-
 @ 7d33ba57:1b82db35
2025-04-23 10:28:49
@ 7d33ba57:1b82db35
2025-04-23 10:28:49Lake Bled is straight out of a storybook—an emerald alpine lake with a tiny island crowned by a church, surrounded by forested hills and overlooked by a clifftop castle. Just an hour from Ljubljana, this Slovenian gem is perfect for romantic getaways, outdoor adventures, or a peaceful escape into nature.
🌊 Top Things to Do in Bled
🛶 Bled Island & Church of the Assumption
- Take a traditional pletna boat or rent a rowboat to reach the only natural island in Slovenia
- Ring the church bell and make a wish—it’s a local tradition!
- Enjoy serene lake views from the island’s stone steps
🏰 Bled Castle (Blejski Grad)
- Perched on a cliff 130 meters above the lake
- Explore the medieval halls, museum, and wine cellar
- The terrace views? Absolutely unforgettable—especially at sunset
🚶♂️ Walk or Cycle the Lakeside Path
- A 6 km flat path circles the lake—perfect for a leisurely stroll or bike ride
- Stop for lakeside cafés, photo ops, or a quick swim in summer
🌄 Outdoor Adventures Beyond the Lake
- Hike to Mala Osojnica Viewpoint for the most iconic panoramic view of Lake Bled
- Go paddleboarding, kayaking, or swimming in warmer months
- Nearby Vintgar Gorge offers a stunning wooden path through a narrow, turquoise canyon
🍰 Try the Famous Bled Cream Cake (Kremšnita)
- A must-try dessert with layers of vanilla custard, cream, and crispy pastry
- Best enjoyed with a coffee on a terrace overlooking the lake

🏡 Where to Stay
- Lakeside hotels, cozy guesthouses, or charming Alpine-style B&Bs
- Some even offer views of the lake, castle, or Triglav National Park
🚗 Getting There
- Around 1 hour from Ljubljana by car, bus, or train
- Easy to combine with stops like Lake Bohinj or Triglav National Park
-
 @ fbf0e434:e1be6a39
2025-04-23 08:42:22
@ fbf0e434:e1be6a39
2025-04-23 08:42:22Hackathon 概要
Naija HackAtom 圆满落幕。此次活动共有 160 名开发者注册参与,成功展示 51 个通过审核的项目。该黑客马拉松旨在推动尼日利亚 Web3 社区内 Interchain、Cosmos Hub 和 Atom 经济区(AEZ)的发展,主要目标是培养本土人才、提供资源支持,并开发基于 $ATOM 代币的区块链应用。
活动聚焦 Interchain 安全性、Atom 经济区、CosmWasm 以及 ATOM 的具体发展等关键领域。其中,跨链汇款平台、面向非洲农民的去中心化市场等项目尤为亮眼,充分展现了 Cosmos 技术的创新应用潜力。
本次黑客马拉松设立了 10000 美元的奖金池,用于奖励在 UI/UX 设计、社区参与度及 Atom 创新应用方案等方面表现突出的项目。在系列研讨会与公开教程的辅助下,参赛者提交的项目从技术可行性、创新性、社会影响力和用户体验等维度进行评审。活动凭借广泛的参与度与丰富的创新成果,有力推动了尼日利亚乃至整个非洲区块链生态的发展。
Hackathon 获奖者
Naija HackAtom 作为尼日利亚首个以 Cosmos 和 ATOM 为核心的黑客马拉松,吸引了超 500 人参与,其中开发者达 160 名。在 ATOMAccelerator 的支持下,活动共收到 57 个项目提交,最终 18 个项目脱颖而出,入围决赛。
主奖项获奖者
- Beep: 一个用于Naira代币化的平台,促进了与tAtom无缝交易和交换。
- Padi [Crypto Go Fund Me]: 一个基于区块链的平台,用于进行代币驱动的筹款活动。
- ATwork: 一个去中心化的自由职业平台,通过Cosmos区块链增强自由职业者与客户之间的合作。
独特解决方案/产品奖项获奖者
- LendPro: 一个借贷协议,通过区块链促进合作金融治理。
- Tradi-App: 一个在Secret Network上的隐私AI交易分析平台,提供市场见解。
- Delegated Staking Agent(DSA): 提供Cosmos生态系统中的质押和治理投票,具有AI增强的安全性能。
- Neutron NFT Launch: 通过整合AI、区块链和NFT技术简化NFT的创建和交易。
Secret Network 赏金获奖者
- Prompt Hub: 一个专注隐私、AI生成提示的市场,带有集成功能。
- Delegated Staking Agent(DSA)
- Secret AI Writer: 一个AI写作平台,提供安全的区块链存储和隐私中心的内容生成。
- Tradi-App
ChihuahuaChain 赏金获奖者
- Neutron NFT Launch
- woof-dot-fun: 一个复制Pump.Fun的项目,具有代币和债券曲线功能。
- Vault Quest: 一个无损奖品储蓄协议,利用DeFi策略进行基于收益的奖品分配。
Akash 赏金获奖者
- Jarvis AI: 一个语音激活的助手,旨在高效的云资源管理。
有关Naija HackAtom期间提交的所有项目的完整列表,请访问这里。
关于组织者
Cosmos Hub Africa
Cosmos Hub Africa专注于在非洲推广区块链技术和Cosmos生态系统。该组织在去中心化网络开发和区块链行业内的协作方面发挥着重要作用。其贡献包括提高平台之间可扩展性和互操作性的项目。目前,Cosmos Hub Africa致力于推进该地区的区块链教育和基础设施,旨在促进与传统经济和金融系统的创新和整合。
-
 @ fd06f542:8d6d54cd
2025-04-23 07:51:30
@ fd06f542:8d6d54cd
2025-04-23 07:51:30- 第三章、NIP-03: OpenTimestamps Attestations for Events
- 第四章、NIP-04: Encrypted Direct Message
- 第五章、NIP-05: Mapping Nostr keys to DNS-based internet identifiers
- 第六章、NIP-06: Basic key derivation from mnemonic seed phrase
- 第七章、NIP-07: window.nostr capability for web browsers
- 第八章、NIP-08: Handling Mentions --- unrecommended: deprecated in favor of NIP-27
- 第九章、NIP-09: Event Deletion Request
- 第十章、NIP-10: Text Notes and Threads
- 第十一章、NIP-11: Relay Information Document
- 第十二章、NIP-13: Proof of Work
- 第十三章、NIP-14: Subject tag in text events
- 第十四章、NIP-15: Nostr Marketplace (for resilient marketplaces)
- 第十五章、NIP-17: Private Direct Messages
- 第十六章、NIP-18: Reposts
- 第十七章、NIP-19: bech32-encoded entities
-
 @ da0b9bc3:4e30a4a9
2025-04-23 07:50:49
@ da0b9bc3:4e30a4a9
2025-04-23 07:50:49Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/954269
-
 @ 2b24a1fa:17750f64
2025-04-23 06:53:15
@ 2b24a1fa:17750f64
2025-04-23 06:53:15„Immer wieder ist jetzt“ übertitelt unsere Sprecherin Sabrina Khalil ihren Text, den sie für die Friedensnoten geschrieben hat. Das gleichnamige Gedicht hat Jens Fischer Rodrian vertont.
Sprecher des Textes: Ulrich Allroggen
-
 @ fd06f542:8d6d54cd
2025-04-23 06:39:15
@ fd06f542:8d6d54cd
2025-04-23 06:39:15有时候写点日志,可以 记录一点琐碎的事情。
! 也许这就是 这就是 这个blog存在的原因吧。
如何将docsify 变成一个渲染blog的 工具
我用了很多办法,但是关键点还是这个 方法。 无须配置 window.$docsify ={} ```js $: if (blogItem) {
compiledContent = window.__current_docsify_compiler__.compile(blogItem.content); }```
直接用内容的 功能转换。
但是渲染的时候要注意:
html <article class="markdown-section" id="main"> {@html compiledContent} </article>内容要加上这个外框,这个问题我调试了一天在知道...原来是少了他,导致缺少很多东西。
如何上传背景图片?
- 一定要点击 封面图区域的空白处, 让 编辑框失去焦点。
- 再 把鼠标放在 虚线封面图区域,就可以ctrl+v 粘贴截图了。
其他使用事项,我想起来再写吧。
-
 @ 8d34bd24:414be32b
2025-04-23 03:52:15
@ 8d34bd24:414be32b
2025-04-23 03:52:15I started writing a series on the signs of the End Times and how they align with what we are seeing in the world today. There are some major concerns with predicting the end times, so I decided I should insert a short post on “Can we know when the end times are coming?” Like many principles in the Bible, it takes looking at seemingly contradictory verses to reach the truth.
This Generation
Before I get into “Can we know?” I want to address one point that some will bring up against a future Rapture, Tribulation, and Millennium.
Truly I say to you, this generation will not pass away until all these things take place. (Matthew 24:34) {emphasis mine}
What generation is Jesus talking about. Most Christians that don’t believe in a future Rapture, Tribulation, and Millennium will point to this verse to support their point of view. The important question is, “What is Jesus referring to with the words ‘this generation’?”
Is it referring to the people He was talking to at that time? If so, since that generation died long ago, then Jesus’s predictions must have been fulfilled almost 2 millennia ago. The problem with this interpretation is that nothing resembling these predictions happened during that initial generation. You have to really twist His words to try to support that they were fulfilled. Also, John wrote in Revelation about future fulfillment. By that time, John was the last of the apostles still alive and that whole generation was pretty much gone.
If “this generation” doesn’t refer to the people Jesus was speaking to personally in that moment, then to whom does it refer? The verses immediately preceding talk about the signs that will occur right before the end times. If you take “this generation” to mean the people who saw the signs Jesus predicted, then everything suddenly makes sense. It also parallel’s Paul’s statement of consolation to those who thought they had been left behind,**
But we do not want you to be uninformed, brethren, about those who are asleep, so that you will not grieve as do the rest who have no hope. For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. For this we say to you by the word of the Lord, that we who are alive and remain until the coming of the Lord, will not precede those who have fallen asleep. For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. Therefore comfort one another with these words. (1 Thessalonians 4:13-18) {emphasis mine}
Some believers thought things were happening in their lifetime, but Paul gave them comfort that no believer would miss the end times rapture.
No One Knows
Truly I say to you, this generation will not pass away until all these things take place. Heaven and earth will pass away, but My words will not pass away.
But of that day and hour no one knows, not even the angels of heaven, nor the Son, but the Father alone. For the coming of the Son of Man will be just like the days of Noah. For as in those days before the flood they were eating and drinking, marrying and giving in marriage, until the day that Noah entered the ark, and they did not understand until the flood came and took them all away; so will the coming of the Son of Man be. Then there will be two men in the field; one will be taken and one will be left. Two women will be grinding at the mill; one will be taken and one will be left. (Matthew 24:34-41) {emphasis mine}
This verse very explicitly says that no one, not even angels or Jesus, knows the exact day or hour of His coming.
So when they had come together, they were asking Him, saying, “Lord, is it at this time You are restoring the kingdom to Israel?” He said to them, “It is not for you to know times or epochs which the Father has fixed by His own authority; but you will receive power when the Holy Spirit has come upon you; and you shall be My witnesses both in Jerusalem, and in all Judea and Samaria, and even to the remotest part of the earth.” (Acts 1:6-8)
In this verse Jesus again says that they cannot know the time of His return, but based on context, He is explaining that this generation needs to focus on sharing the Gospel with world and not primarily on the kingdom. Is this Jesus’s way of telling them that they would not be alive to see His return, but they would be responsible for “sharing the Gospel even to the remotest part of the earth?”
Therefore we do know that predicting the exact date of His return is a fool’s errand and should not be attempted, but does this mean we can’t know when it is fast approaching?
We Should Know
There is an opposing passage, though.
The Pharisees and Sadducees came up, and testing Jesus, they asked Him to show them a sign from heaven. But He replied to them, “When it is evening, you say, ‘It will be fair weather, for the sky is red.’ And in the morning, ‘There will be a storm today, for the sky is red and threatening.’ Do you know how to discern the appearance of the sky, but cannot discern the signs of the times? An evil and adulterous generation seeks after a sign; and a sign will not be given it, except the sign of Jonah.” And He left them and went away. (Matthew 16:1-4) {emphasis mine}
In this passage, Jesus reprimands the Pharisees and Sadducees because, although they can rightly read the signs of the weather, they were unable to know and understand the prophecies of His first coming. Especially as the religious leaders, they should’ve been able to determine that Jesus’s coming was imminent and that He was fulfilling the prophetic Scriptures.
In Luke, when Jesus is discussing His second coming with His disciples, He tells this parable:
Then He told them a parable: “Behold the fig tree and all the trees; as soon as they put forth leaves, you see it and know for yourselves that summer is now near. So you also, when you see these things happening, recognize that the kingdom of God is near. (Luke 21:29-31) {emphasis mine}
Jesus would not have given this parable if there were not signs of His coming that we can recognize.
We are expected to know the Scriptures and to study them looking for the signs of His second coming. We can’t know the hour or the day, but we can know that the time is fast approaching. We shouldn’t set dates, but we should search anxiously for the signs of His coming. We shouldn’t be like the scoffers that question His literal fulfillment of His promises:
Know this first of all, that in the last days mockers will come with their mocking, following after their own lusts, and saying, “Where is the promise of His coming? For ever since the fathers fell asleep, all continues just as it was from the beginning of creation.” For when they maintain this, it escapes their notice that by the word of God the heavens existed long ago and the earth was formed out of water and by water, through which the world at that time was destroyed, being flooded with water. But by His word the present heavens and earth are being reserved for fire, kept for the day of judgment and destruction of ungodly men. But do not let this one fact escape your notice, beloved, that with the Lord one day is like a thousand years, and a thousand years like one day. The Lord is not slow about His promise, as some count slowness, but is patient toward you, not wishing for any to perish but for all to come to repentance. (2 Peter 3:3-9) {emphasis mine}
One thing is certain, we are closer to Jesus’s second coming than we have ever been and must be ready as we see the day approaching.
May the God of heaven give you a desire and urgency to share the Gospel with all those around you and to grow your faith, knowledge, and relationship with Him, so you can finish the race well, with no regrets. May the knowledge that Jesus could be coming soon give you an eternal perspective on life, so you put more of your time into things of eternal consequence and don’t get overwhelmed with things of the world which are here today and then are gone.
Trust Jesus.
FYI, I hope to write several more articles on the end times (signs of the times, the rapture, the millennium, and the judgement), but I might be a bit slow rolling them out because I want to make sure they are accurate and well supported by Scripture. You can see my previous posts on the end times on the end times tab at trustjesus.substack.com. I also frequently will list upcoming posts.
-
 @ 9c9d2765:16f8c2c2
2025-04-23 08:54:57
@ 9c9d2765:16f8c2c2
2025-04-23 08:54:57CHAPTER TEN
Gasps rippled through the hall as James strode in confidently, his PA by his side. The expensive fabric of his suit gleaned Helen's jaw dropped, her fingers freezing mid-tap. She instinctively clutched Christopher’s arm under the chandeliers, its impeccable fit accentuating his regal posture. Every eye was locked onto him, disbelief spreading across the faces of those who had once looked down on him.
"That can’t be James… It must be one of rich friends who lent him that suit!"
Christopher remained speechless, his face paling as realization dawned. Robert, sitting across from them, stared wide-eyed at James, his mind racing to piece together what was happening.
James walked straight to the front of the hall, his PA pulling out a chair for him. He sat down calmly, scanning the room with a faint smirk. He could see the stunned expressions, the silent questions dancing in their eyes.
"Ladies and gentlemen," the event host finally announced, clearing his throat. "Please welcome Mr. James, the President of JP Enterprises."
A wave of murmurs swept through the hall, disbelief clashing with admiration. The Ray family sat frozen in place, Helen clutching the armrest so tightly her knuckles turned white.
