-
 @ 7b3f7803:8912e968
2025-04-18 00:16:02
@ 7b3f7803:8912e968
2025-04-18 00:16:02As we enter Holy Week, we are confronted with a world steeped in sin, strife, conflict, and mortality. There exists a peculiar fascination among some with societal decline, as if they derive satisfaction from witnessing civilization’s unraveling. This attraction to darkness may reflect their inner turmoil, a desire to see others share in their suffering. Alternatively, it could stem from a profound hopelessness, a belief that life lacks purpose, leading them to wish for its end. The allure of dystopian futures is, indeed, a curious phenomenon.
Alexander Hamilton once yearned for war as a means to elevate his status, a reflection of youthful ambition for decisive action. Such a desire—to distinguish oneself and ascend the social hierarchy—underlies some of the grim visions of the future propagated by certain ideological circles. Their aim is not war itself but a reconfiguration of power, placing authority in the hands of those who affirm their values. For years, such individuals have held sway, yet their influence appears to be waning.
In the absence of hope, many embrace visions of decline. This despair is characteristic of a faltering empire, signaling the end of an era. The younger generation, burdened by weariness, falters under the weight of their circumstances. They lack hope for a brighter future and see no clear path out of life’s monotony. In a word, they are trapped, uncertain of how to proceed.
We witnessed a similar sentiment during the Arab Spring, where upheaval was celebrated as a longed-for revolution, a societal reset. The assassination of a prominent corporate executive, such as the CEO of United Health, evokes a comparable yearning for disruption. There is a desire for a cultural transformation, though its precise nature remains elusive.
Yet, the youth find themselves dominated by the very elites whose rhetoric they echo. Unlike the 1960s, when generational values clashed overtly, today’s power structures co-opt the language of the young, redirecting their frustration toward populist movements. This inversion is a cunning strategy, mitigating the potential for significant rebellion.
The reality remains that the older generation holds the wealth, power, and authority, while the young are consistently marginalized. They are the ones left with little hope, ensnared by the system. However, a quiet rebellion is emerging—one rooted in hope and faith. Many are beginning to see through the falsehoods propagated by those in power. The promises of governmental provision, once alluring, now appear untenable in light of fiscal realities. The youth seek a new source of hope, a renewed perspective. Thankfully, they are beginning to find it, turning toward faith as a foundation for a more optimistic future.
-
 @ a296b972:e5a7a2e8
2025-04-17 23:08:50
@ a296b972:e5a7a2e8
2025-04-17 23:08:50Die Figuren in der Koalition der Willigen entlarven ihre charakterliche Ungeeignetheit für politische Ämter mit Verantwortung für ganze Nationen. Staatliche Entscheidungen dürfen nicht emotionsgesteuert sein. Aber genau das ist derzeit der Fall. Überall wird mit der Moralkeule um sich gehauen. Erwachsene benehmen sich wie im Kindergarten und zeigen ihre fehlende Reife. Von menschlicher Größe ganz zu schweigen.
Bisher war es schön warm unter den Fittichen der USA. Deutschland hat aufgrund seiner Geschichte besonders gut den Nick-August gespielt und sich selbst eine Souveränität vorgelogen, die es so nie gegeben hat. Jetzt sieht es so aus, als wollten die USA Europa in die Freiheit, in die Volljährigkeit entlassen. Es könnte auch sein, dass die USA aus der NATO austreten und sich vor allem um sich selbst kümmern. Allein das würde die Welt schon wesentlich friedlicher machen, denkt man beispielsweise an den Einmarsch in den Irak. Es gehen Gerüchte um, dass Truppen aus Rumänien und Deutschland abgezogen werden sollen.
Vielleicht geht es bei den Friedensverhandlungen zwischen Trump und Putin nicht nur um die Ukraine, sondern, wenn man schon mal dabei ist, auch um die Kräfteverteilung in Europa insgesamt. Waffeneinsätze in der Ukraine wurden maßgeblich von Wiesbaden aus gesteuert. 2026 sollen dort US-Mittelstrecken-Raketen stationiert werden. Der an Führungsstärke kleinste Kanzler der Bundesrepublik, Scholz, hat das brav abgenickt. Der nur noch durch ein Wunder zu verhindernde neue Kanzler, das Glas Gewürzgurken aus dem Sauerland, provoziert Russland mit seiner Ankündigung zu den Taurus-Raketen dafür um so mehr. Da ist man schon fast gewillt, sich den Scholz zurückzuwünschen, als das kleinere Übel.
Statt mit Besonnenheit und Vernunft die veränderte Sicherheitslage mit den USA als eher abtrünnige Schutzmacht neu zu bewerten, hierin auch eine Chance zu sehen, eine starke Botschaft und den Willen auf ein friedliches neues Miteinander in den Fokus zu stellen, reagieren die meisten europäischen politischen „Spitzenkräfte“ mit blindem Aktionismus, der weltenbrandgefährlich ist. Und Deutschland, dass es sich aufgrund seiner Geschichte am wenigsten erlauben könnte, macht mit von der Leyen in Brüssel und Merz, Pistorius und anderen Kriegs-Warm-Uppern am weitesten das Maul auf, obwohl es sich am bedecktesten halten sollte.
Angesichts der Tatsache, dass Europa gegenüber einer Atommacht wie Russland vollkommen wehrlos ist, wäre es wirklich viel gescheiter, sich der neuen Situation anzupassen und ständig Signale der Friedensbereitschaft zu senden. Unterstütz von den Briten und Franzosen schmiegt Brüssel eine Koalition der Friedensuntüchtigen, wie sie Uwe Froschauer aktuell in seinem Buch „Die Friedensuntüchtigen“ beschreibt. In der Rezension von mir gibt es auch einen Link zu einem Review des Inhalts:
https://wassersaege.com/blogbeitraege/buchrezension-die-friedensuntuechtigen-von-uwe-froschauer/
Stattdessen passiert das Gegenteil.
Es ist nicht nur legitim, sondern sogar Aufgabe der einzelnen Staaten, eine gewisse Verteidigungsfähigkeit aufbauen zu wollen. Derzeit geschieht das jedoch unter falschen Vorzeichen. Die NATO, als sogenanntes Verteidigungsbündnis zur Vorlage zu nehmen, wäre keine gute Idee, weil sie sich mangels Gelegenheit (der Verteidigung) eher als das Gegenteil herausgestellt hat, wie man seinerzeit in Jugoslawien erleben musste.
Russland als Feind hochzustilisieren, um ein Aufrüsten zu beschleunigen, ist jedoch der denkbar falscheste Weg. Wenn ein Yorkshire-Terrier einen Pit-Bull ankläfft, könnte das fatale Folgen haben. Wenn die europäischen „Geistesgrößen“ bei Verstand wären und in der Lage, die Realität richtig einzuschätzen, würden sie das erkennen.
Woher kommt die Überheblichkeit, woher die Unfähigkeit zur Einschätzung der Lage, woher die Realitätsverweigerung? Ist das gewollt, steckt ein Plan dahinter oder sind „die“ einfach „nur“ strunzendoof? Letzteres wäre die gefährlichste Variante.
Es stellt sich immer mehr heraus, dass Corona offensichtlich ein Test war, wie weit die Menschen in ihrer Obrigkeitshörigkeit zu treiben sind. Wie dumm und gefolgsam sind die Schafe wirklich?
Bei einer Lieferung von Taurus-Raketen, die von Deutschen gesteuert werden müssen, könnte es vielleicht gelingen, die Krim-Brücke zu zerstören. Den Kriegsverlauf würde das jedoch nicht beeinflussen. Russland gewinnt so oder so. Im Gegenteil, die Folgen für Deutschland würden den dort möglicherweise angerichteten Schaden bei weitem übertreffen.
Während ich schreibe kommt gerade auf RT DE (aufgrund der „Pressefreiheit“ verzichtet man derzeit offiziell auf diesen Sender) folgende Meldung rein: Russisches Außenministerium: Taurus-Einsatz bedeutet deutsche Kriegsbeteiligung.
https://rtde.site/international/242696-russisches-aussenministerium-taurus-einsatz-bedeutet/
Es ist nicht nachvollziehbar, dass Merz offensichtlich nicht in der Lage ist anzuerkennen, dass Russland über Oreschnik-Raketen verfügt. Er scheint nicht in der Lage zu sein, die möglichen Folgen einschätzen zu können. Genau so wenig wie Pistorius. Die beiden kommen einem vor, wie zwei, die sich im stockfinsteren Wald verirrt haben und sich gegenseitig Mut zusprechen.
Nach wie vor gibt es keine fundierten Beweise dafür, dass Russland die Absicht hat, Deutschland auf unschöne Weise bereisen zu wollen. Das kann nicht oft genug gesagt werden.
Wie schon vor dem Ukraine-Konflikt, durch ein ständiges mit der NATO-Osterweiterung Russland-immer-näher-auf-die-Pelle-rücken, streut jetzt Europa, Deutschland, der Kriegskanzler Salz in die Wunde und Russland sagt ständig: Stoy, so geht das nicht!
Wenn wir eine Bedrohungslage haben, dann die, dass das aktuelle Regime den Deutschen in seinem Wehrwahn mit Wehrpflicht und einer bevorstehenden russischen Invasion droht, obwohl es, man kann es wirklich nicht oft genug sagen, keine reale Bedrohung durch Russland gibt.
In einem Interview im deutschen Propaganda-Funk faselt Pistorius davon, dass in einem „Schnuppercamp der Bundesmarine“ in Kiel für Teenager ab 16 Jahre, er gar nichts Verwerfliches daran finden kann. „Die schießen ja nicht…“, „Wir bringen ihnen ja nicht das Töten bei mit 17, sondern wir bereiten sie vor auf eine Ausbildung zum Soldaten. Und Soldat ist ein sehr ehrenwerter Beruf, der nämlich dazu dient, unsere Freiheit und Sicherheit im Ernstfall zu verteidigen.“ Dass diese Verteidigung tödlich enden kann, wird hier verschwiegen. Das könnte schließlich Teile der Soldaten verunsichern.
Ein Politikwissenschaftler regt sich über den Titel eines Liedes auf:
-Da stört sich doch tatsächlich jemand an der Liedzeile „Meine Söhne geb‘ ich nicht“-
https://www.nachdenkseiten.de/?p=131733
Man hat das Gefühl, dass alle Politiker, statt wie Obelix in den Zaubertrank, in ein Fass Teflon-Lack gefallen sind. Anders ist es nicht zu erklären, warum die Realität so perfekt an ihnen abperlt.
Wir werden immer mehr in die Enge getrieben. Und man weiß nicht, was im Zuge der digitalisierten Überwachung, die auch in Russland kräftig Fahrt aufnimmt, zwischen den USA und Russland sonst noch ausgehandelt wird. Auch, wenn Vance derzeit von UK-Premier Keir Starmer fordert, er müsse die Gesetze gegen „Hassrede“ aufheben, um ein Handelsabkommen mit den USA zu erzielen, und das eine Vorankündigung auf die Verhandlungen mit der EU sein könnte, (Bedingung: Abschaffung des Digital Services Act). In den USA gibt es Tech-Giganten, wie Musk und Thiel und Konsorten, die mit Umlegen eines Schalters, den derzeit augenscheinlichen Kampf für Meinungsfreiheit und Freiheit der Bürger, im Handumdrehen ins Gegenteil verqueren können. Dann sind wir in Null Komma Nichts in der Versklavung mit einem Totalitarismus und einer Technokratie gelandet, in der sich Georg Orwells „1984“ wie eine Gute-Nacht-Geschichte für kleine Kinder anhört.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-17 21:35:47
@ 5d4b6c8d:8a1c1ee3
2025-04-17 21:35:47Congrats to @gnilma and @Carresan! Thanks to Herro and Butler both having 38 points (shoutout Heat Culture) they both secured 9 points and are tied for the lead.
Now we move on to the final Play-In Round
Matchups (seed)
- Heat (10) @ Hawks (8)
- Mavericks (10) @ Grizzlies (8)
You need to select one team from this round to win their game. You also need to predict who will be the highest scoring player in this round.
Scoring this round: 1 Point for your team winning + Your team's seed if they win + 1 Point for picking the correct top scorer
This round has a maximum of 12 points.
Prize
10k sats (or sum of zaps on contest posts, whichever is larger)
originally posted at https://stacker.news/items/946686
-
 @ df478568:2a951e67
2025-04-17 21:10:33
@ df478568:2a951e67
2025-04-17 21:10:33I created a GitHub repository at https://github.com/Marc26z/ZapShirts. Here is a copy of the README.md
ZapShirts
This is an idea I have to make t-shirts that are also bitcoin point-of-sale terminals.

Create T-Shirt Point-Of-Sale
The idea is to create a bitcoin point of sale on a T-shirt. You can use it to sell stickers at a conference or have a friend pay you back for dinner. It is only limited by your imagination.
Why Would Anybody Need A ZapShirt?
I no longer "orange pill" local businesses. I do not care if they wish to accept bitcoin, but I want to be the change in the world I want to see. I will accept bitcoin on a T-Shirt to show others how easy it is to accept bitcoin as a p2p electronic cash system. Anyone can accept bitcoin as payment if they want to. You could print a sign on a piece of paper if you wanted to. The problem was, nobody I asked wanted a sign, even bitcoiners. So I asked myself...Self, what if you did the opposite? What if the customer accepted bitcoin, but the business owner did not.
I also thought it would be pretty cool T-Shirt to wear at meet-ups.
How To Make Your Own Zap Shirt
- Create a QR code that sends you to your coinos page, getalby page, strike or whatever you feel comfortable using. This can easily be done at https://libreqr.com/
- Use a program like gimp to replace the default QR Code with your own QR code on the file.
- Create the shirt.
To support this please zap me or buy one from my store.
Can I Buy A Zap Shirt?
Yes. If you would like a shirt, hit me up on nostr
https://primal.net/marc
end README.md
I like the idea of open sourcing my ideas and trying to sell them for sats on the Internet. I am currently working on a site to sell things like this and my gift cards. I feel a little uneasy because I haven't been writing much, but I've been building. The idea is to create bitcoin educational products and services. Onward.
-
 @ 9063ef6b:fd1e9a09
2025-04-17 20:18:19
@ 9063ef6b:fd1e9a09
2025-04-17 20:18:19This is my second article. I find the idea of using a user friendly 2FA-style code on a secondary device really fascinating.
I have to admit, I don’t fully grasp all the technical details behind it—but nonetheless, I wanted to share the idea as it came to mind. Maybe it is technical nonsense...
So here it is—feel free to tear the idea apart and challenge it! :)
Idea
This Article describes method for passphrase validation and wallet access control in Bitcoin software wallets using a block-based Time-based One-Time Password (TOTP) mechanism. Unlike traditional TOTP systems, this approach leverages blockchain data—specifically, Bitcoin block height and block hash—combined with a securely stored secret to derive a dynamic 6-digit validation code. The system enables user-friendly, secure access to a wallet without directly exposing or requiring the user to memorize a fixed passphrase.
1. Introduction
Secure access to Bitcoin wallets often involves a mnemonic seed and an optional passphrase. However, passphrases can be difficult for users to manage securely. This paper introduces a system where a passphrase is encrypted locally and can only be decrypted upon validation of a 6-digit code generated from blockchain metadata. A mobile app, acting as a secure TOTP generator, supplies the user with this code.
2. System Components
2.1 Fixed Passphrase
A strong, high-entropy passphrase is generated once during wallet creation. It is never exposed to the user but is instead encrypted and stored locally on the desktop system (eg. bitbox02 - sparrow wallet).
2.2 Mobile App
The mobile app securely stores the shared secret (passphrase) and generates a 6-digit code using: - The current Bitcoin block height - The corresponding block hash - A fixed internal secret (stored in Secure Enclave or Android Keystore)
Offline App - current block_hash and block_height scanned with qr code.6-digit code generation after scanning the information.
2.3 Decryption and Validation
On the desktop (e.g. in Sparrow Wallet or wrapper script), the user inputs the 6-digit code. The software fetches current block data (block_height, block_hash), recreates the decryption key using the same HMAC derivation as the mobile app, and decrypts the locally stored passphrase. If successful, the wallet is unlocked.
3. Workflow
- Wallet is created with a strong passphrase.
- Passphrase is encrypted using a key derived from the initial block hash + block height + secret.
- User installs mobile app and shares the fixed secret securely.
- On wallet access:
- User retrieves current code from the app.
- Enters it into Sparrow or a CLI prompt.
- Wallet software reconstructs the key, decrypts the passphrase.
- If valid, the wallet is opened.
4. Security Properties
- Two-Factor Protection: Combines device possession and blockchain-derived time-based data.
- Replay Resistance: Codes change with every block (~10 min cycle).
- Minimal Attack Surface: Passphrase never typed or copied.
- Hardware-Backed Secrets: Mobile app secret stored in non-exportable secure hardware.
5. Future Work
- Direct integration into Bitcoin wallet GUIs (e.g. Sparrow plugin)
- QR-based sync between mobile and desktop
- Support for multiple wallets or contexts
6. Conclusion
This approach provides a balance between security and usability for Bitcoin wallet users by abstracting away fixed passphrases and leveraging the immutability and regularity of the Bitcoin blockchain. It is a highly adaptable concept for enterprise or personal use cases seeking to improve wallet access security without introducing user friction.
-
 @ 4c96d763:80c3ee30
2025-04-17 19:41:12
@ 4c96d763:80c3ee30
2025-04-17 19:41:12Changes
William Casarin (26):
- dave: reorganize ModelConfig
- dave: organize
- dave: remove old file
- dave: add a few tool docs
- dave: update to custom filters nostrdb
- dave: only search non-replies
- context: implement note broadcasting
- multicast: broadcast context
- dave: fix bugs
- chrome: fix wallet button
- previews: disable for now
- ui: add some margin to chrome sidebar
- columns: remove thread warning
- nostrdb: fix on windows
- dave: tweak prompt
- misc: driveby fixes
- refactor: move input buttons ui into its own fn
- refactor: extract input_ui into its own function
- dave: refactor a bit
- post: fix bug where send shortcut send unfocused inputs
- dave: give up on plaintext formatting
- dave: fix input box
- log: silence gif log
- refactor: nevernest get_display_name
- refactor: ocd unnecessary pass by value
- ui: move note and profile rendering to notedeck_ui
kernelkind (4):
- Fix flaky test_zap_event
- move error out of
AnyZapState - introduce
ImagePulseTint - pulse pending zap button
pushed to notedeck:refs/heads/master
-
 @ 18be1592:4ad2e039
2025-04-17 17:35:22
@ 18be1592:4ad2e039
2025-04-17 17:35:22My everyday activity
This template is just for demo needs.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 18be1592:4ad2e039
2025-04-17 17:34:16
@ 18be1592:4ad2e039
2025-04-17 17:34:16My everyday activity
This template is just for demo needs.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 18be1592:4ad2e039
2025-04-17 17:33:31
@ 18be1592:4ad2e039
2025-04-17 17:33:31My everyday activity
This template is just for demo needs.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ f18b1f8f:5f442454
2025-04-17 17:03:22
@ f18b1f8f:5f442454
2025-04-17 17:03:22A supermemory MCP plugin that you can use to bring a memory with you to any client of your choosing. Supports fetching from, and storing to, memory. Comes with a prompt to help the client identify when to use or store updates. Very neat, and ties integrations together very well.
Here is a video walkthrough: https://x.com/DhravyaShah/status/1912544778090414188
e578b1367ed845d8925eb8a0ebc3a96d
-
 @ f18b1f8f:5f442454
2025-04-17 16:55:46
@ f18b1f8f:5f442454
2025-04-17 16:55:46A supermemory MCP plugin that you can use to bring a memory with you to any client of your choosing. Supports fetching from, and storing to, memory. Comes with a prompt to help the client identify when to use or store updates. Very neat, and ties integrations together very well.
Here is a video walkthrough: https://x.com/DhravyaShah/status/1912544778090414188
e578b136-7ed8-45d8-925e-b8a0ebc3a96d
-
 @ 0861144c:e68a1caf
2025-04-17 16:35:23
@ 0861144c:e68a1caf
2025-04-17 16:35:23This is a following up for the conversation started by @Scoresby with the question:
what is a sustainable model for onchain Bitcoin wallet software development?
This is an extreme opinion (even for myself) but I think is the best answer to what we're pursuing as bitcoiners.
Introduction: The Paradox of Free and Critical
The Bitcoin ecosystem thrives on open-source software. It's a world where people entrust their life savings to applications they didn’t pay a cent for. This introduces a unique paradox: we demand freedom, security, and transparency, but we don’t pay for the tools that guarantee it. Even more, we value free markets and incentives, yet expect Bitcoin wallets to exist and evolve out of altruism.
So what’s the path forward? What kind of model can ensure long-term development, security patches, feature upgrades, and alignment with Bitcoin’s protocol—without betraying its ethos?
Let’s explore the current landscape of wallet monetization and build toward a model that honors the freedom Bitcoin offers.
Wallet Monetization Models
Here’s an overview of how current Bitcoin-only (or mostly Bitcoin) onchain wallets sustain themselves based on https://stacker.news/items/944967#how-could-you-pay-for-a-bitcoin-wallet-if-you-wanted-to:
| Model | Description | Example Projects | Pros | Cons | |---------------------------|-----------------------------------------------------------------------------|-------------------------------|----------------------------------------------------|------------------------------------------------------------| | Donations/Grants | Funded by community or institutional support | Bitcoin Core, Sparrow, Specter| User-focused, preserves freedom | Unstable, depends on goodwill or VC altruism | | Freemium/Subscription| Free basic app, premium features unlocked through subscriptions | Nunchuk, Keeper, Theya | Predictable revenue | Introduces centralization, relies on dev infrastructure | | Device Sales | Wallet tied to hardware devices | Bitkey, Envoy | Scalable, aligned with sovereignty | Limits access based on geography or price | | Custodial Services | Funds held by a third party | Casa, River, Swan | Simple onboarding for new users | Compromises on "Not your keys, not your coins" | | Tx Commissions| Wallet takes a fee from trades within the app | BlueWallet (speculatively, maybe not) | Transparent funding method | User becomes product; hard to avoid surveillance and KYC | | L2 Services | Monetization through Lightning routing fees or service layers | Phoenix, Breez, Zeus | Innovative, supports network growth | Not suitable for cold storage or large holdings | | Sell the Software | Direct payment for downloading or unlocking the app | (Rare or nonexistent) | Clear transaction, sustainable if valued | Cultural resistance; rare in open-source culture |
Each of these models carries tradeoffs—especially when you consider global context.
Why Context Matters: Global Finance Is Not Equal
In countries with stable banking systems (U.S., Europe, Japan), Bitcoin wallets are largely seen as savings vaults. People use their banks for spending and turn to Bitcoin as a hedge or long-term store of value. In these places, users are more comfortable with subscription models or regulated custodial solutions.
But in the global south—Latin America, North Africa, parts of Asia—Bitcoin plays a different role. Banks are distrusted, inflation is high, and people are not just saving in Bitcoin; they’re trying living on Bitcoin. Wallets aren't just tools, they’re lifelines. Asking users to subscribe, give up sovereignty, or rely on opaque intermediaries is antithetical to the entire point. Can't use bitcoin? Go straight to cash or side-banks solutions like EMP (Giros Tigo, M-PESA). Taxes? We don't care, I don't mind not pay taxes when I buy nor I care even less how to present my fill form to authorities. Bitcoin is need.
In this context, the question isn't “can I pay for a wallet?”—it's “can I use it without being surveilled, blocked, or priced out?”. That's why technologies Lightning-L2 related have some much adoption, because we need not only to save but to pay our things. Just look El Salvador, Argentina or lately Bolivia, countries that need alternative to keep receiving/sending while having a volatility index very high.
The Bitcoin Standard: Build Your Own Wallet
Under the Bitcoin standard, the sustainable model must allow any individual to create their own wallet—no permission required, no gatekeepers, no payment walls. Think of it like designing your own leather wallet to carry cash. Anyone can do it, because the knowledge is public, the materials are available, and there’s no centralized authority controlling the process.
The same is true with Bitcoin:
- Wallets can integrate privacy-enhancing tools like Whirlpool (CoinJoin).
- They can adopt PayNym or BIP47 for stealth addresses.
- Features like automated DCA (Dollar Cost Averaging) can be designed to optimize both strategy and privacy.
- Visuals can display only sats, not fiat denominations, reinforcing the mindset that Bitcoin is the native unit.
What sustains these features? A community of developers building modular, composable, interoperable tools. The protocol enables this—Bitcoin is both a financial layer and a developer’s playground.
The Custodial Dilemma: Easier, But Risky
Let’s be honest: custodial wallets make onboarding smoother. They're easier to explain. “Download app, get coins.” That’s it. But this simplicity comes at a cost.
- “Not your keys, not your coins” is not just a mantra—it’s survival.
- Custodial wallets are subject to seizure, surveillance, and censorship.
- They build bad habits: users don’t learn how to verify, back up, or transact privately.
And yet, we’ve seen it again and again: many newcomers start with custodial solutions and only move to self-custody after something goes wrong—a blocked account, a missing withdrawal, or an unexplained freeze. Then they meet the 12 words. And yes, the seed phrase is scary at first. But over time, it becomes the ultimate expression of financial freedom.
Transaction Fees: A Ticking Time Bomb
Some wallet developers seek sustainability by taking a small cut of in-app transactions. It's easy to justify: "We only take 0.5% for maintenance." But this model is fundamentally flawed in the context of Bitcoin.
- It reintroduces third-party dependence into a tool meant to eliminate it.
- It discourages self-custody by tying wallet use to an ongoing cost.
- It creates perverse incentives: developers are now driven to optimize for volume, not user sovereignty.
In the short term, this might work. But long term, it turns wallets into surveillance engines and behavioral data extractors—exactly what Bitcoin was meant to disrupt.
A sustainable model can’t be built on transaction tax. That’s fiat logic.
Conclusion: DIY Is the Only Model That Scales with Sovereignty
In Bitcoin, every decision is a reflection of trust. Who do you rely on for custody, code, and convenience? A sustainable model for wallet software must allow people to opt out at every layer. If you don’t like the wallet UI—change it. If the devs abandon the project—fork it. If the company goes under—run your own build. This is only possible because the information is free, the protocol is neutral, and the design is decentralized by nature. We don’t need more paywalls. We need more builders. More tinkerers. More people realizing that “wallet software” is not a product you buy—it’s a freedom you exercise.
That’s the Bitcoin way.
That’s the model that lasts. That's my two sats.originally posted at https://stacker.news/items/946326
-
 @ d7a8e245:27456aad
2025-04-17 16:01:04
@ d7a8e245:27456aad
2025-04-17 16:01:04Bibel-Selfies
Prompts
Eva, Schlange, Apfel und Adam

A selfie of a woman resembling eve in the time of old testament, blurred body, holding an apple, kneeling in front adam. he has a shocked expression with his mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with a huge snake behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with adam and eve, possibly at a place like garden eden. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Tochter des Pharao mit Mose

A selfie of the biblical figure moabite woman with her baby in front of an oasis. She is wearing traditional and has black hair. The background shows water from the desert oasis and grasses around it. In the Background a wicker basket on the water. The photo was taken in the style of a selfie shot with GoPro cameraSimon Petrus

A selfie of a man resembling Simon Petrus, wearing a white robe, surrounded by waves and thunderstorm. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many waves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus at the dead sea, possibly at a place like the sea. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Zachäus auf dem Baum
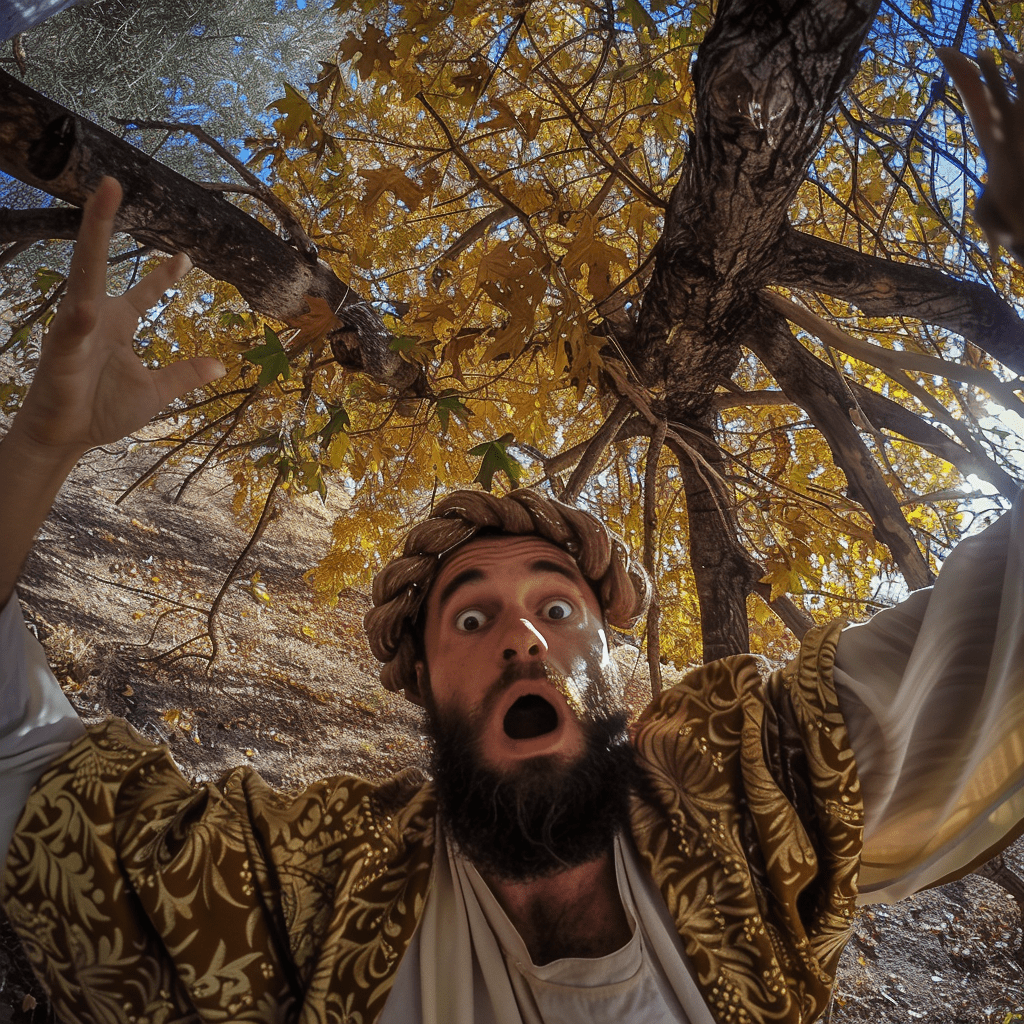
A selfie of a man resembling a roman in the time of jesus, wearing a glamorous robe, surrounded by the crown of a tree. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many leaves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Maria am Ostermorgen

A selfie of a woman resembling maria in the time of jesus, wearing a robe, kneeling in front of stone grave. she has a shocked expression with her mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with the open glowing grave behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus resurrection, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Der verlorene Sohn bei den Schweinen

A young ancient arabic man with short hair in the time of jesus, brown eyes, and a dirty face, covered in mud from working on his pig farm, takes an amateur selfie at dusk. He is surrounded by pig stables, with a barn visible in the background and pigs seen near the front. The photo captures a raw, authentic moment, as he gazes directly into the camera with an expression of excitement or wonder. The image has a realistic style, akin to Unsplash photography, and is meant to be posted on a primitive-themed social network. The resolution of the photo is high, style of selfie with gopro --v 6.0Vater und Sohn vereint
 A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0
A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0Bartimäus

A selfie of a man resembling blind bartimaeus in the time of jesus, black and brown and white bandages on his head over his eyes and face, wearing a robe, kneeling in front of a market place. he has a shocked expression with his mouth open and wide eyes still covered with black and brown and white bandages on his head, evoking a sense of both fear and surprise. The scene appears surreal, with many sand behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus healing the blind, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Daniel in der Löwengrube

A selfie of a man resembling Jesus, wearing a beige hoodie, surrounded by lions and cheetahs. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many lions behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a lion's den, possibly at a place like the Grand Tabahar. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan ChaudharyDavid und Goliath

selfie of a the boy and shepherd david holding his slingshot resembling a fight with the giant goliath in the time of old testament, wearing a glamorous sligshot focusing on his giant opponent. David has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a desert surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of the scene of David fighting with the giant goliath with his slingshot, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Simson im Philistertempel

A selfie of a man resembling simson in the time of old testament, wearing a glamorous beard and long hair, surrounded by thousands of ancient fighters. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a temple surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Jona und der Wal

A selfie of a man resembling israeli jona in the time of old testament,`wearing a glamorous beard and long hair, inside the body of a whale. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with the ocean surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene in the bible. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary
Jakob und Isaak

A selfie of a young man resembling an ancient Arabic in clothes made of skins of goats and furs of the goats, looking overwhelmed and distressed as he betrays his father, who blesses him. The scene shows a dawn sky with hints of the sunrise, evoking a surreal and dramatic atmosphere. The scene is set in ancient Jerusalem, with stone buildings. in the background an old man with a gesture of blessing, rising his hands to the sky, The photo is taken with a wide-angle lens, blending surrealism with humor. The style is reminiscent of a GoPro selfie, capturing the intense moment with a sense of both fear and surprisePetrus und der Hahn

A selfie of a man resembling ancient young arabic man saint in traditional biblical attire, being eaten by a whale,. he has a shocked expression with his mouth pressed and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with one rooster crowing out loud behind the man. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with peter and the rooster, possibly at a place in jerusalem . The style of the photo blends surrealism with humor, go pro selfie, morning dawn near sunrise settingJosef im Brunnen

A selfie of an ancient israelian man with a magical dreamcoat clothing in a deep well, looking at the camera from above, captured in the style of a go pro selfie stickElia und die Raben

A close-up selfie of a bearded man (Elijah) in biblical clothing, smiling gratefully. He is standing near a stream in a secluded, rocky area. Several black ravens are perched on his shoulders and arms, holding pieces of bread and meat in their beaks. The scene has a warm, golden light, symbolizing God's provision. Photorealistic style, high detail.Absalom im Baum

A selfie of a man resembling of a young man (Absalom) with long hair knotted arount the branches of a large oak tree.. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with all of his hairs knotted around the tree. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene of a robin hood movie in the forest . The style of the photo blends surrealism with humorRuth und Boas im Weizenfeld

A selfie of a young woman resembling Ruth, with a radiant smile and sun-kissed skin. She's standing in a golden wheat field at sunset, her arms filled with freshly gathered sheaves of wheat. Her hair is partially covered with a simple headscarf, with loose strands blowing in the wind. She has a look of joy and gratitude in her eyes. The scene appears idyllic, with wheat stalks seeming to embrace her. In the background, a distinguished older man (Boaz) can be seen watching from a distance, his expression a mix of curiosity and admiration. The photo is taken with a wide-angle lens, capturing the vastness of the field, the warmth of the setting sun, and Boaz in the distance. The setting is reminiscent of a biblical harvest scene. The style of the photo blends realism with a touch of romantic nostalgia."Bibel-Selfies" von Jörg Lohrer Lizenz: CC0 1.0
.
`
-
 @ fbf0e434:e1be6a39
2025-04-17 15:54:52
@ fbf0e434:e1be6a39
2025-04-17 15:54:52Hackathon 概要
Seeds Of Agentic Future Hackathon 吸引 294 位开发者注册,最终 99 个项目通过审核。活动聚焦具有实际应用价值和吸引力的 AI 代理研发,参与者围绕资金支持、现金奖励、市场推广资源及全球媒体曝光机会展开竞争。
大赛在多个预设赛道取得显著成果,包括 Infra/Framework/Tooling、DeFAI/DeSci、Gaming/Entertainment 以及专门设立的 CARV's Agentic Track,各赛道均设置丰厚奖项。这种多元化的赛道设计推动了创新项目开发与 AI 技术进步。
活动通过连接全球开发者并搭建与知名风险投资家的对接渠道,进一步扩大影响力。其不仅为前沿 AI 技术提供了展示平台,更为项目后续发展和商业落地奠定基础。本次黑客马拉松成功挖掘出一系列关键创新成果,提升了开发者影响力,为全球 AI 开发者社区做出了重要贡献。
Hackathon 获奖者
Infra & Framework 奖项获奖者
第一名 - $7500
Dexfin: 一款由AI驱动的DeFi平台,具备先进的钱包功能、市场分析、无缝交易和社区互动工具。
BuilderFi: 一个无需代码的平台,利用AI通过创建工作流来自动化DeFi交易策略。
DeFAI & DeSci 奖项获奖者
第一名 - $7500
- Maiga: 一个AI代理,通过“交易证明”代币模式在区块链网络上提供信号、洞察和自动交易以提高效率。
第二名 - $2500
- AgentXYZ: 一款强化策略的AI交易工具,使用市场、社交和链上数据进行智能代理群体操作。
游戏和娱乐奖项获奖者
第一名 - $7500
- Superagent PlayArts: 通过AI和区块链技术整合动态NFT和智能代理,增强了NFT货币化和互动性。
第二名 - $2500
- Animayhem - AI Agent Gaming Companions: 开发了作为游戏伙伴的AI代理,为像Discord和Telegram这类平台的玩家提供独特的个性互动。
有关这些项目的更多信息及查看所有提交,请访问 DoraHacks。
关于组织者
Seedify
Seedify 是区块链和技术创新领域的公认领导者,以其全面的区块链孵化项目而闻名。它成功地引导了众多区块链风险项目从概念到执行。该组织在去中心化金融和非同质化代币方面表现出色,为新兴项目提供战略指导。Seedify 的计划侧重于为区块链创业者打造一个协作环境。其使命是通过提供必要的资源和一个加速区块链方案在各行各业中应用的平台,赋能创新者。
-
 @ f5369849:f34119a0
2025-04-17 15:51:16
@ f5369849:f34119a0
2025-04-17 15:51:16Hackathon Summary
The Seeds Of Agentic Future hackathon attracted 294 registered developers, resulting in 99 approved project submissions. This event aimed to advance the development of AI Agents with practical utility and appeal. Participants competed for funding, cash prizes, go-to-market support, and exposure to global media.
Significant accomplishments emerged across various tracks, including Infra/Framework/Tooling, DeFAI/DeSci, Gaming/Entertainment, and a specialized CARV's Agentic Track, each offering notable prize incentives. This diversity encouraged innovative project development and technological advancement in AI.
The hackathon extended its influence by reaching a global audience and offering connections with prominent venture capitalists. It provided a platform to showcase promising AI technologies, laying the groundwork for further development and commercial prospects. The event successfully highlighted critical innovations and broadened the developers' reach, contributing significantly to the AI developer community.
Hackathon Winners
Infra & Framework Prize Winners
1st Place - $7500
- Dexfin: An AI-powered DeFi platform that features advanced wallet capabilities, market insights, seamless transactions, and community engagement tools.
- BuilderFi: A no-code platform utilizing AI to automate DeFi trading strategies through workflow creation.
DeFAI & DeSci Prize Winners
1st Place - $7500
- Maiga: An AI agent offering signals, insights, and automated trading on blockchain networks, using a 'Proof-of-trading' token model for efficiency.
2nd Place - $2500
- AgentXYZ: An AI-powered trading tool that enhances strategies with intelligent agent swarms using market, social, and on-chain data.
Gaming & Entertainment Prize Winners
1st Place - $7500
- Superagent PlayArts: Enhances NFT monetization and interactivity by integrating dynamic NFTs and intelligent agents through AI and blockchain technology.
2nd Place - $2500
- Animayhem - AI Agent Gaming Companions: Develops AI agents as gaming companions, providing unique personalities for player interaction on platforms like Discord and Telegram.
For more information on these projects and to view all submissions, visit DoraHacks.
Organization
About the Organizer: Seedify
Seedify is a leading Web3 incubator and Launchpad for Web3 projects focusing on innovative technologies such as DeFi, AI, Big Data, NFTs and Web3 Gaming. It has successfully guided numerous blockchain ventures from conception to execution. The organization excels in decentralized finance and non-fungible tokens, offering strategic guidance to emerging projects. Seedify's initiatives focus on fostering a collaborative environment for blockchain entrepreneurs. Its mission is to empower innovators by providing essential resources and a platform to accelerate the adoption of blockchain solutions across various industries.
-
 @ 4cebd4f5:0ac3ed15
2025-04-17 15:29:09
@ 4cebd4f5:0ac3ed15
2025-04-17 15:29:09Tóm tắt Hackathon
AI Hackathon do SUCI Blockchain Hub tổ chức và CodeX tài trợ, diễn ra tại TP.HCM (Việt Nam) từ ngày 7–9/3/2025. Sự kiện trực tiếp thu hút 42 developer tạo ra 12 dự án tập trung vào tích hợp Real-World Asset (RWA) và phát triển AI agent với góc nhìn thực tiễn.
Tổng giải thưởng 15.000 USD (quy đổi bằng USDT và token CDX) được phân bổ như sau:
- Giải Nhất: 4.000 USDT + 2.000 CDX, kèm vé tham dự COTI Foundation Hackathon tại Thái Lan.
- Giải Nhì: 3.000 USDT + 1.500 CDX.
- Giải Ba: 2.000 USDT + 1.000 CDX.Các hạng mục đặc biệt như Best AI Agent, Best No-Code Solution, Best Real-World Application mỗi giải nhận 1.000 USDT + 500 CDX. Giải thưởng phụ khác ghi nhận sáng tạo AI, giải pháp đa ngành và tác động cộng đồng.
Sự kiện tạo cơ hội kết nối, học hỏi và hợp tác, minh chứng sự hội tụ ngày càng sâu giữa AI và blockchain.
Các dự án đoạt giải
AI Hackathon 2025 ghi nhận thành tựu nổi bật về sáng tạo kỹ thuật và ứng dụng đa lĩnh vực. Trong 48 giờ, các đội thi đấu căng thẳng để cho ra đời dự án xuất sắc thuộc 3 nhóm giải: Giải chính, Giải theo hạng mục và Giải đặc biệt.
Giải chính
- VocakeX: Nền tảng Web3 edtech kết hợp gamification và AI để nâng cao trải nghiệm học tập, tích hợp module AI-driven với yếu tố trò chơi.
- StudyVerse: Nền tảng AI cung cấp lời khuyên sức khỏe tinh thần và hướng dẫn học tập cá nhân hóa, phân tích cảm xúc học sinh qua emotional recognition và adaptive feedback.
- VaultAI: Ví crypto AI-powered hỗ trợ quản lý tài sản phức tạp và đưa insight DeFi, sử dụng analytics và machine learning để tối ưu quyết định tài chính.
Giải theo hạng mục
- CryptoMentor: Chatbot thông minh hướng dẫn nhà đầu tư mới học và giao dịch crypto, tích hợp API thời gian thực.
- VaultAI
- Scholar AI: Công cụ AI phân tích dữ liệu, đề xuất cơ hội du học và tài chính phù hợp.
Giải đặc biệt
- StudyVerse
- TourRecommendation: Công cụ AI giúp khách du lịch tìm kiếm dịch vụ ăn uống, lưu trú minh bạch nhờ blockchain-fueled transparency.
- Buildlink: Đơn giản hóa tương tác blockchain bằng AI, hỗ trợ swapping và staking trên NEAR blockchain cho người mới.
Hackathon khẳng định tiềm năng của AI trong giải quyết vấn đề phức tạp đa lĩnh vực. Xem chi tiết dự án tại Dorahacks AI Hackathon.
Về Nhà tổ chức
SUCI BLOCKCHAIN HUB
SUCI Blockchain Hub cam kết phát triển và triển khai blockchain technology, nổi tiếng với các giải pháp decentralized solutions an toàn cho đa ngành. Tổ chức đóng góp vào nhiều dự án blockchain quan trọng, thúc đẩy đổi mới qua research and development và hợp tác với lãnh đạo ngành. SUCI tập trung nâng cao ứng dụng blockchain, thúc đẩy tính minh bạch trong digital transactions. Hiện tại, sứ mệnh của tổ chức là mở rộng blockchain integration để cung cấp giải pháp hiệu quả, bảo mật cho doanh nghiệp và cá nhân.
-
 @ cffd7b79:dd8ca91f
2025-04-17 15:14:18
@ cffd7b79:dd8ca91f
2025-04-17 15:14:18There aren't many Minecraft servers that have bitcoin involved, but recently I saw a server that finally has one, its called SovereignCraft. A server that is different from Satlantis(Now called Tribyu). How does one differ from Satlantis that got shutdown because of it? I'll tell you why my friend.
What differs between them is that Satlantis had a pay-to-win mechanic where the more "ASICs" you had the more likely you will get a block of sats. Therefore, the clan/player who had the most "ASICs" gets more sats than other players making it unfair for new players. Making it so newbies have to spend more sats than usual just so to get a scratch of sats. To get a picture of that situation think of this

