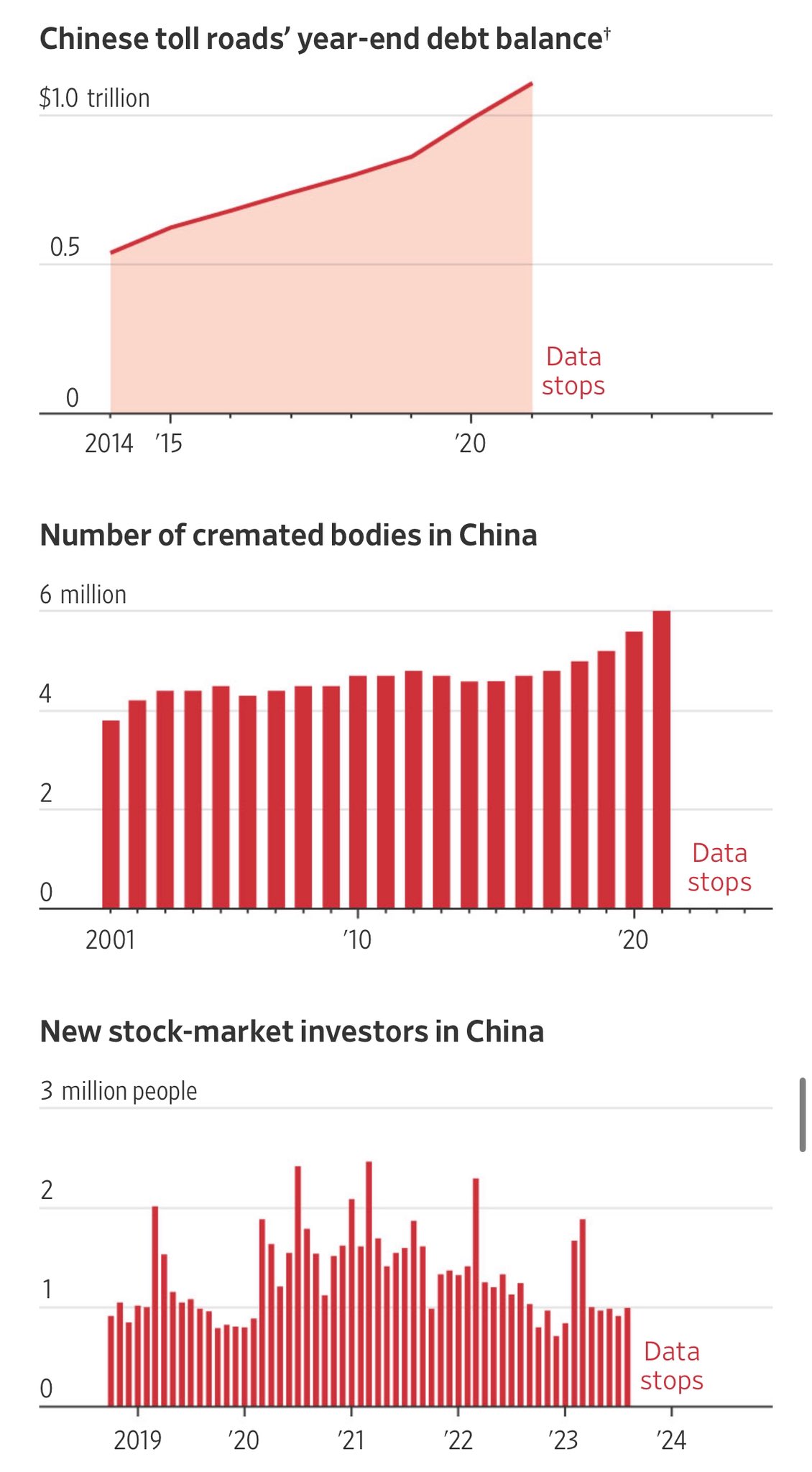
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ 2b24a1fa:17750f64
2025-05-06 07:35:01
@ 2b24a1fa:17750f64
2025-05-06 07:35:01Eine Kolumne von Michael Sailer, jeden ersten Freitag bei Radio München, nachzulesen auf sailersblog.de.
https://soundcloud.com/radiomuenchen/belastigungen-35-das-ist-nicht-meine-regierung?
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ c9badfea:610f861a
2025-05-05 20:16:29
@ c9badfea:610f861a
2025-05-05 20:16:29- Install PocketPal (it's free and open source)
- Launch the app, open the menu, and navigate to Models
- Download one or more models (e.g. Phi, Llama, Qwen)
- Once downloaded, tap Load to start chatting
ℹ️ Experiment with different models and their quantizations (Q4, Q6, Q8, etc.) to find the most suitable one
-
 @ 2b24a1fa:17750f64
2025-05-02 13:40:12
@ 2b24a1fa:17750f64
2025-05-02 13:40:12Das Kriegsgrauen kriecht unter die Haut. Bilder von verstümmelten Beinen und Armen, von Kriegstraumatisierten schweigenden Männern, von Kriegsgräbern steigen auf. Als Mutter, Schwester, Tante, Großmutter wachsen die Ängste, dass sich ein Verwandter von der politischen und medialen Kriegslust anstecken lässt und tatsächlich die Beteiligung an den näher kommenden kriegerischen Auseinandersetzungen in Erwägung zieht. Einen wütenden Kommentar anlässlich der wachsenden Kriegstreiberei verfasste unser Autor Nicolas Riedl.
https://soundcloud.com/radiomuenchen/sofa-soldaten-an-die-front-von-nicolas-riedl?
Bild: KI
-
 @ 04ea4f83:210e1713
2025-05-01 18:22:24
@ 04ea4f83:210e1713
2025-05-01 18:22:2430. November 2022
Sehr geehrter Herr Bindseil und Herr Schaff von der Europäischen Zentralbank,
Ich schreibe Ihnen heute, am Tag der Veröffentlichung Ihres EZB-Blog-Berichts „Bitcoin's Last Stand", sowohl mit Belustigung als auch mit Bestürzung. Ich amüsiere mich darüber, wie albern und hilflos Sie beide erscheinen, indem Sie sich auf müde und längst widerlegte Erzählungen über Bitcoin und seine Nutzlosigkeit und Verschwendung stützen. Und ich bin beunruhigt, weil ich von zwei sehr gut ausgebildeten und etablierten Mitgliedern Ihres Fachgebiets eine viel differenziertere kritische Sichtweise auf den aufkeimenden Bitcoin und die Lightning Skalierungslösung erwartet hätte.
Sie haben sich mit Ihren dilettantischen Versuchen, Angst, Unsicherheit und Zweifel an einem globalen Open-Source-Kooperationsprojekt zu säen, das als ein ständig wachsendes Wertspeicher und -übertragungssystem für viele Millionen Menschen weltweit fungiert, wirklich einen Bärendienst erwiesen. Ein System, das jedes Jahr von mehr und mehr Menschen genutzt wird, da sie von seiner Effektivität und seinem Nutzen erfahren. Und ein System, das noch nie gehackt oder geknackt wurde, das funktioniert, um die „Banklosen" zu versorgen, besonders in den Ländern und Orten, wo sie von finsteren totalitären Regierungen schwer unterdrückt oder von der finanziell „entwickelten" Welt einfach im Stich gelassen wurden. In der Tat ist Bitcoin bereits gesetzliches Zahlungsmittel in El Salvador und der Zentralafrikanischen Republik, und erst gestern erhielt er in Brasilien den Status eines „Zahlungsmittels".
Es entbehrt nicht einer gewissen Ironie, wenn ich schreibe, dass Sie das Ziel so gründlich verfehlen, insbesondere weil die Bank- und Finanzsysteme, zu denen Sie gehören, für eine Energie- und Materialverschwendung verantwortlich sind, die um Größenordnungen größer ist als die Systeme und Ressourcen, die das Bitcoin-Netzwerk antreiben und erhalten. Ich bin mir sicher, dass Sie sich der revolutionären kohlenstoff- und treibhausgasreduzierenden Effekte bewusst sind, die Bitcoin-Mining-Anlagen haben, wenn sie neben Methan-emittierenden Mülldeponien und/oder Ölproduktionsanlagen angesiedelt sind. Und ich weiß, dass Sie auch gut über solar- und windbetriebene Bitcoin-Mining-Cluster informiert sind, die dabei helfen, Mikronetze in unterversorgten Gemeinden einzurichten.
Ich könnte noch weiter darüber sprechen, wie das Lightning-Netzwerk implementiert wird, um Überweisungszahlungen zu erleichtern sowie Finanztechnologie und Souveränität in Gemeinden in Laos und Afrika südlich der Sahara zu bringen. Aber lassen Sie mich zu dem Teil kommen, der einen gewöhnlichen Menschen wie mich einfach zutiefst traurig macht. Bitcoin ist, wie Sie sehr wohl wissen (trotz Ihrer dummen und veralteten Verleumdungen), ein technologisches Netzwerk, das nicht auf nationaler oder internationaler Verschuldung oder der Laune von Politikern basiert oder durch sie entwertet wird. Es ist ein System, das jenseits der Kontrolle einer einzelnen Person, eines Landes oder einer Gruppe von Ländern liegt. Wenn Bitcoin sprechen könnte (was er in der Tat ungefähr alle zehn Minuten tut, durch das elektro-mathematische Knistern und Summen des Wahrheitsfeuers), würde er diese Worte aussprechen:
„Über allen Völkern steht die Menschlichkeit".\ \ Als Bankiers der Europäischen Union, als Menschen von der Erde, als biologische Wesen, die denselben Gesetzen des Verfalls und der Krankheit unterliegen wie alle anderen Wesen, wäre es da nicht erfrischend für Sie beide, das Studium und die Teilnahme an einer Technologie zu begrüßen, die die Arbeit und die Bemühungen der sich abmühenden Menschen auf unserem Planeten bewahrt, anstatt sie zu entwerten? Wie die Bitcoin-Kollegin Alyse Killeen wiederholt gesagt hat: „Bitcoin ist FinTech für arme Menschen".
Ich bin dankbar für Ihre Aufmerksamkeit und hoffe, dass Sie über Bitcoin nachdenken und es gründlicher studieren werden.
Mit freundlichen Grüßen,
Cosmo Crixter
-
 @ 04ea4f83:210e1713
2025-05-01 18:18:36
@ 04ea4f83:210e1713
2025-05-01 18:18:36Digitales Geld ist nur Text, die ganze Zeit
Bei digitalem Geld geht es im Grunde nur um Zahlen in einem Hauptbuch. Die ganze Zeit über sind es die Zahlen, auf die es ankommt. Lange Zahlen sind einfach nur Zeichenketten im PC und diese werden als Nachrichten in einem Netzwerk, das durch Regeln gebildet wird, an gleichwertige Peers gesendet - das ist Bitcoin, das mit einem einzigartigen dezentralen Zeitstempel-Algorithmus kombiniert wird, der durch die Unfälschbarkeit von Energie gesichert ist. Das Ergebnis ist ein Bargeldnetzwerk mit einem festen, vorprogrammierten Zeitplan für die Geldschöpfung, das den ersten absolut knappen digitalen Inhabervermögenswert schafft.\ \ Diese revolutionären Ideen werden bleiben, genauso wie das Feuer, das Rad, die Elektrizität, das Smartphone, das Internet oder die Zahl Null. Technologie entwickelt sich weiter und was machen lebende Organismen? Sie können mutieren, genau wie Viren, und das hat mich zu dem Schluss gebracht, dass es auch in dieser Hinsicht eine Verbindung gibt und das obwohl Gigi bereits einige der vielen Facetten von Bitcoin beschrieben hat. Für mich ist die Grundlage die Abstraktion, dass Bitcoin nur die Summe aller Menschen ist, die Satoshis besitzen oder anderweitig mit dem Bitcoin-Netzwerk interagieren.\ \ Die Technologien werden in einem bestimmten Tempo angenommen. Allerdings gibt es immer frühe oder späte Entdecker von neuer Technologie. Aber was passiert, wenn es zu einer ernsthaften Bedrohung wird, wenn hartes Geld nicht adoptiert wird? Was passiert, wenn die Geschwindigkeit der Preiszunahme so hoch wird, dass es unmöglich ist, jemanden zu finden, der Satoshi in Fiat tauschen möchte? Was passiert, wenn die Hyperbitcoinisierung morgen beginnt? Was wäre, wenn es eine UpSideProtection™️ gäbe, die diesen Prozess noch mehr beschleunigt und dir Bitcoin zu einem Bruchteil seines wahren Wertes sichert?\ \ Wir alle wünschen uns einen sicheren Übergang, um den Krieg aufgrund einer scheiternden Dollar-Hegemonie zu vermeiden, und tatsächlich gibt es ein Rennen, um den Krieg zu vermeiden. Mein größtes Geschenk ist die Zeit, die ich ich investiere, und die monetäre Energie, die ich in Bitcoin spare, und da ich schon eine Weile dabei bin, sehe ich, dass meine Mitstreiter die gleiche Mission verfolgen. Aber das ist NICHT genug. Wir müssen skalieren. Schneller.\ \ Das Erstaunen über den Kurzfilm der große Widerstand hat mich zu dem Schluss gebracht, dass wir alle Werkzeuge und Informationen in Form von Lehrern, Podcasts, Büchern und aufklärenden Videos bereits haben. Der Vorteil einer festen Geldmenge wird aber noch nicht von einer kritischen Masse verstanden, sondern nur von einer intoleranten Minderheit. Diese Minderheit wächst von Tag zu Tag. Ihre Inkarnationen sind die DCA-Armee, die Hodler der letzten Instanz, die unbeirrten Stacker, die Cyberhornets, die Memefactory™️ und Mitglieder der 21 Gruppe auf der ganzen Welt.\ \ Wir Bitcoiner sind räumlich getrennt, aber nicht in der Zeit. Getrennt in der Sprache, aber nicht in der Mission. Vereint müssen wir uns zu Wort melden, aufklären und Bitcoin wie einen Virus verbreiten.\ \ Niemand entscheidet, was Bitcoin für dich ist - dieser Virus des Geistes verfestigt sich in unbestechlichen Zahlen, die zu einer wachsenden Zahl an UTXOs in den Geldbörsen führen, nicht in negativen gesundheitlichen Auswirkungen. Bitcoin ist der Virus der Schuldenindustrie, der Virus, der im 21. Jahrhundert zur größten Definanzialisierung und Auflösung des Kredits führen wird. Da wir noch nicht in einer hyperbitcoinisierten Welt leben, müssen wir den Virus effektiver machen. Bitcoin muss mutieren, aber es ist nicht Bitcoin, der tatsächlich mutiert, sondern die Menschen, die ihn benutzen. Sie werden zu toxischen Maximalisten, die den Virus noch stärker verbreiten und alle Shitcoiner während ihrer Anwesenheit geistig infizieren oder argumentativ töten.\ \ Ich habe mich gefragt, wie wir eine Milliarde Menschen dazu ausbilden und überzeugen können, Bitcoin freiwillig zu nutzen und darin zu sparen, so dass sie Bitcoin als primäres Mittel zur Speicherung und Übermittlung von Werten in Raum und Zeit nutzen? Die Hyperbitcoinisierung braucht nur eine einzige, starke positive Rückkopplungsschleife um wirklich in Gang zu kommen, und diese Rückkopplung gibt es bereits, aber nicht in den Köpfen aller. Ab einer bestimmten Schwelle wird die Schwerkraft von Bitcoins gehärteten monetären Eigenschaften einfach zu hoch sein, als dass die Spieltheorie nicht zu dieser Rückkopplung führen würde, vor allem da Bitcoin im Jahr 2024 Gold in Punkto Knappheit übertrifft.\ \ Die Verbreitung der Idee einer festen dezentralen Geldmenge, die der Macht zentraler Kräfte entzogen ist, ist der Virus. Der Weg, das Spiel zu spielen, ist, Stacker zu stapeln, und Stacker stapeln Sats, wodurch die Geldmenge noch dezentralisierter wird und ein Verbot noch absurder wird. Sats sind endlich und unser Spiel ist es auch. Allein eine bestimmte Anzahl von einfachen Leuten, den Plebs, kann den Preis auf 1.000.000 EURO treiben.\ \ Letztendlich wird sich die Welt an das neue Gleichgewicht der Macht zugunsten des Individuums anpassen. Diese Idee in die Köpfe der Massen zu bringen, ist die wichtigste Aufgabe für 2023, die in das nächste Halving Mitte 2024 führt.\ \ Wir müssen unseren Reproduktionswert erhöhen, um die Akzeptanz zu steigern. Die Verwendung von Bitcoin als Zahlungsmittel und eine Kreislaufwirtschaft ist wichtig. Bildung ist wichtig. Apps und Anwendungsfälle sind wichtig. Die Kaufkraft, d.h. die Moskau Zeit, die sich in Richtung Mitternacht (00:00) bewegt, spielt eine Rolle, und all dies hängt zusammen.\ \ Aber wie genau können Plebs eine Milliarde Menschen überzeugen?\ \ Wie genau hat das Corona-Virus eine Milliarde Menschen infiziert?\ \ Peer-to-Peer.\ \ Erhebe deine Stimme, wer auch immer du bist, sprich über Bitcoin, werde aktiv und BUIDL oder lass uns einfach Spaß daran haben, arm zu bleiben und es genießen, jeden Tag bestohlen zu werden.\ \ Lass uns Yellow mehr Freizeit schenken und Bitcoin bis 100k+ aufkaufen und uns damit ins Stackheaven befördern.
"Don't stop believin' HODL on to that feelin' "
Der Rest wird in die unumstößliche Geschichte der Timechain eingraviert.
„Unter dieser Maske gibt es mehr als nur Fleisch. Unter dieser Maske ist eine Idee. Und Ideen sind kugelsicher." Alan Moore, V wie Vendetta

⚡
Danke für deine Aufmerksamkeit .\ \ #GetShortFiat und #GetOnZero\ \ Es ist immer noch 60 Uhr. Sei weise und stapele unbeirrt. Man kann die Mathematik und Physik nicht austricksen.\ \ Wenn der Post dir Motivation zum Stapeln von Sats oder dem Stapeln von Stackern gemacht hat, freue ich mich, wenn du mir auch etwas beim Stapeln hilfst!
-
 @ 04ea4f83:210e1713
2025-05-01 18:12:30
@ 04ea4f83:210e1713
2025-05-01 18:12:30Was ist ein Meme?
Bevor wir uns in die Materie vertiefen, sollten wir einen genaueren Blick auf die Begriffe werfen, mit denen wir es zu tun haben. Laut dem American Heritage Dictionary of the English Language ist ein Meme „eine Einheit kultureller Informationen, wie z. B. eine kulturelle Praxis oder Idee, die verbal oder durch wiederholte Handlungen von einem Geist zum anderen übertragen wird".
Der Begriff wurde von Richard Dawkins in seinem 1976 erschienenen Buch geprägt und ist eine Anspielung auf das Wort "Gen", die Einheit der biologischen Information, die sexuell von einem Organismus auf einen anderen übertragen wird.
Dawkins erkannte, dass kulturelle Informationen ähnlich wie biologische Informationen sind und sich genauso verbreiten und mutieren, wenn auch auf einer höheren Abstraktionsebene. Genau wie bei biologischen Informationen ist der ultimative Test für kulturelle Informationen das Überleben, und genau wie biologische Informationen müssen sie für die Umwelt geeignet sein, um sich zu verbreiten und am Leben zu gehalten zu werden.
Manche Ideen funktionieren einfach nicht, wenn sie fehl am Platz sind oder die Zeit nicht reif für sie ist. Sie werden schnell sterben, genau wie der sprichwörtliche Fisch auf dem Trockenen. Andere Memes funktionieren vielleicht eine Zeit lang, verblassen aber langsam durch allmähliche Veränderungen in der Umwelt oder brechen plötzlich durch die von ihnen ausgelösten destruktiven Rückkopplungsschleifen zusammen. Wie Gene verbreiten sich Meme langfristig nur dann, wenn sie für den Organismus und seine Umwelt von Nutzen sind.
„In der Wissenschaft der Ökologie lernt man, dass der Mensch nicht ein Organismus in einer Umwelt ist, sondern eine Organismus-Umwelt-Beziehung. Das heißt, ein einheitlicher Bereich des Verhaltens. Wenn man das Verhalten eines Organismus sorgfältig beschreibt, kann man das nicht tun, ohne gleichzeitig das Verhalten der Umwelt zu beschreiben... [...] Der Organismus ist nicht die Marionette der Umwelt, die von ihr herumgeschubst wird. Umgekehrt ist auch die Umwelt nicht die Marionette des Organismus, die vom Organismus herumgeschubst wird. Die Beziehung zwischen ihnen ist, um es mit John Deweys Worten zu sagen, transaktional."\ \ Alan Watts
Was hat das mit Bitcoin zu tun? Nun, du musst dich fragen, wie das Bitcoin-Netzwerk zustande kommt, und wenn du das tust, wirst du feststellen, dass Bitcoin sich nicht allzu sehr von den oben erwähnten Memen und Genen unterscheidet. Bitcoin ist ein instanziierter Computercode, ein digitaler Organismus, der die Menschheit dafür bezahlt, ihn am Leben zu erhalten, wie Ralph Merkle es so treffend formulierte. Die kumulative Arbeit, die in Bitcoins Timechain eingebettet ist, ist das, was Bitcoin real macht und was ihn von gewöhnlicher Information unterscheidet. Und von gewöhnlichen Computerprogrammen, was das betrifft. Genauso wie es einen Unterschied zwischen dir selbst und einem Ausdruck deiner DNA gibt, gibt es einen Unterschied zwischen dem Bitcoin-Code - den Memes, die er sich zu Nutze macht - und der realen Instanziierung von Bitcoin.
Das Bitcoin-Netzwerk instanziiert und validiert sich selbst alle 10 Minuten, Block für Block, wie ein Uhrwerk. Diese Blöcke sind die Informationseinheit, die übertragen wird, und ja, genau wie bei den Memen ist diese Information eine kulturelle Information. Die Tatsache, dass diese Information elektronisch übertragen wird, spielt keine Rolle; sie verkörpert immer noch den Kern der Bitcoin-Kultur, die Seele des Netzwerks. Und genau wie Memes wird diese Information durch wiederholte Aktionen von einem Knotenpunkt zum anderen übertragen. Und davor, von einem Geist zum anderen.
Im ökologischen Sinne handeln wir alle mit Bitcoin, und Bitcoin handelt mit uns. Wenn du von Bitcoin gehört hast, wenn du das Meme „21 Millionen" kennst, dann hat Bitcoin mit dir Geschäfte gemacht. Lange bevor du deine erste Bitcoin-Transaktion gemacht haben.
Memes und ihre Umgebung
Bitcoin sind Menschen, wenn es darauf ankommt. Ja, es ist Software, aber die Menschen müssen die Software ausführen und, was noch wichtiger ist, selbst entscheiden, was Bitcoin ist. Es gibt keine Autorität, wenn es um Bitcoin geht. So muss jeder für sich selbst herausfinden, was Bitcoin ist, und aus der Überschneidung der verschiedenen Standpunkte ergibt sich ein Konsens. Dies ist ein ständiger Prozess, denn es geht nicht nur darum, was Bitcoin derzeit ist, sondern auch darum, was Bitcoin sein könnte. Was Bitcoin sein sollte. Genau darum ging es im Blocksize War. Ein Kampf um die Seele von Bitcoin. Eine Meinungsverschiedenheit über die Zukunft und den ultimativen Zweck von Bitcoin. Ein Unterschied im memetischen Material, der letztendlich zu einer Spaltung des Protokolls führte, was wiederum zu einer Spaltung des Netzwerks und einer Spaltung der Kultur führte.
Aber auch ohne eine Spaltung, selbst wenn ein Konsens besteht, ist die Frage „was Bitcoin ist" nicht eindeutig zu beantworten.
Für dich mag das Lightning Network nicht wichtig sein, und es steht dir frei, eine Vor-SegWit-Version von Bitcoin zu betreiben. Für jemand anderen sind Dickbutts und Fürze auf der Blockchain vielleicht nicht wichtig, und er könnte sich entscheiden, eine Vor-Taproot-Version von Bitcoin zu verwenden (oder eine Version zu verwenden, die Ordnungszahlen (Ordinals) nicht respektiert). Bitcoin ist abwärtskompatibel, und Upgrades sind optional, gerade weil es keine Autorität gibt, die etwas vorschreibt.
So funktioniert Bitcoin, und so wird es immer funktionieren, weshalb Memes wichtig sind und warum es eigentlich durchweg Memes sind.
Um Bitcoin zu nutzen, muss man sich freiwillig entscheiden. Man muss zuerst von der Idee überzeugt werden, von der Idee, Sats zu akzeptieren, damit Fiat fallen zu lassen und Bitcoin zu erwerben. Erst wenn man davon überzeugt ist, dass elektronisches Bargeld mit einer (absolut) festen Menge nützlich sein könnte, wird man es akzeptieren oder damit sparen.
Das Meme „21 Millionen" kommt zuerst, und nachdem unsere Gehirne ausreichend von der Idee infiziert wurden, werden wir deshalb die Software starten, die die 21 Millionen ins Leben rufen.
Natürlich kommen manche Leute - ich glaube, die meisten - auf Umwegen zum Bitcoin. Du denkst, dass es sich um einen spekulativen Vermögenswert handelt, etwas, das existiert, um mehr Dollar zu verdienen, d. h. um mehr Papiergeld zu verdienen. Oder du entdeckst ihn über Online-Glücksspiele oder andere Wege, und auf diese Weise kommen sie zu ihren ersten Sätzen. Aber selbst wenn du auf Umwegen zu Bitcoin kommst, selbst wenn Bitcoin vor deiner Haustür ankommt, ohne dass du verstehst, womit du es zu tun hast, musst du lernen, Bitcoin selbstbestimmt zu nutzen, oder du wirst es nicht schaffen.
Bitcoin auf eine selbstsouveräne Art und Weise zu nutzen, bedeutet, dass du die Memes von Bitcoin absorbieren musst. Zum Beispiel musst du die „21 Millionen" übernehmen und ihnen zustimmen, sonst hast du keinen Bitcoin, sondern einen Shitcoin in den Händen. Bitcoin am Laufen zu halten bedeutet, Bitcoin auszuleben, was wiederum bedeutet, seine eigenen Schlüssel zu besitzen, seinen eigenen Knoten zu betreiben und den zentralen Konsensparametern zuzustimmen, die Bitcoin zu Bitcoin machen.

Mit der Zeit wird ein horizontaler Meme-Transfer stattfinden. Bitcoin wird auf dich abfärben. Du wirst nicht nur den Ideen ausgesetzt sein, die in Bitcoin eingebettet sind; nein, du wirst ein Teil davon sein und das Meme leben, indem du die Satoshi Tag für Tag und Block für Block hältst.
Oder du wirst es nicht. Wenn du mit den Ideen, die in den Konsensparametern von Bitcoin eingebettet sind, nicht einverstanden sind, hast du zwei Möglichkeiten: Du kannst dich abspalten oder unter dem Bitcoin Derangement Syndrom leiden. Man kann sich natürlich auch an die Umwelt anpassen und in Symbiose mit ihr leben, was bedeutet, sich mit dem in Bitcoin eingebetteten memetischen Material zu arrangieren - es zu akzeptieren und ihm langsam zuzustimmen.
Wenn man die zuvor skizzierte ökologische Sichtweise anwendet, bilden Bitcoin und die Bitcoiner selbst den Organismus-Umwelt und beeinflussen sich gegenseitig in 10-Minuten-Intervallen. Das Knifflige daran ist, dass Bitcoin sowohl Organismus als auch Umwelt ist, genau wie wir selbst. Das Bitcoin-Meme lebt in unseren Gehirnen und unsere Vorstellung davon, was Bitcoin ist - und was es sein sollte - ändert sich mit der Zeit. Die ökonomische Erweiterung von uns - unsere Sats - leben in der Umgebung, die Bitcoin ist, eine Umgebung, die wir individuell und kollektiv hervorbringen.
Wir formen unsere Werkzeuge, und unsere Werkzeuge formen uns. Und wir benutzen unsere Werkzeuge, um unsere Umwelt zu formen, die natürlich auch uns formt. Kultur ist das Ergebnis dieser gegenseitigen Beeinflussung, und was ist Kultur anderes als eine Vielzahl von Memen?
Bei Bitcoin haben wir es mit einem unglaublichen meinungsbildenden Werkzeug zu tun, das eng mit uns verwoben ist. Ein Werkzeug, das ein Umfeld schafft, das lächerlich schwer zu ändern ist. Ich würde sogar so weit gehen zu sagen, dass einige Aspekte dieser seltsamen Meme-Werkzeug-Organismus-Umwelt-Schleife unmöglich zu ändern sind, da dies die Identität von Bitcoin und Bitcoinern gleichermaßen zerstören würde.
Für mich wird Bitcoin immer durch 21ismus definiert werden, auch wenn ich der letzte Mensch wäre, der an dieses Meme glauben würde. Anstelle dessen würde ich lieber auf dem Hügel von 21 Millionen sterben - allein und in Armut, mit dem Node in der Hand und zwölf Worten in meinem Kopf - als einer Erhöhung des Bitcoin-Angebots um 1 % zuzustimmen. (Buchvorschlag: Mandibles)
Es gibt diejenigen, die diese unveränderliche Umgebung akzeptieren, und diejenigen, die sie ablehnen, was natürlich zu einer Spaltung der Kultur führt.
Kulturelle Spaltungen
Wir erleben zweifelsohne eine Art Kulturkrieg. Links gegen Rechts, Rot gegen Schwarz, Based gegen Woke, Blue Bird gegen Purple Bird und Furries gegen normale Menschen. Es ist schwer, die Bruchlinien auszumachen, die diesem Krieg zugrunde liegen. Einige glauben, dass es auf Individualismus gegen Kollektivismus hinausläuft. Andere sehen es als Kapitalismus vs. Marxismus, selbstregulierende Ordnung vs. zentrale Planung. Wieder andere spekulieren, dass dieses Chaos mit dem Rückgang des religiösen Glaubens zusammenhängt, der eine Folge der nietzscheanischen Ermordung Gottes ist.
Alle diese Gründe mögen zutreffend oder teilweise zutreffend sein, aber für mich als Bitcoiner - als jemand, der die Graphen des "WTF geschah 1971" viele Male bestaunt hat - ist es schwer, etwas anderes als den Notstand des Fiat-Geldes als den Hauptgrund für das Chaos, das wir erleben, zu benennen. Für mich scheint es offensichtlich, dass diese verrückten Zeiten ein Ergebnis des Fiat-Geldsystems und der wirtschaftlichen sowie memetischen Konsequenzen sind, die es mit sich bringt. Es ist ein System, das völlig von der Realität abgekoppelt ist, ein künstliches und hochpolitisches Umfeld, das, ob wir es erkennen oder nicht, das wirtschaftliche Betriebssystem unserer Welt ist. Für mich lässt sich die Bruchlinie der Gesellschaft am besten als „Bitcoin vs. Fiat" zusammenfassen.
Seit 50 Jahren leben wir die Idee des Fiat-Geldes aus. Das Meme, dass die Art des Basisgeldes keine Rolle spielt, die hartnäckige Überzeugung, dass „wir es uns selbst schulden". Wir scheinen zu glauben, dass unsere kollektive Zukunft ein magischer goldener Topf ist - scheinbar ohne Boden -, aus dem wir uns immer und immer wieder etwas leihen können.
Ich glaube, dass wir uns in der Endphase des großen Fiat-Experiments befinden. Einmal mehr haben die arroganten Könige dieser Welt beschlossen, Gott zu spielen und sich in Kräfte einzumischen, die größer sind als sie, größer als wir. Wieder einmal müssen wir feststellen, dass das Drucken von Geld keinen wirklichen Wert schafft. Einmal mehr wird sich die Gesellschaft wandeln oder ganz zusammenbrechen, wie es in Ägypten, Rom und in vielen anderen Kulturen vor der unseren geschah. Und einmal mehr wird sich die Natur durchsetzen, indem sie Verwüstung anrichtet und alles ausrottet, was nicht mit ihr übereinstimmt. Seien es Ideen oder anderes.
„Als es nun an Geld gebrach im Lande Ägypten und in Kanaan, kamen alle Ägypter zu Josef und sprachen: Schaffe uns Brot! Warum lässt du uns vor dir sterben? Denn das Geld ist zu Ende."\ \ Mose 47:15
Diesmal ist das Fiat-Experiment jedoch nicht lokal begrenzt. Es ist nicht das Geld eines einzelnen Landes, das versagt, sondern das Meme des Fiat-Geldes selbst.
Geld drucken vs. das Geld in Ordnung bringen
Die Erkenntnis der Bedeutung des Geldes sowie der moralischen und kulturellen Implikationen der Natur des Geldes - und der Ethik der Geldproduktion - hat mein Weltbild unwiderruflich verändert. Als ich erkannte, dass Gelddrucken nichts anderes als eine Umverteilung von Reichtum ist und dass eine zentral geplante Umverteilung von Reichtum eine unmögliche Aufgabe ist - nicht nur rechnerisch, sondern auch moralisch -, dämmerte mir, dass Konfiszierung durch Inflation und andere Formen der unfreiwilligen Umverteilung nichts anderes ist als Diebstahl auf Umwegen. Das Fiat-System ist ein System der Sklaverei, und nein, das ist keine Übertreibung.
Aber hier ist die gute Nachricht: Bitcoin schafft hier Abhilfe.

Das ist unsere Meme-Welt, alle anderen leben nur darin.
Es gibt eine bestimmte Ethik, die in Bitcoin eingebettet ist, und es ist diese Ethik, die den Grundstein für die Meme bildet, die wir entstehen und sich verbreiten sehen. Wenn ich es in einem Satz zusammenfassen müsste, dann wäre es dieser: „Du sollst nicht stehlen." Wenn ich es in einer Zahl zusammenfassen müsste, dann wäre es natürlich 21 Millionen.
Die Motivation hinter der Erschaffung von Bitcoin ist zweifelsohne politisch, wie „Kanzlerin am Rande der zweiten Bankenrettung" und verschiedene Kommentare von Satoshi zeigen. So stimmte Satoshi zwar der Aussage zu, dass „sie in der Kryptographie keine Lösung für politische Probleme finden werden", aber er erwähnte auch, dass „wir eine wichtige Schlacht im Wettrüsten gewinnen und ein neues Territorium der Freiheit gewinnen können". Man beachte die Worte, die in dieser Aussage verwendet werden: ein Gebiet (Umfeld) der Freiheit (im Gegensatz zur Sklaverei).
Ich würde argumentieren, dass „eine große Schlacht gewinnen" eine Untertreibung ist, und ich würde auch argumentieren, dass die ursprüngliche Behauptung falsch ist, aber ich werde darauf zurückkommen.
Doch auch ohne diese Kommentare, selbst wenn die in den Genesis-Block eingebettete Botschaft „ooga chaka ooga ooga ooga chaka" lauten würde, wäre Bitcoin immer noch politisch. Ja, das daraus resultierende System ist unpolitisch, genau wie der Sonnenaufgang unpolitisch ist, aber der Akt der Schaffung von bitcoin ist ein politischer Akt. Er ist eine Aussage, eine Manifestation bestimmter Ideen, von Qualitätsmemes.
Vergleiche die in Bitcoin eingebettete Ethik (festes Angebot, keine erzwungene Umverteilung, kein kostenloses Mittagessen, keine Rettungsaktionen) mit der Ethik des Fiat-Geldes (endloses Angebot, zentral geplante Umverteilung, Rettungsaktionen für Freunde, alles ist erfunden) - oder, noch drastischer, mit der „Ethik" der Shitcoins, die nur Fiat-Geld auf Steroiden ist (jeder kann sein eigenes Geld drucken, nichts ist wichtig, Rugpulls sind lustig und Dickbutts sind im Grunde die Mona Lisa).
Ist es eine Überraschung, dass die Kultur rund um diese Phänomene so unterschiedlich ist? Oder ist „du wirst nichts besitzen und du wirst glücklich sein" einfach eine Folge des Mems, das Fiat-Geld ist? Ist der kulturelle Unterschied zwischen Bitcoinern und Shitcoinern ein natürliches Ergebnis der Meme, die in den verschiedenen Organismus-Umgebungen eingebettet sind und von diesen hervorgebracht werden?
Im Klartext bedeutet das Meme des Fiat-Geldes - die Idee, dass wir Geld aus dem Nichts erschaffen können und sollten - einfach zu sagen: „Ich weiß besser als der Markt, wie man Geld verteilt", was bedeutet, dass ich besser als alle anderen weiß, was gut und was schlecht ist, was wertvoll ist und was nicht, was notwendig und was überflüssig ist.
Die Frage, die das Fiat-System beantwortet, ist die folgende: Wer darf Geld fälschen und wie viel? Und wer darf Zugang zu Geld haben, und wer nicht? Die Antwort ist politisch und wird mit Gewalt durchgesetzt.
Das Bitcoin-System beantwortet dieselben Fragen, und die Antworten sind ebenso einfach wie ethisch: Niemand darf Geld fälschen, und jeder kann darauf zugreifen. Keine Ausnahmen.
Dies sind zwei sehr unterschiedliche Ideen, zwei sehr unterschiedliche Memes. Die eine wird im Fiat-System umgesetzt, die andere im Bitcoin-System. Das eine bricht aus den Nähten, das andere tuckert vor sich hin und wächst wirtschaftlich, rechnerisch und memetisch - alle 10 Minuten.
Bitcoin vs. Gold
Wenn es darum geht, die Grundursache vieler unserer Übel zu identifizieren, hatten die Goldanhänger (größtenteils) die richtige Idee. Aber sie hatten keine Möglichkeit, ihre Ideen auf sinnvolle und effektive Weise umzusetzen, die in der vernetzten Welt des 21. Das Meme des „gesunden Geldes" ist das richtige Mem, aber ohne eine Möglichkeit, dieses Meme effizient umzusetzen, hat das Meme keine Möglichkeit, sich in der Bevölkerung zu verbreiten.
So sieht es aus, liebe Goldfresser: Wir werden nicht zu einem Goldstandard zurückkehren. Gold hat in der Vergangenheit versagt, und es würde auch in der Zukunft versagen. Die Nützlichkeit des „Goldstandard"- Memes ist zu einem Ende gekommen. Das Überbleibsel seiner glorreichen Vergangenheit wird nur noch in der Linguistik zu finden sein.
„Warum", fragst du dich? Nun, zunächst einmal verbietet der physische Körper des Goldes die Teleportation, d. h. die elektronische Übertragung von Gold. Er verbietet die Unsichtbarkeit, d. h. die plausible Abstreitbarkeit des Besitzes. Bitcoin kann sofort teleportiert und perfekt versteckt werden. Man kann ihn im Kopf behalten, und niemand kann wissen, ob man Bitcoin tatsächlich besitzt oder nicht. Gold wird allein aus logistischen Gründen immer in Tresoren zentralisiert sein. Bitcoin muss das nicht sein. Gold wird sich immer mit einer bestimmten Rate aufblähen, da eine unbekannte Menge noch unter der Erde (und im Weltraum) liegt. Die Menge, die sich über der Erde befindet, ist ebenfalls unbekannt, da der weltweite Goldvorrat nicht einfach überprüft werden kann.
Im Gegensatz dazu ist Bitcoin absolut knapp und perfekt überprüfbar. Alle 10 Minuten wird der Gesamtvorrat an Bitcoin geprüft. Alle 10 Minuten wird der Emissionsplan überprüft. Alle 10 Minuten werden Milliarden von Sats endgültig und elektronisch, d.h. mit Lichtgeschwindigkeit, abgerechnet. Eine echte, physische Abrechnung. Global und sofort, ohne große Kosten oder Reibungsverluste. Alle 10 Minuten.

Das Gold-Meme wird sich noch eine Weile halten, und das ist auch gut so. Die Menschen sind nostalgisch, besonders wenn sie in ihren Gewohnheiten verhaftet sind. Wie bei wissenschaftlichen Revolutionen wird sich die monetäre Revolution, die derzeit im Gange ist, wahrscheinlich langsam verbreiten: eine Beerdigung nach der anderen.
Ich glaube jedoch, dass Bitcoin die Macht hat, die Köpfe und Herzen der Menschen sehr schnell zu gewinnen, wenn diese Köpfe offen oder kulturell angepasst genug sind; oder wenn die Veränderung in ihrem Umfeld drastisch genug ist.
Politik vs. Kultur
Kehren wir zu der Behauptung zurück, dass "du in der Kryptographie keine Lösung für politische Probleme finden werden". Ich habe bereits erwähnt, dass ich dem nicht zustimme, und hier ist der Grund. Politik ist der Kultur nachgelagert, und Kryptographie im Allgemeinen (und Bitcoin im Besonderen) verändert die Kultur.
Das sollte jedem außer dem blindesten Beobachter des Bitcoin-Bereichs sonnenklar sein. Die Kultur rund um Bitcoin ist durchdrungen von Verantwortung und Selbsteigentum („besitze deine eigenen Schlüssel" & „nicht deine Schlüssel, nicht dein Bitcoin"), Verifizierung und Schlussfolgerungen aus ersten Prinzipien ("vertraue nicht, verifiziere"), langfristigem Denken und Sparen für die Zukunft ("bleibe bescheiden, staple Sats"), sowie einem Fokus auf harte Arbeit, Integrität, Wahrheit und sichtbare Ergebnisse ("Proof-of-work, der Arbeitsnachweis").
Satoshi erkannte in wahrer Cypherpunk-Manier, dass Memes implementiert werden müssen, um sich möglichst effizient zu verbreiten, weshalb er sich hinsetzte und den Code schrieb. Es war auch der erste Test für die Tauglichkeit seiner Ideen, wie er in einem seiner vielen Forenbeiträge erwähnte: „Ich musste den ganzen Code schreiben, bevor ich mich selbst davon überzeugen konnte, dass ich jedes Problem lösen kann, und dann habe ich das Whitepaper geschrieben."
Das ist der Arbeitsnachweis, genau da. Das ist Anti-Fiat. Nicht nur darüber reden, sondern es auch tun. Mit gutem Beispiel vorangehen. Nicht nur über die Ideen spekulieren, die man im Kopf hat, die Memes, die man in der Welt verbreitet sehen möchte, sondern sie auch umsetzen. Das heißt, sie an der Realität zu messen.
„Lass deine Memes keine Träume sein."
Satoshi (paraphrasiert)
Ist es eine Überraschung, dass sich Bitcoin in den Bereichen „gesunde Ernährung", „gesunde Landwirtschaft", „freie Meinungsäußerung und Menschenrechte ausbreitet? Dass Bitcoin schnell und einfach von Menschen verstanden wird, die buchstäblich nahe am Boden sind, verbunden mit der grundlegenden Realität der Dinge? Ist es eine Überraschung, dass Bitcoin von denjenigen genutzt und verstanden wird, die es am meisten brauchen? Von denjenigen, die in Ländern leben, in denen das Geld versagt? Von denjenigen, die vom Fiat-System abgelehnt werden?
Das sollte keine Überraschung sein. Einige Kulturen haben eine natürliche Überschneidung mit der Bitcoin-Kultur, und es sind diese Kulturen, die Bitcoin zuerst annehmen werden. Frühe Beispiele sind die Cypherpunk-Kultur sowie die Kulturen rund um die österreichische Wirtschaft, den Libertarismus und das muslimische Finanzwesen. Wenn diese Kulturen Bitcoin annehmen, wird Bitcoin seinerseits diese Kulturen annehmen und dich beeinflussen. Ein für beide Seiten vorteilhafter Einfluss, wie er für alles, was langfristig überlebt, erforderlich ist, und wie er für die Symbiose, die die Natur darstellt, Standard ist. Der Organismus und das Umfeld, das durch die orangefarbene Münze und ihre Besitzer geschaffen wird, will überleben. Bitcoin: das egoistische Meme.
Natürlich gibt es auch Fiat-Meme. Es ist das, was unsere Kultur in den letzten 50 Jahren geprägt hat: „Fake it till you make it" und „YOLO" kommen mir in den Sinn, was interessanterweise die moderne Version der keynesianischen Idee ist, dass wir auf lange Sicht alle tot sind. Ist es verwunderlich, dass ein Umfeld, das durch falsches Geld geschaffen wurde, zu falschem Essen, falschen Körpern, falscher Gesundheit, falscher Medizin, falschen Beziehungen, falschen Experten und falschen Menschen führt?
Diejenigen, die an der Spitze der Fiat-Pyramide sitzen, sprechen von „nutzlosen Essern" und versuchen uns davon zu überzeugen, dass wir nichts besitzen müssen, aber trotzdem glücklich sein werden. Man muss sich über den Slogan wundern: „Du wirst nichts besitzen und du wirst glücklich sein".
„Du wirst ein glücklicher kleiner Sklave sein", heißt es in diesem Meme. Jemand hat beschlossen, dass Glück das ultimative Ziel ist, das es zu erreichen gilt, und du (und nur du) weißt, wie du es für dich erreichen können.

„Glück"
Als ob Glück das eigentliche Ziel wäre, das A und O, der Grund für unsere Existenz. Was ist mit dem Streben nach etwas Sinnvollem, etwas, das schwer ist, etwas, das Opfer erfordert, das Schmerz und Leid mit sich bringt?
\ „Jeder Mensch ist glücklich, bis das Glück plötzlich ein Ziel ist."
Oder was ist mit der Aussage von Lagarde, dass „wir glücklicher sein sollten, einen Arbeitsplatz zu haben, als dass unsere Ersparnisse geschützt sind?" Das ist Ausdruck eines bestimmten Memes, das sich in ihrem Kopf festgesetzt hat, des Mems, dass Arbeitsplatzsicherheit die meisten anderen Bedürfnisse übertrumpft und dass normale Menschen kein Vermögen anhäufen müssen. Schlimmer noch: Es suggeriert, dass es völlig in Ordnung ist, das zu stehlen, was normale Menschen durch fleißige Arbeit im Laufe ihres Lebens angespart haben.

Wir sollte glücklicher sein einen Job zu haben als das unsere Erparnisse geschützt werden. Christine Largarde Präsidentin der ECB, Oktober 2019
Es gibt einen Grund, warum wir vom „Rattenrennen" oder dem „Hamsterrad" sprechen und warum dieser Teil unserer Kultur in Kunst und Film so stark kritisiert wird. Um Tyler Durden zu zitieren: „Die Werbung bringt uns dazu, Autos und Klamotten zu jagen, Jobs zu machen, die wir hassen, damit wir Scheiß kaufen können, den wir nicht brauchen. Wir sind die mittleren Kinder der Geschichte, Mann. Wir haben keinen Sinn und keinen Platz. Wir haben keinen Großen Krieg. Keine Weltwirtschaftskrise. Unser großer Krieg ist ein spiritueller Krieg... unsere große Depression ist unser Leben. Wir sind alle durch das Fernsehen in dem Glauben erzogen worden, dass wir eines Tages alle Millionäre, Filmgötter und Rockstars sein werden. Aber das werden wir nicht. Und wir lernen diese Tatsache langsam kennen. Und wir sind sehr, sehr wütend."
Ich glaube jedoch nicht, dass die Menschen wütend sind. Ich glaube, dass die meisten Menschen deprimiert und nihilistisch sind. Sie sehen keinen Ausweg, sie sind hoffnungslos und haben sich mit ihrer Position im System abgefunden - ob bewusst oder unbewusst.
Nichts zeigt die Plackerei des Fiat-Rattenrennens besser als der kurze Animationsfilm „Happiness", der eine visuelle Reise durch die unerbittliche Suche des Menschen nach Erfüllung in der modernen Welt darstellt. Er setzt in Bilder um, was viele Menschen nicht in Worte fassen können. Hilflosigkeit, Sucht, Hoffnungslosigkeit. Eine Krise des Selbst, eine Krise des Sinns. Das Fehlen einer hoffnungsvollen Vision für die Zukunft.
„Ehrlich gesagt, ist es ziemlich deprimierend", so ein 44-jähriger Arbeiter, der allein im Wald festsitzt. „Ich habe versucht, einen Gedanken zu formulieren, ihn auszudrücken, ohne zusammenzubrechen und zu weinen. Aber ich bin mir nicht sicher, ob ich ihn weitergeben kann, ohne zu weinen."
„Mein Problem, einer der Gründe, warum ich hierher kommen wollte, war also, dass ich versuchen wollte, über den neuen Aspekt meines Lebens nachzudenken. Mit anderen Worten: nach den Kindern."
„Ein Mensch kann eine Menge Dinge ertragen, für jemanden, den er liebt. Die gleichen Dinge nur für sich selbst zu ertragen, ist nicht so einfach. Ich bin Elektriker. Man könnte meinen, das sei nicht so schwer, aber es sind viele sich wiederholende Aufgaben. Ich weiß, dass jeder seine eigene Arbeit hat, ich weiß, dass das einfach der Lauf der Welt ist. Aber für mich ist der Gedanke, dass ich weitere 15 Jahre meines Lebens damit verbringen muss, auf die Wochenenden zu warten, einfach eine Qual. Einfach nur die banale Qual des Ganzen..."
Schau dir bei Möglichkeit diesen Clip an. Es ist eine Sache, über das Meme des Rattenrennens zu theoretisieren; es ist eine andere Sache, einem erwachsenen Mann zuzusehen, der weinend zusammenbricht, nachdem er über sein Leben, das System, in das er eingebettet ist, und die Zukunft, die dieses System für ihn bereithält, nachgedacht hat. Nachdem er sich die Tränen weggewischt hat, spekuliert er darüber, was der Grund für seine depressive Stimmung sein könnte: „An diesem Ort kenne ich die Regeln. Es ist das Leben außerhalb dieses Ortes, das mich zum Weinen bringt."
Das ist es, nicht wahr? Regeln und Regeländerungen. Wenn du jemanden zutiefst deprimieren wollen, änderst du die Regeln, und zwar häufig. Zwingen du sie, etwas Sinnloses zu tun. Ändere die Regeln willkürlich. Das ist es, was die Menschen wirklich demoralisiert: in einem System willkürlicher Regeländerungen gefangen zu sein. Keine Hoffnung auf Stabilität und kein Ausweg.

