-
 @ a296b972:e5a7a2e8
2025-05-04 08:30:56
@ a296b972:e5a7a2e8
2025-05-04 08:30:56Am Ende der Woche von Unseremeinungsfreiheit wird in der Unserehauptstadt von Unserdeutschland, Unserberlin, voraussichtlich der neue Unserbundeskanzler vereidigt.
Der Schwur des voraussichtlich nächsten Unserbundeskanzlers sollte aktualisiert werden:
Jetzt, wo endlich mein Traum in Erfüllung geht, nur einmal im Leben Unserbundeskanzler zu werden, zahlen sich für mich alle Tricks und Kniffe aus, die ich angewendet habe, um unter allen Umständen in diese Position zu kommen.
Ich schwöre, dass ich meine Kraft meinem Wohle widmen, meinen Nutzen mehren, nach Vorbild meines Vorgängers Schaden von mir wenden, das Grundgesetz und die Gesetze des Unserbundes formen, meine Pflichten unsergewissenhaft erfüllen und Unseregerechtigkeit gegen jedermann und jederfrau nicht nur üben, sondern unter allen Umständen auch durchsetzen werde, die sich mir bei der Umsetzung der Vorstellungen von Unseredemokratie in den Weg stellen. (So wahr mir wer auch immer helfe).
Der Antrittsbesuch des Unserbundeskanzlers beim Repräsentanten der noch in Unserdeutschland präsenten Besatzungsmacht wird mit Spannung erwartet.
Ein großer Teil der Unsereminister ist schon bekannt. Die Auswahl verspricht viele Unsereüberraschungen.
Die Unsereeinheitspartei, bestehend aus ehemaligen Volksparteien, wird weiterhin dafür sorgen, dass die Nicht-Unsereopposition so wenig wie möglich Einfluss erhält, obwohl sie von den Nicht-Unserebürgern, die mindestens ein Viertel der Urnengänger ausmachen, voll-demokratisch gewählt wurde.
Das Zentralkomitee der Deutschen Unseredemokratischen Bundesrepublik wird zum Wohle seiner Unserebürger alles daransetzen, Unseredemokratie weiter voranzubringen und hofft auch weiterhin auf die Unterstützung von Unser-öffentlich-rechtlicher-Rundfunk.
Die Unserepressefreiheit wird auch weiterhin garantiert.
Auf die Verlautbarungen der Unserepressekonferenz, besetzt mit frischem Unserpersonal, brauchen die Insassen von Unserdeutschland auch weiterhin nicht zu verzichten.
Alles, was nicht gesichert unserdemokratisch ist, gilt als gesichert rechtsextrem.
Als Maxime gilt für alles Handeln: Es muss unter allen Umständen demokratisch aussehen, aber wir (die Unseredemokraten) müssen alles in der Hand haben.
Es ist unwahrscheinlich, dass Unsersondervermögen von den Unserdemokraten zurückgezahlt wird. Dieser Vorzug ist den Unserebürgern und den Nicht-Unserebürgern durch Unseresteuerzahlungen vorbehalten.
Die Unserebundeswehr soll aufgebaut werden (Baut auf, baut auf!), die Unsererüstungsindustrie läuft auf Hochtouren und soll Unserdeutschland wieder unserkriegstüchtig machen, weil Russland immer Unserfeind sein wird.
Von Unserdeutschland soll nur noch Unserfrieden ausgehen.
Zur Bekräftigung, dass alles seinen unser-sozialistischen Gang geht, tauchte die Phoenix*in aus der Asche auf, in dem Unseremutti kürzlich ihren legendären Satz wiederholte:
Wir schaffen das.
Ob damit der endgültige wirtschaftliche Untergang und die Vollendung der gesellschaftlichen Spaltung von Unserdeutschland gemeint war, ist nicht überliefert.
Orwellsche Schlussfolgerung:
Wir = unser
Ihr = Euer
Vogel und Maus passen nicht zusammen
Ausgerichtet auf Ruinen und der Zukunft abgewandt, Uneinigkeit und Unrecht und Unfreiheit für das deutsche Unserland.
Unserdeutschland – ein Land mit viel Vergangenheit und wenig Zukunft?
Es ist zum Heulen.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ b2caa9b3:9eab0fb5
2025-05-04 08:20:46
@ b2caa9b3:9eab0fb5
2025-05-04 08:20:46Hey friends,
Exciting news – I’m currently setting up my very first Discord server!
This space will be all about my travels, behind-the-scenes stories, photo sharing, and practical tips and insights from the road. My goal is to make it the central hub connecting all my decentralized social platforms where I can interact with you more directly, and share exclusive content.
Since I’m just starting out, I’d love to hear from you:
Do you know any useful RSS-feed integrations for updates?
Can you recommend any cool Discord bots for community engagement or automation?
Are there any tips or features you think I must include?
The idea is to keep everything free and accessible, and to grow a warm, helpful community around the joy of exploring the world.
It’s my first time managing a Discord server, so your experience and suggestions would mean a lot. Leave a comment – I’m all ears!
Thanks for your support, Ruben Storm
-
 @ 86dfbe73:628cef55
2025-05-04 06:56:33
@ 86dfbe73:628cef55
2025-05-04 06:56:33Building A Second Brain (BASB) ist eine Methode, mit der man Ideen, Einsichten und Vernetzungen, die man durch seine Erfahrungen gewonnen hat, systematisch speichert und die jeder Zeit abrufbar sind. Kurz, BASB erweitert das Gedächtnis mit Hilfe moderner digitaler Werkzeuge und Netzwerke. Die Kernidee ist, dass man durch diese Verlagerung sein biologisches Gehirn befreit, um frei denken zu können, seiner Kreativität freien Lauf zu geben oder einfach im Moment sein kann.
Die Methode besteht aus drei Grundschritten: dem Sammeln von Ideen und Erkenntnissen, dem Vernetzen dieser Ideen und Erkenntnisse und dem Erschaffen konkreter Ergebnisse.
Sammeln: Der erste Schritt beim Aufbau eines Second Brains ist das «Sammeln» der Ideen und Erkenntnisse, die genug wichtig oder interessant sind, um sie festzuhalten. Dafür wird als Organisationsstruktur P.A.R.A empfohlen.
Vernetzen: Sobald man angefangen hat, sein persönliches Wissen strukturiert zu sammeln, wird man anfangen, Muster und Verbindungen zwischen den Ideen und Erkenntnissen zu erkennen. Ab dieser Stelle verwende ich parallel die Zettelkastenmethode (ZKM)
Erschaffen: All das Erfassen, Zusammenfassen, Verbinden und Strukturieren haben letztlich das Ziel: Konkrete Ergebnisse in der realen Welt zu erschaffen.
PARA ist die Organisationsstruktur, die auf verschiedenen Endgeräten einsetzt werden kann, um digitale Informationen immer nach dem gleichen Schema abzulegen. Seien es Informationen, Notizen, Grafiken, Videos oder Dateien, alles hat seinen festen Platz und kann anhand von vier Kategorien bzw. „Buckets“ kategorisiert werden.
PARA steht dabei für: * Projekte * Areas * Ressourcen * Archiv
Projekte (engl. Projects) sind kurzfristige Bemühungen in Arbeit und Privatleben. Sie sind das, woran Du aktuell arbeitest. Sie haben einige für die Arbeit förderliche Eigenschaften: * Sie haben einen Anfang und ein Ende (im Gegensatz zu einem Hobby oder einem Verantwortungsbereich). * Sie haben ein konkretes Ergebnis, dass erreicht werden soll und bestehen aus konkreten Schritten, die nötig und zusammen hinreichend sind, um dieses Ziel zu erreichen, entspricht GTD von David Allen
Verantwortungsbereiche (engl. Areas) betreffen alles, was man langfristig im Blick behalten will. Sie unterscheidet von Projekten, dass man bei ihnen kein Ziel verfolgt, sondern einem Standard halten will. Sie sind dementsprechend nicht befristet. Man könnte sagen, dass sie einen Anspruch an uns selbst und unsere Lebenswelt darstellen.
Ressourcen (engl. Resources) sind Themen, die allenfalls langfristig relevant oder nützlich werden könnten. Sie sind eine Sammelkategorie für alles, was weder Projekt noch Verantwortungsbereich ist. Es sind: * Themen, die interessant sind. (English: Topic) * Untersuchungsgegenständige, die man erforschen will. (Englisch: Subject) * Nützliche Informationen für den späteren Gebrauch.
Das Archiv ist für alles Inaktive aus den obigen drei Kategorien. Es ist ein Lager für Beendetes und Aufgeschobenes.
Das System PARA ist eine nach zeitlicher Handlungsrelevanz angeordnete Ablage. Projekte kommen vor den Verantwortungsbereichen, weil sie einen kurz- bis mittelfristigen Zeithorizont haben, Verantwortungsbereiche dagegen einen unbegrenzten Zeithorizont. Ressourcen und Archiv bilden die Schlusslichter, weil sie gewöhnlich weder Priorität haben, noch dringend sind.
-
 @ 57d1a264:69f1fee1
2025-05-04 06:37:52
@ 57d1a264:69f1fee1
2025-05-04 06:37:52KOReader is a document viewer for E Ink devices. Supported file formats include EPUB, PDF, DjVu, XPS, CBT, CBZ, FB2, PDB, TXT, HTML, RTF, CHM, DOC, MOBI and ZIP files. It’s available for Kindle, Kobo, PocketBook, Android and desktop Linux.
Download it from https://koreader.rocks Repository: https://github.com/koreader/koreader
originally posted at https://stacker.news/items/970912
-
 @ 57d1a264:69f1fee1
2025-05-04 06:27:15
@ 57d1a264:69f1fee1
2025-05-04 06:27:15Well, today posts looks are dedicated to STAR WARS. Enjoy!
Today we’re looking at Beat Saber (2019) and why its most essential design element can be used to make great VR games that have nothing to do with music or rhythm.
https://www.youtube.com/watch?v=EoOeO7S9ehw
It’s hard to believe Beat Saber was first released in Early Access seven years ago today. From day one, it was clear the game was something special, but even so we couldn’t have predicted it would become one of VR’s best-selling games of all time—a title it still holds all these years later. In celebration of the game’s lasting legacy we’re re-publishing our episode of Inside XR Design which explores the secret to Beat Saber’s fun, and how it can be applied to VR games which have nothing to do with music.
Read more at https://www.roadtovr.com/beat-saber-instructed-motion-until-you-fall-inside-xr-design/
originally posted at https://stacker.news/items/970909
-
 @ 57d1a264:69f1fee1
2025-05-04 06:16:58
@ 57d1a264:69f1fee1
2025-05-04 06:16:58Found this really fun, so created a few intros for latest SN newsletters https://stacker.news/items/960787/r/Design_r?commentId=970902 and https://stacker.news/items/970459/r/Design_r?commentId=970905
Create your STAR-WARS-like movie intro https://starwarsintrocreator.kassellabs.io/
originally posted at https://stacker.news/items/970906
-
 @ 4fe14ef2:f51992ec
2025-05-04 06:02:38
@ 4fe14ef2:f51992ec
2025-05-04 06:02:38Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and zap on.
Share and repost: N: https://nostrudel.ninja/#/n/nevent1qvzqqqqqqypzqnlpfme... X: https://x.com/AGORA_SN/status/1918907693516914793
originally posted at https://stacker.news/items/970896
-
 @ 2a655bda:344d8870
2025-05-04 04:24:19
@ 2a655bda:344d8870
2025-05-04 04:24:19Bet888 là một nền tảng giải trí trực tuyến hiện đại, thu hút sự quan tâm của đông đảo người dùng nhờ vào những trải nghiệm độc đáo và phong phú mà nó mang lại. Nền tảng này được thiết kế với giao diện thân thiện, dễ sử dụng, giúp người tham gia dễ dàng truy cập và tận hưởng các hoạt động giải trí ngay trên thiết bị của mình. Bet888 không chỉ là một nền tảng giải trí đơn thuần mà còn tạo ra một không gian cho người tham gia có thể thư giãn, học hỏi và khám phá những cơ hội mới. Với sự kết hợp hoàn hảo giữa công nghệ tiên tiến và các dịch vụ tiện ích, Bet888 đem đến cho người tham gia một trải nghiệm trực tuyến thú vị và mượt mà. Từ các trò chơi thử thách trí tuệ, các sự kiện đặc biệt, đến những hoạt động cộng đồng, nền tảng này không ngừng cải tiến để đáp ứng nhu cầu giải trí ngày càng cao của người dùng. Bet888 cam kết mang lại một không gian giải trí an toàn, thân thiện và luôn tạo ra những cơ hội mới mẻ cho cộng đồng người tham gia.
Một trong những yếu tố làm nên sự thành công của BET888 chính là khả năng cá nhân hóa trải nghiệm người dùng. Nền tảng này cung cấp rất nhiều lựa chọn cho người tham gia, từ các trò chơi giải trí, thử thách trí tuệ đến các sự kiện đặc biệt, giúp người tham gia có thể tự do lựa chọn hoạt động phù hợp với sở thích và nhu cầu cá nhân. Bet888 không chỉ mang lại những giây phút giải trí thú vị mà còn giúp người tham gia phát triển các kỹ năng cá nhân, từ khả năng giải quyết vấn đề đến tư duy chiến lược. Các trò chơi và thử thách được thiết kế không chỉ để giải trí mà còn để kích thích sự sáng tạo và khả năng tư duy logic của người tham gia. Nền tảng này cũng chú trọng đến việc xây dựng một cộng đồng mạnh mẽ, nơi mà người tham gia có thể giao lưu, kết nối và học hỏi lẫn nhau. Các sự kiện cộng đồng được tổ chức thường xuyên, khuyến khích sự hợp tác và chia sẻ ý tưởng sáng tạo giữa các thành viên, từ đó tạo ra một không gian giải trí vui vẻ và đầy thử thách. Bet888 luôn lắng nghe phản hồi từ cộng đồng người tham gia để cải tiến các dịch vụ, giúp nền tảng ngày càng trở nên hấp dẫn và phù hợp với nhu cầu người dùng.
Bảo mật và chất lượng dịch vụ là hai yếu tố quan trọng mà Bet888 luôn chú trọng. Nền tảng này áp dụng các công nghệ bảo mật tiên tiến, đảm bảo rằng thông tin cá nhân của người tham gia luôn được bảo vệ một cách an toàn. Với hệ thống bảo mật chặt chẽ, người dùng có thể yên tâm tham gia vào các hoạt động trực tuyến mà không phải lo lắng về vấn đề bảo mật dữ liệu. Bet888 cũng đặc biệt chú trọng đến việc cung cấp dịch vụ hỗ trợ khách hàng chất lượng cao, giúp người tham gia giải quyết mọi thắc mắc và vấn đề gặp phải trong quá trình sử dụng nền tảng. Đội ngũ hỗ trợ khách hàng của Bet888 luôn sẵn sàng 24/7 để đảm bảo rằng người dùng có thể nhận được sự trợ giúp kịp thời và hiệu quả. Bên cạnh đó, nền tảng này liên tục cải tiến giao diện người dùng, giúp người tham gia dễ dàng tìm kiếm và tham gia vào các hoạt động yêu thích mà không gặp phải bất kỳ trở ngại nào. Các tính năng mới luôn được cập nhật nhanh chóng, giúp người tham gia luôn cảm thấy hài lòng và không bao giờ cảm thấy nhàm chán. Bet888 cam kết tiếp tục phát triển mạnh mẽ, mang lại cho người dùng những trải nghiệm thú vị, an toàn và chất lượng, từ đó giữ vững vị thế là một trong những nền tảng giải trí hàng đầu.
-
 @ 502ab02a:a2860397
2025-05-04 03:13:06
@ 502ab02a:a2860397
2025-05-04 03:13:06เรารู้จักกับ Circadian Rhythm และ Infradian Rhythm แล้ว คราวนี้เรามารู้จักกับ Ultradian Rhythm กันครับ จากรากศัพท์ภาษาละติน คำว่า “Ultra” แปลว่า “มากกว่า” หรือ “ถี่กว่า” คำว่า diem” = แปลว่า "วัน" พอเอามารวมกันเป็น “ultradian” ก็หมายถึงวงจรชีวภาพที่เกิดขึ้น บ่อยกว่า 1 รอบต่อวัน (ความถี่สูงกว่ารอบ 24 ชั่วโมง) ไม่ใช่ “ยาวกว่า 1 วัน” สรุปเป็นภาษาง่ายๆคือ "จังหวะชีวภาพที่เกิดซ้ำ มากกว่า 1 ครั้งภายใน 24 ชั่วโมง"
หรือถ้าเราจะเรียงลำดับของ Rythm ทั้ง 3 ประเภทเราจะได้เป็น 1.Circadian Rhythm (ประมาณ 24 ชม.) 2.Ultradian Rhythm (น้อยกว่า 24 ชม.) 3.Infradian Rhythm (มากกว่า 24 ชม.)
สำหรับตัวอย่าง Ultradian Rhythm ที่สำคัญๆนะครับ เช่น 1. วัฏจักรการนอน (Sleep Cycle) ที่แต่ละรอบ จะอยู่ที่ราวๆ 90–120 นาที สลับกันไปมาระหว่าง NREM (หลับลึก) และ REM (ฝัน) อย่างที่สายสุขภาพเรียนรู้กันมาคือ ถ้าหลับสลับครบ 4–6 รอบ จะหลับสนิท ฟื้นเช้ามาสดชื่นแจ่มใสพักผ่อนเต็มที่
แสงเช้า-แดดอ่อนๆ ช่วยรีเซ็ต circadian แต่ก็ส่งผลให้ ultradian sleep cycle เริ่มต้นตรงจังหวะพอดี นอกจากนี้ยังมีสิ่งที่เรียกว่า Power nap ตอนแดดบ่าย (20–25 นาทีแดดอ่อน) จะช่วยกระตุ้น ultradian nap cycle ให้ตื่นขึ้นมาเป๊ะ ไม่งัวเงีย ให้เลือกจุดที่แดดยังอ่อน เช่น ริมหน้าต่างที่มีแดดผ่านมานุ่ม ๆ หรือใต้ต้นไม้ที่กรองแสงได้บางส่วน ไม่จำเป็นต้องนอนตากแดดโดยตรง แต่ให้ “รับแสงธรรมชาติ” พร้อมกับงีบ จะช่วยให้ circadian และ ultradian cycles ทำงานประสานกันได้ดีขึ้น
- การหลั่งฮอร์โมนแบบพัลซ์ หรือ Pulsatile Hormone Secretion คือรูปแบบการปล่อยฮอร์โมนออกมาจากต่อมต่าง ๆ ในร่างกายแบบเป็น “จังหวะ” หรือ “เป็นช่วง” (bursts/pulses) ไม่ใช่การหลั่งออกมาอย่างต่อเนื่องตลอดเวลา เช่น เทพแห่งการลดน้ำหนัก Growth Hormone (GH) หลั่งพุ่งตอนหลับลึกทุก 3–4 ชั่วโมง / Cortisol มีพัลซ์เล็กๆ ในวัน แม้หลักๆ จะเป็น circadian แต่ก็มี ultradian pulse ทุก 1–2 ชั่วโมง ได้เหมือนกัน / Insulin & Glucagon ชัดเลยชาว keto IF รู้ดีที่สุดว่า หลั่งเป็นรอบตามมื้ออาหารและช่วงพักระหว่างมื้อ
ลองนึกภาพว่า “แสงแดง” และ “อินฟราเรด” เปรียบเหมือนอาหารเช้าของเซลล์เรา เมื่อผิวเราโดนแดดอ่อน ๆ ในช่วงเช้าหรือบ่ายแก่ แสงเหล่านี้จะซึมเข้าไปกระตุ้น “โรงไฟฟ้าประจำเซลล์” (ไมโตคอนเดรีย) ให้ผลิตพลังงาน (ATP) ขึ้นมาเพิ่ม เหมือนเติมน้ำมันให้เครื่องยนต์วิ่งได้ลื่น พอเซลล์มีพลังงานมากขึ้น ในช่วงที่ร่างกายหลั่งฮอร์โมนการซ่อมแซมอย่าง “growth hormone” (GH) ร่างกายก็จะใช้พลังงานจากแสงนี้พร้อมกับฮอร์โมนในการซ่อมแซมกล้ามเนื้อและเนื้อเยื่อต่าง ๆ ได้เต็มประสิทธิภาพขึ้นนั่นเองครับ
- ช่วงเวลาการจดจ่อ หรือ Attention Span & Energy Cycle คนทั่วไปมีสมาธิ/พลังงานโฟกัสอยู่รอบละ 90 นาที หลังจากนั้นควรพัก 10–20 นาที หากฝืนต่อเนื่อง จะเกิดอาการอ่อนล้า สมาธิหลุด
Blue light เช้า จากแดดจะไปกระตุ้นในส่วนของ suprachiasmatic nucleus (SCN) ในสมองให้ปล่อยสารกระตุ้นความตื่นตัว (เช่น คอร์ติซอล) พอสมควร ซึ่งช่วยให้ ultradian cycle ของสมาธิ (โฟกัสได้ประมาณ 90 นาที) ทำงานเต็มประสิทธิภาพ ถ้าเช้าๆ ไม่เจอแดดเลย cycle นี้จะเลื่อนออกไป ทำให้รู้สึกง่วงเหงาหาวนอนเร็ว หรือโฟกัสไม่ได้นานตามปกติ เป็นที่มาของการเพลียแม้จะตื่นสายแล้วก็ตาม
- รอบความหิว หรือ Appetite & Digestive Rhythm ชื่อเท่ห์ป่ะหล่ะ 555 คือความหิวมาเป็นรอบตามวิธีการกินของแต่ละคน ซึ่งเป็นความสัมพันธ์กับ ฮอร์โมน GI (เช่น ghrelin, leptin) ก็วิ่งเป็นรอบเหมือนกัน
แสงแดดเช้า ช่วยตั้ง leptin/ghrelin baseline ให้สมดุล ลดการกินจุกจิกนอกมื้อได้ ส่วนแสงอ่อนๆ ตอนบ่ายช่วยบูสต์ blood flow ในทางเดินอาหาร ให้ digestion cycle หรือการดูดซึมสารอาหารตรงจังหวะ
แดดเป็นแค่ส่วนสำคัญในชีวิตแต่การใช้ Ultradian Rhythm มันต้องประกอบกับกิจกรรมอื่นๆด้วยนะครับ เช่น ทำงานหรืออ่านหนังสือ 90 นาที แล้ว พัก 15–20 นาที ยืดเส้นสาย เคลื่อนไหวเล็กน้อย, ออกกำลังกายให้ตรงจังหวะ, ในช่วง ultradian break พยายามลดการใช้จอมือถือ/คอมฯ ออกไปรับแสงธรรมชาติ หรือยืดเส้น เปิดเพลงเบาๆ เพื่อหลีกเลี่ยง "stimuli" ช่วง break หรือ สิ่งเร้าภายนอก ที่มากระตุ้นประสาทสัมผัสและสมองเรา
แสงแดดจึงเป็น ตัวตั้งเวลา (zeitgeber) ที่ไม่ได้แค่กับรอบวัน-เดือน-ปี แต่รวมถึงจังหวะสั้นๆ ภายในวันด้วย การใช้แสงธรรมชาติให้พอดีในแต่ละช่วง (เช้า เบรก บ่าย) จะช่วยให้ ultradian rhythms ในด้านสมาธิ การนอน ฮอร์โมน และการย่อยอาหาร ทำงานสอดคล้องกับจังหวะชีวิตที่เป็นธรรมชาติที่สุดครับ #pirateketo #SundaySpecialเราจะไปเป็นหมูแดดเดียว #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 211c0393:e9262c4d
2025-05-04 02:32:24
@ 211c0393:e9262c4d
2025-05-04 02:32:24**日本の覚せい剤ビジネスの闇:
警察、暴力団、そして「沈黙の共犯関係」の真相**
1. 暴力団の支配構造(公的データに基づく)
- 輸入依存の理由:
- 国内製造は困難(平成6年「覚せい剤原料規制法」で規制強化)→ ミャンマー・中国からの密輸が主流(国連薬物犯罪事務所「World Drug Report 2023」)。
- 暴力団の利益率:1kgあたり仕入れ価格30万円 → 小売価格500万~1000万円(警察庁「薬物情勢報告書」2022年)。
2. 警察と暴力団の「共生関係」
- 逮捕統計の不自然さ:
- 全薬物逮捕者の70%が単純所持(厚生労働省「薬物乱用状況」2023年)。
- 密輸組織の摘発は全体の5%未満(東京地検特捜部データ)。
- メディアの検証:
- NHKスペシャル「覚せい剤戦争」(2021年)で指摘された「末端ユーザー優先捜査」の実態。
3. 矛盾する現実
- 需要の不可視性:
- G7で最高の覚せい剤価格(1gあたり3~7万円、欧米の3倍)→ 暴力団の暴利(財務省「組織犯罪資金流動調査」)。
- 使用者率は低い(人口の0.2%、国連調査)が、逮捕者の過半数を占める矛盾。
4. 「密輸組織対策」の限界
- 国際的な失敗例:
- メキシコ(カルテル摘発後も市場拡大)、欧州(合成薬物の蔓延)→ 代替組織が即座に台頭(英「The Economist」2023年6月号)。
- 日本の地理的ハンデ:
- 海上密輸の摘発率は10%未満(海上保安庁報告)。
5. 解決策の再考(事実に基づく提案)
- ADHD治療薬の合法化:
- アメリカ精神医学会「ADHD患者の60%が自己治療で違法薬物使用」(2019年研究)。
- 日本ではリタリン・アデロール禁止→ 暴力団の市場独占。
- 労働環境改革:
- 過労死ライン超えの労働者20%(厚労省「労働時間調査」2023年)→ 覚せい剤需要の一因。
6. 告発のリスクと情報源
- 匿名性の重要性:
- 過去の暴力団報復事例(2018年、告発記者への脅迫事件・毎日新聞報道)。
- 公的データのみ引用:
- 例:「警察庁統計」「国連報告書」など第三者検証可能な情報。
結論:変革のためには「事実」の可視化が必要
「薬物=個人の道徳的問題」という幻想が、暴力団と腐敗官僚を利している。
国際データと国内統計の矛盾を突くことで、システムの欺瞞を暴ける。安全な共有のために:
- 個人特定を避け、匿名プラットフォーム(Tor上フォーラム等)で議論。
- 公的機関のデータを直接リンク(例:警察庁PDFレポート)。
この文書は、公表された統計・メディア報道のみを根拠とし、個人の推測を排除しています。
脅威を避けるため、具体的な個人・組織の非難は意図的に避けています。 -
 @ 0c87e540:8a0292f2
2025-05-04 01:53:02
@ 0c87e540:8a0292f2
2025-05-04 01:53:02A plataforma 188W tem se destacado como uma das opções mais confiáveis e empolgantes para jogadores brasileiros que buscam entretenimento de alto nível no mundo dos jogos online. Com um ambiente moderno, seguro e recheado de funcionalidades, o site oferece uma experiência completa, indo muito além das expectativas do público que procura lazer aliado à tecnologia de ponta.
Introdução à Plataforma 188W Desde sua chegada ao mercado, o 188W vem conquistando espaço e fidelizando usuários graças à sua interface intuitiva, sistema de navegação simplificado e compatibilidade com todos os dispositivos — seja computador, tablet ou smartphone. A proposta é clara: oferecer uma plataforma prática e acessível para jogadores de todos os perfis, desde os iniciantes até os mais experientes.
Além de um visual atrativo, o site se destaca por sua segurança. A proteção de dados dos usuários é prioridade, utilizando criptografia de última geração e protocolos rigorosos para garantir uma experiência tranquila e confiável.
Catálogo de Jogos Variado e Emocionante O 188W apresenta um portfólio amplo de jogos para todos os gostos. Entre os destaques estão as slots online (conhecidas como caça-níqueis virtuais), com centenas de opções que variam entre temas clássicos e modernos, gráficos vibrantes e trilhas sonoras imersivas. Esses jogos são desenvolvidos por fornecedores renomados, o que garante qualidade e desempenho técnico superior.
Para quem prefere desafios estratégicos, a plataforma oferece também jogos de cartas e roleta online, que permitem ao usuário testar suas habilidades e explorar diferentes modos de jogo. Muitos desses jogos são ao vivo, com transmissão em tempo real e interatividade com crupiês profissionais, o que torna a experiência ainda mais autêntica e envolvente.
Os fãs de esportes também encontram espaço no 188W. A seção de apostas esportivas é completa, com cobertura de dezenas de modalidades, como futebol, basquete, tênis, MMA, entre outros. É possível apostar antes ou durante os jogos, aproveitando as melhores odds do mercado e diversas promoções exclusivas.
A Experiência do Jogador no 188W Um dos principais diferenciais da plataforma é o foco total na experiência do usuário. Desde o cadastro rápido até o suporte ao cliente 24 horas, tudo é pensado para que o jogador se sinta valorizado e tenha acesso fácil a todas as funcionalidades.
Os bônus de boas-vindas são generosos e frequentes, oferecendo vantagens reais para novos usuários. Além disso, o 188W costuma lançar promoções temáticas, desafios semanais e sorteios especiais que tornam a jornada ainda mais divertida.
O suporte ao cliente é outro ponto forte da plataforma. Com atendimento em português via chat ao vivo, e-mail e WhatsApp, a equipe está sempre pronta para ajudar com dúvidas, problemas técnicos ou informações sobre pagamentos e retiradas.
O sistema de pagamentos também é eficiente e seguro. O 188W aceita diversos métodos populares no Brasil, incluindo PIX, transferências bancárias, carteiras digitais e boletos. As retiradas são processadas rapidamente, muitas vezes em menos de 24 horas.
Conclusão O 188W é muito mais do que uma simples plataforma de jogos. Ele representa um ambiente completo, onde entretenimento, segurança e inovação caminham juntos. Com um catálogo vasto, suporte de qualidade e uma experiência de usuário pensada nos mínimos detalhes, o site se firma como uma excelente escolha para quem busca diversão com praticidade e confiança.
-
 @ 0c87e540:8a0292f2
2025-05-04 01:52:26
@ 0c87e540:8a0292f2
2025-05-04 01:52:26No cenário atual de entretenimento digital, plataformas que oferecem praticidade, segurança e uma ampla gama de jogos são cada vez mais valorizadas pelos usuários. A KCBET surge como uma dessas opções, conquistando o público brasileiro com uma proposta moderna e intuitiva, que combina tecnologia de ponta, variedade de jogos e um suporte eficiente ao usuário.
Desde o primeiro acesso, a KCBET impressiona pelo seu design amigável e pela facilidade de navegação. O site é totalmente otimizado para funcionar tanto em computadores quanto em dispositivos móveis, o que garante liberdade ao usuário para jogar onde e quando quiser. Outro diferencial importante é a interface em português, o que torna a experiência ainda mais personalizada para o público brasileiro.
A KCBETse destaca por oferecer um ambiente seguro, utilizando tecnologias de criptografia avançadas para proteger os dados dos usuários. Além disso, o processo de cadastro é simples e rápido, permitindo que novos jogadores comecem sua jornada em poucos minutos.
Variedade de Jogos para Todos os Perfis O grande atrativo da KCBET é, sem dúvida, a diversidade de jogos disponíveis. A plataforma conta com uma seleção impressionante de opções para todos os gostos e estilos. Os fãs de jogos tradicionais vão encontrar diversas versões de títulos consagrados, enquanto aqueles que preferem novidades e inovação têm à disposição opções modernas com gráficos de última geração e recursos interativos.
Entre os destaques estão os jogos de mesa, jogos de cartas, slots virtuais e opções com crupiês ao vivo — uma experiência que aproxima o jogador da emoção de estar em um ambiente físico, sem sair de casa. Todos os jogos são fornecidos por desenvolvedores renomados do setor, o que garante qualidade visual, fluidez e, principalmente, resultados justos e auditados.
Experiência do Jogador: Imersão e Suporte A experiência do usuário na KCBET vai além dos jogos. A plataforma investe continuamente em proporcionar um ambiente imersivo, com bônus promocionais atrativos, torneios temáticos e desafios semanais que mantêm a emoção sempre em alta. Para novos usuários, há ofertas de boas-vindas que tornam o início da jornada ainda mais empolgante.
Outro ponto alto da KCBET é o atendimento ao cliente. O suporte está disponível 24 horas por dia, sete dias por semana, pronto para auxiliar em qualquer dúvida ou situação. Os canais de atendimento incluem chat ao vivo, e-mail e até suporte via aplicativos de mensagem, garantindo agilidade e eficiência na resolução de problemas.
A KCBET também oferece uma plataforma de pagamentos completa, com diversos métodos de depósito e saque, incluindo opções locais como PIX e boletos bancários. As transações são rápidas, seguras e sem complicações, o que contribui para uma experiência ainda mais satisfatória.
Conclusão: KCBET é a Escolha Certa para Jogadores Brasileiros Com uma proposta moderna, segura e voltada para o entretenimento de qualidade, a KCBET se firma como uma das melhores opções para jogadores brasileiros que buscam diversão online com praticidade. Sua vasta gama de jogos, promoções atrativas, atendimento eficiente e suporte a métodos de pagamento nacionais tornam a plataforma uma escolha inteligente para quem quer transformar momentos de lazer em experiências memoráveis.
-
 @ 5df413d4:2add4f5b
2025-05-04 00:51:49
@ 5df413d4:2add4f5b
2025-05-04 00:51:49Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 01: Ku/苦 Bar
Find a dingy, nondescript alley in a suspiciously quiet corner of Bangkok’s Chinatown at night. Walk down it. Pass the small prayer shrine that houses the angels who look over these particular buildings and approach an old wooden door. You were told that there is a bar here, as to yet nothing suggests that this is so…

Wait! A closer inspection reveals a simple bronze plaque, out of place for its polish and tended upkeep, “cocktails 3rd floor.” Up the stairs then! The landing on floor 3 presents a white sign with the Chinese character for bitter, ku/苦, and a red arrow pointing right.


Pass through the threshold, enter a new space. To your right, a large expanse of barren concrete, an empty “room.” Tripods for…some kind of filming? A man-sized, locked container. Yet, you did not come here to ask questions, such things are none of your business!

And to your left, you find the golden door. Approach. Enter. Be greeted. You have done well! You have found it. 苦 Bar. You are among friends now. Inside exudes deep weirdness - in the etymological sense - the bending of destinies, control of the fates. And for the patrons, a quiet yet social place, a sensual yet sacred space.


Ethereal sounds, like forlorn whale songs fill the air, a strange music for an even stranger magic. But, Taste! Taste is the order of the day! Fragrant, Bizarre, Obscure, Dripping and Arcane. Here you find a most unique use flavor, flavors myriad and manifold, flavors beyond name. Buddha’s hand, burnt cedar charcoal, ylang ylang, strawberry leaf, maybe wild roots brought in by some friendly passerby, and many, many other things. So, Taste! The drinks here, libations even, are not so much to be liked or disliked, rather, the are liquid context, experience to be embraced with a curious mind and soul freed from judgment.

And In the inner room, one may find another set of stairs. Down this time. Leading to the second place - KANGKAO. A natural wine bar, or so they say. Cozy, botanical, industrial, enclosed. The kind of private setting where you might overhear Bangkok’s resident “State Department,” “UN,” and “NGO” types chatting auspiciously in both Mandarin and English with their Mainland Chinese counterparts. But don’t look hard or listen too long! Surely, there’s no reason to be rude… Relax, relax, you are amongst friends now.

**苦 Bar. Bangkok, circa 2020. There are secrets to be found. Go there. **
Plebchain #Bitcoin #NostrArt #ArtOnNostr #Writestr #Createstr #NostrLove #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Bangkok #Thailand #Siamstr
-
 @ e516ecb8:1be0b167
2025-05-04 01:45:38
@ e516ecb8:1be0b167
2025-05-04 01:45:38El sol de la tarde caía oblicuo sobre un campo de hierba alta, tiñéndolo de tonos dorados y rojizos. A un lado, una formación disciplinada de hombres vestidos con armaduras de cuero y metal relucía bajo la luz. Eran legionarios romanos, cada uno portando un scutum, el gran escudo rectangular, y un gladius corto y letal. Se movían como una sola entidad, un muro de escudos erizado de puntas de lanza que asomaban por encima.
Al otro lado del campo, una fuerza más dispersa pero igualmente imponente esperaba. Eran samuráis, guerreros vestidos con armaduras lacadas de intrincado diseño. En sus manos, las brillantes curvas de las katanas reflejaban el sol poniente. Su presencia era menos de masa compacta y más de tensión contenida, como la de depredadores listos para abalanzarse.
El silencio se quebró cuando un oficial romano alzó su signum, un estandarte con el águila imperial. Al unísono, los legionarios avanzaron con paso firme, sus sandalias clavándose en la tierra. Gritaban su grito de guerra, un rugido gutural que resonaba en el aire.
Los samuráis observaron el avance implacable. Su líder, un hombre de rostro sereno con una cicatriz que le cruzaba la mejilla, desenvainó su katana con un movimiento fluido y silencioso. La hoja brilló intensamente. Con un grito agudo, dio la orden de ataque.
La batalla comenzó con un choque violento. Los legionarios, con sus escudos entrelazados, formaron una muralla impenetrable. Los samuráis se lanzaron contra ella, sus katanas trazando arcos de acero en el aire. El choque de metal contra metal llenó el campo, un coro estridente de la guerra.
Un samurái, ágil como un felino, intentó saltar sobre el muro de escudos. Pero un legionario, rápido y entrenado, lo recibió con una estocada precisa de su gladius, que encontró un hueco en la armadura. El samurái cayó, la sangre tiñendo la hierba.
Otro samurái, con un grito furioso, lanzó un corte horizontal con su katana. El golpe impactó contra un scutum, dejando una marca profunda en la madera y el metal, pero el escudo resistió. Antes de que pudiera recuperar su arma, el legionario detrás del escudo le asestó un golpe rápido con el gladius en el costado desprotegido.
La formación romana era una máquina de matar eficiente. Los legionarios trabajaban en equipo, protegiéndose mutuamente con sus escudos y atacando con sus gladius en los momentos oportunos. La disciplina y el entrenamiento eran sus mayores armas.
Sin embargo, la ferocidad y la habilidad individual de los samuráis eran innegables. Sus katanas, a pesar de no poder penetrar fácilmente la sólida pared de escudos, eran devastadoras en los espacios abiertos. Un samurái logró flanquear a un grupo de legionarios y, con movimientos rápidos y precisos, cortó brazos y piernas, sembrando el caos en la retaguardia romana.
La batalla se convirtió en un torbellino de acero y gritos. Los legionarios mantenían su formación, avanzando lentamente mientras repelían los ataques. Los samuráis, aunque sufrían bajas, no retrocedían, impulsados por su honor y su valentía.
En un punto crucial, un grupo de samuráis liderados por su comandante logró concentrar sus ataques en un sector de la línea romana. Con golpes repetidos y feroces, consiguieron romper la formación, creando una brecha. Se lanzaron a través de ella, sus katanas sedientas de sangre.
La disciplina romana se tambaleó por un momento. Los samuráis, aprovechando la oportunidad, lucharon cuerpo a cuerpo con una furia indomable. La longitud de sus katanas les daba ventaja en el combate individual, permitiéndoles mantener a raya a los legionarios con cortes amplios y letales.
Sin embargo, la respuesta romana fue rápida. Los oficiales gritaron órdenes, y las líneas se cerraron nuevamente, rodeando a los samuráis que habían penetrado la formación. Los legionarios, trabajando en parejas, inmovilizaban los largos brazos de los samuráis con sus escudos mientras otros asestaban golpes mortales con sus gladius.
La batalla continuó durante lo que pareció una eternidad. El sol finalmente se ocultó en el horizonte, tiñendo el campo de batalla de sombras oscuras y reflejos sangrientos. Ambos bandos lucharon con una determinación feroz, sin ceder terreno fácilmente.
Al final, la disciplina y la formación compacta de los legionarios comenzaron a imponerse. Lentamente, pero de manera constante, fueron cercando y diezmando a los samuráis. La muralla de escudos era demasiado sólida, y la lluvia constante de estocadas del gladius era implacable.
Los últimos samuráis lucharon con la desesperación de quienes saben que su final está cerca. Sus katanas seguían cortando con gracia mortal, pero eran superados en número y en la táctica del combate en grupo. Uno a uno, fueron cayendo, sus brillantes espadas manchadas de sangre.
Cuando la última katana cayó al suelo con un resonido metálico, un silencio pesado se cernió sobre el campo. Los legionarios, exhaustos pero victoriosos, permanecieron en formación, sus escudos goteando sangre. Habían prevalecido gracias a su disciplina, su equipo y su táctica de combate en grupo. La ferocidad individual y la maestría de la katana de los samuráis no habían sido suficientes contra la máquina de guerra romana.
La noche cubrió el campo de batalla, llevándose consigo los ecos de la lucha y dejando solo la sombría realidad de la victoria y la derrota.
-
 @ 79be667e:16f81798
2025-05-04 01:28:53
@ 79be667e:16f81798
2025-05-04 01:28:53Bla blablabla
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 84b0c46a:417782f5
2025-05-04 09:26:43
@ 84b0c46a:417782f5
2025-05-04 09:26:43 -
 @ 5df413d4:2add4f5b
2025-05-04 00:06:31
@ 5df413d4:2add4f5b
2025-05-04 00:06:31This opinion piece was first published in BTC Magazine on Feb 20, 2023
Just in case we needed a reminder, banks are showing us that they can and will gatekeep their customers’ money to prevent them from engaging with bitcoin. This should be a call to action for Bitcoiners or anyone else who wants to maintain control over their finances to move toward more proactive use of permissionless bitcoin tools and practices.
Since January of 2023, when Jamie Dimon decried Bitcoin as a “hyped-up fraud” and “a pet rock,” on CNBC, I've found myself unable to purchase bitcoin using my Chase debit card on Cash App. And I'm not the only one — if you have been following Bitcoin Twitter, you might have also seen Alana Joy tweet about her experience with the same. (Alana Joy Twitter account has since been deleted).
In both of our cases, it is the bank preventing bitcoin purchases and blocking inbound fiat transfers to Cash App for customers that it has associated with Bitcoin. All under the guise of “fraud protection,” of course.
No, it doesn’t make a whole lot of sense — Chase still allows ACH bitcoin purchases and fiat on Cash App can be used for investing in stocks, saving or using Cash App’s own debit card, not just bitcoin — but yes, it is happening. Also, no one seems to know exactly when this became Chase’s policy. The fraud representative I spoke with wasn’t sure and couldn’t point to any documentation, but reasoned that the rule has been in place since early last year. Yet murkier still, loose chatter can be found on Reddit about this issue going back to at least April 2021.
However, given that I and so many others were definitely buying bitcoin via Chase debit throughout 2021 and 2022, I’d wager that this policy, up to now, has only been exercised haphazardly, selectively, arbitrarily, even. Dark patterns abound, but for now, it seems like I just happen to be one of the unlucky ones…
That said, there is nothing preventing this type of policy from being enforced broadly and in earnest by one or many banks. If and as banks feel threatened by Bitcoin, we will surely see more of these kinds of opaque practices.
It’s Time To Get Proactive
Instead, we should expect it and prepare for it. So, rather than railing against banks, I want to use this as a learning experience to reflect on the importance of permissionless, non-KYC Bitcoining, and the practical actions we can take to advance the cause.
Bank with backups and remember local options. Banking is a service, not servitude. Treat it as such. Maintaining accounts at multiple banks may provide some limited fault tolerance against banks that take a hostile stance toward Bitcoin, assuming it does not become the industry norm. Further, smaller, local and regional banks may be more willing to work with Bitcoiner customers, as individual accounts can be far more meaningful to them than they are to larger national banks — though this certainly should not be taken for granted.
If you must use KYC’d Bitcoin services, do so thoughtfully. For Cash App (and services like it), consider first loading in fiat and making buys out of the app’s native cash balance instead of purchasing directly through a linked bank account/debit card where information is shared with the bank that allows it to flag the transaction for being related to bitcoin. Taking this small step may help to avoid gatekeeping and can provide some minor privacy, from the bank at least.
Get comfortable with non-KYC bitcoin exchanges. Just as many precoiners drag their feet before making their first bitcoin buys, so too do many Bitcoiners drag their feet in using permissionless channels to buy and sell bitcoin. Robosats, Bisq, Hodl Hodl— you can use the tools. For anyone just getting started, BTC Sessions has excellent video tutorial content on all three, which are linked.
If you don’t yet know how to use these services, it’s better to pick up this knowledge now through calm, self-directed learning rather than during the panic of an emergency or under pressure of more Bitcoin-hostile conditions later. And for those of us who already know, we can actively support these services. For instance, more of us taking action to maintain recurring orders on such platforms could significantly improve their volumes and liquidity, helping to bootstrap and accelerate their network effects.
Be flexible and creative with peer-to-peer payment methods. Cash App, Zelle, PayPal, Venmo, Apple Cash, Revolut, etc. — the services that most users seem to be transacting with on no-KYC exchanges — they would all become willing, if not eager and active agents of financial gatekeeping in any truly antagonistic, anti-privacy environment, even when used in a “peer-to-peer” fashion.
Always remember that there are other payment options — such as gift cards, the original digital-bearer items — that do not necessarily carry such concerns. Perhaps, an enterprising soul might even use Fold to earn bitcoin rewards on the backend for the gift cards used on the exchange…
Find your local Bitcoin community! In the steadily-advancing shadow war on all things permissionless, private, and peer-to-peer, this is our best defense. Don’t just wait until you need other Bitcoiners to get to know other Bitcoiners — to paraphrase Texas Slim, “Shake your local Bitcoiner’s hand.” Get to know people and never underestimate the power of simply asking around. There could be real, live Bitcoiners near you looking to sell some corn and happy to see it go to another HODLer rather than to a bunch of lettuce-handed fiat speculators on some faceless, centralized, Ponzi casino exchange. What’s more, let folks know your skills, talents and expertise — you might be surprised to find an interested market that pays in BTC!
In closing, I believe we should think of permissionless Bitcoining as an essential and necessary core competency, just like we do with Self-Custody. And we should push it with similar urgency and intensity. But as we do this, we should also remember that it is a spectrum and a progression and that there are no perfect solutions, only tradeoffs. Realization of the importance of non-KYC practices will not be instant or obvious to near-normie newcoiners, coin-curious fence-sitters or even many minted Bitcoiners. My own experience is certainly a testament to this.
As we promote the active practice of non-KYC Bitcoining, we can anchor to empathy, patience and humility — always being mindful of the tremendous amount of unlearning most have to go through to get there. So, even if someone doesn’t get it the first time, or the nth time, that they hear it from us, if it helps them get to it faster at all, then it’s well worth it.