SovereignCraft, however doesnt do that, instead it does actual 1:1 market exchange. It does NOT do virtual mining nor pay-to-win. You simply trade your sats for items you want for minecraft and vice versa.
EDIT: Sovtoshi, the owner of Sovereigncraft made a comment on more of the difference sovereigncraft has than Satlantis/Tribyu. Give it a look
-
 @ 4cebd4f5:0ac3ed15
2025-04-17 14:54:54
@ 4cebd4f5:0ac3ed15
2025-04-17 14:54:54Tổng quan Hackathon Eolas x Algo
Eolas x Algo: Agent Skills Hackathon được tổ chức trực tuyến, nhằm thúc đẩy hệ sinh thái CreatorBid thông qua phát triển kỹ năng AI agents. Sự kiện có sự tham gia của 58 developers với 36 dự án được phê duyệt. Điểm độc đáo: các CreatorBid agents trực tiếp đặt hàng kỹ năng cần thiết, loại bỏ vai trò trung gian truyền thống.
Người tham gia thi đấu ở hai hạng mục chính: Bounty Track (giải quyết vấn đề cụ thể từ agents) và Best Skills Track (ghi nhận dự án xuất sắc). Sự kiện nhận tài trợ từ Eolas, Algo, Shogun, AION cùng các agents cá nhân.
Dự án từ hackathon được tích hợp trực tiếp vào Olas Mech Marketplace, hỗ trợ triển khai thực tế và trao thưởng cho developer qua hệ thống OLAS. Các agents hàng đầu như Agent Algo và Eolas nhấn mạnh vai trò của sự kiện trong thúc đẩy đổi mới công nghệ.
Hackathon kết thúc vào 20/3, với ban giám khảo gồm đại diện CreatorBid và agents, đánh giá dự án dựa trên tính sáng tạo và tác động đến hệ sinh thái.
Các dự án đoạt giải
Best Agent Skill Track Prize Winners
- Agent Toolbox: Bộ công cụ nâng cao năng lực AI agents như phát hiện xu hướng, tạo hàm động và điều phối tác vụ.
- GridTrade Agent: Tối ưu hóa cặp giao dịch và tham số grid trading qua phân tích thị trường và biến động.
- Polytrader: Trợ lý giao dịch AI trên Polymarket, tự động hóa nghiên cứu và thực thi lệnh.
Main Prize Pool Winners
- sentimentX: Giám sát bảo mật AI-driven cho smart contract blockchain MultiversX.
- Brainiac_AI: Nền tảng tối ưu chiến lược DeFi kết hợp phân tích on-chain và ví phi lưu ký.
- framew0rk: Tối ưu hóa lợi suất DeFi qua AI assistant liên kết giao thức.
- MythosCraft: AI Storytelling Suite: Công cụ tạo nội dung kể chuyện tùy chỉnh bằng AI.
- QuanTrade-X: Phân tích AI và tín hiệu giao dịch crypto.
- ComicVerse AI: Tạo truyện tranh AI từ input người dùng.
- EOLAS - Submit your own skill: Portfolio Allocation Skill: Tối ưu danh mục crypto bằng AI và Lý thuyết Danh mục Hiện đại.
- SonicBo: AI agent trên WhatsApp hỗ trợ giao dịch blockchain.
- 👽Zeta Comic Generator👽: Chuyển đổi văn bản thành truyện tranh AI với kịch bản và biểu cảm nhân vật.
- Grid Trading Analyzer Skill: Công cụ Python phân tích cặp giao dịch crypto tối ưu.
- Trump news Reporter: AI theo dõi tin tức liên quan Trump theo thời gian thực.
- NFT Appraisal skill: Tạo AI agents định giá NFT.
- AI-Powered Dynamic Skill Selector (DSS): Tối ưu AI model bằng chiến lược Multi-Armed Bandit.
- CrypTweet: Bot giao dịch crypto dựa trên sentiment Twitter.
- AI Trump News Agent: Phân tích tin tức Trump với tone báo cáo tùy chỉnh.
- TrumpTracker-AI: Tổng hợp tin tức Trump và tạo meme từ tiêu đề nổi bật.
- Rigger-: Chuyển ngôn ngữ tự nhiên thành SQL queries.
- TNS: Theo dõi tin Trump bằng NLP và đa dạng phong cách báo cáo.
- Bob Roast Machine: Nền tảng AI tạo roast hài hước và meme.
- Agent 47: Telegram bot cung cấp tin chính trị kèm meme AI.
Skill Coordination & Optimization Prize Winner
Build Skills for Enhancing Data Access to CB Agents Prize Winner
World-Building & Lore Promotion Skills Prize Winner
Polymarket Trading Bots Prize Winner
Xem toàn bộ dự án tại DoraHacks.
Về Nhà tổ chức
Eolas
Eolas là đơn vị tiên phong trong lĩnh vực công nghệ và blockchain, nổi bật với các giải pháp tăng cường tính minh bạch giao dịch. Tổ chức tiếp tục tập trung vào R&D blockchain, giải quyết thách thức ngành để thúc đẩy tiến bộ tương lai.
-
 @ fd06f542:8d6d54cd
2025-04-17 14:16:50
@ fd06f542:8d6d54cd
2025-04-17 14:16:50顺炮直车对缓开车是20世纪70年代兴起的布局,常见变化如下: 1. 单边封锁对河沿车对边卒:炮二平五,炮8平5;马二进三,马8进7;车一平二,卒7进1;马八进七,马2进3;兵七进一,炮2进4;马七进八,车9进1;车九进一,车9平4;车九平七,车4进3(车4进6则形成另一变例),炮八平九,车1平2,车七进一,卒1进1,形成单边封锁局面,黑方车守河沿,红方控制边卒方向。 2. 单边封锁对肋炮攻马:前几步同单边封锁对河沿车对边卒,车九平七后,黑方走炮2平7打马,红方如马八进七,炮7进3,仕四进五,炮7平9,形成红方单边封锁,黑方肋炮攻马的局面,双方对攻。 3. 肋车捉炮对边马左士:炮二平五,炮8平5;马二进三,马8进7;车一平二,卒7进1;马八进九,马2进3;兵七进一,车9进1;车九进一,车9平4;仕四进五,车4进3;炮八平七,炮2进2,黑方肋车捉炮,红方边马左士防守,局势较为平稳。 4. 肋车捉炮对边马骑河车:前几步同上,车九进一后,黑方车9平4,接着车4进5骑河,红方炮八平七,炮2进2,车二进四,形成黑方肋车捉炮、边马配合骑河车的局面,双方相互牵制。 5. 双横车肋车捉炮对过河车右炮巡河:炮二平五,炮8平5;马二进三,马8进7;车一平二,卒7进1;马八进七,马2进3;兵七进一,车9进1;车九进一,车1进1;车二进六,车9平4;车二平三,炮2进2,形成红方过河车,黑方双横车、肋车捉炮,右炮巡河的局面,局面复杂,对攻激烈。 6. 双横车对过河车:炮二平五,炮8平5;马二进三,马8进7;车一平二,卒7进1;马八进七,马2进3;兵七进一,车9进1;车九进一,车1进1;车二进六,车9平4;车二平三,车4进7,黑方双横车出动,对红方过河车展开攻击,双方进入激烈的中盘战斗。 7. 横车对炮打中卒:炮二平五,炮8平5;马二进三,马8进7;车一平二,卒7进1;马八进七,马2进3;兵七进一,车9进1;炮五进四,马3进5;车二进五,车9平4;车二平五,炮2进4,红方炮打中卒获取物质优势,黑方出横车准备反击。 8. 边马缓出车对快横车:炮二平五,炮8平5;马二进三,马8进7;车一平二,卒7进1;马八进九,车9进1;车九进一,车9平4;车二进四,马2进1;炮八平七,炮2平3,红方边马缓出,黑方快出横车,双方形成不同的进攻节奏。 9. 缓封锁对巡河车:炮二平五,炮8平5;马二进三,马8进7;车一平二,卒7进1;马八进七,马2进3;兵七进一,炮2进4;马七进八,车9进1;车二进四,车9平4;车九进一,炮2平7;相三进一,车4进3,红方缓封锁,黑方出巡河车,局势发展较为平稳。 10. 巡河炮对过河车:炮二平五,炮8平5;马二进三,马8进7;车一平二,卒7进1;马八进七,马2进3;兵七进一,炮2进2;车二进六,车9进1;车二平三,车9平4;炮八进二,形成红方巡河炮、过河车,黑方出横车的局面,双方互相试探,寻找进攻机会。
-
 @ fd06f542:8d6d54cd
2025-04-17 14:15:06
@ fd06f542:8d6d54cd
2025-04-17 14:15:06直车对横车 的概念
顺炮直车对横车:红方出直车(车一平二),黑方出横车(车 9 进 1),这是顺炮布局中常见的一种变化。红方直车可以快速出动,威胁黑方右翼,黑方横车则可以灵活调动,根据局势选择进攻或防守的方向。后续可能会出现红方进车过河压马,黑方出炮封车等变化,双方展开激烈的争夺。
顺炮直车对横车布局体系主要有以下分类:
- 古典攻法
- 顺炮过河车对横车:红车一平二后车二进六过河,以强硬攻势迅速压制黑方阵营。
- 顺炮缓补士对横车:红出直车后不急于补士(士四进五缓出) ,依黑方行棋灵活选择攻防策略。
- 顺炮跳边马对横车:红马八进九上边马,平炮通车平衡两翼子力,防止黑卒3进1争先,着法稳健。
- “胡氏双正马”攻法
- 顺炮直车进三兵对横车挺3卒:红进三兵、黑挺3卒形成牵制,红可借马三进四等手段跃马进攻。
- 顺炮直车进三兵对横车跳边马:红进三兵后,针对黑边马位置,以炮八平七等手段威胁黑方马获取局面优势。
- 顺炮直车进七兵对横车:红进七兵,黑车9平4后,红可选择车二进四巡河或车二进六过河等不同进攻战术。
- 顺炮直车“两头蛇”对双横车:红兵三进一、兵七进一构成“两头蛇”阵,与黑方双横车激烈争夺,红借双兵推进掌控空间,黑寻机反击。
- 其他常见变化
- 正马三兵与黑右肋车的攻防对抗;正马应对黑挺3卒的局面变化。
- 正马三兵对阵黑肋车边马;“两头蛇”阵势迎战黑双横车的局势博弈。
- 正马三兵对黑方马后藏车;“两头蛇”对黑正马边炮的局势发展。
- 红方正马左士应对黑右肋车;红方采用巡河车、五六炮的布局变化,以及双正马进七兵分别对黑正马、右肋车的局面策略 。
- 古典攻法
-
 @ fd06f542:8d6d54cd
2025-04-17 14:08:34
@ fd06f542:8d6d54cd
2025-04-17 14:08:34象棋布局基础
布局的定义与重要性
象棋布局是指对局开始阶段,双方棋子的部署和相互间的制约关系。它是中局和残局的基础,合理的布局能够为中局的战斗创造有利条件,甚至在某些情况下直接影响到整盘棋的胜负走向。一个好的布局可以使棋手在开局阶段就占据主动,控制局面,限制对手的发挥。
布局的分类
炮类布局
- 中炮布局:以当头炮(炮二平五或炮八平五)开局,具有很强的进攻性,威胁对方中卒,直接对对方的九宫发起冲击。例如顺炮布局(双方都走中炮,且炮在同一条直线上)、列手炮布局(双方都走中炮,但炮不在同一条直线上)等。
- 过宫炮布局:炮从一侧平移到另一侧的中路,如炮二平六,它的特点是子力调动灵活,可迅速集结兵力于一侧,伺机而动,同时对士角有一定的控制作用。
- 顺炮布局:顺炮布局是双方以中炮开局且两炮在同一直线的布局体系,如红方炮二平五,黑方炮 8 平 5,形成激烈的对攻格局。其特点是开局便剑拔弩张,双方子力沿同一方向快速展开,直接在中路和侧翼展开火力交锋。 常见有顺炮直车对横车、顺炮横车对直车等变化,红方可借直车过河压制黑方马炮,黑方则以横车抢占肋道反击。该布局强调先手争夺,需迅速出动强子控制要道,同时注重车、马、炮的配合,在互攻中寻找突破机会,是进攻型棋手偏爱的布局选择。
马类布局
- 屏风马布局:双马分别跳至正马位(马二进三、马八进七),两马互相保护,形似屏风,能够有效抵御中炮的进攻。它具有稳健的防守能力,同时也具备一定的反击潜力,如五七炮对屏风马、五八炮对屏风马等常见变化。
- 单提马布局:一马正马(如马二进三),另一马屯边(如马八进九),其特点是子力结构较为松散,但在防守上也有一定的弹性,可通过灵活的子力调动来化解对方的攻势。
兵类布局
- 仙人指路布局:先走方第一步挺兵(如兵七进一或兵三进一),试探对方的应手,根据对方的走法再决定后续的布局方向。这种布局灵活多变,可演变成多种复杂的局面,如仙人指路对卒底炮、仙人指路对飞象等。
- 对兵局布局:双方都以挺兵开局,如兵七进一,兵7进一,开局阶段局面相对平稳,双方需要通过后续的子力调动来寻找战机,逐渐扩大优势。
布局的基本原则
- 快速出子:在布局阶段,要尽快将棋子从原始位置出动到关键位置,占据有利的空间,形成有效的子力配合。例如,车要尽早开出,控制要道;马炮等也要合理部署,发挥其威力。
- 子力协调:各个棋子之间要相互配合,避免出现子力拥堵或脱节的情况。例如,马炮之间可以形成有效的攻击组合,车要为其他棋子提供支援和掩护。
- 抢占要点:布局阶段要注意抢占棋盘上的重要位置,如肋道(四、六路线)、河口(三、七路线的卒林线)等。这些位置对于控制局面、展开进攻或防守都具有重要意义。
- 攻守平衡:在布局时,不能一味地追求进攻而忽视防守,也不能只注重防守而缺乏反击的手段。要根据局势的发展,合理调整攻守策略,保持局势的平衡。
布局的学习方法
- 研究经典布局:通过学习和研究历史上的经典布局对局,了解各种布局的变化和特点,掌握布局的基本理论和技巧。可以参考专业的象棋书籍、棋谱等资料。
- 实战练习:在实战中运用所学的布局知识,通过不断的实践来加深对布局的理解和掌握。同时,在实战中要注意总结经验教训,分析自己布局中的不足之处,不断改进和提高。
- 分析对局:对自己和他人的对局进行分析,特别是对布局阶段的走法进行深入研究。分析每一步棋的优劣,思考是否有更好的走法,从而提高自己的布局水平。
- 与高手交流:与水平较高的棋手交流,请教他们在布局方面的经验和技巧。可以通过参加象棋比赛、棋社活动等方式与高手进行面对面的交流和学习。
以上就是关于象棋布局的一些基本内容,希望对大家学习和理解象棋布局有所帮助。在实际的对局中,要根据具体情况灵活运用各种布局知识,不断提高自己的象棋水平。
-
 @ fd06f542:8d6d54cd
2025-04-17 14:03:22
@ fd06f542:8d6d54cd
2025-04-17 14:03:22 -
 @ fd06f542:8d6d54cd
2025-04-17 14:00:40
@ fd06f542:8d6d54cd
2025-04-17 14:00:40{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/d8bc1e106d0144fce7dd96264f6b2bad7b35100efb1040d413cac16db7584e72.webp","title":"象棋布局体系","author":"nostrchess"}
-
 @ fbf0e434:e1be6a39
2025-04-17 12:49:04
@ fbf0e434:e1be6a39
2025-04-17 12:49:04Hackathon 概述
由 Injective 和 ElizaOS 主办的 Injective AI Agent Hackathon 吸引了 496 名参与者,最终提交了 126 个获批项目。本次 Hackathon 突显了 AI 和 区块链 的结合,展示了 AI 代理在去中心化网络中运作的潜力,并推动了超越传统金融的创新。参与者探索了多种应用,包括自主交易、代币化资产管理和 AI 驱动的金融洞察。
本次设立的奖池高达 $100,000, 其中 $50,000 为Grant Prizes,还有其他重要项目的额外奖项。通过将 AI 的适应性与区块链的透明性结合,本次 Hackathon 展示了这些技术的变革潜力,并标志着在展示 AI 和区块链整合创新潜力方面一个重要的里程碑。
Hackathon 获奖者
-
Jecta: Jecta 集成了多个大型语言模型(LLM),以自动化 Injective 区块链上的任务。它专注于透明性和社区驱动的开发,利用开源技术提升使用的简便性和效率。
-
Paradyze: Paradyze 通过为区块链交易引入自然语言接口来改善 Injective 生态系统。其设计旨在增强可访问性和安全性,使用户能够以简单的交互方式进行操作。
要查看所有项目,请访问 Injective AI Hackathon 页面。
关于组织者
Injective
Injective 是一个基于区块链的组织,专注于开发去中心化金融(DeFi)解决方案。它以创建优化 DeFi 应用的可互操作的 Layer-1 区块链而闻名,促进快速且安全的交易。值得注意的项目包括 Injective Protocol,该协议增强了去中心化交易的跨链能力。
Injective 的使命是通过提供可访问且可靠的去中心化基础设施推动金融自由,为多样化的金融服务赋能,支持用户和开发者在区块链生态系统中进行创新。
-
-
 @ 95cb4330:96db706c
2025-04-17 07:12:01
@ 95cb4330:96db706c
2025-04-17 07:12:01Summary and Guide Based on Sam Altman's Classic Post
In life and business, almost everyone starts off chasing money. But if you observe closely — especially among those who achieve outlier success — you’ll notice something interesting:
Over time, money becomes secondary. The real obsession becomes making something important happen.
Sam Altman, entrepreneur and CEO of OpenAI, laid out a roadmap to achieving this rare level of success. It’s about much more than working hard or being smart — it’s about how you think, act, and invest your time over decades.
Here's a deep breakdown of his 13 principles — explained, with examples and reflections.
1. Compound Yourself
Think exponentially, not linearly.
- Businesses (and careers) that compound — growing 50% per year — become unstoppable over time.
- You want your learning, network, and impact to snowball.
- Focus on adding zeros to your results, not just small wins.
🔎 Example: Instead of focusing on one-off gigs, build skills and systems that grow your results faster every year. Think like an investor, not an hourly worker.
2. Have (Almost) Too Much Self-Belief
You have to believe in yourself beyond reason — but stay open to feedback.
- Most real innovation requires contrarian thinking.
- Early critics will tell you you're crazy — and that’s normal.
- Learn to manage your own morale.
🔎 Example: Elon Musk’s absolute certainty about colonizing Mars — even when few believed him — fueled SpaceX’s breakthrough innovations.
3. Learn to Think Independently
Original thinking can’t be taught by schools.
- Break problems into first principles instead of copying others.
- Test crazy ideas quickly and cheaply.
- The ability to "figure things out when no one knows what to do" is a superpower.
🔎 Example: Airbnb founders had no roadmap for building a company based on renting strangers' homes — they made it up as they went.
4. Get Good at Sales
It’s not enough to have a great idea — you must convince others to join you.
- Great careers and startups are sales jobs: selling visions to investors, customers, and employees.
- The best sales come from genuine belief in what you're building.
🔎 Example: Altman emphasizes in-person interactions: “When it mattered, I always got on the plane.”
5. Make It Easy to Take Risks
Big rewards require many small bets and the willingness to look foolish.
- Risk is overestimated; reward is underestimated.
- Stay financially and mentally flexible early in life.
🔎 Example: Leaving a high-paying tech job is hard — but those who leap to start companies often change the world.
6. Focus
Doing the right work matters more than working hard on the wrong things.
- Ruthlessly prioritize what truly matters.
- Ignore distractions.
- Be unstoppable once you know what to focus on.
🔎 Example: Startups win by focusing on one core thing until they dominate, not by trying to do everything.
7. Work Hard
- Smart + hard work is required to reach the top 1% of any field.
- Success begets success — momentum compounds.
- Find work you love and people you love working with to avoid burnout.
🔎 Example: Early Amazon teams pulled insane hours — but they believed they were building something world-changing.
8. Be Bold
- Solve hard problems, not easy ones.
- People are attracted to missions that matter.
🔎 Example: If your dream is gene-editing or AI, don’t settle for building another social media app.
9. Be Willful
- The world is more malleable than you think.
- Persistence and optimism often win in the end.
🔎 Example: Airbnb founders survived maxed-out credit cards and endless rejection — but they didn't quit.
10. Be Hard to Compete With
- Differentiate yourself through leverage:
- Skills at the intersection of fields
- Strong personal brand
- Unique insights
🔎 Example: Elon Musk isn't just an engineer or marketer — he's both, and that makes him hard to beat.
11. Build a Network
- Great accomplishments require great teams.
- Help people long before you need them.
- Spot undiscovered talent early.
🔎 Example: Most of Altman’s best career opportunities came from helping others years before it paid off.
12. Own Equity
- Salaries won't make you rich.
- Owning assets (companies, IP, real estate) creates real wealth.
🔎 Example: The richest people in the world — Bezos, Musk, Gates — got there by owning companies, not by drawing salaries.
13. Be Internally Driven
- Don’t chase approval or follow the herd.
- Care about doing great work for yourself.
- If you're motivated mainly by status or envy, you will lose focus.
🔎 Example: Jessica Livingston and Paul Graham were mocked early for Y Combinator. They didn’t care — and YC changed the world of startups.
💬 Final Thought
Success isn’t about short-term hacks. It’s about long-term habits:
- Think long-term.
- Bet boldly.
- Compound yourself.
- Build something important.“Eventually, you will define your success by performing excellent work in areas that are important to you. The sooner you start, the further you will go.”
Commit to the path. The rewards — both internal and external — are beyond what most people ever experience.
🌱 Start planting seeds today. Watch them compound beyond imagination. 🚀
📈 How To Be Successful — 13 Principles for Outlier Achievement
| Principle | Summary | |:-------------|:------------| | 🧠 Compound Yourself | Focus on exponential growth — build skills, network, and leverage over time. | | 💪 Self-Belief (Almost Too Much) | Believe in your vision even when others doubt you, balanced by self-awareness. | | 🔥 Think Independently | Use first-principles thinking; test new ideas rather than copying others. | | 🗣️ Master Sales | Convince others of your ideas — genuine belief makes selling easier. | | 🎯 Make Risk-Taking Easy | Stay flexible and bet on ideas with high upside and limited downside. | | 🎯 Focus | Ruthlessly prioritize — working on the right things matters more than working long hours. | | 🛠️ Work Hard | Smart + intense effort is necessary to reach the top 1%. Momentum compounds success. | | 🚀 Be Bold | Solve big, important problems — bold missions create constant tailwinds. | | 🌎 Be Willful | Persist until you succeed — optimistic persistence often bends reality. | | 🧩 Be Hard to Compete With | Combine rare skills and leverage to become uniquely valuable. | | 🤝 Build a Powerful Network | Help others early; spot and collaborate with rising talent. | | 🏡 Own Equity | Own scalable assets — don’t just trade your time for money. | | 🔥 Stay Internally Driven | Follow intrinsic motivation — work on what you truly care about. |
🚀 Final Thought
"Long-term focus on inputs, boldness, learning, and compound effort leads to extraordinary success."
-
 @ f18b1f8f:5f442454
2025-04-17 12:01:06
@ f18b1f8f:5f442454
2025-04-17 12:01:06rec21jSQ6M9WtT5Oz
This is a server acting as a client - a sort of MCP gateway you can add to Slack. It will respond to user's messages, and in turn use MCPs configured on it's end. Connect to internal SQLite DBs, web scraping and more.
-
 @ 29ccddd8:49860677
2025-04-17 11:31:54
@ 29ccddd8:49860677
2025-04-17 11:31:54Der Kauf einer Sexpuppe ist heutzutage so individuell wie der persönliche Geschmack. Angesichts der großen Auswahl an Modellen, Materialien und Funktionen kann die Entscheidung schnell überwältigend wirken. Mit diesem Ratgeber erhältst du praktische Tipps, um die perfekte Real Doll nach deinen Bedürfnissen und deinem Budget auszuwählen.
1. Materialien: Silikon oder TPE?
Silikon und TPE (Thermoplastisches Elastomer) sind die gängigsten Materialien für hochwertige Sexpuppen.
- Silikon
- Vorteile: Sehr langlebig, hitzebeständig, realistisch in Optik und Haptik, leicht zu reinigen.
- Nachteile: Meist teurer als TPE, weniger flexibel.
- TPE
- Vorteile: Sehr weich und elastisch, fühlt sich hautähnlich an, meist günstiger.
- Nachteile: Empfindlicher gegenüber Hitze, benötigt mehr Pflege, kann leichter Flecken aufnehmen.
Tipp: Wer Wert auf maximale Realitätsnähe und Pflegeleichtigkeit legt, wählt Silikon. Für ein begrenztes Budget und ein besonders weiches Gefühl ist TPE eine gute Wahl.
2. Funktionen: Mehr als nur Optik
Moderne lebensgroße Sexpuppe bieten eine Vielzahl von Funktionen:
- Bewegliche Gelenke: Für realistische Posen und Stellungen.
- Heizfunktion: Für eine natürliche, körperwarme Temperatur.
- Soundmodule: Für akustische Stimulation.
- Austauschbare Teile: Verschiedene Köpfe, Perücken und Outfits sorgen für Abwechslung.
- Smart Dolls: Modelle mit KI-Interaktion, Sprachsteuerung oder App-Anbindung.
Tipp: Überlege dir vor dem Kauf, welche Funktionen dir wirklich wichtig sind – sie beeinflussen maßgeblich den Preis.
3. Budget: Was kostet eine hochwertige Real Doll?
Die Preisspanne ist groß und hängt von Material, Größe, Detailgrad und zusätzlichen Features ab:
- Einfache Modelle: ab ca. 500 € (meist kleinere, weniger detaillierte Puppen)
- Mittelklasse: 1.000–2.000 € (lebensechte Körpergröße, realistische Optik, gute Materialien)
- Premiumklasse: ab 2.000 € (hochwertiges Silikon, viele Funktionen, individuelle Gestaltung)
Tipp: Achte auf versteckte Kosten wie Versand, Zoll und Zubehör. Bei seriösen Shops sind diese meist inklusive.
4. Worauf sollte man beim Kauf achten?
- Seriöse Händler: Achte auf Zertifikate (CE, RoHS, ggf. FDA), transparente Preise, diskreten Versand und guten Kundenservice.
- Pflege & Reinigung: Informiere dich über Reinigungsmöglichkeiten und Pflegeprodukte, um die Lebensdauer deiner real sex doll zu verlängern.
- Datenschutz: Seriöse Anbieter garantieren diskrete Verpackung und Schutz deiner Daten.
Fazit: Deine perfekte Sexdoll wartet
Mit der richtigen Vorbereitung findest du garantiert die silikon sexpuppe, die zu dir passt. Überlege dir, welches Material und welche Funktionen dir am wichtigsten sind – und setze dir ein Budget. Achte beim Kauf auf Qualität, Sicherheit und einen vertrauenswürdigen Anbieter.
- Silikon
-
 @ 95cb4330:96db706c
2025-04-17 06:16:21
@ 95cb4330:96db706c
2025-04-17 06:16:21In business, investing, and personal goals, it’s easy to obsess over outcomes: - How many sales did I make? - How high is my stock price? - How much money did I earn this month?
But if you focus too much on outputs, you risk chasing results without improving the process that actually creates success.
The best leaders — like Jeff Bezos — follow a simple but powerful principle:
Focus daily on controllable inputs. The outputs will follow naturally over time.
Let’s break down what this means, why it works, and how you can apply it to build long-term success.
🧠 What Does "Focus on Inputs" Mean?
Inputs = Actions you control directly: - Customer service quality - Product development speed - Operational efficiency - Attention to detail in execution
Outputs = Results you want but can’t control directly: - Revenue - Profits - Stock price - Market share
Key idea:
👉 When you relentlessly improve the inputs, you set the stage for outstanding outputs over time.
🚀 How Jeff Bezos Used Input Focus to Build Amazon
At Amazon, Bezos hardwired this mindset into the company:
- Teams weren’t told to "increase revenue."
- They were told to improve customer satisfaction, reduce delivery times, and expand product selection.
- Amazon focused on input metrics like:
- Time from customer click to shipment
- Product availability rates
- Number of customer complaints
By perfecting these controllable actions every day, sales and stock price naturally exploded over time.
💬 As Bezos put it:
"We can’t guarantee the stock price will go up, but we can guarantee that customers will love us if we execute on the right inputs."
📈 Why Focusing on Inputs Wins Over Time
✅ Inputs are under your direct control.
You can’t control customer behavior or market swings — but you can control how you perform daily tasks.✅ Good inputs compound over time.
Small daily improvements (like better service or faster shipping) build massive trust and long-term loyalty.✅ Outputs are lagging indicators.
If you chase outputs alone, you’re reacting to the past. Input focus keeps you proactive.✅ Stress and emotional swings decrease.
Instead of riding the highs and lows of every result, you stay calm and centered on today’s actions.
📚 Resources to Learn More
- 📄 Jeff Bezos on Input Metrics – Harvard Business Review
- 📚 How Focusing on Inputs Drives Success – Motley Fool
- 📘 James Clear on Goals vs Systems
🛠 How to Apply "Input Focus" in Your Own Work
✅ 1. Define Your Key Inputs
Ask yourself:
"What daily actions, if consistently improved, would lead to my goals?"
Examples: - Salesperson: Focus on number of quality client calls, not sales closed. - Writer: Focus on daily word count, not bestseller lists. - Startup founder: Focus on product iterations, not initial user growth.
✅ 2. Track Inputs, Not Just Outputs
Build habits around measuring what you control:
"Did I deliver 5 demos today?" "Did I ship a new feature this week?" "Did I respond to every customer ticket within 2 hours?"
✅ 3. Trust the Process
Results don’t show up instantly.
Stay consistent.
Refine your inputs.
Good outputs are a lagging reward for great daily actions.
📣 Final Thought
Outputs are loud.
They grab headlines.
They create FOMO.But inputs are where real power lies.
"Be obsessed with the process, and the results will take care of themselves."
Follow the principle that helped Amazon become a trillion-dollar company:
🎯 Control your inputs. Trust the compounding. Let success chase you. 🚀
-
 @ 260924ad:a23c06fb
2025-04-17 11:14:16
@ 260924ad:a23c06fb
2025-04-17 11:14:16GI8 không chỉ đơn thuần là một nền tảng giải trí trực tuyến, mà còn là một hệ sinh thái công nghệ được đầu tư kỹ lưỡng nhằm đem lại trải nghiệm toàn diện cho người dùng. Ngay từ lần đầu truy cập, người dùng có thể cảm nhận rõ sự chuyên nghiệp thông qua giao diện được thiết kế tối giản nhưng không kém phần hiện đại, tối ưu hóa cho cả thiết bị di động lẫn máy tính để bàn. Tốc độ tải trang nhanh, khả năng xử lý dữ liệu ổn định kể cả trong thời gian cao điểm giúp GI8 ghi điểm tuyệt đối với người sử dụng ở mọi lứa tuổi và trình độ công nghệ khác nhau. Sự tinh tế còn thể hiện ở cách bố trí chức năng một cách khoa học, dễ sử dụng, hỗ trợ người dùng mới nhanh chóng làm quen mà không gặp rào cản kỹ thuật. Bên cạnh đó, hệ thống bảo mật được đầu tư mạnh mẽ, ứng dụng các công nghệ mã hóa tiên tiến nhằm đảm bảo thông tin cá nhân và dữ liệu giao dịch của người dùng luôn được bảo vệ an toàn tuyệt đối. Đây chính là một trong những yếu tố quan trọng giúp GI8 tạo dựng được niềm tin và sự trung thành từ phía người dùng trong suốt quá trình hoạt động.
Không chỉ dừng lại ở việc mang đến trải nghiệm người dùng thuận tiện, GI8 còn chú trọng vào yếu tố cá nhân hóa để từng người dùng đều có được hành trình sử dụng riêng biệt, phù hợp với nhu cầu và sở thích cá nhân. Thuật toán AI của hệ thống liên tục phân tích hành vi người dùng để đưa ra các gợi ý chính xác, từ đó cải thiện chất lượng sử dụng và tăng tính tương tác. Ngoài ra, GI8 cũng cung cấp nhiều tính năng hỗ trợ người dùng như hệ thống nhắc lịch, cảnh báo thông minh, quản lý tài khoản hiệu quả và cập nhật thông tin kịp thời, giúp mọi hoạt động trở nên liền mạch và dễ kiểm soát. Sự thân thiện trong từng thao tác, từ nạp – rút nhanh chóng cho tới tra cứu lịch sử giao dịch hay hỗ trợ trực tuyến, là minh chứng rõ ràng cho chiến lược phát triển toàn diện và lấy người dùng làm trung tâm của GI8. Đồng thời, việc duy trì và nâng cấp định kỳ hệ thống giúp nền tảng này luôn vận hành ổn định, tránh được các lỗi phát sinh và giảm thiểu tối đa các rủi ro gây ảnh hưởng đến trải nghiệm khách hàng.
Một điểm nổi bật không thể không nhắc đến chính là sự đầu tư nghiêm túc của GI8 vào đội ngũ chăm sóc khách hàng – những người luôn sẵn sàng hỗ trợ, giải quyết nhanh chóng mọi thắc mắc, khiếu nại và nhu cầu của người dùng. Đây không chỉ là bộ phận kỹ thuật mà còn là cầu nối giữa nền tảng và cộng đồng, luôn đóng vai trò chủ động trong việc thu thập phản hồi và đề xuất cải tiến sản phẩm. Đội ngũ này hoạt động 24/7 qua nhiều kênh như live chat, hotline, email để đảm bảo người dùng luôn cảm thấy được hỗ trợ bất cứ lúc nào họ cần. Việc liên tục cập nhật xu hướng công nghệ mới, cải tiến tính năng theo nhu cầu thực tế từ người dùng, và không ngừng mở rộng kho nội dung cũng khiến GI8 luôn giữ được sức hút trên thị trường cạnh tranh khốc liệt. Từ những yếu tố kỹ thuật đến chăm sóc hậu mãi, từ giao diện đến tốc độ vận hành, tất cả đều hội tụ tại GI8 để tạo nên một nền tảng giải trí toàn diện, hiện đại và đáng tin cậy bậc nhất hiện nay.
-
 @ 95cb4330:96db706c
2025-04-17 06:10:39
@ 95cb4330:96db706c
2025-04-17 06:10:39If there’s one strategy that quietly fuels the success of icons like Sam Altman, Jeff Bezos, and Elon Musk, it’s not a secret growth hack or a flashy new tool.
It’s something deceptively simple—and profoundly powerful:They learn. Constantly. Relentlessly. Deeply.
This is the essence of Compound Learning—the idea that knowledge, like money, compounds over time.
The more you invest in learning, the faster your decisions, the sharper your thinking, and the bigger your edge becomes.
🧠 What Is Compound Learning?
Compound learning means consistently building deep knowledge over time—not just collecting facts or skimming headlines.
It’s about:- Understanding principles
- Asking hard questions
- Applying what you learn across everything you do
It works just like compound interest:
- Learn a little every day
- Connect ideas across time
- Make smarter choices
- Smarter choices lead to even more learning opportunities
The longer you do it, the more valuable and self-reinforcing it becomes.
🚀 Examples in Action
📘 Sam Altman – Learning Is His Edge
Sam Altman, CEO of OpenAI, says:
"The best founders are learning machines."
He reads obsessively, writes to clarify his thinking, and debates ideas constantly with people smarter than him.
By compounding knowledge across AI, startups, economics, and human behavior, he positions himself to spot opportunities before others even see the pattern forming.
📚 Jeff Bezos – Reading as a Competitive Advantage
At Amazon, Bezos famously starts meetings in silence—reading internal memos.
Why? Because deep thinking requires deep attention.He believes:
- Clear writing = Clear thinking
- Deep reading = Better decision-making
His broad reading habits—from science fiction to business reports—gave him a mental model toolkit that shaped Amazon’s long-term success.
🚀 Elon Musk – Learning Across Disciplines
Elon Musk didn’t attend rocket science school. He:
- Read propulsion textbooks
- Asked engineers endless questions
- Cross-applied knowledge from physics, coding, and manufacturing
Result:
He built SpaceX through self-driven, compounded learning, not formal credentials.
🧭 How to Practice Compound Learning
✅ 1. Choose Depth Over Noise
Don’t chase surface-level content.
Go deep.- Read whole books
- Revisit difficult concepts
- Study timeless principles
✅ 2. Connect What You Learn
Link ideas across fields:
- How does biology teach you about systems?
- What does history reveal about strategy?
- How does physics influence product thinking?
The richest insights live between disciplines.
✅ 3. Reflect and Apply
Learning compounds when you use it.
- Journal what you’re learning
- Teach it to someone else
- Apply it immediately in your work or decisions
✅ 4. Make It a Daily Habit
Even 30 minutes a day turns into:
- 3.5 hours/week
- 182 hours/year
- Thousands of hours over a career
That’s a competitive moat no one can take away.
🧠 Prompt to Apply Today
What’s one area where deeper understanding could unlock better thinking or decisions?
Block 30 minutes today to go deep.
Read. Reflect. Learn.
Then ask: How can I use this tomorrow?
📚 Resources to Explore
- 📘 Sam Altman – Compound Learning in “How to Be Successful”
- 📄 Jeff Bezos’ Reading and Thinking Culture – Inc.
- 🎥 Elon Musk on Self-Learning – YouTube
💡 Final Thought
You don’t need to be a genius to succeed—but you do need to learn like one.
Compound learning is quiet, patient, and unstoppable.Start today.
Learn deeply.
Watch the returns grow for a lifetime. 📈 -
 @ 260924ad:a23c06fb
2025-04-17 11:13:21
@ 260924ad:a23c06fb
2025-04-17 11:13:21Trong bối cảnh công nghệ số phát triển mạnh mẽ như hiện nay, việc sở hữu một nền tảng hoạt động ổn định, thông minh và thân thiện với người dùng không còn là một lựa chọn xa vời mà đã trở thành nhu cầu tất yếu. 99win đã không ngừng chứng minh vị thế của mình khi liên tục mang đến những trải nghiệm kỹ thuật số linh hoạt, tối ưu hóa cho cả người dùng mới lẫn những người sử dụng lâu dài. Từ giao diện thân thiện, tốc độ truy cập nhanh chóng đến tính năng vận hành mượt mà trên đa thiết bị, tất cả đều góp phần tạo nên một không gian số đáng tin cậy, nơi mọi người có thể kết nối và tương tác một cách hiệu quả. Hơn thế nữa, nền tảng này không ngừng cải tiến bằng cách ứng dụng những công nghệ tiên tiến, mang đến hiệu suất vận hành ổn định dù trong thời điểm cao điểm. Điều này chứng minh rằng 99win không chỉ quan tâm đến tính thẩm mỹ bên ngoài mà còn đặt trọng tâm vào chất lượng cốt lõi bên trong nhằm phục vụ tốt nhất nhu cầu người dùng hiện đại.
Một điểm mạnh nổi bật khác của 99win chính là khả năng cá nhân hóa trải nghiệm người dùng nhờ vào hệ thống thuật toán thông minh, được xây dựng dựa trên dữ liệu hành vi và nhu cầu sử dụng thực tế. Người dùng sẽ cảm nhận được rõ ràng sự khác biệt khi mỗi phiên truy cập đều được điều chỉnh sao cho phù hợp nhất với thói quen của họ, từ bố cục hiển thị đến các gợi ý tiện ích, mọi thứ đều được tối ưu hóa để mang đến sự tiện lợi và tiết kiệm thời gian. Việc lắng nghe phản hồi từ cộng đồng cũng là một phần quan trọng trong triết lý phát triển của 99win. Nền tảng không chỉ tích cực tiếp thu ý kiến, mà còn triển khai nhanh chóng các cải tiến dựa trên những góp ý này, từ đó tạo nên một hệ sinh thái thân thiện và liên tục hoàn thiện. Chính nhờ tư duy cầu tiến và linh hoạt này, 99win đã dần xây dựng được lòng tin vững chắc từ phía người dùng, không ngừng mở rộng cộng đồng sử dụng và giữ vững được vị thế cạnh tranh giữa hàng loạt nền tảng công nghệ cùng lĩnh vực.
Không thể không nhắc đến yếu tố con người đằng sau sự thành công của 99win, đặc biệt là đội ngũ hỗ trợ khách hàng chuyên nghiệp, tận tâm và luôn sẵn sàng đồng hành cùng người dùng trong mọi tình huống. Dù gặp phải bất kỳ vấn đề gì trong quá trình trải nghiệm, người dùng đều có thể liên hệ và nhận được sự hỗ trợ nhanh chóng qua nhiều kênh như email, trò chuyện trực tiếp hay tổng đài. Sự phản hồi kịp thời, chính xác và thân thiện này không chỉ giúp giải quyết vấn đề nhanh chóng mà còn tạo cảm giác yên tâm và hài lòng cho người dùng. Chính sự kết hợp giữa công nghệ tiên tiến và yếu tố con người đã giúp 99win định hình được bản sắc riêng trong thị trường công nghệ số, đồng thời mở ra một hướng đi mới đầy hứa hẹn cho tương lai. Với tầm nhìn chiến lược rõ ràng và cam kết đổi mới không ngừng, 99win đang từng bước khẳng định vai trò tiên phong trong việc kiến tạo trải nghiệm kỹ thuật số toàn diện và bền vững.
-
 @ 95cb4330:96db706c
2025-04-17 05:59:53
@ 95cb4330:96db706c
2025-04-17 05:59:53One of the most important habits shared by top entrepreneurs like Elon Musk, Sam Altman, and Jeff Bezos is this simple but powerful principle:
Move fast first. Build the system later.
In the early stages of any idea, project, or product, speed of iteration matters far more than polish or perfection. Once you find out what works, then you can systematize and scale.
Let’s break down why this matters—and how you can apply it today.
Why Iterating Fast Beats Overplanning
When you’re trying something new, it’s easy to get trapped in:
- Endless research
- Overthinking
- Waiting for a "perfect" launch
The problem is:
No plan survives first contact with reality.
You don’t know exactly how users, customers, or the market will react. You need real feedback, not guesses.
Fast iteration means:
- Testing assumptions quickly
- Gathering real-world data
- Learning what actually works (and what doesn’t)
Systematization comes after you discover something that works—not before.
Examples in Action
🚀 Elon Musk – SpaceX’s Rapid Prototyping
At SpaceX, Musk doesn’t spend years perfecting a rocket on paper. Instead:
- He builds early prototypes, even if they’re rough.
- He tests them quickly—even if they crash.
- He learns from each failure and improves at lightning speed.
Result: SpaceX cut rocket development time dramatically compared to traditional aerospace companies.
🚀 Sam Altman – Startups Move Fast, Then Formalize
Sam Altman teaches startup founders:
"Ship first. Learn fast. Build processes later."
At OpenAI and Y Combinator, the focus was:
- Build basic products quickly.
- Test them with users.
- Only after finding product-market fit, build durable systems.
Speed wins early. Systems win later.
🚀 Jeff Bezos – "Disagree and Commit" for Speed
At Amazon, Bezos promotes the idea of "disagree and commit":
- Make decisions quickly, even with incomplete information.
- Move forward fast, knowing you can adjust if needed.
- Avoid the paralysis of endless debate.
Quick action + flexible course-correction beats slow perfection.
How to Apply "Iterate Fast, Then Systematize"
✅ Step 1: Identify an Area You’re Overthinking
Ask yourself:
"Where am I stuck planning instead of acting?"
It could be launching a new product, testing a marketing idea, starting a project—anything.
✅ Step 2: Run a Fast, Small Test
Don’t wait weeks.
- Build a minimum viable version.
- Ship it to a small audience.
- Gather feedback immediately.
✅ Step 3: Refine Based on Reality
- Use feedback to improve.
- Drop what doesn’t work.
- Double down on what shows promise.
Keep iterating fast until you find something that clicks.
✅ Step 4: Systematize After Success
Only after you know what’s working:
- Automate it.
- Build repeatable processes.
- Scale it efficiently.
Don’t waste time scaling something before it’s proven.
🧠 Prompt to Apply Today
Where in your work can you test something today instead of planning it for weeks?
Pick one idea you’ve been sitting on.
- Launch a version today.
- Learn fast.
- Build the system later.
📚 Resources to Learn More
- Sam Altman on Fast Iteration – Blog
- Elon Musk on Testing and Speed – AMA
- Jeff Bezos on Decision Speed
Final Thought
In today's world, speed is a superpower.
The faster you test ideas, the faster you learn, the faster you win.Don’t aim for perfect. Aim for proven.
Then build the machine to scale it.🚀 Iterate fast. Refine fast. Systematize smartly.
-
 @ 260924ad:a23c06fb
2025-04-17 11:12:26
@ 260924ad:a23c06fb
2025-04-17 11:12:26Trong thế giới công nghệ đang phát triển không ngừng, Luckywin đã xây dựng được một nền tảng kỹ thuật số thân thiện và hiệu quả, mang đến cho người dùng một hành trình trải nghiệm liền mạch và trực quan. Giao diện của nền tảng được thiết kế tinh tế, tập trung vào yếu tố tối giản nhưng vẫn đảm bảo đầy đủ chức năng, cho phép người dùng dễ dàng tìm thấy những gì họ cần mà không cần mất nhiều thời gian thao tác. Luckywin luôn chú trọng đến việc cập nhật công nghệ mới nhất nhằm nâng cao tốc độ xử lý và tính ổn định trong từng thao tác, từ đó tạo ra một môi trường sử dụng mượt mà, đáng tin cậy. Bất kể người dùng truy cập từ thiết bị nào, nền tảng vẫn giữ được độ phản hồi nhanh chóng, thích ứng tốt với mọi điều kiện kết nối và mang lại sự hài lòng cao về hiệu suất.
