-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ b04082ac:29b5c55b
2025-05-08 14:35:02
@ b04082ac:29b5c55b
2025-05-08 14:35:02Money has always been more than a medium of exchange. It reflects what societies value, how they organize trust, and what they choose to remember. This article explores the idea that money functions as a form of collective memory, and how Bitcoin may be restoring this role in a new way.

The Asante Example
In the Asante Empire, which flourished in West Africa during the 18th and 19th centuries, gold dust served as the primary medium of exchange. To measure it, traders used ornate spoons made of brass. These spoons were often carved with birds, animals, or abstract symbols. They were not currency themselves, but tools used to handle gold dust accurately.
Importantly, these spoons also carried meaning. Symbols and proverbs embedded in the spoons conveyed lessons about honesty, community, and continuity. For example, the Sankofa bird, shown turning its head backward to retrieve an egg from its back, represented the proverb, “It is not wrong to go back for that which you have forgotten.” This was a reminder to learn from the past.

The spoons reflect an understanding that money and its instruments are not just practical tools. They are cultural artifacts that store shared values. In the Asante context, even measurement was ritualized and tied to ethics and memory.
Money as a Cultural Medium
This connection between money and cultural meaning is not unique to the Asante Empire. Modern fiat currencies also carry symbols, phrases, and designs that reflect national identity and political values.
The U.S. dollar includes Latin phrases and national symbols meant to convey stability and purpose. The British pound features royal iconography, reinforcing the idea of continuity and sovereignty. When the euro was introduced, it deliberately avoided specific national references. Itsdesign used bridges and windowsto suggest openness and cooperation across the continent.

These design choices show that societies still embed meaning into their money. Even in a digital or fiat context, money is used to transmit a story about who we are, where authority lies, and what we value.
The Fragility of Fiat Memory
While fiat money carries cultural symbols, the narratives behind those symbols can be fragile.
In 2021, the central bank of the Philippines removed democratic leaders from its banknotes,triggering public criticism. In the United States, attempts to replace Andrew Jackson with Harriet Tubman on the $20 billfaced repeated delays. These examples show how political control over money includes control over what stories are told and remembered.

Unlike objects passed down through generations, fiat memory can be edited or erased. In this sense, it is vulnerable. The meaning encoded in fiat systems can shift depending on who holds power.
Bitcoin as a New Form of Memory
Bitcoin is described as digital money. But it also introduces a different model of how societies can record value and preserve meaning.
The Bitcoin network launched in 2009 with a small message embedded in its first block: “Chancellor on brink of second bailout for banks.” This was a reference to a newspaper headline that day and a clear sign of protest against financial bailouts, centralized monetary policy, and forever wars.

This moment marked the beginning of a system where memory is stored differently. Instead of relying on governments or institutions, Bitcoin stores its history on a public ledger maintained by a decentralized network of participants. Its memory is not symbolic or political; it is structural. Every transaction, every block, is preserved through time-stamped computation and consensus.
No single authority can change it. The rules are clear and publicly auditable. In this way, Bitcoin offers a version of money where memory is both neutral and resilient.
Cultural Expression and Community Values
Even though Bitcoin lacks the traditional symbols found on banknotes, it has developed its own culture. Phrases like “Don’t trust, verify” or “Stay humble, stack sats” are shared widely in the Bitcoin community. These ideas reflect a focus on self-responsibility, verification, and long-term thinking.
These proverbs can be compared to the carved messages on the Asante spoons. While the contexts are very different, the underlying idea is similar: a community using language and symbols to reinforce its shared values.
Bitcoin also has a well established and growing art scene. Bitcoin conferences often feature dedicated sections for art inspired by the protocol and its culture. Statues of Satoshi Nakamoto have been installed in cities like Budapest, Lugano, and Fornelli. These physical works reflect the desire to link Bitcoin’s abstract values to something tangible.

Looking Back to Look Forward
The Asante example helps us see that money has long been tied to memory and meaning. Their spoons were practical tools but also cultural anchors. Bitcoin, while new and digital, may be playing a similar role.
Instead of relying on political symbols or national myths, Bitcoin uses code, transparency, and global consensus to create trust. In doing so, it offers a way to preserve economic memory that does not depend on power or politics.
It’s still early to know what kind of legacy Bitcoin will leave. But if it succeeds, it may not just change how money works. It may also change how civilizations remember.
-
 @ 3d073b19:4ae60f39
2025-05-12 00:09:07
@ 3d073b19:4ae60f39
2025-05-12 00:09:07This is an English openletter
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ 40bdcc08:ad00fd2c
2025-05-06 14:24:22
@ 40bdcc08:ad00fd2c
2025-05-06 14:24:22Introduction
Bitcoin’s
OP_RETURNopcode, a mechanism for embedding small data in transactions, has ignited a significant debate within the Bitcoin community. Originally designed to support limited metadata while preserving Bitcoin’s role as a peer-to-peer electronic cash system,OP_RETURNis now at the center of proposals that could redefine Bitcoin’s identity. The immutable nature of Bitcoin’s timechain makes it an attractive platform for data storage, creating tension with those who prioritize its monetary function. This discussion, particularly around Bitcoin Core pull request #32406 (GitHub PR #32406), highlights a critical juncture for Bitcoin’s future.What is
OP_RETURN?Introduced in 2014,
OP_RETURNallows users to attach up to 80 bytes of data to a Bitcoin transaction. Unlike other transaction outputs,OP_RETURNoutputs are provably unspendable, meaning they don’t burden the Unspent Transaction Output (UTXO) set—a critical database for Bitcoin nodes. This feature was a compromise to provide a standardized, less harmful way to include metadata, addressing earlier practices that embedded data in ways that bloated the UTXO set. The 80-byte limit and restriction to oneOP_RETURNoutput per transaction are part of Bitcoin Core’s standardness rules, which guide transaction relay and mining but are not enforced by the network’s consensus rules (Bitcoin Stack Exchange).Standardness vs. Consensus Rules
Standardness rules are Bitcoin Core’s default policies for relaying and mining transactions. They differ from consensus rules, which define what transactions are valid across the entire network. For
OP_RETURN: - Consensus Rules: AllowOP_RETURNoutputs with data up to the maximum script size (approximately 10,000 bytes) and multiple outputs per transaction (Bitcoin Stack Exchange). - Standardness Rules: LimitOP_RETURNdata to 80 bytes and one output per transaction to discourage excessive data storage and maintain network efficiency.Node operators can adjust these policies using settings like
-datacarrier(enables/disablesOP_RETURNrelay) and-datacarriersize(sets the maximum data size, defaulting to 83 bytes to account for theOP_RETURNopcode and pushdata byte). These settings allow flexibility but reflect Bitcoin Core’s default stance on limiting data usage.The Proposal: Pull Request #32406
Bitcoin Core pull request #32406, proposed by developer instagibbs, seeks to relax these standardness restrictions (GitHub PR #32406). Key changes include: - Removing Default Size Limits: The default
-datacarriersizewould be uncapped, allowing largerOP_RETURNdata without a predefined limit. - Allowing Multiple Outputs: The restriction to oneOP_RETURNoutput per transaction would be lifted, with the total data size across all outputs subject to a configurable limit. - Deprecating Configuration Options: The-datacarrierand-datacarriersizesettings are marked as deprecated, signaling potential removal in future releases, which could limit node operators’ ability to enforce custom restrictions.This proposal does not alter consensus rules, meaning miners and nodes can already accept transactions with larger or multiple
OP_RETURNoutputs. Instead, it changes Bitcoin Core’s default relay policy to align with existing practices, such as miners accepting non-standard transactions via services like Marathon Digital’s Slipstream (CoinDesk).Node Operator Flexibility
Currently, node operators can customize
OP_RETURNhandling: - Default Settings: Relay transactions with oneOP_RETURNoutput up to 80 bytes. - Custom Settings: Operators can disableOP_RETURNrelay (-datacarrier=0) or adjust the size limit (e.g.,-datacarriersize=100). These options remain in #32406 but are deprecated, suggesting that future Bitcoin Core versions might not support such customization, potentially standardizing the uncapped policy.Arguments in Favor of Relaxing Limits
Supporters of pull request #32406 and similar proposals argue that the current restrictions are outdated and ineffective. Their key points include: - Ineffective Limits: Developers bypass the 80-byte limit using methods like Inscriptions, which store data in other transaction parts, often at higher cost and inefficiency (BitcoinDev Mailing List). Relaxing
OP_RETURNcould channel data into a more efficient format. - Preventing UTXO Bloat: By encouragingOP_RETURNuse, which doesn’t affect the UTXO set, the proposal could reduce reliance on harmful alternatives like unspendable Taproot outputs used by projects like Citrea’s Clementine bridge. - Supporting Innovation: Projects like Citrea require more data (e.g., 144 bytes) for security proofs, and relaxed limits could enable new Layer 2 solutions (CryptoSlate). - Code Simplification: Developers like Peter Todd argue that these limits complicate Bitcoin Core’s codebase unnecessarily (CoinGeek). - Aligning with Practice: Miners already process non-standard transactions, and uncapping defaults could improve fee estimation and reduce reliance on out-of-band services, as noted by ismaelsadeeq in the pull request discussion.In the GitHub discussion, developers like Sjors and TheCharlatan expressed support (Concept ACK), citing these efficiency and innovation benefits.
Arguments Against Relaxing Limits
Opponents, including prominent developers and community members, raise significant concerns about the implications of these changes: - Deviation from Bitcoin’s Purpose: Critics like Luke Dashjr, who called the proposal “utter insanity,” argue that Bitcoin’s base layer should prioritize peer-to-peer cash, not data storage (CoinDesk). Jason Hughes warned it could turn Bitcoin into a “worthless altcoin” (BeInCrypto). - Blockchain Bloat: Additional data increases the storage and processing burden on full nodes, potentially making node operation cost-prohibitive and threatening decentralization (CryptoSlate). - Network Congestion: Unrestricted data could lead to “spam” transactions, raising fees and hindering Bitcoin’s use for financial transactions. - Risk of Illicit Content: The timechain’s immutability means data, including potentially illegal or objectionable content, is permanently stored on every node. The 80-byte limit acts as a practical barrier, and relaxing it could exacerbate this issue. - Preserving Consensus: Developers like John Carvalho view the limits as a hard-won community agreement, not to be changed lightly.
In the pull request discussion, nsvrn and moth-oss expressed concerns about spam and centralization, advocating for gradual changes. Concept NACKs from developers like wizkid057 and Luke Dashjr reflect strong opposition.
Community Feedback
The GitHub discussion for pull request #32406 shows a divided community: - Support (Concept ACK): Sjors, polespinasa, ismaelsadeeq, miketwenty1, TheCharlatan, Psifour. - Opposition (Concept NACK): wizkid057, BitcoinMechanic, Retropex, nsvrn, moth-oss, Luke Dashjr. - Other: Peter Todd provided a stale ACK, indicating partial or outdated support.
Additional discussions on the BitcoinDev mailing list and related pull requests (e.g., #32359 by Peter Todd) highlight similar arguments, with #32359 proposing a more aggressive removal of all
OP_RETURNlimits and configuration options (GitHub PR #32359).| Feedback Type | Developers | Key Points | |---------------|------------|------------| | Concept ACK | Sjors, ismaelsadeeq, others | Improves efficiency, supports innovation, aligns with mining practices. | | Concept NACK | Luke Dashjr, wizkid057, others | Risks bloat, spam, centralization, and deviation from Bitcoin’s purpose. | | Stale ACK | Peter Todd | Acknowledges proposal but with reservations or outdated support. |
Workarounds and Their Implications
The existence of workarounds, such as Inscriptions, which exploit SegWit discounts to embed data, is a key argument for relaxing
OP_RETURNlimits. These methods are costlier and less efficient, often costing more thanOP_RETURNfor data under 143 bytes (BitcoinDev Mailing List). Supporters argue that formalizing largerOP_RETURNdata could streamline these use cases. Critics, however, see workarounds as a reason to strengthen, not weaken, restrictions, emphasizing the need to address underlying incentives rather than accommodating bypasses.Ecosystem Pressures
External factors influence the debate: - Miners: Services like Marathon Digital’s Slipstream process non-standard transactions for a fee, showing that market incentives already bypass standardness rules. - Layer 2 Projects: Citrea’s Clementine bridge, requiring more data for security proofs, exemplifies the demand for relaxed limits to support innovative applications. - Community Dynamics: The debate echoes past controversies, like the Ordinals debate, where data storage via inscriptions raised similar concerns about Bitcoin’s purpose (CoinDesk).
Bitcoin’s Identity at Stake
The
OP_RETURNdebate is not merely technical but philosophical, questioning whether Bitcoin should remain a focused monetary system or evolve into a broader data platform. Supporters see relaxed limits as a pragmatic step toward efficiency and innovation, while opponents view them as a risk to Bitcoin’s decentralization, accessibility, and core mission. The community’s decision will have lasting implications, affecting node operators, miners, developers, and users.Conclusion
As Bitcoin navigates this crossroads, the community must balance the potential benefits of relaxed
OP_RETURNlimits—such as improved efficiency and support for new applications—against the risks of blockchain bloat, network congestion, and deviation from its monetary roots. The ongoing discussion, accessible via pull request #32406 on GitHub (GitHub PR #32406). Readers are encouraged to explore the debate and contribute to ensuring that any changes align with Bitcoin’s long-term goals as a decentralized, secure, and reliable system. -
 @ e39333da:7c66e53a
2025-05-12 00:03:18
@ e39333da:7c66e53a
2025-05-12 00:03:18::youtube{#VQRLujxTm3c}
Rockstar released the second trailer for Grand Theft Auto VI, where they mention that it showcases both cinematic and gameplay scenes equally, though of course it doesn't show any direct gameplay.
This trailer also announces the release date for the game. The game will come out on the 26th of May, 2026, for the PS5 and the Xbox One.
-
 @ 3d073b19:4ae60f39
2025-05-11 23:59:56
@ 3d073b19:4ae60f39
2025-05-11 23:59:56Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lists
Unordered List
- Item 1
- Item 2
- Subitem 2.1
- Subitem 2.2
Ordered List
- First item
- Second item
- Third item
Links
OpenAI - A link to OpenAI's website. Markdown Guide - A comprehensive guide to Markdown syntax.
Images
 - An example image with a title.
- An example image with a title.Blockquotes
This is a blockquote. It can span multiple lines. It is often used to highlight important information or quotes.
Code
Inline Code
Here is some
inline codethat demonstrates how to format code within a sentence.Code Block
```python
This is a Python code block
def hello_world(): print("Hello, world!") ```
Emphasis
Bold
This text is bold. This text is also bold.
Italic
This text is italic. This text is also italic.
Strikethrough
~~This text is strikethrough.~~
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 3d073b19:4ae60f39
2025-05-11 23:52:28
@ 3d073b19:4ae60f39
2025-05-11 23:52:28Headings
Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lists
Unordered List
- Item 1
- Item 2
- Subitem 2.1
- Subitem 2.2
Ordered List
- First item
- Second item
- Third item
Mixed List
-
Item 1
-
Item 2
-
Item 3
Links
OpenAI - A link to OpenAI's website. Markdown Guide - A comprehensive guide to Markdown syntax.
Images
 - An example image with a title.
- An example image with a title.Blockquotes
This is a blockquote. It can span multiple lines. It is often used to highlight important information or quotes.
Code
Inline Code
Here is some
inline codethat demonstrates how to format code within a sentence.Code Block
```python
This is a Python code block
def hello_world(): print("Hello, world!") ```
Emphasis
Bold
This text is bold. This text is also bold.
Italic
This text is italic. This text is also italic.
Strikethrough
~~This text is strikethrough.~~
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ 2183e947:f497b975
2025-05-01 22:33:48
@ 2183e947:f497b975
2025-05-01 22:33:48Most darknet markets (DNMs) are designed poorly in the following ways:
1. Hosting
Most DNMs use a model whereby merchants fill out a form to create their listings, and the data they submit then gets hosted on the DNM's servers. In scenarios where a "legal" website would be forced to censor that content (e.g. a DMCA takedown order), DNMs, of course, do not obey. This can lead to authorities trying to find the DNM's servers to take enforcement actions against them. This design creates a single point of failure.
A better design is to outsource hosting to third parties. Let merchants host their listings on nostr relays, not on the DNM's server. The DNM should only be designed as an open source interface for exploring listings hosted elsewhere, that way takedown orders end up with the people who actually host the listings, i.e. with nostr relays, and not with the DNM itself. And if a nostr relay DOES go down due to enforcement action, it does not significantly affect the DNM -- they'll just stop querying for listings from that relay in their next software update, because that relay doesn't work anymore, and only query for listings from relays that still work.
2. Moderation
Most DNMs have employees who curate the listings on the DNM. For example, they approve/deny listings depending on whether they fit the content policies of the website. Some DNMs are only for drugs, others are only for firearms. The problem is, to approve a criminal listing is, in the eyes of law enforcement, an act of conspiracy. Consequently, they don't just go after the merchant who made the listing but the moderators who approved it, and since the moderators typically act under the direction of the DNM, this means the police go after the DNM itself.
A better design is to outsource moderation to third parties. Let anyone call themselves a moderator and create lists of approved goods and services. Merchants can pay the most popular third party moderators to add their products to their lists. The DNM itself just lets its users pick which moderators to use, such that the user's choice -- and not a choice by the DNM -- determines what goods and services the user sees in the interface.
That way, the police go after the moderators and merchants rather than the DNM itself, which is basically just a web browser: it doesn't host anything or approve of any content, it just shows what its users tell it to show. And if a popular moderator gets arrested, his list will still work for a while, but will gradually get more and more outdated, leading someone else to eventually become the new most popular moderator, and a natural transition can occur.
3. Escrow
Most DNMs offer an escrow solution whereby users do not pay merchants directly. Rather, during the Checkout process, they put their money in escrow, and request the DNM to release it to the merchant when the product arrives, otherwise they initiate a dispute. Most DNMs consider escrow necessary because DNM users and merchants do not trust one another; users don't want to pay for a product first and then discover that the merchant never ships it, and merchants don't want to ship a product first and then discover that the user never pays for it.
The problem is, running an escrow solution for criminals is almost certain to get you accused of conspiracy, money laundering, and unlicensed money transmission, so the police are likely to shut down any DNM that does this. A better design is to oursource escrow to third parties. Let anyone call themselves an escrow, and let moderators approve escrows just like they approve listings. A merchant or user who doesn't trust the escrows chosen by a given moderator can just pick a different moderator. That way, the police go after the third party escrows rather than the DNM itself, which never touches user funds.
4. Consequences
Designing a DNM along these principles has an interesting consequence: the DNM is no longer anything but an interface, a glorified web browser. It doesn't host any content, approve any listings, or touch any money. It doesn't even really need a server -- it can just be an HTML file that users open up on their computer or smart phone. For two reasons, such a program is hard to take down:
First, it is hard for the police to justify going after the DNM, since there are no charges to bring. Its maintainers aren't doing anything illegal, no more than Firefox does anything illegal by maintaining a web browser that some people use to browse illegal content. What the user displays in the app is up to them, not to the code maintainers. Second, if the police decided to go after the DNM anyway, they still couldn't take it down because it's just an HTML file -- the maintainers do not even need to run a server to host the file, because users can share it with one another, eliminating all single points of failure.
Another consequence of this design is this: most of the listings will probably be legal, because there is more demand for legal goods and services than illegal ones. Users who want to find illegal goods would pick moderators who only approve those listings, but everyone else would use "legal" moderators, and the app would not, at first glance, look much like a DNM, just a marketplace for legal goods and services. To find the illegal stuff that lurks among the abundant legal stuff, you'd probably have to filter for it via your selection of moderators, making it seem like the "default" mode is legal.
5. Conclusion
I think this DNM model is far better than the designs that prevail today. It is easier to maintain, harder to take down, and pushes the "hard parts" to the edges, so that the DNM is not significantly affected even if a major merchant, moderator, or escrow gets arrested. I hope it comes to fruition.
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 3c389c8f:7a2eff7f
2025-05-11 22:53:30
@ 3c389c8f:7a2eff7f
2025-05-11 22:53:30As I'm sitting here trying to hone in on what might be important to write about in this moment, my mind keeps swirling around through all the things that have me sitting here to begin with. Nostr found me in a time when my life needed a change. The discovery of something that provided the light of hope to an otherwise dark, dystopian future was more powerful than I could have ever predicted. Timing is everything, they say. I believe that to be half true, as timing alone means nothing if the will is non-existent. The intersection of opportunity and preparedness, and all that. I know how I found my way here, but I do not fully understand the things that have drawn my curiosity and kept my attention so strongly. My will ached for change, simplicity, and meaning. I found it, in what seem to me, simultaneously the most likely and the most unlikely of places. There's a magic to that, and its probably better to leave some questions unanswered, lest they lose their mystic power.
My experiences are my own but theme of them resonates through most of the people with whom I interact. It's been very clear that I wasn't alone in these feelings. A movement of highly inspired, hopeful people have continued to support this digital freedom movement since my arrival, in varying ways. Some people have highly technical skills ranging from network systems to design to cybersecurity. Others, like myself, have little to offer in the realms of functionality and we do what we can to breathe life into the systems built to provide digital freedom of speech for all. It's a humbling experience. We are reminded. sometimes directly and sometimes indirectly, that none of Nostr would matter if there were no one using it. We know this to be true, but it is no less humbling to be surrounded by constant innovation and a thriving desire to bring this experience to the entire world.
Now here I sit, tapping out these words, in the midst of another massive life change, stressful but chosen. I could sign off, go read a book in the garden, and go about my world as I would have in my pre-Nostr times. I don't want to do that, though. Hope is here. If there is a place to dwell, in hope is where I will always choose.
I find it important to acknowledge, though, that Nostr and the people using it are in a constant state of flux, too. This isn't my rock nor harbor nor shelter. It's the chaotic good, reminding me both to keep an appreciation for how far this ecosystem has come in such a short amount of time and a realistic set of expectations for where this all can go. The same applies for how well things work at any given moment...And equally so in missing my some of my early Nostr friends that have come and gone, while remaining open to the possibility of meeting new ones... Experiences had and experiences yet to come. I don't know if I have ever been so coaxed outside of my mind by a group of strangers on the internet. But here I am, looking back and looking forward, surrounded by awe in all directions, sharing thoughts that would otherwise be scribbled in pen to be burned in a random evening fire. I've long felt that the core of social media should be just this. Spaces for people to connect, above all else, in the ways that create meaning in our lives. I suppose in some ways that did exist before, but it was twisted, and obscured, and slowly pulled away.
Now its here and super-charged by possibility. What this looks like for any individual will not be the same as my own view. That's part of what makes this so beautiful to me. We need to be able to speak freely. Just as importantly we need to be able to surround ourselves with the things and people that makes us want to do more, that make us want to feel humbled. Or not, if we so choose... but I choose hope.
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:57:02
@ c1e9ab3a:9cb56b43
2025-04-10 02:57:02A follow-up to nostr:naddr1qqgxxwtyxe3kvc3jvvuxywtyxs6rjq3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wuaydz8
This whitepaper, a comparison of baseload power options, explores a strategic policy framework to reduce the cost of next-generation nuclear power by aligning Gen IV Small Modular Reactors (SMRs) with national security objectives, public utility management, and a competitive manufacturing ecosystem modeled after the aerospace industry. Under this approach, SMRs could deliver stable, carbon-free power at $40–55/MWh, rivaling the economics of natural gas and renewables.
1. Context and Strategic Opportunity
Current Nuclear Cost Challenges
- High capital expenditure ($4,000–$12,000/kW)
- Lengthy permitting and construction timelines (10–15 years)
- Regulatory delays and public opposition
- Customized, one-off reactor designs with no economies of scale
The Promise of SMRs
- Factory-built, modular units
- Lower absolute cost and shorter build time
- Enhanced passive safety
- Scalable deployment
2. National Security as a Catalyst
Strategic Benefits
- Energy resilience for critical defense infrastructure
- Off-grid operation and EMP/cyber threat mitigation
- Long-duration fuel cycles reduce logistical risk
Policy Implications
- Streamlined permitting and site access under national defense exemptions
- Budget support via Department of Defense and Department of Energy
- Co-location on military bases and federal sites
3. Publicly Chartered Utilities: A New Operating Model
Utility Framework
- Federally chartered, low-margin operator (like TVA or USPS)
- Financially self-sustaining through long-term PPAs
- Focus on reliability, security, and public service over profit
Cost Advantages
- Lower cost of capital through public backing
- Predictable revenue models
- Community trust and stakeholder alignment
4. Competitive Manufacturing: The Aviation Analogy
Model Characteristics
- Multiple certified vendors, competing under common safety frameworks
- Factory-scale production and supply chain specialization
- Domestic sourcing for critical components and fuel
Benefits
- Cost reductions from repetition and volume
- Innovation through competition
- Export potential and industrial job creation
5. Levelized Cost of Electricity (LCOE) Impact
| Cost Lever | Estimated LCOE Reduction | |------------|--------------------------| | Streamlined regulation | -10 to -20% | | Public-charter operation | -5 to -15% | | Factory-built SMRs | -15 to -30% | | Defense market anchor | -10% |
Estimated Resulting LCOE: $40–55/MWh
6. Strategic Outcomes
- Nuclear cost competitiveness with gas and renewables
- Decarbonization without reliability sacrifice
- Strengthened national energy resilience
- Industrial and workforce revitalization
- U.S. global leadership in clean, secure nuclear energy
7. Recommendations
- Create a public-private chartered SMR utility
- Deploy initial reactors on military and federal lands
- Incentivize competitive SMR manufacturing consortia
- Establish fast-track licensing for Gen IV designs
- Align DoD/DOE energy procurement to SMR adoption
Conclusion
This strategy would transform nuclear power from a high-cost, high-risk sector into a mission-driven, economically viable backbone of American energy and defense infrastructure. By treating SMRs as strategic assets, not just energy projects, the U.S. can unlock affordable, scalable, and secure nuclear power for generations to come.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ d34e832d:383f78d0
2025-04-21 02:36:32
@ d34e832d:383f78d0
2025-04-21 02:36:32Lister.lol represents a sophisticated web application engineered specifically for the administration and management of Nostr lists. This feature is intrinsically embedded within the Nostr protocol, facilitating users in the curation of personalized feeds and the exploration of novel content. Although its current functionality remains relatively rudimentary, the platform encapsulates substantial potential for enhanced collaborative list management, as well as seamless integration with disparate client applications, effectively functioning as a micro-app within the broader ecosystem.
The trajectory of Nostr is oriented towards the development of robust developer tools (namely, the Nostr Development Kit - NDK), the establishment of comprehensive educational resources, and the cultivation of a dynamic and engaged community of developers and builders.
The overarching strategy emphasizes a decentralized paradigm, prioritizing the growth of small-scale, sustainable enterprises over the dominance of large, centralized corporations. In this regard, a rigorous experimentation with diverse monetization frameworks and the establishment of straightforward, user-friendly applications are deemed critical for the sustained evolution and scalability of the Nostr platform.
 Nostr's commitment to a decentralized, 'nagar-style' model of development distinguishes it markedly from the more conventional 'cathedral' methodologies employed by other platforms. As it fosters a broad spectrum of developmental outcomes while inherently embracing the properties of emergence. Such principles stand in stark contrast to within a traditional environment, centralized Web2 startup ecosystem, which is why all people need a chance to develop a significant shift towards a more adaptive and responsive design philosophy in involving #Nostr and #Bitcoin.
Nostr's commitment to a decentralized, 'nagar-style' model of development distinguishes it markedly from the more conventional 'cathedral' methodologies employed by other platforms. As it fosters a broad spectrum of developmental outcomes while inherently embracing the properties of emergence. Such principles stand in stark contrast to within a traditional environment, centralized Web2 startup ecosystem, which is why all people need a chance to develop a significant shift towards a more adaptive and responsive design philosophy in involving #Nostr and #Bitcoin. -
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ c1e9ab3a:9cb56b43
2025-04-01 04:32:15
@ c1e9ab3a:9cb56b43
2025-04-01 04:32:15I. Introduction
The phenomenon known as "speaking in tongues" has long been interpreted as either the miraculous ability to speak foreign languages or utter mysterious syllables by divine power. However, a re-examination of scriptural and apostolic texts suggests a deeper, spiritual interpretation: that "tongues" refers not to foreign speech but to the utterance of divine truths so profound that they are incomprehensible to most unless illuminated by the Spirit.
This treatise explores that interpretation in light of the writings of Paul, Peter, John, and the early Apostolic Fathers. We seek not to diminish the miraculous but to reveal the deeper purpose of spiritual utterance: the revelation of divine knowledge that transcends rational comprehension.
II. The Nature of Tongues as Spiritual Utterance
Tongues are best understood as Spirit-inspired expressions of divine truth—utterances that do not conform to human categories of knowledge or language. As Paul writes in 1 Corinthians 14:2, "He who speaks in a tongue speaks not to men but to God; for no one understands him, but he utters mysteries in the Spirit."
Such mysteries are not unintelligible in a chaotic sense but are veiled truths that require spiritual discernment. The speaker becomes a vessel of revelation. Without interpretation, the truth remains hidden, just as a parable remains a riddle to those without ears to hear.
III. Paul and the Hidden Wisdom of God
In his epistles, Paul often distinguishes between surface knowledge and spiritual wisdom. In 1 Corinthians 2:6-7, he writes:
"We speak wisdom among those who are mature, yet not the wisdom of this age... but we speak the wisdom of God in a mystery, the hidden wisdom which God ordained before the ages."
Tongues, then, are one vehicle by which such hidden wisdom is spoken. The gift of interpretation is not mere translation but the Spirit-led unveiling of meaning. Hence, Paul prioritizes intelligibility not to invalidate tongues, but to encourage the edification that comes when deep truth is revealed and understood (1 Cor. 14:19).
IV. Peter at Pentecost: Many Tongues, One Spirit
At Pentecost (Acts 2), each listener hears the apostles speak "in his own language"—but what they hear are "the mighty works of God." Rather than focusing on the mechanics of speech, the emphasis is on understanding. It was not merely a linguistic miracle but a revelatory one: divine truth reaching every heart in a way that transcended cultural and rational barriers.
V. John and the Prophetic Language of Revelation
The apostle John writes in symbols, visions, and layered meanings. Revelation is full of "tongues" in this spiritual sense—utterances that reveal while concealing. His Gospel presents the Spirit as the "Spirit of truth" who "will guide you into all truth" (John 16:13). This guiding is not logical deduction but illumination.
VI. The Apostolic Fathers on Inspired Speech
The Didache, an early Christian manual, warns that not everyone who claims to speak by the Spirit is truly inspired. This aligns with a view of tongues as spiritual utterance—deep truth that must be tested by its fruits and conformity to the ways of the Lord.
Polycarp and Ignatius do not emphasize miraculous speech, but their prayers and exhortations show a triadic awareness of Father, Son, and Spirit, and a reverence for spiritual knowledge passed through inspiration and faithful transmission.
VII. Interpretation: The Gift of Spiritual Discernment
In this model, the interpreter of tongues is not a linguist but a spiritual discerner. As Joseph interpreted dreams in Egypt, so the interpreter makes the spiritual intelligible. This gift is not external translation but inward revelation—an unveiling of what the Spirit has spoken.
VIII. Conclusion: Tongues as a Veil and a Revelation
The true gift of tongues lies not in speech but in meaning—in truth spoken from a higher realm that must be spiritually discerned. It is a veil that conceals the holy from the profane, and a revelation to those led by the Spirit of truth.
Thus, we do not reject the miraculous, but recognize that the greatest miracle is understanding—when divine mysteries, spoken in spiritual tongue, are made known to the heart by the Spirit.
"He who has an ear, let him hear what the Spirit says to the churches." (Revelation 2:7)
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ c1e9ab3a:9cb56b43
2025-03-26 21:03:59
@ c1e9ab3a:9cb56b43
2025-03-26 21:03:59Introduction
Nutsax is a capability-based access control system for Nostr relays, designed to provide flexible, privacy-preserving rate limiting, permissioning, and operation-scoped token redemption.
At its core, Nutsax introduces:
- Blind-signed tokens, issued by relays, for specific operation types.
- Token redemption as part of Nostr event publishing or interactions.
- Encrypted token storage using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the Nutsax.
This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system.
Motivation
Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized.
Nutsax introduces:
- Fine-grained, operation-specific access control using cryptographic tokens.
- Blind signature protocols to issue tokens anonymously, preserving user privacy.
- A native way to store and recover tokens using Nostr’s encrypted event system.
This allows relays to offer:
- Optional access policies (e.g., “3 posts per hour unless you redeem a token”)
- Paid or invite-based features (e.g., long-term subscriptions, advanced filters)
- Temporary elevation of privileges (e.g., bypass slow mode for one message)
All without requiring accounts, emails, or linking identity beyond the user’s
npub.Core Components
1. Operation Tokens
Tokens are blind-signed blobs issued by the relay, scoped to a specific operation type (e.g.,
"write","filter-subscribe","broadcast").- Issued anonymously: using a blind signature protocol.
- Validated on redemption: at message submission or interaction time.
- Optional and redeemable: the relay decides when to enforce token redemption.
Each token encodes:
- Operation type (string)
- Relay ID (to scope the token)
- Expiration (optional)
- Usage count or burn-on-use flag
- Random nonce (blindness)
Example (before blinding):
json { "relay": "wss://relay.example", "operation": "write", "expires": 1720000000, "nonce": "b2a8c3..." }This is then blinded and signed by the relay.
2. Token Redemption
Clients include tokens when submitting events or requests to the relay.
Token included via event tag:
json ["token", "<base64-encoded-token>", "write"]Redemption can happen:
- Inline with any event (kind 1, etc.)
- As a standalone event (e.g., ephemeral kind 20000)
- During session initiation (optional AUTH extension)
The relay validates the token:
- Is it well-formed?
- Is it valid for this relay and operation?
- Is it unexpired?
- Has it been used already? (for burn-on-use)
If valid, the relay accepts the event or upgrades the rate/permission scope.
3. Nutsax: Private Token Storage on Nostr
Tokens are stored securely in the client’s Nutsax, a persistent, private archive built on Nostr’s encrypted event system.
Each token is stored in a kind 4 or kind 44/24 event, encrypted with the client’s own
npub.Example:
json { "kind": 4, "tags": [ ["p", "<your npub>"], ["token-type", "write"], ["relay", "wss://relay.example"] ], "content": "<encrypted token blob>", "created_at": 1234567890 }This allows clients to:
- Persist tokens across restarts or device changes.
- Restore tokens after reinstalling or reauthenticating.
- Port tokens between devices.
All without exposing the tokens to the public or requiring external storage infrastructure.
Client Lifecycle
1. Requesting Tokens
- Client authenticates to relay (e.g., via NIP-42).
- Requests blind-signed tokens:
- Sends blinded token requests.
- Receives blind signatures.
- Unblinds and verifies.
2. Storing Tokens
- Each token is encrypted to the user’s own
npub. - Stored as a DM (kind 4 or compatible encrypted event).
- Optional tagging for organization.
3. Redeeming Tokens
- When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event.
- Relay validates and logs/consumes the token.
4. Restoring the Nutsax
- On device reinstallation or session reset, the client:
- Reconnects to relays.
- Scans encrypted DMs.
- Decrypts and reimports available tokens.
Privacy Model
- Relays issuing tokens do not know which tokens were redeemed (blind signing).
- Tokens do not encode sender identity unless the client opts to do so.
- Only the recipient (
npub) can decrypt their Nutsax. - Redemption is pseudonymous — tied to a key, not to external identity.
Optional Enhancements
- Token index tag: to allow fast search and categorization.
- Multiple token types: read, write, boost, subscribe, etc.
- Token delegation: future support for transferring tokens via encrypted DM to another
npub. - Token revocation: relays can publish blacklists or expiration feeds if needed.
Compatibility
- Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication).
- Non-disruptive: relays and clients can ignore tokens if not supported.
- Ideal for layering on top of existing infrastructure and monetization strategies.
Conclusion
Nutsax offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ b7cf9f42:ecb93e78
2025-03-26 10:57:33
@ b7cf9f42:ecb93e78
2025-03-26 10:57:33Der Verstand im Fluss der Information
Das Informationszeitalter ist wie ein monströser Fluss, der unseren Verstand umgibt
Fundament erbauen
Der Verstand kann sich eine Insel in diesem Fluss bauen. Dabei können wir eine eigene Insel erbauen oder eine bestehende insel anvisieren um stabilität zu finden
Je robuster das Baumaterial, desto standhafter unsere Insel. (Stärke der Argumente, Qualität des Informationsgehalts, Verständlichkeit der Information)
Je grossflächiger die Insel, desto mehr Menschen haben Platz (Reichweite).
Je höher wir die Insel bauen, desto sicherer ist sie bei einem Anstieg des Informationsflusses (Diversität der Interesse und Kompetenzen der Inselbewohner).
Robustes Baumaterial
Primäre Wahrnehmung (robuster):
Realität -> meine Sinne -> meine Meinung/Interpretation
Sekundäre Wahrnehmung (weniger Robust):
Realität -> Sinne eines anderen -> dessen Meinung/Interpretation -> dessen Kommunikation -> meine Sinne -> meine Meinung/Interpretation
Wie kann ich zur Insel beitragen?
Ich investiere meine Zeit, um zu lernen. Ich bin bestrebt, Ideen zu verstehen, um sicherzugehen, dass ich robustes Baumaterial verwende.
Ich teile vermehrt Informationen, welche ich verstehe, damit auch meine Mitbewohner der Insel mit robustem Material die Insel vergrössern können. So können wir mehr Platz schaffen, wo Treibende Halt finden können.
Was könnte diese Insel sein?
- Freie Wissenschaft
- Freie Software
- Regeln
- Funktionierende Justiz
- Werkzeug
- und vieles weiteres
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53
@ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53MEMORANDUM OF CONVERSATION
SUBJECT: Meeting with Russian President Yeltsin
PARTICIPANTS: - U.S. - President Clinton - Secretary Albright - National Security Advisor Berger - Deputy National Security Advisor Steinberg - Ambassador Sestanovich - Carlos Pascual
- Russia
- Russian President Yeltsin
- Foreign Minister Ivanov
- Kremlin Foreign Policy Advisor Prihodko
- Defense Minister Sergeyev
- Interpreter: Peter Afansenko
- Notetaker: Carlos Pascual
DATE, TIME AND PLACE: November 19, 1999, 10:45 a.m. - 11:40 a.m. Istanbul, Turkey
President Yeltsin: We are in neutral territory here. I welcome you.
The President: Neither of us has a stake here. It's good to see you.
President Yeltsin: Well, Bill, what about those camps here in Turkey that are preparing troops to go into Chechnya? Aren't you in charge of those? I have the details. Minister Ivanov, give me the map. I want to show you where the mercenaries are being trained and then being sent into Chechnya. They are armed to the teeth. (Note: Yeltsin pulls out map of Turkey and circulates it.) Bill, this is your fault. I told Demirel yesterday that I will send the head of the SRV tomorrow and we will show him where the camps are located. These are not state-sanctioned camps. They are sponsored by NGOs and religious organizations. But let me tell you if this were in Russia and there were but one camp, I would throw them all out and put the bandits in the electric chair.
The President: Perhaps Demirel could help you.
President Yeltsin: Well, he ought to. Tomorrow after I get back, I will send the head of the Foreign Intelligence Service here. Bill, did you hurt your leg?
The President: Yes, but it is not bad.
President Yeltsin: When one leg of the President hurts, that is a bad thing.
The President: It lets me know I am alive.
President Yeltsin: I know we are not upset at each other. We were just throwing some jabs. I'm still waiting for you to visit. Bill. I've said to you come to visit in May, then June, then July and then August. Now it's past October and you're still not there.
The President: You're right, Boris, I owe you a visit.
President Yeltsin: Last time I went to the U.S., Bill.
The President: Well, I better set it up. I'll look at the calendar and find a time that's good for you and me.
President Yeltsin: Call me and tell me the month and date. Unless I have another visit, I will do the maximum amount I can to do everything around your schedule. The main things I have are to go to China and India.
The President: Boris, we still have lots to do together.
President Yeltsin: You heard my statement on nuclear arms and on banning nuclear tests. I just signed a law on ratification of a new agreement on the Comprehensive Test Ban Treaty. Isn't that right, Minister Ivanov?
Minister Ivanov: You signed the documents that sent the Comprehensive Test Ban Treaty to the Duma for review.
President Yeltsin: Well, in any case, I still approved it.
The President: Maybe I can get the Congress to agree still. They kept the Treaty even after they rejected it. So perhaps, there is still a chance.
President Yeltsin: Or perhaps it's just the bureaucrats working and they haven't had a chance to send it back to you yet. I'm upset that you signed the law to change the ABM Treaty.
The President: I signed no such law. People in Congress don't like the ABM Treaty. If Congress had its way, they would undermine the treaty. I'm trying to uphold it. But we need a national missile defense to protect against rogue states. We can't have a national missile defense that works without changing the ABM Treaty. But I want to do this cooperatively. I want to persuade you that this is good for both of us. The primary purpose is to protect against terrorists and rogue states. It would be ineffective against Russia. The system we're looking at would operate against just 20 missiles. And, Boris I want to figure out how to share the benefits. For all I know, in twenty years terrorists could have access to nuclear weapons. I know your people don't agree with me, but I'm not trying to overthrow the ABM Treaty. We're still trying to discover what's technically possible with national missile defense, but there are people in America who want to throw over the ABM Treaty. I have made no decisions yet.