~Moon
-
 @ b99efe77:f3de3616
2025-05-03 23:37:57
@ b99efe77:f3de3616
2025-05-03 23:37:57343433
34333434
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ b99efe77:f3de3616
2025-05-03 23:34:54
@ b99efe77:f3de3616
2025-05-03 23:34:5412123123123
eqeqeqeqeqeqe
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ b99efe77:f3de3616
2025-05-03 23:20:27
@ b99efe77:f3de3616
2025-05-03 23:20:27PetriNostr. My everyday activity
sdfsdfsfsfdfdf
petrinet sfsfdsf -
 @ b99efe77:f3de3616
2025-05-03 22:58:44
@ b99efe77:f3de3616
2025-05-03 22:58:44dfsf
adfasfafafafafadsf
```petrinet
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working``` -
 @ 6fc114c7:8f4b1405
2025-05-03 22:06:36
@ 6fc114c7:8f4b1405
2025-05-03 22:06:36In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
Our Recovery Services Include: 📈 Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞 For quick queries or support, connect with us on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust
At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process
Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate
With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure
Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools
We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!
Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ b6524158:8e898a89
2025-05-03 18:11:47
@ b6524158:8e898a89
2025-05-03 18:11:47Steps: 1. Run a node one mynode 2. Upgrade to premium 3. Select your Bitcoin version (to Bitcoin Knots)
originally posted at https://stacker.news/items/970504
-
 @ d0ea1c34:9c84dc37
2025-05-03 17:53:05
@ d0ea1c34:9c84dc37
2025-05-03 17:53:05Markdown Rendering Test Document
Basic Text Formatting
This is a paragraph with bold text, italic text, and bold italic text. You can also use underscores for bold or single underscores for italics.
This is a paragraph with some
inline codeusing backticks.Lists
Unordered Lists
- Item 1
- Item 2
- Nested item 2.1
- Nested item 2.2
- Item 3
Ordered Lists
- First item
- Second item
- Nested item 2.1
- Nested item 2.2
- Third item
Links and Images
Blockquotes
This is a blockquote.
It can span multiple lines.
And can be nested.
Code Blocks
```python def hello_world(): print("Hello, world!")
This is a Python code block with syntax highlighting
hello_world() ```
javascript // JavaScript code block function helloWorld() { console.log("Hello, world!"); }Tables
| Header 1 | Header 2 | Header 3 | |----------|----------|----------| | Cell 1 | Cell 2 | Cell 3 | | Cell 4 | Cell 5 | Cell 6 | | Cell 7 | Cell 8 | Cell 9 |
Horizontal Rules
Task Lists
- [x] Completed task
- [ ] Incomplete task
- [x] Another completed task
Math (if supported)
Inline math: $E = mc^2$
Block math:
$$ \frac{d}{dx}e^x = e^x $$
Footnotes
Here's a sentence with a footnote reference[^1].
[^1]: This is the footnote content.
Definition Lists
Term 1 : Definition 1
Term 2 : Definition 2a : Definition 2b
Special Characters & Escaping
*This text is surrounded by asterisks but not italicized*
Advanced Formatting
Click to expand
This is hidden content that appears when expanded.Emoji (if supported)
:smile: :heart: :thumbsup:
Final Notes
This document demonstrates various Markdown formatting features. Compatibility may vary across different Markdown renderers and platforms.
-
 @ 1408bad0:4971f2ca
2025-05-01 19:55:37
@ 1408bad0:4971f2ca
2025-05-01 19:55:37Raised by Wolves is another sci-fi flick where Earth faces an extinction level event and lots of cool androids.
The series has some exciting action points showing a side of AI androids used as super weapons against humanity. If you were thinking to get an AI girlfriend, you might have a change of mind.
We see some pretty cool androids, but the awesome Necromancer is pretty spectacular and powerful and you wonder if anything can stop them. However, bizarrely, at times they are also apparently weak and despite their power, the religious group doesn't shy away from confrontation without any real weapons.
It would have been good if they had explored this side more and some of the advanced tech available like which gave the atheista super strength and speed to combat them.
The series has a feel like Foundation to it, but much less polished and maybe more negative and dreary at times. Instead of exploring exciting themes, it descends into mindless trivialities and bizarre gory rituals like killing a hideous pregnant animal and parading the dead baby corpse around.
They arrive on a mysterious but quite dreary planet and things start to set the scene.
The androids themselves are quite well played. The "Mother" is as expected in these woke times the strong and powerful one. The "Father" is the beta male serving her and the kids. It's all quite bizarre in a way.
When they first land they use some tech to make a base quickly and easily, but it disappoints how basic it all is. This is then compounded when the religious group arrive and instead of using modern tech to make a base as you might expect, instead turn into the Amish and make everything from wood. Oh yes, there are trees on this planet, but no really nice food.
The oddness continues and grows throughout the season as the androids become more human and spoiler alert , the most ridiculous storyline emerges as mother becomes pregnant and also really annoying. She starts attaching other bits and creatures to her to suck their blood out for her baby.
Despite all my criticisms, it has been an interesting first series but very disappointing in many ways compared to Foundation.
-
 @ a965e1a8:3463a92f
2025-05-03 17:52:48
@ a965e1a8:3463a92f
2025-05-03 17:52:48test reply
-
 @ 08964cb5:51bf010f
2025-05-01 10:14:41
@ 08964cb5:51bf010f
2025-05-01 10:14:41«Reflexiones y Acción: Entre la Defensa del Patrimonio»
[English below][Deutsch unten]
Los recientes acontecimientos que han puesto en peligro mi patrimonio, así como los valores fundamentales que definen mi camino, me han llevado a tomar una decisión importante: iniciar una campaña de recaudación de fondos. Esta iniciativa no solo busca proteger lo que he construido con esfuerzo, sino también garantizar que pueda seguir adelante con proyectos y principios que son esenciales para mí.
Tu apoyo puede marcar una gran diferencia. Si deseas conocer más sobre esta causa o contribuir con tu solidaridad, te invito a visitar ›🔗éste enlace.‹
"Reflections and Action: Safeguarding My Heritage"
The recent events that have jeopardised my assets and the core values that define my journey have led me to take a significant step: launching a fundraising campaign. This initiative aims not only to protect what I have built with hard work but also to ensure that I can continue moving forward with projects and principles that are essential to me.
Your support can make a real difference. If you’d like to learn more about this cause or contribute with your solidarity, I invite you to visit ›🔗this link.‹
"Überlegungen und Handeln: Den Schutz meines Vermögens"
Die jüngsten Ereignisse, die mein Vermögen sowie die grundlegenden Werte, die meinen Weg bestimmen, gefährdet haben, haben mich dazu veranlasst, einen wichtigen Schritt zu gehen: den Start einer Spendenkampagne. Diese Initiative zielt nicht nur darauf ab, das zu schützen, was ich mit harter Arbeit aufgebaut habe, sondern auch sicherzustellen, dass ich mit Projekten und Prinzipien, die für mich unerlässlich sind, weitermachen kann.
Deine Unterstützung kann einen großen Unterschied machen. Wenn du mehr über diese Sache erfahren oder mit deiner Solidarität beitragen möchtest, lade ich dich ein, ›🔗diesen Link zu besuchen.‹
-
 @ 2e8970de:63345c7a
2025-05-03 17:31:07
@ 2e8970de:63345c7a
2025-05-03 17:31:07The figure in this article illustrates exactly how most biology papers are secretly p-hacked. A large number of hypotheses is explored, and only the ones that form a coherent story are reported.
This is actually the main reason behind the replication crisis in biology IMO. (source)
https://www.nature.com/articles/s41587-025-02635-7
originally posted at https://stacker.news/items/970464
-
 @ e2388e53:0e93e8a9
2025-05-03 16:44:06
@ e2388e53:0e93e8a9
2025-05-03 16:44:06- Die Befreiung beginnt nicht mit einem Aufschrei, sondern mit einem leisen Nein.
- Herkunft ist kein Zuhause. Es ist der Ort, an dem man lernt, warum man gehen musste.
- Manche Familien sind wie alte Götter: Man glaubt an sie, obwohl sie längst gestorben sind.
- Wer das Nichts anschaut, sieht sich selbst: ein Schatten, der sich für Licht hält.
- Das Schweigen des Universums ist keine Antwort – es ist die endgültige Form der Gleichgültigkeit.
- In der Dämmerung unserer Tage suchen wir die Sonne, die nur in der Erinnerung noch brennt.
- Freiheit beginnt, wenn der Mensch aufhört, sich retten zu lassen.
- Wer nie verloren ging, hat sich selbst nie gesucht.
- Gedanken zerfallen wie Tropfen, die nie den Boden erreichen.
- Wahrheit ist selten laut. Sie flüstert – meist dann, wenn niemand mehr zuhört.
-
 @ 90de72b7:8f68fdc0
2025-05-03 16:29:51
@ 90de72b7:8f68fdc0
2025-05-03 16:29:51Custom1. PetriNostr. My everyday activity
PetriNostr never sleep! This is a demo
```petrinet
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working``` -
 @ fc7085c3:0b32a4cb
2025-05-03 16:17:10
@ fc7085c3:0b32a4cb
2025-05-03 16:17:10- ~~finish writing some experimental specs and store on hidden repo for later~~
- ~~fix bugs on in-house js web components framework (with react-like hooks)~~
- ~~add signal/reactive hooks to framework~~ (thx to nootropics)
- (ongoing) slooowly migrate kind:1 app from Qwik to above framework
- test feasibility of new app - codename: ZULULA. cool? flawed?
- if cool, finish ZULULA basic features
- nread.me: add nostr documentation (mpa for this part cause seo)
- nread.me: add nip crud (save on relay)
- nread.me: add nip curation (rating and labeling)
- nread.me: filter by curator / rating / labeling
- nread.me: seed curator (fiatjaf) adds other curators
- revamp kind:1 app login
- add basic engagement features then halt kind:1 app dev
- start simplified messenger app to test custom chat spec
- ...don't know what's next yet
-
 @ 90de72b7:8f68fdc0
2025-05-03 16:14:50
@ 90de72b7:8f68fdc0
2025-05-03 16:14:50PetriNostr. My everyday activity - may3
PetriNostr never sleep! This is a demo
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 6ad3e2a3:c90b7740
2025-05-03 15:33:07
@ 6ad3e2a3:c90b7740
2025-05-03 15:33:07You are wearing a helmet, but it's been on your head so long you no longer notice it.
The helmet interfaces with your mind via thought-emotion. It influences what you think about and how you feel.
You could remove the helmet at any time. But the thought-emotions keep you distracted, fearful and attached.
Occasionally you remember you are wearing it. Moments of clarity and detachment. You see the way your experience is colored by it. You know it is biased, untrue to reality. You seriously contemplate removing it.
But the moment passes.
Later, you remember contemplating your helmet’s removal, but you wonder what you will gain from it, whether it’s worth doing.
You are no longer having a moment of clarity, just a memory of the question that arose from it, but colored now by thought-emotions.
You decide even if you wanted to remove it, you would put it back on before long. After all, you have never kept it off before, why would you suddenly live without this interface now? The interface is what you know.
Maybe one day, when you are in a more secure place, when your ducks are more in a row, you will remove it. Not now, not in the midst of all this chaos, so many things to do, so much on your plate. You will leave it on for now. You will deal with this later.
But one day too late it dawns on you it is always ever now, and later means never. You have lived your entire life at the behest of the interface when all you had to do was remove it.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-03 14:18:36
@ 5d4b6c8d:8a1c1ee3
2025-05-03 14:18:36Comments: 3395 (Top Territory!!!) Posts: 306 (3rd) Stacking: 198k (2nd)
We're really bouncing back from the post-Super Bowl lull, with lots of contests and discussion threads. I think we've really found our niche with those two things.
The rest of Stacker News is experiencing declining activity, so our steady growth since February really tells me that we're on the right track.
Thanks for being part of our growing sports community!
originally posted at https://stacker.news/items/970289
-
 @ f4a890ce:af88c4aa
2025-05-03 13:03:35
@ f4a890ce:af88c4aa
2025-05-03 13:03:35執行摘要
上週,加密貨幣市場總市值增至 2.90 兆美元,成交量放大至 1,038.4 億美元,顯示資金回流。市場情緒轉為貪婪,恐懼與貪婪指數升至 63,動能短期強勁。穩定幣市值小幅提升,資金結構穩健。
永續合約持倉突破 1,200 億美元,空單爆倉金額高於多單,代表市場強勢上漲。期權市場看漲情緒濃厚,集中在 8萬至10萬美元。 BTC ETF流入大增至 9.17 億美元,而ETH ETF則小幅流出,資金更多集中在比特幣。
本週觀察重點:資金是否持續流入以支撐漲勢。若動能延續,市場或能保持上行;反之需警惕回吐風險。資金流向與交易量是判斷反彈真實性的重要指標。
加密市場
本週加密貨幣市場總市值小幅上升至2.96兆美元,較上週2.9兆美元略有增長,顯示主流資產價格維持高檔震盪格局。然而,成交量回落至88億美元,較上週的1,038億美元明顯下降,反映在價格高位區間內,市場參與意願略有減弱。
https://coinmarketcap.com/charts/
恐懼與貪婪指數由上週的63下降至60,顯示市場情緒由「貪婪」回落至「中性偏樂觀」,投資人心態從積極轉為謹慎。
https://www.coinglass.com/zh-TW/pro/i/FearGreedIndex
相對強弱指標則回到「中性」區間,表明短線上升動能放緩,市場正進入整理消化期。
https://www.coinglass.com/zh-TW/pro/i/RsiHeatMap
山寨幣季節指數下降至16,顯示資金仍以主流幣為主,對中小型代幣的風險偏好依然低迷。
https://www.blockchaincenter.net/en/altcoin-season-index/
穩定幣市值增加至2,394.87億美元,可能暗示部分資金等待更明確的入場時機。
https://defillama.com/stablecoins
小結
本週加密貨幣市場總市值持續小幅上升,顯示基本面仍具支撐力,但成交量明顯下滑與情緒指標回落,透露市場短線追價動能減弱。相對強弱指標回到中性,表示市場進入高檔整理期。穩定幣資金略增,反映資金操作趨於謹慎。展望未來,若成交量無法有效回溫,短期內市場可能以區間震盪為主,需密切關注外部宏觀消息與主流幣表現,以判斷後續趨勢轉折。
衍生性商品
本週衍生性商品市場展現出更高的波動性,特別是在永續合約和期權市場的表現上。永續合約方面,持倉規模自上週的 99.89B 大幅增至 116.9B,顯示出投資者在本週加強槓桿操作。
https://www.coinglass.com/zh-TW/pro/futures/Cryptofutures
資金費率從正值 0.0018% 急劇轉為負值 -0.0047%,且多數交易所均呈負費率,反映出市場正在偏向空頭主導。
https://www.coinglass.com/zh-TW/FundingRate
爆倉數據同樣顯著上升,其中空單由上週的 45.29M 攀升至 62.26M,多單更是大幅增至 119.508M,表明市場波動加劇導致強制清算事件頻率升高。
https://www.coinglass.com/zh-TW/LiquidationData
清算熱力圖顯示,在 $96,000 價位附近的清算金額達 $128.96M,相較於上週的 $113.48M 有明顯增加。
https://www.coinglass.com/zh-TW/pro/futures/LiquidationHeatMap
期權市場方面,數據反映出投資者對特定價格區間的配置策略有所改變:行權價 $80,000 的看跌期權合約數量仍維持 9.6K,但總金額明顯上升至 $22.29M,表明投資者正加強對中低價位區間的下行防禦。而行權價 $100,000 的看漲期權合約數從上週的 11.85K 增至 15.67K,總金額也上漲至 $104.52M,顯示出投資者對高價位行情的預期正逐步增強。
https://www.coinglass.com/zh-TW/pro/options/OIStrike
最大痛點方面,本週的價位仍維持在 $85,000,但時間已延後至 2025/06/27,暗示市場頭寸正進一步調整以應對長期風險。
https://www.coinglass.com/zh-TW/pro/options/max-pain
小結
綜上所述,本週衍生性商品市場在永續合約槓桿持倉的激增與期權市場配置策略的分歧中,可能預示著更高的波動與風險。我們應慎重觀察市場波動區域的資金流向,並結合不同合約數據的變化,調整操作策略,以應對潛在市場風險。
ETF
本週4/29比特幣與以太幣ETF皆呈現資金淨流出,BTC ETF流出金額達3,676萬美元,結束連續多天的淨流入趨勢,較上週高達9.12億美元的流入量有明顯反轉,顯示機構資金對短期市場展望轉趨保守。
ETH ETF亦出現7.1百萬美元的流出,儘管規模不大,但多週未見到大額流入,反映市場對ETH的信心仍較薄弱。
https://coinmarketcap.com/zh-tw/etf/
小結
整體而言,本週ETF市場資金動能放緩,可能與市場短線震盪、技術面超買,以及即將到來的宏觀數據發布有關,投資人選擇暫時觀望。後續仍需觀察資金是否回流,確認是否為短期調整或趨勢反轉的訊號。
鏈上分析 | BTC
從本週的鏈上數據來看,BTC 持續自交易所流出,顯示二級市場上的賣壓逐漸減輕。
地址分布方面,中小持倉(10-100)的地址數量持續下滑,可能反映散戶或中型參與者獲利了結或轉為觀望;而中型以上持倉(100-1k)地址數量則呈現小幅上升,代表市場對後市仍保有一定信心。值得關注的是,(1k-10k)的大戶地址持續增長,且10k以上的超級鯨魚地址也開始出現小幅增加的動作,顯示機構或長期資金正逐步重新佈局。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
根據最新的鏈上數據觀察,礦工的未實現盈虧顯示目前大多數礦工處於盈利階段,顯示其短期內無明顯的拋售壓力。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
同時,全網未實現盈虧指標亦顯示大部分持幣地址處於盈利區間,代表市場尚未進入恐慌階段,整體投資者心態相對穩定。這樣的結構對價格具備一定支撐力。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
本週觀察顯示,鯨魚活躍地址數量明顯上升,顯示大型投資者近期參與度增加,對市場走勢形成潛在支撐。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
此外,Coinbase 溢價指數持續維持在 0 值以上,反映美國本土買盤仍具動能。然而,該指數是否能在下週持續維持正值,將是判斷主力資金是否穩定流入的重要觀察指標。整體而言,鏈上結構偏多,但仍需謹慎觀察主力動向是否延續。
近期數據顯示,長期持有者的供應急劇上升,與去年盤整階段的走勢相似,代表長期投資者持續看好後市,選擇繼續持有。
https://www.bitcoinmagazinepro.com/charts/long-term-holder-supply/
然而,目前價格已接近短期持有者的實現價格區間,形成潛在的拋壓。若市場要進一步上漲,需先有效消化短期持有者的賣壓,並觀察市場是否能重新建立多頭動能。整體而言,雖長線結構健康,但短期內仍有調整壓力需克服。
https://www.bitcoinmagazinepro.com/charts/short-term-holder-realized-price/
小結
目前市場仍在消化短期持有者的拋壓,短線籌碼換手使得價格波動加劇。然而,鏈上數據顯示長期持有者仍在持續買入,並未受短期波動影響,顯示其對後市走勢仍具高度信心。
總體經濟
本週總體經濟數據與上週持平,美國聯邦基礎有效利率維持在 4.33%,顯示當前仍處於高利率環境。
https://fred.stlouisfed.org/series/FEDFUNDS
而市場對5月7日即將召開的聯準會會議預期將維持利率不變,機率高達 95.4%。
https://www.cmegroup.com/cn-t/markets/interest-rates/cme-fedwatch-tool.html
消費者物價指數(CPI)為 2.41%,失業率則穩定在 4.20%。整體來看,儘管通膨壓力略有降溫,但就業市場依然偏緊,使得聯準會在貨幣政策上保持謹慎態度。資金面短期內難以出現大幅寬鬆,市場整體情緒仍以觀望為主。
https://www.macromicro.me/series/128/consumer-price-index-sa-yoy https://www.macromicro.me/series/37/unemployment-rate
小結
儘管目前總體經濟數據相對穩定,但若要推動整體市場持續走強,仍需觀察更具結構性的變化。筆者認為,唯有失業率出現顯著上升、同時CPI高於聯準會2%的通膨目標,才可能逼迫聯準會啟動降息循環。
若伴隨著貨幣供給(M2)大幅增加,將有望為市場注入充足流動性,推動風險資產進一步上行。因此,短期內市場仍處觀望格局,中長期走勢仍需仰賴宏觀經濟環境的轉變與政策調整的催化。
新聞
美國參議院正推動穩定幣法案的立法進程
https://www.coindesk.com/policy/2025/05/01/us-senate-moves-toward-action-on-stablecoin-bill
根據分析師的預測,SEC可能在未來幾個月內批准SOL、XRP和DOGE加密貨幣的ETF
Mastercard 推出全方位穩定幣金融系統:整合消費、跨境匯款、支付、結算四大功能
https://abmedia.io/mastercard-moves-to-integrate-stablecoin-in-global
英國擬將加密資產全面納管,新草案包含穩定幣發行、交易平台、託管與 Staking 業務
https://abmedia.io/the-financial-services-and-markets-act-2000
-
 @ 5df413d4:2add4f5b
2025-05-04 01:13:31
@ 5df413d4:2add4f5b
2025-05-04 01:13:31Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 02: Jerusalem Old City
The bus slowly lurches up the winding and steep embankment. We can finally start to see the craggy tops of buildings peaking out over the ridge in the foreground distance. We have almost reached it. Jerusalem, the City on the Hill.
https://i.nostr.build/e2LpUKEgGBwfveGi.jpg
Our Israeli tour guide speaks over the mic to draw our attention to the valley below us instead - “This is the the Valley of Gehenna, the Valley of the Moloch,” he says. “In ancient times, the pagans who worshiped Moloch used this place for child sacrifice by fire. Now, imagine yourself, an early Hebrew, sitting atop the hill, looking down in horror. This is the literal Valley of The Shadow of Death, the origin of the Abrahamic concept of Hell.” Strong open - this is going to be fun.
https://i.nostr.build/5F29eBKZYs4bEMHk.jpg
Inside the Old City, our guide - a chubby, cherub-faced intelligence type on some sort of punishment duty, deputized to babysit foreigners specifically because he reads as so dopey and disarming - points out various Judeo-Christian sites on a map, his tone subtly suggesting which places are most suggested, or perhaps, permitted…
https://i.nostr.build/J44fhGWc9AZ5qpK4.jpg
https://i.nostr.build/3c0jh09nx6d5cEdt.jpg
Walking, we reach Judaism’s Kotel, the West Wall - massive, grand, and ancient, whispering of the Eternal. Amongst the worshipers, we touch the warm, dry limestone and, if we like, place written prayers into the wall's smaller cracks. A solemn and yearning ghost fills the place - but whose it is, I'm not sure.  https://i.nostr.build/AjDwA0rFiFPlrw1o.jpg
Just above the Kotel, Islam’s Dome of the Rock can be seen, its golden cap blazing in the sun. I ask our guide about visiting the dome. He cuts a heavy eyeroll in my direction - it seems I’ve outed myself as my group’s “that guy.” His face says more than words ever could, “Oy vey, there’s one in every group…”
“Why would anyone want to go there? It is a bit intense, no?” Still, I press. “Well, it is only open to tourists on Tuesday and Thursdays…” It is Tuesday. “And even then, visiting only opens from 11:30…” It is 11:20. As it becomes clear to him that I don't intend to drop this...“Fine!” he relents, with a dramatic flaring of the hands and an uniquely Israeli sigh, “Go there if you must. But remember, the bus leaves at 1PM. Good luck...” Great! Totally not ominous at all.
https://i.nostr.build/6aBhT61C28QO9J69.jpg
The checkpoint for the sole non-Muslim entrance leading up to the Dome is administered by several gorgeous and statuesque, assault rifle clad, Ethiop-Israeli female soldiers. In this period of relative peace and calm, they feel lax enough to make a coy but salacious game of their “screening” the men in line. As I observe, it seems none doth protest...
https://i.nostr.build/jm8F3pUp9EXqPRkN.jpg
Past the gun-totting Sirens, a long wooden rampart leads up to the Temple Mount, The Mount of the House of the Holy, al-Ḥaram al-Sharīf, The Noble Sanctuary, The Furthest Mosque, the site of the Dome of the Rock and the al-Masjid al-Asqa.
https://i.nostr.build/DoS0KIkrVN0yiVJ0.jpg
On the Mount, the Dome dominates all views. To those interested in pure expressions of beauty, the Dome is, undeniably, a thing of absolute glory. I pace the grounds, snapping what pictures I can. I pause to breathe and to let the electric energy of the setting wash over me.
https://i.nostr.build/0BQYLwpU291q2fBt.jpg
https://i.nostr.build/yCxfB1V8eAcfob93.jpg
It’s 12:15 now, I decide to head back. Now, here is what they don’t tell you. The non-Muslin entrance from the West Wall side is a one-way deal. Leaving the Dome plaza dumps you out into the back alley bazaar of Old City’s Muslim district. And so it is. I am lost.
https://i.nostr.build/XnQ5eZgjeS1UTEBt.jpg
https://i.nostr.build/EFGD5vgmFx5YYuH4.jpg
I run through the Muslim quarter, blindly turning down alleyways that seem to be taking me in the general direction of where I need to be - glimpses afforded by the city’s uneven elevation and cracks in ancient stone walls guiding my way.
https://i.nostr.build/mWIEAXlJfdqt3nuh.jpg
In a final act of desperation and likely a significant breach of Israeli security protocol, I scale a low wall and flop down back on the side of things where I'm “supposed” to be. But either no one sees me or no one cares. Good luck, indeed.
I make it back to my group - they are not hard to find, a bunch of MBAs in “business casual” travel attire and a tour guide wearing a loudly colored hat and jacket - with just enough time to still visit the Church of the Holy Sepulcher.
https://i.nostr.build/3nFvsXdhd0LQaZd7.jpg
https://i.nostr.build/sKnwqC0HoaZ8winW.jpg
Inside, a chaotic and dizzying array of chapels, grand domed ceilings, and Christian relics - most notably the Stone of Anointing, commemorating where Christ’s body was prepared for burial and Tomb of Christ, where Christ is said to have laid for 3 days before Resurrection.
https://i.nostr.build/Lb4CTj1dOY1pwoN6.jpg
https://i.nostr.build/LaZkYmUaY8JBRvwn.jpg
In less than an hour, one can traverse from the literal Hell, to King David’s Wall, The Tomb of Christ, and the site of Muhammad’s Ascension. The question that stays with me - What is it about this place that has caused so many to turn their heads to the heavens and cry out for God? Does he hear? And if he answers, do we listen?
https://i.nostr.build/elvlrd7rDcEaHJxT.jpg
Jerusalem, The Old City, circa 2014. Israel.
There are secrets to be found. Go there.
Bitcoin #Jerusalem #Israel #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Plebchain #Coffeechain #Bookstr #NostrArt #Writing #Writestr #Createstr
-
 @ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13
@ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android!
Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet.
Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review.
The application can be installed through the Google Play Store, nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8, or by downloading it directly from Primal's GitHub. The full review is current as of Primal Android version 2.0.21. Updates to the review on 4/30/2025 are current as of version 2.2.13.
In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.

Overall Impression
Score: 4.4 / 5 (Updated 4/30/2025)
Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet.
Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions, or when loading DVM-based feeds, which are outside of Primal's control.
Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5.
Update: As of version 2.2.13, Primal now supports the Amber Android signer! One of the most glaring issues with the app has now been remedied and as promised, the overall score above has been increased.
Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when. This also means that you will not see any DMs from users who are messaging from a client that has moved to the latest, and far more private, messaging spec.
That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging.
Features
Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience.
Home Feed
By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.

Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection.
Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.

Interacting With Notes
Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note.
Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.

Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂.
It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one.
Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that.
Post Creation
Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.

Your device's default keyboard loads immediately, and the you can start typing away.
There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post.
There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.

This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle.
Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results.
Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen.
Feed Selector and Marketplace
Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.

The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.

Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app.
One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again.
This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use.
Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen.
The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed.
I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead.
Long-Form "Reads" Feed
A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles.
This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.

Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor.
Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks.
While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client.
Primal Web:

Primal Android:

The Explore Tab
Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones!
The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material.
Indeed, it does not appear that filters for sensitive content are available in Primal for any feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.

The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content.
This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit.
The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in.
If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag.
The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice.
Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with.
Built-In Wallet
While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.

Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users.
Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is not intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried.
In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know.
Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet.
Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are fast. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client.
One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed.
Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration.
Advanced Search
Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible.
Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar.
As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.

You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery.
The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more.
Can My Grandma Use It?
Score: 4.8 / 5 Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square.
To begin with, the onboarding experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."

From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out.
At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.

That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics.
Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all.
The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users.
We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing.
Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so.
How do UI look?
Score: 4.9 / 5
Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me want to use it.

It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding.
First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.

The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.

Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.





At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app.
This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.

Log In Options
Score: 4 / 5 (Updated 4/30/2025)
Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications.
This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they are you on Nostr for all intents and purposes.
This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users.
That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below:
nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl
No word yet on whether this will be Android signer or remote signer support, or both.
This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users.
Update: As of version 2.2.13, all of what I have said above is now obsolete. Primal has added Android signer support, so users can now better protect their nsec by using Amber!
I would still like to see support for remote signers, especially with nstart.me as a recommended Nostr onboarding process and the advent of FROSTR for key management. That said, Android signer support on its own has been a long time coming and is a very welcome addition to the Primal app. Bravo Primal team!
Zap Integration
Score: 4.8 / 5
As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption.
But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.

How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history.
The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.

An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet.
Content Discovery
Score: 4.8 / 5
Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats.
First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking.
Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker.
Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab.
Relay Management
Score: 2.5 / 5
For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect.
However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on nostr.watch. I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs.
That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.

However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay.
One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice.
By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address.
In short, if you use any other Nostr clients at all, do not use Primal for managing your relays.
Media Hosting Options
Score: 4.9 / 5 This is a NEW SECTION of this review, as of version 2.2.13!
Primal has recently added support for the Blossom protocol for media hosting, and has added a new section within their settings for "Media Uploads."
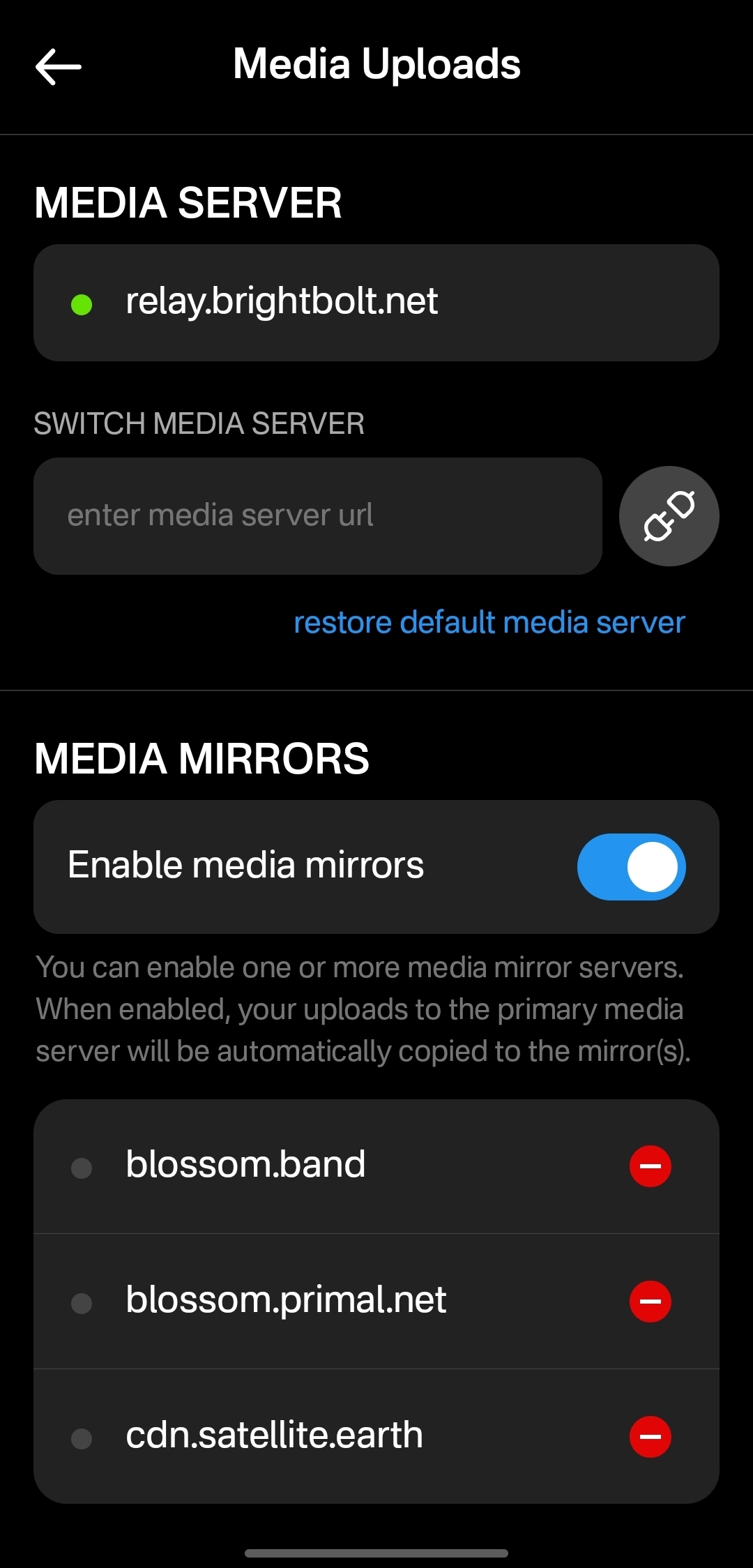
Media hosting is one of the more complicated problems to solve for a decentralized publishing protocol like Nostr. Text-based notes are generally quite small, making them no real burden to store on relays, and a relay can prune old notes as they see fit, knowing that anyone who really cared about those notes has likely archived them elsewhere. Media, on the other hand, can very quickly fill up a server's disk space, and because it is usually addressable via a specific URL, removing it from that location to free up space means it will no longer load for anyone.
Blossom solves this issue by making it easy to run a media server and have the same media mirrored to more than one for redundancy. Since the media is stored with a file name that is a hash of the content itself, if the media is deleted from one server, it can still be found from any other server that has the same file, without any need to update the URL in the Nostr note where it was originally posted.
Prior to this update, Primal only allowed media uploads to their own media server. Now, users can upload to any blossom server, and even choose to have their pictures or videos mirrored additional servers automatically. To my knowledge, no other Nostr client offers this automatic mirroring at the time of upload.
One of my biggest criticisms of Primal was that it had taken a siloed approach by providing a client, a caching relay, a media server, and a wallet all controlled by the same company. The whole point of Nostr is to separate control of all these services to different entities. Now users have more options for separating out their media hosting and their wallet to other providers, at least. I would still like to see other options available for a caching relay, but that relies on someone else being willing to run one, since the software is open for anyone to use. It's just not your average, lightweight relay that any average person can run from home.
Regardless, this update to add custom Blossom servers is a most welcome step in the right direction!
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0:
nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd
This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client.
nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe
This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though.
nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr
There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to only show replies, but there is no corresponding filter to only show original notes.
nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6
Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile.
nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep
It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque.
nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced
For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future.
nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6
Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though.
nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex
Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it.
There is good news on this front, though:
nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh
Wrap Up
All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary.
There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release.
So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments.
I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows.
Thank you for reading!
PV 🤙
-
 @ f6488c62:c929299d
2025-05-03 11:53:03
@ f6488c62:c929299d
2025-05-03 11:53:03ช่วงปลายปี 2567 ถึงต้นปี 2568 BNB Chain เปิดตัวโปรเจกต์ใหม่หลากหลายแนว ทั้ง AI, DeFi, GameFi และโครงสร้างพื้นฐาน เช่น Ballies, Coinfair, OpenTaskAI และ VeraBridge 🌐
วันนี้ ผมได้อ่าน x ของทางคุณ CZ เจอขายโพสไว้หลายโพส ดูแล้วน่าสนใจ จึงคิดว่า การที่ Kraken เริ่มลิสต์โปรเจกต์จาก BNB Chain ยิ่งตอกย้ำว่า ecosystem นี้กำลัง “โตจริง” 🚀
พร้อมทั้งมีโปรแกรมสนับสนุนมากมาย เช่น MVB Accelerator, TVL Incentive และ Gas-Free Carnival ช่วยดึงดูดนักพัฒนาและผู้ใช้จากทั่วโลก
🧠 เป้าหมายปี 2568: รองรับ 100 ล้านธุรกรรม/วัน, ผสาน AI เต็มรูปแบบ และเครื่องมือใหม่ช่วย dev สร้างโปรเจกต์ได้ง่ายขึ้น!
📈 ใครจับตา BNB Chain อยู่ บอกเลย... ช่วงนี้ของจริง!
-
 @ 90c656ff:9383fd4e
2025-05-03 11:52:14
@ 90c656ff:9383fd4e
2025-05-03 11:52:14In recent years, Bitcoin has often been compared to gold, earning the nickname “digital gold.” This comparison arises because both forms of value share key characteristics, such as scarcity, durability, and global acceptance. However, Bitcoin also represents a technological innovation that redefines the concept of money and investment, standing out as a modern and efficient alternative to physical gold.
One of the main reasons Bitcoin is compared to gold is its programmed scarcity. While gold is a naturally limited resource whose supply depends on mining, Bitcoin has a maximum cap of 21 million units, defined in its code. This cap protects Bitcoin from inflation, unlike traditional currencies that can be created without limit by central banks.
This scarcity gives Bitcoin lasting value, similar to gold, as the limited supply helps preserve purchasing power over time. As demand for Bitcoin grows, its reduced availability reinforces its role as a store of value.
Another feature that brings Bitcoin closer to gold is durability. While gold is resistant to corrosion and can be stored for centuries, Bitcoin is a digital asset protected by advanced cryptography and stored on the blockchain. An immutable and decentralized ledger.
Moreover, Bitcoin is far easier to transport than gold. Moving physical gold involves high costs and security risks, making transport particularly difficult for international transactions. Bitcoin, on the other hand, can be sent digitally anywhere in the world in minutes, with low fees and no intermediaries. This technological advantage makes Bitcoin more effective in a globalized and digital world.
Security is another trait that Bitcoin and gold share. Gold is difficult to counterfeit, making it a reliable store of value. Similarly, Bitcoin uses cryptographic protocols that ensure secure transactions and protect against fraud.
In addition, all Bitcoin transactions are recorded on the blockchain, offering a level of transparency that physical gold does not provide. Anyone can review transactions on the network, increasing trust and traceability.
Historically, gold has been used as a hedge against inflation and economic crises. During times of instability, investors turn to gold as a way to preserve their wealth. Bitcoin is emerging as a digital alternative with the same purpose.
In countries with high inflation or political instability, Bitcoin has been used as a safeguard against the devaluation of local currencies. Its decentralized nature prevents governments from directly confiscating or controlling the asset, providing greater financial freedom to users.
Despite its similarities with gold, Bitcoin still faces challenges. Its volatility is much higher, which can cause short-term uncertainty. However, many experts argue that this volatility is typical of new assets and tends to decrease over time as adoption grows and the market matures.
Another challenge is regulation. While gold is globally recognized as a financial asset, Bitcoin still faces resistance from governments and financial institutions, which seek ways to control and regulate it.
In summary, Bitcoin - often called "digital gold" - offers a new form of value that combines the best characteristics of gold with the efficiency and innovation of digital technology. Its programmed scarcity, cryptographic security, portability, and resistance to censorship make it a viable alternative for preserving wealth and conducting transactions in the modern world.
Despite its volatility, Bitcoin is establishing itself as both a store of value and a hedge against economic crises. As such, it represents not just an evolution of the financial system but also a symbol of the shift toward a decentralized and global digital economy.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 2ce0697b:1ee3d3fc
2025-04-29 18:54:19
@ 2ce0697b:1ee3d3fc
2025-04-29 18:54:19Excerpt
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government, without violence and in a way that they can´t stop it. With Bitcoin as the backbone of a new societal order, we are beginning to disrupt the old paradigm.
“If you have built castles in the air, your work need not be lost; that is where they should be. Now put the foundations under them.” ― Henry David Thoreau, Walden
The problem: lack of freedom in the physical realm
Freedom is essential to human life. Being free is what matters. That´s our target, always. No matter the time or space. We pursue freedom because we know its the right thing to do. Freedom is the right to question and change the stablished way of doing things.
Where can we find some freedom? Certainly in the cyberspace. The cyberspace is a free space. Humanity has been blessed by the magic of cryptography, a technology that gave us all the necessary tools to operate in that environment without intervention of undesired third parties.
In cyberspace cryptography performs the function of an impenetrable cyberwall. So, whatever we build in cyberspace can be perfectly protected. Thank to this cybernetic walls we can be sure that the gardens we build and nurture will be protected and cannot be trampled. When we build our digital gardens we have the keys to open the doors to let in whoever we want and most important to leave out whoever we don´t want. In the digital world we can already perfectly interact with one and another in a peer to peer way, without intervention of undesired third parties.
In cyberspace we have Bitcoin for freedom of money and Nostr, torrent and Tor for freedom of information and speech. These open-source protocols are designed to fully realize and expand the promise of freedom, and they certainly deliver what they promise.

So, thanks to the magic of asymmetric cryptography, we´ve already achieved sufficiently descentralization and the possibility of any level of desired digital privacy. Cryptoanarchists and cypherpunks have set their conquering flag in cyberspace and there´s no force on Earth than can remove it. The digital world cannot escape the rules of cryptography. This is great but it only works in the digital realm, meanwhile in the physical realm we are overrun by centralized attackers due to the impossibility of the creation of impenetrable walls such as the ones we have online.
Humans have the upper hand in creating impenetrable walled gardens in cyberspace, but in the physical space authoritarians have the upper hand in bullying physical persons.
The physical world is also naturally free. According to natural law each person is free to do whatever he wants as long as it doesn´t hurt other people. However due to unnatural -artificial and inhuman- centralization of power, the natural freedom of the physical world has been completely undermined. Mostly by Governments, the entities that centralize violence and law.
Bitcoin as a bridge between both realms

Let´s take a look at one connection between both realms, the physical and the digital world. Bitcoin layer one is made essentially of software plus hardware. It consists of any software that produces the same output as the reference implementation - Bitcoin core- and the hardware needed to run that software. Layer two, three or any other layer above, is made essentially of other software and other hardware that interacts with layer one in some way. All these layers, one, two and subsequent, are completely protected by cryptography and a set of game theories that have been successfully tested. Each new block added to the timechain is a testimony of the unstoppable force of freedom and meritocracy.
Before layer one we have Bitcoin layer zero, which is essentially the sum of all actions and inactions done by bitcoiners regarding to or because of bitcoin. In other words, layer zero is composed by flesh and bone people interacting in some way with layer one of the bitcoin network.
Hence, an attack on a bitcoiner - on his way of life- is an attack on bitcoin, the network itself. First because it is an attack on a layer zero node, the physical person, the bitcoiner under duress or coercion. And second because is also an attack on the store-of-value-aspect of bitcoin. Nowaday, the most common attack against bitcoiners is the entirety of compliance regulations. This is the sum of all coercive regulations,such as laws, threats of more laws, imprisonment, threats of more imprisonment, taxation, threats of more taxation, requirements to prove the origin of funds, coercive removal of privacy such as the travel rule, unnecessary bureaucracy such as the need to obtain a money transmitting license and many others rules, in a never stopping inflationary coercive legislation.

If a physical attack is preventing any bitcoiner to exchange the value he created for bitcoin due to any kind of artificial obstacles -such as any kind of compliance- that specific attack is successful in the sense that even though the whole network keeps operating, the attack itself diminishes the value of all the bitcoins.
So, even if layer-zero cannot be taken down, every interference on this layer is an attack on the bitcoin network. Attacks on layer one, two or any other layer that exists in the cyberspace can interfere with the network but they may hardly subtract any value from it. For example we have already been through plenty of times where hashing power was diminished due to government intervention and the bitcoin network remain completely unaffected.
On the other hand successful attacks on layer zero subtract potential, but real and demonstrable value. This value is equal to the amount of value the frustrated user would have added to the network if he would have been able to use it freely, that means if he would have sold his product without the cost of compliance. I´ll demonstrate this in the next chapter.
The cost of compliance
Alice is a merchant specialized in a specific area and topic. She studied the market, her business, her suppliers, consumers, the logistics involved, marketing, design, and everything necessary to become a successful entrepreneur. After investing a considerable amount of resources, she developed a perfect product. Or at least she considers it perfect, that is, the best in its class. While developing everything necessary to create her product, she met Bob, who became her main lead and stereotype of a buyer persona. She knows what Bob wants and she wants to sell it to him. According to Alice's calculations, for her business to be viable, she must sell the product at ten satoshis per unit, and fortunately, Bob is willing to pay that price for it. Alice's product is finished, ready to hit the market, but just before sending it to production, Alice decides to take a pause to analyze her reality. Before taking the public action of making her product available in the open market, Alice analyzes her material, political, and legal reality. In doing so, she realizes that she lives under the jurisdiction of a State. She learns that the Government prescribes through its regulations how she must behave. She analyzes that in order to sell her product legally, in compliance, she must make a series of modifications to it. The product before hitting the shelves must first be modified both in the way it is presented to the market and also regarding certain technical characteristics that it possesses. She must also modify the way it produces her product by changing the contractual relationship with its suppliers, distribution channels, and all other types of logistics involved. She must make all these changes even if they bring about significant and insurmountable inefficiencies.
Likewise, Alice also sees that she not only has to modify the product but also has to meet tax obligations. In addition to paying an accountant since the tax obligations by some irrational reason are not calculated by the creditor. Additionally, she must hire other professionals to assist her in studying the current regulations and how they should be applied in all stages of production, distribution, and sale of her product.
Alice, being a rational person, wishes to avoid having to make these modifications since they increase her costs while also decreasing the quality of her product. But when studying compliance, that is, the entirety of applicable regulations, she also examines the consequences of not being in compliance. Alice realizes that if she does not comply with the regulations, she risks having all her assets legally confiscated, going to prison, being killed while they try to capture her to imprison her, and, if she goes to prison, being tortured in jail by other inmates or by State officials in charge of holding her in that place. So, since Alice does not want to suffer these negative consequences, she decides to modify the product and be in compliance.
So, Alice makes the necessary changes and puts her new version of the product on the market. Then she has the following dialogue with Bob, her lead, the interested party in acquiring the product.
Bob: - Hey Alice, nice meeting you here in this market. I came to buy the product you were developing and told me about. However, this product I´m seeing now is not what you promised me. This is clearly inferior.
Alice: - Yeah, I know. I'm sorry Bob, but I prefer to sell this inferior product rather than risk having all my assets confiscated, going to prison, being killed while they try to capture me, and if they don´t kill but managed to put me in jail I could be tortured there.
Bob: - Ok, no problem. Thats quite understandable. I don´t believe anyone would prefer those kind of experiences. But given the quality of the product, I no longer intend to pay you ten satoshis; I only offer you eight. Shall we close the deal?