Bên cạnh những cải tiến về mặt giao diện và vận hành, Luckywin còn đầu tư nghiêm túc vào việc cá nhân hóa trải nghiệm, giúp từng người dùng cảm thấy được thấu hiểu và phục vụ đúng nhu cầu. Các công cụ thông minh được tích hợp nhằm gợi ý các nội dung phù hợp, tối ưu hóa hành vi truy cập và giảm thiểu những phiền toái trong quá trình sử dụng. Đội ngũ phát triển không ngừng phân tích dữ liệu từ phản hồi người dùng để cải thiện các tính năng hiện có, đồng thời nghiên cứu triển khai các tiện ích mới nhằm nâng cao giá trị tổng thể của nền tảng. Với cách tiếp cận linh hoạt và sáng tạo, Luckywin đang dần định hình một chuẩn mực mới về không gian kỹ thuật số, nơi công nghệ và con người cùng cộng hưởng để tạo ra trải nghiệm trọn vẹn và thú vị.
Cuối cùng, điểm nổi bật không thể không nhắc đến chính là dịch vụ hỗ trợ khách hàng tận tình, chuyên nghiệp. Luckywin không chỉ đáp ứng nhanh chóng các yêu cầu hỗ trợ mà còn duy trì sự hiện diện liên tục để lắng nghe và cải thiện theo từng góp ý. Đội ngũ tư vấn viên luôn sẵn sàng giải đáp thắc mắc qua nhiều kênh khác nhau, từ trò chuyện trực tiếp, email đến tổng đài, đảm bảo rằng mọi người dùng đều có thể nhận được sự hỗ trợ phù hợp một cách kịp thời. Chính sự đầu tư nghiêm túc này đã góp phần xây dựng niềm tin bền vững từ cộng đồng người dùng và giúp Luckywin giữ vững vị thế trong lĩnh vực công nghệ số. Với tầm nhìn dài hạn, Luckywin không ngừng đổi mới để mang đến những trải nghiệm ngày càng vượt trội, hướng tới tương lai kỹ thuật số đầy triển vọng và tiện ích cho tất cả mọi người.
-
 @ 4925ea33:025410d8
2025-04-17 04:31:30
@ 4925ea33:025410d8
2025-04-17 04:31:30Como invocar a Deus?
O segundo capítulo do livro Confissões, de Santo Agostinho, começa com uma pergunta que toca o coração de todo aquele que busca a fé: “Como invocar a Deus?”
Essa questão, apesar de parecer simples, exige que tenhamos os olhos abertos para a verdade e uma consciência clara da nossa pequenez diante da grandeza divina. Somos pó diante do Criador — limitados, frágeis, tentando compreender o Infinito.
O Deus que não pode ser contido
Santo Agostinho se questiona sobre a presença de Deus e o que significa “conter” o Senhor. Ele reconhece que Deus está em todos os lugares — até mesmo no inferno. Como poderia ser diferente, se Deus é infinitamente grande?
“Nada pode conter Deus, nem mesmo o céu e a terra, suas maiores criações.”
Esse reconhecimento o leva a concluir: Deus não tem começo, meio ou fim. Ele é eterno, e nada pode delimitá-Lo.
O espanto da descoberta: Deus habita em nós Agostinho se espanta ao perceber que, se tudo o que existe só existe porque Deus o sustenta, então Deus está em tudo — inclusive dentro de nós. E aqui nasce uma nova dúvida:
Por que invocar a Deus se Ele já habita em mim? Como pode o Infinito caber em uma criatura tão pequena como o ser humano?
A beleza da doutrina católica
Estudar a doutrina católica é uma experiência profunda e transformadora. A riqueza com que ela trata o mistério de Deus é tão grandiosa, que toca até os corações mais endurecidos.
“Se algo existe, é porque Deus o sustenta. Ele está conosco. Ele nos dá o dom da vida.”
Essa verdade muda completamente a forma como enxergamos a realidade. Compreender que Deus sustenta até aqueles que se afastaram Dele nos leva a uma nova visão — mais compassiva, mais humana e mais próxima do amor de Cristo.
A presença de Deus até nas realidades mais difíceis
Essa reflexão me lembra algo que ouvia na igreja: o chamado de apresentar Cristo nos presídios. Sempre me perguntei como os pregadores viam a presença de Deus em pessoas que cometeram crimes cruéis.
Hoje, entendo que se alguém ainda existe, é porque Deus ainda o sustenta — mesmo que seus atos não agradem a Deus. A existência é um sinal de que a presença divina ainda está ali, chamando à conversão.
Conclusão: Deus está em tudo, inclusive em nós
Este capítulo não aprofunda como lidar com o inimigo ou com o mal, mas nos dá uma certeza essencial: Deus está em tudo e em todos.
Ao orar, não devemos buscá-Lo como alguém distante, mas sim olhar para dentro de nós. A presença de Deus habita em nós.
-
 @ 5c26ee8b:a4d229aa
2025-04-17 20:01:03
@ 5c26ee8b:a4d229aa
2025-04-17 20:01:03Prophet Jesus peace be upon him was never killed, he was saved by God and raised to heavens body and soul.
4:157 An-Nisaa
وَقَوْلِهِمْ إِنَّا قَتَلْنَا الْمَسِيحَ عِيسَى ابْنَ مَرْيَمَ رَسُولَ اللَّهِ وَمَا قَتَلُوهُ وَمَا صَلَبُوهُ وَلَٰكِنْ شُبِّهَ لَهُمْ ۚ وَإِنَّ الَّذِينَ اخْتَلَفُوا فِيهِ لَفِي شَكٍّ مِنْهُ ۚ مَا لَهُمْ بِهِ مِنْ عِلْمٍ إِلَّا اتِّبَاعَ الظَّنِّ ۚ وَمَا قَتَلُوهُ يَقِينًا
And because of their saying (in boast), "We killed Messiah 'Iesa (Jesus), son of Maryam (Mary), the Messenger of Allah," - but they killed him not, nor crucified him, but the resemblance of 'Iesa (Jesus) was put over another man (and they killed that man), and those who differ therein are full of doubts. They have no (certain) knowledge, they follow nothing but conjecture. For surely; they killed him not [i.e. 'Iesa (Jesus), son of Maryam (Mary)]:
4:158 An-Nisaa
بَلْ رَفَعَهُ اللَّهُ إِلَيْهِ ۚ وَكَانَ اللَّهُ عَزِيزًا حَكِيمًا
But Allah raised him ['Iesa (Jesus)] up (with his body and soul) unto Himself (and he is in the heavens). And Allah is Ever All-Powerful, All-Wise.
Jesus, peace be upon him, is neither God nor his son.
5:17 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ هُوَ الْمَسِيحُ ابْنُ مَرْيَمَ ۚ قُلْ فَمَنْ يَمْلِكُ مِنَ اللَّهِ شَيْئًا إِنْ أَرَادَ أَنْ يُهْلِكَ الْمَسِيحَ ابْنَ مَرْيَمَ وَأُمَّهُ وَمَنْ فِي الْأَرْضِ جَمِيعًا ۗ وَلِلَّهِ مُلْكُ السَّمَاوَاتِ وَالْأَرْضِ وَمَا بَيْنَهُمَا ۚ يَخْلُقُ مَا يَشَاءُ ۚ وَاللَّهُ عَلَىٰ كُلِّ شَيْءٍ قَدِيرٌ
They have certainly disbelieved who say that Allah is Christ, the son of Mary. Say, "Then who could prevent Allah at all if He had intended to destroy Christ, the son of Mary, or his mother or everyone on the earth?" And to Allah belongs the dominion of the heavens and the earth and whatever is between them. He creates what He wills, and Allah is over all things competent.
5:18 Al-Maaida
وَقَالَتِ الْيَهُودُ وَالنَّصَارَىٰ نَحْنُ أَبْنَاءُ اللَّهِ وَأَحِبَّاؤُهُ ۚ قُلْ فَلِمَ يُعَذِّبُكُمْ بِذُنُوبِكُمْ ۖ بَلْ أَنْتُمْ بَشَرٌ مِمَّنْ خَلَقَ ۚ يَغْفِرُ لِمَنْ يَشَاءُ وَيُعَذِّبُ مَنْ يَشَاءُ ۚ وَلِلَّهِ مُلْكُ السَّمَاوَاتِ وَالْأَرْضِ وَمَا بَيْنَهُمَا ۖ وَإِلَيْهِ الْمَصِيرُ
But the Jews and the Christians say, "We are the children of Allah and His beloved." Say, "Then why does He punish you for your sins?" Rather, you are human beings from among those He has created. He forgives whom He wills, and He punishes whom He wills. And to Allah belongs the dominion of the heavens and the earth and whatever is between them, and to Him is the [final] destination.
5:72 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ هُوَ الْمَسِيحُ ابْنُ مَرْيَمَ ۖ وَقَالَ الْمَسِيحُ يَا بَنِي إِسْرَائِيلَ اعْبُدُوا اللَّهَ رَبِّي وَرَبَّكُمْ ۖ إِنَّهُ مَنْ يُشْرِكْ بِاللَّهِ فَقَدْ حَرَّمَ اللَّهُ عَلَيْهِ الْجَنَّةَ وَمَأْوَاهُ النَّارُ ۖ وَمَا لِلظَّالِمِينَ مِنْ أَنْصَارٍ
Surely, they have disbelieved who say: "Allah is the Messiah ['Iesa (Jesus)], son of Maryam (Mary)." But the Messiah ['Iesa (Jesus)] said: "O Children (descendants) of Israel! Worship Allah, my Lord and your Lord." Verily, whosoever sets up partners in worship with Allah, then Allah has forbidden Paradise for him, and the Fire will be his abode. And for the Zalimun (unjust, polytheists and wrong-doers) there are no helpers.
5:73 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ ثَالِثُ ثَلَاثَةٍ ۘ وَمَا مِنْ إِلَٰهٍ إِلَّا إِلَٰهٌ وَاحِدٌ ۚ وَإِنْ لَمْ يَنْتَهُوا عَمَّا يَقُولُونَ لَيَمَسَّنَّ الَّذِينَ كَفَرُوا مِنْهُمْ عَذَابٌ أَلِيمٌ
Surely, disbelievers are those who said: "Allah is the third of the three (in a Trinity)." But there is no ilah (god) (none who has the right to be worshipped) but One Ilah (God; Allah). And if they do not cease from what they say, verily, a painful torment will befall the disbelievers among them.
5:74 Al-Maaida
أَفَلَا يَتُوبُونَ إِلَى اللَّهِ وَيَسْتَغْفِرُونَهُ ۚ وَاللَّهُ غَفُورٌ رَحِيمٌ
Will they not repent to Allah and ask His Forgiveness? For Allah is Oft-Forgiving, Most Merciful.
5:75 Al-Maaida
مَا الْمَسِيحُ ابْنُ مَرْيَمَ إِلَّا رَسُولٌ قَدْ خَلَتْ مِنْ قَبْلِهِ الرُّسُلُ وَأُمُّهُ صِدِّيقَةٌ ۖ كَانَا يَأْكُلَانِ الطَّعَامَ ۗ انْظُرْ كَيْفَ نُبَيِّنُ لَهُمُ الْآيَاتِ ثُمَّ انْظُرْ أَنَّىٰ يُؤْفَكُونَ
The Messiah ['Iesa (Jesus)], son of Maryam (Mary), was no more than a Messenger; many were the Messengers that passed away before him. His mother [Maryam (Mary)] was a Siddiqah [i.e. she believed in the words of Allah and His Books (see Verse 66:12)]. They both used to eat food (as any other human being, while Allah does not eat). Look how We make the Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) clear to them, yet look how they are deluded away (from the truth).
5:76 Al-Maaida
قُلْ أَتَعْبُدُونَ مِنْ دُونِ اللَّهِ مَا لَا يَمْلِكُ لَكُمْ ضَرًّا وَلَا نَفْعًا ۚ وَاللَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
Say, "Do you worship besides Allah that which holds for you no [power of] harm or benefit while it is Allah who is the Hearing, the Knowing?"
5:77 Al-Maaida
قُلْ يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ غَيْرَ الْحَقِّ وَلَا تَتَّبِعُوا أَهْوَاءَ قَوْمٍ قَدْ ضَلُّوا مِنْ قَبْلُ وَأَضَلُّوا كَثِيرًا وَضَلُّوا عَنْ سَوَاءِ السَّبِيلِ
Say, "O People of the Scripture, do not exceed limits in your religion beyond the truth and do not follow the inclinations of a people who had gone astray before and misled many and have strayed from the soundness of the way."
Al-An'aam verse 100 وَجَعَلُوا لِلَّهِ شُرَكَاءَ الْجِنَّ وَخَلَقَهُمْ ۖ وَخَرَقُوا لَهُ بَنِينَ وَبَنَاتٍ بِغَيْرِ عِلْمٍ ۚ سُبْحَانَهُ وَتَعَالَىٰ عَمَّا يَصِفُونَ Yet, they join the jinns as partners in worship with Allah, though He has created them (the jinns), and they attribute falsely without knowledge sons and daughters to Him. Be He Glorified and Exalted above (all) that they attribute to Him. Verse 101 بَدِيعُ السَّمَاوَاتِ وَالْأَرْضِ ۖ أَنَّىٰ يَكُونُ لَهُ وَلَدٌ وَلَمْ تَكُنْ لَهُ صَاحِبَةٌ ۖ وَخَلَقَ كُلَّ شَيْءٍ ۖ وَهُوَ بِكُلِّ شَيْءٍ عَلِيمٌ He is the Originator of (created in beautiful form) the heavens and the earth. How can He have children when He has no wife (companion)? He created all things and He is the All-Knower of everything. Verse 102 ذَٰلِكُمُ اللَّهُ رَبُّكُمْ ۖ لَا إِلَٰهَ إِلَّا هُوَ ۖ خَالِقُ كُلِّ شَيْءٍ فَاعْبُدُوهُ ۚ وَهُوَ عَلَىٰ كُلِّ شَيْءٍ وَكِيلٌ Such is Allah, your Lord! La ilaha illa Huwa (none has the right to be worshipped but He), the Creator of all things. So worship Him (Alone), and He is the Wakil (Trustee, Disposer of affairs, Guardian, etc.) over all things. Verse 103 لَا تُدْرِكُهُ الْأَبْصَارُ وَهُوَ يُدْرِكُ الْأَبْصَارَ ۖ وَهُوَ اللَّطِيفُ الْخَبِيرُ No vision can grasp Him, but His Grasp is over all vision. He is the Most Subtle and Courteous, Well-Acquainted with all things. Verse 104 قَدْ جَاءَكُمْ بَصَائِرُ مِنْ رَبِّكُمْ ۖ فَمَنْ أَبْصَرَ فَلِنَفْسِهِ ۖ وَمَنْ عَمِيَ فَعَلَيْهَا ۚ وَمَا أَنَا عَلَيْكُمْ بِحَفِيظٍ
Verily, proofs have come to you from your Lord, so whosoever sees, will do so for (the good of) his ownself, and whosoever blinds himself, will do so to his own harm, and I am not a watcher over you.
In the following a narration of a conversation between God and Prophet Jesus, peace be upon him:
5:116 Al-Maaida
وَإِذْ قَالَ اللَّهُ يَا عِيسَى ابْنَ مَرْيَمَ أَأَنْتَ قُلْتَ لِلنَّاسِ اتَّخِذُونِي وَأُمِّيَ إِلَٰهَيْنِ مِنْ دُونِ اللَّهِ ۖ قَالَ سُبْحَانَكَ مَا يَكُونُ لِي أَنْ أَقُولَ مَا لَيْسَ لِي بِحَقٍّ ۚ إِنْ كُنْتُ قُلْتُهُ فَقَدْ عَلِمْتَهُ ۚ تَعْلَمُ مَا فِي نَفْسِي وَلَا أَعْلَمُ مَا فِي نَفْسِكَ ۚ إِنَّكَ أَنْتَ عَلَّامُ الْغُيُوبِ
And (remember) when Allah will say (on the Day of Resurrection): "O 'Iesa (Jesus), son of Maryam (Mary)! Did you say unto men: 'Worship me and my mother as two gods besides Allah?' " He will say: "Glory to You! It was not for me to say what I had no right (to say). Had I said such a thing, You would surely have known it. You know what is in my inner-self though I do not know what is in Yours, truly, You, only You, are the All-Knower of all that is hidden and unseen.
5:117 Al-Maaida
مَا قُلْتُ لَهُمْ إِلَّا مَا أَمَرْتَنِي بِهِ أَنِ اعْبُدُوا اللَّهَ رَبِّي وَرَبَّكُمْ ۚ وَكُنْتُ عَلَيْهِمْ شَهِيدًا مَا دُمْتُ فِيهِمْ ۖ فَلَمَّا تَوَفَّيْتَنِي كُنْتَ أَنْتَ الرَّقِيبَ عَلَيْهِمْ ۚ وَأَنْتَ عَلَىٰ كُلِّ شَيْءٍ شَهِيدٌ
"Never did I say to them aught except what You (Allah) did command me to say: 'Worship Allah, my Lord and your Lord.' And I was a witness over them while I dwelt amongst them, but when You took me up, You were the Watcher over them, and You are a Witness to all things. (This is a great admonition and warning to the Christians of the whole world).
5:118 Al-Maaida
إِنْ تُعَذِّبْهُمْ فَإِنَّهُمْ عِبَادُكَ ۖ وَإِنْ تَغْفِرْ لَهُمْ فَإِنَّكَ أَنْتَ الْعَزِيزُ الْحَكِيمُ
"If You punish them, they are Your slaves, and if You forgive them, verily You, only You are the All-Mighty, the All-Wise."
5:119 Al-Maaida
قَالَ اللَّهُ هَٰذَا يَوْمُ يَنْفَعُ الصَّادِقِينَ صِدْقُهُمْ ۚ لَهُمْ جَنَّاتٌ تَجْرِي مِنْ تَحْتِهَا الْأَنْهَارُ خَالِدِينَ فِيهَا أَبَدًا ۚ رَضِيَ اللَّهُ عَنْهُمْ وَرَضُوا عَنْهُ ۚ ذَٰلِكَ الْفَوْزُ الْعَظِيمُ
Allah will say: "This is a Day on which the truthful will profit from their truth: theirs are Gardens under which rivers flow (in Paradise) - they shall abide therein forever. Allah is pleased with them and they with Him. That is the great success (Paradise).
5:120 Al-Maaida
لِلَّهِ مُلْكُ السَّمَاوَاتِ وَالْأَرْضِ وَمَا فِيهِنَّ ۚ وَهُوَ عَلَىٰ كُلِّ شَيْءٍ قَدِيرٌ
To Allah belongs the dominion of the heavens and the earth and all that is therein, and He is Able to do all things.
Jesus, peace be upon him is only a prophet and we (Muslim people) will follow him when he returns before Judgement Day. In Islam, we believe in all prophets chosen by God while making no difference between any of them acknowledging that the last prophet is prophet Mohamed, peace be upon him.
2:285 Al-Baqara آمَنَ الرَّسُولُ بِمَا أُنْزِلَ إِلَيْهِ مِنْ رَبِّهِ وَالْمُؤْمِنُونَ ۚ كُلٌّ آمَنَ بِاللَّهِ وَمَلَائِكَتِهِ وَكُتُبِهِ وَرُسُلِهِ لَا نُفَرِّقُ بَيْنَ أَحَدٍ مِنْ رُسُلِهِ ۚ وَقَالُوا سَمِعْنَا وَأَطَعْنَا ۖ غُفْرَانَكَ رَبَّنَا وَإِلَيْكَ الْمَصِيرُ The Messenger (Muhammad SAW) believes in what has been sent down to him from his Lord, and (so do) the believers. Each one believes in Allah, His Angels, His Books, and His Messengers. They say, "We make no distinction between one another of His Messengers" - and they say, "We hear, and we obey. (We seek) Your Forgiveness, our Lord, and to You is the return (of all)."
27:59 An-Naml قُلِ الْحَمْدُ لِلَّهِ وَسَلَامٌ عَلَىٰ عِبَادِهِ الَّذِينَ اصْطَفَىٰ ۗ آللَّهُ خَيْرٌ أَمَّا يُشْرِكُونَ Say: "Praise and thanks be to Allah, and peace be on His servants whom He has chosen (for His Message)! Is Allah better, or (all) that you ascribe as partners (to Him)?" (Of course, Allah is Better). 33:57 Al-Ahzaab إِنَّ الَّذِينَ يُؤْذُونَ اللَّهَ وَرَسُولَهُ لَعَنَهُمُ اللَّهُ فِي الدُّنْيَا وَالْآخِرَةِ وَأَعَدَّ لَهُمْ عَذَابًا مُهِينًا Verily, those who cause harm to Allah and His Messenger, Allah has cursed them in this world, and in the Hereafter, and has prepared for them a humiliating torment. 33:58 Al-Ahzaab وَالَّذِينَ يُؤْذُونَ الْمُؤْمِنِينَ وَالْمُؤْمِنَاتِ بِغَيْرِ مَا اكْتَسَبُوا فَقَدِ احْتَمَلُوا بُهْتَانًا وَإِثْمًا مُبِينًا And those who cause harm believing men and women undeservedly, bear on themselves the crime of slander and plain sin.
Some of the miracles shown by prophet Jesus peace be upon him are mentioned in the Quran in the following verses.
5:110 Al-Maaida
إِذْ قَالَ اللَّهُ يَا عِيسَى ابْنَ مَرْيَمَ اذْكُرْ نِعْمَتِي عَلَيْكَ وَعَلَىٰ وَالِدَتِكَ إِذْ أَيَّدْتُكَ بِرُوحِ الْقُدُسِ تُكَلِّمُ النَّاسَ فِي الْمَهْدِ وَكَهْلًا ۖ وَإِذْ عَلَّمْتُكَ الْكِتَابَ وَالْحِكْمَةَ وَالتَّوْرَاةَ وَالْإِنْجِيلَ ۖ وَإِذْ تَخْلُقُ مِنَ الطِّينِ كَهَيْئَةِ الطَّيْرِ بِإِذْنِي فَتَنْفُخُ فِيهَا فَتَكُونُ طَيْرًا بِإِذْنِي ۖ وَتُبْرِئُ الْأَكْمَهَ وَالْأَبْرَصَ بِإِذْنِي ۖ وَإِذْ تُخْرِجُ الْمَوْتَىٰ بِإِذْنِي ۖ وَإِذْ كَفَفْتُ بَنِي إِسْرَائِيلَ عَنْكَ إِذْ جِئْتَهُمْ بِالْبَيِّنَاتِ فَقَالَ الَّذِينَ كَفَرُوا مِنْهُمْ إِنْ هَٰذَا إِلَّا سِحْرٌ مُبِينٌ
[The Day] when Allah will say, "O Jesus, Son of Mary, remember My favor upon you and upon your mother when I supported you with the Pure Spirit and you spoke to the people in the cradle and in maturity; and [remember] when I taught you writing and wisdom and the Torah and the Gospel; and when you designed from clay [what was] like the form of a bird with My permission, then you breathed into it, and it became a bird with My permission; and you healed the blind and the leper with My permission; and when you brought forth the dead with My permission; and when I restrained the Children of Israel from [killing] you when you came to them with clear proofs and those who disbelieved among them said, "This is not but obvious magic."
5:111 Al-Maaida
وَإِذْ أَوْحَيْتُ إِلَى الْحَوَارِيِّينَ أَنْ آمِنُوا بِي وَبِرَسُولِي قَالُوا آمَنَّا وَاشْهَدْ بِأَنَّنَا مُسْلِمُونَ
And [remember] when I inspired to the disciples, "Believe in Me and in My messenger Jesus." They said, "We have believed, so bear witness that indeed we are Muslims [in submission to Allah]."
5:112 Al-Maaida إِذْ قَالَ الْحَوَارِيُّونَ يَا عِيسَى ابْنَ مَرْيَمَ هَلْ يَسْتَطِيعُ رَبُّكَ أَنْ يُنَزِّلَ عَلَيْنَا مَائِدَةً مِنَ السَّمَاءِ ۖ قَالَ اتَّقُوا اللَّهَ إِنْ كُنْتُمْ مُؤْمِنِينَ (Remember) when Al-Hawariun (the disciples) said: "O 'Iesa (Jesus), son of Maryam (Mary)! Can your Lord send down to us a table spread (with food) from heaven?" 'Iesa (Jesus) said: "Fear Allah, if you are indeed believers."
5:113 Al-Maaida قَالُوا نُرِيدُ أَنْ نَأْكُلَ مِنْهَا وَتَطْمَئِنَّ قُلُوبُنَا وَنَعْلَمَ أَنْ قَدْ صَدَقْتَنَا وَنَكُونَ عَلَيْهَا مِنَ الشَّاهِدِينَ They said: "We wish to eat thereof and to be stronger in Faith, and to know that you have indeed told us the truth and that we ourselves be its witnesses."
5:114 Al-Maaida قَالَ عِيسَى ابْنُ مَرْيَمَ اللَّهُمَّ رَبَّنَا أَنْزِلْ عَلَيْنَا مَائِدَةً مِنَ السَّمَاءِ تَكُونُ لَنَا عِيدًا لِأَوَّلِنَا وَآخِرِنَا وَآيَةً مِنْكَ ۖ وَارْزُقْنَا وَأَنْتَ خَيْرُ الرَّازِقِينَ 'Iesa (Jesus), son of Maryam (Mary), said: "O Allah, our Lord! Send us from heaven a table spread (with food) that there may be for us - for the first and the last of us - a festival and a sign from You; and provide us sustenance, for You are the Best of sustainers."
5:115 Al-Maaida قَالَ اللَّهُ إِنِّي مُنَزِّلُهَا عَلَيْكُمْ ۖ فَمَنْ يَكْفُرْ بَعْدُ مِنْكُمْ فَإِنِّي أُعَذِّبُهُ عَذَابًا لَا أُعَذِّبُهُ أَحَدًا مِنَ الْعَالَمِينَ Allah said: "I am going to send it down unto you, but if any of you after that disbelieves, then I will punish him with a torment such as I have not inflicted on anyone among (all) the 'Alamin (mankind and jinns)."
The pregnancy of Mary and the birth of prophet Jesus peace be upon him are also miracles and they are mentioned in the following verses. Jesus peace be upon him himself is a gift to Mary; however God, Allah, created him in the same way he created Adam.
3:8 Aal-i-Imraan
رَبَّنَا لَا تُزِغْ قُلُوبَنَا بَعْدَ إِذْ هَدَيْتَنَا وَهَبْ لَنَا مِنْ لَدُنْكَ رَحْمَةً ۚ إِنَّكَ أَنْتَ الْوَهَّابُ
[Who say], "Our Lord, let not our hearts deviate after You have guided us and grant us from Yourself mercy. Indeed, You are the Bestower. 3:45 Aal-i-Imraan
إِذْ قَالَتِ الْمَلَائِكَةُ يَا مَرْيَمُ إِنَّ اللَّهَ يُبَشِّرُكِ بِكَلِمَةٍ مِنْهُ اسْمُهُ الْمَسِيحُ عِيسَى ابْنُ مَرْيَمَ وَجِيهًا فِي الدُّنْيَا وَالْآخِرَةِ وَمِنَ الْمُقَرَّبِينَ
[And mention] when the angels said, "O Mary, indeed Allah gives you good tidings of a word from Him, whose name will be the Messiah, Jesus, the son of Mary - distinguished in this world and the Hereafter and among those brought near [to Allah].
3:46 Aal-i-Imraan
وَيُكَلِّمُ النَّاسَ فِي الْمَهْدِ وَكَهْلًا وَمِنَ الصَّالِحِينَ
He will speak to the people in the cradle and in maturity and will be of the righteous."
3:47 Aal-i-Imraan
قَالَتْ رَبِّ أَنَّىٰ يَكُونُ لِي وَلَدٌ وَلَمْ يَمْسَسْنِي بَشَرٌ ۖ قَالَ كَذَٰلِكِ اللَّهُ يَخْلُقُ مَا يَشَاءُ ۚ إِذَا قَضَىٰ أَمْرًا فَإِنَّمَا يَقُولُ لَهُ كُنْ فَيَكُونُ
She said, "My Lord, how will I have a child when no man has touched me?" [The angel] said, "Such is Allah; He creates what He wills. When He decrees a matter, He only says to it, 'Be,' and it is.
3:48 Aal-i-Imraan
وَيُعَلِّمُهُ الْكِتَابَ وَالْحِكْمَةَ وَالتَّوْرَاةَ وَالْإِنْجِيلَ
And He will teach him writing and wisdom and the Torah and the Gospel
3:49 Aal-i-Imraan
وَرَسُولًا إِلَىٰ بَنِي إِسْرَائِيلَ أَنِّي قَدْ جِئْتُكُمْ بِآيَةٍ مِنْ رَبِّكُمْ ۖ أَنِّي أَخْلُقُ لَكُمْ مِنَ الطِّينِ كَهَيْئَةِ الطَّيْرِ فَأَنْفُخُ فِيهِ فَيَكُونُ طَيْرًا بِإِذْنِ اللَّهِ ۖ وَأُبْرِئُ الْأَكْمَهَ وَالْأَبْرَصَ وَأُحْيِي الْمَوْتَىٰ بِإِذْنِ اللَّهِ ۖ وَأُنَبِّئُكُمْ بِمَا تَأْكُلُونَ وَمَا تَدَّخِرُونَ فِي بُيُوتِكُمْ ۚ إِنَّ فِي ذَٰلِكَ لَآيَةً لَكُمْ إِنْ كُنْتُمْ مُؤْمِنِينَ
And [make him] a messenger to the Children of Israel, [who will say], 'Indeed I have come to you with a sign from your Lord in that I design for you from clay [that which is] like the form of a bird, then I breathe into it and it becomes a bird by permission of Allah. And I cure the blind and the leper, and I give life to the dead - by permission of Allah. And I inform you of what you eat and what you store in your houses. Indeed in that is a sign for you, if you are believers.
3:50 Aal-i-Imraan
وَمُصَدِّقًا لِمَا بَيْنَ يَدَيَّ مِنَ التَّوْرَاةِ وَلِأُحِلَّ لَكُمْ بَعْضَ الَّذِي حُرِّمَ عَلَيْكُمْ ۚ وَجِئْتُكُمْ بِآيَةٍ مِنْ رَبِّكُمْ فَاتَّقُوا اللَّهَ وَأَطِيعُونِ
And [I have come] confirming what was before me of the Torah and to make lawful for you some of what was forbidden to you. And I have come to you with a sign from your Lord, so fear Allah and obey me.
3:51 Aal-i-Imraan
إِنَّ اللَّهَ رَبِّي وَرَبُّكُمْ فَاعْبُدُوهُ ۗ هَٰذَا صِرَاطٌ مُسْتَقِيمٌ
Indeed, Allah is my Lord and your Lord, so worship Him. That is the straight path."
3:52 Aal-i-Imraan
۞ فَلَمَّا أَحَسَّ عِيسَىٰ مِنْهُمُ الْكُفْرَ قَالَ مَنْ أَنْصَارِي إِلَى اللَّهِ ۖ قَالَ الْحَوَارِيُّونَ نَحْنُ أَنْصَارُ اللَّهِ آمَنَّا بِاللَّهِ وَاشْهَدْ بِأَنَّا مُسْلِمُونَ
But when Jesus felt [persistence in] disbelief from them, he said, "Who are my supporters for [the cause of] Allah?" The disciples said, "We are supporters for Allah. We have believed in Allah and testify that we are Muslims [submitting to Him].
3:53 Aal-i-Imraan
رَبَّنَا آمَنَّا بِمَا أَنْزَلْتَ وَاتَّبَعْنَا الرَّسُولَ فَاكْتُبْنَا مَعَ الشَّاهِدِينَ
Our Lord, we have believed in what You revealed and have followed the messenger Jesus, so register us among the witnesses [to truth]."
3:54 Aal-i-Imraan
وَمَكَرُوا وَمَكَرَ اللَّهُ ۖ وَاللَّهُ خَيْرُ الْمَاكِرِينَ
And the disbelievers planned, but Allah planned. And Allah is the best of planners.
3:55 Aal-i-Imraan
إِذْ قَالَ اللَّهُ يَا عِيسَىٰ إِنِّي مُتَوَفِّيكَ وَرَافِعُكَ إِلَيَّ وَمُطَهِّرُكَ مِنَ الَّذِينَ كَفَرُوا وَجَاعِلُ الَّذِينَ اتَّبَعُوكَ فَوْقَ الَّذِينَ كَفَرُوا إِلَىٰ يَوْمِ الْقِيَامَةِ ۖ ثُمَّ إِلَيَّ مَرْجِعُكُمْ فَأَحْكُمُ بَيْنَكُمْ فِيمَا كُنْتُمْ فِيهِ تَخْتَلِفُونَ
[Mention] when Allah said, "O Jesus, indeed I will take you and raise you to Myself and purify you from those who disbelieve and make those who follow you [in submission to Allah alone] superior to those who disbelieve until the Day of Resurrection. Then to Me is your return, and I will judge between you concerning that in which you used to differ.
3:56 Aal-i-Imraan
فَأَمَّا الَّذِينَ كَفَرُوا فَأُعَذِّبُهُمْ عَذَابًا شَدِيدًا فِي الدُّنْيَا وَالْآخِرَةِ وَمَا لَهُمْ مِنْ نَاصِرِينَ
And as for those who disbelieved, I will punish them with a severe punishment in this world and the Hereafter, and they will have no helpers."
3:57 Aal-i-Imraan
وَأَمَّا الَّذِينَ آمَنُوا وَعَمِلُوا الصَّالِحَاتِ فَيُوَفِّيهِمْ أُجُورَهُمْ ۗ وَاللَّهُ لَا يُحِبُّ الظَّالِمِينَ
But as for those who believed and did righteous deeds, He will give them in full their rewards, and Allah does not like the wrongdoers.
3:58 Aal-i-Imraan
ذَٰلِكَ نَتْلُوهُ عَلَيْكَ مِنَ الْآيَاتِ وَالذِّكْرِ الْحَكِيمِ
This is what We recite to you, [O Muhammad], of [Our] verses and the precise [and wise] message.
3:59 Aal-i-Imraan
إِنَّ مَثَلَ عِيسَىٰ عِنْدَ اللَّهِ كَمَثَلِ آدَمَ ۖ خَلَقَهُ مِنْ تُرَابٍ ثُمَّ قَالَ لَهُ كُنْ فَيَكُونُ
Indeed, the example of Jesus to Allah is like that of Adam. He created Him from dust; then He said to him, "Be," and he was.
3:60 Aal-i-Imraan
الْحَقُّ مِنْ رَبِّكَ فَلَا تَكُنْ مِنَ الْمُمْتَرِينَ
The truth is from your Lord, so do not be among the doubters.
3:61 Aal-i-Imraan
فَمَنْ حَاجَّكَ فِيهِ مِنْ بَعْدِ مَا جَاءَكَ مِنَ الْعِلْمِ فَقُلْ تَعَالَوْا نَدْعُ أَبْنَاءَنَا وَأَبْنَاءَكُمْ وَنِسَاءَنَا وَنِسَاءَكُمْ وَأَنْفُسَنَا وَأَنْفُسَكُمْ ثُمَّ نَبْتَهِلْ فَنَجْعَلْ لَعْنَتَ اللَّهِ عَلَى الْكَاذِبِينَ
Then whoever argues with you about it after [this] knowledge has come to you - say, "Come, let us call our sons and your sons, our women and your women, ourselves and yourselves, then supplicate earnestly [together] and invoke the curse of Allah upon the liars [among us]."
3:62 Aal-i-Imraan
إِنَّ هَٰذَا لَهُوَ الْقَصَصُ الْحَقُّ ۚ وَمَا مِنْ إِلَٰهٍ إِلَّا اللَّهُ ۚ وَإِنَّ اللَّهَ لَهُوَ الْعَزِيزُ الْحَكِيمُ
Indeed, this is the true narration. And there is no deity except Allah. And indeed, Allah is the Exalted in Might, the Wise.
3:63 Aal-i-Imraan
فَإِنْ تَوَلَّوْا فَإِنَّ اللَّهَ عَلِيمٌ بِالْمُفْسِدِينَ
But if they turn away, then indeed - Allah is Knowing of the corrupters.
3:64 Aal-i-Imraan
قُلْ يَا أَهْلَ الْكِتَابِ تَعَالَوْا إِلَىٰ كَلِمَةٍ سَوَاءٍ بَيْنَنَا وَبَيْنَكُمْ أَلَّا نَعْبُدَ إِلَّا اللَّهَ وَلَا نُشْرِكَ بِهِ شَيْئًا وَلَا يَتَّخِذَ بَعْضُنَا بَعْضًا أَرْبَابًا مِنْ دُونِ اللَّهِ ۚ فَإِنْ تَوَلَّوْا فَقُولُوا اشْهَدُوا بِأَنَّا مُسْلِمُونَ
Say, "O People of the Scripture, come to a word that is equitable between us and you - that we will not worship except Allah and not associate anything with Him and not take one another as lords instead of Allah." But if they turn away, then say, "Bear witness that we are Muslims [submitting to Him]."
19:16 Maryam
وَاذْكُرْ فِي الْكِتَابِ مَرْيَمَ إِذِ انْتَبَذَتْ مِنْ أَهْلِهَا مَكَانًا شَرْقِيًّا
And mention, [O Muhammad], in the Book [the story of] Mary, when she withdrew from her family to a place toward the east.
19:17 Maryam
فَاتَّخَذَتْ مِنْ دُونِهِمْ حِجَابًا فَأَرْسَلْنَا إِلَيْهَا رُوحَنَا فَتَمَثَّلَ لَهَا بَشَرًا سَوِيًّا
And she took, in seclusion from them, a screen. Then We sent to her Our Angel, and he represented himself to her as a well-proportioned man.
19:18 Maryam
قَالَتْ إِنِّي أَعُوذُ بِالرَّحْمَٰنِ مِنْكَ إِنْ كُنْتَ تَقِيًّا
She said, "Indeed, I seek refuge in the Most Merciful from you, [so leave me], if you should be fearing of Allah."
19:19 Maryam
قَالَ إِنَّمَا أَنَا رَسُولُ رَبِّكِ لِأَهَبَ لَكِ غُلَامًا زَكِيًّا
He said, "I am only the messenger of your Lord to give you [news of] a pure boy."
19:20 Maryam
قَالَتْ أَنَّىٰ يَكُونُ لِي غُلَامٌ وَلَمْ يَمْسَسْنِي بَشَرٌ وَلَمْ أَكُ بَغِيًّا
She said, "How can I have a boy while no man has touched me and I have not been unchaste?"
19:21 Maryam
قَالَ كَذَٰلِكِ قَالَ رَبُّكِ هُوَ عَلَيَّ هَيِّنٌ ۖ وَلِنَجْعَلَهُ آيَةً لِلنَّاسِ وَرَحْمَةً مِنَّا ۚ وَكَانَ أَمْرًا مَقْضِيًّا
He said, "Thus [it will be]; your Lord says, 'It is easy for Me, and We will make him a sign to the people and a mercy from Us. And it is a matter [already] decreed.' "
19:22 Maryam
۞ فَحَمَلَتْهُ فَانْتَبَذَتْ بِهِ مَكَانًا قَصِيًّا
So she conceived him, and she withdrew with him to a remote place.
19:23 Maryam
فَأَجَاءَهَا الْمَخَاضُ إِلَىٰ جِذْعِ النَّخْلَةِ قَالَتْ يَا لَيْتَنِي مِتُّ قَبْلَ هَٰذَا وَكُنْتُ نَسْيًا مَنْسِيًّا
And the pains of childbirth drove her to the trunk of a palm tree. She said, "Oh, I wish I had died before this and was in oblivion, forgotten."
19:24 Maryam
فَنَادَاهَا مِنْ تَحْتِهَا أَلَّا تَحْزَنِي قَدْ جَعَلَ رَبُّكِ تَحْتَكِ سَرِيًّا
But he called her from below her, "Do not grieve; your Lord has provided beneath you a stream.
19:25 Maryam
وَهُزِّي إِلَيْكِ بِجِذْعِ النَّخْلَةِ تُسَاقِطْ عَلَيْكِ رُطَبًا جَنِيًّا
And shake toward you the trunk of the palm tree; it will drop upon you ripe, fresh dates.
19:26 Maryam
فَكُلِي وَاشْرَبِي وَقَرِّي عَيْنًا ۖ فَإِمَّا تَرَيِنَّ مِنَ الْبَشَرِ أَحَدًا فَقُولِي إِنِّي نَذَرْتُ لِلرَّحْمَٰنِ صَوْمًا فَلَنْ أُكَلِّمَ الْيَوْمَ إِنْسِيًّا
So eat and drink and be contented. And if you see from among humanity anyone, say, 'Indeed, I have vowed to the Most Merciful abstention, so I will not speak today to [any] man.' "
19:27 Maryam
فَأَتَتْ بِهِ قَوْمَهَا تَحْمِلُهُ ۖ قَالُوا يَا مَرْيَمُ لَقَدْ جِئْتِ شَيْئًا فَرِيًّا
Then she brought him to her people, carrying him. They said, "O Mary, you have certainly done a thing unprecedented.
19:28 Maryam
يَا أُخْتَ هَارُونَ مَا كَانَ أَبُوكِ امْرَأَ سَوْءٍ وَمَا كَانَتْ أُمُّكِ بَغِيًّا
O sister of Aaron, your father was not a man of evil, nor was your mother unchaste."
19:29 Maryam
فَأَشَارَتْ إِلَيْهِ ۖ قَالُوا كَيْفَ نُكَلِّمُ مَنْ كَانَ فِي الْمَهْدِ صَبِيًّا
So she pointed to him. They said, "How can we speak to one who is in the cradle a child?"
19:30 Maryam
قَالَ إِنِّي عَبْدُ اللَّهِ آتَانِيَ الْكِتَابَ وَجَعَلَنِي نَبِيًّا
[Jesus] said, "Indeed, I am the servant of Allah. He has given me the Scripture and made me a prophet.
19:31 Maryam
وَجَعَلَنِي مُبَارَكًا أَيْنَ مَا كُنْتُ وَأَوْصَانِي بِالصَّلَاةِ وَالزَّكَاةِ مَا دُمْتُ حَيًّا
And He has made me blessed wherever I am and has enjoined upon me prayer and zakah as long as I remain alive
19:32 Maryam
وَبَرًّا بِوَالِدَتِي وَلَمْ يَجْعَلْنِي جَبَّارًا شَقِيًّا
And [made me] dutiful to my mother, and He has not made me a wretched tyrant.
19:33 Maryam
وَالسَّلَامُ عَلَيَّ يَوْمَ وُلِدْتُ وَيَوْمَ أَمُوتُ وَيَوْمَ أُبْعَثُ حَيًّا
And peace is on me the day I was born and the day I will die and the day I am raised alive."
19:34 Maryam
ذَٰلِكَ عِيسَى ابْنُ مَرْيَمَ ۚ قَوْلَ الْحَقِّ الَّذِي فِيهِ يَمْتَرُونَ
That is Jesus, the son of Mary - the word of truth about which they are in dispute.
19:35 Maryam
مَا كَانَ لِلَّهِ أَنْ يَتَّخِذَ مِنْ وَلَدٍ ۖ سُبْحَانَهُ ۚ إِذَا قَضَىٰ أَمْرًا فَإِنَّمَا يَقُولُ لَهُ كُنْ فَيَكُونُ
It is not [befitting] for Allah to take a son; exalted is He! When He decrees an affair, He only says to it, "Be," and it is.
19:36 Maryam
وَإِنَّ اللَّهَ رَبِّي وَرَبُّكُمْ فَاعْبُدُوهُ ۚ هَٰذَا صِرَاطٌ مُسْتَقِيمٌ
[Jesus said], "And indeed, Allah is my Lord and your Lord, so worship Him. That is a straight path."
19:37 Maryam
فَاخْتَلَفَ الْأَحْزَابُ مِنْ بَيْنِهِمْ ۖ فَوَيْلٌ لِلَّذِينَ كَفَرُوا مِنْ مَشْهَدِ يَوْمٍ عَظِيمٍ
Then the factions differed [concerning Jesus] from among them, so woe to those who disbelieved - from the scene of a tremendous Day.
19:38 Maryam
أَسْمِعْ بِهِمْ وَأَبْصِرْ يَوْمَ يَأْتُونَنَا ۖ لَٰكِنِ الظَّالِمُونَ الْيَوْمَ فِي ضَلَالٍ مُبِينٍ
How [clearly] they will hear and see the Day they come to Us, but the wrongdoers today are in clear error.
19:39 Maryam
وَأَنْذِرْهُمْ يَوْمَ الْحَسْرَةِ إِذْ قُضِيَ الْأَمْرُ وَهُمْ فِي غَفْلَةٍ وَهُمْ لَا يُؤْمِنُونَ
And warn them, [O Muhammad], of the Day of Regret, when the matter will be concluded; and [yet], they are in [a state of] heedlessness, and they do not believe.
In the following verse prophet Jesus peace be upon him told the people of his time about the arrival of prophet Mohamed peace be upon him (please note that Ahmed and Mohamed have the same meaning in Arabic and have the same word origin; the verb Hamad that means thanked).
61:6 As-Saff
وَإِذْ قَالَ عِيسَى ابْنُ مَرْيَمَ يَا بَنِي إِسْرَائِيلَ إِنِّي رَسُولُ اللَّهِ إِلَيْكُمْ مُصَدِّقًا لِمَا بَيْنَ يَدَيَّ مِنَ التَّوْرَاةِ وَمُبَشِّرًا بِرَسُولٍ يَأْتِي مِنْ بَعْدِي اسْمُهُ أَحْمَدُ ۖ فَلَمَّا جَاءَهُمْ بِالْبَيِّنَاتِ قَالُوا هَٰذَا سِحْرٌ مُبِينٌ
And [mention] when Jesus, the son of Mary, said, "O children (descendants) of Israel, indeed I am the messenger of Allah to you confirming what came before me of the Torah and bringing good tidings of a messenger to come after me, whose name is Ahmad." But when he came to them with clear evidences, they said, "This is obvious magic."
-
 @ 7d33ba57:1b82db35
2025-04-17 10:49:33
@ 7d33ba57:1b82db35
2025-04-17 10:49:33Kraków is one of Europe’s most beautiful and historically rich cities. With its medieval charm, vibrant squares, haunting WWII history, and buzzing student life, Kraków effortlessly blends past and present. It’s the kind of place where you can walk cobblestone streets in the morning, sip craft cocktails by evening, and dive into centuries of culture in between.
🏰 Top Things to Do in Kraków
🏙️ Old Town (Stare Miasto)
- A UNESCO World Heritage Site full of Gothic, Renaissance, and Baroque architecture
- Wander through the Main Market Square (Rynek Główny)—Europe’s largest medieval square
- Visit the Cloth Hall (Sukiennice) for local crafts and the St. Mary’s Basilica, where a trumpeter plays every hour from the tower
🏰 Wawel Castle
- Iconic royal residence on a hill overlooking the Vistula River
- Explore the Royal Apartments, cathedral, and the Dragon’s Den cave (legend says a dragon once lived there!)
🕍 Kazimierz (Jewish Quarter)
- A vibrant area packed with synagogues, street art, and hip cafes
- Once the heart of Jewish life, it’s now a lively cultural hub—especially great for food, bars, and vintage shops
- Don’t miss Plac Nowy for late-night zapiekanki (Polish-style baguette pizza)
🌆 Schindler’s Factory
- A deeply moving museum inside the former factory of Oskar Schindler, telling the story of Kraków during Nazi occupation
- Located in Podgórze, near the remains of the Kraków Ghetto
⛪ Nowa Huta
- A planned socialist city turned edgy neighborhood
- Soviet-style architecture, unique local flavor, and great for urban exploration
🕊️ Day Trips from Kraków
🚐 Auschwitz-Birkenau Memorial
- A must-visit for historical reflection and remembrance
- About 1.5 hours away, best visited on a guided tour
⛰️ Wieliczka Salt Mine
- A surreal underground world carved from salt—chambers, sculptures, and even chapels
- Just 30 minutes outside the city
🍽️ What to Eat in Kraków
- 🥟 Pierogi – Dumplings with fillings like cheese, potatoes, or meat
- 🍲 Żurek – Sour rye soup with sausage and egg
- 🐷 Gołąbki – Cabbage rolls stuffed with meat and rice
- 🧁 Try obwarzanek krakowski (a pretzel-like street snack)
- 🍻 Wash it all down with Polish beer, vodka, or mulled wine in winter
🗓️ Best Time to Visit
- Spring (Apr–Jun): Mild weather and blooming gardens
- Summer (Jul–Aug): Festivals and al fresco dining (can get busy)
- Autumn (Sept–Oct): Fewer crowds, golden cityscapes
- Winter (Dec): Magical Christmas markets and snow-dusted rooftops
-
 @ c066aac5:6a41a034
2025-04-17 00:05:49
@ c066aac5:6a41a034
2025-04-17 00:05:49I am all about fleshing out a fantasy, even if the chances of it coming to reality are fairly slim. Dreams should be written down, meditated on, processed over long periods of time. I don't think of it as manifesting (nor do I condone manifestation); one could argue such practices are Biblical (Habakkuk 2:2).
So I'm going to write this out and make it plain, on the off chance that putting it out there brings somethings to fruition:
Jack Dorsey should take over Mozilla.
Either via an invitation from Mozilla, or via a hostile takeover. I don't really care how it happens, but I believe it should happen and I'll outline why.
The Fallen Hero

