-
 @ b0a838f2:34ed3f19
2025-05-23 18:02:28
@ b0a838f2:34ed3f19
2025-05-23 18:02:28- CyTube - Synchronize media, chat, and more for an arbitrary number of channels. (Demo)
MITNodejs - Invidious
⚠- Alternative YouTube front-end. (Demo)AGPL-3.0Docker/Crystal - MediaCMS - Modern, fully featured open source video and media CMS, written in Python/Django/React, featuring a REST API. (Source Code)
AGPL-3.0Python/Docker - OvenMediaEngine - Streaming Server with Sub-Second Latency. (Demo)
AGPL-3.0C++/Docker - Owncast - Decentralized single-user live video streaming and chat server for running your own live streams similar in style to the large mainstream options. (Source Code)
MITGo - PeerTube - Decentralized video streaming platform using P2P (BitTorrent) directly in the web browser. (Source Code)
AGPL-3.0Nodejs - Rapidbay - Self-hosted torrent videostreaming service/torrent client that allows searching and playing videos from torrents in the browser or from a Chromecast/AppleTV/Smart TV.
MITPython/Docker - Restreamer - Restreamer allows you to do h.264 real-time video streaming on your website without a streaming provider. (Source Code)
Apache-2.0Nodejs/Docker - SRS - A simple, high efficiency and real-time video server, supports RTMP, WebRTC, HLS, HTTP-FLV and SRT. (Source Code)
MITDocker/C++ - SyncTube - Lightweight and very simple to setup CyTube alternative to watch videos with friends and chat.
MITNodejs/Haxe - Tube Archivist
⚠- Organize, search, and enjoy your YouTube collection. Subscribe, download, and track viewed content with metadata indexing and a user-friendly interface. (Source Code, Clients)GPL-3.0Docker - Tube - Youtube-like (without censorship and features you don't need!) video sharing app written in Go which also supports automatic transcoding to MP4 H.265 AAC, multiple collections and RSS feed. (Demo)
MITGo - VideoLAN Client (VLC) - Cross-platform multimedia player client and server supporting most multimedia files as well as DVDs, Audio CDs, VCDs, and various streaming protocols. (Source Code)
GPL-2.0C/deb
- CyTube - Synchronize media, chat, and more for an arbitrary number of channels. (Demo)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:02:11
@ b0a838f2:34ed3f19
2025-05-23 18:02:11- ClipBucket - Start your own video sharing website (YouTube/Netflix Clone) in a matter of minutes. (Demo, Source Code)
AALDocker/PHP - Gerbera - UPnP Media Server, which allows you to stream your digital media throughout your home network and listen to/watch it on a variety of UPnP compatible devices. (Source Code)
GPL-2.0Docker/deb/C++ - Icecast 2 - Streaming audio/video server which can be used to create an Internet radio station or a privately running jukebox and many things in between. (Source Code, Clients)
GPL-2.0C - Jellyfin - Media server for audio, video, books, comics, and photos with a sleek interface and robust transcoding capabilities. Almost all modern platforms have clients, including Roku, Android TV, iOS, and Kodi. (Demo, Source Code, Clients)
GPL-2.0C#/deb/Docker - Karaoke Eternal - Host awesome karaoke parties where everyone can easily find and queue songs from their phone's browser. The player is also fully browser-based with support for MP3+G, MP4 and WebGL visualizations. (Source Code)
ISCDocker/Nodejs - Kodi - Multimedia/Entertainment center, formerly known as XBMC. Runs on Android, BSD, Linux, macOS, iOS and Windows. (Source Code)
GPL-2.0C++/deb - Kyoo - Innovative media browser designed for seamless streaming of anime, series and movies, offering advanced features like dynamic transcoding, auto watch history and intelligent metadata retrieval. (Demo)
GPL-3.0Docker - Meelo - Personal Music Server, designed for collectors and music maniacs.
GPL-3.0Docker - MistServer - Public domain streaming media server that works with any device and any format. (Source Code)
UnlicenseC++ - NymphCast - Turn your choice of Linux-capable hardware into an audio and video source for a television or powered speakers (alternative to Chromecast). (Source Code)
BSD-3-ClauseC++ - ReadyMedia - Simple media server software, with the aim of being fully compliant with DLNA/UPnP-AV clients. Formerly known as MiniDLNA. (Source Code)
GPL-2.0C - Rygel - Rygel is a UPnP AV MediaServer that allows you to easily share audio, video, and pictures. Media player software may use Rygel to become a MediaRenderer that may be controlled remotely by a UPnP or DLNA Controller. (Source Code)
GPL-3.0C - Stash - A web-based library organizer and player for your adult media stash, with auto-tagging and metadata scraping support. (Source Code)
AGPL-3.0Docker/Go - µStreamer - Lightweight and very quick server to stream MJPEG video from any V4L2 device to the net.
GPL-3.0C/deb - üWave
⚠- Self-hosted collaborative listening platform. Users take turns playing media—songs, talks, gameplay videos, or anything else—from a variety of media sources like YouTube and SoundCloud. (Demo, Source Code)MITNodejs
- ClipBucket - Start your own video sharing website (YouTube/Netflix Clone) in a matter of minutes. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:01:53
@ b0a838f2:34ed3f19
2025-05-23 18:01:53- Ampache - Web based audio/video streaming application. (Demo, Source Code)
AGPL-3.0PHP - Audiobookshelf - Audiobook and podcast server. It streams all audio formats, keeps and syncs progress across devices. Comes with open-source apps for Android and iOS. (Source Code, Clients)
GPL-3.0Docker/deb/Nodejs - Audioserve - Simple personal server to serve audio files from directories (audiobooks, music, podcasts...). Focused on simplicity and supports sync of play position between clients.
MITRust - AzuraCast - Modern and accessible web radio management suite. (Source Code)
Apache-2.0Docker - Beets - Music library manager and MusicBrainz tagger (command-line and Web interface). (Source Code)
MITPython/deb - Black Candy - Music streaming server.
MITDocker/Ruby - Funkwhale - Modern, web-based, convivial, multi-user and free music server.
BSD-3-ClausePython/Django - gonic - Lightweight music streaming server. Subsonic compatible.
GPL-3.0Go/Docker - HoloPlay
⚠- Listen to Youtube audio sources using Invidious API. (Source Code)MITNodejs/Docker - koel - Personal music streaming server that works. (Demo, Source Code)
MITPHP - LibreTime - Broadcast streaming radio on the web (fork of Airtime). (Source Code)
AGPL-3.0Docker/PHP - LMS - Access your self-hosted music using a web interface.
GPL-3.0Docker/deb/C++ - Maloja - Music scrobble database (alternative to Last.fm). (Demo)
GPL-3.0Python/Docker - moOde Audio - Audiophile-quality music playback for the wonderful Raspberry Pi family of single board computers. (Source Code)
GPL-3.0PHP - Mopidy
⚠- Extensible music server. Offers a superset of the mpd API, as well as integration with 3rd party services like Spotify, SoundCloud etc. (Source Code)Apache-2.0Python/deb - mpd - Daemon to remotely play music, stream music, handle and organize playlists. Many clients available. (Source Code, Clients)
GPL-2.0C++ - mStream - Music streaming server with GUI management tools. Runs on Mac, Windows, and Linux. (Source Code)
GPL-3.0Nodejs - multi-scrobbler - Scrobble plays from multiple sources to multiple scrobbling services. (Source Code)
MITNodejs/Docker - musikcube - Streaming audio server with Linux/macOS/Windows/Android clients. (Source Code)
BSD-3-ClauseC++/deb - Navidrome Music Server - Modern Music Server and Streamer, compatible with Subsonic/Airsonic. (Demo, Source Code, Clients)
GPL-3.0Docker/Go - Pinepods - Podcast management system with multi-user support. Pinepods utilizes a central database so aspects like listen time and themes follow from device to device. (Demo, Source Code)
GPL-3.0Docker - Polaris - Music browsing and streaming application optimized for large music collections, ease of use and high performance.
MITRust/Docker - Snapcast - Synchronous multiroom audio server.
GPL-3.0C++/deb - Stretto
⚠- Music player with Youtube/Soundcloud import and iTunes/Spotify discovery. (Demo, Clients)MITNodejs - Supysonic - Python implementation of the Subsonic server API.
AGPL-3.0Python/deb - SwingMusic - Swing Music is a beautiful, self-hosted music player and streaming server for your local audio files. Like a cooler Spotify ... but bring your own music. (Source Code)
MITPython/Docker - vod2pod-rss
⚠- Convert YouTube and Twitch channels to podcasts, no storage required. Transcodes VoDs to MP3 192k on the fly, generates an RSS feed to use in podcast clients.MITDocker
- Ampache - Web based audio/video streaming application. (Demo, Source Code)
-
 @ eb0157af:77ab6c55
2025-05-23 18:01:42
@ eb0157af:77ab6c55
2025-05-23 18:01:42Bitcoin adoption will come through businesses: neither governments nor banks will lead the revolution.
In recent years, it’s undeniable that Bitcoin has ceased to be just a radical idea born from the minds of cypherpunks. It is now recognized across the board as a global asset, discussed in the upper echelons of finance, accepted even on Wall Street, purchased by banking groups and included as a “strategic reserve” by some nations.
However, the general perception that hovers today regarding Bitcoin’s diffusion is still that of minimal adoption, almost insignificant. Bitcoin exists, certainly, but in fact it is not being used. It is rarely possible to pay in satoshis in commercial establishments. Demand is still extremely low.
Furthermore, the debate on Bitcoin is still practically absent: excluding some local events, some niche media outlets or some timid discussion, today Bitcoin is in fact excluded from general interest. The level of understanding and knowledge of the phenomenon is certainly still very low.
Yet, Bitcoin represents an unprecedented technological improvement, capable of solving many problems inherent in the fiat system in which we live. What could facilitate its diffusion?
Bitcoin becomes familiar when businesses adopt it
When talking about Bitcoin adoption, many look to States. They imagine governments that legislate or accumulate Bitcoin as a “strategic reserve,” or banks perceived as forward-thinking that would lead technological change, opening up to innovation. But the reality is different: bureaucracy, political constraints, and fear of losing control inherently prevent States and central banks from being pioneers.
What really drives Bitcoin adoption are not States, but businesses. It is the forward-looking entrepreneurs, innovative startups and – eventually – even large multinational companies that decide to integrate Bitcoin into their operating systems that drive adoption. Indeed, the business world has always played a key role in the adoption of new technologies. This was the case, for example, with the internet, e-commerce, mobile telephony, and the cloud. It will also be the case with Bitcoin.
Unlike a State, when a company adopts Bitcoin, it does so for concrete reasons: efficiency, savings, protection, access to new markets, independence from traditional banking circuits, or bureaucratic streamlining. It is a rational choice, not an ideological one, dictated by the intent to improve one’s competitiveness against the competition to survive in the market.
What is currently missing to facilitate adoption is, in all likelihood, a significant number of businesses that have decided to integrate Bitcoin into their company systems.
Bitcoin becomes “normal” when it is integrated into the operational flow of businesses. Holding and framing bitcoin on the balance sheet, paying an invoice, paying salaries to employees in satoshis, making value transfers globally thanks to the blockchain, allowing customers to pay via Lightning Network… when all this becomes possible with the same simplicity with which we use the euro or the dollar, Bitcoin stops being alternative and becomes the standard.
Businesses are not just users. They are adoption multipliers. When a company chooses Bitcoin, it is automatically proposing it to customers, employees, suppliers, and institutional stakeholders. Each business adoption equals tens, hundreds, or thousands of new eyes on Bitcoin.
People, after all, trust what they see every day: if your trusted restaurant accepts bitcoin, or if your favorite e-commerce platform uses it to receive international payments, or if your colleague receives it as a salary, then Bitcoin no longer appears to be a mysterious object. It finally begins to be perceived as a real, useful, and functioning tool.
The integration of a technology in companies helps make it understandable, accessible, and legitimate in the eyes of the public. This is how distrust is overcome: by making Bitcoin visible in daily life.
Bitcoin and businesses today
A River Financial report estimates that as of May 2025, only 5% of bitcoin is currently owned by private businesses. A still very small number.

According to research by River, in May 2025 businesses hold just over a million btc (about 5% of available monetary units). More than two-thirds of bitcoin (68.2%) are in the hands of private individuals.
To promote Bitcoin adoption, it is necessary today to support businesses in integrating this standard, leveraging all its enormous opportunities. Among others, this technology allows for fast, economical, and global payments. It eliminates intermediaries, increases transparency and security in value transfers. It removes bureaucratic frictions and allows opening up to a new global market.
Every sector can benefit from Bitcoin: e-commerce, tourism, industry, restaurants, professional services, or any other business. Bitcoin revolutionizes the concept of money, and money is a transversal working tool.
We are still at the beginning, but several signals are encouraging. According to a study by Bitwise and reported by Atlas21, in the first quarter of 2025, a growing number of US companies (+16.11% compared to the previous one) are including Bitcoin in their balance sheets, not just as a financial bet, but as a long-term strategy to protect their assets and access a decentralized monetary system to transfer value worldwide without resorting to financial intermediaries.
Who is driving the change?
Echoing the words of Roy Sheinfeld, CEO of Breez, the true potential of Bitcoin will be unleashed first and foremost from the work of developers, the true architects in designing and refining tools that are increasingly simple and intuitive to use for anyone, regardless of level of expertise. It is the developers – Roy rightly argued – who will enable us to “conquer the world.”
But probably that’s not enough: the next step is to make Bitcoin a globally accepted technological standard, changing its perception towards the general public. And this is where businesses come into play.
Guided by the market, technological innovation, and the desire to meet user demands, entrepreneurs today represent the fulcrum to accelerate the monetary transition from the current fiat system towards the Bitcoin standard. It is entrepreneurs who transform innovations from opportunities for a few to a reality shared by many.
The adoption of Bitcoin will therefore not arise from a sudden event, nor from the exclusive fruit of enthusiasts’ enthusiasm or from arbitrary political choices decreed by States or regulators.
The future of Bitcoin is built in the places where value is created every day: in companies, in their systems, and in their strategic decisions.
“If we conquer developers, we conquer the world. If we conquer businesses, we conquer adoption.”
The post The key to Bitcoin adoption is businesses appeared first on Atlas21.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:01:38
@ b0a838f2:34ed3f19
2025-05-23 18:01:38- ChannelTube
⚠- Download video or audio from YouTube channels on a schedule via yt-dlp.AGPL-3.0Docker - Dagu - Powerful Cron alternative with a Web UI. It allows you to define dependencies between commands as a Directed Acyclic Graph (DAG) in a declarative YAML format. (Source Code)
GPL-3.0Go/Docker - Headphones - Automated music downloader for NZB and Torrent, written in Python. It supports SABnzbd, NZBget, Transmission, µTorrent, Deluge and Blackhole.
GPL-3.0Python - Jellyseerr - Manage requests for your media library, supports Plex, Jellyfin and Emby media servers (fork of Overseerr).
MITDocker/Nodejs - Lidarr - Music collection manager for Usenet and BitTorrent users. (Source Code)
GPL-3.0C#/Docker - LidaTube
⚠- Finding and fetch missing Lidarr albums via yt-dlp.GPL-3.0Docker - Lidify
⚠- Music discovery tool that provides recommendations based on selected Lidarr artists, using Spotify or LastFM.MITDocker - Medusa - Automatic Video library manager for TV Shows. It watches for new episodes of your favorite shows, and when they are posted it does its magic. (Clients)
GPL-3.0Python - MetaTube
⚠- Automatically download music from YouTube add metadata from Spotify, Deezer or Musicbrainz.GPL-3.0Python - MeTube - Web GUI for youtube-dl, with playlist support. Allows downloading videos from dozens of websites.
AGPL-3.0Python/Nodejs/Docker - nefarious - Automate downloading Movies and TV Shows. (Source Code)
GPL-3.0Python - Ombi - Content request system for Plex/Emby, connects to SickRage, CouchPotato, Sonarr, with a growing feature set. (Demo, Source Code)
GPL-2.0C#/deb - Overseerr
⚠- Manage requests for your media library. It integrates with your existing services, such as Sonarr, Radarr, and Plex!. (Source Code)MITDocker - Pinchflat
⚠- Download YouTube content built using yt-dlp.AGPL-3.0Docker - PlexRipper
⚠- Cross-platform Plex media downloader that seamlessly adds media from other Plex servers to your own. (Source Code)GPL-3.0Docker - PodFetch - Sleek and efficient podcast downloader. (Source Code)
Apache-2.0Docker/Rust - Radarr - Radarr is an independent fork of Sonarr reworked for automatically downloading movies via Usenet and BitTorrent, à la Couchpotato. (Source Code)
GPL-3.0C#/Docker - Reiverr
⚠- Clean combined interface for Jellyfin, TMDB, Radarr and Sonarr, as well as a replacement to Overseerr.AGPL-3.0Docker - SickChill - Automatic video library manager for TV shows. It watches for new episodes of your favorite shows, and when they are posted it does its magic. (Source Code)
GPL-3.0Python/Docker - Sonarr - Automatic TV Shows downloader and manager for Usenet and BitTorrent. It can grab, sort and rename new episodes and automatically upgrade the quality of files already downloaded when a better quality format becomes available. (Source Code)
GPL-3.0C#/Docker - tubesync
⚠- Syncs YouTube channels and playlists to a locally hosted media server.AGPL-3.0Docker/Python - Watcharr - Add and track all the shows and movies you are watching. Comes with user authentication, modern and clean UI and a very simple setup. (Demo)
MITDocker - ydl_api_ng - Simple youtube-dl REST API to launch downloads on a distant server.
GPL-3.0Python - YoutubeDL-Server - Web and REST interface to Youtube-DL for downloading videos onto a server.
MITPython/Docker - yt-dlp Web UI - Web GUI for yt-dlp.
MPL-2.0Docker/Go/Nodejs
- ChannelTube
-
 @ b0a838f2:34ed3f19
2025-05-23 18:01:20
@ b0a838f2:34ed3f19
2025-05-23 18:01:20- AdventureLog - Travel tracker and trip planner. (Demo, Source Code)
GPL-3.0Docker - AirTrail - Personal flight tracking system. (Source Code)
GPL-3.0Docker/Nodejs - Bicimon - Bike Speedometer as Progressive Web App. (Demo)
MITJavascript - Dawarich - Visualize your location history, track your movements, and analyze your travel patterns with complete privacy and control (alternative to Google Timeline a.k.a. Google Location History). (Source Code)
AGPL-3.0Docker - Geo2tz - Get the timezone from geo coordinates (lat, lon).
MITGo/Docker - GraphHopper - Fast routing library and server using OpenStreetMap. (Source Code)
Apache-2.0Java - Nominatim - Server application for geocoding (address -> coordinates) and reverse geocoding (coordinates -> address) on OpenStreetMap data. (Source Code)
GPL-2.0C - Open Source Routing Machine (OSRM) - High performance routing engine designed to run on OpenStreetMap data and offering an HTTP API, C++ library interface, and Nodejs wrapper. (Demo, Source Code)
BSD-2-ClauseC++ - OpenRouteService - Route service with directions, isochrones, time-distance matrix, route optimization, etc. (Demo, Source Code)
GPL-3.0Docker/Java - OpenStreetMap - Collaborative project to create a free editable map of the world. (Source Code, Clients)
GPL-2.0Ruby - OpenTripPlanner - Multimodal trip planning software based on OpenStreetMap data and consuming published GTFS-formatted data to suggest routes using local public transit systems. (Source Code)
LGPL-3.0Java/Javascript - OwnTracks Recorder
⚠- Store and access data published by OwnTracks location tracking apps.GPL-2.0C/Lua/deb/Docker - TileServer GL - Vector and raster maps with GL styles. Server side rendering by Mapbox GL Native. Map tile server for Mapbox GL JS, Android, iOS, Leaflet, OpenLayers, GIS via WMTS, etc. (Source Code)
BSD-2-ClauseNodejs/Docker - Traccar - Java application to track GPS positions. Supports loads of tracking devices and protocols, has an Android and iOS App. Has a web interface to view your trips. (Demo, Source Code)
Apache-2.0Java - wanderer - Trail database where you can upload your recorded tracks or create new ones and add various metadata to build an easily searchable catalogue. (Demo)
AGPL-3.0Docker/Go/Nodejs
- AdventureLog - Travel tracker and trip planner. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:01:03
@ b0a838f2:34ed3f19
2025-05-23 18:01:03- CNCjs - Web interface for CNC milling controllers running Grbl, Smoothieware, or TinyG. (Source Code)
MITNodejs - Fluidd - Lightweight & responsive user interface for Klipper, the 3D printer firmware. (Source Code)
GPL-3.0Docker/Nodejs - Mainsail - Modern and responsive user interface for the Klipper 3D printer firmware. Control and monitor your printer from everywhere, from any device. (Source Code)
GPL-3.0Docker/Python - Manyfold - Digital asset manager for 3d print files; STL, OBJ, 3MF and more. (Source Code)
MITDocker - Octoprint - Snappy web interface for controlling consumer 3D printers. (Source Code)
AGPL-3.0Docker/Python
- CNCjs - Web interface for CNC milling controllers running Grbl, Smoothieware, or TinyG. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:00:46
@ b0a838f2:34ed3f19
2025-05-23 18:00:46- Canvas LMS - Learning management system (LMS) that is revolutionizing the way we educate. (Demo, Source Code)
AGPL-3.0Ruby - Chamilo LMS - Create a virtual campus for the provision of online or semi-online training. (Source Code)
GPL-3.0PHP - Digiscreen - Interactive whiteboard/wallpaper for the classroom, in person or remotely (documentation in French). (Demo, Source Code)
AGPL-3.0Nodejs/PHP - Digitools - A set of simple tools to accompany the animation of courses in person or remotely. (documentation in French). (Demo, Source Code)
AGPL-3.0PHP - edX - The Open edX platform is open-source code that powers edX.org. (Source Code)
AGPL-3.0Python - Gibbon - Flexible school management platform designed to make life better for teachers, students, parents and leaders. (Source Code)
GPL-3.0PHP - ILIAS - Learning management system that can cope with anything you throw at it. (Demo, Source Code)
GPL-3.0PHP - INGInious - Intelligent grader that allows secured and automated testing of code made by students. (Source Code, Clients)
AGPL-3.0Python/Docker - Moodle - Learning and courses platform with one of the largest open source communities worldwide. (Demo, Source Code)
GPL-3.0PHP - Open eClass - Open eClass is an advanced e-learning solution that can enhance the teaching and learning process. (Demo, Source Code)
GPL-2.0PHP - OpenOLAT - Learning management system for teaching, education, assessment and communication. (Demo, Source Code)
Apache-2.0Java - QST - Online assessment software. From a quick quiz on your phone to large scale, high stakes, proctored desktop testing, easy, secure and economical. (Demo, Source Code)
GPL-2.0Perl - RELATE - RELATE is a web-based courseware package, includes features such as: flexible rules, statistics, multi-course support, class calendar. (Source Code)
MITPython - RosarioSIS - RosarioSIS, free Student Information System for school management. (Demo, Source Code)
GPL-2.0PHP - Schoco - Online IDE for learning Java programming at school, including automatic JUnit tests. Designed to give coding homework/assignments.
MITDocker - scholarsome - Web-based and open source interactive flashcard learning software studying for the masses. (Demo, Source Code)
GPL-3.0Docker
- Canvas LMS - Learning management system (LMS) that is revolutionizing the way we educate. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:00:28
@ b0a838f2:34ed3f19
2025-05-23 18:00:28- Atomic Server - Knowledge graph database with documents (similar to Notion), tables, search, and a powerful linked data API. Lightweight, very fast and no runtime dependencies. (Demo)
MITDocker/Rust - Digimindmap - Create simple mindmaps (documentation in French). (Demo, Source Code)
AGPL-3.0Nodejs/PHP - LibreKB - Web-based knowledge base solution. A simple web app, it runs on pretty much any web server or hosting provider with PHP and MySQL. (Source Code)
GPL-3.0PHP - memEx - Structured personal knowledge base, inspired by zettlekasten and org-mode.
AGPL-3.0Docker - SiYuan - A privacy-first personal knowledge management software, written in typescript and golang. (Source Code)
AGPL-3.0Docker/Go - TeamMapper - Host and create your own mindmaps. Share your mindmap sessions with your team and collaborate live on mindmaps. (Demo)
MITDocker/Nodejs
- Atomic Server - Knowledge graph database with documents (similar to Notion), tables, search, and a powerful linked data API. Lightweight, very fast and no runtime dependencies. (Demo)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:00:12
@ b0a838f2:34ed3f19
2025-05-23 18:00:12- Cannery - Firearm and ammunition tracker app. (Source Code)
AGPL-3.0Docker - HomeBox (SysAdminsMedia) - Inventory and organization system built for the home user. (Demo, Source Code)
AGPL-3.0Docker/Go - Inventaire - Collaborative resources mapper project, while yet only focused on exploring books mapping with wikidata and ISBNs. (Source Code)
AGPL-3.0Nodejs - Inventree - Inventory management system which provides intuitive parts management and stock control. (Demo, Source Code)
MITPython - Open QuarterMaster - Powerful inventory management system, designed to be flexible and scalable. (Source Code)
GPL-3.0deb/Docker - Part-DB - Inventory management system for your electronic components. (Demo, Source Code)
AGPL-3.0Docker/PHP/Nodejs - Shelf - Asset and equipment tracking software used by teams who value clarity. Shelf is an asset database and QR asset label generator that lets you create, manage and overview your assets across locations. Unlimited assets, free forever. (Source Code)
AGPL-3.0Nodejs - Spoolman - Keep track of your inventory of 3D-printer filament spools.
MITDocker/Python
- Cannery - Firearm and ammunition tracker app. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:59:47
@ b0a838f2:34ed3f19
2025-05-23 17:59:47- Domoticz - Home Automation System that lets you monitor and configure various devices like: Lights, Switches, various sensors/meters like Temperature, Rain, Wind, UV, Electra, Gas, Water and much more. (Source Code, Clients)
GPL-3.0C/C++/Docker/Shell - EMQX - Scalable MQTT broker. Connect 100M+ IoT devices in one single cluster, move and process real-time IoT data with 1M msg/s throughput at 1ms latency. (Demo, Source Code)
Apache-2.0Docker/Erlang - evcc - Extensible Electric Vehicle Charge Controller and home energy management system. (Source Code)
MITdeb/Docker/Go - FHEM - Automate common tasks in the household like switching lamps and heating. It can also be used to log events like temperature or power consumption. You can control it via web or smartphone frontends, telnet or TCP/IP directly. (Source Code)
GPL-3.0Perl - FlowForge - Deploy Node-RED applications in a reliable, scalable and secure manner. The FlowForge platform provides DevOps capabilities for Node-RED development teams. (Source Code)
Apache-2.0Nodejs/Docker/K8S - Gladys - Privacy-first home assistant. (Source Code)
Apache-2.0Nodejs/Docker - Home Assistant - Home automation platform. (Demo, Source Code)
Apache-2.0Python/Docker - ioBroker - Integration platform for the Internet of Things, focused on building automation, smart metering, ambient assisted living, process automation, visualization and data logging. (Source Code)
MITNodejs - LHA - Light Home Automation application that is fully extensible using Blockly, HTML or Lua. It includes extensions such as ConBee, Philips Hue or Z-Wave JS.
MITLua - Node RED - Browser-based flow editor that helps you wiring hardware devices, APIs and online services to create IoT solutions. (Source Code)
Apache-2.0Nodejs/Docker - openHAB - Vendor and technology agnostic open source software for home automation. (Source Code)
EPL-2.0Java - OpenRemote - IoT Asset management, Flow Rules and WHEN-THEN rules, Data visualization, Edge Gateway. (Demo, Source Code)
AGPL-3.0Java - SIP Irrigation Control - Open source software for sprinkler/irrigation control. (Source Code)
GPL-3.0Python - Tasmota - Open source firmware for ESP devices. Total local control with quick setup and updates. Control using MQTT, Web UI, HTTP or serial. Automate using timers, rules or scripts. Integration with home automation solutions. (Source Code)
GPL-3.0C/C++ - Thingsboard - Open-source IoT Platform - Device management, data collection, processing and visualization. (Demo, Source Code)
Apache-2.0Java/Docker/K8S - WebThings Gateway - WebThings is an open source implementation of the Web of Things, including the WebThings Gateway and the WebThings Framework. (Source Code)
MPL-2.0Nodejs
- Domoticz - Home Automation System that lets you monitor and configure various devices like: Lights, Switches, various sensors/meters like Temperature, Rain, Wind, UV, Electra, Gas, Water and much more. (Source Code, Clients)
-
 @ 866e0139:6a9334e5
2025-05-23 17:57:24
@ 866e0139:6a9334e5
2025-05-23 17:57:24Autor: Caitlin Johnstone. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Ich hörte einem jungen Autor zu, der eine Idee beschrieb, die ihn so sehr begeisterte, dass er die Nacht zuvor nicht schlafen konnte. Und ich erinnerte mich daran, wie ich mich früher – vor Gaza – über das Schreiben freuen konnte. Dieses Gefühl habe ich seit 2023 nicht mehr gespürt.
Ich beklage mich nicht und bemitleide mich auch nicht selbst, ich stelle einfach fest, wie unglaublich düster und finster die Welt in dieser schrecklichen Zeit geworden ist. Es wäre seltsam und ungesund, wenn ich in den letzten anderthalb Jahren Freude an meiner Arbeit gehabt hätte. Diese Dinge sollen sich nicht gut anfühlen. Nicht, wenn man wirklich hinschaut und ehrlich zu sich selbst ist in dem, was man sieht.
Es war die ganze Zeit über so hässlich und so verstörend. Es gibt eigentlich keinen Weg, all diesen Horror umzudeuten oder irgendwie erträglich zu machen. Alles, was man tun kann, ist, an sich selbst zu arbeiten, um genug inneren Raum zu schaffen, um die schlechten Gefühle zuzulassen und sie ganz durchzufühlen, bis sie sich ausgedrückt haben. Lass die Verzweiflung herein. Die Trauer. Die Wut. Den Schmerz. Lass sie deinen Körper vollständig durchfließen, ohne Widerstand, und steh dann auf und schreibe das nächste Stück.
Das ist es, was Schreiben für mich jetzt ist. Es ist nie etwas, worüber ich mich freue, es zu teilen, oder wofür ich von Inspiration erfüllt bin. Wenn überhaupt, dann fühlt es sich eher so an wie: „Okay, hier bitte, es tut mir schrecklich leid, dass ich euch das zeigen muss, Leute.“ Es ist das Starren in die Dunkelheit, in das Blut, in das Gemetzel, in die gequälten Gesichter – und das Aufschreiben dessen, was ich sehe, Tag für Tag.
Nichts daran ist angenehm oder befriedigend. Es ist einfach das, was man tut, wenn ein Genozid in Echtzeit vor den eigenen Augen stattfindet, mit der Unterstützung der eigenen Gesellschaft. Alles daran ist entsetzlich, und es gibt keinen Weg, das schönzureden – aber man tut, was getan werden muss. So, wie man es täte, wenn es die eigene Familie wäre, die da draußen im Schutt liegt.
Dieser Genozid hat mich für immer verändert. Er hat viele Menschen für immer verändert. Wir werden nie wieder dieselben sein. Die Welt wird nie wieder dieselbe sein. Ganz gleich, was passiert oder wie dieser Albtraum endet – die Dinge werden nie wieder so sein wie zuvor.
Und das sollten sie auch nicht. Der Holocaust von Gaza ist das Ergebnis der Welt, wie sie vor ihm war. Unsere Gesellschaft hat ihn hervorgebracht – und jetzt starrt er uns allen direkt ins Gesicht. Das sind wir. Das ist die Frucht des Baumes, den die westliche Zivilisation bis zu diesem Punkt gepflegt hat.
Jetzt geht es nur noch darum, alles zu tun, was wir können, um den Genozid zu beenden – und sicherzustellen, dass die Welt die richtigen Lehren daraus zieht. Das ist eines der würdigsten Anliegen, denen man sich in diesem Leben widmen kann.
Ich habe noch immer Hoffnung, dass wir eine gesunde Welt haben können. Ich habe noch immer Hoffnung, dass das Schreiben über das, was geschieht, eines Tages wieder Freude bereiten kann. Aber diese Dinge liegen auf der anderen Seite eines langen, schmerzhaften, konfrontierenden Weges, der in den kommenden Jahren vor uns liegt. Es gibt keinen Weg daran vorbei.