James leaned forward, clasping his hands together. "Shall we begin?" he said, his voice smooth yet firm, carrying the weight of a man who had risen from the ashes.
The meeting commenced, but Helen couldn’t focus. Her mind reeled from the shocking truth James, the man she had humiliated and cast aside, was not just successful; he was now one of the most powerful businessmen in the room.
"How dare you lay your hands on me? Do you know who I am?" Mark roared as the security guards tightened their grip on his arms, dragging him toward the exit of the grand conference hall.
The murmurs in the room grew louder, investors and company representatives whispering among themselves as they watched the Prime Minister's son being forcefully removed. Mark struggled, his face flushed red with anger and embarrassment.
"Sir, please don't make this harder than it has to be. You are not an authorized investor," one of the guards said firmly.
Mark's glare was searing as he turned his head towards James, who stood calmly at the head table, watching the entire scene unfold. "You!" Mark spat. "You planned this, didn’t you? You set me up to be humiliated like this!"
James arched an eyebrow, folding his arms across his chest. "No, Mark. You did this to yourself. You thought you could walk in here, throwing your weight around without proper authorization. This is a professional investment summit, not your playground."
Helen, sitting across the hall, clenched her fists. "How can they do this to Mark? He is a valuable investor!" she whispered furiously to her husband, Christopher, who was too stunned to respond.
Mark twisted in the guards' grip, his voice dripping with venom. "I swear, James, you will regret this. You think you can humiliate me in front of these elites? I will make you pay for this!"
James met his gaze with a calm but firm expression. "Mark, threats won’t change reality. You came here thinking your name alone could buy you a seat at the table. But in business, it's about credibility, not status. And today, you just proved to everyone here that you have none."
The room remained silent as the guards escorted Mark out. His loud protests echoed through the hallway before the grand doors finally shut behind him.
Rita sat in her chair, her heart pounding. She knew Mark was dangerous when scorned. She turned to James, worry evident in her eyes. "James, you know he won’t let this go, right?"
James exhaled slowly, nodding. "I know, Rita. And I'm ready for whatever he plans next."
The hall remained hushed for a moment before the moderator cleared his throat. "Now that the disruption has been handled, let us proceed with the investment discussions. Mr. James, as the President of JP Enterprises, you have the floor."
James stepped forward, commanding the attention of every business mogul in the room. He knew this was just the beginning, but one thing was certain Mark had declared war, and James was ready for battle.
-
 @ f5369849:f34119a0
2025-04-23 08:48:05
@ f5369849:f34119a0
2025-04-23 08:48:05Hackathon Summary
The Naija HackAtom successfully concluded with the participation of 160 registered developers and a presentation of 51 approved projects. This hackathon was designed to advance the Interchain, Cosmos Hub, and Atom Economic Zone (AEZ) within Nigeria’s Web3 communities. The main objectives included nurturing local talent, providing resources, and developing blockchain applications utilizing the $ATOM token.
The primary focus areas encompassed Interchain Security, the Atom Economic Zone, CosmWasm, and developments specific to ATOM. Notable projects included cross-chain remittance platforms and decentralized marketplaces for African farmers, emphasizing innovative applications of Cosmos technologies.
An $10,000 prize pool was established to reward innovation in UI/UX, community engagement, and unique Atom utility solutions. Over the course of various workshops and public tutorials, participants developed projects that were judged on technical feasibility, innovation, impact, and user experience. The event, marked by widespread participation and innovation, effectively contributed to the growth of blockchain ecosystems in Nigeria and across Africa.
Hackathon Winners
The Naija HackAtom marked Nigeria's first hackathon centered on Cosmos and ATOM, drawing over 500 participants, including 160 developers. With support from ATOMAccelerator, a total of 57 projects were submitted, narrowing down to 18 finalists.
Main Prize Winners
- Beep: A platform for Naira tokenization, facilitating seamless transactions and exchanges with tAtom.
- Padi {Crypto Go Fund Me}: A blockchain-based platform for conducting token-driven fundraising campaigns.
- ATwork: A decentralized freelancing platform enhancing collaboration between freelancers and clients through the Cosmos blockchain.
Unique Solution/Product Prize Winners
- LendPro: A lending protocol that fosters cooperative financial governance via blockchain.
- Tradi-App: A confidential AI trading analytics platform on the Secret Network providing market insights.
- Delegated Staking Agent (DSA): Offers staking and governance voting in the Cosmos ecosystem with AI-enhanced security.
- Neutron NFT Launch: Simplifies NFT creation and trading by integrating AI, blockchain, and NFT technology.
Secret Network Bounty Winners
- Prompt Hub: A marketplace for privacy-focused, AI-generated prompts with integration features.
- Delegated Staking Agent (DSA)
- Secret AI Writer: An AI writing platform offering secure blockchain storage and privacy-centric content generation.
- Tradi-App
ChihuahuaChain Bounty Winners
- Neutron NFT Launch
- woof-dot-fun: A project replicating Pump.Fun with token and bond curve functionality.
- Vault Quest: A no-loss prize-saving protocol leveraging DeFi strategies for yield-based prize distribution.
Akash Bounty Winner
- Jarvis AI: A voice-activated assistant designed for efficient cloud resource management.
For a complete list of all projects submitted during the Naija HackAtom, visit here.
Organization
About the Organizer: Cosmos Hub Africa
Cosmos Hub Africa is focused on promoting blockchain technology and the Cosmos ecosystem specifically across Africa. The organization plays a significant role in decentralized network development and collaboration within the blockchain industry. Its contributions include projects that enhance scalability and interoperability across platforms. At present, Cosmos Hub Africa is committed to advancing blockchain education and infrastructure in the region, aiming to foster innovation and integration with the traditional economy and financial system.
-
 @ 1d7ff02a:d042b5be
2025-04-23 02:28:08
@ 1d7ff02a:d042b5be
2025-04-23 02:28:08ທຳຄວາມເຂົ້າໃຈກັບຂໍ້ບົກພ່ອງໃນລະບົບເງິນຂອງພວກເຮົາ
ຫຼາຍຄົນພົບຄວາມຫຍຸ້ງຍາກໃນການເຂົ້າໃຈ Bitcoin ເພາະວ່າພວກເຂົາຍັງບໍ່ເຂົ້າໃຈບັນຫາພື້ນຖານຂອງລະບົບເງິນທີ່ມີຢູ່ຂອງພວກເຮົາ. ລະບົບນີ້, ທີ່ມັກຖືກຮັບຮູ້ວ່າມີຄວາມໝັ້ນຄົງ, ມີຂໍ້ບົກພ່ອງໃນການອອກແບບທີ່ມີມາແຕ່ດັ້ງເດີມ ເຊິ່ງສົ່ງຜົນຕໍ່ຄວາມບໍ່ສະເໝີພາບທາງເສດຖະກິດ ແລະ ການເຊື່ອມເສຍຂອງຄວາມຮັ່ງມີສຳລັບພົນລະເມືອງທົ່ວໄປ. ການເຂົ້າໃຈບັນຫາເຫຼົ່ານີ້ແມ່ນກຸນແຈສຳຄັນເພື່ອເຂົ້າໃຈທ່າແຮງຂອງວິທີແກ້ໄຂທີ່ Bitcoin ສະເໜີ.
ບົດບາດຂອງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ
ລະບົບເງິນຕາປັດຈຸບັນໃນສະຫະລັດອາເມລິກາປະກອບມີການເຊື່ອມໂຍງທີ່ຊັບຊ້ອນລະຫວ່າງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ. ກະຊວງການຄັງສະຫະລັດເຮັດໜ້າທີ່ເປັນບັນຊີທະນາຄານຂອງປະເທດ, ເກັບອາກອນ ແລະ ສະໜັບສະໜູນລາຍຈ່າຍຂອງລັດຖະບານເຊັ່ນ: ທະຫານ, ໂຄງລ່າງພື້ນຖານ ແລະ ໂຄງການສັງຄົມ. ເຖິງຢ່າງໃດກໍຕາມ, ລັດຖະບານມັກໃຊ້ຈ່າຍຫຼາຍກວ່າທີ່ເກັບໄດ້, ເຊິ່ງເຮັດໃຫ້ຕ້ອງໄດ້ຢືມເງິນ. ການຢືມນີ້ແມ່ນເຮັດໂດຍການຂາຍພັນທະບັດລັດຖະບານ, ຊຶ່ງມັນຄືໃບ IOU ທີ່ສັນຍາວ່າຈະຈ່າຍຄືນຈຳນວນທີ່ຢືມພ້ອມດອກເບ້ຍ. ພັນທະບັດເຫຼົ່ານີ້ມັກຖືກຊື້ໂດຍທະນາຄານໃຫຍ່, ລັດຖະບານຕ່າງປະເທດ, ແລະ ທີ່ສຳຄັນ, ທະນາຄານກາງ.
ວິທີການສ້າງເງິນ (ຈາກອາກາດ)
ນີ້ແມ່ນບ່ອນທີ່ເກີດການສ້າງເງິນ "ຈາກອາກາດ". ເມື່ອທະນາຄານກາງຊື້ພັນທະບັດເຫຼົ່ານີ້, ມັນບໍ່ໄດ້ໃຊ້ເງິນທີ່ມີຢູ່ແລ້ວ; ມັນສ້າງເງິນໃໝ່ດ້ວຍວິທີການດິຈິຕອນໂດຍພຽງແຕ່ປ້ອນຕົວເລກເຂົ້າໃນຄອມພິວເຕີ. ເງິນໃໝ່ນີ້ຖືກເພີ່ມເຂົ້າໃນປະລິມານເງິນລວມ. ຍິ່ງສ້າງເງິນຫຼາຍຂຶ້ນ ແລະ ເພີ່ມເຂົ້າໄປ, ມູນຄ່າຂອງເງິນທີ່ມີຢູ່ແລ້ວກໍຍິ່ງຫຼຸດລົງ. ຂະບວນການນີ້ຄືສິ່ງທີ່ພວກເຮົາເອີ້ນວ່າເງິນເຟີ້. ເນື່ອງຈາກກະຊວງການຄັງຢືມຢ່າງຕໍ່ເນື່ອງ ແລະ ທະນາຄານກາງສາມາດພິມໄດ້ຢ່າງຕໍ່ເນື່ອງ, ສິ່ງນີ້ຖືກສະເໜີວ່າເປັນວົງຈອນທີ່ບໍ່ມີທີ່ສິ້ນສຸດ.
ການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ
ເພີ່ມເຂົ້າໃນບັນຫານີ້ຄືການປະຕິບັດຂອງການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ. ເມື່ອທ່ານຝາກເງິນເຂົ້າທະນາຄານ, ທະນາຄານຖືກຮຽກຮ້ອງໃຫ້ເກັບຮັກສາພຽງແຕ່ສ່ວນໜຶ່ງຂອງເງິນຝາກນັ້ນໄວ້ເປັນເງິນສະຫງວນ (ຕົວຢ່າງ, 10%). ສ່ວນທີ່ເຫຼືອ (90%) ສາມາດຖືກປ່ອຍກູ້. ເມື່ອຜູ້ກູ້ຢືມໃຊ້ຈ່າຍເງິນນັ້ນ, ມັນມັກຖືກຝາກເຂົ້າອີກທະນາຄານ, ເຊິ່ງຈາກນັ້ນກໍຈະເຮັດຊ້ຳຂະບວນການໃຫ້ກູ້ຢືມສ່ວນໜຶ່ງຂອງເງິນຝາກ. ວົງຈອນນີ້ເຮັດໃຫ້ເພີ່ມຈຳນວນເງິນທີ່ໝູນວຽນຢູ່ໃນລະບົບໂດຍອີງໃສ່ເງິນຝາກເບື້ອງຕົ້ນ, ເຊິ່ງສ້າງເງິນຜ່ານໜີ້ສິນ. ລະບົບນີ້ໂດຍທຳມະຊາດແລ້ວບອບບາງ; ຖ້າມີຫຼາຍຄົນພະຍາຍາມຖອນເງິນຝາກຂອງເຂົາເຈົ້າພ້ອມກັນ (ການແລ່ນທະນາຄານ), ທະນາຄານກໍຈະລົ້ມເພາະວ່າມັນບໍ່ໄດ້ເກັບຮັກສາເງິນທັງໝົດໄວ້. ເງິນໃນທະນາຄານບໍ່ປອດໄພຄືກັບທີ່ເຊື່ອກັນທົ່ວໄປ ແລະ ສາມາດຖືກແຊ່ແຂງໃນຊ່ວງວິກິດການ ຫຼື ສູນເສຍຖ້າທະນາຄານລົ້ມລະລາຍ (ຍົກເວັ້ນໄດ້ຮັບການຊ່ວຍເຫຼືອ).
ຜົນກະທົບ Cantillon: ໃຜໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ
ເງິນທີ່ຖືກສ້າງຂຶ້ນໃໝ່ບໍ່ໄດ້ກະຈາຍຢ່າງເທົ່າທຽມກັນ. "ຜົນກະທົບ Cantillon", ບ່ອນທີ່ຜູ້ທີ່ຢູ່ໃກ້ກັບແຫຼ່ງສ້າງເງິນໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ. ນີ້ລວມເຖິງລັດຖະບານເອງ (ສະໜັບສະໜູນລາຍຈ່າຍ), ທະນາຄານໃຫຍ່ ແລະ Wall Street (ໄດ້ຮັບທຶນໃນອັດຕາດອກເບ້ຍຕ່ຳສຳລັບການກູ້ຢືມ ແລະ ການລົງທຶນ), ແລະ ບໍລິສັດໃຫຍ່ (ເຂົ້າເຖິງເງິນກູ້ທີ່ຖືກກວ່າສຳລັບການລົງທຶນ). ບຸກຄົນເຫຼົ່ານີ້ໄດ້ຊື້ຊັບສິນ ຫຼື ລົງທຶນກ່ອນທີ່ຜົນກະທົບຂອງເງິນເຟີ້ຈະເຮັດໃຫ້ລາຄາສູງຂຶ້ນ, ເຊິ່ງເຮັດໃຫ້ພວກເຂົາມີຂໍ້ໄດ້ປຽບ.
ຜົນກະທົບຕໍ່ຄົນທົ່ວໄປ
ສຳລັບຄົນທົ່ວໄປ, ຜົນກະທົບຂອງປະລິມານເງິນທີ່ເພີ່ມຂຶ້ນນີ້ແມ່ນການເພີ່ມຂຶ້ນຂອງລາຄາສິນຄ້າ ແລະ ການບໍລິການ - ນ້ຳມັນ, ຄ່າເຊົ່າ, ການດູແລສຸຂະພາບ, ອາຫານ, ແລະ ອື່ນໆ. ເນື່ອງຈາກຄ່າແຮງງານໂດຍທົ່ວໄປບໍ່ທັນກັບອັດຕາເງິນເຟີ້ນີ້, ອຳນາດການຊື້ຂອງປະຊາຊົນຈະຫຼຸດລົງເມື່ອເວລາຜ່ານໄປ. ມັນຄືກັບການແລ່ນໄວຂຶ້ນພຽງເພື່ອຢູ່ໃນບ່ອນເກົ່າ.
Bitcoin: ທາງເລືອກເງິນທີ່ໝັ້ນຄົງ
ຄວາມຂາດແຄນ: ບໍ່ຄືກັບເງິນຕາ fiat, Bitcoin ມີຂີດຈຳກັດສູງສຸດໃນປະລິມານຂອງມັນ. ຈະມີພຽງ 21 ລ້ານ Bitcoin ເທົ່ານັ້ນຖືກສ້າງຂຶ້ນ, ຂີດຈຳກັດນີ້ຝັງຢູ່ໃນໂຄດຂອງມັນ ແລະ ບໍ່ສາມາດປ່ຽນແປງໄດ້. ການສະໜອງທີ່ຈຳກັດນີ້ເຮັດໃຫ້ Bitcoin ເປັນເງິນຫຼຸດລາຄາ; ເມື່ອຄວາມຕ້ອງການເພີ່ມຂຶ້ນ, ມູນຄ່າຂອງມັນມີແນວໂນ້ມທີ່ຈະເພີ່ມຂຶ້ນເພາະວ່າປະລິມານການສະໜອງບໍ່ສາມາດຂະຫຍາຍຕົວ.
