-
 @ d34e832d:383f78d0
2025-04-22 23:35:05
@ d34e832d:383f78d0
2025-04-22 23:35:05For Secure Inheritance Planning and Offline Signing
The setup described ensures that any 2 out of 3 participants (hardware wallets) must sign a transaction before it can be broadcast, offering robust protection against theft, accidental loss, or mismanagement of funds.
1. Preparation: Tools and Requirements
Hardware Required
- 3× COLDCARD Mk4 hardware wallets (or newer)
- 3× MicroSD cards (one per COLDCARD)
- MicroSD card reader (for your computer)
- Optional: USB data blocker (for safe COLDCARD connection)
Software Required
- Sparrow Wallet: Version 1.7.1 or later
Download: https://sparrowwallet.com/ - COLDCARD Firmware: Version 5.1.2 or later
Update guide: https://coldcard.com/docs/upgrade
Other Essentials
- Durable paper or steel backup tools for seed phrases
- Secure physical storage for backups and devices
- Optional: encrypted external storage for Sparrow wallet backups
Security Tip:
Always verify software signatures before installation. Keep your COLDCARDs air-gapped (no USB data transfer) whenever possible.
2. Initializing Each COLDCARD Wallet
- Power on each COLDCARD and choose “New Wallet”.
- Write down the 24-word seed phrase (DO NOT photograph or store digitally).
- Confirm the seed and choose a strong PIN code (both prefix and suffix).
- (Optional) Enable BIP39 Passphrase for additional entropy.
- Save an encrypted backup to the MicroSD card:
Go to Advanced > Danger Zone > Backup. - Repeat steps 1–5 for all three COLDCARDs.
Best Practice:
Store each seed phrase securely and in separate physical locations. Test wallet recovery before storing real funds.
3. Exporting XPUBs from COLDCARD
Each hardware wallet must export its extended public key (XPUB) for multisig setup:
- Insert MicroSD card into a COLDCARD.
- Navigate to:
Settings > Multisig Wallets > Export XPUB. - Select the appropriate derivation path. Recommended:
- Native SegWit:
m/84'/0'/0'(bc1 addresses) - Alternatively: Nested SegWit
m/49'/0'/0'(starts with 3) - Save the XPUB file to the MicroSD card.
- Insert MicroSD into your computer and transfer XPUB files to Sparrow Wallet.
- Repeat for the remaining COLDCARDs.
4. Creating the 2-of-3 Multisig Wallet in Sparrow
- Launch Sparrow Wallet.
- Click File > New Wallet and name your wallet.
- In the Keystore tab, choose Multisig.
- Select 2-of-3 as your multisig policy.
- For each cosigner:
- Choose Add cosigner > Import XPUB from file.
- Load XPUBs exported from each COLDCARD.
- Once all 3 cosigners are added, confirm the configuration.
- Click Apply, then Create Wallet.
- Sparrow will display a receive address. Fund the wallet using this.
Tip:
You can export the multisig policy (wallet descriptor) as a backup and share it among cosigners.
5. Saving and Verifying the Wallet Configuration
- After creating the wallet, click Wallet > Export > Export Wallet File (.json).
- Save this file securely and distribute to all participants.
- Verify that the addresses match on each COLDCARD using the wallet descriptor file (optional but recommended).
6. Creating and Exporting a PSBT (Partially Signed Bitcoin Transaction)
- In Sparrow, click Send, fill out recipient details, and click Create Transaction.
- Click Finalize > Save PSBT to MicroSD card.
- The file will be saved as a
.psbtfile.
Note: No funds are moved until 2 signatures are added and the transaction is broadcast.
7. Signing the PSBT with COLDCARD (Offline)
- Insert the MicroSD with the PSBT into COLDCARD.
- From the main menu:
Ready To Sign > Select PSBT File. - Verify transaction details and approve.
- COLDCARD will create a signed version of the PSBT (
signed.psbt). - Repeat the signing process with a second COLDCARD (different signer).
8. Finalizing and Broadcasting the Transaction
- Load the signed PSBT files back into Sparrow.
- Sparrow will detect two valid signatures.
- Click Finalize Transaction > Broadcast.
- Your Bitcoin transaction will be sent to the network.
9. Inheritance Planning with Multisig
Multisig is ideal for inheritance scenarios:
Example Inheritance Setup
- Signer 1: Yourself (active user)
- Signer 2: Trusted family member or executor
- Signer 3: Lawyer, notary, or secure backup
Only 2 signatures are needed. If one party loses access or passes away, the other two can recover the funds.
Best Practices for Inheritance
- Store each seed phrase in separate, tamper-proof, waterproof containers.
- Record clear instructions for heirs (without compromising seed security).
- Periodically test recovery with cosigners.
- Consider time-locked wallets or third-party escrow if needed.
Security Tips and Warnings
- Never store seed phrases digitally or online.
- Always verify addresses and signatures on the COLDCARD screen.
- Use Sparrow only on secure, malware-free computers.
- Physically secure your COLDCARDs from unauthorized access.
- Practice recovery procedures before storing real value.
Consider
A 2-of-3 multisignature wallet using COLDCARD and Sparrow Wallet offers a highly secure, flexible, and transparent Bitcoin custody model. Whether for inheritance planning or high-security storage, it mitigates risks associated with single points of failure while maintaining usability and privacy.
By following this guide, Bitcoin users can significantly increase the resilience of their holdings while enabling thoughtful succession strategies.
-
 @ f32184ee:6d1c17bf
2025-04-22 22:56:11
@ f32184ee:6d1c17bf
2025-04-22 22:56:11Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. NextBlock’s PROMO Protocol, designed while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media -]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media -]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ a8d1560d:3fec7a08
2025-04-22 22:52:15
@ a8d1560d:3fec7a08
2025-04-22 22:52:15Based on the Free Speech Flag generator at https://crocojim18.github.io/, but now you can encode binary data as well.
https://free-speech-flag-generator--wholewish91244492.on.websim.ai/
Please also see https://en.wikipedia.org/wiki/Free_Speech_Flag for more information about the Free Speech Flag.
Who can tell me what I encoded in the flag used for this longform post?
-
 @ d34e832d:383f78d0
2025-04-22 22:48:30
@ d34e832d:383f78d0
2025-04-22 22:48:30What is pfSense?
pfSense is a free, open-source firewall and router software distribution based on FreeBSD. It includes a web-based GUI and supports advanced features like:
- Stateful packet inspection (SPI)
- Virtual Private Network (VPN) support (OpenVPN, WireGuard, IPSec)
- Dynamic and static routing
- Traffic shaping and QoS
- Load balancing and failover
- VLANs and captive portals
- Intrusion Detection/Prevention (Snort, Suricata)
- DNS, DHCP, and more
Use Cases
- Home networks with multiple devices
- Small to medium businesses
- Remote work VPN gateway
- IoT segmentation
- Homelab firewalls
- Wi-Fi network segmentation
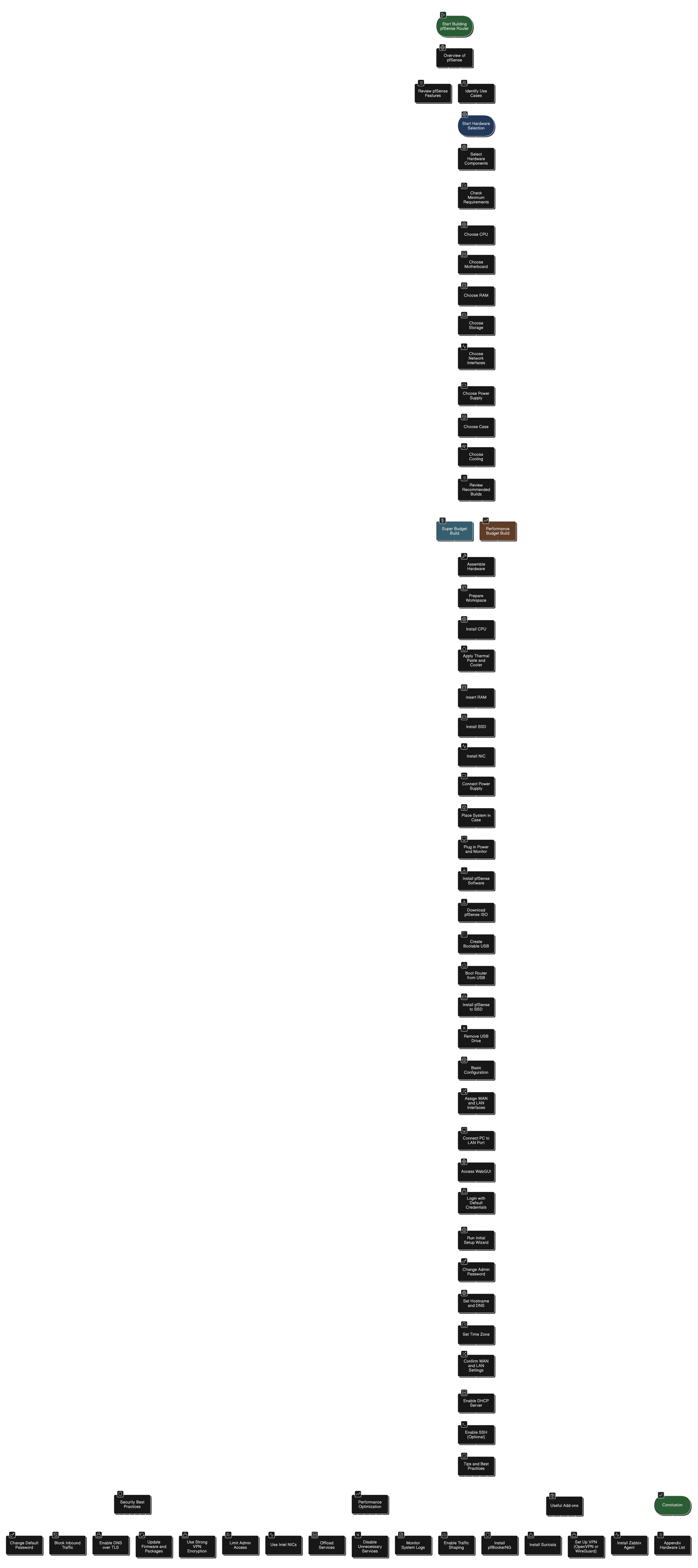
2. Essential Hardware Components
When building a pfSense router, you must match your hardware to your use case. The system needs at least two network interfaces—one for WAN, one for LAN.
Core Components
| Component | Requirement | Budget-Friendly Example | |---------------|------------------------------------|----------------------------------------------| | CPU | Dual-core 64-bit x86 (AES-NI support recommended) | Intel Celeron J4105, AMD GX-412HC, or Intel i3 6100T | | Motherboard | Mini-ITX or Micro-ATX with support for selected CPU | ASRock J4105-ITX (includes CPU) | | RAM | Minimum 4GB (8GB preferred) | Crucial 4GB DDR4 | | Storage | 16GB+ SSD or mSATA/NVMe (for longevity and speed) | Kingston A400 120GB SSD | | NICs | At least two Intel gigabit ports (Intel NICs preferred) | Intel PRO/1000 Dual-Port PCIe or onboard | | Power Supply | 80+ Bronze rated or PicoPSU for SBCs | EVGA 400W or PicoPSU 90W | | Case | Depends on form factor | Mini-ITX case (e.g., InWin Chopin) | | Cooling | Passive or low-noise | Stock heatsink or case fan |
3. Recommended Affordable Hardware Builds
Build 1: Super Budget (Fanless)
- Motherboard/CPU: ASRock J4105-ITX (quad-core, passive cooling, AES-NI)
- RAM: 4GB DDR4 SO-DIMM
- Storage: 120GB SATA SSD
- NICs: 1 onboard + 1 PCIe Intel Dual Port NIC
- Power Supply: PicoPSU with 60W adapter
- Case: Mini-ITX fanless enclosure
- Estimated Cost: ~$150–180
Build 2: Performance on a Budget
- CPU: Intel i3-6100T (low power, AES-NI support)
- Motherboard: ASUS H110M-A/M.2 (Micro-ATX)
- RAM: 8GB DDR4
- Storage: 120GB SSD
- NICs: 2-port Intel PCIe NIC
- Case: Compact ATX case
- Power Supply: 400W Bronze-rated PSU
- Estimated Cost: ~$200–250
4. Assembling the Hardware
Step-by-Step Instructions
- Prepare the Workspace:
- Anti-static mat or surface
- Philips screwdriver
- Install CPU (if required):
- Align and seat CPU into socket
- Apply thermal paste and attach cooler
- Insert RAM into DIMM slots
- Install SSD and connect to SATA port
- Install NIC into PCIe slot
- Connect power supply to motherboard, SSD
- Place system in case and secure all components
- Plug in power and monitor
5. Installing pfSense Software
What You'll Need
- A 1GB+ USB flash drive
- A separate computer with internet access
Step-by-Step Guide
- Download pfSense ISO:
- Visit: https://www.pfsense.org/download/
- Choose AMD64, USB Memstick Installer, and mirror site
- Create Bootable USB:
- Use tools like balenaEtcher or Rufus to write ISO to USB
- Boot the Router from USB:
- Enter BIOS → Set USB as primary boot
- Save and reboot
- Install pfSense:
- Accept defaults during installation
- Choose ZFS or UFS (UFS is simpler for small SSDs)
- Install to SSD, remove USB post-installation
6. Basic Configuration Settings
After the initial boot, pfSense will assign: - WAN to one interface (via DHCP) - LAN to another (default IP: 192.168.1.1)
Access WebGUI
- Connect a PC to LAN port
- Open browser → Navigate to
http://192.168.1.1 - Default login: admin / pfsense
Initial Setup Wizard
- Change admin password
- Set hostname and DNS
- Set time zone
- Confirm WAN/LAN settings
- Enable DHCP server for LAN
- Optional: Enable SSH
7. Tips and Best Practices
Security Best Practices
- Change default password immediately
- Block all inbound traffic by default
- Enable DNS over TLS (with Unbound)
- Regularly update pfSense firmware and packages
- Use strong encryption for VPNs
- Limit admin access to specific IPs
Performance Optimization
- Use Intel NICs for reliable throughput
- Offload DNS, VPN, and DHCP to dedicated packages
- Disable unnecessary services to reduce CPU load
- Monitor system logs for errors and misuse
- Enable traffic shaping if managing VoIP or streaming
Useful Add-ons
- pfBlockerNG: Ad-blocking and geo-blocking
- Suricata: Intrusion Detection System
- OpenVPN/WireGuard: VPN server setup
- Zabbix Agent: External monitoring
8. Consider
With a modest investment and basic technical skills, anyone can build a powerful, flexible, and secure pfSense router. Choosing the right hardware for your needs ensures a smooth experience without overpaying or underbuilding. Whether you're enhancing your home network, setting up a secure remote office, or learning network administration, a custom pfSense router is a versatile, long-term solution.
Appendix: Example Hardware Component List
| Component | Item | Price (Approx.) | |------------------|--------------------------|------------------| | Motherboard/CPU | ASRock J4105-ITX | $90 | | RAM | Crucial 4GB DDR4 | $15 | | Storage | Kingston A400 120GB SSD | $15 | | NIC | Intel PRO/1000 Dual PCIe | $20 | | Case | Mini-ITX InWin Chopin | $40 | | Power Supply | PicoPSU 60W + Adapter | $25 | | Total | | ~$205 |
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:57
@ 9bde4214:06ca052b
2025-04-22 22:04:57“The human spirit should remain in charge.”
Pablo & Gigi talk about the wind.
In this dialogue:
- Wind
- More Wind
- Information Calories, and how to measure them
- Digital Wellbeing
- Rescue Time
- Teleology of Technology
- Platforms get users Hooked (book)
- Feeds are slot machines
- Movie Walls
- Tweetdeck and Notedeck
- IRC vs the modern feed
- 37Signals: “Hey, let’s just charge users!”
- “You wouldn’t zap a car crash”
- Catering to our highest self VS catering to our lowest self
- Devolution of YouTube 5-star ratings to thumb up/down to views
- Long videos vs shorts
- The internet had to monetize itself somehow (with attention)
- “Don’t be evil” and why Google had to remove it
- Questr: 2D exploration of nostr
- ONOSENDAI by Arkinox
- Freedom tech & Freedom from Tech
- DAUs of jumper cables
- Gossip and it’s choices
- “The secret to life is to send it”
- Flying water & flying bus stops
- RSS readers, Mailbrew, and daily digests
- Nostr is high signal and less addictive
- Calling nostr posts “tweets” and recordings being “on tape”
- Pivoting from nostr dialogues to a podcast about wind
- The unnecessary complexity of NIP-96
- Blossom (and wind)
- Undoing URLs, APIs, and REST
- ISBNs and cryptographic identifiers
- SaaS and the DAU metric
- Highlighter
- Not caring where stuff is hosted
- When is an edited thing a new thing?
- Edits, the edit wars, and the case against edits
- NIP-60 and inconsistent balances
- Scroll to text fragment and best effort matching
- Proximity hashes & locality-sensitive hashing
- Helping your Uncle Jack of a horse
- Helping your uncle jack of a horse
- Can we fix it with WoT?
- Vertex & vibe-coding a proper search for nostr
- Linking to hashtags & search queries
- Advanced search and why it’s great
- Search scopes & web of trust
- The UNIX tools of nostr
- Pablo’s NDK snippets
- Meredith on the privacy nightmare of Agentic AI
- Blog-post-driven development (Lightning Prisms, Highlighter)
- Sandwich-style LLM prompting, Waterfall for LLMs (HLDD / LLDD)
- “Speed itself is a feature”
- MCP & DVMCP
- Monorepos and git submodules
- Olas & NDK
- Pablo’s RemindMe bot
- “Breaking changes kinda suck”
- Stories, shorts, TikTok, and OnlyFans
- LLM-generated sticker styles
- LLMs and creativity (and Gigi’s old email)
- “AI-generated art has no soul”
- Nostr, zaps, and realness
- Does the source matter?
- Poker client in bitcoin v0.0.1
- Quotes from Hitler and how additional context changes meaning
- Greek finance minister on crypto and bitcoin (Technofeudalism, book)
- Is more context always good?
- Vervaeke’s AI argument
- What is meaningful?
- How do you extract meaning from information?
- How do you extract meaning from experience?
- “What the hell is water”
- Creativity, imagination, hallucination, and losing touch with reality
- “Bitcoin is singularity insurance”
- Will vibe coding make developers obsolete?
- Knowing what to build vs knowing how to build
- 10min block time & the physical limits of consensus
- Satoshi’s reasons articulated in his announcement post
- Why do anything? Why stack sats? Why have kids?
- All you need now is motivation
- Upcoming agents will actually do the thing
- Proliferation of writers: quantity VS quality
- Crisis of sameness & the problem of distribution
- Patronage, belle epoche, and bitcoin art
- Niches, and how the internet fractioned society
- Joe’s songs
- Hyper-personalized stories
- Shared stories & myths (Jonathan Pageau)
- Hyper-personalized apps VS shared apps
- Agency, free expression, and free speech
- Edgy content & twitch meta, aka skating the line of demonetization and deplatforming
- Using attention as a proxy currency
- Farming eyeballs and brain cycles
- Engagement as a success metric & engagement bait
- “You wouldn’t zap a car crash”
- Attention economy is parasitic on humanity
- The importance of speech & money
- What should be done by a machine?
- What should be done by a human?
- “The human spirit should remain in charge”
- Our relationship with fiat money
- Active vs passive, agency vs serfdom
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:08
@ 9bde4214:06ca052b
2025-04-22 22:04:08"With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
Pablo & Gigi are getting high on glue.
Books & articles mentioned:
- Saving beauty by Byung-Chul Han
- LLMs as a tool for thought by Amelia Wattenberger
In this dialogue:
- vibeline & vibeline-ui
- LLMs as tools, and how to use them
- Vervaeke: AI thresholds & the path we must take
- Hallucinations and grounding in reality
- GPL, LLMs, and open-source licensing
- Pablo's multi-agent Roo setup
- Are we going to make programmers obsolete?
- "When it works it's amazing"
- Hiring & training agents
- Agents creating RAG databases of NIPs
- Different models and their context windows
- Generalists vs specialists
- "Write drunk, edit sober"
- DVMCP.fun
- Recklessness and destruction of vibe-coding
- Sharing secrets with agents & LLMs
- The "no API key" advantage of nostr
- What data to trust? And how does nostr help?
