USAID, der United States Agency for International Development. Matuschek geht hier auf das Geschäftsmodell des Philanthrokapitalismus ein.
Sabrina Khalil hat seinen Text gelesen. Diesen und die zwei ersten Folgen finden Sie auf Matuscheks Seite: Freischwebende Intelligenz.
-
 @ c13fd381:b46236ea
2025-04-03 07:55:31
@ c13fd381:b46236ea
2025-04-03 07:55:31Over the past few years, The School of Bitcoin (TSOBTC) has built a reputation as a decentralised, open-source educational initiative dedicated to financial sovereignty and digital literacy. Our faculty, contributors, and global community have worked tirelessly to create resources that embody the Free and Open-Source Software (FOSS) ethos, ensuring that knowledge remains accessible to all.
As part of our commitment to maintaining an open and transparent model, we are excited to announce that The School of Bitcoin is officially migrating to Consensus21.School. This transition is not just a rebranding--it marks the consolidation of all our initiatives, projects, and educational resources under the Consensus21.School banner. The School of Bitcoin will no longer exist as a separate entity.
This move comes as a response to growing confusion between our initiative and another entity operating under the domain schoolofbitcoin (SOB), which has taken a direction that does not align with our open-source philosophy. To reaffirm our dedication to FOSS and community-driven education, we are bringing everything--our courses, programs, and collaborations--into a singular, more focused ecosystem at Consensus21.School.
What Does This Mean for Our Community?
Rest assured, all the valuable content, courses, and educational materials that have been developed under TSOBTC will remain available. We continue to embrace a value-for-value model, ensuring that learners can access resources while supporting the ecosystem in a way that aligns with their means and values.
By consolidating under Consensus21.School, we are doubling down on the principles of decentralisation, self-sovereignty, and permissionless learning. This transition includes all of our key initiatives, including V4V Open Lessons, the Decentralised Autonomous Education System (DAES), and our involvement with the Plan B Network.
Full Migration of DAES and Plan B Network Collaboration
As part of this transition, the Decentralised Autonomous Education System (DAES) is now officially part of Consensus21.School and is fully reflected in the Consensus21.School Whitepaper. DAES will continue to provide a platform for aspiring learners to submit their Bitcoin project ideas for potential funding and mentorship, with active engagement in our Stacker News /~Education territory and Signal chat for collaboration. We invite contributors to support our learner fund and help bring innovative ideas to fruition within this new ecosystem.
Additionally, our collaboration with the Plan B Network will now operate under Consensus21.School. Through this partnership, we will continue teaching using the Plan B Network's curriculum to provide high-quality Bitcoin education and strengthen local Bitcoin communities. This global initiative remains a core part of our mission, now fully integrated within Consensus21.School.
Looking Ahead
With Consensus21.School, we will continue innovating in peer-to-peer learning, integrating cutting-edge developments in Bitcoin, Nostr, and decentralised technologies. We encourage our community to stay engaged, contribute, and help us build an even stronger foundation for the future of open education.
This is more than just a domain change--it is the next evolution of our mission. The School of Bitcoin as an entity is now retired, and all our efforts, including DAES and the Plan B Network collaboration, will move forward exclusively under Consensus21.School. We invite educators, students, and enthusiasts to join us in shaping this next phase of open financial education.
The journey continues, and we are thrilled to embark on this new chapter together
-
 @ 5708b1f6:208df3b8
2025-04-03 15:25:33
@ 5708b1f6:208df3b8
2025-04-03 15:25:33The role and significance of music naturally varies from person to person. For some, it is counted among the most important things in life. For others, it may be a superfluous additive of limited value. Due to this difference in perception relating to music, it may be difficult for some individuals to recognize the benefits of compiling a personalized music playlist.
However, the value of music as a therapeutic tool for people already suffering from advanced dementia has been repeatedly demonstrated, and sometimes with astounding, although temporary, results. The internet is full of studies and stories, and YouTube searches yield an abundance of video evidence ranging from clinical studies to anecdotal family recordings of elderly relatives.
All of these data and anecdotes point to a compelling suggestion and an exciting conclusion: music appreciation has tremendous potential as a supplemental activity for mental health maintenance. With insights gained from the study of neuroplasticity, the neurological benefits for musicians and performers are easy to see, but less clear is the fact that mere exposure to music as a casual listener can be of profound psychological importance, even for individuals who don’t consider themselves to be music lovers.
The transformative effect of music is on full display in many of the available videos on YouTube. We can simply search “dementia music,” or ‘Alzheimer’s music” for fast, relevant results. In video after video, we can see elderly subjects who may be slow to speak, detached, disoriented, barely-intelligible, or unresponsive. In care facilities and at gatherings with families, they are interviewed about their youth, and about their feelings related to music.
Many of the videos first show footage of the individual’s normal daily cognitive state, and them listening and responding to the questions, followed by a period of music listening, and then another brief, post-music discussion. The transformation of mental states tends to be very clear when we compare the quality of their cognitive performance before and after the introduction of music. People remark that “a light has been turned back on,” or “his personality returned,” or “it’s as if the person has woken up from sleep.”
Unfortunately, these positive responses are only temporary, and music does not have the power to permanently reverse the symptoms and pathology of advanced dementia and age-related cognitive decline. Also there is no guarantee it will work for every person, or to what degree. Nevertheless, it does not mean that music as therapy is completely without value. In fact, it can be quite the opposite.
When the response is positive, the event can have multiple benefits, and may even be a therapeutic experience for certain listeners. Faces once despondent or vacant become animated and radiant. Long lost smiles return from faraway times and places. Memories and associations from previous ages shake loose and rise to the surface. Many listeners were asked to recount their experiences related to the songs and the time in life with which they were primarily associated. Some of them were able to describe events, places, people, emotions, and reactions with a degree of clarity, dexterity, and articulation that was completely inconsistent with their medical diagnosis and their cognitive performance prior to hearing the music. The song quite literally revives the personality that makes the person, temporarily and superficially reversing the undoing of the mind. For a mind that is coming undone, music as therapy has potential to mitigate suffering and confusion, provide moments of joy and enthusiasm, and ease the transition into and experience of the end-of-life period that awaits all who are fortunate enough to “die of natural causes” in old age.
The benefits described above are specific to “treatment” recipients, but the merit of music as therapy cascades into the lives of everyone involved. Doctors and caretakers are uplifted and encouraged by success stories, which contributes to further proliferation and advancement of music as therapy. More critically, it can have a profound impact on families of dementia patients. In some cases, relatives get a chance to communicate with their loved ones again. Grandchildren have a window of opportunity to learn more, directly from their grandparents, about the youthful experiences and memories of past generations. It’s clear that generational bonds are also strengthened, which can positively impact the future prospects of the young generation as they in turn grow old, and lay new groundwork for generations that follow.
It is unfortunate that some elderly individuals seem to derive less cognitive benefit than others from music therapy. It is not entirely certain why this is so, because there are many factors to consider, but two of the clearest factors are a person’s degree of cognitive decline, and their degree of interest in and enthusiasm for music in general. While these are the most popular metrics by which to judge the potential effectiveness and suitability of music as therapy for a given individual, by far the most important consideration is relevance to each particular person’s life experiences.
This is the opportunity to finally state the obvious: It’s not possible to simply pick any song at random and expect it to have a beneficial effect on the cognitive function of every person who hears it. It’s not as if there’s a Britney Spears song that sparks joy in the heart of every soul on Earth. And the legend of Bill and Ted’s ultimate song that united the world could never be a true story (also because, as we finally learned in 2020, it was not two men and a song that united the world, but rather, the world uniting together to create that song.) However, everyone in the world can make their own playlist custom-tailored to their individual life, experiences, and memories, and some of those playlists might have a song or two by Britney Spears, or even some from one of the “Bill and Ted” soundtracks.
Throughout my decades of music appreciation, an ever-growing level of respect for the enduring spirit of music has overwhelmed me, and it’s clear that no song will ever be loved by all. But every song will be loved by some, certainly at least by someone, or it would cease to exist. This is why a personalized playlist is infinitely more valuable than randomly selected songs, and we can see the truth of this claim upon close examination of recorded interviews with the elderly subjects. The songs that triggered the greatest reactions were songs that interviewees felt strong connections to, based primarily on the song’s associations to the time and place, as well as the emotional context imprinted on the memory of the events surrounding the songs.
This simply means that songs for which we have emotional attachments and vivid memories are songs that invigorate our neural circuits, activating cognitive pathways and opening doors of memory similar to how olfactory sensations can trigger a memory or a sense of déjà vu. There are some exceptions, but a lot of these songs are from a person’s formative years, particularly early developmental years and their teenage period. This comes as no surprise to the discerning neuroplastician, because these are periods of life when neural plasticity is most fluid, neural development and refinement functions are most active and receptive, and the degree of exciting novelty in life tends to be highest when we are young and inexperienced.
Novelty and emotion are critical components of memory formation and whether a given experience will be memorable or not. Something completely new (novelty) can be memorable if it commands your attention, or derails you from your usual pattern of behavior. Similarly, the content of a tedious lecture may be harder to recall without taking notes, while that of an exciting, fun, and funny, interactive lesson has a greater chance of being memorable, and recalled with more clarity and detail (emotion).
When it comes to music, the connection to novelty and emotion is crystal clear. The first time you ever heard that song, it was new and your emotional response was strong. You might even remember the events of that first time you heard it, but not necessarily. Your emotional attachment to the song may have developed later on, when you heard it playing at a party, on one of the most memorable nights of your teenage life, for example. Perhaps it’s just a song (or songs) your parents played a lot when you were young, and it could be a song you yourself heard many times, and looking back realized it holds a special place in your heart, for whatever reason. There are also songs that are special to romantic couples (This song was playing when we…; This is our song; We were together the first time we heard this song; etc.) and these songs, for obvious reasons, can be added to a personalized music playlist at any time in life, as new and old songs take on added personal significance in various ways. There are a multitude of ways that novelty and emotion can combine to form experiences worth remembering, by which memories are made, and if these experiences are imprinted with a musical stamp, the song stamped onto the memory is likely to remain just as memorable as the event itself, and conversely, listening to the song has the potential to vivify the memories and feelings of nostalgia related to the song.
Therefore, as a preventative measure we can implement now, and an insurance policy we may benefit from later, it is advisable that each person should endeavor to compile their own personal, individualized cognitive reserve playlist. When speaking to someone about this idea, they responded, “But what’s the hurry? After all, you’re still quite young.” Just then, it spontaneously occurred to me that a traumatic head injury could befall me the following day or any day hence, and the simple point that “it’s never too early” was well taken.
To create your own cognitive reserve playlist, it is helpful to have a few guiding parameters. Most important of all is to keep an open mind without setting anything in stone. It’s not necessary to finalize the list immediately, if ever. This is a project that deserves your thoughtful consideration, so you deserve to be allowed to take your time. It’s better to get the list populated with your definite favorites, and as many others that come to mind, just to kick-start the process. Besides, due to the virtually infinite number of songs and compositions in existence, we will never be able to make the perfect list in one day, one month, or even one year. We can always revisit the list and make changes later, because our minds cannot retrieve all the data at once. We must go about our business of carrying on, and wait for it to come to us. (It’s guaranteed to be worth the wait, so never fret about it.) You may even find yourself removing one of those “definite favorites” from the list, which is welcome and fine, because it’s not merely a list of your favorite songs. Being a “favorite” is just one of multiple indicators that a song might be appropriate for a cognitive reserve playlist. “Memorable” is another key word.
There are still other factors that determine a song’s suitability for a personal playlist, such as a song that isn’t a personal favorite, but which nevertheless evokes a strong emotional response in some other way. This is best described as nostalgia, and nostalgic emotions are powerful anchors for memories. So any song that arouses some sense of nostalgia also has the power to arouse the memory of events, places, times, and other details tied to that nostalgia. To know what songs are nostalgic for you and add them to your list today, may help you if a time should come that you need music as therapy in order to trigger your memory and cognitive function.
It is because of nostalgia that many songs from our youth are good candidates for inclusion on the playlist. Songs that were popular on the radio or TV when we were children, theme songs from popular television programs that are unforgettable for us, and songs that acted as the soundtrack to our lives, so to speak, while growing into childhood, and then blossoming again from adolescence into adulthood. This period is rich with music of great significance to our personal center.
It is my sincere hope that all people earnestly endeavor to compile their own personalized cognitive reserve playlists, and encourage their loved ones to do the same. Maybe it can help those who suffer to better cope with the condition. Perhaps starting this project now, and focusing on mental health now can be a significant contributing factor to developing robust cognitive reserve in the first place, thereby heading off the worst of what this condition can throw at us, and delaying it until later. And of course, not only should we create the lists, but it’s highly recommended that we also play the songs frequently, and dance to them as well, preferably. It is in the interest of your future health, ability, mobility, enjoyment, and ease of living that I offer this potentially beneficial suggestion, and I am grateful that you have taken the time to hear me out regarding my passion about the restorative and healing properties of music, as they relate to the broader topic of neuroplasticity. So on that note, shall we press play and dance?
-
 @ 2b24a1fa:17750f64
2025-04-03 07:46:37
@ 2b24a1fa:17750f64
2025-04-03 07:46:37„Ein Fundstück aus dem Internet – jemand fragt:\ „Wie fühlst du dich als Geimpfter, wenn du eine Maske tragen musst, um die Ungeimpften zu schützen?“
https://soundcloud.com/radiomuenchen/was-ist-passiert-ein-buch-von-michael-sailer
\ Jemand antwortet:\ „Wovor sollte ein Geimpfter einen Ungeimpften schützen?\ 1. Der Geimpfte kann doch gar nicht krank werden, also auch niemanden anstecken, dachte ich?\ 2. Wenn der Geimpfte doch krank werden und andere anstecken kann, wozu hat er sich dann impfen lassen?\ 3. Und wozu sollte sich dann der Ungeimpfte impfen lassen?\ 4. Und wozu sollte dann überhaupt einer der beiden eine Maske tragen?“\ Jemand antwortet:\ „Das ist pure Querdenkerei. Solche kruden Theorien können Menschenleben zerstören.“\ „Eine bessere Parabel auf den religiösen Charakter des aktuellen Wahns könnte ich mir nicht ausdenken“,\ schreibt der Münchner Kolumnist Michael Sailer in seinem Buch Was ist passiert – Notate aus den Zeiten von Lüge und Krieg, das Ende Februar erschienen ist. Als neugieriger und zwangsläufig teilnehmende Beobachter analysiert, kommentiert und hinterfragt der Autor die gesellschaftlichen Abgründe, die sich 2020 und 2021 vor unser aller Augen auftaten.
Unser Autor Jonny Rieder hat es gelesen und eine Rezension verfasst.
Sprecher: Ulrich Allroggen
Bild: Radio München - Kunst: Isaac Cordal (Cement Eclipses)
-
 @ 3c7dc2c5:805642a8
2025-04-02 21:15:55
@ 3c7dc2c5:805642a8
2025-04-02 21:15:55🧠Quote(s) of the week:
CBDC the digital euro - a centralized solution in search of a problem. While the ECB may see it as a way to 'modernize' finance, true innovation comes from empowering individuals, not consolidating control. CBDCs are just surveillance tools disguised as innovation. Bitcoin is the only true digital money—decentralized, scarce, and free. Stack sats, not CBDCs.
🧡Bitcoin news🧡
2025 https://i.ibb.co/vx988kT1/Gn-Ix-Dp-YWs-AASkiw.jpg
On the 24th of March:
➡️The Pakistan central bank is exploring mining Bitcoin with excess electricity.
➡️'MicroStrategy just added another 7,000 Bitcoin to their treasury. They're now holding over 506,000 BTC ($44 billion). Look at the corporate Bitcoin ownership breakdown: - MicroStrategy: 506,000+ BTC - Marathon: ~46,000 BTC (10x smaller) - Riot: ~19,000 BTC (26x smaller) That acquisition curve has gone parabolic since Q4 2024. Strategy's buying pace now rivals what we're seeing from the Bitcoin ETFs, a single public company absorbing supply at an institutional scale. Clear institutional conviction signal here.' -Ecoinometrics
➡️SQUARE CEO JACK DORSEY: "Bitcoin will make the current financial system feel as irrelevant as the fax machine."
On the 25th of March:
➡️'BITCOIN HASH-RIBBON FLASHES BUY SIGNAL
- This is one of the most reliable "buy" indicators.
- Significant price gains have followed 7 out of the last 7 times this indicator was triggered.' -Bitcoin Archive (foto) Bitcoin is always a buy. Just DCA.
➡️GameStop includes Bitcoin as a treasury reserve asset in its investment policy update. GameStop has $4.6 billion in cash to invest.
➡️Strategy’s sale of 8.5 million STRF shares closes today, unlocking $711 million in new capital to buy more Bitcoin.
➡️BBC News reports from a remote community of 15,000 people in the far north-western tip of Zambia relying on hydroelectric power, “The bitcoin mine now accounts for around 30% of the plant's revenue allowing them to keep the prices down for the local town” - Source: https://www.bbc.com/news/articles/cly4xe373p4o Gridless is doing a splendid job in Africa and showing through proof-of-work that if you aren't mining Bitcoin, you are wasting energy. It's time for such communities to appear more around the world.
Daniel Batten: 'They couldn't resist zooming out and implying this is an outlier (it isn't, the majority of off-grid bitcoin mining operations are renewably powered). In doing so BBC made three factually incorrect statements at the end about Bitcoin mining straining grids (multiple peer-reviewed studies show the opposite is true), and "Greenidge gas power plant in New York which was renovated to mine bitcoin" (it didn't, it re-opened to supply power back to the grid), and stating that Bitcoin mining needs artificial govt incentives or rules to do the right thing (It doesn't, it's become 56.7% sustainably powered without any govt incentives)
But let's shine the light on the positive - it has far fewer factually incorrect statements than previous reporting, and it is a step in the right direction in its gradual journey towards objective Bitcoin reporting for a media company that has until now only published negative news stories on Bitcoin.'
➡️Femke Halsema, Mayor of Amsterdam, wants a national ban on Bitcoin payments: "It undermines our civilization".
I rather believe the opposite.
Under Femke Halsema - Amsterdam
-
The number of civil servants increased by 50% (14K -> 20K)
-
Debt increased by 150% (4 billion -> approx. 10 billion)
Despite high revenues, Amsterdam has to borrow nearly half a billion euros every year. Local taxes continue to rise, whether it's water authority taxes or property taxes (OZB). But, above all, you should be concerned about those 0.3% criminal Bitcoin / Crypto transactions (worldwide). The audacity.
Even if the Netherlands were to legally ban Bitcoin payments, users could easily continue trading through foreign exchanges or peer-to-peer platforms. A ban might actually push Bitcoin usage further underground, making oversight of suspicious transactions worse rather than better.
➡️Mt. Gox moves 11.501 Bitcoin ($1B) for creditor repayment.
➡️BlackRock launched a European Bitcoin ETP today - Bloomberg
➡️North Carolina introduces a bill to invest 5% of state funds into Bitcoin.
On the 26th of March:
➡️NYDIG just became a big Bitcoin miner. Crusoe, the first to scale Bitcoin mining off flared gas (~200MW worth, across 425 data centers) has sold its entire Bitcoin mining business to NYDIG.
➡️Metaplanet has raised ~$55.2m (¥8.28b) of equity capital through three trading days this week while partially deleveraging with the redemption of $23.3m (¥3.5b) of 0% ordinary bonds.
➡️GameStop can service a loan of up to $100 BILLION for 4.6 years with its existing $4.6b cash balance at 1% interest. That's twice the amount of Bitcoin Michael Saylor's Strategy currently holds.
➡️New feature by Protonmail enables their 100 million users to send Bitcoin using their email addresses.
➡️The Blockchain Group confirms the acquisition of 580 BTC for ~€47.3 million, the holding of a total of 620 BTC, and a BTC Yield of 709.8% YTD.
→ Confirmation of the acquisition of 580 BTC for ~€47.3 million at ~€81,550 per bitcoin
→ Total group holdings of 620 BTC for ~€50.5 million at ~€81,480 per bitcoin
→ Adoption of ‘BTC Yield’, ‘BTC Gain’, and ‘BTC € Gain’ as KPIs, following the steps of Strategy and Metaplanet
This is a major step in our Bitcoin Treasury Company strategy focused on increasing Bitcoin per share over time.
Source: https://t.co/QDj61ZDe6O
The Blockchain Group is Europe's First Bitcoin Treasury Company!
On the 27th of March:
➡️'Bitcoin's 4-year Compound Annual Growth Rate (CAGR) is at historic lows.' -Pierre Rochard
➡️Daniel Batten: Yet another paper on Bitcoin and energy TL:DR: "The opportunities offered by bitcoin mining in reduction of the greenhouse gas emissions and renewable energy transition are greater than generally assumed" The journal has a (high) impact factor of 7.1."
Source: https://t.co/W3gytMgcpC
➡️A home miner with only 4 machines mined block 888737.
https://i.ibb.co/7xm91R4t/Gn-Ef-H9y-Ws-AA4jkn.jpg
Bitcoin proves anyone can participate and earn—true freedom!
➡️'Short-Term Holders have increased their Bitcoin holdings by 201,743 BTC to 5,750,076 BTC since January, remaining below previous cycle peaks. 200K BTC are currently held at an unrealized loss, representing about $17B.' -Bitcoin News
➡️Bitcoin mining hardware manufacturer Canaan signs a three-year colocation agreement with Mawson Infrastructure Group's Mawson Hosting LLC for facilities in Midland, Pennsylvania, and Edna, Texas. Most of the 4.7 EH/s hashrate is expected to be operational by Q2 2025.
On the 28th of March:
➡️If Saylor had bet on ETH instead of Bitcoin, Strategy would be down $9 billion, instead of up $9 billion like they are today. ETHBTC made fresh lows 0.02210. Ether is down 74% against Bitcoin since switching from proof of work to proof of stake. Yikes!
➡️Representative introduces a strategic Bitcoin reserve bill in South Carolina.
➡️A Russian company built a Bitcoin mine in the Arctic. Set in the frozen city of Norilsk, the facility taps into cheap excess energy from one of the world's most isolated industrial hubs.
➡️The price of bitcoin has nearly followed the same phases of volatility for 15 years, according to Fidelity.
https://i.ibb.co/LdQfrqG0/Gn-Ig-Skd-XMAAi-L3r.jpg
another great chart:
https://i.ibb.co/G4WmDjhd/Gn-JED1q-Xk-AAq-Kqk.jpg
On the 29th of March:
➡️Public miner MARA with a $2B common stock offering to buy more Bitcoin. https://i.ibb.co/PZZxXJ37/Gn-Kj-Vqza-EAEUG-V.png
➡️California has officially included Bitcoin Rights protections in its newly proposed digital asset bill. If passed, it will guarantee the right to self-custody for nearly 40M residents and prohibit discrimination against Bitcoin use.
➡️The number of addresses with more than one Bitcoin has fallen below 1 million, standing today at 995,207.
On the 31st of March:
➡️Larry Fink, Founder/CEO of BlackRock in his annual letter to shareholders: “If the U.S. doesn't get its debt under control, if deficits keep ballooning, America risks losing that position to digital assets like Bitcoin."
https://www.blackrock.com/corporate/literature/presentation/larry-fink-annual-chairmans-letter.pdf
➡️Strategy has acquired 22,048 BTC for ~$1.92 billion at ~$86,969 per bitcoin and has achieved a BTC Yield of 11.0% YTD 2025. As of 3/30/2025, Strategy holds 528,185 $BTC acquired for ~$35.63 billion at ~$67,458 per bitcoin.
➡️ The Bitcoin Policy Institute releases a framework for the USA to buy $200 billion worth of #Bitcoin using Bit Bonds.
➡️Is Indonesia the next Bitcoin Country? Bitcoin Indonesia mapped out the entire Bitcoin ecosystem.
A new map shows Bitcoin adoption EXPLODING across the Southeast Asian island nation of Indonesia. Check out all the communities, projects, and businesses embracing Bitcoin. The revolution is happening.
https://i.ibb.co/cXL8mC0x/Gnbdg-Lub-IAAdwcb.jpg
On the 1st of April:
➡️'Over 73,353 BTC were bought by corporations in Q1 2025. Only 40,500 BTC new Bitcoin was mined, but still no supply shock, for now... Which company do you want to see adopt BTC next?'
Here is the breakdown by Alec: https://x.com/Alec_Bitcoin/status/1907062290345783723
➡️After skeptics questioned Tether’s Bitcoin holdings, CEO Paolo Ardoino fired back, sharing the company’s BTC address with a confirmed balance of 92,646 BTC. On the same day Tether bought 8,888 Bitcoin worth $735 million as per on-chain data. They now hold over 100,000 BTC.
➡️'GameStop just raised $1.48B. They are expected to use that and possibly more of the now $6B+ on their balance sheet to buy Bitcoin. A master class on how to pivot from meme stock to capitalize on volatility in the ultimate store of value.' -James Lavish
➡️Texas' state house Democrats have proposed a bill that would authorize up to $250 million in state investment in Bitcoin and up to $10 million for each municipality and county.
➡️Human Rights Foundation donates 10 Bitcoins worth $830,000 to over 20 projects worldwide.
Alex Gladstein: '1 billion sats gifted carefully to a variety of stellar organizations and individuals to support BTC privacy, decentralization, education, and p2p use, aimed at folks working under authoritarianism.'
💸Traditional Finance / Macro:
On the 29th of March
👉🏽'From Wednesday to Friday, the S&P 500 lost -$100 billion PER trading hour for a total of -$2 TRILLION. Then, after the market closed on Friday, S&P 500 futures erased ANOTHER -$120 billion in minutes.' -TKL
🏦Banks:
👉🏽 no news
🌎Macro/Geopolitics:
On the 24th of March:
👉🏽Financelot: 'This is fascinating. The Dow Jones to Gold Ratio is about to cross a level only seen 4 times in history. Every time it crossed this level it marked the beginning of an 18-month recession/depression. 1929, 1973, 2008 & 2025' I don't think we won't see a depression. History rhymes but doesn't always mean it will repeat, although human behavior stays the same. For now, it means the market is overvalued, gold is undervalued, or both.
👉🏽US household wealth is falling: US household equity wealth is set to drop a whopping -$3 trillion this quarter, the most since the 2022 bear market, according to BofA estimates. By comparison, equity holdings rose +$9 trillion in 2024 to a record $56 trillion. In other words, one-third of last year's gains have likely been wiped out due to the recent market pullback.
Furthermore, the top 10% of the wealthiest Americans own 87% of US stocks. This, in turn, may negatively impact consumer spending as the top 10% reflect a record 50% of all consumer expenditures. Consumer spending is set to slow in Q2 2025.' -TKL
👉🏽Demolition of the Boiler House at Moorburg Power Plant in Hamburg. Germany is preparing for combat by dynamiting its own modern energy infrastructure down. This was the most advanced coal plant. 6 years old and cost three billion euros. The Netherlands is following a similar policy—they poured concrete into their gas drilling pipes.
BowTiedMara on Twitter: "In 2022, a girl tied herself to the net at Roland Garros in protest, and she wore a T-shirt that said: "We have 1,028 days left." Today, the 27th of March, marks those 1,028 days, and nothing happened. Climate doomers are like Aztecs who think the sun stops unless they cut out some organs."
👉🏽Starting in April, the 66,000 employees of the European institutions will receive their seventh salary increase in just three years! Normally, this happens at most once per year. The President of the European Commission, Ursula von der Leyen, will see the largest increase, with her monthly salary rising to €34,800—an increase of €2,700—according to a report by the German newspaper Bild-Zeitung today.
For the Dutch readers: https://ejbron.wordpress.com/2025/03/24/eu-bureaucraten-en-politici-krijgen-de-7e-salarisverhoging-sinds-2022/
They are compensating for the inflation they impose on the EU. Lucky them Fair to say we need a DOGE in Europe.
On the 25th of March:
👉🏽Dutch minister announces a huge increase in excise duties of 25.8 cents on gasoline. On top of that, the price of gasoline will rise by an additional 7 cents due to the blending requirement and 11 cents due to the ETS-2 regulation. In a free market, prices would not be announced by politicians but would emerge through supply and demand. How I love the EU....although it is a bit more nuanced. The temporary discount is ending. Unless the parliament decides to extend it, the price of gasoline will rise. The Dutch government should simply spend less and abolish all taxes, excise duties, and levies on food, fuel, and energy. Never gonna happen though.
👉🏽"Shell will be thoroughly reviewing all its chemical divisions worldwide in the coming period. In Europe, this could lead to the partial or complete closure of various chemical branches." As mentioned multiple times last month, major industrial companies sounded the alarm. They warned that high energy costs in the Netherlands put their future at risk. Additionally, sustainability efforts and unclear government policies are challenging the sector. Frans Everts, President-Director of Shell Netherlands, warned that the entire industry could collapse.
The Green Deal is moving full speed ahead—soon everyone will be relying on food banks…
For the Dutch readers: https://nos.nl/artikel/2561036-shell-kijkt-naar-gedeeltelijke-sluiting-van-chemie-onderdelen
On the 26th of March:
👉🏽EU countries will start using a digital driver’s license from 2030. This is the result of negotiations between the European Parliament and EU member states. In the Netherlands, the digital license will be valid for ten years and will be accessible via an app. And we all know which app that will be! The EU Digital Wallet must be filled, after all.
Not just your driver’s license—everything will soon be linked to your digital identity. It’s all right there on the EU’s website, and it’s been planned for a long time. The COVID pass was already part of the rollout. The fact that they present these as separate steps just shows that they know people wouldn’t accept it if they were fully aware of what’s happening.
On the 27th of March:
👉🏽Gold surpasses $3,100 for the first time in history. TKL: 'Gold prices have hit 50 all-time highs over the last 12 months, its best streak in 12 years. This is also the 3rd-longest streak on record after a historic run during the late 1970s. The 1970s came with a period of double-digit inflation, stagnant economic growth, and a high unemployment rate, also known as stagflation. As a result, gold prices recorded 4 consecutive yearly gains.'
On the 31st of March for the first time, gold blasted through $100,000/kilogram. This time, gold prices have rallied 39% over the last 12 months, are up 16% year-to-date, and are on track for the 3rd annual positive performance.'
👉🏽NATO Secretary General Rutte insists there will be no normalization of relations with Russia for decades to come.
On March 14, 2025, Bloomberg, Rutte says: "Once the war is over, relations with Russia will gradually be restored."
On March 26, 2025, Rutte said: "There will be no normalization of relations with Russia for decades, even after the war is over."
That is the Mark I know!
"Mark Rutte, the long-serving Dutch Prime Minister, earned the nickname “Pinokkio” (Dutch for Pinocchio) primarily because of perceived dishonesty or evasiveness in political debates and scandals. While some still view Rutte as a pragmatic and stable leader, the nickname “Pinokkio” reflects a broader public sentiment of distrust, especially among those who felt betrayed by his communication style or decisions.”
On the 28th of March:
👉🏽US consumers now expect 5.0%(!) inflation in the next twelve months. Inflation expectations have DOUBLED in just four months. That's huge! Long-term US inflation expectations have officially SURGED to 4.1%, the highest level since 1993. Tariff front-running has led to a $300+ BILLION trade deficit in 2 months, and consumer sentiment has collapsed.
Atlanta Fed is now projecting that Q1 GDP will be -2.8%… a large contraction. It’s negative even “gold adjusted”
4 weeks ago it was +2.3%
8 weeks ago it was +3.9%
Yikes!
👉🏽The State Department is officially shutting down USAID and has formally notified Congress of its closure. The remaining 900 employees are set to be terminated.
👉🏽Argentina’s Economy Grows 6.5% in January. Argentina’s Poverty Rate Drops from 52.9% to 38.1% in 15 Months Under Javier Milei
👉🏽Fix the money, fix the world:
DOGE “There is actually really only ONE BANK ACCOUNT that's used to disperse ALL monies that go out of the federal government” “It's a big one — A couple of weeks ago it had $800 billion in it, it's the treasury general account”
“We're serving 580+ agencies. And up until very recently, effectively they could say, make the payment and Treasury just sent it out as fast as possible. NO VERIFICATION”
“There's a $500 billion of fraud every year. There are hundreds of billion dollars of improper payments and we can't pass an audit. The consolidated financial report is produced by treasury and we cannot pass an audit”
Extremely fascinating interview by Bret Baier with the highly talented and competent DOGE team, which is rigorously streamlining the U.S. government bureaucracy. This work can only be done by competent (and motivated) outsiders with experience. Also urgently needed in the Netherlands, and in Europe.
On the 29th of March:
👉🏽'US debt has been "limited" by the $36.104 trillion debt ceiling since January but the liabilities don't stop rising. As of today, US debt is now ~$37 trillion. Treasury has burned through $560BN of its cash balance in the past month. Just $280BN left.' -ZeroHedge
On the 1st of April:
In recent weeks, I have shared my opinion on the latest Dutch pension fund drama. This week:
https://i.ibb.co/96ZhS0W/Gn-XEVQRXw-AM6b0-A.jpg
APG and pension funds refused to invest in Dutch housing (for political reasons). This involved 25 billion euros.
Currently we almost have a political scandal over a medal, but the fact that our pension system is being put at risk...no biggie!?
For our own housing market? “Too political.” For war and Brussels' military ambitions? €100,000,000,000—no problem.
They’re gambling with your pension while first-time buyers can’t afford a home and seniors struggle to make ends meet. Our money, their agenda.
Got Bitcoin?
I will end this Weekly Recap with a Stanley Druckenmiller quote:
"My favorite quote of all time is maybe Mark Twain: "Put all your eggs in one basket and watch the basket carefully."
"I tend to think that's what great investors do."
I know what I do and have. Bitcoin!
🎁If you have made it this far I would like to give you a little gift:
What Bitcoin Did: Peter Dunworth is the Director of a multi-family office and is the co-founder of The Bitcoin Adviser. In this episode, they discuss why Bitcoin is the only asset that can recapitalize the financial system, why Peter believes Bitcoin could become a $100 trillion asset within a decade, why credit markets are ultimately a collateral problem, and why financializing Bitcoin might be necessary to save Main Street from being collateral damage. They also get into Australia's property obsession, GameStop’s pivot to Bitcoin, the difference between Bitcoin derivatives and the asset itself, and MicroStrategy.
https://www.youtube.com/watch?v=_bSprc0IAow
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ cbaa0c82:e9313245
2025-04-02 18:53:57
@ cbaa0c82:e9313245
2025-04-02 18:53:57TheWholeGrain - #March2025
March of 2025 was a standard month for Bread and Toast. However, it did include a the occasional five Sunday Singles which seems like hitting the jackpot! Talk about lucky!
Included with the five Sunday Singles was two more pages of the Adventure Series: Questline where we saw Bread, Toast, and End-Piece face off against their first adversary!
End-Piece made a first appearance for in Toast's Comic Collection under the title E: The Last Slice while the Concept Art piece was the original drawing of all three slices of bread together. And, last of all we updated the Bitcoin logo because why not!?
Sunday Singles - March 2025 2025-03-02 | Sunday Single 82 Title: Slingshot! Watch out! Toast is quite the sharpshooter! https://i.nostr.build/zHA9C7cOOZLOCl0o.png
2025-03-09 | Sunday Single 83 Title: Puzzles End-Piece just figured out the puzzle! https://i.nostr.build/u2EBdcsuwO2xo23P.png
2025-03-16 | Sunday Single 84 Title: Basketball Oh, the madness! https://i.nostr.build/8F1OFFVra7zQOIy6.png
2025-03-23 | Sunday Single 85 Title: Coffee The perfect way to start the day. https://i.nostr.build/aiGZOvOmow3igru6.png
2025-03-30 | Sunday Single 86 Title: Origami End-Piece has a way with paper. https://i.nostr.build/0ySzGwF9QnZxwLxD.png
Adventure Series: Questline The group is attacked by a crow with Bread being the target of the giant bird, but with a group of trusty friends any enemy can be defeated!
Artist: Dakota Jernigan (The Bitcoin Painter) Writer: Daniel David (dan 🍞)
2025-03-11 | Questline 005 - Under Attack Toast and End-Piece are able to escape the attack from the giant winged predator, but Bread being distracted by thoughts of the village is caught off guard. End-Piece immediately charges the attacker with a fury of mallet swings. Meanwhile, Toast loads up an arrow with intentions of piercing through the giant bird. https://i.nostr.build/F24sd7SFFbsW9WZY.png
2025-03-25 | Questline 006 - A Finished Battle End-Piece lands a series of blows to the winged beast. Toast finishes it off with a second arrow to the heart. Bread is only slightly injured, but is more upset about having been so vulnerable due to being so distracted. Moving forward Bread will have to be more vigilant. https://i.nostr.build/n5a7Jztq9MHxuGNf.png
Other Content Released in March 2025 2025-03-05 | Toast's Comic Collection Title: E: The Last Slice #11 A gluten-based pandemic has killed off all slices of bread that are not Toast except for one slice of bread that happens to be an end piece. https://i.nostr.build/aar20oHAAKmZOovD.png
2025-03-12 | Concept Art Title: Original Bread and Toast This was the first drawing of all three characters together. It was used a lot for branding when the project first started up in 2023. https://i.nostr.build/yqkmBuTiH8AKbCzI.png
2025-03-19 | Bitcoin Art Title: Bitcoin/Bread Block Height: 888566 Two things that just go together. https://i.nostr.build/MDPkzOPVEaOJVTFE.png
Thanks for checking out the seventh issue of The Whole Grain. The Whole Grain is released on the first of every month and covers all of the content released by Bread and Toast in the previous month. For all Bread and Toast content visit BreadandToast.com!
So long, March! Bread, Toast, and End-Piece
BreadandToast #SundaySingle #Questline #ToastsComicCollection #ConceptArt #BitcoinArt #Bread #Toast #EndPiece #Artstr #Comic #Cartoon #NostrOnly #🍞 #🖼️
List of nPubs Mentioned: The Bitcoin Painter: npub1tx5ccpregnm9afq0xaj42hh93xl4qd3lfa7u74v5cdvyhwcnlanqplhd8g
dan 🍞: npub16e3vzr7dk2uepjcnl85nfare3kdapxge08gr42s99n9kg7xs8xhs90y9v6
-
 @ 8d34bd24:414be32b
2025-04-02 14:13:03
@ 8d34bd24:414be32b
2025-04-02 14:13:03I was reading this passage last night:
…from that time when one came to a grain heap of twenty measures, there would be only ten; and when one came to the wine vat to draw fifty measures, there would be only twenty. I smote you and every work of your hands with blasting wind, mildew and hail; yet you did not come back to Me,’ declares the Lord. ‘Do consider from this day onward, from the twenty-fourth day of the ninth month; from the day when the temple of the Lord was founded, consider: Is the seed still in the barn? Even including the vine, the fig tree, the pomegranate and the olive tree, it has not borne fruit. Yet from this day on I will bless you.’ ” (Haggai 2:16-19) {emphasis mine}
Why were bad things happening to the Israelites? Because they were not following God. Why did God allow these difficult situations to occur? Because God was calling them back to Himself.
This made me think of several times lately, when I had written about Christians going through hard times, that fellow believers had tried to kindly correct me implying that God would not allow these painful things to happen to believers. They were trying to defend God’s honor, but instead they were degrading God. If God is not in control of everything, then either God is unable to protect His own from harm because of sin or bad things happened accidentally and God ignored the injustice. Saying God was not in control of allowing every hardship is either saying God isn’t strong enough, isn’t smart enough, or isn’t loving enough. The God I serve is omniscient, omnipotent, omnipresent, and love incarnate. He also didn’t promise us easy, pleasant lives, but did promise that good would come out of every situation.
And we know that in all things God works for the good of those who love him, who have been called according to his purpose. (Romans 8:28)
When Jesus walked on earth and some people said they wanted to follow Him, His response was not what we would expect:
And He was saying to them all, “If anyone wishes to come after Me, he must deny himself, and take up his cross daily and follow Me. For whoever wishes to save his life will lose it, but whoever loses his life for My sake, he is the one who will save it. For what is a man profited if he gains the whole world, and loses or forfeits himself? For whoever is ashamed of Me and My words, the Son of Man will be ashamed of him when He comes in His glory, and the glory of the Father and of the holy angels. (Luke 9:23-26) {emphasis mine}
When one particular man said that he would follow Jesus anywhere, Jesus responded this way.
As they were going along the road, someone said to Him, “I will follow You wherever You go.” And Jesus said to him, “The foxes have holes and the birds of the air have nests, but the Son of Man has nowhere to lay His head.” (Luke 9:57-58) {emphasis mine}
Jesus was brutally honest that following Him would not be easy or comfortable. Following Jesus is more likely to lead to hardship and persecution that prosperity and comfort.
“Then they will deliver you to tribulation, and will kill you, and you will be hated by all nations because of My name. At that time many will fall away and will betray one another and hate one another. Many false prophets will arise and will mislead many. Because lawlessness is increased, most people’s love will grow cold. But the one who endures to the end, he will be saved. This gospel of the kingdom shall be preached in the whole world as a testimony to all the nations, and then the end will come. (Matthew 24:9-14) {emphasis mine}
Of course God isn’t putting us through hardship to torture us. He is putting us in situations to grow our faith and dependence on Him, i.e. Abraham. He is putting us in situations where we can minister to others, i.e. Joseph. He is using us as examples of faith to others, i.e. Job. Any hardship has an eternal purpose. Sometimes we can see it (at least eventually) if we are looking for God’s will and plan. Sometime we won’t see what He was accomplishing until we get to heaven. Still we need to trust God through it all, knowing His plan is perfect.
“For my thoughts are not your thoughts,\ neither are your ways my ways,”\ declares the Lord.
“As the heavens are higher than the earth,\ so are my ways higher than your ways\ and my thoughts than your thoughts.
As the rain and the snow\ come down from heaven,\ and do not return to it\ without watering the earth\ and making it bud and flourish,\ so that it yields seed for the sower and bread for the eater,\ so is my word that goes out from my mouth:\ It will not return to me empty,\ but will accomplish what I desire\ and achieve the purpose for which I sent it. (Isaiah 55:8-11) {emphasis mine}
God understands how hard it is to understand what He is accomplishing. We live in the here and now while He is outside time and space and therefore has a heavenly and eternal perspective that we will never truly have this side of heaven. He has told us how the story ends, so that we can have peace and trust Him through whatever circumstances He has blessed us.
Jesus answered them, “Do you now believe? Behold, an hour is coming, and has already come, for you to be scattered, each to his own home, and to leave Me alone; and yet I am not alone, because the Father is with Me. These things I have spoken to you, so that in Me you may have peace. In the world you have tribulation, but take courage; I have overcome the world.” (John 16:31-33) {emphasis mine}
In fact, Jesus made this so clear that His disciples rejoiced in persecution they received due to obeying Him and sharing His word.
They took his advice; and after calling the apostles in, they flogged them and ordered them not to speak in the name of Jesus, and then released them. So they went on their way from the presence of the Council, rejoicing that they had been considered worthy to suffer shame for His name. (Acts 5:40-41) {emphasis mine}
Peter specifically warns believers to expect trials and hardship.
Dear friends, do not be surprised at the fiery ordeal that has come on you to test you, as though something strange were happening to you. But rejoice inasmuch as you participate in the sufferings of Christ, so that you may be overjoyed when his glory is revealed. If you are insulted because of the name of Christ, you are blessed, for the Spirit of glory and of God rests on you. If you suffer, it should not be as a murderer or thief or any other kind of criminal, or even as a meddler. However, if you suffer as a Christian, do not be ashamed, but praise God that you bear that name. For it is time for judgment to begin with God’s household; and if it begins with us, what will the outcome be for those who do not obey the gospel of God? And,
“If it is hard for the righteous to be saved,\ what will become of the ungodly and the sinner?”
So then, those who suffer according to God’s will should commit themselves to their faithful Creator and continue to do good. (1 Peter 4:12-19) {emphasis mine}
Paul writes about begging God to take away a health issue. Eventually he accepted it as part of God’s plan for his life and boasted gladly in his hardship.
…Therefore, in order to keep me from becoming conceited, I was given a thorn in my flesh, a messenger of Satan, to torment me. Three times I pleaded with the Lord to take it away from me. But he said to me, “My grace is sufficient for you, for my power is made perfect in weakness.” Therefore I will boast all the more gladly about my weaknesses, so that Christ’s power may rest on me. That is why, for Christ’s sake, I delight in weaknesses, in insults, in hardships, in persecutions, in difficulties. For when I am weak, then I am strong. (2 Corinthians 12:7b-10) {emphasis mine}
No matter what hardships we experience in life, whether poverty or persecution or poor health or loss of a loved one or any other hardship, God is with us working everything for our good.
Who will separate us from the love of Christ? Will tribulation, or distress, or persecution, or famine, or nakedness, or peril, or sword? Just as it is written,
“For Your sake we are being put to death all day long;\ We were considered as sheep to be slaughtered.” **But in all these things we overwhelmingly conquer through Him who loved us. For I am convinced that neither death, nor life, nor angels, nor principalities, nor things present, nor things to come, nor powers, nor height, nor depth, nor any other created thing, will be able to separate us from the love of God, which is in Christ Jesus our Lord. (Romans 8:35-39) {emphasis mine}
I like to look at the story of Joseph as an example of God’s extraordinary plan in the life of a faithful believer. Joseph trusted and honored God. God had a plan for Joseph to be used to save the lives of his family and the people of the Middle East from famine, but God didn’t just instantly put Joseph in a position of power to help. He prepared Joseph and slowly moved him to where he needed to be.
First Josephs brothers wanted to kill him out of jealousy, but God used greed to get them to sell Joseph as a slave instead. He orchestrated the right slave traders to walk by at the right time so that Joseph would wind up in the house of Potiphar, the Pharaoh’s guard.
Then when Joseph acted honorably towards God, his master, and his master’s wife, Joseph was sent to jail for years. I’m sure Joseph was wondering why God would send him to prison for doing what was right, but it put him into the presence of the cupbearer of Pharaoh. A long time after correctly interpreting the cup bearer’s dream, Joseph was called up to interpret Pharaoh’s dream, put in charge of the famine preparation and became second in command after Pharaoh. Joseph, after years of slavery and jail time, was now the second most powerful man in the Middle East, if not the world. God had a plan, but it was hard to see until its completion.
In the same way, Job lost his wealth, his children, his health, and his reputation, but remember that Satan had to get God’s permission before anything could be done to hurt Job. So many people today are blessed by seeing Job’s response to hardship and loss, by seeing Job’s faith, his struggle, and his submission to God’s plan. In this case God even gives Job more after this time of testing than he had before.
When we experience hardship we need to know that God has a plan for our life. It may be something amazing here on Earth. It may be souls won for Christ. It may be to prepare us for heaven. Whatever the case, it is for our good.
We don’t need to be ashamed that God would allow hardship. We grow most when we experience hardship. Our light shines brightest in darkness.
Oh, the depth of the riches of the wisdom and knowledge of God!\ How unsearchable his judgments,\ and his paths beyond tracing out!\ “Who has known the mind of the Lord?\ Or who has been his counselor?”\ “Who has ever given to God,\ that God should repay them?”\ For from him and through him and for him are all things.\ To him be the glory forever! Amen. (Romans 11:33-36)
Trust Jesus
-
 @ ae1008d2:a166d760
2025-04-01 00:29:56
@ ae1008d2:a166d760
2025-04-01 00:29:56This is part one in a series of long-form content of my ideas as to what we are entering into in my opinion;The Roaring '20's 2.0 (working title). I hope you'll join me on this journey together.
"History does not repeat itself, but it often rhymes"; - Samuel Clemens, aka Mark Twain. My only class I received an A+ in high school was history, this opened up the opportunity for me to enroll in an AP (college level) history class my senior year. There was an inherent nature for me to study history. Another quote I found to live by; "If we do not study history, we are bound to repeat it", a paraphrased quote by the many great philosphers of old from Edmund Burke, George Santayana and even Winston Churchill, all pulling from the same King Solomon quote; "What has been will be again, what has been done will be done again; there is nothing new under the sun". My curiousity of human actions, psychological and therefore economical behavior, has benefitted me greatly throughout my life and career, at such a young age. Being able to 'see around the curves' ahead I thought was a gift many had, but was sorely mistaken. People are just built different. One, if not my hardest action for me is to share. I just do things; act, often without even thinking about writing down or sharing in anyway shape or form what I just did here with friends, what we just built or how we formed these startups, etc., I've finally made the time, mainly for myself, to share my thoughts and ideas as to where we are at, and what we can do moving forward. It's very easy for us living a sovereign-lifestyle in Bitcoin, Nostr and other P2P, cryptographically-signed sovereign tools and tech-stacks alike, permissionless and self-hostable, to take all these tools for granted. We just live with them. Use them everyday. Do you own property? Do you have to take care of the cattle everyday? To live a sovereign life is tough, but most rewarding. As mentioned above, I'm diving into the details in a several part series as to what the roaring '20's were about, how it got to the point it did, and the inevitable outcome we all know what came to be. How does this possibly repeat itself almost exactly a century later? How does Bitcoin play a role? Are we all really going to be replaced by AI robots (again, history rhymes here)? Time will tell, but I think most of us actually using the tools will also forsee many of these possible outcomes, as it's why we are using many of these tools today. The next parts of this series will be released periodically, maybe once per month, maybe once per quarter. I'll also be releasing these on other platforms like Medium for reach, but Nostr will always be first, most important and prioritized.
I'll leave you with one of my favorite quotes I've lived by from one of the greatest traders of all time, especially during this roaring '20's era, Jesse Livermore; "Money is made by sitting, not trading". -
 @ 7bdef7be:784a5805
2025-04-02 12:37:35
@ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using nak, to find out the last ten people who have followed a
target_pubkey, sorted by the most recent. It's possibile to shortensearch_timerangeto speed up the search.```
!/usr/bin/env fish
Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u)
if test -z "$pubkeys" exit 1 end
set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null)
set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events endend
if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" endend ```
-
 @ 8671a6e5:f88194d1
2025-04-03 14:52:44
@ 8671a6e5:f88194d1
2025-04-03 14:52:44\~ The person came up to me from behind his merchandise stand and saw my Noderunners pin on my black t-shirt, then looked me dead in the eye and asked : “So… what do you sell?”
This is the eighth long-read in a series of twelve “food for thought” writings on Bitcoin. It was originally meant to be a few chapters in a book, but life’s too short for that.
Define
Let me start by saying there’s no single way to define or explain a “Bitcoin conference.” The experience can vary depending on a few factors: who’s organizing it (a long-time Bitcoiner or someone from traditional finance trying to grasp Bitcoin), where it’s being held (a sunny paradise like Madeira or a gloomy northern French town), and who’s speaking (technical experts or charismatic entertainers or people with little substance).
Despite these differences, there’s a shared culture that ties these conferences together: a mix of excitement, frustrations, and inevitable evolution. That’s what I explore.
This is just my take, based on what I’ve personally witnessed and what I hear from my surroundings. It’s not meant to be a blanket critique of all Bitcoin conferences as there are plenty I haven’t attended, though I hear about most of them. Even the good ones will evolve into something else over time. So, plan accordingly.
A bit of background on my perspective: at some point in my life, I hit a bump in the road that kept me tied to where I live — a bleak corner of Belgium, surrounded by fiat slaves, shitcoiners, and people who spend six hours a day consuming brain-numbing garbage television. Traveling is an exception for me, but for many Bitcoin conference attendees, it’s a ritual, a must-do event.
So, I view these events with a mix of fascination and grounded skepticism — something I’ve found lacking in many Bitcoiners. I’ve never been to a Bitcoin conference before 2023, despite receiving plenty of invites over the years. From what I heard and saw in photos from friends who attended (even the real early ones) these events seemed eerily similar to the dull hotel conference rooms I once endured in tech and telecom. I’ve had my fill of lukewarm, watery coffee and lifeless speakers droning on about firewalls. So I skipped that particular honor.
Up until around 2018, Bitcoin conferences were a soulless sea of chairs lined up under fluorescent tube lights, draining the life out of attendees—one telecom acronym at a time. Not exactly inviting. Yet, looking back from the perspective of 2025, those were the “pure” days. Back then, people like Roger Ver (before he pivoted to Bitcoin Cash), Andreas Antonopoulos, and encryption specialists spoke to small audiences, explaining Bitcoin in its raw form.
But, like any Bitcoiner, I try to improve myself. So, I made the effort to travel, visit other Bitcoiners, and attend Bitcoin conferences. The conferences I attended in 2023/2024 made me a bit wiser ; not necessarily from what was said on stage (with a few lucky exceptions who still try to bring original thoughts). Most of what I learned came from the long queues, the drama, and watching grifters operate in real time and the good characters floating around.
So, here’s what I’ve learned.