Die Welt kann keinen Frieden und kein Glück finden, solange wir uns nicht vollständig damit auseinandergesetzt haben, was wir Gaza angetan haben.
Dieser Text ist die deutsche Übersetzung dieses Substack-Artikels von Caitlin Johnstone.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ b0a838f2:34ed3f19
2025-05-23 17:59:29
@ b0a838f2:34ed3f19
2025-05-23 17:59:29- admidio - User management system for websites of organizations and groups. The system has a flexible role model so that it’s possible to reflect the structure and permissions of your organization. (Demo, Source Code)
GPL-2.0PHP/Docker - Frappe HR - Complete HRMS solution with over 13 different modules right from employee management, onboarding, leaves, to payroll, taxation, and more. (Source Code)
GPL-3.0Docker/Python/Nodejs - MintHCM - Tool for Human Capital Management based on two popular, well-known business applications SugarCRM Community Edition and SuiteCRM. (Source Code)
AGPL-3.0PHP - OrangeHRM - Comprehensive HRM system that captures all the essential functionalities required for any enterprise. (Demo, Source Code)
GPL-2.0PHP
- admidio - User management system for websites of organizations and groups. The system has a flexible role model so that it’s possible to reflect the structure and permissions of your organization. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:59:13
@ b0a838f2:34ed3f19
2025-05-23 17:59:13- Endurain - Fitness tracking service designed to give users full control over their data and hosting environment. (Source Code)
AGPL-3.0Docker - Fasten Health
⚠- Personal/family electronic medical record aggregator, designed to integrate with hundreds of thousands of insurances/hospitals/clinics in the United States.GPL-3.0Go/Docker - Mere Medical
⚠- Manage all of your medical records from Epic MyChart, Cerner, and OnPatient patient portals in one place. Privacy-focused, self-hosted, and offline-first. (Demo, Source Code)GPL-3.0Docker/Nodejs - OpenEMR - Electronic health records and medical practice management solution. (Demo, Source Code)
GPL-3.0PHP/Docker - wger - Web-based personal workout, fitness and weight logger/tracker. It can also be used as a simple gym management utility and offers a full REST API as well. (Demo, Source Code)
AGPL-3.0Python/Docker
- Endurain - Fitness tracking service designed to give users full control over their data and hosting environment. (Source Code)
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ b0a838f2:34ed3f19
2025-05-23 17:58:58
@ b0a838f2:34ed3f19
2025-05-23 17:58:58- Citadel - Groupware including email, calendar/scheduling, address books, forums, mailing lists, IM, wiki and blog engines, RSS aggregation and more. (Source Code)
GPL-3.0C/Docker/Shell - Cozy Cloud - Personal cloud where you can manage and sync your contact, files and calendars, and manage your budget with an app store full of community contributions. (Source Code)
GPL-3.0Nodejs - Digipad - An online self-hosted application for creating collaborative digital notepads (Documentation in french). (Source Code)
AGPL-3.0Nodejs - Digistorm - Create collaborative surveys, quizzes, brainstorms, and word clouds (documentation in French). (Demo, Source Code)
AGPL-3.0Nodejs - Digiwall - Create multimedia collaborative walls for in-person or remote work (documentation in French). (Source Code)
AGPL-3.0Nodejs - egroupware - Software suite including calendars, address books, notepad, project management tools, client relationship management tools (CRM), knowledge management tools, a wiki and a CMS. (Source Code)
GPL-2.0PHP - Group Office - Enterprise CRM and groupware tool. Share projects, calendars, files and e-mail online with co-workers and clients. (Source Code)
AGPL-3.0PHP - Openmeetings - Video conferencing, instant messaging, whiteboard, collaborative document editing and other groupware tools using API functions of the Red5 Streaming Server for Remoting and Streaming. (Source Code)
Apache-2.0Java - SOGo - SOGo offers multiple ways to access the calendaring and messaging data. CalDAV, CardDAV, GroupDAV, as well as ActiveSync, including native Outlook compatibility and Web interface. (Demo, Source Code)
LGPL-2.1Objective-C - Tine - Software for digital collaboration in companies and organizations. From powerful groupware functionalities to clever add-ons, tine combines everything to make daily team collaboration easier. (Source Code)
AGPL-3.0Docker - Tracim - Collaborative Platform for team collaboration: file,threads,notes,agenda,etc.
AGPL-3.0/LGPL-3.0/MITPython - Zimbra Collaboration - Email, calendar, collaboration server with Web interface and lots of integrations. (Source Code)
GPL-2.0/CPAL-1.0Java
- Citadel - Groupware including email, calendar/scheduling, address books, forums, mailing lists, IM, wiki and blog engines, RSS aggregation and more. (Source Code)
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ b0a838f2:34ed3f19
2025-05-23 17:58:40
@ b0a838f2:34ed3f19
2025-05-23 17:58:40- IOPaint
⚠- Image inpainting tool powered by SOTA AI Model. (Source Code)Apache-2.0Python/Docker - Ollama - Get up and running with Llama 3.3, DeepSeek-R1, Phi-4, Gemma 3, and other large language models. (Source Code)
MITDocker/Python - Open-WebUI - User-friendly AI Interface, supports Ollama, OpenAI API. (Source Code)
BSD-3-ClauseDocker/Python - Perplexica - AI-powered search engine (alternative to Perplexity AI).
MITDocker
- IOPaint
-
 @ b0a838f2:34ed3f19
2025-05-23 17:58:23
@ b0a838f2:34ed3f19
2025-05-23 17:58:23- Genea.app - Genealogy tool designed with privacy in mind that anyone can use to author or edit their family tree. Data is stored in the GEDCOM format and all processing is done in the browser. (Source Code)
MITJavascript - GeneWeb - Genealogy software that can be used offline or as a Web service. (Demo, Source Code)
GPL-2.0OCaml - Gramps Web - Web app for collaborative genealogy, based on and interoperable with Gramps, the open source genealogy desktop application. (Demo, Source Code)
AGPL-3.0Docker - webtrees - Webtrees is the web's leading online collaborative genealogy application. (Demo, Source Code)
GPL-3.0PHP
- Genea.app - Genealogy tool designed with privacy in mind that anyone can use to author or edit their family tree. Data is stored in the GEDCOM format and all processing is done in the browser. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:58:01
@ b0a838f2:34ed3f19
2025-05-23 17:58:01- auto-mcs - Cross-platform Minecraft server manager. (Source Code)
AGPL-3.0Python - Crafty Controller - Minecraft launcher and manager that allows users to start and administer Minecraft servers from a user-friendly interface. (Source Code)
GPL-3.0Docker/Python - EasyWI - Easy-Wi is a Web-interface that allows you to manage server daemons like gameservers. In addition it provides you with a CMS which includes a fully automated game- and voiceserver lending service. (Source Code)
GPL-3.0PHP/Shell - Gaseous Server
⚠- Game ROM manager with a built-in web-based emulator using multiple sources to identify and provide metadata.AGPL-3.0Docker/.NET - Kubek - Web management panel for Minecraft servers. (Source Code)
GPL-3.0Nodejs - Lancache
⚠- LAN Party game caching made easy. (Source Code)MITDocker/Shell - LinuxGSM - CLI tool for deployment and management of dedicated game servers on Linux: more than 120 games are supported. (Source Code)
MITShell - Lodestone - Server hosting tool for Minecraft and other multiplayers.
AGPL-3.0Docker/Rust - Minus Games - Sync games and save files across multiple devices. (Source Code)
MITRust - Pelican Panel - Web application for easy management of game servers, offering a user-friendly interface for deploying, configuring, and managing servers, server monitoring tools, and extensive customization options (fork of Pterodactyl). (Source Code)
AGPL-3.0PHP/Docker - Pterodactyl - Management panel for game servers, with an intuitive UI for end users. (Source Code)
MITPHP - PufferPanel - Game server management panel designed for both small networks and game server providers. (Source Code)
Apache-2.0Go - RconCli - CLI for executing queries on a remote Valve Source dedicated server using the RCON Protocol.
MITGo - Retrom - Private cloud game library distribution server + frontend/launcher.
GPL-3.0Docker/Rust - RomM
⚠- ROM manager for organizing, enriching, and playing retro games, with support for 400+ platforms. (Demo, Source Code)AGPL-3.0Docker - SourceBans++ - Admin, ban, and communication management system for games running on the Source engine. (Source Code)
CC-BY-SA-4.0PHP - Sunshine - Remote game stream host for Moonlight with support up to 120 frames per second and 4K resolution. (Source Code)
GPL-3.0C++/deb/Docker
- auto-mcs - Cross-platform Minecraft server manager. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:57:42
@ b0a838f2:34ed3f19
2025-05-23 17:57:42- 0 A.D. - Cross-platform real-time strategy game of ancient warfare. (Source Code)
MIT/GPL-2.0/ZlibC++/C/deb - A Dark Room - Minimalist text adventure game for your browser. (Demo)
MPL-2.0Javascript - Digibuzzer - Create a virtual game room around a connected buzzer (documentation in French). (Demo, Source Code)
AGPL-3.0Nodejs - Lila - Ad-less chess server powering lichess.org, with official iOS and Android client apps. (Source Code)
AGPL-3.0Scala - Luanti - Voxel game engine (formerly Minetest). Play one of our many games, mod a game to your liking, make your own game, or play on a multiplayer server. (Source Code)
LGPL-2.1/MIT/ZlibC++/Lua/deb - Mindustry - Factorio-like tower defense game. Build production chains to gather more resources, and build complex facilities. (Source Code)
GPL-3.0Java - MTA:SA
⚠- Add network play functionality to Rockstar North's Grand Theft Auto game series, in which this functionality is not originally found. (Source Code)GPL-3.0C++ - OpenTTD - Transport tycoon simulation game. (Source Code, Clients)
GPL-2.0C++/Docker - piqueserver - Server for openspades, the first-person shooter in a destructible voxel world. (Clients)
GPL-3.0Python/C++ - Posio - Geography multiplayer game.
MITPython - Quizmaster - Web application for conducting a quiz, including a page for players to enter their answers.
Apache-2.0Scala - Red Eclipse 2 - A FOSS Arena First-Person Shooter Similar to Unreal Tournament. (Source Code)
Zlib/MIT/CC-BY-SA-4.0C/C++/deb - Scribble.rs - A web-based pictionary game. (Demo)
BSD-3-ClauseGo/Docker - Suroi - An open-source 2D battle royale game inspired by surviv.io. (Demo, Source Code)
GPL-3.0Nodejs - The Battle for Wesnoth - The Battle for Wesnoth is an Open Source, turn-based tactical strategy game with a high fantasy theme, featuring both singleplayer and online/hotseat multiplayer combat.
GPL-2.0C++/deb - Veloren - Multiplayer RPG. Open-source game inspired by Cube World, Legend of Zelda, Dwarf Fortress and Minecraft. (Source Code)
GPL-3.0Rust - Word Mastermind - Wordle clone. A Mastermind-like game, but instead of colors you need to guess words. (Demo)
MITNodejs - Zero-K - Open Source on Springrts engine. Zero-K is a traditional real time strategy game with a focus on player creativity through terrain manipulation, physics, and a large roster of unique units - all while being balanced to support competitive play. (Source Code)
GPL-2.0Lua
- 0 A.D. - Cross-platform real-time strategy game of ancient warfare. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:57:18
@ b0a838f2:34ed3f19
2025-05-23 17:57:18- Apaxy - Theme built to enhance the experience of browsing web directories, using the mod_autoindex Apache module and some CSS to override the default style of a directory listing. (Source Code)
GPL-3.0Javascript - copyparty - Portable file server with accelerated resumable uploads, deduplication, WebDAV, FTP, zeroconf, media indexer, video thumbnails, audio transcoding, and write-only folders, in a single file with no mandatory dependencies. (Demo)
MITPython - DirectoryLister - Simple PHP based directory lister that lists a directory and all its sub-directories and allows you to navigate there within. (Source Code)
MITPHP - filebrowser - Web File Browser with a Material Design web interface. (Source Code)
Apache-2.0Go - FileGator - FileGator is a powerful multi-user file manager with a single page front-end. (Demo, Source Code)
MITPHP/Docker - Filestash - Web file manager that lets you manage your data anywhere it is located: FTP, SFTP, WebDAV, Git, S3, Minio, Dropbox, or Google Drive. (Demo, Source Code)
AGPL-3.0Docker - Gossa - Light and simple webserver for your files.
MITGo - IFM - Single script file manager.
MITPHP - mikochi - Browse remote folders, upload files, delete, rename, download and stream files to VLC/mpv.
MITGo/Docker/K8S - miniserve - CLI tool to serve files and dirs over HTTP.
MITRust - ResourceSpace - ResourceSpace open source digital asset management software is the simple, fast, and free way to organise your digital assets. (Demo, Source Code)
BSD-4-ClausePHP - Surfer - Simple static file server with webui to manage files.
MITNodejs - TagSpaces - TagSpaces is an offline, cross-platform file manager and organiser that also can function as a note taking app. The WebDAV version of the application can be installed on top of a WebDAV servers such as Nextcloud or ownCloud. (Demo, Source Code)
AGPL-3.0Nodejs - Tiny File Manager - Web based File Manager in PHP, simple, fast and small file manager with a single file. (Demo, Source Code)
GPL-3.0PHP
- Apaxy - Theme built to enhance the experience of browsing web directories, using the mod_autoindex Apache module and some CSS to override the default style of a directory listing. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:57:02
@ b0a838f2:34ed3f19
2025-05-23 17:57:02- Chibisafe - File uploader service that aims to to be easy to use and set up. It accepts files, photos, documents, anything you imagine and gives you back a shareable link for you to send to others. (Source Code)
MITDocker/Nodejs - Digirecord - Record and share audio files (documentation in French). (Source Code)
AGPL-3.0Nodejs/PHP - elixire - Simple yet advanced screenshot uploading and link shortening service. (Clients)
AGPL-3.0Python - Enclosed - Minimalistic web application designed for sending private and secure notes. (Demo, Source Code)
Apache-2.0Docker/Nodejs - Files Sharing - File sharing application based on unique and temporary links.
GPL-3.0PHP/Docker - Gokapi - Lightweight server to share files, which expire after a set amount of downloads or days. Similar to the discontinued Firefox Send, with the difference that only the admin is allowed to upload files.
GPL-3.0Go/Docker - goploader - Easy file sharing with server-side encryption, curl/httpie/wget compliant. (Source Code)
MITGo - GoSƐ - Modern file-uploader focusing on scalability and simplicity. It only depends on a S3 storage backend and hence scales horizontally without the need for additional databases or caches.
Apache-2.0Go/Docker - OnionShare - Securely and anonymously share a file of any size.
GPL-3.0Python/deb - Pairdrop - Local file sharing in your browser, inspired by Apple's AirDrop (fork of Snapdrop). (Source Code)
GPL-3.0Docker - PicoShare - Minimalist, easy-to-host service for sharing images and other files. (Demo, Source Code)
AGPL-3.0Go/Docker - Picsur - Simple imaging hosting platform that allows you to easily host, edit, and share images. (Demo)
AGPL-3.0Docker - PictShare - Multi lingual image hosting service with a simple resizing and upload API. (Source Code)
Apache-2.0PHP/Docker - Pingvin Share - File sharing platform that combines lightness and beauty, perfect for seamless and efficient file sharing. (Demo)
BSD-2-ClauseDocker/Nodejs - Plik - Scalable and friendly temporary file upload system. (Demo)
MITGo/Docker - ProjectSend - Upload files and assign them to specific clients you create. Give access to those files to your clients. (Source Code)
GPL-2.0PHP - PsiTransfer - Simple file sharing solution with robust up-/download-resume and password protection.
BSD-2-ClauseNodejs - QuickShare - Quick and simple file sharing between different devices. (Source Code)
LGPL-3.0Docker/Go - Sharry - Share files easily over the internet between authenticated and anonymous users (both ways) with resumable up- and downloads.
GPL-3.0Scala/Java/deb/Docker - Shifter - A simple, self-hosted file-sharing web app, powered by Django.
MITDocker - Slink - Image sharing platform designed to give users complete control over their media sharing experience. (Source Code)
AGPL-3.0Docker - transfer.sh - Easy file sharing from the command line.
MITGo - Uguu - Stores files and deletes after X amount of time.
MITPHP - Uploady - Uploady is a simple file uploader script with multi file upload support.
MITPHP - XBackBone - A simple, fast and lightweight file manager with instant sharing tools integration, like ShareX (a free and open-source screenshot utility for Windows). (Source Code)
AGPL-3.0PHP/Docker - Zipline - A lightweight, fast and reliable file sharing server that is commonly used with ShareX, offering a react-based Web UI and fast API.
MITDocker/Nodejs
- Chibisafe - File uploader service that aims to to be easy to use and set up. It accepts files, photos, documents, anything you imagine and gives you back a shareable link for you to send to others. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:56:45
@ b0a838f2:34ed3f19
2025-05-23 17:56:45- bittorrent-tracker - Simple, robust, BitTorrent tracker (client and server) implementation. (Source Code)
MITNodejs - Deluge - Lightweight, cross-platform BitTorrent client. (Source Code)
GPL-3.0Python/deb - qBittorrent - Free cross-platform bittorrent client with a feature rich Web UI for remote access. (Source Code)
GPL-2.0C++ - Send - Simple, private, end to end encrypted temporary file sharing, originally built by Mozilla. (Clients)
MPL-2.0Nodejs/Docker - slskd
⚠- A modern client-server application for the Soulseek file sharing network.AGPL-3.0Docker/C# - Transmission - Fast, easy, free Bittorrent client. (Source Code)
GPL-3.0C++/deb - Webtor - Web-based torrent client with instant audio/video streaming. (Demo)
MITDocker
- bittorrent-tracker - Simple, robust, BitTorrent tracker (client and server) implementation. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:56:27
@ b0a838f2:34ed3f19
2025-05-23 17:56:27- GarageHQ - Geo-distributed, S3‑compatible storage service that can fulfill many needs. (Source Code)
AGPL-3.0Docker/Rust - Minio - Object storage server compatible with Amazon S3 APIs. (Source Code)
AGPL-3.0Go/Docker/K8S - SeaweedFS - SeaweedFS is an open source distributed file system supporting WebDAV, S3 API, FUSE mount, HDFS, etc, optimized for lots of small files, and easy to add capacity.
Apache-2.0Go - SFTPGo - Flexible, fully featured and highly configurable SFTP server with optional FTP/S and WebDAV support.
AGPL-3.0Go/deb/Docker - Zenko CloudServer - Zenko CloudServer, an open-source implementation of a server handling the Amazon S3 protocol. (Source Code)
Apache-2.0Docker/Nodejs - ZOT OCI Registry - A production-ready vendor-neutral OCI-native container image registry. (Demo, Source Code)
Apache-2.0Go/Docker
- GarageHQ - Geo-distributed, S3‑compatible storage service that can fulfill many needs. (Source Code)
-
 @ 91bea5cd:1df4451c
2025-05-23 17:04:49
@ 91bea5cd:1df4451c
2025-05-23 17:04:49Em nota, a prefeitura justificou que essas alterações visam ampliar a segurança das praias, conforto e organização, para os frequentadores e trabalhadores dos locais. No entanto, Orla Rio, concessionária responsável pelos espaços, e o SindRio, sindicato de bares e restaurantes, ficou insatisfeita com as medidas e reforçou que a música ao vivo aumenta em mais de 10% o ticket médio dos estabelecimentos e contribui para manter os empregos, especialmente na baixa temporada.
De acordo com Paes, as medidas visam impedir práticas ilegais para que a orla carioca continue sendo um espaço ativo econômico da cidade: “Certas práticas são inaceitáveis, especialmente por quem tem autorização municipal. Vamos ser mais restritivos e duros. A orla é de todos”.
Saiba quais serão as 16 proibições nas praias do Rio de Janeiro
- Utilização de caixas de som, instrumentos musicais, grupos ou qualquer equipamento sonoro, em qualquer horário. Apenas eventos autorizados terão permissão.
- Venda ou distribuição de bebidas em garrafas de vidro em qualquer ponto da areia ou do calçadão.
- Estruturas comerciais ambulantes sem autorização, como carrocinhas, trailers, food trucks e barracas.
- Comércio ambulante sem permissão, incluindo alimentos em palitos, churrasqueiras, isopores ou bandejas térmicas improvisadas.
- Circulação de ciclomotores e patinetes motorizados no calçadão.
- Escolinhas de esportes ou recreações não autorizadas pelo poder público municipal.
- Ocupação de área pública com estruturas fixas ou móveis de grandes proporções sem autorização.
- Instalação de acampamentos improvisados em qualquer trecho da orla.
- Práticas de comércio abusivo ou enganosas, incluindo abordagens insistentes. Quiosques e barracas devem exibir cardápio, preços e taxas de forma clara.
- Uso de animais para entretenimento, transporte ou comércio.
- Hasteamento ou exibição de bandeiras em mastros ou suportes.
- Fixação de objetos ou amarras em árvores ou vegetação.
- Cercadinhos feitos por ambulantes ou quiosques, que impeçam a livre circulação de pessoas.
- Permanência de carrinhos de transporte de mercadorias ou equipamentos fora dos momentos de carga e descarga.
- Armazenamento de produtos, barracas ou equipamentos enterrados na areia ou depositados na vegetação de restinga.
- Uso de nomes, marcas, logotipos ou slogans em barracas. Apenas a numeração sequencial da prefeitura será permitida.
-
 @ b0a838f2:34ed3f19
2025-05-23 17:56:09
@ b0a838f2:34ed3f19
2025-05-23 17:56:09- bewCloud - File sharing + sync, notes, and photos (alternative to Nextcloud and ownCloud's RSS reader). (Source Code, Clients)
AGPL-3.0Docker - Git Annex - File synchronization between computers, servers, external drives. (Source Code)
GPL-3.0Haskell - Kinto - Minimalist JSON storage service with synchronisation and sharing abilities. (Source Code)
Apache-2.0Python - Nextcloud - Access and share your files, calendars, contacts, mail and more from any device, on your terms. (Demo, Source Code)
AGPL-3.0PHP/deb - OpenSSH SFTP server - Secure File Transfer Program. (Source Code)
BSD-2-ClauseC/deb - ownCloud - All-in-one solution for saving, synchronizing, viewing, editing and sharing files, calendars, address books and more. (Source Code, Clients)
AGPL-3.0PHP/Docker/deb - Peergos - Secure and private space online where you can store, share and view your photos, videos, music and documents. Also includes a calendar, news feed, task lists, chat and email client. (Source Code)
AGPL-3.0Java - Puter - Web-based operating system designed to be feature-rich, exceptionally fast, and highly extensible. (Demo, Source Code)
AGPL-3.0Nodejs/Docker - Pydio - Turn any web server into a powerful file management system and an alternative to mainstream cloud storage providers. (Demo, Source Code)
AGPL-3.0Go - Samba - Samba is the standard Windows interoperability suite of programs for Linux and Unix. It provides secure, stable and fast file and print services for all clients using the SMB/CIFS protocol. (Source Code)
GPL-3.0C - Seafile - File hosting and sharing solution primary for teams and organizations. (Source Code)
GPL-2.0/GPL-3.0/AGPL-3.0/Apache-2.0C - Syncthing - Syncthing is an open source peer-to-peer file synchronisation tool. (Source Code)
MPL-2.0Go/Docker/deb - Unison - Unison is a file-synchronization tool for OSX, Unix, and Windows. (Source Code)
GPL-3.0deb/OCaml
- bewCloud - File sharing + sync, notes, and photos (alternative to Nextcloud and ownCloud's RSS reader). (Source Code, Clients)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:55:49
@ b0a838f2:34ed3f19
2025-05-23 17:55:49- Bubo Reader - Irrationally minimal RSS feed reader. (Demo)
MITNodejs - CommaFeed - Google Reader inspired self-hosted RSS reader. (Demo, Source Code)
Apache-2.0Java/Docker - FeedCord
⚠- Simple, lightweight & customizable RSS News Feed for your Discord Server.MITDocker - Feedpushr - Powerful RSS aggregator, able to transform and send articles to many outputs. Single binary, extensible with plugins.
GPL-3.0Go/Docker - Feeds Fun - News reader with tags, scoring, and AI. (Source Code)
BSD-3-ClausePython - FreshRSS - Self-hostable RSS feed aggregator. (Demo, Source Code)
AGPL-3.0PHP/Docker - Fusion - Lightweight RSS aggregator and reader.
MITGo/Docker - JARR - JARR (Just Another RSS Reader) is a web-based news aggregator and reader (fork of Newspipe). (Demo, Source Code)
AGPL-3.0Docker/Python - Kriss Feed - Simple and smart (or stupid) feed reader.
CC0-1.0PHP - Leed - Leed (for Light Feed) is a Free and minimalist RSS aggregator.
AGPL-3.0PHP - Miniflux - Minimalist news reader. (Source Code)
Apache-2.0Go/deb/Docker - NewsBlur - Personal news reader that brings people together to talk about the world. A new sound of an old instrument. (Source Code)
MITPython - Newspipe - Web news reader. (Demo)
AGPL-3.0Python - Precis - Extensibility-oriented RSS reader that can use LLMs (including local LLMs) to summarize RSS entries with built-in notification support.
MITPython/Docker - reader - A Python feed reader web app and library (so you can use it to build your own), with only standard library and pure-Python dependencies.
BSD-3-ClausePython - Readflow - Lightweight news reader with modern interface and features: full-text search, automatic categorization, archiving, offline support, notifications... (Source Code)
MITGo/Docker - RSS-Bridge - Generate RSS/ATOM feeds for websites which don't have one.
UnlicensePHP/Docker - RSS Monster - An easy to use web-based RSS aggregator and reader compatible with the Fever API (alternative to Google Reader).
MITPHP - RSS2EMail - Fetches RSS/Atom-feeds and pushes new Content to any email-receiver, supports OPML.
GPL-2.0Python/deb - RSSHub - An easy to use, and extensible RSS feed aggregator, it's capable of generating RSS feeds from pretty much everything ranging from social media to university departments. (Demo, Source Code)
MITNodejs/Docker - Selfoss - New multipurpose rss reader, live stream, mashup, aggregation web application. (Source Code)
GPL-3.0PHP - Stringer - Work-in-progress self-hosted, anti-social RSS reader.
MITRuby - Tiny Tiny RSS - Open source web-based news feed (RSS/Atom) reader and aggregator. (Demo, Source Code)
GPL-3.0Docker/PHP - Yarr - Yarr (yet another rss reader) is a web-based feed aggregator which can be used both as a desktop application and a personal self-hosted server.
MITGo
- Bubo Reader - Irrationally minimal RSS feed reader. (Demo)
-
 @ 5144fe88:9587d5af
2025-05-23 17:01:37
@ 5144fe88:9587d5af
2025-05-23 17:01:37The recent anomalies in the financial market and the frequent occurrence of world trade wars and hot wars have caused the world's political and economic landscape to fluctuate violently. It always feels like the financial crisis is getting closer and closer.
This is a systematic analysis of the possibility of the current global financial crisis by Manus based on Ray Dalio's latest views, US and Japanese economic and financial data, Buffett's investment behavior, and historical financial crises.
Research shows that the current financial system has many preconditions for a crisis, especially debt levels, market valuations, and investor behavior, which show obvious crisis signals. The probability of a financial crisis in the short term (within 6-12 months) is 30%-40%,
in the medium term (within 1-2 years) is 50%-60%,
in the long term (within 2-3 years) is 60%-70%.
Japan's role as the world's largest holder of overseas assets and the largest creditor of the United States is particularly critical. The sharp appreciation of the yen may be a signal of the return of global safe-haven funds, which will become an important precursor to the outbreak of a financial crisis.
Potential conditions for triggering a financial crisis Conditions that have been met 1. High debt levels: The debt-to-GDP ratio of the United States and Japan has reached a record high. 2. Market overvaluation: The ratio of stock market to GDP hits a record high 3. Abnormal investor behavior: Buffett's cash holdings hit a record high, with net selling for 10 consecutive quarters 4. Monetary policy shift: Japan ends negative interest rates, and the Fed ends the rate hike cycle 5. Market concentration is too high: a few technology stocks dominate market performance
Potential trigger points 1. The Bank of Japan further tightens monetary policy, leading to a sharp appreciation of the yen and the return of overseas funds 2. The US debt crisis worsens, and the proportion of interest expenses continues to rise to unsustainable levels 3. The bursting of the technology bubble leads to a collapse in market confidence 4. The trade war further escalates, disrupting global supply chains and economic growth 5. Japan, as the largest creditor of the United States, reduces its holdings of US debt, causing US debt yields to soar
Analysis of the similarities and differences between the current economic environment and the historical financial crisis Debt level comparison Current debt situation • US government debt to GDP ratio: 124.0% (December 2024) • Japanese government debt to GDP ratio: 216.2% (December 2024), historical high 225.8% (March 2021) • US total debt: 36.21 trillion US dollars (May 2025) • Japanese debt/GDP ratio: more than 250%-263% (Japanese Prime Minister’s statement)
Before the 2008 financial crisis • US government debt to GDP ratio: about 64% (2007) • Japanese government debt to GDP ratio: about 175% (2007)
Before the Internet bubble in 2000 • US government debt to GDP ratio: about 55% (1999) • Japanese government debt to GDP ratio: about 130% (1999)
Key differences • The current US debt-to-GDP ratio is nearly twice that before the 2008 crisis • The current Japanese debt-to-GDP ratio is more than 1.2 times that before the 2008 crisis • Global debt levels are generally higher than historical pre-crisis levels • US interest payments are expected to devour 30% of fiscal revenue (Moody's warning)
Monetary policy and interest rate environment
Current situation • US 10-year Treasury yield: about 4.6% (May 2025) • Bank of Japan policy: end negative interest rates and start a rate hike cycle • Bank of Japan's holdings of government bonds: 52%, plans to reduce purchases to 3 trillion yen per month by January-March 2026 • Fed policy: end the rate hike cycle and prepare to cut interest rates
Before the 2008 financial crisis • US 10-year Treasury yield: about 4.5%-5% (2007) • Fed policy: continuous rate hikes from 2004 to 2006, and rate cuts began in 2007 • Bank of Japan policy: maintain ultra-low interest rates
Key differences • Current US interest rates are similar to those before the 2008 crisis, but debt levels are much higher than then • Japan is in the early stages of ending its loose monetary policy, unlike before historical crises • The size of global central bank balance sheets is far greater than at any time in history
Market valuations and investor behavior Current situation • The ratio of stock market value to the size of the US economy: a record high • Buffett's cash holdings: $347 billion (28% of assets), a record high • Market concentration: US stock growth mainly relies on a few technology giants • Investor sentiment: Technology stocks are enthusiastic, but institutional investors are beginning to be cautious
Before the 2008 financial crisis • Buffett's cash holdings: 25% of assets (2005) • Market concentration: Financial and real estate-related stocks performed strongly • Investor sentiment: The real estate market was overheated and subprime products were widely popular
Before the 2000 Internet bubble • Buffett's cash holdings: increased from 1% to 13% (1998) • Market concentration: Internet stocks were extremely highly valued • Investor sentiment: Tech stocks are in a frenzy
Key differences • Buffett's current cash holdings exceed any pre-crisis level in history • Market valuation indicators have reached a record high, exceeding the levels before the 2000 bubble and the 2008 crisis • The current market concentration is higher than any period in history, and a few technology stocks dominate market performance
Safe-haven fund flows and international relations Current situation • The status of the yen: As a safe-haven currency, the appreciation of the yen may indicate a rise in global risk aversion • Trade relations: The United States has imposed tariffs on Japan, which is expected to reduce Japan's GDP growth by 0.3 percentage points in fiscal 2025 • International debt: Japan is one of the largest creditors of the United States
Before historical crises • Before the 2008 crisis: International capital flows to US real estate and financial products • Before the 2000 bubble: International capital flows to US technology stocks
Key differences • Current trade frictions have intensified and the trend of globalization has weakened • Japan's role as the world's largest holder of overseas assets has become more prominent • International debt dependence is higher than any period in history
-
 @ b0a838f2:34ed3f19
2025-05-23 17:55:31
@ b0a838f2:34ed3f19
2025-05-23 17:55:31- Aimeos - E-commerce framework for building custom online shops, market places and complex B2B applications scaling to billions of items with Laravel. (Demo, Source Code)
LGPL-3.0/MITPHP - Bagisto - Leading Laravel open source e-commerce framework with multi-inventory sources, taxation, localization, dropshipping and more exciting features. (Demo, Source Code)
MITPHP - CoreShop - E-commerce plugin for Pimcore. (Source Code)
GPL-3.0PHP - Drupal Commerce - Popular e-commerce module for Drupal CMS, with support for dozens of payment, shipping, and shopping related modules. (Source Code)
GPL-2.0PHP - EverShop
⚠- E-commerce platform with essential commerce features. Modular architecture and fully customizable. (Demo, Source Code)GPL-3.0Docker/Nodejs - Litecart
⚠- Shopping cart in 1 file (with support for payment by card or cryptocurrency).MITGo/Docker - Magento Open Source - Leading provider of open omnichannel innovation. (Source Code)
OSL-3.0PHP - MedusaJs - Headless commerce engine that enables developers to create amazing digital commerce experiences. (Demo, Source Code)
MITNodejs - Microweber - Drag and Drop CMS and online shop. (Source Code)
MITPHP - Open Source POS - Open Source Point of Sale is a web based point of sale system.