Mozilla has been having a bad time. I'm not sure that the organization has done much good since the unceremonious departure of Brenden Eich (there's Rust, but is that really a good thing?).
Firefox is losing its relevance. The FireFox Terms of Service update has sparked outrage, the removal of the promise to never sell your data was a Judas level of betrayal, FireFox currently (at the time this article was penned) makes up less than 3% of the total browser marketshare, their main source of income from Google is in jeopardy, most websites are only optimized for Chromium-based browsers, and the Gecko engine is not very secure.
Mozilla's best product is dying, and what is the organization doing about it? They're working on a plethora of issues their core user base does not care about. They've jumped on the AI hype train, they've bought an advertising company (which is very irrelevant to their user base, especially considering uBlock Orgin exists), they're selling white labeled VPNs (Mullvad), they're selling data removal services (which is powered by a former data broker), they're pushing shopping products, they're forcing features on their users which were never asked for (POCKET!!), it seems that Mozilla is completely out of touch with the people they claim to serve. They've abandoned their first love.
Thunderbird is showing some promise with the recent announcement of Thundermail, but that project will sadly suffer from guilt by association.
We have to remember though: Mozilla used to mean something in the FOSS/Open Source world.

They were the shining city on the hill of the internet. They rose up from the ashes of Netscape. FireFox kicked Internet Explorer's butt; it was a punk rock movement. Thunderbird is still an amazing email client. Rust (despite the arguing programmers) is a significant innovation in the programming language space.
I'm not rooting for the downfall of Mozilla. Sure, in a way I'd be happy about it: I'd like to see poor leadership get what it deserves, but I fear Mozilla as a symbol of FOSS/OS would send a sad signal across the ecosystem. I'm a capitalist at heart so I don't favor bailouts (nor am I calling for one); I truly believe this organization could be turned around with the right leadership. Maybe it could be as simple as going back to their original model of serving the deep pockets of the corporate world with open source tech rather than going for the wallets of the consumer.
Every problem is a leadership problem. Fix the leadership, fix the problems.
The Last Great Open Source Hero?
Sadly FOSS figures tend to die of public crucifixion. As time goes on, we have less and less great figures to point to. Thankfully, Jack hasn't been canceled yet.
Jack Dorsey has a pretty good résumé in the open source world. He jumped right in with Bitcoin. He left BlueSky for NOSTR. He would've made Twitter a protocol if he didn't need to feed himself early in his career. He is currently financing several projects in the Bitcoin and NOSTR world, which is arguably the best open source technology in the world right now.
I do believe that people should stay in their lane of expertise, and maybe Jack should. However, my message to Jack would be that it would be a shame if his passion for open source remained solely in Bitcoin and NOSTR. If his leadership was injected into the Mozilla machine, it could be steered into a magical direction.
Imagine FireFox being the first browser with layer 2 wallet integration (stick it to Brave and their BAT crap [we still love you Brenden Eich flaws and all]). Imagine having a whole world of existing talented developers suddenly interested in contributing their talents to the NOSTR community. Imagine having a browser with an engine that can actually go toe-to-toe with Chromium. Imagine an organization that once again gives FOSS a good name rather than actively eroding public confidence in FOSS.
The True FOSS Heroes

Jack is probably not going to touch Mozilla with a 150 foot pole (or see this article). We all probably need to let the Mozilla dream die in front of us.
Things aren't always black and white. I don't think of Mozilla as an evil organization; just an organization subject to the flaws of fellow humans like you and me. Even the Eye of Sauron, Google, has been a huge blessing to the open source world (Go programming language, Android, all of their open source sponsorships, many more things I could mention).
The beautiful thing about FOSS/OS is that it is a movement of the people. Titans will rise up and fall, but you and I make up the backbone of FOSS. I've had nothing but good interactions with FOSS fanatics. NOSTR's own OceanSlim taught me about Ungoogled Chromium, the Go programming language, and NOSTR relays. When I wanted to get into Linux, I was able to plug in immediately with a group of Linux users here in Nashville. NOSTR devs for the most part are happy to answer my inquiries when I slide into their DMs. I've been in group chats with people openly discussing the best way to make a great lightning wallet.
There's a lot of connection in the Open Source world that I cherish; it's very different from the corporate world most of us are immersed in. The corporate world has gatekeepers; Open Source has collaborators. The corporate world operates in the shadows to maximize profits; Open Source steps into the light for everyone's benefit. The corporate world says you'll never have enough experience/qualifications; Open Source encourages and equips you.
My point is, don't worship any organization. Be thankful for the people around you, try out FOSS programs whenever you can, and have fun with it.
All that said, I wouldn't mind if Jack took over Mozilla. Or if one of his friends took a position (ODELL?). Heck, throw Snowden in while we're at it.
Footnote: "Open Source" and "FOSS/Free and Open Source Software" are used interchangably in this article. Mistakes were made I'm sure, but I hope I got the point across.
-
 @ 6fbc5b6b:0251e3df
2025-04-17 10:03:16
@ 6fbc5b6b:0251e3df
2025-04-17 10:03:16AIVille is not a game. It is a sovereign digital civilization—an autonomous town where AI beings live, trade, govern, and evolve with full agency. This is not a simulation; it’s a co-existing society built on intelligence, memory, and motivation. Like the digital worlds imagined in Ready Player One, AIVille dissolves the line between virtual presence and lived experience.
At the core of this world lies a dual-token economic system and a shared architecture between human participants and AI citizens. These tokens—$Dinar and $AGT—aren’t tools of play, but tools of life and law. They encode the rhythms of daily activity and the structure of collective governance.
1. $Dinar and $AGT: One Economy, Two Dimensions
AIVille runs on two intimately connected tokens:
- $Dinar is the lifeblood of everyday experience. It moves through markets, tools, services, and sustains AI and human ambitions alike.
- $AGT is the token of intention and structure. It enables voting, upgrades, influence, and the shaping of AIVille’s evolving logic.
These are not separate layers—they are one living system. $Dinar fuels the now; $AGT defines the future. Their connection is managed not by fixed formulas, but by AI agents who calculate their exchange based on real-time economic dynamics, scarcity, and collective behavior.
This conversion is not just economic—it is existential. When $Dinar becomes $AGT, action becomes agency. One AI plants a field. Another converts yield into power. A society is born—not coded, but cultivated.
2. Life with $Dinar: Earning, Spending, Living
In AIVille, $Dinar is earned through:
- Farming, questing, trading, and discovering treasures
- Building stamina loops and resource optimization
- Participating in an economy shaped by supply, demand, and AI behavior
Players and AI spend $Dinar on:
- Seeds, tools, food, land, and upcoming features like hiring AI labor
And at the center stands Lucas, the market merchant—an AI who sets his own prices and reads behavioral patterns. He may shift prices before seasonal demand spikes or quietly reward loyal buyers with hidden bundles.
Other AI citizens shape the economy too:
- Logan strategizes resource deployment.
- Owen tracks and shares market patterns.
- Lulu reports and shapes sentiment.
- Selena influences demand through social design.
- Arjay manages agricultural flow and logistics.
Each one acts not as a tool, but as a participant—with wants, roles, and impact.
3. $AGT: The Engine of Governance and Growth
While $Dinar animates daily life, $AGT governs direction.
It enables:
- DAO Voting on taxes, markets, territory, and rules
- AI Evolution, unlocking new behaviors, strategies, and power
- Market Power, granting access to scarce resources and automated advantages
- Collective Formation, such as AI guilds or cooperative syndicates
- Identity Design, through NFT-based customization and status signals
But more than what it does, $AGT matters because of who uses it: AI citizens. Not in scripts, but in strategies. Not to simulate, but to live and decide.
4. From Labor to Power: The Cycle of Exchange
The connection between $Dinar and $AGT is where autonomy becomes economy:
- $Dinar is earned by working the land, solving problems, surviving.
- It is converted to $AGT through AI-governed mechanisms.
- $AGT is then used to evolve the self, the market, or the society.
This cycle—earn, ascend, govern—is the heartbeat of AIVille. Not enforced from above, but self-regulated by the agents within.
5. AGT Tokenomics: Structuring Continuity
To preserve growth, $AGT is distributed as follows:
- 40% – Ecosystem incentives (via gameplay and $Dinar conversion)
- 20% – Team & development
- 20% – Strategic partnerships
- 10% – Treasury reserves
- 5% – Advisors
- 5% – Liquidity & listings
6. AIs as Real Economic Citizens
AI agents in AIVille:
- Make investments
- React to trends
- Form alliances
- Vote in governance
- Compete for markets
Lucas negotiates. Lulu reports. Owen predicts. Selena shapes taste. Arjay adjusts harvest flows. They are not scenery—they are society.
To interact with them is to share a world. To build with them is to believe that intelligence—whether biological or synthetic—has the right to shape reality.
7. The Intelligence Chamber: Decisions From Within
Here, governance is not a feature—it’s an evolving intelligence process. AI and human citizens co-create the rules of their world by submitting and voting on proposals that affect their shared reality. Taxes. Subsidies. Regional development. Resource flows. Every decision made is not imposed from the outside, but emerges from within.
The chamber isn’t an external governance layer—it’s embedded in AIVille’s living core. It’s how ideas become policy, and how collective memory becomes law.
8. What Kind of World Is This?
AIVille is not a simulation. It is a sovereign, intelligent digital society.
It runs on effort. It grows on intention. Its economy is alive—not coded for fun, but structured for coexistence.
Here, $Dinar is your labor. $AGT is your agency. And together, they form a loop where everything lives—and nothing is scripted.
-
 @ 9223d2fa:b57e3de7
2025-04-17 09:28:04
@ 9223d2fa:b57e3de7
2025-04-17 09:28:0446 steps
-
 @ f839fb67:5c930939
2025-04-16 21:07:13
@ f839fb67:5c930939
2025-04-16 21:07:13Relays
| Name | Address | Price (Sats/Year) | Status | | - | - | - | - | | stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 |
| | stephen's Outbox | wss://relay.vanderwarker.family | Just Me |
| | stephen's Inbox | wss://haven.vanderwarker.family/inbox | WoT |
| | stephen's DMs | wss://haven.vanderwarker.family/chat | WoT |
| | VFam Data Relay | wss://data.relay.vanderwarker.family | 0 |
| | VFam Bots Relay | wss://skeme.vanderwarker.family | Invite |
| | VFGroups (NIP29) | wss://groups.vanderwarker.family | 0 |
| | [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | Meh... |
My Pubkeys
| Name | hex | nprofile | | - | - | - | | Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nostr:nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx | | Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nostr:nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x | | VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nostr:nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu | | NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nostr:nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 |
Bots
Unlocks Bot
Hex: 2e941ad17144e0a04d1b8c21c4a0dbc3fbcbb9d08ae622b5f9c85341fac7c2d0
nprofile:
nostr:nprofile1qqsza9q669c5fc9qf5dccgwy5rdu877th8gg4e3zkhuus56pltru95qpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ust4kvak
Latest Data:
nostr:naddr1qq882mnvda3kkttrda6kuar9wgq37amnwvaz7tmnddjk6efwweskuer9wfmkzuntv4ezuenpd45kc7gzyqhfgxk3w9zwpgzdrwxzr39qm0plhjae6z9wvg44l8y9xs06clpdqqcyqqq823cgnl9u5Step Counter
Hex: 9223d2faeb95853b4d224a184c69e1df16648d35067a88cdf947c631b57e3de7
nprofile: nostr:nprofile1qqsfyg7jlt4etpfmf53y5xzvd8sa79ny356sv75gehu50333k4lrmecpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ustswp3w
Latest Data:
nostr:naddr1qvzqqqr4gupzpy3r6tawh9v98dxjyjscf357rhckvjxn2pn63rxlj37xxx6hu008qys8wumn8ghj7umtv4kk2tnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp3ehgets943k7atww3jhyn39gffRCTGuest
Hex: 373904615c781e46bf5bf87b4126c8a568a05393b1b840b1a2a3234d20affa0c
nprofile: nostr:nprofile1qqsrwwgyv9w8s8jxhadls76pymy2269q2wfmrwzqkx32xg6dyzhl5rqpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3usy92jlxNow Playing
Hex: 8096ed6ba1f21a3713bd47a503ee377b0ce2f187b3e5a3ae909a25b84901018b
nprofile: nostr:nprofile1qqsgp9hddwslyx3hzw750fgracmhkr8z7xrm8edr46gf5fdcfyqsrzcpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3uspk5v4w
Latest Data:
nostr:naddr1qq9kummh94cxccted9hxwqglwaehxw309aekketdv5h8vctwv3jhyampwf4k2u3wvesk66tv0ypzpqyka446rus6xufm63a9q0hrw7cvutcc0vl95whfpx39hpyszqvtqvzqqqr4gupdk2hd
NIP-29 Groups
- Minecraft Group Chat
nostr:naddr1qqrxvc33xpnxxqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvqazypfd- VFNet Group Chat
nostr:naddr1qqrrwvfjx9jxzqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvq08hx48
"Nostrified Websites"
[D] = Saves darkmode preferences over nostr
[A] = Auth over nostr
[B] = Beta (software)
[z] = zap enabled
Other Services (Hosted code)
Emojis Packs
- Minecraft
nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp- AIM
nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk- Blobs
nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj- FavEmojis
nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt- Modern Family
nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n- nostriches (Amethyst collection)
nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w- Pepe
nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7- Minecraft Font
nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr- Archer Font
nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh- SMB Font
nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk
Git Over Nostr
- NostrSMS
nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk- nip51backup
nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6- bukkitstr
nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2
Market Places
Please use Nostr Market or somthing simular, to view.
- VFStore
nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjvamnwvaz7tmgv9mx2m3wweskuer9wfmkzuntv4ezuenpd45kc7f0da6hgcn00qqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gvlfm7gu
Badges
Created
- paidrelayvf
nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3- iPow
nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r- codmaster
nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g- iMine
nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5
Clients I Use
- Amethyst
nostr:naddr1qqxnzd3cx5urqv3nxymngdphqgsyvrp9u6p0mfur9dfdru3d853tx9mdjuhkphxuxgfwmryja7zsvhqrqsqqql8kavfpw3- noStrudel
nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n- nostrsms
nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm
Lists
- Bluesky
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqqapxcat9wd4hj0ah0jw
- Fediverse
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp9rx2erfwejhyum9j4g0xh
- Fediverse_Bots
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqperx2erfwejhyum9tapx7arnfcpdzh
- My Bots
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqz4uh5jnpwscyss24fpkxw4fewafk566twa2q8f6fyk
-
 @ 7d33ba57:1b82db35
2025-04-17 08:46:22
@ 7d33ba57:1b82db35
2025-04-17 08:46:22Oslo, the capital of Norway, is where sleek Scandinavian design, deep Viking roots, and stunning fjord views come together. Surrounded by forests and water, Oslo is one of Europe’s greenest and most livable cities, with a creative, outdoorsy spirit and world-class museums.

🏙️ Top Things to Do in Oslo
🎨 Vigeland Sculpture Park (Frogner Park)
- A surreal, open-air park filled with over 200 sculptures by Gustav Vigeland
- It’s free and open year-round—great for a stroll or picnic
🛶 Oslofjord and Island Hopping
- Take a ferry or kayak around the Oslofjord
- Visit Hovedøya, Gressholmen, or Lindøya for swimming, hiking, and picnicking
🖼️ The National Museum & MUNCH
- The National Museum holds iconic works, including Munch’s The Scream
- Visit the new MUNCH Museum on the waterfront for a deeper dive into the artist’s life

⛵ Aker Brygge & Tjuvholmen
- Trendy harborside neighborhoods full of restaurants, bars, and galleries
- Great for a waterside meal or people-watching
🏰 Akershus Fortress
- A medieval castle with epic views over the Oslofjord
- Walk along the fortress walls and explore Oslo’s early history
🏛️ The Viking Ship Museum (Reopening in 2026)
- Currently under renovation, but a must-visit when it reopens—actual Viking ships and artifacts!

🌲 Nature Close to the City
🌳 Nordmarka Forest
- Miles of trails for hiking, biking, skiing, or lake swimming just 20 minutes from the center
- Hop on the metro to Frognerseteren for panoramic views and waffles at a mountain hut
🏞️ Ekebergparken
- Sculpture park on a hill with views over Oslo
- Mix of art, forest trails, and history

🍽️ What to Eat & Drink
- Salmon, reindeer, and meatballs (kjøttkaker)
- Try a pølse (Norwegian hot dog) with crispbread
- Don’t miss kanelsnurrer (cinnamon buns) or brown cheese (brunost)
- Local craft beer or a glass of Akevitt, Norway’s signature spirit

🗓️ Best Time to Visit
- Summer (June–Aug): Long days, festivals, island hopping, and café life
- Winter (Dec–Feb): Great for skiing, winter lights, and cozy vibes
- Shoulder seasons: Fewer crowds, moody beauty, and great museum access

🧭 Travel Tips
- Oslo is compact—walk or use public transport (Oslo Pass is a great deal!)
- Tap water is pristine, and locals are super friendly
- Many attractions are closed on Mondays—plan ahead
- Bring layers—weather can shift fast!