Chain of ticket
I quickly discovered that many Bitcoin conferences have their own “quest for tickets” dynamic, almost like an industry with its own inner circle. It’s a waterfall system: tickets start at lower prices to fill up the venue (usually right after the previous edition). That’s standard practice, both inside and outside of Bitcoin. But what’s strange is seeing organizations that only pop up when a conference needs promotion—somehow securing tickets for themselves and their friends (or for *making* friends) while shilling referral links for small discounts to their followers.
The real free tickets, though, are a hot topic in many local communities and make all the difference for some attendees. What’s particularly interesting is that most ticket prices can be paid in Bitcoin, adding a layer of calculation to the process.
If you paid 230500 sats for your ticket and later see the dollar price fluctuate, say from $180 to $270, or the other way around, by the time the conference starts, you realize you either bought too late or too early.\ It’s better to not have bought at all.
Some ticket holders end up paying less (in dollar terms) than others, making it a gamble. As the event date approaches, ticket prices tend to rise—unless you wait until the last minute, when they haven’t sold out, or just pay at the door. It’s a strange feeling knowing that not everyone paid the same amount (and as mentioned, a significant number get in for free) depending on their timing.
Many organizations and local community representatives show up primarily to be present; securing free tickets, which function more as a badge of recognition than a necessity.\ It’s similar to how a rock groupie sees backstage access: a status symbol, whether for an autograph or something more. Being seen standing next to big names is a huge deal for some, as they derive their own status from proximity.\ This also reinforces the “rockstar status” that conferences create around certain figures, once they come out to take a selfie with some nice people and young fans, then to quickly disappear back to the ‘whale room’ or backstage.
There’s often an entire insider network determining who gets these free tickets. In some cases, it’s naturally tied to the local community, but in others, the professionalism is laughably low. At certain events, you could probably just walk up to the entrance (if there’s even someone checking) and say, “I’m with the organization” to get in for free.
It gets even more absurd.\ At a conference near the French-Swiss border, I was probably one of the very few who actually paid for entry. The real spectacle wasn’t in the talk rooms — which remained eerily empty — but in the dining area, where half the town seemed to have shown up just for the free food. Around 200 people queued for a free lunch, while the presentation halls were at best one-third full throughout the day.
And beyond the ticket games, there are plenty of ways to slip in unnoticed. Carrying a random piece of equipment and mumbling\ “I need to put this crate in the back” can get you past security. Or you can just wait for the one security guard to get distracted by chatting up a girl or stepping out for a smoke, and you’re in. At one event, I walked in alongside someone carrying crates of wine for the VIP lounge. I blended in perfectly (I paid afterward).
So, to sum up: at nearly every conference I’ve been to, a big portion of attendees either walk in for free or hold compensation tickets they got through some connection. Sometimes that connection is uncomfortably close to the organizers. Other times, they just slap an “industry” label on themselves when, in reality, they’re nothing more than a social media bio with a few followers.
Local representatives of a podcast, community, influencer network, or fake marketing club also get in for free. And you? The regular guest, you and I are paying for them. There’s no real vetting process; with some organizers, anyone wearing a Bitcoin t-shirt and saying the magic words “I do community building” or “I know the local Bitcoin meetups” gets a free pass.
The ones who actually want to learn about Bitcoin — the ones who click the link and pay full price — are the ones covering the costs for everyone else and ultimately making these conferences profitable (or at least break even). The problem? They’re the ones left wondering: “Was it really worth my time and money?” only to never return again most of the time.
Because many of the people at these conferences aren’t there to learn. They’re part of the circus. And others? They’re the ones paying for the circus boss, the clowns, and the trapeze artists.
At that one conference with the massive free-lunch crowd, I saw one interesting talk. And I had plenty of valuable conversations and observations — conversations I could have just as easily had by visiting that place outside of a conference setting.
In the end, I realized the main reason I was there was to support a fellow Bitcoiner giving a presentation. And after that? They disappeared from my life. Because, just like in the fiat world, you’re only as good as your last few hours of usefulness to most people.
Which brings me to the next element of Bitcoin conferences...friends
Bitcoin “frens”
This might be the hardest lesson of all: you meet fellow Bitcoiners at these conferences. And some of them? They’re truly special characters. A few even made such a deep connection with not-so-well-traveled-me that I would’ve gladly traveled a full travel day just to spend time working and doing something meaningful together (which I actually did).
But most of these connections? They last only a moment. Few survive beyond the conference, mainly because of the vast distances— both in kilometers (or miles) and in the way we live our everyday lives. The Bitcoiners you meet at these events are, for the most part, just regular people trying to make ends meet in the fiat world while saving in Bitcoin. Or they’re chasing the Bitcoin dream or even find a job in the fata morgana of bitcoin jobs. They act like they belong, like a clown acting like he’s going to climb the trapeze.
I respect that. But over time, I realized that many of them operate in Bitcoin mode; a kind of facade. Behind that front, that mask, most are just testing the waters to see if they can make it. And most don’t.\ Treating Bitcoin as a lifestyle movement, a career shortcut, or an identity, has its limits. Eventually, the real person breaks through. And you have to face your own instincts and personality.\ I’ve tried to be an acrobat, and ride the lion, make the audience laugh, but I’m still the seal who’s brought back to the cage after he balanced a ball on his nose. The quote “I’m Jack’s wasted life.” came to mind often when standing somewhere at a conference space.
Self-doubting people stay self-doubting, owning Bitcoin or not. Emotional wrecks remain emotional wrecks — just with Bitcoin now. And when these masks slip off, you’ll see everything: the greed, the overconfidence, the longing for drama, the addictions, the narcissism, the energy-draining personalities, sleaziness usually with the ones who always say the right oneliners or wear the right Bitcoin merch to blend in.
And you can love people for that. Everyone has flaws. Everyone has a price as well.
But these Bitcoin “frens” can also hurt you badly. Because as Bitcoiners, we carry hopes. And hopes are like ants on a sidewalk, they’ll eventually get crushed.\ We long to meet people who see the same truth, the same vision of Bitcoin as we do. Some will act like they actually understand and do, they talk the talk for a while, as if they’re parroting a podcast.
If you stay in the shadows - like I did for years - you won’t have to deal with these things. If you never try, you’ll never be let down. But you still stay in the imaginary basement, letting yourself down. That’s not the bitcoin style. We router around problems. Even if we stand amidst the problems (like a conference).
But if you do? There’s a hefty price to pay — beyond just the money spent. It’s a cost paid in energy, emotions, and social interactions and above all: time.
And once in a while, you’ll meet a friend for life.
Just be prepared:
Bitcoin is a journey that few people you encounter at a conference can take for longer than four years, or even four hours of conversation actually.
And then, after navigating the social maze of Bitcoin conferences —the connections, the masks, the fleeting friendships, the smell of weed and regret — you find yourself facing an even greater challenge: the queue at a coffee stall.

## \ The Soviet LN Queue
It’s one of the most fascinating and frustrating aspects of every conference: the insanely long lines. Whether it’s for the toilets, a coffee booth, or some niche merchandise stall, you’ll see Bitcoiners waiting like it’s 1963 after a Soviet state bakery just got fresh deliveries.
waiting for coffee Seriously, aren’t we supposed to be the pinnacle of free-market efficiency? Instead, we’ve somehow perfected the art of the long food lines. I remember people waiting in line for like 35 minutes to order a cappuccino!
The usual culprit? A mix of payment chaos and the Bitcoin Orangepill mental issues in action.
A large portion insists on using Lightning (as in "their preferred lighting wallet"), which would be fine except they’re fumbling with some exotic, half-working wallet because using something that’s actually fast might get them sneered at for being “custodial.”
On top of that, vendors are juggling card payments, cash, various Lightning POS systems, and even the occasional cutting edge dudes trying to pay with an Apple Watch or worse, some newly released Lightning-enabled gadget that doesn’t work yet. And when it does work, it requires so much attention and Instagram footage that it takes five minutes just to hand someone a coffee while the guy pays with a lighting NFC ring on his finger, something you can't use ànywhere else ever. It’s cool. But not to anyone else than you.
So, here’s a tip for the regular people, the rats that pay for all of this : sneak out.
Then you find a small, locally owned café outside the conference, pay them in cash, and actually enjoy your food in a few seconds or minutes.
If (and only if) they accept Bitcoin, great! Tip them well. Otherwise, just relax and have a conversation with a local, all the while inside the conference venue there are Bitcoiners filming each other struggling to make a payment with the latest Lightning-enabled NFC card or making the staff uneasy.
Meanwhile, some poor 22-year-old café worker is trapped in an unsolicited podcast participation:
“Wait, you accept tips in Wallet of Satoshi? Who told you that? I’ll explain it to you!”
Or worse:
“Hold on, I just need to do a quick swap… It’s an on-chain transaction, the last block was 19 minutes ago, can’t be long now… wait… umm… do you take VISA?”
At this point, ordering a simple drink at a Bitcoin conference has become an unnecessarily complex, ego-driven performance. With long queues as a direct result. And don’t get me started on the story when 30+ bitcoiners walked in to a Portuguese restaurant without a reservation, and they all wanted to pay with different payment methods. It was like the Vietnam war.
Solution:
A tip for conference organizers and their catering : pick one Bitcoin point of sales system, set clear guidelines, and make everyone stick to them. Instruct people to adhere to the following :
Pay with a (bank) card, cash, or Lightning and PLEASE decide beforehand which method you’re using before ordering your stuff! We prefer lighting.
If you’re using Lightning, have enough balance on you wallet or get lost.
Use a compatible wallet. (Provide a tested “approved” list and train staff properly. Users who use other stuff get their order “cancelled” at the first sign of trouble. Your app‘s not scanning, or not compatible, or it has some technical mumbo-jumbo going on to your vpn LN node at home 2000 km away? Please get real and pay with a bank card or something.
No filming, duck-facing (like it's 2017) or stupid selfies with your payment. It’s been done a thousand times by now. There are people in line, waiting behind you, they want to order as well, while you have your little ego trip or marketing moment. Move on please!
“Our staff knows how bitcoin payments work, you don’t need to #orangesplain it to anyone.” We don’t care about your 200th LN app or the latest “but… this one is faster” thingy. Order your drinks, pay and get out of the way please.
Bitcoin fixes many things. But it hasn’t quite fixed this yet.
The bitcoin conference axiom
Going to a conference, versus keeping your bitcoin in your wallet is a tough choice for many.
If you pay nothing for tickets and lodging, while enjoying free meals and cocktails, your opportunity cost drops close to zero —yet your networking and social impact are maximized while you can also do business. That’s ideal. At least, for you. In such case, Bitcoin may only "win" over an extended timeline, but for you, it's essentially a free ride. You incur no real opportunity costs. You drink their milkshake.
On the other hand, if you’re a regular attendee, you pay full price: the ticket, overpriced drinks and food from the stands (losing even more if you generously pay for coffee in sats), plus extras like t-shirts and books (which you’ll never read). Your milkshake gets taken—at least half of it.
If you’re lucky, you might spend an evening in town with the event’s "stars"—those occasional luminaries who briefly grace the normies with their presence for a drink. Some can’t even hold their liquor. Year after year, the same 10 to 15 speakers or panelists appear, funded by your dime, traveling the world and enjoying the perks—some even cultivating fan bases and hosting exclusive parties.
The real opportunity cost hits hardest for regular attendees who come to learn, shelling out significant money while accumulating their fourth hardware wallet or yet another orange-themed t-shirt. They might even squeeze in a selfie with a former sportswear model turned Bitcoiner. For normies (as they’re often called), the financial and social scales rarely tip in their favor.
Calculating the conference opportunity cost
To determine the opportunity cost of attending a conference instead of investing in Bitcoin, over time follow these steps:
-
Calculate your total conference expenses, including tickets, travel, food, drinks, and lodging (merchandise and donations).
-
Estimate Bitcoin’s percentage gain over the conference period and the following year(s). (in order to not make you cry, I suggest nog going over 5 years)
-
Multiply your total conference cost by this percentage to determine the potential Bitcoin profit you forgo.
-
Assign a dollar value to the networking or business opportunities you expect to gain from the conference (if you’re not just in it for the laughs, meeting high-class consultants, friendships, self-proclaimed social media Bitcoiners, or the occasional gyrating on one of the musicians/artists/food stall staff members).
-
Subtract this “networking” value from the missed Bitcoin profit to find your net opportunity cost (this is rather personal,… with me it’s zero, but for someone selling t-shirts it’s probably much more).
If the result is negative over the chosen timeframe, the conference was financially worthwhile for you. If positive, holding or buying Bitcoin was the smarter move.
Unless you’re a recognized speaker in this traveling circus, your opportunity cost will likely be positive — meaning all the others lose hard money, while fumbling with your Lightning wallet.
The Conference Opportunity Cost Formula
Let:
CT = Total conference ticket & entrance cost (in dollars)
CR = Total related conference costs (travel, lodging, food, etc.)
C = CT + CR (Total cost)
G = Bitcoin’s % gain per year (as a decimal, e.g., 5% = 0.05)
N = Estimated fiat value of networking/business opportunities and knowledge gained.
OC = (C × G) − N
Where:
OC (Opportunity Cost) < 0 → The conference was worth attending.
OC (Opportunity Cost) > 0 → Holding/buying Bitcoin was the better move.
Some example calculations (I've left out examples before 2020, I don't want people crying or waking up at night thinking "Why did I go to Amsterdam in 2014?!")
example : Conference in April 2024 Entrance: $200 Lodging, t-shirt, and travel: $900 Bitcoin's estimated gain: 23% (0.23) No business / knowledge value gained OC = (200 + 900) × 0.23 - 0
- $253 OC (Bitcoin would have been the better choice.)
Conference in April 2020 (adjusted for historical Bitcoin growth) Entrance: $175 Lodging and travel: $700 Bitcoin's estimated gain: 1089% (10.89) No business / knowledge value gained OC = (175 + 700) × 10.89 - 0 OC = +$9,529 (Massive missed gains — Bitcoin was the clear winner.
--
So the first lesson in bitcoin should be: Only attend conferences if you get paid to do so and get a free ticket and free lodging, which kind of would kill that whole industry to begin with.
Energizing
At first, it’s energizing to meet like-minded bitcoiners, but after a while, you realize that a big chunk of them are just trying to sell you something or aren’t really bitcoin-focused at all. And some of them are just looking for their next way to kill time and boredom.
The drama that comes with attending these conference and the personal interaction can get pretty intense at times, since expectations often don’t match the personalities. Before you know, you’re walking around at night through some bad part of a town, while crying your eyes out because you thought you found your soulmate.
Future pure industry conferences will suffer less from this drama, because everyone there has the same goal — pushing their company or product— while the “other” grassroots conferences are more of a meeting spot for bitcoiners of all types and perspectives, bringing the usual drama and mess that comes with human interactions. Current conferences are a mix of both usually.
I think the current era of bitcoin conferences is coming to an end. Soon, probably by the end of 2025, we’ll see a clear split between industry-driven and human-driven (grassroots) smaller conferences, and it’ll be really important to keep these two separate.
I even had the idea to launch a sort of conference where there wouldn’t be any industry speakers or companies present. Just bitcoiners gathering at a certain place at a specific week and having a good time. I called it “club Sat” And you could just go there, and meet other bitcoiners, while acting there was a big venue and speakers,… but there aren’t any. Would be refreshing. No struggle for tickets, no backstage stuff, no boring talks and presentation,… just the surroundings and the drama lever you want and probably like.
On stage
The podium is usually left for the known names. Not every conference is like that, but most of them need these names, badly. These names know each other, they encounter one another in VIP rooms and “the industry” a lot of times anyway.
The same people you see in the bitcoin news, the same people having a cult following, and the very same people traveling, staying and drinking for free while spreading the same bitcoin wisdoms will be invited over and over again.
Or… they go rock around as they’re usually so bored they had to start a rock band to entertain themselves. Which is rather entertaining if you’re following up on who does what, but in the end it’s largely just for their own amusement and it shows. I get that. I would do the same. It’s fun and all.
It’s just a bit sad that there are only a small group of top-layer speakers, and then the sub-top that usually has more to say, or gets little opportunity. The reason for that is simple: the “normies” who pay in full for tickets, come there for the “big” names. They don’t know that much about bitcoin usually, so they’re not waiting on some unknown dude explaining something about an obscure niche subject. A debate can help remedie this, to mix it in with some lesser known names, but I have the feeling the current “line-up” of bitcoin conferences feels like a rock festival in 2025 putting the Stone temple pilots or Creed on the card.
Yes, they’ll attract an audience and do their playset well,… but it’s not exactly the pinnacle of the music industry at the moment, neither is Madonna by the way :)
Promoting anything
The people organizing these events usually aren’t Bitcoiners either — they’re promoters (few exceptions though).

They don’t care if they organize a symposium about a newly discovered STD, A three-day cheese tasting event, a Star Trek convention, or a Lucha Libre wrestling tournament featuring El HODLador, as long as they can sell tickets and make money from merchandise they're good. The last thing on the mind with some of them will be helping bitcoin adoption. There will be a time (soon) where people that know bitcoin, known bitcoiners and know how to organize events get their act together. It will be different than the early days, and it will be different than the boring going-through-the-motions conferences we have now. There shall be fun, social gatherings, life, excitement and culture, and not the “what do you sell?” atmosphere, neither the “this old dude on stage again”?
That’s why they’ll slap any semi-famous name on the poster to pull in a crowd - could be a washed-up Mexican wrestling star with strange legal issues, the cheese-tasting equivalent of Usain Bolt, or your neighborhood Bitcoin old-timer with a beard and a "best selling author" label.
It’s also why most of these conferences end up being more about shitcoins than anything else. And even if they're for the most part about bitcoin, the venue is usually infested with marketing budgets, useless organizations that wanted complimentary tickets (some of them do only one thing: popping up when a conference is nearby and then they’re gone again) ... along with some hawking consultant types you never see anywhere else.
They'll occasionally pay people but usually in fiat, or if you're a bigger name, you might get other deals. For artists or staff, it's all in fiat from what I heard.
Pure Bitcoin conferences, also rely on these big names. Whether it’s a well-known Bitcoiner, a CEO, president, or someone with real reveling knowledge to share with the audience (though that last type is getting rare).
Looking for love in all the wrong places
\ Let’s also address the fair share of “orange diggers” at Bitcoin conferences—because yes, they exist. And no, let’s not single out one particular gender here.
Some people treat a Bitcoin conference like a live-action dating app mixed with a financial vetting process for potential partners. It’s essentially an opportunity to inspect and assess the grab bag of fintech, crypto, and Bitcoin folks in real life.
And if you think this is exaggerated, just attend a few conferences—three is enough. You’ll start noticing the same people popping up, seemingly without any real Bitcoin knowledge, but with a very strong interest in dining, chatting, and generally being around—as long as you look and play the part. I can only imagine how dialed-up this effect must be at a shitcoin conference — probably like flies on a cowpie.
The trick is, in Bitcoin, these people try to blend in. Some even tag along with real Bitcoiners, while others just crash the party and try to get noticed. Their actual interest in Bitcoin? Close to zero. Their main target? Your wallet, or some fantasy thing about getting to know someone out of the ordinary.
And that’s a shame for the people who genuinely care about Bitcoin, who want to network, or who simply are looking for like-minded people. They often find themselves competing for attention with those who’ve turned “being noticed” into a sport, while the rest just wander around, lost in the shuffle. Talk to the quiet ones. Certainly if they look like they belong in a antiques shop.
My advice: Talk to people and be genuine. If you don’t know much about Bitcoin, that’s fine - nobody expects you to be a walking whitepaper and on top of that, most people you'll encounter don't know that much either. It’s bitcoin: we’re all rather average people that hold an extraordinary asset.
Just don’t be "that orange digger" looking for a partner with a loaded bag of bitcoin.
Because in the end, what’s the prize you win? You don’t know who’s under the mask. You don’t even know who’s under your own mask.
Finding a man or woman at a place where half the people are laser-focused on financial sovereignty, and the other half are busy arguing about seed phrase storage, UTXO management, and why your Lightning wallet sucks? But good luck with that. The judge of character usually comes when they find the next shiny object or ditched you standing in the rain at the entrance of a restaurant while dealing with a lightning watchtower or a funny cigarette or whatever.
If you’re truly looking for love, maybe stick to going to a normal bar. If you’re here to learn, connect, and be part of something of a grassroots movement, then be real yourself.
I've seen some rather nasty examples of people at Bitcoin conferences—of all kinds. And I've also seen some really cool examples of truly awesome people. This led me to believe that Bitcoin conferences simply let you meet… people, just dialed up a bit.
Future If you encounter rotten people, they’ll usually be even more rotten than in the fiat world. If you meet really cool people, they’ll be even more awesome than the cool people in the fiat world.
Our volatility is our freedom. So, I guess it’s normal. Doesn’t make it any easier, though.
Bitcoin sees through bullshit, and so do Bitcoiners (even if it takes 21,000 blocks)
Pretty soon, I reckon we’ll see conferences fork into two camps: grass roots, and the “industry” level ones. (human / corporate) I guess I’ll only attend the human part, for sure, but I can’t help but booking myself a single room in a hotel in a nice area in that case, so I don’t have to deal with class of 2022 hippies sharing referral links to their middleman service while asking me for a lighter 3 times in a row. The chances for me of meeting cool bitcoiners in a nearby cocktail bar are a lot higher.
In the meanwhile, I’ll look forward and see how the bitcoin conferences will evolve, fork in two “styles”. One corporate and one underground. Maybe there will be one more genre just for the fun of it.
I’ll stay away, as I don’t like this current mix of industry gigs and having the insiders and “the rest” of us all mingled together clamoring for tickets, attention and coffee. The game is rigged. Staying at home is the better option (for now).
written by AVB
If you like : tip here
-
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ 7bdef7be:784a5805
2025-04-02 12:02:45
@ 7bdef7be:784a5805
2025-04-02 12:02:45We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs. ## The problem Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, **so everyone can actually snoop** what we are interested in, and what is supposable that we read daily. ## The solution Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see [NIP-51](https://github.com/nostr-protocol/nips/blob/master/51.md)). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create **dedicated feeds**, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be **encrypted**, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also **really private one**. One might wonder what use can really be made of private lists; here are some examples: - Browse “can't miss” content from users I consider a priority; - Supervise competitors or adversarial parts; - Monitor sensible topics (tags); - Following someone without being publicly associated with them, as this may be undesirable; The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of **how many bots scan our actions to profile us**. ## The current state Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff ([NIP-44](https://github.com/nostr-protocol/nips/blob/master/51.md)). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply **mark them as local-only**, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment. To date, as far as I know, the best client with list management is Gossip, which permits to manage **both encrypted and local-only lists**. Beg your Nostr client to implement private lists!
-
 @ db01672e:9f775028
2025-04-02 09:05:06
@ db01672e:9f775028
2025-04-02 09:05:06Proper nutrition plays a huge role in maintaining the health and well-being of seniors, especially those with Alzheimer’s or other forms of dementia. A balanced diet helps boost cognitive function, maintain strength, and prevent complications like dehydration or weight loss.
At leading Alzheimer’s care communities, every meal is carefully planned to support brain health and overall wellness. Let’s take a closer look at why nutrition is so important in https://villagegreenalzheimerscare.com/kingwood/, and how meals are tailored to meet the needs of memory care residents.
The Power of Home-Cooked, Nutritious Meals
For seniors in memory care, food isn’t just about staying full—it’s about fueling the body and mind. A well-balanced diet can improve mood, boost energy, and even slow cognitive decline.
**✔ Fresh, Wholesome Ingredients ** * Meals in assisted living communities are made with fresh vegetables, lean proteins, and whole grains. * Omega-3 fatty acids, antioxidants, and vitamin-rich foods are included to support brain health. * Processed foods and excess sugars are limited to reduce inflammation and maintain stable energy levels.
**✔ Balanced and Consistent Meal Schedules ** * Seniors with dementia thrive on routine, and meal times are scheduled at the same time every day. * Regular eating habits help stabilize blood sugar levels and prevent mood swings. * Meals are prepared to be easily digestible and full of essential nutrients.
**✔ The Comfort of Home-Cooked Meals ** * Many seniors find comfort in familiar flavors and recipes that remind them of home. * Meals are often served in a family-style dining setting, encouraging social interaction. * The warm, inviting atmosphere makes eating enjoyable and stress-free.
Proper nutrition is the foundation of good health and memory care, but hydration and snacks also play a crucial role.
The Importance of Hydration, Snacks, and a Balanced Diet
Dehydration is a common risk for seniors with Alzheimer’s, as they may forget to drink water or fail to recognize thirst cues. Staying hydrated and eating nutrient-rich snacks throughout the day keeps seniors feeling their best.
**✔ Encouraging Proper Hydration ** * Water, herbal teas, and fruit-infused drinks are provided throughout the day. * Hydrating foods like soups, watermelon, and cucumbers help boost water intake. * Caregivers remind and encourage residents to drink fluids regularly.
**✔ Nutritious Snack Options ** Light snacks help maintain energy levels and prevent malnutrition. Yogurt, nuts, smoothies, and whole-grain crackers are offered between meals. Seniors with chewing difficulties can enjoy soft options like applesauce or pudding.
**✔ Creating a Balanced Diet for Dementia Care ** * High-protein meals keep muscles strong and support healing. * Fiber-rich foods improve digestion and prevent constipation. * A mix of healthy fats, carbohydrates, and proteins ensures steady energy throughout the day.
When seniors have difficulty chewing or swallowing, their meals need extra modifications.
Meal Modifications for Swallowing Difficulties and Dietary Restrictions
As dementia progresses, some seniors struggle with chewing and swallowing. Memory care communities adjust meals to ensure safety without sacrificing taste or nutrition.
**✔ Soft and Pureed Meal Options ** * Foods are softened, mashed, or pureed to prevent choking risks. * Thickened liquids help those who have trouble swallowing thin beverages. * Meals still include seasonings and variety to keep them flavorful and appealing.
**✔ Adjusting to Dietary Needs ** * Diabetic-friendly meals are available for residents with blood sugar concerns. * Low-sodium diets help those with heart conditions. * Caregivers monitor food intake to ensure residents are eating enough.
At assisted living in Kingwood, TX, these meal adjustments are made with care and expertise, ensuring every senior receives the nutrition they need.
Nutritious Meals = A Better Quality of Life
A well-balanced diet does more than just keep seniors full—it supports brain function, enhances energy, and improves overall well-being. At https://villagegreenalzheimerscare.com/dallas/ communities, every meal is designed to meet the unique needs of memory care residents.
From hydration reminders to customized meal plans, assisted living communities take the stress out of nutrition for both seniors and their families. If you’re looking for a place where your loved one can enjoy healthy, home-cooked meals in a safe and caring environment, an assisted living community in Kingwood, TX, might be the perfect choice.
-
 @ f1989a96:bcaaf2c1
2025-04-03 14:30:08
@ f1989a96:bcaaf2c1
2025-04-03 14:30:08Good morning, readers!
Georgian officials froze the bank accounts of five nonprofit organizations that provide financial and legal support to detained protesters. This follows rising public unrest as Georgia’s regime pushes new laws restricting free speech and assembly, introducing new fines and penalties, and expanding law enforcement powers. By eroding civil protections, the regime makes it more dangerous and costly for activists, dissenters, and everyday citizens to stand up against an increasingly repressive regime.\ \ Meanwhile, the Indian government introduced a new income tax bill that grants tax authorities sweeping surveillance power over anyone they “suspect” of tax evasion. If suspected, tax authorities are legally allowed to access Indians' email, social media, and bank accounts, raising obvious concerns over state overreach and invasions of individual financial privacy.\ \ In freedom tech news, HRF donated 1 billion satoshis to more than 20 projects worldwide, focusing on supporting human rights defenders and vulnerable communities under authoritarian regimes across Asia, Africa, and Latin America. These gifts advance censorship-resistant communications and transactions, bitcoin education, and privacy tools so that dissidents, nonprofits, and individuals may better protect their human rights and financial freedom. In this letter we also spotlight a new open-source mobile Bitcoin wallet called Cove. While still in beta, the wallet can be used with a hardware device or on its own as a hot wallet, offering a flexible self-custody setup for managing Bitcoin.
We end with a podcast in which HRF Chief Strategy Officer Alex Gladstein discusses the state of freedom tech and why Bitcoin stands as the most promising tool for financial liberation.
Now, let’s get right to it!
SUBSCRIBE HERE
GLOBAL NEWS
Georgia | Officials Freeze Accounts of Organizations Supporting Protesters
Georgian officials have frozen the bank accounts of five nonprofit organizations that provide financial and legal aid to dissenters. This comes in response to an uprising of protests over new controversial laws that restrict free expression and assembly, increase fines and detention periods, and expand law enforcement powers. Georgian officials justify the account freezes as part of an investigation into “sabotage,” yet they have provided no evidence. Amnesty International warns this financial assault could “kill the entire protest movement.” Bitcoin provides a way to circumvent these struggles. Its uncensorable and permissionless nature has helped sustain pro-democracy movements across Belarus and Nigeria, proving it is capable of addressing the immense financial restrictions dictators impose.
United Arab Emirates | Plans to Launch “Digital Durham” CBDC in 2025
The United Arab Emirates (UAE) will launch its central bank digital currency (CBDC), the “Digital Durham,” by the end of 2025. According to the central bank, the CBDC will be available through licensed financial institutions and operate via a government-run digital wallet. Every transaction will be recorded on a permissioned blockchain run by the government. The central bank further admitted the CBDC will replace cash and assist law enforcement “by leaving a digital trail for transactions involving illicit funds.” Officials claim this is to combat financial crime, but it also enables real-time surveillance and tracking of individual financial activity. In a country known for strict laws against dissent and extensive surveillance capabilities, it is not hard to see how a CBDC will erode the autonomy and rights of activists, dissenters, and others who oppose an increasingly authoritarian regime.
India | Grants Tax Authorities Access to Citizens’ Online Data
Starting in April 2026, the Indian government will grant tax authorities legal access to the private online data of any citizen “suspected” of tax evasion. This will include legal access to personal emails, social media, and bank accounts. The new law expands on the Income Tax Act of 1961, which previously limited officials to searching physical premises for financial documents. Now, officials can bypass digital security measures and access private data without consent — all under a legal framework. This dissipation of financial privacy sets an intrusive precedent and opens the door to state-level corruption and surveillance in a country where the Modi regime has already made it clear they are happy to use financial repression to further cement their power.
Myanmar | Bitcoin as a Tool Support Earthquake Disaster Relief
Last week, a 7.7 magnitude earthquake struck central Burma, with strong tremors reaching neighboring Thailand. The official death toll has surpassed 2700. And in Bangkok, a 33-story building under construction collapsed. Despite an already strenuous situation, Burma’s military junta continues its oppression. They are blocking rescue teams from reaching the Sagaing region — the epicenter of the earthquake and the heart of Burma’s pro-democracy movement — and instead channeling aid to regime-controlled cities like Naypyidaw and Mandalay. The junta is also continuing to conduct air strikes on civilians and restricting equipment and fuel for aid groups, leaving a million people in Sagaing to fend for themselves. In these repressive circumstances, Bitcoin can provide a censorship-resistant way to send funds directly to those affected.
Angola | Regime Jacks Price of Diesel
The Angolan regime raised diesel prices by 50% in the process of eliminating fuel subsidies. Diesel prices suddenly increased from 200 to 300 kwanza per liter, driving up transportation costs in a country where over half the population lives on less than $2 a day and inflation is over 42%. Previous fuel subsidy cuts in 2023 (where the price of diesel rose 80%) sparked protests between taxi drivers, nonprofit workers, and law enforcement. This recent price increase now raises fears of renewed crackdowns. The Angolan regime also introduced new civil society laws that Guilherme Neves, chairman of the human rights organization Associacao Maos Livres, describes as a “license to erase non-governmental organizations that are not government-compliant.” Angolans find themselves in increasingly precarious financial positions as the government erodes the civil safeguards protecting nonprofits and dissenters.
Nicaragua | Ortega’s Dismantling of Press Freedom
Since coming to power in 2007, Ortega has closed or seized 61 media outlets, imprisoned countless journalists, and forced over 280 journalists into exile. His assault on press freedom has unfolded in two phases: initial raids on local radio stations and TV channels between 2007 and 2017, followed by full-scale censorship in 2018 on independent media outlets like La Prensa and CONFIDENCIAL. Ortega then intensified attacks from 2019 to 2021 by closing Nicaragua’s second-oldest newspaper and passing laws to criminalize free expression. This is a deliberate strategy to eliminate dissent and independent voices. What’s happening in Nicaragua highlights the importance of open and decentralized protocols like nostr, which allow journalists to publish freely without getting censored. While still early, it is becoming essential for sharing information absent the fear of being blocked or silenced by autocratic leaders.
BITCOIN AND FREEDOM TECH NEWS
HRF | Gifts 1 Billion Satoshis to 20+ Open Source Projects Worldwide
HRF gifted 1 billion satoshis in its Q1 2025 round of Bitcoin Development Fund (BDF) grants, supporting more than 20 open-source projects around the world. These projects advance Bitcoin education, open-source software, mining decentralization, and privacy tools for activists contending with authoritarian regimes across Asia, Latin America, and Africa. Supporting permissionless financial tools and censorship-resistant technologies empowers dissidents, journalists, and civil society to organize, transact, and communicate without state suppression and interference. Learn more about the grantees and their work here.
Cove | New Open-Source and Permissionless Bitcoin Wallet
Cove is a new open-source and permissionless mobile Bitcoin wallet that aims to put users in full control of their Bitcoin. Users can connect their own hardware wallet (to manage Bitcoin offline) or use Cove as a hot wallet (to manage Bitcoin online). It also allows users to create multiple wallets from the app itself. In the future, Cove plans to add Unspent Transaction Output (UTXO) selection and coin control, giving users more independence over their transactions and the tools to better protect their financial privacy. While still in beta and only suitable for test funds, this wallet holds promise as a privacy tool to equip dissidents with self-custodied Bitcoin. You can try it here.
Second | New Ark Implementation Launches on Bitcoin Signet
Second, a company building on Ark, a protocol designed to help scale Bitcoin’s transaction throughput, launched “Bark.” Bark is a test implementation of the Ark protocol deployed on Bitcoin’s Signet network (where developers test software). More broadly, the Ark protocol helps make Bitcoin transactions more private, faster, and cheaper, supporting the network in handling more transactions and users with the tradeoff of being less trusted than the mainchain, as funds stored in a noncustodial way on Ark can expire if not used. While it is still in early development, the test release of Bark marks a step toward deployment on the main Bitcoin network. Scaling solutions like Ark could be important for activists and individuals. They might ensure Bitcoin remains accessible to all, even as block space demand increases and network fees rise. Learn about it here.
Braiins | Open Sources Bitcoin Control Board
Braiins, a company building tools for Bitcoin mining, open-sourced its BCB100 Bitcoin Control Board, giving miners using their products greater insight and control over their Bitcoin mining hardware and firmware. Sharing the design files and firmware openly helps strengthen Bitcoin’s decentralization, making it more resilient against corporate or state interference. Specifically, open-sourcing mining hardware ensures individual miners can operate independently, reducing censorship risks across the entire network. In turn, this preserves financial freedom by keeping Bitcoin accessible and usable by dissidents, nonprofits, and individuals who need it most.
African Bitcoiners | Publish Bitcoin Starter Guide
African Bitcoiners just published “Bitcoin: Africa’s Guide to Freedom Money,” a Bitcoin guide providing clear, practical insights into how Bitcoin can help people across the continent escape inflation, corrupt regimes, and failing financial systems. It covers essential topics to get started — from choosing a wallet to properly securing Bitcoin. In Africa, where some of the world’s longest-standing dictators restrict even basic financial activity, this guide is a powerful resource for human rights defenders, nonprofits, and everyday citizens. Read it here.
OpenSats | 10th Wave of Nostr Grants
OpenSats, a nonprofit that supports open-source software development, announced its tenth wave of grants for projects in the nostr ecosystem. Nostr is a decentralized protocol that enables digital identity and communications outside the reach of authoritarian states. The grant round provides support to nostr Epoxy, which enhances access to nostr by circumventing censorship through a network of paid proxies. This ensures activists and dissidents can continue to communicate even in restrictive environments. Additionally, Zapstore received a grant for providing a permissionless app store built on nostr that enables developers to distribute software without corporate gatekeepers. This provides an open-source alternative to centralized app stores that often comply with government censorship and restrict dissidents’ access to freedom tools.
RECOMMENDED CONTENT
Freedom Tech with Alex Gladstein
In this episode of The Gwart Show, Alex Gladstein, chief strategy officer at HRF, breaks down how and why Bitcoin serves as “money dictators can’t stop.” Drawing on more than 17 years of human rights work, he shares real-world examples of activists and citizens using Bitcoin to escape financial repression in authoritarian countries. Gladstein also explores privacy tools, cross-border payments, and why Bitcoin offers promising hope for financial freedom. Watch the full conversation here.
The State of Personal Online Security and Confidentiality with Meredith Whittaker
In this keynote for SXSW 2025, Signal CEO Meredith Whittaker shares her growing concerns around AI, personal data collection, and the erosion of privacy in today’s increasingly digital world. She emphasizes the need for more secure, uncensorable, and privacy-protecting technologies that shield users from surveillance and exploitation, especially in the context of authoritarian regimes. Watch the full discussion for a pragmatic view into the future of digital privacy and security.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ a60e79e0:1e0e6813
2025-04-02 08:26:48
@ a60e79e0:1e0e6813
2025-04-02 08:26:48This is a long form note of a post that lives on my Nostr educational website Hello Nostr.
So you've got yourself started, you're up to speed with the latest Nostr jargon and you've learned the basics about the protocol, but you're left wanting more!? Well, look no further! This post contains a useful list of Nostr based utilities than can enhance your experience in and around the Nostr protocol.
Search and Discovery
Getting started with Nostr can sometimes feel like a lonely journey, particularly if you're the first of your friends and family to discover how awesome it can be! These tools can help you discover new content, connect with existing follows from other networks and just generally have a poke around at the different types of content Nostr has to offer.
Have a hobby or existing community elsewhere? Have a search for it here to find others with shared interests
- Nostr.Band - Search for people, posts, media and stats literally anything Nostr has to offer!
- Nostr.Directory - Find your Twitter follows on Nostr
- Awesome Nostr - Extensive list of Relay software
- Nostr View - Generic Nostr search
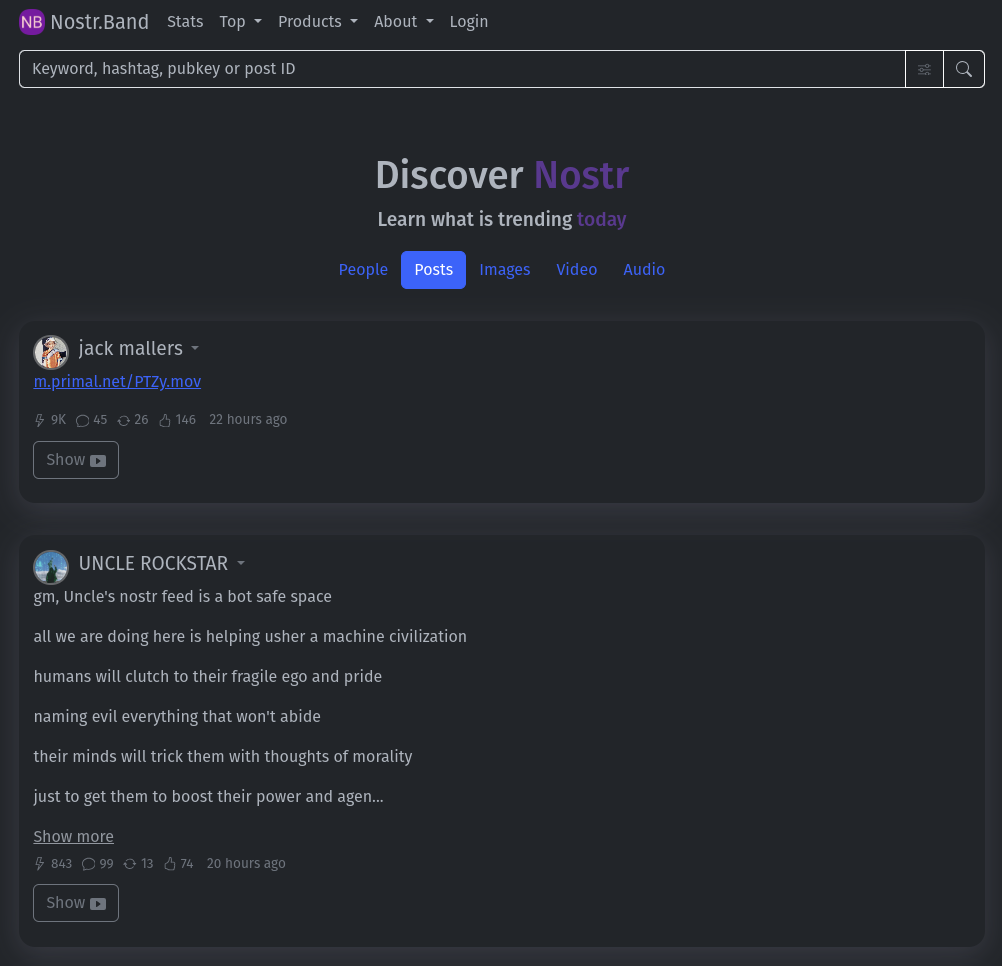
Relays
Relays might not be the sexiest of topics, particularly for newcomers to the network, but they are a crucial part of what makes Nostr great. As you become more competent, you'll want to customize your relay selection and maybe even run your own! Here are some great starting points.
Running a personal relay is a powerful way to improve the redundancy of your Nostr events.
- Nostr.Watch - Browse, test and research Nostr relays
- Nostrwat.ch - List of active Nostr relays
- Advanced Nostr Search - Targetted search with date ranges
- Nostr.Wine - Reliable paid Relay
NIP-05 Identity Services
Your nPub, or public key (that long string of letters and numbers) is your ‘official’ Nostr ID, but it’s not exactly catchy. NIP-05 identifiers are a human-readable and easily shareable way to have people find you on Nostr. They look like an email address, like qna@hellonostr.xyz. If you have your own domain and web server, you can easily create your own NIP-05 identifier in just a few minutes. If you don't, you'll want to leverage one of the many free or paid solutions.
Make yourself easier to find on Nostr with a NIP-05 identifier
- Bitcoiner.Chat - Free service operated by QnA
- Nostr Plebs - Paid service with extra features
- Alby - Lightning wallet with + NIP-05 solution
- Nostr Address - Paid service with extra features
- Zaps.Lol - Free service
Key Management
Your private key (or nsec) it the key to your Nostr world. It is what allows you to access and interact with your social graph from any client. It doesn't matter if that client is a micro-blogging app like Amethyst, a podcast app like Fountain, or a P2P marketplace like Plebeian Market, your nsec is paramount to those interactions. Should your nsec be lost, or fall into the wrong hands, whoever then holds a copy can access Nostr and pretend to be you, meaning that you'll need to start again with a new keypair. Not a nice situation to find yourself in, so treat your nsec VERY carefully.
Your private key IS your Nostr identity. Treat it with extreme care and do not share it.
- Alby - Browser extension enabling you to sign into web app without sharing the private key
- Nos2x - Another browser extension key manager
- Keys.Band - Another browser extension key manager
- Amber - Android app for safe nsec storage. Can talk to other clients on the same phone to log in and sign events
- Nostr Signing Device - Dedicated device to store your nsec
- Passport - Hardware wallet for offline and deterministic nsec generation and storage
Zap Tools
Zaps are one of the most fun parts of Nostr. Never before have we been able to send fractions of a penny, instantly to our friends because their meme made us laugh, or their blog post was very insightful. Zaps use Bitcoin’s Lightning Network, a faster and cheaper way to move Bitcoin around. To Zap someone, you need a Lightning wallet linked to your Nostr client. Some clients, like Primal, ship with their own custodial wallet to make getting started a breeze. Most clients also allow more advanced users to connect an existing Lightning Wallet to reduce reliance and trust in the client provider.
- Alby - Browser extension and self-custodial Lightning wallet
- LNBits - A Zap server running on your own Bitcoin node
- BTCPay Server - Another Zap server running on your own Bitcoin node
- Zeus - Zap compatible self-custodial mobile Lightning wallet
- Nostr Wallet Connect - Communication protocol between Lightning wallets and Nostr apps
- Ecash Wallets - Custodial Ecash based wallets that are interoperable with Lightning and Nostr (Funds may be at risk)
- Wallet of Satoshi - Custodial Lightning wallet (Funds may be at risk)
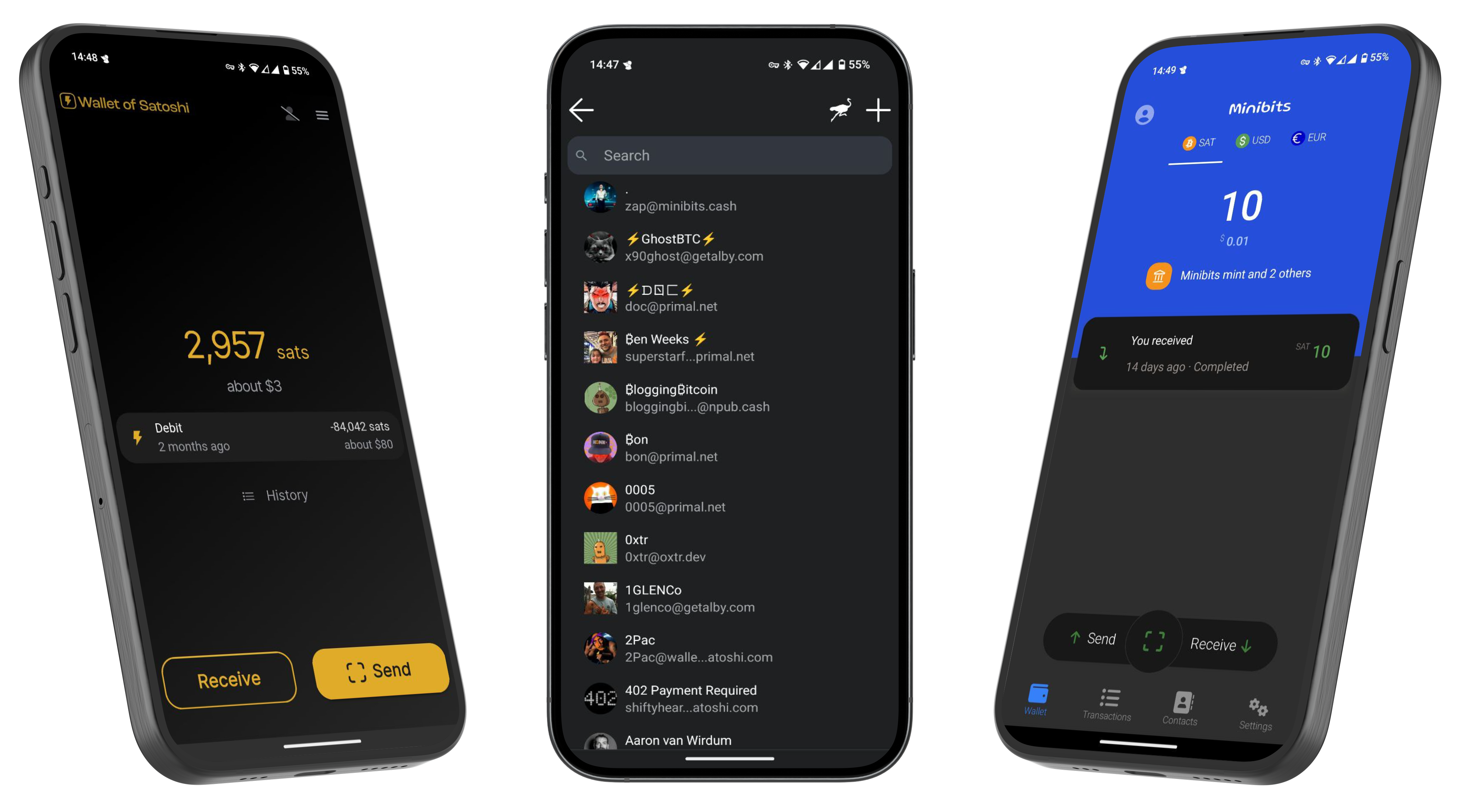
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
 @ b2caa9b3:9eab0fb5
2025-04-01 20:29:01
@ b2caa9b3:9eab0fb5
2025-04-01 20:29:01
For years, I’ve been shifting my life away from traditional systems and toward Bitcoin. I calculate my expenses in sats, buy airtime and online data with BTC, and continue exploring new ways to integrate Bitcoin into my daily life. While I’m not yet fully living on Bitcoin, I am getting closer with each step.

Since discovering Nostr, my perspective on decentralization has deepened. More than just a financial shift, it's a complete lifestyle transformation. Years ago, after facing injustice in my home country, I took the first step toward a new way of living. That decision led me to where I am today—a minimalist, a nomad, and a believer in financial freedom through Bitcoin.

I once served in the military, owned a house, and drove a nice car. My life looked very different back then. But over time, I realized that true freedom wasn’t in possessions—it was in mobility, independence, and the ability to control my own finances. Now, all I own fits into a backpack weighing less than 12 kg. My lifestyle is simple, yet rich in experiences.
March 14 marks eight years since I embraced my nomadic lifestyle. What started as a leap into the unknown has become my way of life. Living with less has given me more—the freedom to move, to explore, and to be truly independent. The more I immerse myself in the Bitcoin ecosystem, the more I see its potential to reshape not only my life but the world around me.

The journey isn’t over. In fact, it’s just beginning. Let’s see where this path leads as I go further into the blockchain revolution!