MITPHP - OpenCart - Shopping cart solution. (Source Code)
GPL-3.0PHP - PrestaShop - Fully scalable e-commerce solution. (Demo, Source Code)
OSL-3.0PHP - Pretix - Ticket sales platform for events. (Source Code)
AGPL-3.0Python/Docker - s-cart - S-Cart is a free e-commerce website project for individuals and businesses, built on top of Laravel Framework. (Demo, Source Code)
MITPHP - Saleor - Django based open-sourced e-commerce storefront. (Demo, Source Code)
BSD-3-ClauseDocker/Python - Shopware Community Edition - PHP based open source e-commerce software made in Germany. (Demo, Source Code)
MITPHP - Solidus - A free, open-source ecommerce platform that gives you complete control over your store. (Source Code)
BSD-3-ClauseRuby/Docker - Spree Commerce - Spree is a complete, modular & API-driven open source e-commerce solution for Ruby on Rails. (Demo, Source Code)
BSD-3-ClauseRuby - Sylius - Symfony2 powered open source full-stack platform for eCommerce. (Demo, Source Code)
MITPHP - Thelia - Thelia is an open source and flexible e-commerce solution. (Demo, Source Code)
LGPL-3.0PHP - Vendure - A headless commerce framework. (Demo, Source Code)
MITNodejs - WooCommerce - WordPress based e-commerce solution. (Source Code)
GPL-3.0PHP
- Aimeos - E-commerce framework for building custom online shops, market places and complex B2B applications scaling to billions of items with Laravel. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:55:13
@ b0a838f2:34ed3f19
2025-05-23 17:55:13- Evergreen - Highly-scalable software for libraries that helps library patrons find library materials, and helps libraries manage, catalog, and circulate those materials. (Source Code)
GPL-2.0PLpgSQL - Koha - Enterprise-class ILS with modules for acquisitions, circulation, cataloging, label printing, offline circulation for when Internet access is not available, and much more. (Demo, Source Code)
GPL-3.0Perl - RERO ILS - Large-scale ILS that can be run as a service with consortial features, intended primarily for library networks. Includes most standard modules (circulation, acquisitions, cataloging,...) and a web-based public and professional interface. (Demo, Source Code)
AGPL-3.0Python/Docker
- Evergreen - Highly-scalable software for libraries that helps library patrons find library materials, and helps libraries manage, catalog, and circulate those materials. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:54:53
@ b0a838f2:34ed3f19
2025-05-23 17:54:53- DSpace - Turnkey repository application providing durable access to digital resources. (Source Code)
BSD-3-ClauseJava - EPrints - Digital document management system with a flexible metadata and workflow model primarily aimed at academic institutions. (Demo, Source Code)
GPL-3.0Perl - Fedora Commons Repository - Robust and modular repository system for the management and dissemination of digital content especially suited for digital libraries and archives, both for access and preservation. (Source Code)
Apache-2.0Java - InvenioRDM - Highly scalable turn-key research data management platform with a beautiful user experience. (Demo, Source Code, Clients)
MITPython - Islandora - Drupal module for browsing and managing Fedora-based digital repositories. (Demo, Source Code)
GPL-3.0PHP - Samvera Hyrax - Front-end for the Samvera framework, which itself is a Ruby on Rails application for browsing and managing Fedora-based digital repositories. (Source Code)
Apache-2.0Ruby
- DSpace - Turnkey repository application providing durable access to digital resources. (Source Code)
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ cae03c48:2a7d6671
2025-05-23 16:01:05
@ cae03c48:2a7d6671
2025-05-23 16:01:05Bitcoin Magazine

Spark Partners with Breez to Launch Bitcoin-Native SDK for Lightning PaymentsToday, Breez and Spark have announced a new implementation of the Breez SDK, built on Spark’s Bitcoin-native Layer 2 infrastructure. According to a press release sent to Bitcoin Magazine, the update is intended to make it easier for developers to integrate self-custodial Bitcoin Lightning payments into everyday apps and services.
Few companies are as good as @Breez_Tech at putting Bitcoin in people’s hands. We’re incredibly humbled to have them building on Spark.
Learn more → https://t.co/KRPpWJa3os pic.twitter.com/QiCfHbWu9d
— Spark (@buildonspark) May 22, 2025
“This is what the future of Bitcoin looks like — fast, open, and embedded in the apps people use every day. By teaming up with Breez, we’re expanding the ecosystem and giving developers powerful, Bitcoin-native tools to build next-generation payment experiences. Together, we’re building the standard for global, peer-to-peer transactions,” said the creator of Spark Kevin Hurley.
The SDK supports LNURL, Lightning addresses, real-time mobile notifications, and includes bindings for all major programming languages and frameworks. It is designed to allow developers to build directly on Bitcoin without relying on bridges or external consensus. This collaboration gives developers tools to add Bitcoin payment features to apps used for monetization social apps, cross-border remittances, and in-game currencies.
“We need developers to bring Bitcoin into apps people use every day,” said the CEO of Breez Roy Sheinfeld. “That’s why we built the Breez SDK. We’re excited to build on Spark’s revolutionary architecture — giving developers a powerful new Bitcoin-native option and continuing to strengthen Lightning as the common language of Bitcoin.”
Breez will also operate as a Spark Service Provider (SSP), alongside Lightspark, to help support payment facilitation and the growth of Spark’s ecosystem. The new implementation is expected to be released later this year.
“We’re excited to see what developers build with Spark; it’s very exciting to see this come to the world,” said the co-founder and CEO of Lightspark David Marcus.
The Breez SDK is expanding

We’re joining forces with @buildonspark to release a new nodeless implementation of the Breez SDK — giving developers the tools they need to bring Bitcoin payments to everyday apps.
Bitcoin-Native
Powered by Spark’s…— Breez
 (@Breez_Tech) May 22, 2025
(@Breez_Tech) May 22, 2025Yesterday, Magic Eden also partnered with Spark to improve Bitcoin trading by addressing issues like slow transaction times, high fees, and poor user experience. The integration will introduce a native settlement system aimed at making transactions faster and more cost-effective, without using bridges or synthetic assets.
“We’re proud to be betting on BTC DeFi,” said the CEO of Magic Eden Jack Lu. “We’re going to lead the forefront of all Bitcoin DeFi to make BTC fast, fun, and for everyone with Magic Eden as the #1 BTC native app on-chain.”
This post Spark Partners with Breez to Launch Bitcoin-Native SDK for Lightning Payments first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ b0a838f2:34ed3f19
2025-05-23 17:54:34
@ b0a838f2:34ed3f19
2025-05-23 17:54:34- Atsumeru - Manga/comic/light novel media server with clients for Windows, Linux, macOS and Android. (Source Code, Clients)
MITJava/Docker - BookLogr - Manage your personal book library with ease. (Demo)
Apache-2.0Docker - Calibre Web - Browse, read and download eBooks using an existing Calibre database.
GPL-3.0Python - Calibre - E-book library manager that can view, convert, and catalog e-books in most of the major e-book formats and provides a built-in Web server for remote clients. (Demo, Source Code)
GPL-3.0Python/deb - Kapowarr - Build and manage a comic book library. Download, rename, move and convert issues of the volume to your liking. (Source Code)
GPL-3.0Docker/Python - Kavita - Cross-platform e-book/manga/comic/pdf server and web reader with user management, ratings and reviews, and metadata support. (Demo, Source Code)
GPL-3.0.NET/Docker - kiwix-serve - HTTP daemon for serving wikis from ZIM files. (Source Code)
GPL-3.0C++ - Komga - Media server for comics/mangas/BDs with API and OPDS support, a modern web interface for exploring your libraries, as well as a web reader. (Source Code)
MITJava/Docker - Librum - Modern e-book reader and library manager that supports most major book formats, runs on all devices and offers great tools to boost productivity. (Source Code)
GPL-3.0C++ - Stump - A fast, free and open source comics, manga and digital book server with OPDS support. (Source Code)
MITRust - The Epube - Self-hosted web EPUB reader using EPUB.js, Bootstrap, and Calibre. (Source Code)
GPL-3.0PHP
- Atsumeru - Manga/comic/light novel media server with clients for Windows, Linux, macOS and Android. (Source Code, Clients)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:54:16
@ b0a838f2:34ed3f19
2025-05-23 17:54:16- DocKing - Document management service/microservice that handles templates and renders them in PDF format, all in one place. (Demo, Source Code)
MITPHP/Nodejs/Docker - Docspell - Auto-tagging document organizer and archive. (Source Code)
GPL-3.0Scala/Java/Docker - Documenso - Digital document signing platform (alternative to DocuSign). (Source Code)
AGPL-3.0Nodejs/Docker - Docuseal - Create, fill, and sign digital documents (alternative to DocuSign). (Demo, Source Code)
AGPL-3.0Docker - EveryDocs - Simple Document Management System for private use with basic functionality to organize your documents digitally.
GPL-3.0Docker/Ruby - Gotenberg - Developer-friendly API to interact with powerful tools like Chromium and LibreOffice for converting numerous document formats (HTML, Markdown, Word, Excel, etc.) into PDF files, and more. (Source Code)
MITDocker - I, Librarian - Organize PDF papers and office documents. It provides a lot of extra features for students and research groups both in industry and academia. (Demo, Source Code)
GPL-3.0PHP - Mayan EDMS - Electronic document management system for your documents with preview generation, OCR, and automatic categorization among other features. (Source Code)
GPL-2.0Docker/K8S - OpenSign
⚠- Document signing software (alternative to DocuSign). (Source Code)AGPL-3.0Nodejs/Docker - Paperless-ngx - Scan, index, and archive all of your paper documents with an improved interface (fork of Paperless). (Demo, Source Code)
GPL-3.0Python/Docker - Papermerge - Document management system focused on scanned documents (electronic archives). Features file browsing in similar way to dropbox/google drive. OCR, full text search, text overlay/selection. (Source Code)
Apache-2.0Docker/K8S - PdfDing - PDF manager, viewer and editor offering a seamless user experience on multiple devices. It's designed to be minimal, fast, and easy to set up using Docker.
AGPL-3.0Docker - SeedDMS - Document Management System with workflows, access rights, fulltext search, and more. (Demo, Source Code)
GPL-2.0PHP - Stirling-PDF - Local hosted web application that allows you to perform various operations on PDF files, such as merging, splitting, file conversions and OCR.
Apache-2.0Docker/Java - Teedy - Lightweight document management system packed with all the features you can expect from big expensive solutions (Ex SismicsDocs). (Demo, Source Code)
GPL-2.0Docker/Java
- DocKing - Document management service/microservice that handles templates and renders them in PDF format, all in one place. (Demo, Source Code)
-
 @ 90152b7f:04e57401
2025-05-23 15:48:58
@ 90152b7f:04e57401
2025-05-23 15:48:58U.S. troops would enforce peace under Army study
The Washington Times - September 10, 2001
by Rowan Scarborough
https://www.ord.io/70787305 (image) https://www.ord.io/74522515 (text)
An elite U.S. Army study center has devised a plan for enforcing a major Israeli-Palestinian peace accord that would require about 20,000 well-armed troops stationed throughout Israel and a newly created Palestinian state. There are no plans by the Bush administration to put American soldiers into the Middle East to police an agreement forged by the longtime warring parties. In fact, Defense Secretary Donald H. Rumsfeld is searching for ways to reduce U.S. peacekeeping efforts abroad, rather than increasing such missions. But a 68-page paper by the Army School of Advanced Military Studies (SAMS) does provide a look at the daunting task any international peacekeeping force would face if the United Nations authorized it, and Israel and the Palestinians ever reached a peace agreement.
Located at Fort Leavenworth, Kan., the School for Advanced Military Studies is both a training ground and a think tank for some of the Army’s brightest officers. Officials say the Army chief of staff, and sometimes the Joint Chiefs of Staff, ask SAMS to develop contingency plans for future military operations. During the 1991 Persian Gulf war, SAMS personnel helped plan the coalition ground attack that avoided a strike up the middle of Iraqi positions and instead executed a “left hook” that routed the enemy in 100 hours.
The cover page for the recent SAMS project said it was done for the Joint Chiefs of Staff. But Maj. Chris Garver, a Fort Leavenworth spokesman, said the study was not requested by Washington. “This was just an academic exercise,” said Maj. Garver. “They were trying to take a current situation and get some training out of it.” The exercise was done by 60 officers dubbed “Jedi Knights,” as all second-year SAMS students are nicknamed.
The SAMS paper attempts to predict events in the first year of a peace-enforcement operation, and sees possible dangers for U.S. troops from both sides. It calls Israel’s armed forces a “500-pound gorilla in Israel. Well armed and trained. Operates in both Gaza . Known to disregard international law to accomplish mission. Very unlikely to fire on American forces. Fratricide a concern especially in air space management.”
Of the Mossad, the Israeli intelligence service, the SAMS officers say: “Wildcard. Ruthless and cunning. Has capability to target U.S. forces and make it look like a Palestinian/Arab act.”
On the Palestinian side, the paper describes their youth as “loose cannons; under no control, sometimes violent.” The study lists five Arab terrorist groups that could target American troops for assassination and hostage-taking. The study recommends “neutrality in word and deed” as one way to protect U.S. soldiers from any attack. It also says Syria, Egypt and Jordan must be warned “we will act decisively in response to external attack.”
It is unlikely either of the three would mount an attack. Of Syria’s military, the report says: “Syrian army quantitatively larger than Israeli Defense Forces, but largely seen as qualitatively inferior. More likely, however, Syrians would provide financial and political support to the Palestinians, as well as increase covert support to terrorism acts through Lebanon.” Of Egypt’s military, the paper says, “Egyptians also maintain a large army but have little to gain by attacking Israel.”
The plan does not specify a full order of battle. An Army source who reviewed the SAMS work said each of a possible three brigades would require about 100 Bradley fighting vehicles, 25 tanks, 12 self-propelled howitzers, Apache attack helicopters, Kiowa Warrior reconnaissance helicopters and Predator spy drones. The report predicts that nonlethal weapons would be used to quell unrest. U.S. European Command, which is headed by NATO’s supreme allied commander, would oversee the peacekeeping operation. Commanders would maintain areas of operation, or AOs, around Nablus, Jerusalem, Hebron and the Gaza strip. The study sets out a list of goals for U.S. troops to accomplish in the first 30 days. They include: “create conditions for development of Palestinian State and security of “; ensure “equal distribution of contract value or equivalent aid” that would help legitimize the peacekeeping force and stimulate economic growth; “promote U.S. investment in Palestine”; “encourage reconciliation between entities based on acceptance of new national identities”; and “build lasting relationship based on new legal borders and not religious-territorial claims.”
Maj. Garver said the officers who completed the exercise will hold major planning jobs once they graduate. “There is an application process” for students, he said. “They screen their records, and there are several tests they go through before they are accepted by the program. The bright planners of the future come out of this program.”
James Phillips, a Middle East analyst at the Heritage Foundation, said it would be a mistake to put peacekeepers in Israel, given the “poor record of previous monitors.” “In general, the Bush administration policy is to discourage a large American presence,” he said. “But it has been rumored that one of the possibilities might be an expanded CIA role.” “It would be a very different environment than Bosnia,” said Mr. Phillips, referring to America’s six-year peacekeeping role in Bosnia-Herzegovina. “The Palestinian Authority is pushing for this as part of its strategy to internationalize the conflict. Bring in the Europeans and Russia and China. But such monitors or peacekeeping forces are not going to be able to bring peace. Only a decision by the Palestinians to stop the violence and restart talks could possibly do that.”
<<https://www.ord.io/70787305>>
<<<https://www.ord.io/74522515>>>
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ b0a838f2:34ed3f19
2025-05-23 17:53:54
@ b0a838f2:34ed3f19
2025-05-23 17:53:54- AdGuard Home - User-friendly ads & trackers blocking DNS server. (Source Code)
GPL-3.0Docker - blocky - Fast and lightweight DNS proxy as ad-blocker for local network with many features (alternative to Pi-hole). (Source Code)
Apache-2.0Go/Docker - Maza ad blocking - Local ad blocker. Like Pi-hole but local and using your operating system. (Source Code)
Apache-2.0Shell - Pi-hole - Blackhole for Internet advertisements with a GUI for management and monitoring. (Source Code)
EUPL-1.2Shell/PHP/Docker - Technitium DNS Server - Authoritative/recursive DNS server with ad blocking functionality. (Source Code)
GPL-3.0Docker/C#
- AdGuard Home - User-friendly ads & trackers blocking DNS server. (Source Code)
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 87e98bb6:8d6616f4
2025-05-23 15:36:32
@ 87e98bb6:8d6616f4
2025-05-23 15:36:32Use this guide if you want to keep your NixOS on the stable branch, but enable unstable application packages. It took me a while to figure out how to do this, so I wanted to share because it ended up being far easier than most of the vague explanations online made it seem.
I put a sample configuration.nix file at the very bottom to help it make more sense for new users. Remember to keep a backup of your config file, just in case!
If there are any errors please let me know. I am currently running NixOS 24.11.
Steps listed in this guide: 1. Add the unstable channel to NixOS as a secondary channel. 2. Edit the configuration.nix to enable unstable applications. 3. Add "unstable." in front of the application names in the config file (example: unstable.program). This enables the install of unstable versions during the build. 4. Rebuild.
Step 1:
- Open the console. (If you want to see which channels you currently have, type: sudo nix-channel --list)
- Add the unstable channel, type: sudo nix-channel --add https://channels.nixos.org/nixpkgs-unstable unstable
- To update the channels (bring in the possible apps), type: sudo nix-channel --update
More info here: https://nixos.wiki/wiki/Nix_channels
Step 2:
Edit your configuration.nix and add the following around your current config:
``` { config, pkgs, lib, ... }:
let unstable = import
{ config = { allowUnfree = true; }; }; in { #insert normal configuration text here } #remember to close the bracket!```
At this point it would be good to save your config and try a rebuild to make sure there are no errors. If you have errors, make sure your brackets are in the right places and/or not missing. This step will make for less troubleshooting later on if something happens to be in the wrong spot!
Step 3:
Add "unstable." to the start of each application you want to use the unstable version. (Example: unstable.brave)
Step 4:
Rebuild your config, type: sudo nixos-rebuild switch
Example configuration.nix file:
```
Config file for NixOS
{ config, pkgs, lib, ... }:
Enable unstable apps from Nix repository.
let unstable = import
{ config = { allowUnfree = true; }; }; in { #Put your normal config entries here in between the tags. Below is what your applications list needs to look like.
environment.systemPackages = with pkgs; [ appimage-run blender unstable.brave #Just add unstable. before the application name to enable the unstable version. chirp discord ];
} # Don't forget to close bracket at the end of the config file!
``` That should be all. Hope it helps.
-
 @ b0a838f2:34ed3f19
2025-05-23 17:53:35
@ b0a838f2:34ed3f19
2025-05-23 17:53:35- Adminer - Database management in a single PHP file. Available for MySQL, MariaDB, PostgreSQL, SQLite, MS SQL, Oracle, Elasticsearch, MongoDB and others. (Source Code)
Apache-2.0/GPL-2.0PHP - Azimutt - Visual database exploration made for real world databases (big and messy). Explore your database schema as well as data, document them, extend them and even get analysis and guidelines. (Demo, Source Code)
MITElixir/Nodejs/Docker - Baserow - Create your own database without technical experience (alternative to Airtable). (Source Code)
MITDocker - Bytebase - Safe database schema change and version control for DevOps teams, supports MySQL, PostgreSQL, TiDB, ClickHouse, and Snowflake. (Demo, Source Code)
MITDocker/K8S/Go - Chartbrew - Connect directly to databases and APIs and use the data to create beautiful charts. (Demo, Source Code)
MITNodejs/Docker - ChartDB - Database diagrams editor that allows you to visualize and design your DB with a single query. (Demo, Source Code)
AGPL-3.0Nodejs/Docker - CloudBeaver - Manage databases, supports PostgreSQL, MySQL, SQLite and more. A web/hosted version of DBeaver. (Source Code)
Apache-2.0Docker - Databunker - Network-based, self-hosted, GDPR compliant, secure database for personal data or PII. (Source Code)
MITDocker - Datasette - Explore and publish data with easy import and export and database management. (Demo, Source Code)
Apache-2.0Python/Docker - Evidence - Code-based BI tool. Write reports using SQL and markdown and they render as a website. (Source Code)
MITNodejs - Limbas - Database framework for creating database-driven business applications. As a graphical database frontend, it enables the efficient processing of data stocks and the flexible development of comfortable database applications. (Source Code)
GPL-2.0PHP - Mathesar - Intuitive UI to manage data collaboratively, for users of all technical skill levels. Built on Postgres – connect an existing DB or set up a new one. (Source Code)
GPL-3.0Docker/Python - NocoDB - No-code platform that turns any database into a smart spreadsheet (alternative to Airtable or Smartsheet). (Source Code)
AGPL-3.0Nodejs/Docker - WebDB - Efficient database IDE. (Demo, Source Code)
AGPL-3.0Docker
- Adminer - Database management in a single PHP file. Available for MySQL, MariaDB, PostgreSQL, SQLite, MS SQL, Oracle, Elasticsearch, MongoDB and others. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:53:11
@ b0a838f2:34ed3f19
2025-05-23 17:53:11- Corteza - CRM including a unified workspace, enterprise messaging and a low code environment for rapidly and securely delivering records-based management solutions. (Demo, Source Code)
Apache-2.0Go - Django-CRM - Analytical CRM with tasks management, email marketing and many more. Django CRM is built for individual use, businesses of any size or freelancers and is designed to provide easy customization and quick development.
AGPL-3.0Python - EspoCRM - CRM with a frontend designed as a single page application, and a REST API. (Demo, Source Code)
AGPL-3.0PHP - Krayin - CRM solution for SMEs and Enterprises for complete customer lifecycle management. (Demo, Source Code)
MITPHP - Monica - Personal relationship manager, and a new kind of CRM to organize interactions with your friends and family. (Source Code)
AGPL-3.0PHP/Docker - SuiteCRM - The award-winning, enterprise-class open source CRM. (Source Code)
AGPL-3.0PHP - Twenty - A modern CRM offering the flexibility of open source, advanced features, and a sleek design. (Source Code)
AGPL-3.0Docker
- Corteza - CRM including a unified workspace, enterprise messaging and a low code environment for rapidly and securely delivering records-based management solutions. (Demo, Source Code)
-
 @ 10f7c7f7:f5683da9
2025-05-23 15:26:17
@ 10f7c7f7:f5683da9
2025-05-23 15:26:17While I’m going to stand by what I said in my previous piece, minimise capital gains payments, don’t fund the government, get a loan against your bitcoin, but the wheels in my left curve brain have continued to turn, well that, and a few more of my 40PW insights. I mentioned about paying attention to the risks involved in terms of borrowing against your bitcoin, and hopefully ending up paying less in bitcoin at the end of the loan, even if you ultimately sold bitcoin to pay off the loan. However, the idea of losing control of the bitcoin I have spent a good deal of time and effort accumulating being out of my control has led me to reconsider. I also realised I didn’t fully flesh out some other topics that I think are relevant, not least time preference, specifically in relation to what you’re buying. The idea of realising a lump some of capital to live your dreams, buy a house or a cool car may be important, but it may be worth taking a step back and looking at what you’re purchasing. Are you only purchasing those things because you had been able to get this new money “tax free”? If that is the case, and the fiat is burning a hold in your pocket, maybe you’ve just found yourself with the same fiat brained mentality you have been working so hard to escape from while you have sacrificed and saved to stack sats.
While it may no longer be necessary to ask yourself whether a particular product or service is worth selling your bitcoin for because you’ve taken out a loan, it may still be worth asking yourself whether a particular loan fuelled purchase is worth forfeiting control of your keys for? Unlike the foolish 18 year-old, released into a world with their newly preapproved credit card, you need to take a moment and ask yourself:
Is the risk worth it?
Is the purchase worth it?
But also take a moment to consider a number of other things, are there fiat options?
Where in the cycle might you be?
Or if I’m thinking carefully about this, will whatever I’m buying hold its value (experiences may be more difficult to run the numbers on)?
The reason for asking these things, is that if you still have a foot in the fiat world, dealing with a fiat bank account, fiat institutions may still be very willing to provide you with a loan at a lower rate than a bitcoin backed loan. Particularly if you’re planning on using that money to buy a house; if you can qualify for a mortgage, get a mortgage, but if you need cash for a deposit, maybe that is where the bitcoin backed loan may come in. Then, it may be worth thinking about where are you in the bitcoin cycle? No one can answer this, but with the historic data we have, it appears logical that after some type of run up, prices may retrace (Dan Held’s supercycle withstanding).
Matteo Pellegrini with Daniel Prince provided a new perspective on this for me. Rather the riding the bull market gains all the way through to the bear market bottom, what happens if I chose to buy an asset that didn’t lose quite as much fiat value as bitcoin, for example, a Swiss Watch, or a tasteful, more mature sports car? If that was the purchase of choice, they suggested that you could enjoy the car, “the experience” for a year or two, then realise the four door estate was likely always the better option, sell it and be able to buy back as many, if not slightly more bitcoin that you originally sold (not financial, classic car or price prediction advice, I’m not accredited to advise pretty much anything). Having said that, it is a scenario I think worth thinking about when the bitcoin denominated dream car begins to make financial sense.
Then, as we begin to look forward to the near inevitable bear market (they are good for both stacking and grinding), if we’ve decided to take out a loan rather than sell, we then may ultimately need to increase our collateral to maintain loan to value requirements, as well as sell more bitcoin to cover repayments (if that’s the route we’re taking). This then moves us back into the domain of saying, well in actual fact we should just sell our bitcoin when we can get most dollar for it (or the coolest car), with a little extra to cover future taxes, it is probably better to sell near a top than a bottom. The balance between these two rather extreme positions could be to take out a fiat loan to buy the item and maybe sell sufficient bitcoin so you’re able to cover the loan for a period of time (less taxable events to keep track of and also deals with future uncertainty of bitcoin price). In this case, if the loan timeframe is longer than the amount of loan your sale can cover, by the time you need to sell anymore, the price should have recovered from a cycle bottom.
In this scenario, apart from the smaller portion of bitcoin you have had to sell, the majority of your stack can remain in cold storage, the loan you took out will be unsecured (particularly against your bitcoin), but even if it isn’t, the value of what you purchase maintains its value, you can in theory exit the loan at any point by selling the luxury item. Then within this scenario, if you had sold near a top, realised the car gave you a bad back or made you realise you staying humble is more important, sold it, paid off the loan, there may even be a chance you could buy back more bitcoin with the money you had left over from selling your bitcoin to fund the loan.
I have no idea of this could actually work, but to be honest, I’m looking forward to trying it out in the next 6-12 months, although I may keep my daily driver outside of my bitcoin strategy (kids still need a taxi service). Having said that, I think there are some important points to consider in addition to not paying capital gains tax (legally), as well as the opportunities of bitcoin loans. They are still very young products and to quote every trad-fi news outlet, “bitcoin is still a volatile asset”, these thought experiments are still worth working through. To push back on the Uber fiat journalist, Katie Martin, “Bitcoin has no obvious use case”, it does, it can be a store of value to hold or sell, it can be liquid and flexible collateral, but also an asset that moves independently of other assets to balance against fiat liabilities. The idea of being able to release some capital, enjoy the benefits of the capital for a period, before returning that capital to store value feels like a compelling one.
The important thing to remember is that there are a variety of options, whether selling for cash, taking out a bitcoin backed loan, taking out a fiat loan or some combination of each. Saying that, what I would think remains an important question to ask irrespective of the option you go for:
Is what I’m planning on buying, worth selling bitcoin for?
If it cannot pass this first question, maybe it isn’t worth purchasing to start with.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ cae03c48:2a7d6671
2025-05-23 14:01:07
@ cae03c48:2a7d6671
2025-05-23 14:01:07Bitcoin Magazine

KindlyMD, Nakamoto, and Anchorage Digital Form Strategic Bitcoin Treasury AllianceNakamoto Holdings Inc., KindlyMD, Inc., and Anchorage Digital today announced a strategic partnership that will see Anchorage become a trading partner for KindlyMD’s Bitcoin treasury. The partnership will officially take effect upon the close of KindlyMD’s merger with Nakamoto, expected in Q3 2025.
NEW! Anchorage Digital
 @Nakamoto @KindlyMD
@Nakamoto @KindlyMD Today we’re thrilled to announce a strategic partnership with Nakamoto Holdings and $KDLY to accelerate the future of corporate Bitcoin adoption. pic.twitter.com/nQueTyutQH
— Anchorage Digital
 (@Anchorage) May 21, 2025
(@Anchorage) May 21, 2025Anchorage Digital, a U.S. federally chartered digital asset bank, will provide institutional-grade custody, 24/7 trading, and deep liquidity to support the Bitcoin strategy of the combined entity.
“In the not-so-distant-future, the omission of Bitcoin on a balance sheet will be more glaring than its inclusion,” said Nathan McCauley, CEO and Co-Founder of Anchorage Digital. “Until then, companies like Nakamoto-KindlyMD are pioneering a new path forward—one in which Bitcoin is at the heart of corporate strategy.”
The future of corporate treasury strategy is Bitcoin-native. We're here to make it happen. Pumped to be partnering with @Nakamoto and @KindlyMD.@DavidFBailey’s vision continues to open new doors.
— Nathan McCauley
 (@nathanmccauley) May 21, 2025
(@nathanmccauley) May 21, 2025The merger between KindlyMD and Nakamoto is backed by approximately $710 million in financing, including $510 million in PIPE funding—the largest ever PIPE for a public crypto-related deal. The goal is to establish a Bitcoin-native corporate treasury strategy that redefines how capital markets engage with digital assets.
“Our goal is to bring Bitcoin to the center of global capital markets within a compliant, transparent structure,” said David Bailey, Founder and CEO of Nakamoto Holdings Inc. “We are excited to partner with Anchorage Digital to implement our vision with the highest levels of security and battle-tested infrastructure and enable us to deliver sustained value to shareholders.”
This announcement follows a key milestone on May 18, when KindlyMD shareholders approved the proposed merger with Nakamoto. The transaction is now expected to close in Q3 2025, pending SEC review and information statement distribution.
“This milestone brings us one step closer to unlocking Bitcoin’s potential for KindlyMD shareholders,” Bailey said yesterday. “We are grateful that KindlyMD shares our vision for a future in which Bitcoin is a core part of the corporate balance sheet.”
With its Bitcoin-first strategy and strategic alliances, the Nakamoto-KindlyMD partnership is set to accelerate institutional Bitcoin adoption—and with Anchorage Digital’s infrastructure behind it, the foundation is now firmly in place.
“By collaborating with Anchorage Digital, we are implementing our Bitcoin treasury strategy with the utmost standards in safety and security for our shareholders,” stated Tim Pickett, CEO of KindlyMD. “Their institutional-grade platform allows us to confidently hold Bitcoin as a treasury asset as we look to unlock access to Bitcoin and drive value for the long term.”
Disclosure: Nakamoto is in partnership with Bitcoin Magazine’s parent company BTC Inc to build the first global network of Bitcoin treasury companies, where BTC Inc provides certain marketing services to Nakamoto. More information on this can be found here.
