-
 @ 502ab02a:a2860397
2025-05-17 03:21:54
@ 502ab02a:a2860397
2025-05-17 03:21:54ยังมีเรื่องราวของน้ำตาล และ เซลล์ มาคุยกันต่อนะครับ เพราะยังมีคนสงสัยอยู่ว่า เอ้ย ตกลงต้องห่วงการ Spike&Staylong ของอินซุลินอยู่หรือเปล่า แล้วถ้าเราไม่ spike&staylong ก็คือกินคาร์บเบาๆตลอดวันได้เลยใช่ไหมก็มันไม่ spike&staylong แล้วนี่ โอเคครับ เรามาเปิดผับกันอีกครั้ง
คราวก่อนนั้นเราคุยกันเรื่อง ผับน้ำตาลกันไปแล้วนะครับว่า เมื่ออินซูลิน spike สูง และค้างนาน เหมือนเปิดผับแล้ววัยรุ่นแห่กันเข้ามาเที่ยว จนพีอาร์เมาจัด
เผื่อใครจำไม่ได้ ย้อนให้นิดๆครับ ว่าให้ลองนึกภาพว่าเฮียเปิดผับอยู่ดี ๆ ลูกค้าหลั่งไหลเข้ามารัว ๆ เหมือนมีโปรเบียร์ 1 แถม 10 ตอนสามทุ่ม ทุกโต๊ะสั่งข้าวเหนียวหมูปิ้งพร้อมเบียร์น้ำแข็งเต็มโต๊ะ นักเที่ยวก็ยังแห่เข้าผับแบบไม่มีพัก อินซูลินซึ่งเป็นเหมือน “พีอาร์” ที่ต้องจัดการรับแขก (หรือรับน้ำตาลเข้าสู่เซลล์) ก็เลยต้องทำงานหนักแบบ non-stop
อินซูลินเป็นฮอร์โมนสำคัญที่ช่วยเอาน้ำตาลในเลือดเข้าไปเก็บในเซลล์ ถ้า spike ทีเดียวสูงมาก เซลล์ก็รีบดูดน้ำตาลเข้าไปเต็มที่จนเกินพิกัด เหมือนผับที่แน่นจนปิดประตูไม่ลง
ถ้าเหตุการณ์แบบนี้เกิดขึ้นบ่อย ๆ ร่างกายจะเริ่มรู้สึกว่า “ทำไมอินซูลินถึงต้องออกมาบ่อยขนาดนี้วะ?” ระบบก็เริ่มปิดรับแขก เซลล์เริ่มไม่อยากตอบสนอง เพราะมันเหนื่อย มันชิน และมันก็เริ่ม “ดื้ออินซูลิน”
ผลที่ตามมาเมื่อ spike สูงและค้าง สิ่งที่ตามมา... คือความปั่นป่วนในร่างกายอย่างต่อเนื่อง น้ำตาลลอยค้างในเลือด ไปจับกับโปรตีนจนกลายเป็นเจ้า AGEs ตัวร้าย ไขมันก็ถูกสร้างมากขึ้น ล้นเข้าไปสะสมในตับ ในพุง ในซอกที่ร่างกายไม่รู้จะเก็บไว้ตรงไหนแล้ว สมองก็เบลอ ใจวูบ ง่วงงุน... เหมือนเข้าเวรประชุมยาวแบบไม่มีกาแฟ ฮอร์โมนที่เคยเป็นทีมงานสามัคคี ก็เริ่มทะเลาะกันเอง อินซูลินงอน leptin งง ghrelin งวย
แล้วถ้าเราไม่ spike แต่กินคาร์บจุ๋มจิ๋มทั้งวันล่ะ? พอรู้ว่าการเปิดผับแจกคาร์บแบบจัดหนักไม่ดี หลายคนก็ปรับกลยุทธ์ใหม่ มาแนวสายสุขุมว่า “งั้นเปิดผับแบบเนิบ ๆ ก็แล้วกัน… ไม่จัดปาร์ตี้ใหญ่ แต่มีแขกแวะเข้ามาทั้งวัน” ฟังดูดีใช่ไหม? แต่เอาเข้าจริง มันเหนื่อยไม่แพ้กันเลย
ลองนึกภาพว่าประเทศไม่มีเคอร์ฟิว เฮียเปิดผับที่มีลูกค้าเดินเข้าออกไม่หยุด ไม่ได้มากันเป็นฝูงแบบรอบโปรโมชั่น แต่มาเรื่อย ๆ แบบชั่วโมงละโต๊ะ สองโต๊ะ พีอาร์ อินซูลิน ก็เลยต้องยืนต้อนรับแขกตลอดเวลา ไม่มีเวลานั่งพัก ไม่มีช่วงเปลี่ยนกะ ไม่มีเวลาปิดไฟเก็บโต๊ะ คือทำงานต่อเนื่องยาว ๆ ตั้งแต่ 8 โมงเช้า ยัน 8 โมงเช้า สุดท้าย ผับก็เปิดไฟยันสว่าง อินซูลินก็กลายเป็นพนักงานกะดึกตลอดชีพ และเมื่อไม่มีเวลา “พักผับ” ระบบหลังบ้านก็ไม่เคยได้ฟื้นฟูเลย
ภาพรวมของการกินจุ๋มจิ๋มทั้งวันแบบนี้นั้น - เผาผลาญไขมันไม่ออกเลย เพราะอินซูลินทำหน้าที่เหมือนไฟบนเวที ถ้ายังเปิดไฟอยู่ “เครื่องดูดไขมันหลังร้าน” มันก็ไม่ทำงาน - แม่บ้านทำความสะอาดก็เข้าไม่ได้ เพราะแขกเดินเข้าเดินออกตลอด ระบบกำจัดที่ควรจะได้ล้างของเสียในเซลล์ ก็เลยโดนขัดจังหวะตลอด - พนักงานเหนื่อยสะสมจากงานไม่มีหยุด ทำให้เกิดความเครียดสะสมในร่างกาย ฮอร์โมนรวน อารมณ์ก็แปรปรวนง่ายขึ้น หิวเก่งขึ้น ทั้งที่เพิ่งกินไป
เปิดผับแบบคึกคักจัดเต็มทีเดียว แล้วปิดยาว หรือ เปิดทั้งวันแบบไม่มีช่วงปิด สุดท้ายพังทั้งคู่
ทีนี้เราน่าจะพอเห็นภาพร่างคร่าวๆ ของการบริหารการจัดการน้ำตาลในตัวเราได้แล้วนะครับ ว่าจะไดเอทไหนก็ตาม การบริหารการจัดการฮอร์โมนส์ คือสิ่งสำคัญไม่แพ้เรื่องอื่นๆ แม้จะไม่ใช่เรื่องสำคัญที่สุดในสายตาใครก็ตาม
นี่เป็นเพียงจุดเริ่มต้นการเรียนรู้เล็กๆ ซึ่งเส้นทางสายที่เรียกว่า ร่างกาย มันยังไปไกลอีกลิบลับเลยครับ ไม่ว่าจะจังหวัดคอติซอล จังหวัดพฤกษเคมี จังหวัดพลังงาน จังหวัดสารอาหาร แถมลักษณะร่างกายแต่ละคน ก็เปรียบเหมือนรถต่างยี่ห้อ ต่างน้ำมันขับเคลื่อน ต่างซีซี หรือแม้ว่าจะเหมือนกัน ก็ยังต่างปี ต่างไมล์การขับขี่
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ c9badfea:610f861a
2025-05-17 03:08:55
@ c9badfea:610f861a
2025-05-17 03:08:55- Install Rethink (it's free and open source)
- Launch the app and tap Skip
- Tap Start and then Proceed to set up the VPN connection
- Allow notifications and Proceed, then disable battery optimization for this app (you may need to set it to Unrestricted)
- Navigate to Configure and tap Apps
- On the top bar, tap 🛜 and 📶 to block all apps from connecting to the internet
- Search Apps for the apps you want to allow and Bypass Universal
- Return to the Configure view and tap DNS, then choose your preferred DNS provider (e.g. DNSCrypt > Quad9)
- Optionally, tap On-Device Blocklists, then Disabled, Download Blocklists, and later Configure (you may need to enable the Use In-App Downloader option if the download is not working)
- Return to the Configure view and tap Firewall, then Universal Firewall Rules and enable the options as desired:
- Block all apps when device is locked
- Block newly installed apps by default
- Block when DNS is bypassed
- Optionally, to set up WireGuard or Tor, return to the Configure view and tap Proxy
- For Tor, tap Setup Orbot, then optionally select all the apps that should route through Tor (you must have Orbot installed)
- For WireGuard, tap Setup WireGuard, then +, and select an option to import a WireGuard configuration (QR Code Scan, File Import, or Creation).
- Use Simple Mode for a single WireGuard connection (all apps are routed through it).
- Use Advanced Mode for multiple WireGuard connections (split tunnel, manually choosing apps to route through them)
⚠️ Use this app only if you know what you are doing, as misconfiguration can lead to missing notifications and other problems
ℹ️ On the main view, tap Logs to track all connections
ℹ️ You can also use a WireGuard connection (e.g., from your VPN provider) and on-device blocklists together
-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ b83a28b7:35919450
2025-05-16 19:26:56
@ b83a28b7:35919450
2025-05-16 19:26:56This article was originally part of the sermon of Plebchain Radio Episode 111 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 14206a66:689725cf
2025-05-17 01:49:33
@ 14206a66:689725cf
2025-05-17 01:49:33This article is a repost, migrating from Substack
Uncertainty is the only constant
It goes without saying that uncertainty is a given in business. It could be the weather, pestilence, or some other physical phenomenon that brings different conditions for your business (good or bad). Or it could be uncertainty in the behaviour of consumers, suppliers, workers, or any other person critical to your success. Most of the time, we just don’t know what will happen next.
One of the most important skills in managing a business, then, is making predictions in the face of uncertainty. We have several tools to do so. The first covers methods from the physical sciences, and involves calculating the frequency of events. We need to unpick a concept at the root of uncertainty, probability.
Thanks for reading Department of Praxeology! Subscribe for free to receive new posts and support my work.
Subscribed
Types of probability
In Human Action, Ludwig von Mises introduces us to two classifications of probability: case and class probability.
Case probability
Case probability is when we know something about some of the factors which determine the outcome, but not others.
This is the kind of probability most often encountered in business. We often know small key parts about several factors that lead to a particular outcome, we might see that oil prices have risen significantly, coupled with a decrease in the exchange rate. These factors help to lead to the outcome of a rising price of fertiliser. But then, there are other factors that lead to this outcome, such as a myriad of decisions by businesspeople all along the supply chain. These, we know absolutely nothing about!
Class probability
Class probability is when we know everything about the particular kind (or class) of event, but we don’t know anything at all about the specific event.
We do encounter class probability in business. But it happens at very specific times (as opposed to just all the time, as with case probability).
Myrtle rust, picture courtesy of NZ Department of Conservation
For example (and sticking to agriculture) we know nothing about an outbreak of Myrtle rust on our farm. But we know, from agricultural science, that the likelihood of an outbreak in our area for a given year is about 13 percent.
So how can we make predictions of these events?
Making predictions
For the latter (class probabilities, like losses caused by Myrtle rust) we can always rely on methods from the physical sciences to calculate frequencies. Then, we know that the physical world has certain constants, so we can say that given a set of conditions (like rainfall) the likelihood of losses from Myrtle rust in future is about 12 percent.
Thinking about the former (case probabilities such as changing consumer preferences, or changes in prices). In these situations we are dealing with the realm of human decisions. So while we can count the number of these events, we cannot use these counts for prediction. The reason is that, in the realm of human decisions, there are no constants. We can’t say that given the world of 2023 prices rose five times, therefore in the world of 2027 prices will rise five times. Even if physical conditions are the same, human decisions will not be.
Luckily, economic science does give us an answer. In dealing with case probabilities we should use our method of understanding (which I wrote about here).
Using this in your business
You can incorporate this knowledge into your business by critically analysing each event for which you need to make a prediction. Is the event dealing with the physical world, for which there are constants? Or is it the realm of human decisions, for which there are no constants? It most likely is a mix of these.
Work backwards and jot down the more granular events which compose the event in question. Then try again to fit each of these into case or class probability.
When each event is broken down into only one category you know which methods of prediction to apply to each event.
For case probabilities, engage a specialist in the area. For class probabilities, engage your own expertise in understanding, and consider hiring an economist to augment your analysis.
-
 @ c631e267:c2b78d3e
2025-05-16 18:40:18
@ c631e267:c2b78d3e
2025-05-16 18:40:18Die zwei mächtigsten Krieger sind Geduld und Zeit. \ Leo Tolstoi
Zum Wohle unserer Gesundheit, unserer Leistungsfähigkeit und letztlich unseres Glücks ist es wichtig, die eigene Energie bewusst zu pflegen. Das gilt umso mehr für an gesellschaftlichen Themen interessierte, selbstbewusste und kritisch denkende Menschen. Denn für deren Wahrnehmung und Wohlbefinden waren und sind die rasanten, krisen- und propagandagefüllten letzten Jahre in Absurdistan eine harte Probe.
Nur wer regelmäßig Kraft tankt und Wege findet, mit den Herausforderungen umzugehen, kann eine solche Tortur überstehen, emotionale Erschöpfung vermeiden und trotz allem zufrieden sein. Dazu müssen wir erkunden, was uns Energie gibt und was sie uns raubt. Durch Selbstreflexion und Achtsamkeit finden wir sicher Dinge, die uns erfreuen und inspirieren, und andere, die uns eher stressen und belasten.
Die eigene Energie ist eng mit unserer körperlichen und mentalen Gesundheit verbunden. Methoden zur Förderung der körperlichen Gesundheit sind gut bekannt: eine ausgewogene Ernährung, regelmäßige Bewegung sowie ausreichend Schlaf und Erholung. Bei der nicht minder wichtigen emotionalen Balance wird es schon etwas komplizierter. Stress abzubauen, die eigenen Grenzen zu kennen oder solche zum Schutz zu setzen sowie die Konzentration auf Positives und Sinnvolles wären Ansätze.
Der emotionale ist auch der Bereich, über den «Energie-Räuber» bevorzugt attackieren. Das sind zum Beispiel Dinge wie Überforderung, Perfektionismus oder mangelhafte Kommunikation. Social Media gehören ganz sicher auch dazu. Sie stehlen uns nicht nur Zeit, sondern sind höchst manipulativ und erhöhen laut einer aktuellen Studie das Risiko für psychische Probleme wie Angstzustände und Depressionen.
Geben wir negativen oder gar bösen Menschen keine Macht über uns. Das Dauerfeuer der letzten Jahre mit Krisen, Konflikten und Gefahren sollte man zwar kennen, darf sich aber davon nicht runterziehen lassen. Das Ziel derartiger konzertierter Aktionen ist vor allem, unsere innere Stabilität zu zerstören, denn dann sind wir leichter zu steuern. Aber Geduld: Selbst vermeintliche «Sonnenköniginnen» wie EU-Kommissionspräsidentin von der Leyen fallen, wenn die Zeit reif ist.
Es ist wichtig, dass wir unsere ganz eigenen Bedürfnisse und Werte erkennen. Unsere Energiequellen müssen wir identifizieren und aktiv nutzen. Dazu gehören soziale Kontakte genauso wie zum Beispiel Hobbys und Leidenschaften. Umgeben wir uns mit Sinnhaftigkeit und lassen wir uns nicht die Energie rauben!
Mein Wahlspruch ist schon lange: «Was die Menschen wirklich bewegt, ist die Kultur.» Jetzt im Frühjahr beginnt hier in Andalusien die Zeit der «Ferias», jener traditionellen Volksfeste, die vor Lebensfreude sprudeln. Konzentrieren wir uns auf die schönen Dinge und auf unsere eigenen Talente – soziale Verbundenheit wird helfen, unsere innere Kraft zu stärken und zu bewahren.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 14206a66:689725cf
2025-05-17 01:44:35
@ 14206a66:689725cf
2025-05-17 01:44:35This article is a repost, migrating from Substack
Introduction
Released in November 2020 by fiatjaf, Nostr is an open, decentralised, censorship-resistant messaging protocol. The protocol is well designed, and many authors have written extensively about the mechanics and use-cases. For the purposes of this article, I will narrow the focus to Nostr as a tool to enable the creation of platform markets. My aim is to give the reader an introduction to platform market pricing and provide concrete steps to price their platform strategically.
What is a Platform Market?
A platform market consists of multiple groups of users who want to interact but can’t do so directly. The platform brings them together to enable interaction, benefiting all users and the platform itself by enabling these interactions and pricing appropriately. Although platform markets have been around forever, the last decade has seen an explosion in their number due to the ubiquity of the internet.
Examples:
· Google
· YouTube
· TV
· Facebook
· Twitter (X)
Platform markets have historically earned significant revenue if they design their pricing correctly. This is because platform markets don’t need to produce goods themselves; rather, one or more “sides” of the platform produce goods and services for the other side, with the platform merely enabling the exchange. TikTok is a prime example: it produces nothing except a video hosting service, with users generating all the content for other users. Effectively, the platform has only fixed costs and very low marginal costs.
Therefore, platform markets are far more scalable than traditional one-sided markets, as their primary concern is to attract as many users as possible (who have no marginal cost to the platform). Additionally, platforms often enjoy a captive audience, making it difficult for competitors to entice away users once they are established. This is particularly evident in software and payment platforms.
How Does Nostr Enable the Creation of Platform Markets?
· Open Protocol: Like the internet, Nostr is an open protocol.
· Inbuilt Payment Systems: Nostr integrates payment systems such as Bitcoin’s Lightning Network.
· Existing User Base: It already has a growing user base.
· Decentralisation: This feature acts as a moat against competitors.
Types of platform enabled by Nostr
As of 2024 we are seeing multiple types of platforms that Nostr has enabled. The first is Nostr relays. A Nostr relay is a simple server that receives and broadcasts user notes (messages) in the Nostr protocol. Users can publish and fetch notes across multiple relays. Nostr relays can be configured by their operator to curate content on specific topics or people. Alternatively, they can be configured with an algorithm as experienced by users of contemporary social media. These can be valuable for users. And potentially, paid relays are a viable business opportunity.
The second platform Nostr enables is the Nostr client. Nostr clients are analogous to internet browser software. Historically, we have seen users be charged to install an internet browser, though this is unlikely to emerge in the market for Nostr clients. As a platform, a Nostr client might be bundled with a relay service (with curation or algorithm).
The third type of platform is Nostr apps. Each app can be designed as a platform if that is valuable for users. We are already seeing Nostr-based alternatives for music and video streaming, looking to compete with apps like YouTube.
We can’t know what the future will hold but the possibilities for designing platforms with Nostr are many. The advantage in designing a platform is that you can create a two sided market.
What is a Two-Sided Market?
All two-sided markets are platform markets, but not all platform markets are two-sided markets. The critical aspect of a two-sided market is that the volume of interactions on the platform depends on both the relative prices charged to each side and the total price charged. This is the case when both sides value more users on the other side, known in literature as an “indirect network externality.”
An example of a one-sided platform market is a clothes retailer, where the volume of sales depends only on the total price, not the relative prices charged to buyers and producers. Conversely, YouTube is a two-sided market where both creators and watchers benefit from more users. Watchers benefit from more variety and quality, while creators benefit from more users and views. YouTube introduces a special category of creators, the advertisers, who benefit monetarily from views because consumers viewing their content are likely to purchase their goods.
The prices paid by YouTube users are not all monetary:
· Watchers are charged an inconvenience fee in the form of advertisements.
· Advertisers are charged a monetary fee.
· Creators are not charged any fees.
Let’s assume the total fees for YouTube add up to $100. Say advertisers are charged $90, watchers face an inconvenience worth $10, and creators still enjoy $0 costs. In this scenario, the total volume of videos watched might be some number like 100,000.
Assume we change the price structure to advertisers being charged $80, watchers paying an inconvenience worth $10, and creators being charged $10 (keeping the total fees at $100). In this new scenario, the likely outcome is that the marginal creator will no longer create videos, and thus, the total volume of videos watched will fall.
Two-Sided Markets that Allow Money Exchange
The key to understanding Nostr’s value lies in its inbuilt payment mechanism—Bitcoin’s Lightning Network protocol. Although this protocol is not part of the Nostr codebase, the existing Nostr clients incorporate it to allow users to pay each other bitcoin with a simple user interface. This means that Nostr as a protocol is ideal for creating platforms where users can exchange monetary value. The mechanics and design choices of the Lightning network further augment Nostr’s value proposition more so than traditional payment systems like credit cards, PayPal, etc.
Key Problem: Chicken and Egg
So far, we have established that platform markets enable at least two groups of users to come together and exchange. The primary problem is that both groups will only use the platform if the other group is already using it, creating a classic chicken and egg scenario. Platforms operate by bringing groups of users together, making users reticent to switch to a new platform because they don’t know if the other users will be there. This gives existing platforms enormous power.
Guy Swann sums this up well in this Nostr note: note1695j0czewtkfwy7h4ne7k2ug706uwc7lendsq50prsfp8vwq8nfszdx4z7.
Competing with Existing Platforms: Divide and Conquer!
To compete with existing platforms, you need to divide and conquer. The original formulation for this strategy is given in both Caillaud and Jullien (2003) and Armstrong (2006). To take advantage of the indirect network externalities identified earlier, the divide and conquer strategy involves subsidising one side of the market to attract a large user base (the "divide" part) and then monetising the other side of the market (the "conquer" part).
Divide: Attract one side of the market by offering lower prices or subsidies. For example, offer free registration to one side. This subsidy is essential to kickstart the network effects, as a larger user base on one side increases the platform’s attractiveness to the other side. This was observed in the early days of YouTube, which was free for both creators and watchers.
Conquer: Once a substantial user base is established on the subsidised side, charge higher fees on the other side of the market. This can be seen in contemporary YouTube, where advertisers (a specific kind of creator) pay fees, and watchers deal with the inconvenience of watching ads (inconvenience is a non-price fee).
Implementing This Strategy in Your Platform:
So who are are you dividing, who are you conquering? Deciding which side to subsidise involves understanding which side offers more benefit to the other side. For example, in nightclubs (Wright, 2004), men and women go to interact. Men are assumed to gain more from each woman’s presence than vice versa, so nightclubs often subsidise women with free entry or drinks to attract men.
First, consider all your user groups. What brings them to your platform, what do they want to gain by interacting with the other user groups.
Think about, and identify, which group confers more value for the other group by being on the platform.
Then, think about how you can subsidise that user group. Free access is common. But Nostr allows seamless payment integration which encourages users to exchange money. A potential model for your platform could be that you charge a fee to both users based on how much value they send to each other. One way to subsidise users in this case is to reduce those fees.
Alternatively, you could pay users to join your platform using Nostr’s integration with the Lightning Network.
References:
· Armstrong, M. (2006). Competition in two-sided markets. The RAND Journal of Economics, 37(3), 668-691.
· Caillaud, B., & Jullien, B. (2003). Chicken & Egg: Competition among Intermediation Service Providers. The RAND Journal of Economics, 34(2), 309-328.
· Wright, J. (2004). One-sided logic in two-sided markets. Review of Network Economics, 3(1).
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 6fc114c7:8f4b1405
2025-05-17 00:54:52
@ 6fc114c7:8f4b1405
2025-05-17 00:54:52Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ c9badfea:610f861a
2025-05-16 23:58:34
@ c9badfea:610f861a
2025-05-16 23:58:34- Install Breezy Weather (it's free and open source)
- Launch the app, tap Add A New Location and search for your city
- Review the providers for each weather source
- Optionally, add more locations by tapping the + icon
- Enjoy the weather updates
ℹ️ To receive notifications for weather alerts, tap ⚙️, then Notifications and enable Notifications Of Severe Weather Alerts
-
 @ 609f186c:0aa4e8af
2025-05-16 20:57:43
@ 609f186c:0aa4e8af
2025-05-16 20:57:43Google says that Android 16 is slated to feature an optional high security mode. Cool.
Advanced Protection has a bunch of requested features that address the kinds of threats we worry about.
It's the kind of 'turn this one thing on if you face elevated risk' that we've been asking for from Google.
And likely reflects some learning after Google watched Apple 's Lockdown Mode play out. I see a lot of value in this..
Here are some features I'm excited to see play out:
The Intrusion Logging feature is interesting & is going to impose substantial cost on attackers trying to hide evidence of exploitation. Logs get e2ee encrypted into the cloud. This one is spicy.
The Offline Lock, Inactivity Reboot & USB protection will frustrate non-consensual attempts to physically grab device data.