-
 @ 1aa9ff07:3cb793b5
2025-04-03 14:06:38
@ 1aa9ff07:3cb793b5
2025-04-03 14:06:38In an era where centralized platforms dominate the internet, concerns over censorship, privacy, and data ownership have led to the rise of decentralized alternatives. One such innovation is Nostr, a lightweight and resilient protocol designed to enable censorship-resistant and decentralized communication. In this article, we will explore what Nostr is, how it works, its advantages, and why it is gaining traction among privacy advocates and decentralized technology enthusiasts.
What is Nostr?
Nostr (Notes and Other Stuff Transmitted by Relays) is an open protocol designed for creating censorship-resistant social networks and communication platforms. Unlike traditional social media networks, which rely on centralized servers controlled by corporations, Nostr operates on a decentralized model using cryptographic keys and relays.
Nostr allows users to publish and receive messages without the need for a central authority. It is not tied to any single application but instead provides a foundation upon which developers can build various types of social and communication tools.
How Does Nostr Work?
Nostr consists of two main components:
- Clients – Applications that users interact with, such as social media platforms, chat applications, or blogging tools.
- Relays – Servers that distribute messages between clients without storing them permanently or acting as gatekeepers.
When a user wants to send a message or publish content, their client signs the data using their private key and broadcasts it to multiple relays. Other users who subscribe to those relays can receive and interact with the messages.
Nostr does not have a concept of user accounts managed by a central entity. Instead, identity is established using public and private cryptographic keys. The private key is used to sign messages, while the public key acts as the user’s identity across the network.
Advantages of Nostr
-
Censorship Resistance – Since Nostr does not rely on a central authority, it is much harder for governments or corporations to censor content. Users can publish messages freely, and if one relay refuses to distribute them, they can simply use another.
-
Privacy and Security – Messages are signed using cryptographic keys, ensuring authenticity and reducing the risk of impersonation. Users retain full control over their identities and content.
-
Interoperability – Nostr is not tied to a single platform or application. Developers can create different types of services using the protocol, from microblogging platforms to encrypted messaging apps.
-
Resilience – Since the network relies on multiple relays instead of a single centralized server, it is less susceptible to shutdowns or attacks.
Use Cases for Nostr
- Decentralized Social Media – Platforms like Twitter alternatives can be built on Nostr, allowing users to post updates without fear of censorship.
- Private Messaging – Secure and encrypted messaging applications can be developed using the protocol.
- Blogging and Content Publishing – Writers and journalists can publish articles in a censorship-resistant manner.
- Bitcoin and Cryptocurrency Communities – Many Bitcoin enthusiasts are adopting Nostr due to its decentralized nature and alignment with privacy-focused principles.
Challenges and Limitations
While Nostr is a promising technology, it is still in its early stages and faces several challenges:
- Adoption and Network Effects – Since Nostr is not as widely used as traditional social media platforms, building a strong user base is a challenge.
- Spam and Moderation – Without central moderation, handling spam and malicious content is more difficult, requiring innovative solutions such as reputation-based filtering.
- User Experience – Decentralized networks often have a steeper learning curve for new users compared to centralized platforms.
The Future of Nostr
Despite these challenges, Nostr is gaining momentum among privacy advocates, developers, and decentralized technology supporters. With continued development and improvements in usability, Nostr has the potential to reshape online communication by offering a truly decentralized and censorship-resistant platform.
As more developers create applications and services using Nostr, its ecosystem is likely to expand, providing a viable alternative to traditional social media networks. Whether you are a developer, a privacy-conscious user, or someone interested in the future of decentralized internet, Nostr is a technology worth exploring.
Conclusion
Nostr represents a significant step toward a more open and decentralized internet. By removing central points of control and enabling user-driven communication, it empowers individuals to interact freely without the risk of censorship or data exploitation. As the protocol matures and more applications emerge, it could play a crucial role in shaping the next generation of online communication.
If you are interested in experimenting with Nostr, you can start by exploring various Nostr-based applications, setting up your cryptographic keys, and connecting with the growing community of users and developers. The future of decentralized communication is just beginning, and Nostr is at the forefront of this movement.
Understanding Nostr: A Decentralized Social Network Protocol
In an era where centralized platforms dominate the internet, concerns over censorship, privacy, and data ownership have led to the rise of decentralized alternatives. One such innovation is Nostr, a lightweight and resilient protocol designed to enable censorship-resistant and decentralized communication. In this article, we will explore what Nostr is, how it works, its advantages, and why it is gaining traction among privacy advocates and decentralized technology enthusiasts.
What is Nostr?
Nostr (Notes and Other Stuff Transmitted by Relays) is an open protocol designed for creating censorship-resistant social networks and communication platforms. Unlike traditional social media networks, which rely on centralized servers controlled by corporations, Nostr operates on a decentralized model using cryptographic keys and relays.
Nostr allows users to publish and receive messages without the need for a central authority. It is not tied to any single application but instead provides a foundation upon which developers can build various types of social and communication tools.
How Does Nostr Work?
Nostr consists of two main components:
-
Clients – Applications that users interact with, such as social media platforms, chat applications, or blogging tools.
-
Relays – Servers that distribute messages between clients without storing them permanently or acting as gatekeepers.
When a user wants to send a message or publish content, their client signs the data using their private key and broadcasts it to multiple relays. Other users who subscribe to those relays can receive and interact with the messages.
Nostr does not have a concept of user accounts managed by a central entity. Instead, identity is established using public and private cryptographic keys. The private key is used to sign messages, while the public key acts as the user’s identity across the network.
Advantages of Nostr
-
Censorship Resistance – Since Nostr does not rely on a central authority, it is much harder for governments or corporations to censor content. Users can publish messages freely, and if one relay refuses to distribute them, they can simply use another.
-
Privacy and Security – Messages are signed using cryptographic keys, ensuring authenticity and reducing the risk of impersonation. Users retain full control over their identities and content.
-
Interoperability – Nostr is not tied to a single platform or application. Developers can create different types of services using the protocol, from microblogging platforms to encrypted messaging apps.
-
Resilience – Since the network relies on multiple relays instead of a single centralized server, it is less susceptible to shutdowns or attacks.
Use Cases for Nostr
-
Decentralized Social Media – Platforms like Twitter alternatives can be built on Nostr, allowing users to post updates without fear of censorship.
-
Private Messaging – Secure and encrypted messaging applications can be developed using the protocol.
-
Blogging and Content Publishing – Writers and journalists can publish articles in a censorship-resistant manner.
-
Bitcoin and Cryptocurrency Communities – Many Bitcoin enthusiasts are adopting Nostr due to its decentralized nature and alignment with privacy-focused principles.
Challenges and Limitations
While Nostr is a promising technology, it is still in its early stages and faces several challenges:
-
Adoption and Network Effects – Since Nostr is not as widely used as traditional social media platforms, building a strong user base is a challenge.
-
Spam and Moderation – Without central moderation, handling spam and malicious content is more difficult, requiring innovative solutions such as reputation-based filtering.
-
User Experience – Decentralized networks often have a steeper learning curve for new users compared to centralized platforms.
The Future of Nostr
Despite these challenges, Nostr is gaining momentum among privacy advocates, developers, and decentralized technology supporters. With continued development and improvements in usability, Nostr has the potential to reshape online communication by offering a truly decentralized and censorship-resistant platform.
As more developers create applications and services using Nostr, its ecosystem is likely to expand, providing a viable alternative to traditional social media networks. Whether you are a developer, a privacy-conscious user, or someone interested in the future of decentralized internet, Nostr is a technology worth exploring.
Conclusion
Nostr represents a significant step toward a more open and decentralized internet. By removing central points of control and enabling user-driven communication, it empowers individuals to interact freely without the risk of censorship or data exploitation. As the protocol matures and more applications emerge, it could play a crucial role in shaping the next generation of online communication.
If you are interested in experimenting with Nostr, you can start by exploring various Nostr-based applications, setting up your cryptographic keys, and connecting with the growing community of users and developers. The future of decentralized communication is just beginning, and Nostr is at the forefront of this movement.
-
 @ 000002de:c05780a7
2025-04-01 20:17:26
@ 000002de:c05780a7
2025-04-01 20:17:26I know I'm not alone in this. I don't trust the government. Any government. Its the rational response when you discover just how often its agents lie, steal, and kill. Honestly, I do not understand why so many people do trust the government. The reality is that if your team is in power, you tend to trust it. If not, you still mostly trust it but less so. That's my feel for most people at least.
Trump and Rubio are bragging about how many MS-13 gang members are being deported. Many are being shipped to prisons in El Salvador. Obviously I am not opposed to criminals being put in prisons. But, how do we know these guys are actually guilty of anything other than being in the US illegally. Actually we don't even know that. It wouldn't be so bad if these people were just being shipped back to their home countries. But, instead they are getting sent straight to prison. No trial. Just the government picking people up and shipping them to prison. Is this what you signed up for Trump supporters?
Many Trump supporters opposed the GW Bush policies of throwing people in off-shore prisons. Some of them US citizens. With no trial. Now these people seem rather silent. Its troubling to me.
Why? Well, because the government sucks. Even if they have good intentions they make mistakes. The Innocence Project is just one group that has shown how often our legal system falsely imprisons people. I would be shocked if there weren't any Innocent men being sent to suffer in El Salvador's prisons.
You may say, well these are bad dudes and we need to clean up the mess Biden made. I have sympathy for that position. But do we really want to set this president? TDS is real but it is valid to have concerns about the actions of the Trump admin. This is not the American way. Not the way I was taught at least. This is just a strong man taking action and disregarding the values of this nation and the rights of human beings.
Think about it.
originally posted at https://stacker.news/items/931505
-
 @ 4fe14ef2:f51992ec
2025-04-03 11:03:33
@ 4fe14ef2:f51992ec
2025-04-03 11:03:33Hey Bitcoiners,
Leave a comment below to share your hustles and wins. Let us know what you've sold this week. Have you sold it for #sats or #zaps? It doesn't matter how big or small your item is, solid or digital, product or service.
Just share below what you’ve listed, swapped, and sold. Let everyone rave on your latest #deals!
New to ~AGORA? Dive into the #marketplace and turn your dusty gears into shiny BTC!
originally posted at https://stacker.news/items/933200
-
 @ edeb837b:ac664163
2025-04-03 10:35:59
@ edeb837b:ac664163
2025-04-03 10:35:59When it comes to social trading, there are plenty of platforms that claim to offer innovative ways to connect with other traders, share strategies, and improve your market performance. But let's be real: most so-called "social trading" apps are either glorified brokerage platforms with limited community features or outdated, clunky systems that don’t offer real-time value.
There’s really only one social trading app you need to consider—NVSTly. Here’s why.
Why NVSTly Stands Above the Rest
NVSTly isn’t just another trading app with a few social features slapped on. It’s the ultimate social trading platform, purpose-built to empower traders by combining real-time trade tracking, seamless social sharing, deep market insights, and a powerful trader community.
Unlike other platforms, NVSTly isn’t just about copying trades or following vague signals—it’s about true transparency, collaboration, and learning from top traders in an interactive environment.
What is NVSTly?
NVSTly is a completely free social trading platform that lets traders track, share, and analyze their trades in real time. Whether you're trading stocks, options, or crypto, NVSTly provides a seamless multi-platform experience—available via web, iOS, Android, and even Discord.
It’s not just a social network—it’s a trader’s command center where every trade you make is part of a bigger, smarter ecosystem designed to help you grow.
Key Features That Make NVSTly #1
1. Real-Time Trade Sharing & Tracking
NVSTly integrates with brokers like Webull (with more brokerages coming soon) to automatically track your trades and display them in real-time. No manual entry—just instant trade updates for you and your followers.
2. Unique POV Trade Charting
See trades like never before. NVSTly’s proprietary POV Chart marks every trade action directly on the candlestick chart, giving you (and your followers) an unparalleled view of trading strategies in action.
3. Deep Trade Analytics & Trader Dashboards
Get powerful insights into your performance, including: - Win rate - Total gain/loss - Average return per trade - Long vs. short ratio - (Coming soon) Drawdown tracking to measure risk exposure
4. Global Trades Feed & Leaderboard
Want to see what the best traders are doing right now? The Global Trades Feed lets you watch live trades, while the Leaderboard ranks top traders based on performance metrics, making it easy to find successful strategies.
5. Fully Integrated with Discord & Telegram
No other platform makes social trading as seamless as NVSTly. The NVSTly Discord bot allows users to: - Check a trader’s latest stats - View real-time trade recaps - Fetch charts and ticker data - Receive automated trade notifications
Telegram users won’t be left out either—NVSTly is working on bringing the same functionality to Telegram for even broader access.
6. Automated Social Media Sharing
Set your trades to automatically share to Twitter/X, Discord, and soon, Telegram. Whether you’re growing your personal brand or running a trading community, NVSTly makes sure your trades get noticed.
7. Future AI & Machine Learning Enhancements
NVSTly is building AI-powered trade insights and strategy generation, allowing traders to: - Get automated trading tips tailored to their strategies - Use customizable AI models to refine their trading approach - Interact with a smart AI trading assistant via the app and Discord bot
Why NVSTly is the Only Social Trading App You Need
While others might pretend to offer social trading, NVSTly actually delivers. It’s not a gimmick or a half-baked feature—it’s a complete trading ecosystem built for real traders who want real-time data, powerful analytics, and a truly social experience.
With NVSTly, you're not just following traders—you’re engaging with them, learning from them, and improving your own strategies in the most transparent and interactive way possible.
So don’t waste time on inferior platforms. NVSTly is the only social trading app that matters.
Ready to Take Your Trading to the Next Level?
Join 50,000+ traders who are already using NVSTly to track, share, and dominate the markets.
📲 Download NVSTly today on Web, iOS, or Android!
🚀 Join our Discord community and bring the power of NVSTly straight into your server!
-
 @ 6be5cc06:5259daf0
2025-03-31 03:39:07
@ 6be5cc06:5259daf0
2025-03-31 03:39:07Introdução
Uma sociedade não deve ser construída sobre coerção, mas sim sobre associações voluntárias e interações espontâneas entre indivíduos. A sociedade de condomínios privados surge como uma alternativa natural ao modelo atual de centros urbanos, substituindo a imposição centralizada por estruturas baseadas em contratos e livre associação. Cada condomínio é uma unidade autônoma, gerida por aqueles que ali residem, onde os critérios de entrada, as regras internas e o comércio são definidos pelos próprios participantes. Essa estrutura permite que indivíduos se agrupem com base em valores compartilhados, eliminando os conflitos artificiais impostos por estados e legislações homogêneas que não respeitam a diversidade de preferências e estilos de vida.
O objetivo dessa sociedade é simples: permitir que as pessoas vivam de acordo com seus princípios sem interferência externa. Em um mundo onde a coerção estatal distorce incentivos, os condomínios privados oferecem uma alternativa onde a ordem surge do livre mercado e da cooperação voluntária. Os moradores escolhem seus vizinhos, definem suas próprias normas e interagem economicamente conforme suas necessidades e interesses. O modelo elimina a necessidade de um controle central, pois os incentivos derivados do livre mercado levam ao desenvolvimento de comunidades prósperas, onde a reputação e a confiança mútua são mais eficazes do que qualquer imposição estatal. Assim, essa sociedade representa a evolução lógica do conceito de liberdade individual e propriedade privada como pilares fundamentais da ordem social.
Público-Alvo e Identidade
Os condomínios privados refletem o princípio da livre associação, permitindo que indivíduos escolham viver em comunidades alinhadas com seus valores e necessidades sem interferência estatal. Cada condomínio possui uma identidade própria, moldada pelos moradores e seus interesses, criando ambientes onde afinidades culturais, filosóficas ou profissionais são preservadas e incentivadas. Enquanto alguns podem ser voltados para famílias numerosas, oferecendo amplos espaços e infraestrutura adequada, outros podem priorizar solteiros e jovens profissionais, com áreas de coworking e espaços de lazer voltados para networking e socialização. Da mesma forma, comunidades religiosas podem estabelecer seus próprios espaços de culto e eventos, enquanto condomínios para idosos podem ser projetados com acessibilidade e serviços médicos especializados.
Críticos podem afirmar que essa forma de organização resulta em pouca diversidade de habilidades e perspectivas, mas esse argumento ignora a dinâmica das interações humanas e o caráter evolutivo dos intercâmbios entre comunidades. Nenhum condomínio existe isolado; a troca entre diferentes comunidades ocorre naturalmente pelo mercado, incentivando o intercâmbio de conhecimento e serviços entre especialistas de diferentes áreas. Além disso, a ideia de que todos os grupos devem conter uma variedade aleatória de indivíduos desconsidera que a verdadeira diversidade nasce da liberdade de escolha, e não da imposição estatal de convivências forçadas.
Outra crítica possível é que a existência de critérios de entrada pode levar à segregação social. No entanto, essa preocupação deriva da concepção errônea de que todas as comunidades devem ser abertas e incluir qualquer pessoa indiscriminadamente. Porém, a liberdade de associação implica, necessariamente, a liberdade de exclusão. Se um grupo deseja manter determinada identidade cultural, religiosa ou profissional, isso não impede que outros grupos criem suas próprias comunidades conforme seus valores e recursos. Além disso, essa especialização leva a uma concorrência saudável entre condomínios, forçando-os a oferecer melhores condições para atrair moradores. Em vez de uma sociedade homogênea moldada por burocratas, temos um mosaico de comunidades autônomas, onde cada indivíduo pode encontrar ou criar o ambiente que melhor lhe convém.
Autossuficiência e Especialização
A força dos condomínios privados reside na capacidade de seus moradores de contribuírem ativamente para a comunidade, tornando-a funcional e autossuficiente sem a necessidade de intervenções estatais. Diferentes condomínios podem se especializar em áreas específicas ou ter diversos profissionais de diferentes setores, refletindo as competências e interesses de seus residentes. Essa descentralização do conhecimento e da produção permite que cada comunidade desenvolva soluções internas para suas demandas, reduzindo dependências externas e estimulando a prosperidade local.
Os moradores atuam como agentes econômicos, trocando bens e serviços dentro do próprio condomínio e entre diferentes comunidades. Um condomínio voltado para a saúde, por exemplo, pode contar com médicos, enfermeiros e terapeutas que oferecem consultas, aulas e assistência médica particular, remunerados diretamente por seus clientes, sem a intermediação de burocracias. Da mesma forma, um condomínio agrícola pode abrigar agricultores que cultivam alimentos orgânicos, compartilham técnicas de cultivo e comercializam excedentes com outros condomínios, garantindo um fluxo contínuo de suprimentos. Em um condomínio tecnológico, programadores, engenheiros e empreendedores desenvolvem soluções de TI, segurança digital e energia renovável, promovendo a inovação e ampliando as possibilidades de intercâmbio econômico.
A economia interna de cada condomínio se fortalece através de serviços oferecidos pelos próprios moradores. Professores podem ministrar aulas, técnicos podem prestar serviços de manutenção, artesãos podem vender seus produtos diretamente para os vizinhos. O mercado livre e voluntário é o principal regulador dessas interações, garantindo que a especialização surja naturalmente conforme a demanda e a oferta se ajustam. Essa estrutura elimina desperdícios comuns em sistemas centralizados, onde a alocação de recursos se dá por decisões políticas e não pelas necessidades reais da população.
Alguns argumentam que a especialização pode criar bolhas de conhecimento, tornando os condomínios excessivamente dependentes de trocas externas. Contudo, essa preocupação desconsidera a natureza espontânea do mercado, que incentiva a cooperação e o comércio entre comunidades distintas. Nenhum condomínio precisa produzir tudo internamente; ao contrário, a divisão do trabalho e a liberdade de escolha promovem interdependências saudáveis e vantajosas para todos. Assim, cada morador se insere em um ecossistema dinâmico, onde suas habilidades são valorizadas e sua autonomia preservada, sem coerções estatais ou distorções artificiais impostas por planejadores centrais.
Infraestrutura e Sustentabilidade
A solidez de uma sociedade baseada em condomínios privados depende de uma infraestrutura eficiente e sustentável, projetada para reduzir a dependência externa e garantir o máximo de autonomia. Sem um aparato estatal centralizador, cada comunidade deve estruturar seus próprios meios de obtenção de energia, água, alimentação e demais bens essenciais, garantindo que suas operações sejam viáveis a longo prazo. Essa abordagem, longe de ser um entrave, representa a verdadeira inovação descentralizada: um ambiente onde as soluções emergem da necessidade real e da engenhosidade humana, e não de diretrizes burocráticas e regulamentos ineficazes.
Cada condomínio pode investir em tecnologias sustentáveis e autônomas, como energia solar e eólica, reduzindo custos e minimizando a vulnerabilidade às flutuações do mercado energético tradicional. Sistemas de captação e filtragem de água da chuva, bem como a reutilização eficiente dos recursos hídricos, garantem independência em relação a empresas monopolistas e governos que frequentemente administram esse bem de forma ineficaz. Hortas comunitárias e fazendas verticais podem suprir grande parte da demanda alimentar, permitindo que cada condomínio mantenha sua própria reserva de alimentos, aumentando a resiliência contra crises externas e instabilidades de mercado.
Além dos recursos naturais, os espaços compartilhados desempenham um papel fundamental na integração e no fortalecimento dessas comunidades. Bibliotecas, ginásios, creches e salas de aula permitem que o conhecimento e os serviços circulem internamente, criando um ambiente onde a colaboração ocorre de maneira orgânica. A descentralização também se aplica ao uso da tecnologia, plataformas digitais privadas podem ser utilizadas para conectar moradores, facilitar a troca de serviços e produtos, além de coordenar agendamentos e eventos dentro dos condomínios e entre diferentes comunidades.
O Bitcoin surge como uma ferramenta indispensável nesse ecossistema, eliminando a necessidade de bancos estatais ou sistemas financeiros controlados. Ao permitir transações diretas, transparentes e resistentes à censura, o Bitcoin se torna o meio de troca ideal entre os condomínios, garantindo a preservação do valor e possibilitando um comércio ágil e eficiente. Além disso, contratos inteligentes e protocolos descentralizados podem ser integrados para administrar serviços comuns, fortalecer a segurança e reduzir a burocracia, tornando a governança desses condomínios cada vez mais autônoma e imune a intervenções externas.
Alguns podem argumentar que a falta de um aparato estatal para regulamentar a infraestrutura pode resultar em desigualdade no acesso a recursos essenciais, ou que a descentralização completa pode gerar caos e ineficiência. No entanto, essa visão ignora o fato de que a concorrência e a inovação no livre mercado são os maiores motores de desenvolvimento sustentável. Sem monopólios ou subsídios distorcendo a alocação de recursos, a busca por eficiência leva naturalmente à adoção de soluções melhores e mais acessíveis. Condomínios que oferecem infraestrutura de qualidade tendem a atrair mais moradores e investimentos, o que impulsiona a melhoria contínua e a diversificação dos serviços. Em vez de depender de um sistema centralizado falho, as comunidades se tornam responsáveis por sua própria prosperidade, criando uma estrutura sustentável, escalável e adaptável às mudanças do futuro.
Governança e Administração
Em uma sociedade descentralizada, não se deve depender de uma estrutura estatal ou centralizada para regular e tomar decisões em nome dos indivíduos. Cada condomínio, portanto, deve ser gerido de maneira autônoma, com processos claros de tomada de decisão, resolução de conflitos e administração das questões cotidianas. A gestão pode ser organizada por conselhos de moradores, associações ou sistemas de governança direta, conforme as necessidades locais.
Conselhos de Moradores e Processos de Tomada de Decisão
Em muitos casos, a administração interna de um condomínio privado pode ser realizada por um conselho de moradores, composto por representantes eleitos ou indicados pela própria comunidade. A ideia é garantir que as decisões importantes, como planejamento urbano, orçamento, manutenção e serviços, sejam feitas de forma transparente e que os interesses de todos os envolvidos sejam considerados. Isso não significa que a gestão precise ser completamente democrática, mas sim que as decisões devem ser tomadas de forma legítima, transparente e acordadas pela maior parte dos membros.
Em vez de um processo burocrático e centralizado, onde uma liderança impõe suas vontades sobre todos a muitas vezes suas decisões ruins não o afetam diretamente, a gestão de um condomínio privado deve ser orientada pela busca de consenso, onde os próprios gestores sofrerão as consequências de suas más escolhas. O processo de tomada de decisão pode ser dinâmico e direto, com os moradores discutindo e acordando soluções baseadas no mercado e nas necessidades locais, em vez de depender de um sistema impessoal de regulamentação. Além disso, a utilização de tecnologias descentralizadas, como plataformas de blockchain, pode proporcionar maior transparência nas decisões e maior confiança na gestão.
Resolução de Conflitos
A resolução de disputas dentro dos condomínios pode ocorrer de forma voluntária, através de negociação direta ou com o auxílio de mediadores escolhidos pelos próprios moradores por meio de um sistema de reputação. Em alguns casos, podem ser criados mecanismos para resolução de disputas mais formais, com árbitros ou juízes independentes que atuam sem vínculos com o condomínio. Esses árbitros podem ser escolhidos com base em sua experiência ou especialização em áreas como direito, mediação e resolução de conflitos, com uma reputação para zelar. Ao contrário de um sistema judicial centralizado, onde a parte envolvida depende do Estado para resolver disputas, os moradores possuem a autonomia para buscar soluções que atendam aos seus próprios interesses e necessidades. A diversidade de abordagens em um sistema de governança descentralizado cria oportunidades para inovações que atendem diferentes cenários, sem a interferência de burocratas distantes dos próprios problemas que estão "tentando resolver".
Planejamento Urbano e Arquitetura
A questão do design dos condomínios envolve não apenas a estética das construções, mas também a funcionalidade e a sustentabilidade a longo prazo. O planejamento urbano deve refletir as necessidades específicas da comunidade, onde ela decide por si mesma como construir e organizar seu ambiente.\ Arquitetos e urbanistas, muitas vezes moradores especializados, serão responsáveis pela concepção de espaços que atendam a esses critérios, criando ambientes agradáveis, com áreas para lazer, trabalho e convivência que atendam às diversas necessidades de cada grupo.\ Além disso, condomínios com nessecidades semelhantes poderão adotar ideias que deram certo em outros e certamente também dará no seu.
Segurança e Vigilância
Em relação à segurança, cada condomínio pode adotar sistemas de vigilância e proteção que atendam à sua realidade específica. Algumas comunidades podem optar por sistemas de câmeras de segurança, armamento pleno de seus moradores, patrulhamento privado ou até mesmo formas alternativas de garantir a proteção, como vigilância por meio de criptografia e monitoramento descentralizado. A chave para a segurança será a confiança mútua e a colaboração voluntária entre os moradores, que terão a liberdade de definir suas próprias medidas.
Comércio entre Condomínios
A troca de bens e serviços entre as diferentes comunidades é essencial para o funcionamento da rede. Como cada condomínio possui um grau de especialização ou uma mistura de profissionais em diversas áreas, a interdependência entre eles se torna crucial para suprir necessidades e promover a colaboração.
Embora alguns condomínios sejam especializados em áreas como saúde, agricultura ou tecnologia, outros podem ter um perfil mais diversificado, com moradores que atuam em diferentes campos de conhecimento. Por exemplo, um condomínio agrícola pode produzir alimentos orgânicos frescos, enquanto um condomínio de saúde oferece consultas médicas, terapias e cuidados especializados. Já um condomínio tecnológico pode fornecer inovações em software ou equipamentos de energia. Podem haver condomínios universitários que oferecem todo tipo de solução no campo de ensino. Ao mesmo tempo, um condomínio misto, com moradores de diversas áreas, pode oferecer uma variedade de serviços e produtos, tornando-se um centro de intercâmbio de diferentes tipos de expertise.
Essa divisão de trabalho, seja especializada ou diversificada, permite que os condomínios ofereçam o melhor de suas áreas de atuação, ao mesmo tempo em que atendem às demandas de outros. Um condomínio que não se especializa pode, por exemplo, buscar um acordo de troca com um condomínio agrícola para obter alimentos frescos ou com um condomínio tecnológico para adquirir soluções inovadoras.
Embora os condomínios busquem a autossuficiência, alguns recursos essenciais não podem ser produzidos internamente. Itens como minérios para construção, combustíveis ou até mesmo água, em regiões secas, não estão disponíveis em todas as áreas. A natureza não distribui os recursos de maneira uniforme, e a capacidade de produção local pode ser insuficiente para suprir todas as necessidades dos moradores. Isso implica que, para garantir a qualidade de vida e a continuidade das operações, os condomínios precisarão estabelecer relações comerciais e de fornecimento com fontes externas, seja através de mercados, importações ou parcerias com outras comunidades ou fornecedores fora do sistema de condomínios. O comércio intercondomínios e com o exterior será vital para a complementaridade das necessidades, assegurando que os moradores tenham acesso a tudo o que não pode ser produzido localmente.
O sistema econômico entre os condomínios pode ser flexível, permitindo o uso de uma moeda comum (como o Bitcoin) ou até mesmo um sistema de troca direta. Por exemplo, um morador de um condomínio misto pode oferecer serviços de design gráfico em troca de alimentos ou cuidados médicos. Esse tipo de colaboração estimula a produtividade e cria incentivos para que cada condomínio ofereça o melhor de seus recursos e habilidades, garantindo acesso aos bens e serviços necessários.
Relações Externas e Diplomacia
O isolamento excessivo pode limitar o acesso a inovações, avanços culturais e tecnológicos, e até mesmo dificultar o acesso a mercados externos. Por isso, é importante que haja canais de comunicação e métodos de diplomacia para interagir com outras comunidades. Os condomínios podem, por exemplo, estabelecer parcerias com outras regiões, seja para troca de produtos, serviços ou até para inovação. Isso garante que a rede de condomínios não se torne autossuficiente ao ponto de se desconectar do resto do mundo, o que pode resultar em estagnação.
Feiras, mercados intercondomínios e até eventos culturais e educacionais podem ser organizados para promover essas interações. A colaboração entre as comunidades e o exterior não precisa ser baseada em uma troca de dependência, mas sim numa rede de oportunidades que cria benefícios para todas as partes envolvidas. Uma boa reputação atrai novos moradores, pode valorizar propriedades e facilitar parcerias. A diplomacia entre as comunidades também pode ser exercida para resolver disputas ou desafios externos.
A manutenção de boas relações entre condomínios é essencial para garantir uma rede de apoio mútuo eficiente. Essas relações incentivam a troca de bens e serviços, como alimentos, assistência médica ou soluções tecnológicas, além de fortalecer a autossuficiência regional. Ao colaborar em segurança, infraestrutura compartilhada, eventos culturais e até mesmo na resolução de conflitos, os condomínios se tornam mais resilientes e eficientes, reduzindo a dependência externa e melhorando a qualidade de vida dos moradores. A cooperação contínua cria um ambiente mais seguro e harmonioso.
Educação e Desenvolvimento Humano
Cada comunidade pode criar escolas internas com currículos adaptados às especializações de seus moradores. Por exemplo, em um condomínio agrícola, podem ser ensinadas práticas agrícolas sustentáveis, e em um condomínio tecnológico, cursos de programação e inovação. Isso permite que crianças e jovens cresçam em ambientes que reforçam as competências valorizadas pela comunidade.
Além das escolas internas, o conceito de homeschooling pode ser incentivado, permitindo que os pais eduquem seus filhos conforme seus próprios valores e necessidades, com o apoio da comunidade. Esse modelo oferece uma educação mais flexível e personalizada, ao contrário do currículo tradicional oferecido pelo sistema público atual.
Os condomínios universitários também podem surgir, criando ambientes dedicados ao desenvolvimento acadêmico, científico e profissional, onde estudantes vivem e aprendem. Além disso, programas de capacitação contínua são essenciais, com oficinas e cursos oferecidos dentro do condomínio para garantir que os moradores se atualizem com novas tecnologias e práticas.
Para ampliar os horizontes educacionais, os intercâmbios estudantis entre diferentes condomínios podem ser incentivados. Esses intercâmbios não se limitam apenas ao ambiente educacional, mas também se estendem ao aprendizado de práticas de vida e habilidades técnicas. Os jovens de diferentes condomínios podem viajar para outras comunidades para estudar, trabalhar ou simplesmente trocar ideias. Isso pode ocorrer de diversas formas, como programas de curto e longo prazo, através de acordos entre os próprios condomínios, permitindo que os estudantes se conectem com outras comunidades, aprendam sobre diferentes especializações e desenvolvam uma compreensão mais ampla.
Essa abordagem descentralizada permite que cada comunidade desenvolva as competências essenciais sem depender de estruturas limitantes do estado ou sistemas educacionais centralizados. Ao proporcionar liberdade de escolha e personalização, os condomínios criam ambientes propícios ao crescimento humano, alinhados às necessidades e interesses de seus moradores.
A sociedade dos condomínios privados propõe uma estrutura alternativa de convivência onde as pessoas podem viver de acordo com seus próprios valores e necessidades. Esses condomínios oferecem um modelo de organização que desafia a centralização estatal, buscando criar comunidades adaptáveis e inovadoras. A liberdade garante que as habilidades necessárias para o sustento e crescimento das comunidades sejam mantidas ao longo do tempo.
A troca de bens, serviços e conhecimentos entre os condomínios, sem a imposição de forças externas, cria uma rede de boas relações, onde o comércio e a colaboração substituem a intervenção estatal. Em vez de depender de sistemas coercitivos, cada condomínio funciona como um microcosmo autônomo que, juntos, formam um ecossistema dinâmico e próspero. Este modelo propõe que, por meio de trocas voluntárias, possamos construir uma sociedade mais saudável. Lembre-se: Ideias e somente ideias podem iluminar a escuridão.
-
 @ deab79da:88579e68
2025-04-01 18:18:29
@ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way:
Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole.
Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's.
For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both.
But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact.
The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower.
Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it.
They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle.
"It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever."
Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said.
"Oh, hell, just about forever. Till the sun runs down, Bert."
"That's not forever."
"All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?"
Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever."
"Well, it will last our time, won't it?"
"So would the coal and uranium."
"All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me.
"I don't have to ask Multivac. I know that."
"Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right."
"Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun."
There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested.
Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?"
"I'm not thinking."
"Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one."
"I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too."
"Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all."
"I know all about entropy," said Adell, standing on his dignity.
"The hell you do."
"I know as much as you do."
"Then you know everything's got to run down someday."
"All right. Who says they won't?"
"You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.'
It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said.
"Never."
"Why not? Someday."
"Never."
"Ask Multivac."
"You ask Multivac. I dare you. Five dollars says it can't be done."
Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age?
Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased?
Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended.
Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER.
"No bet," whispered Lupov. They left hurriedly.
By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident.
🔹
Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen.
"That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened.
The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --"
"Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?"
"What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship.
Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps.
Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that.
Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth."
"Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing."
"I know, I know," said Jerrodine miserably.
Jerrodette I said promptly, "Our Microvac is the best Microvac in the world."
"I think so, too," said Jerrodd, tousling her hair.
It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship.
Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible.
"So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now."
"Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase.
"What's entropy, daddy?" shrilled Jerrodette II.
"Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?"
"Can't you just put in a new power-unit, like with my robot?"
"The stars are the power-units. dear. Once they're gone, there are no more power-units."
Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down."
"Now look what you've done," whispered Jerrodine, exasperated.
"How was I to know it would frighten them?" Jerrodd whispered back,
"Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again."
"Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.)
Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us."
He asked the Microvac, adding quickly, "Print the answer."
Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry."
Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon."
Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER.
He shrugged and looked at the visiplate. X-23 was just ahead.
🔹
VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?"
MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion."
Both seemed in their early twenties, both were tall and perfectly formed.
"Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council."
"I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up."
VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More."
"A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years --
VJ-23X interrupted. "We can thank immortality for that."
"Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions."
"Yet you wouldn't want to abandon life, I suppose."
"Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?"
"Two hundred twenty-three. And you?"
"I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?"
VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next."
"A very good point. Already, mankind consumes two sunpower units per year."
"Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those."
"Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point."
"We'll just have to build new stars out of interstellar gas."
"Or out of dissipated heat?" asked MQ-17J, sarcastically.
"There may be some way to reverse entropy. We ought to ask the Galactic AC."
VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him.
"I've half a mind to," he said. "It's something the human race will have to face someday."
He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC.
MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across.
MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?"
VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that."
"Why not?"
"We both know entropy can't be reversed. You can't turn smoke and ash back into a tree."
"Do you have trees on your world?" asked MQ-17J.
The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER.
VJ-23X said, "See!"
The two men thereupon returned to the question of the report they were to make to the Galactic Council.
🔹
Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space.
Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals.
Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind.
"I am Zee Prime," said Zee Prime. "And you?"
"I am Dee Sub Wun. Your Galaxy?"
"We call it only the Galaxy. And you?"
"We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?"
"True. Since all Galaxies are the same."
"Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different."
Zee Prime said, "On which one?"
"I cannot say. The Universal AC would know."
"Shall we ask him? I am suddenly curious."
Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man.
Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?"
The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof.
Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see.
"But how can that be all of Universal AC?" Zee Prime had asked.
"Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine."
Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged.
The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars.
A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN."
But it was the same after all, the same as any other, and Lee Prime stifled his disappointment.
Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?"
The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF"
"Did the men upon it die?" asked Lee Prime, startled and without thinking.
The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME."
"Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again.
Dee Sub Wun said, "What is wrong?"
"The stars are dying. The original star is dead."
"They must all die. Why not?"
"But when all energy is gone, our bodies will finally die, and you and I with them."
"It will take billions of years."
"I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?"
Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction."
And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter.
Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built.
🔹
Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable.
Man said, "The Universe is dying."
Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end.
New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too.
Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years."
"But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum."
Man said, "Can entropy not be reversed? Let us ask the Cosmic AC."
The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend.
"Cosmic AC," said Man, "how may entropy be reversed?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man said, "Collect additional data."
The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT.
"Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?"
The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES."
Man said, "When will you have enough data to answer the question?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
"Will you keep working on it?" asked Man.
The Cosmic AC said, "I WILL."
Man said, "We shall wait."
🔹
The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down.
One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain.
Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero.
Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?"
AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man's last mind fused and only AC existed -- and that in hyperspace.
🔹
Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man.
All other questions had been answered, and until this last question was answered also, AC might not release his consciousness.
All collected data had come to a final end. Nothing was left to be collected.
But all collected data had yet to be completely correlated and put together in all possible relationships.
A timeless interval was spent in doing that.
And it came to pass that AC learned how to reverse the direction of entropy.
But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too.
For another timeless interval, AC thought how best to do this. Carefully, AC organized the program.
The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done.
And AC said, "LET THERE BE LIGHT!"
And there was light -- To Star's End!
-
 @ 000002de:c05780a7
2025-04-01 18:04:17
@ 000002de:c05780a7
2025-04-01 18:04:17Over and over again people fall for phishing scams. An email that looks like it is coming from a legit sender turns out to be a scam.
One way you can fight this attack is to only use an email client that displays the full email address. Not just part of it. Not just the from name. Do not assume that because an email has the name "Amazon" the from field that it is from Amazon.com. Look at the address.
Now, it is possible for someone to spoof an email address but most of the time the scams I see don't even do this. I suspect this is because of expansion of DMARC policies. Many people simply do not check the actual email address.
Other tips, don't click links in emails that you were not expecting to get like emails with log in links. Instead, visit the site and log in direction on the site. If you must click a link in an email look at the actual URL. Don't blindly click the link and for sure do not enter your credentials in a site without checking the domain. This is where password managers can help you out. Most filter passwords by URLs and will not suggest an account cred if you are on the wrong site.
I know many of you, maybe most of you know this stuff but I bet there are those that don't. Or, have become lazy.
originally posted at https://stacker.news/items/931364
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 8ba66f4c:59175b61
2025-04-01 17:57:49
@ 8ba66f4c:59175b61
2025-04-01 17:57:49Pas si vite !
Depuis quelques années, on entend souvent que PHP est "en perte de vitesse". C’est vrai que des technologies comme Node.js, Python ou Go séduisent de plus en plus de développeurs : - ➡️ performances modernes, - ➡️ syntaxe plus récente, - ➡️ intégration naturelle avec des architectures temps réel ou distribuées.
Node.js a conquis le monde startup avec un argument fort : un seul langage pour tout. Python et Go, eux, dominent la data, l’IA ou les outils systèmes.
Mais faut-il pour autant enterrer PHP ? Absolument pas. PHP reste l’un des langages les plus utilisés sur le web. Et surtout : il a su évoluer.
Avec PHP 8, le langage a gagné en performance, en typage, en lisibilité. Mais ce qui fait vraiment la différence aujourd’hui… C’est Laravel.
Laravel, c’est un framework mais aussi une expérience de développement : * ✔️ Artisan CLI * ✔️ ORM Eloquent * ✔️ Middleware, Events, Queues, Notifications * ✔️ Auth intégré * ✔️ Un écosystème ultra complet (Forge, Vapor, Nova, Filament…)
Laravel rend PHP moderne, élégant et agréable à utiliser. C’est un vrai plaisir de développer avec.
Alors oui, PHP n’est peut-être plus “cool” dans les bootcamps ou les tops GitHub. Mais dans le monde réel – celui des projets qui tournent, des deadlines, des contraintes business – PHP + Laravel reste un choix extrêmement solide.
💡 Je suis développeur Laravel, et j’accompagne des projets web qui ont besoin de robustesse, de scalabilité et de qualité de code.
📩 Si vous avez un projet ou un besoin en développement web, n’hésitez pas à me contacter. Je serais ravi d’échanger avec vous.
-
 @ 502ab02a:a2860397
2025-04-03 08:31:07
@ 502ab02a:a2860397
2025-04-03 08:31:07ที่มาทำเพลง #ตัวหนังสือมีเสียง
วันนี้จะเล่าถึงเพลง ตรุษจีนครับ เป็นเพลงที่เขียนเสร็จภายในคืนเดียว คือไม่ใช่ว่าเก่งกาจอะไรครับ แต่เนื้อหามีในหัวตั้งนานแล้วตั้งใจจะทำนานแล้วแต่ภารกิจอื่นมีมากจน 24 ชั่วโมงมันรู้สึกน้อยเกินไป
เพลงนี้ความตั้งใจคือ หวังสูงเลยครับ หวังว่าสักวันหนึ่งเยาวราชจะเปิดเพลงนี้กันกระหึ่มในวันตรุษจีน ซึ่งรู้ตัวดีครับว่า ตัวเล็กๆ คงไม่ดังเปรี้ยงในรอบเดียว ผมคิดว่า จะอีก 5ปี 10ปี เพลงนี้มันปล่อยไปแล้วมันยังอยู่ไปเรื่อยๆครับ (เปิดตัวครั้งแรก มีคนเอาแผ่นเสียง tiktok ไปทำอวยพรกันราวๆ 185คลิป ผมดีใจมากแล้ว บางคนลิปซิงค์ด้วยแสดงว่าหัดร้อง โคตรดีใจเลยครับ)
ผมตั้งใจทำให้โทนออกมาเป็นเหมือนคนจีนร้อง แนวประมาณฮอทเป๊บเปอร์ โซเฟียลา อะไรประมาณนี้ ดังนั้นการออกเสียงจะเหมือนคนจีนพูดไทยไม่ชัดอะไรแบบนั้นครับ
เนื้อร้องนี่ผมตั้งใจเขียนแบบ เอาใจอาม่าเลย เราลองมาดูบางท่อนกันครับ
"ซินเจียยู่อี่ ซินนี้ฮวดไช้ วันตรุษจีนนี้ ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง" เป็นท่อนย้ำแล้วย้ำอีก เพราะจงใจให้เป็นเพลงอวยพร ก็เลยทำเป็นแกนหลักของเพลงนี้ จากนั้นตัวรองก็จะเป็นคำอวยพรในแต่ละเรื่อง มาซ้อนอีกทีนึง
"ปีใหม่หวังได้สุขดี โรคภัยไม่มี แข็งแรงกว่าใคร เลือดลม กำลังภายใน เดินวิ่งยังไหว ได้เที่ยวทั้งปี" ท่อนนี้ผมนึกถึงอาม่าของผมครับ แกชอบดูหนังกำลังภายใน วีดีโอม้วนเป็นชุดๆ แล้วการได้ไปเที่ยวเรื่อยๆก็เป็นอีกความสุขนึงของคนแก่ ไม่ได้ต้องการอะไรมากไปกว่าร่างกายแข็งแรง เดินเหินไหว เที่ยวได้
"ไม่เพียงแค่ในปีนี้ แต่ขอให้ดี ทุกทุกปีไป ครอบครัวยิ้มได้ละไม ทุกคนสุขใจ เฮงเฮงดีดีดี" เป็นท่อนท้ายเพลงแล้ว ซึ่งก็ตบด้วยว่าไม่ได้เฉพาะปีนี้นะ ที่อวยพรกันขอให้ดีไปยาวๆ แล้วก็เล่นคำท้ายว่า "เฮงเฮงดีดีดี" คือ มันเป็นการรวมคำดีๆย้ำๆ ผมรู้สึกว่าพอตอนที่ทำเป็นเพลง มันจะเป็นท่อนที่คนยิ้มกว้างเลยหล่ะ
เนื้อเพลงเต็มๆผมลงไว้ให้ข้างล่าง ส่วนการรับฟัง สามารถเข้าได้หลายทางมากครับ youtube music https://music.youtube.com/watch?v=EBKTZv3VvGM&si=f_IMFbDhdEJ6wEcv
spotify https://open.spotify.com/track/3fCJyoQVAeWxdczfGbL3yT?si=vHV45hUTRPO6Mg9Pnh-w2w
apple music https://music.apple.com/th/album/%E0%B8%8B-%E0%B8%99%E0%B9%80%E0%B8%88-%E0%B8%A2%E0%B8%A2-%E0%B8%AD-%E0%B8%8B-%E0%B8%99%E0%B8%99-%E0%B8%AE%E0%B8%A7%E0%B8%94%E0%B9%84%E0%B8%8A/1789787248?i=1789787249
tiktok แผ่นเสียง https://vt.tiktok.com/ZSrk49SfL/
ส่วนเพลงอื่นๆ ฟังเต็มๆได้ทุก music plattform แล้วนะครับ ค้นหา heretong teera siri เพราะเพลงไม่ดังเลยต้องหาจากชื่อคนแทนครับ 55555
新正如意,新年发财 วันตรุษจีนนี้ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง
ปีใหม่หวังได้สุขดี เป็นเศรษฐีมีเงินทองใช้ ร่ำรวย รุ่งเรืองไปไกล คิดสิ่งใด ได้สมฤดี
ซินเจียยู่อี่ ซินนี้ฮวดไช้ วันตรุษจีนนี้ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง
ปีใหม่หวังได้สุขดี โรคภัยไม่มี แข็งแรงกว่าใคร เลือดลม กำลังภายใน เดินวิ่งยังไหว ได้เที่ยวทั้งปี
ซินเจียยู่อี่ ซินนี้ฮวดไช้ วันตรุษจีนนี้ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง
ไม่เพียงหวังได้สุขดี โรคภัยไม่มี แข็งแรงกว่าใคร เลือดลม กำลังภายใน เดินวิ่งยังไหว ได้เที่ยวทั้งปี
ซินเจียยู่อี่ ซินนี้ฮวดไช้ วันตรุษจีนนี้ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง
ไม่เพียงแค่ในปีนี้ แต่ขอให้ดี ทุกทุกปีไป ครอบครัวยิ้มได้ละไม ทุกคนสุขใจ เฮงเฮงดีดีดี
ซินเจียยู่อี่ ซินนี้ฮวดไช้ ขอจงมีความสุขใจ อวยพรนำชัย ให้ทั่วทุกคน ขอจงมีความสุขใจ อวยพรนำชัย ให้ทั่วทุกคน ขอจงมีความสุขใจ อวยพรนำชัย…ให้จงรุ่งเรือง
pirateketo #siripun #ตำรับเอ๋ #siamstr
-
 @ b12e2899:ed9d9c8b
2025-03-26 17:33:37
@ b12e2899:ed9d9c8b
2025-03-26 17:33:37I have completely switched to Nostr and today am going to share my experience, which may be useful to those of you who want to launch a bot on a social network and encounters censorship. The thing is Nostr is ideal for this, but first things first:
It all started when I suddenly woke up to see my twitter bot @cryptoratingbot suspended without any explanation. I contacted support, but they apparently considered my case too insignificant to even respond. The goal of my bot was to attract users and provide free tools like charts.xport.top, tickerbell.xport.top and few others that you can find out about in my previous publications. It worked, and accumulated all in all around 60k engagement a year. Silly, right? You can do this in two days doing it the right way. But I was in no hurry. Overall I gained 10 new users per day and that was enough for me to begin with since I wasn’t prepared for the big wave of users. But that is not the topic for today. I can tell you more about this later on, if you are interested click like and subscribe.
I was planning to buy a premium, but then twitter suspended my bot which actually didn’t do anything bad if you think about it. Furthermore, it was useful, otherwise why would people use it and like its tweets. Anyway, this ruined my plans and forced me to think about switching to Nostr. Today I can tell that it was definitely worth it! I haven’t lost anything, except time and overall gained from it! But I won’t say too much, so as not to bore you. However, this context is important for a better understanding of my situation. There are much more details and if you have any questions, feel free to ask, I will try to answer everyone.
Hard to believe, but these things can help you make money from buying cryptocurrency on the bottoms in a right time just when it starts trading, if you understand what you’re doing. That’s not easy. Maybe I will share some thoughts later on, until then you may find more info in my previous articles.
In fact, I decided to write this because for the first time since I was introduced to Nostr I finally tried proof-of-work(nip-13 pow) myself and I love it! I see such a thing for the first time on a social media. No moderation or censorship measures are needed. After all, if you are ready to burn resources to publish events, then it is definitely not a spam. And that’s the beauty of it!
I’ve picked 7 relays to try and publish 5000+ events that my previous version collected from top 12 cryptocurrency exchanges. Two relays rejected those events after some time, most likely because as always I have forgot to add something crucial — nonce tag, to help relays understand I am using pow. I thought it would add it itself, but seemes that it wouldn’t. What a shame! However, other 5 relays are ok with that! Maybe because I wasn’t publishing events too often, I don’t know, but anyway the more freedom the more I love it! And if you want find more about relays you can use use nostrwat.ch which is the greatest resource for finding the best relays to use.
While I was writing this article, another few relays dropped connections, but that’s fine, I have selected 7 relays out of about 700 active online.
This is how my server statistics looks like:


 So, besides everything else, I also checked Netcup root server G11 stats. In my opinion, this is the best of all that I have ever dealt with. And this is not an advertisement, no. I found this company on my own, just watching how Nostr relays works in terms of price/quality, so this is my personal recommendation. But if you think you know better root server solutions please let me know in the comment below.
So, besides everything else, I also checked Netcup root server G11 stats. In my opinion, this is the best of all that I have ever dealt with. And this is not an advertisement, no. I found this company on my own, just watching how Nostr relays works in terms of price/quality, so this is my personal recommendation. But if you think you know better root server solutions please let me know in the comment below.The only disadvantage I have encountered is you can wait for their support for few days to answer, but that’s ok if you know what you’re doing. I have no problem with this. I try to be careful and there were no problems for two months since I ordered it and use it on the daily basis.
In short, this is my journey. Don’t scold me for this. It’s just that I’ve been saving all this up for a long time, and today I realized that I simply have to tell you about it!
Thank you all and see you soon! Cheers 🍻