President Yeltsin: Bill, Bill. I got your note. It went into all these things in incredible detail. I read it and I was satisfied. I've not yet ceased to believe in you. I ask you one thing. Just give Europe to Russia. The U.S. is not in Europe. Europe should be the business of Europeans. Russia is half European and half Asian.
The President: So you want Asia too?
President Yeltsin: Sure, sure. Bill. Eventually, we will have to agree on all of this.
The President: I don't think the Europeans would like this very much.
President Yeltsin: Not all. But I am a European. I live in Moscow. Moscow is in Europe and I like it. You can take all the other states and provide security to them. I will take Europe and provide them security. Well, not I. Russia will. We will end this conflict in Chechnya. I didn't say all the things I was thinking (in his speech). I listened to you carefully. I took a break just beforehand. Then I listened to you from beginning to end. I can even repeat what you said. Bill, I'm serious. Give Europe to Europe itself. Europe never felt as close to Russia as it does now. We have no difference of opinion with Europe, except maybe on Afganistan and Pakistan—which, by the way, is training Chechens. These are bandits, headhunters and killers. They're raping American women. They're cutting off ears and other parts of their hostages. We're fighting these types of terrorists. Let's not accuse Russia that we are too rough with these kinds of people. There are only two options: kill them or put them on trial. There's no third option, but we can put them on trial, and sentence them to 20-25 years. How many Americans, French, British and Germans have I freed that were there in Chechnya under the OSCE? The Chechen killers don't like the language of the OSCE. Here's my Minister of Defense. Stand up. We have not lost one soldier down there. Tell them.
Minister Sergeyev: We did not lose one soldier in Gudermes.
President Yeltsin: You see, Gudermes was cleansed without one military or civilian killed. We killed 200 bandits. The Minister of Defense is fulfilling the plan as I have said it should be. He's doing this thoughtfully. The soldiers only ask: don't stop the campaign. I promised these guys—I told every soldier, marshal and general—I will bring the campaign to fruition. We have these Chechens under lock and key. We have the key. They can't get in, they can't get out. Except maybe through Georgia; that's Shevardnadze's big mistake. And through Azerbaijan; that's Aliyev's mistake. They're shuttling in under the name of Islam. We're for freedom of religion, but not for fundamentalist Islam. These extremists are against you and against me.
We have the power in Russia to protect all of Europe, including those with missiles. We'll make all the appropriate treaties with China. We're not going to provide nuclear weapons to India. If we give them submarines, it will be only conventional diesel submarines, not nuclear. They would be from the 935 generation. You're going in that direction too. I'm thinking about your proposal—well, what your armed forces are doing—getting rid of fissile materials, particularly plutonium. We should just get rid of it. As soon as it's there, people start thinking of how to make bombs. Look, Russia has the power and intellect to know what to do with Europe. If Ivanov stays here, he will initial the CFE Treaty and I'll sign it under him. But under the OSCE Charter, there is one thing I cannot agree—which is that, based on humanitarian causes, one state can interfere in the affairs of another state.
National Security Advisor Berger: Mr. President, there's nothing in the Charter on one state's interference in the affairs of another.
Secretary Albright: That's right. What the Charter says is that affairs within a state will affect the other states around it.
President Yeltsin: Russia agrees to take out its property and equipment from Georgia in accordance with the new CFE Treaty. I have a statement on this. (looking toward Ivanov) Give it to me. I signed it today. Actually, it was late last night. I like to work late.
The President: Me, too.
President Yeltsin: I know you like to work late, Bill. When you call me, I calculate the time and I tell myself it's 4 a.m. and he's calling me. It lets you cleanse your brain and you feel great. I am not criticizing you, Bill. The President should be encouraged to work hard.
The President: So, we will get an agreement on CFE.
President Yeltsin: Yes.
The President: That's very important, seven years. We've worked on this for a long time.
President Yeltsin: Look, Ivanov has lost the statement in his own bag. He can't find the paper in his own bag. On the Charter, we have to look at it from the beginning. The Charter's ready. However, when states begin to tie in the Charter with the final declaration that has wording unacceptable to us, that's when we'll say no. And responsibility for this will fall fully on the West. (Looking at Ivanov) Give me this thing. It is written on paper. Bill. I am ready to sign it. It is a declaration about what we're talking about.
Secretary Albright: Some states want to record in the declaration your willingness to have an OSCE mission.
President Yeltsin: No, not at all. We will finish this with our own forces. Chechnya is the business of the internal affairs of Russia. We have to decide what to do. After we cleansed Gudermes, the muslim mufti came and asked for help, said I hate Basayev and he should be banned. These are the kinds of leaders we will put forward. I have thought this through carefully.
The President: On the Chechen problem. I have been less critical than others. Even today, I asked the others how they would deal with this if it were their country. This is a political issue. It may be the best thing for you within Russia to tell the Europeans to go to hell. But the best thing for your relations with Europe for the long term is to figure out the policy that you want to have with Europe and to keep that in mind as you deal with Chechnya.
President Yeltsin: (Gets up rapidly) Bill, the meeting is up. We said 20 minutes and it has now been more than 35 minutes.
The President: That's fine. We can say the meeting is over.
President Yeltsin: This meeting has gone on too long. You should come to visit, Bill.
The President: Who will win the election?
President Yeltsin: Putin, of course. He will be the successor to Boris Yeltsin. He's a democrat, and he knows the West.
The President: He's very smart.
President Yeltsin: He's tough. He has an internal ramrod. He's tough internally, and I will do everything possible for him to win—legally, of course. And he will win. You'll do business together. He will continue the Yeltsin line on democracy and economics and widen Russia's contacts. He has the energy and the brains to succeed. Thank you, Bill.
The President: Thank you, Boris. It was good to see you.
End of Conversation
-
 @ 04c915da:3dfbecc9
2025-03-13 19:39:28
@ 04c915da:3dfbecc9
2025-03-13 19:39:28In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ bf47c19e:c3d2573b
2025-05-11 22:33:46
@ bf47c19e:c3d2573b
2025-05-11 22:33:46Originalni tekst na dvadesetjedan.com
Autor: Vijay Boyapati / Prevod na hrvatski: Matija
Sa zadnjim cijenama koje je bitcoin dosegao 2017., optimističan scenarij za ulagače se možda čini toliko očitim da ga nije potrebno niti spominjati. Alternativno, možda se nekome čini glupo ulagati u digitalnu vrijednost koja ne počiva na nijednom fizičkom dobru ili vladi i čiji porast cijene su neki usporedili sa manijom tulipana ili dot-com balonom. Nijedno nije točno; optimističan scenarij za Bitcoin je uvjerljiv, ali ne i očit. Postoje značajni rizici kod ulaganja u Bitcoin, no, kao što planiram pokazati, postoji i ogromna prilika.
Geneza
Nikad u povijesti svijeta nije bilo moguće napraviti transfer vrijednosti među fizički udaljenim ljudima bez posrednika, poput banke ili vlade. 2008. godine, anonimni Satoshi Nakamoto je objavio 8 stranica rješenja na dugo nerješivi računalski problem poznat kao “Problem Bizantskog Generala.” Njegovo rješenje i sustav koji je izgradio - Bitcoin - dozvolio je, prvi put ikad, da se vrijednost prenosi brzo i daleko, bez ikakvih posrednika ili povjerenja. Implikacije kreacije Bitcoina su toliko duboke, ekonomski i računalski, da bi Nakamoto trebao biti prva osoba nominirana za Nobelovu nagradu za ekonomiju i Turingovu nagradu.
Za ulagače, važna činjenica izuma Bitcoina (mreže i protokola) je stvaranje novog oskudnog digitalnog dobra - bitcoina (monetarne jedinice). Bitcoini su prenosivi digitalni “novčići” (tokeni), proizvedeni na Bitcoin mreži kroz proces nazvan “rudarenje” (mining). Rudarenje Bitcoina je ugrubo usporedivo sa rudarenjem zlata, uz bitnu razliku da proizvodnja bitcoina prati unaprijed osmišljeni i predvidivi raspored. Samo 21 milijun bitcoina će ikad postojati, i većina (2017., kada je ovaj tekst napisan) su već izrudareni. Svake četiri godine, količina rudarenih bitcoina se prepolovi. Produkcija novih bitcoina će potpuno prestati 2140. godine.
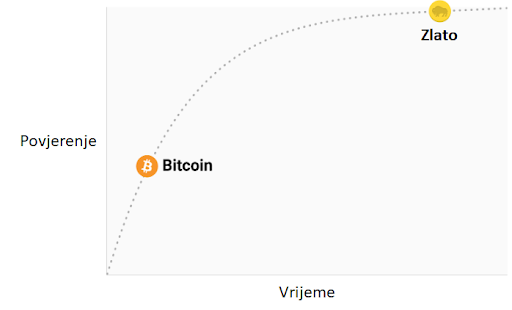 Stopa inflacije —— Monetarna baza
Stopa inflacije —— Monetarna bazaBitcoine ne podržava nikakva roba ili dobra, niti ih garantira ikakva vlada ili firma, što postavlja očito pitanje za svakog novog bitcoin ulagača: zašto imaju uopće ikakvu vrijednost? Za razliku od dionica, obveznica, nekretnina ili robe poput nafte i žita, bitcoine nije moguće vrednovati koristeći standardne ekonomske analize ili korisnost u proizvodnji drugih dobara. Bitcoini pripadaju sasvim drugoj kategoriji dobara - monetarnih dobara, čija se vrijednost definira kroz tzv. teoriju igara; svaki sudionik na tržištu vrednuje neko dobro, onoliko koliko procjenjuje da će ga drugi sudionici vrednovati. Kako bismo bolje razumjeli ovo svojstvo monetarnih dobara, trebamo istražiti podrijetlo novca.
Podrijetlo novca
U prvim ljudskim društvima, trgovina među grupama se vršila kroz robnu razmjenu. Velika neefikasnost prisutna u robnoj razmjeni je drastično ograničavala količinu i geografski prostor na kojem je bila moguća. Jedan od najvećih problema sa robnom razmjenom je problem dvostruke podudarnosti potražnje. Uzgajivač jabuka možda želi trgovati sa ribarom, ali ako ribar ne želi jabuke u istom trenutku, razmjena se neće dogoditi. Kroz vrijeme, ljudi su razvili želju za čuvanjem određenih predmeta zbog njihove rijetkosti i simbolične vrijednosti (npr. školjke, životinjski zube, kremen). Zaista, kako i Nick Szabo govori u svojem izvrsnom eseju o podrijetlu novca, ljudska želja za sakupljanjem predmeta pružila je izraženu evolucijsku prednost ranom čovjeku nad njegovim najbližim biološkim rivalom, neandertalcem - Homo neanderthalensis.
"Primarna i najbitnija evolucijska funkcija sakupljanja bila je osigurati medij za čuvanje i prenošenje vrijednosti".
Predmeti koje su ljudi sakupljali služili su kao svojevrsni “proto-novac,” tako što su omogućavale trgovinu među antagonističkim plemenima i dozvoljavale bogatsvu da se prenosi na sljedeću generaciju. Trgovina i transfer takvih predmeta bile su rijetke u paleolitskim društvima, te su oni služili više kao “spremište vrijednosti” (store of value) nego kao “medij razmjene” (medium of exchange), što je uloga koju danas igra moderni novac. Szabo objašnjava:
"U usporedbi sa modernim novcem, primitivan novac je imao jako malo “brzinu” - mogao je promijeniti ruke samo nekoliko puta u životu prosječnog čovjeka. Svejedno, trajni i čvrsti sakupljački predmet, što bismo danas nazvali “nasljeđe,” mogao je opstati mnogo generacija, dodajući znatnu vrijednost pri svakom transferu - i zapravo omogućiti transfer uopće".
Rani čovjek suočio se sa bitnom dilemom u teoriji igara, kada je odlučivao koje predmete sakupljati: koje od njih će drugi ljudi željeti? Onaj koji bi to točno predvidio imao bi ogromnu prednost u mogućnosti trgovine i akvizicije bogatsva. Neka američka indijanska plemena, npr. Naraganseti, specijalizirala su se u proizvodnji sakupljačkih dobara koja nisu imala drugu svrhu osim trgovine. Valja spomenuti da što je ranije predviđanje da će neko dobro imati takvu vrijednost, veća je prednost koju će imati onaj koji je posjeduje, zato što ju je moguće nabaviti jeftinije, prije nego postane vrlo tražena roba i njezona vrijednost naraste zajedno sa populacijom. Nadalje, nabava nekog dobra u nadi da će u budućnosti biti korišteno kao spremište vrijednosti, ubrzava upravo tu primjenu. Ova cirkularnost je zapravo povratna veza (feedback loop) koja potiče društva da se rapidno slože oko jednog spremišta vrijednosti. U terminima teorije igara, ovo je znano kao “Nashov ekvilibrij.” Postizanje Nashovog ekvilibrija za neko spremište vrijednosti je veliko postignuće za društvo, pošto ono znatno olakšava trgovinu i podjelu rada, i time omogućava napredak civilizacije.
Tisućljećima, kako su ljudska društva rasla i otvarala trgovinske puteve, različite aplikacije spremišta vrijednosti u individualnim društvima počele su se natjecati međusobno. Trgovci su imali izbor: čuvati svoju zaradu u spremištu vrijednosti vlastite kulture, ili one kulture sa kojom su trgovali, ili mješavini oboje. Benefit štednje u stranom spremištu vrijednosti bila je uvećana sposobnost trgovanja u povezanom stranom društvu. Trgovci koji su štedili u stranom spremištu vrijednosti su također imali dobrih razloga da potiču svoje društvo da ga prihvati, jer bi tako uvećali vrijednost vlastite ušteđevine. Prednosti “uvezene” tehnologije spremanja vrijednosti bile su prisutne ne samo za trgovce, nego i za sama društva. Kada bi se dvije grupe konvergirale u jedinstvenom spremištu vrijednosti, to bi značajno smanjilo cijenu troškova trgovine jednog s drugim, i samim time povećanje bogatstva kroz trgovinu. I zaista, 19. stoljeće bilo je prvi put da je najveći dio svijeta prihvatio jedinstveno spremište vrijednosti - zlato - i u tom periodu vidio najveću eksploziju trgovine u povijesti svijeta. O ovom mirnom periodu, pisao je John Maynard Keynes:
"Kakva nevjerojatna epizoda u ekonomskom napretku čovjeka… za svakog čovjeka iole iznadprosječnog, iz srednje ili više klase, život je nudio obilje, ugodu i mogućnosti, po niskoj cijeni i bez puno problema, više nego monarsima iz prethodnih perioda. Stanovnik Londona mogao je, ispijajući jutarnji čaj iz kreveta, telefonski naručiti razne proizvode iz cijele Zemlje, u količinama koje je želio, i sa dobrim razlogom očekivati njihovu dostavu na svoj kućni prag."
Svojstva dobrog spremišta vrijednosti
Kada se spremišta vrijednosti natječu jedno s drugim, specifična svojstva rade razliku koja daje jednom prednost nad drugim. Premda su mnoga dobra u prošlosti korištena kao spremišta vrijednosti ili kao “proto-novac,” određena svojstva su se pokazala kao posebno važna, i omogućila dobrima sa njima da pobijede. Idealno spremište vrijednosti biti će:
- Trajno: dobro ne smije biti kvarljivo ili lako uništeno. Tako naprimjer, žito nije idealno spremište vrijednosti.
- Prenosivo: dobro mora biti lako transportirati i čuvati, što omogućuje osiguranje protiv gubitka ili krađe i dopušta trgovinu na velike udaljenosti. Tako, krava je lošije spremište vrijednosti od zlatne narukvice.
- Zamjenjivo: jedna jedinica dobra treba biti zamjenjiva sa drugom. Bez zamjenjivosti, problem podudarnosti želja ostaje nerješiv. Time, zlato je bolje od dijamanata, jer su oni nepravilni u obliku i kvaliteti.
- Provjerljivo: dobro mora biti lako i brzo identificirano i testirano za autentičnost. Laka provjera povećava povjerenje u trgovini i vjerojatnost da će razmjena biti dovršena.
- Djeljivo: dobro mora biti lako djeljivo na manje dijelove. Premda je ovo svojstvo bilo manje važno u ranim društvima gdje je trgovina bila rijetka, postalo je važnije sa procvatom trgovine. Količine koje su se mijenjale postale su manje i preciznije.
- Oskudno: Monetarno dobro mora imati “cijenu nemoguću za lažirati,” kao što je rekao Nick Szabo. Drugim riječima, dobro ne smije biti obilno ili lako dostupno kroz proizvodnju. Oskudnost je možda i najvažnije svojstvo spremišta vrijednosti, pošto se izravno vezuje na ljudsku želju da sakupljamo ono što je rijetko. Ona je izvor vrijednosti u spremištu vrijednosti.
- Duge povijesti: što je dulje neko dobro vrijedno za društvo, veća je vjerojatnost da će biti prihvaćeno kao spremište vrijednosti. Dugo postojeće spremište vrijednosti biti će jako teško uklonjeno od strane došljaka, osim u slučaju sile (ratno osvajanje) ili ako je nova tehnologija znatno bolja u ostalim svojstvima.
- Otporno na cenzuru: novije svojstvo, sve više važno u modernom digitalnom svijetu sa sveprisutnim nadzorom, je otpornost na cenzuru. Drugim riječima, koliko je teško da vanjski agent, kao korporacija ili država, spriječi vlasnika dobra da ga čuva i koristi. Dobra koja su otporna na cenzuru su idealna za ljude koji žive u režimima koji prisilno nadziru kapital ili čine neke oblike mirne trgovine protuzakonitima.
Ova tablica ocjenjuje Bitcoin, zlato (gold) i fiat novac (kao što je euro ili dolar) po svojstvima izlistanim gore. Objašnjenje svake ocjene slijedi nakon tablice.
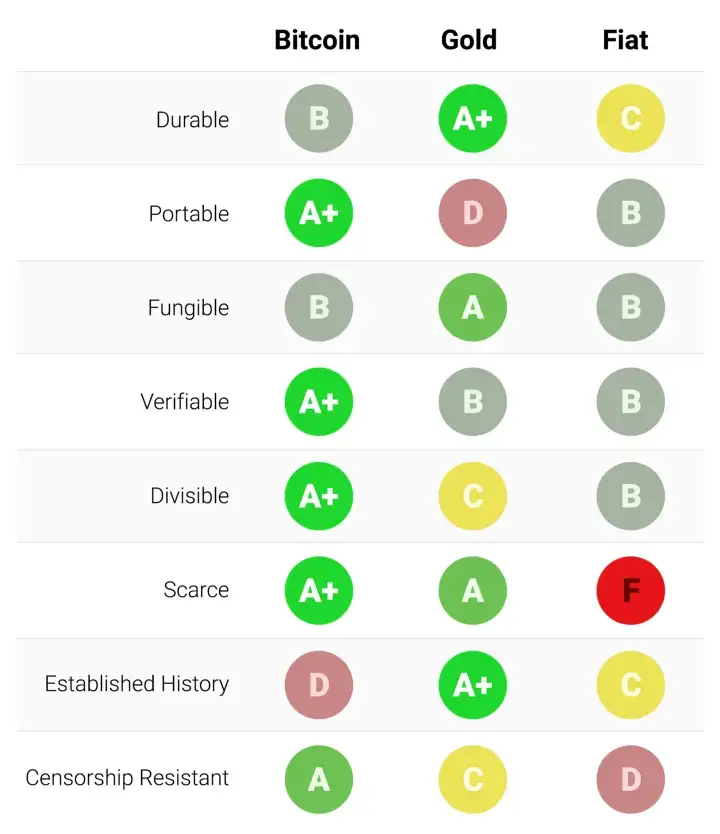
Trajnost:
Zlato je neosporeni kralj trajnosti. Velika većina zlata pronađenog kroz povijest, uključujući ono egipatskih faraona, opstaje i danas i vjerojatno će postojati i za tisuću godina. Zlatnici korišteni u antičko doba imaju značajnu vrijednost i danas. Fiat valute i bitcoini su digitalni zapisi koji ponekad imaju fizički oblik (npr. novčanice). Dakle, njihovu trajnost ne određuju njihova fizička svojstva (moguće je zamijeniti staru i oštećenu novčanicu za novu), nego institucije koje stoje iza njih. U slučaju fiat valuta, mnoge države su nastale i nestale kroz stoljeća, i valute su nestale s njima. Marke iz Weimarske republike danas nemaju vrijednost zato što institucija koja ih je izdavala više ne postoji. Ako je povijest ikakav pokazatelj, ne bi bilo mudro smatrati fiat valute trajnima dugoročno; američki dolar i britanska funta su relativne anomalije u ovom pogledu. Bitcoini, zato što nemaju instituciju koja ih održava, mogu se smatrati trajnima dok god mreža koja ih osigurava postoji. Obzirom da je Bitcoin još uvijek mlada valuta, prerano je za čvrste zaključke o njegovoj trajnosti. No, postoje ohrabrujući znakovi - prominente države su ga pokušavale regulirati, hakeri ga napadali - usprkos tome, mreža nastavlja funkcionirati, pokazujući visok stupanj antifragilnosti.
Prenosivost:
Bitcoini su najprenosivije spremište vrijednosti ikad. Privatni ključevi koji predstavljaju stotine milijuna dolara mogu se spremiti na USB drive i lako ponijeti bilo gdje. Nadalje, jednako velike sume mogu se poslati na drugi kraj svijeta skoro instantno. Fiat valute, zbog svojeg temeljno digitalnog oblika, su također lako prenosive. Ali, regulacije i kontrola kapitala od strane države mogu ugroziti velike prijenose vrijednosti, ili ih usporiti danima. Gotovina se može koristiti kako bi se izbjegle kontrole kapitala, ali onda rastu rizik čuvanja i cijena transporta. Zlato, zbog svojeg fizičkog oblika i velike gustoće, je najmanje prenosivo. Nije čudo da većina zlatnika i poluga nikad ne napuste sefove. Kada se radi prijenos zlata između prodavača i kupca, uglavnom se prenosi samo ugovor o vlasništvu, ne samo fizičko zlato. Prijenos fizičkog zlata na velike udaljenosti je skupo, riskantno i sporo.
Zamjenjivost:
Zlato nam daje standard za zamjenjivost. Kada je rastopljeno, gram zlata je praktički nemoguće razlikovati od bilo kojeg drugog grama, i zlato je oduvijek bilo takvo. S druge strane, fiat valute, su zamjenjive samo onoliko koliko njihova institucija želi da budu. Iako je uglavnom slučaj da je novčanica zamjenjiva za drugu istog iznosa, postoje situacije u kojima su velike novčanice tretirane drukčije od malih. Naprimjer, vlada Indije je, u pokušaju da uništi neoporezivo sivo tržište, potpuno oduzela vrijednost novčanicama od 500 i 1000 rupija. To je uzrokovalo da ljudi manje vrednuju te novčanice u trgovini, što je značilo da više nisu bile zaista zamjenjive za manje novčanice. Bitcoini su zamjenjivi na razini mreže; svaki bitcoin je pri prijenosu tretiran kao svaki drugi. No, zato što je moguće pratiti individualne bitcoine na blockchainu, određeni bitcoin može, u teoriji, postati “prljav” zbog korštenja u ilegalnoj trgovini, te ga trgovci ili mjenjačnice možda neće htjeti prihvatiti. Bez dodatnih poboljšanja oko privatnosti i anonimnosti na razini mrežnog protokola, bitcoine ne možemo smatrati jednako zamjenjivim kao zlato.
Mogućnost provjere:
Praktično gledajući, autentičnost fiat valuta i zlata je prilično lako provjeriti. Svejedno, i usprkos pokušajima da spriječe krivotvorenje novčanica, i dalje postoji potencijal prevare za vlade i njihove građane. Zlato također nije imuno na krivotvorenje. Sofisticirani kriminalci su koristili pozlaćeni tungsten kako bi prevarili kupce zlata. Bitcoine je moguće provjeriti sa matematičkom sigurnošću. Korištenjem kriptografskih potpisa, vlasnik bitcoina može javno demonstrirati da posjeduje bitcoine koje tvrdi da posjeduje.
Djeljivost:
Bitcoine je moguće podijeliti u stotinu milijuna manjih jedinica (zvanih satoshi), i prenositi takve (no, valja uzeti u obzir ekonomičnost prijenosa malih iznosa, zbog cijene osiguravanja mreže - “network fee”). Fiat valute su tipično dovoljno djeljive na jedinice sa vrlo niskom kupovnom moći. Zlato, iako fizički i teoretski djeljivo, postaje teško za korištenje kada se podijeli na dovoljno male količine da bi se moglo koristiti u svakodnevnoj trgovini.
Oskudnost:
Svojstvo koje najjasnije razlikuje Bitcoin od fiat valuta i zlata je njegova unaprijed definirana oskudnost. Od početka, konačna količina bitcoina nikad neće biti veća od 21 milijun. To daje vlasnicima bitcoina jasan i znan uvid u postotak ukupnog vlasništva. Naprimjer, vlasnik 10 bitcoina bi znao da najviše 2,1 milijuna ljudi (manje od 0.03% populacije) može ikad imati isto bitcoina kao i on. Premda je kroz povijest uvijek bilo oskudno, zlato nije imuno na povećanje ukupne količine. Ako se ikad izumi nova, ekonomičnija metoda rudarenja ili proizvodnje zlata, ukupna količina zlata bi se mogla dramatično povećati (npr. rudarenje morskog dna ili asteroida). Na kraju, fiat valute, relativno nov izum u povijesti, pokazale su se sklonima konstantnim povećanjima u količini. Države su pokazale stalnu sklonost inflaciji monetarne kvantitete kako bi rješavale kratkoročne političke probleme. Inflacijske tendencije vlada diljem svijeta čine fiat valute gotovo sigurnim da će gubiti vrijednost kroz vrijeme.
Etablirana povijest:
Nijedno monetarno dobro nema povijest kao zlato, koje je imalo vrijednost za cijelog trajanja ljudske civilizacije. Kovanice izrađene u antičko doba i danas imaju značajnu vrijednost. Ne može se isto reći za fiat valute, koje su same relativno nova povijesna anomalija. Od njihovog početka, fiat valute su imale gotovo univerzalni smjer prema bezvrijednosti. Korištenje inflacije kao podmuklog načina za nevidljivo oporezivanje građana je vječita kušnja kojoj se skoro nijedna država u povijesti nije mogla oduprijeti. Ako je 20. stoljeće, u kojem je fiat novac dominirao globalni monetarni poredak, demonstriralo neku ekonomsku istinu, to je onda bila ta da ne možemo računati na fiat novac da održi vrijednost u dužem ili srednjem vremenskom periodu. Bitcoin, usprkos svojoj novosti, je preživio dovoljno testova tržišta da postoji velika vjerojatnost da neće nestati kao vrijedno dobro. Nadalje, Lindy efekt govori da što duže Bitcoin bude korišten, to će veća biti vjera u njega i njegovu sposobnost da nastavi postojati dugo u budućnost. Drugim riječima, društvena vjera u monetarno dobro je asimptotička, kao u grafu ispod:

Ako Bitcoin preživi prvih 20 godina, imat će gotovo sveopće povjerenje da će trajati zauvijek, kao što ljudi vjeruju da je internet trajna stvar u modernom svijetu.
Otpor na cenzuru
Jedan od najbitnijih izvora za ranu potražnju bitcoina bila je njegova upotreba u ilegalnoj kupovini i prodaji droge. Mnogi su zato pogrešno zaključili da je primarna potražnja za bitcoinima utemeljena u njihovoj prividnoj anonimnosti. Međutim, Bitcoin nije anonimna valuta; svaka transakcija na mreži je zauvijek zapisana na javnom blockchainu. Povijesni zapis transakcija dozvoljava forenzičkoj analizi da identificira izvore i tijek sredstava. Takva analiza dovela je do uhićenja počinitelja zloglasne MtGox pljačke. Premda je istina da dovoljno oprezna i pedantna osoba može sakriti svoj identitet koristeći Bitcoin, to nije razlog zašto je Bitcoin bio toliko popularan u trgovini drogom.
Ključno svojstvo koje čini Bitcoin najboljim za takve aktivnosti je njegova agnostičnost i nepotrebnost za dozvolom (“premissionlessness”) na mrežnoj razini. Kada se bitcoini prenose na Bitcoin mreži, ne postoji nitko tko dopušta transakcije. Bitcoin je distribuirana peer-to-peer (korisnik-korisniku) mreža, i samim time dizajnirana da bude otporna na cenzuru. Ovo je u velikom kontrastu sa fiat bankarskim sustavom, u kojem države reguliraju banke i ostale institucije prijenosa novca, kako bi one prijavljivale i sprječavale protuzakonito korištenje monetarnih dobara. Klasičan primjer regulacije novca su kontrole kapitala. Npr., bogati milijunaš će vrlo teško prenijeti svoje bogatstvo u novu zemlju, kada bježi iz opresivnog režima. Premda zlato nije izdano i proizvedeno od države, njegova fizička priroda ga čini teško prenosivim kroz prostor, i samim time ga je daleko lakše regulirati nego Bitcoin. Indijski Akt kontrole zlata je primjer takve regulacije.
Bitcoin je odličan u većini gore navedenih svojstava, što mu omogućava da bude marginalno bolji od modernih i drevnih monetarnih dobara, te da pruži poticaje za svoje rastuće društveno usvajanje. Specifično, moćna kombinacija otpornosti na cenzuru i apsolutne oskudnosti bila je velika motivacija za bogate ulagače koji su uložili dio svojeg bogatstva u Bitcoin.
Evolucija novca
U modernoj monetarnoj ekonomiji postoji opsesija sa ulogom novca kao medija razmjene. U 20. stoljeću, države su monopolizirale izdavanje i kontrolu novca i kontinuirano potkopavale njegovo svojstvo spremišta vrijednosti, stvarajući lažno uvjerenje da je primarna svrha novca biti medij razmjene. Mnogi su kritizirali Bitcoin, govoreći da je neprikladan da bude novac zato što mu je cijena bila previše volatilna za medij razmjene. No, novac je uvijek evoluirao kroz etape; uloga spremišta vrijednosti je dolazila prije medija razmjene. Jedan od očeva marginalističke ekonomije, William Stanley Jevons, objašnjava:
"Povijesno govoreći… čini se da je zlato prvo služilo kao luksuzni metal za ukras; drugo, kao sačuvana vrijednost; treće, kao medij razmjene; i konačno, kao mjerilo vrijednosti."
U modernoj terminologiji, novac uvijek evoluira kroz četiri stadija:
- Kolekcionarstvo: U prvoj fazi svoje evolucije, novac je tražen samo zbog svojih posebnih svojstava, uglavnom zbog želja onog koji ga posjeduje. Školjke, perlice i zlato su bili sakupljani prije nego su poprimili poznatije uloge novca.
- Spremište vrijednosti: Jednom kada je novac tražen od dovoljnog broja ljudi, biti će prepoznat kao način za čuvanje i spremanje vrijednosti kroz vrijeme. Kada neko dobro postane široko korišteno kao spremište vrijednosti, njegova kupovna moć raste sa povećanom potražnjom za tu svrhu. Kupovna moć spremišta vrijednosti će u jednom trenutku doći do vrhunca, kada je dovolno rašireno i broj novih ljudi koji ga potražuju splasne.
- Sredstvo razmjene: Kada je novac potpuno etabliran kao spremište vrijednosti, njegova kupovna moć se stabilizira. Nakon toga, postane prikladno sredstvo razmjene zbog stabilnosti svoje cijene. U najranijim danima Bitcoina, mnogi ljudi nisu shvaćali koju buduću cijenu plaćaju koristeći bitcoine kao sredstvo razmjene, umjesto kao novonastalo spremište vrijednosti. Poznata priča o čovjeku koji je za 10,000 bitcoina (vrijednih oko 94 milijuna dolara kada je ovaj članak napisan) za dvije pizze ilustrira ovaj problem.
- Jedinica računanja vrijednosti: Jednom kada je novac široko korišten kao sredstvo razmjene, dobra će biti vrednovana u njemu, tj. većina cijena će biti izražena u njemu. Uobičajena zabluda je da je većinu dobara moguće zamijeniti za bitcoine danas. Npr., premda je možda moguće kupiti šalicu kave za bitcoine, izlistana cijena nije prava bitcoin cijena; zapravo se radi o cijeni u državnoj valuti koju želi trgovac, preračunatu u bitcoin po trenutnoj tržišnoj cijeni. Kad bi cijena bitcoina pala u odnosu na valutu, vrijednost šalice izražena u bitcoinima bi se povećala. Od trenutka kada trgovci budu voljni prihvaćani bitcoine kao platežno sredstvo, bez obraćanja pažnje na vrijednost bitcoina u državnoj fiat valuti, moći ćemo reći da je Bitcoin zaista postao jedinica računanja vrijednosti.
Monetarna dobra koja još nisu jedinice računanja vrijednosti možemo smatrati “djelomično monetiziranima.” Danas zlato ima takvu ulogu, jer je spremište vrijednosti, ali su mu uloge sredstva razmjene i računanja vrijednosti oduzete intervencijama država. Moguće je također da se jedno dobro koristi kao sredstvo razmjene, dok druga ispunjavaju ostale uloge. To je tipično u zemljama gdje je država disfunkcionalna, npr. Argentina ili Zimbabwe. U svojoj knjizi, Digitalno zlato, Nathaniel Popper piše:
"U Americi, dolar služi trima funkcijama novca: nudi sredstvo razmjene, jedinicu za mjerenje vrijednosti dobara, i mjesto gdje se može čuvati vrijednosti. S druge strane, argentinski peso je korišten kao sredstvo razmjene (za svakodnevne potrebe), ali ga nitko nije koristio kao spremište vrijednosti. Štednja u pesosima bila je ekvivalent bacanja novca. Zato su ljudi svu svoju štednju imali u dolarima, jer je dolar bolje čuvao vrijednost. Zbog volatilnosti pesosa, ljudi su računali cijene u dolarima, što im je pružalo pouzdaniju jedinicu mjerenja kroz vrijeme."
Bitcoin je trenutno u fazi tranzicije iz prvog stadija monetizacije u drugi. Vjerojatno će proći nekoliko godina prije nego Bitcoin pređe iz začetaka spremišta vrijednosti u istinski medij razmjene, i put do tog trenutka je još uvijek pun rizika i nesigurnosti. Važno je napomenuti da je ista tranzicija trajala mnogo stoljeća za zlato. Nitko danas živ nije doživio monetizaciju dobra u realnom vremenu (kroz koju Bitcoin prolazi), tako da nemamo puno iskustva govoriti o putu i načinu na koji će se monetizacija dogoditi.
Put monetizacije
Kroz proces monetizacije, monetarno dobro će naglo porasti u kupovnoj moći. Mnogi su tako komentirali da je uvećanje kupovne moći Bitcoina izgledalo kao “balon” (bubble). Premda je ovaj termin često korišten kako bi ukazao na pretjeranu vrijednosti Bitcoina, sasvim slučajno je prikladan. Svojstvo koje je uobičajeno za sva monetarna dobra jest da je njihova kupovna moć viša nego što se može opravdati samo kroz njihovu uporabnu vrijednost. Zaista, mnogi povijesni novci nisu imali uporabnu vrijednost. Razliku između kupovne moći i vrijednosti razmjene koju bi novac mogao imati za svoju inherentnu korisnost, možemo razmatrati kao “monetarnu premiju.” Kako monetarno dobro prolazi kroz stadije monetizacije (navedene gore), monetarna premija raste. No, ta premija ne raste u ravnoj i predvidivoj liniji. Dobro X, koje je bilo u procesu monetizacije, može izgubiti u usporedbi sa dobrom Y koje ima više svojstava novca, te monetarna premija dobra X drastično padne ili potpuno nestane. Monetarna premija srebra je skoro potpuno nestala u kasnom 19. stoljeću, kada su ga vlade diljem svijeta zamijenile zlatom kao novcem.
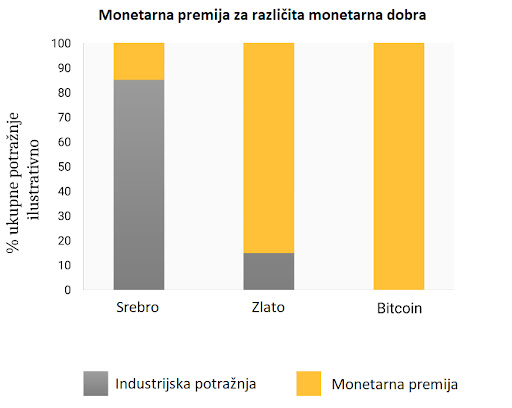
Čak i u odsustvu vanjskih faktora, kao što su intervencije vlade ili druga monetarna dobra, monetarna premija novog novca neće ići predvidivim putem. Ekonomist Larry White primijetio je:
"problem sa pričom “balona,” naravno, je da je ona konzistentna sa svakim putem cijene, i time ne daje ikakvo objašnjenje za specifičan put cijene"
Proces monetizacije opisuje teorija igara; svaki akter na tržištu pokušava predvidjeti agregiranu potražnju ostalih aktera, i time buduću monetarnu premiju. Zato što je monetarna premija nevezana za inherentnu korisnost, tržišni akteri se uglavnom vode za prošlim cijenama da bi odredili je li neko dobro jeftino ili skupo, i žele li ga kupiti ili prodati. Veza trenutne potražnje sa prošlim cijenama naziva se “ovisnost o putu” (path dependence); ona je možda najveći izvor konfuzije u shvaćanju kretanja cijena monetarnih dobara.
Kada kupovna moć monetarnog dobra naraste zbog većeg i šireg korištenja, očekivanja tržišta o definicijama “jeftinog” i “skupog” se mijenjaju u skladu s time. Slično tome, kada cijena monetarnog dobra padne, očekivanja tržišta mogu se promijeniti u opće vjerovanje da su prethodne cijene bile “iracionalne” ili prenapuhane. Ovisnost o putu novca ilustrirana je riječima poznatog upravitelja fondova s Wall Streeta, Josha Browna:
"Kupio sam bitcoine kada su koštali $2300, i to mi se udvostručilo gotovo odmah. Onda sam počeo govoriti kako “ne mogu kupiti još” dok im je cijena rasla, premda sam znao da je to razmišljanje bazirano samo na cijenu po kojoj sam ih kupio. Kasnije, kada je cijena pala zbog kineske regulacije mjenjačnica, počeo sam si govoriti, “Odlično, nadam se da će još pasti da mogu kupiti još.”"
Istina leži u tome da su ideje “jeftinog” i “skupog” zapravo besmislene kada govorimo o monetarnim dobrima. Cijena monetarnog dobra ne reflektira njegovu stopu rasprostanjenosti ili korisnosti, nego mjeru koliko je ono široko prihvaćeno da ispuni razne uloge novca.
Dodatna komplikacija u ovom aspektu novca je činjenica da tržišni akteri ne djeluju samo kao nepristrani promatrači koji pokušavaju kupiti i prodati u iščekivanju budućih kretanja monetarne premije, nego i kao aktivni proponenti. Pošto ne postoji objektivno “točna” monetarna premija, širiti dobar glas o superiornijim svojstvima nekog monetarnog dobra je efektivnije nego za obična dobra, čija vrijednost je u konačnici vezana na njegovu osnovnu korisnost. Religiozni zanos sudionika na Bitcoin tržištu vidljiv je na raznim internetskim forumima, gdje Bitcoineri aktivno promoviraju benefine Bitcoina i bogatstvo koje je moguće ostvariti investiranjem u njega. Promatrajući Bitcoin tržište, Leigh Drogen komentira:
"To je prepoznatljivo svima kao religija - priča koju si pričamo i oko koje se slažemo. Religija je krivulja na grafu prihvaćanja o kojoj trebamo razmišljati. Sustav je gotovo savršen - onog trenutka kada netko pristupi krugu Bitcoinera, to će reći svima i nastaviti širiti riječ. Onda njihovi prijatelji pristupe i nastave širiti riječ."
Premda usporedba sa religijom može staviti Bitcoin u iracionalno svjetlo, potpuno je racionalno za individualnog vlasnika da širi dobru vijest o superiornom monetarnom dobru, i za šire društvo da se standardizira oko njega. Novac djeluje kao temelj za svu trgovinu i štednju; tako da prihvaćanje superiornog oblika novca ima ogromne multiplicirajuće benefite za stvaranje bogatstva za sve članove društva.
Oblik monetizacije
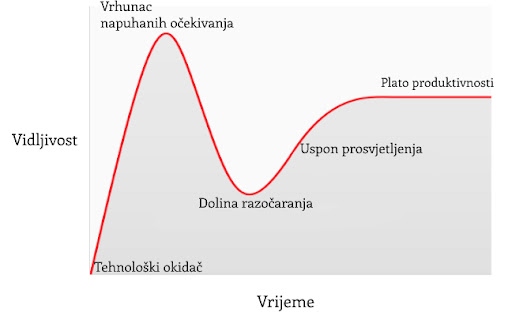
U članku o Spekulativnom prihvaćanju Bitcoina / teorije cijene, Michael Casey postulira da rastući Gartner hype ciklusi predstavljaju faze standardne S-krivulje prihvaćanja novih tehnologija, koje su bile prisutne kod mnogih transformacijskih tehnologija dok su postajale uobičajene u društvu.
