-
 @ 6d5c826a:4b27b659
2025-05-23 21:52:26
@ 6d5c826a:4b27b659
2025-05-23 21:52:26- grml - Bootable Debian Live CD with powerful CLI tools. (Source Code)
GPL-3.0Shell - mitmproxy - A Python tool used for intercepting, viewing and modifying network traffic. Invaluable in troubleshooting certain problems. (Source Code)
MITPython - mtr - Network utility that combines traceroute and ping. (Source Code)
GPL-2.0C - Sysdig - Capture system state and activity from a running Linux instance, then save, filter and analyze. (Source Code)
Apache-2.0Docker/Lua/C - Wireshark - The world's foremost network protocol analyzer. (Source Code)
GPL-2.0C
- grml - Bootable Debian Live CD with powerful CLI tools. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:52:06
@ 6d5c826a:4b27b659
2025-05-23 21:52:06- Docker Compose - Define and run multi-container Docker applications. (Source Code)
Apache-2.0Go - Docker Swarm - Manage cluster of Docker Engines. (Source Code)
Apache-2.0Go - Docker - Platform for developers and sysadmins to build, ship, and run distributed applications. (Source Code)
Apache-2.0Go - LXC - Userspace interface for the Linux kernel containment features. (Source Code)
GPL-2.0C - LXD - Container "hypervisor" and a better UX for LXC. (Source Code)
Apache-2.0Go - OpenVZ - Container-based virtualization for Linux. (Source Code)
GPL-2.0C - Podman - Daemonless container engine for developing, managing, and running OCI Containers on your Linux System. Containers can either be run as root or in rootless mode. Simply put:
alias docker=podman. (Source Code)Apache-2.0Go - Portainer Community Edition - Simple management UI for Docker. (Source Code)
ZlibGo - systemd-nspawn - Lightweight, chroot-like, environment to run an OS or command directly under systemd. (Source Code)
GPL-2.0C
- Docker Compose - Define and run multi-container Docker applications. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:49:50
@ 6d5c826a:4b27b659
2025-05-23 21:49:50- Consul - Consul is a tool for service discovery, monitoring and configuration. (Source Code)
MPL-2.0Go - etcd - Distributed K/V-Store, authenticating via SSL PKI and a REST HTTP Api for shared configuration and service discovery. (Source Code)
Apache-2.0Go - ZooKeeper - ZooKeeper is a centralized service for maintaining configuration information, naming, providing distributed synchronization, and providing group services. (Source Code)
Apache-2.0Java/C++
- Consul - Consul is a tool for service discovery, monitoring and configuration. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:49:30
@ 6d5c826a:4b27b659
2025-05-23 21:49:30- DD-WRT - A Linux-based firmware for wireless routers and access points, originally designed for the Linksys WRT54G series. (Source Code)
GPL-2.0C - OpenWrt - A Linux-based router featuring Mesh networking, IPS via snort and AQM among many other features. (Source Code)
GPL-2.0C - OPNsense - An open source FreeBSD-based firewall and router with traffic shaping, load balancing, and virtual private network capabilities. (Source Code)
BSD-2-ClauseC/PHP - pfSense CE - Free network firewall distribution, based on the FreeBSD operating system with a custom kernel and including third party free software packages for additional functionality. (Source Code)
Apache-2.0Shell/PHP/Other
- DD-WRT - A Linux-based firmware for wireless routers and access points, originally designed for the Linksys WRT54G series. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:49:12
@ 6d5c826a:4b27b659
2025-05-23 21:49:12- Remmina - Feature-rich remote desktop application for linux and other unixes. (Source Code)
GPL-2.0C - Tiger VNC - High-performance, multi-platform VNC client and server. (Source Code)
GPL-2.0C++ - X2go - X2Go is an open source remote desktop software for Linux that uses the NoMachine/NX technology protocol. (Source Code)
GPL-2.0Perl
- Remmina - Feature-rich remote desktop application for linux and other unixes. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:56
@ 6d5c826a:4b27b659
2025-05-23 21:48:56- ActiveMQ - Java message broker. (Source Code)
Apache-2.0Java - BeanstalkD - A simple, fast work queue. (Source Code)
MITC - Gearman - Fast multi-language queuing/job processing platform. (Source Code)
BSD-3-ClauseC++ - NSQ - A realtime distributed messaging platform. (Source Code)
MPL-2.0Go - ZeroMQ - Lightweight queuing system. (Source Code)
GPL-3.0C++
- ActiveMQ - Java message broker. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:36
@ 6d5c826a:4b27b659
2025-05-23 21:48:36- aptly - Swiss army knife for Debian repository management. (Source Code)
MITGo - fpm - Versatile multi format package creator. (Source Code)
MITRuby - omnibus-ruby - Easily create full-stack installers for your project across a variety of platforms.
Apache-2.0Ruby - tito - Builds RPMs for git-based projects.
GPL-2.0Python
- aptly - Swiss army knife for Debian repository management. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:21
@ 6d5c826a:4b27b659
2025-05-23 21:48:21- CapRover - Build your own PaaS in a few minutes. (Demo, Source Code)
Apache-2.0Docker/Nodejs - Coolify - An open-source & self-hostable Heroku / Netlify alternative (and even more). (Source Code)
Apache-2.0Docker - Dokku - An open-source PaaS (alternative to Heroku). (Source Code)
MITDocker/Shell/Go/deb - fx - A tool to help you do Function as a Service with painless on your own servers.
MITGo - Kubero - A self-hosted Heroku PaaS alternative for Kubernetes that implements GitOps. (Demo, Source Code)
GPL-3.0K8S/Nodejs/Go - LocalStack - LocalStack is a fully functional local AWS cloud stack. This includes Lambda for serverless computation. (Source Code)
Apache-2.0Python/Docker/K8S - Nhost - Firebase Alternative with GraphQL. Get a database and backend configured and ready in minutes. (Source Code)
MITDocker/Nodejs/Go - OpenFaaS - Serverless Functions Made Simple for Docker & Kubernetes. (Source Code)
MITGo - Tau - Easily build Cloud Computing Platforms with features like Serverless WebAssembly Functions, Frontend Hosting, CI/CD, Object Storage, K/V Database, and Pub-Sub Messaging. (Source Code)
BSD-3-ClauseGo/Rust/Docker - Trusted-CGI - Lightweight self-hosted lambda/applications/cgi/serverless-functions platform.
MITGo/deb/Docker
- CapRover - Build your own PaaS in a few minutes. (Demo, Source Code)
-
 @ 3c389c8f:7a2eff7f
2025-05-23 21:35:30
@ 3c389c8f:7a2eff7f
2025-05-23 21:35:30Web:
https://shopstr.store/
https://cypher.space/
https://plebeian.market/
Mobile:
https://www.amethyst.social/
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:04
@ 6d5c826a:4b27b659
2025-05-23 21:48:04- GNS3 - Graphical network simulator that provides a variety of virtual appliances. (Source Code)
GPL-3.0Python - OpenWISP - Open Source Network Management System for OpenWRT based routers and access points. (Demo, Source Code)
GPL-3.0Python - Oxidized - Network device configuration backup tool.
Apache-2.0Ruby - phpIPAM - Open source IP address management with PowerDNS integration. (Source Code)
GPL-3.0PHP - RANCID - Monitor network devices configuration and maintain history of changes. (Source Code)
BSD-3-ClausePerl/Shell - rConfig - Network device configuration management tool. (Source Code)
GPL-3.0PHP
- GNS3 - Graphical network simulator that provides a variety of virtual appliances. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:44
@ 6d5c826a:4b27b659
2025-05-23 21:47:44- Adagios - Web based Nagios interface for configuration and monitoring (replacement to the standard interface), and a REST interface. (Source Code)
AGPL-3.0Docker/Python - Alerta - Distributed, scalable and flexible monitoring system. (Source Code)
Apache-2.0Python - Beszel - Lightweight server monitoring platform that includes Docker statistics, historical data, and alert functions. (Source Code)
MITGo - Cacti - Web-based network monitoring and graphing tool. (Source Code)
GPL-2.0PHP - cadvisor - Analyzes resource usage and performance characteristics of running containers.
Apache-2.0Go - checkmk - Comprehensive solution for monitoring of applications, servers, and networks. (Source Code)
GPL-2.0Python/PHP - dashdot - A simple, modern server dashboard for smaller private servers. (Demo)
MITNodejs/Docker - EdMon - A command-line monitoring application helping you to check that your hosts and services are available, with notifications support.
MITJava - eZ Server Monitor - A lightweight and simple dashboard monitor for Linux, available in Web and Bash application. (Source Code)
GPL-3.0PHP/Shell - glances - Open-source, cross-platform real-time monitoring tool with CLI and web dashboard interfaces and many exporting options. (Source Code)
GPL-3.0Python - Healthchecks - Monitoring for cron jobs, background services and scheduled tasks. (Source Code)
BSD-3-ClausePython - Icinga - Nagios fork that has since lapped nagios several times. Comes with the possibility of clustered monitoring. (Source Code)
GPL-2.0C++ - LibreNMS - Fully featured network monitoring system that provides a wealth of features and device support. (Source Code)
GPL-3.0PHP - Linux Dash - A low-overhead monitoring web dashboard for a GNU/Linux machine.
MITNodejs/Go/Python/PHP - Monit - Small utility for managing and monitoring Unix systems. (Source Code)
AGPL-3.0C - Munin - Networked resource monitoring tool. (Source Code)
GPL-2.0Perl/Shell - Naemon - Network monitoring tool based on the Nagios 4 core with performance enhancements and new features. (Source Code)
GPL-2.0C - Nagios - Computer system, network and infrastructure monitoring software application. (Source Code)
GPL-2.0C - Netdata - Distributed, real-time, performance and health monitoring for systems and applications. Runs on Linux, FreeBSD, and MacOS. (Source Code)
GPL-3.0C - NetXMS - Open Source network and infrastructure monitoring and management. (Source Code)
LGPL-3.0/GPL-3.0Java/C++/C - Observium Community Edition - Network monitoring and management platform that provides real-time insight into network health and performance.
QPL-1.0PHP - openITCOCKPIT Community Edition - Monitoring Suite featuring seamless integrations with Naemon, Checkmk, Grafana and more. (Demo, Source Code)
GPL-3.0deb/Docker - Performance Co-Pilot - Lightweight, distributed system performance and analysis framework. (Source Code)
LGPL-2.1/GPL-2.0C - PHP Server Monitor - Open source tool to monitor your servers and websites. (Source Code)
GPL-3.0PHP - PhpSysInfo - A customizable PHP script that displays information about your system nicely. (Source Code)
GPL-2.0PHP - Prometheus - Service monitoring system and time series database. (Source Code)
Apache-2.0Go - Riemann - Flexible and fast events processor allowing complex events/metrics analysis. (Source Code)
EPL-1.0Java - rtop - Interactive, remote system monitoring tool based on SSH.
MITGo - ruptime - Classic system status server.
AGPL-3.0Shell - Scrutiny - Web UI for hard drive S.M.A.R.T monitoring, historical trends & real-world failure thresholds.
MITGo - Sensu - Monitoring tool for ephemeral infrastructure and distributed applications. (Source Code)
MITGo - Status - Simple and lightweight system monitoring tool for small homeservers with a pleasant web interface. (Demo
MITPython - Thruk - Multibackend monitoring web interface with support for Naemon, Nagios, Icinga and Shinken. (Source Code)
GPL-1.0Perl - Wazuh - Unified XDR and SIEM protection for endpoints and cloud workloads. (Source Code)
GPL-2.0C - Zabbix - Enterprise-class software for monitoring of networks and applications. (Source Code)
GPL-2.0C
- Adagios - Web based Nagios interface for configuration and monitoring (replacement to the standard interface), and a REST interface. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:22
@ 6d5c826a:4b27b659
2025-05-23 21:47:22- Chocolatey - The package manager for Windows. (Source Code)
Apache-2.0C#/PowerShell - Clonezilla - Partition and disk imaging/cloning program. (Source Code)
GPL-2.0Perl/Shell/Other - DadaMail - Mailing List Manager, written in Perl. (Source Code)
GPL-2.0Perl - Fog - Cloning/imaging solution/rescue suite. (Source Code)
GPL-3.0PHP/Shell - phpList - Newsletter and email marketing software. (Source Code)
AGPL-3.0PHP
- Chocolatey - The package manager for Windows. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:03
@ 6d5c826a:4b27b659
2025-05-23 21:47:03- Beats - Single-purpose data shippers that send data from hundreds or thousands of machines and systems to Logstash or Elasticsearch. (Source Code)
Apache-2.0Go - Collectd - System statistics collection daemon. (Source Code)
MITC - Diamond - Daemon that collects system metrics and publishes them to Graphite (and others).
MITPython - Grafana - A Graphite & InfluxDB Dashboard and Graph Editor. (Source Code)
AGPL-3.0Go - Graphite - Scalable graphing server. (Source Code)
Apache-2.0Python - RRDtool - Industry standard, high performance data logging and graphing system for time series data. (Source Code)
GPL-2.0C - Statsd - Daemon that listens for statistics like counters and timers, sent over UDP or TCP, and sends aggregates to one or more pluggable backend services.
MITNodejs - tcollector - Gathers data from local collectors and pushes the data to OpenTSDB. (Source Code)
LGPL-3.0/GPL-3.0Python - Telegraf - Plugin-driven server agent for collecting, processing, aggregating, and writing metrics.
MITGo
- Beats - Single-purpose data shippers that send data from hundreds or thousands of machines and systems to Logstash or Elasticsearch. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:46
@ 6d5c826a:4b27b659
2025-05-23 21:46:46- aerc - Terminal MUA with a focus on plaintext and features for developers. (Source Code)
MITGo - Claws Mail - Old school email client (and news reader), based on GTK+. (Source Code)
GPL-3.0C - ImapSync - Simple IMAP migration tool for copying mailboxes to other servers. (Source Code)
NLPLPerl - Mutt - Small but very powerful text-based mail client. (Source Code)
GPL-2.0C - Sylpheed - Still developed predecessor to Claws Mail, lightweight mail client. (Source Code)
GPL-2.0C - Thunderbird - Free email application that's easy to set up and customize. (Source Code)
MPL-2.0C/C++
- aerc - Terminal MUA with a focus on plaintext and features for developers. (Source Code)
-
 @ 3c389c8f:7a2eff7f
2025-05-23 21:27:26
@ 3c389c8f:7a2eff7f
2025-05-23 21:27:26Clients:
https://untype.app
https://habla.news
https://yakihonne.com
https://cypher.space
https://highlighter.com
https://pareto.space/en
https://comet.md/
Plug Ins:
https://github.com/jamesmagoo/nostr-writer
https://threenine.co.uk/products/obstrlish
Content Tagging:
https://labelmachine.org
https://ontolo.social
Blog-like Display and Personal Pages:
https://orocolo.me
https://npub.pro
Personal Notes and Messaging:
https://app.flotilla.social There's an app, too!
https://nosbin.com
RSS Readers:
https://nostrapps.com/noflux
https://nostrapps.com/narr
https://nostrapps.com/feeder
-
 @ 86611181:9fc27ad7
2025-05-23 20:31:44
@ 86611181:9fc27ad7
2025-05-23 20:31:44It's time to secure user data in your identity system This post was also published with the Industry Association of Privacy Professionals.
It seems like every day there is a new report of a major personal data breach. In just the past few months, Neiman Marcus, Ticketmaster, Evolve Bank, TeamViewer, Hubspot, and even the IRS have been affected.
The core issue is that user data is commonly spread across multiple systems that are increasingly difficult to fully secure, including database user tables, data warehouses and unstructured documents.
Most enterprises are already running an incredibly secure and hardened identity system to manage customer login and authorization, commonly referred to as a customer identity access management system. Since identity systems manage customer sign-up and sign-in, they typically contain customer names, email addresses, and phone numbers for multifactor authentication. Commercial CIAMs provide extensive logging, threat detection, availability and patch management.
Identity systems are highly secure and already store customers' personally identifiable information, so it stands to reason enterprises should consider identity systems to manage additional PII fields.
Identity systems are designed to store numerous PII fields and mask the fields for other systems. The Liberty Project developed the protocols that became Security Assertion Markup Language 2.0, the architecture at the core of CIAM systems, 20 years ago, when I was its chief technology officer. SAML 2.0 was built so identity data would be fully secure, and opaque tokens would be shared with other systems. Using tokens instead of actual user data is a core feature of identity software that can be used to fully secure user data across applications.
Most modern identity systems support adding additional customer fields, so it is easy to add new fields like Social Security numbers and physical addresses. Almost like a database, some identity systems even support additional tables and images.
A great feature of identity systems is that they often provide a full suite of user interface components for users to register, login and manage their profile fields. Moving fields like Social Security numbers from your database to your identity system means the identity system can fully manage the process of users entering, viewing and editing the field, and your existing application and database become descoped from managing sensitive data.
With sensitive fields fully isolated in an identity system and its user interface components, the identity system can provide for cumbersome and expensive compliance with standards such as the Health Insurance Portability and Accountability Act for medical data and the Payment Card Industry Data Security Standard for payment data, saving the time and effort to achieve similar compliance in your application.
There are, of course, applications that require sensitive data, such as customer service systems and data warehouses. Identity systems use a data distribution standard called System for Cross-domain Identity Management 2.0 to copy user data to other systems. The SCIM is a great standard to help manage compliance such as "right to be forgotten," because it can automatically delete customer data from other systems when a customer record is deleted from the identity system.
When copying customer data from an identity system to another application, consider anonymizing or masking fields. For example, anonymizing a birthdate into an age range when copying a customer record into a data warehouse can descope the data warehouse from containing personal information.
Most enterprises already run an Application Programming Interface Gateway to manage web services between systems. By combining an API Gateway with the identity system's APIs, it becomes very easy to automatically anonymize and mask customer data fields before they are copied into other systems.
A new set of companies including Baffle, Skyflow, and Piiano have introduced services that combine the governance and field management features of an identity system with extensive field masking. Since these systems do not offer the authentication and authorization features of an identity system, it's important to balance the additional features as they introduce an additional threat surface with PII storage and permissions.
PII sprawl is an increasing liability for companies. The most secure, compliant and flexible central data store to manage PII is the existing CIAM and API Gateway infrastructure that enterprises have already deployed.
Move that customer data into your identity system and lock it down. https://peter.layer3.press/articles/3c6912eb-404a-4630-9fe9-fd1bd23cfa64
-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:28
@ 6d5c826a:4b27b659
2025-05-23 21:46:28- Fluentd - Data collector for unified logging layer. (Source Code)
Apache-2.0Ruby - Flume - Distributed, reliable, and available service for efficiently collecting, aggregating, and moving large amounts of log data. (Source Code)
Apache-2.0Java - GoAccess - Real-time web log analyzer and interactive viewer that runs in a terminal or through the browser. (Source Code)
MITC - Loki - Log aggregation system designed to store and query logs from all your applications and infrastructure. (Source Code)
AGPL-3.0Go - rsyslog - Rocket-fast system for log processing. (Source Code)
GPL-3.0C
- Fluentd - Data collector for unified logging layer. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:11
@ 6d5c826a:4b27b659
2025-05-23 21:46:11- GLPI - Information Resource-Manager with an additional Administration Interface. (Source Code)
GPL-3.0PHP - OCS Inventory NG - Asset management and deployment solution for all devices in your IT Department. (Source Code)
GPL-2.0PHP/Perl - OPSI - Hardware and software inventory, client management, deployment, and patching for Linux and Windows. (Source Code)
GPL-3.0/AGPL-3.0OVF/Python - RackTables - Datacenter and server room asset management like document hardware assets, network addresses, space in racks, networks configuration. (Demo, Source Code)
GPL-2.0PHP - Ralph - Asset management, DCIM and CMDB system for large Data Centers as well as smaller LAN networks. (Demo, Source Code)
Apache-2.0Python/Docker - Snipe IT - Asset & license management software. (Source Code)
AGPL-3.0PHP
- GLPI - Information Resource-Manager with an additional Administration Interface. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:45:53
@ 6d5c826a:4b27b659
2025-05-23 21:45:53- BounCA - A personal SSL Key / Certificate Authority web-based tool for creating self-signed certificates. (Source Code)
Apache-2.0Python - easy-rsa - Bash script to build and manage a PKI CA.
GPL-2.0Shell - Fusion Directory - Improve the Management of the services and the company directory based on OpenLDAP. (Source Code)
GPL-2.0PHP - LDAP Account Manager (LAM) - Web frontend for managing entries (e.g. users, groups, DHCP settings) stored in an LDAP directory. (Source Code)
GPL-3.0PHP - Libravatar - Libravatar is a service which delivers your avatar (profile picture) to other websites. (Source Code)
AGPL-3.0Python - Pomerium - An identity and context aware access-proxy inspired by BeyondCorp. (Source Code)
Apache-2.0Docker/Go - Samba - Active Directory and CIFS protocol implementation. (Source Code)
GPL-3.0C - Smallstep Certificates - A private certificate authority (X.509 & SSH) and related tools for secure automated certificate management. (Source Code)
Apache-2.0Go - ZITADEL - Cloud-native Identity & Access Management solution providing a platform for secure authentication, authorization and identity management. (Source Code)
Apache-2.0Go/Docker/K8S
- BounCA - A personal SSL Key / Certificate Authority web-based tool for creating self-signed certificates. (Source Code)
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-23 19:32:28
@ 5d4b6c8d:8a1c1ee3
2025-05-23 19:32:28https://primal.net/e/nevent1qvzqqqqqqypzp6dtxy5uz5yu5vzxdtcv7du9qm9574u5kqcqha58efshkkwz6zmdqqszj207pl0eqkgld9vxknxamged64ch2x2zwhszupkut5v46vafuhg9833px
Some of my colleagues were talking about how they're even more scared of RFK Jr. than they are of Trump. I hope he earns it.
https://stacker.news/items/987685
-
 @ 3c389c8f:7a2eff7f
2025-05-23 18:23:28
@ 3c389c8f:7a2eff7f
2025-05-23 18:23:28I've sporadically been trying to spend some time familiarizing myself with Nostr marketplace listings and the clients that support them. I have been pleased with what I have encountered. The clients are simple to use, and people have been receptive to transacting with me. I've sold items to both people whom I consider to be close contacts, as well as to people that I barely know.
My first attempt was close to 2 years ago, when I listed one pound bags of coffee for sale. If I remember correctly, there was only one marketplace client then, and it only had support for extension signing. At the time, my old laptop had just died so I couldn't really interact with my listings through that client. (I have never had much luck with extensions on mobile browsers, so I have never attempted to use one for Nostr.) Instead, I used Amethyst to list my product and exchange messages with potential buyers. The Amethyst approach to handling different Nostr events is brilliant to me. You can do some part of each thing but not all. I view it as great introduction to what Nostr is capable of doing and a gateway to discovering other clients. Marketplace listings on Amethyst are handled in that fashion. You can list products for sale. You can browse and inquire about products listed by your contacts or by a more "global" view, which in the case of Nostr, would be products listed by anyone who publishes their listings to any of the relays that I connect with to read. There is no delete option, should a product sell out, and there is no direct purchase option. All sales need to be negotiated through direct messages. Though it has limited functionality, the system works great for items that will be listed for repeated sale, such as my coffee. If one were to list a one-off item and sell it, the flow to delete the listing would be easy enough. Copy the event ID, visit delete.nostr.com , and remove the product. Should there be a price change, it would be necessary to visit a full marketplace client to edit the listing, though one could easily delete and start over as well. Anyway, much to my surprise I sold more coffee than I had anticipated through that listing. People were eager to try out the feature and support a small business. This was an awesome experience and I see no reason to avoid buying or selling products on Nostr, even if the only client available to you is Amethyst. (Which I think might be the only mobile app with marketplace support.) It is completely manageable.
Later, I tried to list a pair of nearly new shoes. Those did not sell. I have a sneaking suspicion that there were very few people that wore size USw6 shoes using Nostr at the time. Even though no one wanted my shoes, I still ended up having some interesting conversations about different styles of running shoes, boots, and other footwear talk. I can't call the listing a total bust, even though I ended up deleting the listing and donating those shoes to the YWCA. After some number of months watching and reading about development in the Nostr marketplace space, I decided to try again.
This second approach, I started with niche rubber duckies that, for reasons unbeknownst to most, I just happen to have an abundance of. It occurred to me that day that I would most likely be creating most of my listings via mobile app since that is also my main method of taking pictures these days. I could sync or send them, but realistically it's just adding extra steps for me. I listed my ducks with Amethyst (all of which are currently still available, surprise, surprise.). I immediately went to check how the listing renders in the marketplace clients. There are 2 where I can view it, and the listing looks nice, clean, organized in both places. That alone is reason enough to get excited about selling on Nostr. Gone are the days of "this item is cross-posted to blah, blah, blah" lest risk being kicked out of the seller groups on silo'd platforms.
Knowing I can't take it personally that literally no one else on Nostr has an affinity for obscure rubber ducks (that they are willing to admit), I leave my duckies listed and move on. My next listing is for artisan bracelets. Ones that I love to make. I made my mobile listing, checked it across clients and this time I noticed that shopstr.store is collecting my listings into a personal seller profile, like a little shop. I spent some time setting up the description and banner, and now it looks really nice. This is great, since the current site acts as an open and categorized market for all sellers. Maybe someone will see the bracelets while browsing the clothing category and stumble upon the rubber ducky of their dreams in the process. That hasn't happened yet, but I was pretty jazzed to sell a few bracelets right away. Most of the sale and exchange happened via DM, for which I switched to Flotilla because it just handles messaging solidly for me. I made some bracelets, waited a few weeks, then visited Shopstr again to adjust the price. That worked out super well. I noticed that a seller can also list in their preferred currency, which is very cool. Meanwhile, back to my social feed, I can see my listing posted again since there was an edit. While not always the best thing to happen with edits, it is great that it happens with marketplace listings. It removes all the steps of announcing a price reduction, which would be handy for any serious seller. I am very happy with the bracelet experience, and I will keep that listing active and reasonably up to date for as long as any interest arises. Since this has all gone so well, I've opted to continue listing saleable items to Nostr first for a few days to a few weeks prior to marketing them anywhere else.
Looking at my listings on cypher.space, I can see that this client is tailored more towards people who are very passionate about a particular set of things. I might not fall into this category but my listings still look very nice displayed with my writing, transposed poetry, and recipes. I could see this being a great space for truly devotional hobbyists or sellers who are both deeply knowledgeable about their craft and also actively selling. My experience with all 3 of these marketplace-integrated clients had been positive and I would say that if you are considering selling on Nostr, it is worth the effort.
As some sidenotes:
-
I am aware that Shopstr has been built to be self-hosted and anyone interested in selling for the long term should at least consider doing so. This will help reduce the chances of Nostr marketplaces centralizing into just another seller-silo.
-
Plebeian Market is out there, too. From the best I could tell, even though this is a Nostr client, those listings are a different kind than listings made from the other clients referenced here. I like the layout and responsiveness of the site but I opted not to try it out for now. Cross-posting has been the bane of online selling for me for quite some time. If they should migrate to an interoperable listing type (which I think I read may happen in the future), I will happily take that for a spin, too.
-
My only purchase over Nostr marketplaces so far was some vinyls, right around the time I had listed my coffee. It went well, the seller was great to work with, everything arrived in good shape. I have made some other purchases through Nostr contacts, but those were conversations that lead to non-Nostr seller sites. I check the marketplace often, though, for things I may want/need. The listings are changing and expanding rapidly, and I foresee more purchases becoming a part of my regular Nostr experience soon enough.
-
I thought about including screenshots for this, but I would much rather you go check these clients out for yourself.
-
-
 @ 6d5c826a:4b27b659
2025-05-23 21:45:34
@ 6d5c826a:4b27b659
2025-05-23 21:45:34- Authelia - The Single Sign-On Multi-Factor portal for web apps. (Source Code)
Apache-2.0Go - Authentik - Flexible identity provider with support for different protocols. (OAuth 2.0, SAML, LDAP and Radius). (Source Code)
MITPython - KeyCloak - Open Source Identity and Access Management. (Source Code)
Apache-2.0Java
- Authelia - The Single Sign-On Multi-Factor portal for web apps. (Source Code)
-
 @ ecda4328:1278f072
2025-05-23 18:16:24
@ ecda4328:1278f072
2025-05-23 18:16:24And what does it mean to withdraw back to Bitcoin Layer 1?
Disclaimer: This post was written with help from ChatGPT-4o. If you spot any mistakes or have suggestions — feel free to reply or zap in feedback!
Let’s break it down — using three popular setups:
1. Wallet of Satoshi (WoS)
Custodial — you don’t touch Lightning directly
Sending sats:
- You open WoS, paste a Lightning invoice, hit send.
- WoS handles the payment entirely within their system.
- If recipient uses WoS: internal balance update.
- If external: routed via their node.
- You never open channels, construct routes, or sign anything.
Withdrawing to L1:
- You paste a Bitcoin address.
- WoS sends a regular on-chain transaction from their custodial wallet.
- You pay a fee. It’s like a bank withdrawal.
You don’t interact with Lightning directly. Think of it as a trusted 3rd party Lightning “bank”.
2. Phoenix Wallet
Non-custodial — you own keys, Phoenix handles channels
Sending sats:
- You scan a Lightning invoice and hit send.
- Phoenix uses its backend node (ACINQ) to route the payment.
- If needed, it opens a real 2-of-2 multisig channel on-chain automatically.
- You own your keys (12-word seed), Phoenix abstracts the technical parts.
Withdrawing to L1:
- You enter your Bitcoin address.
- Phoenix closes your Lightning channel (cooperatively, if possible).
- Your sats are sent as a real Bitcoin transaction to your address.
You’re using Lightning “for real,” with real Bitcoin channels — but Phoenix smooths out the UX.
3. Your Own Lightning Node
Self-hosted — you control everything
Sending sats:
- You manage your channels manually (or via automation).
- Your node:
- Reads the invoice
- Builds a route using HTLCs
- Sends the payment using conditional logic (preimages, time locks).
- If routing fails: retry or adjust liquidity.
Withdrawing to L1:
- You select and close a channel.
- A channel closing transaction is broadcast:
- Cooperative = fast and cheap
- Force-close = slower, more expensive, and time-locked
- Funds land in your on-chain wallet.
You have full sovereignty — but also full responsibility (liquidity, fees, backups, monitoring).
Core Tech Behind It: HTLCs, Multisig — and No Sidechain
- Lightning channels = 2-of-2 multisig Bitcoin addresses
- Payments = routed via HTLCs (Hashed Time-Locked Contracts)
- HTLCs are off-chain, but enforceable on-chain if needed
- Important:
- The Lightning Network is not a sidechain.
- It doesn't use its own token, consensus, or separate blockchain.
- Every Lightning channel is secured by real Bitcoin on L1.
Lightning = fast, private, off-chain Bitcoin — secured by Bitcoin itself.
Summary Table
| Wallet | Custody | Channel Handling | L1 Withdrawal | HTLC Visibility | User Effort | |--------------------|--------------|------------------------|---------------------|------------------|--------------| | Wallet of Satoshi | Custodial | None | Internal to external| Hidden | Easiest | | Phoenix Wallet | Non-custodial| Auto-managed real LN | Channel close | Abstracted | Low effort | | Own Node | You | Manual | Manual channel close| Full control | High effort |
Bonus: Withdrawing from LN to On-Chain
- WoS: sends sats from their wallet — like PayPal.
- Phoenix: closes a real channel and sends your UTXO on-chain.
- Own node: closes your multisig contract and broadcasts your pre-signed tx.
Bitcoin + Lightning = Sovereign money + Instant payments.
Choose the setup that fits your needs — and remember, you can always level up later.P.S. What happens in Lightning... usually stays in Lightning.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:45:15
@ 6d5c826a:4b27b659
2025-05-23 21:45:15- 389 Directory Server - Enterprise-class Open Source LDAP server for Linux. (Source Code)
GPL-3.0C - Apache Directory Server - Extensible and embeddable directory server, certified LDAPv3 compatible, with Kerberos 5 and Change Password Protocol support, triggers, stored procedures, queues and views. (Source Code)
Apache-2.0Java - FreeIPA - Integrated security information management solution combining Linux (Fedora), 389 Directory Server, Kerberos, NTP, DNS, and Dogtag Certificate System (web interface and command-line administration tools). (Source Code)
GPL-3.0Python/C/JavaScript - FreeRADIUS - Multi-protocol policy server (radiusd) that implements RADIUS, DHCP, BFD, and ARP and associated client/PAM library/Apache module. (Source Code)
GPL-2.0C - lldap - Light (simplified) LDAP implementation with a simple, intuitive web interface and GraphQL support.
GPL-3.0Rust - OpenLDAP - Open-source implementation of the Lightweight Directory Access Protocol (server, libraries and clients). (Source Code)
OLDAP-2.8C
- 389 Directory Server - Enterprise-class Open Source LDAP server for Linux. (Source Code)
-
 @ 866e0139:6a9334e5
2025-05-23 17:57:24
@ 866e0139:6a9334e5
2025-05-23 17:57:24Autor: Caitlin Johnstone. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Ich hörte einem jungen Autor zu, der eine Idee beschrieb, die ihn so sehr begeisterte, dass er die Nacht zuvor nicht schlafen konnte. Und ich erinnerte mich daran, wie ich mich früher – vor Gaza – über das Schreiben freuen konnte. Dieses Gefühl habe ich seit 2023 nicht mehr gespürt.
Ich beklage mich nicht und bemitleide mich auch nicht selbst, ich stelle einfach fest, wie unglaublich düster und finster die Welt in dieser schrecklichen Zeit geworden ist. Es wäre seltsam und ungesund, wenn ich in den letzten anderthalb Jahren Freude an meiner Arbeit gehabt hätte. Diese Dinge sollen sich nicht gut anfühlen. Nicht, wenn man wirklich hinschaut und ehrlich zu sich selbst ist in dem, was man sieht.
Es war die ganze Zeit über so hässlich und so verstörend. Es gibt eigentlich keinen Weg, all diesen Horror umzudeuten oder irgendwie erträglich zu machen. Alles, was man tun kann, ist, an sich selbst zu arbeiten, um genug inneren Raum zu schaffen, um die schlechten Gefühle zuzulassen und sie ganz durchzufühlen, bis sie sich ausgedrückt haben. Lass die Verzweiflung herein. Die Trauer. Die Wut. Den Schmerz. Lass sie deinen Körper vollständig durchfließen, ohne Widerstand, und steh dann auf und schreibe das nächste Stück.
Das ist es, was Schreiben für mich jetzt ist. Es ist nie etwas, worüber ich mich freue, es zu teilen, oder wofür ich von Inspiration erfüllt bin. Wenn überhaupt, dann fühlt es sich eher so an wie: „Okay, hier bitte, es tut mir schrecklich leid, dass ich euch das zeigen muss, Leute.“ Es ist das Starren in die Dunkelheit, in das Blut, in das Gemetzel, in die gequälten Gesichter – und das Aufschreiben dessen, was ich sehe, Tag für Tag.