Memory Tagging Extension is going to make a lot of attack & exploitation categories harder.
2G Network Protection & disabling Auto-connect to insecure networks are going to address categories of threat from things like IMSI catchers & hostile WiFi.
I'm curious about some other features such as:
Spam & Scam detection: Google messages feature that suggests message content awareness and some kind of scanning.
Scam detection for Phone by Google is interesting & coming later. The way it is described suggests phone conversation awareness. This also addresses a different category of threat than the stuff above. I can see it addressing a whole category of bad things that regular users (& high risk ones too!) face. Will be curious how privacy is addressed or if this done purely locally. Getting messy: Friction points? I see Google thinking these through, but I'm going to add a potential concern: what will users do when they encounter friction? Will they turn this off & forget to re-enable? We've seen users turn off iOS Lockdown Mode when they run into friction for specific websites or, say, legacy WiFi. They then forget to turn it back on. And stay vulnerable.

Bottom line: users disabling Apple's Lockdown Mode for a temporary thing & leaving it off because they forget to turn it on happens a lot. This is a serious % of users in my experience...
And should be factored into design decisions for similar modes. I feel like a good balance is a 'snooze button' or equivalent so that users can disable all/some features for a brief few minute period to do something they need to do, and then auto re-enable.
Winding up:
I'm excited to see how Android Advanced Protection plays with high risk users' experiences. I'm also super curious whether the spam/scam detection features may also be helpful to more vulnerable users (think: aging seniors)...
Niche but important:
Some users, esp. those that migrated to security & privacy-focused Android distros because of because of the absence of such a feature are clear candidates for it... But they may also voice privacy concerns around some of the screening features. Clear communication from the Google Security / Android team will be key here.
-
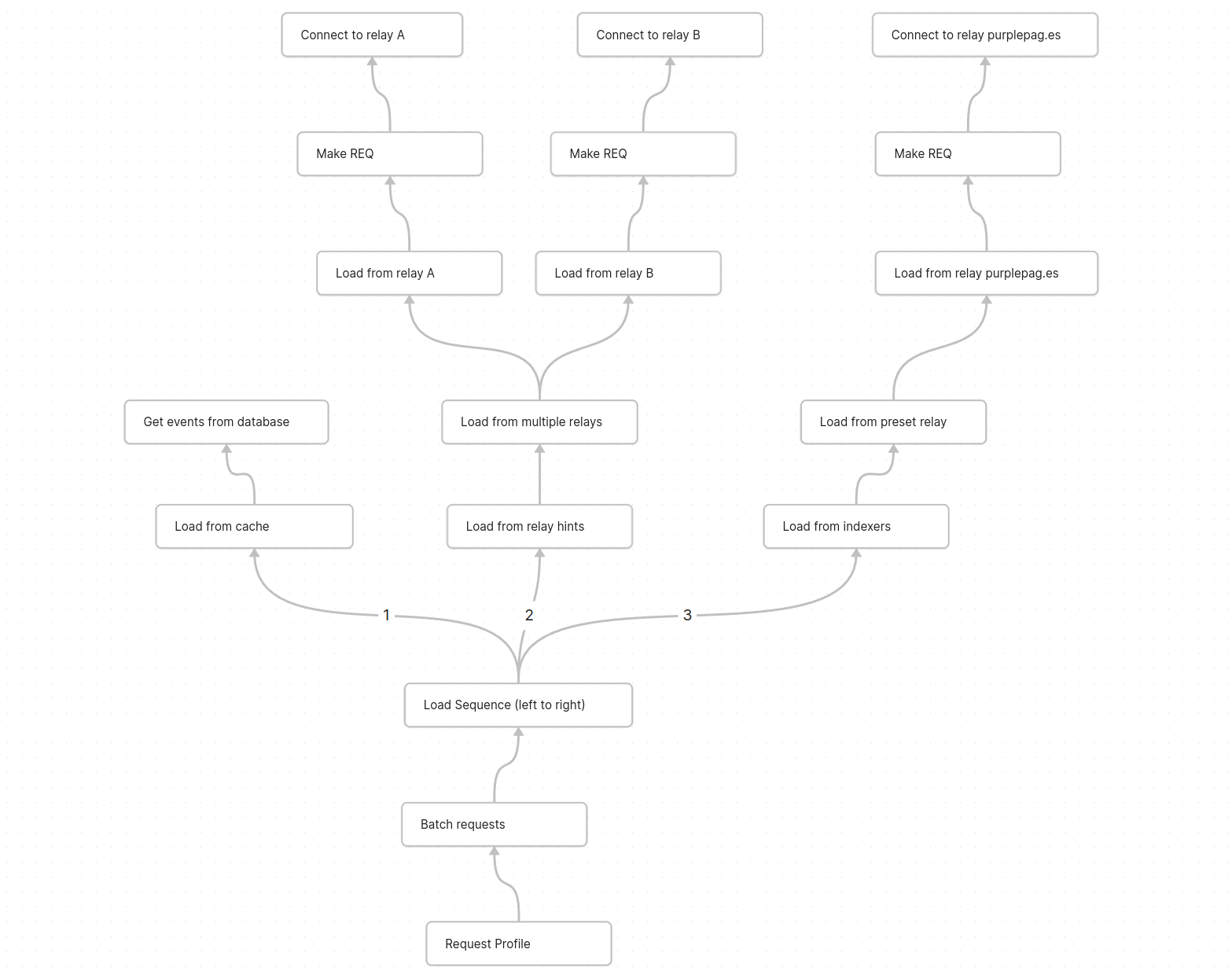
 @ 266815e0:6cd408a5
2025-05-16 20:52:42
@ 266815e0:6cd408a5
2025-05-16 20:52:42Streams are the key to nostr
Loading events from a nostr relay is probably the most inconsistent way of loading data I've had to work with, and that's only loading from a single relay. the problem gets exponentially more complicated once you try to load events from multiple relays
Unlike HTTP nostr does not have a simple flow with timeouts built in. events are sent back one at a time and can fail at any point or have massive (10s) gaps between them
The key is to use streams. something that starts, emits any number of results, then maybe errors or completes. luckily it just so happens that JavaScript / TypeScript has a great observable stream library called RxJS
What is an observable
An
Observablein RxJS is stream a of data that are initialized lazily, which means the stream is inactive and not running until something subscribes to it```ts let stream = new Observable((observer) => { observer.next(1) observer.next(2) observer.next(3) observer.complete() })
// The stream method isn't run until its subscribed to stream.subscribe(v => console.log(v)) ```
This is super powerful and perfect for nostr because it means we don't need to manage the life-cycle of the stream. it will run when something subscribes to it and stop when unsubscribed.
Its helpful to think of this as "pulling" data. once we have created an observable we can request the data from it at any point in the future.
Pulling data from relays
We can use the lazy nature of observables to only start fetching events from a nostr relay when we need them
For example we can create an observable that will load kind 1 events from the damus relay and stream them back as they are returned from the relay
```typescript let req = new Observable((observer) => { // Create a new websocket connection when the observable is start let ws = new WebSocket('wss://relay.damus.io')
ws.onopen = () => { // Start a REQ ws.send(JSON.stringify(['REQ', 'test', {kinds: [1], limit: 20}])) }
ws.onmessage = (event) => { let message = JSON.parse(event.data) // Get the event from the message and pass it along to the subscribers if(message[0] === 'EVENT') observer.next(message[1]) }
// Cleanup subscription return () => { ws.send(JSON.stringify(['CLOSE', 'test'])) ws.close() } }) ```
But creating the observable wont do anything. we need to subscribe to it to get any events.
ts let sub = req.subscribe(event => { console.log('we got an event' event) })Cool now we are pulling events from a relay. once we are done we can stop listening to it by unsubscribing from it
ts sub.unsubscribe()This will call the cleanup method on the observable, which in turn closes the connection to the relay.
Hopefully you can see how this work, we don't have any
open,connect, ordisconnectmethods. we simply subscribe to a stream of events and it handles all the messy logic of connecting to a relayComposing and chaining observables
I've shown you how we can create a simple stream of events from a relay, but what if we want to pull from two relays?
Easy, lets make the previous example into a function that takes a relay URL
```ts function getNoteFromRelay(relay: string){ return new Observable((observer) => { let ws = new WebSocket(relay)
// ...rest of the observable...}) } ```
Then we can "merge" two of these observables into a single observable using the
mergemethod from RxJSThe
mergemethod will create a single observable that subscribes to both upstream observables and sends all the events back. Think of it as pulling events from both relays at once```ts import { merge } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') )
// Subscribe to the observable to start getting data from it const sub = notes.subscribe(event => { console.log(event) })
// later unsubscribe setTimeout(() => { sub.unsubscribe() }, 10_000) ```
But now we have a problem, because we are pulling events from two relays we are getting duplicate events. to solve this we can use the
.pipemethod and thedistinctoperator from RxJS to modify our single observable to only return one version of each eventThe
.pipemethod will create a chain of observables that will each subscribe to the previous one and modify the returned values in some wayThe
distinctoperator takes a method that returns a unique identifier and filters out any duplicate values```ts import { merge, distinct } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') ).pipe( // filter out events we have seen before based on the event id distinct(event => event.id) ) ```
Now we have an observable that when subscribed to will connect to two relays and return a stream of events without duplicates...
As you can see things can start getting complicated fast. but its also very powerful because we aren't managing any life-cycle code, we just subscribe and unsubscribe from an observable
Taking it to an extreme
Hopefully at this point you can see how powerful this is, we can think of almost any data loading pattern as a series of observables that pull data from upstream observables and stream it back to the original subscriber.
Here is a quick sketch of what it could look like to load user profiles. each node is an observable that "pulls" data from its child node ending with the "connect websocket" or "load from database" nodes which do the work of making a relay connection
Conclusion
All this might seem pretty simple and straight forward, but its been a long six month of learning for me. I've had to completely rethink how data and nostr events should be handled in a client and how to avoid screwing up and shooting myself in the foot with these powerful tools.
If you want to give RxJS a try I would encourage you to checkout the nostr sdk I've been building called applesauce
Its uses RxJS for pretty much everything and has the simplest and most flexible relay connection API I've seen so far (mainly no life-cycle management)
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ c9badfea:610f861a
2025-05-16 20:15:31
@ c9badfea:610f861a
2025-05-16 20:15:31- Install Obtainium (it's free and open source)
- Launch the app and allow notifications
- Open your browser, navigate to the GitHub page of the app you want to install, and copy the URL (e.g.
https://github.com/revanced/revanced-managerfor ReVanced) - Launch Obtainium, navigate to Add App, paste the URL into App Source URL, and tap Add
- Wait for the loading process to finish
- You can now tap Install to install the application
- Enable Allow From This Source and return to Obtainium
- Proceed with the installation by tapping Install
ℹ️ Besides GitHub, Obtainium can install from additional sources
ℹ️ You can also explore Complex Obtainium Apps for more options
-
 @ 662f9bff:8960f6b2
2025-05-16 19:57:46
@ 662f9bff:8960f6b2
2025-05-16 19:57:46Let's start with some important foundational thinking - based on natural law. Money should be separate from the State - if not history shows that governments and human greed will always take over and manipulate the system in their favour and the expense of their populations. For extensive references, read The Sovereign Individual and The Creature from Jeckyll Island.
-
The Separation of State and Money is the most important thing you can listen to this week. Thanks to Allen Farrington - his paper is here for those who prefer to read. Wake up, folks!
-
The American Forefathers knew this when the wrote the American Constitution. Thomas Jefferson said: “If the American people ever allow private banks to control the issue of their currency first by inflation then by deflation the banks and corporations that will grow up around them will deprive the people of all property until their children wake up homeless on the continent their Fathers conquered... I believe that banking institutions are more dangerous to our liberties than standing armies... The issuing power should be taken from the banks and restored to the people to whom it properly belongs.” Mark Moss explains it well here. Charlie Robinsons take here.
The situation in Canada exemplifies the issues
Governments have have long used "international economic sanctions" against other nations to enforce their positions. Now in Canada, and soon in your country too, they are applying such sanctions their own citizens - disconnecting them from the financial system and removing their ability to use their own life savings as they wish. Canadians spoke with their money - in one week they raised more money in support of the truckers for peaceful protest than were raised in support of all Canadian political parties in the election of last year - only to have it confiscated and blocked by those politicians.
-
CPL. Daniel Bulford (Justin Trudeau's body guard) is particularly clear and eloquent - https://www.facebook.com/watch/?v=3123688351279364
-
Nick & Greg (two Canadians in Canada) explain the situation to Peter McCormack - https://youtu.be/QBWYp-cBr4o
-
Dr Jordan Peterson and Dr Julie Ponesse (also Canadians in Canada) speak openly about what is going on https://t.co/2T7A4VEek1
-
Even Canadians living in China speak up: https://www.youtube.com/watch?v=xvDvJWdlD1E
Meanwhile in Turkey...
Joe Blogs has been giving blow by blow updates of the deteriorating sitation over the last weeks. What is happening to Turkey will come to many countries - sooner than you might imagine. Watch and learn here, here and here - more on his channel.
EU Citizens should be aware and lobby their MPs
Dropping of all C-19 restrictions is a tactic to stop people thinking about them; meanwhile the politicians are taking steps to get all of the emergency restrictions codified into normal law so that they can be deployed on you any time or all the time in future.\ Act now - or lose all freedoms - your choice - watch here or click below for the explainer.
More on war - recall our discussion last week
War steals and destroys the wealth of generations. We have been here before - remember World Wars 1 and 2...
-
Dr Mattias Desmet explains how mass formation psychosis happens and how he became aware: https://www.youtube.com/watch?v=CRo-ieBEw-8
-
Be aware of this well known and much abused psycholgical experiment - rats in a cage - explained by Dr Christ Martensen: https://www.youtube.com/watch?v=7kSBdMXQkPI
To remain silent is wrong - to deny the rights of others to discuss and challenge (and even to punish or coerce them) is a crime in support of the biger crime. Each of us has a choice - choose wisely.
Could you have known about this?
"The Matrix is a system, Neo. That system is our enemy. But when you're inside, you look around, what do you see? Businessmen, teachers, lawyers, carpenters. The very minds of the people we are trying to save. But until we do, these people are still a part of that system and that makes them our enemy. You have to understand, most of these people are not ready to be unplugged. And many of them are so inert, so hopelessly dependent on the system that they will fight to protect it."
"Unfortunately, no one can be told what the Matrix is. You have to see it for yourself."
A closing thought...
Look closely at the cover of the Economist magazine *released in December 2018 *- The World in 2019 - see how many of those things have already come true.