This post KindlyMD, Nakamoto, and Anchorage Digital Form Strategic Bitcoin Treasury Alliance first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ cae03c48:2a7d6671
2025-05-23 14:01:05
@ cae03c48:2a7d6671
2025-05-23 14:01:05Bitcoin Magazine

How Zeus is Redefining Bitcoin with Cashu Ecash IntegrationThe U.S.-based Bitcoin and Lightning mobile wallet Zeus recently announced an alpha-release integration of Cashu. The move marks the first integration of ecash into a popular Bitcoin wallet, breaking new ground for potential user adoption to Bitcoin.
Cashu is a hot new implementation of Chaumian ecash, a form of digital cash invented by David Chaum in the ’90s that has incredible privacy and scalability properties, with the trade-off of being fundamentally centralized, requiring a significant amount of trust in the issuer.


In a counterintuitive move for Zeus, known as the go-to tool for advanced Lightning users seeking to connect to their home nodes, the integration of Cashu acknowledges a “last mile” challenge Lightning wallets face when delivering Bitcoin to the masses.
“We basically started off as the cypherpunk wallet, right? You got to set up your own Lightning node and connect to it with Zeus. The last two years, we put the node in the phone with one click, you can run it all in a standalone app without a remote node,” Evan Kaloudis, founder and CEO of Zeus, told Bitcoin Magazine.
“Cashu addresses uneconomical self-custody for small bitcoin amounts. On-chain, the dust limit is 546 satoshis, and Layer Two systems like Lightning have costs for channel setup or unilateral exits that aren’t widely discussed,” Evan explained, highlighting a major point of friction in noncustodial Lightning wallets: the need for liquidity and channel management. While these esoteric aspects of the Lightning Network have been mostly abstracted away since its invention in 2016, these fundamental trade-offs continue to manifest even in the most sophisticated and user-friendly wallets.
In the case of both Phoenix and Zeus, two of the most popular noncustodial options in the market, users must pay up to 10,000 sats upfront to gain spending capacity. These fees are necessary to cover the on-chain fees spent to open a channel for the user against the wallet’s liquidity service provider, unlocking a noncustodial experience.
The required up-front fee is difficult to explain and represents a painful onboarding experience for new users who are used to fiat apps giving them money to join instead. The result is the proliferation of custodial Lightning wallets like Wallet of Satoshi (WOS), which gained massive adoption early on by leveraging the global, near-instant settlement power of Bitcoin combined with the excellent user experience centralized wallets can create.
Major developments have been made over seven years after the Lightning Network’s inception, however, and Zeus is pushing the boundaries.
“With Ecash, we make it so easy that anyone can set up a wallet and start participating in our ecosystem, which I really think is going to become more and more prevalent,” Evan explained.
Today, at roughly $100,000 per bitcoin, 1,000 satoshis are equivalent to $1. Transactions of these sizes are known as microtransactions — a popular example are Nostr social media tips known as Zaps. But finding the right tool for this use case is not simple. Self custodied wallets like Phoenix charge transaction fees in the hundreds of satoshis, even with open channels, and on-chain fees often cost the same and are slower to settle. As a result, there’s an entire category of spending that is only served by cheaper alternatives such as custodial lightning wallets like WOS or Blink, but result in significant privacy tradeoffs, often requiring phone numbers from users and in some cases more advanced KYC and IP tracking. Cashu hopes to serve this market with lower privacy costs, the same ease of use, speed and competitive fees.
Digging deeper into the Cashu integration, Evan explained that “for users this means being able to pick and switch between custodians in a single app. For developers this means being able to defer custodial responsibilities to third parties and not have to wire up a new integration when your current custodian halts operations.”
Zaps are satoshi-denominated rewards delivered as “likes” or micro-tips for content in the Nostr social media ecosystem. A Zap can be as small as one satoshi, the smallest amount of bitcoin that can be technically transferred, equivalent today to about a tenth of a penny. “But I think if we look at Nostr and you’re seeing how many people are Zapping and how big a part of that ecosystem it is. It’s like, people are willing to do it,” Evan explained.
“Cashu, while custodial, lets users accumulate small amounts — say, via Nostr Zaps — without needing 6,000 satoshis to open a Lightning channel. Zeus prompts users to upgrade to self-custody as their balance grows,” he concluded, explaining that the wallet will effectively annoy users into self custody, one of several design choices made to mitigate the risks introduced by Cashu.
Ecash
The trade-offs introduced by Cashu challenge the common understanding of custody as an either-or in Bitcoin. Historically you were either a centralized — custodial — exchange, or you were a noncustodial Bitcoin wallet. In the former, you entrust the coins to a third party; in the latter you take personal responsibility for those coins and their corresponding private keys. Cashu changes this paradigm by introducing bitcoin-denominated ecash notes or “nuts,” which are bearer instruments that should be backed by a full bitcoin reserve and Lightning interoperability for instant withdraw.
Similar to fiat cash, you must take control and responsibility over these notes, but there’s also counterparty risk. In the case of Cashu, there are certain things the issuing mint can theoretically do to exploit their users — akin to how a bank can run on a fractional reserve.
The big difference between Cashu or custodial Bitcoin exchanges and fiat currency is that Cashu is open source, is designed around user privacy, and scales very well. It makes the cost of running a mint lower than either alternative, a feature that makes mint competition easier, in theory countering the centralizing network effects of specific mints.
Finally, the user experience of storing Cashu tokens has been attached to known forms of Bitcoin self custody such as the download of 12-words seeds via various mechanisms, though implementations still vary from wallet to wallet and the whole ecosystem is in its early stages.
To further mitigate the custodial risk of Chaumian-style ecash in Bitcoin, the Cashu community has developed various methods for automatically managing custody risk.



“Users can split risk by using multiple mints, switching between them in the user interface. Soon, ZEUS will guide users to select five or six reputable mints, automatically balancing funds to minimize exposure,” Evan explained, referring to a particular approach called automated bank runs. The idea is that as some Cashu mints may hold more of your funds, Zeus de-ranks them and rotates value out to minimize risk.
“I think the idea is going to be that we guide users to pick five or six reputable mints… And from there, users will be able to have the wallet automatically switch between those mints and determine which mint should be receiving the balance depending on the balance of all the mints presently. So you’ll be like, OK. MiniBits has way too much money. Let’s switch the default to one of the mints that doesn’t have a lot. So that way you can sort of mitigate or rather distribute the rug risk there,” Evan explained, adding, “Our Discover Mint feature pulls reviews from bitcoinmints.com, showing vouch counts and user feedback, like mint reliability or longevity,” describing the reputation layer stacked on top of the various other risk management mechanisms.
There is no known way to use Chaumian-style ecash in an entirely noncustodial way. So as long as the custody risk can be minimized, the scaling and privacy upside becomes remarkable.
Microtransactions
One of the opportunities that ecash unlocks is microtransactions, the most popular example of which are Nostr Zaps often in single dollar ranges of value transferred, though it applies to small Lightning transactions as well. This use case triggers an important technical question that predates Bitcoin, do microtransactions actually make economic sense?
There’s a long-standing argu
-
 @ b0a838f2:34ed3f19
2025-05-23 17:52:51
@ b0a838f2:34ed3f19
2025-05-23 17:52:51- Alfresco Community Edition - The open source Enterprise Content Management software that handles any type of content, allowing users to easily share and collaborate on content. (Source Code)
LGPL-3.0Java - Apostrophe - CMS with a focus on extensible in-context editing tools. (Demo, Source Code)
MITNodejs - Backdrop CMS - Comprehensive CMS for small to medium sized businesses and non-profits. (Source Code)
GPL-2.0PHP - BigTree CMS - Straightforward, well documented, and capable CMS. (Source Code)
LGPL-2.1PHP - Bludit
⚠- Build a site or blog in seconds. Bludit uses flat-files (text files in JSON format) to store posts and pages. (Source Code)MITPHP - CMS Made Simple - Faster and easier management of website contents, scalable for small businesses to large corporations. (Source Code)
GPL-2.0PHP - Cockpit - Simple content platform to manage any structured content. (Source Code)
MITPHP - Concrete 5 CMS - Open source content management system. (Source Code)
MITPHP - Contao - Powerful CMS that allows you to create professional websites and scalable web applications. (Demo, Source Code)
LGPL-3.0PHP - CouchCMS - CMS for designers. (Source Code)
CPAL-1.0PHP - Drupal - Advanced open source content management platform. (Source Code)
GPL-2.0PHP - eLabFTW - Online lab notebook for research labs. Store experiments, use a database to find reagents or protocols, use trusted timestamping to legally timestamp an experiment, export as pdf or zip archive, share with collaborators…. (Demo, Source Code)
AGPL-3.0PHP - Expressa - Content Management System for powering database driven websites using JSON schemas. Provides permission management and automatic REST APIs.
MITNodejs - Joomla! - Advanced Content Management System (CMS). (Source Code)
GPL-2.0PHP - KeystoneJS - CMS and web application platform. (Source Code)
MITNodejs - Localess
⚠- Powerful translation management and content management system. Manage and translate your website or app content into multiple languages, using AI to translate faster. (Source Code)MITDocker - MODX - Advanced content management and publishing platform. The current version is called 'Revolution'. (Source Code)
GPL-2.0PHP - Neos - Neos or TYPO3 Neos (for version 1) is a modern, open source CMS. (Source Code)
GPL-3.0PHP - Noosfero - Platform for social and solidarity economy networks with blog, e-Portfolios, CMS, RSS, thematic discussion, events agenda and collective intelligence for solidarity economy in the same system.
AGPL-3.0Ruby - Omeka - Create complex narratives and share rich collections, adhering to Dublin Core standards with Omeka on your server, designed for scholars, museums, libraries, archives, and enthusiasts. (Demo, Source Code)
GPL-3.0PHP - Payload CMS - Developer-first headless CMS and application framework. (Source Code)
MITNodejs - Pimcore - Multi-channel experience and engagement management platform. (Source Code)
GPL-3.0PHP/Docker - Plone - Powerful open-source CMS system. (Source Code)
ZPL-2.0Python/Docker - Publify - Simple but full featured web publishing software. (Source Code)
MITRuby - REDAXO - Simple, flexible and useful content management system (documentation only available in German). (Source Code)
MITPHP/Docker - Roadiz - Modern CMS based on a node system which can handle many types of services. (Source Code)
MITPHP - SilverStripe - Easy to use CMS with powerful MVC framework underlying. (Demo, Source Code)
BSD-3-ClausePHP - SPIP - Publication system for the Internet aimed at collaborative work, multilingual environments, and simplicity of use for web authors. (Source Code)
GPL-3.0PHP - Squidex - Headless CMS, based on MongoDB, CQRS and Event Sourcing. (Demo, Source Code)
MIT.NET - Strapi - The most advanced open-source Content Management Framework (headless-CMS) to build powerful API with no effort. (Source Code)
MITNodejs - Superdesk
⚠- End-to-end news creation, production, curation, distribution, and publishing platform. (Source Code)AGPL-3.0Docker/Python/PHP - Textpattern - Flexible, elegant and easy-to-use CMS. (Demo, Source Code)
GPL-2.0PHP - Typemill - Author-friendly flat-file-cms with a visual markdown editor based on vue.js. (Source Code)
MITPHP - TYPO3 - Powerful and advanced CMS with a large community. (Source Code)
GPL-2.0PHP - Umbraco - The friendly CMS. Free and open source with an amazing community. (Source Code)
MIT.NET - Vvveb CMS - Powerful and easy to use CMS to build websites, blogs or e-commerce stores. (Demo, Source Code)
AGPL-3.0PHP/Docker - Wagtail - Django content management system focused on flexibility and user experience. (Source Code)
BSD-3-ClausePython - WinterCMS - Speedy and secure content management system built on the Laravel PHP framework. (Source Code)
MITPHP - WonderCMS - WonderCMS is the smallest flat file CMS since 2008. (Demo, Source Code)
MITPHP - WordPress - World's most-used blogging and CMS engine. (Source Code)
GPL-2.0PHP
- Alfresco Community Edition - The open source Enterprise Content Management software that handles any type of content, allowing users to easily share and collaborate on content. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:52:28
@ b0a838f2:34ed3f19
2025-05-23 17:52:28- indico - Feature-rich event management system, made @ CERN, the place where the Web was born. (Demo, Source Code)
MITPython - motion.tools (Antragsgrün) - Manage motions and amendments for (political) conventions. (Demo, Source Code)
AGPL-3.0PHP/Docker - OpenSlides - Presentation and assembly system for managing and projecting agenda, motions and elections of an assembly. (Demo, Source Code)
MITDocker - osem - Event management tailored to free Software conferences. (Source Code)
MITRuby/Docker - pretalx - Web-based event management, including running a Call for Papers, reviewing submissions, and scheduling talks. Exports and imports for various related tools. (Source Code)
Apache-2.0Python
- indico - Feature-rich event management system, made @ CERN, the place where the Web was born. (Demo, Source Code)
-
 @ cae03c48:2a7d6671
2025-05-23 14:01:04
@ cae03c48:2a7d6671
2025-05-23 14:01:04Bitcoin Magazine

Bitcoin Liquid Network Surpasses $3.27 Billion in Total Value LockedToday, the Liquid Federation has announced that the Liquid Network has surpassed $3.27 billion in total value locked (TVL), according to a press release shared with Bitcoin Magazine.
“Surpassing the $3 billion threshold marks a pivotal moment for both Liquid and Bitcoin, signaling the evolution of Bitcoinʼs ecosystem into a full-fledged platform for global financial markets,” said the CEO and Co-Founder of Blockstream Dr. Adam Back. “As Bitcoin gains mainstream acceptance, and demand for regulated asset tokenization accelerates, Liquid is better positioned than ever to bridge Bitcoin with traditional finance and drive the next wave of capital markets innovation.”
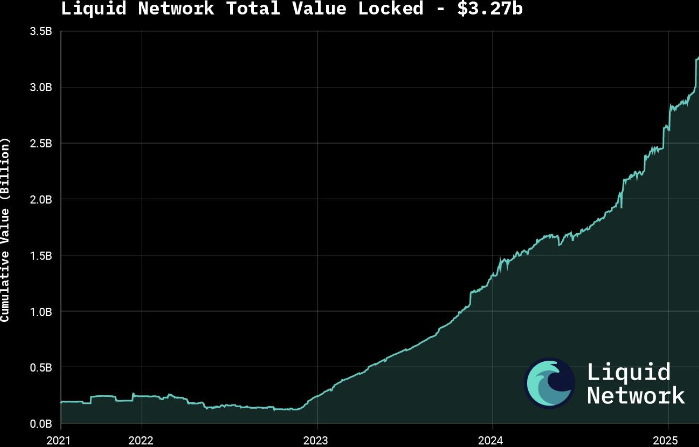
The announcement follows growing interest in tokenizing real-world assets (RWAs), with major moves such as BlackRock’s decision to tokenize a $150 billion Treasury fund. According to a 2025 report by Security Token Market, the tokenized asset market is projected to grow to $30 trillion by 2030.
Liquid supports over $1.8 billion in tokenized private credit and offers products like U.S. Treasury notes and digital currencies through Blockstream’s AMP platform. The network also features fast, low-cost, and confidential transactions, with support for atomic swaps and robust smart contracts.
Governed by over 80 global institutions, Liquid was launched in 2018 as Bitcoin’s first sidechain. It is now preparing for a major upgrade with the mainnet release of Simplicity, aimed at expanding its smart contract capabilities.
To keep up with increasing demand, the Liquid Federation is boosting developer resources and technical onboardings, along with integrations with exchanges, custodians and service providers. Recent bootcamps and important meetings with policy makers in Asia, Europe and Latin America reflect the network’s growing global presence.
This post Bitcoin Liquid Network Surpasses $3.27 Billion in Total Value Locked first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ b0a838f2:34ed3f19
2025-05-23 17:52:10
@ b0a838f2:34ed3f19
2025-05-23 17:52:10- ACP Admin - CSA administration. Manage members, subscriptions, deliveries, drop-off locations, member participation, invoices and emails (documentation in French). (Source Code)
MITRuby - E-Label - Solution for electronic labels, with QR Codes, on wine bottles sold within the European Union. (Source Code)
MITDocker - FoodCoopShop - User-friendly software for food-coops. (Source Code)
AGPL-3.0PHP/Docker - Foodsoft - Manage a non-profit food coop (product catalog, ordering, accounting, job scheduling). (Source Code)
AGPL-3.0Docker/Ruby - juntagrico - Management platform for community gardens and vegetable cooperatives. (Source Code)
LGPL-3.0Python - Open Food Network - Online marketplace for local food. It enables a network of independent online food stores that connect farmers and food hubs with individuals and local businesses. (Source Code)
AGPL-3.0Ruby - OpenOlitor - Administration platform for Community Supported Agriculture groups. (Source Code)
AGPL-3.0Scala - teikei - A web application that maps out community-supported agriculture based on crowdsourced data. (Demo)
AGPL-3.0Nodejs
- ACP Admin - CSA administration. Manage members, subscriptions, deliveries, drop-off locations, member participation, invoices and emails (documentation in French). (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:51:53
@ b0a838f2:34ed3f19
2025-05-23 17:51:53- Converse.js - XMPP chat client in your browser. (Source Code)
MPL-2.0Javascript - JSXC - Real-time XMPP web chat application with video calls, file transfer and encrypted communication. There are also versions for Nextcloud/Owncloud and SOGo. (Source Code)
MITJavascript - Libervia - Web frontend from Salut à Toi.
AGPL-3.0Python - Salut à Toi - Multipurpose, multi frontend, libre and decentralized communication tool. (Source Code)
AGPL-3.0Python
- Converse.js - XMPP chat client in your browser. (Source Code)
-
 @ eed7ca5d:191de8eb
2025-05-23 13:58:46
@ eed7ca5d:191de8eb
2025-05-23 13:58:46Growing up, we were told that in order to build wealth, we need to save little by little. By living below your means, you are providing more for your future.
It is a simple formula that will help you build up the capital necessary to buy a car, a house or start a business… You prioritize long-term benefits and delayed gratification over immediate rewards.
This is called having a low-time preference. In contrast, high-time preference individuals prioritize today over tomorrow, seeking immediate gratification.
Austrian economists explain that civilization growth is driven by low-time preference societies. Groups of individuals who prioritize long-term planning are able to innovate and develop new tools for a better future. Over time, this behavior leads to technological inventions like the light bulb and artistic masterpieces like the Notre Dame cathedral.
***What happens when you realize that the money you save is losing value over time? ***
There is less incentive to save for the future, because in the future your savings will be worth less. You might as well spend it now and enjoy life today.
When the money you save loses its value, you are facing one of two choices:
-
Spend it today and reap the rewards of your hard work;
-
Invest it (stocks, real estate, etc.) with the hope to reap higher rewards later, bearing the risk of losing it all if the investment does not pay off.
There is a distinct difference between saving and investing as the latter approach is riskier than the former. By investing, you are betting on the upside while bearing the downside risk. Saving, in contrast, comes without downside risk. That difference becomes blurry when the money you save is losing value. In fact, saving becomes inherently a losing approach. Logically, you will be forced to place a speculative bet with the hope to outperform the guaranteed loss of value. You are required to find a way to hedge your bet…
Humans over time have always sought out a medium to save their economic energy for a better future. That used to be beads and seashells, and evolved to precious metals like gold and silver.
Money is a tool that we use to save our economic energy over time, and exchange value with each other.
I spend time fishing, you spend time farming, the neighbor spends time building homes, and society rewards us with money for the time and energy we spent being productive
Today, the tool that we use to save our economic energy is clearly losing value over time. The nominal value remains the same, but the purchasing power is decreasing. In other words, the value of our time today will be worth less in the future.
That explains why everyone around us is looking for the next best investment opportunity. We are all needing to become investment experts, speculators, on top of our respective professions. Speculation became necessary, and some of us are forced into a high-time preference lifestyle.
Earn now and spend it all now before you lose it.
This should not be the case…
Time is Money
Our time is the only scarce resource we all have. We use it to be productive and generate economic value, then store that value in the form of money in order to reap the rewards in the future.
Money is the abstract representation of our time. Hence, time is money.
In January 2009, at the height of the global financial crisis, a software protocol called Bitcoin was released pseudonymously by Satoshi Nakamoto. This individual (or group) released a whitepaper a few months prior named “Bitcoin: A Peer-to-Peer Electronic Cash System” outlining how the system enables secure, peer-to-peer transactions without relying on a central authority. (https://bitcoin.org/bitcoin.pdf)
Although there are more technical concepts involved, the bitcoin protocol can be thought of as a language for communicating value. The same way we respect the rules of the English language to communicate ideas with one another, bitcoin users adhere to the network’s consensus rules to communicate value with each other in a peer-to-peer fashion.
There are no physical or digital coins in the bitcoin network. Rather, it is a collection of transactions transferring value from sender to recipient. Transactions are validated and propagated by nodes across the network, before being recorded into the blockchain. The Bitcoin blockchain is a global public ledger of all transactions that cannot be altered.
More importantly, Bitcoin is money that does not lose value overtime.
-
Its supply is capped at 21 million coins.
-
Its scarcity increases over time due to the predictable issuance rate, which halves roughly every 4 years.
-
Its decentralized nature puts the power in the hands of its users.
-
There is no governing body that can devalue or alter it.
It is a tool that we can use to save our economic energy over time, and be able to use it later.
It is the scarcest verifiable commodity: we cannot make more of it no matter how high its demand grows. That cannot be said for any other commodity in the world today.
A savings tool in disguise
See, most people tend to view bitcoin as another speculative investment. They presume they have missed out on another investment opportunity, and it’s now too late to get in.
Meanwhile, it is quite the opposite. Bitcoin’s value will keep growing over time due to its deflationary nature.
With bitcoin, we can save for a better future, for a rainy day, and spend more time with our loved ones or focusing on our craft to build better tools or artistic masterpieces. It takes away the burden of having to speculate on which stock will perform best, or which real estate market will grow the fastest, all while working one or multiple jobs
Bitcoin is not another investment opportunity you missed out on. It is the best savings tool humans have invented (or discovered), while everything else is the speculative bet. Bitcoin is the hedge against the guaranteed devaluation of money, without any counterparty risk.
What we were taught as children is true. With the right tool, the idea that saving will help you build wealth overtime stands true. Bitcoin might seem like an investment today given the volatility during its adoption phase. In reality, it is the perfect way to store your time and economic energy and grow your wealth. Whether you make $1/hour or $1M/hour, you can start saving in the best money humans have invented.
My goal is to help people around me understand this technology and break the stigma around it.
Bitcoin is not the next best investment.
It is the best tool we have found to store our economic energy across time and exchange value with each other.
Bitcoin is Money.
-
-
 @ b0a838f2:34ed3f19
2025-05-23 17:51:36
@ b0a838f2:34ed3f19
2025-05-23 17:51:36- ejabberd - XMPP instant messaging server. (Source Code)
GPL-2.0Erlang/Docker - MongooseIM - Mobile messaging platform with a focus on performance and scalability. (Source Code)
GPL-2.0Erlang/Docker/K8S - Openfire - Real time collaboration (RTC) server. (Source Code)
Apache-2.0Java - Prosody IM - Feature-rich and easy to configure XMPP server. (Source Code)
MITLua - Snikket - All-in-one Dockerized easy XMPP solution, including web admin and clients. (Source Code, Clients)
Apache-2.0Docker - Tigase - XMPP server implementation in Java. (Source Code)
GPL-3.0Java
- ejabberd - XMPP instant messaging server. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:51:16
@ b0a838f2:34ed3f19
2025-05-23 17:51:16- BigBlueButton - Supports real-time sharing of audio, video, slides (with whiteboard controls), chat, and the screen. Instructors can engage remote students with polling, emojis, and breakout rooms. (Source Code)
LGPL-3.0Java - Galene - Video conferencing server that is easy to deploy and that requires moderate server resources. (Source Code)
MITGo - Janus - General-purpose, lightweight, minimalist WebRTC Server. (Demo, Source Code)
GPL-3.0C - Jitsi Meet - WebRTC application that uses Jitsi Videobridge to provide high quality, scalable video conferences. (Demo, Source Code)
Apache-2.0Nodejs/Docker/deb - Jitsi Video Bridge - WebRTC compatible Selective Forwarding Unit (SFU) that allows for multiuser video communication. (Source Code)
Apache-2.0Java/deb - MiroTalk C2C - Real-time cam-2-cam video calls & screen sharing, end-to-end encrypted, to embed in any website with a simple iframe. (Source Code)
AGPL-3.0Nodejs/Docker - MiroTalk P2P - Simple, secure, fast real-time video conferences up to 4k and 60fps, compatible with all browsers and platforms. (Demo, Source Code)
AGPL-3.0Nodejs/Docker - MiroTalk SFU - Simple, secure, scalable real-time video conferences up to 4k, compatible with all browsers and platforms. (Demo, Source Code)
AGPL-3.0Nodejs/Docker - plugNmeet - Scalable and high performance web conferencing system. (Demo, Source Code)
MITDocker/Go
- BigBlueButton - Supports real-time sharing of audio, video, slides (with whiteboard controls), chat, and the screen. Instructors can engage remote students with polling, emojis, and breakout rooms. (Source Code)
-
 @ 47259076:570c98c4
2025-05-23 13:57:28
@ 47259076:570c98c4
2025-05-23 13:57:28"Know thyself and you will know the universe and the gods"
This is the greatest truth.
Knowing yourself is a process that is perhaps eternal.
Knowing yourself means making conscious what is unconscious, in all fields.
Making conscious your material reality, your emotions, your thoughts, your mind, your patterns, your spirit, your flaws, your qualities, etc.
The journey is within.
And in this process, burning everything that is not you.
Burning everything so only the essential remains.
The essential being your higher self.
You are not your body, you are not your emotions, you are not your mind, etc...
You are pure consciousness.
Everyday we can learn from him, but if we are asleep, we will not realize the gold opportunities passing right in front of our eyes.
Everyday he teaches us.
If everyday he teaches us, why stress so much for having an astral projection?
If an astral projection happens with you, it will be a good experience indeed, if you know how to value opportunities.
Otherwise, you may see some """evil"" spirits trying to scare you.
Therefore, don't depend on astral projection for your spiritual growth.
In fact, don't depend on anything.
Don't depend on books, don't depend on people, don't depend on "psychologists", don't depend on "rituals", don't depend on institutions, and of course, don't depend on the "government".
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-23 13:46:21
@ 5d4b6c8d:8a1c1ee3
2025-05-23 13:46:21You'd think I'd be most excited to talk about that awesome Pacers game, but, no. What I'm most excited about this week is that @grayruby wants to continue Beefing with Cowherd.
Still, I am excited to talk about Tyrese Haliburton becoming a legendary Knicks antagonist. Unfortunately, the Western Conference Finals are not as exciting. Also, why was the MVP announcement so dumb?
The T20k cricket contest is tightening up, as we head towards the finish. Can @Coinsreporter hold on to his vanishing lead?
@Carresan has launched Football Madness. Let's see if we understand whatever the hell this is any better than we did last week.
On this week's Blok'd Shots, we'll ridicule Canada for their disgraceful loss in the World Championships and talk about the very dominant American Florida Panthers, who are favorites to win the Stanley Cup.
Are the Colorado the worst team in MLB history?
The Tush Push has survived another season. Will the NFL eventually ban it or will teams adjust?
Plus, whatever else Stackers want to talk about.
https://stacker.news/items/987399
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ 30b99916:3cc6e3fe
2025-05-23 13:16:37
@ 30b99916:3cc6e3fe
2025-05-23 13:16:37sourcegraph #vibecoding #ai #bitcoin #security
After reading the article Revenge of the junior developer, this inspired me to go take a look at Sourcegraph.com to get a better understanding of all this AI stuff.
The first step was installing the VS Code extension called, Cody which is a coding agent. The Cody features explain the code in a file and review and analyze code did an extremely impressive job with VaultApi and BTCwallet.
VaultApi and BTCwallet are PowerShell scripts that are available from my BTCPAY Server
All of the following output was generated by Cody.
Code Analysis of VaultApi.ps1
The VaultApi.ps1 script is generally well-structured and follows many PowerShell best practices. It has comprehensive documentation, version history, and clear parameter definitions. The suggestions below would further enhance what is already a solid codebase. The author has clearly put significant effort into making the script functional and user-friendly, with good attention to cross-platform compatibility and security considerations.
VaultApi.ps1 Explanation
VaultApi.ps1 is a PowerShell script that helps users interact with HashiCorp Vault, which is a tool for securely storing and managing sensitive information like passwords and API keys.
Purpose of the Code
This script makes it easier to use Vault by providing simple commands to start the Vault server, unlock it (unseal), log in, store secrets, retrieve secrets, and shut down the server. Think of it as a friendly interface that simplifies all the complex operations you would otherwise need to do manually with Vault.
Inputs
The script takes several inputs:
- An
actionparameter that tells the script what operation to perform (like "Start", "Stop", "Kv1Create", "Kv1Read") - A
kvpathparameter that specifies where in Vault to store or retrieve information - A
kvalueparameter for the actual secret value you want to store - A
kvkeyparameter that lets you specify a custom name for your secret - Optional switches like
-Infoto show more detailed information and-Rawto display output directly instead of copying to clipboard
Outputs
Depending on the action performed, the script produces different outputs:
- Text messages in the console showing the status of operations
- Secret values retrieved from Vault (either displayed or copied to clipboard)
- Lists of available secret paths
- Status information about the Vault server
- Backup files of your Vault data
How It Works
The script works by:
- First checking if Vault is installed and running
- Setting up communication with the Vault server using its API address
- Performing the requested action by sending the appropriate commands to Vault
- Processing any responses and displaying results to the user
For example, when you use the "Kv1Create" action, the script:
- Checks if you're logged in
- Verifies the path doesn't already exist
- Formats your data correctly
- Sends a request to Vault to create the new secret
- Shows you the result
Important Logic Flows
Some key processes in the script include:
-
Authentication flow: The script helps you log in using either a token or username/password, then stores your authentication token for future commands.
-
Unsealing process: Vault requires multiple keys to unlock (unseal) it after starting. The script can retrieve these keys from a secure file or prompt you to enter them.
-
Secret management: The script handles creating, reading, updating, and deleting secrets, supporting both single values and multiple key-value pairs at a path.
-
Path management: The script can list all available paths and help you search for specific ones, making it easier to organize and find your secrets.
-
Value generation: When creating or updating secrets, you can use the keyword "setvalue" to automatically generate a random 20-character value, which is then copied to your clipboard.
The script uses a configuration file in your home directory to know how to connect to Vault, and it can optionally use encrypted files to store sensitive information like unlock keys. It communicates with Vault using REST API calls, which are like special messages that tell Vault what to do.
In summary, VaultApi.ps1 is a helper tool that makes it much easier to use HashiCorp Vault for securely storing and managing your sensitive information, without needing to remember all the complex commands and procedures.
Code Analysis of BTCwallet.ps1
The script generally follows sound design principles with good organization, comments, and documentation. It demonstrates thoughtful error checking and user interaction. The identified opportunities for enhancement would primarily improve security, maintainability, and robustness rather than addressing fundamental flaws. The script author has clearly put significant effort into creating a comprehensive tool with good documentation and practical functionality.
BTCwallet.ps1 Explanation
The BTCwallet.ps1 script is a PowerShell tool designed to help Bitcoin users manage different wallet applications on a Linux system. It provides a convenient way to start, stop, and check the status of Bitcoin wallets while adding security features.
Purpose
The main purpose of this script is to securely manage Bitcoin wallets, particularly focusing on "cold storage" solutions. Cold storage means keeping your Bitcoin wallet data in an encrypted container that's only mounted when needed, which is more secure than keeping it always accessible ("hot storage").
Inputs
The script takes one main input parameter:
$action: This can be "start", "stop", or "check" (default), telling the script what operation to perform on your Bitcoin wallet.
Outputs
The script doesn't return data but produces several visible outputs:
- Status messages showing whether wallets are running or stopped
- Prompts for user input when decisions are needed
- Confirmation messages when actions are completed
How It Works
-
When you run the script, it first loads a configuration file (BTCwalletCfg.xml) that contains information about which wallets you have installed.
-
Based on the
$actionparameter, it performs one of three main functions:- Check: Shows if your wallet application is currently running
- Start: Launches your wallet application, with options for hot or cold storage
- Stop: Closes your wallet application and securely dismounts any encrypted containers
- For security, the script can use HashiCorp Vault (a secure password manager) to store sensitive information like passwords for encrypted containers.
-
The script also verifies its own integrity by checking its file hash against a previously stored value, alerting you if the script has been modified.