Der Dritte Weltkrieg wird ein Guerilla-Informationskrieg sein, bei dem es keine Trennung zwischen militärischer und ziviler Beteiligung gibt. - Marshall McLuhan
Das Meme ist die Nachricht.
"Weißt du, jetzt habe ich es endlich verstanden. Über den Unterschied zwischen einem echten Krieg und einem globalen Guerillakrieg. Denn was wir jetzt haben, ist kein konventioneller Krieg mit scharfen Waffen. Mit militärischer Ehre, militärischen Rängen, militärischer Aktivität... Das ist ein Kulturkrieg. Wir haben die Unruhen. Wir haben die Unordnung. Und jetzt weiß ich wirklich, wie das funktioniert. Wenn die Unruhen vorbei sind, kann man nicht mehr sagen: „Ich habe mit Stolz gedient. Es spielt keine Rolle, auf welcher Seite man steht. Denn die Unruhen sind ein Krieg gegen den Stolz. Es ist ein Krieg gegen die Moral der Menschen. Man kann dem Feind nicht als Gleicher gegenübertreten. Jeder lebt im Schatten. Es ist immer verdeckt. Es ist immer gefälscht. Er ist immer erfunden. Und es kann keine Geschichte darüber geschrieben werden, weil alles abgeschottet ist."\ \ Bruce Sterling
Für die Geldpolitik gibt es im Fiat-System keine Regeln. „Die Regeln sind erfunden, und die Punkte sind egal", um Drew Carey zu zitieren. Die Realität hat Regeln, und wenn ein Fiat-System erst einmal aus dem Ruder gelaufen ist, dann ist es die Realität, die die Konsequenzen zieht, nicht das Fiat-System selbst.
Das Fiat-System ist kaputt; sein Geld ist wertlos; seine Kultur ist deprimiert und hoffnungslos. Wenn die Politik der Kultur nachgelagert ist, ist es dann eine Überraschung, dass unsere Politik größtenteils eine Clownshow ist, die nur auf Äußerlichkeiten und kurzfristige Ziele ausgerichtet ist? Wo gibt es Hoffnung in der hoffnungslosen Welt des fiat everything? Kaputte Ideen führen zu kaputten Umgebungen, die wiederum zu kaputten Organismen führen. Ist der Mensch erst einmal kaputt, wird er nicht in der Lage sein, seine Umwelt auf eine für alle Seiten vorteilhafte Weise zu verändern. Ganz im Gegenteil. Er wird in einer Abwärtsspirale aus Verzweiflung und Zerstörung feststecken und versuchen, „um jeden Preis" zu tun, was nötig ist.
Ohne Bitcoin sind die Aussichten für unsere Zukunft düster. Ohne Bitcoin hast du zwei Möglichkeiten: die schwarze Pille des Pessimismus oder das Soma des Nihilismus.
Es gibt einen Grund, warum die Leute sagen, dass Bitcoin Hoffnung ist.
Schwarze Pille vs. Orange Pille
Bitcoin ist Hoffnung, weil die Regeln von Bitcoin bekannt und stabil sind. Das Bitcoin-System ist wahnsinnig zuverlässig, funktioniert wie ein Uhrwerk, mit Regeln, die bekannt und in Stein gemeißelt sind. Es ist eine Umgebung mit eisenharten Zwängen, die ohne Herrscher durchgesetzt werden.
Es ist nicht nur das Gegenteil des Fiat-Systems, sondern auch sein Gegengift. Es ist nicht nur ein Rettungsboot, in das jeder einsteigen kann, der in Not ist, sondern auch ein Heilmittel, das Sinn und Optimismus gibt, wo es vorher keinen gab.
Es ist leicht, depressiv zu werden, wenn man die Übel des Fiat-Systems erkannt hat. Viele Bitcoiner, die heute von Optimismus erfüllt sind, waren hoffnungslos und fatalistisch, bevor sie die orangefarbene Pille schluckten. Viele Menschen sind es immer noch, Lionel Shriver und die meisten Goldfresser eingeschlossen.
Aber man muss bereit sein. Man kann sich nur selbst eine orangefarbene Pille geben, wie man sagt. Niemand kann dir Bitcoin aufzwingen.
Du müsstest eine Erleuchtung haben, dieselbe Erleuchtung wie unser 44-jähriger Elektriker im Wald, der über sein Leben nachdenkt. Kurz nach seinem Zusammenbruch und seinem Monolog darüber, dass er im Rattenrennen feststeckt, kommt er zu einer plötzlichen Erkenntnis: „Ich muss etwas ändern. Es ist nicht die Welt, die sich ändern muss. Es bin ich, der sich ändern muss. Es ist meine Einstellung zum Leben."
Ja. Was für ein Chad.
Das ist buchstäblich die Funktionsweise von Bitcoin.
Fiat Denkweise vs. Bitcoin Denkweise
\ Das Fiat-System wird nicht einfach verschwinden, und es wird auch nicht still und leise verschwinden. Zu viele Menschen sind immer noch mit dem Gedanken an leicht verdientes Geld infiziert, arbeiten in Scheißjobs und führen ein Fiat-Leben. Der Tod des Fiat-Organismus ist jedoch unausweichlich. Er ist selbstzerstörerisch, und wie alle Tiere, die in die Enge getrieben werden und am Rande des Todes stehen, wird er in einem letzten Versuch, das Unvermeidliche zu verhindern, um sich schlagen.

Piggies von artdesignbysf
„Unser großer Krieg ist ein spiritueller Krieg", wie Tyler Durden es so treffend formulierte. Und wir sind mittendrin in diesem Krieg.
Mit jedem Tag wird es offensichtlicher, dass dies ein geistiger Krieg ist. Ein Zusammenprall von Ideen, ein Kampf der unterschiedlichen Weltanschauungen.
Selbst der letzte Boss von Bitcoin, Augustin Carstens, weiß, dass dies ein Krieg ist. Warum sonst würde er, die Verkörperung des Fiat-Standards, im Fernsehen auftreten und Folgendes sagen?
„Vor ein paar Jahren wurden Kryptowährungen als Alternative zu Papiergeld dargestellt. Ich denke, diese Schlacht ist gewonnen. Eine Technologie macht noch kein vertrauenswürdiges Geld."
Augustin Carstens
Wenn wir uns nicht in einem memetischen Krieg befänden, warum wäre es dann notwendig zu erklären, dass eine Schlacht gewonnen wurde?
Wenn wir uns nicht mitten in einem spirituellen Krieg befinden würden, warum würde Christine Lagarde, eine Person, die wegen Fahrlässigkeit und Missbrauchs öffentlicher Gelder verurteilt wurde - eine Person, die jetzt Präsidentin der Europäischen Zentralbank ist - öffentlich erklären, dass wir Bitcoin auf globaler Ebene regulieren müssen, denn „wenn es einen Ausweg gibt, wird dieser Ausweg genutzt werden?"
Warum würde Stephen Lynch behaupten, dass Bitcoin „auf Null gehen wird, wenn wir ein CBDC entwickeln, das den vollen Glauben und Kredit der Vereinigten Staaten hinter sich hat?"
Warum würde Neel Kashkari, verrückt wie er ist, vor eine Kamera treten, um das Mem zu verbreiten, dass „es unendlich viel Bargeld in der Federal Reserve gibt", in der Hoffnung, dass diese Aussage das Vertrauen in das zusammenbrechende Fiat-System stärken würde?

Es ist fast unmöglich, sich diese Interviews anzusehen, ohne den Kopf zu schütteln. Glauben diese Menschen wirklich, was sie sagen? Ist es Böswilligkeit oder ist es Unwissenheit? Oder ist es einfach ein Auswuchs der verzerrten Weltsicht des Fiat-Verstandes? Sind diese Menschen nicht mehr zu retten, oder könnte Bitcoin sie sogar demütigen und sie auf den Pfad der Verantwortung und der Finanzdisziplin bringen?
Wie auch immer die Antwort lauten mag, die bloße Existenz von Bitcoin ist eine Beleidigung für ihr Denken, oder für jedes Fiat-Denken, was das betrifft. Bitcoin setzt die Idee außer Kraft, dass Geld vom Staat geschaffen werden muss. Seine Architektur sagt: „Jeder sollte Zugang zum Geldsystem haben". Sein Design sagt: „Wir sehen, was ihr getan habt, Fiat-Leute, und wir werden dem ein Ende setzen."
„Die Existenz von Bitcoin ist eine Beleidigung für den Fiat-Verstand."
\ Es ist ironisch, dass das, was die meisten Fiat-Leute zuerst sehen, die Schlachtrufe der Bitcoiner sind, die „HODL!" schreien und „wir werden euch obsolet machen" von den Dächern schreien. Du übersiehst die tiefere Wahrheit dieser Memes, die Tatsache, dass diese Meme der tiefen Überzeugung entspringen, dass ein mathematisch und thermodynamisch gesundes System einem politischen System vorzuziehen ist. Sie hören weder das Brummen der ASICs, noch achten sie auf die gültigen Blöcke, die unaufhörlich eintreffen. Alle 10 Minuten wird leise geflüstert: „Du sollst nicht stehlen."
Das laute und prahlerische Oberflächenphänomen lässt sich leicht ins Lächerliche ziehen und abtun. Der zutiefst technische, wirtschaftliche und spieltheoretische Organismus, der die 21 Millionen zustande bringt, nicht so sehr. Beide sind im Wachstum begriffen. Beide sind miteinander verwoben. Das eine kann ohne das andere nicht existieren.
Fiat-Selbst vs. Bitcoin-Selbst
\ Beim ersten Kontakt wird der Bitcoin von den meisten abgetan. In einer Welt, die vom Fiat-Standard beherrscht wird, sind die meisten Menschen nicht in der Lage, die orangefarbene Münze zu verstehen, wenn sie zum ersten Mal über sie stolpern. Ich denke, man kann mit Sicherheit sagen, dass die meisten Bitcoiner es nicht sofort „verstanden" haben. Ich habe es anfangs sicherlich nicht verstanden.
Die Reise vieler Bitcoiner lässt sich wie folgt zusammenfassen:
- Was zum Teufel ist das?
- Was zum Teufel ist das?
- Was zur Hölle?
- Die Scheiße?
- Scheiße...
- All in.
Der Prozess des Verstehens und der Annahme von Bitcoin ist der Prozess des Verlassens deines Fiat-Selbst hinter sich. Man muss die Fiat-Memes aus dem Kopf bekommen und die Bitcoin-Memes hineinlassen. Du musst dein Fiat-Selbst ausbrennen und dein Bitcoin-Selbst aufbauen. Tag für Tag, Aktion für Aktion, Block für Block.
Indem du am System der Fiat-Schuldensklaverei teilnimmst, verstärkst du das Meme der sofortigen Befriedigung, der Diskontierung der Zukunft für die Gegenwart, des falschen Geldes und des kurzfristigen Denkens. Indem du am Bitcoin-System teilnimmst, stärkst du das Mem des gesunden Geldes, des unelastischen Angebots, des langfristigen Denkens, der Verantwortung und der unveräußerlichen Eigentumsrechte.
„Man kann die Revolution nicht kaufen. Man kann die Revolution nicht machen. Du kannst nur die Revolution sein. Sie ist in deinem Geist, oder sie ist nirgendwo." - Ursula K. Le Guin
Verstehe mich nicht falsch. Es ist nichts falsch daran, in den Fiat-Minen zu arbeiten und bescheiden Sats zu stapeln. Es ist eines der wichtigsten Dinge, die du tun kannst. Das Stapeln von Sats gibt dir Freiheit, Kontrolle und Selbstständigkeit. Es ermöglicht dir, sich in eine Position der Stabilität und Stärke zu manövrieren, und ehe du dich versiehst, wird der einfache Akt des demütigen Stapelns und der Liebe zu deinem zukünftigen dich selbst verändern.
Der wahre Kampf ist ein persönlicher Kampf. Den Drang zu unterdrücken, etwas umsonst haben zu wollen. Die Gewohnheit der sofortigen Befriedigung aufzugeben und eine Kultur des langfristigen Denkens aufzubauen. Ablehnung von impulsiven Ausgaben, Akzeptanz von Opfern und Einschränkungen.
Die Beziehung zwischen Ihnen und der Welt ist transaktional, wie John Dewey uns lehrte. Nicht nur unsere physischen Körper sind an unsere physische Umgebung gebunden, sondern wir sind auch über die ebenso reale wirtschaftliche Umgebung, an der wir uns beteiligen, miteinander verbunden. Und mit jedem Dollar, den wir ausgeben, und jedem Satoshi, den wir sparen, erschaffen wir unsere Zukunft.
Es gibt eine Weggabelung. Das Schild auf der einen Seite sagt: „Du wirst nichts besitzen und du wirst glücklich sein". Das Schild auf der anderen Seite sagt: „Du wirst Bitcoin besitzen und du wirst die beste Version deiner selbst sein."

Die Wahl liegt bei dir.
Bitcoin hat die Macht, die beste Version von sich selbst hervorzubringen, weil die Anreize von Bitcoin auf gegenseitige Verbesserung ausgerichtet sind. Auf individueller Ebene erfordert der Besitz von Bitcoin eine Änderung der Zeitpräferenz und der Verantwortung. Der Besitz impliziert, dass man seine eigenen Schlüssel besitzt. Wenn du das nicht tun, besitzts du keine Bitcoin, sondern Schuldscheine. Es bedeutet auch, dass du deinen eigenen Knotenpunkt betreiben, um zu überprüfen, ob du tatsächlich Bitcoin besitzen. Wenn man das nicht tut, vertraut man auf das Wort eines anderen, verlässt sich auf seine Sicht von Bitcoin, seine Weltsicht und darauf, dass er einen nicht anlügt.
Darüber hinaus bedeutet der fortgesetzte Besitz von Bitcoin, dass man die Verantwortung übernimmt, einen Wert für die Gesellschaft zu schaffen. Geld tut nichts anderes, als zu zirkulieren, also musst etwas leisten, das andere Menschen als wertvoll empfinden. Wenn du das nicht tust, wirst du bald keine Bitcoin mehr haben. Die Natur wird dich dazu zwingen, dich von deinen Sats zu trennen, denn jeder - auch du - muss essen.
„Beschäftige dich mit dem Sinn des Lebens, wirf leere Hoffnungen beiseite, engagiere dich für deine eigene Rettung - wenn du dich überhaupt um dich selbst kümmerst - und tue es, solange du kannst."\ \ Marcus Aurelius
Der Bitcoin-Weg ist kein einfacher Weg, aber ein erfüllender. Er ist erfüllend, weil du die Regeln kennst, du kennst die Konsequenzen, und du hast die Verantwortung. Es ist ein Weg, der es dir erlaubt, dein Leben so zu gestalten, wie du es für richtig hältst, aber du musstes auch selbst gestalten. Es ist ein Weg, der es dir ermöglicht, sich vor Übergriffen und Diebstahl zu schützen, und der langfristige Sicherheit und Stabilität bietet. Aber du musst ihn gehen. Du musst mitmachen. Du musst ihn ausleben.
Du musst dein Fiat-Selbst ausbrennen und die einfachen Antworten, die Abkürzungen und den Scheinwert hinter dir lassen. Du musst etwas Reales anbieten, jemand Reales sein und im Falle des Scheiterns die realen Konsequenzen tragen.
Die Grenze zwischen Gut und Böse verläuft nicht nur in jedermanns Herzen, sondern auch die Grenze zwischen Fiat und Bitcoin verläuft ebenfalls in jedermanns Herzen. Es geht nicht um „wir gegen sie". Es geht um unser Fiat-Selbst gegen unser Bitcoin-Selbst. Persönliche Verantwortung vs. vorsätzliche Ignoranz. Systemische Fragilität vs. langfristige Stabilität. Mit jeder Handlung triffst du eine Entscheidung, und du hast keine andere Wahl als zu handeln.
Es gibt eine Weggabelung, und jeder Einzelne von uns muss sich entscheiden, welchen Weg er einschlagen will. Den scheinbar bequemen Weg, den die Machthaber vorgeben, oder den Bitcoin-Weg: hart, steinig, mit Höhen und Tiefen, ohne Sicherheitsnetze und ohne Rettungsaktionen. Es ist kein einfacher Weg, aber es ist ein schöner Weg. Ein Weg, der Geduld, Verantwortung und Disziplin lehrt. Ein Weg, der dich demütig macht. Ein sinnvoller Weg. Ein Weg, den zu gehen sich lohnt.
Früher war es ein einsamer Weg, aber das ist er nicht mehr. Früher war es ein verrückter Weg. Heute ist der Weg zu mehr Freiheit der verrückte Weg. Es ist ein langer Weg, ein täglicher Kampf. Und niemand außer dir kann diesen Weg gehen. Ich würde dir gerne sagen, dass ich dich auf dem Gipfel treffe, aber ich fürchte, es gibt keinen Gipfel. Ich treffe dich stattdessen auf dem Weg.