- Identity, web of trust, and signing data
- How to fight AI slop
- Marketplaces of code snippets
- Restricting agents with expert knowledge
- Trusted sources without a central repository
- Zapstore as the prime example
- "How do you fight off re-inventing GitHub?"
- Using large context windows to help with refactoring
- Code snippets for Olas, NDK, NIP-60, and more
- Using MCP as the base
- Using nostr as the underlying substrate
- Nostr as the glue & the discovery layer
- Why is this important?
- Why is this exciting?
- "With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
- How to single-shot nostr applications
- "Go and create this app"
- The agent has money, because of NIP-60/61
- PayPerQ
- Anthropic and the genius of mcp-tools
- Agents zapping & giving SkyNet more money
- Are we going to run the mints?
- Are agents going to run the mints?
- How can we best explain this to our bubble?
- Let alone to people outside of our bubble?
- Building pipelines of multiple agents
- LLM chains & piped Unix tools
- OpenAI vs Anthropic
- Genius models without tools vs midwit models with tools
- Re-thinking software development
- LLMs allow you to tackle bigger problems
- Increased speed is a paradigm shift
- Generalists vs specialists, left brain vs right brain
- Nostr as the home for specialists
- fiatjaf publishing snippets (reluctantly)
- fiatjaf's blossom implementation
- Thinking with LLMs
- The tension of specialization VS generalization
- How the publishing world changed
- Stupid faces on YouTube thumbnails
- Gaming the algorithm
- Will AI slop destroy the attention economy?
- Recency bias & hiding publication dates
- Undoing platform conditioning as a success metric
- Craving realness in a fake attention world
- The theater of the attention economy
- What TikTok got "right"
- Porn, FoodPorn, EarthPorn, etc.
- Porn vs Beauty
- Smoothness and awe
- "Beauty is an angel that could kill you in an instant (but decides not to)."
- The success of Joe Rogan & long-form conversations
- Smoothness fatigue & how our feeds numb us
- Nostr & touching grass
- How movement changes conversations
- LangChain & DVMs
- Central models vs marketplaces
- Going from assembly to high-level to conceptual
- Natural language VS programming languages
- Pablo's code snippets
- Writing documentation for LLMs
- Shared concepts, shared language, and forks
- Vibe-forking open-source software
- Spotting vibe-coded interfaces
- Visualizing nostr data in a 3D world
- Tweets, blog posts, and podcasts
- Vibe-producing blog posts from conversations
- Tweets are excellent for discovery
- Adding context to tweets (long-form posts, podcasts, etc)
- Removing the character limit was a mistake
- "Everyone's attention span is rekt"
- "There is no meaning without friction"
- "Nothing worth having ever comes easy"
- Being okay with doing the hard thing
- Growth hacks & engagement bait
- TikTok, theater, and showing faces and emotions
- The 1% rule: 99% of internet users are Lurkers
- "We are socially malnourished"
- Web-of-trust and zaps bring realness
- The semantic web does NOT fix this LLMs might
- "You can not model the world perfectly"
- Hallucination as a requirement for creativity
-
 @ 9bde4214:06ca052b
2025-04-22 22:01:34
@ 9bde4214:06ca052b
2025-04-22 22:01:34"The age of the idea guys has begun."
Articles mentioned:
- LLMs as a tool for thought by Amelia Wattenberger
- Micropayments and Mental Transaction Costs by Nick Szabo
- How our interfaces have lost their senses by Amelia Wattenberger
Talks mentioned:
- The Art of Bitcoin Rhetoric by Bitstein
Books mentioned:
- Human Action by Ludwig von Mises
- Working in Public by Nadia Eghbal
In this dialogue:
- nak
- Files
- SyncThing (and how it BitTorrent Sync became Resilio Sync)
- Convention over configuration
- Changes & speciation
- File systems as sources of truth
- Vibe-coding shower thoughts
- Inspiration and The Muse
- Justin's LLM setup
- Tony's setup (o1-pro as the architect)
- Being okay with paying for LLMs
- Anthropomorphising LLMs
- Dialog, rubber-duck debugging, and the process of thinking
- Being nice and mean to LLMs
- Battlebots & Gladiators
- Hedging your bets by being nice to Skynet
- Pascal's Wager for AI
- Thinking models vs non-thinking faster models
- Sandwich-style LLM prompting, again (waterfall stuff, HLDD / LLDD)
- Cursor rules & Paul's Prompt Buddy
- Giving lots of context vs giving specific context
- The benefit of LLMs figuring out obscure bugs in minutes (instead of days)
- The phase change of fast iteration and vibe coding
- Idea level vs coding level
- High-level vs low-level languages
- Gigi's "vibeline"
- Peterson's Logos vs Vervaeke's Dia-Logos
- Entering into a conversation with technology
- Introducing MCPs into your workflow
- How does Claude think?
- How does it create a rhyme?
- How does thinking work?
- And how does it relate to dialogue?
- Gzuuus' DVMCP & using nostr as an AI substrate
- Language Server Protocols (LSPs)
- VAAS: Vibe-coding as a service
- Open models vs proprietary models
- What Cursor got right
- What ChatGPT got right
- What Google got right
- Tight integration of tools & remaining in a flow state
- LLMs as conversational partners
- The cost of context switching
- Conversational flow & how to stay in it
- Prompts VS diary entries
- Solving technical vs philosophical models
- Buying GPUs & training your own models
- Training LLMs to understand Zig
- Preventing entryism by writing no documentation
- Thin layers & alignment layers
- Working in public & thinking in public
- Building a therapist / diary / notes / idea / task system
- "The age of the idea guys has begun."
- Daemons and spirits
- Monological VS dialogical thinking
- Yes-men and disagreeable LLMs
- Energy cost vs human cost
- Paying by the meter vs paying a subscription
- The equivalence of storage and compute
- Thinking needs memory, and memory is about the future
- Nostr+ecash as the perfect AI+human substrate
- Real cost, real consequence, and Human Action
- The cost of words & speaking
- Costly signals and free markets
- From shitcoin tokens to LLM tokens to ecash tokens
- Being too close to the metal & not seeing the forest for the trees
- Power users vs engineers
- Participatory knowing and actually using the tools
- Nostr as the germination ground for ecash
- What is Sovereign Engineering?
- LLVM and the other side of the bell-curve
- How nostr gives you users, discovery, mircopayments, a backend, and many other things for free
- Echo chambers & virality
- Authenticity & Realness
- Growing on the edges, catering to the fringe
- You don't own your iPhone
- GrapheneOS
- WebRTC and other monolithic "open" standards
- Optimizing for the wrong thing
- Building a nostr phone & Gigi's dream flow
- Using nostr to sync dotfile setups and other things
- "There are no solutions, only trade-offs"
- Cross-platform development
- Native vs non-native implementations
- Vitor's point on what we mean by native
- Does your custom UI framework work for blind people?
- Ladybird browser & how to build a browser from scratch
- TempleOS
- Form follows function & 90's interfaces
- Lamentations on the state of modern browsers
- Complexity & the downfall of the Legacy Web
- Nostr as the "new internet"
- Talks by Ladybird developer Andreas Kling
- Will's attempt of building it from scratch with Notedeck & nostr-db
- Justin's attempt with rust-multiplatform
- "If it doesn't have a rust implementation, you shouldn't use it."
- Native in terms of speed vs native in terms of UI/UX
- Engineer the logic, vibe-code the UI
- From Excalidraw to app in minutes
- What can you one-shot?
- What do you need to care about?
- Pablo's NDK snippets
- 7GUIs and GUI benchmarks for LLMs
- "Now we're purpose-building tools to make it easier for LLMs"
- "Certain tools really make your problems go away."
- Macros and meta-programming
- Zig's comptime
- UNIX tools and pipes
- Simple tools & composability
- Nostr tools for iOS & sharing developer signing keys
- Building 10 apps as one guy
- Simplicity in a community context
- Most people are on phones
- Most people don't install PWAs
- Zapstore & building our own distribution channels
- Web-of-trust and pushing builds quickly
- Improving homebrew by 10x
- (Micro)payments for package managers
- Guix and bitcoin-core
- Nix vs Guix
- Reproducible builds & web-of-trust
- Keet vs "calling an npub"
- Getting into someone's notifications
- Removing the character limit was a mistake
-
 @ d34e832d:383f78d0
2025-04-22 21:32:40
@ d34e832d:383f78d0
2025-04-22 21:32:40The Domain Name System (DNS) is a foundational component of the internet. It translates human-readable domain names into IP addresses, enabling the functionality of websites, email, and services. However, traditional DNS is inherently insecure—queries are typically sent in plaintext, making them vulnerable to interception, spoofing, and censorship.
DNSCrypt is a protocol designed to authenticate communications between a DNS client and a DNS resolver. By encrypting DNS traffic and validating the source of responses, it thwarts man-in-the-middle attacks and DNS poisoning. Despite its security advantages, widespread adoption remains limited due to usability and deployment complexity.
This idea introduces an affordable, lightweight DNSCrypt proxy server capable of providing secure DNS resolution in both home and enterprise environments. Our goal is to democratize secure DNS through low-cost infrastructure and transparent architecture.
2. Background
2.1 Traditional DNS Vulnerabilities
- Lack of Encryption: DNS queries are typically unencrypted (UDP port 53), exposing user activity.
- Spoofing and Cache Poisoning: Attackers can forge DNS responses to redirect users to malicious websites.
- Censorship: Governments and ISPs can block or alter DNS responses to control access.
2.2 Introduction to DNSCrypt
DNSCrypt mitigates these problems by: - Encrypting DNS queries using X25519 + XSalsa20-Poly1305 or X25519 + ChaCha20-Poly1305 - Authenticating resolvers via public key infrastructure (PKI) - Supporting relay servers and anonymized DNS, enhancing metadata protection
2.3 Current Landscape
DNSCrypt proxies are available in commercial routers and services (e.g., Cloudflare DNS over HTTPS), but full control remains in the hands of centralized entities. Additionally, hardware requirements and setup complexity can be barriers to entry.
3. System Architecture
3.1 Overview
Our system is designed around the following components: - Client Devices: Use DNSCrypt-enabled stub resolvers (e.g., dnscrypt-proxy) - DNSCrypt Proxy Server: Accepts DNSCrypt queries, decrypts and validates them, then forwards to recursive resolvers (e.g., Unbound) - Recursive Resolver (Optional): Provides DNS resolution without reliance on upstream services - Relay Support: Adds anonymization via DNSCrypt relays
3.2 Protocols and Technologies
- DNSCrypt v2: Core encrypted DNS protocol
- X25519 Key Exchange: Lightweight elliptic curve cryptography
- Poly1305 AEAD Encryption: Fast and secure authenticated encryption
- UDP/TCP Fallback: Supports both transport protocols to bypass filtering
- DoH Fallback: Optional integration with DNS over HTTPS
3.3 Hardware Configuration
- Platform: Raspberry Pi 4B or x86 mini-PC (e.g., Lenovo M710q)
- Cost: Under $75 total (device + SD card or SSD)
- Operating System: Debian 12 or Ubuntu Server 24.04
- Memory Footprint: <100MB RAM idle
- Power Consumption: ~3-5W idle
4. Design Considerations
4.1 Affordability
- Hardware Sourcing: Use refurbished or SBCs to cut costs
- Software Stack: Entirely open source (dnscrypt-proxy, Unbound)
- No Licensing Fees: FOSS-friendly deployment for communities
4.2 Security
- Ephemeral Key Pairs: New keypairs every session prevent replay attacks
- Public Key Verification: Resolver keys are pre-published and verified
- No Logging: DNSCrypt proxies are configured to avoid retaining user metadata
- Anonymization Support: With relay chaining for metadata privacy
4.3 Maintainability
- Containerization (Optional): Docker-compatible setup for simple updates
- Remote Management: Secure shell access with fail2ban and SSH keys
- Auto-Updating Scripts: Systemd timers to refresh certificates and relay lists
5. Implementation
5.1 Installation Steps
- Install OS and dependencies:
bash sudo apt update && sudo apt install dnscrypt-proxy unbound - Configure
dnscrypt-proxy.toml: - Define listening port, relay list, and trusted resolvers
- Enable Anonymized DNS, fallback to DoH
- Configure Unbound (optional):
- Run as recursive backend
- Firewall hardening:
- Allow only DNSCrypt port (default: 443 or 5353)
- Block all inbound traffic except SSH (optional via Tailscale)
5.2 Challenges
- Relay Performance Variability: Some relays introduce latency; solution: geo-filtering
- Certificate Refresh: Mitigated with daily cron jobs
- IP Rate-Limiting: Mitigated with DNS load balancing
6. Evaluation
6.1 Performance Benchmarks
- Query Resolution Time (mean):
- Local resolver: 12–18ms
- Upstream via DoH: 25–35ms
- Concurrent Users Supported: 100+ without degradation
- Memory Usage: ~60MB (dnscrypt-proxy + Unbound)
- CPU Load: <5% idle on ARM Cortex-A72
6.2 Security Audits
- Verified with dnsleaktest.com and
tcpdump - No plaintext DNS observed over interface
- Verified resolver keys via DNSCrypt community registry
7. Use Cases
7.1 Personal/Home Use
- Secure DNS for all home devices via router or Pi-hole integration
7.2 Educational Institutions
- Provide students with censorship-free DNS in oppressive environments
7.3 Community Mesh Networks
- Integrate DNSCrypt into decentralized networks (e.g., Nostr over Mesh)
7.4 Business VPNs
- Secure internal DNS without relying on third-party resolvers
8. Consider
This idea has presented a practical, affordable approach to deploying a secure DNSCrypt proxy server. By leveraging open-source tools, minimalist hardware, and careful design choices, it is possible to democratize access to encrypted DNS. Our implementation meets the growing need for privacy-preserving infrastructure without introducing prohibitive costs.
We demonstrated that even modest devices can sustain dozens of encrypted DNS sessions concurrently while maintaining low latency. Beyond privacy, this system empowers individuals and communities to control their own DNS without corporate intermediaries.
9. Future Work
- Relay Discovery Automation: Dynamic quality-of-service scoring for relays
- Web GUI for Management: Simplified frontend for non-technical users
- IPv6 and Tor Integration: Expanding availability and censorship resistance
- Federated Resolver Registry: Trust-minimized alternative to current resolver key lists
References
- DNSCrypt Protocol Specification v2 – https://dnscrypt.info/protocol
- dnscrypt-proxy GitHub Repository – https://github.com/DNSCrypt/dnscrypt-proxy
- Unbound Recursive Resolver – https://nlnetlabs.nl/projects/unbound/about/
- DNS Security Extensions (DNSSEC) – IETF RFCs 4033, 4034, 4035
- Bernstein, D.J. – Cryptographic Protocols using Curve25519 and Poly1305
- DNS over HTTPS (DoH) – RFC 8484
-
 @ d34e832d:383f78d0
2025-04-22 21:14:46
@ d34e832d:383f78d0
2025-04-22 21:14:46Minecraft remains one of the most popular sandbox games in the world. For players who wish to host private or community-based servers, monthly hosting fees can quickly add up. Furthermore, setting up a server from scratch often requires technical knowledge in networking, system administration, and Linux.
This idea explores a do-it-yourself (DIY) method for deploying a low-cost Minecraft server using common secondhand hardware and a simple software stack, with a focus on energy efficiency, ease of use, and full control over the server environment.
2. Objective
To build and deploy a dedicated Minecraft server that:
- Costs less than $75 in total
- Consumes minimal electricity (<10W idle)
- Is manageable via a graphical user interface (GUI)
- Supports full server management including backups, restarts, and plugin control
- Requires no port forwarding or complex network configuration
- Delivers performance suitable for a small-to-medium number of concurrent players
3. Hardware Overview
3.1 Lenovo M710Q Mini-PC (~$55 used)
- Intel Core i5 (6th/7th Gen)
- 8GB DDR4 RAM
- Compact size and low power usage
- Widely available refurbished
3.2 ID Sonics 512GB NVMe SSD (~$20)
- Fast storage with sufficient capacity for multiple Minecraft server instances
- SSDs reduce world loading lag and improve backup performance
Total Hardware Cost: ~$75
4. Software Stack
4.1 Ubuntu Server 24.04
- Stable, secure, and efficient operating system
- Headless installation, ideal for server use
- Supports automated updates and system management via CLI
4.2 CasaOS
- A lightweight operating system layer and GUI on top of Ubuntu
- Built for managing Docker containers with a clean web interface
- Allows app store-like deployment of various services
4.3 Crafty Controller (via Docker)
- Web-based server manager for Minecraft
- Features include:
- Automatic backups and restore
- Scheduled server restarts
- Plugin management
- Server import/export
- Server logs and console access
5. Network and Remote Access
5.1 PlayIt.gg Integration
PlayIt.gg creates a secure tunnel to your server via a relay node, removing the need for traditional port forwarding.
Benefits: - Works even behind Carrier-Grade NAT (common on mobile or fiber ISPs) - Ideal for users with no access to router settings - Ensures privacy by hiding IP address from public exposure
6. Setup Process Summary
- Install Ubuntu Server 24.04 on the M710Q
- Install CasaOS via script provided by the project
- Use CasaOS to deploy Crafty Controller in a Docker container
- Configure Minecraft server inside Crafty (Vanilla, Paper, Spigot, etc.)
- Integrate PlayIt.gg to expose the server to friends
- Access Crafty via browser for daily management
7. Power Consumption and Performance
- Idle Power Draw: ~7.5W
- Load Power Draw (2–5 players): ~15W
- M710Q fan runs quiet and rarely under load
- Performance sufficient for:
- Vanilla or optimized Paper server
- Up to 10 concurrent players with light mods
8. Cost Analysis vs Hosted Services
| Solution | Monthly Cost | Annual Cost | Control Level | Mods Support | |-----------------------|--------------|-------------|----------------|---------------| | Commercial Hosting | $5–$15 | $60–$180 | Limited | Yes | | This Build (One-Time) | $75 | $0 | Full | Yes |
Return on Investment (ROI):
Break-even point reached in 6 to 8 months compared to lowest hosting tiers.
9. Advantages
- No Subscription: Single upfront investment
- Local Control: Full access to server files and environment
- Privacy Respecting: No third-party data mining
- Modular: Can add mods, backups, maps with full access
- Low Energy Use: Ideal for 24/7 uptime
10. Limitations
- Not Ideal for >20 players: CPU and RAM constraints
- Local Hardware Dependency: Physical failure risk
- Requires Basic Setup Time: CLI familiarity useful but not required
11. Future Enhancements
- Add Dynmap with reverse proxy and TLS via CasaOS
- Integrate Nextcloud for managing world backups
- Use Watchtower for automated container updates
- Schedule daily email logs using system cron
12. Consider
This idea presents a practical and sustainable approach to self-hosting Minecraft servers using open-source software and refurbished hardware. With a modest upfront cost and minimal maintenance, users can enjoy full control over their game worlds without recurring fees or technical hassle. This method democratizes game hosting and aligns well with educational environments, small communities, and privacy-conscious users.
-
 @ 3ad01248:962d8a07
2025-04-22 21:09:52
@ 3ad01248:962d8a07
2025-04-22 21:09:52The trade war between Trump and the rest of the world has kicked of in earnest with Trump's unveiling of sweeping tariffs on so called "Liberation Day". The entire world was essentially put on notice that there is a new sheriff in town and things will be done different from now on.
The is the sentiment that won Trump the election so it is no wonder that Trump would follow through on changing how the world relates to America. President Trump hit the entire world with reciprocal tariffs and some places where people don't live which I find hilarious
I wonder who was in charge of making this tariff list because they need fired to be honest. Screams incompetence but that for another day. Will Bitcoin benefit from the trade war?
Bitcoin will benefit because the world now believes that the United States can not be trusted to honor its word or commitments. Why would any country want to to business with a country that says one thing and does another. Trump has upended the very economic order that the US created in the first place! Is this a smart idea? Only time will tell to be honest.
The worst thing Trump did was created doubt and uncertainty for the bond market. The bond market is the main engine of economic power for the US government. Having the world buy your bonds gives the United States unparalleled economic power to flex all around the world. The US might have military bases all over the world and uses it to conduct foreign policy but its the economic power of the US that gives it the influence that it has right now.