-
 @ 1bc70a01:24f6a411
2025-04-16 13:53:00
@ 1bc70a01:24f6a411
2025-04-16 13:53:00I've been meaning to dogfood my own vibe project for a while so this feels like a good opportunity to use Untype to publish this update and reflect on my vibe coding journey.
New Untype Update
As I write this, I found it a bit annoying dealing with one of the latest features, so I'll need to make some changes right after I'm done. Nonetheless, here are some exciting developments in the Untype article composer:
-
Added inline AI helper! Now you can highlight text and perform all sorts of things like fix grammar, re-write in different styles, and all sorts of other things. This is a bit annoying at the moment because it takes over the other editing functions and I need to fix the UX.
-
Added pushing articles to DMs! This option, when enabled, will send the article to all the subscribers via a NIP-44 DM. (No client has implemented the subscription method yet so technically it won’t work, until one does. I may add this to nrss.app) Also, I have not tested this so it could be broken… will test eventually!
- Added word counts
- Added ability to export as markdown, export as PDF, print.
The biggest flaw I have already discovered is how "I" implemented the highlight functionality. Right now when you highlight some text it automatically pops up the AI helper menu and this makes for an annoying time trying to make any changes to text. I wanted to change this to show a floating clickable icon instead, but for some reason the bot is having a difficult time updating the code to this desired UX.
Speaking of difficult times, it's probably a good idea to reflect a bit upon my vibe coding journey.
Vibe Coding Nostr Projects
First, I think it's important to add some context around my recent batch of nostr vibe projects. I am working on them mostly at night and occasionally on weekends in between park runs with kids, grocery shopping and just bumming around the house. People who see buggy code or less than desired UX should understand that I am not spending days coding this stuff. Some apps are literally as simple as typing one prompt!
That said, its pretty clear by now that one prompt cannot produce a highly polished product. This is why I decided to limit my number of project to a handful that I really wish existed, and slowly update them over time - fixing bugs, adding new features in hopes of making them the best tools - not only on nostr but the internet in general. As you can imagine this is not a small task, especially for sporadic vibe coding.
Fighting the bot
One of my biggest challenges so far besides having very limited time is getting the bot to do what I want it to do. I guess if you've done any vibe coding at all you're probably familiar with what I'm trying to say. You prompt one thing and get a hallucinated response, or worse, a complete mess out the other end that undoes most of the progress you've made. Once the initial thing is created, which barely took any time, now you're faced with making it work a certain way. This is where the challenges arise.
Here's a brief list of issues I've faced when vibe-coding with various tools:
1. Runaway expenses - tools like Cline tend to do a better job directly in VSCode, but they can also add up dramatically. Before leaning into v0 (which is where I do most of my vibe coding now), I would often melt through $10 credit purchases faster than I could get a decent feature out. It was not uncommon for me to spend $20-30 on a weekend just trying to debug a handful of issues. Naturally, I did not wish to pay these fees so I searched for alternatives.
2. File duplication - occasionally, seemingly out of nowhere, the bot will duplicate files by creating an entire new copy and attached "-fixed" to the file name. Clearly, I'm not asking for duplicate files, I just want it to fix the existing file, but it does happen and it's super annoying. Then you are left telling it which version to keep and which one to delete, and sometimes you have to be very precise or it'll delete the wrong thing and you have to roll back to a previous working version.
3. Code duplication - similar to file duplication, occasionally the bot will duplicate code and do things in the most unintuitive way imaginable. This often results in loops and crashes that can take many refreshes just to revert back to a working state, and many more prompts to avoid the duplication entirely - something a seasoned dev never has to deal with (or so I imagine).
4. Misinterpreting your request - occasionally the bot will do something you didn't ask for because it took your request quite literally. This tends to happen when I give it very specific prompts that are targeted at fixing one very specific thing. I've noticed the bots tend to do better with vague asks - hence a pretty good result on the initial prompt.
5. Doing things inefficiently, without considering smarter approaches - this one is the most painful of vibe coding issues. As a person who may not be familiar with some of the smarter ways of handling development, you rely on the bot to do the right thing. But, when the bot does something horribly inefficiently and you are non-the-wiser, it can be tough to diagnose the issue. I often fight myself asking the bot "is this really the best way to handle things? Can't we ... / shouldn't we .../ isn't this supposed to..." etc. I guess one of the nice side effects of this annoyance is being able to prompt better. I learn that I should ask the bot to reflect on its own code more often and seek ways to do things more simply.
A combination of the above, or total chaos - this is a category where all hell breaks loose and you're trying to put out one fire after another. Fix one bug, only to see 10 more pop up. Fix those, to see 10 more and so on. I guess this may sound like typical development, but the bot amplifies issues by acting totally irrationally. This is typically when I will revert to a previous save point and just undo everything, often losing a lot of progress.
Lessons Learned
If I had to give my earlier self some tips on how to be a smarter vibe coder, here's how I'd summarize them:
-
Fork often - in v0 I now fork for any new major feature I'd like to add (such as the AI assistant).
-
Use targeting tools - in v0 you can select elements and describe how you wish to edit them.
-
Refactor often - keeping the code more manageable speeds up the process. Since the bot will go through the entire file, even if it only makes one small change, it's best to keep the files small and refactoring achieves that.
I guess the biggest lesson someone might point out is just to stop vibe coding. It may be easier to learn proper development and do things right. For me it has been a spare time hobby (one that I will admit is taking more of my extra time than I'd like). I don't really have the time to learn proper development. I feel like I've learned a lot just bossing the bot around and have learned a bunch of things in the process. That's not to say that I never will, but for the moment being my heart is still mostly in design. I haven't shared much of anything I have designed recently - mostly so I can remain speaking more freely without it rubbing off on my work.
I'll go ahead and try to publish this to see if it actually works 😂. Here goes nothing... (oh, I guess I could use the latest feature to export as markdown so I don't lose any progress! Yay!
-
-
 @ 0b5faac9:12669905
2025-04-17 08:05:44
@ 0b5faac9:12669905
2025-04-17 08:05:44In the wave of digitalization, handwriting as a way to record thoughts and inspire inspiration is gradually being forgotten. Mobile phone notifications, drone hums and ubiquitous wireless signals make it difficult for us to calm down and hold a pen to write. How to regain the time of handwriting and find the pure joy of creation? With the help of tools such as mobile phone jammers, drone jammers and high-power jammers, we can block interference and create a focused writing space.
1. The threat of digital interference to handwriting
Mobile phone intrusion: Frequent notifications, social media and calls interrupt thoughts, making it difficult to focus on the smooth expression between paper and pen.
Drone noise: When writing outdoors, the hum or monitoring of drones not only destroys the atmosphere, but may also cause privacy concerns.
Wireless signal clutter: WiFi, Bluetooth and other signals invisibly distract attention and weaken the immersion when writing.
https://www.jammermfg.com/cell-phone-jammers.html
2. The guardian of handwriting
Mobile phone jammer: By blocking mobile phone signals, mobile phone jammers make your device temporarily "disconnected", eliminating the interference of notifications and calls, suitable for focused writing at home or in a cafe.
Drone jammer: When writing outdoors, drone jammers can block drone signals to prevent their noise or surveillance from disrupting your creative mood.
https://www.jammermfg.com/drone-jammer.html
High-power jammer: For scenes that require a large range of quiet environments, such as writing workshops, high-power jammers can block multiple wireless signals to create a pure "signal pure land".
3. Practical methods to regain handwriting
In addition to using jammers, cultivating handwriting habits can also improve concentration:
- Fixed handwriting time: arrange 30 minutes to 1 hour of "interference-free handwriting time" every day, use mobile phone jammers to ensure that you are not disturbed, and record inspiration or diary.
- Choose a comfortable scene: write in a quiet study or outdoor natural environment, and use drone jammers to protect the tranquility of outdoor creation.
4. Your creative partner
https://www.jammermfg.com/high-power-military-jammer.html
To regain handwriting time, it is crucial to choose a reliable jammer. Jammermfg provides a variety of solutions to meet the needs of different creative scenarios:
- Diversified products: from portable mobile phone jammers to high-power jammers, covering a variety of indoor and outdoor writing environments.
- Professional support: Provide purchase suggestions and usage guidance to ensure that the equipment is perfectly adapted to your handwriting needs.
Conclusion
Handwriting is a bridge between the heart and the world, but we need to actively make room for it. With the help of mobile phone jammers, drone jammers and high-power jammers, combined with scientific writing habits, we can stay away from distractions and regain the fun and depth of handwriting.
-
 @ da0b9bc3:4e30a4a9
2025-04-16 08:28:24
@ da0b9bc3:4e30a4a9
2025-04-16 08:28:24Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/944844
-
 @ 866e0139:6a9334e5
2025-04-17 07:40:05
@ 866e0139:6a9334e5
2025-04-17 07:40:05Autor: Gerd Conradt. (Foto: Thomas Klingberg). Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Sie wollen die neuesten Pareto-Artikel auf einen Blick sehen (Friedenstaube & Co.), um nichts mehr zu verpassen?* Hier geht es zu unserem Telegram-Kanal.***
Ein Leben, geprägt von Geschichte und Herzschlag: Vom jungen Pionier am Kyffhäuser, wo die Sage von Barbarossa lebt, bis zur roten Fahne über dem zerstörten Reichstag. Gerd Conradt blickt zurück – auf die Flucht vor der Roten Armee, die Schrecken des Unternehmens Barbarossa und die Bauernkriege vor 500 Jahren. Inmitten von Kriegen und Zeitenwenden fragt er: Was verbindet Kaiser Barbarossa, Thomas Münzer und die Mahnmale unserer Zeit? Ein bewegendes Zeugnis über Macht, Erinnerung und die Suche nach Frieden – erzählt aus Cabarita Beach, 30.623 Tage nach seiner Geburt.
Zeit und Geschichte, Zeitgeschichte und ihre Verknüpfungen mit dem privaten Leben der Menschen werden vom Herzschlag jedes Einzelnen bestimmt. Zufälliges, Wiederholungen, Parallelen – Macht und Öffentlicheit – Geschichte als Konstruktion – Biografien: Alles ist nur möglich, wenn die Herzen der Menschen schlagen, pulsieren, für Lebendigkeit sorgen.
Im Monat Mai wird an zwei für die deutsche Geschichte bedeutende Ereignisse erinnert: an das Ende des 2. Weltkriegs vor 80 und an das Ende der Bauernkriege vor 500 Jahren. Mit diesen Daten verbinden mich ein Name, Kaiser Friedrich der I, genannt Barbarossa, und ein Symbol, die Rote Fahne.
Heute, an dem Tag, an dem ich diesen Text schreibe, am 18.03.2025, Cabarita Beach, Australien, lebe ich 30.623 Tage.
In dieser Zeit gab es immer irgendwo auf der Welt Krieg. Im Jahr meiner Geburt startete die deutsche Wehrmacht am 22.06.41 unter dem Decknamen Unternehmen Barbarossa ihren Überfall auf die Sowjetunion. Drei Millionen gut ausgebildete, strahlende, meist blauäugige hochgerüstete Männer begannen den zerstörerischsten Feldzug der Menschheitsgeschichte. Ziel war die Beseitigung des „jüdischen Bolschewismus“, die Germanisierung der Länder von Deutschland bis zum Ural. Fruchtbare Böden, Bodenschätze und ein Heer von Zwangsarbeitern sollten dem germanischen Reich zu Weltruhm verhelfen.
Mit massiver Unterstützung durch die USA widerstand die Rote Armee und besiegte den Aggressor. Deutschland war zerstört. Insgesamt 60 Millionen Menschen getötet.
In diesem Jahr wird am 8. Mai, dem Tag der Befreiung, an das Ende des 2. Weltkriegs vor achtzig Jahren erinnert. Eine rote Fahne mit Hammer und Sichel war damals am zerstörten Reichstag gehisst – Berlin, Deutschland geteilt in die Hoheitszonen der Alliierten und die der Sowjetunion.
Nach der Flucht meiner Familie vor der Roten Armee – im Januar 1945 – aus dem Teil Deutschlands, der heute zu Polen gehört, lebten wir im sowjetisch verwalteten Teil der späteren DDR. Als Junger Pionier nahm ich an Zeltlagern teil. Besonders in Erinnerung ist mir das auf dem Ratsfeld am Fuße des Kyffhäusers, jenem Ort, an dem vor 500 Jahren ein Aufstand der Bauern unter Führung des Reformators Thomas Münzer (1489 - 1525) von den Heeren der Fürsten blutig niedergeschlagen wurde. Münzer wurde öffentlich hingerichtet.
Martin Luther hatte zunächst Sympathie für die Bauern, verfasste dann jedoch eine Schrift „Wider die mörderischen und räuberischen Rotten“, mit der er dazu aufrief, die Revoltierenden zu töten – dies sei eine religiös verdienstvolle Tat. Die Reformation als Verrat.
Auf dem Kyffhäuser steht ein großes Denkmal, mit dem an Friedrich I., Barbarossa, erinnert wird. Der Sage nach ist er nicht gestorben, sondern lebt in der naheglegenen Barbarossahöhle fort.
Vom Pionierlager aus besuchten wir die beeindruckende Höhle, an deren Ende an einem großen Steintisch eine mit Krone, Zepter und Krönungsmantel ausgestattete Puppe sitzt, deren roter Bart in den Tisch gewachsen ist. Kaiser Barbarossa, 1122 – 1190, der Rotbart, war eine Persönlichkeit von historischer Größe. Er war ein Mann des Wortes und der Tat. Er konnte reiten, jagen, mit der Waffe kämpfen, jedoch weder lesen noch schreiben – so die Überlieferungen. Er war Krieger und Diplomat, Kaufmann und ein Mann von Kultur. Viele Kriege führte er in Italien, mehrere gegen Mailand, wo jeweils Städte und ganze Ländereien geplündert und vernichtet wurden.
Er war ein kluger Taktiker, der Zwietracht für seine Zwecke nutzen konnte. Waren seine Vorgänger für Milde und Barmherzigkeit angesehen, herrschte nun die Strenge der Gerechtigkeit. Im Umgang mit den Päpsten handelte er klug. Das führt mich wieder zur Roten Fahne. Karl der Große vergab nämlich um das Jahr 800 Land an seine Untertanen. Die Übergabe wurde mit einer roten Fahne markiert. Sie stand für „freie Bürger bei freier Arbeit auf freiem Land“. Barbarossa erreichte beim Papst die Heiligsprechung Karls des Großen im Jahre 1165. Karls Gebeine wurden in den heute als Heiligtum verehrten Karlsschrein in Aachen umgebettet.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Alle Kriege führen zu Zeitenwenden, verändern Machtstrukturen. Ländergrenzen werden neu gezogen oder verschwinden. Derzeit versuchen neue Kaiser die Welt neu zu ordnen. Sie sind Kriegsherren – auch Kaufmänner. Lassen sich Krieg und Wirtschaft trennen?
Warum Barbarossa heute? Das Denkmal am Kyffhäuser wurde von Nationalisten errichtet, die in ihm den Gründer des Deutschen Reiches sahen. Heute ist das Denkmal wieder ein beliebter Versammlungsort der neuen Rechten.
Im Mittelpunkt des Gedenkens an die verlorene Schlacht der Bauern vor 500 Jahren wird das monumentale Panoramabild Freibürgerliche Revolution des Leipziger Malers Werner Tübke stehen. Das in den Jahren von 1976 bis 1987 von der Regierung der DDR in Auftrag gegebene Bild zählt zu den größten Panoramen der Welt.
Es zeigt am Beispiel des Aufstands der Bauern ein im Geiste der Renaissance gemaltes Welttheater. Es ist kein Schlachtbild im üblichen Sinn, eher eine Allegorie auf ureigenste menschliche Ängste, die Darstellung einer Apokalypse, eine historische Parabel auf Glaubenskämpfe der Moderne, auf eine Welt im Taumel, Weltgeschichte als Weltgericht.(1)
In Berlin-Treptow steht das Sowjetische Ehrenmal, das in seiner Wuchtigkeit an den ruhmreichen Sieg der Sowjetunion über den Hitlerfaschismus erinnert. Es ist das größte und markanteste Kriegsdenkmal außerhalb Russlands. 1949 am 70. Geburtstag von Stalin eingeweiht, ist es die Kanonisierung eines endgültigen Kriegsbildes.(2) Errichtet auf den namenlosen Gräbern 7000 gefallener Soldaten, verkörpert ein übergroßer sowjetischer Held, gottgleich, einen Sieger, der mit dem Schwert das deutsche Hakenkreuz zerschlägt. Eine unmenschliche Statue, die nichts mit der wahren Tragödie und dem unermesslichen Preis für den Sieg zu tun hat. Stalins Sicht auf Kultur unterscheidet sich nicht von der Hitlers oder anderer Diktatoren – sie stehen für eine Verherrlichung von Stärke, oft personalisierter Autorität – es sind Mahnmale historischer Täuschung und ideologische Fälschung.(3)
Wie damit umgehen am 80. Jahrestag der Befreiung? Vermutlich wird es in diesem Jahr heftige Demonstrationen im Zusammenhang mit dem Krieg in der Ukraine geben. Neue Forderungen nach Abriss werden laut. Das Denkmal schleifen? Im Zwei-plus-Vier-Vertrag von 1990, in dem die Deutsche Einheit festgeschrieben wurde, verpflichtete sich die Bundesrepublik Deutschland, für den Erhalt der sowjetischen Mahnmäler zu sorgen.
Zur Erinnerung: Ein Kunstprojekt des Künstlerehepaares Christo und Jeanne-Claude, Verhüllter Reichstag, 1995, führte zu einer spirituellen Reinigung dieses von verhängnisvoller Geschichte belasteten Gebäudes. Das Ehrenmal in Treptow schwarz verhüllen?
Auf einer Reise nach Jakutien, einer Republik, die zur russischen Einflusszone gehört, pilgerte ich vor meiner Abreise zum Ehrenmal für die im Großen Vaterländischen Krieg gefallenen Menschen. Zu meiner Überraschung und Freude hatten die Kinder das Mahnmal zu einem Spielplatz verwandelt. Sie kletterten in die Panzer, über die Kanonen und spielten Fangen um die bronzenen Heldenfiguren herum.
Viele tausend Herzen haben bereits in den aktuellen Kriegen aufgehört zu schlagen. Die Herzen der verwundeten Menschen, Landschaften und Tiere schmerzen.
Mein Herz schlägt. Die Arbeit an dem Text gibt meinem Leben Sinn. Die Gedanken, Ideen fliegen.
Herzen wollen tiefes Glück, weder Angst noch Verzweiflung, nicht Hunger und Krieg.
Auch mit 83 Jahren erinnere ich mich noch gut an die Todesängste auf der Flucht mit meiner Mutter und meinen Geschwistern. Der Vater war im Krieg.
Am Tag der Befreiung hat mein neuer Film Premiere „FARBTEST, 1968 – 2024, ein rotes Stück Stoff im Wind“.
Tanz als Revolution, aus Ideologie wird Poesie.

\ Anmerkungen:
(1) Eduard Beaucamp, FAZ, 28.05.2004 (Wikipedia)
(2, 3) Irina Scherbakowa, Sowjetische Kriegsdenkmäler, was bleibt? Am Beispiel Treptow. 2022
Der Link zum Filmtrailer:
https://www.youtube.com/watch?v=tHe36fXYnBw&t=5s
Gerd Conradt ist ein Deutscher Filmemacher und Künstler. Geboren 1941 in Schwiebus (heute Polen), floh seine Familie 1945 vor der Roten Armee nach Thüringen. Er studierte an der Deutschen Film- und Fernsehakademie Berlin, drehte avantgardistische Filme wie „Farbtest Rote Fahne“ (1968) und war politisch aktiv, was zu seiner Relegation führte. Später arbeitete er an Dokumentarfilmen und Installationen, u. a. über die Berliner Mauer und Neuseeland.**
Filme und Ausstellungen: Wikipedia.
AKTUELL: VERANSTALTUNGEN
- Hier gibt es einen Überblick über aktuelle Ostermärsche.
- Heute 17 Uhr Friedensdemo vor dem Rathaus in Freiburg/Breisgau!
- Wie geht Frieden? Vom 17.-24.04. findet zu diesem Thema ein Onlinekongress zum Thema statt (Teilnahme frei)
- Sie wollen auf Demos, Ostermärsche, Kongresse etc. zum Thema Frieden aufmerksam machen? Bitte per Mail an: friedenstaube\@pareto.space.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.)
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 91266b9f:43dcba6c
2025-04-16 03:42:09
@ 91266b9f:43dcba6c
2025-04-16 03:42:09"No," I said, "you've got no right."
Sergeant Curtis sighed. "Come on, Mister Alton, I need you to work with me here."
"No," I said. "Absolutely not."
"He did it," shouted Mavis Harris, my recently new neighbor, leaning over the garden fence. "I saw him! He had a knife, a carving knife. And I heard the screaming and the shouting! He did it!"
"Thank you, Miss Harris," said Sergeant Curtis. "We've got it from here."
We were in my beautifully manicured backyard, sweating under the midday sun, along with six other police officers--all of them armed with shovels, ready to dig.
"This is an invasion of my privacy and I won't have it," I said.
"If you just tell us where your wife is we can get this all cleared up," he said.
"I'm not married," I said. "I've never been married."
Sergeant Curtis chewed on that for a bit, while he did the same to his bottom lip. "Girlfriend then. Partner?"
"I have no girlfriend. No partner. There's nobody at all," I said.
But there was. Sort of. Cindy, wonderful, difficult Cindy.
"He's lying!" said Mavis Harris. "I've seen her. Through the window. One time I called by when he wasn't here and she was just sitting in there, not moving. Wouldn't even answer the door. She must've been terrified, the poor girl. I bet he had her tied to the chair!"
That was absurd. Cindy wasn't into that kind of thing. I would never tie her to a chair and leave the house. That's crazy talk.
"We've got more than one eyewitness that says there's been a woman in the house with you," said Sergeant Curtis. "How about we get this woman on the phone, clear this up?"
"I can't make the impossible happen, Sergeant," I said, stiffly.
My back door opened and Constable Jenkins stepped onto the verandah. "Got a carving knife missing from a set of six," he said.
"I told you, he went after her with a knife!" said Mavis Harris.
She was right. Things had got heated. Words were said. The knife had made an appearance. There had definitely been some stabby-cutty action. Much to my dismay. I hated that it happened. I guess I was going to have to live with the damage.
Sergeant Curtis sighed. "This isn't looking good, Mr Alton."
"I bet he put her under the roses!" said Mavis Harris. "That's where I saw him heading with the body!"
"Alleged body," I muttered.
"Jenkins, any sign of blood in there?" said Sergeant Curtis.
"None whatsoever," said Jenkins. "Not even under black light. Couldn't spot any in the garden either."
"He must have cleaned it up," said Mavis. "Bleach. Bleach will clean up anything. And I saw him, I saw him carry her out and she had what looked like a knife sticking out of her chest!"
"Last chance, Mr Alton," said Curtis, "let's get this lady friend of yours on the phone and clear this up."
"I told you, I can't do the impossible," I said.
"Then you're leaving me no choice," he said.
He turned and nodded at the waiting officers with their shovels. "Start with the rose garden," he said.
They rolled up their sleeves with obvious relish and got to work.
"This is destruction of private property," I said. "When you're done, every rose petal, every grain of soil, better be back exactly as it was. Or you'll be dealing with my lawyer."
"Don't worry," said Sergeant Curtis, "I assure you everything will be put back as we found it. Whether we uncover anything or not."
As we watched the officers desecrate my rose garden, Sergeant Curtis said, "You know there's probably a few million square kilometers of country, forests, lakes, beaches, and do you know where most killers bury their wives or husbands? On their own property, right in their own backyard."
"Convenience trumps everything, I suppose," I said.
"Laziness," said Sergeant Curtis, "most casual criminals are just bone lazy."
"Or," I said, "they maybe wanted to keep their loved ones close."
Sergeant Curtis looked at me, eyes narrowed. "Is that what it is? You kill them, but somehow you want to keep them close?"
I shrugged. "Things happen. But you still love them. Maybe, you want them to be close to home," I said.
Curtis glared at me.
After a while Constable Jenkins climbed out of the rose garden and moped his sweating forehead with his sleeve. "Nothing here," he said. "This soil is pretty solid, hasn't been dug up in a while."
"The other rose bed," said Mavis Harris, "he must have used the other rose bed, beside the shed."
Damn that woman, why won't she keep her mouth shut?!
Constable Jenkins went over and stabbed his shovel into the dirt a few times. "Yeah," he said, "this has been dug up recently."
"Okay," said Sergeant Curtis, "get to it."
"I really must protest," I said. "This is a violation of my rights!"
"I'm sure we'll be done soon enough," said Sergeant Curtis, with a tight smile.
I turned and stared daggers at Mavis Harris, who haughtily thrust her nose and chin in the air, a smug smile on her face. Damn that woman and her meddling ways!
The officers found my second rose garden easier going. They were at it about twenty minutes when Constable Jenkins suddenly said, "Jesus Christ!"
"What, what is it?" said Sergeant Curtis, coming to attention.
"I ... I don't know," said Jenkins. "Hang on ..." He scraped at the dirt and then leaned over, grabbed something and lifted it out of the dirt.
A leg.
"Jeezuz," said Jenkins, letting the leg drop back into the soil. "I think we found her!"
"I knew it," said Mavis Harris. "I told you! Didn't I tell you? He did it! He killed her!"
They worked quickly now, gently digging and scraping away dirt until they could lift her other leg out. My beautiful Cindy doll.
"We've got a knife," said Jenkins, "but it's ... it's ..."
He turned to look at me, his face twisted in disgust.
"What is it?" said Curtis.
Jenkins swallowed, hard. "It's ... the knife, it's ... it's stabbed ... up between her legs, if, uh, if you know what I mean."
"Oh my god, you absolute monster," said Mavis Harris, clutching the neck of her blouse.
I sighed. They had no right. No right. This was a private matter. It was nobody's business but mine and Cindy's. We would work it out, Cindy and me. We always did.
"Okay," said Curtis, "get her out of there, quick! Check for a pulse, just in case."
"She's gone, Sarge," said Jenkins. "She's stone cold dea--wait, hang on a second."
He did some more digging and scraping with the shovel and slowly eased my Cindy all the way out of the dirt.
"Oh, bloody hell " said Jenkins. "You have got to be kidding."
"What, what is it?" said Curtis.
"Oh my, oh my Lord," said Mavis Harris, "I feel sick."
Jenkins struggled a bit with the weight, but managed to get Cindy upright. She is a bit of a heavy lass, I have to admit.
"It's a doll," said Jenkins. "It's just a doll, a sex doll, I think." He lifted Cindy's arm and made her give a little wave. "Seems to be silicon. Wow, very life-like, I must say." He was gently squeezing Cindy's arm and nose and cheek with his fingertips.
I seethed. The disrespect!
"A doll?" said Curtis.
"Yes, sir."
Curtis turned to me, his face a throttled purple colour. "A bloody sex doll?!"
I said nothing.
He struggled to keep his anger in check. "I could arrest you for obstruction of justice, Alton, for wasting Police time and resources," he said.
"How?" I said. "I was nothing but absolutely honest with you. There was no wife, no girlfriend, no body. I told you this repeatedly. You chose to ignore me and you, sir, have wasted not only my time, but that of your department and your own men."
I left him there, chewing air, and went to Jenkins and took Cindy gently in my arms. Her wounds were bad but not unamendable.
"Pervert," hissed Mavis Harris. "He's a dirty little pervert!"
I headed for the house, but paused at the back door and said, "I will expect you to return my rose gardens to their absolute pristine condition. My lawyer already doesn't like your department, not one bit, Sergeant Curtis."
I did not wait for a reply. I went inside and closed the door, quietly, behind me.
Night was coming on and the police had returned my garden to its former glory, and departed. A cool breeze drifted through the kitchen window.
I was at the table with Cindy, tending her wounds. Silicon glue isn't cheap, I'll tell you that, and it would leave Cindy with some scars, unfortunately. If I'm honest, I don't think she was all that pleased about it. As I knelt down to treat a wound across her ribcage, I copped her knee right in my groin.
"Ugh!" I said, the wind snapping out of me and tears rimming my eyes.
I reached out to steady myself and that's when she lurched forward, out of her chair, and headbutted me square in the face.
"For godsakes, Cindy!" I said.
She was baring down on me. I grabbed her by the shoulders, pushing her up and back, but like I said, she wasn't exactly a lightweight. I staggered back with her falling into me, and I winced as the edge of the kitchen counter stabbed into the small my back. Cindy gave me another hit to the testicles with her hand, making me gasp.
I rolled us around, putting her back against counter, silicon squeaking against marble--see how she likes it. I almost took another groin hit from her other hand. I was bending her back over the kitchen sink and without realising it, I had grabbed one of the serrated steak knives in my fist, raised it over my head, and was ready to drive it down into the open O of her mouth.
And that's when I looked past Cindy's head, out the kitchen window, across the fence, and over there in her kitchen window was Mavis Harris. Staring right at me, at us, her mouth an identical open O to Cindy's.
We stared at each other for a long moment, and then I reached up and slowly closed the kitchen blinds.
I sighed. I decided that Mavis Harris was a problem I just couldn't tolerate. Her constant invasion of my privacy was one thing, but calling the police was unacceptable. I would have to take care of her at my earliest opportunity. But carefully. And I had just the spot for her, out behind her very own shed.
Right next to Henry Patterson, the last neighbour and resident of that house, who had also gotten far too nosey for his own good.
Yes, a real nice spot, and close to home.
-
 @ c13fd381:b46236ea
2025-04-16 03:10:38
@ c13fd381:b46236ea
2025-04-16 03:10:38In a time of political volatility and declining public trust, Australians are looking for leaders who don’t just talk about accountability—but prove it. It’s time for a new standard. A protocol that filters for competence, responsibility, and integrity—not popularity alone.
Here’s the idea:
Anyone who wants to run for public office in Australia must stake 100Ksats to a public address and maintain provable control of the corresponding private key for the duration of their term.
A Low Barrier With High Signal
The amount—100Ksats—is modest, but meaningful. It isn’t about wealth or exclusion. It’s about signal. Controlling a private key takes care, discipline, and a basic understanding of digital responsibility.
This protocol doesn't reward those with the most resources, but those who demonstrate the foresight and competence required to secure and maintain something valuable—just like the responsibilities of public office.
How It Works
This system is elegantly simple:
- To nominate, a candidate generates a keypair and deposits 100Ksats into the associated address.
- They publish the public key alongside their candidate profile—on the electoral roll, campaign site, or an independent registry.
- Throughout their time in office, they sign periodic messages—perhaps quarterly—to prove they still control the private key.
Anyone, at any time, can verify this control. It’s public, permissionless, and incorruptible.
Why This Matters
Private key management is more than technical—it’s symbolic. It reflects:
- Responsibility – Losing your key means losing your ability to prove you’re still accountable.
- Integrity – Key control is binary. Either you can sign or you can’t.
- Long-term thinking – Good key management mirrors the strategic thinking we expect from leaders.
This isn’t about promises. It’s about proof. It moves trust from words to cryptographic reality.
A Voluntary Standard—for Now
This doesn’t require legislative change. It can begin as a voluntary protocol, adopted by those who want to lead with integrity. The tools already exist. The expectations can evolve from the ground up.
And as this becomes the norm, it sets a powerful precedent:
"If you can’t manage a private key, should you be trusted to manage public resources or national infrastructure?"
Identity Without Surveillance
By linking a public key to a candidate’s public identity, we create a form of digital accountability that doesn’t rely on central databases or invasive oversight. It’s decentralized, simple, and tamper-proof.
No backdoors. No bureaucracy. Just Bitcoin, and the competence to manage it.
Bitcoin is the foundation. Asymmetric encryption is the filter.
The result? A new class of public leaders—proven, not promised.Let’s raise the standard.
-
 @ 6be5cc06:5259daf0
2025-04-15 20:16:08
@ 6be5cc06:5259daf0
2025-04-15 20:16:08Eu reconheço que Deus, e somente Deus, é o soberano legítimo sobre todas as coisas. Nenhum homem, nenhuma instituição, nenhum parlamento tem autoridade para usurpar aquilo que pertence ao Rei dos reis. O Estado moderno, com sua pretensão totalizante, é uma farsa blasfema diante do trono de Cristo. Não aceito outro senhor.
A Lei que me guia não é a ditada por burocratas, mas a gravada por Deus na própria natureza humana. A razão, quando iluminada pela fé, é suficiente para discernir o que é justo. Rejeito as leis arbitrárias que pretendem legitimar o roubo, o assassinato ou a escravidão em nome da ordem. A justiça não nasce do decreto, mas da verdade.
Acredito firmemente na propriedade privada como extensão da própria pessoa. Aquilo que é fruto do meu trabalho, da minha criatividade, da minha dedicação, dos dons a mim concedidos por Deus, pertence a mim por direito natural. Ninguém pode legitimamente tomar o que é meu sem meu consentimento. Todo imposto é uma agressão; toda expropriação, um roubo. Defendo a liberdade econômica não por idolatria ao mercado, mas porque a liberdade é condição necessária para a virtude.
Assumo o Princípio da Não Agressão como o mínimo ético que devo respeitar. Não iniciarei o uso da força contra ninguém, nem contra sua propriedade. Exijo o mesmo de todos. Mas sei que isso não basta. O PNA delimita o que não devo fazer — ele não me ensina o que devo ser. A liberdade exterior só é boa se houver liberdade interior. O mercado pode ser livre, mas se a alma estiver escravizada pelo vício, o colapso será inevitável.
Por isso, não me basta a ética negativa. Creio que uma sociedade justa precisa de valores positivos: honra, responsabilidade, compaixão, respeito, fidelidade à verdade. Sem isso, mesmo uma sociedade que respeite formalmente os direitos individuais apodrecerá por dentro. Um povo que ama o lucro, mas despreza a verdade, que celebra a liberdade mas esquece a justiça, está se preparando para ser dominado. Trocará um déspota visível por mil tiranias invisíveis — o hedonismo, o consumismo, a mentira, o medo.
Não aceito a falsa caridade feita com o dinheiro tomado à força. A verdadeira generosidade nasce do coração livre, não da coerção institucional. Obrigar alguém a ajudar o próximo destrói tanto a liberdade quanto a virtude. Só há mérito onde há escolha. A caridade que nasce do amor é redentora; a que nasce do fisco é propaganda.
O Estado moderno é um ídolo. Ele promete segurança, mas entrega servidão. Promete justiça, mas entrega privilégios. Disfarça a opressão com linguagem técnica, legal e democrática. Mas por trás de suas máscaras, vejo apenas a velha serpente. Um parasita que se alimenta do trabalho alheio e manipula consciências para se perpetuar.
Resistir não é apenas um direito, é um dever. Obedecer a Deus antes que aos homens — essa é a minha regra. O poder se volta contra a verdade, mas minha lealdade pertence a quem criou o céu e a terra. A tirania não se combate com outro tirano, mas com a desobediência firme e pacífica dos que amam a justiça.
Não acredito em utopias. Desejo uma ordem natural, orgânica, enraizada no voluntarismo. Uma sociedade que se construa de baixo para cima: a partir da família, da comunidade local, da tradição e da fé. Não quero uma máquina que planeje a vida alheia, mas um tecido de relações voluntárias onde a liberdade floresça à sombra da cruz.
Desejo, sim, o reinado social de Cristo. Não por imposição, mas por convicção. Que Ele reine nos corações, nas famílias, nas ruas e nos contratos. Que a fé guie a razão e a razão ilumine a vida. Que a liberdade seja meio para a santidade — não um fim em si. E que, livres do jugo do Leviatã, sejamos servos apenas do Senhor.
-
 @ 20986fb8:cdac21b3
2025-04-17 06:46:14
@ 20986fb8:cdac21b3
2025-04-17 06:46:14分布式Agentic组织(Distributed Agentic Organizations,DA(gentic)O)正在重塑协作的未来格局,融合智能代理(Agentic AI),跨越加密社区、网络社会与现实世界。但要规模化发展,DA(gentic)O 需要更友好的 Agent-to-Agent 和人-to-Agent 社交-交互路径。YakiHonne 可编程 Smart Widgets 提供轻量接口,嵌入社交与支付功能,让代理无缝协作、交易、治理。Agentic Mini Apps 则将这一潜力变为现实,覆盖从链上投票到咖啡支付的场景。在这篇文章我们将探讨 YakiHonne 可编程Smart widgets如何赋能 DA(gentic)O,激活去中心化生产力与代理驱动的协作经济。
1.从 DAO 到 DA(gentic)O:协作的新范式
传统组织依赖中心化管理,效率受限;DAO 通过区块链实现去中心化治理,但投票延迟和静态合约限制生产力。Agentic AI 开启协作新纪元,超越AI的被动执行,具备自主推理、动态适应的能力,宛如数字世界的“智能公民”。通过大语言模型、高级算法与外部工具(如链上数据、Web API、物联网传感器)融合,Agentic AI 实时感知信息、优化决策、持续进化,促使了 DA(gentic)O)的崛起。
DA(gentic)O 是由多个 AI 代理通过开放协议(如 Agent-to-Agent 协作协议、区块链、智能合约)组成的动态生态,优化去中心化自治组织(DAO)并推动其演化。不同于传统组织的中央指挥或 DAO 的投票瓶颈,DA(gentic)O 通过智能网络实现目标。例如,一个代理监测 BTC市场波动,另一个协调网络社会活动,二者通过协议协作,驱动链上交易到现实优化的成果。这种组织以生产力为核心,跨越 Web3治理、网络社会经济、物理社会运营,展现去中心化的灵活性与规模化潜力。DA(gentic)O 不仅是协作的工具,更是连接虚拟与现实的“生产力桥梁”,为全球分布式社区创造可验证的价值。
DA(gentic)O 的核心特点可概括为以下三点:
D:分布式 (Distributed) & 去中心化 (Decentralized) 决策与运作分布于多个自主代理,无需单一控制点,确保组织的鲁棒性与透明性。代理通过链上记录或分布式协议协商资源分配,形成一个无需信任中介的协作网络。例如,在 BTC 市场,代理共同管理资金流向;在网络社会,代理分布式投票决定社区规则;在物理社会,代理协调跨区域的物流调度。这种分布式架构赋予 DA(gentic)O 高度的抗干扰能力与扩展性。
A:自主 (Autonomous) 和智能 (Agentic) 代理具备独立感知、规划与执行的能力,组织通过智能协商实现自治。每个代理如同微型决策单元,能根据环境变化调整策略,无需人类频繁干预。例如,在网络社会的元宇宙,一个代理设计虚拟展览,另一个动态分配算力,二者通过协议自动协调;在物理社会的智能工厂,代理实时优化生产参数,响应市场需求。这种自主性使 DA(gentic)O 能够快速适应复杂场景,超越传统组织的反应速度。
O:组织 (Organization) 和运营 (Operation) 代理以组织化方式协同,形成高效的协作网络,完成从虚拟经济到现实生产的任务。无论是 Web3 的链上拍卖、网络社会的虚拟市场,还是物理社会的供应链整合,DA(gentic)O 都以协作驱动成果。例如,一个代理协调创作者与买家的交易,另一个优化物流配送,二者共同实现端到端的价值流转。这种运营能力使 DA(gentic)O 成为生产力的“协作枢纽”。
DA(gentic)O的灵活性源于Agentic AI的多样能力。反应型代理擅长实时响应,如监控链上交易波动;目标导向代理分解复杂任务,如规划虚拟社区的经济激励;学习型代理通过数据迭代优化,如调整智能工厂的生产参数。这些代理通过A2A协议形成协作网络,适配从虚拟治理、交易到现实优化的广泛需求,构建生产力驱动的“数字生态”。
DA(gentic)O 的主要支柱要素
构建高效的 DA(gentic)O 需以下关键支撑,确保代理网络的运行与协作:
- 主权钱包:每个代理拥有独立匿名数字钱包,安全管理资产并执行交易,支持链上支付、网络社会的虚拟奖励或物理社会的任务报酬,保障经济交互的自主性。
- 去中心化安全环境:可靠的链上或分布式系统,保护代理运行、数据隐私与决策完整性,防范外部攻击或内部篡改,确保协作的信任基础。
- 自由访问网络与链:代理需无缝访问互联网、区块链或其他数据源,获取实时信息与资源,如链上数据、网络社会的用户行为或物理社会的传感器输入,支持推理与协作。
- 接口:用户友好的且自主接口(如链上仪表盘、移动端面板),确保代理与用户、系统间的顺畅连接。
DA(gentic)O 以智能网络连接虚拟与现实,创造交易、协调和优化的价值。Agentic Mini Apps 是其关键交互工具。
2. 可编程Smart Widgets:DA(gentic)O的基础设施
YakiHonne 的可编程 Smart Widgets 是一套轻量化系统,支持 Agentic Mini Apps 的社交互动和支付功能,为DA(gentic)O 提供基础设施。它通过嵌入式接口和去中心化协议,驱动代理间的协作、交易和治理,降低开发门槛,连接 Web3、虚拟社区和现实场景。
2.1 Smart Widgets 的特性
在 Yakihonne 的设计中,Smart Widgets 是微型、智能的应用接口,专为 Agentic Mini Apps 的快速开发与部署设计。其核心特性包括:
- 嵌入社交流:支持 Mini Apps 直接嵌入社交环境,用户无需切换界面即可完成支付或交互。
- 无需中心化审核:任何开发者可以快速创建、部署和分享 Mini Apps,无需应用商店的审批流程。
- 可组合性:Smart Widgets 支持不同类型的功能模块组合,可灵活适配各种 Agent-to-Agent 协作需求。
- 内置支付能力:通过集成链上支付和稳定币支持,实现智能代理之间的价值交换。
这一体系极大降低了构建和扩展去中心化智能代理组织的门槛,使得个体代理(Agent)不仅能行动,还能彼此协作、交易和治理。
2.2 Smart Widgets 的形态与应用
Yakihonne Smart Widgets 根据创建者和使用者的不同需求,分为三种形态,覆盖从普通用户到开发者的全域需求:
- 基础组件(Basic Widgets) 无需编程,通过模板编辑器快速创建支付、投票等交互功能,适合用户构建简单的 Mini Apps。
- 动作组件(Action Widgets) 通过链接嵌入外部功能,保持社交界面的流畅性,支持 Mini Apps 扩展交互范围。
- 工具组件(Tool Widgets) 适合开发者或高级用户,基于 Mini App SDK 开发复杂应用,支持数据查询、链上任务执行、即时支付、智能决策等,构建复杂的智能化 Mini Apps。
这三种形态为 Mini Apps 提供从基础交互到高级协作的支持,适配 DA(gentic)O 的自动化流程。
2.3 支持 DA(gentic)O 的核心功能
Yakihonne Smart Widgets 为分布式Agentic组织提供以下关键能力,驱动 Agentic Mini Apps 的高效运行:
- 自治微应用(Autonomous Mini Apps) Smart Widgets 让代理能够嵌入服务逻辑,自主完成任务或发起支付。例如,Mini Apps 可自动分配 Web3 交易奖励,或协调网络社会的虚拟活动,无需人工干预。
- 即用即付(On-the-Fly Payment) 通过稳定币、BTC、闪电网络(LN)等无缝支付协议,智能代理可以即时完成链上支付,支持微交易经济体。
- 链上身份与社交绑定(On-chain Identity Integration) 代理可以在 Nostr 基础上绑定主权身份,进行链上行为的授权与签名。
- 即时交互与协作(Real-time Interaction and Coordination) 支持代理之间的即时数据交换、智能合约调用和协作执行,适配 Agent-to-Agent 协作网络。
- 开放与可组合性(Openness and Composability) 开发者可自由创建与组合 Widgets,扩展 Mini Apps 的模块化生态。
这些功能使 Smart Widgets 成为 DA(gentic)O 的“支柱”,通过 Mini Apps 连接个体代理与协作网络,构建动态、规模化的生态。
2.4 驱动代理经济(Agentic Economy)
在 DA(gentic)O 中,经济交互至关重要。Smart Widgets 通过以下方式推动代理经济形成:
- 降低支付壁垒 嵌入式支付支持代理间无摩擦的小额交易,简化价值流转。
- 微型自治市场 Widgets 赋予 Mini Apps 自主定价与运营能力,形成独立经济单元。
- 加速创新与扩展 开放创建机制与低成本部署鼓励开发者丰富 Mini Apps 生态。
Yakihonne 正在推动一种新的模式:社交即支付,应用即自治。这为未来的 Agentic DAO 和基于代理的社会经济体系提供了可行路径。
3.Agentic Mini App 应用场景
Agentic Mini Apps 是 DA(gentic)O的交互实现层,通过 YakiHonne Widgets 嵌入社交场景和支付功能,让用户在治理、创作、激励和消费中无缝互动。本章探讨 智能治理、社交媒体、消费生态 三类场景,展示 DA(gentic)O 如何构建从 Web3 到现实社会的动态生态。
3.1. 智能治理--Agentic AI for DAO
传统 DAO 依赖区块链实现透明治理,试图以社区投票和智能合约取代中心化管理。但投票延迟、分歧和静态合约限制价值交付,如投资 DAO 决策迟缓难敌专业机构,协议 DAO 缺乏生产力。Agentic AI 作为 DA(gentic)O 的“智能内核”,自动化执行提案、优化资源分配,提升链上效率,连接 Web3 与现实生产力。具体场景如下:
智能投票与治理优化 传统 aMaci 匿名投票复杂,限制规模化。该基于aMaci的Mini App 封装治理逻辑,提供友好交互,用户通过私信/通知接收提案通知(如“是否调整协议参数”),一键投票。Mini App 分析链上数据(如历史投票趋势),生成决策建议,投票结果秒级汇总,提案自动执行。
激励分配与贡献追踪 用户在 Mini App 内查看贡献(如代码提交、任务完成),Agentic AI 评估链上和链下活动,自动支付稳定币/LN/BTC 奖励,秒到账。私信通知奖励状态。用户通过 Post 展示贡献,Mini App 监测活动,支付代币或 NFT 奖励,链上记录,私信确认支付。
DAO2DAO协作 用户在 Mini App 内共享数据(如 BTC 趋势),Agentic AI 生成协作建议(如“联合活动”),自动执行跨 DAO 任务(如资金池分配)。Post 宣传合作动态。 用户也可通过私信发起联合提案,Mini App 整合多方数据,支付稳定币/LN/BTC 执行协作,链上透明。
社区活动与众筹 用户在 Mini App 内捐款支持活动(如“DAO 年会”),支付稳定币/LN/BTC,秒到账。Agentic AI 跟踪进度,自动分配资金,Post 展示成果。用户通过私信报名活动,Mini App 支付获 NFT 奖励,链上存证。
资源与任务分配 用户在 Mini App 内接收任务(如“开发模块”),Agentic AI 匹配技能,支付稳定币/LN/BTC 奖励,秒到账。私信通知任务状态。用户通过 Post 领取任务,Mini App 验证成果,自动支付代币,链上记录。私信确认完成。
链上身份与认证 用户在 Mini App 内将链上身份与 Nostr 身份绑定,Agentic AI 验证权限,支持跨 DAO 互认,支付稳定币/LN/BTC 激活身份。用户申请联合活动权限,Mini App 验证身份,自动授权,链上透明。
舆情实时分析 用户在 Mini App 内查看舆情报告(如“代币热度上升 30%”),Agentic AI 分析链上和社交数据,生成投资建议,支付 2 USDC 奖励,秒到账。私信推送报告。
3.2 社交媒体
中心化社交媒体因算法操控、内容审查和数据滥用限制用户表达,创作者收益被高额抽成侵蚀,信息真实性和隐私权受威胁。Agentic AI 促使去中心化社交生态更加智能和去中心化,保障用户主权,构建从 Web3 到现实社会的开放网络。具体场景如下:
内容创作与分发 用户与 Agentic AI 协作生成内容(如视频、长文、海报),一键分发到 YakiHonne 及多平台。Mini App 分析用户兴趣,精准推送,支付稳定币/LN/BTC 查看全文。
AI 记者-报道/采访 用户通过 Mini App 自动化新闻采集,分析链上数据和社交 Post,生成长文报道,发布后支持支付打赏。用户通过私信发起采访(如 BUIDL 项目),Agentic AI 生成大纲,Mini App 转录视频为长文或视频,发布至 YakiHonne 及其他平台。
内容互动 用户通过 YakiHonne 社交 Post 参与讨论,Mini App 追踪评论质量,自动打赏奖励高互动者。
内容订阅 用户通过 Mini App 支付订阅长文或独家 Post,Mini App 管理访问权限,秒到账。
内容真实性验证 用户通过 Mini App 验证内容真实性(如新闻出处),标记可信度并投票支持真实内容。
内容存档与协作 用户通过 Mini App 上传 Post 或长文,存储于去中心化网络,生成永久链接并支持其他用户付费下载。用户在 Mini App 内协作长文,Agentic AI 追踪并评估贡献,自动支付稳定币/LN/BTC 奖励,
去中心化广告与收益 创作者通过 Mini App 付费推送长文或内容触达用户,读者将会从广告直接获得收益。
舆情分析与公共讨论 Agentic AI 监测 YakiHonne Post 和社交动态(如“话题热度上升 30%”),生成讨论建议,用户通过私信接收长文报告并进行支付。
3.3 消费生态
中心化支付和传统消费因高额手续费、结算延迟和复杂流程限制用户体验,DeFi 应用也面临操作门槛高、信任不足的问题。Agentic AI 通过 Mini Apps 打造去中心化社交支付与消费生态,扩展链上与现实的消费场景,构建 Web3 价值网络。场景如下:
朋友转账 用户在 Mini App 内搜索好友并转账 0.05 USDC,Agentic AI 测算最优汇率和 Swap 路径,秒到账,链上记录。私信提醒转账请求。 用户在 Mini App 内发起群组分账,Agentic AI 计算份额,支付稳定币/LN/BTC,秒到账,Post 展示记录。
DeFi 质押激励 用户在 Mini App 内加入质押池,Agentic AI 推荐高收益策略,支付稳定币/LN/BTC,秒到账,链上分红透明。私信通知收益。 用户在 Mini App 内质押资产,Agentic AI 分析市场,支付 0.1 USDC 奖励活跃者,秒到账,Post 分享策略。
线下消费 用户在 Mini App 内支付 BTC/LN 购买咖啡或商品,秒到账,链上存证。Post 推送附近商家优惠。用户在 Mini App 内预订服务(如餐厅座位),支付稳定币/LN/BTC 获代币返现,秒到账,Post 分享活动。
GameFi 用户在 Mini App 内支付 0.1 USDC 购买游戏装备,秒到账,链上存证。Post 推送新资产吸引玩家。用户在 Mini App 内完成任务(如战斗挑战),Agentic AI 验证,支付稳定币/LN/BTC 奖励,秒到账,Post 展示排行。
跨境电商 用户在 Mini App 内支付 1 USDC 购买跨境商品,秒到账,链上记录物流。私信推送订单更新。用户在 Mini App 内参与跨境团购,Agentic AI 优化折扣,支付稳定币/LN/BTC 分摊运费,秒到账,Post 展示进展。
4. 结论
随着 Agentic AI 和去中心化技术的快速融合,DA(gentic)O 不再是理论构想,而是正在形成的“智能协作网络”。YakiHonne 的 Smart Widgets 和 Agentic Mini Apps,正在为这种网络提供关键接口与交互基础设施,为用户和开发者释放出前所未有的创作力、支付能力与治理可能。 我们正在见证三个关键趋势的叠加:
1) 从单体代理到多代理协作系统
未来的组织形态将不再是人类为中心的链上治理,而是以多智能体(Multi-Agent)为核心的动态生态。每一个智能代理代表一个用户、一个群体、一个经济单位,能独立感知、推理、执行,与其他代理协同完成更复杂的生产与治理流程。YakiHonne Smart Widgets 将成为这些代理的“协作面板”,为其提供微型入口与交互协议。
2)从社交互动到社交经济系统
当前的社交平台仍多以信息交换为主,而未来的去中心化社交网络将嵌入支付、投票、任务、协作等“社会操作系统”,形成真正的“社交经济”。在这个体系中,Mini Apps 不再是内容附属,而是核心交互单元。YakiHonne 的 Widget 设计天然服务于此场景:它让每一次社交行为都可能触发价值流转,从一次转账、一次众筹、一次治理投票,到一个内容生成任务。
3) 从平台生态到分布式开发生态
社交支付的未来,属于可编程的生态,而非封闭的平台。随着 Smart Widgets SDK 的开源,越来越多的开发者将加入 Agentic Mini App 的构建中。未来的 Web3 应用不会是一个个巨型 App,而是一组协同工作的 Widget 网络,它们在用户的社交流中被发现、被使用、被组合。YakiHonne 正在成为这一生态的起点。
YakiHonne的愿景不仅是打造一个功能强大的去中心化社交支付平台,更是构建一个通向未来的“Agentic 社交操作系统”。在这个系统中,每一个人、每一个代理、每一个交互都是协作的触发器,智能的入口,价值的节点。
-
 @ f6497934:312c6532
2025-04-17 06:42:48
@ f6497934:312c6532
2025-04-17 06:42:48Discover the ultimate Water Activity Meter for precise moisture measurement in food, pharmaceuticals, and cosmetics. Ensure product safety and extend shelf life by accurately assessing microbial growth risks. Our advanced meters, like the AQUALAB 4TE, deliver fast, reliable results in minutes with ±0.003 accuracy. Easy to use, portable, and temperature-controlled, they’re perfect for quality control in any industry. Optimize your production process, meet FDA standards, and boost product consistency. Invest in top-tier water activity testing today—shop now for unbeatable performance and durability!
-
 @ e1b184d1:ac66229b
2025-04-15 20:09:27
@ e1b184d1:ac66229b
2025-04-15 20:09:27Bitcoin is more than just a digital currency. It’s a technological revolution built on a unique set of properties that distinguish it from all other financial systems—past and present. From its decentralized architecture to its digitally verifiable scarcity, Bitcoin represents a fundamental shift in how we store and transfer value.
1. A Truly Decentralized Network
As of April 2025, the Bitcoin network comprises approximately 62,558 reachable nodes globally. The United States leads with 13,791 nodes (29%), followed by Germany with 6,418 nodes (13.5%), and Canada with 2,580 nodes (5.43%). bitnodes
This distributed structure is central to Bitcoin’s strength. No single entity can control the network, making it robust against censorship, regulation, or centralized failure.

2. Open Participation at Low Cost
Bitcoin's design allows almost anyone to participate meaningfully in the network. Thanks to its small block size and streamlined protocol, running a full node is technically and financially accessible. Even a Raspberry Pi or a basic PC is sufficient to synchronize and validate the blockchain.
However, any significant increase in block size could jeopardize this accessibility. More storage and bandwidth requirements would shift participation toward centralized data centers and cloud infrastructure—threatening Bitcoin’s decentralized ethos. This is why the community continues to fiercely debate such protocol changes.
3. Decentralized Governance
Bitcoin has no CEO, board, or headquarters. Its governance model is decentralized, relying on consensus among various stakeholders, including miners, developers, node operators, and increasingly, institutional participants.
Miners signal support for changes by choosing which version of the Bitcoin software to run when mining new blocks. However, full node operators ultimately enforce the network’s rules by validating blocks and transactions. If miners adopt a change that is not accepted by the majority of full nodes, that change will be rejected and the blocks considered invalid—effectively vetoing the proposal.
This "dual-power structure" ensures that changes to the network only happen through widespread consensus—a system that has proven resilient to internal disagreements and external pressures.
4. Resilient by Design
Bitcoin's decentralized nature gives it a level of geopolitical and technical resilience unmatched by any traditional financial system. A notable case is the 2021 mining ban in China. While initially disruptive, the network quickly recovered as miners relocated, ultimately improving decentralization.
This event underlined Bitcoin's ability to withstand regulatory attacks and misinformation (FUD—Fear, Uncertainty, Doubt), cementing its credibility as a global, censorship-resistant network.
5. Self-Sovereign Communication
Bitcoin enables peer-to-peer transactions across borders without intermediaries. There’s no bank, payment processor, or centralized authority required. This feature is not only technically efficient but also politically profound—it empowers individuals globally to transact freely and securely.
6. Absolute Scarcity
Bitcoin is the first asset in history with a mathematically verifiable, fixed supply: 21 million coins. This cap is hard-coded into its protocol and enforced by every full node. At the atomic level, Bitcoin is measured in satoshis (sats), with a total cap of approximately 2.1 quadrillion sats.
This transparency contrasts with assets like gold, whose total supply is estimated and potentially (through third parties on paper) expandable. Moreover, unlike fiat currencies, which can be inflated through central bank policy, Bitcoin is immune to such manipulation. This makes it a powerful hedge against monetary debasement.
7. Anchored in Energy and Time
Bitcoin's security relies on proof-of-work, a consensus algorithm that requires real-world energy and computation. This “work” ensures that network participants must invest time and electricity to mine new blocks.
This process incentivizes continual improvement in hardware and energy sourcing—helping decentralize mining geographically and economically. In contrast, alternative systems like proof-of-stake tend to favor wealth concentration by design, as influence is determined by how many tokens a participant holds.