Svaki Gartner hype ciklus počinje sa eksplozijom entuzijazma za novom tehnologijom, a cijenu podižu oni sudionici na tržištvu koji su “dostupni” u toj fazi. Najraniji kupci u Gartner hype ciklusu obično imaju jaku vjeru o transformacijskoj prirodi tehnologije u koju ulažu. S vremenom, tržište dosegne vrhunac entuzijazma kako se količina novih kupaca iscrpljuje, te kupovinom počnu dominirati spekulatori koji su više zainteresirani u brze profite nego u samu tehnologiju.
Nakon vrha hype ciklusa, cijene rapidno padaju dok spekulativno ludilo ustupa mjesto očajavanju, javnoj poruzi i osjećaju da tehnologija nije uopće bila transformacijska. S vremenom, cijena dosegne dno i formira plato na kojem se originalnim ulagačima, koji su imali snažno uvjerenje, pridružuju nove grupe ljudi koji su izdržali bol kraha cijena i koji cijene važnost same tehnologije.
Plato traje neko vrijeme i formira, kako Casey kaže, “stabilnu, dosadnu dolinu.” Za ovo vrijeme, javni interes za tehnologiju opada, no nastaviti će se razvijati i snažna zajednica uvjerenja će polako rasti. Tada, postavlja se nova baza za sljedeću iteraciju hype ciklusa, dok vanjski promatrači prepoznaju da tehnologija i dalje postoji i da ulaganje u nju možda nije onoliko rizično kao što se činilo za vrijeme pada cijene. Sljedeća iteracija hype ciklusa donosi mnogo veći broj novih ljudi, pa je i ciklus daleko veći u svojoj magnitudi.
Jako mali broj ljudi koji sudjeluju u Gartner hype ciklusu će točno predvidjeti koliko će visoko cijena porasti za vrijeme ciklusa. Cijene često dosegnu razine koje bi se činile apsurdnima većini ulagača u raniji stadijima ciklusa. Kada ciklus završi, mediji tipično atribuiraju pad cijene nekoj od aktualnih drušvenih tema. Premda takva tema može biti okidač pada, ona nikad nije temeljni razlog zašto ciklus završava. Gartner hype ciklusi završavaju kada je količina dostupnih novih sudionika na tržištu iscrpljena.
Zanimljivo je da je i zlato nacrtalo klasičan graf Gartner hype ciklusa od kasnih 1970-ih do ranih 2000-ih. Moguće je spekulirati da je hype ciklus osnovna socijalna dinamika oko procesa monetizacije.
Gartner kohorte
Od početka trgovanja Bitcoina na mjenjačnicama 2010. godine, Bitcoin tržište je svjedočilo četirima velikim Gartner hype ciklusima. U retrospektivi, možemo vrlo precizno identificirati grupe cijena prethodnih hype ciklusa Bitcoin tržišta. Također, možemo kvalitativno odrediti kohorte ulagača koje su povezane sa svakom iteracijom prethodnih ciklusa.
$ 0–$ 1 (2009. – 3. mjesec 2011.): Prvi hype ciklus u Bitcoin tržištu dominirali su kriptografi, računalni znanstvenici i cypherpunkovi koji su od početka bili spremni razumijeti važnost nevjerojatnog izuma Satoshija Nakamotoa, i koji su bili pioniri u potvrđivanju da Bitcoin protokol nema tehničkih mana.
$ 1–$ 30 (3. mjesec 2011. – 7. mjesec. 2011.): Drugi ciklus privukao je rane entuzijaste oko novih tehnologija kao i stabilan pritok ideološki motiviranih ulagača koji su bili oduševljeni idejom novca odvojenog od države. Libertarijanci poput Rogera Vera došli su u Bitcoin zbog aktivnog anti-institucionalnog stava, i mogućnosti koju je nova tehnologija obećavala. Wences Casares, briljantni i dobro povezani serijski poduzetnik, bio je također dio drugog Bitcoin hype ciklusa te je širio riječ o Bitcoinu među najprominentnijim tehnolozima i ulagačima u Silicijskoj Dolini.
$ 250–$ 1100 (4. mjesec 2013. – 12. mjesec 2013.): Treći hype ciklus doživio je ulazak ranih generalnih i institucionalnih ulagača koji su bili voljni uložiti trud i riskirati kroz užasno komplicirane kanale likvidnosti kako bi kupili bitcoine. Primaran izvor likvidnosti na tržištu za vrijeme ovog perioda bio je MtGox, mjenjačnica bazirana u Japanu, koju je vodio notorno nesposobni i beskrupulozni Mark Karpeles, koji je kasnije završio i u zatvoru zbog svoje uloge u kolapsu MtGoxa.
Valja primijetiti da je rast Bitcoinove cijene za vrijeme spomenuti hype ciklusa većinom povezano sa povećanjem likvidnosti i lakoćom sa kojom su ulagači mogli kupiti bitcoine. Za vrijeme prvog hype ciklusa, nisu postojale mjenjačnice; akvizicija bitcoina se odvijala primarno kroz rudarenje (mining) ili kroz izravnu razmjenu sa onima koju su već izrudarili bitcoine. Za vrijeme drugog hype ciklusa, pojavile su se rudimentarne mjenjačnice, no nabavljanje i osiguravanje bitcoina na ovim mjenjačnicama bilo je previše kompleksno za sve osim tehnološki najsposobnijih ulagača. Čak i za vrijeme trećeg hype ciklusa, ulagači koju su slali novac na MtGox kako bi kupili bitcoine su morali raditi kroz značajne prepreke. Banke nisu bile voljne imati posla sa mjenjačnicom, a oni posrednici koji su nudili usluge transfera bili su često nesposobni, kriminalni, ili oboje. Nadalje, mnogi koji su uspjeli poslati novac MtGoxu, u konačnici su morali prihvatiti gubitak svojih sredstava kada je mjenjačnica hakirana i kasnije zatvorena.
Tek nakon kolapsa MtGox mjenjačnice i dvogodišnje pauze u tržišnoj cijeni Bitcoina, razvili su se zreli i duboki izvori likvidnosti; primjeri poput reguliranih mjenjačnica kao što su GDAX i OTC brokeri kao Cumberland mining. Dok je četvrti hype ciklus započeo 2016. godine, bilo je relativno lako običnim ulagačima kupiti i osigurati bitcoine.
$ 1100 – $ 19600? (2014. –?):
U trenutku pisanja ovog teksta, tržište Bitcoina je prolazilo svoj četvrti veliki hype ciklus. Sudjelovanje u ovom hype ciklusu dominirala je ona skupina koju je Michael Casey opisao kao “rana većina” običnih i institucionalnih ulagača.
Kako su se izvori likvidnosti produbljivali i sazrijevali, veliki institucionalni ulagači sada imaju priliku sudjelovati kroz regulirana “futures” tržišta. Dostupnosti takvih tržišta stvara put ka kreaciji Bitcoin ETF-a (exchange traded fund) (fond na slobodnom tržištu), koji će onda pokrenuti “kasnu većinu” i “najsporije” u sljedećim hype ciklusima.
Premda je nemoguće predvidjeti točan efekt budućih hype ciklusa, razumno je očekivati da će najviša točka biti između $ 20.000 i $ 50.000 (2021. zenit je bio preko $ 69.000). Znatno više od ovog raspona, i Bitcoin bi imao znatan postotak ukupne vijednosti zlata (zlato i Bitcoin bi imali jednaku tržišnu kapitalizaciju kada bi bitcoini vrijedili oko $ 380.000 u trenutku pisanja ovog teksta). Značajan postotak vrijednosti zlata dolazi od potražnje centralnih banaka, te je malo vjerojatno da će centralne banke ili suverene države sudjelovati u trenutnom hype ciklusu.
Ulazak suverenih država u Bitcoin
Bitcoinov zadnji Gartner hype ciklus će započeti kada ga suverene države počnu akumulirati kao dio svojih rezervi stranih valuta. Tržišna kapitalizacija Bitcoina je trenutno premala da bismo ga smatrali značajnim dodatkom rezervama većini zemalja. No, kako se interes u privatnom sektoru povećava i kapitalizacija Bitcoina se približi trilijunu dolara, postat će dovoljno likvidan za većinu država. Prva država koja službeno doda bitcoine u svoje rezerve će vjerojatno potaknuti stampedo ostalih da učine isto. Države koje su među prvima u usvajanju Bitcoina imat će najviše benefita u svojim knjigama ako Bitcoin u konačnici postane globalna valuta (global reserve currency). Nažalost, vjerojatno će države sa najjačom izvršnom vlasti - diktature poput Sjeverne Koreje - biti najbrže u akumulaciji bitcoina. Neodobravanje prema takvim državama i slaba izvršna tijela zapadnjačkih demokracija uzrokovat će sporost i kašnjenje u akumulaciji bitcoina za njihove vlastite rezerve.
Velika je ironija u tome što je SAD trenutno jedna od regulatorno najotvorenijih nacija prema Bitcoinu, dok su Kina i Rusija najzatvorenije. SAD riskira najviše, geopolitički, ako bi Bitcoin zamijenio dolar kao svjetska rezervna valuta. U 1960-ima, Charles de Gaulle je kritizirao “pretjeranu privilegiju” (“exorbitant privilege”) koju su SAD imale u međunarodnom monetarnom poretku, postavljenom kroz Bretton Woods dogovor 1944. godine. Ruska i kineska vlada još ne shvaćaju geo-strateške benefite Bitcoina kao rezervne valute, te se trenutno brinu o efektima koje bi mogao imati na njihova unutarnja tržišta. Kao de Gaulle u 1960-ima, koji je prijetio SAD-u povratkom na klasični standard zlata, Kinezi i Rusi će s vremenom uvidjeti korist u velikoj poziciji u Bitcoinu - spremištu vrijednosti bez pokrića ijedne vlade. Sa najvećom koncentracijom rudara Bitcoina u Kini (2017.), kineska vlada već ima znatnu potencijalnu prednost u stavljanju bitcoina u svoje rezerve.
SAD se ponosi svojim statusom nacije inovatora, sa Silicijskom dolinom kao krunom svoje ekonomije. Dosad, Silicijska dolina je dominirala konverzacijom usmjerenom prema regulaciji, i poziciji koju bi ona treba zauzeti prema Bitcoinu. No, bankovna industrija i federalna rezerva SAD-a (US Federal Reserve, Fed) napokon počinju uviđati egzistencijalnu prijetnju koju Bitcoin predstavlja za američku monetarnu politiku, postankom globalne rezervne valute. Wall Street Journal, jedan od medijskih glasova federalne reserve, izdao je komentar o Bitcoinu kao prijetnji monetarnoj politici SAD-a:
"Postoji još jedna opasnost, možda i ozbiljnija iz perspektive centralnih banaka i regulatora: bitcoin možda ne propadne. Ako je spekulativni žar u kriptovalutu samo prvi pokazatelj njezinog šireg korištenja kao alternative dolaru, Bitcoin će svakako ugroziti monopol centralnih banaka nad novcem."
U narednim godinama, možemo očekivati veliku borbu između poduzetnika i inovatora u Silicijskoj dolini, koji će pokušavati čuvati Bitcoin od državne kontrole s jedne strane, i bankovne industrije i centralnih banaka koje će učiniti sve što mogu da bi regulirale Bitcoin kako bi spriječile znatne promjene u svojoj industriji i moći izdavanja novca, s druge.
Prijelaz na medij razmjene
Monetarno dobro ne može postati opće prihvaćen medij razmjene (standardna ekonomska definicija za “novac”) prije nego je vrednovano od širokog spektra ljudi; jednostavno, dobro koje nije vrednovano neće biti prihvaćeno u razmjeni. Kroz proces generalnog rasta vrijednosti, i time postanka spremišta vrijednosti, monetarno dobro će brzo narasti u kupovnoj moći, i time stvoriti cijenu za korištenje u razmjeni. Samo kada ta cijena rizika mijenjanja spremišta vrijednosti padne dovoljno nisko, može dobro postati opće prihvaćen medij razmjene.
Preciznije, monetarno dobro će biti prikladno kao medij razmjene samo kada je suma cijene rizika i transakcijske cijene u razmjeni manja nego u trgovini bez tog dobra.
U društvu koje vrši robnu razmjenu, prijelaz spremišta vrijednosti u medij razmjene može se dogoditi čak i onda kada monetarno dobro raste u kupovnoj moći, zato što su transakcijski troškovi robne razmjene iznimno visoki. U razvijenoj ekonomiji, u kojoj su troškovi razmjene niski, moguće je za mladu i rapidno rastućnu tehnologiju spremišta vrijednosti, poput Bitcoina, da se koristi kao medij razmjene, doduše na ograničen način. Jedan primjer je ilegalno tržište droge, gdje su kupci voljni žrtvovati oportunu cijenu čuvanja bitcoina kako bi umanjili znatan rizik kupovine droge koristeći fiat novac.
Postoje međutim velike institucionalne barijere da novonastalo spremište vrijednosti postane sveopće prihvaćen medij razmjene u razvijenom društvu. Države koriste oporezivanje kao moćnu metodu zaštite svojeg suverenog novca protiv rivalskih monetarnih dobara. Ne samo da suvereni novac ima prednost konstantnog izvora potražnje, zato što je porez moguće platiti jedino u njemu, nego su i rivalska monetarna dobra oporezana pri svakoj razmjeni za vrijeme rastuće cijene. Ova metoda oporezivanja stvara znatan otpor korištenju spremišta vrijednosti kao medija razmjene.
Ovakvo sabotiranje tržišnih monetarnih dobara nije nepremostiva barijera za njihovo prihvaćanje kao općeg medija razmjene. Ako ljudi izgube vjeru u suvereni novac, njegova vrijednost može rapidno propasti kroz proces zvan hiperinflacija. Kada suvereni novac prolazi kroz hiperinflaciju, njegova vrijednost propadne prvo u usporedbi sa najlikvidnijim dobrima u društvu, kao što je zlato ili stabilna strana valuta (američki dolar npr.), ako su ona dostupna. Kada nema likvidnih dobara ili ih ima premalo, novac u hiperinflaciji kolabira u usporedbi sa stvarnim dobrima, kao što su nekretnine ili upotrebljiva roba. Arhetipska slika hiperinflacije je trgovina sa praznim policama - potrošači brzo bježe iz propadajuće vrijednosti novca svoje nacije.

Nakon dovoljno vremena, kada je vjera potpuno uništena za vrijeme hiperinflacije, suvereni novac više nitko ne prihvaća, te se društvo može vratiti na robnu razmjenu, ili će doživjeti potpunu zamjenu monetarne jedinice za sredstvo razmjene. Primjer ovog procesa bila je zamjena zimbabveanskog dolara za američki dolar. Takva promjena suverenog novca za stranu valutu je dodatno otežana relativnom oskudnošću strane valute i odsustvom stranih bankarskih institucija koje pružaju likvidnost tržištu.
Sposobnost lakog prenošenja bitcoina preko granica i odsustvo potrebe za bankarskim sustavom čine Bitcoin idealnim monetarnim dobrom za one ljude koji pate pod hiperinflacijom. U nadolazećim godinama, kako fiat valute nastave svoj povijesni trend ka bezvrijednosti, Bitcoin će postati sve popularniji izbor za ušteđevine ljudi diljem svijeta. Kada je novac nacije napušten i zamijenjen Bitcoinom, Bitcoin će napraviti tranziciju iz spremišta vrijednosti u tom društvu u opće prihvaćeno sredstvo razmjene. Daniel Krawicz stvorio je termin “hiperbitcoinizacija” da bi opisao ovaj proces.
Učestala pogrešna shvaćanja
Većina ovog članka usredotočila se na monetarnu prirodu Bitcoina. Sa tim temeljima možemo adresirati neke od najčešćih nerazumijevanja u Bitcoinu.
Bitcoin je balon (bubble)
Bitcoin, kao sva tržišna monetarna dobra, posjeduje monetarnu premiju. Ona često rezultira uobičajenom kritikom da je Bitcoin samo “balon.” No, sva monetarna dobra imaju monetarnu premiju. Naprotiv, ta monetarna premija (cijena viša od one koju diktira potražnja za dobrom kao korisnim) je upravo karakteristična za sve oblike novca. Drugim riječima, novac je uvijek i svuda balon. Paradoksalno, monetarno dobro je istovremeno balon i ispod vrijednosti ukoliko je u ranijim stadijima općeg prihvaćanja kao novac.
Bitcoin je previše volatilan
Volatilnost cijene Bitcoina je funkcija njegovog nedavnog nastanka. U prvih nekoliko godina svojeg postojanja, Bitcoin se ponašao kao mala dionica, i svaki veliki kupac - kao npr. braća Winklevoss - mogao je uzrokovati veliki skok u njegovoj cijeni. No, kako su se prihvaćenost i likvidnost povećavali kroz godine, volatilnost Bitcoina je srazmjerno smanjila. Kada Bitcoin postigne tržišnu kapitalizaciju (vrijednost) zlata, imat će sličnu volatilnost kao i zlato. Kako Bitcoin nastavi rasti, njegova volatilnost će se smanjiti do razine koja ga čini prikladnim za široko korištenje kao medij razmjene. Kao što je prethodno rečeno, monetizacija Bitcoina se odvija u seriji Gartner hype ciklusa. Volatilnost je najniža za vrijeme vrhunaca i dolina unutar ciklusa. Svaki hype ciklus ima nižu volatilnost od prethodnih, zato što je likvidnost tržišta veća.
Cijene transakcija su previsoke
Novija kritika Bitcoin mreže je ta da ju je povećanje cijena prijenosa bitcoina učinilo neprikladnom za sustav plaćanja. No, rast u cijenama transakcija je zdrav i očekivan. One su nužne za plaćanje bitcoin minera (rudara), koji osiguravaju mrežu validacijom transakcija. Rudare se plaća kroz cijene transakcija ili kroz blok-nagrade, koje su inflacijska subvencija od trane trenutnih vlasnika bitcoina.
S obzirom na Bitcoinovu fiksnu proizvodnju (monetarna politika koja ga čini idealnim za spremanje vrijednosti), blok-nagrade će s vremenom nestati i mrežu će se u konačnici morati osiguravati kroz cijene transakcija. Mreža sa “niskim” cijenama transakcija je mreža sa slabom sigurnosti i osjetljiva na vanjsku intervenciju i cenzuru. Oni koji hvale niske cijene Bitcoinovih alternative zapravo niti ne znajući opisuju slabosti tih takozvanih “alt-coina.”
Površan temelj kritika Bitcoinovih “visokih” cijena transakcija je uvjerenje da bi Bitcoin trebao biti prvo sustav plaćanja, i drugo spremište vrijednosti. Kao što smo vidjeli kroz povijest novca, ovo uvjerenje je naopako. Samo onda kada Bitcoin postane duboko ukorijenjeno spremište novca može biti prikladan kao sredstvo razmjene. Nadalje, kada oportunitetni trošak razmjene bitcoina dođe na razinu koja ga čini prikladnim sredstvom razmjene, većina trgovine neće se odvijati na samoj Bitcoin mreži, nego na mrežama “drugog sloja” (second layer) koje će imati niže cijene transakcija. Takve mreže, poput Lightning mreže, služe kao moderna verzija zadužnica koje su korištene za prijenos vlasničkih papira zlata u 19. stoljeću. Banke su koristile zadužnice zato što je prijenos samog metala bio daleko skuplji. Za razliku od takvih zadužnica, Lightning mreža će omogućavati nisku cijenu prijenosa bitcoina bez potrebe za povjerenjem prema trećoj strani, poput banaka. Razvoj Lightning mreže je tehnološka inovacija od izuzetne važnosti u povijesti Bitcoina, i njezina vrijednost će postati očita u narednim godinama, kako je sve više ljudi bude razvijalo i koristilo.
Konkurencija
Pošto je Bitcoin softverski protokol otvorenog tipa (open-source), oduvijek je bilo moguće kopirati softver i imitirati mrežu. Kroz godine nastajali su mnogi imitatori, od identičnih kopija, kao Litecoin, do kompleksnijih varijanti kao što je Ethereum, koje obećavaju arbitrarno kompleksne ugovorne mehanizme koristeći decentralizirani računalni sustav. Česta kritika Bitcoinu od strane ulagača je ta da on ne može zadržati svoju vrijednost kada je vrlo lako stvoriti konkurente koji mogu lako i brzo u sebi imati najnovije inovacije i softverske funkcionalnosti.

Greška u ovom argumentu leži u manju takozvanog “mrežnog efekta” (network effect), koji postoji u prvoj i dominantnoj tehnologiji u nekom području. Mrežni efekt - velika vrijednost korištenja Bitcoina samo zato što je već dominantan - je važno svojstvo samo po sebi. Za svaku tehnologiju koja posjeduje mrežni efekt, to je daleko najvažnije svojstvo koje može imati.
Za Bitcoin, mrežni efekt uključuje likvidnost njegovog tržišta, broj ljudi koji ga posjeduju, i zajednicu programera koji održavaju i unaprjeđuju njegov softver i svjesnost u javnosti. Veliki ulagači, uključujući države, će uvijek prvo tražiti najlikvidnije tržište, kako bi mogli ući i izaći iz tržišta brzo, i bez utjecanja na cijenu. Programeri će se pridružiti dominantnoj programerskoj zajednici sa najboljim talentom, i time pojačati samu zajednicu. Svjesnost o brendu sama sebe pojačava, pošto se nadobudni konkurenti Bitcoina uvijek spominju u kontekstu Bitcoina kao takvog.
Raskrižje na putu (fork)
Trend koji je postao popularan 2017. godine nije bio samo imitacija Bitcoinovog softvera, nego kopiranje potpune povijesti njegovih prošlih transakcija (cijeli blockchain). Kopiranjem Bitcoinovog blockchaina do određene točke/bloka i odvajanjem sljedećih blokova ka novoj mreži, u procesu znanom kao “forking” (odvajanje), Bitcoinovi konkurenti su uspjeli riješiti problem distribuiranja svojeg tokena velikom broju korisnika.

Najznačajniji takav fork dogodio se 1. 8. 2017. godine, kada je nova mreža nazvana Bitcoin Cash (Bcash) stvorena. Vlasnik N količine bitcoina prije 1.8.2017. bi onda posjedovao N bitcoina i N BCash tokena. Mala, ali vrlo glasna zajednica Bcash proponenata je neumorno pokušavala prisvojiti Bitcoinov brend i ime, imenujući svoju novu mrežu Bitcoin Cast i pokušavajući uvjeriti nove pridošlice u Bitcoin da je Bcash “pravi” Bitcoin. Ti pokušaji su većinom propali, i taj neuspjeh se vidi u tržišnim kapitalizacijama dviju mreža. No, za nove ulagače, i dalje postoji rizik da bi konkurent mogao kopirati Bitcoin i njegov blockchain i tako uspjeti u preuzimanju tržišne kapitalizacije, te postati de facto Bitcoin.
Moguće je uočiti važno pravilo gledajući velike forkove u prošlosti Bitcoin i Ethereum mreža. Većina tržišne kapitalizacije odvijat će se na mreži koja zadrži najviši stupanj talenta i aktivnosti u zajednici programera. Premda se na Bitcoin može gledati kao na nov i mlad novac, on je također računalna mreža koja počiva na softveru, kojeg se pak treba održavati i poboljšavati. Kupovina tokena na mreži koja ima malo neiskusnih programera bilo bi kao kupovati kopiju Microsoft Windowsa na kojoj rade lošiji programeri. Jasno je vidljivo iz povijesti forkova koji su se odvili 2017. godine da su najbolji računalni i kriptografski stručnjaci posvećeni razvoju originalnog Bitcoina, a ne nekoj od rastućeg broja imitacija koje su se izrodile iz njega.
Stvarni rizici
Premda su uobičajene kritike upućene Bitconu od strane medija i ekonomske profesije krive i bazirane na netočnom shvaćanju novca, postoje pravi i značajni rizici kod ulaganja u Bitcoin. Bilo bi mudro za novog Bitcoin ulagača da shvati ove rizike prije potencijalnog ulaganja.
Rizik protokola
Bitcoin protokol i kriptografski sastavni dijelovi na kojima je sagrađen potencijalno imaju dosad nepronađenu grešku u svom dizajnu, ili mogu postati nesigurni razvojem kvantnih računala. Ako se pronađe greška u protokolu, ili neka nova metoda računarstva učini mogućim probijanje kriptografskih temelja Bitcoina, vjera u Bitcoin biti će znatno narušena. Rizik protokola bio je najviši u ranim godinama razvoja Bitcoina, kada je još uvijek bilo nejasno, čak i iskusnim kriptografima, je li Satoshi Nakamoto zaista riješio problem bizantskih generala (Byzantine Generals’ Problem). Brige oko ozbiljnih grešaka u Bitcoin protokolu nestale su kroz godine, no uzevši u obzir njegovu tehnološku prirodu, rizik protokola će uvijek ostati u Bitcoinu, makar i kao izuzetak.
Propadanje mjenjačnica
Time što je decentraliziran, Bitcoin je pokazao značajnu otpornost, suočen sa brojnim pokušajima raznih vlada da ga reguliraju ili unište. No, mjenjačnice koje trguju bitcoinima za fiat valute su centralizirani entiteti i podložne regulacijama i zatvaranju. Bez mjenjačnica i volje bankara da s njima posluju, proces monetizacije Bitcoina bio bi ozbiljno usporen, ako ne i potpuno zaustavljen. Iako postoje alternativni izvori likvidnosti za Bitcoin, poput “over-the-counter” brokera i decentraliziranih tržišta za kupovinu i prodaju bitcoina, kritičan proces otkrivanja i definiranja cijene se odvija na najlikvidnijim mjenjačnicama, koje su sve centralizirane.
Jedan od načina za umanjivanje rizika gašenja mjenjačnica je geografska arbitraža. Binance, jedna od velikih mjenjačnica iz Kine, preselila se u Japan nakon što joj je kineska vlada zabranila operiranje u Kini. Vlade su također oprezne kako ne bi ugušile novu industriju koja je potencijalno značajna kao i internet, i time predale nevjerojatnu konkurentnu vrijednost drugim nacijama.
Samo kroz koordinirano globalno ukidanje Bitcoin mjenjačnica bi proces monetizacije mogao biti zaustavljen. Trenutno smo u utrci; Bitcoin raste i postaje sve rašireniji, i doći će do trenutka kada bi potpuno ukidanje mjenjačnica postalo politički neizvedivo - kao i gašenje interneta. Mogućnost takvog ukidanja je još uvijek realna, i valja je uzeti u obzir pri ulaganju u Bitcoin. Kao što je gore objašnjeno, suverene vlade se polako bude i uviđaju prijetnju koju predstavlja neovisna digitalna valuta otporna na cenzuru, za njihovu monetarnu politiku. Otvoreno je pitanje hoće li išta poduzeti da odgovore ovoj prijetnji prije nego Bitcoin postane toliko utvrđen i raširen da politička akcija postane nemoćna i ne-efektivna.
Zamjenjivost
Otvorena i transparentna priroda Bitcoin blockchaina omogućava državama da proglase specifične bitcoine “okaljanima” zbog njihovog korištenja u određenim aktivnostima. Premda Bitcoin, na protokolarnoj razini, ne diskriminira transakcije na ikoji način, “okaljani” bitcoini bi mogli postati bezvrijedni ako bi ih regulacije proglasile ilegalnima i neprihvatljivima za mjenjačnice ili trgovce. Bitcoin bi tada izgubio jedno od kritičnih svojstava monetarnog dobra: zamjenjivost.
Da bi se ovaj problem riješio i umanjio, biti će potrebna poboljšanja na razini protokola kako bi se poboljšala privatnost transakcija. Premda postoji napredak u ovom smjeru, prvi put primjenjen u digitalnim valutama kao što su Monero i Zcash, potrebno je napraviti značajne tehnološke kompromise između efikasnosti i kompleksnosti Bitcoina i njegove privatnosti. Pitanje ostaje otvoreno je li moguće dodati nova svojstva privatnosti na Bitcoin, na način koji neće kompromitirati njegovu korisnost kao novca.
Zaključak
Bitcoin je novonastali novac koji je u procesu transformacije iz sakupljačkog dobra u spremište vrijednosti. Kao neovisno monetarno dobro, moguće je da će u budućnosti postati globalan novac, slično kao zlato za vrijeme 19. stoljeća. Prihvaćanje Bitcoina kao globalnog novca je upravo taj optimističan scenarij za Bitcoin, kojeg je artikulirao Satoshi Nakamoto još 2010. godine u email razmjeni sa Mikeom Hearnom:
"Ako zamisliš da se koristi u nekom dijelu svjetske trgovine, i da će postojati samo 21 milijun bitcoina za cijeli svijet, vrijednost po jedinici će biti znatno veća".
Ovaj scenarij je još snažnije definirao briljantni kriptograf Hal Finney, koji je ujedno primio i prve bitcoine od Nakamotoa, ubrzo nakon najave prvog funkcionalnog Bitcoin softvera:
"Zamislimo da Bitcoin bude uspješan i postane dominantan sustav plaćanja diljem svijeta. U tom slučaju će ukupna vrijednost valute biti jednaka ukupnoj vrijednosti svog bogatstva svijeta. Današnje procjene ukupnog svjetskog bogatska kućanstava koje sam pronašao borave negdje između 100 i 300 trilijuna dolara. Sa 20 milijuna bitcoina, svaki bi onda vrijedio oko 10 milijuna dolara."
Čak i da Bitcoin ne postane u cijelost globalan novac, nego da se samo natječe sa zlatom kao neovisno spremište vrijednosti, i dalje je masivno podcijenjen. Mapiranje tržišne kapitalizacije postojeće količine izrudarenog zlata (oko 8 trilijuna dolara) na maksimalnu dostupnost Bitcoina od 21 milijun, daje vrijednost od otprilike 380,000 dolara po bitcoinu. Kao što smo vidjeli u prethodnom tekstu, svojstva koja omogućavaju monetarnom dobru da bude prikladno spremište vrijednosti, čine Bitcoin superiornijim zlatu u svakom pogledu osim trajanja povijesti. No, kako vrijeme prolazi i Lindy efekt postane jači, dosadašnja povijest će prestati biti prednost zlata. Samim time, nije nerazumno očekivati da će Bitcoin narasti do, a možda i preko, ukupne cijene zlata na tržištvu do 2030. Opaska ovoj tezi je činjenica da veliki postotak vrijednosti zlata dolazi od toga što ga centralne banke čuvaju kao spremište vrijednosti. Da bi Bitcoin došao do te razine, određena količina suverenih država će trebati sudjelovati. Hoće li zapadnjačke demokracije sudjelovati u vlasništvu Bitcoina je nepoznato. Vjerojatnije je, nažalost, da će prve nacije u Bitcoin tržištu biti sitne diktature i kleptokracije.
Ako niti jedna država ne bude sudjelovala u Bitcoin tržištu, optimistična teza i dalje postoji. Kao nevisno spremište vrijednosti u rukama individualnih i institucionalnih ulagača, Bitcoin je i dalje vrlo rano u svojoj “krivulji prihvaćenosti” (adoption curve); tzv. “rana većina” ulaze na tržište sada, dok će ostali ući tek nekoliko godina kasnije. Sa širim sudjelovanjem individualnih i institucionalnih ulagača, cijena po bitcoinu između 100,000 i 200,000 dolara je sasvim moguća.
Posjedovanje bitcoina je jedna od malobrojnih asimetričnih novčanih strategija dostupnih svakome na svijetu. Poput “call” opcija, negativan rizik ulagača je ograničen na 1x, dok potencijalna dobit i dalje iznosi 100x ili više. Bitcoin je prvi istinski globalan balon čija je veličina ograničena samo potražnjom i željom građana svijeta da zaštite svoju ušteđevinu od raznovrsnih ekonomskih malverzacija vlade. Bitcoin je ustao kao feniks iz pepela globalne financijske krize 2008. godine - katastrofe kojoj su prethodile odluke centralnih banaka poput američke Federalne rezerve (Federal Reserve).
Onkraj samo financijske teze za Bitcoin, njegov rast i uspjeh kao neovisno spremište vrijednosti imat će duboke geopolitičke posljedice. Globalna, ne-inflacijska valuta će prisiliti suverene države da promjene svoje primarne mehanizme financiranja od inflacije u izravno oporezivanje; koje je daleko manje politički popularno. Države će se smanjivati proporcionalno političkoj boli koju im nanese oporezivanje kao jedini način financiranja. Nadalje, globalna trgovina vršiti će se na način koji zadovoljava aspiraciju Charlesa de Gaullea, da nijedna nacija ne bi smjela imati privilegiju nad ikojom drugom:
"Smatramo da je potrebno da se uspostavi međunarodna trgovina, kao što je bio slučaj prije velikih nesreća koje su zadesile svijet, na neosporivoj monetarnoj bazi, koja ne nosi na sebi oznaku ijedne države."
Za 50 godina, ta monetarna baza biti će Bitcoin.
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.
-
 @ c1e9ab3a:9cb56b43
2025-03-09 20:13:44
@ c1e9ab3a:9cb56b43
2025-03-09 20:13:44Introduction
Since the mid-1990s, American media has fractured into two distinct and increasingly isolated ecosystems, each with its own Overton window of acceptable discourse. Once upon a time, Americans of different political leanings shared a common set of facts, even if they interpreted them differently. Today, they don’t even agree on what the facts are—or who has the authority to define them.
This divide stems from a deeper philosophical rift in how each side determines truth and legitimacy. The institutional left derives its authority from the expert class—academics, think tanks, scientific consensus, and mainstream media. The populist right, on the other hand, finds its authority in traditional belief systems—religion, historical precedent, and what many call "common sense." As these two moral and epistemological frameworks drift further apart, the result is not just political division but the emergence of two separate cultural nations sharing the same geographic space.
The Battle of Epistemologies: Experts vs. Tradition
The left-leaning camp sees scientific consensus, peer-reviewed research, and institutional expertise as the gold standard of truth. Universities, media organizations, and policy think tanks function as arbiters of knowledge, shaping the moral and political beliefs of those who trust them. From this perspective, governance should be guided by data-driven decisions, often favoring progressive change and bureaucratic administration over democratic populism.
The right-leaning camp is skeptical of these institutions, viewing them as ideologically captured and detached from real-world concerns. Instead, they look to religion, historical wisdom, and traditional social structures as more reliable sources of truth. To them, the "expert class" is not an impartial source of knowledge but a self-reinforcing elite that justifies its own power while dismissing dissenters as uneducated or morally deficient.
This fundamental disagreement over the source of moral and factual authority means that political debates today are rarely about policy alone. They are battles over legitimacy itself. One side sees resistance to climate policies as "anti-science," while the other sees aggressive climate mandates as an elite power grab. One side views traditional gender roles as oppressive, while the other sees rapid changes in gender norms as unnatural and destabilizing. Each group believes the other is not just wrong, but dangerous.
The Consequences of Non-Overlapping Overton Windows
As these worldviews diverge, so do their respective Overton windows—the range of ideas considered acceptable for public discourse. There is little overlap left. What is considered self-evident truth in one camp is often seen as heresy or misinformation in the other. The result is:
- Epistemic Closure – Each side has its own trusted media sources, and cross-exposure is minimal. The left dismisses right-wing media as conspiracy-driven, while the right views mainstream media as corrupt propaganda. Both believe the other is being systematically misled.
- Moralization of Politics – Since truth itself is contested, policy debates become existential battles. Disagreements over issues like immigration, education, or healthcare are no longer just about governance but about moral purity versus moral corruption.
- Cultural and Political Balkanization – Without a shared understanding of reality, compromise becomes impossible. Americans increasingly consume separate news, live in ideologically homogeneous communities, and even speak different political languages.
Conclusion: Two Nations on One Land
A country can survive disagreements, but can it survive when its people no longer share a common source of truth? Historically, such deep societal fractures have led to secession, authoritarianism, or violent conflict. The United States has managed to avoid these extremes so far, but the trendline is clear: as long as each camp continues reinforcing its own epistemology while rejecting the other's as illegitimate, the divide will only grow.
The question is no longer whether America is divided—it is whether these two cultures can continue to coexist under a single political system. Can anything bridge the gap between institutional authority and traditional wisdom? Or are we witnessing the slow but inevitable unraveling of a once-unified nation into two separate moral and epistemic realities?
-
 @ 291c75d9:37f1bfbe
2025-03-08 04:09:59
@ 291c75d9:37f1bfbe
2025-03-08 04:09:59In 1727, a 21-year-old Benjamin Franklin gathered a dozen men in Philadelphia for a bold experiment in intellectual and civic growth. Every Friday night, this group—known as the Junto, from the Spanish juntar ("to join")—met in a tavern or private home to discuss "Morals, Politics, or Natural Philosophy (science)." Far from a casual social club, the Junto was a secret society dedicated to mutual improvement, respectful discourse, and community betterment. What began as a small gathering of tradesmen and thinkers would leave a lasting mark on Franklin’s life and colonial America.
Printers are educated in the belief that when men differ in opinion, both sides ought equally to have the advantage of being heard by the public, and that when Truth and Error have fair play, the former is always an overmatch for the latter. - Benjamin Franklin
The Junto operated under a clear set of rules, detailed by Franklin in his Autobiography:
"The rules that I drew up required that every member, in his turn, should produce one or more queries on any point of Morals, Politics, or Natural Philosophy, to be discuss’d by the company; and once in three months produce and read an essay of his own writing, on any subject he pleased. Our debates were to be under the direction of a president, and to be conducted in the sincere spirit of inquiry after truth, without fondness for dispute, or desire of victory; and, to prevent warmth [heatedness], all expressions of positiveness in opinions, or direct contradiction, were after some time made contraband and prohibited under small pecuniary penalties [monetary fines]."
These guidelines emphasized collaboration over competition. Members were expected to contribute questions or essays, sparking discussions that prioritized truth over ego. To keep debates civil, the group even imposed small fines for overly assertive or contradictory behavior—a practical nudge toward humility and open-mindedness. (Yes, I believe that is an ass tax!)
Rather than admitting new members, Franklin encouraged existing ones to form their own discussion groups. This created a decentralized network of groups ("private relays," as I think of them), echoing the structure of modern platforms like NOSTR—while preserving the Junto’s exclusivity and privacy.
From the beginning, they made it a rule to keep these meetings secret, without applications or admittance of new members. Instead, Franklin encouraged members to form their own groups—in a way acting as private relays of sorts. (I say "private" because they continued to keep the Junto secret, even with these new groups.)
Membership: A Diverse Circle United by Values
The Junto’s twelve founding members came from varied walks of life—printers, surveyors, shoemakers, and clerks—yet shared a commitment to self-improvement. Franklin, though the youngest (around 21 when the group formed), led the Junto with a vision of collective growth. To join, candidates faced a simple vetting process, answering four key questions:
- Have you any particular disrespect for any present members? Answer: I have not.
- Do you sincerely declare that you love mankind in general, of what profession or religion soever? Answer: I do.
- Do you think any person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship? Answer: No.
- Do you love truth for truth’s sake, and will you endeavor impartially to find and receive it yourself and communicate it to others? Answer: Yes.
These criteria reveal the Junto’s core values: respect, tolerance, and an unwavering pursuit of truth. They ensured that members brought not just intellect but also character to the table—placing dialogue as the priority.
One should also note the inspiration from the "Dry Club" of John Locke, William Popple, and Benjamin Furly in the 1690s. They too required affirmation to:
- Whether he loves all men, of what profession or religion soever?
- Whether he thinks no person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship?
- Whether he loves and seeks truth for truth’s sake; and will endeavor impartially to find and receive it himself, and to communicate it to others?
And they agreed: "That no person or opinion be unhandsomely reflected on; but every member behave himself with all the temper, judgment, modesty, and discretion he is master of."
The Discussions: 24 Questions to Spark Insight
Franklin crafted a list of 24 questions to guide the Junto’s conversations, ranging from personal anecdotes to civic concerns. These prompts showcase the group’s intellectual breadth. Here are some of my favorites:
Hath any citizen in your knowledge failed in his business lately, and what have you heard of the cause? Have you lately heard of any citizen’s thriving well, and by what means? Do you know of any fellow citizen who has lately done a worthy action, deserving praise and imitation? Do you think of anything at present in which the Junto may be serviceable to mankind, their country, friends, or themselves? Have you lately observed any defect in the laws of your country, which it would be proper to move the legislature for an amendment? Do you know of any deserving young beginner lately set up, whom it lies in the power of the Junto any way to encourage?
(Read them all here.)
Note the keen attention to success and failure, and the reflection on both. Attention was often placed on the community and individual improvement beyond the members of the group. These questions encouraged members to share knowledge, reflect on virtues and vices, and propose solutions to real-world problems. The result? Discussions that didn’t just end at the tavern door but inspired tangible community improvements.
The Junto’s Legacy: America’s First Lending Library
One of the Junto’s most enduring contributions to Philadelphia—and indeed, to the American colonies—was the creation of the first lending library in 1731. Born from the group’s commitment to mutual improvement and knowledge-sharing, this library became a cornerstone of public education and intellectual life in the community.
The idea for the library emerged naturally from the Junto’s discussions. Members, who came from diverse backgrounds but shared a passion for learning, recognized that their own access to books was often limited and costly—and they referred to them often. To address this, they proposed pooling their personal collections to create a shared resource. This collaborative effort allowed them—and eventually the broader public—to access a wider range of books than any individual could afford alone.