All that comes into question now. When you shit on your friends and buddy up with your adversaries it not a good look and allies will respond accordingly. Why piss off Canada and Mexico? What policy objective is that accomplishing? Picking fights with Europe? Not smart politics. I get wanting allies to pick up the slack on their end or have better trade relations but there is the right way to do it and a wrong way to do it. Trump undoubtedly goes about it the wrong way.
Has he not heard the saying 'You catch more flies with honey than vinegar?" When you are cordial with people and they like you its a lot easier to get people to do things for you or see things from you perspective versus talking shit and bullying them into submission.
Most countries are not going to tolerate this type of political brinkmanship and will decide that they need to take their money elsewhere. You can expect for them to withdraw their money from the stock market and the bond market over the next 12-24 months. Guess what happens after that? Bond yields go through the roof and the stock market takes a shit! You can kiss your 401k goodbye! You'd have to be suicidal to have your money in the stock market right now.
In this scenario which is mostly likely to occur, Bitcoin goes to the moon because governments are going to be looking for a neutral reserve asset that can't be manipulated like US bonds. Bitcoin is the perfect solution to their problem. Once one major government or central bank puts Bitcoin on the balance sheet its game over for the dollar and the bonds. We might be closer to the end game than we think, and that is scary to think about. "Sometimes there are decades where nothing happens and there are weeks where decades happen." ~ Lenin
Crazy to quote a communist but he isn't wrong about history. We are living through a life alter paradigm shift. It is scary and exhilarating all at the same time. What a time to be alive ladies and gentlemen! Buckle up! Its going to get interesting!
-
 @ ba36d0f7:cd802cba
2025-04-22 20:30:45
@ ba36d0f7:cd802cba
2025-04-22 20:30:45| Pieza | Movimiento | Reglas Especiales | | --------- | ---------------------------------- | --------------------------- | | Peón | 1 casilla adelante (o 2 al inicio) | Captura al paso, coronación | | Torre | Líneas rectas | Enroque | | Caballo | En "L" (2+1) | Salta piezas | | Alfil | Diagonales | Atrapado en un color | | Dama | Cualquier dirección | Ninguna | | Rey | 1 casilla en cualquier dirección | Enroque, jaque mate |
1. Peón (♙ / ♟️)
- Mueve: 1 casilla adelante (o 2 en su primer movimiento).

- Captura: En diagonal (1 casilla).
 > Especial:
>- Captura al paso: Si un peón rival avanza 2 casillas, puedes capturarlo como si hubiera movido 1.
> - Coronación: Al llegar a la 8ª fila, se convierte en cualquier pieza (¡usualmente Dama!).
> Especial:
>- Captura al paso: Si un peón rival avanza 2 casillas, puedes capturarlo como si hubiera movido 1.
> - Coronación: Al llegar a la 8ª fila, se convierte en cualquier pieza (¡usualmente Dama!).
2. Torre (♖ / ♜)
- Mueve: Líneas rectas (sin límite de casillas).

- Especial: Participa en el enroque.
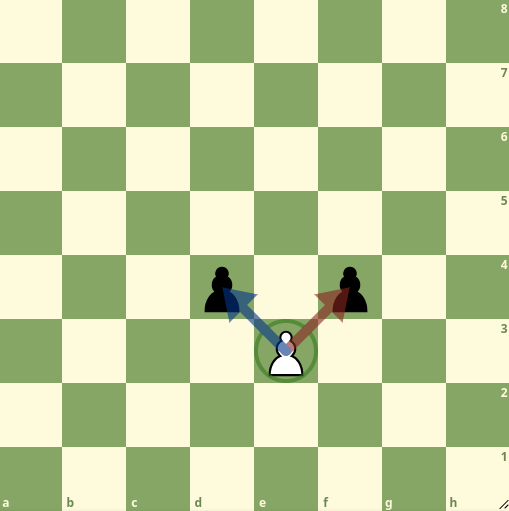
3. Caballo (♘ / ♞)
-
Mueve: En "L" (2 casillas en una dirección + 1 perpendicular).
-
Única pieza que salta sobre otras.
4. Alfil (♗ / ♝)
-
Mueve: Diagonales (sin límite).
-
Siempre permanece en el mismo color de casilla.

5. Dama (♕ / ♛)
- Mueve: Cualquier dirección (recto o diagonal).

- ¡La pieza más poderosa!
6. Rey (♔ / ♚)
- Mueve: 1 casilla en cualquier dirección.

Especial:
- Enroque: Cambia de lugar con una torre (si no hay obstáculos/jaques). - Jaque mate: Pierde si queda atrapado sin escapatoria.
Cómo mover
-
Un movimiento por turno.
-
Elige tu pieza y colócala en una casilla legal.
-
Solo tu color: Blancas mueven primero, luego negras, alternando.
-
No pasar: Debes mover si es tu turno.
Cómo capturar ("comer")
-
Ocupa la casilla de una pieza rival: Reemplázala con tu pieza.
-
Peones capturan solo en diagonal (no de frente).
-
Los reyes no pueden ser capturados (el jaque mate termina el juego).
✔ Jaque: Ataca al rey enemigo (debe escapar en su siguiente turno).
❌ Ilegal: Mover a jaque o dejar a tu rey en jaque.
Movimientos especiales
|Movimiento|Regla Clave|Notación| |---|---|---| |Enroque|Rey + torre, sin movimientos previos|
0-0| |Coronación|Peón→cualquier pieza en 8ª fila|e8=D| |Captura al paso|Captura un peón que avanzó 2 casillas|exd6 a.p.|
1. Enroque ("La escapatoria del rey")
-
Qué: Rey y torre se mueven juntos en un turno.
Cómo: -
Rey mueve 2 casillas hacia una torre.
-
Torre "salta" al lado opuesto del rey.

Reglas: - Sin jaques: El rey no puede estar en jaque ni pasar por casillas atacadas. - Sin movimientos previos: Ni el rey ni esa torre deben haberse movido antes.
Tipos:
- Corto (lado del rey, rápido):0-0- Largo (lado de la dama, seguro):0-0-0
2. Coronación ("Coronar")
-
Qué: Peón llega a la 8ª fila → se convierte en cualquier pieza (usualmente Dama).
-
Cómo: Reemplaza el peón (incluso si ya tienes esa pieza).
Dato curioso: Puedes tener 9 damas (1 original + 8 coronaciones).
Ejemplo: Peón en h8 se convierte en Dama →h8=D.
3. Captura al paso (Del francés "en passant")
-
Cuándo: Un peón rival avanza 2 casillas y queda al lado del tuyo.
-
Cómo: Captúralo en diagonal (como si hubiera movido 1 casilla).

Regla: Debes hacerlo inmediatamente (solo en el turno siguiente)
Recurso digitales
Guia para principiantes - Lichess.org https://lichess.org/study/Hmb28fbv/QRyxzgre
Ajedrez desde cero - Youtube.com https://www.youtube.com/watch?v=YPf9fSY_K2k&list=PLWgqlpb234bHv38g6zXoi3WIJJonzZSAl&index=8
- Mueve: 1 casilla adelante (o 2 en su primer movimiento).
-
 @ 9223d2fa:b57e3de7
2025-04-22 20:02:06
@ 9223d2fa:b57e3de7
2025-04-22 20:02:069,322 steps
-
 @ 7d33ba57:1b82db35
2025-04-22 19:43:27
@ 7d33ba57:1b82db35
2025-04-22 19:43:27Welcome to Hortobágy National Park, Hungary’s oldest and largest national park, and a UNESCO World Heritage Site that showcases the wild, open heart of the Puszta—the vast steppe of Eastern Europe. Spanning over 800 km², this park is a land of windswept grasslands, grazing animals, traditional herding culture, and incredible birdlife.
🌾 What to See & Do in Hortobágy
🐃 Explore the Puszta Landscape
- Ride through the grasslands in a horse-drawn cart or take a bike tour
- See iconic gray cattle, racka sheep with spiral horns, water buffalo, and traditional herdsmen in wide-brimmed hats
🐎 Horse Shows & Herding Traditions
- Visit a csikós show, where Hungarian horsemen perform riding tricks and herding techniques
- Learn about the unique pastoral culture that has existed here for centuries
🐦 Birdwatching Paradise
- Hortobágy is one of Europe’s best spots for birdwatching
- See cranes, eagles, storks, and rare migratory species, especially in spring and autumn
- Visit the Hortobágy Bird Hospital and crane observation sites
🌉 Hortobágy Nine-Arch Bridge (Kilenclyukú híd)
- An iconic stone bridge built in the 19th century, stretching over the river Hortobágy
- The symbolic center of the park and a great photo spot
- Nearby you’ll find the Hortobágy Village, with museums, markets, and local food
🧀 Local Culture & Cuisine
- Taste slambuc (a traditional shepherd’s stew), cheeses, and local smoked meats
- Check out folk art and handmade crafts in local markets and heritage centers
🚶♂️ How to Visit
- Closest city: Debrecen (around 30 minutes by car or bus)
- The park offers guided tours, bike rentals, and wildlife safaris
- Great for day trips or overnight stays in nearby guesthouses or rural lodges
Hortobágy is more than a landscape—it’s a living cultural heritage site, where ancient traditions, wildlife, and wide horizons stretch as far as the eye can see. Perfect for nature lovers, culture seekers, or anyone looking to experience a different side of Hungary.
-
 @ 7d33ba57:1b82db35
2025-04-22 19:29:59
@ 7d33ba57:1b82db35
2025-04-22 19:29:59Tucked into the foothills of the Bükk Mountains, Eger is one of Hungary’s most charming and historic towns. Famous for its Baroque architecture, thermal baths, and Egri Bikavér (“Bull’s Blood”) red wine, Eger offers a perfect blend of culture, relaxation, and rustic charm all just a couple of hours from Budapest.
🏰 Top Things to Do in Eger
🏯 Eger Castle (Egri Vár)
- A key site in Hungary’s defense against the Ottoman Empire
- Learn about the 1552 Siege of Eger, when outnumbered locals held off the Turks
- Climb the walls for views of the old town’s red rooftops and spires
⛪ Eger’s Baroque Old Town
- Wander elegant streets lined with pastel facades, cute cafés, and small boutiques
- Don’t miss the Minorite Church and Dobó Square, the lively heart of the city
🛁 Thermal Baths
- Relax in the Eger Turkish Bath, built during the Ottoman period and still in use today
- Or soak at Eger Thermal Spa, great for families and wellness seekers
🍷 Wine Tasting in the Valley of the Beautiful Women (Szépasszony-völgy)
- A short walk or ride from town, this valley is lined with wine cellars built into the hillside
- Taste the iconic Egri Bikavér (a full-bodied red blend) and Egri Csillag (a refreshing white)
- Most cellars offer generous tastings and hearty local snacks
🧀 Local Food to Try
- Goulash, Lángos, and hearty meat dishes
- Pair local cheeses and sausages with regional wines
- Cozy cellar restaurants and rustic taverns set the mood
🚆 Getting There
- About 2 hours by train or car from Budapest
- Walkable town, no car needed once you’re there
-
 @ df478568:2a951e67
2025-04-22 18:56:38
@ df478568:2a951e67
2025-04-22 18:56:38"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." --Satoshi Nakamoto The Cryptography Mailing List--January 17, 2009
Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial. --Satoshi Nakamoto Bitcoin Talk-- August 5, 2010
I very be coded some HTML buttons using Claude and uploaded it to https://github.com/GhostZaps/ It's just a button that links to zapper.fun.
I signed up for Substack to build an email address, but learned adding different payment options to Substack is against their terms and services. Since I write about nostr, these terms seem as silly as someone saying Craig Wright is Satoshi. It's easy to build an audience on Substack however, or so I thought. Why is it easier to build an audience on Subtack though? Because Substack is a platform that markets to writers. Anyone with a ~~pen~~ ~~keyboard~~ smartphone and an email can create an account with Substack. There's just one problem: You are an Internet serf, working the land for your Internet landlord--The Duke of Substack.
Then I saw that Shawn posted about Substack's UX.
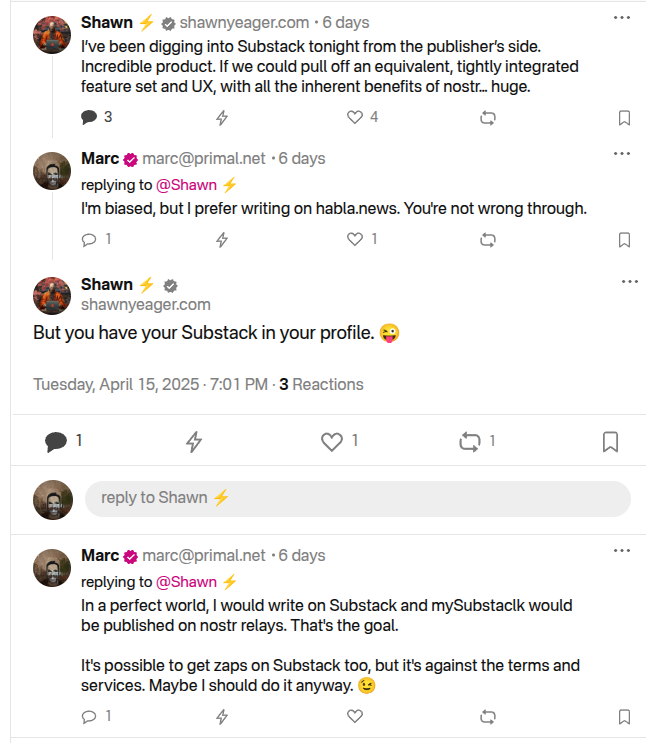
I should have grabbed my reading glasses before pushing the post button, but it occurred to me that I could use Ghost to do this and there is probably a way to hack it to accept bitcoin payments over the lightning network and host it yourself. So I spun my noddle, doodled some plans...And then it hit me. Ghost allows for markdown and HTML. I learned HTML and CSS with free-code camp, but ain't nobody got time to type CSS so I vibe-coded a button that ~~baits~~ sends the clicker to my zapper.fun page. This can be used on any blog that allows you to paste html into it so I added it to my Ghost blog self-hosted on a Start 9. The blog is on TOR at http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/, but most people around me have been conditioned to fear the dark web so I used the cloudflared to host my newsletter on the clear net at https://marc26z.com/
Integrating Nostr Into My Self-Hosted Ghost Newsletter
I would venture to say I am more technical than the average person and I know HTML, but my CSS is fuzzy. I also know how to print("Hello world!") in python, but I an NPC beyond the basics. Nevertheless, I found that I know enough to make a button. I can't code well enough to create my own nostr long-form client and create plugins for ghost that send lightning payments to lighting channel, but I know enough about nostr to know that I don't need to. That's why nostr is so F@#%-ing cool! It's all connected. ** - One button takes you to zapper.fun where you can zap anywhere between 1 and ,000,000 sats.** - Another button sends you to a zap planner pre-set to send 5,000 sats to the author per month using nostr. - Yet another button sends you to a zap planner preset to send 2,500 sats per month.
The possibilities are endless. I entered a link that takes the clicker to my Shopstr Merch Store. The point is to write as self-sovereign as possible. I might need to change my lightning address when stuff breaks every now and then, but I like the idea of busking for sats by writing on the Internet using the Value 4 Value model. I dislike ads, but I also want people to buy stuff from people I do business with because I want to promote using bitcoin as peer-to-peer electronic cash, not NGU porn. I'm not prude. I enjoy looking at the price displayed on my BlockClock micro every now and then, but I am not an NGU porn addict.
This line made this pattern, that line made this pattern. All that Bolinger Bart Simpson bullshit has nothing to with bitcoin, a peer-to-peer electronic cash system. It is the musings of a population trapped in the fiat mind-set. Bitcoin is permissionless so I realized I was bieng a hipocryte by using a permissioned payment system becaue it was easier than writing a little vibe code. I don't need permission to write for sats. I don't need to give my bank account number to Substack. I don't need to pay a 10$ vig to publish on a a platform which is not designed for stacking sats. I can write on Ghost and integrate clients that already exist in the multi-nostr-verse.
Nostr Payment Buttons
The buttons can be fouund at https://github.com/Marc26z/GhostZapButton
You can use them yourself. Just replace my npub with your npub or add any other link you want. It doesn't technically need to be a nostr link. It can be anything. I have a link to another Ghost article with other buttons that lead down different sat pledging amounts. It's early. Everyone who spends bitcoin is on nostr and nostr is small, but growing community. I want to be part of this community. I want to find other writers on nostr and stay away from Substack.
Here's what it looks like on Ghost: https://marc26z.com/zaps-on-ghost/
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ d34e832d:383f78d0
2025-04-22 18:15:42
@ d34e832d:383f78d0
2025-04-22 18:15:42Proof Of Concept
In a world where decentralization often hinges on the strength of its weakest node, the idea of federation—applied not to content moderation or identity, but strictly to communication protocols—opens up intriguing possibilities. In this model, Nostr relays do not operate in total isolation, nor do they function in a single cohesive mesh. Instead, they form selective, encrypted alliances, communicating through secure tunnels while preserving autonomy.
💡 The Core Idea
Relays remain sovereign, but may establish peer-to-peer encrypted channels with other trusted relays using Elliptic Curve Diffie-Hellman (ECDH) to generate shared secrets. These secrets are then used to encrypt communication tunnels—facilitating a federated communication layer.
Each relay is free to choose: - Whom it speaks to - How often - What types of events are relayed through the tunnel
But never must it rely on a central coordinator.
🔁 Schnorr for Authentication
While ECDH can create the secure tunnel, Schnorr signatures (already a part of Nostr’s pubkey-based design) can be used to authenticate the origin of the data inside. This keeps the integrity of messages intact even when traveling over shared or hostile networks.
Use case: - Relay A and Relay B establish an ECDH-based shared key. - All communication is tunnel-encrypted with this shared key. - Inside the tunnel, every message still carries a Schnorr signature, proving its source.
This separation of transport-level encryption from message-level authenticity provides an elegant layering of security.
🌐 Practical Benefits
- Obfuscation: Encrypted tunnels reduce visibility into relay-to-relay traffic patterns.
- Privacy: Federation over encrypted channels shields metadata and protects against surveillance.
- Resilience: Relays can route around censorship by tunneling through less obvious peers.
- Synergy: Specific relay clusters can form ephemeral or long-term alliances—say, art relays or academic relays—without disclosing their full graph to the world.
🧩 Optional Enhancements
- Noise Protocol Framework to standardize encrypted relay tunnels.
- Tor Hidden Services or I2P for transport obfuscation.
- Relay Reputation Systems to gauge trust before federation.
- Dynamic Federation Negotiation: using NIP-like proposals over encrypted handshakes to initiate or terminate communication agreements.
🌱 Case In Point
This is not about governing content, users, or identities—this is about strengthening how relays talk. By embracing federated communication via ECDH and Schnorr-secured tunnels, Nostr relays could evolve into a resilient underground of trust-minimized, pseudonymous routers that defy surveillance while amplifying decentralization.
federated communication via ECDH and Schnorr-authenticated encrypted tunnels between Nostr relays:
markdown NIP-xyz: Federated Encrypted Relay Communication Status: Draft Type: Relay Created: 2025-04-22
Summary
This NIP proposes a method for encrypted, authenticated communication between Nostr relays using ECDH-based tunnels for transport encryption and Schnorr signatures for payload integrity. This federation model allows relays to communicate securely while maintaining full autonomy, enhancing privacy, censorship resistance, and interoperability.
Motivation
Nostr’s decentralized architecture relies heavily on relays, which currently operate in isolated or broadcast modes. There is no standard for secure, peer-to-peer communication between relays themselves, outside of client interactions.
Introducing encrypted tunnels between relays offers:
- Privacy: Reduces metadata leakage across public or adversarial networks.
- Resilience: Allows relays to forward events and metadata through trusted peers when direct access is blocked or filtered.
- Autonomy: Federation is opt-in and purely communicational—no centralized authority or directory is involved.
- Extensibility: Enables experimental protocols or content-specific subnets without altering the global Nostr model.
Specification
1. Key Exchange via ECDH
Each relay maintains: - A persistent relay keypair:
relay_pubkey,relay_privkey- Optionally: rotating session keys for forward secrecyWhen two relays (A and B) wish to establish communication: - They exchange their public keys (
relay_pubkey_Aandrelay_pubkey_B) - Both calculate a shared secret using ECDH oversecp256k1:plaintext shared_secret = SHA256(ECDH(relay_privkey_A, relay_pubkey_B))This
shared_secretis used to derive an encryption key for an authenticated symmetric cipher, such as AES-GCM or ChaCha20-Poly1305.