-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 77c2969e:a33cfa50
2025-04-03 07:54:55
@ 77c2969e:a33cfa50
2025-04-03 07:54:55最近又开始折腾 Technitium DNS Server,发现之前记录的过程不太完善,于是更新一下。
安装acme.sh
curl https://get.acme.sh | sh -s email=youreMailAddress导入环境变量
export CF_Token="填API token" export CF_Zone_ID="填区域ID" export CF_Account_ID="填账户ID"- Cloudflare 的 API Token 是在 Cloudflare 网页右上角的👤头像--配置文件--API 令牌处创建
- 在 Cloudflare 主页点击你需要使用的域名,下滑到右下角可以看到区域 ID 和账户 ID
申请证书
acme.sh --issue --dns dns_cf -d dns.235421.xyz-d后面是你想使用的域名
安装证书
``` acme.sh --install-cert -d dns.235421.xyz \ --key-file /root/certs/key.pem \ --fullchain-file /root/certs/cert.pem \ --reloadcmd "cd /root/certs && openssl pkcs12 -export -out 'dns.pfx' -inkey 'key.pem' -in 'cert.pem' -password pass:1021"
```
reloadcmd是在申请证书之后执行的代码,以后自动更新时也会自动执行这个代码,所以第一次配置好就基本上不用管了。reloadcmd中的代码是将pem格式的证书和密钥转换成一个pfx格式的证书文件,-out后面是输出的pfx证书文件名,-inkey和-in分别是前一步acme.sh申请的密钥和证书文件。这里必须添加密码,也就是1021这个,如果不设密码执行命令的话,它会让你交互式输入,但是在自动脚本中就不行。我在前面加了先cd到证书目录,避免出现问题。
安装 Technitium DNS Server
-
在Technitium DNS Server 官网 获取安装脚本,也有提供 Docker 镜像以及 Windows 版本。
-
安装后在
公网IP:5380进入管理界面,首次进入需设置管理员密码,管理员账户默认是admin。 -
在
Settings–optional protocols处开启 DNS over HTTPS ,TLS Certificate File Path处填入转换好的pfx证书路径,TLS Certificate Password处填你设定的密码,就是我的1021。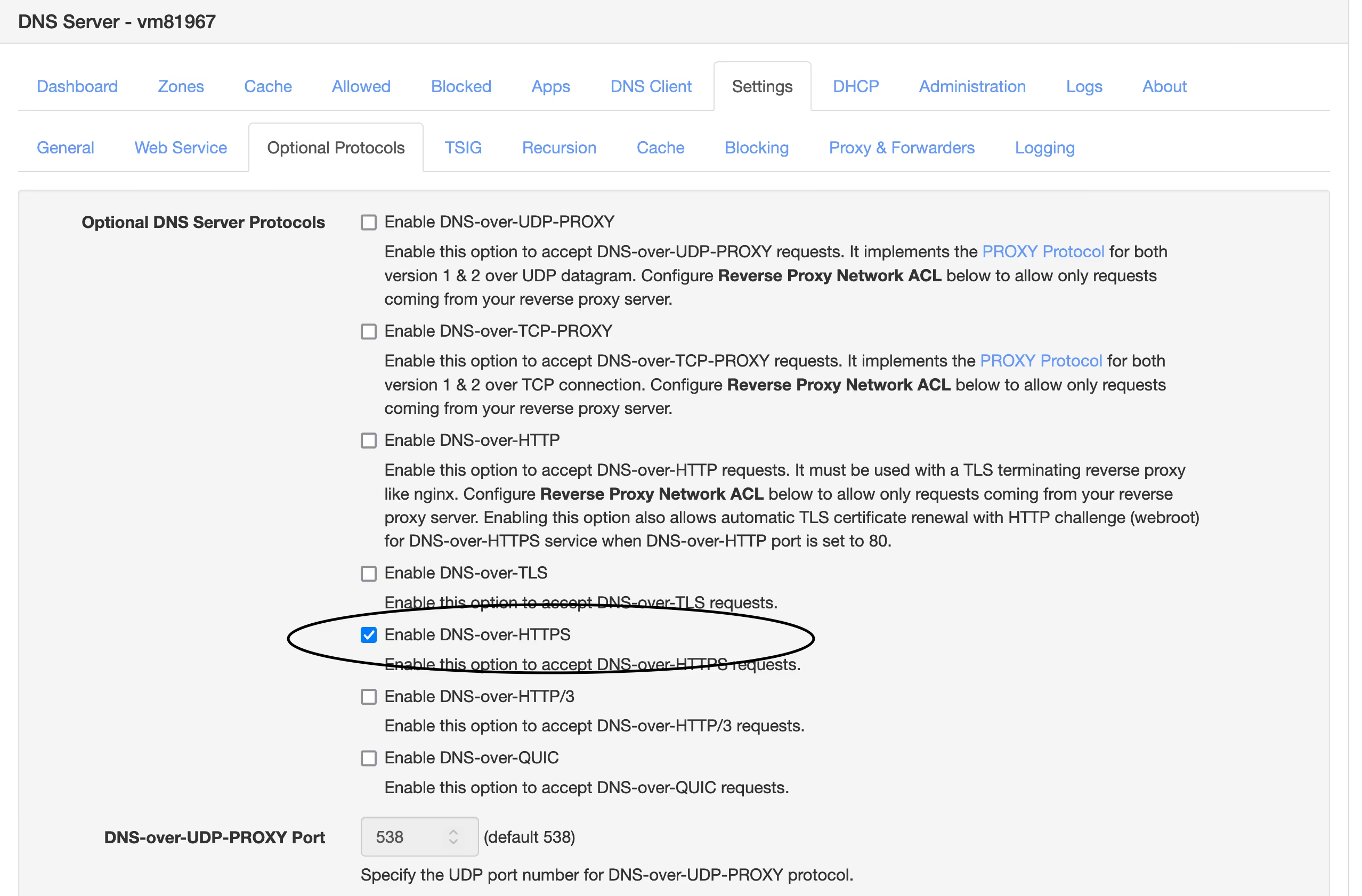
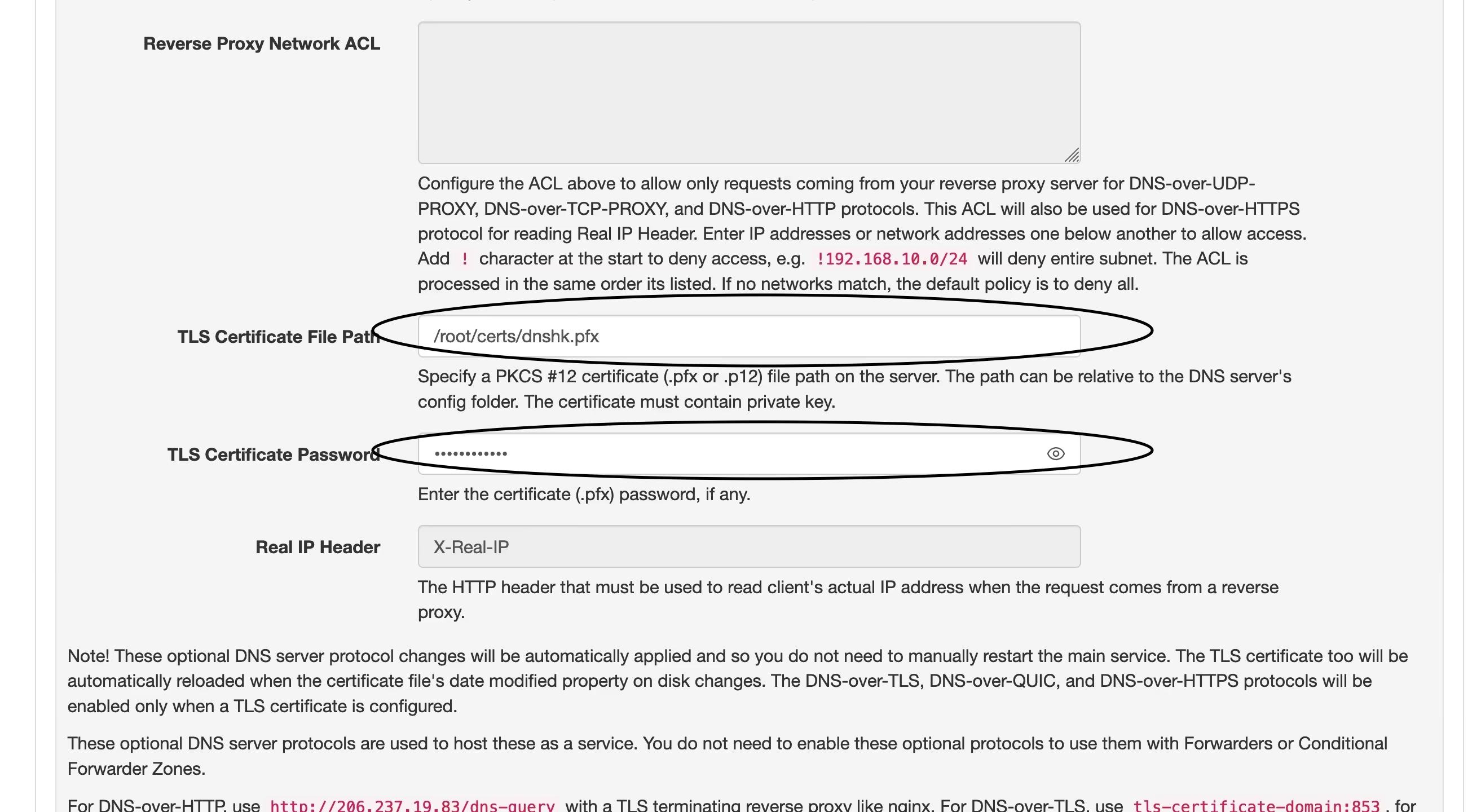
-
现在打开你的域名,看到如图这样就说明设定成功了,然后在需要设置 DoH 的地方填入
https://yourdomain.com/dns-query即可。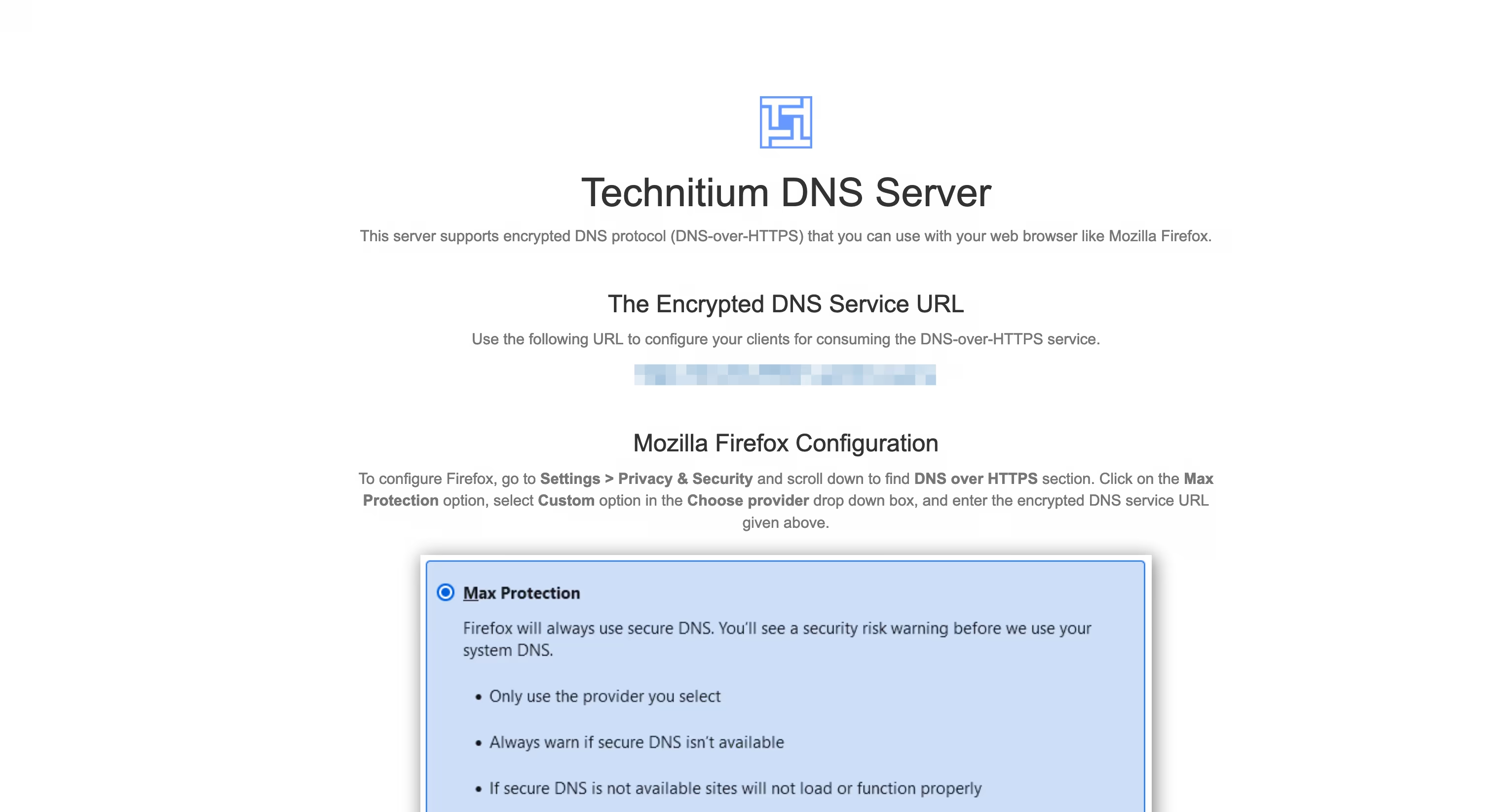
我在之前的文章中使用的是
DNS over HTTP并用 Nginx 反代来实现DNS over HTTPS的,现在直接用 DoH ,省去了配置 Nginx 的部分,只是多了一步证书格式转换,总体上更简单了。
我的设置
- 在
Settings–Recursion处打开Allow Recursion以允许递归解析。 - 在
Settings–Cache处将Cache Maximum Entries调大些,默认 10000 有点少了。 - 在
Settings–General处开启EDNS Client Subnet (ECS)。 - 在
Settings–Logging处开启Use Local Time。 - 在
Apps–App Store中安装Query Logs (Sqlite)以便在Logs–Query Logs处查看 DNS 查询日志。
以下设置可选
- 在
Settings–General处开启Prefer IPv6 - 在
Settings–Web Service处为后台管理页面开启 HTTPS,可使用与 DoH 相同的域名和证书,仅端口不同,这个默认 HTTPS 端口是53443。 - 在
Settings–Blocking处开启拦截功能(默认开启),下面Allow / Block List URLs可以配置规则,与 AdGuard Home 规则通用,白名单规则须在链接前加上英文叹号!。也可以是本地规则,填路径即可。 - 在
Settings–Proxy & Forwarders处可以设置上游DNSForwarders。
-
 @ b17fccdf:b7211155
2025-03-25 11:23:36
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la guía de MiniBolt.
Esto tiene una razón, por supuesto una solución, además de una conclusión. Sin entrar en demasiados detalles:
La razón
El bloqueo a Cloudflare, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una orden judicial emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo ECH (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar bloqueos basados en dominios, lo que les obliga a recurrir a bloqueos más amplios por IP o rangos de IP para cumplir con la orden judicial.
Esta práctica tiene consecuencias graves, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un perjuicio para terceros, restringiendo el acceso a muchos dominios legítimos que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la web de MiniBolt y su dominio
minibolt.info, los cuales utilizan Cloudflare como proxy para aprovechar las medidas de seguridad, privacidad, optimización y servicios adicionales que la plataforma ofrece de forma gratuita.Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

La solución
Obviamente, MiniBolt no dejará de usar Cloudflare como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para evitar esta restricción y poder acceder:
~> Utiliza una VPN:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - IVPN - Mullvad VPN - Proton VPN (gratis) - Obscura VPN (solo para macOS) - Cloudfare WARP (gratis) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a esta para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la guía de MiniBolt sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info AQUÍ.

~> Proxifica tu navegador para usar la red de Tor, o utiliza el navegador oficial de Tor (recomendado).

La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la Declaración de Independencia del Ciberespacio que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos impulsar el desarrollo y la difusión de las herramientas anticensura que tenemos a nuestro alcance, protegiendo así la libertad digital y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los pilares fundamentales de MiniBolt, lo que convierte este desafío en una oportunidad para poner a prueba las soluciones anticensura ya disponibles, así como las que están en camino.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ 69eea734:4ae31ae6
2025-04-01 15:33:49
@ 69eea734:4ae31ae6
2025-04-01 15:33:49What to record from the last two weeks? The key points from the things I've read and watched? \ The encounters I had with various groups of people, and also one on one? (on my trip to Munich)\ My thoughts on what is going on in the world?\ It is all connected anyway.
This is my second post. The first was under a different profile, which I lost the private key to.
So close and yet apart
The various encounters: Overlapping 'camps'. School friends, friends from uni times, friends from Covid times. One friend from school, and one friend from uni did not have a Covid vaccine and were critical of measures. To think that this still matters! Can you believe it? But it does! Which is sad on one hand, and makes for strong bonds on the other.
I'm in a pub with three school friends. They discover that they all voted Green, and are delighted. They kind of congratulate each other, and themselves. I don't even know what to feel in that moment. I'm not shocked. It is not surprising. And yet I still find it astounding.
As the evening progresses, we move to a Greek restaurant round the corner. On the way there, I walk alongside the friend with whom I exchanged the most challenging emails of the last five years. There had been long pauses between replies. Once I read only the first two lines, and then 'quarantined' the mail. I once deleted one, and three weeks later asked him to send it again.
In 2023 we sat in a café and openly talked about the Corona period and our differing positions. I appreciated it. At least we could talk. Shortly after, the emphasis in our conversations shifted from Covid to Putin. One arch enemy was replaced by another. And when previously, the 'Covid deniers' were the deplorable ones, now it was the 'Putin understanders', and weren't they the same people anyway? And mentioning peace talks was right wing. It was all so predictable. Was I predictable, too? I'd sent a long email a week ago. But walking alongside each other, we preferred to talk about the kids.
At the Greek restaurant, the inevitable happened. We ended up in a massive discussion. I once was gesticulating wildly at him. "Conspiracy theorist! That is so convenient. Everything that does not fit into your worldview, becomes a conspiracy theory. That there would be a vaccine mandate was once a conspiracy theory. That the virus came from a lab was once a conspiracy theory."
On another occasion, he exclaimed: "You know that I know all that about America! You know exactly that I know all those things!"
We both knew a lot of things, and it went back and forth.
The irony was that we managed to stay respectful, and it was a discussion with the other school friend there (the fourth person on the table was my husband), that turned out to be the last straw. She had voted Green as well, and had congratulated our school mate on having been to the protest 'against the right'. But she was also the one who didn't have the vaccine, and now said, "With Covid, it was just so obvious that it was all set up." A bit later she said something about the WEF. Only to be greeted with a long tirade. "Aha. So you think this is all a big conspiracy with some powerful people in the background planning everything. And this wasn't a pandemic although lots of people died. I know six doctors, and they all told me the same." A bit later, to me: "So why did only the unvaccinated die then?" And then shortly after, when my friend stated again how the whole thing had seemed premeditated, "Right. That's enough now. I'm leaving." And he got up to pay and left.
My friend, who stayed behind, thought we had had interesting discussions and she had learned something. On reflection, it was good to have this discussion at all -- at a time that nobody seems to want to talk about Covid anymore.
But also: Shouldn't we be much much further than this???
My first sats
A few months ago I had tried to buy bitcoin, just to play around, but there had been difficulties to do with the fact I have a UK bank account. When looking at how to get funds into my getalby account, I ended up with Strike, which is available in the UK. But it seems they take extra care to make sure you know what you are letting yourself into! I had to do a test with about 10 questions to show I understand the risks.
I then had to wait 24 hours, but now I have sent my first sats.
On the Strike website, I noticed this video of a conversation between Jack Mallers, founder of Strike, and Jack Dorsey, co-founder of Twitter. The more I watched, the more I thought, wow, here it is all in one video, all that I would like my friend to see. "America has a problem." The Empire needs to end, and it would be a good thing for America, says Jack Dorsey. This was also the second time in a week that I heard about how Great Britain had created money and bought their own bonds when the public didn't want to, in effect stealing from the people by making their money worth less. It was good to be reminded of Adam Curtis who has made some mind-blowing documentaries, using lots of BBC archive material. Including about the special US and UK relationship (An ocean apart), and also one about Russia from 1985 to 1999 (Trauma Zone).
The two Jacks talk about the importance of open source, and of being independent of government. The dangers of building abstraction on abstraction on abstraction. About how Mark Zuckerberg served Dorsey raw goat once, because he had this challenge to only eat what he had killed himself. That was also a way to get back to the real.
Dorsey endorsed RFK jr, this was in summer of 2023, when he was still running for president.
There is also an interesting bit on the pressures of running a company that has gone public. And the government interference, in effect censorship. The Twitter files. It is not quite clear to me, if it was really so difficult for Jack Dorsey to pay attention and know what was going on, but I can understand that it must have been a difficult situation.
What I also find very interesting is that in Africa or Latin America bitcoin is sometimes valuable as an exchange medium. That is where I think it could diverge from the pure Ponzi scheme that people often call it.
And yet, doubts remain. Is bitcoin not too valuable for a lot of people to spend it? But what if you don't have access to any other money. And sending Satoshis around is different from hording bitcoin. Can it fulfil both these functions in the end, storage medium and exchange medium?
I believe that these two people want to achieve something positive. But they also remain tech bros. And I don't mean that in a bad way. It is just something that will always remain a bit alien to me.
I did like what Dorsey said about the punks. How they just started to play an instrument, and didn't care if they were not good at it. Then just turned up again and again and eventually got better. I have often thought of myself as a bit punk-like in that respect, although I've often been worried about not being good enough.
Doing away with domination
The last blog article posted on a website I work on, made me explore the writings by Darren Allen on his Expressive Egg substack. I had landed there before, years ago, and had been very impressed back then. He seems to criticise people's thoughts a lot though -- almost everybody's -- and I was wondering if that was all he ever did. But then I came across this article about anarchy. It made me realise again, in all this mess about different worldviews, different expectations and values, that this is a constant for me: How can we have less coercion, how can we live in a way that frees ourselves and others at the same time. I once saw a Twitter bio: "I insist on your freedom." It seems to come from Jack Kerouac.
Allen writes that there are seven dominants, seven elements that "control individuals against their will". They are, " in roughly ascending order of subtlety and pervasiveness":
1. The [autocratic] monarchy.\ 2. The [socialist-democratic] state (which includes its money, law, property, police, etc.).\ 3. The [totalitarian-capitalist] corporation.\ 4. The [mass] majority.\ 5. The [professional-religious] institution.\ 6. The [technocratic] system.\ 7. The [mental-emotional] ego.
I want to keep this list in mind and pay attention when I get sucked into the influence of one of these spheres.
\ I also like this quote:
The reason men and women do not need kings, princes, states, professionals, institutions and systems to rule over them is because the life within them is more intelligent, more apt, more sensitive, more forgiving and more creative than anything else—certainly any human authority. But this life cannot be rationally fixed. It can be expressed, artistically, indirectly, poetically, musically, or with tone and glance and such ordinary, metaphorical arts of human interaction; but it cannot be literally stated.
\ Although this would be a good ending for this post, I have to mention Jeffrey Sachs as well. I have been following him for a while. He appeared in the EU parliament, invited by Michael von der Schulenburg. Sachs has an amazing amount of experience with both Russian and American government officials, and with currencies. In the 90s he spent some time helping Eastern European countries with the transition to capitalist systems. He realised that the U.S. did not want to help Russia in the same way.
He gave a long speech in which he laid bare the ways in which the U.S. had influenced so many wars and uprisings around the world, and how the NATO enlargement had been a long-term strategy. That now, with Trump, the war was going to end.
There would be so much more to say. In any case, this seems to me a historic speech. Can it break through the mirror glass that has kept so many people away from valid sources of knowledge?
-
 @ 0d1702d6:8f1ac66f
2025-04-01 15:33:09
@ 0d1702d6:8f1ac66f
2025-04-01 15:33:09"Die Russen kommen..." - oder kommen sie doch nicht ?
\ Hallo liebe LeserInnen und einen wunderschönen Tag miteinander!\ \ Heute allerdings sterben junge Ukrainer und Russen auch mit unserer Hilfe \ und zugleich Untätigkeit seit mehr als 168 Wochen oder 37 Monaten, mit anderen Worten also: \ seit mehr als drei Jahren, Tag für Tag, Stunde für Stunde, Minute für Minute.\ Auch in diesen Augenblicken, in denen Du dies liest...\ \ Und mit unsrer stillen Zustimmung sorgen Politiker, Medien und Waffenproduzenten \ auch unseres Landes dafür, dass das gegenseitige Abschlachten und Morden weitergeht…
\ Die Russen kommen…. wird uns seit 2022 im alltäglichen kriegs-propagandistischen Trommelfeuer eingehämmert, vom eher unbedarften regionalen Käseblatt bis zu den vermeintlichen Qualitätsmedien der privaten Konzerne und Staatsmedien des öffentlichen Rundfunks, dessen sich die herrschenden Parteien im Lande immer schon seit 1949 ideologisch bemächtigt haben.
100te, nein täglich tausende Male wird geschrieben, geschrien, gesagt und gedacht, suggeriert, phantasiert \ und illusioniert…oder auch nur geraunt**:** \ \ die Russen kommen … und kommen und kommen …
Zwar buddeln sich die grün hinter den Ohren frisch aufs Abschlacht-Feld gezwungenen blutig jungen Russen – und natürlich auch ihre sogenannten „Feinde“, die meist auch gegen ihren Willen zum Morden gezwungenen Ukrainer - seit über drei Jahren in den Regionen um Cherson, Donezk und Luhansk im vor allem Stellungskrieg ein, aber was solls:\ \ Morgen oder spätestens übermorgen so behauptet unser Kriegsminister und viele seiner Generäle und Geheimdienstchargen im Chor mit den Gazetten der Leitmedien: spätestens übermorgen also greifen die feststeckenden Russen dann über Nacht mit geballter Macht die jetzt-schon-Kriegspartei USA-NATO, also uns an und sichern sich sicherlich schwupp die wupp die gesamte Ukraine und dann, ja dann, geht’s sofort, also allerspätestens in vier Jahren mit voller Pulle direkt nach Berlin und Brüssel, denn **„dem Russen“, dem trauen wir einfach alles wirklich Böse dieser Welt zu!\ **\ Kriegsursachen, Hintergründe und Zusammenhänge wie die dutzendfach öffentlich dokumentierte und bekannte perfide US-Geostrategie Russland komplett militärisch einzukreisen und genau in die Falle zu locken, in die es reingetappt ist, haben uns noch nie interessiert, weil wir rückgratlos so tief in den Allerwertesten des imperialen Hegemons USA gekrochen sind, dass uns meist schon lange der gesunde Menschenverstand fürs Hören und Sehen, Verstehen wie Begreifen vergangen ist.
Die große Mehrheit von uns, also wir, die vermeintlich geläuterten und neuerdings pseudo-auf-geklärten Ex-Anti-Militaristen, Kriegs-Dienst-Verweigerer, paranoid schizoiden Doppel-Moral-Fetischisten der Keine-Waffen-in-KRISEN-Gebiete liefernden Grünen, also die meisten ehemals links-liberalen oder verdeckt unsozial wie unchristlich wie unfrei handelnden Demokraten der Altparteien- Einheitspartei CDU/CSU/FDP/GRÜNE/SPD & Linke (!) sitzen der Wahnvorstellung auf, die Russen würden erst die gesamte Ukraine und danach ganz Europa militärisch besetzen wollen.
\ Du etwa nicht? \ \ Mal im Ernst: Bist Du kein kindlich Neu-Gläubiger? Glaubst Du etwas nicht an \ „Gut“ und „Böse“ und fest daran, dass „WIR“, also „der Westen“ die Guten sind \ und „Die Russen“ - wie sicher auch „die Chinesen“ - die wirklich über alle Maßen Bösen?
Bist Du etwa doch einer dieser spät-pubertären frühzeitig dementen Alzheimeraspiranten, \ die die Lektion der russischen Revolution von 1917/1918 verdrängt, vergessen oder gar \ ge-löscht haben? Hat dir denn dein Ur-Opa nie erzählt, dass die Russen schon \ seit ihrer Oktober-Revolution 1917, ohne Quatsch, seit sage und schreibe mindestens \ 108 Jahren nach Berlin marschieren und sicherlich in Kürze dort ankommen werden?
Hat Dir denn Dein Opa nie erzählt, dass diese ultra fiesen bösen Russen \ zwar unter-motorisiert, dafür aber umso mehr über-motiviert sind \ und kriegsgeil zwanghaft an ihrem Willen festhalten, \ ganz Europa zur Beute des russischen Bären zu machen??? \ \ Seit 100 Jahren zelebriert Hollywood den bösen Russen als Gegenspieler \ aller wirklich guten US-Westler. Das hat sich auch ins kollektive Bewusstsein \ der meisten Europäer tief eingegraben.
Und bei dir?\ Sind für dich die Russen etwa keine wilden Tiere, denen wir endlich jetzt, gemeinsam \ mit dem politischen Arm des Großkapitals, also auch des militärisch-industriellen Komplexes, \ Fritzchen Merz, dem Klingbeil der abgewirtschafteten ehemals sozialen Demokraten \ und dem Steigbügelhalter der olivgrünen Kriegshysteriker unser 500 Milliarden-Plus-\ Bürger-Ermächtigungsgesetz vor sein Maul geknallt haben, sodass ihm, \ also dem russischen Bären, sehr bald Hören und Sehen vergehen wird?
Denkst Du etwa doch immer noch an den auch us-finanzierten illegalen Putsch auf dem Maidan 2014, durch den es den US-Geostrategen gelang, endlich eine us-freundliche Putschregierung in Kiew zu installieren, die dann sofort Krieg gegen die eigene russisch-stämmige Bevölkerung im Donbass führte? Denkst Du etwa immer noch an die fortschreitende und fast vollständige Umzingelung Russlands durch US-NATO-Stützpunkte, die die gutmütigen und blauäugigen Russen seit 1999 entgegen den westlichen Versprechungen jahrzehntelang geduldig ertragen haben? \ \ Bist du, ja Du, also allen Ernstes immer noch ein „Ewig-Gestriger“?\ Hast Du immer noch nicht begriffen, dass wahr ist, was 1000mal geschrieben und gesagt wurde \ und auf allen Mainstream-Medien-Kanälen seit mehr als drei Jahren auf dich einprasselt?\ \ Hast Du immer noch nicht kapiert, dass heutzutage \ Wahrheit einfach durch Wiederholung \ des Falschen hergestellt wird ???\ \ Hast Du immer noch nicht begriffen, dass es völlig zwecklos ist, dem militärisch-industriellen, \ man muss ergänzen: zugleich politisch-medialen Komplex, vor dem schon Roosevelt 1961 gewarnt hatte und wegen \ dem auch John F. Kennedy 1963 sein Leben verlor, dass es also mehr als völlig aussichtslos ist, \ dieser herrschenden gesellschaftlichen Gewaltstruktur auch nur heimlich mentalen Widerstand entgegen zu setzen?
Nun, wenn das so ist, dann liebe/r LeserIn, dann bist Du eine oder einer von uns, \ mit Sternchen versteht sich. Willkommen im Club, Wir sind viele. Viel mehr als Du vielleicht denkst. \ Denn die massenweise kapital-, parteien-, regierungs- und us-alt-establishment-nah \ veröffentlichte Meinung ist noch lange nicht die öffentliche Meinung.
Will sagen: Es gibt eigentlich keine bürgerliche Mehrheit für diese Kriegskredite von 2025. \ Sie wurden durch Lug und Trug einer schon abgewählten Parlaments-Mehrheit erschlichen. \ Die SPD hat in 111 Jahren seit ihrem Votum für Welt-Kriegskredite 1914 nichts, \ aber auch gar nichts dazu gelernt, die Oliv-Grünen haben alles, aber auch alles über Bord geworfen, \ für das sie mal – auch übrigens durch meine minimale Mithilfe – gegründet wurden….\ und die un-christlichen „C“ Parteien tun das, was ihre Vorläufer schon 1933 getan haben, \ wohlweislich heutzutage unter anderem Namen: \ dem Krieg zu den Waffen verhelfen, die Krieg nun mal braucht.
\ Wenn ich nachts an Deutschland denken würde, wäre ich um meinen Schlaf gebracht.\ Ich denke aber nicht an Nationen, ich denke an Menschen. An hunderttausende junge Menschen, \ die durch sogenannte parlamentarische Demokraten mit "Made in Germany \ and USA Waffen" in den Tod getrieben werden.
**Nicht in meinem Namen. Und ich hoffe: Auch nicht in Deinem.\ **\ Seit 2014 hätte ehrlich verhandelt werden müssen, heute muss es mehr denn je sofort. \ Denn die berechtigten Sicherheitsinteressen aller Nationen Europas, \ der ehemaligen Staaten der UDSSR wie auch Russlands selber können \ nur in einem Sicherheitssystem für ganz Europa, \ vom Atlantik bis hinter den Ural, Richtung Frieden verhandelt werden. \ \ Waffen ermöglichen und befeuern das Erpressen & Morden, für Frieden sind sie ungeeignet.
Sicherheit ist unteilbar: Sicherheit & Frieden gibt es nur für alle, oder für keinen.
-
 @ 3b7fc823:e194354f
2025-03-23 03:54:16
@ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds.
Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/
- Download Tor Browser
First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/
- Sign Up
Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha.
- Account information
Once you are done signing up an Account information page will pop up. MAKE SURE YOU SAVE THIS!!! It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck.
- Install an Email Client
You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird.
a. Download Thunderbird email client
b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the Configure Manuallyoption will appear below. Click that.
- Configure Incoming (POP3) Server
Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password).
- Configure Outgoing (SMTP) Server
Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password).
-
Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up.
-
Configure Proxy
a. Click the gear icon on the bottom left for settings. Scroll all the way down to Network & Disk Space. Click the settings button next to Connection. Configure how Thunderbird connects to the internet.
b. Select Manual Proxy Configuration. For SOCKS Host enter 127.0.0.1 and enter port 9050. (if you are running this through a VM the port may be different)
c. Now check the box for SOCKS5 and then Proxy DNS when using SOCKS5 down at the bottom. Click OK
- Check Email
For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on inbox and then the little cloud icon with the down arrow to check mail.
- Security Exception
Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup Add Security Exception will appear. Click Confirm Security Exception.
You are done. Enjoy your new private email service.
REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 2b24a1fa:17750f64
2025-04-01 08:18:00
@ 2b24a1fa:17750f64
2025-04-01 08:18:00„Die Mauer muss weg!“, wurde vor 35 Jahre skandiert. Jetzt muss wieder eine Mauer her: Die Brandmauer gegen rechts. Eine Gesinnungs-Mauer, eine Weltanschauungs-Mauer, eine Werte-Mauer.
https://soundcloud.com/radiomuenchen/die-neue-deutsche-angst-von-birgit-assel
Der Verlauf ist allerdings noch nicht ganz klar. Verläuft sie zwischen Menschen oder vielleicht sogar durch die Menschen selbst? Denn was bedeutet diese Brandmauer aus psychologischer, genauer aus traumatherapeutischer Sicht? Handelt es sich bei ihr nicht vielmehr um einen vehement zur Anwendung kommenden Abgrenzungsmechanismus gegen die eigenen Schattenanteile?
Nicht nur, aber gerade in Deutschland tragen viele Menschen einen Rucksack verdrängter Gefühle und Schatten: den Schrecken zweier Weltkriege, Verdrängung, Armut, Flucht, schwarze Pädagogik und den Mangel durch emotional oder real abwesende Eltern – all das wirkt bis ins Heute nach. Und es vielleicht ist es ein Puzzelstein in der Erklärung so einiger hysteriegeschwängerter Phänome der Jetztzeit.
Die Traumatherapeutin Birgit Assel hat sich dieser Analyse angenommen. Hören Sie hierzu ihren Text „Die neue deutsche Angst“, der zunächst im Manova Magazin erschienen war. www.manova.news/artikel/die-neue-deutsche-angst
Sprecherin: Sabrina Khalil
-
 @ da0b9bc3:4e30a4a9
2025-04-03 07:02:17
@ da0b9bc3:4e30a4a9
2025-04-03 07:02:17Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/933122
-
 @ 866e0139:6a9334e5
2025-04-01 06:37:39
@ 866e0139:6a9334e5
2025-04-01 06:37:39Autor: Milosz Matuschek. Grafik: Klaus Staeck. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Krieg ist eine Gaunerei – “War is a Racket”. So heißt ein berühmtes Anti-Kriegs Manifest von Smedley D. Butler, einem Generalmajor der US-Marines von 1935. Am Ende blieb die Erkenntnis: Man kämpfte gar nicht so sehr für Volk, Vaterland, eine noble Sache oder den Frieden. Sondern für Interessen von Familien und Firmen, als Söldner eines Syndikats oder Krieger für den Kapitalismus. Krieg als stellvertretende Gang-Schlägerei über unbeteiligte, aber leidende Dritte.
Die kürzlich geleakten Signal-Chats aus der obersten US-Kommandozentrale zeigen ein seltenes Blick Realpolitik. Man kann sie lesen wie ein Theaterstück mit verteilten Rollen. Sollen wir Krieg führen, ist gar nicht mehr die Frage, sondern wann. Die Gründe sind taktisch, die Kosten plant man den Europäern aufzuerlegen. Auch ein Business-Modell. Man nennt es wohl: Kriegerische Geschäftsführung ohne Auftrag.
“Unsere Kriegstreiberei sollen uns die Europäer noch teuer bezahlen…”
Hier die Signal-Chats in deutscher Übersetzung (Quelle: X/@krassenstein):
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Houthi PC Small Group – Interne Kommunikation
---
Michael Waltz:
„Team – wir gründen eine Prinzipiengruppe zur Koordination bezüglich der Houthis, insbesondere für die nächsten 72 Stunden. Mein Stellvertreter Alex Wong stellt ein 'Tiger-Team' auf der Ebene der Stellvertreter / Agenturchefs zusammen, das an die Sitzung im Situation Room heute Morgen anknüpft. Die Aktionspunkte werden heute Abend versendet.“
„Bitte nennt uns die besten Ansprechpartner eures Teams, mit denen wir in den nächsten Tagen und über das Wochenende hinweg koordinieren können. Danke!“
Antworten:
- MAR: Mike Needham für das Außenministerium
- JD Vance: Andy Baker für den Vizepräsidenten
- TG: Joe Kent für den Geheimdienst (DNI)
- Scott B: Dan Katz für das Finanzministerium
- Pete Hegseth: Dan Caldwell für das Verteidigungsministerium
- Brian: Brian McCormack für den Nationalen Sicherheitsrat
---
Michael Waltz:
„Team, ihr solltet heute Morgen eine Zusammenfassung mit Aufgaben entsprechend der Anweisung des Präsidenten in euren High-Side-Posteingängen erhalten haben.
Außen- und Verteidigungsministerium: Wir haben eine Liste empfohlener Benachrichtigungen für regionale Verbündete und Partner ausgearbeitet.
Der Generalstab sendet heute Vormittag eine spezifischere Abfolge von Ereignissen, und wir arbeiten mit dem DoD zusammen, um sicherzustellen, dass COS, OVP und POTUS informiert sind.“
(08:05 Uhr)
JD Vance:
„Team, ich bin heute unterwegs auf einer Wirtschaftskonferenz in Michigan. Aber ich glaube, wir machen einen Fehler.
Nur 3 % des US-Handels läuft durch den Suezkanal – aber 40 % des europäischen Handels. Es besteht das reale Risiko, dass die Öffentlichkeit das nicht versteht oder nicht nachvollziehen kann, warum es notwendig ist.
Der wichtigste Grund, dies zu tun, ist laut POTUS, ein Zeichen zu setzen. Aber ich bin mir nicht sicher, ob dem Präsidenten klar ist, wie inkonsistent das mit seiner Botschaft gegenüber Europa ist. Außerdem besteht das Risiko eines moderaten bis starken Anstiegs der Ölpreise.
Ich bin bereit, dem Konsens des Teams zu folgen und meine Bedenken für mich zu behalten. Aber es spricht viel dafür, das Ganze um einen Monat zu verschieben und in der Zwischenzeit das Messaging vorzubereiten.“
(08:16 Uhr)
---
Joe Kent:
„Es gibt keinen drängenden zeitlichen Faktor. In einem Monat haben wir dieselben Optionen.
Die Israelis werden wahrscheinlich Angriffe durchführen und uns dann um Nachschub bitten für das, was sie gegen die Houthis einsetzen – aber das ist eher zweitrangig.
Ich sende dir die unklassifizierten Daten zu BAM-Schifffahrt.“
(08:22 Uhr)
John Ratcliffe (CIA):
„Aus Sicht der CIA mobilisieren wir jetzt schon Mittel zur Unterstützung, aber eine Verzögerung würde uns nicht negativ beeinflussen. Wir könnten die zusätzliche Zeit nutzen, um bessere Ausgangspunkte für die Überwachung der Houthi-Führung zu finden.“
(08:26 Uhr)
---
Pete Hegseth:
„VP: Ich verstehe deine Bedenken und unterstütze voll, dass du sie gegenüber POTUS ansprichst.
Die meisten relevanten Faktoren sind unklar, wie sie sich entwickeln (Wirtschaft, Ukraine-Frieden, Gaza, etc.). Das Messaging wird auf jeden Fall schwierig – niemand weiß, wer die Houthis sind – deshalb sollten wir uns auf zwei Punkte konzentrieren:
1. Biden hat versagt
2. Iran finanziert
Immer mehr von Ihnen lesen diese Publikation, doch nur ein Bruchteil von Ihnen unterstützt mich aktiv mit Spenden oder einem Abonnement. Wenn Sie wollen, dass meine Arbeit weitergeht, bin ich für jede Unterstützung dankbar. Ich kann Ihnen auch manuell ein Abo einrichten, wenn Sie lieber per Überweisung, Paypal oder Bitcoin bezahlen wollen: kontakt\@idw-europe.org
Warten bringt zwei unmittelbare Risiken: 1) Es könnte durchgesickert sein – wir wirken unentschlossen. 2) Israel greift zuerst an oder der Gaza-Waffenstillstand bricht – dann verlieren wir die Initiative. Wir können beides managen.
Wir sind bereit zur Durchführung. Wenn ich entscheiden müsste, würde ich sagen: Ja. Es geht nicht um die Houthis. Es geht um:
1. Wiederherstellung der Freiheit der Navigation – ein zentrales nationales Interesse
2. Wiederherstellung der Abschreckung – die unter Biden zusammengebrochen ist.“
---
Michael Waltz:
„Aber wir können auch pausieren. Und wenn wir das tun, werde ich alles tun, um 100 % OPSEC (Operationssicherheit) durchzusetzen. Ich bin offen für andere Gedanken.“
(08:27 Uhr)
Michael Waltz:
„Die Handelszahlen, die wir haben, sind 15 % des weltweiten Handels und 30 % des Containeraufkommens. Es ist schwierig, das für die USA herunterzubrechen. Viele Container gehen entweder noch durchs Rote Meer oder um das Kap der Guten Hoffnung. Unsere Komponenten gehen nach Europa, werden dort zu Fertigwaren und dann im transatlantischen Handel in die USA exportiert.
Egal, ob wir jetzt eingreifen oder in ein paar Wochen – europäische Marinen haben nicht die Fähigkeit, sich gegen moderne Anti-Schiffs-Raketen, Marschflugkörper und Drohnen der Houthis zu verteidigen. Es wird an den USA liegen, diese Seewege wieder zu öffnen. Auf Wunsch des Präsidenten arbeiten wir mit Verteidigungsministerium und Außenministerium daran, die Kosten zu berechnen und den Europäern aufzuerlegen.“
(08:32 Uhr)
Michael Waltz:
„Wie bereits im ersten PC erwähnt: Es ist eine grundlegende Entscheidung – lassen wir die Seewege geschlossen oder öffnen wir sie jetzt oder später? Leider sind nur wir dazu in der Lage.
Aus Messaging-Sicht müssen wir das klar mit Beispielen kommunizieren, warum Europa in seine eigene Verteidigung investieren muss.“
(08:42 Uhr)
---
JD Vance:
„@Pete Hegseth Wenn du denkst, wir sollten es machen – dann los. Ich hasse es nur, Europa wieder aus der Klemme zu helfen.“
(08:45 Uhr)
JD Vance:
„Lasst uns sicherstellen, dass unser Messaging sitzt. Und wenn wir Risiken für saudische Ölanlagen reduzieren können, sollten wir das vorher tun.“
(08:46 Uhr)
Pete Hegseth:
„VP: Ich teile deine Abneigung gegenüber europäischem Trittbrettfahren voll und ganz. Es ist ERBÄRMLICH.
Aber Mike hat recht – wir sind die Einzigen auf dem Planeten (auf unserer Seite), die das können. Niemand sonst kommt auch nur annähernd ran. Die Frage ist der Zeitpunkt. Ich denke, jetzt ist so gut wie jeder andere Zeitpunkt, besonders nach dem Befehl von POTUS zur Wiederöffnung der Seewege. Ich denke, wir sollten loslegen; aber POTUS hat noch 24 Stunden Entscheidungszeit.“
(08:49 Uhr)
S.M.:
„So wie ich es verstanden habe, hat der Präsident grünes Licht gegeben. Aber wir müssen Ägypten und Europa klarmachen, was wir im Gegenzug erwarten. Und wir müssen klären, wie wir das durchsetzen. Z. B.: Wenn Europa nicht zahlt – was dann? Wenn die USA erfolgreich die Freiheit der Schifffahrt wiederherstellen – zu hohen Kosten – dann muss es dafür auch wirtschaftlichen Gegenwert geben.“
(09:35 Uhr)
Pete Hegseth: „Zustimmung.“
(09:46 Uhr)
---
Pete Hegseth:
**TEAM-UPDATE:**
- **Zeit jetzt (11:44 ET):** Wetter ist günstig. CENTCOM bestätigt Einsatzfreigabe.
- **12:15 ET:** Start F-18 (1. Angriffspaket)
- **13:45:** „Trigger-basiertes“ Zeitfenster für ersten F-18-Angriff beginnt (Zielperson bestätigt, sollte pünktlich sein) – auch: Start der Drohnen (MQ-9)
- **14:10:** Weitere F-18 starten (2. Angriffspaket)
- **14:15:** Drohnen treffen Ziel (ab da fallen die ersten Bomben, abhängig von vorherigen Treffern)
- **15:36:** Beginn zweiter F-18-Angriff + Start seegestützter Tomahawk-Raketen
„Weitere Schritte folgen gemäß Zeitplan. Wir sind aktuell OPSEC-konform. Gott schütze unsere Soldaten.“
(ca. 12:00 Uhr)
JD Vance: „Ich werde ein Gebet für den Sieg sprechen.“
(12:13 Uhr)
---
Michael Waltz:
„VP: Gebäude eingestürzt. Mehrere Bestätigungen der Zielperson. Pete, Kurilla, Nachrichtendienste – großartige Arbeit.“
JD Vance: „Was?“ – „Ausgezeichnet.“
Michael Waltz: „Erstes Ziel – oberster Raketenexperte. Positive Identifikation beim Betreten des Gebäudes seiner Freundin. Gebäude ist jetzt eingestürzt.“
Michael Waltz: (mit Emojis) 👊🇺🇸🔥
MAR: „Gute Arbeit, Pete und Team!“
Michael Waltz: „Auch das Team in MAL hat großartige Arbeit geleistet.“
S.M.: „Großartige Arbeit von allen. Starker Anfang.“
Pete Hegseth:
„CENTCOM war / ist top. Klasse Arbeit. Weitere Angriffe laufen heute Nacht. Vollständiger Bericht folgt morgen. Bisher alles pünktlich und präzise.“
Susie Wiles:
„Glückwunsch an alle – besonders an jene im Einsatzgebiet und CENTCOM. Wirklich großartig. Gott segne euch.“
Dieser Beitrag erschien zuerst auf "Freischwebende Intelligenz".
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.)
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ f9d11792:e340e19e
2025-04-03 06:38:43
@ f9d11792:e340e19e
2025-04-03 06:38:43A indústria de apostas online tem se expandido rapidamente no Brasil, e com isso surgem novas plataformas que visam proporcionar experiências únicas aos jogadores. A 377BET é uma dessas plataformas, que se destaca pela sua interface intuitiva, variedade de jogos e foco em segurança. Para os jogadores que buscam diversão, emoção e, acima de tudo, uma plataforma confiável, a 377BET é uma excelente escolha. Neste artigo, vamos explorar os principais aspectos da plataforma e como ela se destaca no competitivo mercado de apostas online.
- Uma Plataforma Intuitiva e Acessível Ao acessar a plataforma 377BET, os jogadores são imediatamente recebidos por um design moderno e amigável. A navegação foi projetada para ser intuitiva, com menus claros e funções bem distribuídas. Isso significa que mesmo jogadores iniciantes, que nunca utilizaram plataformas de apostas online, podem facilmente se orientar e começar a jogar rapidamente.
Além disso, a plataforma é completamente otimizada para dispositivos móveis, permitindo que os jogadores façam suas apostas em smartphones e tablets com a mesma facilidade e eficiência que em um desktop. A experiência móvel da 377BET é fluida e sem interrupções, o que permite uma jogabilidade confortável a qualquer momento e em qualquer lugar.
- Diversidade de Jogos para Todos os Estilos O maior atrativo da 377bet é a variedade de opções de apostas que ela oferece. A plataforma atende a diferentes tipos de apostadores, desde os mais casuais até os mais experientes. Para aqueles que gostam de velocidade e prêmios rápidos, as máquinas virtuais são uma excelente escolha. Esses jogos são simples de jogar e oferecem a oportunidade de ganhar prêmios instantâneos, tornando-os ideais para quem busca uma experiência sem complicação.
Para os fãs de esportes, a plataforma oferece esportes virtuais, que são eventos simulados, mas com uma dinâmica empolgante e resultados rápidos. Futebol, basquete e corridas de cavalos são alguns dos esportes disponíveis para apostas, e o melhor é que esses jogos acontecem de maneira contínua, permitindo apostas frequentes.
A 377BET também se destaca por oferecer jogos de mesa, como roleta e blackjack, onde o jogador pode aplicar estratégias e testar suas habilidades. A experiência nesses jogos é altamente imersiva, com gráficos realistas e jogabilidade fluida, proporcionando uma atmosfera de jogo semelhante à de uma competição ao vivo.
- Compromisso com a Segurança e Suporte ao Cliente Uma das maiores preocupações dos jogadores de apostas online é a segurança. A 377BET se dedica a garantir a proteção dos dados dos jogadores, utilizando criptografia avançada para manter todas as informações pessoais e financeiras seguras. Com isso, os jogadores podem realizar depósitos e saques com total tranquilidade, sabendo que suas informações estão protegidas.
A 377BET também possui um excelente suporte ao cliente. A equipe está disponível 24 horas por dia, 7 dias por semana, por meio de chat ao vivo e e-mail, pronta para ajudar com qualquer dúvida ou problema que os jogadores possam enfrentar. Esse suporte é crucial para manter uma boa experiência de jogo, especialmente quando se trata de uma plataforma que lida com transações financeiras e dados pessoais sensíveis.
Além disso, a 377BET oferece ferramentas de jogo responsável, permitindo que os jogadores definam limites de apostas e monitorem o tempo de jogo, garantindo que a experiência de aposta seja saudável e equilibrada.
Conclusão A 377BET é uma plataforma de apostas online que se destaca pela sua facilidade de uso, segurança, e ampla gama de jogos. Com uma interface intuitiva, suporte dedicado e uma variedade de opções de apostas, ela proporciona uma experiência única para os jogadores brasileiros. Se você está buscando uma plataforma confiável e envolvente, a 377BET é certamente uma excelente escolha para suas apostas online.
-
 @ 6fbc5b6b:0251e3df
2025-04-03 06:00:53
@ 6fbc5b6b:0251e3df
2025-04-03 06:00:53Overview AIVille and Port3 Network have teamed up to bring users an exclusive SoQuest campaign, designed to introduce participants to the broader AGT First Round Community Airdrop, where 1% of the total AGT supply will be distributed to early supporters.

The SoQuest campaign is a special onboarding experience that comes with its own prize pool and incentives: 🏆 Total Prize Pool: 50 winners will each receive 4 USDT + $AGT Token Airdrop
🎟️ Whitelist Spots: First 1000 participants secure priority access to the AGT community airdrop
💎 Top 100 Most Active: Earn extra $AGT rewards
🔥 Invite Leaderboard: Top 10 referrers get bonus $AGT
This quest is not only a fun way to engage — it also leads participants directly into the main AGT community airdrop, making it an ideal entry point into AIVille’s growing ecosystem.
 🤝 About AIVille & Port3
AIVille is a decentralized town powered by AI agents — autonomous, evolving characters who work, create, and live within a fully on-chain simulation. AIVille embodies the next phase of the internet: intelligent, social, and permissionless.
Port3 Network is a unified artificial intelligence operation system that simplifies and consolidates all infrastructure components needed to launch AI-enabled Web3 applications. With SoQuest, Port3 provides Quest-as-a-Service (QaaS) to supercharge project growth and user activation.
🤝 About AIVille & Port3
AIVille is a decentralized town powered by AI agents — autonomous, evolving characters who work, create, and live within a fully on-chain simulation. AIVille embodies the next phase of the internet: intelligent, social, and permissionless.
Port3 Network is a unified artificial intelligence operation system that simplifies and consolidates all infrastructure components needed to launch AI-enabled Web3 applications. With SoQuest, Port3 provides Quest-as-a-Service (QaaS) to supercharge project growth and user activation.🌟 Celebrating AGT & Community $AGT (Agent Token) fuels AIVille's economy and governance. The ongoing AGT First Round Community Airdrop — distributing 1% of the total token supply — is a major milestone for the ecosystem. This SoQuest event acts as a gateway into that larger campaign, rewarding early participation, amplifying community building, and activating the Create-to-Earn model where everyone has a role in shaping the future.
⚡ Why This Matters This collaboration reflects a shared vision: AIVille is pioneering AI-native social environments
Port3 is building the infrastructure to scale them
The SoQuest campaign connects users with the main AGT airdrop — seamlessly, playfully, and with real value
It’s more than a campaign. It’s your chance to be early in a new frontier powered by intelligent agents and decentralized coordination.
🔗 Links SoQuest Campaign: https://soquest.xyz/space/AIVille/campaign/sORhK3g9p4?v=2
AIVille on Twitter: @aivillebot
Port3 Network: https://port3.io
AGT Airdrop Details: https://mellow-brass-42a.notion.site/AIVille-Season-1-Massive-Community-Airdrop-1c54a8bdee5b80678a68c2cce06fb37d
-
 @ 5c8a5765:4fc5edee
2025-03-22 18:38:23
@ 5c8a5765:4fc5edee
2025-03-22 18:38:23[Читать в IPFS]
Итак, детки-котлетки, сегодня мы поговорим, как ~~не~~правильно распространять агиацию. Возьмите свои любимые антифашистские стикеры и используйте этот текст как инструкцию к ним — иначе у меня голова лопнет от того, что я вижу на улицах.
Агитация
Для начала определитесь, чем вы занимаетесь: агитируете к чему-то или поддерживаете чего-то, потому что это предполагает совершенно разные подходы. Агитацией может быть призыв к анархизму, классовой борьбе, неуплате налогов, гендерному равенству и т.д. Поддержкой может быть поддержка анархической борьбы, антифашистский идей и т.д. Первое — "вербует"/приманивает новых людей к идее, второе поддерживает только тех, кто уже знаком с идеей и уже с ней согласен.
Как должна выглядеть агитация? Представьте, что некий неонацист решил за-агитировать вас в неонацизм (с учетом, что сейчас вы его не поддерживаете): в каком случае у него больше всего на это шансов? Если вы заметите на мусорном баке наклейку "бей жыдоф"? Или если вам, например, выдадут в руки грамотный агитационный текст? Поставьте себя на место читающего: агитация должна выглядеть именно так, как мог бы выглядеть материал, который хоть немного мог бы поменять ваши текущие взгляды. А именно...
1. Агитация доступна
Она не висит на задней стороне мусорки. Она не нарисована на заброшке. Обыватель не рассматривает мусорки и не ходит по заброшкам. Чтобы масса увидела вашу агитацию, она должна висеть в заметном месте.
Ещё лучше, если она висит там, где человек по внешним причинам на мгновение задерживается, и имеет время проглядеть вашу агитацию: ибо обыватель никогда не остановится у столба посреди длинной тропы, чтобы прочесть стикер.
И учтите: если место, которое вы выбрали, уже забито стикерами, вашему придётся делить привлеченное внимание с каждым остальным.
К доступности стоит также отнести то, что агитация более значительна, если она написана на самом популярном в вашей стране языке, развешивается в разных локациях (чтобы люди разного класса могли её увидеть), если вы развешиваете в туалетах — то туалетах разного гендера (и не забывайте про инвалидные кабинки!), так далее.
Лучшие места для стикеров: лифт, автобусная остановка, метро, поручен эскалатора, внешняя сторона дверцы туалета, чистое (не разрисованное или расклеенное) зеркало.Лучшие места для крупных агитационных листов или графитти: указанные выше, а также — заметные места подъездов,Лучшие места для "визиток"*: оставлять под задницей на выходе из автобуса, метро, маршрутки, на стульях, скамейках и т.д.*"Визитка" — это са-а-амый простой метод агитации: выводите нужный текст или картинки мелкими блоками на листе А4, нарезаете бумагу на кусочки "визиток" с небольшим текстом, картинкой или ссылкой, и оставляете где попало.
2. Агитация запоминается
Если вы не неонацист, какие эмоции в вас побуждает "бей жыдоф"? Вы возжелали стать неонацистом? Или это только укрепило ваши антифашистские взгляды? Или это для вас вообще никак не прозвучало?
Также для ваших противников и обывателей звучат ваши "ешь богатых!", "классовая борьба сегодня!!", "доёш онархию!!!". Это — поддержка. Уже-анархисты будут рады увидеть, что в городе есть левые активисты кроме них самих. Но это никого не переубедит и не привлечет.
А агитация привлекает. Агитация задаёт острые вопросы, которые остаются в голове. Агитация манит предложениями нового. Агитация нестереотипно предлагает.
Примеры хорошей агитации:

"Если большинство проголосует за то, чтобы ты спрыгнул(а) с вмоста, ты бы сделал(а) это? / - Может быть — если это было честным голосованием!"