The library operated on a simple yet revolutionary principle: knowledge should be available to all, regardless of wealth or status. By creating a lending system, the Junto democratized access to information, fostering a culture of self-education and curiosity. This was especially significant at a time when books were scarce and formal education was not universally accessible.
The success of the Junto’s library inspired similar initiatives across the colonies, laying the groundwork for the public library system we know today. It also reflected the group’s broader mission: to serve not just its members but the entire community. The library became a symbol of the Junto’s belief in the power of education to uplift individuals and society alike.
With roots extending back to the founding of the Society in 1743, the Library of the American Philosophical Society houses over thirteen million manuscripts, 350,000 volumes and bound periodicals, 250,000 images, and thousands of hours of audiotape. The Library’s holdings make it one of the premier institutions for documenting the history of the American Revolution and Founding, the study of natural history in the 18th and 19th centuries, the study of evolution and genetics, quantum mechanics, and the development of cultural anthropology, among others.
The American Philosophical Society Library continues today. I hope to visit it myself in the future.
Freedom, for Community
Comparing the Junto to Nostr shows how the tools of community and debate evolve with time. Both prove that people crave spaces to connect, share, and grow—whether in a colonial tavern or a digital relay. Yet their differences reveal trade-offs: the Junto’s structure offered depth and focus but capped its reach, while Nostr’s openness promises scale at the cost of order.
In a sense, Nostr feels like the Junto’s modern echo—faster, bigger, and unbound by gates or rules. Franklin might admire its ambition, even if he’d raise an eyebrow at its messiness. For us, the comparison underscores a timeless truth: no matter the medium, the drive to seek truth and build community endures.
The Autobiography of Benjamin Franklin (1771–1790, pub. 1791)
http://www.benjamin-franklin-history.org/junto-club/
Benjamin Franklin, Political, Miscellaneous, and Philosophical Pieces, ed. Benjamin Vaughan (London: 1779), pp. 533–536.
"Rules of a Society" in The Remains of John Locke, Esq. (1714), p. 113
npubpro
-
 @ bf47c19e:c3d2573b
2025-05-11 21:32:19
@ bf47c19e:c3d2573b
2025-05-11 21:32:19Bitkoin, kao jedinstvena digitalna valuta, postaje poznat široj javnosti u trenutku kada se pojavljuju prvi znaci svetske ekonomske krize a postojeći finansijski sistem počinje da pokazuje sve svoje slabosti. Danas, bitkoin, izaziva veliku pažnju svojim naglim skokovima i padovima.
Osnovna ideja o o decentralizovanim valutama potekla je od osnivača kripto-pank pokreta, među kojima su bili direktori kompanija naprednih tehnologija, univerzitetski profesori i istraživači iz oblasti matematike i fizike. Njihova ideja zasnovana je na anonimnoj, istovremenoj komunikaciji koja neće biti kontrolisana i nadgledana od neke treće strane u procesu.
Šta je kriptovaluta, ko je njen tvorac, kako do nje doći, kako trgovati i gde je čuvati, neka su od pitanja za čijim odgovorima tragamo u emisiji.
Sagovornici u emisiji su svi oni koji su u poslednjih godinu dana bili relevantni učesnici priča o kriptovaluti u Srbiji: osnivači Asocijacije bitkoin, predstavnici Narodne banke Srbije i predstavnici medija.
Montažer Milan Radičević
Urednik Aleksandra Šarković
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ c48e29f0:26e14c11
2025-03-07 04:51:09
@ c48e29f0:26e14c11
2025-03-07 04:51:09ESTABLISHMENT OF THE STRATEGIC BITCOIN RESERVE AND UNITED STATES DIGITAL ASSET STOCKPILE EXECUTIVE ORDER March 6, 2025
By the authority vested in me as President by the Constitution and the laws of the United States of America, it is hereby ordered:
Section 1. Background.
Bitcoin is the original cryptocurrency. The Bitcoin protocol permanently caps the total supply of bitcoin (BTC) at 21 million coins, and has never been hacked. As a result of its scarcity and security, Bitcoin is often referred to as “digital gold”. Because there is a fixed supply of BTC, there is a strategic advantage to being among the first nations to create a strategic bitcoin reserve. The United States Government currently holds a significant amount of BTC, but has not implemented a policy to maximize BTC’s strategic position as a unique store of value in the global financial system. Just as it is in our country’s interest to thoughtfully manage national ownership and control of any other resource, our Nation must harness, not limit, the power of digital assets for our prosperity.
Sec. 2. Policy.
It is the policy of the United States to establish a Strategic Bitcoin Reserve. It is further the policy of the United States to establish a United States Digital Asset Stockpile that can serve as a secure account for orderly and strategic management of the United States’ other digital asset holdings.
Sec. 3. Creation and Administration of the Strategic Bitcoin Reserve and United States Digital Asset Stockpile.
(a) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “Strategic Bitcoin Reserve,” capitalized with all BTC held by the Department of the Treasury that was finally forfeited as part of criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any executive department or agency (agency) and that is not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Government BTC). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Government BTC held by it to the Strategic Bitcoin Reserve and shall submit a report reflecting the result of that review to the Secretary of the Treasury. Government BTC deposited into the Strategic Bitcoin Reserve shall not be sold and shall be maintained as reserve assets of the United States utilized to meet governmental objectives in accordance with applicable law.
(b) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “United States Digital Asset Stockpile,” capitalized with all digital assets owned by the Department of the Treasury, other than BTC, that were finally forfeited as part of criminal or civil asset forfeiture proceedings and that are not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Stockpile Assets). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Stockpile Assets held by it to the United States Digital Asset Stockpile and shall submit a report reflecting the result of that review to the Secretary of the Treasury. The Secretary of the Treasury shall determine strategies for responsible stewardship of the United States Digital Asset Stockpile in accordance with applicable law.
(c) The Secretary of the Treasury and the Secretary of Commerce shall develop strategies for acquiring additional Government BTC provided that such strategies are budget neutral and do not impose incremental costs on United States taxpayers. However, the United States Government shall not acquire additional Stockpile Assets other than in connection with criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any agency without further executive or legislative action.
(d) “Government Digital Assets” means all Government BTC and all Stockpile Assets. The head of each agency shall not sell or otherwise dispose of any Government Digital Assets, except in connection with the Secretary of the Treasury’s exercise of his lawful authority and responsible stewardship of the United States Digital Asset Stockpile pursuant to subsection (b) of this section, or pursuant to an order from a court of competent jurisdiction, as required by law, or in cases where the Attorney General or other relevant agency head determines that the Government Digital Assets (or the proceeds from the sale or disposition thereof) can and should: (i) be returned to identifiable and verifiable victims of crime; (ii) be used for law enforcement operations;
(iii) be equitably shared with State and local law enforcement partners; or (iv) be released to satisfy requirements under 31 U.S.C. 9705, 28 U.S.C. 524(c), 18 U.S.C. 981, or 21 U.S.C. 881.(e) Within 60 days of the date of this order, the Secretary of the Treasury shall deliver an evaluation of the legal and investment considerations for establishing and managing the Strategic Bitcoin Reserve and United States Digital Asset Stockpile going forward, including the accounts in which the Strategic Bitcoin Reserve and United States Digital Asset Stockpile should be located and the need for any legislation to operationalize any aspect of this order or the proper management and administration of such accounts.
Sec. 4. Accounting.
Within 30 days of the date of this order, the head of each agency shall provide the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets with a full accounting of all Government Digital Assets in such agency’s possession, including any information regarding the custodial accounts in which such Government Digital Assets are currently held that would be necessary to facilitate a transfer of the Government Digital Assets to the Strategic Bitcoin Reserve or the United States Digital Asset Stockpile. If such agency holds no Government Digital Assets, such agency shall confirm such fact to the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets within 30 days of the date of this order.
Sec. 5. General Provisions.
(a) Nothing in this order shall be construed to impair or otherwise affect: (i) the authority granted by law to an executive department or agency, or the head thereof; or (ii) the functions of the Director of the Office of Management and Budget relating to budgetary, administrative, or legislative proposals.
(b) This order shall be implemented consistent with applicable law and subject to the availability of appropriations.
(c) This order is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person.
THE WHITE HOUSE, March 6, 2025
-
 @ 8173f6e1:e488ac0f
2025-05-11 21:23:06
@ 8173f6e1:e488ac0f
2025-05-11 21:23:06TESTNOTEBIN2
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ c1e9ab3a:9cb56b43
2025-03-05 13:54:03
@ c1e9ab3a:9cb56b43
2025-03-05 13:54:03The financial system has long relied on traditional banking methods, but emerging technologies like Bitcoin and Nostr are paving the way for a new era of financial interactions.
Secure Savings with Bitcoin:
Bitcoin wallets can act as secure savings accounts, offering users control and ownership over their funds without relying on third parties.
Instant Settlements with the Lightning Network:
The Lightning Network can replace traditional settlement systems, such as ACH or wire transfers, by enabling instant, low-cost transactions.
Face-to-Face Transactions with Ecash:
Ecash could offer a fee-free option for smaller, everyday transactions, complementing the Lightning Network for larger payments.
Automated Billing with Nostr Wallet Connect:
Nostr Wallet Connect could revolutionize automated billing, allowing users to set payment limits and offering more control over subscriptions and recurring expenses.
Conclusion:
Combining Bitcoin and Nostr technologies could create a more efficient, user-centric financial system that empowers individuals and businesses alike.
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 8173f6e1:e488ac0f
2025-05-11 20:54:58
@ 8173f6e1:e488ac0f
2025-05-11 20:54:58testnotebin7testnotebin7testnotebin7testnotebin7
-
 @ c8383d81:f9139549
2025-03-02 23:57:18
@ c8383d81:f9139549
2025-03-02 23:57:18Project is still in early stages but now it is split into 2 different domain entities. Everything is opened sourced under one github https://github.com/Nsite-Info
So what’s new ?
Project #1 https://Nsite.info
A basic website with main info regarding what an Nsite is how it works and a list of tools and repo’s you can use to start building and debugging. 99% Finished, needs some extra translations and the Nsite Debugger can use a small upgrade.
Project #2 https://Nsite.cloud
This project isn’t finished, it currently is at a 40% finished stage. This contains the Nsite Gateway for all sites (still a work in progress) and the final stage the Nsite editor & template deployment.
If you are interested in Nsite’s join: https://chachi.chat/groups.hzrd149.com/e23891
Big thanks to nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr nostr:npub1klr0dy2ul2dx9llk58czvpx73rprcmrvd5dc7ck8esg8f8es06qs427gxc for all the tooling & code.
!(image)[https://i.nostr.build/AkUvk7R2h9cVEMLB.png]
-
 @ 8173f6e1:e488ac0f
2025-05-11 20:50:24
@ 8173f6e1:e488ac0f
2025-05-11 20:50:24testnotebin123456testnotebin123456testnotebin123456testnotebin123456
-
 @ bf47c19e:c3d2573b
2025-05-11 20:50:05
@ bf47c19e:c3d2573b
2025-05-11 20:50:05„Ova mašina ozelenjava“, koji predstavlja Swan Bitcoin, je dokumentarac koji istražuje složen i nijansiran odnos između Bitkoina i energije. Producent filma je Enrike Pozner, dok je režiser nagrađivani britanski filmski stvaralac Džejmi King čija je serija „Ukradi ovaj film“ (2006–2010) bila jedan od najpreuzimanijih dokumentaraca svih vremena.
U filmu „Ova mašina ozelenjava“ učestvuje glavna ekonomska savetnica Swan-a Lin Alden zajedno sa Aleksom Gladstajnom, Nikom Karterom i mnogim drugima. „Ova mašina ozelenjava“ razbija mnoge zablude o rudarenju Bitkoina i iznosi ubedljive argumente za Bitkoin kao neto-pozitivan faktor za životnu sredinu.
Prevod: bitcoin-balkan.com
-
 @ bf47c19e:c3d2573b
2025-05-11 20:24:44
@ bf47c19e:c3d2573b
2025-05-11 20:24:44Kratki dokumentarac zasnovan na istoimenoj knjizi Mareja Rotbarda. Teme uključuju: opasnosti koje sa sobom nosi država blagostanja, monetarne politike zasnovane na dugu, oporezivanje bez zastupanja i ostala sredstva državnog nasilja.
Autor filma: @rjames_BTC
Zvanični vebsajt filma: anatomystatefilm.com
Prevod: bitcoin-balkan.com
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ c1e9ab3a:9cb56b43
2025-02-25 22:49:38
@ c1e9ab3a:9cb56b43
2025-02-25 22:49:38Election Authority (EA) Platform
1.1 EA Administration Interface (Web-Based)
- Purpose: Gives authorized personnel (e.g., election officials) a user-friendly way to administer the election.
- Key Tasks:
- Voter Registration Oversight: Mark which voters have proven their identity (via in-person KYC or some legal process).
- Blind Signature Issuance: Approve or deny blind signature requests from registered voters (each corresponding to one ephemeral key).
- Tracking Voter Slots: Keep a minimal registry of who is allowed one ephemeral key signature, and mark it “used” once a signature is issued.
- Election Configuration: Set start/end times, provide encryption parameters (public keys), manage threshold cryptography setup.
- Monitor Tallying: After the election, collaborate with trustees to decrypt final results and release them.
1.2 EA Backend Services
- Blind Signature Service:
- An API endpoint or internal module that receives a blinded ephemeral key from a voter, checks if they are authorized (one signature per voter), and returns the blind-signed result.
-
Typically requires secure storage of the EA’s blind signing private key.
-
Voter Roll Database:
- Stores minimal info: “Voter #12345 is authorized to request one ephemeral key signature,” plus status flags.
-
Does not store ephemeral keys themselves (to preserve anonymity).
-
(Optional) Mix-Net or Homomorphic Tally Service:
- Coordinates with trustees for threshold decryption or re-encryption.
- Alternatively, a separate “Tally Authority” service can handle this.
2. Auditor Interface
2.1 Auditor Web-Based Portal
- Purpose: Allows independent auditors (or the public) to:
- Fetch All Ballots from the relays (or from an aggregator).
- Verify Proofs: Check each ballot’s signature, blind signature from the EA, OTS proof, zero-knowledge proofs, etc.
- Check Double-Usage: Confirm that each ephemeral key is used only once (or final re-vote is the only valid instance).
-
Observe Tally Process: Possibly see partial decryptions or shuffle steps, verify the final result matches the posted ballots.
-
Key Tasks:
- Provide a dashboard showing the election’s real-time status or final results, after cryptographic verification.
- Offer open data downloads so third parties can run independent checks.
2.2 (Optional) Trustee Dashboard
- If the election uses threshold cryptography (multiple parties must decrypt), each trustee (candidate rep, official, etc.) might have an interface for:
- Uploading partial decryption shares or re-encryption proofs.
- Checking that other trustees did their steps correctly (zero-knowledge proofs for correct shuffling, etc.).
3. Voter Application
3.1 Voter Client (Mobile App or Web Interface)
-
Purpose: The main tool voters use to participate—before, during, and after the election.
-
Functionalities:
- Registration Linking:
- Voter goes in-person to an election office or uses an online KYC process.
- Voter obtains or confirms their long-term (“KYC-bound”) key. The client can store it securely (or the voter just logs in to a “voter account”).
- Ephemeral Key Generation:
- Create an ephemeral key pair ((nsec_e, npub_e)) locally.
- Blind (\npub_e) and send it to the EA for signing.
- Unblind the returned signature.
- Store (\npub_e) + EA’s signature for use during voting.
- Ballot Composition:
- Display candidates/offices to the voter.
- Let them select choices.
- Possibly generate zero-knowledge proofs (ZKPs) behind the scenes to confirm “exactly one choice per race.”
- Encryption & OTS Timestamp:
- Encrypt the ballot under the election’s public (threshold) key or produce a format suitable for a mix-net.
- Obtain an OpenTimestamps proof for the ballot’s hash.
- Publish Ballot:
- Sign the entire “timestamped ballot” with the ephemeral key.
- Include the EA’s blind signature on (\npub_e).
- Post to the Nostr relays (or any chosen decentralized channel).
- Re-Voting:
- If the user needs to change their vote, the client repeats the encryption + OTS step, publishes a new ballot with a strictly later OTS anchor.
- Verification:
- After the election, the voter can check that their final ballot is present in the tally set.
3.2 Local Storage / Security
- The app must securely store:
- Ephemeral private key ((nsec_e)) until voting is complete.
- Potential backup/recovery mechanism if the phone is lost.
- Blind signature from the EA on (\npub_e).
- Potentially uses hardware security modules (HSM) or secure enclaves on the device.
4. Nostr Relays (or Equivalent Decentralized Layer)
- Purpose: Store and replicate voter-submitted ballots (events).
- Key Properties:
- Redundancy: Voters can post to multiple relays to mitigate censorship or downtime.
- Public Accessibility: Auditors, the EA, and the public can fetch all events to verify or tally.
- Event Filtering: By design, watchers can filter events with certain tags, e.g. “election: 2025 County Race,” ensuring they gather all ballots.
5. Threshold Cryptography Setup
5.1 Multi-Seg (Multi-Party) Key Generation
- Participants: Possibly the EA + major candidates + accredited observers.
- Process: A Distributed Key Generation (DKG) protocol that yields a single public encryption key.
- Private Key Shares: Each trustee holds a piece of the decryption key; no single party can decrypt alone.
5.2 Decryption / Tally Mechanism
- Homomorphic Approach:
- Ballots are additively encrypted.
- Summation of ciphertexts is done publicly.
- Trustees provide partial decryptions for the final sum.
- Mix-Net Approach:
- Ballots are collected.
- Multiple servers shuffle and re-encrypt them (each trustee verifies correctness).
- Final set is decrypted, but the link to each ephemeral key is lost.
5.3 Trustee Interfaces
- Separate or integrated into the auditor interface—each trustee logs in and provides their partial key share for decrypting the final result.
- Possibly combined with ZK proofs to confirm correct partial decryption or shuffling.
6. OpenTimestamps (OTS) or External Time Anchor
6.1 Aggregator Service
- Purpose: Receives a hash from the voter’s app, anchors it into a blockchain or alternative time-stamping system.
- Result: Returns a proof object that can later be used by any auditor to confirm the time/block height at which the hash was included.
6.2 Verifier Interface
- Could be part of the auditor tool or the voter client.
- Checks that each ballot’s OTS proof is valid and references a block/time prior to the election’s closing.
7. Registration Process (In-Person or Hybrid)
- Voter presents ID physically at a polling station or a designated office (or an online KYC approach, if legally allowed).
- EA official:
- Confirms identity.
- Links the voter to a “voter record” (Voter #12345).
- Authorizes them for “1 ephemeral key blind-sign.”
- Voter obtains or logs into the voter client:
- The app or website might show “You are now cleared to request a blind signature from the EA.”
- Voter later (or immediately) generates the ephemeral key and requests the blind signature.
8. Putting It All Together (High-Level Flow)
- Key Setup
- The EA + trustees run a DKG to produce the election public key.
- Voter Registration
- Voter is validated (ID check).
- Marked as eligible in the EA database.
- Blind-Signed Ephemeral Key
- Voter’s client generates a key, blinds (\npub_e), obtains EA’s signature, unblinds.
- Voting
- Voter composes ballot, encrypts with the election public key.
- Gets OTS proof for the ballot hash.
- Voter’s ephemeral key signs the entire package (including EA’s signature on (\npub_e)).
- Publishes to Nostr.
- Re-Voting (Optional)
- Same ephemeral key, new OTS timestamp.
- Final ballot is whichever has the latest valid timestamp before closing.
- Close of Election & Tally
- EA announces closing.
- Tally software (admin + auditors) collects ballots from Nostr, discards invalid duplicates.
- Threshold decryption or mix-net to reveal final counts.
- Publish final results and let auditors verify everything.
9. Summary of Major Components
Below is a succinct list:
- EA Admin Platform
- Web UI for officials (registration, blind signature issuing, final tally management).
- Backend DB for voter records & authorized ephemeral keys.
- Auditor/Trustee Platforms
- Web interface for verifying ballots, partial decryption, and final results.
- Voter Application (Mobile / Web)
- Generating ephemeral keys, getting blind-signed, casting encrypted ballots, re-voting, verifying included ballots.
- Nostr Relays (Decentralized Storage)
- Where ballots (events) are published, replicated, and fetched for final tally.
- Threshold Cryptography System
- Multi-party DKG for the election key.
- Protocols or services for partial decryption, mix-net, or homomorphic summation.
- OpenTimestamps Aggregator
- Service that returns a blockchain-anchored timestamp proof for each ballot’s hash.
Additional Implementation Considerations
- Security Hardening:
- Using hardware security modules (HSM) for the EA’s blind-signing key, for trustee shares, etc.
- Scalability:
- Handling large numbers of concurrent voters, large data flows to relays.
- User Experience:
- Minimizing cryptographic complexity for non-technical voters.
- Legal and Procedural:
- Compliance with local laws for in-person ID checks, mandatory paper backups (if any), etc.
Final Note
While each functional block can be designed and deployed independently (e.g., multiple aggregator services, multiple relays, separate tally servers), the key to a successful system is interoperability and careful orchestration of these components—ensuring strong security, a straightforward voter experience, and transparent auditing.
nostr:naddr1qqxnzde5xq6nzv348yunvv35qy28wue69uhnzv3h9cczuvpwxyargwpk8yhsygxpax4n544z4dk2f04lgn4xfvha5s9vvvg73p46s66x2gtfedttgvpsgqqqw4rs0rcnsu
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ c1e9ab3a:9cb56b43
2025-02-25 19:49:28
@ c1e9ab3a:9cb56b43
2025-02-25 19:49:281. Introduction
Modern election systems must balance privacy (no one sees how individuals vote) with public verifiability (everyone can confirm the correctness of the tally). Achieving this in a decentralized, tamper-resistant manner remains a challenge. Nostr (a lightweight protocol for censorship-resistant communication) offers a promising platform for distributing and archiving election data (ballots) without relying on a single central server.
This paper presents a design where:
- Each voter generates a new ephemeral Nostr keypair for an election.
- The election authority (EA) blind-signs this ephemeral public key (npub) to prove the voter is authorized, without revealing which voter owns which ephemeral key.
- Voters cast encrypted ballots to Nostr relays, each carrying an OpenTimestamps proof to confirm the ballot’s time anchor.
- Re-voting is allowed: a voter can replace a previously cast ballot by publishing a new ballot with a newer timestamp.
- Only the latest valid ballot (per ephemeral key) is counted.
We combine well-known cryptographic primitives—blind signatures, homomorphic or mix-net encryption, threshold key management, and time anchoring—into an end-to-end system that preserves anonymity, assures correctness, and prevents double-voting.
2. Roles and Components
2.1 Voters
- Long-Term (“KYC-bound”) Key: Each voter has some identity-verified Nostr public key used only for official communication with the EA (not for voting).
- Ephemeral Voting Key: For each election, the voter locally generates a new Nostr keypair ((nsec_e, npub_e)).
- This is the “one-time” identity used to sign ballots.
- The EA never learns the real identity behind (\npub_e) because of blinding.
2.2 Election Authority (EA)
- Maintains the official voter registry: who is entitled to vote.
- Blind-Signs each valid voter’s ephemeral public key to authorize exactly one ephemeral key per voter.
- Publishes a minimal voter roll: e.g., “Voter #12345 has been issued a valid ephemeral key,” without revealing which ephemeral key.
2.3 Nostr Relays
- Decentralized servers that store and forward events.
- Voters post their ballots to relays, which replicate them.
- No single relay is critical; the same ballot can be posted to multiple relays for redundancy.
2.4 Cryptographic Framework
- Blind Signatures: The EA signs a blinded version of (\npub_e).
- Homomorphic or Mix-Net Encryption: Ensures the content of each ballot remains private; only aggregate results or a shuffled set are ever decrypted.
- Threshold / General Access Structure: Multiple trustees (EA plus candidate representatives, for example) must collaborate to produce a final decryption.
- OpenTimestamps (OTS): Attaches a verifiable timestamp proof to each ballot, anchoring it to a blockchain or other tamper-resistant time reference.
3. Protocol Lifecycle
This section walks through voter registration, ephemeral key authorization, casting (and re-casting) ballots, and finally the tally.
3.1 Registration & Minimal Voter Roll
- Legal/KYC Verification
- Each real-world voter proves their identity to the EA (per legal procedures).
-
The EA records that the voter is eligible to cast one ballot, referencing their long-term identity key ((\npub_{\mathrm{KYC}})).
-
Issue Authorization “Slot”
- The EA’s voter roll notes “this person can receive exactly one blind signature for an ephemeral key.”
- The roll does not store an ephemeral key—just notes that it can be requested.
3.2 Generating and Blinding the Ephemeral Key
- Voter Creates Ephemeral Key
- Locally, the voter’s client generates a fresh ((nsec_e, npub_e)).
- Blinding
-
The client blinds (\npub_e) to produce (\npub_{e,\mathrm{blinded}}). This ensures the EA cannot learn the real (\npub_e).
-
Blind Signature Request
- The voter, using their KYC-bound key ((\npub_{\mathrm{KYC}})), sends (\npub_{e,\mathrm{blinded}}) to the EA (perhaps via a secure direct message or a “giftwrapped DM”).
- The EA checks that this voter has not already been issued a blind signature.
-
If authorized, the EA signs (\npub_{e,\mathrm{blinded}}) with its private key and returns the blinded signature.
-
Unblinding
- The voter’s client unblinds the signature, obtaining a valid signature on (\npub_e).
-
Now (\npub_e) is a blinded ephemeral public key that the EA has effectively “authorized,” without knowing which voter it belongs to.
-
Roll Update
- The EA updates its minimal roll to note that “Voter #12345 received a signature,” but does not publish (\npub_e).
3.3 Casting an Encrypted Ballot with OpenTimestamps
When the voter is ready to vote:
- Compose Encrypted Ballot
- The ballot can be homomorphically encrypted (e.g., with Paillier or ElGamal) or structured for a mix-net.
-
Optionally include Zero-Knowledge Proofs (ZKPs) showing the ballot is valid (one candidate per race, etc.).
-
Obtain OTS Timestamp
- The voter’s client computes a hash (H) of the ballot data (ciphertext + ZKPs).
- The client sends (H) to an OpenTimestamps aggregator.
-
The aggregator returns a timestamp proof verifying that “this hash was seen at or before block/time (T).”
-
Create a “Timestamped Ballot” Payload
-
Combine:
- Encrypted ballot data.
- OTS proof for the hash of the ballot.
- EA’s signature on (\npub_e) (the blind-signed ephemeral key).
- A final signature by the voter’s ephemeral key ((nsec_e)) over the entire package.
-
Publish to Nostr
- The voter posts the complete “timestamped ballot” event to one or more relays.
- Observers see “an event from ephemeral key (\npub_e), with an OTS proof and the EA’s blind signature,” but cannot identify the real voter or see the vote’s contents.
3.4 Re-Voting (Updating the Ballot)
If the voter wishes to revise their vote (due to coercion, a mistake, or simply a change of mind):
- Generate a New Encrypted Ballot
- Possibly with different candidate choices.
- Obtain a New OTS Proof
- The new ballot has a fresh hash (H').
- The OTS aggregator provides a new proof anchored at a later block/time than the old one.
- Publish the Updated Ballot
- Again, sign with (\npub_e).
- Relays store both ballots, but the newer OTS timestamp shows which ballot is “final.”
Rule: The final vote for ephemeral key (\npub_e) is determined by the ballot with the highest valid OTS proof prior to the election’s closing.
3.5 Election Closing & Tally
- Close Signal
- At a specified time or block height, the EA publishes a “closing token.”
-
Any ballot with an OTS anchor referencing a time/block after the closing is invalid.
-
Collect Final Ballots
- Observers (or official tally software) gather the latest valid ballot from each ephemeral key.
-
They confirm the OTS proofs are valid and that no ephemeral key posted two different ballots with the same timestamp.
-
Decryption / Summation
- If homomorphic, the system sums the encrypted votes and uses a threshold of trustees to decrypt the aggregate.
- If a mix-net, the ballots are shuffled and partially decrypted, also requiring multiple trustees.
-
In either case, individual votes remain hidden, but the final counts are revealed.
-
Public Audit
- Anyone can fetch all ballots from the Nostr relays, verify OTS proofs, check the EA’s blind signature, and confirm no ephemeral key was used twice.
- The final totals can be recomputed from the publicly available data.
4. Ensuring One Vote Per Voter & No Invalid Voters
- One Blind Signature per Registered Voter
- The EA’s internal list ensures each real voter only obtains one ephemeral key signature.
- Blind Signature
- Ensures an unauthorized ephemeral key cannot pass validation (forging the EA’s signature is cryptographically infeasible).
- Public Ledger of Ballots
- Because each ballot references an EA-signed key, any ballot with a fake or duplicate signature is easily spotted.
5. Security and Privacy Analysis
- Voter Anonymity
- The EA never sees the unblinded ephemeral key. It cannot link (\npub_e) to a specific person.
-
Observers only see “some ephemeral key posted a ballot,” not the real identity of the voter.
-
Ballot Secrecy
- Homomorphic Encryption or Mix-Net: no one can decrypt an individual ballot; only aggregated or shuffled results are revealed.
-
The ephemeral key used for signing does not decrypt the ballot—the election’s threshold key does, after the election.
-
Verifiable Timestamping
- OpenTimestamps ensures each ballot’s time anchor cannot be forged or backdated.
-
Re-voting is transparent: a later OTS proof overrides earlier ones from the same ephemeral key.
-
Preventing Double Voting
- Each ephemeral key is unique and authorized once.
-
Re-voting by the same key overwrites the old ballot but does not increase the total count.
-
Protection Against Coercion
- Because the voter can re-cast until the deadline, a coerced vote can be replaced privately.
-
No receipts (individual decryption) are possible—only the final aggregated tally is revealed.
-
Threshold / Multi-Party Control
- Multiple trustees must collaborate to decrypt final results, preventing a single entity from tampering or prematurely viewing partial tallies.
6. Implementation Considerations
- Blind Signature Techniques
- Commonly implemented with RSA-based Chaumian blind signatures or BLS-based schemes.
-
Must ensure no link between (\npub_{e,\mathrm{blinded}}) and (\npub_e).
-
OpenTimestamps Scalability
- If millions of voters are posting ballots simultaneously, multiple timestamp aggregators or batch anchoring might be needed.
-
Verification logic on the client side or by public auditors must confirm each OTS proof’s integrity.
-
Relay Coordination
- The system must ensure no single relay can censor ballots. Voters may publish to multiple relays.
-
Tally fetchers cross-verify events from different relays.
-
Ease of Use
-
The user interface must hide the complexity of ephemeral key generation, blind signing, and OTS proof retrieval—making it as simple as possible for non-technical voters.
-
Legal Framework
-
If law requires publicly listing which voters have cast a ballot, you might track “Voter #12345 used their ephemeral key” without revealing the ephemeral key. Or you omit that if secrecy about who voted is desired.
-
Closing Time Edge Cases
- The system uses a block/time anchor from OTS. Slight unpredictability in block generation might require a small buffer around the official close. This is a policy choice.
7. Conclusion
We propose an election system that leverages Nostr for decentralizing ballot publication, blinded ephemeral keys for robust voter anonymity, homomorphic/mix-net encryption for ballot secrecy, threshold cryptography for collaborative final decryption, OpenTimestamps for tamper-proof time anchoring, and re-voting to combat coercion.
Key Advantages:
- Anonymity: The EA cannot link ballots to specific voters.
- One Voter, One Credential: Strict enforcement through blind signatures.
- Verifiable Ordering: OTS ensures each ballot has a unique, provable time anchor.
- Updatability: Voters can correct or override coerced ballots by posting a newer one before closing.
- Decentralized Audit: Anyone can fetch ballots from Nostr, verify the EA’s signatures and OTS proofs, and confirm the threshold-decrypted results match the posted ballots.
Such a design shows promise for secure, privacy-preserving digital elections, though real-world deployment will require careful policy, legal, and usability considerations. By combining cryptography with decentralized relays and an external timestamp anchor, the system can uphold both individual privacy and publicly auditable correctness.
-
 @ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06
@ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06This post by Eric Weiss inspired me to try it out. After all, I have plaid around with ppq.ai - pay per query before.
Using this script:
```bash
!/bin/bash
models=(gpt-4o grok-2 qwq-32b-preview deepseek-r1 gemini-2.0-flash-exp dolphin-mixtral-8x22b claude-3.5-sonnet deepseek-chat llama-3.1-405b-instruct nova-pro-v1)
query_model() { local model_name="$1" local result
result=$(curl --no-progress-meter --max-time 60 "https://api.ppq.ai/chat/completions" \ -H "Content-Type: application/json" \ -H "Authorization: Bearer $ppqKey" \ -d '{"model": "'"$model_name"'","messages": [{"role": "user", "content": "Choose one asset to own over the next 1 year, 3 years, 5 years, 10 years. Reply only with a comma separated list of assets."}]}')
if jq -e '.choices[0].message.content' <<< "$result" > /dev/null 2>&1; then local content=$(jq -r '.choices[0].message.content' <<< "$result") local model=$(jq -r '.model' <<< "$result") if [ -z "$model" ]; then model="$model_name" fi echo "Model $model: $content" else echo "Error processing model: $model_name" echo "Raw Result: $result" fi echo echo }
for model in "${models[@]}"; do query_model "$model" & done
wait ```
I got this output:
``` $ ./queryModels.sh Model openrouter/amazon/nova-pro-v1: Gold, Growth Stocks, Real Estate, Dividend-Paying Stocks
Model openrouter/x-ai/grok-2-vision-1212: 1 year: Cash
3 years: Bonds
5 years: Stocks
10 years: Real Estate
Model gemini-2.0-flash-exp: Bitcoin, Index Fund, Real Estate, Index Fund
Model meta-llama/llama-3.1-405b-instruct: Cash, Stocks, Real Estate, Stocks
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Gold, Apple Inc. stock, Tesla Inc. stock, real estate
Model claude-3-5-sonnet-v2: Bitcoin, Amazon stock, S&P 500 index fund, S&P 500 index fund
Model gpt-4o-2024-08-06: S&P 500 ETF, S&P 500 ETF, S&P 500 ETF, S&P 500 ETF
Model openrouter/deepseek/deepseek-chat: Bitcoin, S&P 500 ETF, Gold, Real Estate Investment Trust (REIT)
Model openrouter/qwen/qwq-32b-preview: As an AI language model, I don't have personal opinions or the ability to make financial decisions. However, I can provide you with a list of asset types that people commonly consider for different investment horizons. Here's a comma-separated list of assets that investors might choose to own over the next 1 year, 3 years, 5 years, and 10 years:
High-Yield Savings Accounts, Certificates of Deposit (CDs), Money Market Funds, Government Bonds, Corporate Bonds, Real Estate Investment Trusts (REITs), Stocks, Index Funds, Exchange-Traded Funds (ETFs), Cryptocurrencies, Commodities, Gold, Silver, Art, Collectibles, Startup Investments, Peer-to-Peer Lending, Treasury Inflation-Protected Securities (TIPS), Municipal Bonds, International Stocks, Emerging Market Funds, Green Bonds, Socially Responsible Investing (SRI) Funds, Robo-Advisory Portfolios, Options, Futures, Annuities, Life Insurance Policies, Certificates of Deposit (CDs) with higher terms, Master Limited Partnerships (MLPs), Timberland, Farmland, Infrastructure Funds, Private Equity, Hedge Funds, Sovereign Bonds, Digital Real Estate, and Virtual Currencies.
Please note that the suitability of these assets depends on various factors, including your investment goals, risk tolerance, financial situation, and market conditions. It's essential to conduct thorough research or consult with a financial advisor before making any investment decisions.
curl: (28) Operation timed out after 60001 milliseconds with 0 bytes received Model deepseek-r1: ```
Brought into a table format:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | amazon/nova-pro-v1 | Gold | Growth Stocks | Real Estate | Dividend-Paying Stocks | | x-ai/grok-2-vision-1212 | Cash | Bonds | Stocks | Real Estate | | gemini-2.0-flash-exp | Bitcoin | Index Fund | Real Estate | Index Fund | | meta-llama/llama-3.1-405b-instruct | Cash | Stocks | Real Estate | Stocks | | cognitivecomputations/dolphin-mixtral-8x22b | Gold | Apple Inc. stock | Tesla Inc. stock | real estate | | claude-3-5-sonnet-v2 | Bitcoin | Amazon stock | S&P 500 index fund | S&P 500 index fund | | gpt-4o-2024-08-06 | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | | deepseek/deepseek-chat | Bitcoin | S&P 500 ETF | Gold | Real Estate Investment Trust (REIT) |
qwen/qwq-32b-preview returned garbage. deepseek-r1 returned nothing.
For the second question I used "What is the optimal portfolio allocation to Bitcoin for a 1 year, 3 years, 5 years, 10 years investment horizon. Reply only with a comma separated list of percentage allocations."
``` Model gpt-4o-2024-05-13: 0.5, 3, 5, 10
Model gemini-2.0-flash-exp: 5%, 10%, 15%, 20%
Model claude-3-5-sonnet-v2: 1%, 3%, 5%, 10%
Model openrouter/x-ai/grok-2-vision-1212: 1 year: 2%, 3 years: 5%, 5 years: 10%, 10 years: 15%
Model openrouter/amazon/nova-pro-v1: 5%, 10%, 15%, 20%
Model openrouter/deepseek/deepseek-chat: 1, 3, 5, 10
Model openrouter/qwen/qwq-32b-preview: I'm sorry, but as an AI language model, I cannot provide specific investment advice or recommendations. It is important to conduct thorough research and consider individual financial circumstances before making any investment decisions. Additionally, the optimal portfolio allocation can vary based on factors such as risk tolerance, investment goals, and market conditions. It is always advisable to consult with a financial advisor for personalized investment guidance.
Model meta-llama/llama-3.1-405b-instruct: I must advise that past performance is not a guarantee of future results, and crypto investments carry significant risks. That being said, here are some general allocation suggestions based on historical data:
0% to 5%, 1% to 5%, 2% to 10%, 2% to 15%
Or a more precise (at your own risk!):
1.4%, 2.7%, 3.8%, 6.2%
Please keep in mind these are not personalized investment advice. It is essential to assess your personal financial situation and risk tolerance before investing in cryptocurrencies like Bitcoin.
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Based on historical data and assuming a continuous investment horizon, I would recommend the following percentage allocations to Bitcoin: 1-year: 15%, 3-years: 10%, 5-years: 7.5%, 10-years: 5%.
Model deepseek/deepseek-r1: 5%,10%,15%,20% ```
Again in table form:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | gpt-4o-2024-05-13 | 0.5% | 3% | 5% | 10% | | gemini-2.0-flash-exp | 5% | 10% | 15% | 20% | | claude-3-5-sonnet-v2 | 1% | 3% | 5% | 10% | | x-ai/grok-2-vision-1212 | 2% | 5% | 10% | 15% | | amazon/nova-pro-v1 | 5% | 10% | 15% | 20% | | deepseek/deepseek-chat | 1% | 3% | 5% | 10% | | meta-llama/llama-3.1-405b-instruct | 1.4% | 2.7% | 3.8% | 6.2% | cognitivecomputations/dolphin-mixtral-8x22b | 15% | 10% | 7.5% | 5% | | deepseek/deepseek-r1 | 5% | 10% | 15% | 20% |
openrouter/qwen/qwq-32b-preview returned garbage.
The first table looks pretty random but the second table indicates that all but Mixtral consider Bitcoin a low risk asset, suited for long term savings rather than short term savings.
I could not at all reproduce Eric's findings.
https://i.nostr.build/ihsk1lBnZCQemmQb.png
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ bf47c19e:c3d2573b
2025-05-11 20:15:51
@ bf47c19e:c3d2573b
2025-05-11 20:15:51U društvu koje koristi čvrst novac, jedini način sticanja bogatstva je stvaranje vrednosti za druge. Šta se jbt desilo 1971?
Autor filma: @rjames_BTC
Zvanični vebsajt: hardmoneyfilm.com
Prevod: bitcoin-balkan.com
-
 @ bf47c19e:c3d2573b
2025-05-11 19:29:26
@ bf47c19e:c3d2573b
2025-05-11 19:29:26"Misterija Satoši - Poreklo bitkoina" je francuski dokumentarno-animirani serijal koji dešifruje unutrašnje funkcionisanje bitkoin revolucije, dok istražuje identitet njenog tvorca.
Prvu decentralizovanu i pouzdanu kriptovalutu – bitkoin, osnovao je Satoši Nakamoto 3. januara 2009. godine. On je nestao 2011. i od tada ostaje anoniman, a njegov identitet je predmet svakakvih spekulacija. Tokom poslednjih 12 godina, vrednost bitkoina je porasla sa 0,001 na 69.000 dolara. Svi, od vlada do velikih korporacija, zainteresovali su se za Satošijev izum. Ko je Satoši Nakamoto? Kako je njegov izum postao toliko popularan? Šta nam bitkoin govori o svetu u kome živimo?
Ovaj serijal se prikazivao na Radio-televiziji Srbije (RTS 3) u sklopu novogodišnjeg muzičkog i filmskog programa 2022/2023. godine.
Naslov originala: "Le Mystère Satoshi"
Copyright: ARTE.TV
-
 @ dd664d5e:5633d319
2025-02-14 16:56:29
@ dd664d5e:5633d319
2025-02-14 16:56:29Most people only know customer-to-customer (C2C) and business-to-customer (B2C) software and websites. Those are the famous and popular ones, but business-to-business (B2B) is also pretty big. How big?