Gigi ist ein professioneller Shitposter und Meme-Kenner. Er ist vor kurzem aus der woken Höllenlandschaft der Vogel-App in das lila gelobte Land des Straußen-Protokolls umgezogen. Wenn er nicht gerade Shitposting betreibt, ist er meistens damit beschäftigt, ein Bitcoin-Genießer zu sein und seine Pflaumen im Glanz der orangefarbenen Münze zu baden. Du kannst ihn herbeirufen, indem du seinem npub in den Kartenschlitz eines stillgelegten Geldautomaten flüsterst:
npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc
-
 @ 04ea4f83:210e1713
2025-05-01 17:59:51
@ 04ea4f83:210e1713
2025-05-01 17:59:51In nicht allzu vielen Jahren wird die Zahl der Bitcoiner in den Vereinigten Staaten von Amerika zehn Millionen überschreiten. Wenn wir diesen Meilenstein erreichen, ist das Spiel vorbei: Bitcoin gewinnt.
Mein Lieblingsautor und -denker, Nassim Nicholas Taleb, schrieb in seinem Buch Skin in the Game über "die unnachgiebige Minderheit". Das Konzept funktioniert folgendermaßen: Auf fast allen verpackten Lebensmitteln, die in den USA verkauft werden, ist außen ein kleines U in einem Kreis aufgedruckt. Nur sehr wenige US-Bürger benötigen die durch dieses U gekennzeichnete Koscher-Zertifizierung, aber für die Lebensmittelhersteller ist es einfacher, nicht für jedes Produkt zwei separate Versionen zu produzieren, so dass sie im Allgemeinen alles koscher machen. Nach Taleb gilt die Regel: „Ein koscherer Esser wird niemals nicht-koschere Lebensmittel essen, aber einem nicht-koscheren Esser ist es nicht verboten, koscher zu essen."
„Bei den meisten beobachteten komplexen Systemen liegt der Anteil der Minderheit, der erforderlich ist, um die Bevölkerung von ihrer unnachgiebigen Meinung abzubringen, in der Größenordnung von 3 bis 4%. Bei einer US-Bevölkerung von 325 Millionen sind 3% 10 Millionen." - Nassim Nicholas Taleb
Ein Fintech-Fonds, der seit 2012 im Bitcoin-Bereich tätig ist, hat kürzlich eine intensive Analyse durchgeführt, die zur besten Schätzung des Bitcoin-Besitzes geführt hat, die ich kenne. Nur 7 Millionen Menschen weltweit haben einen Wert von 100 Dollar oder mehr im Bitcoin-Protokoll gespeichert. Um die Zahlen zu runden, nehmen wir an, dass die Hälfte dieser Menschen in den USA lebt und dass ein Siebtel von ihnen einen höheren Wert als $2500 in BTC speichert. Das sind gerade einmal 500.000 US-Bürger mit einer bedeutenden Menge an Bitcoin. Und wie viel Prozent davon verstehen und interessieren sich tatsächlich so sehr für Bitcoin, dass sie dafür kämpfen würden? Lass uns großzügig sein und sagen wir 20%.
Es gibt ungefähr 100.000 Bitcoiner in den Vereinigten Staaten. Das bedeutet, dass wir eine 100-fache Steigerung benötigen, um das Niveau einer "unnachgiebigen Minderheit" zu erreichen. Das ist der Grund, warum die Akzeptanz alle anderen Prioritäten für Bitcoin dominiert.
„Bitcoiner haben bereits so viele potentielle Angriffsvektoren ausgeschaltet und so viel FUD gehandhabt, dass es nicht mehr viel Abwärtsrisiko für Bitcoin gibt." - Cory Klippsten
Ein weiteres Konzept, auf das sich Taleb in den fünf Bänden seines Incerto bezieht, ist: Schütze dich vor dem Abwärtsrisiko. Bitcoiner haben bereits so viele potentielle Angriffsvektoren ausgeschaltet und so viel FUD gehandhabt, dass es nicht mehr viel Abwärtsrisiko für Bitcoin gibt. Aber es gibt ein gewisses Risiko, egal ob man es mit unter 1%, unter 10% oder mehr beziffert. Und der bei weitem bedrohlichste Angriffsvektor wäre meiner Meinung nach eine konzertierte Aktion der US-Regierung auf vielen Ebenen, die versucht, Bitcoin auszurotten, um die Hegemonie des Dollars auf der ganzen Welt zu erhalten.
Um es klar zu sagen: Bitcoin würde selbst den konzertiertesten und bösartigsten Angriff der US-Regierung überleben. Er könnte sogar gedeihen, im Stil von Antifragile (ein weiteres Buch von Taleb), mit Menschen auf der ganzen Welt, die massenhaft Sats kaufen, wenn sie sehen, wie der frühere Hegemon ausschlägt. Es könnte aber auch anders kommen, mit einem massiven Rückgang der Netzwerkaktivität und des gespeicherten Wertes, mit Tausenden von Menschenleben, die irreparabel gestört werden, und mit einer Verzögerung unserer leuchtend orangenen Zukunft um Jahrzehnte oder länger.
Das ist für mich nicht hinnehmbar. Deshalb habe ich mein Leben der Rekrutierung der anderen 99% unserer unnachgiebigen Bitcoiner-Minderheit hier in den Vereinigten Staaten gewidmet. Es gibt bereits 100.000 von uns. Helfe mit, die anderen 9,9 Millionen zu rekrutieren.
-
 @ 40bdcc08:ad00fd2c
2025-05-06 14:24:22
@ 40bdcc08:ad00fd2c
2025-05-06 14:24:22Introduction
Bitcoin’s
OP_RETURNopcode, a mechanism for embedding small data in transactions, has ignited a significant debate within the Bitcoin community. Originally designed to support limited metadata while preserving Bitcoin’s role as a peer-to-peer electronic cash system,OP_RETURNis now at the center of proposals that could redefine Bitcoin’s identity. The immutable nature of Bitcoin’s timechain makes it an attractive platform for data storage, creating tension with those who prioritize its monetary function. This discussion, particularly around Bitcoin Core pull request #32406 (GitHub PR #32406), highlights a critical juncture for Bitcoin’s future.What is
OP_RETURN?Introduced in 2014,
OP_RETURNallows users to attach up to 80 bytes of data to a Bitcoin transaction. Unlike other transaction outputs,OP_RETURNoutputs are provably unspendable, meaning they don’t burden the Unspent Transaction Output (UTXO) set—a critical database for Bitcoin nodes. This feature was a compromise to provide a standardized, less harmful way to include metadata, addressing earlier practices that embedded data in ways that bloated the UTXO set. The 80-byte limit and restriction to oneOP_RETURNoutput per transaction are part of Bitcoin Core’s standardness rules, which guide transaction relay and mining but are not enforced by the network’s consensus rules (Bitcoin Stack Exchange).Standardness vs. Consensus Rules
Standardness rules are Bitcoin Core’s default policies for relaying and mining transactions. They differ from consensus rules, which define what transactions are valid across the entire network. For
OP_RETURN: - Consensus Rules: AllowOP_RETURNoutputs with data up to the maximum script size (approximately 10,000 bytes) and multiple outputs per transaction (Bitcoin Stack Exchange). - Standardness Rules: LimitOP_RETURNdata to 80 bytes and one output per transaction to discourage excessive data storage and maintain network efficiency.Node operators can adjust these policies using settings like
-datacarrier(enables/disablesOP_RETURNrelay) and-datacarriersize(sets the maximum data size, defaulting to 83 bytes to account for theOP_RETURNopcode and pushdata byte). These settings allow flexibility but reflect Bitcoin Core’s default stance on limiting data usage.The Proposal: Pull Request #32406
Bitcoin Core pull request #32406, proposed by developer instagibbs, seeks to relax these standardness restrictions (GitHub PR #32406). Key changes include: - Removing Default Size Limits: The default
-datacarriersizewould be uncapped, allowing largerOP_RETURNdata without a predefined limit. - Allowing Multiple Outputs: The restriction to oneOP_RETURNoutput per transaction would be lifted, with the total data size across all outputs subject to a configurable limit. - Deprecating Configuration Options: The-datacarrierand-datacarriersizesettings are marked as deprecated, signaling potential removal in future releases, which could limit node operators’ ability to enforce custom restrictions.This proposal does not alter consensus rules, meaning miners and nodes can already accept transactions with larger or multiple
OP_RETURNoutputs. Instead, it changes Bitcoin Core’s default relay policy to align with existing practices, such as miners accepting non-standard transactions via services like Marathon Digital’s Slipstream (CoinDesk).Node Operator Flexibility
Currently, node operators can customize
OP_RETURNhandling: - Default Settings: Relay transactions with oneOP_RETURNoutput up to 80 bytes. - Custom Settings: Operators can disableOP_RETURNrelay (-datacarrier=0) or adjust the size limit (e.g.,-datacarriersize=100). These options remain in #32406 but are deprecated, suggesting that future Bitcoin Core versions might not support such customization, potentially standardizing the uncapped policy.Arguments in Favor of Relaxing Limits
Supporters of pull request #32406 and similar proposals argue that the current restrictions are outdated and ineffective. Their key points include: - Ineffective Limits: Developers bypass the 80-byte limit using methods like Inscriptions, which store data in other transaction parts, often at higher cost and inefficiency (BitcoinDev Mailing List). Relaxing
OP_RETURNcould channel data into a more efficient format. - Preventing UTXO Bloat: By encouragingOP_RETURNuse, which doesn’t affect the UTXO set, the proposal could reduce reliance on harmful alternatives like unspendable Taproot outputs used by projects like Citrea’s Clementine bridge. - Supporting Innovation: Projects like Citrea require more data (e.g., 144 bytes) for security proofs, and relaxed limits could enable new Layer 2 solutions (CryptoSlate). - Code Simplification: Developers like Peter Todd argue that these limits complicate Bitcoin Core’s codebase unnecessarily (CoinGeek). - Aligning with Practice: Miners already process non-standard transactions, and uncapping defaults could improve fee estimation and reduce reliance on out-of-band services, as noted by ismaelsadeeq in the pull request discussion.In the GitHub discussion, developers like Sjors and TheCharlatan expressed support (Concept ACK), citing these efficiency and innovation benefits.
Arguments Against Relaxing Limits
Opponents, including prominent developers and community members, raise significant concerns about the implications of these changes: - Deviation from Bitcoin’s Purpose: Critics like Luke Dashjr, who called the proposal “utter insanity,” argue that Bitcoin’s base layer should prioritize peer-to-peer cash, not data storage (CoinDesk). Jason Hughes warned it could turn Bitcoin into a “worthless altcoin” (BeInCrypto). - Blockchain Bloat: Additional data increases the storage and processing burden on full nodes, potentially making node operation cost-prohibitive and threatening decentralization (CryptoSlate). - Network Congestion: Unrestricted data could lead to “spam” transactions, raising fees and hindering Bitcoin’s use for financial transactions. - Risk of Illicit Content: The timechain’s immutability means data, including potentially illegal or objectionable content, is permanently stored on every node. The 80-byte limit acts as a practical barrier, and relaxing it could exacerbate this issue. - Preserving Consensus: Developers like John Carvalho view the limits as a hard-won community agreement, not to be changed lightly.
In the pull request discussion, nsvrn and moth-oss expressed concerns about spam and centralization, advocating for gradual changes. Concept NACKs from developers like wizkid057 and Luke Dashjr reflect strong opposition.
Community Feedback
The GitHub discussion for pull request #32406 shows a divided community: - Support (Concept ACK): Sjors, polespinasa, ismaelsadeeq, miketwenty1, TheCharlatan, Psifour. - Opposition (Concept NACK): wizkid057, BitcoinMechanic, Retropex, nsvrn, moth-oss, Luke Dashjr. - Other: Peter Todd provided a stale ACK, indicating partial or outdated support.
Additional discussions on the BitcoinDev mailing list and related pull requests (e.g., #32359 by Peter Todd) highlight similar arguments, with #32359 proposing a more aggressive removal of all
OP_RETURNlimits and configuration options (GitHub PR #32359).| Feedback Type | Developers | Key Points | |---------------|------------|------------| | Concept ACK | Sjors, ismaelsadeeq, others | Improves efficiency, supports innovation, aligns with mining practices. | | Concept NACK | Luke Dashjr, wizkid057, others | Risks bloat, spam, centralization, and deviation from Bitcoin’s purpose. | | Stale ACK | Peter Todd | Acknowledges proposal but with reservations or outdated support. |
Workarounds and Their Implications
The existence of workarounds, such as Inscriptions, which exploit SegWit discounts to embed data, is a key argument for relaxing
OP_RETURNlimits. These methods are costlier and less efficient, often costing more thanOP_RETURNfor data under 143 bytes (BitcoinDev Mailing List). Supporters argue that formalizing largerOP_RETURNdata could streamline these use cases. Critics, however, see workarounds as a reason to strengthen, not weaken, restrictions, emphasizing the need to address underlying incentives rather than accommodating bypasses.Ecosystem Pressures
External factors influence the debate: - Miners: Services like Marathon Digital’s Slipstream process non-standard transactions for a fee, showing that market incentives already bypass standardness rules. - Layer 2 Projects: Citrea’s Clementine bridge, requiring more data for security proofs, exemplifies the demand for relaxed limits to support innovative applications. - Community Dynamics: The debate echoes past controversies, like the Ordinals debate, where data storage via inscriptions raised similar concerns about Bitcoin’s purpose (CoinDesk).
Bitcoin’s Identity at Stake
The
OP_RETURNdebate is not merely technical but philosophical, questioning whether Bitcoin should remain a focused monetary system or evolve into a broader data platform. Supporters see relaxed limits as a pragmatic step toward efficiency and innovation, while opponents view them as a risk to Bitcoin’s decentralization, accessibility, and core mission. The community’s decision will have lasting implications, affecting node operators, miners, developers, and users.Conclusion
As Bitcoin navigates this crossroads, the community must balance the potential benefits of relaxed
OP_RETURNlimits—such as improved efficiency and support for new applications—against the risks of blockchain bloat, network congestion, and deviation from its monetary roots. The ongoing discussion, accessible via pull request #32406 on GitHub (GitHub PR #32406). Readers are encouraged to explore the debate and contribute to ensuring that any changes align with Bitcoin’s long-term goals as a decentralized, secure, and reliable system. -
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ 2b24a1fa:17750f64
2025-05-01 08:26:05
@ 2b24a1fa:17750f64
2025-05-01 08:26:05Ein Gedicht unserer Zeit von Lionne Douce.
Sprecherin: Sabrina Khalil
https://soundcloud.com/radiomuenchen/der-gutmenschzug-ist-da-von?
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 2b24a1fa:17750f64
2025-04-29 08:20:58
@ 2b24a1fa:17750f64
2025-04-29 08:20:58Die Satire Muxmäuchenstill von 2004 erzählt die Geschichte des 30-jährigen Mux, der seine Mitbürgern zu mehr Verantwortungsbewusstsein erziehen möchte. Dazu stellt er Raser, Schwarzfahrer, Graffiti-Sprüher, Falschparker, Ladendiebe und Vergewaltiger, konfrontiert sie mit ihrem Verhalten und bestraft sie.
https://soundcloud.com/radiomuenchen/muxmauschenstill-x-interview-mit-jan-henrik-stahlberg?
Als Mitstreiter gewinnt er Arbeits- und Obdachlose. Mux’ fanatische Ein-Mann-Mission wächst zu einem kleinen Unternehmen. Auch privat kann er seinen Moralismus nicht zügeln und erschießt seine Freundin. Am Ende des Films wird er von einem Raser überfahren.
Ab 1. Mai läuft die Fortsetzung in den Kinos: Muxmäuschenstill X: muxfilm.de/. Nach zwanzig Jahre Wachkoma findet sich Mux in einer Welt wieder, die er nicht mehr versteht: dem wunderbaren Neoliberalismus. Wieder möchte Mux die Menschen erziehen. Doch diesmal kämpft er gegen ein System, das alles durchdringt, die Welt spaltet, unsere Lebensgrundlagen zerstört, die Reichen reicher macht und die Armen ärmer. Mux gründet den Muxismus und schart die Aussortierten des Systems um sich.
Drehbuchautor und Hauptdarsteller Jan Henrik Stahlberg führt diesmal auch Regie. Unser Autor Jonny Rieder hat mit Jan Henrik Stahlberg über seinen neuen Film gesprochen. Zunächst wollte er wissen, wo für ihn die Grenze verläuft zwischen Übergriffigkeit und Zivilcourage und wie er Mux hier einordnet.
Bild: Mux Filmproduktion
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 2b24a1fa:17750f64
2025-04-28 09:11:34
@ 2b24a1fa:17750f64
2025-04-28 09:11:34Eine Stunde Klassik! Der Münchner Pianist und "Musikdurchdringer" Jürgen Plich stellt jeden Dienstag um 20 Uhr bei Radio München (https://radiomuenchen.net/stream/) große klassische Musik vor. Er teilt seine Hör- und Spielerfahrung und seine persönliche Sicht auf die Meisterwerke. Er spielt selbst besondere, unbekannte Aufnahmen, erklärt, warum die Musik so und nicht anders klingt und hat eine Menge aus dem Leben der Komponisten zu erzählen.
Sonntags um 10 Uhr in der Wiederholung. Oder hier zum Nachhören:
-
 @ 04ea4f83:210e1713
2025-04-20 08:46:16
@ 04ea4f83:210e1713
2025-04-20 08:46:16Veröffentlicht auf Youtube am 19.01.2024\ Originalautor: Bitcoin University\ Übersetzt und angepasst von: Sinautoshi am 21.01.2024 - 825611\ \ Dieser Artikel wird auf der Website von European Bitcoiners nur zu Bildungs-, Informations- und Übersetzungszwecken zur Verfügung gestellt und stellt weder eine finanzielle Beratung noch einen Anspruch auf die im Bericht erwähnten Details dar.\ \ Alle Rechte liegen bei dem Autor des Originals.
Du hast auch begrenzte Zeit um Bitcoin zu verstehen und zu nutzen.
Also, wie bestimmst du nun wie du deine begrenzte Zeit sinnvoll einsetzt?
Weg #1: Shitcoiner/Altcoiner
Dein Tag als Shitcoiner:
- Schaue viele Youtube Videos mit den Vorschaubildern von Kerlen mit offenem Mund, weil die dich mit einfach mit den besten Informationen versorgen
- Den Preis von einem dutzend Kryptowährungen mindestens ein paar hundertmal checken
- Ehrfurchtsvoll Krypto Trading Charts lesen
- Sicher gehen, dass du niemals deine Performance in BTC misst, da dies dir zeigen könnte, dass Shitcoins doch nicht so eine gute Idee ist
- Das Internet nach Informationen durchforstest, welcher Coin als nächstes groß rauskommen wird um dabei nach folgenden Schema vorzugehen:\ - Versuche frühzeitig zu kaufen\ - Versuche nicht abgezockt zu werden\ - Dann schnell verkaufen\ - Einen großen Teil des Gewinns direkt ans Finanzamt abdrücken\ - Und nun alles wieder von vorn!\ \ VERTRAU MIR JUNGE, SO WERDEN WIR ALLE MILLIONÄRE!!!!
- Achtung (!), du brauchst nur den passenden Guru oder Online Trading Berater, der dir sagt welche Kryptowährung und dir stündlich, die passenden Trading-Signale schickt
- Das einzig wichtige: schalte niemals dein eigenes Hirn an.
- Versuche nicht zu verstehen wie ein Markt funktioniert
- Springe von Gerücht zu Gerücht und kümmere dich nur um das Allerneuste
Vertraue einfach anderen Leute dir zu sagen was du zu denken hast, denn schließlich hat reich werden nichts damit zu tun an sich zu arbeiten und echte Fähigkeiten zu lernen.
Das Patentrezept ist der Hochfrequenz-Handel während man im Schlafanzug vor dem PC sitzt.
Falls du doch mal abgezogen werden solltest:
Stelle sicher, dass du auf Telegram einen ausgezeichneten Online Wiederherstellungsdienst bezahlst, der dir hilft die Coins wiederzuholen.
Lass dir dabei vorlügen, dass alle Bitcoin und Kryptotransaktionen rückgängig zu machen sind, obwohl sie IRREVERSIBEL sind.
Genieß deine Shitcoinerei - sie könnte nicht von langer Dauer sein.
Immerhin hast du nun ein paar Dopamin Stöße bekommen.
Weg #2: Bitcoiner
Wenn dir der Dopamin Stoß wichtiger ist als harte Arbeit, dann ist dieser Weg sicherlich nichts für dich.
Der Tag im Leben eines Bitcoiners:
- Prüft nicht den Preis
- Kauft ein bisschen BTC, sobald etwas Bargeld reinkommt oder macht einfach regelmäßiges DCA
- Bleibt am Ball um zu verstehen wie Bitcoin funktioniert
- Versteht die Anreize, welche das Bitcoin Netzwerk schützt
- Versteht den Unterschied zwischen Proof of Work und Proof of Stake
- Versteht was Miner, Mining Pools, Nodes, XPubs und UTXO sind
- Versteht die Grundlagen eines asymmetrischen Verschlüsselungsverfahren und was es so nützlich macht
- Versteht wie verschiedene Attacken gegen Bitcoin aussehen könnten und warum sie erfolgreich seien oder fehlschlagen müssten
- Lernt wie man eine Hardware Wallet sicher aufsetzt und wiederherstellt
- Lernt wie man die Hardware Wallet mit Sparrow oder Nunchuk verbindet
- Spielt mit Nodes herum auf einem Desktop, Laptop oder Mini PC
- Versteht wie Wiederherstellungsphrasen und Passphrasen funktionieren
- Versteht die Vor- und Nachteile von Single-Sig und Multi-Sig
- Entwickelt seine persönliche Aufbewahrungsmethode, die ihn vor verschiedenen Szenarien schützt
- Weiß wie man eine Hardware Wallet zurücksetzt und sie wiederherstellt
- Weiß wie man seine Bitcoin schnell und überall in die Welt mitnehmen kann, falls das nötig sein sollte
- Weiß wie man seine Bitcoin zwischen den verschiedenen Ebenen wie Lightning und Liquid bewegen kann
- Weiß wie man eine Bitcoin im Lightning Netzwerk selbst verwahren kann wie z.B. mit Phoenix Wallet
- Lernt wie man eine Lightning Node betreibt
- Weiß wie man Bitcoin ohne Identifizierungsverfahren kauft
- Weiß wie und wann man seine Bitcoin mit einer Coinjoin Transaktion verschleiert
- Arbeitet hart in der echten Welt um seinen Lohn in Bitcoin zu tauschen
- Schaut nach Möglichkeiten Bitcoin direkt zu verdienen, entweder durch den Hauptjob oder einen kleinen Nebenjob
- Lernt wie man Software mit GPG verifiziert
- Versteht wie Lightning, Splicing, Liquid und Fedimint arbeiten
Es gibt einfach so viele zu lernen und du wirst einsehen, dass das Trading von Shitcoins einfach Zeitverschwendung ist, wenn man auch die aufgelisteten Fähigkeiten lernen könnte. Dazu wird die übrige Zeit mit Folgendem verbracht:
- Viel Zeit in der Natur
- Atmen von frischer Luft
- Etwas Sonne abbekommen
- Laufen, Joggen und Gewichtstraining
- Kochen, und das mit guten Zutaten
- Zeit mit den Liebsten verbringen, während man abgekoppelt von den sozialen Medien ist
Man versucht einfach jeden Tag eine schlauere, stärkere und bessere Person im Allgemeinen zu werden.
Was nimmst du nun mit?
Hör auf zu zocken, fang an zu lernen.
Anstatt deine Zeit mit Trading und Shitcoins zu verschwenden, lerne wie du Bitcoin kaufst und sie sicher auf einer Hardware Wallet verwahrst. Lerne sie zu benutzten, sie zu löschen und sie wiederherzustellen. Schaue dir regelmäßig dein Sicherheitskonzept an und falls nötig, mache eine Upgrade zu etwas besserem, damit du sicherer und privater unterwegs bist.
Übe deine Bitcoin zu bewegen. Schicke sie dir selbst, konsolidiere deine UTXO und stelle deine Bitcoin wieder her über deinen Seed.
Höre auf mit dem Glückspiel und #studybitcoin.
Bitcoin ist die Revolution.
Bitcoin ist der nächste Bitcoin.
Also, wirst du dich dem Gewinnerteam anschließen?
Wirst du lernen wie du auf einem Bitcoin Standard als selbst souveränes Individuum lebst?
Oder wirst du weiter von Coin zu Coin hüpfen um den nÄcHsTen Bitcoin zu finden ohne etwas an deinen echten Fähigkeiten oder deiner Expertise zu arbeiten während du die größte Menge an Bitcoin, die du je verdient hättest und die in den nächsten 1000 Jahren in Kaufkraft steigt, einfach links liegen lässt.
Selbst wenn du keine Bitcoin haben solltest, oder eine sehr kleine Menge hast, sei dir bewusst es ist nicht zu spät.
Wir sind noch sehr früh dabei.
Wähle weise wie du deine Tage und Wochen verbringst
Die heutigen Entscheidungen werden einen nachhaltigen Einfluss auf den Rest deines Lebens und wahrscheinlich sogar, das deiner Kinder.
Bist du neugierig geworden oder weißt du schon alles über Bitcoin? Ich fordere dich heraus mehr über Bitcoin zu Lernen. Hier findest du eine große Menge an weiterem Material.
-
 @ 0d97beae:c5274a14
2025-01-11 16:52:08
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-
 @ 37fe9853:bcd1b039
2025-01-11 15:04:40
@ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa
-
 @ 04ea4f83:210e1713
2025-04-20 08:45:14
@ 04ea4f83:210e1713
2025-04-20 08:45:14Veröffentlicht auf Nakamoto Portfolio am 06.04.2023\ Originalautor: Alpha Zeta\ Übersetzt von: Sinautoshi am 24.06.2023 - 795682
Einführung
Bitcoin wurde mit verschiedenen Formen von Eigentum und anderen Vermögenswerten verglichen, die traditionell zur Wertaufbewahrung verwendet werden. In der Abwesenheit von gesundem Geld weisen rationale Investoren\ Kapital in Immobilien, Aktien und andere alternativen Wertaufbewahrungsmittel auf. Inspiriert von „Bitcoin as Property" von Michael Saylor, diskutiert dieses Whitepaper das Potenzial von Bitcoin, das monetäre Premium (Anm. den Aufschlag für die Geldartigkeit des Vermögenswertes) von traditionellen Vermögenswerten einzufangen, und seine Auswirkungen auf deren zukünftige Bewertung.
Die Verlagerung vom traditionellen Sparen zu alternativen Anlagen
In der Vergangenheit haben weniger erfahrene Anleger ihr Geld auf Sparkonten gespart, während erfahrenere Anleger nach Hebelwirkung und Effizienz durch Immobilien und Risikoinvestitionen suchten. In den letzten zehn Jahren haben sich die Anleger aufgrund des Rückgangs der Zinssätze und der Ausweitung der Finanzinstrumente haben sich die Anleger für Aktien, Immobilien und\ börsengehandelte Fonds (ETFs) als ihre primären Wertaufbewahrungsmittel entschieden. Die explosionsartige Zunahme von ETFs und die Beliebtheit von Zweitimmobilien (zur Vermietung) oder Real Estate Investment Trusts (REITs) haben zu einer Monetarisierung zahlreicher Vermögenswerte geführt.\ Bis Ende 2021 wurden viele Vermögenswerte, darunter auch Immobilien, weit über ihrem Nutzwert gehandelt. Die Zentralbanken haben mit überschüssigem Geld den Wert des Geldes grundlegend zerstört, was die Anleger dazu veranlasst, nach Vermögenswerten zu suchen, die einen Schutz gegen die negativen Auswirkungen des Gelddruckens bieten. Dieses Phänomen hat zu einer Finanzialisierung der Wirtschaft geführt, bei der die Anleger keine andere Wahl haben, als nach anderen Formen des Sparens zu suchen.
Bitcoin: Der optimale Vermögenswert für die Monetarisierung
Bitcoin hat das Potenzial, der optimale Vermögenswert für die Monetarisierung zu werden und die traditionellen Wertaufbewahrungsmittel wie Währungen, Anleihen, Immobilien, Aktien und Gold konsequent zu demonetisieren.
Immobilien werden aufgrund ihres inhärenten Nutzwerts oft als begehrter Vermögenswert betrachtet, aber ihr Wert wird auch stark von der Monetarisierung beeinflusst, die dazu geführt hat, dass viele Menschen mehrere Immobilien besitzen, was die Nachfrage und die Preise in die Höhe treibt. Es ist jedoch zu beachten, dass der Besitz von Immobilien mit einer Reihe von Problemen verbunden ist. So können beispielsweise die Grundsteuer und die Instandhaltungskosten die potenziellen Renditen erheblich schmälern. Außerdem können Immobilien im Laufe der Zeit an Wert verlieren, was ihren Wert weiter schmälert. Auch wenn man eine Urkunde für eine Immobilie besitzt, ist man nicht der eigentliche Eigentümer der Immobilie; die Zusage des Eigentums kann unter bestimmten Umständen widerrufen werden. Wenn beispielsweise die Regierung beschließt, die Immobilie für die öffentliche Nutzung zu beschlagnahmen, kann der Immobilieneigentümer seine Investition vollständig verlieren. All diese Faktoren haben Anleger dazu veranlasst, nach Alternativen zum Schutz ihres Vermögens zu suchen, insbesondere in einem Umfeld mit geringem Risiko und niedriger Inflation.
Im Gegensatz dazu bietet Bitcoin ein „Konstrukt", das nicht zerstört werden kann, keine Wartung erfordert und eine hervorragende Wertaufbewahrung bietet. Als dezentralisierter, sicherer und knapper digitaler Vermögenswert hat Bitcoin das Potenzial, den monetären Aufschlag traditioneller Vermögenswerte zu übernehmen, was möglicherweise zu deren Demonetisierung führt.
Bitcoin wird aus mehreren Gründen zunehmend als überlegenes Wertaufbewahrungsmittel anerkannt:
- Knappheit: Bitcoin hat einen festen Vorrat von 21 Millionen Münzen, was zu einem Grad an Knappheit führt, der seinen Wert vor Inflation schützt.
- Übertragbarkeit: Bitcoin lässt sich leicht digital übertragen und aufbewahren, was ihn praktischer macht als physische Vermögenswerte wie Gold.
- Sicherheit: Die dezentralisierte Natur der Blockchain-Technologie, die Bitcoin zugrunde liegt, gewährleistet seine Sicherheit und seinen Schutz vor Manipulationen.
- Transparenz: Alle Transaktionen werden in der Blockchain aufgezeichnet, wodurch ein transparenter und überprüfbarer Eigentumsnachweis entsteht.
- Zugänglichkeit: Bitcoin ist für jeden zugänglich, der über einen Internetanschluss verfügt, was ihn zu einem umfassenden Wertaufbewahrungsmittel macht.
- Unveränderlichkeit oder Widerstand gegen Zensur: Die Aufzeichnung des Eigentums ist durch ein massives und wachsendes Computernetzwerk gesichert, was es nahezu unmöglich macht, Transaktionen zu verändern oder zu zensieren. Dies bietet eine zusätzliche Sicherheitsebene und stärkt den Status von Bitcoin als zuverlässiges und vertrauenswürdiges Wertaufbewahrungsmittel.
Das Modell
Das Schrödinger-Münzmodell basiert auf dem Konzept der Quantensuperposition, bei dem ein Objekt gleichzeitig in mehreren Zuständen existieren kann, bis es beobachtet wird. In diesem Fall wird davon ausgegangen, dass Bitcoin zwei mögliche Ergebnisse hat: Entweder scheitert er und ist wertlos (das Dan-Peña-Szenario) oder er erobert erfolgreich die Geldprämie traditioneller Wertaufbewahrungsmittel (das Saylor-Szenario).
Anstatt sich auf absolute Gewissheit wie in den obigen Szenarien zu verlassen, ordnet dieses Modell jedem dieser Szenarien Wahrscheinlichkeiten zu, um einen fairen Wert für Bitcoin zu ermitteln. Wenn du die Box öffnest und eine Welt beobachtest, in der Saylor Recht hatte, was passiert dann? Was wäre, wenn Dan Recht hätte?
Modell-Komponenten
Das Modell berechnet den Marktwert von Bitcoin heute anhand der folgenden Komponenten:
a. Marktkapitalisierung der Vermögenswerte: Der aktuelle Marktwert jedes traditionellen Wertaufbewahrungsmittels (z.B. Gold, Immobilien, Aktien, Anleihen).
b. Prozentsatz des monetären Aufschlags: Der Anteil der Marktkapitalisierung eines Vermögenswerts, der auf seinen Status als Wertaufbewahrungsmittel zurückzuführen ist.
c. Wahrscheinlichkeit der Vereinnahmung: Die Wahrscheinlichkeit, dass Bitcoin die monetäre Prämie jedes Vermögenswerts vereinnahmt.
d. Zeit bis zur Vereinnahmung: Die erwartete Zeit, bis Bitcoin die Geldprämie eines jeden Vermögenswerts erbeutet. Dies kann auch als Vektor mit verschiedenen Prozentsätzen der eingefangenen Prämie über die Zeit modelliert werden.
e. Abzinsungsrate: Der Prozentsatz, mit dem die zukünftig erwarteten Erfassungswerte auf den Gegenwartswert abgezinst werden, um den heutigen Marktwert zu berechnen.
Modell-Berechnung
Der Zeitwert von Bitcoin wird als Summe des erwarteten Erfassungswerts der einzelnen Vermögenswerte berechnet:
wobei der Zeitwert jedes Vermögenswerts definiert ist als:
- mcap: Aktuelle Marktkapitalisierung der einzelnen Vermögenswerte
- mp: Prozentualer Anteil der Marktkapitalisierung, der Monetarisierungscharakter hat (nicht Nutzwert)\ prob: Wahrscheinlichkeit, dass Bitcoin diesen Wert erfasst
- r: Abzinsungssatz
- n: Anzahl der Perioden, bis die Monetarisierung realisiert wird
Denke daran, dass wir mit diesem Rahmen auch den heutigen Bitcoin-Preis verwenden könnten, um die aktuell implizierte Wahrscheinlichkeit des Marktes zu berechnen.
Modell-Inputs
Potenzielle Vermögensklassen und geschätzte Werte - Daten vom April 2023
- Aktien: a. Angenommener Marktwert: $100 Billionen b. Quelle: Die Börsenkapitalisierung kann der Weltbank und Statista entnommen werden.Die Daten stellen eine ungefähre Schätzung dar, da die Börsenkapitalisierung mit den Marktbewegungen schwankt.
- Anleihen: a. Angenommener Marktwert: $130 Billionen b. Quelle: Die Kapitalisierung des globalen Anleihemarktes wurde aus Quellen wie der Bank für Internationalen Zahlungsausgleich abgeleitet. Die Daten stellen eine ungefähre Schätzung dar, da sich die Kapitalisierung des Anleihemarktes durch Neuemissionen und Tilgungen ändert. Sie umfassen nur die Gesamtsumme für „fortgeschrittene Volkswirtschaften".
- Gold: a. Angenommener Marktwert: $10 Billionen b. Quelle: Die Gesamtmarktkapitalisierung von Gold wurde anhand der Daten des World Gold Council zu den oberirdischen Goldbeständen und dem durchschnittlichen Goldpreis pro Unze zum Zeitpunkt der Erstellung dieses Berichts berechnet. Die Daten sollten aktualisiert werden, um den aktuellen Goldpreis für eine genaue Bewertung widerzuspiegeln.
- Silber: a. Angenommener Marktwert: $1,3 Billionen b. Quelle: Die gesamte Marktkapitalisierung von Silber wurde anhand der Daten des Silver Institute zu den oberirdischen Silberbeständen und dem durchschnittlichen Silberpreis pro Unze zum Zeitpunkt der Erstellung dieses Berichts geschätzt. Die Daten sollten aktualisiert werden, um den aktuellen Silberpreis für eine genaue Bewertung widerzuspiegeln.
- Immobilien: a. Angenommener Marktwert: $320 Billionen b. Quelle: Savills Research
- Kryptowährungen (ausgenommen BTC): a. Angenommener Marktwert: $500 Mrd. b. Quelle: Coinmarketcap.com
Parallelen zum Black-Scholes-Modell für die Optionsbewertung
Die Black-Scholes-Formel wird verwendet, um den fairen Preis von Optionen zu berechnen. Dabei handelt es sich um Finanzkontrakte, die dem Käufer das Recht (aber nicht die Verpflichtung) geben, einen Basiswert, z. B. eine Aktie oder einen Rohstoff, zu einem bestimmten Preis und Zeitpunkt zu kaufen oder zu verkaufen.
Die Formel umfasst fünf Inputs: den aktuellen Kurs des Basiswerts, den Ausübungspreis (den Preis, zu dem die Option ausgeübt werden kann), die Zeit bis zum Ablauf, den risikofreien Zinssatz und die Volatilität des Kurses des Basiswerts. Hier ist die Formel für den Preis einer Call-Option:
Die Formel selbst ist etwas kompliziert, aber in einfachen Worten funktioniert sie, indem sie die Wahrscheinlichkeit verschiedener Zukunftsszenarien für den Kurs des Basiswerts auf der Grundlage seiner Volatilität (wie stark sein Kurs im Laufe der Zeit zu schwanken pflegt) schätzt. Die Formel berechnet dann den erwarteten Wert der Option auf der Grundlage dieser Wahrscheinlichkeiten, abgezinst auf den heutigen Wert unter Verwendung des risikofreien Zinssatzes.
Die linke Seite der Gleichung stellt den Wert der Call-Option dar (das Recht, den Basiswert zu kaufen), während die rechte Seite die Summe aus dem Gegenwartswert des Ausübungspreises (der bei Ausübung der Option garantiert wird) und dem erwarteten Wert des Kurses des Basiswerts bei Fälligkeit darstellt. Der Erwartungswert wird berechnet, indem der aktuelle Kurs des Basiswerts mit einer Wahrscheinlichkeitsdichtefunktion multipliziert wird, die auf der Volatilität des Kurses des Basiswerts basiert.
Ein wesentlicher Unterschied zwischen den beiden Modellen besteht darin, dass die Black-Scholes-Formel auf der Annahme einer kontinuierlichen Zeit und einer bekannten Verteilung der Preise von Vermögenswerten beruht, während das Schrödinger-Münzmodell auf dem Konzept der Quantensuperposition basiert, bei dem ein Objekt in mehreren Zuständen existieren kann, bis es beobachtet wird. Das Schrödinger-Münzmodell ordnet jedem möglichen Ergebnis Wahrscheinlichkeiten zu, um einen fairen Wert für Bitcoin zu ermitteln, während die Black-Scholes-Formel eine Wahrscheinlichkeitsdichtefunktion verwendet, die auf der Volatilität des Preises des zugrunde liegenden Vermögenswerts basiert.
Ein weiterer Unterschied besteht darin, dass die Black-Scholes-Formel eine geschlossene Gleichung ist, was bedeutet, dass sie analytisch gelöst werden kann, während das Schrödinger-Münzen-Modell ein komplexeres Modell ist, das mehrere Eingaben und Berechnungen umfasst.
Trotz dieser Unterschiede zielen beide Modelle darauf ab, den beizulegenden Zeitwert eines Vermögenswerts zu schätzen, indem sie verschiedene Faktoren wie den aktuellen Preis des Vermögenswerts, die Zeit bis zum Verfall, die Zinssätze und die Volatilität berücksichtigen. Beide Modelle berücksichtigen auch das Potenzial für extreme Ergebnisse und die Ungewissheit künftiger Ereignisse, die zur Volatilität des Vermögenswerts beitragen können.
Schrödingers Münze und Volatilität als Merkmal, nicht als Fehler
Einer der meistdiskutierten Aspekte von Bitcoin und anderen Kryptowährungen ist ihre inhärente Preisvolatilität. In diesem Abschnitt argumentieren wir, dass das Schrödinger-Münzmodell die Volatilität von Bitcoin als ein natürliches Merkmal seiner Bewertung erklärt und nicht als Fehler oder Schwachstelle. Darüber hinaus werden wir diskutieren, wie diese Volatilität abnehmen kann, wenn wir uns der Hyperbitcoinisierung nähern.
- Extreme Ergebnisse Das Schrödinger Modell basiert auf zwei extremen Ergebnissen für Bitcoin: entweder sch-eitert er und wird wertlos (das Dan Peña Szenario), oder er erobert erfolgreich die Geldprämie traditioneller Wertaufbewahrungsmittel (das Saylor Szenario). Infolgedessen sagt das Modell von Natur aus erhebliche Wertschwankungen voraus, die von der Marktstimmung und externen Faktoren abhängen, die die Wahrnehmung der Anleger hinsichtlich der Wahrscheinlichkeit dieser Ergebnisse beeinflussen.
- Kleine Änderungen in der Wahrscheinlichkeit, große Änderungen im fairen Wert Angesichts der extremen Natur der beiden möglichen Ergebnisse können kleine Änderungen in der wahrgenommenen Wahrscheinlichkeit des Eintretens eines der beiden Szenarien zu erheblichen Änderungen im fairen Wert von Bitcoin führen. Zum Beispiel könnte ein leichter Anstieg des Vertrauens des Marktes in den Erfolg von Bitcoin zu einem signifikanten Anstieg des Preises führen, während ein Rückgang des Vertrauens zu einem starken Rückgang führen könnte.
- Ungewissheit der Zeit Ein weiterer Faktor, der zur Volatilität von Bitcoin beiträgt, ist die Ungewissheit über die Zeit, die benötigt wird, um die Hyperbitcoinisierung zu erreichen. Während Hausse-Märkten nimmt die Zeitwahrnehmung (t) tendenziell ab, da die Anleger optimistischer werden, was die Akzeptanz von Bitcoin und die Geschwindigkeit angeht, mit der Bitcoin die Geldprämie von traditionellen Vermögenswerten erreichen wird. Umgekehrt steigt die wahrgenommene Zeit bis zur Hyperbitcoinisierung während Baisse-Märkten, wenn die Marktstimmung negativ wird. Diese Fluktuation in der Zeitwahrnehmung fügt dem Bitcoin-Kurs eine weitere Ebene der Volatilität hinzu.
- Abnehmende Volatilität bei zunehmender Hyperbitcoinisierung Je näher wir der Hyperbitcoinisierung kommen, desto geringer dürfte die Volatilität von Bitcoin werden. Dies liegt daran, dass der Markt im Laufe der Zeit mehr Informationen über die Akzeptanz von Bitcoin, das regulatorische Umfeld und die technologischen Entwicklungen erhalten wird. Infolgedessen wird die Wahrnehmung des Marktes hinsichtlich der Wahrscheinlichkeit der beiden extremen Ergebnisse stabiler werden, was zu geringeren Preisschwankungen führt.
Zusammenfassend erklärt das Schrödinger-Münzen-Modell die Volatilität von Bitcoin als eine natürliche Folge seiner Bewertung, die auf extremen Ergebnissen, kleinen Veränderungen der Wahrscheinlichkeit und der Ungewissheit der Zeit bis zur Hyperbitcoinisierung beruht. Wenn der Markt mehr Informationen erhält und mehr Vertrauen in die Zukunft von Bitcoin gewinnt, wird erwartet, dass seine Volatilität abnimmt und gegen Null tendiert. Das Verständnis dieses Aspekts des Modells kann Anlegern helfen, fundiertere Entscheidungen über die mit einer Investition in Bitcoin verbundenen Risiken und Erträge zu treffen.
Schlussfolgerung
Schrödingers-Münzmodell bietet einen Rahmen für die Bewertung von Bitcoin, indem es sein Potenzial berücksichtigt, den monetäre Aufschlag von traditionellen Vermögenswerten wie Immobilien, Aktien und Anleihen einzufangen. Als überlegenes Wertaufbewahrungsmittel hat Bitcoin das Potenzial, Investitionen in traditionelle Vermögenswerte konsequent zu demonetisieren, was zu einer Verschiebung der Kapitalallokation und einer Neubewertung ihres Wertes führt.
Das Modell beleuchtet auch die inhärente Volatilität von Bitcoin, die sich aus den extremen Ergebnissen, kleinen Veränderungen der Wahrscheinlichkeit und der Ungewissheit der Zeit bis zur Hyperbitcoinisierung ergibt. Da der Markt jedoch mehr Informationen erhält und mehr Vertrauen in die Zukunft von Bitcoin gewinnt, wird erwartet, dass seine Volatilität abnimmt und gegen Null tendiert.
Darüber hinaus unterstreicht das Modell, wie wichtig es ist, die Risiken zu verstehen, die mit einer Investition in Bitcoin verbunden sind, wie regulatorische Änderungen, technologische Herausforderungen und potenzielle Konkurrenz durch andere Kryptowährungen oder alternative Wertaufbewahrungsmittel.
Durch das Verständnis der Dynamik des Schrödinger-Münzmodells sowie der Faktoren, die zur Volatilität von Bitcoin und den damit verbundenen Risiken beitragen, können Anleger fundiertere Entscheidungen über das potenzielle Wachstum und die mit Bitcoin und anderen Vermögenswerten verbundenen Risiken treffen. Dieser ganzheitliche Bewertungsansatz ermöglicht eine umfassendere Beurteilung des Potenzials von Bitcoin sowohl als Investition als auch als transformative Technologie.
-
 @ 62033ff8:e4471203
2025-01-11 15:00:24
@ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。
所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。
https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。
我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛
幸运的是npub.pro 建站这样的,我觉得有点意思。
yakihonne 智能widget 也有意思
我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
-
 @ 04ea4f83:210e1713
2025-04-20 08:41:34
@ 04ea4f83:210e1713
2025-04-20 08:41:34Veröffentlicht auf Bitcoin Magazine am 11.01.2024\ Originalautor: Josh von BlueCollarBitcoin\ Übersetzt von: Sinautoshi am 13.01.2024 - 825611
Wir alle haben einen Werdegang in Bezug auf Bitcoin. Einige begannen als Verfechter des gesunden Geldes, die die österreichische Schule der Nationalökonomie und Gold verehrten. Andere sind aus der TradFi-Welt herausgefallen, als sie merkten, dass etwas nicht ganz richtig war. Die meisten Bitcoiner haben die Irrungen und Wirrungen der Altcoin-Hölle durchlaufen. Wie auch immer du es hierher und zu Bitcoin geschafft hast, willkommen und schnall dich verdammt nochmal an.
Als ich mich zum ersten Mal für Bitcoin interessierte, war das im Juli 2017, und der Bullenmarkt des Jahres war bereits in vollem Gange. Ich kaufte etwas Bitcoin und sah zu, wie der Wert stieg. Dann kaufte ich mehr. Wie es bei diesen parabolischen Aufwärtsbewegungen üblich ist, beobachtete ich, wie der Preis stieg und mein Gemütszustand veränderte sich:
Von Interesse zu Unglauben zu Verliebtheit zu ausgearteten Käufen zu Verzweiflung.
Dies ist eine Entwicklung, die du während der nächsten Aufwärtsbewegung vermeiden kannst, wenn du dich richtig vorbereitest.
Wenn du dies in der Hoffnung liest, alle Antworten zu finden, habe ich leider schlechte Nachrichten. Es gibt keine richtigen Antworten in Bitcoin oder im Leben. Wir sind alle auf einer Reise, um herauszufinden, was wir tun und wie wir vorgehen sollen. Ich hoffe, dass ich dir einen Leitfaden an die Hand geben kann, aber letztendlich werden deine persönlichen Ziele und deine Veranlagung bestimmen, wie du mit der Volatilität umgehst. Bitcoin wird deine Entschlossenheit auf die Probe stellen.
In der späteren Phase des Bullemarkts 2017 sprach ich mit jedem in meinem Leben über Bitcoin - völlig besessen. Mein damaliger Nachbar war älter als ich und hatte den Dot-Com-Boom erlebt. Den Rat, den er mir gab, werde ich nie vergessen, denn er hatte während der Dot-Com-Blase eine Menge Geld gewonnen (und verloren). Er hörte sich mein glühendes Interesse an Bitcoin an und ging sehr maßvoll mit meiner offensichtlichen LIEBE für diesen Vermögenswert um. Er erzählte mir, dass er während des Dot-Com-Booms mehr Geld verdient hat, als er jemals geglaubt hätte, und am Ende war er wieder genau da, wo er angefangen hatte - weil er den Bullenmarkt über den Gipfel geritten und nichts verkauft hatte. Sein Rat war: "Ich freue mich, dass es dir gut geht, aber vergiss nicht, etwas Gewinn mitzunehmen." Er riet mir, 50 % zu verkaufen und 50 % zu behalten - eine einfache Absicherungsstrategie. Kurz nachdem Bitcoin sein Allzeithoch erreicht hatte, beherzigte ich seinen Rat und verkaufte einige meiner Bestände in der Nähe des lokalen Höchststands.
Ich weiß, dass dies für viele Hodler ein Frevel ist. Wir verkaufen unsere Bitcoin doch nicht, oder? Nun, das ist eine persönliche Entscheidung, und je nach deiner Risikotoleranz und deinem Platz im Leben, möchtest du vielleicht ein gewisses Risiko vom Tisch nehmen. Das ist Teil des Investierens, und wie das alte Sprichwort sagt, verliert niemand Geld, wenn er mit Gewinn verkauft. Dieser Artikel soll den Rat geben, den ich mir gewünscht hätte, als ich Bitcoin zum ersten Mal entdeckte. Ich hoffe, er hilft Neulingen in diesem Bereich zu verstehen, wie man sich in dem bombastischen Umfeld zurechtfindet, das Bitcoin während seiner Bullenmärkte erzeugt.
Ich habe zwei Bullenmärkte erlebt, einen im Jahr 2017 und einen im Jahr 2021. Diese Bullenmärkte waren SEHR unterschiedlich, und ich vermute, wenn du mit denjenigen sprichst, die bei Bullenmärkten vor 2017 dabei waren, wirst du feststellen, dass sie sich auch sehr unterschiedlich anfühlten.
Das erste, was ich loswerden möchte, ist Folgendes - niemand weiß, was passieren wird:
- Balaji spricht von 1 Million in 3 Monaten
- Nobelpreisträger sagen, Bitcoin wird auf Null sinken
- Buffett und Munger (RIP) nennen es Rattengift
Egal, wem Du zuhörst, egal, wie lange sie schon in dem Bereich tätig sind oder wie korrekt sie in der Vergangenheit waren, es spielt keine Rolle. Sie haben keine Ahnung, was die Zukunft bringt.
Bei Investitionen gibt es eine Idee, die als Überlebensbias bezeichnet wird. Diejenigen, die richtig lagen, haben überlebt, und sie erscheinen wie Genies, weil sie richtig lagen. Die überwiegende Mehrheit derjenigen, die sich geirrt haben, ist vergessen. Man hört nichts über sie. Ich will hier niemanden in die Pfanne hauen, aber es gab prominente Bitcoin-Leute, die VIEL höhere Preise riefen, als wir im Jahr 2021 bei 68K waren. Ich sage nicht, dass sie schlechte Menschen sind; ich bin mir sicher, dass sie einen guten Grund hatten, diese Zahlen zu prognostizieren, aber wenn man damals ihren Ratschlägen gefolgt wäre, hätte man zum denkbar schlechtesten Zeitpunkt gekauft und wäre für JAHRE unter die Räder gekommen.
Meiner Meinung nach gibt es verschiedene Arten von Kristallkugelbesitzern, und die unterste Kategorie sind die technischen Analysten. Das sind die ein Dutzend Leute, die man auf Twitter sieht, die über Momentum, Preisniveaus, Tassen und Griffe usw. schwadronieren. Diese Leute riefen für 10K Bitcoin, wo der Boden bei 16k lag. Ich sage nicht, dass TA Unsinn ist; im Grunde ist es ein System zur Vorhersage menschlicher Handlungen durch Wahrscheinlichkeit. Es ist bestenfalls eine Überlegung. Sie sollte nie in einem Vakuum verwendet werden, um Ihre Allokationen zu bestimmen. Wenn du es in Verbindung mit den Fundamentaldaten verwendest, kann es viel hilfreicher sein. Worauf ich hier hinaus will, ist, dass es GANZ viele TA-Analysten gibt, die Ihnen raten, bei 68 K zu kaufen und nicht bei 16 K. Sie werfen probabilistische Darts. Setze deine finanzielle Zukunft nicht auf eine fundierte Vermutung von irgendjemandem.
Die zweite Art von Kristallkugel-Liebhabern sind Makro-Analysten. Diese Leute sind meiner Meinung nach glaubwürdiger, weil sie den allgemeinen Trend in der Wirtschaft einschätzen. Sie berücksichtigen die Zinssätze, die Bewegungen der Fed und die Wirtschaftsdaten. Diese Leute sind viel näher an der Realität, weil sie den Finger am Puls des wirtschaftlichen Geschehens haben. Aber wie bei den TA-Analysten können sich auch diese Leute VÖLLIG irren. Viele sagten, dass die Leitzinsen nicht über x oder y steigen könnten, da sonst die gesamte Wirtschaft zusammenbrechen würde. Nun, die Zinssätze wurden auf ein Niveau angehoben, das weit über ihren Weltuntergangsprognosen liegt, und wir haben keinen Zusammenbruch erlebt.
Ob du nun einem TA-Analysten oder einem Makro-Analysten folgst, sie können wegen eines schwarzen Schwans völlig FALSCH liegen. Nicholas Taleb - bekanntlich von Bitcoinern gehasst - hat den Begriff "schwarzer Schwan" geprägt, um Ereignisse zu bezeichnen, die von Zeit zu Zeit eintreten und mit Standardmodellen einfach nicht vorhergesagt werden können, weil sie so unwahrscheinlich sind. Covid war ein schwarzer Schwan. Der Krieg in der Ukraine war ein schwarzer Schwan. Und rate mal, was passiert: Morgen könnte es einen weiteren unvorhersehbaren schwarzen Schwan geben, der alle TA- und Makro-Analysten völlig auf den Kopf stellt. In der Welt gibt es jede Menge Zufälle. Übrigens sind schwarze Schwäne nicht immer schlecht. Sie können genauso gut auch positive Katalysatoren sein.
Heißt das also, dass wir vor Angst gelähmt bleiben und niemandem trauen sollten?
Ganz und gar nicht. Es bedeutet, dass wir uns die Mühe machen sollten, UNS SELBST zu BILDEN! Du musst die Verantwortung für dich und deine Entscheidungen übernehmen. Du kannst die Informationen der TA-Analysten und der Makro-Analysten nehmen und deine eigenen fundierten Entscheidungen treffen. DAS IST VON GRÖSSTER WICHTIGKEIT.
BILDE DICH SELBST WEITER
Bitcoin ist ein unglaublich einfaches und doch unendlich komplexes Wesen. Deine Ausbildung wird nie vollständig sein, aber du kannst dein Verständnis Schritt für Schritt erweitern. Wir haben eine 10-teilige Bitcoin-Grundlagen-Serie mit Dazbea und Seb Bunney gemacht, und ich habe das Gefühl, dass wir nicht einmal an der Oberfläche gekratzt haben!
Du solltest gut ausgebildet sein, um widerstandsfähig zu werden. Wenn du ein solides Verständnis von Bitcoin und seiner Funktionsweise hast, wirst du nicht so leicht zu erschüttern sein. Die Psychologie ist hier SEHR WICHTIG. Wenn du verstehst, in was du investierst, und der Markt von einem Börsenausfall betroffen ist, ähnlich dem, der FTX passiert ist, wirst du einige Dinge verstehen, die die Durchschnittsperson vielleicht nicht versteht.
- Bitcoin ist davon nicht betroffen
- Der Preisverfall ist vorübergehend und unbegründet
- Deshalb ist jetzt ein guter Zeitpunkt, um Bitcoin zu akkumulieren
Aber auch das Gegenteil ist der Fall. Wenn du siehst, wie die Mainstream-Schlagzeilen über Bitcoin schwärmen und die Gewinne kein Ende zu nehmen scheinen, und du das Gefühl hast, dass du jedes bisschen Geld in Bitcoin investieren solltest, weil der Preis nirgendwo hin geht, außer nach oben - dann sei VORSICHTIG. Ich habe festgestellt, dass meine Psychologie typisch ist. Ich habe Angst, wenn der Preis nach unten geht, und ich habe irrationalen Überschwang, wenn der Preis schnell steigt. Wenn ich GENAU das Gegenteil von dem tue, was mein Affenhirn mir sagt, stelle ich fest, dass ich oft das Richtige tue. Das heißt, wenn du extreme Angst verspürst, ist dies der richtige Zeitpunkt zum Kaufen, und wenn du dich überschwänglich fühlst, ist dies der richtige Zeitpunkt zum Verkaufen.
Panikkäufe sind gefährlich. Wenn du einen unkontrollierbaren Drang verspürst, Bitcoin zu kaufen, atme tief durch. Ich kann dir versichern, dass du in der Lage sein wirst, etwas Bitcoin zu kaufen, und wenn du den Drang so stark verspürst, ist der Markt wahrscheinlich reif für einen Rücksetzer. Das ist keine Garantie, aber nach meiner Erfahrung ist dies der wahrscheinliche Fall. Ich plädiere nicht für den Handel mit BTC, ganz und gar nicht. Ich kann ehrlich sagen, dass ich durch den Handel mehr BTC verloren als gewonnen habe, und wenn die meisten Leute ehrlich sind, werden sie das auch zugeben. Das Trading ist eine Fähigkeit und Disziplin, die nur sehr wenige Menschen beherrschen.
Die typischen psychologischen Hindernisse, die den Menschen im Weg stehen, sind Angst und Gier. Denk über deine Gefühle nach und erkenne, wann du diese Emotionen erlebst. Sie werden dich dazu bringen, Fehler zu machen. Der einfachste Weg, all dies zu mildern, ist einfach der Dollar-Cost-Average. Dollar-Cost Averaging nimmt den ganzen Stress heraus. Basta. Wenn du in diesem Moment in diesen Schatz einsteigst und er über Nacht auf 30 % fällt, frage dich ehrlich: Habe ich den Mut dazu? Habe ich die nötige Überzeugung dafür? Habe ich das nötige Wissen, um zu verstehen, warum der Dollarpreis kurzfristig keine Rolle spielt? Werde ich in Panik verkaufen? Wenn du nicht überzeugt bist, wird dich das Dollar-Cost-Averaging retten. Du bekommst den Durchschnittspreis über einen langen Zeitraum.
Ich habe eine kleine DCA-Taktik, die einfach ist und bei mir funktioniert:
Wenn der Preis sich entspannt, erhöhe ich meinen DCA, und wenn der Preis in die Höhe schießt, ziehe ich mich zurück und kaufe im Durchschnitt weniger. Über Monate und Jahre hinweg führt dies zu einem optimalen Durchschnittswert.
FÜHLE DICH NICHT WIE EIN VERRÄTER, WENN DU BTC VERKAUFST
Habe einen Plan und sei bereit, ihn auszuführen. Der Plan meines Nachbarn ist ein guter Anfang. Sobald du dein Geld verdoppelt hast, nimmst du die Anfangsinvestition heraus. Dabei gibt es ein erhebliches Sternchen - was willst du anstelle von Bitcoin kaufen? Inflationäres Bargeld? Die Möglichkeiten, sein Geld woanders anzulegen, sind heutzutage sehr begrenzt. Das mag für viele in diesem Bereich kontrovers sein, aber ich denke, es ist absolut vernünftig, Bitcoin zu verkaufen. Wenn du Bitcoin seit JAHREN hältst und dein Stack dein Leben sinnvoll verbessern könnte, solltest du auf jeden Fall einen Teil verkaufen.
Zeit ist das einzige Gut, das wertvoller ist als BTC; wir haben wirklich nur eine begrenzte Menge an Zeit auf dieser Erde. Wenn du deine BTC hortest und dann friedlich einschläfst was war dann der Sinn? Wenn du einen Teil deines Stacks verkaufen kannst, um dein Haus abzubezahlen oder dich von erdrückenden Schulden zu befreien, halte ich das für eine gute Entscheidung. Es ist vielleicht nicht die BESTE finanzielle Entscheidung, vor allem, wenn Ihr Haus mit einem zinsgünstigen Darlehen belastet ist, aber es ist eine nachvollziehbare Entscheidung, weil man dadurch beruhigt sein kann. Man muss jedoch auch bedenken, dass der Verkauf von Bitcoin auf lange Sicht sehr wahrscheinlich eine schmerzhafte Entscheidung sein wird.
Bitcoin für Spielzeug zu verkaufen, ist hingegen kein guter Schachzug. Wenn du den 250.000 Dollar teuren Lamborghini kaufst, der in 3 Jahren 50% seines Wertes verliert, während Bitcoin um mehr als diesen Prozentsatz zugelegt hat, wird das Bedauern unerträglich sein. Robert Kiyosaki kommt mir in den Sinn. Sein Buch Rich Dad Poor Dad hat mich sehr beeinflusst, und seine Beschreibung von Vermögenswerten und Verbindlichkeiten hat mich sehr beeindruckt:
- Ein Vermögenswert erzeugt Cashflow
- Eine Verbindlichkeit zieht den Cashflow ab
Wenn du Vermögenswerte kaufst, wird dein Nettovermögen auf einer exponentiellen Kurve erheblich ansteigen. Wenn du Verbindlichkeiten kaufst, wirst du einfach ärmer. Wenn du Bitcoin verkaufst, wirst du es wahrscheinlich langfristig bereuen.
ZEITPRÄFERENZ
Die Zeitpräferenz ist ein Thema, das in Bitcoin oft angesprochen wird. Eine niedrige Zeitpräferenz zu haben bedeutet, dass man bereit ist, für eine bessere Zukunft auf die Annehmlichkeiten von heute zu verzichten. Jede sehenswerte Kathedrale, jedes klassische Kunstwerk, alles Schöne auf dieser Welt wurde gebaut, weil Menschen mit Blick auf die Zukunft und nicht auf die Gegenwart gearbeitet haben. Hätte DaVinci Bananen an die Wand geklebt, hätten wir uns nie an ihn erinnert. Wären die großen Pyramiden aus Lehm gebaut worden, gäbe es sie heute nicht mehr. Wenn die Zivilisation ihren gesamten Reichtum für das Hier und Jetzt ausgeben würde, ohne in die Zukunft zu investieren, würde sie nicht überleben.
Bitcoin selbst ist ein digitales Artefakt, das von einem geheimnisvollen Architekten bis zur Perfektion entwickelt wurde. Er ist so konzipiert, dass er Äonen überdauert; wenn die Zivilisation überdauert, wird er bis in die Zukunft hinein perfekte Treue beweisen. Da niemand ihn verändern oder kontrollieren kann, ist Bitcoin anti-entropisch. Das ist der Inbegriff von Handwerkskunst der geringen Zeitpräferenz. Bitcoin ist ein Da Vinci in einer Welt der an die Wand geklebten Bananen. Es ist so offensichtlich, wenn die Arbeit erst einmal geleistet ist, dass es peinlich ist, dass nicht mehr Menschen den Wert verstehen, den er bietet.
Im krassen Gegensatz zu diesem Bitcoin-Meisterwerk stehen die Schrotthaufen, die wir Altcoins oder Shitcoins nennen. Diese wurden mit der Technologie von Bitcoin gebaut, führen aber Entropie ein. Die Treue geht bei den Altcoins verloren, weil sie jeweils von einem Gründer oder einer Gruppe kontrolliert werden. Wenn Menschen etwas kontrollieren können, manipulieren sie es unweigerlich zu ihrem Vorteil. Und ob bewusst oder unbewusst, es wird sich verschlechtern. Die meisten dieser Shitcoins waren von Anfang an darauf ausgelegt, dich zu betrügen. Einige dieser Altcoins haben eine Führung, die vielleicht gute Absichten hat, aber sie sind menschlich und können beeinflusst und genötigt werden. Das Problem ist die FÜHRUNG. Bitcoin und seine Zeitkette wurden entwickelt, um das menschliche Element als primäre Eigenschaft zu entfernen. Die Einführung von Menschen in den Mix verursacht Entropie, die den Wert durch Seigniorage zerstört.
Die Erfindung von Bitcoin war die der NICHT-INTERVENTION durch Menschen.
Das sind Erkenntnisse, die für viele Menschen Jahre dauern, um sie vollständig zu verstehen. Wenn du das Kurzfassung über Altcoins wissen willst, ist es einfach. Bemühe dich einfach nicht. Du bist besser dran, wenn du dein Geld in ein Casino bringst und Glücksspiel machst. Die Karten sind in der Kryptowelt schwer gegen Dich ausgelegt; du hast einfach Glück, wenn du Geld verdienst. Nimm den Weg der geringen Zeitpräferenz und staple Bitcoin, während du lernst, wie deine Investition wächst. Ich kann mit Zuversicht sagen, dass du in 5 Jahren viel weiter vorne sein wirst, wenn du in Bitcoin Dollar-Cost-Averaging betreibst, als wenn du mit Shitcoins spielen würdest.
5-JAHRES-AUSSICHTEN MINIMUM
Die meisten Menschen interessieren sich für Bitcoin während einer seiner parabolischen Bullenläufe. Ich war einer von ihnen. Wir sind alle daran interessiert, finanziell voranzukommen, besonders wenn das Gespenst der Inflation über unseren Köpfen schwebt.
Wenn du neu bei Bitcoin bist und dies dein erster Versuch ist, dann stelle sicher, dass du bereit bist, diesen Vermögenswert für mindestens 5 Jahre zu halten. Du bist wahrscheinlich während einer Aufwärtsbewegung hier, und wenn du kein Glück hattest, ist es wahrscheinlich am Ende der Aufwärtsbewegung. Zum Zeitpunkt der Erstellung dieses Berichts im Dezember 2023 stehen wir meiner Meinung nach am Anfang der nächsten Aufwärtsbewegung. Mit der Zulassung der ETFs, der Halbierung im April 2024 und der Aussicht, dass die US-Notenbank ihre Geldpolitik zurückfahren wird, sind viele Katalysatoren aufeinander abgestimmt. Das bedeutet jedoch NICHT, dass dies unvermeidlich ist. Schwarze Schwäne sind immer eine Möglichkeit. Abgesehen von diesem schwarzen Schwan scheinen wir für einen massiven Kursanstieg in den nächsten Jahren bereit zu sein.
SELBSTVERWAHRUNG
Wenn du zum ersten Mal Bitcoin an der Börse deiner Wahl kaufst, wird es sich anfühlen wie der Kauf eines beliebigen anderen Vermögenswerts bei einem Broker. Du kaufst Bitcoin, und die Zahl auf dem Bildschirm spiegelt die Menge an Bitcoin wider, die du jetzt "besitzt".
Es ist von entscheidender Bedeutung, dass du deine Bitcoin in Verwahrung nimmst. Wir haben in jüngster Zeit Fehler beim Umtausch und regelrechte Betrugsfälle erlebt. Wenn diese Betrügereien aufgedeckt und strafrechtlich verfolgt werden und der Preis von Bitcoin unter Druck gerät, weil viele Menschen den Vermögenswert Bitcoin mit den Börsen in Verbindung bringen, die ihn verkaufen, wird dies zu einer RIESIGEN Kaufgelegenheit. Als FTX vor einem Jahr scheiterte, wurde der Preis von Bitcoin negativ beeinflusst, und diejenigen, die verstanden, dass Bitcoin kein fundamentales Problem hatte, kauften mehr. Du hast verstanden, dass die Angst durch den Markt strömte (womit wir wieder bei dem Punkt wären, warum es in diesem Bereich SO WICHTIG ist, gut informiert zu sein). Wer damals Bitcoin kaufte (um 16k), sicherte sich innerhalb eines Jahres einen Gewinn von weit über 100%!
Stell dir die Seed Keys als das Passwort zu deinem Bitcoin vor, das geschützt werden muss, denn wenn jemand anderes es bekommt, kann er deine Bitcoin in Besitz nehmen - nicht gut für dich. Bitcoin-Seed-Keys werden in der Regel durch eine Hardware-Wallet oder ein Signiergerät geschützt. Dieses Gerät schützt deine Schlüssel vor Hackern oder schlechten Akteuren. Ich verwende seit Jahren Coldcards, und sie gehören zu den besten Geräten zum Schutz von privaten Schlüsseln. Es funktioniert sehr einfach. Du erstellst auf dem Gerät die geheimen Schlüssel; es speichert sie und bewahrt sie offline auf, d. h. ohne Verbindung zum Internet. Dieser letzte Punkt ist WICHTIG. Du darfst diese Wörter NIEMALS auf einem Computer mit Internetanschluss speichern. Der einzige Ort, an dem du deine Schlüssel sicher aufbewahren kannst, ist ein dafür vorgesehenes Gerät. Wenn der Computer kompromittiert wird (und glauben Sie mir, es ist SEHR WÄHRLICH, dass er kompromittiert wird), wird das Signiergerät deine Bitcoin schützen.
Das mag sich alles sehr schwierig und komplex anhören, wenn du es noch nie gemacht hast, aber glaub mir, es ist ganz einfach. Ich würde empfehlen, dass du dir die Videos von BTC Sessions über die Verwendung des Signiergeräts deiner Wahl ansiehst. Er hat unglaubliche Walk-Through-Videos auf YouTube, die alles im Detail erklären.
Eine gemeinsame Verwahrung mit einem Unternehmen wie Swan Bitcoin oder Unchained Capital ist auch eine gute Idee für diejenigen, die neu in diesem Bereich sind. Sie werden dir die Hand halten und dich davor schützen, einfache Fehler zu machen, die zu Problemen führen können. Die gemeinschaftliche Verwahrung ist die Kosten wert, wenn du dir Sorgen machst, deine Bitcoin zu verlieren. Unchained bietet ein Produkt zur gemeinschaftlichen Verwahrung an, das mehrere Schlüssel enthalten kann und deinen Verwandten helfen kann, deine Bitcoin im Falle deines Ablebens wiederzuerlangen.
GEBE NICHT MIT DEINEN BITCOIN AN. Es besteht die Versuchung, mit dem Erfolg zu prahlen. Wenn du fünf Jahre lang durchhältst, wirst du ihn wahrscheinlich haben. Du bist stolz darauf, dass du die Disziplin und Selbstbeherrschung hattest, dich selbst zu beherrschen und erfolgreich das zu erwerben, was du als eine bedeutende Menge an Bitcoin ansiehst. Teile nicht, wie viel du hast, mit anderen. Das sollte offensichtlich sein, aber es gibt Leute, die sich nicht so sehr für dich freuen. Sie könnten es ihren Freunden erzählen, und früher oder später könnte jemand, den du nicht kennst und der vielleicht gewaltbereit ist, feststellen, dass du ein attraktives Ziel bist. Dies ist ein weiterer Grund für die Verwendung einer Konfiguration mit mehreren Signaturen. Selbst wenn jemand 1 von 3 Schlüsseln erhalten hat, kann er deine Bitcoin nicht stehlen.
KAUFE KEINE BITCOIN, DIE DU NICHT KONTROLLIEREN KANNST
Kaufe nicht den glänzenden neuen ETF, den die Wall Street anbietet. Kaufe Bitcoin nur bei Anbietern, die es dir ermöglichen, deine Bitcoin tatsächlich in Verwahrung zu nehmen. Lege deine Bitcoin nicht bei irgendeinem Dienst an, der eine Rendite bietet, insbesondere wenn diese Rendite unrealistisch hoch erscheint. Als allgemeine Faustregel gilt: Lass es einfach bleiben.
Der erste und wichtigste Grund, warum du deine Bitcoin in Verwahrung nehmen solltest, ist, dass du die absolute und vollständige Kontrolle über sie hast. Es gibt in Bitcoin ein Sprichwort: "Nicht deine Schlüssel, nicht deine Coins". Wenn du deine Bitcoin nicht verwahrst, hast du einfach einen Schuldschein. Das ist der ganze Grund für die Existenz von Bitcoin. Um Zwischenhändler auszuschalten und den Menschen zu ermöglichen, ihr finanzielles Schicksal selbst in die Hand zu nehmen.
Wenn du den Besitz hast, fallen keine Gebühren an wie bei einem ETF. Diese Gebühren können niedrig erscheinen, aber mit der Zeit können sie SIGNIFIKANT sein. GBTC ist ein Trust, der einem Bitcoin-ETF am ähnlichsten ist. GBTC erhebt eine Gebühr von 2 % PRO JAHR (jetzt 1,5 % mit dem ETF). Im Laufe der Zeit kann dies erheblich sein. Außerdem erlauben es die ETF-Produkte, die die Wall Street verkauft, nicht, den Bitcoin JEMALS zu verwahren. Ein ETF könnte für einige Leute in bestimmten Szenarien Sinn machen, aber für jeden, der ein Lego-Set bauen kann, ist die Verwahrung von Bitcoin ähnlich komplex. Nimm es selbst in die Hand.
Wenn sich Bitcoin mehr und mehr durchsetzt, wird es möglich sein, ihn als Sicherheiten zu verwenden. Ja, ich verstehe, dass die Verwendung deines Bitcoin als Sicherheit ihn aus deinem Besitz nimmt und Vertrauen in eine dritte Partei erfordert. Dies ist ein weiterer Fall, in dem du dich informieren und SICHER sein solltest, dass der von dir gewählte Kreditgeber vertrauenswürdig ist und nicht pleite gehen wird. Im Zweifelsfall solltest du dich immer auf die Selbstverwahrung verlassen.
Eine Kreditaufnahme gegen deine Bitcoin ist unmöglich, wenn du ihn nicht selbst verwahrst. Du kannst den Bitcoin, den Blackrock in deinem Namen hält, nicht ausleihen. Dies ist von Bedeutung. Es hat steuerliche Vorteile, Bitcoin zu beleihen, anstatt sie zu verkaufen. Wenn du keine Kontrolle über deine Bitcoin hast, schließt du dich selbst von einigen vorhersehbaren Anwendungsfällen in der nahen Zukunft aus und von vielen unvorhersehbaren Anwendungen, die noch erfunden werden müssen. Programmierbares Geld ist nicht nützlich, wenn du es nicht in deiner Hand hältst.
Der letzte Grund, warum du deine Bitcoin aufbewahren solltest, ist ein wenig düsterer. Bitcoin wurde entwickelt, um unzensierbar und nicht konfiszierbar zu sein. Wenn der Staat merkt, dass er die Kontrolle über das Geld verliert, wird er sich wahrscheinlich dein Bitcoin holen. Dies ist ein Präzedenzfall in der Geschichte der USA. Im Jahr 1933 wurde mit der Executive Order 6102 der Besitz von Gold für US-Bürger illegal. Sie zwangen die Menschen, Gold abzugeben und 20 Dollar pro Unze zu erhalten. Die Regierung setzte dann den Goldpreis auf 35 Dollar pro Unze herauf. Für den Besitz von Goldmünzen konnte man in den USA von 1933 bis Mitte der 1970er Jahre ins Gefängnis kommen. Das könnte wieder passieren, und du hast die Wahl, wenn du Bitcoin selbst hältst. Depotbanken WERDEN in diesem Szenario gezwungen sein, der Regierung deine Bitcoin zu geben. Was du in dieser Situation mit deinem Bitcoin tust, sollte DEINE Entscheidung sein, nicht die eines Verwahrers.
VERANTWORTUNG
Wenn du die Schritte unternimmst, um deine Bitcoin selbst zu verwahren, bist du verantwortlich. Dies ist eine Art von radikaler Verantwortung, die Menschen beunruhigen kann. Wenn du deine Schlüssel verlierst, ist dein Bitcoin für immer verloren. Es gibt keine Nummer, die du anrufen kannst, und niemanden, der dir helfen kann. SIE. SIND. WEG.
Im Jahr 2017 verlor einer meiner Freunde auf der Feuerwache Bitcoin im Wert von 1300 Dollar, weil er die Bitcoin in einer Papier-Wallet aufbewahrte. Diese werden nicht mehr verwendet, weil sie so unsicher sind, aber man kann einen QR-Code ausdrucken, der die Bitcoin enthält. Er ließ das Stück Papier in seinem Auto liegen. Dann räumte er sein Auto aus und saugte die Papier-Wallet auf. Diese Bitcoin sind für immer weg. Sie sind jetzt irgendwo zwischen 4 und 5 Tausend Dollar wert, und sie sind einfach weg. Nun, technisch gesehen sind sie nicht weg, sie sind immer noch da, nur für niemanden zugänglich. Ohne die Schlüssel kann niemand die Bitcoin bewegen, also sind die Bitcoin praktisch für immer eingefroren.
Ein anderer guter Freund von mir verlor eine beträchtliche Menge an Bitcoin bei einem Unternehmen namens BlockFi. Dabei handelte es sich um eine Börse, die Renditen für Bitcoin anbot, die bei ihrer Börse aufbewahrt wurden. Dieser Bitcoin ist nicht eingefroren, aber er ist jetzt für die absehbare Zukunft in einem Rechtsstreit eingesperrt. Um dem Ganzen noch die Krone aufzusetzen - da der Bitcoin, als er von BlockFi gehalten wurde, technisch gesehen nicht ihm gehörte, sondern aufgrund der "Vereinbarung", die er bei der Eröffnung des Kontos unterschrieben hat, ihnen gehört, wird er irgendwann in der Zukunft den Dollarwert dieses Bitcoins zu dem Preis erhalten, zu dem BlockFi pleite ging - also 16.000 Dollar -, sind wir wieder bei dem Punkt angelangt, warum du die Selbstverwahrung ernst nehmen solltest!
Das alte Bitcoin-Sprichwort lautet: "Nicht deine Schlüssel, nicht deine Coins".
Bitcoin ist eine endlose Lernreise. Wenn du ein Kaninchenloch erforschen willst, hast du Glück! Die Menge an soliden Inhalten, die in diesem Bereich angeboten werden, ist um Lichtjahre besser als im Jahr 2017. Man kann in einem Bruchteil der Zeit, die man damals gebraucht hätte, von null auf kompetent umsteigen. Wie oben bereits angedeutet, haben wir bei Blue Collar Bitcoin eine Grundlagenreihe zusammengestellt, die du für den Einstieg nutzen kannst. Die Liste der großartigen Inhaltsersteller und Ressourcen ist so lang, dass wir sie nicht alle aufzählen können. Geh einfach auf Entdeckungsreise und achte darauf, zu überprüfen, nicht zu vertrauen.
Lerne weiter, und vor allem - denke selbst!
Erinnere dich an die Weisheit von Matt Odell: "Bleib bescheiden und staple Sats".
-
 @ 04ea4f83:210e1713
2025-04-20 08:38:43
@ 04ea4f83:210e1713
2025-04-20 08:38:43Bei dem Begriff "Midlife-Crisis" denkt man oft an Menschen mittleren Alters, die sich Sportwagen kaufen, ihre Ehepartner für jüngere Partner verlassen oder sich in einem verzweifelten Versuch, ihre Jugend wiederzuerlangen, plötzlich auf ausgefallene Abenteuer einlassen. Im Bitcoin Space zeichnet sich jedoch ein neues Phänomen ab - die Bitcoiner Midlife-Crisis.
Für diejenigen, die tief in den Kaninchen Bau eingetaucht sind kommt ein Punkt auf ihrer Reise, an dem sie ein Plateau erreichen. Sie haben ein außerordentliches Vermögen in Form von Sats angehäuft und verfügen über ein klares Verständnis der Technologie und des Marktes. Aber trotz alledem fühlen sie sich unerfüllt, so als ob der nächste Kauf von Bitcoin einfach keinen wirklichen Unterschied mehr macht.
Dieses Gefühl wird durch die extreme Volatilität des Bitcoin-Marktes noch verstärkt. An einem Tag kann das Nettovermögen in neue Höhen steigen, nur um am nächsten Tag wieder deutlich zu fallen. Die Schwankungen können so drastisch sein, dass ihr Jahresgehalt im Vergleich zu den nicht realisierten Gewinnen und Verlusten, die sie an einem einzigen Tag erleben, verblasst. Es wird schwierig, die Achterbahnfahrt der finanziellen Freiheit mit der Stabilität einer traditionellen Festanstellung in Einklang zu bringen.
Die traditionellen Vorstellungen von Erfolg und Erfüllung verlieren für Bitcoiner, die diese Midlife-Crisis erleben, an Bedeutung. Die Verlockung von materiellen Besitztümern oder beruflichen Fortschritten hat nicht mehr das gleiche Gewicht im Vergleich zu den potenziellen Gewinnen und Verlusten der Bitcoin. Die Vorstellung, für jemand anderen zu arbeiten und Zeit gegen Geld zu tauschen, wird zunehmend unattraktiver, wenn sie das Potenzial für finanzielle Unabhängigkeit durch ihre überlegene Spar-Technologie sehen.
Infolgedessen können Bitcoiner in der Mitte ihrer Lebenskrise ihre Prioritäten und Werte in Frage stellen. Sie könnten beginnen, die gesellschaftlichen Normen und Erwartungen zu hinterfragen, die ihr Leben bis zu diesem Zeitpunkt bestimmt haben. Das Bedürfnis nach Anerkennung oder Bestätigung durch andere hat nicht mehr den gleichen Stellenwert, da sie erkennen, dass ihr Wohlstand und ihr Erfolg nicht durch traditionelle Maßstäbe definiert werden.
Diese veränderte Denkweise kann zu einem Mangel an Filter oder Selbstzensur in ihren Interaktionen mit anderen führen. Bitcoiner, die eine Midlife-Crisis durchleben, werden möglicherweise offener und selbstbewusster, wenn es darum geht, ihre Überzeugungen und Meinungen zu äußern, unabhängig davon, wie sie von ihrem Umfeld wahrgenommen werden. Sie haben vielleicht nicht mehr das Bedürfnis, sich an gesellschaftliche Normen anzupassen oder sich an konventionelle Weisheiten zu halten, was zu Konflikten mit Freunden, Familie oder Arbeitskollegen führt, die ihre Ansichten nicht verstehen oder teilen.
Die emotionale Loslösung, die mit der Bitcoiner-Midlife-Crisis einhergeht, kann sich auch in einem allgemeinen Gefühl der Apathie oder Gleichgültigkeit gegenüber äußeren Ereignissen oder Umständen äußern. Themen oder Herausforderungen, die früher vielleicht eine starke emotionale Reaktion hervorgerufen haben, werden jetzt kaum noch wahrgenommen. Die Höhen und Tiefen des alltäglichen Fiat-Jobs scheinen im Vergleich zur Volatilität des Bitcoin-Marktes unbedeutend zu sein.
Mitten in dieser Midlife-Crisis könnten sich Bitcoiner an einem Scheideweg wiederfinden und sich mit Fragen der Identität, des Zwecks und der Erfüllung auseinandersetzen. Sie könnten gezwungen sein, sich mit ihrer eigenen Sterblichkeit und dem Erbe, das sie hinterlassen wollen, auseinanderzusetzen. Die traditionellen Meilensteine des Erfolgs, wie ein Haus, staatliche Altersvorsorge oder berufliche Erfolge, haben vielleicht nicht mehr die gleiche Anziehungskraft, wenn man sie mit dem Potenzial für finanzielle Freiheit und Souveränität vergleicht, das der Bitcoin bietet.
Die Midlife-Crisis der Bitcoiner ist nicht nur ein persönlicher Kampf, sondern ein Spiegelbild der breiteren gesellschaftlichen Veränderungen und Umwälzungen, die durch den Aufstieg eines digitalen Geldes ausgelöst wurden, welches die Gesellschaft von monetärer Entwertung und finanzieller Unterdrückung befreit. Sie ist eine Herausforderung für die etablierten Normen und Strukturen der Finanzwelt und eine Neudefinition dessen, was es bedeutet, in der modernen Zeit Erfolg und Erfüllung zu finden.
Während Bitcoiner durch diese Midlife-Crisis schreiten, können sie Trost darin finden, sich mit anderen zu verbinden, die ihre Reise und Erfahrungen teilen. Online-Communities, Meetups und Konferenzen bieten einen Raum für Gleichgesinnte, um zusammenzukommen und sich gegenseitig durch die Höhen und Tiefen des Bitcoin-Marktes zu unterstützen. Indem sie ihre Kämpfe, Erfolge und Einsichten miteinander teilen, können Bitcoiner ein Gefühl der Kameradschaft und ein Ziel auf ihrem Weg zur finanziellen Unabhängigkeit und Selbstverwirklichung finden.
Zusammenfassend lässt sich sagen, dass die Midlife-Crisis der Bitcoiner ein komplexes und vielschichtiges Phänomen ist, das die einzigartigen Herausforderungen und Chancen der Einführung von gesundem Geld widerspiegelt. Sie stellt einen Wendepunkt im Leben derjenigen dar, die tief in die Welt des Bitcoin eingetaucht sind, wo traditionelle Maßstäbe für Erfolg und Erfüllung im Lichte des Potenzials für Selbstständigkeit und finanzielle Freiheit neu bewertet werden. Indem sie sich mit ihren eigenen Werten, Überzeugungen und Prioritäten auseinandersetzen, können Bitcoiner aus dieser Midlife-Crisis mit einem neuen Sinn für Ziel und Richtung auf ihrer Reise zu finanzieller Unabhängigkeit und Selbstverwirklichung hervorgehen.
-
 @ 04ea4f83:210e1713
2025-04-20 08:37:09
@ 04ea4f83:210e1713
2025-04-20 08:37:09Veröffentlicht auf Medium am 07.06.2021\ Originalautor: Tomer Strolight\ Übersetzt von: Sinautoshi am 04.05.2023 - 788249\
Reden wir über Dinge, die man mit Geld nicht kaufen kann.
Ehrlichkeit kann man mit Geld nicht kaufen. Tatsächlich sind Menschen, die versuchen, dich davon zu überzeugen, ihnen dein Geld zu geben, oft nicht ganz ehrlich zu dir.
Freundschaft kann man mit Geld nicht kaufen. Du kannst nicht in ein Geschäft oder eine Bar gehen und einen Freund kaufen – jemanden, der deine Werte teilt, der dich respektiert, den du respektierst. Und aus den gleichen Gründen kann man sich damit keine Liebe kaufen , die eine besonders tiefe Form der Freundschaft ist.
Vor allem kann Geld dir keine Dinge kaufen, die in dir selbst sind: Es kann dir kein Selbstwertgefühl, Intelligenz, Mut oder Integrität kaufen, um nur einige Beispiele zu nennen. Gebe einer unsicheren Person einen Haufen Geld und sie wird es verschwenden, um vor anderen anzugeben oder sich selbst zu zerstören. Gib einem intellektuell faulen Menschen Geld und er wird nicht schlauer. Gebe einem Feigling Geld und er hat nur noch eine Sache, vor der er Angst haben muss: das Geld zu verlieren. Und gebe einem Betrüger Geld, und er wird versuchen, es zu verwenden, um einen unehrlichen Plan auszuhecken, durch den er mehr bekommen kann.
Die Dinge, die man für Geld kaufen kann
Geld wird dir ein schönes Outfit, einen tollen Haarschnitt, ein schickes Auto und ein schönes Haus kaufen, aber das Glück selbst wird unerreichbar bleiben ohne echte Freunde und Liebhaber, denen du vertrauen kannst, und ohne in der Lage zu sein, dich selbst zu lieben und zu respektieren.
Geld kauft nämlich kein Glück. Nicht von alleine. Es ist nicht ausreichend.
Warum arbeiten wir dann so hart für Geld? Warum messen manche Menschen ihren Wert in Dollar?
Es ist wahr, dass wir viele der Dinge brauchen, die man mit Geld kaufen kann, wie Nahrung, Unterkunft, Kleidung und sogar Unterhaltung, die uns ein wenig glücklicher macht.
Geld kann ein Wegbereiter sein. Es kann verwendet werden, um Dinge zu kaufen, die grundlegende Überlebensbedürfnisse befriedigen, und uns dadurch die Zeit verschaffen, diesen anderen Werten nachzugehen, die Geld selbst nicht kaufen kann.
Es ist jedoch immer noch sehr falsch, unseren Wert anhand einer einzigen Zahl zu messen, geschweige denn an einer Zahl, von der wir wissen, dass sie Freundschaft, Liebe, Selbstwertgefühl, Intelligenz, Mut, Integrität und viele andere Tugenden und Werte, die wir zeigen und verfolgen sollten, auslässt.
Was hat das mit Bitcoin zu tun?
Nehmen wir uns nun eine Minute Zeit, um uns die Gemeinschaft der Bitcoiner anzusehen. Bitcoiner sind überzeugt von einer neue Form von Geld, Bitcoin.
Wir unternehmen große Anstrengungen, um zu erklären, warum wir denken, dass es die beste Form von Geld ist, die es je gegeben hat und wahrscheinlich jemals geben wird.
Um dies erklären zu können, müssen wir zunächst große Anstrengungen unternehmen, um zu verstehen, was Geld ist und wie Bitcoin die Anforderungen erfüllt, Geld zu sein.
Dazu müssen wir einen sehr ehrlichen Blick auf die Geschichte und die Gegenwart werfen . Wir müssen erforschen, was viele Menschen für selbstverständlich halten. Wir müssen harte Fragen stellen und nach ehrlichen, vertretbaren Antworten suchen.
Wir müssen etwas über die Mathematik lernen, auf die sich Bitcoin stützt.
Wir müssen etwas über die Energieproduktion lernen, auf die Bitcoin angewiesen ist.
Wir lernen etwas über Ökonomie, die Lehre davon, wie Menschen mit den Dingen umgehen, die man mit Geld kaufen kann.
Wir entwickeln eine tiefe Überzeugung, die von all diesem Lernen und unseren Beobachtungen und Argumenten über das, was um uns herum passiert, geprägt ist.
Wir bilden Ansichten darüber aus, wohin die Welt steuert .
Wir kommen zu dem Schluss, dass eine Welt mit Bitcoin als Geld oder auch nur als das Geld, das von uns, welche sich für Bitcoin entscheiden, verwendet wird, eine bessere Welt ist.
Wir schließen daraus, dass es eine bessere Welt ist, weil sie ehrlich und transparent ist. Es ist eine Welt ohne Geheimnisse, Intrigen und Täuschungen darüber, was Geld ist.
Es ist eine Welt ohne mächtige Leute, die die Kontrolle über das Geldsystem ausüben, um die Schwachen zu kontrollieren.
Wir finden dann eine moralische Mission in Bitcoin.
Wir übernehmen die Verantwortung, das Wissen zu verbreiten.
Dazu braucht es Mut. Wir müssen unser Geld dort einsetzen, wo unser Mund ist, indem wir Bitcoin mit unseren Euro kaufen. Dies ist ein Akt der Risikobereitschaft oder des Mutes. Es ist ein Akt der Integrität – unsere Worte an unseren Taten auszurichten.
Wir müssen standhaft bleiben. Wir werden ausgelacht. Mächtige Menschen und Institutionen verspotten uns und versuchen, uns zu diskreditieren. Sie bezeichnen uns als Unterstützer von Kriminellen und Terroristen. Entweder stärken wir unseren Mut und unsere Überzeugung oder verlassen Bitcoin.
Diejenigen von uns, die bleiben, wissen, dass unsere Mit-Bitcoiner, die die gleichen Schwierigkeiten durchgemacht haben oder durchmachen wie wir, ehrlich, intelligent und mutig sind.
Wir respektieren einander. Wir werden Freunde.
Wir alle tragen bei, was wir können, wie wir können. Wir bauen die Welt, die wir uns vorstellen.
All dies tun wir unbeirrt, während Millionen an der Seitenlinie stehen, einige neugierig zusehen, uns verspotten und einige aktiv angreifen und versuchen, uns aufzuhalten. Ab und zu rennt einer rüber und sagt „Ich will so sein wie du!“ Und wir empfangen sie mit offenen Armen.
Ein Bitcoiner zu werden ist ein Prozess, durch den du Dinge erhältst, die man mit Geld nicht kaufen kann.
Schau mal. Ehrlichkeit kann man mit Geld nicht kaufen. Freundschaft kann man damit nicht kaufen. Selbstachtung, Mut, Intelligenz oder Integrität kann man damit auch nicht kaufen. Doch diese Bitcoiner mit ihren Ideen, ihren Idealen, Bemühungen und ihren Errungenschaften haben sich all diese Dinge angeeignet. Bitcoiner sind ehrlich. Sie haben authentische Freundschaften. Sie glauben an sich. Sie sind mutig. Sie sind schlau. Und sie besitzen eine Integrität, die all diese Dinge über jeden Reichtum stellt, der in einem monetären Wert gemessen wird.
Kein Bitcoiner beurteilt einen anderen danach, wie viel Bitcoin diese andere Person wert ist.
Es ist ein Fauxpas in der Community, überhaupt danach zu fragen.
Ich liebe meine Mit-Bitcoiner. Sie sind die besten Menschen auf Erden. Einige mögen finanziell reich sein, andere nicht. Aber sie sind mir alle viel mehr wert als Geld.
Bitcoin hat uns allen eine Fülle von Dingen gegeben, die man mit Geld nicht kaufen kann.
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ 42342239:1d80db24
2025-03-09 15:22:43
@ 42342239:1d80db24
2025-03-09 15:22:43Last fall, Italian economist Mario Draghi, former head of the European Central Bank (ECB), published his 400-page report on Europe's (actually the EU's) competitiveness. Draghi's verdict was harsh: Europe is facing an "existential challenge." It's hard to disagree. While the EU is launching new regulations on plastic corks and hiding text messages from the public, Elon Musk is changing the world with groundbreaking innovations in the automotive, robotics, and space industries.
At the same time that the EU is not only preventing people from trying new things but also preventing them from even thinking about trying, Musk's space company SpaceX is capturing massive star rockets with "chopstick grips". While the EU is stuck in an ocean of meaningless bureaucratic details, Musk is engaged in a process of constant testing and improvement, reminiscent of the natural course of decentralized systems.
The EU's meager economic growth can be compared to a ticking time bomb that threatens to explode in all of our faces. Disposable incomes have increased nearly twice as much in the US compared to the EU since 2000, and this is a difference that is noticeable not only in our standard of living but also in our opportunities for leisure time. As the late economist Robert Lucas said, "Once you start thinking about growth, it's hard to think about anything else." Perhaps the best thing that can be said about the report is that its abundance of words, numbers, and images underscores how bad things are. And perhaps it has therefore become impossible for the EU's leaders to continue ignoring the union's problems.
Like giving a shark responsibility for beach safety
However, asking a former EU president to investigate and propose changes is like giving a shark responsibility for beach safety. Among other things, he proposes larger allocations for research and development, even though the EU already spends more than the US as a percentage of GDP - it's thus impossible for this to be the problem. It comes as no surprise that the proposals are about more centralization, harmonization, and streamlining - i.e., continuing in the same old tracks. While Musk seems to have an intuitive understanding of how knowledge arises through real-world experiments , what is proposed here is more of the administrative bureaucracy's preconceived five-year plans. The bureaucracy is to be given free rein, and the nations are to be pushed back - a repeat of a theme we know all too well. Centralization undermines real knowledge growth, which may explain why the EU is falling behind.
A venomous snake that is ignored
Rent-seeking is like a venomous snake that slithers through the EU's corridors, but the concept is conspicuous by its absence in Draghi's report. It is a well-known phenomenon where companies spend resources on influencing decision-makers to gain advantages instead of creating value. The EU bureaucracy has produced a total of 13,000 legislative acts since 2019 - more than four times as many as the US. How many of these have received an invisible stamp of approval from lobbyists? Economist Jeffrey Sachs has warned that American lobbying in Brussels is so dominant that it affects all decision-making in the digital economy, which may be one of the EU's biggest problems. GDPR regulations, for example, are estimated to have reduced small tech companies' profits by 15% (!).
Size is not everything
Small businesses are the invisible heroes that contribute most to productivity and employment growth. These are being suffocated by the ECB's actions and the constantly increasing and inefficient regulatory mess. The ECB's war on small banks hampers growth for small businesses because large banks prioritize large transactions. Big computers' algorithms cannot replace small banks' local knowledge. Harmful regulations and grandiose dreams lead to a loss of both knowledge and growth.
What should the end goal be?
Sweden's daily Dagens Industri's editorial page recently wrote that "Defeat is not an option" on the theme of green transition. It asked whether "free democracies or a Chinese dictatorship should lead the way." Large-scale industrial projects and plans can undoubtedly provide benefits. But it's worth questioning whether Europe should really have the same end goal as China.
During both the Renaissance and the Industrial Revolution, decentralized power structures played a crucial role. During the Renaissance, states and cities were relatively independent. Power was decentralized to princes, nobles, and merchants. The Church had an important role, but it was not as centralized as it would become. Florence, Venice, and Amsterdam could develop different scientific and artistic traditions. When one region encountered problems, other regions could continue to develop and grow, and so on. At that time - even if the concept did not exist - it seemed to be understood that the economy is a complex system of the second order. Or a computationally irreducible one, as Stephen Wolfram would have expressed it.
In the book "The Art of War," Chinese General Sun Tzu wrote that "He who chooses the battlefield first will win. He who lets his opponent choose the battlefield will lose." Instead of striving to play on China's (alleged) centralized battlefield, perhaps we Europeans should consider returning to our roots. Do away with the bureaucracy's heavy foot and give power back to the individual! Scrap the monster banks and create conditions for small local banks instead. Stop subsidizing American IT giants' data centers and give every European an AI in their own hand. Forget the five-year plans and invest in decentralized economic experiments instead. Does that sound radical?
The word "radical" comes from the Latin word for root, radix . The word used to have a positive connotation because it implied a willingness to go to the root of the problem or to return to one's roots.
More of us should dare to question the modern structures that brought us to today's sad situation. Roots are a plant's strength - without them, it cannot grow and flourish. So it is with Europe. Our continent, which was once a thriving garden where ideas and innovations bloomed, needs to return to its roots to regain its former strength. This may be exactly what is required.
Put simply: a more radical Europe.
-
 @ 8671a6e5:f88194d1
2025-05-07 16:31:50
@ 8671a6e5:f88194d1
2025-05-07 16:31:50Users are not employees Continued from (part 1)