Important Logic Flows
Starting a Wallet
When starting a wallet, the script:
- Asks which wallet you want to use (Sparrow, GreenWallet, or Wasabi)
- Checks if HashiCorp Vault is running and starts it if needed
- Verifies the script's integrity by comparing file hashes
- Asks if you want to use hot or cold storage
- For cold storage, it:
- Retrieves the encrypted container's location and password
- Mounts the encrypted container using VeraCrypt
- Starts the wallet application pointing to the mounted container
- For hot storage, it simply starts the wallet application with default settings
Stopping a Wallet
When stopping a wallet, the script:
- Checks if the wallet is still running and asks you to close it first if needed
- For cold storage wallets, it moves any wallet files back to the encrypted container
- Dismounts the encrypted container
- Optionally stops the HashiCorp Vault service
The script handles different wallet applications (Sparrow, GreenWallet, and Wasabi) slightly differently based on how each one stores its data and what command-line options they support.
In summary, BTCwallet.ps1 provides a secure way to manage Bitcoin wallets by combining wallet applications with encrypted storage and password management, all controlled through simple commands.
- An
-
 @ b0a838f2:34ed3f19
2025-05-23 17:50:59
@ b0a838f2:34ed3f19
2025-05-23 17:50:59- Akkoma - Federated microblogging server with Mastodon, GNU social, and ActivityPub compatibility. (Source Code)
AGPL-3.0Elixir/Docker - Answer - Knowledge-based community software. You can use it to quickly build your Q&A community for product technical support, customer support, user communication, and more. (Source Code)
Apache-2.0Docker/Go - Artalk - Comment system built in Golang, providing a lightweight and highly customizable solution for adding comments to your website. (Source Code)
MITGo/Docker - AsmBB - Fast, SQLite-powered forum engine written in ASM. (Source Code)
EUPL-1.2Assembly - BuddyPress - Powerful plugin that takes your WordPress.org powered site beyond the blog with social-network features like user profiles, activity streams, user groups, and more. (Source Code)
GPL-2.0PHP - Chirpy - Privacy-friendly and customizable Disqus (comment system) alternate. (Demo, Source Code)
AGPL-3.0Docker/Nodejs - Coral - A better commenting experience from Vox Media. (Source Code)
Apache-2.0Docker/Nodejs - diaspora* - Distributed social networking server. (Source Code)
AGPL-3.0Ruby - Discourse - Advanced forum / community solution based on Ruby and JS. (Demo, Source Code)
GPL-2.0Docker - Elgg - Powerful open source social networking engine. (Source Code)
GPL-2.0PHP - Enigma 1/2 BBS - Enigma 1/2 is a modern, multi-platform BBS engine with unlimited "callers" and legacy DOS door game support. (Source Code)
BSD-2-ClauseShell/Docker/Nodejs - Flarum - Delightfully simple forums. Flarum is the next-generation forum software that makes online discussion fun again. (Source Code)
MITPHP - Friendica - Social Communication Server. (Source Code)
AGPL-3.0PHP - GoToSocial - ActivityPub federated social network server implementing the Mastodon client API. (Source Code)
AGPL-3.0Docker/Go - Hatsu - Bridge that interacts with Fediverse on behalf of your static site. (Source Code)
AGPL-3.0Docker/Rust - Hubzilla - Decentralized identity, privacy, publishing, sharing, cloud storage, and communications/social platform. (Source Code)
MITPHP - HumHub - Flexible kit for private social networks. (Source Code)
AGPL-3.0PHP - Isso - Lightweight commenting server written in Python and Javascript. It aims to be a drop-in replacement for Disqus. (Source Code)
MITPython/Docker - Lemmy - Link aggregator for the fediverse (alternative to Reddit). (Source Code)
AGPL-3.0Docker/Rust - Loomio - Collaborative decision-making tool that makes it easy for anyone to participate in decisions which affect them. (Source Code)
AGPL-3.0Docker - Mastodon - Federated microblogging server. (Source Code, Clients)
AGPL-3.0Ruby - Misago - Fully featured modern forum application that is fast, scalable and responsive. (Source Code)
GPL-2.0Docker - Misskey - Decentralized app-like microblogging server/SNS for the Fediverse, using the ActivityPub protocol like GNU social and Mastodon. (Source Code)
AGPL-3.0Nodejs/Docker - Movim - Modern, federated social network based on XMPP, with a fully featured group-chat, subscriptions and microblogging. (Source Code)
AGPL-3.0PHP/Docker - MyBB - Free, extensible forum software package. (Source Code)
LGPL-3.0PHP - NodeBB - Forum software built for the modern web. (Demo, Source Code)
GPL-3.0Nodejs/Docker - OSSN - Social networking software that allows you to make a social networking website and helps your members build social relationships, with people who share similar professional or personal interests. (Source Code)
CAL-1.0PHP - phpBB - Flat-forum bulletin board software solution that can be used to stay in touch with a group of people or can power your entire website. (Source Code)
GPL-2.0PHP - PixelFed - Ethical photo sharing platform, powered by ActivityPub federation (alternative to Instagram). (Source Code)
AGPL-3.0PHP - Pleroma - Federated microblogging server, Mastodon, GNU social, & ActivityPub compatible. (Source Code)
AGPL-3.0Elixir - qpixel - Q&A-based community knowledge-sharing software. (Source Code)
AGPL-3.0Ruby - Redlib
⚠- An alternative private front-end to Reddit, with its origins in Libreddit.AGPL-3.0Rust - remark42 - A lightweight and simple comment engine, which doesn't spy on users. It can be embedded into blogs, articles or any other place where readers add comments. (Demo, Source Code)
MITDocker/Go - Retrospring - A free, open-source social network following the Q/A (question and answer) principle of sites like Formspring, ask.fm or CuriousCat. (Demo)
AGPL-3.0Ruby/Nodejs - Scoold - Stack Overflow in a JAR. An enterprise-ready Q&A platform with full-text search, SAML, LDAP integration and social login support. (Demo, Source Code)
Apache-2.0Java/Docker/K8S - Simple Machines Forum - Free, professional grade software package that allows you to set up your own online community within minutes. (Source Code)
BSD-3-ClausePHP - Socialhome - Federated and decentralized profile builder and social network engine. (Demo, Source Code)
AGPL-3.0Docker/Python - Takahē - Federated microblogging server. Mastodon, & ActivityPub compatible. (Source Code)
BSD-3-ClauseDocker - Talkyard - Create a community, where your users can suggest ideas and get questions answered. And have friendly open-ended discussions and chat (Slack/StackOverflow/Discourse/Reddit/Disqus hybrid). (Demo, Source Code)
AGPL-3.0Docker/Scala - yarn.social - Self-Hosted, Twitter™-like Decentralised micro-logging platform. No ads, no tracking, your content, your data. (Source Code)
MITGo - Zusam - Free and open-source way to self-host private forums for groups of friends or family. (Demo)
AGPL-3.0PHP
- Akkoma - Federated microblogging server with Mastodon, GNU social, and ActivityPub compatibility. (Source Code)
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ 63d59db8:be170f6f
2025-05-23 12:53:00
@ 63d59db8:be170f6f
2025-05-23 12:53:00In a world overwhelmed by contradictions—climate change, inequality, political instability, and social disconnection—absurdity becomes an unavoidable lens through which to view the human condition. Inspired by Albert Camus' philosophy, this project explores the tension between life’s inherent meaninglessness and our persistent search for purpose.\ \ The individuals in these images embody a quiet defiance, navigating chaos with a sense of irony and authenticity. Through the act of revolt—against despair, against resignation—they find agency and resilience. These photographs invite reflection, not on solutions, but on our capacity to live meaningfully within absurdity.
Visit Katerina's website here.
Submit your work to the NOICE Visual Expression Awards for a chance to win a few thousand extra sats:
-
 @ b0a838f2:34ed3f19
2025-05-23 17:50:31
@ b0a838f2:34ed3f19
2025-05-23 17:50:31- Asterisk - Easy to use but advanced IP PBX system, VoIP gateway and conference server. (Source Code)
GPL-2.0C/deb - Eqivo - Eqivo implements an API layer on top of FreeSWITCH facilitating integration between web applications and voice/video-enabled endpoints such as traditional phone lines (PSTN), VoIP phones, webRTC clients etc. (Source Code)
MITDocker/PHP - Flexisip - Complete, modular and scalable SIP server, includes a push gateway, to deliver SIP incoming calls or text messages on mobile device platforms where push notifications are required to receive information when the app is not active in the foreground. (Source Code)
AGPL-3.0C/Docker - Freepbx - Web-based open source GUI that controls and manages Asterisk. (Source Code)
GPL-2.0PHP - FreeSWITCH - Scalable open source cross-platform telephony platform. (Source Code)
MPL-2.0C - FusionPBX - Web interface for multi-platform voice switch called FreeSWITCH. (Source Code)
MPL-1.1PHP - Kamailio - Modular SIP server (registrar/proxy/router/etc). (Source Code)
GPL-2.0C/deb - openSIPS - SIP proxy/server for voice, video, IM, presence and any other SIP extensions. (Source Code)
GPL-2.0C - Routr - A lightweight sip proxy, location server, and registrar for a reliable and scalable SIP infrastructure. (Source Code)
MITDocker/K8S - SIP3 - VoIP troubleshooting and monitoring platform. (Demo, Source Code)
Apache-2.0Java - SIPCAPTURE Homer - Troubleshooting and monitoring VoIP calls. (Source Code)
AGPL-3.0Nodejs/Go/Docker - Wazo - Full-featured IPBX solution built atop Asterisk with integrated Web administration interface and REST-ful API. (Source Code)
GPL-3.0Python - Yeti-Switch - Transit class4 softswitch(SBC) with integrated billing and routing engine and REST API. (Demo, Source Code)
GPL-2.0C++/Ruby
- Asterisk - Easy to use but advanced IP PBX system, VoIP gateway and conference server. (Source Code)
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ a296b972:e5a7a2e8
2025-05-23 12:42:10
@ a296b972:e5a7a2e8
2025-05-23 12:42:10Was Rudolf Steiner vor gut 110 Jahren an Informationen zusammengetragen und kommentiert hat, liest sich in großen Abschnitten so, als ob es in der heutigen Zeit geschrieben worden wäre. Man trifft auf eine ganze Reihe von „guten, alten Bekannten“, die auch heute noch maßgeblich an den Strippen ziehen. Deutlich wird, dass ein Krieg nicht aus heiterem Himmel ausbricht, sondern das im Vorfeld schon Kräfte wirken, die auf einen Krieg hinarbeiten. Wie jetzt wieder im Ukraine-Krieg wird diese Vorgeschichte gerne versucht unter den Teppich zu kehren und hochkompetente, sauber recherchierende, akribisch Quellen angebende Journalisten, wie z. B. Frau Gabriele Krone-Schmalz oder Herr Patrik Baab, der sich auf eigene Kosten einen Eindruck von vor Ort verschafft hat, werden versucht mundtot zu machen und mittlerweile gar nicht mehr zu Gesprächen im öffentlich-rechtlichen Rundfunk eingeladen, weil sie die fortlaufende Gehirnwäsche des Ministeriums für Wahrheit und Narrative mit ihren Aussagen gefährden. Andere kommen auf die Sanktionsliste.
Auch heute ist von den „Guten“ und den „Bösen“ die Rede, was darauf schließen lässt, dass man durchaus eingesteht, dass hier geistige Kräfte am Werk sind. Rudolf Steiner kommt auf diese immer wieder zu sprechen. Aus der von ihm gegebenen anthroposophischen Geisteswissenschaft heraus, beleuchtet er die Vorgänge innerhalb der gesamten Menschheitsentwicklung. Mancher stört sich hier an Begriffen, die man heute so nicht mehr verwenden würde. Dabei ist immer zu berücksichtigen, zu welcher Zeit die Vorträge gehalten wurden. Die Anthroposophie von Rudolf Steiner gilt heute bei vielen auch als „umstritten“, aber was ist das heute nicht? Fast könnte man es schon als Auszeichnung sehen, wenn etwas „umstritten“ ist, denn das ist mittlerweile ein Beweis dafür, dass es Ansichten, Meinungen und Einschätzungen gibt, die in einer gesunden Demokratie innerhalb einer Kontroverse zu einem Dialog und Austausch beitragen können, der jedoch leider derzeit weder gewünscht ist, noch gepflegt wird, was an der „Spaltung“ deutlich zu sehen ist. Und auch unter den Anthroposophen hat die „Spaltung“ Einzug gehalten.
Um das aktuelle, viele Bereiche umschließende, gigantische Lügenkonstrukt aufrecht zu erhalten, ist mittlerweile jedes Mittel recht, von der Deutungshoheit der Wahrheit durch systemkonforme Begutachter, bis hin zu infantil-kleingeistigen Kindergartenspielchen, um gegenläufige Meinungen oder Oppositionelle in ihrem Wirken zu behindern.
Der gesunde Hausverstand wird ausgetrocknet, und der Garten des Wahnsinns wird durch immer neue Ideen kranker Geister weiter gegossen, gehegt und gepflegt.
Die Zeitgeschichtlichen Betrachtungen von Rudolf Steiner bestehen aus 3 Bänden aus der GA (Gesamtausgabe):
GA 173 a – Wege zu einer objektiven Urteilsbildung
GA 173 b – Das Karma der Unwahrhaftigkeit
GA 173 c – Die Wirklichkeit okkulter Impulse
Sie bestehen aus niedergeschriebenen Vorträgen und einem sehr umfangreichen Anhang mit näheren Erläuterungen und einer Schilderung der Entstehung dieser drei Bände.
Es bedarf einiger Eingewöhnung in die zur damaligen Zeit verwendete Sprache Rudolf Steiners, der ein Meister im Bilden von Schachtelsätzen war. Der Inhalt jedoch, und auf den kommt es ja an, berührt immer wieder den in allen Menschen vorhandenen Wahrheitssinn.
Hier nur eine kleine Kostprobe, die vielleicht das Interesse wecken kann, sich mit diesem derzeit besonders aktuellen Werk näher zu beschäftigen.
GA 173a, 6. Vortrag, Seite 205 und Seite 206, Dornach, 17. Dezember 1916:
„Viel intimer, viel verborgener liegen die Dinge bei der englischen Politik, die ja ganz beeinflußt ist von dem, was in solcher Weise hinter ihr steckt. Da handelt es sich darum, daß man die Wege findet, um die entsprechenden Menschen an die richtigen Plätze zu befördern. Okkultistische Menschen, im Hintergrunde stehend, sind oftmals – na, verzeihen Sie – Einser, bloße Einser, und bedeuten für sich nichts Besonderes; sie brauchen noch etwas anderes – sie brauchen Nullen. Nullen sind ja nicht Einser, aber (fügt man eine Null zu einer Eins), dann wird gleich eine Zehn daraus. Und wenn man noch mehr Nullen hinzufügt – jede Null ist nur eine Null, aber wenn die Eins irgendwo steckt, dann ist gar mancherlei da, zum Beispiel die Tausend, und wenn man die Eins zudeckt, dann sind (scheinbar) nur die Nullen da; die Nullen brauchen aber nur in der entsprechenden Weise mit den Einsern kombiniert zu sein, und sie brauchen nicht einmal viel zu wissen von der Art, wie sie mit den Einsern kombiniert sind.“
Schildert diese 108 Jahre alte Beschreibung nicht genau das, was sich heute vor unseren Augen abspielt?
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ b0a838f2:34ed3f19
2025-05-23 17:50:11
@ b0a838f2:34ed3f19
2025-05-23 17:50:11- Convos - Always online web IRC client. (Demo, Source Code)
Artistic-2.0Perl/Docker - Ergo - Modern IRCv3 server written in Go, combining the features of an ircd, a services framework, and a bouncer. (Source Code)
MITGo/Docker - Glowing Bear - A web frontend for WeeChat. (Demo)
GPL-3.0Nodejs - InspIRCd - Modular IRC server written in C++ for Linux, BSD, Windows, and macOS. (Source Code)
GPL-2.0C++/Docker - Kiwi IRC - Responsive web IRC client with theming support. (Demo, Source Code)
Apache-2.0Nodejs - ngircd - Portable and lightweight Internet Relay Chat server for small or private networks. (Source Code)
GPL-2.0C/deb - Quassel IRC - Distributed IRC client, meaning that one (or multiple) client(s) can attach to and detach from a central core. (Source Code)
GPL-2.0C++ - Robust IRC - RobustIRC is IRC without netsplits. Distributed IRC server, based on RobustSession protocol. (Source Code)
BSD-3-ClauseGo - The Lounge - Self-hosted web IRC client. (Demo, Source Code)
MITNodejs/Docker - UnrealIRCd - Modular, advanced and highly configurable IRC server written in C for Linux, BSD, Windows, and macOS. (Source Code)
GPL-2.0C - Weechat - Fast, light and extensible chat client. (Source Code)
GPL-3.0C/Docker/deb - ZNC - Advanced IRC bouncer. (Source Code)
Apache-2.0C++/deb
- Convos - Always online web IRC client. (Demo, Source Code)
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ b0a838f2:34ed3f19
2025-05-23 17:49:53
@ b0a838f2:34ed3f19
2025-05-23 17:49:53- Cypht - Feed reader for your email accounts. (Source Code)
LGPL-2.1PHP - Roundcube - Browser-based IMAP client with an application-like user interface. (Source Code)
GPL-3.0PHP/deb - SnappyMail - Simple, modern, lightweight & fast web-based email client (fork of RainLoop). (Demo, Source Code)
AGPL-3.0PHP - SquirrelMail - Another browser-based IMAP client. (Source Code)
GPL-2.0PHP
- Cypht - Feed reader for your email accounts. (Source Code)
-
 @ cae03c48:2a7d6671
2025-05-23 12:00:53
@ cae03c48:2a7d6671
2025-05-23 12:00:53Bitcoin Magazine

Not ECDSA. Not Schnorr. Meet DahLIAS.Aggregate signatures aren’t new. They’ve been around since the early 2000s. But building one that actually works in Bitcoin’s security model, with Bitcoin’s elliptic curve, has never been proven. Developers speculated it might be possible. They shared hand-wavy sketches and said, “maybe it’d work like MuSig2, but across transaction inputs.” The idea lingered for years as developer folklore, close, never provably confirmed.
That changed recently, when Jonas Nick and Tim Ruffing of Blockstream Research, together with Yannick Seurin of Ledger, published a paper that turned this cryptographic ghost story into a concrete, provable result. DahLIAS is the first formal, secure construction of a full constant-size aggregate signature (CISA) scheme that works on Bitcoin’s native curve!
But that’s a lot of words, so let’s break that down:
- Full aggregation: Multiple signatures across different inputs are combined into one — and the result is a 64 byte signature whose size stays constant, no matter how many signers or inputs.
- Cross-input: Each signer can authorize different inputs, and all combine into one signature.
It adds no significant new assumptions beyond those already relied on by Bitcoin. DahLIAS builds a new cryptographic primitive using the same math Bitcoin already relies on, unlocking an entirely new kind of signature.
Let’s Talk About Curves and Signatures
Digital signatures are how Bitcoin proves that a user has authorized a transaction. When you go to spend bitcoin, your wallet uses a private key to sign a message, and the network verifies that signature using the matching public key.
Bitcoin uses the secp256k1 curve. It is fast, efficient, and has been battle-tested over time. It supports signature schemes like ECDSA (Bitcoin’s original signature algorithm) and Schnorr (added through Taproot in 2021), which are currently the only signature schemes permitted by Bitcoin consensus.
Traditionally, full signature aggregation relied on mathematical operations not supported by Bitcoin’s curve, secp256k1, which made it seem out of reach. These features have typically relied on other types of elliptic curves. For example, BLS (Boneh–Lynn–Shacham) signatures use a special kind of curve called a pairing-friendly curve, which enables advanced operations like combining many signatures, even on different messages, into one.
The problem is that BLS signatures do not work on secp256k1. While Schnorr was a natural upgrade from ECDSA, since both rely on the same kind of elliptic curve, adding BLS would be a much bigger leap and a departure from Bitcoin’s existing security model. Though technically possible, it would introduce new cryptographic assumptions and add significant complexity to the protocol. Supporting a curve that is pairing-friendly, like BLS12-381, would be a major change for Bitcoin.
This is part of why full signature aggregation has never been done on secp256k1.
Until now.
What Aggregate Signatures Actually Do
Most Bitcoin users are familiar with multisignatures. In a multisig wallet, multiple people jointly authorize the spending of a single UTXO or some specific “coin”. Everyone signs the same input data. This setup is useful for things like shared custody wallets.
Aggregate signatures work differently. Instead of multiple people signing the same input or coin, each signer authorizes a different UTXO in a transaction. These separate signatures are then compressed into one compact proof. With DahLIAS, that means a single 64-byte signature on Bitcoin’s secp256k1 curve that verifies all inputs at once.
That means if you have five inputs from five different people, the transaction needs five different signatures. With an aggregate signature, all of those can be bundled into one. Even if each signer is spending a different input and signing a different part of the transaction, the result is one signature that proves the entire transaction was properly authorized.
It’s like zipping a whole list of approvals into one file. The signature is compact, but still verifiably proves that each signer authorized their specific UTXO.
Instead of verifying 10 separate signatures, you verify one.
This helps realign incentives for privacy. By reducing the signature overhead to a single 64-byte proof, DahLIAS lowers the cost of combining inputs in CoinJoins, making it financially smarter to choose privacy than to go without it.
Why Half-Aggregation Got Close
Shortly after Schnorr signatures were introduced on Bitcoin, developers explored half-aggregation, as a way to compress multiple signatures but they were not fixed size. Each input contributes to the size of the signature, so the transaction still grows with every participant. DahLIAS fixes this by enabling full-aggregation across inputs and signers. No matter how many people are involved or what they’re signing, all their signatures compress into one constant-size, 64-byte proof.
What DahLIAS Actually Unlocks
The main benefit here is that DahLIAS are reducing the size of complex transactions.
DahLIAS uses a two-round interactive signing process. It’s similar to MuSig2 in that regard, but it isn’t a multisignature protocol because it doesn’t require all participants to co-sign the same message. Instead, it aggregates different signatures on different messages across the transaction.
DahLIAS is also faster to verify than checking each signature individually, up to twice as fast in some cases. Lower verification costs make it easier for more people to run full nodes, which helps preserve Bitcoin’s decentralization over time.
Importantly, DahLIAS comes with strong cryptographic guarantees. The scheme includes formal security proofs. Earlier ‘folklore’ approaches to full signature aggregation lacked this, and some were even later shown to be insecure. Fortunately they weren’t adopted prematurely.
It’s worth repeating: DahLIAS is not a multisig protocol. It isn’t comparable to MuSig2 or FROST from a functional standpoint, even if it shares similar cryptographic building blocks. It serves a different purpose. It offers a new way to encode many independent approvals into one clean, verifiable package.
Future Directions
You might think: if DahLIAS is so powerful, why isn’t it a BIP? Why not propose it for Bitcoin consensus?
DahLIAS signatures don’t look like Schnorr or ECDSA signatures. The verification algorithm is different. Instead of taking a single public key, message, and signature, a DahLIAS verifier takes lists of public keys and messages, and a single 64-byte proof.
This makes DahLIAS incompatible with Bitcoin’s current consensus rules. Supporting it at the base layer would require a consensus change. This paper doesn’t propose that change, but it does something equally important.
This paper shows that a full signature aggregation scheme for Bitcoin’s native curve is possible.
That alone is a major step forward.
To make DahLIAS part of Bitcoin, someone would need to write a Bitcoin Improvement Proposal (BIP), maybe even using secp256k1lab. That means specifying the scheme in detail, considering its implications for consensus and implementation, and building community support. This paper lays the cryptographic foundation for that conversation.
The real value of the DahLIAS paper is what it proves. Full signature aggregation on secp256k1 is not just a thought experiment. It’s concrete. It’s efficient. It’s secure. For years, the idea lived in developer folklore. Now, it’s written down, analyzed, and proven. All that’s left is to bring it to Bitcoin—if we want it.
This is a guest post by Kiara Bickers. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.
This post Not ECDSA. Not Schnorr. Meet DahLIAS. first appeared on Bitcoin Magazine and is written by Kiara Bickers.
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ 1c5ff3ca:efe9c0f6
2025-05-23 10:13:57
@ 1c5ff3ca:efe9c0f6
2025-05-23 10:13:57Auto-Deployment on a VPS with GitHub Actions
Introduction
This tutorial describes how you can deploy an application on a VPS using GitHub Actions. This way, changes in your GitHub repository are automatically deployed to your VPS.
Prerequisites
- GitHub Account
- GitHub Repository
- Server + SSH access to the server
Step 1 - SSH Login to Server
Open a terminal and log in via SSH. Then navigate to the
.sshdirectoryssh user@hostname cd ~/.sshStep 2 - Create an SSH Key
Now create a new SSH key that we will use for auto-deployment. In the following dialog, simply press "Enter" repeatedly until the key is created.
ssh-keygen -t ed25519 -C "service-name-deploy-github"Step 3 - Add the Key to the
authorized_keysFilecat id_ed25519.pub >> authorized_keys(If you named the key file differently, change this accordingly)
Step 4 - GitHub Secrets
In order for the GitHub Action to perform the deployment later, some secrets must be stored in the repository. Open the repository on GitHub. Navigate to "Settings" -> "Secrets And Variables" -> "Actions". Add the following variables:
HOST: Hostname or IP address of the serverUSERNAME: Username you use to log in via SSHSSHKEY: The private key (copy the content fromcat ~/.ssh/id_ed25519)PORT: 22
Step 5 - Create the GitHub Action
Now create the GitHub Action for auto-deployment. The following GitHub Action will be used: https://github.com/appleboy/scp-action In your local repository, create the file
.github/workflows/deploy.yml:```yaml name: Deploy on: [push] jobs: build: runs-on: ubuntu-latest steps: - uses: actions/checkout@v1 - name: Copy repository content via scp uses: appleboy/scp-action@master with: host: ${{ secrets.HOST }} username: ${{ secrets.USERNAME }} port: ${{ secrets.PORT }} key: ${{ secrets.SSHKEY }} source: "." target: "/your-target-directory"
- name: Executing a remote command uses: appleboy/ssh-action@master with: host: ${{ secrets.HOST }} username: ${{ secrets.USERNAME }} port: ${{ secrets.PORT }} key: ${{ secrets.SSHKEY }} script: | ls```
This action copies the repository files to your server using
scp. Afterwards, thelscommand is executed. Here you can add appropriate commands that rebuild your service or similar. To rebuild and start a docker service you could use something like this or similar:docker compose -f target-dir/docker-compose.yml up --build -dNow commit this file and in the "Actions" tab of your repository, the newly created action should now be visible and executed. With every future change, the git repository will now be automatically copied to your server.Sources
I read this when trying out, but it did not work and I adapted the
deploy.ymlfile: https://dev.to/knowbee/how-to-setup-continuous-deployment-of-a-website-on-a-vps-using-github-actions-54im -
 @ eb0157af:77ab6c55
2025-05-23 10:01:28
@ eb0157af:77ab6c55
2025-05-23 10:01:28A Chinese printer company inadvertently distributed malware that steals Bitcoin through its official drivers, resulting in the theft of over $950,000.
According to local media outlet Landian News, a Chinese printer manufacturer was found to have unknowingly distributed malware designed to steal Bitcoin through its official device drivers.
Procolored, a Shenzhen-based printer company, distributed malware capable of stealing Bitcoin alongside the official drivers for its devices. The company reportedly used USB devices to spread infected drivers and uploaded the compromised software to globally accessible cloud storage services.
Crypto security and compliance firm SlowMist explained how the malware works in a post on X:
 The official driver provided by this printer carries a backdoor program. It will hijack the wallet address in the user's clipboard and replace it with the attacker's address: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj
The official driver provided by this printer carries a backdoor program. It will hijack the wallet address in the user's clipboard and replace it with the attacker's address: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj  According to @MistTrack_io, the attacker has stolen 9.3086… https://t.co/DHCkEpHhuH pic.twitter.com/W1AnUpswLU
According to @MistTrack_io, the attacker has stolen 9.3086… https://t.co/DHCkEpHhuH pic.twitter.com/W1AnUpswLU— MistTrack
 (@MistTrack_io) May 19, 2025
(@MistTrack_io) May 19, 2025The consequences of the breach have been significant, with a total of 9.3 BTC stolen — equivalent to over $950,000.
The issue was first flagged by YouTuber Cameron Coward, whose antivirus software detected malware in the drivers during a test of a Procolored UV printer. The software identified both a worm and a trojan virus named Foxif.
When contacted, Procolored denied the accusations, dismissing the antivirus warning as a false positive. Coward then turned to Reddit, where he shared the issue with cybersecurity professionals, drawing the attention of security firm G Data.
G Data’s investigation revealed that most of Procolored’s drivers were hosted on the MEGA file-sharing platform, with uploads dating back to October 2023. Their analysis confirmed the presence of two separate malware strains: the Win32.Backdoor.XRedRAT.A backdoor and a crypto-stealer designed to replace clipboard wallet addresses with those controlled by the attacker.
G Data reached out to Procolored, which stated that it had removed the infected drivers from its storage as of May 8 and had re-scanned all files. The company attributed the malware to a supply chain compromise, saying the malicious files were introduced via infected USB devices before being uploaded online.
Landian News recommended that users who downloaded Procolored drivers in the past six months “immediately run a full system scan using antivirus software.” However, given that antivirus tools are not always reliable, the Chinese media outlet suggested that a full system reset is the safest option when in doubt.
The post Bitcoin malware discovered: Chinese printer manufacturer involved appeared first on Atlas21.
-
 @ b0a838f2:34ed3f19
2025-05-23 17:49:32
@ b0a838f2:34ed3f19
2025-05-23 17:49:32- HyperKitty - Access GNU Mailman v3 archives. (Demo, Source Code)
GPL-3.0Python - Keila - Reliable and easy-to-use newsletter tool (alternative to Mailchimp or Sendinblue). (Demo, Source Code)
AGPL-3.0Docker - Listmonk - High performance, self-hosted newsletter and mailing list manager with a modern dashboard. (Source Code)
AGPL-3.0Go/Docker - Mailman - Manage electronic mail discussion and e-newsletter lists. (Source Code)
GPL-3.0Python - Mautic - Marketing automation software (email, social and more). (Source Code)
GPL-3.0PHP - phpList - Newsletter and email marketing with advanced management of subscribers, bounces, and plugins. (Source Code)
AGPL-3.0PHP - Postorius - Web user interface to access GNU Mailman. (Source Code)
GPL-3.0Python - Schleuder - GPG-enabled mailing list manager with resending-capabilities. (Source Code)
GPL-3.0Ruby - Sympa - Mailing list manager. (Source Code)
GPL-2.0Perl
- HyperKitty - Access GNU Mailman v3 archives. (Demo, Source Code)
-
 @ f6488c62:c929299d
2025-05-23 09:48:20
@ f6488c62:c929299d
2025-05-23 09:48:20ในวันที่ 23 พฤษภาคม 2568 The Wall Street Journal รายงานข่าวที่น่าสนใจว่า ธนาคารยักษ์ใหญ่ของสหรัฐฯ เช่น JPMorgan Chase, Bank of America, Citigroup และ Wells Fargo กำลังพิจารณาความเป็นไปได้ในการพัฒนา Stablecoin ร่วมกัน เพื่อก้าวเข้าสู่โลกของคริปโตเคอเรนซีอย่างเต็มตัว การเคลื่อนไหวครั้งนี้ไม่เพียงสะท้อนถึงการยอมรับสินทรัพย์ดิจิทัลในระบบการเงินกระแสหลัก แต่ยังเป็นก้าวสำคัญในการรักษาความเป็นผู้นำของเงินดอลลาร์สหรัฐในยุคการเงินดิจิทัล.
Stablecoin: อนาคตของการชำระเงินดิจิทัล Stablecoin เป็นสกุลเงินดิจิทัลที่ออกแบบมาเพื่อลดความผันผวนโดยผูกมูลค่ากับสินทรัพย์ที่มีเสถียรภาพ เช่น เงินดอลลาร์สหรัฐ ทำให้เหมาะสำหรับการใช้ในระบบการชำระเงิน การโอนเงินข้ามพรมแดน และการเงินแบบกระจายศูนย์ (DeFi). การที่ธนาคารใหญ่ของสหรัฐฯ หันมาสนใจ Stablecoin ร่วมกัน แสดงถึงความพยายามในการปรับตัวให้เข้ากับความต้องการของผู้บริโภคยุคใหม่ที่ต้องการความรวดเร็วและประหยัดต้นทุนในการทำธุรกรรมทางการเงิน.