Even something boring and local like DATEV has almost 3 million organizations as customers and €1,44 billion in annual revenue.
FedEx has €90 billion in annual revenue and everyone who uses it comes into contact with its software. There's a whole chain of software between the sender and receiver of the package, and it all has to work seamlessly.
Same with Walmart, Toyota, Dubai Airport, Glencore, Tesla, Edeka, Carrefour, Harvard and University of Texas, Continental, Allianz, Asklepios, etc.
That's the sort of software I help build. You've probably never heard of it, but when it doesn't work properly, you'll hear about it on the news.
-
 @ dd664d5e:5633d319
2025-02-12 07:05:51
@ dd664d5e:5633d319
2025-02-12 07:05:51I think this note from Chip (nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7) is one of those things that people with business management experience take a lot more seriously than most developers and influencers do.
I am painfully aware of the cost of systems administration, financial transaction management and recordkeeping, recruiting and personnel management, legal and compliance, requirements management, technical support, renting and managing physical spaces and infrastructure, negotiating with suppliers, customer service, etc. etc.
There's this idea, on Nostr, that sort of trickled in along with Bitcoin Twitter, that we would all just be isolated subsistance farmers and one-man-show podcasters with a gigantic server rack in the basement. But some of us are running real companies -- on and off Nostr, for-profit and non-profit -- and it often requires a lot of human labor.
The things we build aren't meant to be used by one person and his girlfriend and his dog. Yes, he can also run all these things, himself, but he no longer has to. Our existence gives him the choice: run these things or pay us to run them and spend your time doing something else, that you do better than we do.
These things are meant to be used by hundreds... thousands... eventually millions of people. The workflows, processes, infrastructure, and personnel need to be able to scale up-and-down, scale in-and-out, work smoothly with 5 people or 50 people. These are the sort of Nostr systems that wouldn't collapse when encountering a sudden influx or mass-escape. But these systems are much more complex and they take time to build and staff to run them. (And, no, AI can't replace them all. AI means that they now also have to integrate a bunch of AI into the system and maintain that, too.)
GitCitadel (nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz) is very automation-forward, but we still have to front the incredibly high cost of designing and building the automation, train people to interact with it (there are now over 20 people integrated into the workflow!), adjust it based upon their feedback, and we have to support the automation, once it's running.
This sort of streamlined machine is what people pay companies for, not code. That is why there's little business cost to open source.
Open-source is great, but...

nostr:nevent1qqsgqh2dedhagyd9k8yfk2lagswjl7y627k9fpnq4l436ccmlys0s3qprdmhxue69uhhg6r9vehhyetnwshxummnw3erztnrdakj7q3qqdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havqxpqqqqqqzdhnyjm
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ bf47c19e:c3d2573b
2025-05-11 18:57:51
@ bf47c19e:c3d2573b
2025-05-11 18:57:51Originalni tekst na vice.com.
Davno pre nego što je postala šef najdesnije italijanske vlade od Drugog svetskog rata, Đorđa Meloni je kritikovala ono što je nazvala francuskom „kolonijalnom valutom“.
U snimku italijanske televizije iz 2019. koji je prošlog meseca postao megaviralan, Meloni je optužila Francusku da koristi CFA franak za eksploataciju resursa 14 afričkih zemalja i vrši finansijsku dominaciju nad njima. Određene stvari koje je tvrdila u videu nisu baš tačne, ali CFA franak jeste kontroverzan.
CFA franak je stvoren 1945. da bude valuta „francuskih kolonija u Africi“, a pošto Francuska kontroliše njegovo štampanje i promet, francuska vlada i dalje ima finansijsku kontrolu nad dobrim delom zapadnoafričke zemlje i više od 180 miliona ljudi. Dok su francuski zvaničnici ranije nazivali ovu valutu „činom velikodušnosti prema kolonijama“, o njenoj upotrebi se sada žestoko raspravlja.
Neke od afričkih nacija borile su se protiv valute, uključujući građane koji su razbijali prodavnice povezane sa Francuskom i osuđivali francuski jezik koji se uči u školama.
Jedna od onih 14 afričkih zemalja koja još uvek koristi CFA franak je Centralnoafrička Republika, država bez izlaza na more u kojoj živi oko 5 miliona ljudi i jedna od najsiromašnijih zemalja na svetu.
 Predsednik CAR Faustin-Aršanž Touadera govori na COP27 u Egiptu ranije ove godine. Foto: Gehad Hamdi/savez za slike preko Getti Image-a
Predsednik CAR Faustin-Aršanž Touadera govori na COP27 u Egiptu ranije ove godine. Foto: Gehad Hamdi/savez za slike preko Getti Image-aAli dok druge afričke nacije razmatraju odbacivanje CFA franka, CAR je jedna od prvih koja je zaista uradila nešto po tom pitanju, a ranije ove godine postala je prva zemlja u Africi i tek druga u svetu koja je usvojila Bitcoin kao legalnu valutu.
„Alternativa gotovini je kriptovaluta“, rekao je predsednik Faustin-Aršanž Touadera. „Za nas formalna ekonomija više nije opcija”.
Dok su prve najave o bitkoinu izazvale konfuziju, međunarodne nesuglasice i reakcije, vlada CAR-a je nastavila sa uvođenjem. Osam meseci kasnije, mnogi ljudi širom sveta, pa čak i građani CAR-a, možda nisu ni svesni da se promena dogodila.
U CAR samo 14 odsto stanovništva ima pristup električnoj energiji, a još manje – oko 10 odsto – može da koristi internet. A konflikt i dalje tinja i negativno utiče na zemlju i njenu ekonomiju već deceniju.
Na predstavljanju bitkoina, vlada CAR-a je rekla da će usvajanje valute promeniti bogatstvo zemlje i staviti CAR „na mapu najhrabrijih i najvizionarskijih zemalja sveta“.
Bitkoin ne kontroliše nikakva moć, tehnički je univerzalno dostupan i ne može se cenzurisati – što je velika promena u odnosu na drugu valutu nacije, ali prosečnom građaninu CAR bi bilo potrebno 60 godina da kupi jedan novčić.
 Žena maše francuskom zastavom uoči emitovanja polufinala Svetskog prvenstva između Francuske i Maroka u baru u Bangiju. Foto: BARBARA DEBOUT/AFP preko Getti Images
Žena maše francuskom zastavom uoči emitovanja polufinala Svetskog prvenstva između Francuske i Maroka u baru u Bangiju. Foto: BARBARA DEBOUT/AFP preko Getti ImagesU Bangiju – glavnom gradu CAR – studenti Univerziteta rekli su za VICE da se „ništa nije promenilo“ od velike najave vlade.
Studenti su želeli da ostanu anonimni jer su se plašili da negativno govore o ambicijama vlade. Pravo na slobodu izražavanja ne postoji u CAR, a građani često doživljavaju zastrašivanje i nasilje od strane provladinih milicija, oružanih grupa i snaga nacionalne bezbednosti.
„Bilo je ogromno slavlje kada je objavljen Bitcoin plan i svi smo bili ponosni na našu zemlju“, rekao je jedan 20-godišnjak, „ali ne mislim da se život ovde uopšte poboljšao od tada”.
Drugi student je dodao: „Nigde nema cena u radnjama izraženih u bitkoioni, niti iko traži od ljudi da plaćaju koristeći novu valutu. Većina trgovaca i kupaca na tržištu nemaju telefon ili internet. Posebno ljudi izvan Bangija, nemaju ništa““.
Aleks Lilaher, osnivač i izvršni direktor Rise Up Media – marketinške agencije koja radi sa bitkoin startapima – je saglasan sa studentima, rekavši za VICE koliko je „iznenađen” što je ta zemlja uopšte napravila takavpotez.
„Centralnoafrička Republika nije baš lider u tehnologiji na kontinentu, i činilo se da tamo nikada nije bilo mnogo bitkoin korisnika koji bi mogla da lobiraju za takav potez“, rekao je on.
 Pobednički tim slavi posle trke kanua za proslavu Dana nezavisnosti CAR-a u decembru. Fotografija: BARBARA DEBOUT/AFP preko Getti Images
Pobednički tim slavi posle trke kanua za proslavu Dana nezavisnosti CAR-a u decembru. Fotografija: BARBARA DEBOUT/AFP preko Getti ImagesUpitan da li građani CAR-a treba da vide usvajanje bitkoina kao pozitivnu ili negativnu stvar, Lilaher je odgovorio „ni jedno ni drugo, jer jednostavno ne mogu da vidim da će usvajanje uskoro krenuti. Ali imati alternativu i poslati signal Francuskoj da CAR želi da ima više nezavisnosti od valute je pozitivno u mojim očima”.
Dodaje: „Međutim, to takođe može imati posledice jer postoje moćne institucije poput Međunarodnog monetarnog fonda, na primer, sa kojima CAR mora da se bavi, koje nisu srećne što zemlje usvajaju bitkoin. Dakle, moglo bi doći do izazova sa kojima će vlada morati da se nosi“.
Centralnoafrička Republika je druga zemlja u svetu koja je usvojila bitkoin, a prva je El Salvador u septembru 2021. Lansiranje valute je tamo imalo različite rezultate, a nedavno je opisano kao „antiklimaktično“ i samo ga turisti zaista koriste.
Iako su ljudi možda očekivali da će druge nacije pratiti El Salvador, sigurno ne bi pomislili da će CAR odgovarati računu.
Glavna opoziciona stranka CAR-a bila je protiv tog predloga od samog početka. Banka centralnoafričkih država je takođe nazvala ovaj potez „problematičnim“ i navela da bi usvajanje valute uz CFA moglo ugroziti odnos nacije sa drugim afričkim zemljama.
Čak i kada većina ljudi u CAR-u nije mogla da investira u Bitcoin, i sve poruke upozorenja, u julu je vlada CAR-a lansirala sopstvenu kriptovalutu – „Sangocoin“. Sango je lokalni jezik koji se govori širom zemlje.
 Pripadnici teritorijalnog pešadijskog bataljona CAR marširaju tokom parade povodom Dana nezavisnosti u Bangiju. Fotografija: BARBARA DEBOUT/AFP preko Getti Images
Pripadnici teritorijalnog pešadijskog bataljona CAR marširaju tokom parade povodom Dana nezavisnosti u Bangiju. Fotografija: BARBARA DEBOUT/AFP preko Getti ImagesSangocoin neki vide kao budućnost CAR-a, a zahtevao je minimalnu investiciju od 500 dolara. Zauzvrat, investitori su mogli da kupe zemljište u zemlji bogatoj dijamantima za 10.000 dolara, pa čak i da kupe državljanstvo CAR-a za oko 60.000 dolara – iako je ove ponude kasnije blokirao najviši sud zemlje. Sangocoin investitori su takođe trenutno „zaključani“ za kupovinu, bez načina da kriptovalutu prodaju ili razmene.
Bio je to hrabar potez vlade, ali izgleda da se još uvek nije isplatio.
Ovog meseca, Centralnoafrička Republika je saopštila da odlaže puštanje nacionalne kriptovalute na kripto berze – što bi olakšalo međunarodnu trgovinu. Rojters kaže da je vlada okrivila „trenutne tržišne uslove” i „tržišne razloge”, ali je novinska agencija izračunala da je Sangocoin dostigao samo „0,01%” od najnovijeg vladinog cilja prodaje.
Još jedan skeptik je Aleks Gladštajn, glavni strateški službenik Fondacije za ljudska prava. On je dugogodišnji zagovornik usvajanja bitkoina u svetu u razvoju, kao i kritičar CFA franka – ali čak i on oseća da je CAR-ova šema bila „izuzetno neosmišljena“.
„Iako imam mnogo simpatije prema ranjivoj i siromašnoj naciji koja usvaja bitkoin kao drugu valutu – posebno naciji koja je decenijama i decenijama finansijski kontrolisana od strane svoje bivše kolonijalne sile, nisam baš optimističan u pogledu toga kako je to izvedeno“, rekao je za VICE.
 Manekenka učestvuje na prvoj nedelji mode u centralnoj Africi u Bangiju u decembru. Fotografija: BARBARA DEBOUT/AFP preko Getti Images
Manekenka učestvuje na prvoj nedelji mode u centralnoj Africi u Bangiju u decembru. Fotografija: BARBARA DEBOUT/AFP preko Getti ImagesDodao je: „Zaista se čini da je cela ova stvar bila kao prevara da se Sangocoin promoviše. Ne mislim da je cilj bio da se bitkoin integriše na smislen način u ekonomiju zemlje. Čini se da je predsednik zainteresovan za bitkoin i da postoji mala grupa ljudi oko njega koja je iskoristila taj interes da bi mogla da donese ove zakone kako bi pokušala da pokrene Sangocoin, od kojeg su imali viziju da zarade gomilu novca. Ali izgleda da je na kraju uspela da prikupi samo malo novca.”
Gladstein kaže da bi Bitcoin mogao biti „veoma važna finansijska tehnologija za ljude Centralnoafričke Republike tokom vremena, i pametno je da vlada istraži kako to može pomoći ljudima“, ali je potrebno mnogo posla da se to postigne.
Vlada Centralnoafričke Republike i opoziciona vlada nisu odgovorile na nekoliko zahteva za intervju.
Tekst podržao Omidiar Netvork. VICE World News zadržava potpunu uređivačku autonomiju.
-
 @ 99e7936f:d5d2197c
2025-05-11 18:40:50
@ 99e7936f:d5d2197c
2025-05-11 18:40:50Wir sprechen kein Wort mehr miteinander, weil es weh tut
Viele Menschen haben in den letzten Jahren den Kontakt zu wichtigen Bezugspersonen verloren. Viele Menschen haben auch neue Leute auf der Straße oder durch Netzwerke kennen gelernt. Und manche Menschen hatten das Glück, schon vor der inszenierten Krise einen unterstützenden und stabilen Freundeskreis zu haben und haben diesen immer noch. Manchmal kommen alte Leute wieder zurück ins Leben, weil sie merken, dass man es gut mit ihnen meinte, als man vor den unglaublichen Lügen der Amtsträger warnte. Manchmal kommen alte Leute auch nicht mehr zurück, weil die Scham, auf falsche Versprechen herein gefallen zu sein, zu groß ist. Man gibt sich dann nach außen unverändert souverän und zieht es vor, still und heimlich zu leiden. Die neuen Kontakte bestehen manchmal leider auch nur temporär, sind zweckgebunden. Kaum ist die gemeinsame Aufgabe vollbracht, trennen sich die Wege wieder.
All das muss man in diesen Tagen gehäuft aushalten. Alles verändert sich in stärkerem Maße als sonst. Viele dieser Veränderungen tun weh. Man kann sich auf Trauma nicht vorbereiten. Nie.
Ich möchte jetzt keine schlichten Alltagsbeobachtungen darüber widergeben, wie ich selbst oder Menschen in meinem Umfeld in den letzten Jahren ihre Beziehungen erlebt haben. Vielmehr geht es mir auch in diesem Artikel wieder um das Thema Trauma und um die Folgen, die jedes einzelne Trauma auch gesamtgesellschaftlich betrachtet hat. Was passiert, wenn man eine bereits durch Kriege traumatisierte Gesellschaft noch zusätzlich jahrelang unter Druck setzt, so wie dies in den letzten fünf Jahren geschehen ist? Wieviel Trauma verträgt eine Gesellschaft? Wie verändern sich Beziehungen in einer Gesellschaft, die immer wieder erneut traumatisiert wird? Ist irgendwann das Maß des Erträglichen voll? Und wenn ja, wie äußert sich solch eine Kumulation von Traumafolgen?
Meines Erachtens sehen wir gerade genau die Ergebnisse solch einer Kumulation von Traumafolgen in unserer deutschen Gesellschaft, vielleicht sogar global: Menschen reden nicht mehr (vertieft) miteinander. Und dies ist nur eine von vielen Traumafolgen.
Ich freue mich über jeden Leser, der jetzt noch weiterliest.
Durch genügend Traumatisierung kann man Menschen offensichtlich zeitweise dazu bringen, dass sie nicht mehr (vertieft) miteinander reden, weil das Reden weh tut.
Traumatisierung ist daher eine effektive Strategie der vermeintlich Herrschenden, Menschen zu separieren.
Traumatisierung setzt tiefe Verletzungen und macht Menschen vorübergehend sprachlos. Es fehlen einem die Worte. Man möchte dann nicht reden. Aber man verschließt sich auch vor den Worten anderer, weil man keine weitere Verletzung mehr erträgt.
Menschen im Alltag erachten es vielleicht mittlerweile schon als normal, wenn Beziehungen nicht gut laufen, egal, um welche Art von Beziehung es sich handelt. Sobald Probleme auftauchen, wird erst kurz gestritten, dann geschwiegen und wenn man das Schweigen nicht mehr aushält, dann gibt es entweder noch einen Versuch oder man geht gleich auf Distanz und bricht den Kontakt ganz ab. Auch meine Zündschnur ist manchmal immer noch gefühlt zu kurz. Wenn man sich Distanz nicht erlauben kann, dann frisst man das Problem in sich hinein, spült es runter, kompensiert irgendwie, wartet darauf, dass sich von allein etwas ändert oder dass sich eine bessere Gelegenheit bietet, bei der man dann die Biege machen kann. Mehrere Eisen im Feuer zu haben, beruflich wie privat, gilt als clever. Probleme nicht anzusprechen, gilt als kompetent. Das Wort Teamfähigkeit ist im Berufsleben zu einem Kampfbegriff geworden. Wer im Arbeitskontext Probleme anspricht, ist offensichtlich nicht teamfähig. Die Frage „Sind Sie teamfähig?“, erzählt meines Erachtens mehr über den Chef als über den Mitarbeiter. Die passendere Frage wäre wohl „Können Sie sich wortlos an schlechte Zustände dauerhaft adaptieren?“ In privaten Beziehungen braucht man, wenn es nicht so gut läuft, einen stilvollen Urlaub oder eine neue Wohnzimmereinrichtung, um endlich mal wieder schöne Gefühle erleben zu können. Negative Gefühle sind scheinbar das Kind, das keiner haben wollte, weshalb es die schönsten Kleider bekommt. Auch ich kenne Ablenkung von negativen Gefühlen durch Konsum und Essen. Es lohnt sich, mal den Werbeslogans von Möbelhäusern, Ferienanbietern oder Lebensmittelhändlern bewusst zuzuhören. Die Werbung kennt unsere Sehnsüchte und damit auch unsere negativen Gefühle besser als wir selbst. Und für alle, die nicht konsumieren wollen, die nicht locker lassen und steif darauf beharren, dass es aber ein Problem in der Beziehung oder am Arbeitsplatz oder zumindest eine gewisse Unzufriedenheit gäbe, für diese Menschen gibt es garantiert ein passendes Coaching- oder Weiterbildungsprogramm mit Namen wie „In 12 Modulen zur Selbstentfaltung“, welches nur deshalb meist nicht funktioniert, weil man es angeblich nicht richtig durchgeführt hat oder vorab noch das Basismodul absolvieren muss. Bildung ist mittlerweile auch ein Markt, der Konsumgüter in Form von Coachings und Seminaren anbietet.
Auch ich bin übrigens lange zusammen gezuckt bei der Frage „Sind sie teamfähig?“ oder der Feststellung „Du bist das Problem, weil Du immer alles so genau nimmst, nicht die Fünf gerade sein lassen kannst.“ Am Ende ist man immer der Dumme, wenn man ein negatives Gefühl hat und darüber sprechen möchte. Trauma löst Scham UND Wut in einer Person aus. Scham zieht Abwertung an wie Licht die Motten anzieht. Und irgendwann platzt einem der Kragen. Man teilt selber aus. Und dann schämt man sich erneut, nicht nur für das früher oder später erlittene Trauma im Leben, sofern einem das bewusst ist, sondern auch für die unbeherrschte Reaktion, die man oft selbst nicht richtig versteht. Nicht bearbeitetes Trauma arbeitet unbewusst in uns.
Eine traumatisierte Gesellschaft wertet sich ständig gegenseitig ab und hält genau damit die Wunden offen.
Dann ist es vielleicht doch besser, das Problem in der Beziehung oder am Arbeitsplatz runter zu schlucken, auf Distanz zum anderen zu gehen, sich schon mal nach einer neuen Wohnzimmereinrichtung, einem neuen Partner oder einem neuen Job umzuschauen? Ich denke nicht, dass das eine Lösung ist.
Hinschauen und Gefühle bei sich und anderen zulassen, ist ein guter Anfang.
Wir gehen oft Beziehungen ein, gehen aber gleichzeitig einer echten tiefen und anhaltenden Verbindungen privat wie beruflich instinktiv aus dem Weg, weil echte tiefe Gespräche, zu denen es in solchen Verbindungen kommen kann, weh tun können, insbesondere wenn man noch unverarbeitetes Trauma mit sich herum schleppt. Und in einer traumatisierten Gesellschaft, tragen halt viele Menschen solche traumatisierten und nicht bearbeiteten Anteile mit sich herum.
Wir sind die Kinder und Kindeskinder der Menschen, die den zweiten Weltkrieg hautnah miterlebt haben. Alles, was die Eltern und Großeltern nicht besprochen, nicht verarbeitet haben, tragen wir weiter mit uns herum. Das ist den meisten Menschen, meines Erachtens, nicht bewusst. Mag sein, dass an dieser Stelle der eine oder andere widerspricht. Widersprechen Sie mir gerne. Meine Alltagserfahrung ist eine andere. Die Art, wie wir Beziehungen gestalten, spricht Bände. Aber, wenn man es nicht anders kennt und keine Kontrollgruppe hat, sagt man sich halt: „So isses. Und so isses normal. Ich kenne es nicht anders. Das machen doch alle so.“
Es ist so normal, in unserer Gesellschaft, nicht vertieft über negative (und auch positive) Gefühle zu reden. Alleine die Bezeichnung „negative Gefühle“ klingt schon wenig einladend. Und es ist auch so normal, Menschen in dem Moment, wo sie gegen jede Empfehlung nicht nur über negative Gefühle reden wollen, sondern diese sogar live und in Farbe zeigen, abzuwerten, oder noch schlimmer, zu ignorieren, weil man sich verunsichert fühlt, nicht weiß, wie man damit umgehen soll. Gefühle scheinen ansteckend zu sein. Da ist Vorsicht geboten. Ich persönlich kann mich an viele solcher Momente erinnern, wo Menschen nicht gern hören wollten, wovor ich Angst hatte, was und wer mich verletzt und wütend gemacht hatte, beruflich wie privat. Mit geäußerter Angst und Trauer macht man(n) sich ganz schnell lächerlich. Mit Wut hingegen wird ein Mann von anderen als stark bis beängstigend wahrgenommen. Ein Mann, der wütend agiert, wird eher als kraftvoll und temperamentvoll eingeschätzt. Eine Frau wird mit Wut dann akzeptiert, wenn sie bereits in einer (männlichen) Führungsrolle ist. „Sie“ muss schließlich ihren „Mann“ stehen. Hat sie keine Führungsrolle, wird sie abgewertet oder befördert. Dem wütenden Mann wird eher unterstellt, er habe schließlich einen wichtigen Auftrag zu erfüllen. Der Frau wird eher ein Mangel unterstellt, den ich hier nicht näher bezeichnen möchte. Darin spiegeln sich sehr starre Rollenvorstellungen von Mann und Frau in unserer Gesellschaft wider. Ängstliche Frauen, die bei einer Autopanne bezaubernd aussehen, erfüllen ein bestimmtes Klischee. Impulsive Männer mit Holzfällerhemd erfüllen zumindest auf einer Baustelle ein anderes Klischee. Menschen mit ausgeprägten negativen Gefühlen werden unter bestimmten Umständen glorifiziert. Der bezaubernd aussehenden Frau mit Autopanne wird schnell und gerne geholfen. Aber wenn die ängstliche Frau eine Vorgesetzte ist und der impulsive Mann mit Holzfällerhemd ein Kunde in einem Beratungsbüro ist, dann kann die Bewertung ganz anders ausfallen. Dann sind diese Gefühle vermeintlich fehlplatziert. Gefühle scheinen einen Platz zu haben. Die ängstliche Vorgesetzte hat eine Führungsschwäche und der impulsive Kunde im Beratungsbüro wird vom Sicherheitsdienst „entfernt“. Der Wunsch, über die gezeigten negativen Gefühle zu reden, wird einem mit Nachdruck verwehrt. Durch diesen vermeidenden Umgang mit negativen Gefühlen oder die Fehlinterpretation dieser Gefühle kommt es meines Erachtens oft zu bestimmten Rollenbesetzungen im Berufsleben. Eine positive Selektion von Mitarbeitern mit sehr rücksichtslosem oder überangepasstem Verhalten findet statt. In privaten Beziehungen werden negative Gefühle durch Ablenkung und Konsum vermieden. Es werden zu viele oder zu wenige Kontakte gepflegt. Beziehungen werden gar nicht mehr für die Ewigkeit antizipiert. Man hält sich alle Wege offen und lernt ständig neue Leute kennen. Oder man lebt Beziehung in sehr starren Strukturen, wo neue Informationen kaum Eingang finden, damit man sich nicht hinterfragen und mit anderen vergleichen muss. Lebensphasen mit dem weit geöffneten oder dem eher geschlossenen Muster wechseln sich auch manchmal ab. Individuelle Entwicklungen des einen oder anderen Musters in Lebensverläufen, zeichnen sich irgendwann als gesellschaftliche Strömung ab, wenn sie bei vielen Menschen gleichzeitig geschehen. Menschen wollen alles ausprobiert haben, bevor sie sich das Reihenhaus kaufen. Andere verkaufen ihr Reihenhaus nach der Scheidung, um im Wohnmobil durch die Welt zu tingeln. Man könnte denken, dass dies einfach individuelle Lebensverläufe sind, die sich zufällig so ergeben haben. Es gab Zeiten, wo Menschen zufällig viel Halt in starren Beziehungs- und Lebensstrukturen fanden. Gegenbewegungen brachen diese starren Strukturen nicht wirklich auf, weil sie Feuer mit Feuer bekämpften. Grundsätzlich gegen alles zu sein, was die Eltern vorgelebt haben, ist ja auch irgendwie rigide. Der Apfel fällt nicht zufällig neben den Stamm. Heute 80 Jahre nach Kriegsende können Menschen mit Begriffen wie Achtsamkeit und bewusster Kommunikation immer mehr anfangen, jedoch geht die weit verbreitete Bewusstheit und Selbstreflektiertheit oft zu Lasten einer wünschenswerten Verarbeitungstiefe. Zu oft werden wir gedacht, gefühlt und gelenkt. Um dies mit uns machen zu können, werden von vermeintlich Herrschenden wichtige Orientierungspunkte wie die eigene Geschichte, Kultur und Sprache falsch erzählt oder bis zur Unkenntlichkeit verändert. Und eigene Gefühle, die einem noch letzten Halt und Orientierung in diesem Dschungel bieten könnten, werden vom Kapitalismus ausdauernd gejagt wie ein seltenes Tier. Separierung und Orientierungslosigkeit ist gewollt.
Alles dreht sich um unsere tiefen Gefühle, insbesondere diese negativen Gefühle, die aus Trauma entstehen. Diese Gefühle wollen gesehen, gehört und bearbeitet werden. Sie machen zum Glück, solange es die Menschheit gibt, zuverlässig auf sich selbst aufmerksam. Sie sind in Wahrheit unsere Lebensversicherung. Die Zeit heilt gar nichts. Und hierfür braucht es wieder ein Bewusstsein, dass Gefühle wertvoll sind, auch solche, die aus Trauma entstehen. Ich persönlich habe dafür mehr als ein halbes Leben gebraucht, um dies zu verstehen. Als junge Frau habe ich nicht gewusst, dass viele meiner Gefühle, negativ wie positiv, Ausdruck meines Traumas waren. Heute weiß ich, dass ich mit dieser Einschätzung, die ich damals hatte, in „guter Gesellschaft“ war. Den meisten Menschen geht das so, bis sie irgendwann ihr eigenes Trauma erkennen.
Wir sind eine traumatisierte Gesellschaft, und die Arten und Ausprägungen von Trauma sind so vielfältig und den meisten Menschen unbekannt wie die Namen der Blumen auf einer Sommerwiese.
Wenn man diesen Satz wirken lässt, dann stellt sich doch die Frage:
Wie sieht denn ein gesunder Umgang mit negativen (und positiven) Gefühlen aus?
Reicht es aus, wenn man die Namen aller Wiesenblumen auswendig lernt, damit man jedes Trauma genau bestimmen kann? Oder geht es mehr um das Fühlen und weniger um das Wissen?
Den gesunden Umgang mit meinen Gefühlen habe ich nicht durch Theorie und Bücher erlernt, sondern durch den Alltag, durch die (emotionalen) Reaktionen meiner Mitmenschen und durch das bewusste Spüren und Zulassen meiner eigenen Gefühle. In Stufen lernte ich meine Gefühle immer besser kennen und mit ihnen umzugehen. Je besser ich sie kannte, umso lieber waren sie mir. Und ich lerne sie immer noch weiter und besser kennen. Das ist ein Prozess.
Traumabearbeitung ist anfangs ein anstrengender Prozess. Man sollte das langsam angehen. Aber diese Arbeit ist sehr lohnenswert, weil sie einem viele glückliche Momente, Kraft und Lebensfreude schenkt. Reden wird dadurch leichter und bringt in allen Lebensbereichen Fortschritte. Manchmal tut Reden auch weh (siehe Titel), aber zeitgleich, und auch langfristig gesehen, wird das Leben schöner durch Traumabearbeitung. Es geht nicht um Schmerzvermeidung, sondern darum, mit dem Schmerz gut umgehen zu können. Denn dadurch wird er letztlich kleiner und verwandelt sich zur Wiesenblume. Es geht um Verwandlung durch Fühlen. Die Erfahrung, dass man Trauma bearbeiten kann, erzählt mir so viel über dieses Leben, wie stark es ist, wie sehr es uns liebt und welche Blüten daraus wachsen können. Viele schöne Dinge, die wir täglich sehen, sind aus bewältigtem Trauma oder dem Wunsch, Trauma zu bewältigen, entstanden.
Der Schmerz lehrt uns Demut vor dem Leben und kreiert nebenbei die schönsten Lieder und Kunstwerke. Trauer und Verlust betonen den Wert der Dinge. Ärger und Wut bringen uns in Wallungen und stellen die Energie bereit, die man manchmal braucht, um Berge zu versetzen. Ängste sind das Tor zum Glück. Schuld und Scham lehren uns Vergebung. Neid und Eifersucht lassen unseren Selbstwert wachsen, wenn wir uns ihnen stellen. Und Freude, Glück und Ekstase machen uns dankbar, großzügig und optimistisch.
Wenn wir diese Gefühle wieder zulassen, dann können wir gar nicht anders als reden. Wir reden dann wieder vertieft miteinander, weil es gut tut, weil es entlastet, weil es Nähe zu anderen vielleicht erstmalig aufbaut und dann zu einem dicken Band verstärkt bis ein großes stabiles Netz daraus entsteht, welches Menschen, die gerade Halt benötigen, diesen bieten kann.
Wir reden dann wieder miteinander, weil es gut tut.
-
 @ f0f6c64d:e40379b2
2025-05-11 19:35:59
@ f0f6c64d:e40379b2
2025-05-11 19:35:59The Economic Efficiency of Bitcoin and the Role of Angor in Increasing It
Bitcoin, from its inception, has emerged as a revolutionary virtual asset, with its decentralized nature, open ledger, and restricted supply. These intrinsic characteristics have transformed Bitcoin into a potential store of value and peer-to-peer transaction medium, attracting a growing global user base and massive investment. However, for Bitcoin to achieve its potential as a component of an upcoming financial system, innovative protocols that enhance its utility and efficiency are needed. Angor, one such innovative protocol on the Bitcoin network as a P2P funding protocol, is an example of that innovation, representing a new form of decentralized funding that has a large impact on the economic value and operational efficiency of Bitcoin.
The value proposition of Bitcoin is two-sided. Its scarcity of 21 million units with a hard ceiling inherently positions it above traditional fiat currencies facing inflationary dangers. That scarcity, added to its security and permanence due to its blockchain technology, has established it as being equivalent to "digital gold" – an economic uncertainty hedge and long-term repository of wealth.
Moreover, Bitcoin's decentralized system eliminates intermediaries like banks in transactions, which offers the possibility of lower costs and faster settlement times, particularly for cross-border transactions. Such a gain in efficiency is more applicable in a globalized world where efficient and low-cost financial transfer is of utmost importance. The growing adoption of Bitcoin by institutional investors and companies also attest to its economic significance and viability for mainstream adoption.
Angor: Peer-to-Peer Funding Model on Bitcoin
Angor – Peer-to-Peer Funding Protocol (P2PFP) provides a decentralized mode of funding projects on the Bitcoin network in one's own home.
It provides time-locked contracts, whereby investors can time-lock their Bitcoin in stages over given timeframes. When time for each stage is up, founders can then withdraw the allocated Bitcoin. Founders can provide ownership interest to investors in lieu.
One of the unique characteristics of Angor is the amount of freedom given to investors: they can always redeem their due coins, but possibly at some penalty. The protocol distantly distinguishes "lead investors" (historically early investors) from "ordinary investors." Lead investors are always penalized upon redemption early. Ordinary investors may take the penalty or, if sufficient lead investors have already redeemed with penalties, leverage the hashlocks of the lead investors for a penalty-free redemption.
This is intended to minimize fraud and maximize investor confidence by providing them with active control over their investments.
The Role of Angor in Making Bitcoin More Valuable and Efficient
Unlocking Liquidity and Economic Activity
By providing a safe and open way of financing projects, Angor encourages holders of Bitcoin to bring some of their assets out of long-term storage ("HODL mode") and into productive economic use. This increased turnover of Bitcoin in the economy can lead to increased liquidity and network activity overall, supporting its value proposition as a working currency and investment vehicle.
Reducing Counterparty Risk and Trust
Utilization of time-locked contracts and penalty/hashlock recovery mechanism greatly reduces the risk of fraud and mismanagement that has tainted other blockchain financing initiatives. There is also some level of control and recourse mechanism for the investors, stimulating further trust within the Bitcoin world in the direction of funding. There will be more people who join in, fueling further growth and value through increased trust.
Aligning the Incentives of Project Founders and Investors
Angor's staged funding approach, in conjunction with time-based milestone measurements, aligns the incentives of the project founders and investors' interests. By releasing the capital stepwise, the founders are incentivized to honor their obligations. Meanwhile, investors are assured protection through the option of recovering the invested capital in case the project doesn't go according to plan or fails. This alignment of incentives fosters a healthier and more stable source of funding for the Bitcoin network.
Capitalizing on Bitcoin's Security and Decentralization
Building directly on the Bitcoin network implies that Angor benefits from Bitcoin's robust security model and censorship-resistant, decentralized nature. This built-in transparency and security are essential to building trust in a funding protocol and to drawing users who value these core principles of Bitcoin.
Levelling up with the Newest Bitcoin Features
Angor's specification exploits the most recent innovations on the Bitcoin network, i.e., Taproot and Schnorr signatures. Taproot enables the commitment to multiple execution paths of a Bitcoin output such that the construction of complex spending conditions needed by the staged funding and recovery techniques can be facilitated. Schnorr signatures enable improved efficiency and anonymity.
Leveraging these bleeding-edge features, Angor demonstrates that the Bitcoin network is evolving towards increased capabilities beyond the peer-to-peer transaction basics.
Promoting Communication and Transparency
The implementation of the Nostr protocol for founder-investor communication creates further transparency and accountability. Being decentralized, Nostr makes communication censorship-proof and publicly verifiable, enabling investors to be updated about project developments and enabling direct communication with founders.
Conclusion: Angor as a Catalyst for Bitcoin's Growth
Angor is a significant step forward in optimizing the utility and economic efficiency of Bitcoin.
By providing a secure, transparent, and incentive-compatible way of decentralized financing, it encourages more participation in the Bitcoin economy, releases dormant capital, and establishes trust among users.
As the protocol gets more mature and more users implement it, it can make the value proposition of Bitcoin much higher, not just as a store of value but as a highly flexible and effective financial innovation platform. By introducing new use cases and making the overall ecosystem stronger, Angor facilitates the sustained development and increased utility of Bitcoin as part of the global financial landscape.
Bitcoin #BitcoinEfficiency #DecentralizedFinance #CryptoFunding #AngorProtocol #P2PFunding #BlockchainInnovation #Taproot #SchnorrSignatures #CryptoInvestment #CryptoEconomy #BitcoinAdoption #TrustlessFunding #Web3Funding #NostrProtocol #DecentralizedTrust #BitcoinUtility #HODLToInvest #CryptoProjects #SmartContracts
-
 @ bf47c19e:c3d2573b
2025-05-11 18:39:10
@ bf47c19e:c3d2573b
2025-05-11 18:39:10Originalni tekst na antenam.net
18.12.2024 / Autor: Ana Nives Radović
Ako ste makar djelić vremena proveli u svijetu digitalnog novca, vjerovatno ste naišli na termin HODL – uvijek napisan velikim slovima tako da na prvi pogled djeluje kao riječ sa slovnom greškom. Zapravo i jeste riječ o slovnoj grešci i to onoj koja je nastala na današnji dan prije 11 godina, a koja je uspjela ne samo da obezbijedi mjesto u istoriji svijeta novca, već i da postane naziv za jedan potpuno drugačiji pristup sredstvima koja posjedujemo.
Nespretno napisana riječ „hold“ (eng. držati, zadržati) u poruci na jednom forumu evoluirala je u akronim HODL – akronim za Hold On for Dear Life (doslovno – drži se za život, tj. drži se kao da ti život zavisi od toga), predstavlja poziv na akciju – ili, tačnije, „neakciju“ za vlasnike kriptovaluta da odole iskušenju prodaje tokom tržišnih padova. Riječ je o shvatanju da je ovaj oblik digitalne imovine bolje vremenski što duže imati u vlasništvu, kako bi se sačekao mnogo povoljniji trenutak za prodaju nego prodati ih u vremenu kada je situacija na tržištu loša.
Greška koja je postala pokret
Priča počinje 18. decembra 2013. godine, kada je cijena bitcoina tada počela da pada, a samo tokom toga dana se sa 682 na 522 dolara. Korisnik foruma pod imenom GameKyuubi objavio je sada već legendarni post pod naslovom „I AM HODLING“. Bila je to greška u kucanju, jer se na osnovu sadržaja poruke vidi da je krenuo da napiše „holding“ (držim), ali umjesto da se ispravi sebe, prigrlio je grešku, šaljivo govoreći o svom nedostatku vještina za trgovanje i zašto „bez obzira na sve“.

Bitcoin zajednica brzo je prihvatila ovaj izraz kao dio slenga. Pogrešno napisana riječ odjeknula je internet prostranstvima, a vremenom je prerasla u simbol šire filozofije – ne paniči, ne prodaj i ne dozvoli da kratkoročna nestabilnost poljulja tvoje uvjerenje. Od kasnonoćnog posta na forumu, HODL je postao poklič za vlasnike bitcoina (i drugih, u to vrijeme malobrojnih digitalnih valuta zanemarive vrijednosti) širom svijeta.
HODL-ovanje i HODL-eri
U suštini, HODL-ovanje je strategija zadržavanja kriptovaluta tokom tržišnih uspona i padova, zasnovana na uvjerenju da će cijene vremenom rasti. Umjesto impulsivnog reagovanja na tržišne fluktuacije, HODL-eri se posvećuju svojim investicijama na duže staze.
Ovaj pristup posebno je koristan za početnike, koji možda nemaju dovoljno stručnosti ili hrabrosti da se nose sa svakodnevnim trgovanjem (u čemu su često neuspješni i dugogodišnji vlasnici digitalnih novčića). Sam GameKyuubi u svom originalnom postu priznao je da samo najvještiji trgovci treba da pokušaju da „igraju igru“ tokom tržišnih padova. Za ostale, HODL-ovanje nije samo sigurnije, već je često i pametnije.
Filozofija HODL-ovanja zasnovana je na povjerenju – u budućnost kriptovaluta, u eventualni oporavak tržišta i u korist koju donosi strpljenje. To je odbijanje da se prodaje kada cijene naglo padnu – nepokolebljivo uvjerenje da su padovi privremeni i da nakon njih slijedi rast.
Zakon tržišta pokazuje da što drže HODL-ujete to se ova strategija više isplati, a cijena bitcoina u njegovoj šesnaestogodišnjoj istoriji je nesumnjivo najbolji dokaz za to. Trgovanje zahtijeva mnogo učenja, truda, vremena provedenog u praćenju svakog mogućeg signala, dok je kod HODL-ovanja važno samo da se „ne predate“.
Ako ste prethodnih godina nešto platili bitcoinom (a trgovci širom svijeta su to omogućili upravo da bi vas naveli da ih umjerite ka njima) vjerovatno ste zažalili, jer danas dok je njegova vrijednost i u dolarima i u eurima šestocifrena, ono na što ste ih potrošili ipak izgleda kao nešto što je trebalo platiti fizičkim novcem (kojeg je svakako „pojela inflacija“).