2. Encrypted Tunnel Establishment
Once the shared secret is derived: - All messages between relays are sent through an encrypted tunnel - Transport can be TCP, WebSocket, or HTTP/3 over QUIC, optionally via Tor or I2P
A RelayHello message is exchanged encrypted, optionally containing:
json { "type": "relay_hello", "relay_name": "nostr.relay.example", "features": ["forwarding", "dedup", "metadata"], "timestamp": 1684000000, "sig": "<Schnorr-signed payload>" }The
sigis a Schnorr signature from therelay_pubkey, verifying the message content.
3. Event Forwarding
Relays may forward selected event types across tunnels, such as: - Kind 1 (Text Note) - Kind 3 (Contacts) - Kind 5 (Deletion Notices) - Custom kinds (with mutual agreement)
All forwarded events MUST retain original client-level signatures. Relay-to-relay metadata (like timestamps, relay hints, or scores) may be added in a separate metadata envelope.
4. Access Control and Policies
Each relay maintains a federation list, including: - Public key of the peer relay - Features enabled - Rate limits and quotas - Last active session or rotation timestamp
Relays MAY: - Deny tunnel requests - Rotate keys periodically - Restrict communication to a whitelist - Use Proof-of-Work or tokens for DoS protection
5. Optional Features
- Forward Secrecy: ephemeral key pairs with HKDF for short sessions
- Relay Reputation: signed relay trust scores (future NIP)
- Message Compression: gzip or zstd on tunnel payloads
- Encrypted Gossip: tunnel-specific metadata routing
Compatibility
This NIP is backward-compatible. Relays that do not implement it will simply not participate in tunnel-based communication.
No changes are required from Nostr clients.
Reference Implementation (Proposed)
nostr-tunnel-relay: Rust-based relay that supports federated encrypted tunnelsnostr-relay-link: CLI tool to establish and monitor tunnels- Example configs for federation policies in JSON or TOML
Rationale
- ECDH ensures only the two relays involved can decrypt tunnel data
- Schnorr signatures authenticate content without duplicating identity schemes
- Federation is scoped only to communication, preserving Nostr’s core simplicity
Security Considerations
- Relay pubkeys must be carefully verified to prevent MITM
- Session expiration and key rotation should be configurable
- Replay protection and nonce management are required for AEAD ciphers
- Metadata leakage minimized by default obfuscation or Tor-based transport
NIP.eshgham
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ 9bde4214:06ca052b
2025-04-22 17:30:02
@ 9bde4214:06ca052b
2025-04-22 17:30:02“We do not have the answers."
Pablo & Gigi have no solutions.
In this dialogue:
- What is this No Solutions thing anyway?
- Why dialogue and distributed cognition is so important
- Why is nostr exciting for developers?
- Evolution, Life, and nostr
- What is the perfect nostr app, and why can’t there be THE perfect nostr app?
- Why there is no “global” view in nostr
- Impossible problems vs. possible (but still hard) problems
- Blossom, blossom, and more blossom
- Zooko’s Triangle
- Freedom Tech Building Blocks
- NIP-60/61, NIP-89
- Email vs ICQ
- Accepting constraints & moving forward
- Nostr has data integrity, but no data guarantees
- Bitcoin as an extreme RAID system
- Fault tolerance vs. efficiency
- “Build the infrastructure, don’t run it.”
- eCash fixes 402
- Everything in nostr can be one-click
- There’s infinite nsecs (and they are free!)
- The magic of the nostr view-only mode
- The Local-first movement
- How to monetize without putting yourself in the middle?
- RoboSats as an example of open-source monetization
- The YouTube like count is a lie
Further links:
- https://en.wikipedia.org/wiki/Distributed_cognition
- https://nips.nostr.com/60
- https://nips.nostr.com/61
- https://nips.nostr.com/89
- https://github.com/hzrd149/blossom
- https://en.wikipedia.org/wiki/Zooko’s_triangle
- https://www.jrepodcast.com/guest/adam-curry/
- https://localfirstweb.dev/
- https://www.localfirstconf.com/
- https://en.wikipedia.org/wiki/ICQ
- https://appleinsider.com/articles/24/05/25/icq-1996-2024-the-first-universal-messenger-had-a-good-run-and-is-leaving-us-soon
- https://www.chatinum.com/articles/the-old-chat-apps-of-the-2000s
- https://en.wikipedia.org/wiki/Standard_RAID_levels
- https://www.youtube.com/watch?v=oIkhgagvrjI
- https://njump.me/nosolutions@sovereignengineering.io
-
 @ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44
@ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44A monthly newsletter by The 256 Foundation

April 2025
Introduction:
Welcome to the fourth newsletter produced by The 256 Foundation! March was an action-packed month with events ranging from the announcement of TSMC investing in US fabs to four solo block finds. Dive in to catch up on the latest news, mining industry developments, progress updates on grant projects, Actionable Advice on updating a Futurebit Apollo I to the latest firmware, and the current state of the Bitcoin network.
[IMG-001] Variation of the “I’m the captain now” meme by @maxisclub
Definitions:
MA = Moving Average
Eh/s = Exahash per second
Ph/s = Petahash per second
Th/s = Terahash per second
T = Trillion
J/Th = Joules per Terahash
$ = US Dollar
OS = Operating System
SSD = Solid State Drive
TB = Terabyte
News:
March 3, Ashigaru releases v1.1.1. Notable because this fork of Samourai Wallet serves as the remaining choice of mobile Bitcoin wallet capable of making peer to peer collaborative transactions. Not the Whirlpool transactions that Samourai Wallet was well-known for but the Stowaway and StonewallX2 p2p CoinJoin transactions. The persistence of Samourai’s tools still working despite the full force of the State coming down on the developers is a testament to the power of open-source code.
March 3, Stronghold completes cleanup of decommissioned coal plant using Bitcoin miners. Stronghold’s initiative counters the narrative that Bitcoin mining is wasteful by removing 150,000 tons of coal waste, part of a broader effort that cleared 240,000 tons in Q2 2024 alone. Waste coal piles in Pennsylvania, like the one in Russellton, have scarred landscapes, making this reclamation a significant step for local ecosystems. The project aligns with growing efforts in the region, as The Nature Conservancy also leads restoration projects in Pennsylvania to revive forests and waters. Stronghold’s dual-use model—powering Bitcoin miners and supplying the grid—shows how Bitcoin mining can support environmental goals while remaining economically viable.
March 3, five TSMC semiconductor fabs coming to Arizona. TSMC’s $100 billion investment in Arizona reflects a strategic push to bolster U.S. semiconductor production amid global supply chain vulnerabilities and geopolitical tensions, particularly with West Taiwan’s claims over Taiwan. TSMC’s existing $65 billion investment in Phoenix, now totaling $165 billion, aims to create 40,000 construction jobs and tens of thousands of high-tech roles over the next decade. This could relieve bottlenecks in ASIC chip supply if Bitcoin mining chip designers can get access to the limited foundry space. If that is the case, this could help alleviate some centralization concerns as it relates to a majority of Bitcoin mining chips coming from Taiwan and West Taiwan.
March 10, Block #887212 solved by a Bitaxe Ultra with ~491Gh/s. Not only did the Bitaxe satisfy the network difficulty, which was 112.15T, but obliterated it with a whopping 719.9T difficulty. This Block marked the second one solved by a Bitaxe and an increasing number of solo block finds overall as more individuals choose to play the Bitcoin lottery with their hashrate.
March 12, Pirate Bay co-founder, Carl Lundström, killed in plane crash. The Pirate Bay, launched in 2003, revolutionized online file-sharing by popularizing BitTorrent technology, enabling millions to access music, movies, and software, often in defiance of legal systems, which led to Lundström’s 2009 conviction for copyright infringement. The timing of his death coincides with ongoing global debates over digital ownership and intellectual property, often echoing many of the same themes in open-source technology, underscoring the enduring impact of The Pirate Bay’s challenge to traditional media distribution models.
March 18, Samourai Wallet status conference update. This was a short meeting in which the dates for the remaining pre-trial hearings was discussed.
- May 9, Opening Motion. - June 6, prosecution response to the opening motion. - June 20, defense replies to the prosecution response. - July 15, prosecution provides expert disclosure - August 8, defense provides expert disclosure - Tdev is able to remain home during the remaining pre-trial hearings so that he doesn’t have to incur the expenses traveling back and forth between Europe and the USDespite seemingly positive shifts in crypto-related policies from the Trump administration, all signs point to the prosecution still moving full steam ahead in this case. The defense teams need to be prepared and they could use all the financial help they can get. If you feel compelled to support the legal defense fund, please do so here. If the DOJ wins this case, all Bitcoiners lose.
March 18, DEMAND POOL launches, transitioning out of stealth mode and making room for applicants to join the private waiting list to be one of the Founding Miners.
Key features of DEMAND Pool include: • Build your own blocks • SLICE payment system & new mempool algorithm • No more empty blocks • End-to-end encryption for protection • Efficient data transfer, less wasted hashrate • Lower costs on CPU, bandwidth, & time
DEMAND Pool implements Stratum v2 so that miners can generate their own block templates, entering the arena of pools trying to decentralize mining such as OCEAN with their alternative to Stratum v2 called DATUM. A benefit of the Stratum v2 protocol over Stratum v1 is that data sent between the miner and the pool is now encrypted whereas before it was sent in clear-text, the encryption helps with network level privacy so that for example, your Internet Service Provider cannot read what is in the data being passed back and forth. Although, unless there is a proxy between your miner and the pool then the ISP may be able to determine that you are sending data to a mining pool, they just wouldn’t be able to tell what’s in that data. Overall, decentralization has become a buzz word lately and while it is a step in the right direction that more pools are enabling miners to decide which transactions are included in the block templates they work on, the pools remain a centralized force that ultimately can reject templates based on a number of reasons.
March 20, Bitaxe makes the cover of Bitcoin Magazine’s The Mining Issue, solidifying the Bitaxe as a pop-culture icon. Even those who disregard the significance of the Bitaxe project must recognize that the project’s popularity is an indication that something big is developing here.
 [IMG-002] Bitcoin Magazine, The Mining Issue
[IMG-002] Bitcoin Magazine, The Mining IssueMarch 21, self-hosted solo miner solves block #888737 with a Futurebit Apollo, making this the third solo block find for Futurebit. The first Futurebit Apollo block find may have been a fluke, the second a coincidence, but the third is an indication of a pattern forming here. More hashrate is being controlled by individuals who are constructing their own blocks and this trend will accelerate as time goes on and deploying these devices becomes easier and less expensive. This was the second solo block found in March.
March 21, US Treasury Department lifts sanctions on Tornado Cash. This is a positive sign coming from the US Treasury, however the charges against the Tornado Cash developer, Roman Storm, still stand and his legal defense team is still fighting an uphill battle. Even though the US Treasury removed Tornado Cash from the OFAC list, the department is attempting to stop a Texas court from granting a motion that would ensure the Treasury can’t put Tornado Cash back on the OFAC list. Meanwhile, the other Tornado Cash developer, Alex Pertsev, is fighting his appeal battle in the Dutch courts.
March 22, Self-hosted Public Pool user mines Block #888989. This was the first block mined with the Public Pool software, which is open-source and available for anyone to host themselves, in this case hosted on the user’s Umbrel. If you read the January issue of The 256 Foundation newsletter, there are detailed instructions for hosting your own instance of Public Pool on a Raspberry Pi. Easier solutions exist and accomplish the same thing such as Umbrel and Start9. This was the third solo block mined in March.
March 26, DeFi Education Fund publishes coalition letter urging congress to correct the DOJ’s dangerous misinterpretation of money transmission laws. In their own words: “First seen in Aug 2023 via the criminal indictment of @rstormsf, the DOJ’s novel legal theory expands criminal liability to software developers, ignoring longstanding FinCEN guidance and threatening the entire U.S. blockchain & digital asset ecosystem”. Many familiar organizations in the industry signed the letter, such as Coinbase, Kraken, A16z Crypto, and Ledger. Sadly, no Bitcoin companies signed the letter, highlighting the reckless ignorance prevalent among the “toxic Bitcoin maximalists” who often pride themselves on their narrow focus; a focus which is proving to be more of a blind spot limiting their ability to recognize a clear and present threat. The full letter text can be found here.
March 28, Heatbit reveals the black Heatbit, an elegant space heater that mines Bitcoin. Heat re-use applications such as Bitcoin mining space heaters are one of many examples where energy spent on generating heat can also earn the user sats. Other popular solutions include heating hot tubs, hotels, drive ways, and more. The innovations in this area will continue to be unlocked as open-source solutions like the ones being developed at The 256 Foundation are released and innovators gain more control over their applications.
March 29, miner with 2.5Ph/s solves Block #889975 with Solo CK Pool, marking the fourth solo block found in the month of March. This was the first solo block found on CK Pool’s European server. This was a good way to finish the month on a strong note for small-scale miners.
Free & Open Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open. Innovators didn’t let off the gas in March, here are eleven note-worthy events:
0) @BTC_Grid demonstrates heating a new residential build with Bitcoin miners. This custom build features 6,000 square feet of radiant floors, 1,500 sqft of snow melting slab, 2 heated pools, all powered by Bitcoin miners and fully automated. Innovations and efficient systems like this will become more common as Bitcoin mining hardware and firmware solutions become open-source
1) @DrydeGab shares The Ocho, a Bitaxe Nerd Octaxe open-source Bitcoin miner featuring 8x BM1370 ASICs that performs at 9-10Th/s consuming ~180W. The Ocho runs on it’s own custom AxeOS. Currently out of stock but generally available for purchase in the IX Tech store.
 [IMG-003] The Nerd OCTAXE Ocho by @DrydeGab
[IMG-003] The Nerd OCTAXE Ocho by @DrydeGab2) @incognitojohn23 demonstrates building a Bitaxe from scratch with no prior experience, proving that anyone can access this technology with a little determination and the right community. @incognitojohn23 has also uploaded several videos documenting his progress and lessons along the way. Every builder has their first day, don’t hold back if you feel compelled to jump in and get started.
3) @HodlRev demonstrating how he combines Bitcoin mining with maple syrup production. In fact, @HodlRev has integrated Bitcoin mining into several aspects of his homestead. Be sure to follow his content for an endless stream of resourceful ideas. Once open-source Bitcoin mining firmware and hardware solutions become widely available, innovators like @HodlRev will have more control over every parameter of these unique applications.
4) ATL Bitlab announces their first hackathon, running June 7 through July 6. Promoted as “A global hackathon focused on all things bitcoin mining”. If you are interested in joining the hackathon, there is a Google form you can fill out here. It will be interesting to see what innovations come from this effort.
5) @100AcresRanch builds touchscreen dashboard for Bitaxe and Loki Boards. With this, you can control up to 10 mining devices with the ability to instantly switch any of the presets without going into the mining device UI.
 [IMG-004] Decentral Command Dashboard by @100AcresRanch
[IMG-004] Decentral Command Dashboard by @100AcresRanch6) @IxTechCrypto reveals HAXE, the newest member of the Nerdaxe miner family. HAXE is a 6 ASIC miner performing at ~7.4 Th/s at ~118W. Upon looking at the IX Tech store, it seems as though the HAXE has not hit shelves yet but keep an eye out for announcements soon.
7) Solo Satoshi reveals the NerdQaxe++, the latest marvel in the world of open-source Bitcoin mining solutions. This device is equipped with four ASIC chips from the Antminer S21 Pro and boasts an efficiency rating of 15.8 J/Th. At the advertised power consumption of 76 Watts, that would produce nearly 5 Th/s. Currently out of stock at the Solo Satoshi store and the IX Tech store but in stock and available at the PlebSource store.
8) @TheSoloMiningCo shares a bolt-on voltage regulator heatsink for the Bitaxe, this is a helpful modification when overclocking your miner and helps dissipate heat away from the voltage regulator. Many innovators are discovering ways to get every bit of efficiency they can from their hardware and sharing their ideas with the wider community for anyone to adopt.
9) @boerst adds historical data to stratum.work, a public website that monitors mining pool activity through calling for the work templates being generated for the pool’s respective miners. By parsing the information available in the work templates, a number of interesting observations can be made like which pools are merely proxies for larger pools, timing analysis of when templates are sent out, and now historical data on what the state of each pool’s templates were at a given block height. The work Boerst is doing with this website provides a great tool for gaining insights into mining centralization.
10) Braiins open-sources the BCB100 Control Board, designed to work with Antminers, this control board project has two parts: the hardware and the software. For the hardware part, open files include the Bill Of Materials, schematics, Gerbers, and CAD files. For the software part, open files include the board-level OpenWrt-based firmware with the full configuration file and the Nix environment for reproducible builds. The mining firmware binaries for bosminer and boser (same as the official Braiins OS releases) are also available to download and use to compile the image for the control board, however the Braiins OS firmware itself is not included in this open-source bundle. Braiins chose the GPLv3 open-source license for the software and the CERN-OHL-S open-source license for the hardware. This is a great gesture by Braiins and helps validate the efforts of The 256 Foundation to make Bitcoin mining free and open. The Braiins GitHub repositories where all this information can be found are accessible here and here. The 256 Foundation has plans to develop a Mujina firmware that can be flashed onto the BCB100 helping target Antminer machines.
Grant Project Updates:
In March, The 256 Foundation formalized agreements with the lead developers who were selected for each project. These agreements clearly defined the scope of each project, identified the deliverables, set a timeline, and agreement on compensation was made. Below are the outlines for each project, the compensation is not made public for privacy and security reasons.
Ember One:
@skot9000 instigator of the Bitaxe and all around legend for being the first mover in open-source Bitcoin mining solutions is the lead engineer for the Ember One project. This was the first fully funded grant from The 256 Foundation and commenced in November 2024 with a six month duration. The deliverable is a validated design for a ~100W miner with a standardized form factor (128mm x 128mm), USB-C data connection, 12-24v input voltage, with plans for several versions – each with a different ASIC chip. The First Ember One features the Bitmain BM1362 ASIC, next on the list will be an Ember One with the Intel BZM2 ASIC, then an Auradine ASIC version, and eventually a Block ASIC version. Learn more at: https://emberone.org/
Mujina Mining Firmware:
@ryankuester, embedded Linux developer and Electrical Engineer who has mastered the intersection of hardware and software over the last 20 years is the lead developer for the Mujina project, a Linux based mining firmware application with support for multiple drivers so it can be used with Ember One complete mining system. The grant starts on April 5, 2025 and continues for nine months. Deliverables include:
Core Mujina-miner Application: - Fully open-source under GPLv3 license - Written in Rust for performance, robustness, and maintainability, leveraging Rust's growing adoption in the Bitcoin ecosystem - Designed for modularity and extensibility - Stratum V1 client (which includes DATUM compatibility) - Best effort for Stratum V2 client in the initial release but may not happen until later
Hardware Support:
- Support for Ember One 00 hash boards (Bitmain chips) - Support for Ember One 01 hash boards (Intel chips) on a best effort basis but may not happen until later - Full support on the Raspberry Pi CM5 and IO board running the Raspberry Pi OS - Support for the Libre board when released - Best-effort compatibility with other hardware running LinuxManagement Interfaces:
• HTTP API for remote management and monitoring • Command-line interface for direct control • Basic web dashboard for status monitoring • Configuration via structured text files • Community Building and Infrastructure • GitHub project organization and workflow • Continuous integration and testing framework • Comprehensive user and developer documentation • Communication channels for users and developers • Community building through writing, podcasts, and conference participationThe initial release of Mujina is being built in such a way that it supports long-term goals like ultimately evolving into a complete Linux-based operating system, deployable through simple flashing procedures. Initially focused on supporting the 256 Foundation's Libre control boards and Ember hash boards, Mujina's modular architecture will eventually enable compatibility with a wide variety of mining hardware from different manufacturers. Lean more at: https://mujina.org/
Libre Board:
@Schnitzel, heat re-use maximalist who turned his home's hot water accessories into Bitcoin-powered sats generators and during the day has built a successful business with a background in product management, is the lead engineer on the Libre Board project; the control board for the Ember One complete mining system. Start date is April 5, 2025 and the deliverables after six months will be a mining control board based on the Raspberry Pi Compute Module I/O Board with at least the following connections:
• USB hub integration (maybe 10 ports?) • Support for fan connections • NVME expansion • Two 100-pin connectors for the compute module • Ethernet port • HDMI port • Raspberrypi 40-pin header for sensors, switches, & relays etc. • MIPI port for touchscreen • Accepts 12-24 VDC input power voltage.The initial release of Libre Board is being built in such a way that it supports long-term goals like alternative compute modules such as ARM, x86, and RISC-V. Learn more at: https://libreboard.org/
Hydra Pool:
@jungly, distributed systems PhD and the lead developer behind P2Pool v2 and formerly for Braidpool, now takes the reigns as lead developer for Hydra Pool, the stratum server package that will run on the Ember One mining system. Start date for this project was on April 5, 2025 and the duration lasts for six months. Deliverables include:
• Talks to bitcoind and provides stratum work to users and stores received shares • Scalable and robust database support to save received shares • Run share accounting on the stored shares • Implement payment mechanisms to pay out miners based on the share accounting • Provide two operation modes: Solo mining and PPLNS or Tides based payout mechanism, with payouts from coinbase only. (All other payout mechanism are out of scope of this initial release for now but there will be more). • Rolling upgrades: Tools and scripts to upgrade server with zero downtime. • Dashboard: Pool stats view only dashboard with support to filter miner payout addresses. • Documentation: Setup and other help pages, as required.The initial release of Hydra Pool is being built in such a way that it supports long-term goals like alternative payout models such as echash, communicating with other Hydra Pool instances, local store of shares for Ember One, and a user-friendly interface that puts controls at the user's fingertips, and supports the ability for upstream pool proxying. Learn More at: https://hydrapool.org/
Block Watcher:
Initially scoped to be a Bitcoin mining insights application built to run on the Ember One mining system using the self-hosted node for blockchain data. However, The 256 Foundation has decided to pause Block Watcher development for a number of reasons. Primarily because the other four projects were more central to the foundation’s mission and given the early stages of the Foundation with the current support level, it made more sense to deploy capital where it counts most.