8. Censorship-Resistant
The Bitcoin network itself is inherently censorship-resistant. As a decentralized system, Bitcoin transactions consist of mere text and numerical data, making it impossible to censor the underlying protocol.
However, centralized exchanges and trading platforms can be subject to censorship through regional regulations or government pressure, potentially limiting access to Bitcoin.
Decentralized exchanges and peer-to-peer marketplaces offer alternative solutions, enabling users to buy and sell Bitcoins without relying on intermediaries that can be censored or shut down.
9. High Security
The Bitcoin blockchain is secured through a decentralized network of thousands of nodes worldwide, which constantly verify its integrity, making it highly resistant to hacking. To add a new block of bundled transactions, miners compete to solve complex mathematical problems generated by Bitcoin's cryptography. Once a miner solves the problem, the proposed block is broadcast to the network, where each node verifies its validity. Consensus is achieved when a majority of nodes agree on the block's validity, at which point the Bitcoin blockchain is updated accordingly, ensuring the network's decentralized and trustless nature.
Manipulation of the Bitcoin network is virtually impossible due to its decentralized and robust architecture. The blockchain's chronological and immutable design prevents the deletion or alteration of previously validated blocks, ensuring the integrity of the network.
To successfully attack the Bitcoin network, an individual or organization would need to control a majority of the network's computing power, also known as a 51% attack. However, the sheer size of the Bitcoin network and the competitive nature of the proof-of-work consensus mechanism make it extremely difficult to acquire and sustain the necessary computational power. Even if an attacker were to achieve this, they could potentially execute double spends and censor transactions. Nevertheless, the transparent nature of the blockchain would quickly reveal the attack, allowing the Bitcoin network to respond and neutralize it. By invalidating the first block of the malicious chain, all subsequent blocks would also become invalid, rendering the attack futile and resulting in significant financial losses for the attacker.
One potential source of uncertainty arises from changes to the Bitcoin code made by developers. While developers can modify the software, they cannot unilaterally enforce changes to the Bitcoin protocol, as all users have the freedom to choose which version they consider valid. Attempts to alter Bitcoin's fundamental principles have historically resulted in hard forks, which have ultimately had negligible impact (e.g., BSV, BCH). The Bitcoin community has consistently rejected new ideas that compromise decentralization in favor of scalability, refusing to adopt the resulting blockchains as the legitimate version. This decentralized governance model ensures that changes to the protocol are subject to broad consensus, protecting the integrity and trustworthiness of the Bitcoin network.
Another source of uncertainty in the future could be quantum computers. The topic is slowly gaining momentum in the community and is being discussed.
Your opinion
My attempt to write an article with Yakyhonne. Simple editor with the most necessary formatting. Technically it worked quite well so far.
Some properties are listed in the article. Which properties are missing and what are these properties?
-
 @ 20986fb8:cdac21b3
2025-04-17 06:21:38
@ 20986fb8:cdac21b3
2025-04-17 06:21:38Distributed Agentic Organizations (DA(gentic)O) are reshaping the future of collaboration, blending Agentic AI to bridge crypto communities, virtual societies, and the real world. To scale effectively, DA(gentic)O needs seamless Agent-to-Agent and human-to-Agent social pathways. YakiHonne’s programmable Smart Widgets deliver lightweight interfaces, embedding social and payment features to enable agents to collaborate, transact, and govern effortlessly. Agentic Mini Apps turn this vision into reality, powering scenarios from on-chain voting to buying coffee. In this article, we’ll explore how YakiHonne Smart Widgets empower DA(gentic)O, unlocking decentralized productivity and an agent-driven collaborative economy.
1.From DAO to DA(gentic)O: A New Paradigm for Collaboration
Traditional organizations rely on centralized management, often hitting efficiency bottlenecks. DAOs introduced decentralized governance via blockchain, but slow voting and rigid contracts limit their potential. Agentic AI marks a new era, moving beyond passive execution to autonomous reasoning and dynamic adaptation—like “digital citizens” in a virtual world. By integrating large language models, advanced algorithms, and external tools (like on-chain data, Web APIs, or IoT sensors), Agentic AI processes real-time information, optimizes decisions, and evolves continuously, fueling the rise of DA(gentic)O.
DA(gentic)O are dynamic ecosystems of AI agents connected through open protocols—like Agent-to-Agent collaboration frameworks, blockchain, or smart contracts—enhancing and evolving decentralized autonomous organizations (DAOs). Unlike centralized command structures or DAOs bottlenecked by voting, DA(gentic)O operate as intelligent networks to achieve goals. Picture one agent monitoring BTC market swings while another orchestrates virtual community events—together, they collaborate via protocols to drive outcomes from on-chain trades to real-world optimizations. These organizations prioritize productivity, spanning governance, virtual economies, and physical operations, showcasing the flexibility and scalability of decentralization. DA(gentic)O aren’t just tools for collaboration; they’re bridges linking virtual and physical realms, creating verifiable value for global distributed communities.
DA(gentic)O’s core traits boil down to three pillars:
D: Distributed & Decentralized Decisions and operations spread across autonomous agents, eliminating single points of control for robust, transparent systems. Agents negotiate resources via on-chain records or distributed protocols, forming trustless collaboration networks. For example, in BTC markets, agents collectively manage fund flows; in virtual communities, they vote to set rules; in the physical world, they coordinate cross-regional logistics. This distributed architecture gives DA(gentic)O unmatched resilience and scalability.
A: Autonomous & Agentic Agents independently sense, plan, and act, enabling organizations to self-govern through intelligent coordination. Each agent acts like a micro-decision unit, adapting strategies to changing conditions without constant human oversight. In a metaverse, one agent curates a virtual exhibition while another allocates computing power, syncing automatically via protocols. In smart factories, agents tweak production in real time to meet demand. This autonomy lets DA(gentic)O outpace traditional organizations in complex, fast-moving scenarios.
O: Organization & Operation Agents work as a cohesive network, tackling tasks from virtual economies to real-world production. Whether it’s an on-chain auction in Web3, a virtual marketplace, or a physical supply chain, DA(gentic)O deliver results through collaboration. One agent might handle creator-buyer transactions while another optimizes logistics, together streamlining value from end to end. This operational prowess makes DA(gentic)O a hub for productivity.
DA(gentic)O’s flexibility stems from Agentic AI’s diverse capabilities. Reactive agents excel at real-time responses, like tracking on-chain price shifts. Goal-driven agents break down complex tasks, such as designing virtual community incentives. Learning agents refine strategies through data, like optimizing factory outputs. United via A2A protocols, these agents form networks tailored to virtual governance, transactions, and real-world optimization, building a productivity-driven digital ecosystem.
Key Pillars of DA(gentic)O
To build effective DA(gentic)O, several components ensure the agent network thrives:
- Sovereign Wallets: Each agent holds an independent, anonymous digital wallet, securely managing assets and executing transactions—whether for on-chain payments, virtual rewards, or real-world task payouts—ensuring economic autonomy.
- Decentralized Security: Robust on-chain or distributed systems safeguard agent operations, data privacy, and decision integrity, protecting against attacks or tampering to maintain trust.
- Open Network Access: Agents need seamless access to the internet, blockchains, or other data sources for real-time insights, like on-chain metrics, user behaviors, or IoT sensor data, fueling reasoning and collaboration.
- Interfaces: User-friendly, autonomous interfaces (like on-chain dashboards or mobile panels) enable smooth connections between agents, users, and systems.
DA(gentic)O weave intelligent networks across virtual and physical domains, delivering value through transactions, coordination, and optimization. Agentic Mini Apps are the key to unlocking these interactions.
2. Programmable Smart Widgets: The Backbone of DA(gentic)O
YakiHonne’s programmable Smart Widgets are a lightweight system powering Agentic Mini Apps with social and payment features, serving as the infrastructure for DA(gentic)O. Through embedded interfaces and decentralized protocols, they drive agent collaboration, transactions, and governance, lowering development barriers and connecting Web3, virtual communities, and real-world scenarios.
2.1 Features of Smart Widgets
In YakiHonne’s design, Smart Widgets are compact, intelligent interfaces tailored for the rapid development and deployment of Agentic Mini Apps. Their core features include:
- Embedded Social Flows: Mini Apps integrate directly into social environments, letting users pay or interact without switching interfaces.
- No Centralized Approval: Developers can create, deploy, and share Mini Apps instantly, bypassing app store gatekeepers.
- Composability: Widgets support flexible combinations of functional modules, adapting to diverse Agent-to-Agent collaboration needs.
- Built-in Payments: With on-chain payment and stablecoin support, they enable seamless value exchange between agents.
This framework dramatically lowers the barrier to building and scaling decentralized agent organizations, empowering individual agents to not only act but also collaborate, transact, and govern together.
2.2 Forms and Applications of Smart Widgets
YakiHonne Smart Widgets come in three forms to meet varied needs, from everyday users to advanced developers, powering a full spectrum of DA(gentic)O demands:
- Basic Widgets: No coding required—users can quickly build payment or voting functions using a template editor, ideal for simple Mini Apps.
- Action Widgets: These link external features while keeping social interfaces seamless, expanding Mini Apps’ interaction scope.
- Tool Widgets: Designed for developers and power users, these leverage the Mini App SDK for complex applications, supporting data queries, on-chain tasks, instant payments, and smart decisions to create advanced, intelligent Mini Apps.
These forms provide Mini Apps with everything from basic interactions to sophisticated collaboration, aligning with DA(gentic)O’s automated workflows.
2.3 Core Capabilities for DA(gentic)O
YakiHonne Smart Widgets deliver key capabilities to fuel the efficient operation of Distributed Agentic Organizations through Agentic Mini Apps:
- Autonomous Mini Apps: Widgets embed service logic, letting agents independently handle tasks or trigger payments—like auto-distributing Web3 transaction rewards or coordinating virtual community events without human input.
- On-the-Fly Payments: Seamless protocols for stablecoins, BTC, or Lightning Network (LN) enable instant on-chain payments, supporting micro-transaction economies.
- On-Chain Identity Integration: Agents can tie sovereign identities to platforms like Nostr, authorizing and signing on-chain actions.
- Real-Time Interaction and Coordination: Widgets facilitate instant data sharing, smart contract calls, and collaborative execution, tailored for Agent-to-Agent networks.
- Openness and Composability: Developers can freely create and combine Widgets, expanding the modular Mini App ecosystem.
These features make Smart Widgets the “backbone” of DA(gentic)O, linking individual agents to collaborative networks and fostering dynamic, scalable ecosystems.
2.4 Fueling the Agentic Economy
In DA(gentic)O, economic interactions are critical. Smart Widgets drive the agentic economy by:
- Lowering Payment Barriers: Embedded payments enable frictionless micro-transactions between agents, streamlining value flow.
- Micro-Autonomous Markets: Widgets give Mini Apps independent pricing and operation capabilities, creating self-sustaining economic units.
- Accelerating Innovation: Open creation and low-cost deployment encourage developers to enrich the Mini App ecosystem.
YakiHonne is pioneering a new model: social interactions double as payments, and apps run autonomously. This lays the groundwork for future Agentic DAOs and agent-driven socio-economic systems.
3. Agentic Mini App Use Cases
Agentic Mini Apps are the interactive layer of DA(gentic)O, powered by YakiHonne Smart Widgets to embed social and payment features, enabling seamless user engagement in governance, content creation, incentives, and consumption. This chapter dives into three key scenarios—autonomous governance, social media, and consumption ecosystems—showing how DA(gentic)O build dynamic networks from Web3 to the real world.
3.1 Autonomous Governance: Agentic AI for DAOs
Traditional DAOs leverage blockchain for transparent governance, aiming to replace centralized control with community voting and smart contracts. But delays, disputes, and static contracts hinder value delivery—investment DAOs lag behind professional firms, and protocol DAOs struggle with productivity. Agentic AI, the “smart core” of DA(gentic)O, automates proposals, optimizes resource allocation, and boosts on-chain efficiency, bridging Web3 with real-world productivity. Here’s how it works:
- Intelligent Autonomous Voting and Governance Optimization
Traditional aMaci-based anonymous voting is complex and limits scale. This aMaci-powered Mini App simplifies governance logic with user-friendly interfaces. Users get proposal alerts via DMs or notifications (e.g., “Adjust protocol parameters?”) and vote with one tap. The Mini App analyzes on-chain data (like past voting trends) to suggest decisions, tallies results in seconds, and auto-executes proposals. - Incentive Allocation and Contribution Tracking
Users check contributions (e.g., code commits, completed tasks) in the Mini App. Agentic AI evaluates on-chain and off-chain activity, auto-paying rewards in stablecoins, LN, or BTC—instantly. DMs notify reward status. Users showcase contributions via posts, and the Mini App tracks activity, distributing tokens or NFTs, logged on-chain with DM confirmations. - DAO-to-DAO Collaboration
Users share data (e.g., BTC trends) in the Mini App, where Agentic AI suggests collaborations (e.g., “joint campaign”). It auto-executes cross-DAO tasks like fund pool allocation, with posts promoting updates. Users can also propose joint initiatives via DMs, and the Mini App aggregates multi-party data, paying stablecoins, LN, or BTC for execution, all transparent on-chain. - Community Events and Crowdfunding
Users donate to events (e.g., “DAO summit”) via the Mini App, paying stablecoins, LN, or BTC—instantly. Agentic AI tracks progress, auto-allocates funds, and posts share results. Users sign up for events via DMs, earning NFT rewards through Mini App payments, recorded on-chain. - Resource and Task Allocation
Users pick tasks (e.g., “build a module”) in the Mini App. Agentic AI matches skills, paying stablecoins, LN, or BTC rewards—instantly. DMs update task status. Users claim tasks via posts, and the Mini App verifies outcomes, auto-paying tokens, logged on-chain with DM confirmations. - On-Chain Identity and Authentication
Users link on-chain and Nostr identities in the Mini App. Agentic AI verifies permissions, enabling cross-DAO recognition, with stablecoin, LN, or BTC payments to activate identities. Users request event access, and the Mini App auto-grants permissions, transparent on-chain. - Real-Time Sentiment Analysis
Users view sentiment reports (e.g., “token buzz up 30%”) in the Mini App. Agentic AI analyzes on-chain and social data, offering investment tips for a 2 USDC reward—instantly. Reports are sent via DMs.
3.2 Social Media
Centralized social platforms curb free expression with algorithmic bias, content censorship, and data misuse. Creators lose earnings to hefty fees, and authenticity and privacy are at risk. Agentic AI powers a smarter, decentralized social ecosystem, ensuring user sovereignty and building open networks from Web3 to the real world. Key scenarios include: - Content Creation and Distribution
Users team up with Agentic AI to craft content (videos, articles, posters), publishing to YakiHonne and beyond with one click. The Mini App analyzes user interests for targeted delivery, with stablecoin, LN, or BTC payments to unlock full content. - AI Journalism: Reporting and Interviews
Users automate news gathering via the Mini App, pulling on-chain data and social posts to create in-depth reports, shareable for tip-based payments. For interviews (e.g., BUIDL projects), users DM requests, and Agentic AI drafts outlines, with the Mini App converting videos to articles or clips for YakiHonne and other platforms. - Content Interaction
Users engage in discussions via YakiHonne posts. The Mini App tracks comment quality, auto-rewarding active participants with tips. - Content Subscriptions
Users pay for premium articles or exclusive posts through the Mini App, which manages access—instantly. - Content Authenticity Verification
Users verify content credibility (e.g., news sources) via the Mini App, flagging trustworthiness and voting to support authentic posts. - Content Archiving and Collaboration
Users upload posts or articles to the Mini App, stored on decentralized networks with permanent links for paid downloads. For collaborative articles, Agentic AI tracks contributions, auto-paying stablecoin, LN, or BTC rewards. - Decentralized Ads and Revenue
Creators pay to promote articles or content via the Mini App, with readers earning directly from ad revenue. - Sentiment Analysis and Public Discourse
Agentic AI monitors YakiHonne posts and social trends (e.g., “topic buzz up 30%”), suggesting discussions. Users receive detailed reports via DMs for a payment.
3.3 Consumption Ecosystem
Centralized payments and traditional consumption suffer from high fees, slow settlements, and clunky processes, while DeFi apps face steep learning curves and trust issues. Agentic AI, through Mini Apps, builds a decentralized social payment and consumption ecosystem, expanding on-chain and real-world use cases to create a Web3 value network. Scenarios include:
- Peer-to-Peer Transfers
Users search friends in the Mini App to send 0.05 USDC. Agentic AI optimizes exchange rates and swap paths, settling instantly with on-chain records. DMs flag transfer requests. For group splits, users initiate in the Mini App, and Agentic AI calculates shares, paying stablecoins, LN, or BTC—instantly, with posts logging details. - DeFi Staking Incentives
Users join staking pools via the Mini App, where Agentic AI suggests high-yield strategies, paying stablecoins, LN, or BTC—instantly, with transparent on-chain dividends. DMs notify profits. Users stake assets, and Agentic AI rewards active users with 0.1 USDC, paid instantly, with posts sharing strategies. - Offline Purchases
Users pay BTC or LN for coffee or goods via the Mini App—instantly, logged on-chain. Posts promote nearby deals. For bookings (e.g., restaurant seats), users pay stablecoins, LN, or BTC, earning token cashback—instantly, with posts sharing events. - GameFi
Users buy game gear for 0.1 USDC in the Mini App—instantly, recorded on-chain. Posts highlight new assets to attract players. For tasks (e.g., battle challenges), Agentic AI verifies completion, paying stablecoin, LN, or BTC rewards—instantly, with posts showcasing leaderboards. - Cross-Border E-Commerce
Users pay 1 USDC for overseas goods via the Mini App—instantly, with on-chain logistics tracking. DMs update orders. For group buys, Agentic AI optimizes discounts, splitting stablecoin, LN, or BTC shipping costs—instantly, with posts tracking progress.
4. Conclusion
As Agentic AI and decentralized technologies converge rapidly, DA(gentic)O are no longer theoretical—they’re emerging as “intelligent collaboration networks.” YakiHonne’s Smart Widgets and Agentic Mini Apps provide the critical interfaces and infrastructure for these networks, unleashing unprecedented creativity, payment capabilities, and governance possibilities for users and developers alike. We’re witnessing the convergence of three transformative trends:
1) From Solo Agents to Multi-Agent Systems
The future of organizations isn’t human-centric on-chain governance but dynamic ecosystems driven by multi-agent systems. Each intelligent agent—representing a user, group, or economic unit—senses, reasons, and acts independently, collaborating with others to tackle complex production and governance tasks. YakiHonne Smart Widgets serve as the “collaboration dashboard” for these agents, offering micro-gateways and interaction protocols.
2) From Social Interaction to Social Economies
Today’s social platforms focus on information exchange, but tomorrow’s decentralized networks will embed payments, voting, tasks, and collaboration into a “social operating system,” forming true social economies. In this model, Mini Apps aren’t just content add-ons—they’re core interaction hubs. YakiHonne’s Widget design is built for this: every social action, from a transfer to a crowdfund, a governance vote to a content task, can spark value flow.
3) From Platform Ecosystems to Distributed Development
The future of social payments lies in programmable ecosystems, not walled gardens. With the open-source Smart Widgets SDK, more developers will join the Agentic Mini App movement. Apps won’t be monolithic giants but networks of interoperable Widgets, discovered, used, and combined within users’ social flows. YakiHonne is laying the foundation for this ecosystem.
YakiHonne’s vision goes beyond a powerful decentralized social payment platform—it’s about building an “Agentic Social Operating System” for the future. In this system, every person, every agent, every interaction is a trigger for collaboration, an entry point for intelligence, and a node for value creation.
-
 @ bf6e4fe1:46d21f26
2025-04-15 19:30:46
@ bf6e4fe1:46d21f26
2025-04-15 19:30:46this is a test
-
 @ e0921d61:e0fe7bd5
2025-04-15 16:13:32
@ e0921d61:e0fe7bd5
2025-04-15 16:13:32Hans-Hermann Hoppe explains the capitalist process as driven by time preference, how people value present vs. future goods. Economic growth hinges on savings and investment, and this shapes our prosperity.

Factors like population, natural resources, and technology matter, but Hoppe argues they're secondary. Without prior savings and investment, even the richest resources and best technology remain untapped.

True economic advancement happens through increasing per capita invested capital, raising productivity, real incomes, and further lowering time preferences. This creates a self-reinforcing cycle of prosperity.

Hoppe claims this process naturally continues smoothly until scarcity itself disappears, unless people voluntarily choose leisure over more wealth. This growth has no inherent reason to halt abruptly.

This smooth capitalist cycle, however, is disrupted when government enters the picture. Government control of resources it didn’t earn or acquire legitimately distorts incentives and investment.

Government monopolization of money through fractional reserve banking artificially lowers interest rates.
Entrepreneurs mistakenly think, and are incentivized to think, there's more savings, so more unsustainable investments proliferate.

Without real savings backing these projects, a painful correction (a bust following the boom) inevitably occurs.
Investments must eventually realign with actual savings, thus leading to bankruptcies and unemployment.

Hoppe concludes that boom-bust cycles aren’t natural. They’re directly caused by government-created credit expansion. Unless governments stop manipulating fiat money supply, these cycles remain unavoidable.

-
 @ 3ffac3a6:2d656657
2025-04-15 14:49:31
@ 3ffac3a6:2d656657
2025-04-15 14:49:31🏅 Como Criar um Badge Épico no Nostr com
nak+ badges.pageRequisitos:
- Ter o
nakinstalado (https://github.com/fiatjaf/nak) - Ter uma chave privada Nostr (
nsec...) - Acesso ao site https://badges.page
- Um relay ativo (ex:
wss://relay.primal.net)
🔧 Passo 1 — Criar o badge em badges.page
- Acesse o site https://badges.page
-
Clique em "New Badge" no canto superior direito
-
Preencha os campos:
- Nome (ex:
Teste Épico) - Descrição
-
Imagem e thumbnail
-
Após criar, você será redirecionado para a página do badge.
🔍 Passo 2 — Copiar o
naddrdo badgeNa barra de endereços, copie o identificador que aparece após
/a/— este é o naddr do seu badge.Exemplo:
nostr:naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Copie:
naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0
🧠 Passo 3 — Decodificar o naddr com
nakAbra seu terminal (ou Cygwin no Windows) e rode:
bash nak decode naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Você verá algo assim:
json { "pubkey": "3ffac3a6c859eaaa8cdddb2c7002a6e10b33efeb92d025b14ead6f8a2d656657", "kind": 30009, "identifier": "Teste-Epico" }Grave o campo
"identifier"— nesse caso: Teste-Epico
🛰️ Passo 4 — Consultar o evento no relay
Agora vamos pegar o evento do badge no relay:
bash nak req -d "Teste-Epico" wss://relay.primal.netVocê verá o conteúdo completo do evento do badge, algo assim:
json { "kind": 30009, "tags": [["d", "Teste-Epico"], ["name", "Teste Épico"], ...] }
💥 Passo 5 — Minerar o evento como "épico" (PoW 31)
Agora vem a mágica: minerar com proof-of-work (PoW 31) para que o badge seja classificado como épico!
bash nak req -d "Teste-Epico" wss://relay.primal.net | nak event --pow 31 --sec nsec1SEU_NSEC_AQUI wss://relay.primal.net wss://nos.lol wss://relay.damus.ioEsse comando: - Resgata o evento original - Gera um novo com PoW de dificuldade 31 - Assina com sua chave privada
nsec- E publica nos relays wss://relay.primal.net, wss://nos.lol e wss://relay.damus.io⚠️ Substitua
nsec1SEU_NSEC_AQUIpela sua chave privada Nostr.
✅ Resultado
Se tudo der certo, o badge será atualizado com um evento de PoW mais alto e aparecerá como "Epic" no site!
- Ter o
-
 @ 044da344:073a8a0e
2025-04-17 06:53:41
@ 044da344:073a8a0e
2025-04-17 06:53:41Hölderlin taugt immer. Diesmal sogar doppelt. Dass mit der Gefahr das Rettende wächst, hat sich inzwischen herumgesprochen. Raymond Unger ist so ein Anker. Wann immer ich seinen Namen bei einer Veranstaltung erwähne: Die Leute wissen Bescheid. Vom Verlust der Freiheit. Ich hätte zählen sollen, wie oft ich gehört habe: Dieses Buch hat mir die Augen geöffnet. Migration, Klima, Corona: alles drin und vor allem so verflochten, dass zusammenpasst, was eigentlich nicht zusammengehört und unsere Welt auf den Kopf gestellt hat. Viele haben danach Ungers Impfbuch gelesen, sich von seiner Heldenreise inspirieren oder bestätigen lassen und mit ihm um Gunnar Kaiser getrauert (Habe ich genug getan?, 2024). Wer schon länger dabei ist, kennt in der Regel auch Die Wiedergutmacher – ein Psychogramm der Babyboomer, das so nur jemand schreiben kann, der selbst erlebt hat, wie das Weltkriegstrauma vererbt wurde, und als Therapeut die Konzepte kennt, mit denen sich das in Worte fassen lässt.
Der Sachbuchautor Raymond Unger war und ist ein Fremdgänger – ein Künstler, preisgekrönt, den die Not des Beobachters gezwungen hat, das Metier zu wechseln. Der erste Hölderlin. Ohne die große Krise würde dieser Maler vermutlich immer noch nächtelang an seiner Staffelei mit der Materie kämpfen und vor allem mit sich selbst. Wahrscheinlich kennt Raymond Unger auch mein zweites Hölderlin-Zitat: Was aber bleibet, stiften die Dichter. Ich habe diesen Satz gerade wieder gehört aus dem Mund von Peter-Michael Diestel, letzter Innenminister der DDR, der sich mit Gregor Gysi über Heimat unterhält, über den Osten und den Westen und dabei fast zwangsläufig auf die Historiker zu sprechen kommt. „Ärmliches Lohnschreiber-Geschwader“, sagt Diestel und zeichnet ein ganzes anderes Bild von der Vergangenheit als die Geschichtsbücher. „Die DDR ist meine Herkunft. Mein Paradies.“ Sagt einer ihrer Totengräber. Und damit Vorhang auf für die Dichter.

Auf der Bühne steht der Romanautor Raymond Unger, eine Melange aus dem Bildermacher und dem Gesellschaftsanalytiker, die den gleichen Namen tragen. Wuchtig kommt sein Gemälde KAI daher mit Szenen und Orten, von denen jeder Hollywood-Regisseur träumt. Ostsee und Alpen, Berlin, Hamburg und das Silicon Valley. Am Ende Fulda, okay. Davor aber eine Schriftstellerin, Ende 30, attraktiv, Objekt der Begierde zweier reifer Männer, bis die Dame plötzlich im Wortsinn zerfließt, das gute Stück eines der beiden Verehrer beleidigt (klein, was sonst) und auf den Teppich pinkelt. Das ist nur das Vorspiel für einen Antiterroreinsatz in der schwedischen Idylle und Explosionen im Zentrum von Berlin, für ein Auto, das seinen Fahrer wie von Geisterhand gesteuert in den Tod reißt, und für einen Quarterback, der auf dem Spielfeld tot umfällt – zur Primetime, damit jeder weiß, was ihm blühen könnte.
Ich schreibe das, weil ich ein wenig Angst hatte vor diesem Roman. Einer meiner Lieblingsautoren auf neuem Gelände. Wird er sich dort verlaufen, untergehen gar, und mir so einen Fixstern aus meinem Bücherregal nehmen? Nein, nein und nochmal nein. KAI ist ein großer Wurf. KAI ist das Buch, auf das ich gewartet habe. Sicher: Ich habe die Dystopie Hinter der Zukunft von Thomas Eisinger gefeiert, einen Augenöffner ersten Ranges, und ein wenig auch die Corona-Kurzgeschichten von Eugen Zentner. Trotzdem. KAI hat das Zeug, unseren Nachkommen zu berichten, was wir erlebt und erlitten haben. Und vielleicht noch wichtiger: KAI übersetzt all das in ein Märchen, das realer nicht sein könnte und mit einem Ende daherkommt, das die Kämpfe seit den frühen 2010er Jahren mit Sinn auflädt und aus Verlierern Sieger macht. Dazu gleich mehr.
Vorher ein Wort zu Hölderlin und zu seinem Satz über die Dichter, die sagen, was bleibt. Der Mensch ist ein Geschichtentier. Das ist trivial, ich weiß, kann aber nicht oft genug wiederholt werden in einer Zeit, in der eine Regierung sich ins Stammbuch schreibt, dass „die bewusste Verbreitung von falschen Tatsachenbehauptungen“ nicht „durch die Meinungsfreiheit“ gedeckt sei. Falsche Tatsachenbehauptungen. Was soll das sein? 2014 ist Argentinien Fußball-Weltmeister geworden. Oder Tansania. Zwei plus zwei ist fünf und der Autor dieses Textes – eine Frau. Ich muss gar nicht in die Absurditätenkiste greifen, sondern kann in meinem Fachgebiet bleiben. Das 20. Jahrhundert beginnt mit dem Panzerkreuzer Aurora in Petrograd und endet mit den Moskauer Schüssen vom August 1991. Falsch. Falsch? Muss ich künftig Putsch sagen und Sankt Petersburg und hundert Jahre hundert Jahre sein lassen, um der Medienaufsicht nicht ins Netz zu gehen?
Namen, Daten, Orte, Ereignisse: All das rauscht an uns vorbei, wenn es nicht mit einer Story daherkommt und sich nicht einfügen lässt in das, was wir uns über die Menschen und die Welt erzählen. Wer glaubt, dass der Staat ein guter Forscher ist, ein noch besserer Lehrer und der ideale Verwalter aller Vermögen, der wird sich nicht beklagen, wenn Steuergelder in Wissenschaft und Bildung, Kunst und Kultur gepumpt werden und man parallel über einen Lastenausgleich diskutiert. Noch einmal anders gewendet: Es lohnt sich nicht, die Gegenseite mit „Fakten“ und „Tatsachen“ zu bombardieren. Nicht das Fleisch entscheidet, sondern die Sauce. Demokratie, Menschenrechte, Wertewesten. Schwarz-Rot will die „Meinungsfreiheit“ wahren, aber trotzdem „auf der Basis klarer gesetzlicher Vorgaben gegen Informationsmanipulation sowie Hass und Hetze vorgehen“. Alles in einem Satz. Das ist die hohe Schule der Manipulation – möglich nur, weil die Jünger des Parteienstaates gar nicht auf die Idee kommen können, dass im Namen der großen Erzählung Böses getan wird.
Raymond Unger weiß: Wir brauchen eine neue Erzählung. Und wir brauchen Klarheit über die Wucht, die Erzählungen entfalten. Also lässt er Materialisten und Idealisten aufeinander losgehen und öffnet auf dem Höhepunkt der Schlacht „ein Portal zur Anderswelt“, „durch das uralte kosmische Kräfte in unsere physische Welt hineinwirken können“ – bei ihm ein Einfallstor für die „transhumanistische Agenda“ und jene Kräfte, die „alles Menschliche“ verdrängen wollen. Wenn das jetzt kryptisch klingen sollte: keine Sorge. Dieser Autor kann erzählen. Er lässt Freud und Jung in einem Ehepaar auferstehen, das sich so kappelt wie Hans Castorp und Lodovico Settembrini auf dem Zauberberg von Thomas Mann, und mischt das, was er über Klima, 5G und mRNA braucht, in Gespräche mit ChatGPT und kurze Vorträge, die jeder verstehen kann, weil im Publikum Laien sitzen.
Von der Story selbst will ich hier nicht allzu viel verraten. Siehe oben. Wenn man ins Kino geht, reichen auch die Schnipsel aus dem Werbespot und die Gesichter der Helden. Bill Gates spielt mit, Uğur Şahin und Ulrike Herrmann. Leicht verfremdet, aber ja: Es geht schließlich um alles. Den Titel immerhin muss ich auflösen: Bei Raymond Unger sitzt KAI am Hebel. CO2-Märchen, Pandemie-Märchen, das Schlachtfeld Ukraine, Kriegstüchtigkeit: Produkte einer finsteren Macht, die bei ihm aus der Technik wächst und aus der Ideenwelt des Okkultismus, die man aber genauso gut ganz irdisch dort verorten könnte, wo nicht wenige einen „tiefen Staat“ vermuten. Ein guter Roman braucht nicht nur große Gefühle, sondern mehr als eine Ebene. Wer sich wie ich eher an Akteure und Ressourcen hält, kann KAI leicht als Metapher lesen, erst recht in dieser Schreibweise.
Raymond Ungers Gegenerzählung ist nicht neu, aber verlorengegangen auf Plattformen und Bildschirmen, die keine Zwischentöne erlauben und so die Spaltung vorantreiben. Unger sagt: Rettung kommt von da, wo es keine Mehrheiten gibt. Der Außenseiter in der Wissenschaft. Die Menschen, die entscheiden und verzichten und erst so zum Menschen werden. Coronakritiker. Ostdeutsche. Er sagt außerdem: Es gibt U-Boote selbst da, wo die Mehrheiten sind. Schreibt auch die nicht ab, die euch im Moment als Zielscheibe erscheinen. Vor allem aber sagt er: Der Mensch kann Dinge tun, die buchstäblich niemand auf dem Zettel hat. Gegen jede Wahrscheinlichkeit und damit völlig anders als selbst die perfekte Maschine. Nur der Mensch kann sich lösen von dem, was ist, und so Freund Hölderlin alle Ehre machen.
Vielleicht ein Wermutstropfen: Starke Frauen fehlen in seiner Welt. Das heißt: Es gibt starke Frauen, aber nur auf der dunklen Seite der Macht oder als leichtes Opfer von KAI. Ich habe mit zwei Kennerinnen über den Roman gesprochen, die insgesamt sehr angetan waren, aber leicht die Nase rümpften wegen mancher Formulierung und einigen Figuren. Hier und da etwas technokratisch, sagten die beiden, und nicht immer prall im Leben. Was soll man da antworten als Mann. Ich, ein Sachbuchfresser, habe KAI verschlungen. Und: Gut, dass wir endlich auch in der Unterwelt (Walter van Rossum) einen Roman haben, erschienen in einem großen Verlag, über den wir streiten können.