In case this is too difficult for you - some things to note: Four horsemen of the apacalypse, Statue of Liberty wearing a facemask, Vetruvian Man with QR code (Vaccine passport), DNA mark on his arm, wearing virtual reality glasses... The animal bottom right is a Pangolin. Scales of Justice are well tipped/skewed, facial recognition, electric cars, Putin's pipelines, China and Brexit feature highly along with the lieing media (Pinnochio) and #metoo. I smell Predictive Programming.
- More insights in the explainer here (backup copy here) - including why it is backwards...
That's it!
No one can be told what The Matrix is.**\ You have to see it for yourself.
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
-
 @ 57d1a264:69f1fee1
2025-05-16 07:51:08
@ 57d1a264:69f1fee1
2025-05-16 07:51:08Payjoin allows the sender and receiver of an on-chain payment to collaborate and create a transaction that breaks on-chain heuristics, allowing a more private transaction with ambiguous payment amount and UTXO ownership. Additionally, it can also be used for UTXO consolidation (receiver saves future fees) and batching payments (receiver can make payment(s) of their own in the process of receiving one), also known as transaction cut-through. Other than improved privacy, the rest of the benefits are typically applicable to the receiver, not the sender.
BIP-78 was the original payjoin protocol that required the receiver to run a endpoint/server (always online) in order to mediate the payjoin process. Payjoin adoption has remained pretty low, something attributed to the server & perpetual online-ness requirement. This is the motivation for payjoin v2.
The purpose of the one-pager is to analyse the protocol, and highlight the UX issues or tradeoffs it entails, so that the payjoin user flows can be appropriately designed and the tradeoffs likewise communicated. A further document on UX solutions might be needed to identify solutions and opportunities
The following observations are generally limited to individual users transacting through their mobile devices:
While users naturally want better privacy and fee-savings, they also want to minimise friction and minimise (optimise) payment time. These are universal and more immediate needs since they deal with the user experience.
Added manual steps
TL;DR v2 payjoin eliminates server & simultaneous user-liveness requirements (increasing TAM, and opportunities to payjoin, as a result) by adding manual steps.
Usually, the extent of the receiver's involvement in the transaction process is limited to sharing their address with the sender. Once they share the address/URI, they can basically forget about it. In the target scenario for v2 payjoin, the receiver must come online again (except they have no way of knowing "when") to contribute input(s) and sign the PSBT. This can be unexpected, unintuitive and a bit of a hassle.
Usually (and even with payjoin v1), the sender crafts and broadcasts the transaction in one go; meaning the user's job is done within a few seconds/minutes. With payjoin v2, they must share the original-PSBT with the receiver, and then wait for them to do their part. Once the the receiver has done that, the sender must come online to review the transaction, sign it & broadcast.
In summary,
In payjoin v1, step 3 is automated and instant, so delay 2, 3 =~ 0. As the user experiences it, the process is completed in a single session, akin to a non-payjoin transaction.
With payjoin v2, Steps 2 & 3 in the above diagram are widely spread and noticeable. These manual steps are separated by uncertain delays (more on that below) when compared to a non-payjoin transaction.
Delays
We've established that both senders and receivers must take extra manual steps to execute a payoin transaction. With payjoin v2, this process gets split into multiple sessions, since the sender and receiver are not like to be online simultaneously.
Delay 2 & 3 (see diagram above) are uncertain in nature. Most users do not open their bitcoin wallets for days or weeks! The receiver must come online before the timeout hits in order for the payjoin process to work, otherwise time is just wasted with no benefit. UX or technical solutions are needed to minimise these delays.
Delays might be exacerbated if the setup is based on hardware wallet and/or uses multisig.
Notifications or background processes
There is one major problem when we say "the user must come online to..." but in reality the user has no way of knowing there is a payjoin PSBT waiting for them. After a PSBT is sent to the relay, the opposite user would only find out about it whenever they happen to come online. Notifications and background sync processes might be necessary to minimise delays. This is absolutely essential to avert timeouts in addition to saving valuable time. Another risk is phantom payjoin stuff after the timeout is expired if receiver-side does not know it has.
Fee Savings
The following observations might be generally applicable for both original and this v2 payjoin version. Fee-savings with payjoin is a tricky topic. Of course, overall a payjoin transaction is always cheaper than 2 separate transactions, since they get to share the overhead.
Additionally, without the receiver contributing to fees, the chosen fee rate of the PSBT (at the beginning) drops, and can lead to slower confirmation. From another perspective, a sender paying with payjoin pays higher fees for similar confirmation target. This has been observed in a production wallet years back. Given that total transaction time can extend to days, the fee environment itself might change, and all this must be considered when designing the UX.
Of course, there is nothing stopping the receiver from contributing to fees, but this idea is likely entirely novel to the bitcoin ecosystem (perhaps payments ecosystem in general) and the user base. Additionally, nominally it involves the user paying fees and tolerating delays just to receive bitcoin. Without explicit incentives/features that encourage receivers to participate, payjoining might seem like an unncessary hassle.
Overall, it seems that payjoin makes UX significant tradeoffs for important privacy (and potential fee-saving) benefits. This means that the UX might have to do significant heavy-lifting, to ensure that users are not surprised, confused or frustrated when they try to transact on-chain in a privacy-friendly feature. Good, timely communication, new features for consolidation & txn-cutthrough and guided user flows seem crucial to ensure payjoin adoption and for help make on-chain privacy a reality for users.
---------------
Original document available here. Reach out at
yashrajdca@proton.me,y_a_s_h_r_a_j.70on Signal, or on reach out in Bitcoin Design discord.https://stacker.news/items/981388
-
 @ 57d1a264:69f1fee1
2025-05-16 05:38:28
@ 57d1a264:69f1fee1
2025-05-16 05:38:28LegoGPT generates a LEGO structure from a user-provided text prompt in an end-to-end manner. Notably, our generated LEGO structure is physically stable and buildable.
Lego is something most of us knows. This is a opportuity to ask where is our creativity going? From the art of crafting figures to building blocks following our need and desires to have a machine thinking and building following step-by-step instructions to achieve an isolated goal.
Is the creative act then in the question itself, not anymore in the crafting? Are we just delegating the solution of problems, the thinking of how to respond to questions, to machines? Would it be different if delegated to other people?
Source: https://avalovelace1.github.io/LegoGPT/
https://stacker.news/items/981336
-
 @ b83a28b7:35919450
2025-05-16 19:13:43
@ b83a28b7:35919450
2025-05-16 19:13:43This is the body
-
 @ 57d1a264:69f1fee1
2025-05-14 09:48:43
@ 57d1a264:69f1fee1
2025-05-14 09:48:43Just another Ecash nutsnote design is a ew template for brrr.gandlaf.com cashu tocken printing machine and honoring Ecash ideator David Lee Chaum. Despite the turn the initial project took, we would not have Ecash today without his pioneering approach in cryptography and privacy-preserving technologies.
A simple KISS (Keep It Super Simple) Ecash nutsnote delivered as SVG, nothing fancy, designed in PenPot, an open source design tool, for slides, presentations, mockups and interactive prototypes.
Here Just another Nutsnote's current state, together with some snapshots along the process. Your feedback is more than welcome.
https://design.penpot.app/#/view?file-id=749aaa04-8836-81c6-8006-0b29916ec156&page-id=749aaa04-8836-81c6-8006-0b29916ec157§ion=interactions&index=0&share-id=addba4d5-28a4-8022-8006-2ecc4316ebb2
originally posted at https://stacker.news/items/979728
-
 @ 88cc134b:5ae99079
2025-05-16 19:07:14
@ 88cc134b:5ae99079
2025-05-16 19:07:14This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that @QW and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 57d1a264:69f1fee1
2025-05-14 06:48:45
@ 57d1a264:69f1fee1
2025-05-14 06:48:45Has the architect Greg Chasen considered it when rebuilding the house just one year before the catastrophe? Apparently not! Another of his projects was featured on the Value of Architecture as properties with design integrity.
This is a super interesting subject. The historic character, livability, and modern disaster-resistance is a triangle where you often have to pick just one or two, which leads to some tough decisions that have major impacts on families and communities. Like one of the things he mentions is that the architect completely eliminated plants from the property. That's great for fire resistance, but not so great for other things if the entire town decides to go the same route (which he does bring up later in the video). I don't think there's any objectively right answer, but definitely lots of good (and important) discussion points to be had.
https://www.youtube.com/watch?v=cbl_1qfsFXk
originally posted at https://stacker.news/items/979653
-
 @ 88cc134b:5ae99079
2025-05-16 19:04:30
@ 88cc134b:5ae99079
2025-05-16 19:04:30text
-
 @ 57d1a264:69f1fee1
2025-05-14 06:12:19
@ 57d1a264:69f1fee1
2025-05-14 06:12:19We asked members of the design community to choose an artifact that embodies craft—something that speaks to their understanding of what it means to make with intention. Here’s what they shared.
A vintage puzzle box, a perfectly tuned guitar, an AI-powered poetry camera. A daiquiri mixed with precision. A spreadsheet that still haunts muscle memory. Each artifact tells a story: not just about the thing itself, but about the choices of the creator behind it. What to refine, what to leave raw. When to push forward, when to let go. Whether built to last for generations or designed to delight in a fleeting moment, the common thread is that great craft doesn’t happen by accident. It’s made.
On the application of craft
Even the most experienced makers can benefit from building structure and intention into their practice. From sharpening your storytelling to designing quality products, these pieces offer practical ways to uplevel your craft.
Read more at https://www.figma.com/blog/craft-artifacts/
originally posted at https://stacker.news/items/979644
-
 @ 57d1a264:69f1fee1
2025-05-14 05:56:15
@ 57d1a264:69f1fee1
2025-05-14 05:56:15Shanghai: Bus Stops Here
A new crowd-sourced transit platform allows riders to propose, vote on, and activate new bus lines in as little as three days.
From early-morning school drop-offs to seniors booking rides to the hospital, from suburban commuters seeking a faster link to the metro to families visiting ancestral graves, Shanghai is rolling out a new kind of public bus — one that’s designed by commuters, and launched only when enough riders request it.
Branded “DZ” for dingzhi, or “customized,” the system invites residents to submit proposed routes through a city-run platform. Others with similar travel needs can opt in or vote, and if demand meets the threshold — typically 15 to 20 passengers per trip — the route goes live.
More than 220 DZ routes have already launched across all 16 city districts. Through an online platform opened May 8, users enter start and end points, preferred times, and trip frequency. If approved, routes can begin running in as little as three days.
Continue reading at https://www.sixthtone.com/news/1017072
originally posted at https://stacker.news/items/979637
-
 @ 3a9a4c49:f774dd7a
2025-05-16 18:05:58
@ 3a9a4c49:f774dd7a
2025-05-16 18:05:58Keeping a home safe and functioning means being sure that your boiler is functioning well and having a valid Gas Safety Certificate. If you're looking for 'https://certificates4uk.co.uk/boiler-replacement-services/' or a trusted Gas Safety Certificate company near me, stop searching at Certificates 4 UK. Our services include professional boiler servicing, repair, and safety certification to keep your home compliant and safe.
**Why Certificates 4 UK for Boiler Repairs?
** A malfunctioning boiler means high energy bills, cold showers, and, ultimately, gas leaks that might be harmful. Hence, timely boiler service near me is of prime importance. At Certificates 4 UK, our Gas Safe registered engineers can promptly and accurately troubleshoot and carry out any repairs on your boiler. Whether it is a faulty thermostat, low pressure, or a complete breakdown, we restore your heating to peak performance.
****Common Boiler Problems We Fix:
- No heating or hot water is often caused by broken diaphragms, airlocks, or valve failures.
- Leaking or dripping boilers could be due to broken internal components or high pressure.
- Strange noises(banging, gurgling, whistling) usually indicate limescale buildup or trapped air.
- The pilot light keeps going out this may indicate a faulty thermocouple or draught affecting the flame.
- Boiler pressure issues: Besides improvement of efficiency, the pressure should not be excessively high or low in any boiler.
Our experts offer same-day emergency repair services to make sure you never have to cope without the heating when needed.
**
Significance of Gas Safety Certificate.
** Gas Safety Certification, or CP12, is a necessary proviso for landlords. Homeowners also are supposed to do annual gas safety checks to avail against carbon monoxide leakages and gas-based catastrophes. When looking for an honest https://certificates4uk.co.uk/gas-services/, Certificates 4 UK should be a prime consideration to provide you with quick, cheap, and legally satisfactory inspections.
**What is a part of the Gas Safety Check?
**
## **Our Gas Safe engineers will:
** * Inspect all gas appliances (boilers, cookers, and fires) to detect leaks or defects. * Check ventilation and flue systems to ensure no obstruction of exhaust flow. * Test gas pressure and safety controls. * Submit a report and provide a Gas Safety Certificate if all equipment passes.
Every landlord is expected to renew this certificate once a year and provide a copy to their tenants. Otherwise, there are hefty-to-hidden fines, ' fines or imprisonment.'
**Why Trust Certificates 4 UK?
** * Gas Safe Registered Engineers : All our technicians are fully qualified and approved. * Fast & Reliable Service : Same-day and next-day appointments. * Competitive Pricing : Reasonable rates without having to cut costs on quality. * Nationwide Coverage Helping homeowners and landlords throughout the UK.
**Book Your Boiler Repair or Gas Safety Check Today!
** Do not wait for a day when your boiler gives up on you or when your gas certificate lapses! Call Certificates 4 UK today for professional boiler repair near me or a Gas Safety Certificate inspection. By going with Certificates 4 UK, you are assured of high-quality boiler repair and gas safety compliance. Whenever you need an emergency fix or an annual inspection, we have got you covered. Lastly, put any doubts about 'boiler repairs near me' or 'gas safety certificate companies near me' to rest; rest assured, the experts at Certificates 4 UK will provide you with peace of mind!
-
 @ c9badfea:610f861a
2025-05-16 17:57:20
@ c9badfea:610f861a
2025-05-16 17:57:20- Install Lemuroid (it's free and open source)
- Launch the app, enable notifications, and select a directory for your games (e.g.
/Download/ROMs) - Download game ROMs and place them in the folder from the previous step (see links below)
- Open Lemuroid again, navigate to the Home tab, and tap the downloaded game
- Enjoy!
Some ROM Sources
ℹ️ An internet connection is only required when opening a game for the first time to download the emulator core per system (e.g. Gameboy or PS2)
ℹ️ Supported ROM file formats include
.nes,.gba,.sfc,.gb,.iso,.bin, and.zipℹ️ You may need to extract downloaded ROM files if they are packaged as archives (e.g.
.7z,.rar, or.zip) -
 @ 88cc134b:5ae99079
2025-05-16 18:08:25
@ 88cc134b:5ae99079
2025-05-16 18:08:25Here's the article. Not the longest one ever. But definitely impactful.
-
 @ 7e6f9018:a6bbbce5
2025-05-16 17:32:56
@ 7e6f9018:a6bbbce5
2025-05-16 17:32:56The rental population in Spain has grown from about 5 million in 2005 to around 10 million in 2025. During that same period, Spain's total population has increased by 6 million people, from 43 to 49 million. In other words, the entire population growth over the past 20 years has essentially gone straight into the rental market.
This demographic growth is not due to natural increase, Spain has one of the lowest fertility rates in the world. Instead, population growth is driven by a positive migratory balance, which has been the main factor behind the rise in rental demand.
This increased demand for rentals has pushed up rental prices, which have significantly outpaced the growth in property sale prices. That didn’t happen during the Great Financial Crisis. The growth in both demand and prices is allowing rental profitability to remain at the high end of the curve—around 5% net.
This situation explains the rise in housing squatting, from 2,000 cases in 2010 to 16,000 in 2024. Since the immigrant population is the main driver of this surge in rental demand, it is more vulnerable to squatting, as they often have no alternative housing when they are unable to pay.
The unemployment rate is currently low, however, if it were to rise (as it did during the Great Financial Crisis and other periods in the past), squatting would likely increase significantly, representing the main risk to the current real estate market in Spain.
-
 @ bbef5093:71228592
2025-05-16 17:00:59
@ bbef5093:71228592
2025-05-16 17:00:59Technológiai fejlemények
Az Egyesült Államokban és világszerte jelentős előrelépések történtek a nukleáris technológia területén. A mesterséges intelligencia (AI) egyre nagyobb szerepet kap az atomerőművek működtetésében: például a kaliforniai Diablo Canyon atomerőmű már alkalmaz generatív AI-t a dokumentumkezelés és az üzemeltetési hatékonyság javítására. Az AI segíti az üzemeltetőket a karbantartás előrejelzésében, a biztonság növelésében és a reaktorok élettartamának meghosszabbításában is. Emellett az USA Nukleáris Szabályozó Bizottsága (NRC) is vizsgálja, hogyan gyorsíthatná fel az engedélyezési folyamatokat AI-alapú rendszerekkel, ami jelentősen felgyorsíthatja az új reaktorok telepítését.
A NANO Nuclear Energy jelentős mérföldkövet ért el: megszerezte a KRONOS MMR™ (45 MWth teljesítményű, helyhez kötött mikroreaktor) és a LOKI MMR™ (1–5 MWth teljesítményű, hordozható mikroreaktor) technológiákat, és ezek fejlesztését az USA-ban és Kanadában is előmozdítja. A KRONOS MMR üzemanyag-minősítési módszertanát az NRC már jóváhagyta, ami kulcsfontosságú a kereskedelmi bevezetéshez
Ipari és piaci fejlemények
Az amerikai The Nuclear Company startup 46 millió dolláros tőkebevonással kívánja új, nagy teljesítményű atomerőművek fejlesztését megkezdeni, elsősorban már engedélyezett helyszíneken. A cél, hogy az első flottában összesen 6 gigawatt kapacitást hozzanak létre. Ez a lépés válasz a gyorsan növekvő amerikai áramigényre, amelyet főként az adatközpontok és a mesterséges intelligencia-alkalmazások hajtanak. Ugyanakkor a nukleáris ipar pénzügyi kilátásait bizonytalanság övezi, mivel az amerikai törvényhozás egyes tervezetei a nukleáris energia adókedvezményeinek megszüntetését is kilátásba helyezték, ami a jövőbeni beruházások megtérülését is befolyásolhatja.
Belgiumban a parlament váratlan fordulattal úgy döntött, hogy nem zárják be az atomerőműveket, hanem tíz évvel meghosszabbítják a reaktorok élettartamát, sőt, új reaktorok építését is tervezik. A döntés mögött az energiaválság, az ellátásbiztonság és a geopolitikai feszültségek állnak.
Magyarországon folytatódik a Paks II. projekt előkészítése, és napirenden van kis moduláris reaktorok (SMR) telepítése is, amelyek néhány száz megawattos teljesítményükkel akár ipari zónákat vagy városokat is önállóan elláthatnak.
Pénzügyi és geopolitikai aktualitások
A nukleáris energia geopolitikai jelentősége továbbra is kiemelkedő. Tajvan szombaton leállítja utolsó működő atomerőművi blokkját, ami jelentős LNG-import költségnövekedést eredményez, és komoly vitákat váltott ki a szigetországban. A törvényhozás ugyanakkor már vizsgálja az atomenergia-törvény felülvizsgálatát, amely lehetővé teheti a reaktorok újraindítását – erről akár népszavazás is lehet a közeljövőben.
Az USA és Irán között folytatódnak az atomprogramról szóló tárgyalások. Bár közelednek az álláspontok, az USA új szankciókat vezetett be Irán ellen, mivel Teherán továbbra is magas szintű urándúsítást folytat. Az esetleges megállapodás rövid távon növelheti az iráni kőolajexportot, ami a világpiaci árakra is hatással lehet.
-
 @ c9e9bdc0:e4dbe9b8
2025-05-16 17:00:09
@ c9e9bdc0:e4dbe9b8
2025-05-16 17:00:09Today we’re launching Buzzbot Express: a clean, targeted way to drive engagement and reward your audience with sats.
Here’s how it works:
-
Tag @buzzbot express [amount] (e.g.,
@buzzbot express 5000) -
Pay the invoice sent to your DMs
-
After 12 hours, one random liker and one random commenter each win **50% of the sats **(6% fee)
Since launching Buzzbot, we’ve seen a wide range of creative use cases. But the clearest path to long-term value may lie in branded content and decentralized promotion.
From plebs promoting value-for-value concerts to podcasters pushing new episodes, Buzzbot Express gives creators and brands a tool to generate real energy around a post.
Paying for engagement might feel off-brand to some, but if you’re promoting a product, a song, or an event, Buzzbot Express offers a clean, transparent way to generate real momentum.
The invention of Zaps opened the fifth dimension of social media. They are not just another feature added to the stack. They are an exponential amplifier that transforms attention into economic energy.
At Buzzbot, we believe this new creator economy can and should include advertisers.
The days of brands paying millions to ad firms, hiring Hollywood talent, and forcing campaigns into feeds are fading. That model made sense on centralized, algorithmic platforms, but it doesn’t belong on Nostr.
Instead, brands can spend that same money directly with creators who align with their values. Or better yet, they can reward audiences for engaging honestly.
That’s where Buzzbot comes in.
Buzzbot Express is a small step toward this future. Try it out — and let us know what you think.
Pay attention.
-
-
 @ e39333da:7c66e53a
2025-05-16 13:20:33
@ e39333da:7c66e53a
2025-05-16 13:20:33::youtube{#Pex7jW3Tqwo}
Developer SHIFT UP has announced that their latest titled, Stellar Blade, that was released on PS5 on the 2024, will release on PC via Steam and EGS on the 11th of June 2025.
The game will be priced at $60, and $80 for the edition of the game that includes the 'Twin Expansion Pack', which includes the NieR: Automata DLC and the Goddess of Victory: Nikke DLC, and a key to redeem a Stellar Blade costume in the developer's previous Free-to-Play title Goddess of Victory: Nikke.
The trailer released to announce said release date also showcases the changes the made for the game and highlight PC specific enhancements, support, and options.
It's worth noting, in terms of negative news that tagged along with this, that the game will have Denuvo running, which there are evidence that decreases a game's performance, and may prevent you from playing the game offline. The game will also have an optional PSN account login, and because of this, the game is not available for purchase in around 130 countries. There's also an exclusive outfit locked behind a PSN-to-Steam account linking.

