-
 @ a296b972:e5a7a2e8
2025-05-24 09:35:09
@ a296b972:e5a7a2e8
2025-05-24 09:35:09„Aaaach, was für ein herrlicher Tag!“
In Berlin geht man hochmotiviert an die Arbeit, in der tiefen Überzeugung stets die richtigen Entscheidungen zu treffen, die Steuern der Einzahler ausschließlich für wohlüberlegte, notwendige Investitionen auszugeben und Entscheidungen zu treffen, die im dem Umfeld, in dem man sich bewegt, als höchst sinnvoll erachtet werden. Zustimmung von allen Seiten, dann muss es ja richtig sein.
Man fährt im Dienstwagen ins Regierungsviertel, sieht die vielen geschäftigen Menschen, wie sie ebenfalls zur Arbeit eilen. Man freut sich darüber, dass alles so gut läuft, dank der überragenden Kompetenz, die man einbringen darf und die das alles ermöglicht.
In Gedanken klopft man sich auf die Schulter und sagt sich im Stillen: „Bist schon ein geiler Typ, der richtig was bewegen kann, bewegen kann.“
Man hat auch schon erkannt, dass die zunehmende Kriminalität, vorzugsweise mit einem unsachgemäß gebrauchten Messer, durch den schlechten Einfluss der sozialen Medien entstanden ist und schon entsprechende Maßnahmen auf den Weg gebracht, um das durch geleitete Meinungsäußerungen, selbstverständlich zum Wohle aller, zu unterbinden. Man ist ja nicht umsonst in diese verantwortungsvolle Position gelangt. „Endlich am Ziel!“
„Messerattacken sind unschön, unschön, aber man muss auch berücksichtigen, dass viele der Attentäter und Attentäterinnen in ihren Herkunftsländern Schlimmes erlebt haben und dadurch traumatisiert wurden. Den betroffenen Traumaopfern kann ja nichts Besseres passieren, als in eine deutsche Psychiatrie zu kommen, wo sie die allerbeste Therapie erfahren, um wieder glückliche Menschen der Gesellschaft zu werden.
** **
Und jeder, der nicht die große soziale Aufgabe erkennt, die wir uns gestellt haben und auch effizient umsetzen, muss es eben noch besser erklärt bekommen, erklärt bekommen. Daran müssen wir noch arbeiten. (Muss ich mir notieren, damit ich meinem Sekretär die Anweisung erteile, das in die Wege zu leiten). Und jeder, der sich dagegen sträubt, zeigt damit eindeutig, dass er zum rechten Rand gehört. Was denen nur einfällt? Da müssen klare Zeichen gesetzt werden, und das muss unter allen Umständen unterbunden werden, unterbunden werden.
** **
Sowas schadet der Demokratie, es delegitimiert sie“.
Zum Schutz der braven Bürger arbeitet man auch fleißig daran, Deutschland, in neuem Selbstbewusstsein, zur stärksten Kraft in Europa zu machen. Mit der Stationierung von deutschen Soldaten an der Ostfront, pardon, an der Ostflanke, zeigt man dem bösen, aggressiven Russen schon mal, was eine Harke ist. „Und das ist ja erst der Anfang, der Anfang. Warte nur ab!“
„Was noch? Ach ja, die Wirtschaft. Solange die nicht auf die Barrikaden geht, das sehe ich derzeit nicht, scheint es ja noch keinen akuten Handlungsbedarf zu geben. Darum kümmern wir uns später. Immerhin halten sich die Wirtschaftsprognosen in einem akzeptablen Rahmen und die Priorität (die kann auch nicht jeder richtig setzen) der Investitionen muss derzeit auf dem wichtigsten Bereich, der Aufrüstung liegen, Aufrüstung liegen. Schließlich werden wir bald angegriffen.
** **
Ich darf nicht vergessen, meinen Sekretär zu beauftragen, meine Bestellung im Feinkostladen abholen zu lassen, sonst gibt’s Zuhause Ärger. Ach ja, und die Anzüge und die Wäsche muss auch noch aus der Reinigung abgeholt werden. Darf ich nicht vergessen, nicht vergessen.
** **
Wie viele Reinigungen gäbe es nicht, wenn wir Politiker nicht wären, nicht wären. Viele sichere Arbeitsplätze, gut so!
** **
Was, schon da? Das ging aber heute schnell. Kein Stau. Ja, der Chauffeur ist schon ein Guter, der weiß, wo man lang muss, um Baustellen zu umfahren. Allerdings muss ich ihm bei nächster Gelegenheit noch einmal deutlich sagen, dass er bitte die Sitzheizung früher anzuschalten hat, anzuschalten hat! Dass der sich das immer noch nicht gemerkt hat, unmöglich!“
Wen wundert es, wenn in dieser Wonnewelt der Selbstüberschätzung von Unsererdemokratie gesprochen wird, so entrückt vom Alltag, in einem Raumschiff, dass völlig losgelöst von der Realität über allem schwebt.
„Ich müsste ja verrückt sein, wenn ich an diesen Zuständen etwas ändern wollte. Warum auch, es läuft doch und mir geht es doch gut. Ich habe ein gutes Einkommen, kann mir allerhand leisten, Haus ist bezahlt, Frau ist gut untergebracht, Kinder sind versorgt, wie die Zeit vergeht. Und wenn ich mal ausscheide, erhalte ich weiter meine Bezüge und muss nicht an mein Vermögen ran, man will ja auch den Kindern was hinterlassen. Schadet ja nicht, wenn ich mich etwas einschränke, und der eine oder andere Job wird schon an mich herangetragen werden, schließlich habe ich ja erstklassige Kontakte, die dem einen oder anderen sicher etwas wert sein werden.
** **
Na, dann woll’n wir mal wieder, woll’n wir mal wieder!“
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 0e9491aa:ef2adadf
2025-05-24 09:01:14
@ 0e9491aa:ef2adadf
2025-05-24 09:01:14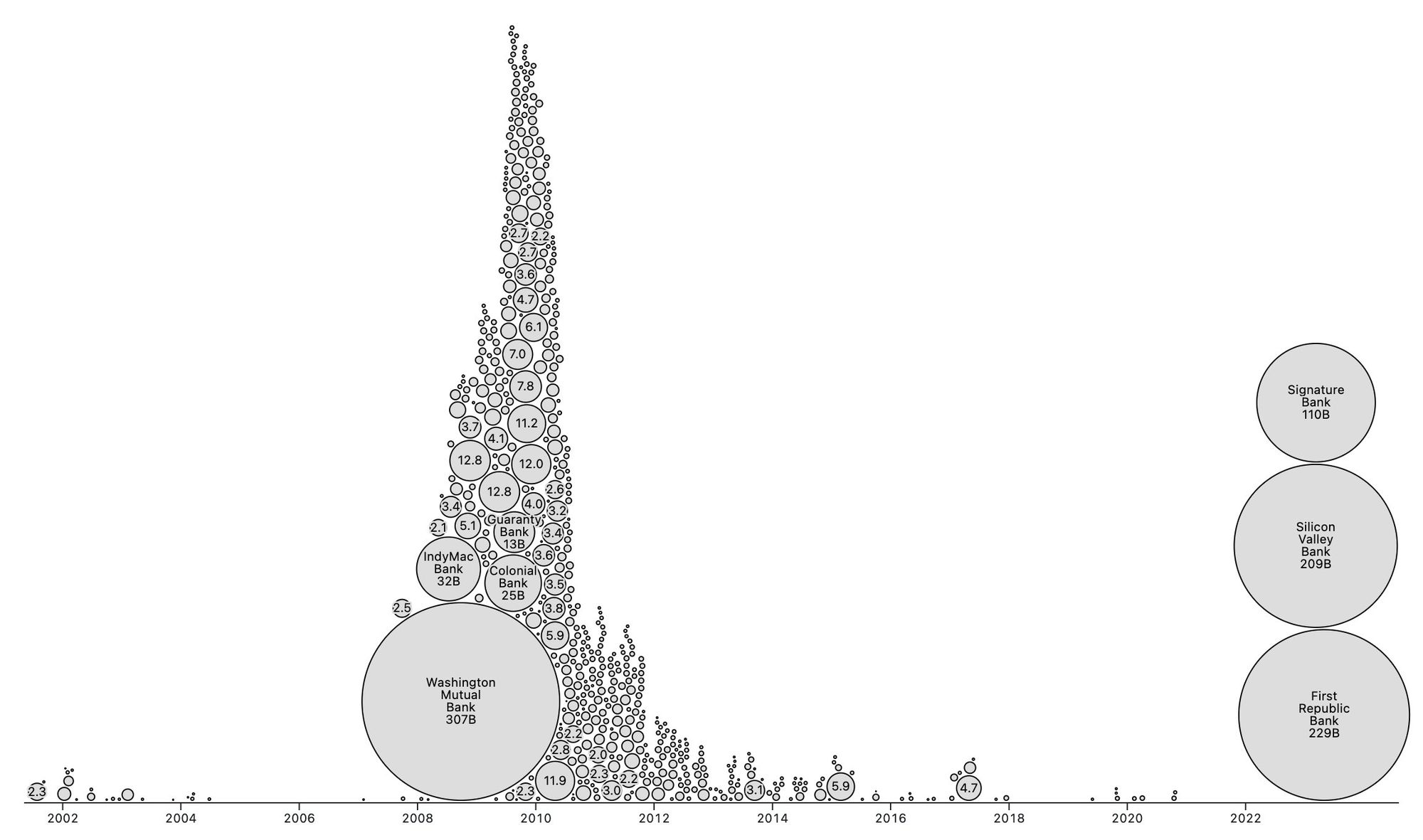
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ 6a6be47b:3e74e3e1
2025-05-24 08:21:35
@ 6a6be47b:3e74e3e1
2025-05-24 08:21:35Hi, frens!
🥳 This is my first post over here, yaaay! I’m very excited to start this journey. I have lots of posts on my website https://samhainsam.art/ , but I decided to give you a short introduction to me and my artwork. Shall we?
But first, how’s your weekend going? Already dreading Monday, or just enjoying the moment? I hope it’s the latter, but if not, that’s okay too. Everything passes, and while that might not be the most comforting thought, knowing that it will eventually pass—and, most importantly, that we get to decide how to respond—makes a big difference. Either way, we’re all going to die, so take it as you wish! 😅
Anyway, I wanted to share a little something. If you’ve visited my shop on Ko-fi https://ko-fi.com/samhainsam/shop , you might have wondered why it seems a bit all over the place. Or maybe you haven’t noticed or don’t care—but either way, I thought I’d clarify.
🖼️ I’m a self-taught artist who loves everything related to religion, occultism, paganism, animals, and esotericism—and how all these themes intertwine in our lives. I paint and illustrate inspired by these ideas.
Most of my recent paintings come with a blog post explaining their background. Even before, I always researched the subjects I painted, but lately, I’ve been diving much deeper.
🎨 My “Wheel of the Year” series has completely fascinated me. I’ve been learning so many nuggets of wisdom, and discovering how Christianity borrowed or even erased many symbols and traditions to create new narratives. For example, Imbolc was rebranded as Candlemas, and my blog post about the Spanish Inquisition touches on some of these symbols and their impact on both past and present society.
🐦 I also have some paintings just about birds—I'm a bit of a sucker for them! Shoebills and cassowaries are among my favorites, and I might end up painting them again soon. But you get the picture! If not, why not take a peek at my blog? https://samhainsam.art/blog/
🖋️ You can read something fun and interesting while enjoying my artwork.
Come on over, and let’s have some cool and healthy fun.
Enjoy your weekend, my friends!
Godspeed ⚡
https://stacker.news/items/988069
-
 @ 1b9fc4cd:1d6d4902
2025-05-24 08:19:41
@ 1b9fc4cd:1d6d4902
2025-05-24 08:19:41Music in media is like audio umami, the perfect seasoning in a recipe. It has the ability to enhance flavor and provide depth. Daniel Siegel Alonso examines how music is indispensable in enchanting consumers, from the memorable jingles of television commercials to the emotionally charged earworms in viral videos. Its influence is ubiquitous, transforming ordinary content into unforgettable experiences, evoking emotions, and molding cultural trends.
Television Commercials: The Jingle Jungle
Siegel Alonso begins by considering the television commercial. Music is the secret weapon in advertising and marketing, where attention spans can be shorter than the length of a cat video on TikTok. With its catchy melody and simple lyrics, the classic jingle is a masterclass in auditory branding. Do you remember 1971's "I'd Like to Buy the World a Coke"? That was more than just a tune; it was a cultural touchstone.
Today, in modern advertising, music's role transcends nostalgic jingles. Brands now curate full-fledged soundtracks to build an emotional narrative. Take Apple's commercials, for example. They often spotlight indie artists whose songs capture the essence of innovation and simplicity. These choices aren't random; they align with the brand's identity and leave a lasting impression.
Music Videos: The Visual Symphony
Music videos are the perfect union of audio and visual storytelling and have revolutionized how people consume music. These clips are not merely promotional tools but are art forms. At its peak, music videos were cultural events. Nobody took advantage of the medium better than Madonna. Think of her "Justify My Love" video—a short film that was so subversive that MTV banned it. (Ever the businesswoman, The Material Girl decided to make the controversial video available commercially as a video single, marking the first time a musician released a single in this format in the United States.)
Daniel Siegel Alonso fast forwards to the current age of social media, with channels like YouTube and TikTok breathing new life into the music video. Artists can now connect directly with their audience, bypassing cautious publicists and conservative record company executives. This democratization has led to a surge in creativity. Think about Childish Gambino's cinematic "This is America." The music video sparked widespread discussion and analysis with its in-your-face imagery and complex themes. It wasn't just a song but a statement.
Social Media: The Viral Soundtrack
Music is the magical ingredient in social media that can instantly catapult content into viral fame. Platforms like TikTok have turned short, catchy music clips into a global phenomenon. A 15-second snippet can lead to myriad dance challenges, lip-sync clips, and memes, propelling relatively obscure singers to stardom overnight.
Daniel Siegel Alonso uses Lil Nas X's "Old Town Road" as a key example. With its genre-blending sound, the song became a sensation largely thanks to TikTok. Users created countless videos featuring the song, and the track's infectious energy spread like wildfire. The result was a record-breaking run on the Billboard Hot 100—and a Grammy win!
Even Instagram's Stories and Reels leverage songs to enrich their user experience. Whether it's a tearjerker ballad emphasizing heartfelt memories or an aggressive track fueling a workout video, music layers in emotional content that words and images can't achieve.
The Emotional Manipulator
Music's influence in media lies in its power to manipulate emotions—the invisible puppeteer tugs at the heartstrings, stirring nostalgia, joy, sadness, or excitement. Filmmakers and content creators understand this well. Imagine watching a horror flick without a creepy soundtrack.
In television shows, music often acts as an additional character on screen. Netflix's "Stranger Things" and HBO's "Game of Thrones" have iconic soundtracks that are instantly recognizable and have even revitalized musicians' careers (think Kate Bush and her iconic song "Running Up That Hill"). These scores aren't just background fodder; they are crucial to storytelling by creating tension and enhancing dramatic moments.
Cultural Shaper
Beyond its emotional impact, music in media also serves as a cultural shaper. It impacts everything from fashion to language and even social movements. Consider MTV's influence and reach at its height in the 1980s and 1990s. The cable channel didn't just air music videos; it created superstars and defined an era, influencing everything from hairdos to political views.
While MTV may not be the behemoth it once was, social media platforms continue the tradition today. Viral music trends can spark global discussions. For instance, the Black Lives Matter movement saw numerous musicians penning powerful anthems that became rallying cries, shared widely on social media. In this context, music transcends entertainment; it's a vehicle for evolution.
Conclusion
In the grand tapestry of media, Daniel Siegel Alonso asserts that music is the thread that weaves everything together. It turns commercials into cultural icons, music videos into visual feasts, and social media content into viral sensations. Its power to elicit emotion, contribute to culture, and tell unique stories makes it an invaluable tool for creators.
If there are stories to tell and products to sell, music will remain at the heart of media, striking the right chords and leaving an unforgettable mark on our collective psyche. Ultimately, it's not just about the notes and melodies; it's about the feelings and memories they arouse, making music the unsung hero in the ever-changing media landscape.
-
 @ 0e9491aa:ef2adadf
2025-05-24 07:01:14
@ 0e9491aa:ef2adadf
2025-05-24 07:01:14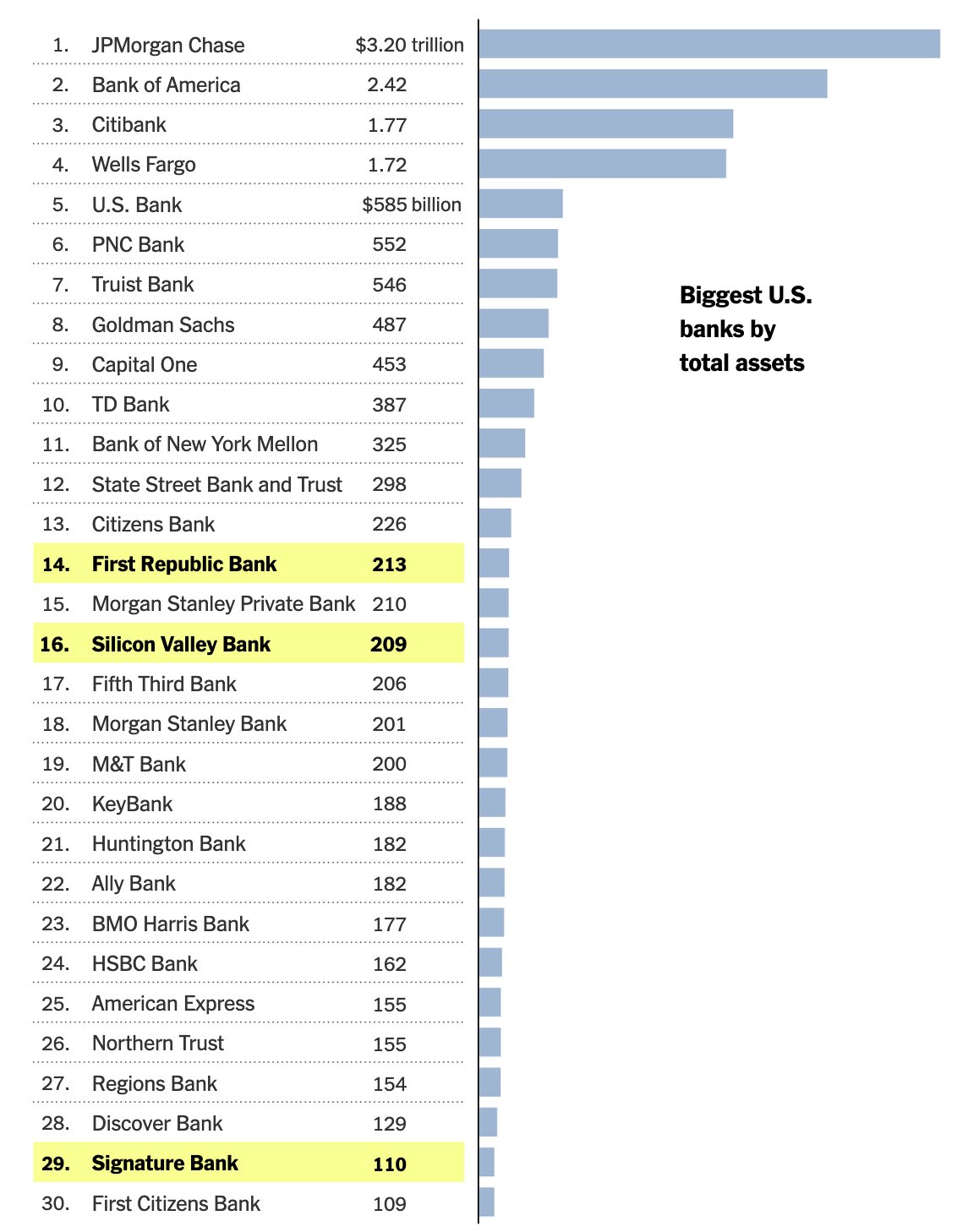
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ 57d1a264:69f1fee1
2025-05-24 06:07:19
@ 57d1a264:69f1fee1
2025-05-24 06:07:19Definition: when every single person in the chain responsible for shipping a product looks at objectively horrendous design decisions and goes: yup, this looks good to me, release this. Designers, developers, product managers, testers, quality assurance... everyone.
I nominate Peugeot as the first example in this category.
Continue reading at https://grumpy.website/1665
https://stacker.news/items/988044
-
 @ 0e9491aa:ef2adadf
2025-05-24 06:01:20
@ 0e9491aa:ef2adadf
2025-05-24 06:01:20
The newly proposed RESTRICT ACT - is being advertised as a TikTok Ban, but is much broader than that, carries a $1M Fine and up to 20 years in prison️! It is unconstitutional and would create massive legal restrictions on the open source movement and free speech throughout the internet.
The Bill was proposed by: Senator Warner, Senator Thune, Senator Baldwin, Senator Fischer, Senator Manchin, Senator Moran, Senator Bennet, Senator Sullivan, Senator Gillibrand, Senator Collins, Senator Heinrich, and Senator Romney. It has broad support across Senators of both parties.
Corrupt politicians will not protect us. They are part of the problem. We must build, support, and learn how to use censorship resistant tools in order to defend our natural rights.
The RESTRICT Act, introduced by Senators Warner and Thune, aims to block or disrupt transactions and financial holdings involving foreign adversaries that pose risks to national security. Although the primary targets of this legislation are companies like Tik-Tok, the language of the bill could potentially be used to block or disrupt cryptocurrency transactions and, in extreme cases, block Americans’ access to open source tools or protocols like Bitcoin.
The Act creates a redundant regime paralleling OFAC without clear justification, it significantly limits the ability for injured parties to challenge actions raising due process concerns, and unlike OFAC it lacks any carve-out for protected speech. COINCENTER ON THE RESTRICT ACT
If you found this post helpful support my work with bitcoin.

-
 @ 57d1a264:69f1fee1
2025-05-24 05:53:43
@ 57d1a264:69f1fee1
2025-05-24 05:53:43This talks highlights tools for product management, UX design, web development, and content creation to embed accessibility.
Organizations need scalability and consistency in their accessibility work, aligning people, policies, and processes to integrate it across roles. This session highlights tools for product management, UX design, web development, and content creation to embed accessibility. We will explore inclusive personas, design artifacts, design systems, and content strategies to support developers and creators, with real-world examples.
https://www.youtube.com/watch?v=-M2cMLDU4u4
https://stacker.news/items/988041
-
 @ b1ddb4d7:471244e7
2025-05-24 10:00:42
@ b1ddb4d7:471244e7
2025-05-24 10:00:42Asia has emerged as a powerhouse for bitcoin adoption, with diverse countries across the region embracing the world’s leading digital currency in unique ways.
From institutional investors in Singapore to grassroots movements in Indonesia, the Asian bitcoin ecosystem presents a fascinating tapestry of innovation, regulation, and community-driven initiatives.
We dive deep into the current state of bitcoin adoption across key Asian markets, providing investors with actionable insights into this dynamic region.
The Numbers: Asia’s Bitcoin Dominance
As of early 2025, over 500 million people worldwide hold some form of digital currency, with bitcoin remaining the most widely adopted digital asset. Asia stands at the forefront of this adoption wave, with the Central & Southern Asia and Oceania (CSAO) region leading the world in digital currency adoption according to Chainalysis’s 2024 Global Crypto Adoption Index.
The statistics paint a compelling picture:
- Seven of the top 20 countries in global crypto adoption are located in the CSAO region.
- India and China together comprise almost half of the world’s digital currency user base.
- Japan’s digital currency market is expected to reach 19.43 million users by the end of 2025, with a penetration rate of 15.93%.
Behind these impressive numbers lies a complex ecosystem shaped by diverse factors including regulatory environments, technological infrastructure, economic necessities, and vibrant community initiatives.
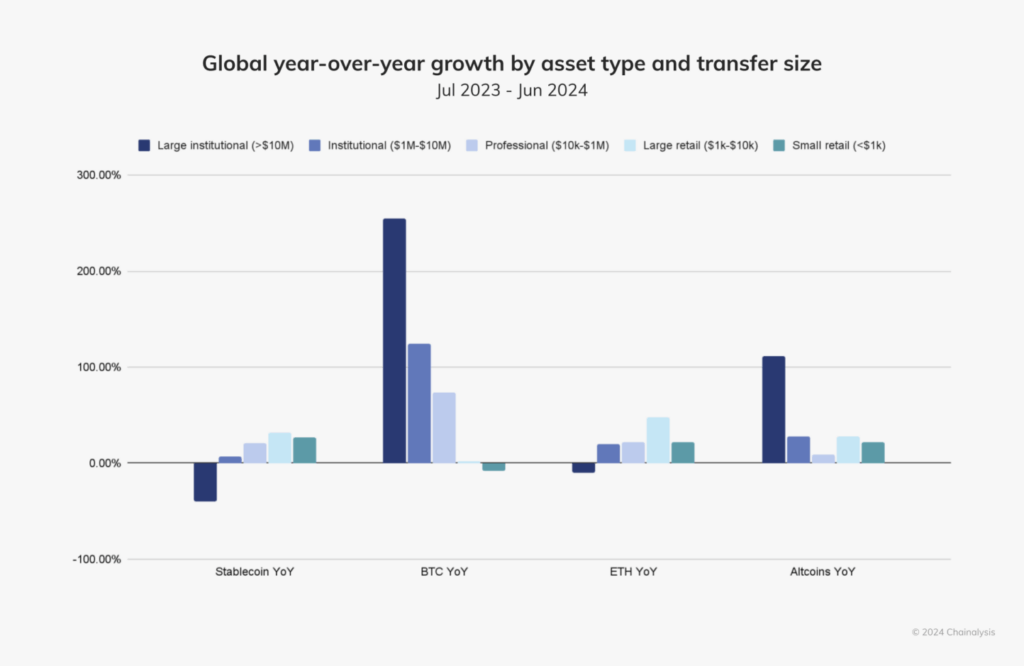
Photo Source: Chainalysis
Country-by-Country Analysis
India: The Grassroots Powerhouse
India ranks first in Chainalysis’s Global Crypto Adoption Index, with bitcoin adoption thriving particularly in tier-2 and tier-3 cities. This grassroots movement is driven primarily by:
- Financial inclusion: Bitcoin offers banking-like services to India’s large unbanked population.
- Remittance solutions: Lower fees for the significant Indian diaspora sending money home.
- Mobile wallet proliferation: India’s high smartphone penetration enables easy access to bitcoin services.
Japan: The Regulatory Pioneer
Japan has long played a significant role in bitcoin’s evolution, from hosting some of the earliest exchanges to pioneering regulatory clarity. In 2025, Japan finds itself at a fascinating crossroads:
- The Japan Financial Services Agency is considering reclassifying digital currency assets as financial products akin to stocks, potentially enhancing user protection.
- Major corporations like Metaplanet Inc. are expanding their bitcoin holdings, with plans to increase holdings by 470% to reach 10,000 BTC in 2025.
- The country boasts a thriving grassroots bitcoin community and a strong developer ecosystem.
Bitcoin adoption in Japan is uniquely balanced between institutional involvement and community enthusiasm, with initiatives like Blockstream’s Tokyo office working to promote layer-2 solutions, self-custody, and developer education.
Vietnam: The P2P Leader
Vietnam consistently ranks among the top countries for bitcoin adoption per capita. The country’s relationship with bitcoin is characterized by:
- Strong peer-to-peer (P2P) platform usage for daily transactions and remittances.
- High mobile wallet adoption driving grassroots usage.
- Bitcoin serving as a hedge against local currency fluctuations.
- Relatively favorable regulatory attitude compared to some neighboring countries.
Singapore: The Institutional Hub
Singapore has established itself as Asia’s premier institutional bitcoin destination through:
- Clear and forward-thinking regulatory frameworks, particularly the Payment Services Act.
- Growing presence of global digital currency firms including Gemini, OKX, and HashKey, which have received regulatory approvals.
- A robust financial infrastructure catering to high-net-worth individuals and institutional investors.
While Singapore’s consumer protection-focused framework restricts promotional activities and public advertising by digital currency service providers, the city-state remains a beacon for institutional bitcoin adoption in Asia.
South Korea: Retail Dominance Transitioning to Institutional
South Korea presents a fascinating case study of a market in transition:
- Retail investors currently dominate digital currency trading volume, while institutional participation significantly lags behind.
- Experts expect institutional involvement to increase, though a significant shift may not occur until around 2027.
- The local finance watchdog recently launched a crypto committee to assess permissions for corporate digital currency investors and ETFs.
- Users must access fiat-to-digital currency services through local exchanges with official banking partnerships, linking digital currency activities to legal identities.
Bitcoin Communities: The Grassroots Movements
What truly sets Asia apart in the global bitcoin landscape is the vibrant tapestry of community-driven initiatives across the region. These grassroots movements are instrumental in driving adoption from the ground up.
Bitcoin House Bali: A Community Hub
In Indonesia, the Bitcoin House Bali project exemplifies grassroots innovation. This initiative has transformed an old mining container into a vibrant hub for bitcoin education and community engagement.
Key features include:
- Free workshops (including “Bitcoin for Beginners” and “Bitcoin for Kids”).
- Developer programs including online classes, BitDevs Workshops, and Hackathons.
- A closed-loop economic system that turns bitcoin into community points.
- Merchant onboarding—from restaurants and drivers to scooter rentals and street vendors.