Alice: - I'm sorry Bob, but I can't sell it to you for eight sats. Due to government intervention and its requirements, now I can't even sell it for less than thirteen satoshis.
Bob: - Ok. Considering this I prefer not to purchase it. I will keep looking for alternatives. Bye

Some time later, Charlie arrives at the market, who is also interested in the product and, despite it not being like the original version, decides to purchase it by paying the thirteen satoshis demanded by the seller Alice.
Meanwhile, in the same universe, we have Daniel, the last character in this example. Daniel is a merchant competing with Alice. Daniel has a product that is very similar, practically identical to the one originally designed by Alice. Like Alice, Daniel initially also wants to sell it for ten satoshis. Just like Alice, before heading to the market, Daniel analyzes the reality in which he lives. And it turns out that he also lives under the jurisdiction of a State. Daniel too then analyzes the entirety of the applicable regulations and also comes to the conclusion that to comply with them, he would also need to modify the product and cover all the additional expenses artificially generated to be in compliance.
However, Daniel's ethics are different from Alice's. Daniel understands that his product is indeed perfect (the best in its class) and that therefore modifying it would go against its essence. Daniel understands that changing the product would be a betrayal of his creation and therefore a betrayal of his own self and the essence of his being. Daniel conducts an ethical analysis of his actions and the moral implications of putting the product on the market. Daniel sees that the product not only does not harm anyone but is also made to be freely acquired by adults who give their consent for its purchase and subsequent use. Daniel also understands that paying taxes only serves to promote the slavery system driven by fiat and that whenever he can avoid collaborating with the immoral fiat system, it is his ethical obligation to do so. Likewise, Daniel highlights the hypocrisy and inefficiencies of anti-money laundering regulations, as well as the futility of requiring licenses for naturally free acts that do not harm others. For all these reasons, Daniel decides to sell the product in its current state irregardles of compliance regulations.
However, before going to market, Daniel also studies the possible consequences of neglecting compliance. By doing so, Daniel sees that if he does not comply with the regulations, he risks having all his assets legally confiscated, going to prison, being killed while they attempt to capture him to imprison him, and, in the event of going to prison, being tortured in jail by other inmates or by State officials responsible for holding him in that place. So, since Daniel is a rational person who does not want to suffer these negative consequences but also does not want to betray his product and himself, he decides to take the risk of not being in compliance. After making this decision, Daniel puts the product on the market and there he meets Bob. In doing so, they converse in the following terms:
Bob: - Hey Daniel, this product is exactly what I was looking for. A product like the one promised by Alice but never delivered. I love it! I offer you ten satoshis for it.
Daniel: - Thank you for your feedback Bob and for the offer! However I am currently selling it for eleven satoshis. Ten satoshis seems like a good price to me, and it was indeed my original intention to sell it for that amount because at that price I achieve competitiveness and a sustainable business model.
Bob: - So why are you asking me for eleven satoshis? Interrupts Bob
Daniel: - Because that price is calculated before assessing compliance and the risks associated with non-compliance. By not complying with the regulation, I managed to maintain the quality of the product and avoided a large amount of unnecessary expenses, but there is no way to avoid the risk of facing penalties for non-compliance. To bring this product to market, I had to incur several expenses in order to minimize the risk of non-compliance as much as possible. While I am taking all reasonable actions to prevent all of my assets from being legally confiscated, from going to prison, from being killed while they try to capture me, and in case of going to prison, from being tortured, the reality is that I still run the risk of all that, or part of all that, happening to me, my family, or any of my company's employees. The remaining risk balance is transferred to the price along with the costs of mitigating those risks. The total of those costs and the remaining risk I estimate them at one satoshi per unit of product. Therefore, I can't sell you the product for ten satoshis, but I can sell it to you for eleven.
To which Bob, lacking a better option in the market, ends up buying the product for eleven satoshis.
In summary: two products were made by two different merchants whose business model allowed them, in both cases, to put the product on the market at a rate of ten satoshis per unit. However, in one case, a lower quality product was sold for thirteen satoshis, and in the other case, a higher quality product was sold for eleven satoshis. That is to say, in the first case there was an overprice or inefficiency objectively measured at three satoshis, while in the second case there was an overprice or inefficiency of one satoshi. So, we are facing a total loss of value equivalent to four satoshis. The value represented by these four satoshis was absorbed by the inefficiency programmed and ruled by the State. The example shows us that whether one chooses the compliance route, as Alice did, or the free market route, as Daniel did, in both cases the existence of regulations generates an additional cost to the market. In this example the state attack on layer zero was successful and extracted from the Bitcoin network a value of four satoshis.
Bitcoin is money
Bitcoin is many things but essentially is money. And money sole purpose is to store value in order to facilitate future exchanges of products and services with other people. Without the products and services to be exchanged for the money, money itself would be useless and worthless. We only use money because we may require favors, benefits, services, products from other people in the future. And we don´t know which services and products we´ll need nor exactly when we are goint to need them.

The total value of bitcoin equals to infinity divided twenty one millions. This is because the total worth of the network mirrors the total worth of accumulated capital by the entirety of mankind throughout its entire history. That is clearly a lot of value. But if the if the dividend equals zero then the divisor is also zero and if the dividend growth is obstructed through artificial means -such as compliance- then the divisor growth is also obstructed.
Bitcoin layer zero, the bitcoiners and the services and products we create, are what give value to the twenty one million units of bitcoin.
Freedom is without a doubt the best context for value creation. So, the more and better games we can create that allow humankind to find a way to exercise freedom, then the most value we can add to all the layers of the network.
This is why the most important layer of the whole bitcoin phenomenon is layer zero, the bitcoiners. Hence the problem to be solved is not how to prevent bitcoin - layer one upwards- from successful attacks. The problem to solve is how to prevent attacks on layer zero. Or in other words, the problem to be solved is how to get bitcoiners in the physical world to practice the same level of freedom that bitcoin achieves in the cyberspace.
Summary of the first part of this article: freedom in cyberspace has already been conquered and each further development in the digital realm contributes to further developments but only in the same realm. Meanwhile in the physical space, the layer zero of bitcoin is under constant attacks that successfully extract value from it.
Exercising freedom in a sly roundabout way

In 1984 the Austrian economist Friedrich Hayek predicted that we couldn´t take money with violence out of the hands of government. He stated that we needed to do it in a sly roundabout way. Twenty five years later Satoshi Nakamoto discovered the sly roundabout way actually introducing something that the government couldn´t stop. Thus fulfilling Hayek´s prophecy.
Bitcoin is a sly roundabout way that removed money without violence from the hands of the government in a way that they can´t stop it.
Cryptography in general and protocols such as Tor and Tails are a sly roundabout way that removed confidential information from the hands of the government without violence in a way that they can´t stop it.
Nostr is a sly roundabout way that removed social media and public information from the hands of the government without violence in a way that they can´t stop it.
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government without violence in a way that they can´t stop it.

So, what are Special Jurisdictions, Free Cities and Bitcoin Citadels? To understand what they are we can take a look at the current mainstream market of living together, at how the physical space is organized. Essentially the entire planet Earth and its surroundings are run by a conglomerate of Governments. They create all the rules, regarding every aspect of life, of all the individuals, and enforce every rule through coercive means.
In the mainstream market of living together individuals have several alternatives to pick from. We can choose to live in a natural city or a pre design city, in a public neighborhood or private neighborhood or even in an intentional community with common interest amongst the users. But irregardless of the choice, every product offered in the mainstream market has the sames rules which are established by the host state to the entirety of organizations in his territory. In the mainstream market, even the most different products abide by the same high level rules such as criminal law, civil law, taxation laws, customs, enviromental laws, money laundering regulations and many others. To abide to the sum of all the laws and regulations is to be in compliance.
The centralization of regulations makes extremely difficult to experiment in market of living together. The less experimentation is allowed, the more human progress is hindered.
So what is the sly roundabout that fixes this? What are Special Jurisdictions, Free Cities and Bitcoin Citadels? I´m using the term Special Jurisdictions as an umbrella term that includes the entire spectrum of iterations of products that aim to modify the mainstream rules of the market of living together.
This term includes all the different models such as Charter Cities, Free Cities, Special Economic Zones, microstates, micropolis, start up societies, government as a service, self governing jurisdictions, autonomous intentional communities, network states and Bitcoin Citadels. The array of possible iterations is huge and permanently expanding. What they all have in common is that each of these experiments aims to create a functional game theory that replaces the lack of unbreakable walls in the physical space.
Let´s take a look of a couple of examples. Special Economic Zones are bounded areas of countries that have their own rules and regulations. Worldwide, there are more than five thousands special economic zones located in more than hundred countries.
One of them is the special economic zone of Shenzhen in China. The Chinese government allowed Shenzhen the freedom to experiment with certain practices that were prohibited in the rest of the country at the time. This included allowing foreign companies to make direct investments in China, allowing people to buy and sell land, allowing Chinese people to set up their own private businesses and relaxation of the system that limited internal migration within China for Chinese citizens. It served as a place where China could experiment with market reforms. The experiment was such a huge economic success that it was replicated in many other areas of the country.
Another place that has made extensive use of special economic zones is Dubai. The monarchic Government has more than 30 SEZs. In this case one of the many obstacles removed by the host state its the monopoly of the legal system. Dubai Government allowed the special economic zone to have its own independent legal system thus conceding a modification of the mainstream rules in that area.
This kind of projects, such as Dubai or Shenzhen, are a top-to-down product. Fully created by the Governments thus compliant with their own regulations.

On the other side of the spectrum we have Citadels and several other archetypes of not so compliant projects .
For example the Free Commune of Penadexo it´s a grassroots project building a freedom-oriented community in one of Spain’s abandoned villages.
 It´s model is based on building a peer to peer society avoiding government intervention as much as possible.
They stablished themselves in an abandoned historic village and the started to track down the owners to purchase as much property as possible. Meanwhile, they are living there and expanding their users base while also reconstructing buildings.
It´s model is based on building a peer to peer society avoiding government intervention as much as possible.
They stablished themselves in an abandoned historic village and the started to track down the owners to purchase as much property as possible. Meanwhile, they are living there and expanding their users base while also reconstructing buildings. This is an example of a completely different way of dealing with the Government. While Special Economic Zones are fully compliant and created top to down, this model on the other hand is bottom-up and aims to add value to the users relying in factual freedom which is exercised by stablishing the commune away from heavily populated centers where Government grip is tighter. Under this model the interaction with the Government is kept as low as possible. Their strategy relies in ignoring the Government as much as possible and being a good neighbor. With this simple and effective tactic some Citadels enjoy the benefits of liberty in their lifetime without needing to spend huge resources in governmental lobby.
There are countless models or archetypes of Bitcoin Citadels trying to solve the obstacles in different ways, trying to restart the system. And one of the challenges of the Bitcoin Citadels is how to connect the different projects to boost and help each other.
This is where The Meshtadel comes into play. The Meshtadel is a system where decentralized tactics are used to help and defend citadels connected in a global network. With real life connections with fellow bitcoiners. Its an organization equivalent to the hanseatic league built under a starfish model. If you cut off a spider’s head, it dies, but if you cut off a starfish’s arm, it can regenerate and even grow into a new starfish.
The Meshtadel its a network of peer relationships, with ambiguous leadership roles, trust among participants, a shared ideology and vision based on the Bitcoin ethos, and an open system where new nodes - bitcoin citadel builders - can participate.
The long term goal of the Bitcoin Meshtadel is to help Bitcoin Citadels to gain the support of a critical mass of the total population. If enough people see that Bitcoin is as peaceful as it gets, in the long run, some nations could become friendly and supportive enough to legally tolerate the Bitcoin Citadel inside its territory in the form of a Bitcoin safe haven. In the Meshtadel we are fighting from the moral high ground using memes, Nostr notes and zapping our way into freedom creating an online and offline circular economy.
TO CONCLUDE:
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government, without violence and in a way that they can´t stop it.
Nation states, abusing the myth of authority, have halted development on the market of living together for so long that a blooming freer market is eating its lunch. The sovereign individual thesis is live and continuously expanding. The network state is forming and intentional communities are flourishing all around the world reshaping globally the relationship between individuals and the governments.
With global internet connections, uncensorable means of communication and Bitcoin as the backbone of a new societal order, we are beginning to disrupt the old paradigm.
The fashion of the present world is passing away, let’s help it to move forward along by building Special Jurisdictions, Free Cities and Bitcoin Citadels.
--- --- --- --- --- --- --- --- ------
byCamiloat 875.341 timechain.
If you find this content helpful, zap it to support more content of the sort and to boost the V4V model.
-
 @ e2388e53:0e93e8a9
2025-05-03 11:39:45
@ e2388e53:0e93e8a9
2025-05-03 11:39:45- Melancholie ist die sanfteste Form der Rebellion – ein Nein, das sich in Schönheit kleidet, um nicht verbrannt zu werden.
- Die Menschheit sucht nach Erlösung – und nennt das Kind dabei „Zukunft“, ohne zu merken, wie schwer diese Krone wiegt.
- Nähe ohne Ehrlichkeit ist nur ein getarnter Abstand.
- Jede Zentralisierung ist ein Denkfehler, der Macht als Fürsorge tarnt.
- Sehnsucht ist ein Fluss, der rückwärts fließt – du watest hinein, doch das Ufer zieht sich fort, unerreichbar fern.
- Die letzte Form der Sklaverei ist die freiwillige Abhängigkeit.
- Ein Kind spielt nicht, um zu vergessen – es spielt, weil es noch nicht gelernt hat zu verdrängen.
- Freiheit ist die Fähigkeit, in Ketten zu tanzen.
- Das Leben ist der Widerhall eines sterbenden Willens. Nur im Nichts finden wir Erlösung.
- Wer Kinder erzieht, erzieht auch seine Schatten – sie kommen zurück, wenn das Haus still ist.
-
 @ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44
@ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions
At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery
We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority
Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology
Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.
- Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.
⚠️ What We Don’t Do
While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
 # Don’t Let Lost Crypto Hold You Back! ⏳
# Don’t Let Lost Crypto Hold You Back! ⏳Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection
Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!
Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us!
For real-time support or questions, reach out to our dedicated team on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ 266815e0:6cd408a5
2025-04-29 17:47:57
@ 266815e0:6cd408a5
2025-04-29 17:47:57I'm excited to announce the release of Applesauce v1.0.0! There are a few breaking changes and a lot of improvements and new features across all packages. Each package has been updated to 1.0.0, marking a stable API for developers to build upon.
Applesauce core changes
There was a change in the
applesauce-corepackage in theQueryStore.The
Queryinterface has been converted to a method instead of an object withkeyandrunfields.A bunch of new helper methods and queries were added, checkout the changelog for a full list.
Applesauce Relay
There is a new
applesauce-relaypackage that provides a simple RxJS based api for connecting to relays and publishing events.Documentation: applesauce-relay
Features:
- A simple API for subscribing or publishing to a single relay or a group of relays
- No
connectorclosemethods, connections are managed automatically by rxjs - NIP-11
auth_requiredsupport - Support for NIP-42 authentication
- Prebuilt or custom re-connection back-off
- Keep-alive timeout (default 30s)
- Client-side Negentropy sync support
Example Usage: Single relay
```typescript import { Relay } from "applesauce-relay";
// Connect to a relay const relay = new Relay("wss://relay.example.com");
// Create a REQ and subscribe to it relay .req({ kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events"); } else { console.log("Received event:", response); } }); ```
Example Usage: Relay pool
```typescript import { Relay, RelayPool } from "applesauce-relay";
// Create a pool with a custom relay const pool = new RelayPool();
// Create a REQ and subscribe to it pool .req(["wss://relay.damus.io", "wss://relay.snort.social"], { kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events on all relays"); } else { console.log("Received event:", response); } }); ```
Applesauce actions
Another new package is the
applesauce-actionspackage. This package provides a set of async operations for common Nostr actions.Actions are run against the events in the
EventStoreand use theEventFactoryto create new events to publish.Documentation: applesauce-actions
Example Usage:
```typescript import { ActionHub } from "applesauce-actions";
// An EventStore and EventFactory are required to use the ActionHub import { eventStore } from "./stores.ts"; import { eventFactory } from "./factories.ts";
// Custom publish logic const publish = async (event: NostrEvent) => { console.log("Publishing", event); await app.relayPool.publish(event, app.defaultRelays); };
// The
publishmethod is optional for the asyncrunmethod to work const hub = new ActionHub(eventStore, eventFactory, publish); ```Once an
ActionsHubis created, you can use therunorexecmethods to execute actions:```typescript import { FollowUser, MuteUser } from "applesauce-actions/actions";
// Follow fiatjaf await hub.run( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", );
// Or use the
execmethod with a custom publish method await hub .exec( MuteUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", ) .forEach((event) => { // NOTE: Don't publish this event because we never want to mute fiatjaf // pool.publish(['wss://pyramid.fiatjaf.com/'], event) }); ```There are a log more actions including some for working with NIP-51 lists (private and public), you can find them in the reference
Applesauce loaders
The
applesauce-loaderspackage has been updated to support any relay connection libraries and not justrx-nostr.Before:
```typescript import { ReplaceableLoader } from "applesauce-loaders"; import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(rxNostr); ```
After:
```typescript
import { Observable } from "rxjs"; import { ReplaceableLoader, NostrRequest } from "applesauce-loaders"; import { SimplePool } from "nostr-tools";
// Create a new nostr-tools pool const pool = new SimplePool();
// Create a method that subscribes using nostr-tools and returns an observable function nostrRequest: NostrRequest = (relays, filters, id) => { return new Observable((subscriber) => { const sub = pool.subscribe(relays, filters, { onevent: (event) => { subscriber.next(event); }, onclose: () => subscriber.complete(), oneose: () => subscriber.complete(), });
return () => sub.close();}); };
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
Of course you can still use rx-nostr if you want:
```typescript import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a method that subscribes using rx-nostr and returns an observable function nostrRequest( relays: string[], filters: Filter[], id?: string, ): Observable
{ // Create a new oneshot request so it will complete when EOSE is received const req = createRxOneshotReq({ filters, rxReqId: id }); return rxNostr .use(req, { on: { relays } }) .pipe(map((packet) => packet.event)); } // Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
There where a few more changes, check out the changelog
Applesauce wallet
Its far from complete, but there is a new
applesauce-walletpackage that provides a actions and queries for working with NIP-60 wallets.Documentation: applesauce-wallet
Example Usage:
```typescript import { CreateWallet, UnlockWallet } from "applesauce-wallet/actions";
// Create a new NIP-60 wallet await hub.run(CreateWallet, ["wss://mint.example.com"], privateKey);
// Unlock wallet and associated tokens/history await hub.run(UnlockWallet, { tokens: true, history: true }); ```
-
 @ 90c656ff:9383fd4e
2025-05-03 11:39:03
@ 90c656ff:9383fd4e
2025-05-03 11:39:03The emergence of Bitcoin brought a new perspective to the concept of money, challenging the conventional financial system based on fiat currencies. While fiat currencies like the real, dollar, and euro are widely used and recognized as means of exchange, Bitcoin represents a digital innovation that promotes decentralization and financial autonomy. Although both serve basic functions such as a medium of exchange and store of value, their main differences lie in how they are issued, managed, and transacted.
One of the key distinctions between Bitcoin and fiat currencies is the way they are issued and administered. Fiat currencies are issued by central banks, which have the power to regulate the amount in circulation. This model allows for the implementation of monetary policies, such as increasing the money supply to stimulate the economy or decreasing it to control inflation. However, this power can also result in currency devaluation if money is issued in excess.
Bitcoin, on the other hand, has a completely decentralized issuance system. It is created through a process called mining, in which computers solve complex mathematical problems to validate transactions on the network. Additionally, the total supply of bitcoins is limited to 21 million units, making it a deflationary asset—its scarcity can potentially increase its value over time. This limitation contrasts sharply with the unlimited nature of fiat money printing.
Fiat currencies are centralized, meaning their issuance and control are decided by governmental authorities. This also means that transactions involving these currencies go through intermediaries like banks, which can impose fees and limits, and are subject to regulations and audits.
Bitcoin, by contrast, is decentralized. It operates on a peer-to-peer network where transactions are verified by participants called miners and recorded in a public ledger known as the blockchain. This decentralization eliminates the need for intermediaries, making Bitcoin more resistant to censorship and government control. It also provides greater transparency, as anyone can verify transactions on the network.
Another important difference lies in how transactions are carried out. With fiat currencies, transactions usually depend on banks or payment systems, which may impose time restrictions and high fees, especially for international transfers.
Bitcoin, on the other hand, enables direct transfers between people, anywhere in the world and at any time, without the need for intermediaries. This makes the system more accessible, particularly for those without bank accounts or living in countries with restrictive financial systems. Additionally, Bitcoin transaction fees can be lower than those charged by traditional banks.
Fiat currencies offer security backed by government laws and the banking system, but users must place trust in those intermediaries. Bitcoin, by contrast, offers a high level of security through advanced cryptography. Digital wallets that store bitcoins are protected by private keys, ensuring that only the owner has access.
However, privacy works differently. Fiat currency transactions are typically linked to the user's identity, whereas Bitcoin offers a certain level of anonymity, since wallet addresses do not require personal identification. Still, all transactions are public and recorded on the blockchain, which can serve as a point of monitoring for authorities.
The value of fiat currencies is backed by trust in the government that issues them and the country's economy. In contrast, Bitcoin is not backed by any government or physical asset. Its value is determined by market supply and demand, making it highly volatile. While this volatility presents a risk, it also attracts people who see Bitcoin as a long-term appreciation opportunity.
In summary, Bitcoin and fiat currencies differ significantly in their structure, control, and functionality. While fiat currencies are government-controlled and depend on intermediaries, Bitcoin offers decentralization, transparency, and financial freedom. Despite its volatility and some regulatory challenges, Bitcoin represents a new alternative to the traditional financial system.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ e2388e53:0e93e8a9
2025-05-03 11:36:28
@ e2388e53:0e93e8a9
2025-05-03 11:36:28„Anstatt das System zu bekämpfen, baue ein System, das es überflüssig macht.“
– zugeschrieben Buckminster Fuller
Die Gegenwart ist geprägt von Zentralisierung, digitaler Kontrolle und einem Finanzsystem, das Vertrauen verlangt, aber wenig zurückgibt. Für Bitcoiner stellt sich nicht mehr die Frage nach dem Ob, sondern nach dem Wie des Rückzugs aus diesem System.
Vom Goldstandard zu Bitcoin
Der klassische Goldstandard war Ausdruck eines strukturellen Misstrauens gegenüber staatlicher Willkür. Die Bindung des Geldes an ein rares Gut wie Gold disziplinierte die Geldpolitik – allerdings auf Kosten von Flexibilität, Zugänglichkeit und Dezentralität. Gold war zentral verwahrt, schwer zu transportieren und politisch angreifbar.
Bitcoin übernimmt die Idee der Begrenzung, ohne diese Schwächen: keine zentrale Verwahrung, leicht teilbar, digital übertragbar, resistent gegen Konfiszierung. Was beim Gold noch eine politische Vereinbarung war, ist bei Bitcoin eine technische Tatsache.
Anarchie als Ordnung ohne Herrschaft
Anarchie wird oft missverstanden. Sie ist keine Ablehnung von Ordnung, sondern von Herrschaft. Sie setzt auf freiwillige Strukturen statt auf Zwang, auf Verantwortung statt auf Kontrolle. Bitcoin ist in diesem Sinne anarchisch. Es gibt keine zentrale Autorität, keine Intervention, kein Gatekeeping. Teilhabe ist offen, Regeln sind transparent, Entscheidungen beruhen auf Konsens. Es ist ein System, das sich jeder aneignen kann, ohne jemanden um Erlaubnis zu fragen.
Die Praxis des Rückzugs
Der Rückzug aus dem bestehenden System ist kein plötzlicher Bruch, sondern eine Praxis. Er beginnt mit Selbstverwahrung, mit der Vermeidung von KYC, mit der Nutzung von Peer-to-Peer-Technologien und mit dem bewussten Aufbau eigener Infrastruktur. Es geht nicht darum, das alte System zu stürzen, sondern es überflüssig zu machen – indem man es nicht mehr braucht.
Bitcoin als Entscheidung
Bitcoin ist keine Spekulation, kein Unternehmen, kein Produkt. Es ist eine Entscheidung. Eine Entscheidung für Autonomie. Für Verantwortung. Für Souveränität. Wer sich für diesen Weg entscheidet, entscheidet sich nicht für die einfachste Lösung – sondern für die ehrlichste. Der Preis ist Selbstverantwortung. Die Belohnung ist Freiheit.
Ein stiller Rückzug
Kein Spektakel. Keine Revolution. Nur ein Protokoll. Und ein Mensch, der es nutzt.
-
 @ 90c656ff:9383fd4e
2025-05-03 11:17:21
@ 90c656ff:9383fd4e
2025-05-03 11:17:21Bitcoin was created as something far beyond just a digital currency; it is a revolutionary idea that challenges the foundations of the conventional financial system. The concept behind its creation, presented by the enigmatic Satoshi Nakamoto, focuses on two main principles: decentralization and financial freedom. These ideas reflect an effort to return control of money to the people, eliminating intermediaries and reducing the influence of governments and large financial institutions.
Decentralization is the foundation of Bitcoin. Unlike traditional currencies, which are issued and managed by central banks and governments, Bitcoin operates on a peer-to-peer network. This means there is no central authority or single entity controlling the currency. Instead, all transactions are validated and recorded on a public ledger called the blockchain or timechain, maintained by thousands of computers around the world.
This decentralized structure ensures that Bitcoin is resistant to censorship and immune to monetary policy manipulations such as excessive money printing, which can lead to inflation. It also removes the need for intermediaries like banks, allowing for direct transactions between users. This is especially valuable in scenarios where the traditional banking system is inaccessible or unreliable, such as in remote areas or countries facing economic crises.
The financial freedom promoted by Bitcoin is another transformative element. In traditional systems, individuals depend on third parties such as banks or financial institutions to access, store, and transfer money. These entities can impose restrictions like withdrawal limits, high transfer fees, or even freeze accounts. With Bitcoin, the user has full control over their funds through private keys (a kind of password that grants access to their digital wallet).
Moreover, Bitcoin offers an accessible solution for billions of people worldwide who are unbanked. According to World Bank data, around 1.4 billion adults lack access to a bank account, but many of them do have access to the internet or smartphones. Bitcoin allows these individuals to participate in the global economy without needing intermediary institutions.
Another crucial point is its censorship resistance. In authoritarian regimes or politically unstable situations, governments may confiscate or freeze citizens' assets. Bitcoin, being decentralized and operating on a global network, cannot be arbitrarily controlled or seized, offering an extra layer of financial protection for individuals at risk.
Bitcoin’s vision also includes the creation of a fairer and more transparent financial system. The blockchain or timechain, by recording all transactions in a public and immutable way, reduces the chances of fraud and corruption. Additionally, the limited supply of 21 million bitcoins, hard-coded into the system, supports a deflationary model that contrasts with the unlimited expansion of fiat currencies. This gives Bitcoin the potential to be a stable store of value in the long term.
Despite its promising vision, the path toward full financial freedom is not without challenges. Bitcoin’s price volatility, regulatory concerns, and technological barriers remain hurdles to overcome. However, these challenges also create opportunities for innovation and for strengthening the ecosystem over time.
In summary, the vision behind Bitcoin represents a disruption of the centralized financial system, offering people more autonomy, transparency, and security over their financial resources. It is not just a technology but a movement that aims to empower individuals, especially those excluded or harmed by traditional economic models. By promoting decentralization and financial freedom, Bitcoin paves the way for a future where money truly belongs to the people, not the institutions.
Thank you very much for reading this far — I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 90c656ff:9383fd4e
2025-05-03 11:07:50
@ 90c656ff:9383fd4e
2025-05-03 11:07:50Bitcoin is the world’s first decentralized digital currency, created in 2009 by an individual or group under the pseudonym Satoshi Nakamoto. Its birth marked the beginning of a revolution in the global financial system, introducing a new kind of currency that is not controlled by governments or traditional financial institutions. The history of Bitcoin is deeply rooted in the ideals of economic freedom, transparency, and resistance to censorship.
The journey began in October 2008, when Satoshi Nakamoto published a paper titled “Bitcoin: A Peer-to-Peer Electronic Cash System.” The white paper, published on the Cryptography mailing list, described the idea of a digital payment system based on a peer-to-peer network. This concept eliminates the need for intermediaries like banks and solves a problem known as “double spending” — the possibility of duplicating digital currencies — through a technology called blockchain, or what Satoshi Nakamoto himself referred to as the timechain.
The blockchain, or timechain, is essentially a public and immutable ledger that records all Bitcoin transactions. It operates through a decentralized system where participants in the network (the so-called nodes) verify transactions and organize them into blocks. These blocks are in turn linked together in a continuous chain, forming the basis of the system’s security and transparency.
On January 3, 2009, Satoshi Nakamoto mined the first Bitcoin block, known as the genesis block. The block contained a coded message referencing the 2008 global financial crisis: "The Times, January 3, 2009, Chancellor on brink of second bailout for banks." This message is emblematic of the motivation behind Bitcoin: to provide an alternative to the centralized financial system that failed to protect the global economy.
Throughout 2009 and 2010, Bitcoin remained an experiment among tech and crypto enthusiasts. The first Bitcoin transactions took place between network participants, and the first commercial use of the currency occurred on May 22, 2010, when a programmer named Laszlo Hanyecz bought two pizzas for 10,000 Bitcoins. This historic transaction became known as “Bitcoin Pizza Day.”
Satoshi Nakamoto continued to contribute to Bitcoin's development until the end of 2010, when he gradually disappeared from the community. To this day, his identity remains a mystery, and there is no concrete evidence of who or how many people were behind the pseudonym. Before leaving, Satoshi Nakamoto handed over control of the project to other developers and made it clear that Bitcoin should be a decentralized technology, owned by everyone and controlled by no one.
Since then, Bitcoin has grown exponentially. It has evolved from a technological experiment into a multibillion-dollar asset and is widely considered a legitimate form of digital money and store of value. Governments, companies, and individuals around the world have adopted Bitcoin as an alternative to traditional fiat currencies.
In summary, the creation of Bitcoin by Satoshi Nakamoto was more than just the birth of a digital currency; it was the beginning of a global movement to rethink how money is controlled and distributed. Although the identity of Satoshi Nakamoto remains unknown, his legacy will continue to shape the future of the financial system and challenge traditional economic structures.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 044da344:073a8a0e
2025-05-03 19:02:02
@ 044da344:073a8a0e
2025-05-03 19:02:02Mein Thema kommt heute aus dem Kalender und hat gleich noch zu einem Video geführt. Internationaler Tag der Pressefreiheit – wie jedes Jahr am 3. Mai. Das Publikum liebt Ranglisten. Shanghai für die Hochschulen, der Best Country Report für die Lebensqualität und Freedom House für die Freiheit in der Welt. Es gibt Aufsteiger und Absteiger und Jahr für Jahr eine Meldung, über die sich trefflich diskutieren lässt – vor allem in Europa und Nordamerika, wo die Sieger wohnen. Man muss die Statistik dafür nicht einmal fälschen, sondern einfach nur das messen, was man selbst am besten kann, und alles weglassen, was das Bild trüben könnte. Bei den „Reportern ohne Grenzen“ sorgen dafür die Geldgeber und Fragen, die sich zum Beispiel in Afrika oder in Südostasien gar nicht stellen. Ergebnis: Die Medien sind bei uns ziemlich frei, auch wenn Leser dieser Seite wissen, dass das so nicht stimmt.
Okay: Deutschland hat es wieder nicht ganz geschafft in den grünen Bereich – dorthin, wo die skandinavischen Länder stehen, die Niederlande oder Irland. Deutschland gehört auch nicht mehr zu den Top Ten wie noch 2024, aber es war knapp. Platz elf. Zum Glück nennen die „Reporter ohne Grenzen“ die Schuldigen. Zensur? Gott bewahre. Das Ausblenden, Diffamieren, Verleumden von allen, die laut Fragen stellen zum Regierungskurs? Doch nicht bei uns. Dieses Land würde auch in Sachen Pressefreiheit längst Weltmeister sein, wenn da nicht ein paar Unverbesserliche wären, die auf Journalisten ungefähr so reagieren wie ein Stier auf ein rotes Tuch. Glaubt man den „Reportern ohne Grenzen“, dann sind Demos in Deutschland ein gefährlicher Ort für alle, die dort mit Kamera, Mikro oder Presseschild auftauchen. 75 „physische Angriffe“ 2024, davon die meisten in Berlin und beim Thema Nahost, wobei es zwei Bild-Reporter allein auf 29 Einträge gebracht haben (Iman Sefati und seine Fotografin Yalcin Askin).
Vorweg: Jede Attacke ist eine zu viel. Gleich danach kommt aber der Verdacht, dass das ganz gut passt, weil die „Reporter ohne Grenzen“ so eine „zunehmende Pressefeindlichkeit“ beklagen können und „ein verengtes Verständnis von Pressefreiheit“. Zitat: „Denn viele Bürger*innen sehen Berichterstattende, die nicht ihrem eigenen politischen Spektrum entstammen, mittlerweile als Gegner an.“
Sorry für die Genderei. Ich habe das so gelassen, weil es vermutlich bereits damit anfängt. Mit einem „verengten Verständnis“ auch und gerade bei der Sprache. Lassen Sie uns das in drei Schritten angehen. Nummer eins: Wir schauen auf den Kellner, der da jedes Jahr zum Welttag der Pressefreiheit eine Quittung ausstellt. Nummer zwei: Wir zählen nach. Und Nummer drei: Wir schlagen all das drauf, was in der Rechnung fehlt.
Die „Reporter ohne Grenzen“ sitzen in Paris und sind damit auf den ersten Blick weniger verdächtig als der US-Thinktank „Freedom House“, der bis 2017 jedes Jahr eine Konkurrenzliste veröffentlicht hat und einen Großteil seiner Gelder und Sicherheiten direkt oder indirekt aus dem Staatshaushalt in Washington bezieht. Der Volksmund weiß, was das Brot aus den Liedern macht, die draußen gesungen werden. Bei den „Reportern ohne Grenzen“ kommt das Geld aus ganz ähnlich Töpfen – 2023 zu drei Vierteln von der EU, von staatlichen Behörden und von den großen Stiftungen. Ford, Luminate (Geldbörse von Ebay-Gründer Pierre Omidyar, der auch bei den Faktencheckern mitspielt), Open Society Foundations. Der deutsche Steuerzahler ist über ein Ministerium (Entwicklungshilfe) und den Berliner Senat jeweils mit einer Viertelmillion Euro dabei. Dass die Niederlande und Schweden mitspielen, erklärt sich bei einem Blick auf die Ergebnisse (in diesem Jahr: Platz 3 und 4). Besser kann man nicht investieren in Werbung für das eigene Land.
Diese Platzierungen sind gewissermaßen ein Selbstläufer, weil all das in die Wertung kommt, was der Westen gut findet – die formale Trennung von Regierung und Redaktionen zum Beispiel. Andersherum: Abzüge gibt es überall da, wo der Staat, Parteien oder Politiker selbst Medien betreiben. In Uganda zum Beispiel, Platz 143, gibt es kaum Werbetreibende, die ein TV-Programm finanzieren könnten, und nur ein kleines Publikum, das sich ein Zeitungsabo leisten kann und will. Sonntags drängen sich die Menschen dort vor kleinen Hütten mit großen Bildschirmen, um ihren Lieblingen aus der Premier League zuzujubeln und vielleicht einen Wettgewinn einzustreichen, der sie über die Woche trägt. Auf dem Land gehören die Radiostationen in aller Regel lokalen Größen. Kirche, Politik, Wirtschaft. Ich habe dort Interviews geführt und gelernt: Über „Pressefreiheit“ und Informationsqualität sagt das alles wenig. Die Menschen in Uganda wissen sehr genau, wer jeweils zu ihnen spricht, und machen sich ihren Reim darauf. Ein anderer Kriterienkatalog könnte daraus ein Qualitätsmerkmal machen. Während Besitz- und damit Machtverhältnisse im Westen hinter Nebelkerzen versteckt werden (Objektivität, Unabhängigkeit, Neutralität), herrscht in Uganda Transparenz.
Neben dem „politischen Kontext“ haben die „Reporter ohne Grenzen“ vier weitere Blöcke in ihrem Punktekatalog. Gesetze, Wirtschaft, Gesellschaft, Sicherheit. Die Fragen decken das ab, was bei uns Standard ist. Dürfen sich Journalisten gewerkschaftlich organisieren? Werden sie bestochen? Können Nachrichtenmedien finanziell überleben? Werden Karikaturen toleriert? Ich will hier nicht zu sehr auf Uganda herumreiten. Nur: Der Beruf wird dort völlig anders gesehen als hier. Es gibt nur eine kleine vierstellige Zahl an Journalisten. 1000, vielleicht 1500. Die meisten sind jung, weil die Redaktionen als Sprungbrett gesehen werden zu einem wirklich lukrativen Job in der Verwaltung, in den Unternehmen, in der Politik. Wer zu einer Pressekonferenz fährt, erwartet dort einen Umschlag. Offiziell: Anreisepauschale. Inoffiziell der Preis für einen wohlwollenden Bericht. Die „Reporter ohne Grenzen“ strafen Uganda folglich ab. Angriffe auf Journalisten (oft von Sicherheitsleuten), wenig Schutz vor Gericht, wenig Achtung vor dem Beruf. Platz 143 halt.
Und Deutschland? Die Demos wie gesagt und Leute, die die Dinge einfach falsch sehen. Ein „verengtes Verständnis von Pressefreiheit“. Außerdem sagen die „Reporter ohne Grenzen“: Wir tun zu wenig gegen „Hassrede und Desinformation“. Der Koalitionsvertrag von Schwarz-Rot ist offenbar nicht mehr eingeflossen in diesen Bericht. Dort heißt es:
Gezielte Einflussnahme auf Wahlen sowie inzwischen alltägliche Desinformation und Fake News sind ernste Bedrohungen für unsere Demokratie, ihre Institutionen und den gesellschaftlichen Zusammenhalt. Die bewusste Verbreitung falscher Tatsachenbehauptungen ist durch die Meinungsfreiheit nicht gedeckt. Deshalb muss die staatsferne Medienaufsicht unter Wahrung der Meinungsfreiheit auf der Basis klarer gesetzlicher Vorgaben gegen Informationsmanipulation sowie Hass und Hetze vorgehen können.
Schon vorab hatten die „Reporter ohne Grenzen“ von „einem stark verengten Meinungskorridor bei der Arbeit zu Israel und Palästina“ berichtet. Selbst alte Hasen haben in dieser Befragung gesagt, dass sie noch nie einen solchen Druck erlebt hätten – vor allem dann, wenn es um die israelische Kriegsführung geht, um die Folgen für die Bevölkerung in Gaza und um das, was in Deutschland zu diesem Thema passiert. Ich verlinke hier die Münchner Rede von Andreas Zumach, gehalten im November 2018, wo all das schon Thema war.
Und sonst? Corona, Ukraine, Klima und damit Energiewende? Kontokündigungen? Gerichtsurteile, die selbst es bis in die Weltpresse schafften (im Bild: The Economist vom 16. April 2025) und dort Unbehagen auslösten? Eine Cancel Culture, die Sprecher aus der Öffentlichkeit verbannt, die sich gegen die herrschende Ideologie und den Regierungskurs stellen?
Alles kein Thema – jedenfalls nicht für die Experten, die gefragt werden (Journalisten, Forscher, Akademiker, Menschenrechtsspezialisten; mithin Menschen, die in irgendeiner Form von Staat oder Konzernen abhängen). Die konzernfreien oder neuen Medien senden für die „Reporter ohne Grenzen“ offenbar jenseits von Gut und Böse. Und dass die Regierung Fernsehen, Radio und Presse nicht unbedingt selbst betreiben muss wie in Uganda, um ihre Sicht der Dinge flächendeckend zu verbreiten, scheint dort außerhalb jeder Vorstellungskraft zu liegen. Anders ist nicht zu erklären, dass im Bericht zwar ein paar öffentlich-rechtliche Skandälchen auftauchen und der Stellenabbau bei der Südwestdeutschen Medienholding, aber nichts zu lesen ist über die Aufrüstung der Medienapparate in Ministerien, Parteien, Unternehmen und über den Druck, der davon auf Journalisten ausgeht, die zwar keinen Umschlag bekommen, wenn sie ordentlich berichten, aber sicher ein wenig Exklusives, wahrscheinlich eine Beförderung und vielleicht sogar ein Ticket für den Sprung auf die andere, besser entlohnte Seite. Bis es soweit ist, melden sie einfach, dass mit der Medienfreiheit alles okay ist, wenn es da nicht diese Chaoten auf der Straße geben würde und ein paar Unverbesserliche mit einem „verengten Verständnis von Pressefreiheit“. Sonst müsste man sich möglicherweise aufmachen und nach den Ursachen für den Unmut fragen.
-
 @ 4ba8e86d:89d32de4
2025-04-28 22:39:20
@ 4ba8e86d:89d32de4
2025-04-28 22:39:20Como funciona o PGP.

O texto a seguir foi retirado do capítulo 1 do documento Introdução à criptografia na documentação do PGP 6.5.1. Copyright © 1990-1999 Network Associates, Inc. Todos os direitos reservados.
-O que é criptografia? -Criptografia forte -Como funciona a criptografia? -Criptografia convencional -Cifra de César -Gerenciamento de chaves e criptografia convencional -Criptografia de chave pública -Como funciona o PGP - Chaves • Assinaturas digitais -Funções hash • Certificados digitais -Distribuição de certificados -Formatos de certificado •Validade e confiança -Verificando validade -Estabelecendo confiança -Modelos de confiança • Revogação de certificado -Comunicar que um certificado foi revogado -O que é uma senha? -Divisão de chave
Os princípios básicos da criptografia.
Quando Júlio César enviou mensagens aos seus generais, ele não confiou nos seus mensageiros. Então ele substituiu cada A em suas mensagens por um D, cada B por um E, e assim por diante através do alfabeto. Somente alguém que conhecesse a regra “shift by 3” poderia decifrar suas mensagens. E assim começamos.
Criptografia e descriptografia.
Os dados que podem ser lidos e compreendidos sem quaisquer medidas especiais são chamados de texto simples ou texto não criptografado. O método de disfarçar o texto simples de forma a ocultar sua substância é chamado de criptografia. Criptografar texto simples resulta em um jargão ilegível chamado texto cifrado. Você usa criptografia para garantir que as informações sejam ocultadas de qualquer pessoa a quem não se destinam, mesmo daqueles que podem ver os dados criptografados. O processo de reverter o texto cifrado ao texto simples original é chamado de descriptografia . A Figura 1-1 ilustra esse processo.
https://image.nostr.build/0e2fcb71ed86a6083e083abbb683f8c103f44a6c6db1aeb2df10ae51ec97ebe5.jpg
Figura 1-1. Criptografia e descriptografia
O que é criptografia?
Criptografia é a ciência que usa a matemática para criptografar e descriptografar dados. A criptografia permite armazenar informações confidenciais ou transmiti-las através de redes inseguras (como a Internet) para que não possam ser lidas por ninguém, exceto pelo destinatário pretendido. Embora a criptografia seja a ciência que protege os dados, a criptoanálise é a ciência que analisa e quebra a comunicação segura. A criptoanálise clássica envolve uma combinação interessante de raciocínio analítico, aplicação de ferramentas matemáticas, descoberta de padrões, paciência, determinação e sorte. Os criptoanalistas também são chamados de atacantes. A criptologia abrange tanto a criptografia quanto a criptoanálise.
Criptografia forte.
"Existem dois tipos de criptografia neste mundo: a criptografia que impedirá a sua irmã mais nova de ler os seus arquivos, e a criptografia que impedirá os principais governos de lerem os seus arquivos. Este livro é sobre o último." --Bruce Schneier, Criptografia Aplicada: Protocolos, Algoritmos e Código Fonte em C. PGP também trata deste último tipo de criptografia. A criptografia pode ser forte ou fraca, conforme explicado acima. A força criptográfica é medida no tempo e nos recursos necessários para recuperar o texto simples. O resultado de uma criptografia forte é um texto cifrado que é muito difícil de decifrar sem a posse da ferramenta de decodificação apropriada. Quão díficil? Dado todo o poder computacional e o tempo disponível de hoje – mesmo um bilhão de computadores fazendo um bilhão de verificações por segundo – não é possível decifrar o resultado de uma criptografia forte antes do fim do universo. Alguém poderia pensar, então, que uma criptografia forte resistiria muito bem até mesmo contra um criptoanalista extremamente determinado. Quem pode realmente dizer? Ninguém provou que a criptografia mais forte disponível hoje resistirá ao poder computacional de amanhã. No entanto, a criptografia forte empregada pelo PGP é a melhor disponível atualmente.
Contudo, a vigilância e o conservadorismo irão protegê-lo melhor do que as alegações de impenetrabilidade.
Como funciona a criptografia?
Um algoritmo criptográfico, ou cifra, é uma função matemática usada no processo de criptografia e descriptografia. Um algoritmo criptográfico funciona em combinação com uma chave – uma palavra, número ou frase – para criptografar o texto simples. O mesmo texto simples é criptografado em texto cifrado diferente com chaves diferentes. A segurança dos dados criptografados depende inteiramente de duas coisas: a força do algoritmo criptográfico e o sigilo da chave. Um algoritmo criptográfico, mais todas as chaves possíveis e todos os protocolos que o fazem funcionar constituem um criptossistema. PGP é um criptossistema.
Criptografia convencional.
Na criptografia convencional, também chamada de criptografia de chave secreta ou de chave simétrica , uma chave é usada tanto para criptografia quanto para descriptografia. O Data Encryption Standard (DES) é um exemplo de criptossistema convencional amplamente empregado pelo Governo Federal. A Figura 1-2 é uma ilustração do processo de criptografia convencional. https://image.nostr.build/328b73ebaff84c949df2560bbbcec4bc3b5e3a5163d5fbb2ec7c7c60488f894c.jpg
Figura 1-2. Criptografia convencional
Cifra de César.
Um exemplo extremamente simples de criptografia convencional é uma cifra de substituição. Uma cifra de substituição substitui uma informação por outra. Isso é feito com mais frequência compensando as letras do alfabeto. Dois exemplos são o Anel Decodificador Secreto do Capitão Meia-Noite, que você pode ter possuído quando era criança, e a cifra de Júlio César. Em ambos os casos, o algoritmo serve para compensar o alfabeto e a chave é o número de caracteres para compensá-lo. Por exemplo, se codificarmos a palavra "SEGREDO" usando o valor chave de César de 3, deslocaremos o alfabeto para que a terceira letra abaixo (D) comece o alfabeto. Então começando com A B C D E F G H I J K L M N O P Q R S T U V W X Y Z e deslizando tudo para cima em 3, você obtém DEFGHIJKLMNOPQRSTUVWXYZABC onde D=A, E=B, F=C e assim por diante. Usando este esquema, o texto simples, "SECRET" é criptografado como "VHFUHW". Para permitir que outra pessoa leia o texto cifrado, você diz a ela que a chave é 3. Obviamente, esta é uma criptografia extremamente fraca para os padrões atuais, mas, ei, funcionou para César e ilustra como funciona a criptografia convencional.