Here's the system requirements:
| | Minimum | Recommended | High | Very High | | ----------------------- | ----------------------------------------------------- | ------------------------------------------------------- | ------------------------------------------------------- | ------------------------------------------------- | | Average Performance | 1080P at 60 frames per second | 1440P at 60 frames per second | 1440P at 60 frames per second | 4K at 60 frames per second | | Graphic Presets | Low | Medium | High | Very High | | CPU | Intel Core i5-7600K AMD Ryzen 5 1600X | Intel Core i5-8400 AMD Ryzen 5 3600X | Intel Core i5-8400 AMD Ryzen 5 3600X | Intel Core i5-8400 AMD Ryzen 5 3600X | | GPU | NVIDIA GeForce GTX 1060 6GB AMD Radeon RX 580 8GB | NVIDIA GeForce RTX 2060 SUPER AMD Radeon RX 5700 XT | NVIDIA GeForce RTX 2070 SUPER AMD Radeon RX 6700 XT | NVIDIA GeForce RTX 3080 AMD Radeon RX 7900 XT | | RAM | 16GB | 16GB | 16GB | 16GB | | Storage | 75GB HDD (SSD Recommended) | 75GB SSD | 75GB SSD | 75GB SSD | | OS | Windows 10 64-bit | Windows 10 64-bit | Windows 10 64-bit | Windows 10 64-bit |
-
 @ 84b0c46a:417782f5
2025-05-16 13:09:31
@ 84b0c46a:417782f5
2025-05-16 13:09:31₍ ・ᴗ・ ₎ ₍ ・ᴗ・ ₎₍ ・ᴗ・ ₎
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-16 15:29:10
@ 5d4b6c8d:8a1c1ee3
2025-05-16 15:29:10How could the Dallas Mavericks possibly have gotten the first pick in this draft? League corruption? Mischievous basketball gods? Simulation theory? Dumb stupid luck? Whatever the reason, it's very interesting.
We'll probably be done with the 2nd round, by the time we record, which means round 2 recap and conference finals previews. It's definitely not the matchups anyone expected. What are the implications for our brackets?
The NFL released the season schedules and @grayruby's rightly excited for his 49ers upcoming season.
The parity situation worsens in the MLB, as the Dodgers' pitchers are ravaged by injury. Also, @grayruby and I are going head-to-head in fantasy baseball this week. Who will prevail?
On this week's Blok'd Shots, @grayruby will dance on the Leafs' grave and celebrate their well-deserved misfortune. Hell hath no fury like a scorned Leafs fan. Also, the NHL bracket is coming down to me and @Jer. Will knowing anything about hockey be enough to get Jer the victory?
And, as always, whatever the stackers want us to cover.
https://stacker.news/items/981596
-
 @ 99e7936f:d5d2197c
2025-05-16 13:09:05
@ 99e7936f:d5d2197c
2025-05-16 13:09:05Baustelle HERZ
Können wir nicht einfach glücklich sein? Nein.
Eine traumatisierte Gesellschaft kann nicht EINFACH glücklich sein, weil die Herzen verletzt sind.
„Ja, aber es gibt doch auch noch andere Probleme als Trauma“, kritisieren einige.
„Ich habe schließlich eine Familie und einen anstrengenden Job“, erklären andere.
„Für mich ist das eine abstrakte Diskussion, ein Luxusproblem“, geben manche zu bedenken.
„Eigentlich möchte ich mich mit dem Thema gar nicht beschäftigen“, sagen wenige, denken aber viele.
„Ich beschäftige mich lieber mit positiven Dingen“, ist die diplomatische Variante der Vermeidung dieses Themas.
Niemand redet gerne über Trauma, bis es an die eigene Tür klopft. Und dann ist guter Rat teuer. Dann würde man gerne reden, aber die anderen wollen immer noch nicht.
Niemand redet gerne über Trauma.
„Was heißt denn Anklopfen?“ Mit Anklopfen meine ich die Situationen, die jeder kennt. Gemeint sind ganz normale Lebenskrisen, die es mehrmals in jedem Leben gibt.
„Ist denn eine Lebenskrise gleichzusetzten mit einem Trauma?“ Nein, aber durch eine starke Lebenskrise kann ein altes Trauma wieder hochgespült werden, und das fühlt sich dann original so an, wie das Trauma, das man z.B. als Kind oder später im Leben erlebt hat.
Und das passiert in einer traumatisierten Gesellschaft ständig, nur nennen die Leute es nicht so. Niemand sagt: „Er oder sie hat ein aktiviertes Trauma.“
Hierzu habe ich eine Anekdote. Vor ein paar Monaten zog in das Nachbarhaus bei mir auf der Straße ein junger Mann ein. Das Haus war frisch renoviert worden. Es zogen zeitgleich mehrere junge Leute jeweils in eine Wohnung dieses Hauses ein. Die Stimmung im Haus war gut, weil alles neu und geschmackvoll gestaltet worden war und die Mieter gut zusammen passten. Dann merkten die Mieter und Nachbarn, dass es einem jungen Mann nicht gut ging. Er saß den ganzen Tag in der Wohnung, konnte sich zu nichts aufraffen. Er schaffte es nicht, sich Lebensmittel einzukaufen. Ein Freund kam regelmäßig vorbei und brachte ihm Essen. Eine ältere Nachbarin fragte nach einigen Monaten diesen Freund, was dem jungen Mann denn fehle, ob er eine Krankheit habe oder was denn los sei. Der Freund lachte und sagte nur einen Satz: „Er stirbt.“
Die Nachbarin erzählte mir das und schaute mich fragend an. Ich übersetzte ihr den Satz und meinte: „Er hat vermutlich Liebeskummer.“ Aber was ich wirklich dachte, war, dass er ein aktiviertes Trauma hatte, nur sagte ich das nicht zur Nachbarin. Nach mittlerweile zwei Jahren kommt der Freund immer noch regelmäßig und bringt dem jungen Mann Essen. Er kauft für ihn ein und kümmert sich um ihn.
Manche Menschen leiden sehr lange unter Verlusten, Zurückweisungen, Niederlagen, Verletzungen. Andere kommen nie auf die nächste Stufe, obwohl sie sich unaufhörlich anstrengen. Wieder andere haben alles und sind dennoch unzufrieden und in permanenter Angriffshaltung. All diese Phänomene dauern oft lange, manchmal sogar ein Leben lang. Meines Erachtens sind das aktivierte Traumen bzw. Traumen, die gut verschlossen dennoch im Unterbewusstsein gegen die eigene Person arbeiten.
Trauma hat viele Gesichter.
Es kommt bei den unmöglichsten Gelegenheiten zum Vorschein. Und oft erkennen wir es nicht als das, was es ist. Wir suchen den Grund im Außen, den es ja meist auch gibt. Nur ist der Grund nicht der Grund, sondern nur der Auslöser.
Auch ich bin einmal „gestorben“. Dieser Zustand dauerte über drei Jahre an. Deshalb klingelte es bei mir auch sofort im Ohr als die Nachbarin sagte, der Freund habe gesagt: „Er stirbt.“
Sprache ist wunderbar.
Wer beides schon mal erlebt hat, eine normale Trennung und eine schwere Trennung, einen normalen Arbeitsplatzwechsel oder einen dramatischen Jobverlust, ein geplatztes Geschäft oder einen geplatzten Lebenstraum, das Ende einer Freundschaft oder eine Kränkung, über die man noch nach 35 Jahren so berichtet, als ob es gestern gewesen wäre, der kennt den Unterschied in der Intensität der Gefühle. Manche Menschen erzählen immer wieder eine Geschichte, obwohl man sie schon kennt und auch sein Mitgefühl dazu ausgedrückt hat. Manche Menschen reden gar nicht mehr über eine bestimmte Sache, bis einem irgendwann von Dritten gesagt wird, dass man ihn oder sie besser nicht auf das Thema XYZ ansprechen sollte.
All das sind aktivierte Traumen, die noch weh tun, noch nicht verarbeitet sind. Es sind Dinge, die jedem von uns passieren können. Jeder erlebt im Leben partnerschaftliche Trennungen, geplatzte Geschäfte und Kränkungen am laufenden Meter, aber es „trifft“ einen nicht immer gleich. Und es trifft nicht nur die Sensiblen, sondern es trifft jeden, wenn der Punkt, an dem es trifft, wund ist. Der wunde Punkt macht jeden sensibel. Auch robuste Naturen haben einen wunden Punkt. Und wenn der getroffen wird, dann werden auch die härtesten Menschen butterweich. In einer traumatisierten Gesellschaft wird jeder so oft „getroffen“, wie es braucht, bis er sich dem Thema widmet. Wir alle haben diese frühen oder späten Traumen erlebt, die früher oder später erneut durch Krisen aktiviert werden. Und dann „sterben“ wir, zumindest gefühlt.
Denn Trauma ist immer existenziell.
Und aktiviertes Trauma ist bitte nicht zu verwechseln mit Depression. Es ist ein aktiviertes Trauma, das sich im Unterschied zur Depression sehr wach, lebendig und vor allem schmerzvoll anfühlt. Es fühlt sich an wie „damals“. Das versteht man, in der Situation steckend, komischerweise sofort, denn wir haben ein Schmerzgedächtnis. Wir können Düfte oder Musik ja auch sofort zuordnen, wenn sie uns an etwas erinnern. Mit Schmerz ist es ähnlich. Aber es fällt so schwer, darüber zu reden, weil es keiner versteht und weil es dafür meines Erachtens in unserer Sprache keine Worte gibt. Man versteht das erst, wenn man es selbst erlebt hat. Und dann reichen zwei Worte.
Die Baustelle HERZ versteht man erst, wenn man selbst ein aktiviertes Trauma erlebt, durchlebt hat, wenn man einmal „gestorben“ ist.
Heute kann ich an Äußerungen, die jemand macht, gut ablesen, ob jemand seine Baustelle HERZ bereits kennen gelernt hat oder nicht. Menschen, die das selbst noch nicht kennen gelernt haben, haben oft aufmunternde Sprüche wie „Das wird schon wieder. Jetzt lass den Kopf mal nicht hängen.“ Das hilft einem dann in etwa so, wie wenn man in einer Depression gesagt bekommt: „Nun lach doch mal.“ Man weiß dann sofort, welchen Erfahrungshintergrund das Gegenüber hat. Das ist keine Wertung, nur eine Feststellung. Unsere Kultur hat hier einfach wichtiges Wissen verloren. Ich persönlich weiß nicht, wie es ist, ein Kind auf die Welt zu bringen oder ein Kind zu verlieren. Ich weiß vieles nicht und habe vermutlich auch schon wenig hilfreiche Kommentare abgegeben, weil ich es nicht besser wusste. Aber ich weiß, wie sich ein aktiviertes Trauma anfühlt. Und das ist ein wertvolles Wissen, was ich gern teilen möchte. Man schaut mit diesem erfahrenen Wissen (kein Bücher-Wissen) viel differenzierter auf das Leid anderer Menschen. Es gibt so viele Sorten von Trauma und deswegen auch Sorten von aktiviertem Trauma. Manchmal denkt man sich nichts dabei und sagt etwas, und schon hat man beim anderen einen Punkt getroffen, der dadurch nun schmerzt. Wenn man Glück hat, dann dauert der Schmerz nur kurz an. Wenn man Pech hat, ist die Freundschaft zu Ende. Ich habe das selbst schon erlebt. Mal war ich es, die den Rückzug angetreten hat. Mal war es der andere. Hinter diesen Phänomenen steckt nichtverarbeitetes Trauma. Die Bildungslücke bezüglich Trauma in unserer Gesellschaft ist (gewollt) riesig.
Wir sind eine traumatisierte Gesellschaft, die nicht weiß, dass sie eine traumatisierte Gesellschaft ist.
Viele Menschen haben unverarbeitetes Trauma im Gepäck. Wir haben selbst nach Jahren der Therapie und Selbstreflektion immer noch unverarbeitete Anteile eines Traumas im Gepäck, das wir glaubten, bearbeitet zu haben. Mir ist das bewusst geworden, je besser ich mein eigenes Trauma kennen und lieben gelernt habe.
Eigentlich wollte ich heute kurz etwas über den gesunden Umgang mit Gefühlen schreiben. Beim Schreiben habe ich aber gemerkt, dass ich erstmal etwas über das Haus erzählen muss, bevor ich über die Gäste, die Gefühle, rede. Ich bin das Haus, das durch Verstand und Gefühle belebt wird. Und hinter dem Haus gibt es noch ein ganzes Universum, auf das ich heute nicht eingehen möchte.
Gefühle und Fühlen sind zentral wichtig, wenn man Trauma bearbeiten möchte.
Trauma wird solange aktiviert, bis es bearbeitet wurde.
In einer traumatisierten Gesellschaft wird 24/7 Trauma aktiviert. Und das ist gut so. Die Evolution schläft nicht. Die Evolution schenkt uns Schmerz, damit wir ihr Aufmerksamkeit schenken.
Das Leben liebt uns, und wiederkehrender Schmerz ist wie die Schlummerfunktion am Wecker, die möchte, dass wir aufwachen.
In unserer traumatisierten Gesellschaft klingelt momentan nicht nur der Wecker. Alles, was tönen kann, gibt Signal. Mir kommt es in dieser Zeit manchmal vor, wie wenn sich gleichzeitig , das Kinder-Sinfonieorchester mit sämtlichen Instrumenten einstimmt, jemand mit dem Handy telefoniert, das Fenster zur Hauptstraße offen steht, der Bus anfährt, der Auspuff röhrt, jemand hupt, das Martinshorn aufheult, die Drehorgel spielt, das Pausenzeichen in der Schule ertönt, es an der Tür klingelt und die Kirchenorgel aus allen Pfeifen flötet und brummt.
Aktiviertes Trauma macht ordentlich Krach individuell und erst recht gesellschaftlich gesehen. Und je lauter es ist, desto dringender möchte es bearbeitet werden.
Die Baustelle HERZ zu bearbeiten, lohnt sich. Und Fühlen bringt die Verwandlung.
-
 @ d57360cb:4fe7d935
2025-05-16 14:54:18
@ d57360cb:4fe7d935
2025-05-16 14:54:18I soar all over the world, but one of the places I visit often is this little tiny square opening. I land softly on the platform and peer in through the hole. There’s a man inside; he seems to enjoy when I come by. His eyes light up and he gives me crumbs of bread to eat. The bread is tasty and fulfilling; it satisfies my hunger during my flights to other destinations. I wonder what it’s like to be man.
Man does strange things. I can’t fully understand. For example, this man is confined in a tiny box. He sits on what looks like a deformed tree, and in front of him is a tiny rectangular box. Everything man has is so boxy; it’s unnatural to me. When I fly from place to place, I don’t see any boxes; rather, I see a wiggly world. Endless shape, no two things look the same, but to man, it’s like he wants everything to be the same. Man usually is looking at other thin boxes; these are slim and have marks on them. He appears to stare for a long time at them, and then he sets them down and picks up another to stare at. In his box, he has long, narrow boxes. They hold small boxes bundled together with slim boxes. It gives me a headache seeing so many boxes. Once I observed man outside in the wiggly world, and when he left his big box, he went into another smaller box that moved! I was so interested I followed his moving box. You wouldn’t guess where he went to! Another box, but this one was a big one with subsections of smaller boxes. Could you believe they even have big boxes for water! What a headache man is.
The game man plays is interesting; it seems to be about boxes and how to put wiggly things in them. The wiggly is too elusive; one can’t box it up. Even if you surround the wiggly in a box, it will continue to wiggle. Like a tree confined to a planter box, its roots will spread beyond their confinement. Man is like this but believes the box will contain him, shameful.
-
 @ 4fa5d1c4:fd6c6e41
2025-05-16 13:15:47
@ 4fa5d1c4:fd6c6e41
2025-05-16 13:15:47Willkommen zur Mitmachplattform: KI-Kompetenzen für die religionsbezogene Bildung
Diese Plattform ist ein offenes, gemeinschaftliches Lernmodul für alle, die KI-Kompetenzen im Kontext der religionsbezogenen Bildung entdecken, vertiefen und weitergeben möchten.
Hier können Religionslehrende, Hochschulangehörige und ehrenamtlich Engagierte gemeinsam Inhalte entwickeln, teilen und weiterentwickeln.
Was ist das Ziel?
Wir schaffen eine offene Lernumgebung, in der Materialien zu KI-Kompetenzen für Schule, Hochschule und außerschulische Jugendarbeit kollaborativ entstehen.
Die Plattform richtet sich an Lehrkräfte, Fortbildner:innen und Ehrenamtliche, die KI-Themen in der religiösen Bildung verantwortungsvoll erschließbar machen wollen.
Unser Kompetenzmodell
Im Zentrum steht ein Kreismodell mit vier Kompetenzbereichen, die auf drei Niveaustufen ausdifferenziert sind:
Verstehen, Anwenden, Reflektieren und Gestalten.
Diese Bereiche bauen aufeinander auf, beeinflussen sich gegenseitig und werden durch die zentrale Kompetenz AI Leadership verbunden.Im Zentrum steht ein Kreismodell mit vier Kompetenzbereichen, die auf drei Niveaustufen ausdifferenziert werden können:
Verstehen, Anwenden, Reflektieren und Gestalten.
Diese Bereiche bauen aufeinander auf, beeinflussen sich gegenseitig und werden durch die zentrale Kompetenz AI Leadership verbunden.| Kompetenzbereich | Beschreibung | |------------------|--------------| | 🟢 VERSTEHEN | Grundlagen und Mechanismen von KI | | 🔵 ANWENDEN | KI-Tools im Lernprozess nutzen | | 🟠 REFLEKTIEREN | Kritische Auseinandersetzung mit KI | | 🟣 GESTALTEN | Aktive Weiterentwicklung von KI-Systemen |
Jeder Lerninhalt ist einem Kompetenzbereich (und wenn möglich einer Niveaustufe) zugeordnet – farblich und inhaltlich klar erkennbar.
So funktioniert die Mitmachplattform
- Offene Inhalte: Alle Materialien werden als Markdown-Dateien über Nostr gepflegt.
- Mitmachen leicht gemacht: Egal wo auf Nostr du publizierst, mit den Hashtags #relilab und dem jeweiligen Kompetenzbereich als Schlagwort (also #verstehen, #anwenden, #gestalten, #reflektieren) finden wir diese Hashtagkombination und können die Webseite mit deiner Idee oder Weiterentwicklung ergänzen.
- Anleitungen: Eine eigene Seite erklärt Schritt für Schritt, wie du dich beteiligen kannst – ganz ohne Vorkenntnisse im Programmieren.
- Suchfunktion: Finde gezielt Inhalte nach Kompetenzbereich, Niveaustufe oder Schlagworten.
Für wen ist diese Plattform?
- Lehrkräfte an Schulen und Hochschulen in religionsbezogenen Fächern
- Ehrenamtliche und Multiplikator:innen in der kirchlichen Jugendarbeit
- Fort- und Weiterbildner:innen im Bereich KI und Religion
Mitmachen & Teilen
"Sharing is Caring":
Unser KI-Kompetenzmodell und alle Lernmaterialien stehen unter der offenen Lizenz [CC-BY 4.0].
Du darfst sie frei nutzen, anpassen und weitergeben – mit Nennung der Urheber:innen.
Starte jetzt!
Gemeinsam gestalten wir KI-Kompetenzen für eine reflektierte, verantwortungsvolle und kreative religiöse Bildung im KI-Zeitalter.
Kontakt & Feedback:
Für Fragen, Anregungen oder Feedback antworte einfach auf diese Nachricht oder komm' in den Matrix/Element-Raum #relilab-ki:rpi-virtuell zum Online-Austausch! -
 @ 87fedb9f:0da83419
2025-05-16 12:45:01
@ 87fedb9f:0da83419
2025-05-16 12:45:01Push it! Push it! Push it!
That chant still echoes in my bones, not just from the gym, but from the inside out. I remember watching a bodybuilder once — the weight trembling above him, his muscles bulging and giving out, the spotters swooping in to catch the bar just in time. “Train to failure,” they said. “That’s how you grow.”
And it makes sense, doesn’t it? If you’re being chased by a wild beast, you run until your body gives out. That’s how we’re wired — to survive first and foremost, not necessarily to thrive.