Bitcoin Seoul 2025: Bringing the Community Together
The upcoming Bitcoin Seoul 2025 conference (June 4-6, 2025) represents Asia’s largest bitcoin-focused gathering, bringing together global leaders, executives, and community members.
The event will feature:
- The Bitcoin Policy Summit: Seoul Edition, providing insights into regulatory trends.
- The Bitcoin Finance Forum, addressing institutional investment and treasury management.
- A Global Bitcoin Community Assembly for bitcoin grassroots and community leaders.
- Live Lightning Network payments demonstrations at the on-site Lightning Market.
This event underscores South Korea’s emerging role in the global Bitcoin ecosystem and highlights the growing institutional interest in the region.
Regulatory Landscapes: A Mixed Picture
The regulatory environment for bitcoin across Asia presents a complex and evolving picture that significantly impacts adoption patterns.
Japan’s Regulatory Evolution
Japan is considering tightening regulations on digital asset transactions by reclassifying them as financial products similar to stocks. If implemented, these changes would:
- Require issuers to disclose more detailed information on their corporate status.
- Potentially enhance user protection.
- Come into effect after June 2025, following policy direction outlines by the administration.
Current regulations in Japan are relatively digital currency-friendly, with bitcoin recognized as a legal form of payment under the Payment Services Act since 2016.
Singapore’s Balanced Approach
Singapore maintains a regulatory framework that emphasizes market stability and consumer protection, including:
- Restrictions on promoting digital services in public areas.
- The Payment Services Act that regulates digital currency exchanges.
- A general approach that supports institutional adoption while carefully managing retail exposure.
This balanced approach has helped establish Singapore as a trusted hub for bitcoin businesses and institutional investors.
South Korea’s Transitional Framework
South Korea’s regulatory landscape is in flux, with several developments impacting the bitcoin ecosystem:
- Corporate access to digital currenc
-
 @ f6488c62:c929299d
2025-05-24 05:10:20
@ f6488c62:c929299d
2025-05-24 05:10:20คุณเคยจินตนาการถึงอนาคตที่ AI มีความฉลาดเทียบเท่ามนุษย์หรือไม่? นี่คือสิ่งที่ Sam Altman ซีอีโอของ OpenAI และทีมพันธมิตรอย่าง SoftBank, Oracle และ MGX กำลังผลักดันผ่าน โครงการ Stargate! โครงการนี้ไม่ใช่แค่เรื่องเทคโนโลยี แต่เป็นก้าวกระโดดครั้งใหญ่ของมนุษยชาติ! Stargate คืออะไร? Stargate เป็นโปรเจกต์สร้าง ศูนย์ข้อมูล AI ขนาดยักษ์ที่ใหญ่ที่สุดในประวัติศาสตร์ ด้วยเงินลงทุนเริ่มต้น 100,000 ล้านดอลลาร์ และอาจสูงถึง 500,000 ล้านดอลลาร์ ภายในปี 2029! เป้าหมายคือการพัฒนา Artificial General Intelligence (AGI) หรือ AI ที่ฉลาดเทียบเท่ามนุษย์ เพื่อให้สหรัฐฯ ครองความเป็นผู้นำด้าน AI และแข่งขันกับคู่แข่งอย่างจีน โครงการนี้เริ่มต้นที่เมือง Abilene รัฐเท็กซัส โดยจะสร้างศูนย์ข้อมูล 10 แห่ง และขยายไปยังญี่ปุ่น สหราชอาณาจักร และสหรัฐอาหรับเอมิเรตส์ ทำไม Stargate ถึงสำคัญ?
นวัตกรรมเปลี่ยนโลก: AI จาก Stargate จะช่วยพัฒนาวัคซีน mRNA รักษามะเร็งได้ใน 48 ชั่วโมง และยกระดับอุตสาหกรรมต่าง ๆ เช่น การแพทย์และความมั่นคงแห่งชาติสร้างงาน: คาดว่าจะสร้างงานกว่า 100,000 ตำแหน่ง ในสหรัฐฯ
พลังงานมหาศาล: ศูนย์ข้อมูลอาจใช้พลังงานถึง 1.2 กิกะวัตต์ เทียบเท่ากับเมืองขนาดใหญ่!
ใครอยู่เบื้องหลัง? Sam Altman ร่วมมือกับ Masayoshi Son จาก SoftBank และได้รับการสนับสนุนจาก Donald Trump ซึ่งผลักดันนโยบายให้ Stargate เป็นจริง การก่อสร้างดำเนินการโดย Oracle และพันธมิตรด้านพลังงานอย่าง Crusoe Energy Systems ความท้าทาย? ถึงจะยิ่งใหญ่ แต่ Stargate ก็เจออุปสรรค ทั้งปัญหาการระดมทุน ความกังวลเรื่องภาษีนำเข้าชิป และการแข่งขันจากคู่แข่งอย่าง DeepSeek ที่ใช้โครงสร้างพื้นฐานน้อยกว่า แถม Elon Musk ยังออกมาวิจารณ์ว่าโครงการนี้อาจ “ไม่สมจริง” แต่ Altman มั่นใจและเชิญ Musk ไปดูไซต์งานที่เท็กซัสเลยทีเดียว! อนาคตของ Stargate ศูนย์ข้อมูลแห่งแรกจะเริ่มใช้งานในปี 2026 และอาจเปลี่ยนโฉมวงการ AI ไปตลอดกาล นี่คือก้าวสำคัญสู่ยุคใหม่ของเทคโนโลยีที่อาจเปลี่ยนวิถีชีวิตของเรา! และไม่ใช่ประตูดวงดาวแบบในหนังนะ! ถึงชื่อ Stargate จะได้แรงบันดาลใจจากภาพยนตร์ sci-fi อันโด่งดัง แต่โครงการนี้ไม่ได้พาเราไปยังดวงดาวอื่น มันคือการเปิดประตูสู่โลกแห่ง AI ที่ทรงพลัง และอาจเปลี่ยนอนาคตของมนุษยชาติไปเลย! และไม่เหมือน universechain ของ star ของผมนะครับ
Stargate #AI #SamAltman #OpenAI #อนาคตของเทคโนโลยี
-
 @ c1d77557:bf04ec8b
2025-05-24 05:02:26
@ c1d77557:bf04ec8b
2025-05-24 05:02:26O 567br é uma plataforma de entretenimento online que tem se destacado pela sua inovação, variedade de jogos e foco na experiência do jogador. Com uma interface amigável e recursos de alta qualidade, a plataforma oferece uma jornada divertida e segura para os seus usuários. Neste artigo, vamos explorar os principais aspectos do 567br, incluindo a introdução da plataforma, os jogos que ela oferece e como a experiência do jogador é aprimorada em cada detalhe.
O 567br foi desenvolvido com o objetivo de proporcionar aos jogadores uma experiência imersiva e prazerosa. Sua interface é simples, intuitiva e de fácil navegação, permitindo que os usuários encontrem rapidamente seus jogos favoritos. A plataforma também é otimizada para dispositivos móveis, o que significa que os jogadores podem acessar seus jogos em qualquer lugar e a qualquer momento, seja no computador ou no smartphone.
Além disso, o 567brse preocupa com a segurança de seus usuários, implementando tecnologias de criptografia de ponta para garantir que todos os dados pessoais e financeiros estejam protegidos. A plataforma também oferece suporte ao cliente de alta qualidade, disponível 24/7, para resolver quaisquer dúvidas ou problemas que possam surgir durante a experiência de jogo.
Jogos Empolgantes e Variedade para Todos os Gostos No 567br, a diversidade de jogos é um dos pontos fortes da plataforma. Desde jogos de mesa e cartas até opções de entretenimento mais dinâmicas e inovadoras, há algo para todos os gostos e preferências. Os jogos disponíveis são desenvolvidos por alguns dos melhores fornecedores de conteúdo da indústria, garantindo gráficos de alta qualidade, jogabilidade fluida e mecânicas envolventes.
Os jogadores podem escolher entre diferentes categorias, como:
Jogos de Mesa: Para quem gosta de uma experiência mais estratégica e de tomada de decisões, os jogos de mesa são uma excelente opção. São oferecidas diversas variantes de jogos populares, como pôquer, blackjack, roleta, entre outros.
Jogos de Ação e Aventura: Para os que buscam adrenalina e emoção, a plataforma oferece uma seleção de jogos de ação e aventura com temas envolventes e gráficos impressionantes. Esses jogos garantem uma experiência de jogo emocionante e desafiadora.
Jogos de Arcade: Se você está em busca de algo mais descontraído e divertido, os jogos de arcade são uma excelente escolha. Eles são rápidos, fáceis de entender e proporcionam diversão instantânea.
A plataforma está sempre atualizando seu portfólio de jogos para garantir que os jogadores tenham acesso às últimas novidades e inovações do mundo do entretenimento online.
A Experiência do Jogador: Personalização e Interatividade O 567br não se limita a oferecer apenas uma plataforma de jogos, mas também busca criar uma experiência personalizada e interativa para cada jogador. A plataforma possui funcionalidades que permitem que os usuários ajustem sua experiência de jogo de acordo com suas preferências individuais.
A personalização da interface é um exemplo claro disso. O jogador pode escolher o tema e a disposição dos elementos na tela, criando um ambiente que seja confortável e agradável de usar. Além disso, o 567br oferece recursos interativos, como chats ao vivo, onde os jogadores podem interagir com outros usuários e até mesmo com os dealers, proporcionando uma sensação de comunidade.
Outro aspecto importante é a possibilidade de acompanhar o desempenho e os resultados de jogo. A plataforma oferece relatórios detalhados, permitindo que os jogadores monitorem seu progresso, analisem suas vitórias e perdas, e façam ajustes em sua estratégia de jogo.
Promoções e Benefícios para os Jogadores O 567br também oferece uma série de promoções e benefícios que tornam a experiência de jogo ainda mais atrativa. Novos jogadores podem aproveitar bônus de boas-vindas e outras ofertas especiais, enquanto jogadores regulares podem se beneficiar de programas de fidelidade e promoções exclusivas.
Essas ofertas ajudam a aumentar a diversão e proporcionam mais oportunidades para que os jogadores explorem novos jogos e tenham uma experiência ainda mais rica. Além disso, o sistema de recompensas é transparente e justo, garantindo que todos os jogadores tenham as mesmas oportunidades de aproveitar os benefícios.
Conclusão: Uma Plataforma Completa para Todos os Gostos Com sua interface intuitiva, variedade de jogos e foco na experiência do jogador, o 567br se consolida como uma plataforma de entretenimento online de alta qualidade. Seja para quem busca jogos estratégicos, ação intensa ou diversão casual, o 567br tem algo para todos.
A segurança, o suporte ao cliente e a personalização da experiência de jogo tornam o 567br uma opção atraente para jogadores que buscam mais do que apenas uma plataforma de jogos – buscam uma jornada de entretenimento envolvente e segura. Se você está procurando por uma experiência completa e agradável, o 567br é, sem dúvida, uma excelente escolha.
-
 @ c1d77557:bf04ec8b
2025-05-24 05:01:44
@ c1d77557:bf04ec8b
2025-05-24 05:01:44O P11Bet é uma plataforma inovadora que chega para oferecer uma experiência de jogo única, reunindo uma variedade de opções para os entusiastas de diferentes tipos de entretenimento online. Com uma interface moderna e fácil de usar, ela se destaca por proporcionar uma jornada divertida e segura para os jogadores, com um foco especial na qualidade da experiência e no atendimento às necessidades do público.
Uma Plataforma Completa e Acessível Ao acessar o P11Bet, os usuários encontram uma plataforma intuitiva, que facilita a navegação e oferece uma variedade de recursos para tornar o jogo mais agradável. A estrutura do site é otimizada para fornecer uma experiência fluida, seja no desktop ou em dispositivos móveis. Além disso, a plataforma se preocupa em manter um ambiente seguro, garantindo a proteção dos dados dos jogadores e permitindo que se concentrem na diversão.
A plataforma é projetada para todos os tipos de jogadores, desde os iniciantes até os mais experientes. A simplicidade de uso é uma das grandes vantagens, permitindo que qualquer pessoa possa se registrar e começar a jogar sem dificuldades. Além disso, a p11betoferece suporte ao cliente em português, o que facilita a comunicação e garante um atendimento de alta qualidade para os usuários brasileiros.
Diversidade de Jogos para Todos os Gostos O P11Bet se destaca pela vasta gama de opções de jogos que oferece aos seus usuários. A plataforma abriga uma seleção diversificada que vai desde jogos clássicos até as opções mais modernas, atendendo a todos os estilos e preferências. Entre as opções mais procuradas estão jogos de mesa, apostas esportivas, slots, e outras modalidades que garantem horas de entretenimento.
Um dos principais atrativos do P11Bet são os jogos de habilidade e de sorte, que exigem tanto estratégia quanto um pouco de sorte. As opções variam desde os mais simples aos mais complexos, oferecendo algo para todos os gostos. Os jogadores podem se aventurar em diversas modalidades, testando suas habilidades em jogos que vão de roletas e blackjack a versões mais inovadoras e dinâmicas.
Para aqueles que preferem algo mais emocionante e competitivo, as apostas esportivas são uma das maiores atrações. O P11Bet oferece uma ampla variedade de eventos esportivos ao vivo para apostar, com odds atrativas e uma plataforma que permite realizar apostas de forma rápida e eficiente. Seja em esportes populares como futebol, basquete ou até mesmo esportes menos tradicionais, há sempre algo para os apostadores mais exigentes.
A Experiência do Jogador: Diversão e Segurança O P11Bet não apenas se preocupa com a diversidade de jogos, mas também com a experiência do jogador. A plataforma foi desenvolvida para garantir que os jogadores possam desfrutar de seus jogos favoritos com a maior segurança e conforto possível. Além de um design intuitivo, a plataforma oferece diversas opções de pagamento, incluindo métodos populares no Brasil, para facilitar depósitos e retiradas. Isso garante que o processo de transações seja simples, rápido e seguro.
Outro ponto positivo do P11Bet é a experiência imersiva que ele oferece aos jogadores. A plataforma está sempre atualizada com novas funcionalidades, com promoções atraentes e bônus especiais que aumentam ainda mais a diversão. A interação com outros jogadores também é um diferencial, com espaços que permitem competir, conversar e trocar experiências com pessoas de todo o mundo.
Além disso, o suporte ao cliente da P11Bet é um dos mais elogiados pelos usuários. A equipe está sempre disponível para resolver dúvidas e fornecer assistência de maneira eficaz e amigável. Isso garante que os jogadores tenham sempre uma experiência tranquila, sem se preocupar com questões técnicas ou problemas relacionados à plataforma.
Conclusão Em resumo, o P11Bet é uma excelente escolha para quem busca uma plataforma completa e de qualidade para se divertir e desafiar suas habilidades. Com uma grande variedade de jogos, uma interface de fácil navegação e um suporte excepcional, ele garante que cada momento na plataforma seja único e prazeroso. Para quem deseja se aventurar no mundo dos jogos online, o P11Bet é uma opção que combina segurança, inovação e diversão.
-
 @ c1d77557:bf04ec8b
2025-05-24 05:01:11
@ c1d77557:bf04ec8b
2025-05-24 05:01:11Se você está em busca de uma experiência de jogo dinâmica e diversificada, o 59h é a plataforma que você precisa conhecer. Com um foco claro na satisfação dos jogadores, ela oferece uma ampla variedade de opções de entretenimento, além de uma interface amigável e segura. Neste artigo, vamos explorar a plataforma 59h, destacando suas principais funcionalidades, jogos emocionantes e a experiência do usuário.
O Que é a Plataforma 59h? O 59h é uma plataforma inovadora que oferece uma vasta gama de jogos e experiências digitais para os entusiastas do entretenimento online. A plataforma se destaca pela sua interface intuitiva, que permite aos jogadores navegar com facilidade entre as diferentes categorias de jogos. Ela é ideal para quem busca uma experiência divertida e acessível, sem complicações.
Desde o momento em que você acessa o 59h, fica evidente o compromisso com a qualidade. A plataforma é projetada para ser acessível em diversos dispositivos, seja no seu computador, tablet ou smartphone. Isso garante que os jogadores possam aproveitar seus jogos favoritos a qualquer momento e em qualquer lugar, com a mesma qualidade e desempenho.
Uma Grande Variedade de Jogos para Todos os Gostos O 59h se destaca por sua impressionante variedade de jogos. Independentemente do tipo de jogo que você prefere, certamente encontrará algo que se adapte ao seu estilo. A plataforma oferece desde jogos de habilidade, até opções mais relaxantes e divertidas para aqueles que buscam algo mais descontraído.
Entre as opções mais populares, destacam-se os jogos de mesa, onde os jogadores podem testar suas habilidades em jogos como pôquer, blackjack e outros. Para quem prefere algo mais voltado para a sorte, o 59h também oferece jogos com elementos de sorte que podem garantir grandes recompensas.
Além disso, a plataforma está sempre atualizando seu portfólio de jogos, trazendo novidades para os jogadores. Isso significa que você nunca ficará entediado, já que sempre haverá algo novo e emocionante para experimentar.
A Experiência do Jogador no 59h Uma das maiores qualidades da plataforma 59h é sua atenção à experiência do usuário. Desde o processo de registro até a escolha de um jogo, tudo foi pensado para garantir uma navegação tranquila e sem estresse.
A plataforma é completamente segura, oferecendo métodos de pagamento rápidos e confiáveis. Isso significa que os jogadores podem depositar e retirar seus fundos com confiança, sem se preocupar com a segurança de suas informações pessoais. Além disso, o suporte ao cliente está sempre disponível para ajudar em caso de dúvidas ou problemas, garantindo que sua experiência seja o mais fluida possível.
Outro ponto que merece destaque é a comunidade de jogadores. A interação com outros jogadores é uma parte importante da plataforma, permitindo que você compartilhe dicas, participe de torneios e crie amizades. A plataforma 59h se esforça para criar um ambiente amigável e inclusivo, onde todos podem se divertir e aprender uns com os outros.
Acessibilidade e Facilidade de Uso O 59h não é apenas sobre a diversidade de jogos; também se trata de tornar o acesso o mais simples possível. A plataforma oferece um design responsivo, que se adapta perfeitamente a qualquer tipo de dispositivo. Isso significa que você pode jogar no computador, smartphone ou tablet com a mesma facilidade.
O processo de cadastro é simples e rápido, permitindo que você comece a jogar em questão de minutos. Além disso, a plataforma oferece uma série de recursos adicionais, como promoções e bônus exclusivos, que tornam a experiência ainda mais empolgante.
Conclusão O 59h se posiciona como uma plataforma de entretenimento online completa, oferecendo uma vasta gama de jogos, uma experiência de usuário de alta qualidade e um ambiente seguro e amigável para jogadores de todos os níveis. Se você procura uma plataforma confiável, diversificada e divertida, o 59h é a escolha ideal. Não importa se você é um iniciante ou um jogador experiente, há sempre algo novo para descobrir e aproveitar no 59h.
-
 @ 348e7eb2:3b0b9790
2025-05-24 05:00:33
@ 348e7eb2:3b0b9790
2025-05-24 05:00:33Nostr-Konto erstellen - funktioniert mit Hex
Was der Button macht
Der folgende Code fügt einen Button hinzu, der per Klick einen Nostr-Anmeldedialog öffnet. Alle Schritte sind im Code selbst ausführlich kommentiert.
```html
```
Erläuterungen:
- Dynamisches Nachladen: Das Script
modal.jswird nur bei Klick nachgeladen, um Fehlermeldungen beim Initial-Load zu vermeiden. -
Parameter im Überblick:
-
baseUrl: Quelle für API und Assets. an: App-Name für den Modal-Header.aa: Farbakzent (Foerbico-Farbe als Hex).al: Sprache des Interfaces.am: Licht- oder Dunkelmodus.afb/asb: Bunker-Modi für erhöhten Datenschutz.aan/aac: Steuerung der Rückgabe privater Schlüssel.arr/awr: Primal Relay als Lese- und Schreib-Relay.-
Callbacks:
-
onComplete: Schließt das Modal, zeigt eine Bestätigung und bietet die Weiterleitung zu Primal an. onCancel: Schließt das Modal und protokolliert den Abbruch.
Damit ist der gesamte Code sichtbar, kommentiert und erklärt.
- Dynamisches Nachladen: Das Script
-
 @ 06830f6c:34da40c5
2025-05-24 04:21:03
@ 06830f6c:34da40c5
2025-05-24 04:21:03The evolution of development environments is incredibly rich and complex and reflects a continuous drive towards greater efficiency, consistency, isolation, and collaboration. It's a story of abstracting away complexity and standardizing workflows.
Phase 1: The Bare Metal & Manual Era (Early 1970s - Late 1990s)
-
Direct OS Interaction / Bare Metal Development:
- Description: Developers worked directly on the operating system's command line or a basic text editor. Installation of compilers, interpreters, and libraries was a manual, often arcane process involving downloading archives, compiling from source, and setting environment variables. "Configuration drift" (differences between developer machines) was the norm.
- Tools: Text editors (Vi, Emacs), command-line compilers (GCC), Makefiles.
- Challenges: Extremely high setup time, dependency hell, "works on my machine" syndrome, difficult onboarding for new developers, lack of reproducibility. Version control was primitive (e.g., RCS, SCCS).
-
Integrated Development Environments (IDEs) - Initial Emergence:
- Description: Early IDEs (like Turbo Pascal, Microsoft Visual Basic) began to integrate editors, compilers, debuggers, and sometimes GUI builders into a single application. This was a massive leap in developer convenience.
- Tools: Turbo Pascal, Visual Basic, early Visual Studio versions.
- Advancement: Improved developer productivity, streamlined common tasks. Still relied on local system dependencies.
Phase 2: Towards Dependency Management & Local Reproducibility (Late 1990s - Mid-2000s)
-
Basic Build Tools & Dependency Resolvers (Pre-Package Managers):
- Description: As projects grew, manual dependency tracking became impossible. Tools like Ant (Java) and early versions of
autoconf/makefor C/C++ helped automate the compilation and linking process, managing some dependencies. - Tools: Apache Ant, GNU Autotools.
- Advancement: Automated build processes, rudimentary dependency linking. Still not comprehensive environment management.
- Description: As projects grew, manual dependency tracking became impossible. Tools like Ant (Java) and early versions of
-
Language-Specific Package Managers:
- Description: A significant leap was the emergence of language-specific package managers that could fetch, install, and manage libraries and frameworks declared in a project's manifest file. Examples include Maven (Java), npm (Node.js), pip (Python), RubyGems (Ruby), Composer (PHP).
- Tools: Maven, npm, pip, RubyGems, Composer.
- Advancement: Dramatically simplified dependency resolution, improved intra-project reproducibility.
- Limitation: Managed language-level dependencies, but not system-level dependencies or the underlying OS environment. Conflicts between projects on the same machine (e.g., Project A needs Python 2.7, Project B needs Python 3.9) were common.
Phase 3: Environment Isolation & Portability (Mid-2000s - Early 2010s)
-
Virtual Machines (VMs) for Development:
- Description: To address the "it works on my machine" problem stemming from OS-level and system-level differences, developers started using VMs. Tools like VMware Workstation, VirtualBox, and later Vagrant (which automated VM provisioning) allowed developers to encapsulate an entire OS and its dependencies for a project.
- Tools: VMware, VirtualBox, Vagrant.
- Advancement: Achieved strong isolation and environment reproducibility (a true "single environment" for a project).
- Limitations: Resource-heavy (each VM consumed significant CPU, RAM, disk space), slow to provision and boot, difficult to share large VM images.
-
Early Automation & Provisioning Tools:
- Description: Alongside VMs, configuration management tools started being used to automate environment setup within VMs or on servers. This helped define environments as code, making them more consistent.
- Tools: Chef, Puppet, Ansible.
- Advancement: Automated provisioning, leading to more consistent environments, often used in conjunction with VMs.
Phase 4: The Container Revolution & Orchestration (Early 2010s - Present)
-
Containerization (Docker):
- Description: Docker popularized Linux Containers (LXC), offering a lightweight, portable, and efficient alternative to VMs. Containers package an application and all its dependencies into a self-contained unit that shares the host OS kernel. This drastically reduced resource overhead and startup times compared to VMs.
- Tools: Docker.
- Advancement: Unprecedented consistency from development to production (Dev/Prod Parity), rapid provisioning, highly efficient resource use. Became the de-facto standard for packaging applications.
-
Container Orchestration:
- Description: As microservices and container adoption grew, managing hundreds or thousands of containers became a new challenge. Orchestration platforms automated the deployment, scaling, healing, and networking of containers across clusters of machines.
- Tools: Kubernetes, Docker Swarm, Apache Mesos.
- Advancement: Enabled scalable, resilient, and complex distributed systems development and deployment. The "environment" started encompassing the entire cluster.
Phase 5: Cloud-Native, Serverless & Intelligent Environments (Present - Future)
-
Cloud-Native Development:
- Description: Leveraging cloud services (managed databases, message queues, serverless functions) directly within the development workflow. Developers focus on application logic, offloading infrastructure management to cloud providers. Containers become a key deployment unit in this paradigm.
- Tools: AWS Lambda, Azure Functions, Google Cloud Run, cloud-managed databases.
- Advancement: Reduced operational overhead, increased focus on business logic, highly scalable deployments.
-
Remote Development & Cloud-Based IDEs:
- Description: The full development environment (editor, terminal, debugger, code) can now reside in the cloud, accessed via a thin client or web browser. This means developers can work from any device, anywhere, with powerful cloud resources backing their environment.
- Tools: GitHub Codespaces, Gitpod, AWS Cloud9, VS Code Remote Development.
- Advancement: Instant onboarding, consistent remote environments, access to high-spec machines regardless of local hardware, enhanced security.
-
Declarative & AI-Assisted Environments (The Near Future):
- Description: Development environments will become even more declarative, where developers specify what they need, and AI/automation tools provision and maintain it. AI will proactively identify dependency issues, optimize resource usage, suggest code snippets, and perform automated testing within the environment.
- Tools: Next-gen dev container specifications, AI agents integrated into IDEs and CI/CD pipelines.
- Prediction: Near-zero environment setup time, self-healing environments, proactive problem identification, truly seamless collaboration.
web3 #computing #cloud #devstr
-
-
 @ 90152b7f:04e57401
2025-05-24 03:47:24
@ 90152b7f:04e57401
2025-05-24 03:47:24"Army study suggests U.S. force of 20,000"
The Washington Times - Friday, April 5, 2002
The Bush administration says there are no active plans to put American peacekeepers between Palestinians and Israelis, but at least one internal military study says 20,000 well-armed troops would be needed.
The Army’s School of Advanced Military Studies (SAMS), an elite training ground and think tank at Fort Leavenworth, Kan., produced the study last year. The 68-page paper tells how the major operation would be run the first year, with peacekeepers stationed in Gaza, Hebron, Jerusalem and Nablus.
One major goal would be to “neutralize leadership of Palestine dissenting factions [and] prevent inter-Palestinian violence.”
The military is known to update secret contingency plans in the event international peacekeepers are part of a comprehensive Middle East peace plan. The SAMS study, a copy of which was obtained by The Washington Times, provides a glimpse of what those plans might entail.
Defense Secretary Donald H. Rumsfeld repeatedly has said the administration has no plans to put American troops between the warring factions. But since the escalation of violence, more voices in the debate are beginning to suggest that some type of American-led peace enforcement team is needed.
Sen. Arlen Specter, Pennsylvania Republican, quoted U.S. special envoy Gen. Anthony Zinni as saying there is a plan, if needed, to put a limited number of American peacekeepers in the Israeli-occupied territories.
Asked on CBS whether he could envision American troops on the ground, Mr. Specter said Sunday: “If we were ever to stabilize the situation, and that was a critical factor, it’s something that I would be willing to consider.”
Added Sen. Joseph R. Biden Jr., Delaware Democrat and Senate Foreign Relations Committee chairman, “In that context, yes, and with European forces as well.”
The recent history of international peacekeeping has shown that it often takes American firepower and prestige for the operation to work. The United Nations made futile attempts to stop Serbian attacks on the Muslim population in Bosnia.
The U.S. entered the fray by bombing Serbian targets and bringing about a peace agreement that still is being backed up by American soldiers on the ground. U.S. combat troops are also in Kosovo, and they have a more limited role in Macedonia.
But James Phillips, a Middle East analyst at the Heritage Foundation, used the word “disaster” to describe the aftermath of putting an international force in the occupied territories.
“I think that would be a formula for sucking us into the violence,” he said. “United States troops would be a lightening rod for attacks by radical Islamics and other Palestinian extremist groups. The United States cannot afford to stretch its forces any thinner. They’re very busy as it is with the war against international terrorism.”
Mr. Phillips noted that two Norwegian observers in Hebron were killed this week. U.N. representatives on the Lebanon border have been unable to prevent terrorists from attacking Israel.
The SAMS paper tries to predict events in the first year of peacekeeping and the dangers U.S. troops would face.
It calls the Israeli armed forces a “500-pound gorilla in Israel. Well armed and trained. Operates in both Gaza [and the West Bank]. Known to disregard international law to accomplish mission. Very unlikely to fire on American forces.”
On the Mossad, the Israeli intelligence service, the Army study says, “Wildcard. Ruthless and cunning. Has capability to target U.S. forces and make it look like a Palestinian/Arab act.”