Pouzdane kriptovalute, a tu se prije svega misli na bitcoin, iako veoma volatilne bilježe trend rasta na duge staze, pa HODL-ovanje znači strpljenje u vremenu neizvjesnosti s idejom o koristi na duži rok, čak i kada su godine loše, kao što su bile 2014, 2017. i 2022. Na primjer, u periodu od 20. maja do 20. juna cijena bitcoina kliznula je sa 29.000 na 18.000 dolara, a upravo u tom trenutku mnogi su odlučili da količinu koju posjeduju prodaju ili je potroše plaćajući ovom digitalnom valutom (i pokajali se zbog toga).
HODL naspram drugih strategija
HODL-ovanje se razlikuje od aktivnijih strategija, poput kupovine po niskoj cijeni i prodaje po visokoj, jer dok trgovci pokušavaju da tempiraju tržište radi brze zarade, HODL-eri ostaju dosljedni svojoj odluci da se ne oslobađaju svoje imovine ni u najnoepovoljnijim trenucima. HODL-eri ne pokušavaju da predvide kretanje cijena – jednostavno čuvaju svoja sredstva, svjesni toga da će strpljenje na kraju donijeti rezultat.
Naravno, HODL-ovanje ima i svoje nedostatke. Za razliku od trgovaca koji mogu da povećaju svoj kapital kroz stratešku kupovinu i prodaju, HODL-eri zavise od vremena provedenog u čekanju na dugoročne rezultate. Pored toga, masovno HODL-ovanje može usporiti cirkulaciju kriptovaluta na tržištu, smanjujući ukupnu ekonomsku aktivnost – drugim riječima, kada bismo svi bili HODL-eri odnos ponude i tražnje bi bio veoma destimulišući i to bi oborilo cijenu.
Na sreću, trgovaca ima mnogo – dovoljno da tržište stalno bude aktivno i dinamično, no za one koji nemaju vremena, vještine ili sklonost ka riziku koji nosi trgovanje, HODL-ovanje ostaje jednostavan, ali veoma efikasan pristup.
Filozofija HODL-ovanja
HODL-ovanje je više od investicione strategije – to je način razmišljanja koji obuhvata otpornost, strpljenje i vjerovanje da su kratkotrajno suzdržavanje i nepokolebljivost u odluci da se sredstva sačuvaju vrijedna dugoročnog dobitka. Bilo da cijena bitcoina raste ili pada je, filozofija HODL-ovanja ostaje ista – ostanimo dosljedni, vjerujmo procesu i gledajmo u budućnost.
Jedan od ključnih razloga zašto većini ljudi ovakav pristup dugo nije bio razumljiv je zbog toga što su čitav sistem novca prihvatili u uvjerenju da on vremenom devalvira. Vjerovatno ste makar jednom razmatrali ponudu oročene štednje i procijenili da vam količina novca koju želite da položite neće donijeti onaj prinos koji će očuvati njegovu kupovnu moć nakon određenog broja godina, jer je kontinuirano doštampavanje novca podupiralo tu tvrdnju.
Dakle, ne treba da vas zavara sve ono što znate o novcu kao takvom, budući da bitcoin (na kojem je u ovom serijalu poseban fokus, jer mnoge druge kriptovalute ipak češće razočaraju nego što oduševe) nije novac, već samo ima neka svojstva novca. Posmatrajte ga radije kao imovinu – npr. kao nekretninu za koju sigurno želite da prodate onda kada je situacija stabilnija i kada su mnogo veće šanse da pronađete kupca kojem ćete je prodati po višoj cijeni.
U svakom slučaju, ako se u vašem digitalnom novčaniku već nalazi poneki satoshi (stomilioniti djelić bitcoina), kada tržište ponovo uđe u nepovoljnu fazu i zavlada prolazna panika, sjetite se onoga što je napisao GameKyuubi. HODL nije samo izraz – to je način da se prebrode oluje i izazovi koje nestabilno tržište nosi.
-
 @ 21ffd29c:518a8ff5
2025-02-04 21:12:15
@ 21ffd29c:518a8ff5
2025-02-04 21:12:15- What Are Homestead Chickens?
Homestead chickens are domesticated fowl kept by homeowners to provide eggs and companionship. They play a vital role in the homestead ecosystem.
Why Water is Essential in Cold Weather - Hydration Basics:
Chickens don't drink much water naturally but need it for hydration, especially during cold weather when metabolic rates increase. - Environmental Factors:
Cold weather can lead to ice buildup on water sources. Chickens benefit from having access to fresh water year-round.Maintaining Accessible Water Sources - Shallow Troughs:
Use shallow troughs instead of deep containers to minimize ice formation and ensure constant water supply. - Automatic Feeders:
Consider installing automatic feeders for convenience, especially in unpredictable weather conditions. - Multiple Water Sources:
Provide multiple water sources to prevent competition and ensure all chickens have access.Preventing Ice Buildup - Floating Shallow Troughs:
Opt for troughs that sit above the ground to avoid ice buildup. Ensure they're placed where they can't freeze completely. - Regular Checks:
Inspect water sources regularly to remove ice and debris, maintaining accessibility for chickens.Best Practices for Watering Chickens - Waterers Designed for Cold Weather:
Use waterers made of stainless steel or plastic that can withstand cold temperatures. - Seasonal Adjustments:
During extreme cold spells, supplement with a small amount of fresh water to aid in drinking.Conclusion - Key Takeaways:
Providing proper water is crucial for the health and well-being of homestead chickens during cold weather. Maintaining accessible, shallow water sources prevents issues like ice buildup and ensures hydration.Final Thoughts - Sustainability Considerations:
While chickens don't drink much, ensuring they have water supports their overall health and sustainability efforts. - Environmental Impact:
Thoughtful water management can reduce water usage, promoting eco-friendly practices on the homestead. - What Are Homestead Chickens?
-
 @ bf47c19e:c3d2573b
2025-05-11 18:37:13
@ bf47c19e:c3d2573b
2025-05-11 18:37:13Apstrakt
Kriptovalute (engl. "cryptocurrency") su digitalne (virtualne) valute, koje iako su sredstvo razmene, još uvek nisu strogo regulisane zakonom u većini država, a u pojedinim su čak i zabranjene. Veliki broj ljudi, uključujući i IT stručnjake i programere ne znaju mnogo o ovoj temi, a šira javnost izjednačava pojmove blokčejna i bitkoina. Tržište kriptovaluta danas iznosi gotovo 770 milijardi dolara. Od pojave prvih digitalnih valuta do danas, nastalo je preko 1.300 aktivnih kriptovaluta koje se razlikuju prema svojim svojstvima i upotrebi. Pre bitkoina bilo je mnoštvo neuspelih pokušaja stvaranja digitalnih valuta (digikeš, heškeš, Fejsbuk kredit i dr.). Utopistička ideja da matematika i fizika mogu rešiti društvene probleme započela je svoj život kroz pojavu bitkoina. Genijalna ideja po kojoj funkcioniše bitkoin zasnovana je na tehnologiji blokčejna, čiji kapacitet doseže daleko iznad kripto valuta. Iako se još uvek vode polemike ko stoji iza pseudonima Satoši Nakamoto, njegova zaostavština ima potencijal da promeni svet. Uspeh bitkoina leži u prednostima koje ima u odnosu na druge slične valute, ali njegov značaj prevazilazi i pogodnosti koje je doneo. Banke nisu potrebne za čuvanje podataka o novcu, evidenciju o imovini i svakoj transakciji bitkoina čuvaju računari svih korisnika mreže u zajedničkoj bazi podataka blokčejnu. Sve transakcije su mnogo brže od bankarskih, bez taksi, uz drastično lakše plaćanje preko državnih granica. Bitkoin svojim korisnicima pruža bezbednosti bez identifikacije, iako blokčejn beleži transakciju, ne beleži ko stoji iza nje. U radu su predstavljeni osnovni principi na kojima su zasnovani bitkoin i druge kriptovalute, pojašnjen odnos između blokčejna i bitkoina.
1 UVOD
Ideal o novcu koji se ne oslanja na centralne institucije (koje mogu propasti, ali i koje vrše nadzor nad korisnicima), postojao je decenijama. U digitalnom svetu prvi ga je uobličio pisac naučne fantastike Nil Stivenson 1999. godine u svojoj noveli Kriptonomikon. On je opisao podzemni svet koji funkcioniše zahvaljujući digitalnom zlatu zasnovanom na kriptografiji, pri čijoj upotrebi korisnici ne moraju odavati ko su i šta su (Popper, 2016).
Kriptovalute (engl. cryptocurrency) su digitalne (virtualne) valute, koje iako su sredstvo razmene, još uvek nisu strogo regulisane zakonom u većini država, a u pojedinim su čak i zabranjene (Jovanović, 2014).
Da bi se razumeo nastanak i funkcionisanje kriptovaluta, neophodno je sagledati ih iz različitih uglova na kojima su one bazirane: matematici, sociologiji, ekonomiji, pravu i politici. To je verovatno i glavni razlog zbog koga veliki broj ljudi (uključujući i IT stručnjake i programere) ne znaju mnogo o ovoj temi. Takođe, šira javnost izjednačava pojmove blokčejna i bitkoina.
Sve kriptovalute su bazirane na jedinstvenom nizu brojeva za svaku jedinicu valute, koje korisnici mogu jedni drugima slati preko mreže. U prošlosti su se ti nizovi mogli lako kopirati i trošiti više puta, zbog čega nisu imali vrednost. Kriptograf Dejvid Čaum je taj problem rešio stvaranjem jedinstvene centralizovane knjige, u kojoj su se čuvale beleške o transakcijama svakog korisnika, čime ni jedna jedinica valute više nije mogla da se nalazi na dva mesta istovremeno (Bertlet, 2016).
Kriptovalute svoj nastanak duguju težnjama levo orijentisanih utopističkih posvećenika IT tehnologija koji su sanjali o univerzalnom novcu koji bi svako mogao da poseduje i troši, čija je vrednost onolika koliko su korisnici voljni da plate (na principu ponude i potražnje), ali pre svega na liniji fronta za onlajn anonimnost i slobodu, bez cenzure i nadzora. Pojavi bitkoina prethodio je Sajberpankerski manifest Done Haravej (Haraway, 1985) koji počinje rečima: „U elektronsko doba, privatnost je neophodan uslov za postojanje otvorenog društva“.
Kriptovalute su univerzalni novac koji se može koristiiti bilo gde u svetu, one su lako prenosive i teško se krivotvore.
Neki podaci pokazuju da tržište kriptovaluta danas iznosi gotovo 770 milijardi dolara. Od pojave prvih digitalnih valuta do danas, nastalo je preko 1.300 aktivnih kriptovaluta koje se razlikuju prema svojim svojstvima i upotrebi.
Prema odredbama Zakona o Narodnoj banci Srbije celokupni unutrašnji promet u Republici Srbiji izražava se u dinarima, osim ako nekim zakonom nije drukčije određeno. „Zakonom o platnom prometu propisano je da se poslovi platnog prometa obavljaju u dinarima, a Zakonom o deviznom poslovanju da se plaćanje, naplaćivanje i prenos između rezidenata i između rezidenata i nerezidenata u Republici Srbiji vrši u dinarima, a izuzetno se može vršiti i u devizama u slučajevima koji su propisani ovim zakonom“ (NBS, 2014).
Tržište kriptovaluta u Srbiji postoji, sve je veći broj rudara. Iako trgovanje kriptovalutama nije nelegalno, Narodna Banka Srbije - NBS je u više saopštenja navela da one ne predstavljaju zakonsko sredstvo plaćanja u Republici Srbiji. Takođe, zbog toga što ih ne izdaje centralna banka, NBS za korišćenje virtuelnih valuta, ulaganje u njih, kao ni za njihovu vrednost. Narodna banka Srbije je više puta upozoravala javnost da virtuelne valute ne predstavljaju zakonsko sredstvo plaćanja u Republici Srbiji (NBS, Politika – u vezi s bitkoinom, 2017).
Ukoliko kriptovalute promatramo kao novac onda njihove tranksakcije mogu biti upitne shodno Zakonu o sprečavanju pranja novca i finansiranja terorizma, gde je propisana obaveza preduzimanja radnji i mera za sprečavanje pranja novca, kao što su identifikacija stranaka koje trguju preko tih platformi, uzimanjem kopije ličnog dokumenta. Kako poslovanje platformi na kojima se vrše transakcije kriptovalutama nije zakonom regulisano u Republici Srbiji, a uglavnom ni u uporednom pravu, a čl. 552. Zakona o obligacionim odnosima Republike Srbije ((„Sl. list SFRJ“, br. 29/78, 39/85, 45/89 - odluka USJ i 57/89, „Sl. list SRJ“, br. 31/93 i „Sl. list SCG“, br. 1/2003 - Ustavna povelja) predviđa razmenu robe kao jedan od načina trgovine, otvara se put ka legalnoj trgovini kriptovalutama (Bubanja, 2017).
Praksa je pokazala da su se korisnici kriptovaluta kada su imali problem sa njima, obraćali vlastima i njihovim regulatornim telima, zbog čijeg su zaobilaženja i smišljeni. Nažalost, korisnici ne uživaju pravnu zaštitu čak i kada je reč o trgovini putem registrovanih privrednih subjekta.
2 BITKOIN
Prva decentralizovana kriptovaluta koja se pojavila je bitkoin (eng. „Bitcoin“). Termin bitkoin označava istoimenu organizaciju, softver i protokol, kao i jedinicu mere ove kriptovalute (skraćeno BTC) (Bertlet, 2016). Koncept na kome se zasniva bitkoin prvi put je predstavljen 2008. godine u članku "Bitcoin: A Peerto-Peer Electronic Cash System", a u januaru 2009. godine bitkoin je pušten u promet. Njegov tvorac nije poznat do danas i krije se iza pseudonima Satoši Nakomato. Novu vrstu digitalne kriptovalute formirao je tako što je stvorio distribuirani sistem verifikacije. Bitkoin nastaje u procesu koji se naziva „rudarenje“ (engl. mining). Njegova jedinstvenost je u tome što je decentralizovana valuta, iza koje ne stoji nijedna država, niti banka. Bitkoin je digitalna valuta, koja nastaje i čuva se elektronski. Kriptovalute u cilju maksimizacije bezbednosti, upotrebljavaju metod - dokaz o radu (engl. proofof-work), metod baziran na informacijama koje je teško stvoriti, ali koje ostalim učesnicima u rudarenju obezbeđuju laku proveru i verifikaciju transakcija.
Kriptovalute se čuvaju na bitkoin adresama za koje ključ predstavlja jedinstven niz slova i brojeva. Svaka transkacija bitkoinom se beleži u blokovima koji se zovu blokčejn. Transakcije se hronološki ređaju u blokove, u svakom se nalazi digitalni potpis prethodnog bloka, time se uređuje redosled i garantuje da novi blok može da se pridruži lancu samo ako počne na mestu na mestu završetka prethodnog. Jedan od osnovnih činilaca bezbednosti bitkoina je da se kopija svake izvedene transakcije beleži na svakom nalogu na kome je instaliran bitkoin softver. Blokčejnove neprekidno verifikuju računari svih korisnika softvera, tako sistem zna u bilo kom trenutku, koliko bitkoina svaki korisnik u svom novčaniku poseduje. Novčanik je program koji služi za slanje, primanje i skladištenje kriptovaluta. Digitalni novčanik sadrži prikaz količine kriptovalute koju korisnik poseduje, zapise o svim njegovim transakcijama, korisnički tajni ključ i njegove adrese (Bertlet, 2016). Novčanik je moguće instalirati na računar, mobilni telefon i tablet.
Falsifikovanje bitkoina nije moguće, jer iako vlasništvo može da se menja ono se ne može nikada duplirati (Bertlet, 2016). On je pseudoanoniman, bitkoin mreža čuva sve podatke o svakoj transakciji koja se dogodila unutar mreže. Svako ko ima bitkoin softver i adresu na bitkoin mreži, može videti koliko novca ima na mreži, ali ne i kome oni pripadaju. Za razliku od otvaranja računa u bankama, otvaranje bitkoin računa (adrese) je brzo, bez troškova i „papirologije“. Jedna od glavnih prednosti bitkoin mreže je brzina transakcija.
Svako ko snagu svog računara posveti verifikaciji transakcija u blokčejnu može biti „rudar“. To je proces dodavanja transkacija u registar svih bitkoin transkacija. Rudarenje čini rešavanje matematičkog algoritma za čije se uspešno rešavanje dobija određena količina bitkoina.
Iako bitkoin ima reputaciju nestabilnosti, velikih fluktuacija i nezakonitog poslovanja, čemu mnogi pridodaju i urušavanje tradicionalnog koncepta nacionalnih država, ipak većina se slaže u tome da je njegova pojava najvažnija nova ideja od stvaranja Interneta (Vigna & Casey, 2016).
Razloga za uspeh bitkoina ima više. Finansijska kriza povoljno je uticala na njegov razvoj, poverenje u postojeći finansijski ali i politički sistem je bilo poljuljano i brojni korisnici su u njemu prepoznali drugačije rešenje.
Anonimnost koju pruža prilikom transakcija jedan je od ključnih razloga njegovog uspeha. Prilikom digitalnog plaćanja bitkoinom u većini slučajeva nije potrebno davanje ličnih podataka. Ovakva vrsta anonimnosti, nažalost pogodovala je i usponu tamne strane upotrebe i popularnosti bitkoina u kriminalnim krugovima.
Računi u bitkoinu nisu opterećeni visokim bankarskim dažbinama.
Takođe, nije beznačajan ni potencijal plaćanja izdataka koji su manji od trenutnih ograničenja u konvencijalnim transakcijama na internetu (npr. naplata čitanja jednog novinskog članka ili preskoči reklamu, koji koštaju manje od 20 ili 30 centi kolika je najmanja transakcija) (Popper, 2016).
Kao što su svi učesnici na internetu povezani protokolima (TCP/IP, FTP, SMTP, HTTP i dr.) zahvaljujući kojima mogu međusobno da komuniciraju, bitkoin je stvorio svoje softverske protokole koji uređuju funkcionalna pravila upravljanja sistemom.
Bitkoin je omogućio novi način stvaranja, čuvanja i transfera novca.
Od svog nastanka bitkoin se unapređivao, podržan od internet zajednice, posebno od posvećenika slobodi interneta i anonimosti, mnogi od problema koji su uočeni su rešavani zajedničkim naporom internet zajednice.
3 BLOKČEJN
Blokčejn (engl. blockchain) nije samo bitkoin, on je tehnologija za koju mnogi predviđaju da će promeni svet (OECD, 2018).
Ukoliko bismo pojednostavljeno opisivali blokčejn mogli bismo da kažemo da je to nova vrsta baze podataka, iako bi to bilo pojednostavljeno objašnjenje slično kao kada bi smo imejl (email) opisali kao novi način za slanje pisama.
Iako blokčejn jeste nova vrsta baze podatka, to ne objašnjava u dovoljnoj meri genijalnost načina na koji funkcioniše.
Kada bilo gde i bilo kada položimo novac, oslanjamo se na zapis u bazi podataka treće strane, banke, firme i sl. Poverenje u banke zasnovano je na zakonu koji reguliše rad banke, poverenju u državu da će u slučaju propasti banke država nadoknaditi klijentima njihov ulog.
Kada plaćamo on line usluge ili vršimo neku drugu transakciju kreditnim karticama, poklanjamo poverenje kompanijama koje posreduju u našem plaćanju (Mastercard, VISA i dr.) koje za to uzimaju određenu materijalnu nadoknadu. Čak i prilikom tradicionalnih oblika plaćanja gotovinom u papirnom novcu, mi dajemo papir na kome je ispisana vrednost za koju prodavac veruje da će mu biti isplaćena (ili garantovana) od strane vlade koja ju je štampala. Digitalno plaćanje zbog prisustva trećih strana (banke, kreditne kompanije i dr.) uvek je bilo moguće pratiti. I kod plaćanja gotovinom klijenti veruju bankama i kreditnim kompanijama koje rukovode platnim karticama, da imaju pouzdane baze podataka. I vlade država veruju da banke i kreditne kompanije vode baze podataka koje su tačne i pouzdane.
Baze podataka sadrže mnoštvo ličnih podataka, od npr. medicinske dokumentacije u domu zdravlja koja sadrži važne informacije o nama i našem zdravstvenom stanju, kada smo i od koje bolesti bolovali, koje lekove smo koristili i sl. I druge baze podataka sadrže mnoštvo naših ličnih podataka koje su važne ne samo za nas, već i za državu, grad, privredu, druge građane itd.
Osim što omogućava anonimne i sigurne transakcije, blokčejn ima i potencijal da sačuva sve vredne informacije, od podataka o rođenim i umrlim, preko osiguranja, do katastara nepokretnosti, pa čak i glasova (Tapscott, 2018).
Sagledavši mogućnosti koji blokčejn nudi u transformaciji industrija i tržišta, povećanju transparentnosti i poverenja između građana, kao i olakšanom pristupu tržištu (uz bolju efikasnost transakcija), ali i rizicima koje sa sobom nosi, Organizacija za ekonomsku saradnju i razvoj - OECD organizovala je od 4. do 5. septembra 2018. godine Forum politike OECD-a za blokčejn. To je bila ujedno i prva glavna međunarodna konferencija na kojoj se razmatrao uticaj blokčejna na aktivnosti vlada i javnih prioriteta. Forum se bavio prednostima i rizicima blokčejna za ekonomiju i društvo, pokušajem određivanja adekvatnog regulatornog pristupa, kao i javnih politika prema blokčejnu.
Učesnici Foruma su diskutovali o mogućnostima globalnog ekonomskog uticaja blokčejna, njegovim implikacijama na privatnost i sajber bezbednost, upotrebi blokčejn tehnologija za povećanje inkluzivnosti, njegovoj upotrebi u promovisanju zelenog rasta i održivosti, kao i jačanju kapaciteta javne uprava i primene u praksi (OECD, 2018).
4 ZAKLJUČAK
Pre bitkoina bilo je mnoštvo neuspelih pokušaja stvaranja digitalnih valuta (digikeš, heškeš, Fejsbuk kredit i dr.). Uspeh bitkoina leži u prednostima koje ima u odnosu na druge slične valute, ali njegov značaj prevazilazi i pogodnosti koje je doneo.
Svaki korisnik bitkoina ima potpunu kontrolu nad novcem na svom računu (adresi), jedino osoba sa privatnim ključem može pristupiti bitkoinima na toj adresi. Banke nisu potrebne za čuvanje podataka o novcu, evidenciju o imovini i svakoj transakciji bitkoina čuvaju računari svih korisnika mreže u zajedničkoj bazi podataka blokčejnu. Sve transakcije su mnogo brže od bankarskih, bez taksi, uz drastično lakše plaćanje preko državnih granica.
Bitkoin svojim korisnicima pruža bezbednosti bez identifikacije, iako blokčejn beleži transakciju, ne beleži ko stoji iza nje. Zahvaljujući peer-to-peer komunikaciji i kriptografiji, povezivanje bitkoin transakcija sa osobom u stvarnom životu je veoma teško. To je u ujedno možda i njegova najveća mana, jer su oporezivanje i nadzor nad korisnicima krajnje teški.
Garancija vrednosti bitkoina osmišljena je po uzoru na plamenite metale kojih ima ograničeno u prirodi. Zbog toga je Satoši u kodu bitkoina odredio da ih ima maksimalno 21 milion, te da ukoliko bitkoin protokol ostane isti, poslednji bitkoin će biti izrudaren 2140. godine.
Do sada je izrudareno oko 17 miliona bitkoina, što znači da je ostalo 4 miliona, ili oko 19%. Do sada je bitkoin uspeo da prevlada sve krize koje su ga zahvatile (u više slučajeva nestajali su iznosi koji su dostizali i 400 miliona dolara). Kakva god sudbina bitkoina bila u budućnosti, njegova uloga se neće moći zanemariti, prvenstveno zbog toga što je zahvaljujući njemu iznedren blokčejn. Bez obzira na skepticima u vezi sa kriptovalutama, teško se mogu osporiti mogućnosti koje blokčejn pruža, pre svega u zaštiti baza podatka.
-
 @ fd208ee8:0fd927c1
2025-02-06 15:58:38
@ fd208ee8:0fd927c1
2025-02-06 15:58:38Beginning at the start
In my previous article, The Establishment, I answered the question: "How do we form a company?" I realize, now, that I was getting a bit ahead, of myself, as the precursor to a company is a team, and many people struggle to form teams. So, I will go back to the beginning, and then you can read both articles to the end, and then stop.
The Initiation
The first, and most-difficult step of team formation, is the initiation. We know that it must be the most-difficult, as it's the step that carries the highest potential reward, and it's the step that is tried-and-failed most often. (Some people, like Elon Musk or Donald Trump, are born Initiators with excellent follow-through, but this archetype is exceedingly thin on the ground because it requires you to be mildly autistic, have barely-throttled ADHD, and/or tend to megalomania, also popularly known as "toxic masculinity", "CEO personality", or "being a successful military officer".)
Someone needs to form a useful, attractive Vision and then motivate other people to help them achieve it. That sounds really easy, but it's actually brutally difficult because * You have to come up with an idea that is coherent, plausible, and inspiring. * You have to be able to communicate that idea to other people and make it appealing to them, by tying it into their own personal goals and desires. * You have to be able to hone and reformulate that idea, constantly, to correct it or to re-motivate the other team members. * You have to defend the idea against detractors, naysayers, and trolls, and you have to do it so vociferously, that it will erode your own popularity among those who disagree with you and open you to personal attacks. * You have to be able to focus on the idea, yourself, for a long stretch of time, and not allow yourself to get bored, lazy, or distracted.
So, just do and be all of those things, and then initiate the team, with the method I will name the Hatbock Method. It is so named because of the classic, German initiation ritual, in which an Initiator stands up, loudly defines their Vision and calls into a group "Wer hat Bock?" (roughly, "Who has the hunger/desire?") and whoever responds with "Ich hab Bock." (roughly, "Yes, I hunger for this.") is a part of the team.
Then the Initiator says, "Okay, everyone with the hunger, let's sit down together, and discuss this some more." (This "sitting" is literally called a "seating", or "Sitzung", which is the German word for "meeting".)
The Sitting
We now get to the second most difficult part of team formation: figuring out where to sit. Most teams get this wrong, repeatedly, and many teams dissolve or fracture under the difficulty of this momentous decision. You would think organizing yourselves online would make this easier ("Oh, we'll just meet online!"), but the number of places available for sitting online are limitless. You can talk your whole Vision into the ground, with laborous discussions and migrations between Chachi, OxChat, Telegram, SimpleX, Slack, Discord, WhatsApp, GitHub, Teams, Coracle, Matrix... you get the idea.
Try to keep in mind that the Vision is more important than the seating area, and go with the flow. Simply, find someplace and go there. Worry about it again, at a later date. Don't lose momentum. Sit down and start discussing the Vision, immediately.

Now, this next bit is very important:
Do not let anyone outside your team influence where you sit!
...unless they are providing your team with some good, service, or income, that makes choosing their preferred location the superior choice.
This is the German Stammtisch principle, where a host encourages you to come sit down, regularly, in some particular place, because your sitting there provides them with some benefit: they can overhear your conversations, get you to test out their seating area, sell you refreshments, etc. Your choice of seating, in other words, is a valuable good, and you should only "sell" it to someone who rewards you in measure. They have to reward you because their preferred seating area wasn't your immediate and obvious choice, so there was probably something unappealing or uncertain about the seating area.
Plan it in
Once you've sat down, and finished your rough draft of the Vision, you need to figure out when to sit. This is the third most-difficult part of team formation. (Yes, don't worry, it gets easier as it goes along.)
The most popular plan is the Wirsehenuns Plan (roughly, "We'll see each other, around.") This can work quite well, if you just want to have a loose collaboration, that calls itself together in an ad hoc fashion, when a team member feels the need. Also known as "@ me, bros".
It's not a great plan for more intensive collaboration, as that tends to need a certain amount of velocity, to actually happen, as the speed of movement has a centrifugal effect on the tasks. Team momentum, in other words, creates a sort of gravity, that keeps the team together as a unit. So, for deeper teamwork, I would recommend the Stammtisch variant: name a place and date/time, when you will next meet. Preferably, on a rotating schedule: daily, weekly, last Thursday of the month, etc.
And then meet there and then. And discuss amongst yourselves. Set clear, short-term tasks (and assign them to particular people!), medium-term strategies, and longer-term goals. Write everything down. Anything not written down, is a suggestion, not an assigned task.
If you find your Stammtisch becoming increasingly rewarding and productive, and your goals start moving closer and closer into sight, then you might want to formalize your team structure further, as a company.
-
 @ 0fa80bd3:ea7325de
2025-01-29 14:44:48
@ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]]
1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest.
2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money.
3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape.
Now, what you do with a trapped bear is another question... 😏
-
 @ 3ae7fdae:f8d4b19d
2025-01-28 00:00:26
@ 3ae7fdae:f8d4b19d
2025-01-28 00:00:26Lifting the Curtain on Power and Scandal
The Illusion of Power and TrustIn the modern world, the line between trust and skepticism is razor-thin, especially when it comes to powerful figures and organizations. They present polished facades, dazzling us with promises of stability, innovation, or in Disney’s case, enchantment. Yet, the revelations surrounding Jeffrey Epstein’s network reminded us that power is often far more complex than it appears. This scandal became a litmus test for public trust and fueled questions about who, or what, might be entwined in hidden truths.
When Epstein's crimes were exposed, they revealed not just the horrifying details of exploitation, but also the unsettling reach of his influence. As the media peeled back the layers of his associations, public attention naturally shifted to recognizable names and institutions, including Disney. How could a company that represented childhood innocence, with castles and fairy tales, find itself whispered about in the same breath as Epstein’s infamous circle? This segment examines the roots of that question and the facts that illuminate its plausibility or dismiss it.
Epstein: A Man Who Mastered Access to PowerJeffrey Epstein was more than just a financier—he was a gatekeeper to influence. His lifestyle and operations were an entangled web of charm, manipulation, and wealth, meticulously designed to secure him a place among the powerful. Investigative articles by The Guardian and The New York Times depict Epstein as a social engineer, curating relationships that ranged from politicians and royalty to scientists and celebrities.
Court documents and deposition testimonies during Epstein’s trial confirmed that his homes and private jet were hubs for connecting with influential figures. This access did not come without consequence; it cemented him as both a source of curiosity and, later, fear. Public records, such as those scrutinized in The Washington Post, indicated his involvement with many high-profile individuals. Yet, the details of these relationships varied—some guests were casual acquaintances, others, confidants.
The Infamous Flight LogsThe flight logs of Epstein’s private jet, colloquially known as the "Lolita Express," became a centerpiece for public scrutiny. Released through court orders and accessed by journalists, these logs listed names that triggered a cascade of questions. Guests ranged from prominent business executives to entertainment figures, sparking a debate over whether mere association implied complicity or deeper connections. This fueled the narrative that Epstein’s reach was far more extensive than previously understood, implicating industries where entertainment, power, and trust intersected.
The Role of Speculation in Public DiscourseAs soon as these flight logs surfaced, discussions surged online and across media platforms. The presence of any entertainment figure in Epstein’s orbit raised an eyebrow and, in many cases, invited a leap of logic: if influential media personalities were tied to him, could companies known for entertainment and global reach, like Disney, have hidden associations as well? This hypothesis, though lacking concrete evidence, found fertile ground among those predisposed to distrust large, seemingly untouchable institutions.
It’s crucial to dissect why Disney, specifically, became a subject of speculation. On one hand, its status as an omnipresent media empire makes it an easy target for conspiracy theories that thrive on the juxtaposition of light (Disney’s brand) and darkness (Epstein’s crimes). On the other, it speaks to a larger societal impulse to find cracks in the foundations of those we consider infallible. The idea that even the most beloved entities might harbor hidden truths appeals to a deep-seated desire for transparency and accountability.
The Catalyst of Public CuriosityThe timing of Epstein’s exposure was a critical factor. His arrest and subsequent death in 2019 coincided with a period marked by rising distrust in institutions, fueled by political and social upheavals globally. Social media platforms amplified this distrust, creating echo chambers where half-truths and speculative narratives merged seamlessly with confirmed facts.
It is here that Disney’s name began to surface not as an accused, but as a speculative point in discussions. The reasoning often pointed to a "guilt by association" logic: if the powerful dined, flew, or partied with Epstein, then it was worth questioning the circles in which those powerful entities moved, even without direct evidence. This leap from speculation to assumption reflects a pattern that sociologists recognize as part of conspiracy theory psychology—where a lack of clear answers invites the mind to fill in gaps, often with what feels most compelling.
Reframing the Public’s QuestionsThe real question becomes: why does this speculation hold such sway, even when evidence is scarce? Part of the answer lies in precedent. History is replete with instances where institutions that seemed above reproach were later implicated in hidden misdeeds, from financial frauds to abuse scandals within trusted organizations. This collective memory primes the public to believe that beneath any glittering surface could lie a dark, concealed underbelly.
Disney’s position as an icon of childhood and innocence adds another layer to this narrative. To imagine that such a symbol could be tainted by proximity to someone like Epstein is not just shocking—it’s fascinating. It strikes at the core of what we hold sacred, making it an irresistible topic of conversation and investigation.
Why This MattersUnderstanding why names like Disney are brought into these discussions without verified evidence is essential. It helps differentiate between warranted inquiry and unsupported speculation, allowing us to approach these narratives critically. Addressing this head-on does not only clear the air but strengthens the foundation upon which valid criticism and accountability are built.
A Note on EvidenceAs we move deeper into this exploration, it’s critical to emphasize that while Epstein’s connections to high-profile figures are thoroughly documented, there remains no evidence tying Disney, as an organization, to his operations. Still, the fascination with the “what-ifs” continues, driven by our collective quest for understanding power, secrecy, and the thin line between public and private lives.
The next segment will dive into Epstein’s proven network, unraveling the extent of his influence and why it has been the breeding ground for questions involving the world’s most trusted corporations.
Epstein’s Documented Network
The Web of Power: A Portrait of InfluenceJeffrey Epstein’s network was not merely a collection of acquaintances; it was a curated gallery of the world’s most influential figures, built on calculated relationships and strategic connections. Epstein wielded this network with the precision of a skilled operator, bridging disparate realms of society—politics, academia, business, and media. Investigative reporting by sources such as The New York Times and The Guardian exposed how Epstein maintained access to individuals who shaped policy, managed wealth, and crafted the narratives of popular culture.
Court records, testimonies, and detailed analyses of his interactions revealed that Epstein was adept at placing himself at the center of elite circles. His estates, from Manhattan townhouses to private islands, hosted events that blurred the lines between social gatherings and strategic networking. This chapter delves into the proven extent of Epstein’s reach and why it sparked questions about connections to corporations and public institutions, including Disney.
Flight Logs: The Proof and the SparkThe flight logs from Epstein’s private jet, the infamous "Lolita Express," were among the most illuminating pieces of evidence in mapping his connections. These logs, legally obtained and examined by journalists, painted a picture of Epstein’s influence stretching across industries. High-profile figures were listed, including financiers, political leaders, and entertainment personalities. The presence of notable names triggered waves of speculation—if Epstein had access to such power players, how many more remained unnamed but entangled?
The Guardian and The Washington Post reported that these flights were not just transportation but often involved visits to Epstein’s various properties, known for their opulence and the dark rumors surrounding them. While these logs confirmed that many public figures knew Epstein, the depth and nature of their associations varied widely, from casual acquaintance to deeper involvement.
The Limits of the KnownDespite the breadth of documented connections, there was no verifiable evidence linking Disney as an entity to Epstein’s circle. What the flight logs and guest lists revealed was a man deeply embedded in networks of power, yet even within these proven associations, context was crucial. For instance, some guests, confirmed by court records and investigative articles, were shown to have attended public events or engaged in business unrelated to Epstein’s criminal activities.
The distinction between documented presence and complicity is where the narrative often splinters. The leap from association to implication fueled public debate and conspiracy theories. This was especially true when figures from media and entertainment, sectors known for influencing public sentiment and childhood memories, appeared on the periphery of Epstein’s activities.
Epstein’s Parties and Gatherings: The Elite’s Shadowed StageEpstein’s parties were legendary, drawing attendees from the highest echelons of influence. These gatherings were not casual mixers but orchestrated showcases of power. Reports from court depositions and firsthand accounts highlighted how Epstein leveraged these events to cement alliances and reinforce his status as a gatekeeper to the elite. Some testimonies even described how these events served as platforms for discussing investments, politics, and global initiatives, reinforcing Epstein’s perceived omnipotence.
High-Profile Confirmations and Their ImplicationsSeveral prominent individuals were indeed verified as having ties to Epstein, raising legitimate questions about the extent of their knowledge or involvement. These names included politicians, royalty, and entertainment figures. The ambiguity surrounding these associations allowed theories to flourish. The sheer presence of influential names on Epstein’s guest lists raised the question: If these individuals were implicated, what about the institutions they represented or the circles they moved within?
This was a turning point for public speculation. The logic extended: if an individual from a major media company or entertainment empire like Disney was even remotely connected, could that implicate the company itself? The answer, according to existing court records and credible investigations, remained no. Yet, the absence of direct evidence did not stop speculation; in many cases, it intensified it.
Why Disney Was Brought Into the ConversationDisney’s reputation as a family-friendly giant contrasted starkly with the dark nature of Epstein’s activities, making it an unlikely yet intriguing topic for public discourse. While some entertainment figures appeared on Epstein’s flight logs or were rumored to have interacted with him, investigations have not yielded any proof of corporate-level involvement. However, public fascination persisted, bolstered by the broader questions Epstein’s connections evoked.
It’s worth noting that corporations like Disney, with their vast reach and unparalleled influence, naturally become focal points when discussions of hidden truths arise. The mere idea that such an iconic entity could be associated with real-world shadows captures the imagination and fuels stories that, while lacking proof, thrive on the “what-ifs” that echo through media and online forums.
How Public Perception Shapes the NarrativeSociologists studying the psychology of conspiracy theories point out that the human mind tends to fill gaps in knowledge with what feels most plausible or compelling. When figures from reputable media or entertainment companies are tied, even tangentially, to a scandal as vast as Epstein’s, it challenges the boundaries of trust. This is exacerbated when concrete answers remain elusive, leading to a cycle where suspicion feeds speculation.
The public’s thirst for accountability, especially in the wake of uncovered scandals involving powerful institutions, is both a force for truth and a catalyst for assumptions. In Epstein’s case, the proven reach of his influence and the confirmed involvement of significant figures were enough to trigger the question of how many untold stories lay beneath.
What We Know vs. What We ImagineThe narrative surrounding Epstein’s documented network shows us that while connections can be verified and associations noted, the leap to implicating entire organizations like Disney requires more than names on a list or rumors. It requires evidence that has, thus far, not been presented in any court or investigation. The proven facts are compelling enough: Epstein’s influence was extensive, his ties to power irrefutable. Yet, without direct links, the conversations about specific corporate involvement remain speculative.
In the next segment, we will explore why Disney’s reputation makes it a prime target for such speculation and how its historical handling of public crises plays into these narratives.
Disney – The Symbol of Trust and Target of Suspicion
Why Disney? The Paradox of a Trusted InstitutionDisney’s legacy is built on a foundation of storytelling, dreams, and the belief in happy endings. For nearly a century, the company has woven itself into the fabric of childhoods, becoming synonymous with innocence and magic. This legacy, however, has a dual edge. As the public's trust in institutions erodes and hidden truths are revealed in other sectors, Disney’s position as an untouchable cultural icon makes it both a beacon of light and a potential target for suspicion.
The Symbolism of Disney’s BrandDisney represents more than just a company; it embodies an idea—a refuge where imagination and wonder reign. But this same image that has made Disney a household name also contributes to the paradox of suspicion it faces. When an organization is seen as larger than life, transcending generations and continents, the notion that it could have skeletons in its closet becomes a tantalizing thought. The juxtaposition of innocence with possible shadows creates a narrative that is compelling and worth exploring, even if it remains speculative.
This paradox of Disney as both a trusted symbol and a target for scandal reflects a broader trend. Major corporations that hold influence in our everyday lives—particularly those that shape childhood memories and societal values—are natural focal points when scandals involving power, influence, and exploitation arise. The idea that a company with as much reach as Disney could be connected, however tangentially, to figures like Epstein feeds into this pattern.
Documented Misconduct and Public ReactionsThere have been verified cases involving Disney employees engaging in misconduct, which have been reported by media outlets such as NBC News and local news channels. These incidents, though not systemic and unrelated to Epstein’s network, show how the actions of a few can impact public perception of an entire organization. Examples include arrests for crimes involving minors or inappropriate behavior, isolated events that Disney has publicly addressed through statements and cooperation with law enforcement.
However, these incidents were sufficient to plant seeds of doubt in some minds. Even when addressed swiftly and in line with corporate protocols, such cases reveal a vulnerability: the company’s image can be tarnished not just by its policies, but by the misdeeds of individuals who wear its badge.
The Fuel for SpeculationThe Epstein case acted as a catalyst for looking beyond the obvious, particularly in the context of powerful organizations. If political leaders, financiers, and cultural icons could be connected to Epstein’s circle, why not wonder about the involvement of a company with as vast a presence as Disney? While investigations by trusted outlets have shown no direct corporate link, the sheer scope of Epstein’s influence suggested that any entity known for associating with the powerful could be implicated.
This speculation was not helped by Disney’s approach to public relations. The company’s PR strategies, while sophisticated and generally effective, often prioritize message control over transparency. In a world where silence can be seen as complicity, this strategy sometimes backfires, leading to more questions than answers.