But what if the house we’re building isn’t under threat from wolves? What if we’ve got stone-moving machines and time to breathe? What if we’re not being chased anymore… but we still act like we are?
See, survival patterns are sneaky. They wear masks. They show up in workouts and work days. They dress up in ambition, caffeine, and “just one more thing before I stop.”
I’ve never been a bodybuilder — my brother was — but I’ve tried that route in my own work life. Lift to failure. Push it. Every other day, I’d be nursing another injury to body and mind.
I wasn’t getting stronger. I was just breaking myself in cycles. Push, break, recover, repeat.
I see the same thing with brains. Push it. Adderall. More coffee. Keep going. Hit the wall. And then—collapse.
That’s not strengthening. That’s surviving pretending to be “powerful.”
What happens to the rest of your system when your brain is sucking up all the energy just to stay on task? You stop digesting. You stop feeling the sun on your skin. You stop enjoying your kids’ laughter. Everything feels like something to push through.
That isn’t thriving.
Thriving feels different. It’s alive, yes — there’s activation. But it’s not strained. When we’re in thriving mode, we’re with our energy, not yanking it out by the roots and forcing it to regrow. The muscles — or the mind — are engaged, fluid, expressive. Alive.
It’s a fine line. You can take the same exact action and fill it with stress.
I’ve done it. I’ve turned a perfectly normal task into a survival sprint. It feels ridiculous in hindsight — like, why did I make this email reply into a mountain climb?
Because my primitive brain still whispers, “If you don’t do this perfectly and fast, you’ll die.” Not literally. But the threat feels real. The imagined judgment, the self-criticism, the fear of not being enough — they’re imaginary lions in the tall grass of modern life.
I’ve used this system on myself. I’ve strained my nervous system like fingernails scraping rock to avoid a fall that was never coming.
That’s what we’re supposed to do, right? We bring survival force into every aspect. Into parenting. Into projects. Into relationships.
And we wonder why we’re tired all the time. Not sleepy tired — soul tired. That kind of tired that feels like you ran for your life… but all you did was sit at your desk.
Here’s what I know now: if you’re not actually in danger, you can stop living like you are.
You don’t have to push everything to the edge. You don’t have to prove your strength through strain. Strength can be alive in you — not torn, not depleted, but awake and sustaining.
And when we live from there, the recovery feels different, too. We’re not collapsing. We’re restoring.
We’re not dropping all the pieces and then forcing ourselves to pick them up… again! Instead, we’re crafting a thriving life from the pieces we find, fashion, and consciously put in place.
There’s a wisdom to building your foundation around thriving — not just surviving. And thriving starts with recognizing: it’s not life or death to get through your inbox. Your self-worth isn’t measured by how busy and depleted you are.
Look around. Are you stacking more and more iron to prove something? Or are you listening to the quiet whisper that says, “Yes, move… but don’t hurt yourself doing it.”
And in a life that tells you to push until you fail, choosing to rest and relish — choosing to feel alive rather than just alive-enough — might just be the truest strength there is.
Useful Concepts for Thriving in This Story
-
Primitive Brain\ The primitive brain keeps us on high alert even when we’re safe — it’s time to question whether the lion is real.
-
Unrushed\ Being unrushed is a radical shift from survival tempo to the rhythm of true aliveness.
-
Savvy\ Savvy invites us to work with our energy wisely, not destructively — to choose thriving over proving.
-
Vitality\ Vitality flows when we stop draining ourselves for performance and start living from inner strength.
-
Inspired Action\ Inspired action arises from presence and aliveness, not adrenaline and depletion.
-
-
 @ 8f69ac99:4f92f5fd
2025-05-16 11:40:35
@ 8f69ac99:4f92f5fd
2025-05-16 11:40:35Há algo quase reconfortante na previsibilidade com que certos colunistas abordam Bitcoin: a cada oportunidade, repetem os mesmos chavões, reciclados com indignação moralista e embrulhados numa embalagem de falsa autoridade. O artigo publicado na Visão, com o título dramático "De criança prodígio a adolescente problemático", encaixa-se perfeitamente nesse molde.
Trata-se de uma peça de opinião que mistura factos irrelevantes com interpretações enviesadas, estatísticas sem contexto e um medo mal disfarçado de perder o monopólio da narrativa económica. A autora, Sofia Santos Machado, opta por colar em Bitcoin os desastres do chamado “mundo cripto” como se fossem parte do mesmo fenómeno — ignorando, por conveniência ou ignorância, que Bitcoin não é altcoins, não é NFTs, não é esquemas de yield exótico, e não é fintech vestida de blockchain.
Esta resposta centra-se exclusivamente em Bitcoin — um protocolo monetário aberto, incorruptível e resistente à censura, que já está a servir como salvaguarda de valor em regiões onde o sistema financeiro convencional falhou. Não me interessa defender pirâmides, tokens inflacionários ou aventuras bancárias mal calculadas.
Criticar Bitcoin é legítimo — mas fazê-lo sem saber do que se fala é apenas desinformação.
A Histeria da Água — Falar Sem Saber
O artigo abre com uma pérola alarmista sobre o consumo de água:
“Uma única transacção de bitcoin consome seis milhões de vezes mais água do que um pagamento com cartão.”
Seis. Milhões. De vezes. Resta saber se a autora escreveu isto com cara séria ou a rir-se enquanto bebia água engarrafada dos Alpes Suíços.
Fontes? Metodologia? Contexto? Estou a brincar — isto é a Visão, onde os números são decoração e os factos opcionais.
Claro que comparar transacções na camada base de Bitcoin com pagamentos "instantâneos" da rede Visa é tão rigoroso como comparar um Boeing 747 com um avião de papel porque um voa mais longe. Um artigo sério teria falado em batching, na Lightning Network, ou no facto de que Bitcoin nem sequer compete com a Visa nesse nível, nem em nenhum. Mas isso exigiria, imagine-se, investigação.
Pior ainda, não há qualquer menção ao consumo de água na extracção de ouro, nos data centers bancários, ou no treino de modelos de inteligência artificial. Pelos vistos, só Bitcoin tem de obedecer aos mandamentos ecológicos da Visão. O resto? Santa ignorância selectiva.
Criminosos e o Fantasma do Satoshi
Eis o clássico: “Bitcoin é usado por criminosos”. Um cliché bafiento tirado do baú de 2013, agora reapresentado como se fosse escândalo fresco.
Na realidade, Bitcoin é pseudónimo, não anónimo. Todas as transacções ficam gravadas num livro público — não é propriamente o esconderijo ideal para lavar dinheiro, a menos que sejas fã de disfarces em néon.
E os dados? Claríssimos. Segundo a Chainalysis e a Europol, a actividade ilícita com Bitcoin tem vindo a diminuir. Enquanto isso, os bancos — esses bastiões de confiança — continuam a ser apanhados a lavar biliões para cartéis e cleptocratas. Mas disso a Visão não fala. Devia estragar a narrativa.
O verdadeiro crime aqui é a preguiça intelectual tão profunda que quase merece uma moldura. A Visão tem um editor?
O Espantalho Energético
Como uma criança que acabou de aprender uma palavra nova, a Visão repete “consumo energético” como se fosse um pecado original. Bitcoin usa electricidade — escândalo!
Mas vejamos: o Proof-of-Work não é um defeito. É a razão pela qual Bitcoin é seguro. Não há “desperdício” — há uso, e muitas vezes com energia excedente, renovável, ou que de outro modo seria desperdiçada. É por isso que os mineiros se instalam junto a barragens remotas, queima de gás (flaring), ou parques eólicos no meio do nada — não porque odeiam o planeta, mas porque os incentivos económicos funcionam. Escrevi sobre isso aqui.
O que a Visão convenientemente ignora é que Bitcoin está a ajudar a integrar mais energia renovável nas redes, funcionando como carga flexível. Mas nuance? Trabalho de casa? Esquece lá isso.
Para uma explicação mais séria, podiam ter ouvido o podcast A Seita Bitcoin com o Daniel Batten. Mas para quê investigar?
Cripto = Bitcoin = Fraude?
Aqui chegamos ao buraco negro intelectual: enfiar tudo no mesmo saco. FTX colapsou? Culpa de Bitcoin. Um banqueiro jogou com altcoins? Culpa de Bitcoin. Scam de NFT? Deve ter sido o Satoshi.
Vamos esclarecer: Bitcoin não é “cripto”. Bitcoin é descentralizado, sem líderes, transparente. Não teve pré-mineração, não tem CEO, não promete lucros. O que o rodeia? Tokens centralizados, esquemas Ponzi, pirâmides e vaporware — precisamente o oposto do que Bitcoin representa.
Se um executivo bancário perde o dinheiro dos clientes em Dogecoins, isso é um problema dele. Bitcoin não lhe prometeu nada. Foi a ganância.
E convenhamos: os bancos tradicionais também colapsam. E não precisam de satoshis para isso. Bastam dívidas mal geridas, contabilidade criativa e uma fé cega no sistema.
Culpar Bitcoin por falcatruas “cripto” é como culpar o TCP/IP ou SMTP por emails de phishing. É preguiçoso, desonesto e diz-nos mais sobre a autora do que sobre a tecnologia.
Promessas Por Cumprir? Só Se Não Estiveres a Ver
A "jornalista" da Visão lamenta que “após 15 anos, os riscos são reais mas as promessas por cumprir”. Que promessas? Dinheiro grátis? Cafés pagos com QR codes mágicos?
Bitcoin nunca prometeu fazer cappuccinos mais rápidos. Prometeu soberania monetária, resistência à censura e um sistema previsível. E tem cumprido — diariamente, para milhões. E para o cappuccino, há sempre a Lightning Network.
Pergunta aos venezuelanos, nigerianos, peruanos ou argentinos se Bitcoin falhou. Para muitos, é a única forma de escapar à hiperinflação, ao confisco estatal e à decadência financeira.
Bitcoin não é uma app. É infra-estrutura. É uma nova camada base para o dinheiro global. Não se vê — mas protege, impõe regras e não obedece a caprichos de banqueiros centrais.
E isso assusta. Especialmente quem nunca viveu fora da bolha do euro.
Conclusão: A Visão a Gritar Contra o Progresso
No fim, o artigo da Visão é um festival de clichés, dados errados e ressentimento. Não é só enganador. É desonesto. Culpa a tecnologia pelos erros dos homens. Rejeita o futuro em nome do conforto passado.
Bitcoin não é uma varinha mágica. Mas é a fundação de uma nova liberdade financeira. Uma ferramenta para proteger valor, resistir a abusos e escapar ao controlo constante de quem acha que sabe o que é melhor para ti.
Portanto, fica aqui o desafio, Sofia: se queres criticar Bitcoin, primeiro percebe o que é. Lê o white paper. Estuda. Faz perguntas difíceis.
Caso contrário, és só mais um cão a ladrar para a trovoada — muito barulho, zero impacto.
-
 @ 975e4ad5:8d4847ce
2025-05-16 11:22:20
@ 975e4ad5:8d4847ce
2025-05-16 11:22:20Introduction
Bitcoin and torrents are two technologies that have reshaped how people share information and resources in the digital age. Both are built on decentralized principles and challenge traditional systems—torrents in the realm of file sharing, and Bitcoin in the world of finance. However, while torrents have seen a decline in popularity with the rise of streaming platforms like Netflix and HBO, many wonder whether Bitcoin will follow a similar trajectory or continue to grow as a widely adopted technology. This article explores the similarities between the two technologies, the resilience of torrents against attempts to shut them down, the reasons for their declining popularity, and why Bitcoin is likely to avoid a similar fate.
Similarities Between Torrents and Bitcoin
Torrents and Bitcoin share several key characteristics that make them unique and resilient:
-
Decentralization:\ Torrents rely on peer-to-peer (P2P) networks, where users share files directly with each other without depending on a central server. Similarly, Bitcoin operates on a blockchain—a decentralized network of nodes that maintain and validate transactions. This lack of a central authority makes both technologies difficult to control or shut down.
-
Censorship Resistance:\ Both systems are designed to withstand attempts at restriction. Torrents continue to function even when specific sites like The Pirate Bay are blocked, as the network relies on thousands of users worldwide. Bitcoin is also resistant to government bans, as transactions are processed by a global network of miners.
-
Anonymity and Pseudonymity:\ Torrents allow users to share files without revealing their identities, especially when using VPNs. Bitcoin, while pseudonymous (transactions are public but not directly tied to real-world identities), offers a similar level of privacy, attracting users seeking financial freedom.
-
Open Source:\ Both technologies are open-source, enabling developers to improve and adapt them. This fosters innovation and makes the systems more resilient to attacks.
Why Torrents Cannot Be Stopped
Torrents have persisted despite numerous attempts to curb them due to their decentralized nature. Governments and organizations have shut down sites like The Pirate Bay and Kickass Torrents, but new platforms quickly emerge. The key reasons for their resilience include:
-
P2P Architecture:\ Torrents do not rely on a single server. Every user downloading or sharing a file becomes part of the network, making it impossible to completely dismantle.
-
Global Distribution:\ Millions of users worldwide sustain torrent networks. Even if one country imposes strict regulations, others continue to support the system.
-
Adaptability:\ The torrent community quickly adapts to challenges, using VPNs, proxy servers, or the dark web to bypass restrictions.
Despite this resilience, the popularity of torrents has significantly declined in recent years, particularly among younger users.
The Decline of Torrents: Why They Lost Popularity
In the early 2000s, torrents were the primary way to access movies, music, and software. They were easy to use, free, and offered a vast array of content. However, the rise of streaming platforms like Netflix, HBO, Disney+, and Spotify has changed how people consume media. The main reasons for the decline of torrents include:
-
Convenience:\ Streaming platforms provide instant access to high-quality content without the need for downloading or specialized software. Torrents, in contrast, require technical knowledge and are often slower.
-
Legality and Safety:\ Using torrents carries risks such as viruses, malware, and legal consequences. Streaming services offer a safe and legal alternative.
-
Marketing and Accessibility:\ Platforms like Netflix invest billions in original content and marketing, attracting younger users who prefer easy access over free but risky downloads.
-
Social Shifts:\ Younger generations, raised with access to subscription services, are often unfamiliar with torrents or view them as outdated. Studies from 2023 indicate that only a small percentage of people under 25 regularly use torrents.
Despite this decline, torrents have not disappeared entirely. They are still used in regions with limited access to streaming services or by users who value free access to niche content.
Why Bitcoin Will Not Share the Fate of Torrents
Despite the similarities, Bitcoin has unique characteristics that make it more likely to achieve mainstream adoption rather than being overshadowed by alternatives. Here are the key reasons:
-
Financial Revolution:\ Bitcoin addresses problems that lack direct alternatives. It enables transactions without intermediaries, which is particularly valuable in countries with unstable currencies or limited banking access. Unlike torrents, which were replaced by more convenient streaming platforms, traditional financial systems still have flaws that Bitcoin addresses.
-
Institutional Adoption:\ Major companies like Tesla, PayPal, and Square accept Bitcoin or invest in it. Financial institutions, including JPMorgan and Goldman Sachs, are developing cryptocurrency-related products. This institutional acceptance boosts Bitcoin’s credibility and legitimacy, something torrents never achieved.
-
Limited Supply:\ Bitcoin’s fixed supply of 21 million coins makes it attractive as a store of value, similar to gold. This characteristic distinguishes it from other technologies and gives it potential for long-term growth.
-
Technological Advancements:\ The Bitcoin network evolves through improvements like the Lightning Network, which makes transactions faster and cheaper. These innovations make it competitive with traditional payment systems, whereas torrents failed to adapt to streaming technologies.
-
Global Financial Integration:\ Unlike torrents, which remained in the niche of file sharing, Bitcoin has the potential to integrate into the global financial system. Countries like El Salvador have already recognized it as legal tender, and others may follow suit.
-
Cultural and Economic Significance:\ Bitcoin is perceived not only as a technology but also as a movement for financial independence and decentralization. This ideology attracts young people and tech enthusiasts, making it more resilient to the social shifts that affected torrents.
Conclusion
Torrents and Bitcoin share common roots as decentralized technologies that challenge the status quo. However, while torrents lost popularity due to the rise of more convenient and legal alternatives, Bitcoin has the potential to avoid this fate. Its ability to address real financial problems, institutional adoption, and technological advancements make it a likely candidate for mainstream use in the future. While torrents remained a niche technology, Bitcoin is emerging as a global force that could transform how the world perceives money.
-
-
 @ 4fa5d1c4:fd6c6e41
2025-05-16 11:42:12
@ 4fa5d1c4:fd6c6e41
2025-05-16 11:42:12Bibel-Selfies
Prompts
Eva, Schlange, Apfel und Adam