Bitcoiners know how a lot of stuff works, so we think everybody knows. That’s a project management assumption that belongs more in the hobby-code project sphere (where it’s even cool to do so). And sure, I enjoy that myself when I’m building a small tool for fun with no one to answer to. But that mindset doesn’t scale when the goal is to make Bitcoin more accessible and structurally sound for new users. Some argue we don’t need new users at all—that Bitcoin is so good, so perfect, that people will eventually come around. Imagine being forced to use bitcoin by economic and monetary circumstances, to realize you hate to work with things like Nunchuk ‘s multisig or a Trezor hardware wallet from 2025.
An impression: Bitcoiners know that opening a Lightning channel comes with an on-chain fee—unless the provider covers it and claws it back through subscriptions or service charges. But the average user doesn’t. So when that fee appears out of nowhere, or gets buried in cryptic devspeak jargon, so they bounce, often left confused, frustrated, and unlikely to return.
That’s not that bad on itself, as long as companies know who their audience is and take care of the way you inform users. You have to “raise” your customers. Not scare them away with a wall of nonsense.
Same goes for onboarding people into Nostr sometimes by the way.
If features like this or natural onboarding hurdles were explained with more than just puzzling error codes or vague on-screen prompts, half the users wouldn’t vanish in the first 10 seconds, confused and frustrated. It’s the same story we’ve seen with PGP: people stumble during the initial key creation, or get lost trying to sign a message with someone’s public key. The tech works; the experience doesn’t. Have trust in what you’ve build underneath!
It’s a barrier for newcomers. Just keep it in mind. Take care of the user. They do like to come on board! Most people do want to come on board. Our goal is to help free them from fiat, not drown them in confusing UX or half-baked tools. Bitcoin's underlying value might be incredible, but that doesn’t matter to someone still trapped in the fiat bubble. They won’t get onboarded through broken apps or confusing flows, just like they’ll use something like SimpleX on Linux.
To make it even worse, some bitcoin organizations and companies don’t seem to grasp the extent of this alienation of the user — because it’s always brushed off as ‘niche’ or just an edge case. It’s all so obvious for them on how to use it. But it adds up. Sites like Highlighter.com (I like their underlying service by the way!) is not working properly with Nos2x (a key handler) on the first try. A user needs to know to reload, re-try, re-load again after selecting the public key, then maybe it works). These are exactly the kind of small annoyances that new users won’t wade through. It’s also not that difficult to tackle it with proper testing.
Users who encounter such thing, certainly when they just wanted to see what the site or service did, just leave. Let someone who just discovered Nostr try logging in there for example, and unless they're unusually determined, they'll get stuck immediately, wondering why pasting their public key and clicking “login” doesn’t lead anywhere. It’s a brick wall; and the creators think it’s a nice landing page.
These things also lead to other frustrations and eventual software cycling through the interested users’ hands.
About a year ago I “onboarded” a friend of mine, and she already tried four wallets since I introduced her to the wonderful world of Bitcoin/LN wallets. First just to get things going she used Wallet of Satoshi, then when the custodial story was getting traction for this user, we moved to Phoenix (which failed due to upfront money). Next, Aqua wallet, which was too cumbersome and had hiccups, and then moving on to Mutiny wallet, which shut down a bit later.
And so we ended up back with Wallet of Satoshi, with Blink being a second choice but having to give a telephone number was too much for the user (yes, you can skip that if you carefully read and put it in test / demo mode or whatever it’s called).
People kept recommending other wallet brands, other names to try, … there are always other names. “Try Muun” “Get Zeus”, “Why don’t you go for CoinOs, just as a web app?” (that last one is actually good) … but it’s always like that … if you talk to ten bitcoiners, then you’ll have heard five different ‘best wallets’ to try, and you’ve had probably get about four referral links from all of these people. (Or some Relai squad member trying to get a few sats out of your genuine interest:)
Real testing is a ghost town
We saw in part 1 that Bitcoin companies do some testing these days—but it lacks specialization. It’s often so superficial that the cracks are visible in the software itself: clumsy onboarding flows, unclear settings, or unexpected fields asking for information users don’t have and don’t know how to get. Much of this stems from the habit of pulling in a handful of “fans” or supporters to try out a beta version.
That’s the wrong way to go (the fiat companies that do this, usually get bad or inconclusive results as well, unless you’re doing it a scale and a very diverse audience).
Most of the people brought in this way have no background in structured testing, let alone in reporting bugs clearly or identifying critical failure points. The feedback you get is vague and surface-level: “I like the colors,” “the buttons feel small,” or “I got an error when I tried to send something.”
But rarely do you hear what caused it, what preceded it, or what device or settings were involved. That kind of insight doesn’t come from random fans trying to get their hands on some products or perks. You’ll have to pay professionals to do it. And even when meaningful feedback does come in, it often ends up on the wrong or overworked hands, forwarded to whichever developer drew the short straw that weekend. There's usually no structured triage, no internal testing culture that treats usability or edge cases as part of the real product. Just a sigh, a shrug, and back to building features that sound cool when they dreamed it up.
I keep hammering this point because this might be the only time you’ll actually read about it. No company—bitcoin or fiat—tries to win users by focusing on boring but critical details like onboarding clarity or robust edge-case handling. They’ll avoid claiming “this just works,” because saying so invites scrutiny and backlash. The only company bold (or arrogant) enough to occasionally say that is Apple—and even they drop the ball more often than they like to admit.
By design
The dream I have, is “Usability by design”. And that dream is close to non-existent in the realm and everyday reality of Bitcoin. From the moment something gets drawn up or is being created, the design and user flow, the easy adoption, should be kept in mind as well as the real implementation factors for the intended purpose (and beyond even). Then you hardly have any discussions like “yeah, but technically the user has to make an input here, so we can’t do otherwise, and it works on my machine”
Users that have to trial and error, are maybe bitcoin-natives, and like that sort of stuff. Other people just want to try something out (wallet, nostr, an exchange, a node, lightning …) and expect it to work smooth. It gives them trust in the system.
These issues all create enormous opportunity for companies that would start to take software delivery quality more serious. But I’m afraid that would cost them two things most Bitcoin companies already lack: time and proper funding.
Many are stuck in a “pump-my-bags” mindset, focused more on hype than durability, while others simply don’t have the resources to invest in thoughtful UX, thorough testing, or long-term support.
The very few companies that do “get it”, and make something that just works, with good leadership and a focus on clear, usable interfaces—often catch flack for it. They’re criticized for making things “too easy,” “too centralized,” or for “lowering the bar,” as if simplicity and accessibility are somehow problems. But in reality, these are the companies pushing the space forward, making it easier for people to use Bitcoin without the constant headache. And newsflash: you can do so with keeping bitcion’s ethos alive I think, even without a company as a middleman. Which raises another problem about funding and hard money, something I’ll write more about in chapter 12 of this series.
Back to the software…. Protonmail’s wallet comes to mind where most bitcoiners I know just scoffed at like “it doesn’t have lightning”, or “why do we need another wallet?”. While they deliver an excellent product that just works.
Exactly. Take the Stack Wallet project, for example. They had the audacity to incorporate Monero, and because of that, they’re shunned by many Bitcoiners — despite offering a solid, open-source, multi-platform wallet that actually works. It’s a perfect example of how Bitcoiners can sometimes reject the very things that could help bring more users into the space, all because they don’t align perfectly with some purist ideology. While on the other hand these same bitcoiners support middlemen multi-level-marketing tactics from questionable companies.
But I guess yelling “oooh shiiiitcoooooin” is the easier answer, instead of making something that works fine. And by the way, if you want, you can fork that wallet and take a bitcoin-only version to market, however, the same people say “Oh, but that’s no my task”. (Yeah, we all know what your “task” is, gluing a sticker on a pole).
Another nice illustration is the kind of reaction you get if you “provoke the beast” by using the really usable, always working, always compatible, fast starting, lightning wallet “Wallet of Satoshi”. If you use that wallet at a bitcoin meetup, you’ll get clever remarks (from people that ar technically right, I mind saying) like: “You know… that’s custodial right?” (this came after I gave a presentation, and some smartass walked in when I ordered a beer from the honesty bar at the local meetup…) “Yeah I know man, but I’m scanning an LNurl here, so I just want it to work fine” (like I have to defend myself to them) “But you’re supporting these custodial thieves, they have already so much power man”, … said the dude that never even lifted a finger at the meetups to help anyone out or get things set up. “So… make something better.” I answered “Yeah, there’s like Zeus and stuff” “Uhuh, I tried it… I never got it to work properly. I just use this WoS today”
They usually get mad. Because they want everyone to follow their lead, and that lead is always the way of most resistance and acting like a normal user-repellent. I know we’re all rat-poison in bitcoin, but not take it too far please.
Other discussions like this always evolve into the “you’re dumb” argument (I like to provoke these types at meetups by scanning a qr and getting a payment through, while they’re fiddling with their whatever it is that runs on a node they need to reboot every few hours or so). calling out the ones who act like they know it all, but don’t have a solid grasp on the fundamentals themselves. We all make mistakes, and that’s where the real growth happens.
The other answer you can give is: “Hey why are you sending me a WhatsApp message man? Why don’t you use a Free BDS and a GNUPGP encrypted message brought to me on a micro-sd card through a sneaker net currier?” And they would be like “eh now, I just send you a WhatsApp message” “Oh you know these are all collecting your meta data right?”…
The double standard among bitcoiners these days regarding usability is incredible.
I know there’s plenty of software trying to be both non-custodial and user-friendly—don’t remind me. My point is: in the Bitcoin world, usability is often treated like a dirty word, something suspicious or even dangerous. But it’s the opposite—we're the hope, and usability is our fire starter, the spark that lights the fuse for real adoption. Without it, we’ll just be another niche tool used by a few, and not the global movement we could be.
Nod to the Node So, I can finally say it like I think it is: 90% of bitcoin software sucks donkey balls when it comes to usability, UX and UI.
A few things I want to mention in that regard, because things move too fast to write it all down in a book to keep up with.
Some examples of bad UX and/or rotten software experiences:
In Sparrow 2.0, commonly praised as as a “good” wallet, lacks of good interface. Try to create a multisig wallet there, and you’ll soon be met with a persistent bug that frustrates users when signing a transaction. The software prompts for a hardware wallet for example, even when a software wallet's seed is loaded, creating a confusing and poorly designed user interface experience. And yes, for bitcoin this is considered a good wallet, as the others are even worse (Nunchuk and Electrum don’t do much better).
Or Blue Wallet, which finally in 2025 fixed a few UI bugs and annoyances, but otherwise has a few really rotten design choices which makes using it not intuitive enough. Users don’t get much further on some aspects without looking anything up in youtube tutorials. And only bitcoiners do that anyway. Users just stop opening the app after a while.
Try to create a multi-sig wallet for example in Blue wallet, then take a random part away from the setup and try to use it with the leftover parts. It works. But you’ll be really pressed to get it done within 40 minutes. (Unless that’s your job and you demo it every so often in a studio).
Bitcoin Core, is also a prime example of bitcoin software, that has a command line interface repelling users like it’s a steaming turd on the street. It has a (let’s say) “spartan” way of working. And yes, I know this piece of software is not meant to be the next Instagram-like user interface for everyday use by the masses, but it’s a far cry from being usable in the really real world. Getting anything done inside that software is a constant battle against clunky commands, and their cryptic error messages. Even getting a private key out for one of your addresses of your own wallet, is hell. bitcoin core’s infamous command line at work
Also puzzling to me is the “success” of Bitcoin Core’s wallet. It’s command line “help” is enough to frustrate even the most willing of new users.
For example (and there are a dozen things like this) , try to get a command like “dumppriv” key (to see the private key from a wallet address) working.
And some more:
Jade wallet’s inability to store BIP39 compatible seed phrases (at the time of testing, beginning of 2024), when the seed contained a double word. Don’t know if they ever fixed it, as I couldn’t get into my Jade wallet v1 anymore after the pin code entry screen froze and was not even coming back after a factory reset.
We have Phoenix (where finding the right URL for downloading it, is already a first hurdle to take by the way:) try to tell the URL by heart to another person, without searching online… I’ll wait.
And Strike app, alongside the much despised Wallet of Satoshi (in my opinion the only people in bitcoin together with the creators of the Minibits.cash creators) that get the importance of a simple to use interface and a good well-thought out inner working.
And when I took a shot at the new Trezor Safe 5 wallet I got some critique because I “tested it like an end user” (yeah, it was my fault… I made the exact same mistakes than the end user that had this wallet and asked me for help, after 30 min. of trying, we figured out that the words were in fact not seed words but some verification method that also created a 20 words SLIP39 seed by default… and we fat fingered the stupid interface design a few times, on which the whole thing had to be restarted after a reset to defaults… Try to explain that to a new user that just wanted to have a wallet and had about 1 hour time…
But I guess people demonstrating such things in a studio don’t mind that. It’s just “what do you sell?” now. If the hardware with the unknown supply chain attack vectors sells well, then everyone is happy… the manufacturer, the marketing team, the podcasts that get sponsorship and the events that can have a budget; the user is really at the very back-end last in line… usually queuing up for coffee with the rest of the liquidity-cows.
Also it had accompanying software that kept hanging though some updating loops, it has a clumsy swipe/touch (and sometimes) hold, then swipe again-interface that no one I tested it with, could get through when creating a new wallet. But of course, it’s always the dumb users’ fault I guess.
The Zeus wallet that claims to be super user friendly and cool, is also something… weird. Where you can’t really set it up, without some very technical guidance. To their advantage: the very first thing you read on their website is “To start using ZEUS you will need to be running your own Bitcoin lightning node.” (they at least mention it, that’s progress) But… there it ends for most users of course. Babysitting a Lightning node is absolutely not something you want to entrust a new user with. Not in order to get a wallet up and running at least :)
Then you get the Linuxsplaining : “Then you’re not the intended user”.
NWC (nostr wallet connect) is some very promising tool, and it has features and way of working I like in theory. But I’ve yet have to see the first smooth implementation that can be understood by normal non-tech people (even the wording of the text fields it completely unclear).
A small example of making your software unusable? Well… do like NWC does and indicate that the user needs to “connect” through this service with : “nostr+walletconnect://”
So when I asked some people what I needed to fill in there, and how I would get these values… they said “it’s a string”. which tells me nothing. And so, the user left
Tip: add real user guidance. When you connect to a service, at least point to WHERE people get explained how to create such a wallet string, or where to get it, from which website or service.
It’s the same as telling someone “hey you have to call a number to reach our catering service” ”Ok, your website says “phone us“ ”yeah, its a number man.. a phone number” ”Ok; but where do I get which phone number I need to call” ”It’s like… a number man, duh you’re so dumb”
So, if there’s no user guidance, the user will leave. After searching for a few minutes I just gave up.
Nostr is also starting to feel like that usability-averse stance is getting traction, although there are promising signs, as they need new users to thrive and seem to realize that all too well. But still… it has it’s moments of user-repelling snags. Nostr relay lists don’t allow you to copy relay addresses, making it a hassle to set up on mobile. No one seems to realize that users want to simply copy these values rather than struggle to recall if it’s “ssw,” “wss,” or “wws://” and type them out manually. And make mistakes eventually.
puzzling for people who don’t have Alby and want to get such code Arrays are not human Then there’s the BIP39 seed system (12 or 24 words representing a key derived via a KDF and mapped through a lookup table). Mathematically, this wordlist is an array—and arrays start at 0. So, word 0 = "abandon". But most humans naturally count from 1, making "abandon" word 1 in their eyes. Both are valid depending on perspective: 0 is technically correct, 1 is intuitive. There’s no clear winner—both versions float around in Bitcoinland. Same mess with compressed vs. uncompressed keys (don’t get me started). So, when I made bip39tool.com I gave users the option: go full math mode with 0 = abandon, or go human mode and start with 1 (the default). Even hardware makers don’t agree. Blockplate starts at 1 = abandon (source), While the widely used master BIP39 list has no number attached (just a raw list), but appears to be starting at 1 because of Githubs’s line numbering (source) while some others use 0 = abandon
As one user (Codebender) excellently put it: ”Array is an offset, not a cardinal number. The first entry is zero away from the beginning of the array, the second entry is one away.”
Sink through the ceiling

Most tools today cater purely to Bitcoiners, built with a 'Bitcoin' mindset that expects non-Bitcoin users to adapt instead of being taken along for the ride.
That works as we’ve seen, but hits an “orange colored glass ceiling” at some point. You can build the next “Lotus notes” and be really happy about Lotus notes enthusiasts and the consultants that got hired to implement and migrate that office note system, and it’s e-mail software at a hefty fee. But you’re still in your own niche bubble, thinking your software owns the world and you can be bothered to look further than your own audience.
The same way people that were into Lotus Notes were very keen on a big player like IBM acquiring the software and brand to build on it some more.
And of course,… Bitcoin is bitcoin, there can’t be a second best, there can’t be a replacement that comes in and swoops up the market share or replaces the functions like Lotus Notes was replaced by Google workspace, Microsoft Exchange or Slack.
I don’t want to make the point that bitcoin will be replaced by a new player (I’m not a shitcoiner). I do however, want to make the point that we’ve become collectively lazy, complacent about usability, to the point that we’re actually the Google, Microsoft and so on… but with the interface of our own underlying “Lotus Notes” or PGP .
If We Don’t Fix UX, Bitcoin Becomes the next PGP
To understand how bad it is, we again need to take a small look at the past. To better understand the now, and to avoid some future mistakes.
Let’s quickly recall some examples from the '90s, like Microsoft’s Clippy, Bob, Vista, and Netscape Navigator 4—failures driven by poor usability, feature creep, or mishaps that eroded trust. Lotus Notes serves as a warning: even widely used platforms can lose their edge if usability and modernization are neglected, leaving room for competitors. Bitcoin doesn’t face competition in the traditional sense, but it does face something worse: the erosion of usability and trust, which threatens the very foundation of hard money we rely on. It’s our only shot at hard money we’re ever going to have. It’s do-or-die.
And that’s our Achilles heel: we stand or die with that trust.
For now, Bitcoin’s trust comes from its decentralized, secure network and its value propositions. But usability has been sidelined for years, largely due to a lack of serious testing. Some companies recently hired 14 new team members: - 4 Software Engineers - 3 R&D Engineers - 2 Data Scientists - 1 Machine Learning Engineer - 1 Talent Acquisition Specialist - 1 Global Controller, 2 Marketeers… No testers.
I’m serious about this: when the broader bitcoin space (from Bitcoin Core to the newest coolest and latest Nostr plugin) don’t take testing more serious, then we’ll end up just being the creators of the software equivalent of a “Bonzi Buddy” or the next “Lotus Notes”.
Because we’ll be catering to the same people that liked the system 10+ years ago, and have no clue why new users don’t flock to it anymore. Then our core value we’re so proud of right now, will be nothing more than a laughing stock because it stands only through trust.
If we don’t take this seriously, Bitcoin’s core value will fade, and we’ll lose trust—not to altcoins, but to our own neglect.
Fiat parasites and our own complacency is our real “competitor”.
When we lose this battle for usability and relevancy, then the math, code and the core of bitcoin would still go on to exist, with more and more users being locked out because the complexity rises. While others would reluctantly try to make efforts to get in. This will impact how you interact with and maintain nodes, as well as manage lightning channels and participate in the P2P economy of the Bitcoin standard. We would become a small island that “gets it”. A curiosum. We’de be the Moloka‘i1 of decentralization. (Make your own ‘Father Damien’ joke here if you like).
You can’t see me
This is happening right now.
The real usability repels new users, with only a few exceptions holding the fort.
It doesn’t bother the store-of-value and pump-my-bags crowd—they're not using Bitcoin anyway and don’t care either way, as long as they make their fiat gains in a quarterly report or at the end of a year. When you onboard a business and teach them self custody, they’re usually set... then forget. You encounter the real issues along the way. There’s little real use, as average people still need a "specialist" to hold their hand.
After a while, Bitcoiners who explain things end up like Lotus Notes consultants, trying to make a buck on a system no one else understands or really cares about.
Usability in the Bitcoin ecosystem is stagnating. The so-called "studio usability" presented by Bitcoin influencers with nice podcasts, who demo new stuff and ignore flaws to stay “positive,” is part of the problem. It's the same with the flood of metal plate seed bearers (as an example) We have about 25 products that aren’t as innovative as they’re made out to be. And it’s all fan-tas-tic and cool on every review. Unless you really test it. (luckily some actually do that)
The real issue is that nobody dares saying: “This hardware wallet sucks” or “This product is too buggy to trust.”
On the flip side of that coin we’ve got the LinuxSplaining crowd—treating lack of usability like a virtue. For them, being one of the ten people on a metaphorical Bitcoin leper colony who can navigate some convoluted tool is a badge of honor. They’ll call it a success even if the other eight billion people can’t—or won’t—bother opening the app, dismissing those users as simply too clueless to matter.
These folks would happily sit beside the 30th Satoshi Nakamoto statue, ignoring the peanuts tossed at their face by passersby. Some will reach 60, sporting stained Star Wars t-shirts, proud to be the only ones who still understand Bitcoin. To them, that’s success — because Bitcoin was always meant to be their obscure triumph and it’s becoming a way of life for them to be that weird uncle that’s into computers and stuff like “crypto”. ’No man, it’s bitcoin, not cryptooh!’
I want bitcoin to open the door to freedom and abundance of ideas and real-life solutions, and not becoming a barbed wire fence around a lepper colony. Even in that grim outpost, you’d still find two Bitcoiners barricaded in their hut without AC, boycotting the òther eight because one tweaked their node settings the wrong way.
Let’s build tools and bridges towards bitcoin, as a "usable bitcoin” (because that’s bitcoin too!) Build tools that invite everyone to the table, not just the converted, the Linuxsplainers and know-it-alls.
Only then will we move onwards, to a thriving, open ecosystem where you’re not feeling like a Lotus Notes consultant that ran away from 1994, but a bitcoiner who’s part of positive changes in the world. ”Fix your bugs, before you try to fix the world.”
by AVB
Support my work here : coinos / avb
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 2e8970de:63345c7a
2025-05-07 15:26:35
@ 2e8970de:63345c7a
2025-05-07 15:26:35Beijing has stopped publishing hundreds of statistics, making it harder to know what’s going on in the country
Data stops. Data stops. Data stops.
https://www.wsj.com/world/china/china-economy-data-missing-096cac9a?st=j7V11b&reflink=article_copyURL_share
originally posted at https://stacker.news/items/973942
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 42342239:1d80db24
2025-03-02 14:13:43
@ 42342239:1d80db24
2025-03-02 14:13:43With the rapid development of artificial intelligence (AI), we face a future where we may soon have access to almost everything we desire – at least in the digital realm. But unfortunately, what we wish for doesn’t always align with what we truly need, or what would benefit us.
The Dutch ethologist Niko Tinbergen was awarded the Nobel Prize in Physiology or Medicine in 1973 for his studies of animal behaviour patterns. While earlier scientists had primarily focused on learning as the main explanation for animal behaviour, Tinbergen instead emphasised instincts.
Tinbergen studied, among other things, what makes newly hatched bird chicks beg for food from their parents. This was investigated by presenting parentless chicks with various painted beak models to see which ones they would seek food from. Several objects proved more popular than real gull beaks.
Artificial eggs were also created and placed in bird nests. Black-headed gulls that received wooden eggs before laying their own were found to actually refrain from laying real eggs. Fake eggs were painted in different colours and patterns, and made in various sizes. The gulls always preferred trying to incubate eggs of absurd sizes – for example eggs with eight times the volume of real ones. The poor gulls made desperate attempts to sit on these giant eggs – but often slid off.
The explanation for the gulls’ self-destructive behaviour was that they had a hardwired ability (instinct) to respond to specific stimuli (appearance of beaks and eggs with particular colours/sizes). Researchers exaggerated these stimuli, creating stronger but ultimately misguided reactions. The concept of "superstimuli" was hatched. Nothing in the gulls’ evolution had prepared them for these experiments, explaining their self-destructive behaviors.
Psychologist Deirdre Barrett has translated this concept to a human context. She argues that superstimuli govern human behaviours much like they do other animals’, citing junk food consumption, addictive social media use, and pornography consumption as examples. Nothing in Homo sapiens’ evolution prepared us for modern society’s stimuli, which might explain our frequently self-destructive behaviours.
When the Liberal Party (Swedish political party Liberalerna) proposes mandatory porn filters on all mobile phones "to protect children and youth," it might appear they’re on the right track. However, these issues deserve more profound discussions.
How do we create technical solutions that meet our fundamental needs for health, education, and human connection – rather than just supplying mindless scrolling entertainment? How can we ensure those collecting our data don’t exploit it for their own interests, selling us things we don’t need? Is the current model of centralisation, corporate giants, and profit maximisation really compatible with our best interests?
In summary: How can we ensure future technology serves our real needs, rather than mislead us - much like Niko Tinbergen deceived the poor gulls?
-
 @ 0e29efc2:ff142af2
2025-05-07 15:09:46
@ 0e29efc2:ff142af2
2025-05-07 15:09:46Table of Contents
- Intro
- Important Terminology
- Getting Started
- Where do I buy bitcoin?
- Okay, I bought some bitcoin-now what?
- Less than 0.01 BTC
- More than 0.01 BTC and less than 0.1 BTC
- More than 0.1 BTC
- How Bitcoin Works
- Skepticism
- Someone will hack it
- The government will try to stop it
- It’s not backed by anything
- Conclusion
Intro
Maybe you saw an article in Forbes, a news segment about MicroStrategy (MSTR), or you glanced at the bitcoin price chart; whatever the spark, your curiosity led you here. Enough friends and relatives keep asking me about bitcoin that I finally organized my thoughts into a single reference. This is not a comprehensive guide—it assumes you trust me as a heuristic.
Important Terminology
Sat (satoshi) – the smallest unit of bitcoin. One bitcoin (₿) equals 100 000 000 sats.
Getting Started
Where do I buy bitcoin?
I use River because it publishes proof‑of‑reserves, supports the Lightning Network, and pays interest on idle USD balances (currently 3.8 %).
Okay, I bought some bitcoin-now what?
Withdraw it immediately. Centralized exchanges can and do fail. Your next step depends on how much bitcoin you hold.
If at any point you're struggling, please reach out to me.
Less than 0.01 BTC
- On your phone open Safari (iOS) or Chrome (Android).
- Paste
https://wallet.cashu.me?mint=https://mint.westernbtc.com. Confirm the prompt that asks whether you trusthttps://mint.westernbtc.com. I run this mint so beginners can skip the gnarly parts. - Complete setup.
- Tap Receive → LIGHTNING → enter amount → COPY.
- In River choose Send → Send to a Bitcoin wallet, paste the invoice, verify, and send.
- Return to the wallet; your sats should appear.
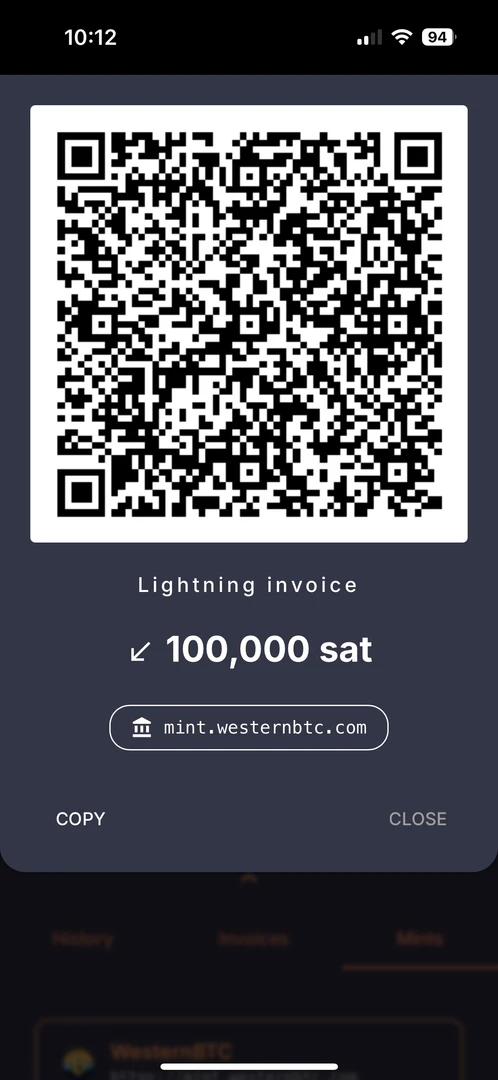
More than 0.01 BTC and less than 0.1 BTC
It's time for cold storage. Cold storage means a dedicated signing device not connected to the internet. Think of it like keys to a house. If you have the keys (your cold storage signing device), you can get into your house (the bitcoin). I recommend and use the COLDCARD Q or COLDCARD MK4 from COLDCARD. See this thorough walkthrough.
The creator nostr:npub1rxysxnjkhrmqd3ey73dp9n5y5yvyzcs64acc9g0k2epcpwwyya4spvhnp8 makes reliable content.
More than 0.1 BTC
The next security upgrade involves something called multisig. It requires the use of multiple devices instead of one. Think of those nuclear launch silos in movies where two keys need to be turned in order to launch the missile. One person can't reach both keys, so you need two people. Like the two keys needing to be turned, we need a certain number of keys (signing devices) to be used.

This offers a number of benefits. Say you have a 2-of-3 multisig setup. You would need two of the three keys to move the bitcoin. If you were to lose one, you could use the two others to move it instead. Many choose to geographically distribute the keys; choosing to keep one at a friend’s house or with a bank.
The previous video I linked covers multisig as well. Again, please reach out to me if you need help.
How Bitcoin Works
I'm going to paint a scene portraying the basics of how bitcoin works. Picture a race that's supposed to take 10 minutes to run start-to-finish, and there's a crowd of people spectating. When the fastest runner crosses the finish line, they're awarded 50 bitcoin. Everyone in the crowd recognizes who won, and writes it down on their own scoreboard. Then, the next race begins.
Now, let's say more racers who've had special training join. They start winning consistently because of it, and now the race only lasts about 9 minutes. There's a special rule everyone in the crowd agreed to, that they can make the race harder to ensure it's around 10 minutes long. So they make the race harder to counteract the faster runners.