ทำไมธนาคารถึงสนใจ Stablecoin? ในปี 2568 ตลาดคริปโตเคอเรนซีกำลังร้อนแรง โดยมูลค่าตลาดรวมของคริปโตทั่วโลกอยู่ที่ 3.64 ล้านล้านดอลลาร์ ซึ่งในจำนวนนี้ Bitcoin มีมูลค่าตลาดสูงสุดที่ 2.2 ล้านล้านดอลลาร์ และราคา Bitcoin ล่าสุดพุ่งแตะ 111,160.66 ดอลลาร์ (ข้อมูล ณ วันที่ 23 พฤษภาคม 2568 เวลา 16:44 น. ตามเขตเวลา +07) นอกจากนี้ ยังมีเม็ดเงินไหลเข้าสู่กองทุนสินทรัพย์ดิจิทัลในสหรัฐฯ กว่า 7.5 พันล้านดอลลาร์ การที่ธนาคารยักษ์ใหญ่ที่มีมูลค่ารวมกันถึง 8 ล้านล้านดอลลาร์เข้ามาในสนามนี้ แสดงถึงศักยภาพในการเปลี่ยนแปลงภูมิทัศน์ของอุตสาหกรรมการเงิน. นโยบายที่เอื้ออำนวยต่อคริปโตในยุคของประธานาธิบดีโดนัลด์ ทรัมป์ และการลดดอกเบี้ยนโยบายของ Fed ยังเป็นปัจจัยสนับสนุนที่สำคัญ.
โอกาสและความท้าทาย การพัฒนา Stablecoin ร่วมกันของธนาคารเหล่านี้เปิดโอกาสให้สหรัฐฯ รักษาความเป็นผู้นำในระบบการเงินดิจิทัล และเพิ่มประสิทธิภาพในระบบการชำระเงินทั่วโลก อย่างไรก็ตาม ความท้าทายที่รออยู่คือการแข่งขันกับ Stablecoin ที่ครองตลาด เช่น USDT และ USDC รวมถึงความไม่แน่นอนด้านกฎระเบียบและความผันผวนของเศรษฐกิจโลกจากนโยบายการค้าของสหรัฐฯ. ธนาคารจะต้องลงทุนในโครงสร้างพื้นฐานที่ปลอดภัยและสอดคล้องกับกฎหมาย เพื่อสร้างความไว้วางใจจากผู้ใช้.
มองไปข้างหน้า การที่ธนาคารชั้นนำของสหรัฐฯ หันมาสนใจ Stablecoin เป็นสัญญาณที่ชัดเจนว่าโลกการเงินกำลังเปลี่ยนผ่านสู่ยุคดิจิทัลอย่างเต็มรูปแบบ การเคลื่อนไหวครั้งนี้อาจเป็นจุดเปลี่ยนที่ทำให้คริปโตเคอเรนซีกลายเป็นส่วนสำคัญของระบบการเงินกระแสหลัก อย่างไรก็ตาม ความสำเร็จจะขึ้นอยู่กับความสามารถในการสร้างนวัตกรรมที่ตอบโจทย์ผู้บริโภคและการจัดการกับความท้าทายด้านกฎระเบียบและการแข่งขันในตลาด. ในอนาคตอันใกล้ Stablecoin จากธนาคารยักษ์ใหญ่อาจกลายเป็นตัวเปลี่ยนเกมในวงการการเงินโลก และเป็นเครื่องมือสำคัญในการเชื่อมโยงระบบการเงินแบบดั้งเดิมเข้ากับโลกดิจิทัล นักลงทุนและผู้บริโภคควรจับตาดูความคืบหน้าของโครงการนี้อย่างใกล้ชิด เพราะมันอาจเป็นก้าวแรกสู่การปฏิวัติครั้งใหญ่ในวงการการเงิน.
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ b0a838f2:34ed3f19
2025-05-23 17:49:07
@ b0a838f2:34ed3f19
2025-05-23 17:49:07- chasquid - SMTP (email) server with a focus on simplicity, security, and ease of operation. (Source Code)
Apache-2.0Go - Courier MTA - Fast, scalable, enterprise mail/groupware server providing ESMTP, IMAP, POP3, webmail, mailing list, basic web-based calendaring and scheduling services. (Source Code)
GPL-3.0C/deb - DragonFly - A small MTA for home and office use. Works on Linux and FreeBSD.
BSD-3-ClauseC - EmailRelay - A small and easy to configure SMTP and POP3 server for Windows and Linux. (Source Code)
GPL-3.0C++ - Exim - Message transfer agent (MTA) developed at the University of Cambridge. (Source Code)
GPL-3.0C/deb - Haraka - Fast, highly extensible, and event driven SMTP server. (Source Code)
MITNodejs - MailCatcher - Deploy a simply SMTP MTA gateway that accepts all mail and displays in web interface. Useful for debugging or development. (Source Code)
MITRuby - OpenSMTPD - Secure SMTP server implementation from the OpenBSD project. (Source Code)
ISCC/deb - OpenTrashmail - Complete trashmail solution that exposes an SMTP server and has a web interface to manage received emails. Works with multiple and wildcard domains and is fully file based (no database needed). Includes RSS feeds and JSON API.
Apache-2.0Python/PHP/Docker - Postfix - Fast, easy to administer, and secure Sendmail replacement.
IPL-1.0C/deb - Sendmail - Message transfer agent (MTA).
SendmailC/deb
- chasquid - SMTP (email) server with a focus on simplicity, security, and ease of operation. (Source Code)
-
 @ 21ffd29c:518a8ff5
2025-02-04 21:12:15
@ 21ffd29c:518a8ff5
2025-02-04 21:12:15- What Are Homestead Chickens?
Homestead chickens are domesticated fowl kept by homeowners to provide eggs and companionship. They play a vital role in the homestead ecosystem.
Why Water is Essential in Cold Weather - Hydration Basics:
Chickens don't drink much water naturally but need it for hydration, especially during cold weather when metabolic rates increase. - Environmental Factors:
Cold weather can lead to ice buildup on water sources. Chickens benefit from having access to fresh water year-round.Maintaining Accessible Water Sources - Shallow Troughs:
Use shallow troughs instead of deep containers to minimize ice formation and ensure constant water supply. - Automatic Feeders:
Consider installing automatic feeders for convenience, especially in unpredictable weather conditions. - Multiple Water Sources:
Provide multiple water sources to prevent competition and ensure all chickens have access.Preventing Ice Buildup - Floating Shallow Troughs:
Opt for troughs that sit above the ground to avoid ice buildup. Ensure they're placed where they can't freeze completely. - Regular Checks:
Inspect water sources regularly to remove ice and debris, maintaining accessibility for chickens.Best Practices for Watering Chickens - Waterers Designed for Cold Weather:
Use waterers made of stainless steel or plastic that can withstand cold temperatures. - Seasonal Adjustments:
During extreme cold spells, supplement with a small amount of fresh water to aid in drinking.Conclusion - Key Takeaways:
Providing proper water is crucial for the health and well-being of homestead chickens during cold weather. Maintaining accessible, shallow water sources prevents issues like ice buildup and ensures hydration.Final Thoughts - Sustainability Considerations:
While chickens don't drink much, ensuring they have water supports their overall health and sustainability efforts. - Environmental Impact:
Thoughtful water management can reduce water usage, promoting eco-friendly practices on the homestead. - What Are Homestead Chickens?
-
 @ 0fa80bd3:ea7325de
2025-01-29 14:44:48
@ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]]
1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest.
2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money.
3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape.
Now, what you do with a trapped bear is another question... 😏
-
 @ dfc7c785:4c3c6174
2025-05-23 09:42:37
@ dfc7c785:4c3c6174
2025-05-23 09:42:37Where do I even start? Sometimes it's best to just begin writing whatever comes into your head. What do I do for a living? It used to be easy to explain, I write JavaScript, I build front-end code, in order to build apps. I am more than that though. Over the past eight years, I moved from writing Angular, to React and then to Vue. However my background was originally in writing full-stack projects, using technologies such as .NET and PHP. The thing is - the various jobs I've had recently have pigeon-holed me as front-end developer but nowadays I am starting to feel distracted by a multitude of other interesting, pivotal technologies both in my "day job" and across my wider experience as a Technologist; a phrase I prefer to use in order to describe who I am, more gernerally.
I have used untype.app to write this today, it looks great.
More to come...
-
 @ b0a838f2:34ed3f19
2025-05-23 17:48:32
@ b0a838f2:34ed3f19
2025-05-23 17:48:32- Cyrus IMAP - Email (IMAP/POP3), contacts and calendar server. (Source Code)
BSD-3-Clause-AttributionC - DavMail
⚠- POP/IMAP/SMTP/Caldav/Carddav/LDAP exchange gateway allowing users to use any mail/calendar client with an Exchange server, even from the internet or behind a firewall through Outlook Web Access. (Source Code)GPL-2.0Java - Dovecot - IMAP and POP3 server written primarily with security in mind. (Source Code)
MIT/LGPL-2.1C/deb - Piler - Feature-rich email archiving solution. (Source Code)
GPL-3.0C
- Cyrus IMAP - Email (IMAP/POP3), contacts and calendar server. (Source Code)
-
 @ 3eba5ef4:751f23ae
2025-05-23 09:33:55
@ 3eba5ef4:751f23ae
2025-05-23 09:33:55The article below brings together some of the Q&A from our recent AMA on Reddit. Thanks so much for sending in your questions—we love chatting with you and being part of this awesome community!
Meepo Hardfork Features
What does Meepo bring to CKB, in simple terms?
Imagine upgrading from wooden blocks to LEGO bricks. That’s what the
spawnsyscall in Meepo does for CKB smart contracts, enabling script interoperability.Spawn and a series of related syscalls are introduced as a major upgrade to CKB-VM, enabling interoperability, modularity, and better developer experience, by letting scripts call other scripts, like modular apps in an operating system.
Key features of the upgraded VM?
The upgraded CKB-VM Meepo version unlocks true decoupling and reuse of CKB scripts, enhancing modularity and reusability in smart contract development.
For instance, before Meepo, if developers wanted to build a new time lock in CKB, they had to bundle all necessary functionalities—like signature algorithms—directly into a single lock or type script. This often led to bloated scripts where most of the code was unrelated to the developer's original design goal (time lock). With the spawn syscall, scripts can now delegate tasks—such as signature checks—to other on-chain scripts. As new algorithms emerge, the time lock can adopt them without being redeployed—just by calling updated signature scripts, as long as a shared protocol is followed.
This separation allows developers to: - Focus solely on their core logic. - Reuse independently deployed signature verification scripts. - Upgrade cryptographic components without modifying the original script. - Embrace a more OS-like model where smart contracts can call each other to perform specialized tasks.
By enabling true decoupling and reuse, the spawn syscall makes CKB scripts significantly more composable, maintainable, and adaptable.
Besides Spawn, other improvements in Meepo include:
- Block Extension Fields: Enables reading extension fields in blocks, opening new possibilities like community voting on hardforks (as this ckb-zero-lock prototype). More use cases are expected.
- CKB-VM Optimization: Reduces cycle consumption for common compiler-generated code, making scripts faster and more efficient.
A practical example: IPC on Spawn
Here's an example building an entire Inter-Process Communication (IPC) layer on top of spawn syscalls: - GitHub Repo - Blog post: Transforming IPC in CKB On-Chain Script: Spawn and the Custom Library for Simplified Communication
What does “every wallet will become a CKB wallet because of ckb-auth” mean?
Current CKB-VM already comes with the power to build omnilock / ckb-auth, spawn just makes them easier to reuse in new scripts through decoupling and improved modularity.
Upgrade Compatibility Concerns
Will Meepo require a new address format?
No. Meepo does not introduce breaking changes like address format switching. The only required upgrade is support for a new hash type (
data2). We aim to keep upgrades smooth and backwards-compatible wherever possible.RISC-V & CKB’s Long-Term Design Philosophy
Ethereum is exploring RISC-V—CKB has been doing this for years. What’s your take?
The discussion about RISC-V in Ethereum, is partly about the ease of building zk solutions on Ethereum. And it's easy to mix two different use cases of RISC-V in zk:
- Use RISC-V as the language to write programs running in a zk engine. In this case, we use zero knowledge algorithms to build a RISC-VM and prove programs running inside these RISC-V VMs.
- Use RISC-V as the underlying engine to run cryptographic algorithms, we then compile the verifier / prover code of zero knowledge algorithm into RISC-V, then we run those verifiers / provers inside RISC-V. Essentially, we run the verifying / proving algorithms of zero knowledge algorithms in RISC-V, the programs running inside ZK VMs can be written in other languages suiting the zk algorithms.
When most people talk about RISC-V in zk, they mean the first point above. As a result, we see a lot of arguments debating if RISC-V fits in zk circuits. I couldn't get a direct confirmation from Vitalik, but based on what I read, when Vitalik proposes the idea of RISC-V in Ethereum, he's at least partly thinking about the second point here. The original idea is to introduce RISC-V in Ethereum, so we can just compile zk verifiers / provers into RISC-V code, so there is no need to introduce any more precompiles so as to support different zk algorithms in Ethereum. This is indeed a rare taken path, but I believe it is a right path, it is also the path CKB chose 7 years ago for the initial design of CKB-VM.
CKB believes that a precompile-free approach is the only viable path if we’re serious about building a blockchain that can last for decades—or even centuries. Cryptographic algorithms evolve quickly; new ones emerge every few years, making it unsustainable for blockchains to keep adding them as precompiles. In contrast, hardware evolves more slowly and lives longer.
By choosing RISC-V, we’ve committed to a model that can better adapt to future cryptographic developments. CKB may be on an uncommon path, but I believe it's the right one—and it's encouraging to see Ethereum now moving in a similar direction. Hopefully, more will follow.
CKB already stands out as the only blockchain VM built on RISC-V and entirely free from cryptographic precompiles. Meepo, with its spawn syscall, builds on this foundation—pushing for even greater modularity and reuse. We're also closely watching progress in the RISC-V ecosystem, with the goal of integrating hardware advances into CKB-VM, making it even more future-proof and a state-of-the-art execution environment for blockchain applications.
Will CKB run directly on RISC-V chips? What are the implications?
The "CKB on RISC-V"comes in several stages:
- For now, CKB-VM can already be compiled into RISC-V architecture and run on a RISC-V CPU (e.g. StarFive board), though optimized native implementations are still in development.
- That said, one key issue in the previous stage was that CKB-VM lacks a high-performance, assembly based VM on RISC-V architecture. Ironically, despite CKB-VM being based on RISC-V, we ended up running a Rust-based VM interpreter on RISC-V CPUs—which is far from ideal.
The root of the problem is that RISC-V CPUs come in many configurations, each supporting a different set of extensions. Porting CKB-VM to run natively on real RISC-V chips isn’t trivial—some extensions used by CKB-VM might not be available on the target hardware. With enough time and effort, a performant native implementation could be built, but it’s a non-trivial challenge that still needs significant work.
How do you see the RISC-V narrative expanding?
We are delighted to see the growing recognition of RISC-V in the blockchain space. For CKB, we firmly believe RISC-V is the best choice. Consensus is costly, so only essential data should be on-chain, with the chain serving as a universal verification layer—this is CKBʼs philosophy, and we have consistently designed and developed in this direction.
CKB Roadmap & Ecosystem Growth
Any plan to boost the usage of the CKB network in the next 6 - 24 months?
Growth starts with better developer experience. Spawn in Meepo significantly lowers the barrier to building complex apps. With better tools and documentation, more devs can experiment on CKB, leading to better apps and more users.
What would you focus on if the secondary issuance budget was huge?
If funding were abundant, we'd expand the Spark Program, support more grassroots projects, and even evolve toward a fully decentralized DAO structure—aligning with our long-term vision of a permissionless, community-owned network.
What’s next for Nervos after Meepo?
We're exploring new RISC-V extensions like CFI, which could boost script security and defend against ROP attacks. Still early-stage, but promising. Check out this: Against ROP Attacks: A Blockchain Architect’s Take on VM-Level Security.
Resources
Take a deeper look at the VM upgrades introduced in the Meepo hardfork:
Explore the CFI (Control Flow Integrity) extension on RISC-V:
Check out the Inter-Process Communication (IPC) layer built on top of spawn syscalls:
-
 @ b0a838f2:34ed3f19
2025-05-23 17:48:10
@ b0a838f2:34ed3f19
2025-05-23 17:48:10- AnonAddy - Email forwarding service for creating aliases. (Source Code)
MITPHP/Docker - DebOps - Your Debian-based data center in a box. A set of general-purpose Ansible roles that can be used to manage Debian or Ubuntu hosts. (Source Code)
GPL-3.0Ansible/Python - docker-mailserver - Production-ready fullstack but simple mail server (SMTP, IMAP, LDAP, Antispam, Antivirus, etc.) running inside a container. Only configuration files, no SQL database. (Source Code)
MITDocker - Dovel - SMTP server that sends and receives emails according to a simple configuration file, with an optional web interface that you can use to browse your emails. (Source Code)
LGPL-3.0Go - emailwiz - Luke Smith's bash script to completely automate the setup of a Postfix/Dovecot/SpamAssassin/OpenDKIM server on debian.
GPL-3.0Shell - homebox - Suite of Ansible scripts to deploy a fully functional mail server on Debian. Unobtrusive and automatic as much as possible, focusing on stability and security.
GPL-3.0Shell - Inboxen - Lets you have an infinite number of unique inboxes. (Source Code)
GPL-3.0Python - iRedMail - Full-featured mail server solution based on Postfix and Dovecot. (Source Code)
GPL-3.0Shell - Maddy Mail Server - All-in-one mail server that implements SMTP (both MTA and MX) and IMAP. Replaces Postfix, Dovecot, OpenDKIM, OpenSPF, OpenDMARC with single daemon. (Source Code)
GPL-3.0Go - Mail-in-a-Box - Turns any Ubuntu server into a fully functional mail server with one command. (Source Code)
CC0-1.0Shell - Mailcow - Mail server suite based on Dovecot, Postfix and other open source software, that provides a modern Web UI for administration. (Source Code)
GPL-3.0Docker/PHP - Mailu - Simple yet full-featured mail server as a set of Docker images. (Source Code)
MITDocker/Python - Modoboa - Mail hosting and management platform including a modern and simplified web user interface. (Source Code)
ISCPython - Mox - Complete e-mail solution with IMAP4, SMTP, SPF, DKIM, DMARC, MTA-STS, DANE and DNSSEC, reputation-based and content-based junk filtering, Internationalization (IDNA), automatic TLS with ACME and Let's Encrypt, account autoconfiguration, and webmail. (Source Code)
MITGo - Postal - Complete and fully featured mail server for use by websites & web servers. (Source Code)
MITDocker/Ruby - Simple NixOS Mailserver - Complete mailserver solution leveraging the Nix Ecosystem.
GPL-3.0Nix - SimpleLogin - Open source email alias solution to protect your email address. Comes with browser extensions and mobile apps. (Source Code)
MITDocker/Python - Stalwart Mail Server - All-in-one mail server with JMAP, IMAP4, and SMTP support and a wide range of modern features. (Source Code)
AGPL-3.0Rust/Docker - wildduck - Scalable no-SPOF IMAP/POP3 mail server. (Source Code)
EUPL-1.2Nodejs/Docker
- AnonAddy - Email forwarding service for creating aliases. (Source Code)
-
 @ 82b30d30:40c6c003
2025-05-23 09:02:28
@ 82b30d30:40c6c003
2025-05-23 09:02:28nostr:nevent1qqsyeyycax9qgrr4qvtty4h62x96vc6lydh8yg7jl5er99zg7wlpdrch4np3n nostr:nevent1qqs0sqhtzc4p3vysz5k7l29x2lcnedeys55t7mqp2mz7ugrmw0v725cskvqau nostr:nevent1qqsq74xd6qzp9fp8nt8wqpredynnx9t59w9gmzs69jemwu24vjvx78c7wqsl6 nostr:nevent1qqsx6uaegtvy8y47w4fn4dsa0dzkrkjhmwyz9kgq8zw7s3hcg6fuhqg9yywsj nostr:nevent1qqspze6lekfau8063lcup5z0sq62fjhjgr5qjhqy29th28ghsjdendgpvh0ev nostr:nevent1qqsds5j8zk2cx0z4c7ndmq7pgnhtt9hxxu3ee8lq7j69xkpf68u44xgx0v9ux nostr:nevent1qqs20740qquqtt7mrxsqdhftg6rghselqmz8ewp7xsr4v3ltw8ha64scu0suh nostr:nevent1qqsr6sekrmed9g6m7fussfeg4ye5wupplx2wkrul6u8w7yykq6gs7cgz5lwj9 nostr:nevent1qqsfthry2n8yrevtuu8e83gjz2cjv9yh5p43t992h9dx8zy7xs49npq5rp89x nostr:nevent1qqs2rsq8g63z86vw5ta6rcjhtm94u92hhgdv5u7l6ymhy6nulq4awwq58f2af nostr:nevent1qqsdjqf2rwen0sqxvftqg9r6k6404n6ufhl89rn0kyga890ssx7a9pqhvw9z7 nostr:nevent1qqs9j53hpsdpt08f258hnm2sjrgx2anvd7qdrrvqx6ryppslr6lcqdqnammt4 nostr:nevent1qqsx2cs5gf2mlk4a524k2fk0f2fs80t7ryppe0qxyzvexyyh0z2xq0q9ckpgk nostr:nevent1qqsvtkg68twtgm6659v76rxc703qruq6awdxjfdjjcvlwu2r3k4r27sa9qexz nostr:nevent1qqs82g7s2u3560xu95zf55yf4suw52zy5sa6d3p7x2rt8trhcneul7qyze3qd nostr:nevent1qqs2zypn5lpuprgede5ncv0z23ewy8wqf8hqx8ltsdhkmv29jgg3svgc7rv4x nostr:nevent1qqsr9mpqw59703y5dltlycd7yxx9ndkx7xe80emd74nzv7f8uvj9y9saugvlp nostr:nevent1qqsr707sa8jns2ppuyh7kp2jxv6ax4vq7c2y5c2a57y0ewhw2qmpgjc935qgp nostr:nevent1qqsv8gj48n085jtqrr2kaygzcltq026cdn4p448h6s9u25eje8ytvfgu6yyh9 nostr:nevent1qqst2zc68sad5kvklacaqwrh09ghderycqreszwc9schd9zt6z8snzcxzwnwq nostr:nevent1qqszq6fhmm7vuva5ptyflkdstdcknvamlt3j3jj829s59x9d8qw65vslvs39k nostr:nevent1qqst7e22rz3m23mweqdv7ra2mwd7zf4cm3wmvr3hvlc3n2ep6peqjfs753ple nostr:nevent1qqs94rt2exfeuh9v03lftw0s67s0ymuxn8d9vahm08kf2adpwn0h3kgzmfrqw nostr:nevent1qqsysaa7s4apg77tgdx449zwrh86cgrrgm8nl75rk5ezfhk08gemcfq7m7kde nostr:nevent1qqs29glqa5sf3d6nrapqhdlqmmj64xdejf4ky5902s0rcfzyr34gx5s6z9vh2 nostr:nevent1qqswnwcakyyef405uq84u529axlftmc2hq6ejgkefpha38t9fg0tf7ceqarnt nostr:nevent1qqsgpztjppvz0e4lackz9zgutvgtszl9hw6dahlfrmg0u7p3epk9lvgutulpm nostr:nevent1qqszqlx6a695hjnv3m2hwphx2vmu6euw0rmnzqzdgy9d6ud97d9etqshlw6zv nostr:nevent1qqsgfesj07k75v7y5sx070808kd6rr4nf8ptsx685z8kwem7quhk3uc2nhlre nostr:nevent1qqs9qq0tu5t2mrpe8n0f98zewvednrdzqdwsj9vhja9sjtuyjfkmlcswxmjz6 nostr:nevent1qqsfjsjkeq9ux0mjlpzkkcl26vdk7p96paxzlmnp0uckzd3gwtsf9gc32t9ya nostr:nevent1qqs0clwat2zwn4nurlgx9ghlrly8jkk6094hjsz0hd2esxfnkqhcdscnv0xuq nostr:nevent1qqs9vvydt9y0ph230at8mgd4x4juqw89wze2sjthmr4h0rsrg0vmwkc68fass nostr:nevent1qqs8gg9rqrw05hx4a2nmjc7kgc4fxrsd0fqpvz4hg73qel3pxz7yqecwefmha nostr:nevent1qqs9lmvurhnyp0pr8x0ckxnjpt9c6dtnwc0tuczl7uujsc2mf7drfvgjm7s5t nostr:nevent1qqs9n0fvpjl4qmp6nq7s697trhlp9cqydmfwtv0hyevfmnkkjq53ldcp2ue30 nostr:nevent1qqstphjtlec767x53cd0hycul0up5nccje54gyxdakp6rj6jdczw66st3rh78 nostr:nevent1qqstk68pvck7lv6dqlgx9eszmx4h3vyurfxwjgwgg2fw258ws7y7u0s0k28re nostr:nevent1qqs8m2sql8nnzfzpmgqer3vhaxejjeqsyam4q7dt5h58czzezffnsrq7tf2e7 nostr:nevent1qqs2gxp2p69m4xn0z8fmhg7s7krhcu60yszes3sapa9rz89qt8t6zas56lwvq nostr:nevent1qqs9esesyzs2mq93tkcy3wcvtu85rwj5e4m8dh4mk6zma86zz9vv06scurxue nostr:nevent1qqswprrqxz0smcrzn8qexp480jhkg4zjd0n0uphc2wx8pyte4dfavjqjyg7rn nostr:nevent1qqspltzt54qxxu3yjpazxyssm3s6xl8gwxr5eyvuvl8c8epj02e7dkclx3xy7 nostr:nevent1qqsp5ye5klfkf5fzapwscq26jaq84emcd8lku0q2vdky2spf0rhh2as83nnjn nostr:nevent1qqsxsrjh8m77eh3lpn9kacssn7k0mza4z4e9g68q70mqa78p4xjv2tqx28avg nostr:nevent1qqs2h9sg90jxzs08qancaj08qzeu7hh8lss32ny8uaww5m96xp25uus9z5rkz nostr:nevent1qqs2w7us0ef22ervcpya2rk24q5zcjaccae3d5rh9tt5jphfwax493c9pjs86 nostr:nevent1qqs2zr67e5pca9m3lqjw9w72v2h9507d62eya53n8pysle0fhu7adfqkd6hrq nostr:nevent1qqs87zlw6cas3my02fndu2rnfxyzrayqa7g5ptyhsjr37ewmk9jaqwclnp9n5 nostr:nevent1qqsqwpjhgp02jp878c5ftuuxt6czwf5sxcp25ma7p6y9x0sagpwz4tck0cjrt nostr:nevent1qqsyvtujm282xpmstttexzz2u0jxuts0e88t4vcnvg327vw5ju4x74q4wwjh7 nostr:nevent1qqsx6ulpc88x7nqpur3gagkp5uewn3t3a6qelzflejfy86j2y4pqv8gugmhu9 nostr:nevent1qqs9xgvwqy4ephxmfne62d7vucg6mvt8r9vlajw660eq590xnhrg5agv8q4s4 nostr:nevent1qqs9wpg4d0xd8dksnejdewus562f2t2vepyp8fdm6fft4k8t3j4tasguatjx5 nostr:nevent1qqs8lp0skjc83ky4lysegx3cnzxfvy3myskdfwcqs9v7564970ru29qsyc0np nostr:nevent1qqs2vle2yawtsrfftltp9nnzs65vcl4qjtyakap7qkvzd5mg8va4jjqtys34s nostr:nevent1qqsxm5q0xvnrlseh9x2t4k3cr207hzv9veyyt4vtht04yxlgcjk9cpq60l7jw nostr:nevent1qqsvqez6v63mglzj0xwy5d2tqy4956edvtqctncmmhxthgufefsw6wshuvlza nostr:nevent1qqsvk95ngt7u9jfx8l9det80qx39vrlfgkatn3cz3y5pk0g7qu7p2fctqrd2r nostr:nevent1qqsrknzln82etu0pqzhtakemt4c4thszw7kh9zzc85wx9q7y2ltee7gcl4gpu nostr:nevent1qqspws9jvjsj3lzksqvxtche9tvnz55lvurund04pltq92cyrpm3dzqe4zxzt nostr:nevent1qqsf2cmj0txt9l23a2jx9jr0pwsmsr7js2nztgygknltu3alad8mpxqmkm75p nostr:nevent1qqsdh8zc5ydx4nvv4vxgg40xuatg5vdccdy5pn8nqz4x8gchke6sqns2v5ed2 nostr:nevent1qqsptqnt63mntkthndn8ganaatjh08xqrz6fx8y28r85elgrwfk97qsnasax5 nostr:nevent1qqsqp4l0mw3lm0mznvn37dk7wfxsr3e9fvp220v4zjy7fs5u3km5h6cl2u28m nostr:nevent1qqs09m70m33lkafu89xjfpyjft9p3dmcywjsmm7tx30ppxzwy6t3aaq959lff nostr:nevent1qqswpnrgahzcxnqg886gx9vgvsf7tenxgw9uqmtsv95r38m4xu90zwgaekq5s
-
 @ 5c26ee8b:a4d229aa
2025-05-23 08:47:45
@ 5c26ee8b:a4d229aa
2025-05-23 08:47:45Generally mentioning God, Allah, by reciting/reading the Quran or performing Salat (compulsory prayer), for instance, brings tranquility to the heart of the believer. The Salat, other than being the first deed a Muslim would be questioned about on Judgement Day, it keeps the person away from the forbidden wrong deeds too. The Salat is sufficient for obtaining God’s provision as he decrees the means for it to reach the person. Wasting or missing performing the Salat or mentioning God (Allah) by reciting/reading the Quran or Tasbieh, can lead to following the desires only and a depressed life as well as punishment in the Thereafter.
13:28 Ar-Ra'd
الَّذِينَ آمَنُوا وَتَطْمَئِنُّ قُلُوبُهُمْ بِذِكْرِ اللَّهِ ۗ أَلَا بِذِكْرِ اللَّهِ تَطْمَئِنُّ الْقُلُوبُ
Those who have believed and whose hearts are assured (tranquillised) by the remembrance of Allah. Unquestionably, by the remembrance of Allah hearts are assured (tranquillised)."
29:45 Al-Ankaboot
اتْلُ مَا أُوحِيَ إِلَيْكَ مِنَ الْكِتَابِ وَأَقِمِ الصَّلَاةَ ۖ إِنَّ الصَّلَاةَ تَنْهَىٰ عَنِ الْفَحْشَاءِ وَالْمُنْكَرِ ۗ وَلَذِكْرُ اللَّهِ أَكْبَرُ ۗ وَاللَّهُ يَعْلَمُ مَا تَصْنَعُونَ
Recite, [O Muhammad], what has been revealed to you of the Book and establish prayer. Indeed, prayer prohibits immorality and wrongdoing, and the remembrance of Allah is greater. And Allah knows that which you do.
11:114 Hud
وَأَقِمِ الصَّلَاةَ طَرَفَيِ النَّهَارِ وَزُلَفًا مِنَ اللَّيْلِ ۚ إِنَّ الْحَسَنَاتِ يُذْهِبْنَ السَّيِّئَاتِ ۚ ذَٰلِكَ ذِكْرَىٰ لِلذَّاكِرِينَ
And establish prayer at the two ends of the day and at the approach of the night. Indeed, good deeds do away with misdeeds. That is a reminder for those who remember.
20:132 Taa-Haa
وَأْمُرْ أَهْلَكَ بِالصَّلَاةِ وَاصْطَبِرْ عَلَيْهَا ۖ لَا نَسْأَلُكَ رِزْقًا ۖ نَحْنُ نَرْزُقُكَ ۗ وَالْعَاقِبَةُ لِلتَّقْوَىٰ
And enjoin prayer upon your family [and people] and be steadfast therein. We ask you not for provision; We provide for you, and the [best] outcome is for [those of] righteousness.