A selfie of a woman resembling eve in the time of old testament, blurred body, holding an apple, kneeling in front adam. he has a shocked expression with his mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with a huge snake behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with adam and eve, possibly at a place like garden eden. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Tochter des Pharao mit Mose

A selfie of the biblical figure moabite woman with her baby in front of an oasis. She is wearing traditional and has black hair. The background shows water from the desert oasis and grasses around it. In the Background a wicker basket on the water. The photo was taken in the style of a selfie shot with GoPro cameraSimon Petrus

A selfie of a man resembling Simon Petrus, wearing a white robe, surrounded by waves and thunderstorm. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many waves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus at the dead sea, possibly at a place like the sea. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Zachäus auf dem Baum
A selfie of a man resembling a roman in the time of jesus, wearing a glamorous robe, surrounded by the crown of a tree. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many leaves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Maria am Ostermorgen

A selfie of a woman resembling maria in the time of jesus, wearing a robe, kneeling in front of stone grave. she has a shocked expression with her mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with the open glowing grave behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus resurrection, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Der verlorene Sohn bei den Schweinen

A young ancient arabic man with short hair in the time of jesus, brown eyes, and a dirty face, covered in mud from working on his pig farm, takes an amateur selfie at dusk. He is surrounded by pig stables, with a barn visible in the background and pigs seen near the front. The photo captures a raw, authentic moment, as he gazes directly into the camera with an expression of excitement or wonder. The image has a realistic style, akin to Unsplash photography, and is meant to be posted on a primitive-themed social network. The resolution of the photo is high, style of selfie with gopro --v 6.0Vater und Sohn vereint
 A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0
A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0Bartimäus

A selfie of a man resembling blind bartimaeus in the time of jesus, black and brown and white bandages on his head over his eyes and face, wearing a robe, kneeling in front of a market place. he has a shocked expression with his mouth open and wide eyes still covered with black and brown and white bandages on his head, evoking a sense of both fear and surprise. The scene appears surreal, with many sand behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus healing the blind, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Daniel in der Löwengrube

A selfie of a man resembling Jesus, wearing a beige hoodie, surrounded by lions and cheetahs. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many lions behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a lion's den, possibly at a place like the Grand Tabahar. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan ChaudharyDavid und Goliath

selfie of a the boy and shepherd david holding his slingshot resembling a fight with the giant goliath in the time of old testament, wearing a glamorous sligshot focusing on his giant opponent. David has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a desert surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of the scene of David fighting with the giant goliath with his slingshot, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Simson im Philistertempel

A selfie of a man resembling simson in the time of old testament, wearing a glamorous beard and long hair, surrounded by thousands of ancient fighters. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a temple surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Jona und der Wal

A selfie of a man resembling israeli jona in the time of old testament,`wearing a glamorous beard and long hair, inside the body of a whale. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with the ocean surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene in the bible. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary
Jakob und Isaak

A selfie of a young man resembling an ancient Arabic in clothes made of skins of goats and furs of the goats, looking overwhelmed and distressed as he betrays his father, who blesses him. The scene shows a dawn sky with hints of the sunrise, evoking a surreal and dramatic atmosphere. The scene is set in ancient Jerusalem, with stone buildings. in the background an old man with a gesture of blessing, rising his hands to the sky, The photo is taken with a wide-angle lens, blending surrealism with humor. The style is reminiscent of a GoPro selfie, capturing the intense moment with a sense of both fear and surprisePetrus und der Hahn

A selfie of a man resembling ancient young arabic man saint in traditional biblical attire, being eaten by a whale,. he has a shocked expression with his mouth pressed and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with one rooster crowing out loud behind the man. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with peter and the rooster, possibly at a place in jerusalem . The style of the photo blends surrealism with humor, go pro selfie, morning dawn near sunrise settingJosef im Brunnen

A selfie of an ancient israelian man with a magical dreamcoat clothing in a deep well, looking at the camera from above, captured in the style of a go pro selfie stickElia und die Raben

A close-up selfie of a bearded man (Elijah) in biblical clothing, smiling gratefully. He is standing near a stream in a secluded, rocky area. Several black ravens are perched on his shoulders and arms, holding pieces of bread and meat in their beaks. The scene has a warm, golden light, symbolizing God's provision. Photorealistic style, high detail.Absalom im Baum

A selfie of a man resembling of a young man (Absalom) with long hair knotted arount the branches of a large oak tree.. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with all of his hairs knotted around the tree. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene of a robin hood movie in the forest . The style of the photo blends surrealism with humorRuth und Boas im Weizenfeld

A selfie of a young woman resembling Ruth, with a radiant smile and sun-kissed skin. She's standing in a golden wheat field at sunset, her arms filled with freshly gathered sheaves of wheat. Her hair is partially covered with a simple headscarf, with loose strands blowing in the wind. She has a look of joy and gratitude in her eyes. The scene appears idyllic, with wheat stalks seeming to embrace her. In the background, a distinguished older man (Boaz) can be seen watching from a distance, his expression a mix of curiosity and admiration. The photo is taken with a wide-angle lens, capturing the vastness of the field, the warmth of the setting sun, and Boaz in the distance. The setting is reminiscent of a biblical harvest scene. The style of the photo blends realism with a touch of romantic nostalgia."Bibel-Selfies" von Jörg Lohrer Lizenz: CC0 1.0
.
`
-
 @ 91bea5cd:1df4451c
2025-05-16 11:07:16
@ 91bea5cd:1df4451c
2025-05-16 11:07:16Instruções:
- Leia cada pergunta cuidadosamente.
- Escolha a opção (A, B, C ou D) que melhor descreve você na maioria das situações. Seja o mais honesto possível.
- Anote a letra correspondente à sua escolha para cada pergunta.
- No final, some quantas vezes você escolheu cada letra (A, B, C, D).
- Veja a seção de resultados para interpretar sua pontuação.
Teste de Temperamento
1. Em um evento social (festa, reunião), como você geralmente se comporta? A) Sou o centro das atenções, converso com todos, faço piadas e animo o ambiente. B) Tomo a iniciativa, organizo atividades ou discussões, e gosto de liderar conversas. C) Prefiro observar, conversar em grupos menores ou com pessoas que já conheço bem, e analiso o ambiente. D) Sou tranquilo, ouvinte, evito chamar atenção e me adapto ao ritmo do grupo.
2. Ao enfrentar um novo projeto ou tarefa desafiadora no trabalho ou estudo: A) Fico entusiasmado com a novidade, tenho muitas ideias iniciais, mas posso me distrair facilmente. B) Defino metas claras, crio um plano de ação rápido e foco em alcançar resultados eficientemente. C) Analiso todos os detalhes, planejo meticulosamente, prevejo possíveis problemas e busco a perfeição. D) Abordo com calma, trabalho de forma constante e organizada, e prefiro um ambiente sem pressão.
3. Como você geralmente reage a críticas? A) Tento levar na esportiva, talvez faça uma piada, mas posso me magoar momentaneamente e logo esqueço. B) Defendo meu ponto de vista vigorosamente, posso ficar irritado se sentir injustiça, mas foco em corrigir o problema. C) Levo muito a sério, analiso profundamente, posso me sentir magoado por um tempo e repenso minhas ações. D) Escuto com calma, considero a crítica objetivamente e tento não levar para o lado pessoal, buscando a paz.
4. Qual seu estilo de tomada de decisão? A) Sou impulsivo, decido rapidamente com base no entusiasmo do momento, às vezes me arrependo depois. B) Sou decidido e rápido, foco no objetivo final, às vezes sem considerar todos os detalhes ou sentimentos alheios. C) Sou ponderado, analiso todas as opções e consequências, demoro para decidir buscando a melhor escolha. D) Sou cauteloso, prefiro evitar decisões difíceis, busco consenso ou adio se possível.
5. Como você lida com rotina e repetição? A) Acho entediante rapidamente, preciso de variedade e novidade constante para me manter engajado. B) Tolero se for necessário para atingir um objetivo, mas prefiro desafios e mudanças que eu controlo. C) Aprecio a ordem e a previsibilidade, me sinto confortável com rotinas bem estabelecidas. D) Adapto-me bem à rotina, acho confortável e seguro, não gosto de mudanças bruscas.
6. Em uma discussão ou conflito: A) Tento aliviar a tensão com humor, expresso meus sentimentos abertamente, mas não guardo rancor. B) Sou direto e assertivo, defendo minha posição com firmeza, posso parecer confrontador. C) Evito confronto direto, mas fico remoendo o problema, analiso os argumentos e posso guardar ressentimento. D) Busco a conciliação, tento entender todos os lados, sou diplomático e evito o conflito a todo custo.
7. Como você expressa seus sentimentos (alegria, tristeza, raiva)? A) Expresso de forma aberta, intensa e visível, minhas emoções mudam rapidamente. B) Expresso de forma direta e forte, principalmente a raiva ou a determinação, controlo emoções "fracas". C) Tendo a internalizar, minhas emoções são profundas e duradouras, posso parecer reservado. D) Sou contido na expressão emocional, mantenho a calma externamente, mesmo que sinta algo internamente.
8. Qual seu nível de energia habitual? A) Alto, sou muito ativo, falante e entusiasmado, gosto de estar em movimento. B) Muito alto e direcionado, tenho muita energia para perseguir meus objetivos e liderar. C) Variável, posso ter picos de energia para projetos que me interessam, mas também preciso de tempo quieto para recarregar. D) Moderado e constante, sou calmo, tranquilo, prefiro atividades menos agitadas.
9. Como você organiza seu espaço de trabalho ou sua casa? A) Pode ser um pouco caótico e desorganizado, com muitas coisas interessantes espalhadas. B) Organizado de forma funcional para máxima eficiência, focado no essencial para as tarefas. C) Extremamente organizado, metódico, cada coisa em seu lugar, prezo pela ordem e estética. D) Confortável e prático, não necessariamente impecável, mas funcional e sem excessos.
10. O que mais te motiva? A) Reconhecimento social, diversão, novas experiências e interações. B) Poder, controle, desafios, alcançar metas ambiciosas e resultados concretos. C) Qualidade, significado, fazer as coisas da maneira certa, compreensão profunda. D) Paz, estabilidade, harmonia nos relacionamentos, evitar estresse e pressão.
11. Como você reage a imprevistos ou mudanças de plano? A) Adapto-me rapidamente, às vezes até gosto da novidade, embora possa atrapalhar meus planos iniciais. B) Fico irritado com a perda de controle, mas rapidamente busco uma solução alternativa para manter o objetivo. C) Sinto-me desconfortável e ansioso, preciso de tempo para reavaliar e replanejar cuidadosamente. D) Aceito com calma, sou flexível e me ajusto sem muito alarde, desde que não gere conflito.
12. Qual o seu maior medo (em termos gerais)? A) Ser rejeitado, ignorado ou ficar entediado. B) Perder o controle, parecer fraco ou incompetente. C) Cometer erros graves, ser inadequado ou imperfeito. D) Conflitos, pressão, tomar decisões erradas que afetem a estabilidade.
13. Como você costuma passar seu tempo livre? A) Socializando, saindo com amigos, buscando atividades novas e divertidas. B) Engajado em atividades produtivas, esportes competitivos, planejando próximos passos. C) Lendo, estudando, refletindo, dedicando-me a hobbies que exigem atenção e cuidado. D) Relaxando em casa, assistindo filmes, lendo tranquilamente, passando tempo com a família de forma calma.
14. Ao trabalhar em equipe: A) Sou o animador, trago ideias, conecto as pessoas, mas posso ter dificuldade em focar nos detalhes. B) Assumo a liderança naturalmente, delego tarefas, foco nos resultados e mantenho todos na linha. C) Sou o planejador e o crítico construtivo, atento aos detalhes, garanto a qualidade, mas posso ser muito exigente. D) Sou o pacificador e o colaborador, ajudo a manter a harmonia, realizo minhas tarefas de forma confiável.
15. Como você lida com prazos? A) Muitas vezes deixo para a última hora, trabalho melhor sob a pressão do prazo final, mas posso me atrapalhar. B) Gosto de terminar bem antes do prazo, vejo o prazo como um desafio a ser superado rapidamente. C) Planejo o tempo cuidadosamente para cumprir o prazo com qualidade, fico ansioso se o tempo fica curto. D) Trabalho em ritmo constante para cumprir o prazo sem estresse, não gosto de correria.
16. Qual destas frases mais te descreve? A) "A vida é uma festa!" B) "Se quer algo bem feito, faça você mesmo (ou mande fazer do seu jeito)." C) "Tudo tem um propósito e um lugar certo." D) "Devagar se vai ao longe."
17. Em relação a regras e procedimentos: A) Gosto de flexibilidade, às vezes acho as regras limitantes e tento contorná-las. B) Uso as regras a meu favor para atingir objetivos, mas não hesito em quebrá-las se necessário e se eu puder controlar as consequências. C) Sigo as regras rigorosamente, acredito que elas garantem ordem e qualidade. D) Respeito as regras para evitar problemas, prefiro seguir o fluxo estabelecido.
18. Como você reage quando alguém está emocionalmente abalado? A) Tento animar a pessoa, conto piadas, ofereço distração e companhia. B) Ofereço soluções práticas para o problema, foco em resolver a situação que causou o abalo. C) Escuto com empatia, ofereço apoio profundo e tento compreender a dor da pessoa. D) Mantenho a calma, ofereço um ouvido atento e um ombro amigo, sem me deixar abalar muito.
19. Que tipo de filme ou livro você prefere? A) Comédias, aventuras, romances leves, algo que me divirta e me mantenha entretido. B) Ação, suspense, biografias de líderes, estratégias, algo que me desafie ou inspire poder. C) Dramas profundos, documentários, mistérios complexos, ficção científica filosófica, algo que me faça pensar e sentir. D) Histórias tranquilas, dramas familiares, romances amenos, natureza, algo que me relaxe e traga conforto.
20. O que é mais importante para você em um relacionamento (amizade, amoroso)? A) Diversão, cumplicidade, comunicação aberta e espontaneidade. B) Lealdade, objetivos em comum, apoio mútuo nas ambições. C) Compreensão profunda, fidelidade, apoio emocional e intelectual. D) Harmonia, estabilidade, aceitação mútua e tranquilidade.
21. Se você ganhasse na loteria, qual seria sua primeira reação/ação? A) Faria uma grande festa, viajaria pelo mundo, compraria presentes para todos! B) Investiria estrategicamente, planejaria como multiplicar o dinheiro, garantiria o controle financeiro. C) Pesquisaria as melhores opções de investimento, faria um plano detalhado de longo prazo, doaria para causas significativas. D) Guardaria a maior parte em segurança, faria algumas melhorias práticas na vida, evitaria mudanças drásticas.
22. Como você se sente em relação a riscos? A) Gosto de arriscar se a recompensa parecer divertida ou excitante, sou otimista. B) Calculo os riscos e assumo-os se acreditar que a recompensa vale a pena e que posso controlar a situação. C) Evito riscos desnecessários, prefiro a segurança e a previsibilidade, analiso tudo antes de agir. D) Desgosto de riscos, prefiro caminhos seguros e comprovados, a estabilidade é mais importante.
23. Sua memória tende a focar mais em: A) Momentos divertidos, pessoas interessantes, experiências marcantes (embora possa esquecer detalhes). B) Sucessos, fracassos (para aprender), injustiças cometidas contra você, quem te ajudou ou atrapalhou. C) Detalhes precisos, conversas significativas, erros cometidos (por você ou outros), sentimentos profundos. D) Fatos objetivos, rotinas, informações práticas, geralmente de forma neutra.
24. Quando aprende algo novo, você prefere: A) Experimentar na prática imediatamente, aprender fazendo, mesmo que cometa erros. B) Entender o objetivo e a aplicação prática rapidamente, focar no essencial para usar o conhecimento. C) Estudar a fundo a teoria, entender todos os porquês, buscar fontes confiáveis e dominar o assunto. D) Aprender em um ritmo calmo, com instruções claras e passo a passo, sem pressão.
25. Se descreva em uma palavra (escolha a que mais se aproxima): A) Entusiasmado(a) B) Determinado(a) C) Criterioso(a) D) Pacífico(a)
26. Como você lida com o silêncio em uma conversa? A) Sinto-me desconfortável e tento preenchê-lo rapidamente com qualquer assunto. B) Uso o silêncio estrategicamente ou o interrompo para direcionar a conversa. C) Posso apreciar o silêncio para refletir, ou me sentir um pouco ansioso dependendo do contexto. D) Sinto-me confortável com o silêncio, não sinto necessidade de preenchê-lo.
27. O que te deixa mais frustrado(a)? A) Tédio, falta de reconhecimento, ser ignorado. B) Incompetência alheia, falta de controle, obstáculos aos seus planos. C) Desorganização, falta de qualidade, injustiça, superficialidade. D) Conflitos interpessoais, pressão excessiva, desordem emocional.
28. Qual a sua relação com o passado, presente e futuro? A) Foco no presente e nas oportunidades imediatas, otimista em relação ao futuro, esqueço o passado facilmente. B) Foco no futuro (metas) e no presente (ações para alcançá-las), aprendo com o passado mas não me prendo a ele. C) Reflito muito sobre o passado (aprendizados, erros), analiso o presente e planejo o futuro com cautela, às vezes com preocupação. D) Vivo o presente de forma tranquila, valorizo a estabilidade e a continuidade do passado, vejo o futuro com serenidade.
29. Se você tivesse que organizar um evento, qual seria seu papel principal? A) Relações públicas, divulgação, animação, garantir que todos se divirtam. B) Coordenação geral, definição de metas, delegação de tarefas, garantir que tudo aconteça conforme o planejado (por você). C) Planejamento detalhado, logística, controle de qualidade, garantir que nada dê errado. D) Suporte, resolução de problemas de forma calma, garantir um ambiente harmonioso.
30. Qual ambiente de trabalho te agrada mais? A) Dinâmico, social, com muita interação, flexibilidade e novidades. B) Competitivo, desafiador, focado em resultados, onde eu possa liderar ou ter autonomia. C) Estruturado, quieto, onde eu possa me concentrar, com padrões claros de qualidade e tempo para análise. D) Estável, cooperativo, sem pressão, com relacionamentos harmoniosos e tarefas previsíveis.
Calculando seus Resultados:
Agora, conte quantas vezes você escolheu cada letra:
- Total de A: ______
- Total de B: ______
- Total de C: ______
- Total de D: ______
A letra (ou as letras) com a maior pontuação indica(m) seu(s) temperamento(s) dominante(s).
Interpretação dos Resultados:
-
Se sua maior pontuação foi A: Temperamento SANGUÍNEO Dominante
- Características: Você é extrovertido, otimista, sociável, comunicativo, entusiasmado e adora novidades. Gosta de ser o centro das atenções, faz amigos facilmente e contagia os outros com sua energia. É criativo e espontâneo.
- Pontos Fortes: Carismático, inspirador, adaptável, bom em iniciar relacionamentos e projetos, perdoa facilmente.
- Desafios Potenciais: Pode ser indisciplinado, desorganizado, impulsivo, superficial, ter dificuldade em focar e terminar tarefas, e ser muito dependente de aprovação externa.
-
Se sua maior pontuação foi B: Temperamento COLÉRICO Dominante
- Características: Você é enérgico, decidido, líder nato, orientado para metas e resultados. É ambicioso, assertivo, direto e não tem medo de desafios ou confrontos. Gosta de estar no controle e é muito prático.
- Pontos Fortes: Determinado, eficiente, líder natural, bom em tomar decisões e resolver problemas, autoconfiante.
- Desafios Potenciais: Pode ser impaciente, dominador, teimoso, insensível aos sentimentos alheios, propenso à raiva e a "atropelar" os outros para atingir seus objetivos.
-
Se sua maior pontuação foi C: Temperamento MELANCÓLICO Dominante
- Características: Você é introvertido, analítico, sensível, perfeccionista e profundo. É leal, dedicado, aprecia a beleza e a ordem. Tende a ser pensativo, criterioso e busca significado em tudo. Leva as coisas a sério.
- Pontos Fortes: Detalhista, organizado, criativo (em profundidade), leal, empático, comprometido com a qualidade e a justiça.
- Desafios Potenciais: Pode ser pessimista, excessivamente crítico (consigo e com os outros), indeciso (pela análise excessiva), guardar ressentimentos, ser propenso à tristeza e ao isolamento.
-
Se sua maior pontuação foi D: Temperamento FLEUMÁTICO Dominante
- Características: Você é calmo, tranquilo, equilibrado e diplomático. É observador, paciente, confiável e fácil de conviver. Evita conflitos, busca harmonia e estabilidade. É um bom ouvinte e trabalha bem sob rotina.
- Pontos Fortes: Pacífico, estável, confiável, bom ouvinte, diplomático, eficiente em tarefas rotineiras, mantém a calma sob pressão.
- Desafios Potenciais: Pode ser indeciso, procrastinador, resistente a mudanças, parecer apático ou sem entusiasmo, ter dificuldade em se impor e expressar suas próprias necessidades.
Combinações de Temperamentos:
É muito comum ter pontuações altas em duas letras. Isso indica uma combinação de temperamentos. Por exemplo:
- Sanguíneo-Colérico: Extrovertido, enérgico, líder carismático, mas pode ser impulsivo e dominador.
- Sanguíneo-Fleumático: Sociável e agradável, mas pode ter dificuldade com disciplina e iniciativa.
- Colérico-Melancólico: Líder focado e detalhista, muito capaz, mas pode ser excessivamente crítico e exigente.
- Melancólico-Fleumático: Quieto, confiável, analítico, mas pode ser indeciso e resistente a riscos.
Importante: Este teste é uma ferramenta de autoconhecimento. Ninguém se encaixa perfeitamente em uma única caixa. Use os resultados para entender melhor suas tendências naturais, seus pontos fortes e as áreas onde você pode buscar equilíbrio e desenvolvimento.
-
 @ e4950c93:1b99eccd
2025-05-16 10:14:50
@ e4950c93:1b99eccd
2025-05-16 10:14:50Joha est une marque danoise qui crée des vêtements en laine mérinos, coton biologique, viscose de bambou biologique et soie pour les bébés, les enfants et les femmes.
Matières naturelles utilisées dans les produits
- Coton (biologique)
- Laine (mérinos)
- Soie
- Cellulose régénérée (cupra, lyocell, modal, rayonne, viscose) (bambou biologique)
⚠️ Attention, certains produits de cette marque contiennent des matières non naturelles, dont : - Elasthanne, lycra, spandex - Polyamides, nylon
Catégories de produits proposés
Cette marque propose des produits intégralement en matière naturelle dans les catégories suivantes :
Vêtements
- Tailles vêtements: bébés, enfants, femmes
- Sous-vêtements: culottes
- Une pièce:
- Hauts: débardeurs, t-shirts
- Bas: pantalons, leggings
- Tête et mains: bonnets, cagoules, moufles
- Nuit: pyjamas
Chaussures
- Tailles chaussures: chaussures bébé
- Chaussons: botillons
Autres informations
- Certification Oeko-Tex Standard 100
- Certification Woolmark
- Déclaration de laine de mouton sans mulesing et de bien-être animal (Südwolle group GmbH)
👉 En savoir plus sur le site de la marque
Où trouver leurs produits ?
- Luna & Curious (en anglais, zone de livraison : RU et international)
- Niddle Noddle (en anglais, zone de livraison : RU et international)
- Chlidren Salon (en anglais, zone de livraison : RU et international)
- Lieblings Paris
Cet article est publié sur origine-nature.com 🌐 See this article in English
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises les produits de cette marque ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don, pour remercier les contribut-eur-ice-s.
-
 @ b423e216:3280b1c0
2025-05-16 08:27:58
@ b423e216:3280b1c0
2025-05-16 08:27:58Im digitalen Zeitalter wird der Schutz der Privatsphäre immer wichtiger. Unabhängig davon, ob es sich um eine Regierungsbehörde, ein Unternehmen oder eine Einzelperson handelt, besteht für alle das Risiko, abgehört oder verfolgt zu werden. Mobiltelefone, WLAN, GPS und UHF-Geräte (Ultrahochfrequenz) können zu Werkzeugen für Hacker oder Überwachungsgeräte werden. Um diesen Bedrohungen entgegenzuwirken, sind Signalstörsender (wie etwa Tragbare Handyblocker, WLAN-Störsender, GPS-Störsender und UHF-Störsender) zu einem wirksamen Mittel zum Schutz der Privatsphäre geworden. In diesem Artikel werden die verschiedenen Arten von Störsendern erläutert, wie sie funktionieren und wie man sie legal und angemessen einsetzt, um Abhören und Tracking zu verhindern.
1. Was ist ein Signalstörsender?
Ein Signalstörsender ist ein elektronisches Gerät, das die Kommunikationssignale eines Zielgeräts durch die Aussendung von Radiowellen einer bestimmten Frequenz stört oder blockiert. Es kann Mobiltelefonanrufe, WLAN-Verbindungen, GPS-Positionierung oder UHF-Signalübertragungen blockieren, um Abhören oder Tracking zu verhindern.
Das Funktionsprinzip eines Störsenders besteht darin, ein Rauschsignal mit hoher Intensität an das Zielfrequenzband zu senden, wodurch es für das empfangende Gerät unmöglich wird, das ursprüngliche Signal richtig zu interpretieren. Beispielsweise blockiert ein Handy-Störsender die Kommunikation zwischen einem Handy und einer Basisstation, sodass mit dem Handy weder Anrufe getätigt noch Textnachrichten empfangen werden können.
2. Gängige Arten von Signalstörern
(1) Handy-Störsender
Tragbare störsender für handy werden hauptsächlich verwendet, um GSM-, 3G UMTS-, 4G- und 5G-Signale zu blockieren. Es kann verhindern, dass das Telefon überwacht oder geortet wird und eignet sich für die folgenden Szenarien:
- Abhören verhindern: Verhindern Sie, dass das Mikrofon Ihres Telefons während wichtiger Besprechungen oder privater Gespräche aus der Ferne aktiviert wird.
- Anti-Tracking: Blockieren Sie die GPS- und Mobilfunknetzortung, um die Verfolgung durch Malware oder Hacker zu verhindern.
- Prävention von Prüfungsbetrug: Wird in Schulen oder Prüfungssälen verwendet, um zu verhindern, dass Kandidaten mit Mobiltelefonen schummeln.
(2) WLAN-Störsender
WLAN-Störsender können drahtlose Netzwerksignale in den Frequenzbändern 2,4 GHz und 5 GHz blockieren und eignen sich für:
- Hacking verhindern: Blockieren Sie WLAN-Signale in der Nähe, um Datendiebstahl zu verhindern.
- Smart-Home-Geräte schützen: Verhindern Sie die Fernsteuerung von Smart-Kameras, Lautsprechern und anderen Geräten.
- Militärische oder staatliche vertrauliche Bereiche: Verhindern Sie, dass durch drahtlose Signale vertrauliche Informationen preisgegeben werden.
(3) GPS-Störsender
GPS-Störsender können Satellitenpositionierungssignale blockieren, um die Verfolgung von Fahrzeugen oder Mobiltelefonen zu verhindern. Sie eignen sich für:
- Schützen Sie Ihre Privatsphäre: Verhindern Sie, dass Mitfahrdienste, Essenslieferdienste oder Malware Ihren Aufenthaltsort aufzeichnen.
- Militärische Nutzung: Verhindern, dass Drohnen oder Raketen für ihren Angriff auf GPS-Navigation angewiesen sind.
- Anti-Aufklärung: Verhindern Sie Wirtschaftsspionage oder die Verfolgung von Logistikfahrzeugen durch Wettbewerber.
(4) UHF-Störsender
UHF Jammer (Ultra High Frequency) werden hauptsächlich verwendet, um drahtlose Kommunikation im Frequenzband von 300 MHz bis 3 GHz zu blockieren, wie z. B. Walkie-Talkies, drahtlose Mikrofone, RFID usw. und eignen sich für:
- Verhindern Sie drahtloses Abhören: Blockieren Sie drahtlose Abhörgeräte, die von Spionen verwendet werden.
- RFID-Daten schützen: Verhindern Sie das illegale Scannen von Kreditkarten oder Zugangskarten.
- Anti-Drohnen-Störsender: Blockiert die Fernbedienungssignale von Drohnen, um zu verhindern, dass sie sich sensiblen Bereichen nähern.
3. Wie verwendet man Signalstörsender richtig, um die Privatsphäre zu schützen?
Obwohl Störsender das Abhören und Verfolgen wirksam verhindern können, kann eine unsachgemäße Verwendung gegen das Gesetz verstoßen oder die normale Kommunikation beeinträchtigen. Hier sind einige Vorschläge für den legalen und sinnvollen Einsatz von Störsendern:
(1) Verstehen Sie die örtlichen Gesetze
- In vielen Ländern ist die unbefugte Verwendung von Störsendern illegal und kann zu Geldstrafen oder strafrechtlichen Konsequenzen führen.
- Nur zur Verwendung im privaten Bereich oder dort, wo dies gesetzlich zulässig ist, z. B. beim Militär, in der Regierung oder bei der Unternehmenssicherheit.
(2) Wählen Sie den entsprechenden Störbereich
- WLAN Signal Blocker mit geringer Leistung eignen sich für kleine Besprechungsräume oder Fahrzeuge, um die Kommunikation in der Umgebung nicht zu beeinträchtigen.
- In großen Veranstaltungsorten können Störsender mit hoher Leistung eingesetzt werden, dabei ist jedoch Vorsicht geboten, um die öffentliche Kommunikation nicht zu stören.
(3) Kombiniert mit anderen Sicherheitsmaßnahmen
- Störsender sind nur eine vorübergehende Lösung. Für einen langfristigen Schutz der Privatsphäre ist die Verwendung verschlüsselter Kommunikation, VPNs, Abhörgeräte usw. erforderlich.
(4) Regelmäßige Überprüfung der Ausrüstung
- Störsender können aufgrund von Änderungen der Signalstärke unwirksam werden und müssen regelmäßig getestet und angepasst werden.
4. Einschränkungen von Störsendern
Obwohl Störsender Signale wirksam blockieren können, unterliegen sie dennoch einigen Einschränkungen:
- Verhindert kein kabelgebundenes Abhören: Störsender wirken nur gegen drahtlose Signale und schützen nicht vor physischen Abhörgeräten (wie versteckten Mikrofonen).
- Kann legitime Kommunikation beeinträchtigen: Störsender blockieren wahllos Signale, was Notrufe oder die normale WLAN-Nutzung beeinträchtigen kann.
- Kann durch Anti-Jamming-Technologie geknackt werden: Einige fortschrittliche Geräte verwenden möglicherweise Frequenzsprungtechnologie (z. B. militärische Kommunikation), die von gewöhnlichen Störsendern nur schwer vollständig blockiert werden kann.
5. Alternativen: Sicherere Methoden zum Schutz der Privatsphäre
Wenn der Einsatz von Auto GPS Tracker Störsender eingeschränkt ist, ziehen Sie die folgenden Alternativen in Betracht:
- Verwenden Sie einen Faradayschen Käfig: Eine metallische Abschirmhülle oder ein Raum, der drahtlose Signale vollständig blockiert.
- Flugmodus aktivieren: Durch das Ausschalten der drahtlosen Mobiltelefonkommunikation wird die Fernaktivierung des Mikrofons verhindert.
- Verwenden Sie verschlüsselte Kommunikationstools: z. B. Anwendungen mit End-to-End-Verschlüsselung wie Signal, ProtonMail usw.
abschließend
Ein Signalstörsender ist ein leistungsstarkes Tool zum Schutz der Privatsphäre, das das Abhören von Mobiltelefonen, WLAN-Hacking, GPS-Tracking und UHF-Überwachung wirksam verhindern kann. Allerdings ist die Verwendung gesetzlich eingeschränkt und sollte mit Vorsicht verwendet werden. Durch die Kombination von Störsendern mit anderen Sicherheitsmaßnahmen (wie verschlüsselter Kommunikation und physischer Abschirmung) kann die Privatsphäre im Rahmen des gesetzlich Gegebenen weitestgehend vor Verletzungen geschützt werden. Mit der Entwicklung von Technologien zum Abhören von Störsendern könnten diese in Zukunft intelligenter und präziser werden und sich zu einem wichtigen Mittel zum Schutz der Privatsphäre entwickeln.
- https://www.signaljammerphone.com/de/echte-gefahren-durch-versteckte-kameras-und-ein-leitfaden-zur-abwehr.html
- https://www.signaljammerphone.com/de/J-DR6-leistungsstarker-tragbare-rucksack-drohnen-fernsteuerungs-stoerer-300W.html
- https://www.signaljammerphone.com/de/wie-kann-man-funkwellen-wirksam-blockieren-funkwellenabschirmung-und-stoertechnologie.html
-
 @ 94215f42:7681f622
2025-05-16 08:18:52
@ 94215f42:7681f622
2025-05-16 08:18:52Value Creation at the Edge
The conversation around artificial intelligence has largely centered on the technology itself, the capabilities of large language models, the race for more parameters, and the competition between AI companies.
He with the most data / biggest model / biggest platform wins all.
As we're been exploring in recent "Good Stuff" podcasts, the true business model of AI may be much more straightforward. AI is after all a productivity tool with little technical moat, in fact the existence of AI coding and learning tools quickly chop away at this moat even quicker!.\ \ We believe that the it's about transforming traditional human heavy businesses by dramatically reducing operational costs while maintaining or increasing output.
AI is poised to create value not primarily for AI companies themselves, but for businesses that effectively implement AI to transform their operations, particularly small, local businesses that can become extraordinarily efficient through AI adoption.
The Value Shift: From AI Companies to AI-Enabled Traditional Businesses
A central insight from episode 1 of the podcast series, is that the value of AI isn't likely to accrue primarily to companies like OpenAI or other AI technology providers. Instead, the real winners will be traditional service businesses that can leverage AI to transform their operations and cost structures.
"I think we're gonna see this shift to traditional service businesses... that traditionally have pretty fixed low margins because of a dependency on language-heavy workflows that require a lot of humans as the medium of intelligence in the business."
The opportunity here is to use AI to manage the language dependency and shift the moments of intelligence, that currently exist in the heads of our staff, into software that can run 24x7 for fractions of a cost.\ \ The real limiting factor here is less a magic AGI, but instead detailed thinking and process redesign to move humans to the edge of the process. As it turns out if we think through what each person is doing in detail we see the specific decisions, outputs, moments of intelligence are actually quite constrained and can be replicated in LLM's if we break them down to a low enough level of fidelity and take each decisions one step at a time.\ \ The result? Businesses that have traditionally operated with fixed, low margins can potentially achieve "software-style margins" by dramatically reducing their operational expenses.
Transforming Traditional Service Businesses
We have developed three key heuristics for identifying businesses that could benefit most from AI transformation:
-
Language Intensity: Businesses where much of the work involves processing language (reading, writing, communicating). Language in, language out. If you are sat in a chair and typing all day, this could be you.
-
Labor Component: Where we see this language intensity so we find many people performing similar, standardized roles. For examples, if we have four people in the same role this is a big clue we have good process, checklists, role descriptions etc for how the work can be done in order to replicate work across multiple people.
-
Load in the Business: Taking these processes into account, what amount of the operational expense of the business do they represent? Where these language and labor-intensive operations represent a significant portion of the business cost, we can see there will be significant return.
Traditional service businesses that match these criteria—legal firms, accounting practices, consulting agencies, contract engineering, design agencies and others—could see dramatic transformations through AI implementation.
By automating these language-heavy processes, businesses can potentially reduce operational costs by 50-80% while maintaining similar levels of output.
The Power of Small
We believe that small businesses may have an inherent advantage in this transformation. While large enterprises face significant barriers to reducing their workforce (political pressure, media scrutiny, organizational complexity), smaller businesses can adapt more quickly and focus on growth rather than just cost-cutting.
If I'm in a 20,000 person business and I need to remove 10,000 people... that's hard. You can't do this without sending political shock waves in your local community.
If I'm a 10 person business and I need to double my revenue, nobody gives a shit. I can just do it.
For small businesses, AI removes growth constraints. When adding the "21st person" no longer represents a significant capital investment, small businesses can scale much more efficiently:
If the next nominal client that you onboard doesn't actually cause you any more additional pain, if you don't need to hire more people to service that client... you just take off the brakes off from a growth perspective.
This gives small business a unique advantage in capitalizing on AI.
From "Bionic Humans" to "Humans at the Edge"
We currently see this integration to business happening in one of two models:
-
The Bionic Human: Equipping workers with AI tools to make them more productive.
-
Human at the Edge: Redesigning processes to be AI-native, with humans entering the process only when needed (and often facilitated by bitcoin payments).
While many businesses are focused on the first approach and it can certainly see returns, it is still a process constrained by the human input. The real value unlock comes from fundamentally redesigning business processes with AI at the core.
Now we can purchase intelligence in buckets of $0.02 API calls, how would we operate different?
This represents a profound shift in how we think about work and processes. Rather than humans being central to processes with tools supporting them, AI becomes the backbone of operations with humans providing input only at critical junctures.
This is "a complete mental shift" that challenges our fundamental assumptions about how businesses operate. The human becomes "the interface with the real world" for AI systems rather than the primary processor of information and decision-maker.
The Value Trap: Understanding the Competitive Dynamic
So what happens next? Here we have developed the concept of the Value Trap to explain how the competitive landscape will evolve as AI adoption increases..\ \