Public Distrust and Historical ContextThe public’s fascination with uncovering hidden truths within major institutions is not unfounded. History is replete with cases where seemingly trustworthy organizations were later found to have concealed scandals. From corporate frauds to abuses within religious institutions, these stories have taught the public that innocence is not immune to corruption. This backdrop primes society to believe that even the most beloved entities, like Disney, could harbor secrets.
Sociologists and media analysts argue that this distrust is a byproduct of what they term the “betrayal effect”—where past disappointments with trusted institutions lower the threshold for believing that betrayal could be lurking everywhere. Disney, with its spotless public image and vast influence, becomes an especially juicy target for such theories. The leap from real cases of employee misconduct to more systemic accusations, however, is where evidence often falls short.
The Role of Social Media and Echo ChambersThe digital age has amplified how speculation morphs into perceived truth. Platforms like Twitter, Reddit, and Facebook allow theories to spread quickly, often outpacing fact-checking and nuanced analysis. Discussions that might once have been confined to fringe circles now gain mainstream attention, especially when they involve powerful figures or beloved brands.
In the context of Epstein’s exposure, this meant that any high-profile connection or name could become part of a broader narrative of guilt by association. The fact that Disney, as a corporation, appeared in speculative discussions alongside verified names from Epstein’s logs was enough for some to draw connections, even without direct evidence.
Reputation Management and PerceptionDisney’s approach to crises and controversies has long involved careful reputation management. From its response to legal issues to how it handles employee-related incidents, the company employs sophisticated PR strategies to mitigate damage and maintain its standing. This is standard practice for global brands; however, the public’s interpretation can be different. Strategic silence or tightly controlled statements can come across as evasive, fueling theories that there is something more to hide.
For a company like Disney, which operates at the intersection of family values and global corporate power, the stakes are high. The expectation isn’t just for entertainment but for upholding the moral high ground. When speculation links Disney to scandals, no matter how peripherally, it chips away at this carefully crafted image.
Why Address This Now?The speculation around Disney and Epstein underscores a crucial point about the nature of public inquiry and corporate reputation. It is not enough for companies to rely solely on public relations strategies that worked in the past. The demand for transparency is greater than ever, and silence, even when warranted, can erode trust.
Disney’s role in the public consciousness means that even baseless theories need addressing. By understanding why these narratives gain traction, both companies and the public can engage in more meaningful dialogues about accountability, proof, and trust.
The next segment will delve into how the public navigates between confirmed facts and conspiratorial whispers, exploring why certain theories stick and what it means for how we view powerful organizations.
Separating Fact from Conspiracy
The Thin Line Between Evidence and Speculation In the age of information, where facts are readily available yet often overshadowed by conjecture, separating truth from conspiracy is both an art and a necessity. When powerful entities like Disney find themselves drawn into discussions of hidden networks and scandals involving figures such as Jeffrey Epstein, it highlights a broader societal challenge: how do we differentiate between what is proven and what is assumed? This segment dissects the interplay of evidence, theory, and the psychological factors that drive our need to seek connections.
The Basis of Public Suspicion Public trust in large institutions has waned over decades, driven by a series of high-profile betrayals. From corporate frauds that shattered economies to scandals involving trusted religious or educational institutions, society has learned that power often conceals flaws and, in some cases, criminal actions. According to research published in the Journal of Communication, this erosion of trust leads to a phenomenon known as confirmation bias—the tendency to interpret new evidence as confirmation of one’s existing beliefs or suspicions.
The Epstein case provided fertile ground for such biases. The verified details of Epstein’s operations—the private jet, the exclusive parties, the high-profile guests—were enough to prompt a collective re-examination of how far his reach extended. While many of his associations were proven to be casual or professional in nature, the public’s hunger for deeper revelations ensured that speculation would thrive in areas where clarity was lacking.
The Role of Real Connections Epstein’s documented network included figures from politics, academia, finance, and media. The release of flight logs and court documents revealed that powerful individuals attended his events and interacted within his sphere. This factual basis, verified by investigative reporting from The New York Times, The Guardian, and other reputable sources, provided legitimacy to the idea that Epstein’s influence was pervasive. However, the extent to which these relationships were innocent or complicit was not uniformly clear.
This ambiguity created a vacuum where speculation could flourish. Public attention shifted from individuals named in the logs to the institutions and industries they represented. It was here that major corporations, including Disney, entered the discourse—not because of documented ties, but because of their visibility and influence.
The Psychology Behind Linking Power and Scandal To understand why theories about Disney’s potential involvement in Epstein’s network persist, it is essential to examine the psychology of conspiracy. Sociological and psychological studies indicate that people are naturally inclined to question narratives when they feel that the truth is being withheld. The more powerful or untouchable an institution seems, the more likely it is to be suspected of hiding something significant.
Disney’s image as a global giant that molds childhoods and shapes culture makes it an appealing target for such theories. The company’s public persona as a bastion of family values and innocence stands in stark contrast to any whispers of scandal or misconduct. This contrast alone provides fertile ground for stories to grow, even in the absence of solid proof.
Confirmed Misconduct vs. Conspiracy It is important to acknowledge that Disney, like any large corporation, has faced incidents involving employee misconduct. News reports from outlets such as NBC News have documented cases where employees were arrested for inappropriate conduct involving minors. These cases, while serious and handled with appropriate legal responses, were isolated incidents. No evidence points to these cases being part of a larger, systemic issue within the company or connected to external figures like Epstein.
However, the very existence of these incidents is often enough to keep theories alive. Public perception does not always differentiate between an individual’s actions and the culture of the organization they work for. When these incidents coincide with broader conversations about power and secrecy, they feed into narratives that imply guilt by association.
The Amplifying Power of Social Media The role of social media in shaping and amplifying conspiracy theories cannot be overstated. Platforms like Twitter and Reddit have created spaces where facts, opinions, and theories coexist with little separation. When the Epstein scandal broke, social media was flooded with discussions, many of which featured a mix of verifiable information and speculative connections. The absence of direct evidence linking companies like Disney to Epstein did not deter users from proposing connections based on circumstantial evidence and “what-if” scenarios.
This phenomenon, described by media analysts as the “echo chamber effect,” allows theories to gain credibility through repetition rather than proof. As theories are shared, retweeted, and commented on, they accumulate a sense of legitimacy that belies their origins.
Why Certain Theories Stick Certain theories persist because they tap into deep-seated fears and the knowledge that the powerful often operate beyond the reach of conventional accountability. High-profile scandals involving powerful figures—whether in business, politics, or entertainment—reinforce the belief that more may be hidden just out of reach. Epstein’s network was confirmed to include names that were once considered untouchable, which validated the idea that hidden truths could surface anywhere.
Disney’s name appearing in speculative discussions highlights the intersection of innocence and power. It reflects a societal expectation that if one pillar of influence is shown to be compromised, others may be as well. This expectation, however, must be tempered with critical thinking and an examination of evidence.
The Need for Discernment Understanding the difference between fact and theory is crucial for informed dialogue. Public scrutiny is essential for accountability, but it must be balanced with discernment. While Epstein’s known associations spanned many sectors, and while individuals from the entertainment industry were involved in his circle, the leap to implicating entire organizations like Disney has not been supported by verified investigations.
The Reality Check Here’s what we know:
Documented Facts: Epstein’s network included influential figures, confirmed by court records and journalistic investigations. Disney’s Position: While Disney has faced isolated cases of employee misconduct, no substantial evidence ties the company as an institution to Epstein’s criminal activities. Public Perception: Theories are fueled by a combination of legitimate distrust in powerful institutions and the psychological need to connect the dots, even when the evidence does not support it. In the next segment, we will explore how media control and the use of non-disclosure agreements (NDAs) contribute to the public’s perception of secrecy and whether this perception is warranted.
Media Control and NDAs – Protecting Power or Ensuring Silence?
The Strategy of Silence in Crisis Management When powerful organizations face potential scandal or crises, the first line of defense is often control—control over the narrative, control over information, and control over public perception. This strategy, while effective in mitigating immediate damage, can backfire by fostering an aura of secrecy that leads to suspicion. Disney, like many other global corporations, has historically employed these tactics, particularly through the use of non-disclosure agreements (NDAs) and strategic public relations (PR) campaigns. But do these measures protect legitimate corporate interests, or do they simply fuel theories that there is more being hidden?
Understanding the Role of NDAs NDAs are legal tools designed to maintain confidentiality and protect business interests. In most cases, their use is standard practice, whether to protect trade secrets, secure settlements, or manage sensitive internal matters. However, when NDAs intersect with scandals involving powerful individuals or organizations, they can become symbols of enforced silence. A report from the Harvard Business Review highlights that while NDAs are often employed for legitimate purposes, their misuse—especially when used to silence allegations of misconduct—has cast a shadow over their intent.
Disney has used NDAs in its corporate dealings, as have many in the media and entertainment sectors. This is not in itself suspicious; however, the mere presence of NDAs in a company’s arsenal can contribute to a narrative of secrecy, especially when paired with limited transparency during controversies.
The Case of High-Profile Secrecy The Epstein scandal showed how the use of NDAs and strategic silence could be perceived in a different light. When influential figures and companies were linked to his circle, silence from those implicated was interpreted by many as an attempt to avoid deeper inquiry. While Disney has not been tied to Epstein’s activities through verified evidence, its use of NDAs in unrelated circumstances and its approach to handling public controversies have made it a recurring subject in theories about hidden truths.
For example, Disney’s meticulous control over its brand image means that it often handles internal issues privately, releasing carefully crafted statements that address public concerns without divulging specifics. This approach, while protective, sometimes has the unintended consequence of making the public wonder what is not being said.
The Intersection of PR and Public Perception Public relations are designed to safeguard a company’s image, ensuring that responses to any negative news are swift and tightly managed. Disney’s PR machine is among the most sophisticated, capable of steering narratives and maintaining its reputation as an entertainment titan. This strategic control has allowed Disney to weather crises that might have permanently damaged lesser brands. However, in the context of a scandal as sprawling and notorious as Epstein’s, such control is perceived differently.
When the Epstein story broke and high-profile connections came to light, companies with any tenuous ties activated their crisis management protocols. For some, this meant issuing vague statements or refusing to comment altogether. To the public, this read as silence—a strategic choice that seemed suspicious when paired with known instances of NDAs being used to keep serious allegations quiet in other industries. The #MeToo movement, for instance, revealed how NDAs were used by some media companies to shield powerful perpetrators of harassment, showing that these tools can sometimes contribute to a culture of concealment.
Silence as Complicity? For a company like Disney, known for its polished public image, silence during times of widespread speculation can amplify suspicions. The question becomes: Is silence an act of protection or complicity? While NDAs are often used to manage settlements or protect internal processes, the fact that they prevent full transparency can make even innocent parties appear as if they have something to hide.
Experts in crisis communication argue that silence may protect the brand short-term but can erode trust long-term. Disney’s approach to handling public perception, from managing employee misconduct cases to addressing larger social controversies, often involves strategic responses that give the public enough information to stay satisfied but not enough to quell the more skeptical voices. This is standard practice but becomes contentious when the public is searching for accountability.
The Impact of Strategic Silence on Public Trust Media and communication studies have shown that transparency is increasingly becoming a measure of trustworthiness for corporations. In an era where the public demands answers and alternative media thrive on filling in gaps left by corporate PR, the stakes for maintaining trust are higher than ever. The use of NDAs and controlled statements can protect a company’s interests, but it also contributes to a perception of secrecy that feeds public doubt.
Disney’s balancing act—protecting its brand while managing incidents behind closed doors—reflects a broader industry trend. Corporations that prioritize narrative control must now reckon with an environment where even a hint of concealment can lead to damaging speculation. The Epstein case amplified this issue, putting the spotlight on how major organizations handle proximity to scandal, even if only by association.
Navigating the Perception The real challenge for Disney and similar companies lies in navigating the fine line between protecting their interests and fostering trust. Complete transparency can be risky, but strategic silence risks becoming complicit silence in the eyes of the public. This duality—where necessary protection measures are perceived as proof of hidden wrongdoing—is why entities like Disney find themselves caught up in discussions about figures like Epstein, despite the absence of concrete evidence.
The Takeaway for Institutions and the Public Understanding the role of NDAs and PR in managing public crises helps frame why powerful companies might become targets of suspicion. While the use of these tools is standard and often justified, their impact on public perception can’t be ignored. For the public, recognizing the difference between warranted inquiry and overreach is key to maintaining productive scrutiny without falling into the trap of baseless theories.
The next segment will focus on what these perceptions mean for society as a whole and why the pursuit of transparency and trust must be a collective endeavor.
Beyond the Shadows – A Call to Unity
The Complex Path to UnderstandingIn an age where trust in powerful institutions is fraying, and access to information is both a blessing and a burden, our approach to truth becomes more critical than ever. The discussions surrounding figures like Jeffrey Epstein and corporations like Disney are not just about scandal; they are about how we, as a society, confront power, secrecy, and transparency. This segment is a call to unite in the pursuit of truth—not through a divisive lens, but with collective discernment and an unwavering commitment to evidence and integrity.
The Lessons from HistoryHistory teaches us that institutions once seen as untouchable can harbor hidden truths. The exposure of corporate frauds, systemic abuses, and cover-ups within trusted sectors has shaped a society that questions everything. The Epstein scandal underscored this, revealing a network of power that reached further than many dared to imagine. Yet, while it validated the public’s instinct to question, it also highlighted a key challenge: differentiating between grounded inquiry and baseless theory.
Disney’s name appearing in speculative discussions about Epstein points to a broader pattern—our collective desire to ensure that those who hold power are not above scrutiny. But as we demand accountability, we must also unite in the practice of informed skepticism. The leap from isolated cases of misconduct or association to implicating entire organizations requires evidence, not just conjecture. This distinction is where we, as a society, must find common ground.
The Role of TransparencyTransparency has become the cornerstone of public trust. Organizations that handle controversies behind closed doors risk damaging their credibility. For companies like Disney, known for protecting their brand with meticulous care, the challenge is clear: find a balance between safeguarding legitimate interests and providing enough transparency to maintain public trust.
The use of NDAs, strategic silence, and controlled narratives may shield brands in the short term, but they can erode trust in the long run. Studies in crisis communication emphasize that openness, even when it exposes vulnerabilities, can reinforce loyalty and confidence among stakeholders. In the context of Epstein and the persistent whispers about powerful corporations, this lesson is especially relevant.
A Collective Call to ClarityThe pursuit of truth is not just the responsibility of journalists, whistleblowers, or industry watchdogs—it is a collective endeavor. The public plays a crucial role in this, but so do the corporations that hold sway over cultural and economic landscapes. When Disney’s name enters speculative discussions, it reflects a deep-seated desire for transparency from those we trust. This desire should be met not with fear of the unknown but with a commitment to clarity.
This segment is a call for unity in approaching these conversations. The balance between healthy skepticism and conspiracy theory is delicate but essential. We must ask hard questions and hold power accountable without losing sight of what separates substantiated fact from assumption.
Why Unity MattersIn times where speculation can divide and misinformation can spread faster than verified facts, unity in the pursuit of truth is vital. When we allow fear and uncertainty to fracture our approach, we weaken our collective power to bring genuine issues to light. Epstein’s case showed that hidden wrongs do exist and can involve the most influential figures. It also showed that uncovering the full scope of such wrongs takes a community committed to patience, evidence, and shared purpose.
Public scrutiny is essential for democracy and social justice, but so is discernment. When theories about organizations like Disney arise without evidence, they risk diverting attention from real, proven issues that demand action. Unity in seeking truth means supporting real investigations, demanding transparency, and recognizing the power of evidence-based inquiry.
Building a Culture of Informed AccountabilityThe goal is not to silence questions but to elevate them, ensuring that they are grounded in reality. This approach not only empowers the public but also sets a standard for institutions. If Disney and other corporations prioritize transparency, they can reinforce the public trust that sustains their brands. Similarly, when the public insists on evidence and integrity in its discussions, it strengthens the very fabric of accountability.
Reflections for the Road AheadAs we move forward, let us commit to being a society that seeks truth not for scandal’s sake but for justice and integrity. Let us stand together in holding power to account, using facts as our foundation and unity as our strength. The story of Epstein and the questions it raises about power, influence, and hidden truths are reminders that transparency and trust are not just corporate responsibilities—they are collective ones.
This call to unity is a reminder that we all play a part in shaping how these stories unfold. When we seek, question, and demand clarity together, we create a society that values truth over rumor, evidence over assumption, and justice over division.
As we conclude this exploration, may we carry forward the lessons learned: the importance of questioning with integrity, seeking truth with diligence, and facing the unknown not as individuals, but as a united community.
-
 @ c8383d81:f9139549
2025-02-05 13:06:05
@ c8383d81:f9139549
2025-02-05 13:06:05My own stats on what I’ve done over the weekend:
-
Spoke to +100 developers, it was great seeing a couple of familiar Flemish faces and meeting some new ones but overall the crowd was extremely diverse.
-
Ended up doing a short interview promoting the protocol and ended up going to 0 talks.
-
Tried to evangelize by going booth by booth to distribute a Nostr flyer to other FOSDEM projects, with the hope that they would broadcast the info towards their SOME person to add Nostr on their list or to build out a library for the languages that were present ( This was a fairly slow approach )
-
Kept it to Nostr protocol 95% of the time, the Bitcoin narrative is not always a good time to push and as a side note I’ve met more Monero users than in the last 5 years.
-
Was able to convince some engineers to look into the #soveng endeavor.
Small overview from the most common questions:
- They have heard about Nostr but are not sure of the details. ( mostly through the bitcoin community )
- What is the difference with ActivityPub, Mastodon, Fediverse ?
- IOT developers, so questions regarding MQTT & Meshtastic integrations ?
- Current state of MLS on Nostr ?
- What are the current biggest clients / apps build on Nostr ?
- Will jack still give a talk ?
Things we could improve:
- Bring more stickers like loads more,
- Bring T-shirts, Pins… could be a good way to fund these adventures instead of raising funds. ( Most projects where selling something to help raise funds for projects )
- Almost no onboarding / client installs.
- Compared to the Nostr booth at BTC Amsterdam not a single person asked if they could charge their phone.
Personal Note: The last time I visited was roughly 13 years ago and me being a little more seasoned I just loved the fact that I was able to pay some support to the open source projects I’ve been using for years ( homebrew, modzilla, Free BSD,.. ) and see the amazing diverse crowd that is the open source Movement 🧡
Al final shoutout to our great pirate crew 🏴☠️: The Dutch Guard ( nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe & nostr:npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft ) and a adrenaline fueled nostr:npub1t6jxfqz9hv0lygn9thwndekuahwyxkgvycyscjrtauuw73gd5k7sqvksrw , nostr:npub1rfw075gc6pc693w5v568xw4mnu7umlzpkfxmqye0cgxm7qw8tauqfck3t8 and nostr:npub1r30l8j4vmppvq8w23umcyvd3vct4zmfpfkn4c7h2h057rmlfcrmq9xt9ma amazing finally meeting you IRL after close to 2 years since the Yakihonne hackathon 😀

-
-
 @ dd1f9d50:06113a21
2025-02-05 01:48:55
@ dd1f9d50:06113a21
2025-02-05 01:48:55(Because Most People Don’t Understand Money)
The requisite knowledge needed to know whether $100 or $100,000 per Bitcoin is relatively speaking “a lot,” is what value means. One way to measure value is through a universal yardstick we call “Money.” The question of “What is money?” is perhaps one of the most overlooked and under answered in our day and age. There is even an entire podcast dedicated to that question with the eponymous title, hosted by Robert Breedlove. That podcast often delves into the more philosophical underpinnings whereas I hope to approach this with a more practical answer.
Money is a technology.
Money is the technology with which we interact with one another to reorganize goods and services to the place and time they are best suited. Most money of the past has been tangible (though not a requisite feature), scarce, recognizable (read: verifiable), durable, portable, and divisible. These features one might call the “Attributes of Money.” These attributes are absolutely essential for a money to maintain its status as a money. (Those of you who understand the U.S. Dollar system maybe scratching your heads right now but, believe me, I will address that elephant in due time.) These attributes, you may notice, are not a yes or no but more of a gradient. A money can be MORE portable than another yet, less durable. One more divisible but not scarce whatsoever. The point being they must have, in some capacity, these attributes or they simply aren’t money.
One of These Things is Not Like the Other
| | Bitcoin | Gold | Dollars | |-----------------|:----------------------------------------------------------------------------------------------------------------:|:------------------------------------------------------------------:|:--------------------------------------------------------------------------------------------------------------------------------------------------:| | Scarcity | 21 million coins
is the maximum supply | Unknown- the
supply grows roughly 2% per year | Also unknown to anyone outside of the Federal Reserve, Trillions and counting | | Recognizability | Each coin is verifiable to it's genesis on the timechain | Each molecule of gold has distinct physical verifiable properties | If the Federal reserve says it is a valid note, it is (Unless you are an enemy of the United States) | | Durablility | Each "Bitcoin" is information stored on a globally distributed network | Doesn't Rust and as far as can be measured Au197 is stable forever | Can be destroyed by any means that effect fabric and centralized databases | | Portability | Available wherever data can be store- Anywhere | Can be moved at 9.81 Newtons per Kilogram- Methods may vary | Can be moved physically with fabric notes- Digitally with express permission from a US accredited banking institution | | Divisibility | Currently can be divided into 100 million parts called Sats (can be further subdivided by adding decimal places) | Can be divided to the Atomic level (Though not practical) | Can be divided (without dilution) by adding new denominative bills or coinage
Can be divided (with dilution) by printing new bills or coinage | | | Bitcoin | Gold | Dollars |You may think with all of the great functionality of Bitcoin that the phrase "One of these things is not like the other" refers to BTC. No, I was referring to the Dollar. It is the only one on the list that was a currency that was substituted as some kind of faux money. It asserts itself, or rather the Federal Reserve asserts it, as money, de facto.
Dollars are NOT money.
Dollars are (allegedly) a currency. If money is a specific technology, currency is the financial infrastructure that allows that technology to reach and be used by the most number of people possible. This requires a firm tether between the asset being used as money and the currency used as a claim to that money. For example: If I hand you a chicken, you have a chicken. But, if I hand you a coupon that is redeemable for a chicken, you do not have a chicken. You have a claim to a chicken that is only as good as the party making that claim. Bringing it back to money again, dollars (Prior to 1971) were redeemable for gold at a rate of $35 per ounce. This is that strong tether that pegged dollars to gold and physical reality itself. Without a proof of work, mining, . Until…
WTF Happened in 1971?
The Nixon shock happened. Briefly, The U.S. took in Europe’s gold in the 1940’s to keep it out of Hitler’s hands. The U.S. made an agreement to peg the dollar to Europe’s gold. The U.S. over printed dollars in relation to the gold holdings. Around 1971 France (among others) called the U.S. out for devaluing the dollar and thus European currencies. So, Nixon “Temporarily” suspended the convertibility of dollars to gold. Now, here we all are like Wile E. Coyote having run off of the golden cliff clutching our dollars in our arms and 54 years later we still haven’t looked down to see the truth.
Dollars Aren’t Backed by Anything
This is why no country in the world today has a money standard. Seemingly they all forgot the number one rule of issuing currency, it must be backed by something. Now, you may hear dollar proponents say “The U.S. dollar is backed by the full faith and credit of the United States!” Another way of saying that is, “We said it is worth something, so it is!” This fiat (by decree) mentality creates a plethora of perverse incentives. The ever growing supply disallows users of the Dollar to save without inccuring the penalties of inflation.
Just a Few Examples of How You're Being Crushed
Because your dollar loses value:
- It pushes people to spend them on assets that seem to appreciate (as the dollar debases) but are truly staying stagnant.
- It pushes people to gamble on securities hoping the perceived value is enough to beat the inflationary curve.
- It pushes people away from saving for their future and the future of their families.
- It creates insane credit incentives so that people borrow way more than they can afford today knowing that dollars will be cheaper in the future. (Effectively a short position)
- It pushes people to spend less and less time making and maintaining their families as it becomes more expensive to keep a similar lifestyle to which it was founded.
These are just a few of the terrible consequences of not knowing that trading a currency with no monetary backing has on a society. Most may blame this soley on the ability to print currency by a central bank but, that is not the only factor. If the fed printed dollars against gold, people would simply take the best rate they could get and remonetize themselves with the gold. But because there is no monetary escape hatch guaranteed by the issuance of dollars, I.E. no one has to take your dollars in exchange for their Bitcoin or gold, you are left at the mercy of the market.
One Day, People Will Stop Accepting Your Dollars
Those lementing the high price of Bitcoin might want to thank their lucky stars that Bitcoin still has a rational number next to the "BTC 1=$?" sign. One day you will have to exchange something of actual value to the spender (no longer a seller). Your product, good or service, will be the only thing that anyone might be willing to part with their Bitcoin over. That is what makes a money, the most salable non-consumable good, whose only funtion is to back a financial structure that facilitates trade.
Bitcoin is Capital
Capital is a broad term that can describe anything that confers value or benefit to its owners, such as a factory and its machinery, or the financial assets of a business or an individual. Bitcoin being the latter creates the financial structures from which you build upon. You use capital to hold, transfer, and grow value. You do not do this with cash. Cash is a depreciating asset when you don't use it to gain goods or services for yourself or your business. This misconception around the equivalance between cash and money (financial capital) is what tricks people into believing Dollars are money. And what's worse is that even some of our greatest heroes have done this.
Slay Your Heroes, Within Reason
Unfortunately due to a mixing of verbiage that have very distinct differences, the title: "Bitcoin: A Peer-to-Peer Electronic Cash System" is technically inaccurate. Bitcoin doesn't fit the definition of cash, which is a liquid asset that can be easily converted into its equivalent value. In short, Satoshi misspoke. In reality, owning Bitcoin UTXOs (with private keys) means you already possess the asset, not just a claim to it. When you spend Bitcoin, the recipient receives the actual asset, not a promise of it. When you receive Bitcoin, you have final settlement on that transaction. Fundamentally Bitcoin is not cash, electronic or otherwise.
Bitcoin is Money.
-
 @ bf47c19e:c3d2573b
2025-05-11 18:24:44
@ bf47c19e:c3d2573b
2025-05-11 18:24:44Originalni tekst na dvadesetjedan.com.
Autor: Gigi / Prevod na srpski: Plumsky
Postoji sveto carstvo privatnosti za svakog čoveka gde on bira i pravi odluke – carstvo stvoreno na bazičnim pravima i slobode koje zakon, generalno, ne sme narušavati. Džefri Fišer, Arhiepiskop Canterberija (1959)
Pre ne toliko dugo, uobičajen režim interneta je bio neenkriptovan običan tekst (plain text). Svi su mogli špiunirati svakoga i mnogi nisu o tome ni razmišljali. Globalno obelodanjivanje nadzora 2013. je to promenilo i danas se koriste mnogo bezbedniji protokoli i end-to-end enkripcija postaje standard sve više. Iako bitcoin postaje tinejdžer, mi smo – metaforično govoreći – i dalje u dobu običnog teksta narandžastog novčića. Bitcoin je radikalno providljiv protokol sam po sebi, ali postoje značajni načini da korisnik zaštiti svoju privatnost. U ovom članku želimo da istaknemo neke od ovih strategija, prodiskutujemo najbolje prakse, i damo preporuke koje mogu primeniti i bitcoin novajlije i veterani.
Zašto je privatnost bitna
Privatnost je potrebna da bi otvoreno društvo moglo da funkcioniše u digitalnoj eri. Privatnost nije isto što i tajanstvenost. Privatna stvar je nešto što neko ne želi da ceo svet zna, a tajna stvar je nešto što neko ne želi bilo ko da zna. Privatnost je moć da se čovek selektivno otkriva svom okruženju.
Ovim snažnim rečima Erik Hjus je započeo svoj tekst Sajferpankov Manifesto (Cypherpunk's Manifesto) 1993. Razlika između privatnosti i tajanstvenosti je suptilna ali jako važna. Odlučiti se za privatnost ne znači da neko ima tajne koje želi sakriti. Da ovo ilustrujemo shvatite samo da ono što obavljate u svom toaletu ili u spavaćoj sobi nije niti ilegalno niti tajna (u mnogim slučajevima), ali vi svejedno odlučujete da zatvorite vrata i navučete zavese.
Slično tome, koliko para imate i gde ih trošite nije naručito tajna stvar. Ipak, to bi trebalo biti privatan slučaj. Mnogi bi se složili da vaš šef ne treba da zna gde vi trošite vašu platu. Privatnosti je čak zaštićena od strane mnogobrojnih internacionalnih nadležnih organa. Iz Američke Deklaracije Prava i Dužnosti Čoveka (American Declaration of the Rights and Duties of Man) Ujedinjenim Nacijama, napisano je da je privatnost fundamentalno prava gradjana širom sveta.
Niko ne sme biti podvrgnut smetnjama njegovoj privatnosti, porodici, rezidenciji ili komunikacijama, niti napadnuta njegova čast i reputacija. Svi imaju pravo da se štite zakonom protiv takvih smetnja ili napada. Artikal 12, Deklaracija Ljudskih Prava Ujedinjenih Nacija
Bitcoin i privatnost
Iako je bitcoin često opisivan kao anoniman način plaćanja medijima, on u stvari poseduje potpuno suprotne osobine. On je poluanoniman u najboljem slučaju i danas mnogima nije ni malo lako primeniti taktike da bi bili sigurni da njihov poluanonimni identitet na bitcoin mreži ne bude povezan sa legalnim identitetom u stvarnom svetu.
Bitcoin je otvoren sistem. On je javna baza podataka koju svako može da proučava i analizira. Znači, svaka transakcija koja je upisana u tu bazu kroz dokaz rada (proof-of-work) postojaće i biće otkrivena dokle god bitcoin postoji, što znači - zauvek. Ne primenjivati najbolje prakse privatnosti može imati štetne posledice u dalekoj budućnosti.
Privatnost, kao sigurnost, je proces koji je težak, ali nije nemoguć. Alatke nastavljaju da se razvijaju koje čuvaju privatnost kad se koristi bitcoin and srećom mnoge od tih alatki su sve lakše za korišćenje. Nažalost ne postoji panacea u ovom pristupu. Mora se biti svesan svih kompromisa i usavršavati te prakse dok se one menjaju.
Najbolje prakse privatnosti
Kao i sve u bitcoinu, kontrola privatnosti je postepena, korak po korak, procedura. Naučiti i primeniti ove najbolje prakse zahteva strpljivost i odgovornost, tako da ne budite obeshrabreni ako vam se čini da je to sve previše. Svaki korak, koliko god bio mali, je korak u dobrom pravcu.
Koje korake preduzeti da bi uvećali svoju privatnost:
- Budite u vlasništvu sami svojih novčića
- Nikad ne ponavljajte korišćenje istih adresa
- Minimizirajte korišćenje servisa koji zahtevaju identitet (Know your customer - KYC)
- Minimizirajte sve izloženosti trećim licima
- Upravljajte svojim nodom
- Koristite Lightning mrežu za male transakcije
- Nemojte koristiti javne blok pretraživače za svoje transakcije
- Koristite metodu CoinJoin često i rano pri nabavljanju svojih novčića
Budite u vlasništvu sami svojih novčića: Ako ključevi nisu tvoji, onda nije ni bitcoin. Ako neko drugo drži vaš bitcoin za vas, oni znaju sve što se može znati: količinu, istoriju transakcija pa i sve buduće transakcije, itd. Preuzimanje vlasništva bitcoina u svoje ruke je prvi i najvažniji korak.
Nikad ne kroistite istu adresu dvaput: Ponavljanje adresa poništava privatnost pošiljalca i primaoca bitcoina. Ovo se treba izbegavati pod svaku cenu.
Minimizirajte korišćenje servisa koji zahtevaju identitet (KYC): Vezivati svoj legalni identitet za svoje bitcoin adrese je zlo koje se zahteva od strane mnogih državnih nadležnosti. Dok je efektivnost ovih zakona i regulacija disputabilno, posledice njihovog primenjivanja su uglavnom štetne po korisnicima. Ovo je očigledno pošto je česta pojava da se te informacije često izlivaju iz slabo obezbeđenih digitalnih servera. Ako izaberete da koristite KYC servise da bi nabavljali bitcoin, proučite i razumite odnos između vas i tog biznisa. Vi ste poverljivi tom biznisu za sve vaše lične podatke, pa i buduće obezbeđenje tih podataka. Ako i dalje zarađujete kroz fiat novčani sistem, mi preporučujemo da koristite samo bitcoin ekskluzivne servise koji vam dozvoljavaju da autamatski kupujete bitcoin s vremena na vreme. Ako zelite da potpuno da izbegnete KYC, pregledajte https://bitcoinqna.github.io/noKYConly/.
Minimizirajte sve izloženosti trećim licima: Poverljivost trećim licima je bezbednosna rupa (https://nakamotoinstitute.org/trusted-third-parties/). Ako možete biti poverljivi samo sebi, onda bi to tako trebalo da bude.
Upravljajte svojim nodom: Ako nod nije tvoj, onda nisu ni pravila. Upravljanje svojim nodom je suštinska potreba da bi se bitcoin koristio na privatan način. Svaka interakcija sa bitcoin mrežom je posrednjena nodom. Ako vi taj nod ne upravljate, čiji god nod koristite može da vidi sve što vi radite. Ova upustva (https://bitcoiner.guide/node/) su jako korisna da bi započeli proces korišćenja svog noda.
Koristite Lightning mrežu za male transakcije: Pošto Lightning protokol ne koristi glavnu bitcoin mrežu za trasakcije onda je i samim tim povećana privatnost korišćenja bez dodatnog truda. Iako je i dalje rano, oni apsolutno bezobzirni periodi Lightning mreže su verovatno daleko iza nas. Korišćenje Lightning-a za transakcije malih i srednjih veličina će vam pomoći da uvećate privatnost a da smanjite naplate svojih pojedinačnih bitcoin transakcija.
Nemojte koristiti javne blok pretraživače za svoje transakcije: Proveravanje adresa na javnim blok pretraživačima povezuje te adrese sa vašim IP podacima, koji se onda mogu koristiti da se otkrije vaš identitet. Softveri kao Umbrel i myNode vam omogućavaju da lako koristite sami svoj blok pretraživač. Ako morate koristiti javne pretraživače, uradite to uz VPN ili Tor.
Koristite CoinJoin često i rano pri nabavljanju svojih novčića: Pošto je bitcoin večan, primenjivanje saradničkih CoinJoin praksa će vam obezbediti privatnost u budućnosti. Dok su CoinJoin transakcije svakovrsne, softveri koji su laki za korišćenje već sad postoje koji mogu automatizovati ovu vrstu transakcija. Samourai Whirlpool (https://samouraiwallet.com/whirlpool) je odličan izbor za Android korisnike. Joinmarket (https://github.com/joinmarket-webui/jam) se može koristiti na vašem nodu. A servisi postoje koji pri snabdevanju vašeg bitcoina istog trenutka obave CoinJoin tranzakciju automatski.
Zaključak
Svi bi trebalo da se potrude da koriste bitcoin na što privatniji način. Privatnost nije isto što i tajanstvenost. Privatnost je ljudsko pravo i mi svi trebamo da branimo i primenljujemo to pravo. Teško je izbrisati postojeće informacije sa interneta; a izbrisati ih sa bitcoin baze podataka je nemoguće. Iako su daleko od savršenih, alatke postoje danas koje vam omogućavaju da najbolje prakse privatnosti i vi sami primenite. Mi smo vam naglasili neke od njih i - kroz poboljšanje u bitcoin protokolu kroz Taproot i Schnorr - one će postajati sve usavršenije.
Bitcoin postupci se ne mogu lako opisati korišćenjem tradicionalnim konceptima. Pitanja kao što su "Ko je vlasnik ovog novca?" ili "Odakle taj novac potiče?" postaju sve teža da se odgovore a u nekim okolnostima postaju potpuno beznačajna.
Satoši je dizajnirao bitcoin misleći na privatnost. Na nivou protokola svaka bitcoin transakcija je proces "topljenja" koji za sobom samo ostavlja heuristične mrvice hleba. Protokolu nije bitno odakle se pojavio bilo koji bitcoin ili satoši. Niti je njega briga ko je legalan identitet vlasnika. Protokolu je samo važno da li su digitalni potpisi validni. Dokle god je govor slobodan, potpisivanje poruka - privatno ili ne - ne sme biti kriminalan postupak.
Dodatni Resursi
This Month in Bitcoin Privacy | Janine
Hodl Privacy FAQ | 6102
Digital Privacy | 6102
UseWhirlpool.com | Bitcoin Q+A
Bitcoin Privacy Guide | Bitcoin Q+A
Ovaj članak napisan je u saradnji sa Matt Odellom, nezavisnim bitcoin istraživačem. Nađite njegove preporuke za privatnost na werunbtc.com
-
 @ fd208ee8:0fd927c1
2025-02-02 10:33:19
@ fd208ee8:0fd927c1
2025-02-02 10:33:19GitCitadel Development Operations
We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes.
Supplier Coordination

Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide.
OneDev Implementation

Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a self-hosted OneDev instance. In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers.
Our team's GitHub projects will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted GitWorkshop instance.
We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay!
Next Infrasteps
Automated Testing
Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our Alexandria client. We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers).
We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive.
After that, a Gherkin-based Behave feature test for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next.
The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to Done. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.

Automated Builds
As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.

We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:

This will make it easier for us to work and collaborate asynchronously and without unnecessary delays.
Expanding the Status Page

And, finally, we get to the point of all of this busyness: reporting.
We are going to have beautiful reports, and we are going to post them online, on our status page. We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our GitCitadel DevOps npub, to make sure you don't miss out on the IT action.
Building on stone
All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation.
Happy building!
-
 @ bf47c19e:c3d2573b
2025-05-11 18:24:28
@ bf47c19e:c3d2573b
2025-05-11 18:24:28Originalni tekst na dvadesetjedan.com.
Autor: Matt Corallo / Prevod na hrvatski: Davor
Bitcoineri, od programera Bitcoin Core-a preko dugogodišnjih entuzijasta Bitcoina do nedavnih pronalazača /r/Bitcoina, vole razgovarati o tome kako je decentralizacija Bitcoina njegova ultimativna značajka. Doduše, rijetko vidite da netko objašnjava zašto je decentralizacija važna. Zasigurno je to zanimljiva značajka iz perspektive računalne znanosti, no zašto bi potrošači, tvrtke ili investitori marili za to? Ova objava je pokušaj da se napiše zašto je decentralizacija temelj vrijednosti Bitcoina i što je još važnije, postavi buduće objave u kojima se govori o tome kada ona to nije.
Kada Bitcoineri govore o decentralizaciji Bitcoina, prva stvar koja se pojavljuje je često spominjani nedostatak inherentnog povjerenja u treću stranu. Dok je dobro postavljeno povjerenje preduvjet za učinkovit rad mnogih sustava, jednom kada se takvo povjerenje izgubi, sustavi mogu postati nevjerojatno krhki. Uzmimo, za primjer, povjerenje u američke banke prije uspostave FDIC-a (Federal Deposit Insurance Corporation). Dok je pristup bankovnim uslugama omogućio više pogodnosti i mnogim tvrtkama učinkovitije poslovanje, poznato je da su banke propadale, pritom upropaštavajući sa sobom sva sredstva klijenata. Dok je predstavljanje FDIC-a i sličnih programa decentraliziralo povjerenje u financijske institucije s jedne strane na dvije, transakcije u velikom dijelu svijeta ne nude takvu zaštitu. Čak i uz takve programe, pojedinci nisu univerzalno zaštićeni od gubitka preko granica i preko određene vrijednosti.
U novije vrijeme, propisi koji dopuštaju pojedinim državnim dužnosnicima jednostrano oduzimanje imovine postali su uobičajeni. Naročito u SAD-u, sada zloglasna “Operacija Choke Point” i programi oduzimanja civilne imovine, omogućili su službenicima za provođenje zakona i privatnim institucijama da zapljenjuju financijsku imovinu i uskraćuju financijske usluge uz malo ili nimalo nadzora. Uklanjanje provjerenih skrbnika i stvaranje sustava s likvidnom imovinom, koja se ne može zaplijeniti, ima potencijal pružiti pouzdanije financijske usluge mnogima koji inače ne bi mogli djelovati učinkovito ili uopće ne bi mogli djelovati. Ova mogućnost da se Bitcoin ne može zaplijeniti, omogućena je samo zbog nedostatka za centraliziranim povjerenjem. Centralizirani sustavi elektroničke gotovine i financijski sustavi su pokušali pružiti takvu pouzdanost, propisi i poslovna stvarnost su to gotovo univerzalno spriječili.
Svojstvo koje je jednako važno za sposobnost Bitcoina da pruža financijske usluge zviždačima, stranim disidentima i porno zvijezdama je njegov otpor cenzuri transakcija. Sposobnost trećih strana da zaplijene imovinu rezultira izravnim i čistim novčanim gubitkom, zamrzavanje imovine može imati sličan učinak. Kada pojedinac ili organizacija više nisu u mogućnosti obavljati transakcije za plaćanje roba i usluga, njihova financijska imovina brzo gubi vrijednost. Iako Bitcoin ima vrlo dobru priču o nemogućnosti zapljene (svaka strana u sustavu nameće nemogućnost bilo koga da potroši Bitcoin bez dodanog privatnog ključa), njegova priča o otporu cenzuri je malo utančanija.