ຄວາມທົນທານ: Bitcoin ຢູ່ໃນ blockchain, ເຊິ່ງເປັນປຶ້ມບັນຊີສາທາລະນະທີ່ແບ່ງປັນກັນຂອງທຸກການເຮັດທຸລະກຳທີ່ແທບຈະເປັນໄປບໍ່ໄດ້ທີ່ຈະລຶບ ຫຼື ປ່ຽນແປງ. ປຶ້ມບັນຊີນີ້ຖືກກະຈາຍໄປທົ່ວພັນຄອມພິວເຕີ (nodes) ທົ່ວໂລກ. ແມ້ແຕ່ຖ້າອິນເຕີເນັດລົ້ມ, ເຄືອຂ່າຍສາມາດຢູ່ຕໍ່ໄປໄດ້ຜ່ານວິທີການອື່ນເຊັ່ນ: ດາວທຽມ ຫຼື ຄື້ນວິທະຍຸ. ມັນບໍ່ໄດ້ຮັບຜົນກະທົບຈາກການທຳລາຍທາງກາຍະພາບຂອງເງິນສົດ ຫຼື ການແຮັກຖານຂໍ້ມູນແບບລວມສູນ.
ການພົກພາ: Bitcoin ສາມາດຖືກສົ່ງໄປໃນທຸກບ່ອນໃນໂລກໄດ້ທັນທີ, 24/7, ດ້ວຍການເຊື່ອມຕໍ່ອິນເຕີເນັດ, ໂດຍບໍ່ຈຳເປັນຕ້ອງມີທະນາຄານ ຫຼື ການອະນຸຍາດຈາກພາກສ່ວນທີສາມ. ທ່ານສາມາດເກັບຮັກສາ Bitcoin ຂອງທ່ານໄດ້ດ້ວຍຕົນເອງໃນອຸປະກອນທີ່ເອີ້ນວ່າກະເປົາເຢັນ, ແລະ ຕາບໃດທີ່ທ່ານຮູ້ວະລີກະແຈລັບຂອງທ່ານ, ທ່ານສາມາດເຂົ້າເຖິງເງິນຂອງທ່ານຈາກກະເປົາທີ່ເຂົ້າກັນໄດ້, ເຖິງແມ່ນວ່າອຸປະກອນຈະສູນຫາຍ. ສິ່ງນີ້ສະດວກສະບາຍກວ່າ ແລະ ມີຄວາມສ່ຽງໜ້ອຍກວ່າການພົກພາເງິນສົດຈຳນວນຫຼາຍ ຫຼື ການນຳທາງການໂອນເງິນສາກົນທີ່ຊັບຊ້ອນ.
ການແບ່ງຍ່ອຍ: Bitcoin ສາມາດແບ່ງຍ່ອຍໄດ້ສູງ. ໜຶ່ງ Bitcoin ສາມາດແບ່ງເປັນ 100 ລ້ານໜ່ວຍຍ່ອຍທີ່ເອີ້ນວ່າ Satoshis, ເຊິ່ງອະນຸຍາດໃຫ້ສົ່ງ ຫຼື ຮັບຈຳນວນນ້ອຍໄດ້.
ຄວາມສາມາດໃນການທົດແທນກັນ: ໜຶ່ງ Bitcoin ທຽບເທົ່າກັບໜຶ່ງ Bitcoin ໃນມູນຄ່າ, ໂດຍທົ່ວໄປ. ໃນຂະນະທີ່ເງິນໂດລາແບບດັ້ງເດີມອາດສາມາດຖືກຕິດຕາມ, ແຊ່ແຂງ, ຫຼື ຍຶດໄດ້, ໂດຍສະເພາະໃນຮູບແບບດິຈິຕອນ ຫຼື ຖ້າຖືກພິຈາລະນາວ່າໜ້າສົງໄສ, ແຕ່ລະໜ່ວຍຂອງ Bitcoin ໂດຍທົ່ວໄປຖືກປະຕິບັດຢ່າງເທົ່າທຽມກັນ.
ການພິສູດຢັ້ງຢືນ: ທຸກການເຮັດທຸລະກຳ Bitcoin ຖືກບັນທຶກໄວ້ໃນ blockchain, ເຊິ່ງທຸກຄົນສາມາດເບິ່ງ ແລະ ພິສູດຢັ້ງຢືນ. ຂະບວນການພິສູດຢັ້ງຢືນທີ່ກະຈາຍນີ້, ດຳເນີນໂດຍເຄືອຂ່າຍ, ໝາຍຄວາມວ່າທ່ານບໍ່ຈຳເປັນຕ້ອງເຊື່ອຖືທະນາຄານ ຫຼື ສະຖາບັນໃດໜຶ່ງແບບມືດບອດເພື່ອຢືນຢັນຄວາມຖືກຕ້ອງຂອງເງິນຂອງທ່ານ.
ການຕ້ານການກວດກາ: ເນື່ອງຈາກບໍ່ມີລັດຖະບານ, ບໍລິສັດ, ຫຼື ບຸກຄົນໃດຄວບຄຸມເຄືອຂ່າຍ Bitcoin, ບໍ່ມີໃຜສາມາດຂັດຂວາງທ່ານຈາກການສົ່ງ ຫຼື ຮັບ Bitcoin, ແຊ່ແຂງເງິນຂອງທ່ານ, ຫຼື ຍຶດມັນ. ມັນເປັນລະບົບທີ່ບໍ່ຕ້ອງຂໍອະນຸຍາດ, ເຊິ່ງໃຫ້ຜູ້ໃຊ້ຄວບຄຸມເຕັມທີ່ຕໍ່ເງິນຂອງເຂົາເຈົ້າ.
ການກະຈາຍອຳນາດ: Bitcoin ຖືກຮັກສາໂດຍເຄືອຂ່າຍກະຈາຍຂອງບັນດາຜູ້ຂຸດທີ່ໃຊ້ພະລັງງານການຄິດໄລ່ເພື່ອຢັ້ງຢືນການເຮັດທຸລະກຳຜ່ານ "proof of work". ລະບົບທີ່ກະຈາຍນີ້ຮັບປະກັນວ່າບໍ່ມີຈຸດໃດຈຸດໜຶ່ງທີ່ຈະລົ້ມເຫຼວ ຫຼື ຄວບຄຸມ. ທ່ານບໍ່ໄດ້ເພິ່ງພາຂະບວນການທີ່ບໍ່ໂປ່ງໃສຂອງທະນາຄານກາງ; ລະບົບທັງໝົດໂປ່ງໃສຢູ່ໃນ blockchain. ສິ່ງນີ້ເຮັດໃຫ້ບຸກຄົນມີອຳນາດທີ່ຈະເປັນທະນາຄານຂອງຕົນເອງແທ້ ແລະ ຮັບຜິດຊອບຕໍ່ການເງິນຂອງເຂົາເຈົ້າ.
-
 @ 3ffac3a6:2d656657
2025-04-23 01:57:57
@ 3ffac3a6:2d656657
2025-04-23 01:57:57🔧 Infrastructure Overview
- Hardware: Raspberry Pi 5 with PCIe NVMe HAT and 2TB NVMe SSD
- Filesystem: ZFS with separate datasets for each service
- Networking: Docker bridge networks for service segmentation
- Privacy: Tor and I2P routing for anonymous communication
- Public Access: Cloudflare Tunnel to securely expose LNbits
📊 Architecture Diagram
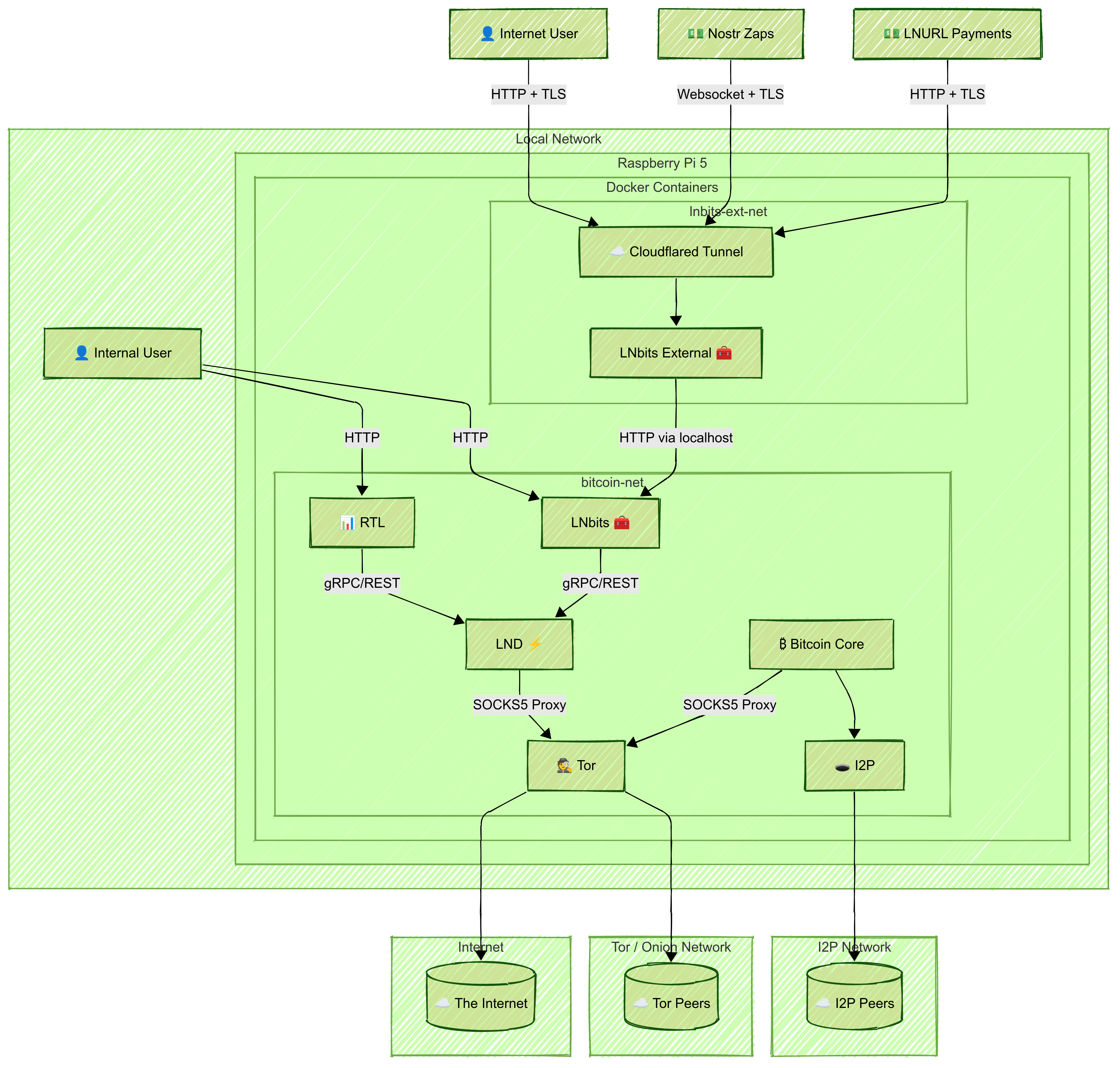
🛠️ Setup Steps
1. Prepare the System
- Install Raspberry Pi OS (64-bit)
- Set up ZFS on the NVMe disk
- Create a ZFS dataset for each service (e.g.,
bitcoin,lnd,rtl,lnbits,tor-data) - Install Docker and Docker Compose
2. Create Shared Docker Network and Privacy Layers
Create a shared Docker bridge network:
bash docker network create \ --driver=bridge \ --subnet=192.168.100.0/24 \ bitcoin-netNote: Connect
bitcoind,lnd,rtl, internallnbits,tor, andi2pto thisbitcoin-netnetwork.Tor
- Run Tor in a container
- Configure it to expose LND's gRPC and REST ports via hidden services:
HiddenServicePort 10009 192.168.100.31:10009 HiddenServicePort 8080 192.168.100.31:8080 - Set correct permissions:
bash sudo chown -R 102:102 /zfs/datasets/tor-data
I2P
- Run I2P in a container with SAM and SOCKS proxies
- Update
bitcoin.conf:i2psam=192.168.100.20:7656 i2pacceptincoming=1
3. Set Up Bitcoin Core
- Create a
bitcoin.confwith Tor/I2P/proxy settings and ZMQ enabled - Sync the blockchain in a container using its ZFS dataset
4. Set Up LND
- Configure
lnd.confto connect tobitcoindand use Tor: ```ini [Bitcoind] bitcoind.rpchost=bitcoin:8332 bitcoind.rpcuser=bitcoin bitcoind.rpcpass=very-hard-password bitcoind.zmqpubrawblock=tcp://bitcoin:28332 bitcoind.zmqpubrawtx=tcp://bitcoin:28333
[Application Options] externalip=xxxxxxxx.onion
`` - Don’t expose gRPC or REST ports publicly - Mount the ZFS dataset at/root/.lnd` - Optionally enable Watchtower5. Set Up RTL
- Mount
RTL-Config.jsonand data volumes - Expose RTL's web interface locally:
```yaml
ports:
- "3000:3000" ```
6. Set Up Internal LNbits
- Connect the LNbits container to
bitcoin-net - Mount the data directory and LND cert/macaroons (read-only)
- Expose the LNbits UI on the local network:
```yaml
ports:
- "5000:5000" ```
- In the web UI, configure the funding source to point to the LND REST
.onionaddress and paste the hex macaroon - Create and fund a wallet, and copy its Admin Key for external use
7. Set Up External LNbits + Cloudflare Tunnel
- Run another LNbits container on a separate Docker network
- Access the internal LNbits via the host IP and port 5000
- Use the Admin Key from the internal wallet to configure funding
- In the Cloudflare Zero Trust dashboard:
- Create a tunnel
- Select Docker, copy the
--tokencommand - Add to Docker Compose:
yaml command: tunnel --no-autoupdate run --token eyJ...your_token...
💾 Backup Strategy
- Bitcoin Core: hourly ZFS snapshots, retained for 6 hours
- Other Services: hourly snapshots with remote
.tar.gzbackups - Retention: 7d hourly, 30d daily, 12mo weekly, monthly forever
- Back up ZFS snapshots to avoid inconsistencies
🔐 Security Isolation Benefits
This architecture isolates services by scope and function:
- Internal traffic stays on
bitcoin-net - Sensitive APIs (gRPC, REST) are reachable only via Tor
- Public access is controlled by Cloudflare Tunnel
Extra Security: Host the public LNbits on a separate machine (e.g., hardened VPS) with strict firewall rules:
- Allow only Cloudflare egress
- Allow ingress from your local IP
- Allow outbound access to internal LNbits (port 5000)
Use WireGuard VPN to secure the connection between external and internal LNbits:
- Ensures encrypted communication
- Restricts access to authenticated VPN peers
- Keeps the internal interface isolated from the public internet
✅ Final Notes
- Internal services communicate over
bitcoin-net - LND interfaces are accessed via Tor only
- LNbits and RTL UIs are locally accessible
- Cloudflare Tunnel secures external access to LNbits
Monitor system health using
monit,watchtower, or Prometheus.Create all configuration files manually (
bitcoin.conf,lnd.conf,RTL-Config.json), and keep credentials secure. Test every component locally before exposing it externally.⚡
-
 @ 33baa074:3bb3a297
2025-04-23 06:07:54
@ 33baa074:3bb3a297
2025-04-23 06:07:54Soil water potential refers to the potential energy of water in the soil, which is the driving force for the movement and distribution of water in the soil. It reflects the activity and energy level of soil water, and has a direct impact on plant water absorption and soil water retention capacity. Changes in soil water potential can reflect the effectiveness of soil water, which in turn affects plant growth and the effectiveness of soil nutrients. The following are the specific effects of soil water potential on soil:
Effects on plant water absorption Soil water potential directly affects the water absorption process of plants. Increases in osmotic potential and matrix potential can promote plant water absorption, while increases in gravity potential and pressure potential can hinder plant water absorption. For example, when soil water potential is high, the ability of water to move from high concentration to low concentration is enhanced, which is conducive to plant roots absorbing water.