20:124 Taa-Haa
وَمَنْ أَعْرَضَ عَنْ ذِكْرِي فَإِنَّ لَهُ مَعِيشَةً ضَنْكًا وَنَحْشُرُهُ يَوْمَ الْقِيَامَةِ أَعْمَىٰ
And whoever turns away from My remembrance - indeed, he will have a depressed life, and We will gather him on the Day of Resurrection blind."
20:125 Taa-Haa
قَالَ رَبِّ لِمَ حَشَرْتَنِي أَعْمَىٰ وَقَدْ كُنْتُ بَصِيرًا
He will say, "My Lord, why have you raised me blind while I was [once] seeing?"
20:126 Taa-Haa
قَالَ كَذَٰلِكَ أَتَتْكَ آيَاتُنَا فَنَسِيتَهَا ۖ وَكَذَٰلِكَ الْيَوْمَ تُنْسَىٰ
[Allah] will say, "Thus did Our signs come to you, and you forgot them; and thus will you this Day be forgotten."
20:127 Taa-Haa
وَكَذَٰلِكَ نَجْزِي مَنْ أَسْرَفَ وَلَمْ يُؤْمِنْ بِآيَاتِ رَبِّهِ ۚ وَلَعَذَابُ الْآخِرَةِ أَشَدُّ وَأَبْقَىٰ
And thus do We recompense he who transgressed and did not believe in the signs of his Lord. And the punishment of the Hereafter is more severe and more enduring.
20:128 Taa-Haa
أَفَلَمْ يَهْدِ لَهُمْ كَمْ أَهْلَكْنَا قَبْلَهُمْ مِنَ الْقُرُونِ يَمْشُونَ فِي مَسَاكِنِهِمْ ۗ إِنَّ فِي ذَٰلِكَ لَآيَاتٍ لِأُولِي النُّهَىٰ
Then, has it not become clear to them how many generations We destroyed before them as they walk among their dwellings? Indeed in that are signs for those of intelligence.
49:17 Al-Hujuraat
يَمُنُّونَ عَلَيْكَ أَنْ أَسْلَمُوا ۖ قُلْ لَا تَمُنُّوا عَلَيَّ إِسْلَامَكُمْ ۖ بَلِ اللَّهُ يَمُنُّ عَلَيْكُمْ أَنْ هَدَاكُمْ لِلْإِيمَانِ إِنْ كُنْتُمْ صَادِقِينَ
They consider it a favor to you that they have accepted Islam. Say, "Do not consider your Islam a favor to me. Rather, Allah has conferred favor upon you that He has guided you to the faith, if you should be truthful."
53:29 An-Najm
فَأَعْرِضْ عَنْ مَنْ تَوَلَّىٰ عَنْ ذِكْرِنَا وَلَمْ يُرِدْ إِلَّا الْحَيَاةَ الدُّنْيَا
So turn away from whoever turns his back on Our message and desires not except the worldly life.
53:30 An-Najm
ذَٰلِكَ مَبْلَغُهُمْ مِنَ الْعِلْمِ ۚ إِنَّ رَبَّكَ هُوَ أَعْلَمُ بِمَنْ ضَلَّ عَنْ سَبِيلِهِ وَهُوَ أَعْلَمُ بِمَنِ اهْتَدَىٰ
That is their sum of knowledge. Indeed, your Lord is most knowing of who strays from His way, and He is most knowing of who is guided.
53:62 An-Najm
فَاسْجُدُوا لِلَّهِ وَاعْبُدُوا ۩
So prostrate to Allah and worship [Him].
-
 @ b0a838f2:34ed3f19
2025-05-23 17:47:51
@ b0a838f2:34ed3f19
2025-05-23 17:47:51- AnyCable - Realtime server for reliable two-way communication over WebSockets, Server-sent events, etc. (Demo, Source Code)
MITGo/Docker - Apprise - Apprise allows you to send a notification to almost all of the most popular notification services available to us today such as: Telegram, Discord, Slack, Amazon SNS, Gotify, etc.
MITPython/Docker/deb - Centrifugo - Language-agnostic real-time messaging (Websocket or SockJS) server. (Demo, Source Code)
MITGo/Docker/K8S - Chitchatter - Peer-to-peer chat app that is serverless, decentralized, and ephemeral. (Source Code)
GPL-2.0Nodejs - Conduit - A simple, fast, and reliable chat server powered by Matrix. (Source Code)
Apache-2.0Rust - Databag - Federated, end-to-end encrypted messaging service for the web, iOS, and Android, supporting text, photos, video, and WebRTC video and audio calls. (Demo)
Apache-2.0Docker - Element - Fully-featured Matrix client for Web, iOS & Android. (Source Code)
Apache-2.0Nodejs - GlobaLeaks - Whistleblowing software enabling anyone to easily set up and maintain a secure reporting platform. (Demo, Source Code)
AGPL-3.0Python/deb/Docker - GNUnet - Software framework for decentralized, peer-to-peer networking. (Source Code)
GPL-3.0C - Gotify - Notification server with Android and CLI clients (alternative to PushBullet). (Source Code, Clients)
MITGo/Docker - Hyphanet - Anonymously share files, browse and publish freesites (web sites accessible only through Hyphanet) and chat on forums. (Source Code)
GPL-2.0Java - Jami - Universal communication platform which preserves the user's privacy and freedoms. (Source Code)
GPL-3.0C++ - Live Helper Chat - Live Support chat for your website. (Source Code)
Apache-2.0PHP - Mattermost - Platform for secure collaboration across the entire software development lifecycle, can be integrated with Gitlab (alternative to Slack). (Source Code)
AGPL-3.0/Apache-2.0Go/Docker/K8S - MiAOU - Multi-room persistent chat server. (Source Code)
MITNodejs - Mumble - Low-latency, high quality voice/text chat software. (Source Code, Clients)
BSD-3-ClauseC++/deb - Notifo - Multichannel notification server with support for Email, Mobile Push, Web Push, SMS, messaging and a javascript plugin.
MITC# - Novu - Notification infrastructure for developers. (Source Code)
MITDocker/Nodejs - ntfy - Push notifications to phone or desktop using HTTP PUT/POST, with Android app, CLI and web app, similar to Pushover and Gotify. (Demo, Source Code, Clients)
Apache-2.0/GPL-2.0Go/Docker/K8S - One Time Secret - Share sensitive information securely with self-destructing links that are only viewable once. (Demo, Source Code)
MITDocker/Ruby/Nodejs - OTS - One-Time-Secret sharing platform with a symmetric 256bit AES encryption in the browser. (Source Code)
Apache-2.0Go - PushBits - Notification server for relaying push notifications via Matrix, similar to PushBullet and Gotify.
ISCGo - RetroShare - Secured and decentralized communication system. Offers decentralized chat, forums, messaging, file transfer. (Source Code)
GPL-2.0C++ - Revolt - Revolt is a user-first chat platform built with modern web technologies. (Source Code)
AGPL-3.0Rust - Rocket.Chat - Teamchat solution similar to Gitter.im or Slack. (Source Code)
MITNodejs/Docker/K8S - SAMA - Next-Gen self-hosted chat server and clients. (Demo, Source Code, Clients)
GPL-3.0Nodejs/Docker - Screego - Screego is a simple tool to quickly share your screen to one or multiple people via web browser. (Demo, Source Code)
GPL-3.0Docker/Go - Shhh - Keep secrets out of emails or chat logs, share them using secure links with passphrase and expiration dates.
MITPython - SimpleX Chat - The most private and secure chat and applications platform - now with double ratchet E2E encryption.
AGPL-3.0Haskell - Spectrum 2 - Spectrum 2 is an open source instant messaging transport. It allows users to chat together even when they are using different IM networks. (Source Code)
GPL-3.0C++ - Synapse - Server for Matrix, an open standard for decentralized persistent communication. (Source Code)
Apache-2.0Python/deb - Syndie - Syndie is a libre system for operating distributed forums.
CC0-1.0Java - Tailchat - Next generation noIM application in your own workspace, not only another Slack/Discord/rocket.chat. (Demo, Source Code)
Apache-2.0Docker/K8S/Nodejs - Tiledesk - All-in-one customer engagement platform from lead-gen to post-sales, from WhatsApp to your website. With omni-channel live agents and AI-powered chatbots (alternative to Intercom, Zendesk, Tawk.to and Tidio). (Source Code)
MITDocker/K8S - Tinode - Instant messaging platform. Backend in Go. Clients: Swift iOS, Java Android, JS webapp, scriptable command line; chatbots. (Demo, Source Code, Clients)
GPL-3.0Go - Tox - Distributed, secure messenger with audio and video chat capabilities. (Source Code)
GPL-3.0C - Typebot - Conversational app builder (alternative to Typeform or Landbot). (Source Code)
AGPL-3.0Docker - WBO - Web Whiteboard to collaborate in real-time on schemas, drawings, and notes. (Demo)
AGPL-3.0Nodejs/Docker - Zulip - Zulip is a powerful, open source group chat application. (Source Code)
Apache-2.0Python
- AnyCable - Realtime server for reliable two-way communication over WebSockets, Server-sent events, etc. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:47:26
@ b0a838f2:34ed3f19
2025-05-23 17:47:26- Baïkal - Lightweight CalDAV and CardDAV server based on sabre/dav. (Source Code)
GPL-3.0PHP - DAViCal - Server for calendar sharing (CalDAV) that uses a PostgreSQL database as a data store. (Source Code)
GPL-2.0PHP/deb - Davis - A simple, dockerizable and fully translatable admin interface for sabre/dav based on Symfony 5 and Bootstrap 4, largely inspired by Baïkal.
MITPHP - Etebase (EteSync) - End-to-end encrypted and journaled personal information server supporting calendar and contact data, offering its own clients. (Source Code)
AGPL-3.0Python/Django - Manage My Damn Life - Manage my Damn Life (MMDL) is a self-hosted front end for managing your CalDAV tasks and calendars. (Source Code)
GPL-3.0Nodejs/Docker - Radicale - Simple calendar and contact server with extremely low administrative overhead. (Source Code)
GPL-3.0Python/deb - SabreDAV - Open source CardDAV, CalDAV, and WebDAV framework and server. (Source Code)
MITPHP - Xandikos - Open source CardDAV and CalDAV server with minimal administrative overhead, backed by a Git repository.
GPL-3.0Python/deb
- Baïkal - Lightweight CalDAV and CardDAV server based on sabre/dav. (Source Code)
-
 @ 3ae7fdae:f8d4b19d
2025-01-28 00:00:26
@ 3ae7fdae:f8d4b19d
2025-01-28 00:00:26Lifting the Curtain on Power and Scandal
The Illusion of Power and TrustIn the modern world, the line between trust and skepticism is razor-thin, especially when it comes to powerful figures and organizations. They present polished facades, dazzling us with promises of stability, innovation, or in Disney’s case, enchantment. Yet, the revelations surrounding Jeffrey Epstein’s network reminded us that power is often far more complex than it appears. This scandal became a litmus test for public trust and fueled questions about who, or what, might be entwined in hidden truths.
When Epstein's crimes were exposed, they revealed not just the horrifying details of exploitation, but also the unsettling reach of his influence. As the media peeled back the layers of his associations, public attention naturally shifted to recognizable names and institutions, including Disney. How could a company that represented childhood innocence, with castles and fairy tales, find itself whispered about in the same breath as Epstein’s infamous circle? This segment examines the roots of that question and the facts that illuminate its plausibility or dismiss it.
Epstein: A Man Who Mastered Access to PowerJeffrey Epstein was more than just a financier—he was a gatekeeper to influence. His lifestyle and operations were an entangled web of charm, manipulation, and wealth, meticulously designed to secure him a place among the powerful. Investigative articles by The Guardian and The New York Times depict Epstein as a social engineer, curating relationships that ranged from politicians and royalty to scientists and celebrities.
Court documents and deposition testimonies during Epstein’s trial confirmed that his homes and private jet were hubs for connecting with influential figures. This access did not come without consequence; it cemented him as both a source of curiosity and, later, fear. Public records, such as those scrutinized in The Washington Post, indicated his involvement with many high-profile individuals. Yet, the details of these relationships varied—some guests were casual acquaintances, others, confidants.
The Infamous Flight LogsThe flight logs of Epstein’s private jet, colloquially known as the "Lolita Express," became a centerpiece for public scrutiny. Released through court orders and accessed by journalists, these logs listed names that triggered a cascade of questions. Guests ranged from prominent business executives to entertainment figures, sparking a debate over whether mere association implied complicity or deeper connections. This fueled the narrative that Epstein’s reach was far more extensive than previously understood, implicating industries where entertainment, power, and trust intersected.
The Role of Speculation in Public DiscourseAs soon as these flight logs surfaced, discussions surged online and across media platforms. The presence of any entertainment figure in Epstein’s orbit raised an eyebrow and, in many cases, invited a leap of logic: if influential media personalities were tied to him, could companies known for entertainment and global reach, like Disney, have hidden associations as well? This hypothesis, though lacking concrete evidence, found fertile ground among those predisposed to distrust large, seemingly untouchable institutions.
It’s crucial to dissect why Disney, specifically, became a subject of speculation. On one hand, its status as an omnipresent media empire makes it an easy target for conspiracy theories that thrive on the juxtaposition of light (Disney’s brand) and darkness (Epstein’s crimes). On the other, it speaks to a larger societal impulse to find cracks in the foundations of those we consider infallible. The idea that even the most beloved entities might harbor hidden truths appeals to a deep-seated desire for transparency and accountability.
The Catalyst of Public CuriosityThe timing of Epstein’s exposure was a critical factor. His arrest and subsequent death in 2019 coincided with a period marked by rising distrust in institutions, fueled by political and social upheavals globally. Social media platforms amplified this distrust, creating echo chambers where half-truths and speculative narratives merged seamlessly with confirmed facts.
It is here that Disney’s name began to surface not as an accused, but as a speculative point in discussions. The reasoning often pointed to a "guilt by association" logic: if the powerful dined, flew, or partied with Epstein, then it was worth questioning the circles in which those powerful entities moved, even without direct evidence. This leap from speculation to assumption reflects a pattern that sociologists recognize as part of conspiracy theory psychology—where a lack of clear answers invites the mind to fill in gaps, often with what feels most compelling.
Reframing the Public’s QuestionsThe real question becomes: why does this speculation hold such sway, even when evidence is scarce? Part of the answer lies in precedent. History is replete with instances where institutions that seemed above reproach were later implicated in hidden misdeeds, from financial frauds to abuse scandals within trusted organizations. This collective memory primes the public to believe that beneath any glittering surface could lie a dark, concealed underbelly.
Disney’s position as an icon of childhood and innocence adds another layer to this narrative. To imagine that such a symbol could be tainted by proximity to someone like Epstein is not just shocking—it’s fascinating. It strikes at the core of what we hold sacred, making it an irresistible topic of conversation and investigation.
Why This MattersUnderstanding why names like Disney are brought into these discussions without verified evidence is essential. It helps differentiate between warranted inquiry and unsupported speculation, allowing us to approach these narratives critically. Addressing this head-on does not only clear the air but strengthens the foundation upon which valid criticism and accountability are built.
A Note on EvidenceAs we move deeper into this exploration, it’s critical to emphasize that while Epstein’s connections to high-profile figures are thoroughly documented, there remains no evidence tying Disney, as an organization, to his operations. Still, the fascination with the “what-ifs” continues, driven by our collective quest for understanding power, secrecy, and the thin line between public and private lives.
The next segment will dive into Epstein’s proven network, unraveling the extent of his influence and why it has been the breeding ground for questions involving the world’s most trusted corporations.
Epstein’s Documented Network
The Web of Power: A Portrait of InfluenceJeffrey Epstein’s network was not merely a collection of acquaintances; it was a curated gallery of the world’s most influential figures, built on calculated relationships and strategic connections. Epstein wielded this network with the precision of a skilled operator, bridging disparate realms of society—politics, academia, business, and media. Investigative reporting by sources such as The New York Times and The Guardian exposed how Epstein maintained access to individuals who shaped policy, managed wealth, and crafted the narratives of popular culture.
Court records, testimonies, and detailed analyses of his interactions revealed that Epstein was adept at placing himself at the center of elite circles. His estates, from Manhattan townhouses to private islands, hosted events that blurred the lines between social gatherings and strategic networking. This chapter delves into the proven extent of Epstein’s reach and why it sparked questions about connections to corporations and public institutions, including Disney.
Flight Logs: The Proof and the SparkThe flight logs from Epstein’s private jet, the infamous "Lolita Express," were among the most illuminating pieces of evidence in mapping his connections. These logs, legally obtained and examined by journalists, painted a picture of Epstein’s influence stretching across industries. High-profile figures were listed, including financiers, political leaders, and entertainment personalities. The presence of notable names triggered waves of speculation—if Epstein had access to such power players, how many more remained unnamed but entangled?
The Guardian and The Washington Post reported that these flights were not just transportation but often involved visits to Epstein’s various properties, known for their opulence and the dark rumors surrounding them. While these logs confirmed that many public figures knew Epstein, the depth and nature of their associations varied widely, from casual acquaintance to deeper involvement.
The Limits of the KnownDespite the breadth of documented connections, there was no verifiable evidence linking Disney as an entity to Epstein’s circle. What the flight logs and guest lists revealed was a man deeply embedded in networks of power, yet even within these proven associations, context was crucial. For instance, some guests, confirmed by court records and investigative articles, were shown to have attended public events or engaged in business unrelated to Epstein’s criminal activities.
The distinction between documented presence and complicity is where the narrative often splinters. The leap from association to implication fueled public debate and conspiracy theories. This was especially true when figures from media and entertainment, sectors known for influencing public sentiment and childhood memories, appeared on the periphery of Epstein’s activities.
Epstein’s Parties and Gatherings: The Elite’s Shadowed StageEpstein’s parties were legendary, drawing attendees from the highest echelons of influence. These gatherings were not casual mixers but orchestrated showcases of power. Reports from court depositions and firsthand accounts highlighted how Epstein leveraged these events to cement alliances and reinforce his status as a gatekeeper to the elite. Some testimonies even described how these events served as platforms for discussing investments, politics, and global initiatives, reinforcing Epstein’s perceived omnipotence.
High-Profile Confirmations and Their ImplicationsSeveral prominent individuals were indeed verified as having ties to Epstein, raising legitimate questions about the extent of their knowledge or involvement. These names included politicians, royalty, and entertainment figures. The ambiguity surrounding these associations allowed theories to flourish. The sheer presence of influential names on Epstein’s guest lists raised the question: If these individuals were implicated, what about the institutions they represented or the circles they moved within?
This was a turning point for public speculation. The logic extended: if an individual from a major media company or entertainment empire like Disney was even remotely connected, could that implicate the company itself? The answer, according to existing court records and credible investigations, remained no. Yet, the absence of direct evidence did not stop speculation; in many cases, it intensified it.
Why Disney Was Brought Into the ConversationDisney’s reputation as a family-friendly giant contrasted starkly with the dark nature of Epstein’s activities, making it an unlikely yet intriguing topic for public discourse. While some entertainment figures appeared on Epstein’s flight logs or were rumored to have interacted with him, investigations have not yielded any proof of corporate-level involvement. However, public fascination persisted, bolstered by the broader questions Epstein’s connections evoked.
It’s worth noting that corporations like Disney, with their vast reach and unparalleled influence, naturally become focal points when discussions of hidden truths arise. The mere idea that such an iconic entity could be associated with real-world shadows captures the imagination and fuels stories that, while lacking proof, thrive on the “what-ifs” that echo through media and online forums.
How Public Perception Shapes the NarrativeSociologists studying the psychology of conspiracy theories point out that the human mind tends to fill gaps in knowledge with what feels most plausible or compelling. When figures from reputable media or entertainment companies are tied, even tangentially, to a scandal as vast as Epstein’s, it challenges the boundaries of trust. This is exacerbated when concrete answers remain elusive, leading to a cycle where suspicion feeds speculation.
The public’s thirst for accountability, especially in the wake of uncovered scandals involving powerful institutions, is both a force for truth and a catalyst for assumptions. In Epstein’s case, the proven reach of his influence and the confirmed involvement of significant figures were enough to trigger the question of how many untold stories lay beneath.
What We Know vs. What We ImagineThe narrative surrounding Epstein’s documented network shows us that while connections can be verified and associations noted, the leap to implicating entire organizations like Disney requires more than names on a list or rumors. It requires evidence that has, thus far, not been presented in any court or investigation. The proven facts are compelling enough: Epstein’s influence was extensive, his ties to power irrefutable. Yet, without direct links, the conversations about specific corporate involvement remain speculative.
In the next segment, we will explore why Disney’s reputation makes it a prime target for such speculation and how its historical handling of public crises plays into these narratives.
Disney – The Symbol of Trust and Target of Suspicion
Why Disney? The Paradox of a Trusted InstitutionDisney’s legacy is built on a foundation of storytelling, dreams, and the belief in happy endings. For nearly a century, the company has woven itself into the fabric of childhoods, becoming synonymous with innocence and magic. This legacy, however, has a dual edge. As the public's trust in institutions erodes and hidden truths are revealed in other sectors, Disney’s position as an untouchable cultural icon makes it both a beacon of light and a potential target for suspicion.
The Symbolism of Disney’s BrandDisney represents more than just a company; it embodies an idea—a refuge where imagination and wonder reign. But this same image that has made Disney a household name also contributes to the paradox of suspicion it faces. When an organization is seen as larger than life, transcending generations and continents, the notion that it could have skeletons in its closet becomes a tantalizing thought. The juxtaposition of innocence with possible shadows creates a narrative that is compelling and worth exploring, even if it remains speculative.
This paradox of Disney as both a trusted symbol and a target for scandal reflects a broader trend. Major corporations that hold influence in our everyday lives—particularly those that shape childhood memories and societal values—are natural focal points when scandals involving power, influence, and exploitation arise. The idea that a company with as much reach as Disney could be connected, however tangentially, to figures like Epstein feeds into this pattern.
Documented Misconduct and Public ReactionsThere have been verified cases involving Disney employees engaging in misconduct, which have been reported by media outlets such as NBC News and local news channels. These incidents, though not systemic and unrelated to Epstein’s network, show how the actions of a few can impact public perception of an entire organization. Examples include arrests for crimes involving minors or inappropriate behavior, isolated events that Disney has publicly addressed through statements and cooperation with law enforcement.
However, these incidents were sufficient to plant seeds of doubt in some minds. Even when addressed swiftly and in line with corporate protocols, such cases reveal a vulnerability: the company’s image can be tarnished not just by its policies, but by the misdeeds of individuals who wear its badge.
The Fuel for SpeculationThe Epstein case acted as a catalyst for looking beyond the obvious, particularly in the context of powerful organizations. If political leaders, financiers, and cultural icons could be connected to Epstein’s circle, why not wonder about the involvement of a company with as vast a presence as Disney? While investigations by trusted outlets have shown no direct corporate link, the sheer scope of Epstein’s influence suggested that any entity known for associating with the powerful could be implicated.
This speculation was not helped by Disney’s approach to public relations. The company’s PR strategies, while sophisticated and generally effective, often prioritize message control over transparency. In a world where silence can be seen as complicity, this strategy sometimes backfires, leading to more questions than answers.
Public Distrust and Historical ContextThe public’s fascination with uncovering hidden truths within major institutions is not unfounded. History is replete with cases where seemingly trustworthy organizations were later found to have concealed scandals. From corporate frauds to abuses within religious institutions, these stories have taught the public that innocence is not immune to corruption. This backdrop primes society to believe that even the most beloved entities, like Disney, could harbor secrets.
Sociologists and media analysts argue that this distrust is a byproduct of what they term the “betrayal effect”—where past disappointments with trusted institutions lower the threshold for believing that betrayal could be lurking everywhere. Disney, with its spotless public image and vast influence, becomes an especially juicy target for such theories. The leap from real cases of employee misconduct to more systemic accusations, however, is where evidence often falls short.
The Role of Social Media and Echo ChambersThe digital age has amplified how speculation morphs into perceived truth. Platforms like Twitter, Reddit, and Facebook allow theories to spread quickly, often outpacing fact-checking and nuanced analysis. Discussions that might once have been confined to fringe circles now gain mainstream attention, especially when they involve powerful figures or beloved brands.
In the context of Epstein’s exposure, this meant that any high-profile connection or name could become part of a broader narrative of guilt by association. The fact that Disney, as a corporation, appeared in speculative discussions alongside verified names from Epstein’s logs was enough for some to draw connections, even without direct evidence.
Reputation Management and PerceptionDisney’s approach to crises and controversies has long involved careful reputation management. From its response to legal issues to how it handles employee-related incidents, the company employs sophisticated PR strategies to mitigate damage and maintain its standing. This is standard practice for global brands; however, the public’s interpretation can be different. Strategic silence or tightly controlled statements can come across as evasive, fueling theories that there is something more to hide.
For a company like Disney, which operates at the intersection of family values and global corporate power, the stakes are high. The expectation isn’t just for entertainment but for upholding the moral high ground. When speculation links Disney to scandals, no matter how peripherally, it chips away at this carefully crafted image.
Why Address This Now?The speculation around Disney and Epstein underscores a crucial point about the nature of public inquiry and corporate reputation. It is not enough for companies to rely solely on public relations strategies that worked in the past. The demand for transparency is greater than ever, and silence, even when warranted, can erode trust.
Disney’s role in the public consciousness means that even baseless theories need addressing. By understanding why these narratives gain traction, both companies and the public can engage in more meaningful dialogues about accountability, proof, and trust.
The next segment will delve into how the public navigates between confirmed facts and conspiratorial whispers, exploring why certain theories stick and what it means for how we view powerful organizations.
Separating Fact from Conspiracy
The Thin Line Between Evidence and Speculation In the age of information, where facts are readily available yet often overshadowed by conjecture, separating truth from conspiracy is both an art and a necessity. When powerful entities like Disney find themselves drawn into discussions of hidden networks and scandals involving figures such as Jeffrey Epstein, it highlights a broader societal challenge: how do we differentiate between what is proven and what is assumed? This segment dissects the interplay of evidence, theory, and the psychological factors that drive our need to seek connections.
The Basis of Public Suspicion Public trust in large institutions has waned over decades, driven by a series of high-profile betrayals. From corporate frauds that shattered economies to scandals involving trusted religious or educational institutions, society has learned that power often conceals flaws and, in some cases, criminal actions. According to research published in the Journal of Communication, this erosion of trust leads to a phenomenon known as confirmation bias—the tendency to interpret new evidence as confirmation of one’s existing beliefs or suspicions.
The Epstein case provided fertile ground for such biases. The verified details of Epstein’s operations—the private jet, the exclusive parties, the high-profile guests—were enough to prompt a collective re-examination of how far his reach extended. While many of his associations were proven to be casual or professional in nature, the public’s hunger for deeper revelations ensured that speculation would thrive in areas where clarity was lacking.
The Role of Real Connections Epstein’s documented network included figures from politics, academia, finance, and media. The release of flight logs and court documents revealed that powerful individuals attended his events and interacted within his sphere. This factual basis, verified by investigative reporting from The New York Times, The Guardian, and other reputable sources, provided legitimacy to the idea that Epstein’s influence was pervasive. However, the extent to which these relationships were innocent or complicit was not uniformly clear.
This ambiguity created a vacuum where speculation could flourish. Public attention shifted from individuals named in the logs to the institutions and industries they represented. It was here that major corporations, including Disney, entered the discourse—not because of documented ties, but because of their visibility and influence.
The Psychology Behind Linking Power and Scandal To understand why theories about Disney’s potential involvement in Epstein’s network persist, it is essential to examine the psychology of conspiracy. Sociological and psychological studies indicate that people are naturally inclined to question narratives when they feel that the truth is being withheld. The more powerful or untouchable an institution seems, the more likely it is to be suspected of hiding something significant.
Disney’s image as a global giant that molds childhoods and shapes culture makes it an appealing target for such theories. The company’s public persona as a bastion of family values and innocence stands in stark contrast to any whispers of scandal or misconduct. This contrast alone provides fertile ground for stories to grow, even in the absence of solid proof.
Confirmed Misconduct vs. Conspiracy It is important to acknowledge that Disney, like any large corporation, has faced incidents involving employee misconduct. News reports from outlets such as NBC News have documented cases where employees were arrested for inappropriate conduct involving minors. These cases, while serious and handled with appropriate legal responses, were isolated incidents. No evidence points to these cases being part of a larger, systemic issue within the company or connected to external figures like Epstein.
However, the very existence of these incidents is often enough to keep theories alive. Public perception does not always differentiate between an individual’s actions and the culture of the organization they work for. When these incidents coincide with broader conversations about power and secrecy, they feed into narratives that imply guilt by association.
The Amplifying Power of Social Media The role of social media in shaping and amplifying conspiracy theories cannot be overstated. Platforms like Twitter and Reddit have created spaces where facts, opinions, and theories coexist with little separation. When the Epstein scandal broke, social media was flooded with discussions, many of which featured a mix of verifiable information and speculative connections. The absence of direct evidence linking companies like Disney to Epstein did not deter users from proposing connections based on circumstantial evidence and “what-if” scenarios.
This phenomenon, described by media analysts as the “echo chamber effect,” allows theories to gain credibility through repetition rather than proof. As theories are shared, retweeted, and commented on, they accumulate a sense of legitimacy that belies their origins.
Why Certain Theories Stick Certain theories persist because they tap into deep-seated fears and the knowledge that the powerful often operate beyond the reach of conventional accountability. High-profile scandals involving powerful figures—whether in business, politics, or entertainment—reinforce the belief that more may be hidden just out of reach. Epstein’s network was confirmed to include names that were once considered untouchable, which validated the idea that hidden truths could surface anywhere.
Disney’s name appearing in speculative discussions highlights the intersection of innocence and power. It reflects a societal expectation that if one pillar of influence is shown to be compromised, others may be as well. This expectation, however, must be tempered with critical thinking and an examination of evidence.
The Need for Discernment Understanding the difference between fact and theory is crucial for informed dialogue. Public scrutiny is essential for accountability, but it must be balanced with discernment. While Epstein’s known associations spanned many sectors, and while individuals from the entertainment industry were involved in his circle, the leap to implicating entire organizations like Disney has not been supported by verified investigations.
The Reality Check Here’s what we know:
Documented Facts: Epstein’s network included influential figures, confirmed by court records and journalistic investigations. Disney’s Position: While Disney has faced isolated cases of employee misconduct, no substantial evidence ties the company as an institution to Epstein’s criminal activities. Public Perception: Theories are fueled by a combination of legitimate distrust in powerful institutions and the psychological need to connect the dots, even when the evidence does not support it. In the next segment, we will explore how media control and the use of non-disclosure agreements (NDAs) contribute to the public’s perception of secrecy and whether this perception is warranted.
Media Control and NDAs – Protecting Power or Ensuring Silence?
The Strategy of Silence in Crisis Management When powerful organizations face potential scandal or crises, the first line of defense is often control—control over the narrative, control over information, and control over public perception. This strategy, while effective in mitigating immediate damage, can backfire by fostering an aura of secrecy that leads to suspicion. Disney, like many other global corporations, has historically employed these tactics, particularly through the use of non-disclosure agreements (NDAs) and strategic public relations (PR) campaigns. But do these measures protect legitimate corporate interests, or do they simply fuel theories that there is more being hidden?
Understanding the Role of NDAs NDAs are legal tools designed to maintain confidentiality and protect business interests. In most cases, their use is standard practice, whether to protect trade secrets, secure settlements, or manage sensitive internal matters. However, when NDAs intersect with scandals involving powerful individuals or organizations, they can become symbols of enforced silence. A report from the Harvard Business Review highlights that while NDAs are often employed for legitimate purposes, their misuse—especially when used to silence allegations of misconduct—has cast a shadow over their intent.
Disney has used NDAs in its corporate dealings, as have many in the media and entertainment sectors. This is not in itself suspicious; however, the mere presence of NDAs in a company’s arsenal can contribute to a narrative of secrecy, especially when paired with limited transparency during controversies.
The Case of High-Profile Secrecy The Epstein scandal showed how the use of NDAs and strategic silence could be perceived in a different light. When influential figures and companies were linked to his circle, silence from those implicated was interpreted by many as an attempt to avoid deeper inquiry. While Disney has not been tied to Epstein’s activities through verified evidence, its use of NDAs in unrelated circumstances and its approach to handling public controversies have made it a recurring subject in theories about hidden truths.
For example, Disney’s meticulous control over its brand image means that it often handles internal issues privately, releasing carefully crafted statements that address public concerns without divulging specifics. This approach, while protective, sometimes has the unintended consequence of making the public wonder what is not being said.