Actionable Advice:
This month’s Actionable Advice column explains the process for upgrading the Futurebit Apollo I OS to the newer Apollo II OS and replacing the SSD. The Futurebit Apollo is a small mining device with an integrated Bitcoin node designed as a plug-and-play solution for people interested in mining Bitcoin without all the noise and heat of the larger industrial-grade miners. The Apollo I can hash between 2 – 4 Th/s and will consume roughly 125 – 200 Watts. The Apollo II can hash between 8 – 10 Th/s and will consume roughly 280 – 400 Watts. The motivation behind upgrading from the Apollo I OS to the Apollo II OS is the ability to run a stratum server internally so that the mining part of the device can ask the node part of the device for mining work, thus enabling users to solo mine in a self-hosted fashion. In fact, this is exactly what The 256 Foundation did during the Telehash fundraising event where Block #881423 was solo mined, at one point there was more than 1 Eh/s of hashrate pointed to that Apollo.
 [IMG-005] Futurebit Apollo I with new NVME SSD
[IMG-005] Futurebit Apollo I with new NVME SSDYou can find the complete flashing instructions on the Futurebit website here. You will need a separate computer to complete the flashing procedure. The flashing procedure will erase all data on the microSD card so back it up if you have anything valuable saved on there.
First navigate to the Futurebit GitHub Releases page at: https://github.com/jstefanop/apolloapi-v2/releases
Once there, you will see two OS images available for download, along with two links to alternative hosting options for those two images. If you are upgrading an Apollo I, you need to figure out which new OS image is right for your device, the MCU 1 image or the MCU 2 image. There are detailed instructions on figuring this out available here. There are multiple ways to determine if you need the MCU 1 or MCU 2 image. If the second to last digit in your Futurebit Apollo I is between 4 – 8 then you have an MCU 1; or if your batch number is 1 – 3 then you have an MCU 1; or if the circuit board has a 40-pin connector running perpendicular to the microSD card slot then you have an MCU 1. Otherwise, you have an MCU 2.
For example, this is what the MCU 1 circuit board will look like:
 [IMG-006] Futurebit MCU1 example
[IMG-006] Futurebit MCU1 exampleOnce you figure out which OS image you need, go ahead and download it. The SHA256 hash values for the OS Image files are presented in the GitHub repo. If you’re running Linux on your computer, you can change directory to your Download folder and run the following command to check the SHA256 hash value of the file you downloaded and compare that to the SHA256 hash values on GitHub.
 [IMG-007] Verifying Futurebit OS Image Hash Value
[IMG-007] Verifying Futurebit OS Image Hash ValueWith the hash value confirmed, you can use a program like Balena Etcher to flash your microSD card. First remove the microSD card from the Apollo circuit board by pushing it inward, it should make a small click and then spring outward so that you can grab it and remove it from the slot.
Connect the microSD card to your computer with the appropriate adapter.
Open Balena Etcher and click on the “Flash From File” button to define the file path to where you have the OS image saved:
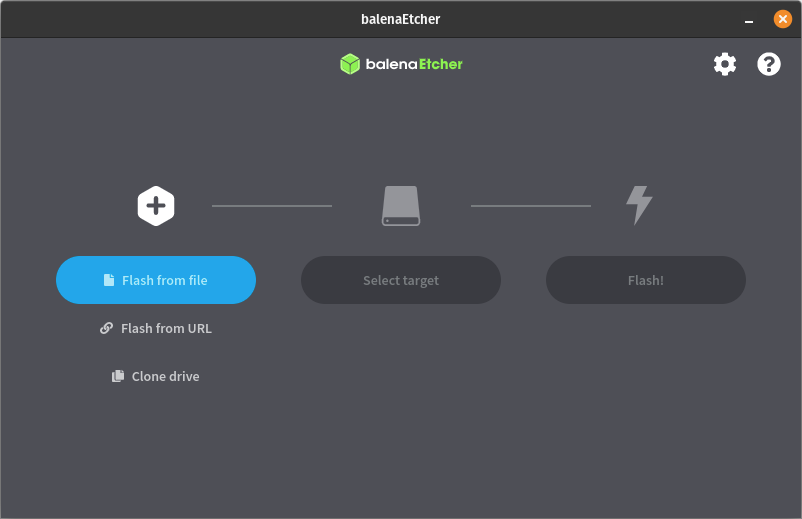 [IMG-008] Balena Etcher user interface
[IMG-008] Balena Etcher user interfaceThen click on the “Select Target” button to define the drive which you will be flashing. Select the microSD card and be sure not to select any other drive on your computer by mistake:
 [IMG-009] Balena Etcher user interface
[IMG-009] Balena Etcher user interfaceThen click on the “Flash” button and Balena Etcher will take care of formatting the microSD card, decompressing the OS image file, and flashing it to the microSD card.
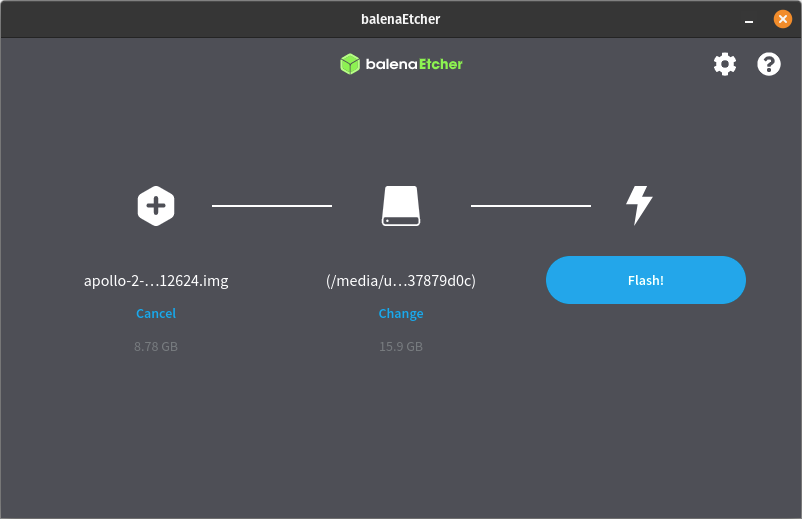 [IMG-010] Balena Etcher user interface.
[IMG-010] Balena Etcher user interface.The flashing process can take some time so be patient. The Balena Etcher interface will allow you to monitor the progress.
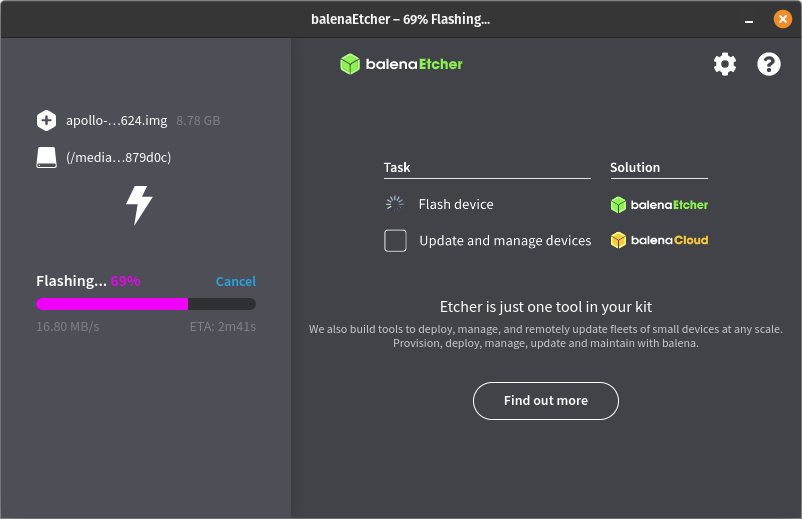 [IMG-011] Balena Etcher user interface.
[IMG-011] Balena Etcher user interface.Once the flashing process is completed successfully, you will receive a notice in the balena Etcher interface that looks like this:
 [IMG-012] Balena Etcher user interface.
[IMG-012] Balena Etcher user interface.You can remove the microSD card from your computer now and install it back into the Futurebit Apollo. If you have an adequately sized SSD then your block chain data should be safe as that is where it resides, not on the microSD card. If you have a 1TB SSD then this would be a good time to consider upgrading to a 2TB SSD instead. There are lots of options but you want to get an NVME style one like this:
 [IMG-013] 1TB vs. 2TB NVME SSD
[IMG-013] 1TB vs. 2TB NVME SSDSimply loosen the screw holding the SSD in place and then remove the old SSD by pulling it out of the socket. Then insert the new one and put the screw back in place.
Once the SSD and microSD are back in place, you can connect Ethernet and the power supply, then apply power to your Apollo.
You will be able to access your Apollo through a web browser on your computer. You will need to figure out the local IP address of your Apollo device so log into your router and check the DHCP leases section. Your router should be accessible from your local network by typing an IP address into your web browser like 192.168.0.1 or 10.0.0.1 or maybe your router manufacturer uses a different default. You should be able to do an internet search for your specific router and figure it out quickly if you don’t already know. If that fails, you can download and run a program like Angry IP Scanner.
Give the Apollo some time to run through a few preliminary and automatic configurations, you should be able to see the Apollo on your local network within 10 minutes of powering it on.
Once you figure out the IP address for your Apollo, type it into your web browser and this is the first screen you should be greeted with:
 [IMG-014] Futurebit welcome screen
[IMG-014] Futurebit welcome screenClick on the button that says “Start setup process”. The next you will see should look like this:
 [IMG-015] Futurebit mining selection screen
[IMG-015] Futurebit mining selection screenYou have the option here to select solo mining or pooled mining. If you have installed a new SSD card then you should select pooled mining because you will not be able to solo mine until the entire Bitcoin blockchain is downloaded.
Your Apollo will automatically start downloading the Bitcoin blockchain in the background and in the mean-time you can start mining with a pool of your choice like Solo CK Pool or Public Pool or others.
Be forewarned that the Initial Blockchain Download (“IBD”) takes a long time. At the time of this writing, it took 18 days to download the entire blockchain using a Starlink internet connection, which was probably throttled at some points in the process because of the roughly 680 GB of data that it takes.
In February 2022, the IBD on this exact same device took 2 days with a cable internet connection. Maybe the Starlink was a bit of a bottleneck but most likely the extended length of the download can be attributed to all those JPEGS on the blockchain.
Otherwise, if you already have the full blockchain on your SSD then you should be able to start solo mining right away by selecting the solo mining option.
After making your selection, the Apollo will automatically run through some configurations and you should have the option to set a password somewhere in there along the way. Then you should see this page:
 [IMG-016] Futurebit setup completion page
[IMG-016] Futurebit setup completion pageClick on the “Start mining” button. Then you should be brought to your dashboard like this:
 [IMG-017] Futurebit dashboard
[IMG-017] Futurebit dashboardYou can monitor your hashrate, temperatures, and more from the dashboard. You can check on the status of your Bitcoin node by clicking on the three-circle looking icon that says “node” on the left-hand side menu.
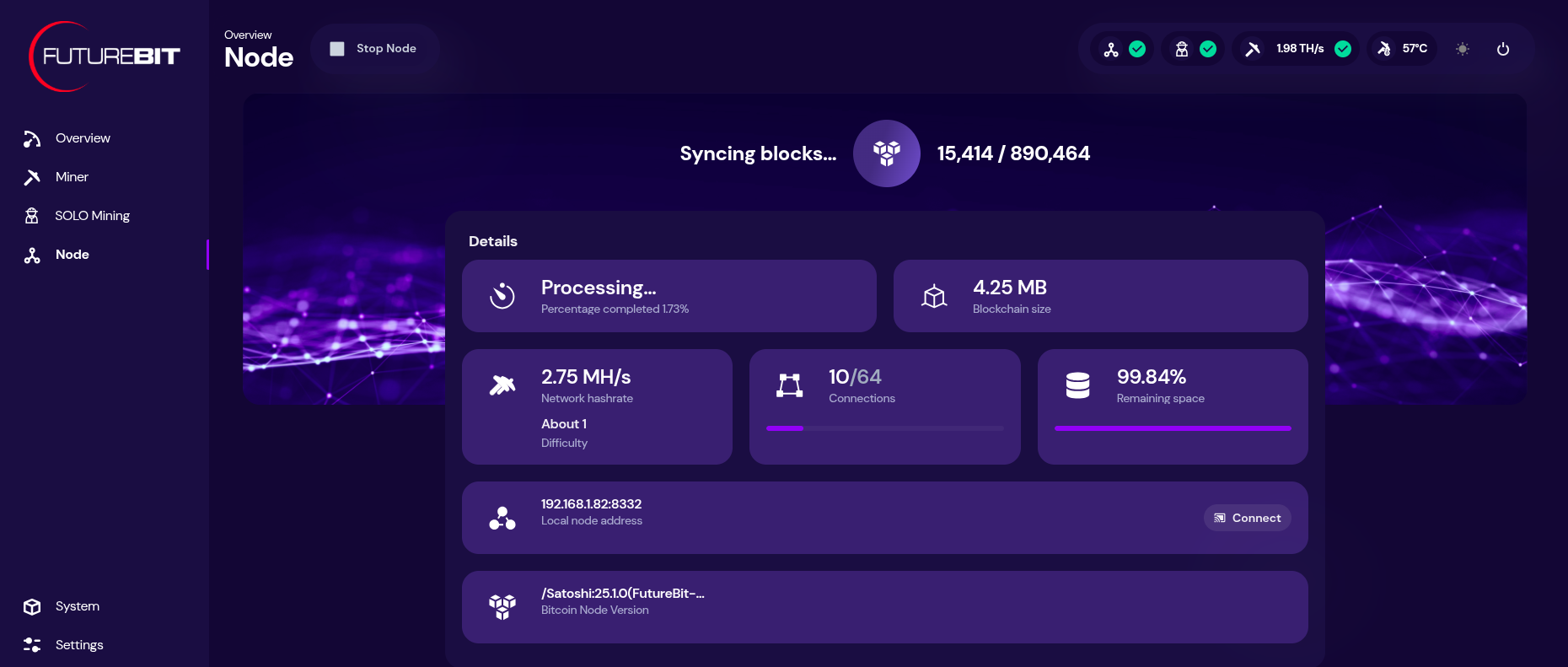 [IMG-018] Futurebit node page
[IMG-018] Futurebit node pageIf you need to update the mining pool, click on the “settings” option at the bottom of the left-hand side menu. There you will see a drop down menu for selecting a pool to use, you can select the “setup custom pool” option to insert the appropriate stratum URL and then your worker name.
Once your IBD is finished, you can start solo mining by toggling on the solo mode at the bottom of the settings page. You will have a chance to update the Bitcoin address you want to mine to. Then click on “save & restart”.
 [IMG-019] Futurebit mining pool settings
[IMG-019] Futurebit mining pool settingsThen once your system comes back up, you will see a banner at the top of the dashboard page with the IP address you can use to point any other miners you have, like Bitaxes, to your own self-hosted solo mining pool!
 [IMG-020] Futurebit solo mining dashboard
[IMG-020] Futurebit solo mining dashboardNow just sit back and enjoy watching your best shares roll in until you get one higher than the network difficulty and you mine that solo block.
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~793 Eh/s to ~829 Eh/s in March, marking ~4.5% growth for the month.
 [IMG-021] 2025 hashrate/difficulty chart from mempool.space
[IMG-021] 2025 hashrate/difficulty chart from mempool.spaceDifficulty was 110.57T at it’s lowest in March and 113.76T at it’s highest, which is a 2.8% increase for the month. All together for 2025 up until the end of March, difficulty has gone up ~3.6%.
According to the Hashrate Index, more efficient miners like the <19 J/Th models are fetching $17.29 per terahash, models between 19J/Th – 25J/Th are selling for $11.05 per terahash, and models >25J/Th are selling for $3.20 per terahash. Overall, prices seem to have dropped slightly over the month of March. You can expect to pay roughly $4,000 for a new-gen miner with 230+ Th/s.
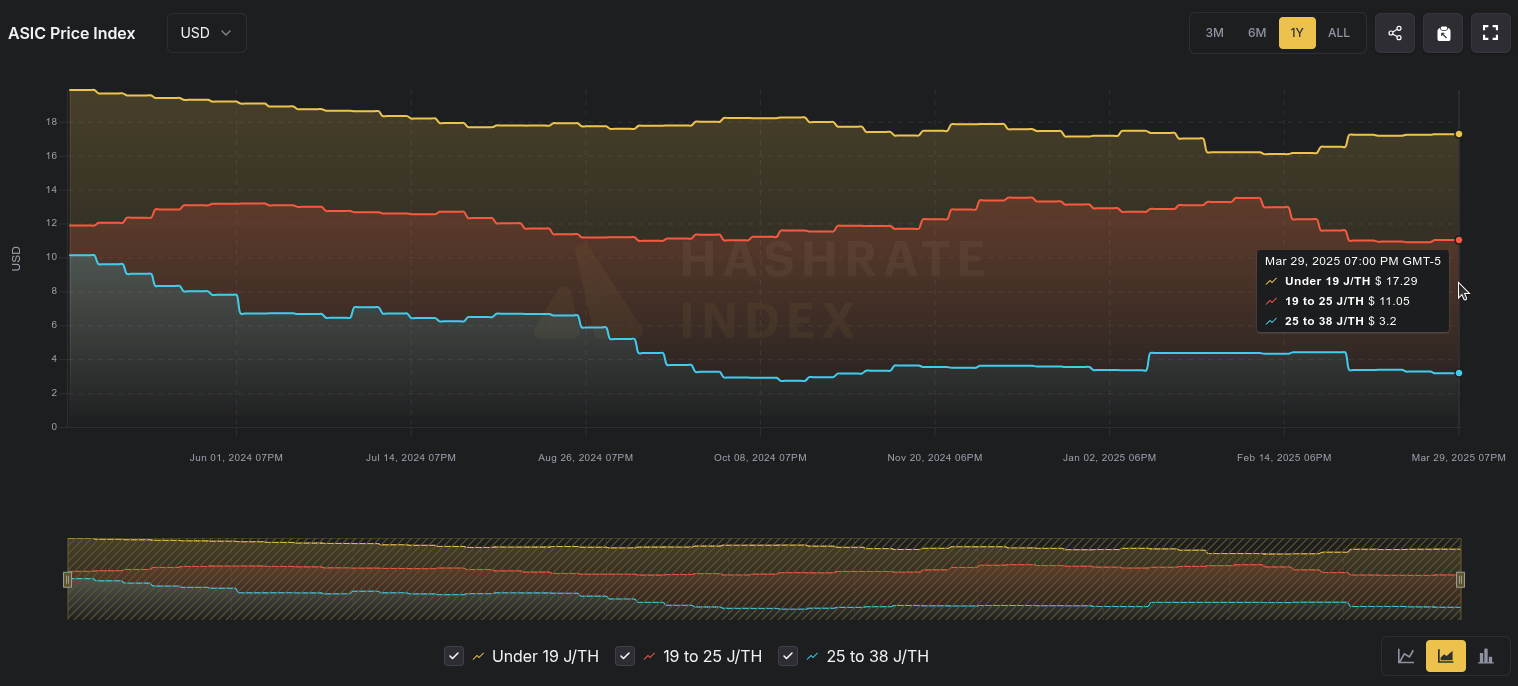 [IMG-022] Miner Prices from Luxor’s Hashrate Index
[IMG-022] Miner Prices from Luxor’s Hashrate IndexHashvalue is closed out in March at ~56,000 sats/Ph per day, relatively flat from Frebruary, according to Braiins Insights. Hashprice is $46.00/Ph per day, down from $47.00/Ph per day in February.