Effects on soil water distribution Soil texture has a great influence on water permeability and water retention, thereby affecting soil water potential. Clay soils are more likely to form high water potential, while sandy soils are more likely to form low water potential. The amount of rainfall will also affect soil water potential. A lot of rainfall will increase the moisture in the soil, leading to an increase in soil water potential, while a lot of rainfall will reduce soil water potential.
Impact on soil temperature Soil water potential is also related to soil temperature. Soil temperature affects the evaporation and infiltration rate of water in the soil, thereby affecting soil water potential. In addition, the moisture content in the soil will also affect the heat capacity of the soil. Soil with high moisture content has the slowest heating and cooling rates.
Impact on soil fertility There is a close relationship between soil water potential and soil fertility. Appropriate soil water potential is conducive to soil microbial activity, nutrient conversion, and root absorption of water and nutrients. Changes in groundwater levels will also affect soil fertility. When the groundwater level rises, dissolved substances in the groundwater will enter the soil and increase soil fertility; on the contrary, when the groundwater level drops, the nutrients in the soil will decrease with the loss of groundwater.
Impact on soil structure Changes in soil water potential can affect soil structure. For example, the rise and fall of the groundwater level can cause particles in the soil to move and change the soil texture. Clay particles become more sticky under the action of water, and sandy soil may be lost due to water erosion. Therefore, measures need to be taken to strengthen soil conservation, such as covering with plants and building dams to reduce soil loss.
In summary, soil water potential has many effects on soil, including plant water absorption, soil moisture distribution, soil temperature, soil fertility, and soil structure. Understanding and managing soil water potential is of great significance to agricultural production, environmental protection, and ecological balance.
-
 @ f32184ee:6d1c17bf
2025-04-23 01:15:09
@ f32184ee:6d1c17bf
2025-04-23 01:15:09Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. NextBlock’s PROMO Protocol, designed while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ 872982aa:8fb54cfe
2025-04-23 06:04:20
@ 872982aa:8fb54cfe
2025-04-23 06:04:20NIP-28
Public Chat
draftoptionalThis NIP defines new event kinds for public chat channels, channel messages, and basic client-side moderation.
It reserves five event kinds (40-44) for immediate use:
40 - channel create41 - channel metadata42 - channel message43 - hide message44 - mute user
Client-centric moderation gives client developers discretion over what types of content they want included in their apps, while imposing no additional requirements on relays.
Kind 40: Create channel
Create a public chat channel.
In the channel creation
contentfield, Client SHOULD include basic channel metadata (name,about,pictureandrelaysas specified in kind 41).jsonc { "content": "{\"name\": \"Demo Channel\", \"about\": \"A test channel.\", \"picture\": \"https://placekitten.com/200/200\", \"relays\": [\"wss://nos.lol\", \"wss://nostr.mom\"]}", // other fields... }Kind 41: Set channel metadata
Update a channel's public metadata.
Kind 41 is used to update the metadata without modifying the event id for the channel. Only the most recent kind 41 per
etag value MAY be available.Clients SHOULD ignore kind 41s from pubkeys other than the kind 40 pubkey.
Clients SHOULD support basic metadata fields:
name- string - Channel nameabout- string - Channel descriptionpicture- string - URL of channel picturerelays- array - List of relays to download and broadcast events to
Clients MAY add additional metadata fields.
Clients SHOULD use NIP-10 marked "e" tags to recommend a relay.
It is also possible to set the category name using the "t" tag. This category name can be searched and filtered.
jsonc { "content": "{\"name\": \"Updated Demo Channel\", \"about\": \"Updating a test channel.\", \"picture\": \"https://placekitten.com/201/201\", \"relays\": [\"wss://nos.lol\", \"wss://nostr.mom\"]}", "tags": [ ["e", <channel_create_event_id>, <relay-url>, "root"], ["t", <category_name-1>], ["t", <category_name-2>], ["t", <category_name-3>], ], // other fields... }Kind 42: Create channel message
Send a text message to a channel.
Clients SHOULD use NIP-10 marked "e" tags to recommend a relay and specify whether it is a reply or root message.
Clients SHOULD append NIP-10 "p" tags to replies.
Root message:
jsonc { "content": <string>, "tags": [["e", <kind_40_event_id>, <relay-url>, "root"]], // other fields... }Reply to another message:
jsonc { "content": <string>, "tags": [ ["e", <kind_40_event_id>, <relay-url>, "root"], ["e", <kind_42_event_id>, <relay-url>, "reply"], ["p", <pubkey>, <relay-url>], // rest of tags... ], // other fields... }Kind 43: Hide message
User no longer wants to see a certain message.
The
contentmay optionally include metadata such as areason.Clients SHOULD hide event 42s shown to a given user, if there is an event 43 from that user matching the event 42
id.Clients MAY hide event 42s for other users other than the user who sent the event 43.
(For example, if three users 'hide' an event giving a reason that includes the word 'pornography', a Nostr client that is an iOS app may choose to hide that message for all iOS clients.)
jsonc { "content": "{\"reason\": \"Dick pic\"}", "tags": [["e", <kind_42_event_id>]], // other fields... }js function add(a,b){ returun a+b; }Kind 44: Mute user
User no longer wants to see messages from another user.
The
contentmay optionally include metadata such as areason.Clients SHOULD hide event 42s shown to a given user, if there is an event 44 from that user matching the event 42
pubkey.Clients MAY hide event 42s for users other than the user who sent the event 44.
jsonc { "content": "{\"reason\": \"Posting dick pics\"}", "tags": [["p", <pubkey>]], // other fields... }Relay recommendations
Clients SHOULD use the relay URLs of the metadata events.
Clients MAY use any relay URL. For example, if a relay hosting the original kind 40 event for a channel goes offline, clients could instead fetch channel data from a backup relay, or a relay that clients trust more than the original relay.
Motivation
If we're solving censorship-resistant communication for social media, we may as well solve it also for Telegram-style messaging.
We can bring the global conversation out from walled gardens into a true public square open to all.
Additional info
-
 @ 502ab02a:a2860397
2025-04-23 01:04:54
@ 502ab02a:a2860397
2025-04-23 01:04:54ช่วงหลัง ๆ มานี้ ถ้าใครเดินผ่านชั้นนมในซูเปอร์ฯ แล้วสะดุดตากับกล่องสีเรียบ ๆ สไตล์สแกนดิเนเวียนที่เขียนคำว่า "OATLY!" ตัวใหญ่ ๆ ไม่ต้องแปลกใจ เพราะนี่คือเครื่องดื่มที่กำลังพยายามจะทำให้ทุกบ้านเชื่อว่า "ดื่มข้าวโอ๊ตแทนนมวัวคือสิ่งที่ดีต่อสุขภาพ ต่อโลก และต่อเด็ก ๆ"
Oatly ไม่ได้มาเล่น ๆ เป็นดาวรุ่งของวงการ plant-based dairy ทางเลือก ด้วยการตลาดที่เฉียบคมและอารมณ์ขันแบบขบถ เพราะบริษัทนี้เขาวางโพสิชั่นของตัวเองว่าเป็นนักสู้เพื่อสิ่งแวดล้อม ต่อต้านโลกร้อน และเป็นทางเลือกที่รักสัตว์รักโลกจนพืชยังปรบมือให้ แต่เบื้องหลังที่ดูคลีน ๆ กลับซ่อนกลยุทธ์ทางการตลาดที่แสบสันไม่เบา โดยเฉพาะการรณรงค์ในโรงเรียน และเทคนิคในการ “ซ่อนความหวาน” ได้อย่างแนบเนียนจนน้ำตาลยังงง
หวานแบบซ่อนรูปสูตรลับที่ไม่อยู่ในช่อง Sugar โอ๊ตมิลค์ของ Oatly มีคาร์บต่ำจริงตามฉลาก แต่ที่หลายคนไม่รู้คือ Oatly ใช้ เอนไซม์ย่อยแป้งจากข้าวโอ๊ต ให้กลายเป็นน้ำตาลมอลโทส ซึ่งมีรสหวานพอ ๆ กับน้ำตาลทราย แต่ไม่ต้องแสดงในช่อง Total Sugar บนฉลากโภชนาการ เพราะมันเกิดขึ้น "ตามธรรมชาติจากกระบวนการ" ซึ่งตรงตามเกณฑ์ FDA เป๊ะ
ความเจ้าเล่ห์ของระบบนี้คือ มอลโตสที่เกิดจากการย่อยแป้งด้วยเอนไซม์ ไม่ต้องนับเป็น “น้ำตาล” ในช่อง Sugar ของฉลากโภชนาการ เพราะมันถือเป็น “naturally occurring sugar” หรือ “น้ำตาลที่เกิดขึ้นเองตามธรรมชาติ” พูดง่ายๆ คือ หวานเหมือนโค้ก แต่ไม่ต้องบอกว่าใส่น้ำตาลเลยแม้แต่นิดเดียว! ในขณะที่เด็กๆ ดื่มแล้วบอกว่า “อร่อยมาก!” ผู้ใหญ่ก็เห็นฉลากแล้วบอกว่า “น้ำตาลแค่นิดเดียวเอง ดีจัง”… ความเข้าใจผิดแบบสองชั้นนี้คือการตลาดที่ชาญฉลาดแต่แฝงความไม่โปร่งใส
และเมื่อคุณไปอ่านงานวิจัยจะเจอว่า น้ำตาลมอลโตสที่ได้จากโอ๊ตผ่านกระบวนการย่อยแบบนี้ มีค่าดัชนีน้ำตาลสูงถึง 105-110 ซึ่งสูงกว่าโค้กเสียอีก (Coke อยู่ประมาณ 63) ส่งผลให้ระดับน้ำตาลในเลือดพุ่งอย่างรวดเร็ว และถ้าใครมีภาวะดื้อต่ออินซูลินหรืออยู่ในขอบเขต prediabetes ก็ยิ่งน่ากังวลเข้าไปใหญ่ พูดง่าย ๆ คือ Oatly หวาน แต่ไม่ต้องบอกว่าใส่น้ำตาล คนทั่วไปเลยเข้าใจผิดว่า “อ้าว มันไม่หวานนี่นา”
บางโรงเรียนในอังกฤษและสวีเดนเริ่มตั้งคำถามว่า การเปลี่ยนนมวัวที่อุดมไปด้วยไขมันดี โปรตีนสมบูรณ์ และแคลเซียม เข้าสู่ร่างกายเด็กๆ ให้กลายเป็น “นมโอ๊ตหวานแบบซ่อนรูป” แบบนี้ มันคือความยั่งยืนจริงๆ หรือเป็นเพียงการใช้ภาพรักษ์โลกบังหน้า แล้วขายคาร์บอย่างแนบเนียน โดยเฉพาะ The Telegraph ได้เผยแพร่บทความชื่อ “The truth about the great oat milk 'con'” ซึ่งกล่าวถึงการที่หน่วยงานกำกับดูแลโฆษณาในสหราชอาณาจักร (Advertising Standards Authority - ASA) สั่งห้ามโฆษณาบางรายการของบริษัท Oatly เนื่องจากพบว่ามีการให้ข้อมูลที่ทำให้ผู้บริโภคเข้าใจผิดเกี่ยวกับประโยชน์ต่อสิ่งแวดล้อมของการเปลี่ยนจากนมวัวเป็นนมจากพืช รวมถึง ภาพลักษณ์ “plant-based ดีต่อโลก” ถูกใช้เป็น เครื่องมือโฆษณาเชิงอารมณ์ โดยลดคุณค่าของนมวัวแท้ ๆ และสิ่งที่น่าตลกร้ายก็คือ…บริษัท Oatly เคยออกมาโจมตีอุตสาหกรรมนมวัวว่า “ไม่โปร่งใส” ขณะเดียวกันพวกเขาเองกลับโดนฟ้องร้องเรื่องการใช้โฆษณาเกินจริง และพยายามซุกซ่อนกระบวนการผลิตที่ทำให้เกิดน้ำตาลแบบ “ซ่อนในตาราง” เสียเอง
ไม่แปลกที่หลายคนในแวดวงโภชนาการแซวว่า "Oatmilk is the new Coke" เพราะมันหวานแบบไม่รู้ตัว ดื่มเพลินเหมือนน้ำอัดลม แต่สื่อสารราวกับเป็นน้ำเต้าหู้สายโยคะ โอเคเรื่องพวกนี้เอาจริงๆเคยคุยกันแล้วในรายการ ลองไปดูย้อนได้ครับ
แต่นั่นยังไม่เท่ากับสิ่งนี้ครับ “Normalize It!”: รณรงค์เข้ารร.แบบซอฟต์พาวเวอร์ ถ้าคิดว่าแค่ขายในซูเปอร์คือจุดหมาย ขอบอกว่า Oatly เล่นเกมไกลกว่านั้น เพราะเขาเปิดแคมเปญชื่อ “Normalize it!” ในหลายประเทศในยุโรป เช่น เยอรมนี สวีเดน และเนเธอร์แลนด์ โดยรณรงค์ให้ เครื่องดื่มจากพืชถูกบรรจุเป็นส่วนหนึ่งของ "โครงการนมโรงเรียน" ที่มีอยู่เดิมในระบบรัฐ ซึ่งแต่เดิมให้เฉพาะนมวัวเท่านั้น
ในโฆษณาแคมเปญนี้ มีการเล่นภาพเด็ก ๆ ที่แอบเอาโอ๊ตมิลค์ใส่กล่องนมโรงเรียน พร้อมประโยคชวนสะอึกว่า “เด็กควรต้องทำเองเหรอ?” (เหมือนจะบอกว่ารัฐควรรับหน้าที่แทน) ดูความแสบได้ที่นี่ https://youtu.be/D3d_GfGVq_I?si=3pi6VKnlJC2SDleW
มันฟังดูดีใช่ไหม...แต่ประเด็นคือ ใครเป็นคนได้ประโยชน์? คำตอบคือ บริษัทที่ขายโอ๊ตมิลค์นั่นแหละ
เพราะหากสำเร็จ โรงเรียนจำนวนมากในยุโรปจะต้องซื้อผลิตภัณฑ์จากพืชแทนหรือควบคู่กับนมวัว ทำให้บริษัทที่ขายเครื่องดื่มพืชกลายเป็นผู้ได้สัมปทานทางอ้อมในชื่อ “ความยั่งยืน”
Lobby แบบ “รักษ์โลก” แต่ก็ไม่ลืมรักษาผลประโยชน์ แคมเปญนี้ไม่ได้แค่โฆษณาเล่น ๆ แต่ยังมีการล็อบบี้ทางนโยบายในระดับสหภาพยุโรป (EU) โดยผลักดันให้เครื่องดื่มจากพืชที่มีการเสริมแคลเซียมได้รับการยอมรับเท่าเทียมกับนมวัว Oatly จึงไม่ได้แค่เป็นแบรนด์ข้าวโอ๊ตอีกต่อไป แต่กลายเป็น "นักกิจกรรม" ที่มีเป้าหมายใหญ่คือการเข้าไปอยู่ในระบบอาหารภาครัฐ โดยเฉพาะสำหรับเด็ก ๆ
ปัญหาคือไม่ใช่แค่ “พืช” แต่คือ “วิธีการสื่อสาร” ไม่มีใครเถียงว่าเด็กควรมีทางเลือกในอาหาร แต่เมื่อ “ข้อมูล” ที่ใช้สร้างภาพลักษณ์ผลิตภัณฑ์ถูกเรียบเรียงให้ดูดีเกินจริง โดยเฉพาะเมื่อซ่อนความหวานไว้ในกลไกทางเคมี และรณรงค์ให้เข้าสู่ระบบโรงเรียน มันก็กลายเป็นประเด็นที่เราควรถามว่า “เรากำลังให้เด็กกินอะไร เพราะอะไร และใครได้ประโยชน์จากสิ่งนั้น?” เครื่องดื่มจากพืชไม่ใช่ปีศาจ และนมวัวก็ไม่ใช่เทวดา แต่สิ่งที่น่ากลัวคือกลยุทธ์ที่หลอกให้คนเชื่อว่าทางเลือกหนึ่ง “ดีกว่า” โดยไม่ให้ข้อมูลครบถ้วน หรือยิ่งแย่กว่านั้นถ้าเป็นการตัดริดรอนสิทธิ์ในการเลือก
วันหนึ่งถ้าเด็ก ๆ ทุกคนได้ดื่มโอ๊ตมิลค์ที่หวานแต่ไม่เรียกว่าน้ำตาล เพราะใครบางคนบอกว่า “ดีต่อสุขภาพ” เราควรถามว่า “สุขภาพของใคร?” และ “ใครนิยามว่าอะไรคือดี?” เพราะบางครั้ง โลกที่ดูยั่งยืน อาจมีรากฐานมาจากการตลาดที่ยืนนาน
เรื่องนี้ไม่ได้เกี่ยวกับการเกลียดพืช หรือรังเกียจข้าวโอ๊ต หรือนมโอ้ต แต่มันเกี่ยวกับ ความจริงที่ถูกแต่งหน้าให้ดูดีเกินจริง ในนามของสุขภาพและสิ่งแวดล้อม ซึ่งอาจกลายเป็นการเปลี่ยนเด็กๆ ให้คุ้นชินกับเครื่องดื่มหวานแบบไม่รู้ตัว ในขณะที่เราเคยพยายามลดโค้กจากโรงเรียนไปเมื่อสิบปีก่อน
อย่าลืมว่า ไม่ใช่แค่น้ำตาลที่ต้องดู แต่ต้องดูว่ามันมาจากไหน ถูกสร้างขึ้นอย่างไร และร่างกายตอบสนองอย่างไร
สำคัญที่สุดคือ เรามีสิทธิ์ในการเลือกไหม ในอนาคต
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 866e0139:6a9334e5
2025-04-23 04:54:00
@ 866e0139:6a9334e5
2025-04-23 04:54:00Autor: Caitlin Johnstone. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Sie schicken Milliardäre und Popstars ins All, während der Planet brennt und Amerikaner ihr Insulin rationieren.