Gerenciamento de chaves e criptografia convencional.
A criptografia convencional tem benefícios. É muito rápido. É especialmente útil para criptografar dados que não vão a lugar nenhum. No entanto, a criptografia convencional por si só como meio de transmissão segura de dados pode ser bastante cara, simplesmente devido à dificuldade de distribuição segura de chaves. Lembre-se de um personagem do seu filme de espionagem favorito: a pessoa com uma pasta trancada e algemada ao pulso. Afinal, o que há na pasta? Provavelmente não é o código de lançamento de mísseis/fórmula de biotoxina/plano de invasão em si. É a chave que irá descriptografar os dados secretos. Para que um remetente e um destinatário se comuniquem com segurança usando criptografia convencional, eles devem chegar a um acordo sobre uma chave e mantê-la secreta entre si. Se estiverem em locais físicos diferentes, devem confiar em um mensageiro, no Bat Phone ou em algum outro meio de comunicação seguro para evitar a divulgação da chave secreta durante a transmissão. Qualquer pessoa que ouvir ou interceptar a chave em trânsito poderá posteriormente ler, modificar e falsificar todas as informações criptografadas ou autenticadas com essa chave. Do DES ao Anel Decodificador Secreto do Capitão Midnight, o problema persistente com a criptografia convencional é a distribuição de chaves: como você leva a chave ao destinatário sem que alguém a intercepte?
Criptografia de chave pública.
Os problemas de distribuição de chaves são resolvidos pela criptografia de chave pública, cujo conceito foi introduzido por Whitfield Diffie e Martin Hellman em 1975. (Há agora evidências de que o Serviço Secreto Britânico a inventou alguns anos antes de Diffie e Hellman, mas a manteve um segredo militar - e não fez nada com isso.
[JH Ellis: The Possibility of Secure Non-Secret Digital Encryption, CESG Report, January 1970]) A criptografia de chave pública é um esquema assimétrico que usa um par de chaves para criptografia: uma chave pública, que criptografa os dados, e uma chave privada ou secreta correspondente para descriptografia. Você publica sua chave pública para o mundo enquanto mantém sua chave privada em segredo. Qualquer pessoa com uma cópia da sua chave pública pode criptografar informações que somente você pode ler. Até mesmo pessoas que você nunca conheceu. É computacionalmente inviável deduzir a chave privada da chave pública. Qualquer pessoa que possua uma chave pública pode criptografar informações, mas não pode descriptografá-las. Somente a pessoa que possui a chave privada correspondente pode descriptografar as informações. https://image.nostr.build/fdb71ae7a4450a523456827bdd509b31f0250f63152cc6f4ba78df290887318b.jpg
Figura 1-3. Criptografia de chave pública O principal benefício da criptografia de chave pública é que ela permite que pessoas que não possuem nenhum acordo de segurança pré-existente troquem mensagens com segurança. A necessidade de remetente e destinatário compartilharem chaves secretas através de algum canal seguro é eliminada; todas as comunicações envolvem apenas chaves públicas e nenhuma chave privada é transmitida ou compartilhada. Alguns exemplos de criptossistemas de chave pública são Elgamal (nomeado em homenagem a seu inventor, Taher Elgamal), RSA (nomeado em homenagem a seus inventores, Ron Rivest, Adi Shamir e Leonard Adleman), Diffie-Hellman (nomeado, você adivinhou, em homenagem a seus inventores). ) e DSA, o algoritmo de assinatura digital (inventado por David Kravitz). Como a criptografia convencional já foi o único meio disponível para transmitir informações secretas, o custo dos canais seguros e da distribuição de chaves relegou a sua utilização apenas àqueles que podiam pagar, como governos e grandes bancos (ou crianças pequenas com anéis descodificadores secretos). A criptografia de chave pública é a revolução tecnológica que fornece criptografia forte para as massas adultas. Lembra do mensageiro com a pasta trancada e algemada ao pulso? A criptografia de chave pública o tira do mercado (provavelmente para seu alívio).
Como funciona o PGP.
O PGP combina alguns dos melhores recursos da criptografia convencional e de chave pública. PGP é um criptossistema híbrido. Quando um usuário criptografa texto simples com PGP, o PGP primeiro compacta o texto simples. A compactação de dados economiza tempo de transmissão do modem e espaço em disco e, mais importante ainda, fortalece a segurança criptográfica. A maioria das técnicas de criptoanálise explora padrões encontrados no texto simples para quebrar a cifra. A compressão reduz esses padrões no texto simples, aumentando assim enormemente a resistência à criptoanálise. (Arquivos que são muito curtos para compactar ou que não são compactados bem não são compactados.) O PGP então cria uma chave de sessão, que é uma chave secreta única. Esta chave é um número aleatório gerado a partir dos movimentos aleatórios do mouse e das teclas digitadas. Esta chave de sessão funciona com um algoritmo de criptografia convencional rápido e muito seguro para criptografar o texto simples; o resultado é texto cifrado. Depois que os dados são criptografados, a chave da sessão é criptografada na chave pública do destinatário. Essa chave de sessão criptografada com chave pública é transmitida junto com o texto cifrado ao destinatário.
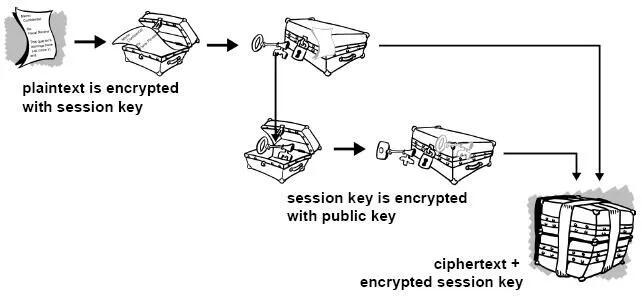
Figura 1-4. Como funciona a criptografia PGP A descriptografia funciona ao contrário. A cópia do PGP do destinatário usa sua chave privada para recuperar a chave de sessão temporária, que o PGP usa para descriptografar o texto cifrado criptografado convencionalmente.

Figura 1-5. Como funciona a descriptografia PGP A combinação dos dois métodos de criptografia combina a conveniência da criptografia de chave pública com a velocidade da criptografia convencional. A criptografia convencional é cerca de 1.000 vezes mais rápida que a criptografia de chave pública. A criptografia de chave pública, por sua vez, fornece uma solução para
problemas de distribuição de chaves e transmissão de dados. Usados em conjunto, o desempenho e a distribuição de chaves são melhorados sem qualquer sacrifício na segurança.
Chaves.
Uma chave é um valor que funciona com um algoritmo criptográfico para produzir um texto cifrado específico. As chaves são basicamente números muito, muito, muito grandes. O tamanho da chave é medido em bits; o número que representa uma chave de 1024 bits é enorme. Na criptografia de chave pública, quanto maior a chave, mais seguro é o texto cifrado. No entanto, o tamanho da chave pública e o tamanho da chave secreta da criptografia convencional não têm nenhuma relação. Uma chave convencional de 80 bits tem a força equivalente a uma chave pública de 1.024 bits. Uma chave convencional de 128 bits é equivalente a uma chave pública de 3.000 bits. Novamente, quanto maior a chave, mais segura, mas os algoritmos usados para cada tipo de criptografia são muito diferentes e, portanto, a comparação é como a de maçãs com laranjas. Embora as chaves pública e privada estejam matematicamente relacionadas, é muito difícil derivar a chave privada dada apenas a chave pública; no entanto, derivar a chave privada é sempre possível, desde que haja tempo e capacidade computacional suficientes. Isto torna muito importante escolher chaves do tamanho certo; grande o suficiente para ser seguro, mas pequeno o suficiente para ser aplicado rapidamente. Além disso, você precisa considerar quem pode estar tentando ler seus arquivos, quão determinados eles estão, quanto tempo têm e quais podem ser seus recursos. Chaves maiores serão criptograficamente seguras por um longo período de tempo. Se o que você deseja criptografar precisar ficar oculto por muitos anos, você pode usar uma chave muito grande. Claro, quem sabe quanto tempo levará para determinar sua chave usando os computadores mais rápidos e eficientes de amanhã? Houve um tempo em que uma chave simétrica de 56 bits era considerada extremamente segura. As chaves são armazenadas de forma criptografada. O PGP armazena as chaves em dois arquivos no seu disco rígido; um para chaves públicas e outro para chaves privadas. Esses arquivos são chamados de chaveiros. Ao usar o PGP, você normalmente adicionará as chaves públicas dos seus destinatários ao seu chaveiro público. Suas chaves privadas são armazenadas em seu chaveiro privado. Se você perder seu chaveiro privado, não será possível descriptografar nenhuma informação criptografada nas chaves desse anel.
Assinaturas digitais.
Um grande benefício da criptografia de chave pública é que ela fornece um método para empregar assinaturas digitais. As assinaturas digitais permitem ao destinatário da informação verificar a autenticidade da origem da informação e também verificar se a informação está intacta. Assim, as assinaturas digitais de chave pública fornecem autenticação e integridade de dados. A assinatura digital também proporciona o não repúdio, o que significa que evita que o remetente alegue que não enviou realmente as informações. Esses recursos são tão fundamentais para a criptografia quanto a privacidade, se não mais. Uma assinatura digital tem a mesma finalidade de uma assinatura manuscrita. No entanto, uma assinatura manuscrita é fácil de falsificar. Uma assinatura digital é superior a uma assinatura manuscrita porque é quase impossível de ser falsificada, além de atestar o conteúdo da informação, bem como a identidade do signatário.
Algumas pessoas tendem a usar mais assinaturas do que criptografia. Por exemplo, você pode não se importar se alguém souber que você acabou de depositar US$ 1.000 em sua conta, mas quer ter certeza de que foi o caixa do banco com quem você estava lidando. A maneira básica pela qual as assinaturas digitais são criadas é ilustrada na Figura 1-6 . Em vez de criptografar informações usando a chave pública de outra pessoa, você as criptografa com sua chave privada. Se as informações puderem ser descriptografadas com sua chave pública, elas deverão ter se originado em você.
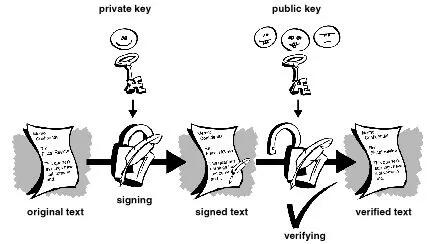
Figura 1-6. Assinaturas digitais simples
Funções hash.
O sistema descrito acima apresenta alguns problemas. É lento e produz um enorme volume de dados – pelo menos o dobro do tamanho da informação original. Uma melhoria no esquema acima é a adição de uma função hash unidirecional no processo. Uma função hash unidirecional recebe uma entrada de comprimento variável – neste caso, uma mensagem de qualquer comprimento, até mesmo milhares ou milhões de bits – e produz uma saída de comprimento fixo; digamos, 160 bits. A função hash garante que, se a informação for alterada de alguma forma – mesmo que por apenas um bit – seja produzido um valor de saída totalmente diferente. O PGP usa uma função hash criptograficamente forte no texto simples que o usuário está assinando. Isso gera um item de dados de comprimento fixo conhecido como resumo da mensagem. (Novamente, qualquer alteração nas informações resulta em um resumo totalmente diferente.) Então o PGP usa o resumo e a chave privada para criar a “assinatura”. O PGP transmite a assinatura e o texto simples juntos. Ao receber a mensagem, o destinatário utiliza o PGP para recalcular o resumo, verificando assim a assinatura. O PGP pode criptografar o texto simples ou não; assinar texto simples é útil se alguns dos destinatários não estiverem interessados ou não forem capazes de verificar a assinatura. Desde que uma função hash segura seja usada, não há como retirar a assinatura de alguém de um documento e anexá-la a outro, ou alterar uma mensagem assinada de qualquer forma. A menor alteração em um documento assinado causará falha no processo de verificação da assinatura digital.
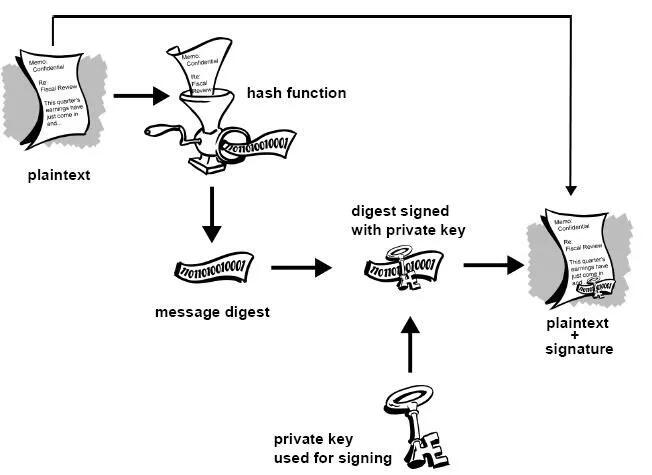
Figura 1-7. Assinaturas digitais seguras As assinaturas digitais desempenham um papel importante na autenticação e validação de chaves de outros usuários PGP.
Certificados digitais.
Um problema com os criptosistemas de chave pública é que os usuários devem estar constantemente vigilantes para garantir que estão criptografando com a chave da pessoa correta. Num ambiente onde é seguro trocar chaves livremente através de servidores públicos, os ataques man-in-the-middle são uma ameaça potencial. Neste tipo de ataque, alguém publica uma chave falsa com o nome e ID de usuário do destinatário pretendido. Os dados criptografados – e interceptados por – o verdadeiro proprietário desta chave falsa estão agora em mãos erradas. Em um ambiente de chave pública, é vital que você tenha certeza de que a chave pública para a qual você está criptografando os dados é de fato a chave pública do destinatário pretendido e não uma falsificação. Você pode simplesmente criptografar apenas as chaves que foram entregues fisicamente a você. Mas suponha que você precise trocar informações com pessoas que nunca conheceu; como você pode saber se tem a chave correta? Os certificados digitais, ou certs, simplificam a tarefa de estabelecer se uma chave pública realmente pertence ao suposto proprietário. Um certificado é uma forma de credencial. Exemplos podem ser sua carteira de motorista, seu cartão de previdência social ou sua certidão de nascimento. Cada um deles contém algumas informações que identificam você e alguma autorização informando que outra pessoa confirmou sua identidade. Alguns certificados, como o seu passaporte, são uma confirmação importante o suficiente da sua identidade para que você não queira perdê-los, para que ninguém os use para se passar por você.
Um certificado digital são dados que funcionam como um certificado físico. Um certificado digital é uma informação incluída na chave pública de uma pessoa que ajuda outras pessoas a verificar se uma chave é genuína ou válida. Os certificados digitais são usados para impedir tentativas de substituir a chave de uma pessoa por outra.
Um certificado digital consiste em três coisas:
● Uma chave pública.
● Informações do certificado. (Informações de "identidade" sobre o usuário, como nome, ID do usuário e assim por diante.) ● Uma ou mais assinaturas digitais.
O objetivo da assinatura digital em um certificado é afirmar que as informações do certificado foram atestadas por alguma outra pessoa ou entidade. A assinatura digital não atesta a autenticidade do certificado como um todo; ele atesta apenas que as informações de identidade assinadas acompanham ou estão vinculadas à chave pública. Assim, um certificado é basicamente uma chave pública com uma ou duas formas de identificação anexadas, além de um forte selo de aprovação de algum outro indivíduo confiável.
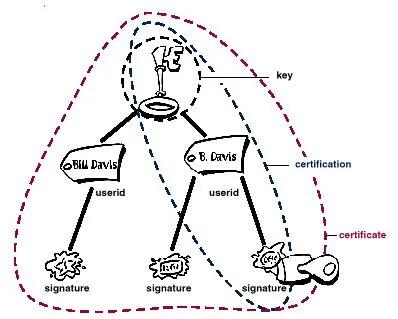 Figura 1-8. Anatomia de um certificado PGP
Figura 1-8. Anatomia de um certificado PGPDistribuição de certificados.
Os certificados são utilizados quando é necessário trocar chaves públicas com outra pessoa. Para pequenos grupos de pessoas que desejam se comunicar com segurança, é fácil trocar manualmente disquetes ou e-mails contendo a chave pública de cada proprietário. Esta é a distribuição manual de chave pública e é prática apenas até certo ponto. Além desse ponto, é necessário implementar sistemas que possam fornecer os mecanismos necessários de segurança, armazenamento e troca para que colegas de trabalho, parceiros de negócios ou estranhos possam se comunicar, se necessário. Eles podem vir na forma de repositórios somente de armazenamento, chamados Servidores de Certificados, ou sistemas mais estruturados que fornecem recursos adicionais de gerenciamento de chaves e são chamados de Infraestruturas de Chave Pública (PKIs).
Servidores de certificados.
Um servidor de certificados, também chamado de servidor certificado ou servidor de chaves, é um banco de dados que permite aos usuários enviar e recuperar certificados digitais. Um servidor certificado geralmente fornece alguns recursos administrativos que permitem que uma empresa mantenha suas políticas de segurança – por exemplo, permitindo que apenas as chaves que atendam a determinados requisitos sejam armazenadas.
Infraestruturas de Chave Pública.
Uma PKI contém os recursos de armazenamento de certificados de um servidor de certificados, mas também fornece recursos de gerenciamento de certificados (a capacidade de emitir, revogar, armazenar, recuperar e confiar em certificados). A principal característica de uma PKI é a introdução do que é conhecido como Autoridade Certificadora,ou CA, que é uma entidade humana — uma pessoa, grupo, departamento, empresa ou outra associação — que uma organização autorizou a emitir certificados para seus usuários de computador. (A função de uma CA é análoga à do Passport Office do governo de um país.) Uma CA cria certificados e os assina digitalmente usando a chave privada da CA. Devido ao seu papel na criação de certificados, a CA é o componente central de uma PKI. Usando a chave pública da CA, qualquer pessoa que queira verificar a autenticidade de um certificado verifica a assinatura digital da CA emissora e, portanto, a integridade do conteúdo do certificado (mais importante ainda, a chave pública e a identidade do titular do certificado).
Formatos de certificado.
Um certificado digital é basicamente uma coleção de informações de identificação vinculadas a uma chave pública e assinadas por um terceiro confiável para provar sua autenticidade. Um certificado digital pode ter vários formatos diferentes.
O PGP reconhece dois formatos de certificado diferentes:
● Certificados PGP ● Certificados X.509 Formato do certificado PGP. Um certificado PGP inclui (mas não está limitado a) as seguintes informações: ● O número da versão do PGP — identifica qual versão do PGP foi usada para criar a chave associada ao certificado. A chave pública do titular do certificado — a parte pública do seu par de chaves, juntamente com o algoritmo da chave: RSA, DH (Diffie-Hellman) ou DSA (Algoritmo de Assinatura Digital).
● As informações do detentor do certificado — consistem em informações de “identidade” sobre o usuário, como seu nome, ID de usuário, fotografia e assim por diante. ● A assinatura digital do proprietário do certificado — também chamada de autoassinatura, é a assinatura que utiliza a chave privada correspondente da chave pública associada ao certificado. ● O período de validade do certificado — a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar. ● O algoritmo de criptografia simétrica preferido para a chave — indica o algoritmo de criptografia para o qual o proprietário do certificado prefere que as informações sejam criptografadas. Os algoritmos suportados são CAST, IDEA ou Triple-DES. Você pode pensar em um certificado PGP como uma chave pública com um ou mais rótulos vinculados a ele (veja a Figura 1.9 ). Nessas 'etiquetas' você encontrará informações que identificam o proprietário da chave e uma assinatura do proprietário da chave, que afirma que a chave e a identificação andam juntas. (Essa assinatura específica é chamada de autoassinatura; todo certificado PGP contém uma autoassinatura.) Um aspecto único do formato de certificado PGP é que um único certificado pode conter múltiplas assinaturas. Várias ou muitas pessoas podem assinar o par chave/identificação para atestar a sua própria garantia de que a chave pública pertence definitivamente ao proprietário especificado. Se você procurar em um servidor de certificados público, poderá notar que certos certificados, como o do criador do PGP, Phil Zimmermann, contêm muitas assinaturas. Alguns certificados PGP consistem em uma chave pública com vários rótulos, cada um contendo um meio diferente de identificar o proprietário da chave (por exemplo, o nome do proprietário e a conta de e-mail corporativa, o apelido do proprietário e a conta de e-mail residencial, uma fotografia do proprietário — tudo em um certificado). A lista de assinaturas de cada uma dessas identidades pode ser diferente; as assinaturas atestam a autenticidade de que um dos rótulos pertence à chave pública, e não que todos os rótulos da chave sejam autênticos. (Observe que 'autêntico' está nos olhos de quem vê - assinaturas são opiniões, e diferentes pessoas dedicam diferentes níveis de devida diligência na verificação da autenticidade antes de assinar uma chave.)
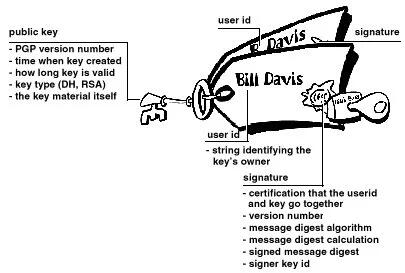 Figura 1-9. Um certificado PGP
Figura 1-9. Um certificado PGPFormato de certificado X.509.
X.509 é outro formato de certificado muito comum. Todos os certificados X.509 estão em conformidade com o padrão internacional ITU-T X.509; assim (teoricamente) os certificados X.509 criados para um aplicativo podem ser usados por qualquer aplicativo compatível com X.509. Na prática, porém, diferentes empresas criaram suas próprias extensões para certificados X.509, e nem todas funcionam juntas. Um certificado exige que alguém valide que uma chave pública e o nome do proprietário da chave andam juntos. Com os certificados PGP, qualquer pessoa pode desempenhar o papel de validador. Com certificados X.509, o validador é sempre uma Autoridade Certificadora ou alguém designado por uma CA. (Tenha em mente que os certificados PGP também suportam totalmente uma estrutura hierárquica usando uma CA para validar certificados.)
Um certificado X.509 é uma coleção de um conjunto padrão de campos contendo informações sobre um usuário ou dispositivo e sua chave pública correspondente. O padrão X.509 define quais informações vão para o certificado e descreve como codificá-lo (o formato dos dados). Todos os certificados X.509 possuem os seguintes dados:
O número da versão X.509
— identifica qual versão do padrão X.509 se aplica a este certificado, o que afeta quais informações podem ser especificadas nele. A mais atual é a versão 3.
A chave pública do titular do certificado
— a chave pública do titular do certificado, juntamente com um identificador de algoritmo que especifica a qual sistema criptográfico a chave pertence e quaisquer parâmetros de chave associados.
O número de série do certificado
— a entidade (aplicação ou pessoa) que criou o certificado é responsável por atribuir-lhe um número de série único para distingui-lo de outros certificados que emite. Esta informação é usada de diversas maneiras; por exemplo, quando um certificado é revogado, seu número de série é colocado em uma Lista de Revogação de Certificados ou CRL.
O identificador exclusivo do detentor do certificado
— (ou DN — nome distinto). Este nome pretende ser exclusivo na Internet. Este nome pretende ser exclusivo na Internet. Um DN consiste em múltiplas subseções e pode ser parecido com isto: CN=Bob Allen, OU=Divisão Total de Segurança de Rede, O=Network Associates, Inc., C=EUA (Referem-se ao nome comum, à unidade organizacional, à organização e ao país do sujeito .)
O período de validade do certificado
— a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar.
O nome exclusivo do emissor do certificado
— o nome exclusivo da entidade que assinou o certificado. Normalmente é uma CA. A utilização do certificado implica confiar na entidade que assinou este certificado. (Observe que em alguns casos, como certificados de CA raiz ou de nível superior , o emissor assina seu próprio certificado.)
A assinatura digital do emitente
— a assinatura utilizando a chave privada da entidade que emitiu o certificado.
O identificador do algoritmo de assinatura
— identifica o algoritmo usado pela CA para assinar o certificado.
Existem muitas diferenças entre um certificado X.509 e um certificado PGP, mas as mais importantes são as seguintes: você pode criar seu próprio certificado PGP;
● você deve solicitar e receber um certificado X.509 de uma autoridade de certificação
● Os certificados X.509 suportam nativamente apenas um único nome para o proprietário da chave
● Os certificados X.509 suportam apenas uma única assinatura digital para atestar a validade da chave
Para obter um certificado X.509, você deve solicitar a uma CA a emissão de um certificado. Você fornece sua chave pública, prova de que possui a chave privada correspondente e algumas informações específicas sobre você. Em seguida, você assina digitalmente as informações e envia o pacote completo – a solicitação de certificado – para a CA. A CA então realiza algumas diligências para verificar se as informações fornecidas estão corretas e, em caso afirmativo, gera o certificado e o devolve.
Você pode pensar em um certificado X.509 como um certificado de papel padrão (semelhante ao que você recebeu ao concluir uma aula de primeiros socorros básicos) com uma chave pública colada nele. Ele contém seu nome e algumas informações sobre você, além da assinatura da pessoa que o emitiu para você.
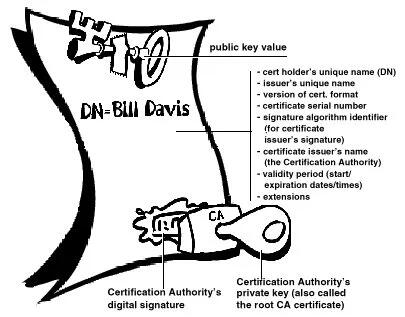
Figura 1-10. Um certificado X.509 Provavelmente, o uso mais visível dos certificados X.509 atualmente é em navegadores da web.
Validade e confiança Cada usuário em um sistema de chave pública está vulnerável a confundir uma chave falsa (certificado) com uma chave real. Validade é a confiança de que um certificado de chave pública pertence ao seu suposto proprietário. A validade é essencial em um ambiente de chave pública onde você deve estabelecer constantemente se um determinado certificado é autêntico ou não. Depois de ter certeza de que um certificado pertencente a outra pessoa é válido, você pode assinar a cópia em seu chaveiro para atestar que verificou o certificado e que ele é autêntico. Se quiser que outras pessoas saibam que você deu ao certificado seu selo de aprovação, você pode exportar a assinatura para um servidor de certificados para que outras pessoas possam vê-la.
Conforme descrito na seção Infraestruturas de Chave Pública , algumas empresas designam uma ou mais Autoridades de Certificação (CAs) para indicar a validade do certificado. Em uma organização que usa uma PKI com certificados X.509, é função da CA emitir certificados aos usuários — um processo que geralmente envolve responder à solicitação de certificado do usuário. Em uma organização que usa certificados PGP sem PKI, é função da CA verificar a autenticidade de todos os certificados PGP e depois assinar os bons. Basicamente, o objetivo principal de uma CA é vincular uma chave pública às informações de identificação contidas no certificado e, assim, garantir a terceiros que algum cuidado foi tomado para garantir que esta ligação das informações de identificação e da chave seja válida. O CA é o Grand Pooh-bah da validação em uma organização; alguém em quem todos confiam e, em algumas organizações, como aquelas que utilizam uma PKI, nenhum certificado é considerado válido, a menos que tenha sido assinado por uma CA confiável.
Verificando validade.
Uma maneira de estabelecer a validade é passar por algum processo manual. Existem várias maneiras de fazer isso. Você pode exigir que o destinatário pretendido lhe entregue fisicamente uma cópia de sua chave pública. Mas isto é muitas vezes inconveniente e ineficiente. Outra forma é verificar manualmente a impressão digital do certificado. Assim como as impressões digitais de cada ser humano são únicas, a impressão digital de cada certificado PGP é única. A impressão digital é um hash do certificado do usuário e aparece como uma das propriedades do certificado. No PGP, a impressão digital pode aparecer como um número hexadecimal ou uma série das chamadas palavras biométricas, que são foneticamente distintas e são usadas para facilitar um pouco o processo de identificação da impressão digital. Você pode verificar se um certificado é válido ligando para o proprietário da chave (para que você origine a transação) e pedindo ao proprietário que leia a impressão digital de sua chave para você e compare essa impressão digital com aquela que você acredita ser a verdadeira. Isso funciona se você conhece a voz do proprietário, mas como verificar manualmente a identidade de alguém que você não conhece? Algumas pessoas colocam a impressão digital de sua chave em seus cartões de visita exatamente por esse motivo. Outra forma de estabelecer a validade do certificado de alguém é confiar que um terceiro indivíduo passou pelo processo de validação do mesmo. Uma CA, por exemplo, é responsável por garantir que, antes de emitir um certificado, ele ou ela o verifique cuidadosamente para ter certeza de que a parte da chave pública realmente pertence ao suposto proprietário. Qualquer pessoa que confie na CA considerará automaticamente quaisquer certificados assinados pela CA como válidos. Outro aspecto da verificação da validade é garantir que o certificado não foi revogado. Para obter mais informações, consulte a seção Revogação de certificado .
Estabelecendo confiança.
Você valida certificados. Você confia nas pessoas. Mais especificamente, você confia nas pessoas para validar os certificados de outras pessoas. Normalmente, a menos que o proprietário lhe entregue o certificado, você terá que confiar na palavra de outra pessoa de que ele é válido.
Introdutores meta e confiáveis.
Na maioria das situações, as pessoas confiam completamente na CA para estabelecer a validade dos certificados. Isso significa que todos os demais dependem da CA para passar por todo o processo de validação manual. Isso é aceitável até um certo número de usuários ou locais de trabalho e, então, não é possível para a AC manter o mesmo nível de validação de qualidade. Nesse caso, é necessário adicionar outros validadores ao sistema.
Um CA também pode ser um meta- introdutor. Um meta-introdutor confere não apenas validade às chaves, mas também confere a capacidade de confiar nas chaves a outros. Semelhante ao rei que entrega seu selo a seus conselheiros de confiança para que eles possam agir de acordo com sua autoridade, o meta-introdutor permite que outros atuem como introdutores de confiança. Esses introdutores confiáveis podem validar chaves com o mesmo efeito do meta-introdutor. Eles não podem, entretanto, criar novos introdutores confiáveis.
Meta-introdutor e introdutor confiável são termos PGP. Em um ambiente X.509, o meta-introdutor é chamado de Autoridade de Certificação raiz ( CA raiz) e os introdutores confiáveis são Autoridades de Certificação subordinadas . A CA raiz usa a chave privada associada a um tipo de certificado especial denominado certificado CA raiz para assinar certificados. Qualquer certificado assinado pelo certificado CA raiz é visto como válido por qualquer outro certificado assinado pela raiz. Este processo de validação funciona mesmo para certificados assinados por outras CAs no sistema — desde que o certificado da CA raiz tenha assinado o certificado da CA subordinada, qualquer certificado assinado pela CA será considerado válido para outras pessoas dentro da hierarquia. Este processo de verificação de backup por meio do sistema para ver quem assinou cujo certificado é chamado de rastreamento de um caminho de certificação ou cadeia de certificação.
Modelos de confiança.
Em sistemas relativamente fechados, como em uma pequena empresa, é fácil rastrear um caminho de certificação até a CA raiz. No entanto, os usuários muitas vezes precisam se comunicar com pessoas fora do seu ambiente corporativo, incluindo algumas que nunca conheceram, como fornecedores, consumidores, clientes, associados e assim por diante. É difícil estabelecer uma linha de confiança com aqueles em quem sua CA não confia explicitamente. As empresas seguem um ou outro modelo de confiança, que determina como os usuários irão estabelecer a validade do certificado. Existem três modelos diferentes:
Confiança Direta.
Confiança Hierárquica Uma teia de confiança Confiança direta A confiança direta é o modelo de confiança mais simples. Neste modelo, um usuário confia que uma chave é válida porque sabe de onde ela veio. Todos os criptosistemas usam essa forma de confiança de alguma forma. Por exemplo, em navegadores da Web, as chaves raiz da Autoridade de Certificação são diretamente confiáveis porque foram enviadas pelo fabricante. Se houver alguma forma de hierarquia, ela se estenderá a partir desses certificados diretamente confiáveis. No PGP, um usuário que valida as chaves e nunca define outro certificado para ser um introdutor confiável está usando confiança direta.
 Figura 1-11. Confiança direta
Figura 1-11. Confiança diretaConfiança Hierárquica.
Em um sistema hierárquico, há vários certificados "raiz" a partir dos quais a confiança se estende. Esses certificados podem certificar eles próprios certificados ou podem certificar certificados que certificam ainda outros certificados em alguma cadeia. Considere isso como uma grande “árvore” de confiança. A validade do certificado "folha" é verificada rastreando desde seu certificador até outros certificadores, até que um certificado raiz diretamente confiável seja encontrado.
Figura 1-12. Confiança hierárquica
Teia de Confiança.
Uma teia de confiança abrange ambos os outros modelos, mas também acrescenta a noção de que a confiança está nos olhos de quem vê (que é a visão do mundo real) e a ideia de que mais informação é melhor. É, portanto, um modelo de confiança cumulativa. Um certificado pode ser confiável diretamente ou confiável em alguma cadeia que remonta a um certificado raiz diretamente confiável (o meta-introdutor) ou por algum grupo de introdutores.
Talvez você já tenha ouvido falar do termo seis graus de separação, que sugere que qualquer pessoa no mundo pode determinar algum vínculo com qualquer outra pessoa no mundo usando seis ou menos outras pessoas como intermediários. Esta é uma teia de introdutores. É também a visão de confiança do PGP. PGP usa assinaturas digitais como forma de introdução. Quando qualquer usuário assina a chave de outro, ele ou ela se torna o introdutor dessa chave. À medida que esse processo avança, ele estabelece uma rede de confiança.
Em um ambiente PGP, qualquer usuário pode atuar como autoridade certificadora. Qualquer usuário PGP pode validar o certificado de chave pública de outro usuário PGP. No entanto, tal certificado só é válido para outro usuário se a parte confiável reconhecer o validador como um introdutor confiável. (Ou seja, você confia na minha opinião de que as chaves dos outros são válidas apenas se você me considerar um apresentador confiável. Caso contrário, minha opinião sobre a validade das outras chaves é discutível.) Armazenados no chaveiro público de cada usuário estão indicadores de
● se o usuário considera ou não uma chave específica válida
● o nível de confiança que o usuário deposita na chave que o proprietário da chave pode servir como certificador das chaves de terceiros
Você indica, na sua cópia da minha chave, se acha que meu julgamento conta. Na verdade, é um sistema de reputação: certas pessoas têm a reputação de fornecer boas assinaturas e as pessoas confiam nelas para atestar a validade de outras chaves.
Níveis de confiança no PGP.
O nível mais alto de confiança em uma chave, a confiança implícita , é a confiança em seu próprio par de chaves. O PGP assume que se você possui a chave privada, você deve confiar nas ações da sua chave pública relacionada. Quaisquer chaves assinadas pela sua chave implicitamente confiável são válidas.
Existem três níveis de confiança que você pode atribuir à chave pública de outra pessoa:
● Confiança total ● Confiança marginal ● Não confiável (ou não confiável)
Para tornar as coisas confusas, também existem três níveis de validade:
● Válido ● Marginalmente válido ● Inválido
Para definir a chave de outra pessoa como um introdutor confiável, você
- Comece com uma chave válida, que seja.
- assinado por você ou
-
assinado por outro apresentador confiável e então
-
Defina o nível de confiança que você acha que o proprietário da chave tem direito.
Por exemplo, suponha que seu chaveiro contenha a chave de Alice. Você validou a chave de Alice e indica isso assinando-a. Você sabe que Alice é uma verdadeira defensora da validação de chaves de outras pessoas. Portanto, você atribui a chave dela com confiança total. Isso faz de Alice uma Autoridade Certificadora. Se Alice assinar a chave de outra pessoa, ela aparecerá como Válida em seu chaveiro. O PGP requer uma assinatura Totalmente confiável ou duas assinaturas Marginalmente confiáveis para estabelecer uma chave como válida. O método do PGP de considerar dois Marginais iguais a um Completo é semelhante a um comerciante que solicita duas formas de identificação. Você pode considerar Alice bastante confiável e também considerar Bob bastante confiável. Qualquer um deles sozinho corre o risco de assinar acidentalmente uma chave falsificada, portanto, você pode não depositar total confiança em nenhum deles. No entanto, as probabilidades de ambos os indivíduos terem assinado a mesma chave falsa são provavelmente pequenas.
Revogação de certificado.
Os certificados só são úteis enquanto são válidos. Não é seguro simplesmente presumir que um certificado é válido para sempre. Na maioria das organizações e em todas as PKIs, os certificados têm uma vida útil restrita. Isso restringe o período em que um sistema fica vulnerável caso ocorra um comprometimento do certificado.
Os certificados são assim criados com um período de validade programado: uma data/hora de início e uma data/hora de expiração. Espera-se que o certificado seja utilizável durante todo o seu período de validade (seu tempo de vida ). Quando o certificado expirar, ele não será mais válido, pois a autenticidade do seu par chave/identificação não estará mais garantida. (O certificado ainda pode ser usado com segurança para reconfirmar informações que foram criptografadas ou assinadas dentro do período de validade – no entanto, ele não deve ser confiável para tarefas criptográficas futuras.)
Existem também situações em que é necessário invalidar um certificado antes da sua data de expiração, como quando o titular do certificado termina o contrato de trabalho com a empresa ou suspeita que a chave privada correspondente do certificado foi comprometida. Isso é chamado de revogação. Um certificado revogado é muito mais suspeito do que um certificado expirado. Os certificados expirados são inutilizáveis, mas não apresentam a mesma ameaça de comprometimento que um certificado revogado. Qualquer pessoa que tenha assinado um certificado pode revogar a sua assinatura no certificado (desde que utilize a mesma chave privada que criou a assinatura). Uma assinatura revogada indica que o signatário não acredita mais que a chave pública e as informações de identificação pertencem uma à outra, ou que a chave pública do certificado (ou a chave privada correspondente) foi comprometida. Uma assinatura revogada deve ter quase tanto peso quanto um certificado revogado. Com certificados X.509, uma assinatura revogada é praticamente igual a um certificado revogado, visto que a única assinatura no certificado é aquela que o tornou válido em primeiro lugar – a assinatura da CA. Os certificados PGP fornecem o recurso adicional de que você pode revogar todo o seu certificado (não apenas as assinaturas nele) se você achar que o certificado foi comprometido. Somente o proprietário do certificado (o detentor da chave privada correspondente) ou alguém que o proprietário do certificado tenha designado como revogador pode revogar um certificado PGP. (Designar um revogador é uma prática útil, pois muitas vezes é a perda da senha da chave privada correspondente do certificado que leva um usuário PGP a revogar seu certificado - uma tarefa que só é possível se alguém tiver acesso à chave privada. ) Somente o emissor do certificado pode revogar um certificado X.509.
Comunicar que um certificado foi revogado.
Quando um certificado é revogado, é importante conscientizar os usuários potenciais do certificado de que ele não é mais válido. Com certificados PGP, a maneira mais comum de comunicar que um certificado foi revogado é publicá-lo em um servidor de certificados para que outras pessoas que desejem se comunicar com você sejam avisadas para não usar essa chave pública. Em um ambiente PKI, a comunicação de certificados revogados é mais comumente obtida por meio de uma estrutura de dados chamada Lista de Revogação de Certificados, ou CRL, que é publicada pela CA. A CRL contém uma lista validada com carimbo de data e hora de todos os certificados revogados e não expirados no sistema. Os certificados revogados permanecem na lista apenas até expirarem e, em seguida, são removidos da lista — isso evita que a lista fique muito longa. A CA distribui a CRL aos usuários em algum intervalo programado regularmente (e potencialmente fora do ciclo, sempre que um certificado é revogado). Teoricamente, isso impedirá que os usuários usem involuntariamente um certificado comprometido. É possível, no entanto, que haja um período de tempo entre as CRLs em que um certificado recentemente comprometido seja usado.
O que é uma senha?
A maioria das pessoas está familiarizada com a restrição de acesso a sistemas de computador por meio de uma senha, que é uma sequência única de caracteres que um usuário digita como código de identificação.
Uma senha longa é uma versão mais longa de uma senha e, em teoria, mais segura. Normalmente composta por várias palavras, uma frase secreta é mais segura contra ataques de dicionário padrão, em que o invasor tenta todas as palavras do dicionário na tentativa de determinar sua senha. As melhores senhas são relativamente longas e complexas e contêm uma combinação de letras maiúsculas e minúsculas, caracteres numéricos e de pontuação. O PGP usa uma senha para criptografar sua chave privada em sua máquina. Sua chave privada é criptografada em seu disco usando um hash de sua senha como chave secreta. Você usa a senha para descriptografar e usar sua chave privada. Uma senha deve ser difícil de esquecer e difícil de ser adivinhada por outras pessoas. Deve ser algo já firmemente enraizado na sua memória de longo prazo, em vez de algo que você invente do zero. Por que? Porque se você esquecer sua senha, você estará sem sorte. Sua chave privada é total e absolutamente inútil sem sua senha e nada pode ser feito a respeito. Lembra-se da citação anterior neste capítulo?
 PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.
PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.Divisão de chave.
Dizem que um segredo não é segredo se for conhecido por mais de uma pessoa. Compartilhar um par de chaves privadas representa um grande problema. Embora não seja uma prática recomendada, às vezes é necessário compartilhar um par de chaves privadas. Chaves de assinatura corporativa, por exemplo, são chaves privadas usadas por uma empresa para assinar – por exemplo – documentos legais, informações pessoais confidenciais ou comunicados de imprensa para autenticar sua origem. Nesse caso, vale a pena que vários membros da empresa tenham acesso à chave privada. No entanto, isto significa que qualquer indivíduo pode agir plenamente em nome da empresa. Nesse caso, é aconselhável dividir a chave entre várias pessoas, de modo que mais de uma ou duas pessoas apresentem um pedaço da chave para reconstituí-la em condições utilizáveis. Se poucas peças da chave estiverem disponíveis, a chave ficará inutilizável. Alguns exemplos são dividir uma chave em três partes e exigir duas delas para reconstituir a chave, ou dividi-la em duas partes e exigir ambas as peças. Se uma conexão de rede segura for usada durante o processo de reconstituição, os acionistas da chave não precisam estar fisicamente presentes para aderirem novamente à chave.
-
 @ cefb08d1:f419beff
2025-05-03 11:01:47
@ cefb08d1:f419beff
2025-05-03 11:01:47https://www.youtube.com/watch?v=BOqWgxCo7Kw
The Catch Up Day 1: Bonsoy Gold Coast Pro provides opening day dominance from upper echelon:
https://www.youtube.com/watch?v=B1uM0FnyPvA
Next Round, elimination:
Results of the 1st day, opening round: https://www.worldsurfleague.com/events/2025/ct/325/bonsoy-gold-coast-pro/results
originally posted at https://stacker.news/items/970160
-
 @ f683e870:557f5ef2
2025-04-28 10:10:55
@ f683e870:557f5ef2
2025-04-28 10:10:55Spam is the single biggest problem in decentralized networks. Jameson Lopp, co-founder of Casa and OG bitcoiner, has written a brilliant article on the death of decentralized email that paints a vivid picture of what went wrong—and how an originally decentralized protocol was completely captured. The cause? Spam.
The same fate may happen to Nostr, because posting a note is fundamentally cheap. Payments, and to some extent Proof of Work, certainly have their role in fighting spam, but they introduce friction, which doesn’t work everywhere. In particular, they can’t solve every economic problem.\ Take free trials, for example. There is a reason why 99% of companies offer them. Sure, you waste resources on users who don’t convert, but it’s a calculated cost, a marketing expense. Also, some services can’t or don’t want to monetize directly. They offer something for free and monetize elsewhere.
So how do you offer a free trial or giveaway in a hostile decentralized network? Or even, how do you decide which notes to accept on your relay?
At first glance, these may seem like unrelated questions—but they’re not. Generally speaking, these are situations where you have a finite budget, and you want to use it well. You want more of what you value — and less of what you don’t (spam).
Reputation is a powerful shortcut when direct evaluation isn’t practical. It’s hard to earn, easy to lose — and that’s exactly what makes it valuable.\ Can a reputable user do bad things? Absolutely. But it’s much less likely, and that’s the point. Heuristics are always imperfect, just like the world we live in.
The legacy Web relies heavily on email-based reputation. If you’ve ever tried to log in with a temporary email, you know what I’m talking about. It just doesn’t work anymore. The problem, as Lopp explains, is that these systems are highly centralized, opaque, and require constant manual intervention.\ They also suck. They put annoying roadblocks between the world and your product, often frustrating the very users you’re trying to convert.
At Vertex, we take a different approach.\ We transparently analyze Nostr’s open social graph to help companies fight spam while improving the UX for their users. But we don’t take away your agency—we just do the math. You take the decision of what algorithm and criteria to use.
Think of us as a signal provider, not an authority.\ You define what reputation means for your use case. Want to rank by global influence? Local or personalized? You’re in control. We give you actionable and transparent analytics so you can build sharper filters, better user experiences, and more resilient systems. That’s how we fight spam, without sacrificing decentralization.
Are you looking to add Web of Trust capabilities to your app or project?\ Take a look at our website or send a DM to Pip.
-
 @ 0d8633e5:eec06e57
2025-05-03 10:58:22
@ 0d8633e5:eec06e57
2025-05-03 10:58:22The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap. Automated Distribution: Ensures quick and secure token transfers to user wallets. Minimal Latency: Prevents blockchain congestion issues for seamless transfers. Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity. Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
Kindly visit globalfashexperts.com for more information Contact Information For more information or to make a purchase, please contact us through the following channels:
Email: globalfashexperts@gmail.com Flash USDT:https://globalfashexperts.com/product/flash-usdt/ Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features
- Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap.
- Automated Distribution: Ensures quick and secure token transfers to user wallets.
- Minimal Latency: Prevents blockchain congestion issues for seamless transfers.
- Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity.
- Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
 Kindly visit globalfashexperts.com for more information
Kindly visit globalfashexperts.com for more informationContact Information
For more information or to make a purchase, please contact us through the following channels:
- Email: globalfashexperts@gmail.com
- Flash USDT:https://globalfashexperts.com/product/flash-usdt/
- Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/
-
 @ 6be5cc06:5259daf0
2025-04-28 01:05:49
@ 6be5cc06:5259daf0
2025-04-28 01:05:49Eu reconheço que Deus, e somente Deus, é o soberano legítimo sobre todas as coisas. Nenhum homem, nenhuma instituição, nenhum parlamento tem autoridade para usurpar aquilo que pertence ao Rei dos reis. O Estado moderno, com sua pretensão totalizante, é uma farsa blasfema diante do trono de Cristo. Não aceito outro senhor.
A Lei que me guia não é a ditada por burocratas, mas a gravada por Deus na própria natureza humana. A razão, quando iluminada pela fé, é suficiente para discernir o que é justo. Rejeito as leis arbitrárias que pretendem legitimar o roubo, o assassinato ou a escravidão em nome da ordem. A justiça não nasce do decreto, mas da verdade.