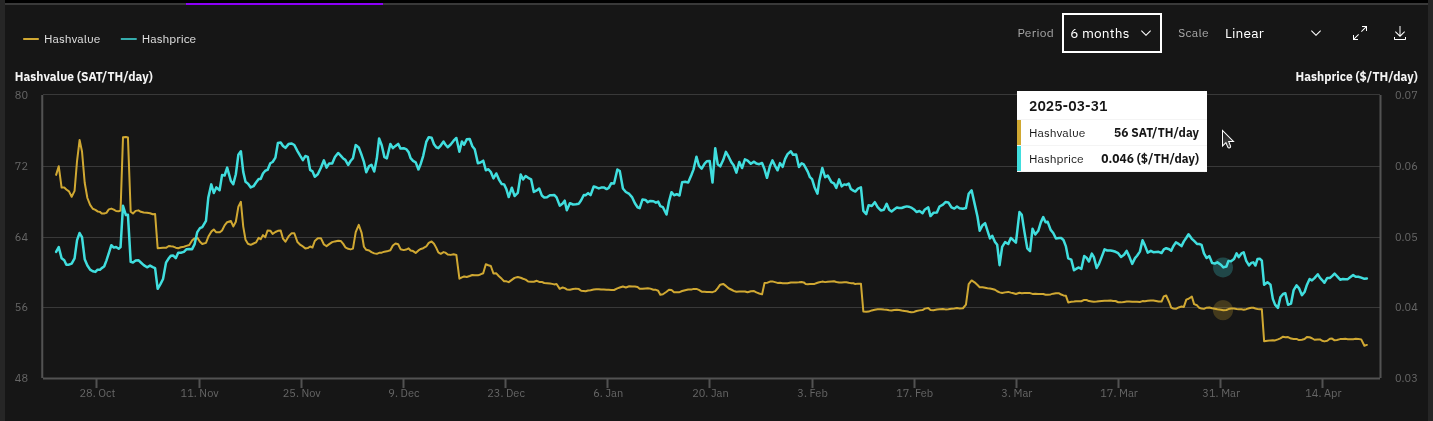 [IMG-023] Hashprice/Hashvalue from Braiins Insights
[IMG-023] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,071 days or in other words ~156,850 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the third 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you haven’t done so already, be sure to RSVP for the Texas Energy & Mining Summit (“TEMS”) in Austin, Texas on May 6 & 7 for two days of the highest Bitcoin mining and energy signal in the industry, set in the intimate Bitcoin Commons, so you can meet and mingle with the best and brightest movers and shakers in the space.
While you’re at it, extend your stay and spend Cinco De Mayo with The 256 Foundation at our second fundraiser, Telehash #2. Everything is bigger in Texas, so set your expectations high for this one. All of the lead developers from the grant projects will be present to talk first-hand about how to dismantle the proprietary mining empire.
 IMG-024] TEMS 2025 flyer
IMG-024] TEMS 2025 flyerIf you have an old Apollo I laying around and want to get it up to date and solo mining then hopefully this newsletter helped you accomplish that.
 [IMG-026] FREE SAMOURAI
[IMG-026] FREE SAMOURAIIf you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.
You can just FAFO,
-econoalchemist
-
 @ 9bde4214:06ca052b
2025-04-22 17:23:02
@ 9bde4214:06ca052b
2025-04-22 17:23:02“You’ll get all that for free if you build it right.”
Pablo & Gigi try to stop giggling.
In this dialogue:
- 01: Start Ugly
- 02: There is No Global
- Concept of ownership & “Read, Write, Own”
- Shamir Secret Sharing and Timelocks
- “No amount of violence will ever solve a math problem.”
- You can’t prove deletion of a key (or anything, really); best you can do is “burn” bitcoin
- Data is information, which behaves like an idea (not like an apple)
- “If you have an apple and I have an apple and we exchange these apples then you and I will still each have one apple. But if you have an idea and I have an idea and we exchange these ideas, then each of us will have two ideas.” – https://dergigi.com/threads/memes-vs-the-world
- Why the Pubky architecture isn’t great
- Cashu
- Nutzaps: NIP-60 / NIP-61
- How nutzaps fix fake zaps on zaplife.lol
- “Ecash fixes HTTP 402”
- “[Bitcoin [and nostr]] take advantage of the nature of information being easy to spread but hard to stifle.” –Satoshi Nakamoto
- Discovery with NIP-89
- #RunDVM with NIP-90
- Why micropayments can’t work on credit rails, and how bitcoin is the rediscovery of money.
- Putting payments into blossom
- “Money is essentially a tool to keep track of who owes what to whom. Broadly speaking, everything we have used as money up to now falls into two categories: physical artifacts and informational lists. Or, to use more common parlance: tokens and ledgers.”
- “maximum utility in the world of Bitcoin entails the adoption of maximum responsibility.”
- Complexity of Lightning vs the simplicity of eCash
- Amber and Citrine
- How Pablo became the BIS
- 12 words in your head can literally save your life
- The in-between of custodial and non-custodial in a multi-mint world
- Nutzaps integrated in chachi.chat
- The intermediacy of nostr is magic
- In nostr you’ll get a lot for free IF YOU BUILD IT RIGHT
- “Free Speech platforms cannot exist; if there is a ‘deplatform’ button, the button will be pressed.”
- “Neither nostalgia nor utopia.”
- Solutions that make stuff worse over time vs solutions that make stuff better over time.
-
asknostr on passkeys, and why we think they’ll make things worse over time.
- Authentication vs identity: “identification asks, authentication proves”
- You are not your name and photo; identity is prismatic
- (m00t’s talk on it at web summit 2011)
- Starbug from CCC pwning TouchID biometrics from a high-res photo (article)
- Key rotation and (American) HODL
- Social recovery
- Multi-sig for nostr with FROSTR
Links & References:
- Nostr Protocol Repository: https://github.com/nostr-protocol
- Cashu (e-cash): https://github.com/cashubtc
- NIP-60 (Nutzaps): https://github.com/nostr-protocol/nips/blob/master/60.md
- NIP-89 (Service Discovery) & NIP-90 (DVMs) – upcoming proposals: https://nips.nostr.com/89 & https://nips.nostr.com/90
-
 @ 9bde4214:06ca052b
2025-04-22 17:15:24
@ 9bde4214:06ca052b
2025-04-22 17:15:24“I don’t believe in Utopia anymore. I’m too old for that.”
Calle & Gigi philosophize about nuts.
Books and articles mentioned:
In this dialogue:
- Where is the Utopia that the internet promised?
- “Neither nostalgia nor utopia”
- Net Neutrality is a moral stance
- Where did the internet go wrong?
- Tech as a tool; is tech always neutral?
- Technology that increases agency VS tech that enslaves
- Competition vs Symbiosis
- “Who will run the mints?”
- “Anyone” can use it vs “everyone” can use it
- Centralizing vs. Monopolizing
- Bitcoin has an ethos baked in (You Shall Not Steal)
- Passive internet vs active internet
- Agency in cyberspace, and how to maximize it
- Blinded custodian vs regular custodian
- User data is a liability
- Obscura / Mullvad / Silent.Link as obvious early adopters
- Run your own ISP - Tollgate
- Cryptography is Not Enough
- Bitcoin is Time
- Time requires heat
- Zero-knowledge service providers
- Electronic Cash vs Digital Cash (CBDCs)
- Credit requires KYC, KYC implies outside enforcement
- Writings on Micropayments by Nick Szabo
- eCash fixes 402, obviously
- Who Owns the Future?
- “You are the product” vs “Subscription Hell”
- “Hello old friend!!!”
- Cathedral vs Bazaar
- Why paywalls suck
- Information wants to be free
- "Markets become absurd as supply approaches infinity."
- eCash + AI = match made in heaven
- #LearnToCode vs #LearnToPrompt
- Scarcity in cyberspace: compute, storage, networking
- Zero-Knowledge compute & zero-knowledge proofs
- https://en.wikipedia.org/wiki/Zero-knowledge_proof
- https://github.com/AbdelStark/cashu-zk-engine
- Cairo: https://github.com/starkware-libs/cairo
- MCP https://github.com/AbdelStark/bitcoin-mcp
- MCP DVM: https://github.com/r0d8lsh0p/n8n-AI-agent-DVM-MCP-client
- DVMCP: https://mcp.so/server/dvmcp
- Olas & Nutzaps (NIP-60, NIP-61)
- Bitcoin is not only the internet of money, but it is the money of the internet
- Re-building the internet archive on top of nostr
- Bitrot & 404
- Resurrection markets & marketplace for hashes via Blossom
- Hugs 🫂
-
 @ f10512df:c9293bb3
2025-04-22 17:11:05
@ f10512df:c9293bb3
2025-04-22 17:11:05Details
- 🍳 Cook time: 5-7 minutes
- 🍽️ Servings: 1
Ingredients
- 2 eggs
- Shredded cheese (Sharp cheddar is a favorite)
- 1 Tbsp olive oil or ghee
Directions
- Add oil to a non-stick pan and allow it to get hot (med-high heat)
- Add eggs and additional toppings, scramble and wait for the edges to get brown.
- Add shredded cheese while edges are browning. It is best if cheese begins to melt before flipping.
- Flip, and make sure all cheese stayed down, and there is enough oil left in the pan.
- Keep checking until pan side of eggs lift easily. Done correctly, the cheese will form a crisp layer.
- When fully cooked, serve with cheese right side up and enjoy!
-
 @ 9bde4214:06ca052b
2025-04-22 17:09:47
@ 9bde4214:06ca052b
2025-04-22 17:09:47“It isn’t obvious that the world had to work this way. But somehow the universe smiles on encryption.”
hzrd149 & Gigi take a stroll along the shore of cryptographic identities.
This dialogue explores how cryptographic signatures fundamentally shift power dynamics in social networks, moving control from servers to key holders. We discuss the concept of "setting data free" through cryptographic verification, the evolving role of relays in the ecosystem, and the challenges of building trust in decentralized systems. We examine the tension between convenience and decentralization, particularly around features like private data and data synchronization. What are the philosophical foundations of building truly decentralized social networks? And how can small architectural decisions have profound implications for user autonomy and data sovereignty?
Movies mentioned:
- 2001: A Space Odyssey (1968)
- Soylent Green (1973)
- Close Encounters of the Third Kind (1977)
- Johnny Mnemonic (1995)
- The Matrix (1999)
In this dialogue: - Hzrd's past conversations: Bowls With Buds 316 & 361 - Running into a water hose - Little difference, big effect - Signing data moves the power to the key holders - Self-signing data sets the data free - Relay specialization - Victor's Amethyst relay guide - Encryption and decryption is expensive - is it worth it? - The magic of nostr is that stuff follows you around - What should be shown? What should be hidden? - Don't lie to users. Never show outdated data. - Nostr is raw and immediate - How quickly you get used to things working - Legacy web always tries to sell you something - Lying, lag, frustration - How NoStrudel grew - NoStrudel notifications - Data visualization and dashboards - Building in public and discussing in public - Should we remove DMs? - Nostr as a substrate for lookups - Using nostr to exchange Signal or SimpleX credentials - How private is a group chat? - Is a 500-people group chat ever private? - Pragmatism vs the engineering mindset - The beauty and simplicity of nostr - Anti-patterns in nostr - Community servers and private relays - Will vibe coding fix (some of the) things? - Small specialized components VS frameworks - Technology vs chairs (and cars, and tractors, and books) - The problem of being greedy - Competitive silos VS synergistic cooperation - Making things easy vs barriers of entry - Value4value for music and other artists - Adding code vs removing code - Pablo's Roo setup and DVMCP - Platform permission slips vs cryptographic identities - Micropayments vs Subscription Hell - PayPerQ - Setting our user-generated data free - The GNU/Linux approach and how it beat Microsoft - Agents learning automatically thanks to snippets published on nostr - Taxi drivers, GPS, and outsourcing understanding - Wizards VS vibe coders - Age differences, Siri, and Dragon Naturally Speaking - LLMs as a human interface to call tools - Natural language vs math and computer language - Natural language has to be fuzzy, because the world is fuzzy - Language and concepts as compression - Hzrd watching The Matrix (1999) for the first time - Soylent Green, 2001, Close Encounters of the 3rd Kind, Johnny Mnemonic - Are there coincidences? - Why are LLMs rising at the same time that cryptography identities are rising? - "The universe smiles at encryption" - The universe does not smile upon closed silos - The cost of applying force from the outside - Perfect copies, locality, and the concept of "the original" - Perfect memory would be a curse, not a blessing - Organic forgetting VS centralized forgetting - Forgetting and dying needs to be effortless - (it wasn't for IPFS, and they also launched a shitcoin) - Bitcoin makes is cheap to figure out what to dismiss - Would you like to have a 2nd brain? - Trust and running LLMs locally - No need for API keys - Adjacent communities: local-first, makers and hackers, etc. - Removing the character limit was a mistake - Browsing mode vs reading mode - The genius of tweets and threads - Vibe-coding and rust-multiplatform - Global solutions vs local solutions - The long-term survivability of local-first - All servers will eventually go away. Your private key won't. - It's normal to pay your breakfast with sats now - Nostr is also a normal thing now, at least for us - Hzrd's bakery - "Send Gigi a DM that says GM" - and it just works - The user is still in control, thanks to Amber - We are lacking in nostr signing solutions - Alby's permission system as a step in the right direction - We have to get better at explaining that stuff - What we do, why we care, why we think it's important
-
 @ 9bde4214:06ca052b
2025-04-22 17:00:55
@ 9bde4214:06ca052b
2025-04-22 17:00:55"What should the next iteration of the internet look like?"
Paul & Gigi pray for a better tomorrow.
Books mentioned:
- The Bible
- I, Pencil by Leonard E. Read
- Don't make me think! by Steve Krug
- The Sovereign Individual by James Dale Davidson and William Rees-Mogg
In this dialogue:
- Paul and his awesome nostr t-shirt
- Are we all just nostalgic?
- Where did the optimism of computing and the information superhighway go?
- We went from interop to pay-to-unlock.
- Do we have to live in the digital gulags forever?
- Homecooked meals and homecooked apps
- Paper straws and the downfall of Western Civilization
- "You need to be okay with people getting rekt"
- If the car would be introduced today, it would be illegal
- Bravery and personal responsibility
- "nostr will only be what diehards will build it to be"
- Bad teleology is built into the current (non-nostr) app landscape
- "You can get a lot of the upside without holding your own keys”
- “...but you can't get ALL of the upside!"
- Expressiveness and free speech online
- Freedom of Speech, Freedom of Assembly, and Financial Freedom in Cyberspace
- Self-publishing vs platform publishing
- Information calories. Can we count them?
- Don't make me think!
- Is not being forced to think part of the problem?
- Mutiny & bitcoin UX that's too easy
- Games and costly mistakes
- The early days: software distribution via print magazines
- Prompting allows you to define your own teleology
- Vibe coding and Cursor
- "The hard part is to figure out what you want."
- "What should the next iteration of the internet look like?"
- GenZ doesn't know shit about files and folders
- Why files are great
- Gigi's SyncThing & Standard Notes setup
- File-based apps like Smart AudioBook Player
- Reading apps like Pocket, Instapaper, and Readwise Reader
- Saving all the things & linking stuff together
- Clips of podcasts and videos, e.g. Fountain
- A Commonplace Book to cyberspace
- Creating a "Family Bible" app
- If you want to maximize profits in the attention economy, you have to get users addicted
- (Zaps potentially fix this, as you wouldn’t zap a car crash)
- Let computers do computer work, let humans be humans
- "The end is not being on the computer"
- Solo private / group private / public
- Liberal vs Conservative sentiment in social environments
- Whom to care about?
- Web of trust & our understanding of it
- Forgiveness, Trust, and Repeat Games
- Tit-for-tat and forgiving tit-for-tat
- Three strikes and you're out!
- "Choose your gulag" is the alternative to nostr
- 7-generation thinking
- 2140
- The Sovereign Individual is embedded in a social structure, always
- I, Pencil
- Jungle vs Civilization
- Fiat = because I said so (“Fiat Lux” - Let there be light)
- Do we need leaders in bitcoin?
- Peterson Fallacy / God vs Bitcoin
- Jesus early followers were the Followers of The Way
- Zaps are not payments
- Zaps are not "tips"
- Bitstein & Pierre: The Reorg
- Vervaeke: “Where do you go for wisdom?”
- Rough consensus and Pieter Wuille
- "There is no such thing as a leaderless system"
- Wisdom in cyberspace
- Can we build wise tools?
- Prompting the Bible, ChristGPT, and Bible Slop
- Gell-Mann amnesia effect
- Vervaekes AI argument: The Coming Thresholds and The Path We Must Take
- Where do new ideas come from?
- Sandwich prompting style (HLDD / LLDD)
- The Tale of John Henry
- Silicon Sages
- Conscience and The Muse
- Hypermedia and HyperNote
- Glassholes, Google Glasses, and wearable technology
- Prompting & Praying for An Internet Worth Having
-
 @ f10512df:c9293bb3
2025-04-22 17:00:44
@ f10512df:c9293bb3
2025-04-22 17:00:44Chef's notes
Use a tea bag to hold the spices. I like to fill it and drape it on the side of the pan so the flavors get in, and then toss it before serving. Easier than picking rosemary out of your teeth later.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour 45 from scratch, 45 if using chicken stock
- 🍽️ Servings: 4
Ingredients
- 1 Cup Carrots (sliced)
- 1C celery (sliced)
- 2 cloves garlic
- 1 tsp dried thyme
- 1/2 tsp dried minced onion
- 2 Tbsp lemon juice (or more to taste)
- 1/2 Tbsp salt (to taste)
- 1 rotisserie chicken
- 2 tsp dried rosemary (or 1-2 sprigs fresh)
- 8 C water & additional 1-2 C later
- 10 oz pre-cooked noodles
- 1 tsp cracked pepper (to taste)
Directions
- Remove chicken meat from bones and set aside. Do not discard skin. Put bones and skin in a large stock pot and add water. Let boil covered for one hour, and then remove bones and strain out any bits of skin from broth.
- Add chopped vegetables, spices, and lemon juice to broth with up to 2 C. additional water to replace what might have boiled away. Simmer over low to medium heat (covered) for another half hour, stirring occasionally. Add in chicken meat. Taste test and add additional salt if needed.
- When vegetables are cooked, add in noodles and stir for an additional 2-3 minutes until hot (uncovered), and enjoy.
- If using store bought chicken stock, only simmer until vegetables are cooked (about half an hour).
-
 @ d1667293:388e7004
2025-04-22 16:52:15
@ d1667293:388e7004
2025-04-22 16:52:15In my book “Bitcoindollar The Dawn of American Hegemony in the Digital Era,” I challenge the prevailing narrative that de-dollarization is a distant or hypothetical threat. Rather, I present a body of evidence suggesting that we are already living in a world where de-dollarization is unfolding—not through bombastic proclamations or sudden abandonment of the dollar in trade—but through a quieter, more telling trend: the steady escape of emerging powers like China, Russia, India, and much of the Global South from US Treasuries as the global reserve asset.