With this in mind, let's get to the skepticism you might have.
Skepticism
Someone will hack it
Think of bitcoin as the people in the crowd. If someone tries to cheat and writes on their scoreboard that they have a billion bitcoin, their scoreboard is going to look different than everybody else’s. The other people in the crowd will cross-reference with each other and decide to ignore that person who cheated.
The government will try to stop it
Again, think of the crowd. In reality, the "crowd participants" are scattered all around the world. You might be able to stop many of them, but it would be almost impossible to stop everyone. Imagine people are watching the race on TV, can you find everyone who's spectating? Ironically, attempted bans often increase interest.
It’s not backed by anything.
Think of the runners. The runners are bitcoin miners. They have to expend real energy to participate in the race. The more bitcoin miners, the more secure the network. In summary, it's backed by electricity and work.
Conclusion
There are too many topics to cover in one article. I haven't even touched on the history of money, what money is, scarcity, etc. The best way to learn is to research the topics you're interested in for yourself. It took months of deep diving before I was sold on bitcoin, and I had many touch points before that.
Once you see it though, you can't unsee it.
-
 @ 4523be58:ba1facd0
2025-02-27 22:20:33
@ 4523be58:ba1facd0
2025-02-27 22:20:33NIP-117
The Double Ratchet Algorithm
The Double Ratchet is a key rotation algorithm for secure private messaging.
It allows us to 1) communicate on Nostr without revealing metadata (who you are communicating with and when), and 2) keep your message history and future messages safe even if your main Nostr key is compromised.
Additionally, it enables disappearing messages that become undecryptable when past message decryption keys are discarded after use.
See also: NIP-118: Nostr Double Ratchet Invites
Overview
"Double ratchet" means we use 2 "ratchets": cryptographic functions that can be rotated forward, but not backward: current keys can be used to derive next keys, but not the other way around.
Ratchet 1 uses Diffie-Hellman (DH) shared secrets and is rotated each time the other participant acknowledges a new key we have sent along with a previous message.
Ratchet 2 generates encryption keys for each message. It rotates after every message, using the previous message's key as input (and the Ratchet 1 key when it rotates). This process ensures forward secrecy for consecutive messages from the same sender in between Ratchet 1 rotations.
Nostr implementation
We implement the Double Ratchet Algorithm on Nostr similarly to Signal's Double Ratchet with header encryption, but encrypting the message headers with NIP-44 conversation keys instead of symmetric header keys.
Ratchet 1 keys are standard Nostr keys. In addition to encryption, they are also used for publishing and subscribing to messages on Nostr. As they are rotated and not linked to public Nostr identities, metadata privacy is preserved.
Nostr event format
Message
Outer event
typescript { kind: 1060, content: encryptedInnerEvent, tags: [["header", encryptedHeader]], pubkey: ratchetPublicKey, created_at, id, sig }We subscribe to Double Ratchet events based on author public keys which are ephemeral — not used for other purposes than the Double Ratchet session. We use the regular event kind
1060to differentiate it from other DM kinds, retrieval of which may be restricted by relays.The encrypted header contains our next nostr public key, our previous sending chain length and the current message number.
Inner event
Inner events must be NIP-59 Rumors (unsigned Nostr events) allowing plausible deniability.
With established Nostr event kinds, clients can implement all kinds of features, such as replies, reactions, and encrypted file sharing in private messages.
Direct message and encrypted file messages are defined in NIP-17.
Algorithm
Signal's Double Ratchet with header encryption document is a comprehensive description and explanation of the algorithm.
In this NIP, the algorithm is only described in code, in order to highlight differences to the Signal implementation.
External functions
We use the following Nostr functions (NIP-01):
generateSecretKey()for creating Nostr private keysfinalizeEvent(partialEvent, secretKey)for creating valid Nostr events with pubkey, id and signature
We use NIP-44 functions for encryption:
nip44.encryptnip44.decryptnip44.getConversationKey
- createRumor
Key derivation function:
```typescript export function kdf( input1: Uint8Array, input2: Uint8Array = new Uint8Array(32), numOutputs: number = 1 ): Uint8Array[] { const prk = hkdf_extract(sha256, input1, input2);
const outputs: Uint8Array[] = []; for (let i = 1; i <= numOutputs; i++) { outputs.push(hkdf_expand(sha256, prk, new Uint8Array([i]), 32)); } return outputs; } ```
Session state
With this information you can start or continue a Double Ratchet session. Save it locally after each sent and received message.
```typescript interface SessionState { theirCurrentNostrPublicKey?: string; theirNextNostrPublicKey: string;
ourCurrentNostrKey?: KeyPair; ourNextNostrKey: KeyPair;
rootKey: Uint8Array; receivingChainKey?: Uint8Array; sendingChainKey?: Uint8Array;
sendingChainMessageNumber: number; receivingChainMessageNumber: number; previousSendingChainMessageCount: number;
// Cache of message & header keys for handling out-of-order messages // Indexed by Nostr public key, which you can use to resubscribe to unreceived messages skippedKeys: { [pubKey: string]: { headerKeys: Uint8Array[]; messageKeys: { [msgIndex: number]: Uint8Array }; }; }; } ```
Initialization
Alice is the chat initiator and Bob is the recipient. Ephemeral keys were exchanged earlier.
```typescript static initAlice( theirEphemeralPublicKey: string, ourEphemeralNostrKey: KeyPair, sharedSecret: Uint8Array ) { // Generate ephemeral key for the next ratchet step const ourNextNostrKey = generateSecretKey();
// Use ephemeral ECDH to derive rootKey and sendingChainKey const [rootKey, sendingChainKey] = kdf( sharedSecret, nip44.getConversationKey(ourEphemeralNostrKey.private, theirEphemeralPublicKey), 2 );
return { rootKey, theirNextNostrPublicKey: theirEphemeralPublicKey, ourCurrentNostrKey: ourEphemeralNostrKey, ourNextNostrKey, receivingChainKey: undefined, sendingChainKey, sendingChainMessageNumber: 0, receivingChainMessageNumber: 0, previousSendingChainMessageCount: 0, skippedKeys: {}, }; }
static initBob( theirEphemeralPublicKey: string, ourEphemeralNostrKey: KeyPair, sharedSecret: Uint8Array ) { return { rootKey: sharedSecret, theirNextNostrPublicKey: theirEphemeralPublicKey, // Bob has no ‘current’ key at init time — Alice will send to next and trigger a ratchet step ourCurrentNostrKey: undefined, ourNextNostrKey: ourEphemeralNostrKey, receivingChainKey: undefined, sendingChainKey: undefined, sendingChainMessageNumber: 0, receivingChainMessageNumber: 0, previousSendingChainMessageCount: 0, skippedKeys: {}, }; }
```
Sending messages
```typescript sendEvent(event: Partial
) { const innerEvent = nip59.createRumor(event) const [header, encryptedData] = this.ratchetEncrypt(JSON.stringify(innerEvent)); const conversationKey = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, this.state.theirNextNostrPublicKey); const encryptedHeader = nip44.encrypt(JSON.stringify(header), conversationKey);
const outerEvent = finalizeEvent({ content: encryptedData, kind: MESSAGE_EVENT_KIND, tags: [["header", encryptedHeader]], created_at: Math.floor(now / 1000) }, this.state.ourCurrentNostrKey.privateKey);
// Publish outerEvent on Nostr, store inner locally if needed return {outerEvent, innerEvent}; }
ratchetEncrypt(plaintext: string): [Header, string] { // Rotate sending chain key const [newSendingChainKey, messageKey] = kdf(this.state.sendingChainKey!, new Uint8Array([1]), 2); this.state.sendingChainKey = newSendingChainKey; const header: Header = { number: this.state.sendingChainMessageNumber++, nextPublicKey: this.state.ourNextNostrKey.publicKey, previousChainLength: this.state.previousSendingChainMessageCount }; return [header, nip44.encrypt(plaintext, messageKey)]; } ```
Receiving messages
```typescript handleNostrEvent(e: NostrEvent) { const [header, shouldRatchet, isSkipped] = this.decryptHeader(e);
if (!isSkipped) { if (this.state.theirNextNostrPublicKey !== header.nextPublicKey) { // Received a new key from them this.state.theirCurrentNostrPublicKey = this.state.theirNextNostrPublicKey; this.state.theirNextNostrPublicKey = header.nextPublicKey; this.updateNostrSubscriptions() }
if (shouldRatchet) { this.skipMessageKeys(header.previousChainLength, e.pubkey); this.ratchetStep(header.nextPublicKey); }}
decryptHeader(event: any): [Header, boolean, boolean] { const encryptedHeader = event.tags[0][1]; if (this.state.ourCurrentNostrKey) { const conversationKey = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, event.pubkey); try { const header = JSON.parse(nip44.decrypt(encryptedHeader, conversationKey)) as Header; return [header, false, false]; } catch (error) { // Decryption with currentSecret failed, try with nextSecret } }
const nextConversationKey = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, event.pubkey); try { const header = JSON.parse(nip44.decrypt(encryptedHeader, nextConversationKey)) as Header; return [header, true, false]; } catch (error) { // Decryption with nextSecret also failed }
const skippedKeys = this.state.skippedKeys[event.pubkey]; if (skippedKeys?.headerKeys) { // Try skipped header keys for (const key of skippedKeys.headerKeys) { try { const header = JSON.parse(nip44.decrypt(encryptedHeader, key)) as Header; return [header, false, true]; } catch (error) { // Decryption failed, try next secret } } }
throw new Error("Failed to decrypt header with current and skipped header keys"); }
ratchetDecrypt(header: Header, ciphertext: string, nostrSender: string): string { const plaintext = this.trySkippedMessageKeys(header, ciphertext, nostrSender); if (plaintext) return plaintext;
this.skipMessageKeys(header.number, nostrSender);
// Rotate receiving key const [newReceivingChainKey, messageKey] = kdf(this.state.receivingChainKey!, new Uint8Array([1]), 2); this.state.receivingChainKey = newReceivingChainKey; this.state.receivingChainMessageNumber++;
return nip44.decrypt(ciphertext, messageKey); }
ratchetStep(theirNextNostrPublicKey: string) { this.state.previousSendingChainMessageCount = this.state.sendingChainMessageNumber; this.state.sendingChainMessageNumber = 0; this.state.receivingChainMessageNumber = 0; this.state.theirNextNostrPublicKey = theirNextNostrPublicKey;
// 1st step yields the new conversation key they used const conversationKey1 = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, this.state.theirNextNostrPublicKey!); // and our corresponding receiving chain key const [theirRootKey, receivingChainKey] = kdf(this.state.rootKey, conversationKey1, 2); this.state.receivingChainKey = receivingChainKey;
// Rotate our Nostr key this.state.ourCurrentNostrKey = this.state.ourNextNostrKey; const ourNextSecretKey = generateSecretKey(); this.state.ourNextNostrKey = { publicKey: getPublicKey(ourNextSecretKey), privateKey: ourNextSecretKey };
// 2nd step yields the new conversation key we'll use const conversationKey2 = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, this.state.theirNextNostrPublicKey!); // And our corresponding sending chain key const [rootKey, sendingChainKey] = kdf(theirRootKey, conversationKey2, 2); this.state.rootKey = rootKey; this.state.sendingChainKey = sendingChainKey; }
skipMessageKeys(until: number, nostrSender: string) { if (this.state.receivingChainMessageNumber + MAX_SKIP < until) { throw new Error("Too many skipped messages"); }
if (!this.state.skippedKeys[nostrSender]) { this.state.skippedKeys[nostrSender] = { headerKeys: [], messageKeys: {} };
if (this.state.ourCurrentNostrKey) { const currentSecret = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, nostrSender); this.state.skippedKeys[nostrSender].headerKeys.push(currentSecret); } const nextSecret = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, nostrSender); this.state.skippedKeys[nostrSender].headerKeys.push(nextSecret);}
while (this.state.receivingChainMessageNumber < until) { const [newReceivingChainKey, messageKey] = kdf(this.state.receivingChainKey!, new Uint8Array([1]), 2); this.state.receivingChainKey = newReceivingChainKey; this.state.skippedKeys[nostrSender].messageKeys[this.state.receivingChainMessageNumber] = messageKey; this.state.receivingChainMessageNumber++; } }
trySkippedMessageKeys(header: Header, ciphertext: string, nostrSender: string): string | null { const skippedKeys = this.state.skippedKeys[nostrSender]; if (!skippedKeys) return null;
const messageKey = skippedKeys.messageKeys[header.number]; if (!messageKey) return null;
delete skippedKeys.messageKeys[header.number];
if (Object.keys(skippedKeys.messageKeys).length === 0) { delete this.state.skippedKeys[nostrSender]; }
return nip44.decrypt(ciphertext, messageKey); } ```
-
 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52Necessário
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
Algumas coisas que você precisa saber
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
O tutorial será dividido em dois módulos:
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
No final, teremos:
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

Módulo 1 - Criando uma carteira fria/assinador
-
Baixe o APK do Electrum na aba de downloads em https://electrum.org/. Fique à vontade para verificar as assinaturas do software, garantindo sua autenticidade.
-
Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

- Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

- Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o modo avião.\ (Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)

- Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

- No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. (Aqui entra seu método pessoal de backup.)

Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
-
Criar uma carteira somente leitura em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em https://electrum.org/ ou da própria Play Store. (ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)
-
Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção Usar uma chave mestra.

- Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em Carteira > Detalhes da carteira > Compartilhar chave mestra pública.

-
Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
-
Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: Carteira > Addresses/Coins.
-
Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

- No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

- No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
Conclusão
Pontos positivos do setup:
- Simplicidade: Basta um dispositivo Android antigo.
- Flexibilidade: Funciona como uma ótima carteira fria, ideal para holders.
Pontos negativos do setup:
- Padronização: Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- Interface: A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
-
 @ 04ea4f83:210e1713
2025-02-24 06:42:36
@ 04ea4f83:210e1713
2025-02-24 06:42:36Erschienen im The Bitstein Brief | Veröffenlichung 10.12.2022 |\ Author: Bitstein (Michael Goldstein)\ Übersetzt von: Sinautoshi am 11.12.2022 - 766906
„Die gesellschaftliche Funktion der Wirtschaftswissenschaft besteht gerade darin, solide Wirtschaftstheorien zu entwickeln und die Irrtümer bösartiger Denkweisen zu entlarven. Bei der Verfolgung dieser Aufgabe zieht der Wirtschaftswissenschaftler die tödliche Feindschaft aller Schwindler und Scharlatane auf sich, deren Abkürzungen zum irdischen Paradies er entlarvt. Je weniger diese Quacksalber in der Lage sind, plausible Einwände gegen die Argumente eines Ökonomen vorzubringen, desto wütender beschimpfen sie ihn.“
- Ludwig von Mises, „Nationalökonomie, Theorie des Handelns und Wirtschaftens”
Das „toxischste" an einem Bitcoin-Maximalisten ist seine unerschütterliche Bereitschaft, „Nein” zu sagen. Nach dem Studium der Geldtheorie und -geschichte und der Erfahrung mit den unerbittlichen Kräften des Marktes, hat der Bitcoiner ein Verständnis für die Realität des monetären Wettbewerbs, ein Bewusstsein für die kritische Natur dezentraler Systeme, einen Fokus auf die Lösung der wichtigsten monetären Probleme und eine strikte Ablehnung der unvermeidlichen Ablenkungen, Opportunitätskosten und ethischen Bedenken bei der Einführung und Förderung von Altcoin-Projekten.
Einige Kritiker bemängeln unhöfliche rhetorische Schnörkel, die als Hindernis für die Gewinnung neuer Bitcoin-Nutzer angesehen werden. Wenn das wahr wäre, gäbe es in der Arbeitsteilung eine Chance für eine qualitativ hochwertigere Bitcoin-Ausbildung, die die Bitcoiner meiner Meinung nach gerne wahrnehmen würden, vor allem die Kritiker, die die bestehenden Unzulänglichkeiten besser erkennen. Doch egal, wie höflich die Bitcoiner ihre Ansichten darlegen, bestimmte Möchtegern-Unternehmer und Influencer werden immer im Streit mit einer leidenschaftlichen Bevölkerungsgruppe stehen, die einfach nicht interessiert ist - und ihr Desinteresse lautstark kundtut. Die „toxischsten" Bitcoiner sind oft diejenigen, die die Weisheit der Bitcoiner erst erkannt haben, nachdem sie von Shitcoins verbrannt wurden und ihr neu gefundenes Desinteresse unmissverständlich zum Ausdruck bringen wollen.
Was soll man also als Bitcoiner tun? Ich empfehle, sich der Wahrheit und der Förderung der Wahrheit zu verschreiben und die Wirksamkeit von Rhetorik an ihrem langfristigen Einfluss und nicht an ihrer kurzfristigen Popularität zu messen.
In dieser Hinsicht sollten sich die Bitcoiner von dem ursprünglichen toxischen Maximalisten inspirieren lassen: Ludwig von Mises. Der bedeutende Wirtschaftswissenschaftler setzte sich unbeirrt für die Wahrheit, freie Märkte und gesundes Geld ein und scheute sich nicht, das zu sagen, was gesagt werden musste, auch wenn er sich damit keine Freunde machte. Langfristig wurde er zu einem der einflussreichsten Ökonomen und Denker des 20. Jahrhunderts, und seine Arbeit hat den Weg für den Bitcoin geebnet.
Mises, der Geldmaximalist
Einer der Hauptkritikpunkte an den Bitcoin-Maximalisten ist die Behauptung, dass die Welt auf Bitcoin (als Geld) konvergieren wird und es generell keine Verwendung für andere Währungen gibt. Dies wird als normative Aussage betrachtet. In Wirklichkeit machen die Bitcoiner eine positive, beschreibende Aussage darüber, wie der monetäre Wettbewerb funktioniert.
In der 1912 veröffentlichten Theorie des Geldes und der Umlaufmittel schrieb Mises:
„So haben die Erfordernisse des Marktes allmählich dazu geführt, dass bestimmte Waren als gemeinsame Tauschmittel ausgewählt wurden. Die Gruppe der Waren, aus der diese ausgewählt wurden, war ursprünglich sehr groß und unterschied sich von Land zu Land; sie wurde aber immer mehr eingeschränkt. Wann immer ein direkter Tausch nicht in Frage kam, war jede der an einem Geschäft beteiligten Parteien bestrebt, ihre überflüssigen Waren nicht nur gegen marktgängigere Waren im Allgemeinen, sondern gegen die marktgängigsten Waren einzutauschen, und von diesen wiederum bevorzugte sie natürlich die marktgängigste Ware. Je größer die Marktfähigkeit der zuerst im indirekten Tausch erworbenen Waren ist, desto größer ist die Aussicht, das endgültige Ziel ohne weitere Manöver erreichen zu können. So gäbe es die unvermeidliche Tendenz, dass die weniger marktfähigen Güter aus der Reihe der als Tauschmittel verwendeten Waren nach und nach verworfen würden, bis schließlich nur noch ein einziges Gut übrig bliebe, das allgemein als Tauschmittel verwendet würde: das Geld.“
Mises zufolge wählen die Akteure zunehmend das marktgängigste Gut als Tauschmittel aus und der natürliche Verlauf des Marktes geht in Richtung Vereinheitlichung zu einem einzigen Geldgut. Das ist schlicht und einfach monetärer Maximalismus.
Mises unterscheidet sich von den Bitcoinern lediglich durch die Stärke der Behauptungen, die er über die tatsächlichen empirischen Entscheidungen der Wirtschaftsakteure zu treffen bereit ist. Mises weist darauf hin, dass sowohl Gold als auch Silber an vielen Orten zu Geld gemacht wurden, wahrscheinlich wegen ihrer ähnlichen Eigenschaften, und dass es den Rahmen der Geldtheorie sprengt, zu sagen, ob Gold oder Silber letztlich besser verkäuflich ist. Trotzdem sagt er:
„Denn es ist ziemlich sicher, dass die Vereinheitlichung auch dann ein wünschenswertes geldpolitisches Ziel gewesen wäre, wenn die ungleiche Marktfähigkeit der als Tauschmittel verwendeten Güter kein Motiv geboten hätte. Die gleichzeitige Verwendung mehrerer Geldarten bringt so viele Nachteile mit sich und verkompliziert die Technik des Tauschens so sehr, dass das Bestreben, das Geldsystem zu vereinheitlichen, in jedem Fall unternommen worden wäre.“
Die natürliche Tendenz zu einem einzigen Geldgut ist so stark, dass seiner Meinung nach die Vereinheitlichung der Geldsysteme auch dann angestrebt würde, wenn zwei Güter genau gleich marktfähig wären. Zuvor stellt er außerdem fest:
„Das endgültige Urteil könnte erst gefällt werden, wenn alle Hauptteile der bewohnten Erde ein einziges Handelsgebiet bilden, denn erst dann wäre es unmöglich, dass andere Nationen mit unterschiedlichen Geldsystemen sich anschließen und die internationale Organisation verändern.“
Jede neue Handelsbeziehung eröffnet die Möglichkeit, ein brandneues Geldgut einzuführen, das bisher nicht verwendet wurde. Wenn seine Qualitäten ein höheres Maß an Marktfähigkeit aufrechterhalten könnten, ist es möglich, dass sich die gesamte internationale Währungsordnung aufgrund seiner natürlichen Überlegenheit bei der Bewältigung der Funktionen des Geldes um ihn herum neu organisieren könnte.
Im Bitcoin Standard liefert Saifedean Ammous zahlreiche Argumente dafür, warum Gold dem Silber als Geldwert überlegen war, obwohl Mises nicht bereit oder nicht daran interessiert war, diesen Punkt zu diskutieren, und warum Bitcoin ein noch besserer Geldwert ist. Mises hat die Einführung von Bitcoin in die Weltwirtschaft zwar nicht mehr erlebt, aber seine Wirtschaftstheorie erklärt genau, warum Bitcoin an Wert gewinnen würde und warum es plausibel ist, dass die gesamte internationale Währungsordnung auf einen Bitcoin-Standard umgestellt wird. Er gibt auch den theoretischen Rahmen, um zu verstehen, warum Altcoins Bitcoin nicht allein durch ihre Eigenschaften ausstechen können. Sie müssen eine bessere Marktfähigkeit in Bezug auf Raum, Zeit und Größe bieten, um einen ausreichenden Vorteil gegenüber Bitcoin zu haben. Wie bereits an anderer Stelle beschrieben, ist dies einfach nicht gelungen, und nur Bitcoin bietet ein stark dezentralisiertes, überprüfbares und glaubwürdig knappes digitales Geldgut.
Mises, der Marktmaximalist
Die Geldtheorie ist nicht der einzige Ort, an dem der Leser eine Art „Maximalismus" in Mises' Denken spüren kann. Sein gesamtes Werk läuft auf einen unverhohlenen Marktmaximalismus hinaus, der sich weigert, durch rigorose ökonomische Theorie und Analyse sozialistischen oder interventionistischen Argumenten nachzugeben.
Ein großartiges Beispiel für seine Verteidigung des freien Marktes findet sich in einem Vortrag aus dem Jahr 1950 mit dem Titel „Die Mitte des Weges führt zum Sozialismus". In dieser Vorlesung greift Mises Interventionisten an, die behaupten, eine Politik der „Mitte" zwischen den beiden Extremen Kapitalismus und Sozialismus zu favorisieren. Durch strategische Interventionen kann der Staat die Auswüchse beider Systeme verhindern.
Mises betrachtet Kapitalismus und Sozialismus jedoch als diametral entgegengesetzte und unvereinbare Organisationssysteme und nicht als ein Spektrum der Wohlstandsverteilung:
„Der Konflikt der beiden Prinzipien ist unüberbrückbar und lässt keinen Kompromiss zu. Kontrolle ist unteilbar. Entweder entscheidet die Nachfrage der Verbraucher, die sich auf dem Markt manifestiert, für welche Zwecke und wie die Produktionsfaktoren eingesetzt werden sollen, oder der Staat kümmert sich um diese Angelegenheiten. Es gibt nichts, was den Gegensatz zwischen diesen beiden widersprüchlichen Prinzipien abmildern könnte. Sie schließen sich gegenseitig aus. Der Interventionismus ist kein goldener Mittelweg zwischen Kapitalismus und Sozialismus. Er ist der Entwurf für ein drittes System der wirtschaftlichen Organisation der Gesellschaft und muss als solches gewürdigt werden.“
Dieses dritte System ist jedoch im Grunde nur ein längerer Marsch zum Sozialismus, indem es ein falsches Lippenbekenntnis zu Privateigentum und freier Marktwirtschaft ablegt. Auf jeden Eingriff, der stattfindet, müssen weitere folgen. Die Festsetzung eines Preises hier erfordert die Festsetzung eines anderen Preises dort, und so geht es die ganze Lieferkette entlang. Am Ende hat der Interventionismus die gesamte „Marktwirtschaft" im Würgegriff.
Der Interventionismus kann nicht als ein Wirtschaftssystem betrachtet werden, das dazu bestimmt ist, zu bleiben. Er ist eine Methode zur Umwandlung des Kapitalismus in den Sozialismus in mehreren aufeinanderfolgenden Schritten. Damit unterscheidet er sich von den Bemühungen der Kommunisten, den Sozialismus auf einen Schlag zu verwirklichen. Der Unterschied bezieht sich nicht auf das letztendliche Ziel der politischen Bewegung, sondern vor allem auf die Taktik, die zur Erreichung des von beiden Gruppen angestrebten Ziels angewandt wird.
Trotzdem sind selbst die meisten vermeintlichen Befürworter einer freien Marktwirtschaft in Wirklichkeit von interventionistischen Ideologien und Denkweisen durchdrungen, und ihre Strategien sind immer zum Scheitern und zu Kompromissen verurteilt.
„Dies hat zur Folge, dass praktisch kaum etwas getan wird, um das System der Privatwirtschaft zu erhalten. Es gibt nur Mittelsmänner, die glauben, erfolgreich gewesen zu sein, wenn sie eine besonders ruinöse Maßnahme eine Zeit lang hinausgezögert haben. Sie sind immer auf dem Rückzug. Sie nehmen heute Maßnahmen in Kauf, die sie noch vor zehn oder zwanzig Jahren für undiskutabel gehalten hätten. In ein paar Jahren werden sie sich mit anderen Maßnahmen abfinden, die sie heute noch für undiskutabel halten. Was den totalitären Sozialismus verhindern kann, ist nur ein grundlegender Wandel der Ideologien.\ \ Was wir brauchen, ist weder Antisozialismus noch Antikommunismus, sondern eine offene Befürwortung des Systems, dem wir all den Wohlstand verdanken, der unser Zeitalter von den vergleichsweise beengten Verhältnissen vergangener Zeiten unterscheidet.“
Mises nimmt kein Blatt vor den Mund, wenn er eine interventionistische Politik fordert, und es gibt viele Lehren, die Bitcoiner daraus ziehen können.
Erstens ist das Bitcoin-Netzwerk nicht einfach nur eine andere Art des Werttransfers als eine bestehende zentralisierte Lösung, eine Art PayPal 2.0. Es ist ein strukturell anderer Ansatz für das gesamte Problem der doppelten Ausgaben. „Blockchain, nicht Bitcoin" ist eine Mogelpackung, weil sie den Kern dessen, was Bitcoin einzigartig macht (Dezentralisierung, unabhängige Überprüfbarkeit usw.), wegnimmt, während sie behauptet, „die zugrundeliegende Technologie" zu nutzen, ähnlich wie ein nationalsozialistisches oder faschistisches Regime die staatliche Kontrolle über die Produktion übernehmen könnte, während es behauptet, für Privateigentum zu sein. Wenn du die Vorteile des Marktes nutzen willst, musst du tatsächlich einen Markt haben, und wenn du die Vorteile von Bitcoin nutzen willst, musst du Bitcoin tatsächlich nutzen.
Außerdem sollte die Dezentralisierung als binäres System betrachtet werden. Entweder ist ein System dezentralisiert, oder es ist dazu verdammt, zentralisiert zu werden, manchmal mit einem Hard Fork nach dem anderen (vgl. Ethereum). Bitcoin-Maximalisten werden regelmäßig als toxisch bezeichnet, weil sie entschlossen an bestimmten Netzwerkparametern festhalten, selbst wenn diese willkürlich oder trivial erscheinen. Ein ganzer Krieg über die Blockgröße wurde um eine Begrenzung von 1 MB geführt. Die Zahl schien willkürlich und die Lösung trivial zu sein, aber die Bitcoiner weigerten sich, davon abzuweichen. Und warum? Eine höhere Blockgröße würde die Kosten für den Betrieb eines vollständigen Knotens (Full Node) erhöhen, der für eine unabhängige Validierung und Dezentralisierung notwendig ist. Ein Hard Fork würde einen vernichtenden Präzedenzfall schaffen und alle zukünftigen Ansprüche auf Abwärtskompatibilität gefährden, die für die Glaubwürdigkeit der Geldpolitik und die Fähigkeit der Nodes, sich vertrauensvoll mit dem Netzwerk zu synchronisieren, erforderlich sind. Die Blockkapazität stieg zwar an, aber nur, weil SegWit, dessen Vorteile weit über die bloße Verbesserung der Skalierung hinausgingen, über einen Soft Fork aktiviert werden konnte, sodass denjenigen, die dies nicht wollten, keine neuen Kosten auferlegt wurden.
Andere Projekte hingegen akzeptieren nicht, dass die Kompromisse bei Bitcoin nicht wirklich willkürlich sind. Sie bieten Turing-complete Smart Contracts, schnellere Blockzeiten, größere Blöcke oder alle möglichen anderen „Features" an. Die Features werden nicht mit demselben extrem konservativen Engagement für Sicherheit produziert wie Bitcoin und bedrohen oft die Fähigkeit, überhaupt einen vollständigen Knoten (Full-Node) zu betreiben. Nur bei Bitcoin kümmern sich die Leute darum, dass die Geldmenge tatsächlich überprüft werden kann. Mit der Zeit verlieren die Projekte, wenn sie überhaupt aufrechterhalten werden, jeden Anschein einer glaubwürdigen Dezentralisierung. Ethereum, das einst mit unaufhaltsamen Anwendungen und der Aussage „Code ist Gesetz" warb, erlebte den DAO-Hack und ist nach der Einführung von Proof-of-Stake (das von Natur aus zentralisierend ist) der OFAC-Zensur in unterschiedlichem Maße unterworfen.
Bitcoin akzeptiert nichts von alledem. Er beugt seine Regeln für niemanden. Bitcoiner wissen auch, dass das System gar kein Bitcoin mehr wäre, wenn die Regeln gebogen würden. Mises hilft uns zu verstehen, dass eine Politik des Mittelweges zu Shitcoinerei führt. Eine Währung ist entweder Bitcoin oder dazu verdammt, ein Shitcoin zu sein.
Mises, der toxische Maximalist
Im Jahr 1947 fand in der Schweiz das erste Treffen der Mont Pèlerin Society statt. Bei diesem Treffen trafen sich viele der einflussreichsten Verfechter der freien Märkte und des klassischen Liberalismus, von Ludwig von Mises über F. A. Hayek bis hin zu Milton Friedman und vielen anderen, um darüber zu diskutieren, wie man die steigende Flut des Totalitarismus und seiner Wirtschaftsideologien durch die Förderung freier Märkte und des Privateigentums bekämpfen kann. Man könnte meinen, dass Mises genau in diese Diskussionen passt. Doch wie Milton Friedman berichtete, kam es anders:
„Die Geschichte, an die ich mich am besten erinnere, ereignete sich auf dem ersten Treffen in Mont Pèlerin, als [Mises] aufstand und sagte: „Ihr seid alle ein Haufen Sozialisten." Wir diskutierten über die Einkommensverteilung und darüber, ob man progressive Einkommenssteuern haben sollte. Einige der Anwesenden vertraten die Ansicht, dass es eine Rechtfertigung dafür geben könnte.\ \ Eine andere Gelegenheit, die ebenso aufschlussreich ist: Fritz Machlup war ein Schüler von Mises, einer seiner treuesten Jünger. Bei einem der Treffen in Mont Pèlerin hielt Machlup einen Vortrag, in dem er, glaube ich, die Idee eines Goldstandards in Frage stellte; er sprach sich für freie Wechselkurse aus. Mises war so wütend, dass er drei Jahre lang nicht mit Machlup sprechen wollte. Einige Leute mussten die beiden wieder zusammenbringen. Es ist schwer zu verstehen; man kann es einigermaßen nachvollziehen, wenn man sich vor Augen führt, wie Menschen wie Mises in seinem Leben verfolgt wurden.“
Wie bereits erwähnt, hielt Mises drei Jahre später einen Vortrag, in dem er eindrucksvoll erklärte, warum sie tatsächlich alle ein Haufen Sozialisten waren. Wer staatliche Eingriffe in die Einkommensverteilung akzeptiert, ist dem Sozialismus bereits verfallen, sobald genug Zeit vergangen ist. Mises war einfach nicht bereit, den sozialistischen Irrtümern, die er im Laufe seiner intellektuellen Karriere so akribisch aufgespießt hatte, Glauben zu schenken. Jörg Guido Hülsmann stellt in Mises: The Last Knight of Liberalism fest, dass „Mises zwar in der Lage war, Sozialisten hoch zu schätzen, aber der Vorfall zeigte, dass er wenig Geduld mit Sozialisten hatte, die sich als Liberale ausgaben."
Doch Mises' giftiges Verhalten blieb nicht ohne Folgen. Laut Hülsmann:
„Der Schlagabtausch zwischen Mises und seinen neoliberalen Gegnern prägte den Ton in der Mont Pèlerin Society für die kommenden Jahre.... Obwohl die Libertären um Mises eine kleine Minderheit waren, hatten sie die finanzielle Unterstützung der amerikanischen Hauptsponsoren wie dem Volker Fund, ohne die die Gesellschaft in jenen frühen Jahren schnell ausgestorben wäre. Solange Mises aktiv an den Treffen teilnahm, war es daher unmöglich, die technischen Details eines genehmigten staatlichen Interventionismus zu diskutieren. Das Laissez-faire hatte ein Comeback gefeiert. Es war zwar nicht die Mehrheitsmeinung, aber es war eine diskutierbare und diskutierte politische Option - zu viel für einige anfängliche Mitglieder wie Maurice Allais, der die Gesellschaft genau aus diesem Grund bald wieder verließ.“
Indem er toxisch war, konnte Mises dazu beitragen, den Ton für eine wirklich laissez-faire Mont Pèlerin Society zu setzen, die ihrem erklärten Ziel gerecht werden konnte, und sie wählten F. A. Hayek zu ihrem Präsidenten. Er hatte keine Angst, Klartext zu reden, aber lautstark, sogar gegenüber Leuten, die vermutlich zu seinem „eigenen Team" gehörten. Ludwig von Mises war ein Mann, der seine Ideen ernst nahm und die Wahrheit noch viel ernster.
In seinen Memoiren schreibt Mises über seine Zeit in der österreichischen Handelskammer in den 1910er und 1920er Jahren:
„Ich wurde manchmal beschuldigt, meinen Standpunkt zu schroff und unnachgiebig zu vertreten. Es wurde auch behauptet, dass ich mehr hätte erreichen können, wenn ich eine größere Kompromissbereitschaft gezeigt hätte.... Die Kritik war ungerechtfertigt; ich konnte nur dann effektiv sein, wenn ich die Dinge so darstellen konnte, wie sie mir erschienen. Wenn ich heute auf meine Arbeit bei der Handelskammer zurückblicke, bedauere ich nur meine Kompromissbereitschaft und nicht meine Unnachgiebigkeit.“
In dieser Zeit trug sein Rat dazu bei, die Hyperinflation in Österreich aufzuhalten und ihre Auswirkungen im Vergleich zur Weimarer Republik abzuschwächen.
Bitcoiner werden von endlosen „Krypto-" und „Shitcoin"-Betrügern geplagt, die auf dem Rücken der innovativen Technologie und des wirtschaftlichen Erfolgs von Bitcoin reiten wollen. Den Bitcoinern wird gesagt, dass sie alle im selben Team sind. In den Augen der Öffentlichkeit sind sie das auch. Das Ergebnis ist eine getäuschte Öffentlichkeit, der zentralisierte Pump-and-Dump-Systeme und Rugpulls, Affen-Jpegs und Rube-Goldberg-Maschinen verkauft werden, die auf Schlagwörtern basieren und die Vorstellung vermitteln, dass sie in der gleichen Liga spielen wie die großartigste Geldtechnologie, die je geschaffen wurde. „Krypto" profitiert vom Erfolg von Bitcoin, und die Bekanntheit von Bitcoin sinkt mit den Misserfolgen von „Krypto". Doch wenn Bitcoiner die Unterschiede ansprechen und diese Projekte ablehnen, die sie uninteressant oder sogar verabscheuungswürdig finden, wird das als schädlich angesehen. Den Bitcoinern schadet das nicht, denn sie können weiter (Satoshis) stapeln und bauen, aber die Menschen, die unter Fiat-Regimen leben müssen, leiden darunter, dass ihnen kein Weg zu Freiheit und Wohlstand gezeigt wird.
Abgesehen davon, dass das Geld des Einzelnen in Gefahr ist, kann die Offenheit für Shitcoins auch Veränderungen im Netzwerk fördern, die die Dezentralisierung beeinträchtigen. Wenn es Unterstützung für einen Shitcoin gibt, der auf einem bestimmten Merkmal basiert, warum sollte das Merkmal dann nicht in Bitcoin existieren? Wenn es tatsächlich eine Tendenz zu einer einzigen Währung gibt, ist die Förderung einer alternativen Kryptowährung selbst ein Angriff auf das Potenzial von Bitcoin. Wirtschaft und Technik sind mit gnadenlosen Konsequenzen konfrontiert. Eine falsche Abfolge von Schritten kann zu absoluter Verwüstung führen. Bitcoiner nehmen das sehr ernst und machen keinen Hehl daraus, dass sie diese Konsequenzen fürchten. Wenn sie das tun, lehnen sie ganze unternehmerische Vorhaben ab und stellen ihre gesamte Einnahmequelle in Frage. Das ist toxisch.
Bitcoiners sollten immer den Mut haben, Mises zu zitieren und jedem zu sagen: „Ihr seid alle ein Haufen Shitcoiner."
Der aufgehende Stern von Mises
Obwohl er aus einer adligen Familie stammte und in Österreich hohe Positionen innehatte, hatte Mises, als er auf der Flucht vor den Nazis in die Vereinigten Staaten emigrierte, nur wenige Möglichkeiten. Bis zu seiner Pensionierung war er „Gastprofessor" an der New York University. Er arbeitete im Grunde genommen im stillen Kämmerlein und unterrichtete hauptsächlich in seinen inzwischen berühmten informellen Seminaren, an denen auch Murray Rothbard und andere teilnahmen. Er benötigte die Unterstützung verschiedener philanthropischer Fonds. Hinzu kam, dass die Wirtschaftswissenschaften, wie alle Sozialwissenschaften, dem Szientismus und der Technokratie erlegen waren, so dass Mises' strenge logisch-deduktive Methoden im Vergleich zu mathematischen Formeln und statistischen Modellen als altmodisch galten. Der Goldstandard wurde zugunsten eines Fiat-Systems abgeschafft, und als Mises starb, hatte der US-Dollar keinerlei Verbindung mehr zu Edelmetallen oder realen Ersparnissen, so dass die Geldpolitik allein den Launen der Politik überlassen blieb.
Es gab allen Grund, Ludwig von Mises völlig in Vergessenheit geraten zu lassen. Doch seine Schüler, wie Murray Rothbard, hielten die österreichische Schule am Leben. Im Jahr 1982 wurde das Ludwig von Mises Institute von Rothbard und Lew Rockwell gegründet und von Dr. Ron Paul finanziert (beide wurden von ihren Kritikern als „toxisch" bezeichnet). Dr. Paul selbst wurde zu einem legendären Verfechter der Ideen von Mises und anderen, sowohl im Kongress als auch im Präsidentschaftswahlkampf. In letzterem machte Dr. Paul die von der Federal Reserve verursachte wirtschaftliche Zerstörung zu einem zentralen Bestandteil seines Programms und zum ersten Mal seit Jahrzehnten zu einem wichtigen Thema in der politischen Debatte, was den Diskurs danach für immer veränderte.
Es ist also kein Wunder, dass viele Menschen, die sich als erste für Bitcoin begeisterten, treue Schüler von Mises waren und dass seine Ideen mit dem Wachstum von Bitcoin noch mehr an Bedeutung gewonnen haben. Seine rigorose Erläuterung der Wahrheiten des Wirtschaftsrechts, die auf Subjektivismus, Marginalismus und methodologischem Individualismus beruht, gab den Menschen den Rahmen, um zu verstehen, wie Bitcoin die Geldpolitik veranschaulicht, die zu Frieden, Wohlstand und Freiheit führt. Anstatt irrelevant zu werden, ist Mises heute wichtiger denn je. Wie Ron Paul bemerkte: „Wir sind jetzt alle Österreicher."
Fazit
Das Toxische liegt im Auge des Betrachters oder des Bagholders. Die Wirtschaftswissenschaft ist, wie jedes Streben nach Wahrheit, kein Beliebtheitswettbewerb, und die Wahrheit wird immer von denen bekämpft werden, deren Geschäft und Status von der Verbreitung von Irrtümern und Unwahrheiten abhängt.\ \ Ludwig von Mises stand fest zu seinen gründlichen Analysen der Wirtschaftswissenschaften und des klassischen Liberalismus und scheute sich nicht, das zu verteidigen, was er für wahr hielt, selbst auf Kosten von Prestige und Popularität. Heute steht er weit über fast jedem anderen Sozialwissenschaftler des 20. Jahrhunderts.
Ich habe an anderer Stelle über Memes und Rhetorik gesprochen, und es gibt viel zu diskutieren über bestimmte Strategien und ihre Wirksamkeit. Aber vor allem muss jede Strategie die Wahrheit in den Mittelpunkt stellen. Die Wahrheit ist zeitlos, so dass ihre Relevanz nicht auf kurzfristige Popularität beschränkt ist. Wenn dies der Fall ist, ist der Vorwurf der „Toxizität" entweder eine Aufforderung zur Verbesserung oder ein Ehrenzeichen dafür, dass man trotz aller Widrigkeiten für die Wahrheit einsteht. Wie das Motto von Ludwig von Mises schon sagte: tu ne cede malis, sed contra audentior ito. Weiche dem Bösen nicht, trete ihm umso mutiger entgegen.
-
 @ 04ea4f83:210e1713
2025-02-23 17:38:11
@ 04ea4f83:210e1713
2025-02-23 17:38:11Erschienen in Citadel 21 Vol. 21 | Veröffentlichung 21.03.2023 \ Autor: Knut Svanholm\ Übersetzt von: Sinautoshi am 24.03.2023 - 782344\ \ Rückblickend sieht das Jahr 2022 wie eine Art Höhepunkt aus. Während der Großteil der Gesellschaft weitgehend vergessen hat, was die politische Klasse ihren Untertanen während der sogenannten Pandemie angetan hat, kotzte Hollywood weiterhin Inhalte aus, die von „diversen" Regisseuren und Drehbuchautoren produziert wurden und bis zum Rand mit nicht ganz so subtilen Botschaften und Verachtung für ihr Publikum gefüllt waren.
Star Wars und Marvel haben nach der Übernahme durch Disney auf diese Weise Franchise-Mord begangen, und auch das Erbe von Der Herr der Ringe wurde von der linken Idiotie vergewaltigt und für immer befleckt. Jetzt gibt es von jedem männlichen Avenger eine weibliche Version. Hugh Jackman, der Schauspieler, der früher die Hauptrolle des X-Men-Mutanten Wolverine spielte, empfahl seinen Anhängern in den sozialen Medien kürzlich Bill Gates' Buch über den Klimawandel.
Als Frauen verkleidete Männer gewinnen Sportmeisterschaften für Frauen, und alle haben so viel Angst davor, als bigott bezeichnet zu werden, dass sich niemand traut, auf die Absurdität hinzuweisen, dass ein Mann alle Mädchen schlägt. Diese so genannten Sportler werden als „mutig" bezeichnet, obwohl sie alles andere als das sind.
Die Tatsache, dass es in einigen Berufen mehr Männer als Frauen gibt, wird als Problem angesehen, aber warum genau das ein Problem ist, wird selten erwähnt. Die Verdienste und die tatsächliche Meinungsvielfalt werden auf dem Altar der „Vielfalt und Integration" geschlachtet.
Die Gesellschaft ist an einem Punkt angelangt, an dem die Verbraucher Ärzten und Anwälten gerade wegen ihrer Hautfarbe misstrauen, da sie vermuten, dass sie deshalb in ihre Positionen gekommen sind und nicht wegen ihrer Kompetenz oder ihrer Verdienste. Noch vor zwanzig Jahren war die normale Bauchreaktion das Gegenteil: „Wow, ein Arzt aus einer Minderheit! Sie müssen hart gearbeitet haben, um dorthin zu gelangen, wo sie heute sind!"
Als ich aufgewachsen bin, wurde ein „Rassist" als jemand definiert, der sich einen Dreck um die Hautfarbe oder die ethnische Zugehörigkeit einer anderen Person scherte. Dasselbe galt für das Wort „Sexist" - man war ein Sexist, wenn man das Geschlecht einer Person bei der Beurteilung berücksichtigte.
Ich hatte das Gefühl, dass die Welt seit den Gräueltaten des Zweiten Weltkriegs im Kampf gegen diese Vorurteile einen weiten Weg zurückgelegt hatte und dass jeder eine anständige Karriere in jedem Beruf machen konnte, wenn er sich nur anstrengte und sich Mühe gab. Doch irgendwann in den frühen 2000er Jahren änderte sich etwas.
Plötzlich begannen die Worte das Gegenteil von dem zu bedeuten, was sie ursprünglich bedeuteten. Plötzlich war jeder, der sich einen Dreck um seine Hautfarbe scherte, ein Rassist. Jeder, dem es egal war, ob der CEO eines großen Unternehmens ein Mann oder eine Frau war, war ein Sexist.
Im Jahr 2023 behaupten manche sogar, man sei ein „Transphobe", wenn man nicht gelegentlich Fellatio an einem „weiblichen Penis" betreiben will. Die Tugendwächter laufen in der Tat Amok, und die Medienunternehmen lieben es. Sie lieben es, weil sie alles lieben, was die Kluft zwischen den Menschen schürt. Je verrückter die Aktionen der Clownwelt® sind, desto wütender sind die Reaktionen der leichtgläubigen, verärgerten Menschen auf der „vernünftigen" Seite des politischen Spektrums.
Die Menschheit neigt dazu, sich wie ein Pendel oder eine Abrissbirne zu verhalten, wenn es um politische Meinungen oder „die aktuelle Sache" geht.
Wenn es zu viele blauhaarige, übergewichtige, lesbische, glutenintolerante, vegane Umweltschützer gibt, taucht von irgendwoher eine Welle von Skinheads auf, die mit Steroiden vollgepumpt sind und gegen Samenöl und Fleischfresser sind.
Für jede Hillary Clinton gibt es einen Donald Trump. Für jede Greta Thunberg gibt es einen Andrew Tate. Für jeden CNN-Reporter gibt es einen Alex Jones.
Auch im Bitcoin-Bereich gibt es immer ein „aktuelles Thema", an das man sich klammern kann, wenn auch oft eine männlichere Idee als das „aktuelle Thema" des Mainstreams. Was nur wenige wissen, ist, wie faul diese Art des Denkens ist.
Wissenschaft ist nicht automatisch schlecht, nur weil „die Wissenschaft" schlecht ist.
Nur weil man gelernt hat, dass alles, was die Regierung sagt, eine Lüge ist, ist nicht automatisch auch das Gegenteil wahr. Die Welt ist nuanciert; die meisten Dinge sind nicht schwarz oder weiß.
Was wahr und sehr schwarz-weiß ist, ist das Geld - es gibt Bitcoin und es gibt Shitcoins. Nur wenn wir letztere für erstere aufgeben, können wir die Politik aus dem menschlichen Handeln entfernen und uns auf eine gewisse Wahrheit in der Basisschicht der Zivilisation zurück arbeiten. Bitcoin belohnt weder Rent-Seeking noch faules Denken.
Die positiven Aspekte vieler moderner Technologien werden oft übersehen. Auch wenn sich die Clownwelt® und die lächerlichen Ideen, die ihr folgen, wie ein Lauffeuer verbreiten, gibt es Gründe für einen ungetrübten Optimismus für die Zukunft.
Wir hören oft von den Gefahren der sozialen Medien und wie sie die Gehirne unserer Kinder schädigen, aber wir werden selten an die Kehrseite der Medaille erinnert. Soziale Medien verbinden Menschen in einem Ausmaß, das der Menschheit nie zuvor zugänglich war. Jeder Mensch auf der Welt kann heute mit jedem anderen in Kontakt treten und mit einem Mausklick einen Videoanruf starten. Das ist ein enorm wichtiges Instrument für den Frieden. In Kombination mit Bitcoin haben die Bösewichte keine Chance mehr.
Wenn jeder auf diese Weise vernetzt ist, wird überdeutlich, wie absurd es ist, dass wir in Staaten mit unterschiedlichen Gesetzen und Vorschriften leben. Warum gelten für meine Mitmenschen auf der anderen Seite dieses Teiches, dieses Flusses, dieses Gebirges oder sogar dieser imaginären Linie in der Erde andere Regeln?
Jeden Tag wachen mehr und mehr Menschen auf und erkennen, dass es nur ein einziges Menschenrecht gibt - das Recht, in Ruhe gelassen zu werden.
Immer mehr Menschen erkennen, dass die Geldentwertung kein natürliches Phänomen ist, sondern eine bewusste Politik. Es ist nur eine Frage der Zeit, bis die alte Welt verschwindet. Solange wir kommunizieren dürfen, gibt es Hoffnung. Das Internet hat bewiesen, dass sich jede Kommunikation auf eine Reihe von Einsen und Nullen reduzieren lässt, und Bitcoin hat bewiesen, dass Geld nichts anderes als Information ist.
-
 @ 207ad2a0:e7cca7b0
2025-01-07 03:46:04
@ 207ad2a0:e7cca7b0
2025-01-07 03:46:04Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my free to read/share attempt to write a novel, but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.
Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end.
Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:

and after a number of outputs, selected this one to work on:

The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.