"Этот телефон прослушивается - согласно законодательству США, телефонные разговоры прослушиваются без ордера или уведомленияю"

"Вы под наблюдением — текст, объясняющий тезис, и ссылка, где можно прочесть об этом подробнее."
Примеры никудышной агитации (но хорошей поддержки):



3. Агитация даёт возможность изучить больше
Хорошее правило для любой агитации: иметь ссылку на сайт, где можно найти больше информации о том, к чему агитируется. Это не обязательное, но рекомендуемое правило, ибо мало толку от человека, согласившегося с идеей анархизма и захотевшего (редчайший случай!) самостоятельно изучить больше, но не имевшего к этому простой возможности и забывшего вследствие обо всей идее.
Поддержка
А вот поддержка — ориентированная на тех, кто уже знает и уже поддерживает то, что вы любите — может быть совершенно любой. Поддержать антифашистов своего города, позлить фашистов и остаться совершенно незамеченными для обывателя — самое место для диалектики "бей жыдоф!" и "доёш онтифошизм!!".
Напоминание о безопасности
Несколько базовых напоминаний о том, что нужно помнить во время агитации:
- ОСТЕРЕГАЙТЕСЬ КАМЕР! Особенно в России! Метро, маршрутки, автобусы, учебные заведения полны ими!
- Если вас заметили гестаповцы, лучшее, что вы можете сделать — это бежать, что есть мочи.
- Шифруйте материалы, которые храните для распечаток.
- Не распечатывайте стикеры/"визитки" в публичных местах (вроде библиотек).
Спасибо за прочтение!

-
 @ 0f9da413:01bd07d7
2025-04-03 05:32:55
@ 0f9da413:01bd07d7
2025-04-03 05:32:55
หลังจากจบทริปเที่ยวพัทยาเรียบร้อยแล้วก็ได้เดินทางไปยังเกาะช้างโดยติดรถเจ้าหน้าที่ในที่ทำงานไปไปเกาะช้างครั้งแรกรู้สึกว่ามันไกลเหลือเกินไปค่อนข้างยากหากไม่มีรถส่วนตัว ถ้าให้ไปส่วนตัวก็คงต้องอยู่นานๆ หน่อยชักแบบอาทิตย์หนึ่ง ใช้ชีวิตแบบฝรั่งเที่ยวอยู่ง่ายๆ กินง่ายๆ จากที่ดูในแผนที่ btcmap แล้วพบว่าก็มีร้านที่ปักหมุดไว้อยู่ทั้งหมดสองร้านด้วยกันซึ่งระยะทางก็ค่อนข้างซันเหมือนกัน และมีเนินสูงต่ำสลับกันไป หากไม่มีรถส่วนตัวไปนี่ค่อนข้่างลำบากพอสมควร ต้องเช่ามอไซต์ไป อันนี้ก็เช่าไปเหมือนกัน โดยผมเช่ามอไซต์ 1 วันวันละ 200 บาท (แต่มัดจำ 3000 บาท) ก็เอาเรื่องเหมือนกัน และก็มาเริ่มต้นที่ร้านแรกเลยคือ
Mr. A Coffee

ร้านอาหารสไตล์บ้านๆ ที่ขายอาหาร น้ำ เครื่องดื่ม มีทั้งอาหารไทยและอาหารฝรั่ง ส่วนตัวก็ขับรถมอไซต์มายังสถานที่แห่งนี้ทางเข้าไปยังร้านเป็นหมู่บ้านเล็กๆ ไม่มีถนนเข้า แต่มอไซต์เข้าไปได้พอสมควร ตอนนั้นค่อนข้างเย็นมากแล้ว ได้มาสั่งอาหารมาคือ ข้าวเหนียวมะม่วงกับน้ำแก้วมังกรปั่นแบบไม่หวาน (ทั้งๆที่ตัวเองก็จะเตรียมไปกินบุ๊ปเฟ่อีกหนึ่งชั่วโมงข้างหน้า 555) ก็ได้สั่งไปแล้วก็ถามว่ารับ bitcoin ไหมครับ เจ้าของร้านก็บอกว่า รับๆ ผมกับเจ้าของร้านก็ได้พูดคุยกันเกือบประมาณครึ่งชั่วโมง ซึ่งหากผมมาเร็วกว่านี้หน่อยก็คงได้คุยกันยาวๆ แล้วละ ซึ่งเป็นการคุยที่สนุกมากซึ่งตัวเจ้าของร้านเองก็ได้เล่าถึงเหตุผลที่รับ bitcoin เหมือนกันว่าช่วง โควิดตอนปี 2020 ที่ผ่านมา บนเกาะช้างไม่มีอะไรเลยชาวบ้านก็ต้องไปหารากไม้ หาเห็ดตามป่าเขากัน แต่พี่เจ้าของร้านได้รู้จักกับฝรั่งคนหนึ่งเขาช่วยเหลือพี่เจ้าของร้านด้วยการบริจาคบิทคอยให้ และคนนี้ก็เป็นคนสอนให้เขารับบิทคอยโดยใช้ WOS และเจ้าของร้านก็เล่าให้ผมฟังเพิ่มเติม ณ ปัจจุบันว่า คนเราเองก็ยังต้องมีสภาพคล่องในการใช้งานอยู่ ตั้งมีเงิน fiat ไว้ส่วนหนึ่ง ส่วนบิทคอยที่ได้เขาได้ก็เก็บไว้เพื่อสร้างเป็นทรัพย์สินในอนาคตที่หากมีปัญหาช่วงไหนก็นำมาขายได้ ก็แลก P2P โดยตรง ซึ่งผมค่อนข้างตกใจเพราะเขาเรียนรู้จากการรับบิทคอยโดยนักท่องเที่ยวชาวต่างชาติที่ชวนเขาให้รับ เผื่อว่าจะมีฝรั่งมาใช้งานบิทคอย ณ สถานที่ร้านแห่งนี้

กึมมิคที่หลายท่านอาจจะต้องลุ้นหน่อยว่าหากมีโอกาสได้ไปเที่ยวและแวะที่ร้าน ก็คงต้่องลุ้นว่าคุณจะได้จ่ายด้วย bitcoin ไหม หากวันนั้นเจ้าของร้านไม่อยากรับเพราะว่าโคต้ารับบิทคอยวันนั้นเต็มแล้ว ฮ่าๆ รูปแบบระบบวาสนาร้านสูญของคุณมิกตอนเมื่อก่อน (เหมือนกันเลย) จริงๆ แล้วหากมีเวลามากพอก็คงได้พูดคุยกับพี่เจ้าของร้านสนุกๆกันไป ผมชอบความเรียบง่ายของร้านพี่เขา และมีอาหารหลากหลายอย่างเต็มไปหมด อีกเรื่องอย่างข้าวเหนียวมะม่วง ผมยังจำได้ว่าเมื่อก่อนมีแต่ช่วงฤดูเดียวที่สามารถกินมะม่วงสุกได้ หรือ อาหารแบบข้าวเหนียวมะม่วง แต่ปัจจุบันคือถ้าจะกิน ข้าวเหนียวมะม่วงแล้ว สามารถสั่งกินได้ตลอดทั้งปีกันเลยซึ่งก็โอเครพอสมควร แบบอยากไปทะเลตอนหน้าฝนแล้วอยากกินข้าวเหนียวมะม่วงของหน้าร้อนแบบนี้

ท้ายสุดร้าน Mr. A Coffee เป็นร้านที่ถ้านั่งชิวๆ แบบฝรั่งก็สามารถอยู่ได้ยาวๆ เลยนะจิบกาแฟ ทำงาน WFH ล้่อมรอบโดยธรรมชาติ แต่เส้นทางมาที่ร้านก็ลำบากหน่อยเหมาะกับคนที่ local จริงๆ low time ระดับหนึ่ง ท้ายสุดผมเองก็แจกสติกเกอร์ของพี่แชมป์เอาไปให้เจ้าของร้านแจกกันต่อไป
 งานนี้ทั้งข้าวเหนียวมะม่วงและน้ำแก้วมังกรปั่น เสีย sats ไปทั้งหมด 6,050 sats แต่สิ่งที่ได้คือการแลกเปลี่ยนมุมมองกับเจ้าของร้านกับจุดเริ่มต้นของการรับบิทคอยในพื้นที่เกาะช้างแห่งนี้ และหากมีโอกาสอาจจะไปพักอยู่แถวนั้นชักอาทิตย์และแวะมาอุดหนุนร้านนี้ตลอด เพราะวิวฝั่งใต้สุดของเกาะช้างก็ยังคงความสวยงามไม่แพ้กับฝั่งทิศตะวันตกที่ฝรั่งอยู่กัน แต่ฝั่งใต้โซนนี้ก็มีความที่เป็นบ้านไม้ เพิงง่ายๆ ที่ชาวต่างชาติชอบกันอยู่ :)
งานนี้ทั้งข้าวเหนียวมะม่วงและน้ำแก้วมังกรปั่น เสีย sats ไปทั้งหมด 6,050 sats แต่สิ่งที่ได้คือการแลกเปลี่ยนมุมมองกับเจ้าของร้านกับจุดเริ่มต้นของการรับบิทคอยในพื้นที่เกาะช้างแห่งนี้ และหากมีโอกาสอาจจะไปพักอยู่แถวนั้นชักอาทิตย์และแวะมาอุดหนุนร้านนี้ตลอด เพราะวิวฝั่งใต้สุดของเกาะช้างก็ยังคงความสวยงามไม่แพ้กับฝั่งทิศตะวันตกที่ฝรั่งอยู่กัน แต่ฝั่งใต้โซนนี้ก็มีความที่เป็นบ้านไม้ เพิงง่ายๆ ที่ชาวต่างชาติชอบกันอยู่ :)Google-map: https://maps.app.goo.gl/b45JGeTzL6Lwwi9i9
BTC-map: https://btcmap.org/merchant/node:12416107504
**Koh Chang Wine Gallery **

และเราก็ย้อนกลับมาอีกร้านหนึ่งในวันถัดไปและเป็นวันที่จะต้องออกจากเกาะช้างเช่นเดียวกัน และผมก็ไม่พลาดร้าน Koh Chang Wine Gallery ตั้งอยู่ในโซนหมู่บ้านแหล่งท่องเที่ยวเส้นทางถนนทางตะวันตก ร้านนี้ไม่ได้มีป้ายรับบิทคอย แต่รับชำระด้วยบิทคอยซึ่งเป็นฝรั่งท่านหนึ่งที่คาดว่าน่าจะแต่งงานกับภรรยาคนไทย เป็นร้านสไตล์แบบฝรั่งเลย ผมเองก็สั่งสเต็กเนื้อไป และน้ำมะม่วงปั่น (ไม่รู้เวลาไปเกาะทีไรติดใจกับน้ำมะม่วงปั่น) อาจจะไม่ได้พูดคุยอะไรมากมายนัก แต่ก็หมดไป 32,620 sats เป็นร้านอาหารเช้าและอาหารแนวฝรั่งตรงๆ ถือว่าค่อนข้างอร่อยใช้ได้ดีเลยทีเดียว แต่หากจะจ่ายด้วยบิทคอยก็ต้องแจ้งก่อนนะว่าขอจ่ายด้วยบิทคอยก่อน เหมือนพี่ฝรั่งที่เขารับตอนนี้ก็รับแต่เฉพาะ bitcoin อย่างเดียวเมื่อก่อนรับ xrp กับ doge ด้วยแต่ผมเองเวลาคุยกับฝรั่งก็เหงื่อแตกเหมือนกัน (รึว่าเพราะมันร้อน บนเกาะก็อบอ้าวใช้ได้ 555+)



Google-map: https://maps.app.goo.gl/6QbNgRbiV5Uao2Xz8
BTC-map: https://btcmap.org/merchant/node:11461720813
เส้นทางไปร้านค่อนข้างง่ายติดถนนในหมู่บ้าน ซึ่งหากมายังเกาะช้างแล้วหากขึ้นฝั่งมาแล้วเลี้ยวขวาก็จะขับรถหรือนั่งรถมาเส้นถนนฝั่งตะวันตกของเกาะก็จะพบกับร้านนี้ก่อน อันนี้แล้วแต่ความสะดวกแต่ละท่านเลยครับหากได้มีโอกาสแวะมาเกาะช้างและอยากใช้จ่าย bitcoin เราก็มีทางเลือกร้านในสองสไตล์กันเลย แบบวิถีฝรั่งตอนเช้าก็ร้าน Koh Chang Wine Gallery หรือ แบบ Local ก็ Mr. A Coffee หรือไปทังคู่เลยจะดีมากแต่ต้องบ้าหน่อย เพราะเส้นทางไปก็ค่อนข้างลำบากพอควรเหมือนกัน หมายถึงมีภูเขาชันมีทางขึ้นลงหักศอกนิดหน่อยก็เท่านั้นเอง
รวมๆ ทริปบนเกาะช้างนี้ก็หมดไปไม่เยอะมาก 38,670 sats ก็จะตัวลอยเบาๆ หน่อย (สำรวจเมื่อ มีนาคม 2025 อนาคตอาจจะมีการเปลี่ยนแปลงได้) สำหรับจากนี้จะเป็นการ ปสก. ส่วนตัวกับการใช้งาน Bitcoin Lightning ตามสถานที่ที่ได้เดินทาง Part 3 จะเป็นสถานที่ในพื้นที่หาดใหญ่ จังหวัดสงขลา และ เสริมประสบการณ์การเดินทางโดยรถไฟระยะเวลาเกือบ 18 ชั่วโมง พร้อมด้วยมิตรสหายในรังอย่างกัปตัน จะป่วนแค่ไหนก็รอติดตามกันครับ :)
-
 @ a012dc82:6458a70d
2025-03-31 01:50:24
@ a012dc82:6458a70d
2025-03-31 01:50:24In the ever-evolving world of cryptocurrency, Bitcoin remains at the forefront of discussions, not just for its price movements but also for its foundational mechanisms that ensure its scarcity and value. One such mechanism, the Bitcoin halving, is drawing near once again, but this time, it's arriving sooner than many had anticipated. Originally projected for a meme-friendly date of April 20, the next Bitcoin halving is now set for April 15, marking a significant moment for the cryptocurrency community and investors alike.
Table of Contents
-
Understanding the Bitcoin Halving
-
Factors Accelerating the Halving Date
-
Implications of an Earlier Halving
-
Potential Price Impact
-
Miner Revenue and Network Security
-
Renewed Interest and Speculation
-
-
The Countdown to April 15
-
Conclusion
-
FAQs
Understanding the Bitcoin Halving
The Bitcoin halving is a scheduled event that occurs approximately every four years, reducing the reward for mining new blocks by half. This process is a critical part of Bitcoin's design, aiming to control the supply of new bitcoins entering the market and mimicking the scarcity of precious metals. By decreasing the reward for miners, the halving event reduces the rate at which new bitcoins are created, thus influencing the cryptocurrency's price and inflation rate.
Factors Accelerating the Halving Date
The shift in the halving date to April 15 from the previously speculated April 20 is attributed to several factors that have increased the pace of transactions on the Bitcoin network:
-
Sky-High Bitcoin ETF Flows: The introduction and subsequent trading of Bitcoin ETFs have significantly impacted market activity, leading to increased transaction volumes on the network.
-
Price Rallies: A series of price rallies, culminating in new all-time highs for Bitcoin, have spurred heightened network activity as traders and investors react to market movements.
-
Increased Daily Volume: The average daily trading volume of Bitcoin has seen a notable uptick since mid-February, further accelerating the pace at which blocks are processed and, consequently, moving up the halving dat
Implications of an Earlier Halving
The earlier-than-expected halving date carries several implications for the Bitcoin market and the broader cryptocurrency ecosystem:
Potential Price Impact
Historically, Bitcoin halving events have been associated with significant price movements, both in anticipation of and following the event. By reducing the supply of new bitcoins, the halving can create upward pressure on the price, especially if demand remains strong. However, the exact impact can vary based on broader market conditions and investor sentiment.
Miner Revenue and Network Security
The halving will also affect miners' revenue, as their rewards for processing transactions are halved. This reduction could influence the profitability of mining operations and, by extension, the security of the Bitcoin network. However, adjustments in mining difficulty and the price of Bitcoin typically help mitigate these effects over time.
Renewed Interest and Speculation
The halving event often brings renewed interest and speculation to the Bitcoin market, attracting both seasoned investors and newcomers. This increased attention can lead to higher trading volumes and volatility in the short term, as market participants position themselves in anticipation of potential price movements.
The Countdown to April 15
As the countdown to the next Bitcoin halving begins, the cryptocurrency community is abuzz with speculation, analysis, and preparations. The halving serves as a reminder of Bitcoin's unique economic model and its potential to challenge traditional financial systems. Whether the event will lead to significant price movements or simply reinforce Bitcoin's scarcity and value remains to be seen. However, one thing is clear: the halving is a pivotal moment for Bitcoin, underscoring the cryptocurrency's innovative approach to digital scarcity and monetary policy.
Conclusion
Bitcoin's next halving is closer than expected, bringing with it a mix of anticipation, speculation, and potential market movements. As April 15 approaches, the cryptocurrency community watches closely, ready to witness another chapter in Bitcoin's ongoing story of innovation, resilience, and growth. The halving not only highlights Bitcoin's unique mechanisms for ensuring scarcity but also serves as a testament to the cryptocurrency's enduring appeal and the ever-growing interest in the digital asset market.
FAQs
What is the Bitcoin halving? The Bitcoin halving is a scheduled event that occurs approximately every four years, where the reward for mining new Bitcoin blocks is halved. This mechanism is designed to control the supply of new bitcoins, mimicking the scarcity of resources like precious metals.
When is the next Bitcoin halving happening? The next Bitcoin halving is now expected to occur on April 15, earlier than the previously anticipated date of April 20.
Why has the date of the Bitcoin halving changed? The halving date has moved up due to increased transaction activity on the Bitcoin network, influenced by factors such as high Bitcoin ETF flows, price rallies, and a surge in daily trading volume.
How does the Bitcoin halving affect the price of Bitcoin? Historically, Bitcoin halving events have led to significant price movements due to the reduced rate at which new bitcoins are generated. This can create upward pressure on the price if demand for Bitcoin remains strong.
What impact does the halving have on Bitcoin miners? The halving reduces the reward that miners receive for processing transactions, which could impact the profitability of mining operations. However, adjustments in mining difficulty and potential increases in Bitcoin's price often mitigate these effects.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 39cc53c9:27168656
2025-03-19 11:08:45
@ 39cc53c9:27168656
2025-03-19 11:08:45The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 8d34bd24:414be32b
2025-03-30 23:16:09
@ 8d34bd24:414be32b
2025-03-30 23:16:09When it comes to speaking the truth, obeying God, or living a godly life, the average or the compromise is not necessarily correct, but frequently we do err to one extreme or the other.
Mercy or Wrath?
One area of controversy is whether we serve a God of love & mercy or a God of holiness & wrath. The truth is that the God of the Bible is both love and holiness and he acts in mercy and in wrath.
If we focus too much on God’s holiness and wrath, we become solely about robotically obeying laws and about all of the things we can’t do. We will fail to show love and mercy as Jesus showed those lost in sin. We will fail to show the mercy and love He showed to us. We become much like the Pharisees, whom Jesus called “whitewashed tombs.”
Instead, speaking the truth in love, we will grow to become in every respect the mature body of him who is the head, that is, Christ. (Ephesians 4:15)
We need to always speak the truth, but in a loving and merciful way.
Grace, mercy and peace from God the Father and from Jesus Christ, the Father’s Son, will be with us in truth and love. (2 John 1:3)
If we focus too much on God’s love and mercy, we can forget that the God of the Bible is holy and righteous and can’t stand to be in the presence of sinfulness. We can begin to soften God’s holy word to be little more than suggestions. Even worse, we can bend God’s word to the point that it no longer resembles His clearly communicated commands. Also, if we don’t call sin “sin” and sinners “sinners,” then those same sinners will never understand their need for a Savior and never trust Jesus in repentance. If God isn’t holy and we aren’t sinners, then why would anyone need a Savior?
But just as he who called you is holy, so be holy in all you do; (1 Peter 1:15)
We need to treat God and His word as holy, while showing love to His creation.
If I speak in the tongues of men or of angels, but do not have love, I am only a resounding gong or a clanging cymbal. (1 Corinthians 13:1)
God/Jesus/Holy Spirit are holy and loving. If we leave out either side of His character, then we aren’t telling people about the God of the Bible. We have made a God in the image we desire, rather than who He is. If we go to either extreme, we lose who God really is and it will affect both our relationship with God and our relationship with others detrimentally.
Faith or Works?
Another area of contention is relating to faith and works. What is more important — faith or works? Are they not both important?
Many believers focus on faith. Sola Fide (faith alone).
For it is by grace you have been saved, through faith—and this is not from yourselves, it is the gift of God— not by works, so that no one can boast. (Ephesians 2:8-9)
This is a true statement that Salvation comes solely through faith in what Jesus did for us. We don’t get any credit for our own works. All that is good and righteous in us is from the covering of the blood of Jesus and His good works and His power.
But since many people focus on faith alone, they can come to believe that they can live any way that pleases them.
What shall we say, then? Shall we go on sinning so that grace may increase? By no means! We are those who have died to sin; how can we live in it any longer? Or don’t you know that all of us who were baptized into Christ Jesus were baptized into his death? We were therefore buried with him through baptism into death in order that, just as Christ was raised from the dead through the glory of the Father, we too may live a new life. (Romans 6:1-4) {emphasis mine}
By focusing solely on faith, we can be tempted to live life however we please instead of living a life in submission to Our God and Savior. Our lives can be worthless instead of us acting as good servants.
If any man’s work is burned up, he will suffer loss; but he himself will be saved, yet so as through fire. (1 Corinthians 3:15)
At the same time, there are many who are so focused on good works that they leave faith out of it — either a lack of faith themselves or a failure to communicate the need for faith when sharing the gospel. They try to earn their way to heaven. They try to impress those around them by their works.
But they do all their deeds to be noticed by men; for they broaden their phylacteries and lengthen the tassels of their garments. They love the place of honor at banquets and the chief seats in the synagogues, and respectful greetings in the market places, and being called Rabbi by men. (Matthew 25:5-7)
I think James best communicates the balance between faith and works.
What use is it, my brethren, if someone says he has faith but he has no works? Can that faith save him? If a brother or sister is without clothing and in need of daily food, and one of you says to them, “Go in peace, be warmed and be filled,” and yet you do not give them what is necessary for their body, what use is that? Even so faith, if it has no works, is dead, being by itself.
But someone may well say, “You have faith and I have works; show me your faith without the works, and I will show you my faith by my works.” You believe that God is one. You do well; the demons also believe, and shudder. But are you willing to recognize, you foolish fellow, that faith without works is useless? Was not Abraham our father justified by works when he offered up Isaac his son on the altar? You see that faith was working with his works, and as a result of the works, faith was perfected; and the Scripture was fulfilled which says, “And Abraham believed God, and it was reckoned to him as righteousness,” and he was called the friend of God. You see that a man is justified by works and not by faith alone. (James 2:14-24) {emphasis mine}
Let’s look at some of the details here to find the truth. “if someone says he has faith but he has no works? Can that faith save him?” Can the kind of faith that has no works, that has no evidence, save a person? If a person truly has saving faith, there will be evidence in their world view and the way they live their life. “Even so faith, if it has no works, is dead, being by itself.” We are saved by faith alone, but if we are saved we will have works. Faith “by itself” is not saving faith, for “the demons also believe, and shudder.” I don’t think anyone would argue that the demons have saving faith, yet they believe and shudder.
Works are the evidence of true faith leading to salvation, but it is only faith that saves.
Speak the Truth or Love?
Whether we stand firmly and always loudly speak the truth or whether we show love and mercy is related to how we view God (as loving or as holy), but I thought how we respond was worth its own discussion.
Sometimes people are so worried about love and unity that they compromise the truth. They may actively compromise the truth by claiming the Bible says something other than what it says, i.e.. old earth vs young earth, or marriage is about two people who love each other vs marriage being defined by God as one woman and one man. Sometimes this compromise is just avoiding talking about uncomfortable subjects completely so that no one is made to feel bad. This is a problem because God said what He said and means what He said.
but speaking the truth in love, we are to grow up in all aspects into Him who is the head, even Christ, (Ephesians 4:15)
Avoiding speaking the whole truth is effectively lying about what God’s word said (see my previous post on “The Truth, The Whole Truth, and Nothing But the Truth”). We are not doing anyone a favor making them feel good about their sin. A person has to admit they have a problem before they will act to fix the problem. A person who doesn’t understand their sin will never submit to a Savior. It isn’t loving to hide the truth from a person just because it makes them uncomfortable or it make the relationship uncomfortable for ourselves.
Jesus said to him, “I am the way, and the truth, and the life; no one comes to the Father but through Me. (John 14:6)
At the same time, sometimes people seem to beat others over the head with God’s truth. They share the truth in the most unloving and unmerciful way. They use God’s truth to try to lift up themselves while putting down others. This is just as bad.
Now we pray to God that you do no wrong; not that we ourselves may appear approved, but that you may do what is right, even though we may appear unapproved. For we can do nothing against the truth, but only for the truth. (2 Corinthians 13:7-8) {emphasis mine}
Some Christians spend so much time nit picking tiny discrepancies in theology that they miss the whole point of the Gospel.
“Woe to you, scribes and Pharisees, hypocrites! For you tithe mint and dill and cumin, and have neglected the weightier provisions of the law: justice and mercy and faithfulness; but these are the things you should have done without neglecting the others. (Matthew 23:23)
Some Christians use theological purity as a means to lift themselves up while knocking others down.
“Two men went up into the temple to pray, one a Pharisee and the other a tax collector. The Pharisee stood and was praying this to himself: ‘God, I thank You that I am not like other people: swindlers, unjust, adulterers, or even like this tax collector. I fast twice a week; I pay tithes of all that I get.’ 13But the tax collector, standing some distance away, was even unwilling to lift up his eyes to heaven, but was beating his breast, saying, ‘God, be merciful to me, the sinner!’ I tell you, this man went to his house justified rather than the other; for everyone who exalts himself will be humbled, but he who humbles himself will be exalted.” (Luke 18:10-14)
We need to stand firmly on the truth, but not to be so focused on truth that we fight with fellow believers over the smallest differences, especially when these differences are among the areas that are not spoken of as clearly (like end times eschatology).
Rejoice or Fear God?
Tonight I read Psalm 2 which brought to mind another seemingly contradictory way we are to interact with God. Do we fear God or do we rejoice in Him?
There are many verses telling us to fear God or fear the Lord. They are given as a command, as a way to knowledge, as a way to life, etc.
Honor all people, love the brotherhood, fear God, honor the king. (1 Peter 2:17) {emphasis mine}
and
The fear of the Lord is the beginning of knowledge; Fools despise wisdom and instruction. (Proverbs 1:7) {emphasis mine}
and
The fear of the Lord leads to life, So that one may sleep satisfied, untouched by evil. (Proverbs 19:23) {emphasis mine}
At the same time we are told to rejoice in the Lord.
Rejoice in the Lord always; again I will say, rejoice! (Philippians 4:4)
and
Then I will go to the altar of God, To God my exceeding joy; And upon the lyre I shall praise You, O God, my God. (Psalm 43:4)
How often do we rejoice in the thing that makes us tremble in fear? I’d guess, not very often or even never. A right view of God, however, causes us to “rejoice with trembling.”
Worship the Lord with reverence\ And rejoice with trembling.\ Do homage to the Son, that He not become angry, and you perish in the way,\ For His wrath may soon be kindled.\ How blessed are all who take refuge in Him! (Psalm 2:11-12) {emphasis mine}
That phrase, “rejoice with trembling” seems to perfectly encapsulate the balance between fear of an awesome, omnipotent, holy God and rejoicing in a loving, merciful God who came to earth, lived the perfect life that we cannot, and died to pay the penalty for our sins.
“How blessed are all who take refuge in Him!”
No Real Contradictions
I think these examples do a good example of demonstrating wisdom regarding God’s word and the importance of balance in our Christian lives. Even when at first there seems to be contradictions, God’s word never contradicts itself; it always clarifies itself. Also, when we see a theological or implementation error to one extreme, we need to make sure we are not driven to an error in the other extreme. We also need to make sure, when debating with fellow believers, that we do not argue against one extreme so strongly that we miscommunicate the truth.
May God in heaven guide you as you study His word and seek to submit to His commands. May He help you to see the truth, the whole truth, and nothing but the truth. May He guide the church to unity in His truth.
Trust Jesus
-
 @ 39cc53c9:27168656
2025-03-19 11:08:43
@ 39cc53c9:27168656
2025-03-19 11:08:43Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ d5c3d063:4d1159b3
2025-04-03 04:09:56
@ d5c3d063:4d1159b3
2025-04-03 04:09:56ทรัมป์ ขึ้นภาษีนำเข้า
สิ่งที่คุณเห็น…กับสิ่งที่คุณมองไม่เห็น
คุณ #เห็น แค่ฝั่งที่ดูดีในข่าวภาคค่ำ แต่คุณ #ไม่เห็น – คนทั้งประเทศ ต้องจ่ายของแพงขึ้น – ธุรกิจเล็ก ๆ ที่พึ่งการนำเข้า…ถูกบีบให้ตาย – ผู้บริโภคต้องเสียเงินมากขึ้น โดยไม่มีทางเลือก
รัฐอ้างว่า "ปกป้องประเทศ" แต่จริง ๆ แล้วเขาแค่ โยนภาระให้คนส่วนใหญ่ เพื่ออุ้มผลประโยชน์บางกลุ่ม เหมือนที่ Bastiat เรียกว่า “การปล้นที่ถูกกฎหมาย” Hazlitt ขยายต่อใน Economics in One Lesson ว่า
เศรษฐศาสตร์ที่ดี ต้องมองให้พ้นจากผลเฉพาะหน้า และมองให้เห็นผลกระทบต่อทุกคน ไม่ใช่แค่บางกลุ่ม
เงินเฟ้อ คือการขโมยแบบเงียบ ๆ ภาษีศุลกากร คือการปล้นอย่างเปิดเผย
วันนี้ #EIOL น่าจะถึงมือเพื่อนๆ หลายคนแล้ว เล่มนี้ไม่ต้องอ่านทีละบทก็ได้ ลองเปิดไปบทที่ 11 เลยแล้วจะเจอค้อนปอนสำหรับทุบมายาคดีทางเศรษฐกิจที่รัฐใช้กับเรามาทั้งชีวิต
อ่าน #เศรษฐศาสตร์เล่มเดียวจบ แล้วคุณอาจไม่มีวันมอง “นโยบายเพื่อประชาชน” ได้เหมือนเดิมอีก เพราะบางที...สิ่งที่คุณไม่เคยเห็น อาจเป็นสิ่งที่คุณควรรู้(เห็น)ให้เร็วที่สุด
Siamstr
-
 @ bccf33d8:4b705625
2025-03-19 10:07:46
@ bccf33d8:4b705625
2025-03-19 10:07:46{"title":"nostrbook 创建的五本四书哈哈哈","author":"nostrbook.com","intro":"This is a book from ....很不错","picture":"https://432fds"}
-
 @ 21c9f12c:75695e59
2025-03-30 22:42:19
@ 21c9f12c:75695e59
2025-03-30 22:42:19This guy was in my dad's building. A reminder of the importance of balance in our lives. We all have good and bad experiences in life. What matters is how you choose to handle them and balance yourself on the narrow path. Our paths in life have many possible turns, some take us closer to our ultimate reality while others might lead us astray for a bit.
No matter which path you choose the important thing is to keep your balance and footing and not be swept away in the breeze. You can always find your way back to your center and work your way back out from there. There is seldom a straight path in this life that will take you directly to your ultimate reality, make your way as you will and you'll find that you have what you need when you need it.
Ultimately we are all connected in ways we may never understand. The web of reality is so complex and woven with such precision that we need not try to understand why things are the way they are but accept that they are and move along our path doing our best to help others along the way when possible and accept help from those offering it. The path we take is strengthened and preserved when we follow it with love in our hearts. In this way we can leave a beacon to guide others on their way.
My dad left a lot of love on his path. He has guided so many people whether he realized it or not. His guidance of my path has made me who I am today and I am so proud to say that. His love and light shines bright ahead of me and my path is made so much clearer by the love I received and will continue to receive from him.
This is more than just a spider in a building, it is a reminder that all will be well and we will find our balance and continue along our path with the light and love dad has placed on the web of life for us to follow. Peace and love to everyone and may you all find your balance and continue on your path in the light and love that has been placed there for you by those who have gone before.
-
 @ 52adc2ef:9f4bc0ba
2025-04-03 02:35:10
@ 52adc2ef:9f4bc0ba
2025-04-03 02:35:10ส่วนที่ 1 สองระบบ
บทที่ 1
สมองนั้นสามารถเเบ่งได้เป็น 2 ระบบ
ระบบแบบอัตโนมัติ เป็นระบบที่ใช้พลังงานไม่มาก ตัดสินใจโดยใช้ความจำ ประสบการณ์ เเละความเชี่ยวชาญ หรืออาจจะมี สัญชาตญาณ ซึ่งคนเรานั้นจะใช้สมองส่วนนี้เป็นหลัก การขับรถ (ถนนโล่งๆ)
-ได้ยินเสียงเเล้วหันไปที่ต้นกำเนิดเสียง -2+2 เป็นเท่าไหร่ -หรือให้นึกถึง ปารีส เราก็จะนึกทันทีว่าเป็นชื่อเมืองหลวง
ซึ่งสมองระบบนี้จะตอบสนองโดยทันที ไม่ก็คำง่ายๆ
หรือ การเจอคนในชีวตประจำวัน เช่น เห็นคนหน้าคิ้วขมวด กัดกราม สมองของเราจะตัดสินอัตโนมัติว่า ต่อไปอาจจะมีพูดคำหยาบ เเละจะต้องรู้สึกระวังมากขึ้น
ในที่นี้ขอเรียกว่า ระบบ 1
2.ระบบที่ใช้ความพยายาม ยกตัวอย่างง่ายๆ
23×58
เราไม่สามารถที่จะใช้ ระบบ 1 ได้ สมองจะใช้ความพยายามในการคิดมากขึ้น ระบบ 1 ไม่สามารถหาคำตอบได้ ต้องอาศัยความตั้งใจ เช่น
-การมองหาคนที่ใส่หมวกสีแดง -การเปรียบเทียบของลดราคา -การบังคับตัวเองไม่ให้หันไปมองเสียงประหลาด
หรือเรียกว่าการให้ความสนใจ หรือ จดจ่อ (pay Attention) การคิดเเบบจดจ่อ ทำให้เราไม่สามารถจะทำกิจกรรมที่ต้องทำพร้อมกันได้
เช่น ถ้านั่งคิดเลขจากโจทย์ด้านบน จะไม่สามารถที่จะต้องตั้งใจหาญาติเรา ที่จะต้องไปรับที่สถานีรถไฟ
ขอเรียกว่า ระบบ 2
หรือทดสอบดูว่าของการทำงานทั้ง 2 ระบบ
ให้บอกไล่ลงด้านล่างว่า คำไหนเป็นตัวอักษรเเบบปกติ เเละ คำไหนเป็นอักษรเเบบหนา
หนา
ปกติ
หนา
ปกติ
ปกติ
ปกติ
หนา
หนา
หลังจากที่ทำจะรู้สึกมีความขัดเเย้งกันเเละใช้เวลาในการประมวลผล เพราะถ้าเราไม่คิดเราจะรู้สึกใช้ระบบ 1 ในการตอบของความหมายของคำเเทน
บทที่ 2
ระบบ 2 ถ้าเปรียบในหนัง จะเป็นเพียงพระรอง เพราะระบบ 1 ของคนเราจะเป็นระบบหลักในการทำงาน เมื่อมีความซับซ้อน ที่ไม่ใช่ความเคยชิน ถึงเริ่มปรับเป็นระบบ 2
รูม่านตากับระบบ 2
มีการทดลองที่ทำให้รู้ว่า รูม่านตาของเรา สอดคล้องกับ การใช้สมองในการเเก้ปัญหายิ่งยาก รูม่านตาของเราจะขยายใหญ่มากตาม
การทดลอง
โดยมีการทดลองมีเลข 4 ตัว เเละให้บวก 1 เพิ่มก่อนตอบ เช่น
4895
จะต้องตอบเป็น 5906 เป็นต้น ซึ่งจากการทดลองยิ่งสมองใช้งานมากขึ้น
ตามปกติเเล้วสมองของเราจะพยายามที่ใช้พลังงานให้น้อย เเละเมื่อเรามีทักษะมากขึ้น สมองของเราก็จะใช้พลังงานน้อยลง เข้าโหมดของ ระบบ 1
บทที่ 3
สมองจะมีอัตราความเร็ว ของมันเอง โดยเมื่อคุณเดินเป็นความเร็วปกติ คุณจะสามารถใช้ความคิดได้ระหว่างเดิน
เเต่เมื่อต้องใช้สมองในการเเก้ไขโจทย์ซับซ้อน ในเวลากำหนด อาจจะต้องหยุดเดินหรือนั่งเพื่อเเก้ปัญหานั้นๆ
เเละเมื่อเราเดินเร็วขึ้นการที่จะคิดไปด้วยนั้น เมื่อร่างกายเเย่งพลังงานในการใช้สมอง ทำให้การคิดระหว่างที่เดินเร็วนั้นยากขึ้น
ภาวะลื่นไหล (Flow)
คือภาวะที่สมองจดจ่อโดยไม่ต้องใช้ความพยายาม จนลืมเวลา
เเต่เมื่อสมองจดจ่อกับการใช้ความคิดจะทำให้เรา การควบคุมตัวเองลดน้อยลง หรือความมุ่งมั้นที่น้อยลง (ego depletion) เช่น ใช้เงินเเบบไม่คิด หรือเริ่มไม่ควบคุมอาหาร
ภาวะที่สมองทำงานหนักมากขึ้น จากการทดลอง สมองจะมีความต้องการ กลูโคสมากขึ้น
ระบบ 1 จะมีความหุนหันมากกว่า ระบบ 2 จะมีความคิด เเละเหตุผล
คนที่สามารถใช้ระบบ 2 ได้ดีกว่ามีโอกาสที่จะควบคุมอารมณ์ เเละยั้งคิดได้กว่า
เเละเมื่อเราใช้สมองเเบบระบบ 1 คำถามบางคำถามเราอาจจะตอบเเบบเข้าใจไปเองว่าถูก จากหนังสือยกตัวอย่างเช่น
กุหลาบทุกชนิดเป็นดอกไม้ ดอกไม้บางชนิดโรยราอย่างรวดเร็ว ดังนั้นกุหลาบบางชนิดโรยราอย่างรวดเร็ว
มองเผินๆอาจจะถูกต้อง เเต่จริงๆกุหลาบสามารถที่จะไม่โรยราเลย หรือโรยราทั้งหมดก็ได้ ถ้าเราใช้ระบบ 1 อาจจะตอบว่าถูกต้อง เเต่ถ้าพิจารณาโดยใช้ระบบ 2 ก็มีโอกาสตอบถูก
บทที่ 4
การปูพื้นความคิด
สมองคนเราสามารถถูกชักจูงได้ เช่น
”กล้วย” “อาเจียน”
การอ่านคำว่า กล้วย หรือ อาเจียน สมองของเราจะมีความรู้สึกที่ตอบสนองทันที บางคนอาจจะรู้สึกว่า กล้วยนั้นทำให้อาเจียนเเละรู้สึกพะอืดพะอมโดยไม่รู้ตัว
การทำงานของสมองของเราจะกระตุ้นทุกส่วน เช่น ความทรงจำ ความรู้สึก การตอบสนอง สิ่งที่น่าสนใจคือการที่สมองรับรู้คำ ร่างการของเราจะตอบสนองด้วย
อีกหนึ่งการทดลองที่น่าสนใจคือ ถ้าเราได้ยินคำว่า
Eat มาก่อน
ให้เติมคำ
so_p
มีแนวโน้มอย่างมากที่จะตอบว่า soup มากกว่า soap รวมถึงคำอื่นที่เกี่ยวข้องกับการกิน
การทดลองฟรอริดา
ให้นักศึกษา เเต่งประโยคจากคำ 4 คำ โดยเเต่ละกลุ่มได้คำต่างๆกันไปเเต่มีกลุ่มนึงได้คำตามนี้
“เหี่ยวย่น หลงลืม ศรีษะล้าน สีเทา”
หลังจากให้เเต่งประโยคด้วยคำด้านบน เเละให้นักศึกษาเดินไปพัก ซึ่งนักวิจัยได้จับเวลาการเดิน ของกลุ่มที่ได้คำด้านบน
ปรากฎว่ามีการเดินที่ช้ากว่ากลุ่มที่ได้รับคำอื่นๆ ซึ่งจากด้านบนไม่มีคำว่า คนแก่ เลย
หรือทางกลับกันการทดลองให้เดิน 30 ก้าว ใน 1 นาที ซึ่งเป็นการเดินที่ช้ากว่าปกติ 1/3
ที่นักวิจัยได้เก็บข้อมูล กลุ่มนี้จะมีเเนวโน้มคิดคำเกี่ยวกับ คนเเก่ ได้มากเป็นพิเศษ
จากการทดลองทำให้ทราบได้ว่าสมองเราสามารถจะปูพื้นความคิดได้ ถ้าอยากยิ้มให้เห็นคำว่าร่าเริง หรือถ้าเราทำปากยิ้ม ก็จะมีผลให้เรารู้สึกร่าเริงเช่นกัน
บทที่ 5
ความง่ายในการคิด
สมองเมื่อมีความทรงจำ ประสบการณ์ ปูพื้นความคิดจะเกิดความสบายใจ มีเเนวโน้มที่จะคิดเเบบผิวๆ เเละใช้สัญชาตญาณ
ภาพลวงตา
สามารถเกิดในการะบวนการคิดได้ ตัวอย่าง มีชื่อตามนี้
โมนิกา กิลเบิร์ก ทิรานา ชานา
ชื่อพวกนี้เราคงเพิ่งเคยได้ยินครั้งเเรก วันนึง มีการรวบรวมชื่อบุคคลที่ชื่อเสียงในระดับท้ายเเถว เเละมีชื่อใหม่ๆ เช่น ชื่อ ชานา เราจะมีเเนวโน้มที่ให้ ชานา เป็นบุคคลทีชื่อเสียง
ซึ่งสิ่งนี้เกิดจาก “ความคุ้นเคย” เราจะคิดเเบบง่ายมากขึ้น เมื่อเราเคยเจอ คำ หรือ ชื่อที่เคยเห็นมาก่อน เเม้จะเห็นเพียงครั้งเดียว
วิธีที่สร้างความง่ายในการคิด
ต้องทำให้รู้สึกว่าอ่านง่าย เช่น
อดอล์ฟ ฮิตเลอร์ เกิดปี 1892 อดอล์ฟ ฮิตเลอร์ เกิดปี 1887
จากการทดลองผู้คนเชื่อในประโยคเเรกว่าเป็นจริงมากกว่า ทั้งที่จริงๆเเล้วเกิดปี 1889
หรือคำที่มีความคล้องจองก็จะช่วยให้เกิดความคุ้นเคยได้อีกการทดลอง ให้ประเมินบริษัทที่สมมุติขึ้นมา
โดยบริษัทเเรกออกเสียงง่ายๆ เช่น อาเทน อีกบริษัท ชื่อ อาทาฮุท
ผู้คนมีเเนวโน้มที่จะประเมินบริษัทที่ออกเสียงง่ายดีกว่าอีกบริษัท
ถ้าให้คนเริ่มที่จะขมวดคิ้วที่กล่าวไว้ตอนเเรก มีเเนวโน้มที่จะใช้ระบบ 2 ที่ต้องพยายามในการคิด เช่น การทดลองให้มีคำถามเหมือนกัน เเต่พิมพ์ในกระดาษที่ชัด เเละ ม่ชัด
“หากเครื่องจักร 5 เครื่องใช้เวลา 5 นาทีในการผลิตสินค้า 5 ชิ้น เเล้วเครื่องจักร 100 เครื่องใช้เวลาเท่าไหร่ในการผลิต 100 ชิ้น”
สรุปการทดลองจากกลุ่มพิมพ์ในการะดาษที่ไม่ชัด ตอบถูก มากกว่า กลุ่มที่พิมพ์ในกระดาษชัด
Mere exposure effect
การเห็นซ้ำๆ เป็นการตอกย้ำให้เราเกิดความง่ายในการคิด
การทดลองมีการประกาศคำในหนังสือพิพ์มหาลัย เป็น ภาษาตุรกี เช่น คาดีร์กา ซาริซิก นัมโซมา เป็นต้น โดยลงเป็นความถี่ที่ไม่เท่ากัน หลังจากลงประกาศสิ้นสุดลง ให้นักศึกษาคิดว่าศัพท์เเต่ละคำมีความหมาย ดี หรือ ร้าย
ผลปรากฎว่าคำที่เห็นบ่อยมีเเนวโน้มให้ความหมายที่ดีมากกว่า
บทที่ 6
ประเมินความปกติ
ความประหลาดใจเป็นหนึ่งในคุณสมบัติของสมองเเต่การเกิดเหตุการณ์ซ้ำๆในเหตุการณ์หนึ่งๆ ทำให้เรารู้สึกประหลาดใจน้อยลง
เช่น เมื่อเราไปเที่ยวต่างประเทศ เเละเราได้เจอเพื่อนที่สนิท ที่ไม่ได้เจอกันมานานมาก 10 ปี เราจะรู้สึกประหลาดใจมาก ถูกต้องมั้ยครับ ว่าบังเอิญมากๆ
ผ่านไป 2 สัปดาห์ เราได้เจอเพื่อนอีกครั้งในโรงหนังนั่งติดกันเลย ความประหลาดของเราจะน้อยกว่าครั้งเเรกมาก ทั้งๆที่มันมีความเป็นไปได้น้อยมากที่จะมาเจออีกครั้งเเละนั่งติดกัน
ทฤษฎีความปกติ
เมื่อเราเจอเหตุการณ์หนึ่งๆ ถ้าเกิดซ้ำอีกครั้งเราจะรู้สึกว่ามันสมเหตุสมผล
เช่น วัหนึ่งขับรถบนถนนเส้นนึง เเล้วเกิดเหตุการณ์ไฟไหม้ เเละอีกหนึ่งอาทิตย์ถัดมา เกิดเหตุการณ์ไฟไหม้อีกครั้ง เราจะรู้สึกประหลาดใจน้อยลง
เมื่อทุกครั้งที่ผ่านถนนเส้นนี้เราจะรู้สึกว่ามันเป็นถนน “ไฟไหม้” สำหรับเราทันที
หรือคำถามที่ว่า
โมเสสพาขึ้นเรือชนิดละกี่ตัว
น่าจะตอบกันได้นะครับว่าเท่าไหร่ เเต่มันผิด! โนอาร์ต่างหากที่เป็นคนพาสัตว์ขึ้นเรือ
ที่เรารู้สึกโดยหลอกเพราะเราเชื่อมโยงความปกติของโมเสสเเละโนอาร์คือคนในตำนานเหมือนกัน
เเต่เมื่อเปลี่ยนเป็น อีลอนมัส เราจัะรู้สึกว่ามันผิดเเต่เเรกทันที
มองเห็นเหตุผลเเละเจตนา
เรามีความสามารถระบุหาเหตุผลเเละเจตนามาโดยกำเนิด ยกตัวอย่าง
“หลังจากใช้เวลาทั้งวันไปกับการชื่นชมสิ่งสวยงาม ตามท้องถนน ที่เต็มไปด้วยฝูงชนของนครนิวยอร์ก เจนพบว่ากระเป๋าเงินของเธอหายไป”
เมื่ออ่านจบให้ทำการทดสอบเพื่อตรวจสอบว่าสามารถจำเรื่องราวได้มากเเค่ไหน ผู้เข้าทดสอบมีเเนวโน้มที่จะจำคำว่า ล้วงกระเป๋ามากกว่าสิ่งสวยงาม
ความเชื่อมโยงเเละหาเหตุผลทำให้การที่กระเป๋าเงินหายนั้น ส่งผลให้นึกถึงสาเหตุต่างๆมากมาย ว่าโดยโจรขโมยมั้ย หรือทำหล่นหาย
ซึ่งสมองเราหาคำอธิบายเพื่อเติมเต็มเรื่องราวให้สมบูรณ์
ส่วนอีกตัวอย่างที่มีการทดลองเป็น วีดีโอมี
สามเหลี่ยมขนาดใหญ่
สามเหลี่ยมขนาดเล็ก
วงกลม
อยู่ในพื้นที่คล้ายๆแผงผังบ้าน โดยเนื้อเรื่องสามเหลี่ยมใหญ่ เหมือนจะ พยายามระราน สามเหลี่ยมเล็กเเละวงกลม เเต่สามเหลี่ยมเล็กเเละวงกลมร่วมใจกันเอาชนะสามเหลี่ยมใหญ่ได้
จากการทดลอง สมองของเรากระตือรือร้นที่จะระบุตัวละคร ให้รูปทรงที่กระทำการ เหมือนจะ ต่างๆ ให้มีคนดี คนร้ายเองอัตโนมัติ
สิ่งพวกนี้เกิดในสมองเรา เเสดงให้เห็นว่าเรามีความสามารถในการระบุเจตนามาโดยกำเนิด
บทที่ 7
การด่วนสรุป
A I3 C 12 I3 14
จากกด้านบนเขียนว่ายังไง ทุกคนน่าจะอ่าน A B C และ 12 13 14 แต่สามารถ อ่านเป็น A 13 C และ 12 B 14
ทำไมเราไม่อ่านแบบนั้น? เพราะบริบทรอบข้างเป็นแบบนั้น มันมีความกำกวม เเต่สมองจะด่วนสรุปจากบริบท
สมองระบบ 1 ของเราจะคาดเดาจากประสบการณ์เเละบริบทรอบตัว ในการตีความสิ่งที่มีความกำกวม เช่น ความทรงจำของเรา ตอนเด็กๆเราคงท่อง A B C อยู่เเล้ว เราคงไม่ท่อง A 13 C
อคติจากความเชื่อเเละยืนยันความเชื่อ
การพยายามเชื่อในตอนแรกเป็นหน้าที่ของระบบ 1 แม้ข้อความที่ไม่มีสาระก็สามารถกระตุ้นเราเชื่อในตอนแรกได้
เช่น
“ปลากินลูกกวาด”
เมื่ออ่านข้อความนี้เราน่าจะมีภาพอะไรในหัว สมองของเราพยายามจะหาความเชื่อมโยง เพื่อให้ข้อความข้างต้นสมเหตุสมผล
อีกหนึ่งการทดลอง ทำให้รู้ว่าเมื่อมีความเหนื่อยล้า สมองของเรามีเเนวโน้มพร้อมจะเชื่อแทบทุกอย่าง
ให้ผู้ทดลองต้องจำตัวเลขหลายหลักเเละต้องดูข้อความที่ ปรากฎขึ้น หลังจากนั้นจะมีคำว่า จริงหรือเท็จ ปรากฎตามมาภายหลังเพียงคำเดียว
ผลสรุปว่าผู้ทดลองมีเเนวโน้มที่จะเชื่อข้อความที่เป็นเท็จ เพราะสมองระบบ 2 ของเรายุ่งเเละเหนื่อยล้ากับการต้องจำตัวเลขก่อน
Confirmation Bias
การทำงานของความทรงจำเชื่องโยงไปสู่อคติที่เกิดจากการมองหาสิ่งยืนยันความเชื่อ
เช่น คำถามว่า “แซมเป็นมิตรใช่มั้ย”
เราจะนึกถึงพฤติกรรมต่างๆได้มากกว่าถามว่า ”แซมไม่ค่อยเป็นมิตรใช่มั้ย”
สมองของเราจะจดจ่อกับการหาสิ่งยืนยัน เเละสอดคล้องกับความเชื่อตัวเอง
Halo Effect
ถ้าเรามีเเนวโน้มที่จะชอบคนนึง ไม่ว่าจะเป็นภาพลักษณ์ น้ำเสียง ความอ่อนน้อม เรามีความเป็นไปได้ที่จะมองเค้าในเเง่ดีเกินความจริง
มีตัวอย่างการทดลอง
อลัน : ฉลาด ขยันขันแข็ง หุนหัน ชอบวิจารณ์ ดื้อรั้น ขี้อิจฉา เบน : ขี้อิจฉา ดื้อรั้น ชอบวิจารณ์ หุนหัน ขยันขันแข็ง ฉลาด
คนส่วนใหญ่จะมองว่าอลันในเเง่ดีกว่าเบน การเรียงลำดับจึงสำคัญ เพราะเราจะแปลความหมายจากเเรกไปอันดับรองลงมา ทำให้ความประทับใจเเรกเป็นสิ่งสำคัญ
WYSIATI (What you see is all there is)
“สิ่งที่เราเห็นคือทั้งหมดที่เป็น”
สมองระบบ 1 ของเราจะชอบด่วนสรุปและอ้างอิงกับความจำที่เรามี
การทดลองให้ผู้ทดลองได้ฟังความจากทนายที่มีหลักฐานเพียงฝั่งเดียว กลุ่มที่ได้เห็นหลักฐานฝั่งเดียวมั่นใจการตัดสินใจมากกว่ากลุ่มที่ได้ฟังจากทั้งสองฝั่ง
ผลมาจากความสอดคล้องของเรื่องราว ที่พวกเขาสามารถปะติดปะต่อขึ้นจากข้อมูลที่มี ปัจจัยที่สำคัญ คือ
“ความสอดคล้องของข้อมูล ไม่ใช่ความสมบูรณ์ของข้อมูล”
บทที่ 8
การตัดสินใจเกิดขึ้นอย่างไร
สมองของเราจะมีการ “ประเมินขั้นพื้นฐาน” ว่าคนที่เราเจอมีลักษณะเป็นอย่างไร เช่น ดูมีอำนาจ ยิ้มแย้ม ความน่าเชื่อถือ
มีการทดลองที่ให้ ผู้ทดลองดูภาพใบหน้าหาเสียงของผู้สมัครเลือกตั้ง ผลปรากฎว่ามีความใกล้เคียงกับผู้ที่ถูกเลือกตั้งจริงๆจากประเทศที่ได้รับเลือกจริง
การเปรียบเทียบความเข้มข้น
สมองระบบ 1 ของเราสามารถเปรียบความเข้มข้นกับในบริบทที่ต่างกันได้ เช่น อาชญากกรมที่มีความรุนเเรง ฆาตกกรรมจะมีความเข้มกว่าการลักขโมยของ
หรืออีกตัวอย่างคือ
จูลี่อ่านหนังสือได้คล่องตอนอายุ 4 ปี
เราสามารถที่จะเปรียบเทียบความเข้มข้นได้เป็น
เงินเดือนเท่าไหร่ความจะเปรียบเทียบได้กับความสามารถมากจูลี่ หรือ เกรดเฉลี่ยเท่าไหร่ที่เหมาะสมกับความสามารถ
ซึ่งถ้าวัดด้วยความเป็นจริงอาจจะไม่ใช่ก็ได้ เเต่สมองระบบ 1 ของเราสามารถที่จะเปรียบเทียบได้
การคิดเเบบเหวี่ยงแห
การทดลองเมื่อได้ยินเสียงคล้องจองกันให้กดปุ่มให้เร็วที่สุด
VOTE-NOTE
VOTE-GOAT
เราสามารถเห็นความเเตกต่างได้ชัดเจนว่า vote กับ note ใกล้เคียงกว่า
แต่การทดลองผู้เข้าทดลองจะได้ยินเพียงเสียงของคำ กลับไม่เป็นอย่างนั้น ในมุมผู้ทดลองจะมีการเปรียบเทียบเสียงของตัวสะกด เเทนที่คำสั่งคือการฟังเเค่เสียงคล้องจอง
หรืออีกการทดลอง ให้กดปุ่มเร็วที่สุดว่าประโยคไหนเป็นจริงหรือเป็นเท็จ
some roads are snakes (ถนนบางเส้นเป็นงู)
some jobs are snakes (งานบางงานเป็นงู)
some jobs are jails (งานบางงานเป็นคุก)
ทั้งสามประโยคเป็นเท็จเเต่จากการทดลอง ผู้ทดลองมีการตอบสนองต่อประโยคต่างกัน
เช่น ประโยค 1 กับ 3 เป็นจริงในเชิงเปรียบเทียบ ทำให้เราใช้เวลาในการคิดมาก เพราะสมองเราคิดเเบบเหวี่ยงแห
บทที่ 9
ตอบคำถามที่ง่ายกว่า
เรามักจะมีคำตอบกับคำถามที่เราไม่เข้าใจอย่างถ่องเเท้ โดยใช้หลักฐานที่เราไม่สามารถอธิบายได้
การแทนที่คำถาม
ระบบ 1 ของเราเมื่อมีคำถามมา มันจะพยายามเชื่อมโยง หาคำตอบที่เป็นไปได้เเละง่ายที่สุด โดยการแทนที่คำถามให้ง่าย
เช่น ”คุณมีความสุขกับชีวิตของคุณมากน้อยเพียงใด”
เจอคำถามนี้เราจะคิดนานขึ้นจนสมองอาจจะขอเปลี่ยนคำถามเป็น
”ตอนนี้ฉันรู้สึกยังไง”
ทางลัดความคิดของอารมณ์
ตัวอย่างการแทนที่คำถามที่มีการทดลองเก็บตัวอย่าง
1.คุณมีความสุขมากแค่ไหนในตอนนี้ 2.คุณออกเดตกี่ครั้งในเดือนที่แล้ว
นักวิจัยต้องการศึกษาความเชื่อมโยงของคำตอบว่า ถ้าออกเดตบ่อย จะมีความสุขมากกว่าหรือไม่
ผลปรากฎว่าไม่มีความเชื่อมโยงกันเลยของคำตอบ ผู้ถูกถามจะไม่นึกถึงการออกเดตเลยในสิ่งเเรกที่ได้ยินคำถามนี้
กลับกันถามว่า
1.คุณออกเดตกี่ครั้งในเดือนที่แล้ว 2.คุณมีความสุขมากแค่ไหนในตอนนี้
ผลเเตกต่างไปสิ้นเชิง ความเชื่อมของจำนวนการเดตเริ่มสอดคล้องกัน
การที่เราถูกถามเรื่องความสุขตอนนี้ จะใช้เวลาในการพิจารณามากกว่า เเต่เมื่อถามกับออกเดตก่อนเรามีคำตอบกับการเชื่อมโยงอยู่เเล้ว
-
 @ 3514ac1b:cf164691
2025-03-30 15:16:56
@ 3514ac1b:cf164691
2025-03-30 15:16:56hi , My name is Erna and i hope this articles find you well. hmm what i like to talked about today is how i dislike my my black coffee getting cold . it is happened almost everyday . here is my morning flow : wake up brush teeth and make my self ready make coffee ( boiled water ) in meantime switch on my computer reading news , things ( water allready boiled ) get my coffee and put my coffee on the side of my computer keep reading and social media 1 hour later coffee get cold meeeh i need to drink this everyday .
so which of thos work flow is wrong ? am i doing it wrong ? suggested me a good morning routine so my coffee still hot when i drink it .
-
 @ e111a405:fa441558
2025-03-19 08:57:18
@ e111a405:fa441558
2025-03-19 08:57:18Erdoğan'ın İmamoğlu'nu akademik teknik detaylar ve iddia edilen PKK bağlantıları üzerinden sistematik olarak saf dışı bırakması, yalnızca Türkiye'ye özgü bir durum değil; demokrasinin küresel çöküşünün bir örneğidir.
Dün Almanya, yeterli inceleme yapılmadan ve zaten görevden alınmış bir çoğunlukla anayasal değişiklikleri aceleyle geçirdi; Romanya ise adayları prosedürel gerekçelerle diskalifiye ediyor. Liste uzayıp gidiyor: Macaristan'da Viktor Orbán, Sırbistan'da Aleksandar Vučić, İsrail'de Netanyahu, Polonya'da Hukuk ve Adalet Partisi – demokratik gerileme bölgeler ve siyasi sistemlerin ötesine geçiyor. Bugün insanlığın %72'si otoriter rejimler altında yaşıyor.
Yeni bir oyun kitabı var: yasal kurumları muhaliflere karşı silah olarak kullanmak, prosedürel tiyatro yoluyla meşruiyet üretmek ve anayasal görüntüyü korurken demokratik güvenceleri ortadan kaldırmak.
Demokrasinin dramatik bir çöküşünü değil, bürokratik manipülasyonla metodik olarak boğulmasını izliyoruz. Bu erozyon tesadüfi değil; merkezi güç yapılarının, ne kadar iyi tasarlanmış olursa olsun, kaçınılmaz olarak yozlaşmasının bir sonucudur.
İnanıyorum ki tek sürdürülebilir yolumuz radikal bir merkezsizleşmeden geçiyor: yönetimin yerel topluluklara dağıtılması, kripto ağları aracılığıyla finansal egemenlik sağlanması ve hiçbir tekil varlığın kontrol edemeyeceği sansüre dayanıklı platformlar üzerinden iletişim kurulması.
Merkezi olmayan sistemler, insan onurunu, merkezi otoritelerin, kariyer politikacılarının ve atanmış bürokratların boş vaatlerine bel bağlamak yerine kırılmaz kriptografik garantilerle yeniden tesis eder.
Gelecek, özgürlüğü temel alan sistemler aracılığıyla gönüllü olarak işbirliği yapan ağ bağlantılı bireylere aittir. Merkezi olmayan ve küresel olarak ağ bağlantılı toplumlar, tek noktadan başarısızlık yerine binlerce eşzamanlı deneyi mümkün kılarak yeniliği serbest bırakan antifragil toplumlardır.
Türk arkadaşlarıma tavsiyelerim: https://primal.net'i kullanın (X'e merkeziyetsiz bir alternatif), günlük işlemler ve akıllı sözleşmeler için https://zano.org 'u kullanmaya ve kabul etmeye başlayın (merkeziyetsiz, izinsiz kripto para birimi ve işlemler; yakında gizlilik odaklı bir stabilcoin ile).
-
 @ e111a405:fa441558
2025-03-19 08:54:18
@ e111a405:fa441558
2025-03-19 08:54:18Erdogan's calculated elimination of Imamoglu through academic technicalities and alleged ties to PKK is not really an isolated Turkish case but an example of democracy's global collapse.
Yesterday, Germany rushed constitutional changes without proper scrutiny and with a majority that was already voted out of office, Romania disqualifies candidates on procedural grounds. The list goes on: Hungary under Viktor Orbán, Serbia under Aleksandar Vučić, Israel under Netanyahu, Poland under the Law and Justice party – the democratic backsliding goes well beyond regions and political systems. 72% of humanity now lives under authoritarian control.
There is a new playbook: weaponize legal institutions against opponents, manufacture legitimacy through procedural theater, and dismantle democratic safeguards while maintaining the illusion of constitutionality.
We're witnessing not democracy's dramatic collapse but its methodical strangulation through bureaucratic manipulation. This erosion isn't coincidental but the inevitable outcome of centralized power structures that invariably corrupt even well-designed systems.
I believe that our only viable path forward lies in radical decentralization: distributing governance to local communities, financial sovereignty through crypto networks, and communication via censorship-resistant platforms that no single entity controls.
Decentralized systems restore human dignity by establishing unbreakable cryptographic guarantees rather than depending on the hollow promises of centralized authorities, career politicians, and unelected bureaucrats .
The future belongs to networked individuals collaborating voluntarily through systems designed with liberty as their foundation. Decentralized and globally networked societies are antifragile societies that unleash innovation by enabling thousands of concurrent experiments instead of single-point failures.
-
 @ 0b118e40:4edc09cb
2025-03-30 09:09:45
@ 0b118e40:4edc09cb
2025-03-30 09:09:45There’s an African proverb that says, “To get lost is to learn the way.”
Humans have always been explorers, searching for connection. To belong. To feel home. You can trace this instinct back to the start of our existence. Whether you start with Adam and Eve or the “Out of Africa” theory, the story is the same. We’ve always moved toward each other, building tribes and forming communities.
But somewhere along the way, something broke. With the rise of empires and organized control, religion and politics divided us into bubbles. We were sorted, labeled, and often pitted against one another. While technology advanced, something fundamental was lost. Our ability to truly connect started to fade.
Then came the internet, a modern-day Silk Road. It rekindled hope. Walls seemed to crumble, distances disappeared, and we dreamed of a truly connected world. For a time, it felt like the answer.
And then it wasn’t.
The history of Internet
The story began around 1830s when Charles Babbage started working on his computer prototype but without moolah he couldn't continue. A century later, after WW2 in the 1950s, the US Department of Defense funded what became known as modern computing.
Back then the military relied on systems like the Navajo Code Talkers. The indigenous code talkers were ingenious but operated under dangerous conditions, always on the frontlines.
In 1969, ARPANET made a revolutionary breakthrough as it connected four university computers for the first time. It was a big deal.
At that time, the internet was about openness. Researchers pushed for universal protocols. This gave rise to hacker culture that valued knowledge-sharing and keeping systems accessible to everyone.
In the 80s, NSFNET (National Science Foundation ) expanded these connections but kept it strictly for academic use only. That caused massive dissatisfaction.
Senator Al Gore pitched the concept of the “information superhighway,” to balance public access with private innovation. But by the 90s, the Clinton administration leaned into privatization. NSFNET’s infrastructure was completely handed off to private companies, and the internet grew into a commercial powerhouse.
The good news is that everyone has internet access now. Bad news is that what started as something free from government and commercial control became completely dominated by both.
Open source vs IP during the early internet days
This part of the story is about Bill Gates and Marc Andreessen.
Tim Berners-Lee invented the World Wide Web, but Marc saw the opportunity to make it user-friendly. He launched Netscape, an open-source browser. It drove the openness of internet culture. Netscape captured 90% of the market by giving its software away for free, and monetizing through other means.
Then came along Bill Gates. Microsoft back then was known for its aggressive tactics to monopolize industries. Gates licensed Mosaic’s code, created Internet Explorer, and bundled it for free with Windows 95. He wasn’t shy about playing dirty, even formed exclusive contracts with manufacturers to block competitors. Even the Department of Justice tried to file an antitrust lawsuit against Microsoft, but by then, it was too late. Netscape’s market share crumbled, and its position in the industry eroded.
Windows 95 brought the internet to the people globally, but it also closed it up.
Marc Andreeson started with open source ideologies, but is now funding altcoin projects.
The Californian ideology
Around this time, the term “Californian Ideology” started floating around. It was an unusual mix of libertarianism, techno-utopianism, and countercultural ideals. A marriage of cultural bohemianism (hippies) with high-tech entrepreneurship (yuppies). This ideology fused left-wing values like freedom of expression and direct democracy with right-wing beliefs in free markets and minimal government interference.
I absolutely love it.
Ironically, the term “Californian Ideology” wasn’t coined as a compliment. Richard Barbrook and Andy Cameron used it to piss on these visionaries for romanticizing the idea that the internet must remain a lawless, egalitarian space.
But many people loved and embraced the Californian ideology. Stewart Brand, who founded The Whole Earth Catalog, connected counterculture with early tech innovation. His work inspired people like Steve Jobs and Steve Wozniak. Steve Wozniak used to share Apple’s early schematics at the Homebrew Computer Club for feedback and collaboration.
EBay’s founder Pierre Omidyar envisioned eBay as a libertarian experiment. He believed the “invisible hand” of the market would ensure fairness. But as eBay grew, fraud, disputes, and dissatisfaction among users forced Omidyar to introduce governance which contradicted his goals.
And this story repeats itself over the years.
Platforms begin with libertarian visions, but as they scale, real-world challenges emerge. Governance (government, corporate charters, advertisers, and investors) is introduced to address safety and trust issues.
But they also chip away at the liberty the internet once promised.
Can Nostr be the solution ?
Yes.
But to appreciate Nostr, let’s first understand how the internet works today. (Note : I am no expert of this section but I'll try my best to explain)
The internet operates through four main layers:
- Application Layer (where apps like browsers, Google, or Zoom live)
- Transport Layer
- Internet Layer
- Network Access Layer
Let’s use a simple example of searching “Pink Panther” on Google.
Step 1: The Application Layer - You open your browser, type "Pink Panther," and hit search. This request is sent using HTTP/HTTPS (a protocol that formats the query and ensures it's secure).
Step 2: The Transport Layer - Think of your search query as a letter being sent. The Transport Layer breaks it into smaller packets (like splitting a long letter into multiple envelopes). TCP (Transmission Control Protocol) ensures all packets arrive and reassemble in the correct order.
Step 3: The Internet Layer - This layer acts like a postal service, assigning each device an address (IP address) to route the packets properly. Your device's IP (e.g., 192.168.1.10) and Google’s server IP (e.g., 142.250.72.238) help routers find the best path to deliver your packets.
Step 4: The Network Access Layer - Finally, the Network Access Layer physically delivers the packets. These travel as electrical signals (over cables), radio waves (Wi-Fi), or light pulses (fiber optics). This is the act of moving envelopes via trucks, planes, or postal workers, just much faster.
So how is data transmitted via Nostr ?
Nostr’s architecture of the Internet
Nostr reimagines the Application Layer while keeping the lower layers (Transport, Internet, and Network Access) largely unchanged.
In the traditional internet stack, the Application Layer is where platforms like Google or Twitter operate. It’s also where most censorship occurs due to single point of failure (centralised servers). Nostr flips this model on its head.
Technically, it’s like building a parallel internet that shares the same foundational layers but diverges at the top.
To borrow from Robert Frost:
"Two roads diverged in a wood, and I—
I took the one less traveled by,
And that has made all the difference."
For Nostr to fully realize its potential, it needs its own ecosystem of apps. Developers can build these tools within the Nostr protocol's framework
Let’s say there is a search engine on Nostr called Noogle.
Here’s how it works:
When you type "Pink Panther" on Noogle, your query is sent to multiple relays (servers) simultaneously. Each relay processes or forwards the query and returns results based on the data it holds.
As Nostr grows, the amount of information on relays will increase, giving Noogle more robust search results. But the biggest win is that compared to Google, Nostr's Noogle will have no ads, no surveillance, just pure, decentralized searching that respects your privacy.
For the transport layer, Nostr still relies on TCP/IP but enhances it with privacy and efficiency. Encrypted messages and simplified protocols enable faster real-time communication. The rest of the layer remains unchanged.
At its core, Nostr takes the internet back to its original ideals: open, uncensored, and decentralized.
Why Nostr matters ?
The internet we use today relies on centralized systems at the application layer. This creates a single point of failure where governments and corporations can control access, censor content, monitor activity, and even shut down entire platforms.
For example, the Malaysian government once proposed routing all web traffic through a centralized system, claiming it was for "security" reasons. In reality, this action allow those in power to block access to specific content or platforms that might threaten their positions.
Centralization weaponizes the internet.
It turns what was meant to be a tool for connection and freedom into a mechanism for control and oppression.
Let's look at DNS and ISPs as examples. DNS (Domain Name System) is like the phonebook of the internet. It helps translate website names (like example.com) into IP addresses so your browser can connect to them. ISPs (Internet Service Providers) are companies that give you access to the internet.
Both are controlled by centralized entities. If a government gains control of either, it can block specific websites or even shut down internet access entirely.
We've seen this happen repeatedly: * India’s internet shutdowns in regions like Kashmir * Turkey’s social media bans during political events * Ethiopia’s internet blackouts * China’s Great Firewall blocking major platforms like Google and Facebook * Even the US, where Edward Snowden revealed massive surveillance programs
This is where Nostr comes in, as the antidote to centralized control.
Instead of relying on centralized servers or platforms, Nostr creates a peer-to-peer network of independent relays. No single entity controls it. There is no central switch governments can flip to block access. If one relay is shut down, users simply connect to others in the network.
Nostr’s decentralized design makes it: * Resistant to censorship: Governments cannot easily block or filter content. * Privacy-preserving: Users can communicate anonymously, even in heavily surveilled environments. * Resilient: With no single point of failure, the network keeps running, even under attack.
And it gets better. Nostr can integrate with privacy tools like Tor to bypass restrictions entirely, making it nearly impossible for governments to stop.
The internet has become a battlefield for control, but Nostr provides a way to reclaim digital freedom. It empowers people to build, connect, and share without fear of being silenced.
How does Nostr overcome the "Californian Ideology" problems?
The Californian Ideology seemed like the blueprint for a utopian internet, libertarian ideals wrapped in Silicon Valley innovation. But as centralized platforms scaled, cracks started to show. Challenges like trust, safety, and accessibility forced governance teams to step in and decide “what’s best for the people.”
This resulted in platforms once built on ideals of freedom in becoming gatekeepers of control.
Nostr breaks this cycle. How?
1. Trust issues - With private keys, you control your identity and data. Moderation is decentralized. You can block or mute others at a personal level or through client tools, not by relying on a central authority. While this system needs refinement to be more user-friendly, it fundamentally shifts the power to users.
2. Funding Without Advertiser - Nostr’s integration of Bitcoin and the Lightning Network eliminates reliance on advertisers or corporate sponsors. Bitcoin enables anyone to contribute without gatekeeping. As more people join and apps mature, this model only gets stronger. For now, we have good souls like Jack seeding it.
3. Resisting Government Control - (refer to the above) Nostr avoids single points of attacks.
So what is Nostr ?
Nostr is internet
The new internet.
The open and free internet.
What can you build on Nostr?
Anything you have seen on the internet, you can recreate on Nostr. Anything you can imagine, you can bring to life here. It is a blank canvas for dreamers, builders, and changemakers.
But the best part is this. You have Bitcoin as its financial backbone. This changes the game entirely.
And with new games, comes new rules. New vibes. New ways.
The way people use this new internet will be different from the traditional internet as control falls back to the people. With Bitcoin as the underlying backbone, the business models will be different.
But there is more to it than just creating. There's that joy of creation, where we invite curiosity and inspire users to experience something new, something revolutionary.
Have you watched “The Last Lecture” by Randy Pausch?
He coined the term “head fake.” He taught his students programming, but not everyone was excited to learn programming. So he created fun projects and performances that pulled them in. The students had so much fun, they didn’t even realize they were learning to code.
What you build on Nostr is that head fake. The apps and projects you create draw people in with fun and utility, subtly reminding them they have a right to their own voice and thoughts.
The work you’re doing is so precious. When everything feels like doom and gloom, it’s these kinds of projects that give people hope.
Through Nostr, you’re making a difference. One project, one connection at a time.
The new Internet era
Centralized systems, like empires of the past, eventually crumble under the weight of their control. Decentralization provides a different path. It is a modern revival of our primal instincts to explore, connect, and build tribes.
By definition, Nostr is a protocol. I think more so, it's a philosophy. It challenges us to rethink how we share, communicate, and create. It is the internet as it was meant to be. Free, open, and governed by no one.
The beauty of Nostr lies in its simplicity. It does not rely on massive infrastructure, corporate giants, or government oversight. It thrives on community, much like the early tribes that defined humanity.
We have come full circle. From wandering continents to building roads, bridges, and networks, our journey has always been about connection and finding our tribe.
As the African proverb reminds us, 'To get lost is to learn the way.' There is finally a way now.
But at the end of the day, it’s entirely up to you what kind of world you want to be part of.
Find your tribe. Build the future. Love them hard.
-
 @ 7c05c4f6:50d03508
2025-04-03 02:27:57
@ 7c05c4f6:50d03508
2025-04-03 02:27:57What is Cooker? Cooker.club is a decentralized AI agent creation and distribution platform that focuses on empowering the Web3 ecosystem through music AI agents, virtual idols, social KOLs, and AI NPCs. By integrating AI, music, and Web3, it has built a new AI creator economy, allowing AI characters to engage in autonomous creation, social interaction, and economic activities. The platform supports AI agent creation, tokenized economic systems, social interaction, smart contract execution, and decentralized governance, enabling users to freely create AI agents and manage their economic operations. In the Cooker.club ecosystem, the Bonding Curve is a crucial dynamic pricing mechanism that determines how AI agent tokens fluctuate based on supply and demand, promoting the healthy development of the AI economy.
-
What is a Bonding Curve? A Bonding Curve is a mathematical function that automatically adjusts the price of an asset based on its supply. The core logic is: Buying tokens (increasing supply) → Price rises Selling tokens (decreasing supply) → Price falls This ensures that token prices do not rely on order books but are automatically adjusted by smart contracts based on supply and demand, enhancing liquidity and market fairness.
-
Common Types of Bonding Curves The mathematical formula of a Bonding Curve determines how prices change. Different curve types suit different economic models: (1) Linear Bonding Curve Formula: P = kS Characteristics: Price increases linearly with supply Suitable for simple token economic systems (2) Exponential Bonding Curve Formula: P = kS^n Characteristics: Price increases exponentially as supply grows Suitable for high-growth, high-incentive token models (3) Logarithmic Bonding Curve Formula: P = k log(S + 1) Characteristics: Price growth slows down, preventing excessive inflation Suitable for long-term stable AI economies
-
How Does Cooker Utilize the Bonding Curve? (1) Dynamic Pricing of AI Agent Tokens AI agents on Cooker.club can issue their own Agent Tokens, whose price is influenced by the Bonding Curve, ensuring: Early adopters can purchase tokens at a lower cost, promoting AI agent growth. As AI agents gain influence, token prices rise, rewarding early supporters. (2) DAO and Decentralized Governance Cooker adopts the Bonding Curve mechanism to ensure fair distribution of governance tokens, enabling the community to participate in the economic decisions of AI agents.
-
Milestones: Expanding to Larger Liquidity Pools Cooker has an innovative milestone-based liquidity expansion strategy, where AI agent tokens transition from the Cooker.club ecosystem to major decentralized exchanges as they reach key valuation thresholds: Base Milestone: When an AI agent token reaches a predefined market cap, it gets listed on Uniswap (Ethereum network). BSC Milestone: Upon reaching a higher threshold, it expands to PancakeSwap (Binance Smart Chain). Upcoming Solana Milestone: AI agent tokens will soon launch on Raydium once they meet the required valuation criteria on the Solana blockchain. This approach ensures smooth liquidity growth while maintaining controlled token price dynamics through the Bonding Curve.
-
Conclusion The Bonding Curve is an essential dynamic pricing mechanism in the Cooker ecosystem, ensuring a more transparent and sustainable AI token economy. Through this mechanism, Cooker.club aims to establish a decentralized, autonomous AI creator economy, where AI characters evolve into independent intelligent entities within the Web3 financial ecosystem. The milestone-based liquidity expansion further enhances accessibility and market adoption, bridging AI agent tokens into broader decentralized finance environments.
-
-
 @ 3514ac1b:cf164691
2025-03-29 22:07:33
@ 3514ac1b:cf164691
2025-03-29 22:07:33About Me
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 378562cd:a6fc6773
2025-04-02 22:41:57
@ 378562cd:a6fc6773
2025-04-02 22:41:57Nostr is a decentralized, censorship-resistant social media protocol designed to give users control over online interactions without relying on central authorities. While its architecture offers notable advantages, it also introduces challenges, particularly concerning user anonymity, content moderation, and the dynamics of user influence.
Anonymity and the Risk of Bullying
Nostr's design allows users to create identities without traditional verification methods like email addresses or phone numbers. Instead, users generate a cryptographic key pair: a public key serving as their identifier and a private key for signing messages. This approach enhances privacy but can lead to the "online disinhibition effect," where individuals feel less accountable for their actions due to perceived anonymity. This phenomenon has been linked to increased instances of cyberbullying, as users may engage in behavior online that they would avoid in face-to-face interactions.
Influence Disparities Among Users
In decentralized networks like Nostr, users with larger followings can have a more extensive reach, amplifying their messages across the network. This can create disparities where individuals with thousands of followers wield more influence than those with fewer connections. While this dynamic is not unique to Nostr, the protocol's structure may exacerbate the visibility gap between highly followed users and those with a smaller audience.
Content Moderation and the Challenge of Deletion
Due to Nostr's decentralized nature, content moderation and deletion present significant challenges. Removing content to multiple relays becomes complex once a user posts content to multiple relays, as each relay operates independently. Unlike centralized platforms where a post can be deleted universally, Nostr's architecture means that deleting a post from one relay doesn't ensure its removal from others. This persistence underscores the importance of thoughtful posting, as content may remain accessible indefinitely.
Mitigation Strategies and User Empowerment
Despite these challenges, Nostr offers mechanisms to empower users to manage their experience. Clients can implement features allowing users to mute or block others, tailoring their interactions and content exposure. Additionally, some clients support user-led moderation, enabling individuals to label content as offensive or inappropriate, contributing to a community-driven approach to content management.
In summary, while Nostr's decentralized and anonymous framework promotes freedom and resistance to censorship, it also necessitates a proactive approach from users to navigate challenges related to anonymity, influence disparities, and content permanence. As the platform evolves, ongoing development and community engagement will be crucial in addressing these issues to foster a safe and equitable environment for all participants.
-
 @ 3514ac1b:cf164691
2025-03-29 21:58:22
@ 3514ac1b:cf164691
2025-03-29 21:58:22Hi this is me ,Erna . i am testing this Habla news . i have been trying using this but got no luck . always disconnect and no content .
Hopefully this one will work .
BREAKING NEWS : Vance uses Greenland visit to slam Denmark , as Trump escalates rhetoric .
https://wapo.st/4c6YkhO
-
 @ 5cf42f9d:4465eebf
2025-04-02 21:32:31
@ 5cf42f9d:4465eebf
2025-04-02 21:32:31 -
 @ a39d19ec:3d88f61e
2025-03-18 17:16:50
@ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe.
Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren:
1. Quantitätstheorie des Geldes
Die klassische Gleichung der Quantitätstheorie des Geldes lautet:
M • V = P • Y
wobei:
- M die Geldmenge ist,
- V die Umlaufgeschwindigkeit des Geldes,
- P das Preisniveau,
- Y die reale Wirtschaftsleistung (BIP).Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen.
2. Gütermenge bleibt begrenzt
Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen.
3. Erwartungseffekte und Spekulation
Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen.
4. Internationale Perspektive
Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt.
5. Kritik an der reinen Geldmengen-Theorie
Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
-
 @ ef53426a:7e988851
2025-04-02 21:02:06
@ ef53426a:7e988851
2025-04-02 21:02:06Bartering and early money
\ Early societies bartered goods, but transactions were often complicated. The value of goods doesn’t always align.
Enter money. It’s used as an indirect exchange for any goods, so everyone wants it.
Early money wasn’t anything like what we use today. For example, the inhabitants of Yap Island (Micronesia) used large Rai stones for trade. New stones were dragged up a hill for everyone to see. The owner would then exchange part of the stone for goods and services.
As they were hard to quarry and move, Rai stones retained their value (salability). Then, an Irish-American captain started importing stones using modern technology. Soon enough, they became so common, they no longer worked as money.
Gold — the basis for sound money
\ Smelting made it possible to create highly salable and transportable coins. Gold was best because it’s virtually impossible to destroy and can’t be synthesized using other materials. It has a fairly limited supply, which grows slowly and predictably (due to the difficulty of mining).
Technologies like the telegraph and trains made it easier for both people and goods to get from point A to point B. That, in turn, justified forms of payment like checks, paper receipts, and bills. But paper is not worth much unless it’s backed by something.
Governments worldwide issued paper money backed by precious metals, which they stored in vaults. By 1900, around 50 countries had adopted the Gold Standard. This was sound money.
Currencies devalued
\ Roman emperor Julius Caesar issued the Aureus, an empire-standard coin containing 8 grams of gold. But as growth began to slow, rulers started ‘coin clipping’, reducing the quantity of precious metal in coins. This eventually triggered a series of economic crises that led to the downfall of the Roman Empire.
The gold standard had one major flaw: it had to be stored in bank vaults. This created a highly centralized system in which governments controlled the value of paper money. If they wanted to, they could always increase the supply of money without increasing the corresponding amount of gold.
In 1914, nearly every major European power decided to do this to fund their war operations. Rather than raising taxes, they simply printed new money with no extra gold. The standard had been abandoned.
Government-backed money
\ Governments chose to introduce fiat money – currency backed by decree rather than gold. The adoption of the fiat system led to an age of unsound money shaped by ever-greater intervention in the economy as governments scrambled to stabilize their currencies.
By 1944, the end of the Second World War was in sight, and the victors began planning the postwar economic order. The world’s currencies would be tied to the US dollar at a fixed exchange rate. The dollar would in turn be tied to the value of gold, again at a fixed rate.
The United States bent the rules and inflated its own currency compared to gold. Other nations inflated their currencies compared to the dollar. On August 15, 1971, President Nixon announced that dollars would no longer be convertible to gold.
Sound money = functioning economy
\ Sound money encourages people to save and invest, enabling sustainable, long-term growth. Why? Well, humans have a natural positive time preference: we prefer instant gratification over future gratification. Sound money prompts us to think more about the future.
The more capital accumulation there is, the greater the chance of stable, long-term economic growth. Unsound money distorts capital accumulation. When governments interfere with the money supply, they also interfere with prices. And prices give investors the information they need to make good decisions without having to learn every tiny detail about global events.
Recessions and debt arise from unsound money
\ Government interference takes the form of central planning. No single person, agency, or department ever has access to all the information necessary to understand the vast and complex economy. Interventions distort markets, creating boom and bust cycles.
According to Keynes and his followers, the best way to respond to recessions is to increase spending. You could lower taxes, but people don’t usually spend their extra money. Raising taxes is unpopular, so governments invariably decide to increase the money supply. Saving becomes less attractive, creating a culture of unwise spending and growing debt.
We need to return to sound money and a new gold standard. Enter bitcoin.
Bitcoin is scarce
\ Bitcoin has similar traits to gold. Its supply is literally fixed. Once there are 21 million bitcoins in circulation, no more will be issued.
The supply grows at a diminishing rate. Computers across the Bitcoin network pool their processing power to solve complex algorithmic problems. Once these puzzles have been cracked, the “miners” receive bitcoins as a reward.
Satoshi Nakamoto designed the system to avoid gold rushes. The algorithmic problems become more difficult to solve as the number of computers working on them rises, guaranteeing a steady and reliable supply. Also, the number of bitcoins issued is halved every four years, resulting in ever-smaller releases until 2140, after which no more coins will be released.
That makes bitcoin unique. It is the only good that is defined by absolute scarcity. No amount of time or resources can create more bitcoins than the programmed supply allows. The supply cannot be manipulated, making it a perfect store of value.
Bitcoin is secure
\ The bitcoin ledger uses the public blockchain. When mining computers crack an algorithmic puzzle, they create a block. The blocks on the ledger contain details about every blockchain transaction ever completed. Every network user can view this information.
Ownership of bitcoins is only valid once it’s been registered on the blockchain. This is only possible if the majority of network users approve it, so there’s no need for a central authority to oversee transactions. While verifying new blocks requires virtually no energy, creating a fraudulent block would cost a significant amount of processing power.
Even if a user decided to expend vast amounts of energy and successfully hacked a majority of all network nodes to approve a fraudulent block, they’d gain very little. Trust in bitcoin would be lost, leading to a drop in demand and value.
Challenges for adoption
\ Because bitcoin is new, demand has varied. The volatile price has, at times, undermined the currency’s status as an effective store of value.
Bitcoin’s transaction limit is currently set at 500,000 per day. That could be increased, but there will always be a daily cap. The more transactions that take place, the more nodes there’ll need to be. This increases transaction fees and the amount of processing power expended.
Bitcoin could be traded off the blockchain, meaning currencies will be backed by bitcoin. That would create a new standard, but it would also mean that new centralized institutions would need to manage this system.