It described Palestinian youth as “loose cannons; under no control, sometimes violent.” The study was done by 60 officers dubbed the “Jedi Knights,” as all second-year SAMS students are called. The Times first reported on their work in September. Recent violence in the Middle East has raised questions about what type of force it would take to keep the peace.
In the past, SAMS has done studies for the Army chief of staff and the Joint Chiefs. SAMS personnel helped plan the allied ground attack that liberated Kuwait.
The Middle East study sets goals that a peace force should accomplish in the first 30 days. They include “create conditions for development of Palestinian State and security of [Israel],” ensure “equal distribution of contract value or equivalent aid” and “build lasting relationships based on new legal borders and not religious-territorial claims.”
The SAMS report does not specify a full order of battle for the 20,000 troops. An Army source who reviewed the paper said each of three brigades would require about 100 armored vehicles, 25 tanks and 12 self-propelled howitzers, along with attack helicopters and spy drones.
The Palestinians have supported calls for an international force, but Tel Aviv has opposed the idea.
https://www.washingtontimes.com/news/2002/apr/5/20020405-041726-2086r/
-
 @ 2b998b04:86727e47
2025-05-24 03:40:36
@ 2b998b04:86727e47
2025-05-24 03:40:36Solzhenitsyn Would Have Loved Bitcoin
I didn’t plan to write this. But a comment from @HODL stirred something in me — a passing thought that took root and wouldn’t let go:
> “Solzhenitsyn would have understood Bitcoin.”
The more I sat with it, the more I realized: he wouldn’t have just understood it — he would have loved it.
A Life of Resistance
Aleksandr Solzhenitsyn didn’t just survive the Soviet gulags — he exposed them. Through The Gulag Archipelago and other works, he revealed the quiet machinery of evil: not always through brutality, but through systemic lies, suppressed memory, and coerced consensus.
His core belief was devastatingly simple:
> “The line dividing good and evil cuts through the heart of every human being.”
He never let anyone off the hook — not the state, not the system, not even himself. Evil, to Solzhenitsyn, was not “out there.” It was within. And resisting it required truth, courage, and deep personal responsibility.
Bitcoin: Truth That Resists
That’s why I believe Solzhenitsyn would have resonated with Bitcoin.
Not the hype. Not the coins. Not the influencers.
But the heart of it:
-
A system that resists coercion.
-
A ledger that cannot be falsified.
-
A network that cannot be silenced.
-
A protocol that doesn't care about party lines — only proof of work.
Bitcoin is incorruptible memory.\ Solzhenitsyn fought to preserve memory in the face of state erasure.\ Bitcoin cannot forget — and it cannot be made to lie.
Responsibility and Sovereignty
Bitcoin demands what Solzhenitsyn demanded: moral responsibility. You hold your keys. You verify your truth. You cannot delegate conscience.
He once wrote:
> “A man who is not inwardly prepared for the use of violence against him is always weaker than his opponent.”
Bitcoin flips that equation. It gives the peaceful man a weapon: truth that cannot be seized.
I’ve Felt This Line Too
I haven’t read all of The Gulag Archipelago — it’s long, and weighty — but I’ve read enough to know Solzhenitsyn’s voice. And I’ve felt the line he describes:
> That dividing line between good and evil… that runs through my own heart.
That’s why I left the noise of Web3. That’s why I’m building with Bitcoin. Because I believe the moral architecture of this protocol matters. It forces me to live in alignment — or walk away.
Final Word
I think Solzhenitsyn would have seen Bitcoin not as a tech innovation, but as a moral stand. Not a replacement for Christ — but a quiet echo of His justice.
And that’s why I keep stacking, writing, building — one block at a time.
Written with help from ChatGPT (Dr. C), and inspired by a comment from @HODL that sparked something deep.
If this resonated, feel free to zap a few sats — not because I need them, but because signal flows best when it’s shared with intention.
HODL mentioned this idea in a note — their Primal profile:\ https://primal.net/hodl
-
-
 @ 58537364:705b4b85
2025-05-24 03:25:05
@ 58537364:705b4b85
2025-05-24 03:25:05Ep 228 "วิชาชีวิต"
คนเราเมื่อเกิดมาแล้ว ไม่ได้หวังแค่มีชีวิตรอดเท่านั้น แต่ยังปรารถนา "ความเจริญก้าวหน้า" และ "ความสุขในชีวิต"
จึงพากันศึกษาเล่าเรียนเพื่อให้มี "วิชาความรู้" สำหรับการประกอบอาชีพ โดยเชื่อว่า การงานที่มั่นคงย่อมนำ "ความสำเร็จ" และ "ความเจริญก้าวหน้า" มาให้
อย่างไรก็ตาม...ความสำเร็จในวิชาชีพหรือความเจริญก้าวหน้าในชีวิต ไม่ได้เป็นหลักประกันความสุขอย่างแท้จริง
แม้เงินทองและทรัพย์สมบัติจะช่วยให้ชีวิตมีความสุข สะดวก สบาย แต่ไม่ได้ช่วยให้สุขใจในสิ่งที่ตนมี หากยังรู้สึกว่า "ตนยังมีไม่พอ"
ขณะเดียวกันชื่อเสียงเกียรติยศที่ได้มาก็ไม่ช่วยให้คลายความทุกข์ใจ เมื่อต้องเผชิญปัญหาต่างๆ นาๆ
ทั้งการพลัดพราก การสูญเสียบุคคลผู้เป็นที่รัก ความเจ็บป่วย และความตายที่ต้องเกิดขึ้นกับทุกคน
ยิ่งกว่านั้น...ความสำเร็จในอาชีพและความเจริญก้าวหน้าในชีวิต ล้วนเป็น "สิ่งไม่เที่ยง" แปรผันตกต่ำ ไม่สามารถควบคุมได้
วิชาชีพทั้งหลายช่วยให้เราหาเงินได้มากขึ้น แต่ไม่ได้ช่วยให้เราเข้าถึง "ความสุขที่แท้จริง"
คนที่ประสบความสำเร็จในวิชาชีพไม่น้อย ที่มีชีวิตอมทุกข์ ความเครียดรุมเร้า สุขภาพเสื่อมโทรม
หากเราไม่อยากเผชิญกับสิ่งเหล่านี้ ควรเรียน "วิชาชีวิต" เพื่อเข้าใจโลก เข้าใจชีวิต รู้เท่าทันความผันแปรไปของสรรพสิ่ง
วิชาชีวิต...เรียนจากประสบการณ์ชีวิต เมื่อมีปัญหาต่างๆ ขอให้คิดว่า คือ "บททดสอบ"
จงหมั่นศึกษาหาบทเรียนจากวิชานี้อยู่เสมอ สร้าง "ความตระหนักรู้" ถึงความสำคัญในการมีชีวิต
ช่วงที่ผ่านมา เมื่อมีปัญหาฉันไม่สามารถหาทางออกจากทุกข์ได้เศร้า เสียใจ ทุรน ทุราย สอบตก "วิชาชีวิต"
โชคดีครูบาอาจารย์ให้ข้อคิด กล่าวว่า เป็นเรื่องธรรมดาหากเรายังไม่เข้าใจชีวิต ทุกสิ่งล้วนผันแปร เกิด-ดับ เป็นธรรมดา ท่านเมตตาส่งหนังสือเล่มนี้มาให้
เมื่อค่อยๆ ศึกษา ทำความเข้าใจ นำความทุกข์ที่เกิดขึ้นมาพิจารณา เห็นว่าเมื่อ "สอบตก" ก็ "สอบใหม่" จนกว่าจะผ่านไปได้
วิชาทางโลกเมื่อสอบตกยังเปิดโอกาสให้เรา "สอบซ่อม" วิชาทางธรรมก็เช่นเดียวกัน หากเจอปัญหา อุปสรรค หรือ ความทุกข์ถาโถมเข้ามา ขอให้เราตั้งสติ ว่า จะตั้งใจทำข้อสอบนี้ให้ผ่านไปให้จงได้
หากเราสามารถดำเนินชีวิตด้วยความเข้าใจ เราจะค้นพบ "วิชาชีวิต" ที่สามารถทำให้หลุดพ้นจากความทุกข์ได้แน่นอน
ด้วยรักและปรารถนาดี ปาริชาติ รักตะบุตร 21 เมษายน 2566

น้อมกราบขอบพระคุณพระ อ.ไพศาล วิสาโล เป็นอย่างสูง ที่ท่านเมตตา ให้ข้อธรรมะยามทุกข์ใจและส่งหนังสือมาให้ จึงตั้งใจอยากแบ่งปันเป็นธรรมทาน
-
 @ 2b998b04:86727e47
2025-05-24 03:16:38
@ 2b998b04:86727e47
2025-05-24 03:16:38Most of the assets I hold—real estate, equities, and businesses—depreciate in value over time. Some literally, like physical buildings and equipment. Some functionally, like tech platforms that age faster than they grow. Even cash, which should feel "safe," quietly loses ground to inflation. Yet I continue to build. I continue to hold. And I continue to believe that what I’m doing matters.
But underneath all of that — beneath the mortgages, margin trades, and business pivots — I’ve made a long-term bet:
Bitcoin will outlast the decay.
The Decaying System I Still Operate In
Let me be clear: I’m not a Bitcoin purist. I use debt. I borrow to acquire real estate. I trade with margin in a brokerage account. I understand leverage — not as a sin, but as a tool that must be used with precision and respect. But I’m also not naive.
The entire fiat-based financial system is built on a slow erosion of value. Inflation isn't a bug — it’s a feature. And it's why most business models, whether in real estate or retail, implicitly rely on asset inflation just to stay solvent.
That’s not sustainable. And it’s not honest.
The Bitcoin Thesis: Deflation That Works for You
Bitcoin is fundamentally different. Its supply is fixed. Its issuance is decreasing. Over time, as adoption grows and fiat weakens, Bitcoin’s purchasing power increases.
That changes the game.
If you can hold even a small portion of your balance sheet in BTC — not just as an investment, but as a strategic hedge — it becomes a way to offset the natural depreciation of your other holdings. Your buildings may age. Your cash flow may fluctuate. But your Bitcoin, if properly secured and held with conviction, becomes the anchor.
It’s not about day trading BTC or catching the next ATH. It’s about understanding that in a world designed to leak value, Bitcoin lets you patch the hole.
Why This Matters for Builders
If you run a business — especially one with real assets, recurring costs, or thin margins — you know how brutal depreciation can be. Taxes, maintenance, inflation, replacement cycles… it never stops.
Adding BTC to your long-term treasury isn’t about becoming a "crypto company." It’s about becoming anti-fragile. It’s about building with a component that doesn’t rot.
In 5, 10, or 20 years, I may still be paying off mortgages and navigating property cycles. But if my Bitcoin allocation is still intact, still growing in real purchasing power… then I haven’t just preserved wealth. I’ve preserved optionality. I’ve created a counterbalance to the relentless decay of everything else.
Final Word
I still play the fiat game — because for now, I have to. But I’m no longer betting everything on it. Bitcoin is my base layer now. Quiet, cold-stored, and uncompromising.
It offsets depreciation — not just financially, but philosophically. It reminds me that not everything has to erode. Not everything has to be sacrificed to time or policy or inflation.
Some things can actually hold. Some things can last.
And if I build right — maybe what I build can last too.
If this resonated, feel free to send a zap — it helps me keep writing and building from a place of conviction.
This article was co-written with the help of ChatGPT, a tool I use to refine and clarify what I’m working through in real time.
-
 @ 502ab02a:a2860397
2025-05-24 01:14:43
@ 502ab02a:a2860397
2025-05-24 01:14:43ในสายตาคนรักสุขภาพทั่วโลก “อโวคาโด” คือผลไม้ในฝัน มันมีไขมันดี มีไฟเบอร์สูง ช่วยลดคอเลสเตอรอลได้ มีวิตามินอี มีโพแทสเซียม และที่สำคัญคือ "ดูดี" ทุกครั้งที่ถูกปาดวางบนขนมปังโฮลวีตในชามสลัด หรือบนโฆษณาอาหารคลีนสุดหรู
แต่ในสายตาชาวไร่บางคนในเม็กซิโกหรือชุมชนพื้นเมืองในโดมินิกัน อโวคาโดไม่ใช่ผลไม้แห่งสุขภาพ แต่มันคือสัญลักษณ์ของความรุนแรง การกดขี่ และการสูญเสียเสรีภาพในผืนดินของตัวเอง
เมื่ออาหารกลายเป็นทองคำ กลุ่มอิทธิพลก็ไม่เคยพลาดจะเข้าครอบครอง
เรามักได้ยินคำว่า "ทองคำเขียว" หรือ Green Gold ใช้เรียกอโวคาโด เพราะในรอบ 20 ปีที่ผ่านมา ความต้องการบริโภคของมันพุ่งสูงขึ้นเป็นเท่าตัว โดยเฉพาะในสหรัฐฯ และยุโรป จากผลการวิจัยของมหาวิทยาลัยฮาร์วาร์ดและข้อมูลการส่งออกของ USDA พบว่า 90% ของอโวคาโดที่บริโภคในอเมริกา มาจากรัฐมิโชอากังของเม็กซิโก พื้นที่ซึ่งควบคุมโดยกลุ่มค้ายาเสพติดไม่ต่างจากเจ้าของสวนตัวจริง
พวกเขาเรียกเก็บ “ค่าคุ้มครอง” จากเกษตรกร โดยใช้วิธีเดียวกับมาเฟีย คือ ถ้าไม่จ่าย ก็เจ็บตัวหรือหายตัว ไม่ว่าจะเป็นกลุ่ม CJNG (Jalisco New Generation Cartel), Familia Michoacana หรือ Caballeros Templarios พวกเขาไม่ได้สนใจว่าใครปลูกหรือใครรดน้ำ ตราบใดที่ผลผลิตสามารถเปลี่ยนเป็นเงินได้
องค์กรอาชญากรรมเหล่านี้ไม่ได้แค่ “แฝงตัว” ในอุตสาหกรรม แต่ ยึดครอง ห่วงโซ่การผลิตทั้งหมด ตั้งแต่แปลงปลูกไปจนถึงโรงบรรจุและเส้นทางขนส่ง คนที่ไม่ยอมเข้าระบบมืดอาจต้องพบจุดจบในป่า หรือไม่มีชื่ออยู่ในทะเบียนบ้านอีกต่อไป
จากรายงานของเว็บไซต์ Food is Power องค์กรไม่แสวงกำไรด้านความยุติธรรมด้านอาหารในสหรัฐฯ เผยว่า ในปี 2020 มีเกษตรกรในเม็กซิโกจำนวนมากที่ถูกข่มขู่ บางรายถึงขั้นถูกฆาตกรรม เพราะปฏิเสธจ่ายค่าคุ้มครองจากกลุ่มค้ายา
การปลูกอโวคาโดไม่ใช่เรื่องเบาๆ กับธรรมชาติ เพราะมันต้องการ “น้ำ” มากถึง 272 ลิตรต่อผลเดียว! เรามาดูว่า “272 ลิตร” นี้ เท่ากับอะไรบ้างในชีวิตจริง อาบน้ำฝักบัวนาน 10–12 นาที (โดยเฉลี่ยใช้น้ำ 20–25 ลิตรต่อนาที) ใช้น้ำซักเสื้อผ้าเครื่องหนึ่ง (เครื่องซักผ้า 1 ครั้งกินประมาณ 60–100 ลิตร) น้ำดื่มของคนหนึ่งคนได้นานเกือบ เดือน (คนเราต้องการน้ำดื่มประมาณ 1.5–2 ลิตรต่อวัน)
ถ้าเราใช้ข้อมูลจาก FAO และ Water Footprint Network การผลิตเนื้อวัว 1 กิโลกรัม ต้องใช้น้ำ 15,000 ลิตร (รวมทั้งการปลูกหญ้า อาหารสัตว์ การดื่มน้ำของวัว ฯลฯ) ได้โปรตีนราว 250 กรัม อโวคาโด 1 กิโลกรัม (ราว 5 ผล) ใช้น้ำประมาณ 1,360 ลิตร ได้โปรตีนเพียง 6–8 กรัมเท่านั้น พูดง่ายๆคือ เมื่อเทียบอัตราส่วนเป็นลิตรต่อกรัมโปรตีนแล้วนั้น วัวใช้น้ำ 60 ลิตรต่อกรัมโปรตีน / อโวคาโด ใช้น้ำ 194 ลิตรต่อกรัมโปรตีน แถมการเลี้ยงวัวในระบบธรรมชาติ (เช่น pasture-raised หรือ regenerative farming) ยังสามารถเป็นส่วนหนึ่งของระบบหมุนเวียนน้ำและคาร์บอนได้ พอเห็นภาพแล้วใช่ไหมครับ ดังนั้นเราควรระมัดระวังการเสพสื่อเอาไว้ด้วยว่า คำว่า "ดีต่อโลก" ไม่ได้หมายถึงพืชอย่างเดียว ทุกธุรกิจถ้าทำแบบที่ควรทำ มันยังสามารถผลักดันโลกไม่ให้ตกอยู่ในมือองค์กร future food ได้ เพราะมูลค่ามันสูงมาก
และเมื่อราคาสูง พื้นที่เพาะปลูกก็ขยายอย่างไร้การควบคุม ป่าธรรมชาติในรัฐมิโชอากังถูกแอบโค่นแบบผิดกฎหมายเพื่อแปลงสภาพเป็นไร่ “ทองเขียว” ข้อมูลจาก Reuters พบว่าผลไม้ที่ถูกส่งออกไปยังสหรัฐฯ บางส่วนมาจากแปลงปลูกที่บุกรุกป่าคุ้มครอง และรัฐบาลเองก็ไม่สามารถควบคุมได้เพราะอิทธิพลของกลุ่มทุนและมาเฟีย
ในโดมินิกันก็เช่นกัน มีรายงานจากสำนักข่าว Gestalten ว่าพื้นที่ป่าสงวนหลายพันไร่ถูกเปลี่ยนเป็นไร่อโวคาโด เพื่อป้อนตลาดผู้บริโภคในอเมริกาและยุโรปโดยตรง โดยไม่มีการชดเชยใดๆ แก่ชุมชนท้องถิ่น
สุขภาพที่ดีไม่ควรได้มาจากการทำลายสุขภาพของคนอื่น ไม่ควรมีผลไม้ใดที่ดูดีในจานของเรา แล้วเบื้องหลังเต็มไปด้วยคราบเลือดและน้ำตาของคนปลูก
เฮียไม่ได้จะบอกให้เลิกกินอโวคาโดเลย แต่เฮียอยากให้เรารู้ทัน ว่าความนิยมของอาหารสุขภาพวันนี้ กำลังเป็นสนามใหม่ของกลุ่มทุนโลก ที่พร้อมจะครอบครองด้วย “อำนาจอ่อน” ผ่านแบรนด์อาหารธรรมชาติ ผ่านกฎหมายสิ่งแวดล้อม หรือแม้แต่การครอบงำตลาดเสรีด้วยกำลังอาวุธ
นี่ไม่ใช่เรื่องไกลตัว เพราะเมื่อกลุ่มทุนเริ่มฮุบเมล็ดพันธุ์ คุมเส้นทางขนส่ง คุมฉลาก Certified Organic ทั้งหลาย พวกเขาก็ “ควบคุมสุขภาพ” ของผู้บริโภคเมืองอย่างเราไปด้วยโดยอ้อม
คำถามสำคัญที่มาทุกครั้งเวลามีเนื้อหาอะไรมาฝากคือ แล้วเราจะทำอะไรได้? 555555 - เลือกบริโภคผลไม้จากแหล่งที่โปร่งใสหรือปลูกเองได้ - สนับสนุนเกษตรกรรายย่อยที่ไม่อยู่ภายใต้กลุ่มทุน - ใช้เสียงของผู้บริโภคกดดันให้มีระบบตรวจสอบต้นทางจริง ไม่ใช่แค่ฉลากเขียวสวยๆ - และที่สำคัญ อย่าเชื่อว่า “ทุกสิ่งที่เขาวางให้ดูสุขภาพดี” จะดีจริง (ข้อนี่ละตัวดีเลยครับ)
สุขภาพไม่ใช่สินค้า และอาหารไม่ควรเป็นอาวุธของกลุ่มทุน หากเราเริ่มตระหนักว่าอาหารคือการเมือง น้ำคืออำนาจ และแปลงเกษตรคือสนามรบ เฮียเชื่อว่าผู้บริโภคอย่างเราจะไม่ยอมเป็นหมากอีกต่อไป #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ b1ddb4d7:471244e7
2025-05-24 10:00:40
@ b1ddb4d7:471244e7
2025-05-24 10:00:40Global fintech leader Revolut has announced a landmark partnership with Lightspark, a pioneer in blockchain infrastructure solutions, to integrate bitcoin’s Lightning Network into its platform.
This collaboration, now live for Revolut users in the UK and select European Economic Area (EEA) countries, marks a transformative leap toward frictionless, real-time transactions—eliminating delays and exorbitant fees traditionally associated with digital asset transfers.
 Major update: @RevolutApp is now partnering with @lightspark pic.twitter.com/OUblgrj6Xr
Major update: @RevolutApp is now partnering with @lightspark pic.twitter.com/OUblgrj6Xr— Lightspark (@lightspark) May 7, 2025
Breaking Barriers in Digital Currency Usability
By adopting Lightspark’s cutting-edge technology, Revolut empowers its 40+ million customers to execute bitcoin transactions instantly at a fraction of current costs.
This integration addresses longstanding pain points in digital currency adoption, positioning bitcoin as a practical tool for everyday payments. Users can now seamlessly send, receive, and store bitcoin with the same ease as traditional fiat currencies, backed by Revolut’s secure platform.
The partnership also advances Revolut’s integration into the open Money Grid, a decentralized network enabling universal interoperability between financial platforms.
This move aligns Revolut with forward-thinking fintechs adopting next-gen solutions like Lightning transactions and Universal Money Addresses (UMA), which simplify cross-border payments by replacing complex wallet codes with human-readable addresses (e.g., $john.smith).
Why This Matters
The collaboration challenges conventional payment rails, which often incur delays of days and high fees for cross-border transfers. By contrast, Lightning Network transactions settle in seconds for minimal cost, revolutionizing peer-to-peer payments, remittances, and merchant settlements. For Revolut users, this means:
- Instant transactions: Send bitcoin globally in under three seconds.
- Near-zero fees: Dramatically reduce costs compared to traditional crypto transfers.
- Enhanced utility: Use bitcoin for daily spending, not just as a speculative asset.
The Road Ahead
Revolut plans to expand Lightning Network access to additional markets in 2025, with ambitions to integrate UMA support for seamless fiat and digital currency interactions. Lightspark will continue optimizing its infrastructure to support Revolut’s scaling efforts, further bridging the gap between blockchain innovation and mainstream finance.
About Revolut
Revolut is a global financial app serving over 40 million customers worldwide. Offering services ranging from currency exchange and stock trading to digital assets and insurance, Revolut is committed to building a borderless financial ecosystem.
About Lightspark
Founded by former PayPal and Meta executives, Lightspark develops enterprise-grade solutions for the Lightning Network. Its technology stack empowers institutions to harness bitcoin’s speed and efficiency while maintaining regulatory compliance.
-
 @ 611021ea:089a7d0f
2025-05-24 00:00:04
@ 611021ea:089a7d0f
2025-05-24 00:00:04The world of health and fitness data is booming. Users are tracking more aspects of their well-being than ever before, from daily steps and workout intensity to sleep patterns and caloric intake. But for developers looking to build innovative applications on this data, significant hurdles remain: ensuring user privacy, achieving interoperability between different services, and simply managing the complexity of diverse health metrics.
Enter the NIP-101h Health Profile Framework and its companion tools: the HealthNote SDK and the HealthNote API. This ecosystem is designed to empower developers to create next-generation health and fitness applications that are both powerful and privacy-preserving, built on the decentralized and user-centric principles of Nostr.
NIP-101h: A Standardized Language for Health Metrics
At the core of this ecosystem is NIP-101h. It's a Nostr Improvement Proposal that defines a standardized way to represent, store, and share granular health and fitness data. Instead of proprietary data silos, NIP-101h introduces specific Nostr event kinds for individual metrics like weight (kind
1351), height (kind1352), step count (kind1359), and many more.Key features of NIP-101h:
- Granularity: Each piece of health information (e.g., weight, caloric intake) is a distinct Nostr event, allowing for fine-grained control and access.
- User Control: Built on Nostr, the data remains under user control. Users decide what to share, with whom, and on which relays.
- Standardization: Defines common structures for units, timestamps, and metadata, promoting interoperability.
- Extensibility: New metrics can be added as new NIP-101h.X specifications, allowing the framework to evolve.
- Privacy by Design: Encourages the use of NIP-04/NIP-44 for encryption and includes a
consenttag for users to specify data-sharing preferences.
You can explore the full NIP-101h specification and its metric directory in the main project repository.
The HealthNote SDK: Simplifying Client-Side Integration
While NIP-101h provides the "what," the HealthNote SDK provides the "how" for client-side applications. This (currently draft) TypeScript SDK aims to make it trivial for developers to:
- Create & Validate NIP-101h Events: Easily construct well-formed Nostr events for any supported health metric, ensuring they conform to the NIP-101h specification.
- Handle Encryption: Seamlessly integrate with NIP-44 to encrypt sensitive health data before publication.
- Manage Consent: Automatically include appropriate
consenttags (e.g., defaulting toaggregate-only) to respect user preferences. - Publish to Relays: Interact with Nostr relays to publish the user's health data.
- Prepare Data for Analytics: Extract minimal, privacy-preserving "stat-blobs" for use with the HealthNote API.
The SDK's goal is to abstract away the low-level details of Nostr event creation and NIP-101h formatting, letting developers focus on their application's unique features.
The HealthNote API: Powerful Insights, Zero Raw Data Exposure
This is where things get really exciting for developers wanting to build data-driven features. The HealthNote API (detailed in
HealthNote-API.md) is a server-side component designed to provide powerful analytics over aggregated NIP-101h data without ever accessing or exposing individual users' raw, unencrypted metrics.Here's how it achieves this:
- Privacy-Preserving Ingestion: The SDK sends only "stat-blobs" to the API. These blobs contain the numeric value, unit, timestamp, and metric kind, but not the original encrypted content or sensitive user identifiers beyond what's necessary for aggregation.
- Aggregation at its Core: The API's endpoints are designed to return only aggregated data.
GET /trend: Provides time-series data (e.g., average daily step count over the last month).GET /correlate: Computes statistical correlations between two metrics (e.g., does increased activity duration correlate with changes in workout intensity?).GET /distribution: Shows how values for a metric are distributed across the user base.
- Built-in Privacy Techniques:
- k-Anonymity: Ensures that each data point in an aggregated response represents at least 'k' (e.g., 5) distinct users, preventing re-identification.
- Differential Privacy (Optional): Can add statistical noise to query results, further protecting individual data points while preserving overall trends.
- No Raw Data Access for Developers: Developers querying the API receive only these aggregated, anonymized results, perfect for powering charts, dashboards, and trend analysis in their applications.
A Typical Workflow
- A user records a workout in their NIP-101h-compatible fitness app.
- The app uses the HealthNote SDK to create NIP-101h events for metrics like distance, duration, and calories burned. Sensitive data is encrypted.
- The SDK publishes these events to the user's configured Nostr relays.
- The SDK also extracts stat-blobs (e.g.,
{ kind: 1363, value: 5, unit: 'km', ... }) and sends them to the HealthNote API for ingestion, tagged with anaggregate-onlyconsent. - Later, the app (or an authorized third-party service) queries the HealthNote API:
GET /trend?kind=1363&bucket=week&stat=sum. - The API returns a JSON object like:
{"series": [{"date": "2024-W20", "value": 15000}, ...]}showing the total distance run by all consenting users, week by week. This data can directly populate a trend chart.
Benefits for the Ecosystem
- For Users:
- Greater control and ownership of their health data.
- Ability to use a diverse range of interoperable health and fitness apps.
- Confidence that their data can contribute to insights without sacrificing personal privacy.
- For Developers:
- Easier to build sophisticated health and fitness applications without becoming privacy experts or building complex data aggregation pipelines.
- Access to rich, aggregated data for creating compelling user-facing features (trends, benchmarks, correlations).
- Reduced burden of storing and securing sensitive raw health data for analytical purposes.
- Opportunity to participate in an open, interoperable ecosystem.
The Road Ahead
The NIP-101h framework, the HealthNote SDK, and the HealthNote API are foundational pieces for a new generation of health and fitness applications. As these tools mature and gain adoption, we envision a vibrant ecosystem where users can seamlessly move their data between services, and developers can innovate rapidly, all while upholding the highest standards of privacy and user control.