Es gibt Firmen, die KI-Liebhaber an einsame Menschen vermarkten und dabei ihre Daten ernten.
Gestern Nacht bombardierte Israel ein Zeltlager in Gaza, Frauen und Kinder verbrannten lebendig.
Dies ist ein seltsamer, dunkler Ort. Seltsame, dunkle Zeiten in einer seltsamen, dunklen Welt.
Zünde eine Kerze an für die, die gestorben sind.
Zünde eine Kerze an für die, die innerlich tot sind.
Zünde eine Kerze an für die, die Algorithmen in den Augen tragen.
Zünde eine Kerze an für die, die KI in ihren Seelen tragen.
Zünde eine Kerze an für die schreienden roten Kinder.
Zünde eine Kerze an für die stummen grauen Kinder.
Zünde eine Kerze an für den Großen Pazifischen Müllstrudel.
Zünde eine Kerze an für die Lieder der Wale.
Zünde eine Kerze an für die Herzen wie gegossenes Blei.
Zünde eine Kerze an für die Herzen wie überfahrene Wallabys.
Zünde eine Kerze an für die Herzen wie Weihrauchkathedralen.
Zünde eine Kerze an für die Herzen wie nasse Himmel.
Zünde eine Kerze an für die Eier in unseren Brustkörben.
Zünde eine Kerze an für die Samen in unseren Köpfen.
Zünde eine Kerze an für die Atompilzwolke am Horizont.
Zünde eine Kerze an für die schlafenden Buddhas.
Ich stehe da, mit offenem Mund und trockenem Hals, in einer Welt, die ich nicht verstehe, auf dem Weg in eine Zukunft, die ich nicht erkenne.
Feuerlicht tanzt an meiner Wand — von den Kerzen, oder vielleicht von Gaza, oder vielleicht von der Biosphäre, oder vielleicht von irgendwo unter meiner Haut.
Dieser Text erschien zuerst auf englisch auf dem Substack-Blog der Autorin.
(Den Text kann man hier als Kurzlink abrufen und teilen.)
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ d34e832d:383f78d0
2025-04-22 23:35:05
@ d34e832d:383f78d0
2025-04-22 23:35:05For Secure Inheritance Planning and Offline Signing
The setup described ensures that any 2 out of 3 participants (hardware wallets) must sign a transaction before it can be broadcast, offering robust protection against theft, accidental loss, or mismanagement of funds.
1. Preparation: Tools and Requirements
Hardware Required
- 3× COLDCARD Mk4 hardware wallets (or newer)
- 3× MicroSD cards (one per COLDCARD)
- MicroSD card reader (for your computer)
- Optional: USB data blocker (for safe COLDCARD connection)
Software Required
- Sparrow Wallet: Version 1.7.1 or later
Download: https://sparrowwallet.com/ - COLDCARD Firmware: Version 5.1.2 or later
Update guide: https://coldcard.com/docs/upgrade
Other Essentials
- Durable paper or steel backup tools for seed phrases
- Secure physical storage for backups and devices
- Optional: encrypted external storage for Sparrow wallet backups
Security Tip:
Always verify software signatures before installation. Keep your COLDCARDs air-gapped (no USB data transfer) whenever possible.
2. Initializing Each COLDCARD Wallet
- Power on each COLDCARD and choose “New Wallet”.
- Write down the 24-word seed phrase (DO NOT photograph or store digitally).
- Confirm the seed and choose a strong PIN code (both prefix and suffix).
- (Optional) Enable BIP39 Passphrase for additional entropy.
- Save an encrypted backup to the MicroSD card:
Go to Advanced > Danger Zone > Backup. - Repeat steps 1–5 for all three COLDCARDs.
Best Practice:
Store each seed phrase securely and in separate physical locations. Test wallet recovery before storing real funds.
3. Exporting XPUBs from COLDCARD
Each hardware wallet must export its extended public key (XPUB) for multisig setup:
- Insert MicroSD card into a COLDCARD.
- Navigate to:
Settings > Multisig Wallets > Export XPUB. - Select the appropriate derivation path. Recommended:
- Native SegWit:
m/84'/0'/0'(bc1 addresses) - Alternatively: Nested SegWit
m/49'/0'/0'(starts with 3) - Save the XPUB file to the MicroSD card.
- Insert MicroSD into your computer and transfer XPUB files to Sparrow Wallet.
- Repeat for the remaining COLDCARDs.
4. Creating the 2-of-3 Multisig Wallet in Sparrow
- Launch Sparrow Wallet.
- Click File > New Wallet and name your wallet.
- In the Keystore tab, choose Multisig.
- Select 2-of-3 as your multisig policy.
- For each cosigner:
- Choose Add cosigner > Import XPUB from file.
- Load XPUBs exported from each COLDCARD.
- Once all 3 cosigners are added, confirm the configuration.
- Click Apply, then Create Wallet.
- Sparrow will display a receive address. Fund the wallet using this.
Tip:
You can export the multisig policy (wallet descriptor) as a backup and share it among cosigners.
5. Saving and Verifying the Wallet Configuration
- After creating the wallet, click Wallet > Export > Export Wallet File (.json).
- Save this file securely and distribute to all participants.
- Verify that the addresses match on each COLDCARD using the wallet descriptor file (optional but recommended).
6. Creating and Exporting a PSBT (Partially Signed Bitcoin Transaction)
- In Sparrow, click Send, fill out recipient details, and click Create Transaction.
- Click Finalize > Save PSBT to MicroSD card.
- The file will be saved as a
.psbtfile.
Note: No funds are moved until 2 signatures are added and the transaction is broadcast.
7. Signing the PSBT with COLDCARD (Offline)
- Insert the MicroSD with the PSBT into COLDCARD.
- From the main menu:
Ready To Sign > Select PSBT File. - Verify transaction details and approve.
- COLDCARD will create a signed version of the PSBT (
signed.psbt). - Repeat the signing process with a second COLDCARD (different signer).
8. Finalizing and Broadcasting the Transaction
- Load the signed PSBT files back into Sparrow.
- Sparrow will detect two valid signatures.
- Click Finalize Transaction > Broadcast.
- Your Bitcoin transaction will be sent to the network.
9. Inheritance Planning with Multisig
Multisig is ideal for inheritance scenarios:
Example Inheritance Setup
- Signer 1: Yourself (active user)
- Signer 2: Trusted family member or executor
- Signer 3: Lawyer, notary, or secure backup
Only 2 signatures are needed. If one party loses access or passes away, the other two can recover the funds.
Best Practices for Inheritance
- Store each seed phrase in separate, tamper-proof, waterproof containers.
- Record clear instructions for heirs (without compromising seed security).
- Periodically test recovery with cosigners.
- Consider time-locked wallets or third-party escrow if needed.
Security Tips and Warnings
- Never store seed phrases digitally or online.
- Always verify addresses and signatures on the COLDCARD screen.
- Use Sparrow only on secure, malware-free computers.
- Physically secure your COLDCARDs from unauthorized access.
- Practice recovery procedures before storing real value.
Consider
A 2-of-3 multisignature wallet using COLDCARD and Sparrow Wallet offers a highly secure, flexible, and transparent Bitcoin custody model. Whether for inheritance planning or high-security storage, it mitigates risks associated with single points of failure while maintaining usability and privacy.
By following this guide, Bitcoin users can significantly increase the resilience of their holdings while enabling thoughtful succession strategies.
-
 @ f5836228:1af99dad
2025-04-23 03:27:27
@ f5836228:1af99dad
2025-04-23 03:27:27Se você está em busca de uma plataforma moderna, confiável e repleta de opções de entretenimento digital, a 7788bet é a escolha ideal. Com uma proposta inovadora, a plataforma se destaca por unir tecnologia de ponta, uma ampla variedade de jogos e uma experiência de usuário fluida, pensada para agradar tanto iniciantes quanto jogadores mais experientes.
A 7788bet chegou ao mercado com o objetivo de oferecer um ambiente seguro, intuitivo e divertido. A navegação é simples e responsiva, funcionando perfeitamente em dispositivos móveis e desktops. Tudo é estruturado para que o usuário encontre rapidamente o que procura, desde os jogos populares até promoções atrativas.
Outro diferencial da 7788beté o seu compromisso com a transparência e a confiabilidade. A plataforma opera com tecnologias de segurança de última geração, protegendo os dados pessoais e financeiros de seus usuários. Além disso, o suporte ao cliente é eficiente e disponível em diversos canais, incluindo chat ao vivo e atendimento via e-mail, garantindo assistência rápida sempre que necessário.
Um dos grandes atrativos da 7788bet é a diversidade de jogos oferecidos. São centenas de títulos das melhores desenvolvedoras do mercado, com gráficos envolventes e mecânicas modernas. Entre as categorias mais populares estão:
Slots de Vídeo: Jogos com temas variados, rodadas bônus e prêmios acumulados. Perfeitos para quem busca adrenalina e recompensas.
Jogos de Mesa: Clássicos como roleta, blackjack e bacará estão disponíveis em versões digitais e com crupiês ao vivo, proporcionando uma experiência mais imersiva.
Apostas Esportivas: Para os apaixonados por esportes, a 7788bet oferece uma seção completa para palpites em eventos esportivos do mundo todo, com odds competitivas e diversas modalidades.
Jogos Instantâneos: Ideais para quem quer jogar de forma rápida e descomplicada, os jogos instantâneos são leves, dinâmicos e garantem diversão em poucos cliques.
Todos os jogos passam por auditorias e seguem padrões internacionais de justiça, garantindo que os resultados sejam sempre aleatórios e imparciais.
A Experiência do Jogador em Primeiro Lugar Na 7788bet, cada detalhe é pensado para oferecer a melhor experiência ao jogador. Desde o primeiro acesso, é possível notar a atenção ao design, à facilidade de uso e à personalização da conta do usuário. A plataforma permite definir preferências, salvar jogos favoritos e acompanhar o histórico de apostas de forma organizada.
Além disso, as promoções são atualizadas frequentemente, com bônus de boas-vindas, giros grátis, cashbacks e programas de fidelidade. Essas iniciativas recompensam os jogadores frequentes e incentivam a explorar novos títulos dentro da plataforma.
Os métodos de pagamento também são variados e acessíveis ao público brasileiro, incluindo opções populares como Pix, transferências bancárias e carteiras digitais. Os depósitos são processados de forma ágil, e os saques são liberados com rapidez, valorizando o tempo do jogador.
Conclusão A 7788bet se consolida como uma plataforma completa de entretenimento online. Com uma interface amigável, uma coleção impressionante de jogos e um atendimento de qualidade, ela conquista a confiança de seus usuários a cada dia. Seja você um veterano do mundo dos jogos ou um novato em busca de diversão, a 7788bet oferece tudo o que é necessário para uma jornada emocionante, segura e repleta de prêmios.
-
 @ a8d1560d:3fec7a08
2025-04-22 22:52:15
@ a8d1560d:3fec7a08
2025-04-22 22:52:15Based on the Free Speech Flag generator at https://crocojim18.github.io/, but now you can encode binary data as well.
https://free-speech-flag-generator--wholewish91244492.on.websim.ai/
Please also see https://en.wikipedia.org/wiki/Free_Speech_Flag for more information about the Free Speech Flag.
Who can tell me what I encoded in the flag used for this longform post?
-
 @ f5836228:1af99dad
2025-04-23 03:26:00
@ f5836228:1af99dad
2025-04-23 03:26:00A cada dia que passa, novas plataformas surgem com o objetivo de proporcionar experiências de jogo mais completas, seguras e empolgantes. Entre essas novidades, a 136Bet se destaca como uma das opções mais promissoras no cenário de entretenimento online. Com uma proposta moderna, interface intuitiva e uma variedade de jogos capaz de agradar todos os perfis de usuários, o site tem conquistado rapidamente a confiança de jogadores em todo o Brasil.
Logo ao acessar a 136Bet, é possível perceber o cuidado com o design e a navegação. A plataforma foi desenvolvida pensando na experiência do usuário, oferecendo um ambiente digital fluido, seguro e de fácil compreensão até mesmo para quem está começando. Seja no computador, tablet ou smartphone, a navegação é ágil, com menus bem organizados e respostas rápidas.
Outro ponto positivo é o suporte técnico disponível. A equipe da 136bet oferece atendimento ágil, seja por chat ou e-mail, garantindo que dúvidas e problemas sejam resolvidos rapidamente. Isso aumenta ainda mais a confiança dos jogadores na plataforma.
Diversidade de Jogos para Todos os Gostos Um dos grandes diferenciais da 136Bet é a variedade de jogos disponíveis. A plataforma conta com opções para quem busca jogos de sorte, desafios estratégicos e experiências imersivas. Entre os destaques, estão os populares jogos de cartas, roletas virtuais, slots temáticos e alternativas interativas ao vivo, onde o jogador participa em tempo real com resultados transmitidos ao vivo.