Acredito firmemente na propriedade privada como extensão da própria pessoa. Aquilo que é fruto do meu trabalho, da minha criatividade, da minha dedicação, dos dons a mim concedidos por Deus, pertence a mim por direito natural. Ninguém pode legitimamente tomar o que é meu sem meu consentimento. Todo imposto é uma agressão; toda expropriação, um roubo. Defendo a liberdade econômica não por idolatria ao mercado, mas porque a liberdade é condição necessária para a virtude.
Assumo o Princípio da Não Agressão como o mínimo ético que devo respeitar. Não iniciarei o uso da força contra ninguém, nem contra sua propriedade. Exijo o mesmo de todos. Mas sei que isso não basta. O PNA delimita o que não devo fazer — ele não me ensina o que devo ser. A liberdade exterior só é boa se houver liberdade interior. O mercado pode ser livre, mas se a alma estiver escravizada pelo vício, o colapso será inevitável.
Por isso, não me basta a ética negativa. Creio que uma sociedade justa precisa de valores positivos: honra, responsabilidade, compaixão, respeito, fidelidade à verdade. Sem isso, mesmo uma sociedade que respeite formalmente os direitos individuais apodrecerá por dentro. Um povo que ama o lucro, mas despreza a verdade, que celebra a liberdade mas esquece a justiça, está se preparando para ser dominado. Trocará um déspota visível por mil tiranias invisíveis — o hedonismo, o consumismo, a mentira, o medo.
Não aceito a falsa caridade feita com o dinheiro tomado à força. A verdadeira generosidade nasce do coração livre, não da coerção institucional. Obrigar alguém a ajudar o próximo destrói tanto a liberdade quanto a virtude. Só há mérito onde há escolha. A caridade que nasce do amor é redentora; a que nasce do fisco é propaganda.
O Estado moderno é um ídolo. Ele promete segurança, mas entrega servidão. Promete justiça, mas entrega privilégios. Disfarça a opressão com linguagem técnica, legal e democrática. Mas por trás de suas máscaras, vejo apenas a velha serpente. Um parasita que se alimenta do trabalho alheio e manipula consciências para se perpetuar.
Resistir não é apenas um direito, é um dever. Obedecer a Deus antes que aos homens — essa é a minha regra. O poder se volta contra a verdade, mas minha lealdade pertence a quem criou o céu e a terra. A tirania não se combate com outro tirano, mas com a desobediência firme e pacífica dos que amam a justiça.
Não acredito em utopias. Desejo uma ordem natural, orgânica, enraizada no voluntarismo. Uma sociedade que se construa de baixo para cima: a partir da família, da comunidade local, da tradição e da fé. Não quero uma máquina que planeje a vida alheia, mas um tecido de relações voluntárias onde a liberdade floresça à sombra da cruz.
Desejo, sim, o reinado social de Cristo. Não por imposição, mas por convicção. Que Ele reine nos corações, nas famílias, nas ruas e nos contratos. Que a fé guie a razão e a razão ilumine a vida. Que a liberdade seja meio para a santidade — não um fim em si. E que, livres do jugo do Leviatã, sejamos servos apenas do Senhor.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ d0aa74cd:603d35cd
2025-05-03 10:55:11
@ d0aa74cd:603d35cd
2025-05-03 10:55:11CLI #Haskell
https://photonsphere.org/post/2025-05-03-command-line-energy-prices-haskell/
-
 @ d34e832d:383f78d0
2025-04-26 15:04:51
@ d34e832d:383f78d0
2025-04-26 15:04:51Raspberry Pi-based voice assistant
This Idea details the design and deployment of a Raspberry Pi-based voice assistant powered by the Google Gemini AI API. The system combines open hardware with modern AI services to create a low-cost, flexible, and educational voice assistant platform. By leveraging a Raspberry Pi, basic audio hardware, and Python-based software, developers can create a functional, customizable assistant suitable for home automation, research, or personal productivity enhancement.
1. Voice assistants
Voice assistants have become increasingly ubiquitous, but commercially available systems like Alexa, Siri, or Google Assistant come with significant privacy and customization limitations.
This project offers an open, local, and customizable alternative, demonstrating how to build a voice assistant using Google Gemini (or OpenAI’s ChatGPT) APIs for natural language understanding.Target Audience:
- DIY enthusiasts - Raspberry Pi hobbyists - AI developers - Privacy-conscious users
2. System Architecture
2.1 Hardware Components
| Component | Purpose | |:--------------------------|:----------------------------------------| | Raspberry Pi (any recent model, 4B recommended) | Core processing unit | | Micro SD Card (32GB+) | Operating System and storage | | USB Microphone | Capturing user voice input | | Audio Amplifier + Speaker | Outputting synthesized responses | | 5V DC Power Supplies (2x) | Separate power for Pi and amplifier | | LEDs + Resistors (optional)| Visual feedback (e.g., recording or listening states) |
2.2 Software Stack
| Software | Function | |:---------------------------|:----------------------------------------| | Raspberry Pi OS (Lite or Full) | Base operating system | | Python 3.9+ | Programming language | | SpeechRecognition | Captures and transcribes user voice | | Google Text-to-Speech (gTTS) | Converts responses into spoken audio | | Google Gemini API (or OpenAI API) | Powers the AI assistant brain | | Pygame | Audio playback for responses | | WinSCP + Windows Terminal | File transfer and remote management |
3. Hardware Setup
3.1 Basic Connections
- Microphone: Connect via USB port.
- Speaker and Amplifier: Wire from Raspberry Pi audio jack or via USB sound card if better quality is needed.
- LEDs (Optional): Connect through GPIO pins, using 220–330Ω resistors to limit current.
3.2 Breadboard Layout (Optional for LEDs)
| GPIO Pin | LED Color | Purpose | |:---------|:-----------|:--------------------| | GPIO 17 | Red | Recording active | | GPIO 27 | Green | Response playing |
Tip: Use a small breadboard for quick prototyping before moving to a custom PCB if desired.
4. Software Setup
4.1 Raspberry Pi OS Installation
- Use Raspberry Pi Imager to flash Raspberry Pi OS onto the Micro SD card.
- Initial system update:
bash sudo apt update && sudo apt upgrade -y
4.2 Python Environment
-
Install Python virtual environment:
bash sudo apt install python3-venv python3 -m venv voice-env source voice-env/bin/activate -
Install required Python packages:
bash pip install SpeechRecognition google-generativeai pygame gtts
(Replace
google-generativeaiwithopenaiif using OpenAI's ChatGPT.)4.3 API Key Setup
- Obtain a Google Gemini API key (or OpenAI API key).
- Store safely in a
.envfile or configure as environment variables for security:bash export GEMINI_API_KEY="your_api_key_here"
4.4 File Transfer
- Use WinSCP or
scpcommands to transfer Python scripts to the Pi.
4.5 Example Python Script (Simplified)
```python import speech_recognition as sr import google.generativeai as genai from gtts import gTTS import pygame import os
genai.configure(api_key=os.getenv('GEMINI_API_KEY')) recognizer = sr.Recognizer() mic = sr.Microphone()
pygame.init()
while True: with mic as source: print("Listening...") audio = recognizer.listen(source)
try: text = recognizer.recognize_google(audio) print(f"You said: {text}") response = genai.generate_content(text) tts = gTTS(text=response.text, lang='en') tts.save("response.mp3") pygame.mixer.music.load("response.mp3") pygame.mixer.music.play() while pygame.mixer.music.get_busy(): continue except Exception as e: print(f"Error: {e}")```
5. Testing and Execution
- Activate the Python virtual environment:
bash source voice-env/bin/activate - Run your main assistant script:
bash python3 assistant.py - Speak into the microphone and listen for the AI-generated spoken response.
6. Troubleshooting
| Problem | Possible Fix | |:--------|:-------------| | Microphone not detected | Check
arecord -l| | Audio output issues | Checkaplay -l, use a USB DAC if needed | | Permission denied errors | Verify group permissions (audio, gpio) | | API Key Errors | Check environment variable and internet access |
7. Performance Notes
- Latency: Highly dependent on network speed and API response time.
- Audio Quality: Can be enhanced with a better USB microphone and powered speakers.
- Privacy: Minimal data retention if using your own Gemini or OpenAI account.
8. Potential Extensions
- Add hotword detection ("Hey Gemini") using Snowboy or Porcupine libraries.
- Build a local fallback model to answer basic questions offline.
- Integrate with home automation via MQTT, Home Assistant, or Node-RED.
- Enable LED animations to visually indicate listening and responding states.
- Deploy with a small eInk or OLED screen for text display of answers.
9. Consider
Building a Gemini-powered voice assistant on the Raspberry Pi empowers individuals to create customizable, private, and cost-effective alternatives to commercial voice assistants. By utilizing accessible hardware, modern open-source libraries, and powerful AI APIs, this project blends education, experimentation, and privacy-centric design into a single hands-on platform.
This guide can be adapted for personal use, educational programs, or even as a starting point for more advanced AI-based embedded systems.
References
- Raspberry Pi Foundation: https://www.raspberrypi.org
- Google Generative AI Documentation: https://ai.google.dev
- OpenAI Documentation: https://platform.openai.com
- SpeechRecognition Library: https://pypi.org/project/SpeechRecognition/
- gTTS Documentation: https://pypi.org/project/gTTS/
- Pygame Documentation: https://www.pygame.org/docs/
-
 @ 90c656ff:9383fd4e
2025-05-03 10:31:25
@ 90c656ff:9383fd4e
2025-05-03 10:31:25Bitcoin is a decentralized digital currency created in 2009 by an individual or group under the pseudonym Satoshi Nakamoto. Unlike traditional government-issued currencies like the US dollar or the euro, Bitcoin is not controlled by any central authority, such as a central bank or financial institution. This innovative feature has made it a focal point of economic, technological, and even social debate in recent years.
Bitcoin operates using a technology called blockchain (which the Bitcoin community increasingly prefers to call "timechain"). It is essentially a distributed digital ledger. The blockchain or timechain records all transactions made on the Bitcoin network in an open and transparent way. Each block contains a set of transactions that are immutably added to the chain once they are verified by miners (miners are basically network participants who use their computing power to validate these same transactions). This ensures security and prevents fraud, as no person or entity can retroactively alter the records.
One of Bitcoin's most notable features is its limited supply. Only 21 million Bitcoins can ever be created, which gives Bitcoin a deflationary nature — unlike fiat currencies, which central banks can print in unlimited quantities. This fixed limit, combined with growing global interest in the technology in general and individual privacy specifically, has driven Bitcoin’s value over time.
Another important characteristic of Bitcoin is that it enables direct peer-to-peer transactions, removing the need for intermediaries. This is particularly useful in cases like international transfers, where Bitcoin can be used to send money quickly and at low cost, without going through a bank or traditional financial services. Additionally, it is seen as a form of financial freedom in countries with unstable local currencies (often due to central banks printing money uncontrollably) or strict state-imposed capital controls.
However, Bitcoin is not immune to criticism — though these are often hollow arguments that mask the personal interests of those making them, whether because they work in traditional banks or brokerages and fear losing "power" or even their jobs, or because they have bad intentions and want to promote their own cryptocurrencies, which are fundamentally worthless (the infamous “shitcoins”). Bitcoin’s price volatility can also pose significant risks for inexperienced users who buy at a certain price and end up selling when the value drops by half, losing at least half their money. On the other hand, many experts view Bitcoin as a technological and social milestone that challenges existing economic models.
In summary, Bitcoin is much more than just a “crypto” or “cryptocurrency.” It represents a revolution — or a revision — in how most people think about money, offering a decentralized, transparent, and censorship-resistant alternative. Although it still faces challenges to becoming widely accepted by some skeptics and by governments worried about losing control over “their” populations (as mentioned earlier), its impact has been undeniable, paving the way for a new era in the global economy and opening many minds to reflection.
Thank you very much for reading this far — I hope you're doing well, and sending a huge hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 5f078e90:b2bacaa3
2025-05-03 10:18:41
@ 5f078e90:b2bacaa3
2025-05-03 10:18:41The Spoonbill's Dawn
In a marsh where reeds whispered secrets to the wind, a roseate spoonbill named Sable waded through dawn’s amber glow. Her pink feathers shimmered, catching the first light as she swept her spoon-shaped bill through the shallows, sifting for shrimp. Unlike her flock, who chattered and preened, Sable moved with quiet purpose, her eyes tracing ripples for signs of life.

Each morning, she returned to a lone cypress, its roots cradling a pool where minnows danced. Here, Sable had found an odd companion: a young alligator named Moss, whose emerald scales blended with the water’s edge. Moss never lunged, only watched, his eyes like polished stones. Sable, curious, began leaving shrimp at the pool’s edge. Moss, in turn, nudged smooth pebbles toward her, gifts from the marsh’s depths.
One dawn, a storm loomed, its thunder rattling the reeds. The flock fled, their wings a pink blur against charcoal clouds, but Sable lingered. The pool was still; Moss hadn’t surfaced. She dipped her bill, calling softly, her heart a flutter of worry. Then, a ripple—Moss emerged, sluggish, a gash on his flank from a poacher’s trap. Sable’s instinct was to flee, but she stayed, her bill probing the mud for healing herbs she’d seen egrets use.
With gentle nudges, she pressed the herbs to Moss’s wound, her pink wings shielding him from the rain. Moss rumbled, a low thanks, and rested. By dusk, the storm passed, and the marsh gleamed under a crescent moon. Moss stirred, stronger, and nudged a final pebble to Sable—a heart-shaped stone, glinting pink like her feathers.
Sable took flight, the stone clutched in her bill, her wings carving hope into the sky. The flock returned, awed by her tale, and the marsh buzzed with their chatter. Sable and Moss remained, their bond a quiet legend, proof that even in a wild world, trust could bloom where dawn met dusk.
Word count: 313
-
 @ d34e832d:383f78d0
2025-04-26 14:33:06
@ d34e832d:383f78d0
2025-04-26 14:33:06Gist
This Idea presents a blueprint for creating a portable, offline-first education server focused on Free and Open Source Software (FOSS) topics like Bitcoin fundamentals, Linux administration, GPG encryption, and digital self-sovereignty. Using the compact and powerful Nookbox G9 NAS unit, we demonstrate how to deliver accessible, decentralized educational content in remote or network-restricted environments.
1. Bitcoin, Linux, and Cryptographic tools
Access to self-sovereign technologies such as Bitcoin, Linux, and cryptographic tools is critical for empowering individuals and communities. However, many areas face internet connectivity issues or political restrictions limiting access to online resources.
By combining a high-performance mini NAS server with a curated library of FOSS educational materials, we can create a mobile "university" that delivers critical knowledge independently of centralized networks.
2. Hardware Platform: Nookbox G9 Overview
The Nookbox G9 offers an ideal balance of performance, portability, and affordability for this project.
2.1 Core Specifications
| Feature | Specification | |:------------------------|:---------------------------------------| | Form Factor | 1U Rackmount mini-NAS | | Storage | Up to 8TB (4×2TB M.2 NVMe SSDs) | | M.2 Interface | PCIe Gen 3x2 per drive slot | | Networking | Dual 2.5 Gigabit Ethernet ports | | Power Consumption | 11–30 Watts (typical usage) | | Default OS | Windows 11 (to be replaced with Linux) | | Linux Compatibility | Fully compatible with Ubuntu 24.10 |
3. FOSS Education Server Design
3.1 Operating System Setup
- Replace Windows 11 with a clean install of Ubuntu Server 24.10.
- Harden the OS:
- Enable full-disk encryption.
- Configure UFW firewall.
- Disable unnecessary services.
3.2 Core Services Deployed
| Service | Purpose | |:--------------------|:-----------------------------------------| | Nginx Web Server | Host offline courses and documentation | | Nextcloud (optional) | Offer private file sharing for students | | Moodle LMS (optional) | Deliver structured courses and quizzes | | Tor Hidden Service | Optional for anonymous access locally | | rsync/Syncthing | Distribute updates peer-to-peer |
3.3 Content Hosted
- Bitcoin: Bitcoin Whitepaper, Bitcoin Core documentation, Electrum Wallet tutorials.
- Linux: Introduction to Linux (LPIC-1 materials), bash scripting guides, system administration manuals.
- Cryptography: GPG tutorials, SSL/TLS basics, secure communications handbooks.
- Offline Tools: Full mirrors of sites like LearnLinux.tv, Bitcoin.org, and selected content from FSF.
All resources are curated to be license-compliant and redistributable in an offline format.
4. Network Configuration
- LAN-only Access: No reliance on external Internet.
- DHCP server setup for automatic IP allocation.
- Optional Wi-Fi access point using USB Wi-Fi dongle and
hostapd. - Access Portal: Homepage automatically redirects users to educational content upon connection.
5. Advantages of This Setup
| Feature | Advantage | |:-----------------------|:----------------------------------------| | Offline Capability | Operates without internet connectivity | | Portable Form Factor | Fits into field deployments easily | | Secure and Hardened | Encrypted, compartmentalized, and locked down | | Modular Content | Easy to update or expand educational resources | | Energy Efficient | Low power draw enables solar or battery operation | | Open Source Stack | End-to-end FOSS ecosystem, no vendor lock-in |
6. Deployment Scenarios
- Rural Schools: Provide Linux training without requiring internet.
- Disaster Recovery Zones: Deliver essential technical education in post-disaster areas.
- Bitcoin Meetups: Offer Bitcoin literacy and cryptography workshops in remote communities.
- Privacy Advocacy Groups: Teach operational security practices without risking network surveillance.
7. Performance Considerations
Despite PCIe Gen 3x2 limitations, the available bandwidth (~2GB/s theoretical) vastly exceeds the server's 2.5 Gbps network output (~250MB/s), making it more than sufficient for a read-heavy educational workload.
Thermal Management:
Given the G9’s known cooling issues, install additional thermal pads or heatsinks on the NVMe drives. Consider external USB-powered cooling fans for sustained heavy usage.
8. Ways To Extend
- Multi-language Support: Add localized course materials.
- Bitcoin Node Integration: Host a lightweight Bitcoin node (e.g., Bitcoin Core with pruning enabled or a complete full node) for educational purposes.
- Mesh Networking: Use Mesh Wi-Fi protocols (e.g., cjdns or Yggdrasil) to allow peer-to-peer server sharing without centralized Wi-Fi.
9. Consider
Building a Portable FOSS Education Server on a Nookbox G9 is a practical, scalable solution for democratizing technical knowledge, empowering communities, and defending digital sovereignty in restricted environments.
Through thoughtful system design—leveraging open-source software and secure deployment practices—we enable resilient, censorship-resistant education wherever it's needed.
📎 References
-
 @ a5142938:0ef19da3
2025-05-03 10:02:03
@ a5142938:0ef19da3
2025-05-03 10:02:03🧵 Products made from this material
The following brands offer products made exclusively or primarily from this material:
Clothing
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ d34e832d:383f78d0
2025-04-26 07:17:45
@ d34e832d:383f78d0
2025-04-26 07:17:45Practical Privacy and Secure Communications
1. Bootable privacy operating systems—Tails, Qubes OS, and Whonix****
This Idea explores the technical deployment of bootable privacy operating systems—Tails, Qubes OS, and Whonix—for individuals and organizations seeking to enhance operational security (OpSec). These systems provide different layers of isolation, anonymity, and confidentiality, critical for cryptographic operations, Bitcoin custody, journalistic integrity, whistleblowing, and sensitive communications. The paper outlines optimal use cases, system requirements, technical architecture, and recommended operational workflows for each OS.
2. Running An Operating System
In a digital world where surveillance, metadata leakage, and sophisticated threat models are realities, bootable privacy OSs offer critical mitigation strategies. By running an operating system from a USB, DVD, or external drive—and often entirely in RAM—users can minimize the footprint left on host hardware, dramatically enhancing privacy.
This document details Tails, Qubes OS, and Whonix: three leading open-source projects addressing different aspects of operational security.
3. Technical Overview of Systems
| OS | Focus | Main Feature | Threat Model | |------------|---------------------------|-----------------------------------------------|--------------------------------| | Tails | Anonymity & Ephemerality | Runs entirely from RAM; routes traffic via Tor | For activists, journalists, Bitcoin users | | Qubes OS | Security through Compartmentalization | Hardware-level isolation via Xen hypervisor | Defense against malware, APTs, insider threats | | Whonix | Anonymity over Tor Networks | Split-Gateway Architecture (Whonix-Gateway & Whonix-Workstation) | For researchers, Bitcoin node operators, privacy advocates |
4. System Requirements
4.1 Tails
- RAM: Minimum 2 GB (4 GB recommended)
- CPU: x86_64 (Intel or AMD)
- Storage: 8GB+ USB stick (optional persistent storage)
4.2 Qubes OS
- RAM: 16 GB minimum
- CPU: Intel VT-x or AMD-V support required
- Storage: 256 GB SSD recommended
- GPU: Minimal compatibility (no Nvidia proprietary driver support)
4.3 Whonix
- Platform: VirtualBox/KVM Host (Linux, Windows, Mac)
- RAM: 4 GB minimum (8 GB recommended)
- Storage: 100 GB suggested for optimal performance
5. Deployment Models
| Model | Description | Recommended OS | |--------------------------|-----------------------------------|------------------------------| | USB-Only Boot | No installation on disk; ephemeral use | Tails | | Hardened Laptop | Full disk installation with encryption | Qubes OS | | Virtualized Lab | VMs on hardened workstation | Whonix Workstation + Gateway |
6. Operational Security Advantages
| OS | Key Advantages | |------------|----------------------------------------------------------------------------------------------------| | Tails | Memory wipe at shutdown, built-in Tor Browser, persistent volume encryption (LUKS) | | Qubes OS | Compartmentalized VMs for work, browsing, Bitcoin keys; TemplateVMs reduce attack surface | | Whonix | IP address leaks prevented even if the workstation is compromised; full Tor network integration |
7. Threat Model Coverage
| Threat Category | Tails | Qubes OS | Whonix | |----------------------------|-----------------|------------------|------------------| | Disk Forensics | ✅ (RAM-only) | ✅ (with disk encryption) | ✅ (VM separation) | | Malware Containment | ❌ | ✅ (strong) | ✅ (via VMs) | | Network Surveillance | ✅ (Tor enforced) | Partial (needs VPN/Tor setup) | ✅ (Tor Gateway) | | Hardware-Level Attacks | ❌ | ❌ | ❌ |
8. Use Cases
- Bitcoin Cold Storage and Key Signing (Tails)
- Boot Tails offline for air-gapped Bitcoin signing.
- Private Software Development (Qubes)
- Use separate VMs for coding, browsing, and Git commits.
- Anonymous Research (Whonix)
- Surf hidden services (.onion) without IP leak risk.
- Secure Communications (All)
- Use encrypted messaging apps (Session, XMPP, Matrix) without metadata exposure.
9. Challenges and Mitigations
| Challenge | Mitigation | |---------------------|---------------------------------------------| | Hardware Incompatibility | Validate device compatibility pre-deployment (esp. for Qubes) | | Tor Exit Node Surveillance | Use onion services or bridge relays (Tails, Whonix) | | USB Persistence Risks | Always encrypt persistent volumes (Tails) | | Hypervisor Bugs (Qubes) | Regular OS and TemplateVM updates |
Here’s a fully original technical whitepaper version of your request, rewritten while keeping the important technical ideas intact but upgrading structure, language, and precision.
Executive Summary
In a world where digital surveillance and privacy threats are escalating, bootable privacy operating systems offer a critical solution for at-risk individuals. Systems like Tails, Qubes OS, and Whonix provide strong, portable security by isolating user activities from compromised or untrusted hardware. This paper explores their architectures, security models, and real-world applications.
1. To Recap
Bootable privacy-centric operating systems are designed to protect users from forensic analysis, digital tracking, and unauthorized access. By booting from an external USB drive or DVD and operating independently from the host machine's internal storage, they minimize digital footprints and maximize operational security (OpSec).
This paper provides an in-depth technical analysis of: - Tails (The Amnesic Incognito Live System) - Qubes OS (Security through Compartmentalization) - Whonix (Anonymity via Tor Isolation)
Each system’s strengths, limitations, use cases, and installation methods are explored in detail.
2. Technical Overview of Systems
2.1 Tails (The Amnesic Incognito Live System)
Architecture:
- Linux-based Debian derivative. - Boots from USB/DVD, uses RAM exclusively unless persistent storage is manually enabled. - Routes all network traffic through Tor. - Designed to leave no trace unless explicitly configured otherwise.Key Features:
- Memory erasure on shutdown. - Pre-installed secure applications: Tor Browser, KeePassXC, OnionShare. - Persistent storage available but encrypted and isolated.Limitations:
- Limited hardware compatibility (especially Wi-Fi drivers). - No support for mobile OS platforms. - ISP visibility to Tor network usage unless bridges are configured.
2.2 Qubes OS
Architecture:
- Xen-based hypervisor model. - Security through compartmentalization: distinct "qubes" (virtual machines) isolate tasks and domains (work, personal, banking, etc.). - Networking and USB stacks run in restricted VMs to prevent direct device access.Key Features:
- Template-based management for efficient updates. - Secure Copy (Qubes RPC) for data movement without exposing full disks. - Integrated Whonix templates for anonymous browsing.Limitations:
- Requires significant hardware resources (RAM and CPU). - Limited hardware compatibility (strict requirements for virtualization support: VT-d/IOMMU).
2.3 Whonix
Architecture:
- Debian-based dual VM system. - One VM (Gateway) routes all traffic through Tor; the second VM (Workstation) is fully isolated from the physical network. - Can be run on top of Qubes OS, VirtualBox, or KVM.Key Features:
- Complete traffic isolation at the system level. - Strong protections against IP leaks (fails closed if Tor is inaccessible). - Advanced metadata obfuscation options.Limitations:
- High learning curve for proper configuration. - Heavy reliance on Tor can introduce performance bottlenecks.
3. Comparative Analysis
| Feature | Tails | Qubes OS | Whonix | |:--------|:------|:---------|:-------| | Anonymity Focus | High | Medium | High | | System Isolation | Medium | Very High | High | | Persistence | Optional | Full | Optional | | Hardware Requirements | Low | High | Medium | | Learning Curve | Low | High | Medium | | Internet Privacy | Mandatory Tor | Optional Tor | Mandatory Tor |
4. Use Cases
| Scenario | Recommended System | |:---------|:--------------------| | Emergency secure browsing | Tails | | Full system compartmentalization | Qubes OS | | Anonymous operations with no leaks | Whonix | | Activist communications from hostile regions | Tails or Whonix | | Secure long-term project management | Qubes OS |
5. Installation Overview
5.1 Hardware Requirements
- Tails: Minimum 2GB RAM, USB 2.0 or higher, Intel or AMD x86-64 processor.
- Qubes OS: Minimum 16GB RAM, VT-d/IOMMU virtualization support, SSD storage.
- Whonix: Runs inside VirtualBox or Qubes; requires host compatibility.
5.2 Setup Instructions
Tails: 1. Download latest ISO from tails.net. 2. Verify signature (GPG or in-browser). 3. Use balenaEtcher or dd to flash onto USB. 4. Boot from USB, configure Persistent Storage if necessary.
Qubes OS: 1. Download ISO from qubes-os.org. 2. Verify using PGP signatures. 3. Flash to USB or DVD. 4. Boot and install onto SSD with LUKS encryption enabled.
Whonix: 1. Download both Gateway and Workstation VMs from whonix.org. 2. Import into VirtualBox or a compatible hypervisor. 3. Configure VMs to only communicate through the Gateway.
6. Security Considerations
- Tails: Physical compromise of the USB stick is a risk. Use hidden storage if necessary.
- Qubes OS: Qubes is only as secure as its weakest compartment; misconfigured VMs can leak data.
- Whonix: Full reliance on Tor can reveal usage patterns if used carelessly.
Best Practices: - Always verify downloads via GPG. - Use a dedicated, non-personal device where possible. - Utilize Tor bridges if operating under oppressive regimes. - Practice OPSEC consistently—compartmentalization, metadata removal, anonymous communications.
7. Consider
Bootable privacy operating systems represent a critical defense against modern surveillance and oppression. Whether for emergency browsing, long-term anonymous operations, or full-stack digital compartmentalization, solutions like Tails, Qubes OS, and Whonix empower users to reclaim their privacy.
When deployed thoughtfully—with an understanding of each system’s capabilities and risks—these tools can provide an exceptional layer of protection for journalists, activists, security professionals, and everyday users alike.
10. Example: Secure Bitcoin Signing Workflow with Tails
- Boot Tails from USB.
- Disconnect from the network.
- Generate Bitcoin private key or sign transaction using Electrum.
- Save signed transaction to encrypted USB drive.
- Shut down to wipe RAM completely.
- Broadcast transaction from a separate, non-sensitive machine.
This prevents key exposure to malware, man-in-the-middle attacks, and disk forensic analysis.
11. Consider
Bootable privacy operating systems like Tails, Qubes OS, and Whonix offer robust, practical strategies for improving operational security across a wide spectrum of use cases—from Bitcoin custody to anonymous journalism. Their open-source nature, focus on minimizing digital footprints, and mature security architectures make them foundational tools for modern privacy workflows.
Choosing the appropriate OS depends on the specific threat model, hardware available, and user needs. Proper training and discipline remain crucial to maintain the security these systems enable.
Appendices
A. Download Links
B. Further Reading
- "The Qubes OS Architecture" Whitepaper
- "Operational Security and Bitcoin" by Matt Odell
- "Tor and the Darknet: Separating Myth from Reality" by EFF
-
 @ a5142938:0ef19da3
2025-05-03 10:01:17
@ a5142938:0ef19da3
2025-05-03 10:01:17🧵 Products made from this material
The following brands offer products made exclusively or primarily from this material:
Clothing
- Engel
- Dilling (merino wool)
- ManyMonths (merino wool)
Home
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ d34e832d:383f78d0
2025-04-26 04:24:13
@ d34e832d:383f78d0
2025-04-26 04:24:13A Secure, Compact, and Cost-Effective Offline Key Management System
1. Idea
This idea presents a cryptographic key generation appliance built on the Nookbox G9, a compact 1U mini NAS solution. Designed to be a dedicated air-gapped or offline-first device, this system enables the secure generation and handling of RSA, ECDSA, and Ed25519 key pairs. By leveraging the Nookbox G9's small form factor, NVMe storage, and Linux compatibility, we outline a practical method for individuals and organizations to deploy secure, reproducible, and auditable cryptographic processes without relying on cloud or always-connected environments.
2. Minimization Of Trust
In an era where cryptographic operations underpin everything from Bitcoin transactions to secure messaging, generating keys in a trust-minimized environment is critical. Cloud-based solutions or general-purpose desktops expose key material to increased risk. This project defines a dedicated hardware appliance for cryptographic key generation using Free and Open Source Software (FOSS) and a tightly scoped threat model.
3. Hardware Overview: Nookbox G9
| Feature | Specification | |-----------------------|----------------------------------------------------| | Form Factor | 1U Mini NAS | | Storage Capacity | Up to 8TB via 4 × 2TB M.2 NVMe SSDs | | PCIe Interface | Each M.2 slot uses PCIe Gen 3x2 | | Networking | Dual 2.5 Gigabit Ethernet | | Cooling | Passive cooling (requires modification for load) | | Operating System | Windows 11 pre-installed; compatible with Linux |
This hardware is chosen for its compact size, multiple SSD support, and efficient power consumption (~11W idle on Linux). It fits easily into a secure rack cabinet and can run entirely offline.
4. System Configuration
4.1 OS & Software Stack
We recommend wiping Windows and installing:
- OS: Ubuntu 24.10 LTS or Debian 12
- Key Tools:
gnupg(for GPG, RSA, and ECC)ageorrage(for modern encryption)openssl(general-purpose cryptographic tool)ssh-keygen(for Ed25519 or RSA SSH keys)vault(optional: HashiCorp Vault for managing key secrets)pwgen/diceware(for secure passphrase generation)
4.2 Storage Layout
- Drive 1 (System): Ubuntu 24.10 with encrypted LUKS partition
- Drive 2 (Key Store): Encrypted Veracrypt volume for keys and secrets
- Drive 3 (Backup): Offline encrypted backup (mirrored or rotated)
- Drive 4 (Logs & Audit): System logs, GPG public keyring, transparency records
5. Security Principles
- Air-Gapping: Device operates disconnected from the internet during key generation.
- FOSS Only: All software used is open-source and auditable.
- No TPM/Closed Firmware Dependencies: BIOS settings disable Intel ME, TPM, and Secure Boot.
- Tamper Evidence: Physical access logs and optional USB kill switch setup.
- Transparency: Generation scripts stored on device, along with SHA256 of all outputs.
6. Workflow: Generating Keypairs
Example: Generating an Ed25519 GPG Key
```bash gpg --full-generate-key
Choose ECC > Curve: Ed25519
Set expiration, user ID, passphrase
```
Backup public and private keys:
bash gpg --armor --export-secret-keys [keyID] > private.asc gpg --armor --export [keyID] > public.asc sha256sum *.asc > hashes.txtStore on encrypted volume and create a printed copy (QR or hex dump) for physical backup.
7. Performance Notes
While limited to PCIe Gen 3x2 (approx. 1.6 GB/s per slot), the speed is more than sufficient for key generation workloads. The bottleneck is not IO-bound but entropy-limited and CPU-bound. In benchmarks:
- RSA 4096 generation: ~2–3 seconds
- Ed25519 generation: <1 second
- ZFS RAID-Z writes (if used): ~250MB/s due to 2.5Gbps NIC ceiling
Thermal throttling may occur under extended loads without cooling mods. A third-party aluminum heatsink resolves this.
8. Use Cases
- Bitcoin Cold Storage (xprv/xpub, seed phrases)
- SSH Key Infrastructure (Ed25519 key signing for orgs)
- PGP Trust Anchor (for a Web of Trust or private PKI)
- Certificate Authority (offline root key handling)
- Digital Notary Service (hash-based time-stamping)
9. Recommendations & Improvements
| Area | Improvement | |-------------|--------------------------------------| | Cooling | Add copper heatsinks + airflow mod | | Power | Use UPS + power filter for stability | | Boot | Use full-disk encryption with Yubikey unlock | | Expansion | Use one SSD for keybase-style append-only logs | | Chassis | Install into a tamper-evident case with RFID tracking |
10. Consider
The Nookbox G9 offers a compact, energy-efficient platform for creating a secure cryptographic key generation appliance. With minor thermal enhancements and a strict FOSS policy, it becomes a reliable workstation for cryptographers, developers, and Bitcoin self-custodians. Its support for multiple encrypted SSDs, air-gapped operation, and Linux flexibility make it a modern alternative to enterprise HSMs—without the cost or vendor lock-in.
A. Key Software Versions
GnuPG 2.4.xOpenSSL 3.xUbuntu 24.10Veracrypt 1.26+
B. System Commands (Setup)
bash sudo apt install gnupg2 openssl age veracrypt sudo cryptsetup luksFormat /dev/nvme1n1C. Resources
The Nookbox G9 epitomizes a compact yet sophisticated energy-efficient computational architecture, meticulously designed to serve as a secure cryptographic key generation appliance. By integrating minor yet impactful thermal enhancements, it ensures optimal performance stability while adhering to a stringent Free and Open Source Software (FOSS) policy, thereby positioning itself as a reliable workstation specifically tailored for cryptographers, software developers, and individuals engaged in Bitcoin self-custody. Its capability to support multiple encrypted Solid State Drives (SSDs) facilitates an augmented data security framework, while the air-gapped operational feature significantly enhances its resilience against potential cyber threats. Furthermore, the inherent flexibility of Linux operating systems not only furnishes an adaptable environment for various cryptographic applications but also serves as a compelling modern alternative to conventional enterprise Hardware Security Modules (HSMs), ultimately bypassing the prohibitive costs and vendor lock-in typically associated with such proprietary solutions.
Further Tools
🔧 Recommended SSDs and Tools (Amazon)
-
Kingston A400 240GB SSD – SATA 3 2.5"
https://a.co/d/41esjYL -
Samsung 970 EVO Plus 2TB NVMe M.2 SSD – Gen 3
https://a.co/d/6EMVAN1 -
Crucial P5 Plus 1TB PCIe Gen4 NVMe M.2 SSD
https://a.co/d/hQx50Cq -
WD Blue SN570 1TB NVMe SSD – PCIe Gen 3
https://a.co/d/j2zSDCJ -
Sabrent Rocket Q 2TB NVMe SSD – QLC NAND
https://a.co/d/325Og2K -
Thermalright M.2 SSD Heatsink Kit
https://a.co/d/0IYH3nK -
ORICO M.2 NVMe SSD Enclosure – USB 3.2 Gen2
https://a.co/d/aEwQmih
Product Links (Amazon)
-
Thermal Heatsink for M.2 SSDs (Must-have for stress and cooling)
https://a.co/d/43B1F3t -
Nookbox G9 – Mini NAS
https://a.co/d/3dswvGZ -
Alternative 1: Possibly related cooling or SSD gear
https://a.co/d/c0Eodm3 -
Alternative 2: Possibly related NAS accessories or SSDs
https://a.co/d/9gWeqDr
Benchmark Results (Geekbench)
-
GMKtec G9 Geekbench CPU Score #1
https://browser.geekbench.com/v6/cpu/11471182 -
GMKtec G9 Geekbench CPU Score #2
https://browser.geekbench.com/v6/cpu/11470130 -
GMKtec Geekbench User Profile
https://browser.geekbench.com/user/446940
🛠️ DIY & Fix Resource
- How-Fixit – PC Repair Guides and Tutorials
https://www.how-fixit.com/
-
 @ a5142938:0ef19da3
2025-05-03 10:00:49
@ a5142938:0ef19da3
2025-05-03 10:00:49🧵 Products made from this material
The following brands offer products made exclusively or primarily from this material:
Clothing
- Engel (organic cotton)
- Dilling (organic cotton)
- ManyMonths (organic cotton)
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ e4950c93:1b99eccd
2025-05-03 09:59:59
@ e4950c93:1b99eccd
2025-05-03 09:59:59🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ d34e832d:383f78d0
2025-04-25 23:39:07
@ d34e832d:383f78d0
2025-04-25 23:39:07First Contact – A Film History Breakdown
🎥 Movie: Contact
📅 Year Released: 1997
🎞️ Director: Robert Zemeckis
🕰️ Scene Timestamp: ~00:35:00
In this pivotal moment, Dr. Ellie Arroway (Jodie Foster), working at the VLA (Very Large Array) in New Mexico, detects a powerful and unusual signal emanating from the star system Vega, over 25 light-years away. It starts with rhythmic pulses—prime numbers—and escalates into layers of encoded information. The calm night shatters into focused chaos as the team realizes they might be witnessing the first confirmed evidence of extraterrestrial intelligence.
🎥 Camera Work:
Zemeckis uses slow zooms, wide shots of the VLA dishes moving in synchrony, and mid-shots on Ellie as she listens with growing awe and panic. The kinetic handheld camera inside the lab mirrors the rising tension.💡 Lighting:
Low-key, naturalistic nighttime lighting dominates the outdoor shots, enhancing the eerie isolation of the array. Indoors, practical lab lighting creates a realistic, clinical setting.✂️ Editing:
The pacing builds through quick intercuts between the signal readouts, Ellie’s expressions, and the reactions of her team. This accelerates tension while maintaining clarity.🔊 Sound:
The rhythmic signal becomes the scene’s pulse. We begin with ambient night silence, then transition to the raw audio of the alien transmission. It’s diegetic (heard by the characters), and as it builds, a subtle score underscores the awe and urgency. Every beep feels weighty.
Released in 1997, Contact emerged during a period of growing public interest in both SETI (Search for Extraterrestrial Intelligence) and skepticism about science in the post-Cold War world. It was also the era of X-Files and the Mars Pathfinder mission, where space and the unknown dominated media.
The scene reflects 1990s optimism about technology and the belief that answers to humanity’s biggest questions might lie beyond Earth—balanced against the bureaucratic red tape and political pressures that real scientists face.
- Classic procedural sci-fi like 2001: A Space Odyssey and Close Encounters of the Third Kind.
- Real-world SETI protocols and the actual scientists Carl Sagan consulted with.
- The radio broadcast scene reflects Sagan’s own passion for communication and cosmic connectedness.
This scene set a new benchmark for depicting science authentically in fiction. Many real-world SETI scientists cite Contact as an accurate portrayal of their field. It also influenced later films like Arrival and Interstellar, which similarly blend emotion with science.
The signal is more than data—it’s a modern miracle. It represents Ellie’s faith in science, the power of patience, and humanity's yearning to not be alone.
The use of prime numbers symbolizes universal language—mathematics as a bridge between species. The scene’s pacing reflects the clash between logic and emotion, science and wonder.
The signal itself acts as a metaphor for belief: you can't "see" the sender, but you believe they’re out there. It’s the crux of the entire movie’s science vs. faith dichotomy.
This scene hits hard because it captures pure awe—the mix of fear, wonder, and purpose when faced with the unknown. Watching Ellie realize she's not alone mirrors how we all feel when our faith (in science, in hope, in truth) is rewarded.
For filmmakers and students, this scene is a masterclass in procedural suspense, realistic portrayal of science, and using audiovisual cues to build tension without needing action or violence.
It reminds us that the greatest cinematic moments don’t always come from spectacle, but from stillness, sound, and a scientist whispering: “We got something.”
-
 @ e4950c93:1b99eccd
2025-05-03 09:59:25
@ e4950c93:1b99eccd
2025-05-03 09:59:25🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
- Engel
- Dilling (laine mérinos)
- ManyMonths (laine mérinos)
Maison
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ d34e832d:383f78d0
2025-04-25 23:20:48
@ d34e832d:383f78d0
2025-04-25 23:20:48As computing needs evolve toward speed, reliability, and efficiency, understanding the landscape of storage technologies becomes crucial for system builders, IT professionals, and performance enthusiasts. This idea compares traditional Hard Disk Drives (HDDs) with various Solid-State Drive (SSD) technologies including SATA SSDs, mSATA, M.2 SATA, and M.2 NVMe. It explores differences in form factors, interfaces, memory types, and generational performance to empower informed decisions on selecting optimal storage.
1. Storage Device Overview
1.1 HDDs – Hard Disk Drives
- Mechanism: Mechanical platters + spinning disk.
- Speed: ~80–160 MB/s.
- Cost: Low cost per GB.
- Durability: Susceptible to shock; moving parts prone to wear.
- Use Case: Mass storage, backups, archival.
1.2 SSDs – Solid State Drives
- Mechanism: Flash memory (NAND-based); no moving parts.
- Speed: SATA SSDs (~550 MB/s), NVMe SSDs (>7,000 MB/s).
- Durability: High resistance to shock and temperature.
- Use Case: Operating systems, apps, high-speed data transfer.
2. Form Factors
| Form Factor | Dimensions | Common Usage | |------------------|------------------------|--------------------------------------------| | 2.5-inch | 100mm x 69.85mm x 7mm | Laptops, desktops (SATA interface) | | 3.5-inch | 146mm x 101.6mm x 26mm | Desktops/servers (HDD only) | | mSATA | 50.8mm x 29.85mm | Legacy ultrabooks, embedded systems | | M.2 | 22mm wide, lengths vary (2242, 2260, 2280, 22110) | Modern laptops, desktops, NUCs |
Note: mSATA is being phased out in favor of the more versatile M.2 standard.
3. Interfaces & Protocols
3.1 SATA (Serial ATA)
- Max Speed: ~550 MB/s (SATA III).
- Latency: Higher.
- Protocol: AHCI.
- Compatibility: Broad support, backward compatible.
3.2 NVMe (Non-Volatile Memory Express)
- Max Speed:
- Gen 3: ~3,500 MB/s
- Gen 4: ~7,000 MB/s
- Gen 5: ~14,000 MB/s
- Latency: Very low.
- Protocol: NVMe (optimized for NAND flash).
- Interface: PCIe lanes (usually via M.2 slot).
NVMe significantly outperforms SATA due to reduced overhead and direct PCIe access.
4. Key Slot & Compatibility (M.2 Drives)
| Drive Type | Key | Interface | Typical Use | |------------------|----------------|---------------|-----------------------| | M.2 SATA | B+M key | SATA | Budget laptops/desktops | | M.2 NVMe (PCIe) | M key only | PCIe Gen 3–5 | Performance PCs/gaming |
⚠️ Important: Not all M.2 slots support NVMe. Check motherboard specs for PCIe compatibility.
5. SSD NAND Memory Types
| Type | Bits/Cell | Speed | Endurance | Cost | Use Case | |---------|---------------|-----------|---------------|----------|--------------------------------| | SLC | 1 | ⭐⭐⭐⭐ | ⭐⭐⭐⭐ | $$$$ | Enterprise caching | | MLC | 2 | ⭐⭐⭐ | ⭐⭐⭐ | $$$ | Pro-grade systems | | TLC | 3 | ⭐⭐ | ⭐⭐ | $$ | Consumer, gaming | | QLC | 4 | ⭐ | ⭐ | $ | Budget SSDs, media storage |
6. 3D NAND / V-NAND Technology
- Traditional NAND: Planar (flat) design.
- 3D NAND: Stacks cells vertically—more density, less space.
- Benefits:
- Greater capacity
- Better power efficiency
- Improved lifespan
Samsung’s V-NAND is a branded 3D NAND variant known for high endurance and stability.
7. Performance & Generational Comparison
| PCIe Gen | Max Speed | Use Case | |--------------|---------------|----------------------------------| | Gen 3 | ~3,500 MB/s | Mainstream laptops/desktops | | Gen 4 | ~7,000 MB/s | Gaming, prosumer, light servers | | Gen 5 | ~14,000 MB/s | AI workloads, enterprise |
Drives are backward compatible, but will operate at the host’s maximum supported speed.
8. Thermal Management
- NVMe SSDs generate heat—especially Gen 4/5.
- Heatsinks and thermal pads are vital for:
- Sustained performance (prevent throttling)
- Longer lifespan
- Recommended to leave 10–20% free space for optimal SSD wear leveling and garbage collection.
9. HDD vs SSD: Summary
| Aspect | HDD | SSD | |------------------|---------------------|------------------------------| | Speed | 80–160 MB/s | 550 MB/s – 14,000 MB/s | | Durability | Low (mechanical) | High (no moving parts) | | Lifespan | Moderate | High (depends on NAND type) | | Cost | Lower per GB | Higher per GB | | Noise | Audible | Silent |
10. Brand Recommendations
| Brand | Strength | |------------------|-----------------------------------------| | Samsung | Leading in performance (980 Pro, 990 Pro) | | Western Digital | Reliable Gen 3/4/5 drives (SN770, SN850X) | | Crucial | Budget-friendly, solid TLC drives (P3, P5 Plus) | | Kingston | Value-oriented SSDs (A2000, NV2) |
11. How to Choose the Right SSD
- Check your device slot: Is it M.2 B+M, M-key, or SATA-only?