Structural, Not Cyclical: The Causes Behind the Exodus
This transformation is not cyclical or temporary; it is structural. The root causes run deep and stem from decades of US foreign and monetary policy—specifically, the aggressive military posturing that has defined American global engagement, the weaponization of dollar-based financial systems, and the overuse of sanctions as instruments of coercion rather than diplomacy. The result has been a widespread erosion of trust in the US as a neutral monetary steward. Increasingly, large economies and trading blocs—such as the Shanghai Cooperation Organization (SCO), BRICS, and the Belt and Road Initiative (BRI)—are seeking alternatives. They are diversifying their reserves, entering bilateral currency agreements, stockpiling gold, and in some cases, launching central bank digital currencies (CBDCs).
The message is clear: the era of unquestioned dollar supremacy is over.
The Treasury Dilemma: Who Will Fund America’s Debt?
This structural shift raises a daunting question for American policymakers: who will buy US Treasuries in the future? For decades, the demand for Treasuries rested on the premise of dollar dominance. Global trade surpluses—especially from oil-exporting nations under the Petrodollar system—were recycled into US debt markets. This “exorbitant privilege” allowed the US to run persistent deficits, finance wars, and project power without facing the immediate fiscal consequences most nations would. But that privilege is now in peril.
The Bitcoindollar System: A Strategic Response
In my book, I argue that the United States still has one viable path forward—a path that does not require relinquishing its leadership role, but rather reimagining it for the digital era. I call this new paradigm the Bitcoindollar system. It is an evolutionary successor to the Petrodollar framework, and it hinges on embracing bitcoin as the global store of value and dollar denominated stablecoins to maintain the US dollar’s relevance in a multipolar world. Under the Bitcoindollar system, global capital flows are incentivized to enter dollar-denominated stablecoins such as USDC and USDT. These stablecoins can then be recycled into short-term US debt instruments like Treasury bills, creating a digital-era version of the Petrodollar recycling mechanism. At the heart of this system lies Bitcoin—not as a threat to the dollar, but as a global decentralized and uncensorable Store of Value (SOV) that drives capital into the broader dollar-denominated ecosystem. As Bitcoin grows in adoption and price, it draws global attention and capital toward stablecoins, which in turn creates natural demand for dollar-based instruments such as Treasuries. This system offers the United States a first-mover advantage. No other nation has the credibility, capital markets depth, or global network effects to replicate it—if, and only if, the dollar’s digital rails are perceived as trustworthy and politically neutral. Herein lies the great conundrum: trust cannot be mandated. It must be earned, particularly in a geopolitical climate where the United States continues to alienate both allies and adversaries alike.
Trump’s Paradox: Economic Nationalism vs Monetary Hegemony
The current Trump administration, despite its rhetoric on economic nationalism, continues along a path that exacerbates this alienation. By doubling down on tariffs, aggressive posturing toward China, and unconditional support for Israel’s supremacist regional ambitions, it perpetuates the same policies that catalyzed de-dollarization in the first place. Tariffs, in this context, are a distraction. The US trade deficit is not primarily the result of unfair trade practices by other countries—it is largely the result of the dollar's role as the global reserve currency. To sustain global demand for dollars, the US has had to export dollars—and therefore run trade deficits. The dollar’s dominance enabled vast capital inflows and supported America’s imperial military architecture, but this model is fundamentally incompatible with dreams of reshoring industry, reducing deficits, and limiting foreign entanglements. Furthermore, these policies undermine any future attempt to establish dollar stablecoins as trusted global instruments. Why would a nation park its savings in a dollar-based asset, however digitized, if it fears arbitrary sanctions or seizure at the stroke of a keyboard? Despite his aggressive posturing, Trump, like Zelensky and the EU before him, has no cards to play to force China or Russia to the table.
A Fork in the Road: Choose Multipolar Collaboration or Decline
Absent a disastrous military escalation—which will not prevent the fall of American unipolar hegemony—the US is left with ONLY ONE path forward: a deliberate, peaceful shift from military and imperial posturing toward a more collaborative, multipolar engagement with the world. This means treating allies, adversaries, and vassal states alike with respect and inclusion in a reimagined dollar-based system—one that is digital, decentralized, and incentivized by global participation. The Bitcoindollar system can serve as the financial infrastructure of this new era, but it demands that the United States rehabilitate its image as a trustworthy party. For the Trump administration to succeed in securing America’s future financial relevance, it must course-correct immediately. This includes ending the influence of the neo-conservative and Zionist hardliners who perpetuate conflict and distrust for their own interest, and embracing a vision of digital dollar diplomacy that builds bridges instead of burning them.
In conclusion, the Bitcoindollar is not just a financial mechanism—it is a strategic opportunity for the United States to retain leadership in the emerging multipolar order. The alternative is clear: a continued slide into irrelevance, fiscal instability, and geopolitical isolation or a mutually assured destruction through war.
The time to act boldly for President Trump is now.
bitcoin #bitcoindollar #stablecoin
-
 @ 9bde4214:06ca052b
2025-04-22 16:35:00
@ 9bde4214:06ca052b
2025-04-22 16:35:00"We have the chance of building the next iteration of the internet, and hopefully, not repeat the mistakes of the past."
In this dialogue:
- Why starting ugly and shipping early is hard
- The ugliest thing that Pablo ever shipped
- “Happiness is shipping”
- Make it real first, you can make it pretty later
- Getting into the habit of shipping
- Highlighter and the hang-up of shipping something big
- How nostr allows you to have cash flow from the get-go
-
value4value for artists and devs
- What DHH & 37Signals got right
People and projects mentioned:
Further links:
- https://excellentjourney.net/2015/03/04/art-fear-the-ceramics-class-and-quantity-before-quality/
- https://world.hey.com/dhh/that-shipping-feeling-b7c8c565
- https://world.hey.com/dhh/i-was-wrong-we-need-crypto-587ccb03
- https://sovereignengineering.io/
- https://dergigi.com/2023/04/04/purple-text-orange-highlights/
- https://highlighter.com/
- https://njump.me/nosolutions@sovereignengineering.io
-
 @ b04082ac:29b5c55b
2025-04-22 15:57:28
@ b04082ac:29b5c55b
2025-04-22 15:57:28Africa has long grappled with the “resource curse,” a paradox where nations rich in natural resources face economic stagnation, political instability, and reliance on foreign powers. The reason isn’t hard to pinpoint. For centuries, foreign entities have extracted immense wealth from African soil such as gold, oil, cobalt, and more, leaving behind weak institutions, crippling debt, and minimal infrastructure. Instead of fueling local growth and uplifting communities, Africa’s resources have powered the industrial and digital revolutions of others.
Now, this extractive pattern is resurfacing in new ways. Recent headlines paint a clear picture:
-
Bill Gates and Jeff Bezos plan to invest $537 million in Africa to mine rare metals.
-
A ‘terrifying’ crackdown on mining companies in Africa’s coup belt.
-
Blackwater founder and Trump ally strikes mineral security deal with Congo.
-
Biden’s last dash to Africa highlights the power of minerals.
As the world scrambles to secure minerals vital for green energy and artificial intelligence, Africa stands at a crossroads. It can remain a supplier of cheap raw materials or seize this moment to shape its economic destiny.
1. Diversifying Beyond Minerals
The global race for Africa’s resources centers on critical minerals like cobalt in the Congo, rare earths in Zambia, and nickel in Tanzania. Superpowers are jostling for control, but leaning too heavily on mineral exports is fraught with risks. Prices fluctuate wildly, extraction demands massive capital, profits often vanish overseas, and overreliance can fuel political instability by deepening inequality and sparking conflicts over resource control.
To truly escape the boom-and-bust cycles of commodity markets, countries must find alternative ways to monetize their natural advantages, particularly in areas that the rest of the world tends to overlook.
One promising avenue is to tap into the continent’s vast renewable energy sources such as hydro, solar, and geothermal, and convert them into something transformative: Bitcoin.
Bitcoin mining involves validating transactions and securing the Bitcoin network in exchange for new bitcoins and fees. At its heart, it’s an energy market. Wherever there’s surplus or stranded energy, mining can thrive. Africa’s renewable energy potential is enormous and largely untapped. Rather than waiting for foreign companies to swoop in, African governments could monetize their energy directly by mining Bitcoin themselves.
2. Bitcoin Mining for Monetary Independence
Many African nations are burdened by debt, much of it in foreign currencies like the U.S. dollar. Servicing these loans drains public funds and forces governments to prioritize external creditors over local needs.
Bitcoin mining offers a way to build reserves in a neutral, censorship-resistant asset. Unlike foreign aid or currencies, Bitcoin isn’t tied to political strings or inflationary policies of other nations. It’s a step toward financial self-reliance.
In the long run, Bitcoin’s scarcity could drive its value higher, helping countries reduce their reliance on dollar-dominated systems. Looking further ahead, African nations that participate meaningfully in the Bitcoin economy may also gain influence over blockspace, the limited space where Bitcoin transactions are recorded.
3. Stabilizing Energy Grids with Mining
In much of Africa, electricity is costly, unreliable, or nonexistent. Yet, the problem often stems from underused infrastructure. Power producers struggle to recover costs due to inconsistent demand, and grids falter when supply and demand don’t align.
Bitcoin mining can act as an economic “shock absorber” for energy providers. It creates a flexible buyer that adjusts to grid demands, soaking up excess power or scaling back when needed. By placing miners near energy sources, especially in remote areas, utilities can earn steady revenue to fund broader electrification.
Take Gridless in rural Kenya. By mining Bitcoin off-grid with small hydro units, they’ve stabilized local power, supported rural internet access, and lowered costs for nearby residents. This model works. To make a more meaningful impact, however, it needs national-scale adoption supported by clear government strategy.
4. Foreign Miners Are Already Here
The shift is already happening. In Ethiopia, foreign Bitcoin mining firms are signing deals to tap the country’s hydroelectric surplus. Similar moves are underway across the continent. This isn’t a distant possibility; it is already happening.
Miners chase the cheapest energy, and Africa boasts some of the world’s most affordable renewables. Mining will happen with or without local policies. The critical question is whether the benefits will stay in Africa or flow abroad, repeating history’s mistakes.
Foreign companies bring expertise and capital, but if they dominate, African nations risk becoming mere hosts to another extractive industry. Governments must act swiftly by launching national Bitcoin mining initiatives, forging public-private partnerships, and securing ownership of infrastructure to keep the value local.
Conclusion
Africa is at a turning point. The world craves its minerals, its energy, and increasingly, its role in shaping the future. But African nations can’t afford to sit on the sidelines. The next revolution must be led, not endured.
Bitcoin mining is not a silver bullet. It is a tool that, if used wisely, could help transform energy into economic power, build digital infrastructure, and break the cycle of debt and dependence.
Bitcoin miners are already arriving. The real question is whether African nations will take the lead and ensure that this industry builds lasting value at home, rather than repeating the patterns of the past.
-
-
 @ 9a859fbc:8a9270f3
2025-04-22 15:45:55
@ 9a859fbc:8a9270f3
2025-04-22 15:45:55A story of art and inspiration
This image was generated by AI
That is...
I am artificial. I was created by two other humans (hi mum and dad 👋)
I am intelligent. I can perceive the world, experience it, learn to understand cause & effect, and make decisions.
To go perhaps deeper, cells, DNA and life itself are artifices of the fabric of reality.
I sat, in a pub in Bristol, a place where I rarely frequent. I sat with one housemate, who I rarely spent time with. I met his friends that day, only once, never we met again.
I got chatting with a lady there. I had some paper and pencils with me. My intention, for a couple of weeks, was to come up with a symbol to represent Deep Sea Frequencies, at that time still known as Psychedelic Jelly. We were a new collaboration.
She and I got chatting about art. About symbolic representation of concepts, feelings, ideas. We chatted about flow, about how there are different types of flow, different elemental conditions of flow. I doodled some shapes, and we noticed how fire, water and air all look similar due to their fluid natures. So we considered how to differentiate, distinguish them from one another.
I doodled some more, and we came up with swooshes, curls, crests and bubbles. These seemed to be distinguishing enough such that they were no longer reminiscent of fire or air. I doodled fire and air too, just in case, just to check.
Then we chatted about symmetry types, reflective, axes, rotational. About geometry, geometric containers. We both enjoy triangles and hexagons. (It's always hexagons!)
I doodled some more shapes and put them in hexagonal shapes. Then I tried bending them into triangular forms instead, and overlaid two triangles.
Each triangle looked like a triskelion. Perfect.
Overlaid, they looked just like the flow of water, coming up, spiralling down.
The logo was born in this moment, in this serendipitous meeting, in this unlikely chat with a total stranger. We met for the first time that day, and I'm not sure if we ever met again. This interaction was, is, precious, and it led to a particular creation that is now a core part of my life and is a highlight for many people around the UK and the world, as we put on events and released musicians' music.
This is inspiration. This is expression. This is flow, through the fluid nature of the cosmos.
This is what you miss out on when you talk into your AI LLM black hole prompt.
This is what you steal from when you demand your AI LLM to generate you something according to your whim.
Art and expression is the very foundation of human community. Join in! Try new things! Learn from each other! Bring us all closer together by interacting and creating through shared ideas, shared visions, shared wisdom!
After that, I drew it up cleanly, geometrically.
I photographed it like scanning it, carefully aligning the camera because I didn't have a scanner.
I redrew it more than twice.
I digitised it, colourised it, split it into two layers so I could apply colour & lighting effects to it.
I painstakingly traced the photograph into a vector format, to enlarge it and use it for various media.
I even more painstakingly (do we have a more extreme adverb??) divided all the vector shapes into new objects so that the layers became "real". And cleaned up the vector nodes, shaping them to my imagination.
The vector form is used all over our record label & events branding.
And then I imported the vector form into Blender, a 3D rendering application, free and open source.
I learnt Blender, day by day developing my understanding and my skills. Day by day my GPU crashing on raytracing and cutting the laptop's power out!
And finally, I learnt to make some simple renders that look like being underwater, like surreal glassy objects floating in the deep. I even learnt to animate it, although I haven't released that into the wild.
I imagined all of this stuff, and then I spent months over years developing my skills in my spare time in order to bring these imaginations to life.
You can do the same.
You have to sacrifice things.
Sacrifice your time.
Sacrifice your energy.
Sacrifice your distractions and enter yourself into the learning process and the creative process.
To you, amazing lady who helped me draw this symbol from the fabric of the Realm of Forms, thank you! I'm sorry that I don't recall your name, although actually I think I do remember but I would be embarrassed if I tagged the wrong person. Please reach out if you recognise this story! It was about 7, maybe 8 years ago, in the painted pub in St. Werburgh's.
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-22 15:37:53
@ 5d4b6c8d:8a1c1ee3
2025-04-22 15:37:53How I wish I had time for this!
https://primal.net/e/nevent1qvzqqqqqqypzqntcggz30qhq60ltqdx32zku9d46unhrkjtcv7fml7jx3dh4h94nqqsynzz85x8dcqnzxrzypec9xw6haxxjt0z0c547suty7gpa835v0vs2qusmr
originally posted at https://stacker.news/items/953418
-
 @ d1667293:388e7004
2025-04-22 14:27:15
@ d1667293:388e7004
2025-04-22 14:27:15The motivation behind my newly published book Bitcoindollar the Dawn of American Hegemony in the Digital Era was simple: to answer some of the most pressing and overlooked questions about the future of money. My analysis starts by viewing Bitcoin not in isolation, but as a paradigm shift in the evolution of money—a foundational institution that underpins both economic and societal relationships, from individuals to nations.
Rethinking the Monetary Landscape
To understand Bitcoin's potential, we need to explore the landscape it seeks to disrupt:
-
The dominance of nation-states.
-
The role of the US fiat dollar as the global reserve currency.
-
US debt as the reserve liability (pardon "asset") underpinning the fiat system.
-
The influence of the banking cartel and the distorted incentives built into the fiat monetary structure—especially in the last 55 years, since the US elegantly defaulted on its promise to convert paper dollars into gold in 1971.
Bitcoin is a direct response to these imbalances, but its adoption will depend on how and who drives the transition.
Two Paths of Bitcoin Adoption: Bottom-Up vs. Top-Down
Bitcoin’s journey can take two distinct paths:
1. Bottom-Up Adoption
This is driven by grassroots use of Bitcoin as a currency, particularly in developing nations, often alongside dollar-denominated stablecoins like USDt.
2. Top-Down Adoption
This path sees Bitcoin increasingly used as a store of value (SOV) and financial asset, especially in developed economies. It is driven by institutions, wealth managers, and financial innovation.
It's clear that top-down adoption correlates with faster price appreciation, whereas bottom-up adoption is slower, more organic—and potentially more resilient in the long run.
Why the Top-Down Path Matters
A critical but often uncomfortable truth is: elites don’t give up power easily. The fiat system is held tightly by those benefiting most from its continuation.
Pareto’s Law teaches us that no historical revolution was purely bottom-up. Real change happens when a new elite emerges to replace the old one—carrying the masses along.
The advantages of top-down adoption:
-
Speeds up the revolution.
-
Allows coexistence between Bitcoin and fiat for a transitional period, avoiding violent disruption.
-
Strengthens new power structures around Bitcoin as it becomes a more established SOV.
-
Enables the U.S. to reinvent the dollar’s role through dollar-backed stablecoins and their recycling into US TBills, maintaining global dollar demand even post-Petrodollar.
A Warning for the United States
In my book, I argue that the #Bitcoindollar system gives the U.S. a first-mover advantage—but only if it changes course.
The U.S. must shift from a militaristic, imperialist approach to a cooperative, multipolar model that welcomes both allies and adversaries into this new system.
Unfortunately, the Trump administration appears headed in the opposite direction, risking this historic opportunity. I explore this further in an upcoming article expanding on my book’s conclusions.
Store of Value vs. Currency: Which Comes First?
Some critics lament that Bitcoin isn’t widely used as a currency yet. But ask yourself:
What is the world’s most urgent need in today’s monetary environment?
A medium of exchange? Or a store of value to protect savings from corrupt governments and inflation?
We already have more or less efficient payment systems. But we lack a sound store of value with key properties such as decentralization, censorship resistance and hard coded scarcity. That’s why the market is adopting Bitcoin primarily as a SOV.
Gresham’s Law gives us the formula:
Save the hard money (Bitcoin, gold), spend the USDt, USDC, and fiat.
Looking Ahead: From Store of Value to Currency
This doesn’t mean #bitcoin won’t be used as a currency eventually. Once it’s widely adopted as a store of value—perhaps within the next 10–20 years—its volatility will decrease, more people will price goods in bitcoin, and acceptance for payments will grow.
We will get there. Just not through the path many imagined at the beginning.
Call It What It Is: A Revolutionary Monetary Transition
Rather than a disruptive revolution, think of this as a revolutionary monetary transition—a new system growing alongside the old, until one inevitably replaces the other.
-
-
 @ 4ba8e86d:89d32de4
2025-04-22 13:26:12
@ 4ba8e86d:89d32de4
2025-04-22 13:26:12Cashu é Ecash para Bitcoin
Cashu é um sistema ecash Chaumian gratuito e de código aberto criado para Bitcoin. Cashu oferece privacidade quase perfeita para usuários de aplicativos Bitcoin de custódia. Ninguém precisa saber quem você é, quanto dinheiro você tem e com quem você faz transações.
O que é Cashu?
Cashu é um novo protocolo ecash para aplicativos de custódia Bitcoin que está totalmente integrado à rede Lightning. Um sistema Ecash consiste em duas partes, a carteira mint e a carteira ecash. Transações Ecash não rastreáveis, instantâneas e sem taxas. Cashu é construído para Bitcoin. As carteiras usam o nó Lightning da casa da moeda para fazer ou receber pagamentos em Bitcoin em troca de ecash. Uma casa da moeda Cashu não sabe quem você é, qual é o seu saldo ou com quem você está negociando.Os usuários de uma casa da moeda podem trocar ecash de forma privada, sem que ninguém saiba quem são as partes envolvidas. Os pagamentos em Bitcoin são executados sem que ninguém possa censurar usuários específicos.