As animações são envolventes, os gráficos são de alta qualidade e os efeitos sonoros contribuem para criar um ambiente dinâmico e realista. Além disso, a 136Bet colabora com fornecedores renomados de software de jogos, garantindo a confiabilidade e a justiça nos resultados.
Experiência do Jogador: Simples, Rápida e Segura Outro grande destaque da 136Bet é o foco na experiência do usuário. O processo de cadastro é simples e rápido, permitindo que o novo jogador comece a se divertir em poucos minutos. A plataforma também oferece métodos variados e seguros para depósitos e saques, com transações processadas de forma ágil.
A transparência da 136Bet é um ponto que merece ser mencionado. Os termos de uso são claros e as regras dos jogos estão sempre acessíveis, o que demonstra o compromisso da empresa com a responsabilidade e a honestidade.
Os bônus e promoções também fazem parte da estratégia da plataforma para valorizar seus usuários. Jogadores frequentes têm acesso a recompensas, rodadas grátis e benefícios especiais, tornando a jornada ainda mais empolgante.
Por que Escolher a 136Bet? Segurança: Sistema criptografado que protege os dados dos usuários.
Variedade: Jogos para todos os gostos, com atualizações frequentes.
Acessibilidade: Compatível com dispositivos móveis e desktops.
Atendimento de qualidade: Suporte ativo e prestativo.
Promoções atrativas: Benefícios constantes para novos e antigos jogadores.
Conclusão A 136Bet chegou com força total ao mercado brasileiro e tem tudo para se consolidar como uma das plataformas mais completas de entretenimento online. Seja você um iniciante curioso ou um jogador experiente, o ambiente amigável, os jogos variados e a experiência segura tornam a 136Bet uma excelente escolha para momentos de lazer e diversão.
Se você procura uma plataforma confiável, moderna e feita para proporcionar entretenimento de qualidade, vale a pena conhecer tudo o que a 136Bet tem a oferecer.
-
 @ d34e832d:383f78d0
2025-04-22 22:48:30
@ d34e832d:383f78d0
2025-04-22 22:48:30What is pfSense?
pfSense is a free, open-source firewall and router software distribution based on FreeBSD. It includes a web-based GUI and supports advanced features like:
- Stateful packet inspection (SPI)
- Virtual Private Network (VPN) support (OpenVPN, WireGuard, IPSec)
- Dynamic and static routing
- Traffic shaping and QoS
- Load balancing and failover
- VLANs and captive portals
- Intrusion Detection/Prevention (Snort, Suricata)
- DNS, DHCP, and more
Use Cases
- Home networks with multiple devices
- Small to medium businesses
- Remote work VPN gateway
- IoT segmentation
- Homelab firewalls
- Wi-Fi network segmentation
2. Essential Hardware Components
When building a pfSense router, you must match your hardware to your use case. The system needs at least two network interfaces—one for WAN, one for LAN.
Core Components
| Component | Requirement | Budget-Friendly Example | |---------------|------------------------------------|----------------------------------------------| | CPU | Dual-core 64-bit x86 (AES-NI support recommended) | Intel Celeron J4105, AMD GX-412HC, or Intel i3 6100T | | Motherboard | Mini-ITX or Micro-ATX with support for selected CPU | ASRock J4105-ITX (includes CPU) | | RAM | Minimum 4GB (8GB preferred) | Crucial 4GB DDR4 | | Storage | 16GB+ SSD or mSATA/NVMe (for longevity and speed) | Kingston A400 120GB SSD | | NICs | At least two Intel gigabit ports (Intel NICs preferred) | Intel PRO/1000 Dual-Port PCIe or onboard | | Power Supply | 80+ Bronze rated or PicoPSU for SBCs | EVGA 400W or PicoPSU 90W | | Case | Depends on form factor | Mini-ITX case (e.g., InWin Chopin) | | Cooling | Passive or low-noise | Stock heatsink or case fan |
3. Recommended Affordable Hardware Builds
Build 1: Super Budget (Fanless)
- Motherboard/CPU: ASRock J4105-ITX (quad-core, passive cooling, AES-NI)
- RAM: 4GB DDR4 SO-DIMM
- Storage: 120GB SATA SSD
- NICs: 1 onboard + 1 PCIe Intel Dual Port NIC
- Power Supply: PicoPSU with 60W adapter
- Case: Mini-ITX fanless enclosure
- Estimated Cost: ~$150–180
Build 2: Performance on a Budget
- CPU: Intel i3-6100T (low power, AES-NI support)
- Motherboard: ASUS H110M-A/M.2 (Micro-ATX)
- RAM: 8GB DDR4
- Storage: 120GB SSD
- NICs: 2-port Intel PCIe NIC
- Case: Compact ATX case
- Power Supply: 400W Bronze-rated PSU
- Estimated Cost: ~$200–250
4. Assembling the Hardware
Step-by-Step Instructions
- Prepare the Workspace:
- Anti-static mat or surface
- Philips screwdriver
- Install CPU (if required):
- Align and seat CPU into socket
- Apply thermal paste and attach cooler
- Insert RAM into DIMM slots
- Install SSD and connect to SATA port
- Install NIC into PCIe slot
- Connect power supply to motherboard, SSD
- Place system in case and secure all components
- Plug in power and monitor
5. Installing pfSense Software
What You'll Need
- A 1GB+ USB flash drive
- A separate computer with internet access
Step-by-Step Guide
- Download pfSense ISO:
- Visit: https://www.pfsense.org/download/
- Choose AMD64, USB Memstick Installer, and mirror site
- Create Bootable USB:
- Use tools like balenaEtcher or Rufus to write ISO to USB
- Boot the Router from USB:
- Enter BIOS → Set USB as primary boot
- Save and reboot
- Install pfSense:
- Accept defaults during installation
- Choose ZFS or UFS (UFS is simpler for small SSDs)
- Install to SSD, remove USB post-installation
6. Basic Configuration Settings
After the initial boot, pfSense will assign: - WAN to one interface (via DHCP) - LAN to another (default IP: 192.168.1.1)
Access WebGUI
- Connect a PC to LAN port
- Open browser → Navigate to
http://192.168.1.1 - Default login: admin / pfsense
Initial Setup Wizard
- Change admin password
- Set hostname and DNS
- Set time zone
- Confirm WAN/LAN settings
- Enable DHCP server for LAN
- Optional: Enable SSH
7. Tips and Best Practices
Security Best Practices
- Change default password immediately
- Block all inbound traffic by default
- Enable DNS over TLS (with Unbound)
- Regularly update pfSense firmware and packages
- Use strong encryption for VPNs
- Limit admin access to specific IPs
Performance Optimization
- Use Intel NICs for reliable throughput
- Offload DNS, VPN, and DHCP to dedicated packages
- Disable unnecessary services to reduce CPU load
- Monitor system logs for errors and misuse
- Enable traffic shaping if managing VoIP or streaming
Useful Add-ons
- pfBlockerNG: Ad-blocking and geo-blocking
- Suricata: Intrusion Detection System
- OpenVPN/WireGuard: VPN server setup
- Zabbix Agent: External monitoring
8. Consider
With a modest investment and basic technical skills, anyone can build a powerful, flexible, and secure pfSense router. Choosing the right hardware for your needs ensures a smooth experience without overpaying or underbuilding. Whether you're enhancing your home network, setting up a secure remote office, or learning network administration, a custom pfSense router is a versatile, long-term solution.
Appendix: Example Hardware Component List
| Component | Item | Price (Approx.) | |------------------|--------------------------|------------------| | Motherboard/CPU | ASRock J4105-ITX | $90 | | RAM | Crucial 4GB DDR4 | $15 | | Storage | Kingston A400 120GB SSD | $15 | | NIC | Intel PRO/1000 Dual PCIe | $20 | | Case | Mini-ITX InWin Chopin | $40 | | Power Supply | PicoPSU 60W + Adapter | $25 | | Total | | ~$205 |
-
 @ f5836228:1af99dad
2025-04-23 03:25:26
@ f5836228:1af99dad
2025-04-23 03:25:26A 4444win vem se destacando no cenário de entretenimento online no Brasil por oferecer uma experiência inovadora, segura e repleta de oportunidades para os jogadores. Com uma interface intuitiva, ampla variedade de jogos e suporte eficiente, a plataforma se consolida como uma das melhores opções para quem busca diversão com a chance de conquistar prêmios reais.
Desde sua criação, a 4444win tem como objetivo proporcionar um ambiente moderno e confiável para seus usuários. Com tecnologia de ponta, o site foi desenvolvido para ser acessível tanto em computadores quanto em dispositivos móveis, permitindo que os jogadores se divirtam de onde estiverem. Além disso, a navegação é fluida e bem organizada, o que facilita a busca por jogos e serviços disponíveis.
Outro ponto que merece destaque é o compromisso com a segurança dos dados dos usuários. A plataforma utiliza criptografia avançada e segue rigorosos protocolos de proteção de informações, garantindo uma experiência tranquila e sem preocupações.
Jogos para Todos os Gostos A grande estrela da 4444win é, sem dúvida, sua diversidade de jogos. O catálogo foi cuidadosamente selecionado para agradar a diferentes perfis de jogadores, desde os iniciantes até os mais experientes. Entre as opções disponíveis, estão:
Slots temáticos: com gráficos envolventes, animações vibrantes e uma mecânica fácil de entender, os slots são ideais para quem busca partidas rápidas e empolgantes.
Jogos de cartas: clássicos como pôquer, blackjack e baccarat estão disponíveis em versões modernas e dinâmicas, com regras claras e possibilidades de ganhos atrativas.
Roletas virtuais: com diferentes estilos e formatos, a roleta oferece uma experiência emocionante com cada giro, sempre com resultados aleatórios e justos.
Jogos ao vivo: para quem busca uma experiência mais imersiva, os jogos com transmissão em tempo real permitem interações com apresentadores e outros jogadores, trazendo um toque social à diversão.
Todos os jogos são fornecidos por desenvolvedores renomados internacionalmente, o que garante qualidade gráfica, mecânicas bem elaboradas e resultados auditáveis.
Experiência do Jogador: Diversão com Responsabilidade Um dos diferenciais da 4444win é o cuidado com a experiência do usuário. A plataforma oferece bônus de boas-vindas e promoções frequentes, que aumentam as chances de jogar por mais tempo sem precisar fazer grandes investimentos. Além disso, o sistema de fidelidade recompensa os jogadores frequentes com vantagens exclusivas.
O suporte ao cliente funciona 24 horas por dia, sete dias por semana, e está disponível em português. Seja por chat ao vivo, e-mail ou redes sociais, a equipe de atendimento está sempre pronta para resolver dúvidas e auxiliar em qualquer etapa da jornada do usuário.
A 4444win também promove o jogo responsável, oferecendo ferramentas como limites de depósito, autoexclusão temporária e acesso a informações educativas para garantir que a diversão aconteça de forma saudável e equilibrada.
Conclusão Com uma estrutura sólida, ampla variedade de jogos e foco total no bem-estar do usuário, a 4444win se firma como uma das plataformas de entretenimento mais completas e confiáveis do Brasil. Seja para quem está começando ou para quem já tem experiência no universo dos jogos online, a 4444win oferece tudo o que é necessário para momentos emocionantes, recompensadores e seguros.
Explore, jogue e descubra as oportunidades que a 4444win tem a oferecer. A diversão está só começando!
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:57
@ 9bde4214:06ca052b
2025-04-22 22:04:57“The human spirit should remain in charge.”
Pablo & Gigi talk about the wind.
In this dialogue:
- Wind
- More Wind
- Information Calories, and how to measure them
- Digital Wellbeing
- Rescue Time
- Teleology of Technology
- Platforms get users Hooked (book)
- Feeds are slot machines
- Movie Walls
- Tweetdeck and Notedeck
- IRC vs the modern feed
- 37Signals: “Hey, let’s just charge users!”
- “You wouldn’t zap a car crash”
- Catering to our highest self VS catering to our lowest self
- Devolution of YouTube 5-star ratings to thumb up/down to views
- Long videos vs shorts
- The internet had to monetize itself somehow (with attention)
- “Don’t be evil” and why Google had to remove it
- Questr: 2D exploration of nostr
- ONOSENDAI by Arkinox
- Freedom tech & Freedom from Tech
- DAUs of jumper cables
- Gossip and it’s choices
- “The secret to life is to send it”
- Flying water & flying bus stops
- RSS readers, Mailbrew, and daily digests
- Nostr is high signal and less addictive
- Calling nostr posts “tweets” and recordings being “on tape”
- Pivoting from nostr dialogues to a podcast about wind
- The unnecessary complexity of NIP-96
- Blossom (and wind)
- Undoing URLs, APIs, and REST
- ISBNs and cryptographic identifiers
- SaaS and the DAU metric
- Highlighter
- Not caring where stuff is hosted
- When is an edited thing a new thing?
- Edits, the edit wars, and the case against edits
- NIP-60 and inconsistent balances
- Scroll to text fragment and best effort matching
- Proximity hashes & locality-sensitive hashing
- Helping your Uncle Jack of a horse
- Helping your uncle jack of a horse
- Can we fix it with WoT?
- Vertex & vibe-coding a proper search for nostr
- Linking to hashtags & search queries
- Advanced search and why it’s great
- Search scopes & web of trust
- The UNIX tools of nostr
- Pablo’s NDK snippets
- Meredith on the privacy nightmare of Agentic AI
- Blog-post-driven development (Lightning Prisms, Highlighter)
- Sandwich-style LLM prompting, Waterfall for LLMs (HLDD / LLDD)
- “Speed itself is a feature”
- MCP & DVMCP
- Monorepos and git submodules
- Olas & NDK
- Pablo’s RemindMe bot
- “Breaking changes kinda suck”
- Stories, shorts, TikTok, and OnlyFans
- LLM-generated sticker styles
- LLMs and creativity (and Gigi’s old email)
- “AI-generated art has no soul”
- Nostr, zaps, and realness
- Does the source matter?
- Poker client in bitcoin v0.0.1
- Quotes from Hitler and how additional context changes meaning
- Greek finance minister on crypto and bitcoin (Technofeudalism, book)
- Is more context always good?
- Vervaeke’s AI argument
- What is meaningful?
- How do you extract meaning from information?
- How do you extract meaning from experience?
- “What the hell is water”
- Creativity, imagination, hallucination, and losing touch with reality
- “Bitcoin is singularity insurance”
- Will vibe coding make developers obsolete?
- Knowing what to build vs knowing how to build
- 10min block time & the physical limits of consensus
- Satoshi’s reasons articulated in his announcement post
- Why do anything? Why stack sats? Why have kids?
- All you need now is motivation
- Upcoming agents will actually do the thing
- Proliferation of writers: quantity VS quality
- Crisis of sameness & the problem of distribution
- Patronage, belle epoche, and bitcoin art
- Niches, and how the internet fractioned society
- Joe’s songs
- Hyper-personalized stories
- Shared stories & myths (Jonathan Pageau)
- Hyper-personalized apps VS shared apps
- Agency, free expression, and free speech
- Edgy content & twitch meta, aka skating the line of demonetization and deplatforming
- Using attention as a proxy currency
- Farming eyeballs and brain cycles
- Engagement as a success metric & engagement bait
- “You wouldn’t zap a car crash”
- Attention economy is parasitic on humanity
- The importance of speech & money
- What should be done by a machine?
- What should be done by a human?
- “The human spirit should remain in charge”
- Our relationship with fiat money
- Active vs passive, agency vs serfdom
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:08
@ 9bde4214:06ca052b
2025-04-22 22:04:08"With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
Pablo & Gigi are getting high on glue.
Books & articles mentioned:
- Saving beauty by Byung-Chul Han
- LLMs as a tool for thought by Amelia Wattenberger
In this dialogue:
- vibeline & vibeline-ui
- LLMs as tools, and how to use them
- Vervaeke: AI thresholds & the path we must take
- Hallucinations and grounding in reality
- GPL, LLMs, and open-source licensing
- Pablo's multi-agent Roo setup
- Are we going to make programmers obsolete?
- "When it works it's amazing"
- Hiring & training agents
- Agents creating RAG databases of NIPs
- Different models and their context windows
- Generalists vs specialists
- "Write drunk, edit sober"
- DVMCP.fun
- Recklessness and destruction of vibe-coding
- Sharing secrets with agents & LLMs
- The "no API key" advantage of nostr
- What data to trust? And how does nostr help?
- Identity, web of trust, and signing data
- How to fight AI slop
- Marketplaces of code snippets
- Restricting agents with expert knowledge
- Trusted sources without a central repository
- Zapstore as the prime example
- "How do you fight off re-inventing GitHub?"
- Using large context windows to help with refactoring
- Code snippets for Olas, NDK, NIP-60, and more
- Using MCP as the base
- Using nostr as the underlying substrate
- Nostr as the glue & the discovery layer
- Why is this important?
- Why is this exciting?
- "With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
- How to single-shot nostr applications
- "Go and create this app"
- The agent has money, because of NIP-60/61
- PayPerQ
- Anthropic and the genius of mcp-tools
- Agents zapping & giving SkyNet more money
- Are we going to run the mints?
- Are agents going to run the mints?
- How can we best explain this to our bubble?
- Let alone to people outside of our bubble?
- Building pipelines of multiple agents
- LLM chains & piped Unix tools
- OpenAI vs Anthropic
- Genius models without tools vs midwit models with tools
- Re-thinking software development
- LLMs allow you to tackle bigger problems
- Increased speed is a paradigm shift
- Generalists vs specialists, left brain vs right brain
- Nostr as the home for specialists
- fiatjaf publishing snippets (reluctantly)
- fiatjaf's blossom implementation
- Thinking with LLMs
- The tension of specialization VS generalization
- How the publishing world changed
- Stupid faces on YouTube thumbnails
- Gaming the algorithm
- Will AI slop destroy the attention economy?
- Recency bias & hiding publication dates
- Undoing platform conditioning as a success metric
- Craving realness in a fake attention world
- The theater of the attention economy
- What TikTok got "right"
- Porn, FoodPorn, EarthPorn, etc.
- Porn vs Beauty
- Smoothness and awe
- "Beauty is an angel that could kill you in an instant (but decides not to)."
- The success of Joe Rogan & long-form conversations
- Smoothness fatigue & how our feeds numb us
- Nostr & touching grass
- How movement changes conversations
- LangChain & DVMs
- Central models vs marketplaces
- Going from assembly to high-level to conceptual
- Natural language VS programming languages
- Pablo's code snippets
- Writing documentation for LLMs
- Shared concepts, shared language, and forks
- Vibe-forking open-source software
- Spotting vibe-coded interfaces
- Visualizing nostr data in a 3D world
- Tweets, blog posts, and podcasts
- Vibe-producing blog posts from conversations
- Tweets are excellent for discovery
- Adding context to tweets (long-form posts, podcasts, etc)
- Removing the character limit was a mistake
- "Everyone's attention span is rekt"
- "There is no meaning without friction"
- "Nothing worth having ever comes easy"
- Being okay with doing the hard thing
- Growth hacks & engagement bait
- TikTok, theater, and showing faces and emotions
- The 1% rule: 99% of internet users are Lurkers
- "We are socially malnourished"
- Web-of-trust and zaps bring realness
- The semantic web does NOT fix this LLMs might
- "You can not model the world perfectly"
- Hallucination as a requirement for creativity
-
 @ 9bde4214:06ca052b
2025-04-22 22:01:34
@ 9bde4214:06ca052b
2025-04-22 22:01:34"The age of the idea guys has begun."
Articles mentioned:
- LLMs as a tool for thought by Amelia Wattenberger
- Micropayments and Mental Transaction Costs by Nick Szabo
- How our interfaces have lost their senses by Amelia Wattenberger
Talks mentioned:
- The Art of Bitcoin Rhetoric by Bitstein
Books mentioned:
- Human Action by Ludwig von Mises
- Working in Public by Nadia Eghbal
In this dialogue:
- nak
- Files
- SyncThing (and how it BitTorrent Sync became Resilio Sync)
- Convention over configuration
- Changes & speciation
- File systems as sources of truth
- Vibe-coding shower thoughts
- Inspiration and The Muse
- Justin's LLM setup
- Tony's setup (o1-pro as the architect)
- Being okay with paying for LLMs
- Anthropomorphising LLMs
- Dialog, rubber-duck debugging, and the process of thinking
- Being nice and mean to LLMs
- Battlebots & Gladiators
- Hedging your bets by being nice to Skynet
- Pascal's Wager for AI
- Thinking models vs non-thinking faster models
- Sandwich-style LLM prompting, again (waterfall stuff, HLDD / LLDD)
- Cursor rules & Paul's Prompt Buddy
- Giving lots of context vs giving specific context
- The benefit of LLMs figuring out obscure bugs in minutes (instead of days)
- The phase change of fast iteration and vibe coding
- Idea level vs coding level
- High-level vs low-level languages
- Gigi's "vibeline"
- Peterson's Logos vs Vervaeke's Dia-Logos
- Entering into a conversation with technology
- Introducing MCPs into your workflow
- How does Claude think?
- How does it create a rhyme?
- How does thinking work?
- And how does it relate to dialogue?
- Gzuuus' DVMCP & using nostr as an AI substrate
- Language Server Protocols (LSPs)
- VAAS: Vibe-coding as a service
- Open models vs proprietary models
- What Cursor got right
- What ChatGPT got right
- What Google got right
- Tight integration of tools & remaining in a flow state
- LLMs as conversational partners
- The cost of context switching
- Conversational flow & how to stay in it
- Prompts VS diary entries
- Solving technical vs philosophical models
- Buying GPUs & training your own models
- Training LLMs to understand Zig
- Preventing entryism by writing no documentation
- Thin layers & alignment layers
- Working in public & thinking in public
- Building a therapist / diary / notes / idea / task system
- "The age of the idea guys has begun."
- Daemons and spirits
- Monological VS dialogical thinking
- Yes-men and disagreeable LLMs
- Energy cost vs human cost
- Paying by the meter vs paying a subscription
- The equivalence of storage and compute
- Thinking needs memory, and memory is about the future
- Nostr+ecash as the perfect AI+human substrate
- Real cost, real consequence, and Human Action
- The cost of words & speaking
- Costly signals and free markets
- From shitcoin tokens to LLM tokens to ecash tokens
- Being too close to the metal & not seeing the forest for the trees
- Power users vs engineers
- Participatory knowing and actually using the tools
- Nostr as the germination ground for ecash
- What is Sovereign Engineering?
- LLVM and the other side of the bell-curve
- How nostr gives you users, discovery, mircopayments, a backend, and many other things for free
- Echo chambers & virality
- Authenticity & Realness
- Growing on the edges, catering to the fringe
- You don't own your iPhone
- GrapheneOS
- WebRTC and other monolithic "open" standards
- Optimizing for the wrong thing
- Building a nostr phone & Gigi's dream flow
- Using nostr to sync dotfile setups and other things
- "There are no solutions, only trade-offs"
- Cross-platform development
- Native vs non-native implementations
- Vitor's point on what we mean by native
- Does your custom UI framework work for blind people?
- Ladybird browser & how to build a browser from scratch
- TempleOS
- Form follows function & 90's interfaces
- Lamentations on the state of modern browsers
- Complexity & the downfall of the Legacy Web
- Nostr as the "new internet"
- Talks by Ladybird developer Andreas Kling
- Will's attempt of building it from scratch with Notedeck & nostr-db
- Justin's attempt with rust-multiplatform
- "If it doesn't have a rust implementation, you shouldn't use it."
- Native in terms of speed vs native in terms of UI/UX
- Engineer the logic, vibe-code the UI
- From Excalidraw to app in minutes
- What can you one-shot?
- What do you need to care about?
- Pablo's NDK snippets
- 7GUIs and GUI benchmarks for LLMs
- "Now we're purpose-building tools to make it easier for LLMs"
- "Certain tools really make your problems go away."
- Macros and meta-programming
- Zig's comptime
- UNIX tools and pipes
- Simple tools & composability
- Nostr tools for iOS & sharing developer signing keys
- Building 10 apps as one guy
- Simplicity in a community context
- Most people are on phones
- Most people don't install PWAs
- Zapstore & building our own distribution channels
- Web-of-trust and pushing builds quickly
- Improving homebrew by 10x
- (Micro)payments for package managers
- Guix and bitcoin-core
- Nix vs Guix
- Reproducible builds & web-of-trust
- Keet vs "calling an npub"
- Getting into someone's notifications
- Removing the character limit was a mistake
-
 @ 57d56d16:458edffd
2025-04-22 23:43:13
@ 57d56d16:458edffd
2025-04-22 23:43:13Hello. I've had a look at shopstr. You can find my instance of shopstr here so you can have a look yourself: https://shopstr.tectumordo.com/marketplace
Wondering your thoughts on Shopstr. I'm looking to start selling some things. Handcrafted Items / Services.
Anyone have any insights into shopstr, or something similar.
originally posted at https://stacker.news/items/953976
-
 @ d34e832d:383f78d0
2025-04-22 21:32:40
@ d34e832d:383f78d0
2025-04-22 21:32:40The Domain Name System (DNS) is a foundational component of the internet. It translates human-readable domain names into IP addresses, enabling the functionality of websites, email, and services. However, traditional DNS is inherently insecure—queries are typically sent in plaintext, making them vulnerable to interception, spoofing, and censorship.
DNSCrypt is a protocol designed to authenticate communications between a DNS client and a DNS resolver. By encrypting DNS traffic and validating the source of responses, it thwarts man-in-the-middle attacks and DNS poisoning. Despite its security advantages, widespread adoption remains limited due to usability and deployment complexity.
This idea introduces an affordable, lightweight DNSCrypt proxy server capable of providing secure DNS resolution in both home and enterprise environments. Our goal is to democratize secure DNS through low-cost infrastructure and transparent architecture.
2. Background
2.1 Traditional DNS Vulnerabilities
- Lack of Encryption: DNS queries are typically unencrypted (UDP port 53), exposing user activity.
- Spoofing and Cache Poisoning: Attackers can forge DNS responses to redirect users to malicious websites.
- Censorship: Governments and ISPs can block or alter DNS responses to control access.
2.2 Introduction to DNSCrypt
DNSCrypt mitigates these problems by: - Encrypting DNS queries using X25519 + XSalsa20-Poly1305 or X25519 + ChaCha20-Poly1305 - Authenticating resolvers via public key infrastructure (PKI) - Supporting relay servers and anonymized DNS, enhancing metadata protection
2.3 Current Landscape
DNSCrypt proxies are available in commercial routers and services (e.g., Cloudflare DNS over HTTPS), but full control remains in the hands of centralized entities. Additionally, hardware requirements and setup complexity can be barriers to entry.
3. System Architecture
3.1 Overview
Our system is designed around the following components: - Client Devices: Use DNSCrypt-enabled stub resolvers (e.g., dnscrypt-proxy) - DNSCrypt Proxy Server: Accepts DNSCrypt queries, decrypts and validates them, then forwards to recursive resolvers (e.g., Unbound) - Recursive Resolver (Optional): Provides DNS resolution without reliance on upstream services - Relay Support: Adds anonymization via DNSCrypt relays
3.2 Protocols and Technologies
- DNSCrypt v2: Core encrypted DNS protocol
- X25519 Key Exchange: Lightweight elliptic curve cryptography
- Poly1305 AEAD Encryption: Fast and secure authenticated encryption
- UDP/TCP Fallback: Supports both transport protocols to bypass filtering
- DoH Fallback: Optional integration with DNS over HTTPS
3.3 Hardware Configuration
- Platform: Raspberry Pi 4B or x86 mini-PC (e.g., Lenovo M710q)
- Cost: Under $75 total (device + SD card or SSD)
- Operating System: Debian 12 or Ubuntu Server 24.04
- Memory Footprint: <100MB RAM idle
- Power Consumption: ~3-5W idle
4. Design Considerations
4.1 Affordability
- Hardware Sourcing: Use refurbished or SBCs to cut costs
- Software Stack: Entirely open source (dnscrypt-proxy, Unbound)
- No Licensing Fees: FOSS-friendly deployment for communities
4.2 Security
- Ephemeral Key Pairs: New keypairs every session prevent replay attacks
- Public Key Verification: Resolver keys are pre-published and verified
- No Logging: DNSCrypt proxies are configured to avoid retaining user metadata
- Anonymization Support: With relay chaining for metadata privacy
4.3 Maintainability
- Containerization (Optional): Docker-compatible setup for simple updates
- Remote Management: Secure shell access with fail2ban and SSH keys
- Auto-Updating Scripts: Systemd timers to refresh certificates and relay lists
5. Implementation
5.1 Installation Steps
- Install OS and dependencies:
bash sudo apt update && sudo apt install dnscrypt-proxy unbound - Configure
dnscrypt-proxy.toml: - Define listening port, relay list, and trusted resolvers
- Enable Anonymized DNS, fallback to DoH
- Configure Unbound (optional):
- Run as recursive backend
- Firewall hardening:
- Allow only DNSCrypt port (default: 443 or 5353)
- Block all inbound traffic except SSH (optional via Tailscale)
5.2 Challenges
- Relay Performance Variability: Some relays introduce latency; solution: geo-filtering
- Certificate Refresh: Mitigated with daily cron jobs
- IP Rate-Limiting: Mitigated with DNS load balancing
6. Evaluation
6.1 Performance Benchmarks
- Query Resolution Time (mean):
- Local resolver: 12–18ms
- Upstream via DoH: 25–35ms
- Concurrent Users Supported: 100+ without degradation
- Memory Usage: ~60MB (dnscrypt-proxy + Unbound)
- CPU Load: <5% idle on ARM Cortex-A72
6.2 Security Audits
- Verified with dnsleaktest.com and
tcpdump - No plaintext DNS observed over interface
- Verified resolver keys via DNSCrypt community registry
7. Use Cases
7.1 Personal/Home Use
- Secure DNS for all home devices via router or Pi-hole integration
7.2 Educational Institutions
- Provide students with censorship-free DNS in oppressive environments
7.3 Community Mesh Networks
- Integrate DNSCrypt into decentralized networks (e.g., Nostr over Mesh)
7.4 Business VPNs
- Secure internal DNS without relying on third-party resolvers
8. Consider
This idea has presented a practical, affordable approach to deploying a secure DNSCrypt proxy server. By leveraging open-source tools, minimalist hardware, and careful design choices, it is possible to democratize access to encrypted DNS. Our implementation meets the growing need for privacy-preserving infrastructure without introducing prohibitive costs.
We demonstrated that even modest devices can sustain dozens of encrypted DNS sessions concurrently while maintaining low latency. Beyond privacy, this system empowers individuals and communities to control their own DNS without corporate intermediaries.
9. Future Work
- Relay Discovery Automation: Dynamic quality-of-service scoring for relays
- Web GUI for Management: Simplified frontend for non-technical users
- IPv6 and Tor Integration: Expanding availability and censorship resistance
- Federated Resolver Registry: Trust-minimized alternative to current resolver key lists
References
- DNSCrypt Protocol Specification v2 – https://dnscrypt.info/protocol
- dnscrypt-proxy GitHub Repository – https://github.com/DNSCrypt/dnscrypt-proxy
- Unbound Recursive Resolver – https://nlnetlabs.nl/projects/unbound/about/
- DNS Security Extensions (DNSSEC) – IETF RFCs 4033, 4034, 4035
- Bernstein, D.J. – Cryptographic Protocols using Curve25519 and Poly1305
- DNS over HTTPS (DoH) – RFC 8484
-
 @ d34e832d:383f78d0
2025-04-22 21:14:46
@ d34e832d:383f78d0
2025-04-22 21:14:46Minecraft remains one of the most popular sandbox games in the world. For players who wish to host private or community-based servers, monthly hosting fees can quickly add up. Furthermore, setting up a server from scratch often requires technical knowledge in networking, system administration, and Linux.