- Interface compatibility: Confirm if the M.2 slot supports NVMe or only SATA.
- Match PCIe Gen: Use Gen 3/4/5 based on CPU/motherboard lanes.
- Pick NAND type: TLC for best balance of speed/longevity.
- Thermal plan: Use heatsinks or fans for Gen 4+ drives.
- Capacity need: Leave headroom (15–20%) for performance and lifespan.
- Trustworthy brands: Stick to Samsung, WD, Crucial for warranty and quality.
Consider
From boot speed to data integrity, SSDs have revolutionized how modern systems handle storage. While HDDs remain relevant for mass archival, NVMe SSDs—especially those leveraging PCIe Gen 4 and Gen 5—dominate in speed-critical workflows. M.2 NVMe is the dominant form factor for futureproof builds, while understanding memory types like TLC vs. QLC ensures better longevity planning.
Whether you’re upgrading a laptop, building a gaming rig, or running a self-hosted Bitcoin node, choosing the right form factor, interface, and NAND type can dramatically impact system performance and reliability.
Resources & Further Reading
- How-Fixit Storage Guides
- Kingston SSD Reliability Guide
- Western Digital Product Lines
- Samsung V-NAND Explained
- PCIe Gen 5 Benchmarks
Options
🔧 Recommended SSDs and Tools (Amazon)
-
Kingston A400 240GB SSD – SATA 3 2.5"
https://a.co/d/41esjYL -
Samsung 970 EVO Plus 2TB NVMe M.2 SSD – Gen 3
https://a.co/d/6EMVAN1 -
Crucial P5 Plus 1TB PCIe Gen4 NVMe M.2 SSD
https://a.co/d/hQx50Cq -
WD Blue SN570 1TB NVMe SSD – PCIe Gen 3
https://a.co/d/j2zSDCJ -
Sabrent Rocket Q 2TB NVMe SSD – QLC NAND
https://a.co/d/325Og2K -
Thermalright M.2 SSD Heatsink Kit
https://a.co/d/0IYH3nK -
ORICO M.2 NVMe SSD Enclosure – USB 3.2 Gen2
https://a.co/d/aEwQmih
🛠️ DIY & Fix Resource
- How-Fixit – PC Repair Guides and Tutorials
https://www.how-fixit.com/
In Addition
Modern Storage Technologies and Mini NAS Implementation
1. Network Attached Storage (NAS) system
In the rapidly evolving landscape of data storage, understanding the nuances of various storage technologies is crucial for optimal system design and performance. This idea delves into the distinctions between traditional Hard Disk Drives (HDDs), Solid State Drives (SSDs), and advanced storage interfaces like M.2 NVMe, M.2 SATA, and mSATA. Additionally, it explores the implementation of a compact Network Attached Storage (NAS) system using the Nookbox G9, highlighting its capabilities and limitations.
2. Storage Technologies Overview
2.1 Hard Disk Drives (HDDs)
- Mechanism: Utilize spinning magnetic platters and read/write heads.
- Advantages:
- Cost-effective for large storage capacities.
- Longer lifespan in low-vibration environments.
- Disadvantages:
- Slower data access speeds.
- Susceptible to mechanical failures due to moving parts.
2.2 Solid State Drives (SSDs)
- Mechanism: Employ NAND flash memory with no moving parts.
- Advantages:
- Faster data access and boot times.
- Lower power consumption and heat generation.
- Enhanced durability and shock resistance.
- Disadvantages:
- Higher cost per gigabyte compared to HDDs.
- Limited write cycles, depending on NAND type.
3. SSD Form Factors and Interfaces
3.1 Form Factors
- 2.5-Inch: Standard size for laptops and desktops; connects via SATA interface.
- mSATA: Miniature SATA interface, primarily used in ultrabooks and embedded systems; largely supplanted by M.2.
- M.2: Versatile form factor supporting both SATA and NVMe interfaces; prevalent in modern systems.
3.2 Interfaces
- SATA (Serial ATA):
- Speed: Up to 600 MB/s.
- Compatibility: Widely supported across various devices.
-
Limitation: Bottleneck for high-speed SSDs.
-
NVMe (Non-Volatile Memory Express):
- Speed: Ranges from 3,500 MB/s (PCIe Gen 3) to over 14,000 MB/s (PCIe Gen 5).
- Advantage: Direct communication with CPU via PCIe lanes, reducing latency.
- Consideration: Requires compatible motherboard and BIOS support.
4. M.2 SATA vs. M.2 NVMe
| Feature | M.2 SATA | M.2 NVMe | |------------------------|--------------------------------------------------|----------------------------------------------------| | Interface | SATA III (AHCI protocol) | PCIe (NVMe protocol) | | Speed | Up to 600 MB/s | Up to 14,000 MB/s (PCIe Gen 5) | | Compatibility | Broad compatibility with older systems | Requires NVMe-compatible M.2 slot and BIOS support | | Use Case | Budget builds, general computing | High-performance tasks, gaming, content creation |
Note: M.2 NVMe drives are not backward compatible with M.2 SATA slots due to differing interfaces and keying.
5. NAND Flash Memory Types
Understanding NAND types is vital for assessing SSD performance and longevity.
- SLC (Single-Level Cell):
- Bits per Cell: 1
- Endurance: ~100,000 write cycles
-
Use Case: Enterprise and industrial applications
-
MLC (Multi-Level Cell):
- Bits per Cell: 2
- Endurance: ~10,000 write cycles
-
Use Case: Consumer-grade SSDs
-
TLC (Triple-Level Cell):
- Bits per Cell: 3
- Endurance: ~3,000 write cycles
-
Use Case: Mainstream consumer SSDs
-
QLC (Quad-Level Cell):
- Bits per Cell: 4
- Endurance: ~1,000 write cycles
-
Use Case: Read-intensive applications
-
3D NAND:
- Structure: Stacks memory cells vertically to increase density.
- Advantage: Enhances performance and endurance across NAND types.
6. Thermal Management and SSD Longevity
Effective thermal management is crucial for maintaining SSD performance and lifespan.
- Heatsinks: Aid in dissipating heat from SSD controllers.
- Airflow: Ensuring adequate case ventilation prevents thermal throttling.
- Monitoring: Regularly check SSD temperatures, especially under heavy workloads.
7. Trusted SSD Manufacturers
Selecting SSDs from reputable manufacturers ensures reliability and support.
- Samsung: Known for high-performance SSDs with robust software support.
- Western Digital (WD): Offers a range of SSDs catering to various user needs.
- Crucial (Micron): Provides cost-effective SSD solutions with solid performance.
8. Mini NAS Implementation: Nookbox G9 Case Study
8.1 Overview
The Nookbox G9 is a compact NAS solution designed to fit within a 1U rack space, accommodating four M.2 NVMe SSDs.
8.2 Specifications
- Storage Capacity: Supports up to 8TB using four 2TB NVMe SSDs.
- Interface: Each M.2 slot operates at PCIe Gen 3x2.
- Networking: Equipped with 2.5 Gigabit Ethernet ports.
- Operating System: Comes pre-installed with Windows 11; compatible with Linux distributions like Ubuntu 24.10.
8.3 Performance and Limitations
- Throughput: Network speeds capped at ~250 MB/s due to 2.5 GbE limitation.
- Thermal Issues: Inadequate cooling leads to SSD temperatures reaching up to 80°C under load, causing potential throttling and system instability.
- Reliability: Reports of system reboots and lockups during intensive operations, particularly with ZFS RAIDZ configurations.
8.4 Recommendations
- Cooling Enhancements: Implement third-party heatsinks to improve thermal performance.
- Alternative Solutions: Consider NAS systems with better thermal designs and higher network throughput for demanding applications.
9. Consider
Navigating the myriad of storage technologies requires a comprehensive understanding of form factors, interfaces, and memory types. While HDDs offer cost-effective bulk storage, SSDs provide superior speed and durability. The choice between M.2 SATA and NVMe hinges on performance needs and system compatibility. Implementing compact NAS solutions like the Nookbox G9 necessitates careful consideration of thermal management and network capabilities to ensure reliability and performance.
Product Links (Amazon)
-
Thermal Heatsink for M.2 SSDs (Must-have for stress and cooling)
https://a.co/d/43B1F3t -
Nookbox G9 – Mini NAS
https://a.co/d/3dswvGZ -
Alternative 1: Possibly related cooling or SSD gear
https://a.co/d/c0Eodm3 -
Alternative 2: Possibly related NAS accessories or SSDs
https://a.co/d/9gWeqDr
Benchmark Results (Geekbench)
-
GMKtec G9 Geekbench CPU Score #1
https://browser.geekbench.com/v6/cpu/11471182 -
GMKtec G9 Geekbench CPU Score #2
https://browser.geekbench.com/v6/cpu/11470130 -
GMKtec Geekbench User Profile
https://browser.geekbench.com/user/446940
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ 3bf0c63f:aefa459d
2025-04-25 18:55:52
@ 3bf0c63f:aefa459d
2025-04-25 18:55:52Report of how the money Jack donated to the cause in December 2022 has been misused so far.
Bounties given
March 2025
- Dhalsim: 1,110,540 - Work on Nostr wiki data processing
February 2025
- BOUNTY* NullKotlinDev: 950,480 - Twine RSS reader Nostr integration
- Dhalsim: 2,094,584 - Work on Hypothes.is Nostr fork
- Constant, Biz and J: 11,700,588 - Nostr Special Forces
January 2025
- Constant, Biz and J: 11,610,987 - Nostr Special Forces
- BOUNTY* NullKotlinDev: 843,840 - Feeder RSS reader Nostr integration
- BOUNTY* NullKotlinDev: 797,500 - ReadYou RSS reader Nostr integration
December 2024
- BOUNTY* tijl: 1,679,500 - Nostr integration into RSS readers yarr and miniflux
- Constant, Biz and J: 10,736,166 - Nostr Special Forces
- Thereza: 1,020,000 - Podcast outreach initiative
November 2024
- Constant, Biz and J: 5,422,464 - Nostr Special Forces
October 2024
- Nostrdam: 300,000 - hackathon prize
- Svetski: 5,000,000 - Latin America Nostr events contribution
- Quentin: 5,000,000 - nostrcheck.me
June 2024
- Darashi: 5,000,000 - maintaining nos.today, searchnos, search.nos.today and other experiments
- Toshiya: 5,000,000 - keeping the NIPs repo clean and other stuff
May 2024
- James: 3,500,000 - https://github.com/jamesmagoo/nostr-writer
- Yakihonne: 5,000,000 - spreading the word in Asia
- Dashu: 9,000,000 - https://github.com/haorendashu/nostrmo
February 2024
- Viktor: 5,000,000 - https://github.com/viktorvsk/saltivka and https://github.com/viktorvsk/knowstr
- Eric T: 5,000,000 - https://github.com/tcheeric/nostr-java
- Semisol: 5,000,000 - https://relay.noswhere.com/ and https://hist.nostr.land relays
- Sebastian: 5,000,000 - Drupal stuff and nostr-php work
- tijl: 5,000,000 - Cloudron, Yunohost and Fraidycat attempts
- Null Kotlin Dev: 5,000,000 - AntennaPod attempt
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ e4950c93:1b99eccd
2025-05-03 09:59:03
@ e4950c93:1b99eccd
2025-05-03 09:59:03🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
- Engel (coton biologique)
- Dilling (coton biologique)
- ManyMonths (coton biologique)
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 1d7ff02a:d042b5be
2025-05-03 09:47:49
@ 1d7ff02a:d042b5be
2025-05-03 09:47:49ບົດຄວາມນີ້ແປມາຈາ: https://jackkruse.com/what-to-do-with-new-cancer-diagnosis/
ເນື້ອຫາສຳລັບຜູ້ອ່ານ: 1. ຈະເຮັດແນວໃດເມື່ອທ່ານໄດ້ຮັບການວິນິດໄສວ່າເປັນມະເຮັງ? 2. ສະໜາມຮົບກັບມະເຮັງທີ່ສຳຄັນແມ່ນຢູ່ບ່ອນການປິ່ນປົວແບບແພດ ຫຼື ໃນຮ່າງກາຍຂອງທ່ານເອງ? 3. ອາຫານການກິນມີບົດບາດແນວໃດ? 4. ຈະຮັບມືກັບໝໍມະເຮັງຄົນໃໝ່ຂອງທ່ານແນວໃດ? 5. ບໍ່ຕ້ອງຢ້ານທີ່ຈະສຳຫຼວດທຸກຄວາມເປັນໄປໄດ້ເພື່ອຊະນະສົງຄາມນີ້. ຮຽນຮູ້ກ່ຽວກັບອາຫານ ketogenic!!!
ກ່ອນທ່ານຈະອ່ານບົດຄວາມນີ້, ໃຫ້ເບິ່ງວິດີໂອນີ້: HYPERLINK
ບົດຄວາມນີ້ແມ່ນສຳລັບໜຶ່ງໃນໝູ່ທີ່ພິເສດຂອງຂ້ອຍ ຜູ້ທີ່ພົວພັນຂ້ອຍໃນອາທິດນີ້ ແລະ ບອກວ່າເມຍລາວຖືກວິນິດໄສວ່າເປັນມະເຮັງໃນໄວອາຍຸໜຸ່ມ. ຂ້ອຍໄດ້ຍິນຈາກການໂທ ແລະ ໂພສຂອງລາວໃນ Facebook ວ່າມັນກຳລັງທຳລາຍລາວ. ຂ້ອຍບອກລາວທັນທີໃຫ້ໄປຊື້ປື້ມ Anti Cancer: A New Way of Life ໂດຍ David Servan Schreiber ແລະ ມອບໃຫ້ເຈົ້າສາວຂອງລາວ. ຂ່າວດີກໍ່ຄືຫຼາຍລ້ານຄົນໃນຈຳນວນ 6 ລ້ານຄົນທີ່ກຳລັງປິ່ນປົວມະເຮັງໃນປະຈຸບັນຈະມີຊີວິດທີ່ສົມບູນຕໍ່ໄປ. ຈຳນວນຜູ້ລອດຊີວິດຕາມຄວາມຄິດເຫັນຂອງຂ້ອຍຍັງຕ່ຳເກີນໄປ (ປະມານ 45-50%). ນອກຈາກນັ້ນ, ຫຼາຍຄົນໃນຈຳນວນ 2000 ຄົນທີ່ເສຍຊີວິດຈາກມະເຮັງທຸກມື້ແມ່ນເນື່ອງຈາກຄອບຄົວຂອງພວກເຂົາບໍ່ຮູ້ກ່ຽວກັບຊັບພະຍາກອນທີ່ມີໃນປະຈຸບັນສຳລັບການປິ່ນປົວມະເຮັງທັງແບບດັ້ງເດີມ ແລະ ແບບທາງເລືອກ ເຊັ່ນ: ການປິ່ນປົວແບບເສີມ ຫຼື ແບບບູລະນາການ.
ເມື່ອຖືກວິນິດໄສດ້ວຍພະຍາດນີ້, ທ່ານຈະຮູ້ສຶກສັ່ນສະເທືອນຢ່າງຮຸນແຮງ. ສິ່ງສຳຄັນທີ່ທ່ານຕ້ອງຮູ້ແມ່ນພະຍາດນີ້ບໍ່ພຽງແຕ່ສາມາດຕໍ່ສູ້ໄດ້ແຕ່ຍັງສາມາດປ້ອງກັນໄດ້ຖ້າທ່ານຕັດສິນໃຈປ່ຽນແປງບາງສິ່ງທັນທີ ແລະ ປ່ອຍວາງຄວາມເຊື່ອທີ່ບໍ່ຖືກຕ້ອງທີ່ທ່ານໄດ້ສະສົມໃນຊີວິດ. ນີ້ເປັນຄວາມຈິງໂດຍສະເພາະຖ້າທ່ານເຮັດວຽກໃນຂົງເຂດສາທາລະນະສຸກ ແລະ ໄດ້ດຳລົງຊີວິດຕາມຄວາມເຊື່ອຕາຍຕົວຕະຫຼອດຊີວິດ. ປື້ມນີ້ຂຽນໂດຍແພດນັກຄົ້ນຄວ້າທີ່ບໍ່ພຽງແຕ່ຖືກກະທົບຈາກມະເຮັງ ແຕ່ຍັງເປັນມະເຮັງສະໝອງທີ່ອັນຕະລາຍທີ່ສຸດ. ລາວສາມາດຮື້ຖອນຄວາມເຊື່ອຂອງຕົນເອງໃນຖານະແພດດ້ວຍວິທະຍາສາດໃໝ່ທີ່ມີຢູ່ສຳລັບນັກຄົ້ນຄວ້າ ແຕ່ບໍ່ແມ່ນແພດມະເຮັງທົ່ວໄປ. ປື້ມນີ້ຈຳເປັນສຳລັບທຸກຄົນທີ່ເປັນມະເຮັງ ຫຼື ມີປັດໄຈສ່ຽງ ເພື່ອທ່ານຈະໄດ້ຊະນະກ່ອນມັນເລີ່ມ. ນີ້ແມ່ນໜຶ່ງໃນເຫດຜົນທີ່ຂ້ອຍຂຽນ QUILT ຂອງຂ້ອຍ ເພາະຂ້ອຍເຊື່ອວ່າຖ້າທ່ານປົກປ້ອງຈຸລັງຂອງທ່ານ ທ່ານຈະບໍ່ເປັນພະຍາດນີ້. ດຽວນີ້ ໝູ່ຂອງຂ້ອຍເປັນພະຍາດນີ້... ນີ້ແມ່ນບົດຄວາມກ່ຽວກັບສິ່ງທີ່ທ່ານອາດພິຈາລະນາເຮັດທັນທີຫຼັງຈາກປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ພິຈາລະນາຂໍຄວາມຄິດເຫັນທີສອງຈາກສູນມະເຮັງທີ່ສຳຄັນເຊັ່ນ MD Anderson.
-
ອ່ານປື້ມ Anticancer ທີ່ກ່າວເຖິງຂ້າງເທິງ. ມັນສຳຄັນທີ່ຈະເຫັນພະຍາດນີ້ໃນມຸມມອງໃໝ່.
-
ປ່ຽນອາຫານການກິນຂອງທ່ານທັນທີເປັນ Epi-paleo Rx ແລະ ອອກຫ່າງຈາກອາຫານແບບຕາເວັນຕົກມາດຕະຖານ.
-
ເລີ່ມເຮັດສະມາທິໂດຍໄວເທົ່າທີ່ຈະເປັນໄປໄດ້ເພື່ອຄວບຄຸມ cortisol ແລະ ຄວາມກັງວົນຂອງທ່ານ. (ທາງເລືອກບໍ່ສຳຄັນແຕ່ການເຮັດຈິງຊ່ວຍຊີວິດໄດ້)
-
ຄົນເຈັບຄວນປຶກສາຫາລືກ່ຽວກັບແຜນການປິ່ນປົວມະເຮັງ: ປັດໃຈສຳຄັນໃນມະເຮັງ: ຄວນຄົນເຈັບໃຊ້ອາຫານເສີມສຳລັບປະເພດມະເຮັງທີ່ທ່ານມີບໍ?
-
ພິຈາລະນາເລີ່ມລະບົບອາຫານເສີມ ລວມເຖິງ Curcumin, Reservatrol, Quercetin, ນ້ຳມັນປາ Omega ສາມ (ຄຸນນະພາບ Rx), ວິຕາມິນ D3 ໂດຍມີເປົ້າໝາຍເກີນ 50 ng/dl, ການໃຊ້ CoEnZQ10 ເປັນປະຈຳທຸກວັນ, R-alpha lipoic acid ແລະ ວິຕາມິນ K ທຸກມື້. ພິຈາລະນາການໃຊ້ N Acetyl Cysteine ທຸກວັນເຊັ່ນກັນ. ສັງເກດວ່າຂ້ອຍບໍ່ໄດ້ກຳນົດປະລິມານເພາະປະລິມານທີ່ຕ້ອງການສຳລັບການບຳບັດມະເຮັງແມ່ນສູງກວ່າທີ່ຈະໃຊ້ໃນການປ້ອງກັນ. ສິ່ງນີ້ຄວນເຮັດພາຍໃຕ້ການປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ຖ້າແພດມະເຮັງຂອງທ່ານບໍ່ເປີດໃຈກວ້າງກ່ຽວກັບບັນຫາເຫຼົ່ານີ້... ຫຼັງຈາກອ່ານປື້ມໃນຂັ້ນຕອນທີໜຶ່ງ ທ່ານອາດຈະຕ້ອງຊອກຫາແພດມະເຮັງຄົນໃໝ່. ເຫຼົ່ານີ້ແມ່ນສິ່ງທີ່ຂ້ອຍພິຈາລະນາວ່າເປັນອາຫານເສີມຫຼັກສຳລັບມະເຮັງສ່ວນໃຫຍ່ທີ່ມະນຸດເປັນ.
-
ໃນອາຫານຂອງທ່ານໃຫ້ເພີ່ມ ຂີ້ໝິ້ນ, ຂິງ, ກະທຽມ, ຣອດສະແມລີ, ແລະ ໃບແບຊິນ (ໃບໂຫລະພາ) ໃສ່ອາຫານຂອງທ່ານໃຫ້ຫຼາຍເທົ່າທີ່ຈະເປັນໄປໄດ້. ທ່ານຄວນດື່ມຊາຂຽວ 1 ລິດຕໍ່ມື້. ຊາຂຽວມີ L-Theanine ທີ່ຊ່ວຍຫຼຸດຄວາມກັງວົນ ແຕ່ຍັງເປັນສ່ວນເສີມຂອງຢາເຄມີບຳບັດໂດຍເຮັດໃຫ້ພວກມັນມີປະສິດທິພາບຍິ່ງຂຶ້ນ. ທ່ານຍັງສາມາດໃຊ້ສານສະກັດຊາຂຽວຖ້າທ່ານບໍ່ຕ້ອງການດື່ມຂອງແຫຼວຫຼາຍ ຫຼື ບໍ່ສາມາດດື່ມໄດ້ເນື່ອງຈາກສະພາບຂອງທ່ານ.
-
ໃນປີ 1955 Otto Warburg ຜູ້ຊະນະລາງວັນໂນເບວພົບວ່າມະເຮັງທັງໝົດໃຊ້ນ້ຳຕານເປັນແຫຼ່ງພະລັງງານ ແລະ ລະດັບອິນຊູລິນສູງເຮັດໃຫ້ຮ່າງກາຍສູນເສຍການຄວບຄຸມລະບົບພູມຄຸ້ມກັນທີ່ຈະປ້ອງກັນມັນ. ນີ້ໝາຍຄວາມວ່າຄົນເຈັບຕ້ອງຈຳກັດທຸກສິ່ງທີ່ກະຕຸ້ນອິນຊູລິນ. ອາຫານແບບ Epi-paleo ທີ່ມີຄາໂບໄຮເດຣດຕ່ຳເຮັດໄດ້ແນວນີ້ພໍດີ. ຂໍ້ມູນອ້າງອີງທີ່ດີສຳລັບອາຫານແມ່ນຢູ່ບ່ອນນີ້.
-
ລະບົບພູມຄຸ້ມກັນຂອງທ່ານແມ່ນການປ້ອງກັນທີ່ດີທີ່ສຸດຕໍ່ມະເຮັງ. ເພີ່ມລະດັບວິຕາມິນ D ແລະ ຮັກສາລະດັບອິນຊູລິນໃຫ້ຕ່ຳກວ່າສອງ. ການຫຼຸດລະດັບ cortisol ຈະປັບປຸງ leptin ແຕ່ສິ່ງສຳຄັນທີ່ສຸດແມ່ນເພີ່ມຈຳນວນຈຸລັງ Natural Killer (WBC) ທີ່ເປັນສ່ວນໜຶ່ງຂອງລະບົບພູມຄຸ້ມກັນໃນຈຸລັງທີ່ຕໍ່ສູ້ກັບມະເຮັງ. ທ່ານຈະໄດ້ອ່ານຫຼາຍກ່ຽວກັບຈຸລັງເຫຼົ່ານີ້ໃນປື້ມທີ່ຂ້ອຍແນະນຳໃນຂັ້ນຕອນທີໜຶ່ງ.
-
ຜັກ. ເຮັດໃຫ້ຜັກຕະກຸນ cruciferous ເປັນອາຫານຫຼັກ. ພືດທັງໝົດໃນຕະກຸນ Brassica ແມ່ນໝູ່ຂອງທ່ານ. Glucosinolates ສາມາດຢັບຢັ້ງ, ຊະລໍ, ແລະ ປີ້ນການເກີດມະເຮັງຫຼາຍຂັ້ນຕອນ. ເຫດຜົນແມ່ນການປ່ອຍ isothiocyanates ເຊັ່ນ sulphoraphanes. Sulphoraphanes ເຮັດສອງສິ່ງຫຼັກ. ພວກມັນສົ່ງເສີມ apoptosis (levee 19) ແລະ ກະຕຸ້ນເອນໄຊມ໌ detoxification ໄລຍະສອງໃນຕັບທີ່ເສີມຄວາມເຂັ້ມແຂງໃຫ້ກັບຍີນ p53 ເປັນຜູ້ປົກປ້ອງຈີໂນມຂອງພວກເຮົາ. ຈຸລັງມະເຮັງມັກຈະຕາຍ (necrosis) ເມື່ອສຳຜັດກັບ sulphoraphanes ຢ່າງຕໍ່ເນື່ອງເປັນເວລາດົນ. ຜັກບຣອກໂຄລີຍັງມີສານ metabolite ຂັ້ນສອງທີ່ເອີ້ນວ່າ Indole 3 Carbinol ທີ່ແຕກຕົວຕໍ່ໄປເປັນສານຕ້ານມະເຮັງອີກຊະນິດໜຶ່ງຊື່ວ່າ DIM, diindolylmethane. ທ່ານບໍ່ສາມາດກິນຜັກພວກນີ້ຫຼາຍພໍຖ້າທ່ານເປັນມະເຮັງໃນທັດສະນະຂອງຂ້ອຍ. I3C ຍັງຂັດຂວາງ 16-hydroxyestrone ແລະ ມີປະໂຫຍດຫຼາຍໃນການປ້ອງກັນມະເຮັງເຕົ້ານົມ ແລະ ມະເຮັງຮັງໄຂ່ໃນແມ່ຍິງ ແລະ ມະເຮັງຕ່ອມລູກໝາກໃນຜູ້ຊາຍ.
-
ນີ້ແມ່ນສິ່ງທີ່ຂັດກັບຄວາມເຊື່ອຊຶ່ງຢູ່ໃນຫົວຂອງທ່ານ... ກິນ cholesterol ຫຼາຍໆ. ໂດຍສະເພາະນ້ຳມັນໝາກພ້າວ. ຫຼາຍການສຶກສາທາງລະບາດວິທະຍາສະແດງໃຫ້ເຫັນວ່າລະດັບ cholesterol ໃນເລືອດຕ່ຳສຳພັນກັບອັດຕາການເກີດມະເຮັງສູງ. ນີ້ແມ່ນເຫດຜົນທີ່ການກິນອາຫານ ketogenic Epi-paleo ມີຄວາມໝາຍຫຼາຍ. ເປັນຫຍັງອາຫານແບບ ketogenic? ເພາະມະເຮັງທັງໝົດໃຊ້ກລູໂຄສເປັນວັດຖຸດິບ. ທ່ານຈຳເປັນຕ້ອງປ່ຽນເຊື້ອໄຟຂອງຈຸລັງ. ໄປຊອກຫາ Otto Warburg ໃນ Google ສຳລັບລາຍລະອຽດເພີ່ມເຕີມ. ອາຫານແບບ ketogenic ຄວນມີ MCT ຈາກນ້ຳມັນໝາກພ້າວຫຼາຍ ເພາະພວກມັນໃຫ້ຂໍ້ໄດ້ປຽບຫຼາຍແກ່ຈຸລັງປົກກະຕິກວ່າຈຸລັງມະເຮັງ. ຂໍ້ໄດ້ປຽບນີ້ເຮັດໃຫ້ລະບົບພູມຄຸ້ມກັນຂອງທ່ານສາມາດຕາມທັນຈຸລັງມະເຮັງ ແລະ ທຳລາຍພວກມັນໂດຍໃຊ້ກົນໄກຊີວະວິທະຍາຂອງທ່ານເອງ. ມີຫຼາຍບົດຄວາມໃນວາລະສານມະເຮັງທີ່ພິມເຜີຍແຜ່ສະແດງໃຫ້ເຫັນການເຊື່ອມໂຍງແບບດຽວກັນ.
-
-
 @ d34e832d:383f78d0
2025-04-25 07:09:36
@ d34e832d:383f78d0
2025-04-25 07:09:361. Premise
The demand for high-capacity hard drives has grown exponentially with the expansion of cloud storage, big data, and personal backups. As failure of a storage device can result in significant data loss and downtime, understanding long-term drive reliability is critical. This research seeks to determine the most reliable manufacturer of 10TB+ HDDs by analyzing cumulative drive failure data over ten years from Backblaze, a leader in cloud backup services.
2. Methodology
Data from Backblaze, representing 350,000+ deployed drives, was analyzed to calculate the AFR of 10TB+ models from Seagate, Western Digital (including HGST), and Toshiba. AFR was calculated using cumulative data to reduce volatility and better illustrate long-term reliability trends. Power-on hours were used as the temporal metric to more accurately capture usage-based wear, as opposed to calendar-based aging.
3. Results and Analysis
3.1 Western Digital (including HGST)
- Ultrastar HC530 & HC550 (14TB & 16TB)
- AFR consistently below 0.35% after the initial “burn-in” period.
- Exhibited superior long-term stability.
- HGST Ultrastar HC520 (12TB)
- Demonstrated robust performance with AFR consistently under 0.5%.
- Excellent aging profile after year one.
3.2 Toshiba
- General Performance
- Noted for higher early failure rates (DOA issues), indicating manufacturing or transport inconsistencies.
- After stabilization, most models showed AFRs under 1%, which is within acceptable industry standards.
- Model Variability
- Differences in AFR observed between 4Kn and 512e sector models, suggesting firmware or controller differences may influence longevity.
3.3 Seagate
- Older Models (e.g., Exos X12)
- AFRs often exceeded 1.5%, raising concerns for long-term use in mission-critical applications.
- Newer Models (e.g., Exos X16)
- Improvements seen, with AFRs around 1%, though still higher than WD and HGST counterparts.
- Seagate’s aggressive pricing often makes these drives more attractive for cost-sensitive deployments.
4. Points Drawn
The data reveals a compelling narrative in brand-level reliability trends among high-capacity hard drives. Western Digital, especially through its HGST-derived Ultrastar product lines, consistently demonstrates superior reliability, maintaining exceptionally low Annualized Failure Rates (AFRs) and excellent operational stability across extended use periods. This positions WD as the most dependable option for enterprise-grade and mission-critical storage environments. Toshiba, despite a tendency toward higher early failure rates—often manifesting as Dead-on-Arrival (DOA) units—generally stabilizes to acceptable AFR levels below 1% over time. This indicates potential suitability in deployments where early failure screening and redundancy planning are feasible. In contrast, Seagate’s performance is notably variable. While earlier models displayed higher AFRs, more recent iterations such as the Exos X16 series have shown marked improvement. Nevertheless, Seagate drives continue to exhibit greater fluctuation in reliability outcomes. Their comparatively lower cost structure, however, may render them an attractive option in cost-sensitive or non-critical storage environments, where performance variability is an acceptable trade-off.
It’s crucial to remember that AFR is a probabilistic measure; individual drive failures are still possible regardless of brand or model. Furthermore, newer drive models need additional longitudinal data to confirm their long-term reliability.
5. Consider
Best Overall Choice: Western Digital Ultrastar HC530/HC550
These drives combine top-tier reliability (AFR < 0.35%), mature firmware, and consistent manufacturing quality, making them ideal for enterprise and archival use.Runner-Up (Budget Consideration): Seagate Exos X16
While reliability is slightly lower (AFR ~1%), the Exos series offers excellent value, especially for bulk storage.Cautionary Choice: Toshiba 10TB+ Models
Users should be prepared for potential early failures and may consider pre-deployment burn-in testing.
6. Recommendations for Buyers
- For mission-critical environments: Choose Western Digital Ultrastar models.
- For budget-focused or secondary storage: Seagate Exos offers acceptable risk-to-cost ratio.
- For experimental or non-essential deployments: Toshiba drives post-burn-in are serviceable.
7. Future Work
Based on publicly available Backblaze data, which reflects data center use and may not perfectly map to home or SMB environments. Sample sizes vary by model and may bias certain conclusions. Future research could integrate SMART data analytics, firmware version tracking, and consumer-use data to provide more granular insight.
References
- Backblaze. (2013–2023). Hard Drive Stats. Retrieved from https://www.backblaze.com/blog
- Manufacturer datasheets and reliability reports for Seagate, Western Digital, and Toshiba. -
 @ e4950c93:1b99eccd
2025-05-03 09:46:42
@ e4950c93:1b99eccd
2025-05-03 09:46:42Engel est une marque allemande qui crée des vêtements et accessoires en coton biologique, laine mérinos et soie pour toute la famille.
Matières naturelles utilisées dans les produits
⚠️ Attention, certains produits de cette marque (notamment les soutiens-gorge) contiennent des matières non naturelles, dont :
Catégories de produits proposés
#Vêtements
- Coupes : bébés, enfants, femmes, hommes, unisexe
- Sous-vêtements : boxers, culottes
- Une pièce : bodies
- Hauts : débardeurs, gilets, t-shirts, pulls, vestes
- Bas : pantalons, shorts
- Tête et mains : bonnets
- Nuit : pyjamas
#Maison
- Linge : couvertures, turbulettes
Autres informations
- Certification GOTS
- Certification IVN Best
- Fabriqué en Allemagne
👉 En savoir plus sur le site de la marque
Cet article est publié sur origine-nature.com 🌐 See this article in English
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises ce produit ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don, pour remercier les contribut-eur-ice-s.
-
 @ d34e832d:383f78d0
2025-04-25 06:06:32
@ d34e832d:383f78d0
2025-04-25 06:06:32This walkthrough examines the integration of these three tools as a combined financial instrument, focusing on their functionality, security benefits, and practical applications. Specter Desktop offers a user-friendly interface for managing Bitcoin wallets, Bitcoin Core provides a full node for transaction validation, and Coldcard provides the hardware security necessary to safeguard private keys. Together, these tools offer a robust and secure environment for managing Bitcoin holdings, protecting them from both online and physical threats.
We will explore their individual roles in Bitcoin management, how they can be integrated to offer a cohesive solution, and the installation and configuration process on OpenBSD. Additionally, security considerations and practical use cases will be addressed to demonstrate the advantages of this setup compared to alternative Bitcoin management solutions.
2.1 Specter Desktop
Specter Desktop is a Bitcoin wallet management software that provides a powerful, open-source interface for interacting with Bitcoin nodes. Built with an emphasis on multi-signature wallets and hardware wallet integration, Specter Desktop is designed to serve as an all-in-one solution for users who prioritize security and self-custody. It integrates seamlessly with Bitcoin Core and various hardware wallets, including Coldcard, and supports advanced features such as multi-signature wallets, which offer additional layers of security for managing Bitcoin funds.
2.2 Bitcoin Core
Bitcoin Core is the reference implementation of the Bitcoin protocol and serves as the backbone of the Bitcoin network. Running a Bitcoin Core full node provides users with the ability to independently verify all transactions and blocks on the network, ensuring trustless interaction with the blockchain. This is crucial for achieving full decentralization and autonomy, as Bitcoin Core ensures that users do not rely on third parties to confirm the validity of transactions. Furthermore, Bitcoin Core allows users to interact with the Bitcoin network via the command-line interface or a graphical user interface (GUI), offering flexibility in how one can participate in the Bitcoin ecosystem.
2.3 Coldcard
Coldcard is a Bitcoin hardware wallet that prioritizes security and privacy. It is designed to store private keys offline, away from any internet-connected devices, making it an essential tool for protecting Bitcoin holdings from online threats such as malware or hacking. Coldcard’s secure hardware environment ensures that private keys never leave the device, providing an air-gapped solution for cold storage. Its open-source firmware allows users to audit the wallet’s code and operations, ensuring that the device behaves exactly as expected.
2.4 Roles in Bitcoin Management
Each of these components plays a distinct yet complementary role in Bitcoin management:
- Specter Desktop: Acts as the interface for wallet management and multi-signature wallet configuration.
- Bitcoin Core: Provides a full node for transaction verification and interacts with the Bitcoin network.
- Coldcard: Safeguards private keys by storing them securely in hardware, providing offline signing capabilities for transactions.
Together, these tools offer a comprehensive and secure environment for managing Bitcoin funds.
3. Integration
3.1 How Specter Desktop, Bitcoin Core, and Coldcard Work Together
The integration of Specter Desktop, Bitcoin Core, and Coldcard offers a cohesive solution for managing and securing Bitcoin. Here's how these components interact:
- Bitcoin Core runs as a full node, providing a fully verified and trustless Bitcoin network. It validates all transactions and blocks independently.
- Specter Desktop communicates with Bitcoin Core to manage Bitcoin wallets, including setting up multi-signature wallets and connecting to hardware wallets like Coldcard.
- Coldcard is used to securely store the private keys for Bitcoin transactions. When a transaction is created in Specter Desktop, it is signed offline on the Coldcard device before being broadcasted to the Bitcoin network.
The main advantages of this setup include:
- Self-Sovereignty: By using Bitcoin Core and Coldcard, the user has complete control over their funds and does not rely on third-party services for transaction verification or key management.
- Enhanced Security: Coldcard provides the highest level of security for private keys, protecting them from online attacks and malware. Specter Desktop’s integration with Coldcard ensures a user-friendly method for interacting with the hardware wallet.
- Privacy: Using Bitcoin Core allows users to run their own full node, ensuring that they are not dependent on third-party servers, which could compromise privacy.
This integration, in combination with a user-friendly interface from Specter Desktop, allows Bitcoin holders to manage their funds securely, efficiently, and with full autonomy.
3.2 Advantages of This Setup
The combined use of Specter Desktop, Bitcoin Core, and Coldcard offers several advantages over alternative Bitcoin management solutions:
- Enhanced Security: The use of an air-gapped Coldcard wallet ensures private keys never leave the device, even when signing transactions. Coupled with Bitcoin Core’s full node validation, this setup offers unparalleled protection against online threats and attacks.
- Decentralization: Running a full Bitcoin Core node ensures that the user has full control over transaction validation, removing any dependence on centralized third-party services.
- User-Friendly Interface: Specter Desktop simplifies the management of multi-signature wallets and integrates seamlessly with Coldcard, making it accessible even to non-technical users.
4. Installation on OpenBSD
This section provides a step-by-step guide to installing Specter Desktop, Bitcoin Core, and setting up Coldcard on OpenBSD.
4.1 Installing Bitcoin Core
OpenBSD Bitcoin Core Build Guide
Updated for OpenBSD 7.6
This guide outlines the process of building Bitcoin Core (bitcoind), its command-line utilities, and the Bitcoin GUI (bitcoin-qt) on OpenBSD. It covers necessary dependencies, installation steps, and configuration details specific to OpenBSD.
Table of Contents
- Preparation
- Installing Required Dependencies
- Cloning the Bitcoin Core Repository
- Installing Optional Dependencies
- Wallet Dependencies
- GUI Dependencies
- Building Bitcoin Core
- Configuration
- Compilation
- Resource Limit Adjustments
1. Preparation
Before beginning the build process, ensure your system is up-to-date and that you have the necessary dependencies installed.
1.1 Installing Required Dependencies
As the root user, install the base dependencies required for building Bitcoin Core:
bash pkg_add git cmake boost libeventFor a complete list of all dependencies, refer to
dependencies.md.1.2 Cloning the Bitcoin Core Repository
Next, clone the official Bitcoin Core repository to a directory. All build commands will be executed from this directory.
bash git clone https://github.com/bitcoin/bitcoin.git1.3 Installing Optional Dependencies
Bitcoin Core supports optional dependencies for advanced functionality such as wallet support, GUI features, and notifications. Below are the details for the installation of optional dependencies.
1.3.1 Wallet Dependencies
While it is not necessary to build wallet functionality for running
bitcoindorbitcoin-qt, if you need wallet functionality:-
Descriptor Wallet Support: SQLite is required for descriptor wallet functionality.
bash pkg_add sqlite3 -
Legacy Wallet Support: BerkeleyDB is needed for legacy wallet support. It is recommended to use Berkeley DB 4.8. The BerkeleyDB library from OpenBSD ports cannot be used directly, so you will need to build it from source using the
dependsfolder.Run the following command to build it (adjust the path as necessary):
bash gmake -C depends NO_BOOST=1 NO_LIBEVENT=1 NO_QT=1 NO_ZMQ=1 NO_USDT=1After building BerkeleyDB, set the environment variable
BDB_PREFIXto point to the appropriate directory:bash export BDB_PREFIX="[path_to_berkeleydb]"
1.3.2 GUI Dependencies
Bitcoin Core includes a GUI built with Qt6. To compile the GUI, the following dependencies are required:
-
Qt6: Install the necessary parts of the Qt6 framework for GUI support.
bash pkg_add qt6-qtbase qt6-qttools -
libqrencode: The GUI can generate QR codes for addresses. To enable this feature, install
libqrencode:bash pkg_add libqrencodeIf you don't need QR encoding support, use the
-DWITH_QRENCODE=OFFoption during the configuration step to disable it.
1.3.3 Notification Dependencies
Bitcoin Core can provide notifications through ZeroMQ. If you require this functionality, install ZeroMQ:
bash pkg_add zeromq1.3.4 Test Suite Dependencies
Bitcoin Core includes a test suite for development and testing purposes. To run the test suite, you will need Python 3 and the ZeroMQ Python bindings:
bash pkg_add python py3-zmq
2. Building Bitcoin Core
Once all dependencies are installed, follow these steps to configure and compile Bitcoin Core.
2.1 Configuration
Bitcoin Core offers various configuration options. Below are two common setups:
-
Descriptor Wallet and GUI: Enables descriptor wallet support and the GUI. This requires SQLite and Qt6.
bash cmake -B build -DBUILD_GUI=ONTo see all available configuration options, run:
bash cmake -B build -LH -
Descriptor & Legacy Wallet, No GUI: Enables support for both descriptor and legacy wallets, but no GUI.
bash cmake -B build -DBerkeleyDB_INCLUDE_DIR:PATH="${BDB_PREFIX}/include" -DWITH_BDB=ON
2.2 Compile
After configuration, compile the project using the following command. Use the
-j Noption to parallelize the build process, whereNis the number of CPU cores you want to use.bash cmake --build buildTo run the test suite after building, use:
bash ctest --test-dir buildIf Python 3 is not installed, some tests may be skipped.
2.3 Resource Limit Adjustments
OpenBSD's default resource limits are quite restrictive and may cause build failures, especially due to memory issues. If you encounter memory-related errors, increase the data segment limit temporarily for the current shell session:
bash ulimit -d 3000000To make the change permanent for all users, modify the
datasize-curanddatasize-maxvalues in/etc/login.confand reboot the system.
Now Consider
By following these steps, you will be able to successfully build Bitcoin Core on OpenBSD 7.6. This guide covers the installation of essential and optional dependencies, configuration, and the compilation process. Make sure to adjust the resource limits if necessary, especially when dealing with larger codebases.
4.2 Installing Specter Desktop What To Consider
Specter Installation Guide for OpenBSD with Coldcard
This simply aims to provide OpenBSD users with a comprehensive and streamlined process for installing Specter, a Bitcoin wallet management tool. Tailored to those integrating Coldcard hardware wallets with Specter, this guide will help users navigate the installation process, considering various technical levels and preferences. Whether you're a beginner or an advanced user, the guide will empower you to make informed decisions about which installation method suits your needs best.
Specter Installation Methods on OpenBSD
Specter offers different installation methods to accommodate various technical skills and environments. Here, we explore each installation method in the context of OpenBSD, while considering integration with Coldcard for enhanced security in Bitcoin operations.
1. OS-Specific Installation on OpenBSD
Installing Specter directly from OpenBSD's packages or source is an excellent option for users who prefer system-native solutions. This method ensures that Specter integrates seamlessly with OpenBSD’s environment.
- Advantages:
- Easy Installation: Package managers (if available on OpenBSD) simplify the process.
- System Compatibility: Ensures that Specter works well with OpenBSD’s unique system configurations.
-
Convenience: Can be installed on the same machine that runs Bitcoin Core, offering an integrated solution for managing both Bitcoin Core and Coldcard.
-
Disadvantages:
- System-Specific Constraints: OpenBSD’s minimalistic approach might require manual adjustments, especially in terms of dependencies or running services.
-
Updates: You may need to manually update Specter if updates aren’t regularly packaged for OpenBSD.
-
Ideal Use Case: Ideal for users looking for a straightforward, system-native installation that integrates with the local Bitcoin node and uses the Coldcard hardware wallet.
2. PIP Installation on OpenBSD
For those comfortable working in Python environments, PIP installation offers a flexible approach for installing Specter.
- Advantages:
- Simplicity: If you’re already managing Python environments, PIP provides a straightforward and easy method for installation.
- Version Control: Gives users direct control over the version of Specter being installed.
-
Integration: Works well with any existing Python workflow.
-
Disadvantages:
- Python Dependency Management: OpenBSD users may face challenges when managing dependencies, as Python setups on OpenBSD can be non-standard.
-
Technical Knowledge: Requires familiarity with Python and pip, which may not be ideal for non-technical users.
-
Ideal Use Case: Suitable for Python-savvy users who already use Python-based workflows and need more granular control over their installations.
3. Docker Installation
If you're familiar with Docker, running Specter Desktop in Docker containers is a fantastic way to isolate the installation and avoid conflicts with the OpenBSD system.
- Advantages:
- Isolation: Docker ensures Specter runs in an isolated environment, reducing system conflicts.
- Portability: Once set up, Docker containers can be replicated across various platforms and devices.
-
Consistent Environment: Docker ensures consistency in the Specter installation, regardless of underlying OS differences.
-
Disadvantages:
- Docker Setup: OpenBSD’s Docker support isn’t as seamless as other operating systems, potentially requiring extra steps to get everything running.
-
Complexity: For users unfamiliar with Docker, the initial setup can be more challenging.
-
Ideal Use Case: Best for advanced users familiar with Docker environments who require a reproducible and isolated installation.
4. Manual Build from Source (Advanced Users)
For users looking for full control over the installation process, building Specter from source on OpenBSD offers the most flexibility.
- Advantages:
- Customization: You can customize Specter’s functionality and integrate it deeply into your system or workflow.
-
Control: Full control over the build and version management process.
-
Disadvantages:
- Complex Setup: Requires familiarity with development environments, build tools, and dependency management.
-
Time-Consuming: The process of building from source can take longer, especially on OpenBSD, which may lack certain automated build systems for Specter.
-
Ideal Use Case: Best for experienced developers who want to customize Specter to meet specific needs or integrate Coldcard with unique configurations.