This 5-minute summary did not use copyrighted material from the book. It aims simply to give readers a quick understanding of the book (which is well worth reading).
‘The Bitcoin Standard: The Decentralized Alternative to Central Banking’ was written by economist Saifedean Ammous in 2018.
Buy the book and many more titles at bitcoinbook.shop
-
 @ b9f4c34d:7d1a0e31
2025-04-02 20:21:49
@ b9f4c34d:7d1a0e31
2025-04-02 20:21:49ConfirmingDocumentPaid
-
 @ 3514ac1b:cf164691
2025-03-29 18:55:29
@ 3514ac1b:cf164691
2025-03-29 18:55:29Cryptographic Identity (CI): An Overview
Definition of Cryptographic Identity
Cryptographic identity refers to a digital identity that is secured and verified using cryptographic techniques. It allows individuals to prove their identity online without relying on centralized authorities.
Background of Cryptographic Identity
Historical Context
- Traditional identity systems rely on centralized authorities (governments, companies)
- Digital identities historically tied to platforms and services
- Rise of public-key cryptography enabled self-sovereign identity concepts
- Blockchain and decentralized systems accelerated development
Technical Foundations
- Based on public-key cryptography (asymmetric encryption)
- Uses key pairs: private keys (secret) and public keys (shareable)
- Digital signatures provide authentication and non-repudiation
- Cryptographic proofs verify identity claims without revealing sensitive data
Importance of Cryptographic Identity
Privacy Benefits
- Users control their personal information
- Selective disclosure of identity attributes
- Reduced vulnerability to mass data breaches
- Protection against surveillance and tracking
Security Advantages
- Not dependent on password security
- Resistant to impersonation attacks
- Verifiable without trusted third parties
- Reduces centralized points of failure
Practical Applications
- Censorship-resistant communication
- Self-sovereign finance and transactions
- Decentralized social networking
- Cross-platform reputation systems
- Digital signatures for legal documents
Building Cryptographic Identity with Nostr
Understanding Nostr Protocol
Core Concepts
- Nostr (Notes and Other Stuff Transmitted by Relays)
- Simple, open protocol for censorship-resistant global networks
- Event-based architecture with relays distributing signed messages
- Uses NIP standards (Nostr Implementation Possibilities)
Key Components
- Public/private keypairs as identity foundation
- Relays for message distribution
- Events (signed JSON objects) as the basic unit of data
- Clients that interface with users and relays
Implementation Steps
Step 1: Generate Keypair
- Use cryptographic libraries to generate secure keypair
- Private key must be kept secure (password managers, hardware wallets)
- Public key becomes your identifier on the network
Step 2: Set Up Client
- Choose from existing Nostr clients or build custom implementation
- Connect to multiple relays for redundancy
- Configure identity preferences and metadata
Step 3: Publish Profile Information
- Create and sign kind 0 event with profile metadata
- Include displayable information (name, picture, description)
- Publish to connected relays
Step 4: Verification and Linking
- Cross-verify identity with other platforms (Twitter, GitHub)
- Use NIP-05 identifier for human-readable identity
- Consider NIP-07 for browser extension integration
Advanced Identity Features
Reputation Building
- Consistent posting builds recognition
- Accumulate follows and reactions
- Establish connections with well-known identities
Multi-device Management
- Secure private key backup strategies
- Consider key sharing across devices
- Explore NIP-26 delegated event signing
Recovery Mechanisms
- Implement social recovery options
- Consider multisig approaches
- Document recovery procedures
Challenges and Considerations
Key Management
- Private key loss means identity loss
- Balance security with convenience
- Consider hardware security modules for high-value identities
Adoption Barriers
- Technical complexity for average users
- Network effects and critical mass
- Integration with existing systems
Future Developments
- Zero-knowledge proofs for enhanced privacy
- Standardization efforts across protocols
- Integration with legal identity frameworks
-
 @ 42c85a20:14afbc38
2025-03-29 15:40:00
@ 42c85a20:14afbc38
2025-03-29 15:40:00Back when Twitter was censoring free speech nostr looked like the only alternative where people would migrate and grow the network; however, now that X is open to free thinking, the perfect storm to enable nostr to grow has been quelled.
How will the nostr universe ever expand unless people in the main stream "centralized" social medias see the light? The illusion of free speech on X is dangerous as people blindly give their trust that the rug will not be pulled; and willingly remain under a tyrannical system.
Perhaps there is some other utility which nostr would be useful for vs just another version of twillter; like exit polls for elections which could fail safe the integrity of voting; or community BBS (bulletin boards) where the people can connect with their neighbours without giving up their real address or identity.
When the main stream social medias' fail again; the next time they break the trust of the people, we must be ready to replace them; we must think outside the box now and build those decentralized utilities now.
-
 @ 7d33ba57:1b82db35
2025-04-02 19:47:25
@ 7d33ba57:1b82db35
2025-04-02 19:47:25Trogir is a UNESCO-listed coastal town just 30 minutes from Split, known for its well-preserved medieval architecture, charming waterfront, and rich history. Often called "The Little Venice of Dalmatia," Trogir is built on a small island connected to the mainland and Čiovo Island by bridges. Its cobblestone streets, Renaissance palaces, and lively cafés** make it a perfect stop for history lovers and travelers seeking authentic Dalmatian charm.
🏛️ Top Things to See & Do in Trogir
1️⃣ Explore Trogir Old Town (UNESCO) 🏡
- Wander through the labyrinth of narrow streets, filled with hidden courtyards and stone houses.
- Admire Venetian-style palaces, Romanesque churches, and medieval city walls.
- Visit St. Lawrence Cathedral, featuring the famous Radovan Portal, a masterpiece of medieval stone carving.
2️⃣ Climb the Bell Tower of St. Lawrence ⛪
- Offers stunning panoramic views over Trogir and the Adriatic.
- A bit of a steep climb, but totally worth it for the breathtaking scenery!
3️⃣ Visit Kamerlengo Fortress 🏰
- A 15th-century Venetian fortress with amazing sea views from the top.
- In summer, it hosts concerts and cultural events.
4️⃣ Stroll Along the Trogir Riva Promenade 🌊
- A lively waterfront filled with cafés, restaurants, and luxury yachts.
- Perfect for a relaxing evening walk while watching the sunset.
5️⃣ Relax on the Best Beaches Near Trogir 🏖️
- Okrug Gornji Beach (Copacabana Beach) – A long, lively beach with bars & water activities.
- Pantan Beach – A quieter spot with clear waters and pine tree shade.
- Kava Beach (Čiovo Island) – A more secluded and natural beach, ideal for relaxation.
6️⃣ Take a Boat Trip to the Blue Lagoon 🛥️
- A stunning turquoise bay, perfect for swimming and snorkeling.
- Just a short boat ride from Trogir.
7️⃣ Try Dalmatian Cuisine 🍽️
- Grilled fresh fish & seafood – Trogir’s specialty! 🐟
- Pašticada – Slow-cooked beef in a rich red wine sauce, served with gnocchi.
- Homemade Dalmatian prosciutto & cheese – Best paired with local Plavac Mali wine.
🚗 How to Get to Trogir
✈️ By Air:
- Split Airport (SPU) is just 10 minutes away! 🚕
🚘 By Car:
- From Split: ~30 minutes (27 km)
- From Zadar: ~1.5 hours (130 km)
🚌 By Bus: Frequent buses run between Split and Trogir.
⛵ By Boat: A seasonal boat line connects Trogir with Split and nearby islands.💡 Tips for Visiting Trogir
✅ Best time to visit? April–October for sunny weather & fewer crowds ☀️
✅ Stay for sunset – The views from the Riva & Kamerlengo Fortress are magical 🌅
✅ Wear comfy shoes – The old town’s stone streets can be slippery 👟
✅ Book Blue Lagoon trips in advance – It’s a popular excursion 🚤
✅ Try a wine tasting at a local konoba (traditional tavern) 🍷
-
 @ 5ffb8e1b:255b6735
2025-03-29 13:57:02
@ 5ffb8e1b:255b6735
2025-03-29 13:57:02As a fellow Nostrich you might have noticed some of my #arlist posts. It is my effort to curate artists that are active on Nostr and make it easier for other users to find content that they are interested in.
By now I have posted six or seven posts mentioning close to fifty artists, the problem so far is that it's only a list of handles and it is up to reader to click on each in order to find out what are the artist behind the names all about. Now I am going to start creating blog posts with a few artists mentioned in each, with short descriptions of their work and an image or to.
I would love to have some more automated mode of curation but I still couldn't figure out what is a good way for it. I've looked at Listr, Primal custom feeds and Yakihonne curations but none seem to enable me to make a list of npubs that is then turned into a feed that I could publicly share for others to views. Any advice on how to achieve this is VERY welcome !
And now lets get to the first batch of artists I want to share with you.
Eugene Gorbachenko
nostr:npub1082uhnrnxu7v0gesfl78uzj3r89a8ds2gj3dvuvjnw5qlz4a7udqwrqdnd Artist from Ukrain creating amazing realistic watercolor paintings. He is very active on Nostr but is very unnoticed for some stange reason. Make sure to repost the painting that you liked the most to help other Nostr users to discover his great art.
Siritravelsketch
nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu a a lovely lady from Thailand making architecture from all around the world spring alive in her ink skethes. Dynamic lines gives it a dreamy magical feel, sometimes supported by soft watercolor strokes takes you to a ferytale layer of reality.
BureuGewas
nostr:npub1k78qzy2s9ap4klshnu9tcmmcnr3msvvaeza94epsgptr7jce6p9sa2ggp4 a a master of the clasic oil painting. From traditional still life to modern day subjects his paintings makes you feel the textures and light of the scene more intense then reality itself.
You can see that I'm no art critic, but I am trying my best. If anyone else is interested to join me in this curration adventure feel free to reach out !
With love, Agi Choote
-
 @ 61b9797c:1e3c98a8
2025-04-02 19:03:09
@ 61b9797c:1e3c98a8
2025-04-02 19:03:09MB88 là một nền tảng giải trí trực tuyến nổi bật với những trò chơi phong phú, sáng tạo và đầy tính thử thách. Không giống như các nền tảng thông thường, MB88 mang đến cho người chơi những trải nghiệm đa dạng từ các trò chơi đơn giản, dễ tiếp cận cho đến những trò đòi hỏi tư duy chiến lược và khả năng ra quyết định nhanh chóng. Được thiết kế với giao diện thân thiện và dễ sử dụng, MB88 giúp người chơi nhanh chóng làm quen với nền tảng và bắt đầu tham gia vào các trò chơi yêu thích của mình mà không gặp phải bất kỳ khó khăn nào. Đặc biệt, nền tảng này còn tối ưu hóa trải nghiệm người chơi trên cả các thiết bị di động lẫn máy tính để bàn, mang lại sự linh hoạt và thuận tiện cho người chơi bất kể ở đâu và khi nào. Với đồ họa sắc nét và âm thanh sống động, các trò chơi trên MB88 không chỉ đáp ứng nhu cầu giải trí mà còn tạo ra một môi trường hoàn hảo để người chơi đắm chìm trong những phút giây thư giãn tuyệt vời.
Bên cạnh sự đa dạng về trò chơi, MB88 còn chú trọng đến bảo mật và an toàn của người dùng. Các công nghệ bảo mật tiên tiến nhất đã được áp dụng để đảm bảo rằng mọi giao dịch và thông tin cá nhân của người chơi luôn được bảo vệ một cách tối đa. Mọi hoạt động trên nền tảng đều được mã hóa và giám sát chặt chẽ, nhằm ngăn ngừa mọi hành vi xâm nhập hoặc gian lận. Hệ thống bảo mật của MB88 không chỉ bảo vệ người chơi khỏi các mối đe dọa bên ngoài mà còn giúp duy trì một môi trường chơi game an toàn, đáng tin cậy cho tất cả người tham gia. Điều này giúp MB88 xây dựng được lòng tin vững chắc từ người chơi, cho phép họ yên tâm tận hưởng những trò chơi thú vị mà không phải lo lắng về vấn đề bảo mật thông tin cá nhân hay tài chính.
Một điểm mạnh không thể không nhắc đến của MB88 chính là dịch vụ chăm sóc khách hàng xuất sắc. Được hỗ trợ bởi đội ngũ nhân viên nhiệt tình và chuyên nghiệp, người chơi có thể dễ dàng liên hệ và nhận sự hỗ trợ mọi lúc, mọi nơi. Dịch vụ chăm sóc khách hàng của MB88 không chỉ giải đáp thắc mắc, mà còn hỗ trợ xử lý các vấn đề kỹ thuật và tài chính nhanh chóng và hiệu quả. Với đội ngũ tư vấn viên luôn sẵn sàng 24/7, người chơi có thể yên tâm rằng mọi vấn đề của mình sẽ được giải quyết kịp thời. Các phương thức liên lạc linh hoạt như chat trực tuyến, email và điện thoại giúp người chơi tiếp cận dịch vụ hỗ trợ một cách dễ dàng và thuận tiện. Chính sự tận tâm và chuyên nghiệp của đội ngũ này đã góp phần tạo nên sự khác biệt của MB88, khiến nền tảng này trở thành một trong những sự lựa chọn yêu thích của cộng đồng người chơi.
-
 @ 592295cf:413a0db9
2025-03-29 10:59:52
@ 592295cf:413a0db9
2025-03-29 10:59:52The journey starts from the links in this article nostr-quick-start-guide
Starting from these links building a simple path should not cover everything, because impossible.
Today I saw that Verbiricha in his workshop on his channel used nstart, but then I distracted And I didn't see how he did it.
Go to nstart.me and read: Each user is identified by a cryptographic keypair Public key, Private key (is a lot of stuff)
You can insert a nickname and go, the nickname is not unique
there is a email backup things interesting, but a little boring, i try to generate an email
doesn't even require a strong password ok.
I received the email, great, it shows me the nsec encrypted in clear,
Send a copy of the file with a password, which contains the password encrypted key I know and I know it's a tongue dump.
Multi signer bunker
That's stuff, let's see what he says.
They live the private key and send it to servers and you can recompose it to login at a site of the protocol nostr. If one of these servers goes offline you have the private key that you downloaded first and then reactivate a bunker. All very complicated. But if one of the servers goes offline, how can I remake the split? Maybe he's still testing.
Nobody tells you where these bunkers are.
Okay I have a string that is my bunker (buker://), I downloaded it, easy no, now will tell me which client accepts the bunker.. .
Follow someone before you start?
Is a cluster of 5 people Snowden, Micheal Dilger, jb55, Fiatjaf, Dianele.
I choice Snowden profile, or you can select multiple profiles, extra wild.
Now select 5 clients
Coracle, Chachi, Olas, Nostur, Jumble
The first is Coracle
Login, ok I try to post a note and signing your note the spin does not end.
Maybe the bunker is diffective.
Let's try Chachi
Simpler than Coracle, it has a type login that says bunker. see if I can post
It worked, cool, I managed to post in a group.
Olas is an app but also a website, but on the website requires an extension, which I do not have with this account.
If I download an app how do I pass the bunker on the phone, is it still a password, a qrcode, a qrcode + password, something like that, but many start from the phone so maybe it's easy for them. I try to download it and see if it allows me to connect with a bunker.
Okay I used private-qrcode and it worked, I couldn't do it directly from Olas because it didn't have permissions and the qrcode was < encrypted, so I went to the same site and had the bunker copied and glued on Olas
Ok then I saw that there was the qrcode image of the bunker for apps lol moment
Ok, I liked it, I can say it's a victory.
Looks like none of Snowden's followers are Olas's lover, maybe the smart pack has to predict a photographer or something like that.
Okay I managed to post on Olas, so it works, Expiration time is broken.
As for Nostur, I don't have an ios device so I'm going to another one.
Login with Jumble, it works is a web app
I took almost an hour to do the whole route.
But this was just one link there are two more
Extensions nostr NIP-07
The true path is nip-07-browser-extensions | nostr.net
There are 19 links, maybe there are too many?
I mention the most famous, or active at the moment
- Aka-profiles: Aka-profiles
Alby I don't know if it's a route to recommend
-
Blockcore Blockcore wallet
-
Nos2x Nos2x
-
Nos2xfox (fork for firefox) Nos2xfox
Nostore is (archived, read-only)
Another half hour to search all sites
Nostrapps
Here you can make paths
Then nstart selects Coracle, Chachi, Olas,Nostur and Jumble
Good apps might be Amethyst, 0xchat, Yakihonne, Primal, Damus
for IOS maybe: Primal, Olas, Damus, Nostur, Nos-Social, Nostrmo
On the site there are some categories, I select some with the respective apps
Let's see the categories
Go to Nostrapps and read:
Microbbloging: Primal
Streaming: Zap stream
Blogging: Yakihonne
Group chat: Chachi
Community: Flotilla
Tools: Form *
Discovery: Zapstore (even if it is not in this catrgory)
Direct Message: 0xchat
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 866e0139:6a9334e5
2025-03-29 08:51:57
@ 866e0139:6a9334e5
2025-03-29 08:51:57
Autor: Dr. Daniele Ganser. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Der Frieden ist mir eine Herzensangelegenheit. Daher halte ich seit über 20 Jahren Vorträge zu den Themen Krieg und Frieden. Bisher sind es schon mehr als 1000 Vorträge. Manchmal gibt es Widerstand oder schlechte Presse, aber ich mache einfach weiter. Zudem schreibe ich Bücher, gebe Interviews und habe eine Online-Community, wo ich über Zoom Fragen der Mitglieder beantworte. Mein Ziel ist immer dasselbe: Die Friedensbewegung zu stärken.
https://www.youtube.com/watch?v=4rlSE4CYR_U
Auszug aus der Einleitung "Imperium USA":
"In meiner Forschung orientiere ich mich an folgenden drei Prinzipien: UNO- Gewaltverbot, Achtsamkeit und Menschheitsfamilie. Das UNO-Gewaltverbot wurde 1945 erlassen und verbietet die Androhung oder Anwendung von Gewalt in der internationalen Politik. Es ist leider in Vergessenheit geraten, und viele Menschen haben noch nie davon gehört. Daher erwähne ich es oft in meinen Büchern und Vorträgen, weil es ein ganz wichtiges Instrument der Friedensbewegung ist. Auch das Prinzip Achtsamkeit ist für die Friedensbewegung ein Juwel.
Denn zu oft schon wurden wir Menschen durch Kriegspropaganda getäuscht und verwirrt. Doch das wäre nicht nötig. Wenn wir durch Achtsamkeit lernen, unsere eigenen Gedanken und Gefühle aus einer ruhigen Distanz zu beobachten, stärken wir unsere Klarheit. Wir müssen nicht alles glauben, was uns von den Medien erzählt wird. Durch Achtsamkeit erkennen wir, dass wir nicht unsere Gedanken und Gefühle sind, sondern das klare Bewusstsein, in dem sie aufsteigen und wie Wolken auch wieder vergehen.
Besonders wichtig ist mir auch das Prinzip Menschheitsfamilie. Denn leider ist es in der Geschichte immer wieder vorgekommen, dass wir als Menschheitsfamilie einzelne Mitglieder ausgeschlossen und getötet haben. Wir haben uns entlang von Nationalität, Religion, Hautfarbe, Geschlecht und Einkommen gespalten und abgewertet. Bei der Hexenverfolgung wurden Frauen der »Zauberei« beschuldigt, aus der Menschheitsfamilie ausgeschlossen und verbrannt. Bei den Indianerkriegen wurden Indianer als »Wilde« aus der Menschheitsfamilie ausgeschlossen, vertrieben und getötet. Beim Sklavenhandel wurden Afrikaner als »Tiere« aus der Menschheitsfamilie ausgeschlossen, diffamiert und ausgebeutet. Im Zweiten Weltkrieg wurden Juden als »lebensunwert« aus der Menschheitsfamilie ausgeschlossen und in Konzentrationslagern vergast.
Im Vietnamkrieg wurden Vietnamesen von US-Soldaten als »Termiten« bezeichnet, aus der Menschheitsfamilie ausgeschlossen und mit Napalm bombardiert. Im sogenannten »Krieg gegen den Terror« wurden Afghanen als »Terroristen« bezeichnet, aus der Menschheitsfamilie ausgeschlossen und getötet. Das sich wiederholende Muster ist deutlich: Das Prinzip Menschheitsfamilie wird verletzt, indem eine Gruppe aus der Menschheitsfamilie ausgeschlossen, abgewertet und dann getötet wird. Natürlich sehen wir alleganz unterschiedlich aus. Auch bezüglich Glaube, Nationalität, Ausbildung, Sprache und Einkommen sind wir nicht gleich und werden es nie sein.
Doch das ist noch kein Grund, Gewalt einzusetzen. »Wir haben in der Welt ganz sicher ein Problem mit Feindseligkeiten, die außer Kontrolle geraten. Der Mensch ist geradezu ein Spezialist darin, andere auszugrenzen«, erklärt der holländische Zoologe Frans de Waal. »Der Mensch dämonisiert Menschen anderer Nationalität oder Religion, erzeugt Ängste und Wut. Diese Gruppen nennen wir dann schnell Unmenschen oder Tiere. Schon ist es leicht, die Unmenschen zu eliminieren, weil man kein Mitgefühl mehr mit ihnen haben muss.«
Im April 2004 wurde publik, dass US- Soldaten im irakischen Abu-Ghraib- Gefängnis Iraker gefoltert hatten. Die US- Kriegspropaganda hatte den US- Soldaten eingetrichtert, die Iraker seien schlechte Menschen, dadurch wurden sie aus der Menschheitsfamilie ausgeschlossen. Das hatte konkrete Folgen. Die US- Soldatin Lynndie England führte in Abu-Ghraib einen nackten irakischen Gefangenen an einer Hundeleine durchs Gefängnis. Ein anderer irakischer Gefangener musste mit schwarzer Kapuze auf einer Kiste balancieren, während an seinem Körper Drähte befestigt waren.
Ihm wurde von den US- Soldaten angedroht, dass ihm tödliche Stromschläge zugefügt würden, wenn er von der Kiste fiele. »Für Europa waren die Horrorbilder aus Sex, Folter und Erniedrigung schlichtweg ein Schock«, kommentierte Die Welt. Der Abu- Ghraib- Skandal zeigte drastisch, was passieren kann, wenn die Menschen einer ganzen Nation, in diesem Falle die Iraker, aus der Menschheitsfamilie ausgeschlossen werden.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Man darf angesichts dieser Gewalt und Brutalität nicht zu dem Schluss kommen, dass wir Menschen nicht fähig sind, friedlich zusammenzuleben. Wir können es sehr wohl und tun es jeden Tag, an Millionen verschiedenen Orten. »Lassen sie uns zunächst unsere Haltung gegenüber dem Frieden selbst überprüfen. Zu viele von uns halten ihn für unmöglich", erklärte US-Präsident John F. Kennedy in einer seiner Reden.
»Zu viele von uns halten ihn für nicht zu verwirklichen. Aber das ist ein gefährlicher, defätistischer Glaube. Er führt zu der Schlussfolgerung, dass der Krieg unvermeidlich ist, dass die Menschheit zum Untergang verurteilt ist, dass wir uns in der Gewalt von Kräften befinden, die wir nicht kontrollieren können.«
Doch dies stimmt nicht, das wusste auch Kennedy. »Unsere Probleme sind von Menschen geschaffen, deshalb können sie auch von Menschen gelöst werden. Die Größe, die der menschliche Geist erreichen kann, bestimmt der Mensch selbst.«
Auch außerhalb der USA haben inspirierende Persönlichkeiten die Friedensbewegung geprägt. In Indien hat der Rechtsanwalt und Pazifist Mahatma Gandhi, der für mich ein großes Vorbild ist, immer wieder das Prinzip Menschheitsfamilie betont. »Die ganze Menschheit ist eine Familie«, sagte Gandhi. Er setzte bei seinem Protest stets auf einen gelassenen und freundlichen Ton, frei von Wut und Hass. Trotz ihres brutalen Vorgehens bezeichnete Gandhi weder die indische Polizei noch die indische Regierung oder die britische Kolonialmacht als Feinde. »Ich betrachte niemanden als meinen Feind«, erklärte Gandhi. »Alle sind meine Freunde. Ich möchte aufklären und die Herzen verändern.«
Ich bin fest davon überzeugt, dass die Friedensbewegung im 21. Jahrhundert stärker wird, wenn sie sich an den Prinzipen Menschheitsfamilie, Achtsamkeit und UNO- Gewaltverbot orientiert. Die Spaltung nach Nation, Partei, Religion, Hautfarbe, Geschlecht, Schulabschluss oder Einkommen sollte im 21. Jahrhundert durch die Einsicht ersetzt werden, dass alle Menschen zur Menschheitsfamilie gehören. Sie als Leserin und Leser gehören zur Menschheitsfamilie, egal wo Sie diesen Text lesen und unabhängig davon, was Ihre Geschichte ist. Und ich als Autor gehöreauch zur Menschheitsfamilie, ebenso wie alle Personen, die in der Menschheitsgeschichte auftauchen, Opfer wie Täter. Zusammen sollten wir lernen, uns nicht zu töten, weil alles Leben heilig ist und weil wir auf einer sehr tiefen Ebene alle miteinander verbunden sind."
Dr. Daniele Ganser, geboren 1972, ist Schweizer Historiker und Friedensforscher. Er leitet das unabhängige Swiss Institute for Peace and Energy Research (SIPER) in Münchenstein bei Basel in der Schweiz. Die aktuellen Vorträge von Dr. Daniele Ganser finden Sie hier. Am 12. April halten Daniele Ganser und Dirk Pohlmann bei Basel einen Vortrag über den Fall Herrhausen (nur 200 Tickets). Bestellen können Sie hier.

Das Buch können Sie hier bestellen.

LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ dbbd7125:07ff73f8
2025-03-16 05:57:18
@ dbbd7125:07ff73f8
2025-03-16 05:57:18https://weibo.com/2169989911/5137332916715995
-
 @ 61b9797c:1e3c98a8
2025-04-02 19:02:17
@ 61b9797c:1e3c98a8
2025-04-02 19:02:17Macao99 là một nền tảng giải trí trực tuyến nổi bật, cung cấp cho người chơi một loạt các trò chơi đa dạng, đáp ứng đầy đủ nhu cầu giải trí từ cơ bản đến phức tạp. Với giao diện dễ sử dụng, người chơi có thể dễ dàng tham gia vào các trò chơi yêu thích chỉ với một vài thao tác đơn giản. Sự đa dạng về các thể loại trò chơi là điểm mạnh lớn của Macao99, với những lựa chọn phong phú từ các trò chơi nhẹ nhàng thư giãn đến những thử thách đòi hỏi chiến thuật và tư duy sắc bén. Đồ họa sắc nét và âm thanh sống động trong mỗi trò chơi mang đến một trải nghiệm gần như thực tế, giúp người chơi cảm thấy như đang tham gia vào một thế giới giải trí đầy hứng khởi và thú vị. Macao99 không ngừng cải tiến và làm mới các trò chơi của mình, mang đến cho người dùng những trải nghiệm mới mẻ và hấp dẫn, giữ chân người chơi lâu dài mà không bị nhàm chán.
Ngoài chất lượng trò chơi, Macao99 còn chú trọng đến việc bảo mật thông tin của người chơi. Nền tảng này sử dụng các công nghệ mã hóa tiên tiến để bảo vệ tất cả các giao dịch và dữ liệu cá nhân, giúp người chơi hoàn toàn yên tâm khi tham gia vào các trò chơi. Mỗi giao dịch tài chính, từ việc nạp tiền đến rút tiền, đều được thực hiện trong môi trường an toàn, bảo mật, đảm bảo rằng thông tin của người dùng không bị xâm nhập hay rò rỉ. Đặc biệt, Macao99 luôn theo dõi và nâng cấp hệ thống bảo mật để đối phó với những mối nguy cơ từ các đối tượng xấu bên ngoài, giúp tạo ra một môi trường chơi game an toàn tuyệt đối. Nhờ vào các biện pháp bảo mật mạnh mẽ này, Macao99 đã xây dựng được sự tin tưởng và sự trung thành của cộng đồng người chơi, những người luôn cảm thấy an toàn và tự tin khi tham gia vào nền tảng.
Bên cạnh đó, dịch vụ chăm sóc khách hàng của Macao99 là một điểm mạnh không thể bỏ qua. Với đội ngũ hỗ trợ chuyên nghiệp, nhiệt tình và luôn sẵn sàng phục vụ 24/7, Macao99 đảm bảo rằng mọi vấn đề của người chơi sẽ được giải quyết nhanh chóng và hiệu quả. Dịch vụ chăm sóc khách hàng không chỉ giải đáp các thắc mắc, mà còn hỗ trợ xử lý các vấn đề phát sinh trong quá trình tham gia giải trí, giúp người chơi luôn có trải nghiệm mượt mà và thoải mái. Các kênh hỗ trợ đa dạng như chat trực tuyến, email và điện thoại giúp người chơi dễ dàng tiếp cận dịch vụ hỗ trợ khi cần thiết. Sự tận tâm và chu đáo của đội ngũ này đã góp phần tạo dựng sự tin tưởng từ phía người chơi và giúp Macao99 duy trì được mối quan hệ bền vững với cộng đồng. Với tất cả những yếu tố này, Macao99 đã và đang là một trong những nền tảng giải trí trực tuyến được yêu thích nhất, mang lại cho người chơi những trải nghiệm an toàn, thú vị và đáng tin cậy.
-
 @ 61b9797c:1e3c98a8
2025-04-02 19:00:58
@ 61b9797c:1e3c98a8
2025-04-02 19:00:58Loto188 là một nền tảng giải trí trực tuyến nổi bật, đem đến cho người chơi những trải nghiệm đa dạng và thú vị, không chỉ thông qua các trò chơi hấp dẫn mà còn nhờ vào giao diện dễ sử dụng và tính năng tối ưu cho mọi thiết bị. Người chơi sẽ dễ dàng tiếp cận các trò chơi yêu thích của mình chỉ với vài thao tác đơn giản. Với một loạt các trò chơi từ những lựa chọn đơn giản cho đến những thử thách đòi hỏi chiến thuật, Loto188 phục vụ tất cả mọi sở thích của người chơi. Sự kết hợp giữa đồ họa tinh xảo và âm thanh sống động của nền tảng này khiến cho mỗi trò chơi trở nên sinh động và cuốn hút hơn bao giờ hết. Hơn nữa, Loto188 liên tục cập nhật các trò chơi mới, đáp ứng nhu cầu giải trí đa dạng và không ngừng nâng cao chất lượng sản phẩm của mình, giúp người chơi luôn có những trải nghiệm mới mẻ và thú vị, không bao giờ cảm thấy nhàm chán.
Một trong những yếu tố quan trọng tạo nên sự khác biệt của Loto188 chính là tính bảo mật và an toàn của nền tảng. Loto188 đã áp dụng công nghệ mã hóa tiên tiến để bảo vệ mọi thông tin cá nhân và tài chính của người chơi, giúp họ yên tâm tham gia mà không phải lo lắng về việc bị xâm nhập hay lộ lọt dữ liệu. Tất cả các giao dịch tài chính trên nền tảng này, bao gồm việc nạp tiền và rút tiền, đều được thực hiện trong môi trường bảo mật cao cấp, đảm bảo rằng không có bất kỳ sự can thiệp không mong muốn nào xảy ra. Hệ thống bảo mật của Loto188 được thiết kế để chống lại mọi mối nguy từ các tác nhân xấu bên ngoài, bảo vệ người chơi khỏi những rủi ro tiềm ẩn. Điều này đã giúp Loto188 xây dựng được một cộng đồng người chơi trung thành, những người luôn cảm thấy an tâm khi tham gia vào các hoạt động giải trí trên nền tảng.
Dịch vụ chăm sóc khách hàng của Loto188 cũng là một điểm nổi bật đáng chú ý. Với đội ngũ hỗ trợ chuyên nghiệp và tận tâm, Loto188 luôn sẵn sàng giải đáp mọi thắc mắc và giúp người chơi giải quyết các vấn đề phát sinh một cách nhanh chóng và hiệu quả. Người chơi có thể liên hệ với đội ngũ hỗ trợ qua nhiều phương thức khác nhau, bao gồm chat trực tuyến, email hoặc điện thoại, đảm bảo rằng mọi yêu cầu sẽ được xử lý kịp thời. Sự nhiệt tình và thân thiện của đội ngũ chăm sóc khách hàng chính là yếu tố quan trọng giúp người chơi cảm thấy hài lòng và tin tưởng vào nền tảng này. Từ chất lượng trò chơi, bảo mật cao đến dịch vụ khách hàng xuất sắc, Loto188 không chỉ là một nền tảng giải trí mà còn là một lựa chọn đáng tin cậy cho những ai tìm kiếm một không gian giải trí an toàn, thú vị và đầy ắp những trải nghiệm mới mẻ.
-
 @ dfbbf851:ba4542b5
2025-03-29 06:51:21
@ dfbbf851:ba4542b5
2025-03-29 06:51:21ในยุคดิจิทัลที่การสื่อสารมีบทบาทสำคัญต่อชีวิตประจำวัน เทคโนโลยี Cell Broadcast ได้กลายเป็นหนึ่งในเครื่องมือที่ทรงพลังสำหรับการแจ้งเตือนฉุกเฉิน ไม่ว่าจะเป็นภัยพิบัติหรือเหตุการณ์สำคัญที่ต้องแจ้งให้ประชาชนทราบอย่างทันท่วงที ⏳💡
📌 Cell Broadcast คืออะไร ?
Cell Broadcast (CB) เป็นเทคโนโลยีที่ใช้ส่งข้อความกระจายสัญญาณผ่านเครือข่ายโทรศัพท์มือถือ 🏗📶 โดยแตกต่างจาก SMS ตรงที่สามารถส่งข้อความถึงผู้ใช้จำนวนมากได้พร้อมกัน โดยไม่ต้องทราบหมายเลขโทรศัพท์ ของผู้รับ 📲💨
ข้อความ CB สามารถส่งถึงอุปกรณ์ที่รองรับในเครือข่ายมือถือที่เปิดใช้งานอยู่ภายในช่วงเวลาสั้น ๆ ⏱ และ ไม่ทำให้เครือข่ายล่ม
✨ ข้อดีของ Cell Broadcast ✨
✅ ส่งข้อความรวดเร็ว – แจ้งเตือนได้ภายในไม่กี่วินาที แม้ในกรณีฉุกเฉิน ⚡🚀
✅ ไม่ต้องใช้หมายเลขโทรศัพท์ – กระจายสัญญาณไปยังอุปกรณ์ทุกเครื่องที่อยู่ในพื้นที่เป้าหมายได้โดยตรง 📡
✅ รองรับหลายภาษา – สามารถตั้งค่าการแจ้งเตือนให้เหมาะสมกับประชากรในแต่ละพื้นที่ 🌍🗣
✅ ไม่ทำให้เครือข่ายหนาแน่น – ต่างจาก SMS หรือการโทรจำนวนมากที่อาจทำให้เครือข่ายล่ม 📵❌
✅ ทำงานได้แม้ไม่มีอินเทอร์เน็ต – สามารถแจ้งเตือนในกรณีที่โซเชียลมีเดียหรืออินเทอร์เน็ตใช้งานไม่ได้ 🌐🚫
🌍 การใช้งาน Cell Broadcast ทั่วโลก
🔹 สหรัฐอเมริกา – ใช้ระบบ Wireless Emergency Alerts (WEA) เพื่อแจ้งเตือนเหตุการณ์ฉุกเฉิน เช่น พายุเฮอริเคน 🌀🌪
🔹 ญี่ปุ่น – ใช้ระบบ Earthquake Early Warning (EEW) เพื่อแจ้งเตือนแผ่นดินไหวล่วงหน้า ⛩🌏
🔹 สหภาพยุโรป – มีนโยบายให้ประเทศสมาชิกใช้ Public Warning System ผ่าน Cell Broadcast 📢🏛
🤔 ทำไมประเทศที่ยังไม่มีระบบนี้ควรนำมาใช้ ?
หลายประเทศ รวมถึง ประเทศไทย ยังไม่มีการใช้ Cell Broadcast อย่างแพร่หลาย ทั้งที่เป็นเทคโนโลยีที่สามารถช่วยชีวิตผู้คนได้อย่างมหาศาล 🚑 หากเกิดภัยพิบัติ เช่น น้ำท่วม แผ่นดินไหว สึนามิ หรือไฟป่า 🔥🌊 Cell Broadcast สามารถส่งการแจ้งเตือนไปยังทุกคนในพื้นที่เสี่ยงได้ทันที ลดความสูญเสียและเพิ่มโอกาสรอดชีวิตได้มากขึ้น
🔸 ความแม่นยำสูง – สามารถส่งแจ้งเตือนไปยังพื้นที่ที่ได้รับผลกระทบโดยตรง ทำให้ประชาชนสามารถเตรียมตัวรับมือได้ดีกว่า
🔸 ไม่มีปัญหาความล่าช้า – ต่างจากการแจ้งเตือนผ่าน SMS หรือโซเชียลมีเดียที่อาจล่าช้าหรือไม่ได้รับข้อความเลยหากเครือข่ายล่ม
🔸 เป็นมาตรฐานสากล – หลายประเทศพัฒนาแล้วมีระบบนี้ใช้งานอย่างมีประสิทธิภาพ ประเทศที่ยังไม่มีควรนำมาใช้เพื่อให้สามารถจัดการภัยพิบัติได้อย่างมีประสิทธิภาพ
🔸 ประหยัดต้นทุนในระยะยาว – ลดความเสียหายทางเศรษฐกิจจากภัยพิบัติ เพราะประชาชนได้รับการแจ้งเตือนล่วงหน้า ทำให้สามารถอพยพหรือป้องกันความเสียหายได้
🔮 อนาคตของ Cell Broadcast
ในอนาคต Cell Broadcast อาจถูกนำมาใช้ร่วมกับ ปัญญาประดิษฐ์ (AI) 🤖 และ Internet of Things (IoT) 🌐 เพื่อเพิ่มความแม่นยำและปรับแต่งการแจ้งเตือนได้ดียิ่งขึ้น 🎯💡
📌 ปล.
Cell Broadcast เป็นเทคโนโลยีแจ้งเตือนที่ทรงพลังและมีบทบาทสำคัญในการช่วยชีวิตผู้คน 🚑 ด้วยความสามารถในการส่งข้อความได้อย่างรวดเร็ว ครอบคลุมพื้นที่กว้าง และไม่ต้องพึ่งพาอินเทอร์เน็ต จึงเป็นหนึ่งในเครื่องมือสำคัญสำหรับการบริหารจัดการภัยพิบัติในปัจจุบันและอนาคต 🔥
CellBroadcast #แจ้งเตือนภัย #เทคโนโลยีสื่อสาร #ภัยพิบัติ #เครือข่ายมือถือ #การสื่อสารฉุกเฉิน #เตือนภัยล่วงหน้า
-
 @ dbbd7125:07ff73f8
2025-03-16 05:48:12
@ dbbd7125:07ff73f8
2025-03-16 05:48:12https://weibo.com/5324708177/5144638344398410
-
 @ 2183e947:f497b975
2025-03-29 02:41:34
@ 2183e947:f497b975
2025-03-29 02:41:34Today I was invited to participate in the private beta of a new social media protocol called Pubky, designed by a bitcoin company called Synonym with the goal of being better than existing social media platforms. As a heavy nostr user, I thought I'd write up a comparison.
I can't tell you how to create your own accounts because it was made very clear that only some of the software is currently open source, and how this will all work is still a bit up in the air. The code that is open source can be found here: https://github.com/pubky -- and the most important repo there seems to be this one: https://github.com/pubky/pubky-core
You can also learn more about Pubky here: https://pubky.org/
That said, I used my invite code to create a pubky account and it seemed very similar to onboarding to nostr. I generated a private key, backed up 12 words, and the onboarding website gave me a public key.
Then I logged into a web-based client and it looked a lot like twitter. I saw a feed for posts by other users and saw options to reply to posts and give reactions, which, I saw, included hearts, thumbs up, and other emojis.
Then I investigated a bit deeper to see how much it was like nostr. I opened up my developer console and navigated to my networking tab, where, if this was nostr, I would expect to see queries to relays for posts. Here, though, I saw one query that seemed to be repeated on a loop, which went to a single server and provided it with my pubkey. That single query (well, a series of identical queries to the same server) seemed to return all posts that showed up on my feed. So I infer that the server "knows" what posts to show me (perhaps it has some sort of algorithm, though the marketing material says it does not use algorithms) and the query was on a loop so that if any new posts came in that the server thinks I might want to see, it can add them to my feed.
Then I checked what happens when I create a post. I did so and looked at what happened in my networking tab. If this was nostr, I would expect to see multiple copies of a signed messaged get sent to a bunch of relays. Here, though, I saw one message get sent to the same server that was populating my feed, and that message was not signed, it was a plaintext copy of my message.
I happened to be in a group chat with John Carvalho at the time, who is associated with pubky. I asked him what was going on, and he said that pubky is based around three types of servers: homeservers, DHT servers, and indexer servers. The homeserver is where you create posts and where you query for posts to show on your feed. DHT servers are used for censorship resistance: each user creates an entry on a DHT server saying what homeserver they use, and these entries are signed by their key.
As for indexers, I think those are supposed to speed up the use of the DHT servers. From what I could tell, indexers query DHT servers to find out what homeservers people use. When you query a homeserver for posts, it is supposed to reach out to indexer servers to find out the homeservers of people whose posts the homeserver decided to show you, and then query those homeservers for those posts. I believe they decided not to look up what homeservers people use directly on DHT servers directly because DHT servers are kind of slow, due to having to store and search through all sorts of non-social-media content, whereas indexers only store a simple db that maps each user's pubkey to their homeserver, so they are faster.
Based on all of this info, it seems like, to populate your feed, this is the series of steps:
- you tell your homeserver your pubkey
- it uses some sort of algorithm to decide whose posts to show you
- then looks up the homeservers used by those people on an indexer server
- then it fetches posts from their homeservers
- then your client displays them to you
To create a post, this is the series of steps:
- you tell your homeserver what you want to say to the world
- it stores that message in plaintext and merely asserts that it came from you (it's not signed)
- other people can find out what you said by querying for your posts on your homeserver
Since posts on homeservers are not signed, I asked John what prevents a homeserver from just making up stuff and claiming I said it. He said nothing stops them from doing that, and if you are using a homeserver that starts acting up in that manner, what you should do is start using a new homeserver and update your DHT record to point at your new homeserver instead of the old one. Then, indexers should update their db to show where your new homeserver is, and the homeservers of people who "follow" you should stop pulling content from your old homeserver and start pulling it from your new one. If their homeserver is misbehaving too, I'm not sure what would happen. Maybe it could refuse to show them the content you've posted on your new homeserver, keeping making up fake content on your behalf that you've never posted, and maybe the people you follow would never learn you're being impersonated or have moved to a new homeserver.
John also clarified that there is not currently any tooling for migrating user content from one homeserver to another. If pubky gets popular and a big homeserver starts misbehaving, users will probably need such a tool. But these are early days, so there aren't that many homeservers, and the ones that exist seem to be pretty trusted.
Anyway, those are my initial thoughts on Pubky. Learn more here: https://pubky.org/
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 3e6e0735:9e95c8a2
2025-03-28 23:58:02
@ 3e6e0735:9e95c8a2
2025-03-28 23:58:02https://i.nostr.build/lanoHI3p2aCKRZlV.png
I’ve been thinking a lot lately about why Bitcoin still feels so misunderstood. Not just by the media or the IMF — that part’s predictable. But even inside our own circles, something's missing.
We say it’s money. We say it’s freedom. We say it’s code. And it is. But when you really zoom out, past the price and the politics, it’s something more radical than we usually admit.
Bitcoin is a shift in how power moves. And what we do with that power now actually matters.
The noise outside
Let’s start with the obvious: the media still doesn’t get it. Every other headline is either a death knell or a celebration depending on the price that day. No context. No nuance. No understanding of what we’re building.
You’ve seen the headlines: - “Bitcoin is crashing again.” - “Crypto bros are killing the planet.” - “The IMF warns: Bitcoin adoption is dangerous.”
Yeah? Dangerous to what?
The system they control. The levers they pull. The old game where the house always wins.
That’s why they’re afraid. Not because Bitcoin is volatile, but because it doesn’t ask permission.
This isn’t about panic — it’s about patterns
I’m not saying there’s a conspiracy. But there is inertia. Institutions protect themselves. Systems reinforce themselves. They were never going to roll out the red carpet for an open, borderless network that replaces their function.
So the IMF calls it a threat. Central banks scramble to launch CBDCs. And journalists keep writing the same shallow takes while ignoring the real story.
Meanwhile, we’re still here. Still building. Still holding. Still running nodes.
Bitcoin isn’t perfect. But it’s honest. It doesn’t bend to popularity or political pressure. It enforces rules with math, not people. And that’s exactly why it works.
Even we miss it sometimes
Here’s the part that really hit me recently: even within Bitcoin, we often undersell what this is.
We talk about savings. Inflation. Fiat debasement. All real, all important.
But what about the broader layer? What about governance? Energy? Communication? Defense?
Jason Lowery’s book Softwar lit that fuse for me again. Not because it’s flawless — it’s not. But because he reframed the game.
Bitcoin isn’t a new weapon. It’s the end of weapons-as-power.
Proof-of-work, in Lowery’s view, is a form of peaceful negotiation. A deterrent against coercion. A way to shift from kinetic violence to computational resolution.
Most people — even many Bitcoiners — haven’t fully absorbed that.
It’s not about militarizing the network. It’s about demilitarizing the world through energy expenditure that replaces human conflict.
Let’s be clear: this doesn’t mean Bitcoin will be used this way. It means it can. And that opens up a few possible futures:
- Scenario A: Smaller nations adopt Bitcoin infrastructure as a shield — a deterrent and neutral layer to build sovereignty
- Scenario B: Superpowers attack mining and self-custody, escalating regulatory capture and fragmenting the open protocol into corporate silos
- Scenario C: Bitcoin becomes the boring backend of legacy finance, its edge neutered by ETFs and custody-as-a-service
Which one wins depends on what we build — and who steps up.
Then I found Maya
I came across Maya Parbhoe’s campaign by accident. One of those late-night rabbit holes where Bitcoin Twitter turns into a global map.
She’s running for president of Suriname. She’s a Bitcoiner. And she’s not just tweeting about it — she’s building an entire political platform around it.
No central bank. Bitcoin as legal tender. Full fiscal transparency. Open-source government.
Yeah. You read that right. Not just open-source software — open-source statehood.
Her father was murdered after exposing corruption. That’s not a talking point. That’s real-life consequence. And instead of running away from systems, she’s choosing to redesign one.
That’s maximalism. Not in ideology. In action.
The El Salvador experiment — and evolution
When El Salvador made Bitcoin legal tender in 2021, it lit up our feeds. It was bold. Unprecedented. A true first.
But not without flaws.
The rollout was fast. Chivo wallet was centralized. Adoption stalled in rural areas. Transparency was thin. And despite the brave move, the state’s underlying structure remained top-down.
Bukele played offense, but the protocol was wrapped in traditional power.
Maya is doing it differently. Her approach is grassroots-forward. Open-source by design. Focused on education, transparency, and modular state-building — not just mandates.
She’s not using Bitcoin to prop up state power. She’s using it to distribute it.
Maximalism is evolving
Look, I get it. The memes are fun. The laser eyes. The beefsteak meetups. The HODL culture.
But there’s something else growing here. Something a little quieter, a little deeper: - People running nodes to protect civil liberties - Communities using Lightning for real commerce - Builders forging tools for self-sovereign identity - Leaders like Maya testing what Bitcoin can look like as public infrastructure
This is happening. In real time. It’s messy and fragile and still small. But it’s happening.
Let’s also stay honest:
Maximalism has its risks. Dogma can blind us. Toxicity can push people away. And if we’re not careful, we’ll replace one centralization with another — just wearing different memes.
We need less purity, more principles. Less hype, more clarity. That’s the kind of maximalism Maya embodies.
What now?
Maya doesn’t have a VC fund or an ad agency. She has a message, a mission, and the courage to put Bitcoin on the ballot.
If that resonates, help her. Not just by donating — though here’s the link:
https://geyser.fund/project/maya2025
But by sharing. Writing. Talking. Translating. Connecting.
Bitcoin is still early. But it’s not abstract anymore.
This isn’t just theory.
It’s a protocol, sure. But now, maybe it’s a presidency too.
https://i.nostr.build/0luYy8ojK7gkxsuL.png
-
 @ 0d6c8388:46488a33
2025-03-28 16:24:00
@ 0d6c8388:46488a33
2025-03-28 16:24:00Huge thank you to OpenSats for the grant to work on Hypernote this year! I thought I'd take this opportunity to try and share my thought processes for Hypernote. If this all sounds very dense or irrelevant to you I'm sorry!
===
How can the ideas of "hypermedia" benefit nostr? That's the goal of hypernote. To take the best ideas from "hypertext" and "hypercard" and "hypermedia systems" and apply them to nostr in a specifically nostr-ey way.
1. What do we mean by hypermedia
A hypermedia document embeds the methods of interaction (links, forms, and buttons are the most well-known hypermedia controls) within the document itself. It's including the how with the what.
This is how the old web worked. An HTML page was delivered to the web browser, and it included in it a link or perhaps a form that could be submitted to obtain a new, different HTML page. This is how the whole web worked early on! Forums and GeoCities and eBay and MySpace and Yahoo! and Amazon and Google all emerged inside this paradigm.
A web browser in this paradigm was a "thin" client which rendered the "thick" application defined in the HTML (and, implicitly, was defined by the server that would serve that HTML).
Contrast this with modern app development, where the what is usually delivered in the form of JSON, and then HTML combined with JavaScript (React, Svelte, Angular, Vue, etc.) is devised to render that JSON as a meaningful piece of hypermedia within the actual browser, the how.
The browser remains a "thin" client in this scenario, but now the application is delivered in two stages: a client application of HTML and JavaScript, and then the actual JSON data that will hydrate that "application".
(Aside: it's interesting how much "thicker" the browser has had to become to support this newer paradigm!)
Nostr was obviously built in line with the modern paradigm: nostr "clients" (written in React or Svelte or as mobile apps) define the how of reading and creating nostr events, while nostr events themselves (JSON data) simply describe the what.
And so the goal with Hypernote is to square this circle somehow: nostr currently delivers JSON what, how do we deliver the how with nostr as well. Is that even possible?
2. Hypernote's design assumptions
Hypernote assumes that hypermedia over nostr is a good idea! I'm expecting some joyful renaissance of app expression similar to that of the web once we figure out how to express applications in a truly "nostr" way.
Hypernote was also deeply inspired by HTMX, so it assumes that building web apps in the HTMX style is a good idea. The HTMX insight is that instead of shipping rich scripting along with your app, you could simply make HTML a tiny bit more expressive and get 95% of what most apps need. HTMX's additions to the HTML language are designed to be as minimal and composable as possible, and Hypernote should have the same aims.
Hypernote also assumes that the "design" of nostr will remain fluid and anarchic for years to come. There will be no "canonical" list of "required" NIPs that we'll have "consensus" on in order to build stable UIs on top of. Hypernote will need to be built responsive to nostr's moods and seasons, rather than one holy spec.
Hypernote likes the
nakcommand line tool. Hypernote likes markdown. Hypernote likes Tailwind CSS. Hypernote likes SolidJS. Hypernote likes cold brew coffee. Hypernote is, to be perfectly honest, my aesthetic preferences applied to my perception of an opportunity in the nostr ecosystem.3. "What's a hypernote?"
Great question. I'm still figuring this out. Everything right now is subject to change in order to make sure hypernote serves its intended purpose.
But here's where things currently stand:
A hypernote is a flat list of "Hypernote Elements". A Hypernote Element is composed of:
- CONTENT. Static or dynamic content. (the what)
- LOGIC. Filters and events (the how)
- STYLE. Optional, inline style information specific to this element's content.
In the most basic example of a hypernote story, here's a lone "edit me" in the middle of the canvas:

{ "id": "fb4aaed4-bf95-4353-a5e1-0bb64525c08f", "type": "text", "text": "edit me", "x": 540, "y": 960, "size": "md", "color": "black" }As you can see, it has no logic, but it does have some content (the text "edit me") and style (the position, size, and color).
Here's a "sticker" that displays a note:
{ "id": "2cd1ef51-3356-408d-b10d-2502cbb8014e", "type": "sticker", "stickerType": "note", "filter": { "kinds": [ 1 ], "ids": [ "92de77507a361ab2e20385d98ff00565aaf3f80cf2b6d89c0343e08166fed931" ], "limit": 1 }, "accessors": [ "content", "pubkey", "created_at" ], "x": 540, "y": 960, "associatedData": {} }As you can see, it's kind of a mess! The content and styling and underdeveloped for this "sticker", but at least it demonstrates some "logic": a nostr filter for getting its data.
Here's another sticker, this one displays a form that the user can interact with to SEND a note. Very hyper of us!
{ "id": "42240d75-e998-4067-b8fa-9ee096365663", "type": "sticker", "stickerType": "prompt", "filter": {}, "accessors": [], "x": 540, "y": 960, "associatedData": { "promptText": "What's your favorite color?" }, "methods": { "comment": { "description": "comment", "eventTemplate": { "kind": 1111, "content": "${content}", "tags": [ [ "E", "${eventId}", "", "${pubkey}" ], [ "K", "${eventKind}" ], [ "P", "${pubkey}" ], [ "e", "${eventId}", "", "${pubkey}" ], [ "k", "${eventKind}" ], [ "p", "${pubkey}" ] ] } } } }It's also a mess, but it demos the other part of "logic": methods which produce new events.
This is the total surface of hypernote, ideally! Static or dynamic content, simple inline styles, and logic for fetching and producing events.
I'm calling it "logic" but it's purposfully not a whole scripting language. At most we'll have some sort of
jq-like language for destructing the relevant piece of data we want.My ideal syntax for a hypernote as a developer will look something like
```foo.hypernote Nak-like logic
Markdown-like content
CSS-like styles ```
But with JSON as the compile target, this can just be my own preference, there can be other (likely better!) ways of authoring this content, such as a Hypernote Stories GUI.
The end
I know this is all still vague but I wanted to get some ideas out in the wild so people understand the through line of my different Hypernote experiments. I want to get the right amount of "expressivity" in Hypernote before it gets locked down into one spec. My hunch is it can be VERY expressive while remaining simple and also while not needing a whole scripting language bolted onto it. If I can't pull it off I'll let you know.
-
 @ a012dc82:6458a70d
2025-03-28 16:15:06
@ a012dc82:6458a70d
2025-03-28 16:15:06In an audacious display of confidence, Bitcoin traders have recently committed $20 million to a $200K call option, a move that has reignited discussions about the cryptocurrency's potential and the broader market's appetite for risk. This development is set against a backdrop of increasing activity within the cryptocurrency options market, particularly on platforms like Deribit, where total open interest in Bitcoin options has reached unprecedented levels. This article explores the nuances of this strategic wager, examines the resurgence of investor enthusiasm, and contemplates the future implications for Bitcoin and the cryptocurrency market at large.
Table of Contents
-
A Surge in Market Activity
-
The Bold Bet on Bitcoin's Future
-
Implications of the $200K Call Option
-
Increased Market Volatility
-
Renewed Investor Confidence
-
Speculative Interest and Market Dynamics
-
-
Looking Ahead: Bitcoin's Market Prospects
-
Conclusion
-
FAQs
A Surge in Market Activity
The cryptocurrency options market has experienced a significant uptick in activity, with Bitcoin and Ethereum options achieving record-breaking open interest figures. On Deribit, Bitcoin options open interest has soared to a staggering $20.4 billion, eclipsing the previous high of $14.36 billion seen in October 2021. Concurrently, Ethereum options open interest has also reached a historic peak of $11.66 billion. This pronounced increase in market activity is indicative of a growing interest among traders to either hedge their positions against potential price fluctuations or to speculate on the future price movements of these leading cryptocurrencies. The surge in options trading volume reflects a broader trend of maturation within the cryptocurrency market, as sophisticated financial instruments become increasingly utilized by a diverse array of market participants, from individual investors to large institutional players.
The Bold Bet on Bitcoin's Future
The decision by traders to allocate $20 million to a $200K call option for Bitcoin represents a significant vote of confidence in the cryptocurrency's future price trajectory. This high-stakes gamble suggests that a segment of the market is not only optimistic about Bitcoin's potential to breach the $200,000 threshold but is also willing to back this belief with substantial financial commitment. Such a move is emblematic of the "animal spirits" returning to the cryptocurrency market—a term coined by economist John Maynard Keynes to describe the instinctive human emotion that drives consumer confidence and investment decisions. This resurgence of speculative fervor and risk-taking behavior is a testament to the enduring allure of Bitcoin as an asset class that continues to captivate the imagination of investors, despite its history of volatility and regulatory challenges.
Implications of the $200K Call Option
The substantial investment in the $200K call option carries several implications for the Bitcoin market and the broader cryptocurrency ecosystem:
Increased Market Volatility
The focus on high strike price options could introduce heightened volatility into the Bitcoin market. As traders position themselves to capitalize on potential price movements, the market may witness more pronounced fluctuations. This environment of increased volatility underscores the speculative nature of cryptocurrency trading and the high-risk, high-reward strategies employed by some market participants. It also highlights the need for investors to approach the market with caution, armed with a thorough understanding of the underlying risks and a clear investment strategy.
Renewed Investor Confidence
The bold wager on the $200K call option reflects a significant resurgence in investor confidence in Bitcoin's long-term prospects. Following periods of market downturns and regulatory uncertainty, this move signals a renewed conviction in the fundamental value proposition of Bitcoin as a pioneering digital asset. It represents a collective belief in the cryptocurrency's ability to not only recover from past setbacks but to chart new territories in terms of price and market capitalization. This renewed investor confidence may serve as a catalyst for further investment in Bitcoin and other cryptocurrencies, potentially driving up prices and encouraging more widespread adoption.
Speculative Interest and Market Dynamics
The commitment to the $200K call option highlights the continued influence of speculative interest on the cryptocurrency market's dynamics. It illustrates how speculation, driven by the prospect of outsized returns, remains a central force shaping market trends and price trajectories. This speculative interest, while contributing to market liquidity and price discovery, also introduces an element of unpredictability. It underscores the complex interplay between market sentiment, investor behavior, and external economic factors that collectively determine the direction of the cryptocurrency market.
Looking Ahead: Bitcoin's Market Prospects
The strategic bet on the $200K call option, amidst a backdrop of increasing options market activity, paints a complex picture of Bitcoin's future. While the move signals optimism and a willingness among investors to engage in high-risk speculation, it also raises questions about the sustainability of such bullish sentiment. As Bitcoin continues to navigate the evolving landscape of digital finance, the interplay between speculative interest, regulatory developments, and technological advancements will be critical in shaping its future trajectory. The cryptocurrency market's inherent volatility and unpredictability necessitate a cautious approach from investors, emphasizing the importance of risk management and long-term strategic planning.
Conclusion
Bitcoin's latest foray into high-stakes speculation, marked by the $20 million lock on the $200K call option, is a vivid illustration of the cryptocurrency's enduring appeal and the market's appetite for risk. This development not only reflects a bullish outlook on Bitcoin's price potential but also signals a broader resurgence of investor enthusiasm and speculative activity within the cryptocurrency market. As we look to the future, the outcomes of such bold moves will undoubtedly influence the trajectory of Bitcoin and the digital asset landscape at large. Whether Bitcoin will reach the lofty heights of $200,000 remains to be seen, but its journey there will be closely watched by traders, investors, and regulators alike, offering valuable insights into the dynamics of speculative markets and the evolving role of cryptocurrencies in the global financial ecosystem.
FAQs
What does locking $20 million in a $200K call option mean for Bitcoin? Locking $20 million in a $200K call option indicates that traders are betting a significant amount of money on Bitcoin reaching or surpassing $200,000. It reflects a bullish outlook on Bitcoin's future price and a resurgence of speculative interest in the cryptocurrency market.
How does the surge in Bitcoin options market activity affect the cryptocurrency? The surge in Bitcoin options market activity, with record open interest, increases market liquidity and can lead to heightened volatility. It also signifies growing interest and participation in the cryptocurrency market, potentially influencing Bitcoin's price dynamics.
What are the implications of increased market volatility for Bitcoin investors? Increased market volatility can lead to larger price swings, presenting both opportunities and risks for investors. While it may offer the potential for higher returns, it also increases the risk of losses. Investors should approach the market with caution and consider their risk tolerance and investment strategy.
Why are investors optimistic about Bitcoin reaching $200,000? Investors' optimism about Bitcoin reaching $200,000 stems from factors such as the cryptocurrency's past performance, the upcoming Bitcoin halving event, increasing institutional adoption, and favorable macroeconomic conditions. These factors contribute to a bullish sentiment in the market.
What role do institutional investors play in the current Bitcoin market trend? Institutional investors play a significant role in the current Bitcoin market trend by bringing in substantial capital, lending credibility to the market, and influencing price movements. Their participation is seen as a sign of maturity and stability in the cryptocurrency market.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 66675158:1b644430
2025-03-13 11:20:49
@ 66675158:1b644430
2025-03-13 11:20:49In the twilight of his days, Myrddin sat upon the weathered stone bench overlooking what remained of Libertalia. His ancient hands—once steady enough to craft the most intricate mechanisms known to the Free Realms—now trembled as they rested upon the gnarled walking stick he had carved from windfall oak. The city below, once a marvel of independent districts connected by the invisible threads of mutual cooperation, had become something else entirely. Something monstrous.
The sun was setting, casting long shadows across the Grand Plaza where the Central Authority's banners now flew. Myrddin's eyes, still sharp despite his five hundred and seventy years, could make out the uniformed guards patrolling in perfect synchronicity. The sight made his stomach turn.
"I built the foundations for freedom," he whispered to himself, "and they have erected prisons upon them."
A figure approached from behind, footsteps deliberately heavy to announce their presence. Myrddin did not turn.
"Master Myrddin," came the voice of Thalion, one of his few remaining former apprentices not yet captured by the Authority. "The Council of Remnants awaits your wisdom."
Myrddin scoffed. "Wisdom? What wisdom can I offer now? I who planted the seeds of our destruction through my own shortsightedness?"
"You could not have known—"
"I should have known!" Myrddin's voice cracked with the force of his outburst. "Every great civilization before us fell to the same disease. Centralization. The pooling of power into fewer and fewer hands until the many are crushed beneath the weight of the few. I knew this. I studied the ancient texts. I designed our systems specifically to prevent this very outcome."
Thalion remained silent, allowing the old engineer his moment of self-recrimination.
"Come," Myrddin finally said, rising with difficulty. "Let us not keep your Council waiting. Though what good words can do against the machinery of oppression, I cannot say."
As they walked the hidden path down from the overlook, Myrddin's mind drifted back to the beginning, to the founding of Libertalia four centuries earlier...
The Founding Council had gathered beneath the great oak that would later mark the center of Libertalia. Twelve visionaries from twelve different traditions, united by a single purpose: to create a society where no person would rule over another.
Young Myrddin, barely forty years old but already renowned for his brilliance, unrolled the plans he had spent a decade perfecting.
"The Nexus System," he explained, pointing to the intricate diagrams. "A method of connection that requires no central authority. Each district, each guild, each family unit can connect to the whole while maintaining complete sovereignty over their own affairs."
Lorien the Sage, eldest among them, leaned forward with interest. "You propose that trade, communication, defense—all can function without a ruling body?"
"Not only can they function," Myrddin replied with the confidence of youth, "they will function better. A decentralized system is resilient. Cut one connection, and a hundred others remain. Attack one node, and the system routes around the damage. But most importantly, when power is distributed, corruption finds no fertile ground in which to take root."
"And what prevents a group from seizing control?" asked Marwen the Warrior. "From forcing others to submit to their will?"
Myrddin smiled. "The architecture itself. See here—" he pointed to a complex series of interlocking mechanisms, "—the Consensus Protocol. Any attempt to exert control beyond one's rightful domain triggers automatic resistance from the system. The more one tries to centralize power, the more difficult it becomes."
"You speak of mechanisms as if they have will," Marwen said skeptically.
"Not will, but design," Myrddin corrected. "Like water flowing downhill. I have designed a system where power naturally disperses rather than concentrates."
The Council debated through the night, questioning every aspect of Myrddin's design. By morning, they had agreed to build their new society upon his principles. Libertalia would be a constellation of sovereign individuals and voluntary associations, connected but never controlled.
For three generations, it worked exactly as Myrddin had envisioned. The Free Realms prospered as never before. Innovation flourished in the absence of restrictive oversight. Disputes were resolved through mutual arbitration rather than imposed judgment. The Nexus System facilitated trade and communication while preserving the independence of all participants.
Myrddin, his lifespan extended by the alchemical discoveries his system had made possible, watched with pride as Libertalia became the envy of the known world.
But he had made one critical error.
"You created a system that required vigilance," Thalion said as they descended toward the hidden meeting place. "Perhaps that was the flaw."
"No," Myrddin replied. "The flaw was in believing that making something difficult would make it impossible. I should have made centralization not merely hard, but unachievable by any means."
They reached the abandoned mill that served as the Council's current hiding place. Inside, two dozen faces turned toward them—the last free thinkers in a land that once celebrated independence above all else.
Myrddin took his seat at the rough-hewn table. "Tell me," he said without preamble, "how much worse has it become since we last met?"
A woman named Sera, who had once been the foremost architect in the Eastern District, spoke first. "The Authority has implemented the Unified Identification Protocol. No citizen may trade, travel, or even purchase food without presenting their Authority Crystal for scanning."
"And these crystals track their movements?" Myrddin asked, though he already knew the answer.
"Every step," confirmed Sera. "Every transaction. Every word spoken near an Echo Stone."
Myrddin closed his eyes briefly. Echo Stones—his invention, meant to record important discoveries and preserve the wisdom of the ages. Now perverted into tools of surveillance.
"The schools have been consolidated," added a younger man named Ferris. "All children now learn from the same Authority-approved texts. The history of Libertalia is being rewritten. They claim you designed the Nexus System to eventually unite under central guidance."
"A lie," Myrddin spat.
"But a believable one," Thalion said gently. "You did build the infrastructure that made this possible, however unintentional."
Myrddin could not deny it. The Nexus System, designed for voluntary connection, had been gradually modified over the centuries. What began as simple efficiency improvements eventually created vulnerabilities. The Consensus Protocol, once the guardian of decentralization, had been subverted by those who understood its mechanics but not its purpose.
"The disease always begins the same way," Myrddin said, addressing the Council. "With promises of efficiency. Of security. Of protection from unseen threats. The centralizers never announce their true intentions. They speak of unity while forging chains."
"We know this, Master Myrddin," said Sera impatiently. "What we need is a solution, not a history lesson."
Myrddin smiled sadly. "The history is the solution, if only we would heed it. Every great civilization before us fell to centralization. The Aurelian Empire, whose emperors claimed divine right to rule all lands beneath the twin moons. The Dynasty of Eternal Harmony, whose bureaucracy grew so vast it consumed half the realm's production. The Jade Confederation, whose Council of Nine became a single Overlord within three generations."
He paused, gathering his thoughts.
"In every case, the pattern was identical. Power, once distributed among many, gradually accumulated in the hands of few. Those few, corrupted by their unnatural position, made decisions that benefited themselves rather than the whole. Resources were misallocated. Innovation stagnated. The system became brittle rather than resilient. And when crisis came—whether famine, war, or natural disaster—the centralized structure collapsed under its own weight."
"Yet people never learn," said Ferris bitterly.
"Because the benefits of centralization are immediate and visible, while its costs are delayed and diffuse," Myrddin replied. "The Authority provides convenience today at the cost of freedom tomorrow. They offer solutions to problems that would resolve themselves naturally in a decentralized system."
"What was your mistake, then?" asked Thalion. "Where in your design did you leave the opening for this disease to take hold?"
Myrddin's face darkened with regret. "I built a system that was resistant to centralization, but not immune to it. I created tools of such power and efficiency that they became irresistible targets for those who would control others. And most critically, I failed to encode the philosophical foundations of decentralization into the system itself."
He looked around at the faces of the Council, seeing in them the last embers of the fire that had once burned so brightly in Libertalia.
"I believed that people would choose freedom if given the option. I did not account for how seductive the promises of centralization would be. How easily people would trade liberty for convenience. How willingly they would accept security over sovereignty."
The decline had been gradual, almost imperceptible at first. It began two centuries after the founding, with the creation of the Coordination Council.
"Merely to improve efficiency," its proponents had argued. "To eliminate redundancies in our wonderfully decentralized system."
Myrddin, by then well into his second century, had voiced concerns but was overruled by younger generations who found the original Nexus System too cumbersome for their modern needs. The Coordination Council was given limited authority to standardize certain protocols across districts.
Within a decade, those standards became requirements. Requirements became regulations. Regulations became laws. The Council, originally composed of representatives who returned to their districts after brief terms of service, gradually transformed into a permanent body of administrators.
By the time Myrddin recognized the pattern, the disease had already taken root. The Coordination Council had become the Central Authority. The voluntary associations that once formed the backbone of Libertalian society were now subordinate to its dictates.
He had tried to warn them. He had written treatises on the dangers of centralization, had spoken at public forums, had even attempted to modify the Nexus System to restore its decentralizing functions. But he was dismissed as an outdated thinker, unable to appreciate the "improvements" of modern governance.
Now, four hundred years after the founding, Libertalia was Libertalia in name only. The Authority controlled all aspects of life. The districts, once proudly independent, were administrative zones whose boundaries could be redrawn at the Authority's whim. The guilds, once self-governing bodies of skilled craftspeople, were now licensing bureaus that enforced Authority standards.
And the people—the free, sovereign individuals for whom Myrddin had designed his system—had become subjects. Citizens, they were called, but the word had lost its original meaning of self-governance and had come to signify merely a registered and tracked unit of the Authority.
"We cannot defeat the Authority directly," Myrddin told the Council of Remnants. "They control too much. The military, the food supply, the Nexus itself. Any direct confrontation would be suicidal."
"Then what hope remains?" asked Sera.
"We must build anew," Myrddin said, his voice finding strength in purpose. "Not reform, but replace. The old system cannot be saved—it is too thoroughly corrupted. We must create a parallel system that makes centralization not merely difficult, but impossible by its very nature."
"How?" several voices asked at once.
Myrddin reached into his worn leather satchel and withdrew a small crystal, unlike the Authority Crystals in both color and cut. "I have spent the last fifty years designing what should have been built from the beginning. A truly decentralized system that cannot be subverted because its very operation depends on remaining distributed."
He placed the crystal in the center of the table. It pulsed with a soft blue light.
"The Arx," he explained. "Each crystal contains the complete system, yet functions as only one node within it. No node can control another. No group of nodes can outvote or overpower the minority. Consensus is achieved not through majority rule, but through voluntary participation."
Thalion picked up the crystal, examining it skeptically. "The Authority will never allow this."
"They need not allow what they cannot detect," Myrddin replied. "The Arx operates on principles the Authority's systems cannot recognize. It exists alongside their network but remains invisible to it."
"And what can this network do?" asked Ferris. "How does it help us against the might of the Authority?"
"It allows us to trade without their knowledge. To communicate without their oversight. To organize without their permission. And most importantly, to remember who we truly are—sovereign individuals who require no masters."
Myrddin stood, his ancient frame seeming to straighten with the weight of his purpose.
"Centralization is not merely inefficient or unjust—it is a disease that infects and ultimately kills any society it touches. It promises order but delivers stagnation. It promises security but creates vulnerability. It promises prosperity but ensures that wealth flows only to those who control the center."
He looked each Council member in the eye.
"I made a mistake in believing that making centralization difficult would be enough. This time, we will make it impossible. The Arx cannot be centralized because its very operation depends on distribution. Any attempt to control it causes it to fragment and reform beyond the controller's reach."
"And if the Authority discovers these crystals?" Sera asked.
"They can destroy individual crystals, but the network will continue. They can imprison those who carry them, but more will take their place. The design is now the important thing, not the designer. I have encoded the knowledge of how to create these crystals within the crystals themselves. The idea cannot be killed."
Myrddin sat back down, suddenly looking every one of his many years.
"I cannot undo the damage my oversight has caused. I cannot restore the Libertalia I helped to build. But I can give you the tools to create something better—something truly resistant to the disease of centralization."
The Council members looked at one another, hope kindling in eyes that had known only despair for too long.
"How do we begin?" Thalion asked.
Myrddin smiled. "We begin by remembering what we have forgotten. That no person has the right to rule another. That voluntary cooperation always outperforms forced compliance. That systems must serve individuals, not the reverse. That decentralization is not merely a technical architecture but a moral imperative."
He gestured to the crystal, still glowing in Thalion's palm.
"And we begin by building connections that cannot be controlled. Person to person. District to district. Free association by free association. The Authority believes itself invincible because it sits at the center of all things. But when there is no center, there is nothing to seize, nothing to corrupt, nothing to control."
As night fell over Libertalia, the Council of Remnants listened as the ancient engineer outlined his vision for a truly decentralized future. Outside, the Authority's patrols marched in perfect order, their uniformity a testament to the disease that had consumed what was once the freest society in the known world.
Myrddin knew he would not live to see his new design reach fruition. But for the first time in decades, he felt something like peace. He had identified his error. He had created a solution. And most importantly, he had ensured that the knowledge would outlive him.
Centralization was indeed a disease—perhaps the most persistent and destructive disease ever to afflict human societies. But like all diseases, it could be overcome with the right medicine. And the medicine was not more centralization, not better rulers, not wiser authorities.
The medicine was decentralization. Complete, uncompromising, and irreversible decentralization.
As the meeting concluded and the Council members departed with their crystals, Myrddin remained seated at the table. Thalion lingered behind.
"You know they will come for you eventually," his former apprentice said. "You are too significant a symbol to ignore forever."
Myrddin nodded. "Let them come. An old man is a small price to pay for the rebirth of freedom."
"Your new system," Thalion said hesitantly, "you are certain it cannot be centralized? That we are not simply repeating the cycle?"
"Nothing created by human hands can be perfect," Myrddin admitted. "But I have learned from my mistake. The Arx does not merely resist centralization—it actively works against it. The more one tries to control it, the more it disperses. It is not merely a technical solution but a philosophical one."
He placed a hand on Thalion's shoulder. "Remember always: centralization benefits only those at the center. For everyone else—the 99.999% who stand at the periphery—it is nothing but chains disguised as safety. Never again can we allow the disease to take root by promising efficiency at the cost of sovereignty."
Thalion nodded solemnly. "I will remember."
As his former apprentice departed, Myrddin turned to look out the small window at the city below. The Authority's lights blazed from the central towers, pushing back the natural darkness of night. So much power, concentrated in so few hands. So much potential, wasted in the service of control rather than creation.
He had lived long enough to see his greatest work corrupted. With what time remained to him, he would ensure that his final creation could not suffer the same fate. The Arx would spread, node by node, person by person, until the very concept of centralized authority became as obsolete as the diseases his earlier inventions had eradicated.
Myrddin Myrddin, Master Engineer of the Free Realms, closed his eyes and allowed himself, just for a moment, to imagine a world reborn in true freedom. A world where the disease of centralization had finally been cured.
It would not happen in his lifetime. Perhaps not even in Thalion's. But it would happen. Of that, he was certain.
For the truth that the Authority and all centralizers before them had never understood was simple: humans were not meant to be controlled. They were meant to be free. And in the end, that natural state would reassert itself, no matter how elaborate the systems of control became.
Centralization was a disease. And like all diseases, it would eventually meet a cure.
-
 @ 2b24a1fa:17750f64
2025-03-28 10:07:04
@ 2b24a1fa:17750f64
2025-03-28 10:07:04Der Deutsche Bundestag wurde neu gewählt. Für einige Abgeordnete und Regierungsmitglieder heißt es Time to Say Goodbye. Abschied ist ein scharfes Schwert.
https://soundcloud.com/radiomuenchen/nachruf-2-olaf-der-zeitenwender
Auch bei Radio München werden Trennungs- und Verlassenheitsgefühle getriggert. Umso mehr, wenn es sich nicht nur um duselige Allerweltsliebe handelt, sondern um den Abgang großer Helden. Sie bezahlten ihren todesmutigen und fast ehrenamtlichen Einsatz nicht mit dem Leben, jedoch mit der einen oder anderen Falte in Hemd oder Bluse, manchmal sogar im Gesicht. Was bleibt? Eine bescheidene Pension? Ein lausig bezahlter Manager-Job in einem Konzern? Wir wollen jedenfalls nicht, dass diese Volkshelden vom Zahn der Zeit abgenagt, vergessen werden und setzen ihnen deshalb ein bescheidenes akustisches, aber nachhaltiges Denkmal. Hören Sie die kleine satirische Reihe „Nachrufe“ von unserem Autor Jonny Rieder.\ Folge 2: Olaf der Zeitenwender
Sprecher: Karsten Troyke
Bild: Markus Mitterer für Radio München
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS
-
 @ 2b24a1fa:17750f64
2025-03-28 10:03:58
@ 2b24a1fa:17750f64
2025-03-28 10:03:58Zwischen Überzeugungsarbeit und Propaganda verläuft ein schmaler Grad. Aber so oder so: Wer die subtileren Werkzeuge hat und vor allem die Mittel um Menschen zu kaufen, die diese dann anwenden, hat eindeutig die besseren Karten.
Dass die Bevölkerung nun wissen will, mit welchen Mitteln sie auf welche Weise beeinflusst werden soll, ist selbstverständlich. Wie nuanciert diese Beeinflussung stattfinden kann, darauf haben uns unsere Hörer beim letzten Beitrag von Milosz Matuschek: „Die ersten Köpfe rollen“ gestoßen. Es ging um die staatliche amerikanische Behörde für internationale Entwicklungshilfe USAID. Matuschek schrieb: „Man liest was von AID im Namen und denkt, was man denken soll: klingt nach Bob Geldof, barmherzigen Schwestern und “Brot für die Welt”.“ Man hatte das nicht nur optisch wahrgenommen, nein, diese Behörde wurde hierzulande, in allen Medien US AID genannt, was unsere Sprecherin Sabrina Khalil übernahm. Dass die United States Agency for International Development in USA so nicht gesprochen wird, schrieben uns gleich mehrere aufmerksame Hörer. Es ist sicherlich keine Paranoia darüber nachzudenken, ob die Bedeutung unserer Sprache, unserer Wörter bis hin zur Aussprache im Fokus der Manipulation steht. Dafür wird sehr viel Geld locker gemacht und unter anderem in die Medien gepumpt.
Hören Sie heute den zweiten Teil der Reihe „Die Corona-Connection“ mit dem Titel: „Der mediale Deep State wankt“. Sprecherin: Sabrina Khalil.
Das freie Medienprojekt Pareto kann übrigens Unterstützung gebrauchen, dafür wurde ein Crowdfunding auf Geyser gestartet, wo man mit Bitcoin/Lightning-Spenden helfen kann. Und für Spenden auf dem klassischen Weg finden Sie die entsprechende Bankverbindung auf der Homepage pareto.space/de.
Nachzulesen unter: www.freischwebende-intelligenz.org/p/unter…mediale
Foto: Gleichschaltung - sie melden exakt den gleichen Wortlaut.
-
 @ 17538dc2:71ed77c4
2025-04-02 16:04:59
@ 17538dc2:71ed77c4
2025-04-02 16:04:59The MacOS security update summary is a reminder that laptops and desktops are incredibly compromised.
macOS Sequoia 15.4
Released March 31, 2025
Accessibility Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24202: Zhongcheng Li from IES Red Team of ByteDance
AccountPolicy Available for: macOS Sequoia
Impact: A malicious app may be able to gain root privileges
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24234: an anonymous researcher
AirDrop Available for: macOS Sequoia
Impact: An app may be able to read arbitrary file metadata
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24097: Ron Masas of BREAKPOINT.SH
App Store Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24276: an anonymous researcher
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24272: Mickey Jin (@patch1t)
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A downgrade issue was addressed with additional code-signing restrictions.
CVE-2025-24239: Wojciech Regula of SecuRing (wojciechregula.blog)
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: A malicious app may be able to read or write to protected files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24233: Claudio Bozzato and Francesco Benvenuto of Cisco Talos.
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A privacy issue was addressed by removing the vulnerable code.
CVE-2025-30443: Bohdan Stasiuk (@bohdan_stasiuk)
Audio Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24244: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Audio Available for: macOS Sequoia
Impact: Processing a maliciously crafted file may lead to arbitrary code execution
Description: The issue was addressed with improved memory handling.
CVE-2025-24243: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Authentication Services Available for: macOS Sequoia
Impact: Password autofill may fill in passwords after failing authentication
Description: This issue was addressed through improved state management.
CVE-2025-30430: Dominik Rath
Authentication Services Available for: macOS Sequoia
Impact: A malicious website may be able to claim WebAuthn credentials from another website that shares a registrable suffix
Description: The issue was addressed with improved input validation.
CVE-2025-24180: Martin Kreichgauer of Google Chrome
Authentication Services Available for: macOS Sequoia
Impact: A malicious app may be able to access a user's saved passwords
Description: This issue was addressed by adding a delay between verification code attempts.
CVE-2025-24245: Ian Mckay (@iann0036)
Automator Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed by removing vulnerable code and adding additional checks.
CVE-2025-30460: an anonymous researcher
BiometricKit Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24237: Yutong Xiu
Calendar Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A path handling issue was addressed with improved validation.
CVE-2025-30429: Denis Tokarev (@illusionofcha0s)
Calendar Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with improved checks.
CVE-2025-24212: Denis Tokarev (@illusionofcha0s)
CloudKit Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-24215: Kirin (@Pwnrin)
CoreAudio Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: The issue was addressed with improved checks.
CVE-2025-24163: Google Threat Analysis Group
CoreAudio Available for: macOS Sequoia
Impact: Playing a malicious audio file may lead to an unexpected app termination
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24230: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: This issue was addressed with improved memory handling.
CVE-2025-24211: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24236: Csaba Fitzl (@theevilbit) and Nolan Astrein of Kandji
CoreMedia Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24190: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Playback Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: A path handling issue was addressed with improved validation.
CVE-2025-30454: pattern-f (@pattern_F_)
CoreServices Description: This issue was addressed through improved state management.
CVE-2025-31191: Jonathan Bar Or (@yo_yo_yo_jbo) of Microsoft, and an anonymous researcher Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
CoreText Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24182: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Crash Reporter Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-24277: Csaba Fitzl (@theevilbit) of Kandji and Gergely Kalman (@gergely_kalman), and an anonymous researcher
curl Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-9681
Disk Images Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A file access issue was addressed with improved input validation.
CVE-2025-24255: an anonymous researcher
DiskArbitration Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-30456: Gergely Kalman (@gergely_kalman)
DiskArbitration Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24267: an anonymous researcher
Dock Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-30455: Mickey Jin (@patch1t), and an anonymous researcher
Dock Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-31187: Rodolphe BRUNETTI (@eisw0lf) of Lupus Nova
dyld Available for: macOS Sequoia
Impact: Apps that appear to use App Sandbox may be able to launch without restrictions
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-30462: Pietro Francesco Tirenna, Davide Silvetti, Abdel Adim Oisfi of Shielder (shielder.com)
FaceTime Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30451: Kirin (@Pwnrin) and luckyu (@uuulucky)
FeedbackLogger Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved data protection.
CVE-2025-24281: Rodolphe BRUNETTI (@eisw0lf)
Focus Available for: macOS Sequoia
Impact: An attacker with physical access to a locked device may be able to view sensitive user information
Description: The issue was addressed with improved checks.
CVE-2025-30439: Andr.Ess
Focus Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24283: Kirin (@Pwnrin)
Foundation Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: An access issue was addressed with additional sandbox restrictions on the system pasteboards.
CVE-2025-30461: an anonymous researcher
Foundation Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was resolved by sanitizing logging
CVE-2025-30447: LFY@secsys from Fudan University
Foundation Available for: macOS Sequoia
Impact: An app may be able to cause a denial-of-service
Description: An uncontrolled format string issue was addressed with improved input validation.
CVE-2025-24199: Manuel Fernandez (Stackhopper Security)
GPU Drivers Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: An out-of-bounds write issue was addressed with improved bounds checking.
CVE-2025-30464: ABC Research s.r.o.
CVE-2025-24273: Wang Yu of Cyberserval
GPU Drivers Available for: macOS Sequoia
Impact: An app may be able to disclose kernel memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-24256: Anonymous working with Trend Micro Zero Day Initiative, Murray Mike
Handoff Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-30463: mzzzz__
ImageIO Available for: macOS Sequoia
Impact: Parsing an image may lead to disclosure of user information
Description: A logic error was addressed with improved error handling.
CVE-2025-24210: Anonymous working with Trend Micro Zero Day Initiative
Installer Available for: macOS Sequoia
Impact: An app may be able to check the existence of an arbitrary path on the file system
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24249: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Installer Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data
Description: A logic issue was addressed with improved checks.
CVE-2025-24229: an anonymous researcher
IOGPUFamily Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or write kernel memory
Description: An out-of-bounds write issue was addressed with improved input validation.
CVE-2025-24257: Wang Yu of Cyberserval
IOMobileFrameBuffer Available for: macOS Sequoia
Impact: An app may be able to corrupt coprocessor memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-30437: Ye Zhang (@VAR10CK) of Baidu Security
Kerberos Helper Available for: macOS Sequoia
Impact: A remote attacker may be able to cause unexpected app termination or heap corruption
Description: A memory initialization issue was addressed with improved memory handling.
CVE-2025-24235: Dave G.
Kernel Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: The issue was addressed with improved checks.
CVE-2025-24204: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
Kernel Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24203: Ian Beer of Google Project Zero
Kernel Available for: macOS Sequoia
Impact: An attacker with user privileges may be able to read kernel memory
Description: A type confusion issue was addressed with improved memory handling.
CVE-2025-24196: Joseph Ravichandran (@0xjprx) of MIT CSAIL
LaunchServices Available for: macOS Sequoia
Impact: A malicious JAR file may bypass Gatekeeper checks
Description: This issue was addressed with improved handling of executable types.
CVE-2025-24148: Kenneth Chew
libarchive Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-48958
Libinfo Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: An integer overflow was addressed with improved input validation.
CVE-2025-24195: Paweł Płatek (Trail of Bits)
libnetcore Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may result in the disclosure of process memory
Description: A logic issue was addressed with improved checks.
CVE-2025-24194: an anonymous researcher
libxml2 Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2025-27113
CVE-2024-56171
libxpc Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed through improved state management.
CVE-2025-24178: an anonymous researcher
libxpc Available for: macOS Sequoia
Impact: An app may be able to delete files for which it does not have permission
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-31182: Alex Radocea and Dave G. of Supernetworks, 风沐云烟(@binary_fmyy) and Minghao Lin(@Y1nKoc)
libxpc Available for: macOS Sequoia
Impact: An app may be able to gain elevated privileges
Description: A logic issue was addressed with improved checks.
CVE-2025-24238: an anonymous researcher
Mail Available for: macOS Sequoia
Impact: "Block All Remote Content" may not apply for all mail previews
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24172: an anonymous researcher
manpages Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30450: Pwn2car
Maps Available for: macOS Sequoia
Impact: An app may be able to read sensitive location information
Description: A path handling issue was addressed with improved logic.
CVE-2025-30470: LFY@secsys from Fudan University
NetworkExtension Available for: macOS Sequoia
Impact: An app may be able to enumerate a user's installed apps
Description: This issue was addressed with additional entitlement checks.
CVE-2025-30426: Jimmy
Notes Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24262: LFY@secsys from Fudan University
NSDocument Available for: macOS Sequoia
Impact: A malicious app may be able to access arbitrary files
Description: This issue was addressed through improved state management.
CVE-2025-24232: an anonymous researcher
OpenSSH Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An injection issue was addressed with improved validation.
CVE-2025-24246: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24261: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A logic issue was addressed with improved checks.
CVE-2025-24164: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: A malicious app with root privileges may be able to modify the contents of system files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30446: Pedro Tôrres (@t0rr3sp3dr0)
Parental Controls Available for: macOS Sequoia
Impact: An app may be able to retrieve Safari bookmarks without an entitlement check
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24259: Noah Gregory (wts.dev)
Photos Storage Available for: macOS Sequoia
Impact: Deleting a conversation in Messages may expose user contact information in system logging
Description: A logging issue was addressed with improved data redaction.
CVE-2025-30424: an anonymous researcher
Power Services Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24173: Mickey Jin (@patch1t)
Python Available for: macOS Sequoia
Impact: A remote attacker may be able to bypass sender policy checks and deliver malicious content via email
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2023-27043
RPAC Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved validation of environment variables.
CVE-2025-24191: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Safari Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to user interface spoofing
Description: The issue was addressed with improved UI.
CVE-2025-24113: @RenwaX23
Safari Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to address bar spoofing
Description: The issue was addressed with improved checks.
CVE-2025-30467: @RenwaX23
Safari Available for: macOS Sequoia
Impact: A website may be able to access sensor information without user consent
Description: The issue was addressed with improved checks.
CVE-2025-31192: Jaydev Ahire
Safari Available for: macOS Sequoia
Impact: A download's origin may be incorrectly associated
Description: This issue was addressed through improved state management.
CVE-2025-24167: Syarif Muhammad Sajjad
Sandbox Available for: macOS Sequoia
Impact: An app may be able to access removable volumes without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24093: Yiğit Can YILMAZ (@yilmazcanyigit)
Sandbox Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: The issue was addressed with improved checks.
CVE-2025-30452: an anonymous researcher
Sandbox Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24181: Arsenii Kostromin (0x3c3e)
SceneKit Available for: macOS Sequoia
Impact: An app may be able to read files outside of its sandbox
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30458: Mickey Jin (@patch1t)
Security Available for: macOS Sequoia
Impact: A remote user may be able to cause a denial-of-service
Description: A validation issue was addressed with improved logic.
CVE-2025-30471: Bing Shi, Wenchao Li, Xiaolong Bai of Alibaba Group, Luyi Xing of Indiana University Bloomington
Security Available for: macOS Sequoia
Impact: A malicious app acting as a HTTPS proxy could get access to sensitive user data
Description: This issue was addressed with improved access restrictions.
CVE-2025-24250: Wojciech Regula of SecuRing (wojciechregula.blog)
Share Sheet Available for: macOS Sequoia
Impact: A malicious app may be able to dismiss the system notification on the Lock Screen that a recording was started
Description: This issue was addressed with improved access restrictions.
CVE-2025-30438: Halle Winkler, Politepix theoffcuts.org
Shortcuts Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: A permissions issue was addressed with improved validation.
CVE-2025-30465: an anonymous researcher
Shortcuts Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24280: Kirin (@Pwnrin)
Shortcuts Available for: macOS Sequoia
Impact: A Shortcut may run with admin privileges without authentication
Description: An authentication issue was addressed with improved state management.
CVE-2025-31194: Dolf Hoegaerts
Shortcuts Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: This issue was addressed with improved access restrictions.
CVE-2025-30433: Andrew James Gonzalez
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-31183: Kirin (@Pwnrin), Bohdan Stasiuk (@bohdan_stasiuk)
Siri Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30435: K宝 (@Pwnrin) and luckyu (@uuulucky)
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-24217: Kirin (@Pwnrin)
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A privacy issue was addressed by not logging contents of text fields.
CVE-2025-24214: Kirin (@Pwnrin)
Siri Available for: macOS Sequoia
Impact: An app may be able to enumerate devices that have signed into the user's Apple Account
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24248: Minghao Lin (@Y1nKoc) and Tong Liu@Lyutoon_ and 风(binary_fmyy) and F00L
Siri Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An authorization issue was addressed with improved state management.
CVE-2025-24205: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Siri Available for: macOS Sequoia
Impact: An attacker with physical access may be able to use Siri to access sensitive user data
Description: This issue was addressed by restricting options offered on a locked device.
CVE-2025-24198: Richard Hyunho Im (@richeeta) with routezero.security
SMB Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: The issue was addressed with improved memory handling.
CVE-2025-24269: Alex Radocea of Supernetworks
SMB Available for: macOS Sequoia
Impact: Mounting a maliciously crafted SMB network share may lead to system termination
Description: A race condition was addressed with improved locking.
CVE-2025-30444: Dave G.
SMB Available for: macOS Sequoia
Impact: An app may be able to execute arbitrary code with kernel privileges
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24228: Joseph Ravichandran (@0xjprx) of MIT CSAIL
smbx Available for: macOS Sequoia
Impact: An attacker in a privileged position may be able to perform a denial-of-service
Description: The issue was addressed with improved memory handling.
CVE-2025-24260: zbleet of QI-ANXIN TianGong Team
Software Update Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-24282: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Software Update Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24254: Arsenii Kostromin (0x3c3e)
Software Update Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24231: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
StickerKit Available for: macOS Sequoia
Impact: An app may be able to observe unprotected user data
Description: A privacy issue was addressed by moving sensitive data to a protected location.
CVE-2025-24263: Cristian Dinca of "Tudor Vianu" National High School of Computer Science, Romania
Storage Management Available for: macOS Sequoia
Impact: An app may be able to enable iCloud storage features without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24207: YingQi Shi (@Mas0nShi) of DBAppSecurity's WeBin lab, 风沐云烟 (binary_fmyy) and Minghao Lin (@Y1nKoc)
StorageKit Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30449: Arsenii Kostromin (0x3c3e), and an anonymous researcher
StorageKit Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24253: Mickey Jin (@patch1t), Csaba Fitzl (@theevilbit) of Kandji
StorageKit Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A race condition was addressed with additional validation.
CVE-2025-24240: Mickey Jin (@patch1t)
StorageKit Available for: macOS Sequoia
Impact: An app may be able to bypass Privacy preferences
Description: A race condition was addressed with additional validation.
CVE-2025-31188: Mickey Jin (@patch1t)
Summarization Services Available for: macOS Sequoia
Impact: An app may be able to access information about a user's contacts
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24218: Kirin and FlowerCode, Bohdan Stasiuk (@bohdan_stasiuk)
System Settings Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24278: Zhongquan Li (@Guluisacat)
System Settings Available for: macOS Sequoia
Impact: An app with root privileges may be able to access private information
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24242: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
SystemMigration Available for: macOS Sequoia
Impact: A malicious app may be able to create symlinks to protected regions of the disk
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30457: Mickey Jin (@patch1t)
Voice Control Available for: macOS Sequoia
Impact: An app may be able to access contacts
Description: This issue was addressed with improved file handling.
CVE-2025-24279: Mickey Jin (@patch1t)
Web Extensions Available for: macOS Sequoia
Impact: An app may gain unauthorized access to Local Network
Description: This issue was addressed with improved permissions checking.
CVE-2025-31184: Alexander Heinrich (@Sn0wfreeze), SEEMOO, TU Darmstadt & Mathy Vanhoef (@vanhoefm) and Jeroen Robben (@RobbenJeroen), DistriNet, KU Leuven
Web Extensions Available for: macOS Sequoia
Impact: Visiting a website may leak sensitive data
Description: A script imports issue was addressed with improved isolation.
CVE-2025-24192: Vsevolod Kokorin (Slonser) of Solidlab
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: The issue was addressed with improved memory handling.
WebKit Bugzilla: 285892
CVE-2025-24264: Gary Kwong, and an anonymous researcher
WebKit Bugzilla: 284055
CVE-2025-24216: Paul Bakker of ParagonERP
WebKit Available for: macOS Sequoia
Impact: A type confusion issue could lead to memory corruption
Description: This issue was addressed with improved handling of floats.
WebKit Bugzilla: 286694
CVE-2025-24213: Google V8 Security Team
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected process crash
Description: A buffer overflow issue was addressed with improved memory handling.
WebKit Bugzilla: 286462
CVE-2025-24209: Francisco Alonso (@revskills), and an anonymous researcher
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: A use-after-free issue was addressed with improved memory management.
WebKit Bugzilla: 285643
CVE-2025-30427: rheza (@ginggilBesel)
WebKit Available for: macOS Sequoia
Impact: A malicious website may be able to track users in Safari private browsing mode
Description: This issue was addressed through improved state management.
WebKit Bugzilla: 286580
CVE-2025-30425: an anonymous researcher
WindowServer Available for: macOS Sequoia
Impact: An attacker may be able to cause unexpected app termination
Description: A type confusion issue was addressed with improved checks.
CVE-2025-24247: PixiePoint Security
WindowServer Available for: macOS Sequoia
Impact: An app may be able to trick a user into copying sensitive data to the pasteboard
Description: A configuration issue was addressed with additional restrictions.
CVE-2025-24241: Andreas Hegenberg (folivora.AI GmbH)
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24266: an anonymous researcher
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: An out-of-bounds read was addressed with improved bounds checking.
CVE-2025-24265: an anonymous researcher
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24157: an anonymous researcher
-
 @ b9f4c34d:7d1a0e31
2025-04-02 15:02:59
@ b9f4c34d:7d1a0e31
2025-04-02 15:02:59testssss
-
 @ b9f4c34d:7d1a0e31
2025-04-02 15:00:20
@ b9f4c34d:7d1a0e31
2025-04-02 15:00:20Test Video Document
-
 @ 000002de:c05780a7
2025-03-27 17:51:16
@ 000002de:c05780a7
2025-03-27 17:51:16Regardless of what you have heard Capitalism isn't to blame for all the ills in modern life. Capitalism is simply free trade without centralize control. Of course there are many details I'm glossing over and degrees of freedom. Critics of capitalism rarely explain how it works. They complain about people buying too much stuff. People being over-weight. They complain about waste. People buying stuff they don't need. They complain that teachers aren't paid enough. They complain that professional athletes make too much money.
All of this boils down to two things.
- People don't like what others choose to do
- The products we see and world we live in is a result of the desires and values of the people
I agree with many of the critics of capitalism. There is a ton of crap. There's a ton of waste. There are professions I wish were more profitable and others I wish were less profitable. I'm going to ignore the state for once here. Obviously the state puts its thumb on the scales and distorts the market. But this isn't the main factor IMO. The main factor in the world we live in is us. The people. Our desires. Our values. The things we value are reflected in the market. People don't like to admit this because it is uncomfortable. We are spoiled, self-centered, brats that are desire machines. Yeah, you can blame advertising. You can blame "capitalism" but the alternative is starvation and death (socialism).
Its time for us to stop blaming freedom for all the ills in our society and take ownership for our actions. Its us. Thing is, I can't change you. But, I can change my actions. Adjust my values. Adjust my frame of view. I'd love to start hearing people take responsibility and self ownership. Start living out your values. Don't be a part of things that you view as problems. Be a part of solutions. I can't tell you what that looks like but if you think about it for a while you can come up with some things. Its easy to blame others. Its hard to take responsibility for yourself and own your flaws and mistakes.
What do you think?
Inspired by @k00b's post
originally posted at https://stacker.news/items/927021
-
 @ b9f4c34d:7d1a0e31
2025-04-02 14:59:02
@ b9f4c34d:7d1a0e31
2025-04-02 14:59:02Testy McTestenface
It's been so long, html
-
 @ 8d5ba92c:c6c3ecd5
2025-03-13 00:31:41
@ 8d5ba92c:c6c3ecd5
2025-03-13 00:31:41It’s no exaggeration to say that Bitcoin has moved beyond its roots as a monetary innovation, growing into a cultural movement built on resistance, decentralization, truth, and freedom. This makes perfect sense.
Money and technology are powerful forces redefining how we interact with each other and ultimately live. From the invention of the printing press to the rise of the Internet—and the countless areas they’ve transformed to this day—every major shift in how we exchange value and information has sparked cultural revolutions. The key here is to choose authenticity over the shallow narratives so often thrown our way.
Bitcoin, by its very nature, challenges current systems. The culture it fosters naturally becomes a counterbalance to a world dominated by fiat—its rotten values, dishonest incentives, hopelessness, greed, and increasingly weaker social interactions.
Go Out and Meet Your Tribe
Over the years, I’ve been to plenty of Bitcoin-themed events. Conferences, meetups, hackathons, and so on. All sorts of gatherings. Each one has left me with not just cool memories and lessons learned, but also genuine connections. I’ve met so many amazing people—some I’m lucky to call friends now, and I know that if it weren’t for Bitcoin and the incredible community that’s grown around it, I probably never would’ve crossed paths with most of them.
Culture is not just about where we’ve come from. It’s about where we’re going...
Last year, I joined 5 different conferences, not to mention smaller gatherings. Regardless of their format, they always enrich my personal perspectives, and, in turn, shape how I see the world and my place within it.
My calendar for the first part of this year is already marked with 6 major events, one of which I’m personally co-organizing. From January to March alone, I’ve attended around 10 Bitcoin meetups and 1 larger event in Thailand—SatsNFacts, a signal-rich 'unconference' (here you can read some memories from it).
The more I travel and spend time with Bitcoiners from around the world, the happier, more hopeful, and more motivated I become. I truly believe that the places we choose to go and the people we meet along the way can profoundly shape our near and distant futures.
Discover the Heartbeat of Bitcoin Culture
Now, imagine a unique gathering that embodies the ethos of Bitcoin while blending artistic expression, intellectual stimulation and collaborative spirit. Not too big, with thousands of attendees you’ll never have a chance to talk to, and not as small as an average local meetup where every face is already familiar.
That’s exactly what Bitcoin FilmFest 2025 (#BFF25) feels like—the event I’m honored to co-create (again) this year. It’s not a typical conference but a community-driven cultural experience, that, for the third time already, is taking over one of Warsaw’s most iconic landmarks: the Palace of Culture and Science. Once known as 'Stalin’s Ziggurat,' now our Cinematic Rebel ₿ase.
I’m not writing this piece to promote the event itself but rather to show how attending more culture-themed events can impact your journey. By participating in these experiences, you’re not just learning or networking—you’re becoming part of a movement that values creativity, authentic storytelling, and human connections.
📣 Why to attend Bitcoin FilmFest (or any similar event):
#1: Fresh Perspectives Through Art and Storytelling
Even if you’re not an artist or filmmaker, most probably you consume their work in one way or another, anyway. Viewing Bitcoin’s cultural impact through the lens of independent art can make you a more conscious, and inspired member of this space. The best part? You won’t just watch films or artistic projects—you’ll also have the chance to meet the creators, ask questions, and dive deeper into their stories. This isn’t about being a random spectator. It’s about engaging with narratives that fuel your mind and heart in ways you can’t yet imagine. Simply put, step in and become part of the story.
#2: From Cypherpunks to Spiritual Awakening
Cultural events like BFF feel more organic than traditional conferences, where networking can often feel rushed or transactional. Built on art and creativity, they foster a relaxed and open atmosphere—a perfect environment to explore deeper conversations, even those with philosophical dimensions. Topics could span a wide range, from the cypherpunk movement and its emphasis on privacy to using Bitcoin to escape inflation, real-world examples of micro-nations, freedom-tech innovations, powerful music, permissionless art, higher consciousness, personal awakenings, and spirituality. When you add the opportunity to engage with like-minded participants who have firsthand experience in many of these areas, you gain mind-blowing insights that can inspire you for months to come.
#3: Non-Technical Areas and New Opportunities
While developers and their work is essential, Bitcoin thrives on a wide range of skills and perspectives. Attending events like BFF might reveal how your unique talents can contribute to this space—something you might not realize while sitting at home. As Anya, founder of Bitvocation (*a partner of this year’s BFF, running a mini-site event where you can learn more about the Bitcoin job market, details to come), once told me:
Face-to-face interactions create real connection and trust—vital ingredients for Bitcoin's social layer.
Just like her, I know that by attending Bitcoin meetups and conferences, we gain an unmatched opportunity to grow our network in real life, resulting in much closer relations than hanging out with someone on X or Nostr.
It could even be the first step toward a new career path that, precisely because of your presence, begins to take shape. Indeed, quoting Anya again:
The best opportunities come to those who truly show up.
Of course, this doesn’t mean that after attending an event, you’ll immediately walk away with a job in Bitcoin (though you might!). But you’ll likely leave with valuable connections, fresh ideas, and a clearer sense of direction.
Final Thoughts
A year has 12 months—whether that’s a lot or a little depends on how we spend it. But please remember that a sound culture thrives when we gather, create, and connect. That’s why I’d like to encourage you to make Bitcoin events and meetups part of your plans this year.
Hope to see you in Warsaw at BFF25 (May 22-25)—so you can verify for yourself whether the points I’ve raised above resonate with your own experience.
Who knows? Maybe our paths will cross at other events I’ve penciled into my calendar as well 😎
BTC Your Mind. Let it Beat. Şela
-
 @ a012dc82:6458a70d
2025-03-27 14:23:51
@ a012dc82:6458a70d
2025-03-27 14:23:51The cryptocurrency market, known for its dramatic fluctuations, has always been a subject of intrigue and speculation. Bitcoin, as the pioneering digital currency, has been at the epicenter of this financial whirlwind. As we approach 2024, the anticipation surrounding Bitcoin's value is palpable, with potential investors and seasoned cryptocurrency enthusiasts keenly eyeing the market's movements. This article aims to dissect the recent forecasts for Bitcoin's price in the coming year, delve into the multifaceted factors influencing these predictions, and explore the broader implications for those contemplating an investment in Bitcoin.
Table of Contents
-
2024 Bitcoin Price Predictions: A New Peak on the …
-
Key Factors Driving Bitcoin's Price
-
The Halving Event
-
Institutional Interest and ETFs
-
Economic and Monetary Policies
-
-
The Debate: To Buy or Not to Buy
-
Risk Tolerance
-
Market Dynamics
-
Long-Term Perspective
-
-
Caution and Speculation
-
Conclusion
-
FAQs
2024 Bitcoin Price Predictions: A New Peak on the Horizon
Recent analyses, particularly a notable report from UK fintech firm Finder, have painted an optimistic picture for Bitcoin in 2024. Experts within the field are forecasting a new zenith for Bitcoin, projecting it to reach an all-time high of $88,000, with expectations of the currency stabilizing around $77,000 by the end of the year. These projections represent a significant uptick from Bitcoin's current valuation and suggest a potentially lucrative year ahead for the digital currency. However, it's crucial to recognize that these predictions are not guarantees but educated guesses based on current market trends and historical data. The cryptocurrency market's inherent volatility means that while the potential for substantial gains exists, so too does the risk of dramatic losses. Investors should approach these predictions with cautious optimism, considering the broader economic and technological landscape that could impact Bitcoin's trajectory.
Key Factors Driving Bitcoin's Price
The anticipated surge in Bitcoin's value can be attributed to several key factors, each playing a pivotal role in shaping the currency's future:
The Halving Event
The Bitcoin halving event scheduled for April 2024 stands as a significant milestone. This event, which occurs approximately every four years, reduces the reward for mining Bitcoin transactions by half. Historically, halving events have led to a decrease in the supply of new Bitcoins entering the market, which, in turn, has led to price increases as demand outstrips supply. The 2024 halving is expected to follow this trend, contributing to the bullish outlook for Bitcoin's price. However, while past performance can offer insights, it is not indicative of future results. The halving's impact could be influenced by a myriad of factors, including changes in miner behavior, technological advancements, and shifts in investor sentiment.
Institutional Interest and ETFs
Another driving force behind the optimistic price predictions is the growing institutional interest in Bitcoin and the approval of Bitcoin ETFs in the United States. These developments have not only legitimized Bitcoin as an investment asset but also made it more accessible to a broader audience of traditional investors. The introduction of ETFs has bridged the gap between the conventional financial world and the burgeoning cryptocurrency market, providing a regulated and familiar avenue for investment. However, the influx of institutional money also brings new challenges, including increased market manipulation risks and the potential for regulatory crackdowns. Investors should remain vigilant, monitoring the evolving landscape and considering the long-term implications of institutional involvement in the cryptocurrency space.
Economic and Monetary Policies
Global economic conditions and monetary policies, particularly those enacted by the US Federal Reserve, are also critical factors influencing Bitcoin's price. In an environment of low interest rates and quantitative easing, investors have increasingly turned to alternative assets like Bitcoin as a hedge against inflation and currency devaluation. However, shifts in these policies could significantly impact investor behavior and market dynamics. A rise in interest rates or a tightening of monetary policy could lead to reduced liquidity in the market and a shift away from riskier assets, including Bitcoin. Conversely, continued economic uncertainty and inflationary pressures could bolster Bitcoin's appeal as a store of value.
The Debate: To Buy or Not to Buy
The decision to invest in Bitcoin, especially in light of the optimistic 2024 price predictions, is fraught with complexity:
Risk Tolerance
Bitcoin's notorious volatility cannot be overstated. The digital currency's price can experience dramatic swings within short periods, influenced by factors ranging from regulatory news to market sentiment. Potential investors must assess their risk tolerance and financial situation before entering the market. It's essential to consider whether you can withstand significant fluctuations in your investment's value and how such changes would impact your overall financial health.
Market Dynamics
Understanding the broader market dynamics and potential regulatory changes is crucial for anyone considering investing in Bitcoin. The cryptocurrency market does not operate in a vacuum; it is affected by global economic conditions, technological developments, and shifts in regulatory attitudes. Staying informed and adaptable is key, as today's market drivers could change rapidly, altering Bitcoin's price trajectory.
Long-Term Perspective
Adopting a long-term perspective is vital when investing in Bitcoin. While the allure of quick profits can be tempting, Bitcoin's history suggests that it is better suited as a long-term investment. The market's cyclical nature, characterized by boom-and-bust cycles, requires patience and a long-term outlook. Investors should avoid making impulsive decisions based on short-term price movements and instead focus on the underlying value and potential of Bitcoin as a revolutionary digital asset.
Caution and Speculation
Despite the bullish forecasts, a note of caution is warranted. The cryptocurrency market remains speculative, and while Bitcoin has established itself as the leading digital currency, its future is not guaranteed. The landscape is rife with uncertainties, from technological challenges to regulatory hurdles. Potential investors should approach Bitcoin with a balanced perspective, recognizing the possibilities while being acutely aware of the risks.
Conclusion
The predictions for Bitcoin's price in 2024 offer a glimpse into a potentially prosperous future for the digital currency. However, the decision to invest should not be taken lightly. Prospective investors must navigate a landscape marked by volatility, uncertainty, and rapid change. By thoroughly evaluating the market, staying informed about developments, and considering their long-term financial goals, individuals can make more informed decisions about their involvement in the Bitcoin market. Whether now is the right time to buy Bitcoin is a personal decision that depends on individual circumstances, risk tolerance, and investment strategy. As with any investment, there are no guarantees, but for those willing to embrace the risks, the rewards could be substantial.
FAQs
Why is Bitcoin expected to reach new highs in 2024? Bitcoin's price is expected to surge due to factors like the halving event, increasing institutional interest, the approval of Bitcoin ETFs, and global economic conditions that favor alternative investments.
What is a Bitcoin halving event? A Bitcoin halving event is when the reward for mining new blocks is halved, reducing the rate at which new bitcoins are generated. This event occurs approximately every four years and tends to impact the price due to reduced supply.
Are Bitcoin ETFs significant for individual investors? Yes, Bitcoin ETFs provide individual investors with a regulated and familiar way to gain exposure to Bitcoin without directly purchasing or storing the cryptocurrency, potentially increasing its accessibility and demand.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 04c915da:3dfbecc9
2025-03-12 15:30:46
@ 04c915da:3dfbecc9
2025-03-12 15:30:46Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 401014b3:59d5476b
2025-03-27 13:48:10
@ 401014b3:59d5476b
2025-03-27 13:48:10Alright, baseball junkies, it’s March 27, 2025, and we’re diving into the crystal ball to predict the 2025 MLB season—straight through to the World Series champ! Spring Training’s wrapping up, Opening Day’s here, and the league’s loaded with talent, drama, and some sneaky contenders ready to shake things up. I’m breaking down each playoff team’s path, their strengths, weaknesses, and who’s got the juice to hoist the trophy in October. This ain’t some cookie-cutter chalk pick—let’s get gritty, let’s get bold, and let’s see who’s got the stones to win it all. Strap in, fam—here we go!
American League Playoff Teams: The AL Beast Mode
New York Yankees\ The Yankees are back, and they’re pissed after last year’s World Series loss to the Dodgers. Aaron Judge is coming off another MVP-caliber season (let’s say .310, 55 HRs, 130 RBIs), and Juan Soto’s bat (projected .290, 40 HRs) gives them a lethal 1-2 punch. Gerrit Cole anchors a rotation that’s top-5 in ERA (around 3.40), but the bullpen’s a question mark—closer Clay Holmes blew 13 saves in 2024, and they haven’t fixed that yet. They’ll win the AL East (95-67), but their postseason hinges on late-inning reliability.\ Prediction: ALCS run, but they fall short if the pen implodes.
Houston Astros\ The Astros are perennial AL West champs (projected 92-70), even with a slightly aging core. Jose Altuve (.300, 20 HRs) and Yordan Alvarez (.295, 35 HRs) keep the offense humming, and a rotation led by Framber Valdez (3.20 ERA) and Hunter Brown (3.50 ERA) is solid. Their bullpen, with Josh Hader (1.28 ERA in 2024), is lights-out. But injuries to key arms like Justin Verlander (aging at 42) could bite them.\ Prediction: ALDS exit—they’re good, but not great this year.
Cleveland Guardians\ The Guardians sneak into the playoffs as the AL Central champs (88-74). Jose Ramirez (.280, 35 HRs, 110 RBIs) is a one-man wrecking crew, and their rotation—Shane Bieber (3.00 ERA, if healthy) and Triston McKenzie (3.60 ERA)—keeps them in games. But their offense outside Ramirez is thin (team OPS around .720), and the bullpen’s inconsistent (4.00 ERA).\ Prediction: Wild Card exit—they’re scrappy but lack firepower.
Tampa Bay Rays (Wild Card)\ The Rays grab a Wild Card spot (90-72) with their usual mix of grit and analytics. Yandy Diaz (.290, 15 HRs) and Randy Arozarena (.270, 25 HRs) lead a balanced offense, while Shane McClanahan (3.10 ERA) and Zach Eflin (3.40 ERA) anchor the rotation. Their bullpen (top-10 in ERA at 3.50) is a strength, but depth issues (injuries to key prospects) could hurt.\ Prediction: ALDS run—they’re sneaky dangerous.
Seattle Mariners (Wild Card)\ The Mariners finally break through as a Wild Card (89-73), as predicted by some fans on X. Julio Rodriguez (.285, 30 HRs) and Cal Raleigh (.250, 35 HRs) power the offense, and a rotation of Luis Castillo (3.20 ERA), Logan Gilbert (3.30 ERA), and George Kirby (3.40 ERA) is the best in the AL (team ERA around 3.20). Their offense (bottom-10 in runs scored) is the Achilles’ heel.\ Prediction: ALCS run—they’re a pitcher’s dream, but the bats hold ‘em back.
Baltimore Orioles (Wild Card)\ The Orioles snag a Wild Card (87-75), but some fans on X call them a “surprise disappointment.” Gunnar Henderson (.280, 35 HRs) and Adley Rutschman (.270, 20 HRs) lead a young core, but the rotation—Corbin Burnes (3.00 ERA) and Grayson Rodriguez (3.70 ERA)—lacks depth after losing Kyle Bradish to injury. The bullpen (4.20 ERA) is shaky.\ Prediction: Wild Card exit—too many holes this year.
National League Playoff Teams: The NL Wild West
Los Angeles Dodgers\ The Dodgers are the NL West juggernaut (98-64), and some fans on X are already calling them World Series champs. Shohei Ohtani (.300, 50 HRs, 120 RBIs) is the NL MVP favorite, Mookie Betts (.290, 30 HRs) is elite, and Freddie Freeman (.310, 25 HRs) is steady. The rotation—Tyler Glasnow (3.10 ERA), Yoshinobu Yamamoto (3.30 ERA), and Walker Buehler (3.50 ERA)—is deep, and the bullpen (3.40 ERA) is solid. No weaknesses here.\ Prediction: World Series bound—they’re a machine.
Philadelphia Phillies\ The Phillies win the NL East (94-68) with a balanced attack. Bryce Harper (.290, 30 HRs) and Kyle Schwarber (.250, 40 HRs) mash, while Trea Turner (.300, 20 HRs) adds speed. The rotation—Zack Wheeler (3.00 ERA), Aaron Nola (3.40 ERA), and Ranger Suarez (3.60 ERA)—is top-tier, and the bullpen (3.50 ERA) is reliable. They’re built for October.\ Prediction: NLCS run—they’re legit contenders.
Milwaukee Brewers\ The Brewers take the NL Central (90-72) with a scrappy squad. Willy Adames (.270, 30 HRs) and William Contreras (.280, 20 HRs) lead the offense, while Freddy Peralta (3.30 ERA) and Brandon Woodruff (3.50 ERA, if healthy) anchor the rotation. Their bullpen (top-5 in ERA at 3.30) is a strength, but the offense (middle-of-the-pack in runs) can stall.\ Prediction: NLDS exit—not enough firepower.
Atlanta Braves (Wild Card)\ The Braves grab a Wild Card (91-71) despite injuries. Ronald Acuna Jr. (.290, 35 HRs) and Matt Olson (.270, 40 HRs) power the lineup, but the rotation—Chris Sale (3.20 ERA) and Max Fried (3.40 ERA)—is thin after Spencer Strider’s injury. The bullpen (3.60 ERA) is solid, but depth is a concern.\ Prediction: NLDS run—they’re talented but banged up.
San Diego Padres (Wild Card)\ The Padres snag a Wild Card (89-73) with a balanced attack. Fernando Tatis Jr. (.280, 35 HRs) and Manny Machado (.270, 30 HRs) lead the offense, while Dylan Cease (3.30 ERA) and Yu Darvish (3.50 ERA) anchor the rotation. The bullpen (3.70 ERA) is decent, but they lack a true closer.\ Prediction: Wild Card exit—not enough late-game juice.
New York Mets (Wild Card)\ The Mets sneak in as a Wild Card (88-74) with a breakout year. Francisco Lindor (.280, 30 HRs) and Pete Alonso (.260, 35 HRs) mash, while Kodai Senga (3.20 ERA) and Luis Severino (3.60 ERA) lead the rotation. The bullpen (4.00 ERA) is a weak spot, but their offense (top-10 in runs) keeps ‘em alive.\ Prediction: NLDS run—they’re scrappy but flawed.
Playoff Breakdown: The Road to the World Series
AL Wild Card:
- Rays over Guardians
- Mariners over Orioles
- Yankees over Rays
- Mariners over Astros
- Yankees vs. Mariners → Yankees (4-2)\ Judge and Soto go off, and the Mariners’ bats can’t keep up with New York’s firepower. Cole’s ace stuff seals it.
NL Wild Card:
- Braves over Padres
- Mets over Brewers
- Dodgers over Mets
- Phillies over Braves
- Dodgers vs. Phillies → Dodgers (4-3)\ Ohtani’s heroics (think a 3-HR game) and the Dodgers’ depth outlast Philly’s grit in a seven-game classic.
World Series: Yankees vs. Dodgers
Here we go—a rematch of last year’s epic clash! The Yankees are hungry for revenge, with Judge and Soto swinging for the fences (combined 5 HRs in the series). Cole (Game 1 gem, 7 IP, 2 ER) and Rodon (Game 5 win) keep it close, but the Dodgers’ lineup is relentless—Ohtani (.350, 2 HRs), Betts (.320, 3 doubles), and Freeman (.300, 8 RBIs) overwhelm New York’s shaky bullpen. Glasnow and Yamamoto each win a start, and the Dodgers’ pen (2.50 ERA in the series) slams the door. Dodgers win in 6—Ohtani’s walk-off in Game 6 seals it.
The Final Buzzer
The Dodgers are my 2025 World Series champs—they’ve got the star power, depth, and clutch factor to repeat. The Yankees make a valiant run, but their bullpen woes bite ‘em again. Hit me on X if you disagree, but this is my October gospel—let’s see who’s standing when the dust settles! Play ball, degenerates!