This idea explores a do-it-yourself (DIY) method for deploying a low-cost Minecraft server using common secondhand hardware and a simple software stack, with a focus on energy efficiency, ease of use, and full control over the server environment.
2. Objective
To build and deploy a dedicated Minecraft server that:
- Costs less than $75 in total
- Consumes minimal electricity (<10W idle)
- Is manageable via a graphical user interface (GUI)
- Supports full server management including backups, restarts, and plugin control
- Requires no port forwarding or complex network configuration
- Delivers performance suitable for a small-to-medium number of concurrent players
3. Hardware Overview
3.1 Lenovo M710Q Mini-PC (~$55 used)
- Intel Core i5 (6th/7th Gen)
- 8GB DDR4 RAM
- Compact size and low power usage
- Widely available refurbished
3.2 ID Sonics 512GB NVMe SSD (~$20)
- Fast storage with sufficient capacity for multiple Minecraft server instances
- SSDs reduce world loading lag and improve backup performance
Total Hardware Cost: ~$75
4. Software Stack
4.1 Ubuntu Server 24.04
- Stable, secure, and efficient operating system
- Headless installation, ideal for server use
- Supports automated updates and system management via CLI
4.2 CasaOS
- A lightweight operating system layer and GUI on top of Ubuntu
- Built for managing Docker containers with a clean web interface
- Allows app store-like deployment of various services
4.3 Crafty Controller (via Docker)
- Web-based server manager for Minecraft
- Features include:
- Automatic backups and restore
- Scheduled server restarts
- Plugin management
- Server import/export
- Server logs and console access
5. Network and Remote Access
5.1 PlayIt.gg Integration
PlayIt.gg creates a secure tunnel to your server via a relay node, removing the need for traditional port forwarding.
Benefits: - Works even behind Carrier-Grade NAT (common on mobile or fiber ISPs) - Ideal for users with no access to router settings - Ensures privacy by hiding IP address from public exposure
6. Setup Process Summary
- Install Ubuntu Server 24.04 on the M710Q
- Install CasaOS via script provided by the project
- Use CasaOS to deploy Crafty Controller in a Docker container
- Configure Minecraft server inside Crafty (Vanilla, Paper, Spigot, etc.)
- Integrate PlayIt.gg to expose the server to friends
- Access Crafty via browser for daily management
7. Power Consumption and Performance
- Idle Power Draw: ~7.5W
- Load Power Draw (2–5 players): ~15W
- M710Q fan runs quiet and rarely under load
- Performance sufficient for:
- Vanilla or optimized Paper server
- Up to 10 concurrent players with light mods
8. Cost Analysis vs Hosted Services
| Solution | Monthly Cost | Annual Cost | Control Level | Mods Support | |-----------------------|--------------|-------------|----------------|---------------| | Commercial Hosting | $5–$15 | $60–$180 | Limited | Yes | | This Build (One-Time) | $75 | $0 | Full | Yes |
Return on Investment (ROI):
Break-even point reached in 6 to 8 months compared to lowest hosting tiers.
9. Advantages
- No Subscription: Single upfront investment
- Local Control: Full access to server files and environment
- Privacy Respecting: No third-party data mining
- Modular: Can add mods, backups, maps with full access
- Low Energy Use: Ideal for 24/7 uptime
10. Limitations
- Not Ideal for >20 players: CPU and RAM constraints
- Local Hardware Dependency: Physical failure risk
- Requires Basic Setup Time: CLI familiarity useful but not required
11. Future Enhancements
- Add Dynmap with reverse proxy and TLS via CasaOS
- Integrate Nextcloud for managing world backups
- Use Watchtower for automated container updates
- Schedule daily email logs using system cron
12. Consider
This idea presents a practical and sustainable approach to self-hosting Minecraft servers using open-source software and refurbished hardware. With a modest upfront cost and minimal maintenance, users can enjoy full control over their game worlds without recurring fees or technical hassle. This method democratizes game hosting and aligns well with educational environments, small communities, and privacy-conscious users.
-
 @ 3ad01248:962d8a07
2025-04-22 21:09:52
@ 3ad01248:962d8a07
2025-04-22 21:09:52The trade war between Trump and the rest of the world has kicked of in earnest with Trump's unveiling of sweeping tariffs on so called "Liberation Day". The entire world was essentially put on notice that there is a new sheriff in town and things will be done different from now on.
The is the sentiment that won Trump the election so it is no wonder that Trump would follow through on changing how the world relates to America. President Trump hit the entire world with reciprocal tariffs and some places where people don't live which I find hilarious
I wonder who was in charge of making this tariff list because they need fired to be honest. Screams incompetence but that for another day. Will Bitcoin benefit from the trade war?
Bitcoin will benefit because the world now believes that the United States can not be trusted to honor its word or commitments. Why would any country want to to business with a country that says one thing and does another. Trump has upended the very economic order that the US created in the first place! Is this a smart idea? Only time will tell to be honest.
The worst thing Trump did was created doubt and uncertainty for the bond market. The bond market is the main engine of economic power for the US government. Having the world buy your bonds gives the United States unparalleled economic power to flex all around the world. The US might have military bases all over the world and uses it to conduct foreign policy but its the economic power of the US that gives it the influence that it has right now.
All that comes into question now. When you shit on your friends and buddy up with your adversaries it not a good look and allies will respond accordingly. Why piss off Canada and Mexico? What policy objective is that accomplishing? Picking fights with Europe? Not smart politics. I get wanting allies to pick up the slack on their end or have better trade relations but there is the right way to do it and a wrong way to do it. Trump undoubtedly goes about it the wrong way.
Has he not heard the saying 'You catch more flies with honey than vinegar?" When you are cordial with people and they like you its a lot easier to get people to do things for you or see things from you perspective versus talking shit and bullying them into submission.
Most countries are not going to tolerate this type of political brinkmanship and will decide that they need to take their money elsewhere. You can expect for them to withdraw their money from the stock market and the bond market over the next 12-24 months. Guess what happens after that? Bond yields go through the roof and the stock market takes a shit! You can kiss your 401k goodbye! You'd have to be suicidal to have your money in the stock market right now.
In this scenario which is mostly likely to occur, Bitcoin goes to the moon because governments are going to be looking for a neutral reserve asset that can't be manipulated like US bonds. Bitcoin is the perfect solution to their problem. Once one major government or central bank puts Bitcoin on the balance sheet its game over for the dollar and the bonds. We might be closer to the end game than we think, and that is scary to think about. "Sometimes there are decades where nothing happens and there are weeks where decades happen." ~ Lenin
Crazy to quote a communist but he isn't wrong about history. We are living through a life alter paradigm shift. It is scary and exhilarating all at the same time. What a time to be alive ladies and gentlemen! Buckle up! Its going to get interesting!
-
 @ ba36d0f7:cd802cba
2025-04-22 20:30:45
@ ba36d0f7:cd802cba
2025-04-22 20:30:45| Pieza | Movimiento | Reglas Especiales | | --------- | ---------------------------------- | --------------------------- | | Peón | 1 casilla adelante (o 2 al inicio) | Captura al paso, coronación | | Torre | Líneas rectas | Enroque | | Caballo | En "L" (2+1) | Salta piezas | | Alfil | Diagonales | Atrapado en un color | | Dama | Cualquier dirección | Ninguna | | Rey | 1 casilla en cualquier dirección | Enroque, jaque mate |
1. Peón (♙ / ♟️)
- Mueve: 1 casilla adelante (o 2 en su primer movimiento).

- Captura: En diagonal (1 casilla).
 > Especial:
>- Captura al paso: Si un peón rival avanza 2 casillas, puedes capturarlo como si hubiera movido 1.
> - Coronación: Al llegar a la 8ª fila, se convierte en cualquier pieza (¡usualmente Dama!).
> Especial:
>- Captura al paso: Si un peón rival avanza 2 casillas, puedes capturarlo como si hubiera movido 1.
> - Coronación: Al llegar a la 8ª fila, se convierte en cualquier pieza (¡usualmente Dama!).
2. Torre (♖ / ♜)
- Mueve: Líneas rectas (sin límite de casillas).

- Especial: Participa en el enroque.
3. Caballo (♘ / ♞)
-
Mueve: En "L" (2 casillas en una dirección + 1 perpendicular).
-
Única pieza que salta sobre otras.
4. Alfil (♗ / ♝)
-
Mueve: Diagonales (sin límite).
-
Siempre permanece en el mismo color de casilla.

5. Dama (♕ / ♛)
- Mueve: Cualquier dirección (recto o diagonal).

- ¡La pieza más poderosa!
6. Rey (♔ / ♚)
- Mueve: 1 casilla en cualquier dirección.

Especial:
- Enroque: Cambia de lugar con una torre (si no hay obstáculos/jaques). - Jaque mate: Pierde si queda atrapado sin escapatoria.
Cómo mover
-
Un movimiento por turno.
-
Elige tu pieza y colócala en una casilla legal.
-
Solo tu color: Blancas mueven primero, luego negras, alternando.
-
No pasar: Debes mover si es tu turno.
Cómo capturar ("comer")
-
Ocupa la casilla de una pieza rival: Reemplázala con tu pieza.
-
Peones capturan solo en diagonal (no de frente).
-
Los reyes no pueden ser capturados (el jaque mate termina el juego).
✔ Jaque: Ataca al rey enemigo (debe escapar en su siguiente turno).
❌ Ilegal: Mover a jaque o dejar a tu rey en jaque.
Movimientos especiales
|Movimiento|Regla Clave|Notación| |---|---|---| |Enroque|Rey + torre, sin movimientos previos|
0-0| |Coronación|Peón→cualquier pieza en 8ª fila|e8=D| |Captura al paso|Captura un peón que avanzó 2 casillas|exd6 a.p.|
1. Enroque ("La escapatoria del rey")
-
Qué: Rey y torre se mueven juntos en un turno.
Cómo: -
Rey mueve 2 casillas hacia una torre.
-
Torre "salta" al lado opuesto del rey.

Reglas: - Sin jaques: El rey no puede estar en jaque ni pasar por casillas atacadas. - Sin movimientos previos: Ni el rey ni esa torre deben haberse movido antes.
Tipos:
- Corto (lado del rey, rápido):0-0- Largo (lado de la dama, seguro):0-0-0
2. Coronación ("Coronar")
-
Qué: Peón llega a la 8ª fila → se convierte en cualquier pieza (usualmente Dama).
-
Cómo: Reemplaza el peón (incluso si ya tienes esa pieza).
Dato curioso: Puedes tener 9 damas (1 original + 8 coronaciones).
Ejemplo: Peón en h8 se convierte en Dama →h8=D.
3. Captura al paso (Del francés "en passant")
-
Cuándo: Un peón rival avanza 2 casillas y queda al lado del tuyo.
-
Cómo: Captúralo en diagonal (como si hubiera movido 1 casilla).

Regla: Debes hacerlo inmediatamente (solo en el turno siguiente)
Recurso digitales
Guia para principiantes - Lichess.org https://lichess.org/study/Hmb28fbv/QRyxzgre
Ajedrez desde cero - Youtube.com https://www.youtube.com/watch?v=YPf9fSY_K2k&list=PLWgqlpb234bHv38g6zXoi3WIJJonzZSAl&index=8
- Mueve: 1 casilla adelante (o 2 en su primer movimiento).
-
 @ 9223d2fa:b57e3de7
2025-04-22 20:02:06
@ 9223d2fa:b57e3de7
2025-04-22 20:02:069,322 steps
-
 @ 7d33ba57:1b82db35
2025-04-22 19:43:27
@ 7d33ba57:1b82db35
2025-04-22 19:43:27Welcome to Hortobágy National Park, Hungary’s oldest and largest national park, and a UNESCO World Heritage Site that showcases the wild, open heart of the Puszta—the vast steppe of Eastern Europe. Spanning over 800 km², this park is a land of windswept grasslands, grazing animals, traditional herding culture, and incredible birdlife.
🌾 What to See & Do in Hortobágy
🐃 Explore the Puszta Landscape
- Ride through the grasslands in a horse-drawn cart or take a bike tour
- See iconic gray cattle, racka sheep with spiral horns, water buffalo, and traditional herdsmen in wide-brimmed hats
🐎 Horse Shows & Herding Traditions
- Visit a csikós show, where Hungarian horsemen perform riding tricks and herding techniques
- Learn about the unique pastoral culture that has existed here for centuries
🐦 Birdwatching Paradise
- Hortobágy is one of Europe’s best spots for birdwatching
- See cranes, eagles, storks, and rare migratory species, especially in spring and autumn
- Visit the Hortobágy Bird Hospital and crane observation sites
🌉 Hortobágy Nine-Arch Bridge (Kilenclyukú híd)
- An iconic stone bridge built in the 19th century, stretching over the river Hortobágy
- The symbolic center of the park and a great photo spot
- Nearby you’ll find the Hortobágy Village, with museums, markets, and local food
🧀 Local Culture & Cuisine
- Taste slambuc (a traditional shepherd’s stew), cheeses, and local smoked meats
- Check out folk art and handmade crafts in local markets and heritage centers
🚶♂️ How to Visit
- Closest city: Debrecen (around 30 minutes by car or bus)
- The park offers guided tours, bike rentals, and wildlife safaris
- Great for day trips or overnight stays in nearby guesthouses or rural lodges
Hortobágy is more than a landscape—it’s a living cultural heritage site, where ancient traditions, wildlife, and wide horizons stretch as far as the eye can see. Perfect for nature lovers, culture seekers, or anyone looking to experience a different side of Hungary.
-
 @ 7d33ba57:1b82db35
2025-04-22 19:29:59
@ 7d33ba57:1b82db35
2025-04-22 19:29:59Tucked into the foothills of the Bükk Mountains, Eger is one of Hungary’s most charming and historic towns. Famous for its Baroque architecture, thermal baths, and Egri Bikavér (“Bull’s Blood”) red wine, Eger offers a perfect blend of culture, relaxation, and rustic charm all just a couple of hours from Budapest.
🏰 Top Things to Do in Eger
🏯 Eger Castle (Egri Vár)
- A key site in Hungary’s defense against the Ottoman Empire
- Learn about the 1552 Siege of Eger, when outnumbered locals held off the Turks
- Climb the walls for views of the old town’s red rooftops and spires
⛪ Eger’s Baroque Old Town
- Wander elegant streets lined with pastel facades, cute cafés, and small boutiques
- Don’t miss the Minorite Church and Dobó Square, the lively heart of the city
🛁 Thermal Baths
- Relax in the Eger Turkish Bath, built during the Ottoman period and still in use today
- Or soak at Eger Thermal Spa, great for families and wellness seekers
🍷 Wine Tasting in the Valley of the Beautiful Women (Szépasszony-völgy)
- A short walk or ride from town, this valley is lined with wine cellars built into the hillside
- Taste the iconic Egri Bikavér (a full-bodied red blend) and Egri Csillag (a refreshing white)
- Most cellars offer generous tastings and hearty local snacks
🧀 Local Food to Try
- Goulash, Lángos, and hearty meat dishes
- Pair local cheeses and sausages with regional wines
- Cozy cellar restaurants and rustic taverns set the mood
🚆 Getting There
- About 2 hours by train or car from Budapest
- Walkable town, no car needed once you’re there

