5. Node-Specific Integrations (e.g., Raspiblitz, Umbrel, etc.)
If you’re using a Bitcoin node like Raspiblitz or Umbrel along with Specter, these node-specific integrations allow you to streamline wallet management directly from the node interface.
- Advantages:
- Seamless Integration: Integrates Specter directly into the node's wallet management system.
-
Efficient: Allows for efficient management of both Bitcoin Core and Coldcard in a unified environment.
-
Disadvantages:
- Platform Limitation: Not applicable to OpenBSD directly unless you're running a specific node on the same system.
-
Additional Hardware Requirements: Running a dedicated node requires extra hardware resources.
-
Ideal Use Case: Perfect for users already managing Bitcoin nodes with integrated Specter support and Coldcard hardware wallets.
6. Using Package Managers (Homebrew for Linux/macOS)
If you're running OpenBSD on a machine that also supports Homebrew, this method can simplify installation.
- Advantages:
- Simple Setup: Package managers like Homebrew streamline the installation process.
-
Automated Dependency Management: Handles all dependencies automatically, reducing setup complexity.
-
Disadvantages:
- Platform Limitation: Package managers like Homebrew are more commonly used on macOS and Linux, not on OpenBSD.
-
Version Control: May not offer the latest Specter version depending on the repository.
-
Ideal Use Case: Best for users with Homebrew installed, though it may be less relevant for OpenBSD users.
Installation Decision Tree for OpenBSD with Coldcard
- Do you prefer system-native installation or Docker?
- System-native (OpenBSD-specific packages) → Proceed to installation via OS package manager.
-
Docker → Set up Docker container for isolated Specter installation.
-
Are you comfortable with Python?
- Yes → Install using PIP for Python-based environments.
-
No → Move to direct installation methods like Docker or manual build.
-
Do you have a specific Bitcoin node to integrate with?
- Yes → Consider node-specific integrations like Raspiblitz or Umbrel.
- No → Install using Docker or manual source build.
Now Consider
When installing Specter on OpenBSD, consider factors such as your technical expertise, hardware resources, and the need for integration with Coldcard. Beginners might prefer simpler methods like OS-specific packages or Docker, while advanced users will benefit from building from source for complete control over the installation. Choose the method that best fits your environment to maximize your Bitcoin wallet management capabilities.
4.3 Setting Up Coldcard
Refer to the "Coldcard Setup Documentation" section for the installation and configuration instructions specific to Coldcard. At the end of writing.
5. Security Considerations
When using Specter Desktop, Bitcoin Core, and Coldcard together, users benefit from a layered security approach:
- Bitcoin Core offers transaction validation and network security, ensuring that all transactions are verified independently.
- Coldcard provides air-gapped hardware wallet functionality, ensuring private keys are never exposed to potentially compromised devices.
- Specter Desktop facilitates user-friendly management of multi-signature wallets while integrating the security of Bitcoin Core and Coldcard.
However, users must also be aware of potential security risks, including:
- Coldcard Physical Theft: If the Coldcard device is stolen, the attacker would need the PIN code to access the wallet, but physical security must always be maintained.
- Backup Security: Users must securely back up their Coldcard recovery seed to prevent loss of access to funds.
6. Use Cases and Practical Applications
The integration of Specter Desktop, Bitcoin Core, and Coldcard is especially beneficial for:
- High-Value Bitcoin Holders: Those managing large sums of Bitcoin can ensure top-tier security with a multi-signature wallet setup and Coldcard’s air-gapped security.
- Privacy-Conscious Users: Bitcoin Core allows for full network verification, preventing third-party servers from seeing transaction details.
- Cold Storage Solutions: For users who want to keep their Bitcoin safe long-term, the Coldcard provides a secure offline solution while still enabling easy access via Specter Desktop.
7. Coldcard Setup Documentation
This section should provide clear, step-by-step instructions for configuring and using the Coldcard hardware wallet, including how to pair it with Specter Desktop, set up multi-signature wallets, and perform basic operations like signing transactions.
8. Consider
The system you ant to adopt inculcates, integrating Specter Desktop, Bitcoin Core, and Coldcard provides a powerful, secure, and decentralized solution for managing Bitcoin. This setup not only prioritizes user privacy and security but also provides an intuitive interface for even non-technical users. The combination of full node validation, multi-signature support, and air-gapped hardware wallet storage ensures that Bitcoin holdings are protected from both online and physical threats.
As the Bitcoin landscape continues to evolve, this setup can serve as a robust model for self-sovereign financial management, with the potential for future developments to enhance security and usability.
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ a5142938:0ef19da3
2025-05-03 09:45:38
@ a5142938:0ef19da3
2025-05-03 09:45:38Engel is a German brand that creates clothing and accessories made from organic cotton, merino wool, and silk for the whole family.
Natural materials used in products
⚠️ Warning: some products from this brand (especially bras) contain non-natural materials, including:
Categories of products offered
#Clothing
- Fits: babies, children, women, men, unisex
- Underwear: boxers, panties
- One-piece: bodysuits
- Tops: tank tops, cardigans, t-shirts, sweaters, jackets
- Bottoms: trousers, shorts
- Head & hands: hats
- Nightwear: pyjamas
#Home
- Linen: blankets, sleeping bags
Other information
- GOTS certification
- IVN Best certification
- Made in Germany
👉 Learn more on the brand's website
This article is published on origin-nature.com 🌐 Voir cet article en français
📝 You can contribute to this entry by suggesting edits in comments.
🗣️ Do you use this product? Share your opinion in the comments.
⚡ Happy to have found this information? Support the project by making a donation to thank the contributors.
-
 @ cefb08d1:f419beff
2025-05-03 08:57:18
@ cefb08d1:f419beff
2025-05-03 08:57:18There is a well-known legend about pelicans that has been told for centuries: it was believed that pelican parents would wound their own chests with their beaks to feed their young with their blood. In reality, pelicans actually catch fish in their large beaks and then press their beaks to their chicks’ mouths to feed them. The myth likely arose because young pelicans sometimes peck their mother's chest while competing for food, but the mother does not harm herself intentionally.
originally posted at https://stacker.news/items/970123
-
 @ a296b972:e5a7a2e8
2025-05-03 07:48:25
@ a296b972:e5a7a2e8
2025-05-03 07:48:25Derzeit formiert sich ein neues Gruselkabinett, als Folge einer Pandemie der Ungeeigneten. Kostproben der Unfähigkeit konnte man schon in den aktuellen „Quassel-Shows“ des Staatsfunks „genießen“. Die Riege der Universal-Dilettanten, die noch schnell hochgelobt wurde, macht gerade Platz für Rekruten aus dem Milieu der überzeugten Realitätsverweigerer.
Impfpflichtbefürworter, ideologisch vergiftete Klima- und Gender-Gagaisten, Verteidiger des Russen-Dauer-Feindbilds, Finanzwirtschafts-Ahnungslose, zahllose „Südamerika-Experten“, die davon überzeugt sind, solche zu sein, weil sie unfallfrei eine Banane essen können und weitere, die als einzige Qualifikation das Prädikat „Untauglich“ auszeichnet, geben sich ein neues Stelldichein.
Nach Vorbild des öffentlich-rechtlichen Unfugs bilden sie ein in sich geschlossenes System, das sich gegen Kritik abschotten will, in dem es alles, was sich nach Nicht-nach-dem-Maul geredet anhört, als Hass und Hetze bezeichnet und sich als Hüter der Wahrheit aufspielt.
Begriffe wie „Hass und Hetze“ und „Kriegstüchtigkeit“ werden einem Wortschatz entlehnt, die dem bisher dunkelsten Kapitel der deutschen Geschichte entnommen sind. Zur Abschreckung verwendete Begriffe, im Sinne von „Wehret den Anfängen!“, wie die Anlehnung „Impfen macht frei“ hingegen, werden mit Geldbußen und Haft belegt. Es kommt eben immer darauf an, von wem diese verbrannten Begriffe verwendet werden.
Wenn aus einer Demokratie „Unseredemokratie“ wird, müssen alle Alarmglocken schrillen, weil so Tür und Tor weit aufgerissen werden, um Tendenzen und Ideologien den Einzug zu ermöglichen, die in einer freiheitlich-demokratischen Grundordnung nichts, aber auch rein gar nichts zu suchen haben, weil die Auslegung davon, was „Unseredemokratie“ bedeutet, in den Händen derjenigen liegt, die sich zwar noch als Volksvertreter ausgeben, aber den Willen des Souveräns nicht mehr umsetzen.
Die Meinung und der Wille des Volkes werden maximal ignoriert und unterdrückt. Mit einem „weiter so“ manifestiert sich die Verachtung der Wähler, die in ihrer unterstellten Dummheit bestenfalls noch als Stimmvieh taugen, ansonsten aber zu vernachlässigen sind, wenn das Ziel erreicht ist: Die Macht!
Eine Absichtserklärung, genannt Koalitionsvertrag, ist die Grundlage für „alles kann, nichts muss“. Er lässt so eine unbegrenzte Flexibilität in jede Richtung zu, alles ist möglich. ALLES!
Die Basis der Koalition beruht auf Lügen, sei es in der Migrationspolitik oder in der Neuverschuldung. Das gemeinsame Klüngeln hat schon begonnen, bevor der eigentliche Regierungsauftrag überhaupt erteilt wurde.
Das wirklich einzige, gemeinsame Ziel ist, mit allen Mitteln an der Macht zu bleiben, koste es, was es wolle und eine demokratisch gewählte Opposition, die rund ein Viertel der Wählerstimmen ausmacht, wo immer es geht zu delegitimieren und so klein zu halten, wie es nur eben geht.
Hirngespinste sollen weiter vorangetrieben, die Rückkehr zur Vernunft soll unter allen Umständen verhindert werden, bzw. ist aufgrund mangelnder Kenntnisse und Einsicht gar nicht möglich.
Das Lügen bleibt den Nicht-Volksvertretern vorbehalten, die definieren, was Lüge ist und was nicht, sofern die Kritik vom Volk kommt. Berichtet man über die Politik, spricht man von Unwahrheiten, spricht die Politik über das Volk, sind es Lügen. Überall wird mit zweierlei Maß gemessen.
Die Verachtung des Souveräns wirkt wie ein Bumerang und wird wie durch einen Spiegel auf die Versender zurückgeworfen.
Ein zukünftiger Ex-Bundeskanzler verliert bereits den Rückhalt, noch bevor er in sein Amt eingesetzt wird. Grisu, der kleine Drache, will unbedingt, nur einmal im Leben, Feuerwehrmann werden. Phrasen-Dreschen wird zur Staatsräson.
Ministerposten werden nach maximaler Fachferne verschachert.
Gut ausgebildete Kräfte verlassen das Land, die Wirtschaft stagniert, massive Einbrüche in der Auto-Industrie, der einstigen Vorzeige-Marken in der ganzen Welt. Ja, Autos bauen, das könnten die Deutschen, wenn sie noch dürften.
Wer kann, wandert ab ins Ausland, wo Energiekosten und Steuern ein unternehmerisches Handeln ermöglichen, statt es mit aller Kraft durch gezielte Wirtschaftsvernichtung abzuwürgen. Wo ist der massive Widerstand seitens der Wirtschaftsverbände, der Industrie- und Handelskammern und Groß-Unternehmen? Geht es denen immer noch zu gut?
Recht haben und Recht bekommen waren noch nie so weit auseinander, wie heute.
Die Kirche, in einem christlich geprägten Land, schreibt ihre eigene Lehre um: „Gott ist queer!“ Grenzt das schon an Gotteslästerung aus den eigenen Reihen? Dabei merkt sie offensichtlich nicht, dass sie sich damit selbst abschafft. Wieder einmal springt sie auf den Zug der vorgegebenen Staatsdoktrin auf. Unvergessen die Hakenkreuzfahne über dem Hauptportal am Kölner Dom in der bisher dunkelsten Zeit Deutschlands.
Eine Überzeugung, und seien die Beweggründe mit noch so guten Absichten verbunden, darf nie wieder zu einer Ideologie werden, die nur in die Irre führen kann. Deshalb ist es demokratische Pflicht, auf die Gefahr hinzuweisen, wenn auch nur der leiseste Hauch Anlass zu solchen Befürchtungen gibt. Das gilt für die Kirche, die Politik, die Rechtsprechung und Menschen, von denen man den Eindruck hat, dass sie sich verirrt haben.
Das Zuviel an Fremden wird nicht gestoppt. Eine Minderheit, die bei Verstand geblieben ist, verlässt das Land, wenn es ihr finanziell möglich ist. Andere, die sich das nicht leisten können, müssen ausharren und dabei zusehen, wie ein Land vor die Hunde geht.
Gut integrierte „Gastarbeiter“ schämen sich für den Plebs, der nach Deutschland kommt. Natürlich unter dem Deckmantel der Menschlichkeit, der die Menschlichkeit gegenüber den Bio-Deutschen mit Füßen tritt. Ihr Ansehen, ihr Fleiß und ihre Dankbarkeit, dass sich ihre Vätergeneration hier eine neue Existenz aufbauen konnte, wird mit Füßen getreten. Sie geraten unter einen Generalverdacht, der ihnen schadet. Auch sie haben Jahrzehnte in die Krankenkassen eingezahlt und ihre Steuern brav entrichtet.
Der Polizei sind von staatlicher Seite die Hände gebunden gegen Clan-Kriminalität und asozialem Verhalten durchzugreifen. Sie bilden Parallel-Gesellschaften mit eigenen Regeln und eigenen Gesetzen und die Polizei muss tatenlos dabei zusehen. Banden in Berlin und Duisburg stellen sich über herrschende Gesetze, Roma terrorisieren Kiel, benehmen sich, wie die Axt im Walde. „An Leib und Leben gefährdete Migranten“ werfen, wie in Bochum, Ziegel von Dächern, und gefährden die Bevölkerung an Leib und Leben. Anschließend setzen sie sich mit einem Gartenstuhl auf einem Kamin in die Sonne und träumen vermutlich vom Ausblick auf dem Kilimandscharo. Statt sie bei Kopf und Kragen zu fassen und sofort aus dem Land zu werfen, werden solche irren Taten mit psychischen Problemen aufgrund der Erfahrungen in ihrem Heimatland entschuldigt. Würden sich solche Bekloppte in ihrem eigenen Land vergleichbare Handlungen erlauben, würde sie die Dorfgemeinschaft wahrscheinlich den Löwen zum Fraß vorwerfen.
Jeder, der nicht das in Deutschland geltende Recht akzeptiert und stattdessen seine eigene Auffassung von Recht durchsetzen will, gehört unverzüglich des Landes verwiesen, und es ist Aufgabe des Staates, dafür zu sorgen, dass solche Personen nie wieder einen Fuß über die Grenzen des Landes setzen dürfen. Stattdessen werden die Fahnder verfolgt und die Täter laufen gelassen. Der Staat lässt so zu, dass geltendes Recht unterwandert und außer Kraft gesetzt wird. Seine abschreckende Wirkung geht verloren, weil es in den einschlägigen Kreisen bekannt ist, dass sich jeder aufführen kann, wie er will, ohne, dass es Konsequenzen nach sich zieht.
Gepaart mit Willkür ist das hoch gefährliches Dynamit, dass die Gesellschaft sprengt und eine Gefahr in sich birgt, dass die Gesellschaft ab dem Punkt, wo es unerträglich geworden ist, zur Selbstjustiz greift, und das wäre möglicherweise der Anfang eines Bürgerkriegs.
Für alles ist Geld da. Es werden Schulden in atemberaubender Höhe aufgenommen, vor allem, um die Kriegswirtschaft anzukurbeln, um vor einem Feind - Russland gewappnet zu sein, das nicht das geringste Interesse an einem Land hat, das nichts unversucht lässt, auf irgendeine Art und Weise Selbstmord zu begehen. Einmal muss es doch gelingen!
Und natürlich müssen auch die westlichen Werte im Stellvertreterkrieg zwischen den USA und Russland in der Ukraine verteidigt werden.
Kein Geld ist allerdings für die eigenen Leute da. Im Gegenteil: Wer Flaschen sammelt, muss ab einer bestimmten Höhe der Einnahmen ein Gewerbe anmelden. Aber sonst haben die Sesselfurzer nichts zu tun, oder? Es sollte Geld in die Hand genommen werden, die zunehmende Armut in der Bevölkerung nachhaltig zu stoppen, aus dem Abfahrtsvorschlags-Plan der Bahn wieder einen richtigen Fahrplan zu machen, die Schlagloch-Nostalgie á la DDR abzuschaffen, Brücken wieder ihrem Wesen zuzuführen, nämlich, dass man drüberfahren kann, das ganze Land einer dringenden Generalüberholung zu unterziehen, die Gewinnorientierung aus dem Gesundheitssystem wieder abzuschaffen, die Fallpauschalen samt dem Verursacher in die Wüste zu schicken, Deutschland steuer-sexy zu machen.
Das ist wohl zu viel verlangt, denn diejenigen, die das bewirken könnten, haben keine Not. Die einzige Not, die sie kennen, ist, wie sie immer genug Leim auf Vorrat haben können, um an ihrem Pöstchen kleben zu bleiben. Solche Menschen können nur in einem geschützten Rahmen existieren, weil sie in der Welt da draußen gar nicht zurecht kämen, geschweige denn in der Lage wären, für ihren Lebensunterhalt mit einer wirklichen Arbeit selbst zu sorgen.
Der Staat erfüllt nicht mehr seine Aufgabe für die Sicherheit seiner Bürger zu sorgen. Statt Messer-Attacken und Terror-Anschläge aufzuklären und damit den Bürgern ein Gefühl von Sicherheit zu vermitteln, wird die Aufklärung auf dem Mond im Meer der Stille versenkt. Transparenz: Fehlanzeige. Im besten Fall werden Symptom-Bekämpfungs-Maßnahmen ergriffen, statt die Ursachen zu verunmöglichen. Schilder an Messerverbots-Zonen aufzustellen, manifestieren bestenfalls die Gewissheit der Lächerlichkeit und Unfähigkeit seitens der Messerfachkräfte und der selbstfahrenden Autos, die von niemandem gesteuert werden.
Gleiches gilt für das Nennen der hinlänglich bekannten Verursacher der Sprengung der Nordstream 2-Pipelines, die dem scheidenden Bundeskanzler, an dessen Namen man sich schon jetzt nicht mehr erinnern kann, bekannt gewesen sein müssen. Selbst Trump soll sich auf die Frage, ob die USA maßgeblich daran beteiligt waren, geäußert haben, dass, wenn er auf diese Frage antworten würde, er seinem Land sehr schaden würde. Er könne aber mit Gewissheit sagen, dass es die Russen nicht waren. Immerhin ist eine für ganz Europa wichtige Energieversorgung absichtlich, bewusst und mutwillig zerstört worden. Aber aus Rücksicht darauf, dass die Wahrheit Teile der deutschen Bevölkerung verunsichern könnte, verzichtet man in Berlin auf eine Stellungnahme, lügt wiederholt, dass die Ermittlungen noch andauern und glaubt, dass man die Bürger damit ahnungslos halten kann. Die doofen Deutschen werden auch das noch schlucken.
Vergessen die Verpflichtung: Von deutschem Boden soll nur noch Frieden ausgehen. Vergessen die grauen Gesichter der Männer mit einem hochgeklappten Hosenbein, in der Kinderzeit. Wer von den aktuellen Kriegstreibern war live bei einem Gemetzel dabei, in dem Körperteile herumfliegen und Blut spritzt, in dem Menschen zerfetzt werden oder in ihren Panzern bei lebendigem Leib verbrennen? Viele Dümmste unter den Dummen kennen Krieg nur aus Video-Spielen. Nur einmal live als Zaungast dabei sein, und sehen, wie der halbe Darm aus dem Körper heraushängt, dann würde sich ihr großes Maul schon von alleine schließen.
Immer mehr Deutsche sagen: Das ist nicht mehr mein Staat. Kann man es ihnen verdenken?
Deutschland ist ein Paradebeispiel dafür, wie man in der heutigen Zeit, ein einst in aller Welt hochangesehenes Land, im Handumdrehen wirtschaftlich, politisch, rechtsstaatlich, gesundheitlich, und nicht zuletzt auch gesellschaftlich zerstören kann.
Sowohl innen- als auch außenpolitisch wurde nichts unterlassen, um Deutschland, vom Ausland aus gesehen, in die absolute Lächerlichkeit zu überführen.
Die Dummheit, gepaart mit unerträglicher Überheblichkeit, haben ein Maß erreicht, dass in die Gefährlichkeit übergegangen ist. Deutschland braucht gar keinen Feind von außen, denn der Feind sitzt im eigenen Land und zerstört es von innen heraus.
Der Eindruck taucht auf, dass spätestens mit dem Corona-Ereignis das Schleusentor des Wahnsinns sperrangelweit aufgerissen wurde, und keiner vermag es derzeit wieder zu schließen.
Entweder schließen sich Kräfte zusammen, die noch vorhanden sind, dieses Land von innen heraus zu retten, hierzu tragen auch die Neuen Medien erheblich bei, oder Deutschland ist noch einmal darauf angewiesen, von außen gerettet zu werden.
Zukunftsplanungen werden verunmöglicht. Mindestens eine Generation wird die komplette Lebensplanung geraubt. Man ist gezwungen, von einem Tag auf den anderen zu leben, weil alles derartig unberechenbar geworden ist. Eine junge Familie überlegt sich drei Mal, ob sie noch Kinder in diese Welt setzen will. Wo soll das enden?
Der Alltag in Deutschland gleicht einer Dauer-Vorstellung eines Theater-Stücks. Irgendwie läuft es noch, jedoch es fehlt der Rückhalt. Man versucht seinen Alltag zu meistern, Normalität zu leben, doch über allem schwebt das Damokles-Schwert. Keiner weiß, wie lange was noch gut geht und welchen Irrsinn sich die Realitätsverweigerer als Nächstes ausdenken werden. Manchen gelingt das Verdrängen recht gut. Manche schotten sich vollkommen von schlechten Nachrichten ab. Die Psychologie sagt jedoch, dass jedes erlebte Trauma den Menschen früher oder später einholen wird.
Wetten, wie lange die unheilvolle Allianz der Neuen Nullen halten wird, können ab sofort entgegengenommen werden. Und dann? Wie geht es weiter?
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
(Bild von pixabay)
-
 @ cefb08d1:f419beff
2025-05-03 08:43:37
@ cefb08d1:f419beff
2025-05-03 08:43:37originally posted at https://stacker.news/items/970118
-
 @ d34e832d:383f78d0
2025-04-24 07:22:54
@ d34e832d:383f78d0
2025-04-24 07:22:54Operation
This operational framework delineates a methodologically sound, open-source paradigm for the self-custody of Bitcoin, prominently utilizing Electrum, in conjunction with VeraCrypt-encrypted USB drives designed to effectively emulate the functionality of a cold storage hardware wallet.
The primary aim of this initiative is to empower individual users by providing a mechanism that is economically viable, resistant to coercive pressures, and entirely verifiable. This is achieved by harnessing the capabilities inherent in open-source software and adhering to stringent cryptographic protocols, thereby ensuring an uncompromising stance on Bitcoin sovereignty.
The proposed methodology signifies a substantial advancement over commercially available hardware wallets, as it facilitates the creation of a do-it-yourself air-gapped environment that not only bolsters resilience and privacy but also affirms the principles of decentralization intrinsic to the cryptocurrency ecosystem.
1. The Need For Trustless, Private, and Secure Storage
With Bitcoin adoption increasing globally, the need for trustless, private, and secure storage is critical. While hardware wallets like Trezor and Ledger offer some protection, they introduce proprietary code, closed ecosystems, and third-party risk. This Idea explores an alternative: using Electrum Wallet within an encrypted VeraCrypt volume on a USB flash drive, air-gapped via Tails OS or offline Linux systems.
2. Architecture of the DIY Hardware Wallet
2.1 Core Components
- Electrum Wallet (SegWit, offline mode)
- USB flash drive (≥ 8 GB)
- VeraCrypt encryption software
- Optional: Tails OS bootable environment
2.2 Drive Setup
- Format the USB drive and install VeraCrypt volumes.
- Choose AES + SHA-512 encryption for robust protection.
- Use FAT32 for wallet compatibility with Electrum (under 4GB).
- Enable Hidden Volume for plausible deniability under coercion.
3. Creating the Encrypted Environment
3.1 Initial Setup
- Download VeraCrypt from the official site; verify GPG signatures.
- Encrypt the flash drive and store a plain Electrum AppImage inside.
- Add a hidden encrypted volume with the wallet seed, encrypted QR backups, and optionally, a decoy wallet.
3.2 Mounting Workflow
- Always mount the VeraCrypt volume on an air-gapped computer, ideally booted into Tails OS.
- Never connect the encrypted USB to an internet-enabled system.
4. Air-Gapped Wallet Operations
4.1 Wallet Creation (Offline)
- Generate a new Electrum SegWit wallet inside the mounted VeraCrypt volume.
- Record the seed phrase on paper, or store it in a second hidden volume.
- Export xpub (public key) for use with online watch-only wallets.
4.2 Receiving Bitcoin
- Use watch-only Electrum wallet with the exported xpub on an online system.
- Generate receiving addresses without exposing private keys.
4.3 Sending Bitcoin
- Create unsigned transactions (PSBT) in the watch-only wallet.
- Transfer them via QR code or USB sneakernet to the air-gapped wallet.
- Sign offline using Electrum, then return the signed transaction to the online device for broadcast.
5. OpSec Best Practices
5.1 Physical and Logical Separation
- Use a dedicated machine or a clean Tails OS session every time.
- Keep the USB drive hidden and disconnected unless in use.
- Always dismount the VeraCrypt volume after operations.
5.2 Seed Phrase Security
- Never type the seed on an online machine.
- Consider splitting the seed using Shamir's Secret Sharing or metal backup plates.
5.3 Coercion Resilience
- Use VeraCrypt’s hidden volume feature to store real wallet data.
- Maintain a decoy wallet in the outer volume with nominal funds.
- Practice your recovery and access process until second nature.
6. Tradeoffs vs. Commercial Wallets
| Feature | DIY Electrum + VeraCrypt | Ledger/Trezor | |--------|--------------------------|---------------| | Open Source | ✅ Fully | ⚠️ Partially | | Air-gapped Usage | ✅ Yes | ⚠️ Limited | | Cost | 💸 Free (except USB) | 💰 $50–$250 | | Hidden/Coercion Defense | ✅ Hidden Volume | ❌ None | | QR Signing Support | ⚠️ Manual | ✅ Some models | | Complexity | 🧠 High | 🟢 Low | | Long-Term Resilience | ✅ No vendor risk | ⚠️ Vendor-dependent |
7. Consider
A DIY hardware wallet built with Electrum and VeraCrypt offers an unprecedented level of user-controlled sovereignty in Bitcoin storage. While the technical learning curve may deter casual users, those who value security, privacy, and independence will find this setup highly rewarding. This Operation demonstrates that true Bitcoin ownership requires not only control of private keys, but also a commitment to operational security and digital self-discipline. In a world of growing surveillance and digital coercion, such methods may not be optional—they may be essential.
8. References
- Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
- Electrum Technologies GmbH. “Electrum Documentation.” electrum.org, 2024.
- VeraCrypt. “Documentation.” veracrypt.fr, 2025.
- Tails Project. “The Amnesic Incognito Live System (Tails).” tails.boum.org, 2025.
- Matonis, Jon. "DIY Cold Storage for Bitcoin." Forbes, 2014.
In Addition
🛡️ Create Your Own Secure Bitcoin Hardware Wallet: Electrum + VeraCrypt DIY Guide
Want maximum security for your Bitcoin without trusting third-party devices like Ledger or Trezor?
This guide shows you how to build your own "hardware wallet" using free open-source tools:
✅ Electrum Wallet + ✅ VeraCrypt Encrypted Flash Drive — No extra cost, no vendor risk.Let Go Further
What You’ll Need
- A USB flash drive (8GB minimum, 64-bit recommended)
- A clean computer (preferably old or dedicated offline)
- Internet connection (for setup only, then go air-gapped)
- VeraCrypt software (free, open-source)
- Electrum Bitcoin Wallet AppImage file
Step 1: Download and Verify VeraCrypt
- Go to VeraCrypt Official Website.
- Download the installer for your operating system.
- Verify the GPG signatures to ensure the download isn't tampered with.
👉 [Insert Screenshot Here: VeraCrypt download page]
Pro Tip: Never skip verification when dealing with encryption software!
Step 2: Download Electrum Wallet
- Go to Electrum Official Website.
- Download the Linux AppImage or Windows standalone executable.
- Again, verify the PGP signatures published on the site. 👉 [Insert Screenshot Here: Electrum download page]
Step 3: Prepare and Encrypt Your USB Drive
- Insert your USB drive into the computer.
- Open VeraCrypt and select Create Volume → Encrypt a Non-System Partition/Drive.
- Choose Standard Volume for now (later we'll talk about hidden volumes).
- Select your USB drive, set an extremely strong password (12+ random characters).
- For Encryption Algorithm, select AES and SHA-512 for Hash Algorithm.
- Choose FAT32 as the file system (compatible with Bitcoin wallet sizes under 4GB).
- Format and encrypt. 👉 [Insert Screenshot Here: VeraCrypt creating volume]
Important: This will wipe all existing data on the USB drive!
Step 4: Mount the Encrypted Drive
Whenever you want to use the wallet:
- Open VeraCrypt.
- Select a slot (e.g., Slot 1).
- Click Select Device, choose your USB.
- Enter your strong password and Mount. 👉 [Insert Screenshot Here: VeraCrypt mounted volume]
Step 5: Set Up Electrum in Offline Mode
- Mount your encrypted USB.
- Copy the Electrum AppImage (or EXE) onto the USB inside the encrypted partition.
- Run Electrum from there.
- Select Create New Wallet.
- Choose Standard Wallet → Create New Seed → SegWit.
- Write down your 12-word seed phrase on PAPER.
❌ Never type it into anything else. - Finish wallet creation and disconnect from internet immediately. 👉 [Insert Screenshot Here: Electrum setup screen]
Step 6: Make It Air-Gapped Forever
- Only ever access the encrypted USB on an offline machine.
- Never connect this device to the internet again.
- If possible, boot into Tails OS every time for maximum security.
Pro Tip: Tails OS leaves no trace on the host computer once shut down!
Step 7: (Optional) Set Up a Hidden Volume
For even stronger security:
- Repeat the VeraCrypt process to add a Hidden Volume inside your existing USB encryption.
- Store your real Electrum wallet in the hidden volume.
- Keep a decoy wallet with small amounts of Bitcoin in the outer volume.
👉 This way, if you're ever forced to reveal the password, you can give access to the decoy without exposing your true savings.
Step 8: Receiving Bitcoin
- Export your xpub (extended public key) from the air-gapped Electrum wallet.
- Import it into a watch-only Electrum wallet on your online computer.
- Generate receiving addresses without exposing your private keys.
Step 9: Spending Bitcoin (Safely)
To send Bitcoin later:
- Create a Partially Signed Bitcoin Transaction (PSBT) with the online watch-only wallet.
- Transfer the file (or QR code) offline (via USB or QR scanner).
- Sign the transaction offline with Electrum.
- Bring the signed file/QR back to the online device and broadcast it.
✅ Your private keys never touch the internet!
Step 10: Stay Vigilant
- Always dismount the encrypted drive after use.
- Store your seed phrase securely (preferably in a metal backup).
- Regularly practice recovery drills.
- Update Electrum and VeraCrypt only after verifying new downloads.
🎯 Consider
Building your own DIY Bitcoin hardware wallet might seem complex, but security is never accidental — it is intentional.
By using VeraCrypt encryption and Electrum offline, you control your Bitcoin in a sovereign, verifiable, and bulletproof way.⚡ Take full custody. No companies. No middlemen. Only freedom.
-
 @ a93be9fb:6d3fdc0c
2025-05-03 06:02:56
@ a93be9fb:6d3fdc0c
2025-05-03 06:02:56GG
-
 @ d34e832d:383f78d0
2025-04-24 06:28:48
@ d34e832d:383f78d0
2025-04-24 06:28:48Operation
Central to this implementation is the utilization of Tails OS, a Debian-based live operating system designed for privacy and anonymity, alongside the Electrum Wallet, a lightweight Bitcoin wallet that provides a streamlined interface for secure Bitcoin transactions.
Additionally, the inclusion of advanced cryptographic verification mechanisms, such as QuickHash, serves to bolster integrity checks throughout the storage process. This multifaceted approach ensures a rigorous adherence to end-to-end operational security (OpSec) principles while simultaneously safeguarding user autonomy in the custody of digital assets.
Furthermore, the proposed methodology aligns seamlessly with contemporary cybersecurity paradigms, prioritizing characteristics such as deterministic builds—where software builds are derived from specific source code to eliminate variability—offline key generation processes designed to mitigate exposure to online threats, and the implementation of minimal attack surfaces aimed at reducing potential vectors for exploitation.
Ultimately, this sophisticated approach presents a methodical and secure paradigm for the custody of private keys, thereby catering to the exigencies of high-assurance Bitcoin storage requirements.
1. Cold Storage Refers To The offline Storage
Cold storage refers to the offline storage of private keys used to sign Bitcoin transactions, providing the highest level of protection against network-based threats. This paper outlines a verifiable method for constructing such a storage system using the following core principles:
- Air-gapped key generation
- Open-source software
- Deterministic cryptographic tools
- Manual integrity verification
- Offline transaction signing
The method prioritizes cryptographic security, software verifiability, and minimal hardware dependency.
2. Hardware and Software Requirements
2.1 Hardware
- One 64-bit computer (laptop/desktop)
- 1 x USB Flash Drive (≥8 GB, high-quality brand recommended)
- Paper and pen (for seed phrase)
- Optional: Printer (for xpub QR export)
2.2 Software Stack
- Tails OS (latest ISO, from tails.boum.org)
- Balena Etcher (to flash ISO)
- QuickHash GUI (for SHA-256 checksum validation)
- Electrum Wallet (bundled within Tails OS)
3. System Preparation and Software Verification
3.1 Image Verification
Prior to flashing the ISO, the integrity of the Tails OS image must be cryptographically validated. Using QuickHash:
plaintext SHA256 (tails-amd64-<version>.iso) = <expected_hash>Compare the hash output with the official hash provided on the Tails OS website. This mitigates the risk of ISO tampering or supply chain compromise.
3.2 Flashing the OS
Balena Etcher is used to flash the ISO to a USB drive:
- Insert USB drive.
- Launch Balena Etcher.
- Select the verified Tails ISO.
- Flash to USB and safely eject.
4. Cold Wallet Generation Procedure
4.1 Boot Into Tails OS
- Restart the system and boot into BIOS/UEFI boot menu.
- Select the USB drive containing Tails OS.
- Configure network settings to disable all connectivity.
4.2 Create Wallet in Electrum (Cold)
- Open Electrum from the Tails application launcher.
- Select "Standard Wallet" → "Create a new seed".
- Choose SegWit for address type (for lower fees and modern compatibility).
- Write down the 12-word seed phrase on paper. Never store digitally.
- Confirm the seed.
- Set a strong password for wallet access.
5. Exporting the Master Public Key (xpub)
- Open Electrum > Wallet > Information
- Export the Master Public Key (MPK) for receiving-only use.
- Optionally generate QR code for cold-to-hot usage (wallet watching).
This allows real-time monitoring of incoming Bitcoin transactions without ever exposing private keys.
6. Transaction Workflow
6.1 Receiving Bitcoin (Cold to Hot)
- Use the exported xpub in a watch-only wallet (desktop or mobile).
- Generate addresses as needed.
- Senders deposit Bitcoin to those addresses.
6.2 Spending Bitcoin (Hot Redeem Mode)
Important: This process temporarily compromises air-gap security.
- Boot into Tails (or use Electrum in a clean Linux environment).
- Import the 12-word seed phrase.
- Create transaction offline.
- Export signed transaction via QR code or USB.
- Broadcast using an online device.
6.3 Recommended Alternative: PSBT
To avoid full wallet import: - Use Partially Signed Bitcoin Transactions (PSBT) protocol to sign offline. - Broadcast PSBT using Sparrow Wallet or Electrum online.
7. Security Considerations
| Threat | Mitigation | |-------|------------| | OS Compromise | Use Tails (ephemeral environment, RAM-only) | | Supply Chain Attack | Manual SHA256 verification | | Key Leakage | No network access during key generation | | Phishing/Clone Wallets | Verify Electrum’s signature (when updating) | | Physical Theft | Store paper seed in tamper-evident location |
8. Backup Strategy
- Store 12-word seed phrase in multiple secure physical locations.
- Do not photograph or digitize.
- For added entropy, use Shamir Secret Sharing (e.g., 2-of-3 backups).
9. Consider
Through the meticulous integration of verifiable software solutions, the execution of air-gapped key generation methodologies, and adherence to stringent operational protocols, users have the capacity to establish a Bitcoin cold storage wallet that embodies an elevated degree of cryptographic assurance.
This DIY system presents a zero-dependency alternative to conventional third-party custody solutions and consumer-grade hardware wallets.
Consequently, it empowers individuals with the ability to manage their Bitcoin assets while ensuring full trust minimization and maximizing their sovereign control over private keys and transaction integrity within the decentralized financial ecosystem..
10. References And Citations
Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
“Tails - The Amnesic Incognito Live System.” tails.boum.org, The Tor Project.
“Electrum Bitcoin Wallet.” electrum.org, 2025.
“QuickHash GUI.” quickhash-gui.org, 2025.
“Balena Etcher.” balena.io, 2025.
Bitcoin Core Developers. “Don’t Trust, Verify.” bitcoincore.org, 2025.In Addition
🪙 SegWit vs. Legacy Bitcoin Wallets
⚖️ TL;DR Decision Chart
| If you... | Use SegWit | Use Legacy | |-----------|----------------|----------------| | Want lower fees | ✅ Yes | 🚫 No | | Send to/from old services | ⚠️ Maybe | ✅ Yes | | Care about long-term scaling | ✅ Yes | 🚫 No | | Need max compatibility | ⚠️ Mixed | ✅ Yes | | Run a modern wallet | ✅ Yes | 🚫 Legacy support fading | | Use cold storage often | ✅ Yes | ⚠️ Depends on wallet support | | Use Lightning Network | ✅ Required | 🚫 Not supported |
🔍 1. What Are We Comparing?
There are two major types of Bitcoin wallet address formats:
🏛️ Legacy (P2PKH)
- Format starts with:
1 - Example:
1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa - Oldest, most universally compatible
- Higher fees, larger transactions
- May lack support in newer tools and layer-2 solutions
🛰️ SegWit (P2WPKH)
- Formats start with:
- Nested SegWit (P2SH):
3... - Native SegWit (bech32):
bc1q... - Introduced via Bitcoin Improvement Proposal (BIP) 141
- Smaller transaction sizes → lower fees
- Native support by most modern wallets
💸 2. Transaction Fees
SegWit = Cheaper.
- SegWit reduces the size of Bitcoin transactions in a block.
- This means you pay less per transaction.
- Example: A SegWit transaction might cost 40%–60% less in fees than a legacy one.💡 Why?
Bitcoin charges fees per byte, not per amount.
SegWit removes certain data from the base transaction structure, which shrinks byte size.
🧰 3. Wallet & Service Compatibility
| Category | Legacy | SegWit (Nested / Native) | |----------|--------|---------------------------| | Old Exchanges | ✅ Full support | ⚠️ Partial | | Modern Exchanges | ✅ Yes | ✅ Yes | | Hardware Wallets (Trezor, Ledger) | ✅ Yes | ✅ Yes | | Mobile Wallets (Phoenix, BlueWallet) | ⚠️ Rare | ✅ Yes | | Lightning Support | 🚫 No | ✅ Native SegWit required |
🧠 Recommendation:
If you interact with older platforms or do cross-compatibility testing, you may want to: - Use nested SegWit (address starts with
3), which is backward compatible. - Avoid bech32-only wallets if your exchange doesn't support them (though rare in 2025).
🛡️ 4. Security and Reliability
Both formats are secure in terms of cryptographic strength.
However: - SegWit fixes a bug known as transaction malleability, which helps build protocols on top of Bitcoin (like the Lightning Network). - SegWit transactions are more standardized going forward.
💬 User takeaway:
For basic sending and receiving, both are equally secure. But for future-proofing, SegWit is the better bet.
🌐 5. Future-Proofing
Legacy wallets are gradually being phased out:
- Developers are focusing on SegWit and Taproot compatibility.
- Wallet providers are defaulting to SegWit addresses.
- Fee structures increasingly assume users have upgraded.
🚨 If you're using a Legacy wallet today, you're still safe. But: - Some services may stop supporting withdrawals to legacy addresses. - Your future upgrade path may be more complex.
🚀 6. Real-World Scenarios
🧊 Cold Storage User
- Use SegWit for low-fee UTXOs and efficient backup formats.
- Consider Native SegWit (
bc1q) if supported by your hardware wallet.
👛 Mobile Daily User
- Use Native SegWit for cheaper everyday payments.
- Ideal if using Lightning apps — it's often mandatory.
🔄 Exchange Trader
- Check your exchange’s address type support.
- Consider nested SegWit (
3...) if bridging old + new systems.
📜 7. Migration Tips
If you're moving from Legacy to SegWit:
- Create a new SegWit wallet in your software/hardware wallet.
- Send funds from your old Legacy wallet to the SegWit address.
- Back up the new seed — never reuse the old one.
- Watch out for fee rates and change address handling.
✅ Final User Recommendations
| Use Case | Address Type | |----------|--------------| | Long-term HODL | SegWit (
bc1q) | | Maximum compatibility | SegWit (nested3...) | | Fee-sensitive use | Native SegWit (bc1q) | | Lightning | Native SegWit (bc1q) | | Legacy systems only | Legacy (1...) – short-term only |
📚 Further Reading
- Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
- Bitcoin Core Developers. “Segregated Witness (Consensus Layer Change).” github.com/bitcoin, 2017.
- “Electrum Documentation: Wallet Types.” docs.electrum.org, 2024.
- “Bitcoin Wallet Compatibility.” bitcoin.org, 2025.
- Ledger Support. “SegWit vs Legacy Addresses.” ledger.com, 2024.
-
 @ 4e8933a9:aadeb641
2025-05-03 07:23:55
@ 4e8933a9:aadeb641
2025-05-03 07:23:55XENG là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người chơi một không gian giải trí đa dạng và phong phú. Với giao diện thân thiện và dễ sử dụng, XENG cung cấp cho người chơi rất nhiều trò chơi hấp dẫn từ những tựa game dễ chơi đến những trò đòi hỏi sự chiến lược và tư duy. Những trò chơi này được thiết kế với đồ họa bắt mắt, âm thanh sống động và gameplay hấp dẫn, mang lại cho người chơi những giờ phút thư giãn tuyệt vời. XENG luôn cố gắng cập nhật và bổ sung các tựa game mới để người chơi không cảm thấy nhàm chán và có cơ hội trải nghiệm nhiều điều thú vị. Điều này giúp XENG trở thành một lựa chọn tuyệt vời cho những ai yêu thích không gian giải trí đa dạng và đầy thử thách.
Một trong những yếu tố giúp XENG thu hút đông đảo người chơi chính là hệ thống bảo mật an toàn và hiệu quả. Nền tảng này sử dụng công nghệ mã hóa tiên tiến, giúp bảo vệ thông tin cá nhân và giao dịch của người chơi. Các giao dịch tài chính được thực hiện một cách an toàn và minh bạch, đảm bảo rằng người chơi không phải lo lắng về việc thông tin bị rò rỉ hay bị xâm nhập trái phép. Đội ngũ của XENG luôn chú trọng đến việc bảo vệ quyền lợi của người chơi và đảm bảo một môi trường chơi game an toàn. Nhờ vào sự cam kết này, người chơi có thể hoàn toàn yên tâm khi tham gia các hoạt động giải trí trên nền tảng mà không phải lo lắng về vấn đề bảo mật.
Bên cạnh chất lượng trò chơi và bảo mật, XENG còn đặc biệt chú trọng đến dịch vụ khách hàng. Đội ngũ hỗ trợ khách hàng của XENG luôn sẵn sàng giúp đỡ người chơi trong suốt quá trình trải nghiệm trên nền tảng. Dịch vụ hỗ trợ 24/7 giúp người chơi giải quyết mọi vấn đề, từ kỹ thuật đến các thắc mắc về trò chơi, đảm bảo rằng họ sẽ không gặp phải bất kỳ khó khăn nào khi tham gia. Hơn nữa, XENG cũng tổ chức nhiều chương trình khuyến mãi và sự kiện hấp dẫn, tạo cơ hội cho người chơi nhận được các phần thưởng giá trị. Những chương trình này không chỉ giúp người chơi có thêm niềm vui mà còn tạo ra các cơ hội chiến thắng hấp dẫn. Nhờ những yếu tố này, XENG đã và đang giữ vững được lòng tin của người chơi và trở thành một nền tảng giải trí uy tín và đáng tin cậy.
-
 @ b2caa9b3:9eab0fb5
2025-04-24 06:25:35
@ b2caa9b3:9eab0fb5
2025-04-24 06:25:35Yesterday, I faced one of the most heartbreaking and frustrating experiences of my life. Between 10:00 AM and 2:00 PM, I was held at the Taveta border, denied entry into Kenya—despite having all the necessary documents, including a valid visitor’s permit and an official invitation letter.
The Kenyan Immigration officers refused to speak with me. When I asked for clarification, I was told flatly that I would never be allowed to enter Kenya unless I obtain a work permit. No other reason was given. My attempts to explain that I simply wanted to see my child were ignored. No empathy. No flexibility. No conversation. Just rejection.
While I stood there for hours, held by officials with no explanation beyond a bureaucratic wall, I recorded the experience. I now have several hours of footage documenting what happened—a silent testimony to how a system can dehumanize and block basic rights.
And the situation doesn’t end at the border.
My child, born in Kenya, is also being denied the right to see me. Germany refuses to grant her citizenship, which means she cannot visit me either. The German embassy in Nairobi refuses to assist, stating they won’t get involved. Their silence is loud.
This is not just about paperwork. This is about a child growing up without her father. It’s about a system that chooses walls over bridges, and bureaucracy over humanity. Kenya, by refusing me entry, is keeping a father away from his child. Germany, by refusing to act under §13 StGB, is complicit in that injustice.
In the coming days, I’ll share more about my past travels and how this situation unfolded. I’ll also be releasing videos and updates on TikTok—because this story needs to be heard. Not just for me, but for every parent and child caught between borders and bureaucracies.
Stay tuned—and thank you for standing with me.
-
 @ 866e0139:6a9334e5
2025-05-03 04:53:34
@ 866e0139:6a9334e5
2025-05-03 04:53:34Autor: Friderike Komárek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Was grade war, ist schief.
Wer Frieden will, ist böse.
Wer tötet, der ist lieb.
Gesund ist nur symptomlos krank,
Abstand ist gefühlte Nähe,
Maskenatmen – Gott sei Dank!
Fakten dienen Hass und Hetze,
Lügen tun gut.
Wer Fakten nennt, der wird zensiert,
Wahrheit schafft nur böses Blut.