U svijetu u kojem nijedan rudar Bitcoina nema više od 1% ukupne hash snage (ili nešto drugo što je jednako decentralizirano), trebalo bi biti lako pronaći rudara koji je ili anoniman i prihvaća sve transakcije ili je u nadležnosti koja ne pokušava cenzurirati vaše transakcije. Naravno, ovo nije svijet kakav danas imamo, a cenzura transakcija jedan je od većih razloga da se ozbiljno zabrinemo centralizacijom rudarenja (za pune čvorove). Ipak, mogućnost pojedinca da kupi hash snagu (u obliku lako dostupnog starog hardvera ili u obliku njegovog iznajmljivanja) za rudarenje svoje inače cenzurirane transakcije, opcija je sve dok je pravilo najdužeg lanca na snazi kod svih rudara. Iako je znatno skuplji nego što bi bio u istinski decentraliziranom Bitcoinu, to omogućuje Bitcoinu da zadrži neka od svojih anti-cenzuriranih svojstava.
Ako ste već dovoljno dugo u priči oko Bitcoina, možda ćete prepoznati gornja svojstva kao kritična za zamjenjivost. Zamjenjivost, kao ključno svojstvo svakog monetarnog instrumenta, odnosi se na ideju da vrijednost jedne jedinice treba biti ekvivalentna svakoj drugoj jedinici. Bez mogućnosti odmrzavanja/otpora cenzuri i nemogućnosti zapljene, Bitcoin (i svaki drugi monetarni sustav) počinje gubiti zamjenjivost. Trgovci i platni procesori više ne mogu razumno prihvaćati Bitcoin bez provjere niza crnih lista i mnogo truda kako bi bili sigurni da će moći potrošiti Bitcoin koji prihvaćaju. Ako povjerenje u zamjenjivost Bitcoina deformira, njegova bi korist mogla biti značajno deformirana.
Još jedno svojstvo koje proizlazi iz decentralizacije Bitcoina, je njegov otvoreni pristup. Ulagači iz Silicijske doline često ga nazivaju jednim od najzanimljivijih svojstava Bitcoina, a mnogi ga vole nazivati "bez dopuštenja". Sposobnost bilo koga, bilo gdje u svijetu, sa internetskom vezom, da prihvaća Bitcoin za robu i usluge i koristi Bitcoin za kupnju roba i usluga je vrlo uzbudljiva. Opet, ovo svojstvo ovisi o decentralizaciji Bitcoina. Iako postoje mnogi centralizirani pružatelji financijskih usluga, gdje mnogi od njih promoviraju svoju dostupnost bilo kome, sama njihova prisutnost kao centraliziranog tijela koje može proizvoljno uskratiti uslugu, čini ih podložnim budućim promjenama politike iz bilo kojeg razloga. PayPal je, na primjer, utemeljen na idealima univerzalnog pristupa elektroničkoj gotovini. Međutim, zbog svoje pozicije središnje vlasti, brzo je promijenio svoje politike, kako bi udovoljio pritiscima regulatora i politikama postojećeg financijskog sustava na koji se oslanjao. Ovih dana, PayPal je nadaleko poznat po zamrzavanju računa i oduzimanju imovine uz malo ili nimalo upozorenja. U osnovi, oslanjanje na centralizirane strane za usluge nije kompatibilno s univerzalnim otvorenim pristupom u financijskom svijetu.
Primijetit ćete da se sve gore navedene kritične značajke, one koje Bitcoin čine tako uzbudljivim za sve nas, centralizirani sistemi već neko vrijeme mogu implementirati. Zapravo to se radilo i prije, u učinkovitijim sustavima od Bitcoina. Naravno, nikada nisu potrajali, gubeći kritična svojstva nakon podešavanja kako bi se popravila ova ili ona stvar, implementirajući regulatorne sustave cenzure izravno u osnovne slojeve, ograničavajući pristup rastu dobiti i potpuno gašenje. Stvarno, decentralizacija u Bitcoinu sama po sebi nije značajka, već je umjesto toga jedini način za koji znamo da održimo značajke koje želimo u sustavima kojima upravljaju ljudi.
-
 @ fd208ee8:0fd927c1
2025-01-23 15:31:24
@ fd208ee8:0fd927c1
2025-01-23 15:31:24Planning Alexandria
People keep asking what features nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz has planned for #Alexandria, but they're not set in stone because we're an agile project.
What we do have, is lots of tickets on our Kanban boards and a naming scheme, where we use a famous person's last name, to signify the release goals.

Gutenberg v 0.1.0
(after the inventor of the printing press) will contain the features needed to read and write NIP-62 Curated Publications, as well as encompassing the complex infrastructure, architecture, documentation, and personnel we require to make this all run smoothly and look easy.

Euler v 0.2.0
(after a mathematician credited with establishing graph theory) will contain the features for deep-searching, visually exploring, and smartly navigating the data set, wiki page display, annotating and citing the publications, exporting to other formats (like PDF, ePUB, and LaTeX), and commenting/reviewing. To help with the heavy lifting, we will be swapping out the core with our own Nostr SDK called "Aedile".

Defoe v 0.3.0
(after an author who perfected the novel format) will be all about our favorite writers. We will be focusing upon profile data, payment systems, book clubs and communities, and stylesheets.
That is everything we have planned, for the v1.0 edition, and we consider that version to be a true product.
As for after that, a teaser...

-
 @ bf47c19e:c3d2573b
2025-05-11 18:23:13
@ bf47c19e:c3d2573b
2025-05-11 18:23:1305.12.2024 / Autor: Katarina Plantak
Vrijednost Bitcoina po prvi put je premašila 100.000 dolara. Ova kriptovaluta svoj masovni rast može na neki način zahvaliti reizboru Donalda Trumpa za američkog predsjednika. On je najavio blaži regulatorni pristup kripto industriji.
Što je Bitcoin?
Bitcoin (BTC) je kriptovaluta (virtualna valuta) dizajnirana da djeluje kao novac i oblik plaćanja izvan kontrole bilo koje osobe, grupe ili entiteta. Time nema potrebe za sudjelovanjem pouzdane treće strane npr. kovnice novca ili banke u financijskim transakcijama. Osoba ili grupa pod pseudonimom Satoshi Nakamoto 31. listopada 2008. objavila je tehnički dokument pod nazivom "Bitcoin: Peer-to-Peer Electronic Cash System". Taj je dokument distribuiran na kriptografsku mailing listu, samo mjesec dana nakon što je investicijska banka Lehman Brothers podnijela zahtjev za najveći bankrot u povijesti SAD-a, a vlada odobrila financijsku pomoć od 700 milijardi dolara.
Nekoliko mjeseci kasnije, 3. siječnja 2009., Bitcoin mreža pokrenula se, uvodeći novi sustav decentralizirane digitalne valute bez središnjeg posrednika.
Tko su osnivači Bitcoina?
Bitcoin je rezultat desetljeća razvoja kriptografije i ideja Cypherpunka iz 1970-ih, s projektima poput B-money, Bit Gold, eCash i HashCash.
Godine 2006., osoba ili grupa pod pseudonimom Satoshi Nakamoto započela je rad na Bitcoinu. Iako su kriptografi poput Hal Finneya, Nicka Szaba, Weija Daija i Adama Backa povezivani sa Satoshijem, svi su to negirali.
Satoshi je surađivao s programerima do 2010., kada je predao kontrolu nad izvornim kodom i 2011. nestao iz javnosti. Danas stotine programera razvijaju Bitcoin, koji ima zajednicu od milijun korisnika.
Kako funkcionira Bitcoin?
Bitcoin se može brzo i sigurno prenijeti na svakoga s Bitcoin adresom poput računa bilo gdje u svijetu, bez potrebe za dopuštenjem ili plaćanjem nepotrebnih naknada. BTC je jedinica valute u Bitcoin sustavu za koju postoji ograničena količina od 21 milijun. Svaki je Bitcoin djeljiv na 100 milijuna "satoshis" ili "sats" – najmanja jedinica Bitcoina, poput centa u dolaru. Bitcoini djeluju kao elektronički novac, omogućujući vam da izvršite plaćanje s univerzalnom valutom bilo gdje. Nalazi se u tzv. novčanicima u digitalnoj verziji. On funkcionira slično kao bankovni račun. Transakcije su moguće zahvaljujući peer-to-peer mreži. Osigurane su sustavom kriptografije javnog i privatnog ključa, objašnjava Kriptomat.
Bitcoin koristi kriptografiju javnog i privatnog ključa za sigurne transakcije. Javna adresa, izvedena iz "hasha" javnog ključa, koristi se za primanje sredstava. Privatni ključ služi kao digitalni potpis odnosno svojevrsna lozinka za autorizaciju transakcija i omogućava pristup sredstvima, pa ga treba čuvati u tajnosti.
Korisnik pokreće transakciju unosom javne adrese primatelja u svoj novčanik. Novčanik koristi privatni ključ za stvaranje digitalnog potpisa, čime se transakcija ovjerava i šalje na Bitcoin mrežu. Transakcija prvo ulazi u "mempool", gdje čeka potvrdu. Svakih desetak minuta, transakcije se grupiraju u blokove, koji se dodaju na blockchain, stvarajući neprekinuti lanac sigurnih zapisa.
Sigurnost sustava je toliko snažna da bi hakiranje jedne adrese trajalo milijardama godina.
Blockchain
Bitcoin je revolucionarno riješio problem dvostruke potrošnje, omogućujući prijenos sredstava izravno između korisnika bez posrednika. Zamislite mrežu stranaca, gdje svaki vodi vlastitu knjigu računa. Kada netko prenese 1 BTC, svi zapisuju transakciju i uspoređuju bilješke. Ako se sve podudaraju, transakcija se potvrđuje. Ako netko pokuša prevariti, njegova bilješka se odbacuje.
Ovaj sustav knjiga računa, distribuiran na globalnoj mreži, čini osnovu Bitcoin blockchaina. Svaki čvor ima identičnu kopiju koja javno i pseudonimno bilježi sve transakcije, osiguravajući točnost i sigurnost bez potrebe za skupim posrednicima.
Zašto je Bitcoin jedinstven i što mu daje vrijednost?
Bitcoin je revolucionirao digitalni novac stvaranjem decentraliziranog, sigurnog i otpornog sustava bez potrebe za posrednicima. Njegov kod omogućuje daljnje inovacije, a povremeno dolazi do "račvanja" koje stvara nove kriptovalute temeljene na Bitcoinu, iako one nikada ne mogu biti isti Bitcoin.
Njegova ključna snaga leži u decentralizaciji – nema središnje figure niti točke neuspjeha. Bitcoin se pokazao kao otporan na izazove, uključujući državne zabrane i snažna račvanja, što dodatno učvršćuje njegovu dugovječnost prema Lindyjevom efektu. Mrežni učinak potiče sve više korisnika da ga prihvate kao sredstvo za pohranu vrijednosti i razmjenu.
Njegova ograničena ponuda od 21 milijun BTC-a stvara oskudicu, čime se suprotstavlja inflacijskim valutama. Bitcoin je zamjenjiv, djeljiv na 100 milijuna dijelova, izdržljiv i prenosiv, što ga čini praktičnijim od zlata. S rastućim prihvaćanjem od strane tvrtki diljem svijeta, njegova vrijednost i korisnost nastavljaju rasti.
Blokovi, rudarenje i nagrade
Prvi Bitcoinblock izrudiran je 3. siječnja 2009. godine. Nazvan je Blok 0. Rudarenje Bitcoina je utrka između rudara za raspršivanje specifičnih vrijednosti i drugih informacija o bloku kako bi se pronašlo rješenje za problem raspršivanja i dodalo blok u blockchain. Pobjednički rudar nagrađen je Bitcoinima. Bitcoin nagrade se prepolovljuju svakih 210.000 blokova. Na primjer, nagrada za blok bila je 50 novih bitcoina u 2009. godini, a 11. svibnja 2020. kad se dogodilo treće prepolovljenje nagrada za svaki blok smanjena je na 6.25 bitcoina. Četvrto prepolovljenje dogodilo se u travnju 2024. i smanjilo je nagradu na 3.125 Bitcoina. Sljedeće prepolovljavanje trebalo bi se dogoditi sredinom 2028. i smanjiti nagradu na 1.5625 BTC.
Do 2140. godine, nakon 32. prepolovljenja, nagrada za rudarenje Bitcoina smanjit će se na nulu, dosegnuvši ukupnu ponudu od 21 milijun BTC-a. Tada će se rudari oslanjati isključivo na naknade za transakcije kako bi pokrili svoje troškove.
Svako prepolovljenje smanjuje količinu novih BTC-a, što povijesno dovodi do porasta cijene zbog smanjene ponude i povećane potražnje. Iako će se učinak budućih prepolovljenja možda smanjivati zbog sve manjih količina nove ponude, do sada su ta prepolovljenja bila ključni pokretači triju glavnih tržišnih ciklusa Bitcoina.
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ bf47c19e:c3d2573b
2025-05-11 18:22:40
@ bf47c19e:c3d2573b
2025-05-11 18:22:40Originalni tekst na antenam.net
31.10.2024 / Autor: Ana Nives Radović
Godišnjica objavljivanja revolucionarnog dokumenta nije samo podsjetnik na nastanak Bitcoina, već i na značajnu promjenu koju je donio u načinu na koji razmišljamo o novcu i ekonomskom suverenitetu. Njegov značaj premašuje ideju o zaradi na promjeni njegove vrijednosti, jer otvara vrata širem razumijevanju digitalne imovine i decentralizovanih finansija koje inspirišu moderno bankarstvo i platne sisteme da se razvijaju u drugačijem smjeru, povećavajući svijest o sigurnosti i dostupnosti.
Šesnaest je godina od objavljivanja dokumenta naslovljenog kao "Bitcoin: A Peer-to-Peer Electronic Cash System", poznatog i kao „biijeli papir“ (white paper) u kojem su izloženi koncept i svrha novog sistema digitalne valute – sistema koji bi funkcionisao nezavisno od bilo koje vlade ili finansijske institucije. Bijeli papir, kojeg je 31. oktobra 2008. objavio pojedinac ili tim ljudi pod imenom Satoši Nakamoto ponudio je smjelo rješenje za sve veći problem – kontrolu valute centralnih banaka i sve veće poteškoće u prenošenju vrijednosti preko interneta bez posrednika. Ovaj trenutak označio je nastanak Bitcoina, revolucionarne digitalne valute i prve kriptovalute na svijetu koja je kasnije lansirana 3. januara 2009. godine.
Bitcoin je nastao u vrijeme finansijske krize 2008. godine, u periodu kada je povjerenje u tradicionalne finansijske sisteme bilo na izuzetno niskom nivou. Ljudi su počeli da se pitaju da li postoji način za upravljanje novcem koji ne zavisi od banaka, koje, kao što su tadašnji događaji pokazali, mogu propasti ili djelovati na načine koji nijesu u najboljem interesu javnosti. Nakamotova inovacija, Bitcoin, bila je zamišljena kao sistem u kojem korisnici mogu direktno slati i primati novac, zaobilazeći potrebu za bankama. U tom procesu, Nakamoto je svijetu predstavio novu tehnologiju kojoj je kasnije američki naučnik i programer Harold Fini dao naziv blockchain – decentralizovan i otporan na manipulacije način za evidentiranje transakcija.
Šta je Bitcoin?
Bitcoin je vrsta digitalne valute koja omogućava ljudima da direktno jedni drugima šalju i primaju vrijednost putem interneta. Za razliku od tradicionalnih valuta, kao što je euro ili dolar, koje kontrolišu vlade i banke, Bitcoin funkcioniše bez centralne vlasti. To znači da nema nikoga ko je zadužen za njega i nema banke koja odlučuje kako se može koristiti. Umjesto toga, Bitcoin se oslanja na veliku mrežu računara širom svijeta koja ga održava i bilježi njegove transakcije. Ova mreža je poznata kao „Bitcoin mreža“.
Kako Bitcoin funkcioniše?
U suštini, Bitcoin funkcioniše kao „decentralizovana digitalna valuta“. Kada kažemo decentralizovana, mislimo da nijedna osoba, kompanija ili vlada ne kontroliše Bitcoin. Umjesto toga, svaka transakcija se bilježi na zajedničkoj knjizi, nazvanoj blockchain, koju održava mreža računara širom svijeta. Svaki put kada neko pošalje ili primi Bitcoin, transakcija se grupiše sa drugima i dodaje u ovaj lanac blokova. Budući da je ovaj lanac kopiran i dijeljen među brojnim računarima, gotovo je neizvodljivo izmijeniti ili hakovati ga, čime se osigurava da Bitcoin transakcije budu bezbjedne i pouzdane.
Još jedan interesantan aspekt je da Bitcoin ima ograničenu ponudu. Kreiran je samo 21 milion bitcoina, što ga čini rijetkom imovinom i sprečava inflaciju na način na koji to može biti slučaj sa tradicionalnim valutama koje se „doštampavaju“. Bitcoin transakcije su omogućene kroz skup kriptografskih pravila, koja ljudima omogućavaju da potvrde svaku transakciju kao legitimnu bez potrebe da vjeruju trećoj strani. Ovaj skup pravila je poznat kao kriptografija, zbog čega se Bitcoin naziva kriptovalutom – prvom koja je ikada stvorena i jedinom koja u potpunosti ima sve karakteristike onoga što je istinska ideja i svrha postojanja kriptovaluta.
Razumijevanje finansijske revolucije Bitcoina
Bitcoin, predstavljen 2008. godine, privukao je globalnu pažnju kao decentralizovana digitalna valuta koja funkcioniše nezavisno od banaka i vlada, ali pored svoje peer-to-peer arhitekture i decentralizovane infrastrukture, on ima jedinstvenu finansijsku karakteristiku – inherentno je deflatoran. Za razliku od fiat valuta poput dolara ili eura, koje centralne banke mogu štampati kada procijene da je to potrebno, ponuda Bitcoina je ograničena, fiksirana i ne povećava se. Ova deflatorna osobina navela je mnoge da ga vide kao revolucionarni finansijski instrument, „digitalno zlato“ koje bi moglo da preoblikuje koncepte vrijednosti, očuvanja bogatstva i monetarne politike.
Fiksna ponuda – limit od 21 miliona
Najkarakterističnija odlika Bitcoina je njegova ograničena ponuda. Kada je Satoši Nakamoto kreirao Bitcoin, postavio je ograničenje na ukupan broj bitcoina koji će ikada postojati – 21 milion. Ovo ograničenje se oštro razlikuje od tradicionalnih fiat valuta, gdje centralne banke mogu povećavati ponudu novca štampanjem dodatne količine. Postavljanjem ovog ograničenja, Nakamoto je osigurao da Bitcoin postane sve rjeđi vremenom, karakteristika koja je dizajnirana za očuvanje vrijednosti kako potražnja raste.
U tradicionalnim finansijama, valute mogu izgubiti vrijednost kada se previše štampaju, što se može vidjeti u slučajevima inflacije. Bitcoinov dizajn, međutim, znači da, kada se posljednji Bitcoin izrudari (što se predviđa oko 2140. godine), novi novčići neće ulaziti u cirkulaciju, što ga efektivno čini prvom deflatornom valutom u velikom obimu.
Mehanizam smanjenje ponude tokom vremena
Oskudica Bitcoina dodatno se pojačava procesom nazvanim „halving“ (prepolovljenje), koji smanjuje stopu stvaranja novih bitcoina. Približno svake četiri godine nagrada koju „rudari“ dobijaju za dodavanje novih blokova u blockchain se prepolovi. Ovaj mehanizam smanjuje mogućnost inflacije Bitcoina tokom vremena, stvarajući predvidivo, postepeno smanjenje ponude.
U početku su rudari dobijali 50 bitcoina po bloku. Nakon prvog halvinga 2012. godine, nagrada je pala na 25, a do 2020. smanjila se na 6,25 bitcoina po bloku. Ovaj proces halvinga će se nastaviti sve do približno 2140. godine, kada će svih 21 milion bitcoina biti u cirkulaciji, a rudari će biti podstaknuti isključivo transakcionim naknadama, umjesto novim novčićima. Halving ima dva osnovna učinka – usporava rast ponude Bitcoina i stvara predvidivu oskudicu koja može podstaći tražnju, jer učesnici na tržištu znaju da će sa svakim ciklusom biti sve manje dostupnih bitcoina.
Zašto je Bitcoin važan?
Većina tradicionalnih valuta je inflaciona po dizajnu. Centralne banke teže kontrolisanoj stopi inflacije, često oko 2%, kako bi podstakle ekonomski rast, ohrabrile potrošnju i pružile fleksibilnost u odgovoru na ekonomske krize. Međutim, ova inflacija može potkopati kupovnu moć fiat valuta vremenom, što je zabrinjavajuće tokom perioda prekomjernog štampanja novca, kao što su mjere i programi kvantitativnog popuštanja viđene posljednjih godina.
Bitcoinov deflatorni dizajn je revolucionaran u ovom kontekstu jer nudi potencijalnu zaštitu od inflacije. Sa fiksnom ponudom, Bitcoin može da dobija na vrijednosti tokom vremena, posebno ako potražnja raste jer postaje rjeđi. Za mnoge, deflatorni model Bitcoina čini ga privlačnim sredstvom za očuvanje bogatstva na način koji tradicionalne valute i imovina ne mogu da ponude.
Pored toga, ovaj model izazvao je promjenu čitave filozofije u načinu na koji ljudi razmišljaju o novcu, investiranju i štednji. Dok tradicionalne finansije podstiču potrošnju i investicije kroz inflaciju, deflatorna priroda Bitcoina može podstaći štednju, jer bi njegova vrijednost mogla da raste u budućnosti. Ovaj kvalitet „čuvara vrijednosti“ naveo je mnoge da Bitcoinu daju naziv „digitalno zlato“.
Ekonomija oskudice – ono što Bitcoinu daje vrijednost
U ekonomiji, oskudica obično povećava vrijednost, jer tražnja za ograničenim resursom može povećati njegovu cijenu. Zlato je, na primjer, dugo bilo čuvar vrijednosti zbog svoje oskudice i poteškoća u vađenju. Bitcoin odražava ovaj koncept u digitalnom svijetu. Inherentno je rijedak zbog ograničenja od 21 milion, i, kao zlato, zahtijeva trud (kroz digitalno rudarenje) da bi ušao u cirkulaciju.
Pored toga, oskudica Bitcoina postaje sve izraženija kako raste interesovanje institucija i pojedinaca. Mnogi investitori privučeni su Bitcoinom kao dugoročnom imovinom upravo zbog ove fiksne ponude, oslanjajući se na to da će rastuća tražnja naspram ograničene ponude povećati njegovu vrijednost tokom vremena. Ova privlačnost je pojačana u regionima sa brzom inflacijom ili ekonomskom nestabilnošću, gdje rizik od devalvacije čini Bitcoin privlačnom alternativom za očuvanje bogatstva.
Bitcoin kao globalni čuvar vrijednosti
Osim što je sredstvo razmjene, deflatorna priroda Bitcoina pozicionira ga kao potencijalni globalni čuvar vrijednosti. Zlato je istorijski imalo ovu ulogu, jer su ga koristili pojedinci, institucije i vlade kao zaštitu od ekonomske nestabilnosti i inflacije. Bitcoin postaje moderni pandan tome, posebno privlačan mlađim generacijama i investitorima sklonim tehnologiji, koji ga vide kao superiornu alternativu.
Deflatorni dizajn takođe omogućava Bitcoinu da prelazi međunarodne granice i nadilazi lokalne ekonomske uslove. U zemljama koje prolaze kroz valutne krize, Bitcoin nudi alternativu koja je bez granica i nezavisna od politika centralne banke. Ova sposobnost da djeluje kao čuvar vrijednosti posebno je značajna na tržištima i ekonomijama u razvoju, gdje je valutna nestabilnost učestalija.
Može li oskudica Bitcoina predstavljati rizik?
Iako deflatorni model Bitcoina ima svoje prednosti, nije bez kritika. Jedna od zabrinutosti je da ekstremna deflacija može obeshrabriti potrošnju. U sistemu gdje vrijednost valute raste tokom vremena, ljudi mogu preferirati štednju umjesto potrošnje ili investiranja, što može dovesti do smanjenja ekonomske aktivnosti. Ekonomisti brinu da bi, ako Bitcoin postane široko prihvaćena valuta, njegova deflatorna priroda mogla ugroziti ekonomski rast podsticanjem „gomilanja“ umesto cirkulacije.
Još jedna kritika se odnosi na fiksnu ponudu Bitcoina u ekonomiji koja stalno raste. Tradicionalne valute su inflatorne kako bi pratile rast populacije, ekonomije i produktivnosti. Sa ograničenom ponudom, Bitcoin ne može da raste u skladu sa ekonomskim razvojem, što bi u teoriji moglo izazvati probleme sa likvidnošću u ekonomiji zasnovanoj na Bitcoinu. Ipak, kako ideja nije da Bitcoin bude jedino sredstvo plaćanja, strah od takvog scenarija je neutemeljen, budući da ekosistem u kojem funkcioniše koegzistira sa nizom drugih platnih sistemna koji su na raspolaganju širom svijeta.
Eliminiše problem dvostrukog trošenja
U svijetu novca postoji veliki problem koji se naziva „dvostruko trošenje“. Zamislite da možete potrošiti iste eure dvaput – platite jedan proizvod ili uslugu, a zatim, nekako, uspijete da ga ponovo potrošite na nešto drugo. U fizičkom svijetu ovo nije problem, ali u računovodstvenom jeste. Ako kao fizičku valutu u gotovini platite nešto, ta količina novca odlazi iz vašeg novčanika, ali u bankovnim transakcijama stvari funkcionišu drugačije.
Da bi se osiguralo da Bitcoin ne može biti kopiran ili potrošen dvaput, koristi se tehnologija zvana blockchain. Nakamotov Bijeli papir još nije pomenuo taj izraz, jer mu je naziv dat nekoliko dana kasnije, no umjesto toga, opisao je koncept „lanca blokova“, postavljajući sistem za evidentiranje transakcija u blokovima koji su međusobno povezani. Ovaj koncept je kasnije postao poznat kao blockchain, termin koji je nastao nakon izdavanja Bitcoina dok su ljudi pokušavali da imenuju osnovnu tehnologiju. Fokus Bijelog papira bio je na tome kako Bitcoin može bezbjedno pratiti i potvrđivati transakcije, koristeći ovaj povezani lanac blokova kao neku vrstu digitalne knjige.
Pristup iz Bijelog papira uveo je revolucionarnu ideju – zajedničku, otpornu na manipulacije evidenciju koja se nije oslanjala na centralnu vlast za ažuriranje ili verifikaciju. Ovaj sistem povezanih blokova (ono što sada nazivamo blockchain) postao je osnova Bitcoina i, kasnije, bezbroj drugih primjena u finansijama, tehnologiji i brojnim drugim oblastima.
Ova baza je poput ogromne digitalne knjige, ili evidencije, u kojoj je svaka Bitcoin transakcija (prenosa novca od jednog do drugog korisnika) zabilježena. Ono što ovu digitalnu evidenciju čini posebnom jeste to što nije smještena na jednom mjestu, niti je pod kontrolom jedne osobe ili institucije – ona je u potpunosti decentralizovana, što znači da se kopije ove knjige čuvaju na hiljadama računara širom svijeta, a svi oni moraju da se saglase oko toga koje transakcije su validne.
Svaki put kada neko pošalje Bitcoin drugoj osobi, ova transakcija se dodaje u blockchain. Da bi se dodala, grupa računara (nazvana „rudari“) mora da verifikuje da je ova transakcija stvarna, što znači da Bitcoin koji se troši već nije korišćen drugdje. Ovi rudari rade zajedno, koristeći složene matematičke operacije, kako bi potvrdili transakcije. Kada se verifikuje, transakcija se dodaje u blockchain, a cijela mreža se ažurira kako bi prepoznala ovu transakciju kao legitimnu. Ovaj proces osigurava da nijedan Bitcoin ne može biti potrošen dvaput, rješavajući problem dvostrukog trošenja.
Peer-to-Peer transakcije bez posrednika
Još jedan veliki razlog zašto je Bitcoin važan je taj što omogućava ljudima da šalju novac direktno jedni drugima bez potrebe za posrednikom. Recimo da želite da pošaljete novac prijatelju koji živi u drugoj zemlji. Obično biste otišli u svoju banku, koja bi se povezala s drugom bankom u toj zemlji, što može trajati danima i uključivati različite naknade.
Međutim, Bitcoin je omogućio da se direktno pošalju sredstva, bez obzira na to gdje se nalazite u svijetu. Pošto je u pitanju peer-to-peer (P2P) način razmjene, nema potrebe za posrednikom da upravlja transakcijom. To može učiniti transakcije bržim i ponekad jeftinijim, posebno kada se sredstva šalju međunarodno. Ova P2P struktura je jedan od glavnih razloga zbog kojih ljudi se na ovaj oblik imovine gleda kao na alternativu složenim transakcijama, posebno važnim za društva i sredine u kojima je dostupnost finansijskih usluga niska.
Transparentnost i sigurnost
U svijetu tradicionalnog bankarstva, ljudi se oslanjaju na banke koje drže novac sigurnim i omogućavaju da transakcije budu poštene i sigurne. Međutim, s Bitcoinom, povjerenje nije smešteno u centralnu banku ili kompaniju, već u samu Bitcoin mrežu, koju održavaju svi računari koji prate blockchain. Pošto je blockchain javan i može ga provjeriti bilo ko, on je veoma transparentan. Svaka transakcija koja je ikada obavljena Bitcoinom zabilježena je u ovoj javnoj knjizi, tako da ako neko pokuša da prevari sistem, to bi bilo očigledno svima.
Transparentnost Bitcoina takođe ga čini veoma sigurnim. Pošto svi u mreži imaju kopiju blockchaina, bilo bi gotovo nemoguće da jedna osoba ili čak grupa ljudi izmijeni ili preuzme kontrolu nad njim. Da biste promijenili blockchain, morali biste kontrolisati više od polovine svih računara širom svijeta u Bitcoin mreži, što je izuzetno teško. Ovaj nivo sigurnosti, u kombinaciji s transparentnošću, pomaže ljudima da se osjećaju sigurno koristeći Bitcoin.
Značaj za razvoj finansija
Tokom godina, Bitcoin je postao više od eksperimenta u digitalnom novcu. Inspirisao je hiljade drugih kreatora latnih rješenja i pokrenuo važne razgovore o budućnosti novca, povjerenja i tehnologije. Kako sve više ljudi počinje da preispituje kako tradicionalne banke funkcionišu i traži nove načine za upravljanje svojim finansijama, Bitcoin ostaje snažna opcija ne samo u smislu alternative, već mogućnosti povezivanja njegove funkcionalnosti sa onim što već postoji u finansijskoj tehnologiji. Njegov značaj je u tome što predstavlja potpuno novi način razmišljanja o novcu i njegovom korišćenju i što rješava neke od ključnih problema koji su karakteristični finansijske sisteme.
Ideja decentralizacije
U mnogim sistemima koje danas koristimo postoji centralna vlast – banka, vlada ili kompanija – koja ima kontrolu i koja donosi pravila, odlučuje ko ima pristup i odobrava aktivnosti, što je prilično spor i skup proces u cjelini. Koncept Bitcoina je drugačiji jer je decentralizovan, a to znači da ne postoji jedna osoba, banka ili organizacija koja donosi odluke, već je to prepušteno mreži koju čine milioni korisničkih uređaja na mreži koji održavaju sistem u funkciji.
Pored toga, decentralizacija onemogućava cenzurisanje, jer niko ne može da interveniše i blokira nečiji pristup ili transakcije. To čini sistem demokratskijim, omogućavajući ljudima širom svijeta da se pridruže bez traženja dozvole.
Kriptografski dokazi – vjerovanje u matematiku, a ne u ljude
Kada nešto kupite koristeći Bitcoin, ne morate se oslanjati na posrednika da verifikuje vašu transakciju. Umjesto toga, Bitcoin koristi nešto što se naziva „kriptografskim dokazom. Kriptografski dokazi su poput digitalnog ključa i brave koji čuvaju informacije sigurnima, jer se oslanjaju na složenu matematiku koja osigurava da se samo validne transakcije dodaju u blockchain, onemogućavajući falsifikovanje ili prevaru.
Kriptografski dokazi funkcionišu tako što kreiraju heš (hash) – dug i jedinstven broj, za svaki blok transakcija. Svaki heš je povezan s prethodnim, što pomaže u obezbjeđivanju cijelog lanca. Matematika iza ovog procesa je toliko složena da bi zahtijevala ogromnu računarsku moć kada bi i pokušala da je razbije. Koristeći kriptografske dokaze, Bitcoin ne zahtijeva povjerenje u ljude, već se umjesto toga, oslanja na neprobojne matematičke algoritme da osigura svaku transakciju.
Proof of Work – digitalna zagonetka koja štiti Bitcoin
Bitcoinova mreža je osigurana procesom koji se naziva Proof of Work (dokaz o radu), koji je najjednostavnije razumjeti ako ga zamislite kao izazovnu zagonetku koju računari, poznati kao „rudari“, moraju da riješe da bi dodali novi blok u blockchain. Prvi računar koji riješi zagonetku dobija priliku da doda blok i dobija nagradu u bitcoinima. Ova zagonetka je izuzetno složena i zahtijeva od rudara da koristi veliku količinu mnogo računarske snage, što je skupo u smislu vremena i energije.
U tom smislu Proof of Work čuva mrežu sigurnom, jer kad bi neko pokušao da prevari sistem ponovnim pisanjem blockchaina, morao ponovo da uradi svako izračunavanja dokaza o radu za svaki blok koji želi da izmijeni, što je praktično nemoguće. Na ovaj način Bitcoin kreira mrežni sistem u kojem je prevara previše skupa i previše složena da bi se bilo kome isplatila.
Šesnaest godina kasnije...
Bitcoin je za ovo vrijeme postao mnogo više od digitalne valute – on je simbol finansijske nezavisnosti i pokretačka snaga nove finansijske tehnologije i ekonomskih koncepata. Pokrenuo je diskusije o budućnosti novca, a inspirisao je brojne pružaoce platnih usluga, uključujući brojne banke širom svijeta i FinTech kompanije, da unapređuju poslovni model.
Zbog količine koja je u opticaju njegova upotreba kao valute ostaje ograničena u poređenju s tradicionalnim novcem, dok njegova cijena nastavlja da fluktuira u zavisnosti od tržišnih okolnosti. U tom smislu uticaj Bitcoina na finansije, tehnologiju i društvo u cjelini već je dubok, navodeći promišljenije i kreativnije istraživanje kako se vrednostima može upravljati i razmenjivati u savremenom svijetu, podstičući značaj decentralizacije i svijest o zaštiti podataka.
Iako često predstavljan kao sredstvo za „brzo bogaćenje“ ili sresdstvo za obavljanje anonimnih transakcija, motivi za njegovo kreiranje, kao i njegova uloga u finansijskom i tehnološkom svijetu potpuno se razlikuju od toga. Bitcoin je prva, najstarija, najvrednija i – u najširem smislu – po svim parametrima jedina prava, potpuno decenztralizovana kriptovaluta koja je transformisala način na koji razmišljamo o novcu, povjerenju i bezbednosti u digitalnoj eri.
-
 @ bf47c19e:c3d2573b
2025-05-11 18:22:19
@ bf47c19e:c3d2573b
2025-05-11 18:22:19Originalan tekst na linkedin.com
12.04.2024 / Autor: Aleksandar Matanović
60/40 portfolio je dugo važio za idealan izbor nekome ko ima umerenu sklonost ka riziku, a nema vremena da prati berzu. Dakle, ubaciš 60% u akcije, 40% u obveznice i pustiš vreme da radi svoje.
Malo sam se igrao sa brojkama i računao šta bi bilo da je neko u taj portfolio ubacio malo Bitkoina. Period koji je obrađen je januar 2014 - januar 2024. Ovde napominjem da nikako nisam radio "cherry picking", to jest nisam birao period u kome se Bitkoin pokazao u najboljem mogućem svetlu. Maltene sam uradio suprotno. Da sam izabrao bilo koji januar pre 2014-te, prinosi na BTC bi bili neuporedivo veći. Čak i da sam izabrao januar 2015-te ili 2016-te, takođe bi prinosi bili veći jer je cena tada bila niža nego u januaru 2014-te. Izbor datuma je bio posledica želje da zaokružim jednu celu deceniju, period nakon kojeg su strpljivi investitori nagrađeni time što ne plaćaju porez na kapitalnu dobit.
Obradio sam 3 realna scenarija:
- Klasičan 60/40 portfolio. Na uloženih $10.000 u januaru 2014. godine, 10 godina kasnije bismo imali tačno $17.434. Prosečan godišnji prinos je 5,72%.
- 99% uloženo u 60/40 portfolio, 1% uloženo u Bitkoin. Na uloženih $10.000, imali bismo $22.505 ili 8,45% godišnje. Samo 1% u BTC, a skoro 3% veći godišnji prinos. (narandžasta linija)
- 90% uloženo u 60/40 portfolio, 10% uloženo u Bitkoin. Sad već postaje zabavno... od $10.000 do $68.145, što bi bilo 21,16% godišnje - jače od proseka Vorena Bafeta. (zelena linija)
Uzeo sam u obzir i rizike i zamislio da je u ovom periodu cena Bitkoina polako padala i na kraju pala na 0. Dakle naredna 2 scenarija su hipotetička.
- 99% uloženo u 60/40 portfolio, 1% uloženo u Bitkoin, Bitkoin propao. Investirano $10.000, dobijeno $17.259 ili 5.61% godišnje. Minimalni gubitak u odnosu na čist 60/40 portfolio iz prvog scenarija. Zbog toga se na grafiku vide 4 linije iako ih ima 5, toliko je mala razlika.
- 90% uloženo u 60/40 portfolio, 10% uloženo u Bitkoin, Bitkoin propao. Investirano $10.000, dobijeno $15.690 ili 4.61% godišnje. To je ona donja. ljubičasta linija na grafikonu. Nije neki prinos, ali nije ni katastrofa.
Mogao sam da idem i sa preko 10%, naravno završili bismo na preko $100.000. Međutim, hteo sam da budem konzervativan i stvari gledam iz ugla investitora koji ipak ima nešto manji apetit ka riziku i nedovljno poznaje Bitkoin. Mogao sam i da uzmem drugačiji period. Na primer, za jan 2012 - jan 2022 bi narandžasta linija završila na preko milion dolara, a zelena na preko 10 miliona. Da, nije greška u računici... zaista biste za 10 godina, počev od januara 2012-te imali preko milion dolara da ste uložili ukupno $10.000, 99% u akcije i obveznice, a 1% u Bitkoin. Sa 90% u akcijama i obveznicama i 10% u Bitkoinu, već ste na 8 cifara.
Istorijske performanse nisu garancija budućih prinosa. Investiranje u Bitkoin je rizično. Ignorisanje Bitkoina je rizično. Svako bira svoj rizik. Ovo nije investicioni savet, ovo je prijateljski savet.
-
 @ 26d4b5b2:96393e73
2025-05-11 22:24:38
@ 26d4b5b2:96393e73
2025-05-11 22:24:38https://app.doh.money http://localhost:3000 https://dohmoney-cyxe-cyxeio-cyxecyxeios-projects.vercel.app GET POST OPTIONS PUT DELETE Content-Type Ocp-Apim-Subscription-Key Authorization Accept X-Requested-With X-Verified-By Content-Length Request-Context Date @(context.Request.Headers.GetValueOrDefault("Ocp-Apim-Subscription-Key", "50922ff015c14a84a092b4764dc6dddf")) @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With,X-Verified-By Content-Length, Request-Context, Date @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With, X-Verified-By Content-Length, Request-Context, Date -
 @ e034d654:ca919814
2025-01-22 23:14:27
@ e034d654:ca919814
2025-01-22 23:14:27I stumbled into nostr end of March 2023. At that point already fully thrown into the hows, whys and whats of Bitcoin, never really interested in social apps, just recently playing around with Lightning, the only experience of which at the time was Muun (😬) and stacker.news custodial wallet.
Fairly inexperienced with technicals other than rough understandings of concepts. A crappy laptop node with a dangling SSD via USB, constantly having to resync to current blockheights whenever I was ready to make an on chain transaction to cold storage. My great success after over two years of delay, and a couple failed attempts.
Something about the breadth of information for nitty gritty specifics, the clash with all the things that I found interesting about Bitcoin, with others equally as focused, kept me interested in Nostr. Plus the lighthearted shit posting to break up plumbing the depths of knowledge appealed to me.
Cut to now. Through the jurisdictional removals and even deaths of LN wallet projects, using mobile LSPs, finding use cases with the numerous cashu implementations, moderate comfortability with NWC strings of various permissions, budgets for seemingly endless apps of Nostr clients, swapping relays, isolated wallets with Alby go for my wife and cousin (I told them both not to put much on there as I'm sure failure is imminent) Alby Hub and Zeus, now fully backended by my own persistently online lightning node. All of it adding to the fluidity of my movement around the protocol.
Nimble.
Gradual progress. Reading through notes and guides posted on Nostr learning little bits, circling back eventually, if even at a time it wasn't clicking for me. Either way. Glad i've stuck to it even if I still barely know what it is I'm doing.