The Intersection of PR and Public Perception Public relations are designed to safeguard a company’s image, ensuring that responses to any negative news are swift and tightly managed. Disney’s PR machine is among the most sophisticated, capable of steering narratives and maintaining its reputation as an entertainment titan. This strategic control has allowed Disney to weather crises that might have permanently damaged lesser brands. However, in the context of a scandal as sprawling and notorious as Epstein’s, such control is perceived differently.
When the Epstein story broke and high-profile connections came to light, companies with any tenuous ties activated their crisis management protocols. For some, this meant issuing vague statements or refusing to comment altogether. To the public, this read as silence—a strategic choice that seemed suspicious when paired with known instances of NDAs being used to keep serious allegations quiet in other industries. The #MeToo movement, for instance, revealed how NDAs were used by some media companies to shield powerful perpetrators of harassment, showing that these tools can sometimes contribute to a culture of concealment.
Silence as Complicity? For a company like Disney, known for its polished public image, silence during times of widespread speculation can amplify suspicions. The question becomes: Is silence an act of protection or complicity? While NDAs are often used to manage settlements or protect internal processes, the fact that they prevent full transparency can make even innocent parties appear as if they have something to hide.
Experts in crisis communication argue that silence may protect the brand short-term but can erode trust long-term. Disney’s approach to handling public perception, from managing employee misconduct cases to addressing larger social controversies, often involves strategic responses that give the public enough information to stay satisfied but not enough to quell the more skeptical voices. This is standard practice but becomes contentious when the public is searching for accountability.
The Impact of Strategic Silence on Public Trust Media and communication studies have shown that transparency is increasingly becoming a measure of trustworthiness for corporations. In an era where the public demands answers and alternative media thrive on filling in gaps left by corporate PR, the stakes for maintaining trust are higher than ever. The use of NDAs and controlled statements can protect a company’s interests, but it also contributes to a perception of secrecy that feeds public doubt.
Disney’s balancing act—protecting its brand while managing incidents behind closed doors—reflects a broader industry trend. Corporations that prioritize narrative control must now reckon with an environment where even a hint of concealment can lead to damaging speculation. The Epstein case amplified this issue, putting the spotlight on how major organizations handle proximity to scandal, even if only by association.
Navigating the Perception The real challenge for Disney and similar companies lies in navigating the fine line between protecting their interests and fostering trust. Complete transparency can be risky, but strategic silence risks becoming complicit silence in the eyes of the public. This duality—where necessary protection measures are perceived as proof of hidden wrongdoing—is why entities like Disney find themselves caught up in discussions about figures like Epstein, despite the absence of concrete evidence.
The Takeaway for Institutions and the Public Understanding the role of NDAs and PR in managing public crises helps frame why powerful companies might become targets of suspicion. While the use of these tools is standard and often justified, their impact on public perception can’t be ignored. For the public, recognizing the difference between warranted inquiry and overreach is key to maintaining productive scrutiny without falling into the trap of baseless theories.
The next segment will focus on what these perceptions mean for society as a whole and why the pursuit of transparency and trust must be a collective endeavor.
Beyond the Shadows – A Call to Unity
The Complex Path to UnderstandingIn an age where trust in powerful institutions is fraying, and access to information is both a blessing and a burden, our approach to truth becomes more critical than ever. The discussions surrounding figures like Jeffrey Epstein and corporations like Disney are not just about scandal; they are about how we, as a society, confront power, secrecy, and transparency. This segment is a call to unite in the pursuit of truth—not through a divisive lens, but with collective discernment and an unwavering commitment to evidence and integrity.
The Lessons from HistoryHistory teaches us that institutions once seen as untouchable can harbor hidden truths. The exposure of corporate frauds, systemic abuses, and cover-ups within trusted sectors has shaped a society that questions everything. The Epstein scandal underscored this, revealing a network of power that reached further than many dared to imagine. Yet, while it validated the public’s instinct to question, it also highlighted a key challenge: differentiating between grounded inquiry and baseless theory.
Disney’s name appearing in speculative discussions about Epstein points to a broader pattern—our collective desire to ensure that those who hold power are not above scrutiny. But as we demand accountability, we must also unite in the practice of informed skepticism. The leap from isolated cases of misconduct or association to implicating entire organizations requires evidence, not just conjecture. This distinction is where we, as a society, must find common ground.
The Role of TransparencyTransparency has become the cornerstone of public trust. Organizations that handle controversies behind closed doors risk damaging their credibility. For companies like Disney, known for protecting their brand with meticulous care, the challenge is clear: find a balance between safeguarding legitimate interests and providing enough transparency to maintain public trust.
The use of NDAs, strategic silence, and controlled narratives may shield brands in the short term, but they can erode trust in the long run. Studies in crisis communication emphasize that openness, even when it exposes vulnerabilities, can reinforce loyalty and confidence among stakeholders. In the context of Epstein and the persistent whispers about powerful corporations, this lesson is especially relevant.
A Collective Call to ClarityThe pursuit of truth is not just the responsibility of journalists, whistleblowers, or industry watchdogs—it is a collective endeavor. The public plays a crucial role in this, but so do the corporations that hold sway over cultural and economic landscapes. When Disney’s name enters speculative discussions, it reflects a deep-seated desire for transparency from those we trust. This desire should be met not with fear of the unknown but with a commitment to clarity.
This segment is a call for unity in approaching these conversations. The balance between healthy skepticism and conspiracy theory is delicate but essential. We must ask hard questions and hold power accountable without losing sight of what separates substantiated fact from assumption.
Why Unity MattersIn times where speculation can divide and misinformation can spread faster than verified facts, unity in the pursuit of truth is vital. When we allow fear and uncertainty to fracture our approach, we weaken our collective power to bring genuine issues to light. Epstein’s case showed that hidden wrongs do exist and can involve the most influential figures. It also showed that uncovering the full scope of such wrongs takes a community committed to patience, evidence, and shared purpose.
Public scrutiny is essential for democracy and social justice, but so is discernment. When theories about organizations like Disney arise without evidence, they risk diverting attention from real, proven issues that demand action. Unity in seeking truth means supporting real investigations, demanding transparency, and recognizing the power of evidence-based inquiry.
Building a Culture of Informed AccountabilityThe goal is not to silence questions but to elevate them, ensuring that they are grounded in reality. This approach not only empowers the public but also sets a standard for institutions. If Disney and other corporations prioritize transparency, they can reinforce the public trust that sustains their brands. Similarly, when the public insists on evidence and integrity in its discussions, it strengthens the very fabric of accountability.
Reflections for the Road AheadAs we move forward, let us commit to being a society that seeks truth not for scandal’s sake but for justice and integrity. Let us stand together in holding power to account, using facts as our foundation and unity as our strength. The story of Epstein and the questions it raises about power, influence, and hidden truths are reminders that transparency and trust are not just corporate responsibilities—they are collective ones.
This call to unity is a reminder that we all play a part in shaping how these stories unfold. When we seek, question, and demand clarity together, we create a society that values truth over rumor, evidence over assumption, and justice over division.
As we conclude this exploration, may we carry forward the lessons learned: the importance of questioning with integrity, seeking truth with diligence, and facing the unknown not as individuals, but as a united community.
-
 @ 975e4ad5:8d4847ce
2025-05-23 08:47:08
@ 975e4ad5:8d4847ce
2025-05-23 08:47:08Bitcoin Is Not Just an Asset
When Satoshi Nakamoto introduced Bitcoin in 2009, the vision was clear: a decentralized currency for everyday transactions, from buying coffee to paying bills. It was designed to bypass banks and governments, empowering individuals with financial freedom. But when Bitcoin is treated as “digital gold” and locked away in wallets, it fails to fulfill this vision. Instead of replacing fiat currencies, it becomes just another investment, leaving people reliant on dollars, euros, or other traditional currencies for their daily needs.
The Problem with HODLing and Loans
Some Bitcoin enthusiasts advocate holding their coins indefinitely and taking loans against them rather than spending. This approach may seem financially savvy—Bitcoin’s value often rises over time, and loans provide liquidity without selling. But this prioritizes personal gain over the broader goal of financial revolution. Someone who holds Bitcoin while spending fiat isn’t supporting Bitcoin’s mission; they’re merely using it to stay wealthy within the existing system. This undermines the dream of a decentralized financial future.
Lightning Network: Fast and Cheap Transactions
One common argument against using Bitcoin for daily purchases is the high fees and slow transaction times on the main blockchain. Enter the Lightning Network, a second-layer solution that enables near-instant transactions with minimal fees. Imagine paying for groceries or ordering a pizza with Bitcoin, quickly and cheaply. This technology makes Bitcoin practical for everyday use, paving the way for widespread adoption.
Why Using Bitcoin Matters
If Bitcoin is only hoarded and not spent, it will remain a niche asset that shields against inflation but doesn’t challenge the fiat system. For Bitcoin to become a true alternative currency, it must be used everywhere—in stores, online platforms, and peer-to-peer exchanges. The more people and businesses accept Bitcoin, the closer we get to a world where decentralized currency is the norm. This isn’t just an investment; it’s a movement for financial freedom.\ \ Bitcoin wasn’t created to sit idly in wallets or serve as collateral for loans. It’s a tool for change that demands active use. If we want a world where individuals control their finances, we must start using Bitcoin—not just to avoid poverty, but to build a new financial reality.
-
 @ b0a838f2:34ed3f19
2025-05-23 17:47:03
@ b0a838f2:34ed3f19
2025-05-23 17:47:03- Briefkasten - Modern app for saving and managing your own bookmarks. Includes a browser extension. (Demo)
MITNodejs/Docker - Buku - Powerful bookmark manager and a personal textual mini-web.
GPL-3.0Python/deb - Digibunch - Create bunches of links to share with your learners or colleagues. (Demo, Source Code)
AGPL-3.0Nodejs/PHP - Espial - An open-source, web-based bookmarking server.
AGPL-3.0Haskell - Firefox Account Server - Host your own Firefox accounts server. (Source Code)
MPL-2.0Nodejs/Java - Grimoire - Bookmark manager with a modern UI, automatic content & metadata extraction, categorization, filtering, and more. It has fully documented REST API, and Docker image for easy deployment. (Source Code)
MITNodejs/Docker - Karakeep - Bookmark-everything app with a touch of AI for the data hoarders out there. (Demo, Source Code)
AGPL-3.0Docker - LinkAce - Bookmark archive with automatic backups to the Internet Archive, link monitoring, and a full REST API. Installation is done via Docker, or as a simple PHP application. (Demo, Source Code)
GPL-3.0Docker/PHP - linkding - Minimal bookmark management with a fast and clean UI. Simple installation through Docker and can run on your Raspberry Pi. (Demo, Source Code)
MITDocker - LinkWarden - Bookmark and archive manager to store your useful links. (Source Code)
MITDocker/Nodejs - NeonLink - Bookmark service with unique design and simple installation with Docker.
MITDocker - Readeck - Readeck is a simple web application that lets you save the precious readable content of web pages you like and want to keep forever. See it as a bookmark manager and a read later tool. (Source Code, Clients)
AGPL-3.0Go/Docker - Servas - A self-hosted bookmark management tool. It allows organization with tags, groups, and a list specifically for later access. It supports multiple users with 2FA. Companion browser extensions are available for Firefox and Chrome. (Clients)
GPL-3.0Docker/Nodejs/PHP - Shaarli - Personal, minimalist, super-fast, no-database bookmarking and link sharing platform. (Demo)
ZlibPHP/deb - Shiori - Simple bookmark manager built with Go.
MITGo/Docker - Slash - An open source, self-hosted bookmarks and link sharing platform.
GPL-3.0Docker - SyncMarks - Sync and manage your browser bookmarks from Edge, Firefox and Chromium. (Clients)
AGPL-3.0PHP
- Briefkasten - Modern app for saving and managing your own bookmarks. Includes a browser extension. (Demo)
-
 @ b0a838f2:34ed3f19
2025-05-23 17:46:16
@ b0a838f2:34ed3f19
2025-05-23 17:46:16- Alf.io - Ticket reservation system. (Demo, Source Code)
GPL-3.0Java - Cal.com - Online appointment scheduling system. (Demo, Source Code)
AGPL-3.0Nodejs - Easy!Appointments - Allows your customers to book appointments with you via the web. (Demo, Source Code)
GPL-3.0PHP - Hi.Events - Event management and ticketing platform for conferences, concerts, and more. Offering customizable event pages and embeddable ticket widgets. (Demo, Source Code)
AGPL-3.0Docker - QloApps - Customizable and intuitive web-based hotel reservation system and a booking engine. (Demo, Source Code)
OSL-3.0PHP/Nodejs - Rallly - Create polls to vote on dates and times (alternative to Doodle). (Demo, Source Code)
AGPL-3.0Nodejs/Docker - Seatsurfing - Webbased app to book seats, desks and rooms for offices. (Source Code)
GPL-3.0Docker
- Alf.io - Ticket reservation system. (Demo, Source Code)
-
 @ eb0157af:77ab6c55
2025-05-23 08:01:20
@ eb0157af:77ab6c55
2025-05-23 08:01:20According to CEO Jamie Dimon, the banking giant will open the door to spot Bitcoin ETFs.
As reported by CNBC, JPMorgan has announced that it will allow its clients to buy Bitcoin, without offering custody services. The bank will give clients access to exchange-traded funds (spot ETFs) on Bitcoin, according to sources familiar with the matter.
During a recent investor event, CEO Jamie Dimon confirmed that the bank will open up to Bitcoin for its clients, while refraining from taking on the responsibility of asset custody. “I am not a fan” of Bitcoin, Dimon clarified during the event.
This decision marks a shift from the position Dimon held in 2017, when he labeled Bitcoin a “fraud,” compared it to the tulip mania bubble, and predicted its imminent collapse. At the time, Dimon had even threatened to fire any JPMorgan employee caught trading Bitcoin, calling such activity “stupid” and against company policy.
Despite this operational turnaround, Dimon continues to personally maintain a skeptical stance toward the cryptocurrency. In a 2024 interview with CNBC, he stated he no longer wanted to discuss Bitcoin publicly, emphasizing that, in his view, it lacks “intrinsic value” and is used for criminal activities such as sex trafficking, money laundering, and ransomware.
These comments from Dimon contrast with the recent optimism shown by JPMorgan analysts regarding Bitcoin’s market prospects. According to reports from the bank, Bitcoin could continue gaining ground at the expense of gold in the second half of the year, driven by rising corporate demand and growing support from various U.S. states.
The post JPMorgan to allow clients to buy Bitcoin ETFs: no custody services appeared first on Atlas21.
-
 @ b0a838f2:34ed3f19
2025-05-23 17:45:55
@ b0a838f2:34ed3f19
2025-05-23 17:45:55- Antville - Free, open source project aimed at the development of a high performance, feature rich weblog hosting software. (Source Code)
Apache-2.0Javascript - Castopod - Podcast management hosting platform that includes the latest podcast 2.0 standards, an automated Fediverse feed, analytics, an embeddable player, and more. (Source Code)
AGPL-3.0PHP/Docker - Chyrp Lite - Extra-awesome, extra-lightweight blog engine. (Source Code)
BSD-3-ClausePHP - Dotclear - Take control over your blog.
GPL-2.0PHP - FlatPress - A lightweight, easy-to-set-up flat-file blogging engine. (Source Code)
GPL-2.0PHP - Ghost - Just a blogging platform. (Source Code)
MITNodejs - Haven - Private blogging system with markdown editing and built in RSS reader. (Demo, Source Code)
MITRuby - HTMLy - Databaseless PHP blogging platform. A flat-file CMS that allows you to create a fast, secure, and powerful website or blog in seconds. (Demo, Source Code)
GPL-2.0PHP - Known - Collaborative social publishing platform. (Source Code)
Apache-2.0PHP - Mataroa - Naked blogging platform for minimalists. (Source Code)
MITPython - PluXml - XML-based blog/CMS platform. (Source Code)
GPL-3.0PHP - Serendipity - Serendipity (s9y) is a highly extensible and customizable PHP blog engine using Smarty templating. (Source Code)
BSD-3-ClausePHP - WriteFreely - Writing software for starting a minimalist, federated blog — or an entire community. (Source Code)
AGPL-3.0Go
- Antville - Free, open source project aimed at the development of a high performance, feature rich weblog hosting software. (Source Code)
-
 @ 662f9bff:8960f6b2
2025-05-23 07:38:51
@ 662f9bff:8960f6b2
2025-05-23 07:38:51I have been really busy this week with work - albeit back in Madeira - so I had little time to read or do much other than work. In the coming weeks I should have more time - I am taking a few weeks off work and have quite a list of things to do.
First thing is to relax a bit and enjoy the pleasant weather here in Funchal for a few days. With 1st May tomorrow it does seem that there will be quite a bit to do..
Some food for thought for you. Who takes and makes your decisions? Do you make them yourself based on information that you have and know to be true or do you allow other people to take and make decisions for you? For example - do you allow governments or unaccountable beaureaucrats and others to decide for you and even to compell you?
In theory Governments should respect Consent of the Governed and the 1948 Universal Declaration of Human Rights states that "The will of the people shall be the basis of the authority of government". For you to decide if and to what extent governments today are acting in line with these principles. If not, what can you do about it? I dive into this below and do refer back to letter 9 - section: So What can you do about it.
First, a few things to read, watch and listen to
-
I Finance the Current Thing by Allen Farrington - when money is political, everything is political...
-
Prediction for 2030 (the Great Reset). Sorelle explains things pretty clearly if you care to watch and listen...
-
The Global Pandemic Treaty: What You Need to Know . James Corbett is pretty clear too... is this being done with your support? Did you miss something?
-
Why the Past 10 Years of American Life Have Been Uniquely Stupid - fascinating thinking on how quite a few recent things came about...
And a few classics - you ought to know these already and the important messages in them should be much more obvious now...
-
1984 by George Orwell - look for the perpetual war & conflict, ubiquitous surveillance and censorship not to mention Room 101
-
Animal farm - also by George Orwell - note how the pigs end up living in the farmhouse exceeding all the worst behaviour of the farmer and how the constitution on the wall changes. Things did not end well for loyal Boxer.
-
Brave New World by Aldous Huxley- A World State, inhabited by genetically modified citizens and an intelligence-based social hierarchy - the novel anticipates large scale psychological manipulation and classical conditioning that are combined to make a dystopian society which is challenged by only a single individual who does not take the Soma.
For more - refer to the References and Reading List
The 7 Habits of Highly Effective People
One of the most transformative books that I ever read was 7 Habits of Highly Effective People by Steven Covey. Over many years and from researching hstorical literature he found seven traits that successful people typically display. By default everyone does the opposite of each of these! Check how you do - be honest...
-
Habits 1-3 are habits of Self - they determine how you behave and feel
-
Habits 4-6 are habits of interpersonal behaviour - they determine how you deal with and interact with others
-
Habit 7 is about regeneration and self care - foundation for happy and healthy life and success
One: Be proactive
Choose your responses to all situations and provocations - your reaction to a situation determines how you feel about it.
By default people will be reactive and this controls their emotions
Two: Begin with the end in mind
When you start to work on something, have a clear view of the goal to be achieved; it should be something substantial that you need and will value.
By default people will begin with what is in front of them or work on details that they can do or progress without having a clear view on the end result to be achieved
Three: Put First things First
Be clear on, and begin with, the Big Rocks- the most important things. If you do not put the Big Rocks into your planning daily activities, your days will be full of sand and gravel! All things can be categorised as Urgent or Not-Urgent and Important or Not-Important.
By Default people will focus on Urgent regardless of importance - all of the results come from focusing on Important Non-Urgent things. All of the 7 Habits are in this category!
Four: Seek Win-Win in all dealings with people and in all negotiations
This is the only sustainable outcome; if you cannot achieve Win-Win then no-deal is the sustainable alternative.
By default people will seek Win-Loose - this leads to failed relationships
Five: Seek first to understand - only then to be understood.
Once you visibly understand the needs and expectations of your counterpart they will be open to listening to your point of view and suggestions/requests - not before!
By default people will expound their point of view or desired result causing their counterpart to want to do the same - this ends in "the dialogue of the deaf"
Six: Synergise - Seek the 3rd alternative in all problems and challenges
Work together to find a proposal that is better than what each of you had in mind
By default people will focus on their own desired results and items, regardless of what the other party could bring to help/facilitate or make available
Seven: Sharpen the saw
Take time to re-invigorate and to be healthy - do nothing to excess. Do not be the forrester who persists in cutting the tree with a blunt saw bcause sharpening it is inconvenient or would "take too much time"!
By default people tend to persist on activities and avoid taking time to reflect, prepare and recover
Mindaps - a technique by Tony Buzan
Many years ago I summarised this in a Mind Map (another technique that was transformative for me - a topic for another Letter from around the world!) see below. Let me know if this interests you - happy to do an explainer video on this!
That's it!
No one can be told what The Matrix is.\ You have to see it for yourself.**
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
-
 @ 05a0f81e:fc032124
2025-05-23 17:45:46
@ 05a0f81e:fc032124
2025-05-23 17:45:46The evolution of money has been a long journey, transforming from primitive bartering systems to sophisticated digital currencies. Here's a breakdown of the major stages:
- Barter System (circa 6000 BCE).
In the early days, people exchanged goods and services without using money. This system had limitations, as it required a double coincidence of wants, where both parties had to want what the other offered. Bartering was used in ancient Mesopotamia, and it's still used today in some parts of the world.
- Commodity Money (3000 BCE - 500 BCE).
As societies grew, commodity money emerged as a medium of exchange. Items like salt, cattle, grains, and shells were widely accepted due to their intrinsic value. These commodities were used to buy goods and services, but they had limitations due to their bulk and perishable nature.
- Metal Coins (600 BCE)
The introduction of metal coins revolutionized trade. Coins were made from precious metals like gold, silver, and copper, and were stamped with symbols or images to guarantee their authenticity. The first coins were minted in ancient Lydia (modern-day Turkey) and quickly spread to other civilizations.
- Paper Money (11th century CE)
Paper money was first introduced in China during the Song Dynasty. Initially, it was used as a convenient alternative to heavy metal coins. Over time, paper money evolved into fiat money, where its value was determined by government decree rather than a physical commodity.
- Banking and Fiat Money (17th century CE).
The development of banking systems allowed for the issuance of banknotes and the facilitation of financial transactions. Fiat money emerged as a dominant form of currency, where its value was determined by government decree and public trust.
- Digital Currencies (20th century CE).
The rise of digital technologies led to the emergence of digital currencies like cryptocurrencies (e.g., Bitcoin) and online payment systems. These digital currencies operate independently of central banks and offer a new way to conduct transactions.
Key Milestones:
- First coins: Ancient Lydia (modern-day Turkey), 600 BCE
- First paper money: China, 11th century CE.
- Gold standard: England, 1816.
- Fiat money: Global adoption, 20th century CE.
- Digital currencies: Emerged in the late 20th century CE, with Bitcoin launching in 2009.
The evolution of money reflects human innovation and the need for efficient and convenient ways to conduct transactions. From bartering to digital currencies, money has come a long way, shaping economies and societies along the way.
-
 @ 502ab02a:a2860397
2025-05-23 07:35:13
@ 502ab02a:a2860397
2025-05-23 07:35:13แหม่ ต้องรีบแวะมาเขียนไว้ก่อน ของกำลังร้อนๆ #ตัวหนังสือมีเสียง เพลง ลานกรองมันส์ นั้นเรื่องที่มาที่ไปน่าจะไปตามอ่านในเพจ ลานกรองมันส์ ได้ครับ recap คร่าวๆคือมันคือ พื้นที่สร้างสรรค์ที่เปิดให้มาทำกิจกรรมต่างๆนานากันได้ครับ
วันนี้เลยจะมาเล่าเรื่องวิธีการใช้คำ ซึ่งมันส์ดีตามชื่อลาน ฮาๆๆๆ ผมตั้งโจทย์ไว้เลยว่า ต้องมีคำว่า ลานกรองมันส์ แน่ๆแล้ว เพราะเป็นชื่อสถานที่ จากนั้นก็เอาคำว่า ลานกองมัน มาแตกขยายความเพราะมันคือต้นกำเนิดเดิมของพื้นที่นั้น คือเป็นลานที่เอาหัวมันมากองกันเอาไว้ รอนำไปผลิตต่อเป็นสินค้าการเกษตรต่างๆ
ตอนนี้เขาเลิกทำไปแล้ว จึงกลายมาเป็น ลานกรองมันส์ ที่เอาชื่อเดิมมาแปลง
เมื่อได้คำหลักๆแล้วผมก็เอาพยัญชนะเลย ลอลิง กอไก่ มอม้า คือตัวหลักของเพลง
โทนดนตรีไม่ต้องเลือกเลยหนีไม่พ้นสามช่าแน่นอน โทนมันมาตั้งแต่เริ่มคิดจะเขียนเลยครับ ฮาๆๆๆ
ผมพยายามแบ่งวรรคไว้ชัดๆ เผื่อไว้เลยว่าอนาคตอาจมีการทำดนตรีแบบแบ่งกันร้อง วรรคของมันเลยเป็น หมู่ เดี่ยว หมู่ เดี่ยว หมู่ เดี่ยว หมู่ แบบสามโทนเลย
ท่อนหมู่นั้น คิดแบบหลายชั้นมากครับ โดยเฉพาะคำว่า มัน เอามันมากอง มันที่ว่าได้ทั้งเป็นคำกิริยา คือ เอามันมากองๆ หรือ มันที่ว่าอาจหมายถึงตัวความฝันเองเป็นคำลักษณะนามเรียกความฝัน "ลานกรองมันส์ เรามาลองกัน มาร่วมกันมอง ลานกรองมันส์ มาร่วมสร้างฝัน เอามันมากอง"
หรือแม้แต่ท่อนต่างๆ ก็เล่นคำว่า มัน กอง เพื่อให้รู้สึกย้ำท่อนหมู่ ที่มีคำว่ามัน เป็นพระเอกหลายหน้า ทั้งความสนุก ทั้งลักษณะนามความฝัน ทั้งกิริยา "ทุกคน ต่างมี ความฝัน เอามา รวมกัน ให้มันเป็นกอง"
อีกท่อนที่ชอบมากตอนเขียนคือ ทำที่ ลานกรองมันส์ idea for fun everyone can do เพราะรู้สึกว่า การพูดภาษาอังกฤษสำเนียงไทยๆ มันตูดหมึกดี ฮาๆๆๆๆ
หัวใจของเพลงคือจะบอกว่า ใครมีฝันก็มาเลย มาทำฝันกัน เรามีที่ให้คุณ ไม่ต้องกลัวอะไรที่จะทำฝันของตัวเอง เล็กใหญ่ ผิดถูก ขอให้ทำมัน อย่าให้ใครหยุดฝันของคุณ นอกจากตัวคุณเอง
เพลงนี้ไม่ได้ลงแพลทฟอร์ม เพราะส่งมอบให้ทาง ลานกรองมันส์เขาครับ ใช้ตามอิสระไปเลย ดังนั้นก็อาจต้องฟังในโพสนี้ หรือ ในยูทูปนะครับ https://youtu.be/W-1OH3YldtM?si=36dFbHgKjiI_9DI8
เนื้อเพลง "ลานกรองมันส์"
ลานกรองมันส์ ขอเชิญทุกท่าน มามันกันดู นะโฉมตรู มาลองดูกัน อ๊ะ มาลันดูกอง
มีงาน คุยกัน สังสรรค์ ดื่มนม ชมจันทร์ ปันฝัน กันเพลิน ทุกคน ต่างล้วน มีดี เรานั้น มีที่ พี่นี้มีโชว์ เอ้า
ลานกรองมันส์ เรามาลองกัน มาร่วมกันมอง ลานกรองมันส์ มาร่วมสร้างฝัน เอามันมากอง
จะเล็ก จะใหญ่ ให้ลอง เราเป็น พี่น้อง เพื่อนพ้อง ต้องตา ทุกคน ต่างมี ความฝัน เอามา รวมกัน ให้มันเป็นกอง เอ้า
ลานกรองมันส์ เรามาลองกัน มาร่วมกันมอง ลานกรองมันส์ มาร่วมสร้างฝัน เอามันมากอง
ชีวิต เราคิดเราทำ ทุกสิ่งที่ย้ำ คือทำสุดใจ จะเขียน จะเรียน จะรำ ทำที่ ลานกรองมันส์ idea for fun everyone can do
ลานกรองมันส์ เรามาลองกัน มาร่วมกันมอง ลานกรองมันส์ มาร่วมสร้างฝัน เอามันมากอง
เรามา ลั่นกลองให้มัน เฮไหนเฮกัน ที่ลานกรองมันส์ ให้ฝัน บันเทิง…
ตัวหนังสือมีเสียง #pirateketo #siamstr
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ b0a838f2:34ed3f19
2025-05-23 17:45:36
@ b0a838f2:34ed3f19
2025-05-23 17:45:36- Activepieces - No-code business automation tool like Zapier or Tray. For example, you can send a Slack notification for each new Trello card. (Source Code)
MITDocker - Apache Airflow - Platform to programmatically author, schedule, and monitor workflows. (Source Code)
Apache-2.0Python/Docker - Automatisch - Business automation tool that lets you connect different services like Twitter, Slack, and more to automate your business processes (alternative to Zapier). (Source Code)
AGPL-3.0Docker - BookBounty
⚠- Retrieve missing Readarr books from Library Genesis.MPL-2.0Docker - changedetection.io - Stay up-to-date with web-site content changes. (Source Code)
Apache-2.0Python/Docker - ChiefOnboarding - Employee onboarding platform that allows you to provision user accounts and create sequences with todo items, resources, text/email/Slack messages, and more! Available as a web portal and Slack bot. (Source Code)
AGPL-3.0Docker - Discount Bandit
⚠- Track pricing, stock status of products across multiple stores such as Amazon, Ebay, Walmart, etc. (Source Code)GPL-3.0PHP/Docker - Dittofeed - Omni-channel customer engagement and messaging automation platform (alternative to Braze, Customer.io, Iterable). (Demo, Source Code)
MITDocker - feedmixer - Micro web service which takes a list of feed URLs and returns a new feed consisting of the most recent n entries from each given feed (returns Atom, RSS, or JSON). (Demo)
WTFPLPython - Github Ntfy
⚠- Push notifications to NTFY when a new release is available on Docker Hub or Github. (Clients)GPL-3.0Docker - HandBrake Web - Use one or more instances of HandBrake video transcoder on a headless device via a web interface.
AGPL-3.0Docker - Healthchecks - Listen for pings and sends alerts when pings are late. (Source Code)
BSD-3-ClausePython/Docker - HRConvert2 - Drag-and-drop file conversion server with session based authentication, automatic temporary file maintenance, and logging capability.
GPL-3.0PHP - Huginn - Build agents that monitor and act on your behalf.
MITRuby - Kestra - Event-driven, language-agnostic platform to create, schedule, and monitor workflows. In code. Coordinate data pipelines and tasks such as ETL and ELT. (Source Code)
Apache-2.0Docker - Kibitzr - Lightweight personal web assistant with powerful integrations. (Source Code)
MITPython - LazyLibrarian
⚠- Follow authors and grab metadata for all your digital reading needs. It uses a combination of Goodreads, Librarything and optionally GoogleBooks as sources for author info and book info.GPL-3.0Python - Leon - Personal assistant who can live on your server. (Source Code)
MITNodejs - Matchering - Automated music mastering (alternative to LANDR, eMastered, and MajorDecibel).
GPL-3.0Docker - Mylar3 - Automated Comic Book (cbr/cbz) downloader program for use with NZB and torrents. (Source Code)
GPL-3.0Python/Docker - OliveTin - Web interface for running Linux shell commands. (Source Code)
AGPL-3.0Go - pyLoad - Lightweight, customizable and remotely manageable downloader for 1-click-hosting sites like rapidshare.com or uploaded.to. (Source Code)
AGPL-3.0Python - StackStorm - StackStorm (aka IFTTT for Ops) is event-driven automation for auto-remediation, security responses, troubleshooting, deployments, and more. Includes rules engine, workflow, 160 integration packs with 6000+ actions and ChatOps. (Source Code)
Apache-2.0Python - µTask - Automation engine that models and executes business processes declared in yaml.
BSD-3-ClauseGo/Docker
- Activepieces - No-code business automation tool like Zapier or Tray. For example, you can send a Slack notification for each new Trello card. (Source Code)