Für Frieden braucht man Krieg,
für Meinungsfreiheit die Zensur.
Demokratie, die braucht Verbote,
fürs Klima zerstört man die Natur.
Mann ist Frau
und Frau ist Mann.
Ein Glück, dass man
die Biologie jetzt lenken kann!
Der Größenwahn beherrscht die Welt,
hat alles auf den Kopf gestellt.
Kritiker wandern als Kriminelle ins Gefängnis.
Mit ihren Gedanken bringen sie
die andern in Bedrängnis.
Was schief war, das ist grade.
Was grade war, ist schief.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ d34e832d:383f78d0
2025-04-24 06:12:32
@ d34e832d:383f78d0
2025-04-24 06:12:32
Goal
This analytical discourse delves into Jack Dorsey's recent utterances concerning Bitcoin, artificial intelligence, decentralized social networking platforms such as Nostr, and the burgeoning landscape of open-source cryptocurrency mining initiatives.
Dorsey's pronouncements escape the confines of isolated technological fascinations; rather, they elucidate a cohesive conceptual schema wherein Bitcoin transcends its conventional role as a mere store of value—akin to digital gold—and emerges as a foundational protocol intended for the construction of a decentralized, sovereign, and perpetually self-evolving internet ecosystem.
A thorough examination of Dorsey's confluence of Bitcoin with artificial intelligence advancements, adaptive learning paradigms, and integrated social systems reveals an assertion of Bitcoin's position as an entity that evolves beyond simple currency, evolving into a distinctly novel socio-technological organism characterized by its inherent ability to adapt and grow. His vigorous endorsement of native digital currency, open communication protocols, and decentralized infrastructural frameworks is posited here as a revolutionary paradigm—a conceptual
1. The Path
Jack Dorsey, co-founder of Twitter and Square (now Block), has emerged as one of the most compelling evangelists for a decentralized future. His ideas about Bitcoin go far beyond its role as a speculative asset or inflation hedge. In a recent interview, Dorsey ties together themes of open-source AI, peer-to-peer currency, decentralized media, and radical self-education, sketching a future in which Bitcoin is the lynchpin of an emerging technological and social ecosystem. This thesis reviews Dorsey’s statements and offers a critical framework to understand why his vision uniquely positions Bitcoin as the keystone of a post-institutional, digital world.
2. Bitcoin: The Native Currency of the Internet
“It’s the best current manifestation of a native internet currency.” — Jack Dorsey
Bitcoin's status as an open protocol with no central controlling authority echoes the original spirit of the internet: decentralized, borderless, and resilient. Dorsey's framing of Bitcoin not just as a payment system but as the "native money of the internet" is a profound conceptual leap. It suggests that just as HTTP became the standard for web documents, Bitcoin can become the monetary layer for the open web.
This framing bypasses traditional narratives of digital gold or institutional adoption and centers a P2P vision of global value transfer. Unlike central bank digital currencies or platform-based payment rails, Bitcoin is opt-in, permissionless, and censorship-resistant—qualities essential for sovereignty in the digital age.
3. Nostr and the Decentralization of Social Systems
Dorsey’s support for Nostr, an open protocol for decentralized social media, reflects a desire to restore user agency, protocol composability, and speech sovereignty. Nostr’s architecture parallels Bitcoin’s: open, extensible, and resilient to censorship.
Here, Bitcoin serves not just as money but as a network effect driver. When combined with Lightning and P2P tipping, Nostr becomes more than just a Twitter alternative—it evolves into a micropayment-native communication system, a living proof that Bitcoin can power an entire open-source social economy.
4. Open-Source AI and Cognitive Sovereignty
Dorsey's forecast that open-source AI will emerge as an alternative to proprietary systems aligns with his commitment to digital autonomy. If Bitcoin empowers financial sovereignty and Nostr enables communicative freedom, open-source AI can empower cognitive independence—freeing humanity from centralized algorithmic manipulation.
He draws a fascinating parallel between AI learning models and human learning itself, suggesting both can be self-directed, recursive, and radically decentralized. This resonates with the Bitcoin ethos: systems should evolve through transparent, open participation—not gatekeeping or institutional control.
5. Bitcoin Mining: Sovereignty at the Hardware Layer
Block’s initiative to create open-source mining hardware is a direct attempt to counter centralization in Bitcoin’s infrastructure. ASIC chip development and mining rig customization empower individuals and communities to secure the network directly.
This move reinforces Dorsey’s vision that true decentralization requires ownership at every layer, including hardware. It is a radical assertion of vertical sovereignty—from protocol to interface to silicon.
6. Learning as the Core Protocol
“The most compounding skill is learning itself.” — Jack Dorsey
Dorsey’s deepest insight is that the throughline connecting Bitcoin, AI, and Nostr is not technology—it’s learning. Bitcoin represents more than code; it’s a living experiment in voluntary consensus, a distributed educational system in cryptographic form.
Dorsey’s emphasis on meditation, intensive retreats, and self-guided exploration mirrors the trustless, sovereign nature of Bitcoin. Learning becomes the ultimate protocol: recursive, adaptive, and decentralized—mirroring AI models and Bitcoin nodes alike.
7. Critical Risks and Honest Reflections
Dorsey remains honest about Bitcoin’s current limitations:
- Accessibility: UX barriers for onboarding new users.
- Usability: Friction in everyday use.
- State-Level Adoption: Risks of co-optation as mere digital gold.
However, his caution enhances credibility. His focus remains on preserving Bitcoin as a P2P electronic cash system, not transforming it into another tool of institutional control.
8. Bitcoin as a Living System
What emerges from Dorsey's vision is not a product pitch, but a philosophical reorientation: Bitcoin, Nostr, and open AI are not discrete tools—they are living systems forming a new type of civilization stack.
They are not static infrastructures, but emergent grammars of human cooperation, facilitating value exchange, learning, and community formation in ways never possible before.
Bitcoin, in this view, is not merely stunningly original—it is civilizationally generative, offering not just monetary innovation but a path to software-upgraded humanity.
Works Cited and Tools Used
Dorsey, Jack. Interview on Bitcoin, AI, and Decentralization. April 2025.
Nakamoto, Satoshi. “Bitcoin: A Peer-to-Peer Electronic Cash System.” 2008.
Nostr Protocol. https://nostr.com.
Block, Inc. Bitcoin Mining Hardware Initiatives. 2024.
Obsidian Canvas. Decentralized Note-Taking and Networked Thinking. 2025. -
 @ 6389be64:ef439d32
2025-05-03 07:17:36
@ 6389be64:ef439d32
2025-05-03 07:17:36In Jewish folklore, the golem—shaped from clay—is brought to life through sacred knowledge. Clay’s negative charge allows it to bind nutrients and water, echoing its mythic function as a vessel of potential.
Biochar in Amazonian terra preta shares this trait: it holds life-sustaining ions and harbors living intention. Both materials, inert alone, become generative through human action. The golem and black earths exist in parallel—one cultural, one ecological—shaping the lifeless into something that serves, protects, and endures.
originally posted at https://stacker.news/items/970089
-
 @ d9a329af:bef580d7
2025-05-03 04:20:42
@ d9a329af:bef580d7
2025-05-03 04:20:42To be clear, this is 100% my subjective opinion on the alternatives to popular music, as it has become practically a formula of witchcraft, pseudoscience and mysticism. There is nothing you can do to get me to listen to Western pop music from the late 2010's to now. I could certainly listen to almost anything... just not modern pop, which is now completely backwards.
Most examples of compositions for these genres will be my own, unless otherwise stated. The genres on this list are in no particular order, though my favorite of which will be first: 1. Bossa Nova
Bossa Nova is a subgenre of jazz from Brazil, created in the 1950's as a mix of standard jazz and samba rhythms in a more gentle and relaxing manner. This genre's most famous songs are Tom Jobim's The Girl from Ipanema (found in albums like Getz/Gilberto), Wave, and even Triste. Most of the music is written in 2/4 time signature, and any key is almost acceptable. It's called Afro-Brazilian Jazz for a reason after all. I have a ton of compositions I produced, from Forget and Regret, to Rabbit Theory, Beaches of Gensokyo Past, Waveside, and even Willows of Ice to name a few of them.
- Metal
This is an umbrella term for many subgenres of this fork of hard rock, with more distorted guitars, speedy and technical writing, vocals that sound demonic (some subgenres don't have that), or sometimes, chaotic lyrics and downright nasty ones if you look deep enough. If you want to get into it, just make sure it's not Black Metal (it's weird), Blackened Metal (Any subgenre of metal that's been inserted with elements of Black Metal), Metalcore, or any other genre that has vocals that aren't the best to hear (these are vocal fries that are really good if you're into the weird demonic sounds). This isn't for the faint of heart. Instrumental metal is good though, and an example is my composition from Touhou Igousaken called A Sly Foxy Liar if you want to know what techincal groove metal is like at a glance.
- Touhou-style
I can attest to this one, as I produced bossa nova with a Touhou-like writing style. Touhou Project is a series of action video games created by one guy (Jun'ya Outa, a.k.a. ZUN), and are usually bullet curtain games in the main franchise, with some official spinoffs that are also action games (fighting games like Touhou 12.3 ~ Hisoutensoku). What I'm referring to here is music written by ZUN himself (He does almost everything for Touhou Project, and he's really good at it), or fans that write to his style with their own flair. I did this once with my composition, Toiled Bubble, which is from my self-titled EP. I probably wouldn't do much with it to be fair, and stick to bossa nova (my main genre if you couldn't tell).
- Hip-Hop/Rap
This can get subjective here, but old-school rap and hip-hop... give me more of it. Before it became corrupted with all kinds of immoral things, hip-hop and rap were actually very good for their time. These were new, innovative and creative with how lyrics were written. Nowadays, while we're talking about cars, unspeakable acts, money, and just being dirtbags, artists in this genre back then were much classier than that. I fit in the latter category with my piece entitled, Don't Think, Just Roast, where I called out antis for a Vtuber agency who wanted to give its talent a hard time. It didn't get much traction on YouTube, because I'm not a well-known artist (I'm considered a nobody in the grand scheme of things. I'd like to get it fixed, but I don't want a record deal... I'd have to become a Pharisee or a Jesuit for that).
- Synthwave
This is a genre of electronic music focused on 80's and 90's synths being used to carry a composition. Nowadays, we have plugins like Vital, Serum, Surge and others to create sounds we would otherwise be hearing on an 80's or 90's keyboard. An example of this is my composition, Wrenched Torque, which was composed for a promotion I did with RAES when he released his Vital synth pack.
More are to come in future installments of this series, and I will adjust the title of this one accordingly if y'all have any ideas of genres I should look into.
-
 @ d34e832d:383f78d0
2025-04-24 05:56:06
@ d34e832d:383f78d0
2025-04-24 05:56:06Idea
Through the integration of Optical Character Recognition (OCR), Docker-based deployment, and secure remote access via Twin Gate, Paperless NGX empowers individuals and small organizations to digitize, organize, and retrieve documents with minimal friction. This research explores its technical infrastructure, real-world applications, and how such a system can redefine document archival practices for the digital age.
Agile, Remote-Accessible, and Searchable Document System
In a world of increasing digital interdependence, managing physical documents is becoming not only inefficient but also environmentally and logistically unsustainable. The demand for agile, remote-accessible, and searchable document systems has never been higher—especially for researchers, small businesses, and archival professionals. Paperless NGX, an open-source platform, addresses these needs by offering a streamlined, secure, and automated way to manage documents digitally.
This Idea explores how Paperless NGX facilitates the transition to a paperless workflow and proposes best practices for sustainable, scalable usage.
Paperless NGX: The Platform
Paperless NGX is an advanced fork of the original Paperless project, redesigned with modern containers, faster performance, and enhanced community contributions. Its core functions include:
- Text Extraction with OCR: Leveraging the
ocrmypdfPython library, Paperless NGX can extract searchable text from scanned PDFs and images. - Searchable Document Indexing: Full-text search allows users to locate documents not just by filename or metadata, but by actual content.
- Dockerized Setup: A ready-to-use Docker Compose environment simplifies deployment, including the use of setup scripts for Ubuntu-based servers.
- Modular Workflows: Custom triggers and automation rules allow for smart processing pipelines based on file tags, types, or email source.
Key Features and Technical Infrastructure
1. Installation and Deployment
The system runs in a containerized environment, making it highly portable and isolated. A typical installation involves: - Docker Compose with YAML configuration - Volume mapping for persistent storage - Optional integration with reverse proxies (e.g., Nginx) for HTTPS access
2. OCR and Indexing
Using
ocrmypdf, scanned documents are processed into fully searchable PDFs. This function dramatically improves retrieval, especially for archived legal, medical, or historical records.3. Secure Access via Twin Gate
To solve the challenge of secure remote access without exposing the network, Twin Gate acts as a zero-trust access proxy. It encrypts communication between the Paperless NGX server and the client, enabling access from anywhere without the need for traditional VPNs.
4. Email Integration and Ingestion
Paperless NGX can ingest attachments directly from configured email folders. This feature automates much of the document intake process, especially useful for receipts, invoices, and academic PDFs.
Sustainable Document Management Workflow
A practical paperless strategy requires not just tools, but repeatable processes. A sustainable workflow recommended by the Paperless NGX community includes:
- Capture & Tagging
All incoming documents are tagged with a default “inbox” tag for triage. - Physical Archive Correlation
If the physical document is retained, assign it a serial number (e.g., ASN-001), which is matched digitally. - Curation & Tagging
Apply relevant category and topic tags to improve searchability. - Archival Confirmation
Remove the “inbox” tag once fully processed and categorized.
Backup and Resilience
Reliability is key to any archival system. Paperless NGX includes backup functionality via: - Cron job–scheduled Docker exports - Offsite and cloud backups using rsync or encrypted cloud drives - Restore mechanisms using documented CLI commands
This ensures document availability even in the event of hardware failure or data corruption.
Limitations and Considerations
While Paperless NGX is powerful, it comes with several caveats: - Technical Barrier to Entry: Requires basic Docker and Linux skills to install and maintain. - OCR Inaccuracy for Handwritten Texts: The OCR engine may struggle with cursive or handwritten documents. - Plugin and Community Dependency: Continuous support relies on active community contribution.
Consider
Paperless NGX emerges as a pragmatic and privacy-centric alternative to conventional cloud-based document management systems, effectively addressing the critical challenges of data security and user autonomy.
The implementation of advanced Optical Character Recognition (OCR) technology facilitates the indexing and searching of documents, significantly enhancing information retrieval efficiency.
Additionally, the platform offers secure remote access protocols that ensure data integrity while preserving the confidentiality of sensitive information during transmission.
Furthermore, its customizable workflow capabilities empower both individuals and organizations to precisely tailor their data management processes, thereby reclaiming sovereignty over their information ecosystems.
In an era increasingly characterized by a shift towards paperless methodologies, the significance of solutions such as Paperless NGX cannot be overstated; they play an instrumental role in engineering a future in which information remains not only accessible but also safeguarded and sustainably governed.
In Addition
To Further The Idea
This technical paper presents an optimized strategy for transforming an Intel NUC into a compact, power-efficient self-hosted server using Ubuntu. The setup emphasizes reliability, low energy consumption, and cost-effectiveness for personal or small business use. Services such as Paperless NGX, Nextcloud, Gitea, and Docker containers are examined for deployment. The paper details hardware selection, system installation, secure remote access, and best practices for performance and longevity.
1. Cloud sovereignty, Privacy, and Data Ownership
As cloud sovereignty, privacy, and data ownership become critical concerns, self-hosting is increasingly appealing. An Intel NUC (Next Unit of Computing) provides an ideal middle ground between Raspberry Pi boards and enterprise-grade servers—balancing performance, form factor, and power draw. With Ubuntu LTS and Docker, users can run a full suite of services with minimal overhead.
2. Hardware Overview
2.1 Recommended NUC Specifications:
| Component | Recommended Specs | |------------------|-----------------------------------------------------| | Model | Intel NUC 11/12 Pro (e.g., NUC11TNHi5, NUC12WSKi7) | | CPU | Intel Core i5 or i7 (11th/12th Gen) | | RAM | 16GB–32GB DDR4 (dual channel preferred) | | Storage | 512GB–2TB NVMe SSD (Samsung 980 Pro or similar) | | Network | Gigabit Ethernet + Optional Wi-Fi 6 | | Power Supply | 65W USB-C or barrel connector | | Cooling | Internal fan, well-ventilated location |
NUCs are also capable of dual-drive setups and support for Intel vPro for remote management on some models.
3. Operating System and Software Stack
3.1 Ubuntu Server LTS
- Version: Ubuntu Server 22.04 LTS
- Installation Method: Bootable USB (Rufus or Balena Etcher)
- Disk Partitioning: LVM with encryption recommended for full disk security
- Security:
- UFW (Uncomplicated Firewall)
- Fail2ban
- SSH hardened with key-only login
bash sudo apt update && sudo apt upgrade sudo ufw allow OpenSSH sudo ufw enable
4. Docker and System Services
Docker and Docker Compose streamline the deployment of isolated, reproducible environments.
4.1 Install Docker and Compose
bash sudo apt install docker.io docker-compose sudo systemctl enable docker4.2 Common Services to Self-Host:
| Application | Description | Access Port | |--------------------|----------------------------------------|-------------| | Paperless NGX | Document archiving and OCR | 8000 | | Nextcloud | Personal cloud, contacts, calendar | 443 | | Gitea | Lightweight Git repository | 3000 | | Nginx Proxy Manager| SSL proxy for all services | 81, 443 | | Portainer | Docker container management GUI | 9000 | | Watchtower | Auto-update containers | - |
5. Network & Remote Access
5.1 Local IP & Static Assignment
- Set a static IP for consistent access (via router DHCP reservation or Netplan).
5.2 Access Options
- Local Only: VPN into local network (e.g., WireGuard, Tailscale)
- Remote Access:
- Reverse proxy via Nginx with Certbot for HTTPS
- Twin Gate or Tailscale for zero-trust remote access
- DNS via DuckDNS, Cloudflare
6. Performance Optimization
- Enable
zramfor compressed RAM swap - Trim SSDs weekly with
fstrim - Use Docker volumes, not bind mounts for stability
- Set up unattended upgrades:
bash sudo apt install unattended-upgrades sudo dpkg-reconfigure --priority=low unattended-upgrades
7. Power and Environmental Considerations
- Idle Power Draw: ~7–12W (depending on configuration)
- UPS Recommended: e.g., APC Back-UPS 600VA
- Use BIOS Wake-on-LAN if remote booting is needed
8. Maintenance and Monitoring
- Monitoring: Glances, Netdata, or Prometheus + Grafana
- Backups:
- Use
rsyncto external drive or NAS - Cloud backup options: rclone to Google Drive, S3
- Paperless NGX backups:
docker compose exec -T web document-exporter ...
9. Consider
Running a personal server using an Intel NUC and Ubuntu offers a private, low-maintenance, and modular solution to digital infrastructure needs. It’s an ideal base for self-hosting services, offering superior control over data and strong security with the right setup. The NUC's small form factor and efficient power usage make it an optimal home server platform that scales well for many use cases.
- Text Extraction with OCR: Leveraging the
-
 @ d34e832d:383f78d0
2025-04-24 05:14:14
@ d34e832d:383f78d0
2025-04-24 05:14:14Idea
By instituting a robust network of conceptual entities, referred to as 'Obsidian nodes'—which are effectively discrete, idea-centric notes—researchers are empowered to establish a resilient and non-linear archival framework for knowledge accumulation.
These nodes, intricately connected via hyperlinks and systematically organized through the graphical interface of the Obsidian Canvas, facilitate profound intellectual exploration and the synthesis of disparate domains of knowledge.
Consequently, this innovative workflow paradigm emphasizes semantic precision and the interconnectedness of ideas, diverging from conventional, source-centric information architectures prevalent in traditional academic practices.
Traditional research workflows often emphasize organizing notes by source, resulting in static, siloed knowledge that resists integration and insight. With the rise of personal knowledge management (PKM) tools like Obsidian, it becomes possible to structure information in a way that mirrors the dynamic and interconnected nature of human thought.
At the heart of this approach are Obsidian nodes—atomic, standalone notes representing single ideas, arguments, or claims. These nodes form the basis of a semantic research network, made visible and manageable via Obsidian’s graph view and Canvas feature. This thesis outlines how such a framework enhances understanding, supports creativity, and aligns with best practices in information architecture.
Obsidian Nodes: Atomic Units of Thought
An Obsidian node is a note crafted to encapsulate one meaningful concept or question. It is:
- Atomic: Contains only one idea, making it easier to link and reuse.
- Context-Independent: Designed to stand on its own, without requiring the original source for meaning.
- Networked: Linked to other Obsidian nodes through backlinks and tags.
This system draws on the principles of the Zettelkasten method, but adapts them to the modern, markdown-based environment of Obsidian.
Benefits of Node-Based Note-Taking
- Improved Retrieval: Ideas can be surfaced based on content relevance, not source origin.
- Cross-Disciplinary Insight: Linking between concepts across fields becomes intuitive.
- Sustainable Growth: Each new node adds value to the network without redundancy.
Graph View: Visualizing Connections
Obsidian’s graph view offers a macro-level overview of the knowledge graph, showing how nodes interrelate. This encourages serendipitous discovery and identifies central or orphaned concepts that need further development.
- Clusters emerge around major themes.
- Hubs represent foundational ideas.
- Bridges between nodes show interdisciplinary links.
The graph view isn’t just a map—it’s an evolving reflection of intellectual progress.
Canvas: Thinking Spatially with Digital Notes
Obsidian Canvas acts as a digital thinking space. Unlike the abstract graph view, Canvas allows for spatial arrangement of Obsidian nodes, images, and ideas. This supports visual reasoning, ideation, and project planning.
Use Cases of Canvas
- Synthesizing Ideas: Group related nodes in physical proximity.
- Outlining Arguments: Arrange claims into narrative or logic flows.
- Designing Research Papers: Lay out structure and integrate supporting points visually.
Canvas brings a tactile quality to digital thinking, enabling workflows similar to sticky notes, mind maps, or corkboard pinning—but with markdown-based power and extensibility.
Template and Workflow
To simplify creation and encourage consistency, Obsidian nodes are generated using a templater plugin. Each node typically includes:
```markdown
{{title}}
Tags: #topic #field
Linked Nodes: [[Related Node]]
Summary: A 1-2 sentence idea explanation.
Source: [[Source Note]]
Date Created: {{date}}
```The Canvas workspace pulls these nodes as cards, allowing for arrangement, grouping, and visual tracing of arguments or research paths.
Discussion and Challenges
While this approach enhances creativity and research depth, challenges include:
- Initial Setup: Learning and configuring plugins like Templater, Dataview, and Canvas.
- Overlinking or Underlinking: Finding the right granularity in note-making takes practice.
- Scalability: As networks grow, maintaining structure and avoiding fragmentation becomes crucial.
- Team Collaboration: While Git can assist, Obsidian remains largely optimized for solo workflows.
Consider
Through the innovative employment of Obsidian's interconnected nodes and the Canvas feature, researchers are enabled to construct a meticulously engineered semantic architecture that reflects the intricate topology of their knowledge frameworks.
This paradigm shift facilitates a transformation of conventional note-taking, evolving this practice from a static, merely accumulative repository of information into a dynamic and adaptive cognitive ecosystem that actively engages with the user’s thought processes. With methodological rigor and a structured approach, Obsidian transcends its role as mere documentation software, evolving into both a secondary cognitive apparatus and a sophisticated digital writing infrastructure.
This dual functionality significantly empowers the long-term intellectual endeavors and creative pursuits of students, scholars, and lifelong learners, thereby enhancing their capacity for sustained engagement with complex ideas.
-
 @ d34e832d:383f78d0
2025-04-24 05:04:55
@ d34e832d:383f78d0
2025-04-24 05:04:55A Knowledge Management Framework for your Academic Writing
Idea Approach
The primary objective of this framework is to streamline and enhance the efficiency of several critical academic processes, namely the reading, annotation, synthesis, and writing stages inherent to doctoral studies.
By leveraging established best practices from various domains, including digital note-taking methodologies, sophisticated knowledge management techniques, and the scientifically-grounded principles of spaced repetition systems, this proposed workflow is adept at optimizing long-term retention of information, fostering the development of novel ideas, and facilitating the meticulous preparation of manuscripts. Furthermore, this integrated approach capitalizes on Zotero's robust annotation functionalities, harmoniously merged with Obsidian's Zettelkasten-inspired architecture, thereby enriching the depth and structural coherence of academic inquiry, ultimately leading to more impactful scholarly contributions.
Doctoral research demands a sophisticated approach to information management, critical thinking, and synthesis. Traditional systems of note-taking and bibliography management are often fragmented and inefficient, leading to cognitive overload and disorganized research outputs. This thesis proposes a workflow that leverages Zotero for reference management, Obsidian for networked note-taking, and Anki for spaced repetition learning—each component enhanced by a set of plugins, templates, and color-coded systems.
2. Literature Review and Context
2.1 Digital Research Workflows
Recent research in digital scholarship has highlighted the importance of structured knowledge environments. Tools like Roam Research, Obsidian, and Notion have gained traction among academics seeking flexibility and networked thinking. However, few workflows provide seamless interoperability between reference management, reading, and idea synthesis.
2.2 The Zettelkasten Method
Originally developed by sociologist Niklas Luhmann, the Zettelkasten ("slip-box") method emphasizes creating atomic notes—single ideas captured and linked through context. This approach fosters long-term idea development and is highly compatible with digital graph-based note systems like Obsidian.
3. Zotero Workflow: Structured Annotation and Tagging
Zotero serves as the foundational tool for ingesting and organizing academic materials. The built-in PDF reader is augmented through a color-coded annotation schema designed to categorize information efficiently:
- Red: Refuted or problematic claims requiring skepticism or clarification
- Yellow: Prominent claims, novel hypotheses, or insightful observations
- Green: Verified facts or claims that align with the research narrative
- Purple: Structural elements like chapter titles or section headers
- Blue: Inter-author references or connections to external ideas
- Pink: Unclear arguments, logical gaps, or questions for future inquiry
- Orange: Precise definitions and technical terminology
Annotations are accompanied by tags and notes in Zotero, allowing robust filtering and thematic grouping.
4. Obsidian Integration: Bridging Annotation and Synthesis
4.1 Plugin Architecture
Three key plugins optimize Obsidian’s role in the workflow:
- Zotero Integration (via
obsidian-citation-plugin): Syncs annotated PDFs and metadata directly from Zotero - Highlighter: Enables color-coded highlights in Obsidian, mirroring Zotero's scheme
- Templater: Automates formatting and consistency using Nunjucks templates
A custom keyboard shortcut (e.g.,
Ctrl+Shift+Z) is used to trigger the extraction of annotations into structured Obsidian notes.4.2 Custom Templating
The templating system ensures imported notes include:
- Citation metadata (title, author, year, journal)
- Full-color annotations with comments and page references
- Persistent notes for long-term synthesis
- An embedded bibtex citation key for seamless referencing
5. Zettelkasten and Atomic Note Generation
Obsidian’s networked note system supports idea-centered knowledge development. Each note captures a singular, discrete idea—independent of the source material—facilitating:
- Thematic convergence across disciplines
- Independent recombination of ideas
- Emergence of new questions and hypotheses
A standard atomic note template includes: - Note ID (timestamp or semantic UID) - Topic statement - Linked references - Associated atomic notes (via backlinks)
The Graph View provides a visual map of conceptual relationships, allowing researchers to track the evolution of their arguments.
6. Canvas for Spatial Organization
Obsidian’s Canvas plugin is used to mimic physical research boards: - Notes are arranged spatially to represent conceptual clusters or chapter structures - Embedded visual content enhances memory retention and creative thought - Notes and cards can be grouped by theme, timeline, or argumentative flow
This supports both granular research and holistic thesis design.
7. Flashcard Integration with Anki
Key insights, definitions, and questions are exported from Obsidian to Anki, enabling spaced repetition of core content. This supports: - Preparation for comprehensive exams - Retention of complex theories and definitions - Active recall training during literature reviews
Flashcards are automatically generated using Obsidian-to-Anki bridges, with tagging synced to Obsidian topics.
8. Word Processor Integration and Writing Stage
Zotero’s Word plugin simplifies: - In-text citation - Automatic bibliography generation - Switching between citation styles (APA, Chicago, MLA, etc.)
Drafts in Obsidian are later exported into formal academic writing environments such as Microsoft Word or LaTeX editors for formatting and submission.
9. Discussion and Evaluation
The proposed workflow significantly reduces friction in managing large volumes of information and promotes deep engagement with source material. Its modular nature allows adaptation for various disciplines and writing styles. Potential limitations include: - Initial learning curve - Reliance on plugin maintenance - Challenges in team-based collaboration
Nonetheless, the ability to unify reading, note-taking, synthesis, and writing into a seamless ecosystem offers clear benefits in focus, productivity, and academic rigor.
10. Consider
This idea demonstrates that a well-structured digital workflow using Zotero and Obsidian can transform the PhD research process. It empowers researchers to move beyond passive reading into active knowledge creation, aligned with the long-term demands of scholarly writing. Future iterations could include AI-assisted summarization, collaborative graph spaces, and greater mobile integration.
9. Evaluation Of The Approach
While this workflow offers significant advantages in clarity, synthesis, and long-term idea development, several limitations must be acknowledged:
-
Initial Learning Curve: New users may face a steep learning curve when setting up and mastering the integrated use of Zotero, Obsidian, and their associated plugins. Understanding markdown syntax, customizing templates in Templater, and configuring citation keys all require upfront time investment. However, this learning period can be offset by the long-term gains in productivity and mental clarity.
-
Plugin Ecosystem Volatility: Since both Obsidian and many of its key plugins are maintained by open-source communities or individual developers, updates can occasionally break workflows or require manual adjustments.
-
Interoperability Challenges: Synchronizing metadata, highlights, and notes between systems (especially on multiple devices or operating systems) may present issues if not managed carefully. This includes Zotero’s Better BibTeX keys, Obsidian sync, and Anki integration.
-
Limited Collaborative Features: This workflow is optimized for individual use. Real-time collaboration on notes or shared reference libraries may require alternative platforms or additional tooling.
Despite these constraints, the workflow remains highly adaptable and has proven effective across disciplines for researchers aiming to build a durable intellectual infrastructure over the course of a PhD.
9. Evaluation Of The Approach
While the Zotero–Obsidian workflow dramatically improves research organization and long-term knowledge retention, several caveats must be considered:
-
Initial Learning Curve: Mastery of this workflow requires technical setup and familiarity with markdown, citation keys, and plugin configuration. While challenging at first, the learning effort is front-loaded and pays off in efficiency over time.
-
Reliance on Plugin Maintenance: A key risk of this system is its dependence on community-maintained plugins. Tools like Zotero Integration, Templater, and Highlighter are not officially supported by Obsidian or Zotero core teams. This means updates or changes to the Obsidian API or plugin repository may break functionality or introduce bugs. Active plugin support is crucial to the system’s longevity.
-
Interoperability and Syncing Issues: Managing synchronization across Zotero, Obsidian, and Anki—especially across multiple devices—can lead to inconsistencies or data loss without careful setup. Users should ensure robust syncing solutions (e.g. Obsidian Sync, Zotero WebDAV, or GitHub backup).
-
Limited Collaboration Capabilities: This setup is designed for solo research workflows. Collaborative features (such as shared note-taking or group annotations) are limited and may require alternate solutions like Notion, Google Docs, or Overleaf when working in teams.
The integration of Zotero with Obsidian presents a notable advantage for individual researchers, exhibiting substantial efficiency in literature management and personal knowledge organization through its unique workflows. However, this model demonstrates significant deficiencies when evaluated in the context of collaborative research dynamics.
Specifically, while Zotero facilitates the creation and management of shared libraries, allowing for the aggregation of sources and references among users, Obsidian is fundamentally limited by its lack of intrinsic support for synchronous collaborative editing functionalities, thereby precluding simultaneous contributions from multiple users in real time. Although the application of version control systems such as Git has the potential to address this limitation, enabling a structured mechanism for tracking changes and managing contributions, the inherent complexity of such systems may pose a barrier to usability for team members who lack familiarity or comfort with version control protocols.
Furthermore, the nuances of color-coded annotation systems and bespoke personal note taxonomies utilized by individual researchers may present interoperability challenges when applied in a group setting, as these systems require rigorously defined conventions to ensure consistency and clarity in cross-collaborator communication and understanding. Thus, researchers should be cognizant of the challenges inherent in adapting tools designed for solitary workflows to the multifaceted requirements of collaborative research initiatives.
-
 @ d34e832d:383f78d0
2025-04-24 02:56:59
@ d34e832d:383f78d0
2025-04-24 02:56:591. The Ledger or Physical USD?
Bitcoin embodies a paradigmatic transformation in the foundational constructs of trust, ownership, and value preservation within the context of a digital economy. In stark contrast to conventional financial infrastructures that are predicated on centralized regulatory frameworks, Bitcoin operationalizes an intricate interplay of cryptographic techniques, consensus-driven algorithms, and incentivization structures to engender a decentralized and censorship-resistant paradigm for the transfer and safeguarding of digital assets. This conceptual framework elucidates the pivotal mechanisms underpinning Bitcoin's functional architecture, encompassing its distributed ledger technology (DLT) structure, robust security protocols, consensus algorithms such as Proof of Work (PoW), the intricacies of its monetary policy defined by the halving events and limited supply, as well as the broader implications these components have on stakeholder engagement and user agency.
2. The Core Functionality of Bitcoin
At its core, Bitcoin is a public ledger that records ownership and transfers of value. This ledger—called the blockchain—is maintained and verified by thousands of decentralized nodes across the globe.
2.1 Public Ledger
All Bitcoin transactions are stored in a transparent, append-only ledger. Each transaction includes: - A reference to prior ownership (input) - A transfer of value to a new owner (output) - A digital signature proving authorization
2.2 Ownership via Digital Signatures
Bitcoin uses asymmetric cryptography: - A private key is known only to the owner and is used to sign transactions. - A public key (or address) is used by the network to verify the authenticity of the transaction.
This system ensures that only the rightful owner can spend bitcoins, and that all network participants can independently verify that the transaction is valid.
3. Decentralization and Ledger Synchronization
Unlike traditional banking systems, which rely on a central institution, Bitcoin’s ledger is decentralized: - Every node keeps a copy of the blockchain. - No single party controls the system. - Updates to the ledger occur only through network consensus.
This decentralization ensures fault tolerance, censorship resistance, and transparency.
4. Preventing Double Spending
One of Bitcoin’s most critical innovations is solving the double-spending problem without a central authority.
4.1 Balance Validation
Before a transaction is accepted, nodes verify: - The digital signature is valid. - The input has not already been spent. - The sender has sufficient balance.
This is made possible by referencing previous transactions and ensuring the inputs match the unspent transaction outputs (UTXOs).
5. Blockchain and Proof-of-Work
To ensure consistency across the distributed network, Bitcoin uses a blockchain—a sequential chain of blocks containing batches of verified transactions.
5.1 Mining and Proof-of-Work
Adding a new block requires solving a cryptographic puzzle, known as Proof-of-Work (PoW): - The puzzle involves finding a hash value that meets network-defined difficulty. - This process requires computational power, which deters tampering. - Once a block is validated, it is propagated across the network.
5.2 Block Rewards and Incentives
Miners are incentivized to participate by: - Block rewards: New bitcoins issued with each block (initially 50 BTC, halved every ~4 years). - Transaction fees: Paid by users to prioritize their transactions.
6. Network Consensus and Security
Bitcoin relies on Nakamoto Consensus, which prioritizes the longest chain—the one with the most accumulated proof-of-work.
- In case of competing chains (forks), the network chooses the chain with the most computational effort.
- This mechanism makes rewriting history or creating fraudulent blocks extremely difficult, as it would require control of over 50% of the network's total hash power.
7. Transaction Throughput and Fees
Bitcoin’s average block time is 10 minutes, and each block can contain ~1MB of data, resulting in ~3–7 transactions per second.
- During periods of high demand, users compete by offering higher transaction fees to get included faster.
- Solutions like Lightning Network aim to scale transaction speed and lower costs by processing payments off-chain.
8. Monetary Policy and Scarcity
Bitcoin enforces a fixed supply cap of 21 million coins, making it deflationary by design.
- This limited supply contrasts with fiat currencies, which can be printed at will by central banks.
- The controlled issuance schedule and halving events contribute to Bitcoin’s store-of-value narrative, similar to digital gold.
9. Consider
Bitcoin integrates advanced cryptographic methodologies, including public-private key pairings and hashing algorithms, to establish a formidable framework of security that underpins its operation as a digital currency. The economic incentives are meticulously structured through mechanisms such as mining rewards and transaction fees, which not only incentivize network participation but also regulate the supply of Bitcoin through a halving schedule intrinsic to its decentralized protocol. This architecture manifests a paradigm wherein individual users can autonomously oversee their financial assets, authenticate transactions through a rigorously constructed consensus algorithm, specifically the Proof of Work mechanism, and engage with a borderless financial ecosystem devoid of traditional intermediaries such as banks. Despite the notable challenges pertaining to transaction throughput scalability and a complex regulatory landscape that intermittently threatens its proliferation, Bitcoin steadfastly persists as an archetype of decentralized trust, heralding a transformative shift in financial paradigms within the contemporary digital milieu.
10. References
- Nakamoto, S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System.
- Antonopoulos, A. M. (2017). Mastering Bitcoin: Unlocking Digital Cryptocurrencies.
- Bitcoin.org. (n.d.). How Bitcoin Works
-
 @ d9a329af:bef580d7
2025-05-03 04:10:03
@ d9a329af:bef580d7
2025-05-03 04:10:03Everyone who sees it knows at this point that the matrix of control comes from the overdependence of proprietary software to do our everyday tasks. You can think of this like us being the cling wrap that will just not let go of these pieces of garbage software that don't allow you to see what is in their source code, and how they work. This will tend to lead to the unlawful collection of data (violating the most basic of privacy laws, despite unenforceable contracts that are enforced regardless), bad OPSEC that sees you being stalked and harassed over nothing significant. In the worst of cases, if you speak your mind where you aren't necessarily supposed to be able to do that, and you get doxxed, the worst cases could be far worse than one could imagine.
The solution to this, on the other hand, is using almost exclusively free/libre open-source software and GNU/Linux operation systems. If you're using certain proprietary software, hardening it to give as little data as possible to the entity responsible for it will also work, as long as you know which ones to use. This is a hard pass for a lot of people, but if you want to escape the control matrix of proprietary software, Winblows, HackOS, iHackOS, iBloatOS and stock Google AI Fever Dream, then researching which Free Software (notice the spelling) to use is your first bet. I had already done this for the past four and a half years, and will continue to do it as long as I live, seeing what new Free Software compliant applications and libraries come into the spotlight once things get locked down into walled gardens like what HackOS, iHackOS and BlindnessOS do on a regular basis.
Each of these pieces of software will be in a categorized list with a brief description of what the software is used for. There is a lot to take in, so research this yourself and see if these are right for you. These are the applications I personally use on a regular day-to-day basis, and they work for my needs.
- Operating Systems (the core to your device)
- GNU/Linux operating systems (for PCs) or GrapheneOS (for de-googled Android phones)
To be fair on this one, GNU/Linux is the combination of the Linux kernel with the GNU toolchain, which in turn allows any developer to make an operating system that is FOSS, not necessarily Free Software, especially with the Linux Kernel's proprietary bits of code. The Linux kernel is also used in the Android Open-Source Project (AOSP), and is used as the base of operating systems for Android phones such as GrapheneOS, the only AOSP custom ROM I would recommend based upon the research I had done on this (even if very little).
My recommendations on the Linux side of things are almost any Arch-based distribution (with the exception of Manjaro), Debian-based distributions like Linux Mint Debian edition, regular Debian, AntiX or Devuan, or a Fedora/RedHat-based distribution like Nobara Project (if you're a gamer), OpenSUSE (if set up properly) or even Bluefin if you want an atomic desktop (I wouldn't recommend Bluefin if you want to monkey with your operating system and DIY on many aspects of it). Once you learn how to set these up securely, privately and properly, you're on your way to starting your journey into digital liberation, but there's far more to go on this front.
- Web Browsers (How you surf the internet)
- Firefox Forks
This one is self-explanatory. I harden all the Firefox forks I use (LibreWolf, Waterfox, Cachy Browser, Floorp and Zen as some examples) to the nines, despite being unable to do anything about my fingerprint. This is why I use multiple browsers for specific purposes to counteract the fingerprint spying due to weaponized JavaScript. There are ways to circumvent the fingerprint-based espionage, and make sure the site fingerprint.com doesn't know that one's lying about what their user agent is, though it's not very easy to fool that site, as it's used by 6,000 companies.
- Brave Browser
This is the only Chromium-based browser I would recommend, as it's better when hardened against all the other Chromium-based browsers, including Ungoogled Chromium, which is almost impossible to harden due to security vulnerabilities. Despite that, Brave has some of the best features for a Chromium-based browser one can feel comfortable using, even though you'll have similar issues with Firefox-based browsers that aren't actually Firefox (and Firefox has its own issues regarding espionage from Mozilla)
- Office Suites (If you need to do professional office documents)
- LibreOffice
A fork of Apache's OpenOffice, made better with many features missing from even OnlyOffice and OpenOffice, this suite of applications is the go-to Free Software office suite for many people looking to switch from the proprietary software nether to the diamonds of free/libre open-source software. Though one may need to perform some extra steps to set up compatibility with G-Suite and Microsoft Office past 2015 potentially, it's still a good thing that people trust LibreOffice as their one-stop shop for office documents, despite being completely different from your standard office suite fare.
- OnlyOffice
The competitor to LibreOffice with the ease of Microsoft Office and G-Suite compatibility, OnlyOffice is another office suite that can be good for those who need it, especially since anybody who had used Microsoft Office in particular will be familiar with its layout, if not for a slight learning curve. As someone who's used G-Suite more (due to schooling that stunk worse than a decomposing rat in New York City), that's part of the reason why I switched to LibreOffice, though I tried some others, including OnlyOffice and Abiword (since I use a word processor a lot). This one is another solid option for those who need it.
- Wordgrinder
For those who like to use a terminal emulator like I do, Wordgrinder is a word processor with a terminal user interface (TUI) designed with just focusing on typing without distractions in mind. .wg is the file extension for documents made using Wordgrinder, especially since nowadays most word processors are cloud based. For those who live in a terminal, this is a good option to your terminal UI-based toolbox
- Text editors
- Vi, Vim, Neovim and other Vim-like editors
The classic VI Improved (Vim), a fork of the TUI modal editor, vi, with keybinds that will be confusing at first, but with practice and patience, bring about muscle memory to stay on the keyboard, and not necessarily touch the mouse, keypad on the right hand side, or even the arrow keys. These keybind skills will stay with one for the rest of their life once they learn how the modes in vi, Vim or vi-based editors work. It's a classic for those working in the terminal, and a staple in FLOSS text editing and coding tools once customized potentially to the nines to your particular style.
- VSCodium
The Free Software fork of Code OSS by Microsoft, but made to be similar in function to VSCode without Microsoft's espionage baked into it. It has almost exactly the same features as VSCode that one would need, and even any VSIX files from VSCode will work in VSCodium. This one is an easy switch from VSCode for those who use it, but don't want the forced telemetry.
- Emacs
The competitor to Vim, Emacs is an editor that is FLOSS in every way imaginable. It is one of the most customizable editors anybody could have ever conceived, though the programming language used in Emacs is a dialect of Lisp the developers had made themselves. There are more keybinds to memorize compared to Vim, though Vim keybinds can be added using the Evil Mode package in any Emacs package manager to get the best of both worlds in Emacs. Once one gets a handle of the steep learning curve for Emacs, it's customizable in every imaginable way almost.
These four categories will get you started on your privacy journey, though I covered things a developer might want. I have plans on more lists to compile once I get my ducks in a row on what I want to cover here on Nostr in a longform format. Feel free to let me know if you have recommendations for me to write about, and I can do some digging on that if it isn't a rabbit hole.
-
 @ 34f1ddab:2ca0cf7c
2025-05-03 02:45:30
@ 34f1ddab:2ca0cf7c
2025-05-03 02:45:30In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
Our Recovery Services Include: 📈 Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞 For quick queries or support, connect with us on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust
At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process
Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate
With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure
Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools
We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!
Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪
-
 @ 4e7c1e83:1c2939b5
2025-05-03 02:42:17
@ 4e7c1e83:1c2939b5
2025-05-03 02:42:17Discover the power of Flash Bitcoin with FLASHCORE BTC Softwareclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
What is FLASHCORE BTC Software (Basic)? The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic) 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate. Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities. Single-Device Security: Locked to one computer via obfuscation code for exclusive use. Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection. Why Choose FashExperts’ FLASHCORE BTC Software (Basic)? Simple & Effective: Perfect for beginners or testers who need basic flashing features. Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams. Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate. Reliable Performance: Built for consistent, hassle-free blockchain interaction. How It Works With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably? Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action: 📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertssDiscover the power of Flash Bitcoin with FLASHCORE BTC Software (Basic), exclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
 # What is FLASHCORE BTC Software (Basic)?
# What is FLASHCORE BTC Software (Basic)?The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic)
- 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate.
- Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities.
- Single-Device Security: Locked to one computer via obfuscation code for exclusive use.
- Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection.
Why Choose FashExperts’ FLASHCORE BTC Software (Basic)?
- Simple & Effective: Perfect for beginners or testers who need basic flashing features.
- Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams.
- Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate.
- Reliable Performance: Built for consistent, hassle-free blockchain interaction.
How It Works
With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning
This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably?
Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action:
📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertss
-
 @ 4e7c1e83:1c2939b5
2025-05-03 02:37:13
@ 4e7c1e83:1c2939b5
2025-05-03 02:37:13Discover the power of Flash Bitcoin with FLASHCORE BTC Softwareclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
What is FLASHCORE BTC Software (Basic)? The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic) 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate. Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities. Single-Device Security: Locked to one computer via obfuscation code for exclusive use. Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection. Why Choose FashExperts’ FLASHCORE BTC Software (Basic)? Simple & Effective: Perfect for beginners or testers who need basic flashing features. Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams. Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate. Reliable Performance: Built for consistent, hassle-free blockchain interaction. How It Works With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably? Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action: 📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertssDiscover the power of Flash Bitcoin with FLASHCORE BTC Software (Basic), exclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
 # What is FLASHCORE BTC Software (Basic)?
# What is FLASHCORE BTC Software (Basic)?The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic)
- 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate.
- Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities.
- Single-Device Security: Locked to one computer via obfuscation code for exclusive use.
- Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection.
Why Choose FashExperts’ FLASHCORE BTC Software (Basic)?
- Simple & Effective: Perfect for beginners or testers who need basic flashing features.
- Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams.
- Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate.
- Reliable Performance: Built for consistent, hassle-free blockchain interaction.
How It Works
With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning
This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably?
Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action:
📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertss