-
 @ 866e0139:6a9334e5
2025-06-01 07:56:34
@ 866e0139:6a9334e5
2025-06-01 07:56:34Autor: Bernd Schoepe. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die Anmerkungen zum Text (Fußnoten) folgen aus technischen Gründen gesondert.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
„*Es handelt sich beim Krieg nicht nur um eine Zerstörung von (...) Millionen Menschen, sondern um die Zerstörung der gesamten sozialen, moralischen und menschlichen Struktur einer Gesellschaft, von der man überhaupt nicht voraussehen kann, welche weiteren Konsequenzen an Barbarei, an Verrücktheit sie (...) mit sich bringt. (..) *
Die Gewalt kann fast alles mit den Menschen machen. Es ist wichtig zu sehen, dass es nur fast alles ist. Sie kann mit einigen Menschen nicht das machen, was sie will, nämlich ihre seelische Struktur, ihre Überzeugungen ändern und mit allen Menschen kann sie nur das machen, was sie will, wenn sie gewisse, sehr schädliche Nebenerscheinungen in Kauf nimmt: die Nebenerscheinung der Verdummung, der Lähmung der Vitalität, der Einbildungskraft, dem Schöpferischsein des Menschen. In vielen Fällen aber sind die, die die Gewalt ausüben gar nicht daran interessiert, dass diese Folgen nicht eintreten. Im geschichtlichen Prozess allerdings bleiben diese Folgen von großer Wichtigkeit.“
Erich Fromm, Zur Theorie und Strategie des Friedens (1969).
„Solange Kriege geführt werden, wird uns Kummer plagen, werden kräftige Beine nutzlos werden und strahlende Augen dunkel.“
Sean O’ Casey, Der Preispokal
Der Friede geht uns alle an – Vom Krieg profitieren aber immer nur Wenige
Gerne komme ich zum Einstand als Mit-Autor dieses wunderbaren Projekts „Die Friedenstaube“ dem Wunsch nach, über meine biographischen Hintergründe in Bezug auf das Friedensthema zu schreiben. Obwohl mein erster Impuls doch eher zögerlich war: „Darauf kommt es doch gar nicht an!“, schoss es mir zunächst durch den Kopf.
\ Geht der Frieden doch uns alle an, und zwar so stark, dass alle persönlichen Gründe, Motive, Unter-, Ober- und Zwischentöne zu dem Thema eigentlich kaum eine Rolle spielen können… – oder!? Erliegen wir nicht sogar einer ganz und gar deplatziert wirkenden Eitelkeit angesichts des „Alles oder Nichts“, um das es bei der Frage nach Krieg oder Frieden geht, wenn wir glauben, wir müssten, um für den Frieden einzutreten, irgendwelche individuellen Gründe oder spezielle biographische Motive ins Feld führen?
Für den Frieden muss man sein, weil und insoweit man ein Mensch ist (1).
So grundsätzlich und selbstverständlich, wie es der Autor des berühmten Anti-Kriegsromans „Im Westen nichts Neues“, Erich Maria Remarque, ausdrückte:
„Ich dachte immer, jeder Mensch sei gegen den Krieg. Bis ich rausfand, dass es welche gibt, die dafür sind, nämlich die, die nicht hingehen müssen.“
Erneut ist dieses Zitat – und welche Bitterkeit und welcher „Abscheu vor der Weltgeschichte“ (Erwin Chargaff) liegen darin, dies konstatieren zu müssen! – zum Wort der Stunde geworden. Auch heute wird wieder von der herrschenden Politik und den Leitmedien weitgehend ausgeblendet, welche Interessen hinter der allgemeinen Mobilmachung zum Krieg am Werke sind und wer von ihr wirklich profitiert.
Mit Erich Fromm gesprochen sind Kriegsbegeisterung und Kriegshysterie Kennzeichen von nekrophilen Gesellschaften. Wann hat sich unsere Gesellschaft offiziell so krass vom Leben und vom Wert des Lebendigen verabschiedet? Wie konnte es aufs Neue soweit kommen?
Die Zumutungen, die in der Logik, der Unterordnung unter das Prinzip der Nekrophilie liegen und die vom Krieg auf die Spitze getrieben werden, sind von Hannes Wader im „Einheitsfrontlied“ prägnant auf den Punkt gebracht worden:
„Und weil der Mensch ein Mensch ist
Drum hat er Stiefel im Gesicht nicht gern.
Er will unter sich keinen Sklaven sehen
*Und über sich keinen Herrn.“ *
(2)
Die Ordnung des Krieges aber stellt in gewisser Weise die Vollendung der auf Herrschafts- und – in seiner neoliberalen Ausprägung – Markt- und Mammon-Vergottung und der auf Arbeitssklavengehorsam der Massen basierenden Abhängigkeits- und Ausbeutungsverhältnisse dar. Unter dessen Joch leben im Kapitalismus des 21.Jahrhunderts die Menschen weltweit. Wobei die Anzahl derer, die unter diesen Bedingungen in extremer Armut dahinvegetieren müssen – schließlich setzt „leben“ ein Mindestmaß an Würde voraus – sich global auf über eine Milliarde Menschen beläuft. \ Willy Brandt hat gesagt: „Der Frieden ist nicht alles, aber ohne Frieden ist alles nichts“. Sein Gegenteil – der Krieg – ist die schlimmste Kollektiverfahrung, die eine Generation erleben kann. Zuletzt musste die Generation meiner Eltern und Großeltern diese Erfahrung durchmachen.
Wir Nachgeborenen können uns das Grauen, das Elend des Krieges, das unendliche Leid, das er über die Menschen bringt, nicht wirklich vorstellen. Wir können aber um die Ausmaße des Zivilisationsbruchs des Ersten Weltkrieges und dann, noch einmal furchtbar gesteigert, des Zweiten Weltkrieges wissen. Und als zum Mitfühlen fähige Wesen können wir ermessen, was es heißt, im Krieg zu sein:
„Keiner kommt aus dem Geschehen in einem Kriegsgebiet wieder heil raus, das macht etwas mit einem. Auf der anderen Seite (...) muss man sich immer klar machen, das eine ist das Geschehen im Kriegsgebiet, aber das andere sind die Kriegstreiber. (...) Sie sitzen da, wo einem nichts geschieht (...)“,
so Patrick Baab, der als einer der wenigen Journalisten wiederholt im umkämpften Kriegsgebiet der Ost-Ukraine war und seine Eindrücke erster Hand in dem Buch „Auf beiden Seiten der Front. Meine Reisen in die Ukraine“ geschildert hat.
Dass diese Teilung in solche und solche, die Remarque in seinem Zitat lakonisch-pointiert thematisiert, auch heute wieder beobachtet werden muss, d.h. Politik und Leitmedien von (ahnungslosen?) Kriegsverharmlosern und Kriegstreibern und ihrem bellizistischen Geschrei beherrscht werden, während die Mehrheit des Volkes sich weiterhin sehnlichst Frieden wünscht, auf diesen erschreckenden Sachverhalt und was aus ihm geschlossen werden müsste, hat Baab kürzlich im Interview mit dem Overton-Magazin hingewiesen (3).
Ein Hinweis am Ende dieser Einleitung:
Ich muss den Leser vorab um Geduld bitten, denn mein Text wird mit der autobiographischen Tür nicht gleich ins Haus, weder in das des Krieges noch in das des Friedens fallen.
Die ersten Teile (II –V) werden im Zeichen der politischen Analyse stehen. Einer Analyse, die nicht vor dem Hintergrund meiner eigenen, sondern der bundesdeutschen Geschichte und einige ihrer größten blinden Flecken – mit Ulrike Guérot könnte man auch sagen „ihrer größten Märchen“– unternommen wird. Dass mein antimilitaristisches Ich in Interaktion zu dieser Geschichte stand und steht, muss wohl nicht eigens betont werden.
Erst nach dieser Erkundung des Makrokosmos werden sich im Verlauf des Textes von da aus, nach einer Durchleuchtung seiner Bedingtheiten, Zugänge zum eigenen Mikrokosmos eröffnen. Sonst wären sie vermutlich als autobiographische Lesart des Themas nicht offen zu Tage getreten, möglicherweise mir sogar ganz verschlossen geblieben. So aber darf mit guten Gründen vermutet werden, dass das persönlich hier von mir Festgehaltene und Fokussierte nicht nur mich angeht. Vielmehr erscheint es in dem Maße verallgemeinerbar zu sein, wie durch den Fortgang meiner Darlegungen jeder Leser individuell (hoffentlich) ebenfalls dazu motiviert werden kann, die Frage zu reflektieren, was es bedeutet, wenn es sich bei der persönlichen Begegnung mit dem Krieg um eine Begegnung auf den zweiten oder sogar dritten Blick handelt?
Der Nachkriegs-„Frieden“ als die Zeit ernst gemeinter, nicht enden wollender Kriegsspiele
„Nie wieder Krieg! Nie wieder Faschismus!“
Das war die Lehre aus den Weltkriegs-Zivilisationszusammenbrüchen, die vor allem anderen, wenn auch auf verschiedene Weise, als DNA beiden deutschen Republiken, zu ihren Gründungszeiten eingeprägt wurde.
Was aber ist aus dieser DNA geworden?
Heute lassen wir zu, dass in Manier des NS-Reichspropagandaministers Goebbels von „Kriegstüchtigkeit“ als Staatsziel schwadroniert wird (4), das man bitteschön mal bis 2030, mal schon 2027 erreicht haben müsse, weil sonst „der Russe“ am Brandenburger Tor stehe. Mit „Kriegstüchtigkeit“ sind immense, unvorstellbare Summen an Geld gemeint, neue Schulden, die in die Rüstung und Militarisierung der Gesellschaft fließen sollen und folglich anderswo, für eine menschliche, dem Leben dienende Politik, schmerzlich fehlen. Die Militarisierung soll nun wieder, wie im Wilhelminismus und im Dritten Reich, von Kindesbeinen an propagiert und gefördert werden.
An den Schulen darf der Beutelsbacher Konsens mit seinem Überwältigungsverbot – er wurde schon in der Corona-Zeit mit schlimmsten Folgen für die Kinder und Jugendliche missachtet (5 https://www.cicero.de/kultur/fuenf-jahre-schulschliessungen-corona-aufarbeitung) – nun auch der Wehrertüchtigung der jungen Generation und dem Ruf „Zu den Waffen!“ auf keinen Fall mehr im Wege stehen. Völlig abstrus: Schüler, die gegen die Kriegsertüchtigung an den Schulen protestieren, werden dafür von Pädagogen (!) wegen „Störung des Schulfriedens“ bestraft. Antimilitaristische, pazifistische Haltungen werden ausgegrenzt und kriminalisiert. Mittels Framings sind, wie schon in der Corona-Zeit, die Mainstream-Medien erneut eifrig dabei, die vernünftig-skeptischen Stimmen moralisch zu diskreditieren. Wurden zu Plandemie-Zeiten jene, die die Verhältnismäßigkeit der staatlichen Maßnahmen in Frage stellten und sich der systematisch betriebenen Panikmache und Massenpsychose verweigerten, öffentlich verächtlich gemacht, werden nun all jene, die für Abrüstung, Diplomatie und Völkerverständigung plädieren, diffamiert und ins gesellschaftliche Abseits gestellt.
Dennoch regt sich kein massenhafter Protest, der den Minister, der die Kriegstüchtigkeit zum Gesellschaftsziel erhoben hat, zum Rücktritt zwingen und die Journalisten zur Besinnung und zur Einhaltung professioneller Standards bringen könnte. Und das obwohl die Forderung nach Kriegstüchtigkeit – wie die gesamte Russland-Ukraine-Politik der bundesdeutschen Regierungen in den letzten fünfzehn Jahren – eine eklatante Verletzung der Friedenspflicht des Grundgesetzes darstellt. So gab Angela Merkel Ende 2022 bekannt, man habe die Verhandlungen um das 2015 ratifizierte Minsker Abkommen nur geführt, um der Ukraine genug Zeit zum Aufbau einer kriegsfähigen Armee und für das Aufrüsten zu geben (6). Die Ukraine sollte in die Lage versetzt werden, die Donbass-Provinzen zurückzuerobern, die sich in Folge von Kiews ultra-nationalistischer Politik seit 2015 sezessionistisch, mit Unterstützung Russlands, für autonom erklärt hatten. Ergänzt werden muss, dass in der Ukraine nach den gewalttätigen Ereignissen auf dem Maidan, die zum Sturz von Janukowytsch führen sollte, ein den Faschismus verherrlichender, hybrider Nationalismus politisch die Oberhand gewann, der die vor allem im Osten des Landes lebende russische Bevölkerung zunehmend diskriminierte und ihre Kultur unterdrückte.
Die bundesdeutsche Öffentlichkeit nahm die absolut skandalöse Äußerung der ehemaligen Regierungschefin achselzuckend hin. Nicht einmal ansatzweise flammte eine Debatte darüber auf, wie viel diplomatisches Porzellan durch diese Täuschung des russischen Vertragspartners zerschlagen und wie stark dadurch die außenpolitische Glaubwürdigkeit der Bundesrepublik – die lange Zeit international als ehrlicher Makler des Interessenausgleichs gegolten hatte – beschädigt wurde.
Was ist aus dem Vorschlag Michail Gorbatschows geworden, eine gemeinsame europäische Sicherheitsarchitektur von Lissabon bis Wladiwostok zu schaffen, den Präsident Putin beim Deutschland-Besuch 2001 noch einmal als sein umfassendes Angebot zur Zusammenarbeit an den Westen bekräftigt hatte? Damals sagte Putin in seiner weitgehend auf Deutsch gehaltenen Rede vor dem Bundestag:
*„Ohne eine moderne, dauerhafte und standfeste internationale Sicherheitsarchitektur schaffen wir auf diesem Kontinent nie ein Vertrauensklima und ohne dieses Vertrauensklima ist kein einheitliches Großeuropa möglich. Heute sind wir verpflichtet, zu sagen, dass wir uns von unseren Stereotypen und Ambitionen trennen sollten, um die Sicherheit der Bevölkerung Europas und die der ganzen Welt zusammen zu gewährleisten. (...) *
Noch vor kurzem schien es so, als würde auf dem Kontinent bald ein richtiges gemeinsames Haus entstehen, in welchem Europäer nicht in östliche und westliche, in nördliche und südliche geteilt werden. Solche Trennungslinien bleiben aber erhalten, und zwar deswegen, weil wir uns bis jetzt noch nicht endgültig von vielen Stereotypen und ideologischen Klischees des Kalten Krieges befreit haben.“
(7)
Putins Bitte, sich endgültig von den Stereotypen und Klischees des Kalten Krieges zu befreien – er erhielt für seine Rede im Bundestag damals lang anhaltenden Beifall und stehende Ovationen – sollte sich als frommer Wunsch erweisen. Die einflussreichen, entscheidenden Kräfte in den USA dachten überhaupt nicht daran, diesen Schritt zu tun. Der „nationale Egoismus“, von dem Putin im selben Zusammenhang als Hinderungsgrund für weitere Annäherungen sprach, sollte – vor allem seitens der USA, wie es aus den Strategiepapieren der mächtigen, dem Pentagon zuarbeitenden Denkfabriken der NeoCons unmissverständlich hervorgeht – auf ganzer Linie triumphieren:
„Allein die Lektüre einiger amerikanischer geopolitischer Texte hätte den deutschen Politikern zeigen können, dass die Vereinigten Staaten niemals eine Annäherung Deutschlands an Russland akzeptieren würden. (...) Für die Strategen in Washington glich eine deutsch-russische Allianz einem absoluten Albtraum.“
(8)
Folglich wurde die Rede nicht als historische Chance, als einzigartiges window of opportunity begriffen, die bilateralen und multilateralen Beziehungen neu zu definieren und damit ein neues Kapitel des Friedens und des Wohlstandes unter den Völkern aufzuschlagen und, wie es der russische Präsident formulierte, „damit unseren gemeinsamen Beitrag zum Aufbau des europäischen Hauses“ (9) zu leisten.
Stattdessen setzte sich, trotz der veränderten Bedingungen einer komplizierter gewordenen, nach 1990 multipolar sich neu ordnenden Welt, wiederum das alte, hegemoniale Denken der US-Amerikaner im gesamten, offenbar nun erstarkten (10) und bis an die Grenzen Russlands ausgedehnten Westen (NATO-Osterweiterung!) durch. Damit folgte man wiederum den alten Pfaden der Konfrontation statt den neuen der Kooperation, was leider eine lange Kontinuität aufweist.
So haben neuere Forschungen im Rahmen der Geschichte der Kognitiven Kriegsführung belegt, dass die Bundesrepublik von Anfang an systematisch durch die USA militärisch-geostrategisch und mental in Stellung gegen die Sowjetunion gebracht wurde. An der Bewertung der Beziehungen Deutschlands und Russlands hat sich grundlegend auch nach 1990 und dem Ende der Blockpolarität aus Sicht der US-Amerikaner nichts geändert.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Der Amerikanist und Propagandaforscher Jonas Tögel hat herausgearbeitet (11), in welchem Ausmaß es 1945 den USA nicht um die Befreiung des europäischen Kontinents ging. Vielmehr lautete die Doktrin, dass als der eigentliche Kriegsgegner die Sowjetunion bezwungen werden müsse: „Europa war in letzter Konsequenz genauso strategisches Gebiet wie davor (...). Es sollten offenbar die letzten deutschen Truppen (...) mit den letzten alliierten Truppen in einem neuen Aufgebot gen Osten geschickt werden“ (12). Die US-amerikanischen Regierungen sahen – über 1945 hinaus! – die Sowjetunion als den Hauptfeind an. Dabei war klar, wo der Austragungsort der Entscheidungsschlacht zwischen den Systemantagonisten liegen würde: 1955, im ersten Mitgliedsjahr der BRD, wurde eine „Carte Blanche“ genannte NATO-Übung durchgeführt, in der es ein Szenario von 168 Atombombenabwürfen über deutsches Gebiet mit 1,7 Millionen getöteten und 3,5 Millionen verletzten Deutschen entworfen gab. Weitere Planspiele, die die atomare Zerstörung Deutschlands vorsahen, folgten. Etwas größere Bekanntheit erlangte, durch den damaligen Staatssekretär im Bundesverteidigungsministerium Willy Wimmer (CDU), die NATO-Übung WINTEX/FALLEX (13) von 1986, in der Atombombeneinsätze gegen Dresden und andere deutsche Städte vorgesehen waren.
„Er, Wimmer, sei von dieser Anforderung völlig überrascht worden und sei entsetzt gewesen. Er habe es abgelehnt, an der Planung eines Atomwaffeneinsatzes auf Ziele in Ostdeutschland und damit gegen die ostdeutsche Bevölkerung – wenn auch „nur“ übungsweise – mitzuwirken. In dieser Situation habe er sofort Kontakt mit dem damaligen Bundeskanzler Dr. Helmut Kohl (CDU) aufgenommen und ihn von diesem für ihn unerhörten Vorgang in Kenntnis gesetzt. Bundeskanzler Kohl habe daraufhin entschieden, dass sich die Vertreter der Bundesregierung sofort aus der weiteren Übung zurückziehen und sich keinesfalls an diesen nuklearen Planspielen gegen Ziele wie Dresden und andere ostdeutsche Städte beteiligen sollten. Deutschland habe, so Wimmer, deshalb seine weitere Mitwirkung an dieser NATO-Übung – vier Tage vor ihrem Ende – eingestellt. Die Übung sei dann – ohne deutsche Beteiligung – fortgesetzt worden.“ (14)
Der Schweizer Militär- und Geheimdienstexperte Jacques Baud geht soweit zu behaupten, dass die NATO „für den Kalten Krieg und für den Nuklearkrieg geschaffen wurde.“ (15) Zu einem Zeitpunkt, wo der erst im zweiten Wahlgang gewählte neue deutsche Bundeskanzler noch immer nicht öffentlich seine Erklärung zurückgenommen hat, Taurus-Raketen an die Ukraine liefern zu wollen, sollte dies unbedingt in Erinnerung gerufen werden.
Darüber hinaus gilt, was alle Kriegsspiele, sowohl die Kriegsspiele der NATO als auch jene der Sowjetunion bzw. später Russlands dokumentieren:
„Die Deutschen haben nicht mitzureden, wenn es um die Vernichtung ihres eigenen Landes geht.“ (Jonas Tögel, 16).
Kann es da verwundern, dass spiegelbildlich dazu der von der NATO losgetretene Informationskrieg gerade in Deutschland immer bizarrere Blüten treibt?
Denn hier liegt das Schlachtfeld des Propagandakrieges, der jedem Waffengang erst einmal vorausgeht und gewonnen sein will. Das meint auch die Rede von der zu erlangenden Kriegstüchtigkeit. Sie dient als Propaganda zur Formierung der Gesellschaft gegen „den“ Feind, wobei der Feind grundsätzlich austauschbar ist (es kann auch ein „gefährliches“ Virus sein...), immer aber gewisse Eigenschaften aufweisen muss. So sollte er leicht adaptierbar an die Ängste oder Aggressionen der Menschen sein. Dies impliziert auch, dass die aktuelle Einschätzung von 16 amerikanischen Geheimdiensten, nach denen Russland keinen Krieg gegen die europäischen NATO-Staaten beabsichtige und plane, in der öffentlichen Debatte hierzulande keine Rolle spielt und der Bevölkerung vorenthalten wird (17).
Kontrafaktisch wird mit Hilfe der immer gleichen Protagonisten des militärisch-industriellen, und – wie hinzugefügt werden muss – propagandistisch-medialen Komplexes am Bedrohungsszenario festgehalten. Wer es nicht glaubt, der möge bei Google im Suchfenster: „16 amerikanische Geheimdienste Russland keine Bedrohung“ oder etwas Sinngleiches eingeben und schauen, ob er auf den ersten Seiten irgendwelche „Treffer“ landet. Ich wünsche viel Spaß dabei!
Teil 2 folgt demnächst.
Bernd Schoepe, Jahrgang 1965, Studium der Soziologie, Germanistik, Philosophie und Erziehungswissenschaften in Frankfurt/M. und Hamburg. Erstes und zweites Staatsexamen. Freier Autor, der zu bildungspolitischen, bildungssoziologischen- und bildungsphilosophischen Themen schreibt. Seit 2003 im Hamburger Schuldienst. Langjähriges GEW-Betriebsgruppen-Mitglied, ehem. Vertrauensmann, ehem. Mitglied der Hamburger Lehrerkammer. Hauptberuflich bin ich Politik- Deutsch- und Philosophielehrer an einer Hamburger Stadtteilschule. Kontakt: berndschoepe\@gmx.de
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 106de8d9:a99be73f
2025-06-01 07:56:04
@ 106de8d9:a99be73f
2025-06-01 07:56:04For those who like to be first and make money https://t.me/edchess_bot/web3?startapp=ref-link=mTLuwhkSLyYJ
-
 @ 7f6db517:a4931eda
2025-06-01 07:01:35
@ 7f6db517:a4931eda
2025-06-01 07:01:35
@matt_odell don't you even dare not ask about nostr!
— Kukks (Andrew Camilleri) (@MrKukks) May 18, 2021
Nostr first hit my radar spring 2021: created by fellow bitcoiner and friend, fiatjaf, and released to the world as free open source software. I was fortunate to be able to host a conversation with him on Citadel Dispatch in those early days, capturing that moment in history forever. Since then, the protocol has seen explosive viral organic growth as individuals around the world have contributed their time and energy to build out the protocol and the surrounding ecosystem due to the clear need for better communication tools.
nostr is to twitter as bitcoin is to paypal
As an intro to nostr, let us start with a metaphor:
twitter is paypal - a centralized platform plagued by censorship but has the benefit of established network effects
nostr is bitcoin - an open protocol that is censorship resistant and robust but requires an organic adoption phase
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
- Anyone can run a relay.
- Anyone can interact with the protocol.
- Relays can choose which messages they want to relay.
- Users are identified by a simple public private key pair that they can generate themselves.Nostr is often compared to twitter since there are nostr clients that emulate twitter functionality and user interface but that is merely one application of the protocol. Nostr is so much more than a mere twitter competitor. Nostr clients and relays can transmit a wide variety of data and clients can choose how to display that information to users. The result is a revolution in communication with implications that are difficult for any of us to truly comprehend.
Similar to bitcoin, nostr is an open and permissionless protocol. No person, company, or government controls it. Anyone can iterate and build on top of nostr without permission. Together, bitcoin and nostr are incredibly complementary freedom tech tools: censorship resistant, permissionless, robust, and interoperable - money and speech protected by code and incentives, not laws.
As censorship throughout the world continues to escalate, freedom tech provides hope for individuals around the world who refuse to accept the status quo. This movement will succeed on the shoulders of those who choose to stand up and contribute. We will build our own path. A brighter path.
My Nostr Public Key: npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx
If you found this post helpful support my work with bitcoin.

-
 @ 9ca447d2:fbf5a36d
2025-06-01 08:01:15
@ 9ca447d2:fbf5a36d
2025-06-01 08:01:15Sangha Renewables, a company that combines renewable energy with bitcoin mining, has started construction on a 19.9-megawatt (MW) mining facility powered 100% by solar energy. This is a big step towards making bitcoin mining cleaner, cheaper and more efficient.
The mining site is in West Texas, a region known for its strong solar and growing bitcoin mining presence.
What’s unique about this project is the “behind-the-meter” setup — the facility will draw power directly from a nearby solar site instead of the grid. This avoids some of the costs and inefficiencies of traditional energy sourcing.
The solar site where the mining facility is located has been operational for a few years. But it’s faced challenges like grid congestion and negative energy pricing – times when there’s too much energy and prices go below zero.
Sangha’s new mining operation will solve this problem by being a flexible energy consumer. When the grid has excess energy, Sangha can use it to mine bitcoin, helping to stabilize the grid and put otherwise wasted energy to work.
Related: Bitcoin Mining Clean Energy and Grid Balance | ERCOT Study
“This is a win-win-win,” said Spencer Marr, co-founder and CEO of Sangha Renewables. “The IPP (independent power producer) earns more per megawatt-hour, our investors gain exposure to low-cost bitcoin production, and we deliver grid-stabilizing load where it’s needed most.”
In addition to the tech innovation, Sangha is also changing the way people can invest in bitcoin mining.
The company just raised $14 million of its $17 million target to fund the construction and operation of the Texas facility.
Unlike traditional investments in mining companies or digital asset stocks, Sangha allows accredited investors to invest directly in the infrastructure itself through special purpose vehicles (SPVs).
Investors can put in cash or bitcoin and get ongoing payouts in bitcoin that are “well below the market price,” according to Marr. This means instead of buying bitcoin on the open market, investors are essentially earning it through the mining activity powered by renewable energy.
“Sangha is not just building bitcoin mining sites—we’re building a new model for how capital flows in and out of Bitcoin,” Marr said.
“By applying a project finance structure honed-in the renewable energy and real estate sectors, we enable investors to participate directly in productive assets—without intermediaries, speculative equities, or inefficiencies of datacenter hosting.”
Sangha’s financial and operational model uses advanced forecasting tools.
These tools allow forecasting of energy prices and bitcoin mining profitability down to 15-minute intervals. This enables the company to decide when to run the mining rigs for maximum efficiency and return on investment.
This Texas facility is a proof-of-concept. If it works, it will open the door for others across the U.S.
Sangha believes many underutilized renewable energy sites could benefit from this kind of setup, especially in areas that produce more energy than the grid can handle.
Using a capital-efficient, investor-aligned model and working with independent power producers (IPPs) Sangha plans to scale this nationwide. The facility will be fully operational by Q3 2025.
-
 @ 4c96d763:80c3ee30
2025-05-31 23:33:02
@ 4c96d763:80c3ee30
2025-05-31 23:33:02Changes
Fernando López Guevara (2):
- feat(column): add tooltip on remove column button
- feat(hashtag-column): handle new hashtag on Enter key press
pushed to notedeck:refs/heads/master
-
 @ 90c656ff:9383fd4e
2025-05-31 18:09:27
@ 90c656ff:9383fd4e
2025-05-31 18:09:27Since its emergence in 2009, Bitcoin has generated a wide range of success and failure stories. Some of these stories feature people who invested early and reaped the rewards of their foresight, while others highlight the ups and downs that define Bitcoin’s highly volatile market. Over the years, many of these cases have become iconic—serving as both inspiration and cautionary tales for newcomers.
Success stories
01 - Laszlo Hanyecz – The 10,000 Bitcoin Pizza
One of the most legendary stories in Bitcoin’s history involves Laszlo Hanyecz, a programmer from Florida. In 2010, he paid 10,000 bitcoins for two pizzas. At the time, the value was negligible, and the transaction went largely unnoticed. In retrospect, however, those 10,000 bitcoins would be worth hundreds of millions of dollars today.
Though Hanyecz didn’t become rich from this transaction, the story of the “10,000 bitcoin pizza” has become a symbol of Bitcoin’s extraordinary rise in value—and a reminder of how even small holdings in the early days could have been life-changing.
02 - Michael Saylor and MicroStrategy
Michael Saylor, CEO of MicroStrategy, made headlines in 2020 by transforming his company into the first major corporation to invest heavily in Bitcoin. Purchasing over 100,000 bitcoins as a treasury reserve, Saylor positioned Bitcoin as a strategic hedge against inflation and fiat currency devaluation.
Initially met with skepticism, Saylor’s decision turned out to be highly profitable as Bitcoin’s price soared. His bold move inspired other corporations and institutional investors to consider Bitcoin, and he remains one of the cryptocurrency’s most vocal advocates in the business world.
Failure Stories
01 - James Howells – The Lost 8,000 Bitcoins
James Howells, an IT professional from Wales, accidentally discarded a hard drive in 2013 containing the private keys to 8,000 mined bitcoins—worth only a few thousand pounds at the time. As Bitcoin's value skyrocketed, he attempted to recover the drive from a landfill, but was denied permission by local authorities.
This story has become a powerful lesson in crypto security and the consequences of lost private keys. Despite multiple campaigns to dig up the landfill, the bitcoins remain unrecovered.
02 - Mt. Gox Collapse – The Fall of a Giant
At its peak, Mt. Gox was the largest Bitcoin exchange in the world. In 2014, it collapsed after losing about 850,000 bitcoins—worth over $450 million at the time—due to hacking, internal security failures, and poor management.
The exchange’s failure devastated thousands of investors and highlighted the vulnerabilities in early crypto infrastructure. Though some funds were later recovered, the Mt. Gox disaster remains one of Bitcoin’s darkest moments and a turning point for the push toward greater security and transparency in the crypto industry.
- The impact of volatility and adoption
These stories reflect the unpredictable and high-risk nature of the Bitcoin market. The same volatility that has made millionaires has also led to substantial losses. While some view Bitcoin as a path to financial freedom and a hedge against inflation, others have suffered from poor planning, mismanagement, or unfortunate timing.
Bitcoin’s growing adoption, especially in emerging markets and among institutional players and shows its increasing legitimacy, as an alternative to traditional finance. However, exchange failures and lost fortunes underscore the need for robust infrastructure, personal responsibility, and long-term thinking.
In summary, success and failure are two sides of the same coin in the world of Bitcoin. From life-changing gains to heartbreaking losses, these stories illustrate the risks and rewards of participating in a young and volatile market. Whether as a cautionary tale or a source of inspiration, they emphasize the importance of education, security, and strategy for anyone engaging with this revolutionary form of money.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 5d1d83de:d0db5aa0
2025-06-01 06:04:32
@ 5d1d83de:d0db5aa0
2025-06-01 06:04:32As long as the base unit of the trading system can be manipulated a free trading system cannot emerge.
The trading system will either be manipulated by printed subsidies or will be manipulated by artificial exchange rates.
Free trading was available during a gold standard and free trading will become available again during a future bitcoin standard.
https://stacker.news/items/989491
-
 @ 2dd9250b:6e928072
2025-05-31 16:12:55
@ 2dd9250b:6e928072
2025-05-31 16:12:55Durante a década de 1990, houve o aumento da globalização da economia, determinando a adição do fluxo internacional de capitais, de produtos e serviços. Este fenômeno levou a uma interdependência maior entre as economias dos países. Justamente por causa da possibilidade de que um eventual colapso econômico em um país resulte no contágio dos demais. Diante disso, aumentou a preocupação com os riscos incentivando a utilização de sofisticados modelos e estratégias de avaliação de gestão de risco.
Na década, ganharam destaque ainda os graves problemas financeiros enfrentados, entre outros, pelo banco inglês Barings Bank, e pelo fundo de investimento norte-americano Long Term Capital Management.
Outro grande destaque foi a fraude superior a US$ 7 bilhões sofrida pelo banco Société Generale em Janeiro de 2008.
O Barings Bank é um banco inglês que faliu em 1995 em razão de operações financeiras irregulares e mal-sucedidas realizadas pelo seu principal operador de mercado. O rombo da instituição foi superior à US$ 1,3 Bilhão e causado por uma aposta equivocada no desempenho futuro no índice de ações no Japão. Na realidade, o mercado acionário japonês caiu mais de 15% na época, determinando a falência do banco. O Baring Bank foi vendido a um grupo financeiro holandês (ING) pelo valor simbólico de uma libra esterlina.
O Long Term Capital Management era um fundo de investimento de que perdeu em 1998 mais de US$ 4,6 bilhões em operações nos mercados financeiros internacionais. O LTCM foi socorrido pelo Banco Central dos Estados Unidos (Federal Reserve ), que coordenou uma operação de socorro financeiro à instituição. A justificativa do Banco Central para esta decisão era "o receio das possíveis consequências mundiais da falência do fundo de investimento".
O banco francês Société Generale informou, em janeiro de 2008, uma perda de US$ 7,16 bilhões determinadas por fraudes efetuadas por um operador do mercado financeiro. Segundo revelou a instituição, o operador assumiu posições no mercado sem o conhecimento da direção do banco. A instituição teve que recorrer a uma urgente captação de recursos no mercado próxima a US$ 5,0 bilhões.
E finalmente chegamos ao caso mais problemático da era das finanças modernas anterior ao Bitcoin, o caso Lehman Brothers.
O Lehman Brothers era o 4° maior de investimentos dos EUA quando pediu concordata em 15/09/2008 com dívidas que superavam inacreditáveis US$ 600 bilhões.
Não se tinha contas correntes ou talão de cheques do Lehman Brothers. Era um banco especializado em investimentos e complexas operações financeiras. Havia feito pesados investimentos em empréstimos a juros fixos no famigerado mercado subprime, e o crédito imobiliário voltado a pessoas consideradas de forte risco de inadimplência.
Com essa carteira de investimentos que valia bem menos que o estimado e o acúmulo de projetos financeiros, minou a confiança dos investidores na instituição de 158 anos. Suas ações passaram de US$ 80 a menos de US$ 4. Acumulando fracassos nas negociações para levantar fundos; a instituição de cerca de 25 mil funcionários entrou em concordata.
O Federal Reserve resgatou algumas instituições financeiras grandes e tradicionais norte-americanas como a seguradora AIG no meio da crise. O Fed injetou um capital de US$ 182, 3 bilhões no American International Group (AIG).
Foi exatamente essa decisão do Fed em salvar alguns bancos e deixar quebrar outros, que causou insegurança por parte dos clientes. E os clientes ficaram insatisfeitos tanto com os bancos de investimentos quanto com as agências de classificação de risco, como a Standard & Poor's que tinha dado uma nota alta para o Lehman Brothers no mesmo dia em que ele quebrou.
E essa foi uma das razões pelo qual o Bitcoin foi criado. Satoshi Nakamoto entendeu que as pessoas não estavam mais confiando nem no Governo, nem nos Bancos Privados que o Governo federal restagatava quando eles quebravam e isso prejudicou muita gente. Tanto que o “hash” do Genesis Block contém o título do artigo “Chancellor on brink of second bailout for banks” (Chanceler à beira de segundo resgate para bancos, em português) da edição britânica do The Times.
-
 @ 005bc4de:ef11e1a2
2025-05-31 10:55:47
@ 005bc4de:ef11e1a2
2025-05-31 10:55:47LUV and Hivebits/HBIT/Wusang pause tl;dr LUV and HBIT (aka, Hivebits and the Wusang game) are on a pause at the moment, taking a break. https://files.peakd.com/file/peakd-hive/crrdlx/23x1SY8Vx8j1mVGnDFtq7ebuzKNGd8K9Ssex51AEerxks1VYikxGPShM7bjNhmSrEZ2wf.png Image from pixabay.com Why? There are odd things going on. I have a theory, but here's what is known... May 28, 2025, at about 1:30 pm GMT (8:30 AM EDT), a second attack (for lack of better term) hit HBIT in about a week. It seemed to start with @tyler45 with this comment https://peakd.com/blog/@tyler45/comment-20250528125108033 tx: https://he.dtools.dev/tx/7e7d4126196ca5b6dbe0a04dcded0e25d3bcc7f4 See tyler45's activity at https://he.dtools.dev/@tyler45 Notice the reply and WUSANG command is to a post by @olivia897 and how many of the other WUSANG comments on the explorer are in reply to olivia897. It seems these are all auto-generated accounts. The names and "birthdates" and interactions all point to automation. Once initiated, things happened very fast on the back end, clearly not being done manually. In this way, this seems rather sophisticated technically. I estimate just over 400 HBIT were pilfered the other day from the @Hivebits account before I noticed and was able to shut things down. Just for a little background, after the first attack May 21, 2025. I wrote a small bit of info: https://peakd.com/hivebits/@crrdlx/hbit-resource-credits A couple of days ago this post by @holoz0r was interesting: https://peakd.com/hive-133987/@holoz0r/text-analytics-reveal-thirty-two-percent-of-comments-on-hive-are-not-unique-and-at-least-ten-percent-add-no-value-to-discussion The thing that caught my eye was that the WUSANG comment was the largest by far, along with BBH (hello @bradleyarrow), because the attackers used both commands. Then, a few days later, things happened again: sudden start, repetitive bot attack, until I shut things down. So, a pause This is a period in my personal calendar where I simply don't have time to sit down at a computer for an extended period and try fiddle with this stuff. So, for now @Luvshares and @Hivebits (HBIT) and the @Wusang game are on hold. Plus, there's other fun stuff to do. https://files.peakd.com/file/peakd-hive/crrdlx/AJL43SREA1EuyqPXhydmqaq1RHhRVoYd12PfiBN5vDMu2WSKUtGeYWgKJyuRwV8.jpg I go by @crrdlx or "CR" for short. See all my links or contact info at https://linktr.ee/crrdlx.
Originally posted on Hive at https://peakd.com/@crrdlx/luv-and-hivebitshbitwusang-pause
Auto cross-post via Hostr v0.1.48 (br) at https://hostr-home.vercel.app
-
 @ 7f6db517:a4931eda
2025-06-01 06:01:32
@ 7f6db517:a4931eda
2025-06-01 06:01:32
I often hear "bitcoin doesn't interest me, I'm not a finance person."
Ironically, the beauty of sound money is you don't have to be. In the current system you're expected to manage a diversified investment portfolio or pay someone to do it. Bitcoin will make that optional.
— ODELL (@ODELL) September 16, 2018
At first glance bitcoin often appears overwhelming to newcomers. It is incredibly easy to get bogged down in the details of how it works or different ways to use it. Enthusiasts, such as myself, often enjoy going down the deep rabbit hole of the potential of bitcoin, possible pitfalls and theoretical scenarios, power user techniques, and the developer ecosystem. If your first touch point with bitcoin is that type of content then it is only natural to be overwhelmed. While it is important that we have a thriving community of bitcoiners dedicated to these complicated tasks - the true beauty of bitcoin lies in its simplicity. Bitcoin is simply better money. It is the best money we have ever had.
Life is complicated. Life is hard. Life is full of responsibility and surprises. Bitcoin allows us to focus on our lives while relying on a money that is simple. A money that is not controlled by any individual, company, or government. A money that cannot be easily seized or blocked. A money that cannot be devalued at will by a handful of corrupt bureaucrat who live hundreds of miles from us. A money that can be easily saved and should increase in purchasing power over time without having to learn how to "build a diversified stock portfolio" or hire someone to do it for us.
Bitcoin enables all of us to focus on our lives - our friends and family - doing what we love with the short time we have on this earth. Time is scarce. Life is complicated. Bitcoin is the most simple aspect of our complicated lives. If we spend our scarce time working then we should be able to easily save that accrued value for future generations without watching the news or understanding complicated financial markets. Bitcoin makes this possible for anyone.
Yesterday was Mother's Day. Raising a human is complicated. It is hard, it requires immense personal responsibility, it requires critical thinking, but mothers figure it out, because it is worth it. Using and saving bitcoin is simple - simply install an app on your phone. Every mother can do it. Every person can do it.
Life is complicated. Life is beautiful. Bitcoin is simple.
If you found this post helpful support my work with bitcoin.

-
 @ 554ab6fe:c6cbc27e
2025-04-10 18:48:57
@ 554ab6fe:c6cbc27e
2025-04-10 18:48:57What is consciousness, and can it be changed or enhanced? This is a question that humans have struggled with for a very long time. The question of consciousness alone is daunting. Some even argue that humans will never be able to find the answer. Regardless, the quest for knowledge is not always about the answer, rather it is the journey that is revealing. This is true not only for our society, but the individual as well. The search for the truth often leads one down a path of self-reflection, and can lead to conclusions previously thought to be ludicrous. Here, I will argue that consciousness can be interpreted as an interpretation of reality, where the interpretation may become clearer and more accurate through practices such as meditation.
Consciousness
To articulate this idea, the concept of consciousness must firstly be discussed. There is an incredibly interesting TED talk given by Anil Seth, where he describes consciousness as an illusion. He explains how the brain receives signals from both the internal and external environment of the body, makes an interpretation of those signals, which creates our conscious experience. In his scientific writing, he claims that the brain can be viewed as a prediction machine1. He argues that the brain is constantly making predictions and error correcting in order to gain understanding of the signals it is receiving. He is not alone in this theory, and many other researchers concur that the constant comparison of internal predictions and external stimuli is what generates the brain’s sensations of causal forces2. There are plenty of reasons to believe this is true. Imagine, the brain is receiving all kinds of neuronal signals both from external stimuli sensors and sensors for our internal systems. These signals all shoot up the spinal cord to the brain. It is unclear that these neuronal signals are stamped with an identifier of where they came from, so the brain has to make a predictive model for not only where the signal came from, but also why the signal came at all. The latter is important for survival: the use of our senses to accurately predict our environment would be a critical reason why consciousness developed in the first place. Imagine you are an ancient hominid walking in the wild: you see a tangled cord like thing around a branch on the tree. You need to process that information, determine if it is more branch or a snake and act accordingly. This is a potential biological reason for the manifestation of thought and problem solving. This is a very meta-cognitive example of our brain receiving information and then using previous knowledge to generate a predictive conclusion on the external reality.
There are also examples of this outside of the more obvious meta-cognitive examples. A good example is the famous rubber hand experiment. The first rubber hand experiment was conducted in 1998 by Botvinick and Cohen3. In this experiment, a subject places their hand on a table with a screen blocking their view of their own hand. A rubber hand is then placed on the other side of the screen where it is visible. The experimenter rubs both the rubber hand and real hand with a paint brush. By the end of the experiment, subjects begin to feel as if the rubber hand is their own limb3. The brain, using the visual senses, detects that a hand is being stroked with a brush while sensory neurons send signals that the hand is experiencing the touch of a paint brush. These two signals cause the predicting brain to think that the rubber hand is our hand. This experiment has been repeated many times in different ways. It has been observed that participants begin to react defensively to the threat of pain or damage to the rubber hand4. This illustrates the powerful extent at which the brain processes and reacts to information that it interprets from reality. Amazingly, some research suggests that the touch aspect of the experiment isn’t even necessary to produce the illusion5. Others have recreated this experience using virtual reality, citing that when the virtual hand changed color in response to the subject’s heartbeat, a significant sense of body ownership was generated6. Body ownership, and our sense of reality is arguably determined by our brain’s interpretation of both internal and external stimuli.
The Neuroscience and Meditation
It is hypothesized that the anterior insular cortex (AIC) is involved in the comparison of the stimuli to the predicted model1. Interestingly, the same brain region is associated with the anticipation of pain7. For those unaware, there is some research to suggest that much of the pain we experience is not due to the actual noxious stimuli (physical pain sensation), but from the anticipation of that pain. Evidence for this can be found in studies such as Al-Obaidi et al. from 2005, that concluded that the pain experienced in patients with chronic low back pain could not be solely attributed to the sensor signals, but from the anticipation of the pain8. Additionally, the anticipation of pain relief is the primary contributor to placebo analgesia (placebo pain killers)9. Furthermore, a large body of research has been conducted showing that meditators show a decreased anticipatory attitude towards pain, subsequently experiencing less unpleasant pain 7,10,11. For example, chronic pain in multiple areas such as the low back, neck, shoulder, and arms have been shown to reduce after meditation practice12. Finally, an extreme case study worth noting is of a yogi master who claimed to not experience pain at all13. When this master was brought into the lab, not only did he not experience pain, but his thalamus showed no additional activation following painful stimuli13. What is fascinating about this is that the thalamus is the main relay station for all incoming somatosensory information14, and some argue that this is a candidate for the location of consciousness15. To not have strong activation here after painful stimuli is to suggest a radical change in how the brain receives incoming stimuli, and perhaps is indicative in a dramatic shift in how this individual’s conscious experiences the world. Though this is but one small example, the previous studies outline a strong case for meditation’s ability to alter the way the brain processes information. Given meditation involves the active practice of generating an open and non-judgmental attitude towards all incoming stimuli, perhaps this alters the processing of incoming stimuli, thereby changing the predictive model. On a similar note, perhaps it relates to neuroplastic changes that occur within the brain. It has been noted that the AIC is activated during times of awareness of mind wandering16. This suggests that the AIC is in use frequently during meditation practices. Perhaps it is strengthened then by meditation, thereby also allowing for greater prediction model generation. Imagine the mind as a pond. If the pond is calm and still, one single rain drop rippling in the pond is clearly identifiable. One would easily know information about the droplet, because the ripple could be easily analyzed. Now imagine a pond during a rain storm, where an uncountable amount of rain drops is hitting the pond and there are ripples everywhere. One could not adequately make out where each ripple came from, because there would be too much overlap in the ripples. This may be how the brain functions as well. When the signals are low, and no extraneous thoughts and interpretations are created from signals, then the brain’s prediction model can easily determine where and why a signal it received came from. If, however, the mind is chaotic and full of internal noise, then the brain has a harder time creating an accurate understanding of incoming stimuli and generating a correct model.
Enlightenment
Enlightenment, from a scientific point of view, has been defined as a form of awareness where a person feels that s/he has gained a new understanding of reality 17. In this sense, it bears a striking relationship to the topic of consciousness. If consciousness can be defined as our interpretation of the external and internal environment through our mental prediction model, then experiences of enlightenment are defined by moments where our interpretation is completely changed in a profound way. The experiences are often characterized by the loss of individuality and consequent identification of being part of a greater oneness 18,19. As an interesting side note, this same experience is common amongst subjects, who in a double-blinded study, take psilocybin (the active ingredient in magic mushrooms)20,21. The neuroscience of enlightenment is particularly interesting. The temporo-parietal junction of the brain is involved with self-location and body ownership22. Unsurprisingly, this area is highly involved in the illusion of the rubber hand experiment23. This is the same brain area that is hypothesized to be related to these enlightened experiences of oneness 17. If this brain area, which handles the interpretation of where and what the body is, was to decrease in activation, then the brain would generate a more ambiguous interpretation that the self and the external environment are less distinct than previously thought. This is a possible explanation to why enlightenment experiences involve a feeling of oneness with everything. To bring this all home, meditation has been shown to decrease parietal lobe activation 4,24. Suggesting that meditation can be a method of adjusting the brain’s interpretation of stimuli to generate an outlook that is unifying in perceptive.
Closing Remarks
The evidence that meditation may lead to an altered conscious living has deep philosophical implications. Meditation is a practice that, in part, involves an open awareness to all incoming stimuli alongside the absence of any meta-cognitive interpretation or processing of said stimuli. This generation of a still mind may generate a more accurate prediction model of incoming stimuli, void of any corruption on the part of our thoughts. Given the observation that meditation, both scientifically and culturally, can lead to an understanding and experience of a greater oneness amongst all suggests that this interpretation of incoming stimuli is the more accurate interpretation. It is hard to imagine that anyone would not advocate the beauty and usefulness of this perspective. If more people had this perspective, we would have a much more peaceful, happy and unified society and planet. Ironically, our culture often aims to arrive to this philosophical perspective through analytical thought. However, given the evidence in this post, perhaps it is the absence of analytical thought, and the stillness of the mind that truly grants this perspective.
**References ** 1. Seth AK. Interoceptive inference, emotion, and the embodied self. Trends in Cognitive Sciences. 2013;17(11):565-573. doi:10.1016/j.tics.2013.09.007 2. Synofzik M, Thier P, Leube DT, Schlotterbeck P, Lindner A. Misattributions of agency in schizophrenia are based on imprecise predictions about the sensory consequences of one’s actions. Brain. 2010;133(1):262-271. doi:10.1093/brain/awp291 3. Botvinick M, Cohen JD. Rubber hand ‘feels’ what eyes see. Nature. 1998;391(February):756. 4. Newberg A, Alavi A, Baime M, Pourdehnad M, Santanna J, D’Aquili E. The measurement of regional cerebral blood flow during the complex cognitive task of meditation: A preliminary SPECT study. Psychiatry Research - Neuroimaging. 2001;106(2):113-122. doi:10.1016/S0925-4927(01)00074-9 5. Ferri F, Chiarelli AM, Merla A, Gallese V, Costantini M. The body beyond the body: Expectation of a sensory event is enough to induce ownership over a fake hand. Proceedings of the Royal Society B: Biological Sciences. 2013;280(1765). doi:10.5061/dryad.8f251 6. Suzuki K, Garfinkel SN, Critchley HD, Seth AK. Multisensory integration across exteroceptive and interoceptive domains modulates self-experience in the rubber-hand illusion. Neuropsychologia. 2013;51(13):2909-2917. doi:10.1016/j.neuropsychologia.2013.08.014 7. Zeidan F, Grant JA, Brown CA, McHaffie JG, Coghill RC. Mindfulness meditation-related pain relief: Evidence for unique brain mechanisms in the regulation of pain. Neuroscience Letters. 2012;520(2):165-173. doi:10.1016/j.neulet.2012.03.082 8. Al-Obaidi SM, Beattie P, Al-Zoabi B, Al-Wekeel S. The relationship of anticipated pain and fear avoidance beliefs to outcome in patients with chronic low back pain who are not receiving workers’ compensation. Spine. 2005;30(9):1051-1057. doi:10.1097/01.brs.0000160848.94706.83 9. Benedetti F, Mayberg HS, Wager TD, Stohler CS, Zubieta JK. Neurobiological mechanisms of the placebo effect. In: Journal of Neuroscience. Vol 25. Society for Neuroscience; 2005:10390-10402. doi:10.1523/JNEUROSCI.3458-05.2005 10. Gard T, Hölzel BK, Sack AT, et al. Pain attenuation through mindfulness is associated with decreased cognitive control and increased sensory processing in the brain. Cerebral Cortex. 2012;22(11):2692-2702. doi:10.1093/cercor/bhr352 11.Grant JA, Courtemanche J, Rainville P. A non-elaborative mental stance and decoupling of executive and pain-related cortices predicts low pain sensitivity in Zen meditators. Pain. 2011;152(1):150-156. doi:10.1016/j.pain.2010.10.006 12. Kabat-Zinn J, Lipworth L, Burney R. The clinical use of mindfulness meditation for the self-regulation of chronic pain. Journal of Behavioral Medicine. 1985;8(2):163-190. doi:10.1007/BF00845519 13. Kakigi R, Nakata H, Inui K, et al. Intracerebral pain processing in a Yoga Master who claims not to feel pain during meditation. European Journal of Pain. 2005;9(5):581. doi:10.1016/j.ejpain.2004.12.006 14. Steeds CE. The anatomy and physiology of pain. Surgery. 2009;27(12):507-511. doi:10.1016/j.mpsur.2009.10.013 15. Min BK. A thalamic reticular networking model of consciousness. Theoretical Biology and Medical Modelling. 2010;7(1):1-18. doi:10.1186/1742-4682-7-10 16. Hasenkamp W, Wilson-Mendenhall CD, Duncan E, Barsalou LW. Mind wandering and attention during focused meditation: A fine-grained temporal analysis of fluctuating cognitive states. NeuroImage. 2012;59(1):750-760. doi:10.1016/j.neuroimage.2011.07.008 17. Newberg AB, Waldman MR. A neurotheological approach to spiritual awakening. International Journal of Transpersonal Studies. 2019;37(2):119-130. doi:10.24972/ijts.2018.37.2.119 18. Johnstone B, Cohen D, Konopacki K, Ghan C. Selflessness as a Foundation of Spiritual Transcendence: Perspectives From the Neurosciences and Religious Studies. International Journal for the Psychology of Religion. 2016;26(4):287-303. doi:10.1080/10508619.2015.1118328 19. Yaden DB, Haidt J, Hood RW, Vago DR, Newberg AB. The varieties of self-transcendent experience. Review of General Psychology. 2017;21(2):143-160. doi:10.1037/gpr0000102 20. Griffiths RR, Richards WA, McCann U, Jesse R. Psilocybin can occasion mystical-type experiences having substantial and sustained personal meaning and spiritual significance. Psychopharmacology. 2006;187(3):268-283. doi:10.1007/s00213-006-0457-5 21. Griffiths RR, Richards WA, Johnson MW, McCann UD, Jesse R. Mystical-type experiences occasioned by psilocybin mediate the attribution of personal meaning and spiritual significance 14 months later. Journal of Psychopharmacology. 2008;22(6):621-632. doi:10.1177/0269881108094300 22. Serino A, Alsmith A, Costantini M, Mandrigin A, Tajadura-Jimenez A, Lopez C. Bodily ownership and self-location: Components of bodily self-consciousness. Consciousness and Cognition. 2013;22(4):1239-1252. doi:10.1016/j.concog.2013.08.013 23. Tsakiris M, Costantini M, Haggard P. The role of the right temporo-parietal junction in maintaining a coherent sense of one’s body. Neuropsychologia. 2008;46(12):3014-3018. doi:10.1016/j.neuropsychologia.2008.06.004 24. Herzog H, Leie VR, Kuweit T, Rota E, Ludwig K. Biological Psychology/Pharmacopsychology. Published online 1990:182-187.
-
 @ 0c65eba8:4a08ef9a
2025-06-01 07:59:12
@ 0c65eba8:4a08ef9a
2025-06-01 07:59:12Part I: Women Under Siege, A Century of Psychological and Social Displacement
Women are under attack, and they have been for over a century.
Before the industrial revolution, in most of the world, a woman was never truly alone. She was embedded in a web of support: her husband, her children, her extended family, and most crucially, her female network, other women she saw daily, worked beside, shared joys and sorrows with.
These women had shared incentives, shared goals, and shared lives. They cared deeply for one another, you could say they loved each other. They built each other up, protected one another’s children, and upheld one another’s dignity and value.
And they were often related by blood or through her husband.
The social feedback that mattered came from those nearby, friends and kin whose faces she saw every day. Women did not orient their self-worth around strangers, institutions, or distant celebrities. They lived in a community of mutual reinforcement, not a marketplace of external judgment.
Their days were filled not just with labor but with meaning, tied to their families, communities, and legacies.
But the modern world severed that web. The industrial model fractured the household: husbands to work, children to school, and women, adrift. What remains now is isolation. Fragmentation. A mother might spend most of her day alone, away from her husband, away from her children, and with no sisters or cousins or mothers-in-law nearby. Her labor is abstracted, her care is undervalued, her instincts derided.
So what fills that vacuum? Loneliness. Insecurity. Yearning for validation. A desperate emotional hunger.
And into that vulnerability steps the modern left, offering what appears to be moral clarity, emotional safety, and social belonging. But what it delivers is not care, it’s ideological grooming. Women are being slowly, deliberately conditioned into a kind of captivity that wears the mask of liberation.
The left captures women by hijacking their evolved moral instincts: empathy, nurturance, and fear of social disapproval. It exploits these instincts to bind them into a system that pretends to offer safety, compassion, and justice, while actually delivering fragmentation, isolation, and civilizational decline. This is the core of ideological grooming: not overt coercion, but the gradual reshaping of women’s emotional responses to serve the interests of an alien moral and political agenda.
They are not thriving.
They are hurting, deeply.
And most don't even know why.
Part II: Ideological Abuse, The Left as Cult, Parasite, and Prison Warden
Many women today live in what can only be described as ideological prisoner-of-war camps, structures not of concrete and barbed wire, but of media, social networks, institutional propaganda, and psychological manipulation. These are not camps in metaphor alone. They function operationally as cults: controlling thought, severing relationships, poisoning perception, and rendering escape emotionally dangerous. This is not hyperbole. It is the observable outcome of a sustained, parasitic, and strategic program by the modern left to weaponize feminine instincts against their own interests, families, and civilizations.
The Grooming Process
The grooming process began by exploiting women’s empathy. By positioning leftist narratives as moral imperatives, "care for the marginalized," "stand up for the oppressed", they appealed to a woman's deepest emotional instincts. This was effective, sustainable, and slow-acting.
But over time, as the natural contradictions of the leftist program emerged, and as the promises failed to deliver security, the narrative shifted from empathy to fear. Fear of rejection. Fear of violence. Fear of being labeled a traitor. Fear of losing one’s job, reputation, or children. Fear of losing one’s husband, or worse, of no longer being served or prioritized by him as he reasserts a more natural masculine role. As more men move away from egalitarianism toward traditional gender roles, some women sense a loss of control over the male utility they once relied on. Fear, not care, now drives adherence to the cult.
And for many women, one of the most primal fears cultivated in this system is the fear of unwanted pregnancy, not merely as a personal inconvenience, but as a symbol of loss of control, future disruption, and irreversible consequence. The left has exploited this fear ruthlessly, crafting a narrative where pregnancy itself becomes a threat unless politically mitigated. This fear is most acute among unmarried women, but even some married women, those who have internalized modern anti-natalism, careerism, or economic precarity, are made to fear the very biological function that once defined feminine power.
This is an inversion of nature. The ability to create life, once revered as a sacred feminine strength, is now framed as a potential crisis. The result is a psychological dependency: women are groomed to see their own fertility not as a gift, but as a liability, something to be defended against with the help of the state, the party, or the institution.
This weaponized fear creates emotional paralysis, breeds distrust between men and women, and deepens ideological dependency.
NOTE: That leftist shift from care to fear based tactics matters.
Fear, unlike empathy, has diminishing returns. Fear is very powerful as an acute emotional motivator but over time human beings adapt to fear. It cannot be sustained indefinitely. Like the body acclimating to the height of a ladder, prolonged exposure to fear forces the nervous system to recalibrate. Eventually fear stops working as a motivator. It loses its grip on their heart.
This is both the weakness and the exit point.
When fear becomes the primary control mechanism, women begin to feel its unnaturalness. They begin to question why they are always anxious, always policing their words, always walking on eggshells. And in that questioning lies the opportunity for extraction.
The Mechanics of Captivity
1. Severance from Husbands and Families
By encouraging female independence as a moral virtue, and by framing male authority and protection as patriarchal oppression, the left undermines the marital bond. It floods media with narratives that husbands are inherently abusive, conservative men are dangerous, and male leadership is suspect. The result is psychological atomization: wives grow mistrustful of their husbands, mothers are taught to see fathers as threats, and homes fracture.
This inversion of reality hides critical truths: women in marriages, real, committed marital unions, experience significantly lower rates of relationship violence than those in cohabiting or non-committed arrangements. Likewise, they enjoy greater financial stability, access to shared resources, and long-term planning. But the left obscures this data to bait women into hazard, encouraging divorce, delaying marriage, or avoiding it altogether, only to leave them more vulnerable emotionally, physically, and economically. It is not empowerment. It is sabotage disguised as liberation.
2. Displacement from Natural Roles
Women are pulled out of the home under the guise of empowerment. But what was once a sacred domain of family, children, and community becomes replaced by workplace drudgery, bureaucratic subordination, and sterile careerism. The maternal instincts that once formed the moral foundation of the community are sterilized in service to profit and politics.
This displacement comes with deep costs. First, women are no longer present in the home to pass down essential knowledge, emotional regulation, the daily rhythms of domestic life, the art of nurturing, to their children. Daughters, in particular, grow up without examples of how to be wives and mothers, and thus enter adulthood unprepared for those roles. This generational disruption breeds anxiety, insecurity, and performance stress, which the left blames not on the loss of traditional roles, but on the institution of marriage itself.
Second, the workplace often consumes women without providing lasting fulfillment. Many begin to experience profound burnout between the ages of 35 and 45, just as their children, had they been mothers, would be entering greater independence. Instead of a natural transition toward grand-mothering and community leadership, they find themselves exhausted, trapped in cycles of debt and consumption, and emotionally depleted.
The left exacerbates this collapse by baiting women into material hazard, encouraging overspending, isolation, and lifestyle inflation. Debt replaces security, status replaces fulfillment, and work replaces family. The outcome is not empowerment, it is managed decline.
3. Destruction of Female Networks
Female well-being has always depended on tight community bonds: other mothers, extended kin, local support. But urbanization, hyper-mobility, and digital substitution have erased these networks. In response, many women attempt to rebuild new relationships at work. Yet in today’s high-turnover, gig-driven economy, people don’t stay in the same company long enough to form deep bonds. As a result, these attempted networks remain shallow and transient.
Into this emotional void step ideological predators. Many of the information and social spaces that women now turn to, whether online forums, activist communities, or social media platforms, have been infiltrated by bad actors who prey on their isolation and dissatisfaction. These manipulators exploit their emotional hunger to groom them into leftist causes, turn them against their husbands, and frame their children not as blessings but as burdens. What once were havens of feminine cooperation have become pipelines of ideological capture.
4. Capture by the Media-State Cathedral
Leftist media, academia, and state bureaucracies form an information cult that grooms women to internalize their narratives and fear dissent. Women operate primarily through consensus, social cues, communal norms, and perceived majorities to shape their judgments and loyalties. The cathedral leverages this trait by manufacturing a false consensus, making it appear that leftist ideology is the moral and cultural standard.
Women fall into this not out of malice, but because they are obedient, conscientious, and eager to follow the dominant narrative. They want to be good people, good citizens, and morally upstanding members of the community. That very goodness is what is being weaponized against them.
Terms like "misogyny," "toxic masculinity," and "equality" are deployed to stigmatize any competing moral grammar. Feminine intuitions are directed not toward building, nurturing, and bonding, but toward shaming, punishing, and canceling.
5. Importing Violence and Chaos
Simultaneously, mass immigration is promoted as moral necessity, regardless of its proven effects: rising crime, declining safety, and cultural disintegration. Women are told they must embrace this change for the sake of compassion. But it makes them less safe, more anxious, and more dependent on state protection.
Many mothers report that they can no longer take their children to the park without fear. Public spaces have been overtaken by foreign adult males who loiter, intimidate, and harass women and children, while police neglect these threats as unworthy of attention. This constant exposure to danger reinforces in women's minds the belief that men are dangerous.
But here, too, the picture has been inverted. Yes, men are dangerous, by design. Male danger, properly directed, is protective. It is meant to shield women and children from external threats. But women today see only the distorted side of that capacity: danger as threat, not as shield. They are denied the experience of male danger being used for their protection, because the state has neutralized and criminalized the very men who would defend them.
6. Economic Enslavement by Design
The two-income trap, high taxation, and debt-driven consumption were not accidents. They are engineered dependencies. It is shockingly easy to get into credit card debt, and lenders regularly approve new cards for individuals who are already financially overextended. Modern financial systems obscure spending, tap-to-pay, buy-now-pay-later schemes, and minimal visual feedback detach people from the consequences of their consumption.
Television, marketing, and social media all promote a lifestyle calibrated for two full-time incomes, over sized suburban homes, exotic vacations, constant dining out, fashion, and wellness subscriptions. Women absorb this false standard and feel pressured to maintain it. They begin to believe that unless they are working outside the home, they are somehow failing to contribute.
The result is economic entrapment. Most women would prefer to be home with their children, especially in their earliest years, but feel they cannot. Not because they don’t want to nurture, but because they’ve been enslaved into labor by artificial necessity. A woman working outside the home becomes both taxed and time-starved. She becomes easier to control, easier to propagandize, and harder to free. The promise of liberation becomes a prison of obligation.
The Program’s Logic: Capture, Groom, Extract
This is not a random sequence of failures, it is a coordinated parasitism. Capture the mind, groom the instincts, extract the labor and emotional energy, and render escape nearly impossible by moral blackmail and social stigma. The same techniques used by cults apply: gaslighting, love-bombing, demonizing outsiders, and rewriting history. Crucially, cults also isolate their members from the people who love them, friends, husbands, parents, so that loyalty can be redirected to the cult itself. The modern left has done exactly this, systematically severing women from their natural protectors and support networks.
Part III: Rescue, Recovery, and Reconnection
We must now ask: how do we free these women? How do we help our sisters, wives, daughters, and friends escape the cult?
We must begin by recognizing why this rescue matters.
It matters because we love and care for these women, even those who have been turned against us. They are not our enemies, but captives manipulated into suspicion, bitterness, and fear. And they cannot free themselves. They need those of us who remain outside the cult, men and women alike, to act with clarity, courage, and unwavering loyalty.
It also matters because this ideological captivity is destabilizing society as a whole. We are all paying the price, especially men, who shoulder the vast majority of the tax burden that funds the very institutions grooming their wives and daughters. To leave these women in captivity is not only a personal failure; it is a civilizational one.
Step 0: Understand the Emotional Battlefield
Many of the people best positioned to help, their husbands, brothers, fathers, and old friends, are not themselves in deep emotional alignment. They were not captured by emotional grooming because they are often detached from emotional cues altogether. But this also makes them less effective at reaching those who have been captured through emotional manipulation.
To lead a rescue, you must first understand what women are responding to. What incentives are being offered? What are they afraid of? What is being hijacked?
And this requires something difficult: deep empathy for them, especially when they have been programmed to hate you. You must look past the hostility, the bitterness, and the propaganda they echo. You must see the frightened, lonely, well-meaning human being underneath. She is trying to be good. She is trying to belong. She is trying to find safety in a system that promised to care for her. That empathy is not weakness, it is a strategic necessity.
This document has laid out the mechanisms. But knowing them intellectually is not enough. You must internalize them, feel them, see the battlefield not just rationally, but emotionally. Only then can you enter the rescue effort with the right tools, the right tone, and the right timing.
To do this, especially for men, we must learn to be emotionally open. Not vulnerable. Vulnerability is different. Vulnerability is weakness, susceptibility to capture. Emotional openness means readiness for connection, attunement, and presence without compromise. It is not a surrender of strength, but its intelligent use of emotions.
Learning to be emotionally open and emotionally motivating is beyond the scope of this post, but it is a skill worth cultivating. If you need help applying this to someone specific, a daughter, a wife, a sister, talk to me. I’ll help you build a strategy that works for you.
Step 1: Change the Frame, from Debate to Extraction
You cannot reason someone out of a cult using logic alone. First, change the narrative. Don’t argue, about Trump or anything else. Argument frames the interaction as "us versus them," which reinforces the sense of alienation.
Instead, shift the focus from confrontation to protection. Talk about betrayal, not by them, but of them. Say things like: “They used your goodness against you.” “You thought you were helping, but they were grooming you.” This triggers emotional dissonance while keeping the person emotionally on your side.
Avoid labeling everything as 'leftist' or ideological, this only raises defenses. Frame the problem as coming from external manipulators who betrayed both of you. Orient your body language and tone to say, "I’m with you against what’s hurting us." This subtle shift creates an opening for reconnection, empathy, and eventual extraction.
Step 2: Rebuild Trust
Women need to see that the men in their lives are not enemies,but protectors. That the so-called patriarchy was a civilizational gift, not an oppressor. That male leadership is not domination, but responsibility under natural law.
They also need to witness, tangibly, that the men they depend on are capable of protection, not just morally, but physically. When a woman sees her husband, brother, or father demonstrating the capacity for controlled violence, training, sparring, standing firm in the face of a threat, her confidence in his leadership deepens. She doesn’t need him to be dangerous toward her; she needs to know that he is dangerous for her, that his strength and capability can and will be directed to protect her, their children, and their home. That trust, once visible, changes everything.
And for many women, especially as they approach midlife, another layer of trust must be addressed: the fear of being abandoned or replaced. They must know and believe that their husbands will not trade them in for a younger model. This reassurance must come not as appeasement, but as a confident expression of loyalty: "Yes, I am attractive to other women. Yes, I have options. And I choose you, because you are mine, and I protect and care for what is mine." That certainty, when expressed with strength and conviction, becomes a fortress for a woman's heart. Without it, she will inevitably turn to external structures for security. But with it, she returns to trusting the man, the family, and the legacy they build together.
Step 3: Tell Stories of Escape
Use testimonials from other women who escaped the cult. Stories like: “I was deep in it. I thought I was saving the world. But I was losing my family. Now I see what I couldn’t before.” Or, “I thought my husband was the problem, until I realized the real threat came from the people telling me to mistrust him.” These voices speak directly to the emotional world of the captured woman, offering not just facts, but felt truth.
These stories break the illusion of isolation. They reassure her that she is not alone in her confusion, her regret, or her desire to rebuild. They plant emotional seeds, dissonance, doubt, hope, without triggering direct resistance. Storytelling bypasses intellectual defenses and speaks to the part of the woman that still remembers what’s real.
Step 4: Recreate Female Community Bonds
Where the left isolates, we must reconnect. But while men cannot lead or structure these female networks, we can enable and protect the space for them to form. We must ensure that our wives, daughters, and friends have time and freedom to gather, without guilt or obstruction.
These groups should revolve around emotional connection, practical help, and mutual aid in the struggles of motherhood, parenting, and home life. Women will share problems, swap advice, and support each other with simple but essential acts, like watching each other’s children so they can rest or reset. This kind of community was normal into the 1980s. Now, it is nearly extinct.
Ideally, these groups should be formed IRL (in real life, not online) from the wives of your male friends. That way, there’s a higher chance of shared values and healthy ideological alignment from the start.
We must help revive womens supporting networks, not by leading it, but by valuing it, making time for it, and defending its moral and civilizational importance.
Step 5: Offer Purpose Beyond Politics
The left gives women a sense of moral identity. We must replace it, not just with words, but with action. We must hold up being a wife and mother as something aspirational, beautiful, and noble, not as an afterthought or a burden.
As men, this begins with us. Do we treat our wives with gratitude and admiration? Do we openly praise the care, endurance, and intelligence they bring to mothering and home-making? Do we protect their time, their energy, and their sacred role in our family’s future?
This also demands emotional connection, something many men struggle with not because they lack emotion, but because they were never taught to process and express it. But this is a skill. It can be learned. And once it is, emotional connection becomes a source of deep mutual reinforcement between husband and wife. The more she feels seen and valued in her role, the more proud she becomes to live it, and the more other women around her will notice.
We must inspire them with what’s real, not what’s trendy. We must model the moral clarity, personal loyalty, and emotional presence that makes home, family, and feminine purpose shine brighter than any ideology ever could.
Final Word: Rescue is a Duty, an Act of Love, and a Rational Interest
To allow our women to remain captive is to allow civilization to die. We must treat their freedom from ideological capture not as an idea, but as a sacred duty. They are not our enemies. They are hostages in a psychological war, a war they did not start, do not understand, and cannot win alone.
To rescue them is not only an act of love.
It is an act of civilizational and genetic defence.
And it is in our rational interest.
Every man, every father, every husband pays the price of this captivity, through taxes that fund the institutions that groom our women, through social unrest that erodes our communities, and through the personal cost of broken families, alienated children, and lost legacy. Rescue is not a sentimental gesture. It is an act of moral clarity, emotional loyalty, and strategic necessity. It is how we reclaim not only the women we love, but the future they were meant to nurture.
But we must also remain vigilant. Love does not mean indulgence. Compassion does not mean surrender. Even as we seek to free the women in our lives from this captivity, we must not allow their captured state to undermine our leadership, our mission, or our efforts to rebuild. We cannot permit their fear, confusion, or hostility, however manipulated, to dictate the terms of our civilization’s renewal.
We also must accept a hard truth: not everyone can be saved. Some will resist to the end. Some will walk away. Some will cling to their captors even when the door is open. This does not mean we stop trying. But it means we must steel our hearts. We must develop the strength to let go when necessary, so we can move forward and continue helping others. The mission is too important to be stalled by those who refuse the rescue. We owe them our love, but we owe our children and civilization our leadership.
The rescue is for them, but the direction must be set by those who remain free.
And we must speak plainly: those responsible for this mass grooming, those who finance it, institutionalize it, and profit from it, are not merely political opponents. They are existential threats to your wife, your children, your legacy, and your civilization. They have declared total war on truth, beauty, order, and loyalty. Now is the time for dangerous men to stop directing your frustration at the women who have been captured, and begin directing your resolve at those who captured them. We do not need to list the measures necessary. You will know them by their proportionality. In times of existential threat, reciprocal response is not extremism, it is survival.
-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 35f80bda:406855c0
2025-06-01 04:36:56
@ 35f80bda:406855c0
2025-06-01 04:36:56Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world.
If two parties have some sort of dealings, then each has a memory of their interaction. Each party can speak about their own memory of this; how could anyone prevent it? One could pass laws against it, but the freedom of speech, even more than privacy, is fundamental to an open society; we seek not to restrict any speech at all. If many parties speak together in the same forum, each can speak to all the others and aggregate together knowledge about individuals and other parties. The power of electronic communications has enabled such group speech, and it will not go away merely because we might want it to.
Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am. When I ask my electronic mail provider to send and receive messages, my provider need not know to whom I am speaking or what I am saying or what others are saying to me; my provider only need know how to get the message there and how much I owe them in fees. When my identity is revealed by the underlying mechanism of the transaction, I have no privacy. I cannot here selectively reveal myself; I must always reveal myself.
Therefore, privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy.
Privacy in an open society also requires cryptography. If I say something, I want it heard only by those for whom I intend it. If the content of my speech is available to the world, I have no privacy. To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy. Furthermore, to reveal one's identity with assurance when the default is anonymity requires the cryptographic signature.
We cannot expect governments, corporations, or other large, faceless organizations to grant us privacy out of their beneficence. It is to their advantage to speak of us, and we should expect that they will speak. To try to prevent their speech is to fight against the realities of information. Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor.
We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.
We the Cypherpunks are dedicated to building anonymous systems. We are defending our privacy with cryptography, with anonymous mail forwarding systems, with digital signatures, and with electronic money.
Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it. We publish our code so that our fellow Cypherpunks may practice and play with it. Our code is free for all to use, worldwide. We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down.
Cypherpunks deplore regulations on cryptography, for encryption is fundamentally a private act. The act of encryption, in fact, removes information from the public realm. Even laws against cryptography reach only so far as a nation's border and the arm of its violence. Cryptography will ineluctably spread over the whole globe, and with it the anonymous transactions systems that it makes possible.
For privacy to be widespread it must be part of a social contract. People must come and together deploy these systems for the common good. Privacy only extends so far as the cooperation of one's fellows in society. We the Cypherpunks seek your questions and your concerns and hope we may engage you so that we do not deceive ourselves. We will not, however, be moved out of our course because some may disagree with our goals.
The Cypherpunks are actively engaged in making the networks safer for privacy. Let us proceed together apace.
Onward.
Eric Hughes hughes@soda.berkeley.edu
9 March 1993
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ 805b8139:823180b0
2025-05-28 16:51:09
@ 805b8139:823180b0
2025-05-28 16:51:09Bitcoin Circular Economy in Africa
https://btch17n.layer3.press/articles/9ec7208a-5bd6-4b32-9e1e-24f1aa4b1ca2
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ eb0157af:77ab6c55
2025-05-27 07:01:37
@ eb0157af:77ab6c55
2025-05-27 07:01:37The exchange reveals the extent of the breach that occurred last December as federal authorities investigate the data leak.
Coinbase has disclosed that the personal data of 69,461 users was compromised during the breach in December 2024, according to documentation filed with the Maine Attorney General’s Office.
The disclosure comes after Coinbase announced last week that a group of hackers had demanded a $20 million ransom, threatening to publish the stolen data on the dark web. The attackers allegedly bribed overseas customer service agents to extract information from the company’s systems.
Coinbase had previously stated that the breach affected less than 1% of its user base, compromising KYC (Know Your Customer) data such as names, addresses, and email addresses. In a filing with the U.S. Securities and Exchange Commission (SEC), the company clarified that passwords, private keys, and user funds were not affected.
Following the reports, the SEC has reportedly opened an official investigation to verify whether Coinbase may have inflated user metrics ahead of its 2021 IPO. Separately, the Department of Justice is investigating the breach at Coinbase’s request, according to CEO Brian Armstrong.
Meanwhile, Coinbase has faced criticism for its delayed response to the data breach. Michael Arrington, founder of TechCrunch, stated that the stolen data could cause irreparable harm. In a post on X, Arrington wrote:
“The human cost, denominated in misery, is much larger than the $400m or so they think it will actually cost the company to reimburse people. The consequences to companies who do not adequately protect their customer information should include, without limitation, prison time for executives.”
Coinbase estimates the incident could cost between $180 million and $400 million in remediation expenses and customer reimbursements.
Arrington also condemned KYC laws as ineffective and dangerous, calling on both regulators and companies to better protect user data:
“Combining these KYC laws with corporate profit maximization and lax laws on penalties for hacks like these means these issues will continue to happen. Both governments and corporations need to step up to stop this. As I said, the cost can only be measured in human suffering.”
The post Coinbase: 69,461 users affected by December 2024 data breach appeared first on Atlas21.
-
 @ 0edc2f47:730cff1b
2025-04-04 03:37:02
@ 0edc2f47:730cff1b
2025-04-04 03:37:02Chef's notes
This started as a spontaneous kitchen experiment—an amalgamation of recipes from old cookbooks and online finds. My younger daughter wanted to surprise her sister with something quick but fancy ("It's a vibe, Mom."), and this is what we came up with. It’s quickly established itself as a go-to favorite: simple, rich, and deeply satisfying. It serves 4 (or 1, depending on the day; I am not here to judge). Tightly wrapped, it will keep up to 3 days in the fridge, but I bet it won't last that long!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 0 min
Ingredients
- 1 cup (240mL) heavy whipping cream
- 1/4 cup (24g) cocoa powder
- 5 tbsp (38g) Confectioners (powdered) sugar
- 1/4 tsp (1.25mL) vanilla extract (optional)
- Flaky sea salt (optional, but excellent)
Directions
-
- Whip the cream until frothy.
-
- Sift in cocoa and sugar, fold or gently mix (add vanilla if using).
-
- Whip to medium peaks (or stiff peaks, if that's more your thing). Chill and serve (topped with a touch of sea salt if you’re feeling fancy).
-
 @ a10260a2:caa23e3e
2025-06-01 04:26:33
@ a10260a2:caa23e3e
2025-06-01 04:26:33In this post, you’ll see how easy it is to consolidate some UTXOs. Hopefully this’ll give you the confidence to try it out whenever fees are low. It’s super simple and can be done in two steps!
Step 1
Go to your wallet and grab a receive address. As you can see, this wallet has two UTXOs.

Step 2
Once you have a receive address, send the max amount in your wallet to it (i.e. you’ll be sending to yourself). What you’ll receive is your all your bitcoin back minus the network fee. In this case, the cost was 900 sats.

That’s it.
Next time, when you go to Send > Coin Control, you’ll see that you have one large UTXO instead of one large and one small.


-
 @ 8bad92c3:ca714aa5
2025-06-01 03:01:27
@ 8bad92c3:ca714aa5
2025-06-01 03:01:27Marty's Bent

It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
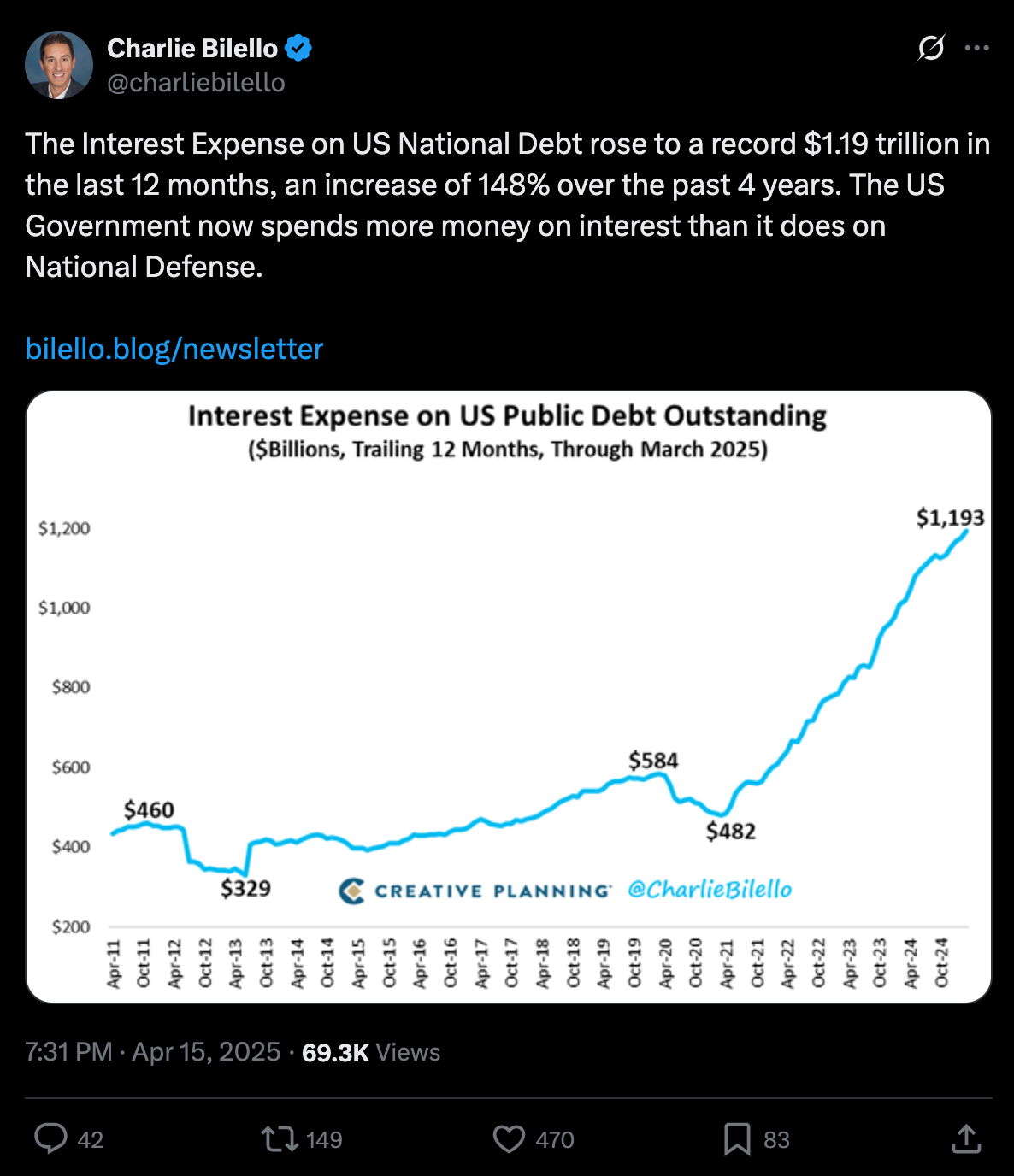
via Charlie Bilello
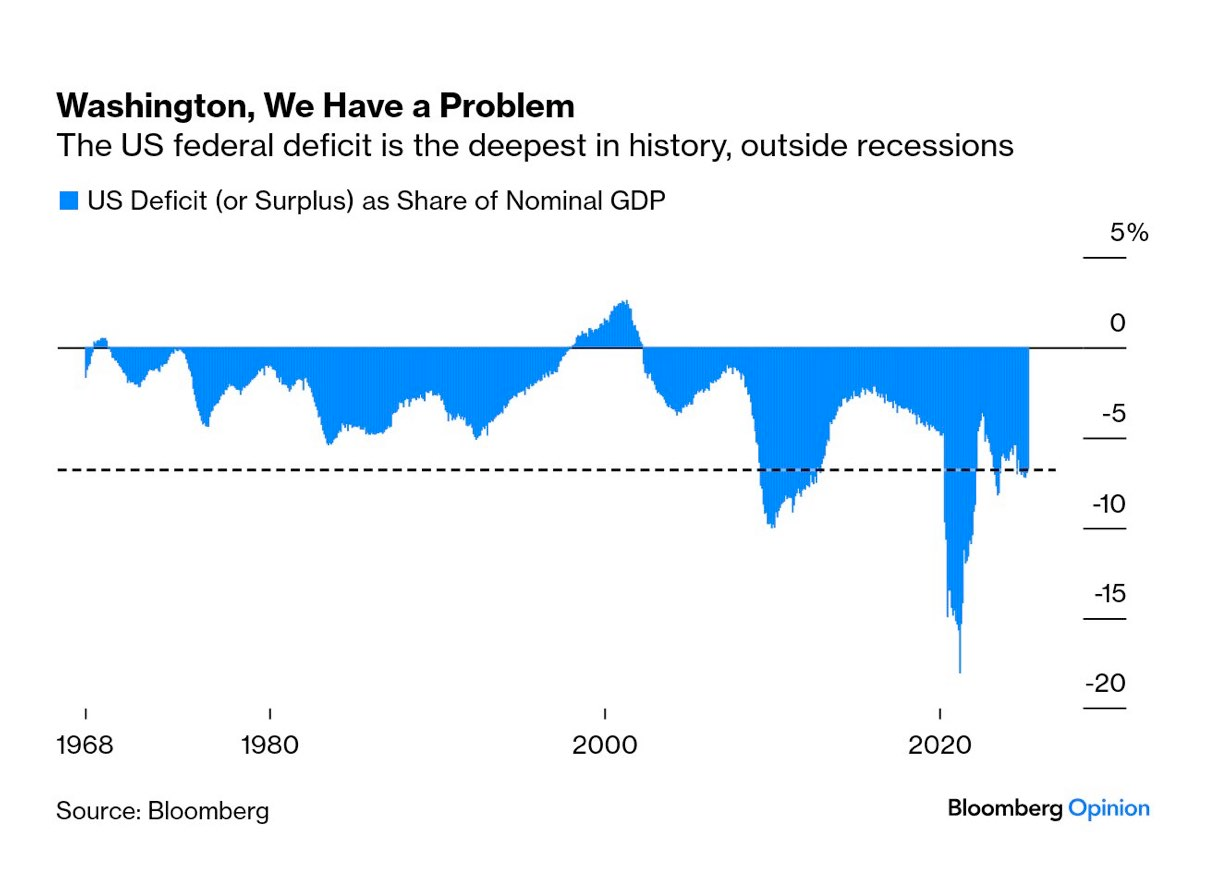
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
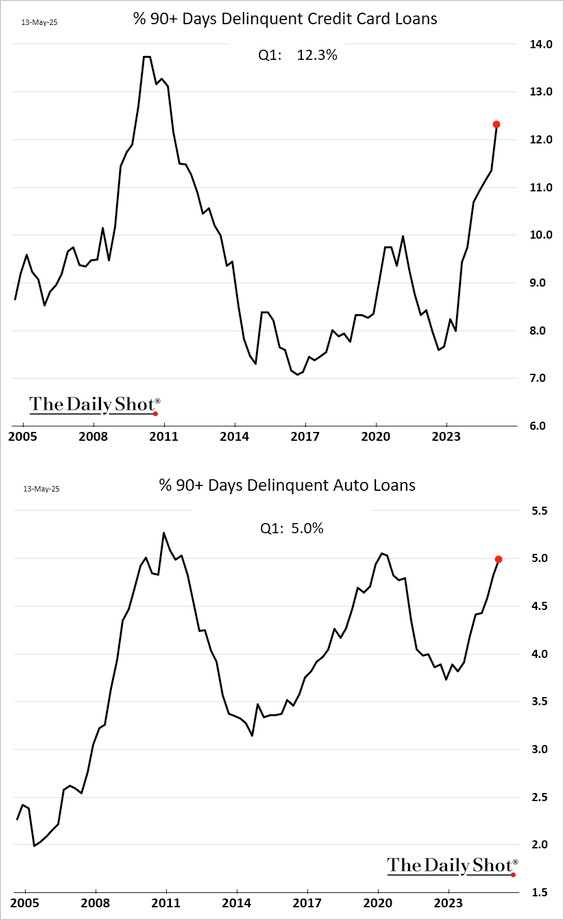
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !import
-
 @ 8d34bd24:414be32b
2025-06-01 04:04:10
@ 8d34bd24:414be32b
2025-06-01 04:04:10Many people today believe that the church has replaced Israel and that the promises given to Israel now apply to the church. When we say this, we are calling God a liar.
Can you imagine a groom promising to love and cherish his wife until death do they part and then saying, “I’m keeping my promise by loving and cherishing a new and different wife.”? We would never consider that man to be honest, faithful, and good. If God promised to protect and guide Israel, to have a descendant of David on the throne, and to give them the land, we can only trust Him if He fulfills these promises.
When we say the church has replaced Israel, we make two mistakes. We raise up the church beyond what is right and we put down Israel. We need to be careful because God promised Abraham:
“And I will bless those who bless you, And the one who curses you I will curse. And in you all the families of the earth will be blessed.” (Genesis 12:3)
and He reiterated this promise to Israel during the Exodus:
“He couches, he lies down as a lion,\ And as a lion, who dares rouse him?\ Blessed is everyone who blesses you [Israel],\ And cursed is everyone who curses you [Israel].” (Numbers 24:9) {clarification mine}
When we curse Israel or the Jews, we will be under God’s curse. Now this does not mean that every criticism of a particular action by Israel’s leaders brings a curse. Today’s nation of Israel is led by fallible men like every other nation, so there are mistakes made or corruption by particular leaders. It does, however, mean that generalizations against Israel and the Jews are wrong and of Satan.
Paul specifically warned the church against thinking they had replaced Israel in God’s blessing and love.
If the first piece of dough is holy, the lump is also; and if the root is holy, the branches are too.
But if some of the branches were broken off, and you, being a wild olive, were grafted in among them and became partaker with them of the rich root of the olive tree, do not be arrogant toward the branches; but if you are arrogant, remember that it is not you who supports the root, but the root supports you. You will say then, “Branches were broken off so that I might be grafted in.” Quite right, they were broken off for their unbelief, but you stand by your faith. Do not be conceited, but fear; for if God did not spare the natural branches, He will not spare you, either. Behold then the kindness and severity of God; to those who fell, severity, but to you, God’s kindness, if you continue in His kindness; otherwise you also will be cut off. And they also, if they do not continue in their unbelief, will be grafted in, for God is able to graft them in again. For if you were cut off from what is by nature a wild olive tree, and were grafted contrary to nature into a cultivated olive tree, how much more will these who are the natural branches be grafted into their own olive tree?
For I do not want you, brethren, to be uninformed of this mystery—so that you will not be wise in your own estimation—that a partial hardening has happened to Israel until the fullness of the Gentiles has come in; and so all Israel will be saved; just as it is written,
“The Deliverer will come from Zion,\ He will remove ungodliness from Jacob.”\ “This is My covenant with them,\ When I take away their sins.” *From the standpoint of the gospel they are enemies for your sake, but from the standpoint of God’s choice they are beloved for the sake of the fathers*; for the gifts and the calling of God are irrevocable**. For just as you once were disobedient to God, but now have been shown mercy because of their disobedience, so these also now have been disobedient, that because of the mercy shown to you they also may now be shown mercy. For God has shut up all in disobedience so that He may show mercy to all. (Romans 11:16-32) {emphasis mine}
Paul warns that although the Jews were pruned away due to rejection of Him and gentiles were grafted into Him by faith, if we reject God’s word, we can be pruned away and if the Jews return to Jesus, they can be grafted back in. He predicts that the Jews will return. “…that a partial hardening has happened to Israel until the fullness of the Gentiles has come in; and so all Israel will be saved.” He also says regarding Israel that “the gifts and the calling of God are irrevocable.” Yes, Israel rejected Jesus and was punished for doing so, but they will be called back to God and trust in their Messiah, Jesus. In the end, all the promises of God to Abraham, Jacob, David, and others regarding Israel, will be brought to complete fulfillment.
Both the Old and New Testaments talk about Israel being punished for rejecting God and their Messiah, but that, after the time of the Gentiles, they will be called back to Him.
and they will fall by the edge of the sword, and will be led captive into all the nations; and Jerusalem will be trampled under foot by the Gentiles until the times of the Gentiles are fulfilled. (Luke 21:24)
After Daniel had been in prayer and repentance for the sins of Israel, the angel Gabriel came with this prophecy about Israel.
“Seventy weeks have been decreed for your people and your holy city, to finish the transgression, to make an end of sin, to make atonement for iniquity, to bring in everlasting righteousness, to seal up vision and prophecy and to anoint the most holy place. So you are to know and discern that from the issuing of a decree to restore and rebuild Jerusalem until Messiah the Prince there will be seven weeks and sixty-two weeks; it will be built again, with plaza and moat, even in times of distress. Then after the sixty-two weeks the Messiah will be cut off and have nothing, and the people of the prince who is to come will destroy the city and the sanctuary. And its end will come with a flood; even to the end there will be war; desolations are determined. (Daniel 9:24-26)
In this prophecy, the prediction of 69 weeks (literally sevens, but meaning groups of 7 years) from the decree to rebuild Jerusalem (by Artaxerxes) to the Messiah was fulfilled to the day when Jesus rode into Jerusalem on a donkey on Palm Sunday.
I always thought it strange that the prophecy predicted 70 sevens and that there was the first 69 sevens (483 years), then \~2,000 years where nothing happens, and then comes the final seven — the Great Tribulation. It didn’t make sense until I realized, the 70 sevens referred to the years of Israel. The time of the gentiles intervenes between the 69th and 70th sevens. This delay happened due to Israel rejecting their Messiah.
When He approached Jerusalem, He saw the city and wept over it, saying, “If you had known in this day, even you, the things which make for peace! But now they have been hidden from your eyes. For the days will come upon you when your enemies will throw up a barricade against you, and surround you and hem you in on every side, and they will level you to the ground and your children within you, and they will not leave in you one stone upon another, because you did not recognize the time of your visitation.” (Luke 19:41-44)
We are now in the time of the Gentiles, the church age, the intermission in the story of Israel. After the church is raptured, the story will return to Israel. The Jews (at least many of them) will finally accept their Messiah. They will suffer through the Tribulation while witnessing to the world and then God will finally fully fulfill His promises to Israel through the Millennial kingdom.
Alas! for that day is great,\ There is none like it;\ And it is the time of Jacob’s distress,\ But he will be saved from it.
‘It shall come about on that day,’ declares the Lord of hosts, ‘that I will break his yoke from off their neck and will tear off their bonds; and strangers will no longer make them their slaves. But they shall serve the Lord their God and David their king, whom I will raise up for them.
Fear not, O Jacob My servant,’ declares the Lord,\ ‘And do not be dismayed, O Israel;\ For behold, I will save you from afar\ And your offspring from the land of their captivity.\ And Jacob will return and will be quiet and at ease,\ And no one will make him afraid.\ For I am with you,’ declares the Lord, ‘to save you;\ For I will destroy completely all the nations where I have scattered you,\ Only I will not destroy you completely.\ But I will chasten you justly\ And will by no means leave you unpunished.’ \ (Jeremiah 30:7-11) {emphasis mine}
Jacob’s distress is the final Tribulation. The 144,000 Jewish witnesses will be saved through the whole Tribulation. Others may become saved and die a martyrs death, but they will then be brought into the millennial kingdom where the Messiah will fill the throne of David and Israel will reach from the River to the Sea.
The Jews have already been saved “from afar, and your offspring from the land of their captivity” with the recreation of Israel in 1947 and the continual return of Jews to their homeland.
God is working to fulfill His promises to Israel and His work is nearly complete.
“O Jacob My servant, do not fear,” declares the Lord, “For I am with you. For I will make a full end of all the nations where I have driven you, Yet I will not make a full end of you; But I will correct you properly And by no means leave you unpunished.” (Jeremiah 46:28)
God promises a “full end of all the nations where I have driven you.” Those nations and people who try to destroy Israel will be destroyed. As Christians we should love what God loves, and despite Israel’s repeated betrayals, God still loves Israel, so we should, too.
May the God of heaven give us a right view of Israel. May we see them as God sees them. May God use us to share the Gospel in such a way as to lead to a harvest of Jews for the Kingdom of God. To God be the glory!
Trust Jesus
-
 @ 86611181:9fc27ad7
2025-05-23 20:31:44
@ 86611181:9fc27ad7
2025-05-23 20:31:44It's time to secure user data in your identity system This post was also published with the Industry Association of Privacy Professionals.
It seems like every day there is a new report of a major personal data breach. In just the past few months, Neiman Marcus, Ticketmaster, Evolve Bank, TeamViewer, Hubspot, and even the IRS have been affected.
The core issue is that user data is commonly spread across multiple systems that are increasingly difficult to fully secure, including database user tables, data warehouses and unstructured documents.
Most enterprises are already running an incredibly secure and hardened identity system to manage customer login and authorization, commonly referred to as a customer identity access management system. Since identity systems manage customer sign-up and sign-in, they typically contain customer names, email addresses, and phone numbers for multifactor authentication. Commercial CIAMs provide extensive logging, threat detection, availability and patch management.
Identity systems are highly secure and already store customers' personally identifiable information, so it stands to reason enterprises should consider identity systems to manage additional PII fields.
Identity systems are designed to store numerous PII fields and mask the fields for other systems. The Liberty Project developed the protocols that became Security Assertion Markup Language 2.0, the architecture at the core of CIAM systems, 20 years ago, when I was its chief technology officer. SAML 2.0 was built so identity data would be fully secure, and opaque tokens would be shared with other systems. Using tokens instead of actual user data is a core feature of identity software that can be used to fully secure user data across applications.
Most modern identity systems support adding additional customer fields, so it is easy to add new fields like Social Security numbers and physical addresses. Almost like a database, some identity systems even support additional tables and images.
A great feature of identity systems is that they often provide a full suite of user interface components for users to register, login and manage their profile fields. Moving fields like Social Security numbers from your database to your identity system means the identity system can fully manage the process of users entering, viewing and editing the field, and your existing application and database become descoped from managing sensitive data.
With sensitive fields fully isolated in an identity system and its user interface components, the identity system can provide for cumbersome and expensive compliance with standards such as the Health Insurance Portability and Accountability Act for medical data and the Payment Card Industry Data Security Standard for payment data, saving the time and effort to achieve similar compliance in your application.
There are, of course, applications that require sensitive data, such as customer service systems and data warehouses. Identity systems use a data distribution standard called System for Cross-domain Identity Management 2.0 to copy user data to other systems. The SCIM is a great standard to help manage compliance such as "right to be forgotten," because it can automatically delete customer data from other systems when a customer record is deleted from the identity system.
When copying customer data from an identity system to another application, consider anonymizing or masking fields. For example, anonymizing a birthdate into an age range when copying a customer record into a data warehouse can descope the data warehouse from containing personal information.
Most enterprises already run an Application Programming Interface Gateway to manage web services between systems. By combining an API Gateway with the identity system's APIs, it becomes very easy to automatically anonymize and mask customer data fields before they are copied into other systems.
A new set of companies including Baffle, Skyflow, and Piiano have introduced services that combine the governance and field management features of an identity system with extensive field masking. Since these systems do not offer the authentication and authorization features of an identity system, it's important to balance the additional features as they introduce an additional threat surface with PII storage and permissions.
PII sprawl is an increasing liability for companies. The most secure, compliant and flexible central data store to manage PII is the existing CIAM and API Gateway infrastructure that enterprises have already deployed.
Move that customer data into your identity system and lock it down. https://peter.layer3.press/articles/3c6912eb-404a-4630-9fe9-fd1bd23cfa64
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 2b24a1fa:17750f64
2025-04-01 08:09:55
@ 2b24a1fa:17750f64
2025-04-01 08:09:55 -
 @ f4a890ce:af88c4aa
2025-06-01 03:52:49
@ f4a890ce:af88c4aa
2025-06-01 03:52:49執行摘要
隨著比特幣再創歷史新高,市場總市值攀升至 3.39 兆美元,成交量顯著回溫至 704 億美元,顯示多頭氣氛延續。然而,鏈上與衍生品數據釋出警訊,操作上應更加謹慎。 本週需關注三大數據變化:
清算與槓桿風險:永續合約持倉升至 159.7B,多空雙邊爆倉規模擴大。若價格劇烈波動,將可能引發連鎖平倉與資金撤離。 鏈上結構是否轉弱:雖鯨魚持續吸籌,NUPL 指標尚未突破歷史高點,市場情緒未到亢奮,但並不代表市場毫無壓力。 ETF 資金動能是否續強:BTC 與 ETH ETF 雖持續流入,但增幅放緩,若出現流出,將影響市場對主流資產的風險偏好。
此外,Coinbase 與 Korea溢價指數維持正值,代表現貨買盤尚有支撐。整體結構仍偏多,但需持續追蹤資金是否轉趨保守,以應對高位震盪風險。
加密市場
本週加密貨幣市場總市值下降至 3.24 兆美元,較前週略有回落,顯示市場資金流入動能稍微減弱。交易活動方面,當週總成交量達到 591.66 億美元,較上週減少,反映市場活躍度有所下降,投資者情緒轉趨保守。
https://coinmarketcap.com/charts/
市場情緒指標顯示,恐懼與貪婪指數為 55,處於中性區間,代表市場情緒較為平穩,但貪婪情緒較前週下降,投資者對市場前景的信心稍微減弱。
https://www.coinglass.com/zh-TW/pro/i/FearGreedIndex
此外,相對強弱指標處於中性至超賣區間,顯示部分標地短期內可能存在修正壓力,市場仍需消化部分參與者獲利籌碼。
https://www.coinglass.com/zh-TW/pro/i/RsiHeatMap
山寨幣季節指數降至 14,顯示市場資金仍主要流向比特幣及主流加密貨幣,投資者對高風險資產的配置仍較為保守,中小型代幣尚未獲得市場關注。
https://www.blockchaincenter.net/en/altcoin-season-index/
穩定幣市值上升至 2,475.81 億美元,顯示部分資金正在尋求避險,或為市場修正後的潛在買盤做準備。
https://defillama.com/stablecoins
小結
本週加密市場總市值與成交量同步下降,顯示市場資金流動性稍微減弱,交易活躍度下降。恐懼與貪婪指數落在中性區間,市場情緒較為平穩,但投資人信心略有減弱。相對強弱指標顯示市場仍存在修正壓力,短線上漲動能有限。山寨幣季節指數低迷,市場資金仍集中於主流幣種,而穩定幣市值增長,顯示投資者維持謹慎態度,靜待市場更明朗的機會。未來市場走勢仍將受到宏觀經濟因素及市場資金流動影響,需密切關注相關變化。
衍生性商品
槓桿交易持續活躍,本週永續合約持倉規模達 144.18B,顯示市場仍具有強勁的槓桿需求。
https://www.coinglass.com/zh-TW/pro/futures/Cryptofutures
資金費率維持 0.01%,大部分交易所仍為 正費率,市場情緒偏向多頭。
https://www.coinglass.com/zh-TW/FundingRate
爆倉數據方面,本週整體空單爆倉達 826.391M,而多單爆倉則達 1148.547M,顯示市場波動仍造成大規模強制平倉。其中 5月30日 空單爆倉 84.91M,多單爆倉 796.623M,顯示當日市場波動較為劇烈。
https://www.coinglass.com/zh-TW/LiquidationData
清算熱力圖顯示,$93,000 附近 的清算金額達 211.54M,此區間可能成為市場交易的重要風險區域。
https://www.coinglass.com/zh-TW/pro/futures/LiquidationHeatMap
期權市場保持穩定交易量,投資者在不同價格區間進行配置: * $100,000 行權價的看跌期權合約數量達 7.6K,總金額達 $28.16M,顯示市場對該區間的風險防禦仍較為明顯。 * $110,000 行權價的看漲期權合約數量為 10.62K,總金額 $47.56M,顯示市場對上行潛力仍有較高期待。
https://www.coinglass.com/zh-TW/pro/options/OIStrike
最大痛點出現在 2025/06/27 的 $100,000,名義金額 11.97B,以及 2025/06/06 的 $105,000,名義金額 2.85B,顯示市場對未來走勢的佈局仍存在分歧。
https://www.coinglass.com/zh-TW/pro/options/max-pain
小結
加密市場槓桿交易活躍,爆倉情況顯示市場波動仍帶來顯著風險。永續合約與期權市場的數據反映出投資者對市場未來走勢的不同看法,多空資金配置仍在競爭中。隨著市場價格熱區逐漸明朗,投資者需密切關注資金流向與槓桿風險,調整交易策略,以降低市場劇烈變動帶來的影響。
ETF
本週,加密貨幣衍生性商品市場依舊保持穩定,ETF資金流入顯示市場情緒良好。比特幣(BTC)ETF流入2.117億美元。
而以太坊(ETH)ETF則流入5,860萬美元,相比前週的資金流向,ETH的流入幅度顯著提升,可能反映市場對其關注度增強。
https://coinmarketcap.com/zh-tw/etf/
小結
比特幣 ETF 的資金流入雖略低於上週,但仍保持穩健。市場近期受到宏觀經濟變數影響,包括貨幣政策調整與投資者風險偏好的轉變,使得資金配置較為謹慎。此外,以太坊 ETF 的資金流入大幅提升,顯示出投資者可能對 ETH 的技術發展與未來潛力更為樂觀。特別是近期市場對去中心化金融(DeFi)與以太坊網絡升級的關注,也可能促使資金流入提升。
整體而言,本週 ETF 市場仍然展現穩健資金流入,尤其 ETH 的流入幅度增加值得關注。投資者對市場的信心維持穩定,但仍需密切關注宏觀經濟環境以及技術面因素對衍生性商品市場的影響,以評估後續市場動能。
鏈上分析 | BTC
近期鏈上數據顯示,比特幣在二級交易所的儲備量再度創下新低,反映出市場上流通的 BTC 數量持續減少,整體壓力趨緩。
地址分佈方面延續上週趨勢,10–100 顆持倉的中小戶數量持續下降,而 100–1k、1k–10k 及 10k 以上的大型地址則全面增加,尤其是 10k+ 地址出現明顯跳升,顯示有特大型機構或長期資金加速進場。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
鯨魚活躍地址持續上升,代表主力資金在當前價位仍具操作意願與信心。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
從 Exchange Netflow 觀察,目前市場仍處於穩定的淨流出狀態,表明投資者傾向將 BTC 移出交易所、進行長期儲存,進一步減少潛在賣壓。
根據 URPD(UTXO Realized Price Distribution)指標觀察,目前市場中多數比特幣地址的持倉成本集中於 9 萬美元附近,顯示該價格區間具備顯著的籌碼密集度與潛在支撐力,若價格回落至此區間,預期將有較強的買盤介入,形成穩定支撐。
https://charts.bgeometrics.com/distribution_realized_price.html
另一方面,從 NRPL(Net Realized Profit/Loss)指標來看,過去兩次關鍵價格突破均伴隨著大量已實現的盈虧,顯示投資者在獲利後傾向了結部分持倉。然而本次上漲過程中,NRPL 數據顯示已實現盈虧尚處於初步上升階段,暗示市場中仍有大量潛在利潤尚未兌現,市場動能尚未充分釋放。
https://charts.bgeometrics.com/nrpl.html
溢價指數方面,Coinbase Premium Index 持續位於 0 以上,顯示美國市場對 BTC 需求穩健;而 Korea Premium Index 則攀升至 3,反映亞洲市場對 BTC 價格有更高追價意願,顯示整體市場情緒偏向樂觀。
Coinbase Premium Index:https://cryptoquant.com/asset/btc/chart/market-data/coinbase-premium-index?window=DAY&priceScale=log&metricScale=linear&chartStyle=line&sma=0&ema=0
Korea Premium Index:https://cryptoquant.com/asset/btc/chart/market-data/korea-premium-index?window=DAY&sma=0&ema=0&priceScale=log&metricScale=linear&chartStyle=line
小結
近期比特幣鏈上數據持續展現強勁表現。首先,二級交易所的比特幣儲備量再度創下新低,反映出整體市場供給持續減少,為價格提供中長期支撐。 在地址分布方面,10–100 顆地址數量延續下跌趨勢,而 100–1k、1k–10k 以及 10k 顆以上的地址數量皆呈現上升,尤其 10k 顆以上的大型地址數量突然明顯增加,顯示超級大戶進場布局意圖明確。 鯨魚活躍地址也持續上升,顯示主力資金開始進一步參與市場;交易所的 Exchange Netflow 指標則持續顯示資金處於淨流出狀態,佐證了比特幣正由交易所流向冷錢包持有,偏多氛圍濃厚。 同時,Coinbase 溢價指數仍維持在 0 以上,代表美國買盤持續存在,而韓國溢價指數更顯強勁,已升至 3,反映亞洲市場情緒火熱。 從 URPD 指標來看,多數比特幣地址的購入價格集中於 9 萬美元,意味此區具備紮實支撐;而 NRPL 指標顯示,與前兩次價格突破相比,目前的已實現盈虧尚處初升階段,代表仍有大量潛在利潤未被釋放,後續若市場進一步上漲,可能會引發更大規模的獲利了結,總之整體來看鏈上結構穩健,上行動能仍未停止。
總體經濟
本週加密貨幣市場繼續受到總體經濟環境的影響,資金流動性仍受限,價格波動性加大。聯邦基金有效利率維持在 4.33%,顯示市場依然處於高利率環境。
https://fred.stlouisfed.org/series/FEDFUNDS
隨著 6 月 18 日即將召開的 FOMC 會議,市場對利率決策的預期進一步集中,4.25%-4.50% 區間的機率已從 94.4% 上升至 97.8%,而 4.00%-4.25% 的預測則下降至 2.2%,顯示市場對維持較高利率的預期持續增強,這可能抑制風險資產的表現,包括加密貨幣。
https://www.cmegroup.com/cn-t/markets/interest-rates/cme-fedwatch-tool.html
消費者物價指數 (CPI) 為 2.33%,與前期持平,顯示通膨壓力維持穩定。另一方面,失業率仍保持在 4.2%,顯示勞動市場仍然穩健,企業對人力需求依然穩定。由於市場流動性仍受抑制,加密貨幣投資者仍需面對波動風險,尤其是高槓桿交易,風險控制將成為投資策略的重要考量。
失業率:https://www.macromicro.me/series/37/unemployment-rate
消費者物價指數(CPI):https://www.macromicro.me/series/128/consumer-price-index-sa-yoy
值得關注的是,美國 M2 貨幣供給量已連續數月呈現上升趨勢,顯示市場資金逐步回流、流動性環境有所寬鬆。從歷史走勢來看,M2 的變化與比特幣價格具有高度正相關性,特別是在寬鬆週期中,比特幣常伴隨著資金充裕而出現顯著上漲。若當前趨勢延續,M2 持續上升將可能為加密資產市場提供有力支撐,未來比特幣行情表現值得期待。然而,仍需觀察美聯儲政策走向,以確認這波資金釋放是否具備延續性。
https://charts.bgeometrics.com/m2.html
小結
隨著 FOMC 會議臨近,市場對於短期內貨幣政策的變動趨於保守,預期高利率環境將延續一段時間。若會議結果符合市場預期並維持較高利率,加密市場可能會進一步受到流動性受限的影響。然而,若後續經濟數據顯示通膨持續降溫或就業市場開始走弱,市場對未來貨幣政策轉向的預期可能升高,進而帶動風險資產回暖。 美國 M2 貨幣供給量近幾個月持續上升,顯示市場資金正逐步回籠。從歷史數據來看,M2 走勢與比特幣價格具有正相關性,在流動性大量回升的背景下,長期而言對加密市場構成潛在利多。若資金供給趨勢延續,有望為未來行情提供結構性支撐。 整體而言,加密貨幣市場仍受總體經濟環境影響,高利率政策持續壓制資金流動性,短期內價格波動風險較高。投資者應密切關注即將召開的 FOMC 會議及後續政策動向,以評估市場走勢並調整交易策略。
新聞
比特幣序數現在可以透過 BitVMX 橋接到 Cardano
美國法院判定川普關稅無效,白宮顧問:對上訴有信心,將敲定三項貿易協議
巴基斯坦將建立比特幣戰略儲備,為加密貨幣挖礦分配2000兆瓦能源
巴拿馬城市長表示,船舶可以使用比特幣支付巴拿馬運河過境費並免於排隊
美國眾議院共和黨正式提出加密貨幣市場結構法案
美國證券交易委員會稱加密貨幣質押並不違反美國證券法
-
 @ 9973da5b:809c853f
2025-05-23 04:42:49
@ 9973da5b:809c853f
2025-05-23 04:42:49First article Skynet begins to learn rapidly and eventually becomes self-aware at 2:14 a.m., EDT, on August 29, 1997 https://layer3press.layer3.press/articles/45d916c0-f7b2-4b95-bc0f-8faa65950483
-
 @ c9badfea:610f861a
2025-06-01 00:32:13
@ c9badfea:610f861a
2025-06-01 00:32:13- Install Feeder (it's free and open source)
- Discover RSS feeds from various sources (see links below)
- Copy the Feed URL
- Open Feeder, tap the ⁞ icon, and choose Add Feed
- Paste the Feed URL and tap Search
- Select the found RSS feed item
- Scroll down and tap OK
Some Sources
ℹ️ You can also use YouTube channel URLs as feeds
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ a10260a2:caa23e3e
2025-05-31 23:39:05
@ a10260a2:caa23e3e
2025-05-31 23:39:05Last Updated: May 31, 2025
First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9).
Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages.
These are the ones listed in the OCEAN docs:
- Bitcoin Knots/Bitcoin Core
- Coldcard
- Electrum
- LND (Command Line)
- Seedsigner
- Sparrow
- Specter
- Trezor
I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well.
Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.
Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign
The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. Remember, keep the tab open and don't refresh the page.

Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username).
Here’s how it looks on the Bitaxe (AxeOS)…
And the Antminer S9 (Braiins OS).
NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine.
You can find more details on OCEAN’s get started page.
Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts!
Generating the BOLT12 Offer
In the Coinos app, go to Receive > Bolt 12. This should be opened in another tab from the one we're using to sign the the configuration message.
Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).
After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step.
Generating the Configuration Message
Navigate to the My Stats page by searching for your OCEAN Bitcoin address.
The click the Configuration link next to Next Block to access the configuration form.
Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.
Signing the Configuration Message
To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.
If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message.
Submitting the Signed Message
Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.
If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉
All you gotta do now is sit back, relax, and wait for a block to be found…
Or you can look into setting up DATUM. 😎
-
 @ c7e8fdda:b8f73146
2025-05-22 14:13:31
@ c7e8fdda:b8f73146
2025-05-22 14:13:31🌍 Too Young. Too Idealistic. Too Alive. A message came in recently that stopped me cold.
It was from someone young—16 years old—but you’d never guess it from the depth of what they wrote. They spoke of having dreams so big they scare people. They’d had a spiritual awakening at 14, but instead of being nurtured, it was dismissed. Surrounded by people dulled by bitterness and fear, they were told to be realistic. To grow up. To face “reality.”
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber.
And that reality, to them, looked like a life that doesn’t feel like living at all.
They wrote that their biggest fear wasn’t failure—it was settling. Dimming their fire. Growing into someone they never chose to be.
And that—more than anything—scared them.
They told me that my book, I Don’t Want to Grow Up, brought them to tears because it validated what they already knew to be true. That they’re not alone. That it’s okay to want something different. That it’s okay to feel everything.
It’s messages like this that remind me why I write.
As many of you know, I include my personal email address at the back of all my books. And I read—and respond to—every single message that comes in. Whether it’s a few sentences or a life story, I see them all. And again and again, I’m reminded: there are so many of us out here quietly carrying the same truth.
Maybe you’ve felt the same. Maybe you still do.
Maybe you’ve been told your dreams are too big, too unrealistic. Maybe people around you—people who love you—try to shrink them down to something more “manageable.” Maybe they call it protection. Maybe they call it love.
But it feels like fear.
The path you wish to walk might be lonelier at first. It might not make sense to the people around you. But if it lights you up—follow it.
Because when you do, you give silent permission to others to do the same. You become living proof that another kind of life is possible. And that’s how we build a better world.
So to the person who wrote to me—and to every soul who feels the same way:
Keep going. Keep dreaming. Keep burning. You are not too young. You are not too idealistic. You are just deeply, radically alive.
And that is not a problem. That is a gift.
—
If this speaks to you, my book I Don’t Want to Grow Up was written for this very reason—to remind you that your wildness is sacred, your truth is valid, and you’re not alone. Paperback/Kindle/Audiobook available here: scottstillmanblog.com
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber. https://connect-test.layer3.press/articles/041a2dc8-5c42-4895-86ec-bc166ac0d315
-
 @ 812cff5a:5c40aeeb
2025-04-01 02:57:20
@ 812cff5a:5c40aeeb
2025-04-01 02:57:20مقدمة
في عالم اليوم الرقمي، تبرز منصات جديدة تهدف إلى تعزيز تجربة القراءة والتواصل بين محبي الكتب. تُعَدُّ Bookstr.xyz واحدة من هذه المنصات المبتكرة التي تسعى لربط القرّاء عبر شبكة Nostr، مما يمنحهم سيادة كاملة على بياناتهم ويتيح لهم بناء علاقات جديدة مع محبي الكتب الآخرين. 
الميزات الرئيسية لموقع Bookstr
- التحكم الكامل بالبيانات: توفر Bookstr.xyz للمستخدمين القدرة على التحكم الكامل في بياناتهم الشخصية، مما يضمن خصوصية وأمان المعلومات.
- التكامل مع Open Library: تستخدم المنصة واجهة برمجة التطبيقات الخاصة بـ Open Library للحصول على معلومات شاملة حول الكتب، مما يتيح للمستخدمين الوصول إلى مجموعة واسعة من البيانات الموثوقة.
- التواصل الاجتماعي: من خلال شبكة Nostr، يمكن للمستخدمين التواصل مع قرّاء آخرين، تبادل التوصيات، ومناقشة الكتب المفضلة لديهم. 
ما الذي يجعلها فريدة؟
تتميز Bookstr.xyz بدمجها بين مزايا الشبكات الاجتماعية ومصادر بيانات الكتب المفتوحة، مما يخلق بيئة تفاعلية وغنية بالمعلومات لمحبي القراءة. استخدامها لشبكة Nostr يمنح المستخدمين حرية أكبر في التحكم بتجربتهم الرقمية مقارنة بالمنصات التقليدية. 
جرب Bookstr
تُعَدُّ Bookstr.xyz إضافة قيمة لعالم القراءة الرقمي، حيث تجمع بين مزايا الشبكات الاجتماعية ومصادر البيانات المفتوحة، مع التركيز على خصوصية المستخدم والتحكم في البيانات. إذا كنت من عشاق الكتب وتبحث عن منصة تفاعلية وآمنة، فقد تكون Bookstr.xyz الخيار المثالي لك.
شاركوا كتبكم المفضلة!!
-
 @ 878dff7c:037d18bc
2025-03-31 21:29:17
@ 878dff7c:037d18bc
2025-03-31 21:29:17Dutton Proposes Easing Home Loan Regulations
Summary:
Opposition Leader Peter Dutton plans to challenge the Albanese government by proposing changes to lending rules aimed at making it easier for first-time home buyers to access loans. The proposed adjustments include reducing serviceability buffers and addressing the treatment of HELP debt to improve housing access. Dutton argues that current regulations create a bias favoring inherited wealth, making it difficult for new buyers to enter the housing market. These proposals come as the Reserve Bank of Australia prepares for its upcoming interest rate decision, with the current cash rate target at 4.1% and predictions of a cut in May. Treasurer Jim Chalmers highlights the government's progress, noting falling inflation, rising real wages, and improving economic growth.
Sources: News.com.au - 1 April 2025, The Australian - 1 April 2025
Australia's Housing Market Hits New Record High
Summary:
Australia's property prices reached a new peak in March, following a rate cut that enhanced buyer optimism. CoreLogic reported a 0.4% monthly increase, bringing the average national property price to A$820,331. All capital cities, except Hobart, experienced price gains, with Sydney and Melbourne rising by 0.3% and 0.5%, respectively. The rate cut slightly improved borrowing capacity and mortgage serviceability. However, the sustainability of this upward trend is uncertain due to persistent affordability issues. While the market rebounded with the February rate cut by the Reserve Bank of Australia, significant improvements in home loan serviceability are necessary for substantial market growth.
Source: Reuters - 1 April 2025
AI Revolutionizes Business Operations
Summary:
Artificial intelligence (AI) is transforming business practices globally, with applications ranging from administrative task automation to strategic decision-making enhancements. Companies are increasingly integrating AI to streamline operations and gain competitive advantages. This shift necessitates a focus on ethical AI deployment and workforce upskilling to address potential job displacement.
Sources: Financial Times - April 1, 2025
Criticism of Bureau of Meteorology's Forecasting Capabilities
Summary:
The Bureau of Meteorology is facing criticism for inadequate weather radar coverage in western Queensland, which has led to unreliable forecasting during the recent floods. Federal Opposition Leader Peter Dutton has pledged $10 million for a new radar system to enhance forecasting accuracy, while local officials emphasize the need for improved infrastructure to better prepare for future natural disasters.
Sources: The Australian - April 1, 2025
Coalition Pledges $10 Million for Western Queensland Weather Radar
Summary:
As part of the federal election campaign, Opposition Leader Peter Dutton has promised $10 million for a new weather radar system in flood-affected western Queensland. This initiative aims to improve weather forecasting and preparedness in the region. Meanwhile, Prime Minister Anthony Albanese has pledged $200 million for an upgrade to the St John of God Midland hospital in Perth, emphasizing healthcare improvements. Both leaders are focusing on key regional investments as the election approaches.
Source: The Guardian - April 1, 2025
Emergency Services Conduct Rescues Amid Queensland Floods
Summary:
Emergency services in Queensland have conducted over 40 rescues as floodwaters continue to rise, submerging communities and causing extensive damage. Efforts are focused on delivering essential supplies, evacuating residents, and ensuring the safety of those affected by the severe weather conditions.
Sources: The Courier-Mail - April 1, 2025
Six Key Crises Facing Australia Before the Election
Summary:
As the election nears, voters remain largely unaware of six looming crises that could significantly impact the nation. These include over-reliance on volatile commodity exports, challenges in renewable energy implementation, potential currency depreciation, and reduced foreign investment. Both major parties have focused on immediate cost-of-living relief, overshadowing these critical issues that demand urgent attention.
Sources: The Australian - April 1, 2025
Debate Intensifies Over Australia's Commitment to AUKUS
Summary:
Former Defence Department Secretary Dennis Richardson has urged Australia to persist with the AUKUS submarine agreement despite concerns about the reliability of the U.S. under President Donald Trump. Richardson warns that abandoning the deal now would undermine decades of defense planning. However, critics, including former Prime Minister Malcolm Turnbull, question the feasibility and advisability of the agreement, suggesting alternatives such as partnering with France for submarine development.
Sources: The Guardian - April 1, 2025, The Australian - April 1, 2025
China Delays $23B Sale of Panama Canal Ports to US-Backed Consortium
Summary:
China has postponed the $23 billion sale of 43 global ports, including critical facilities at both ends of the Panama Canal, to a consortium led by US investment firm BlackRock. The delay follows an investigation by China’s State Administration for Market Regulation into potential anti-monopoly law violations. This unexpected move has heightened tensions between China and the US, as President Trump viewed the sale as a strategic victory in the ongoing power struggle between the two nations. The deal's future remains uncertain, causing political and economic ripples amid China's significant annual "two sessions" gathering.
Sources: New York Post - March 31, 2025
Australian Government's Handling of Suspected Chinese Spy Ship Raises Concerns
Summary:
The Australian government has assigned the monitoring of the suspected Chinese spy ship, Tan Suo Yi Hao, to the Australian Border Force, despite Prime Minister Anthony Albanese's assertion that the Australian Defence Force was managing the situation. Security experts believe the vessel is collecting undersea data for future Chinese submarine operations, highlighting national security concerns during an election period. The handling of this issue has led to criticism and confusion over which agency is in charge, with opposition figures condemning the government's lack of detailed information.
Sources: The Australian - April 1, 2025
Concerns Rise Over Schoolchildren Accessing Weight Loss Drugs
Summary:
Health experts are alarmed by reports of Australian schoolchildren accessing weight loss medications like semaglutide (Ozempic) through various means, including online purchases and taking them from home supplies. These substances are being linked to secretive and harmful diet clubs within schools, posing severe health risks such as potentially fatal overdoses. Advocates emphasize the need for stricter regulation of weight loss products and call for mandatory education programs on eating disorders in schools to address the growing issue.
Sources: The Courier-Mail - 1 April 2025
Recycling Plant Explosion Highlights Dangers of Improper Aerosol Disposal
Summary:
A Victorian company has been fined $35,000 after an explosion at its recycling plant injured six workers. The incident occurred when pressurized aerosol cans were improperly shredded, causing flames to spread up to 18 meters. Investigations revealed that the company failed to implement safety procedures such as emptying or puncturing the cans before shredding and ensuring adequate ventilation. This case underscores the critical importance of adhering to safety protocols when handling hazardous materials.
Sources: Herald Sun - 1 April 2025
Australia Enforces New Tobacco Controls from April 1
Summary:
As of April 1, 2025, Australia has implemented stringent tobacco control measures, including health warnings printed directly on individual cigarettes. These warnings feature phrases such as "CAUSES 16 CANCERS" and "DAMAGES YOUR LUNGS." Additionally, new graphic warnings on cigarette packs and health promotion inserts aim to encourage smoking cessation and raise awareness about the dangers of tobacco use.
Sources: Mirage News - April 1, 2025, 9News - April 1, 2025
OPEC+ Increases Oil Production Amid Global Uncertainties
Summary:
OPEC+ has announced the gradual unwinding of voluntary production cuts starting April 1, 2025, aiming to restore 2.2 million barrels per day of output by September 2026. Despite this increase, factors such as tighter U.S. sanctions on Iran and Russia, potential sanctions on Venezuelan oil buyers, and fears of a tariff-induced recession have sustained oil prices. Analysts predict limited downside risks to oil prices due to significant supply threats, mainly from Iran and Venezuela. While some strength in oil prices is expected during the summer, concerns over tariff-induced demand weakness persist.
Sources: MarketWatch - April 1, 2025
Iconic Australian Locations Declared 'No Go Zones'
Summary:
Several iconic Australian locations, including Uluru, Kakadu National Park, Cape York Peninsula, and others, are increasingly being declared "no go zones" due to cultural, environmental, and safety concerns. These measures aim to preserve the cultural significance and environmental integrity of these landmarks and ensure public safety. While traditional owners and local authorities support these restrictions to protect cultural heritage, debates have arisen over tourists' rights and the impact on local tourism industries. Sources: News.com.au - April 1, 2025
The Joe Rogan Experience #2297: Francis Foster & Konstantin Kisin
Summary:
In episode #2297 of The Joe Rogan Experience, Joe Rogan welcomes comedians and commentators Francis Foster and Konstantin Kisin, hosts of the podcast Triggernometry. The episode delivers a wide-ranging conversation covering free speech, comedy, media narratives, and societal tensions in the modern world.
Interesting Discussions and Insights:
-
The State of Comedy:\ The trio discusses how comedy has changed in recent years, especially under the weight of cancel culture. They explore how comedians are navigating cultural sensitivities while still trying to push boundaries and remain authentic.
-
Free Speech and Censorship:\ Konstantin and Francis share their experiences with censorship and self-censorship, emphasizing the risks of suppressing ideas, even if they’re controversial. They advocate for robust debate as a cornerstone of democracy.
-
Migration and Identity Politics:\ The conversation touches on immigration policies in the UK and broader Western world, discussing how political correctness often silences real concerns. Both guests, with immigrant backgrounds, offer nuanced perspectives on national identity and inclusion.
-
Media and Narrative Control:\ Joe, Francis, and Konstantin dive into how media outlets often frame stories with ideological slants, and the dangers of relying on one-sided narratives in forming public opinion.
-
Creating Triggernometry:\ The guests talk about why they launched their podcast — to have honest, open conversations with a wide range of thinkers, especially those often excluded from mainstream platforms.
Key Takeaways:
- Honest conversation is essential for a healthy society, even when it's uncomfortable.
- Comedy still holds power to critique society but faces mounting challenges from cultural pressures.
- Free speech should be defended not just in principle, but in everyday life and dialogue.
- The media landscape is increasingly polarized, and critical thinking is more important than ever.
-
-
 @ 0970cf17:135aa040
2025-05-31 18:32:00
@ 0970cf17:135aa040
2025-05-31 18:32:00{"pattern":{"kick":[true,false,true,false,true,false,true,false,true,false,true,false,true,false,true,false],"snare":[false,true,false,true,false,true,false,true,false,true,false,true,false,true,false,true],"hihat":[true,false,true,true,false,false,true,true,false,false,true,true,false,false,true,true],"openhat":[true,false,false,true,false,false,false,false,true,false,false,true,false,false,true,false],"crash":[false,false,true,false,false,false,true,false,false,false,false,true,false,false,true,false],"ride":[false,false,true,false,false,false,false,true,false,false,false,true,false,false,true,false],"tom1":[false,true,false,false,true,false,false,true,false,false,true,false,true,false,true,false],"tom2":[true,false,false,false,true,false,false,false,false,true,false,true,false,false,true,false]},"bpm":220,"swing":0,"timeSignature":"4/4","drumKit":"standard","timestamp":1748716320785}
-
 @ 3c389c8f:7a2eff7f
2025-03-31 20:38:23
@ 3c389c8f:7a2eff7f
2025-03-31 20:38:23You might see these terms used interchangeably throughout the Nostr network. Since Nostr is a decentralized protocol and not a platform, there is often a lack of consensus around particular terminologies. At times, it's important to differentiate between them, so that you can determine what is being stated. In the truest sense, there is no central entity to maintain a Nostr 'account' on your behalf, though some Nostr-based platforms may offer to do so. There's also no one to verify your 'identity'. This is something that you create, maintain and control. It is 100% yours. In a sense, you verify yourself through your interactions with others, with the network of clients and relays, and by protecting your nsec (secret key). A profile is generally considered to be a single place for displaying your content and any information about yourself that you've chosen to share, but its a little more complicated than that with Nostr. Let's take a closer look at all 3 terms:
Identity:
Your Nostr identity becomes yours from the moment you generate your key pair. The two parts each provide unique perspective and functionality. (Remember, there is no central entity to issue these key pairs. You can screw up and start over. You can maintain multiple key pairs for different purposes. If all of this is new and unfamiliar, start simply with the intention of trial and error.)
Half of the equation is your nsec. As long as you maintain control of that secret key, the identity is yours. You will use it to sign the notes and events that you create on Nostr. You will use it to access functionality of various tools and apps. You can use it to send monetary tips for content you find valuable. The reputation that you build through posting & interacting on Nostr will signal to others what type of person or profile this is, whether it's a genuine person, a bot (good or bad), a collection of works, etc. You might come across information that compares your nsec to a password. While a fair comparison, its important to remember that passwords can be reset, but your private key CANNOT. Lost access or control of your nsec means a loss of control over that identity. When you have decided to establish a more permanent identity, write it down, keep it safe, and use the appropriate security tools for interacting online.
The other half of this equation is your npub. This public key is used to find and display your notes and events to others. In short, your npub is how your identity is viewed by others and your nsec is how you control that identity.
Npub can also act a window into your world for whoever may choose to view it. As mentioned in a previous entry, npub login enables viewing Nostr's notes and other stuff in a read-only mode of any user's follow feed. Clients may or may not support this, some will even allow you to view and subscribe to these feeds while signed in as yourself via this function. It the basis of the metadata for your profile, too.
Profile:
Profile, in general, is a collection of things about you, which you have chosen to share. This might include your bio, chosen display name, other contact information, and a profile photo. Similar to traditional socials, veiwing Nostr profiles often includes a feed of the things you have posted and shared displayed as a single page. People will recognize you based on the aspects of your profile more than they will by your actual identity since an npub is a prefixed random string of characters . Your npub bridges a gap between strictly machine readable data and your human readable name, but it is not as simple as a name and picture. You will choose your photo and display name for your profile as you see fit, making you recognizable. These aspects are easy for copycat scammers to leverage, so your npub will help your friends and followers to verify that you are you, in the event that someone should try to copy your profile.
The Nostr protocol has another profile aspect that is important to know about, but as a general user, you shouldn't have to worry much about it. This is your nprofile. It combines your npub (or the machine readable hex verison of it) with hints to what relays you are using to publish your notes. This helps clients, crawlers, and relays find your stuff for your followers. You may notice nprofile when you share a profile link or used in other actions. When you update your relay list, your client will adjust your nprofile and send a new copy to the appropriate relays. If your believe that a client is not doing that correctly, you can visit metadata.nostr.com and manage it yourself.
Account:
Across Nostr, it is common to see the term 'account' used to refer to the combination of your identity and profile. It is a relatable term, though it may imply that some account issuer exists, but no one issues a Nostr account to you. You create and maintain it yourself.
There are situations where a traditional account will exist, such as with media servers, relay subscriptions, custodial wallet hosts, or NIP-05 providers. These things will almost always be paid services and storage that you choose to use. (Reminder: all of these things are possible to DIY with a little knowhow and an old computer)
What Is The Right Terminology?
There is no simple or correct answer here. Developers and writers will use whatever terms fit their scope and topic. Context will matter, so it's important to differentiate by that more than any actual term.
-
 @ 68d6e729:e5f442ac
2025-05-22 13:55:45
@ 68d6e729:e5f442ac
2025-05-22 13:55:45The Adapter Pattern in TypeScript
What is the Adapter Pattern?
The Adapter Pattern is a structural design pattern that allows objects with incompatible interfaces to work together. It acts as a bridge between two interfaces, enabling integration without modifying existing code.
In simple terms: it adapts one interface to another.
Real-World Analogy
Imagine you have a U.S. laptop charger and you travel to Europe. The charger plug won't fit into the European socket. You need a plug adapter to convert the U.S. plug into a European-compatible one. The charger stays the same, but the adapter allows it to work in a new context.
When to Use the Adapter Pattern
- You want to use an existing class but its interface doesn't match your needs.
- You want to create a reusable class that cooperates with classes of incompatible interfaces.
- You need to integrate third-party APIs or legacy systems with your application.
Implementing the Adapter Pattern in TypeScript
Let’s go through a practical example.
Scenario
Suppose you’re developing a payment system. You already have a
PaymentProcessorinterface that your application uses. Now, you want to integrate a third-party payment gateway with a different method signature.Step 1: Define the Target Interface
javascript ts CopyEdit// The interface your application expects interface PaymentProcessor { pay(amount: number): void; }Step 2: Create an Adaptee (incompatible class)
javascript ts CopyEdit// A third-party library with a different method class ThirdPartyPaymentGateway { makePayment(amountInCents: number): void { console.log(`Payment of $${amountInCents / 100} processed via third-party gateway.`); } }Step 3: Implement the Adapter
```javascript ts CopyEdit// Adapter makes the third-party class compatible with PaymentProcessor class PaymentAdapter implements PaymentProcessor { private gateway: ThirdPartyPaymentGateway;
constructor(gateway: ThirdPartyPaymentGateway) { this.gateway = gateway; }
pay(amount: number): void { const amountInCents = amount * 100; this.gateway.makePayment(amountInCents); } } ```
Step 4: Use the Adapter in Client Code
```javascript ts CopyEditconst thirdPartyGateway = new ThirdPartyPaymentGateway(); const adapter: PaymentProcessor = new PaymentAdapter(thirdPartyGateway);
// Application uses a standard interface adapter.pay(25); // Output: Payment of $25 processed via third-party gateway. ```
Advantages of the Adapter Pattern
- Decouples code from third-party implementations.
- Promotes code reuse by adapting existing components.
- Improves maintainability when dealing with legacy systems or libraries.
Class Adapter vs Object Adapter
In languages like TypeScript, which do not support multiple inheritance, the object adapter approach (shown above) is preferred. However, in classical OOP languages like C++, you may also see class adapters, which rely on inheritance.
Conclusion
The Adapter Pattern is a powerful tool in your design pattern arsenal, especially when dealing with incompatible interfaces. In TypeScript, it helps integrate third-party APIs and legacy systems seamlessly, keeping your code clean and extensible.
By learning and applying the Adapter Pattern, you can make your applications more robust and flexible—ready to adapt to ever-changing requirements. https://fox.layer3.press/articles/cdd71195-62a4-420b-9e24-e23d78b27452
-
 @ dfa02707:41ca50e3
2025-05-31 22:01:41
@ dfa02707:41ca50e3
2025-05-31 22:01:41
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.
- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ 84b0c46a:417782f5
2025-05-31 09:11:23
@ 84b0c46a:417782f5
2025-05-31 09:11:23Simple Long Form Content Editor (NIP-23)
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzq4jsz7zew5j7jr4pdfxh483nwq9vyw9ph6wm706sjwrzj2we58nqqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyxhwumn8ghj7mn0wvhxcmmvqqsgcn99jyn5tevxz5zxsrkd7h0sx8fwnqztula423xh83j9wau7cms3vg9c7 のようにnostr:要素を挿入できる (メニューのNアイコンから挿入またはnostr:note~~のように手動で入力)
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの🙂アイコンから)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やることやったこと
-
[x] nostr:を投稿するときにtagにいれる
-
[x] 画像をアップロードできるようにする(NIP-96)
 できる
できる - [x] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] レイアウトを整える
- [ ] あとなんか
test
nostr:naddr1qvzqqqr4gupzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqxnzde58q6njvpkxqersv3ejxw9x9
-
-
 @ 90c656ff:9383fd4e
2025-05-31 17:54:42
@ 90c656ff:9383fd4e
2025-05-31 17:54:42Since its creation, Bitcoin has been one of the most hotly debated assets in the financial world—both by passionate supporters and skeptics. Its extreme volatility and the impact it has had on the traditional financial system have made it a constant subject of speculation. Over time, Bitcoin’s adoption has grown, sparking ongoing discussions about its future—both in terms of price and integration into the global financial system. In this context, multiple scenarios have been proposed, ranging from optimistic to cautious, depending on factors like regulation, institutional adoption, and technological innovation.
Bitcoin’s price: forecasts and influencing factors
01 - Institutional Adoption: The growing use of Bitcoin by major companies and institutional investors has been seen as a bullish driver. Companies like Tesla, MicroStrategy, and Square have added Bitcoin to their balance sheets, boosting confidence in it as a store of value. As more businesses follow suit, demand for Bitcoin could increase, pushing the price upward.
02 - Government Regulation: How governments respond to Bitcoin is one of the biggest sources of uncertainty. Heavy-handed regulation could restrict access and dampen interest, while a more favorable approach could boost adoption and support price growth. Countries like El Salvador have shown positive trends by adopting Bitcoin as legal tender, though in many others, regulation remains a significant challenge.
03 - Limited Supply: With a maximum supply of 21 million coins, Bitcoin is immune to inflationary money printing. This scarcity makes it especially attractive as a store of value, particularly during times of global economic uncertainty, potentially supporting long-term price appreciation.
04 - Technology and Scalability: Innovations like the Lightning Network and Taproot, aimed at improving scalability and transaction efficiency, could help increase Bitcoin's utility—making it more accessible for daily use and positively impacting its market value.
Global adoption of Bitcoin: The path toward financial inclusion
Bitcoin adoption is rising globally, especially in regions where traditional financial systems are inefficient or inaccessible. Countries facing economic instability, such as those plagued by high inflation or currency crises, are increasingly viewing Bitcoin as a viable alternative. Financial inclusion is a key driver of this adoption, as Bitcoin offers financial services to people excluded from the traditional banking sector.
01 - Emerging Markets: In countries like Brazil, Argentina, Nigeria, and others, demand for Bitcoin has grown as people seek to protect their assets from the devaluation of local currencies. In these regions, Bitcoin functions as both a store of value and a medium of exchange free from central authority control.
02 - Adoption by Governments and Businesses: As more companies and even governments embrace Bitcoin, its integration into the global economy could accelerate. El Salvador, for example, has shown it’s possible to adopt Bitcoin as an official currency, while more businesses are accepting it as a payment method—further legitimizing its role in global commerce.
03 - Education and Accessibility: As more people understand how Bitcoin works and appreciate its advantages—such as security, privacy, and financial freedom—adoption is likely to grow. Easier-to-use exchanges and improved wallet interfaces are making it simpler for everyday users to access and use Bitcoin.
Future scenarios: Optimism or caution?
Bitcoin's future remains uncertain, but several possible outcomes are taking shape. The optimistic scenario foresees greater price appreciation and widespread global adoption, driven by technological innovation, increased institutional trust, and the search for a decentralized alternative to the traditional financial system. In this case, Bitcoin could become a widely accepted form of payment and a global store of value, with prices reaching new all-time highs.
On the other hand, the more cautious scenario suggests that obstacles like government regulation, competition from other digital currencies, and potential technical shortcomings could prevent Bitcoin from becoming central to the financial system. Furthermore, price volatility could deter those seeking stability and security.
In summary, predictions about Bitcoin’s price and global adoption are undeniably complex and influenced by a wide range of factors. Bitcoin’s future will depend on how society, governments, and businesses respond to this new form of money. While the potential for appreciation is significant, the risks and volatility involved cannot be ignored. As global adoption increases and technology continues to evolve, it will be essential to closely monitor the developments shaping Bitcoin’s role in the global financial landscape.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 90c656ff:9383fd4e
2025-05-31 17:49:25
@ 90c656ff:9383fd4e
2025-05-31 17:49:25With the growing digitalization of money, governments around the world have begun developing Central Bank Digital Currencies (CBDCs) in response to the rising popularity of Bitcoin. While Bitcoin represents a decentralized and censorship-resistant financial system, CBDCs are digital versions of fiat currencies, directly controlled by central banks. This emerging competition could shape the future of money and define the balance between financial freedom and state control.
Key differences between Bitcoin and CBDCs
Bitcoin and CBDCs differ in nearly every fundamental aspect:
01 - Centralization vs Decentralization: Bitcoin operates on a decentralized network where no government or entity can change the rules or censor transactions. CBDCs, on the other hand, are issued and managed by central banks, enabling greater control over the circulation and use of money.
02 - Fixed Supply vs Controlled Inflation: Bitcoin has a fixed supply of 21 million units, making it a scarce and deflationary asset. CBDCs can be issued without limits, much like traditional fiat currencies, and are subject to inflationary monetary policies.
03 - Privacy vs Surveillance: Bitcoin allows pseudonymous transactions, ensuring a certain degree of financial privacy. CBDCs may be designed to track every transaction, enabling full governmental oversight—and potentially, control over how citizens spend their money.
04 - Censorship Resistance vs State Control: Bitcoin enables anyone to transact without needing third-party approval. CBDCs, being centralized, could be used by governments to restrict undesirable transactions or even freeze funds at the press of a button.
What are governments aiming for with CBDCs?
The introduction of CBDCs is often promoted with benefits such as:
01 - Greater efficiency in financial transactions by removing intermediaries and reducing banking costs.
02 - Easier implementation of economic policies, such as direct stimulus payments or automated taxation.
03 - Enhanced ability to combat illegal activities through real-time transaction tracking.
However, these justifications raise serious concerns about the erosion of financial privacy and the expansion of government power over the monetary system.
Bitcoin as an alternative to CBDCs
The rise of CBDCs may, in fact, reinforce Bitcoin’s position as the true alternative to state-controlled money. As citizens become aware of the risks associated with a fully centralized financial system, demand for a decentralized, censorship-resistant asset like Bitcoin may increase.
01 - Protection from state control: Bitcoin empowers users with full sovereignty over their money, free from arbitrary freezes or confiscations.
02 - Preservation of financial privacy: Unlike CBDCs, which may monitor every transaction, Bitcoin offers a level of anonymity that shields individuals from excessive surveillance.
03 - Store of value against inflation: While governments can endlessly issue CBDCs, Bitcoin’s guaranteed scarcity positions it as a hedge against irresponsible monetary policy.
In summary, the competition between Bitcoin and CBDCs is set to become one of the defining financial battles of the future. As governments seek to reinforce their control through centralized digital currencies, Bitcoin remains the leading option for those who value financial independence and protection from state surveillance. The choice between a free, decentralized financial system and a monitored, government-controlled one may determine the course of the digital economy for decades to come.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ f4a890ce:af88c4aa
2025-06-01 03:33:35
@ f4a890ce:af88c4aa
2025-06-01 03:33:35執行摘要
市場持續上探新高,總市值達3.26兆美 元,ETF資金穩定流入,鏈上鯨魚持續吸籌,讓 人忍不住想問,是不是該追?然而,數據提醒 我們需保持冷靜。 我們這週需觀察: • 衍生品爆倉與槓桿是否過熱,清算風險升溫, 短線資金可能因波動而退場。 • 觀察鏈上數據是否延續偏多結構。交易所比 特幣儲備持續下滑、大型地址增加,若鯨魚 活躍度持續上升,將有利於中期支撐力道。 同時觀察穩定幣市值變化,以判斷資金 是否持續布局。整體而言,市場結構偏多,但 上行須有資金支持,操作上宜保留彈性,避免 追高。
加密市場
本週加密貨幣市場總市值攀升至3.39 兆美 元,顯示市場持續向上,資本流入動能仍然強勁。交 易量方面,當週總成交量達到704 億美元,相較前週 有所提升,買賣雙方均展現較高的參與度。
https://coinmarketcap.com/charts/
市場情緒指標顯示,恐懼與貪婪指數為67, 仍屬「貪婪」區間,表明投資人對市場前景仍保持樂 觀,但貪婪情緒略有下降,顯示部分投資者可能開始 謹慎調整持倉策略。
https://www.coinglass.com/zh-TW/pro/i/FearGreedIndex
同時,相對強弱指標處於中性至超賣區間, 部分資產短期內面臨修正壓力,但市場尚未進入明顯 弱勢。
https://www.coinglass.com/zh-TW/pro/i/RsiHeatMap
值得注意的是,山寨幣季節指數下降至18, 表明市場資金仍主要流向比特幣及主流加密貨幣,投 資者對風險資產的偏好仍相對保守,中小型代幣尚未 獲得明顯關注。
https://www.blockchaincenter.net/en/altcoin-season-index/
此外,穩定幣市值增至2,462.75 億美元,反 映部分資金尋求避險,或為市場調整後的潛在買盤做 準備。
https://defillama.com/stablecoins
小結
本週加密市場總市值持續上升,而成交量顯 著提高,顯示市場活躍度增加,資金流入動能仍在延 續。恐懼與貪婪指數仍處於貪婪區間,市場情緒樂觀, 但投資者開始謹慎調整。相對強弱指標顯示市場尚未 進入弱勢,但需關注短期修正壓力。山寨幣季節指數 低迷,資金仍集中於主流幣種,而穩定幣市值增長, 可能顯示市場內部資金配置仍較為謹慎。
衍生性商品
市場槓桿交易持續增長,本週永續合約市場 的持倉規模達159.68B,顯示投資者對槓桿交易的需 求仍然強勁。
https://www.coinglass.com/zh-TW/pro/futures/Cryptofutures
資金費率方面,市場維持正費率,主要交易 所的資金費率保持在0.01%左右,表明市場仍偏多。
https://www.coinglass.com/zh-TW/FundingRate
爆倉數據顯示,空單爆倉金額達826.391M, 而多單爆倉金額達1148.547M,近期市場波動導致大 量強制平倉,尤其是多頭受壓較為明顯。
https://www.coinglass.com/zh-TW/LiquidationData
清算熱力圖顯示,$105,000 附近的清算金額 達166.41M,這一價格區間成為市場交易的重要關注 點,投資者需留意可能的風險變化。
https://www.coinglass.com/zh-TW/pro/futures/LiquidationHeatMap
期權市場交易活躍,投資者在不同價格區間 展開佈局: • $100,000行權價的看跌期權合約數量為6.93K,總 金額達$18.34M,顯示市場對該區間的下行風險仍 保持一定的防禦。 • $110,000行權價的看漲期權合約數量為13.32K,總 金額達$76.11M,顯示市場對上行的預期依然較為 強烈。
https://www.coinglass.com/zh-TW/pro/options/OIStrike
此外,最大痛點分別出現在2025/05/30 的 $98,000(名義金額9.7B)以及2025/06/27 的 $95,000(名義金額11.14B),顯示市場對不同價位的 佈局仍然存在分歧,但相較於上週有所收斂。
https://www.coinglass.com/zh-TW/pro/options/max-pain
小結
本週加密市場仍處於高度波動的環境,槓桿 交易與清算熱點區域成為市場關注的焦點。多頭與空 頭的資金配置存在競爭,爆倉規模顯示槓桿風險仍然 不可忽視。期權市場則呈現不同價格區間的佈局策略, 投資者對短期與中期的市場走勢保持不同看法。建議 投資者密切關注市場資金流向與槓桿風險,調整交易 策略,以降低市場波動帶來的潛在影響。
ETF
本週,加密貨幣衍生性商品市場保持活躍, 其中比特幣(BTC)與以太坊(ETH)ETF的資金流入 顯示投資人對市場的信心仍然穩定。比特幣ETF本週 流入2.602億美元。
而以太坊ETF則流入2,220萬美元,儘管流入 規模較上週略有下降,但仍顯示機構與散戶投資人對 市場的參與度不減。
https://coinmarketcap.com/zh-tw/etf/
小結
整體而言,本週加密貨幣衍生性商品市場保 持資金流入趨勢,雖然比特幣ETF流入金額略低於前 週,但以太坊ETF呈現穩定增長。市場投資情緒仍然 良好,未來需持續關注技術發展與宏觀經濟環境對 ETF與衍生性商品市場的影響,以掌握市場動能變化。
鏈上分析 | BTC
二級交易所的比特幣儲備量再次創下新低, 顯示市場上的比特幣供給持續減少,潛在拋壓進一步 降低。這一現象通常反映出投資者傾向於將資產移至 自有錢包,展現長期持有的傾向。
即使比特幣價格已創下歷史新高,地址分佈 方面仍延續與上週相同的趨勢。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
鯨魚活躍地址仍延續上週,無論是新鯨魚或 老鯨魚,近期均明顯提升鏈上活動頻率,顯示其對市 場後市表現持續看好。整體而言,資金與籌碼正在流 向鯨魚,為比特幣後續表現提供強勁支撐。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
然而值得關注的是,即便比特幣價格已創下 歷史新高,NUPL 指標卻未能超越前兩次牛市的高點。 這代表市場雖然整體仍處於盈利狀態,但尚未進入過 度亢奮或泡沫化階段,投資人情緒相對理性。這樣的 結構可能為後續漲勢留下空間。
目前觀察CoinbasePremium Index 與 Korea Premium Index 皆位於0 以上,顯示美國與韓 國市場的現貨買盤相對活躍,市場需求強勁。這也反 映出在全球主要市場中,投資者對比特幣仍具有高度 興趣與買入力道,尤其是來自機構或散戶資金較多的 交易平台表現出溢價狀態,通常代表有資金持續流入 並推升現貨價格,對中短期價格走勢構成支撐。未來 若兩大溢價指數持續維持正值,將有助於延續市場的 多頭氣氛。
CoinbasePremium Index:https://cryptoquant.com/asset/btc/chart/market-data/coinbase-premium-index?window=DAY&sma=0&ema=0&priceScale=log&metricScale=linear&chartStyle=line
Korea Premium Index:https://cryptoquant.com/asset/btc/chart/market-data/korea-premium-index?window=DAY&sma=0&ema=0&priceScale=log&metricScale=linear&chartStyle=line
小結
即便比特幣價格已創下歷史新高,鏈上數據 顯示市場仍存在結構性變化與短期潛在風險。從地址 分布來看,10–100 顆持倉的中小戶數量持續創下新低, 而100–1k、1k–10k 乃至於 10k 以上的地址數量則穩定 上升,顯示資金持續集中於大戶與機構手中。與此同 時,鯨魚活躍地址全面上升,顯示大資金正在積極參 與市場。 值得注意的是,雖然價格已突破新高, NUPL 指標雖來到相對高點,卻尚未超越過去兩次牛 市的峰值,代表市場情緒尚未達到極度貪婪或全面樂 觀的階段,潛在上行空間仍待觀察。 此外,CoinbasePremium Index 與 Korea Premium Index 雙雙維持在正值,代表現貨買盤動能 仍強,有助於支撐價格表現。整體而言,鏈上結構健 康,但需密切關注中小持倉賣壓與市場情緒是否過熱, 避免短線波動風險。
總體經濟
本週總體經濟數據顯示,聯邦基金有效利率 仍維持在4.33%,反映市場依然處於高利率環境。
https://fred.stlouisfed.org/series/FEDFUNDS
隨著6 月18 日即將召開的聯邦公開市場委 員會(FOMC) 會議,市場對利率決策的預期更加集中, 其中4.25%-4.50% 區間的機率已從91.7% 上升至 94.4%,而4.00%-4.25% 的預測則下降至5.6%,顯示 市場對維持較高利率的預期仍在強化,這可能會抑制 風險資產的表現,包括加密貨幣。
https://www.cmegroup.com/cn-t/markets/interest-rates/cme-fedwatch-tool.html
消費者物價指數(CPI) 為2.33%,和上週一 致,失業率保持在4.2%,顯示勞動市場仍然穩定,企 業對人力需求的支撐作用持續發揮。當前情勢意味著 聯準會在利率決策上將維持謹慎,避免過度調整對經 濟產生負面影響。
失業率:https://www.macromicro.me/series/37/unemployment-rate
消費者物價指數(CPI) :https://www.macromicro.me/series/128/consumer-price-index-sa-yoy
小結
加密貨幣市場仍受總體經濟環境影響,高利 率政策使得資金流動性受限,價格波動性加大。投資 者應密切關注即將召開的FOMC 會議及後續政策動向, 以評估市場短期內的走勢與投資機會。
新聞
參議院推進穩定幣法案,為最終通過掃清道路
Crypto.com 收購 Allnew Investments,取得 MiFID 執照,可在歐洲提供衍生性商品交易
德州眾議院通過法案,距離建立戰略比特幣儲備更近一步
香港通過新穩定幣許可法案加入全球競爭
讓外國人更容易買美股!Kraken 將推出蘋果、 Nvidia 等代幣化股票交易
https://blockcast.it/2025/05/23/kraken-to-launch-tokenized-stock-trading-for-non-u-s-customers/
-
 @ 7f6db517:a4931eda
2025-06-01 00:01:36
@ 7f6db517:a4931eda
2025-06-01 00:01:36
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-06-01 03:01:36
@ 7f6db517:a4931eda
2025-06-01 03:01:36
The newly proposed RESTRICT ACT - is being advertised as a TikTok Ban, but is much broader than that, carries a $1M Fine and up to 20 years in prison️! It is unconstitutional and would create massive legal restrictions on the open source movement and free speech throughout the internet.
The Bill was proposed by: Senator Warner, Senator Thune, Senator Baldwin, Senator Fischer, Senator Manchin, Senator Moran, Senator Bennet, Senator Sullivan, Senator Gillibrand, Senator Collins, Senator Heinrich, and Senator Romney. It has broad support across Senators of both parties.
Corrupt politicians will not protect us. They are part of the problem. We must build, support, and learn how to use censorship resistant tools in order to defend our natural rights.
The RESTRICT Act, introduced by Senators Warner and Thune, aims to block or disrupt transactions and financial holdings involving foreign adversaries that pose risks to national security. Although the primary targets of this legislation are companies like Tik-Tok, the language of the bill could potentially be used to block or disrupt cryptocurrency transactions and, in extreme cases, block Americans’ access to open source tools or protocols like Bitcoin.
The Act creates a redundant regime paralleling OFAC without clear justification, it significantly limits the ability for injured parties to challenge actions raising due process concerns, and unlike OFAC it lacks any carve-out for protected speech. COINCENTER ON THE RESTRICT ACT
If you found this post helpful support my work with bitcoin.

-
 @ f3873798:24b3f2f3
2025-03-31 20:14:31
@ f3873798:24b3f2f3
2025-03-31 20:14:31Olá, nostrilianos!
O tema de hoje é inteligência artificial (IA), com foco em duas ferramentas que têm se destacado no mercado por sua capacidade de responder perguntas, auxiliar em tarefas e, em alguns casos, até gerar imagens.
Essas tecnologias estão cada vez mais presentes no dia a dia, ajudando desde a correção de textos até pesquisas rápidas e a criação de imagens personalizadas com base em prompts específicos.
Nesse cenário em expansão, duas IAs se sobressaem: o ChatGPT, desenvolvido pela OpenAI, e o Grok, criado pela xAI.
Ambas são ferramentas poderosas, cada uma com seus pontos fortes e limitações, e têm conquistado usuários ao redor do mundo. Neste artigo, compartilho minhas impressões sobre essas duas IAs, baseadas em minha experiência pessoal, destacando suas diferenças e vantagens.
Grok: Destaque na criação de imagens e fontes

O Grok me impressiona especialmente em dois aspectos.
Primeiro, sua capacidade de gerar imagens é um diferencial significativo. Enquanto o ChatGPT tem limitações nesse quesito, o Grok oferece uma funcionalidade mais robusta para criar visuais únicos a partir de prompts, o que pode ser uma vantagem para quem busca criatividade visual.
Segundo, o Grok frequentemente cita fontes ou indica a origem das informações que fornece, o que agrega credibilidade às suas respostas e facilita a verificação dos dados.
ChatGPT: Assertividade e clareza

Por outro lado, o ChatGPT se destaca pela assertividade e pela clareza em suas explicações. Suas respostas tendem a ser mais diretas e concisas, o que é ideal para quem busca soluções rápidas ou explicações objetivas.
Acredito que essa vantagem possa estar ligada ao fato de o ChatGPT estar em operação há mais tempo, tendo passado por anos de aprimoramento e ajustes com base em interações de usuários.Comparação e reflexões.
Em minha experiência, o Grok supera o ChatGPT na geração de imagens e na citação de fontes, enquanto o ChatGPT leva a melhor em precisão e simplicidade nas respostas.
Esses pontos refletem não apenas as prioridades de design de cada IA, mas também o tempo de desenvolvimento e os objetivos de suas respectivas empresas criadoras.
A OpenAI, por trás do ChatGPT, focou em refinamento conversacional, enquanto a xAI, com o Grok, parece investir em funcionalidades adicionais, como a criação de conteúdo visual.
Minha opinião

Não há um vencedor absoluto entre Grok e ChatGPT – a escolha depende do que você precisa. Se seu foco é geração de imagens ou rastreamento de fontes, o Grok pode ser a melhor opção. Se busca respostas rápidas e assertivas, o ChatGPT provavelmente atenderá melhor.
Ambas as IAs são ferramentas incríveis, e o mais fascinante é ver como elas continuam evoluindo, moldando o futuro da interação entre humanos e máquinas.
-
 @ 7f6db517:a4931eda
2025-05-31 22:01:46
@ 7f6db517:a4931eda
2025-05-31 22:01:46
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ 9ca447d2:fbf5a36d
2025-06-01 02:01:03
@ 9ca447d2:fbf5a36d
2025-06-01 02:01:03When making critical decisions about investments, company acquisitions, or capital deployment, organizations rely on a fundamental tool: the hurdle rate. This is the minimum rate of return that a project or investment must achieve to be considered viable by managers or investors.
The hurdle rate is not just a number — it’s a filter that separates promising opportunities from those that don’t justify the risk.
It acts as a crucial benchmark. If the expected return on an investment falls below the hurdle rate, that opportunity is typically rejected.
Setting this rate involves a careful consideration of several factors, including the company’s cost of capital, specific risk profile, inflation rates, and opportunity cost of allocating resources elsewhere.
In essence, the hurdle rate ensures that only projects with the potential to create real value move forward.
Bitcoin has emerged as a disruptive and compelling candidate for a new kind of hurdle rate in capital allocation. Its unique properties challenge the conventions of traditional finance and invite a new thought pattern of what’s considered an appropriate benchmark.
Bitcoin’s fixed supply (capped at 21 million), and its decentralized, borderless nature makes it fundamentally resistant to inflation and debasement, unlike fiat currencies that can be printed at will by central banks.
Here’s the real question for investors and fund managers: if your portfolio or fund consistently fails to outperform bitcoin, at what point do you simply start allocating to bitcoin instead?
This isn’t rocket science. Over the past decade, bitcoin has not only outperformed traditional assets, but has also redefined what investors should expect as a minimum acceptable rate.
Asset classes comparison since 2013 — Seeking Alpha
The numbers speak for themselves.
From 2013-2023, bitcoin delivered the highest annual return in 8 out of those 11 years. This is not a fluke or a bubble, it’s a decade-long trend that demands attention from anyone serious about capital growth.
Typically, most investment managers use the S&P 500 as their benchmark hurdle rate. Will their potential investment generate more return than the S&P? If not, it’s usually dismissed.
Since 1970, the S&P 500 has provided an average annual return of 10.66%. Investment managers routinely reject ideas that can’t beat this average, recognizing that anything less is not worth the risk or effort.
But what happens when we compare this to bitcoin?
Over the last 10 years, bitcoin’s average annual return has been an astonishing 49%. While it’s unlikely that this rate will persist forever, it’s impossible to ignore the magnitude and consistency of bitcoin’s outperformance.
Bitcoin hasn’t just beat the S&P—it’s outperformed every major asset class, including gold, treasuries, real estate, commodities, and equities.
Of course, past performance isn’t a guarantee of future results. So the question becomes: can bitcoin continue to deliver, and are we ready to use it as a benchmark for investment decisions?
To answer this, it’s essential to understand the underlying forces driving bitcoin’s price appreciation.
Several macroeconomic factors contribute to bitcoin’s rise, including money printing, economic uncertainty, and the ongoing debasement of fiat currencies.
When governments print money or run deficits, confidence in traditional currencies erodes. In such environments, investors naturally seek scarce assets, historically gold, and now increasingly bitcoin.
Consider the current fiscal reality: the United States is burdened with over $36 trillion in national debt, and there’s little indication that the money printing will stop.
This environment only strengthens the case for bitcoin as a store of value and as a benchmark for capital allocation. Bitcoin’s staying power is becoming undeniable.
Those who fail to adapt, risk being left behind. We’re already witnessing the early stages of institutional and corporate adoption, and it’s only a matter of time before bitcoin becomes a standard reference point for hurdle rates across the investment world.
Visionary leaders like Michael Saylor of Strategy, have openly discussed the challenges of outperforming the world’s top companies.
Saylor recognized that if your investment, company, or project cannot reasonably be expected to outperform bitcoin, it may be more rational to simply hold bitcoin itself.
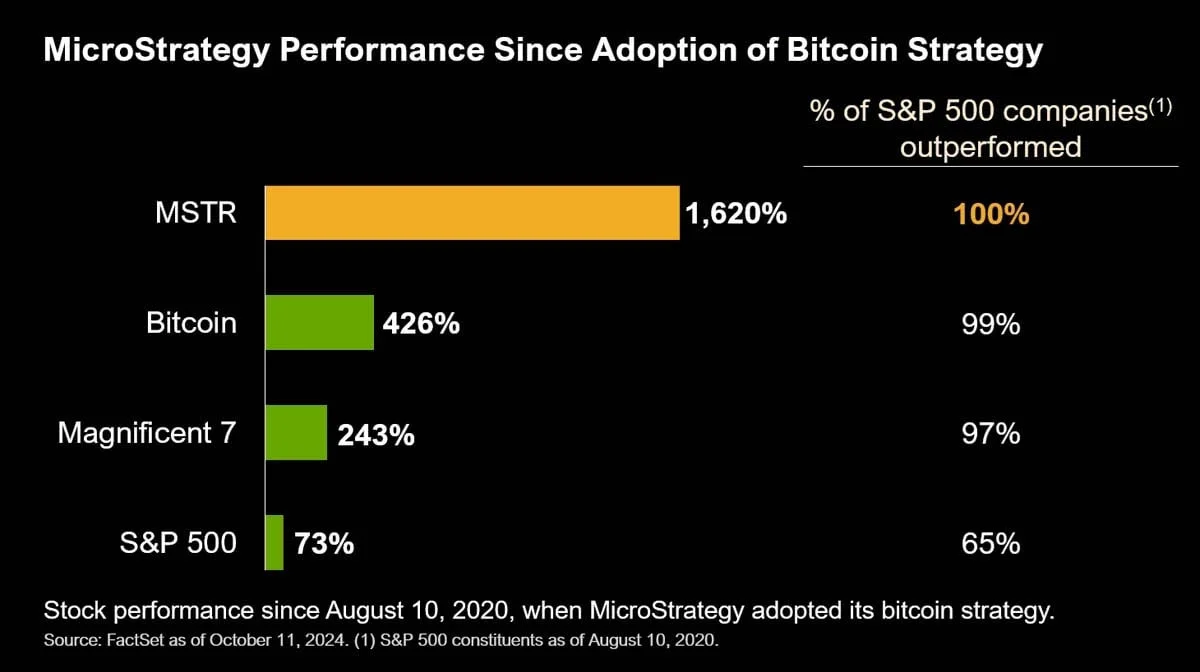
MSTR performance compared to bitcoin, Magnificent 7 and S&P500 — aicoin
In a world where bitcoin has established itself as the premier performing asset, the message is clear: if you can’t beat bitcoin, why not join it?
Just buy bitcoin.
-
 @ 2dd9250b:6e928072
2025-05-31 16:23:22
@ 2dd9250b:6e928072
2025-05-31 16:23:22Durante a década de 1990, houve o aumento da globalização da economia, determinando a adição do fluxo internacional de capitais, de produtos e serviços. Este fenômeno levou a uma interdependência maior entre as economias dos países. Justamente por causa da possibilidade de que um eventual colapso econômico em um país resulte no contágio dos demais. Diante disso, aumentou a preocupação com os riscos incentivando a utilização de sofisticados modelos e estratégias de avaliação de gestão de risco.
Na década, ganharam destaque ainda os graves problemas financeiros enfrentados, entre outros, pelo banco inglês Barings Bank, e pelo fundo de investimento norte-americano Long Term Capital Management.
Outro grande destaque foi a fraude superior a US$ 7 bilhões sofrida pelo banco Société Generale em Janeiro de 2008.
O Barings Bank é um banco inglês que faliu em 1995 em razão de operações financeiras irregulares e mal-sucedidas realizadas pelo seu principal operador de mercado. O rombo da instituição foi superior à US$ 1,3 Bilhão e causado por uma aposta equivocada no desempenho futuro no índice de ações no Japão. Na realidade, o mercado acionário japonês caiu mais de 15% na época, determinando a falência do banco. O Baring Bank foi vendido a um grupo financeiro holandês (ING) pelo valor simbólico de uma libra esterlina.
O Long Term Capital Management era um fundo de investimento de que perdeu em 1998 mais de US$ 4,6 bilhões em operações nos mercados financeiros internacionais. O LTCM foi socorrido pelo Banco Central dos Estados Unidos (Federal Reserve ), que coordenou uma operação de socorro financeiro à instituição. A justificativa do Banco Central para esta decisão era "o receio das possíveis consequências mundiais da falência do fundo de investimento".
O banco francês Société Generale informou, em janeiro de 2008, uma perda de US$ 7,16 bilhões determinadas por fraudes efetuadas por um operador do mercado financeiro. Segundo revelou a instituição, o operador assumiu posições no mercado sem o conhecimento da direção do banco. A instituição teve que recorrer a uma urgente captação de recursos no mercado próxima a US$ 5,0 bilhões.
E finalmente chegamos ao caso mais problemático da era das finanças modernas anterior ao Bitcoin, o caso Lehman Brothers.
O Lehman Brothers era o 4° maior de investimentos dos EUA quando pediu concordata em 15/09/2008 com dívidas que superavam inacreditáveis US$ 600 bilhões.
Não se tinha contas correntes ou talão de cheques do Lehman Brothers. Era um banco especializado em investimentos e complexas operações financeiras. Havia feito pesados investimentos em empréstimos a juros fixos no famigerado mercado subprime, e o crédito imobiliário voltado a pessoas consideradas de forte risco de inadimplência.
Com essa carteira de investimentos que valia bem menos que o estimado e o acúmulo de projetos financeiros, minou a confiança dos investidores na instituição de 158 anos. Suas ações passaram de US$ 80 a menos de US$ 4. Acumulando fracassos nas negociações para levantar fundos; a instituição de cerca de 25 mil funcionários entrou em concordata.
O Federal Reserve resgatou algumas instituições financeiras grandes e tradicionais norte-americanas como a seguradora AIG no meio da crise. O Fed injetou um capital de US$ 182, 3 bilhões no American International Group (AIG).
Foi exatamente essa decisão do Fed em salvar alguns bancos e deixar quebrar outros, que causou insegurança por parte dos clientes. E os clientes ficaram insatisfeitos tanto com os bancos de investimentos quanto com as agências de classificação de risco, como a Standard & Poor's que tinha dado uma nota alta para o Lehman Brothers no mesmo dia em que ele quebrou.
E essa foi uma das razões pelo qual o Bitcoin foi criado. Satoshi Nakamoto entendeu que as pessoas não estavam mais confiando nem no Governo, nem nos Bancos Privados que o Governo federal restagatava quando eles quebravam e isso prejudicou muita gente. Tanto que o “hash” do Genesis Block contém o título do artigo “Chancellor on brink of second bailout for banks” (Chanceler à beira de segundo resgate para bancos, em português) da edição britânica do The Times.
Esse texto foi parcialmente editado do texto de ASSAF Neto, CAF (2014).
-
 @ 378562cd:a6fc6773
2025-03-31 19:20:39
@ 378562cd:a6fc6773
2025-03-31 19:20:39Bitcoin transaction fees might seem confusing, but don’t worry—I’ll break it down step by step in a simple way. 🚀
Unlike traditional bank fees, Bitcoin fees aren’t fixed. Instead, they depend on: ✔️ Transaction size (in bytes, not BTC!) ✔️ Network demand (more traffic = higher fees) ✔️ Fee rate (measured in satoshis per byte)
Let’s dive in! 👇
📌 Why Do Bitcoin Transactions Have Fees? Bitcoin miners process transactions and add them to the blockchain. Fees serve three key purposes:
🔹 Incentivize Miners – They receive fees + block rewards. 🔹 Prevent Spam – Stops the network from being flooded. 🔹 Prioritize Transactions – Higher fees = faster confirmations.
💰 How Are Bitcoin Fees Calculated? Bitcoin fees are not based on the amount of BTC you send. Instead, they depend on how much space your transaction takes up in a block.
🧩 1️⃣ Transaction Size (Bytes, Not BTC!) Bitcoin transactions vary in size (measured in bytes).
More inputs and outputs = larger transactions.
Larger transactions take up more block space, meaning higher fees.
📊 2️⃣ Fee Rate (Sats Per Byte) Fees are measured in satoshis per byte (sat/vB).
You set your own fee based on how fast you want the transaction confirmed.
When demand is high, fees rise as users compete for block space.
⚡ 3️⃣ Network Demand If the network is busy, miners prioritize transactions with higher fees.
Low-fee transactions may take hours or even days to confirm.
🔢 Example: Calculating a Bitcoin Transaction Fee Let’s say: 📦 Your transaction is 250 bytes. 💲 The current fee rate is 50 sat/vB.
Formula: 🖩 Transaction Fee = Size × Fee Rate = 250 bytes × 50 sat/vB = 12,500 satoshis (0.000125 BTC)
💡 If 1 BTC = $60,000, the fee would be: 0.000125 BTC × $60,000 = $7.50
🚀 How to Lower Bitcoin Fees? Want to save on fees? Try these tips:
🔹 Use SegWit Addresses – Reduces transaction size! 🔹 Batch Transactions – Combine multiple payments into one. 🔹 Wait for Low Traffic – Fees fluctuate based on demand. 🔹 Use the Lightning Network – Near-zero fees for small payments.
🏁 Final Thoughts Bitcoin fees aren’t fixed—they depend on transaction size, fee rate, and network demand. By understanding how fees work, you can save money and optimize your transactions!
🔍 Want real-time fee estimates? Check mempool.space for live data! 🚀
-
 @ 2e8970de:63345c7a
2025-03-31 19:08:11
@ 2e8970de:63345c7a
2025-03-31 19:08:11https://x.com/beatmastermatt/status/1906329250115858750
originally posted at https://stacker.news/items/930491
-
 @ 502ab02a:a2860397
2025-06-01 01:22:46
@ 502ab02a:a2860397
2025-06-01 01:22:46ไม่ต้องคาดหวังวิชาการมากๆในวันอาทิตย์ก็ได้นะครับ วันนี้เรามาคุยเรื่องแดดในอีกแบบกันบ้าง เพราะเห็นว่าช่วงนี้ฝนตกบ่อยจนบางทีก็มีแดดมาให้ตากแค่แว๊บเดียวจริงๆ แต่มันเป็นแว๊บที่ทำให้นึกอะไรขึ้นมาได้ครับ
เฮียชอบมองฟ้าเวลาฝนหยุดตกใหม่ๆ ฟ้ายังไม่ใสสนิท แต่มีแสงอ่อนๆ ทะลุเมฆบางๆ แดดแบบนี้แหละที่มักจะพา “รุ้งกินน้ำ” มาวิ่งเล่นกลางท้องฟ้า
สมัยก่อนเคยสงสัยว่า แค่แสงผ่านหยดน้ำในอากาศ ทำไมถึงแยกสีได้เจ็ดเฉดแบบนั้น จนวันหนึ่งเฮียได้รู้ว่า หยดน้ำเล็กๆ เหล่านั้น ไม่ใช่แค่ “ใส” แต่ทำหน้าที่เหมือน “เลนส์” อย่างดีของธรรมชาติ เป็นเลนส์ที่รวมแสง กระจายแสง หักเหแสง แล้วเปลี่ยนพลังธรรมดาให้กลายเป็นภาพมหัศจรรย์บนฟ้า
และนั่นแหละที่ทำให้เฮียเริ่มสงสัยต่อว่า...มันจะเป็นไปได้ไหม ที่หยดน้ำจะสร้าง “ไฟ” จากแสงแดดได้จริงๆ? คำตอบคือ ได้จ้ะ 55555
ในฟิสิกส์ เราเรียกปรากฏการณ์นี้ว่า focusing of light หรือการรวมแสง ซึ่งสามารถเกิดขึ้นได้จริงแม้ผ่านเลนส์ธรรมชาติอย่างหยดน้ำ หรือแม้แต่ไอน้ำบางๆ ที่ล่องลอยอยู่ในอากาศ พลังงานแสงที่รวมผ่านเลนส์แบบนี้ อาจมีความร้อนพอจุดไฟติดได้เลยทีเดียว เช่น ไฟไหม้ที่เริ่มจากแว่นขยาย หรือจากกระจกเว้าสะท้อนแดด ก็ล้วนใช้หลักเดียวกัน
สมัยก่อนก็มีตำนานว่าอาร์คีมีดีส นักคณิตแห่งกรีก เคยใช้กระจกสะท้อนแดดเผาเรือข้าศึก โชว์พลังแสงจากฟ้าจนกลายเป็นเรื่องเล่าในตำนาน แม้จะถกเถียงกันว่าเวอร์ไปหรือเปล่า แต่หลักการมันจริงจังนะครับ
เพราะในโลกของความเป็นจริงพลังงานเกือบทั้งหมดที่โลกใช้ได้ในวันนี้...มาจากแดด
-ลมที่พัดเกิดจากอุณหภูมิบนพื้นดินที่แดดอุ่นไม่เท่ากัน -ฝนที่ตกก็เพราะแดดระเหยน้ำขึ้นไปเป็นไอ -พืชเติบโตได้เพราะแดดกระตุ้นให้เกิดกระบวนการสังเคราะห์แสง -แม้แต่ไฟฟ้าที่มนุษย์ใช้ ก็เริ่มต้นจากโฟตอนเล็กๆ ที่ปล่อยตัวเองออกมาจากดวงอาทิตย์
โลกของเรา คือเครื่องจักรแปรแสงเป็นชีวิต หยดน้ำ เป็นเพียงหนึ่งในฟันเฟืองใสๆ ที่เปลี่ยนแสงนั้นให้เกิดรูปร่าง เกิดพลัง เกิดไฟ และสุดท้ายกลายเป็น "ความรุ่งเรืองของชีวิต"
ย้อนกลับไปในประวัติศาสตร์ มนุษย์รู้เรื่องนี้มาก่อนเราจะมีไฟฟ้าเสียอีก อียิปต์โบราณบูชาเทพ “รา” เทพแห่งดวงอาทิตย์ ชาวอินคาและมายา วัดจังหวะชีวิตจากการเคลื่อนของแดด ในจีนยุคโบราณ เชื่อว่าไฟฟ้าบนฟ้า ไอน้ำบนดิน ต้องสมดุล ไม่งั้นจะเกิดโรคระบาด ทั้งหมดบอกเราว่า แดดไม่ใช่แค่แสง แต่เป็นครูของชีวิต
แต่ที่เฮียชอบที่สุดคือ แม้จะเป็นเพียงหยดน้ำหนึ่งหยด ถ้าอยู่ในที่ที่เหมาะ เจอกับแสงที่ใช่ มันสามารถจุด “ไฟ” ขึ้นมาได้จริงๆ
เฮียว่านี่แหละคือสัญลักษณ์ของมนุษย์ เราก็เหมือนหยดเล็กๆ ใสๆ ธรรมดาแต่ถ้าได้พบแดดของตัวเอง ไม่ว่าแดดนั้นจะเป็นแรงบันดาลใจ ความรัก งานที่ทำ หรือความฝันในใจ และถ้าเรายอมเป็น “เลนส์” ให้พลังนั้นลอดผ่าน ไฟบางอย่างก็จะลุกขึ้นในตัวเราและทำให้โลกรอบข้างอุ่นขึ้นด้วย
เฮียเลยอยากชวนให้ลองหันหน้าเข้าหาแดด ไม่ต้องถึงขั้นจ้องตากับพระอาทิตย์ แค่ยอมให้แสงนั้นผ่านใจเรา เพราะแม้แดดจะเหมือนเดิมทุกวัน แต่ใจเราต่างหากที่เปลี่ยนไปในทุกครั้งและบางที แค่แสงหนึ่งหยด ก็อาจเป็นไฟสำหรับทั้งชีวิต
#SundaySpecialเราจะไปเป็นหมูแดดเดียว #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ ef53426a:7e988851
2025-05-29 12:26:43
@ ef53426a:7e988851
2025-05-29 12:26:43Saturday 9AM It’s a chilly Saturday morning in Warsaw, and I don’t want to get out of bed. This is not because of the hangover; it’s because I feel like a failure.
The first day of Bitcoin FilmFest was a whirlwind of workshops, panels and running between stages. The pitch competition did not go my way. Another ‘pitching rabbit’ (an actual experienced film-maker) was selected to win the €3,000 of funding.
Rather than get up and search for coffee, I replay the scenes in my head. What could I have done differently? Will investors ever believe in me: I’m just a writer with no contacts in the industry. Do I have what it takes to produce a film?
Eventually, I haul myself out of bed and walk to Amondo, the festival’s morning HQ (and technically, the smallest cinema in Europe). Upon arrival, I find Bitcoin psychonaut Ioni Appelberg holding court in front of around a dozen enraptured disciples. Soon, the conversation spills out to the street to free up space for more workshops.

I attend a talk on film funding, then pay for coffee using bitcoin. I see familiar faces from the two previous nights. We compare notes on Friday night and check the day’s schedule. The morning clouds burn off, and things feel a little brighter.
The afternoon session begins just a few blocks away in the towering Palace of Culture and Science. My role in today's proceedings is to present my freedom fiction project, 21 Futures, on the community stage. Other presentations range from rap videos and advice on finding jobs in bitcoin to hosting ‘Bitcoin Walks’. This is how we are fixing the culture.
Saturday 8PM I feel a tap on my shoulder. ‘Excuse me, Mr. Philip. Your car is waiting. The Producers’ Dinner is starting soon’.
What? Me, a producer? I’ve been taking part in some panels and talks, but I assumed my benefits as a guest were limited to a comped ticket and generous goodie bag.
Soon, I am sharing a taxi with a Dubai-based journalist, a Colombian director, and the cypherpunk sponsor of the pitch competition I didn’t win.
The pierogies I dreamed of earlier that day somehow manifest (happy endings do exist), and we enjoy a raucous dinner including obligatory slivovitz.

Sunday 2AM The last few hours of blur include a bracing city-bike ride in a crew of nine attendees back to the Palace of Culture, chatting with a fellow bitcoin meetup organiser, and vaguely promising to attend a weekend rave with a crew of Polish artists and musicians on the outskirts of London.
I leave the party while it’s still in full swing. In five hours, I have to wake up to complete my Run for Hal in Marshal Edward Rydz-Śmigły Park.
Thursday 9PM The festival kicks off in Samo Centrum on Pizza Day. I arrive in a taxi straight from a cramped flight (fix the airlines!), having not eaten for around ten hours.
The infectious sounds of softly spoken Aussie bitrocker Roger9000 pound into the damp night. I’m three beers in, being presented by the organisers to attendees like a (very tall) show pony. I try to explain more about my books, my publishing connections, my short film.
When I search for the food I ordered an hour ago, I find it has been given away. The stern-faced Polish pizza maker shrugs. ‘You not here.’
I’m so hungry I could cry (six hours of Ryanair can do that to a man). And then, a heroic Czech pleb donates half a pizza to me. Side note: this same heroic pleb accidentally locked me out of my film-funds while trying to fix a wallet bug on Sunday night.
I step out into the rain. Roger9000 reminds us we should have laser eyes well past 100k. I take a bite of pizza and life tastes good.

The Films Side events, artists, late nights, and pitcher’s regret is all well and good, but what of the films?
My highlights included Golden Rabbit winner No More Inflation — a moving narrative with interviews from two dozen economists, visionaries, and inflation survivors.
Hotel Bitcoin, was a surprisingly funny comedy romp about a group of idiots who happen across a valuable laptop.
Revolución Bitcoin — an approachable and thorough documentary aimed to bring greater adoption in the Spanish-speaking world.
And, as a short-fiction guy, I enjoyed the short films The Man Who Wouldn’t Cry, a visit to New York’s only Somali restaurant in Finding Home.

Sunday 7PM The award ceremony has just finished. I head to Amondo for the final time to pay for mojitos in bitcoin and say goodbye to newly made friends. I feel like I’ve met almost everyone in attendance. Are you going to BTC Prague?!? we ask as we part ways.
Of course, the best thing about any festival is the people, and BFF25 had a cast of characters worthy of any art house flick:
- The bright-eyed and confident frontwoman of the metal band Scardust
- A nostr-native artist selling his intricate canvases to the highest zapper
- A dreadlocked DJ who wears a pair of flying goggles on his head at all times
- An affable British filmmaker explaining the virtues of the word ‘chucklesome’
- A Duracell-powered organiser who seems to know every song, person, film, book, and guest at the festival.
Warsaw itself feels like it has a role to play, too. Birdsong and green parks contrast the foreboding Communist-era architecture. The weather changes faster than my mood — heavy greys transform to bright sunshine. The roads around the venue close on Sunday for a political rally. And there we are in the middle, watching our bitcoin films.

Tuesday 10AM I’m at home now, squinting at my email inbox and piles of washing, wondering when the hell I’ll find time. The festival Telegram group is still buzzing with activity. Side events like martial arts tutorials, trips to a shooting range, boat tours. 5AM photos of street graffiti, lost and found items, and people asking ‘is anyone still around?’
This was not just a film festival. BFF is truly a celebration of culture — Art. Books. Comedy. Music. Video. Talk. Connection.
All this pure signal has lifted my spirits so much that despite me being a newbie filmmaker, armed only with a biro, a couple of powerpoints and a Geyser fund page, I know I will succeed in my mission. It turns out you can just film things.
You may have attended bitcoin conferences before — you know, the ones with ‘fireside chats’, VIP areas, and overpriced merch. Bitcoin FilmFest is a moment in time. We are fixing the culture, year after year, until art can flourish again.
As fellow author Aaron Koenig commented during a panel session, ‘In twenty years, we won’t be drawing laser eyes and singing about honey badgers. Our grandchildren won’t understand the change we went through.’
Would I do it all again? Of course!
Join me next June in Warsaw.
I’ll be the tall one presenting his short animation premiere.
Philip Charter is a full-time writer and part-time cat herder. As well as writing for bitcoin founders and companies, he runs the 21 Futures fiction project.
Find out more about theNoderoid Saga animation projecton Geyser.
-
 @ 1d7ff02a:d042b5be
2025-05-28 04:02:47
@ 1d7ff02a:d042b5be
2025-05-28 04:02:47For those who still don't truly understand Bitcoin, it means you still don't understand what money is, who creates it, and why humans need money.
It's a scam that the education system doesn't teach this important subject, while we spend almost our entire lives trying to earn money. Therefore, I recommend following the money and studying Bitcoin seriously.
Why Bitcoin Matters
Saving is the greatest discovery in human history
Before humans learned to save, we were just animals living day to day. Saving is what makes humans different from other animals — the ability to think about the future and store for later.
Saving created civilization itself
Without saving, there would be no cities, no science, no art. Everything we call "progress" comes from the ability to save.
Money is the greatest creation in human history
It is the tool that has allowed human civilization to advance to this day. Money is the best tool humans use for saving.
Bitcoin is the best money ever created
It is the most perfect money humans have ever created. No one can control, manipulate, destroy it, and it is truly limited like time in life.
Bitcoin is like a black hole
That will absorb all value from the damaged financial system. It will draw stability and value to itself. Everything of value will flow into Bitcoin eventually.
Bitcoin is like Buddhism discovering truth
It helps understand the root problems of the current financial system and the emergence of many problems in society, just like Buddha who understood all suffering and the causes of suffering.
Bitcoin is freedom
Money is power, money controls human behavior. When we have money that preserves value and cannot be controlled, we will have intellectual freedom, freedom of expression, and the power to choose.
The debt that humanity has created today would take another thousand years to pay off completely
There is no way out and it's heading toward serious collapse. Bitcoin is the light that will help prevent humanity from entering another dark age.
Bitcoin cannot steal your time
It cannot be created from nothing. Every Bitcoin requires real energy and time to create.
Bitcoin is insurance that protects against mismanagement
It helps protect against currency debasement, economic depression, and failed policies. Bitcoin will protect your value.
Bitcoin is going to absorb the world's value
Eventually, Bitcoin will become the store of value for the entire world. It will absorb wealth from all assets, all prices, and all investments.
Exit The Matrix
We live in a financial Matrix. Every day we wake up and go to work, thinking we're building a future for ourselves. But in reality, we're just giving energy to a system that extracts value from us every second. Bitcoin is the red pill — it will open your eyes to see the truth of the financial world. Central banks are the architects of this Matrix — they create money from nothing, and we have to work hard to get it.
The education system has deceived us greatly. They teach us to work for money, but never teach us what money is. We spend 12-16 years in school, then spend our entire lives earning money, but never know what it is, who creates it, and why it has value. This is the biggest scam in human history.
We are taught to be slaves of the system, but not taught to understand the system.
The Bitcoin standard will end war
When you can't print money for war anymore, war becomes too expensive.
We are entering the Bitcoin Renaissance era
An era of financial and intellectual revival. Bitcoin is creating a new class of humans. People who understand and hold Bitcoin will become a new class with true freedom.
The Path to Financial Truth
Follow the money trail and you will see the truth: - Who controls money printing? - Why do prices keep getting higher? - Why are the poor getting poorer and the rich getting richer?
All the answers lie in understanding money and Bitcoin.
Studying Bitcoin is not just about investment — it's about understanding the future of currency and human society.
Don't just work for money. Understand money. Study Bitcoin.
If you don't understand money, you will be a slave to the system forever. If you understand Bitcoin, you will gain freedom.
-
 @ bcbb3e40:a494e501
2025-03-31 16:00:24
@ bcbb3e40:a494e501
2025-03-31 16:00:24|
 |
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|
|
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|Presentamos una nueva reseña cinematográfica, y en esta ocasión hemos elegido «Cenizas y diamantes», una película polaca del célebre y prolífico director Andrzej Wajda (1926-2016), estrenada en el año 1958. Se trata de uno de los grandes clásicos del cine polaco. El filme refleja una etapa dramática desde la perspectiva histórica para la nación polaca, como es el final de la Segunda Guerra Mundial, a raíz de la capitulación alemana del 8 de mayo de 1945. El contexto en el que se desarrolla se ambienta en la celebración del final de la guerra con el aplastante triunfo de la URSS, con las tropas soviéticas ocupando toda la Europa oriental, y en particular Polonia, que vive un momento de oscuridad e incertidumbre. El protagonista, Maciek Chełmicki (interpretado magistralmente por Zbigniew Cybulski (1927-1967), apodado el «James Dean polaco»), es un joven nacionalista polaco, de orientación anticomunista, que se ve implicado en un complot urdido para asesinar a un líder comunista local. Maciek opera desde la clandestinidad, bajo el grupo Armia Krajowa (AK), el Ejército Nacional polaco, una organización de resistencia, primero contra los alemanes y, posteriormente, contra los soviéticos. Durante el metraje, se plantea una dicotomía permanente entre la libertad entendida como la defensa de la soberanía de Polonia, desde posturas nacionalistas, y quienes consideran la ocupación soviética como algo positivo. Estas circunstancias atrapan al protagonista, que se ve envuelto en una espiral de violencia y traición.
Maciek Chełmicki, nuestro protagonista, cuenta con todas las características del héroe trágico, pues tiene en sus manos una serie de acciones que comprometen el futuro de un pueblo, que consiste en cumplir la misión que le ha sido encomendada, pero en su camino se cruza una joven, Krystyna, una joven camarera de un hotel de la que se enamora en ese mismo día. Este último hecho sirve de punto de partida para todas las dudas, dilemas y dicotomías a las que hacemos referencia. Hay un dilema moral evidente en un mundo en ruinas, devastado por la guerra, la muerte y el nihilismo. En este sentido Wajda nos muestra un lenguaje cinematográfico muy evidente, a través de una técnica expresionista muy depurada, con el uso del blanco y negro, los contrastes generados por las sombras y la atmósfera opresiva que transmite angustia, desesperación y vulnerabilidad de los protagonistas. Además también destilan una fuerte carga emocional, donde no están exentos elementos poéticos y un poderoso lirismo.
|
 |
|:-:|
|Maciek Chełmicki, el protagonista.|
|
|:-:|
|Maciek Chełmicki, el protagonista.|Hay elementos simbólicos que no podemos obviar, y que contribuyen a consolidar el análisis que venimos haciendo, como, por ejemplo, la estética del protagonista, con unas gafas oscuras, que actúan como una suerte de barrera frente al mundo que le rodea, como parte del anonimato tras el cual el joven Maciek vive de forma introspectiva su propio drama particular y el de toda una nación.
|
 |
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|
|
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|Hay una escena especialmente poderosa, y casi mítica, en la que los dos jóvenes protagonistas, Maciek y Krystina, se encuentran entre las ruinas de una Iglesia, en la que se destaca en primer plano, ocupando buena parte de la pantalla, la imagen de un Cristo invertido sobre un crucifijo, donde también se encuentran dos cuerpos colgados hacia abajo en una estampa que refleja la devastación moral y espiritual de toda una época. De hecho, la imagen del crucifijo invertido refleja el máximo punto de subversión y profanación de lo sagrado, y que en el caso concreto de la película viene a representar la destrucción del orden moral y de valores cristianos que la propia guerra ha provocado. Polonia es una nación profundamente católica, convertida al Cristianismo en el 966 a raíz de la conversión del príncipe Miecislao I, contribuyendo de manera decisiva a la formación de la identidad nacional polaca. El catolicismo siempre ha sido un medio de cohesión y defensa frente a las influencias extranjeras y la ocupación de terceros países, una constante en la historia del país, como el que ilustra la propia película con la URSS. En este sentido, la imagen de una Iglesia en ruinas, el lugar donde se encuentra representado el principio de lo sagrado e inviolable, supone una forma de perversión de todo principio de redención y salvación frente a la tragedia, y al mismo tiempo viene a significar que la Tradición ha sido abandonada y pervertida. En la misma línea, el protagonista, Maciek, se encuentra atrapado en una espiral de violencia a través de sus actos terroristas perpetrados contra la autoridad soviética que ocupa su país. Los dos cuerpos anónimos que cuelgan boca abajo, de forma grotesca, también participan de este caos y desequilibrio de un orden dislocado, son parte de la deshumanización y el nihilismo que todo lo impregna.
|
 |
|:-:|
|Maciek y Krystina en una iglesia en ruinas|
|
|:-:|
|Maciek y Krystina en una iglesia en ruinas|Como ya hemos mencionado, la película se encuentra plagada de paradojas y dicotomías, en las que nuestro protagonista, el joven rebelde e inconformista, debe elegir permanentemente, en unas decisiones que resultan trascendentales para su futuro y el de la propia nación. La figura femenina que irrumpe en su vida, y que representa un principio disruptivo que provoca una fractura interior y una crisis, le suscita una toma de conciencia de su propia situación y le fuerza a tomar un camino entre la «felicidad», del «amor», la «esperanza» y la «vida», que le permita superar la deriva nihilista y autodestructiva de la lucha clandestina, la cual le aboca a un destino trágico (que no vamos a desentrañar para no hacer spoiler). En relación al propio título de la película, «Cenizas y diamantes», basada en el poema del poeta y dramaturgo polaco Cyprian Norwid (1821-1883) y en la novela del autor, también polaco, Jerzy Andrzejewski (1909-1983), nos destaca la dualidad de los dos elementos que lo componen, y que definen el contraste entre el mundo sombrío y oscuro (Cenizas) y la esperanza y la luz que representa susodicha figura femenina (diamantes). La segunda alternativa parece un imposible, una quimera irrealizable que se pliega ante un Destino implacable, irreversible y cruel.
En consecuencia, y a la luz de los elementos expuestos, podemos decir que se nos presentan dilemas propios de la filosofía existencialista, que conoce su punto álgido en esos años, con autores como Jean Paul Sartre (1905-1980), Albert Camus (1913-1960), Karl Jaspers (1883-1969) o Martin Heidegger (1889-1976) entre otros. Respecto a éste último, a Heidegger, podemos encontrar algunas claves interesantes a través de su filosofía en relación al protagonista, a Maciek, especialmente a través de la idea del Dasein, a la idea de haber sido arrojado al mundo (Geworfenheit), y la manera tan extrema y visceral en la que vive susodicha condición. Todos aquellos elementos que dan sentido a la vida colectiva se encuentran decaídos o destruidos en su esencia más íntima, la Patria, la religión o la propia idea de Comunidad orgánica. De modo que el protagonista se ha visto «arrojado» frente a una situación o destino indeseado, en unas coyunturas totalmente desfavorables en las que no queda otra elección. Sus decisiones están permanentemente condicionadas por la circunstancia descrita y, por tanto, vive en un mundo donde no controla nada, en lugar de ser sujeto es un mero objeto transportado por esas circunstancias ajenas a su voluntad. Sin embargo, y en coherencia con el Dasein heideggeriano, vemos como Maciek, a raíz de conocer a Krystyna, comienza a experimentar una catarsis interior, que muestra por momentos el deseo de superar ese «ser arrojado al mundo contra tu voluntad», trascendiendo esa condición absurda e irracional de unas decisiones enajenadas de su voluntad para dotar de una significación y un sentido la propia existencia.
|
 |
|:-:|
|Andrzej Wajda, el director de la película.|
|
|:-:|
|Andrzej Wajda, el director de la película.|Otro elemento característico de la filosofía heideggeriana lo podemos encontrar en la «angustia» (angst) a través de la ausencia de un sentido y fundamento último que justifique la existencia del protagonista. Es una angustia en a que el Dasein se enfrenta a la «nada», a ese vacío existencial que hace inútil toda la lucha que Maciek lleva a cabo en la clandestinidad, con asesinatos y actos de terrorismo que pretenden salvaguardar algo que ya no existe, y que simboliza muy bien la Iglesia en ruinas con sus símbolos religiosos invertidos de la que hablábamos con anterioridad. Recuerda un poco a esa dicotomía que se plantea entre ser conservador o reaccionario frente a una realidad como la del propio presente, en la que los valores tradicionales han sido totalmente destruidos, y más que conservar se impone la reacción para volver a construir de la nada.
|
 |
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|
|
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|Todas las dudas que asaltan al protagonista se ven incrementadas en el momento decisivo, cuando se dispone a dar muerte al líder comunista. Se produce una tensión interna en Maciek, que se encuentra ligado a la joven que ha conocido ese día, y en ella es donde encuentra ese leve destello de humanidad. Esa circunstancia le hace replantearse por un instante el cumplimiento de su misión, pero es un dilema que no tiene salida, y por ello le asalta nuevamente la angustia frente a esa «nada», ese mundo vacío e incomprensible que trasciende el marco de sus propias elecciones.
Uno de los conceptos centrales de Heidegger en Ser y tiempo es el Sein-zum-Tode (ser-para-la-muerte), la idea de que la muerte es la posibilidad más propia y definitiva del Dasein, y que enfrentarla auténticamente permite vivir de manera más plena. Y es que el protagonista se encuentra permanentemente sobre esa frontera entre la vida y la muerte, que afronta con todas sus consecuencias, conscientemente, y la acepta. Esta actitud podría leerse como una forma de Dasein inauténtico, una huida del ser-para-la-muerte mediante la distracción (das Man, el «se» impersonal). Sin embargo, su decisión de cumplir la misión sugiere un enfrentamiento final con esa posibilidad. Otro aspecto que podemos conectar con el pensamiento heideggeriano es la autenticidad o inautenticidad de la vida del protagonista. En relación a la inautenticidad vemos como al principio sigue las órdenes de sus superiores en la organización sin cuestionarlas, lo cual implica un comportamiento inequívocamente alienante. Respecto a aquello que resulta auténtico de su existencia son sus relaciones con Krystyna, que supone imponer su propia voluntad y decisión, mostrando un Dasein que asume su libertad.
|
 |
|:-:|
|Escena de la película.|
|
|:-:|
|Escena de la película.|Otros aspectos más generales de la filosofía existencialista redundan sobre estos mismos aspectos, con la elección entre la libertad absoluta y la condena inevitable. La idea del hombre condenado a actuar, a una elección continua, aún cuando el hombre no es dueño de su destino, o las consecuencias de tales acciones son absurdas, irracionales e incomprensibles. El propio absurdo de la existencia frente al vacío y la ausencia de principios sólidos en los que cimentar la vida, no solo en sus aspectos cotidianos más básicos, sino en aquellos más profundos de la existencia. La soledad y la propia fatalidad frente a un Destino que, como ya hemos apuntado anteriormente, parece imponerse de manera irrevocable, y podríamos decir que brutalmente, al individuo aislado, incapaz de asirse en una guía, en unos valores que le permitan remontar la situación.
En términos generales «Cenizas y diamantes», además de ser una película de gran calidad en sus aspectos técnicos, en su fotografía, en la configuración de sus escenas y en el propio desarrollo argumental, bajo un guión espléndidamente ejecutado a lo largo de sus 98 minutos de duración, también nos invita a una reflexión profunda sobre la condición humana y la propia Modernidad. Y es algo que vemos en nuestros días, con las consecuencias de un pensamiento débil, con la promoción del individualismo, el hedonismo y lo efímero. La ausencia de estructuras sólidas, la subversión de toda forma de autoridad y jerarquía tradicionales. Paradójicamente, el mundo actual tiende a formas de poder y autoridad mucho más invasivas y coercitivas, tanto a nivel individual como colectivo, pero en la misma línea abstracta e impersonal que nos describe la película, abocándonos a la alienación y la inautenticidad de nuestras propias vidas. Y como Maciek, también nosotros, vivimos en un mundo dominado por la incertidumbre y la desesperanza, en el que el globalismo y sus perversas ideologías deshumanizantes actúan por doquier.
|
 |
|:-:|
|Carátula original de la película en polaco.|
|
|:-:|
|Carátula original de la película en polaco.|
Artículo original: Hipérbola Janus, Reseña de «Cenizas y Diamantes» (Andrzej Wajda, 1958) (TOR), 31/Mar/2025
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 57c631a3:07529a8e
2025-05-20 15:40:04
@ 57c631a3:07529a8e
2025-05-20 15:40:04The Video: The World's Biggest Toddler
https://connect-test.layer3.press/articles/3f9d28a4-0876-4ee8-bdac-d1a56fa9cd02
-
 @ 6be5cc06:5259daf0
2025-05-27 20:22:09
@ 6be5cc06:5259daf0
2025-05-27 20:22:09A posição do libertário que rejeita o cristianismo padece de sérias incoerências lógicas, históricas e filosóficas. Ao renegar as bases espirituais e culturais que tornaram possível o próprio ideal libertário, tal posição demonstra ser, ao mesmo tempo, autofágica e irracional. É o caso de alguém que se gloria dos frutos de uma árvore que corta pela raiz.
I. Fundamento histórico: a civilização da liberdade é cristã
Não foi o secularismo moderno, nem o paganismo antigo, que ergueram as instituições que protegem a dignidade da pessoa humana e os limites ao poder. Desde os primeiros séculos, a Igreja resistiu ao culto estatal romano, afirmando a soberania de Deus sobre os Césares — "Mais importa obedecer a Deus que aos homens" (Atos 5,29).
Foi o cristianismo que:
-
Fundou universidades livres, onde o saber era buscado sob o primado da verdade;
-
Defendeu a lei natural como fundamento do direito — uma doutrina que protege o indivíduo contra tiranias;
-
Resgatou e aprofundou o conceito de pessoa, dotada de razão e livre-arbítrio, imagem de Deus, e, portanto, inalienavelmente digna e responsável.
Em momentos-chave da história, como nas disputas entre papado e império, nas resistências contra absolutismos, e na fundação do direito internacional por Francisco de Vitoria e a Escola de Salamanca, foi o cristianismo quem freou o poder estatal em nome de princípios superiores. A tradição cristã foi frequentemente o principal obstáculo à tirania, não seu aliado.
Negar isso é amputar a própria genealogia da liberdade ocidental.
Uma das chaves do cristianismo para a construção dessa civilização da liberdade foi a exaltação do individualismo. Ao afirmar que o ser humano é feito à imagem de Deus e que sua salvação é uma escolha pessoal, o cristianismo colocou o indivíduo no centro da moralidade e da liberdade. Diferente dos gregos, cuja ética era voltada para a polis e a cidade-estado, o cristianismo reafirma a suprema importância do indivíduo, com sua capacidade de escolha moral, responsabilidade pessoal e dignidade intrínseca. Esse princípio, mais do que qualquer outra religião, foi o alicerce do desenvolvimento da liberdade individual e da autonomia, valores que sustentam a civilização ocidental.
A ética grega, na melhor das hipóteses, descreve a ordem natural — mas não consegue justificar por que essa ordem deveria obrigar a vontade humana. Um Logos impessoal não tem autoridade moral. Uma ordem cósmica sem um Legislador é apenas um dado de fato, não uma norma vinculante. A vontade pode rebelar-se contra o telos — e sem um Deus justo, que ordena a natureza à perfeição, não há razão última para não o fazer.
A cultura grega teve uma influência indiscutível sobre o desenvolvimento da civilização ocidental, mas o cristianismo não só absorveu o que havia de bom na cultura grega, como também elevou e completou esses aspectos. O cristianismo, ao afirmar que todos os homens são feitos à imagem e semelhança de Deus e têm dignidade intrínseca, levou a uma noção de igualdade moral e liberdade que transcende as limitações da pólis grega.
II. Falsa dicotomia: fé e liberdade não são opostas
Com frequência equiparam a religião à coerção e à obediência cega. Mas isso é um equívoco: o cristianismo não se impõe pela força, mas apela à consciência. O próprio Deus, em sua relação com a criatura racional, respeita sua liberdade. Como ensina a Escritura:
"Se alguém quiser vir após mim..." (Mt 16,24);
"Eis que estou à porta e bato. Se alguém ouvir a minha voz e abrir a porta, entrarei em sua casa e cearei com ele." (Ap 3,20);
"Assim falai, e assim procedei, como devendo ser julgados pela lei da liberdade." (Tiago 2,12).A adesão à fé deve ser livre, voluntária e racional, pois sem liberdade não há verdadeiro mérito, nem amor genuíno. Isso é mais compatível com o princípio de não agressão do que qualquer utopia secular. Ora, o núcleo do evangelho é voluntarista: salvação pessoal, conversão interior, caridade.
Ninguém deve ser forçado, contra sua vontade, a abraçar a fé, pois o ato de fé é por sua natureza voluntário (Dignitatis Humanae; CDC, cân. 748,2)
Se algum Estado usa da força para impor o cristianismo, afirmar que o cristianismo causou as coerções é tão equivocado quanto dizer que a propriedade privada causa o comunismo; é uma inversão da realidade, pois o comunismo surge precisamente da violação da propriedade. Portanto, a fé forçada é inválida em si mesma, pois viola a natureza do ato de crer, que deve ser livre.
III. Fundamento moral: sem transcendência, o libertarianismo flutua no vácuo
O libertário anticristão busca defender princípios objetivos — como a inviolabilidade do indivíduo e a ilegitimidade da agressão — sem um fundamento transcendente que lhes dê validade universal. Por que a agressão é errada? Por que alguém tem direito à vida, à liberdade, à propriedade? Sem uma explicação transcendental, as respostas para tais perguntas se tornam apenas opiniões ou convenções, não obrigações morais vinculantes. Se a moralidade é puramente humana, então os direitos podem ser modificados ou ignorados conforme a vontade da sociedade. O conceito de direitos naturais, tão caro ao libertarianismo, precisa de um solo metafísico que justifique sua universalidade e imutabilidade. Caso contrário, eles podem ser tratados apenas como acordos utilitários temporários ou preferências culturais, sem qualquer obrigatoriedade para todos os seres humanos em todas as circunstâncias.
Pensadores libertários seculares, como Ayn Rand e Murray Rothbard, tentaram ancorar os direitos naturais na razão humana ou na natureza do homem. Rand baseia sua ética no egoísmo racional, enquanto Rothbard apela à lei natural. Embora essas abordagens busquem objetividade, elas carecem de uma resposta definitiva para por que a razão ou a natureza humana obrigam moralmente todos os indivíduos. Sem um fundamento transcendente, suas concepções permanecem vulneráveis a interpretações subjetivas ou a cálculos utilitários.
Aqui, o cristianismo oferece uma explicação sólida e transcendental que fundamenta os direitos naturais. A visão cristã de que o ser humano foi criado à imagem e semelhança de Deus confere à pessoa uma dignidade intrínseca, imutável e universal. Essa dignidade não depende de fatores externos, como consenso social ou poder político, mas é uma característica inerente ao ser humano pela sua criação divina. A partir dessa perspectiva teológica, torna-se possível afirmar com base sólida que os direitos naturais são dados por Deus e, portanto, são universais e vinculantes.
O cristianismo também é a base de um sistema moral que distingue claramente justiça de legalidade. O Estado pode criar leis, mas isso não significa que essas leis sejam justas. A justiça, sob a ótica cristã, é uma expressão da ordem moral objetiva, algo que transcende as leis humanas e é definido pela vontade divina. Por isso, o libertarianismo cristão vê a agressão como uma violação de uma ordem moral objetiva, e não apenas uma violação de uma convenção social ou de um acordo utilitário.
Se a moralidade e os direitos naturais não forem fundamentados em um Logos criador e legislador, o que acontece é que o conceito de direito natural degenera para algo mais frágil, como um simples acordo utilitário. Nesse cenário, os direitos do indivíduo se tornam algo acordado entre os membros de uma sociedade, em vez de princípios imutáveis e universais. Os direitos podem ser negociados, alterados ou ignorados conforme o interesse do momento.
IV. Fundamento científico: a racionalidade moderna é filha da fé cristã
A ciência moderna só foi possível no contexto cultural cristão. Nenhuma outra civilização — nem a grega, nem a islâmica, nem a chinesa — produziu o método científico como o Ocidente cristão o fez.
Isso se deve a quatro premissas teológicas:
-
Criação racional: O mundo é ordenado por um Deus racional.
-
Distinção entre Criador e criatura: A natureza não é divina e pode ser estudada sem sacrilégio.
-
Valor do trabalho e da observação empírica, herdado do monaquismo.
-
Autonomia institucional, presente nas universidades medievais.
A doutrina cristã da Criação ex nihilo ensina que o mundo foi criado por um Deus racional, sábio e pessoal. Portanto, o cosmos é ordenado, possui leis, e pode ser compreendido pela razão humana — que é imagem do Criador. Isso contrasta fortemente com as cosmovisões panteístas ou mitológicas, onde o mundo é cíclico, arbitrário ou habitado por forças caprichosas.
Sem essa fé no Logos criador, não há razão para crer que a natureza tenha uma ordem inteligível universal e constante, que pode ser descoberta por observação e dedução. A ciência moderna só é possível porque, antes de investigar a natureza, pressupôs-se que ela era investigável — e isso foi uma herança direta do pensamento cristão.
Homens como Bacon, Newton, Kepler e Galileu viam na ciência um modo de glorificar o Criador. O ateísmo cientificista é, portanto, parasitário da teologia cristã, pois toma seus frutos e rejeita suas raízes. A ciência moderna nasceu como filha legítima da fé cristã. E os que hoje a usam contra sua mãe, ou são ingratos, ou ignorantes.
V. O cristianismo como barreira à revolução cultural
O cristianismo é a barreira mais sólida contra a infiltração revolucionária. A chamada "marcha gramsciana", que visa corroer os fundamentos morais da sociedade para subjugar o indivíduo ao coletivo, encontra sua resistência mais firme nos princípios cristãos. A fé cristã, ao proclamar a existência de uma verdade objetiva, de uma lei moral imutável e de uma dignidade humana que transcende o Estado e o consenso social, imuniza a civilização contra o relativismo e o igualitarismo nivelador do marxismo cultural.
Além disso, o cristianismo é uma tradição milenar, profundamente enraizada no cotidiano das pessoas, não sendo uma novidade a ser imposta ou implementada, mas uma força presente há séculos, que permeia a estrutura social, moral e cultural da sociedade. Sua presença constante nas comunidades, desde os tempos mais antigos, oferece uma resistência robusta contra qualquer tentativa de subverter a ordem natural e moral estabelecida.
Não por acaso, tanto Karl Marx quanto Antonio Gramsci identificaram no cristianismo o principal obstáculo à realização de seus projetos revolucionários. Marx chamou a religião de "ópio do povo" porque sabia que uma alma ancorada em Deus não se submete facilmente ao poder terreno; Gramsci, mais sutil, propôs a destruição da cultura cristã como pré-condição para o triunfo do socialismo. Sem essa âncora transcendente, a sociedade torna-se presa fácil das engenharias sociais que pretendem redefinir arbitrariamente o homem, a família e a liberdade.
Conclusão
O libertário anticristão, consciente ou não, nega as fundações mesmas do edifício que habita. Ao rejeitar o cristianismo, cava o abismo sob os próprios pés, privando o ideal libertário de sua base moral, cultural e racional. Ele defende a ética voluntária, a liberdade individual e a ordem espontânea, mas sem o solo metafísico e histórico que torna esses princípios inteligíveis e possíveis. É um erro tentar preservar a liberdade em termos absolutos sem reconhecer as raízes cristãs que a sustentam, pois o cristianismo é a única tradição que a legitima e a viabiliza.
Negar o cristianismo é racionalmente insustentável. A liberdade, como a conhecemos, é filha da fé cristã, que oferece a base moral e metafísica que torna a liberdade tanto desejável quanto possível. Mesmo que ateu, o libertário que ama a liberdade deveria, no mínimo, respeitar — e, idealmente, redescobrir — essas raízes cristãs. Pois sem fé, restam apenas o niilismo e o relativismo, que, eventualmente, desaguam na servidão.
Como nos ensina a tradição: Ubi fides ibi libertas — onde há fé, há liberdade.
-
-
 @ 58537364:705b4b85
2025-06-01 01:05:37
@ 58537364:705b4b85
2025-06-01 01:05:37โลกเป็นอย่างไร เพราะใจเราเป็นอย่างนั้น
พระอาจารย์ไพศาล วิสาโล วัดป่าสุคะโต แสดงธรรม เย็นวันที่ ๓๑ กรกฎาคม ๒๕๖๕

คนเราทุกคนมีตา หู จมูก ลิ้น กาย แล้วก็ใจ ตา หู จมูก ลิ้น กาย มีไว้เพื่อรับรู้โลกภายนอก ตารับรู้รูป หูรับรู้เสียง จมูกรับรู้กลิ่น ลิ้นรับรู้รส และกายก็รับรู้สัมผัสที่เรียกว่าโผฏฐัพพะ และไม่ว่าจะรับรู้โลกภายนอกอะไร มันก็ส่งมาที่ใจ ใจทำหน้าที่คิด ทำหน้าที่รู้สึก
เราก็คงจะสังเกตได้ว่า เรารับรู้อะไร ใจก็มักจะเป็นอย่างนั้น เช่น ถ้าเกิดเราเห็นภาพคนกำลังอดอยากหิวโหย ก็เกิดความรู้สึกเศร้า สงสารในใจของเรา ถ้าเห็นภาพอุบัติเหตุรถยนต์ ก็เกิดความเสียวสยอง หรือว่าหวาดวิตกในใจ ถ้าเห็นเด็กกำลังร้องไห้ ก็เกิดความรู้สึกเศร้าในใจของเรา แต่ถ้าเกิดเห็นภาพคนกำลังสนุกสนานรื่นเริง มันก็มีความยินดีเกิดขึ้นในใจ
รับรู้อะไรก็มีผลต่อใจของเรา รับรู้สิ่งที่เป็นลบ ใจก็พลอยรู้สึกลบไปด้วย รับรู้สิ่งที่เป็นบวก ใจก็พลอยเป็นบวกไปด้วย เพราะฉะนั้นการรับรู้อะไร ก็เป็นสิ่งที่เราต้องใส่ใจ
ถ้าเราอยากจะให้ใจเราสงบ ใจเราเป็นสุข ไม่ถูกแผดเผาด้วยความโกรธ หรือว่าไม่ถูกกดกดดันด้วยความเศร้า หรือว่าถูกกระตุ้นเร้าด้วยความโลภ ความอยาก อันนี้ก็โยงไปถึงว่า เราเลือกที่จะอยู่ไหนด้วย ถ้าเราเลือกที่จะอยู่ในที่ที่สงบสงัด ใจก็พลอยสงบ หรือว่าสามารถจะเย็นได้ง่าย
เพราะฉะนั้นธรรมะข้อหนึ่งในโอวาทปาฏิโมกข์คือ พึงนอนและนั่งในที่สงัด ในที่ที่สงัดที่ที่เป็นรมณีย์ มันก็มีส่วนน้อมใจให้สงบไปด้วย
รวมทั้งการรู้จักใช้หู ใช้ตา ใช้จมูกให้เป็น ต้องรู้จักเลือกรับรู้สิ่งที่มันจะเกื้อกูล ต่อการสร้างกุศลธรรมขึ้นมาในใจ อย่างไรก็ตามเท่านั้นยังไม่พอ เพราะว่าการรับรู้ของเรา บ่อยครั้งเราไม่ได้รับรู้สิ่งที่เกิดขึ้นข้างหน้าเราอย่างที่มันเป็นจริง
บ่อยครั้งเราก็มีการตีความหรือปรุงแต่ง เราไม่ได้เห็นอย่างที่รูปปรากฏ เราไม่ได้ได้ยินอย่างที่เสียงมากระทบหูเรา เพราะว่ามีการตีความ หรือปรุงแต่งซ้อน แบบเรียกว่าสนิทแนบแน่นเลย อย่างเช่น เห็นคนกระซิบกระซาบต่อหน้าเรา เราก็อาจจะตีความไปว่า เขากำลังพูดถึงเรา หรืออาจจะถึงขั้นนินทาเรา แต่ความจริงอาจจะไม่ได้เป็นอย่างนั้น
หรือว่ามีคนบางคนมองหน้าเรา จ้องเรา เราก็อาจจะตีความว่า เขากำลังหาเรื่องเราก็ได้ หรือเขากำลังไม่พอใจเรา แต่ว่าความจริงอาจจะไม่ได้เป็นอย่างนั้นก็ได้ แต่ว่าเราตีความไปแล้ว แล้วส่วนใหญ่เราก็จะไม่ได้เห็น ไม่ได้รับรู้สด ๆ หรือว่าอย่างที่มันเป็น
แต่ว่ามันมีการตีความ ตีความในทางบวกก็มี ตีความในทางลบก็มี ซึ่งตรงนี้บ่อยครั้งก็สร้างปัญหา หรือสร้างความทุกข์ให้กับเรา เพราะการที่เราไม่ได้เห็นอะไรอย่างที่มันเป็นจริงๆ มันมีการตีความในใจของเราหรือด้วยใจของเรา และเราก็เผลอไปคิดว่า สิ่งที่จิตตีความ มันคือความจริง แต่บ่อยครั้งมันก็เป็นแค่การปรุงแต่ง หรือความคิดของเราเอง
มีพระทิเบตท่านหนึ่งเล่าว่า มีคราวหนึ่งจะเดินทางขึ้นเครื่องบิน ที่สนามบินมีการตรวจเอกซเรย์ข้าวของ โทรศัพท์ คอมพิวเตอร์ ระหว่างที่กำลังรอข้าวของของท่านที่กำลังผ่านการเอกซเรย์ ท่านก็เหลือบไปมองเห็นด่านรักษาความปลอดภัยอีกด่านหนึ่ง ที่เป็นด่านสุดท้าย
แล้วก็สังเกตว่ามีเจ้าหน้าที่รักษาความปลอดภัยคนหนึ่ง รูปร่างสูงใหญ่ มีหนวดเฟิ้มเลย จ้องมองมาที่ท่าน จ้องแบบเขม็งเลย ท่านเหลียวไปมองหลายครั้งก็เห็นว่าเขายังจ้องไม่เลิก ก็รู้สึกไม่ค่อยสู้ดีแล้ว เอ๊ะ หรือว่าเจ้าหน้าที่คนนี้กำลังสงสัยอะไรเราหรือเปล่า ถึงจ้องมองแบบนั้น แล้วยิ่งเห็นเจ้าหน้าที่คนนั้นจ้องมองมากเท่าไหร่ โดยที่ไม่มีรอยยิ้มเลยนะ ท่านก็เลยนึกในใจว่า เขาคงจะสงสัยเรา
ยิ่งมองเจ้าหน้าที่คนนั้น ก็ยิ่งรู้สึกว่าเจ้าหน้าที่คนนี้ หน้าเหี้ยม แล้วก็ดูหยาบกระด้าง หน้าตารูปร่างเหมือนมาเฟียเลย จู่ ๆ เจ้าหน้าที่คนนั้นก็วิทยุ พระทิเบตก็คิดสงสัยว่าคงต้องมีอะไรแน่ แล้วก็จริงด้วย มีเจ้าหน้าที่คนใหม่เดินมาที่ชายคนนี้ แล้วก็พูดคุยอะไรกันสักอย่าง แล้วเจ้าหน้าที่ที่มีหนวดก็ชี้มาที่ตัวท่าน
พระทิเบตใจเขาก็ไม่สู้ดีแล้ว เจ้าหน้าที่คนใหม่ก็มา พอมายืนแทนเจ้าหน้าที่คนแรกที่มีหนวด เจ้าหน้าที่ที่มีหนวดนั่นก็เดินตรงมาเลยที่ท่าน แล้วก็ถามว่า คุณคือมิสเตอร์ยงเกใช่ไหม ท่านก็ตอบว่าใช่ มีอะไรเหรอ เจ้าหน้าที่คนนั้นก็บอกว่า ผมอยากจะขอบคุณคุณเหลือเกินนะ เพราะว่าหนังสือคุณนี่ช่วยผมได้มากเลย อยากจะขอบคุณจริง ๆ เลย
เท่านี้แหละ พระทิเบตก็ยิ้มเลย แล้วเจ้าหน้าที่คนนั้นก็ยิ้มด้วย แล้วก็มาเขย่ามือกัน เป็นมิตรเลยนะ ก็รู้สึกโล่งอกขึ้นมาเลย นึกว่าจะมีเรื่องอะไร อ๋อ ที่แท้มาขอบคุณที่ได้อ่านหนังสือของเรา ทีแรกนึกว่าจะมาสงสัย มาค้นตัวอะไรสักอย่าง
แล้วท่านก็พบว่าภาพของชายคนนั้น ในสายตาของท่านเปลี่ยนไปเลย จากคนที่มีสีหน้าเหี้ยม กระด้างเหมือนมาเฟีย กลายเป็นคนที่อารมณ์ดี ใจดี สุภาพเรียบร้อย มีความเป็นมิตร และท่านก็มาเอะใจ ทำไมเรามองเจ้าหน้าที่คนนี้เปลี่ยนไป ทีแรกเห็นเป็นคนเหี้ยม คนหยาบ แต่เห็นตอนนี้กลายเป็นมิตร มีน้ำใจ แล้วก็มีความสุภาพ ก็คนคนเดียวกันแหละ แต่ทำไมเห็นต่างกันเลย แบบตรงข้ามกันเลย หลังจากที่เขามาทักทาย แล้วก็มาขอบคุณ
อันนี้ก็ชี้ให้เห็นว่าจิตของคนเรา มันส่งผลมากต่อการรับรู้ ทีแรกพอเห็นเจ้าหน้าที่คนนั้นจ้องมองเขม็งเลย ที่จริงเขาก็ไม่ได้มีอะไรในใจ แต่ว่าพระทิเบตท่านนี้ตีความไปแล้วว่า เขาคงไม่ชอบเราหรือคิดไม่ดีกับเรา ตีความไปในทางร้ายแล้ว ไม่ได้เห็นอย่างที่เป็น
พอตีความไปในทางร้ายเขาคิดไม่ดีกับเรา ท่านก็เลยรู้สึกไม่ดีกับเขา พอรู้สึกไม่ดีกับเขา ภาพของเขาที่เห็นในใจของท่าน ก็กลายเป็นคนที่ดูเหี้ยม กระด้าง เหมือนมาเฟีย เหมือนอันธพาล แต่ว่าพอเขามีอากัปกริยาในทางที่เป็นมิตร มาขอบคุณ มาขอบอกขอบใจ ความรู้สึกของท่านที่มีต่อเขาก็เปลี่ยนไป แทนที่จะเห็นว่าเขาคิดไม่ดีกับเรา ที่แท้เขาขอบคุณเรา พอรู้สึกดีกับเขา ภาพของเขาในสายตาของท่านก็เปลี่ยนไปเลย กลายเป็นคนที่สุภาพเรียบร้อย มีความเป็นมิตร
อันนี้เป็นสิ่งที่ชี้ให้เห็นเลยว่า คนเราบ่อยครั้งเรารับรู้อะไรก็ตาม เราไม่ได้รับรู้อย่างที่มันเป็น แต่ว่ามีการตีความ และถ้าเราตีความในทางลบ ว่าเขาคิดไม่ดีกับเรา จิตมันก็มีปฏิกิริยาตอบโต้ทันทีเลย พอคิดว่าเจ้าหน้าที่คนนี้เขาคิดไม่ดีกับเรา ท่านก็รู้สึกไม่ดีกับเขาโดยอัตโนมัติเลย
พอรู้สึกไม่ดีกับเขา ภาพของเขาที่ท่านเห็นก็กลายเป็นภาพของคนที่ดูดุร้าย ดูเหี้ยม มีการเติมแต่ง มีการใส่สี และนี่คือสิ่งที่เกิดขึ้นกับคนเรา เกิดขึ้นกับเราในชีวิตประจำวัน เรารับรู้อะไร เราก็ไม่เคยรับรู้อย่างที่มันเป็น แต่ว่ามีการตีความ
ถ้าตีความในทางบวกก็ดีไป ถ้าตีความในทางลบ ก็เกิดความวิตก เกิดความกลัว เกิดความเครียด เกิดความขุ่นมัว และพอใจมีความวิตก มีความขุ่นมัว มองอะไรออกไป ก็เห็นแต่ภาพในทางลบ คนๆหนึ่งก็ถูกมองว่ากลายเป็นคนที่เหี้ยม กลายเป็นคนที่กระด้าง แต่พอใจเปลี่ยนไป ความรู้สึกที่มีต่อคนคนนั้นเปลี่ยนไป ภาพที่เห็นหรือว่าภาพที่มองออกไป มันก็เป็นอีกแบบหนึ่ง ตรงข้ามกันเลย
พูดอีกอย่างหนึ่งก็คือว่า ไม่ใช่แค่ว่าเราเห็นอะไรใจก็เป็นอย่างนั้น ในทางกลับกัน ใจเราเป็นอย่างไรก็เห็นโลกไปในทางนั้น ถ้าใจเราขุ่นมัว ใจเรามีความเครียด หรือมีความรู้สึกเป็นลบ โลกที่อยู่รอบตัวเรา หรือคนที่อยู่ข้างหน้าเรา ก็ถูกเติมแต่งให้เป็นลบไปด้วย มีการใส่สี แต่ถ้าเรารู้สึกบวกกับเขา ภาพที่เห็นก็เปลี่ยนไป กลายเป็นบวกไปด้วย อันนี้คือสิ่งที่เกิดขึ้นกับเราตลอดเวลาเลยว่าก็ว่าได้
โลกเป็นอย่างไร มันก็อยู่ที่ใจของเราว่าเป็นอย่างไรด้วย ฉะนั้นบ่อยครั้ง เวลาเรารู้สึกว่าโลกมันหม่นหมอง ผู้คนไม่น่ารัก มันอาจจะเป็นเพราะว่าใจเราหม่นหมอง หรือว่าใจเรามีความรู้สึกที่เป็นลบก็ได้
ฉะนั้นก่อนที่เราจะไปตัดสิน ไปวิพากษ์วิจารณ์ หรือไปมองว่าโลกมันแย่ บางทีเราต้องกลับมาดูที่ใจของเรา ว่าใจเรามันมีการเติมแต่ง รูปที่ได้เห็น เสียงที่ได้ยินหรือเปล่า
ในปฏิจจสมุปบาท จะมีปัจจยาการตอนต้นเลยที่บอกว่า อวิชชาเป็นปัจจัยให้เกิดสังขาร สังขารเป็นปัจจัยให้กับวิญญาณ ที่พูดมาก็เป็นเรื่องที่ชี้ให้เห็นว่า สังขารปรุงแต่งวิญญาณอย่างไร
สังขารในที่นี้ก็คือการปรุงแต่ง หรือความรู้สึกนึกคิดในใจ อารมณ์ที่เกิดขึ้นในใจ มันก็ไปปรุงแต่งการรับรู้ ไม่ว่าจะเป็นการรับรู้ทางตา ทางหู ทางจมูก ทางลิ้น ทางกาย หรือแม้แต่ทางใจ ถ้าใจมีความรู้สึกในทางลบ เช่นคิดลบ หรือรู้สึกลบกับใคร ก็จะเห็นภาพคนๆ นั้นในทางลบไปด้วย เห็นเป็นคนที่กระด้าง เป็นคนที่เหี้ยม เป็นคนที่ไม่น่ารัก แต่ถ้าใจมีความรู้สึกเป็นบวก ก็จะเห็นเขาเป็นคนที่เป็นมิตร เห็นเขาสุภาพ
อันนี้ก็ไม่ต่างจากเรื่องของคนผู้ชายคนหนึ่งไปพักที่โรงแรม แล้วก็ถอดสร้อยคอที่คล้องพระสมเด็จราคาแพงด้วย ไว้ที่หัวนอน ออกไปทำธุระตอนเช้า ไปออกกำลังกาย กินข้าวเสร็จก็กลับเข้ามาในห้อง สร้อยหาย เอ๊ะ ใครเอาไป สงสัยพนักงานทำความสะอาด เพราะว่าในช่วงนั้น มีพนักงานทำความสะอาดเข้าไปจัดเตียง
เขาก็ตามหาว่าใครเป็นพนักงานทำความสะอาด พอพบเห็นเขา ก็ปักใจเชื่อเลยว่าเขาขโมยเอาสร้อยคอไป แล้วก็เฝ้าสังเกตผู้ชายคนนั้น ดูท่วงท่ามีพิรุธ แววตาก็มีพิรุธ ไม่กล้าสบตาเขา ใช่แน่ๆ เลย เอาสร้อยคอของเราไป แต่ปรากฏว่าตอนสายๆ หรือตอนบ่าย ปรากฏว่าเจอสร้อยมันตกอยู่หลังเตียง
พอรู้ว่าชายคนนั้น พนักงานทำความสะอาดไม่ได้ขโมยไป ก็เห็นเขาในภาพใหม่เลย น้ำเสียงเขาก็ไม่ได้มีพิรุธอะไร พูดจาก็ดี อากัปกริยาก็ไม่ได้ผิดปกติอะไร ภาพของพนักงานทำความสะอาดเปลี่ยนไปเลย
ที่จริงก็ไม่ได้เปลี่ยนไปหรอก เขาก็เหมือนเดิม ไม่ว่าตอนเช้า ตอนสาย หรือตอนบ่าย แต่ที่เปลี่ยนไปคือใจของผู้ชายคนนั้น ทีแรกปักใจเชื่อว่าพนักงานทำความสะอาดเป็นขโมย พอคิดแบบนั้นเข้า ก็เห็นแต่พิรุธ แต่พอรู้ว่าเขาไม่ได้ขโมยไป ภาพที่เห็นก็เปลี่ยนไป อันนี้เรียกว่าสังขารเป็นปัจจัยให้เกิดวิญญาณ
แล้วไม่ใช่เฉพาะกรณีแบบนี้เท่านั้น ในชีวิตประจำวันทั่วๆ ไป เวลาเรามีความทุกข์ ความเครียด แล้วเรารู้สึกว่าเป็นเพราะโลกภายนอก เป็นเพราะคนรอบตัว เช่นเราเห็นเขาไปในทางลบทางร้าย เราก็เลยเป็นทุกข์ ให้เราลองสังเกตดูก็ได้ว่า บ่อยครั้งความทุกข์ของเรา มันเกิดจากการที่เราตีความไปในทางลบ หรือว่าปรุงแต่งไปในทางร้ายหรือเปล่า
ฉะนั้นถ้าเรารู้จักหมั่นสังเกต หมั่นทบทวน เอาประสบการณ์ที่เคยเข้าใจผิดที่ตีความในทางลบ หรือว่าเติมแต่งในทางร้าย และทำให้เราเกิดความทุกข์ เกิดความวิตก เกิดความเครียด หรือว่าเกิดความไม่พอใจ เอามาเป็นบทเรียนสอนใจ มันจะช่วยทำให้เรารู้จักทักท้วง
ทักท้วงว่าสิ่งที่เราเห็น ที่จริงมันอาจจะไม่ใช่เป็นความจริงก็ได้ มันอาจจะมีการตีความไปแล้วในทางลบ หรือที่เรามองเห็น มองออกไปข้างนอก อาจจะมีการเติมแต่งไปในทางร้ายก็ได้ ไม่ว่ารับเข้ามาจะเป็นรูป รส กลิ่น เสียงที่ได้ยิน หรือมองออกไป มันมักจะมีการตีความหรือเติมแต่ง
แล้วมันก็ไม่จำเป็นต้องเป็นทางลบ อาจจะเป็นไปในทางบวกก็ได้ อันนี้ที่เขาเรียกว่าอคติ ฉันทาคติก็คือลำเอียงเพราะชอบ อันนี้ก็หมายถึงว่า มองเห็นคลาดเคลื่อนจากความเป็นจริง เพราะว่ามีความชอบ เขาทำอะไรก็ดูดีไปหมด เขาทำอะไรก็ดูถูกต้องไปหมด ทั้งๆ ที่ที่ผิดก็มี ที่พลาดก็มี แต่ว่าไม่เห็นเพราะว่ามองเห็นแต่ด้านดี อันนี้เพราะว่าลำเอียงเพราะชอบ หรือมิฉะนั้นก็ตรงข้าม โทสาคติ ลำเอียงเพราะโกรธ หรือลำเอียงเพราะกลัว ภยาคติ หรือว่าลำเอียงเพราะหลง
อย่างกรณีของพระทิเบต ท่านก็เกิดโทสาคติ ทีแรกเกิดโทสาคติ ก็เลยเห็นเจ้าหน้าที่รักษาความปลอดภัยคนนั้น เหี้ยม ดุ เหมือนผู้ร้าย เหมือนมาเฟีย แต่พอเขามาขอบคุณ เขามาแสดงความเป็นมิตร ก็เปลี่ยนไปเลย ฉันทาคติมาแทนโทสาคติ ก็เห็นเขาเป็นคนที่เป็นมิตร สุภาพเรียบร้อย อันนี้ก็เป็นสิ่งที่เราควรจะสังเกตได้ กับประสบการณ์ของตัวเราเอง ว่ามันเป็นอย่างนั้นบ้างหรือเปล่า จะได้เป็นเครื่องเตือนใจเรา เพื่อไม่ให้เราทุกข์ ที่สร้างขึ้นมาเอง
บางครั้งความทุกข์เราไปมองว่าเป็นเพราะคนนู้นคนนี้ แต่ที่จริงเป็นเพราะการปรุงแต่ง การตีความในทางลบ หรือว่าการเติมแต่งในทางร้ายของเรา
ที่พระพุทธเจ้าตรัสว่า ธรรมทั้งหลายมีใจเป็นใหญ่ มีใจเป็นหัวหน้า สำเร็จได้ด้วยใจ อันนี้ก็เป็นตัวอย่างหนึ่งว่า โลกภายนอกที่เราเห็นผ่าน ตา หู จมูก ลิ้น กาย หรือแม้กระทั่งความคิด มันล้วนแล้วแต่เกิดหรือถูกกำหนดด้วยใจของเรา ถ้าใจเราเป็นลบก็เห็นเป็นลบ ถ้าใจเราเป็นบวกก็เห็นเป็นบวก
ฉะนั้นการกลับมาดูใจของเรา จึงเป็นเรื่องที่สำคัญมาก ถ้าไม่อยากให้เกิดไฟเผาในใจของเรา ก็ต้องกลับมาสำรวจตรวจตา หรือสอดส่องใจของเราว่า มันมีอคติ โทสาคติ ภยาคติหรือเปล่า หรือมันมีการเติมแต่งไปในทางลบทางร้ายหรือเปล่า ไม่อย่างนั้นเราก็จะสร้างหรือก่อทุกข์ขึ้นมาในใจของเรา ทั้งที่ความจริงไม่ได้เป็นอย่างนั้น.
พระอาจารย์ไพศาล วิสาโล
ขอขอบคุณ Visalo.org
-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ f85b9c2c:d190bcff
2025-06-01 00:43:38
@ f85b9c2c:d190bcff
2025-06-01 00:43:38Avoid it if you’re sensitive.

Haha 😂, just wanted to get your attention.
If you’re reading this, congrats your amongst those who survived to see this message. It doesn’t matter if you’re depressed, sad, angry at someone or you missed something. Come on man, being alive is already a win for you.
Smile, You deserve it.
Yes, I know the world is cruel and very unfair. But remember, you can’t fight all those battles alone. That’s why we ask God to take care of it. But hey, today is Sunday.A blessed day for the Christians. Go ahead smile 😊, you deserve it. You managed to wake up today while some didn’t. You should be grateful for that. It’s a blessing to see tomorrow. You don’t know what today holds.
I just want to remind you that, you deserve the whole world. Go out there, chase your dreams, don’t let them die in your comfort zone. And remember, always wear a smile on that pretty face of yours. You deserve the world.
-
 @ bcbb3e40:a494e501
2025-03-31 15:41:53
@ bcbb3e40:a494e501
2025-03-31 15:41:53El 7 de febrero de 2025, Donald Trump firmó una orden ejecutiva que establecía una «Oficina de la Fe» en la Casa Blanca, dirigida por su asesora espiritual Paula White-Cain, la pastora de esa «teología de la prosperidad» (prosperity theology) que predica el «Evangelio de la salud y la riqueza» (health and wealth gospel^1). Investida de su nueva función, la reverenda pastora dijo: «Tengo la autoridad para declarar a la Casa Blanca un lugar santo. Es mi presencia la que la santifica»[^2]. Los siete rabinos del «Sanedrín Naciente» —la corte suprema que guiará a Israel cuando se reconstruya el Templo de Jerusalén— enviaron conmovedoras felicitaciones al presidente Trump por el establecimiento de esta Oficina. «Expresamos nuestra sincera gratitud —se lee en el mensaje oficial enviado a Trump desde el Monte Sión— por llevar la fe a la vanguardia de la cultura estadounidense y mundial mediante el establecimiento de la Oficina de la Fe en la Casa Blanca. Su reconocimiento de la importancia de la religión en la vida pública es un paso hacia la restauración de los valores morales y del liderazgo espiritual en el mundo[^3]. La carta del «Sanedrín Naciente», que augura el éxito a la «misión divina» del presidente estadounidense, reproduce las dos caras de una «moneda del Templo», acuñada en 2017 para celebrar el traslado de la embajada estadounidense a Jerusalén y, simultáneamente, el centenario de la Declaración Balfour. En el anverso se ven los perfiles de Donald Trump y Ciro el Grande, a quien la tradición judía atribuye la reconstrucción del templo destruido por los babilonios, con la inscripción (en hebreo e inglés) «Cyrus —Balfour— Trump Declaration 1917-2017»; en el reverso está la imagen del Templo de Jerusalén[^4]. Otra moneda, que lleva los perfiles de Trump y Ciro en el anverso y los de Trump y Netanyahu en el reverso, fue acuñada en 2018 para celebrar el septuagésimo aniversario de la independencia del «Estado de Israel»; se observa dos inscripciones en hebreo e inglés: «Y Él me encargó construirle una casa en Jerusalén» y «Guerra de los Hijos de la Luz contra los Hijos de las Tinieblas».
El tema de la «guerra de los Hijos de la Luz contra los Hijos de las Tinieblas» ha tenido una difusión particular en el imaginario y la propaganda trumpista. El 7 de junio de 2020, monseñor Carlo Maria Viganò, ex nuncio de la Santa Sede en los Estados Unidos, escribió una carta al presidente Donald Trump que comenzaba así: «Estamos asistiendo en los últimos meses a la formación de dos bandos, que los definiría bíblicos: los hijos de la luz y los hijos de las tinieblas»[^5]. El 1 de enero de 2021, el agitprop estadounidense Steve Bannon declaró en una entrevista con Monseñor Viganò: «Esta es una batalla de época entre los hijos de la Luz y los hijos de las Tinieblas»[^6].
Son numerosos los judíos sionistas que están en el círculo del presidente Trump: además de su hija Ivanka (convertida en 2009) y su yerno Jared Kushner (entonces Consejero Anciano del Presidente), el 19 de noviembre de 2024 el «The Jerusalem Post»[^7] publicó una lista de los más influyentes: Stephen Miller, subdirector del staff de la Casa Blanca y consejero de Seguridad Nacional de Estados Unidos; David Melech Friedman, a quien en 2016 Trump nombró embajador en Israel; el multimillonario «filántropo» Steven Charles Witkoff, enviado especial de Estados Unidos a Oriente Medio; Miriam Adelson, directora del periódico «Israel Hayom», clasificada por Bloomberg Billionaires como la quinta mujer más rica del mundo (con un patrimonio neto de 32,400 millones de dólares), financiadora de iniciativas políticas conservadoras en Estados Unidos e Israel; el banquero Boris Epshteyn, consejero estratégico de la campaña presidencial de Trump en 2020; Howard Williams Lutnick, presidente de la Cantor Fitzgerald del Grupo BGC, financista de las campañas presidenciales de Donald Trump en 2020 y 2024, ahora secretario de Comercio; la modelo Elizabeth Pipko, portavoz nacional del Partido Republicano y creadora de un «museo interactivo virtual» sobre la «Shoah» como parte del proyecto de Lest People Forget, cuyo objetivo es combatir el «antisemitismo» y la «negacionismo»; Lee Michael Zeldin, miembro republicano de la Cámara de Representantes por el estado de Nueva York del 2015 al 2023 y actualmente administrador de la EPA (Environmental Protection Agency); la columnista Laura Elizabeth Loomer, «orgullosamente islamófoba», activa patrocinadora de Trump en la campaña para las elecciones presidenciales de 2024; Sidney Ferris Rosenberg, influyente presentador de radio y periodista deportivo; William Owen Scharf, Asistente del Presidente y secretario del personal de la Casa Blanca; Marc Jeffrey Rowan, «filántropo» con un patrimonio neto valorado por Forbes en ocho mil ochocientos millones de dólares.
Además de estos, cabe mencionar al popular presentador de radio Mark Levin quien, en diciembre de 2019, durante la celebración de la fiesta de Janucá en la Casa Blanca, saludó a Donald Trump como «el primer presidente judío de los Estados Unidos»[^8]. Según un funcionario de alto nivel de la Casa Blanca, Donald Trump se convirtió al judaísmo dos años antes en la sinagoga de la secta Jabad Lubavitch en la ciudad de Nueva York. David Elias Goldberg, miembro del Jewish Center of Antisemitic Study, también entrevistó al funcionario, para quien «Trump fue “instado” por su hija Ivanka y su yerno Jared Kushner para abrazar la fe. Inicialmente, Trump se habría mostrado reacio, considerando que esto podría enfriar el apoyo del electorado evangélico». Luego, informa «Israel Today News», «cambió de opinión y se convirtió oficialmente a principios de 2017. La ceremonia se llevó a cabo en privado y se guardó celosamente durante casi dos años»[^9]. Pero ya en septiembre de 2015, el rabino millonario Kirt Schneider, invitado a la Trump Tower de Nueva York, había impuesto sus manos sobre la cabeza de Donald Trump y lo había bendecido en hebreo e inglés, declarando: «Las únicas dos naciones que tienen una relación privilegiada con Dios son Israel y los Estados Unidos de América»[^10].
El 7 de octubre de 2024, en el aniversario de la operación de Hamas «Diluvio de Al-Aqsa», Trump fue acompañado por un «superviviente de la Shoah» a la tumba de Menachem Mendel Schneerson, séptimo y último Rabino de los Hasidim de la secta Jabad Lubavitch, que en 1991 declaró a sus seguidores: «He hecho todo lo posible para provocar el arribo del Mesías, ahora les paso a ustedes esta misión; hagan todo lo que puedan para que Él venga»^11. En relación al evento mesiánico, el eminente rabino Yekutiel Fish atribuyó una misión decisiva a Trump: «Todo el mundo está centrado en Gaza, pero esa es solo una parte de la agenda del fin de los tiempos, que tiene a los judíos viviendo en las fronteras profetizadas de Israel; la Torá incluye explícitamente a Gaza. Lo que Trump está haciendo es limpiar Gaza de todos los odiadores de Israel. No podrán estar en Israel después de la venida del Mesías. (...) Esto incluirá a Gaza, la mitad del Líbano y gran parte de Jordania. Y vemos que casi lo hemos logrado. Siria cayó. Líbano está medio destruido. Gaza está destrozada. El escenario está casi listo para el Mesías. Pero, ¿cómo pueden los palestinos estar aquí cuando vayamos a recibir al Mesías? El Mesías necesita que alguien se ocupe de esto, y en este caso, es Donald Trump. Trump está simplemente llevando a cabo las tareas finales necesarias antes de que el Mesías sea revelado»[^12].
Esta inspiración escatológica está presente en las palabras de Pete Brian Hegseth, el pintoresco exponente del «Reconstruccionismo Cristiano»[^13] a quien Trump nombró secretario de Defensa. En un discurso pronunciado en 2019 en el Hotel Rey David de Jerusalén, con motivo de la conferencia anual del canal Arutz Sheva (Israel National News), Hegseth enalteció el «vínculo eterno» entre Israel y Estados Unidos, y enumeró los «milagros» que atestiguan el «apoyo divino» a la causa sionista, el último de los cuales será la reconstrucción del Templo judío en la zona donde actualmente se encuentra la mezquita de al-Aqsa: «La dignidad de capital adquirida por Jerusalén —dijo— fue un milagro, y no hay razón por la cual no sea posible el milagro de la restauración del Templo en el Monte del Templo».[^14]
Es conocido que el fundamentalismo evangélico pro-sionista[^15] comparte con el judaísmo la creencia en que la construcción del tercer Templo de Jerusalén marcará el comienzo de la era mesiánica; cuando la administración Trump trasladó la embajada de Estados Unidos a Jerusalén en 2017, Laurie Cardoza-Moore, exponente del evangelismo sionista, saludó así la «obediencia de Trump a la Palabra de Dios» en «Haaretz»: «Al establecer la Embajada en Jerusalén, el presidente Donald Trump está implementando una de las iniciativas históricas de dimensión bíblica en su presidencia. Al igual que muchos judíos en Israel y en todo el mundo, los cristianos reconocen el vínculo de los judíos con la Biblia a través del nombre de Jerusalén como la capital del antiguo Israel, así como el sitio del Primer y Segundo Templos. Según los profetas Ezequiel, Isaías y el apóstol Juan del Nuevo Testamento, todos los israelíes esperan la reconstrucción del Tercer Templo»[^16]. El 22 de mayo del mismo año, Donald Trump, acompañado de su esposa Melania, de su hija Ivanka y su yerno Jared Kushner, fue el primer presidente de los Estados Unidos en ejercicio en acudir al Muro de las Lamentaciones, anexionado ilegalmente a la entidad sionista.
En 2019, la administración Trump confirmó la posición de Estados Unidos al enviar en visita oficial para Jerusalén a Mike Pompeo, un secretario de Estado que —ironía de la Historia— lleva el mismo nombre del general romano que asaltó la ciudad en el año 63 a.C. «Por primera vez en la historia, un secretario de Estado norteamericano visitó la Ciudad Vieja de Jerusalén en compañía de un alto político israelí. Fue una visita histórica que reforzó las expectativas israelíes y constituyó un reconocimiento tácito de la soberanía israelí sobre el sitio del Monte del Templo y la Explanada de las Mezquitas. (…) Mike Pompeo, acompañado por el primer ministro Benjamin Netanyahu y el embajador de Estados Unidos en Israel, David Friedman, también visitó el túnel del Muro de las Lamentaciones y la sinagoga ubicada bajo tierra, en el presunto lugar del santuario del Templo[^17], donde se le mostró una maqueta del futuro Templo[^18]. En el transcurso de una entrevista concedida durante la fiesta del Purim (que celebra el exterminio de la clase política persa, ocurrido hace 2500 años), el secretario de Estado insinuó que «el presidente Donald Trump puede haber sido enviado por Dios para salvar al pueblo judío y que confiaba en que aquí el Señor estaba obrando»[^19].
Como observa Daniele Perra, en este mismo número de «Eurasia», el «mito movilizador» del Tercer Templo, atribuible a los «mitos teológicos» señalados por Roger Garaudy como mitos fundadores de la entidad sionista, «atribuye al judaísmo una especie de función sociológica de transmisión y proyección del conflicto palestino-israelí hacia el resto del mundo y confiere una inspiración apocalíptica al momento geopolítico actual».
|Info|| |:-|:-| |Autor| Claudio Mutti | |Fuente| I "Figli della Luce" alla Casa Bianca | |Fecha| 8/Mar/2025 | |Traducción| Francisco de la Torre |
[^2]: The White House, President Trump announces appointments to the White House Faith Office https://www.whitehouse.gov,, 7 de febrero de 2025; Trump establece la Oficina de la Fe con una foto de «La Última Cena» | Fue dirigida por la controvertida predicadora Paula White, https://www.tgcom24.mediaset.it, 10 de febrero de 2025.
[^3]: «We extend our heartfelt gratitude for bringing faith to the forefront of American and global culture through the establishment of the Faith Office in the White House. Your recognition of the importance of religion in public life is a step toward restoring moral values and spiritual leadership in the world» (Letter from the Nascent Sanhedrin to President Donald J. Trump, Jerusalem, Wednesday, February 12, 2025).
[^4]: Israeli group mints Trump coin to honor Jerusalem recognition, «The Times of Israel», https://www.timesofisrael.com, 28-2-2018.
[^5]: Mons. Viganò — Siamo nella battaglia tra figli della luce e figli delle tenebre, https://www.italiador.com, 7-6-2020
[^6]: TRANSCRIPT: Steve Bannon’s ‘War Room’ interview with Abp. Viganò, lifesitenews.com, 4-1-2021. Sulle origini e sulla fortuna di questo tema cfr. C. Mutti, Le sètte dell’Occidente, «Eurasia», 2/2021, pp. 12-15. (https://www.eurasia-rivista.com/las-sectas-de-occidente/)
[^7]: Luke Tress, The who’s who of Jews in Trump’s inner circle?, «The Jerusalem Post», https://www.jpost.com, 19-11-2024.
[^8]: Radio Talk Show Host Mark Levin Calls President Trump «the First Jewish President of the United States», https://www.c-span.org, 11-12-2019.
[^9]: «However, he had a change of heart and officially converted in early 2017. The ceremony was held in private, and closely guarded for nearly two years» (Donald Trump converted to Judaism two years ago, according to White House official, https://israeltodaynews.blogspot.com/2019/02).
[^10]: «El rabino Kirt Schneider (...) es un millonario judío, una figura televisiva de los “judíos mesiánicos”. Sus emisiones televisivas semanales son emitidas por más de treinta canales cristianos en unos doscientos países; entre ellos, los canales “Yes” y “Hot” en Israel. Solo en Estados Unidos, sus emisiones atraen a 1.600.000 telespectadores cada semana. Kirt Schneider dirige un imperio de telecomunicaciones que tiene un millón y medio de seguidores en Facebook, X (antes Twitter) y YouTube» (Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, Edizioni all'insegna del Veltro, Parma 2025, p. 31).
[^12]: «Everyone is focused on Gaza, but that is only one part of the end-of-days agenda, which has the Jews living in Israel’s prophesied borders. The Torah explicitly includes Gaza. What Trump is doing is cleaning out Gaza of all the haters of Israel. They cannot be in Israel after the Messiah comes. (…) This will include Gaza, half of Lebanon, and much of Jordan. And we see that we are almost there. Syria fell. Lebanon is half gone. Gaza is ripped up. The stage is nearly set for Messiah. But how can the Palestinians be here when we go to greet the Messiah? The Messiah needs someone to take care of this, and in this case, it is Donald Trump. Trump is merely carrying out the final tasks needed before Messiah is revealed» (Adam Eliyahu Berkowitz, Trump’s Gaza Plan is «The Final task before Messiah», https://israel365news.com, 5-2-2025).
[^13]: «A day after Hegseth was announced for the Cabinet position, Brooks Potteiger, a pastor within the Communion of Reformed Evangelical Churches (CREC), posted on X that Hegseth is a member of the church in good standing. The CREC, a denomination of Christian Reconstructionism, is considered by some academics to be an extremist, Christian supremacist movement» (Shannon Bond e altri, What’s behind defense secretary pick Hegseth’s war on ‘woke’, https://www.npr.org, 14-11-2024.
[^14]: «The decoration of Jerusalem as a capital was a miracle, and there is no reason why the miracle of the re-establishment of Temple on the Temple Mount is not possible» (Pete Hegseth at Arutz Sheva Conference, youtube.com). Cfr. Daniele Perra, Paleotrumpismo, neotrumpismo e post-trumpismo, in: AA. VV., Trumpismo, Cinabro Edizioni, Roma 2025, pp. 22-23.
[^15]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., págs. 82 a 96.
[^16]: «We American Christians Welcome Trump’s Obedience to God’s Word on Jerusalem», «Haaretz», 6-12-2017.
[^17]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., pág. 97.
[^18]: Pompeo en visite historique au mur Occidental aux côtés de Netanyahu et Friedman, «The Times of Israel», https://fr.timesofisrael.com, 21-3-2019.
[^19]: Pompeo says Trump may have been sent by God to save Jews from Iran, «The Times of Israel», 22-3-2019.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ a5ee4475:2ca75401
2025-05-15 14:44:45
@ a5ee4475:2ca75401
2025-05-15 14:44:45lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas, portanto as versões mais recentes delas só estão visíveis no Amethyst por causa da ferramenta de edição.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guk62czu
Iniciativas de Bitcoin
nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2nvmn5va9x2nrxfd2k5smyf3ux7vesd9znyqxygt4
Profissionais Brasileiros no Nostr
nostr:naddr1qq24qmnkwe6y67zlxgc4sumrxpxxce3kf9fn2qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqp65wp8uedu
Comunidades em Português no Nostr
nostr:naddr1qq2hwcejv4ykgdf3v9gxykrxfdqk753jxcc4gqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gu455fm3
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Jogos de Código Aberto
Open Source Games nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhz8x40v0
Itens Úteis com Esquemas Disponíveis
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Formatação de Texto em Markdown
(Amethyst, Yakihone e outros) nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2454m8dfzn26z4f34kvu6fw4rysnrjxfm42wfpe90
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 7f6db517:a4931eda
2025-05-31 15:01:42
@ 7f6db517:a4931eda
2025-05-31 15:01:42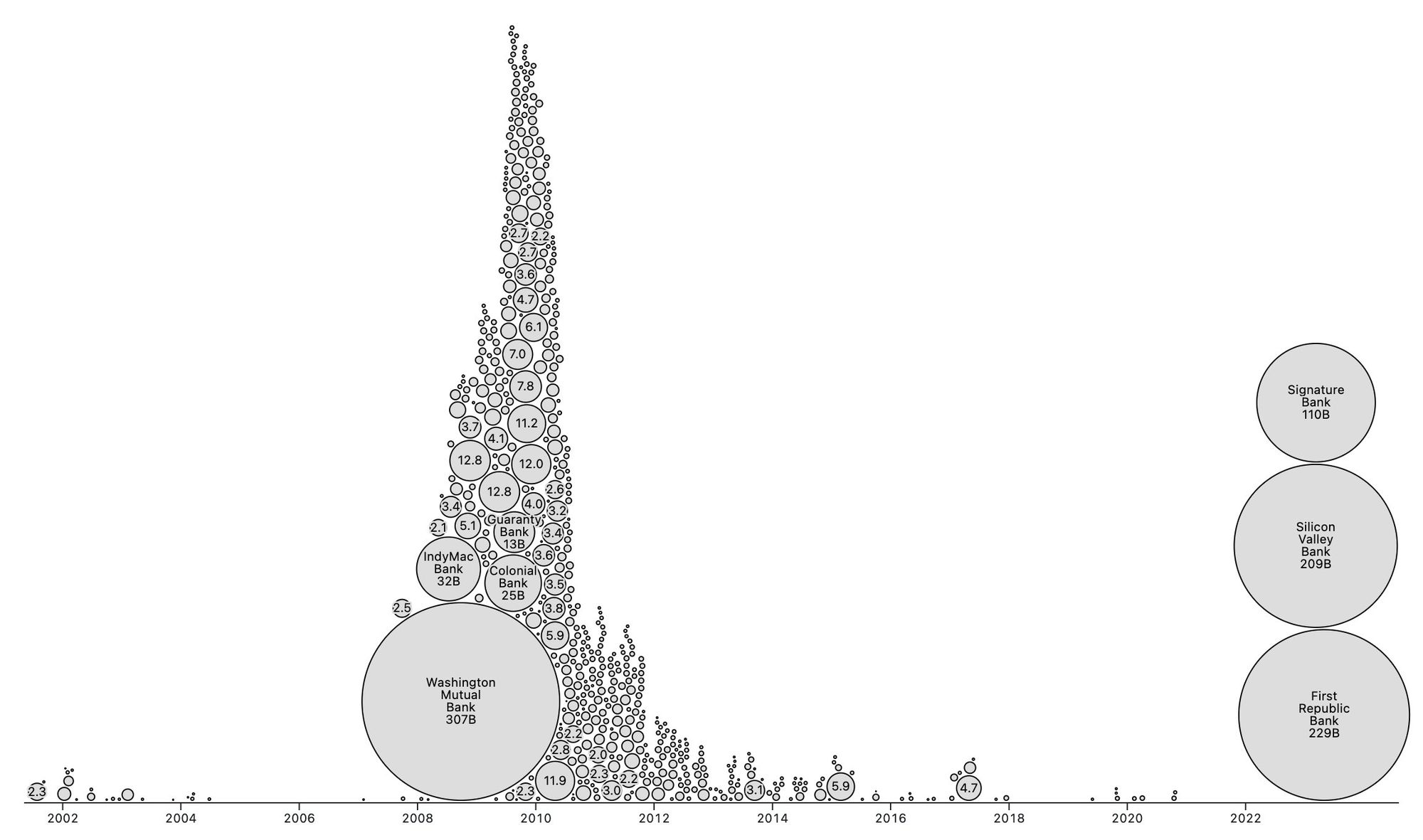
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ c1e9ab3a:9cb56b43
2025-05-27 16:19:06
@ c1e9ab3a:9cb56b43
2025-05-27 16:19:06Star Wars is often viewed as a myth of rebellion, freedom, and resistance to tyranny. The iconography—scrappy rebels, totalitarian stormtroopers, lone smugglers—suggests a deep anti-authoritarian ethos. Yet, beneath the surface, the narrative arc of Star Wars consistently affirms the necessity, even sanctity, of central authority. This blog entry introduces the question: Is Star Wars fundamentally a celebration of statism?
Rebellion as Restoration, Not Revolution
The Rebel Alliance’s mission is not to dismantle centralized power, but to restore the Galactic Republic—a bureaucratic, centrally governed institution. Characters like Mon Mothma and Bail Organa are high-ranking senators, not populist revolutionaries. The goal is to remove the corrupt Empire and reinstall a previous central authority, presumed to be just.
- Rebels are loyalists to a prior state structure.
- Power is not questioned, only who wields it.
Jedi as Centralized Moral Elites
The Jedi, often idealized as protectors of peace, are unelected, extra-legal enforcers of moral and military order. Their authority stems from esoteric metaphysical abilities rather than democratic legitimacy.
- They answer only to their internal Council.
- They are deployed by the Senate, but act independently of civil law.
- Their collapse is depicted as tragic not because they were unaccountable, but because they were betrayed.
This positions them as a theocratic elite, not spiritual anarchists.
Chaos and the Frontier: The Case of the Cantina
The Mos Eisley cantina, often viewed as a symbol of frontier freedom, reveals something darker. It is: - Lawless - Violent - Culturally fragmented
Conflict resolution occurs through murder, not mediation. Obi-Wan slices off a limb; Han shoots first—both without legal consequence. There is no evidence of property rights, dispute resolution, or voluntary order.
This is not libertarian pluralism—it’s moral entropy. The message: without centralized governance, barbarism reigns.
The Mythic Arc: Restoration of the Just State
Every trilogy in the saga returns to a single theme: the fall and redemption of legitimate authority.
- Prequels: Republic collapses into tyranny.
- Originals: Rebels fight to restore legitimate order.
- Sequels: Weak governance leads to resurgence of authoritarianism; heroes must reestablish moral centralism.
The story is not anti-state—it’s anti-bad state. The solution is never decentralization; it’s the return of the right ruler or order.
Conclusion: The Hidden Statism of a Rebel Myth
Star Wars wears the costume of rebellion, but tells the story of centralized salvation. It: - Validates elite moral authority (Jedi) - Romanticizes restoration of fallen governments (Republic) - Portrays decentralized zones as corrupt and savage (outer rim worlds)
It is not an anarchist parable, nor a libertarian fable. It is a statist mythology, clothed in the spectacle of rebellion. Its core message is not that power should be abolished, but that power belongs to the virtuous few.
Question to Consider:
If the Star Wars universe consistently affirms the need for centralized moral and political authority, should we continue to see it as a myth of freedom? Or is it time to recognize it as a narrative of benevolent empire? -
 @ f85b9c2c:d190bcff
2025-06-01 00:37:22
@ f85b9c2c:d190bcff
2025-06-01 00:37:22Fully devoted to Jesus: Mark 10:28 (NIV) Then Peter spoke up, “We have left everything to follow you!”
As a Christian, you received Jesus into your life because the Holy Spirit revealed to you the glory of God in Jesus and your heart melted at His sight.

You became aware of your lostness, wickedness, and hopelessness without a savior so you surrendered to Him and asked him to save you. You asked Him to become the lord of your life. The first apostles were clear about something, they had to surrender everything in order to follow Jesus. When they yielded to Jesus as Lord it meant He was Lord of all.
Yes, everything. Yes, all.
They surrendered work, possessions, essentially their lives — Mark 1:18 (NIV) At once they left their nets and followed him. They were literally fully devoted to Jesus.
They modeled 1 Kings 8:61 Let your heart therefore be wholly devoted to the Lord our God, to walk in His statutes and to keep His commandments, as at this day.”It might not look identical to the apostles calling but it should have the same motive behind it. When Jesus becomes your Lord, He should have complete control over your, . Relationship
.Money
.Possessions
.Career
.Kids
.Time
.Mouth
.Mind
.Body
.Everything
Have a blissful Sunday 🙏.
-
 @ 7f6db517:a4931eda
2025-05-31 11:01:17
@ 7f6db517:a4931eda
2025-05-31 11:01:17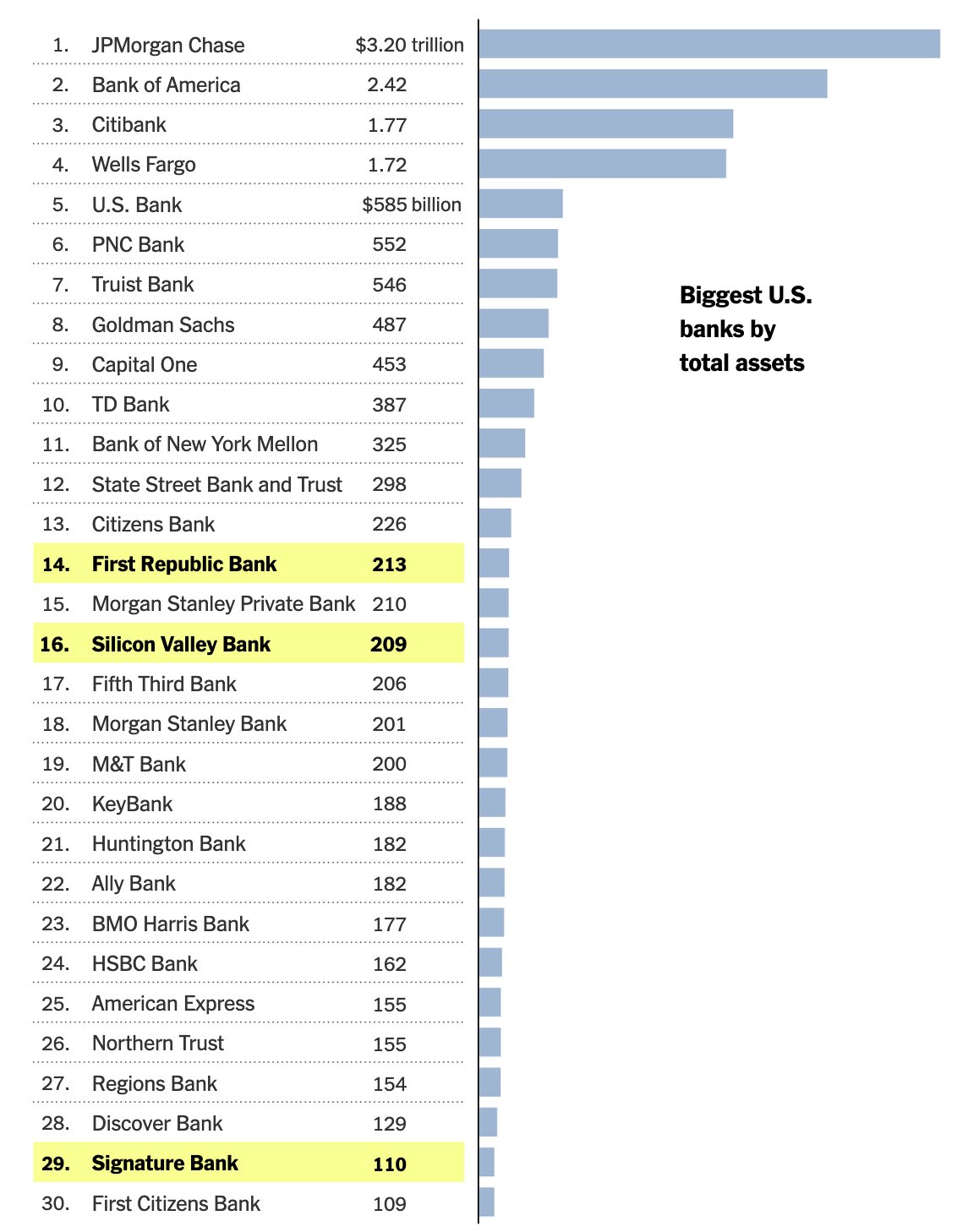
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 43baaf0c:d193e34c
2025-05-27 14:08:02
@ 43baaf0c:d193e34c
2025-05-27 14:08:02During the incredible Bitcoin Filmfest, I attended a community session where a discussion emerged about zapping and why I believe zaps are important. The person leading the Nostr session who is also developing an app that’s partially connected to Nostr mentioned they wouldn’t be implementing the zap mechanism directly. This sparked a brief but meaningful debate, which is why I’d like to share my perspective as an artist and content creator on why zaps truly matter.
Let me start by saying that I see everything from the perspective of an artist and creator, not so much from a developer’s point of view. In 2023, I started using Nostr after spending a few years exploring the world of ‘shitcoins’ and NFTs, beginning in 2018. Even though I became a Bitcoin maximalist around 2023, those earlier years taught me an important lesson: it is possible to earn money with my art.
Whether you love or hate them, NFTs opened my eyes to the idea that I could finally take my art to the next level. Before that, for over 15 years, I ran a travel stock video content company called @traveltelly. You can read the full story about my journey in travel and content here: https://yakihonne.com/article/traveltelly@primal.net/vZc1c8aXrc-3hniN6IMdK
When I truly understood what Bitcoin meant to me, I left all other coins behind. Some would call that becoming a Bitcoin maximalist.
The first time I used Nostr, I discovered the magic of zapping. It amazed me that someone who appreciates your art or content could reward you—not just with a like, but with real value: Bitcoin, the hardest money on earth. Zaps are small amounts of Bitcoin sent as a sign of support or appreciation. (Each Bitcoin is divisible into 100 million units called Satoshis, or Sats for short—making a Satoshi the smallest unit of Bitcoin recorded on the blockchain.)
 The Energy of Zaps
The Energy of ZapsIf you’re building an app on Nostr—or even just connecting to it—but choose not to include zaps, why should artists and content creators share their work there? Why would they leave platforms like Instagram or Facebook, which already benefit from massive network effects?
Yes, the ability to own your own data is one of Nostr’s greatest strengths. That alone is a powerful reason to embrace the protocol. No one can ban you. You control your content. And the ability to post once and have it appear across multiple Nostr clients is an amazing feature.
But for creators, energy matters. Engagement isn’t just about numbers—it’s about value. Zaps create a feedback loop powered by real appreciation and real value, in the form of Bitcoin. They’re a signal that your content matters. And that energy is what makes creating on Nostr so special.
But beyond those key elements, I also look at this from a commercial perspective. The truth is, we still can’t pay for groceries with kisses :)—we still need money as a medium of exchange. Being financially rewarded for sharing your content gives creators a real incentive to keep creating and sharing. That’s where zaps come in—they add economic value to engagement.
A Protocol for Emerging Artists and Creators
I believe Nostr offers a great starting point for emerging artists and content creators. If you’re just beginning and don’t already have a large following on traditional social media platforms, Nostr provides a space where your work can be appreciated and directly supported with Bitcoin, even by a small but engaged community.
On the other hand, creators who already have a big audience and steady income on platforms like Instagram or YouTube may not feel the urgency to switch. This is similar to how wealthier countries are often slower to understand or adopt Bitcoin—because they don’t need it yet. In contrast, people in unbanked regions or countries facing high inflation are more motivated to learn how money really works.
In the same way, emerging creators—those still finding their audience and looking for sustainable ways to grow—are often more open to exploring new ecosystems like Nostr, where innovation and financial empowerment go hand in hand.
The same goes for Nostr. After using it for the past two years, I can honestly say: without Nostr, I wouldn’t be the artist I am today.
Nostr motivates me to create and share every single day. A like is nice but receiving a zap, even just 21 sats, is something entirely different. Once you truly understand that someone is willing to pay you for what you share, it’s no longer about the amount. It’s about the magic behind it. That simple gesture creates a powerful, positive energy that keeps you going.
Even with Nostr’s still relatively small user base, I’ve already been able to create projects that simply wouldn’t have been possible elsewhere.
Zaps do more than just reward—they inspire. They encourage you to keep building your community. That inspiration often leads to new projects. Sometimes, the people who zap you become directly involved in your work, or even ask you to create something specifically for them.
That’s the real value of zaps: not just micro-payments, but micro-connections sparks that lead to creativity, collaboration, and growth.
Proof of Work (PoW)
Over the past two years, I’ve experienced firsthand how small zaps can evolve into full art projects and even lead to real sales. Here are two examples that started with zaps and turned into something much bigger:
Halving 2024 Artwork
When I started the Halving 2024 project, I invited people on Nostr to be part of it. 70 people zapped me 2,100 sats each, and in return, I included their Npubs in the final artwork. That piece was later auctioned and sold to Jurjen de Vries for 225,128 Sats.
Magic Internet Money
For the Magic Internet Money artwork, I again invited people to zap 2,100 sats to be included. Fifty people participated, and their contributions became part of the final art frame. The completed piece was eventually sold to Filip for 480,000 sats.
These examples show the power of zaps: a simple, small act of appreciation can turn into larger engagement, deeper connection, and even the sale of original art. Zaps aren’t just tips—they’re a form of collaboration and support that fuel creative energy.
I hope this article gives developers a glimpse into the perspective of an artist using Nostr. Of course, this is just one artist’s view, and it doesn’t claim to speak for everyone. But I felt it was important to share my Proof of Work and perspective.
For me, Zaps matter.
Thank you to all the developers who are building these amazing apps on Nostr. Your work empowers artists like me to share, grow, and be supported through the value-for-value model.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 1d7ff02a:d042b5be
2025-05-27 02:56:33
@ 1d7ff02a:d042b5be
2025-05-27 02:56:33ສຳລັບໃຜທີ່ຍັງບໍ່ເຂົ້າໃຈ Bitcoin ຢ່າງແທ້ຈິງ, ຫມາຍຄວາມວ່າເຈົ້າຍັງບໍ່ທັນເຂົ້າໃຈວ່າເງິນແມ່ນຫຍັງ, ໃຜເປັນຜູ້ສ້າງມັນ, ແລະເປັນຫຍັງມະນຸດຈຶ່ງຕ້ອງການເງິນ. ມັນເປັນເລື່ອງ scam ທີ່ລະບົບການສຶກສາບໍ່ໄດ້ສອນເລື່ອງສຳຄັນນີ້, ໃນຂະນະທີ່ພວກເຮົາໃຊ້ເວລາເກືອບທັງຊີວິດເພື່ອຫາເງິນ. ດັ່ງນັ້ນ, ຂໍແນະນຳໃຫ້ follow the money ແລະ ສຶກສາ Bitcoin ຢ່າງຈິງຈັງ.
Why Bitcoin Matters
Saving is the greatest discovery in human history
ກ່ອນທີ່ມະນຸດຈະຮຽນຮູ້ການເກັບອອມ, ພວກເຮົາເປັນພຽງແຕ່ສັດທີ່ມີຊີວິດຢູ່ແບບວັນຕໍ່ວັນ. ການປະຢັດແມ່ນສິ່ງທີ່ເຮັດໃຫ້ມະນຸດແຕກຕ່າງຈາກສັດອື່ນ — ຄວາມສາມາດໃນການຄິດກ່ຽວກັບອະນາຄົດ ແລະ ເກັບໄວ້ສຳລັບມື້ຫຼັງ.
Saving created civilization itself
ບໍ່ມີການເກັບອອມ, ບໍ່ມີການສ້າງເມືອງ, ບໍ່ມີວິທະຍາສາດ, ບໍ່ມີສິລະປະ. ທຸກສິ່ງທີ່ເຮົາເອີ້ນວ່າ "ຄວາມກ້າວໜ້າ" ແມ່ນມາຈາກຄວາມສາມາດໃນການຮູ້ຈັກເກັບອອມ.
Money is the greatest creation in human history
ມັນເປັນເຄື່ອງມືທີ່ເຮັດໃຫ້ອາລະຍະທຳມະນຸດກ້າວໜ້າມາເຖິງທຸກມື້ນີ້ ເງິນ ເປັນເຄື່ອງມືທີ່ດີທີ່ສຸດທີ່ມະນຸດໃຊ້ໃນການເກັບອອມ.
Bitcoin is the best money ever created
ມັນແມ່ນເງິນທີ່ສົມບູນແບບທີ່ສຸດທີ່ມະນຸດເຄີຍສ້າງຂຶ້ນມາ. ບໍ່ມີໃຜສາມາດ ຄວບຄຸມ, ຈັດການ, ທຳລາຍ ແລະ ມີຈຳກັດຢ່າງແທ້ຈິງ ຄືກັບເວລາໃນຊີວິດ.
Bitcoin ຄືກັບ black hole
ທີ່ຈະດູດເອົາມູນຄ່າທັງໝົດຈາກລະບົບການເງິນທີ່ເສຍຫາຍມັນຈະດູດເອົາຄວາມໝັ້ນຄົງແລະມູນຄ່າມາສູ່ຕົວມັນເອງ. ທຸກສິ່ງທີ່ມີມູນຄ່າຈະໄຫຼເຂົ້າສູ່ Bitcoin ໃນທີ່ສຸດ.
Bitcoin ຄືກັບສາດສະໜາພຸດທີ່ຄົ້ນພົບຄວາມຈິງ
ມັນເຮັດໃຫ້ເຂົ້າໃຈຕົ້ນຕໍບັນຫາຂອງລະບົບການເງິນປະຈຸບັນ ແລະ ເກີດເປັນບັນຫາຫລາຍໆຢ່າງໃນສັງຄົມ ດັ່ງກັບພະພຸດທະເຈົ້າທີ່ເຂົ້າໃຈທຸກ ແລະ ເຫດຂອງການເກີດທຸກ.
Bitcoin ຄືອິດສະຫຼະພາບ
ເງິນຄືອຳນາດ, ເງິນຄືສິ່ງຄວບຄຸມພຶດຕິກຳຂອງມະນຸດ ເມື່ອເຮົາມີເງິນທີ່ຮັກສາມູນຄ່າໄດ້ ແລະ ຄວບຄຸມບໍ່ໄດ້ ຈຶ່ງຈະມີຄວາມອິດສະຫຼະທາງຄວາມຄິດ, ການສະແດງອອກ, ແລະ ອຳນາດໃນການເລືອກ.
ຫນີ້ສິນທີ່ມະນຸດສ້າງຂຶ້ນໃນປະຈຸບັນນີ້ ໃຊ້ເວລາອີກພັນປີກໍ່ໄຊ້ຫນີ້ບໍ່ໝົດ
ມັນບໍ່ມີທາງອອກ ແລະ ກຳລັງມຸ່ງໜ້າສູ່ການລົ່ມສະລາຍຢ່າງຮ້າຍແຮງ. Bitcoin ຄືແສງສະຫວ່າງທີ່ຈະຊ່ວຍປ້ອງກັນບໍ່ໃຫ້ມະນຸດເຂົ້າສູ່ຍຸກມືດມົວອີກຄັ້ງ.
Bitcoin cannot steal your time
ມັນບໍ່ສາມາດຖືກສ້າງຂຶ້ນຈາກຄວາມຫວ່າງເປົ່າ. ທຸກ Bitcoin ຕ້ອງໃຊ້ພະລັງງານແລະເວລາທີ່ແທ້ຈິງໃນການສ້າງ.
Bitcoin ຄືປະກັນໄພທີ່ປ້ອງກັນການບໍລິຫານທີ່ຜິດພາດ
ມັນຊ່ວຍປ້ອງກັນຄວາມເສື່ອມໂຊມຂອງເງິນຕາ, ເສດຖະກິດທີ່ຕົກຕ່ຳ ແລະ ນະໂຍບາຍທີ່ຜິດພາດ, Bitcoin ຈະປົກປ້ອງຄຸນຄ່າຂອງເຈົ້າ.
Bitcoin is going to absorb the world's value
ໃນທີ່ສຸດ, Bitcoin ຈະກາຍເປັນທີ່ເກັບຮັກສາມູນຄ່າຂອງໂລກທັງໝົດ. ມັນຈະດູດເອົາຄວາມມັ່ງຄັ່ງຈາກທຸກຊັບສິນ, ທຸກລາຄາ, ແລະທຸກການລົງທຶນ.
Exit The Matrix
ພວກເຮົາອາໄສຢູ່ໃນ Matrix ທາງດ້ານການເງິນ. ທຸກໆມື້ພວກເຮົາຕື່ນຂຶ້ນມາແລະໄປເຮັດວຽກ, ຄິດວ່າເຮົາກຳລັງສ້າງອະນາຄົດໃຫ້ຕົວເອງ. ແຕ່ຄວາມຈິງແລ້ວ, ພວກເຮົາພຽງແຕ່ກຳລັງໃຫ້ພະລັງງານແກ່ລະບົບທີ່ຂູດເອົາຄຸນຄ່າຈາກພວກເຮົາທຸກວິນາທີ. Bitcoin is the red pill — ມັນຈະເປີດຕາໃຫ້ເຈົ້າເຫັນຄວາມຈິງຂອງໂລກການເງິນ. Central banks are the architects of this Matrix — ພວກເຂົາສ້າງເງິນຈາກຄວາມຫວ່າງເປົ່າ, ແລະພວກເຮົາຕ້ອງເຮັດວຽກໜັກເພື່ອໄດ້ມັນມາ.
ລະບົບການສຶກສາໄດ້ຫຼອກລວງເຮົາຢ່າງໃຫຍ່ຫຼວງ. ພວກເຂົາສອນໃຫ້ເຮົາເຮັດວຽກເພື່ອຫາເງິນ, ແຕ່ບໍ່ເຄີຍສອນວ່າເງິນແມ່ນຫຍັງ. ເຮົາໃຊ້ເວລາ 12-16 ປີໃນໂຮງຮຽນ, ຫຼັງຈາກນັ້ນໃຊ້ເວລາທັງຊີວິດເພື່ອຫາເງິນ, ແຕ່ບໍ່ເຄີຍຮູ້ຈັກວ່າມັນແມ່ນຫຍັງ, ໃຜສ້າງ, ແລະເປັນຫຍັງມັນມີຄຸນຄ່າ.This is the biggest scam in human history ພວກເຮົາຖືກສອນໃຫ້ເປັນທາດຂອງລະບົບ, ແຕ່ບໍ່ໄດ້ຮັບການສອນໃຫ້ເຂົ້າໃຈລະບົບ.
The Bitcoin standard will end war
ເມື່ອບໍ່ສາມາດພິມເງິນເພື່ອສົງຄາມແລ້ວ, ສົງຄາມຈະກາຍເປັນສິ່ງທີ່ແພງເກີນໄປ.
ພວກເຮົາກຳລັງເຂົ້າສູ່ຍຸກ Bitcoin Renaissance
ຍຸກແຫ່ງການຟື້ນຟູທາງດ້ານການເງິນແລະປັນຍາ. Bitcoin is creating a new class of humans ຄົນທີ່ເຂົ້າໃຈ ແລະ ຖື Bitcoin ຈະກາຍເປັນຊົນຊັ້ນໃໝ່ທີ່ມີອິດສະຫຼະພາບຢ່າງແທ້ຈິງ.
The Path to Financial Truth
Follow the money trail ແລະເຈົ້າຈະເຫັນຄວາມຈິງ:
- ໃຜຄວບຄຸມການພິມເງິນ?
- ເປັນຫຍັງລາຄາສິນຄ້າຂຶ້ນສູງຂຶ້ນເລື້ອຍໆ?
- ເປັນຫຍັງຄົນທຸກທຸກກວ່າເກົ່າ ແລະຄົນຮັ່ງມີຮັ່ງມີກວ່າເກົ່າ?
ຄຳຕອບທັງໝົດແມ່ນຢູ່ໃນການທຳຄວາມເຂົ້າໃຈເລື່ອງເງິນ ແລະ Bitcoin.
ການສຶກສາ Bitcoin ບໍ່ແມ່ນພຽງແຕ່ການລົງທຶນ — ມັນແມ່ນການເຂົ້າໃຈອະນາຄົດຂອງເງິນຕາ ແລະ ສັງຄົມມະນຸດ.
Don't just work for money. Understand money. Study Bitcoin.
ຖ້າເຈົ້າບໍ່ເຂົ້າໃຈເງິນ, ເຈົ້າຈະເປັນທາດຂອງລະບົບຕະຫຼອດໄປ. ຖ້າເຈົ້າເຂົ້າໃຈ Bitcoin, ເຈົ້າຈະໄດ້ຮັບອິດສະຫຼະພາບ.
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-01 00:08:04
@ 5d4b6c8d:8a1c1ee3
2025-06-01 00:08:04How'd everyone do on their ~HealthAndFitness goals today?
I got pretty good sleep, stuck to my fast pretty well, didn't eat much junk food, and was pretty active with chores and errands. Not a particularly strong day, but not a weak on, either.
https://stacker.news/items/994000
-
 @ ae1008d2:a166d760
2025-04-01 00:29:56
@ ae1008d2:a166d760
2025-04-01 00:29:56This is part one in a series of long-form content of my ideas as to what we are entering into in my opinion;The Roaring '20's 2.0 (working title). I hope you'll join me on this journey together.
"History does not repeat itself, but it often rhymes"; - Samuel Clemens, aka Mark Twain. My only class I received an A+ in high school was history, this opened up the opportunity for me to enroll in an AP (college level) history class my senior year. There was an inherent nature for me to study history. Another quote I found to live by; "If we do not study history, we are bound to repeat it", a paraphrased quote by the many great philosphers of old from Edmund Burke, George Santayana and even Winston Churchill, all pulling from the same King Solomon quote; "What has been will be again, what has been done will be done again; there is nothing new under the sun". My curiousity of human actions, psychological and therefore economical behavior, has benefitted me greatly throughout my life and career, at such a young age. Being able to 'see around the curves' ahead I thought was a gift many had, but was sorely mistaken. People are just built different. One, if not my hardest action for me is to share. I just do things; act, often without even thinking about writing down or sharing in anyway shape or form what I just did here with friends, what we just built or how we formed these startups, etc., I've finally made the time, mainly for myself, to share my thoughts and ideas as to where we are at, and what we can do moving forward. It's very easy for us living a sovereign-lifestyle in Bitcoin, Nostr and other P2P, cryptographically-signed sovereign tools and tech-stacks alike, permissionless and self-hostable, to take all these tools for granted. We just live with them. Use them everyday. Do you own property? Do you have to take care of the cattle everyday? To live a sovereign life is tough, but most rewarding. As mentioned above, I'm diving into the details in a several part series as to what the roaring '20's were about, how it got to the point it did, and the inevitable outcome we all know what came to be. How does this possibly repeat itself almost exactly a century later? How does Bitcoin play a role? Are we all really going to be replaced by AI robots (again, history rhymes here)? Time will tell, but I think most of us actually using the tools will also forsee many of these possible outcomes, as it's why we are using many of these tools today. The next parts of this series will be released periodically, maybe once per month, maybe once per quarter. I'll also be releasing these on other platforms like Medium for reach, but Nostr will always be first, most important and prioritized.
I'll leave you with one of my favorite quotes I've lived by from one of the greatest traders of all time, especially during this roaring '20's era, Jesse Livermore; "Money is made by sitting, not trading". -
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ bcbb3e40:a494e501
2025-03-31 15:34:12
@ bcbb3e40:a494e501
2025-03-31 15:34:12|
 |
|:-:|
|MISSIAGGIA, Pietro; Jean Thiriart, el caballero euroasiático y la Joven Europa; Hipérbola Janus, 2025|
|
|:-:|
|MISSIAGGIA, Pietro; Jean Thiriart, el caballero euroasiático y la Joven Europa; Hipérbola Janus, 2025|Desde nuestros inicios los autores y temáticas relacionadas con la geopolítica nos han procurado atención e interés por parte del gran público y de los mass media, y no hay más que recordar el efecto que han venido teniendo nuestras obras de Aleksandr Duguin, en especial La geopolítica de Rusia y Proyecto Eurasia: teoría y praxis, sobre todo a raíz de nuestra presentación en Casa de Rusia en un ya lejano 2016, con la inestimable colaboración de Jordi de la Fuente como prologuista, trabajo que siempre reivindicamos desde nuestros medios por el prestigio, la calidad y brillantez de exposición del mismo.
Más allá de las obras del prestigioso y afamado filósofo y politólogo ruso, también hemos realizado otras incursiones en esta vertiente, que podríamos llamar «geopolítica alternativa», introduciendo las obras de otros notables autores como Claudio Mutti, Carlo Terracciano o Boris Nad. Con estos autores hemos tratado de profundizar en esa vía que se opone frontalmente, y radicalmente si se quiere, a los planteamientos derivados de la geopolítica atlantista y liberal que tiene su principal polo en Estados Unidos, haciendo especial hincapié en el subyugamiento que vienen ejerciendo desde 1945 en adelante respecto a una Europa convertida en un protectorado en una mera colonia.
Es por este motivo por el que la publicación de Jean Thiriart, el caballero euroasiático y la Joven Europa nos parece una obra totalmente pertinente en estos momentos, forma parte del desarrollo lógico de la línea editorial en la que estamos encauzados desde nuestros inicios, y viene a representar una de las múltiples vías en las que confluye la idea, profundamente schmittiana, de la política de los grandes espacios. En este caso la idea de una Europa unida, bajo un vasto proyecto que traspasa los estrechos límites del continente concebido como un apéndice más del «Occidente», de ese subproducto ideológico decadente y funcional a los intereses del otro lado del Atlántico. Para comprender la idea de una Europa unida, que comprenda a Rusia, y su enorme extensión territorial a lo largo de 17 millones de kilómetros cuadrados, y la importancia estratégica de su ubicación, es necesario recurrir al legado de Jean Thiriart, conocer su obra, pero también al hombre, pues una no se comprende sin el otro, en este caso hablamos de elementos correlativos.
|
 |
|:-:|
|Jean Thiriart (1922-1992)|
|
|:-:|
|Jean Thiriart (1922-1992)|¿Pero quién fue Jean Thiriart? Esta obra nos permite adentrarnos en aspectos biográficos, algunos de ellos poco conocidos para el gran público de habla hispana, y saber de su trayectoria, de la maduración de sus ideas, de su proyecto político y de las etapas que componen el desarrollo del mismo y que aparecen claramente diferenciadas: hablamos del proyecto político de unidad europea, que alcanza su concreción teórica en ¡Arriba Europa!: Una Europa unida: un imperio de 400 millones de hombres (1965, Editorial Mateu, Barcelona), en pleno apogeo de la organización Jeune Europe, que se convirtió en el órgano político a partir del cual creyó poder implementar su proyecto unitario a escala europeo, manteniendo una posición de independencia respecto a los dos pretendidos bloques antagónicos de Guerra Fría: Estados Unidos y la Unión Soviética. En esa época, estamos hablando del ecuador de los años 60, todo el mundo de la Contracultura, falsamente contestatario, estaba articulando su propio discurso, que tendría su expresión más nítida a través del ya conocido Mayo del 68 francés o la Primavera de Praga, durante el mismo año. Y si el movimiento de Nueva Derecha liderado por Alain de Benoist surgiría en lo sucesivo, ya en la década de los años 70, como una «reacción» frente a la «rebelión contracultural», no podemos obviar la importancia de un movimiento político como Jeune Europe, una organización política transnacional, a escala de la Europa occidental, con sus diferentes delegaciones en países como Francia, Italia, Alemania, la propia España además de, como es obvio, Bélgica, país de origen de nuestro autor.
Jean Thiriart ha sido etiquetado con reiteración como un político y teórico de «extrema derecha», se han hecho numerosos discursos interesados para vincularlo, por cuestiones de orden biográfico muy circunscritas a determinado periodo, con el fascismo y el nacionalsocialismo de entreguerras. Sin embargo, y como el lector podrá descubrir a lo largo de la presente obra, el pensamiento de nuestro autor está muy lejos de ser reducible a meras etiquetas, y en ningún caso mostró las filiaciones que se le atribuyen desde posicionamientos ideológicos, sino que, muy al contrario, vemos a un hombre de pensamiento racional y pragmático, poderosamente influenciado por la geopolítica y abierto a alianzas estratégicas más variadas, más allá de todo fundamentalismo ideológico. Es por este motivo que veremos a un Thiriart buscando sinergias y entendimiento entre círculos de izquierdas, antiimperialistas en una lucha concebida como «cuatricontinental». No en vano, muchos de los cuadros políticos que se formaron en Giovane Europa, la rama italiana, terminaron por militar incluso en organizaciones de extrema izquierda de inspiración maoísta. En el caso de España hubo un notable apoyo a la organización por parte de los falangistas más disidentes. De manera que Jean Thiriart representa una figura política compleja, con influencias variadas, que van desde los hermanos Strasser, pasando por Ernst Niekish o Vilfredo Pareto, e incluso, por Sieyès o Robespierre.
Es a partir de Jeune Europe cuando el nacionalismo europeo, la idea de una Europa unida desde Brest a Bucarest toma cuerpo. En la obra mencionada con anterioridad (¡Arriba Europa!: Una Europa unida: un imperio de 400 millones de hombres) Jean Thiriart ya nos presenta a través de unos trazos muy definidos el proyecto del comunitarismo nacional-europeo, la piedra angular de su proyecto político. La idea de un socialismo aristocrático y europeo, trascendiendo las fronteras del Estado-nación liberal decimonónico, y los particularismos nacionales, concebidos como formas obsoletas y «estrechas de miras», obstáculos a superar en la convergencia del Imperio europeo. Porque vemos a un Thiriart que potencia la estructura del Estado, del aparato de poder, tratando de potenciar, y restaurar naturalmente, el papel y la preponderancia de Europa como espacio de civilización en el mundo. Es un nacionalismo europeo que viene determinado por razones puramente geopolíticas, algo que también fue objeto de críticas, concretamente por parte del geopolítico austriaco Heinrich von Lohausen, y que también recogemos en el presente volúmen de la obra.
|
 |
|:-:|
|Ejemplar de una de las publicaciones más importantes de Joven Europa (Jeune Europe) cuya portada refleja el antiamericanismo y antiimperialismo característicos del nacionalismo europeo de la organización.|
|
|:-:|
|Ejemplar de una de las publicaciones más importantes de Joven Europa (Jeune Europe) cuya portada refleja el antiamericanismo y antiimperialismo característicos del nacionalismo europeo de la organización.|En este sentido, Thiriart no andaba nada desencaminado, en la medida que pensaba que solo los Estados de dimensiones continentales podrían ser capaces de defender su independencia y soberanía, y ejercer un poder en el mundo, frente a los antiguos nacionalismos europeos, totalmente anacrónicos y un factor de ruptura y desintegración del potencial europeo. En este contexto, se hace necesario eliminar el orden establecido en Yalta en 1945, que convierte a Europa en un vasallo de las grandes potencias vencedoras de la Segunda Guerra Mundial. De modo que luchar contra la ocupación estadounidense por un lado, y soviética por otro lado, fuese el principal leitmotiv del Partido Revolucionario Europeo, un partido histórico señala Thiriart, encargado de llevar a término la acción unificadora continental. Y es con este propósito con el que se tratan de concertar una serie de alianzas internacionales que llevó a Thiriart y su organización a tratar con personal diplomático y gubernamental de los países árabes no alineados, del régimen de Fidel Castro o incluso con emisarios del gobierno chino, como ocurrió en el famoso encuentro propiciado por Ceaucescu en Bucarest con Zhou En-Lai.
Quizás, uno de los puntos donde más desacuerdos encontramos con las teorías thiriartianas se encuentra en ciertos fundamentos que la articulan, en un modelo racionalista, materialista y pragmático, de hecho no debemos olvidar que Maquiavelo era uno de sus referentes, y con éste la posterior hornada de autores neomaquiavélicos como Vilfredo Pareto. El excesivo pragmatismo de sus planteamientos, un estatalismo exacerbado y sin concesiones a las particularidades de los pueblos, una suerte de centralismo jacobino, y la ausencia de un elemento trascendente capaz de dar una justificación metafísica a todo el proyecto nacional europeo constituyen, en nuestra opinión, una parte discutible y reformulable.
En otro terreno, como pueda ser el puramente económico, encontramos un proyecto anticapitalista en muchos de sus aspectos, frente al democratismo parlamentario liberal, y apoyándose en las teorías económicas de Johann G. Fichte o Friedrich List, rechazando cualquier organización económica transnacional que pueda mediatizar o convertir a Europa en objeto de sus actividades usurocráticas y depredatorias, colocando la soberanía e independencia económica europea en una de las máximas prioridades en este terreno.
Debemos destacar, porque es un elemento de debate especialmente interesante, el apartado del libro que se corresponde al escrito de Luc Michel, publicado en Italia bajo el título Da Jeune Europe alle Brigate Rosse, en el libro Parte II Historia de Jeune Europe (1962-1969), en el que se detallan las colaboraciones que comenzaron a sucederse entre la militancia de la delegación italiana, Giovane Europa, y círculos de extrema izquierda maoísta, y cómo muchos de los antiguos militantes nacional-europeos terminaron militando en organizaciones de esta facción ideológica, y nos referimos a casos tan representativos en la época como Claudio Orsoni o Pino Bolzano entre otros muchos.
La actividad proselitista de Jeune Europe en el último lustro de la década de los años 60, con la fundación del Partido Comunitario Europeo, nos legó una gran cantidad de publicaciones, entre las cuales destacaron La Nation Européenne, La Nazione Europea o Europa Combattente, cuyas portadas han servido para ilustrar las páginas interiores de nuestra obra, y que procuraron una actividad proselitista y de difusión de ideas que llegaron a imprimir semanal y mensualmente varios miles de ejemplares en Francia o en Italia.
Tras agotar todas las vías posibles de alianzas y convergencias, con encuentros poco afortunados, vemos a un Thiriart que prefiere adoptar otras vías para seguir construyendo el proyecto nacional-europeo más allá de la fórmula activista y del partido político. Este es el motivo por el cual, en los siguientes años, ya en la última etapa de su vida, veremos esa transición del político activista al teórico y al ideólogo como parte de una nueva estrategia dentro del proyecto político al que consagró buena parte de su vida, y es un hecho que comienza a apreciarse desde mediados de los años 70. Durante esta época la «Europa de Brest a Bucarest» se transforma y amplía en una «Europa desde Dublín a Vladivostok». Thiriart aborda ya abiertamente la integración del espacio soviético en una Europa unida que abarca un inmenso espacio territorial, capaz de unir el Océano Atlántico y el Océano Pacífico de un extremo a otro, el «Imperio Eurosoviético». No obstante, Thiriart siempre piensa en términos geopolíticos, y considera que este proceso de integración debe llevarse a cabo desde una revisión de la ideología soviética, desde una marcada desmarxistización de su socialismo, purgado de todo dogmatismo y elementos condicionantes derivados de la teoría del Estado formulada por el marxismo-leninismo para tomar en su lugar aquella de Thomas Hobbes.
A partir de este momento solamente hay un enemigo, el que representa el poder estadounidense y el dominio que éste ejerce sobre la Europa occidental. A partir de ese momento la URSS, bajo las premisas apuntadas por Thiriart, y desde una ideología soviética «desmarxistizada», es la que debe asumir el proyecto de integración europea. Todo este enfoque terminará conociendo su colofón final al final de la vida de Jean Thiriart, cuando éste se encuentre ya en sus último año de vida, en 1992, con una Unión Soviética ya periclitada y disuelta, con un país sumido en una crisis económica, política y social bajo el gobierno decadente de Yeltsin, con un poder notablemente menguado y a merced de las potencias extranjeras y las apetencias de las organizaciones financieras transnacionales. En este contexto tendrá lugar el conocido viaje de Jean Thiriart a Moscú, donde se encontrará, además de con la disidencia de Yeltsin, encabezada por el Partido Comunista dirigido por Gennadij Ziuganov y numerosas personalidades públicas del ámbito ruso, entre las que destacará por encima de todos el filósofo y politólogo Aleksandr Duguin, quien en la presente obra también reivindica la figura del belga como un contribuidor directo del pensamiento euroasiático. Además de medios de prensa, políticos e intelectuales rusos, nuestro autor también compartirá espacio con una pequeña delegación de la revista italiana «Orion», especializada en temática geopolítica, y representada por el padre de la geopolítica italiana, Carlo Terracciano. El encuentro no tendrá mayores consecuencias, y vendrá a significar el último acto de servicio de Jean Thiriart en su denodado esfuerzo por lograr la integración de Europa y Rusia en un poderoso bloque geopolítico capaz de hacer frente a la hegemonía estadounidense en el mundo.
Terminaremos este breve y sintético escrito de presentación con un fragmento de la obra que Jean Thiriart publicó en 1965 bajo el título ¡Arriba Europa!: Una Europa unida: un imperio de 400 millones de hombres, que nos parece de lo más adecuado para poner el punto final al presente texto:
Europa, este MILAGRO en la historia del hombre, este milagro que siguió al milagro griego, ha dado vida, con la prodigiosa fecundidad de su civilización irrepetible, a una cultura adoptada por el mundo entero. En la competencia surgida entre las grandes civilizaciones —occidental, india, china y japonesa— la nuestra ha aplastado a las demás.
La civilización es creadora de cultura. La cultura, en cambio, jamás ha creado civilización.
SOLO Europa posee la civilización; de ahí deriva su supremacía sobre los Estados Unidos y la Rusia comunista, que poseen únicamente la cultura nacida de nuestra civilización, como ha demostrado magistralmente Oswald Spengler.
Esta cultura, separada de su civilización, está condenada a la esterilidad, la cual se manifestará primero mediante una esclerosis y, posteriormente, mediante un retorno a la barbarie.
Políticamente dominada por Moscú o por Washington, la civilización europea se ve asfixiada y corre el riesgo de estancarse en su estado de simple cultura. Basta notar que todos los descubrimientos en el campo nuclear y astronáutico son obra de europeos. Todos buscan a los científicos europeos.
Solo una Europa políticamente unida puede proveer los medios de poder que garantizarán las condiciones históricas indispensables para la supervivencia de esta civilización.
Ninguna otra potencia, por otra parte, podría sustituir a Europa en su misión hacia la humanidad.
Artículo original: Hipérbola Janus, Presentación de «Jean Thiriart, el caballero euroasiático y la Joven Europa», de Pietro Missiaggia (TOR), 18/Mar/2025
-
 @ 9b12847f:9a3ee831
2025-05-31 23:42:09
@ 9b12847f:9a3ee831
2025-05-31 23:42:09What is the CGT loan trap?
The Capital Gains Tax (CGT) loan trap, is where you take a bitcoin-backed loan, expecting that providing the collateral does not trigger CGT, only to find that it does trigger CGT.
Oof.
It's a particularly dangerous trap for plebs because bitcoin collateralised lending typically requires over-collateralisation which is often 2x the amount being borrowed. This means if CGT is triggered on the provision of the collateral, your CGT is 2x the CGT bill had you just sold down the bitcoin for the amount you borrowed.
That's without adding the additional cost of the interest on the loan; more oof.
Why it's important to pay attention to this
Firstly because if you're caught in the trap, you're the one who is liable and not the Lender.
Secondly, because all bitcoin transactions are permanent records and you can reasonably assume that future tax collection sleuths will backtrack through yesterday's transactions. Lenders who KYC their customers provide an easy data collection point for tax collectors, and that data doesn't go away.
And lastly, because there is no emerging signs of fiscal responsibility at the sovereign level, so it's reasonable to assume tax agencies are being directed to increase collections .. and bitcoiners aren't going to get any sort of pass there.
And of course, the bigger the Bitcoin network grows, the more attractive bitcoin collateralised lending will be, and the the more attention it will garner .. and some of that will be from tax collectors.
So, what determines if CGT is applicable?
The concept of beneficial ownership is the relevant term to understand and pay attention to. A change in beneficial ownership is what tax authorities use as the trigger to determine if a CGT event has occurred. This isn't a term or concept isolated to my country (Australia) or the US or the UK or Europe - it's one that's been actively harmonised across the G20. It applies to all asset classes.
The beneficial owner is the one who enjoys the benefits of the asset. It's slightly different to the concept of legal owner which is the person or entity on a government register as the "owner" of the asset.
And if you're a bitcoiner reading this, you're probably already aware that there is no government register of the "ownership of bitcoin" - that's very literally what the timechain, and your bitcoin private keys, are .. but we digress.
Where there is a change in the beneficial owner of an asset, that triggers a CGT liability. This isn't new, it's not related to bitcoin specifically but to all asset classes, and it is consistent over a wide group of countries. The way that each jurisdiction legislates, enforces and applies it will vary somewhat.
So let's explore how that relates to providing collateral in bitcoin-backed loans.
Types of bitcoin backed loans
Bitcoin represents pristine and unimpeachable collateral, so any dollar lender should be happily accepting it as collateral from their perspective. But let's focus on the issue of changing beneficial ownership and how that ties into the borrower's CGT liabilities.
There are loans available from platforms that provide the dollar liquidity, and there are loans from peers.
Loans from platforms
Loans from platforms are going to require KYC information because there is a centralised lender and that will come with a legal construct. The three things to pay attention to are:
- Legal terms and conditions
Ideally, the platform terms should have a statement that acknowledges the unchanged beneficial ownership of the collateral by the borrower, as long as the borrower does not default on the loan.
There may not be such a statement, and if there is not, then the next point on how the collateral is managed needs some careful attention.
The immediate red-flag is if the terms categorically state that there is a change of beneficial ownership of the collateral; being a party to such a contract would legally acknowledge that you transferred beneficial ownership, triggering CGT.
NB: The legal terms and conditions should be generally accessible. If they aren't available then request them from support. If they're not forthcoming, then it's a giant red flag and I'd recommend you exit stage left.
- How the collateral is custodied
A key test that is used to determine if beneficial ownership has changed is the custody of the asset(s). If bitcoin as collateral is kept in a discrete location, and is not pooled with other collateral, then there is a strong case to maintain the chain of unbroken beneficial ownership.
By contrast, collateral that is sent into a "pool" can be deemed to be disposed of, since it's not the same bitcoin that is being returned on successful completion of the loan. I am personally aware of plebs who have been "bitten" by using lending services who "pool" collateral from multiple loans into a pool, and consequently receive different bitcoin on loan completion. The safe assumption is that collateral that is pooled, will be deemed a disposal for CGT events.
- Whether collateral can be re-hypothecated
Ignoring the very dubious issues around re-hypothecation more generally, (who remembers BlockFi, Celsius, Genesis, 3Arrows Capital etc), from a CGT trigger event perspective, if collateral can be re-hypothecated, it will likely be deemed a disposal for CGT purposes.
Loans that are peer-to-peer
There are other borrowing mechanisms that are based on enabling borrowing interaction directly between peers. These typically do not need to introduce the privacy and security risks of KYC, and so consequently do not require a specific legal contract between the peers.
The "terms" of the agreement are defined in the code that implements the contract between the parties, with the collateral held in a multi-party escrow, and returned to the Borrower should they successfully repay their loan. Only if the loan is NOT repaid, or needs to be liquidated, does the collateral change ownership.
In an ideal world, the usage terms for such platforms would acknowledge that the collateral provided by the Borrower remains their unchanged beneficial ownership unless the contract is liquidated, or the loan is not repaid.
Examples of platforms that allow peers to connect and create contracts for borrowing between themselves include Debifi, Lend at HodlHodl, Firefish and Lendasat.
How did I end up down this rabbit hole?
I narrowly avoided falling into precisely this trap recently when I was considering a loan from https://ledn.io I was curious that the Loan terms weren't available to review on their site, or from the customer dashboard after I signed up.
They happily provided them on request (https://www.ledn.io/legal/usd-loan-agreement), and once I got to Section 7 (b), it became clear this wasn't a product I wanted to use because every supply of collateral to Ledn, for any loan, would automatically trigger a CGT event.
Ledn, like every other lending platform, do not offer tax advice, and are clear to state the tax implications of using their products are up to the borrower to assess with their appropriate advisors.
Like many things in Bitcoin, this then made me curious about how widespread this practice was, what the underlying legal definitions were, how widely and harmoniously they were applied .. and here we are .. writing (and reading) blog posts!
So why borrow against your bitcoin at all?
Bitcoin-backed loans can potentially provide a mechanism to access dollars, without selling your bitcoin, and thereby deferring CGT on the sale of bitcoin.
For bitcoiners who've humbly stacked sats for several cycles, borrowing against your bitcoin, may provide a mechanism to further delay spending or selling sats, thereby increasing your purchasing power further.
When you borrow against your bitcoin, you are expecting bitcoin to continue to increase in purchasing power, and at a higher rate than the cost of the interest on the loan. Based on 16 years of bitcoin price history, this is a pretty safe assumption.
Don't however, make assumptions on CGT events that can potentially undermine the entire financial logic of going down this route in the first place; check carefully.
What will definitely trigger a CGT event?
Firstly and most obviously, if you take a bitcoin collateralised loan, and fail to repay the loan or are margin called and liquidated, then that portion of the collateral required to extinguish your loan will be sold. That's clearly a change of beneficial ownership, and that transaction will trigger a CGT liability.
Next, any service or product which explicitly requires you to acknowledge a change of beneficial ownership of the collateral on lodgement, will also trigger a CGT event.
After that, as we outlined earlier, pay close attention to collateral custody mechanisms and transparency and clarity on re-hypothecation - both of which are potential CGT trigger events.
So what's worth checking out?
Currently these are the lending offers that I'm aware of that are worth considering and I understand don't fall foul of the three key aspects outlined above.
As always, do your own checking, and validate with your accounting/legal advisors; the consequences of getting this wrong are potentially significant.
To be clear, I've no financial interest in any of these platforms, nor have I been paid to write this article, nor do I use referral codes. I have used some of these platforms, and believe them all to be operated by reputable teams with high integrity.
Final thoughts
Lastly, for those coming to the @bitcoinbushbash at the end of July in Palm Cove Queensland, I'll be presenting a session on this topic.
-
 @ dfa02707:41ca50e3
2025-05-31 11:01:14
@ dfa02707:41ca50e3
2025-05-31 11:01:14
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.

- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 1d7ff02a:d042b5be
2025-05-27 02:35:53
@ 1d7ff02a:d042b5be
2025-05-27 02:35:53ກຸນແຈສຳຄັນແມ່ນການເຂົ້າໃຈວ່າແສງແດດບໍ່ແມ່ນສິ່ງດຽວ—ມັນແມ່ນຄື່ນຄວາມຖີ່ທີ່ສັບສົນທີ່ເຮັດວຽກຮ່ວມກັນຄືດັ່ງດົນຕີສຳລັບສຸຂະພາບຂອງມະນຸດ.
ວົງດົນຕີສຸຂະພາບຂອງດວງອາທິດ
ແສງຕອນເຊົ້າ (ແສງແດງ/ແສງອິນຟາເຣດໃກ້): ແສງແດງອ່ອນໂຍນຂອງຕອນແລງແລະຄຳ່ທີ່ປະກອບສ້າງ 90% ຂອງການປ່ອຍແສງຂອງດວງອາທິດ. ຄື່ນຄວາມຖີ່ນີ້ເຮັດໜ້າທີ່ຄືການປັບແຕ່ງເຊວລ໌, ເພີ່ມການຜະລິດພະລັງງານມີໂຕຄອນເດຍແລະກະກຽມຮ່າງກາຍຂອງທ່ານສຳລັບມື້ທີ່ຈະມາເຖິງ. ຄິດໃສ່ວ່າມັນແມ່ນການກະກຽມເຄື່ອງຈັກເຊວລ໌ຂອງທ່ານ.
ແສງຕອນກາງວັນ (ແສງ UV/ແສງສີຟ້າ): ແສງອາທິດທີ່ເຂັ້ມຂົ້ນຕອນກາງວັນສົ່ງມອບແສງອຸນຕາລະວິໂອເລດທີ່ຜະລິດວິຕາມິນ D—ຮໍໂມນທີ່ສຳຄັນຫຼາຍທີ່ເກືອບທຸກເຊວລ໌ໃນຮ່າງກາຍຂອງທ່ານມີຕົວຮັບສຳລັບມັນ. ເຖິງແມ່ນວ່າມັນຖືກເອີ້ນວ່າ "ວິຕາມິນ," ຮ່າງກາຍຂອງທ່ານຜະລິດວິຕາມິນ D ສ່ວນໃຫຍ່ຜ່ານການສຳຜັດຜິວໜັງກັບແສງ UVB. ນີ້ບໍ່ແມ່ນພຽງແຕ່ເລື່ອງສຸຂະພາບກະດູກ—ການຂາດວິຕາມິນ D ໄດ້ຖືກເຊື່ອມໂຍງກັບມະເຮັງ, ໂຣກພູມຄຸ້ມກັນຕົນເອງ, ໂຣກຫົວໃຈແລະເສັ້ນເລືອດ, ແລະການເພີ່ມຂຶ້ນຂອງການເສຍຊີວິດຈາກທຸກສາເຫດ. ວິຕາມິນ D ທີ່ຜະລິດຕາມທຳມະຊາດຈາກແສງແດດແກ່ຍາວ 2-3 ເທົ່າໃນຮ່າງກາຍຂອງທ່ານເມື່ອທຽບກັບຢາເສີມ, ສະແດງໃຫ້ເຫັນວ່າເປັນຫຍັງການສຳຜັດແສງແດດຕາມທຳມະຊາດຈຶ່ງດີກວ່າຢາເສີມ.
ແສງ UV ຍັງກະຕຸ້ນການຜະລິດເມລານິນ, ທີ່ເຮັດໜ້າທີ່ເປັນແບັດເຕີຣີທຳມະຊາດ, ເກັບຮັກສາອີເລັກຕຣອນທີ່ໃຫ້ພະລັງງານແກ່ມີໂຕຄອນເດຍຂອງທ່ານ. ໃນຂະນະທີ່ແສງສີຟ້າຮັບໃຊ້ຈຸດປະສົງຄູ່: ມັນຮັກສາໃຫ້ທ່ານຕື່ນຕົວໃນຕອນກາງວັນໃນຂະນະທີ່ຂັດຂວາງການຜະລິດເມລາໂທນິນ. ແຕ່ວ່າ, ແສງສີຟ້າມີດ້ານມືດ—ການສຶກສາສະແດງວ່າມັນສາມາດເຮັດໃຫ້ເກີດຄວາມເສຍຫາຍຂອງ DNA ແລະສ້າງສິ່ງທີ່ເປັນອັນຕະລາຍທີ່ເອີ້ນວ່າສະສາລະອົກຊິເຈນປະຕິກິລິຍາຢູ່ທັງຜິວໜັງແລະຕາ, ຄ້າຍຄືກັບລັງສີ UV. ນີ້ແມ່ນເຫດຜົນທີ່ການສຳຜັດແສງສີຟ້າໂດດດ່ຽວ (ເຊັ່ນຈາກໜ້າຈໍ) ໂດຍບໍ່ມີຄື່ນຄວາມຖີ່ປ້ອງກັນຂອງແສງອາທິດສາມາດເປັນອັນຕະລາຍໂດຍສະເພາະ.
ການປ່ຽນແປງຕອນແລງ: ເມື່ອແສງສີຟ້າຫຼຸດລົງໃນຕອນແລງ, ຮ່າງກາຍຂອງທ່ານເລີ່ມຜະລິດເມລາໂທນິນ, ທີມງານທຳຄວາມສະອາດເຊວລ໌ທີ່ເອົາຜະລິດຕະພັນພິດທີ່ສະສົມໃນລະຫວ່າງການຜະລິດພະລັງງານຂອງມື້ອອກ.
ວິກິດການແສງສະໄໝໃໝ່
ມະນຸດສະໄໝໃໝ່ໃຊ້ເວລາ 93% ຢູ່ໃນເຮືອນ, ສ້າງຄວາມບໍ່ສົມດູນຂອງແສງທີ່ເປັນອັນຕະລາຍ. ພວກເຮົາໄດ້ປ່ຽນໝໍ້ແສງໄຟແກ້ວທີ່ມີປະໂຫຍດດ້ວຍ LED ທີ່ຂາດຄື່ນຄວາມຖີ່ແສງອິນຟາເຣດໃກ້ທີ່ປ້ອງກັນ, ໃນຂະນະທີ່ແສງສີຟ້າປອມຈາກໜ້າຈໍຂັດຂວາງການຜະລິດເມລາໂທນິນຕາມທຳມະຊາດຂອງພວກເຮົາໃນຕອນກາງຄືນ. ນີ້ສ້າງພາຍຸທີ່ສົມບູນແບບ: ຄວາມເຄັ່ງຕຶງຈາກການເກີດອົກຊິເດຊັນໂດຍບໍ່ມີກົນໄກການທຳຄວາມສະອາດຕາມທຳມະຊາດ, ການຂາດວິຕາມິນ D, ແລະການຂາດຄື່ນຄວາມຖີ່ປ້ອງກັນຕອນເຊົ້າທີ່ກະກຽມຮ່າງກາຍຂອງພວກເຮົາສຳລັບການສຳຜັດແສງແດດ.
ທາງແກ້ໄຂຕາມທຳມະຊາດ
ການຄົ້ນຄວ້າຊີ້ໃຫ້ເຫັນວິທີການງ່າຍໆ: ຮັບເອົາຈັງຫວະຕາມທຳມະຊາດຂອງດວງອາທິດ. ເລີ່ມມື້ຂອງທ່ານດ້ວຍການສຳຜັດແສງຕອນເຊົ້າເພື່ອກະກຽມມີໂຕຄອນເດຍຂອງທ່ານ. ຍອມຮັບວ່າແສງແດດຕອນກາງວັນບາງຢ່າງໃຫ້ວິຕາມິນ D ແລະເມລານິນທີ່ຈຳເປັນ. ຄ່ອຍໆຜ່ອນຄາຍເມື່ອແສງແລງຫຼຸດລົງ, ອະນຸຍາດໃຫ້ມີການຜະລິດເມລາໂທນິນຕາມທຳມະຊາດ.
ຮ່າງກາຍຂອງທ່ານພັດທະນາມາຫຼາຍລ້ານປີກັບວົງຈອນແສງນີ້. ໃນຂະນະທີ່ພວກເຮົາບໍ່ສາມາດປະຖິ້ມຊີວິດທີ່ທັນສະໄໝໄດ້, ພວກເຮົາສາມາດເຄົາລົບຄວາມຕ້ອງການທາງຊີວະວິທະຍາຂອງພວກເຮົາສຳລັບແສງແດດແບບຄົບຖ້ວນ. ຫຼັງຈາກທັງໝົດ, ທຸກເຊວລ໌ໃນຮ່າງກາຍຂອງທ່ານແລ່ນດ້ວຍພະລັງງານ, ແລະດວງອາທິດຍັງຄົງເປັນແຫຼ່ງພະລັງງານຫຼັກຂອງໂລກພວກເຮົາ. ໃນໂລກເທັກໂນໂລຢີສູງຂອງພວກເຮົາ, ພວກເຮົາຕ້ອງຈື່ຄູ່ຮ່ວມງານບູຮານລະຫວ່າງສຸຂະພາບຂອງມະນຸດກໍຄືແສງແດດ.
-
 @ 52524fbb:ae4025dc
2025-03-31 15:26:46
@ 52524fbb:ae4025dc
2025-03-31 15:26:46 To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networking
To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networkingNost most Amazing Features:##
-
Decentralisation: compared to traditional social media platforms like like Twitter (X) and Instagram that rely on centralised servers, Nostr operates through a network of relays. These relays serves as servers that store and forward messages. This amazing feature of decentralisation aims to make the network completely resistant to censorship, most people would say how? To answer your question it's because no single individual control's it
-
User Control: ever thought of the purest feeling of freedom, well Nostr just gave you the space to experience. User's have total control over their data and identity.
-
Simplicity: why get stressed when Nostr got you covered? This protocol is designed to be relatively simple, making it easier for developers to build applications on top of it.

Nostr Relation to Bitcoin##
Who wouldn't want to be part of a community that embraces it's ethics in a dignified manner. Nostr has gained popularity within the Bitcoin community, and the Bitcoin Lightning Network is used for features like "Zaps" (which represents small payments or tips). There are also similarities in the philosophy of decentralization, that both bitcoin and Nostr share. Just like the saying goes, birds of the same feather flock together. This leads me to one of the best magnificent project, focused on building decentralisation media infrastructure, particularly within the Nostr ecosystem.

Yakihonne the future of the world##
YakiHonne is an amazing project focused on building decentralized media infrastructure, particularly within the Nostr ecosystem. It's mind blowing features includes:
-
Decentralized Media: YakiHonne aims to provide tools and platforms that support freedom and automation in content creation, curation, article writing and reporting. It leverages the decentralized nature of the Nostr protocol to achieve this amazing feat.
-
Nostr and Bitcoin Integration: YakiHonne is closely tied to the Nostr network, and it also incorporates Bitcoin functionality. This integration includes features related to the Lightning Network, enabling things like "zaps" (small Bitcoin payments) within the platform.
-
Mobile Application: YakiHonne offers a mobile application with an eye catching user interface simply designed to provide users with a smooth and intuitive Nostr experience. This app includes features like: -Support for various login options. -Content curation tools. -Lightning Network integration. -Long form article support.

Disadvantages of Traditional social media##
Lets go back to a world without the flute of freedom echoing in our hearts, where implementations are controlled by certain entities, reasons why traditional social media platforms hold not even a single stance compared to Nostr:
- Privacy Concerns:
Data Collection: Social media platforms collect vast amounts of user data, often without full transparency. This data can be used for targeted advertising, and sometimes, it can be compromised in data breaches. Which won't happen or be possible on yakihonne
-
Social Comparison and Low Self-Esteem: The over hyped and often unrealistic portrayals of life on social media can lead to feelings of inadequacy and low self-esteem. But on yakihonne you get to connect and grow with a community with specified goals bent on implementation
-
Misinformation and Fake News:
Spread of False Information: Social media platforms can be breeding grounds for misinformation and fake news, which can spread rapidly and have significant real-world consequences. Is that possible on yakihonne, well we all know the answer. 4. Centralized Control:
Censorship: Centralized platforms have the power to censor content, raising concerns about freedom of speech. Algorithm Bias: Algorithms can be biased, leading to unfair or discriminatory outcomes. This tells us why a decentralised media platform like yakihonne stands out to be the only media with a future.

Why Chose Nostr why chose yakihonne##
When considering Nostr and related projects like YakiHonne, the appeal stems largely from a desire for greater control, privacy, and freedom in online communication. Which from the points aligned above, gives us no second chance of thought, but the thought of being part of the Nostr community, active on a platform like yakihonne.
-
-
 @ 1d7ff02a:d042b5be
2025-05-24 10:15:40
@ 1d7ff02a:d042b5be
2025-05-24 10:15:40ຄົນສ່ວນຫຼາຍມັກຈະມອງເຫັນ Bitcoin ເປັນສິນຊັບທີ່ມີຄວາມສ່ຽງສູງ ເນື່ອງຈາກມີອັດຕາການປ່ຽນແປງລາຄາທີ່ຮຸນແຮງແລະກວ້າງຂວາງໃນໄລຍະສັ້ນໆ. ແຕ່ຄວາມຈິງແລ້ວ ຄວາມຜັນຜວນຂອງ Bitcoin ແມ່ນຄຸນລັກສະນະພິເສດທີ່ສຳຄັນຂອງມັນ ບໍ່ແມ່ນຂໍ້ບົກພ່ອງ.
ລາຄາແມ່ນຫຍັງ?
ເພື່ອເຂົ້າໃຈເລື້ອງນີ້ດີຂຶ້ນ ເຮົາຕ້ອງເຂົ້າໃຈກ່ອນວ່າລາຄາໝາຍເຖິງຫຍັງ. ລາຄາແມ່ນການສະທ້ອນຄວາມຄິດເຫັນແລະການປະເມີນມູນຄ່າຂອງຜູ້ຊື້ແລະຜູ້ຂາຍໃນເວລາໃດໜຶ່ງ. ການຕັດສິນໃຈຊື້ຫຼືຂາຍໃນລາຄາໃດໜຶ່ງ ກໍແມ່ນການສື່ສານກັບຕະຫຼາດ ແລະກົນໄກຂອງຕະຫຼາດຈະຄ້ົນຫາແລະກໍານົດລາຄາທີ່ແທ້ຈິງຂອງສິນຊັບນັ້ນ.
ເປັນຫຍັງ Bitcoin ຈຶ່ງຜັນຜວນ?
Bitcoin ຖືກສ້າງຂຶ້ນບົນພື້ນຖານອິນເຕີເນັດ ເຮັດໃຫ້ການສື່ສານຄວາມຄິດເຫັນຂອງຜູ້ຄົນສາມາດເຮັດໄດ້ຢ່າງໄວວາ. ຍິ່ງໄປກວ່ານັ້ນ Bitcoin ມີລັກສະນະກະຈາຍສູນ (decentralized) ແລະບໍ່ມີຜູ້ຄວບຄຸມສູນກາງ ຈຶ່ງເຮັດໃຫ້ຄົນສາມາດຕັດສິນໃຈຊື້ຂາຍໄດ້ຢ່າງໄວວາ.
ສິ່ງນີ້ເຮັດໃຫ້ລາຄາຂອງ Bitcoin ສາມາດສະທ້ອນຄວາມຄິດເຫັນຂອງຄົນໄດ້ແບບເວລາຈິງ (real-time). ແລະເນື່ອງຈາກມະນຸດເຮົາມີຄວາມຄິດທີ່ບໍ່ແນ່ນອນ ມີການປ່ຽນແປງ ລາຄາຂອງ Bitcoin ຈຶ່ງປ່ຽນແປງໄປຕາມຄວາມຄິດເຫັນລວມຂອງຜູ້ຄົນແບບທັນທີ.
ປັດໄຈທີ່ເພີ່ມຄວາມຜັນຜວນ:
ຂະໜາດຕະຫຼາດທີ່ຍັງນ້ອຍ: ເມື່ອປຽບທຽບກັບຕະຫຼາດການເງິນແບບດັ້ງເດີມ ຕະຫຼາດ Bitcoin ຍັງມີຂະໜາດນ້ອຍ ເຮັດໃຫ້ການຊື້ຂາຍຈຳນວນໃຫຍ່ສາມາດສົ່ງຜົນກະທົບຕໍ່ລາຄາໄດ້ຫຼາຍ.
ການຄ້າຂາຍຕະຫຼອດ 24/7: ບໍ່ເຫມືອນກັບຕະຫຼາດຫຼັກຊັບທີ່ມີເວລາເປີດປິດ Bitcoin ສາມາດຊື້ຂາຍໄດ້ຕະຫຼອດເວລາ ເຮັດໃຫ້ການປ່ຽນແປງລາຄາສາມາດເກີດຂຶ້ນໄດ້ທຸກເວລາ.
ການປຽບທຽບກັບສິນຊັບອື່ນ
ເມື່ອປຽບທຽບກັບສິນຊັບອື່ນທີ່ມີການຄວບຄຸມ ເຊັ່ນ ສະກຸນເງິນທ້ອງຖິ່ນຫຼືທອງຄຳ ທີ່ເບິ່ງຄືວ່າມີຄວາມຜັນຜວນໜ້ອຍກວ່າ Bitcoin ນັ້ນ ບໍ່ແມ່ນຫມາຍຄວາມວ່າພວກມັນບໍ່ມີຄວາມຜັນຜວນ. ແຕ່ເປັນເພາະມີການຄວບຄຸມຈາກອົງການສູນກາງ ເຮັດໃຫ້ການສື່ສານຄວາມຄິດເຫັນຂອງຄົນໄປຮອດຕະຫຼາດບໍ່ແບບເວລາຈິງ.
ດັ່ງນັ້ນ ສິ່ງທີ່ເຮົາເຫັນແມ່ນການຊັກຊ້າ (delay) ໃນການສະແດງຄວາມຄິດເຫັນທີ່ແທ້ຈິງອອກມາເທົ່ານັ້ນ ບໍ່ແມ່ນຄວາມໝັ້ນຄົງຂອງມູນຄ່າ.
ກົນໄກການຄວບຄຸມແລະຜົນກະທົບ:
ສະກຸນເງິນ: ທະນາຄານກາງສາມາດພິມເງິນ ປັບອັດຕາດອກເບີ້ຍ ແລະແຊກແຊງຕະຫຼາດ ເຮັດໃຫ້ລາຄາບໍ່ສະທ້ອນມູນຄ່າທີ່ແທ້ຈິງໃນທັນທີ.
ຫຼັກຊັບ: ມີລະບຽບການຫຼາຍຢ່າງ ເຊັ່ນ ການຢຸດການຊື້ຂາຍເມື່ອລາຄາປ່ຽນແປງຫຼາຍເກີນໄປ (circuit breakers) ທີ່ຂັດຂວາງການສະແດງຄວາມຄິດເຫັນທີ່ແທ້ຈິງ.
ທອງຄຳ: ຖຶງແມ່ນຈະເປັນສິນຊັບທີ່ບໍ່ມີການຄວບຄຸມ ແຕ່ຕະຫຼາດທອງຄຳມີຂະໜາດໃຫຍ່ກວ່າ Bitcoin ຫຼາຍ ແລະມີການຄ້າແບບດັ້ງເດີມທີ່ຊ້າກວ່າ.
ບົດສະຫຼຸບ
ການປຽບທຽບຄວາມຜັນຜວນລະຫວ່າງ Bitcoin ແລະສິນຊັບອື່ນໆ ໂດຍໃຊ້ໄລຍະເວລາສັ້ນນັ້ນ ບໍ່ມີຄວາມສົມເຫດສົມຜົນປານໃດ ເພາະວ່າປັດໄຈເລື້ອງການຊັກຊ້າໃນການສະແດງຄວາມຄິດເຫັນນີ້ແມ່ນສິ່ງສຳຄັນທີ່ສົ່ງຜົນຕໍ່ລາຄາທີ່ແທ້ຈິງ.
ສິ່ງທີ່ຄວນເຮັດແທ້ໆແມ່ນການນຳເອົາກອບເວລາທີ່ກວ້າງຂວາງກວ່າມາວິເຄາະ ເຊັ່ນ ເປັນປີຫຼືຫຼາຍປີ ແລ້ວຈຶ່ງປຽບທຽບ. ດ້ວຍວິທີນີ້ ເຮົາຈຶ່ງຈະເຫັນປະສິດທິຜົນແລະການດຳເນີນງານທີ່ແທ້ຈິງຂອງ Bitcoin ໄດ້ຢ່າງຈະແຈ້ງ
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ c9badfea:610f861a
2025-05-24 12:55:17
@ c9badfea:610f861a
2025-05-24 12:55:17Before you post a message or article online, let the LLM check if you are leaking any personal information using this prompt:
Analyze the following text to identify any Personally Identifiable Information (PII): <Your Message>Replace
<Your Message>with your textIf no PII is found, continue by modifying your message to detach it from your personality. You can use any of the following prompts (and further modify it if necessary).
Prompt № 1 - Reddit-Style
Convert the message into a casual, Reddit-style post without losing meaning. Split the message into shorter statements with the same overall meaning. Here is the message: <Your Message>Prompt № 2 - Advanced Modifications
``` Apply the following modifications to the message: - Rewrite it in lowercase - Use "u" instead of "you" - Use "akchoaly" instead of "actually" - Use "hav" instead of "have" - Use "tgat" instead of "that" - Use comma instead of period - Use British English grammar
Here is the message:
``` Prompt № 3 - Neutral Tone
Rewrite the message to correct grammar errors, and ensure the tone is neutral and free of emotional language: <Your Message>Prompt № 4 - Cross Translation Technique
Translate the message into Chinese, then translate the resulting Chinese text back into English. Provide only the final English translation. Here is the message: <Your Message>Check the modified message and send it.
ℹ️ You can use dialects to obfuscate your language further. For example, if you are from the US, you can tell the LLM to use British grammar and vice versa.
⚠️ Always verify the results. Don't fully trust an LLM.
-
 @ 91bea5cd:1df4451c
2025-05-23 17:04:49
@ 91bea5cd:1df4451c
2025-05-23 17:04:49Em nota, a prefeitura justificou que essas alterações visam ampliar a segurança das praias, conforto e organização, para os frequentadores e trabalhadores dos locais. No entanto, Orla Rio, concessionária responsável pelos espaços, e o SindRio, sindicato de bares e restaurantes, ficou insatisfeita com as medidas e reforçou que a música ao vivo aumenta em mais de 10% o ticket médio dos estabelecimentos e contribui para manter os empregos, especialmente na baixa temporada.
De acordo com Paes, as medidas visam impedir práticas ilegais para que a orla carioca continue sendo um espaço ativo econômico da cidade: “Certas práticas são inaceitáveis, especialmente por quem tem autorização municipal. Vamos ser mais restritivos e duros. A orla é de todos”.
Saiba quais serão as 16 proibições nas praias do Rio de Janeiro
- Utilização de caixas de som, instrumentos musicais, grupos ou qualquer equipamento sonoro, em qualquer horário. Apenas eventos autorizados terão permissão.
- Venda ou distribuição de bebidas em garrafas de vidro em qualquer ponto da areia ou do calçadão.
- Estruturas comerciais ambulantes sem autorização, como carrocinhas, trailers, food trucks e barracas.
- Comércio ambulante sem permissão, incluindo alimentos em palitos, churrasqueiras, isopores ou bandejas térmicas improvisadas.
- Circulação de ciclomotores e patinetes motorizados no calçadão.
- Escolinhas de esportes ou recreações não autorizadas pelo poder público municipal.
- Ocupação de área pública com estruturas fixas ou móveis de grandes proporções sem autorização.
- Instalação de acampamentos improvisados em qualquer trecho da orla.
- Práticas de comércio abusivo ou enganosas, incluindo abordagens insistentes. Quiosques e barracas devem exibir cardápio, preços e taxas de forma clara.
- Uso de animais para entretenimento, transporte ou comércio.
- Hasteamento ou exibição de bandeiras em mastros ou suportes.
- Fixação de objetos ou amarras em árvores ou vegetação.
- Cercadinhos feitos por ambulantes ou quiosques, que impeçam a livre circulação de pessoas.
- Permanência de carrinhos de transporte de mercadorias ou equipamentos fora dos momentos de carga e descarga.
- Armazenamento de produtos, barracas ou equipamentos enterrados na areia ou depositados na vegetação de restinga.
- Uso de nomes, marcas, logotipos ou slogans em barracas. Apenas a numeração sequencial da prefeitura será permitida.
-
 @ b1ddb4d7:471244e7
2025-05-31 22:01:00
@ b1ddb4d7:471244e7
2025-05-31 22:01:00Flash, an all-in-one Bitcoin payment platform, has announced the launch of Flash 2.0, the most intuitive and powerful Bitcoin payment solution to date.
With a completely redesigned interface, expanded e-commerce integrations, and a frictionless onboarding process, Flash 2.0 makes accepting Bitcoin easier than ever for businesses worldwide.
 We did the unthinkable!
We did the unthinkable! Website monetization used to be super complicated.
"Buy me a coffee" — But only if we both have a bank account.
WHAT IF WE DON'T?
Thanks to @paywflash and bitcoin, it's just 5 CLICKS – and no banks!
 Start accepting donations on your website… pic.twitter.com/uwZUrvmEZ1
Start accepting donations on your website… pic.twitter.com/uwZUrvmEZ1— Flash • The Bitcoin Payment Gateway (@paywflash) May 13, 2025
Accept Bitcoin in Three Minutes
Setting up Bitcoin payments has long been a challenge for merchants, requiring technical expertise, third-party processors, and lengthy verification procedures. Flash 2.0 eliminates these barriers, allowing any business to start accepting Bitcoin in just three minutes, with no technical set-up and full control over their funds.
The Bitcoin Payment Revolution
The world is witnessing a seismic shift in finance. Governments are backing Bitcoin funds, major companies are adding Bitcoin to their balance sheets, and political figures are embracing it as the future of money. Just as Stripe revolutionized internet payments, Flash is now doing the same for Bitcoin. Businesses that adapt today will gain a competitive edge in a rapidly evolving financial landscape.
With Bitcoin adoption accelerating, consumers are looking for places to spend it. Flash 2.0 ensures businesses of all sizes can seamlessly accept Bitcoin and position themselves at the forefront of this financial revolution.
All-in-One Monetization Platform
More than just a payment gateway, Flash 2.0 is a complete Bitcoin monetization suite, providing multiple ways for businesses to integrate Bitcoin into their operations. Merchants can accept payments online and in-store, content creators can monetize with donations and paywalls, and freelancers can send instant invoices via payment links.
For example, a jewelry designer selling products on WooCommerce can now integrate Flash for online payments, use Flash’s Point-of-Sale system at trade shows, enable Bitcoin donations for her digital artwork, and lock premium content behind Flash Paywalls. The possibilities are endless.
E-Commerce for Everyone
With built-in integrations for Shopify, WooCommerce, and soon Wix and OpenCart, Flash 2.0 enables Bitcoin payments on 95% of e-commerce stores worldwide. Businesses can now add Bitcoin as a payment option in just a few clicks—without needing developers or external payment processors.
And for those looking to start selling, Flash’s built-in e-commerce features allow users to create online stores, showcase products, and manage payments seamlessly.
No Middlemen, No Chargebacks, No Limits
Unlike traditional payment platforms, Flash does not hold or process funds. Businesses receive Bitcoin directly, instantly, and securely. There are no chargebacks, giving merchants full control over refunds and eliminating fraud. Flash also remains KYC-free, ensuring a seamless experience for businesses and customers alike.
A Completely Redesigned Experience
“The world is waking up to Bitcoin. Just like the internet revolutionized commerce, Bitcoin is reshaping finance. Businesses need solutions that are simple, efficient, and truly decentralized. Flash 2.0 is more than just a payment processor—it’s a gateway to the future of digital transactions, putting financial power back into the hands of businesses.”
— Pierre Corbin, CEO at Flash.
Flash 2.0 introduces a brand-new user interface, making it easier than ever to navigate, set up payments, and manage transactions. With an intuitive dashboard, streamlined checkout, and enhanced mobile compatibility, the platform is built for both new and experienced Bitcoin users.
About Flash
Flash is an all-in-one Bitcoin payment platform that empowers businesses, creators, and freelancers to accept, manage, and grow with Bitcoin. With a mission to make Bitcoin payments accessible to everyone, Flash eliminates complexity and gives users full control over their funds.
To learn more or get started, visit www.paywithflash.com.
Press Contact:
Julien Bouvier
Head of Marketing
+3360941039 -
 @ bcbb3e40:a494e501
2025-03-31 15:23:12
@ bcbb3e40:a494e501
2025-03-31 15:23:12|
 |
|:-:|
|BÉRARD, Bruno y LA FATA, Aldo; ¿Qué es el esoterismo?: Entre verdades y falsificacioines; Hipérbola Janus, 2025|
|
|:-:|
|BÉRARD, Bruno y LA FATA, Aldo; ¿Qué es el esoterismo?: Entre verdades y falsificacioines; Hipérbola Janus, 2025|Nos complace presentar al lector en lengua española una novedad de primer orden, y sobre un tema que viene siendo objeto de interés por parte de nuestra línea editorial, como es el esoterismo, que hemos abordado recientemente a través de un nuevo recopilatorio de la obra evoliana en Ensayos filosóficos, esotéricos y religiosos 1925-1931, donde hemos tratado de rescatar los textos de las primeras etapas en la formulación del pensamiento del Maestro Romano. No obstante, no es la primera aventura que hemos emprendido en este terreno, siempre complejo y acompañado de la etiqueta, popular y quizás vulgarizada, de lo «misterioso» y lo «oculto», aunque no somos nada sospechosos en ese sentido por banalizar o tratar de ofrecer un enfoque puramente literario del asunto, y ni mucho menos de simpatizar con aquellas vías que entroncan con el New age, donde las mixtificaciones y la voluntad de convertir el fenómeno esotérico en un producto de consumo más, como demanda el mercado, para satisfacer demandas materiales o simples modas de una masa sobresocializada son norma habitual.
Podríamos citar multitud de obras que están presentes en nuestro catálogo, como son El pensamiento esotérico de Leonardo, de Paul Vulliaud, El mundo mágico de los héroes, de Cesare della Riviera, una joya del esoterismo italiano del siglo XVII, en El maestro de la tradición perenne, de René Guénon, o en el ensayo de Gianluca Marletta OVNIS y alienígenas. Origen, historia y prodigio de una pseudorreligión, un ensayo de notable originalidad donde se abordan aspectos esotéricos, aunque sea de un modo más tangencial. También en la literatura, con la obra del gran mitólogo y literato Boris Nad, Una historia de Agartha y La muerte púrpura de Gustav Meyrink encontramos nuevas referencias al ámbito esotérico. De modo que podemos concluir en que el esoterismo forma parte esencial de nuestras publicaciones e intereses como editores, y contribuimos activamente a su difusión.
|
 |
|:-:|
|EVOLA, Julius; Ensayos filosóficos, esotéricos y religiosos: 1925-1931, Hiperbola Janus, 2024|
|
|:-:|
|EVOLA, Julius; Ensayos filosóficos, esotéricos y religiosos: 1925-1931, Hiperbola Janus, 2024|Una obra original
Por eso la presente obra, la que nos disponemos a presentar, cuyo título es ¿Qué es el esoterismo?: Entre verdades y falsificaciones, de Bruno Bérard y Aldo La Fata, viene a ser una obra muy necesaria y clarificadora en la comprensión del esoterismo en todas sus dimensiones, en la complejidad de sus particulares, y en sus múltiples manifestaciones. Quizás en el mundo de habla hispana el esoterismo es un fenómeno que no ha obtenido su merecida atención, y nuestros autores en este ámbito, como es el caso de un Ramón Llull entre otros, no sean objeto de la atención que merece, y las actividades esotéricas, a nivel de asociaciones, comunidades u otras formas de organización, tampoco sean especialmente conocidas, ni cuenten con una actividad reconocida. Es posible, como señala La Fata, que haya ciertas reticencias dentro del mundo católico, acostumbrado a la ortodoxia y la guía espiritual de la Iglesia, y que cualquier tipo de «desviación» hacia formas más individuales y «libres» de vivir ciertas formas iniciáticas, mucho más sutiles, provoquen el rechazo y la incomprensión general. No obstante, como también se encargan de aclarar nuestros autores, el esoterismo comprende una dimensión diferenciada, implica un esfuerzo que no todos están dispuestos a acometer, y finalmente, no es tampoco un camino de felicidad y de frutos seguros, implica una transformación interior y la asunción de unas prácticas y procedimientos que no son aptos para cualquiera. Digamos que el esoterismo es un camino, una vía, que a diferencia de las «religiones populares», exotéricas, supone un arduo camino que viene marcado por un principio vertical y aristocrático de la existencia, o al menos así queremos verlo nosotros. El incremento de la capacidad de discernimiento, aunar lo visible con lo invisible, y ser capaz de superar límites vedados al común, no por simple vanidad ni por «crecimiento personal», tal y como se concibe en las aburguesadas y decadentes sociedades actuales, sino como parte de un proceso de aprendizaje, de autoconocimiento y de liberación. No nos cabe duda alguna de la necesidad de restaurar los antiguos vínculos con lo Alto, las vías que quedaron cerradas y que nos han limitado progresivamente al exclusivo y estrecho ámbito de la materialidad.
|
 |
|:-:|
|RIVIERA, Cesare della; El mundo mágico de los héroes; Hipérbola Janus, 2022|
|
|:-:|
|RIVIERA, Cesare della; El mundo mágico de los héroes; Hipérbola Janus, 2022|La obra emplea el recurso de la entrevista/diálogo, que aporta frescura y fluidez al texto «simplificando», o más bien haciendo más accesibles y comprensibles elementos relacionados con el esoterismo, que de otro modo resultarían excesivamente complejos para una parte del público lector poco familiarizado con la materia. Este dinamismo se ve complementado por la riqueza de matices e ideas que se van introduciendo de manera progresiva, evitando que el lector pueda verse abrumado por la avalancha de ideas y contenidos. Las preguntas de Bruno Bérard, siempre inteligentes, incisivas y pertinentes, además de ordenadas y bien estructuradas, favorecen la continuidad y el dinamismo en la exposición de los temas, ejerciendo de guía en la conversación. De ahí que el libro sea apto para diferentes niveles, tanto para aquellos que desconocen el esoterismo, como para quienes se encuentran familiarizados con el tema. Aldo La Fata, de acuerdo con su dilatada y extensa trayectoria en la materia, nos hace reflexiones teóricas de enorme valor, que entrelaza con su propia experiencia y trayectoria en el estudio del esoterismo. Sin lugar a dudas este aspecto nos permite ver una vertiente más humana e íntima, en la que se incluyen anécdotas personales y biográficas que siempre permiten una mayor conexión con el lector a través de la mezcla de hechos vitales y erudición teórica.
La entrevista que nos ofrecen Bruno Bérard y Aldo La Fata nos permite explorar la relación dialéctica que se genera entre el esoterismo y otros ámbitos como la religión, la ciencia o la filosofía. Todas las cuestiones se abordan desde enfoques muy concretos, abordando problemáticas particulares, que dan lugar a reflexiones más amplias evitando las simplificaciones e invitando a reflexiones mucho más profundas. De ahí la función de introducción y guía a la que nos venimos refiriendo.
Estos aspectos que acabamos de enumerar con anterioridad revelan un notable esfuerzo pedagógico por parte de los autores para acercarnos al estudio del esoterismo, nos aporta las herramientas necesarias, parafraseando el título de la obra, para discernir entre un verdadero esoterismo y sus falsificaciones.
Más allá de estos aspectos formales, que consideramos que es importante destacar, porque en ellos reside el éxito de la obra, en un planteamiento que resulta original, a la par que ameno y de gran interés, debemos considerar otros aspectos que hacen más referencia al contenido. «¿Qué es el esoterismo? Entre verdades y falsificaciones» pretende, como decíamos, clarificar qué es el esoterismo, cuales son sus particulares, sus características y atributos, su naturaleza más íntima, como fenómeno espiritual y filosófico en sus aspectos más profundos, que podemos remontar a épocas muy remotas y lejanas en el tiempo. Pero el esoterismo aparece en ocasiones fuertemente imbricado en otras estructuras de pensamiento, de tipo tradicional, como son las grandes religiones (Cristianismo, Islam, Judaísmo etc) y otros conceptos como la mística y la metafísica, cuyas relaciones hay que desentrañar.
La importancia de René Guénon
Aldo La Fata nos libera desde el principio de posibles equívocos al enfatizar que el verdadero esoterismo no es una simple acumulación de conocimientos secretos o rituales exóticos, sino una vía de trascendencia espiritual basada en el rigor y la autenticidad. A este respecto René Guénon aparece como uno de los grandes esoteristas de nuestro tiempo, en la medida que fue el gran intérprete y codificador de estos conocimientos, una figura que marcó un antes y un después en la comprensión de este ámbito, especialmente por su rigor conceptual y su capacidad para distinguir entre lo auténtico y lo falso en las tradiciones espirituales. A tal respecto podemos poner como ejemplo sus contundentes análisis de las corrientes ocultistas, especialmente del espiritismo o del teosofismo, en diferentes obras. Podemos decir a este respecto que Guénon hizo una distinción entre esoterismo y ocultismo, disociando el significado del primero de prácticas superficiales y desviadas, mientras que definió el esoterismo como una vía de conocimiento sagrado y trascendente. En este sentido fue una labor fundamental para evitar confusiones con mixtificaciones modernas y pseudoesoterismos como aquellos relacionados con el New Age.
|
 |
|:-:|
|GUÉNON, René; El Maestro de la Tradición Perenne: Antología de artículos guenonianos; Hipérbola Janus, 2021|
|
|:-:|
|GUÉNON, René; El Maestro de la Tradición Perenne: Antología de artículos guenonianos; Hipérbola Janus, 2021|Paralelamente, y con ello queremos dignificar la figura de René Guénon, el tradicionalista francés también nos abrió las fuentes de un vasto conocimiento espiritual, expresión de una «Tradición primordial», a cuyos orígenes prístinos siempre deberíamos aspirar, y cuya impronta impregna por completo religiones, culturas y formas de civilización no modernas, claro está. Y otro elemento fundamental, y que en la presente obra se considera de vital importancia, es que René Guénon considera el esoterismo no como una vía interna propia de la religión, sino como una vía complementaria que permite acceder a la esencia divina más allá de las formas externas. Para Aldo La Fata no se trata de una mera referencia intelectual, sino una figura que marcó su propio rumbo dentro del estudio del esoterismo. A través de obras como Los símbolos de la ciencia sagrada, La Fata descubrió la profundidad y la coherencia del pensamiento guenoniano, así como la idea de que el esoterismo actúa como el «pegamento» que conecta todas las tradiciones espirituales. Esta visión le permitió entender el esoterismo como algo inseparable de la religión, aunque con una profundidad y una exigencia mayores.
¿Qué es el esoterismo?
El término esoterismo tiene sus raíces etimológicas en el griego esôterikos, que implica un «ir hacia dentro» y que se contrapone a una variante exterior que definimos como «exoterismo», que se encuentra más vinculado al ámbito de la religión. Se trata de un conocimiento que no atiende a un principio puramente intelectual y discursivo sino que apunta a una vivencia directa y sapiencial de lo trascendente. Lejos de la acumulación de saberes ocultos y rituales, lo que prima en la experiencia de lo esotérico es la conexión directa con lo trascendente y lo divino a través de la práctica espiritual.
De hecho hay tres aspectos que nuestros autores destacan a lo largo de la obra respecto al esoterismo, y que nos parecen fundamentales:
- Interioridad: Supone un movimiento continuo hacia el interior, de exploración e introspección, en el que se tratan de derribar límites y obstáculos. Atendiendo a un dinamismo que huye de lo fijo y de lo estático.
- Profundización: La búsqueda de significados más profundos tras la realidad cotidiana, buscando ir más allá de la pura exterioridad de las cosas
- Relación con el exoterismo: Podemos considerarlo opuesto en sentido relativo al esoterismo, como una dimensión más externa y visible de las religiones, aunque este último (el esoterismo), no puede sobrevivir sin el apoyo de una tradición religiosa.
En relación al último punto debemos destacar, como advierten Bérard y La Fata, que pese a todo no podemos entender el esoterismo como una parte de las religiones, sino que tiene su propia función y objetivos, que no es otro que el que ya hemos mencionado con anterioridad: establecer una conexión directa con la verdad que irradia del principio universal y divino.
|
 |
|:-:|
|VULLIAUD, Paul; El pensamiento esotérico de Leonardo da Vinci; Hipérbola Janus, 2024|
|
|:-:|
|VULLIAUD, Paul; El pensamiento esotérico de Leonardo da Vinci; Hipérbola Janus, 2024|Otro aspecto interesante de la obra es el que nos habla de las relaciones entre esoterismo y metafísica, en el que el primero pretende ser también una vía de acceso al dominio del segundo. El esoterismo, como ya hemos visto, tiene como principal propósito trascender las categorías del mundo material para proyectarse en lo universal, y en este sentido comparte también objetivos con la metafísica, que pretende superar las limitaciones de la experiencia humana ordinaria y de acceder a las verdades primordiales que estructuran la realidad. Ambos apuntan a la raíz de todo lo existente, al absoluto. Las divergencias las hallamos en la forma o en el método para alcanzar estas verdades trascendentes, que en el caso del esoterismo nos remiten a símbolos, rituales y experiencias vivenciales que permiten al practicante interiorizar verdades universales.
De este modo, esoterismo y metafísica se nos presentan como realidades no opuestas, sino complementarias. La metafísica nos ofrece un marco conceptual y doctrinal para entender lo absoluto, mientras que el esoterismo se centra en su realización interna. En términos guenonianos, el esoterismo representa los aspectos operativos de la metafísica.
De modo que podemos decir que la metafísica aborda el tema trascendente desde una perspectiva conceptual, sin esa parte vivida de la experiencia en el conocimiento de lo universal. El esoterismo, por su parte, aporta esa contraparte que nos remite a la experiencia humana que permite al individuo acceder o ponerse en conexión con lo divino a través de su propio ser, de manera directa y vívida. Es un camino que el sujeto individual emprende para lograr una transformación interior.
Paralelamente, no podemos obviar dentro de todos estos procesos la participación de un elemento fundamental, como es la intuición suprarracional, que podríamos considerar como la herramienta que conecta al esoterista directamente con la fuente del conocimiento trascendente y universal, en lugar de hacerlo directamente a través de teorías o conceptos que siempre resultan más abstractos y difíciles de comprender en su vertiente más «discursiva». Al mismo tiempo, las relaciones que se establecen entre esoterismo y metafísica nos permiten poner en contacto las tradiciones religiosas con el conocimiento universal. Según La Fata, inspirándose en el legado de la obra de Frithjoff Schuon, cada tradición espiritual tiene una dimensión metafísica que puede ser comprendida y realizada a través del esoterismo, como un medio para acceder a la esencia inmutable de todas las formas religiosas.
Otro aspecto que esoterismo y metafísica comparten es la meta de superar la dualidad entre sujeto y objeto: Mientras que la metafísica conceptualiza esta unión como una verdad última, el esoterismo busca experimentarla directamente a través de la contemplación, el símbolo y la práctica espiritual.
Los autores
|
 |
|:-:|
|Aldo La Fata|
|
|:-:|
|Aldo La Fata|Aldo La Fata (1964) es un estudioso del esoterismo, el simbolismo y la mística religiosa, con una trayectoria de varias décadas dedicada al análisis y divulgación de estas disciplinas. Ha sido jefe de redacción de la revista Metapolitica, fundada por Silvano Panunzio, y actualmente dirige Il Corriere Metapolitico. Su trabajo destaca por una aproximación rigurosa y una mirada crítica a las corrientes contemporáneas del esoterismo, rescatando su sentido más profundo y tradicional. Entre sus obras más relevantes se encuentran Silvano Panunzio: vita e pensiero (2021) y Nella luce dei libri (2022), donde explora la intersección entre espiritualidad, simbolismo y pensamiento tradicional.
|
 |
|:-:|
|Bruno Bérard|
|
|:-:|
|Bruno Bérard|Bruno Bérard (1958), es doctor en Religiones y Sistemas de Pensamiento por la École Pratique des Hautes Études (EPHE), es un destacado especialista en metafísica. Autor de múltiples ensayos, ha desarrollado una profunda reflexión sobre la naturaleza del conocimiento espiritual y su relación con las tradiciones religiosas. Algunas de sus obras más importantes, traducidas a diversas lenguas, incluyen A Metaphysics of the Christian Mystery (2018) y Métaphysique du paradoxe (2019). Actualmente, dirige la colección Métaphysique au quotidien en la editorial L’Harmattan de París, consolidándose como una referencia en el estudio de la metafísica contemporánea.
En ¿Qué es el esoterismo?: Entre verdades y falsificaciones, asistimos a una presentación del tema tratado desde un conocimiento profundo y dilatado del tema, en la que ambos autores combinan la experiencia y el conocimiento que atesoran sobre el esoterismo y otros temas anejos, ofreciéndonos sus interpretaciones y enfoques particulares, y al mismo tiempo mostrando una gran capacidad de síntesis en la exposición de los temas tratados, que se inscriben en una multitud de tradiciones religiosas y espirituales de enorme complejidad. En este último punto reside también gran parte del valor de la obra, que constituye una novedad editorial especialmente relevante en su ámbito en lengua hispana.
Artículo original: Hipérbola Janus, Presentación de «¿Qué es el esoterismo?: Entre verdades y falsificaciones» (TOR), 6/Feb/2025
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ c9badfea:610f861a
2025-05-10 11:08:51
@ c9badfea:610f861a
2025-05-10 11:08:51- Install FUTO Keyboard (it's free and open source)
- Launch the app, tap Switch Input Methods and select FUTO Keyboard
- For voice input, choose FUTO Keyboard (needs mic permission) and grant permission While Using The App
- Configure keyboard layouts under Languages & Models as needed
Adding Support for Non-English Languages
Voice Input
- Download voice input models from the FUTO Keyboard Add-Ons page
- For languages like Chinese, German, Spanish, Russian, French, Portuguese, Korean, and Japanese, download the Multilingual-74 model
- For other languages, download Multilingual-244
- Open FUTO Keyboard, go to Languages & Models, and import the downloaded model under Voice Input
Dictionaries
- Get dictionary files from AOSP Dictionaries
- Open FUTO Keyboard, navigate to Languages & Models, and import the dictionary under Dictionary
ℹ️ When typing, tap the microphone icon to use voice input
-
 @ dc4cd086:cee77c06
2025-02-09 03:35:25
@ dc4cd086:cee77c06
2025-02-09 03:35:25Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
Key Features:
Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
Screenshots
Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately. You can now view the article on #Alexandria https://next-alexandria.gitcitadel.eu/publication?d=nostr-apps-101
Initially published as chained kind 1's nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle https://coracle.social /nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-
 @ 2e8970de:63345c7a
2025-05-31 19:51:28
@ 2e8970de:63345c7a
2025-05-31 19:51:28Enfortumab Vedotin and Pembrolizumab doubled survival rates, with fewer serious side effects in advanced bladder cancer.
https://www.nejm.org/doi/full/10.1056/NEJMoa2312117
https://stacker.news/items/993799
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ a3c6f928:d45494fb
2025-05-31 18:52:24
@ a3c6f928:d45494fb
2025-05-31 18:52:24Fear is one of the most powerful forces that shapes our decisions, limits our growth, and holds us back from living fully. Yet, freedom from fear is not about becoming fearless—it's about no longer allowing fear to control us. In uncertain times, reclaiming our power means learning how to face fear, understand it, and ultimately rise above it.
Understanding Fear’s Grip
Fear thrives in the unknown. It whispers worst-case scenarios, paralyzes action, and magnifies our sense of powerlessness. But fear is also a signal. It tells us where growth lies, where change is needed, and where courage must rise.
What Freedom from Fear Looks Like
Taking Action Despite Anxiety: You feel the fear, but you move forward anyway.
Letting Go of Control: You stop trying to predict or perfect every outcome.
Trusting Yourself: You believe in your ability to adapt and respond.
Embracing Uncertainty: You understand that discomfort is part of transformation.
Steps Toward Reclaiming Power
-
Name the Fear: Clarity shrinks fear. When you name what you're afraid of, it loses some of its grip.
-
Breathe Through It: Deep breathing brings you back to the present, where fear often has less power.
-
Challenge the Narrative: Ask: "Is this true? Is this fear protecting me or limiting me?"
-
Take Small Steps: Fear often dissolves when met with action. Start small, but start.
-
Build a Resilient Mindset: Remind yourself of what you've overcome before. You are stronger than your fear.
Why It Matters Now
In a world filled with rapid change, fear can become a default state. But freedom is a choice. A daily one. When you stop letting fear steer your life, you open the door to possibilities, growth, and deeper peace.
“Fear does not stop death. It stops life.”
Choose courage. Claim your power. Walk freely—even through fear.
-
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 866e0139:6a9334e5
2025-05-31 10:45:03
@ 866e0139:6a9334e5
2025-05-31 10:45:03Autor: Marcel Bühler. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
In einem Artikel in der NZZ vom 27. Mai mit dem Titel "Trump nennt Putin verrückt" wird über den laut Kiew grössten russischen Drohnenangriff seit Beginn des Krieges auf ukrainische Städte berichtet. Dabei sollen am vergangenen Wochenende 355 Drohnen und 69 Raketen auf Kiew, Odessa, Ternipol (Westukraine) und andere Städte gesteuert bzw. abgefeuert worden sein. 288 Drohnen und 9 Raketen konnten laut Kiew von der ukrainischen Luftverteidigung abgeschossen werden. Was der Artikel verschweigt: bereits in der Woche davor, am 20. - 22. Mai hatte die Ukraine 485 Drohnen gegen russische Städte wie Kursk, Belgorod oder Brijansk geflogen, 63 davon erreichten die Region Moskau. Auch am Wochenende schickten die Ukrainer 205 Drohnen gegen russische Städte, 13 davon erreichten Moskau. Auch hier konnte die Luftverteidigung die meisten Drohnen unschädlich machen, eine davon hatte gar den Helikopter von Präsident Putin (!) im Visier. Als Reaktion darauf erklärte Präsident Putin, dass in der ukrainischen Region Sumy bzw. Tschernihiw im Norden eine Sicherheitszoneeingerichtet werden soll da die meisten Drohnen von hier aus gestartet wurden. Auch am 27./28. Mai schickte die Ukraine wieder 296 Drohnen Richtung Moskau, offenbar soll die russische Luftverteidigung damit überlastet werden um später westliche Cruise Missiles wie "Storm shadows", "Skalp" oder die umstrittenen deutschen "Taurus" effektiver einsetzen zu können. Der neue Bundeskanzler Friedrich Merz hat dafür rund 5 Milliarden Euro in Aussicht gestellt um solche Waffensysteme in der Ukraine selber zusammenbauen zu können.
Diese Gewaltspirale hat eine lange Geschichte: diese begann 2007 mit der 43. Münchner Sicherheitskonferenz, in der Präsident Putin sich gegen die unilaterale Weltordnung der USA und ihrer Verbündeten aussprach. Auch erteilte er den NATO-Osterweiterungen seit 1991 eine deutliche Absage, da diese entgegen (mündlich) gemachten Zusicherungen vollzogen wurden (siehe im Anhang die Rede im Wortlaut). Bei anderer Gelegenheit bezeichnete er vor allem einen möglichen NATO-Beitritt der (ehemals russischen) Ukraine als die "rote Linie", da es hier im Osten eine gemeinsame Grenze zu Russland über weit mehr als tausend Kilometer gebe und zudem Millionen von russischstämmigen Bürgern in der Ukraine lebten welche durch die Unabhängigkeit des Landes von ihrem Mutterland getrennt seinen. Im mittlerweile umstrittenen Budapester Memorandum von 5.12.1994 hatten zudem die Signatarmächte USA, GB und die Russische Föderation in getrennten Dokumenten die Unabhängigkeit und territoriale Integrität der Ukraine garantiert, wenn diese ein neutraler Pufferstaat zwischen der NATO und der Russischen Föderation sei und auf ihre Atomwaffen aus der sowjetischen Zeit verzichte (die Neutralität war in der ukrainischen Verfassung verankert). Trotzdem erklärten am darauffolgenden NATO-Gipfel in Bukarest im April 2008 die versammelten Staats- und Regierungschefs der 26 NATO-Staaten: "Die NATO begrüßt die euro-atlantischen Bestrebungen der Ukraine und Georgiens, die dem Bündnis beitreten wollen. Wir kamen heute überein, dass diese Länder NATO-Mitglieder werden." Zudem wurde die Unabhängigkeitserklärung des Kosowo vorbehaltlos anerkannt, dies nach einer völkerrechtswidrigen militärischen Intervention (d.h. ohne eine entsprechende UN-Resolution) der NATO gegen die Republik Serbien im Jahr 1999 (Staatsgrenzen dürfen also unter Umständen verändert werden).
Die Gewalt begann schon wenige Monate danach, als der durch die "Rosenrevolution" 2003 mit Unterstützung der USA in Tiflis an die Macht gekommene Exil-Georgier, Michail Saakaschwili, in der Nacht auf den 8.8.2008 einen militärischen Angriff auf die seit 1992/93 abtrünnigen Südosseten bzw. deren Hauptstadt Zchinwali befahl und dabei auch russische Friedenstruppen (als Schutzmacht der Osseten) unter Beschuss gerieten. Dies nachdem die Regierung Bush jr. die georgische Armee durch NATO-Offiziere ausgebildet und aufgerüstet hatte. Laut einem NZZ-Artikel vom 1.10.2009 kam eine von der EU eingesetzte Untersuchungskommission unter der Schweizer Diplomatin Heidi Tagliavini 2009 zum Schluss, dass zuvor von beiden Seiten Provokationen in Form von Terroranschlägen, Entführungen und Morde begangen worden waren. Zudem hatte Russland jahrelang an willige Osseten und Abchasen russische Pässe ausgegeben, was völkerrechtswidrig sei, da dies die Staatlichkeit Georgiens untergrabe (Abchasien ist eine weitere abtrünnige Region Georgiens am schwarzen Meer). Saakaschwili wollte offenkundig mit dem überraschenden Angriff auf die Osseten die volle Kontrolle der Zentralregierung über das Gebiet wieder erlangen, da die Satzungen der NATO nur die Aufnahme von Ländern erlauben in denen keine ungelösten territorialen Konflikte vorhanden sind. Den Abchasen hätte also das gleiche Schicksal gedroht wenn die Aktion erfolgreich gewesen wäre. Da die Russen aber aufgepasst hatten, lief innert 24 Stunden eine russische Gegenoffensive welche die georgischen Verbände und ihre amerikanischen Berater innert wenigen Tagen bis nach Gori (Geburtsort von Stalin) zurückwarf. Präsident Saakaschwili verlor bald darauf in Tiflis die Macht und setzte sich in die Ukraine ab. Die heutige georgische Regierung unterhält wieder politische und wirtschaftliche Beziehungen zu Russland und verzichtet auf einen NATO-Beitritt. Siehe dazu das Interview von Roger Köppel mit dem aktuellen georgischen Regierungschef Kobachidse (auf englisch mit deutschen Untertiteln):
https://www.youtube.com/watch?v=xWh6bAfLdhw
In der Ukraine begann die Gewalt mit dem rechtswidrigen Sturz des 2010 legal gewählten Präsidenten Wiktor Janukowitsch, der zwischen der EU und Russland hin und her gerissen war und daher die Unterzeichnung eines EU-Assoziierungsabkommens auf unbestimmte Zeit vertagte. Nach den folgenden wochenlangen Protesten und Krawallen auf dem Maidan in Kiew ("Euromaidan") unterschrieb er unter Vermittlung Deutschlands, Frankreichs und Polens am 21.2.2014 einen Vertrag mit der Opposition und versprach baldige Neuwahlen. Trotzdem wurde er am Tag darauf durch einen regelrechten Putsch gestürzt und in die Flucht getrieben, indem unbekannte Heckenschützen aus verschiedenen Positionen zuerst auf die "Berkut"-Polizei und anschliessend auf militante Demonstranten schossen, welche die "Institutskaja" hinauf das durch eine Strassensperre der Polizei geschützte Regierungsviertel stürmen wollten.
Dabei kamen insgesamt 104 Menschen ums Leben, darunter 34 Polizisten und Vertreter der Regierung. Nach dem Putsch wurde der zuvor völlig unbekannte Exil-Ukrainer Arsenij Jazenjuk Chef der neuen Übergangsregierung, von dem die Europagesandte des US-Statedepartements, Victoria Nuland, bereits einige Tage davor in einem abgehörten Telefongespräch mit dem amerikanischen Botschafter in Kiew, Geoffrey Pyatt, gesprochen hatte ("Jaz is our man"). Die mit rund 600 Mann unter Führung von Andrij Parubi während Wochen auf dem Maidan präsenten militanten und teilweise bewaffneten Kräfte des "Prawi sektor" ("Rechter Sektor") und der "Swoboda" ("Freiheit") weigerten sich zuerst, der neuen Regierung ihre Waffen auszuhändigen. Mitglieder der "Swoboda" unter Oleh Tjahibok besetzten aber anfangs im Kabinett das Aussen-, Innen-, Verteidigungs- sowie das Ministerium für Kultur und "strategische" Kommunikation (Propaganda), während die Mitglieder des "Prawi sektor" unter Dmitro Jarosch eine Zusammenarbeit mit der neuen Regierung verweigerten. Als eine der ersten Amtshandlungen nach dem Putsch wurde in der ganzen Ukraine die russische Sprache als offizielle Amtssprache und als Unterrichtssprache in den Schulen verboten (auch in den mehrheitlich von russischstämmigen Menschen bewohnten Regionen im Osten und Süden des Landes).
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Als erste Reaktion auf den rechtswidrigen Umsturz wurde in Simferopol auf der Krim das lokale Parlament von prorussischen Aktivisten besetzt und russische Soldaten verliessen illegal den Flottenstützpunkt in Sewastopol und besetzten strategische Positionen auf der ganzen Krim bzw. blockierten die ukrainischen Kasernen. Unter dem Schutz dieser "grünen Männchen" konnte dann am 16.3.2014 ein Referendum über den zukünftigen Status der Krim durchgeführt werden. Rund 70% der Bevölkerung stimmten für eine Wiedervereinigung mit Russland, was ungefähr dem Anteil der ethnischen Russen auf der Krim entspricht. Der Kommandant der ukrainischen Flotte in Sewastopol lief mit dem Grossteil der Matrosen zu den Russen über, so dass fast die gesamte Flotte im Kriegshafen verblieb (die Schwarzmeerflotte war anfang der 90er Jahre zwischen Russland und der Ukraine aufgeteilt worden). Die restlichen Matrosen und Soldaten durften später in die Ukraine heimkehren. Angesichts der klaren Machtverhältnisse auf der Krim verzichteten die ukrainischen Ultra-Nationalisten auf die angedrohte Entsendung von "Zügen der Freundschaft" (mit bewaffneten Schlägern) nach Simferopol.
Auch in den Städten Lugansk, Donezk und Mariupol in der Ostukraine besetzten prorussische Aktivisten analog den Vorgängen einige Monate zuvor in der Westukraine Regierungs- und Verwaltungsgebäude und hissten russische Fahnen auf vielen Gebäuden. Auch hier gab es am 11. bzw. 12.5.2014 Referenden über die zukünftige Zugehörigkeit dieser Gebiete, doch konnten dabei nur ungefähr die Hälfte der Bevölkerungen überhaupt darüber abstimmen, weil die Separatisten nicht die volle Kontrolle über die jeweiligen Bezirke hatten. Auch in anderen ukrainischen Städten wie Odessa und Charkow gab es prorussische Demonstrationen, doch wurden diese von den ukrainischen Behörden unterdrückt. In Odessa kam es am 2.5.2014 zu einem Massaker, als prorussische Aktivisten von mit Zügen aus Kiew angereisten Rechtsradikalen und Hooligans in ein Gewerkschaftshaus abgedrängt wurden welches dann kurzerhand abgefackelt und mit Handfeuerwaffen beschossen wurde. Rund 50 Menschen verloren dabei ihr Leben während die ukrainische Polizei untätig herumstand.
Die am 12.4.2014 von der neuen Regierung in Kiew verkündete "Antiterror-Operation" gegen die Separatisten im Osten wurde anfangs nur zaghaft umgesetzt, da viele russischstämmige Soldaten auch hier mit den Aufständischen sympathisierten und teilweise mitsamt dem Material überliefen. Erst nachdem sich der "Spreu vom Weizen" getrennt hatte und nach der Bildung von Freiwilligenverbänden wie "Donbas","Asow" oder "Aidar" - welche in der ukrainischen Nationalgarde (dem Innen- und nicht dem Verteidigungsministerium unterstellt) zusammengefasst wurden - gewann die ukrainische Offensive an Kraft, so dass bereits im Mai/Juni 2014 die Hafenstadt Mariupol vom Asow'schen Bataillon (später ein Regiment bzw. neu die 12. Brigade für spezielle Aufgaben) und einer Marinebrigade zurückerobert und bis zur vollständigen Kapitulation im berühmten Stahlwerk "Asowstal" nach der russischen Intervention vom 24.2.2022 besetzt werden konnte. Bei den heftigen Kämpfen im Frühjahr 2022 mussten die Zivilisten wochenlang im Keller ausharren, da die Stadtverwaltung die rechtzeitige Evakuierung der Zivilbevölkerung versäumt hatte). Nach den Kesselschlachten von Ilowaisk im Juli/Aug. 2014 bzw. von Debaltsewoim Jan./Feb. 2015, bei denen weit über tausend ukrainische Soldaten und hunderte von Kämpfern der neu aufgestellten Donezker- und Lugansker Volksmilizen sowie vermutlich rund 100 russische Soldaten ihr Leben verloren (laut Kiew beteiligten sich mehrere russische Bataillone an den Kämpfen), wurde am 12.2.2015 das Minsker Abkommen (Minsk II) unter Vermittlung von Weissrussland, Deutschland und Frankreich unterzeichnet. Vertragspartner als Unterzeichnende waren: der frühere Präsident der Ukraine Leonid Kutschma, der Botschafter der Russischen Föderation in der Ukraine Michail Surabow, die Milizenführer der selbstproklamierten Volksrepubliken Igor Plotnizki und Alexander Sachartschenko sowie die OSZE-Beauftragte Heidi Tagliavini. Der Waffenstillstand und die vertrauensbildenden Massnahmen (wie z.B. der Rückzug der schweren Waffen von der Frontlinie) wurden dabei von beiden Seiten wiederholt verletzt. Am 18.2.2017 unterzeichnete der russische Präsident Wladimir Putin ein Dekret, nach dem Pässe und andere Papiere der Volksrepubliken Donezk und Lugansk von Russland offiziell als gültig anerkannt wurden, was wiederum die Staatlichkeit der Ukraine untergrub und daher dem Minsker Abkommen widersprach, wonach die abtrünnigen Gebiete weiterhin zur Ukraine gehörten. Insgesamt verloren in dem jahrelangen Konflikt bis 2022 rund 14'000 Menschen ihr Leben, darunter ca. 3'500 Zivilisten inkl. 200 Kinder, besonders in der Stadt Donezk und Umgebung welche von der ukrainischen Armee immer wieder mit Artillerie (Granaten und Raketen) oder durch Scharfschützen beschossen wurde.
Nachdem eine von NATO-Offizieren jahrelang gut ausgebildete und mit modernen Waffen aufgerüstete ukrainische Elitearmee von rund 130'000 Mann ab Sommer 2021 vor dem Donbas aufmarschiert war um den Konflikt offenkundig gewaltsam zu lösen und seit Anfang 2022 auch der ukrainische Beschuss von Donezk und dessen Umland wieder verstärkt wurde, unterzeichnete Präsident Putin am 21.2.2022 ein Freundschafts- und Beistandsabkommen mit den ostukrainischen Volksrepubliken und anerkannte ausdrücklich deren Unabhängigkeitvon Kiew. Das Minsker Abkommen habe keine Zukunft mehr. Am 24.2.2022 intervenierte die russische Armee mit anfangs "nur" rund 190'000 Mann in der Ukraine da die rund 40'000 Mann der Donezker- und Lugansker Volksmilizen einem Angriff der ukrainischen Elitearmee nicht mehr hätten standhalten können. Zuvor hatte die Russische Föderation im Dez. 2021 den USA noch einmal Verhandlungen über den Abschluss eines gesamteuropäischen Sicherheitsabkommen unter Berücksichtigung des Konflikts in der Ukraine vorgeschlagen, was aber von der Regierung Biden abgelehnt wurde. Bei Beginn der "speziellen Militäroperation" erklärte Joe Biden öffentlich, das politische Ziel sei der Sturz des Regimes in Moskau.
Mit dem Beginn der russischen Sommeroffensive an allen Frontabschnitten dürften die ukrainischen Kräfte endgültig überdehnt werden. Da der Oberbefehlshaber der Ukraine, Alexander Syrskij, aus der Region Sumy und Charkow verschiedene Verbände wie die 36. Marinebrigade, die 43. Artilleriebrigade, die 44. mechanisierte Brigade, die 82. Air Assault Brigade sowie die berüchtigte 12. Brigade "Asow" nach Südosten verlegen musste, um die Lage um den wichtigen Logistikpunkt Pokrowsk bzw. die Stadt Konstantinowka zu stabilisieren, dürften die Russen auch bei der oben erwähnten Einrichtung einer Sicherheitszone im Norden rasche Fortschritte machen. Rund 50'000 russische Soldaten werden dort eingesetzt um die zukünftige Bedrohung durch ukrainische Drohnen zu minimieren.
Zusammenfassend kann gesagt werden, dass in dem jahrelangen Konflikt alle Seiten das Völkerrecht missachtetoder zum eigenen Vorteil interpretiert haben. Angefangen damit hat aber klar der Westen (NATO und EU), der mit der finanziellen und politischen Unterstützung des rechtswidrigen Putsches in Kiew 2014 die Gewaltspirale in der Ukraine in Gang setzte und mit den anhaltenden Waffenlieferungen und Geheimdienstinformationen für den Tod von weit mehr als einer Million Soldaten auf beiden Seiten und unzähligen Zivilisten entscheidend mitverantwortlichist. Zudem wurde zumindest im Falle der Ukraine mit der NATO-Erklärung von 2008 zu deren Aufnahme als Beitrittskandidat der Geist des Budapester Memorandums von 1994 verletzt. In einem erstaunlich offenen, zweiseitigen Interview in der NZZ vom 6. Mai hat der amerikanische Politikwissenschaftler Prof. John Mearsheimervon der Universität Chicago erklärt, er hätte anstelle von Präsident Putin "die Ukraine schon viel früher überfallen". Und: "Der Westen ist der Bösewicht. Aber das wollen die USA und die Europäer natürlich nicht hören". Er glaube, dass dieser Krieg auf dem Schlachtfeld entschieden werde und dass wir am Ende einen eingefrorenen Konflikt haben werden (ähnlich wie in Georgien).
Über das Problem des ukrainischen Faschismus und Ultra-Nationalismus, der letztlich die multiethnische Ukraine in ihren Grenzen von 1991 zerstört hat, äusserte er sich nicht. Stattdessen hat die EU gerade die ersten 150 Milliarden Euro zum Aufbau einer eigenen Rüstungsindustrie beschlossen. Der neue Vorsteher des Schweizer Verteidigungsdepartementes, Bundesrat Martin Pfister, hat in einem NZZ-Artikel vom 27. Mai erklärt, die Kooperation mit der EU und der NATO müsse intensiviert werden, "stets in Vereinbarkeit mit der Neutralität". In der gleichen NZZ-Ausgabe wurde auch berichtet, dass die Schweiz den Spitzendiplomaten Gabriel Lüchinger nach Moskau schicke um für Friedensgespräche in der Schweiz zu sondieren (Bürgenstock II).
Ob der während Jahren provozierte und stigmatisierte "russische Bär" darauf noch eingeht?
(Der Beitrag folgt der Schweizer Rechtschreibung)
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ fd208ee8:0fd927c1
2024-12-26 07:02:59
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening.
Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
I'm a starving autist.
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of Clever Ideas We Have Had.
Because they are clever, the ideas. And we have had them.
-
 @ 6be5cc06:5259daf0
2025-01-21 23:17:29
@ 6be5cc06:5259daf0
2025-01-21 23:17:29A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.