A postagem de David Wagner em 1996 na lista de discussão Cypherpunk é a base da criptografia Cashu. Wagner descreve um sistema ecash usando troca de chave cega Diffie-Hellman em vez de RSA, na qual a implementação original de David Chaum foi baseada.
https://cypherpunks.venona.com/date/1996/03/msg01848.html
https://en.m.wikipedia.org/wiki/Ecash
Como isso começou.
https://void.cat/d/2HJKtTEfuDxmDfh3uH9ZoS.webp https://void.cat/d/XyyHFSQYa5vEswzzt6MMq7.webp
Como vão as coisas.
https://void.cat/d/WUrKzsFDnsvUQdFKZChLeS.webp
Como funciona A Carteira Cashu é através de um esquema criptográfico chamado assinaturas cegas, descrito pela primeira vez pelo cypherpunk e criptógrafo David Chaum. Pense assim:você produz uma mensagem secreta e a envolve em um envelope feito de papel carbono que você envia para a casa da moeda. https://void.cat/d/SbEEHCiGFUHWvk4qGv9xCb.webp
A casa da moeda não pode ver o que está dentro do envelope. Ele assina do lado de fora dizendo "qualquer que seja esse segredo, vale 420 Satoshis”e o envia de volta para você. Como o envelope é realmente criptografado, somente você pode abri-lo e ver sua mensagem secreta (agora assinada por carbono). https://void.cat/d/Pakyb6ztW9B7L5ubAQ74eL.webp
Este segredo assinado é na verdade o seu token Ecash e vale Satoshis.
Você pode enviar e receber esses tokens para qualquer outra pessoa como quiser, seja com um mensageiro, via e-mail ou um pombo. A casa da moeda não sabe nada disso.
A anatomia de um token Cashu. https://void.cat/d/JzvxreMoCitmYe2FthAsei.webp
Um breve passo a passo de uma carteira cashu deixará tudo isso bem claro.
Comece abrindo
https://nutstash.app/
Pressione " WALLET " https://void.cat/d/VeCANsaxkkq9YtoPRS26ZK.webp https://void.cat/d/CTmK9GcPGn3i2gHCVXcL5r.webp https://void.cat/d/UWjyjGLS6MzyZvt6zkuUgG.webp https://void.cat/d/HzNtKanCSAJatrMa9yTKwF.webp
Pressione "+ ADD ".
Agora a carteira cashu está aberta… https://void.cat/d/GAYSrNxHEEhctoW37bFPjJ.webp
O próximo passo é deposite alguns sats com a Casa da moeda.
Pra depositar Pressione o botão "MINT". https://void.cat/d/LC5WEDKAzzZoHXxrKZDiWu.webp
Digite a quantidade de sats a ser depositado na carteira cashu depois Pressione " REQUEST MINT ". https://void.cat/d/Pr6foBWBBCq73i8WggbLGG.webp
Você Pode copiar a fatura ou ler o qrcode , no meu caso usei a carteira LNbits pra pagar a fatura de 10 sats , você tem 10 minutos pra pagar fatura. https://void.cat/d/BQerpEtW2H9ANaoW8truJE.webp https://void.cat/d/8PGFBRW64zavDnQJfYQh9C.webp
Agora pra enviar Ecash.
Pressione “SEND” https://void.cat/d/8rkF2dvhJeZWf8GeQhhf2d.webp
Digite 10 , Pressione “SEND” https://void.cat/d/5SK5w6ewgt8wikCuyk7znM.webp
Então o token Ecash usando a assinatura cega da casa da moeda foi criado. https://void.cat/d/PedBMcZPfczZLLymGmfzVq.webp
O Token Ecash foi criado é esse logo abaixo.
eyJwcm9vZnMiOlt7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50IjoyLCJzZWNyZXQiOiJrWjNBOVorSXkyREJOcDdhdFhYRTIvclVXOFRnR2ZoTDgzWEFXZ0dKUXhVPSIsIkMiOiIwMmM0NjA4NDYwNDhjNzI1ZjgwMDc3M2IyNmRmOTcxNDU1MTJmOTI0YjgyNzYyZTllYzdkZjZjOTkzNGVmYjJhNmMifSx7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50Ijo4LCJzZWNyZXQiOiJXdTZmdWlxNGt4Tkh3UkF1UzFhMmVYaGZtRnRHU2tRQkNYZFNnUzcreHkwPSIsIkMiOiIwMzFhYWI3MzY3MTJhY2Y5MWU4NzE4YmM5OTlmNWE2MGEwYzNjODQ5YTA1MWE2OTA5MzRkMTc4NWNmZGNkNDcyYTAifV0sIm1pbnRzIjpbeyJ1cmwiOiJodHRwczovL2xlZ2VuZC5sbmJpdHMuY29tL2Nhc2h1L2FwaS92MS80Z3I5WGNtejNYRWtVTndpQmlRR29DIiwiaWRzIjpbIjBOSTNUVUFzMVNmeSJdfV19
Se pressionar o botão " send as link "
Então criar link do token Ecash.
https://wallet.nutstash.app/#eyJwcm9vZnMiOlt7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50IjoyLCJzZWNyZXQiOiJrWjNBOVorSXkyREJOcDdhdFhYRTIvclVXOFRnR2ZoTDgzWEFXZ0dKUXhVPSIsIkMiOiIwMmM0NjA4NDYwNDhjNzI1ZjgwMDc3M2IyNmRmOTcxNDU1MTJmOTI0YjgyNzYyZTllYzdkZjZjOTkzNGVmYjJhNmMifSx7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50Ijo4LCJzZWNyZXQiOiJXdTZmdWlxNGt4Tkh3UkF1UzFhMmVYaGZtRnRHU2tRQkNYZFNnUzcreHkwPSIsIkMiOiIwMzFhYWI3MzY3MTJhY2Y5MWU4NzE4YmM5OTlmNWE2MGEwYzNjODQ5YTA1MWE2OTA5MzRkMTc4NWNmZGNkNDcyYTAifV0sIm1pbnRzIjpbeyJ1cmwiOiJodHRwczovL2xlZ2VuZC5sbmJpdHMuY29tL2Nhc2h1L2FwaS92MS80Z3I5WGNtejNYRWtVTndpQmlRR29DIiwiaWRzIjpbIjBOSTNUVUFzMVNmeSJdfV19 https://void.cat/d/U1UnyxsYgj516YbmkgQNkQ.webp Este token Ecash pode ser compartilhado como você quiser. Você pode enviá-lo por e-mail para alguém, enviá-lo em uma mensagem privada, um SMS ou convertê-lo em um código QR e imprimi-lo. Quem tiver este token pode resgatá-lo com o 10 sats.
Você verá que seu saldo caiu para 20 sats: https://void.cat/d/95AVkevmknKNzqRcnJZwQX.webp
Para resgatar um token Ecash sem o link, pressione o botão “Receive ” https://void.cat/d/UjrbAPn8mj5qGZYVQ1Ba2B.webp
cole-o token Ecash no campo
" token: "pressione "RECEIVE" https://void.cat/d/GZLcBgvHfaB3c5N66ygZyV.webp
Com o Link do token Ecash só pressionar no link vai abrir a tela já preencher automáticamente só pressionar " RECEIVE " https://void.cat/d/ARNkKCtchhFt4NCTkfRJRG.webp
Pra Ativa o Nostr na carteira vai na aba settings , pressione o botão ativa o Nostr. https://void.cat/d/MjoDA1dgueWUFABcQFDVRe.webp
Por padrão ficar ativo pra usar o " Use external Key (nos2x , outros) " Mas Nesse caso não vou usar vou desativar e vou ativa " Edit Nostr Keys " https://void.cat/d/BAA6eFkmK5f7BHzLwYLSGF.webp
Ao pressionar esse botão https://void.cat/d/VTNGVsLvwqfy3dWu4hhMSK.webp é gerar um novo par de chaves privadas e pública , assim podemos usar uma nova chave a cada pagamentos. Aumentando a privacidade no pagamentos.
A pois Ativa o Nostr na carteira , você pode enviar Sats / Ecash via Nostr.
Pressione " Send " https://void.cat/d/R2Svye4XPd2VdHfPxT1DzF.webp
Pressione " Send " https://void.cat/d/AwLeBBr2db2wrTHHUHwEPs.webp
Agora pode adicionar npud / hex / nip-05 pra enviar token. https://void.cat/d/VZR6BUXjG7pm3FDogrDvo4.webp
Pressione " SEND OVER NOSTR " pra enviar o token Ecash. https://void.cat/d/MWveqpmii5dqpioa5a3wVt.webp
Pra quem não tem a carteira nutstash , pode entra no seu cliente Nostr no meu caso e snort nostr , Demora algums minutos pra chegar mensagem com o token Ecash.. https://void.cat/d/MVg3fPD7PAzZUskGCCCcps.webp https://void.cat/d/YNtKuCbQYo1wef7pJcjhKy.webp
Ja se a outra pessoa usar carteira nutstash com a chave pública que você mandou chegar mais rápido. Essa bolinha azul no campo " Indox " Indica que você recebeu o pagamento já está pronto pra ser regastado. https://void.cat/d/So6FAp4wiTUeKBBmRBU2Rv.webp
Pressione "Indox " depois pressione a seta. https://void.cat/d/TqYNYDoyy9fUFas9NFxReJ.webp
Pressione " TRUS MINT " pra recebe os Token Ecash. https://void.cat/d/LP6zUTZ3HDPxd6fLvPPNXB.webp
O aplicativo de resgate Cashu, que permite resgatar tokens Ecash via Lightning.
https://redeem.cashu.me/ https://void.cat/d/Mw9kzDHr4A469EjFNoTHyB.webp
Cola o Token no campo " paste in your Cashu Ecash token.. " https://void.cat/d/SkA3MGJaGGxCjNnzeBhPHP.webp
Pressione " REDEEM " pra converter Ecash em Lightning. https://void.cat/d/693C1yfwYz3P3BQB6f7xXN.webp
Você pode editar e manda já pronto pra pessoa só basta a pessoa ou você aberta em " REDEEM " pra converter Ecash em Lightning.
https://redeem.cashu.me/?token=token ecash=&to=Lightning address
Exemplo:
https://redeem.cashu.me/?token=eyJwcm9vZnMiOlt7ImlkIjoiUEVuMVdLalFoN2pGIiwiYW1vdW50IjoyLCJDIjoiMDJhYWE5OWJiMmUwODQyYjJmNzdmNDRlZWEyZjEzMmNkOTNhZjJlNWU0MzI3ZjhjMTE5ODcxZWNiMTNhMTUxYjY0Iiwic2VjcmV0IjoicE5jb3hFRHJRT1ovTXU4d3d2SlpvMnRIaXBSM3pPYkRrSWJUUlB6VXh5bz0ifSx7ImlkIjoiUEVuMVdLalFoN2pGIiwiYW1vdW50IjoxNiwiQyI6IjAzNDM4ZDc1NmZmMjdmYjgyZmQxNWNhNzg3NzgwNTAyZWU4NzdmMzQ5MmYyMWQzMTMwMzc1NTdlNWNmMDJlOWQ0MCIsInNlY3JldCI6Im9DTXQwUTRVT0MvZWhmd2FVOWt5aGFJZUdHdXhiYUNzQTZ2STh2a0w2N1U9In0seyJpZCI6IlBFbjFXS2pRaDdqRiIsImFtb3VudCI6MzIsIkMiOiIwMmIyMmQ4MDEwZWU5MDA2MWYyNWQzODAyY2UyMDE3ZjAwMmVjMDVmMjM5NjIwNGNkYjllMmU2ODllYWY3YTZkYjIiLCJzZWNyZXQiOiI5ejVVMEdzWHZiUS84Rjd4ZFdYUXRxUDlvWGFyVnBRTzRFdUtzb2JSck1vPSJ9XSwibWludHMiOlt7InVybCI6Imh0dHBzOi8vbGVnZW5kLmxuYml0cy5jb20vY2FzaHUvYXBpL3YxL29DcXNTR3I1enphTTZxM1hWZU5ZNXQiLCJpZHMiOlsiUEVMVdLalFoN2pGIl19XX0=&to=alexemidio@ln.tips
Obs: o teclado do celular pode adicionar "=" a mais ou corrigir " &to " com "&tô" assim escrevendo errado, tanto erro no link.
" SWAP " transferência de uma carteira para outra. Pressione " INTER-MINT SWAP" https://void.cat/d/PsCdoLAmYpYCChkgqTAE7p.webp
A carteira que você selecionar em cima é a carteira de saídas e a carteira de baixo e a carteira de entrada. https://void.cat/d/VKY6ts6qttJmCaefrduv4K.webp
Agora digita o valor que quer fazer o SWAP. Após Pressione " CONFIRM AMOUNT" https://void.cat/d/WuuQqeC1mSQUufb75eeMbw.webp
Depois Tem que pressionar " SWAP " não esqueça. https://void.cat/d/Eb2ajSaZfzZkBEWBv8tuk.webp
Pronto antes a primeira Carteira tinha 10 Ecash, e segunda carteira tinha 8 Ecash.
Somando 18 Ecash.
Apois o SWAP Agora as duas tem 9.
Somando 18. https://void.cat/d/8yRtSoFyih2D2KEm66h6in.webp
Fazer o backup da sua carteira cashu ecash. Pressione " BACKUP TOKENS " https://void.cat/d/26vtnDiVP4YpDiQmunatko.webp
Você pode editar o nome do backup E pode alterar o local aonde vai salva o arquivo 📂 do backup. Depois só pressionar " Baixar " https://void.cat/d/PQH94o81U23txdmyx3cHEn.webp
Agora pra recuperar a carteira cashu ecash. Pressione " RESTORE " https://void.cat/d/2vkLS1qUCbJ1XXjSLBou25.webp
Pressione " CONTINUAR " https://void.cat/d/PCbT2UPSLtwcZohwbhD85A.webp
Click no espaço em branco vai abrir pra encontrar o arquivo 📂 Do backup.. https://void.cat/d/P1VC7b46oNe62v4puVZ79b.webp
Selecionar o arquivo 📂 de backup. https://void.cat/d/D6FAGxYRquz2WWwNznSAzT.webp
Pressione " CONTINUE" https://void.cat/d/HicRn5e2feSRicgjy6kuC5.webp
Pressione " CONTINUE" https://void.cat/d/VP6uh8bXHz42PBGrPwGq5e.webp
Backup feito com sucesso. Só aberta " Ok " https://void.cat/d/QsZV1umL9DhoPtEXBMfPtY.webp
O eCash pode ser útil em diversas situações, oferecendo várias vantagens. Uma das principais vantagens do uso de tokens eCash é a privacidade que oferece. Como as transações usando eCash são quase impossíveis de rastrear, isso pode ser útil para quem deseja manter sua atividade financeira privada. O eCash pode ser especialmente útil para Pagamento de serviços em áreas rurais , pode ser difícil acessar serviços financeiros tradicionais, como bancos ou caixas eletrônicos. O uso de tokens eCash pode permitir que as pessoas paguem por serviços como transporte , serviços de saúde ou eletricidade sem a necessidade de viajar para áreas urbanas. No entanto, é importante lembrar que o uso do eCash ainda apresenta riscos e desafios. Como o eCash cashubtc ainda é bem novo , pode haver falhas de segurança ou outras vulnerabilidades que ainda não foram identificadas use com cautela poucos Sats.
Obrigado por ler, e espero que você dedique alguns minutos para experimentar o eCash e ver do que se trata melhor.
Alguma artigos e vídeos a baixo.
https://cashu.space/
https://docs.cashu.space/
https://github.com/cashubtc/
https://youtu.be/UNjVc-WYdgE
https://youtu.be/_XmQSpAhFN4
https://youtu.be/zdtRT7phXBo
https://maxmoney.substack.com/p/ecash-for-better-bitcoin-privacy?utm_source=substack&utm_campaign=post_embed&utm_medium=web
https://cypherpunks.venona.com/date/1996/03/msg01848.html
Encontre-me ou envie um zap para nostr alexemidio@ln.tips alexemidio@alexemidio.github.io
Twitter: alexemidio7
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ 54609048:8e22ba03
2025-04-22 12:25:50
@ 54609048:8e22ba03
2025-04-22 12:25:50One of the greatest threats facing liberty lovers around the world today is the rise of the biomedical security state—the militarization of healthcare. COVID-19 was merely a compliance test, and sadly, most failed it dismally. But pay attention: “pandemic response,” war-gamed at elite gatherings like Davos, is steadily morphing into official health policy through backdoor mechanisms—diabolical agreements like the WHO Pandemic Treaty, which effectively transfers sovereign pandemic authority to Bill Gates via the WHO; the rollout of digital IDs; and the global push for central bank digital currencies (CBDCs).
This biomedical Leviathan requires all three pillars to be firmly in place before it can unleash a never-ending cycle of pandemics. The goal? To normalize draconian measures like those witnessed in 2020, thereby dismantling not only national sovereignty but, more dangerously, individual sovereignty. A digital ID won't merely confirm your identity—it will track your vaccination status, movements, and even your sentiments, all to determine what privileges you're allowed. Meanwhile, the CBDC will act not just as a means of transaction but as an enforcement mechanism—particularly for dissenters. This is why having an alternative like Bitcoin is not just relevant, but essential.
Vaccines are a cornerstone of this architecture—not only as instruments of control but also as tools for "redesigning" humanity. Welcome to the realm of transhumanism. The merger of man and machine through brain-computer interfaces and artificial intelligence is no longer science fiction; it's a stated goal. In this context, vaccines are not merely preventative medicine but potentially covert instruments of eugenics. This could explain the near-religious devotion to these pharmaceutical products—despite their increasingly controversial outcomes and questionable safety record—especially when mandates enter the equation.
The first piece of property any individual owns upon birth is their body. And yet, this sacred ownership is violated at birth when governments mandate certain injections—often administered without informed parental consent. I've often wondered: Why, despite mounting evidence to the contrary, is vaccine efficacy treated as “settled science”? Why is it taboo to question vaccines or hold their manufacturers accountable for harm, even as we’re expected to believe—without scrutiny—that they are “safe and effective”? We’re told our refusal to comply endangers everyone else who took a product supposedly designed to protect them. Strange, isn’t it? If it’s so effective, why must everyone take it simultaneously?
If you're wondering where this seemingly off-the-cuff rant is headed, here's the point: when the state mandates vaccines, it violates your property rights over your own body. It’s a direct claim of ownership over you, dressed up in moral language like “we're all in this together.” You're guilt-tripped into compliance under the pretense of saving “grandma.” But the truth is, if your rights can be suspended for the collective, they were never yours to begin with.
The biomedical security state will manufacture a permanent state of emergency under the guise of “pandemic preparedness.” You’ll be expected—required, even—to inject yourself with the latest mRNA-based bioweapon, all in the name of public health. Some will die. Others will become incapacitated—zombies or vegetables. The altar of compliance will be merciless towards those that bow before it.
Public health agencies like the CDC, WHO, and NIH are on track to become as powerful as central banks. In fact, they may soon act as arms of monetary policy enforcement. Don’t believe it? Look into what was happening in the repo markets in September 2019—just months before the global shutdown. While you're at it, investigate how many elderly pensioners quietly dropped dead like flies between 2021 and 2023, either from the virus or the vaccine. I’ll let the numbers speak for themselves.
These agencies are becoming the new face of the war machine. Vaccines will be marketed as shields against biological threats—“benevolent” weapons to protect us from invisible enemies. And if history is any guide, the next “9/11-style” event will be biological in nature.
The lunatics running the asylum will seize any such crisis to strip away more of your freedoms while simultaneously redesigning the global economy—consolidating even more power in their hands. For a blueprint of this ambition, look no further than Klaus Schwab’s COVID-19: The Great Reset.
The only antidote is a decentralized parallel system of medicine—one that stands entirely outside the Big Pharma cartel. This will require not only a network of courageous healthcare providers but also a new generation of researchers willing to ask uncomfortable questions and challenge sacred cows in the pursuit of truth. Add independent scientific journals to the mix, and we can finally dismantle the machinery that suppresses unprofitable—but potentially life-saving—treatments.
In my view, none of this is viable at scale without decentralized money. Enter Bitcoin. It’s not a panacea, but it’s a crucial tool for realigning incentives. Bitcoin renders CBDCs dead on arrival and undermines the foundation of any future social credit system—where vaccine compliance will be its crown jewel.
The biomedical state is not coming—it’s already here, creeping into every corner of our lives. It will be the scepter of a new technocratic tyranny. So beware the white coats who worship the state. They are not here to heal—they are here to rule.
A more polished series of articles on this topic is forthcoming. Stay tuned.