The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.

At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.

At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:

Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story.
The AI Generated Elephant in the Room
If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it.
I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points.
I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs.
-
 @ 04ea4f83:210e1713
2025-02-23 10:43:38
@ 04ea4f83:210e1713
2025-02-23 10:43:38Veröffentlicht auf Discreetlog.com am 17.04.2023\ Originalautor: Matt Odell\ Übersetzt von: Sinautoshi am 20.05.2023 - 790600
„Privatsphäre ist für eine offene Gesellschaft im elektronischen Zeitalter notwendig. Privatsphäre ist keine Geheimhaltung. Eine private Angelegenheit ist etwas, von dem man nicht möchte, dass es die ganze Welt erfährt, aber eine geheime Angelegenheit ist etwas, von dem man nicht möchte, dass es irgendjemand erfährt." Privatsphäre ist die Macht, sich der Welt selektiv zu offenbaren.“ - Eric Hughes, A Cypherpunk's Manifesto , 1993
Privatsphäre ist für die Freiheit unerlässlich. Ohne Privatsphäre ist der Einzelne nicht in der Lage, frei von Überwachung und Kontrolle Entscheidungen zu treffen. Mangelnde Privatsphäre führt zum Verlust der Selbstbestimmung. Wenn Einzelpersonen ständig überwacht werden, schränkt dies unsere Fähigkeit ein, uns auszudrücken und Risiken einzugehen. Alle Entscheidungen, die wir treffen, können negative Auswirkungen auf diejenigen haben, die uns überwachen. Ohne die Freiheit, Entscheidungen zu treffen, kann der Einzelne nicht wirklich frei sein.
Freiheit ist für den Erwerb und Erhalt von Wohlstand von entscheidender Bedeutung. Wenn der Einzelne nicht die Freiheit hat, Entscheidungen zu treffen, hindern uns Einschränkungen und Beschränkungen daran, wirtschaftliche Chancen zu nutzen. Wenn es uns in einem solchen Umfeld irgendwie gelingt, Wohlstand zu erlangen, kann mangelnde Freiheit zur direkten Beschlagnahme von Vermögenswerten durch Regierungen oder andere böswillige Organisationen führen. Wenn die Freiheit gefährdet wird, führt dies im großen Maßstab zu weitverbreiteter wirtschaftlicher Stagnation und Armut. Der Schutz der Freiheit ist für den wirtschaftlichen Wohlstand von wesentlicher Bedeutung.
Der Zusammenhang zwischen Privatsphäre, Freiheit und Wohlstand ist entscheidend. Ohne Privatsphäre verliert der Einzelne die Freiheit, frei von Überwachung und Kontrolle Entscheidungen zu treffen. Während der Mangel an Freiheit den Einzelnen daran hindert, wirtschaftliche Chancen wahrzunehmen, und den Vermögenserhalt nahezu unmöglich macht. Keine Privatsphäre? Keine Freiheit. Keine Freiheit? Kein Wohlstand.
Rechte werden nicht gewährt. Sie werden eingenommen und verteidigt. Rechte werden oft als Erlaubnis der Machthaber missverstanden, etwas zu tun. Wenn dir jedoch jemand etwas geben kann, kann er es dir grundsätzlich nach Belieben wegnehmen. Im Laufe der Geschichte haben Menschen zwangsläufig für Grundrechte gekämpft, darunter Privatsphäre und Freiheit. Diese Rechte wurden nicht von den Machthabern gegeben, sondern durch Kampf eingefordert und erkämpft. Selbst nachdem diese Rechte erlangt wurden, müssen sie kontinuierlich verteidigt werden, um sicherzustellen, dass sie nicht weggenommen werden. Rechte werden nicht gewährt – sie werden durch Kampf erworben und durch Opfer verteidigt.
-
 @ bbef5093:71228592
2025-05-07 15:09:39
@ bbef5093:71228592
2025-05-07 15:09:39Az Európai Bizottság terve az orosz urán- és energiafüggőség felszámolására
Az Európai Bizottság bejelentette, hogy korlátozni kívánja az új urán-, dúsított urán- és egyéb, Oroszországból származó nukleáris anyagokra vonatkozó ellátási szerződéseket, ezzel is elősegítve, hogy az Európai Unió „teljesen megszüntesse” az orosz energiától való függését[8][6][2].
A Bizottság új ütemtervet mutatott be, amely részletesen tartalmazza, hogyan kívánja megszüntetni az orosz energiafüggőséget, miközben biztosítja az EU energiaellátásának és árainak stabilitását[6][2][15].
Főbb intézkedések és célok
- Az EU az orosz gázimport arányát 45%-ról 19%-ra csökkentette a 2022 májusában indított REPowerEU tervnek köszönhetően, de 2024-ben ismét növekedett az orosz gáz behozatala[2][20].
- Az új ütemterv szerint az orosz olaj, gáz és nukleáris energia fokozatosan, összehangoltan és biztonságosan kerül ki az uniós piacokról, miközben az EU a tiszta energiára való átállást gyorsítja fel[6][15][7].
- Az EU-tagállamoknak 2025 végéig nemzeti terveket kell készíteniük arról, hogyan járulnak hozzá az orosz gáz, nukleáris energia és olaj importjának megszüntetéséhez[13][7][18].
- Az orosz eredetű urán, dúsított urán és egyéb nukleáris anyagok esetében új korlátozásokat vezetnek be: az Euratom Ellátási Ügynökség (ESA) nem hagy jóvá új orosz beszállítási szerződéseket, és gazdasági eszközökkel is igyekeznek visszaszorítani az importot[4][5][16].
- A meglévő rövid távú szerződéseket 2025 végéig meg kell szüntetni, új szerződéseket pedig nem lehet kötni; a hosszú távú szerződéseket 2027 végéig kell felmondani[5][7][6].
- Az intézkedések célja, hogy a teljes orosz gáz- és olajimport 2027 végéig megszűnjön, az orosz atomenergia pedig fokozatosan kivezetésre kerüljön[3][9][17].
Nukleáris háttér
- Az ESA jelentése szerint 2023-ban az EU-ban felhasznált természetes urán 23,4%-a érkezett Oroszországból, ami 72,6%-os növekedést jelentett, főként a VVER típusú orosz atomerőművek üzemanyag-felhalmozása miatt[16].
- Az EU-ban 19 VVER reaktor működik (Bulgáriában, Csehországban, Finnországban, Magyarországon és Szlovákiában).
- Az EU természetes uránszükséglete a globális igények mintegy 22%-át teszi ki, a beszerzések 91%-a Kanadából, Oroszországból, Kazahsztánból és Nigerből származik[16].
Célkitűzés és indoklás
A Bizottság szerint az orosz energiafüggőség felszámolása nemcsak gazdasági, hanem biztonságpolitikai kérdés is, mivel Oroszország többször is eszközként használta az energiát az EU-val szemben[2][12]. A lépések célja, hogy az EU energiaellátása biztonságos, stabil és kiszámítható maradjon, miközben az orosz energiaimportból származó bevételek ne finanszírozhassák tovább az Ukrajna elleni háborút[6][2][12].
Források alapján készült magyar összefoglaló és fordítás
Citations: [1] Döntött az Európai Bizottság: teljes mértékben megszüntetik ... - 444 https://444.hu/2025/05/06/dontott-az-europai-bizottsag-teljes-mertekben-megszuntetik-az-orosz-energiatol-valo-fuggest [2] Három éven belül felszámolná az orosz energiafüggőséget az ... https://hu.euronews.com/my-europe/2025/05/06/harom-even-belul-felszamolna-az-orosz-energiafuggoseget-az-europai-bizottsag [3] 2027-re teljesen leállítaná az Európai Bizottság az orosz ... - Új Szó https://ujszo.com/kozelet/2027-re-teljesen-leallitana-az-europai-bizottsag-az-orosz-energiabehozatalt-a-nuklearis [4] Bejelentették Brüsszelben: megkerülik Magyarországot, teljesen ... https://www.portfolio.hu/gazdasag/20250506/bejelentettek-brusszelben-megkerulik-magyarorszagot-teljesen-levalik-az-orosz-olajrol-es-gazrol-az-eu-759267 [5] Érik az újabb ütközés: Brüsszel betiltaná az orosz energiát https://www.valaszonline.hu/2025/05/06/energia-szankcio-oroszorszag-haboru-eu-olaj-gaz-uran/ [6] Az EU teljes mértékben megszünteti az orosz energiától való függését https://hungary.representation.ec.europa.eu/az-eu-teljes-mertekben-megszunteti-az-orosz-energiatol-valo-fuggeset-2025-05-06_hu?prefLang=en [7] Megvan az ütemterv, végleg betiltaná az orosz energiát az Európai ... https://index.hu/kulfold/2025/05/06/orosz-energiafuggoseg-orosz-gaz-olaj-import-europai-unio-repowereu/ [8] European Commission Unveils Plans To Restrict New Uranium ... https://www.nucnet.org/news/european-commission-unveils-plans-to-restrict-new-uranium-deals-with-russia-5-3-2025 [9] Az EU teljes mértékben megszünteti az orosz energiától való ... https://infostart.hu/belfold/2025/05/06/az-eu-teljes-mertekben-megszunteti-az-orosz-energiatol-valo-fuggoseget-a-nap-hirei [10] [PDF] EURÓPAI BIZOTTSÁG Brüsszel, 2025.4.9. COM(2025) 159 final ... https://secure.ipex.eu/IPEXL-WEB/download/file/082d29089612ec1e019619f955940250 [11] Kiszivárgott az Európai Bizottság 2025-ös munkaprogramja https://www.eu-monitor.hu/hu/cikk/20250206-kiszivargott-az-europai-bizottsag-2025-os-munkaprogramja [12] EU says it will end dependency on Russian energy supplies https://www3.nhk.or.jp/nhkworld/en/news/20250507_B4/ [13] Végleg leválik az orosz energiáról az Európai Unió ... - Népszava https://nepszava.hu/3278673_oroszorszag-europai-unio-foldgaz-koolaj-levalas-terv [14] Egyre több európai ország támogatja az atomenergiát https://www.vg.hu/nemzetkozi-gazdasag/2025/03/atomenergia-energiatarolas-europa [15] Az EU teljes mértékben megszünteti az orosz energiától való ... https://karpatinfo.net/energiafuggetlenseg-orosz-foldgaz-orosz-energiafuggoseg-2025-05-07 [16] EU outlines measures to end Russian gas, oil imports by end-2027 https://balkangreenenergynews.com/eu-outlines-measures-to-end-russian-gas-oil-imports-by-end-2027/ [17] Az Európai Unió 2027 végére betiltaná az orosz gáz importját https://www.korkep.sk/cikkek/gazdasag/2025/05/05/az-europai-unio-2027-vegere-betiltana-az-orosz-gazimportot/ [18] Ficónak és Orbánnak sem tetszik, hogy az EU teljesen kitiltaná az ... https://napunk.dennikn.sk/hu/4623240/ficonak-es-orbannak-sem-tetszik-hogy-az-eu-teljesen-kitiltana-az-orosz-energiat/ [19] Várhelyi Olivér késlelteti az EU orosz energiafüggőségét felszámoló ... https://telex.hu/kulfold/2025/05/05/varhelyi-oliver-europai-bizottsag-orosz-energia-kivaltas-hatraltatas [20] REPowerEU roadmap - Energy - European Commission https://energy.ec.europa.eu/strategy/repowereu-roadmap_en
-
 @ e6817453:b0ac3c39
2025-01-05 14:29:17
@ e6817453:b0ac3c39
2025-01-05 14:29:17The Rise of Graph RAGs and the Quest for Data Quality
As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence.
Booming Interest in Graph RAGs
Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can:
- Enhance LLM Outputs: By grounding responses in structured knowledge, graphs significantly reduce hallucinations.
- Support Complex Queries: Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving.
Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs?
Data Quality: The Foundation of Effective Graphs
A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why:
- Richness of Entities: Effective retrieval depends on graphs populated with rich, detailed entities.
- Freedom from Hallucinations: Poorly constructed graphs amplify inaccuracies rather than mitigating them.
Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs.
Hybrid Graph RAGs and Variations
While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that:
- Handle diverse data sources with ease.
- Offer improved adaptability to complex queries.
Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing.
Ontology: The Key to Graph Construction Quality
Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for:
- Defining Relationships: Clarifying how concepts connect within a domain.
- Validating Graph Structures: Ensuring constructed graphs are logically sound and align with domain-specific realities.
Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs?
How to Build Ontology Expertise in a Startup Team
For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach:
- Assign a Knowledge Champion: Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering.
- Provide Training: Invest in courses, workshops, or certifications in knowledge graph and ontology creation.
- Leverage Partnerships: Collaborate with academic institutions, domain experts, or consultants to build initial frameworks.
- Utilize Tools: Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process.
- Iterate with Feedback: Continuously refine ontologies through collaboration with domain experts and iterative testing.
So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts.
You could read about barefoot experts in my article :
Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise.
How to Find or Create Ontologies
For teams venturing into Graph RAGs, several strategies can help address the ontology gap:
-
Leverage Existing Ontologies: Many industries and domains already have open ontologies. For instance:
-
Public Knowledge Graphs: Resources like Wikipedia’s graph offer a wealth of structured knowledge.
- Industry Standards: Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields.
-
Business Framework Ontology (BFO): A valuable resource for enterprises looking to define business processes and structures.
-
Build In-House Expertise: If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation.
-
Utilize LLMs for Ontology Construction: Interestingly, LLMs themselves can act as a starting point for ontology development:
-
Prompt-Based Extraction: LLMs can generate draft ontologies by leveraging their extensive training on graph data.
- Domain Expert Refinement: Combine LLM-generated structures with insights from domain experts to create tailored ontologies.
Parallel Ontology and Graph Extraction
An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as:
- Detecting Hallucinations: Differentiating between genuine insights and AI-generated inaccuracies.
- Ensuring Completeness: Ensuring no critical concepts are overlooked during extraction.
Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method.
LLMs as Ontologists
While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to:
- Generate Skeleton Ontologies: Prompt LLMs with domain-specific information to draft initial ontology structures.
- Validate and Refine Ontologies: Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance.
However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes.
Final Thoughts: Unlocking the Power of Graph RAGs
The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools.
As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding.
Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 42342239:1d80db24
2025-02-23 10:00:20
@ 42342239:1d80db24
2025-02-23 10:00:20Europe's economic framework requires restructuring grounded in realism. The Commission's Competitiveness Compass, alas, reveals dangerous left-hemisphere dominance and risks repeating Mao's mistakes.
The European Commission presented its "competitiveness compass" in January. There will be massive investments in biotechnology, materials technology, medicines, space, and the defence industry. AI gigafactories are to be established, while Europe will "maintain its leadership in quantum technologies" (a leadership that few seem to be aware of). This will be achieved through more environmental labelling schemes, nature credits, procurement rules, platforms, cooperation plans, and coordination systems. Although the report contains some bright spots, such as promises to ease the regulatory burden, the overall picture is strikingly lacking in creativity. Instead, we are mainly met with the usual thought patterns of the European technocracy, which manifest in additional centralised frameworks, quantifiable goals, and annual reports. Mao's ghost haunts Brussels.
The Missing Half of Europe's Brain
Iain McGilchrist, a British psychiatrist and philosopher, has launched the hemispheric hypothesis (a theory about how the two hemispheres of the brain work). The left hemisphere is more detail- and control-oriented, while the right hemisphere is holistic and creative. A society dominated by the left hemisphere, like our own according to McGilchrist, "would see it as its task to control everything maximally." The Commission's compass appears similarly lobotomised , prioritising measurable processes over imaginative solutions.
In an earlier text, I mentioned that Europe might need to return to its roots and asked if Europe should have "the same end goal as China." This is still a relevant and justified question. But if we are honest, China has implemented a series of well-thought-out reforms since the 1980s, in addition to its many well-known and large-scale investments. It is not necessarily wrong to be inspired by China, as many believe; it depends on which China you are inspired by.
Lessons from the Cat Theory
When Deng Xiaoping returned to power in the late 1970s, he chose a more pragmatic approach than his predecessors. China left Mao Zedong's purges of dissidents behind. Instead, he launched the cat theory: "it doesn't matter what colour the cat is as long as it catches mice", regarding economic development. It was now free to experiment with different models. Instead of ideological conformity, the most important thing was to increase productivity and material prosperity.
What was done in China?
- Companies and individuals were given more freedom
- Provinces and municipalities were given more autonomy
- Special economic zones were established, with different conditions and rules
- Programs to increase the number of banks were introduced
- The banking sector was deregulated
- Property rights and contract law began to be respected
China has since gone from being an economic backwater to not only being the world's largest economy in terms of purchasing power but also a global tech contender (leading in 37 out of 44 key technologies per ASPI).
EU's Compliance Obsession vs Chinese Pragmatism
And today, when China is astonishing the world with surprisingly cheap and competent AI systems, which recently set American tech stocks in motion, in the EU one is met with advertisements for yet another compliance training, this time about AI. Every new compliance training echoes Mao's ghost – ideological correctness overriding practical results. Is prosperity really built with certifications, directives, requirements, and penalties?
When we compare the Chinese experience with today's EU, the contrast is clear:
- Freedoms are curtailed. The right to privacy is undermined (Chat Control, etc.)
- Member states' ability to self-govern is reduced, year by year
- Streamlining and harmony are popular buzzwords in the bureaucracy
- The ECB is actively working to reduce the number of banks
- The banking sector is being regulated more and more
- Property rights and contract law are being eroded, which can be partly attributed to developments in payment systems
Deng's cat theory was an example of when the right hemisphere was involved in decision-making. Rather than just focusing on details (the cat's colour), the whole (the result) was important. The Chinese proverb "cross the river by feeling the stones" is another example of more holistic thinking. Under Deng's leadership, reforms were first tested in a free zone or a province. After a while, the reforms could be evaluated before they were possibly implemented on a larger scale. "Try before you buy" is also a wise principle that follows from complexity research. In sharp contrast to this approach was Mao's "Great Leap Forward," a part of a disastrous five-year plan that shows what can happen when the left hemisphere is given too much power. A tragedy of historic proportions - a mass famine - resulted. While Deng exorcized Mao's ghost through pragmatic experimentation, Brussels seems determined to resurrect. Today's EU risks repeating Mao's mistake of letting political abstractions ("green transition! digital decade!") override reality – Mao's ghost surely smiles at nature credit schemes replacing actual market signals.
Mao's ghost trives on the ontological mistake
The serious problems that the EU is facing have been built up over decades and stem from incorrect assumptions. The economy is not complicated. It is complex. The concepts are often confused, but they describe two fundamentally different things. The complicated refers to something composite, but which can still be unfolded and then folded back up again without changing its essence. The complex, on the other hand, refers to something entangled, where every attempt to divide it changes its character. Compare, for example, an airplane engine with a béarnaise sauce. If you mix up the concepts, you make an ontological mistake, a philosopher would say. A programmer would say: garbage in, garbage out. Mao's ghost thrives on this ontological error, convincing technocrats they can blueprint society like a Soviet tractor factory.
When a system is complicated, predictable, and linear, centralised coordination and control by the left hemisphere can work well. But in complex systems, it can never be a solution because it leads to reduced adaptability and increased system risks. Instead, the goal should be diversity and decentralisation, which provide greater adaptability! The faster the changes of the system or in the environment, the greater the demands on adaptability and flexibility - if the system is to survive, that is. Increased diversity and decentralisation would not only increase adaptability and flexibility but also promote creativity, an ability that will likely become increasingly important in a world where AI and automation are changing the rules.
A better path forward
Europe's economic framework requires restructuring grounded in realism. The Commission's competitiveness compass - fixated on metrics and control - reveals dangerous left-hemisphere dominance, echoing Maoist central planning's epistemological errors. Our path forward demands:
- Dual-brain governance (prioritising creativity over control)
- Banishing of category mistakes (acknowledging the complex adaptive nature of the economy)
- Pragmatism over ideology (policy sandboxes inspired by China's special economic zones)
- Anti-fragile design (increased autonomy of EU nations, within states, and decentralised banking)
- Sunset clauses on all bureaucracy (regulators cannot originate breakthroughs)
The alternative? Another technocratic Great Leap Forward - eco-certified, AI-monitored, but economically brittle and fundamentally maladapted to the complex global economy. As Deng's reformers understood: no institutional architecture, not even the First Emperor's Terracotta Army, can withstand modernity's tide.
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ fe32298e:20516265
2024-12-16 20:59:13
@ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install NVapi to monitor my GPUs in Home Assistant.

NVApi is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions.
- GPU Utilization Monitoring: Utilization, memory usage, temperature, fan speed, and power consumption.
- Automated Power Limiting: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally.
- Cross-GPU Coordination: Total power budget applies across multiple GPUs in the same system.
- PCIe Link Speed Management: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization.
- Home Assistant Integration: Uses the built-in RESTful platform and template sensors.
Getting the Data
sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpuResponse for a single GPU:
[ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ]Response for multiple GPUs:
[ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ]Start at Boot
Create
/etc/systemd/system/nvapi.service:``` [Unit] Description=Run NVapi After=network.target
[Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible
Environment="GPU_TEMP_CHECK_INTERVAL=5"
Environment="GPU_TOTAL_POWER_CAP=400"
Environment="GPU_0_LOW_TEMP=40"
Environment="GPU_0_MEDIUM_TEMP=70"
Environment="GPU_0_LOW_TEMP_LIMIT=135"
Environment="GPU_0_MEDIUM_TEMP_LIMIT=120"
Environment="GPU_0_HIGH_TEMP_LIMIT=100"
Environment="GPU_1_LOW_TEMP=45"
Environment="GPU_1_MEDIUM_TEMP=75"
Environment="GPU_1_LOW_TEMP_LIMIT=140"
Environment="GPU_1_MEDIUM_TEMP_LIMIT=125"
Environment="GPU_1_HIGH_TEMP_LIMIT=110"
[Install] WantedBy=multi-user.target ```
Home Assistant
Add to Home Assistant
configuration.yamland restart HA (completely).For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds
- platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ```
For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature
-
platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C"
-
platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C"
```
Basic entity card:
type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updatedAnsible Role
```
-
name: install go become: true package: name: golang-go state: present
-
name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true
go run main.go -port 9999 -rate 1
-
name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service
-
name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ```
-
 @ 83279ad2:bd49240d
2025-05-07 14:22:43
@ 83279ad2:bd49240d
2025-05-07 14:22:43 -
 @ 9223d2fa:b57e3de7
2025-04-15 02:54:00
@ 9223d2fa:b57e3de7
2025-04-15 02:54:0012,600 steps
-
 @ 83279ad2:bd49240d
2025-05-07 14:20:50
@ 83279ad2:bd49240d
2025-05-07 14:20:50 -
 @ 42342239:1d80db24
2025-02-16 08:39:59
@ 42342239:1d80db24
2025-02-16 08:39:59Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a sceptre of power, compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - the journalist or editor could become a ruler.
Times had certainly changed compared to a few hundred years earlier. Before Gutenberg's invention of the printing press, it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many.
However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. The power over information dissemination was decentralised.
Ten years ago, Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that journalism was now downstream of social media. Five years later, NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: from tanks to tweets." This finally underscores the importance of social media.
Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that citizen journalism is the future.
While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("freedom of speech does not mean freedom of reach "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that it's impossible to know which code is actually used and what adjustments are made by humans or algorithms.
William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods?
Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task - not even well-ventilated computers.
-
 @ 6f6b50bb:a848e5a1
2024-12-15 15:09:52
@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
-
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
-
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!
Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
-
-
 @ 005bc4de:ef11e1a2
2025-05-07 14:19:15
@ 005bc4de:ef11e1a2
2025-05-07 14:19:15The beautiful evil of horse racing

Horse racing intrigues me. And, it appalls me. I find it to be both gloriously beautiful and brutally cruel.
One of the fun facts shared tirelessly around social media for Kentucky Derby #151 was something like this: "This is the first Derby where every horse is in the bloodline of Secretariat." Secretariat, if you don't know, won the Triple Crown in 1973 (KY Derby, Preakness, Belmont) and still holds the fastest times in all three of those races.
That's really a nice fun fact when you first hear it, but maybe it shouldn't be too surprising. After a successful racing career, a male racehorse "retires" to a life of studding himself out, which is where the real horse money is. His post-racing stats: he bred 60 mares per year, he sired 660 foals, and he earned an estimated $120 million in stud fees. When you start branching out the Secretariat family tree over several generations, well, the sheer numbers must be very large. That means the chances that any given Thoroughbred might have a hint of Secretariat blood must get rather high. Grok AI estimates there are 500,000 Thoroughbreds today worldwide, and that beteen 250,000 to 400,000 are in Secretariat's lineage, that's 50% to 80% of every Thoroughbred. Suddenly, the social media snippet from Derby #151 is less surprising, less cool.

Secretariat, retired from racing.
The beautiful side of horse racing
Horse racing is beautiful. This is the easy part to write. If you've ever been to a horse track, especially on a big race day, it's a true multi-sensory experience.
- There are smells that we typically don't smell often in this modern world...especially if you hang out near the paddock. Personally, I don't find horse dung particularly stinky, but earthy.
- There are tastes and good smells. Food and drink are a huge part of horse racing. There is a reason that the Derby has its own pie (a chocolate pecan pie) and each major race has its own drink. Feasting and tailgating are huge parts of horse racing.
- There are things to feel, actually to bodily feel. Aside from crowds of people to bump into, if you stand close to the track, you can feel the reverberation of hooves beating the dirt. We hear the term "thundering herd" sometimes in college sports, but, that term is not just words. You can actually feel the thunder of those hooves.
- The sounds are distinctly horse racing. The announcer's calls of "Less than a minute," "They're in the gates," and "And they're off!" are iconic, not to mention the terms "down to the wire," "won by a nose," or "photo finish." And then there's the bugle's announcement, the singing of "My Old Kentucky Home" at the Derby, the roar of the crowd, and moans of loss from bad bets, shrieks of joy from good bets, and that thunder from the herd, of course.
- The visuals are just stunning. People-wise, the women in their pastel sundresses, the men are snazzy in their colors too (though some go too over-the-top for my liking; they move from classy to clownish), and then there are the hats which are their own category altogether. There's the track, and the spires, and the grass and dirt (or mud) and roses. And there's the jockeys and their colorful silks. But, mostly, there's the horses. A Thoroughbred racehorse at full speed, in full stride, is incredible to look upon. It is a beast that is entirely built for one pure reason: speed. You might be familiar with ESPN's "The Body Issue" that features elite, pro athletes in the nude so that their incredible physiques are displayed. Horse racing is the same thing, equine style. The Derby, in particular, is a sports photographer's bonanza. If you actually know what you're doing, you can't not get great results. Below are some photos amateur me point-and-clicked on Derby Day at a horse track (not Churchill Downs):
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/Eq7LSG39v5H5NpQppxhzwhfAtJVQikYVppRJsgZXh6KxGXU2YochRXqoJaW7NMZ8Yd8.jpg]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/23wWw7ZbXPJxKFAyLwuraK1QypVcLV6QpsyG6Ccr6ZLiPYgNtUBa3ALWx1XR4wPYayhmT.png]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/2432HqW3ZtUCjvGD7WTkg2z2ngoByX2rV6htgENN1eytUYXycRCaQdevL7xn1mdKC8qG8.gif]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/245HijMM8pQ7c2EdJwrzUPa3LDjm1P51WqU6j5mYkAJnAXJrkbAn6XBNCzR7G28MSR62u.png]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/EpVAhnScSoAVCYvw2Faf7ZyipskYLvu9MuBXzmHN3jdVPoDBVAVR8yqrrGf1c7Apxzb.jpg]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/245Hm6k5HafqiMfzUiNK7Z3pUG752f4CmLc5pMVuonkQVY1sKG9ucSrdGgvNVQGNud628.gif]
Horse racing appeals to all senses and is viscerally exhilarating in so many ways. It is beautiful.
Genetics
But, let's get back to the real point: this game is all about Brave New World-like breeding and genetics. It is horse eugenics. The idea is simple: fast Mommy horse and fast Daddy horse means fast baby horse. In horse racing, a horse's blood lineage is called its dosage. Personally, I pay zero attention to dosage (I focus on track length and closing the long races), but dosage is a mathematical stat that tries to answer, "How much is this horse truly a Thoroughbred and a genetic winner?" This question of dosage begs another question, "What actually is a Thoroughbred?"
A Thoroughbred is a horse breed. There are a lot of horse breeds, a lot. For a novice like me, it's very hard to distinguish one from another. I think most people can see a difference between a draft horse, bred for pulling heavy loads, and a Thoroughbred, bred for speed. I think most people, if betting on a foot race, would bet on the Thoroughbred below, left and not on "Jupiter, the largest draft horse in America" on the right. If betting on hauling a wagon load of beer up a steep hill, most would bet Jupiter.
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/23yx8AjtVZkpE7jXJ2RXzV78hhXSvsgU97i2FkvfcFcEZevfshNgwPw2diJNhmL344gmR.png]
But, when comparing racing horses, there are also Sandardbreds which are bred for harness racing and thus have a heavier build than Thoroughbreds. The two breeds are shown below, but their distinctions are not particularly outstanding to my novice eye. Can you tell the difference, which is the Standardbred versus the Thoroughbred? (Answer at the bottom of page.) Maybe side-by-side you can tell, but could you tell if you saw one standing alone? If you saw two of the same breed, could you judge by appearance which one runs faster? If you can, I tip my cap to you.
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/23zbTqFJgYpKyXwxbGsVeQiKv4tTZSj8S8QboTJWEhTETPqjnaUVDtX2BirjBXH5KVNo6.png]
I imagine most people are much more familiar with, and can more readily notice, the differences in dog breeds. For instance, take the French Bulldog, the Greyhound, or the world's best dog breed, the Labrador Retriever (totally unbiased here).
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/244oozGkxAwS4sqoWiT8phQv8ssrqq4caB9bHgDufsogds7scUUfhp54WTKmosDzfL5WT.png]
The French Bulldog is bred for cosmetics, the greyhound for pure speed, and the Labrador for all-around everything...intelligence, sturdy athleticism, loyal companionship (totally unbiased here). In these three dogs, we can clearly see the differences that have resulted from breeding.
The evil side of horse racing
Horse racing is evil. And, it is cruel. But, for now, let's step back to the dogs. Dog breeding can be cruel as well.
The French Bulldog is something of the "it" dog right now. A quick Google Gemini search reported it as the most popular breed in 2025.

I remember when "101 Dalmatians" came out 1996. Dalmatians skyrocketed in popularity. But, that popularity was anything but a blessing for Dalmatian pups. They were overbred (and are too inbred as it is), oversold, and were taken in by people eager to get in on the "it" dog then and scoop up the cute spotted pups. But, Dalmatians are very active pups that grow into very active dogs. When the novelty of the spotted pup wore off, many were returned or given away or taken to shelters as being uncontrollable.
The French Poodle situation is not too different. The dogs were bred for little purpose beyond the sin of human vanity. People wanted a short, stocky, smoosh-faced dog that they perceived as cute. And, that's what they got: an unathletic dog that looked a certain way, with middle-of-the-road intelligence, and little use aside from its appearance.
Worse, seeking out this certain "toy dog" look, French Bulldogs suffer from a plethora of health issues. Summed up, they have the lowest life expectancy "by a large margin" of all dogs at only 4.5 years (average is 11.2. years).
There is a neighbor near to me who breeds French Bulldogs. Evidently, it's a lucrative business as they apparently sell for an estimated $2,000 to $8,000 dollars each. I don't know how many litters the neighbor's have bred and pawned, but it has been several. The breeder bitch is constantly given a little trot outside before being hauled to the vet for insemination. (Sadly, this seems to be about the only time she is taken out for exercise and family "fun.") Considering he and his wife have no real job, this seems to be their job. Breed, advertise (complete with foofy tutu outfit photos), market, sell, repeat. With only a 4.5 year life span, I see the lucrative nature in this business.
All told, it's basically a sin and a shame that humans do this to these dogs. A certain segment of people desire a certain unnatural smooshed face in a dog. And because we vainly want a certain look in a dog, so as to accessorize our own look, we breed them into forms unnatural to a canine, curse them with severe breathing difficulties and other serious health issues, and short lives.
A Greyhound is essentially a canine Thoroughbred. From generations of selective breeding, it has a massive chest, long body with a narrow waist, and long, spindly legs. It's sole purpose is speed. Ironically, both the Thoroughbred and Greyhound can race at about the same speed...44 mph, give or take.
Man's sinful nature has abused the Greyhound too. These hounds are racing dogs and racing means gambling. So, dog tracks for have been common. The pups are bred, they race a few years, then they are hopefully adopted out. A good friend of mine once adopted a retired racer to become the family dog. "Bandit" initially had a post-race job as a business's guard dog. But, due to him constantly doing nothing but laying around and sleeping, he was fired as a guard dog (who gets a Greyhound for a guard dog anyway?). Bandit eventually went to my friend, was a bit neurotic, but turned out to be a good family dog.
I think most Greyhounds don't have the fortunate story of Bandit. Once raced out, they're done and forgotten. Man's thrills are fleeting, whatever sparkles in his eye soon fades. To combat the ills of dog racing, I know that the citizens of Florida voted to outlaw dog racing in 2018 (and it indeed ended Dec. 31, 2020). Now, dog tracks lay rusting away, and Greyhounds are largely forgotten.
And then, there's the Labrador Retriever. What's not to like? These dogs can do it all, and they do it all well. Name a dog task, Labs do that well. Full disclosure: I once had a Lab (or rather, half Lab, and half...Great Dane? Doberman? Something?). Her mother was Lab and my dog looked Lab, though a bit taller and leaner. She was incredible. So, yes, I favor Labs.
But, even my beloved Labs and all that they excel in, even Labs have their issues, such as high rates of hip dysplasia. Selective breeding, and a too-narrow gene pool, have consequences.
Back to horses
Let's try to bring this back to horses. Thoroughbreds and horse racing mirror both of the characteristics seen in the French Bulldog and the Greyhound.
- Thoroughbreds have been, and still are, extremely selectively bred to accentuate certain qualities: speed, speed, speed.
- Thoroughbreds are bred for money. Literally, a champion stud or mare doesn't breed for free.
Regarding speed, Thoroughbreds have a massive muscular chest, almost no waist at all, massive muscular hindquarters, and long, spindly, almost cartoonishly thin legs. And, this built-for-speed physique brings up one of the cruelest aspects of horse racing: Thoroughbreds are prone to "break down."
These horses are structured unnaturally, like aliens. Having such a massive, muscular, powerful architecture stilted on such twig-like legs (and getting more massive and twiggier due to constant selective breeding of these traits) is a recipe for disaster. "Breaking down" in horse terms is a rather correct term. Their leg bones break under the stress and force of running, then the horse's weight and thrust breaks the legs down further.
The name Barabaro might come to memory. Barbaro won the Kentucky Derby in 2006 impressively, by a full 6.5 lengths. Hopes were high for a Triple Crown winner. At the Preakness two weeks later, Barabaro broke down. Actually, in his pre-start excitement he broke through the gate to false start. These animals are bred to run and race, they know when it's race time. He was so jacked up and ready to run while in the starting gate, he bucked up, banged his head hard, then literally broke through the gate to false start. Then, after reentering, he started off the race clean before breaking down in front of the main grandstand of viewers. Horse's can break any of their several leg bones. Barbaro broke the cannon, sesamoid, long pastern, and dislocated the fetlock (ankle joint). In other words, he shattered his leg.
When horses break their legs, they're usually put down. As to why, there are lots of reasons, but it comes down to the fact that horses are built for standing and running, especially Thoroughbreds. They are not built for laying down to recuperate, and actually suffer health consequences for not standing. Understandably, a broken leg causes the horse to favor weight to the other legs while standing and this, in turn, can cause other issues. Altogether, the horse suffers.
In Barbaro's case, they tried to rehab him. I think normally he would have been put down on the track in the equine ambulance (the "meat wagon"), but this was Barbaro. The resources were there, he was beloved, and millions had witnessed his injury live. Not trying to save him would have been a public relations nightmare. Putting him down on live TV would have been even worse. There was surgery, then laminitis (inflammation under the hoof) in his opposite good hoof, the result of standing unnaturally. He rallied, then had more setbacks including laminitis in his front hooves. He was in pain, with no way to stand, and then was euthanized in 2007.
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/23wgoS1v6e2i2gizAqeMeXHf6Zwhz3BTuYMuYNL676tqbPZWwvXUhw7R1J6K4r7DmRj2K.png]
Regarding the money, top studs earn $200 to $400,000 for stud service. A top mare can be bought for $100 to $300,000, then you need the stud service. This is only to breed the foal. This has nothing to do with stabling or training the animals. In other words, it's extremely expensive.
Also regarding the money, there is, of course, the gambling. You might say this is the whole point of horse racing. It's certainly the whole point for breeding Thoroughbreds. It was the whole point for Greyhounds in Florida, before that point was banned.
This year, an estimated $200 million was bet on the Kentucky Derby, the one race alone. $300 million was bet on the races combined. Grok estimated that globally in 2022, horse racing was a $402 billion dollar industry and expects it to grow to $793 billion by 2030.
Those numbers are staggering. But, again, I come back to sinful man. Our love of money is the root of this beautiful evil called horse racing.
I really don't know many scenes more beautiful than a Kentucky horse ranch and a Thoroughbred running across the bluegrass. Add a colt running with his mother, the beauty is staggering. But, underneath that beauty, there is an evil side to horse racing. That side is fueled by sinful man's pride to win and his love of money.
Horse racing is a beautiful evil.


Image sources: https://wikipedia.org, original by me at the track, equine bones at https://www.anatomy-of-the-equine.com/distal-limb-bones.html, the final two images from https://pixabay.com
Note: In the "Can you tell the difference" side-by-side images above, the Thoroughbred was on the left, the Standardbred on the right.
-
 @ 42342239:1d80db24
2025-02-14 08:42:40
@ 42342239:1d80db24
2025-02-14 08:42:40A recent US data leak has brought to light a disturbing reality: our everyday technology has become a powerful tool for surveillance and control. Paradoxically, new technology holds the key to creating a safer, more resilient, and perhaps even more human society.
Preparedness remains a multifaceted topic that continues to spark engagement. The subject is not just about energy infrastructure and food supply but also about seemingly more orthogonal issues like obesity and cybersecurity.
The significant importance of cybersecurity can be illustrated by examples from an American company that was recently subjected to an IT intrusion with a subsequent data leak. The company, Gravy Analytics, specializes in providing mobile phone data that provides exceptionally detailed information about where individuals are located at any given time. Data that can be used, for example, for advertising purposes, but also for more sinister purposes such as extortion or espionage. The company has previously been accused of using misleading methods to collect location data without valid consent from individuals.
Mobile operators have long had the ability to locate their subscribers' positions over time. This leak shows how even apps on your phone risk revealing your location. Analysis of the samples leaked from the leak shows that data has leaked out for users of several well-known mobile applications, including the popular mobile game Candy Crush and the widely used online dating service Tinder.
Even if apps only use an ad ID when collecting data, these collected digital breadcrumbs can often be deanonymized. It is possible, for example, to identify daily routines, workplaces, and where and when an individual usually sleeps. This usually enables identification. But it is also possible to map an individual's social circle and romantic relationships. The mapping risks quickly becoming both sensitive and invasive.
The fact that such data is collected, but especially that it leaks, also poses a threat to preparedness. By mapping military or other sensitive locations (energy supply, water treatment plants, critical infrastructure) along with location and time data, it is potentially possible to identify employees at these locations. Information that can then be used by those who want to cause harm.
It is not written in the stars that citizens must be dependent on a few large IT companies. Our data does not need to be collected and used in a way that does not benefit us, without our knowledge. There are alternatives to large-scale and "super-registers". Technology such as asymmetric encryption and zero-knowledge proofs can be used to give power back to the individual. If the parliament and government are serious about improving preparedness, it is high time to leave old thought patterns like Chat Control 2 behind and instead explore such possibilities.
The primary purpose of the internet was originally to enable information transfer without intermediaries ("peer-to-peer"). Today, intermediaries are everywhere. It is worth remembering that peer-to-peer is not some obscure technical term. In case we have forgotten about it, it simply means: person to person, without intermediaries.
Maybe new technology can not only give us a safer and more resilient society, but also a more human one?
-
 @ e6817453:b0ac3c39
2024-12-07 15:06:43
@ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible.
We model-directed graphs
Also, graphs of entities
We even model hypergraphs
Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge.
So why do we need metagraphs, and what kind of challenge could they help us to solve?
- complex and nested event and temporal context and temporal relations as edges
- multi-mode and multilingual knowledge
- human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks
MetaGraphs
A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context.
Also, in some cases, edges could be referenced as nodes.
This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs.Graph Basics
- A standard graph has a set of nodes (or vertices) and edges (connections between nodes).
- Edges are generally simple and typically represent a binary relationship between two nodes.
- For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes).
Hypergraph
- A hypergraph extends the concept of an edge by allowing it to connect any number of nodes, not just two.
- Each connection, called a hyperedge, can link multiple nodes.
- This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation.
- Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge.
Metagraph
- A metagraph allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures.
- In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph.
- This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship.
Named Graphs and Graph of Graphs
As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem.
If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.
The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature.
It looks complex, but it is not so hard to model it with a slight modification of a directed graph.
So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you
Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free
Meta Graphs in Relational Model
Let’s try to make several attempts to model different meta-graphs with some constraints.
Directed Metagraph where edges are not used as nodes and could not contain subgraphs

In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases.
Directed Metagraph where edges are not used as nodes and could contain subgraphs

Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert.
I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case.Directed Metagraph where edges are used as nodes and could contain subgraphs
As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.

A full-scale metagraph model is way too complex for a relational database.
So we need a better model.Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs.
Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose. -
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ b83a28b7:35919450
2025-05-07 12:46:19
@ b83a28b7:35919450
2025-05-07 12:46:19This article was originally part of the sermon of Plebchain Radio Episode 109 (April 25, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with Noa Gruman from nostr:nprofile1qyv8wumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wsqzqvfdqratfpsvje7f3w69skt34vd7l9r465d5hm9unucnl95yq0ethzx7cf and nostr:nprofile1qye8wumn8ghj7mrwvf5hguewwpshqetjwdshguewd9hj7mn0wd68ycmvd9jkuap0v9cxjtmkxyhhyetvv9usz9rhwden5te0dehhxarj9ehx2cn4w5hxccgqyqj8hd6eed2x5w8pqgx82yyrrpfx99uuympcxmkxgz9k2hklg8te7pq0y72 . You can listen to the full episode here:
https://fountain.fm/episode/gdBHcfDgDXEgALjX7nBu
Let’s start with the obvious: Bitcoin is metal because it’s loud, it’s aggressive, it’s uncompromising. It’s the musical equivalent of a power chord blasted through a wall of amps—a direct challenge to the establishment, to the fiat system, to the sanitized, soulless mainstream. Metal has always been about rebellion, about standing outside the norm and refusing to be tamed. Bitcoin, too, was born in the shadows, dismissed as the currency of outlaws and freaks, and it thrived there, fueled by the energy of those who refused to bow down
But Bitcoin isn’t just any metal. It’s progressive metal. Prog metal is the genre that takes metal’s aggression and fuses it with experimentation, complexity, and a relentless drive to push boundaries. It’s not satisfied with three chords and a chorus. Prog metal is about odd time signatures, intricate solos, unexpected detours, and stories that dig into philosophy, psychology, and the human condition. It’s music for those who want more than just noise—they want meaning, depth, and innovation.
That’s Bitcoin. Bitcoin isn’t just a blunt instrument of rebellion; it’s a living, evolving experiment. It’s code that’s open to anyone, a protocol that invites innovation, a system that’s constantly being pushed, prodded, and reimagined by its community.
Like prog metal, Bitcoin is for the thinkers, the tinkerers, the relentless questioners. It’s for those who see the flaws in the mainstream and dare to imagine something radically different.
Both prog metal and Bitcoin are about freedom — freedom from the tyranny of the predictable, the safe, the centrally controlled. They are countercultures within countercultures, refusing to be boxed in by genre or by law. Both attract those who crave complexity, who aren’t afraid to get lost in the weeds, who want to build something new and beautiful from the chaos.
If you want to reach the heart of Bitcoin’s counterculture, you don’t do it with bland, safe, mainstream pop. You do it with prog metal—with music that refuses to compromise, that demands your attention, that rewards those who dig deeper. Prog metal is the true voice of Bitcoin’s core: the plebs, the builders, the dreamers who refuse to accept the world as it is.
Bitcoin is prog metal. It’s technical, it’s rebellious, it’s unafraid to be different. It’s music and money for those who want to break free—not just from the old systems, but from the old ways of thinking. And as the mainstream tries to water down both, the true counterculture survives at the core, pushing boundaries, making noise, and refusing to die.
The sermon and episode clearly had an impact on people, as evidenced by the fountain charts here (snapshot taken on May 6, 2025)
nostr:nevent1qvzqqqqqqypzqkcpsw4kc03j906dg8rt8thes432z3yy0d6fj4phylz48xs3g437qqsy7rfh8n6vgxppkwzq2ntjps0lmt4njkxjrv3rv5r59l7lkv6ahps2eavd9 And here's the clip of the sermon:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsptkpkd0458yshe7gfshck2f9nfxnqe0nrjz0ptlkm9rhv094rxagapyv4d
-
 @ 7e538978:a5987ab6
2025-05-07 10:25:30
@ 7e538978:a5987ab6
2025-05-07 10:25:30Across Switzerland, customers at SPAR supermarkets are now able to pay for their groceries using Lightning on Bitcoin — a step towards everyday Bitcoin adoption. This rollout was led by DFX, a Bitcoin services company focused on onboarding businesses and individuals to Bitcoin. Behind the scenes LNbits plays a key role.
 ## Lightning at the Checkout
## Lightning at the CheckoutSPAR’s approach is simple: at the till, customers can scan a static QR code to pay in Bitcoin using the Lightning Network. Each checkout in each participating store has its own unique LNURL address — a reusable QR code designed for fast, low-friction Lightning payments.
To manage these LNURLs, DFX leverages LNbits. Using the LNbits Pay Links extension, DFX generates LNURLs for each till across the network of participating SPAR locations. The result is a robust, reliable setup that works at scale. Store staff do not interact with LNbits directly — instead, DFX manages the backend, ensuring each till has a dedicated LNURL without operational overhead for SPAR employees.
At SPAR we use static QR codes that meet the LNURL standard. Therefore we use LNbits. Each checkout has its own personal LNURL address which we generate with LNbits.
— Cyrill Thommen, CEO of DFX.Swiss— Cyrill Thommen, CEO of DFX.Swiss
 ## LNbits in Action
## LNbits in ActionLNbits provided DFX with a modular, open-source solution that allows them to build only what they need, without locking into a rigid platform. For instance, DFX built custom monitoring around payment events using the LNbits API, while keeping full control over wallet infrastructure.
The ability to generate and manage LNURLs through the LNbits API, while layering additional monitoring and business logic on top, made LNbits a practical choice.
DFX’s setup highlights how open source software, Bitcoin and purpose-built tools can underpin enterprise-grade deployments. The system works reliably — without introducing friction for customers or staff.
Bitcoin in the Real World
Switzerland is already one of Europe’s most Bitcoin-friendly environments, with over 1,000 businesses accepting Bitcoin. But SPAR’s implementation is noteworthy for its scale and practicality: everyday purchases, completed with Bitcoin, at a national supermarket chain.
LNbits' flexible architecture, API-first design, and plug-in system make it well suited to precisely this kind of adoption.
As more retailers explore Lightning integration, SPAR’s rollout sets a precedent — showing how modular, open-source tools like LNbits can bring Bitcoin into daily life, seamlessly.

-
 @ 42342239:1d80db24
2025-02-10 08:16:32
@ 42342239:1d80db24
2025-02-10 08:16:32The risks associated with cryptocurrencies have recently received attention in the media, where e.g. the Swedish Financial Supervisory Authority warns of the high volatility and risk of investments in crypto. Within the EU, as usual, significant efforts are being made to expand the already extensive regulatory framework. Meanwhile, in the US, there has been a marked turnaround. Even the presidential family has launched their own cryptocurrencies, resulting in criticism from industry experts .
Important perspectives, however, are conspicuous by their absence in the conversation.
Iain McGilchrist, a British psychiatrist and philosopher, has introduced the hemispheric hypothesis (a theory about how the brain's two hemispheres function). The left hemisphere is more detail- and control-oriented, while the right hemisphere is more holistic. A society dominated by the left hemisphere, such as our own according to McGilchrist , "would see it as its task to control everything maximally and would have a paranoid feeling that we need to have surveillance cameras everywhere...".
During a speech at the World Economic Forum, President Trump recently stated that conservatives complain about big banks, such as Bank of America, not allowing them to conduct business within the bank. Critics argue that the American banking system has been used to persecute political opponents, both during Obama's and Biden's terms. Under Obama, 'Operation Chokepoint' was introduced to limit certain businesses' access to banking services. A subcommittee in the Senate now wants to eradicate this phenomenon.
More and more people are discovering that their money is not always under their control. Non-profit associations and congregations are not allowed to open bank accounts. Sometimes they are even thrown out as bank customers. Others may report being subjected to lengthy interrogations by the bank about what they intend to do with their money, even when they just want to transfer funds between their own accounts. Rejected churches are met with silence, while a bank account is (still!) necessary to fully operate in society.
When leading economists at the International Monetary Fund (IMF) argue that a cashless society can threaten fundamental rights , including property rights, when churches are refused bank accounts in what is described as "a threat to civil society" and when regulations still fail to combat organised crime , is it not reasonable to wonder if we are on the right path?
With cash, people can pay freely without intermediaries, which constitutes a form of financial freedom. The notes you hold in your hand are your own. Cryptocurrencies, such as Bitcoin, offer a similar possibility: an electronic, peer-to-peer cash system (person to person).
A society dominated by the left hemisphere results in a pathological need for control, according to McGilchrist. A more holistic perspective, taking into account the right hemisphere, would acknowledge that too much control can be detrimental, that property rights are a fundamental right, and that financial freedom is a human right. Do these perspectives not deserve more attention?
-
 @ e6817453:b0ac3c39
2024-12-07 15:03:06
@ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans.
The Neurosymbolic Approach: What It Means ?
Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning.
While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in.
Symbolic Calculations and the Early Vision of AI
If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like Lisp emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations.
Lisp: The Earlier AI-Language
Lisp, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.”
Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches.
Prolog: Formal Logic and Deductive Reasoning
In the 1970s, Prolog was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning.
Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s.
The language is declarative in nature, meaning that you define the problem, and Prolog figures out how to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved.
Solvers and Their Role in Complementing LLMs
One of the most powerful features of Prolog and similar logic-based systems is their use of solvers. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning.
For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a solver can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers.
Solvers are also ideal for handling constraint satisfaction problems — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone.
By integrating neurosymbolic methods that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints.
Graph of Rules for Enhanced Reasoning
Another powerful concept that complements LLMs is using a graph of rules. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge.
In a graph of rules, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust.
For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses.
Graphs of rules also enable modular reasoning, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of neural fluency with rule-based structure gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical.
By implementing a graph of rules, LLMs are empowered to perform deductive reasoning alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence.
Enhancing LLMs with Symbolic Reasoning
Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where neurosymbolic approaches shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks.
Personal Knowledge Graphs (PKGs) come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers.
Imagine combining an LLM with a graph of rules that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using deductive databases to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving.
My Research on Deductive Databases and Knowledge Graphs
I recently did some research on modeling knowledge graphs using deductive databases, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning.
Prolog and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a graph of rules that governs how relationships are formed or how logical deductions can be performed.
The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence.
Why It Matters for LLM Employment
Using neurosymbolic RAG (retrieval-augmented generation) in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules.
This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of neural fluency with symbolic accuracy and deductive power is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems.
Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate!
Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
-
 @ 9c35fe6b:5977e45b
2025-05-07 08:49:00
@ 9c35fe6b:5977e45b
2025-05-07 08:49:00Sailing the Nile on the Dahabiya Gorgonia Nile Cruise offers an intimate way to experience the timeless beauty of Egypt. This elegant boat is ideal for travelers who seek calm, charm, and tradition. With only a few cabins onboard, guests can enjoy a more serene atmosphere compared to larger vessels. ETB Tours Egypt offers this unique cruise option as part of its Egypt vacation packages, blending cultural richness with comfort.
Cultural Encounters Along the Nile The Dahabiya Nile Cruises give you a chance to witness life along the riverbanks up close. Onboard the Gorgonia, travelers visit lesser-known villages, ancient temples, and local markets far from the tourist crowds. With ETB Tours Egypt, your itinerary includes authentic experiences guided by knowledgeable Egyptologists—an ideal choice for those seeking Egypt private tours.
Scenic Sailing with Modern Comfort Although traditional in style, the Dahabiya Gorgonia is equipped with modern amenities to ensure a pleasant journey. Guests enjoy spacious decks, elegant dining, and personalized service. Whether part of an All inclusive Egypt vacations or a custom-designed plan, this cruise ensures you travel in style without missing out on comfort.
Smart Choices for Smart Travelers ETB Tours Egypt also makes sure that the Dahabiya Gorgonia Nile Cruise is available as part of their Egypt budget tours, offering excellent value without compromising on experience. It's perfect for those who want to enjoy the best of Egypt without overspending. Flexible options are also available through their wide range of Egypt travel packages, making it easy to match your schedule and interests.
To Contact Us: E-Mail: info@etbtours.com Mobile & WhatsApp: +20 10 67569955 - +201021100873 Address: 4 El Lebeny Axis, Nazlet Al Batran, Al Haram, Giza, Egypt
-
 @ 42342239:1d80db24
2025-01-18 08:31:05
@ 42342239:1d80db24
2025-01-18 08:31:05Preparedness is a hot topic these days. In Europe, Poland has recently introduced compulsory lessons in weapons handling for schoolchildren for war-preparedness purposes. In Sweden, the Swedish Civil Contingencies Agency (MSB) has recently published the brochure on what to do "If crisis or war comes".
However, in the event of war, a country must have a robust energy infrastructure. Sweden does not seem to have this, at least judging by the recent years' electricity price turbulence in southern Sweden. Nor does Germany. The vulnerabilities are many and serious. It's hard not to be reminded of a Swedish prime minister who, just eleven years ago, saw defense as a special interest.
A secure food supply is another crucial factor for a country's resilience. This is something that Sweden lacks. In the early 1990s, nearly 75 percent of the country's food was produced domestically. Today, half of it must be imported. This makes our country more vulnerable to crises and disruptions. Despite our extensive agricultural areas, we are not even self-sufficient in basic commodities like potatoes, which is remarkable.
The government's signing of the Kunming-Montreal Framework for Biological Diversity two years ago risks exacerbating the situation. According to the framework, countries must significantly increase their protected areas over the coming years. The goal is to protect biological diversity. By 2030, at least 30% of all areas, on land and at sea, must be conserved. Sweden, which currently conserves around 15%, must identify large areas to be protected over the coming years. With shrinking fields, we risk getting less wheat, fewer potatoes, and less rapeseed. It's uncertain whether technological advancements can compensate for this, especially when the amount of pesticides and industrial fertilizers must be reduced significantly.
In Danish documents on the "roadmap for sustainable development" of the food system, the possibility of redistributing agricultural land (land distribution reforms) and agreements on financing for restoring cultivated land to wetlands (the restoration of cultivated, carbon-rich soils) are discussed. One cannot avoid the impression that the cultivated areas need to be reduced, in some cases significantly.
The green transition has been a priority on the political agenda in recent years, with the goal of reducing carbon emissions and increasing biological diversity. However, it has become clear that the transition risks having consequences for our preparedness.
One example is the debate about wind power. On the one hand, wind power is said to contribute to reducing carbon emissions and increasing renewable energy. On the other hand, it is said to pose a security risk, as wind turbines can affect radio communication and radar surveillance.
Of course, it's easy to be in favor of biological diversity, but what do we do if this goal comes into conflict with the needs of a robust societal preparedness? Then we are faced with a difficult prioritization. Should we put the safety of people and society before the protection of nature, or vice versa?
“Politics is not the art of the possible. It consists in choosing between the disastrous and the unpalatable” said J. K. Galbraith, one of the most influential economists of the 20th century. Maybe we can’t both eat the cake and have it too?
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ f88e6629:e5254dd5
2025-01-17 14:10:19
@ f88e6629:e5254dd5
2025-01-17 14:10:19...which allow online payments to be sent directly from one party to another without going through a financial institution.
- Without sovereign and accessible payments we are loosing censorship resistance
- Without censorship resistance even other core characteristics are in danger - including scarcity and durability.
- This affects every bitcoiner including sworn hodlers and MSTR followers.
| Property | Description | Fulfillment | | --- | --- | --- | | Scarce | Fixed supply forever. Instantly and costlessly verifiable | 🟢 Good, but can be harmed without censorship resistance | | Portable | Effortless to store and move, with negligible costs | 🟠 Onchain transactions can be expensive, other layers require onchain to be sovereign. Easy portability is offered by custodians only. | | Divisible | Infinitely divisible | 🟠 Smaller units than dust are available only for LN users, which most people can’t use in a sovereign way. | | Durable | Exists forever without deterioration | 🟢 Good, but can be harmed without censorship resistance | | Fungible | Every piece is forever the same as every other piece | 🟡 Onchain bitcoin is not fungible. | | Acceptable | Everyone, anywhere, can send and receive | 🟠 Most people are not able to send and receive in a sovereign way. | | Censorship Resistant | You hold it. Nobody can take it or stop you sending it | 🟠 Custodians are honey-pots that can and will be regulated |
➡️ We need accessible, scalable, and sovereign payment methods
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ e6817453:b0ac3c39
2024-12-07 14:54:46
@ e6817453:b0ac3c39
2024-12-07 14:54:46Introduction: Personal Knowledge Graphs and Linked Data
We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points.
The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management.
In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started.
Intro to RDF
The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent.
RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph.
RDF and Advanced Topics
Lists and Sets in RDF
RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data.
Graph of Graphs
A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling.
Property Graphs
While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges.
For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges).
The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other.
Graph of Graphs and Subgraphs for Entity Modeling
A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties.
For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added.
Hypergraphs and Metagraphs
When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships.
Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts.
Balancing Structure and Properties
One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity.
So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools.
The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage?
Conclusion
Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings.
In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects.
-
 @ 42342239:1d80db24
2025-01-10 09:21:46
@ 42342239:1d80db24
2025-01-10 09:21:46It's not easy to navigate today's heavily polluted media landscape. If it's not agenda-setting journalism, then it's "government by journalism", or "åfanism" (i.e. clickbait journalism)) that causes distortions in what we, as media consumers, get to see. On social media, bot armies and troll factories pollute the information landscape like the German Ruhr area 100 years ago - and who knows exactly how all these opaque algorithms select the information that's placed in front of our eyes. While true information is sometimes censored, as pointed out by the founder of Meta (then Facebook) the other year, the employees of censorship authorities somehow suddenly go on vacation when those in power spread false information.
The need to carefully weigh the information that reaches us may therefore be more important than ever. A principle that can help us follows from what is called costly signaling in evolutionary biology. Costly signaling refers to traits or behaviors that are expensive to maintain or perform. These signals function as honest indicators. One example is the beauty and complexity of a peacock's feathers. Since only healthy and strong males can afford to invest in these feathers, they become credible and honest signals to peahens looking for a partner.
The idea is also found in economics. There, costly signaling refers to when an individual performs an action with high costs to communicate something with greater credibility. For example, obtaining a degree from a prestigious university can be a costly signal. Such a degree can require significant economic and time resources. A degree from a prestigious university can therefore, like a peacock's extravagant feathers, function as a costly signal (of an individual's endurance and intelligence). Not to peahens, but to employers seeking to hire.
News is what someone, somewhere, doesn't want reported: all the rest is advertisement
-- William Randolph Hearst
Media mogul William Randolph Hearst and renowned author George Orwell are both said to have stated that "News is what someone, somewhere, doesn't want reported: all the rest is advertisement." Although it's a bit drastic, there may be a point to the reasoning. "If the spin is too smooth, is it really news?"
Uri Berliner, a veteran of the American public radio station National Public Radio (NPR) for 25 years, recently shared his concerns about the radio's lack of impartiality in public. He argued that NPR had gone astray when it started telling listeners how to think. A week later, he was suspended. His spin was apparently not smooth enough for his employer.
Uri Berliner, by speaking out publicly in this way, took a clear risk. And based on the theory of costly signaling, it's perhaps precisely why we should consider what he had to say.
Perhaps those who resign in protest, those who forgo income, or those who risk their social capital actually deserve much more attention from us media consumers than we usually give them. It is the costly signal that indicates real news value.
Perhaps the rest should just be disregarded as mere advertising.
-
 @ e6817453:b0ac3c39
2024-12-07 14:52:47
@ e6817453:b0ac3c39
2024-12-07 14:52:47The temporal semantics and temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory and semantic memory. And we also have a lot of theories, right?
Declarative Memory of the Human Brain
How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic:
- hippocampus indexing and retrieval
- sanitization of episodic memories
- episodic-semantic shift theory
They all give a different perspective on how different parts of declarative memory cooperate.
We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed.
But, you know, it’s still an open question:
do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different?
It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah?
Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected.
So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory.
Temporal Semantics
It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it.
There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts.
Time in a Semantic context is not a timestamp.
What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that.
You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah.
Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things.
For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events.
I’m more about thinking about the time of semantics, where you have a time model as a hybrid clock or some global clock that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts.
We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between.
Blockchain of connected events and facts
I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events.
Time anchors
We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles.
Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.”
-
 @ 78b3c1ed:5033eea9
2025-05-07 08:23:24
@ 78b3c1ed:5033eea9
2025-05-07 08:23:24各ノードにポリシーがある理由 → ノードの資源(CPU、帯域、メモリ)を守り、無駄な処理を避けるため
なぜポリシーがコンセンサスルールより厳しいか 1.資源の節約 コンセンサスルールは「最終的に有効かどうか」の基準だが、全トランザクションをいちいち検証して中継すると資源が枯渇する。 ポリシーで「最初から弾く」仕組みが必要。
-
ネットワーク健全性の維持 手数料が低い、複雑すぎる、標準でないスクリプトのトランザクションが大量に流れると、全体のネットワークが重くなる。 これを防ぐためにノードは独自のポリシーで中継制限。
-
開発の柔軟性 ポリシーはソフトウェアアップデートで柔軟に変えられるが、コンセンサスルールは変えるとハードフォークの危険がある。 ポリシーを厳しくすることで、安全に新しい制限を試すことができる。
標準ポリシーの意味は何か? ノードオペレーターは自分でbitcoindの設定やコードを書き換えて独自のポリシーを使える。 理論上ポリシーは「任意」で、標準ポリシー(Bitcoin Coreが提供するポリシー)は単なるデフォルト値。 ただし、標準ポリシーには以下の大事な意味がある。
-
ネットワークの互換性を保つ基準 みんなが全く自由なポリシーを使うとトランザクションの伝播効率が落ちる。 標準ポリシーは「大多数のノードに中継される最小基準」を提供し、それを守ればネットワークに流せるという共通の期待値になる。
-
開発・サービスの指針 ウォレット開発者やサービス提供者(取引所・支払いサービスなど)は、「標準ポリシーに準拠したトランザクションを作れば十分」という前提で開発できる。 もし標準がなければ全ノードの個別ポリシーを調査しないと流れるトランザクションを作れなくなる。
-
コミュニティの合意形成の場 標準ポリシーはBitcoin Coreの開発・議論で決まる。ここで新しい制限や緩和を入れれば、まずポリシーレベルで試せる。 問題がなければ、将来のコンセンサスルールに昇格させる議論の土台になる。
つまりデフォルトだけど重要。 確かに標準ポリシーは技術的には「デフォルト値」にすぎないが、実際にはネットワークの安定・互換性・開発指針の柱として重要な役割を果たす。
ビットコインノードにおける「無駄な処理」というのは、主に次のようなものを指す。 1. 承認される見込みのないトランザクションの検証 例: 手数料が極端に低く、マイナーが絶対にブロックに入れないようなトランザクション → これをいちいち署名検証したり、メモリプールに載せるのはCPU・RAMの無駄。
-
明らかに標準外のスクリプトや形式の検証 例: 極端に複雑・非標準なスクリプト(non-standard script) → コンセンサス的には有効だが、ネットワークの他ノードが中継しないため、無駄な伝播になる。
-
スパム的な大量トランザクションの処理 例: 攻撃者が極小手数料のトランザクションを大量に送り、メモリプールを膨張させる場合 → メモリやディスクI/O、帯域の消費が無駄になる。
-
明らかに無効なブロックの詳細検証 例: サイズが大きすぎるブロック、難易度条件を満たさないブロック → 早期に弾かないと、全トランザクション検証や署名検証で計算資源を浪費する。
これらの無駄な処理は、ノードの CPU時間・メモリ・ディスクI/O・帯域 を消耗させ、最悪の場合は DoS攻撃(サービス妨害攻撃) に悪用される。 そこでポリシーによって、最初の受信段階、または中継段階でそもそも検証・保存・転送しないように制限する。 まとめると、「無駄な処理」とはネットワークの大勢に受け入れられず、ブロックに取り込まれないトランザクションやブロックにノード資源を使うこと。
無駄な処理かどうかは、単に「ポリシーで禁止されているか」で決まるわけではない。
本質的には次の2つで判断される 1. ノードの資源(CPU、メモリ、帯域、ディスク)を過剰に使うか 2. 他のノード・ネットワーク・マイナーに受け入れられる見込みがあるか
将来のBitcoin CoreのバージョンでOP_RETURNの出力数制限やデータサイズ制限が撤廃されたとする。 この場合標準ポリシー的には通るので、中継・保存されやすくなる。 しかし、他のノードやマイナーが追随しなければ意味がない。大量に流せばやはりDoS・スパム扱いされ、無駄な資源消費になる。
最終的には、ネットワーク全体の運用実態。 標準ポリシーの撤廃だけでは、「無駄な処理ではない」とは断定できない。 実質的な「無駄な処理」の判定は、技術的制約+経済的・運用的現実のセットで決まる。
-
-
 @ 866e0139:6a9334e5
2025-05-07 08:18:51
@ 866e0139:6a9334e5
2025-05-07 08:18:51Autor: Nicolas Riedl. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Dieser Beitrag erschien zuerst bei Radio München.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Das Kriegsgrauen kriecht unter die Haut. Bilder von verstümmelten Beinen und Armen, von Kriegstraumatisierten schweigenden Männern, von Kriegsgräbern steigen auf. Als Mutter, Schwester, Tante, Großmutter wachsen die Ängste, dass sich ein Verwandter von der politischen und medialen Kriegslust anstecken lässt und tatsächlich die Beteiligung an den näher kommenden kriegerischen Auseinandersetzungen in Erwägung zieht. Einen wütenden Kommentar anlässlich der wachsenden Kriegstreiberei verfasste unser Autor Nicolas Riedl.
Nicolas Riedl, Jahrgang 1993, geboren in München, studierte Medien-, Theater- und Politikwissenschaften in Erlangen. Den immer abstruser werdenden Zeitgeist der westlichen Kultur dokumentiert und analysiert er in kritischen Texten. Darüber hinaus ist er Büchernarr, strikter Bargeldzahler und ein für seine Generation ungewöhnlicher Digitalisierungsmuffel. Entsprechend findet man ihn auf keiner Social-Media-Plattform. Von 2017 bis 2023 war er für die Rubikon-Jugendredaktion und Videoredaktion tätig.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:56:25
@ 57d1a264:69f1fee1
2025-05-07 06:56:25Wild parrots tend to fly in flocks, but when kept as single pets, they may become lonely and bored https://www.youtube.com/watch?v=OHcAOlamgDc
Source: https://www.smithsonianmag.com/smart-news/scientists-taught-pet-parrots-to-video-call-each-other-and-the-birds-loved-it-180982041/
originally posted at https://stacker.news/items/973639
-
 @ f88e6629:e5254dd5
2025-01-08 20:08:17
@ f88e6629:e5254dd5
2025-01-08 20:08:17- Send a transaction, and the recipient uses the coin for another payment. You then merge these two transactions together and save on fees. 🔥
If you have a Trezor, you can try this out on: https://coiner-mu.vercel.app/
But be cautious. This is a hobby project without any guarantee.
How does it work?
- Connect Trezor, enter the passphrase, and select an account.
- The application display your coins, pending transactions, and descendant transactions.
- Then app shows you how much you can save by merging all transactions and removing duplicate information.
- Finally, you can sign and broadcast this more efficient transaction
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 57d1a264:69f1fee1
2025-05-07 06:29:52
@ 57d1a264:69f1fee1
2025-05-07 06:29:52Your device, your data. TRMNL's architecture prevents outsiders (including us) from accessing your local network. TRMNAL achieve this through 1 way communication between client and server, versus the other way around. Learn more.
Learn more at https://usetrmnl.com/
originally posted at https://stacker.news/items/973632
-
 @ 57d1a264:69f1fee1
2025-05-07 06:16:30
@ 57d1a264:69f1fee1
2025-05-07 06:16:30Here’s Sean Voisen writing about how programming is a feeling:
For those of us who enjoy programming, there is a deep satisfaction that comes from solving problems through well-written code, a kind of ineffable joy found in the elegant expression of a system through our favorite syntax. It is akin to the same satisfaction a craftsperson might find at the end of the day after toiling away on well-made piece of furniture, the culmination of small dopamine hits that come from sweating the details on something and getting them just right. Maybe nobody will notice those details, but it doesn’t matter. We care, we notice, we get joy from the aesthetics of the craft.
This got me thinking about the idea of satisfaction in craft. Where does it come from?
Continue Reading https://blog.jim-nielsen.com/2025/craft-and-satisfaction/
originally posted at https://stacker.news/items/973628
-
 @ 77110427:f621e11c
2024-12-02 22:55:12
@ 77110427:f621e11c
2024-12-02 22:55:12All credit to Guns Magazine. Read the full issue here ⬇️











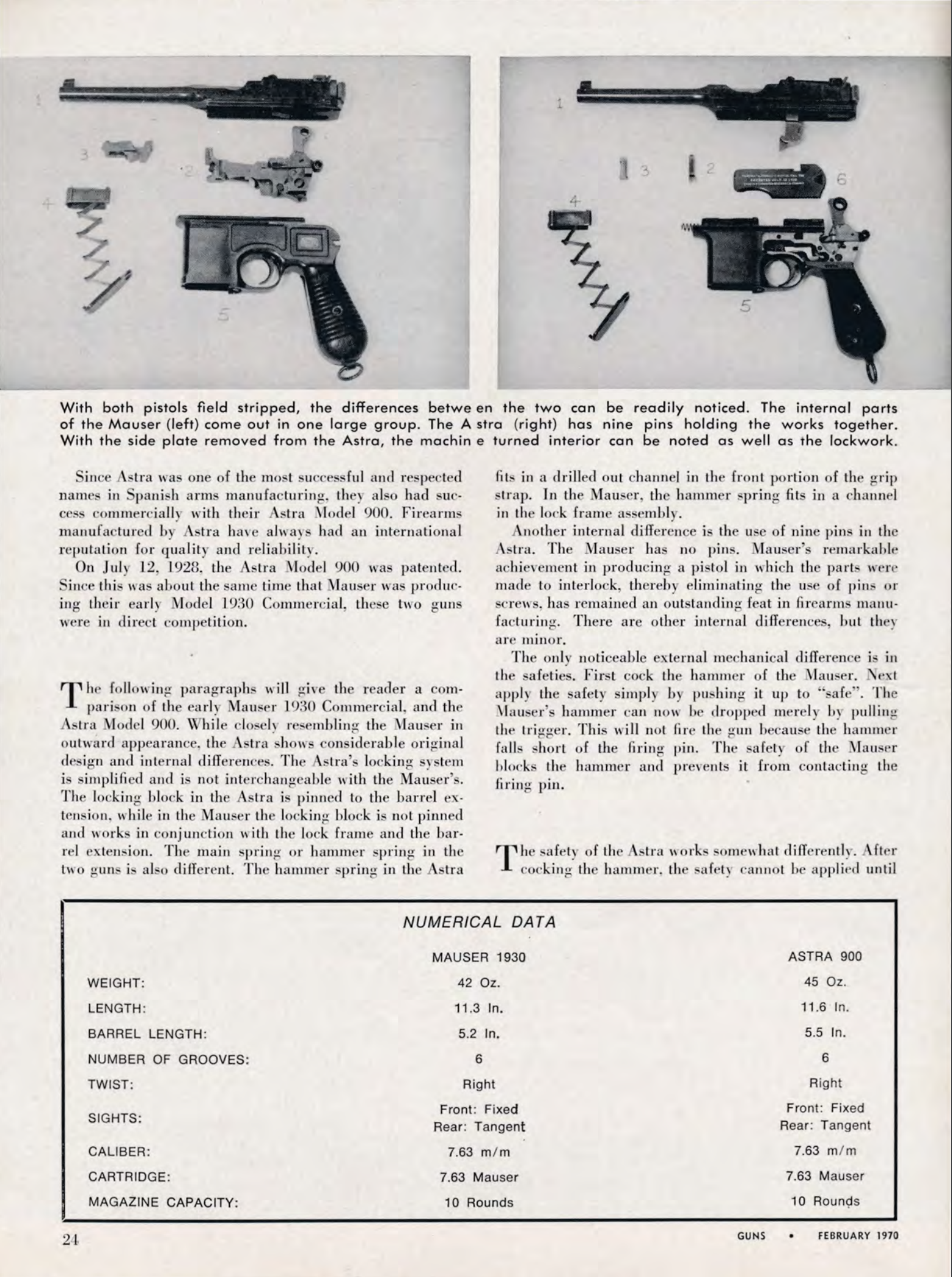








📰 Past Magazine Mondays 📰
⬇️ Follow 1776 HODL ⬇️
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 04c915da:3dfbecc9
2025-03-04 17:00:18
@ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:03:29
@ 57d1a264:69f1fee1
2025-05-07 06:03:29CryptPad
Collaboration and privacy. Yes, you can have both Flagship instance of CryptPad, the end-to-end encrypted and open-source collaboration suite. Cloud administered by the CryptPad development team. https://cryptpad.fr/
ONLYOFFICE DocSpace
Document collaboration made simpler. Easily collaborate with customizable rooms. Edit any content you have. Work faster using AI assistants. Protect your sensitive business data. Download or try STARTUP Cloud (Limited-time offer) FREE https://www.onlyoffice.com/
SeaFile
A new way to organize your files Beyond just syncing and sharing files, Seafile lets you add custom file properties and organize your files in different views. With AI-powered automation for generating properties, Seafile offers a smarter, more efficient way to manage your files. Try it Now, Free for up to 3 users https://seafile.com/
SandStorm
An open source platform for self-hosting web apps Self-host web-based productivity apps easily and securely. Sandstorm is an open source project built by a community of volunteers with the goal of making it really easy to run open source web applications. Try the Demo or Signup Free https://alpha.sandstorm.io/apps
NextCloud Hub
A new generation of online collaboration that puts you in control. Nextcloud offers a modern, on premise content collaboration platform with real-time document editing, video chat & groupware on mobile, desktop and web. Sign up for a free Nextcloud account https://nextcloud.com/sign-up/
LinShare
True Open Source Secure File Sharing Solution We are committed to providing a reliable Open Source file-sharing solution, expertly designed to meet the highest standards of diverse industries, such as government and finance Try the Demo https://linshare.app/
Twake Drive
The open-source alternative to Google Drive. Privacy-First Open Source Workplace. Twake workplace open source business. Improve your effeciency with truly Open Source, all-in-one digital suite. Enhance the security in every aspect of your professional and private life. Sign up https://sign-up.twake.app/
SpaceDrive
One Explorer. All Your Files. Unify files from all your devices and clouds into a single, easy-to-use explorer. Designed for creators, hoarders and the painfully disorganized. Download desktop app (mobile coming soon) https://www.spacedrive.com/
ente
Safe Home for your photos Store, share, and discover your memories with end-to-end encryption. End-to-end encryption, durable storage and simple sharing. Packed with these and much more into our beautiful open source apps. Get started https://web.ente.io
fileStash
Turn your FTP server into... Filestash is the enterprise-grade file manager connecting your storage with your identity provider and authorisations. Try the demo https://demo.filestash.app
STORJ
Disruptively fast. Globally secure. S3-compatible distributed cloud services that make the most demanding workflows fast and affordable. Fast track your journey toward high performance cloud services. Storj pricing is consistent and competitive in meeting or exceeding your cloud services needs. Give the products a try to experience the benefits of the distributed cloud. Get Started https://www.storj.io/get-started
FireFile
The open‑source alternative to Dropbox. Firefiles lets you setup a cloud drive with the backend of your choice and lets you seamlessly manage your files across multiple providers. It revolutionizes cloud storage management by offering a unified platform for all your storage needs. Sign up Free https://beta.firefiles.app
originally posted at https://stacker.news/items/973626
-
 @ 42342239:1d80db24
2025-01-04 20:38:53
@ 42342239:1d80db24
2025-01-04 20:38:53The EU's regulations aimed at combating disinformation raise questions about who is really being protected and also about the true purpose of the "European Democracy Shield".
In recent years, new regulations have been introduced, purportedly to combat the spread of false or malicious information. Ursula von der Leyen, President of the European Commission, has been keen to push forward with her plans to curb online content and create a "European Democracy Shield" aimed at detecting and removing disinformation.
Despite frequent discussions about foreign influence campaigns, we often tend to overlook the significant impact that domestic actors and mass media have on news presentation (and therefore also on public opinion). The fact that media is often referred to as the fourth branch of government, alongside the legislative, executive, and judicial branches, underscores its immense importance.
In late 2019, the Federal Bureau of Investigation (FBI) seized a laptop from a repair shop. The laptop belonged to the son of then-presidential candidate Biden. The FBI quickly determined that the laptop was the son's and did not appear to have been tampered with.
Almost a year later, the US presidential election took place. Prior to the election, the FBI issued repeated warnings to various companies to be vigilant against state-sponsored actors [implying Russia] that could carry out "hack-and-leak campaigns". Just weeks before the 2020 presidential election, an October surprise occurred when the NY Post published documents from the laptop. The newspaper's Twitter account was locked down within hours. Twitter prevented its users from even sharing the news. Facebook (now Meta) took similar measures to prevent the spread of the news. Shortly thereafter, more than 50 former high-ranking intelligence officials wrote about their deep suspicions that the Russian government was behind the story: "if we're right", "this is about Russia trying to influence how Americans vote". Presidential candidate Biden later cited these experts' claims in a debate with President Trump.
In early June this year, the president's son was convicted of lying on a gun license application. The laptop and some of its contents played a clear role in the prosecutors' case. The court concluded that parts of the laptop's contents were accurate, which aligns with the FBI's assessment that the laptop did not appear to have been tampered with. The president's son, who previously filed a lawsuit claiming that the laptop had been hacked and that data had been manipulated, has now withdrawn this lawsuit, which strengthens the image that the content is true.
This raises questions about the true purpose of the "European Democracy Shield". Who is it really intended to protect? Consider the role of news editors in spreading the narrative that the laptop story was Russian disinformation. What impact did social media's censorship of the news have on the outcome of the US election? And if the laptop's contents were indeed true - as appears to be the case - what does it say about the quality of the media's work that it took almost four years for the truth to become widely known, despite the basic information being available as early as 2020?
-
 @ 502ab02a:a2860397
2025-05-07 01:08:58
@ 502ab02a:a2860397
2025-05-07 01:08:58สัปดาห์นี้ถือว่าเป็นเบรคคั่นพักผ่อนแก้เครียดนิดหน่อยแล้วกันครับ เรามาเล่าย้อนอดีตกันนิดหน่อย เหมือนสตาร์วอส์ที่ฉายภาค 4-5-6 แล้วย้อนไป 1-2-3 ฮาๆๆๆ
เคยได้ยินคำว่า Nuremberg Trials ไหมครับ ย้อนความนิดนึงว่า Nuremberg (Nürnberg อ่านว่า เนือร์นแบร์ก) คือชื่อเมืองในเยอรมนีที่เคยเป็นเวทีพิจารณาคดีประวัติศาสตร์หลังสงครามโลกครั้งที่ 2
“Nuremberg Trials” คือการไต่สวนผู้มีส่วนเกี่ยวข้องกับ อาชญากรรมสงครามของนาซีเยอรมัน หลังสงครามโลกครั้งที่ 2 ในปี 1945–46 พันธมิตรผู้ชนะสงครามได้จับตัวผู้นำนาซี นักการเมือง หมอ นักวิทยาศาสตร์ มาขึ้นศาล ข้อหาของพวกเขาไม่ได้แค่ฆ่าคน แต่รวมถึงการละเมิดศีลธรรมมนุษย์ขั้นพื้นฐาน อย่างการทดลองทางการแพทย์กับนักโทษ โดยไม่มีการขอความยินยอม
จากการไต่สวนนี้ จึงเกิดหลักจริยธรรมที่ชื่อว่า “Nuremberg Code” ซึ่งกลายเป็นรากฐานของการทดลองทางการแพทย์ยุคใหม่ หัวใจของโค้ดนี้คือคำว่า “Informed Consent” แปลว่า ถ้าจะทำอะไรกับร่างกายใคร ต้องได้รับความยินยอมจากเขาอย่างเต็มใจ และมีข้อมูลครบถ้วน นี่แหละ คือบทเรียนจากบาดแผลของสงครามโลก
แต่แล้ว...ในปี 2020 โลกก็เข้าสู่ยุคที่ใครบางคนบอกว่า “ต้องเชื่อผู้เชี่ยวชาญ” ใครกังวล = คนไม่รักสังคม ใครถามเยอะ = คนต่อต้านวิทยาศาสตร์ การยินยอมโดยสมัครใจ เริ่มกลายเป็นแค่คำเชิงสัญลักษณ์
ในช่วงหลังนี้เราอาจจะได้ยินข่าวหรือทฤษฎีในอินเตอร์เนทเกี่ยวกับคำว่า Nuremberg 2.0 กันนะครับ เพราะเริ่มผุดขึ้นตามกระทู้เงียบ ๆ คลิปใต้ดิน และเวทีเสวนาแปลก ๆ ที่ไม่มีใครอยากอ้างชื่อบนเวที TED Talk ซึ่ง กลุ่มที่ใช้คำนี้มักจะหมายถึงความต้องการให้มีการ “ไต่สวน” หรือ “เอาผิด” กับนักการเมือง นักวิทยาศาสตร์ แพทย์ หรือองค์กรที่เกี่ยวข้องกับ การออกคำสั่ง การบังคับ การเซ็นเซอร์ข้อมูลที่ขัดแย้งกับแนวทางรัฐ การเผยแพร่ข้อมูลโดยไม่โปร่งใส พวกเขามองว่า นโยบายเหล่านั้นละเมิดสิทธิเสรีภาพของประชาชนในระดับที่เปรียบได้กับ “อาชญากรรมต่อมนุษยชาติ” จึงเสนอแนวคิด “Nuremberg 2.0”
พวกเขาไม่ได้เรียกร้องแค่ความโปร่งใส แต่เขาอยากเห็นการทบทวน ว่าใครกันแน่ที่ละเมิดหลักจริยธรรมที่โลกเคยตกลงกันไว้เมื่อ 80 ปีก่อน
Nuremberg คือการไต่สวนคนที่ใช้อำนาจรัฐฆ่าคนอย่างจงใจ Nuremberg 2.0 คือคำเตือนว่า “การใช้ความกลัวครอบงำเสรีภาพ” อาจไม่ต่างกันนัก
ทีนี้เคยสงสัยไหม แล้วมันเกี่ยวอะไรกับอาหาร?
เพราะจากวิกฤตโรคระบาด เราเริ่มเห็น “วิทยาศาสตร์แบบผูกขาด” คุมเกมส์ บริษัทเทคโนโลยีเริ่มเข้ามาทำอาหาร ชื่อใหม่ของเนื้อสเต๊กกลายเป็น “โปรตีนทางเลือก” อาหารจากแล็บกลายเป็น “ทางรอดของโลก” สารเคมีอัดลงไปแทนเนื้อจริง ๆ แต่มีฉลากติดว่า "รักษ์โลก ปลอดภัย ยั่งยืน"
แต่ถ้ามองให้ลึกลงไปอีกนิด บางกลุ่มคนกลับเริ่มเห็นอะไรบางอย่างที่ขนลุกกว่า เพราะมันคือ “ระบบควบคุมสุขภาพ” ที่อาศัย “ความกลัว” เป็นหัวเชื้อ และ “วิทยาศาสตร์แบบผูกขาด” เป็นกลไก
จากนั้น…ทุกอย่างก็จะถูกเสิร์ฟอย่างสวยงามในรูปแบบ "นวัตกรรมเพื่ออนาคต" ไม่ว่าจะเป็นอาหารเสริมชนิดใหม่ เนื้อสัตว์ปลูกในแล็บ หรืออาหารที่ไม่ต้องเคี้ยว
ลองคิดเล่น ๆครับ ถ้าสารอาหารถูกควบคุมได้ เหมือนที่เราเคยถูกบังคับกับบางอย่างได้ล่ะ? วันหนึ่ง เราอาจถูกขอให้ "กิน" ในสิ่งที่ระบบสุขภาพอนาคตเขาบอกว่าดี แล้วถ้าเฮียบอกว่าไม่อยากกิน...เขาอาจไม่ห้าม แต่ App สุขภาพจะเตือนว่า “คุณมีพฤติกรรมเสี่ยงต่อโลกใบนี้” แต้มเครดิตจะสุขภาพจะลดลงและส่วนลดข้าวกล่องเนื้อจากจุลินทรีย์จะไม่เข้าบัญชีเฮียอีกเลย
ใช่…มันไม่เหมือนการบังคับ แต่มันคือการสร้าง “ระบบทางเดียว” ที่ทำให้คนที่อยากเดินออกนอกแถว เหมือนเดินลงเหว
Nuremberg 2.0 จึงไม่ใช่แค่เรื่องของอดีตหรือโรคระบาด แต่มันเป็นกระจกที่สะท้อนว่า “ถ้าเราไม่เรียนรู้จากประวัติศาสตร์ เราอาจกินซ้ำรอยมันเข้าไปในมื้อเย็น”
อนาคตของอาหารอาจไม่ได้อยู่ในจาน แต่อยู่ในนโยบาย อยู่ในบริษัทที่ผลิตโปรตีนจากอากาศ อยู่ในทุนที่ซื้อนักวิทยาศาสตร์ไว้ทั้งวงการ และถ้าเราหลับตาอีกครั้ง หลายคนก็กลัวว่า...บทไต่สวน Nuremberg รอบใหม่ อาจไม่สามารถเกิดขึ้นอีกต่อไป เพราะคราวนี้ คนร้ายจะไม่ได้ถือปืน แต่อาจถือใบรับรองโภชนาการระดับโลกในมือแทน
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ ee11a5df:b76c4e49
2024-12-24 18:49:05
@ ee11a5df:b76c4e49
2024-12-24 18:49:05China
I might be wrong, but this is how I see it
This is a post within a series I am going to call "I might be wrong, but this is how I see it"
I have repeatedly found that my understanding of China is quite different from that of many libertarian-minded Americans. And so I make this post to explain how I see it. Maybe you will learn something. Maybe I will learn something.
It seems to me that many American's see America as a shining beacon of freedom with a few small problems, and China is an evil communist country spreading communism everywhere. From my perspective, America was a shining beacon of freedom that has fallen to being typical in most ways, and which is now acting as a falling empire, and China was communist for about a decade, but turned and ran away from that as fast as they could (while not admitting it) and the result is that the US and China are not much different anymore when it comes to free markets. Except they are very different in some other respects.
China has a big problem
China has a big problem. But it is not the communism problem that most Westerners diagnose.
I argue that China is no longer communist, it is only communist in name. And that while it is not a beacon of free market principles, it is nearly as free market now as Western nations like Germany and New Zealand are (being somewhat socialist themselves).
No, China's real problem is authoritarian one-party rule. And that core problem causes all of the other problems, including its human rights abuses.
Communism and Socialism
Communism and Socialism are bad ideas. I don't want to argue it right here, but most readers will already understand this. The last thing I intend to do with this post is to bolster or defend those bad ideas. If you dear reader hold a candle for socialism, let me know and I can help you extinguish it with a future "I might be wrong, but this is how I see it" installment.
Communism is the idea of structuring a society around common ownership of the means of production, distribution, and exchange, and the idea of allocating goods and services based on need. It eliminates the concept of private property, of social classes, ultimately of money and finally of the state itself.
Back under Mao in 1958-1962 (The Great Leap Forward), China tried this (in part). Some 50+ million people died. It was an abject failure.
But due to China's real problem (authoritarianism, even worship of their leaders), the leading classes never admitted this. And even today they continue to use the word "Communist" for things that aren't communist at all, as a way to save face, and also in opposition to the United States of America and Europe.
Authorities are not eager to admit their faults. But this is not just a Chinese fault, it is a fault in human nature that affects all countries. The USA still refuses to admit they assassinated their own president JFK. They do not admit they bombed the Nord Stream pipeline.
China defines "socialism with Chinese characteristics" to mean "the leadership of the Communist Party of China". So they still keep the words socialism and communism, but they long ago dropped the meanings of those words. I'm not sure if this is a political ploy against us in the West or not.
China's Marketplace Today
Today China exhibits very few of the properties of communism.
They have some common ownership and state enterprises, but not much differently than Western countries (New Zealand owns Air New Zealand and Kiwibank and Kiwirail, etc). And there are private enterprises all over China. They compete and some succeed and some fail. You might hear about a real-estate bank collapsing. China has private property. They have mostly free markets. They have money, and the most definitely have social classes and a very strong state.
None of that is inline with what communist thinkers want. Communist thinkers in China moan that China has turned away from communism.
Deng Xiaoping who succeeded Mao and attempted to correct the massive mistake, did much when he said "to get rich is glorious."
China achieved staggering rates of economic growth. 10% annually on average since 1977. Chinese economic reform started in 1979 and has continued through successive administrations (Deng, Jiang, Hu and now Xi).
China is now the world's largest economy (by GDP in PPP terms) since 2016.
I was first made aware of China's economic growth by Jim Rogers, an American commodities expert who travelled through China (and the rest of the world from 1990-1992) and in 2007 moved to Singapore where he ensured his daughters learned to speak Mandarin, because Jim knew where the economic growth was going to happen. Jim always spoke positively of China's economic prospects, and his view was so different from the "China is a nasty communist place" view that I had grown up with that my mind opened.
How can anybody believe they are still a communist country? In what world does it make sense that communism can produce such a massively booming economy? It doesn't make sense because it is simply wrong.
What does happen is that the CPC interferes. It lets the market do what markets do, but it interferes where it thinks oversight and regulation would produce a better result.
Western nations interfere with their markets too. They have oversight and regulation. In fact some of China's planned reforms had to be put on hold by Xi due to Donald Trump's trade war with China. That's right, they were trying to be even more free market than America, but America's protectionism prodded Xi to keep control so he could fight back efficiently.
Government oversight and regulation IMHO is mostly bad because it gets out of control, and there are no market forces to correct this. This gets even more extreme in a one-party system, so I can judge that China's oversight and regulation problems are very likely worse than those in Western nations (but I have no first hand experience or evidence).
Why do you keep saying CPC?
The Communist Party of China (CPC) is the ruling party in China. That is their official name. To call them the CCP is to concede to the idea that the British and Americans get to name everybody. I'm not sure who is right, since CPC or CCP is their "English" name (in Chinese it is 中国共产党 and Westernized it is Zhōngguó Gòngchǎndǎng). Nonetheless, I'll call them CPC because that is their wish.
Social Credit System
China moved from a planned economy to a market economy in stages. They didn't want any more sudden changes (can you blame them?). In the process, many institutions that have existed in the West for a long time didn't exist in China and they had to arise somehow. IMHO market forces would have brought these about in the private sector, but the one-party CP of China instead decided to create these.
One of those institutions was a credit score system. In the West we have TransUnion and Equifax that maintain credit ratings on people, and we have S&P, Moody's and Fitch that maintain credit ratings on companies. The domain of these ratings is their financial credit-worthiness.
So the People's Bank of China developed a credit information database for it's own needs. The government picked up on the idea and started moving towards a National Credit Management System. In 2004 it became an official goal to establish a credit system compatible with a modern market system. By 2006 banks were required to report on consumer creditworthiness.
But unchecked one-party governmental power will often take a good idea (credit worthiness data shared among private parties) and systematize it and apply it top-down, creating a solution and a new problem at the same time.
Nonetheless, originally it was about credit worthiness and also criminal convictions. That is no big scary thing that some right-wing American commentators will lead you to believe. In the US for example criminal records are public, so China's Social Credit System started out being no more over-reaching in scope than what Americans have lived under their entire lives, its only fault (a severe one) being centrally planned. And that remained the case up until about 2016 (in my estimation).
But of course there is always scope creep. As it exists today, I have reason to believe that CPC officials and even A.I. use judgement calls to score someone on how moral that person has been! Of course that is not a good idea, and IMHO the problem stems from one-party rule, and authoritarian administration of ideas that should instead be handled by the private sector.
Environmental, Social, and Governance
ESG is a system that came out of a couple basic ideas. The first is that many two-party transactions actually have externalities. They don't just affect the two parties, they also affect everybody else. When you fly in an airplane, you increase the CO2 in the atmosphere that everybody has to pay for (eventually). You may dispute that example, but that is no doubt one of the motivations of ESG.
But of course the recognition of this basic issue didn't lead all people towards market solutions (well it did, but those have been mostly messed up by others), but instead led many people towards ESG, which is a social credit scoring system which applies scores based on environmental and social side-effects of market transactions.
This is not at all the same as China's social credit system, which I described above. I hope you can see the difference.
In fact, China imported ESG from the West. Chinese companies, of their free will, in an attempt to court Western capital, achieve ESG goals for those Western investors. They have been playing this ESG game for 20 years just like the entire world has, because the West has imposed this faux-morality upon them. It isn't something China exported to us, it is something we exported to them.
I think China has avoided Woke-ism
My understanding of Chinese people, based on what I've heard many Chinese people say, is that China isn't affected by the Western woke-ism epidemic. They deride Western white woke people with the term "Baizuo". They have never sent an incompetent break dancer to the Olympics because of wok-ism. Competence is highly respected as is the competition to be the most competent, which (when augmented by a one-child policy which is no longer) has produced child prodigies like no other country has.
What about predatory loans of the Belt and Road initiative?
Predatory is an odd name for loans to people in need. The World Bank makes loans to people in need. China does too. China stands in opposition to Western Empire, and in that regard they produce their own alternative BRICS institutions. This is one of them.
There is AFAIK nothing more predatory about them. It is just that in some cases the borrowers have trouble paying them back and they get foreclosed upon. I don't think this is worthy of much discussion, except that the term "predatory" seems to me to be a propaganda device.
What about foreign influence from China?
China wants to influence the world, especially its own trading partners and potential trading partners. Doing that above board is fine by me.
But some of it is undoubtedly covert. Sometimes Chinese-born people run for public office in Western countries. In New Zealand we stood down some when it became clear they were being influenced too much by the CPC while being charged with representing their local town (dual loyalty issues). If only the USA would do the same thing to their dually-loyal politicians.
And all large nations run influence operations. The USA has the CIA, for example, and claims this "soft power" is actually the better alternative to what would otherwise be military intervention (but IMHO shouldn't be either). I'm not defending such operations (I despise them), I'm just explaining how China's position of exerting influence is not only no big deal and totally expected, it pales in comparison to the United States' influence operations which often become military excursions (something China rarely ever does).
What about the Great Firewall?
Yeah, that sucks. Again, single-party authoritarian control gone to extremes.
What about Human Rights Abuses? What about the Uyghur Genocide?
I don't like them. To the extent they are occurring (and I lean towards the belief that they are occurring), I condemn them.
China has anti-terrorism and anti-extremism policies that go too far. They end up oppressing and/or criminalizing cultures that aren't Chinese enough. But especially, China punishes dissent. Disagreement with the CPC is the high crime. It is the one-party rule that causes this problem. Anybody who speaks out against the CPC or goes against the state in any way is harshly punished. This happens to Uyghurs, to Falun Gong, to Tibetans, and to any religion that is seen as subversive.
Amnesty International and the UN OHCHR have documented issues around the Xinjiang Uyghur autonomous region, Tibet, LGBT rights, death penalty, workers rights, and the Hong Kong special administrative region. I am not about to pretend I know better than they do, but to some extent they go too far.
Amnesty International says this about the USA: Discrimination and violence against LGBTI people were widespread and anti-LGBTI legislation increased. Bills were introduced to address reparations regarding slavery and its legacies. Multiple states implemented total bans on abortion or severely limited access to it. Gender-based violence disproportionately affected Indigenous women. Access to the USA for asylum seekers and migrants was still fraught with obstacles, but some nationalities continued to enjoy Temporary Protected Status. Moves were made to restrict the freedom to protest in a number of states. Black people were disproportionately affected by the use of lethal force by police. No progress was made in the abolition of the death penalty, apart from in Washington. Arbitrary and indefinite detention in the US naval base Guantánamo Bay, Cuba, continued. Despite extensive gun violence, no further firearm reform policies were considered, but President Biden did announce the creation of the White House Office of Gun Violence Prevention. The USA continued to use lethal force in countries around the world. Black people, other racialized groups and low-income people bore the brunt of the health impacts of the petrochemical industry, and the use of fossil fuels continued unabated.
Amnesty international didn't even point out that the US government quashes free speech via pressure on social media corporations (because Amnesty International is far too lefty).
So who is worse, China or the US? I'm not going to make that judgement call, but suffice it to say that in my mind, China is not obviously worse.
China violates freedom of expression, association, and assembly of all people. This is bad, and a consequence mainly of one-party rule (again, what I think is the root cause of most of their ills). They arrest, detain, potentially kill anybody who publicly disagrees openly with their government. Clearly this is an excess of authoritarianism, a cancer that is very advanced in China.
As to organ harvesting of Uyghur Muslims, I think this is a myth.
China has dealt harshly with Muslim extremism. They don't offer freedom of religion to ISIS. And Amnesty International complains about that. But practically speaking you probably shouldn't respect the extremist religion of people who want to force everybody into a global caliphate through threat of violence. As you are well aware, some extremist Muslims (<1% of Islam) believe in using violence to bring about a global caliphate. Those extremists pop up in every country and are usually dealt with harshly. China has had to deal with them too.
I have watched two different Western YouTubers travel to Xinjiang province trying to find the oppressed Uyghurs and interview them. They can't find them. What they find instead are Uyghur Muslims doing their prayers five times a day at the local mosque. And also stories that the CPC pitched in some money to help them renovate the mosque. Maybe they were afraid it was a CPC trap and so they wouldn't speak freely. Amnesty International and the UN OHCHR say more than a million are "arbitrarily detained" and I'm not going to argue otherwise. But I'd be more convinced if there were a stream of pictures and news like there is out of Gaza, and it is suspicious that there isn't.
Conclusion
China is more like a Western nation that Westerners realize. Economically, militarily, socially. It still has a very serious obstacle to overcome: one-party rule. I don't think the one-party is going to voluntarily give up power. So most probably at some point in the future there will be a revolution. But in my opinion it won't happen anytime soon. For the most part Chinese people are living high on the hog, getting rich, enjoying the good life, in positive spirits about life, and are getting along with their government quite well at present.
-
 @ a367f9eb:0633efea
2024-11-05 08:48:41
@ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters
When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies
In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement
If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Originally published on the website of the Consumer Choice Center.
-
 @ 42342239:1d80db24
2024-12-22 09:07:27
@ 42342239:1d80db24
2024-12-22 09:07:27Knappheit statt Slogans: eine Dosis ökonomischer Realität für die politischen Debatten
Die EU-Wirtschaft steht vor zahlreichen Herausforderungen, von hohen Energiekosten bis hin zu geringer Produktivität. Doch hinter der offiziellen Rhetorik verbirgt sich eine Annahme, die kaum hinterfragt wird: dass der grüne Wandel automatisch zu Wirtschaftswachstum und mehr Wohlstand führen wird. Aber stimmt das wirklich?
Eine englische Fassung dieses Textes finden Sie hier.
In Deutschland, das wieder einmal das Etikett „Kranker Mann Europas" tragen muss, kämpft Bundeskanzler Olaf Scholz vor der Wahl im Februar mit alarmierend niedrigen Vertrauenswerten. Aber vielleicht ist das gar nicht so überraschend. ****Die deutsche Industrieproduktion ist rückläufig, seit die grüne Agenda in Mode gekommen ist. ****Die energieintensive Produktion ist in nur wenigen Jahren um ganze 20 Prozent zurückgegangen. Volkswagen schließt Fabriken, Thyssenkrupp entlässt massiv Mitarbeiter und mehr als drei Millionen Rentner sind von Armut bedroht .
Wenn dies Europas „Mann auf dem Mond"-Moment ist, wie EU-Kommissarin von der Leyen ****es 2019 ausdrückte ****, dann ist das nicht viel, womit man angeben kann . Zumindest nicht, wenn man kein Sadist ist.
Der Bericht des ehemaligen EZB-Chefs Mario Draghi über die Wettbewerbsfähigkeit der EU wurde bereits früher diskutiert. Eines der Probleme, auf die hingewiesen wurde, war, dass europäische Unternehmen erheblich höhere Energiekosten haben als ihre amerikanischen Konkurrenten. Die Strompreise sind zwei- bis dreimal so hoch und die Erdgaspreise vier- bis fünfmal so hoch.
Deutschland ist vielleicht am schlimmsten dran, was zum Teil an der Entscheidung der ehemaligen Bundeskanzlerin Angela Merkel liegt, vollständig aus der Atomkraft auszusteigen (eine Entscheidung, die nicht nur keine breite Unterstützung fand , sondern die sie auch nicht als Fehler eingestehen will). Die Sabotage der Nord Stream 2 hat die Situation noch verschlimmert.
Ohne Realkapital kein wirtschaftlicher Wohlstand
Der Ausstieg aus der Atomenergie in Deutschland ist ein Beispiel dafür, wie politische Entscheidungen zur Verringerung der Kapazität der Wirtschaft beigetragen haben. Dasselbe gilt für die Sabotage der Nord Stream. Realkapital, wie Gebäude, Maschinen und Ausrüstung, ist für die Produktivität der Wirtschaft von entscheidender Bedeutung (z. B. Kennzahlen wie das BIP pro Arbeitsstunde). Ein größerer und effizienterer Kapitalstock ermöglicht die Herstellung von mehr Waren und Dienstleistungen mit der gleichen Menge an Arbeit, was zu mehr Produktion, höheren Löhnen und größerem materiellen Wohlstand führt. Das ist grundlegende Ökonomie. ****Wenn andererseits Realkapital aufgrund politischer Entscheidungen für obsolet erklärt wird, wie im Fall der Abschaltung der Atomkraft, verringert dies die Kapazität der Wirtschaft. ****Dasselbe gilt, wenn Realkapital zerstört wird, wie dies bei Nord Stream der Fall war.
Weiteres reales Betriebskapital wird zurückgestellt
EU-Kommissarin von der Leyen verspricht Besserung. Sie scheint überzeugt, dass der Niedergang der EU durch eine Verdreifachung der grünen Ziele des Blocks umgekehrt werden kann, und hat die Dekarbonisierung als eine der drei wichtigsten Säulen eines neuen „Wettbewerbsfähigkeitskompasses" aufgeführt. Wenn die Realität nicht den Erwartungen entspricht, kann man immer noch „Strg+Alt+Slogan" drücken und hoffen, dass niemand merkt, dass sich nichts verbessert hat.
Ihre Pläne bedeuten jedoch, dass bestehendes und derzeit funktionierendes Realkapital in Zukunft in noch größerem Umfang abgeschrieben wird. Dies lässt sich mit einer Nation vergleichen, die Jahr für Jahr ihre Naturschutzgebiete schrittweise erweitert. Tatsächlich geschieht dies auch. Der Kunming-Montreal-Rahmen für die Artenvielfalt sieht vor, dass bis 2030 30 % aller Flächen an Land und im Meer geschützt werden müssen. Ein Land, das derzeit weniger schützt, muss daher zusätzliche Gebiete identifizieren, die geschützt werden können. ****Der Prozess, 30 % aller Flächen zu schützen, wird wahrscheinlich das Produktionspotenzial der Wirtschaft verringern. ****Mit schrumpfenden Feldern wird es weniger Karotten geben (es sei denn, es werden bedeutende technologische Fortschritte erzielt).
Konsequenzen für Sicherheitspolitik und -vorsorge
Auf dem derzeitigen Weg wird mehr Realkapital auf die lange Bank geschoben, was weitreichende Folgen haben kann, nicht zuletzt für unsere Sicherheitspolitik. Wenn Russland beispielsweise Artilleriegeschosse etwa dreimal schneller produzieren kann, und zwar zu Kosten, die etwa ein Viertel der Kosten betragen, die die westlichen Verbündeten der Ukraine dafür aufbringen , dann ist klar, dass dies sicherheitspolitische Konsequenzen hat. Ebenso wird es negative sicherheitspolitische Konsequenzen haben, wenn die Strompreise in Deutschland fünfmal höher sind als in China, was derzeit der Fall ist . Im Vergleich zur EU hat China tatsächlich einen höheren Kohlendioxidausstoß pro Kopf, wobei der Unterschied den ****verfügbaren Daten zufolge etwa 50 % beträgt ****. Bereinigt um den internationalen Handel emittiert China pro Kopf 10 % mehr als Schweden .
Auch eine Perspektive der Vorsorge ist zu finden. Anfang der 1990er Jahre produzierten schwedische Landwirte fast 75 % der Nahrungsmittel des Landes. Heute ist Schwedens Bevölkerung deutlich gewachsen, aber die Nahrungsmittelproduktion hat nicht Schritt gehalten. Jeder zweite Bissen wird heute importiert. In Schweden können wir uns sogar rühmen, dass wir uns nicht einmal mit der einfachsten aller Feldfrüchte versorgen können -- Kartoffeln . Können wir wirklich sicher sein, dass deutlich erweiterte Naturschutzgebiete, wie sie im Kunming-Montreal-Rahmenwerk für Schweden vorgeschrieben sind, unsere Nahrungsmittelvorsorge nicht noch weiter verschlechtern werden?
Erinnert an kleine Gnome
Ich erinnere mich an eine Folge der 90er-Jahre-Serie South Park, in der kleine Gnome Unterhosen sammeln . Als sie nach ihrem Plan gefragt wurden, beschrieben sie ihre Methode:
- Unterhosen sammeln
- ???
- profitieren!
Übersetzt auf die grüne **Energiewende **:
- reales Kapital zerstören und Land und Meer erhalten
- ???
- wirtschaftlicher Wohlstand!
Was kann sich die EU wirklich leisten?
In der Wirtschaft geht es im Grunde um die Verwaltung knapper Ressourcen, was viele Menschen offenbar vergessen haben. Es ist höchste Zeit, zu hinterfragen, was sich die EU wirklich leisten kann. Können wir es uns wirklich leisten, uns für einen Krieg gegen Russland, China und den Iran zu rüsten und uns gleichzeitig mit grünen Versprechen von reduzierten Kohlendioxidemissionen und erhöhter Artenvielfalt selbst die Hände zu binden? Und das in einer Situation, in der die nächste US-Regierung wahrscheinlich massiv in die Steigerung ihrer Wettbewerbsvorteile durch Deregulierung, niedrigere Energiepreise, Steuersenkungen und einen Rückzug aus dem Pariser Abkommen investieren wird ?
Als von der Leyen für das deutsche Militär verantwortlich war, sei die Lage " katastrophal " gewesen. Alle sechs U-Boote des Landes waren außer Gefecht gesetzt . Zeitweise war kein einziges der 14 Transportflugzeuge des Landes flugfähig. Bei Übungen mussten deutsche Soldaten Besen statt Gewehren verwenden .
Hoffentlich wird von der Leyen in ihrem Umgang mit der Wirtschaft, der Verteidigung und der Abwehrbereitschaft der EU mehr Erfolg zeigen als in ihrer Rolle als deutsche Verteidigungsministerin. Es könnte jedoch auch an der Zeit sein, dass mehr Menschen die vorherrschenden Narrative, die unsere Politik prägen, in Frage stellen. Was, wenn die Fakten nicht ganz mit der Wahrheit übereinstimmen, die uns erzählt wird?
-
 @ 42342239:1d80db24
2024-12-22 08:38:02
@ 42342239:1d80db24
2024-12-22 08:38:02The EU's economy is facing a number of challenges, from high energy costs to low productivity. But behind the official rhetoric lies an assumption that is rarely questioned: that the green transition will automatically lead to economic growth and increased prosperity. But is this really true?
In Germany, which is once again forced to bear the label "Europe's sick man", Chancellor Olaf Scholz is struggling with alarmingly low confidence figures ahead of the election in February. But perhaps this is not so surprising. German industrial production has been trending downward since the green agenda became fashionable. Energy-intensive production has decreased by a full 20% in just a few years. Volkswagen is closing factories, Thyssenkrupp is massively laying off employees, and more than three million pensioners are at risk of poverty.
If this is Europe's "man on the moon" moment, as EU Commissioner von der Leyen expressed it in 2019, then it's not much to brag about. At least, not if you're not a sadist.
The former ECB chief Mario Draghi's report on the EU's competitiveness has been discussed previously in Affärsvärlden, among other things by the author and by Christian Sandström. One of the problems pointed out was that European companies have significantly higher energy costs than their American competitors, with electricity prices 2-3 times higher and natural gas prices 4-5 times higher.
Germany is perhaps worst off, thanks in part to former Chancellor Angela Merkel's decision to completely phase out nuclear power (a decision that not only lacked popular support but which she also refuses to acknowledge as a mistake). The sabotage of Nord Stream made the situation worse.
Without Real Capital, No Economic Prosperity
Germany's phasing out of nuclear power plants is an example of how political decisions have contributed to reducing the economy's capacity. The same applies to the sabotage of Nord Stream. Real capital, such as buildings, machinery, and equipment, is crucial for the economy's productivity (e.g., measures such as GDP per hour worked). A larger and more efficient capital stock enables the production of more goods and services with the same amount of labor, leading to greater production, higher wages, and increased material prosperity. This is basic economics. On the other hand, when real capital is declared obsolete due to political decisions, as in the case of the shutdown of nuclear power, it reduces the economy's capacity. The same applies when real capital is destroyed, as was the case with Nord Stream.
More Working Real Capital Will Be Put on the Back Burner
EU Commissioner von der Leyen promises improvement. She seems convinced that the EU's decline can be reversed by tripling down on the bloc's green goals, and listed decarbonization as one of three key pillars in a new "Competitiveness Compass". When reality does not live up to expectations, you can always press "Ctrl+Alt+Slogan" and hope that no one notices that nothing has improved.
However, her plans mean that existing and currently functioning real capital will be written off to an even greater extent in the future. This can be compared to a nation that gradually expands its nature reserves year after year. As it happens, this is also taking place. The Kunming-Montreal framework for biodiversity means that 30% of all areas, on land and at sea, must be protected by 2030. A country that currently conserves less than that must therefore identify additional areas that can be protected. The process of protecting 30% of all areas will likely reduce the economy's productive potential. With shrinking fields, there will be fewer carrots (unless significant technological progress is made).
Security Policy and Preparedness Consequences
On the current path, more real capital will be put on the back burner, which can have far-reaching consequences, not least for our security policy. For example, if Russia can produce artillery shells about three times faster, at a cost that is roughly a quarter of what it costs Ukraine's Western allies, then it's clear that this has security policy consequences. Similarly, if electricity prices in Germany are five times higher than in China, which is currently the case, then this will also have negative security policy consequences. Compared to the EU, China actually has a higher carbon dioxide emission level per capita, with a difference of about 50% according to available data. Adjusted for international trade, China emits 10% more than Sweden per capita.
A preparedness perspective can also be found. In the early 1990s, Swedish farmers produced nearly 75% of the country's food. Today, Sweden's population has increased significantly, but food production has not kept pace. Every other bite is imported today. In Sweden, we can even boast that we cannot even provide for ourselves with the simplest of crops - potatoes. Can we really be sure that significantly expanded nature reserves, as prescribed by the Kunming-Montreal framework for Sweden, will not further deteriorate our food preparedness?
Reminds One of Little Gnomes
I am reminded of an episode from the 90s TV series South Park, where little gnomes collect underpants. When asked about their plan, they described their method:
- collect underpants
- ???
- profit!
Translated to the green transition (the German Energiewende):
- destroy real capital and conserve land and sea
- ???
- economic prosperity!
What Can the EU Really Afford?
Economics is fundamentally about managing scarce resources, which many people seem to have forgotten. It's high time to question what the EU can really afford. Can we really afford to arm ourselves for war against Russia, China, and Iran while at the same time tying our own hands with green promises of reduced carbon dioxide emissions and increased biodiversity? This in a situation where the next US administration is likely to invest heavily in increasing its competitive advantages through deregulation, lower energy prices, tax cuts, and a withdrawal from the Paris Agreement?
When von der Leyen was responsible for the German military, the situation became "catastrophic". All six of the country's submarines were out of commission. At times, not a single one of the country's 14 transport aircraft could fly. German soldiers had to use broomsticks instead of guns during exercises.
Hopefully, von der Leyen will show more success in her handling of the EU's economy, defense, and preparedness than she has shown in her role as German Defense Minister. However, it may also be time for more people to challenge the prevailing narratives that shape our policies. What if the facts don't quite add up to the truth we're being told?
-
 @ a9e24cc2:597d8933
2025-05-07 01:06:44
@ a9e24cc2:597d8933
2025-05-07 01:06:44𝐌𝐄𝐒𝐒𝐀𝐆𝐄 BlackHat_Nexus 𝐅𝐎𝐑 𝐀𝐍𝐘 𝐊𝐈𝐍𝐃 𝐎𝐅 𝐒𝐄𝐑𝐕𝐈𝐂𝐄 𝐑𝐄𝐂𝐎𝐕𝐄𝐑 𝐘𝐎𝐔𝐑 𝐀𝐂𝐂𝐎𝐔𝐍𝐓Fast, Available and Reliable for any of the following services 🤳 Recovery of lost funds🤳 Facebook Hack🤳 WhatsApp Hack 🤳 Instagram Hack🤳 Spying🤳 Windows Hacking🤳 Recover lost wallet 🤳 Credit score trick 🤳 Recover Password🤳 Gmail Hack🤳 SnapChat Hacking 🤳 Cellphone Monitoring 🤳 Tik Tok Hack🤳 Twitter Hack🤳 Lost Phone Tracking🤳 Lost IaptopTracking🤳 Lost Car Tracking🤳 Cloning WhatsApp🤳 Cryptocurrency Wallet🤳 Hacking🤳 Iphone unlock 🤳 Got banned 🤳 Private Number available🤳 Telegram hacking 🤳 Websites hacking 🤳 Hack University 🤳 IOS and Android hack 🤳 Wifi Hacking 🤳 CCTV hacking🤳 Hack Bot Game 🤳 Free fire hack 🤳 Changing of school grades 🤳 Cards 💳hackingNo 🆓 services 🚫WhatsApp +1 3606068592Send a DM https://t.me/BlackHat_Nexus@BlackHat_Nexus
-
 @ 42342239:1d80db24
2024-12-19 15:26:01
@ 42342239:1d80db24
2024-12-19 15:26:01Im Frühjahr kündigte EU-Kommissarin Ursula von der Leyen an, sie wolle einen „ Europäischen Demokratieschild " schaffen, um die EU vor ausländischer Einflussnahme zu schützen. Von der Leyens Demokratieschild befindet sich derzeit in der Planungsphase. Die erklärte Absicht besteht darin, eine „ spezielle Struktur zur Bekämpfung ausländischer Informationsmanipulation und -einmischung" zu schaffen. Obwohl es als Instrument zum Schutz der Demokratie angepriesen wird, vermuten einige, dass es sich in Wirklichkeit um einen verschleierten Versuch handelt, abweichende Meinungen zu unterdrücken. Der im vergangenen Jahr verabschiedete Digital Services Act (DSA) der EU ist eng mit diesem Schild verbunden. Durch den DSA riskieren große Social-Media-Plattformen wie Elon Musks X erhebliche Geldstrafen, wenn sie den Forderungen der EU-Bürokraten nach Zensur und Moderation nicht nachkommen.
Note: This text is also available in English at substack.com. Many thanks to
stroger1@iris.tofor this German translation.Im krassen Gegensatz dazu hat sich der künftige US-Präsident Donald Trump als klarer Befürworter der Meinungsfreiheit und entschiedener Gegner der Zensur hervorgetan. Er wurde bereits von YouTube gesperrt, hat jedoch erklärt, er wolle „das linke Zensurregime zerschlagen und das Recht auf freie Meinungsäußerung für alle Amerikaner zurückfordern" . Er hat auch behauptet: „Wenn wir keine freie Meinungsäußerung haben, dann haben wir einfach kein freies Land."
Sein künftiger Vizepräsident J.D. Vance hat sogar angedeutet, dass er bereit sei, US-Militärhilfe von der Achtung der Meinungsfreiheit in den europäischen NATO-Ländern abhängig zu machen. Vances Aussage erfolgte, nachdem EU-Binnenmarktkommissar Thierry Breton vor seinem geplanten Gespräch mit Trump einen umstrittenen Brief an Musk geschickt hatte. Heute erscheint dies als unkluger Schritt, nicht zuletzt, weil er als Versuch gewertet werden kann, die US-Wahl zu beeinflussen -- etwas, das paradoxerweise dem erklärten Zweck von von der Leyens Demokratieschild (d. h. ausländische Manipulationen zu bekämpfen) widerspricht.
Wenn die NATO möchte, dass wir sie weiterhin unterstützen, und die NATO möchte, dass wir weiterhin ein gutes Mitglied dieses Militärbündnisses sind, warum respektieren Sie dann nicht die amerikanischen Werte und die freie Meinungsäußerung?
- J.D. Vance
In der EU sind Verfechter der Meinungsfreiheit in der Öffentlichkeit weniger verbreitet. In Deutschland hat Vizekanzler Robert Habeck kürzlich erklärt, er sei „überhaupt nicht glücklich darüber, was dort [auf X] passiert ... seit Elon Musk das Amt übernommen hat", und wünscht sich eine strengere Regulierung der sozialen Medien. Die Wohnung eines deutschen Rentners wurde kürzlich von der Polizei durchsucht, nachdem er ein Bild von Habeck mit einem abfälligen Kommentar veröffentlicht hatte . Die deutsche Polizei verfolgt auch einen anderen Kontoinhaber, der einen Minister als „übergewichtig" bezeichnet hat. Dieser überhaupt nicht übergewichtige Minister hat kürzlich eine Zeitung verboten , die mit der laut Meinungsumfragen zweitgrößten Partei Deutschlands, der Alternative für Deutschland (AfD), verbündet ist. Eine Partei, die 113 deutsche Parlamentarier nun offiziell verbieten wollen .
Nach dem US-Wahlergebnis stellen sich viele unbeantwortete Fragen. Wird das Weiße Haus seine Aufmerksamkeit auf die restriktivere Haltung der EU richten, die als Untergrabung der freien Meinungsäußerung angesehen werden kann? Oder droht Musks X und Chinas TikTok stattdessen ein EU-Verbot? Können EU-Länder noch mit militärischer Unterstützung aus den USA rechnen? Und wenn große amerikanische Plattformen verboten werden, wohin sollten sich die EU-Bürger stattdessen wenden? Abgesehen von russischen Alternativen gibt es keine großen europäischen Plattformen. Und wenn die Frage der Meinungsfreiheit neu überdacht wird, was bedeutet das für die Zukunft von Parteien wie der deutschen AfD?
-
 @ 752f5d10:88491db3
2025-05-07 00:25:29
@ 752f5d10:88491db3
2025-05-07 00:25:29Opinion about Trendo: Forex Trading & Broker (android)
L o s i n g $111,555 overnight was a crushing blow. The account lockout and subpar customer service that followed left me stunned. However, I gained invaluable insights from this ordeal : Conduct thorough research before committing Verify credentials and read reviews from multiple sources Be c a u t i o u s of un realistic promises Demand responsive and reliable support. Fortunately, I found chelsy__desmarais__54__A T__g=m=a=i=l__D=o=t__c_o_m, which helped me re-cover from this financial setback. W_h_a_t_s_A_p_p ; +1=8=5=9=4=3=6=4=2=1=1
WalletScrutiny #nostrOpinion
-
 @ 8671a6e5:f88194d1
2025-05-06 16:23:25
@ 8671a6e5:f88194d1
2025-05-06 16:23:25"I tried pasting my login key into the text field, but no luck—it just wouldn't work. Turns out, the login field becomes completely unusable whenever the on-screen keyboard shows up on my phone. So either no one ever bothered to test this on a phone, or they did and thought, ‘Eh, who needs to actually log in anyway?’."

### \ \ Develop and evolve
Any technology or industry at the forefront of innovation faces the same struggle. Idealists, inventors, and early adopters jump in first, working to make things usable for the technical crowd. Only later do the products begin to take shape for the average user.
Bitcoin’s dropping the Ball on usability (and user-experience)
First, we have to acknowledge the progress we've made. Bitcoin has come a long way in terms of usability—no doubt about it. Even if I still think it’s bad, it’s nowhere near as terrible as it was ten or more years ago. The days of printing a paper wallet from some shady website and hoping it would still work months or years later are behind us. The days of buggy software never getting fixed are mostly over.
The Bitcoin technology itself made progress through many BIPs (Bitcoin Improvement Proposals) and combined with an increasing number of apps, devs, websites and related networks (Liquid, Lightning, Nostr, ....) we can say that we're seeing a strong ecosystem going its way. The ecosystem is alive and expanding, and technically, things are clearly working. The problem is that we’re still building with a mindset where developers and project managers consider usability—but don’t truly care about it in practice. They don’t lead with it. (Yes, there are always exceptions.)
All that progress looks cool, when you see the latest releases of hardware wallets, software wallets, exchanges, nostr clients and services built purely for bitcoin, you're usually thinking that we've progressed nicely. But I want to focus on the downside of all these shiny tools. Because if Bitcoin has made it this far, it’s mostly thanks to people who deeply understand its value and are stubborn enough to push through the friction. They don’t give up when the user experience sucks.
Many bitcoiners completely lost their perspective on the software front in my opinion. Because we could have been so much further ahead, and we didn't because some of the most important components on the user-facing side of Bitcoin (arguably the most important part) hasn’t kept pace with the popularity and possible growth. And that should be a great concern, because Bitcoin is meant to be open and accessible. The blockchain is public. This is supposed to be for everyone. This is an open ledger technology so in theory everything is user-facing to one extent or another. Yet we fail on that front to make the glue stick. Somewhere, we’re easily amused by the tools we create, and often contains hurdles we can’t see or feel. While users reject it after 5 seconds tops.
We didn’t came a lot further yet, because we’ve ignored usability at its core (pun intended).
I’m not talking about usability in the “it works on my machine” sense. I’m talking about usability that meets the standard of modern apps. Think Spotify, Instagram, Uber, Gmail. Products that ordinary people use without reading a manual or digging through forums.
That’s the bar. We’re still far from it.
Bad UX scares your grandma away
… and that’s how many bitcoiners apparently like it.
Subsequently, when I say usability, I’m using it as an umbrella term. For me, it covers user experience, user interface, and real-life, full-cycle testing—from onboarding a brand new user to rolling out a new version of the app. And oh boy, our onboarding is so horrible. (“Hey wanna try bitcoin? Here’s an app that takes up to 4 minutes or more to get though, but wait, you’ll have to install a plugin, or wait I’ll send you an on-chain transaction…)
Take a look at the listings on Bitvocation, an excellent job board for Bitcoiners and related projects. You’ll quickly notice a pattern: almost no companies are hiring software testers. It’s marketing, more marketing, some sales, and of course, full-stack developers. But … No testers.
Because testing has become something that’s often skipped or automated in a hurry. Maybe the devs run a test locally to confirm that the feature they just built doesn’t crash outright. That’s it. And if testing does happen at a company, it’s usually shallow—focused only on the top five percent of critical bugs. The finer points that shape real user experience, like button placement, navigation flow, and responsiveness, are dumped on “the community.”
Which leads to some software being rushed out to production, and only then do teams discover how many problems exist in the real world. If there’s anyone left to care that is, since most teams are scattered all over the world and get paid by the hour by some VC firm on a small runway to a launch date.
This has real life consequences I’ve seen for myself with new users. Like a lightning wallet having a +5 minute onboarding time, and a fat on-screen error for the new users, or a hardware wallet stuck in an endless upgrade loop, just because nobody tested it on a device that was “old” (as in, one year old).
The result is clear: usability and experience testing are so low on the priority list, they may as well not exist. And that’s tragic, because the enthusiasm of new users gets crushed the moment they run into what I call Linux’plaining.
That’s when something obvious fails — like a lookup command that’s copied straight from their own help documentation but doesn’t work — and the answer you get as a user is something like: “Yeah, but first you have to…” followed by an explanation that isn’t mentioned anywhere in the interface or documentation. You were just supposed to know. No one updates the documentation, and no one cares. As most of the projects are very temporary or don’t really care if it succeeds or not, because they’re bitcoiners and bitcoin always wins. Just like PGP always was super cool and good, and users should just be smarter.
Lessons from the past usability disasters
We can always learn from the past especially when its precedents are still echoing through the systems we use today
So here goes, some examples from the legacy / fiat industry:
Lotus Notes, for example. Once a titan in enterprise communication software, which managed to capture about 145 million mailboxes. But its downfall is an example of what happens when you ignore and keep ignoring real-life user needs and fail to evolve with the market. Software like that doesn’t just fade, it collapses under the weight of its own inertia and bloat. If you think bitcoin can’t have that, yes… we’re of course not having a competitor in the market (hard money is hard money, not a mailbox or office software provider of course). But we can erode trust to the extent that it becomes LotusNotes’d.
Its archaic 1990s interface came with clunky navigation and a chaotic document management system. Users got frustrated fast—basic tasks took too long. Picture this: you're stuck in a cubicle, trying to find the calendar function in Lotus Notes while a giant office printer hisses and spits out stacks of paper behind you. The platform never made the leap to modern expectations. It failed to deliver proper mobile clients and clung to outdated tech like LotusScript and the Domino architecture, which made it vulnerable to security issues and incompatible with the web standards of the time. By 2012, IBM pulled the plug on the Lotus brand, as businesses moved en masse to cloud-based alternatives.
Another kind of usability failure has plagued PGP1 (and still does so after 34 years). PGP (Pretty Good Privacy) is a time-tested and rock-solid method for encryption and key exchange, but it’s riddled with usability problems, especially for anyone who isn’t technically inclined.
Its very nature and complexity are already steep hurdles (and yes, you can’t make it fully easy without compromising how it’s supposed to work—granted). But the real problem? Almost zero effort has gone into giving even the most eager new users a manageable learning curve. That neglect slowly killed off any real user base—except for the hardcore encryption folks who already know what they’re doing.
Ask anyone in a shopping street or the historic center of your city if they’ve heard of PGP. And on the off chance someone knows it’s not a trendy new fast-food joint called “Perfectly Grilled Poultry,” the odds of them having actually used it in the past six months are basically zero, unless you happen to bump into that one neckbeard guy in his 60s wearing a stained Star Wars T-shirt named Leonard.
The builders of PGP made one major mistake: they never treated usability as a serious design goal (that’s normal for people knee deep in encryption, I get that, it’s the way it is). PGP is fantastic on itself. Other companies and projects tried to build around it, but while they stumbled, tools like Signal and ProtonMail stepped in; offering the same core features of encryption and secure messaging, minus the headache. They delivered what PGP never could: powerful functionality wrapped in something regular people can actually use. Now, we’ve got encrypted communication flowing through apps like Signal, where all the complex tech is buried so deep in the background, the average user doesn’t even realize it’s there. ProtonMail went one step further even, integrating PGP so cleanly that users never need to exchange keys or understand the cryptography behind it all, yet still benefit from bulletproof encryption.
There’s no debate—this shift is a good thing. History shows that unusable software fades into irrelevance. Whether due to lack of interest, failure to reach critical mass, or a competitor swooping in to eat market share, clunky tools don’t survive. Now, to be clear, Bitcoin doesn’t have to worry about that kind of threat. There’s no real competition when it comes to hard money. Unless, of course, you genuinely believe that flashy shitcoins are a viable alternative—in which case, you might as well stop reading here and go get yourself scammed on the latest Solana airdrop or whatever hype train’s leaving the station today for the degens.
The main takeaway here is that Bitcoin must avoid becoming the next Lotus Notes, bloated with features but neglected by users—or the next PGP, sidelined by its own lack of usability. That kind of trajectory would erode trust, especially if usability and onboarding keep falling behind. And honestly, we’re already seeing signs of this in bitcoin. User adoption in Europe, especially in countries like Germany is noticeably lagging. The introduction of the EU’s MiCA regulations isn’t helping either. Most of the companies that were actually pushing adoption are now either shutting down, leaving the EU, or jumping through creative loopholes just to stay alive. And the last thing on anyone’s mind is improving UX. It takes time, effort, and specialized people to seriously think through how to build this properly, from the beginning, with this ease of use and onboarding in mind. That’s a luxury most teams can’t or won’t prioritize right now. Understandably when the lack of funds is still a major issue within the bitcoin space. (for people sitting on hard money, there’s surprisingly little money flowing into useful projects that aren’t hyped up empty boxes)
The number of nodes being set up by end users worldwide isn’t exactly skyrocketing either. Sure, there’s some growth but let’s not overstate it. Based on Bitnodes’ snapshots taken in March of each year, we’re looking at: 2022 : around 10500 2023 : around 17000 2024 : around 18500 2025 : around 21000 (I know there are different methods of measuring these, like read-only nodes, the % change is roughly the same nonetheless)
In my opinion, if we had non-clunky software that was actually released with proper testing and usability in mind, we could’ve easily doubled those node numbers. A bad user experience with a wallet spreads fast—and brings in exactly zero new users. The same goes for people trying to set up a miner or spin up a node, only to give up after a few frustrating steps. Sure, there are good people out there making guides and videos2 to help mitigate those hurdles, and that helps. But let’s be honest: there’s still very little “wow” factor when average users interact with most Bitcoin software. Almost every time they walk away, it’s because of one of two things—usability issues or bugs.
For the record: if a user can’t set up a wallet because the interface is so rotten or poorly tested, so they don’t know where to click or how to even select a seed word from a list, then that’s a problem — that’s a bug. Argue all you want: sure, it’s not a code-level bug and no, it’s not a system crash. But it is a usability failure. Call it onboarding friction, UX flaw, whatever fits your spreadsheet or circus Maximus of failures in your ticketing system. Bottom line: if your software doesn’t help users accomplish its core purpose, it’s broken. It’s a bug. Pretending it’s something a copywriter or marketing team can fix is pure deflection. The solution isn’t to relabel the problem, 1990’s telecom-style, just to avoid dealing with it. It’s to actually sit down, think, collaborate, and go through the issue, and getting real solutions out. ”No it’s not an issue, that’s how it works” like someone from a failing (and by now defunct) wallet told me once, is not a solution.
You got 21 seconds
The user can’t be onboarded because your software has an “issue”? In my book, that’s a bug. The usual response when you report it? “Yeah, that’s not a priority.” Well, guess what? It actually is a priority. All these small annoyances, hurdles, and bits of BS still plague this industry, and they make the whole experience miserable for regular people trying it out for the first time. The first 21 seconds (yeah, you see what I did there) are the most important when someone opens new software. If it doesn’t click right away—if they’re fiddling with sats or dollar signs, or hunting for some hidden setting buried behind a tiny arrow—it’s game over. They’re annoyed. They’re gone.
And this is exactly why we’re seeing a flood of shitcoin apps sweeping new users off their feet with "faster apps" or "nicer designs" apps that somehow can afford the UI specialists and slick, centralized setups to spread their lies and scams.
I hate to say it, but the Phantom wallet for example, for the Solana network, loaded with fake airdrop schemes and the most blatant scams — has a far better UX than most Bitcoin wallets and Lightning Wallets. Learn from it. Download that **** and get to know what we do wrong and how we can learn from the enemy.
That’s a hard truth. So, instead of just screaming “Uh, shitcooooin!” (yes, we know it is), maybe we should start learning from it. Their apps are better than ours in terms of UI and UX. They attract more people 5x faster (we know that’s also because of the fast gains and retardation playing with the marketing) but we can’t keep ignoring that. Somehow these apps attract more than our trustworthiness, our steady, secure, decentralized hard money truth.
It’s like stepping into one of the best Italian restaurants in town—supposedly. But then the menu’s a mess, the staff is scrolling on their phones, and something smells burnt coming from the kitchen. So, what do you do? You walk out. You cross the street to the fast food joint and order a burger and fries. And as you’re walking out with your food, someone from the Italian place yells at you: “Fast food is bad!” ”Yeah man I know, I wanted a nice Spaghetti aglio e olio, but here I am, digesting a cheeseburger that felt rather spongy.” (the problem is so gone so deep now, that users just walk past that Italian restaurant, don’t even recognize it as a restaurant because it doesn’t have cheeseburgers).
Fear of the dark
Technical people, not marketeers built bitcoin, it’s build on hundreds of small building blocks that interacted over time to have the bitcoin network and it’s immer evolving value. At one point David Chaum cooked up eCash, using blind signatures to let people send digital money anonymously — except it was still stuck on clunky centralized servers. Go back even further, to the 1970s, when Diffie, Hellman, and Rivest introduced public-key cryptography—the magic sauce that gave us secure digital signatures and authentication, making sure your messages stayed private and tamper-proof.
Fast forward to the 1990s, where peer-to-peer started to take off, decentralized networks getting started. Adam Back’s Hashcash in ‘97 used proof-of-work to fight email spam, and the cypherpunks were all about sticking it to the man with privacy-first, the invention 199 Human-Readable 128-bit keys3, decentralized systems. We started to swap files over p2p networks and later, torrents.
All these parts—anonymous cash, encryption, and leaderless networks finally clicked into place when Satoshi Nakamoto poured them into a chain of blocks, built on an ingenious “time-stamping” system: the timechain, or blockchain if you prefer. And just like that, Bitcoin was born—a peer-to-peer money system that didn’t need middlemen and actually worked without any central servers.
So yes, it’s only natural that Bitcoin and the many tools, born from math, obscurity, and cryptography, isn’t exactly always a user-interface darling. That’s also it’s charm for me in any case, as the core is robust and valuable beyond belief. That’s why we love to so see more use, more adoption.
But that doesn’t mean we can’t squash critical “show-stopper” bugs before releasing bitcoin-related software. And it sure as hell doesn’t mean we should act like jerks when a user points out something’s broken, confusing, or just doesn’t meet expectations. We can’t be complacent either about our role as builders of the next generations, as the core is hard money, and it would be a fatal mistake for the world to see it being used only for some rockstars from Wall Street and their counterparts to store their debt laden fiat. We can free people, make them better, make them elevate themselves. And yet, the people we try to elevate, we often alienate. All because we don’t test our stuff well enough. We should be so good, we blow the banking apps away. (they’re blowing themselves out of the market luckily with fiat “features” and overly over the top use of “analytics” to measure your carbon footprint for example).
We should be so damn professional that someone using Bitcoin apps for a full year wouldn’t even notice any bugs, because there wouldn’t be much to get annoyed by.
So… we have to do better. I’ve seen it time and time again — on Lightning tipping apps, Nostr plugins, wallets, hardware wallets, even metal plates we can screw up somehow … you name it. “It works on my machine”, isn’t enough anymore! Those days are over.
Even apps built with solid funding and strong dev and test teams like fedi.xyz4 can miss the mark. While the idea was good and the app itself ran fine without too much hurdles and usual bugs. But usability failed on a different front: there was just nothing meaningful to do in the app beyond poking around, chatting a bit, and sending a few sats back and forth. The communities it’s supposed to connect, just aren’t there, or weren’t there “yet”.
It’s a beautifully designed application and a strong proof-of-concept for federated community funds. But then… nothing. No one I know uses it. Their last blogpost was from beginning of October 2024, which doesn’t bode well, writing this than 6 months after. That said, they got some great onboarding going, usually under 20 seconds, which proves it can be done right (even if it was all a front-end for a more complex backend).
As you can see “usability” is a broad terminology, covering technical aspects, user-interface, but also use-cases. Even if you have a cool app that works really well and is well thought-out users won’t use it if there’s no real substance. You can’t get that critical mass by waiting for customers to come in or communities to embrace it. They won’t, because most of the individuals already had past experiences with bitcoin apps or services, and there’s a reason for them not being on-board already.
A lot of bitcoin companies build tools for new people. Never for the lapsed people, the persons that came in, thought of it as an investment or “a coin”… then left because of a bad experience or the price going down in fiat. All the while we have some software that usually isn’t so kind to new people, or causes loss of funds and time. Even if they make one little “mistake” of not knowing the system beforehand.

Bitcoin’s Moby Dick
\ Bitcoin itself has a big issue here. The user base could grow faster, and more robust, if there wasn’t software that worked as a sort of repellent against users.
I especially see a younger and less tech-savvy audience absolutely disliking the software we have now. No matter if it’s Electrum’s desktop wallet (hardly the sexiest tool out there, although I like it myself, but it lacks some features), Sparrow, or any lightning wallet out there (safe for WoS). I even saw people disliking Proton wallet, which I personally thought of as something really slick, well-made and polished. But even that doesn’t cut it for many people, as the “account” and “wallet” system wasn’t clear enough for them. (You see, we all have the same bias, because we know bitcoin, we look at it from a perspective of “facepalm, of course it’s a wallet named “account”, but when you sit next to a new user, it becomes clear that this is a hurdle. (please proton wallet: name a wallet a wallet, not “account”. But most users already in bitcoin, love what you’re doing)
Naturally disliking usability
The same technically brilliant people who maintain Bitcoin and build its apps haven’t quite tapped into their inner Steve Jobs—if that person even exists in the Bitcoin space. Let’s be honest: the next iOS-style wow moment, or the kind of frictionless usability seen in Spotify or Instagram, probably won’t come from hardcore Bitcoin devs alone. In fact, some builders in the space seem to actively disregard—or even look down on—discussions about usability. Just mention names like Wallet of Satoshi (yes, we all know it’s a custodial frontend) or the need for smoother interactions with Bitcoin, and you’ll get eye-rolls or defensive rants instead of curiosity or openness.
Moving more towards a better user interface for things like Sparrow or Bitcoin Core for example, would bring all kinds of “bad things” according to some, and on top of that, bring in new users (noobs) that ask questions like: “Do you burn all these sats when I make a transaction?” (Yes, that’s a real one.)
I get the “usability sucks” gripe — fear of losing key features, dumbing things down, or opening the door to unwanted changes (like BIP proposals real bitcoiners hate) that tweak bitcoin to suit any user’s whim. Close to no one in bitcoin (really in bitcoin!) wants that, including me.
That fear is however largely unfounded; because Bitcoin doesn’t change without consensus. Any change that would undermine its core use or value proposition simply won’t make it through. And let’s be honest: most of the users who crave these “faster,” centralized alternatives—those drawn to slick apps, one-click solutions, and dopamine-driven UI—will either stick with fiat, ape into the shitcoin-of-the-month, or praise the shiny new CBDC once it drops (“much fast, much cool”). These degen types, chasing fiat gains and jackpot dreams, aren’t relevant to this story, No matter what we build for bitcoin, they’ll always love the fiat-story and will always dislike bitcoin because it’s not a jackpot for them. (Honestly, why don’t they just gamble at a casino?)
People who fear that improving usability will somehow bring down the Bitcoin network are being a bit too paranoid—and honestly, they often don’t understand what usability or proper testing actually means.
They treat it like fluff, when in reality it's fundamental. Usability doesn't mean dumbing things down or compromising Bitcoin's core values; it means understanding why your fancy new app isn’t being used by anyone outside of your bubble. Testing is the beating heart of getting things out with confidence. Nothing more satisfying in software building than to proudly show even your beta versions to users, knowing it’s well tested. It’s much more than clicking a few buttons and tossing your code on GitHub. It's about asking real questions: can someone outside your Telegram group actually use this and will it they be using the software at all?
If you create a Nostr app that opens an in-app browser window and then tries to log you in with your NIPS05 or NIPS07 or whatever number it is that authenticates you, then you need to think about how it’s going to work in real life. Have people already visited this underlying website? Is that website using the exact same mechanism? Is it really working like we think it is in the real world? (Some notable good things are happening with the development of Keychat for example, I have the feeling they get it, it’s not all bad). And yes, there are still bugs and things to improve there, they’re just starting. (The browser section and nostr login need some work imho).
Guess what? You can test your stuff. But it takes time and effort. The kind of effort that, if skipped, gets multiplied across thousands of people. Thousands of people wasting their time trying to use your app, hitting errors, assuming they did something wrong, retrying, googling workarounds—only to eventually realize: it’s not them. It’s a bug. A bug you didn’t catch. Because you didn’t test. And now everyone loses. And guess what? Those users? They’re not coming back.
A good example (to stay positive here) is Fountain App, where the first versions were , eh… let’s say not so good, and then quickly evolved into a company and product that works really well, and also listens to their users and fixes their bugs. The interface can still be better in my opinion, but it’s getting there. And it’s super good now.
A bad example? Alby. (Sorry to say.) It still suffers from a bloated, clunky interface and an onboarding flow that utterly confuses new or returning users. It just doesn’t get the job done. Opinions may vary, sure, but hand this app to any non-technical user and ask them to get online and do a Nostr zap. Watch what happens. If they even manage to get through the initial setup, that is.
Another example? Bitkit. When I tried transferring funds from the "savings" to the "spending" account, the wallet silently opened a Lightning channel—no warning, no explanation—and suddenly my coins were locked up. To make things worse, the wallet still showed the full balance as spendable, even though part of it was now stuck in that channel. That was in November 2024, the last time I touched Bitkit. I wasted too much time trying to figure it out, I haven’t looked back (assuming the project is even still alive, I didn’t see them pop up anywhere).
Some metal BIP39 backup tools are great in theory but poorly executed. I bought one that didn’t even include a simple instruction on how to open it. The person I gave it to spent two hours trying to open it with a screwdriver and even attempted drilling. Turns out, it just slides open with some pressure. A simple instruction would’ve saved all that frustration.
Builders often assume users “just get it,” but a small guide could’ve prevented all the hassle. It’s a small step, but it’s crucial for better user experience. So why not avoid such situations and put a friggin cheap piece of paper in the box so people know how to open it? (The creators would probably facepalm if they read this, “how can users nòt see this?”). Yeah,… put a paper in there with instructions.
That’s natural, because as a creator you’re “in” it, you know. You don’t see how others would overlook something so obvious.
Bitcoiners are extremely bad on that front.
I’ll dive deeper into some examples in part 2 of this post.
By AVB
end of part 1
If you like to support independent thought and writings on bitcoin, follow this substack please https://coinos.io/allesvoorbitcoin/receive\ \ footnotes:
1 https://philzimmermann.com/EN/findpgp/
2 BTC sessions: set up a bitcoin node
-
 @ 42342239:1d80db24
2024-12-19 09:00:14
@ 42342239:1d80db24
2024-12-19 09:00:14Germany, the EU's largest economy, is once again forced to bear the label "Europe's sick man". The economic news makes for dismal reading. Industrial production has been trending downward for a long time. Energy-intensive production has decreased by as much as 20% in just a few years. Volkswagen is closing factories. Thyssenkrupp is laying off employees and more than three million pensioners are at risk of poverty according to a study.
Germany is facing a number of major challenges, including high energy costs and increased competition from China. In 2000, Germany accounted for 8% of global industrial production, but by 2030, its share is expected to have fallen to 3%. In comparison, China accounted for 2% of global industrial production in 2000, but is expected to account for nearly half (45%) of industrial production in a few years. This is according to a report from the UN's Industrial Development Organization.
Germany's electricity prices are five times higher than China's, a situation that poses a significant obstacle to maintaining a competitive position. The three main reasons are the phase-out of nuclear power, the sabotage of Nord Stream, and the ongoing energy transition, also known as Energiewende. Upon closer inspection, it is clear that industrial production has been trending downward since the transition to a greener economy began to be prioritized.
Germany's former defense minister, EU Commission President von der Leyen, called the European Green Deal Europe's "man on the moon" moment in 2019. This year, she has launched increased focus on these green goals.
However, the EU as a whole has fallen behind the US year after year. European companies have significantly higher energy costs than their American competitors, with electricity prices 2-3 times higher and natural gas prices 4-5 times higher.
The Environmental Kuznets Curve is a model that examines the relationship between economic growth and environmental impact. The idea is that increased material prosperity initially leads to more environmental degradation, but after a certain threshold is passed, there is a gradual decrease. Decreased material prosperity can thus, according to the relationship, lead to increased environmental degradation, for example due to changed consumption habits (fewer organic products in the shopping basket).
This year's election has resulted in a historic change, where all incumbent government parties in the Western world have seen their popularity decline. The pattern appears to be repeating itself in Germany next year, where Chancellor Olaf Scholz is struggling with low confidence figures ahead of the election in February, which doesn't seem surprising. Adjusted for inflation, German wages are several percent lower than a few years ago, especially in the manufacturing industry.
Germany is still a very rich country, but the current trend towards deindustrialization and falling wages can have consequences for environmental priorities in the long run. Economic difficulties can lead to environmental issues being downgraded. Perhaps the declining support for incumbent government parties is a first sign? Somewhere along the road to poverty, people will rise up in revolt.