We encourage developers to explore the NIP-101h specifications, experiment with the (upcoming) SDK, and review the HealthNote API design. Your feedback and contributions will be invaluable as we build this privacy-first future for health data.
https://github.com/HealthNoteLabs
-
 @ 90152b7f:04e57401
2025-05-23 23:38:49
@ 90152b7f:04e57401
2025-05-23 23:38:49WikiLeaks The Global Intelligence Files
Released on 2013-03-04 00:00 GMT
| Email-ID | 296467 | | -------- | -------------------------- | | Date | 2007-10-29 20:54:22 | | From | <hrwpress@hrw.org> | | To | <responses@stratfor.com> |
Gaza: Israel's Fuel and Power Cuts Violate Laws of War\ \ For Immediate Release\ \ Gaza: Israel's Fuel and Power Cuts Violate Laws of War\ \ Civilians Should Not Be Penalized for Rocket Attacks by Armed Groups\ \ (New York, October 29, 2007) - Israel's decision to limit fuel and\ electricity to the Gaza Strip in retaliation for unlawful rocket attacks\ by armed groups amounts to collective punishment against the civilian\ population of Gaza, in violation of international law, and will worsen the\ humanitarian crisis there, Human Rights Watch said today.\ \ "Israel may respond to rocket attacks by armed groups to protect its\ population, but only in lawful ways," said Sarah Leah Whitson, director of\ Human Rights Watch's Middle East division. "Because Israel remains an\ occupying power, in light of its continuing restrictions on Gaza, Israel\ must not take measures that harm the civilian population - yet that is\ precisely what cutting fuel or electricity for even short periods will\ do."\ \ On Sunday, the Israeli Defense Ministry ordered the reduction of fuel\ shipments from Israel to Gaza. A government spokesman said the plan was to\ cut the amount of fuel by 5 to 11 percent without affecting the supply of\ industrial fuel for Gaza's only power plant.\ \ According to Palestinian officials, fuel shipments into Gaza yesterday\ fell by more than 30 percent.\ \ In response to the government's decision, a group of 10 Palestinian and\ Israeli human rights groups petitioned the Israeli Supreme Court on\ Sunday, seeking an immediate injunction against the fuel and electricity\ cuts. The court gave the government five days to respond but did not issue\ a temporary injunction. On Monday, the groups requested an urgent hearing\ before the five days expire.\ \ Last Thursday, Defense Minister Ehud Barak approved cutting electricity to\ Gaza for increasing periods in response to ongoing rocket attacks against\ civilian areas in Israel, but the government has not yet implemented the\ order.\ \ The rockets fired by Palestinian armed groups violate the international\ legal prohibition on indiscriminate attacks because they are highly\ inaccurate and cannot be directed at a specific target. Because Hamas\ exercises power inside Gaza, it is responsible for stopping indiscriminate\ attacks even when carried out by other groups, Human Rights Watch said.\ \ On Friday, Israeli Prime Minister Ehud Olmert said that Israel would\ respond strongly to the ongoing attacks without allowing a humanitarian\ crisis. But the UN's top humanitarian official, UN Deputy\ Secretary-General John Holmes, said that a "serious humanitarian crisis"\ in Gaza already exists, and called on Israel to lift the economic blockade\ that it tightened after Hamas seized power in June.\ \ Israel's decision to cut fuel and electricity is the latest move aimed\ ostensibly against Hamas that is affecting the entire population of Gaza.\ In September, the Israeli cabinet declared Gaza "hostile territory" and\ voted to "restrict the passage of various goods to the Gaza Strip and\ reduce the supply of fuel and electricity." Since then, Israel has\ increasingly blocked supplies into Gaza, letting in limited amounts of\ essential foodstuffs, medicine and humanitarian supplies. According to\ Holmes, the number of humanitarian convoys entering Gaza had dropped to\ 1,500 in September from 3,000 in July.\ \ "Cutting fuel and electricity obstructs vital services," Whitson said.\ "Operating rooms, sewage pumps, and water well pumps all need electricity\ to run."\ \ Israel sells to Gaza roughly 60 percent of the electricity consumed by the\ territory's 1.5 million inhabitants. In June 2006, six Israeli missiles\ struck Gaza's only power plant; today, for most residents, electricity is\ available during only limited hours.\ \ Israeli officials said they would cut electricity for 15 minutes after\ each rocket attack and then for increasingly longer periods if the attacks\ persist. Deputy Defense Minister Matan Vilnai said Israel would\ "dramatically reduce" the power it supplied to Gaza over a period of\ weeks.\ \ Cutting fuel or electricity to the civilian population violates a basic\ principle of international humanitarian law, or the laws of war, which\ prohibit a government that has effective control over a territory from\ attacking or withholding objects that are essential to the survival of the\ civilian population. Such an act would also violate Israel's duty as an\ occupying power to safeguard the health and welfare of the population\ under occupation.\ \ Israel withdrew its military forces and settlers from the Gaza Strip in\ 2005. Nonetheless, Israel remains responsible for ensuring the well-being\ of Gaza's population for as long as, and to the extent that, it retains\ effective control over the area. Israel still exercises control over\ Gaza's airspace, sea space and land borders, as well as its electricity,\ water, sewage and telecommunications networks and population registry.\ Israel can and has also reentered Gaza for security operations at will.\ \ Israeli officials state that by declaring Gaza "hostile territory," it is\ no longer obliged under international law to supply utilities to the\ civilian population, but that is a misstatement of the law.\ \ "A mere declaration does not change the facts on the ground that impose on\ Israel the status and obligations of an occupying power," said Whitson.\ \ For more information, please contact:\ \ In New York, Fred Abrahams (English, German): +1-917-385-7333 (mobile)\ \ In Washington, DC, Joe Stork (English): +1-202-299-4925 (mobile)\ \ In Cairo, Gasser Abdel-Razek (Arabic, English): +20-2-2-794-5036 (mobile);\ or +20-10-502-9999 (mobile)
-
 @ b1ddb4d7:471244e7
2025-05-24 10:00:39
@ b1ddb4d7:471244e7
2025-05-24 10:00:39In the heart of East Africa, where M-Pesa reigns supreme and innovation pulses through bustling markets, a quiet revolution is brewing—one that could redefine how millions interact with money.
Enter Bitika, the Kenyan startup turning bitcoin’s complexity into a three-step dance, merging the lightning speed of sats with the trusted rhythm of mobile money.
At the helm is a founder whose “aha” moment came not in a boardroom, but at his kitchen table, watching his father grapple with the gap between understanding bitcoin and actually using it.
Bitika was born from that friction—a bridge between M-Pesa’s ubiquity and bitcoin’s borderless promise, wrapped in a name as playful as the Swahili slang that inspired it.
But this isn’t just a story about simplifying transactions. It’s about liquidity battles, regulatory tightropes, and a vision to turn Bitika into the invisible rails powering Africa’s Bitcoin future.
Building on Bitcoin
- Tell us a bit about yourself and how you got into bitcoin/fintech, and what keeps you passionate about this space?
I first came across bitcoin in 2020, but like many at that time, I didn’t fully grasp what it really was. It sounded too complicated, probably with the heavy terminologies. Over time, I kept digging deeper and became more curious.
I started digging into finance and how money works and realised this was what I needed to understand bitcoin’s objectives. I realized that bitcoin wasn’t just a new type of money—it was a breakthrough in how we think about freedom, ownership, and global finance.
What keeps me passionate is how bitcoin can empower people—especially in Africa—to take control of their wealth, without relying on unstable systems or middlemen.
- What pivotal moment or experience inspired you to create Bitika? Was there a specific gap in Kenya’s financial ecosystem that sparked the idea?
Yes, this idea was actually born right in my own home. I’ve always been an advocate for bitcoin, sharing it with friends, family, and even strangers. My dad and I had countless conversations about it. Eventually, he understood the concept. But when he asked, “How do I even buy bitcoin?” or “Can you just buy it for me?” and after taking him through binance—that hit me.
If someone I’d educated still found the buying process difficult, how many others were feeling the same way? That was the lightbulb moment. I saw a clear gap: the process of buying bitcoin was too technical for the average Kenyan. That’s the problem Bitika set out to solve.
- How did you identify the synergy between bitcoin and M-Pesa as a solution for accessibility?
M-Pesa is at the center of daily life in Kenya. Everyone uses it—from buying groceries to paying rent. Instead of forcing people to learn new tools, I decided to meet them where they already are. That synergy between M-Pesa and bitcoin felt natural. It’s about bridging what people already trust with something powerful and new.
- Share the story behind the name “Bitika” – does it hold a cultural or symbolic meaning?
Funny enough, Bitika isn’t a deeply planned name. It came while I was thinking about bitcoin and the type of transformation it brings to individuals. In Swahili, we often add “-ka” to words for flair—like “bambika” from “bamba.”
So, I just coined Bitika as a playful and catchy way to reflect something bitcoin-related, but also uniquely local. I stuck with it because thinking of an ideal brand name is the toughest challenge for me.
- Walk us through the user journey – how does buying bitcoin via M-Pesa in “3 simple steps” work under the hood?
It’s beautifully simple.
1. The user enters the amount they want to spend in KES—starting from as little as 50 KES (about $0.30).
2. They input their Lightning wallet address.
3. They enter their M-Pesa number, which triggers an STK push (payment prompt) on their phone. Once confirmed—pap!—they receive bitcoin almost instantly.
Under the hood, we fetch the live BTC price, validate wallet addresses, check available liquidity, process the mobile payment, and send sats via the Lightning Network—all streamlined into a smooth experience for the user.
- Who’s Bitika’s primary audience? Are you focusing on unbanked populations, tech enthusiasts, or both?
Both. Bitika is designed for everyday people—especially the unbanked and underbanked who are excluded from traditional finance. But we also attract bitcoiners who just want a faster, easier way to buy sats. What unites them is the desire for a seamless and low-barrier bitcoin experience.
Community and Overcoming Challenges
- What challenges has Bitika faced navigating Kenya’s bitcoin regulations, and how do you build trust with regulators?
Regulation is still evolving here. Parliament has drafted bills, but none have been passed into law yet. We’re currently in a revision phase where policymakers are trying to strike a balance between encouraging innovation and protecting the public.
We focus on transparency and open dialogue—we believe that building trust with regulators starts with showing how bitcoin can serve the public good.
- What was the toughest obstacle in building Bitika, and how did you overcome it?
Liquidity. Since we don’t have deep capital reserves, we often run into situations where we have to pause operations often to manually restock our bitcoin supply. It’s frustrating—for us and for users. We’re working on automating this process and securing funding to maintain consistent liquidity so users can access bitcoin at any time, without disruption.
This remains our most critical issue—and the primary reason we’re seeking support.
- Are you eyeing new African markets? What’s next for Bitika’s product?
Absolutely. The long-term vision is to expand Bitika into other African countries facing similar financial challenges. But first, we want to turn Bitika into a developer-first tool—infrastructure that others can build on. Imagine local apps, savings products, or financial tools built using Bitika’s simple bitcoin rails. That’s where we’re heading.
- What would you tell other African entrepreneurs aiming to disrupt traditional finance?
Disrupting finance sounds exciting—but the reality is messy. People fear what they don’t understand. That’s why simplicity is everything. Build tools that hide the complexity, and focus on making the user’s life easier. Most importantly, stay rooted in local context—solve problems people actually face.
What’s Next?
- What’s your message to Kenyans hesitant to try bitcoin, and to enthusiasts watching Bitika?
To my fellow Kenyans: bitcoin isn’t just an investment—it’s a sovereign tool. It’s money you truly own. Start small, learn, and ask questions.
To the bitcoin community: Bitika is proof that bitcoin is working in Africa. Let’s keep pushing. Let’s build tools that matter.
- How can the bitcoin community, both locally and globally, support Bitika’s mission?
We’re currently fundraising on Geyser. Support—whether it’s financial, technical, or simply sharing our story—goes a long way. Every sat you contribute helps us stay live, grow our liquidity, and continue building a tool that brings bitcoin closer to the everyday person in Africa.
Support here: https://geyser.fund/project/bitika
-
 @ b1ddb4d7:471244e7
2025-05-24 10:00:37
@ b1ddb4d7:471244e7
2025-05-24 10:00:37Custodial Lightning wallets allow users to transact without managing private keys or channel liquidity. The provider handles technical complexities, but this convenience comes with critical trade-offs:
- You don’t control your keys: The custodian holds your bitcoin.
- Centralized points of failure: Servers can be hacked or shut down.
- Surveillance risks: Providers track transaction metadata.
Key Risks of Custodial Lightning Wallets
*1. Hacks and Exit Scams*
Custodians centralize large amounts of bitcoin, attracting hackers:
- Nearly $2.2 billion worth of funds were stolen from hacks in 2024.
- Lightning custodians suffered breaches, losing user funds.
Unlike non-custodial wallets, victims have no recourse since they don’t hold keys.
*2. Censorship and Account Freezes*
Custodians comply with regulators, risking fund seizures:
- Strike (a custodial Lightning app) froze accounts of users in sanctioned regions.
- A U.K. court in 2020 ordered Bitfinex to freeze bitcoin worth $860,000 after the exchange and blockchain sleuthing firm Chainalysis traced the funds to a ransomware payment.
*3. Privacy Erosion*
Custodians log user activity, exposing sensitive data:
- Transaction amounts, receiver addresses, and IPs are recorded.
*4. Service Downtime*
Centralized infrastructure risks outages.
*5. Inflation of Lightning Network Centralization*
Custodians dominate liquidity, weakening network resilience:
- At the moment, 10% of the nodes on Lightning control 80% of the liquidity.
- This centralization contradicts bitcoin’s decentralized ethos.
How to Switch to Self-Custodial Lightning Wallets
Migrating from custodial services is straightforward:
*1. Choose a Non-Custodial Wallet*
Opt for wallets that let you control keys and channels:
- Flash: The self-custodial tool that lets you own your keys, control your coins, and transact instantly.
- Breez Wallet : Non-custodial, POS integrations.
- Core Lightning : Advanced, for self-hosted node operators.
*2. Transfer Funds Securely*
- Withdraw funds from your custodial wallet to a bitcoin on-chain address.
- Send bitcoin to your non-custodial Lightning wallet.
*3. Set Up Channel Backups*
Use tools like Static Channel Backups (SCB) to recover channels if needed.
*4. Best Practices*
- Enable Tor: Mask your IP (e.g., Breez’s built-in Tor support).
- Verify Receiving Addresses: Avoid phishing scams.
- Regularly Rebalance Channels: Use tools like Lightning Pool for liquidity.
Why Self-Custodial Lightning Matters
- Self-custody: Control your keys and funds.
- Censorship resistance: No third party can block transactions.
- Network health: Decentralized liquidity strengthens Lightning.
Self-custodial wallets now rival custodial ease.
Custodial Lightning wallets sacrifice security for convenience, putting users at risk of hacks, surveillance, and frozen funds. As bitcoin adoption grows, so does the urgency to embrace self-custodial solutions.
Take action today:
- Withdraw custodial funds to a hardware wallet.
- Migrate to a self-custodial Lightning wallet.
- Educate others on the risks of custodial control.
The Lightning Network’s potential hinges on decentralization—don’t let custodians become its Achilles’ heel.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-23 23:37:17
@ 5d4b6c8d:8a1c1ee3
2025-05-23 23:37:17@grayruby loves to blow up the odds of various sports markets at Predyx. Well, the jig is up, because I finally managed to deposit some sats at BetPlay where I can leverage the mismatched odds.
So, I've now locked in guaranteed wins on the 49ers winning the Super Bowl and the Panthers winning the Stanley Cup.
https://stacker.news/items/987847
-
 @ 34f1ddab:2ca0cf7c
2025-05-23 23:15:14
@ 34f1ddab:2ca0cf7c
2025-05-23 23:15:14Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 0e9491aa:ef2adadf
2025-05-23 23:01:13
@ 0e9491aa:ef2adadf
2025-05-23 23:01:13
I often hear "bitcoin doesn't interest me, I'm not a finance person."
Ironically, the beauty of sound money is you don't have to be. In the current system you're expected to manage a diversified investment portfolio or pay someone to do it. Bitcoin will make that optional.
— ODELL (@ODELL) September 16, 2018
At first glance bitcoin often appears overwhelming to newcomers. It is incredibly easy to get bogged down in the details of how it works or different ways to use it. Enthusiasts, such as myself, often enjoy going down the deep rabbit hole of the potential of bitcoin, possible pitfalls and theoretical scenarios, power user techniques, and the developer ecosystem. If your first touch point with bitcoin is that type of content then it is only natural to be overwhelmed. While it is important that we have a thriving community of bitcoiners dedicated to these complicated tasks - the true beauty of bitcoin lies in its simplicity. Bitcoin is simply better money. It is the best money we have ever had.
Life is complicated. Life is hard. Life is full of responsibility and surprises. Bitcoin allows us to focus on our lives while relying on a money that is simple. A money that is not controlled by any individual, company, or government. A money that cannot be easily seized or blocked. A money that cannot be devalued at will by a handful of corrupt bureaucrat who live hundreds of miles from us. A money that can be easily saved and should increase in purchasing power over time without having to learn how to "build a diversified stock portfolio" or hire someone to do it for us.
Bitcoin enables all of us to focus on our lives - our friends and family - doing what we love with the short time we have on this earth. Time is scarce. Life is complicated. Bitcoin is the most simple aspect of our complicated lives. If we spend our scarce time working then we should be able to easily save that accrued value for future generations without watching the news or understanding complicated financial markets. Bitcoin makes this possible for anyone.
Yesterday was Mother's Day. Raising a human is complicated. It is hard, it requires immense personal responsibility, it requires critical thinking, but mothers figure it out, because it is worth it. Using and saving bitcoin is simple - simply install an app on your phone. Every mother can do it. Every person can do it.
Life is complicated. Life is beautiful. Bitcoin is simple.
If you found this post helpful support my work with bitcoin.

-
 @ 6c05c73e:c4356f17
2025-05-23 22:59:35
@ 6c05c73e:c4356f17
2025-05-23 22:59:35Como a grande maioria dos brasileiros. Eu não comecei um negócio porque “queria empreender”. Diferente disso, eu PRECISAVA para poder pagar contas e manter o básico.
Festas, openbar e camisas
Meu primeiro negócio foi na verdade um combo. Eu tinha saído do último trampo e eu gostava de festas. Então, comecei a organizar uma festa mensalmente na casa do meu pai. Eu pagava a água, energia e dava uma grana para ele. Em troca, organizava festa de sábado para domingo open bar.
A fórmula era simples. Criava o evento da festa no facebook, convidava todo mundo que conhecia. Panfletava na cidade e espalhava cartazes nos pontos de ônibus sobre a festa. E, para fechar com chave de ouro. Mulher era OFF até 20:00. Consequência? Os caras vinham e pagavam o ingresso deles e delas. Kkkkk. E, enchia…
Comecei a notar que a galera se vestia mal. E, pensei: "Porque não vestir eles?” Pimba! Comecei a desenha e confeccionar camisas para vender nas festas. E, pimba denovo! Vendeu, tudo! Fiz 2 coleções e mais algumas festas. Até o dia que um menino deu PT de tanto beber e decidi que era hora de tentar outra coisa.
Como assim a Apple não vai vender mais os carregadores?
Isso, foi durante a pandemia. A Apple decidiu vender o telefone e o cabo. E, você que lute com a fonte. Estava difícil achar dinheiro no mercado naqueles tempos e eu pensei. Vou pesquisar no google trends e validar a ideia. Caixa! Tinha mais de 80 pts de busca. Colei em SP, no Brás e comprei literalmente. Todo meu dinheiro de cabo de iphone, carregador e bateria portátil.
Fiquei com R$100 na conta. Para fazer um lanche e pagar pelo uber para voltar para casa. Chegando aqui, eu tirei foto e fiz várias copys. Anunciei no Olx, Mercado Livre e Facebook. Impulsionei os anúncios no OLX, vendi para familiares e amigos, e; vendia até para quem estava na rua. Fiz entrega de bike, a pé, de ônibus e é isso mesmo. Tem que ralar. Para queimar o resto da mercadoria. Deixei com uma loja de eletrônicos e fiz consignado. E, hora da próxima ideia.
Mulheres, doces e TPM
Meu penúltimo negócio veio depois dos cabos. Eu pesquisei na net, negócios online para começar com pouca grana. (Depois que paguei as contas do dia a dia, sobraram R$3mil). E, achei uma pesquisa mostrando que doces. Tinha baixa barreira de entrada e exigia poucos equipamentos. Eu trabalhei em restaurante por muitos anos e sabia como lucrar com aquilo. Além do mais, mulheres consomem mais doce em uma certa época do mês.
Não deu outra, convidei 2 pessoas para serem sócias. Desenvolvemos os produtos, fotografamos e fizemos as copys. Em sequência, precisávamos vender. Então, lá vamos denovo: Ifood, WPP, 99food (na época), Uber eats (na época), Elo7, famílias e amigos e; por fim começamos a vender consignado com alguns restaurantes e lojas. Foi uma época em que aprendi a prospectar clientes de todas as maneiras possíveis.
De novo, minha maior dificuldade era a locomoção para fazer entregas. Só tinha uma bike. Mas, entregávamos. Os primeiros 3 meses foram difíceis demais. Mas, rolou. No fim, nossas maiores vendas vinham de: Ifood, encomendas de festas e consignados. Mas, como nem tudo são flores. Meus dois sócios tomaram outros caminhos e abandonaram o projeto. Galera, está tudo bem com isso. Isso acontece o tempo todo. A vida muda e temos que aprender a aceitar isso. Vida que segue e fui para frente de novo.
Sobre paixões, paciência e acreditar
Estava eu comemorando meu níver de 30 anos, num misto de realizações e pouco realizado. Como assim? Sabe quando você faz um monte de coisas, mas ainda assim. Não sente que é aquilo? Pois então…
Eu amo investimentos, livros, escrever e sempre curti trocar ideia com amigos e família sobre como se desenvolver. Desde que comecei a usar a internet eu criei: Canal no youtube, páginas no IG e FB, pinterest, steemit, blog e até canal no Telegram. Mas, nunca tinha consistente sabe? Tipo assim, vou fazer isso por um ano e plantar 100 sementes aqui. Enfim, inconsistência te derruba meu amigo…Eu voltei a trabalhar com restaurantes e estava doido para mudar de área. Estava exausto de trabalhar e meu wpp não parava de tocar. Fui estudar ADM e Desenvolvimento de sistemas no Senac. Dois anos depois, formei. Consegui trabalho.
E, comecei a pensar em como criar um negócio online, escalável e multilíngue. Passei os próximos 7 meses desenhando e pensando como. Mas, tinha que dar o primeiro passo. Criei um site e fui escrevendo textos. Os primeiros 30 foram aquilo, os próximos 10 melhoraram muito e os 10 a seguir eu fiquei bem satisfeitos. Hoje, tenho o negócio que estava na cabeça desde 2023. Mas, olha o tamanho da volta que o universo me fez dar e aprender para chegar aqui hoje. Dicas? Só 3:
- Você precisa usar a internet para fazer negócio. Em todos os negócios que falei, sempre teve algo online. Não negligencie isso.
- Tem que aprender a vender e se vender.
- Confia em si mesmo e faz sem medo de errar. Porque, advinha? Você vai errar! Mas, vai aprender e melhorar. Tem que persistir…
Por hoje é isso. Tamo junto!
-
 @ bf47c19e:c3d2573b
2025-05-23 22:14:37
@ bf47c19e:c3d2573b
2025-05-23 22:14:37Originalni tekst na antenam.net
22.05.2025 / Autor: Ana Nives Radović
Da nema besplatnog ručka sigurno ste čuli svaki put kad bi neko poželio da naglasi da se sve na neki način plaća, iako možda tu cijenu ne primjećujemo odmah. Međutim, kada govorimo o događaju od kojeg je prošlo tačno 15 godina onda o „ručku“ ne govorimo u prenešenom smislu, već o porudžbini pice čija tržišna vrijednost iz godine u godinu dostiže iznos koji je čini najskupljom hranom koja je ikad poručena.
Tog 22. maja 2010. godine čovjek sa Floride pod imenom Laslo Hanjec potrošio je 10.000 bitcoina na dvije velike pice. U to vrijeme, ta količina bitcoina imala je tržišnu vrijednost od oko 41 dolar. Ako uzmemo u obzir da je vrijednost jedne jedinice ove digitalne valute danas nešto više od 111.000 dolara, tih 10.000 bitcoina danas bi značilo vrijednost od 1,11 milijardi dolara.
Nesvakidašnji događaj u digitalnoj i ugostiteljskoj istoriji, nastao zbog znatiželje poručioca koji je želio da se uvjeri da koristeći bitcoin može da plati nešto u stvarnom svijetu, pretvorio se u Bitcoin Pizza Day, kao podsjetnik na trenutak koji je označio prelaz bitcoina iz apstraktnog kriptografskog eksperimenta u nešto što ima stvarnu vrijednost.
Hanjec je bio znatiželjan i pitao se da li se prva, a u to vrijeme i jedina kriptovaluta može iskoristiti za kupovinu nečeg opipljivog. Objavio je ponudu na jednom forumu koja je glasila: 10.000 BTC za dvije pice. Jedan entuzijasta se javio, naručio pice iz restorana Papa John’s i ispisao zanimljivu stranicu istorije digitalne imovine.
Taj inicijalni zabilježeni finansijski dogovor dao je bitcoinu prvu široko prihvaćenu tržišnu vrijednost: 10.000 BTC za 41 dolar, čime je bitcoin napravio svoj prvi korak ka onome što danas mnogi zovu digitalnim zlatom.
Šta je zapravo bitcoin?
Bitcoin je oblik digitalnog novca koji je osmišljen da bude decentralizovan, transparentan i otporan na uticaj centralnih banaka. Kreirao ga je 2009. godine anonimni autor poznat kao Satoši Nakamoto, neposredno nakon globalne finansijske krize 2008. godine. U svojoj suštini, bitcoin je protokol, skup pravila koja sprovodi kompjuterski kod, koji omogućava korisnicima da bez posrednika sigurno razmjenjuju vrijednost putem interneta.
Osnova cijelog sistema je blockchain, distribuisana digitalna knjiga koju održavaju hiljade nezavisnih računara (tzv. čvorova) širom svijeta. Svaka transakcija se bilježi u novi „blok“, koji se potom dodaje u lanac (otud naziv „lanac blokova“, odnosno blockchain). Informacija koja se jednom upiše u blok ne može da se izbriše, niti promijeni, što omogućava više transparentnosti i više povjerenja.
Da bi blockchain mreža u kojoj se sve to odvija zadržala to svojstvo, bitcoin koristi mehanizam konsenzusa nazvan dokaz rada (proof-of-work), što znači da specijalizovani računari koji „rudare“ bitcoin rješavaju kompleksne matematičke probleme kako bi omogućili obavljanje transakcija i pouzdanost mreže.
Deflatorna priroda bitcoina
Najjednostavniji način da se razumije deflatorna priroda bitcoina je da pogledamo cijene izražene u valuti kojoj plaćamo. Sigurno ste u posljednje vrijeme uhvatili sebe da komentarišete da ono što je prije nekoliko godina koštalo 10 eura danas košta 15 ili više. Budući da to ne zapažate kada je u pitanju cijena samo određenog proizvoda ili usluge, već kao sveprisutan trend, shvatate da se radi o tome da je novac izgubio vrijednost. Na primjer, kada je riječ o euru, otkako je Evropska centralna banka počela intenzivno da doštampava novac svake godine, pa je od 2009. kada je program tzv. „kvantitativnog popuštanja“ započet euro zabilježio kumulativnu inflaciju od 42,09% zbog povećane količine sredstava u opticaju.
Međutim, kada je riječ o bitcoinu, njega nikada neće biti više od 21 milion koliko je izdato prvog dana, a to nepromjenjivo pravilo zapisano je i u njegovom kodu. Ova ograničena ponuda oštro se suprotstavlja principima koji važe kod monetarnih institucija, poput centralnih banaka, koje doštampavaju novac, često da bi povećale količinu u opticaju i tako podstakle finansijske tokove, iako novac zbog toga gubi vrijednost. Nasuprot tome, bitcoin se zadržava na iznosu od 21 milion, pa je upravo ta konačnost osnova za njegovu deflatornu prirodu i mogućnost da vremenom dobija na vrijednosti.
Naravno, ovo ne znači da je cijena bitcoina predodređena da samo raste. Ona je zapravo prilično volatilna i oscilacije su česte, posebno ukoliko, na primjer, posmatramo odnos cijena unutar jedne godine ili nekoliko mjeseci, međutim, gledano sa vremenske distance od četiri do pet godina bilo koji uporedni period od nastanka bitcoina do danas upućuje na to da je cijena u međuvremenu porasla. Taj trend će se nastaviti, tako da, kao ni kada je riječ o drugim sredstvima, poput zlata ili nafte, nema mjesta konstatacijama da je „vrijeme niskih cijena prošlo“.
Šta zapravo znači ovaj dan?
Bitcoin Pizza Day je za mnoge prilika da saznaju ponešto novo o bitcoinu, jer tada imaju priliku da o njemu čuju detalje sa raznih strana, jer kako se ovaj događaj popularizuje stvaraju se i nove prilike za učenje. Takođe, ovaj dan od 2021. obilježavaju picerije širom svijeta, u više od 400 gradova iz najmanje 75 zemalja, jer je za mnoge ovo prilika da korisnike bitcoina navedu da potroše djelić svoje imovine na nešto iz njihove ponude. Naravno, taj iznos je danasd zanemarljivo mali, a cijena jedne pice danas je otprilike 0,00021 bitcoina.
No, dok picerije širom svijeta danas na zabavan način pokušavaju da dođu do novih gostiju, ovaj dan je za mnoge vlasnike bitcoina nešto poput opomene da svoje digitalne novčiće ipak ne treba trošiti na nešto potrošno, jer je budućnost nepredvidiva. Bitcoin Pizza Day je dan kada se ideja pretvorila u valutu, kada su linije koda postale sredstvo razmjene.