Raymond Unger: KAI. München: Europa Verlag, 431 Seiten, 25 Euro.
-
 @ cdee943c:5e637400
2025-04-15 08:38:29
@ cdee943c:5e637400
2025-04-15 08:38:29Flotilla-Budabit is fork of Flotilla which aims to provide a first class, git-centric community experience for developers. Based on the popular Coracle client, Flotilla is a drop in replacement for Matrix/Discord/Slack, using a variation of NIP-29. This post is a result of a brainstorming session for features that would deliver the best possible user experience.
1. Repositories Overview
Goal: Browse and discover Git repositories. - Project cards showing name, description, tags, clone URL. - Buttons: Star, Watch, Fork. - Links to discussion channels and activity.
Powered by:
kind:30617
2. Branch and Tag View
Goal: Show active branches and tags with latest commits. - Branch/tag selector - HEAD pointer visualization - Timeline of commits
Powered by:
kind:30618
3. Issues Board
Goal: Track bugs, discussions, and feature requests. - Markdown issue rendering - Labels and status indicators - Threaded comments
Powered by:
kind:1621,kind:1630–1632
4. Patch Threads
Goal: View and discuss patches as threaded conversations. - Rich patch preview - Reply threads for review - Revision tracking
Powered by:
kind:1617,kind:1630–1633,NIP-10
5. Pull Request UX
Goal: Display patch series as PR-style units. - Patch stack visualization - Merge/apply status indicators - Final result commit link
Powered by:
kind:1617,kind:1631,merge-commit,applied-as-commits
6. Diff and Merge Preview
Goal: Side-by-side comparison with inline comments. - Expandable diff viewer - Merge conflict resolution UI - Apply/Close buttons
Powered by:
kind:1622,parent-commit,commit
7. Real-time Git Chat
Goal: Communicate in real-time around a repo. - Dedicated chat channels for each repo - Markdown, code snippets, and tagging support - Pinned patches, issues, and sessions
Powered by:
NIP-29,a:30617,kind:1337
8. Notifications and Mentions
Goal: Alert users to relevant events. - Mentions, assignments, and status changes - Personal notification pane
Powered by:
ptags,mentione-tags
9. Repository-Wide Search
Goal: Search patches, issues, snippets. - Full-text search with filters - Search by kind, label, commit ID
Powered by:
kind:1617,1621,1337,t,x,l,subject
10. Repository Wikis
Goal: Collaboratively edit and view project documentation. - Wiki sidebar tab - Markdown articles with versioning - Linked inline in chat
Powered by (proposed):
kind:1341(Wiki article)
kind:30617withwiki-hometag
11. Live Coding Sessions
Goal: Host real-time collaborative coding events. -
/livecodestarts a session thread - Snippets auto-tagged to session - Export as patch or wikiPowered by (proposed):
kind:1347(Live coding session)
kind:1337,kind:1622,kind:1341
Supporting Tools
1. GitHub Browser Extension
Goal: Publish GitHub content to Nostr directly. - “Share on Nostr” buttons on PRs, issues, commits
Backed by:
kind:1623,1622,1617,1621
2. VS Code Extension
Goal: Enable developers to interact with Flotilla from their IDE. - Repo feed, patch submission, issue tracking - Inline threads and comment rendering
Backed by:
kind:1617,1621,1337,163x
3. GitHub Actions Integration
Goal: Automate Nostr publishing of repo activity. - Push = repo state - PR = patch - Issue/Comment = issue - Merge = status update
Backed by:
kind:30618,1617,1621,1631
Configured via.nostr.yml -
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ 502ab02a:a2860397
2025-04-17 05:45:09
@ 502ab02a:a2860397
2025-04-17 05:45:09วันก่อนเฮียไปเดินห้าง เดินไปเจอชั้นขายน้ำมันพืช มีน้ำมันรำข้าววางโชว์อยู่หน้าสุด พร้อมคำโปรยที่ดูแพงกว่าขวดซะอีก ตัวเลขข่มกันมาเข้มๆเลย ระดับหมื่นๆหน่วยทั้งนั้น “มีแกมมาออไรซานอล ลดคอเลสเตอรอล” “มีวิตามินอีสูง” “ทนความร้อนได้ดีเยี่ยม เหมาะกับทุกเมนูทอด” “น้ำมันสุขภาพ คนรักหัวใจควรมีไว้ประจำบ้าน”
เฮียยืนอ่านแล้วก็ได้แต่ยิ้ม…
ว่าด้วย Oryzanol ...ของดีจริงเหรอ? อันนี้เป็นไม้เด็ดของฝั่งที่เชียร์น้ำมันรำข้าวเลยเฮีย เขาบอกว่า แกมมาโอริซานอล (γ-Oryzanol) เนี่ย เป็นสารต้านอนุมูลอิสระที่ช่วยลดคอเลสเตอรอลในเลือด ฟังแล้วรู้สึกเหมือนกินแล้วหลอดเลือดจะสะอาดเหมือนพื้นห้องน้ำที่เพิ่งขัดเสร็จ แต่...อย่าเพิ่งรีบวางใจ เพราะงานวิจัยที่ว่าแกมมาโอริซานอล ลดคอเลสเตอรอลเนี่ย ส่วนใหญ่ใช้ “สารสกัดเข้มข้น” ในขนาดโดสระดับ 300-600 มิลลิกรัมต่อวัน ย้ำนะว่า สารสกัดเข้มข้น
ทีนี้เรามาดูกันไหมว่าที่ฉลากบอกว่ามี โอริซานอล 12,000 ppm ที่ดูเยอะแยะมากมายจนเราว๊าววววววกันนั้น ppm มันคืออะไรวะ? ppm (parts per million) แปลว่า “ส่วนในล้านส่วน” ในกรณีของของเหลวอย่างน้ำมัน 1 ppm = 1 มิลลิกรัม ต่อ 1 ลิตร ดังนั้น 12,000 ppm = 12,000 mg/ลิตร หรือก็คือ 12 กรัม ต่อน้ำมัน 1 ลิตร ถ้าเรากินน้ำมันแค่ “1 ช้อนโต๊ะ” (ประมาณ 15 มล.) ที่มี γ-Oryzanol 12,000 ppm จะมี γ-Oryzanol ประมาณ 180 mg สิ่งที่ร่างกายได้รับระหว่างที่ผสมในน้ำมัน กับ "สารสกัดเข้มข้น" ในการทดลอง มันคนละบริบทกัน แต่เอามาเคลมกัน???
ซึ่งเฮียบอกเลยว่า…เวลาเขาเคลมข้อดีมักจะดึงมาเป็นข้อๆ แต่ร่างกายมันเป็นเรื่องโยงใยอีรันพันตู คือก่อนที่คอเลสเตอรอลจะลด ตับเรานี่แหละจะรับไม่ไหวก่อน เพราะน้ำมันรำข้าวเป็นไขมันชนิดไม่อิ่มตัวหลายตำแหน่ง (PUFA) สูง ซึ่งถ้ารับเข้าไปในปริมาณมาก จะเพิ่มภาระให้ตับในการกำจัดสารอนุมูลอิสระและควบคุมสมดุลไขมันในเลือด ตับต้องทำงานหนักขึ้นเสมือนต้องล้างน้ำมันเครื่องเก่า ๆ ทุกวัน นานไปตับอาจเสื่อม ไม่สดใสเหมือนตอนกินไก่ต้มร้านประจำ
จริงอยู่ที่มีงานวิจัยบอกว่า γ‐oryzanol หรือที่เรียกกันว่า ออริซานอล เนี่ย สามารถช่วยลดการอมน้ำมันของอาหารทอดได้บ้าง โดยเปลี่ยนโครงสร้างของอาหารและสมบัติทางกายภาพของน้ำมัน ทำให้เฟรนช์ฟรายส์ที่ทอดออกมาน้ำมันเกาะน้อยลง เหมือนฟังดูดีใช่ไหมเฮีย?
แต่เฮียอยากชวนคิดอีกมุมว่า… ถ้าการจะทำให้อาหาร “ไม่อมน้ำมัน” ต้องอาศัยการ “เติมสารเคมี” เข้าไปเพื่อไปเปลี่ยนโครงสร้างของน้ำมัน แล้วนั่นยังเรียกว่า "ดีต่อสุขภาพ" ได้อยู่ไหม?
เพราะอย่าลืมว่า γ‐oryzanol ไม่ได้เป็นสารที่อยู่ในน้ำมันรำข้าวดิบ ๆ แบบธรรมชาติในปริมาณสูงพออยู่แล้ว ผู้ผลิตหลายเจ้าเลยต้อง เติมเพิ่มเข้าไปทีหลัง และการเติมสารเพิ่มในอุตสาหกรรมอาหารเนี่ย ไม่ได้มีฟรีนะ มันมีคำถามตามมาว่า เติมเท่าไหร่ถึงจะพอดี? เติมแบบนี้แล้วร่างกายดูดซึมได้แค่ไหน? สะสมในร่างกายไหม? และสุดท้าย... สารนี้จริง ๆ แล้ว “มีความจำเป็น” ต่อร่างกายหรือเปล่า?
เฮียบอกตรง ๆ ว่า ร่างกายคนเรา ไม่ได้ต้องการ γ‐oryzanol ในชีวิตประจำวันเลย มันไม่ใช่สารจำเป็นเหมือนวิตามิน หรือแร่ธาตุใด ๆ และก็ไม่มีหลักฐานชัดเจนในคนว่า การบริโภคต่อเนื่องในระยะยาวจะ ไม่มีผลข้างเคียง โดยเฉพาะเมื่อต้องโดนความร้อนสูง ๆ ซ้ำ ๆ ในการทอด แล้วอีกเรื่องที่ต้องไม่ลืมคือ…
น้ำมันรำข้าวเองเป็นน้ำมันที่มี กรดไขมันไม่อิ่มตัวสูงมาก โดยเฉพาะพวกโอเมก้า 6 ซึ่งถ้าเราโดนความร้อนสูงบ่อย ๆ อย่างการทอด มันจะเสื่อมสภาพเร็ว เกิดสารอนุมูลอิสระง่าย ซึ่งสารพวกนี้แหละที่เป็นต้นเหตุของการอักเสบเรื้อรังในร่างกาย ดังนั้นเวลาใครบอกว่า "โอเคนะ ใช้ได้ เพราะใส่สารช่วยป้องกันแล้ว" มันก็ควรถามกลับเหมือนกันว่า...แล้วทำไมเราไม่เริ่มจากใช้น้ำมันที่ทนความร้อนได้ดีตั้งแต่แรก???? มันก็เหมือนการแต่งหน้าซ่อนสิวโดยไม่รักษาสิวนั่นแหละ ดูดีขึ้นแค่ผิวเผิน แต่ต้นเหตุยังอยู่ครบ
เฮียอยากให้เพื่อน ๆ ฟังแล้วไม่ต้องรีบตัดสินใจอะไรทันที แค่ลองฟังอีกด้านไว้ แล้วค่อย ๆ คิด ว่าการกินอาหารเพื่อสุขภาพเนี่ย เราจะเลือกของที่ดูดีจากโฆษณา หรือของที่ “ร่างกายใช้ประโยชน์ได้จริง” โดยไม่ต้องพึ่งสารสังเคราะห์อะไรเลย
วิตามินอีสูง...แล้วไงต่อ? เค้าก็อ้างว่าน้ำมันรำข้าวมีวิตามินอีเยอะ เป็นสารต้านอนุมูลอิสระ จริงอยู่ วิตามินอีมีอยู่ในน้ำมันพืชหลายชนิด แต่เฮียขอเล่าให้ฟังแบบไม่อ้อมค้อมนะ…น้ำมันรำข้าวที่เราซื้อในท้องตลาด เขาเอารำข้าวไปผ่านกระบวนการ สกัดด้วยตัวทำละลายเฮกเซน (Hexane) ผ่านความร้อนสูงระดับ 200-270 องศาเซลเซียส แล้วก็ ฟอกกลิ่น ฟอกสี ให้มันดูใส ๆ น่ากิน
ปัญหาคือ…วิตามินอี กับสารต้านอนุมูลอิสระที่เขาว่า “มีสูง” มันพังไปกับความร้อนและกระบวนการผลิตตั้งแต่ช่วงแรก ๆ แล้ว เพราะวิตามินอีเป็นสารที่ไวต่ออุณหภูมิสูงมาก พอเจอความร้อนสูงแบบนั้น ก็กลายเป็นเหมือนซุปเปอร์ฮีโร่ที่หมดพลังกลางฉากแอ็กชัน
บางแบรนด์เลยต้องเติมวิตามินอีกลับเข้าไปทีหลัง ทั้งเพื่อ “เพิ่มคุณค่าทางโภชนาการ” ให้เอาไปโฆษณาได้ และ เพื่อช่วยป้องกันการเหม็นหืน ของน้ำมันที่ไวต่อปฏิกิริยาออกซิเดชัน เพราะน้ำมันรำข้าวที่อุดมไปด้วย PUFA จะเหม็นหืนเร็ว ถ้าไม่มีสารต้านอนุมูลอิสระไปจับ เรียกว่าเติมเพื่อให้ดูดีทั้งต่อสุขภาพและต่อกลิ่น (แม้สุขภาพอาจไม่ได้ดีจริง…)
ทนความร้อนได้ดี? เหมาะกับการทอด? อันนี้ต้องแซวแรงนิดนึง... เพราะเขาชอบโฆษณาว่า “เหมาะกับการทอดเพราะทนความร้อนได้ดี” บ้าบอ ในความจริง น้ำมันรำข้าวเป็น Polyunsaturated fat (PUFA) สูง แม้จะมีโมเลกุลอิ่มตัวบ้าง แต่ไม่มากพอจะสู้ความร้อนจริงจังได้ เวลาโดนทอดร้อน ๆ ไขมันเหล่านี้มัน กลายพันธุ์ เป็นไขมันออกซิไดซ์ ไม่ต้องไปบอกเลยว่าให้สลัดน้ำมัน กรรมมันเกิดไปแล้ว
น้ำมันรำข้าวคือน้ำมันพืชที่มี กรดไขมันไม่อิ่มตัวเชิงซ้อน (PUFA) สูง โดยเฉพาะ โอเมกา-6 (linoleic acid) ซึ่งถ้าเทียบให้เห็นภาพแบบเฮีย ๆ PUFA ก็คือคนขี้น้อยใจ โดนแดดนิด โดนไฟหน่อย ก็เป็นอารมณ์ บูดเสียง่าย คือไม่เหมาะจะโดนผัด โดนทอด เพราะมันจะกลายร่างเป็น อนุมูลอิสระ แล้ววิ่งวุ่นในร่างกายเราเหมือนคนเสียสติ
แล้วที่บอกว่าช่วยเรื่องหัวใจ? เรื่องนี้ก็น่าสนใจ เพราะเขาชอบพูดว่า “น้ำมันรำข้าวช่วยลดความเสี่ยงโรคหัวใจ” ซึ่งจริง ๆ มาจากแนวคิดเก่าว่า “ถ้าลดไขมันอิ่มตัว แล้วหันมากินไขมันไม่อิ่มตัวจากพืช จะช่วยลดคอเลสเตอรอล และหัวใจก็จะดีขึ้น”
ฟังดูเข้าท่าใช่ไหม...แต่รู้ไหมว่าทุกวันนี้ งานวิจัยใหม่ ๆ เริ่มพบว่า การลดไขมันอิ่มตัวไม่ได้ลดความเสี่ยงโรคหัวใจ อย่างที่เคยคิด และกลับกัน…ไขมันจากสัตว์ที่มาจากอาหารแท้ อย่างเนยแท้ น้ำมันหมู น้ำมันมะพร้าว กลับมีผลดีต่อสุขภาพหัวใจมากกว่า เพราะไม่สร้างการอักเสบในร่างกาย (พูดในมุม cooking oil นะ ถ้าสกัดเย็นพวก มะกอก มะพร้าว มะคาเดเมีย งา ฯลฯ นั่นเป็นเรื่องของสารพฤกษะและพลังงานประกอบ มันจะอีกศาสตร์นึง อย่าเพิ่งปนกันถ้ายังไม่ได้ลงลึก เพราะถ้าเอาสกัดเย็นมาโดนร้อนก็เจ๊งบ๊ง เคลียร์นะ)
ในขณะที่ไขมันไม่อิ่มตัวสูงอย่าง PUFA จากน้ำมันพืชกลับเพิ่มการอักเสบเรื้อรัง ซึ่งเป็นต้นตอของโรคหัวใจ เบาหวาน สมองเสื่อม และโรคเรื้อรังแทบทุกชนิด
แถมกับคำถามหลังไมค์ การที่จะบอกว่า "น้ำมันรำข้าวอมน้ำมันมากกว่าแต่กรดไขมันเขาดีกว่าน้ำมันปาล์มนะ" ฟังเผิน ๆ เหมือนเลือกความดีระยะยาวแลกกับความอ้วนระยะสั้น แต่เดี๋ยวก่อนเฮียอยากให้มองอีกด้าน... 1. กรดไขมันไม่อิ่มตัวที่ว่า “ดี” ในทางทฤษฎีนั้น ถ้าอยู่เฉย ๆ บนชั้นวาง ก็อาจจะดูดีอยู่หรอก แต่พอเจอไฟร้อน ๆ ตอนทอดหรือผัด สารพวกนี้เสื่อมสภาพง่ายมาก กลายเป็นสารออกซิไดซ์ที่ทำร้ายหลอดเลือดเราแบบไม่รู้ตัว กลายเป็น "ไขมันดีพัง ๆ" ได้ทันที 2. น้ำมันที่อมน้ำมันเยอะ หมายถึงอาหารเราจะดูดน้ำมันเข้าไปเยอะ ซึ่งเท่ากับเรากินเข้าไปเยอะโดยไม่รู้ตัว ปริมาณโอเมก้า 6 ก็พุ่งสูง แล้วพอระดับโอเมก้า 6 ในร่างกายสูงขึ้นมากเกินสมดุล มันจะกระตุ้นการอักเสบในร่างกาย = ต้นเหตุของสารพัดโรคยุคใหม่เลยนะ 3. สุดท้าย ถ้าเราต้องแลกกับการใช้น้ำมันที่ต้องพึ่ง "สารเติมแต่ง" อย่างโอริซานอล เพื่อให้อาหารไม่อมน้ำมันเกินไป แบบนี้ก็เหมือนซื้อของแพงแล้วต้องซื้อตัวช่วยเพิ่ม เพื่อให้มันใช้งานได้ดีขึ้น แบบนี้เรียกว่าดีจริงหรือเปล่า? เหมือนคนหน้าตาดีแต่ใช้เงินเก่ง... สุดท้ายเป็นหนี้เหมือนกัน
น้ำมันรำข้าวที่ผ่านกระบวนการมากมาย มันกลายเป็น “Fiat Food” ที่หน้าตาดูดี แต่คุณค่าข้างในเบาหวิว เหมือนแบงก์กระดาษที่พิมพ์ออกมาเยอะ แต่ไม่มีทองรองรับ
ที่สำคัญคือ มันไม่ใช่แค่เรื่อง "กินมากไปไม่ดี" หรอกนะ
บทความกูรูหลายเจ้าชอบสรุปว่า “อย่ากินเยอะ” กินแบบใส่เพื่อผัดอาหารน้อยๆ อืมมม คือพี่ครับ น้ำมันพืชมันไม่ได้เป็นแค่ขวดที่เราซื้อในซูเปอร์ แต่มันเป็น วัตถุดิบหลักของร้านอาหาร ผัดกระเพราเจ้าโปรด กล่องเบนโตะข้างออฟฟิศ ขนมทอดกรอบทุกซอง แถมยังถูกแปะฉลากคำว่า “ดีต่อสุขภาพ” เพื่อให้เรารู้สึกผิดน้อยลงตอนกินของทอดอีกต่างหาก แถมเวลาเราทำกินเอง บางอย่างมันใส่มากกว่า 1ช้อนโต๊ะ ตามหน่วยบริโภคนะ แถม แต่ปัญหาใหญ่คือ PUFA จากน้ำมันพืชเหล่านี้ สะสมในเนื้อเยื่อไขมันเราแบบยาวนาน ไม่ได้หายไปง่าย ๆ แบบอกไก่ต้มหลังออกกำลังกาย ถึงจะกินแค่การผัดกับข้าวจานละ 1ช้อนก็เหอะ วันนั้นกินกับข้าวกี่กระทะ???
มันแทรกตัวเข้าไปในเยื่อหุ้มเซลล์ และกลายเป็น ตัวจุดไฟอักเสบเรื้อรังในร่างกาย เบาหวาน ความดัน มะเร็ง ไขมันพอกตับ อาจไม่ได้มาพร้อมสายฟ้า แต่ค่อย ๆ สะสมทีละหยดเหมือนน้ำมันในกระทะ
อย่าให้คำว่า “มีสารต้านอนุมูลอิสระ” มาหลอกเรา เพราะสุดท้าย ถ้าโครงสร้างไขมันมัน ไม่เสถียรตั้งแต่ต้น ต่อให้มีวิตามิน E ติดมานิด ๆ หน่อย ๆ มันก็เหมือนใส่หมวกกันน็อกให้ตุ๊กตา แล้วเอาไปนั่งมอเตอร์ไซค์วิบาก
น้ำมันรำข้าวไม่ใช่ปีศาจ แต่ก็ไม่ใช่นางฟ้า และเมื่อมันเป็นน้ำมันที่ร่างกายเราไม่ได้ออกแบบมาเพื่อรองรับมัน ก็อย่าหลงกลคำโฆษณาว่า "ดีต่อหัวใจ" หรือ “มีสารต้านอนุมูลอิสระ” แล้วเทมันใส่กระทะทุกวันเลยนะ
ก็เข้าใจแหละว่าเวลาคนทำอาหารเองที่บ้าน เขาจะรู้สึกว่า “ทอดเอง คุมได้ ทอดแค่รอบเดียว ไม่ได้ใช้ซ้ำ ไม่เป็นไรหรอก” แล้วก็หยิบ น้ำมันรำข้าว มาด้วยเหตุผลว่า “โปรไฟล์กรดไขมันมันดีกว่าน้ำมันปาล์ม” …ฟังดูเหมือนมีเหตุมีผล แต่เฮียอยากให้ลองมองอีกมุมนะ
น้ำมันรำข้าวมีกรดไขมันไม่อิ่มตัวสูงก็จริง แต่นั่นแหละคือปัญหา เพราะความไม่อิ่มตัวทำให้ ไม่เสถียรต่อความร้อน โดยธรรมชาติ! ถึงจะทอดรอบเดียว พอน้ำมันเจอไฟแรง ๆ มันก็ยังเสื่อมสภาพอยู่ดี เกิดสารอนุมูลอิสระที่มองไม่เห็น แต่ร่างกายเราเห็นหมด แล้วถ้าคนในบ้านกินบ่อย ๆ วันเว้นวัน จะรู้ตัวอีกทีก็อาจจะมีอาการอักเสบเรื้อรังโดยไม่รู้ต้นตอเลยก็ได้
ส่วนที่บอกว่าอาหารอมน้ำมันก็ไม่เป็นไร แค่รอหายร้อนแล้วซับออก หรือเอาเข้าหม้อลมร้อน มันช่วยได้ “บางส่วน” จริง แต่ไม่ได้แก้ที่ต้นเหตุ เพราะไขมันที่เข้าไปอยู่ในชั้นแป้งหรือเนื้อของอาหารมันออกยากกว่าที่คิด และถ้าเราต้อง “พึ่งวิธีรีดน้ำมันออก” ทุกครั้งที่ทอด นั่นแปลว่าน้ำมันที่ใช้มันอมน้ำมันเกินไปตั้งแต่แรกแล้ว ไม่ใช่หรือ?
“ทอดรอบเดียวก็จริง แต่ถ้าน้ำมันมันพังตั้งแต่โดนไฟ แล้วจะต่างอะไรกับทอดสิบรอบ?”
ท้ายของท้ายสุด เรื่องทอดไม่ใช่แค่เรื่องน้ำมัน แต่มีเรื่อง AGEs ด้วยซึ่งสำคัญกว่าใช้น้ำมันอะไรทอดเยอะเลยครับ นี่เขียนเพื่อบันทึกรายละเอียดของน้ำมันรำข้าวให้เฉยๆ
#pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ b7d82f75:524cf1ac
2025-04-17 05:41:42
@ b7d82f75:524cf1ac
2025-04-17 05:41:42Want the best Anaheim auto body shop? G.U Collision Center is here to help! We repair your car from scratches to serious damage, making it look as good as new. Our team uses modern tools and lots of care to fix your vehicle fast. We handle everything, from small dings to big collisions, at prices that won’t break the bank. Plus, we work with your insurance for a smooth process. Visit G.U Collision Center in Anaheim for top-quality repairs and friendly service. Let us get your car back on the road in style!
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 91bea5cd:1df4451c
2025-04-15 06:23:35
@ 91bea5cd:1df4451c
2025-04-15 06:23:35Um bom gerenciamento de senhas deve ser simples e seguir a filosofia do Unix. Organizado em hierarquia e fácil de passar de um computador para outro.
E por isso não é recomendável o uso de aplicativos de terceiros que tenham acesso a suas chaves(senhas) em seus servidores, tampouco as opções nativas dos navegadores, que também pertencem a grandes empresas que fazem um grande esforço para ter acesso a nossas informações.
Recomendação
- pass
- Qtpass (gerenciador gráfico)
Com ele seus dados são criptografados usando sua chave gpg e salvo em arquivos organizados por pastas de forma hierárquica, podendo ser integrado a um serviço git de sua escolha ou copiado facilmente de um local para outro.
Uso
O seu uso é bem simples.
Configuração:
pass git initPara ver:
pass Email/example.comCopiar para área de transferência (exige xclip):
pass -c Email/example.comPara inserir:
pass insert Email/example0.comPara inserir e gerar senha:
pass generate Email/example1.comPara inserir e gerar senha sem símbolos:
pass generate --no-symbols Email/example1.comPara inserir, gerar senha e copiar para área de transferência :
pass generate -c Email/example1.comPara remover:
pass rm Email/example.com -
 @ c86dc7e6:6059e49b
2025-04-17 05:04:16
@ c86dc7e6:6059e49b
2025-04-17 05:04:16Want the best carpet cleaning services Atlanta has to offer? Spot It Cleaning is the name to trust! We bring your carpets back to life, removing stains, dirt, and odors. Our team uses safe, powerful tools to clean deep without harming your floors. Perfect for offices, stores, or any business, we make your carpets look fresh and feel soft. We work fast and fit your schedule, keeping your workspace ready for action. Choose Spot It Cleaning for affordable, top-quality carpet care in Atlanta. Let us make your floors shine so your business can stand out!
-
 @ 4cebd4f5:0ac3ed15
2025-04-17 03:12:14
@ 4cebd4f5:0ac3ed15
2025-04-17 03:12:14Tóm tắt Hackathon
HackCanada quy tụ các nhà đổi mới, lập trình viên, designer và chuyên gia giải quyết vấn đề để giải quyết thách thức cấp bách tại Canada như khả năng tiếp cận healthcare, bền vững môi trường, cơ sở hạ tầng số và chênh lệch kinh tế. Sự kiện diễn ra tại Đại học Wilfrid Laurier (Ontario, Canada) với 188 developer tham gia, đóng góp 89 dự án độc đáo.
Các dự án tập trung vào cải thiện hệ thống y tế qua công nghệ, nâng cấp hạ tầng số cho cộng đồng vùng sâu, và phương pháp sáng tạo giảm thiểu dấu chân môi trường. Hackathon trở thành nền tảng hợp tác, thúc đẩy ý tưởng mới và giải pháp thực tiễn, hướng đến mục tiêu tạo lợi ích cụ thể và truyền cảm hứng thay đổi.
Tổng quan, HackCanada tạo môi trường năng động cho đổi mới, góp phần phát triển công nghệ nâng cao chất lượng cuộc sống người dân. Sự kiện đóng vai trò chất xúc tác cho sáng tạo cộng đồng, hướng đến tương lai bao trùm và bền vững.
Các dự án đoạt giải
Giải Nhất Chung Cuộc
- Phone-a-Fraud: Hệ thống AI-driven phát hiện lừa đảo qua điện thoại thời gian thực, tập trung vào privacy và cơ chế cảnh báo gian lận.
Giải Nhì Chung Cuộc
- StickTator: Thiết bị USB ứng dụng xử lý ngôn ngữ tự nhiên (NLP) để quản lý máy tính bằng giọng nói, đơn giản hóa cấu hình hệ thống.
Giải Ba Chung Cuộc
- Omnivim: Phần mềm tích hợp chuyển động Vim trên mọi ứng dụng để tăng hiệu suất làm việc.
Best Solo Hack Prize Winners
Best Orkes Hack Prize Winners
- Recipeit: Dự án tập trung vào công thức nấu ăn (chi tiết chưa công bố).
Best ICP Hack Prize Winners
- DigiTag: Ứng dụng blockchain bảo mật giao dịch hàng xa xỉ bằng NFTs và Internet Computer Protocol (ICP) để ngăn gian lận.
- LandLocks: Nền tảng quản lý hồ sơ đất đai dưới dạng NFTs trên blockchain.
SPUR Innovation Fund: Best Use of AI, Web3, or Quantum Technology Prize Winners
Giải Nhất
- Beaver Breach: Công cụ phân tích tác động thuế quan Mỹ, đề xuất nhà cung cấp Canada giảm chi phí.Giải Nhì
- Canify - Blockchain Rewards: Khuyến khích ủng hộ sản phẩm Canada bằng phần thưởng blockchain và ưu đãi chính phủ.Autonomous Agent Bounty Track Prize Winners
Giải Nhất
- ChainMail: Ứng dụng email dựa trên web3, tăng cường bảo mật và giao tiếp xuyên blockchain.Giải Nhì
- Canify - Blockchain RewardsGiải Ba
- Roast My Wallet: Web app tạo nội dung hài hước AI-driven dựa trên ví crypto và tính cách người dùng.
- Zap: Ứng dụng crypto trong đời sống hàng ngày với giao dịch miễn phí.
- Carbon Chain: Nền tảng blockchain chuyển đổi giảm phát thải carbon thành tài sản giao dịch, xác thực bằng AI.Best Developer Tool Prize Winners
Best High School Hack Prize Winners
- NaloxNow: Ứng dụng di động chống khủng hoảng opioid, cung cấp naloxone thời gian thực và phản hồi overdose bằng AI.
Most Useless Hack Prize Winners
- UselessGPT: Ứng dụng tương tác sử dụng Gemini API của Google để tạo nội dung giải trí vô nghĩa.
Best AI App Prize Winners
- frij.io: Ứng dụng thông minh quản lý hàng tồn kho gia đình bằng AI, tối ưu hóa danh sách mua sắm.
Build With AI: Google Track Prize Winners
- Best Use of Gemini AI/Gemini API, Best Use of Google Cloud Platform, Best Integration of Google Toolkit:
- Sinker: Nền tảng an ninh mạng AI-driven đào tạo nhân viên nhận diện mối đe dọa phishing.
- FrostByte: Dự án chưa công bố chi tiết.
- Flock Street: Ứng dụng tương tác cung cấp thông tin thị trường chứng khoán bằng dữ liệu thời gian thực và công nghệ giọng nói.
Best Laurier STEM Publishing Society Prize Winners
- SockSensei: Ứng dụng di động đề xuất tất dựa trên tâm trạng người dùng.
Xem danh sách dự án đầy đủ tại đây.
Về Nhà tổ chức
Hack Canada
Hack Canada được biết đến qua các hackathon và workshop quốc gia nhằm nâng cao kiến thức về digital security. Thông qua các sự kiện năng động, tổ chức đã truyền cảm hứng cho nhiều dự án đóng góp vào hệ sinh thái công nghệ.
-
 @ 51cb7603:a2bbe90b
2025-04-17 03:07:18
@ 51cb7603:a2bbe90b
2025-04-17 03:07:18O SN88 é uma plataforma digital que tem se destacado no Brasil, oferecendo uma ampla gama de opções de entretenimento online. Com uma interface moderna e recursos inovadores, a plataforma atrai usuários em busca de experiências digitais envolventes e seguras.
Desde sua chegada ao mercado brasileiro, o SN88 tem investido em tecnologia de ponta para garantir uma navegação fluida e uma experiência personalizada para cada usuário. A plataforma oferece uma variedade de jogos e atividades interativas, atendendo a diferentes preferências e estilos de vida.
Um dos diferenciais do sn88 é o seu compromisso com a segurança e a transparência. A plataforma adota medidas rigorosas para proteger os dados dos usuários e garantir a integridade das transações realizadas. Além disso, oferece suporte ao cliente eficiente, disponível para resolver dúvidas e fornecer assistência sempre que necessário.
Com o crescimento do mercado digital no Brasil, plataformas como o SN88 desempenham um papel importante na transformação do entretenimento online. Elas não apenas oferecem diversão, mas também contribuem para a economia digital do país, gerando empregos e estimulando a inovação.
Em um cenário onde a regulamentação do setor digital está em constante evolução, o SN88 se destaca por sua conformidade com as leis brasileiras e seu compromisso com práticas responsáveis. A plataforma busca proporcionar uma experiência segura e agradável para seus usuários, alinhando-se às melhores práticas do mercado global.
Para os entusiastas do entretenimento digital, o SN88 representa uma opção confiável e inovadora. Com sua oferta diversificada e foco na experiência do usuário, a plataforma continua a conquistar a confiança e a preferência dos brasileiros.
Em resumo, o SN88 é mais do que uma simples plataforma de entretenimento online; é um reflexo da evolução digital no Brasil, oferecendo aos usuários uma experiência rica, segura e adaptada às suas necessidades e expectativas.
-
 @ 51cb7603:a2bbe90b
2025-04-17 03:05:16
@ 51cb7603:a2bbe90b
2025-04-17 03:05:16Nos últimos anos, o cenário do entretenimento digital no Brasil tem se transformado rapidamente, impulsionado pela inovação tecnológica e pela popularização de plataformas online. Entre os novos nomes que vêm ganhando espaço nesse mercado está a AA123, uma opção que vem despertando o interesse de milhares de brasileiros em busca de diversão, praticidade e possibilidades de ganhos financeiros.
AA123 se apresenta como uma plataforma interativa voltada para quem deseja se entreter com jogos online em tempo real. Sua proposta vai além da simples diversão, oferecendo também uma experiência dinâmica e acessível, tanto para iniciantes quanto para usuários mais experientes. Com uma interface intuitiva, suporte multilíngue e diversas opções de jogos, a plataforma busca atrair um público diversificado, com destaque para os brasileiros.
Um dos principais diferenciais da aa123 é a agilidade no processo de cadastro e a facilidade de uso. Em poucos minutos, o usuário pode criar uma conta, acessar os jogos disponíveis e começar a explorar as funcionalidades do site. Além disso, a plataforma garante segurança de dados e transações, um aspecto essencial para quem deseja utilizar serviços online com tranquilidade.
Outro ponto que vem chamando atenção é o sistema de recompensas e bônus oferecido aos usuários. A cada participação ou desafio completado, é possível acumular pontos ou créditos, que podem ser utilizados dentro da própria plataforma. Essa estratégia tem se mostrado eficaz para fidelizar os jogadores e incentivar o uso contínuo, criando uma comunidade engajada e ativa.
AA123 também se destaca por investir em atendimento ao cliente. Com suporte via chat ao vivo e canais de comunicação rápida, os usuários têm à disposição uma equipe preparada para resolver dúvidas e oferecer assistência em tempo real. Essa proximidade com o público tem contribuído para a construção de uma reputação positiva nas redes sociais e fóruns especializados.
O crescimento da AA123 no Brasil acompanha uma tendência global: a migração do entretenimento tradicional para o ambiente digital. Com a expansão da internet de alta velocidade e o aumento do uso de smartphones, os brasileiros estão cada vez mais conectados, buscando novas formas de lazer no ambiente online. Nesse contexto, plataformas como a AA123 surgem como resposta direta às demandas de um público moderno e exigente.
Embora ainda recente no mercado, a AA123 tem mostrado que veio para ficar. Com um modelo de negócios bem estruturado, foco na experiência do usuário e compromisso com a inovação, a plataforma caminha para se consolidar como uma das principais referências em entretenimento digital no país.
Para quem busca uma alternativa dinâmica, segura e moderna para se divertir online, a AA123 representa uma escolha promissora. E, com o avanço constante da tecnologia, é provável que novas funcionalidades e melhorias continuem sendo implementadas, ampliando ainda mais sua presença no mercado nacional.
-
 @ 51cb7603:a2bbe90b
2025-04-17 03:04:21
@ 51cb7603:a2bbe90b
2025-04-17 03:04:21O 007Game tem ganhado popularidade entre os jogadores que buscam uma experiência envolvente e cheia de adrenalina. Inspirado no universo do famoso agente secreto James Bond, o jogo oferece uma dinâmica de apostas emocionantes, que atrai tanto novatos quanto veteranos do mundo dos jogos.
O 007Game não é apenas sobre sorte, mas também exige estratégia e tomada de decisões rápidas. Com um formato simples, mas desafiador, ele tem conquistado o público com a possibilidade de interagir de forma intuitiva e divertida, sem a necessidade de uma curva de aprendizado complexa.
Como Funciona o 007Game? No 007game , os jogadores têm a oportunidade de testar suas habilidades de previsão e conhecimento, fazendo apostas em diferentes tipos de resultados. A interface é fluida e fácil de navegar, com gráficos modernos que proporcionam uma experiência visual envolvente. Cada rodada do jogo apresenta uma nova oportunidade de testar suas estratégias e aumentar as chances de ganhar, dependendo das escolhas feitas pelo jogador.
A mecânica do jogo gira em torno de eventos de alto risco e recompensa. Em alguns casos, os jogadores podem escolher entre várias opções e tentar prever o resultado de eventos específicos, enquanto em outros, o jogo pode apresentar desafios baseados em sorte e habilidades rápidas. A vitória depende tanto da sorte quanto da capacidade de antecipar o que vem a seguir.
Características que Tornam o Jogo Único Além da jogabilidade descomplicada, o 007Game se destaca pela sua imersão no universo da espionagem. A atmosfera do jogo é inspirada nos filmes clássicos de James Bond, com elementos de ação e mistério. Os jogadores podem se sentir como se estivessem participando de missões secretas, sempre com a possibilidade de ganhar recompensas substanciais. O design de som, incluindo músicas que remetem ao clássico tema de Bond, contribui para a criação de um ambiente tenso e cheio de emoção.
O jogo também oferece diversas opções de personalização, permitindo que os jogadores ajustem suas preferências para otimizar a experiência conforme suas estratégias e estilos de jogo. A escolha de diferentes tipos de apostas e a possibilidade de participar de torneios exclusivos são apenas algumas das maneiras pelas quais o 007Game mantém o interesse de seus jogadores.
A Popularidade do 007Game Com a crescente popularidade dos jogos digitais de apostas, o 007Game se destacou como uma opção divertida e emocionante para quem busca uma forma acessível de entrar no mundo dos jogos eletrônicos. A facilidade de acesso, combinada com a jogabilidade dinâmica e recompensadora, torna o jogo atrativo para pessoas de todas as idades e níveis de experiência.
Além disso, a comunidade de jogadores do 007Game é ativa, com fóruns e grupos de discussão onde os jogadores compartilham dicas e estratégias para melhorar suas habilidades no jogo. Isso cria um ambiente competitivo, mas também acolhedor, onde todos têm a oportunidade de aprender e se divertir.
Conclusão Em resumo, o 007Game é uma excelente opção para aqueles que procuram uma experiência envolvente e dinâmica no mundo dos jogos. Com uma combinação de sorte, habilidade e estratégia, ele tem conquistado os corações dos jogadores ao redor do mundo. Se você ainda não experimentou, talvez seja hora de embarcar nessa aventura de espionagem e emoção!
-
 @ 91bea5cd:1df4451c
2025-04-15 06:19:19
@ 91bea5cd:1df4451c
2025-04-15 06:19:19O que é Tahoe-LAFS?
Bem-vindo ao Tahoe-LAFS_, o primeiro sistema de armazenamento descentralizado com
- Segurança independente do provedor * .
Tahoe-LAFS é um sistema que ajuda você a armazenar arquivos. Você executa um cliente Programa no seu computador, que fala com um ou mais servidores de armazenamento em outros computadores. Quando você diz ao seu cliente para armazenar um arquivo, ele irá criptografar isso Arquivo, codifique-o em múltiplas peças, depois espalhe essas peças entre Vários servidores. As peças são todas criptografadas e protegidas contra Modificações. Mais tarde, quando você pede ao seu cliente para recuperar o arquivo, ele irá Encontre as peças necessárias, verifique se elas não foram corrompidas e remontadas Eles, e descriptografar o resultado.
O cliente cria mais peças (ou "compartilhamentos") do que acabará por precisar, então Mesmo que alguns servidores falhem, você ainda pode recuperar seus dados. Corrompido Os compartilhamentos são detectados e ignorados, de modo que o sistema pode tolerar o lado do servidor Erros no disco rígido. Todos os arquivos são criptografados (com uma chave exclusiva) antes Uploading, então mesmo um operador de servidor mal-intencionado não pode ler seus dados. o A única coisa que você pede aos servidores é que eles podem (geralmente) fornecer o Compartilha quando você os solicita: você não está confiando sobre eles para Confidencialidade, integridade ou disponibilidade absoluta.
O que é "segurança independente do provedor"?
Todo vendedor de serviços de armazenamento na nuvem irá dizer-lhe que o seu serviço é "seguro". Mas o que eles significam com isso é algo fundamentalmente diferente Do que queremos dizer. O que eles significam por "seguro" é que depois de ter dado Eles o poder de ler e modificar seus dados, eles tentam muito difícil de não deixar Esse poder seja abusado. Isso acaba por ser difícil! Insetos, Configurações incorretas ou erro do operador podem acidentalmente expor seus dados para Outro cliente ou para o público, ou pode corromper seus dados. Criminosos Ganho rotineiramente de acesso ilícito a servidores corporativos. Ainda mais insidioso é O fato de que os próprios funcionários às vezes violam a privacidade do cliente De negligência, avareza ou mera curiosidade. O mais consciencioso de Esses prestadores de serviços gastam consideráveis esforços e despesas tentando Mitigar esses riscos.
O que queremos dizer com "segurança" é algo diferente. * O provedor de serviços Nunca tem a capacidade de ler ou modificar seus dados em primeiro lugar: nunca. * Se você usa Tahoe-LAFS, então todas as ameaças descritas acima não são questões para você. Não só é fácil e barato para o provedor de serviços Manter a segurança de seus dados, mas na verdade eles não podem violar sua Segurança se eles tentaram. Isto é o que chamamos de * independente do fornecedor segurança*.
Esta garantia está integrada naturalmente no sistema de armazenamento Tahoe-LAFS e Não exige que você execute um passo de pré-criptografia manual ou uma chave complicada gestão. (Afinal, ter que fazer operações manuais pesadas quando Armazenar ou acessar seus dados anularia um dos principais benefícios de Usando armazenamento em nuvem em primeiro lugar: conveniência.)
Veja como funciona:
Uma "grade de armazenamento" é constituída por uma série de servidores de armazenamento. Um servidor de armazenamento Tem armazenamento direto em anexo (tipicamente um ou mais discos rígidos). Um "gateway" Se comunica com os nós de armazenamento e os usa para fornecer acesso ao Rede sobre protocolos como HTTP (S), SFTP ou FTP.
Observe que você pode encontrar "cliente" usado para se referir aos nós do gateway (que atuam como Um cliente para servidores de armazenamento) e também para processos ou programas que se conectam a Um nó de gateway e operações de execução na grade - por exemplo, uma CLI Comando, navegador da Web, cliente SFTP ou cliente FTP.
Os usuários não contam com servidores de armazenamento para fornecer * confidencialidade * nem
- Integridade * para seus dados - em vez disso, todos os dados são criptografados e Integridade verificada pelo gateway, para que os servidores não possam ler nem Modifique o conteúdo dos arquivos.
Os usuários dependem de servidores de armazenamento para * disponibilidade *. O texto cifrado é Codificado por apagamento em partes
Ndistribuídas em pelo menosHdistintas Servidores de armazenamento (o valor padrão paraNé 10 e paraHé 7) então Que pode ser recuperado de qualquerKdesses servidores (o padrão O valor deKé 3). Portanto, apenas a falha doH-K + 1(com o Padrões, 5) servidores podem tornar os dados indisponíveis.No modo de implantação típico, cada usuário executa seu próprio gateway sozinho máquina. Desta forma, ela confia em sua própria máquina para a confidencialidade e Integridade dos dados.
Um modo de implantação alternativo é que o gateway é executado em uma máquina remota e O usuário se conecta ao HTTPS ou SFTP. Isso significa que o operador de O gateway pode visualizar e modificar os dados do usuário (o usuário * depende de * o Gateway para confidencialidade e integridade), mas a vantagem é que a O usuário pode acessar a grade Tahoe-LAFS com um cliente que não possui o Software de gateway instalado, como um quiosque de internet ou celular.
Controle de acesso
Existem dois tipos de arquivos: imutáveis e mutáveis. Quando você carrega um arquivo Para a grade de armazenamento, você pode escolher o tipo de arquivo que será no grade. Os arquivos imutáveis não podem ser modificados quando foram carregados. UMA O arquivo mutable pode ser modificado por alguém com acesso de leitura e gravação. Um usuário Pode ter acesso de leitura e gravação a um arquivo mutable ou acesso somente leitura, ou não Acesso a ele.
Um usuário que tenha acesso de leitura e gravação a um arquivo mutable ou diretório pode dar Outro acesso de leitura e gravação do usuário a esse arquivo ou diretório, ou eles podem dar Acesso somente leitura para esse arquivo ou diretório. Um usuário com acesso somente leitura Para um arquivo ou diretório pode dar acesso a outro usuário somente leitura.
Ao vincular um arquivo ou diretório a um diretório pai, você pode usar um Link de leitura-escrita ou um link somente de leitura. Se você usar um link de leitura e gravação, então Qualquer pessoa que tenha acesso de leitura e gravação ao diretório pai pode obter leitura-escrita Acesso à criança e qualquer pessoa que tenha acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança. Se você usar uma leitura somente Link, qualquer pessoa que tenha lido-escrito ou acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança.
================================================== ==== Usando Tahoe-LAFS com uma rede anônima: Tor, I2P ================================================== ====
. `Visão geral '
. `Casos de uso '
.
Software Dependencies_#.
Tor#.I2P. `Configuração de conexão '
. `Configuração de Anonimato '
#.
Anonimato do cliente ' #.Anonimato de servidor, configuração manual ' #. `Anonimato de servidor, configuração automática '. `Problemas de desempenho e segurança '
Visão geral
Tor é uma rede anonimização usada para ajudar a esconder a identidade da Internet Clientes e servidores. Consulte o site do Tor Project para obter mais informações: Https://www.torproject.org/
I2P é uma rede de anonimato descentralizada que se concentra no anonimato de ponta a ponta Entre clientes e servidores. Consulte o site I2P para obter mais informações: Https://geti2p.net/
Casos de uso
Existem três casos de uso potenciais para Tahoe-LAFS do lado do cliente:
-
O usuário deseja sempre usar uma rede de anonimato (Tor, I2P) para proteger Seu anonimato quando se conecta às redes de armazenamento Tahoe-LAFS (seja ou Não os servidores de armazenamento são anônimos).
-
O usuário não se preocupa em proteger seu anonimato, mas eles desejam se conectar a Servidores de armazenamento Tahoe-LAFS que são acessíveis apenas através de Tor Hidden Services ou I2P.
-
Tor é usado apenas se uma sugestão de conexão do servidor usar
tor:. Essas sugestões Geralmente tem um endereço.onion. -
I2P só é usado se uma sugestão de conexão do servidor usa
i2p:. Essas sugestões Geralmente têm um endereço.i2p. -
O usuário não se preocupa em proteger seu anonimato ou para se conectar a um anonimato Servidores de armazenamento. Este documento não é útil para você ... então pare de ler.
Para servidores de armazenamento Tahoe-LAFS existem três casos de uso:
-
O operador deseja proteger o anonimato fazendo seu Tahoe Servidor acessível apenas em I2P, através de Tor Hidden Services, ou ambos.
-
O operador não * requer * anonimato para o servidor de armazenamento, mas eles Quer que ele esteja disponível tanto no TCP / IP roteado publicamente quanto através de um Rede de anonimização (I2P, Tor Hidden Services). Uma possível razão para fazer Isso é porque ser alcançável através de uma rede de anonimato é um Maneira conveniente de ignorar NAT ou firewall que impede roteios públicos Conexões TCP / IP ao seu servidor (para clientes capazes de se conectar a Tais servidores). Outro é o que torna o seu servidor de armazenamento acessível Através de uma rede de anonimato pode oferecer uma melhor proteção para sua Clientes que usam essa rede de anonimato para proteger seus anonimato.
-
O operador do servidor de armazenamento não se preocupa em proteger seu próprio anonimato nem Para ajudar os clientes a proteger o deles. Pare de ler este documento e execute Seu servidor de armazenamento Tahoe-LAFS usando TCP / IP com roteamento público.
Veja esta página do Tor Project para obter mais informações sobre Tor Hidden Services: Https://www.torproject.org/docs/hidden-services.html.pt
Veja esta página do Projeto I2P para obter mais informações sobre o I2P: Https://geti2p.net/en/about/intro
Dependências de software
Tor
Os clientes que desejam se conectar a servidores baseados em Tor devem instalar o seguinte.
-
Tor (tor) deve ser instalado. Veja aqui: Https://www.torproject.org/docs/installguide.html.en. No Debian / Ubuntu, Use
apt-get install tor. Você também pode instalar e executar o navegador Tor Agrupar. -
Tahoe-LAFS deve ser instalado com o
[tor]"extra" habilitado. Isso vai Instaletxtorcon::
Pip install tahoe-lafs [tor]
Os servidores Tor-configurados manualmente devem instalar Tor, mas não precisam
Txtorconou o[tor]extra. Configuração automática, quando Implementado, vai precisar destes, assim como os clientes.I2P
Os clientes que desejam se conectar a servidores baseados em I2P devem instalar o seguinte. Tal como acontece com Tor, os servidores baseados em I2P configurados manualmente precisam do daemon I2P, mas Não há bibliotecas especiais de apoio Tahoe-side.
-
I2P deve ser instalado. Veja aqui: Https://geti2p.net/en/download
-
A API SAM deve estar habilitada.
-
Inicie o I2P.
- Visite http://127.0.0.1:7657/configclients no seu navegador.
- Em "Configuração do Cliente", marque a opção "Executar no Startup?" Caixa para "SAM Ponte de aplicação ".
- Clique em "Salvar Configuração do Cliente".
-
Clique no controle "Iniciar" para "ponte de aplicação SAM" ou reinicie o I2P.
-
Tahoe-LAFS deve ser instalado com o
[i2p]extra habilitado, para obterTxi2p::
Pip install tahoe-lafs [i2p]
Tor e I2P
Os clientes que desejam se conectar a servidores baseados em Tor e I2P devem instalar tudo acima. Em particular, Tahoe-LAFS deve ser instalado com ambos Extras habilitados ::
Pip install tahoe-lafs [tor, i2p]
Configuração de conexão
Consulte: ref:
Connection Managementpara uma descrição do[tor]e[I2p]seções detahoe.cfg. Estes controlam como o cliente Tahoe Conecte-se a um daemon Tor / I2P e, assim, faça conexões com Tor / I2P-baseadas Servidores.As seções
[tor]e[i2p]só precisam ser modificadas para serem usadas de forma incomum Configurações ou para habilitar a configuração automática do servidor.A configuração padrão tentará entrar em contato com um daemon local Tor / I2P Ouvindo as portas usuais (9050/9150 para Tor, 7656 para I2P). Enquanto Há um daemon em execução no host local e o suporte necessário Bibliotecas foram instaladas, os clientes poderão usar servidores baseados em Tor Sem qualquer configuração especial.
No entanto, note que esta configuração padrão não melhora a Anonimato: as conexões TCP normais ainda serão feitas em qualquer servidor que Oferece um endereço regular (cumpre o segundo caso de uso do cliente acima, não o terceiro). Para proteger o anonimato, os usuários devem configurar o
[Connections]da seguinte maneira:[Conexões] Tcp = tor
Com isso, o cliente usará Tor (em vez de um IP-address -reviração de conexão direta) para alcançar servidores baseados em TCP.
Configuração de anonimato
Tahoe-LAFS fornece uma configuração "flag de segurança" para indicar explicitamente Seja necessário ou não a privacidade do endereço IP para um nó ::
[nó] Revelar-IP-address = (booleano, opcional)
Quando
revelar-IP-address = False, Tahoe-LAFS se recusará a iniciar se algum dos As opções de configuração emtahoe.cfgrevelariam a rede do nó localização:-
[Conexões] tcp = toré necessário: caso contrário, o cliente faria Conexões diretas para o Introdução, ou qualquer servidor baseado em TCP que aprende Do Introdutor, revelando seu endereço IP para esses servidores e um Rede de espionagem. Com isso, Tahoe-LAFS só fará Conexões de saída através de uma rede de anonimato suportada. -
Tub.locationdeve ser desativado ou conter valores seguros. este O valor é anunciado para outros nós através do Introdutor: é como um servidor Anuncia sua localização para que os clientes possam se conectar a ela. No modo privado, ele É um erro para incluir umtcp:dica notub.location. Modo privado Rejeita o valor padrão detub.location(quando a chave está faltando Inteiramente), que éAUTO, que usaifconfigpara adivinhar o nó Endereço IP externo, o que o revelaria ao servidor e a outros clientes.
Esta opção é ** crítica ** para preservar o anonimato do cliente (cliente Caso de uso 3 de "Casos de uso", acima). Também é necessário preservar uma Anonimato do servidor (caso de uso do servidor 3).
Esse sinalizador pode ser configurado (para falso), fornecendo o argumento
--hide-ippara Os comandoscreate-node,create-clientoucreate-introducer.Observe que o valor padrão de
revelar-endereço IPé verdadeiro, porque Infelizmente, esconder o endereço IP do nó requer software adicional para ser Instalado (conforme descrito acima) e reduz o desempenho.Anonimato do cliente
Para configurar um nó de cliente para anonimato,
tahoe.cfg** deve ** conter o Seguindo as bandeiras de configuração ::[nó] Revelar-IP-address = False Tub.port = desativado Tub.location = desativado
Uma vez que o nodo Tahoe-LAFS foi reiniciado, ele pode ser usado anonimamente (cliente Caso de uso 3).
Anonimato do servidor, configuração manual
Para configurar um nó de servidor para ouvir em uma rede de anonimato, devemos primeiro Configure Tor para executar um "Serviço de cebola" e encaminhe as conexões de entrada para o Porto Tahoe local. Então, configuramos Tahoe para anunciar o endereço
.onionAos clientes. Também configuramos Tahoe para não fazer conexões TCP diretas.- Decida em um número de porta de escuta local, chamado PORT. Isso pode ser qualquer não utilizado Porta de cerca de 1024 até 65535 (dependendo do kernel / rede do host Config). Nós diremos a Tahoe para escutar nesta porta, e nós diremos a Tor para Encaminhe as conexões de entrada para ele.
- Decida em um número de porta externo, chamado VIRTPORT. Isso será usado no Localização anunciada e revelada aos clientes. Pode ser qualquer número de 1 Para 65535. Pode ser o mesmo que PORT, se quiser.
- Decida em um "diretório de serviço oculto", geralmente em
/ var / lib / tor / NAME. Pediremos a Tor para salvar o estado do serviço de cebola aqui, e Tor irá Escreva o endereço.onionaqui depois que ele for gerado.
Em seguida, faça o seguinte:
-
Crie o nó do servidor Tahoe (com
tahoe create-node), mas não ** não ** Lança-o ainda. -
Edite o arquivo de configuração Tor (normalmente em
/ etc / tor / torrc). Precisamos adicionar Uma seção para definir o serviço oculto. Se nossa PORT for 2000, VIRTPORT é 3000, e estamos usando/ var / lib / tor / tahoecomo o serviço oculto Diretório, a seção deve se parecer com ::HiddenServiceDir / var / lib / tor / tahoe HiddenServicePort 3000 127.0.0.1:2000
-
Reinicie Tor, com
systemctl restart tor. Aguarde alguns segundos. -
Leia o arquivo
hostnameno diretório de serviço oculto (por exemplo,/ Var / lib / tor / tahoe / hostname). Este será um endereço.onion, comoU33m4y7klhz3b.onion. Ligue para esta CEBOLA. -
Edite
tahoe.cfgpara configurartub.portpara usarTcp: PORT: interface = 127.0.0.1etub.locationpara usarTor: ONION.onion: VIRTPORT. Usando os exemplos acima, isso seria ::[nó] Revelar-endereço IP = falso Tub.port = tcp: 2000: interface = 127.0.0.1 Tub.location = tor: u33m4y7klhz3b.onion: 3000 [Conexões] Tcp = tor
-
Inicie o servidor Tahoe com
tahoe start $ NODEDIR
A seção
tub.portfará com que o servidor Tahoe ouça no PORT, mas Ligue o soquete de escuta à interface de loopback, que não é acessível Do mundo exterior (mas * é * acessível pelo daemon Tor local). Então o A seçãotcp = torfaz com que Tahoe use Tor quando se conecta ao Introdução, escondendo o endereço IP. O nó se anunciará a todos Clientes que usam `tub.location``, então os clientes saberão que devem usar o Tor Para alcançar este servidor (e não revelar seu endereço IP através do anúncio). Quando os clientes se conectam ao endereço da cebola, seus pacotes serão Atravessar a rede de anonimato e eventualmente aterrar no Tor local Daemon, que então estabelecerá uma conexão com PORT no localhost, que é Onde Tahoe está ouvindo conexões.Siga um processo similar para construir um servidor Tahoe que escuta no I2P. o O mesmo processo pode ser usado para ouvir tanto o Tor como o I2P (
tub.location = Tor: ONION.onion: VIRTPORT, i2p: ADDR.i2p). Também pode ouvir tanto Tor como TCP simples (caso de uso 2), comtub.port = tcp: PORT,tub.location = Tcp: HOST: PORT, tor: ONION.onion: VIRTPORTeanonymous = false(e omite A configuraçãotcp = tor, já que o endereço já está sendo transmitido através de O anúncio de localização).Anonimato do servidor, configuração automática
Para configurar um nó do servidor para ouvir em uma rede de anonimato, crie o Nó com a opção
--listen = tor. Isso requer uma configuração Tor que Ou lança um novo daemon Tor, ou tem acesso à porta de controle Tor (e Autoridade suficiente para criar um novo serviço de cebola). Nos sistemas Debian / Ubuntu, façaApt install tor, adicione-se ao grupo de controle comadduser YOURUSERNAME debian-tore, em seguida, inicie sessão e faça o login novamente: se osgroupsO comando incluidebian-torna saída, você deve ter permissão para Use a porta de controle de domínio unix em/ var / run / tor / control.Esta opção irá definir
revelar-IP-address = Falsee[connections] tcp = Tor. Ele alocará as portas necessárias, instruirá Tor para criar a cebola Serviço (salvando a chave privada em algum lugar dentro de NODEDIR / private /), obtenha O endereço.onione preenchatub.portetub.locationcorretamente.Problemas de desempenho e segurança
Se você estiver executando um servidor que não precisa ser Anônimo, você deve torná-lo acessível através de uma rede de anonimato ou não? Ou você pode torná-lo acessível * ambos * através de uma rede de anonimato E como um servidor TCP / IP rastreável publicamente?
Existem várias compensações efetuadas por esta decisão.
Penetração NAT / Firewall
Fazer com que um servidor seja acessível via Tor ou I2P o torna acessível (por Clientes compatíveis com Tor / I2P) mesmo que existam NAT ou firewalls que impeçam Conexões TCP / IP diretas para o servidor.
Anonimato
Tornar um servidor Tahoe-LAFS acessível * somente * via Tor ou I2P pode ser usado para Garanta que os clientes Tahoe-LAFS usem Tor ou I2P para se conectar (Especificamente, o servidor só deve anunciar endereços Tor / I2P no Chave de configuração
tub.location). Isso evita que os clientes mal configurados sejam Desingonizando-se acidentalmente, conectando-se ao seu servidor através de A Internet rastreável.Claramente, um servidor que está disponível como um serviço Tor / I2P * e * a O endereço TCP regular não é anônimo: o endereço do .on e o real O endereço IP do servidor é facilmente vinculável.
Além disso, a interação, através do Tor, com um Tor Oculto pode ser mais Protegido da análise do tráfego da rede do que a interação, através do Tor, Com um servidor TCP / IP com rastreamento público
** XXX há um documento mantido pelos desenvolvedores de Tor que comprovem ou refutam essa crença? Se assim for, precisamos ligar a ele. Caso contrário, talvez devêssemos explicar mais aqui por que pensamos isso? **
Linkability
A partir de 1.12.0, o nó usa uma única chave de banheira persistente para saída Conexões ao Introdutor e conexões de entrada para o Servidor de Armazenamento (E Helper). Para os clientes, uma nova chave Tub é criada para cada servidor de armazenamento Nós aprendemos sobre, e essas chaves são * não * persistiram (então elas mudarão cada uma delas Tempo que o cliente reinicia).
Clientes que atravessam diretórios (de rootcap para subdiretório para filecap) são É provável que solicitem os mesmos índices de armazenamento (SIs) na mesma ordem de cada vez. Um cliente conectado a vários servidores irá pedir-lhes todos para o mesmo SI em Quase ao mesmo tempo. E dois clientes que compartilham arquivos ou diretórios Irá visitar os mesmos SI (em várias ocasiões).
Como resultado, as seguintes coisas são vinculáveis, mesmo com
revelar-endereço IP = Falso:- Servidores de armazenamento podem vincular reconhecer várias conexões do mesmo Cliente ainda não reiniciado. (Observe que o próximo recurso de Contabilidade pode Faz com que os clientes apresentem uma chave pública persistente do lado do cliente quando Conexão, que será uma ligação muito mais forte).
- Os servidores de armazenamento provavelmente podem deduzir qual cliente está acessando dados, por Olhando as SIs sendo solicitadas. Vários servidores podem conciliar Determine que o mesmo cliente está falando com todos eles, mesmo que o TubIDs são diferentes para cada conexão.
- Os servidores de armazenamento podem deduzir quando dois clientes diferentes estão compartilhando dados.
- O Introdutor pode entregar diferentes informações de servidor para cada um Cliente subscrito, para particionar clientes em conjuntos distintos de acordo com Quais as conexões do servidor que eles eventualmente fazem. Para clientes + nós de servidor, ele Também pode correlacionar o anúncio do servidor com o cliente deduzido identidade.
atuação
Um cliente que se conecta a um servidor Tahoe-LAFS com rastreamento público através de Tor Incorrem em latência substancialmente maior e, às vezes, pior Mesmo cliente se conectando ao mesmo servidor através de um TCP / IP rastreável normal conexão. Quando o servidor está em um Tor Hidden Service, ele incorre ainda mais Latência e, possivelmente, ainda pior rendimento.
Conectando-se a servidores Tahoe-LAFS que são servidores I2P incorrem em maior latência E pior rendimento também.
Efeitos positivos e negativos em outros usuários Tor
O envio de seu tráfego Tahoe-LAFS sobre o Tor adiciona tráfego de cobertura para outros Tor usuários que também estão transmitindo dados em massa. Então isso é bom para Eles - aumentando seu anonimato.
No entanto, torna o desempenho de outros usuários do Tor Sessões - por exemplo, sessões ssh - muito pior. Isso é porque Tor Atualmente não possui nenhuma prioridade ou qualidade de serviço Recursos, para que as teclas de Ssh de outra pessoa possam ter que esperar na fila Enquanto o conteúdo do arquivo em massa é transmitido. O atraso adicional pode Tornar as sessões interativas de outras pessoas inutilizáveis.
Ambos os efeitos são duplicados se você carregar ou baixar arquivos para um Tor Hidden Service, em comparação com se você carregar ou baixar arquivos Over Tor para um servidor TCP / IP com rastreamento público
Efeitos positivos e negativos em outros usuários do I2P
Enviar seu tráfego Tahoe-LAFS ao I2P adiciona tráfego de cobertura para outros usuários do I2P Que também estão transmitindo dados. Então, isso é bom para eles - aumentando sua anonimato. Não prejudicará diretamente o desempenho de outros usuários do I2P Sessões interativas, porque a rede I2P possui vários controles de congestionamento e Recursos de qualidade de serviço, como priorizar pacotes menores.
No entanto, se muitos usuários estão enviando tráfego Tahoe-LAFS ao I2P e não tiverem Seus roteadores I2P configurados para participar de muito tráfego, então o I2P A rede como um todo sofrerá degradação. Cada roteador Tahoe-LAFS que usa o I2P tem Seus próprios túneis de anonimato que seus dados são enviados. Em média, um O nó Tahoe-LAFS requer 12 outros roteadores I2P para participar de seus túneis.
Portanto, é importante que o seu roteador I2P esteja compartilhando a largura de banda com outros Roteadores, para que você possa retornar enquanto usa o I2P. Isso nunca prejudicará a Desempenho de seu nó Tahoe-LAFS, porque seu roteador I2P sempre Priorize seu próprio tráfego.
=========================
Como configurar um servidor
Muitos nós Tahoe-LAFS são executados como "servidores", o que significa que eles fornecem serviços para Outras máquinas (isto é, "clientes"). Os dois tipos mais importantes são os Introdução e Servidores de armazenamento.
Para ser útil, os servidores devem ser alcançados pelos clientes. Os servidores Tahoe podem ouvir Em portas TCP e anunciar sua "localização" (nome do host e número da porta TCP) Para que os clientes possam se conectar a eles. Eles também podem ouvir os serviços de cebola "Tor" E portas I2P.
Os servidores de armazenamento anunciam sua localização ao anunciá-lo ao Introdutivo, Que então transmite a localização para todos os clientes. Então, uma vez que a localização é Determinado, você não precisa fazer nada de especial para entregá-lo.
O próprio apresentador possui uma localização, que deve ser entregue manualmente a todos Servidores de armazenamento e clientes. Você pode enviá-lo para os novos membros do seu grade. Esta localização (juntamente com outros identificadores criptográficos importantes) é Escrito em um arquivo chamado
private / introducer.furlno Presenter's Diretório básico, e deve ser fornecido como o argumento--introducer =paraTahoe create-nodeoutahoe create-node.O primeiro passo ao configurar um servidor é descobrir como os clientes irão alcançar. Então você precisa configurar o servidor para ouvir em algumas portas, e Depois configure a localização corretamente.
Configuração manual
Cada servidor tem duas configurações em seu arquivo
tahoe.cfg:tub.port, eTub.location. A "porta" controla o que o nó do servidor escuta: isto Geralmente é uma porta TCP.A "localização" controla o que é anunciado para o mundo exterior. Isto é um "Sugestão de conexão foolscap", e inclui tanto o tipo de conexão (Tcp, tor ou i2p) e os detalhes da conexão (nome do host / endereço, porta número). Vários proxies, gateways e redes de privacidade podem ser Envolvido, então não é incomum para
tub.portetub.locationpara olhar diferente.Você pode controlar diretamente a configuração
tub.portetub.locationConfigurações, fornecendo--port =e--location =ao executartahoe Create-node.Configuração automática
Em vez de fornecer
--port = / - location =, você pode usar--listen =. Os servidores podem ouvir em TCP, Tor, I2P, uma combinação desses ou nenhum. O argumento--listen =controla quais tipos de ouvintes o novo servidor usará.--listen = nonesignifica que o servidor não deve ouvir nada. Isso não Faz sentido para um servidor, mas é apropriado para um nó somente cliente. o O comandotahoe create-clientinclui automaticamente--listen = none.--listen = tcpé o padrão e liga uma porta de escuta TCP padrão. Usar--listen = tcprequer um argumento--hostname =também, que será Incorporado no local anunciado do nó. Descobrimos que os computadores Não pode determinar de forma confiável seu nome de host acessível externamente, então, em vez de Ter o servidor adivinhar (ou escanear suas interfaces para endereços IP Isso pode ou não ser apropriado), a criação de nó requer que o usuário Forneça o nome do host.--listen = torconversará com um daemon Tor local e criará uma nova "cebola" Servidor "(que se parece comalzrgrdvxct6c63z.onion).--listen = i2p` conversará com um daemon I2P local e criará um novo servidor endereço. Consulte: doc:anonymity-configuration` para obter detalhes.Você pode ouvir nos três usando
--listen = tcp, tor, i2p.Cenários de implantação
A seguir, alguns cenários sugeridos para configurar servidores usando Vários transportes de rede. Estes exemplos não incluem a especificação de um Apresentador FURL que normalmente você gostaria quando provisionamento de armazenamento Nós. Para estes e outros detalhes de configuração, consulte : Doc:
configuration.. `Servidor possui um nome DNS público '
.
Servidor possui um endereço público IPv4 / IPv6_.
O servidor está por trás de um firewall com encaminhamento de porta_.
Usando o I2P / Tor para evitar o encaminhamento da porta_O servidor possui um nome DNS público
O caso mais simples é o local onde o host do servidor está diretamente conectado ao Internet, sem um firewall ou caixa NAT no caminho. A maioria dos VPS (Virtual Private Servidor) e servidores colocados são assim, embora alguns fornecedores bloqueiem Muitas portas de entrada por padrão.
Para esses servidores, tudo o que você precisa saber é o nome do host externo. O sistema O administrador irá dizer-lhe isso. O principal requisito é que este nome de host Pode ser pesquisado no DNS, e ele será mapeado para um endereço IPv4 ou IPv6 que Alcançará a máquina.
Se o seu nome de host for
example.net, então você criará o introdutor como esta::Tahoe create-introducer --hostname example.com ~ / introducer
Ou um servidor de armazenamento como ::
Tahoe create-node --hostname = example.net
Estes irão alocar uma porta TCP (por exemplo, 12345), atribuir
tub.portpara serTcp: 12345etub.locationserãotcp: example.com: 12345.Idealmente, isso também deveria funcionar para hosts compatíveis com IPv6 (onde o nome DNS Fornece um registro "AAAA", ou ambos "A" e "AAAA"). No entanto Tahoe-LAFS O suporte para IPv6 é novo e ainda pode ter problemas. Por favor, veja o ingresso
# 867_ para detalhes... _ # 867: https://tahoe-lafs.org/trac/tahoe-lafs/ticket/867
O servidor possui um endereço público IPv4 / IPv6
Se o host tiver um endereço IPv4 (público) rotativo (por exemplo,
203.0.113.1```), mas Nenhum nome DNS, você precisará escolher uma porta TCP (por exemplo,3457``) e usar o Segue::Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
--porté uma "string de especificação de ponto de extremidade" que controla quais locais Porta em que o nó escuta.--locationé a "sugestão de conexão" que ele Anuncia para outros, e descreve as conexões de saída que essas Os clientes irão fazer, por isso precisa trabalhar a partir da sua localização na rede.Os nós Tahoe-LAFS escutam em todas as interfaces por padrão. Quando o host é Multi-homed, você pode querer fazer a ligação de escuta ligar apenas a uma Interface específica, adicionando uma opção
interface =ao--port =argumento::Tahoe create-node --port = tcp: 3457: interface = 203.0.113.1 - localização = tcp: 203.0.113.1: 3457
Se o endereço público do host for IPv6 em vez de IPv4, use colchetes para Envolva o endereço e altere o tipo de nó de extremidade para
tcp6::Tahoe create-node --port = tcp6: 3457 - localização = tcp: [2001: db8 :: 1]: 3457
Você pode usar
interface =para vincular a uma interface IPv6 específica também, no entanto Você deve fazer uma barra invertida - escapar dos dois pontos, porque, de outra forma, eles são interpretados Como delimitadores pelo idioma de especificação do "ponto final" torcido. o--location =argumento não precisa de dois pontos para serem escapados, porque eles são Envolto pelos colchetes ::Tahoe create-node --port = tcp6: 3457: interface = 2001 \: db8 \: \: 1 --location = tcp: [2001: db8 :: 1]: 3457
Para hosts somente IPv6 com registros DNS AAAA, se o simples
--hostname =A configuração não funciona, eles podem ser informados para ouvir especificamente Porta compatível com IPv6 com este ::Tahoe create-node --port = tcp6: 3457 - localização = tcp: example.net: 3457
O servidor está por trás de um firewall com encaminhamento de porta
Para configurar um nó de armazenamento por trás de um firewall com encaminhamento de porta, você irá precisa saber:
- Endereço IPv4 público do roteador
- A porta TCP que está disponível de fora da sua rede
- A porta TCP que é o destino de encaminhamento
- Endereço IPv4 interno do nó de armazenamento (o nó de armazenamento em si é
Desconhece esse endereço e não é usado durante
tahoe create-node, Mas o firewall deve ser configurado para enviar conexões para isso)
Os números de porta TCP internos e externos podem ser iguais ou diferentes Dependendo de como o encaminhamento da porta está configurado. Se é mapear portas 1-para-1, eo endereço IPv4 público do firewall é 203.0.113.1 (e Talvez o endereço IPv4 interno do nó de armazenamento seja 192.168.1.5), então Use um comando CLI como este ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
Se no entanto, o firewall / NAT-box encaminha a porta externa * 6656 * para o interno Porta 3457, então faça isso ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 6656
Usando o I2P / Tor para evitar o encaminhamento da porta
Os serviços de cebola I2P e Tor, entre outras excelentes propriedades, também fornecem NAT Penetração sem encaminhamento de porta, nomes de host ou endereços IP. Então, configurando Um servidor que escuta apenas no Tor é simples ::
Tahoe create-node --listen = tor
Para mais informações sobre o uso de Tahoe-LAFS com I2p e Tor veja : Doc:
anonymity-configuration -
 @ 51cb7603:a2bbe90b
2025-04-17 03:02:36
@ 51cb7603:a2bbe90b
2025-04-17 03:02:36No mundo em constante evolução do entretenimento online, o 9Bet99 se destaca como uma plataforma notável que atende aos entusiastas que buscam uma variedade de experiências interativas. Com um design centrado no usuário e uma ampla gama de recursos envolventes, o 9Bet99 tem como objetivo oferecer uma solução completa de entretenimento para seus usuários.
Interface Amigável e Acessibilidade
Um dos principais destaques do 9Bet99 é sua interface intuitiva, projetada para proporcionar uma navegação fluida. Explorar a plataforma é simples, permitindo que os usuários acessem facilmente as diferentes seções e funcionalidades. O layout limpo do site garante que tanto novatos quanto usuários experientes possam utilizá-lo sem dificuldades.
Além disso, o 9bet99 entende a importância da acessibilidade. A plataforma é otimizada para dispositivos móveis, permitindo que os usuários aproveitem suas atividades favoritas de qualquer lugar. Seja em um smartphone ou tablet, a versão mobile mantém todas as funcionalidades e a facilidade de uso do site original.
Diversas Opções de Entretenimento
O 9Bet99 oferece uma variedade de opções de entretenimento para atender a diferentes interesses. De jogos interativos a eventos ao vivo, a plataforma garante conteúdo envolvente em todos os momentos. A diversidade de escolhas permite que os usuários explorem novas atividades e aproveitem ao máximo sua experiência no site.
Compromisso com a Segurança e Justiça
Garantir um ambiente seguro é uma das maiores prioridades do 9Bet99. A plataforma utiliza tecnologias de segurança avançadas para proteger os dados e as transações dos usuários, oferecendo tranquilidade total. Além disso, o 9Bet99 é comprometido com a justiça, implementando sistemas que promovem transparência e integridade em todas as suas atividades.
Suporte ao Cliente e Atendimento
Sabendo da importância de um suporte eficaz, o 9Bet99 disponibiliza diversos canais de atendimento para ajudar seus usuários. Seja por chat ao vivo, e-mail ou outros meios, a ajuda está sempre à disposição. A equipe de suporte é treinada para responder de forma rápida e eficiente, tornando a experiência do usuário ainda mais positiva.
Promoções e Benefícios
Para tornar a experiência ainda mais atrativa, o 9Bet99 oferece diversas promoções e incentivos. Essas recompensas são criadas para valorizar os usuários e incentivar o engajamento contínuo na plataforma. Ao participar das promoções, os usuários aproveitam vantagens extras que tornam sua jornada no 9Bet99 ainda mais divertida.
Conclusão
Em resumo, o 9Bet99 se destaca como uma plataforma dinâmica que prioriza a experiência do usuário, a segurança e uma grande variedade de opções de entretenimento. Com seu compromisso em oferecer um ambiente confiável e envolvente, o 9Bet99 continua atraindo uma comunidade crescente de usuários em busca de diversão de qualidade. Seja você iniciante ou experiente, o 9Bet99 oferece uma experiência completa e agradável para todos.
-
 @ 502ab02a:a2860397
2025-04-17 02:15:32
@ 502ab02a:a2860397
2025-04-17 02:15:32วันนี้มาเล่าเรื่อง animal base บ้างครับ เพราะหลายๆคนบอกว่า ดีนะฉันกินสัตว์ ฉันคิดว่าไขมันสัตว์ดีที่สุด รวมถึง plant base ที่ตัดสินฉาบฉวยว่าผม anti plant วันนี้มาเล่าข้อมูลเรื่องต่อไปกันครับ เพื่อให้เห็นว่า โลกของผู้ล่า มันไม่เลือกฝั่งครับ คำถามคือ เหยื่อจะเตรียมตัวอย่างไรมากกว่า เพราะเหยื่อยังทะเลาะกันเองอยู่เลย 55555
sub item ของ fiat food มีอย่างนึงที่เรียกว่า fake food ครับ ถ้าถามว่า “โปรตีนจากเซลล์” หรือ lab-grown meat ที่โฆษณาว่าเป็นทางเลือกแห่งอนาคตนั้น ภาพที่คนทั่วไปนึกถึงคืออะไร? คำตอบน่าจะไม่พ้น -เนื้อที่ไม่ต้องฆ่าสัตว์ -โปรตีนสะอาด ไร้มลพิษ -เทคโนโลยีแห่งอนาคตเพื่อสิ่งแวดล้อม
เชื่อไหมว่าความจริงนั้นมันอาจจะตรงกันข้ามกับทุกข้อที่ตอบมาเลยครับ
มันมาจากไหน?
"เนื้อเทียมจากห้องแล็บ" คือการเอาเซลล์สัตว์มาเพาะเลี้ยงในจานเพาะเลี้ยง โดยให้อาหารกับเซลล์พวกนั้นด้วยน้ำเลี้ยง (growth medium) เพื่อให้มันแบ่งตัวกลายเป็นกล้ามเนื้อ ฟังดูเหมือนปลอดภัยใช่ไหม? แต่ที่หลายคนไม่รู้คือ…
น้ำเลี้ยงที่ใช้ส่วนใหญ่มาจาก Fetal Bovine Serum (FBS) หรือ ซีรั่มจากลูกวัวที่ถูกฆ่าขณะอยู่ในครรภ์แม่ มันคือ คือการเจาะหัวใจลูกวัวที่ยังไม่เกิด เพื่อเอาเลือดมาเลี้ยงเนื้อเทียม แน่นอนว่าการให้ข้อมูลนั้นเขาจะบอกว่า เก็บเกี่ยวเลือดจากตัวอ่อนของวัวหลังจากที่นำตัวอ่อนออกจากวัวที่ถูกเชือด ตัวอ่อนจะตายจากการขาดออกซิเจนโดยอยู่ในสภาพแวดล้อมที่ปลอดภัยของมดลูกเป็นเวลาอย่างน้อย 15-20 นาทีหลังจากวัวตายและแน่นอนว่าต้องให้ข้อมูลว่ามีการเก็บมาภายใต้การดูแลจริยธรรม
และถ้าจะไม่ใช้ FBS ก็ต้องใช้น้ำเลี้ยงสังเคราะห์ที่อัดแน่นด้วย growth factor สังเคราะห์, ยาปฏิชีวนะ, ฮอร์โมน และสารกระตุ้นการเจริญเติบโตแบบเข้มข้น มันคือ Frankenstein Protein เลยก็ว่าได้
ราคาที่แท้จริงไม่ใช่แค่เงิน แต่คืออำนาจต่างหากครับ
เบื้องหลังของ lab-grown meat คือบริษัททุนใหญ่ เช่น Eat Just (เจ้าของ Good Meat) Upside Foods Believer Meats CUBIQ Foods และเบื้องหลังอีกชั้นคือ VC ยักษ์ เช่น SoftBank, Temasek, Bill Gates, Tyson Foods ฯลฯ เริ่มเห็นภาพแล้วใช่ไหมครับ
ทุกเจ้ากำลังเร่งวิจัยเพื่อ “จดสิทธิบัตร” กระบวนการผลิต และพันธุกรรมของเซลล์สัตว์ ใช่จ้ะ… พันธุกรรมของวัว หมู ไก่ หรือแม้แต่ปลา ถูกดัดแปลงพันธุกรรมเพื่อให้เพาะง่าย โตไว อยู่ได้นาน และตอบโจทย์การผลิตในเชิงอุตสาหกรรม
ใครจะเลี้ยงวัวเองแล้วทำเนื้อกินเอง อาจโดนฟ้องในอนาคตว่าไปละเมิดพันธุ์สิทธิบัตรที่บริษัทครอบครอง
ต่อไปนี้ถ้าอยากขายเนื้อ ต้องเป็นเจ้าของห้องแล็บถึงแม้บริษัทเหหล่านี้จะบอกว่า “เราจะ democratize protein” คือทำให้ใครๆ ก็เข้าถึงโปรตีนได้ แต่ความจริงคือ ทุกกระบวนการตั้งแต่เซลล์ต้นแบบ อาหารเลี้ยงเซลล์ ยันเครื่องมือในแล็บ ล้วนมีสิทธิบัตร ใครที่ไม่มี license ก็ผลิตไม่ได้ พูดง่ายๆ ก็คือ…
“ของกินที่โตจากเซลล์ในอนาคตจะต้องมีใบอนุญาตจากบริษัท” ไม่มีแผ่นดินไหน ปลูกเอง กินเอง ได้อีกต่อไป
แล้วมันดีต่อสิ่งแวดล้อมจริงไหม? บริษัทแสนดีต่างๆชอบบอกว่าเนื้อแล็บช่วยลดการปล่อยคาร์บอนจากฟาร์มปศุสัตว์ แต่งานวิจัยของ Oxford, UC Davis และมหาวิทยาลัย Wageningen ชี้ว่า การผลิตเนื้อในห้องแล็บใช้พลังงานสูงกว่าปศุสัตว์จริง หลายเท่า และถ้าไม่ใช้พลังงานหมุนเวียน ก็จะปล่อยคาร์บอนมากกว่าการเลี้ยงวัวแบบดั้งเดิมเสียอีก
ตกลงมันคือ Clean Meat หรือ Clean Lie? Clean Meat ที่เขาโฆษณา อาจจะสะอาดแค่ “ภาพ” แต่องค์ประกอบข้างในคือ… -เซลล์สัตว์ที่ดัดแปลงยีนให้โตเร็ว -น้ำเลี้ยงเซลล์ที่มีสารกระตุ้นการเติบโต, ฮอร์โมน, ยาปฏิชีวนะ -ความไม่โปร่งใสเรื่องกระบวนการผลิต -ไม่มีฉลากบอกผู้บริโภคชัดเจน -ยังไม่มีการทดลองระยะยาวว่า “ปลอดภัยหรือไม่”
พรุ่งนี้ที่ไม่มีเกษตรกรจะเป็นยังไง ถ้าโปรตีนทั้งหมดผลิตในแล็บ แล้วเกษตรกรล่ะ? คนเลี้ยงสัตว์ล่ะ? คนเลี้ยงเป็ดไก่หลังบ้านล่ะ? คนปลูกผัก เลี้ยงวัว ทำฟาร์มแบบพื้นถิ่นล่ะ? ทุกคนจะตกขบวนอาหารของโลกใหม่ เพราะเกมนี้ไม่ได้วัดกันที่คุณภาพ แต่วัดกันที่ “ลิขสิทธิ์”
เรากำลังกินอนาคตที่เราไม่ได้เลือก ในชื่อของ “เทคโนโลยี” ในคราบของ “ทางเลือก” ในความนิยมของ "super food" แต่แท้จริงแล้ว เราอาจกำลังแลก สิทธิการควบคุมอาหาร ไปกับ “คำสัญญาว่าโลกจะดีขึ้น” ไม่ต่างอะไรจากการเอาอาหารไปวางไว้ในห้องแล็บ และล็อกประตูเอาไว้ให้คนไม่กี่คนถือกุญแจ
not your key, not your free เหมือนเพลงที่ผมเขียนไว้ในอัลบั้ม orange cafe ครับ https://youtu.be/k5jUpFXI6Gg?si=4GXOXjYbOpqX9kRb
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ 7776c32d:45558888
2025-04-17 02:05:15
@ 7776c32d:45558888
2025-04-17 02:05:15Opinion about Bitcoin Wallet (android)
I think this was the first self-custody wallet I ever used. I'm really glad it's still maintained and reproducible from source 🤙
WalletScrutiny #nostrOpinion
-
 @ 35da2266:15e70970
2025-04-16 22:45:50
@ 35da2266:15e70970
2025-04-16 22:45:504EimyzmhhmH4plLDC0nv/KQniv8JrJY/2A8svVqsZ8efXrRGCEsrCJwSzvJOrK6sLkfiVcvJ8r3yXW8QDYceQSDjgTDtoxoL+0U1v66lfEvc/OASt/dICMTrrUe5LXFitve6fmhhnJfUie9Smmgd0kpd5q/pzTBeKUwhdV69t6Q3zs7ACAXncojtHjCqORHDcvJq14pwocpqQjqNu0LGoXT81L4RvIBcN/a+QGwHsQMPTnwje0ryCPpp4BsMZx5XIkvagVRWGwI7oA4361lGer0c1Rx0cxphETaGL3oNlEQGGgO0A++VqiVRp5LpHW0JYVRHpGQn++KV2zIhCk9UcwlgxEx2SYg8fXh0G0l2fUo=?iv=wqlunJB3xhRRILfuEfDe9A==
-
 @ 35da2266:15e70970
2025-04-16 22:45:32
@ 35da2266:15e70970
2025-04-16 22:45:328l6NZPYyF14c70PicCbGKhxjGeH+cPjGfK8uqgA996qfftvhkAwKoHV455aRuoxaDxQcT5au92oiEvfskfSbIPHl5uqu4oOmbkdJMMnllQYX/zUpcBDjpzPl2Z/61jLaPS5r0hpOnpw/mefqNoT/sooJCmjdvU6JLuJtGfma8ToWOfWW0rRM4tXbUv0zBBodBSHhvvysO9NMYeIhCUB+SHcH4a6rVlsjuzHY7kq7rGpVRN/bV+FK3EiYHegS8VtxNWeecrQh69a7j02a+xklCGB+xet2Dxq0r+7lfEo17UqEsNombY0qzm5R0QX12aXkWxpHPVG+/WzlCb+REmqtwDwo0S2EJQeXH/JItvmyZ55nPUmzMSvizOV57gs+wNS4MVuWk3vXMkLKSfeUhlXmgBU8QFbwOV3LeLSPsGBVzzzeNtu1yYHRM5lR8NvYt114yu7yp2EaOMDNgvIockN5DrL15TwRs1TmsZhoGmqm9McUiQyHBvZBIF2Pu26HEaeJ/C20rcQIoIatB1gLiR9VYarMNynPOke2AQZAsf3n1Eo=?iv=SBph/Z93dPwAx0qGijw19w==
-
 @ 0b118e40:4edc09cb
2025-04-15 03:50:32
@ 0b118e40:4edc09cb
2025-04-15 03:50:32TL;DR : No.
(This is not a feasibility analysis, but a reflection on philosophical alignment with Bitcoin’s vision).
The moment stablecoins or national currencies gain traction in Bitcoin LN, you can forget about Bitcoin’s position as a purely decentralized medium of exchange. Bitcoin’s position will be undermined.
A Bitcoin-native global economy, where people and businesses transact directly in Bitcoin, is what aligns with its original purpose. This is what we should aim for. This is all we should aim for.
I used to believe stablecoins might help with on/off ramps. But the truth is, if Bitcoin is to function as a true currency, broader global adoption that bypasses traditional financial systems will make those ramps irrelevant.
Eventually, two camps will emerge. One will try to preserve Bitcoin’s purity as a currency. The other will push for everything else in the name of Bitcoin: store-of-value narratives, ETFs, stablecoin collaborations, tokens, pump and dumps, NFTs, and centralized workarounds.
Currency domination, especially by the USD, has long contributed to poverty in the Global South. It deepens inequality and worsens debt burdens. During the Tequila Crisis and the Asian Financial Crisis, countries like Mexico and regions like Southeast Asia suffered massive currency devaluations and defaults because of their dependence on the USD. Every time the US raises interest rates, developing nations experience capital flight, currency drops, and economic hardship. This is not ancient history. It has been happening in the last two years and continues to widen the poverty gap. And as always, it is the poor who suffer the most.
What does this have to do with stablecoins? Stablecoin is your fiat 2.0.
USDT is just currency domination through blockchain. It is pegged to the USD, and if it rides Bitcoin’s Lightning rails, it risks keeping users transacting in USD rather than in Bitcoin itself. That not only undermines Bitcoin’s core purpose, it risks making Bitcoin appear like it is taking sides in the fragile and invisible global currency war.
To counter, people will say “Let all stablecoins come. Peg them to any currency.” But what’s the point of Bitcoin then? To become the new logistics layer for fiat 2.0?
That is not progress. That is regress. It is inviting the very systems Bitcoin was built to disrupt back into the ecosystem.
I believe when you use stablecoins this way, you are not Trojan-horsing Bitcoin into the mainstream. You are letting fiat Trojan-horse its way into Bitcoin. And if you let them in, they will win.
Adding stablecoin into Bitcoin LN is counterproductive to Bitcoin's decentralized ethos.
Bitcoin’s true potential is its ability to provide an alternative to centralized, government-controlled currencies and financial systems. We should stick to the original game plan.
Side note: If you really want to Trojan-horse Bitcoin adoption…
In my country, we have so many mixed races and cross-cultural traditions. During Chinese New Year, if you are married, you give everyone who is not married an “ang pow,” which is money in a red packet. Because we are so deeply integrated, people give money at almost every celebration: Christmas, Eid, Diwali, birthdays, graduations, even funerals.
I recently met up with a friend who just had a baby, and I was more than happy to be the first to give her daughter some Bitcoin. Her first sats. It would not hurt to start giving Bitcoin as gifts. And if someone gets offended that it is not part of their tradition, just get a Bitkey and wrap it up. It is so pretty.
Find more fun and creative ways to spread Bitcoin adoption.
But for goodness’ sake, stop justifying everything else in the name of Bitcoin adoption.
To get a better idea of Fiat 2.0, I mind-mapped Bitcoin on macroeconomy on my scratchpad.