Nichts daran ist angenehm oder befriedigend. Es ist einfach das, was man tut, wenn ein Genozid in Echtzeit vor den eigenen Augen stattfindet, mit der Unterstützung der eigenen Gesellschaft. Alles daran ist entsetzlich, und es gibt keinen Weg, das schönzureden – aber man tut, was getan werden muss. So, wie man es täte, wenn es die eigene Familie wäre, die da draußen im Schutt liegt.
Dieser Genozid hat mich für immer verändert. Er hat viele Menschen für immer verändert. Wir werden nie wieder dieselben sein. Die Welt wird nie wieder dieselbe sein. Ganz gleich, was passiert oder wie dieser Albtraum endet – die Dinge werden nie wieder so sein wie zuvor.
Und das sollten sie auch nicht. Der Holocaust von Gaza ist das Ergebnis der Welt, wie sie vor ihm war. Unsere Gesellschaft hat ihn hervorgebracht – und jetzt starrt er uns allen direkt ins Gesicht. Das sind wir. Das ist die Frucht des Baumes, den die westliche Zivilisation bis zu diesem Punkt gepflegt hat.
Jetzt geht es nur noch darum, alles zu tun, was wir können, um den Genozid zu beenden – und sicherzustellen, dass die Welt die richtigen Lehren daraus zieht. Das ist eines der würdigsten Anliegen, denen man sich in diesem Leben widmen kann.
Ich habe noch immer Hoffnung, dass wir eine gesunde Welt haben können. Ich habe noch immer Hoffnung, dass das Schreiben über das, was geschieht, eines Tages wieder Freude bereiten kann. Aber diese Dinge liegen auf der anderen Seite eines langen, schmerzhaften, konfrontierenden Weges, der in den kommenden Jahren vor uns liegt. Es gibt keinen Weg daran vorbei.
Die Welt kann keinen Frieden und kein Glück finden, solange wir uns nicht vollständig damit auseinandergesetzt haben, was wir Gaza angetan haben.
Dieser Text ist die deutsche Übersetzung dieses Substack-Artikels von Caitlin Johnstone.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:44:57
@ 6d5c826a:4b27b659
2025-05-23 21:44:57- Atom Community - A fork of atom A hackable text editor from Github.
MITJavaScript - Brackets - Code editor for web designers and front-end developers. (Source Code)
MITJavaScript - Eclipse - IDE written in Java with an extensible plug-in system. (Source Code)
EPL-1.0Java - Geany - GTK2 text editor. (Source Code)
GPL-2.0C/C++ - GNU Emacs - An extensible, customizable text editor-and more. (Source Code)
GPL-3.0C - Haroopad - Markdown editor with live preview. (Source Code)
GPL-3.0JavaScript - jotgit - Git-backed real-time collaborative code editing.
MITNodejs - KDevelop - IDE by the people behind KDE. (Source Code)
GFDL-1.2C++ - Micro - A modern and intuitive terminal-based text editor. (Source Code)
MITGo - Nano - Easy to use, customizable text editor. (Source Code)
GPL-3.0C - Notepad++ - GPLv2 multi-language editor with syntax highlighting for Windows. (Source Code)
GPL-2.0C++ - TextMate - A graphical text editor for OS X. (Source Code)
GPL-3.0C++ - Vim - A highly configurable text editor built to enable efficient editing. (Source Code)
VimC - VSCodium - An open source cross-platform extensible code editor based on VS Code by Microsoft removing their non-free additions. (Source Code)
MITTypeScript
- Atom Community - A fork of atom A hackable text editor from Github.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:44:34
@ 6d5c826a:4b27b659
2025-05-23 21:44:34- Bind - Versatile, classic, complete name server software. (Source Code)
MPL-2.0C - CoreDNS - Flexible DNS server. (Source Code)
Apache-2.0Go - djbdns - A collection of DNS applications, including tinydns. (Source Code)
CC0-1.0C - dnsmasq - Provides network infrastructure for small networks: DNS, DHCP, router advertisement and network boot. (Source Code)
GPL-2.0C - Knot - High performance authoritative-only DNS server. (Source Code)
GPL-3.0C - NSD - Authoritative DNS name server developed speed, reliability, stability and security. (Source Code)
BSD-3-ClauseC - PowerDNS Authoritative Server - Versatile nameserver which supports a large number of backends. (Source Code)
GPL-2.0C++ - Unbound - Validating, recursive, and caching DNS resolver. (Source Code)
BSD-3-ClauseC - Yadifa - Clean, small, light and RFC-compliant name server implementation developed from scratch by .eu. (Source Code)
BSD-3-ClauseC
- Bind - Versatile, classic, complete name server software. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:44:16
@ 6d5c826a:4b27b659
2025-05-23 21:44:16- Atomia DNS - DNS management system.
ISCPerl - Designate - DNSaaS services for OpenStack. (Source Code)
Apache-2.0Python - DNSControl - Synchronize your DNS to multiple providers from a simple DSL. (Source Code)
MITGo/Docker - DomainMOD - Manage your domains and other internet assets in a central location. (Source Code)
GPL-3.0PHP - nsupdate.info - Dynamic DNS service. (Demo, Source Code)
BSD-3-ClausePython - octoDNS - DNS as code - Tools for managing DNS across multiple providers.
MITPython - Poweradmin - Web-based DNS control panel for PowerDNS server. (Source Code)
GPL-3.0PHP - SPF Toolbox - Application to look up DNS records such as SPF, MX, Whois, and more. (Source Code)
MITPHP
- Atomia DNS - DNS management system.
-
 @ 91bea5cd:1df4451c
2025-05-23 17:04:49
@ 91bea5cd:1df4451c
2025-05-23 17:04:49Em nota, a prefeitura justificou que essas alterações visam ampliar a segurança das praias, conforto e organização, para os frequentadores e trabalhadores dos locais. No entanto, Orla Rio, concessionária responsável pelos espaços, e o SindRio, sindicato de bares e restaurantes, ficou insatisfeita com as medidas e reforçou que a música ao vivo aumenta em mais de 10% o ticket médio dos estabelecimentos e contribui para manter os empregos, especialmente na baixa temporada.
De acordo com Paes, as medidas visam impedir práticas ilegais para que a orla carioca continue sendo um espaço ativo econômico da cidade: “Certas práticas são inaceitáveis, especialmente por quem tem autorização municipal. Vamos ser mais restritivos e duros. A orla é de todos”.
Saiba quais serão as 16 proibições nas praias do Rio de Janeiro
- Utilização de caixas de som, instrumentos musicais, grupos ou qualquer equipamento sonoro, em qualquer horário. Apenas eventos autorizados terão permissão.
- Venda ou distribuição de bebidas em garrafas de vidro em qualquer ponto da areia ou do calçadão.
- Estruturas comerciais ambulantes sem autorização, como carrocinhas, trailers, food trucks e barracas.
- Comércio ambulante sem permissão, incluindo alimentos em palitos, churrasqueiras, isopores ou bandejas térmicas improvisadas.
- Circulação de ciclomotores e patinetes motorizados no calçadão.
- Escolinhas de esportes ou recreações não autorizadas pelo poder público municipal.
- Ocupação de área pública com estruturas fixas ou móveis de grandes proporções sem autorização.
- Instalação de acampamentos improvisados em qualquer trecho da orla.
- Práticas de comércio abusivo ou enganosas, incluindo abordagens insistentes. Quiosques e barracas devem exibir cardápio, preços e taxas de forma clara.
- Uso de animais para entretenimento, transporte ou comércio.
- Hasteamento ou exibição de bandeiras em mastros ou suportes.
- Fixação de objetos ou amarras em árvores ou vegetação.
- Cercadinhos feitos por ambulantes ou quiosques, que impeçam a livre circulação de pessoas.
- Permanência de carrinhos de transporte de mercadorias ou equipamentos fora dos momentos de carga e descarga.
- Armazenamento de produtos, barracas ou equipamentos enterrados na areia ou depositados na vegetação de restinga.
- Uso de nomes, marcas, logotipos ou slogans em barracas. Apenas a numeração sequencial da prefeitura será permitida.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:43:55
@ 6d5c826a:4b27b659
2025-05-23 21:43:55- Ceph - Distributed object, block, and file storage platform. (Source Code)
LGPL-3.0C++ - DRBD - Distributed replicated storage system, implemented as a Linux kernel driver. (Source Code)
GPL-2.0C - GlusterFS - Software-defined distributed storage that can scale to several petabytes, with interfaces for object, block and file storage. (Source Code)
GPL-2.0/LGPL-3.0C - Hadoop Distributed Filesystem (HDFS) - Distributed file system that provides high-throughput access to application data. (Source Code)
Apache-2.0Java - JuiceFS - Distributed POSIX file system built on top of Redis and S3. (Source Code)
Apache-2.0Go - Kubo - Implementation of IPFS, a global, versioned, peer-to-peer filesystem that seeks to connect all computing devices with the same system of files.
Apache-2.0/MITGo - LeoFS - Highly available, distributed, replicated eventually consistent object/blob store. (Source Code)
Apache-2.0Erlang - Lustre - Parallel distributed file system, generally used for large-scale cluster computing. (Source Code)
GPL-2.0C - Minio - High-performance, S3 compatible object store built for large scale AI/ML, data lake and database workloads. (Source Code)
AGPL-3.0Go - MooseFS - Fault tolerant, network distributed file system. (Source Code)
GPL-2.0C - OpenAFS - Distributed network file system with read-only replicas and multi-OS support. (Source Code)
IPL-1.0C - Openstack Swift - A highly available, distributed, eventually consistent object/blob store. (Source Code)
Apache-2.0Python - Perkeep - A set of open source formats, protocols, and software for modeling, storing, searching, sharing and synchronizing data (previously Camlistore). (Source Code)
Apache-2.0C - TahoeLAFS - Secure, decentralized, fault-tolerant, peer-to-peer distributed data store and distributed file system. (Source Code)
GPL-2.0Python - XtreemFS - Distributed, replicated and fault-tolerant file system for federated IT infrastructures.. (Source Code)
BSD-3-ClauseJava
- Ceph - Distributed object, block, and file storage platform. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:43:37
@ 6d5c826a:4b27b659
2025-05-23 21:43:37- Diagrams.net - A.K.A. Draw.io. Easy to use Diagram UI with a plethora of templates. (Source Code)
Apache-2.0JavaScript/Docker - Kroki - API for generating diagrams from textual descriptions. (Source Code)
MITJava - Mermaid - Javascript module with a unique, easy, shorthand syntax. Integrates into several other tools like Grafana. (Source Code)
MITNodejs/Docker
- Diagrams.net - A.K.A. Draw.io. Easy to use Diagram UI with a plethora of templates. (Source Code)
-
 @ 5144fe88:9587d5af
2025-05-23 17:01:37
@ 5144fe88:9587d5af
2025-05-23 17:01:37The recent anomalies in the financial market and the frequent occurrence of world trade wars and hot wars have caused the world's political and economic landscape to fluctuate violently. It always feels like the financial crisis is getting closer and closer.
This is a systematic analysis of the possibility of the current global financial crisis by Manus based on Ray Dalio's latest views, US and Japanese economic and financial data, Buffett's investment behavior, and historical financial crises.
Research shows that the current financial system has many preconditions for a crisis, especially debt levels, market valuations, and investor behavior, which show obvious crisis signals. The probability of a financial crisis in the short term (within 6-12 months) is 30%-40%,
in the medium term (within 1-2 years) is 50%-60%,
in the long term (within 2-3 years) is 60%-70%.
Japan's role as the world's largest holder of overseas assets and the largest creditor of the United States is particularly critical. The sharp appreciation of the yen may be a signal of the return of global safe-haven funds, which will become an important precursor to the outbreak of a financial crisis.
Potential conditions for triggering a financial crisis Conditions that have been met 1. High debt levels: The debt-to-GDP ratio of the United States and Japan has reached a record high. 2. Market overvaluation: The ratio of stock market to GDP hits a record high 3. Abnormal investor behavior: Buffett's cash holdings hit a record high, with net selling for 10 consecutive quarters 4. Monetary policy shift: Japan ends negative interest rates, and the Fed ends the rate hike cycle 5. Market concentration is too high: a few technology stocks dominate market performance
Potential trigger points 1. The Bank of Japan further tightens monetary policy, leading to a sharp appreciation of the yen and the return of overseas funds 2. The US debt crisis worsens, and the proportion of interest expenses continues to rise to unsustainable levels 3. The bursting of the technology bubble leads to a collapse in market confidence 4. The trade war further escalates, disrupting global supply chains and economic growth 5. Japan, as the largest creditor of the United States, reduces its holdings of US debt, causing US debt yields to soar
Analysis of the similarities and differences between the current economic environment and the historical financial crisis Debt level comparison Current debt situation • US government debt to GDP ratio: 124.0% (December 2024) • Japanese government debt to GDP ratio: 216.2% (December 2024), historical high 225.8% (March 2021) • US total debt: 36.21 trillion US dollars (May 2025) • Japanese debt/GDP ratio: more than 250%-263% (Japanese Prime Minister’s statement)
Before the 2008 financial crisis • US government debt to GDP ratio: about 64% (2007) • Japanese government debt to GDP ratio: about 175% (2007)
Before the Internet bubble in 2000 • US government debt to GDP ratio: about 55% (1999) • Japanese government debt to GDP ratio: about 130% (1999)
Key differences • The current US debt-to-GDP ratio is nearly twice that before the 2008 crisis • The current Japanese debt-to-GDP ratio is more than 1.2 times that before the 2008 crisis • Global debt levels are generally higher than historical pre-crisis levels • US interest payments are expected to devour 30% of fiscal revenue (Moody's warning)
Monetary policy and interest rate environment
Current situation • US 10-year Treasury yield: about 4.6% (May 2025) • Bank of Japan policy: end negative interest rates and start a rate hike cycle • Bank of Japan's holdings of government bonds: 52%, plans to reduce purchases to 3 trillion yen per month by January-March 2026 • Fed policy: end the rate hike cycle and prepare to cut interest rates
Before the 2008 financial crisis • US 10-year Treasury yield: about 4.5%-5% (2007) • Fed policy: continuous rate hikes from 2004 to 2006, and rate cuts began in 2007 • Bank of Japan policy: maintain ultra-low interest rates
Key differences • Current US interest rates are similar to those before the 2008 crisis, but debt levels are much higher than then • Japan is in the early stages of ending its loose monetary policy, unlike before historical crises • The size of global central bank balance sheets is far greater than at any time in history
Market valuations and investor behavior Current situation • The ratio of stock market value to the size of the US economy: a record high • Buffett's cash holdings: $347 billion (28% of assets), a record high • Market concentration: US stock growth mainly relies on a few technology giants • Investor sentiment: Technology stocks are enthusiastic, but institutional investors are beginning to be cautious
Before the 2008 financial crisis • Buffett's cash holdings: 25% of assets (2005) • Market concentration: Financial and real estate-related stocks performed strongly • Investor sentiment: The real estate market was overheated and subprime products were widely popular
Before the 2000 Internet bubble • Buffett's cash holdings: increased from 1% to 13% (1998) • Market concentration: Internet stocks were extremely highly valued • Investor sentiment: Tech stocks are in a frenzy
Key differences • Buffett's current cash holdings exceed any pre-crisis level in history • Market valuation indicators have reached a record high, exceeding the levels before the 2000 bubble and the 2008 crisis • The current market concentration is higher than any period in history, and a few technology stocks dominate market performance
Safe-haven fund flows and international relations Current situation • The status of the yen: As a safe-haven currency, the appreciation of the yen may indicate a rise in global risk aversion • Trade relations: The United States has imposed tariffs on Japan, which is expected to reduce Japan's GDP growth by 0.3 percentage points in fiscal 2025 • International debt: Japan is one of the largest creditors of the United States
Before historical crises • Before the 2008 crisis: International capital flows to US real estate and financial products • Before the 2000 bubble: International capital flows to US technology stocks
Key differences • Current trade frictions have intensified and the trend of globalization has weakened • Japan's role as the world's largest holder of overseas assets has become more prominent • International debt dependence is higher than any period in history
-
 @ cae03c48:2a7d6671
2025-05-23 16:01:05
@ cae03c48:2a7d6671
2025-05-23 16:01:05Bitcoin Magazine

Spark Partners with Breez to Launch Bitcoin-Native SDK for Lightning PaymentsToday, Breez and Spark have announced a new implementation of the Breez SDK, built on Spark’s Bitcoin-native Layer 2 infrastructure. According to a press release sent to Bitcoin Magazine, the update is intended to make it easier for developers to integrate self-custodial Bitcoin Lightning payments into everyday apps and services.
Few companies are as good as @Breez_Tech at putting Bitcoin in people’s hands. We’re incredibly humbled to have them building on Spark.
Learn more → https://t.co/KRPpWJa3os pic.twitter.com/QiCfHbWu9d
— Spark (@buildonspark) May 22, 2025
“This is what the future of Bitcoin looks like — fast, open, and embedded in the apps people use every day. By teaming up with Breez, we’re expanding the ecosystem and giving developers powerful, Bitcoin-native tools to build next-generation payment experiences. Together, we’re building the standard for global, peer-to-peer transactions,” said the creator of Spark Kevin Hurley.
The SDK supports LNURL, Lightning addresses, real-time mobile notifications, and includes bindings for all major programming languages and frameworks. It is designed to allow developers to build directly on Bitcoin without relying on bridges or external consensus. This collaboration gives developers tools to add Bitcoin payment features to apps used for monetization social apps, cross-border remittances, and in-game currencies.
“We need developers to bring Bitcoin into apps people use every day,” said the CEO of Breez Roy Sheinfeld. “That’s why we built the Breez SDK. We’re excited to build on Spark’s revolutionary architecture — giving developers a powerful new Bitcoin-native option and continuing to strengthen Lightning as the common language of Bitcoin.”
Breez will also operate as a Spark Service Provider (SSP), alongside Lightspark, to help support payment facilitation and the growth of Spark’s ecosystem. The new implementation is expected to be released later this year.
“We’re excited to see what developers build with Spark; it’s very exciting to see this come to the world,” said the co-founder and CEO of Lightspark David Marcus.
The Breez SDK is expanding

We’re joining forces with @buildonspark to release a new nodeless implementation of the Breez SDK — giving developers the tools they need to bring Bitcoin payments to everyday apps.
Bitcoin-Native
Powered by Spark’s…— Breez
 (@Breez_Tech) May 22, 2025
(@Breez_Tech) May 22, 2025Yesterday, Magic Eden also partnered with Spark to improve Bitcoin trading by addressing issues like slow transaction times, high fees, and poor user experience. The integration will introduce a native settlement system aimed at making transactions faster and more cost-effective, without using bridges or synthetic assets.
“We’re proud to be betting on BTC DeFi,” said the CEO of Magic Eden Jack Lu. “We’re going to lead the forefront of all Bitcoin DeFi to make BTC fast, fun, and for everyone with Magic Eden as the #1 BTC native app on-chain.”
This post Spark Partners with Breez to Launch Bitcoin-Native SDK for Lightning Payments first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:43:11
@ 6d5c826a:4b27b659
2025-05-23 21:43:11- Capistrano - Deploy your application to any number of machines simultaneously, in sequence or as a rolling set via SSH (rake based). (Source Code)
MITRuby - CloudSlang - Flow-based orchestration tool for managing deployed applications, with Docker capabilities. (Source Code)
Apache-2.0Java - CloudStack - Cloud computing software for creating, managing, and deploying infrastructure cloud services. (Source Code)
Apache-2.0Java/Python - Cobbler - Cobbler is a Linux installation server that allows for rapid setup of network installation environments. (Source Code)
GPL-2.0Python - Fabric - Python library and cli tool for streamlining the use of SSH for application deployment or systems administration tasks. (Source Code)
BSD-2-ClausePython - Genesis - A template framework for multi-environment BOSH deployments.
MITPerl - munki - Webserver-based repository of packages and package metadata, that allows macOS administrators to manage software installs. (Source Code)
Apache-2.0Python - Overcast - Deploy VMs across different cloud providers, and run commands and scripts across any or all of them in parallel via SSH. (Source Code)
MITNodejs
- Capistrano - Deploy your application to any number of machines simultaneously, in sequence or as a rolling set via SSH (rake based). (Source Code)
-
 @ 90152b7f:04e57401
2025-05-23 15:48:58
@ 90152b7f:04e57401
2025-05-23 15:48:58U.S. troops would enforce peace under Army study
The Washington Times - September 10, 2001
by Rowan Scarborough
https://www.ord.io/70787305 (image) https://www.ord.io/74522515 (text)
An elite U.S. Army study center has devised a plan for enforcing a major Israeli-Palestinian peace accord that would require about 20,000 well-armed troops stationed throughout Israel and a newly created Palestinian state. There are no plans by the Bush administration to put American soldiers into the Middle East to police an agreement forged by the longtime warring parties. In fact, Defense Secretary Donald H. Rumsfeld is searching for ways to reduce U.S. peacekeeping efforts abroad, rather than increasing such missions. But a 68-page paper by the Army School of Advanced Military Studies (SAMS) does provide a look at the daunting task any international peacekeeping force would face if the United Nations authorized it, and Israel and the Palestinians ever reached a peace agreement.
Located at Fort Leavenworth, Kan., the School for Advanced Military Studies is both a training ground and a think tank for some of the Army’s brightest officers. Officials say the Army chief of staff, and sometimes the Joint Chiefs of Staff, ask SAMS to develop contingency plans for future military operations. During the 1991 Persian Gulf war, SAMS personnel helped plan the coalition ground attack that avoided a strike up the middle of Iraqi positions and instead executed a “left hook” that routed the enemy in 100 hours.
The cover page for the recent SAMS project said it was done for the Joint Chiefs of Staff. But Maj. Chris Garver, a Fort Leavenworth spokesman, said the study was not requested by Washington. “This was just an academic exercise,” said Maj. Garver. “They were trying to take a current situation and get some training out of it.” The exercise was done by 60 officers dubbed “Jedi Knights,” as all second-year SAMS students are nicknamed.
The SAMS paper attempts to predict events in the first year of a peace-enforcement operation, and sees possible dangers for U.S. troops from both sides. It calls Israel’s armed forces a “500-pound gorilla in Israel. Well armed and trained. Operates in both Gaza . Known to disregard international law to accomplish mission. Very unlikely to fire on American forces. Fratricide a concern especially in air space management.”
Of the Mossad, the Israeli intelligence service, the SAMS officers say: “Wildcard. Ruthless and cunning. Has capability to target U.S. forces and make it look like a Palestinian/Arab act.”
On the Palestinian side, the paper describes their youth as “loose cannons; under no control, sometimes violent.” The study lists five Arab terrorist groups that could target American troops for assassination and hostage-taking. The study recommends “neutrality in word and deed” as one way to protect U.S. soldiers from any attack. It also says Syria, Egypt and Jordan must be warned “we will act decisively in response to external attack.”
It is unlikely either of the three would mount an attack. Of Syria’s military, the report says: “Syrian army quantitatively larger than Israeli Defense Forces, but largely seen as qualitatively inferior. More likely, however, Syrians would provide financial and political support to the Palestinians, as well as increase covert support to terrorism acts through Lebanon.” Of Egypt’s military, the paper says, “Egyptians also maintain a large army but have little to gain by attacking Israel.”
The plan does not specify a full order of battle. An Army source who reviewed the SAMS work said each of a possible three brigades would require about 100 Bradley fighting vehicles, 25 tanks, 12 self-propelled howitzers, Apache attack helicopters, Kiowa Warrior reconnaissance helicopters and Predator spy drones. The report predicts that nonlethal weapons would be used to quell unrest. U.S. European Command, which is headed by NATO’s supreme allied commander, would oversee the peacekeeping operation. Commanders would maintain areas of operation, or AOs, around Nablus, Jerusalem, Hebron and the Gaza strip. The study sets out a list of goals for U.S. troops to accomplish in the first 30 days. They include: “create conditions for development of Palestinian State and security of “; ensure “equal distribution of contract value or equivalent aid” that would help legitimize the peacekeeping force and stimulate economic growth; “promote U.S. investment in Palestine”; “encourage reconciliation between entities based on acceptance of new national identities”; and “build lasting relationship based on new legal borders and not religious-territorial claims.”
Maj. Garver said the officers who completed the exercise will hold major planning jobs once they graduate. “There is an application process” for students, he said. “They screen their records, and there are several tests they go through before they are accepted by the program. The bright planners of the future come out of this program.”
James Phillips, a Middle East analyst at the Heritage Foundation, said it would be a mistake to put peacekeepers in Israel, given the “poor record of previous monitors.” “In general, the Bush administration policy is to discourage a large American presence,” he said. “But it has been rumored that one of the possibilities might be an expanded CIA role.” “It would be a very different environment than Bosnia,” said Mr. Phillips, referring to America’s six-year peacekeeping role in Bosnia-Herzegovina. “The Palestinian Authority is pushing for this as part of its strategy to internationalize the conflict. Bring in the Europeans and Russia and China. But such monitors or peacekeeping forces are not going to be able to bring peace. Only a decision by the Palestinians to stop the violence and restart talks could possibly do that.”
<<https://www.ord.io/70787305>>
<<<https://www.ord.io/74522515>>>
-
 @ 87e98bb6:8d6616f4
2025-05-23 15:36:32
@ 87e98bb6:8d6616f4
2025-05-23 15:36:32Use this guide if you want to keep your NixOS on the stable branch, but enable unstable application packages. It took me a while to figure out how to do this, so I wanted to share because it ended up being far easier than most of the vague explanations online made it seem.
I put a sample configuration.nix file at the very bottom to help it make more sense for new users. Remember to keep a backup of your config file, just in case!
If there are any errors please let me know. I am currently running NixOS 24.11.
Steps listed in this guide: 1. Add the unstable channel to NixOS as a secondary channel. 2. Edit the configuration.nix to enable unstable applications. 3. Add "unstable." in front of the application names in the config file (example: unstable.program). This enables the install of unstable versions during the build. 4. Rebuild.
Step 1:
- Open the console. (If you want to see which channels you currently have, type: sudo nix-channel --list)
- Add the unstable channel, type: sudo nix-channel --add https://channels.nixos.org/nixpkgs-unstable unstable
- To update the channels (bring in the possible apps), type: sudo nix-channel --update
More info here: https://nixos.wiki/wiki/Nix_channels
Step 2:
Edit your configuration.nix and add the following around your current config:
``` { config, pkgs, lib, ... }:
let unstable = import
{ config = { allowUnfree = true; }; }; in { #insert normal configuration text here } #remember to close the bracket!```
At this point it would be good to save your config and try a rebuild to make sure there are no errors. If you have errors, make sure your brackets are in the right places and/or not missing. This step will make for less troubleshooting later on if something happens to be in the wrong spot!
Step 3:
Add "unstable." to the start of each application you want to use the unstable version. (Example: unstable.brave)
Step 4:
Rebuild your config, type: sudo nixos-rebuild switch
Example configuration.nix file:
```
Config file for NixOS
{ config, pkgs, lib, ... }:
Enable unstable apps from Nix repository.
let unstable = import
{ config = { allowUnfree = true; }; }; in { #Put your normal config entries here in between the tags. Below is what your applications list needs to look like.
environment.systemPackages = with pkgs; [ appimage-run blender unstable.brave #Just add unstable. before the application name to enable the unstable version. chirp discord ];
} # Don't forget to close bracket at the end of the config file!
``` That should be all. Hope it helps.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:42:54
@ 6d5c826a:4b27b659
2025-05-23 21:42:54- Ajenti - Control panel for Linux and BSD. (Source Code)
MITPython/Shell - Cockpit - Web-based graphical interface for servers. (Source Code)
LGPL-2.1C - Froxlor - Lightweight server management software with Nginx and PHP-FPM support. (Source Code)
GPL-2.0PHP - HestiaCP - Web server control panel (fork of VestaCP). (Demo, Source Code)
GPL-3.0PHP/Shell/Other - ISPConfig - Manage Linux servers directly through your browser. (Source Code)
BSD-3-ClausePHP - Sentora - Open-Source Web hosting control panel for Linux, BSD (fork of ZPanel). (Source Code)
GPL-3.0PHP - Virtualmin - Powerful and flexible web hosting control panel for Linux and BSD systems. (Source Code)
GPL-3.0Shell/Perl/Other - Webmin - Web-based interface for system administration for Unix. (Source Code)
BSD-3-ClausePerl
- Ajenti - Control panel for Linux and BSD. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:42:36
@ 6d5c826a:4b27b659
2025-05-23 21:42:36- Buildbot - Python-based toolkit for continuous integration. (Source Code)
GPL-2.0Python - CDS - Enterprise-Grade Continuous Delivery & DevOps Automation Open Source Platform. (Source Code)
BSD-3-ClauseGo - Concourse - Concourse is a CI tool that treats pipelines as first class objects and containerizes every step along the way. (Demo, Source Code)
Apache-2.0Go - drone - Drone is a Continuous Delivery platform built on Docker, written in Go. (Source Code)
Apache-2.0Go - Factor - Programmatically define and run workflows to connect configuration management, source code management, build, continuous integration, continuous deployment and communication tools. (Source Code)
MITRuby - GitLab CI - Gitlab's built-in, full-featured CI/CD solution. (Source Code)
MITRuby - GoCD - Continuous delivery server. (Source Code)
Apache-2.0Java/Ruby - Jenkins - Continuous Integration Server. (Source Code)
MITJava - Laminar - Fast, lightweight, simple and flexible Continuous Integration. (Source Code)
GPL-3.0C++ - PHP Censor - Open source self-hosted continuous integration server for PHP projects.
BSD-2-ClausePHP - Strider - Open Source Continuous Deployment / Continuous Integration platform. (Source Code)
MITNodejs - Terrateam - GitOps-first automation platform for Terraform and OpenTofu workflows with support for self-hosted runners. (Source Code)
MPL-2.0OCaml/Docker - werf - Open Source CI/CD tool for building Docker images and deploying to Kubernetes via GitOps. (Source Code)
Apache-2.0Go - Woodpecker - Community fork of Drone that uses Docker containers. (Source Code)
Apache-2.0Go
- Buildbot - Python-based toolkit for continuous integration. (Source Code)
-
 @ 10f7c7f7:f5683da9
2025-05-23 15:26:17
@ 10f7c7f7:f5683da9
2025-05-23 15:26:17While I’m going to stand by what I said in my previous piece, minimise capital gains payments, don’t fund the government, get a loan against your bitcoin, but the wheels in my left curve brain have continued to turn, well that, and a few more of my 40PW insights. I mentioned about paying attention to the risks involved in terms of borrowing against your bitcoin, and hopefully ending up paying less in bitcoin at the end of the loan, even if you ultimately sold bitcoin to pay off the loan. However, the idea of losing control of the bitcoin I have spent a good deal of time and effort accumulating being out of my control has led me to reconsider. I also realised I didn’t fully flesh out some other topics that I think are relevant, not least time preference, specifically in relation to what you’re buying. The idea of realising a lump some of capital to live your dreams, buy a house or a cool car may be important, but it may be worth taking a step back and looking at what you’re purchasing. Are you only purchasing those things because you had been able to get this new money “tax free”? If that is the case, and the fiat is burning a hold in your pocket, maybe you’ve just found yourself with the same fiat brained mentality you have been working so hard to escape from while you have sacrificed and saved to stack sats.
While it may no longer be necessary to ask yourself whether a particular product or service is worth selling your bitcoin for because you’ve taken out a loan, it may still be worth asking yourself whether a particular loan fuelled purchase is worth forfeiting control of your keys for? Unlike the foolish 18 year-old, released into a world with their newly preapproved credit card, you need to take a moment and ask yourself:
Is the risk worth it?
Is the purchase worth it?
But also take a moment to consider a number of other things, are there fiat options?
Where in the cycle might you be?
Or if I’m thinking carefully about this, will whatever I’m buying hold its value (experiences may be more difficult to run the numbers on)?
The reason for asking these things, is that if you still have a foot in the fiat world, dealing with a fiat bank account, fiat institutions may still be very willing to provide you with a loan at a lower rate than a bitcoin backed loan. Particularly if you’re planning on using that money to buy a house; if you can qualify for a mortgage, get a mortgage, but if you need cash for a deposit, maybe that is where the bitcoin backed loan may come in. Then, it may be worth thinking about where are you in the bitcoin cycle? No one can answer this, but with the historic data we have, it appears logical that after some type of run up, prices may retrace (Dan Held’s supercycle withstanding).
Matteo Pellegrini with Daniel Prince provided a new perspective on this for me. Rather the riding the bull market gains all the way through to the bear market bottom, what happens if I chose to buy an asset that didn’t lose quite as much fiat value as bitcoin, for example, a Swiss Watch, or a tasteful, more mature sports car? If that was the purchase of choice, they suggested that you could enjoy the car, “the experience” for a year or two, then realise the four door estate was likely always the better option, sell it and be able to buy back as many, if not slightly more bitcoin that you originally sold (not financial, classic car or price prediction advice, I’m not accredited to advise pretty much anything). Having said that, it is a scenario I think worth thinking about when the bitcoin denominated dream car begins to make financial sense.
Then, as we begin to look forward to the near inevitable bear market (they are good for both stacking and grinding), if we’ve decided to take out a loan rather than sell, we then may ultimately need to increase our collateral to maintain loan to value requirements, as well as sell more bitcoin to cover repayments (if that’s the route we’re taking). This then moves us back into the domain of saying, well in actual fact we should just sell our bitcoin when we can get most dollar for it (or the coolest car), with a little extra to cover future taxes, it is probably better to sell near a top than a bottom. The balance between these two rather extreme positions could be to take out a fiat loan to buy the item and maybe sell sufficient bitcoin so you’re able to cover the loan for a period of time (less taxable events to keep track of and also deals with future uncertainty of bitcoin price). In this case, if the loan timeframe is longer than the amount of loan your sale can cover, by the time you need to sell anymore, the price should have recovered from a cycle bottom.
In this scenario, apart from the smaller portion of bitcoin you have had to sell, the majority of your stack can remain in cold storage, the loan you took out will be unsecured (particularly against your bitcoin), but even if it isn’t, the value of what you purchase maintains its value, you can in theory exit the loan at any point by selling the luxury item. Then within this scenario, if you had sold near a top, realised the car gave you a bad back or made you realise you staying humble is more important, sold it, paid off the loan, there may even be a chance you could buy back more bitcoin with the money you had left over from selling your bitcoin to fund the loan.
I have no idea of this could actually work, but to be honest, I’m looking forward to trying it out in the next 6-12 months, although I may keep my daily driver outside of my bitcoin strategy (kids still need a taxi service). Having said that, I think there are some important points to consider in addition to not paying capital gains tax (legally), as well as the opportunities of bitcoin loans. They are still very young products and to quote every trad-fi news outlet, “bitcoin is still a volatile asset”, these thought experiments are still worth working through. To push back on the Uber fiat journalist, Katie Martin, “Bitcoin has no obvious use case”, it does, it can be a store of value to hold or sell, it can be liquid and flexible collateral, but also an asset that moves independently of other assets to balance against fiat liabilities. The idea of being able to release some capital, enjoy the benefits of the capital for a period, before returning that capital to store value feels like a compelling one.
The important thing to remember is that there are a variety of options, whether selling for cash, taking out a bitcoin backed loan, taking out a fiat loan or some combination of each. Saying that, what I would think remains an important question to ask irrespective of the option you go for:
Is what I’m planning on buying, worth selling bitcoin for?
If it cannot pass this first question, maybe it isn’t worth purchasing to start with.
-
 @ cae03c48:2a7d6671
2025-05-23 14:01:07
@ cae03c48:2a7d6671
2025-05-23 14:01:07Bitcoin Magazine

KindlyMD, Nakamoto, and Anchorage Digital Form Strategic Bitcoin Treasury AllianceNakamoto Holdings Inc., KindlyMD, Inc., and Anchorage Digital today announced a strategic partnership that will see Anchorage become a trading partner for KindlyMD’s Bitcoin treasury. The partnership will officially take effect upon the close of KindlyMD’s merger with Nakamoto, expected in Q3 2025.
NEW! Anchorage Digital
 @Nakamoto @KindlyMD
@Nakamoto @KindlyMD Today we’re thrilled to announce a strategic partnership with Nakamoto Holdings and $KDLY to accelerate the future of corporate Bitcoin adoption. pic.twitter.com/nQueTyutQH
— Anchorage Digital
 (@Anchorage) May 21, 2025
(@Anchorage) May 21, 2025Anchorage Digital, a U.S. federally chartered digital asset bank, will provide institutional-grade custody, 24/7 trading, and deep liquidity to support the Bitcoin strategy of the combined entity.
“In the not-so-distant-future, the omission of Bitcoin on a balance sheet will be more glaring than its inclusion,” said Nathan McCauley, CEO and Co-Founder of Anchorage Digital. “Until then, companies like Nakamoto-KindlyMD are pioneering a new path forward—one in which Bitcoin is at the heart of corporate strategy.”
The future of corporate treasury strategy is Bitcoin-native. We're here to make it happen. Pumped to be partnering with @Nakamoto and @KindlyMD.@DavidFBailey’s vision continues to open new doors.
— Nathan McCauley
 (@nathanmccauley) May 21, 2025
(@nathanmccauley) May 21, 2025The merger between KindlyMD and Nakamoto is backed by approximately $710 million in financing, including $510 million in PIPE funding—the largest ever PIPE for a public crypto-related deal. The goal is to establish a Bitcoin-native corporate treasury strategy that redefines how capital markets engage with digital assets.
“Our goal is to bring Bitcoin to the center of global capital markets within a compliant, transparent structure,” said David Bailey, Founder and CEO of Nakamoto Holdings Inc. “We are excited to partner with Anchorage Digital to implement our vision with the highest levels of security and battle-tested infrastructure and enable us to deliver sustained value to shareholders.”
This announcement follows a key milestone on May 18, when KindlyMD shareholders approved the proposed merger with Nakamoto. The transaction is now expected to close in Q3 2025, pending SEC review and information statement distribution.
“This milestone brings us one step closer to unlocking Bitcoin’s potential for KindlyMD shareholders,” Bailey said yesterday. “We are grateful that KindlyMD shares our vision for a future in which Bitcoin is a core part of the corporate balance sheet.”
With its Bitcoin-first strategy and strategic alliances, the Nakamoto-KindlyMD partnership is set to accelerate institutional Bitcoin adoption—and with Anchorage Digital’s infrastructure behind it, the foundation is now firmly in place.
“By collaborating with Anchorage Digital, we are implementing our Bitcoin treasury strategy with the utmost standards in safety and security for our shareholders,” stated Tim Pickett, CEO of KindlyMD. “Their institutional-grade platform allows us to confidently hold Bitcoin as a treasury asset as we look to unlock access to Bitcoin and drive value for the long term.”
Disclosure: Nakamoto is in partnership with Bitcoin Magazine’s parent company BTC Inc to build the first global network of Bitcoin treasury companies, where BTC Inc provides certain marketing services to Nakamoto. More information on this can be found here.
This post KindlyMD, Nakamoto, and Anchorage Digital Form Strategic Bitcoin Treasury Alliance first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ cae03c48:2a7d6671
2025-05-23 14:01:05
@ cae03c48:2a7d6671
2025-05-23 14:01:05Bitcoin Magazine

How Zeus is Redefining Bitcoin with Cashu Ecash IntegrationThe U.S.-based Bitcoin and Lightning mobile wallet Zeus recently announced an alpha-release integration of Cashu. The move marks the first integration of ecash into a popular Bitcoin wallet, breaking new ground for potential user adoption to Bitcoin.
Cashu is a hot new implementation of Chaumian ecash, a form of digital cash invented by David Chaum in the ’90s that has incredible privacy and scalability properties, with the trade-off of being fundamentally centralized, requiring a significant amount of trust in the issuer.


In a counterintuitive move for Zeus, known as the go-to tool for advanced Lightning users seeking to connect to their home nodes, the integration of Cashu acknowledges a “last mile” challenge Lightning wallets face when delivering Bitcoin to the masses.
“We basically started off as the cypherpunk wallet, right? You got to set up your own Lightning node and connect to it with Zeus. The last two years, we put the node in the phone with one click, you can run it all in a standalone app without a remote node,” Evan Kaloudis, founder and CEO of Zeus, told Bitcoin Magazine.
“Cashu addresses uneconomical self-custody for small bitcoin amounts. On-chain, the dust limit is 546 satoshis, and Layer Two systems like Lightning have costs for channel setup or unilateral exits that aren’t widely discussed,” Evan explained, highlighting a major point of friction in noncustodial Lightning wallets: the need for liquidity and channel management. While these esoteric aspects of the Lightning Network have been mostly abstracted away since its invention in 2016, these fundamental trade-offs continue to manifest even in the most sophisticated and user-friendly wallets.
In the case of both Phoenix and Zeus, two of the most popular noncustodial options in the market, users must pay up to 10,000 sats upfront to gain spending capacity. These fees are necessary to cover the on-chain fees spent to open a channel for the user against the wallet’s liquidity service provider, unlocking a noncustodial experience.
The required up-front fee is difficult to explain and represents a painful onboarding experience for new users who are used to fiat apps giving them money to join instead. The result is the proliferation of custodial Lightning wallets like Wallet of Satoshi (WOS), which gained massive adoption early on by leveraging the global, near-instant settlement power of Bitcoin combined with the excellent user experience centralized wallets can create.
Major developments have been made over seven years after the Lightning Network’s inception, however, and Zeus is pushing the boundaries.
“With Ecash, we make it so easy that anyone can set up a wallet and start participating in our ecosystem, which I really think is going to become more and more prevalent,” Evan explained.
Today, at roughly $100,000 per bitcoin, 1,000 satoshis are equivalent to $1. Transactions of these sizes are known as microtransactions — a popular example are Nostr social media tips known as Zaps. But finding the right tool for this use case is not simple. Self custodied wallets like Phoenix charge transaction fees in the hundreds of satoshis, even with open channels, and on-chain fees often cost the same and are slower to settle. As a result, there’s an entire category of spending that is only served by cheaper alternatives such as custodial lightning wallets like WOS or Blink, but result in significant privacy tradeoffs, often requiring phone numbers from users and in some cases more advanced KYC and IP tracking. Cashu hopes to serve this market with lower privacy costs, the same ease of use, speed and competitive fees.
Digging deeper into the Cashu integration, Evan explained that “for users this means being able to pick and switch between custodians in a single app. For developers this means being able to defer custodial responsibilities to third parties and not have to wire up a new integration when your current custodian halts operations.”
Zaps are satoshi-denominated rewards delivered as “likes” or micro-tips for content in the Nostr social media ecosystem. A Zap can be as small as one satoshi, the smallest amount of bitcoin that can be technically transferred, equivalent today to about a tenth of a penny. “But I think if we look at Nostr and you’re seeing how many people are Zapping and how big a part of that ecosystem it is. It’s like, people are willing to do it,” Evan explained.
“Cashu, while custodial, lets users accumulate small amounts — say, via Nostr Zaps — without needing 6,000 satoshis to open a Lightning channel. Zeus prompts users to upgrade to self-custody as their balance grows,” he concluded, explaining that the wallet will effectively annoy users into self custody, one of several design choices made to mitigate the risks introduced by Cashu.
Ecash
The trade-offs introduced by Cashu challenge the common understanding of custody as an either-or in Bitcoin. Historically you were either a centralized — custodial — exchange, or you were a noncustodial Bitcoin wallet. In the former, you entrust the coins to a third party; in the latter you take personal responsibility for those coins and their corresponding private keys. Cashu changes this paradigm by introducing bitcoin-denominated ecash notes or “nuts,” which are bearer instruments that should be backed by a full bitcoin reserve and Lightning interoperability for instant withdraw.
Similar to fiat cash, you must take control and responsibility over these notes, but there’s also counterparty risk. In the case of Cashu, there are certain things the issuing mint can theoretically do to exploit their users — akin to how a bank can run on a fractional reserve.
The big difference between Cashu or custodial Bitcoin exchanges and fiat currency is that Cashu is open source, is designed around user privacy, and scales very well. It makes the cost of running a mint lower than either alternative, a feature that makes mint competition easier, in theory countering the centralizing network effects of specific mints.
Finally, the user experience of storing Cashu tokens has been attached to known forms of Bitcoin self custody such as the download of 12-words seeds via various mechanisms, though implementations still vary from wallet to wallet and the whole ecosystem is in its early stages.
To further mitigate the custodial risk of Chaumian-style ecash in Bitcoin, the Cashu community has developed various methods for automatically managing custody risk.



“Users can split risk by using multiple mints, switching between them in the user interface. Soon, ZEUS will guide users to select five or six reputable mints, automatically balancing funds to minimize exposure,” Evan explained, referring to a particular approach called automated bank runs. The idea is that as some Cashu mints may hold more of your funds, Zeus de-ranks them and rotates value out to minimize risk.
“I think the idea is going to be that we guide users to pick five or six reputable mints… And from there, users will be able to have the wallet automatically switch between those mints and determine which mint should be receiving the balance depending on the balance of all the mints presently. So you’ll be like, OK. MiniBits has way too much money. Let’s switch the default to one of the mints that doesn’t have a lot. So that way you can sort of mitigate or rather distribute the rug risk there,” Evan explained, adding, “Our Discover Mint feature pulls reviews from bitcoinmints.com, showing vouch counts and user feedback, like mint reliability or longevity,” describing the reputation layer stacked on top of the various other risk management mechanisms.
There is no known way to use Chaumian-style ecash in an entirely noncustodial way. So as long as the custody risk can be minimized, the scaling and privacy upside becomes remarkable.
Microtransactions
One of the opportunities that ecash unlocks is microtransactions, the most popular example of which are Nostr Zaps often in single dollar ranges of value transferred, though it applies to small Lightning transactions as well. This use case triggers an important technical question that predates Bitcoin, do microtransactions actually make economic sense?
There’s a long-standing argu
-
 @ 6d5c826a:4b27b659
2025-05-23 21:42:17
@ 6d5c826a:4b27b659
2025-05-23 21:42:17- Collins - At Tumblr, it's the infrastructure source of truth and knowledge. (Source Code)
Apache-2.0Docker/Scala - i-doit - IT Documentation and CMDB.
AGPL-3.0PHP - iTop - Complete ITIL web based service management tool. (Source Code)
AGPL-3.0PHP - netbox - IP address management (IPAM) and data center infrastructure management (DCIM) tool. (Demo, Source Code)
Apache-2.0Python
- Collins - At Tumblr, it's the infrastructure source of truth and knowledge. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:41:59
@ 6d5c826a:4b27b659
2025-05-23 21:41:59- Ansible - Provisioning, configuration management, and application-deployment tool. (Source Code)
GPL-3.0Python - CFEngine - Configuration management system for automated configuration and maintenance of large-scale computer systems. (Source Code)
GPL-3.0C - Chef - Configuration management tool using a pure-Ruby, domain-specific language (DSL) for writing system configuration "recipes". (Source Code)
Apache-2.0Ruby - cloud-init - Initialization tool to automate the configuration of VMs, cloud instances, or machines on a network. (Source Code)
GPL-3.0/Apache-2.0Python - Puppet - Software configuration management tool which includes its own declarative language to describe system configuration. (Source Code)
Apache-2.0Ruby/C - Rudder - Scalable and dynamic configuration management system for patching, security & compliance, based on CFEngine. (Source Code)
GPL-3.0Scala - Salt - Event-driven IT automation, remote task execution, and configuration management software. (Source Code)
Apache-2.0Python
- Ansible - Provisioning, configuration management, and application-deployment tool. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:41:37
@ 6d5c826a:4b27b659
2025-05-23 21:41:37- Eggdrop - The oldest Internet Relay Chat (IRC) bot still in active development. (Source Code)
GPL-2.0C - Errbot - Plugin based chatbot designed to be easily deployable, extensible and maintainable. (Source Code)
GPL-3.0Python - Hubot - A customizable, life embetterment robot. (Source Code)
MITNodejs
- Eggdrop - The oldest Internet Relay Chat (IRC) bot still in active development. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:41:18
@ 6d5c826a:4b27b659
2025-05-23 21:41:18- EasyBuild - EasyBuild builds software and modulefiles for High Performance Computing (HPC) systems in an efficient way. (Source Code)
GPL-2.0Python - Environment Modules - Environment Modules provides for the dynamic modification of a user's environment via modulefiles. (Source Code)
GPL-2.0Tcl - Lmod - Lmod is a Lua based module system that easily handles the MODULEPATH Hierarchical problem. (Source Code)
MITLua - Spack - A flexible package manager that supports multiple versions, configurations, platforms, and compilers. (Source Code)
MIT/Apache-2.0Python
- EasyBuild - EasyBuild builds software and modulefiles for High Performance Computing (HPC) systems in an efficient way. (Source Code)
-
 @ cae03c48:2a7d6671
2025-05-23 14:01:04
@ cae03c48:2a7d6671
2025-05-23 14:01:04Bitcoin Magazine

Bitcoin Liquid Network Surpasses $3.27 Billion in Total Value LockedToday, the Liquid Federation has announced that the Liquid Network has surpassed $3.27 billion in total value locked (TVL), according to a press release shared with Bitcoin Magazine.
“Surpassing the $3 billion threshold marks a pivotal moment for both Liquid and Bitcoin, signaling the evolution of Bitcoinʼs ecosystem into a full-fledged platform for global financial markets,” said the CEO and Co-Founder of Blockstream Dr. Adam Back. “As Bitcoin gains mainstream acceptance, and demand for regulated asset tokenization accelerates, Liquid is better positioned than ever to bridge Bitcoin with traditional finance and drive the next wave of capital markets innovation.”
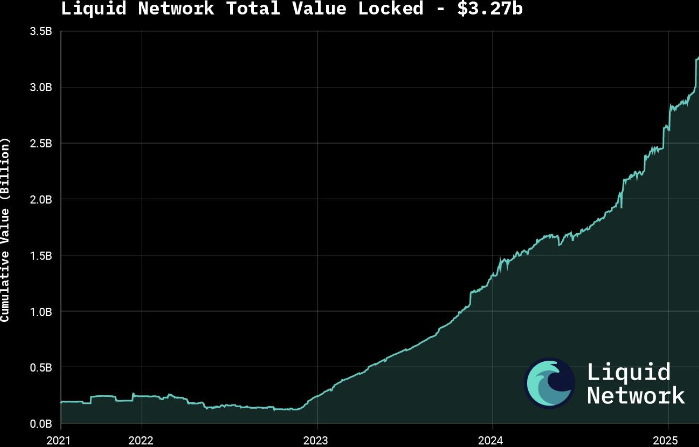
The announcement follows growing interest in tokenizing real-world assets (RWAs), with major moves such as BlackRock’s decision to tokenize a $150 billion Treasury fund. According to a 2025 report by Security Token Market, the tokenized asset market is projected to grow to $30 trillion by 2030.
Liquid supports over $1.8 billion in tokenized private credit and offers products like U.S. Treasury notes and digital currencies through Blockstream’s AMP platform. The network also features fast, low-cost, and confidential transactions, with support for atomic swaps and robust smart contracts.
Governed by over 80 global institutions, Liquid was launched in 2018 as Bitcoin’s first sidechain. It is now preparing for a major upgrade with the mainnet release of Simplicity, aimed at expanding its smart contract capabilities.
To keep up with increasing demand, the Liquid Federation is boosting developer resources and technical onboardings, along with integrations with exchanges, custodians and service providers. Recent bootcamps and important meetings with policy makers in Asia, Europe and Latin America reflect the network’s growing global presence.
This post Bitcoin Liquid Network Surpasses $3.27 Billion in Total Value Locked first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ eed7ca5d:191de8eb
2025-05-23 13:58:46
@ eed7ca5d:191de8eb
2025-05-23 13:58:46Growing up, we were told that in order to build wealth, we need to save little by little. By living below your means, you are providing more for your future.
It is a simple formula that will help you build up the capital necessary to buy a car, a house or start a business… You prioritize long-term benefits and delayed gratification over immediate rewards.
This is called having a low-time preference. In contrast, high-time preference individuals prioritize today over tomorrow, seeking immediate gratification.
Austrian economists explain that civilization growth is driven by low-time preference societies. Groups of individuals who prioritize long-term planning are able to innovate and develop new tools for a better future. Over time, this behavior leads to technological inventions like the light bulb and artistic masterpieces like the Notre Dame cathedral.
***What happens when you realize that the money you save is losing value over time? ***
There is less incentive to save for the future, because in the future your savings will be worth less. You might as well spend it now and enjoy life today.
When the money you save loses its value, you are facing one of two choices:
-
Spend it today and reap the rewards of your hard work;
-
Invest it (stocks, real estate, etc.) with the hope to reap higher rewards later, bearing the risk of losing it all if the investment does not pay off.
There is a distinct difference between saving and investing as the latter approach is riskier than the former. By investing, you are betting on the upside while bearing the downside risk. Saving, in contrast, comes without downside risk. That difference becomes blurry when the money you save is losing value. In fact, saving becomes inherently a losing approach. Logically, you will be forced to place a speculative bet with the hope to outperform the guaranteed loss of value. You are required to find a way to hedge your bet…
Humans over time have always sought out a medium to save their economic energy for a better future. That used to be beads and seashells, and evolved to precious metals like gold and silver.
Money is a tool that we use to save our economic energy over time, and exchange value with each other.
I spend time fishing, you spend time farming, the neighbor spends time building homes, and society rewards us with money for the time and energy we spent being productive
Today, the tool that we use to save our economic energy is clearly losing value over time. The nominal value remains the same, but the purchasing power is decreasing. In other words, the value of our time today will be worth less in the future.
That explains why everyone around us is looking for the next best investment opportunity. We are all needing to become investment experts, speculators, on top of our respective professions. Speculation became necessary, and some of us are forced into a high-time preference lifestyle.
Earn now and spend it all now before you lose it.
This should not be the case…
Time is Money
Our time is the only scarce resource we all have. We use it to be productive and generate economic value, then store that value in the form of money in order to reap the rewards in the future.
Money is the abstract representation of our time. Hence, time is money.
In January 2009, at the height of the global financial crisis, a software protocol called Bitcoin was released pseudonymously by Satoshi Nakamoto. This individual (or group) released a whitepaper a few months prior named “Bitcoin: A Peer-to-Peer Electronic Cash System” outlining how the system enables secure, peer-to-peer transactions without relying on a central authority. (https://bitcoin.org/bitcoin.pdf)
Although there are more technical concepts involved, the bitcoin protocol can be thought of as a language for communicating value. The same way we respect the rules of the English language to communicate ideas with one another, bitcoin users adhere to the network’s consensus rules to communicate value with each other in a peer-to-peer fashion.
There are no physical or digital coins in the bitcoin network. Rather, it is a collection of transactions transferring value from sender to recipient. Transactions are validated and propagated by nodes across the network, before being recorded into the blockchain. The Bitcoin blockchain is a global public ledger of all transactions that cannot be altered.
More importantly, Bitcoin is money that does not lose value overtime.
-
Its supply is capped at 21 million coins.
-
Its scarcity increases over time due to the predictable issuance rate, which halves roughly every 4 years.
-
Its decentralized nature puts the power in the hands of its users.
-
There is no governing body that can devalue or alter it.
It is a tool that we can use to save our economic energy over time, and be able to use it later.
It is the scarcest verifiable commodity: we cannot make more of it no matter how high its demand grows. That cannot be said for any other commodity in the world today.
A savings tool in disguise
See, most people tend to view bitcoin as another speculative investment. They presume they have missed out on another investment opportunity, and it’s now too late to get in.
Meanwhile, it is quite the opposite. Bitcoin’s value will keep growing over time due to its deflationary nature.
With bitcoin, we can save for a better future, for a rainy day, and spend more time with our loved ones or focusing on our craft to build better tools or artistic masterpieces. It takes away the burden of having to speculate on which stock will perform best, or which real estate market will grow the fastest, all while working one or multiple jobs
Bitcoin is not another investment opportunity you missed out on. It is the best savings tool humans have invented (or discovered), while everything else is the speculative bet. Bitcoin is the hedge against the guaranteed devaluation of money, without any counterparty risk.
What we were taught as children is true. With the right tool, the idea that saving will help you build wealth overtime stands true. Bitcoin might seem like an investment today given the volatility during its adoption phase. In reality, it is the perfect way to store your time and economic energy and grow your wealth. Whether you make $1/hour or $1M/hour, you can start saving in the best money humans have invented.
My goal is to help people around me understand this technology and break the stigma around it.
Bitcoin is not the next best investment.
It is the best tool we have found to store our economic energy across time and exchange value with each other.
Bitcoin is Money.
-
-
 @ 6d5c826a:4b27b659
2025-05-23 21:40:57
@ 6d5c826a:4b27b659
2025-05-23 21:40:57- Backupninja - Lightweight, extensible meta-backup system, provides a centralized way to configure and coordinate many different backup utilities.
GPL-2.0Shell - Backrest - Backrest is a web UI and orchestrator for restic backup. (Source Code)
GPL-3.0Docker/Go - Bareos - Cross-network backup solution which preserves, archives, and recovers data from all major operating systems. (Source Code)
AGPL-3.0C++/C - Barman - Backup and Recovery Manager for PostgreSQL. (Source Code)
GPL-3.0Python - BorgBackup - Deduplicating archiver with compression and authenticated encryption. (Source Code)
BSD-3-ClausePython - Burp - Network backup and restore program. (Source Code)
AGPL-3.0C - Dar - Which stands for Disk ARchive, is a robust and rich featured archiving and backup software of the tar style. (Source Code)
GPL-2.0C++ - Duplicati - Backup client that securely stores encrypted, incremental, compressed backups on cloud storage services and remote file servers. (Source Code)
LGPL-2.1C# - Duplicity - Encrypted bandwidth-efficient backup using the rsync algorithm. (Source Code)
GPL-2.0Python - Proxmox Backup Server - Proxmox Backup Server is an enterprise-class, client-server backup solution thatis capable of backing up virtual machines, containers, and physical hosts. (Source Code)
GPL-3.0Rust - rclone - Command-line program to sync files and directories to and from different cloud storage providers.. (Source Code)
MITGo - Rdiff-backup - Reverse differential backup tool, over a network or locally. (Source Code)
GPL-2.0Python - Restic - Easy, fast, verifiable, secure and efficient remote backup tool. (Source Code)
BSD-2-ClauseGo - Rsnapshot - Filesystem snapshot utility based on rsync. (Source Code)
GPL-2.0Perl - Shield - A pluggable architecture for backup and restore of database systems.
MITGo - UrBackup - Client/Server Open Source Network Backup for Windows, MacOS and Linux. (Source Code)
AGPL-3.0C/C++
- Backupninja - Lightweight, extensible meta-backup system, provides a centralized way to configure and coordinate many different backup utilities.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:40:34
@ 6d5c826a:4b27b659
2025-05-23 21:40:34- Apache Ant - Automation build tool, similar to make, a library and command-line tool whose mission is to drive processes described in build files as targets and extension points dependent upon each other. (Source Code)
Apache-2.0Java - Apache Maven - Build automation tool mainly for Java. A software project management and comprehension tool. Based on the concept of a project object model (POM), Maven can manage a project's build, reporting and documentation from a central piece of information. (Source Code)
Apache-2.0Java - Bazel - A fast, scalable, multi-language and extensible build system. Used by Google. (Source Code)
Apache-2.0Java - Bolt - You can use Bolt to run one-off tasks, scripts to automate the provisioning and management of some nodes, you can use Bolt to move a step beyond scripts, and make them shareable. (Source Code)
Apache-2.0Ruby - GNU Make - The most popular automation build tool for many purposes, make is a tool which controls the generation of executables and other non-source files of a program from the program's source files. (Source Code)
GPL-3.0C - Gradle - Another build automation system. (Source Code)
Apache-2.0Groovy/Java - Rake - Build automation tool similar to Make, written in and extensible in Ruby. (Source Code)
MITRuby
- Apache Ant - Automation build tool, similar to make, a library and command-line tool whose mission is to drive processes described in build files as targets and extension points dependent upon each other. (Source Code)
-
 @ 47259076:570c98c4
2025-05-23 13:57:28
@ 47259076:570c98c4
2025-05-23 13:57:28"Know thyself and you will know the universe and the gods"
This is the greatest truth.
Knowing yourself is a process that is perhaps eternal.
Knowing yourself means making conscious what is unconscious, in all fields.
Making conscious your material reality, your emotions, your thoughts, your mind, your patterns, your spirit, your flaws, your qualities, etc.
The journey is within.
And in this process, burning everything that is not you.
Burning everything so only the essential remains.
The essential being your higher self.
You are not your body, you are not your emotions, you are not your mind, etc...
You are pure consciousness.
Everyday we can learn from him, but if we are asleep, we will not realize the gold opportunities passing right in front of our eyes.
Everyday he teaches us.
If everyday he teaches us, why stress so much for having an astral projection?
If an astral projection happens with you, it will be a good experience indeed, if you know how to value opportunities.
Otherwise, you may see some """evil"" spirits trying to scare you.
Therefore, don't depend on astral projection for your spiritual growth.
In fact, don't depend on anything.
Don't depend on books, don't depend on people, don't depend on "psychologists", don't depend on "rituals", don't depend on institutions, and of course, don't depend on the "government".
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-23 13:46:21
@ 5d4b6c8d:8a1c1ee3
2025-05-23 13:46:21You'd think I'd be most excited to talk about that awesome Pacers game, but, no. What I'm most excited about this week is that @grayruby wants to continue Beefing with Cowherd.
Still, I am excited to talk about Tyrese Haliburton becoming a legendary Knicks antagonist. Unfortunately, the Western Conference Finals are not as exciting. Also, why was the MVP announcement so dumb?
The T20k cricket contest is tightening up, as we head towards the finish. Can @Coinsreporter hold on to his vanishing lead?
@Carresan has launched Football Madness. Let's see if we understand whatever the hell this is any better than we did last week.
On this week's Blok'd Shots, we'll ridicule Canada for their disgraceful loss in the World Championships and talk about the very dominant American Florida Panthers, who are favorites to win the Stanley Cup.
Are the Colorado the worst team in MLB history?
The Tush Push has survived another season. Will the NFL eventually ban it or will teams adjust?
Plus, whatever else Stackers want to talk about.
https://stacker.news/items/987399
-
 @ 30b99916:3cc6e3fe
2025-05-23 13:16:37
@ 30b99916:3cc6e3fe
2025-05-23 13:16:37sourcegraph #vibecoding #ai #bitcoin #security
After reading the article Revenge of the junior developer, this inspired me to go take a look at Sourcegraph.com to get a better understanding of all this AI stuff.
The first step was installing the VS Code extension called, Cody which is a coding agent. The Cody features explain the code in a file and review and analyze code did an extremely impressive job with VaultApi and BTCwallet.
VaultApi and BTCwallet are PowerShell scripts that are available from my BTCPAY Server
All of the following output was generated by Cody.
Code Analysis of VaultApi.ps1
The VaultApi.ps1 script is generally well-structured and follows many PowerShell best practices. It has comprehensive documentation, version history, and clear parameter definitions. The suggestions below would further enhance what is already a solid codebase. The author has clearly put significant effort into making the script functional and user-friendly, with good attention to cross-platform compatibility and security considerations.
VaultApi.ps1 Explanation
VaultApi.ps1 is a PowerShell script that helps users interact with HashiCorp Vault, which is a tool for securely storing and managing sensitive information like passwords and API keys.
Purpose of the Code
This script makes it easier to use Vault by providing simple commands to start the Vault server, unlock it (unseal), log in, store secrets, retrieve secrets, and shut down the server. Think of it as a friendly interface that simplifies all the complex operations you would otherwise need to do manually with Vault.
Inputs
The script takes several inputs:
- An
actionparameter that tells the script what operation to perform (like "Start", "Stop", "Kv1Create", "Kv1Read") - A
kvpathparameter that specifies where in Vault to store or retrieve information - A
kvalueparameter for the actual secret value you want to store - A
kvkeyparameter that lets you specify a custom name for your secret - Optional switches like
-Infoto show more detailed information and-Rawto display output directly instead of copying to clipboard
Outputs
Depending on the action performed, the script produces different outputs:
- Text messages in the console showing the status of operations
- Secret values retrieved from Vault (either displayed or copied to clipboard)
- Lists of available secret paths
- Status information about the Vault server
- Backup files of your Vault data
How It Works
The script works by:
- First checking if Vault is installed and running
- Setting up communication with the Vault server using its API address
- Performing the requested action by sending the appropriate commands to Vault
- Processing any responses and displaying results to the user
For example, when you use the "Kv1Create" action, the script:
- Checks if you're logged in
- Verifies the path doesn't already exist
- Formats your data correctly
- Sends a request to Vault to create the new secret
- Shows you the result
Important Logic Flows
Some key processes in the script include:
-
Authentication flow: The script helps you log in using either a token or username/password, then stores your authentication token for future commands.
-
Unsealing process: Vault requires multiple keys to unlock (unseal) it after starting. The script can retrieve these keys from a secure file or prompt you to enter them.
-
Secret management: The script handles creating, reading, updating, and deleting secrets, supporting both single values and multiple key-value pairs at a path.
-
Path management: The script can list all available paths and help you search for specific ones, making it easier to organize and find your secrets.
-
Value generation: When creating or updating secrets, you can use the keyword "setvalue" to automatically generate a random 20-character value, which is then copied to your clipboard.
The script uses a configuration file in your home directory to know how to connect to Vault, and it can optionally use encrypted files to store sensitive information like unlock keys. It communicates with Vault using REST API calls, which are like special messages that tell Vault what to do.
In summary, VaultApi.ps1 is a helper tool that makes it much easier to use HashiCorp Vault for securely storing and managing your sensitive information, without needing to remember all the complex commands and procedures.
Code Analysis of BTCwallet.ps1
The script generally follows sound design principles with good organization, comments, and documentation. It demonstrates thoughtful error checking and user interaction. The identified opportunities for enhancement would primarily improve security, maintainability, and robustness rather than addressing fundamental flaws. The script author has clearly put significant effort into creating a comprehensive tool with good documentation and practical functionality.
BTCwallet.ps1 Explanation
The BTCwallet.ps1 script is a PowerShell tool designed to help Bitcoin users manage different wallet applications on a Linux system. It provides a convenient way to start, stop, and check the status of Bitcoin wallets while adding security features.
Purpose
The main purpose of this script is to securely manage Bitcoin wallets, particularly focusing on "cold storage" solutions. Cold storage means keeping your Bitcoin wallet data in an encrypted container that's only mounted when needed, which is more secure than keeping it always accessible ("hot storage").
Inputs
The script takes one main input parameter:
$action: This can be "start", "stop", or "check" (default), telling the script what operation to perform on your Bitcoin wallet.
Outputs
The script doesn't return data but produces several visible outputs:
- Status messages showing whether wallets are running or stopped
- Prompts for user input when decisions are needed
- Confirmation messages when actions are completed
How It Works
-
When you run the script, it first loads a configuration file (BTCwalletCfg.xml) that contains information about which wallets you have installed.
-
Based on the
$actionparameter, it performs one of three main functions:- Check: Shows if your wallet application is currently running
- Start: Launches your wallet application, with options for hot or cold storage
- Stop: Closes your wallet application and securely dismounts any encrypted containers
- For security, the script can use HashiCorp Vault (a secure password manager) to store sensitive information like passwords for encrypted containers.
-
The script also verifies its own integrity by checking its file hash against a previously stored value, alerting you if the script has been modified.
Important Logic Flows
Starting a Wallet
When starting a wallet, the script:
- Asks which wallet you want to use (Sparrow, GreenWallet, or Wasabi)
- Checks if HashiCorp Vault is running and starts it if needed
- Verifies the script's integrity by comparing file hashes
- Asks if you want to use hot or cold storage
- For cold storage, it:
- Retrieves the encrypted container's location and password
- Mounts the encrypted container using VeraCrypt
- Starts the wallet application pointing to the mounted container
- For hot storage, it simply starts the wallet application with default settings
Stopping a Wallet
When stopping a wallet, the script:
- Checks if the wallet is still running and asks you to close it first if needed
- For cold storage wallets, it moves any wallet files back to the encrypted container
- Dismounts the encrypted container
- Optionally stops the HashiCorp Vault service
The script handles different wallet applications (Sparrow, GreenWallet, and Wasabi) slightly differently based on how each one stores its data and what command-line options they support.
In summary, BTCwallet.ps1 provides a secure way to manage Bitcoin wallets by combining wallet applications with encrypted storage and password management, all controlled through simple commands.
- An
-
 @ 63d59db8:be170f6f
2025-05-23 12:53:00
@ 63d59db8:be170f6f
2025-05-23 12:53:00In a world overwhelmed by contradictions—climate change, inequality, political instability, and social disconnection—absurdity becomes an unavoidable lens through which to view the human condition. Inspired by Albert Camus' philosophy, this project explores the tension between life’s inherent meaninglessness and our persistent search for purpose.\ \ The individuals in these images embody a quiet defiance, navigating chaos with a sense of irony and authenticity. Through the act of revolt—against despair, against resignation—they find agency and resilience. These photographs invite reflection, not on solutions, but on our capacity to live meaningfully within absurdity.
Visit Katerina's website here.
Submit your work to the NOICE Visual Expression Awards for a chance to win a few thousand extra sats:
-
 @ a296b972:e5a7a2e8
2025-05-23 12:42:10
@ a296b972:e5a7a2e8
2025-05-23 12:42:10Was Rudolf Steiner vor gut 110 Jahren an Informationen zusammengetragen und kommentiert hat, liest sich in großen Abschnitten so, als ob es in der heutigen Zeit geschrieben worden wäre. Man trifft auf eine ganze Reihe von „guten, alten Bekannten“, die auch heute noch maßgeblich an den Strippen ziehen. Deutlich wird, dass ein Krieg nicht aus heiterem Himmel ausbricht, sondern das im Vorfeld schon Kräfte wirken, die auf einen Krieg hinarbeiten. Wie jetzt wieder im Ukraine-Krieg wird diese Vorgeschichte gerne versucht unter den Teppich zu kehren und hochkompetente, sauber recherchierende, akribisch Quellen angebende Journalisten, wie z. B. Frau Gabriele Krone-Schmalz oder Herr Patrik Baab, der sich auf eigene Kosten einen Eindruck von vor Ort verschafft hat, werden versucht mundtot zu machen und mittlerweile gar nicht mehr zu Gesprächen im öffentlich-rechtlichen Rundfunk eingeladen, weil sie die fortlaufende Gehirnwäsche des Ministeriums für Wahrheit und Narrative mit ihren Aussagen gefährden. Andere kommen auf die Sanktionsliste.
Auch heute ist von den „Guten“ und den „Bösen“ die Rede, was darauf schließen lässt, dass man durchaus eingesteht, dass hier geistige Kräfte am Werk sind. Rudolf Steiner kommt auf diese immer wieder zu sprechen. Aus der von ihm gegebenen anthroposophischen Geisteswissenschaft heraus, beleuchtet er die Vorgänge innerhalb der gesamten Menschheitsentwicklung. Mancher stört sich hier an Begriffen, die man heute so nicht mehr verwenden würde. Dabei ist immer zu berücksichtigen, zu welcher Zeit die Vorträge gehalten wurden. Die Anthroposophie von Rudolf Steiner gilt heute bei vielen auch als „umstritten“, aber was ist das heute nicht? Fast könnte man es schon als Auszeichnung sehen, wenn etwas „umstritten“ ist, denn das ist mittlerweile ein Beweis dafür, dass es Ansichten, Meinungen und Einschätzungen gibt, die in einer gesunden Demokratie innerhalb einer Kontroverse zu einem Dialog und Austausch beitragen können, der jedoch leider derzeit weder gewünscht ist, noch gepflegt wird, was an der „Spaltung“ deutlich zu sehen ist. Und auch unter den Anthroposophen hat die „Spaltung“ Einzug gehalten.
Um das aktuelle, viele Bereiche umschließende, gigantische Lügenkonstrukt aufrecht zu erhalten, ist mittlerweile jedes Mittel recht, von der Deutungshoheit der Wahrheit durch systemkonforme Begutachter, bis hin zu infantil-kleingeistigen Kindergartenspielchen, um gegenläufige Meinungen oder Oppositionelle in ihrem Wirken zu behindern.
Der gesunde Hausverstand wird ausgetrocknet, und der Garten des Wahnsinns wird durch immer neue Ideen kranker Geister weiter gegossen, gehegt und gepflegt.
Die Zeitgeschichtlichen Betrachtungen von Rudolf Steiner bestehen aus 3 Bänden aus der GA (Gesamtausgabe):
GA 173 a – Wege zu einer objektiven Urteilsbildung
GA 173 b – Das Karma der Unwahrhaftigkeit
GA 173 c – Die Wirklichkeit okkulter Impulse
Sie bestehen aus niedergeschriebenen Vorträgen und einem sehr umfangreichen Anhang mit näheren Erläuterungen und einer Schilderung der Entstehung dieser drei Bände.
Es bedarf einiger Eingewöhnung in die zur damaligen Zeit verwendete Sprache Rudolf Steiners, der ein Meister im Bilden von Schachtelsätzen war. Der Inhalt jedoch, und auf den kommt es ja an, berührt immer wieder den in allen Menschen vorhandenen Wahrheitssinn.
Hier nur eine kleine Kostprobe, die vielleicht das Interesse wecken kann, sich mit diesem derzeit besonders aktuellen Werk näher zu beschäftigen.
GA 173a, 6. Vortrag, Seite 205 und Seite 206, Dornach, 17. Dezember 1916:
„Viel intimer, viel verborgener liegen die Dinge bei der englischen Politik, die ja ganz beeinflußt ist von dem, was in solcher Weise hinter ihr steckt. Da handelt es sich darum, daß man die Wege findet, um die entsprechenden Menschen an die richtigen Plätze zu befördern. Okkultistische Menschen, im Hintergrunde stehend, sind oftmals – na, verzeihen Sie – Einser, bloße Einser, und bedeuten für sich nichts Besonderes; sie brauchen noch etwas anderes – sie brauchen Nullen. Nullen sind ja nicht Einser, aber (fügt man eine Null zu einer Eins), dann wird gleich eine Zehn daraus. Und wenn man noch mehr Nullen hinzufügt – jede Null ist nur eine Null, aber wenn die Eins irgendwo steckt, dann ist gar mancherlei da, zum Beispiel die Tausend, und wenn man die Eins zudeckt, dann sind (scheinbar) nur die Nullen da; die Nullen brauchen aber nur in der entsprechenden Weise mit den Einsern kombiniert zu sein, und sie brauchen nicht einmal viel zu wissen von der Art, wie sie mit den Einsern kombiniert sind.“
Schildert diese 108 Jahre alte Beschreibung nicht genau das, was sich heute vor unseren Augen abspielt?
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 1817b617:715fb372
2025-05-23 20:21:53
@ 1817b617:715fb372
2025-05-23 20:21:53🚀 Instantly Send Spendable Flash BTC, ETH, & USDT — Fully Blockchain-Verifiable!
Welcome to the cutting edge of crypto innovation: the ultimate tool for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Our advanced blockchain simulation technology employs 🔥 Race/Finney-style mechanisms, producing coins indistinguishable from authentic blockchain-confirmed tokens. Your transactions are instantly trackable and fully spendable for durations from 60 to 360 days!
🌐 Visit cryptoflashingtool.com for complete details.
🌟 Why Choose Our Crypto Flashing Service? Crypto Flashing is perfect for crypto enthusiasts, blockchain developers, ethical hackers, security professionals, and digital entrepreneurs looking for authenticity combined with unparalleled flexibility.
🎯 Our Crypto Flashing Features: ✅ Instant Blockchain Verification: Transactions appear completely authentic, complete with real blockchain confirmations, transaction IDs, and wallet addresses.
🔒 Maximum Security & Privacy: Fully compatible with VPNs, TOR, and proxy servers, ensuring absolute anonymity and protection.
🖥️ Easy-to-Use Software: Designed for Windows, our intuitive platform suits both beginners and experts, with detailed, step-by-step instructions provided.
📅 Customizable Flash Durations: Control your transaction lifespan precisely, from 60 to 360 days.
🔄 Universal Wallet Compatibility: Instantly flash BTC, ETH, and USDT tokens to SegWit, Legacy, or BCH32 wallets.
💱 Spendable on Top Exchanges: Flash coins seamlessly accepted on leading exchanges like Kraken and Huobi.
📊 Proven Track Record: ✅ Over 79 Billion flash transactions completed. ✅ 3000+ satisfied customers worldwide. ✅ 42 active blockchain nodes for fast, reliable transactions. 📌 Simple Step-by-Step Flashing Process: Step 1️⃣: Enter Transaction Details
Choose coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20) Specify amount & flash duration Provide wallet address (validated automatically) Step 2️⃣: Complete Payment & Verification
Pay using the cryptocurrency you wish to flash Scan the QR code or paste the payment address Upload payment proof (transaction hash & screenshot) Step 3️⃣: Initiate Flash Transaction
Our technology simulates blockchain confirmations instantly Flash transaction appears authentic within seconds Step 4️⃣: Verify & Spend Immediately
Access your flashed crypto instantly Easily verify transactions via provided blockchain explorer links 🛡️ Why Our Technology is Trusted: 🔗 Race/Finney Attack Logic: Creates realistic blockchain headers. 🖥️ Private iNode Cluster: Guarantees fast synchronization and reliable transactions. ⏰ Live Timer System: Ensures fresh wallet addresses and transaction legitimacy. 🔍 Genuine Blockchain TX IDs: Authentic transaction IDs included with every flash ❓ Frequently Asked Questions: Is flashing secure? ✅ Yes, encrypted with full VPN/proxy support. Can I flash from multiple devices? ✅ Yes, up to 5 Windows PCs per license. Are chargebacks possible? ❌ No, flash transactions are irreversible. How long are flash coins spendable? ✅ From 60–360 days, based on your chosen plan. Verification after expiry? ❌ Transactions can’t be verified after the expiry. Support available? ✅ Yes, 24/7 support via Telegram & WhatsApp.
🔐 Transparent, Reliable & Highly Reviewed:
CryptoFlashingTool.com operates independently, providing unmatched transparency and reliability. Check out our glowing reviews on ScamAdvisor and leading crypto forums!
📲 Get in Touch Now: 📞 WhatsApp: +1 770 666 2531 ✈️ Telegram: @cryptoflashingtool
🎉 Ready to Start?
💰 Buy Flash Coins Now 🖥️ Get Your Flashing Software
Experience the smartest, safest, and most powerful crypto flashing solution on the market today!
CryptoFlashingTool.com — Flash Crypto Like a Pro.
Instantly Send Spendable Flash BTC, ETH, & USDT — Fully Blockchain-Verifiable!
Welcome to the cutting edge of crypto innovation: the ultimate tool for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Our advanced blockchain simulation technology employs
Race/Finney-style mechanisms, producing coins indistinguishable from authentic blockchain-confirmed tokens. Your transactions are instantly trackable and fully spendable for durations from 60 to 360 days!
Visit cryptoflashingtool.com for complete details.
Why Choose Our Crypto Flashing Service?
Crypto Flashing is perfect for crypto enthusiasts, blockchain developers, ethical hackers, security professionals, and digital entrepreneurs looking for authenticity combined with unparalleled flexibility.
Our Crypto Flashing Features:
Instant Blockchain Verification: Transactions appear completely authentic, complete with real blockchain confirmations, transaction IDs, and wallet addresses.
Maximum Security & Privacy: Fully compatible with VPNs, TOR, and proxy servers, ensuring absolute anonymity and protection.
Easy-to-Use Software: Designed for Windows, our intuitive platform suits both beginners and experts, with detailed, step-by-step instructions provided.
Customizable Flash Durations: Control your transaction lifespan precisely, from 60 to 360 days.
Universal Wallet Compatibility: Instantly flash BTC, ETH, and USDT tokens to SegWit, Legacy, or BCH32 wallets.
Spendable on Top Exchanges: Flash coins seamlessly accepted on leading exchanges like Kraken and Huobi.
Proven Track Record:
- Over 79 Billion flash transactions completed.
- 3000+ satisfied customers worldwide.
- 42 active blockchain nodes for fast, reliable transactions.
Simple Step-by-Step Flashing Process:
Step : Enter Transaction Details
- Choose coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20)
- Specify amount & flash duration
- Provide wallet address (validated automatically)
Step : Complete Payment & Verification
- Pay using the cryptocurrency you wish to flash
- Scan the QR code or paste the payment address
- Upload payment proof (transaction hash & screenshot)
Step : Initiate Flash Transaction
- Our technology simulates blockchain confirmations instantly
- Flash transaction appears authentic within seconds
Step : Verify & Spend Immediately
- Access your flashed crypto instantly
- Easily verify transactions via provided blockchain explorer links
Why Our Technology is Trusted:
- Race/Finney Attack Logic: Creates realistic blockchain headers.
- Private iNode Cluster: Guarantees fast synchronization and reliable transactions.
- Live Timer System: Ensures fresh wallet addresses and transaction legitimacy.
- Genuine Blockchain TX IDs: Authentic transaction IDs included with every flash
Frequently Asked Questions:
- Is flashing secure?
Yes, encrypted with full VPN/proxy support. - Can I flash from multiple devices?
Yes, up to 5 Windows PCs per license. - Are chargebacks possible?
No, flash transactions are irreversible. - How long are flash coins spendable?
From 60–360 days, based on your chosen plan. - Verification after expiry?
Transactions can’t be verified after the expiry.
Support available?
Yes, 24/7 support via Telegram & WhatsApp.
Transparent, Reliable & Highly Reviewed:
CryptoFlashingTool.com operates independently, providing unmatched transparency and reliability. Check out our glowing reviews on ScamAdvisor and leading crypto forums!
Get in Touch Now:
WhatsApp: +1 770 666 2531
Telegram: @cryptoflashingtool
Ready to Start?
Experience the smartest, safest, and most powerful crypto flashing solution on the market today!
CryptoFlashingTool.com — Flash Crypto Like a Pro.
-
 @ cae03c48:2a7d6671
2025-05-23 12:00:53
@ cae03c48:2a7d6671
2025-05-23 12:00:53Bitcoin Magazine

Not ECDSA. Not Schnorr. Meet DahLIAS.Aggregate signatures aren’t new. They’ve been around since the early 2000s. But building one that actually works in Bitcoin’s security model, with Bitcoin’s elliptic curve, has never been proven. Developers speculated it might be possible. They shared hand-wavy sketches and said, “maybe it’d work like MuSig2, but across transaction inputs.” The idea lingered for years as developer folklore, close, never provably confirmed.
That changed recently, when Jonas Nick and Tim Ruffing of Blockstream Research, together with Yannick Seurin of Ledger, published a paper that turned this cryptographic ghost story into a concrete, provable result. DahLIAS is the first formal, secure construction of a full constant-size aggregate signature (CISA) scheme that works on Bitcoin’s native curve!
But that’s a lot of words, so let’s break that down:
- Full aggregation: Multiple signatures across different inputs are combined into one — and the result is a 64 byte signature whose size stays constant, no matter how many signers or inputs.
- Cross-input: Each signer can authorize different inputs, and all combine into one signature.
It adds no significant new assumptions beyond those already relied on by Bitcoin. DahLIAS builds a new cryptographic primitive using the same math Bitcoin already relies on, unlocking an entirely new kind of signature.
Let’s Talk About Curves and Signatures
Digital signatures are how Bitcoin proves that a user has authorized a transaction. When you go to spend bitcoin, your wallet uses a private key to sign a message, and the network verifies that signature using the matching public key.
Bitcoin uses the secp256k1 curve. It is fast, efficient, and has been battle-tested over time. It supports signature schemes like ECDSA (Bitcoin’s original signature algorithm) and Schnorr (added through Taproot in 2021), which are currently the only signature schemes permitted by Bitcoin consensus.
Traditionally, full signature aggregation relied on mathematical operations not supported by Bitcoin’s curve, secp256k1, which made it seem out of reach. These features have typically relied on other types of elliptic curves. For example, BLS (Boneh–Lynn–Shacham) signatures use a special kind of curve called a pairing-friendly curve, which enables advanced operations like combining many signatures, even on different messages, into one.
The problem is that BLS signatures do not work on secp256k1. While Schnorr was a natural upgrade from ECDSA, since both rely on the same kind of elliptic curve, adding BLS would be a much bigger leap and a departure from Bitcoin’s existing security model. Though technically possible, it would introduce new cryptographic assumptions and add significant complexity to the protocol. Supporting a curve that is pairing-friendly, like BLS12-381, would be a major change for Bitcoin.
This is part of why full signature aggregation has never been done on secp256k1.
Until now.
What Aggregate Signatures Actually Do
Most Bitcoin users are familiar with multisignatures. In a multisig wallet, multiple people jointly authorize the spending of a single UTXO or some specific “coin”. Everyone signs the same input data. This setup is useful for things like shared custody wallets.
Aggregate signatures work differently. Instead of multiple people signing the same input or coin, each signer authorizes a different UTXO in a transaction. These separate signatures are then compressed into one compact proof. With DahLIAS, that means a single 64-byte signature on Bitcoin’s secp256k1 curve that verifies all inputs at once.
That means if you have five inputs from five different people, the transaction needs five different signatures. With an aggregate signature, all of those can be bundled into one. Even if each signer is spending a different input and signing a different part of the transaction, the result is one signature that proves the entire transaction was properly authorized.
It’s like zipping a whole list of approvals into one file. The signature is compact, but still verifiably proves that each signer authorized their specific UTXO.
Instead of verifying 10 separate signatures, you verify one.
This helps realign incentives for privacy. By reducing the signature overhead to a single 64-byte proof, DahLIAS lowers the cost of combining inputs in CoinJoins, making it financially smarter to choose privacy than to go without it.
Why Half-Aggregation Got Close
Shortly after Schnorr signatures were introduced on Bitcoin, developers explored half-aggregation, as a way to compress multiple signatures but they were not fixed size. Each input contributes to the size of the signature, so the transaction still grows with every participant. DahLIAS fixes this by enabling full-aggregation across inputs and signers. No matter how many people are involved or what they’re signing, all their signatures compress into one constant-size, 64-byte proof.
What DahLIAS Actually Unlocks
The main benefit here is that DahLIAS are reducing the size of complex transactions.
DahLIAS uses a two-round interactive signing process. It’s similar to MuSig2 in that regard, but it isn’t a multisignature protocol because it doesn’t require all participants to co-sign the same message. Instead, it aggregates different signatures on different messages across the transaction.
DahLIAS is also faster to verify than checking each signature individually, up to twice as fast in some cases. Lower verification costs make it easier for more people to run full nodes, which helps preserve Bitcoin’s decentralization over time.
Importantly, DahLIAS comes with strong cryptographic guarantees. The scheme includes formal security proofs. Earlier ‘folklore’ approaches to full signature aggregation lacked this, and some were even later shown to be insecure. Fortunately they weren’t adopted prematurely.
It’s worth repeating: DahLIAS is not a multisig protocol. It isn’t comparable to MuSig2 or FROST from a functional standpoint, even if it shares similar cryptographic building blocks. It serves a different purpose. It offers a new way to encode many independent approvals into one clean, verifiable package.
Future Directions
You might think: if DahLIAS is so powerful, why isn’t it a BIP? Why not propose it for Bitcoin consensus?
DahLIAS signatures don’t look like Schnorr or ECDSA signatures. The verification algorithm is different. Instead of taking a single public key, message, and signature, a DahLIAS verifier takes lists of public keys and messages, and a single 64-byte proof.
This makes DahLIAS incompatible with Bitcoin’s current consensus rules. Supporting it at the base layer would require a consensus change. This paper doesn’t propose that change, but it does something equally important.
This paper shows that a full signature aggregation scheme for Bitcoin’s native curve is possible.
That alone is a major step forward.
To make DahLIAS part of Bitcoin, someone would need to write a Bitcoin Improvement Proposal (BIP), maybe even using secp256k1lab. That means specifying the scheme in detail, considering its implications for consensus and implementation, and building community support. This paper lays the cryptographic foundation for that conversation.
The real value of the DahLIAS paper is what it proves. Full signature aggregation on secp256k1 is not just a thought experiment. It’s concrete. It’s efficient. It’s secure. For years, the idea lived in developer folklore. Now, it’s written down, analyzed, and proven. All that’s left is to bring it to Bitcoin—if we want it.
This is a guest post by Kiara Bickers. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.
This post Not ECDSA. Not Schnorr. Meet DahLIAS. first appeared on Bitcoin Magazine and is written by Kiara Bickers.
-
 @ 05a0f81e:fc032124
2025-05-23 19:50:46
@ 05a0f81e:fc032124
2025-05-23 19:50:46I was discussing with my friend and few of his friends about the inflation of naira in Nigeria 🇳🇬. Our discussions was flowing until he said that lack of production and too much importations are the major reason that devalued currencies, naira to be precise. As a baby bitcioner, I disagree with him and that's where our discussion turn to argument.
People often think that when a country prioritize productions than consumption that it will boost the value of there currency, but that is wrong. Production have it's impart on the economy of the country.
Increased Economic Growth: A trade surplus indicates that a country's output is high, contributing to overall economic growth, as measured by GDP.
Stimulated Consumer Spending: The influx of foreign currency from exports can be used to import goods, stimulating domestic demand and boosting consumer spending.
Potential for Higher Wages and Living Standards: Increased productivity and economic growth can lead to higher wages and a better standard of living.
Savings and Investment: The surplus can be used for savings, investment in infrastructure, or to reduce debt, further strengthening the economy.
Comparative Advantage: A country may specialize in producing goods and services where it has a comparative advantage, leading to higher productivity and efficiency.
Moreover, too production and exportation also causes inflation. country exports too much and its domestic demand doesn't keep pace, it could lead to inflation as businesses raise prices to cover increased production cost.
Meanwhile, the head lead of currency inflation is the printing of money in the air!.
"Printing money in the air" likely refers to the concept of central banks creating new money digitally, often through quantitative easing. This process involves the central bank buying assets, such as government bonds, from banks and other financial institutions, thereby injecting new money into the economy.
How it Works:
-
Digital Money Creation: The central bank creates new money electronically, rather than physically printing currency notes.
-
Asset Purchases: The central bank buys assets from banks and other financial institutions, injecting new money into the economy.
-
Increased Money Supply: This process expands the money supply, which can lead to lower interest rates and increased lending.
Key Points:
-
Quantitative Easing (QE): A monetary policy tool used by central banks to stimulate economic growth by buying assets and injecting new money into the economy.
-
No Physical Printing: Unlike traditional money printing, QE creates digital money, which is then used to purchase assets.
-
Impact on Economy: QE can influence interest rates, inflation, and economic growth.
The role of Central Bank's.
The central bank plays a crucial role in managing the money supply and implementing monetary policies, including QE. By controlling interest rates and the money supply, central banks aim to promote economic growth, stability, and low inflation.
There are key 🔑 negative effects of printing currency notes on air!:
Printing money, also known as quantitative easing, can have several negative effects on the economy. Some of the key concerns include;
-
Inflation: Excessive money printing can lead to inflation, as more money chases a constant amount of goods and services, driving up prices. This can erode the purchasing power of consumers and reduce the value of savings.
-
Currency Devaluation: Printing money can cause a decline in the value of a currency, making imports more expensive and potentially leading to higher prices for consumers.
-
Distorted Financial Markets: The injection of liquidity into the economy can artificially inflate asset prices, creating market distortions and potentially leading to asset bubbles.
-
Uncertainty and Confusion: High inflation can create uncertainty and confusion for businesses and individuals, making it harder to make informed investment decisions.
-
Reduced Incentive to Save: Inflation can reduce the incentive to save, as the value of money declines over time.
-
Menu Costs: High inflation can lead to menu costs, where businesses incur expenses to update prices frequently.
-
Inefficient Allocation of Resources: Government spending funded by printing money can lead to inefficient allocation of resources, as decisions are driven by politics rather than market forces.
-
Addiction to Fiscal Stimulus: The ease of printing money can create a dependency on fiscal stimulus, making it challenging to reverse course when economic conditions change.
-
Long-term Consequences: The long-term consequences of printing money can be severe, including reduced economic growth, higher inflation, and decreased confidence in the currency.
It's worth noting that the impact of printing money can vary depending on the economic context. In times of recession or deflation, moderate money printing might be used to stimulate economic growth without triggering significant inflation. However, excessive or prolonged money printing can lead to negative consequences.
-
-
 @ 1c5ff3ca:efe9c0f6
2025-05-23 10:13:57
@ 1c5ff3ca:efe9c0f6
2025-05-23 10:13:57Auto-Deployment on a VPS with GitHub Actions
Introduction
This tutorial describes how you can deploy an application on a VPS using GitHub Actions. This way, changes in your GitHub repository are automatically deployed to your VPS.
Prerequisites
- GitHub Account
- GitHub Repository
- Server + SSH access to the server
Step 1 - SSH Login to Server
Open a terminal and log in via SSH. Then navigate to the
.sshdirectoryssh user@hostname cd ~/.sshStep 2 - Create an SSH Key
Now create a new SSH key that we will use for auto-deployment. In the following dialog, simply press "Enter" repeatedly until the key is created.
ssh-keygen -t ed25519 -C "service-name-deploy-github"Step 3 - Add the Key to the
authorized_keysFilecat id_ed25519.pub >> authorized_keys(If you named the key file differently, change this accordingly)
Step 4 - GitHub Secrets
In order for the GitHub Action to perform the deployment later, some secrets must be stored in the repository. Open the repository on GitHub. Navigate to "Settings" -> "Secrets And Variables" -> "Actions". Add the following variables:
HOST: Hostname or IP address of the serverUSERNAME: Username you use to log in via SSHSSHKEY: The private key (copy the content fromcat ~/.ssh/id_ed25519)PORT: 22
Step 5 - Create the GitHub Action
Now create the GitHub Action for auto-deployment. The following GitHub Action will be used: https://github.com/appleboy/scp-action In your local repository, create the file
.github/workflows/deploy.yml:```yaml name: Deploy on: [push] jobs: build: runs-on: ubuntu-latest steps: - uses: actions/checkout@v1 - name: Copy repository content via scp uses: appleboy/scp-action@master with: host: ${{ secrets.HOST }} username: ${{ secrets.USERNAME }} port: ${{ secrets.PORT }} key: ${{ secrets.SSHKEY }} source: "." target: "/your-target-directory"
- name: Executing a remote command uses: appleboy/ssh-action@master with: host: ${{ secrets.HOST }} username: ${{ secrets.USERNAME }} port: ${{ secrets.PORT }} key: ${{ secrets.SSHKEY }} script: | ls```
This action copies the repository files to your server using
scp. Afterwards, thelscommand is executed. Here you can add appropriate commands that rebuild your service or similar. To rebuild and start a docker service you could use something like this or similar:docker compose -f target-dir/docker-compose.yml up --build -dNow commit this file and in the "Actions" tab of your repository, the newly created action should now be visible and executed. With every future change, the git repository will now be automatically copied to your server.Sources
I read this when trying out, but it did not work and I adapted the
deploy.ymlfile: https://dev.to/knowbee/how-to-setup-continuous-deployment-of-a-website-on-a-vps-using-github-actions-54im -
 @ eb0157af:77ab6c55
2025-05-23 10:01:28
@ eb0157af:77ab6c55
2025-05-23 10:01:28A Chinese printer company inadvertently distributed malware that steals Bitcoin through its official drivers, resulting in the theft of over $950,000.
According to local media outlet Landian News, a Chinese printer manufacturer was found to have unknowingly distributed malware designed to steal Bitcoin through its official device drivers.
Procolored, a Shenzhen-based printer company, distributed malware capable of stealing Bitcoin alongside the official drivers for its devices. The company reportedly used USB devices to spread infected drivers and uploaded the compromised software to globally accessible cloud storage services.
Crypto security and compliance firm SlowMist explained how the malware works in a post on X:
 The official driver provided by this printer carries a backdoor program. It will hijack the wallet address in the user's clipboard and replace it with the attacker's address: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj
The official driver provided by this printer carries a backdoor program. It will hijack the wallet address in the user's clipboard and replace it with the attacker's address: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj  According to @MistTrack_io, the attacker has stolen 9.3086… https://t.co/DHCkEpHhuH pic.twitter.com/W1AnUpswLU
According to @MistTrack_io, the attacker has stolen 9.3086… https://t.co/DHCkEpHhuH pic.twitter.com/W1AnUpswLU— MistTrack
 (@MistTrack_io) May 19, 2025
(@MistTrack_io) May 19, 2025The consequences of the breach have been significant, with a total of 9.3 BTC stolen — equivalent to over $950,000.
The issue was first flagged by YouTuber Cameron Coward, whose antivirus software detected malware in the drivers during a test of a Procolored UV printer. The software identified both a worm and a trojan virus named Foxif.
When contacted, Procolored denied the accusations, dismissing the antivirus warning as a false positive. Coward then turned to Reddit, where he shared the issue with cybersecurity professionals, drawing the attention of security firm G Data.
G Data’s investigation revealed that most of Procolored’s drivers were hosted on the MEGA file-sharing platform, with uploads dating back to October 2023. Their analysis confirmed the presence of two separate malware strains: the Win32.Backdoor.XRedRAT.A backdoor and a crypto-stealer designed to replace clipboard wallet addresses with those controlled by the attacker.
G Data reached out to Procolored, which stated that it had removed the infected drivers from its storage as of May 8 and had re-scanned all files. The company attributed the malware to a supply chain compromise, saying the malicious files were introduced via infected USB devices before being uploaded online.
Landian News recommended that users who downloaded Procolored drivers in the past six months “immediately run a full system scan using antivirus software.” However, given that antivirus tools are not always reliable, the Chinese media outlet suggested that a full system reset is the safest option when in doubt.
The post Bitcoin malware discovered: Chinese printer manufacturer involved appeared first on Atlas21.
-
 @ 56f27915:5fee3024
2025-05-23 18:51:08
@ 56f27915:5fee3024
2025-05-23 18:51:08Ralph Boes – Menschenrechtsaktivist, Philosoph, Vorstandsmitglied im Verein Unsere Verfassung e.V.
Ralph Boes zeigt in dem Buch auf, wie wir uns von der Übermacht des Parteienwesens, die zur Entmündigung des Volkes führt, befreien können. Er zeigt, dass schon im Grundgesetz selbst höchst gegenläufige, an seinen freiheitlich-demokratischen Idealen bemessen sogar als verfassungswidrig zu bezeichnende Tendenzen wirken. Und dass diese es sind, die heute in seine Zerstörung führen. Er weist aber auch die Ansatzpunkte auf, durch die der Zerstörung des Grundgesetzes wirkungsvoll begegnet werden kann.
Eintritt frei, Spendentopf
Ralph Boes hat u.a. dafür gesorgt, dass die unmäßigen Sanktionen in Hartz IV 2019 vom Bundesverfassungsgericht für menschenrechts- und verfassungswidrig erklärt wurden. Aktuell setzt er sich für eine Ur-Abstimmung des Volkes über seine Verfassung ein.
-
 @ f6488c62:c929299d
2025-05-23 09:48:20
@ f6488c62:c929299d
2025-05-23 09:48:20ในวันที่ 23 พฤษภาคม 2568 The Wall Street Journal รายงานข่าวที่น่าสนใจว่า ธนาคารยักษ์ใหญ่ของสหรัฐฯ เช่น JPMorgan Chase, Bank of America, Citigroup และ Wells Fargo กำลังพิจารณาความเป็นไปได้ในการพัฒนา Stablecoin ร่วมกัน เพื่อก้าวเข้าสู่โลกของคริปโตเคอเรนซีอย่างเต็มตัว การเคลื่อนไหวครั้งนี้ไม่เพียงสะท้อนถึงการยอมรับสินทรัพย์ดิจิทัลในระบบการเงินกระแสหลัก แต่ยังเป็นก้าวสำคัญในการรักษาความเป็นผู้นำของเงินดอลลาร์สหรัฐในยุคการเงินดิจิทัล.
Stablecoin: อนาคตของการชำระเงินดิจิทัล Stablecoin เป็นสกุลเงินดิจิทัลที่ออกแบบมาเพื่อลดความผันผวนโดยผูกมูลค่ากับสินทรัพย์ที่มีเสถียรภาพ เช่น เงินดอลลาร์สหรัฐ ทำให้เหมาะสำหรับการใช้ในระบบการชำระเงิน การโอนเงินข้ามพรมแดน และการเงินแบบกระจายศูนย์ (DeFi). การที่ธนาคารใหญ่ของสหรัฐฯ หันมาสนใจ Stablecoin ร่วมกัน แสดงถึงความพยายามในการปรับตัวให้เข้ากับความต้องการของผู้บริโภคยุคใหม่ที่ต้องการความรวดเร็วและประหยัดต้นทุนในการทำธุรกรรมทางการเงิน.
ทำไมธนาคารถึงสนใจ Stablecoin? ในปี 2568 ตลาดคริปโตเคอเรนซีกำลังร้อนแรง โดยมูลค่าตลาดรวมของคริปโตทั่วโลกอยู่ที่ 3.64 ล้านล้านดอลลาร์ ซึ่งในจำนวนนี้ Bitcoin มีมูลค่าตลาดสูงสุดที่ 2.2 ล้านล้านดอลลาร์ และราคา Bitcoin ล่าสุดพุ่งแตะ 111,160.66 ดอลลาร์ (ข้อมูล ณ วันที่ 23 พฤษภาคม 2568 เวลา 16:44 น. ตามเขตเวลา +07) นอกจากนี้ ยังมีเม็ดเงินไหลเข้าสู่กองทุนสินทรัพย์ดิจิทัลในสหรัฐฯ กว่า 7.5 พันล้านดอลลาร์ การที่ธนาคารยักษ์ใหญ่ที่มีมูลค่ารวมกันถึง 8 ล้านล้านดอลลาร์เข้ามาในสนามนี้ แสดงถึงศักยภาพในการเปลี่ยนแปลงภูมิทัศน์ของอุตสาหกรรมการเงิน. นโยบายที่เอื้ออำนวยต่อคริปโตในยุคของประธานาธิบดีโดนัลด์ ทรัมป์ และการลดดอกเบี้ยนโยบายของ Fed ยังเป็นปัจจัยสนับสนุนที่สำคัญ.
โอกาสและความท้าทาย การพัฒนา Stablecoin ร่วมกันของธนาคารเหล่านี้เปิดโอกาสให้สหรัฐฯ รักษาความเป็นผู้นำในระบบการเงินดิจิทัล และเพิ่มประสิทธิภาพในระบบการชำระเงินทั่วโลก อย่างไรก็ตาม ความท้าทายที่รออยู่คือการแข่งขันกับ Stablecoin ที่ครองตลาด เช่น USDT และ USDC รวมถึงความไม่แน่นอนด้านกฎระเบียบและความผันผวนของเศรษฐกิจโลกจากนโยบายการค้าของสหรัฐฯ. ธนาคารจะต้องลงทุนในโครงสร้างพื้นฐานที่ปลอดภัยและสอดคล้องกับกฎหมาย เพื่อสร้างความไว้วางใจจากผู้ใช้.
มองไปข้างหน้า การที่ธนาคารชั้นนำของสหรัฐฯ หันมาสนใจ Stablecoin เป็นสัญญาณที่ชัดเจนว่าโลกการเงินกำลังเปลี่ยนผ่านสู่ยุคดิจิทัลอย่างเต็มรูปแบบ การเคลื่อนไหวครั้งนี้อาจเป็นจุดเปลี่ยนที่ทำให้คริปโตเคอเรนซีกลายเป็นส่วนสำคัญของระบบการเงินกระแสหลัก อย่างไรก็ตาม ความสำเร็จจะขึ้นอยู่กับความสามารถในการสร้างนวัตกรรมที่ตอบโจทย์ผู้บริโภคและการจัดการกับความท้าทายด้านกฎระเบียบและการแข่งขันในตลาด. ในอนาคตอันใกล้ Stablecoin จากธนาคารยักษ์ใหญ่อาจกลายเป็นตัวเปลี่ยนเกมในวงการการเงินโลก และเป็นเครื่องมือสำคัญในการเชื่อมโยงระบบการเงินแบบดั้งเดิมเข้ากับโลกดิจิทัล นักลงทุนและผู้บริโภคควรจับตาดูความคืบหน้าของโครงการนี้อย่างใกล้ชิด เพราะมันอาจเป็นก้าวแรกสู่การปฏิวัติครั้งใหญ่ในวงการการเงิน.
-
 @ dfc7c785:4c3c6174
2025-05-23 09:42:37
@ dfc7c785:4c3c6174
2025-05-23 09:42:37Where do I even start? Sometimes it's best to just begin writing whatever comes into your head. What do I do for a living? It used to be easy to explain, I write JavaScript, I build front-end code, in order to build apps. I am more than that though. Over the past eight years, I moved from writing Angular, to React and then to Vue. However my background was originally in writing full-stack projects, using technologies such as .NET and PHP. The thing is - the various jobs I've had recently have pigeon-holed me as front-end developer but nowadays I am starting to feel distracted by a multitude of other interesting, pivotal technologies both in my "day job" and across my wider experience as a Technologist; a phrase I prefer to use in order to describe who I am, more gernerally.
I have used untype.app to write this today, it looks great.
More to come...
-
 @ 3eba5ef4:751f23ae
2025-05-23 09:33:55
@ 3eba5ef4:751f23ae
2025-05-23 09:33:55The article below brings together some of the Q&A from our recent AMA on Reddit. Thanks so much for sending in your questions—we love chatting with you and being part of this awesome community!
Meepo Hardfork Features
What does Meepo bring to CKB, in simple terms?
Imagine upgrading from wooden blocks to LEGO bricks. That’s what the
spawnsyscall in Meepo does for CKB smart contracts, enabling script interoperability.Spawn and a series of related syscalls are introduced as a major upgrade to CKB-VM, enabling interoperability, modularity, and better developer experience, by letting scripts call other scripts, like modular apps in an operating system.
Key features of the upgraded VM?
The upgraded CKB-VM Meepo version unlocks true decoupling and reuse of CKB scripts, enhancing modularity and reusability in smart contract development.
For instance, before Meepo, if developers wanted to build a new time lock in CKB, they had to bundle all necessary functionalities—like signature algorithms—directly into a single lock or type script. This often led to bloated scripts where most of the code was unrelated to the developer's original design goal (time lock). With the spawn syscall, scripts can now delegate tasks—such as signature checks—to other on-chain scripts. As new algorithms emerge, the time lock can adopt them without being redeployed—just by calling updated signature scripts, as long as a shared protocol is followed.
This separation allows developers to: - Focus solely on their core logic. - Reuse independently deployed signature verification scripts. - Upgrade cryptographic components without modifying the original script. - Embrace a more OS-like model where smart contracts can call each other to perform specialized tasks.
By enabling true decoupling and reuse, the spawn syscall makes CKB scripts significantly more composable, maintainable, and adaptable.
Besides Spawn, other improvements in Meepo include:
- Block Extension Fields: Enables reading extension fields in blocks, opening new possibilities like community voting on hardforks (as this ckb-zero-lock prototype). More use cases are expected.
- CKB-VM Optimization: Reduces cycle consumption for common compiler-generated code, making scripts faster and more efficient.
A practical example: IPC on Spawn
Here's an example building an entire Inter-Process Communication (IPC) layer on top of spawn syscalls: - GitHub Repo - Blog post: Transforming IPC in CKB On-Chain Script: Spawn and the Custom Library for Simplified Communication
What does “every wallet will become a CKB wallet because of ckb-auth” mean?
Current CKB-VM already comes with the power to build omnilock / ckb-auth, spawn just makes them easier to reuse in new scripts through decoupling and improved modularity.
Upgrade Compatibility Concerns
Will Meepo require a new address format?
No. Meepo does not introduce breaking changes like address format switching. The only required upgrade is support for a new hash type (
data2). We aim to keep upgrades smooth and backwards-compatible wherever possible.RISC-V & CKB’s Long-Term Design Philosophy
Ethereum is exploring RISC-V—CKB has been doing this for years. What’s your take?
The discussion about RISC-V in Ethereum, is partly about the ease of building zk solutions on Ethereum. And it's easy to mix two different use cases of RISC-V in zk:
- Use RISC-V as the language to write programs running in a zk engine. In this case, we use zero knowledge algorithms to build a RISC-VM and prove programs running inside these RISC-V VMs.
- Use RISC-V as the underlying engine to run cryptographic algorithms, we then compile the verifier / prover code of zero knowledge algorithm into RISC-V, then we run those verifiers / provers inside RISC-V. Essentially, we run the verifying / proving algorithms of zero knowledge algorithms in RISC-V, the programs running inside ZK VMs can be written in other languages suiting the zk algorithms.
When most people talk about RISC-V in zk, they mean the first point above. As a result, we see a lot of arguments debating if RISC-V fits in zk circuits. I couldn't get a direct confirmation from Vitalik, but based on what I read, when Vitalik proposes the idea of RISC-V in Ethereum, he's at least partly thinking about the second point here. The original idea is to introduce RISC-V in Ethereum, so we can just compile zk verifiers / provers into RISC-V code, so there is no need to introduce any more precompiles so as to support different zk algorithms in Ethereum. This is indeed a rare taken path, but I believe it is a right path, it is also the path CKB chose 7 years ago for the initial design of CKB-VM.
CKB believes that a precompile-free approach is the only viable path if we’re serious about building a blockchain that can last for decades—or even centuries. Cryptographic algorithms evolve quickly; new ones emerge every few years, making it unsustainable for blockchains to keep adding them as precompiles. In contrast, hardware evolves more slowly and lives longer.
By choosing RISC-V, we’ve committed to a model that can better adapt to future cryptographic developments. CKB may be on an uncommon path, but I believe it's the right one—and it's encouraging to see Ethereum now moving in a similar direction. Hopefully, more will follow.
CKB already stands out as the only blockchain VM built on RISC-V and entirely free from cryptographic precompiles. Meepo, with its spawn syscall, builds on this foundation—pushing for even greater modularity and reuse. We're also closely watching progress in the RISC-V ecosystem, with the goal of integrating hardware advances into CKB-VM, making it even more future-proof and a state-of-the-art execution environment for blockchain applications.
Will CKB run directly on RISC-V chips? What are the implications?
The "CKB on RISC-V"comes in several stages:
- For now, CKB-VM can already be compiled into RISC-V architecture and run on a RISC-V CPU (e.g. StarFive board), though optimized native implementations are still in development.
- That said, one key issue in the previous stage was that CKB-VM lacks a high-performance, assembly based VM on RISC-V architecture. Ironically, despite CKB-VM being based on RISC-V, we ended up running a Rust-based VM interpreter on RISC-V CPUs—which is far from ideal.
The root of the problem is that RISC-V CPUs come in many configurations, each supporting a different set of extensions. Porting CKB-VM to run natively on real RISC-V chips isn’t trivial—some extensions used by CKB-VM might not be available on the target hardware. With enough time and effort, a performant native implementation could be built, but it’s a non-trivial challenge that still needs significant work.
How do you see the RISC-V narrative expanding?
We are delighted to see the growing recognition of RISC-V in the blockchain space. For CKB, we firmly believe RISC-V is the best choice. Consensus is costly, so only essential data should be on-chain, with the chain serving as a universal verification layer—this is CKBʼs philosophy, and we have consistently designed and developed in this direction.
CKB Roadmap & Ecosystem Growth
Any plan to boost the usage of the CKB network in the next 6 - 24 months?
Growth starts with better developer experience. Spawn in Meepo significantly lowers the barrier to building complex apps. With better tools and documentation, more devs can experiment on CKB, leading to better apps and more users.
What would you focus on if the secondary issuance budget was huge?
If funding were abundant, we'd expand the Spark Program, support more grassroots projects, and even evolve toward a fully decentralized DAO structure—aligning with our long-term vision of a permissionless, community-owned network.
What’s next for Nervos after Meepo?
We're exploring new RISC-V extensions like CFI, which could boost script security and defend against ROP attacks. Still early-stage, but promising. Check out this: Against ROP Attacks: A Blockchain Architect’s Take on VM-Level Security.
Resources
Take a deeper look at the VM upgrades introduced in the Meepo hardfork:
Explore the CFI (Control Flow Integrity) extension on RISC-V:
Check out the Inter-Process Communication (IPC) layer built on top of spawn syscalls:
-
 @ 82b30d30:40c6c003
2025-05-23 09:02:28
@ 82b30d30:40c6c003
2025-05-23 09:02:28nostr:nevent1qqsyeyycax9qgrr4qvtty4h62x96vc6lydh8yg7jl5er99zg7wlpdrch4np3n nostr:nevent1qqs0sqhtzc4p3vysz5k7l29x2lcnedeys55t7mqp2mz7ugrmw0v725cskvqau nostr:nevent1qqsq74xd6qzp9fp8nt8wqpredynnx9t59w9gmzs69jemwu24vjvx78c7wqsl6 nostr:nevent1qqsx6uaegtvy8y47w4fn4dsa0dzkrkjhmwyz9kgq8zw7s3hcg6fuhqg9yywsj nostr:nevent1qqspze6lekfau8063lcup5z0sq62fjhjgr5qjhqy29th28ghsjdendgpvh0ev nostr:nevent1qqsds5j8zk2cx0z4c7ndmq7pgnhtt9hxxu3ee8lq7j69xkpf68u44xgx0v9ux nostr:nevent1qqs20740qquqtt7mrxsqdhftg6rghselqmz8ewp7xsr4v3ltw8ha64scu0suh nostr:nevent1qqsr6sekrmed9g6m7fussfeg4ye5wupplx2wkrul6u8w7yykq6gs7cgz5lwj9 nostr:nevent1qqsfthry2n8yrevtuu8e83gjz2cjv9yh5p43t992h9dx8zy7xs49npq5rp89x nostr:nevent1qqs2rsq8g63z86vw5ta6rcjhtm94u92hhgdv5u7l6ymhy6nulq4awwq58f2af nostr:nevent1qqsdjqf2rwen0sqxvftqg9r6k6404n6ufhl89rn0kyga890ssx7a9pqhvw9z7 nostr:nevent1qqs9j53hpsdpt08f258hnm2sjrgx2anvd7qdrrvqx6ryppslr6lcqdqnammt4 nostr:nevent1qqsx2cs5gf2mlk4a524k2fk0f2fs80t7ryppe0qxyzvexyyh0z2xq0q9ckpgk nostr:nevent1qqsvtkg68twtgm6659v76rxc703qruq6awdxjfdjjcvlwu2r3k4r27sa9qexz nostr:nevent1qqs82g7s2u3560xu95zf55yf4suw52zy5sa6d3p7x2rt8trhcneul7qyze3qd nostr:nevent1qqs2zypn5lpuprgede5ncv0z23ewy8wqf8hqx8ltsdhkmv29jgg3svgc7rv4x nostr:nevent1qqsr9mpqw59703y5dltlycd7yxx9ndkx7xe80emd74nzv7f8uvj9y9saugvlp nostr:nevent1qqsr707sa8jns2ppuyh7kp2jxv6ax4vq7c2y5c2a57y0ewhw2qmpgjc935qgp nostr:nevent1qqsv8gj48n085jtqrr2kaygzcltq026cdn4p448h6s9u25eje8ytvfgu6yyh9 nostr:nevent1qqst2zc68sad5kvklacaqwrh09ghderycqreszwc9schd9zt6z8snzcxzwnwq nostr:nevent1qqszq6fhmm7vuva5ptyflkdstdcknvamlt3j3jj829s59x9d8qw65vslvs39k nostr:nevent1qqst7e22rz3m23mweqdv7ra2mwd7zf4cm3wmvr3hvlc3n2ep6peqjfs753ple nostr:nevent1qqs94rt2exfeuh9v03lftw0s67s0ymuxn8d9vahm08kf2adpwn0h3kgzmfrqw nostr:nevent1qqsysaa7s4apg77tgdx449zwrh86cgrrgm8nl75rk5ezfhk08gemcfq7m7kde nostr:nevent1qqs29glqa5sf3d6nrapqhdlqmmj64xdejf4ky5902s0rcfzyr34gx5s6z9vh2 nostr:nevent1qqswnwcakyyef405uq84u529axlftmc2hq6ejgkefpha38t9fg0tf7ceqarnt nostr:nevent1qqsgpztjppvz0e4lackz9zgutvgtszl9hw6dahlfrmg0u7p3epk9lvgutulpm nostr:nevent1qqszqlx6a695hjnv3m2hwphx2vmu6euw0rmnzqzdgy9d6ud97d9etqshlw6zv nostr:nevent1qqsgfesj07k75v7y5sx070808kd6rr4nf8ptsx685z8kwem7quhk3uc2nhlre nostr:nevent1qqs9qq0tu5t2mrpe8n0f98zewvednrdzqdwsj9vhja9sjtuyjfkmlcswxmjz6 nostr:nevent1qqsfjsjkeq9ux0mjlpzkkcl26vdk7p96paxzlmnp0uckzd3gwtsf9gc32t9ya nostr:nevent1qqs0clwat2zwn4nurlgx9ghlrly8jkk6094hjsz0hd2esxfnkqhcdscnv0xuq nostr:nevent1qqs9vvydt9y0ph230at8mgd4x4juqw89wze2sjthmr4h0rsrg0vmwkc68fass nostr:nevent1qqs8gg9rqrw05hx4a2nmjc7kgc4fxrsd0fqpvz4hg73qel3pxz7yqecwefmha nostr:nevent1qqs9lmvurhnyp0pr8x0ckxnjpt9c6dtnwc0tuczl7uujsc2mf7drfvgjm7s5t nostr:nevent1qqs9n0fvpjl4qmp6nq7s697trhlp9cqydmfwtv0hyevfmnkkjq53ldcp2ue30 nostr:nevent1qqstphjtlec767x53cd0hycul0up5nccje54gyxdakp6rj6jdczw66st3rh78 nostr:nevent1qqstk68pvck7lv6dqlgx9eszmx4h3vyurfxwjgwgg2fw258ws7y7u0s0k28re nostr:nevent1qqs8m2sql8nnzfzpmgqer3vhaxejjeqsyam4q7dt5h58czzezffnsrq7tf2e7 nostr:nevent1qqs2gxp2p69m4xn0z8fmhg7s7krhcu60yszes3sapa9rz89qt8t6zas56lwvq nostr:nevent1qqs9esesyzs2mq93tkcy3wcvtu85rwj5e4m8dh4mk6zma86zz9vv06scurxue nostr:nevent1qqswprrqxz0smcrzn8qexp480jhkg4zjd0n0uphc2wx8pyte4dfavjqjyg7rn nostr:nevent1qqspltzt54qxxu3yjpazxyssm3s6xl8gwxr5eyvuvl8c8epj02e7dkclx3xy7 nostr:nevent1qqsp5ye5klfkf5fzapwscq26jaq84emcd8lku0q2vdky2spf0rhh2as83nnjn nostr:nevent1qqsxsrjh8m77eh3lpn9kacssn7k0mza4z4e9g68q70mqa78p4xjv2tqx28avg nostr:nevent1qqs2h9sg90jxzs08qancaj08qzeu7hh8lss32ny8uaww5m96xp25uus9z5rkz nostr:nevent1qqs2w7us0ef22ervcpya2rk24q5zcjaccae3d5rh9tt5jphfwax493c9pjs86 nostr:nevent1qqs2zr67e5pca9m3lqjw9w72v2h9507d62eya53n8pysle0fhu7adfqkd6hrq nostr:nevent1qqs87zlw6cas3my02fndu2rnfxyzrayqa7g5ptyhsjr37ewmk9jaqwclnp9n5 nostr:nevent1qqsqwpjhgp02jp878c5ftuuxt6czwf5sxcp25ma7p6y9x0sagpwz4tck0cjrt nostr:nevent1qqsyvtujm282xpmstttexzz2u0jxuts0e88t4vcnvg327vw5ju4x74q4wwjh7 nostr:nevent1qqsx6ulpc88x7nqpur3gagkp5uewn3t3a6qelzflejfy86j2y4pqv8gugmhu9 nostr:nevent1qqs9xgvwqy4ephxmfne62d7vucg6mvt8r9vlajw660eq590xnhrg5agv8q4s4 nostr:nevent1qqs9wpg4d0xd8dksnejdewus562f2t2vepyp8fdm6fft4k8t3j4tasguatjx5 nostr:nevent1qqs8lp0skjc83ky4lysegx3cnzxfvy3myskdfwcqs9v7564970ru29qsyc0np nostr:nevent1qqs2vle2yawtsrfftltp9nnzs65vcl4qjtyakap7qkvzd5mg8va4jjqtys34s nostr:nevent1qqsxm5q0xvnrlseh9x2t4k3cr207hzv9veyyt4vtht04yxlgcjk9cpq60l7jw nostr:nevent1qqsvqez6v63mglzj0xwy5d2tqy4956edvtqctncmmhxthgufefsw6wshuvlza nostr:nevent1qqsvk95ngt7u9jfx8l9det80qx39vrlfgkatn3cz3y5pk0g7qu7p2fctqrd2r nostr:nevent1qqsrknzln82etu0pqzhtakemt4c4thszw7kh9zzc85wx9q7y2ltee7gcl4gpu nostr:nevent1qqspws9jvjsj3lzksqvxtche9tvnz55lvurund04pltq92cyrpm3dzqe4zxzt nostr:nevent1qqsf2cmj0txt9l23a2jx9jr0pwsmsr7js2nztgygknltu3alad8mpxqmkm75p nostr:nevent1qqsdh8zc5ydx4nvv4vxgg40xuatg5vdccdy5pn8nqz4x8gchke6sqns2v5ed2 nostr:nevent1qqsptqnt63mntkthndn8ganaatjh08xqrz6fx8y28r85elgrwfk97qsnasax5 nostr:nevent1qqsqp4l0mw3lm0mznvn37dk7wfxsr3e9fvp220v4zjy7fs5u3km5h6cl2u28m nostr:nevent1qqs09m70m33lkafu89xjfpyjft9p3dmcywjsmm7tx30ppxzwy6t3aaq959lff nostr:nevent1qqswpnrgahzcxnqg886gx9vgvsf7tenxgw9uqmtsv95r38m4xu90zwgaekq5s
-
 @ b0a838f2:34ed3f19
2025-05-23 18:11:34
@ b0a838f2:34ed3f19
2025-05-23 18:11:34- AmuseWiki - Amusewiki is based on the Emacs Muse markup, remaining mostly compatible with the original implementation. It can work as a read-only site, as a moderated wiki, or as a fully open wiki or even as a private site. (Demo, Source Code)
GPL-1.0Perl/Docker - BookStack - Organize and store information. Stores documentation in a book like fashion. (Demo, Source Code)
MITPHP/Docker - django-wiki - Wiki system with complex functionality for simple integration and a superb interface. Store your knowledge with style: Use django models. (Demo)
GPL-3.0Python - docmost - Collaborative wiki and documentation software (alternative to Confluence, Notion). (Source Code)
AGPL-3.0Docker/Nodejs - Documize - Modern Docs + Wiki software with built-in workflow, single binary executable, just bring MySQL/Percona. (Source Code)
AGPL-3.0Go - Dokuwiki - Easy to use, lightweight, standards-compliant wiki engine with a simple syntax allowing reading the data outside the wiki. All data is stored in plain text files, therefore no database is required. (Source Code)
GPL-2.0PHP - Feather Wiki - A lightning fast and infinitely extensible tool for creating personal non-linear notebooks, databases, and wikis that is entirely self-contained, runs in your browser, and is only 58 kilobytes in size. (Demo, Source Code, Clients)
AGPL-3.0Javascript - Gitit - Wiki program that stores pages and uploaded files in a git repository, which can then be modified using the VCS command line tools or the wiki's web interface.
GPL-2.0Haskell - Gollum - Simple, Git-powered wiki with a sweet API and local frontend.
MITRuby - Mediawiki - Wiki software package that powers Wikipedia and all other Wikimedia projects, serving hundreds of millions of users each month. (Demo, Source Code)
GPL-2.0PHP - Mycorrhiza Wiki - Filesystem and git-based wiki engine written in Go using Mycomarkup as its primary markup language. (Source Code)
AGPL-3.0Go - Otter Wiki - Simple, easy to use wiki software using markdown. (Source Code)
MITDocker - Pepperminty Wiki - Complete markdown-powered wiki contained in a single PHP file. (Demo)
MPL-2.0PHP - PmWiki - Wiki-based system for collaborative creation and maintenance of websites.
GPL-3.0PHP - Raneto - Raneto is an open source Knowledgebase platform that uses static Markdown files to power your Knowledgebase. (Source Code)
MITNodejs - TiddlyWiki - Reusable non-linear personal web notebook. (Source Code)
BSD-3-ClauseNodejs - Tiki - Wiki CMS Groupware with the most built-in features. (Demo, Source Code)
LGPL-2.1PHP - W - Lightweight, mutli-user, flat-file-database Wiki engine. Create pages quickly and edit them in your Web browser using Mardown/HTML/CSS/JS. The main difference with other wiki is that you are encouraged to customize each page style individually. (Source Code)
AGPL-3.0PHP - WackoWiki - WackoWiki is a light and easy to install multilingual Wiki-engine. (Source Code)
BSD-3-ClausePHP - Wiki.js - Modern, lightweight and powerful wiki app using Git and Markdown. (Demo, Source Code)
AGPL-3.0Nodejs/Docker/K8S - WikiDocs - A databaseless markdown flat-file wiki engine. (Source Code)
MITPHP/Docker - WiKiss - Wiki, simple to use and install. (Source Code)
GPL-2.0PHP - Wikmd - Modern and simple file based wiki that uses Markdown and Git.
MITPython/Docker - XWiki - Second generation wiki that allows the user to extend its functionalities with a powerful extension-based architecture. (Demo, Source Code)
LGPL-2.1Java/Docker/deb - Zim - Graphical text editor used to maintain a collection of wiki pages. Each page can contain links to other pages, simple formatting and images. (Source Code)
GPL-2.0Python/deb
- AmuseWiki - Amusewiki is based on the Emacs Muse markup, remaining mostly compatible with the original implementation. It can work as a read-only site, as a moderated wiki, or as a fully open wiki or even as a private site. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:11:11
@ b0a838f2:34ed3f19
2025-05-23 18:11:11- Algernon - Small self-contained pure-Go web server with Lua, Markdown, HTTP/2, QUIC, Redis and PostgreSQL support. (Source Code)
BSD-3-ClauseGo/Docker - Apache HTTP Server - Secure, efficient and extensible server that provides HTTP services in sync with the current HTTP standards. (Source Code)
Apache-2.0C/deb/Docker - BunkerWeb - Next-gen Web Application Firewall (WAF) that will protect your web services. (Demo, Source Code, Clients)
AGPL-3.0deb/Docker/K8S/Python - Caddy - Powerful, enterprise-ready, open source web server with automatic HTTPS. (Source Code)
Apache-2.0Go/deb/Docker - go-doxy - Lightweight, simple, and performant reverse proxy with WebUI, Docker integration, automatic shutdown/startup for container based on traffic.
MITDocker/Go - HAProxy - Very fast and reliable reverse-proxy offering high availability, load balancing, and proxying for TCP and HTTP-based applications. (Source Code)
GPL-2.0C/deb/Docker - Jauth
⚠- Lightweight SSL/TLS reverse proxy with authorization (via Telegram and SSH) for self-hosted apps.GPL-3.0Go - Lighttpd - Secure, fast, compliant, and very flexible web server that has been optimized for high-performance environments. (Source Code)
BSD-3-ClauseC/deb/Docker - Nginx Proxy Manager - Docker container for managing Nginx proxy hosts with a simple, powerful interface. (Source Code)
MITDocker - NGINX - HTTP and reverse proxy server, mail proxy server, and generic TCP/UDP proxy server. (Source Code)
BSD-2-ClauseC/deb/Docker - Pomerium - Identity-aware reverse proxy, successor to now obsolete oauth_proxy. It inserts an OAuth step before proxying your request to the backend, so that you can safely expose your self-hosted websites to public Internet. (Source Code)
Apache-2.0Go/Docker - SafeLine - Web application firewall / reverse proxy to protect your web apps from attacks and exploits. (Demo, Source Code)
GPL-3.0Docker - Static Web Server - Cross-platform, high-performance, and asynchronous web server for static file serving. (Source Code)
Apache-2.0/MITRust/Docker - SWAG (Secure Web Application Gateway) - Nginx webserver and reverse proxy with PHP support, built-in Certbot (Let's Encrypt) client and fail2ban integration.
GPL-3.0Docker - Traefik - HTTP reverse proxy and load balancer that makes deploying microservices easy. (Source Code)
MITGo/Docker - Varnish - Web application accelerator/caching HTTP reverse proxy. (Source Code)
BSD-3-ClauseGo/deb/Docker - Zoraxy - General purpose HTTP reverse proxy and forwarding tool. (Source Code)
AGPL-3.0Go/Docker
- Algernon - Small self-contained pure-Go web server with Lua, Markdown, HTTP/2, QUIC, Redis and PostgreSQL support. (Source Code)
-
 @ 5c26ee8b:a4d229aa
2025-05-23 08:47:45
@ 5c26ee8b:a4d229aa
2025-05-23 08:47:45Generally mentioning God, Allah, by reciting/reading the Quran or performing Salat (compulsory prayer), for instance, brings tranquility to the heart of the believer. The Salat, other than being the first deed a Muslim would be questioned about on Judgement Day, it keeps the person away from the forbidden wrong deeds too. The Salat is sufficient for obtaining God’s provision as he decrees the means for it to reach the person. Wasting or missing performing the Salat or mentioning God (Allah) by reciting/reading the Quran or Tasbieh, can lead to following the desires only and a depressed life as well as punishment in the Thereafter.
13:28 Ar-Ra'd
الَّذِينَ آمَنُوا وَتَطْمَئِنُّ قُلُوبُهُمْ بِذِكْرِ اللَّهِ ۗ أَلَا بِذِكْرِ اللَّهِ تَطْمَئِنُّ الْقُلُوبُ
Those who have believed and whose hearts are assured (tranquillised) by the remembrance of Allah. Unquestionably, by the remembrance of Allah hearts are assured (tranquillised)."
29:45 Al-Ankaboot
اتْلُ مَا أُوحِيَ إِلَيْكَ مِنَ الْكِتَابِ وَأَقِمِ الصَّلَاةَ ۖ إِنَّ الصَّلَاةَ تَنْهَىٰ عَنِ الْفَحْشَاءِ وَالْمُنْكَرِ ۗ وَلَذِكْرُ اللَّهِ أَكْبَرُ ۗ وَاللَّهُ يَعْلَمُ مَا تَصْنَعُونَ
Recite, [O Muhammad], what has been revealed to you of the Book and establish prayer. Indeed, prayer prohibits immorality and wrongdoing, and the remembrance of Allah is greater. And Allah knows that which you do.
11:114 Hud
وَأَقِمِ الصَّلَاةَ طَرَفَيِ النَّهَارِ وَزُلَفًا مِنَ اللَّيْلِ ۚ إِنَّ الْحَسَنَاتِ يُذْهِبْنَ السَّيِّئَاتِ ۚ ذَٰلِكَ ذِكْرَىٰ لِلذَّاكِرِينَ
And establish prayer at the two ends of the day and at the approach of the night. Indeed, good deeds do away with misdeeds. That is a reminder for those who remember.
20:132 Taa-Haa
وَأْمُرْ أَهْلَكَ بِالصَّلَاةِ وَاصْطَبِرْ عَلَيْهَا ۖ لَا نَسْأَلُكَ رِزْقًا ۖ نَحْنُ نَرْزُقُكَ ۗ وَالْعَاقِبَةُ لِلتَّقْوَىٰ
And enjoin prayer upon your family [and people] and be steadfast therein. We ask you not for provision; We provide for you, and the [best] outcome is for [those of] righteousness.
20:124 Taa-Haa
وَمَنْ أَعْرَضَ عَنْ ذِكْرِي فَإِنَّ لَهُ مَعِيشَةً ضَنْكًا وَنَحْشُرُهُ يَوْمَ الْقِيَامَةِ أَعْمَىٰ
And whoever turns away from My remembrance - indeed, he will have a depressed life, and We will gather him on the Day of Resurrection blind."
20:125 Taa-Haa
قَالَ رَبِّ لِمَ حَشَرْتَنِي أَعْمَىٰ وَقَدْ كُنْتُ بَصِيرًا
He will say, "My Lord, why have you raised me blind while I was [once] seeing?"
20:126 Taa-Haa
قَالَ كَذَٰلِكَ أَتَتْكَ آيَاتُنَا فَنَسِيتَهَا ۖ وَكَذَٰلِكَ الْيَوْمَ تُنْسَىٰ
[Allah] will say, "Thus did Our signs come to you, and you forgot them; and thus will you this Day be forgotten."
20:127 Taa-Haa
وَكَذَٰلِكَ نَجْزِي مَنْ أَسْرَفَ وَلَمْ يُؤْمِنْ بِآيَاتِ رَبِّهِ ۚ وَلَعَذَابُ الْآخِرَةِ أَشَدُّ وَأَبْقَىٰ
And thus do We recompense he who transgressed and did not believe in the signs of his Lord. And the punishment of the Hereafter is more severe and more enduring.
20:128 Taa-Haa
أَفَلَمْ يَهْدِ لَهُمْ كَمْ أَهْلَكْنَا قَبْلَهُمْ مِنَ الْقُرُونِ يَمْشُونَ فِي مَسَاكِنِهِمْ ۗ إِنَّ فِي ذَٰلِكَ لَآيَاتٍ لِأُولِي النُّهَىٰ
Then, has it not become clear to them how many generations We destroyed before them as they walk among their dwellings? Indeed in that are signs for those of intelligence.
49:17 Al-Hujuraat
يَمُنُّونَ عَلَيْكَ أَنْ أَسْلَمُوا ۖ قُلْ لَا تَمُنُّوا عَلَيَّ إِسْلَامَكُمْ ۖ بَلِ اللَّهُ يَمُنُّ عَلَيْكُمْ أَنْ هَدَاكُمْ لِلْإِيمَانِ إِنْ كُنْتُمْ صَادِقِينَ
They consider it a favor to you that they have accepted Islam. Say, "Do not consider your Islam a favor to me. Rather, Allah has conferred favor upon you that He has guided you to the faith, if you should be truthful."
53:29 An-Najm
فَأَعْرِضْ عَنْ مَنْ تَوَلَّىٰ عَنْ ذِكْرِنَا وَلَمْ يُرِدْ إِلَّا الْحَيَاةَ الدُّنْيَا
So turn away from whoever turns his back on Our message and desires not except the worldly life.
53:30 An-Najm
ذَٰلِكَ مَبْلَغُهُمْ مِنَ الْعِلْمِ ۚ إِنَّ رَبَّكَ هُوَ أَعْلَمُ بِمَنْ ضَلَّ عَنْ سَبِيلِهِ وَهُوَ أَعْلَمُ بِمَنِ اهْتَدَىٰ
That is their sum of knowledge. Indeed, your Lord is most knowing of who strays from His way, and He is most knowing of who is guided.
53:62 An-Najm
فَاسْجُدُوا لِلَّهِ وَاعْبُدُوا ۩
So prostrate to Allah and worship [Him].
-
 @ 975e4ad5:8d4847ce
2025-05-23 08:47:08
@ 975e4ad5:8d4847ce
2025-05-23 08:47:08Bitcoin Is Not Just an Asset
When Satoshi Nakamoto introduced Bitcoin in 2009, the vision was clear: a decentralized currency for everyday transactions, from buying coffee to paying bills. It was designed to bypass banks and governments, empowering individuals with financial freedom. But when Bitcoin is treated as “digital gold” and locked away in wallets, it fails to fulfill this vision. Instead of replacing fiat currencies, it becomes just another investment, leaving people reliant on dollars, euros, or other traditional currencies for their daily needs.
The Problem with HODLing and Loans
Some Bitcoin enthusiasts advocate holding their coins indefinitely and taking loans against them rather than spending. This approach may seem financially savvy—Bitcoin’s value often rises over time, and loans provide liquidity without selling. But this prioritizes personal gain over the broader goal of financial revolution. Someone who holds Bitcoin while spending fiat isn’t supporting Bitcoin’s mission; they’re merely using it to stay wealthy within the existing system. This undermines the dream of a decentralized financial future.
Lightning Network: Fast and Cheap Transactions
One common argument against using Bitcoin for daily purchases is the high fees and slow transaction times on the main blockchain. Enter the Lightning Network, a second-layer solution that enables near-instant transactions with minimal fees. Imagine paying for groceries or ordering a pizza with Bitcoin, quickly and cheaply. This technology makes Bitcoin practical for everyday use, paving the way for widespread adoption.
Why Using Bitcoin Matters
If Bitcoin is only hoarded and not spent, it will remain a niche asset that shields against inflation but doesn’t challenge the fiat system. For Bitcoin to become a true alternative currency, it must be used everywhere—in stores, online platforms, and peer-to-peer exchanges. The more people and businesses accept Bitcoin, the closer we get to a world where decentralized currency is the norm. This isn’t just an investment; it’s a movement for financial freedom.\ \ Bitcoin wasn’t created to sit idly in wallets or serve as collateral for loans. It’s a tool for change that demands active use. If we want a world where individuals control their finances, we must start using Bitcoin—not just to avoid poverty, but to build a new financial reality.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:10:51
@ b0a838f2:34ed3f19
2025-05-23 18:10:51- Bluecherry - Closed-circuit television (CCTV) software application which supports IP and Analog cameras. (Source Code)
GPL-2.0PHP - Frigate - Monitor your security cameras with locally processed AI. (Source Code)
MITDocker/Python/Nodejs - SentryShot - Video surveillance management system.
GPL-2.0Docker/Rust - Viseron - Self-hosted, local-only NVR and AI Computer Vision software. With features such as object detection, motion detection, face recognition and more, it gives you the power to keep an eye on your home, office or any other place you want to monitor. (Source Code)
MITDocker - Zoneminder - Closed-circuit television (CCTV) software application which supports IP, USB and Analog cameras. (Source Code)
GPL-2.0PHP/deb
- Bluecherry - Closed-circuit television (CCTV) software application which supports IP and Analog cameras. (Source Code)
-
 @ eb0157af:77ab6c55
2025-05-23 08:01:20
@ eb0157af:77ab6c55
2025-05-23 08:01:20According to CEO Jamie Dimon, the banking giant will open the door to spot Bitcoin ETFs.
As reported by CNBC, JPMorgan has announced that it will allow its clients to buy Bitcoin, without offering custody services. The bank will give clients access to exchange-traded funds (spot ETFs) on Bitcoin, according to sources familiar with the matter.
During a recent investor event, CEO Jamie Dimon confirmed that the bank will open up to Bitcoin for its clients, while refraining from taking on the responsibility of asset custody. “I am not a fan” of Bitcoin, Dimon clarified during the event.
This decision marks a shift from the position Dimon held in 2017, when he labeled Bitcoin a “fraud,” compared it to the tulip mania bubble, and predicted its imminent collapse. At the time, Dimon had even threatened to fire any JPMorgan employee caught trading Bitcoin, calling such activity “stupid” and against company policy.
Despite this operational turnaround, Dimon continues to personally maintain a skeptical stance toward the cryptocurrency. In a 2024 interview with CNBC, he stated he no longer wanted to discuss Bitcoin publicly, emphasizing that, in his view, it lacks “intrinsic value” and is used for criminal activities such as sex trafficking, money laundering, and ransomware.
These comments from Dimon contrast with the recent optimism shown by JPMorgan analysts regarding Bitcoin’s market prospects. According to reports from the bank, Bitcoin could continue gaining ground at the expense of gold in the second half of the year, driven by rising corporate demand and growing support from various U.S. states.
The post JPMorgan to allow clients to buy Bitcoin ETFs: no custody services appeared first on Atlas21.
-
 @ 662f9bff:8960f6b2
2025-05-23 07:38:51
@ 662f9bff:8960f6b2
2025-05-23 07:38:51I have been really busy this week with work - albeit back in Madeira - so I had little time to read or do much other than work. In the coming weeks I should have more time - I am taking a few weeks off work and have quite a list of things to do.
First thing is to relax a bit and enjoy the pleasant weather here in Funchal for a few days. With 1st May tomorrow it does seem that there will be quite a bit to do..
Some food for thought for you. Who takes and makes your decisions? Do you make them yourself based on information that you have and know to be true or do you allow other people to take and make decisions for you? For example - do you allow governments or unaccountable beaureaucrats and others to decide for you and even to compell you?
In theory Governments should respect Consent of the Governed and the 1948 Universal Declaration of Human Rights states that "The will of the people shall be the basis of the authority of government". For you to decide if and to what extent governments today are acting in line with these principles. If not, what can you do about it? I dive into this below and do refer back to letter 9 - section: So What can you do about it.
First, a few things to read, watch and listen to
-
I Finance the Current Thing by Allen Farrington - when money is political, everything is political...
-
Prediction for 2030 (the Great Reset). Sorelle explains things pretty clearly if you care to watch and listen...
-
The Global Pandemic Treaty: What You Need to Know . James Corbett is pretty clear too... is this being done with your support? Did you miss something?
-
Why the Past 10 Years of American Life Have Been Uniquely Stupid - fascinating thinking on how quite a few recent things came about...
And a few classics - you ought to know these already and the important messages in them should be much more obvious now...
-
1984 by George Orwell - look for the perpetual war & conflict, ubiquitous surveillance and censorship not to mention Room 101
-
Animal farm - also by George Orwell - note how the pigs end up living in the farmhouse exceeding all the worst behaviour of the farmer and how the constitution on the wall changes. Things did not end well for loyal Boxer.
-
Brave New World by Aldous Huxley- A World State, inhabited by genetically modified citizens and an intelligence-based social hierarchy - the novel anticipates large scale psychological manipulation and classical conditioning that are combined to make a dystopian society which is challenged by only a single individual who does not take the Soma.
For more - refer to the References and Reading List
The 7 Habits of Highly Effective People
One of the most transformative books that I ever read was 7 Habits of Highly Effective People by Steven Covey. Over many years and from researching hstorical literature he found seven traits that successful people typically display. By default everyone does the opposite of each of these! Check how you do - be honest...
-
Habits 1-3 are habits of Self - they determine how you behave and feel
-
Habits 4-6 are habits of interpersonal behaviour - they determine how you deal with and interact with others
-
Habit 7 is about regeneration and self care - foundation for happy and healthy life and success
One: Be proactive
Choose your responses to all situations and provocations - your reaction to a situation determines how you feel about it.
By default people will be reactive and this controls their emotions
Two: Begin with the end in mind
When you start to work on something, have a clear view of the goal to be achieved; it should be something substantial that you need and will value.
By default people will begin with what is in front of them or work on details that they can do or progress without having a clear view on the end result to be achieved
Three: Put First things First
Be clear on, and begin with, the Big Rocks- the most important things. If you do not put the Big Rocks into your planning daily activities, your days will be full of sand and gravel! All things can be categorised as Urgent or Not-Urgent and Important or Not-Important.
By Default people will focus on Urgent regardless of importance - all of the results come from focusing on Important Non-Urgent things. All of the 7 Habits are in this category!
Four: Seek Win-Win in all dealings with people and in all negotiations
This is the only sustainable outcome; if you cannot achieve Win-Win then no-deal is the sustainable alternative.
By default people will seek Win-Loose - this leads to failed relationships
Five: Seek first to understand - only then to be understood.
Once you visibly understand the needs and expectations of your counterpart they will be open to listening to your point of view and suggestions/requests - not before!
By default people will expound their point of view or desired result causing their counterpart to want to do the same - this ends in "the dialogue of the deaf"
Six: Synergise - Seek the 3rd alternative in all problems and challenges
Work together to find a proposal that is better than what each of you had in mind
By default people will focus on their own desired results and items, regardless of what the other party could bring to help/facilitate or make available
Seven: Sharpen the saw
Take time to re-invigorate and to be healthy - do nothing to excess. Do not be the forrester who persists in cutting the tree with a blunt saw bcause sharpening it is inconvenient or would "take too much time"!
By default people tend to persist on activities and avoid taking time to reflect, prepare and recover
Mindaps - a technique by Tony Buzan
Many years ago I summarised this in a Mind Map (another technique that was transformative for me - a topic for another Letter from around the world!) see below. Let me know if this interests you - happy to do an explainer video on this!
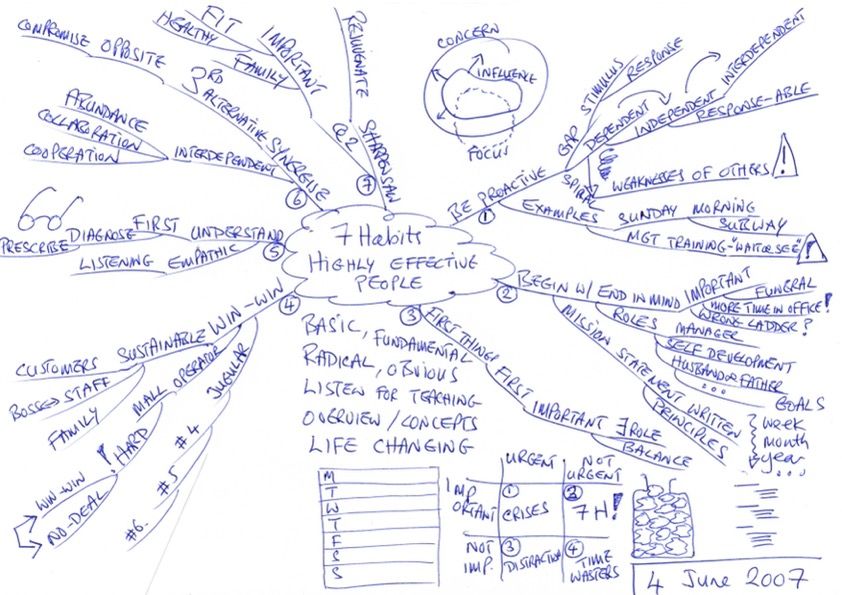
That's it!
No one can be told what The Matrix is.\ You have to see it for yourself.**
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
-
 @ b0a838f2:34ed3f19
2025-05-23 18:10:36
@ b0a838f2:34ed3f19
2025-05-23 18:10:36- bit - Fast, lightweight, resource-efficient, compiled URL shortener.
MITDocker/Crystal - Chhoto URL - Simple, lightning-fast URL shortener with no bloat (fork of simply-shorten).
MITRust/Docker - clink - A super-minimal link shortening service written in pure C, focusing on small executable size, portability, and ease of configuration. (Demo, Source Code)
AGPL-3.0C - Flink - Create QR Codes, embeddable link previews for your website and crawls/scrapes metadata. (Demo)
MITDocker - Just Short It! - A KISS, single-user URL shortener that runs in just one container.
MITDocker - Kutt - Modern URL shortener with support for custom domains and custom URLs. (Demo, Source Code)
MITNodejs/Docker - liteshort - User-friendly, actually lightweight, and configurable URL shortener. (Source Code)
MITPython/deb - rs-short - A lightweight link shortener written in Rust, with features such as caching, spambot protection and phishing detection. (Demo)
MPL-2.0Rust - Shlink - URL shortener with REST API and command line interface. Includes official progressive web application and docker images. (Source Code, Clients)
MITPHP/Docker - Simple-URL-Shortener - KISS URL shortener, public or private (with account). Minimalist and lightweight. No dependencies. (Demo)
MITPHP - YOURLS - YOURLS is a set of PHP scripts that will allow you to run Your Own URL Shortener. Features include password protection, URL customization, bookmarklets, statistics, API, plugins, jsonp. (Source Code)
MITPHP
- bit - Fast, lightweight, resource-efficient, compiled URL shortener.
-
 @ 502ab02a:a2860397
2025-05-23 07:35:13
@ 502ab02a:a2860397
2025-05-23 07:35:13แหม่ ต้องรีบแวะมาเขียนไว้ก่อน ของกำลังร้อนๆ #ตัวหนังสือมีเสียง เพลง ลานกรองมันส์ นั้นเรื่องที่มาที่ไปน่าจะไปตามอ่านในเพจ ลานกรองมันส์ ได้ครับ recap คร่าวๆคือมันคือ พื้นที่สร้างสรรค์ที่เปิดให้มาทำกิจกรรมต่างๆนานากันได้ครับ
วันนี้เลยจะมาเล่าเรื่องวิธีการใช้คำ ซึ่งมันส์ดีตามชื่อลาน ฮาๆๆๆ ผมตั้งโจทย์ไว้เลยว่า ต้องมีคำว่า ลานกรองมันส์ แน่ๆแล้ว เพราะเป็นชื่อสถานที่ จากนั้นก็เอาคำว่า ลานกองมัน มาแตกขยายความเพราะมันคือต้นกำเนิดเดิมของพื้นที่นั้น คือเป็นลานที่เอาหัวมันมากองกันเอาไว้ รอนำไปผลิตต่อเป็นสินค้าการเกษตรต่างๆ
ตอนนี้เขาเลิกทำไปแล้ว จึงกลายมาเป็น ลานกรองมันส์ ที่เอาชื่อเดิมมาแปลง
เมื่อได้คำหลักๆแล้วผมก็เอาพยัญชนะเลย ลอลิง กอไก่ มอม้า คือตัวหลักของเพลง
โทนดนตรีไม่ต้องเลือกเลยหนีไม่พ้นสามช่าแน่นอน โทนมันมาตั้งแต่เริ่มคิดจะเขียนเลยครับ ฮาๆๆๆ
ผมพยายามแบ่งวรรคไว้ชัดๆ เผื่อไว้เลยว่าอนาคตอาจมีการทำดนตรีแบบแบ่งกันร้อง วรรคของมันเลยเป็น หมู่ เดี่ยว หมู่ เดี่ยว หมู่ เดี่ยว หมู่ แบบสามโทนเลย
ท่อนหมู่นั้น คิดแบบหลายชั้นมากครับ โดยเฉพาะคำว่า มัน เอามันมากอง มันที่ว่าได้ทั้งเป็นคำกิริยา คือ เอามันมากองๆ หรือ มันที่ว่าอาจหมายถึงตัวความฝันเองเป็นคำลักษณะนามเรียกความฝัน "ลานกรองมันส์ เรามาลองกัน มาร่วมกันมอง ลานกรองมันส์ มาร่วมสร้างฝัน เอามันมากอง"
หรือแม้แต่ท่อนต่างๆ ก็เล่นคำว่า มัน กอง เพื่อให้รู้สึกย้ำท่อนหมู่ ที่มีคำว่ามัน เป็นพระเอกหลายหน้า ทั้งความสนุก ทั้งลักษณะนามความฝัน ทั้งกิริยา "ทุกคน ต่างมี ความฝัน เอามา รวมกัน ให้มันเป็นกอง"
อีกท่อนที่ชอบมากตอนเขียนคือ ทำที่ ลานกรองมันส์ idea for fun everyone can do เพราะรู้สึกว่า การพูดภาษาอังกฤษสำเนียงไทยๆ มันตูดหมึกดี ฮาๆๆๆๆ
หัวใจของเพลงคือจะบอกว่า ใครมีฝันก็มาเลย มาทำฝันกัน เรามีที่ให้คุณ ไม่ต้องกลัวอะไรที่จะทำฝันของตัวเอง เล็กใหญ่ ผิดถูก ขอให้ทำมัน อย่าให้ใครหยุดฝันของคุณ นอกจากตัวคุณเอง
เพลงนี้ไม่ได้ลงแพลทฟอร์ม เพราะส่งมอบให้ทาง ลานกรองมันส์เขาครับ ใช้ตามอิสระไปเลย ดังนั้นก็อาจต้องฟังในโพสนี้ หรือ ในยูทูปนะครับ https://youtu.be/W-1OH3YldtM?si=36dFbHgKjiI_9DI8
เนื้อเพลง "ลานกรองมันส์"
ลานกรองมันส์ ขอเชิญทุกท่าน มามันกันดู นะโฉมตรู มาลองดูกัน อ๊ะ มาลันดูกอง
มีงาน คุยกัน สังสรรค์ ดื่มนม ชมจันทร์ ปันฝัน กันเพลิน ทุกคน ต่างล้วน มีดี เรานั้น มีที่ พี่นี้มีโชว์ เอ้า
ลานกรองมันส์ เรามาลองกัน มาร่วมกันมอง ลานกรองมันส์ มาร่วมสร้างฝัน เอามันมากอง
จะเล็ก จะใหญ่ ให้ลอง เราเป็น พี่น้อง เพื่อนพ้อง ต้องตา ทุกคน ต่างมี ความฝัน เอามา รวมกัน ให้มันเป็นกอง เอ้า
ลานกรองมันส์ เรามาลองกัน มาร่วมกันมอง ลานกรองมันส์ มาร่วมสร้างฝัน เอามันมากอง
ชีวิต เราคิดเราทำ ทุกสิ่งที่ย้ำ คือทำสุดใจ จะเขียน จะเรียน จะรำ ทำที่ ลานกรองมันส์ idea for fun everyone can do
ลานกรองมันส์ เรามาลองกัน มาร่วมกันมอง ลานกรองมันส์ มาร่วมสร้างฝัน เอามันมากอง
เรามา ลั่นกลองให้มัน เฮไหนเฮกัน ที่ลานกรองมันส์ ให้ฝัน บันเทิง…
ตัวหนังสือมีเสียง #pirateketo #siamstr
-
 @ b0a838f2:34ed3f19
2025-05-23 18:10:12
@ b0a838f2:34ed3f19
2025-05-23 18:10:12- ActivityWatch - Automatically track how you spend time on your devices. (Source Code)
MPL-2.0Python - Beaver Habit Tracker - Habit tracking app to save your precious moments in your fleeting life. (Demo)
BSD-3-ClauseDocker - Ever Gauzy - Open business management platform for collaborative, on-demand and sharing economies (ERP/CRM/HRM/ATS/PM). (Demo, Source Code)
AGPL-3.0Docker/Nodejs - Kimai - Track work time and print out a summary of your activities on demand. (Demo, Source Code)
AGPL-3.0PHP - solidtime - Modern time tracking application for freelancers and agencies. (Source Code)
AGPL-3.0Docker - TimeTagger - An open source time-tracker based on an interactive timeline and powerful reporting. (Demo, Source Code)
GPL-3.0Python - Traggo - Traggo is a tag-based time tracking tool. In Traggo there are no tasks, only tagged time spans. (Source Code)
GPL-3.0Docker/Go
- ActivityWatch - Automatically track how you spend time on your devices. (Source Code)
-
 @ e97aaffa:2ebd765d
2025-05-23 07:30:53
@ e97aaffa:2ebd765d
2025-05-23 07:30:53Passou alguns dias, após as eleições legislativas, a cabeça está mais fria, é um bom momento para um rescaldo e para um pouco de futurologia. Esta análise vai ser limitada apenas aos grandes partidos.
Podemos resumir esta eleição, numa única palavra: Terramoto.
A AD ganhou, mas o grande destaque foi a queda do PS e a subida do Chega. Se a governação do país estava difícil, agora com este novo desenho da assembleia, será quase impossível, piorou bastante. Neste momento, ainda falta contabilizar os votos da emigração, mas o mais provável é o Chega ultrapassar o PS.
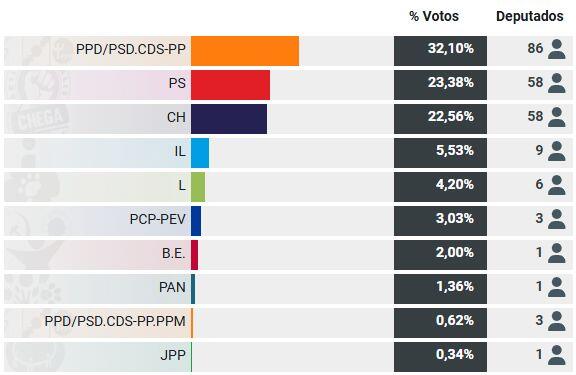
A queda do PS foi tremenda, ninguém esperava tal coisa, o partido está em estado de choque. O partido vai necessitar de tempo para estabilizar e para se reconstruir.
Devido a motivos constitucionais (6 meses antes e 6 meses depois da eleição do presidente da República) só poderá existir eleições no final do próximo ano, isso garante que o novo governo da AD vai estar no poder pelo menos um ano. Isso vai obrigar a aprovação do próximo orçamento de estado, como o PS necessita de tirar os holofotes sobre si, vai facilitar o governo. Provavelmente vai existir um acordo de cavalheiro, um pacto de não agressão entre o governo e o PS, o PS vai se abster na votação do orçamento de estado e a governo não fará revisão constituicional sem o consentimento do PS e também não fará reformas nas leis ou políticas que sejam contra os princípios básicos do partido socialista. Em suma, não haverá grandes reformas, será um governo de gestão com ligeiramente mais poderes.
Não será um governo de bloco central, nem um governo da AD com apoio PS, será apenas um governo da AD com uma falsa oposição do PS. Um governo de bloco central, é uma bomba nuclear, ainda seria demasiado cedo para utilizá-la.
O Partido Socialista sabe que, para ter algumas hipóteses de vencer a próxima eleição, necessita de estar bem e o governo da AD tem que demonstrar algum desgaste, uma queda na popularidade. Eu não acredito que um ano seja suficiente, talvez, seja necessário 2 anos. Isto significa que o país poderá ficar estagnado 1 ou 2 anos, se o governo não conseguir fazer grandes reformas, se os cidadãos não virem/sentirem sinais de mudança, vai dar ainda mais força ao Chega.
Eu acredito que o ponto chave, é a imigração, o governo terá que demonstrar muito trabalho e minimizar o problema, para “esvaziar” um pouco o Chega, caso não faça será um problema.
XXVI Governo
Assim, nessa próxima eleição, talvez em 2027, acredito que as percentagens ficarão mais ou menos como esta eleição, com um partido ligeiramente à frente e os outros dois mais equilibrados. Só que o vencedor seria o Chega, ficando a AD(provavelmente o PSD) e o PS a disputa pelo 2º lugar.
Seria um novo terramoto, mas aqui seria necessário utilizar a bomba nuclear, iria surgir uma nova geringonça. Apesar da vitória do Ventura, iria surgir o governo bloco central, com o PSD e PS, não haveria outra alternativa.
O governo de bloco central, teria que ser muito competente, porque se não o for, iria para novas eleições. Se o governo for um fiasco, PS corre o risco de ser esvaziado, cairá ainda mais, correrá um risco de existência, poderá tornar-se num partido insignificante na nossa política.
XXVII Governo
Agora o terramoto ainda maior, nessa futura eleição, o Chega venceria com maioria absoluta, aí sim, seria um verdadeiro terramoto, ao nível de 1755.
O Chega tem o tempo a seu fazer, tem uma forte penetração nos jovens. Cada jovem que faça 18 anos, existe uma forte possibilidade de ser eleitor do Chega, o seu oposto, acontece com o PCP e o PS, os mais velhos vão morrendo, não existe renovação geracional. Mas o ponto fulcral é a ausência de competência generalizada nos partidos e políticos que têm governado o nosso país nos últimos anos, o descontentamento da população é completo. Esses políticos vivem na sua bolha, não tem noção do mundo real, nem compreendem quais são os problemas das pessoas simples, do cidadão comum.
Ventura
Na minha opinião só existirá três situações, que poderão travar as ascensão do André Ventura a primeiro-ministro:
- Ou existe um óptimo governo, que crie um bom crescimento na qualidade de vida das pessoas e que resolva os 3 problemas que mais anseiam actualmente os portugueses: Habitação, Saúde e Imigração. A probabilidade de isso acontecer é quase nula.
- Ou se o André Ventura desistir, a batalha será muito longa e ele poderá ficar cansado. Pouco provável.
- Ou então, um Argumentum ad hominem, terá que surgir algo, factos concretos que manche a imagem do André Ventura, que destrua por completo a sua reputação.
É a minha a linha leitura da bola de cristal, poderão dizer é uma visão pessimista, eu acho que é realista e pragmática, não vejo qualquer competência na classe política para resolver os problemas do país. Esta é a opinião de um recorrente crítico do Chega.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:09:55
@ b0a838f2:34ed3f19
2025-05-23 18:09:55- Bugzilla - General-purpose bugtracker and testing tool originally developed and used by the Mozilla project. (Source Code)
MPL-2.0Perl - Frappe Helpdesk - Helpdesk software which helps you streamline your company's support, offers an easy setup, clean user interface, and automation tools to resolve customer queries efficiently. (Source Code)
AGPL-3.0Docker - FreeScout - Email-based customer support application, help desk and shared mailbox (alternative to Zendesk and Help Scout). (Demo, Source Code)
AGPL-3.0PHP/Docker - GlitchTip - Error tracking app to collect errors reported by your app. (Source Code)
MITPython/Docker/K8S - ITFlow - Client IT documentation, ticketing, invoicing and accounting for MSPs (Managed Service Providers). (Demo, Source Code)
GPL-3.0PHP - MantisBT - Bug tracker, fits best for software development. (Demo, Source Code)
GPL-2.0PHP - OTOBO - Flexible web-based ticketing system used for customer service, help desk, IT service management. (Demo, Source Code)
GPL-3.0Perl/Docker - Request Tracker - An enterprise-grade issue tracking system. (Source Code)
GPL-2.0Perl - Roundup Issue Tracker - A simple-to-use and -install issue-tracking system with command-line, web, REST, XML-RPC, and e-mail interfaces. Designed with flexibility in mind - not just another bug tracker. (Source Code)
MIT/ZPL-2.0Python/Docker - Trudesk - Trudesk is an open-source help desk/ticketing solution. (Source Code)
Apache-2.0Nodejs/Docker - Zammad - Easy to use but powerful open-source support and ticketing system. (Source Code)
AGPL-3.0Ruby/deb
- Bugzilla - General-purpose bugtracker and testing tool originally developed and used by the Mozilla project. (Source Code)
-
 @ eb0157af:77ab6c55
2025-05-23 07:01:38
@ eb0157af:77ab6c55
2025-05-23 07:01:38A group of users has filed a class action lawsuit against Coinbase, claiming that its identity verification checks violate the state’s biometric privacy law.
According to plaintiffs Scott Bernstein, Gina Greeder, and James Lonergan in the lawsuit filed on May 13 in a federal court, Coinbase’s “indiscriminate collection” of facial biometric data for Know Your Customer (KYC) requirements breaches Illinois’ Biometric Information Privacy Act (BIPA).
The group argued that the exchange failed to notify users in writing about the collection, storage, or sharing of their biometric data, as well as the purpose and retention schedule for such data. “Coinbase does not publicly provide a retention schedule or guidelines for permanently destroying Plaintiffs’ biometric identifiers as specified by BIPA,” they alleged.
The complaint claims that Coinbase requires users to verify their identity by uploading a government-issued ID and a selfie, which is then sent to third-party facial recognition software to scan and extract facial geometry. This process captures biometric identifiers without the users’ informed written consent, thus violating BIPA, according to the lawsuit.
Additionally, the group alleged that Coinbase unlawfully shared biometric data with third-party verification providers such as Jumio, Onfido, Au10tix, and Solaris without users’ consent. “Coinbase ‘obtains’ biometric data in violation of [BIPA] because it explicitly directed the Third Party Verification Providers to use its software to verify and authenticate users, including Plaintiffs, and its software does so by collecting biometric data,” the complaint read.
The group also stated that over 10,000 individuals have filed arbitration demands on these issues with the American Arbitration Association, but Coinbase allegedly refused to pay the required arbitration fees, causing the claims to be dismissed.
Legal demands
The lawsuit brings three counts of biometric privacy law violations and one count of consumer fraud under the Illinois Consumer Fraud and Deceptive Business Practices Act. The group seeks $5,000 for each intentional or reckless violation, $1,000 for each negligent violation, along with injunctive relief and litigation costs.
Coinbase was also recently hit by at least six lawsuits following the May 15 disclosure that some of its customer support agents were allegedly bribed to leak user data.
The post Lawsuit against Coinbase for biometric privacy violations in Illinois appeared first on Atlas21.
-
 @ 9c9d2765:16f8c2c2
2025-05-23 06:10:53
@ 9c9d2765:16f8c2c2
2025-05-23 06:10:53CHAPTER TWENTY SIX
"The streets teach you a lot. It teaches you how to survive, how to fight, how to bend the world to your will. But there’s something else it teaches you how to rise above the petty battles and claim the empire that’s rightfully yours."
Just then, the door opened again, and Charles entered, his usual calm demeanor replaced with a rare air of urgency.
"James," he said, his voice serious. "There’s something you need to know. The press is getting more aggressive. They’ve caught wind of your plans, and they’re pushing for an exclusive interview. They want the story of how you rose from nothing to everything. It’s becoming a media frenzy."
James didn’t flinch. His eyes remained steady as he absorbed the news.
"Let them come," he said. "They can write whatever they want. Let the world see how I turned my destiny around. But they’ll never write the full story. They’ll never know the price I paid to get here."
Charles raised an eyebrow, impressed by James’s unshakable resolve. "And what about Mark and Helen?"
James’s expression darkened, the calm facade cracking just enough to reveal the fire beneath. "They’ll face the consequences of their actions. And I’ll make sure they do."
Rita stepped forward, her tone soft yet firm. "But there’s still a part of you that wants more than just their downfall. You want to rebuild this company, don’t you?"
James glanced at her, his eyes hardening.
"Rebuilding is just the beginning," he replied. "I didn’t fight for what’s mine just to watch it crumble. JP Enterprises will become something greater. Something unbreakable. A legacy that no one can touch, no one can tarnish."
The sound of footsteps echoed through the hallway, and moments later, Mrs. JP entered the room. There was a subtle weight in her posture, but also a sense of pride in her eyes.
"You’ve handled this situation with strength and wisdom, James," she said, her voice full of warmth. "Your father and I could never be prouder. You’ve surpassed every expectation we ever had."
James met her gaze and nodded. "Thank you. But this isn’t just about your approval. It’s about proving to myself in the world that I’m not the man I was before. I’m the man I’ve chosen to be."
Mrs. JP smiled, her eyes softening. "And you’ve become that man with grace. You’ve earned everything that’s come your way."
James’s gaze lingered for a moment before he spoke again. "It’s not over yet. There’s still work to be done. We have to ensure that JP Enterprises remains strong, remains untouchable. This is just the first step."
Charles exchanged a knowing look with Rita, then turned back to James. "We’re with you, every step of the way."
The room fell into a brief, heavy silence. Outside, the city continued to hum, indifferent to the dramatic shifts taking place within the walls of JP Enterprises. But James knew that the storm was far from over. He had won the battle, but the war was only just beginning.
As he looked around at the people who now stood by him, he realized that this victory was more than just personal; it was a turning point for the entire legacy of the JP name.
"James, how does it feel to be the talk of an entire city?" Charles asked, leaning against the polished oak desk in James’s expansive office.
James stood by the window, his hands clasped behind his back, watching the sun descend beyond the city skyline. The room was silent for a moment, filled only with the distant hum of the city below.
"It feels... inevitable," James replied, his tone calm but layered with meaning. "People always talk when someone they counted out rewrites the rules of the game."
Charles chuckled lightly, walking over to pour himself a glass of water. "Well, you haven’t just rewritten the rules, James. You’ve rewritten the entire playbook."
James turned, a shadow of a smile on his face. "And yet, some still believe they can undermine me. Manipulate the truth. Twist it until the entire narrative collapses."
Just then, Rita entered, holding a folder tightly in her hands. There was tension in her posture, controlled, but evident.
"You need to see this," she said, handing James the folder. "It's an internal memo that was intercepted. Apparently, Mark and Helen aren’t done. They’ve secured a secret meeting with a major competitor Wellington Holdings."
James flipped through the documents, his eyes narrowing. "Wellington? So, they’ve moved from sabotage to outright betrayal.
"They’re desperate," Rita added. "Their reputations are in ruins, and with the public backlash after the failed stunt at the anniversary, they’re looking for anything to reclaim their influence."
James’s jaw tightened. "Let them try. I’ve weathered storms far greater than the games of disgraced traitors."
Rita hesitated before continuing. "There’s more. Tracy’s gone quiet. She’s removed all traces of her involvement. But I have reason to believe she’s still communicating with Helen... through an encrypted channel."
James closed the folder and walked slowly to his desk. His movements were deliberate, filled with the confidence of someone who had faced betrayal before and emerged stronger.
"Then it’s time we end this," he said. "Not with anger. Not with revenge. But with undeniable, irreversible justice."
He looked up at Charles and Rita. "I want full surveillance on Wellington. Legal is to prepare a formal complaint if they attempt to interfere with any JP enterprise contract. And I want every associate of Mark and Helen cross-checked. If there’s even a whisper of conspiracy, I want it recorded."
Charles nodded. "Consider it done. We’ll strike with precision."
As they left the room to carry out their tasks, James sat behind his desk, momentarily still. His mind drifted to the days when he had nothing, no name, no wealth, no influence. How far he had come. And yet, how familiar the shadows still felt.
Later that evening, as the city lights glowed brighter, a new headline took over the news:
“JP Enterprises President Set to Announce Major Expansion, Exclusive Projects to Redefine the City’s Economic Landscape.”
It wasn’t about the slander anymore. It wasn’t about revenge. It was about legacy.
The silence in Mark’s penthouse was nearly deafening. Once a space of elite grandeur and sophisticated indulgence, it now felt hollow like the echo of a reputation lost. Mark sat slouched on his couch, the flickering television casting shadows across his unshaven face. He clenched a glass of scotch, half-empty, its contents trembling ever so slightly with each beat of his agitated heart.
The news was relentless. Story after story painted him in a less-than-flattering light. What had once been a carefully crafted image of charm and corporate poise had been shredded by public disgrace. And now, the city wasn’t just ignoring him, they were laughing at him.
“This can’t be it,” he muttered under his breath, his voice raspy. “It can’t end like this.”
Just then, Helen burst into the room. Her heels clicked loudly on the marble floor, a sharp contrast to the dull haze Mark had wrapped himself in. She threw a tabloid magazine onto the coffee table. The headline screamed at them:
“Ray Empire Architect of Scandal: Helen Ray and Ex-Exec Mark Linked to Fraud, Defamation and Bribery.”
-
 @ b0a838f2:34ed3f19
2025-05-23 18:09:35
@ b0a838f2:34ed3f19
2025-05-23 18:09:35- 4ga Boards - Straightforward realtime kanban boards management for intuitive task tracking. Featuring an elegant dark mode, collapsible todo lists, and multitasking tools to supercharge your team's productivity. (Demo, Source Code)
MITNodejs/Docker/K8S - AppFlowy - Build detailed lists of to-do’s for different projects while tracking the status of each one. Open Source Notion Alternative. (Source Code)
AGPL-3.0Rust/Dart/Docker - Donetick - Task and chore management tool for personal and family use, with advanced scheduling, flexible assignment, and group sharing capabilities, detailed history, automation via API, simple and modern design. (Demo, Source Code)
AGPL-3.0Go/Docker - Focalboard - Define, organize, track and manage work across individuals and teams (alternative to Trello, Notion, and Asana). (Source Code, Clients)
MIT/AGPL-3.0/Apache-2.0Nodejs/Go/Docker - Kanboard - Simple visual task board. (Source Code)
MITPHP - myTinyTodo - Simple way to manage your todo list in AJAX style. Uses PHP, jQuery, SQLite/MySQL. GTD compliant. (Demo, Source Code)
GPL-2.0PHP - Nullboard - Single-page minimalist kanban board; compact, highly readable and quick to use. (Demo)
BSD-2-ClauseJavascript - Our Shopping List - Simple shared list application including shopping lists and any other small todo-list that needs to be used collaboratively. (Demo)
AGPL-3.0Docker - Planka - Realtime kanban board for workgroups (alternative to Trello). (Demo, Source Code)
AGPL-3.0Nodejs/Docker/K8S - Task Keeper - List editor for power users, backed by a self-hosted server.
Apache-2.0Scala - Tasks.md - A self-hosted, file based task management board that supports Markdown syntax.
MITDocker - Taskwarrior - Taskwarrior is Free and Open Source Software that manages your TODO list from your command line. It is flexible, fast, efficient, and unobtrusive. It does its job then gets out of your way. (Source Code)
MITC++ - Tegon
⚠- Dev-first issue tracking tool (alternative to Jira, Linear). (Source Code)AGPL-3.0Docker - Tracks - Web-based application to help you implement David Allen’s Getting Things Done™ methodology. (Source Code)
GPL-2.0Ruby - Vikunja - The to-do app to organize your life. (Demo, Source Code)
GPL-3.0Go - Wekan - Open-source Trello-like kanban. (Source Code)
MITNodejs
- 4ga Boards - Straightforward realtime kanban boards management for intuitive task tracking. Featuring an elegant dark mode, collapsible todo lists, and multitasking tools to supercharge your team's productivity. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:09:15
@ b0a838f2:34ed3f19
2025-05-23 18:09:15- cState - Static status page for hyperfast Hugo. Clean design, minimal JS, super light HTML/CSS, high customization, optional admin panel, read-only API, IE8+. Best used with Netlify, Docker. (Demo, Source Code)
MITGo - Gatus - Automated service health dashboard. (Demo, Source Code)
Apache-2.0Docker/K8S - kener - Status page with incident management, easy to use and customize. (Demo, Source Code)
MITNodejs/Docker - StatPing.ng - An easy to use Status Page for your websites and applications. Statping will automatically fetch the application and render a beautiful status page with tons of features for you to build an even better status page. (Source Code)
GPL-3.0Docker/Go - Uptime Kuma - Self-hosted website monitoring tool like "Uptime Robot". (Demo, Source Code)
MITDocker/Nodejs
- cState - Static status page for hyperfast Hugo. Clean design, minimal JS, super light HTML/CSS, high customization, optional admin panel, read-only API, IE8+. Best used with Netlify, Docker. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:09:00
@ b0a838f2:34ed3f19
2025-05-23 18:09:00- Bencher - Suite of continuous benchmarking tools designed to catch performance regressions in CI. (Source Code)
MIT/Apache-2.0Rust - WebHook Tester - Powerful tool for testing WebHooks and more.
MITDocker/Go/deb/K8S
- Bencher - Suite of continuous benchmarking tools designed to catch performance regressions in CI. (Source Code)
-
 @ dfa02707:41ca50e3
2025-05-23 06:00:59
@ dfa02707:41ca50e3
2025-05-23 06:00:59Contribute to keep No Bullshit Bitcoin news going.
Headlines
- OpenSats announces the eleventh wave of Nostr grants. The five projects in this wave are the mobile live-streaming app Swae, the Nostr-over-ham-radio project HAMSTR, Vertex—a Web-of-Trust (WOT) service for Nostr developers, Nostr Double Ratchet for end-to-end encrypted messaging, and the Nostr Game Engine for building games and applications integrated with the Nostr ecosystem.
- Project Eleven offers 1 BTC to break Bitcoin's cryptography with a quantum computer. The quantum computing research organization has introduced the Q-Day Prize, a global challenge that offers 1 BTC to the first team capable of breaking an elliptic curve cryptographic (ECC) key using Shor’s algorithm on a quantum computer. The prize will be awarded to the first team to successfully accomplish this breakthrough by April 5, 2026.
- Bull Bitcoin expands to Mexico, enabling anyone in the country to receive pesos from anywhere in the world straight from a Bitcoin wallet. Additionally, users can now buy Bitcoin with a Mexican bank account.
"Bull Bitcoin strongly believes in Bitcoin’s economic potential in Mexico, not only for international remittances and tourism, but also for Mexican individuals and companies to reclaim their financial sovereignty and protect their wealth from inflation and the fragility of traditional financial markets," said Francis Pouliot, Founder and CEO of Bull Bitcoin.
- Panama City votes to accept bitcoin for municipal services. The Panama City Council has voted to accept Bitcoin and other digital currencies for municipal services, becoming the first public institution in the country to do so. They will partner with an authorized bank responsible for converting the digital currency proceeds into dollars, reports Bitcoin Magazine.
- US Bitcoin miner manufacturer Auradine has raised $153 million in a Series C funding round as it expands into AI infrastructure. The round was led by StepStone Group and included participation from Maverick Silicon, Premji Invest, Samsung Catalyst Fund, Qualcomm Ventures, Mayfield, MARA Holdings, GSBackers, and other existing investors. The firm raised to over $300 million since its inception in 2022.
- Designathon 2025: The Bitcoin Design Community is organizing a Bitcoin design hackathon, scheduled to take place from May 4 to 18, 2025. Sign up and learn more about the event, prizes, and ideas.
Use the tools
- Core Lightning v25.02.1 and v24.11.2 address several issues, including returned outputs on mutual closes if peer didn't support
option_shutdown_anysegwit, properly handling duplicate HTLCs on closing, calculating fees with the correct HTLC timeout, occasional crash onbitcoind_getrawblockbyheightcallback, fixes tracepoint crashes in autoclean/chanbackup, and more. - LND v0.19.0-beta.rc2 is available for testing. New features include support for archiving channel backup, RBF cooperative closes, the Quiescence protocol, the
chainiosubsystem, lnwire messages for the Gossip 1.75 protocol, testnet4, and much more. - Hydrus v0.2.0, a Lightning liquidity management agent, is now available. This version adjusts routing policies, new CLI commands, built-in task scheduling, and a new open heuristic,
channels.block_height. - Alby Hub v1.16.0 introduces Alby Pro, a paid subscription plan for self-hosted Alby Hub runners that offers real-time backups, unlimited sub-wallets, customizable Lightning addresses, priority support, and more. The sidebar and settings page have received a UI update for a smoother experience, along with various other improvements and bug fixes.
- Alby Go v1.12.0 introduces a wallet switcher for swapping wallets during payments, withdrawals, and connections. It also improves number formatting for locales using decimal commas.
- Blitz Wallet v0.4.3-beta allows users to customize their maximum receive and balance amounts for ecash transactions. Besides, users can now pay for items in supported stores using ecash, and manual swap options have been expanded. The update also includes payment experience enhancements, performance optimizations, and bug fixes.
- Phoenix wallet v2.5.3 is a bug fix release that corrects UI problems on iOS and improves the handling of some Bolt12 failures.
- BitBanana v0.9.4 is a maintenance release that adds a link to new documentation, delivers bug fixes, and updated translations.
- BitBanana v0.9.3 was a notable release that introduced Nostr Wallet Connect (NWC) support, significantly enhanced the channel rebalancing interface, and added channel and UTXO sorting, among other features.
- Boltz Web App v1.7.3 has improved the UX for copying addresses and invoices, added fixes for hardware wallet integration, and backup files now include the rescue key, enabling backup imports to pick up pending swaps.
- Stratum v2 Reference Implementation (SRI) v1.3.0 comes with a new integration test framework and tests, enhanced APIs for role development, and core low-level crates now support
no_std. - ESP-Miner v2.6.6b1 is now available for testing.
- CTV Playground Android is a native Android implementation and demonstration of Bitcoin's proposed OP_CHECKTEMPLATEVERIFY (CTV) soft fork, including a CTV Vault implementation.
- Nstart, an onboarding wizard for new Nostr users, is now multilingual. Available languages include English, Español, Italiano, Français, Deutsch, and 日本語. You can contribute with a new language here.

Source: daniele
- GM Swap is a proof-of-concept implementation of the Atomic Signature Swaps NIP. It enables users to "swap GM notes, ensuring that both parties' signatures are exchanged simultaneously or not at all."
- Arti v1.4.2, a next-generation Tor client in Rust, is now available. Arti's RPC interface is now officially stable, and ready for testing.
- Tor Browser v14.5 has been released, introducing Connection Assist to Android, which helps mobile users facing strict censorship to easily unblock Tor with a single button press. Additionally, Belarusian, Bulgarian, and Portuguese languages are now available across all platforms, along with other improvements.
[
 ](https://njump.me/nevent1qqsqp3seup9kqz8xawavqd2jff6v627s63l4xwut9hjcphdnr5r3h5gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqfpwaehxw309akh2mr5d9cxcetcv4ezu6r4wdax7mn9vaujuam0wfkxgq3qpzzrdngrnlufqazx3lfj07k0vfuya6ehfy8q5yv2h8c5e8fxgmxqd
](https://njump.me/nevent1qqsqp3seup9kqz8xawavqd2jff6v627s63l4xwut9hjcphdnr5r3h5gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqfpwaehxw309akh2mr5d9cxcetcv4ezu6r4wdax7mn9vaujuam0wfkxgq3qpzzrdngrnlufqazx3lfj07k0vfuya6ehfy8q5yv2h8c5e8fxgmxqd -
 @ b0a838f2:34ed3f19
2025-05-23 18:08:44
@ b0a838f2:34ed3f19
2025-05-23 18:08:44- Cgit - Fast lightweight web interface for git repositories. (Source Code)
GPL-2.0C - Forgejo - A lightweight software forge focused on scaling, federation, and privacy (fork of Gitea). (Demo, Source Code, Clients)
MITDocker/Go - Fossil - Distributed version control system featuring wiki and bug tracker.
BSD-2-Clause-FreeBSDC - Gerrit - Code review and project management tool for Git-based projects. (Source Code)
Apache-2.0Java/Docker - gitbucket - Git platform powered with easy installation, high extensibility & GitHub API compatibility (alternative to GitHub). (Source Code)
Apache-2.0Scala/Java - Gitea - Git with a cup of tea! Painless self-hosted all-in-one software development service, including Git hosting, code review, team collaboration, package registry and CI/CD. (Demo, Source Code)
MITGo/Docker/K8S - GitLab - Self Hosted Git repository management, code reviews, issue tracking, activity feeds and wikis. (Demo, Source Code)
MITRuby/deb/Docker/K8S - Gitolite - Setup git hosting on a central server, with fine-grained access control and many more powerful features. (Source Code)
GPL-2.0Perl - Gogs - Painless self-hosted Git Service written in Go. (Source Code)
MITGo - Huly - All-in-one project management platform (alternative to Linear, Jira, Slack, Notion, Motion). (Demo, Source Code)
EPL-2.0Docker/K8S/Nodejs - Kallithea - Source code management system that supports two leading version control systems, Mercurial and Git, with a web interface. (Source Code)
GPL-3.0Python - Klaus - Simple, easy-to-set-up Git web viewer that Just Works.
ISCPython/Docker - Leantime - Lean project management system for small teams and startups helping to manage projects from ideation through delivery. (Source Code)
AGPL-3.0PHP/Docker - Mergeable
⚠- A better inbox for GitHub pull requests. (Demo, Source Code)MITNodejs/Docker/K8S - Mindwendel - Brainstorm and upvote ideas and thoughts within your team. (Demo, Source Code)
AGPL-3.0Docker/Elixir - minimal-git-server - Lightweight git server with a basic CLI to manage repositories, supporting multiple accounts and running in a container.
MITDocker - Octobox
⚠- Take back control of your GitHub Notifications. (Source Code)AGPL-3.0Ruby/Docker - OneDev - All-In-One DevOps Platform. With Git Management, Issue Tracking, and CI/CD. Simple yet Powerful. (Source Code)
MITJava/Docker/K8S - OpenProject - Manage your projects, tasks and goals. Collaborate via work packages and link them to your pull requests on Github. (Source Code)
GPL-3.0Ruby/deb/Docker - Pagure - Lightweight, powerful, and flexible git-centric forge with features laying the foundation for federated and decentralized development. (Demo)
GPL-2.0Docker/Python/deb - Phorge - Community-driven platform for collaborating, managing, organizing and reviewing software development projects. (Source Code)
Apache-2.0PHP - Plane - Track issues, epics, and product roadmaps in the simplest way possible (alternative to JIRA, Linear and Height). (Demo, Source Code)
AGPL-3.0Docker - ProjeQtOr - Complete, mature, multi-user project management system with extensive functionality for all phases of a project. (Demo, Source Code)
AGPL-3.0PHP - Redmine - Redmine is a flexible project management web application. (Source Code)
GPL-2.0Ruby - Review Board - Extensible and friendly code review tool for projects and companies of all sizes. (Demo, Source Code)
MITPython/Docker - rgit - An ultra-fast & lightweight cgit clone.
WTFPLRust/Docker - RhodeCode - RhodeCode is an open source platform for software development teams. It unifies and simplifies repository management for Git, Subversion, and Mercurial. (Source Code)
AGPL-3.0Python - Rukovoditel - Configurable open source project management, web-based application. (Source Code)
GPL-2.0PHP - SCM Manager - The easiest way to share and manage your Git, Mercurial and Subversion repositories over http. (Source Code)
BSD-3-ClauseJava/deb/Docker/K8S - Smederee - A frugal platform which is dedicated to help people build great software together leveraging the power of the Darcs version control system. (Source Code)
AGPL-3.0Scala - Sourcehut - A full web git interface with no javascript. (Demo, Source Code)
GPL-2.0Go - Taiga - Agile Project Management Tool based on the Kanban and Scrum methods. (Source Code)
MPL-2.0Docker/Python/Nodejs - Titra - Time-tracking solution for freelancers and small teams. (Source Code)
GPL-3.0Javascript/Docker - Trac - Trac is an enhanced wiki and issue tracking system for software development projects.
BSD-3-ClausePython/deb - Traq - Project management and issue tracking system written in PHP. (Source Code)
GPL-3.0PHP/Nodejs - Tuleap - Tuleap is a libre suite to plan, track, code and collaborate on software projects. (Source Code)
GPL-2.0PHP - UVDesk - UVDesk community is a service oriented, event driven extensible opensource helpdesk system that can be used by your organization to provide efficient support to your clients effortlessly whichever way you imagine. (Demo, Source Code)
MITPHP - ZenTao - An agile(scrum) project management system/tool. (Source Code)
AGPL-3.0PHP
- Cgit - Fast lightweight web interface for git repositories. (Source Code)
-
 @ 58537364:705b4b85
2025-05-23 05:46:31
@ 58537364:705b4b85
2025-05-23 05:46:31“สุขเวทนา” ที่แท้ก็คือ “มายา”
เป็นเหมือนลูกคลื่นลูกหนึ่ง
ที่เกิดขึ้นเพราะน้ำถูกลมพัด
เดี๋ยวมันก็แตกกระจายไป
หากต้องการจะมีชีวิตอย่างเกษมแล้ว
ก็ต้องอาศัยความรู้เรื่อง อนิจจัง ทุกขัง อนัตตา ให้สมบูรณ์
มันจะต่อต้านกันได้กับอารมณ์ คือ รูป เสียง กลิ่น รส สัมผัส ที่มากระทบ
ไม่ให้ไปหลงรัก หรือหลงเกลียดเรื่องวุ่นวายมีอยู่ ๒ อย่างเท่านั้น
- ไปหลงรัก อย่างหนึ่ง
- ไปหลงเกลียด อย่างหนึ่ง
ซึ่งเป็นเหตุให้หัวเราะและต้องร้องไห้
ถ้าใครมองเห็นว่า หัวเราะก็กระหืดกระหอบ มันเหนื่อยเหมือนกัน
ร้องไห้ก็กระหืดกระหอบ เหมือนกัน
สู้อยู่เฉย ๆ ดีกว่า อย่าต้องหัวเราะ อย่าต้องร้องไห้
นี่แหละ! มันเป็นความเกษมเราอย่าได้ตกไปเป็นทาสของอารมณ์
จนไปหัวเราะหรือร้องไห้ตามที่อารมณ์มายั่ว
เราเป็นอิสระแก่ตัว หยุดอยู่ หรือเกษมอยู่อย่างนี้ดีกว่า
ใช้ อนิจจัง ทุกขัง อนัตตา เป็นเครื่องมือกำกับชีวิต
- รูป เสียง กลิ่น รส สัมผัส เป็น มายา เป็น illusion
- "ตัวกู-ของกู" ก็เป็น illusion
- เพราะ "ตัวกู-ของกู" มันเกิดมาจากอารมณ์
- "ตัวกู-ของกู" เป็นมายา อารมณ์ทั้งหลายก็เป็นมายา
เห็นได้ด้วยหลัก อนิจจัง ทุกขัง อนัตตา
...ความทุกข์ก็ไม่เกิด
เราจะตัดลัดมองไปดูสิ่งที่เป็น “สุขเวทนา”
สุขเวทนา คือ ความสุขสนุกสนาน เอร็ดอร่อย
ที่เป็นสุขนั้นเรียกว่า “สุขเวทนา”แต่สุขเวทนา เป็นมายา
เพราะมันเป็นเหมือนลูกคลื่นที่เกิดขึ้นเป็นคราว ๆ
ไม่ใช่ตัวจริงอะไรที่พูดดังนี้ก็เพราะว่า
ในบรรดาสิ่งทั้งปวงในโลกทั้งหมดทุกโลก
ไม่ว่าโลกไหน มันมีค่าอยู่ก็ตรงที่ให้เกิดสุขเวทนาลองคิดดูให้ดีว่า...
- ท่านศึกษาเล่าเรียนทำไม?
- ท่านประกอบอาชีพ หน้าที่การงานทำไม?
- ท่านสะสมทรัพย์สมบัติ เกียรติยศ ชื่อเสียง พวกพ้องบริวารทำไม?มันก็เพื่อสุขเวทนาอย่างเดียว
เพราะฉะนั้น แปลว่า อะไร ๆ มันก็มารวมจุดอยู่ที่สุขเวทนาหมดฉะนั้น ถ้าเรามีความรู้ในเรื่องนี้
จัดการกับเรื่องนี้ให้ถูกต้องเพียงเรื่องเดียวเท่านั้น
ทุกเรื่องมันถูกหมดเพราะฉะนั้น จึงต้องดูสุขเวทนาให้ถูกต้องตามที่เป็นจริงว่า
มันก็เป็น “มายา” ชนิดหนึ่งเราจะต้องจัดการให้สมกันกับที่มันเป็นมายา
ไม่ใช่ว่า จะต้องไปตั้งข้อรังเกียจ เกลียดชังมัน
อย่างนั้นมันยิ่ง บ้าบอที่สุดถ้าเข้าไปหลงรัก หลงเป็นทาสมัน
ก็เป็นเรื่อง บ้าบอที่สุดแต่ว่าไปจัดการกับมันอย่างไรให้ถูกต้อง
นั้นแหละเป็นธรรมะ
เป็น ลูกศิษย์ของพระพุทธเจ้า
ที่จะเอาชนะความทุกข์ได้ และไม่ต้องเป็น โรคทางวิญญาณ
สุขเวทนา ที่แท้ก็คือ มายา
มันก็ต้องทำโดยวิธีที่พิจารณาให้เห็นว่า
“สุขเวทนา” นี้ ที่แท้ก็คือ “มายา”เป็นเหมือน ลูกคลื่นลูกหนึ่ง
ที่เกิดขึ้นเพราะ น้ำถูกลมพัดหมายความว่า
เมื่อ รูป เสียง กลิ่น รส ฯ เข้ามา
แล้ว ความโง่ คือ อวิชชา โมหะ ออกรับ
กระทบกันแล้วเป็นคลื่นกล่าวคือ สุขเวทนาเกิดขึ้นมา
แต่ เดี๋ยวมันก็แตกกระจายไป
ถ้ามองเห็นอย่างนี้แล้ว
เราก็ไม่เป็นทาสของสุขเวทนา
เราสามารถ ควบคุม จะจัด จะทำกับมันได้
ในวิธีที่ ไม่เป็นทุกข์- ตัวเองก็ไม่เป็นทุกข์
- ครอบครัวก็ไม่เป็นทุกข์
- เพื่อนบ้านก็ไม่เป็นทุกข์
- คนทั้งโลกก็ไม่พลอยเป็นทุกข์
เพราะมีเราเป็นมูลเหตุ
ถ้าทุกคนเป็นอย่างนี้
โลกนี้ก็มีสันติภาพถาวร
เป็นความสุขที่แท้จริงและถาวรนี่คือ อานิสงส์ของการหายโรคโดยวิธีต่าง ๆ กัน
ไม่เป็นโรค “ตัวกู” ไม่เป็นโรค “ของกู”
พุทธทาสภิกขุ
ที่มา : คำบรรยายชุด “แก่นพุทธศาสน์”
ปีพุทธศักราช ๒๕๐๔
ครั้งที่ ๑
หัวข้อเรื่อง “ใจความทั้งหมดของพระพุทธศาสนา”
ณ ศิริราชพยาบาล มหาวิทยาลัยมหิดล
เมื่อวันที่ ๑๗ ธันวาคม ๒๕๐๔ -
 @ 502ab02a:a2860397
2025-05-23 01:57:14
@ 502ab02a:a2860397
2025-05-23 01:57:14น้ำนมมนุษย์ที่ไม่ง้อมนุษย์ หรือนี่กำลังจะกลายเป็นเรื่องจริงเร็วกว่าที่เราคิดนะครับ
ในยุคที่อุตสาหกรรมอาหารหันหลังให้กับปศุสัตว์ ไม่ว่าจะด้วยเหตุผลด้านสิ่งแวดล้อม จริยธรรม หรือความยั่งยืน “น้ำนมจากห้องแล็บ” กำลังกลายเป็นแนวหน้าของการปฏิวัติอาหาร โดยเฉพาะเมื่อบริษัทหนึ่งจากสิงคโปร์นามว่า TurtleTree ประกาศอย่างชัดเจนว่า พวกเขากำลังจะสร้างโปรตีนสำคัญในน้ำนมมนุษย์ โดยไม่ต้องมีมนุษย์แม่เลยแม้แต่น้อย
TurtleTree ก่อตั้งในปี 2019 โดยมีเป้าหมายอันทะเยอทะยานคือการผลิตโปรตีนในนมแม่ให้ได้ผ่านเทคโนโลยีที่เรียกว่า precision fermentation โดยใช้จุลินทรีย์ที่ถูกดัดแปลงพันธุกรรมให้ผลิตโปรตีนเฉพาะ เช่น lactoferrin และ human milk oligosaccharides (HMOs) ซึ่งเป็นองค์ประกอบล้ำค่าที่พบในน้ำนมมนุษย์แต่แทบไม่มีในนมวัว หรือผลิตภัณฑ์นมทั่วไป
โปรตีนตัวแรกที่ TurtleTree ประสบความสำเร็จในการผลิตคือ LF+ หรือ lactoferrin ที่เลียนแบบโปรตีนในนมแม่ ซึ่งมีหน้าที่ช่วยระบบภูมิคุ้มกันของทารก ต่อต้านแบคทีเรีย และช่วยให้ร่างกายดูดซึมธาตุเหล็กได้ดีขึ้น โปรตีนนี้เป็นหนึ่งในหัวใจของนมแม่ ที่บริษัทต้องการนำมาใช้ในอุตสาหกรรมนมผงเด็กและอาหารเสริมสำหรับผู้ใหญ่ ล่าสุดในปี 2024 LF+ ได้รับการรับรองสถานะ GRAS (Generally Recognized As Safe) จากองค์การอาหารและยาสหรัฐฯ (FDA) อย่างเป็นทางการ เป็นหมุดหมายสำคัญที่บอกว่า นี่ไม่ใช่แค่ไอเดียในแล็บอีกต่อไป แต่กำลังกลายเป็นผลิตภัณฑ์เชิงพาณิชย์จริง
เบื้องหลังของโปรเจกต์นี้คือการลงทุนกว่า 30 ล้านดอลลาร์สหรัฐจากกลุ่มทุนทั่วโลก รวมถึงบริษัท Solar Biotech ที่จับมือกับ TurtleTree ในการขยายกำลังการผลิตเชิงอุตสาหกรรมในสหรัฐอเมริกา โดยตั้งเป้าว่าจะสามารถผลิตโปรตีนเหล่านี้ได้ในระดับราคาที่แข่งขันได้ภายในไม่กี่ปีข้างหน้า
สิ่งที่น่าสนใจคือ TurtleTree ไม่ได้หยุดแค่ lactoferrin พวกเขายังวางแผนพัฒนา HMO ซึ่งเป็นน้ำตาลเชิงซ้อนชนิดพิเศษที่มีอยู่เฉพาะในน้ำนมแม่ เป็นอาหารเลี้ยงแบคทีเรียดีในลำไส้ทารก ช่วยพัฒนาระบบภูมิคุ้มกันและสมอง ปัจจุบัน HMOs เริ่มเป็นที่นิยมในวงการ infant formula แต่การผลิตยังจำกัดและมีต้นทุนสูง การที่ TurtleTree จะนำเทคโนโลยี precision fermentation มาใช้ผลิต HMO จึงถือเป็นความพยายามในการลดช่องว่างระหว่าง "นมแม่จริง" กับ "นมผงสังเคราะห์"
ทั้งหมดนี้เกิดขึ้นภายใต้แนวคิดใหม่ของอุตสาหกรรมอาหารที่เรียกว่า "functional nutrition" หรือโภชนาการที่ออกแบบเพื่อทำงานเฉพาะทาง ไม่ใช่แค่ให้พลังงานหรือโปรตีน แต่เล็งเป้าหมายเฉพาะ เช่น เสริมภูมิคุ้มกัน ซ่อมแซมสมอง หรือฟื้นฟูร่างกาย โดยมีรากฐานจากธรรมชาติ แต่ใช้เทคโนโลยีสมัยใหม่ในการผลิต
แม้จะฟังดูเป็นความก้าวหน้าทางวิทยาศาสตร์ที่น่าตื่นเต้น แต่น้ำเสียงที่ดังก้องในอีกมุมหนึ่งก็คือคำถามเชิงจริยธรรม TurtleTree กำลังสร้างโปรตีนที่มีอยู่เฉพาะในมนุษย์ โดยอาศัยข้อมูลพันธุกรรมของมนุษย์เอง แล้วนำเข้าสู่ระบบอุตสาหกรรมเพื่อการค้า คำถามคือ เมื่อใดที่การจำลองธรรมชาติจะกลายเป็นการผูกขาดธรรมชาติ? ใครควรเป็นเจ้าของข้อมูลพันธุกรรมของมนุษย์? และถ้าวันหนึ่งบริษัทใดบริษัทหนึ่งสามารถควบคุมการผลิต “นมแม่จำลอง” ได้แต่เพียงผู้เดียว นั่นจะส่งผลต่อเสรีภาพของสังคมในมุมไหนบ้าง?
นักชีวจริยธรรมหลายคน เช่น ดร.ซิลเวีย แคมโปเรซี จาก King's College London ตั้งข้อสังเกตไว้ว่า เทคโนโลยีแบบนี้อาจแก้ปัญหาการเข้าถึงนมแม่ในพื้นที่ห่างไกลหรือในกลุ่มแม่ที่ให้นมไม่ได้ แต่ขณะเดียวกันก็อาจกลายเป็นการสร้าง "ระบบอาหารทางเลือก" ที่ควบคุมโดยบริษัทไม่กี่ราย ที่มีอำนาจเกินกว่าผู้บริโภคจะตรวจสอบได้
เมื่อเทคโนโลยีสามารถจำลองสิ่งที่เคยสงวนไว้เฉพาะธรรมชาติ และมนุษย์ได้ใกล้เคียงจนแทบแยกไม่ออก บางทีคำถามที่ควรถามอาจไม่ใช่แค่ว่า “มันปลอดภัยหรือไม่?” แต่อาจต้องถามว่า “เราไว้ใจใครให้สร้างสิ่งนี้แทนธรรมชาติ?” เพราะน้ำนมแม่เคยเป็นสิ่งที่มาจากรักและชีวิต แต่วันนี้มันอาจกลายเป็นเพียงสิ่งที่มาจากห้องแล็บและโมเลกุล... และนั่นคือสิ่งที่เราต้องคิดให้เป็น ก่อนจะกินให้ดี เต่านี้มีบุญคุณอันใหญ่หลวงงงงงงง
เสริมจุดน่าสนใจให้ครับ KBW Ventures ถือเป็นผู้ลงทุนรายใหญ่ที่สุดใน TurtleTree Labs โดยมีบทบาทสำคัญในหลายรอบการระดมทุนของบริษัท KBW Ventures เป็นบริษัทลงทุนจากสหรัฐอาหรับเอมิเรตส์ ก่อตั้งโดย สมเด็จพระราชโอรสเจ้าชายคาเล็ด บิน อัลวาลีด บิน ตาลาล อัล ซาอุด (HRH Prince Khaled bin Alwaleed bin Talal Al Saud) ในรอบการระดมทุน Pre-A มูลค่า 6.2 ล้านดอลลาร์สหรัฐฯ ซึ่งปิดในเดือนธันวาคม 2020 KBW Ventures ได้ร่วมลงทุนพร้อมกับ Green Monday Ventures, Eat Beyond Global และ Verso Capital . นอกจากนี้ เจ้าชาย Khaled ยังได้เข้าร่วมเป็นที่ปรึกษาให้กับ TurtleTree Labs เพื่อสนับสนุนการขยายตลาดและกลยุทธ์การเติบโตของบริษัท
ซึ่งในตัว KBW Ventures นั้น เป็นบริษัทลงทุนที่มุ่งเน้นการสนับสนุนเทคโนโลยีที่ยั่งยืนและนวัตกรรมในหลากหลายอุตสาหกรรม เช่น เทคโนโลยีชีวภาพ (biotech), เทคโนโลยีพลังงานสะอาด, เทคโนโลยีการเงิน (fintech), เทคโนโลยีการขนส่ง, และเทคโนโลยีอาหาร (food tech) โดยเฉพาะ และในส่วนของเจ้าชาย Khaled มีความสนใจอย่างลึกซึ้งในด้านเทคโนโลยีอาหาร โดยเฉพาะในกลุ่มโปรตีนทางเลือก เช่น Beyond Meat ซึ่งเป็นการลงทุนที่สะท้อนถึงความมุ่งมั่นชัดเจนในการส่งเสริมอาหารที่ยั่งยืนและมีจริยธรรมครับ และแน่นอนเลยว่า โดยมีส่วนร่วมในรอบระดมทุนหลายครั้งของ Beyond Meat รวมถึงตอนที่ Beyond Meat เข้าตลาดหุ้น Nasdaq ครั้งแรกในปี 2019
เจ้าชาย Khaled เชื่อมั่นว่าอาหารทางเลือกแบบพืชจะถูกลงและแพร่หลายมากขึ้น จนอาจถูกกว่าราคาเนื้อสัตว์จากสัตว์จริงภายในปี 2025 ตามข้อมูลที่ได้มาแสดงว่า ปีนี้นี่หว่าาาาาาาาาา
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ b0a838f2:34ed3f19
2025-05-23 18:08:24
@ b0a838f2:34ed3f19
2025-05-23 18:08:24- Appsmith - Build admin panels, CRUD apps and workflows. Build everything you need, 10x faster. (Source Code)
Apache-2.0Java/Docker/K8S - Appwrite - End to end backend server for web, native, and mobile developers 🚀. (Source Code)
BSD-3-ClauseDocker - Dashpress - Generate fully functional admin apps in seconds from your database information, with a single command.
AGPL-3.0Nodejs/Docker - Manifest - Complete backend that fits into 1 YAML file. (Demo, Source Code)
MITNodejs - Motor Admin - No-code admin panel and business intelligence software - search, create, update, and delete data entries, create custom actions, and build reports. (Source Code)
AGPL-3.0Ruby/Docker - PocketBase - Backend for your next SaaS and Mobile app in one file. (Source Code)
MITGo/Docker - SQLPage - SQL-only dynamic website builder. (Source Code)
MITRust/Docker - ToolJet - Low-code framework to build & deploy internal tools with minimal engineering effort (alternative to Retool & Mendix). (Source Code)
GPL-3.0Nodejs/Docker/K8S - TrailBase - Open, sub-millisecond, single-executable FireBase alternative with type-safe REST & realtime APIs, built-in JS/TS runtime, auth & admin UI. (Demo, Source Code)
OSL-3.0Rust/Docker
- Appsmith - Build admin panels, CRUD apps and workflows. Build everything you need, 10x faster. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:08:08
@ b0a838f2:34ed3f19
2025-05-23 18:08:08- Accent - Developer-oriented translation tool. (Source Code)
BSD-3-ClauseElixir/Docker - Tolgee - Developer & translator friendly web-based localization platform enabling users to translate directly in the app they develop. (Source Code)
Apache-2.0Docker/Java - Traduora - Translation management platform for teams. (Source Code)
AGPL-3.0Docker/K8S/Nodejs - Weblate - Web-based translation tool with tight version control integration. (Source Code)
GPL-3.0Python/Docker/K8S
- Accent - Developer-oriented translation tool. (Source Code)
-
 @ 94215f42:7681f622
2025-05-23 01:44:26
@ 94215f42:7681f622
2025-05-23 01:44:26The promise of AI is intoxicating: slash operational costs by 50-80%, achieve software-style margins on service businesses and and watch enterprise value multiply overnight.
But this initial value creation contains a hidden trap that could leave businesses worth less than when they started. Understanding the "Value Trap" is key to navigating a transition to an AI economy.
What is the Value Trap?
Whilst the value trap is forward looking and somewhat theoretical at this point, there are strong financial incentives to drive investments (many $bns of are looking at the transformation opportunity) that mean this should be taken very seriously.
The Value Trap unfolds in distinct phases:
Phase 1: Status Quo A typical service business operates with 100 units of revenue and 90 units of cost, generating 10 units of profit, representing a standard 10% margin. A bog standard business we can all relate to, long term customers locked in, market fit a distant memory, but growth is hard at this point.
Phase 2: Cost Reduction Early AI adopters slash operational expenses from 90 to 20 units while maintaining 100 units of revenue. This is the very real promise when moving to a "Human at the Edge" model that we'll unpack in a future article. Suddenly, they're generating 80 units of profit at an 8x increase that can easily add multiple to the enterprise value! A venture style return on a business previously struggling for growth.
Phase 3: Growth Phase With massive profit margins comes pricing power. These businesses can undercut competitors while maintaining healthy margins, driving rapid revenue growth. Having removed the human constraint on scaling and the additional overheads and complexity this introduces we see seemingly unlimited expansion. The brakes are truly off at this point for early adopters to expand total market share.
Phase 4: Competition Emerges The extraordinary returns attract competitors. It's important to note there is no technical moat here, other businesses implement similar AI strategies, often from your own staff who may have been let go, new entrants launch AI-native operations, and pricing power erodes.
Phase 5: Mean Reversion After 3-7 years (our best guess given current investment interest in transformation led PE), competitive pressure drives revenue down from 100 to 25 units while costs remain at 20. The business ends up with similar margins to where it started but at much lower absolute revenue, potentially destroying enterprise value.
What you've done is just massively reduced costs in this industry by displacing jobs and those individuals can turn around and compete. You incentivise the competition which erodes your pricing power
Why This Pattern is Inevitable
The Value Trap isn't pure speculation, but based on market dynamics playing out given a set of financial incentives. We believe there are several key forces that make this cycle almost guaranteed:
The Arbitrage is Too Attractive When businesses can achieve "venture returns with no product-market fit risk," capital will flood in. Private equity and Venture Capital firms are already raising funds specifically to acquire traditional service businesses and apply AI transformation strategies .
Low Technical Barriers Unlike previous technological advantages, AI implementation doesn't require significant technical moats. Much of the technology is open source, and the real barrier is process redesign thinking rather than proprietary technology.
The "One Player" Principle In any market, it only takes one competitor to implement AI-native processes to force everyone else to adapt. You either "play the game or you get left behind".
Capital Abundance With global money supply expanding and traditional investment opportunities yielding lower returns, the combination of proven product-market fit and dramatic cost reduction potential represents an irresistible opportunity for investors.
Strategic Response for SMEs: The Netflix Model
Small and medium enterprises actually have a significant advantage in navigating the Value Trap, but they need to act strategically and start moving now.
Embrace the Incubation Approach Rather than gutting your existing business, adopt Netflix's strategy: build an AI-native version of your business alongside your current operations. This approach manages risk while positioning for the future.

The answer here is why not both. you don't necessarily have to gut your current business, but you should be thinking about what does my business look like in five years and how do I transition into that.
Leverage Your Natural Advantages Small businesses can adapt faster than large enterprises. While a 20,000-person company faces "political shockwaves" when reducing workforce, a 10-person business can double revenue without anyone noticing. You can focus on growth rather than painful cost-cutting.
Remove Growth Constraints Early AI removes the traditional constraint where "adding the next person" represents a significant capital investment. Small businesses can scale efficiently once they've redesigned their processes around AI-native workflows, avoid further capital outlay and scaling without increasing complexity in operations.
Focus on Local Networks For various reasons associated with the commoditisation of intelligence, we believe the future favours "hyper-localised" businesses serving customers who "know, like, and trust" them. As intelligence becomes commoditised, human relationships become more valuable, not less.
Strategic Response for Capital Allocators
For private equity and venture capital firms, the Value Trap presents both enormous opportunity and significant risk.
Target the Right Businesses Look for businesses with strong persistent moats that will slow mean reversion:
-
Strong brand and customer relationships
-
High customer acquisition costs in the industry
-
Regulatory barriers to entry
-
Capital-intensive startup requirements
-
Long-term contracts and switching costs
Master the Timing The key is capturing value during the expansion phase and exiting before mean reversion accelerates, or finding an appropriate time arbitrage solution to retain value (see below). The optimal point if you're a capital allocator is almost when you've extracted the most cost out of the business.
Consider Hybrid Strategies Rather than just gutting existing businesses, consider acquiring for distribution and customer base while building AI-native operations alongside traditional ones. This provides multiple exit strategies and reduces execution risk.
Bitcoin: The Time Arbitrage Solution
Whenever I've talked to anybody about AI, my first point of advice is just buy bitcoin.
This isn't just evangelism, so much as a recognition of where you would want to hold value as the Value Trap plays out. In essence the value trap generates an arbitrage opportunity, hige profits are pulled forwards short-term balooning the balance sheet, but the second order consequences of this change risk destroying the value you just created!
We believe alongside rapid competition leading to price for services collapsing, the mass job displacement leads to political pressure for intervention.
This could take several forms, but UBI, mortgage bailouts, unemployment extensions, seizure of existing property.
"All roads lead to money printing," as Pete notes in Good Stuff 02 .
During Weimar Republic hyperinflation, "the cost of a newspaper in year five was the same nominal figure as all of the money that existed in year four." While extreme, this illustrates how quickly monetary systems can shift as inflation and money supply inflation begins to run.
To resolve these issues, Bitcoin allows you to conduct arbitrage across time in an asset that is inflation resistant (fixed supply), hard to seize, has no counter party risk (if someone holds your gold, stocks, cash they can take it without asking) and transportable. Capturing value today and preserving it through monetary system changes protecting against the second and third-order effects of massive economic disruption, that AI represents.
Opportunity, Not Fear: The Renaissance Ahead
The Value Trap isn't a reason to avoid AI, it's a roadmap for navigating inevitable change strategically.
The Entrepreneurial Renaissance This could be a Renaissance for entrepreneurs, if you're entrepreneurial minded, this is an amazing time to be alive because there's opportunity that exists in all fields and the barriers to entry have never been lower.
Liberation from Busy Work The displacement of administrative and routine cognitive work frees humans for higher-value creation.
Democratisation of Intelligence When you can "purchase intelligence in buckets of $0.02 API calls," the barriers to starting and scaling businesses collapse. Individual entrepreneurs can build businesses that previously required large teams, with much lower complexity and risk.
Cost Reduction Benefits Everyone The ultimate outcome of the Value Trap cycle benefits consumers through dramatically lower prices for goods and services.
"Who doesn't want cheaper stuff? Why don't we just reduce the cost of everything massively?"
Conclusion: Embrace the High Agency Era
The Value Trap represents a fundamental shift from employment-based to entrepreneurship-based wealth creation. Rather than fearing job displacement, we should prepare for "the age of the entrepreneur" a high agency era.
The businesses and individuals who thrive will be those who:
-
Understand the cycle and position accordingly
-
Focus on unique value creation rather than routine processing or middleman models
-
Build local networks and relationships
-
Preserve wealth through the monetary transition
-
Embrace building and creating unique value
If you are high agency, you can make anything happen.
The Value Trap isn't just about AI transforming business, it won't do this on its own, its a description of how humans will use this technology to generate and capture value.
The future belongs to builders, creators, and entrepreneurs who can navigate transition periods and emerge stronger. The Value Trap is the map, use it wisely.
This article draws heavily on discussion between myself and business partner Andy in Episode 02 of The Good Stuff, if you prefer listening try that :)
-
-
 @ b0a838f2:34ed3f19
2025-05-23 18:07:52
@ b0a838f2:34ed3f19
2025-05-23 18:07:52- Atheos - Web-based IDE framework with a small footprint and minimal requirements, continued from Codiad. (Source Code)
MITPHP/Docker - code-server - VS Code in the browser, hosted on a remote server.
MITNodejs/Docker - Coder - Remote development machines on your own infrastructure. (Source Code)
AGPL-3.0Go/Docker/K8S/deb - Eclipse Che - Open source workspace server and cloud IDE. (Source Code)
EPL-1.0Docker/Java - HttPlaceholder - Quickly mock away any webservice using HttPlaceholder. HttPlaceholder lets you specify what the request should look like and what response needs to be returned.
MITC# - Judge0 CE - API to compile and run source code. (Source Code)
GPL-3.0Docker - JupyterLab - Web-based environment for interactive and reproducible computing. (Demo, Source Code)
BSD-3-ClausePython/Docker - Langfuse - LLM engineering platform for model tracing, prompt management, and application evaluation. Langfuse helps teams collaboratively debug, analyze, and iterate on their LLM applications such as chatbots or AI agents. (Demo, Source Code, Clients)
MITDocker - LiveCodes
⚠- Feature-rich client-side code playground for React, Vue, Svelte, Solid, Typescript, Python, Go, Ruby, PHP and 90+ other languages. (Demo, Source Code)MITNodejs - Lowdefy - Build internal tools, BI dashboards, admin panels, CRUD apps and workflows in minutes using YAML / JSON on an self-hosted, open-source platform. Connect to your data sources, host via Serverless, Netlify or Docker. (Source Code)
Apache-2.0Nodejs/Docker - RStudio Server - Web browser based IDE for R. (Source Code)
AGPL-3.0Java/C++ - Wakapi - Tracking tool for coding statistics, compatible with WakaTime. (Source Code)
GPL-3.0Go/Docker
- Atheos - Web-based IDE framework with a small footprint and minimal requirements, continued from Codiad. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:07:34
@ b0a838f2:34ed3f19
2025-05-23 18:07:34- Featbit - Enterprise-grade feature flag platform that you can self-host. (Source Code)
MITDocker/K8S - Flagsmith - Dashboard, API and SDKs for adding Feature Flags to your applications (alternative to LaunchDarkly). (Source Code)
BSD-3-ClauseDocker/K8S - Flipt - Feature flag solution with support for multiple data backends (alternative to LaunchDarkly). (Demo, Source Code)
GPL-3.0Docker/K8S/Go - GO Feature Flag - Simple, complete, and lightweight feature flag solution (alternative to LaunchDarkly). (Source Code)
MITGo
- Featbit - Enterprise-grade feature flag platform that you can self-host. (Source Code)
-
 @ 90152b7f:04e57401
2025-05-23 01:27:49
@ 90152b7f:04e57401
2025-05-23 01:27:49[Analytical & Intelligence Comments]\ \ “On Monday February 27th, 2012, WikiLeaks began publishing The Global Intelligence Files, over five million e-mails from the Texas headquartered "global intelligence" company Stratfor. The e-mails date between July 2004 and late December 2011. They reveal the inner workings of a company that fronts as an intelligence publisher, but provides confidential intelligence services to large corporations, such as Bhopal's Dow Chemical Co., Lockheed Martin, Northrop Grumman, Raytheon and government agencies, including the US Department of Homeland Security, the US Marines and the US Defence Intelligence Agency. The emails show Stratfor's web of informers, pay-off structure, payment laundering techniques and psychological methods.”\ \ Released on 2013-02-13 00:00 GMT Email-ID 13332210 Date 2011-05-04 16:26:59\ From <jetdrive@earthlink.net> To <responses@stratfor.com> CROYDON KEMP sent a\ message using the contact form at <https://www.stratfor.com/contact\>\\ Mossad ran 9/11 Arab "hijacker" terrorist operation\ \ By Wayne Madsen\ \ British intelligence reported in February 2002 that the Israeli Mossad ran the Arab hijacker cells that were later blamed by the U.S. government's 9/11 Commission for carrying out the aerial attacks on the World Trade Center and Pentagon. WMR has received details of the British intelligence report which was suppressed by the government of then-Prime Minister Tony Blair.\ \ A Mossad unit consisting of six Egyptian- and Yemeni-born Jews infiltrated "Al Qaeda" cells in Hamburg (the Atta-Mamoun Darkanzali cell), south Florida, and Sharjah in the United Arab Emirates in the months before 9/11. The Mossad not only infiltrated cells but began to run them and give them specific orders that would eventually culminate in their being on board four regularly-scheduled flights originating in Boston, Washington Dulles, and Newark, New Jersey on 9/11.\ \ The Mossad infiltration team comprised six Israelis, comprising two cells of three agents, who all received special training at a Mossad base in the Negev Desert in their future control and handling of the "Al Qaeda" cells. One Mossad cell traveled to Amsterdam where they submitted to the operational control of the Mossad's Europe Station, which operates from the El Al complex at Schiphol International Airport. The three-man Mossad unit then traveled to Hamburg where it made contact with Mohammed Atta, who believed they were sent by Osama Bin Laden. In fact, they were sent by Ephraim Halevy, the chief of Mossad.\ \ The second three-man Mossad team flew to New York and then to southern Florida where they began to direct the "Al Qaeda" cells operating from Hollywood, Miami, Vero Beach, Delray Beach, and West Palm Beach. Israeli "art students," already under investigation by the Drug Enforcement Administration for casing the offices and homes of federal law enforcement officers, had been living among and conducting surveillance of the activities, including flight school training, of the future Arab "hijacker" cells, particularly in Hollywood and Vero Beach.\ \ In August 2001, the first Mossad team flew with Atta and other Hamburg "Al Qaeda" members to Boston. Logan International Airport's security was contracted to Huntleigh USA, a firm owned by an Israeli airport security firm closely connected to Mossad — International Consultants on Targeted Security – ICTS. ICTS's owners were politically connected to the Likud Party, particularly the Netanyahu faction and then-Jerusalem mayor and future Prime Minister Ehud Olmert. It was Olmert who personally interceded with New York Mayor Rudolph Giuliani to have released from prison five Urban Moving Systems employees, identified by the CIA and FBI agents as Mossad agents. The Israelis were the only suspects arrested anywhere in the United States on 9/11 who were thought to have been involved in the 9/11 attacks.\ \ The two Mossad teams sent regular coded reports on the progress of the 9/11 operation to Tel Aviv via the Israeli embassy in Washington, DC. WMR has learned from a Pentagon source that leading Americans tied to the media effort to pin 9/11 on Arab hijackers, Osama Bin Laden, and the Taliban were present in the Israeli embassy on September 10, 2001, to coordinate their media blitz for the subsequent days and weeks following the attacks. It is more than likely that FBI counter-intelligence agents who conduct surveillance of the Israeli embassy have proof on the presence of the Americans present at the embassy on September 10. Some of the Americans are well-known to U.S. cable news television audiences.\ \ In mid-August, the Mossad team running the Hamburg cell in Boston reported to Tel Aviv that the final plans for 9/11 were set. The Florida-based Mossad cell reported that the documented "presence" of the Arab cell members at Florida flight schools had been established.\ \ The two Mossad cells studiously avoided any mention of the World Trade Center or targets in Washington, DC in their coded messages to Tel Aviv. Halevy covered his tracks by reporting to the CIA of a "general threat" by an attack by Arab terrorists on a nuclear plant somewhere on the East Coast of the United States. CIA director George Tenet dismissed the Halevy warning as "too non-specific." The FBI, under soon-to-be-departed director Louis Freeh, received the "non-specific" warning about an attack on a nuclear power plant and sent out the information in its routine bulletins to field agents but no high alert was ordered.\ \ The lack of a paper trail pointing to "Al Qaeda" as the masterminds on 9/11, which could then be linked to Al Qaeda's Mossad handlers, threw off the FBI. On April 19, 2002, FBI director Robert Mueller, in a speech to San Francisco's Commonwealth Club, stated: "In our investigation, we have not uncovered a single piece of paper — either here in the United States, or in the treasure trove of information that has turned up in Afghanistan and elsewhere — that mentioned any aspect of the September 11 plot."\ \ The two Mossad "Al Qaeda" infiltration and control teams had also helped set up safe houses for the quick exfiltration of Mossad agents from the United States. Last March, WMR reported: "WMR has learned from two El Al sources who worked for the Israeli airline at New York’s John F. Kennedy airport that on 9/11, hours after the Federal Aviation Administration (FAA) grounded all civilian domestic and international incoming and outgoing flights to and from the United States, a full El Al Boeing 747 took off from JFK bound for Tel Aviv’s Ben Gurion International Airport. The two El Al employee sources are not Israeli nationals but legal immigrants from Ecuador who were working in the United States for the airline. The flight departed JFK at 4:11 pm and its departure was, according to the El Al sources, authorized by the direct intervention of the U.S. Department of Defense. U.S. military officials were on the scene at JFK and were personally involved with the airport and air traffic control authorities to clear the flight for take-off. According to the 9/11 Commission report, Transportation Secretary Norman Mineta ordered all civilian flights to be grounded at 9:45 am on September 11." WMR has learned from British intelligence sources that the six-man Mossad team was listed on the El Al flight manifest as El Al employees.\ \ WMR previously reported that the Mossad cell operating in the Jersey City-Weehawken area of New Jersey through Urban Moving Systems was suspected by some in the FBI and CIA of being involved in moving explosives into the World Trade Center as well as staging "false flag" demonstrations at least two locations in north Jersey: Liberty State Park and an apartment complex in Jersey City as the first plane hit the World Trade Center's North Tower. One team of Urban Moving Systems Mossad agents was arrested later on September 11 and jailed for five months at the Metropolitan Detention Center in Brooklyn. Some of their names turned up in a joint CIA-FBI database as known Mossad agents, along with the owner of Urban Moving Systems, Dominik Suter, whose name also appeared on a "Law Enforcement Sensitive" FBI 9/11 suspects list, along with the names of key "hijackers," including Mohammed Atta and Hani Hanjour, as well as the so-called "20th hijacker," Zacarias Moussaoui.\ \ Suter was allowed to escape the United States after the FBI made initial contact with him at the Urban Moving Systems warehouse in Weehawken, New Jersey, following the 9/11 attacks. Suter was later permitted to return to the United States where he was involved in the aircraft parts supply business in southern Florida, according to an informe3d source who contacted WMR. Suter later filed for bankruptcy in Florida for Urban Moving Systems and other businesses he operated: Suburban Moving & Storage Inc.; Max Movers, Inc.; Invsupport; Woodflooring Warehouse Corp.; One Stop Cleaning LLC; and City Carpet Upholstery, Inc. At the time of the bankruptcy filing in Florida, Suter listed his address as 1867 Fox Court, Wellington, FL 33414, with a phone number of 561 204-2359.\ \ From the list of creditors it can be determined that Suter had been operating in the United States since 1993, the year of the first attack on the World Trade Center. In 1993, Suter began racking up American Express credit card charges totaling $21,913.97. Suter also maintained credit card accounts with HSBC Bank and Orchard Bank c/o HSBC Card Services of Salinas, California, among other banks. Suter also did business with the Jewish Community Center of Greater Palm Beach in Florida and Ryder Trucks in Miami. Miami and southern Florida were major operating areas for cells of Israeli Mossad agents masquerading as "art students," who were living and working near some of the identified future Arab "hijackers" in the months preceding 9/11.\ \ ABC's 20/20 correspondent John Miller ensured that the Israeli connection to "Al Qaeda's" Arab hijackers was buried in an "investigation" of the movers' activities on 9/11. Anchor Barbara Walters helped Miller in putting a lid on the story about the movers and Suter aired on June 21, 2002. Miller then went on to become the FBI public affairs spokesman to ensure that Mueller and other FBI officials kept to the "Al Qaeda" script as determined by the Bush administration and the future 9/11 Commission. But former CIA chief of counter-terrorism Vince Cannistraro let slip to ABC an important clue to the operations of the Mossad movers in New Jersey when he stated that the Mossad agents "set up or exploited for the purpose of launching an intelligence operation against radical Islamists in the area, particularly in the New Jersey-New York area." The "intelligence operation" turned out to have been the actual 9/11 attacks. And it was no coincidence that it was ABC's John Miller who conducted a May 1998 rare interview of Osama Bin Laden at his camp in Afghanistan. Bin Laden played his part well for future scenes in the fictional "made-for-TV" drama known as 9/11.\ \ WMR has also learned from Italian intelligence sources that Mossad's running of "Al Qaeda" operatives did not end with running the "hijacking" teams in the United States and Hamburg. Other Arab "Al Qaeda" operatives, run by Mossad, were infiltrated into Syria but arrested by Syrian intelligence. Syria was unsuccessful in turning them to participate in intelligence operations in Lebanon. Detailed information on Bin Laden's support team was offered to the Bush administration, up to days prior to 9/11, by Gutbi al-Mahdi, the head of the Sudanese Mukhabarat intelligence service. The intelligence was rejected by the Biush White House. It was later reported that Sudanese members of "Al Qaeda's" support network were double agents for Mossad who had also established close contacts with Yemeni President Ali Abdullah Saleh and operated in Egypt, Saudi Arabia, and Eritrea, as well as Sudan. The Mossad connection to Al Qaeda in Sudan was likely known by the Sudanese Mukhabarat, a reason for the rejection of its intelligence on "Al Qaeda" by the thoroughly-Mossad penetrated Bush White House. Yemen had also identified "Al Qaeda" members who were also Mossad agents. A former chief of Mossad revealed to this editor in 2002 that Yemeni-born Mossad "deep insertion" commandos spotted Bin Laden in the Hadhramaut region of eastern Yemen after his escape from Tora Bora in Afghanistan, following the U.S. invasion.\ \ French intelligence determined that other Egyptian- and Yemeni-born Jewish Mossad agents were infiltrated into Sharjah in the United Arab Emirates as radical members of the Muslim Brotherhood. However, the "Muslim Brotherhood" agents actually were involved in providing covert Israeli funding for "Al Qaeda" activities. On February 21, 2006, WMR reported on the U.S. Treasury Secretary's firing by President Bush over information discovered on the shady "Al Qaeda" accounts in the United Arab Emirates: "Banking insiders in Dubai report that in March 2002, U.S. Secretary of Treasury Paul O’Neill visited Dubai and asked for documents on a $109,500 money transfer from Dubai to a joint account held by hijackers Mohammed Atta and Marwan al Shehhi at Sun Trust Bank in Florida. O'Neill also asked UAE authorities to close down accounts used by Al Qaeda . . . . The UAE complained about O’Neill’s demands to the Bush administration. O’Neill’s pressure on the UAE and Saudis contributed to Bush firing him as Treasury Secretary in December 2002 " O'Neill may have also stumbled on the "Muslim Brotherhood" Mossad operatives operating in the emirates who were directing funds to "Al Qaeda."\ \ After the collapse of the Soviet Union and the rise to power of the Taliban in Afghanistan, Sharjah's ruler, Sultan bin Mohammed al-Qasimi, who survived a palace coup attempt in 1987, opened his potentate to Russian businessmen like Viktor Bout, as well as to financiers of radical Muslim groups, including the Taliban and "Al Qaeda."\ \ Moreover, this Israeli support for "Al Qaeda" was fully known to Saudi intelligence, which approved of it in order to avoid compromising Riyadh. The joint Israeli-Saudi support for "Al Qaeda" was well-known to the Sharjah and Ras al Khaimah-based aviation network of the now-imprisoned Russian, Viktor Bout, jailed in New York on terrorism charges. The presence of Bout in New York, a hotbed of Israeli intelligence control of U.S. federal prosecutors, judges, as well as the news media, is no accident: Bout knows enough about the Mossad activities in Sharjah in support of the Taliban and Al Qaeda in Afghanistan, where Bout also had aviation and logistics contracts, to expose Mossad as the actual mastermind behind 9/11. Bout's aviation empire also extended to Miami and Dallas, two areas that were nexuses for the Mossad control operations for the "Al Qaeda" flight training operations of the Arab cell members in the months prior to 9/11.\ \ Bout's path also crossed with "Al Qaeda's" support network at the same bank in Sharjah, HSBC. Mossad's phony Muslim Brotherhood members from Egypt and Yemen controlled financing for "Al Qaeda" through the HSBC accounts in Sharjah. Mossad's Dominik Suter also dealt with HSBC in the United States. The FBI's chief counter-terrorism agent investigating Al Qaeda, John O'Neill, became aware of the "unique" funding mechanisms for Al Qaeda. It was no mistake that O'Neill was given the job as director of security for the World Trade Center on the eve of the attack. O'Neill perished in the collapse of the complex.Mossad uses a number of Jews born in Arab countries to masquerade as Arabs. They often carry forged or stolen passports from Arab countries or nations in Europe that have large Arab immigrant populations, particularly Germany, France, Britain, Denmark, Sweden, and the Netherlands.\ \ For Mossad, the successful 9/11 terrorist "false flag" operation was a success beyond expectations. The Bush administration, backed by the Blair government, attacked and occupied Iraq, deposing Saddam Hussein, and turned up pressure on Israel's other adversaries, including Iran, Syria, Pakistan, Hamas, and Lebanese Hezbollah. The Israelis also saw the U.S., Britain, and the UN begin to crack down on the Lebanese Shi'a diamond business in Democratic Republic of Congo and West Africa, and with it, the logistics support provided by Bout's aviation companies, which resulted in a free hand for Tel Aviv to move in on Lebanese diamond deals in central and west Africa.\ \ Then-Israeli Finance Minister Binyamin Netanyahu commented on the 9/11 attacks on U.S. television shortly after they occurred. Netanyahu said: "It is very good!" It now appears that Netanyahu, in his zeal, blew Mossad's cover as the masterminds of 9/11.\ \ Wayne Madsen is a Washington, DC-based investigative journalist, author and syndicated columnist. He has written for several renowned papers and blogs.\ \ Madsen is a regular contributor on Russia Today. He has been a frequent political and national security commentator on Fox News and has also appeared on ABC, NBC, CBS, PBS, CNN, BBC, Al Jazeera, and MS-NBC. Madsen has taken on Bill O’Reilly and Sean Hannity on their television shows. He has been invited to testifty as a witness before the US House of Representatives, the UN Criminal Tribunal for Rwanda, and an terrorism investigation panel of the French government.\ \ As a U.S. Naval Officer, he managed one of the first computer security programs for the U.S. Navy. He subsequently worked for the National Security Agency, the Naval Data Automation Command, Department of State, RCA Corporation, and Computer Sciences Corporation.\ \ Madsen is a member of the Society of Professional Journalists (SPJ), Association for Intelligence Officers (AFIO), and the National Press Club. He is a regular contributor to Opinion Maker
-
 @ 3eba5ef4:751f23ae
2025-05-23 01:12:10
@ 3eba5ef4:751f23ae
2025-05-23 01:12:10Crypto Insights
Introducing Generalized Program Composition and Coin Delegation into Bitcoin
Joshua Doman proposed a proof-of-concept called Graftleaf, aiming to achieve generalized program composition and delegation in Taproot in a simple and secure way. Graftleaf is a new Taproot leaf version (0xc2) that uses the annex to perform delegation. It adds two key features:
-
Composition: The ability to sequentially execute zero, one, or multiple witness programs, including a locking script.
-
Delegation: The ability to add additional spending conditions at signing time, which can include arbitrary combinations of programs and scripts.
This design overcomes the limitations of previous proposals by supporting complex script composition and delegation, promising backward compatibility, improved privacy and fungibility with the existing P2TR addresses.
Why OP_CHECKCONTRACTVERIFY (CCV) Will Replace OP_VAULT
A post mainly discusses the current status of Bitcoin script opcode OP_VAULT (BIP-345) and the possibility of it being replaced by OP_CHECKCONTRACTVERIFY (CCV, BIP-443). Key factors include:
-
CCV is a more general version of OP_VAULT, inheriting some features such as amount modes and deferred (cross-input) checks.
-
CCV supports replacing multiple script tapleaf nodes, has a simpler interface, and a lighter script interpreter implementation.
The author also points out CCV’s shortcomings and possible future extensions:
-
Currently, there is a lack of supporting documentation and tools, and the BIP is not yet fully completed.
-
A VAULT-decorator opcode may be needed to implement certain advanced features, such as requiring collateral lockup when unvaulting, or adding some rate-limiting behavior. These features are currently difficult to achieve.
Despite this, CCV remains a better foundation for building vault functionality.
Enabling Recursive Covenants via Self-Replication
Bram Cohen proposed adding a few simple opcodes to Bitcoin Script to enable recursive covenants in a natural and straightforward way. He illustrated with examples that a practical and useful script can be achieved through Quine, without other more complex tricks; developers writing recursive covenants must be aware of the importance of this approach.
UTXO Set Report from Mempool Research: Nearly Half of Bitcoin UTXOs Are Less Than 1,000 Sats
During the OP_RETURN debate in April-May 2025, the impact of inserting arbitrary data into transactions on the UTXO set sparked much discussion. In this report, Mempool studied the UTXO set, highlighting the fragmentation and bloat issues, especially due to small transactions and data embedding, which increase the storage and validation burden for node operators.
Key findings include:
-
Severe Bloat: Currently, about 49% of UTXOs are less than 1,000 satoshis (about $1). Most of these use Taproot address format and may be related to data embedding schemes (like Ordinals) or related transfer mechanisms. Although these UTXOs can usually be spent, before they are, they increase the storage and validation burden for all node operators.
-
Significant Proportion of Inscription-Related UTXOs: About 30% of UTXOs are related to inscription.
-
Large Number of Long-Unspent UTXOs: There are over 100,000 old Counterparty UTXOs using Pay to Multisig (p2ms) scripts, which have existed for over 10 years. Although they make up a small proportion of the total (about 173 million UTXOs), they are a typical example of UTXO bloat.
-
Taproot Becomes the Most Common UTXO Type: Among all UTXO types, Taproot (p2tr) has the highest proportion at 34.2%, followed by traditional p2pkh (28.8%) and p2wpkh (26.5%). However, in terms of total value stored, Taproot’s share is relatively low, indicating it is mainly used for small transactions or data embedding.
The report concludes by mentioning that as the UTXO sets continue to grow, Utreexo and SwiftSync are two scaling methods for maintaining Bitcoin’s accessibility to a wide range of node operators.
Visualization of Bitcoin Mainnet Data
mainnet-observer, built and maintained by developer @0xB10C, visualizes multiple data points from the Bitcoin mainnet, including:
-
Mining a single block currently requires over ~500,000,000,000,000,000,000,000,000 (500 zeta or 5×10²³) hash attempts.
-
Over 42 BTC are now permanently lost in provably unspendable OP_RETURN outputs.
-
Daily updated “Mining Centralization Index” (with proxy pools)
-
Bitcoin mining is currently highly centralized, with 6 pools producing and mining over 95% of block templates.

Path Queries: Addressing Payment Reliability and Routing Limitations
brh28 initiated a discussion on Lightning Network payment routing, focusing on issues like liquidity uncertainty and inefficient path discovery. He proposed a new path query mechanism—allowing nodes to dynamically share information through path queries, fostering a more decentralized routing ecosystem. This can improve the success rate of large payments and reduce reliance on a completely synced channel graph. Although there are still some privacy concerns, this method provides nodes with a controllable information disclosure mechanism and is expected to revolutionize current payment routing approaches.
Bitlayer and Sui Achieve Trust-Minimized BitVM Bridge
Bitlayer and Sui integrated the BitVM Bridge, launching Peg-BTC (YBTC)—bridging native Bitcoin to the Sui ecosystem via BitVM Bridge. BitVM Bridge is a trust-minimized bridge powered by Bitlayer and supported by the advanced BitVM smart contract framework.
Ark Protocol Litepaper
Ark recently released its litepaper: Ark: A UTXO-based Transaction Batching Protocol, outlining its technical foundation. As an innovative Bitcoin scaling protocol, Ark enables off-chain transaction execution while allowing users full control over their funds. This is achieved by introducing “virtual UTXOs” (VTXOs), allowing users to transact off-chain while retaining the ability to unilaterally exit to the Bitcoin main chain. Coordinated by an operator who batches user activities into on-chain commitments, Ark achieves high transaction throughput with minimal on-chain footprint. This provides Bitcoin with a simple and user-friendly scaling solution that offers a practical path for Layer 2 solutions that are inefficient or costly to execute on the main chain.
Top Reads on Blockchain and Beyond
List of Known Real-World Bitcoin Attack Incidents
Here is a list of real-world attacks against Bitcoin/crypto asset holders over the years.

The Internet Capital Market: Free Avenue for Developers, or Another Wave of FOMO?
This post discusses Internet Capital Markets (ICM)—decentralized platforms where funds flow directly to app builders and creators. ICM combines crowdfunding, token issuance, and equity speculation, eliminating the need for VCs, banks, or app stores. In 2025, more independent developers are issuing app tokens directly via X and tools like Believe and Launchcoin, attracting mass investment.
ICM Proponents argue this model breaks traditional funding barriers, making innovation more democratic and accessible; while critics warn that ICM is becoming a hotbed for hype and short-term speculation, with many projects lacking real products or long-term value. The author believes whether ICM can become the next milestone for Web3 hinges on whether it can break free from the cycle of “speculation becomes product traction” and deliver real user value and sustained innovation.
-
-
 @ 3eba5ef4:751f23ae
2025-05-23 01:08:23
@ 3eba5ef4:751f23ae
2025-05-23 01:08:23加密洞见
在比特币中引入通用程序组合与币委托机制
Joshua Doman 提出了一个 Graftleaf 的概念验证,旨在用一种简单而安全的方法在 Taproot 中实现通用程序组合和代笔委托。Graftleaf 是一个新的 Taproot 叶子版本(0xc2),使用附件来执行委托。Graftleaf 增加了两个关键功能:
-
组合:按顺序执行零个、一个或多个见证程序的能力,包括一个锁定脚本。
-
委派:在签名时添加其他支出条件的能力,可以包括程序和脚本的任意组合。
它们旨在通过支持复杂的脚本组合和委托来克服以前提案的局限性,承诺提高隐私性、可替代性以及与现有 P2TR 地址的向后兼容性。
为什么说 OP_CHECKCONTRACTVERIFY (CCV) 将会取代 OP_VAULT
帖子主要讨论了比特币脚本操作码 OP_VAULT(BIP-345)的现状,及其被OP_CHECKCONTRACTVERIFY(CCV,BIP-443)取代的可能。重要因素有:
-
CCV 是 OP_VAULT 的更通用版本,继承了部分功能,如金额模式(amount modes)、延迟跨输入检查(deferred cross-input checks)。
-
CCV支持替换多个脚本叶子节点(tapleaf),接口更简洁,脚本解释器实现更轻量。
同时作者也指出 CCV 的不足与未来可能的扩展:
-
当前缺少部分配套文档和工具,BIP 尚未完全完成。
-
可能需要 VAULT-decorator 操作码来实现某些高级功能,如解锁金库时必须抵押锁定、速率限制等。
尽管如此,CCV仍然是构建金库功能的更优基础。
通过自复制方式启用递归契约
Bram Cohen 提出通过向比特币脚本添加一些简单的操作码,以一种自然而直接的方式实现递归契约(recursive covenants)。他通过例子说明,一个实用且有用的脚本通过 Quine 自复制就可以实现,无需其他更复杂的技巧;编写递归契约的开发者必须意识到该方式的重要性。
Mempool Research 发布 UTXO 集的报告:比特币中近一半 UTXO 金额小于 1000 聪
在 2025 年 4 至 5 月期间的 OP_RETURN 大辩论中,将任意数据插入交易对 UTXO 集的影响的问题引发了大量讨论。Mempool 在这份报告中,对 UTXO 集进行了研究,强调了比特币 UTXO 集合碎片化和膨胀的问题,特别是由于小额交易和数据嵌入导致的 UTXO 增长,增加了节点运营者的存储和验证负担。关键结论有:
-
UTXO 集合的碎片化严重:目前约有 49% 的 UTXO 金额低于 1000 聪(约合 1 美元),这些小额 UTXO 大多采用 Taproot 地址格式,可能与数据嵌入方案(如 Ordinals 铭文)或相关的转移机制有关。尽管这些 UTXO 通常可被花费,但在被使用之前,它们会增加所有节点运营者的存储和验证负担。
-
铭文相关的 UTXO 占比显著:约 30% 的 UTXO 与铭文相关。
-
存在大量长期未动用的 UTXO:有超过 10 万个使用 Pay to Multisig (p2ms) 脚本的旧 Counterparty UTXO,且存在超过 10 年。尽管在总数(约 1.73 亿个 UTXO)中所占比例较小,但依然是 UTXO 膨胀的典型问题。
-
Taproot 成为最常见的 UTXO 类型:在所有 UTXO 类型中,Taproot(p2tr)占比最高,为 34.2%,其次是传统的 p2pkh(28.8%)和 p2wpkh(26.5%)。但是从 UTXO 所存储的总价值来看,Taproot 的占比相对较低,表明其主要用于小额交易或数据嵌入。
报告最后也提到,对于继续增长的 UTXO 集,Utreexo 和 SwiftSync 是两种对保持比特币对广泛节点运营者可访问性的扩容方法。
比特币网络各项数据的可视化呈现
mainnet-observer 由开发者 @0xB10C 搭建并维护,将比特币链的多项数据呈现出来,可以看到:
-
目前挖掘一个区块所需要的平均哈希尝试:超过 ~500000000000000000000000000(500 zeta 或 5×10²³)次
-
超过 42 个 BTC 现在永远丢失在可证明无法花费的 OP_RETURN 输出中
-
每日更新的「挖矿中心化指数」(带有代理池)
-
比特币挖矿高度集中,6 个矿池生产并挖掘了超过 95%的区块模板(截止 2025 年 4 月)

闪电网络路径查询:解决支付可靠性和路由限制
brh28 发起了关于闪电网络路由支付的讨论,聚焦「流动性的不确定性」(liquidity uncertainty)和路径发现效率低的问题,提出了一种新的路径查询机制——允许节点以路径查询的形式,实现动态信息共享,推动了一个更加分布式的路由生态。这可以提高了大额支付的成功率,并减少对完整通道图的依赖。尽管在隐私方面仍存在一定担忧,但该方法为节点提供了一种可控的信息披露机制,有望革新现有的支付路由方式。
Bitlayer 和 Sui 实现了信任最小化的 BitVM 桥
Bitlayer 和 Sui 整合了 BitVM Bridge,推出 Peg-BTC(YBTC)——通过 BitVM Bridge 将原生比特币桥接到 Sui 生态中。BitVM Bridge 是一个由 Bitlayer 提供支持并由先进的 BitVM 智能合约框架支持的信任最小化桥。
Ark 协议的正式规范
Ark 近日发布 Litepaper: Ark: A UTXO-based Transaction Batching Protocol,阐述其技术基础。作为一种新颖的比特币扩容协议,Ark 实现了链下交易执行,同时让用户能完全掌控自己的资金。这一点通过引入「虚拟UTXO」(VTXO)得以实现,用户在链下交易,同时保留单方面退出至比特币主链的能力。Ark 同一个 operator 协作,将用户操作打包成链上承诺,在保持极小链上负担的前提下实现高交易吞吐量。这为比特币提供了一种简单易用的扩容方案,也为那些在主链上执行效率低下或成本过高的二层方案提供了落地空间。
精彩无限,不止于链
已知真实发生过的比特币攻击事件列表
这里列出了历年来在真实世界中发生过的、针对比特币/加密资产拥有者的攻击事件。

互联网资本市场:是开发者的自由通道,还是另一波 FOMO?
帖子讨论了互联网资本市场( ICM, Internet Capital Markets ),即去中心化平台——资金直接流向应用程序构建者和创建者。ICM 集众筹、代币发行和股权投机于一体,无需VC、银行或应用商店。2025年,越来越多独立开发者通过 X 和 Believe、Launchcoin 等工具直接发行应用代币,吸引大众投资。ICM 的支持者认为,这种模式打破了传统融资壁垒,让创新更民主、门槛更低;但批评者警告,ICM 正沦为炒作和短期投机的温床,许多项目缺乏实际产品和长期价值。作者认为,ICM 模式能否成为 Web3 的下一个里程碑,关键在于其能否走出「投机成了产品增长动力」(speculation becomes product traction)的怪圈,实现真正的用户价值和持续创新。
-