Prvi let avionom trajao je svega 12 sekundi, a u poređenju sa današnjim transkontinentalnim linijama to djeluje gotovo neuporedivo i čudno, međutim, od nečega je moralo početi. Porudžbina pice plaćene bitcoinom označile su početak razmjene ove vrste, dok se, na primjer, tokom jučerašnjeg dana obim plaćanja bitcoinom premašio 23 milijarde dolara. Nauka i tehnologija nas podsjećaju na to da sve počinje malim, zanemarivim koracima.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:53:16
@ 6d5c826a:4b27b659
2025-05-23 21:53:16- DefGuard - True enterprise WireGuard with MFA/2FA and SSO. (Source Code)
Apache-2.0Rust - Dockovpn - Out-of-the-box stateless dockerized OpenVPN server which starts in less than 2 seconds. (Source Code)
GPL-2.0Docker - Firezone - WireGuard based VPN Server and Firewall. (Source Code)
Apache-2.0Docker - Gluetun VPN client - VPN client in a thin Docker container for multiple VPN providers, written in Go, and using OpenVPN or Wireguard, DNS over TLS, with a few proxy servers built-in.
MITdocker - Headscale - Self-hostable fork of Tailscale, cross-platform clients, simple to use, built-in (currently experimental) monitoring tools.
BSD-3-ClauseGo - Nebula - A scalable p2p VPN with a focus on performance, simplicity and security.
MITGo - ocserv - Cisco AnyConnect-compatible VPN server. (Source Code)
GPL-2.0C - OpenVPN - Uses a custom security protocol that utilizes SSL/TLS for key exchange. (Source Code)
GPL-2.0C - SoftEther - Multi-protocol software VPN with advanced features. (Source Code)
Apache-2.0C - sshuttle - Poor man's VPN.
LGPL-2.1Python - strongSwan - Complete IPsec implementation for Linux. (Source Code)
GPL-2.0C - WireGuard - Very fast VPN based on elliptic curve and public key crypto. (Source Code)
GPL-2.0C
- DefGuard - True enterprise WireGuard with MFA/2FA and SSO. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:52:59
@ 6d5c826a:4b27b659
2025-05-23 21:52:59- Ganeti - Cluster virtual server management software tool built on top of KVM and Xen. (Source Code)
BSD-2-ClausePython/Haskell - KVM - Linux kernel virtualization infrastructure. (Source Code)
GPL-2.0/LGPL-2.0C - OpenNebula - Build and manage enterprise clouds for virtualized services, containerized applications and serverless computing. (Source Code)
Apache-2.0C++ - oVirt - Manages virtual machines, storage and virtual networks. (Source Code)
Apache-2.0Java - Packer - A tool for creating identical machine images for multiple platforms from a single source configuration. (Source Code)
MPL-2.0Go - Proxmox VE - Virtualization management solution. (Source Code)
GPL-2.0Perl/Shell - QEMU - QEMU is a generic machine emulator and virtualizer. (Source Code)
LGPL-2.1C - Vagrant - Tool for building complete development environments. (Source Code)
BUSL-1.1Ruby - VirtualBox - Virtualization product from Oracle Corporation. (Source Code)
GPL-3.0/CDDL-1.0C++ - XCP-ng - Virtualization platform based on Xen Source and Citrix® Hypervisor (formerly XenServer). (Source Code)
GPL-2.0C - Xen - Virtual machine monitor for 32/64 bit Intel / AMD (IA 64) and PowerPC 970 architectures. (Source Code)
GPL-2.0C
- Ganeti - Cluster virtual server management software tool built on top of KVM and Xen. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:52:43
@ 6d5c826a:4b27b659
2025-05-23 21:52:43- Darcs - Cross-platform version control system, like git, mercurial or svn but with a very different approach: focus on changes rather than snapshots. (Source Code)
GPL-2.0Haskell - Fossil - Distributed version control with built-in wiki and bug tracking. (Source Code)
BSD-2-ClauseC - Git - Distributed revision control and source code management (SCM) with an emphasis on speed. (Source Code)
GPL-2.0C - Mercurial - Distributed source control management tool. (Source Code)
GPL-2.0Python/C/Rust - Subversion - Client-server revision control system. (Source Code)
Apache-2.0C
- Darcs - Cross-platform version control system, like git, mercurial or svn but with a very different approach: focus on changes rather than snapshots. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:52:26
@ 6d5c826a:4b27b659
2025-05-23 21:52:26- grml - Bootable Debian Live CD with powerful CLI tools. (Source Code)
GPL-3.0Shell - mitmproxy - A Python tool used for intercepting, viewing and modifying network traffic. Invaluable in troubleshooting certain problems. (Source Code)
MITPython - mtr - Network utility that combines traceroute and ping. (Source Code)
GPL-2.0C - Sysdig - Capture system state and activity from a running Linux instance, then save, filter and analyze. (Source Code)
Apache-2.0Docker/Lua/C - Wireshark - The world's foremost network protocol analyzer. (Source Code)
GPL-2.0C
- grml - Bootable Debian Live CD with powerful CLI tools. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:52:06
@ 6d5c826a:4b27b659
2025-05-23 21:52:06- Docker Compose - Define and run multi-container Docker applications. (Source Code)
Apache-2.0Go - Docker Swarm - Manage cluster of Docker Engines. (Source Code)
Apache-2.0Go - Docker - Platform for developers and sysadmins to build, ship, and run distributed applications. (Source Code)
Apache-2.0Go - LXC - Userspace interface for the Linux kernel containment features. (Source Code)
GPL-2.0C - LXD - Container "hypervisor" and a better UX for LXC. (Source Code)
Apache-2.0Go - OpenVZ - Container-based virtualization for Linux. (Source Code)
GPL-2.0C - Podman - Daemonless container engine for developing, managing, and running OCI Containers on your Linux System. Containers can either be run as root or in rootless mode. Simply put:
alias docker=podman. (Source Code)Apache-2.0Go - Portainer Community Edition - Simple management UI for Docker. (Source Code)
ZlibGo - systemd-nspawn - Lightweight, chroot-like, environment to run an OS or command directly under systemd. (Source Code)
GPL-2.0C
- Docker Compose - Define and run multi-container Docker applications. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:49:50
@ 6d5c826a:4b27b659
2025-05-23 21:49:50- Consul - Consul is a tool for service discovery, monitoring and configuration. (Source Code)
MPL-2.0Go - etcd - Distributed K/V-Store, authenticating via SSL PKI and a REST HTTP Api for shared configuration and service discovery. (Source Code)
Apache-2.0Go - ZooKeeper - ZooKeeper is a centralized service for maintaining configuration information, naming, providing distributed synchronization, and providing group services. (Source Code)
Apache-2.0Java/C++
- Consul - Consul is a tool for service discovery, monitoring and configuration. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:49:30
@ 6d5c826a:4b27b659
2025-05-23 21:49:30- DD-WRT - A Linux-based firmware for wireless routers and access points, originally designed for the Linksys WRT54G series. (Source Code)
GPL-2.0C - OpenWrt - A Linux-based router featuring Mesh networking, IPS via snort and AQM among many other features. (Source Code)
GPL-2.0C - OPNsense - An open source FreeBSD-based firewall and router with traffic shaping, load balancing, and virtual private network capabilities. (Source Code)
BSD-2-ClauseC/PHP - pfSense CE - Free network firewall distribution, based on the FreeBSD operating system with a custom kernel and including third party free software packages for additional functionality. (Source Code)
Apache-2.0Shell/PHP/Other
- DD-WRT - A Linux-based firmware for wireless routers and access points, originally designed for the Linksys WRT54G series. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:49:12
@ 6d5c826a:4b27b659
2025-05-23 21:49:12- Remmina - Feature-rich remote desktop application for linux and other unixes. (Source Code)
GPL-2.0C - Tiger VNC - High-performance, multi-platform VNC client and server. (Source Code)
GPL-2.0C++ - X2go - X2Go is an open source remote desktop software for Linux that uses the NoMachine/NX technology protocol. (Source Code)
GPL-2.0Perl
- Remmina - Feature-rich remote desktop application for linux and other unixes. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:56
@ 6d5c826a:4b27b659
2025-05-23 21:48:56- ActiveMQ - Java message broker. (Source Code)
Apache-2.0Java - BeanstalkD - A simple, fast work queue. (Source Code)
MITC - Gearman - Fast multi-language queuing/job processing platform. (Source Code)
BSD-3-ClauseC++ - NSQ - A realtime distributed messaging platform. (Source Code)
MPL-2.0Go - ZeroMQ - Lightweight queuing system. (Source Code)
GPL-3.0C++
- ActiveMQ - Java message broker. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:36
@ 6d5c826a:4b27b659
2025-05-23 21:48:36- aptly - Swiss army knife for Debian repository management. (Source Code)
MITGo - fpm - Versatile multi format package creator. (Source Code)
MITRuby - omnibus-ruby - Easily create full-stack installers for your project across a variety of platforms.
Apache-2.0Ruby - tito - Builds RPMs for git-based projects.
GPL-2.0Python
- aptly - Swiss army knife for Debian repository management. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:21
@ 6d5c826a:4b27b659
2025-05-23 21:48:21- CapRover - Build your own PaaS in a few minutes. (Demo, Source Code)
Apache-2.0Docker/Nodejs - Coolify - An open-source & self-hostable Heroku / Netlify alternative (and even more). (Source Code)
Apache-2.0Docker - Dokku - An open-source PaaS (alternative to Heroku). (Source Code)
MITDocker/Shell/Go/deb - fx - A tool to help you do Function as a Service with painless on your own servers.
MITGo - Kubero - A self-hosted Heroku PaaS alternative for Kubernetes that implements GitOps. (Demo, Source Code)
GPL-3.0K8S/Nodejs/Go - LocalStack - LocalStack is a fully functional local AWS cloud stack. This includes Lambda for serverless computation. (Source Code)
Apache-2.0Python/Docker/K8S - Nhost - Firebase Alternative with GraphQL. Get a database and backend configured and ready in minutes. (Source Code)
MITDocker/Nodejs/Go - OpenFaaS - Serverless Functions Made Simple for Docker & Kubernetes. (Source Code)
MITGo - Tau - Easily build Cloud Computing Platforms with features like Serverless WebAssembly Functions, Frontend Hosting, CI/CD, Object Storage, K/V Database, and Pub-Sub Messaging. (Source Code)
BSD-3-ClauseGo/Rust/Docker - Trusted-CGI - Lightweight self-hosted lambda/applications/cgi/serverless-functions platform.
MITGo/deb/Docker
- CapRover - Build your own PaaS in a few minutes. (Demo, Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:04
@ 6d5c826a:4b27b659
2025-05-23 21:48:04- GNS3 - Graphical network simulator that provides a variety of virtual appliances. (Source Code)
GPL-3.0Python - OpenWISP - Open Source Network Management System for OpenWRT based routers and access points. (Demo, Source Code)
GPL-3.0Python - Oxidized - Network device configuration backup tool.
Apache-2.0Ruby - phpIPAM - Open source IP address management with PowerDNS integration. (Source Code)
GPL-3.0PHP - RANCID - Monitor network devices configuration and maintain history of changes. (Source Code)
BSD-3-ClausePerl/Shell - rConfig - Network device configuration management tool. (Source Code)
GPL-3.0PHP
- GNS3 - Graphical network simulator that provides a variety of virtual appliances. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:44
@ 6d5c826a:4b27b659
2025-05-23 21:47:44- Adagios - Web based Nagios interface for configuration and monitoring (replacement to the standard interface), and a REST interface. (Source Code)
AGPL-3.0Docker/Python - Alerta - Distributed, scalable and flexible monitoring system. (Source Code)
Apache-2.0Python - Beszel - Lightweight server monitoring platform that includes Docker statistics, historical data, and alert functions. (Source Code)
MITGo - Cacti - Web-based network monitoring and graphing tool. (Source Code)
GPL-2.0PHP - cadvisor - Analyzes resource usage and performance characteristics of running containers.
Apache-2.0Go - checkmk - Comprehensive solution for monitoring of applications, servers, and networks. (Source Code)
GPL-2.0Python/PHP - dashdot - A simple, modern server dashboard for smaller private servers. (Demo)
MITNodejs/Docker - EdMon - A command-line monitoring application helping you to check that your hosts and services are available, with notifications support.
MITJava - eZ Server Monitor - A lightweight and simple dashboard monitor for Linux, available in Web and Bash application. (Source Code)
GPL-3.0PHP/Shell - glances - Open-source, cross-platform real-time monitoring tool with CLI and web dashboard interfaces and many exporting options. (Source Code)
GPL-3.0Python - Healthchecks - Monitoring for cron jobs, background services and scheduled tasks. (Source Code)
BSD-3-ClausePython - Icinga - Nagios fork that has since lapped nagios several times. Comes with the possibility of clustered monitoring. (Source Code)
GPL-2.0C++ - LibreNMS - Fully featured network monitoring system that provides a wealth of features and device support. (Source Code)
GPL-3.0PHP - Linux Dash - A low-overhead monitoring web dashboard for a GNU/Linux machine.
MITNodejs/Go/Python/PHP - Monit - Small utility for managing and monitoring Unix systems. (Source Code)
AGPL-3.0C - Munin - Networked resource monitoring tool. (Source Code)
GPL-2.0Perl/Shell - Naemon - Network monitoring tool based on the Nagios 4 core with performance enhancements and new features. (Source Code)
GPL-2.0C - Nagios - Computer system, network and infrastructure monitoring software application. (Source Code)
GPL-2.0C - Netdata - Distributed, real-time, performance and health monitoring for systems and applications. Runs on Linux, FreeBSD, and MacOS. (Source Code)
GPL-3.0C - NetXMS - Open Source network and infrastructure monitoring and management. (Source Code)
LGPL-3.0/GPL-3.0Java/C++/C - Observium Community Edition - Network monitoring and management platform that provides real-time insight into network health and performance.
QPL-1.0PHP - openITCOCKPIT Community Edition - Monitoring Suite featuring seamless integrations with Naemon, Checkmk, Grafana and more. (Demo, Source Code)
GPL-3.0deb/Docker - Performance Co-Pilot - Lightweight, distributed system performance and analysis framework. (Source Code)
LGPL-2.1/GPL-2.0C - PHP Server Monitor - Open source tool to monitor your servers and websites. (Source Code)
GPL-3.0PHP - PhpSysInfo - A customizable PHP script that displays information about your system nicely. (Source Code)
GPL-2.0PHP - Prometheus - Service monitoring system and time series database. (Source Code)
Apache-2.0Go - Riemann - Flexible and fast events processor allowing complex events/metrics analysis. (Source Code)
EPL-1.0Java - rtop - Interactive, remote system monitoring tool based on SSH.
MITGo - ruptime - Classic system status server.
AGPL-3.0Shell - Scrutiny - Web UI for hard drive S.M.A.R.T monitoring, historical trends & real-world failure thresholds.
MITGo - Sensu - Monitoring tool for ephemeral infrastructure and distributed applications. (Source Code)
MITGo - Status - Simple and lightweight system monitoring tool for small homeservers with a pleasant web interface. (Demo
MITPython - Thruk - Multibackend monitoring web interface with support for Naemon, Nagios, Icinga and Shinken. (Source Code)
GPL-1.0Perl - Wazuh - Unified XDR and SIEM protection for endpoints and cloud workloads. (Source Code)
GPL-2.0C - Zabbix - Enterprise-class software for monitoring of networks and applications. (Source Code)
GPL-2.0C
- Adagios - Web based Nagios interface for configuration and monitoring (replacement to the standard interface), and a REST interface. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:22
@ 6d5c826a:4b27b659
2025-05-23 21:47:22- Chocolatey - The package manager for Windows. (Source Code)
Apache-2.0C#/PowerShell - Clonezilla - Partition and disk imaging/cloning program. (Source Code)
GPL-2.0Perl/Shell/Other - DadaMail - Mailing List Manager, written in Perl. (Source Code)
GPL-2.0Perl - Fog - Cloning/imaging solution/rescue suite. (Source Code)
GPL-3.0PHP/Shell - phpList - Newsletter and email marketing software. (Source Code)
AGPL-3.0PHP
- Chocolatey - The package manager for Windows. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:03
@ 6d5c826a:4b27b659
2025-05-23 21:47:03- Beats - Single-purpose data shippers that send data from hundreds or thousands of machines and systems to Logstash or Elasticsearch. (Source Code)
Apache-2.0Go - Collectd - System statistics collection daemon. (Source Code)
MITC - Diamond - Daemon that collects system metrics and publishes them to Graphite (and others).
MITPython - Grafana - A Graphite & InfluxDB Dashboard and Graph Editor. (Source Code)
AGPL-3.0Go - Graphite - Scalable graphing server. (Source Code)
Apache-2.0Python - RRDtool - Industry standard, high performance data logging and graphing system for time series data. (Source Code)
GPL-2.0C - Statsd - Daemon that listens for statistics like counters and timers, sent over UDP or TCP, and sends aggregates to one or more pluggable backend services.
MITNodejs - tcollector - Gathers data from local collectors and pushes the data to OpenTSDB. (Source Code)
LGPL-3.0/GPL-3.0Python - Telegraf - Plugin-driven server agent for collecting, processing, aggregating, and writing metrics.
MITGo
- Beats - Single-purpose data shippers that send data from hundreds or thousands of machines and systems to Logstash or Elasticsearch. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:46
@ 6d5c826a:4b27b659
2025-05-23 21:46:46- aerc - Terminal MUA with a focus on plaintext and features for developers. (Source Code)
MITGo - Claws Mail - Old school email client (and news reader), based on GTK+. (Source Code)
GPL-3.0C - ImapSync - Simple IMAP migration tool for copying mailboxes to other servers. (Source Code)
NLPLPerl - Mutt - Small but very powerful text-based mail client. (Source Code)
GPL-2.0C - Sylpheed - Still developed predecessor to Claws Mail, lightweight mail client. (Source Code)
GPL-2.0C - Thunderbird - Free email application that's easy to set up and customize. (Source Code)
MPL-2.0C/C++
- aerc - Terminal MUA with a focus on plaintext and features for developers. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:28
@ 6d5c826a:4b27b659
2025-05-23 21:46:28- Fluentd - Data collector for unified logging layer. (Source Code)
Apache-2.0Ruby - Flume - Distributed, reliable, and available service for efficiently collecting, aggregating, and moving large amounts of log data. (Source Code)
Apache-2.0Java - GoAccess - Real-time web log analyzer and interactive viewer that runs in a terminal or through the browser. (Source Code)
MITC - Loki - Log aggregation system designed to store and query logs from all your applications and infrastructure. (Source Code)
AGPL-3.0Go - rsyslog - Rocket-fast system for log processing. (Source Code)
GPL-3.0C
- Fluentd - Data collector for unified logging layer. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:11
@ 6d5c826a:4b27b659
2025-05-23 21:46:11- GLPI - Information Resource-Manager with an additional Administration Interface. (Source Code)
GPL-3.0PHP - OCS Inventory NG - Asset management and deployment solution for all devices in your IT Department. (Source Code)
GPL-2.0PHP/Perl - OPSI - Hardware and software inventory, client management, deployment, and patching for Linux and Windows. (Source Code)
GPL-3.0/AGPL-3.0OVF/Python - RackTables - Datacenter and server room asset management like document hardware assets, network addresses, space in racks, networks configuration. (Demo, Source Code)
GPL-2.0PHP - Ralph - Asset management, DCIM and CMDB system for large Data Centers as well as smaller LAN networks. (Demo, Source Code)
Apache-2.0Python/Docker - Snipe IT - Asset & license management software. (Source Code)
AGPL-3.0PHP
- GLPI - Information Resource-Manager with an additional Administration Interface. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:45:53
@ 6d5c826a:4b27b659
2025-05-23 21:45:53- BounCA - A personal SSL Key / Certificate Authority web-based tool for creating self-signed certificates. (Source Code)
Apache-2.0Python - easy-rsa - Bash script to build and manage a PKI CA.
GPL-2.0Shell - Fusion Directory - Improve the Management of the services and the company directory based on OpenLDAP. (Source Code)
GPL-2.0PHP - LDAP Account Manager (LAM) - Web frontend for managing entries (e.g. users, groups, DHCP settings) stored in an LDAP directory. (Source Code)
GPL-3.0PHP - Libravatar - Libravatar is a service which delivers your avatar (profile picture) to other websites. (Source Code)
AGPL-3.0Python - Pomerium - An identity and context aware access-proxy inspired by BeyondCorp. (Source Code)
Apache-2.0Docker/Go - Samba - Active Directory and CIFS protocol implementation. (Source Code)
GPL-3.0C - Smallstep Certificates - A private certificate authority (X.509 & SSH) and related tools for secure automated certificate management. (Source Code)
Apache-2.0Go - ZITADEL - Cloud-native Identity & Access Management solution providing a platform for secure authentication, authorization and identity management. (Source Code)
Apache-2.0Go/Docker/K8S
- BounCA - A personal SSL Key / Certificate Authority web-based tool for creating self-signed certificates. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:45:34
@ 6d5c826a:4b27b659
2025-05-23 21:45:34- Authelia - The Single Sign-On Multi-Factor portal for web apps. (Source Code)
Apache-2.0Go - Authentik - Flexible identity provider with support for different protocols. (OAuth 2.0, SAML, LDAP and Radius). (Source Code)
MITPython - KeyCloak - Open Source Identity and Access Management. (Source Code)
Apache-2.0Java
- Authelia - The Single Sign-On Multi-Factor portal for web apps. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:45:15
@ 6d5c826a:4b27b659
2025-05-23 21:45:15- 389 Directory Server - Enterprise-class Open Source LDAP server for Linux. (Source Code)
GPL-3.0C - Apache Directory Server - Extensible and embeddable directory server, certified LDAPv3 compatible, with Kerberos 5 and Change Password Protocol support, triggers, stored procedures, queues and views. (Source Code)
Apache-2.0Java - FreeIPA - Integrated security information management solution combining Linux (Fedora), 389 Directory Server, Kerberos, NTP, DNS, and Dogtag Certificate System (web interface and command-line administration tools). (Source Code)
GPL-3.0Python/C/JavaScript - FreeRADIUS - Multi-protocol policy server (radiusd) that implements RADIUS, DHCP, BFD, and ARP and associated client/PAM library/Apache module. (Source Code)
GPL-2.0C - lldap - Light (simplified) LDAP implementation with a simple, intuitive web interface and GraphQL support.
GPL-3.0Rust - OpenLDAP - Open-source implementation of the Lightweight Directory Access Protocol (server, libraries and clients). (Source Code)
OLDAP-2.8C
- 389 Directory Server - Enterprise-class Open Source LDAP server for Linux. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:44:57
@ 6d5c826a:4b27b659
2025-05-23 21:44:57- Atom Community - A fork of atom A hackable text editor from Github.
MITJavaScript - Brackets - Code editor for web designers and front-end developers. (Source Code)
MITJavaScript - Eclipse - IDE written in Java with an extensible plug-in system. (Source Code)
EPL-1.0Java - Geany - GTK2 text editor. (Source Code)
GPL-2.0C/C++ - GNU Emacs - An extensible, customizable text editor-and more. (Source Code)
GPL-3.0C - Haroopad - Markdown editor with live preview. (Source Code)
GPL-3.0JavaScript - jotgit - Git-backed real-time collaborative code editing.
MITNodejs - KDevelop - IDE by the people behind KDE. (Source Code)
GFDL-1.2C++ - Micro - A modern and intuitive terminal-based text editor. (Source Code)
MITGo - Nano - Easy to use, customizable text editor. (Source Code)
GPL-3.0C - Notepad++ - GPLv2 multi-language editor with syntax highlighting for Windows. (Source Code)
GPL-2.0C++ - TextMate - A graphical text editor for OS X. (Source Code)
GPL-3.0C++ - Vim - A highly configurable text editor built to enable efficient editing. (Source Code)
VimC - VSCodium - An open source cross-platform extensible code editor based on VS Code by Microsoft removing their non-free additions. (Source Code)
MITTypeScript
- Atom Community - A fork of atom A hackable text editor from Github.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:44:34
@ 6d5c826a:4b27b659
2025-05-23 21:44:34- Bind - Versatile, classic, complete name server software. (Source Code)
MPL-2.0C - CoreDNS - Flexible DNS server. (Source Code)
Apache-2.0Go - djbdns - A collection of DNS applications, including tinydns. (Source Code)
CC0-1.0C - dnsmasq - Provides network infrastructure for small networks: DNS, DHCP, router advertisement and network boot. (Source Code)
GPL-2.0C - Knot - High performance authoritative-only DNS server. (Source Code)
GPL-3.0C - NSD - Authoritative DNS name server developed speed, reliability, stability and security. (Source Code)
BSD-3-ClauseC - PowerDNS Authoritative Server - Versatile nameserver which supports a large number of backends. (Source Code)
GPL-2.0C++ - Unbound - Validating, recursive, and caching DNS resolver. (Source Code)
BSD-3-ClauseC - Yadifa - Clean, small, light and RFC-compliant name server implementation developed from scratch by .eu. (Source Code)
BSD-3-ClauseC
- Bind - Versatile, classic, complete name server software. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:44:16
@ 6d5c826a:4b27b659
2025-05-23 21:44:16- Atomia DNS - DNS management system.
ISCPerl - Designate - DNSaaS services for OpenStack. (Source Code)
Apache-2.0Python - DNSControl - Synchronize your DNS to multiple providers from a simple DSL. (Source Code)
MITGo/Docker - DomainMOD - Manage your domains and other internet assets in a central location. (Source Code)
GPL-3.0PHP - nsupdate.info - Dynamic DNS service. (Demo, Source Code)
BSD-3-ClausePython - octoDNS - DNS as code - Tools for managing DNS across multiple providers.
MITPython - Poweradmin - Web-based DNS control panel for PowerDNS server. (Source Code)
GPL-3.0PHP - SPF Toolbox - Application to look up DNS records such as SPF, MX, Whois, and more. (Source Code)
MITPHP
- Atomia DNS - DNS management system.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:43:55
@ 6d5c826a:4b27b659
2025-05-23 21:43:55- Ceph - Distributed object, block, and file storage platform. (Source Code)
LGPL-3.0C++ - DRBD - Distributed replicated storage system, implemented as a Linux kernel driver. (Source Code)
GPL-2.0C - GlusterFS - Software-defined distributed storage that can scale to several petabytes, with interfaces for object, block and file storage. (Source Code)
GPL-2.0/LGPL-3.0C - Hadoop Distributed Filesystem (HDFS) - Distributed file system that provides high-throughput access to application data. (Source Code)
Apache-2.0Java - JuiceFS - Distributed POSIX file system built on top of Redis and S3. (Source Code)
Apache-2.0Go - Kubo - Implementation of IPFS, a global, versioned, peer-to-peer filesystem that seeks to connect all computing devices with the same system of files.
Apache-2.0/MITGo - LeoFS - Highly available, distributed, replicated eventually consistent object/blob store. (Source Code)
Apache-2.0Erlang - Lustre - Parallel distributed file system, generally used for large-scale cluster computing. (Source Code)
GPL-2.0C - Minio - High-performance, S3 compatible object store built for large scale AI/ML, data lake and database workloads. (Source Code)
AGPL-3.0Go - MooseFS - Fault tolerant, network distributed file system. (Source Code)
GPL-2.0C - OpenAFS - Distributed network file system with read-only replicas and multi-OS support. (Source Code)
IPL-1.0C - Openstack Swift - A highly available, distributed, eventually consistent object/blob store. (Source Code)
Apache-2.0Python - Perkeep - A set of open source formats, protocols, and software for modeling, storing, searching, sharing and synchronizing data (previously Camlistore). (Source Code)
Apache-2.0C - TahoeLAFS - Secure, decentralized, fault-tolerant, peer-to-peer distributed data store and distributed file system. (Source Code)
GPL-2.0Python - XtreemFS - Distributed, replicated and fault-tolerant file system for federated IT infrastructures.. (Source Code)
BSD-3-ClauseJava
- Ceph - Distributed object, block, and file storage platform. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:43:37
@ 6d5c826a:4b27b659
2025-05-23 21:43:37- Diagrams.net - A.K.A. Draw.io. Easy to use Diagram UI with a plethora of templates. (Source Code)
Apache-2.0JavaScript/Docker - Kroki - API for generating diagrams from textual descriptions. (Source Code)
MITJava - Mermaid - Javascript module with a unique, easy, shorthand syntax. Integrates into several other tools like Grafana. (Source Code)
MITNodejs/Docker
- Diagrams.net - A.K.A. Draw.io. Easy to use Diagram UI with a plethora of templates. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:43:11
@ 6d5c826a:4b27b659
2025-05-23 21:43:11- Capistrano - Deploy your application to any number of machines simultaneously, in sequence or as a rolling set via SSH (rake based). (Source Code)
MITRuby - CloudSlang - Flow-based orchestration tool for managing deployed applications, with Docker capabilities. (Source Code)
Apache-2.0Java - CloudStack - Cloud computing software for creating, managing, and deploying infrastructure cloud services. (Source Code)
Apache-2.0Java/Python - Cobbler - Cobbler is a Linux installation server that allows for rapid setup of network installation environments. (Source Code)
GPL-2.0Python - Fabric - Python library and cli tool for streamlining the use of SSH for application deployment or systems administration tasks. (Source Code)
BSD-2-ClausePython - Genesis - A template framework for multi-environment BOSH deployments.