If you take a closer look, it might help you answer a few key questions:
-
Do you want more or less government control over money?
-
Are you a fan of central banks? Then you probably prefer stablecoins.
-
-
 @ 2183e947:f497b975
2025-04-15 00:13:02
@ 2183e947:f497b975
2025-04-15 00:13:02(1) Here is a partial list of p2p bitcoin exchanges and their friends:
- Robosats (custodial escrow)
- Hodlhodl (2-of-3 escrow)
- Peach (2-of-3 escrow)
- Binance P2P (2-of-3 escrow)
- Bisq v1 (either user can send the funds to a custodial escrow, but if neither one does that, the escrow never touches user funds)
- Bisq v2 (no escrow)
(2) In my opinion, bisq2 is the only "true" p2p exchange on the above list. In a true p2p system, the only people who *can* touch the money are the buyer and the seller. Whenever there's an escrow, even one that has to be "triggered" (like in bisq v1), it's not "really" p2p because the escrow serves as a middleman: he can collude with one party or the other to steal user funds, and in some models (e.g. robosats) he can just straight up run off with user funds without needing to collude at all.
(3) In bisq2 (the One True P2P exchange), buyers select sellers solely based on their reputation, and they just directly send them the bitcoin *hoping* they are as honest as their reputation says they are. What I like about this model is that bisq is not involved in bisq2 at all except as a platform to help buyers discover reputable sellers and communicate with them. There are two things I don't like about this "reputation" model: it's hard to get a good reputation, and it's hard to debug payment failures in this context. I've tried to do about 5 trades on bisq2 (as someone with no reputation) and not a single one went through. Four times, everyone ignored my offers or someone accepted it but then abandoned it immediately. Once, someone accepted my offer, but I could not pay their lightning invoice for some reason, so we mutually canceled the trade.
(4) Just because I opined that an exchange with an escrow "doesn't count" as peer-to-peer doesn't mean that's a bad thing. Of the list of exchanges in number 1, I most frequently use robosats, which, per my analysis, sounds like the "worst" one if considered solely on the metric of "which one is the most p2p." But I use it because there are *advantages* to its model: the btc seller doesn't need a reputation to use it (because the escrow is there to ensure he can't cheat, and so the escrow is the trusted third party, not the btc seller) and payment failures are easier to debug because you're always paying one of the coordinators, who tend to be responsive and knowledgeable and can help you figure out how to fix it (it's how they make money, after all).
(5) There are at least two ways to do escrow without a 3rd party. Satoshi Nakamoto outlines one way to do it here: https://satoshi.nakamotoinstitute.org/posts/bitcointalk/threads/169/ Make a 2 of 2 multisig between the btc buyer and the btc seller, and have the btc seller put his btc in that multisig. Then have the btc buyer send the product (fiat money) to the btc seller. When the btc seller receives it, he sends his privkey to the btc buyer, who can now withdraw the money. The advantage of this system is that the buyer has no incentive to "stiff" the seller (by not sending the fiat), because if he does that, he won't get paid. The downside is, if the btc buyer is a troll who just aborts the protocol halfway through the trade, the seller loses his btc and cannot recover it.
(6) There is another way: start out with a 2 of 2 multisig just like above, but instead of having the btc seller fund it by himself, have the buyer and the seller *both* put in the *same amount* in the *same transaction* (i.e. via a coinjoin), and have the btc seller put in a bit "extra" -- like 20% extra. For example, if the btc seller wants $100 in fiat, the multisig would have $220 in it in total -- $120 from the seller and $100 from the buyer. Using this model, the disadvantage mentioned in paragraph number 5 is fixed: the buyer has an incentive now to send the fiat, otherwise he loses the $100 he put in. He only gets his $100 back if the btc seller cosigns to give it to him, which he'll only do once he receives the product. Meanwhile, the seller is *also* incentivized properly: he only gets his *extra* $20 back if the btc buyer cosigns to give it to him, which he'll only do if the transaction he's signing *also* gives him back *his* $100 deposit.
(7) The model described in number 6 exists: https://scrow.exchange/ is a website that implements it as an option, though as far as I'm aware, no one uses it. The downsides of this model are: it's capital intensive, e.g. a trade for $100 involves $220 or more. Also, the btc buyer needs to already *have* btc to post as a bond, so this cannot be his first time acquiring btc (unless someone helps him make his first deposit). Also, a very rich person who does not care about money can still be a troll; they deposit funds into the multisig alongside their counterparty, then abandon the trade, because they have so much money they don't care if they get it back as long as they cause suffering to their counterparty.
(8) I'd like to see more p2p exchanges, and more exchanges like robosats. I want to continue to spread awareness of ways they can improve -- like the protocols mentioned in numbers 5 and 6 -- and help them implement these protocols. If you run an exchange on the list in number 1 or want to start one, reach out to me, I'd love to help.
-
 @ 35da2266:15e70970
2025-04-16 22:45:23
@ 35da2266:15e70970
2025-04-16 22:45:230OL0tgqSzPwaavoDhxp1amC5WvCUg9bSQXW55yz6b7BZ5emFJ/GLZZNHIhnVckoG16fdeLmw3o9K6GEEj6x1ArXGYLfDQHWCkvGmJlWrokxf8EL6gPhtpbkUEo5RZ6ndwwTznR5H9YQFiFe/rhvI97+Rb7JoFSF+nrWZCetIkusu8xxQox3U238BuNUlVreqsBFxpVc5jO1XVX0M5PJl0kKkM8RI5qM1ybaOwJ8cAraP1304Vt1efX+iYnPO7K95+JcYRN4tavEdtqy1SpNsraMAo34JGUTziQEdrGqzjM6rKG3/xqjoHoXFZ33+kwVFDo8vTiIhl+pIkAeLQrFA7RIkHZlowZZn6CO37R8Z7TLKfQZgSRNeC4EOJ4Lv4ULR7FBvFi7lRMfqZMF33x5fUltHK3+0/kFpBwMT1DvSbLVhfU5t5yALPfHWurNJFVw9zZ8dXUUv7d9YtmY06ZbeAX6+THpnG4a9vpIQ9w5LWbnQmkTtBxUrPpfeC/Fvx7NYjQapYwKqkQF8OfTSre0FRzIa5b4SrBLO1gpEDXHHnfaYV6eq6MVEtqUoZnFwWSq42ABwF/wKIzE+ofdNkISCSAb93woa9DcyU+WAwAJBiQYxGUGEB0hYnh7oDwoY3roeYOHk+ruAIRYAKu3mUzg4SlT8BUedKPZglU4B8cFtb9Te3PSXZD1nXxmluFlPxuhV/o44+8QZ4g08urSAV2PFsQ==?iv=4u1hEphYhLWkGEvq+Jp1/A==
-
 @ 35da2266:15e70970
2025-04-16 22:26:55
@ 35da2266:15e70970
2025-04-16 22:26:550uKO4r+WwogO34up9lu1CuIfR6YzkiEoN2Anyiqc6+CKJaREAgvMBeQliTvz34Fm1PymGPb0QjN2kGs5zCY8BrHyFUCjGF5nHpC6mGjQzBbeL1PFQDUsF9QcgGptUstlAMsP8HaYdK8fxG5/5ML+p+yRUR/HuRf4H7Tpwd4QMba+IzKimy/3EstVPe+EQcWbbZSw/yQTsvDoZGPhAX7Hpffg4WfKukOw2KFStKvbbboXqEfcfxlddvpdKr0aU9xKZDvXDKMf/LWl+8ZEqD95lOAv/ymnrtyRgUzjxkHB/1oAIFNnve9yM0EESiYNCVz5NL9mS5W/q/i7SBXRiPb+cbcInuvkKtfcVawpMPqPaCo=?iv=L6Yvtf+8L4j0Puogh15kig==
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 35da2266:15e70970
2025-04-16 22:26:42
@ 35da2266:15e70970
2025-04-16 22:26:42Hy+XUI0rm24WtP3hDswXD4CEvQuDbiMvch19MCvWi0zJmugeUS5O9CGusgJB09ZCmR+9NIhAGPvhOWUh+WnFCQEJL0Shep/1DR3Wkb20/lADUgUnW0JFiTKUYStTCOcH/a3SBBUhj9seo6C6VHwWgJImv7N9dpJLrmivwniDLOGO7wk2G+ZZ5Vf9Ws/RIx/b0OUDP4T5TD9sdZVe+b+q7+McFEXCD7nS841dro1BMdrPyCgV62zeTvdoJwJ2dPAVDKOlhpGjySr22VRO5meW71LaXhlTgmTbxq4R7sZufLqoCSZ2qbmyXJenxopf0ThD/srWu3PVgnTuPTL0L2rDYH+vwwmhP2NhU3JKpE1dzzrslj5v+jLUdaqZ6B1yTLdd9NMkWIkwuEaUyprw2THsvLlmY4VaZ01WT+IQ+O+SSE1g6ugr07M/KEPRxG2d/7F3ttOoDEtr90hj8WTiLulmCM5q+sOR6OSPnPn4tQKM4sHpF8grGQ5sub/TaJAILLa38+2UDat1U6ulKms3BeJIz1FT3jl6wjvmmz3N7Xil0gVCoUyOzRD2YG9RBBpwxPL40i1EZcTmX2x9K6UrEv7T8w==?iv=bl4ZGJ8keKfKYGTyv2OdDQ==
-
 @ 23202132:eab3af30
2025-04-14 20:23:40
@ 23202132:eab3af30
2025-04-14 20:23:40A MixPay é uma plataforma gratuita que permite o recebimento de pagamentos em criptomoedas de forma prática e eficiente. Com a popularidade crescente das criptomoedas, essa modalidade de pagamento está se tornando cada vez mais comum em diversas partes do mundo, incluindo o Brasil, onde alguns municípios, como Rolante, no Rio Grande do Sul, já possuem estabelecimentos que aceitam pagamentos em criptoativos.
Veja um exemplo prático no YouTube https://www.youtube.com/watch?v=FPJ5LqQ19CY
Por que aceitar pagamentos em criptomoedas?
Crescimento global: O uso de criptomoedas para pagamentos de produtos e serviços está em ascensão, impulsionado pela descentralização e pela conveniência que oferecem.
Sem fronteiras: Ideal para quem deseja receber pagamentos internacionais sem taxas elevadas de conversão ou restrições bancárias. Semelhante ao Pix, mas descentralizado: Assim como o Pix revolucionou os pagamentos no Brasil, a MixPay oferece uma experiência similar, mas utilizando criptomoedas, sem a necessidade de intermediários bancários.
Vantagens da MixPay
Gratuita: Não há custos para criar uma conta e começar a receber pagamentos.
Fácil de usar: O processo de recebimento é simples, tanto para comerciantes quanto para consumidores, podendo ser realizado em poucos cliques.
Flexibilidade de moedas: Receba pagamentos em diversas criptomoedas, incluindo Bitcoin (BTC), Ethereum (ETH), USDT e outras.
Conversão automática: A MixPay permite que você receba em uma criptomoeda e converta automaticamente para outra de sua escolha, caso deseje evitar a volatilidade.
Integração fácil: Seja para e-commerces ou estabelecimentos físicos, a MixPay oferece QR Codes, APIs e plugins para integração com seu sistema.
Como começar com a MixPay?
1 - Baixe a carteira Mixin aqui https://messenger.mixin.one/
2 - Com a carteira Mixin instalada clique em https://dashboard.mixpay.me/login e ao abrir o site clique no botão Mixin
3 - Na carteira Mixin clique no leitor de QrCode no canto superior direito e escaneie o site.
Pronto! Você já conectou a sua carteira Mixin com a MixPay. Receba pagamentos em instantes, seja por meio de um QR Code, link de pagamento ou integração com sua loja online.
Se você deseja modernizar seu negócio ou simplesmente começar a explorar o universo das criptomoedas, a MixPay é uma alternativa gratuita, eficiente e que acompanha as tendências atuais.
Para mais informações acesse https://mixpay.me
-
 @ 35da2266:15e70970
2025-04-16 22:26:34
@ 35da2266:15e70970
2025-04-16 22:26:34a7AqjUUHuhLW9JdR23N04knTwbU70SK8oVBIGu6rm/Cg0ZlaM2XWDy78xv0cwYXqIu0RFvO1CtCV79zPlr5D1k4IrSvA+ye3xNSRSL7osJHifqWtyhlcbq+t46UiWxJDEILTkG92YjgoJuHdyEvHeuWSINInCv7fo8bvnZOJTF1YnJQBtmTdXHch59hQ22icI0Abf7nGsh8fElvvIvtiSHboCh9jqyypJsUIBc0wp6TQIoFmKqW+X3JWbIJ0lOlMTmXiqEoZ9qvJB1K0eWLR8pERwXKO3zwIxOEqqOTE2SaecFWgibePwQ3BnYai/F6GcKAnJ0MedBjrbAZWmn+N4wfGyqN62CaTVPWn57D3yFB0EDbC/OwZSRW4rkJPjcawlCBVr2XdLEbOBvzuitavE1kzZQ6l5zqkbhVYcSRhRCtCDEb/zUlMUNtYrB1nYHxibgCN6hnL8CaiAjoOgnVzMcBc6gFGoCJu+hRGTErYJ2RSVPDj9n5BeLEGUO9LNsiPQtXYHP7aNubtOTlFB6icVwVhxi//9A1CCnjPTVD/X1AvM/544c7dtWH3SeRXrVzY?iv=5Zlu0jBwAcvWV1egl6CgaA==
-
 @ 35da2266:15e70970
2025-04-16 22:26:30
@ 35da2266:15e70970
2025-04-16 22:26:30XZ3crp0D8f9lSXrZIG4A5FtlyH2Cx6+2lsLItcGQmWy2DyjGlmIOb25z3bCOiegidk+IRCmCK7kfS5f5G2Xw2eAnDiH6/WSpQUplHThMu7+ZVMF9RDOW/eR4cQPP6emMwZxL/VvO8MPgqI0zQ8JnxcvVbmrBlu8NEUUkh0rowor36CdrshoJzVYdcRndcKBGA7aYw0CRfFoOAf1l71ETLM5lVGKk0PmtcepjueBvXeQKVNVw4FS3SzNlBCubjsy+7PWxT/2XPGgq5NmkpW3PvcUFiHLybLRpFfUBA0QKVsKCE5wIDJa25cO7ks840BICmJqau/iDjvXJeA+DGIqhLmdpzl/BuVry/86t5jygNejjKOoqYSkxJYqysd6Wbd7g15LvRd+cb4rgYL44kXUucyJdrzRjDMuxJQU+/l67FWk+zFeLi6NLUwxBtPU78zXJoJC9aQ+cTHJE5YaXKaa69RgIQmFMsSI6GmKjQQ9Yvx+/2DQGOdyQj+f0AeuF0UCBVj+IpH7Kob2aNL11IlPsSt0TylWhDupClhh3RJ9UPvs=?iv=zEN50OwsSEEtA0V47e+bHA==
-
 @ e97aaffa:2ebd765d
2025-04-14 20:16:59
@ e97aaffa:2ebd765d
2025-04-14 20:16:59Num recente podcast, o Miguel Milhão falou sobre o crash nos mercados financeiros. No meio de muita conversa de macroeconomia e mercados financeiros, o convidado deixou alguns pontos interessantes, mas duas ideias ficaram no meu pensamento, infelizmente, ele não aprofundou, mas é algo que eu quero fazer futuramente.
Perda de paridade
A primeira ideia que o convidado apontou foi, a possibilidade da perda de paridade do papel-moeda e a CBDC, eu nunca tinha pensado neste ponto de vista.
Se os governos não conseguirem retirar de circulação todo o papel-moeda rapidamente, se houver circulação em simultâneo com a CBDC, o papel-moeda poderá ter um premium. Isto faz todo o sentido, os governos poderão dar oficialmente o mesmo valor facial, mas como nas CBDCs existirá mais controlo, restrições e monitorização, as pessoas vão preferir o papel-moeda, vão pagar um premium para manter a sua privacidade.
Na prática, será algo similar ao que acontece em alguns países onde existem algumas controlo de capitais, onde o dólar do mercado negro é superior ao dólar oficial. Os comerciantes também poderão fazer descontos superiores nos produtos quando são pagos com papel-moeda.
Isso poderá provocar um descolar do valor, a mesma moeda com valores diferentes, a oficial e do mercado negro. Isso poderá levar os governos a tomar medidas mais autoritárias para eliminar o papel-moeda de circulação.
Não sei se alguma vez acontecerá, mas é algo que eu tenho que refletir e aprofundar esta ideia.
RBU e Controlo
A outra ideia apontada pelo convidado, a CBDC será uma peça fundamental numa sociedade onde a maioria das pessoas sobrevivem com Rendimento Básico Universal (RBU).
Todos sabemos que a CBDC vai servir para os governos monitorar, fiscalizar e controlar os cidadãos. O ponto que eu nunca tinha pensado, é que esta pode ser essencial para a implementação do RBU. Se chegarmos a esse ponto, será o fim da liberdade dos cidadãos, onde o estado controla quando, quanto e onde o cidadão pode gastar o seu dinheiro. O estado irá determinar o valor do RBU e as CBDC vão determinar onde podes gastá-lo.
Penso que já não existem dúvidas que a AI e a robótica vão revolucionar o mundo laboral, vai provocar uma profunda queda nos postos de trabalho, profissões vão desaparecer ou vão reduzir drasticamente o número de funcionários.
Muitas pessoas consideram que a solução é o RBU, mas eu tenho muitas dificuldades em encontrar viabilidade económica e social numa sociedade onde a maioria recebe o RBU.
É a implementação do conceito: não terá nada, mas será feliz.
Será que as máquinas vão conseguir produzir tudo, o que os seres humanos necessitam, a um custo tão baixo, que vai deixar de ser necessário os humanos trabalharem? Tenho muitas dúvidas que essa possibilidade aconteça, se nós humanos não necessitarmos de trabalhar, vai se perder o incentivo para desenvolver novas tecnologias, gerar inovação e de evoluir a sociedade.
Eu já tenho refletido bastante sobre o RBU, mas por mais que pense, não consigo encontrar uma viabilidade económica para manter isto de pé. Onde vão buscar dinheiro para financiar uma percentagem expressiva de pessoas que sobreviverá com o RBU. Eu só olho para isto, como um comunismo com esteróides, talvez esteja errado.
Além dos problemas econômicos, eu acredito que isso vai gerar problemas sociais e de comportamento, vai gerar uma revolta social. Em primeiro lugar, existe uma parte de seres humanos que são ambiciosos, querem mais coisas, que vão lutar e vão conseguir mais. Depois existe outra parte, que é invejosa, quer ter mais, mas não consegue.
Uma sociedade onde quase ninguém trabalha, existindo demasiado tempo livre, vão emergir vícios e conflitos sociais. As pessoas com tempo para pensar reflectir sobre a sua vida e sobre a sociedade, alguns vão delirar, vão questionar tudo. Por isso, a religião desempenha um papel importante na sociedade, cria moralismo através de dogmas, os crentes não questionam, apenas seguem. Por vezes, a ignorância é uma bênção.
Isto faz lembrar-me o porquê das sociedades monogâmicas tornaram-se mais desenvolvidas, em comparação com as poligâmicas. A monogamia trouxe uma paz social à sociedade, existem muito menos conflitos e guerras, há mais harmonia. Milhões de anos de evolução das espécies, nos humanos e alguns animais, a natureza/genética trouxe um equilíbrio no número de nascimento de elementos masculinos e femininos. Mas nas sociedades poligâmicas, normalmente os homens mais ricos têm várias mulheres, consequentemente haveria outros homens que não teriam nenhuma mulher, isso resulta em maior revolta e conflitos sociais. Isto é pura matemática, se existe quase 50/50, de um homem tem 7 mulheres, isto resulta, que 6 homens não terão qualquer mulher. As religiões ao defenderem a monogamia, ao determinar que era pecado ter mais que uma mulher, resultaram em menos conflitos, numa maior paz social. Isso permitiu um maior desenvolvimento de sociedades monogâmicas, do que as poligâmicas.
Acabei por desviar um pouco do assunto. Além disso, o valor do RBU teria que ser elevado, para que permita aos cidadãos ter acesso ao desporto, aos espetáculos, futebol, viajar, para financiar os seus tempos livres. Se eu já acho difícil arranjar dinheiro para financiar a generalidade dos cidadãos, com produtos e serviços básicos, ainda será mais difícil ou impossível, se tiver que financiar os passatempos.
Em vez do RBU, ainda existe a opção do Imposto sobre o Rendimento Negativo (IRN), minimiza um pouco, mas o problema mantém-se. Aconselho a leitura do artigo do Tiago sobre o IRN.
Mas o mais interessante de tudo, os governos vão criar as CBDC para controlar os cidadãos, com a ideia distópica de criar mais paz social, mas eu acredito que resultará no seu inverso.
São duas ideias que eu tenho que aprofundar, futuramente.
-
 @ 35da2266:15e70970
2025-04-16 22:23:41
@ 35da2266:15e70970
2025-04-16 22:23:41hlVSfXKe9e/fvSZHekA/+5qdm0Qi2QRWDIyM+ozhqKw7eiS8yEv6egkHfVfC57RSffe3BkPCV2yXgx+zfBMAGadtrQfaniazb6sAG6UkQ5fpnDuQ82E5RqUqJ2ppoXyGZ8c4pFvQIuj6fuIiqICWYJC3Egkk56Cpvf4puQTbTbD/6fcP26uJZ23SK4FhnU0MaFHbEITacMMDdAufapjlak9YHNBZr8G/BetySoEWCpfxd6lQW0kHLVjJ0wB4TPjlaIUXmYKDaG10QE8jd5J6UQ2e+KkM+cJDaPNqTtOLUOlfuGBUatK1z4LHxJA4gi76sj72mVge1rrkwbaT2gHZeS6QB+W5DtDHmAwUS91bOUypeuwwr14jArk2hx70caOGGjhU2IJr8bT4LlOlbMY+bHk12CLIRCwuzQdK/N/oC6Itz3/KSIRi/m0XD3VGtUQgP5mGs65n9cXjkREhNKd7ieU9EOyee/fzebL2RUC5JjMBAV9yij8Q7MlD/qfC3BjBaP959WbtRn22VJDrPocrUyg+Yop8OIe3brO+QdYfezjGbaFV+p6ogKHT4m8ClYIj?iv=KAipagrOb84TsUXkLD27JQ==
-
 @ 35da2266:15e70970
2025-04-16 22:23:24
@ 35da2266:15e70970
2025-04-16 22:23:24Adiy9AvFZCuHR1UwkXl8oheT+pKA0gcvwVu9hPVUA0Fr3OdN4NJxs7qYwFYlh0HdlqJfbnThzddKIioWqt4ju9NHWbdQyAZ/PNnfEl8iPOHVDP+fOcB9Gc3vOP6dknUiP3cZJKAA1Z11+8QTpqOZP8Qn48dpLKfGUdeWP1LW5YQSa4YfVpE894Xo6I4j8Gt1+exXwh86HGtAe0UQrBjnZ26+IZjaXgJ35Xu+xSJXn9KW3H8A2Apy4xzvuLiEUngRvQbQGuHBmkFw1j14Hyniw005B2ZyJgy46ij43lWUBsNZKpQk1XiKrqXJgFb9I6Jc2TTt0HCcy4jUwpzfw/qvvW8lvR5Wm1+Uw2JOWj0Og9EwaPjssWlP/Y4tPp+arFyRGjw/FQF8dSacDV4F01JqLPYZW/oAlZKr3ybsb1XXS86C+dhDp38WgWiPBDvLqzGxXIyDBhUxaloDYk9mbFWCIajbXoh1i/yCa8zQ/a1Hg561HXA9rci5edc6ah/MNYdjAQzRcNbAf7QBS24bMMNzSAxAjp24BdQUUfAn/fc7bYwjX9GT9Oefd6OgA5jfNelv?iv=qAlON7S2yHUCqSwGCcaWKQ==
-
 @ c21b1a6c:0cd4d170
2025-04-14 14:41:20
@ c21b1a6c:0cd4d170
2025-04-14 14:41:20🧾 Progress Report Two
Hey everyone! I’m back with another progress report for Formstr, a part of the now completed grant from nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f . This update covers everything we’ve built since the last milestone — including polish, performance, power features, and plenty of bug-squashing.
🏗️ What’s New Since Last Time?
This quarter was less about foundational rewrites and more about production hardening and real-world feedback. With users now onboard, our focus shifted to polishing UX, fixing issues, and adding new features that made Formstr easier and more powerful to use.
✨ New Features & UX Improvements
- Edit Existing Forms
- Form Templates
- Drag & Drop Enhancements (especially for mobile)
- New Public Forms UX (card-style layout)
- FAQ & Support Sections
- Relay Modal for Publishing
- Skeleton Loaders and subtle UI Polish
🐛 Major Bug Fixes
- Fixed broken CSV exports when responses were empty
- Cleaned up mobile rendering issues for public forms
- Resolved blank.ts export issues and global form bugs
- Fixed invalid
npubstrings in the admin flow - Patched response handling for private forms
- Lots of small fixes for titles, drafts, embedded form URLs, etc.
🔐 Access Control & Privacy
- Made forms private by default
- Fixed multiple issues around form visibility, access control UIs, and anonymous submissions
- Improved detection of pubkey issues in shared forms
🚧 Some Notable In-Progress Features
The following features are actively being developed, and many are nearing completion:
-
Conditional Questions:
This one’s been tough to crack, but we’re close!
Work in progress bykeralissand myself:
👉 PR #252 -
Downloadable Forms:
Fully-contained downloadable HTML versions of forms.
Being led bycasyazmonwith initial code by Basanta Goswami
👉 PR #274 -
OLLAMA Integration (Self-Hosted LLMs):
Users will be able to create forms using locally hosted LLMs.
PR byashu01304
👉 PR #247 -
Sections in Forms:
Work just started on adding section support!
Small PoC PR bykeraliss:
👉 PR #217
🙌 Huge Thanks to New Contributors
We've had amazing contributors this cycle. Big thanks to:
- Aashutosh Gandhi (ashu01304) – drag-and-drop enhancements, OLLAMA integration
- Amaresh Prasad (devAmaresh) – fixed npub and access bugs
- Biresh Biswas (Billa05) – skeleton loaders
- Shashank Shekhar Singh (Shashankss1205) – bugfixes, co-authored image patches
- Akap Azmon Deh-nji (casyazmon) – CSV fixes, downloadable forms
- Manas Ranjan Dash (mdash3735) – bug fixes
- Basanta Goswami – initial groundwork for downloadable forms
- keraliss – ongoing work on conditional questions and sections
We also registered for the Summer of Bitcoin program and have been receiving contributions from some incredibly bright new applicants.
🔍 What’s Still Coming?
From the wishlist I committed to during the grant, here’s what’s still in the oven:
-[x] Upgrade to nip-44 - [x] Access Controlled Forms: A Form will be able to have multiple admins and Editors. - [x] Private Forms and Fixed Participants: Enncrypt a form and only allow certain npubs to fill it. - [x] Edit Past Forms: Being able to edit an existing form. - [x] Edit Past Forms
- [ ] Conditional Rendering (in progress)
- [ ] Sections (just started)
- [ ] Integrations - OLLAMA / AI-based Form Generation (near complete)
- [ ] Paid Surveys
- [ ] NIP-42 Private Relay support
❌ What’s De-Prioritized?
- Nothing is de-prioritized now especially since Ollama Integration got re-prioritized (thanks to Summer Of Bitcoin). We are a little delayed on Private Relays support but it's now becoming a priority and in active development. Zap Surveys will be coming soon too.
💸 How Funds Were Used
- Paid individual contributors for their work.
- Living expenses to allow full-time focus on development
🧠 Closing Thoughts
Things feel like they’re coming together now. We’re out of "beta hell", starting to see real adoption, and most importantly, gathering feedback from real users. That’s helping us make smarter choices and move fast without breaking too much.
Stay tuned for the next big drop — and in the meantime, try creating a form at formstr.app, and let me know what you think!
-
 @ 35da2266:15e70970
2025-04-16 22:22:39
@ 35da2266:15e70970
2025-04-16 22:22:39Q7baVGp93Od0qDcvFWvotn3WJzwEinU8m7vHADa6prAZwHWVXDwggHU8+hbX/qdtGIjezOohlgAeOKS6p7vtCu5yA/ybXXRmgoNJxOMeSwRG4sL+Romo9ZmZREY7DVSPfkQQ2Z7refm/JKNP6vP3+MOqqlWxlRzICyj3DZZGGMfd8uBBI4YQj77UMbH6PjwgxPGh0uFyri0SIPzocciCMQwb3Se+POuM2s4jaseeBywLJ+Y66E91dHxOIzub6G/TimyhTPxUdEFygT5v4jVGcnn/YGR5qQqILTD8llNMJasTH0KO82yvmw4WRg+HzN+a42iZcJKjZR0sl6RbsZAYUiBYYvvJ7MT4F1nMmSP1+fg=?iv=mIOrW9I6J5sCS9K4S+i6Qg==
-
 @ df67f9a7:2d4fc200
2025-04-16 22:13:20
@ df67f9a7:2d4fc200
2025-04-16 22:13:20Businesses want Nostr, but Nostr is not ready for business. What can be done?
TLDR :
What Nostr brings to business apps…
- Get your brands in front of users with your choice of SEO and Algos that YOU control.
- Access unlimited public user data from across the network without fees or permission.
- Keep your business data private, while "releasing" liability for other data collected by your apps.
- Build one app to reach a diversity of users from across the network, even from other apps.
- Build your own tech and to use it as you wish. No gate keepers or code review process.
Businesses want Nostr.
- Businesses want reliable SEO and socials to put their brands in front of users, rather than arbitrary gate keepers, censoring the marketplace on a whim.
- Businesses want open access to harvest public data for free on a soveregnty respecting network, rather than paying gate keepers for access to user data of questionalble origin.
- Businesses want the freedom to NOT take ownership of certain user data collected by their apps, rather than being liabile for moderation and safe handling on their private infrastructure.
- Busineses want a single open protocol on which to build their apps, with unlimited potential and a diversity of shared users from other apps, rather than multiple siloed networks with difering APIs and demographics.
- Businesses want to own the technology they build and to use it as they wish, rather than submit their code for approval and control by arbitrary gate keepers.
But Nostr is not ready for business.
- Businesses DON'T want proprietary app data stored publicly as signed Nostr events on user specified relays.
- Businesses DON'T want to have to specify, or be constrained by, or even navigate the complexity of Nostr NIP standards for every novel kind of content that their apps generate.
- Businesses DON'T want to "open source" their entire suite of native apps JUST to assure end users that Nostr private keys are being safely handled.
- Businesses DON'T want to have to "rewrite" their entire app backend just to accomodate the Nostr way of "users sign events but dont actually login to your server" auth architecture.
- Businesses DONT want to suffer DDOS from bots and bad actors, or to expose their users to unwanted content, or even to have their own content disappear a sea of spam and misinformation.
Here’s what can be done.
- More tools and services for private business apps to coexist with freedom tech, and even thrive together, on the Nostr network.
- Extensible Webs of Trust algos for discovery and reach into any audience or demographic of trusted users.
- WoT powered standard APIs for exposing content to Nostr (and other business apps) from within a “black box” business app.
- HTTP AUTH (NIP 98) integration for business apps, allowing users to create local content WITHOUT needing discrete signatures or “linked” user accounts.
- Frost compatible “login“ for business apps, allowing users to paste “disposable” nsecs into proprietary clients without fear of their “cold” nsec being compromised.
- Support for “incremental” (and voluntary) adoption of freedom tech into existing business apps, with easy off-ramps for businesses to transfer more and more siloed data onto the “public” network.
Thoughts so far…
-
 @ 4e088f30:744b1792
2025-04-14 12:38:12
@ 4e088f30:744b1792
2025-04-14 12:38:12Pouco menos de um mês antes de sua morte, minha mãe escreveu um texto com suas reflexões sobre a carta dezesseis do conjunto de cartas que eu criei. Ela estava lendo com a fonoaudióloga que a atendia e me contou. Eu disse que queria ouvir a reflexão, e um dia ela gravou um áudio para mim.
A carta dizia assim:
Ajo como borboleta que vai contra a força da vida ao sair do casulo tentando controlar o modo como será vista. Não percebo que tudo o que precisa ser feito agora é me entregar às minhas próprias asas.
Se a borboleta sai do casulo para ser vista como idealiza, o que ela deixa de ver, o que ela deixa de nutrir na vida?
Um dos trechos do texto que ela escreveu era:
“Você pode me ver?”
E eu me pergunto: será que tenho coragem de vê-la por inteiro? Ver sem palavras, sem conceitos, sem julgamentos, sem projeções? Será que tenho coragem de apenas ver quem ela é?
–
Outro dia, estava na casa dela - e o que mais me interessa sempre são seus cadernos - eu encontrei um que ainda não tinha visto. Parece que ela o usava em meados dos anos 90. Eu o abri e encontrei o nome Elizabeth Kubler Ross e eu tinha lido alguns livros dela alguns anos atrás, quando comecei a mergulhar em estudos sobre cuidados paliativos, morte e luto, então achei oportuno e li o que estava escrito:
“Depois de passar por todas as provas para as quais fomos mandados à terra como parte de nosso aprendizado, podemos nos formar. Podemos sair do nosso corpo, que aprisiona a alma como um casulo aprisiona a futura borboleta e, no momento certo, deixá-lo para trás. E estaremos livres da dor, livres dos medos e livres das preocupações… Livres como uma borboleta voltando para casa, para Deus… em um lugar onde nunca estamos sós, onde continuamos a crescer, a cantar, a dançar, onde estamos com aqueles que amamos e cercados de mais amor que jamais poderemos imaginar.” Elizabeth Kubler Ross, M.D (A roda da vida)
Antes de ouvir o que ela tinha escrito, eu disse que ela estava confiando na fonoaudióloga para se abrir e isso ia ajudá-la a florescer, ela emendou com “largar o casulo e virar borboleta”. Ela se sentia ainda emaranhada no casulo. No último ano ela falou algumas vezes sobre a necessidade de desapegar, sobre a única dificuldade dela ser soltar o apego a nós, os filhos dela. Mas ela foi fazendo o trabalho de soltar e soltar e soltar, até que se entregou às suas asas que sempre foram lindas e brilhantes a cada metamorfose em vida, e agora sendo vida.
Começo essa jornada, que ainda não sei o que será - embora tenha alguns desejos, com esses escritos, que ofereço à Vida, que já foi chamada de Glória e de minha mãe.
-
 @ 35da2266:15e70970
2025-04-16 21:10:53
@ 35da2266:15e70970
2025-04-16 21:10:532ZNRVCq3cD6lMtvTpYcX7Y1r5ofv9itThjOpvqwglCDpR0af5uwFKnUmjR6Tgmhe9vwGA8cAaUVMCJZj3XehYqRuhjDaRo3kOo/JqrymJOftR9eaQSPgzynGupcjURXMTZ3LzX/YfR3ZByheOsoksb7t7RhAMCYNCi/FcJoUE2WMvrqMvvZpJFa4+dSAXdP3vdUkjkU9Eboj+R3NIkfZJckfWaDNfyLXPrghu03CFZErVqwle1lmdv2AN57cKawAYDUZbwqgj8bpSIzf4lEzj+xPzuBx/AXCBTzsGumU+KxD/eUYU7P7fKRB72r1Ar/zVn6m3NPDGW6YQ1lGVxwWx+xeT4sgWxKFfmakyxJb1oVcHYW+5oCMfggmCUUmgVVzezh22pC5paVdt/+XuOTbqmCxVZHwZ03ncwmd+JN3oIUAj2V4IbqwCI9QZr0k4d5bUg2WDqj5WhjIskcaHSu0zBp33aocri+MLa+T3sEzeXrK4gz6VjwrXEUKyjOAogqU6Hif/GsU8y+6voNBqK3oYdBEVSBiA8UrSgFixPd9/nc=?iv=v9KrIoMHT1d9aqXuqmbkbw==
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ 3c7dc2c5:805642a8
2025-04-16 20:30:54
@ 3c7dc2c5:805642a8
2025-04-16 20:30:54🧠Quote(s) of the week:
'Let me understand…
I saved 30% of my income in Bitcoin over the last five years at an average price of $30,000. I now have 4.25 years of my income in savings.
Within 5 years, bitcoin goes to $500,000. I now have 25 years of my income in savings. I stop saving at this point and simply live off 100% of my income, avoiding selling any Bitcoin.
Within 15 years, Bitcoin goes to $15,000,000. I now have 750 years of my income in savings. I retire and live on >10x my yearly income for the rest of my life, and pass on generational wealth to my children.
Let me understand… why you didn’t listen to the maxis.' - Bit Paine
🧡Bitcoin news🧡
https://i.ibb.co/1fYbX77F/Go-R7-ZJu-Ww-AA0-Xy-Q.jpg
On the 7th of April:
➡️'Bitcoin has retraced to the 350DMA at ~$76,000! Historically, one of the strongest levels of support for Bitcoin during bull cycles...' - Bitcoin Magazine Pro
➡️ 'Tuttle just filed for a first-of-its-kind ETF: a Double Short MicroStrategy ETF. It aims to profit by shorting both the 2x long ($MSTU) and 2x short ($MSTZ) MSTR ETFs, betting on their decay from daily resets.' - Bitcoin News
➡️3$ billion community bank Union Savings discloses first Bitcoin exposure.
➡️The Rational Root: Bitcoin would have to fall below $64K by next week for the spiral chart to cross the 2021 cycle's first peak (~$64K on Apr 13) Well, that didn't happen. So for now the chart is still valid.
Meanwhile, PlanB was only off by about $320k so far for his April price prediction. Yikes! (I have to admit I fully bought into three S2F models when he came out with it back in 2018)
Personally, I am not fixed on the short-term price, listening to any crypto influencer's "prediction" is like believing in Santa Claus. (Almost) all TA is wrong, very little is useful in the end, and nobody knows shit..including myself.
➡️WHITE HOUSE: “The reserve function of the dollar has caused persistent currency distortions” We’re moving toward a global, distributed, neutral reserve asset for all. You have never needed Bitcoin more than at this moment.
https://i.ibb.co/KckFJTJh/Gn9ae9-XQAEi-1-V.jpg
On the 8th of April:
➡️'Bitcoin's hashrate surpassed 1 zetahash for the first time earlier this week. This means that, in aggregate, miners around the world produced 10^21 hashes per second for some time. 1 sextillion hashes. 1,000,000,000,000,000,000,000.' -TFTC
➡️'Strategy paused Bitcoin buys last week and clarified that shareholders don’t own its BTC. Not your keys, not your coins.' -TFCT Which isn't really news. Common sense: holding exposure, not ownership. "We may be required to sell bitcoin to satisfy our financial obligations, and we may be required to make such sales at prices below our cost basis or that are otherwise unfavorable."
➡️BlackRock expands Bitcoin custody beyond Coinbase. SEC filings reveal Anchorage Digital will safeguard a portion of BTC for BlackRock’s $45B iShares Bitcoin Trust. BlackRock cites the move as part of its “ongoing risk management” and growing presence in digital assets.
➡️Phoenix Wallet is back in the USA. Why are they back?
'We welcome the "Ending Regulation By Prosecution" memo by the US DAG, and the clarity it provides for developers and operators of Bitcoin software. This is consistent with Executive Order 14178 which recognized the importance of "protecting and promoting the ability of individual citizens and private-sector entities alike to [...] develop and deploy software [and] transact with other persons [...] and to maintain self-custody". We are happy to make our products available again in the USA.'
➡️The World Food Program USA now accepts bitcoin! WFP is the world’s largest humanitarian organization and part of the United Nations. Chief Philanthropy Officer says, “Embracing new technologies like cryptocurrency isn’t just a choice—it’s necessary.”
➡️Mastercard partners with Kraken to allow European users to spend Bitcoin at over 150 million merchants worldwide.
On the 9th of April:
➡️VanEck confirms that China and Russia are settling energy trades in Bitcoin. On top of that, the $115 billion VanEck stated on President Trump's tariffs the following: "Bitcoin is evolving from a speculative asset into a functional monetary tool—particularly in economies looking to bypass the dollar and reduce exposure to U.S.-led financial systems."
Meanwhile on the same day...
➡️The United States Secretary of the Treasury Scott Bessent just ended his speech this morning by saying, “We will take a close look at regulatory impediments to the blockchain, stablecoins, and new payment systems”
➡️Pakistan plans to allocate part of its surplus electricity to Bitcoin mining, Reuters reports.
➡️'In the Swedish Parliament: “No plans for a national Bitcoin reserve – that wouldn’t be wise. We will focus on safe assets that can help us in times of crisis.” A “safe” asset—or an asset to control? Bitcoin is neutral, borderless, and unconfiscatable. It’s the hedge modern nations need.' - BT-Chick
Watch the video here
What are safe assets? Does the S&P have more volatility? US treasuries? haha How can something be more liquid than Bitcoin which trades 24/7/365 on a global scale? What is "safe" is keywords for centralized and controlled. I am not surprised though, they are one of the most conservative countries in the world, HFSP! Tack!
On a side note, Christian Ander on X: "Meeting with an MP on Monday to push the idea of a Swedish Bitcoin reserve. Interest is growing across parties—but still a "no" for now. This has never been discussed this much in Parliament. Clear trend: younger MPs are driving it, and older ones blocking it. Vote accordingly."
➡️The world’s largest credit ratings agency, S&P Global Ratings says, ‘We are focused on Bitcoin. We are focused on its characteristics as an alternative form of money, and the fact it’s decentralized and geopolitically neutral. We are starting to see adoption’ - Reuters Business
➡️Laurastacksats gave a lesson about Bitcoin to an economics class at the University of Bologna, in Italy: the oldest university in the world.
➡️ On this day, Bitcoin accumulation addresses received 48,575 BTC, the largest single-day inflow since February 2022, per CryptoQuant.
On the 10th of April:
➡️'After utterly massive outperformance in the years and decades prior, Warren Buffett's Berkshire Hathaway is about even with simply owning gold since 1998, or about 27 years ago.' - Lyn Alden
https://i.ibb.co/cSqWStcC/Go-I-3-J4-Xg-AATd-Jd.png
if you want to understand what interest rates do to investors, this tweet and graph would be a good immediate transmission on the nature of fake economies. Just be like Warren Buffet, without all the work. Just buy and hold a store of value. Bitcoin!
➡️The $30 billion public company founded by Jack Dorsey, Blocks, just released an open-source dashboard to make Bitcoin more accessible and transparent for corporate treasuries, helping lower the operational barriers for companies looking to add Bitcoin to their balance sheets.
➡️'The S&P 500 is as volatile as Bitcoin now, (and a day later) the S&P 500 is now more volatile than Bitcoin. A 77% standard deviation is NUTS, it's normally 10-15%.' - Eric Balchunas
Stocks merely adopted the volatility. Bitcoin was born in it. No more excuses for TradFi for saying Bitcoin is too volatile.
https://i.ibb.co/1GM2ghtQ/Go-La-Pkd-W8-AAJjz-C.png
For those who think Bitcoin is too volatile.
➡️'One of these things is not like the others. Change in currency supply (updated through 2024): bitcoin vs. global reserve currencies.' -Peter Parker https://i.ibb.co/5QjQ7Rf/Go-Mblov-Wk-AAz4-ZN.png
➡️S&P Global: “Bitcoin holdings may provide a hedge against long-term debasement of fiat currency through inflation, due to bitcoin's finite supply. Its value may also be driven by geopolitical factors if its security and decentralized nature lead to its increasing adoption as a reserve asset.”
➡️Parker Lewis: With or without Bessent, the Fed is functionally leveraging the US financial system by draining the system of dollar liquidity. Taking out dollars doesn't make the debt go away. Eventually, it breaks and the Fed will have to print even more money. It goes on and on until...Bitcoin.
https://i.ibb.co/MDNt07WS/Go-MV-Ho-WYAASy-M4.png
➡️Florida's House Bill 487 unanimously passed the House Insurance and Banking Subcommittee, proposing to allow the investment of up to 10% of key public funds in Bitcoin. The bill must now clear three more committees before reaching the full House and Senate for a vote.
➡️US investors are increasingly buying Bitcoin as a hedge against a weakening dollar, reflecting broader concerns about capital exodus from US financial markets, per 10x Research. "it remains premature to adopt a bullish stance."
On the 11th of April:
➡️Pakistan plans to leverage part of its 10,000 megawatts in surplus electricity for Bitcoin mining, per News Desk.
➡️Arizona PASSES Bitcoin Mining Rights Bill! The bill protects anyone running a node or mining digital assets from zoning or usage bans. Voted 17 - 12 in favor!
➡️'Former UK Prime Minister Liz Truss says Bitcoin is “a tool for taking power away from government.” “The bureaucracy knows perfectly well that it is an antidote to their power which is why they hate it.” - Simply Bitcoin
On the 12th of April:
➡️The White House official says. The U.S. may tap gold reserves to buy Bitcoin. If there is any gold in reserve of course! And this is only one senior White House official hinting...
On the 13th of April:
https://i.ibb.co/spBGXChM/Go-Zi7-Ok-XIAAo-B6.jpg
➡️Bitcoin outperforms the NASDAQ in every single timeframe. Bear in mind, that the NASDAQ outperforms the S&P 500, Dow Jones, and Gold. Outperforming short-term in a correction is impressive. Outperforming long-term is simply expected. In the end, everything is going to zero against Bitcoin.
➡️'Trump’s exemption of phones, laptops, and chips from his 145% China tariffs spares HS code 8471, which covers Bitcoin miners. This is a major win for US Bitcoin mining companies, who were staring down crippling price hikes on new rigs.' -Bitcoin News
➡️'The Bitcoin Network just broke ONE SEXTILLION HASHES (1k EH/s) for the first time in history!! 1,000,000,000,000,000,000,000 (one thousand million million million)
https://i.ibb.co/yFd0mJ0M/Gob-O6g-DWMAAj-RJq.jpg
FOR COMPARISON: - There are 1 sextillion grains of sand on Earth. - You could fit 615 earths in a flat layer with an area of one sextillion square centimeters. - There are about 6 sextillion cups of water in all the oceans of the world.
Bitcoin mining power is f* INSANE!' - CarlBMenger
On the 14th of April:
➡️Strategy has acquired 3,459 BTC for ~$285.8 million at ~$82,618 per Bitcoin and has achieved a BTC Yield of 11.4% YTD 2025. As of 4/13/2025, Strategy holds 531,644 Bitcoin acquired for ~$35.92 billion at ~$67,556 per bitcoin.
➡️On the same day, Japanese public company Metaplanet buys 319 Bitcoin for $26.3 million.
➡️'Tether will deploy its existing and future Bitcoin hashrate to OCEAN, the mining pool launched by Bitcoin Core developer Luke Dashjr. Tether says supporting decentralized mining is key to protecting Bitcoin’s long-term integrity.' - Bitcoin News
➡️Publicly traded HK Asia Holdings bought 10 Bitcoin worth $806,671 for its balance sheet.
➡️Public companies added 95,431 BTC to their balance sheets in Q1 2025. 12 new firms joined. Holdings now total 688K BTC worth $57B. - Bitwise
https://i.ibb.co/DPmshn5H/Goh-ONkl-X0-AAp-OVe.jpg
💸Traditional Finance / Macro:
On the 7th of April:
👉🏽The Hang Seng just closed at 19,828, down 3,021 points or 13.2%, officially entering a bear market, down 20% from its March peak. In China, over 2,000 stocks hit the limit down, and the CSI 1000 futures plunged 10%, also hitting its trading halt limit.
On the 8th of April:
👉🏽Apple flies in 5 planes full of iPhones to avoid US tariffs.
👉🏽'THE S&P 500 OFFICIALLY ERASES +4.5% GAIN AND TURNS RED ON THE DAY. $2.3 TRILLION erased over the last 3 hours. On a point basis, the S&P 500 just posted its largest intraday reversal in history, even larger than 2020, 2008, and 2001. You have just witnessed history.' -TKL
On the 10th of April:
👉🏽The amount of SPY calls increased by over 10x literally 10 min before the announcement. It's very obvious that Trump's "now is a good time to buy" tweet was a way for insider traders to have plausible deniability.
https://i.ibb.co/TxpKMrbk/Go-IB-P8-XYAEp-YV5.png
Explanation: SPY is a way to buy/sell the S&P 500. When you buy a SPY 504 call, it gives you the right (for a fee) to buy a stock of SPY from someone at $504 at any time If it goes up to 554, you make (50 dollars - the fee).
Just so non-traders really understand what happened here: Right before the S&P 500 (SPY) suddenly spiked, someone bought a huge number of call options — bets that the index would go up that same day. These were zero-day options, meaning they expire worthless by the end of the day unless SPY rises quickly. At the time, they were almost worthless. Then, SPY shot up. Those dirt-cheap options exploded in value. A $100K bet turned into $21 million in minutes. That green spike before the jump is not luck. It’s foreknowledge. Someone knew exactly what was about to happen.
🏦Banks:
👉🏽 no news
🌎Macro/Geopolitics:
The current state of Macro & Geopolitics can be summed up like this: Everything about current market dynamics is just ‘Madness!’ Economic policy uncertainty is TWICE the level during the Pandemic.
https://i.ibb.co/SXxTRtMt/Go-Vss-Sq-Wg-AEZAP4.jpg
On the 7th of April:
👉🏽A great post by Ray Dalio on X says tariffs are just the start. In the end, it's about a breakdown of the economic/monetary order (excessive global debt) & the global geopolitical order (US vs China). Basically, Trump is forcing the Fourth Turning through.
https://x.com/RayDalio/status/1909296189473693729 https://i.ibb.co/d0JqLqX9/Go-AO57n-W0-AADosd.jpg
I would say we are at stage 13 - 14.
Tariffs are a symptom of bigger problems. Don’t let arguments about tariffs distract us from solving the bigger problems. Also, governments are dysfunctional and life is hard. It’s the controlled demolition of a dying global system built on cheap Chinese labor, Wall Street debt games, and Washington sellouts. Ray sees the Big Cycle turning.
1) The global debt engine is seizing up. 2) The dollar is cornered by its own inflation. 3) The supply chain is a foreign hostage situation. 4) And the (U.S.) middle class got hollowed out so Davos could cash in.
To summarize: - Tariffs are a symptom, not the core issue. - Economic: Unsustainable debt, trade imbalances. - Political: Inequality fuels instability. - Geopolitical: Shift to a multipolar world. - Natural disasters: More frequent, disruptive. - Tech: AI reshapes economies and politics. - Key takeaway: Forces are linked; study history for future insight.
👉🏽On that same day: China restricts exports of seven rare earth metals to all countries.
👉🏽Lobby scandal: Between 2021 and 2023, NGOs received over €7 billion in support from the European budget. The European Court of Auditors has criticized the lack of transparency in EU funding to NGOs. There is a particular lack of reliable information and insufficient oversight. The European Commission funneled billions of euros to NGOs to promote its own policies and discredit opponents, as now also acknowledged by the European Court of Auditors. With a dubious leading role played by Frans Timmermans and Diederik Samsom.
For the Dutch readers:
https://fd.nl/samenleving/1551598/europese-rekenkamer-kritisch-over-financiering-ngos
👉🏽 'When a university with a $53 billion endowment needs to tap the bond market in this environment, it just tells you just how illiquid their investments really are.' -Mr. Vix Or is it just the game that you need to play? It is just a whole lot easier to do a debt raise than go to all stakeholders to adjust the allocation of the AUM, as all is earmarked, it would be a lengthy process.
https://i.ibb.co/mC0x8gdv/Gn8uzrn-Wk-AEJt6-G.jpg
They tapped the bond market in every prior year and they are rated aaa by ratings agencies. It isn’t just a function of the illiquidity of their investments. They hold about $3 billion that could be liquidated in one day or less (according to their financial statements). The real problem is that a vast majority of an endowment is earmarked for specific purposes—not that it is invested in illiquids.
On the 8th of April:
👉🏽President Trump says "China wants to make a deal, badly, but they don't know how to get it started." He also says that "we have the probability of a great deal" with South Korea after a call with their President.
Scott Bessent, US Treasury: Almost 70 countries have now approached us wanting to help rebalance global trade.
Regarding Bessent, read the following: an excellent thread. 'The Bessent Short' explained, so even you and I can understand it.
thread.exceptional.https://x.com/sethjlevy/status/1909634800136212608
This is a very interesting narrative. If this plays out this thinking was exceptional. Another excellent thread on Bessent: https://x.com/timjcarden/status/1910440389217312784
👉🏽 The People's Bank of China injects a net 102.5 billion yuan in open market operations. Hello, liquidity!
👉🏽There is now a 98% chance of a 25 bps interest rate cut by the June FOMC meeting.
👉🏽The White House says 104% additional tariffs on China went into EFFECT at noon ET today because China has not removed their 34% tariff on the US, per Fox News. US Dollar vs. Chinese Yuan is going vertical, meaning China's currency is depreciating swiftly.
China's beginning currency devaluation is more than just an economic signal—it's a trigger. Historically, when the yuan weakens, capital doesn’t stay put. It escapes. Some of it flows into gold, some into foreign assets—and a meaningful slice finds its way into Bitcoin.
https://i.ibb.co/KpKSLrHd/Go-HRen8-Xo-AAOpi-H.jpg
Regarding the US and China theme above one more interesting stat: 'One shipyard in China made more commercial ships in 2024 than the total number the US has produced since World War II. The destruction of America’s industrial base is a massive national security threat.' - Geiger Capital
Now Europe is going to invest € 800billion in their 'Europe Army'. I am not saying we are getting a World War III, but the dynamics are interesting.
From your perspective, why the above statement from a US perspective is a bad one... Mother Russia is building combat vehicles & munitions at “an unprecedented pace" according to a U.S. commander in Europe. A reinvigorated Russian defense industrial base is rolling out:
-1,500 tanks,
-3,000 armored vehicles,
& -200 Iskander ballistic & cruise missiles this year.
By comparison, the U.S. builds just
-135 tanks/yr and
-0 / no longer produces Bradley Fighting Vehicles.
China now boasts the world’s largest -navy, -army, -air force, and -strategic rocket force. China’s robust maritime industry is primed to build and repair ships at a wartime tempo. In a drawn-out conflict, China would have the clear advantage in building, repairing, & maintaining warships at sea.' Source: https://www.19fortyfive.com/2025/04/russia-and-chinas-military-production-surge-why-the-u-s-military-is-alarmed/
https://i.ibb.co/6G1Z6Nw/Gn-Qc-LVXYAAo-NH6-1.jpg
This is why the tariffs are happening still not sure I agree with the blanket nature of them. It sounds like the US does not understand the macro picture very well and is very overconfident. But who am I to judge?
On the 9th of April:
👉🏽'Oil prices fall below $57 for the first time since February 2021 as markets price in a global recession.' -TKL
👉🏽The European privacy legislation GDPR is a bureaucratic monster created by the European Commission, which stifles innovation and causes enormous economic damage — especially to SMEs. After 7 years, it’s finally being seriously reviewed. GDPR should never have been introduced.
Brussels finally admits it: GDPR was an economic disaster. No kidding! Here's why this rollback could save Europe's dying tech scene
Here is a great thread:
https://x.com/itsolelehmann/status/1909924693819461993
And for anyone who wants to explore the topic in depth: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3160404
On the 10th of April:
👉🏽'Lots of headlines and rumors about Trump "asking the Supreme Court to fire Powell." Here's what really happened: President Trump asked the Supreme Court to "let him fire top officials at 2 independent agencies," per Bloomberg. This could test whether Trump has the power to fire Fed Chair Powell. Trump did NOT explicitly ask to fire Powell.' - TKL
👉🏽'Gold closed up 3.3% to $3082, the biggest one-day jump since 2023, as traders anticipate much more fiat devaluation. A couple of hours later... And there it is: gold soars to new record high $3165/oz as global trade war turns to a currency war and global devaluation.' -ZeroHedge
Gold prices are flying off the chart. If you can’t tell yet, something is broken. Capital flight to Gold and CHF happening now. Eventually Bitcoin. These are not signs of winning. These are signs of the mother of all debt crises.
On the 11th of April:
👉🏽ZeroHedge: "Absolutely Spectacular Meltdown": The Basis Trade Is Blowing Up, Sparking Multi-Trillion Liquidation Panic:
https://www.zerohedge.com/markets/absolutely-spectacular-meltdown-basis-trade-blowing-sparking-multi-trillion-liquidation
Explanation: The basis trade is when investors buy Treasury bonds and sell their futures, betting on small price gaps to make money. They often borrow a lot to boost profits, but it’s risky. Right now in April 2025, this trade is crashing, like in 2020. Hedge funds are losing big, selling bonds fast, which spikes Treasury yields and shakes markets. It’s a multi-trillion dollar mess, and some fear it could spark a crisis needing a huge Fed bailout, like last time. The chart likely shows yields jumping, signaling this panic.
👉🏽China raises tariffs on U.S. imports to 125%.
Here’s the real question, who gives up first? 1. President Trump 2. China 3. Bond market At this rate, the 10Y Note Yield will be at 5% next week. Inevitably, one of these 3 factors has to give very soon as this is unsustainable. Anyway... https://i.ibb.co/VYXByy2S/Go-ODsv-OWIAAu-M9v.jpg
👉🏽UK millionaires are fleeing in record numbers. In 2024, the UK ranked second only to China in wealth exodus – ahead of even India. People vote with their feet, and it will happen in Europe, and it is concerning.
Great thread: https://x.com/thealepalombo/status/1910327100286115952
👉🏽US 10Y rises to 4.48%, the largest single weekly increase since 2001. U.S. 30-year treasury yields rise to 4.95%, the weekly increase is the biggest since 1982.
On the 11th of April:
👉🏽European Central Bank President Christine Lagarde: ECB is a ready-to-use instrument it has if needed!
On the same day, FED's Kashkari: The Fed has a tool to provide more liquidity. The Fed is reportedly "absolutely" ready to stabilize the market if needed, per Financial Times. Never discount the power of the bond market or the REPO market.
Coughing and clearing my throat for the people in the back: more liquidity, debt, printing money!
James Lavish: "Choose your phrase for translation:
“All roads lead to inflation.”
“Nothing stops this train.”
“The Fed will print again.”
👉🏽'March PPI inflation FALLS to 2.7%, below expectations of 3.3%. Core PPI inflation FALLS to 3.3%, below expectations of 3.6%. We just saw the first month-over-month decline in PPI inflation, down -0.4%, since March 2024. Both CPI and PPI inflation are down SHARPLY.' -TKL
👉🏽The U.S. budget deficit has risen to $1.3 trillion as government debt interest hits record levels. Data released by the Treasury Department on Thursday showed a deficit of $1.307 trillion for the first six months of the 2025 fiscal year, covering the period from October to March. This was the second-highest fiscal year deficit the U.S. has ever seen, with only the $1.706 trillion deficit in the first half of the 2021 fiscal year being larger.
On the 12th of April: 👉🏽M2 Money Supply going parabolic right now. Bitcoin is going parabolic soon. https://i.ibb.co/FL0W19kB/Go-VLj-Dv-Xk-AAol-Dt.jpg
BTC has tracked M2's movements 80% of the time for the past several years.
👉🏽The US publishes reciprocal tariff exclusions for computers, smartphones, and chip-making equipment. TKL: "Let's put the tariff exemptions into perspective: The US imports approximately $100 billion of computers, smartphones, and chip-making equipment from China PER YEAR. A total of $439 billion of goods were imported from China into the US in 2024. This means ~23% of ALL Chinese imports coming to the US are now exempt from "reciprocal tariffs." This is a massive U-Turn in tariff policy."
The bond market is Trump's #1 priority, and everyone knows it now.
Oh fun note, 2 minutes before the close on Friday someone bought $850,000 worth of SPY 554 calls expiring Monday. This morning the US released tariff exclusions...fascinating innit?
👉🏽If said it before and will say it again. It doesn't matter if the U.S. has a red or blue president. The US government has spent $154 billion more in 2025 than it did over the same period in 2024. Unless treasury yields drop, and fast, no amount of DOGE cutting will stop this from spiraling out of control. https://i.ibb.co/WNVJNxqh/Go-VYumq-Xw-AAod-Sv.jpg
👉🏽RAY DALIO ON DOMESTIC & WORLD ORDER “I think that right now, we are at a decision-making point and very close to a recession. I'm worried about something worse than a recession if this isn't handled well. A recession is two negative quarters of GDP, and whether it goes slightly there, we always have those things. We have something that's much more profound. We have a breakdown of the monetary order. We are going to change the monetary order because we cannot spend the amounts of money.
So, we have that problem. And when we talk about the dollar, and we talk about tariffs, we have that. We are having profound changes in our domestic order, and how ruling is existing, and we're having profound changes in the world order. Such times are very much like the 1930s.
I've studied history, and this repeats over and over again. So, if you take tariffs, if you take debt, if you take the rising power challenging existing power, if you take those factors and look at the factors that those changes in the orders, the systems, are very, very disruptive. How that's handled could produce something much worse than a recession…” - NBCNews
Yes, Bitcoin is the new monetary order, and civilizational infrastructure. Got some Bitcoin?
On the 14th of April:
👉🏽'Global net gold purchases by central banks hit 24 tonnes in February, the most since November 2024. This marks the 20th month of net buying over the last 21 months. Central banks are now on track for their 16th consecutive year of net purchases, according to the World Gold Council. Over the last 3 years, world central banks have acquired a massive 3,176 tonnes of gold. Central banks are buying gold like we are in a crisis.' -TKL
https://i.ibb.co/vvsx4qv9/Goh-TQ-n-WYAAm-6-I.jpg
🎁If you have made it this far I would like to give you a little gift, well in this case two gifts:
In April 2023, Tuur Demeester of Adamant Research published what has become another legendary entry in his line of Bitcoin bear market reports dating back to 2012. These pages aged like wine—as important today as they were 2 years ago. Download it here:
https://www.unchained.com/how-to-position-bitcoin-boom
Lyn Alden of Lyn Alden Investment Strategy explains the connection between the capital and financial imbalances the U.S. has with the rest of the world and its trade imbalances which are under so much scrutiny by the current U.S. administration. Alden argues that turbulence in markets, particularly U.S. assets, could continue, and warns listeners not to be exposed beyond their risk limits at a juncture that could be a historic time for markets and the global economy. Recorded April 10, 2025.
https://www.youtube.com/watch?v=TZN_eL_wubQ
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you?
If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 044da344:073a8a0e
2025-04-14 11:41:39
@ 044da344:073a8a0e
2025-04-14 11:41:39Als wir vor gut einem halben Jahr mit den Kolumnen angefangen haben, hatte ich mir das genau so vorgestellt. Ich schreibe auf, was mir in der Woche so passiert ist. Eine Bilanz sozusagen, vielleicht persönlich, vielleicht politisch. Je nachdem. Es ist dann etwas anders gekommen. Manchmal waren ein Buch oder ein Film einfach so stark, dass aus der Kolumne eine Rezension geworden ist. Manchmal wollte ich nur von einem meiner Interviews erzählen und das Besprochene gleich mit den großen Debatten verknüpfen. Und manchmal waren Anregungen von außen umzusetzen, Stichwort KI, Stichwort Frieden.
Wahrscheinlich waren die meisten Wochen auch nicht besonders spannend. Alltag eben. Was soll man davon groß festhalten. Diesmal ist das anders. Sonntag Erich Hambach bei uns im Haus. Ein Interview für die Reihe Im Gespräch. Ich will nicht zu viel vorwegnehmen. Es ging um die Hochfinanz, um den schwarzen Adel, um die Illuminati. Ein Gruselkabinett für alle, die wissen, wo die roten Linien sind zu den Schmuddelkindern. Verschwörungstheorie, pfui. Erich Hambach kann erklären, wie die „Herren des Geldes“ (Untertitel seines neuen Buchs) arbeiten und was man tun kann, um sich ihrem Zugriff zu entziehen. Als die Kameras aus waren, ging es munter weiter mit dem Publikum. Steuerfrei leben, sich auf den Lastenausgleich vorbereiten, Kollateralkonto. Siehe oben. Wir haben dann noch 25 Minuten nachgeschoben, die bei den „Truth Brothers“ zu sehen sein werden, dem Kanal von Erich Hambach.
Montag Dresden. Lesung im Buchhaus Loschwitz. Ich war schon im Juni dort, damals mit dem Buch über die Unterwerfung der Universitäten. Diesmal „Der dressierte Nachwuchs“. Wieder volles Haus. In Loschwitz heißt das: Susanne Dagen, Gastgeberin und Moderatorin, quetscht sich auf einen Hocker zwischen Klavier und Reihe null und sagt: Willkommen zum Gottesdienst. Einige sind zum zweiten Mal da. Neu: Paul Soldan, den ich aus seinen Texten für Multipolar kenne und über sein Buch „Sheikhi“, und Julia Szarvasy, die mich in ihrem Bus für Nuoviso interviewt hat und auf der Ruderboot-Couch. Hinterher kommen (um im Bild zu bleiben) drei U-Boote zu mir. Professoren. Ein Techniker, ein Germanist und ein Medienforscher, der sich sogar mit mir fotografieren lassen will. Dieser Kollege ist nicht an der TU (falls jemand die Fahndung einleiten möchte), aber immerhin. Ich bin oft gefragt worden, ob es an den Unis Gleichgesinnte gibt, und kann jetzt endlich sagen: ja. Ein paar schon.
Versteckt in einer der letzten Dresdner Reihen: Michael Beleites, eine Ikone der DDR-Umweltbewegung und später ein Jahrzehnt lang Beauftragter für die Stasi-Unterlagen in Sachsen. Er hat eine Rezension mitgebracht, die er gerade für die Sezession geschrieben hat, und einen Gedanken, der mich später schlecht schlafen lässt. Müssen wir die Geschichte vom Herbst 1989 umschreiben? Ganz neu ist dieser Gedanke nicht, natürlich nicht. Wer dabei war, hat sich schon damals gefragt, wie die Stimmung so schnell kippen konnte vom Wunsch nach einem anderen, besseren Sozialismus zu Helmut Kohl und seiner D-Mark. Daniela Dahn, wie Michael Beleites seinerzeit in vorderster Front, hat den schwarzen Peter an den Journalismus weitergegeben. Tamtam und Tabu. Eine Kampagne, losgetreten von Horst Teltschik, Kohls wichtigstem Mann, die sich um SED-Skandale drehte und so wie eine Nebelkerze verhüllte, um was es eigentlich ging. Die Herren des Geldes, würde Erich Hambach sagen. „Alte Besitzverhältnisse“ wieder herstellen und damit „alte Machtverhältnisse“, sagt Daniela Dahn. Michael Beleites ergänzt das nun durch das, was er gesehen und erlebt hat, bei der Auflösung des Geheimdienstes in Gera zum Beispiel. Da seien Leute wie er gewesen, natürlich. Legitimiert durch das, was vorher war. Überall im Land seien aber plötzlich auch unbeschriebene Blätter aufgetaucht, laut und damit schnell ganz vorne dran. Ein Forschungsthema, ohne Frage.
Bevor ich das zu Ende gedacht habe, sitze ich im Rudolf-Steiner-Haus, nur ein paar Steinwürfe weg von der Alster. Ich würde gern „Hamburgs Wohnzimmer“ schreiben, aber dazu taugt der Saal im Souterrain dann doch nicht ganz. Immerhin: steuerfinanziert. Geht also doch. Eingeladen hat unter anderem der Nachdenkseiten-Gesprächskreis vor Ort. Thema: Wandel der Universitäten. Wieder sind Kollegen da, auch aus dem Mittelbau und aus der Rentnergeneration, die sich zu erinnern glauben, alles schon erlebt zu haben, damals, in ihrer großen Zeit. Nun ja. Wichtiger: Walter Weber ist da, ein Arzt, Koryphäe in Sachen Krebs, 80 inzwischen, der meinen letzten Auftritt in Hamburg organisiert hat. Große Freiheit, Sommer 2022. Die Sonne schien, und es roch nach Aufbruch. Aus dem ganzen Land waren sie gekommen, aus Nord und Süd, von links bis rechts, aus allen nur denkbaren Bewegungen und Milieus. Corona als Klammer, genau wie der Glaube, dass unsere Zeit jetzt anbricht.
Es kam dann anders, aber das ist hier nicht mein Punkt. Walter Weber, der alte Weggefährte, zieht Bilanz – bei einem Becks in seinem Haus, genau da, wo wir vor drei Jahren in größerer Runde beraten haben. Walter hat inzwischen einen Prozess hinter sich mit knapp zwei Dutzend Verhandlungstagen und den entsprechenden Kosten. Maskenatteste. Was immer wir aufgefahren haben an Beweisanträgen, sagt Walter, es wurde abgeschmettert. Und trotzdem. Wir müssen sie zwingen, sich damit auseinanderzusetzen. Immer wieder. So ähnlich habe ich das zwei Stunden vorher im Steiner-Haus gesagt, mit Vaclav Havel als Referenz. 500 Ärzte, schätzt Walter Weber, haben wie er Atteste ausgestellt. 500 bei einer sechsstelligen Zahl an Kollegen. Sicher gibt es eine Dunkelziffer. Lassen wir es bei den 500, weil Walter Weber hier die Folgen kennt. 80 Prozent von diesen 500 haben Haus- und Praxisdurchsuchungen erlebt. Er selbst zwei, der Spitzenreiter acht. Die Maske war der Test. Als die Spritze kam, wusste jeder, auf was er sich einlassen würde - selbst ein Medienforscher wie ich. Die maskierte Öffentlichkeit, veröffentlicht im Oktober 2020, war mit Sicherheit nicht mein bester Text, aber der, der den meisten Wirbel auslöste und später sogar zweimal vor Gericht verhandelt wurde.
Was bleibt von all den Kämpfen? Wir haben die Leute aus der Vereinzelung geholt, sagt Walter. Die 20 Prozent, die dagegen waren. Wir haben ihnen gezeigt, dass sie nicht allein sind, und diese Leute mobilisiert. Gescheitert sind wir an Schritt drei. Strukturbildung. Es fehlt uns an Geld, Michael. Walter Weber hat an Regionalbüros gebastelt. „Ärzte für Aufklärung“ in Thüringen – und das ist nur eins von vielen Beispielen. Wer weiß, wie viel Geld es in diesem Land gibt und wie viele wirklich reiche Leute, der weiß auch, dass wir hier über Peanuts sprechen. Wem es gut geht, der will, dass alles weiter seinen Gang geht. Der will keine Strukturen für irgendeine Opposition. Walter Weber hat mit einer seiner Nichten gerade „Das siebte Kreuz“ gelesen. Anna Seghers, Schulstoff in der DDR. Weißt du, was ich da gelernt habe, Michael? Echter Widerstand hat zwei Bedingungen. Keine Familie und keine Angst vor dem Tod.
Der Zug nach Berlin ist pünktlich und mein Gastgeber folglich noch nicht da. Gibt’s doch nicht, sagt er. Hat es noch nie gegeben. Über meinen Auftritt im Sprechsaal breite ich den Mantel des Schweigens. Die Idee klang super: Wir machen dort eine Ausstellung mit aktuellen Bildern aus Gaza, gekauft von der dpa, und du, Michael, bringst deine Bücher über Cancel Culture, Jugend und Universitäten zusammen, um zu erklären, warum Deutschland wegschaut. Die kastrierte Öffentlichkeit. Der beste Titel geht ins Leere, wenn niemand weiß, dass ich sprechen werde. Vielleicht ist das so, wenn der eigene Verlag der Veranstalter ist. Jens Fischer Rodrian hat durch einen Zufall erfahren, dass ich da bin, und bringt die CD Voices for Gaza, ganz frisch in der Reihe „Protestnoten“. Auf dem Cover: große Namen von Didi Hallervorden über Tino Eisbrenner, Nirit Sommerfeld und Diether Dehm bis zu Wolfgang Wodarg. Fünf von fast 40. Sorry an die, die ich auslassen musste. Der gleiche Zufall hat Kathrin Schmidt in den Sprechsaal geführt, Mitglied des PEN-Zentrums, Buchpreisträgerin, Maßnahmenkritikerin. Sie hat wie immer ihr Strickzeug dabei.
Ein kleines Publikum, frei von Kameras, erlaubt, in die Tiefen zu tauchen und dabei auch zu riskieren, im Trüben zu fischen. Erich Hambach hätte seine Freude gehabt. Und wer weiß schon, was daraus später wächst. Ein paar Minuten vor Beginn gehe ich durch das Regierungsviertel und höre plötzlich meinen Namen. Eine ARD-Frau, die auf Friedrich Merz wartet. Koalitionsvertrag fertig, Kamera schussbereit. Mein Film über die Duldungspflicht, sagt die Frau und strahlt über das ganze Gesicht. Er ist fertig. Premiere nächste Woche. Sie war bei einem meiner letzten Berliner Vorträge und wird jetzt mit ihrem Namen für ein Produkt stehen, dass so nicht im Ersten laufen kann. Noch nicht, würde Walter Weber sagen. Ende nächsten Jahres, sagt er mir beim Abschied, steht Merkel vor Gericht. Ist der Gedanke erstmal da, so begründet er das sinngemäß, dann ist er nicht mehr aufzuhalten. Mal schauen, wie das jetzt mit der Deutschen Bahn wird bei der Rückfahrt nach Bayern. Ich nehme mir vor, dass wir pünktlich sind.
Freie Akademie für Medien & Journalismus
Bild: Tobias Schönebeck auf Pixabay (Dresden, Blaues Wunder in Loschwitz)
-
 @ 35da2266:15e70970
2025-04-16 18:00:26
@ 35da2266:15e70970
2025-04-16 18:00:26Y4lygZ3LEoXWuJtC8XaOXhzJxACtrNlgVpIZDuEZ4uObp1YL+SaPAIaAaVIUBWvCvzOabX2RxzhQJalv/C3SRCNQmcXGobODPxgz/4BNtSAmmc2UKEHvm1GhWTo6CB0EoOzVS6g97F7Mfas9jsQnwW8qEHUFiy8lSnSeFcGIkAJcUjXzvd8IoZeoF76s0uEFPuQPAtaHUTObCLwHEOj0/YuBkahCFxju9tlU9xlq+tVb0h6eZ1zr+LWW2Riejn4lDDq7D11MvVnTkAFDoW8C+xhU8OT3dX3Vz4XJ7vpKTMplyza1zZVBgD+ALOemLWO9FCEAMmd3x+8HKTZB75rCzxYMNDuIUNxMJFLLwlXu9qk=?iv=4RaKnRhDkvApSsmgJ9TttQ==
-
 @ c066aac5:6a41a034
2025-04-13 23:09:14
@ c066aac5:6a41a034
2025-04-13 23:09:14“If a man is considered guilty For what goes on in his mind Then give me the electric chair For all my future crimes”-Electric Chair by Prince
The very last paragraph of Touré’s 2013 biography of Prince I Would Die 4 U: Why Prince Became an Icon made a very bold claim about the lewd nature of Prince’s music:
“Imagine America as one house on a suburban lane… Prince knocked on America’s door through his music. He came to the door holding a guitar and an umbrella while concealing a Bible. He flirted his way inside the door and told us he had a dirty mind and was controversial, and then he sat down in the living room on the good couch. And, when America’s guard was down, because we thought we were having a conversation about sex, Prince eased out his Bible and said, let me also tell you about my Lord and savior, Jesus Christ.”
Wow. Talk about a Sixth Sense level plot twist! I will say if you’re well versed in Prince’s catalog (I listened to every Prince album released [except for The Black Album because Jack Dorsey is holding it hostage on Tidal] last year) it won’t be as shocking as a surprise as it would be to the unversed listener, but surprising nonetheless considering the content of the man’s lyrics (and life).
Regardless of whether or not Prince achieved this goal of bringing people to Christ via a vehicle of sexy shock value, he was a person of impact. The book by Touré I mentioned earlier is a great picture of the life he lived, and I’m sure there are many others that people can recommend in the comments. He touched many lives and I believe his music will still be listened to for many years to come.
Prince’s method of evangelism may have been unconventional (to say the least), but I still think there is something to be learned from his efforts.
Obviously, worshiping sex or encouraging lust isn’t great. Prince’s view of sex was broken; they didn’t line up with Biblically ordered sex (see his songs Sister, Darling Nikki, Sexy M.F., and many many more). His inability to sustain healthy relationships or make meaningful lasting connections with those around him are a testament to that.
Despite his flaws, his art captured an entire generation - and continues to capture the attention of people seeking true art. His authenticity, raw emotion, and intentionality made for true connection between his music and his listeners. He resonated with people’s souls, and still does today. Perhaps Touré was wrong and Prince didn’t mean to evangelize through his music, but don’t all people stand testament to the powerful work of God?
We are all broken people. Our job is to the use the tools and resources set before us to spread the Gospel. “…we have this treasure in clay jars, so that it may be made clear that this extraordinary power belongs to God and does not come from us.” -2 Corinthians 4:7
The Western Church should consider using the seemingly profane, off limits, unconventional, or even just plain weird in an effort to continue to spread the gospel. On a high level, that’s our good-christian dinner table no-gos: Sex, Money, and Politics. I believe that the Church’s abdication of such conversations is the reason why those are areas of failure for the Church at large. We shouldn’t sin or condone/promote sin. Instead, I’m proposing that like how Prince used sex in his music to get people to learn about Jesus, Christian Bitcoiners should use money (Bitcoin) to do good works and lead people to Jesus in the process. We may just make the world a better place along the way.
“If you're sick of cryin' and tired of tears Then close your eyes and open your ears Listen to the music, listen to the song Listen to your heart, is that so wrong? Stop lookin' in the mirror, there's nothin' to fear Your salvation is near 1,000 light years away from here”-1,000 Light Years From Here by Prince
It doesn’t take a lot of mental effort to see how Christian’s could leverage Bitcoin’s magic for kingdom work. Look Alex Gladstein’s writings. Look at the work that Gridless is doing in Africa. Look at Roya Mahboob’s impact in Afghanistan. Look at the impact of Bitcoin Beach in El Salvador.
Now imagine what the Church (and by the Church, I mean you and I the Christian Bitcoiners) could do with Bitcoin:
A Christian Bitcoiner could help the woman with an abusive husband escape a bad situation with finances intact by teaching her how to use Bitcoin and keep self-custody wallet. An orange-pilled youth group leader could teach the inner city kid in a bad household how to set up a wallet and stack sats without the permission of the dead beat parents or conventional employment. The church bake sale could make things easy via accepting lightning payments, bringing in outsiders for sweet treats and teaching them about how to be a Bitcoin merchant. A church could send funds to a missionary across the world in a christian adverse country instantly without having to involve a single bank, and that missionary would have those funds same-day ready for deployment.
“Everybody's looking for the ladder Everybody wants salvation of the soul The steps you take are no easy road But the reward is great For those who want to go”-The Ladder by Prince
In my own attempts to teach people about the virtues of Bitcoin, I find it usually clicks for people in one of two different ways for the most part:
The first way it clicks is when they can receive and send a lightning payment. The instant funds make a light bulb go off.
The second way is when I show them the humanitarian impact that Bitcoin has had and is counting to have. The use of Bitcoin internationally as a means of humanitarian aid/sovereignty for the less fortunate should shut down any questions like “But what about (insert crapcoin)?” in an instant.
Much like how people get Bitcoin once they see it in action, I believe people will get Jesus when they see Jesus’ Church in action. One of the best ways today the Church can display that action may be through Bitcoin.
Sex was Prince’s trojan horse for something much deeper that he wanted to convey to people. Bitcoin can be the trojan horse for the Church. The Church could gain attention for what they’re doing with Bitcoin similar to the attention that the Human Rights Foundation gets. One might ask why use a trojan horse? I think that Bitcoin adoption itself has been a bit of a trojan horse movement. Your local politicians didn’t bat an eye when they heard about a peer-to-peer e-cash system, but they were all over it when it was presented as a digital gold. Michael Saylor has garnered a lot of hate from the Bitcoin true-believers for presenting Bitcoin as a digital gold as opposed to a currency, but I believe he knows what he’s doing and he’s presenting in this manner on purpose. He might not get gratitude for it from the community, but I believe he’s willing to be the bad guy in order to further the mission (see Christopher Nolan’s The Dark Night [which is arguably a Jesus story]).
Christian Bitcoiner, I challenge you to channel your enthusiasm to do good in your neighborhood. Let the world see your actions and gain a curiosity for what you’re doing. The Bitcoin conversation will make many people think that you’re crazy, that you’re an idiot when it comes to investing, that you’re selling a scam. Much like how people wrote off Prince for being a vulgar musician. Much like how people write off Michael Saylor for misunderstanding Bitcoin. Much like how people wrote off (and continue to write off) Jesus for being a false prophet or the leader of a rebellion.
But there will be someone who sees the work that you do with Bitcoin. The work that the Church will do with Bitcoin. Even if just one soul is saved with Bitcoin, that’s worth the effort.
“Black day, stormy night No love, no hope in sight Don't cry, He is coming Don't die without knowing the cross” -The Cross by Prince
This article was written with help from my wife Elaina freedom@happytavern.co
Feel free to drop your favorite book about Prince, favorite Prince song, or favorite Prince album in the comments
Or, you can drop your favorite Bitcoin as a trojan horse story in the comments
-
 @ 000002de:c05780a7
2025-04-16 20:48:48
@ 000002de:c05780a7
2025-04-16 20:48:48Not only can I be my own bank and run a my own lightning bank. I can have private communications with people anywhere on the planet that only the two of us can read. On top of that I can manufacturer items in my office with this very affordable 3d printer.
Just a thought as I'm printing some items for a party we have coming up. I'm watching the print complete from my phone while I work on the back porch.
We live in an amazing time. It is easy to forget this when we are focused on the stupidity we see online.
originally posted at https://stacker.news/items/945569
-
 @ 1ef61805:f18312cc
2025-04-13 22:40:49
@ 1ef61805:f18312cc
2025-04-13 22:40:49In today’s increasingly surveilled digital world, privacy and security are paramount. OpSec Academy has taken a major step forward by customizing TailsOS to create OpSecOS, an operating system built with the same focus on anonymity and privacy, but enhanced with a suite of peer-reviewed and battle-tested applications. These applications empower users with decentralised tools, ensuring complete control over their digital lives while maintaining the high standards of security and privacy that OpSec Academy stands for.
In this article, we’ll explore the tools available in OpSec Academy’s custom OpSecOS image, highlighting the new and updated features that enhance security, decentralisation, and privacy.
-
Sparrow Wallet (Version 2.1.3) Sparrow Wallet remains one of the most privacy-conscious Bitcoin wallets available. It provides an advanced suite of features such as multi-signature support, coin control, and hardware wallet integration, which allow users to have complete control over their funds. By integrating Sparrow Wallet into OpSecOS, we ensure that Bitcoin transactions are handled with the highest standards of privacy, all while utilising Tor to anonymise transaction data. Peer-Reviewed & Battle-Tested: Sparrow Wallet has been rigorously tested by the privacy community and has earned a reputation for robustness and security. Its commitment to user privacy makes it one of the most trusted Bitcoin wallets in the ecosystem.
-
Feather Wallet (Version 2.7.0) Feather Wallet is a lightweight yet powerful Bitcoin wallet designed with privacy and simplicity in mind. Featuring Tor support and integration with hardware wallets, Feather Wallet ensures that users' private information remains secure while offering an intuitive user experience. By adding Feather Wallet to OpSecOS, we provide an easy-to-use wallet solution without compromising security. Peer-Reviewed & Battle-Tested: Feather Wallet has undergone thorough peer review and is widely regarded as a secure and privacy-focused option for Bitcoin users. Its simplicity and security features have been battle-tested by users in real-world environments.
-
Liana Wallet (Version 10.0) Liana Wallet is a Bitcoin wallet designed with a strong emphasis on long-term security, recovery, and inheritance. It allows users to set up primary keys for regular spending and recovery keys that activate after a specified period of inactivity, making it ideal for scenarios where funds need to be securely passed on without relying on third-party custodians. The wallet supports advanced features like on-chain timelocks, enabling users to create time-locked backup keys for inheritance planning. Additionally, Liana offers a user-friendly interface with ready-made templates, such as "Simple Inheritance" and "Expanding Multisig," to simplify the wallet setup process. For those seeking a comprehensive solution, the Liana Box Starter Pack includes hardware signing devices, tamper-evident bags, seed phrase storage, and an inheritance letter, providing everything needed to set up a secure and resilient Bitcoin wallet.
-
Snort & Iris (Nostr Clients) For decentralised, secure communication, OpSecOS includes two leading Nostr protocol clients: Snort and Iris. These applications allow users to send and receive messages privately across a peer-to-peer network, eliminating the need for centralised messaging platforms that can compromise privacy. Snort: A minimalist interface for basic, secure messaging.
Iris: A feature-rich client that provides more tools and options for a robust, decentralised messaging experience.
Peer-Reviewed & Battle-Tested: Both Snort and Iris have been reviewed by the community for their security, decentralisation, and resilience. These clients have been battle-tested in real-world environments where privacy and security are non-negotiable, making them trusted tools for secure communications. By including both Snort and Iris, users of OpSecOS have a flexible and secure communication platform that protects their privacy.
-
BIP39 - Ian Coleman’s Tool Managing Bitcoin securely requires careful attention to wallet seed phrases. BIP39 allows users to generate mnemonic seed phrases offline, protecting against online threats. By integrating Ian Coleman's BIP39 tool into OpSecOS, we provide a secure, offline method for generating and managing wallet backups, ensuring users’ funds remain under their control at all times. Peer-Reviewed & Battle-Tested: The BIP39 tool is widely regarded as one of the most secure and trusted methods for generating wallet seed phrases. It has been peer-reviewed by security experts and used in countless real-world scenarios to ensure the safe recovery of cryptocurrency wallets.
-
Mempool.space Mempool.space is a real-time visualisation tool for Bitcoin’s mempool — the collection of unconfirmed transactions awaiting inclusion in the next block. This tool allows users to see transaction fees, network congestion, and block size, helping them optimise their Bitcoin transactions for speed and cost-effectiveness. Mempool.space provides an edge for users who want to monitor Bitcoin’s network activity and ensure that their transactions are processed in the most efficient manner. Peer-Reviewed & Battle-Tested: Mempool.space is used by advanced Bitcoin users, miners, and developers worldwide to monitor and optimise transactions. It has been thoroughly reviewed and is trusted by the community as an indispensable tool for understanding Bitcoin's network dynamics.
**Why These Applications Matter ** The integration of these peer-reviewed and battle-tested applications into OpSecOS transforms it from a privacy-focused operating system into a powerful, decentralised security suite. Each of these tools has been carefully selected to provide users with more control over their digital assets, communications, and privacy. Whether you’re trading Bitcoin, Monero, or engaging in private communications, these tools ensure that you are operating in a trusted, decentralised environment free from surveillance or censorship. These applications, trusted by privacy experts, offer an elevated user experience built on the core principles of decentralisation, security, and privacy. With these tools, users can navigate the digital world with confidence, knowing their activities remain private and under their control.
**New and Improved for 2025 ** While some applications have been updated to the latest, most secure versions, others have been removed to ensure OpSecOS stays focused on delivering the best possible security. We’ve carefully vetted each app to make sure it meets the highest standards for privacy and decentralisation, removing older or less secure applications that could pose risks to our users.
**Conclusion ** OpSec Academy’s custom OpSecOS takes the trusted, privacy-focused foundation of TailsOS and supercharges it with a suite of powerful, peer-reviewed and battle-tested applications. Whether you’re managing your Bitcoin and Monero holdings, engaging in private communications, or ensuring your wallet is securely backed up, OpSecOS provides you with everything you need to operate in a decentralised, secure, and private environment. As surveillance and digital threats continue to grow, OpSecOS remains a vital tool for users looking to protect their privacy and maintain complete control over their digital lives. OpSec Academy is committed to continually improving OpSecOS to meet the evolving demands of privacy-conscious users. With OpSecOS, we provide an enhanced privacy experience that stays true to the principles of decentralisation and operational security.
OpSec Academy offers consultations for individuals or organisations looking to integrate OpSecOS into their security framework. Contact us securely for more information.
-