MITPerl - munki - Webserver-based repository of packages and package metadata, that allows macOS administrators to manage software installs. (Source Code)
Apache-2.0Python - Overcast - Deploy VMs across different cloud providers, and run commands and scripts across any or all of them in parallel via SSH. (Source Code)
MITNodejs
- Capistrano - Deploy your application to any number of machines simultaneously, in sequence or as a rolling set via SSH (rake based). (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:42:54
@ 6d5c826a:4b27b659
2025-05-23 21:42:54- Ajenti - Control panel for Linux and BSD. (Source Code)
MITPython/Shell - Cockpit - Web-based graphical interface for servers. (Source Code)
LGPL-2.1C - Froxlor - Lightweight server management software with Nginx and PHP-FPM support. (Source Code)
GPL-2.0PHP - HestiaCP - Web server control panel (fork of VestaCP). (Demo, Source Code)
GPL-3.0PHP/Shell/Other - ISPConfig - Manage Linux servers directly through your browser. (Source Code)
BSD-3-ClausePHP - Sentora - Open-Source Web hosting control panel for Linux, BSD (fork of ZPanel). (Source Code)
GPL-3.0PHP - Virtualmin - Powerful and flexible web hosting control panel for Linux and BSD systems. (Source Code)
GPL-3.0Shell/Perl/Other - Webmin - Web-based interface for system administration for Unix. (Source Code)
BSD-3-ClausePerl
- Ajenti - Control panel for Linux and BSD. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:42:36
@ 6d5c826a:4b27b659
2025-05-23 21:42:36- Buildbot - Python-based toolkit for continuous integration. (Source Code)
GPL-2.0Python - CDS - Enterprise-Grade Continuous Delivery & DevOps Automation Open Source Platform. (Source Code)
BSD-3-ClauseGo - Concourse - Concourse is a CI tool that treats pipelines as first class objects and containerizes every step along the way. (Demo, Source Code)
Apache-2.0Go - drone - Drone is a Continuous Delivery platform built on Docker, written in Go. (Source Code)
Apache-2.0Go - Factor - Programmatically define and run workflows to connect configuration management, source code management, build, continuous integration, continuous deployment and communication tools. (Source Code)
MITRuby - GitLab CI - Gitlab's built-in, full-featured CI/CD solution. (Source Code)
MITRuby - GoCD - Continuous delivery server. (Source Code)
Apache-2.0Java/Ruby - Jenkins - Continuous Integration Server. (Source Code)
MITJava - Laminar - Fast, lightweight, simple and flexible Continuous Integration. (Source Code)
GPL-3.0C++ - PHP Censor - Open source self-hosted continuous integration server for PHP projects.
BSD-2-ClausePHP - Strider - Open Source Continuous Deployment / Continuous Integration platform. (Source Code)
MITNodejs - Terrateam - GitOps-first automation platform for Terraform and OpenTofu workflows with support for self-hosted runners. (Source Code)
MPL-2.0OCaml/Docker - werf - Open Source CI/CD tool for building Docker images and deploying to Kubernetes via GitOps. (Source Code)
Apache-2.0Go - Woodpecker - Community fork of Drone that uses Docker containers. (Source Code)
Apache-2.0Go
- Buildbot - Python-based toolkit for continuous integration. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:42:17
@ 6d5c826a:4b27b659
2025-05-23 21:42:17- Collins - At Tumblr, it's the infrastructure source of truth and knowledge. (Source Code)
Apache-2.0Docker/Scala - i-doit - IT Documentation and CMDB.
AGPL-3.0PHP - iTop - Complete ITIL web based service management tool. (Source Code)
AGPL-3.0PHP - netbox - IP address management (IPAM) and data center infrastructure management (DCIM) tool. (Demo, Source Code)
Apache-2.0Python
- Collins - At Tumblr, it's the infrastructure source of truth and knowledge. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:41:59
@ 6d5c826a:4b27b659
2025-05-23 21:41:59- Ansible - Provisioning, configuration management, and application-deployment tool. (Source Code)
GPL-3.0Python - CFEngine - Configuration management system for automated configuration and maintenance of large-scale computer systems. (Source Code)
GPL-3.0C - Chef - Configuration management tool using a pure-Ruby, domain-specific language (DSL) for writing system configuration "recipes". (Source Code)
Apache-2.0Ruby - cloud-init - Initialization tool to automate the configuration of VMs, cloud instances, or machines on a network. (Source Code)
GPL-3.0/Apache-2.0Python - Puppet - Software configuration management tool which includes its own declarative language to describe system configuration. (Source Code)
Apache-2.0Ruby/C - Rudder - Scalable and dynamic configuration management system for patching, security & compliance, based on CFEngine. (Source Code)
GPL-3.0Scala - Salt - Event-driven IT automation, remote task execution, and configuration management software. (Source Code)
Apache-2.0Python
- Ansible - Provisioning, configuration management, and application-deployment tool. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:41:37
@ 6d5c826a:4b27b659
2025-05-23 21:41:37- Eggdrop - The oldest Internet Relay Chat (IRC) bot still in active development. (Source Code)
GPL-2.0C - Errbot - Plugin based chatbot designed to be easily deployable, extensible and maintainable. (Source Code)
GPL-3.0Python - Hubot - A customizable, life embetterment robot. (Source Code)
MITNodejs
- Eggdrop - The oldest Internet Relay Chat (IRC) bot still in active development. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:41:18
@ 6d5c826a:4b27b659
2025-05-23 21:41:18- EasyBuild - EasyBuild builds software and modulefiles for High Performance Computing (HPC) systems in an efficient way. (Source Code)
GPL-2.0Python - Environment Modules - Environment Modules provides for the dynamic modification of a user's environment via modulefiles. (Source Code)
GPL-2.0Tcl - Lmod - Lmod is a Lua based module system that easily handles the MODULEPATH Hierarchical problem. (Source Code)
MITLua - Spack - A flexible package manager that supports multiple versions, configurations, platforms, and compilers. (Source Code)
MIT/Apache-2.0Python
- EasyBuild - EasyBuild builds software and modulefiles for High Performance Computing (HPC) systems in an efficient way. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:40:57
@ 6d5c826a:4b27b659
2025-05-23 21:40:57- Backupninja - Lightweight, extensible meta-backup system, provides a centralized way to configure and coordinate many different backup utilities.
GPL-2.0Shell - Backrest - Backrest is a web UI and orchestrator for restic backup. (Source Code)
GPL-3.0Docker/Go - Bareos - Cross-network backup solution which preserves, archives, and recovers data from all major operating systems. (Source Code)
AGPL-3.0C++/C - Barman - Backup and Recovery Manager for PostgreSQL. (Source Code)
GPL-3.0Python - BorgBackup - Deduplicating archiver with compression and authenticated encryption. (Source Code)
BSD-3-ClausePython - Burp - Network backup and restore program. (Source Code)
AGPL-3.0C - Dar - Which stands for Disk ARchive, is a robust and rich featured archiving and backup software of the tar style. (Source Code)
GPL-2.0C++ - Duplicati - Backup client that securely stores encrypted, incremental, compressed backups on cloud storage services and remote file servers. (Source Code)
LGPL-2.1C# - Duplicity - Encrypted bandwidth-efficient backup using the rsync algorithm. (Source Code)
GPL-2.0Python - Proxmox Backup Server - Proxmox Backup Server is an enterprise-class, client-server backup solution thatis capable of backing up virtual machines, containers, and physical hosts. (Source Code)
GPL-3.0Rust - rclone - Command-line program to sync files and directories to and from different cloud storage providers.. (Source Code)
MITGo - Rdiff-backup - Reverse differential backup tool, over a network or locally. (Source Code)
GPL-2.0Python - Restic - Easy, fast, verifiable, secure and efficient remote backup tool. (Source Code)
BSD-2-ClauseGo - Rsnapshot - Filesystem snapshot utility based on rsync. (Source Code)
GPL-2.0Perl - Shield - A pluggable architecture for backup and restore of database systems.
MITGo - UrBackup - Client/Server Open Source Network Backup for Windows, MacOS and Linux. (Source Code)
AGPL-3.0C/C++
- Backupninja - Lightweight, extensible meta-backup system, provides a centralized way to configure and coordinate many different backup utilities.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:40:34
@ 6d5c826a:4b27b659
2025-05-23 21:40:34- Apache Ant - Automation build tool, similar to make, a library and command-line tool whose mission is to drive processes described in build files as targets and extension points dependent upon each other. (Source Code)
Apache-2.0Java - Apache Maven - Build automation tool mainly for Java. A software project management and comprehension tool. Based on the concept of a project object model (POM), Maven can manage a project's build, reporting and documentation from a central piece of information. (Source Code)
Apache-2.0Java - Bazel - A fast, scalable, multi-language and extensible build system. Used by Google. (Source Code)
Apache-2.0Java - Bolt - You can use Bolt to run one-off tasks, scripts to automate the provisioning and management of some nodes, you can use Bolt to move a step beyond scripts, and make them shareable. (Source Code)
Apache-2.0Ruby - GNU Make - The most popular automation build tool for many purposes, make is a tool which controls the generation of executables and other non-source files of a program from the program's source files. (Source Code)
GPL-3.0C - Gradle - Another build automation system. (Source Code)
Apache-2.0Groovy/Java - Rake - Build automation tool similar to Make, written in and extensible in Ruby. (Source Code)
MITRuby
- Apache Ant - Automation build tool, similar to make, a library and command-line tool whose mission is to drive processes described in build files as targets and extension points dependent upon each other. (Source Code)
-
 @ 3c389c8f:7a2eff7f
2025-05-23 21:35:30
@ 3c389c8f:7a2eff7f
2025-05-23 21:35:30Web:
https://shopstr.store/
https://cypher.space/
https://plebeian.market/
Mobile:
https://www.amethyst.social/
-
 @ 3c389c8f:7a2eff7f
2025-05-23 21:27:26
@ 3c389c8f:7a2eff7f
2025-05-23 21:27:26Clients:
https://untype.app
https://habla.news
https://yakihonne.com
https://cypher.space
https://highlighter.com
https://pareto.space/en
https://comet.md/
Plug Ins:
https://github.com/jamesmagoo/nostr-writer
https://threenine.co.uk/products/obstrlish
Content Tagging:
https://labelmachine.org
https://ontolo.social
Blog-like Display and Personal Pages:
https://orocolo.me
https://npub.pro
Personal Notes and Messaging:
https://app.flotilla.social There's an app, too!
https://nosbin.com
RSS Readers:
https://nostrapps.com/noflux
https://nostrapps.com/narr
https://nostrapps.com/feeder
-
 @ 86611181:9fc27ad7
2025-05-23 20:31:44
@ 86611181:9fc27ad7
2025-05-23 20:31:44It's time to secure user data in your identity system This post was also published with the Industry Association of Privacy Professionals.
It seems like every day there is a new report of a major personal data breach. In just the past few months, Neiman Marcus, Ticketmaster, Evolve Bank, TeamViewer, Hubspot, and even the IRS have been affected.
The core issue is that user data is commonly spread across multiple systems that are increasingly difficult to fully secure, including database user tables, data warehouses and unstructured documents.
Most enterprises are already running an incredibly secure and hardened identity system to manage customer login and authorization, commonly referred to as a customer identity access management system. Since identity systems manage customer sign-up and sign-in, they typically contain customer names, email addresses, and phone numbers for multifactor authentication. Commercial CIAMs provide extensive logging, threat detection, availability and patch management.
Identity systems are highly secure and already store customers' personally identifiable information, so it stands to reason enterprises should consider identity systems to manage additional PII fields.
Identity systems are designed to store numerous PII fields and mask the fields for other systems. The Liberty Project developed the protocols that became Security Assertion Markup Language 2.0, the architecture at the core of CIAM systems, 20 years ago, when I was its chief technology officer. SAML 2.0 was built so identity data would be fully secure, and opaque tokens would be shared with other systems. Using tokens instead of actual user data is a core feature of identity software that can be used to fully secure user data across applications.
Most modern identity systems support adding additional customer fields, so it is easy to add new fields like Social Security numbers and physical addresses. Almost like a database, some identity systems even support additional tables and images.
A great feature of identity systems is that they often provide a full suite of user interface components for users to register, login and manage their profile fields. Moving fields like Social Security numbers from your database to your identity system means the identity system can fully manage the process of users entering, viewing and editing the field, and your existing application and database become descoped from managing sensitive data.
With sensitive fields fully isolated in an identity system and its user interface components, the identity system can provide for cumbersome and expensive compliance with standards such as the Health Insurance Portability and Accountability Act for medical data and the Payment Card Industry Data Security Standard for payment data, saving the time and effort to achieve similar compliance in your application.
There are, of course, applications that require sensitive data, such as customer service systems and data warehouses. Identity systems use a data distribution standard called System for Cross-domain Identity Management 2.0 to copy user data to other systems. The SCIM is a great standard to help manage compliance such as "right to be forgotten," because it can automatically delete customer data from other systems when a customer record is deleted from the identity system.
When copying customer data from an identity system to another application, consider anonymizing or masking fields. For example, anonymizing a birthdate into an age range when copying a customer record into a data warehouse can descope the data warehouse from containing personal information.
Most enterprises already run an Application Programming Interface Gateway to manage web services between systems. By combining an API Gateway with the identity system's APIs, it becomes very easy to automatically anonymize and mask customer data fields before they are copied into other systems.
A new set of companies including Baffle, Skyflow, and Piiano have introduced services that combine the governance and field management features of an identity system with extensive field masking. Since these systems do not offer the authentication and authorization features of an identity system, it's important to balance the additional features as they introduce an additional threat surface with PII storage and permissions.
PII sprawl is an increasing liability for companies. The most secure, compliant and flexible central data store to manage PII is the existing CIAM and API Gateway infrastructure that enterprises have already deployed.
Move that customer data into your identity system and lock it down. https://peter.layer3.press/articles/3c6912eb-404a-4630-9fe9-fd1bd23cfa64
-
 @ 1817b617:715fb372
2025-05-23 20:21:53
@ 1817b617:715fb372
2025-05-23 20:21:53🚀 Instantly Send Spendable Flash BTC, ETH, & USDT — Fully Blockchain-Verifiable!
Welcome to the cutting edge of crypto innovation: the ultimate tool for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Our advanced blockchain simulation technology employs 🔥 Race/Finney-style mechanisms, producing coins indistinguishable from authentic blockchain-confirmed tokens. Your transactions are instantly trackable and fully spendable for durations from 60 to 360 days!
🌐 Visit cryptoflashingtool.com for complete details.
🌟 Why Choose Our Crypto Flashing Service? Crypto Flashing is perfect for crypto enthusiasts, blockchain developers, ethical hackers, security professionals, and digital entrepreneurs looking for authenticity combined with unparalleled flexibility.
🎯 Our Crypto Flashing Features: ✅ Instant Blockchain Verification: Transactions appear completely authentic, complete with real blockchain confirmations, transaction IDs, and wallet addresses.
🔒 Maximum Security & Privacy: Fully compatible with VPNs, TOR, and proxy servers, ensuring absolute anonymity and protection.
🖥️ Easy-to-Use Software: Designed for Windows, our intuitive platform suits both beginners and experts, with detailed, step-by-step instructions provided.
📅 Customizable Flash Durations: Control your transaction lifespan precisely, from 60 to 360 days.
🔄 Universal Wallet Compatibility: Instantly flash BTC, ETH, and USDT tokens to SegWit, Legacy, or BCH32 wallets.
💱 Spendable on Top Exchanges: Flash coins seamlessly accepted on leading exchanges like Kraken and Huobi.
📊 Proven Track Record: ✅ Over 79 Billion flash transactions completed. ✅ 3000+ satisfied customers worldwide. ✅ 42 active blockchain nodes for fast, reliable transactions. 📌 Simple Step-by-Step Flashing Process: Step 1️⃣: Enter Transaction Details
Choose coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20) Specify amount & flash duration Provide wallet address (validated automatically) Step 2️⃣: Complete Payment & Verification
Pay using the cryptocurrency you wish to flash Scan the QR code or paste the payment address Upload payment proof (transaction hash & screenshot) Step 3️⃣: Initiate Flash Transaction
Our technology simulates blockchain confirmations instantly Flash transaction appears authentic within seconds Step 4️⃣: Verify & Spend Immediately
Access your flashed crypto instantly Easily verify transactions via provided blockchain explorer links 🛡️ Why Our Technology is Trusted: 🔗 Race/Finney Attack Logic: Creates realistic blockchain headers. 🖥️ Private iNode Cluster: Guarantees fast synchronization and reliable transactions. ⏰ Live Timer System: Ensures fresh wallet addresses and transaction legitimacy. 🔍 Genuine Blockchain TX IDs: Authentic transaction IDs included with every flash ❓ Frequently Asked Questions: Is flashing secure? ✅ Yes, encrypted with full VPN/proxy support. Can I flash from multiple devices? ✅ Yes, up to 5 Windows PCs per license. Are chargebacks possible? ❌ No, flash transactions are irreversible. How long are flash coins spendable? ✅ From 60–360 days, based on your chosen plan. Verification after expiry? ❌ Transactions can’t be verified after the expiry. Support available? ✅ Yes, 24/7 support via Telegram & WhatsApp.
🔐 Transparent, Reliable & Highly Reviewed:
CryptoFlashingTool.com operates independently, providing unmatched transparency and reliability. Check out our glowing reviews on ScamAdvisor and leading crypto forums!
📲 Get in Touch Now: 📞 WhatsApp: +1 770 666 2531 ✈️ Telegram: @cryptoflashingtool
🎉 Ready to Start?
💰 Buy Flash Coins Now 🖥️ Get Your Flashing Software
Experience the smartest, safest, and most powerful crypto flashing solution on the market today!
CryptoFlashingTool.com — Flash Crypto Like a Pro.
Instantly Send Spendable Flash BTC, ETH, & USDT — Fully Blockchain-Verifiable!
Welcome to the cutting edge of crypto innovation: the ultimate tool for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Our advanced blockchain simulation technology employs
Race/Finney-style mechanisms, producing coins indistinguishable from authentic blockchain-confirmed tokens. Your transactions are instantly trackable and fully spendable for durations from 60 to 360 days!
Visit cryptoflashingtool.com for complete details.
Why Choose Our Crypto Flashing Service?
Crypto Flashing is perfect for crypto enthusiasts, blockchain developers, ethical hackers, security professionals, and digital entrepreneurs looking for authenticity combined with unparalleled flexibility.
Our Crypto Flashing Features:
Instant Blockchain Verification: Transactions appear completely authentic, complete with real blockchain confirmations, transaction IDs, and wallet addresses.
Maximum Security & Privacy: Fully compatible with VPNs, TOR, and proxy servers, ensuring absolute anonymity and protection.
Easy-to-Use Software: Designed for Windows, our intuitive platform suits both beginners and experts, with detailed, step-by-step instructions provided.
Customizable Flash Durations: Control your transaction lifespan precisely, from 60 to 360 days.
Universal Wallet Compatibility: Instantly flash BTC, ETH, and USDT tokens to SegWit, Legacy, or BCH32 wallets.
Spendable on Top Exchanges: Flash coins seamlessly accepted on leading exchanges like Kraken and Huobi.
Proven Track Record:
- Over 79 Billion flash transactions completed.
- 3000+ satisfied customers worldwide.
- 42 active blockchain nodes for fast, reliable transactions.
Simple Step-by-Step Flashing Process:
Step : Enter Transaction Details
- Choose coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20)
- Specify amount & flash duration
- Provide wallet address (validated automatically)
Step : Complete Payment & Verification
- Pay using the cryptocurrency you wish to flash
- Scan the QR code or paste the payment address
- Upload payment proof (transaction hash & screenshot)
Step : Initiate Flash Transaction
- Our technology simulates blockchain confirmations instantly
- Flash transaction appears authentic within seconds
Step : Verify & Spend Immediately
- Access your flashed crypto instantly
- Easily verify transactions via provided blockchain explorer links
Why Our Technology is Trusted:
- Race/Finney Attack Logic: Creates realistic blockchain headers.
- Private iNode Cluster: Guarantees fast synchronization and reliable transactions.
- Live Timer System: Ensures fresh wallet addresses and transaction legitimacy.
- Genuine Blockchain TX IDs: Authentic transaction IDs included with every flash
Frequently Asked Questions:
- Is flashing secure?
Yes, encrypted with full VPN/proxy support. - Can I flash from multiple devices?
Yes, up to 5 Windows PCs per license. - Are chargebacks possible?
No, flash transactions are irreversible. - How long are flash coins spendable?
From 60–360 days, based on your chosen plan. - Verification after expiry?
Transactions can’t be verified after the expiry.
Support available?
Yes, 24/7 support via Telegram & WhatsApp.
Transparent, Reliable & Highly Reviewed:
CryptoFlashingTool.com operates independently, providing unmatched transparency and reliability. Check out our glowing reviews on ScamAdvisor and leading crypto forums!
Get in Touch Now:
WhatsApp: +1 770 666 2531
Telegram: @cryptoflashingtool
Ready to Start?
Experience the smartest, safest, and most powerful crypto flashing solution on the market today!
CryptoFlashingTool.com — Flash Crypto Like a Pro.
-
 @ 05a0f81e:fc032124
2025-05-23 19:50:46
@ 05a0f81e:fc032124
2025-05-23 19:50:46I was discussing with my friend and few of his friends about the inflation of naira in Nigeria 🇳🇬. Our discussions was flowing until he said that lack of production and too much importations are the major reason that devalued currencies, naira to be precise. As a baby bitcioner, I disagree with him and that's where our discussion turn to argument.
People often think that when a country prioritize productions than consumption that it will boost the value of there currency, but that is wrong. Production have it's impart on the economy of the country.
Increased Economic Growth: A trade surplus indicates that a country's output is high, contributing to overall economic growth, as measured by GDP.
Stimulated Consumer Spending: The influx of foreign currency from exports can be used to import goods, stimulating domestic demand and boosting consumer spending.
Potential for Higher Wages and Living Standards: Increased productivity and economic growth can lead to higher wages and a better standard of living.
Savings and Investment: The surplus can be used for savings, investment in infrastructure, or to reduce debt, further strengthening the economy.
Comparative Advantage: A country may specialize in producing goods and services where it has a comparative advantage, leading to higher productivity and efficiency.
Moreover, too production and exportation also causes inflation. country exports too much and its domestic demand doesn't keep pace, it could lead to inflation as businesses raise prices to cover increased production cost.
Meanwhile, the head lead of currency inflation is the printing of money in the air!.
"Printing money in the air" likely refers to the concept of central banks creating new money digitally, often through quantitative easing. This process involves the central bank buying assets, such as government bonds, from banks and other financial institutions, thereby injecting new money into the economy.
How it Works:
-
Digital Money Creation: The central bank creates new money electronically, rather than physically printing currency notes.
-
Asset Purchases: The central bank buys assets from banks and other financial institutions, injecting new money into the economy.
-
Increased Money Supply: This process expands the money supply, which can lead to lower interest rates and increased lending.
Key Points:
-
Quantitative Easing (QE): A monetary policy tool used by central banks to stimulate economic growth by buying assets and injecting new money into the economy.
-
No Physical Printing: Unlike traditional money printing, QE creates digital money, which is then used to purchase assets.
-
Impact on Economy: QE can influence interest rates, inflation, and economic growth.
The role of Central Bank's.
The central bank plays a crucial role in managing the money supply and implementing monetary policies, including QE. By controlling interest rates and the money supply, central banks aim to promote economic growth, stability, and low inflation.
There are key 🔑 negative effects of printing currency notes on air!:
Printing money, also known as quantitative easing, can have several negative effects on the economy. Some of the key concerns include;
-
Inflation: Excessive money printing can lead to inflation, as more money chases a constant amount of goods and services, driving up prices. This can erode the purchasing power of consumers and reduce the value of savings.
-
Currency Devaluation: Printing money can cause a decline in the value of a currency, making imports more expensive and potentially leading to higher prices for consumers.
-
Distorted Financial Markets: The injection of liquidity into the economy can artificially inflate asset prices, creating market distortions and potentially leading to asset bubbles.
-
Uncertainty and Confusion: High inflation can create uncertainty and confusion for businesses and individuals, making it harder to make informed investment decisions.
-
Reduced Incentive to Save: Inflation can reduce the incentive to save, as the value of money declines over time.
-
Menu Costs: High inflation can lead to menu costs, where businesses incur expenses to update prices frequently.
-
Inefficient Allocation of Resources: Government spending funded by printing money can lead to inefficient allocation of resources, as decisions are driven by politics rather than market forces.
-
Addiction to Fiscal Stimulus: The ease of printing money can create a dependency on fiscal stimulus, making it challenging to reverse course when economic conditions change.
-
Long-term Consequences: The long-term consequences of printing money can be severe, including reduced economic growth, higher inflation, and decreased confidence in the currency.
It's worth noting that the impact of printing money can vary depending on the economic context. In times of recession or deflation, moderate money printing might be used to stimulate economic growth without triggering significant inflation. However, excessive or prolonged money printing can lead to negative consequences.
-
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-23 19:32:28
@ 5d4b6c8d:8a1c1ee3
2025-05-23 19:32:28https://primal.net/e/nevent1qvzqqqqqqypzp6dtxy5uz5yu5vzxdtcv7du9qm9574u5kqcqha58efshkkwz6zmdqqszj207pl0eqkgld9vxknxamged64ch2x2zwhszupkut5v46vafuhg9833px
Some of my colleagues were talking about how they're even more scared of RFK Jr. than they are of Trump. I hope he earns it.
https://stacker.news/items/987685
-
 @ 56f27915:5fee3024
2025-05-23 18:51:08
@ 56f27915:5fee3024
2025-05-23 18:51:08Ralph Boes – Menschenrechtsaktivist, Philosoph, Vorstandsmitglied im Verein Unsere Verfassung e.V.
Ralph Boes zeigt in dem Buch auf, wie wir uns von der Übermacht des Parteienwesens, die zur Entmündigung des Volkes führt, befreien können. Er zeigt, dass schon im Grundgesetz selbst höchst gegenläufige, an seinen freiheitlich-demokratischen Idealen bemessen sogar als verfassungswidrig zu bezeichnende Tendenzen wirken. Und dass diese es sind, die heute in seine Zerstörung führen. Er weist aber auch die Ansatzpunkte auf, durch die der Zerstörung des Grundgesetzes wirkungsvoll begegnet werden kann.
Eintritt frei, Spendentopf
Ralph Boes hat u.a. dafür gesorgt, dass die unmäßigen Sanktionen in Hartz IV 2019 vom Bundesverfassungsgericht für menschenrechts- und verfassungswidrig erklärt wurden. Aktuell setzt er sich für eine Ur-Abstimmung des Volkes über seine Verfassung ein.
-
 @ 3c389c8f:7a2eff7f
2025-05-23 18:23:28
@ 3c389c8f:7a2eff7f
2025-05-23 18:23:28I've sporadically been trying to spend some time familiarizing myself with Nostr marketplace listings and the clients that support them. I have been pleased with what I have encountered. The clients are simple to use, and people have been receptive to transacting with me. I've sold items to both people whom I consider to be close contacts, as well as to people that I barely know.
My first attempt was close to 2 years ago, when I listed one pound bags of coffee for sale. If I remember correctly, there was only one marketplace client then, and it only had support for extension signing. At the time, my old laptop had just died so I couldn't really interact with my listings through that client. (I have never had much luck with extensions on mobile browsers, so I have never attempted to use one for Nostr.) Instead, I used Amethyst to list my product and exchange messages with potential buyers. The Amethyst approach to handling different Nostr events is brilliant to me. You can do some part of each thing but not all. I view it as great introduction to what Nostr is capable of doing and a gateway to discovering other clients. Marketplace listings on Amethyst are handled in that fashion. You can list products for sale. You can browse and inquire about products listed by your contacts or by a more "global" view, which in the case of Nostr, would be products listed by anyone who publishes their listings to any of the relays that I connect with to read. There is no delete option, should a product sell out, and there is no direct purchase option. All sales need to be negotiated through direct messages. Though it has limited functionality, the system works great for items that will be listed for repeated sale, such as my coffee. If one were to list a one-off item and sell it, the flow to delete the listing would be easy enough. Copy the event ID, visit delete.nostr.com , and remove the product. Should there be a price change, it would be necessary to visit a full marketplace client to edit the listing, though one could easily delete and start over as well. Anyway, much to my surprise I sold more coffee than I had anticipated through that listing. People were eager to try out the feature and support a small business. This was an awesome experience and I see no reason to avoid buying or selling products on Nostr, even if the only client available to you is Amethyst. (Which I think might be the only mobile app with marketplace support.) It is completely manageable.
Later, I tried to list a pair of nearly new shoes. Those did not sell. I have a sneaking suspicion that there were very few people that wore size USw6 shoes using Nostr at the time. Even though no one wanted my shoes, I still ended up having some interesting conversations about different styles of running shoes, boots, and other footwear talk. I can't call the listing a total bust, even though I ended up deleting the listing and donating those shoes to the YWCA. After some number of months watching and reading about development in the Nostr marketplace space, I decided to try again.
This second approach, I started with niche rubber duckies that, for reasons unbeknownst to most, I just happen to have an abundance of. It occurred to me that day that I would most likely be creating most of my listings via mobile app since that is also my main method of taking pictures these days. I could sync or send them, but realistically it's just adding extra steps for me. I listed my ducks with Amethyst (all of which are currently still available, surprise, surprise.). I immediately went to check how the listing renders in the marketplace clients. There are 2 where I can view it, and the listing looks nice, clean, organized in both places. That alone is reason enough to get excited about selling on Nostr. Gone are the days of "this item is cross-posted to blah, blah, blah" lest risk being kicked out of the seller groups on silo'd platforms.
Knowing I can't take it personally that literally no one else on Nostr has an affinity for obscure rubber ducks (that they are willing to admit), I leave my duckies listed and move on. My next listing is for artisan bracelets. Ones that I love to make. I made my mobile listing, checked it across clients and this time I noticed that shopstr.store is collecting my listings into a personal seller profile, like a little shop. I spent some time setting up the description and banner, and now it looks really nice. This is great, since the current site acts as an open and categorized market for all sellers. Maybe someone will see the bracelets while browsing the clothing category and stumble upon the rubber ducky of their dreams in the process. That hasn't happened yet, but I was pretty jazzed to sell a few bracelets right away. Most of the sale and exchange happened via DM, for which I switched to Flotilla because it just handles messaging solidly for me. I made some bracelets, waited a few weeks, then visited Shopstr again to adjust the price. That worked out super well. I noticed that a seller can also list in their preferred currency, which is very cool. Meanwhile, back to my social feed, I can see my listing posted again since there was an edit. While not always the best thing to happen with edits, it is great that it happens with marketplace listings. It removes all the steps of announcing a price reduction, which would be handy for any serious seller. I am very happy with the bracelet experience, and I will keep that listing active and reasonably up to date for as long as any interest arises. Since this has all gone so well, I've opted to continue listing saleable items to Nostr first for a few days to a few weeks prior to marketing them anywhere else.
Looking at my listings on cypher.space, I can see that this client is tailored more towards people who are very passionate about a particular set of things. I might not fall into this category but my listings still look very nice displayed with my writing, transposed poetry, and recipes. I could see this being a great space for truly devotional hobbyists or sellers who are both deeply knowledgeable about their craft and also actively selling. My experience with all 3 of these marketplace-integrated clients had been positive and I would say that if you are considering selling on Nostr, it is worth the effort.
As some sidenotes:
-
I am aware that Shopstr has been built to be self-hosted and anyone interested in selling for the long term should at least consider doing so. This will help reduce the chances of Nostr marketplaces centralizing into just another seller-silo.
-
Plebeian Market is out there, too. From the best I could tell, even though this is a Nostr client, those listings are a different kind than listings made from the other clients referenced here. I like the layout and responsiveness of the site but I opted not to try it out for now. Cross-posting has been the bane of online selling for me for quite some time. If they should migrate to an interoperable listing type (which I think I read may happen in the future), I will happily take that for a spin, too.
-
My only purchase over Nostr marketplaces so far was some vinyls, right around the time I had listed my coffee. It went well, the seller was great to work with, everything arrived in good shape. I have made some other purchases through Nostr contacts, but those were conversations that lead to non-Nostr seller sites. I check the marketplace often, though, for things I may want/need. The listings are changing and expanding rapidly, and I foresee more purchases becoming a part of my regular Nostr experience soon enough.
-
I thought about including screenshots for this, but I would much rather you go check these clients out for yourself.
-
-
 @ ecda4328:1278f072
2025-05-23 18:16:24
@ ecda4328:1278f072
2025-05-23 18:16:24And what does it mean to withdraw back to Bitcoin Layer 1?
Disclaimer: This post was written with help from ChatGPT-4o. If you spot any mistakes or have suggestions — feel free to reply or zap in feedback!
Let’s break it down — using three popular setups:
1. Wallet of Satoshi (WoS)
Custodial — you don’t touch Lightning directly
Sending sats:
- You open WoS, paste a Lightning invoice, hit send.
- WoS handles the payment entirely within their system.
- If recipient uses WoS: internal balance update.
- If external: routed via their node.
- You never open channels, construct routes, or sign anything.
Withdrawing to L1:
- You paste a Bitcoin address.
- WoS sends a regular on-chain transaction from their custodial wallet.
- You pay a fee. It’s like a bank withdrawal.
You don’t interact with Lightning directly. Think of it as a trusted 3rd party Lightning “bank”.
2. Phoenix Wallet
Non-custodial — you own keys, Phoenix handles channels
Sending sats:
- You scan a Lightning invoice and hit send.
- Phoenix uses its backend node (ACINQ) to route the payment.
- If needed, it opens a real 2-of-2 multisig channel on-chain automatically.
- You own your keys (12-word seed), Phoenix abstracts the technical parts.
Withdrawing to L1:
- You enter your Bitcoin address.
- Phoenix closes your Lightning channel (cooperatively, if possible).
- Your sats are sent as a real Bitcoin transaction to your address.
You’re using Lightning “for real,” with real Bitcoin channels — but Phoenix smooths out the UX.
3. Your Own Lightning Node
Self-hosted — you control everything
Sending sats:
- You manage your channels manually (or via automation).
- Your node:
- Reads the invoice
- Builds a route using HTLCs
- Sends the payment using conditional logic (preimages, time locks).
- If routing fails: retry or adjust liquidity.
Withdrawing to L1:
- You select and close a channel.
- A channel closing transaction is broadcast:
- Cooperative = fast and cheap
- Force-close = slower, more expensive, and time-locked
- Funds land in your on-chain wallet.
You have full sovereignty — but also full responsibility (liquidity, fees, backups, monitoring).
Core Tech Behind It: HTLCs, Multisig — and No Sidechain
- Lightning channels = 2-of-2 multisig Bitcoin addresses
- Payments = routed via HTLCs (Hashed Time-Locked Contracts)
- HTLCs are off-chain, but enforceable on-chain if needed
- Important:
- The Lightning Network is not a sidechain.
- It doesn't use its own token, consensus, or separate blockchain.
- Every Lightning channel is secured by real Bitcoin on L1.
Lightning = fast, private, off-chain Bitcoin — secured by Bitcoin itself.
Summary Table
| Wallet | Custody | Channel Handling | L1 Withdrawal | HTLC Visibility | User Effort | |--------------------|--------------|------------------------|---------------------|------------------|--------------| | Wallet of Satoshi | Custodial | None | Internal to external| Hidden | Easiest | | Phoenix Wallet | Non-custodial| Auto-managed real LN | Channel close | Abstracted | Low effort | | Own Node | You | Manual | Manual channel close| Full control | High effort |
Bonus: Withdrawing from LN to On-Chain
- WoS: sends sats from their wallet — like PayPal.
- Phoenix: closes a real channel and sends your UTXO on-chain.
- Own node: closes your multisig contract and broadcasts your pre-signed tx.
Bitcoin + Lightning = Sovereign money + Instant payments.
Choose the setup that fits your needs — and remember, you can always level up later.P.S. What happens in Lightning... usually stays in Lightning.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:11:34
@ b0a838f2:34ed3f19
2025-05-23 18:11:34- AmuseWiki - Amusewiki is based on the Emacs Muse markup, remaining mostly compatible with the original implementation. It can work as a read-only site, as a moderated wiki, or as a fully open wiki or even as a private site. (Demo, Source Code)
GPL-1.0Perl/Docker - BookStack - Organize and store information. Stores documentation in a book like fashion. (Demo, Source Code)
MITPHP/Docker - django-wiki - Wiki system with complex functionality for simple integration and a superb interface. Store your knowledge with style: Use django models. (Demo)
GPL-3.0Python - docmost - Collaborative wiki and documentation software (alternative to Confluence, Notion). (Source Code)
AGPL-3.0Docker/Nodejs - Documize - Modern Docs + Wiki software with built-in workflow, single binary executable, just bring MySQL/Percona. (Source Code)
AGPL-3.0Go - Dokuwiki - Easy to use, lightweight, standards-compliant wiki engine with a simple syntax allowing reading the data outside the wiki. All data is stored in plain text files, therefore no database is required. (Source Code)
GPL-2.0PHP - Feather Wiki - A lightning fast and infinitely extensible tool for creating personal non-linear notebooks, databases, and wikis that is entirely self-contained, runs in your browser, and is only 58 kilobytes in size. (Demo, Source Code, Clients)
AGPL-3.0Javascript - Gitit - Wiki program that stores pages and uploaded files in a git repository, which can then be modified using the VCS command line tools or the wiki's web interface.
GPL-2.0Haskell - Gollum - Simple, Git-powered wiki with a sweet API and local frontend.
MITRuby - Mediawiki - Wiki software package that powers Wikipedia and all other Wikimedia projects, serving hundreds of millions of users each month. (Demo, Source Code)
GPL-2.0PHP - Mycorrhiza Wiki - Filesystem and git-based wiki engine written in Go using Mycomarkup as its primary markup language. (Source Code)
AGPL-3.0Go - Otter Wiki - Simple, easy to use wiki software using markdown. (Source Code)
MITDocker - Pepperminty Wiki - Complete markdown-powered wiki contained in a single PHP file. (Demo)
MPL-2.0PHP - PmWiki - Wiki-based system for collaborative creation and maintenance of websites.
GPL-3.0PHP - Raneto - Raneto is an open source Knowledgebase platform that uses static Markdown files to power your Knowledgebase. (Source Code)
MITNodejs - TiddlyWiki - Reusable non-linear personal web notebook. (Source Code)
BSD-3-ClauseNodejs - Tiki - Wiki CMS Groupware with the most built-in features. (Demo, Source Code)
LGPL-2.1PHP - W - Lightweight, mutli-user, flat-file-database Wiki engine. Create pages quickly and edit them in your Web browser using Mardown/HTML/CSS/JS. The main difference with other wiki is that you are encouraged to customize each page style individually. (Source Code)
AGPL-3.0PHP - WackoWiki - WackoWiki is a light and easy to install multilingual Wiki-engine. (Source Code)
BSD-3-ClausePHP - Wiki.js - Modern, lightweight and powerful wiki app using Git and Markdown. (Demo, Source Code)
AGPL-3.0Nodejs/Docker/K8S - WikiDocs - A databaseless markdown flat-file wiki engine. (Source Code)
MITPHP/Docker - WiKiss - Wiki, simple to use and install. (Source Code)
GPL-2.0PHP - Wikmd - Modern and simple file based wiki that uses Markdown and Git.
MITPython/Docker - XWiki - Second generation wiki that allows the user to extend its functionalities with a powerful extension-based architecture. (Demo, Source Code)
LGPL-2.1Java/Docker/deb - Zim - Graphical text editor used to maintain a collection of wiki pages. Each page can contain links to other pages, simple formatting and images. (Source Code)
GPL-2.0Python/deb
- AmuseWiki - Amusewiki is based on the Emacs Muse markup, remaining mostly compatible with the original implementation. It can work as a read-only site, as a moderated wiki, or as a fully open wiki or even as a private site. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:11:11
@ b0a838f2:34ed3f19
2025-05-23 18:11:11- Algernon - Small self-contained pure-Go web server with Lua, Markdown, HTTP/2, QUIC, Redis and PostgreSQL support. (Source Code)
BSD-3-ClauseGo/Docker - Apache HTTP Server - Secure, efficient and extensible server that provides HTTP services in sync with the current HTTP standards. (Source Code)
Apache-2.0C/deb/Docker - BunkerWeb - Next-gen Web Application Firewall (WAF) that will protect your web services. (Demo, Source Code, Clients)
AGPL-3.0deb/Docker/K8S/Python - Caddy - Powerful, enterprise-ready, open source web server with automatic HTTPS. (Source Code)
Apache-2.0Go/deb/Docker - go-doxy - Lightweight, simple, and performant reverse proxy with WebUI, Docker integration, automatic shutdown/startup for container based on traffic.
MITDocker/Go - HAProxy - Very fast and reliable reverse-proxy offering high availability, load balancing, and proxying for TCP and HTTP-based applications. (Source Code)
GPL-2.0C/deb/Docker - Jauth
⚠- Lightweight SSL/TLS reverse proxy with authorization (via Telegram and SSH) for self-hosted apps.GPL-3.0Go - Lighttpd - Secure, fast, compliant, and very flexible web server that has been optimized for high-performance environments. (Source Code)
BSD-3-ClauseC/deb/Docker - Nginx Proxy Manager - Docker container for managing Nginx proxy hosts with a simple, powerful interface. (Source Code)
MITDocker - NGINX - HTTP and reverse proxy server, mail proxy server, and generic TCP/UDP proxy server. (Source Code)
BSD-2-ClauseC/deb/Docker - Pomerium - Identity-aware reverse proxy, successor to now obsolete oauth_proxy. It inserts an OAuth step before proxying your request to the backend, so that you can safely expose your self-hosted websites to public Internet. (Source Code)
Apache-2.0Go/Docker - SafeLine - Web application firewall / reverse proxy to protect your web apps from attacks and exploits. (Demo, Source Code)
GPL-3.0Docker - Static Web Server - Cross-platform, high-performance, and asynchronous web server for static file serving. (Source Code)
Apache-2.0/MITRust/Docker - SWAG (Secure Web Application Gateway) - Nginx webserver and reverse proxy with PHP support, built-in Certbot (Let's Encrypt) client and fail2ban integration.
GPL-3.0Docker - Traefik - HTTP reverse proxy and load balancer that makes deploying microservices easy. (Source Code)
MITGo/Docker - Varnish - Web application accelerator/caching HTTP reverse proxy. (Source Code)
BSD-3-ClauseGo/deb/Docker - Zoraxy - General purpose HTTP reverse proxy and forwarding tool. (Source Code)
AGPL-3.0Go/Docker
- Algernon - Small self-contained pure-Go web server with Lua, Markdown, HTTP/2, QUIC, Redis and PostgreSQL support. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:10:51
@ b0a838f2:34ed3f19
2025-05-23 18:10:51- Bluecherry - Closed-circuit television (CCTV) software application which supports IP and Analog cameras. (Source Code)
GPL-2.0PHP - Frigate - Monitor your security cameras with locally processed AI. (Source Code)
MITDocker/Python/Nodejs - SentryShot - Video surveillance management system.
GPL-2.0Docker/Rust - Viseron - Self-hosted, local-only NVR and AI Computer Vision software. With features such as object detection, motion detection, face recognition and more, it gives you the power to keep an eye on your home, office or any other place you want to monitor. (Source Code)
MITDocker - Zoneminder - Closed-circuit television (CCTV) software application which supports IP, USB and Analog cameras. (Source Code)
GPL-2.0PHP/deb
- Bluecherry - Closed-circuit television (CCTV) software application which supports IP and Analog cameras. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:10:36
@ b0a838f2:34ed3f19
2025-05-23 18:10:36- bit - Fast, lightweight, resource-efficient, compiled URL shortener.
MITDocker/Crystal - Chhoto URL - Simple, lightning-fast URL shortener with no bloat (fork of simply-shorten).
MITRust/Docker - clink - A super-minimal link shortening service written in pure C, focusing on small executable size, portability, and ease of configuration. (Demo, Source Code)
AGPL-3.0C - Flink - Create QR Codes, embeddable link previews for your website and crawls/scrapes metadata. (Demo)
MITDocker - Just Short It! - A KISS, single-user URL shortener that runs in just one container.
MITDocker - Kutt - Modern URL shortener with support for custom domains and custom URLs. (Demo, Source Code)
MITNodejs/Docker - liteshort - User-friendly, actually lightweight, and configurable URL shortener. (Source Code)
MITPython/deb - rs-short - A lightweight link shortener written in Rust, with features such as caching, spambot protection and phishing detection. (Demo)
MPL-2.0Rust - Shlink - URL shortener with REST API and command line interface. Includes official progressive web application and docker images. (Source Code, Clients)
MITPHP/Docker - Simple-URL-Shortener - KISS URL shortener, public or private (with account). Minimalist and lightweight. No dependencies. (Demo)
MITPHP - YOURLS - YOURLS is a set of PHP scripts that will allow you to run Your Own URL Shortener. Features include password protection, URL customization, bookmarklets, statistics, API, plugins, jsonp. (Source Code)
MITPHP
- bit - Fast, lightweight, resource-efficient, compiled URL shortener.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:10:12
@ b0a838f2:34ed3f19
2025-05-23 18:10:12- ActivityWatch - Automatically track how you spend time on your devices. (Source Code)
MPL-2.0Python - Beaver Habit Tracker - Habit tracking app to save your precious moments in your fleeting life. (Demo)
BSD-3-ClauseDocker - Ever Gauzy - Open business management platform for collaborative, on-demand and sharing economies (ERP/CRM/HRM/ATS/PM). (Demo, Source Code)
AGPL-3.0Docker/Nodejs - Kimai - Track work time and print out a summary of your activities on demand. (Demo, Source Code)
AGPL-3.0PHP - solidtime - Modern time tracking application for freelancers and agencies. (Source Code)
AGPL-3.0Docker - TimeTagger - An open source time-tracker based on an interactive timeline and powerful reporting. (Demo, Source Code)
GPL-3.0Python - Traggo - Traggo is a tag-based time tracking tool. In Traggo there are no tasks, only tagged time spans. (Source Code)
GPL-3.0Docker/Go
- ActivityWatch - Automatically track how you spend time on your devices. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:09:55
@ b0a838f2:34ed3f19
2025-05-23 18:09:55- Bugzilla - General-purpose bugtracker and testing tool originally developed and used by the Mozilla project. (Source Code)
MPL-2.0Perl - Frappe Helpdesk - Helpdesk software which helps you streamline your company's support, offers an easy setup, clean user interface, and automation tools to resolve customer queries efficiently. (Source Code)
AGPL-3.0Docker - FreeScout - Email-based customer support application, help desk and shared mailbox (alternative to Zendesk and Help Scout). (Demo, Source Code)
AGPL-3.0PHP/Docker - GlitchTip - Error tracking app to collect errors reported by your app. (Source Code)
MITPython/Docker/K8S - ITFlow - Client IT documentation, ticketing, invoicing and accounting for MSPs (Managed Service Providers). (Demo, Source Code)
GPL-3.0PHP - MantisBT - Bug tracker, fits best for software development. (Demo, Source Code)
GPL-2.0PHP - OTOBO - Flexible web-based ticketing system used for customer service, help desk, IT service management. (Demo, Source Code)
GPL-3.0Perl/Docker - Request Tracker - An enterprise-grade issue tracking system. (Source Code)
GPL-2.0Perl - Roundup Issue Tracker - A simple-to-use and -install issue-tracking system with command-line, web, REST, XML-RPC, and e-mail interfaces. Designed with flexibility in mind - not just another bug tracker. (Source Code)
MIT/ZPL-2.0Python/Docker - Trudesk - Trudesk is an open-source help desk/ticketing solution. (Source Code)
Apache-2.0Nodejs/Docker - Zammad - Easy to use but powerful open-source support and ticketing system. (Source Code)
AGPL-3.0Ruby/deb
- Bugzilla - General-purpose bugtracker and testing tool originally developed and used by the Mozilla project. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:09:35
@ b0a838f2:34ed3f19
2025-05-23 18:09:35- 4ga Boards - Straightforward realtime kanban boards management for intuitive task tracking. Featuring an elegant dark mode, collapsible todo lists, and multitasking tools to supercharge your team's productivity. (Demo, Source Code)
MITNodejs/Docker/K8S - AppFlowy - Build detailed lists of to-do’s for different projects while tracking the status of each one. Open Source Notion Alternative. (Source Code)
AGPL-3.0Rust/Dart/Docker - Donetick - Task and chore management tool for personal and family use, with advanced scheduling, flexible assignment, and group sharing capabilities, detailed history, automation via API, simple and modern design. (Demo, Source Code)
AGPL-3.0Go/Docker - Focalboard - Define, organize, track and manage work across individuals and teams (alternative to Trello, Notion, and Asana). (Source Code, Clients)
MIT/AGPL-3.0/Apache-2.0Nodejs/Go/Docker - Kanboard - Simple visual task board. (Source Code)
MITPHP - myTinyTodo - Simple way to manage your todo list in AJAX style. Uses PHP, jQuery, SQLite/MySQL. GTD compliant. (Demo, Source Code)
GPL-2.0PHP - Nullboard - Single-page minimalist kanban board; compact, highly readable and quick to use. (Demo)
BSD-2-ClauseJavascript - Our Shopping List - Simple shared list application including shopping lists and any other small todo-list that needs to be used collaboratively. (Demo)
AGPL-3.0Docker - Planka - Realtime kanban board for workgroups (alternative to Trello). (Demo, Source Code)
AGPL-3.0Nodejs/Docker/K8S - Task Keeper - List editor for power users, backed by a self-hosted server.
Apache-2.0Scala - Tasks.md - A self-hosted, file based task management board that supports Markdown syntax.
MITDocker - Taskwarrior - Taskwarrior is Free and Open Source Software that manages your TODO list from your command line. It is flexible, fast, efficient, and unobtrusive. It does its job then gets out of your way. (Source Code)
MITC++ - Tegon
⚠- Dev-first issue tracking tool (alternative to Jira, Linear). (Source Code)AGPL-3.0Docker - Tracks - Web-based application to help you implement David Allen’s Getting Things Done™ methodology. (Source Code)
GPL-2.0Ruby - Vikunja - The to-do app to organize your life. (Demo, Source Code)
GPL-3.0Go - Wekan - Open-source Trello-like kanban. (Source Code)
MITNodejs
- 4ga Boards - Straightforward realtime kanban boards management for intuitive task tracking. Featuring an elegant dark mode, collapsible todo lists, and multitasking tools to supercharge your team's productivity. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:09:15
@ b0a838f2:34ed3f19
2025-05-23 18:09:15- cState - Static status page for hyperfast Hugo. Clean design, minimal JS, super light HTML/CSS, high customization, optional admin panel, read-only API, IE8+. Best used with Netlify, Docker. (Demo, Source Code)
MITGo - Gatus - Automated service health dashboard. (Demo, Source Code)
Apache-2.0Docker/K8S - kener - Status page with incident management, easy to use and customize. (Demo, Source Code)
MITNodejs/Docker - StatPing.ng - An easy to use Status Page for your websites and applications. Statping will automatically fetch the application and render a beautiful status page with tons of features for you to build an even better status page. (Source Code)
GPL-3.0Docker/Go - Uptime Kuma - Self-hosted website monitoring tool like "Uptime Robot". (Demo, Source Code)
MITDocker/Nodejs
- cState - Static status page for hyperfast Hugo. Clean design, minimal JS, super light HTML/CSS, high customization, optional admin panel, read-only API, IE8+. Best used with Netlify, Docker. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:09:00
@ b0a838f2:34ed3f19
2025-05-23 18:09:00- Bencher - Suite of continuous benchmarking tools designed to catch performance regressions in CI. (Source Code)
MIT/Apache-2.0Rust - WebHook Tester - Powerful tool for testing WebHooks and more.
MITDocker/Go/deb/K8S
- Bencher - Suite of continuous benchmarking tools designed to catch performance regressions in CI. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:08:44
@ b0a838f2:34ed3f19
2025-05-23 18:08:44- Cgit - Fast lightweight web interface for git repositories. (Source Code)
GPL-2.0C - Forgejo - A lightweight software forge focused on scaling, federation, and privacy (fork of Gitea). (Demo, Source Code, Clients)
MITDocker/Go - Fossil - Distributed version control system featuring wiki and bug tracker.
BSD-2-Clause-FreeBSDC - Gerrit - Code review and project management tool for Git-based projects. (Source Code)
Apache-2.0Java/Docker - gitbucket - Git platform powered with easy installation, high extensibility & GitHub API compatibility (alternative to GitHub). (Source Code)
Apache-2.0Scala/Java - Gitea - Git with a cup of tea! Painless self-hosted all-in-one software development service, including Git hosting, code review, team collaboration, package registry and CI/CD. (Demo, Source Code)
MITGo/Docker/K8S - GitLab - Self Hosted Git repository management, code reviews, issue tracking, activity feeds and wikis. (Demo, Source Code)
MITRuby/deb/Docker/K8S - Gitolite - Setup git hosting on a central server, with fine-grained access control and many more powerful features. (Source Code)
GPL-2.0Perl - Gogs - Painless self-hosted Git Service written in Go. (Source Code)
MITGo - Huly - All-in-one project management platform (alternative to Linear, Jira, Slack, Notion, Motion). (Demo, Source Code)
EPL-2.0Docker/K8S/Nodejs - Kallithea - Source code management system that supports two leading version control systems, Mercurial and Git, with a web interface. (Source Code)
GPL-3.0Python - Klaus - Simple, easy-to-set-up Git web viewer that Just Works.
ISCPython/Docker - Leantime - Lean project management system for small teams and startups helping to manage projects from ideation through delivery. (Source Code)
AGPL-3.0PHP/Docker - Mergeable
⚠- A better inbox for GitHub pull requests. (Demo, Source Code)MITNodejs/Docker/K8S - Mindwendel - Brainstorm and upvote ideas and thoughts within your team. (Demo, Source Code)
AGPL-3.0Docker/Elixir - minimal-git-server - Lightweight git server with a basic CLI to manage repositories, supporting multiple accounts and running in a container.
MITDocker - Octobox
⚠- Take back control of your GitHub Notifications. (Source Code)AGPL-3.0Ruby/Docker - OneDev - All-In-One DevOps Platform. With Git Management, Issue Tracking, and CI/CD. Simple yet Powerful. (Source Code)
MITJava/Docker/K8S - OpenProject - Manage your projects, tasks and goals. Collaborate via work packages and link them to your pull requests on Github. (Source Code)
GPL-3.0Ruby/deb/Docker - Pagure - Lightweight, powerful, and flexible git-centric forge with features laying the foundation for federated and decentralized development. (Demo)
GPL-2.0Docker/Python/deb - Phorge - Community-driven platform for collaborating, managing, organizing and reviewing software development projects. (Source Code)
Apache-2.0PHP - Plane - Track issues, epics, and product roadmaps in the simplest way possible (alternative to JIRA, Linear and Height). (Demo, Source Code)
AGPL-3.0Docker - ProjeQtOr - Complete, mature, multi-user project management system with extensive functionality for all phases of a project. (Demo, Source Code)
AGPL-3.0PHP - Redmine - Redmine is a flexible project management web application. (Source Code)
GPL-2.0Ruby - Review Board - Extensible and friendly code review tool for projects and companies of all sizes. (Demo, Source Code)
MITPython/Docker - rgit - An ultra-fast & lightweight cgit clone.
WTFPLRust/Docker - RhodeCode - RhodeCode is an open source platform for software development teams. It unifies and simplifies repository management for Git, Subversion, and Mercurial. (Source Code)
AGPL-3.0Python - Rukovoditel - Configurable open source project management, web-based application. (Source Code)
GPL-2.0PHP - SCM Manager - The easiest way to share and manage your Git, Mercurial and Subversion repositories over http. (Source Code)
BSD-3-ClauseJava/deb/Docker/K8S - Smederee - A frugal platform which is dedicated to help people build great software together leveraging the power of the Darcs version control system. (Source Code)
AGPL-3.0Scala - Sourcehut - A full web git interface with no javascript. (Demo, Source Code)
GPL-2.0Go - Taiga - Agile Project Management Tool based on the Kanban and Scrum methods. (Source Code)
MPL-2.0Docker/Python/Nodejs - Titra - Time-tracking solution for freelancers and small teams. (Source Code)
GPL-3.0Javascript/Docker - Trac - Trac is an enhanced wiki and issue tracking system for software development projects.
BSD-3-ClausePython/deb - Traq - Project management and issue tracking system written in PHP. (Source Code)
GPL-3.0PHP/Nodejs - Tuleap - Tuleap is a libre suite to plan, track, code and collaborate on software projects. (Source Code)
GPL-2.0PHP - UVDesk - UVDesk community is a service oriented, event driven extensible opensource helpdesk system that can be used by your organization to provide efficient support to your clients effortlessly whichever way you imagine. (Demo, Source Code)
MITPHP - ZenTao - An agile(scrum) project management system/tool. (Source Code)
AGPL-3.0PHP
- Cgit - Fast lightweight web interface for git repositories. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:08:24
@ b0a838f2:34ed3f19
2025-05-23 18:08:24- Appsmith - Build admin panels, CRUD apps and workflows. Build everything you need, 10x faster. (Source Code)
Apache-2.0Java/Docker/K8S - Appwrite - End to end backend server for web, native, and mobile developers 🚀. (Source Code)
BSD-3-ClauseDocker - Dashpress - Generate fully functional admin apps in seconds from your database information, with a single command.
AGPL-3.0Nodejs/Docker - Manifest - Complete backend that fits into 1 YAML file. (Demo, Source Code)
MITNodejs - Motor Admin - No-code admin panel and business intelligence software - search, create, update, and delete data entries, create custom actions, and build reports. (Source Code)
AGPL-3.0Ruby/Docker - PocketBase - Backend for your next SaaS and Mobile app in one file. (Source Code)
MITGo/Docker - SQLPage - SQL-only dynamic website builder. (Source Code)
MITRust/Docker - ToolJet - Low-code framework to build & deploy internal tools with minimal engineering effort (alternative to Retool & Mendix). (Source Code)
GPL-3.0Nodejs/Docker/K8S - TrailBase - Open, sub-millisecond, single-executable FireBase alternative with type-safe REST & realtime APIs, built-in JS/TS runtime, auth & admin UI. (Demo, Source Code)
OSL-3.0Rust/Docker
- Appsmith - Build admin panels, CRUD apps and workflows. Build everything you need, 10x faster. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:08:08
@ b0a838f2:34ed3f19
2025-05-23 18:08:08- Accent - Developer-oriented translation tool. (Source Code)
BSD-3-ClauseElixir/Docker - Tolgee - Developer & translator friendly web-based localization platform enabling users to translate directly in the app they develop. (Source Code)
Apache-2.0Docker/Java - Traduora - Translation management platform for teams. (Source Code)
AGPL-3.0Docker/K8S/Nodejs - Weblate - Web-based translation tool with tight version control integration. (Source Code)
GPL-3.0Python/Docker/K8S
- Accent - Developer-oriented translation tool. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:07:52
@ b0a838f2:34ed3f19
2025-05-23 18:07:52- Atheos - Web-based IDE framework with a small footprint and minimal requirements, continued from Codiad. (Source Code)
MITPHP/Docker - code-server - VS Code in the browser, hosted on a remote server.
MITNodejs/Docker - Coder - Remote development machines on your own infrastructure. (Source Code)
AGPL-3.0Go/Docker/K8S/deb - Eclipse Che - Open source workspace server and cloud IDE. (Source Code)
EPL-1.0Docker/Java - HttPlaceholder - Quickly mock away any webservice using HttPlaceholder. HttPlaceholder lets you specify what the request should look like and what response needs to be returned.
MITC# - Judge0 CE - API to compile and run source code. (Source Code)
GPL-3.0Docker - JupyterLab - Web-based environment for interactive and reproducible computing. (Demo, Source Code)
BSD-3-ClausePython/Docker - Langfuse - LLM engineering platform for model tracing, prompt management, and application evaluation. Langfuse helps teams collaboratively debug, analyze, and iterate on their LLM applications such as chatbots or AI agents. (Demo, Source Code, Clients)
MITDocker - LiveCodes
⚠- Feature-rich client-side code playground for React, Vue, Svelte, Solid, Typescript, Python, Go, Ruby, PHP and 90+ other languages. (Demo, Source Code)MITNodejs - Lowdefy - Build internal tools, BI dashboards, admin panels, CRUD apps and workflows in minutes using YAML / JSON on an self-hosted, open-source platform. Connect to your data sources, host via Serverless, Netlify or Docker. (Source Code)
Apache-2.0Nodejs/Docker - RStudio Server - Web browser based IDE for R. (Source Code)
AGPL-3.0Java/C++ - Wakapi - Tracking tool for coding statistics, compatible with WakaTime. (Source Code)
GPL-3.0Go/Docker
- Atheos - Web-based IDE framework with a small footprint and minimal requirements, continued from Codiad. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:07:34
@ b0a838f2:34ed3f19
2025-05-23 18:07:34- Featbit - Enterprise-grade feature flag platform that you can self-host. (Source Code)
MITDocker/K8S - Flagsmith - Dashboard, API and SDKs for adding Feature Flags to your applications (alternative to LaunchDarkly). (Source Code)
BSD-3-ClauseDocker/K8S - Flipt - Feature flag solution with support for multiple data backends (alternative to LaunchDarkly). (Demo, Source Code)
GPL-3.0Docker/K8S/Go - GO Feature Flag - Simple, complete, and lightweight feature flag solution (alternative to LaunchDarkly). (Source Code)
MITGo
- Featbit - Enterprise-grade feature flag platform that you can self-host. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:07:18
@ b0a838f2:34ed3f19
2025-05-23 18:07:18- DreamFactory - Turns any SQL/NoSQL/Structured data into Restful API. (Source Code)
Apache-2.0PHP/Docker/K8S - form.io - A REST API building platform that utilizes a drag & drop form builder, and is application framework agnostic. Contains open source and enterprise version. (Demo, Source Code)
MITNodejs/Docker - Fusio - Open-source API management platform which helps to build and manage REST APIs. (Demo, Source Code)
AGPL-3.0PHP/Docker - Graphweaver - Turn multiple data sources into a single GraphQL API. (Source Code)
MITNodejs - Hasura - Fast, instant realtime GraphQL APIs on Postgres with fine grained access control, also trigger webhooks on database events. (Source Code)
Apache-2.0Haskell/Docker/K8S - Hoppscotch Community Edition - Fast and beautiful API request builder. (Source Code)
MITNodejs/Docker - Kong - Microservice API Gateway and Platform. (Source Code)
Apache-2.0Lua/Docker/K8S/deb - Lura - High-performance API Gateway. (Source Code)
Apache-2.0Go - Opik
⚠- Evaluate, test, and ship LLM applications with a suite of observability tools to calibrate language model outputs across your dev and production lifecycle. (Source Code)Apache-2.0Docker/Python - Panora
⚠- Add an integration catalog to your SaaS product in minutes (alternative to Merge.dev). (Source Code)AGPL-3.0Nodejs/Docker - Para - Flexible and modular backend framework/server for object persistence, API development and authentication. (Source Code)
Apache-2.0Java/Docker - Svix - Open-source webhooks as a service that makes it super easy for API providers to send webhooks. (Source Code)
MITDocker/Rust - Tyk - Fast and scalable open source API Gateway. Out of the box, Tyk offers an API Management Platform with an API Gateway, API Analytics, Developer Portal and API Management Dashboard. (Source Code)
MPL-2.0Go/Docker/K8S - Yaade - Yaade is an open-source, self-hosted, collaborative API development environment. (Source Code)
MITDocker
- DreamFactory - Turns any SQL/NoSQL/Structured data into Restful API. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:07:01
@ b0a838f2:34ed3f19
2025-05-23 18:07:01- Ansible-NAS - Build a full-featured home server with this playbook and an Ubuntu box.
MITAnsible/Docker - CasaOS - Simple, easy-to-use, elegant Home Cloud system. (Source Code)
Apache-2.0Go/Docker - DietPi - Minimal Debian OS optimized for single-board computers, which allows you to easily install and manage several services for selfhosting at home. (Source Code)
GPL-2.0Shell - DockSTARTer - DockSTARTer helps you get started with home server apps running in Docker. (Source Code)
MITShell - Dropserver - An application platform for your personal web services. (Source Code)
Apache-2.0Go/Deno - FreedomBox - Community project to develop, design and promote personal servers running free software for private, personal, communications. (Source Code)
AGPL-3.0Python/deb - HomelabOS - Offline privacy-centric data-center. Deploy over 100 services with a few commands. (Source Code)
MITDocker - HomeServerHQ - All-in-one home server infrastructure and installer. Have a fully configured email server, VPN, and public website(s) set up in less than an hour, even behind CGNAT. (Source Code)
GPL-3.0Shell - LibreServer - Home server configuration based on Debian. (Source Code)
AGPL-3.0Shell - Mars Server - Managed home server with Docker, Docker Compose, Make and Bash.
MITDocker - Mistborn - Virtual private cloud platform and WebUI that manages self hosted services.
MITShell/Docker - NextCloudPi - Nextcloud preinstalled and preconfigured, with a text and web management interface and all the tools needed to self host private data. With installation images for Raspberry Pi, Odroid, Rock64, Docker, and a curl installer for Armbian/Debian.
GPL-2.0Shell/PHP - OpenMediaVault - Network attached storage (NAS) solution based on Debian Linux. It contains services like SSH, (S)FTP, SMB/CIFS, DAAP media server, RSync, BitTorrent client and many more. (Source Code)
GPL-3.0PHP - Sandstorm - Personal server for running self-hosted apps easily and securely. (Demo, Source Code)
Apache-2.0C++/Shell - Self Host Blocks
⚠- Modular server management based on NixOS modules and focused on best practices.AGPL-3.0Nix - StartOS - Browser-based, graphical Operating System (OS) that makes running a personal server as easy as running a personal computer. (Source Code)
MITRust - Syncloud - Your own online file storage, social network or email server. (Source Code)
GPL-3.0Go/Shell - Tipi - Homeserver manager. One command setup, one click installs for your favorites self-hosted apps. (Source Code)
GPL-3.0Shell - UBOS - Linux distro that runs on indie boxes (personal servers and IoT devices). Single-command installation and management of apps - Jenkins, Mediawiki, Owncloud, WordPress, etc., and other features.
GPL-3.0Perl - Websoft9
⚠- GitOps-driven, multi-application hosting for cloud servers and home servers, one-click deployment of 200+ open source apps. (Demo, Source Code, Clients)LGPL-3.0Shell/Python - WikiSuite - The most comprehensive and integrated Free / Libre / Open Source enterprise software suite. (Source Code)
GPL-3.0/LGPL-2.1/Apache-2.0/MPL-2.0/MPL-1.1/MIT/AGPL-3.0Shell/Perl/deb - xsrv - Install and manage self-hosted services/applications, on your own server(s). (Source Code)
GPL-3.0Ansible/Shell - YunoHost - Server operating system aiming to make self-hosting accessible to everyone. (Demo, Source Code)
AGPL-3.0Python/Shell
- Ansible-NAS - Build a full-featured home server with this playbook and an Ubuntu box.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:06:45
@ b0a838f2:34ed3f19
2025-05-23 18:06:45- Aleph - Tool for indexing large amounts of both documents (PDF, Word, HTML) and structured (CSV, XLS, SQL) data for easy browsing and search. It is built with investigative reporting as a primary use case. (Demo, Source Code)
MITDocker/K8S - Apache Solr - Enterprise search platform featuring full-text search, hit highlighting, faceted search, real-time indexing, dynamic clustering, and rich document (e.g., Word, PDF) handling. (Source Code)
Apache-2.0Java/Docker/K8S - Fess - Powerful and easily deployable Enterprise Search Server. (Demo, Source Code)
Apache-2.0Java/Docker - Jina - Cloud-native neural search framework for any kind of data.
Apache-2.0Python/Docker - Manticore Search - Full-text search and data analytics, with fast response time for small, medium and big data (alternative to Elasticsearch).
GPL-3.0Docker/deb/C++/K8S - MeiliSearch - Ultra relevant, instant and typo-tolerant full-text search API. (Source Code)
MITRust/Docker/deb - OpenSearch - Distributed and RESTful search engine. (Source Code)
Apache-2.0Java/Docker/K8S/deb - SearXNG
⚠- Internet metasearch engine which aggregates results from various search services and databases (Fork of Searx). (Source Code)AGPL-3.0Python/Docker - sist2 - Lightning-fast file system indexer and search tool.
GPL-3.0C/Docker - Sosse - Selenium based search engine and crawler with offline archiving. (Source Code)
AGPL-3.0Python/Docker - Typesense - Blazing fast, typo-tolerant open source search engine optimized for developer happiness and ease of use. (Source Code)
GPL-3.0C++/Docker/K8S/deb - Websurfx
⚠- Aggregate results from other search engines (metasearch engine) without ads while keeping privacy and security in mind. It is extremely fast and provides a high level of customization (alternative to SearX).AGPL-3.0Rust/Docker - Whoogle
⚠- A self-hosted, ad-free, privacy-respecting metasearch engine.MITPython - Yacy - Peer based, decentralized search engine server. (Source Code)
GPL-2.0Java/Docker/K8S - ZincSearch - Search engine that requires minimal resources (alternative to Elasticsearch). (Demo, Source Code)
Apache-2.0Go/Docker/K8S
- Aleph - Tool for indexing large amounts of both documents (PDF, Word, HTML) and structured (CSV, XLS, SQL) data for easy browsing and search. It is built with investigative reporting as a primary use case. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:06:22
@ b0a838f2:34ed3f19
2025-05-23 18:06:22- Dolibarr - Modern CRM software package to manage your company or foundation activity (contacts, suppliers, invoices, orders, stocks, agenda, accounting, ...). (Demo, Source Code)
GPL-3.0PHP/deb - ERPNext - ERP system to help you run your business. (Source Code)
GPL-3.0Python/Docker - farmOS - Web-based farm record keeping application. (Demo, Source Code)
GPL-2.0PHP/Docker - grocy - ERP beyond your fridge. Groceries & household management solution for your home. (Demo, Source Code)
MITPHP/Docker - LedgerSMB - Integrated accounting and ERP system for small and midsize businesses, with double entry accounting, budgeting, invoicing, quotations, projects, orders and inventory management, shipping and more. (Demo, Source Code)
GPL-2.0Docker/Perl - Odoo - Free open source ERP system. (Demo, Source Code)
LGPL-3.0Python/deb/Docker - OFBiz - Enterprise Resource Planning system with a suite of business applications flexible enough to be used across any industry. (Source Code)
Apache-2.0Java - Tryton - Free open source business solution. (Demo, Source Code)
GPL-3.0Python
- Dolibarr - Modern CRM software package to manage your company or foundation activity (contacts, suppliers, invoices, orders, stocks, agenda, accounting, ...). (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:06:04
@ b0a838f2:34ed3f19
2025-05-23 18:06:04- Engity's Bifröst - Highly customizable SSH server with several ways to authorize a user and options where and how to execute a user's session. (Source Code)
Apache-2.0Go/Docker - Firezone - Secure remote access gateway that supports the WireGuard protocol. It offers a Web GUI, 1-line install script, multi-factor auth (MFA), and SSO. (Source Code)
Apache-2.0Elixir/Docker - Guacamole - Clientless remote desktop gateway supporting standard protocols like VNC and RDP. (Source Code)
Apache-2.0Java/C - MeshCentral - Run your own web server to remotely manage and control computers on a local network or anywhere on the internet. (Source Code)
Apache-2.0Nodejs - Remotely - A remote desktop control and remote scripting solution, enterprise level remote support solution with admin web interface and remote control via browser.
GPL-3.0C#/Docker - RustDesk - Remote Desktop Access software that works out-of-the-box (alternative to TeamViewer). (Source Code)
AGPL-3.0Rust/Docker/deb - ShellHub - ShellHub is a modern SSH server for remotely accessing linux devices via command line (using any SSH client) or web-based user interface, designed as an alternative to sshd. (Source Code)
Apache-2.0Docker - Sshwifty - Sshwifty is a SSH and Telnet connector made for the Web. (Demo)
AGPL-3.0Go/Docker - Warpgate - Smart SSH and HTTPS bastion that works with any SSH client.
Apache-2.0Rust/Docker
- Engity's Bifröst - Highly customizable SSH server with several ways to authorize a user and options where and how to execute a user's session. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:05:47
@ b0a838f2:34ed3f19
2025-05-23 18:05:47- Bar Assistant - Manage your home bar while adding your ingredients, searching for cocktails and creating custom cocktail recipes. (Demo, Source Code)
MITPHP/Docker - Fork Recipes - Manage your food recipes with simplicity. (Source Code)
BSD-3-ClauseDocker - KitchenOwl - Cross-platform shopping list, recipe storage, expense tracker, and meal planner following the material design language. (Source Code)
AGPL-3.0Docker/deb - ManageMeals - Manage recipes, import recipes by URL and organize them without any ads or unnecessary text. (Demo, Source Code)
GPL-3.0Docker - Mealie - Material design inspired recipe manager with category and tag management, shopping-lists, meal-planner, and site customizations. Mealie is focused on simple user interactions to keep the whole family using the app. (Source Code)
MITPython - RecipeSage - A recipe keeper, meal plan organizer, and shopping list manager that can import recipes directly from any URL. (Demo)
AGPL-3.0Nodejs - Recipya - A clean, simple and powerful recipe manager your whole family will enjoy. (Demo, Source Code)
GPL-3.0Docker/Go - Specifically Clementines - Grocery shopping app (previously Groceries), providing reliable sync with multiple users/devices (web/Android/iOS), recipes and integration with Tandoor. (Source Code)
MITDocker - Tamari - Recipe manager web app with a built-in collection of recipes. Organize by favorites and categories, create shopping lists, and plan meals. (Demo, Source Code)
GPL-3.0Docker/Python - What To Cook? - Get a recipe to cook today, based on the ingredients you have at home.
AGPL-3.0Docker
- Bar Assistant - Manage your home bar while adding your ingredients, searching for cocktails and creating custom cocktail recipes. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:05:11
@ b0a838f2:34ed3f19
2025-05-23 18:05:11- Bitpoll - Conduct polls about dates, times or general questions. (Demo)
GPL-3.0Docker/Python - Bracket - Flexible tournament system to build a tournament setup, add teams, schedule matches, keep track of scores and present ranking live to the public. (Demo, Source Code)
AGPL-3.0Docker/Nodejs - Christmas Community - Create a simple place for your entire family to use to find gifts that people want, and to avoid double-gifting.
AGPL-3.0Docker/Nodejs - Claper - The ultimate tool to interact with your audience (alternative to Slido, AhaSlides and Mentimeter). (Source Code)
GPL-3.0Elixir/Docker - ClearFlask - Community-feedback tool for managing incoming feedback and prioritizing a public roadmap (alternative to Canny, UserVoice, Upvoty). (Demo, Source Code)
AGPL-3.0Docker - docassemble - A free, open-source expert system for guided interviews and document assembly, based on Python, YAML, and Markdown. (Demo, Source Code)
MITDocker/Python - Fider - Open platform to collect and prioritize feedback (alternative to UserVoice). (Demo, Source Code)
MITDocker - Formbricks - Experience Management Suite built on the largest open source survey stack worldwide. Gracefully gather feedback at every step of the customer journey to know what your customers need. (Demo, Source Code)
AGPL-3.0Nodejs/Docker - Framadate - Online service for planning an appointment or make a decision quickly and easily: Make a poll, Define dates or subjects to choose, Send the poll link to your friends or colleagues, Discuss and make a decision. (Demo, Source Code)
CECILL-BPHP - Gancio - Local community event and agenda sharing. (Demo, Source Code)
AGPL-3.0Nodejs - gathio - Self-destructing, shareable, no-registration event pages. (Demo, Source Code)
GPL-3.0Nodejs/Docker - HeyForm - Form builder that allows anyone to create engaging conversational forms for surveys, questionnaires, quizzes, and polls. (Source Code)
AGPL-3.0Docker - hitobito - Manage complex group hierarchies with members, events and a lot more. (Demo, Source Code)
AGPL-3.0Ruby - Input - Privacy-focused, no-code, open-source form builder designed for simplicity and brand consistency. (Source Code)
AGPL-3.0PHP/Nodejs/Docker - LimeSurvey - Feature-rich web-based polling software. Supports extensive survey logic. (Demo, Source Code)
GPL-2.0PHP - Meetable - Minimal events aggregator. (Source Code)
MITPHP - Mobilizon - Federated tool that helps you find, create and organise events and groups. (Source Code)
AGPL-3.0Elixir/Docker - OpnForm - Beautiful open-source form builder. (Demo, Source Code)
AGPL-3.0PHP/Nodejs/Docker
- Bitpoll - Conduct polls about dates, times or general questions. (Demo)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:04:53
@ b0a838f2:34ed3f19
2025-05-23 18:04:53- Chevereto - Ultimate image sharing software. Create your very own personal image hosting website in just minutes. (Source Code)
AGPL-3.0PHP/Docker - Coppermine - Multilingual photo gallery that integrates with various bulletin boards. Includes upload approval and password protected albums. (Source Code)
GPL-3.0PHP - Damselfly - Fast server-based photo management system for large collections of images. Includes face detection, face & object recognition, powerful search, and EXIF Keyword tagging. Runs on Linux, MacOS and Windows. (Source Code)
GPL-3.0Docker/C#/.NET - Ente - An end-to-end encrypted photo-sharing platform (alternative to Google Photos, Apple Photos). (Source Code)
AGPL-3.0Docker/Nodejs/Go - HomeGallery - Browse personal photos and videos featuring tagging, mobile-friendly, and AI powered image discovery. (Demo, Source Code)
MITNodejs/Docker - Immich Kiosk - Lightweight slideshow for running on kiosk devices and browsers that uses Immich as a data source.
GPL-3.0Docker/Go - Immich - Photo and video backup solution directly from your mobile phone. (Demo, Source Code)
AGPL-3.0Docker - LibrePhotos - Photo management service with a slight focus on cool graphs (alternative to Google Photos). (Clients)
MITPython/Docker - Lychee - Grid and album based photo-management-system. (Source Code)
MITPHP/Docker - Mediagoblin - Media publishing platform that anyone can run (alternative to Flickr, YouTube, SoundCloud, etc). (Source Code)
AGPL-3.0Python - Mejiro - Easy-to-use instant photo publishing.
GPL-3.0PHP - Nextcloud Memories - Fast, modern and advanced photo management suite. Runs as a Nextcloud app. (Demo, Source Code)
AGPL-3.0PHP - Photofield - Experimental fast photo viewer.
MITDocker/Go - PhotoPrism - Personal photo management powered by Go and Google TensorFlow. Browse, organize, and share your personal photo collection, using the latest technologies to automatically tag and find pictures. (Demo, Source Code)
AGPL-3.0Go/Docker - Photoview - Simple and user-friendly photo gallery for personal servers. It is made for photographers and aims to provide an easy and fast way to navigate directories, with thousands of high resolution photos. (Source Code)
GPL-3.0Go/Docker - PiGallery 2 - Directory-first photo gallery website, with a rich UI, optimised for running on low resource servers. (Source Code)
MITDocker/Nodejs - Piwigo - Photo gallery software for the web, built by an active community of users and developers. (Source Code)
GPL-2.0PHP - sigal - Yet another simple static gallery generator.
MITPython - SPIS - A simple, lightweight and fast media server with decent mobile support.
GPL-3.0Docker/Rust - This week in past - Aggregates images taken this week, from previous years and presents them on a web page with a simple slideshow.
MITDocker/Rust - Thumbor - A smart imaging service and enables on-demand cropping, resizing, applying filters and optimizing images. (Source Code)
MITPython/Docker - Zenphoto - Open-source gallery and CMS project. (Source Code)
GPL-2.0PHP
- Chevereto - Ultimate image sharing software. Create your very own personal image hosting website in just minutes. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:04:36
@ b0a838f2:34ed3f19
2025-05-23 18:04:36- Dashy - Feature-rich homepage for your homelab, with easy YAML configuration. (Demo, Source Code)
MITNodejs/Docker - Fenrus - Personal home page that allows for multiple users, guest access and multiple dashboards for each user. It also has "Smart Apps" which display live data for those apps.
GPL-3.0.NET/Docker - Glance - Highly customizable dashboard that puts all your feeds in one place.
AGPL-3.0Docker/Go - Heimdall - Elegant solution to organise all your web applications. (Source Code)
MITPHP - Hiccup - Beautiful static homepage to get to your links and services quickly. It has built-in search, editing, PWA support and localstorage caching to easily organize your start page. (Source Code)
MITJavascript/Docker - Homarr - Sleek, modern dashboard with many integrations and web-based config. (Source Code)
MITDocker/Nodejs - Homepage by gethomepage - Highly customizable homepage (or startpage / application dashboard) with Docker and service API integrations.
GPL-3.0Docker/Nodejs - Homepage by tomershvueli - Simple, standalone, self-hosted PHP page that is your window to your server and the web.
MITPHP - Homer - Dead simple static homepage to expose your server services, with an easy yaml configuration and connectivity check.
Apache-2.0Docker/K8S/Nodejs - Hubleys - Personal dashboards to organize links for multiple users via a central yaml config.
MITDocker - LinkStack - Link all your social media platforms easily accessible on one page, customizable through an intuitive, easy to use user/admin interface (alternative to Linktree and Manylink). (Demo, Source Code)
AGPL-3.0PHP/Docker - LittleLink - Simplistic approach for links in bio with 100+ branded buttons (alternative to Linktree). (Demo, Source Code)
MITJavascript - Mafl - Minimalistic flexible homepage. (Source Code)
MITDocker/Nodejs - portkey - Simple web portal that serves as a startup page, displaying a compilation of links and URLs, while also allowing the addition of custom pages, all managed through a single configuration file. (Demo, Source Code)
AGPL-3.0Go/Docker - ryot - Platform for tracking various facets of your life - media, fitness, etc. (Demo)
GPL-3.0Docker - Starbase 80 - A simple homepage with an iPad-style application grid, for mobile and desktop. One JSON configuration file.
MITDocker - Web-Portal - A python web app designed to allow a easy way to manage the links to all of your web services.
AGPL-3.0Docker/Python - Your Spotify
⚠- Allows you to record your Spotify listening activity and have statistics about them served through a Web application.MITNodejs/Docker
- Dashy - Feature-rich homepage for your homelab, with easy YAML configuration. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:04:16
@ b0a838f2:34ed3f19
2025-05-23 18:04:16- bin - A paste bin that's actually minimalist.
WTFPL/0BSDRust - BinPastes - Minimal pastebin supporting client-side encryption, fulltext search, one-time messages. Intended for one to few users looking for a simple pastebin deployment. (Demo)
Apache-2.0Java - ByteStash - Pastebin and file storage service with a simple web interface. Supports syntax highlighting, optional user authentication and public sharing. (Demo)
GPL-3.0Docker - dpaste - Simple pastebin with multiple text and code option, with short url result easy to remember. (Source Code)
MITDocker/Django - FlashPaper - One-time encrypted zero-knowledge password/secret sharing application focused on simplicity and security. No database or complicated set-up required. (Demo)
MITDocker/PHP - Hemmelig - Share encrypted secrets cross organizations, or as private persons. (Source Code)
MITDocker/Nodejs - lesma - Simple paste app friendly with browser and command line. (Demo, Source Code)
GPL-3.0Rust/Docker - Local Content Share - Store and share text snippets and files within your local network.
MITDocker/Go - not-th.re - Simple paste sharing platform, with client side encryption, featuring the monaco browser-based code editor. (Demo, Source Code)
AGPL-3.0Nodejs/Docker - Opengist - Pastebin powered by Git. (Demo)
AGPL-3.0Docker/Go/Nodejs - paaster - End-to-end encrypted pastebin built with the objective of simplicity. (Source Code)
AGPL-3.0Docker - pacebin - Super-minimal pastebin and file upload service focusing on small executable size, portability, and ease of configuration. (Demo, Source Code)
AGPL-3.0C - Password Pusher - Dead-simple application to securely communicate passwords (or text) over the web. Passwords automatically expire after a certain number of views and/or time has passed. (Source Code)
Apache-2.0Docker/K8S/Ruby - Pastefy - Beautiful, simple and easy to deploy Pastebin with optional client encryption, multitab pastes, an API, a highlighted editor and more. (Source Code, Clients)
MITDocker/K8S/Java - PrivateBin - Minimalist pastebin/discussion board where the server has zero knowledge of hosted data. (Demo, Source Code)
ZlibPHP - rustypaste - A minimal file upload/pastebin service.
MITRust - SnyPy - Open source on-prem code snippet manager. (Demo, Source Code)
MITDocker - Spacebin - Modern Pastebin server written in Go with a JS-free web UI and tons of features. (Demo, Source Code)
Apache-2.0Go/Docker - Sup3rS3cretMes5age - Very simple (to deploy and to use) secret message service using Hashicorp Vault as a secrets storage.
MITGo - Wastebin - Lightweight, minimal and fast pastebin with an SQLite backend. (Demo)
MITRust/Docker - YABin - A pastebin that contains plentiful features while remaining simple. Supports optional E2E encryption, a client-side CLI app, syntax highlighting, minimalistic UI, APIs, keyboard shortcuts, and more. It can even be run in serverless environments. (Demo)
MITNodejs/Docker - ybFeed - Personal micro feed where you can post snippets of text or images.
MITGo/Nodejs/Docker - Yopass - Secure sharing of secrets, passwords and files. (Demo)
Apache-2.0Go/Docker
- bin - A paste bin that's actually minimalist.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:03:56
@ b0a838f2:34ed3f19
2025-05-23 18:03:56- AliasVault - End-to-end encrypted password manager with a built-in email alias generator and server. (Source Code)
MITDocker - Bitwarden
⚠- Password manager with a webapp, browser extension, and mobile app. (Source Code)AGPL-3.0Docker/C# - Passbolt - Collaborative password manager. (Source Code)
AGPL-3.0PHP/deb/K8S/Docker - PassIt - Simple password manage with sharing features by group and user, but no administration interface. (Demo, Source Code)
AGPL-3.0Docker/Django - Passky - Simple and modern password manager with website, browser extension, android and desktop application. (Demo, Source Code)
GPL-3.0PHP/Docker - Psono - Password manager for companies. (Demo, Source Code)
Apache-2.0Python - Teampass - Password manager dedicated for managing passwords in a collaborative way. One symmetric key is used to encrypt all shared/team passwords and stored server side in a file and the database. works on any server Apache, MySQL and PHP. (Source Code)
GPL-3.0PHP - Vaultwarden - Lightweight Bitwarden server API implementation written in Rust.
GPL-3.0Rust/Docker
- AliasVault - End-to-end encrypted password manager with a built-in email alias generator and server. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:03:41
@ b0a838f2:34ed3f19
2025-05-23 18:03:41- Collabora Online Development Edition - Collabora Online Development Edition (CODE) is a powerful LibreOffice-based online office that supports all major document, spreadsheet and presentation file formats, which you can integrate in your own infrastructure. (Source Code)
MPL-2.0C++ - CryptPad - Collaboration suite built to enable collaboration, synchronizing changes to documents in real time. (Source Code)
AGPL-3.0Nodejs/Docker - Digislides - Create multimedia presentations in a quick and easy way. (documentation in French). (Demo, Source Code)
AGPL-3.0Nodejs/PHP - Etherpad - Highly customizable online editor providing collaborative editing in real-time. (Demo, Source Code)
Apache-2.0Nodejs/Docker - Grist - Next-generation spreadsheet with relational structure, formula-based access control, and a portable, self-contained format (alternative to Airtable). (Demo, Source Code)
Apache-2.0Nodejs/Python/Docker - ONLYOFFICE - Office suite that enables you to manage documents, projects, team and customer relations in one place. (Source Code)
AGPL-3.0Nodejs/Docker
- Collabora Online Development Edition - Collabora Online Development Edition (CODE) is a powerful LibreOffice-based online office that supports all major document, spreadsheet and presentation file formats, which you can integrate in your own infrastructure. (Source Code)