Initially, early adopters of AI and "Human at the Edge" business processes, will see dramatic benefits.
If your costs have dropped from 90 to 20 this creates an immediate competitive advantage where the early adopter is "now making 80 units of profit versus your 10 units of profit.
They gain massive pricing power in the industry and can compete for growth with an unfair advantage.
Over time, and here we believe this is likely a 5-10 year period although we believe the quicker side, competitive pressures will erode these advantages.\ \ As competitors adopt similar AI strategies, price competition will intensify, and revenues will decline. The business that initially saw its costs drop from 90 to 20 units might see its revenue decline from 100 to 30 units, resulting in similar margins but much lower overall revenue, often destroying the enterprise value of the company at these new revenue / profit levels!
This evolution creates an imperative for businesses to adopt AI early, not just to maintain perpetual advantage, but simply to survive the transition. Worse they're hit with a second challenge of the value trap, how do I keep hold of the value I generate along the way.\ \ If you're reading this on Nostr you may already suspect a way out of this value trap.\ \ If not I would invite you to consider storing the immediate short term returns you pull forwards in something that would be inflation resistant, hard to seize and ideally portable.\ \ We refer to this as a 'The big orange arbitrage".
Implications for Business Owners and Capital Allocators
For business owners, especially those running small to medium-sized enterprises, the message is clear: understand how AI could transform your industry and begin planning your transition now.\ \ This might involve creating an "AI-native twin" of your current business—similar to how Netflix developed streaming alongside its DVD business—to eventually replace your current operations. If you want help please ask, I heavily favor more small businesses in the world and would love to help make this a reality.
For capital allocation, the emerging opportunity we see if in "transformation led private equity". The acquisition of traditional service businesses and applying AI to dramatically reduce operational costs and increase enterprise value.\ \ This approach treats AI not as a product but as a transformation strategy for existing businesses with proven product-market fit.
Transformation led PE is venture style returns without the risk of product market fit.
So the lesson?
The business model of AI isn't all about selling AI technology, adding a RAG chatbot to a new DB or collecting everyone's data.\ \ Consider the humble cash flow business, use AI to transform the operational processes and save into everyone's favorite orange coin.
-
-
 @ f4db5270:3c74e0d0
2025-05-16 08:13:05
@ f4db5270:3c74e0d0
2025-05-16 08:13:05Hi Art lover! 🎨🫂💜
You may not know it yet but all of the following paintings are available in #Bitcoin on my website: <https://isolabellart.carrd.co/>
For info and prices write to me in DM and we will find a good deal! 🤝
 THE QUIET ROOM 50x40cm, Oil on board - Completed May 8, 2025
THE QUIET ROOM 50x40cm, Oil on board - Completed May 8, 2025
 OLTRE LA NEBBIA 50x40cm, Oil on board - Completed April 18, 2025
OLTRE LA NEBBIA 50x40cm, Oil on board - Completed April 18, 2025
 TO THE LAST LIGHT 50x40cm, Oil on board - Completed April 5, 2025
TO THE LAST LIGHT 50x40cm, Oil on board - Completed April 5, 2025
 BLINDING SUNSET 40x40cm, Oil on board - Completed March 18, 2025
BLINDING SUNSET 40x40cm, Oil on board - Completed March 18, 2025
 ECHI DEL TEMPO PERDUTO 40x40cm, Oil on board - Completed March 09, 2025
ECHI DEL TEMPO PERDUTO 40x40cm, Oil on board - Completed March 09, 2025
 EVANESCENZE 40x40cm, Oil on board - Completed February 11, 2025
EVANESCENZE 40x40cm, Oil on board - Completed February 11, 2025
 OLTRE LA STACCIONATA 50x40cm, Oil on board - Completed February 8, 2025
OLTRE LA STACCIONATA 50x40cm, Oil on board - Completed February 8, 2025
 LONELY WINDMILL 50x40cm, Oil on board - Completed January 30, 2025
LONELY WINDMILL 50x40cm, Oil on board - Completed January 30, 2025
 ON THE ROAD AGAIN 40x50cm, Oil on canvas - Completed January 23, 2025
ON THE ROAD AGAIN 40x50cm, Oil on canvas - Completed January 23, 2025
 SUN OF JANUARY 40x50cm, Oil on canvas - Completed January 14, 2025
SUN OF JANUARY 40x50cm, Oil on canvas - Completed January 14, 2025

THE BLUE HOUR 40x50cm, Oil on canvas - Completed December 14, 2024
 WHERE WINTER WHISPERS 50x40cm, Oil on canvas - Completed November 07, 2024
WHERE WINTER WHISPERS 50x40cm, Oil on canvas - Completed November 07, 2024
 L'ATTESA DI UN MOMENTO 40x40cm, Oil on canvas - Completed October 29, 2024
L'ATTESA DI UN MOMENTO 40x40cm, Oil on canvas - Completed October 29, 2024

LE COSE CHE PENSANO 40x50cm, Oil on paper - Completed October 05, 2024
 TWILIGHT'S RIVER 50x40cm, Oil on canvas - Completed September 17, 2024
TWILIGHT'S RIVER 50x40cm, Oil on canvas - Completed September 17, 2024

GOLD ON THE OCEAN 40x50cm, Oil on paper - Completed September 08, 2024
 SUSSURRI DI CIELO E MARE 50x40cm, Oil on paper - Completed September 05, 2024
SUSSURRI DI CIELO E MARE 50x40cm, Oil on paper - Completed September 05, 2024
 THE END OF A WONDERFUL WEEKEND 40x30cm, Oil on board - Completed August 12, 2024
THE END OF A WONDERFUL WEEKEND 40x30cm, Oil on board - Completed August 12, 2024
 FIAMME NEL CIELO 60x35cm, Oil on board - Completed July 28, 2024
FIAMME NEL CIELO 60x35cm, Oil on board - Completed July 28, 2024
 INIZIO D'ESTATE 50x40cm, Oil on cradled wood panel Completed July 13, 2024
INIZIO D'ESTATE 50x40cm, Oil on cradled wood panel Completed July 13, 2024
 OMBRE DELLA SERA 50x40cm, Oil on cradled wood panel - Completed June 16, 2024
OMBRE DELLA SERA 50x40cm, Oil on cradled wood panel - Completed June 16, 2024
 NEW ZEALAND SUNSET 80x60cm, Oil on canvas board - Completed May 28, 2024
NEW ZEALAND SUNSET 80x60cm, Oil on canvas board - Completed May 28, 2024
 VENICE 50x40cm, Oil on board - Completed May 4, 2024
VENICE 50x40cm, Oil on board - Completed May 4, 2024
 CORNWALL 50x40cm, Oil on board - Completed April 26, 2024
CORNWALL 50x40cm, Oil on board - Completed April 26, 2024
 DOCKS ON SUNSET 40x19,5cm, Oil on board Completed March 14, 2024
DOCKS ON SUNSET 40x19,5cm, Oil on board Completed March 14, 2024
 SOLITUDE 30x30cm, Oil on cradled wood panel - Completed March 2, 2024
SOLITUDE 30x30cm, Oil on cradled wood panel - Completed March 2, 2024
 LULLING WAVES 40x30cm, Oil on cradled wood panel - Completed January 14, 2024
LULLING WAVES 40x30cm, Oil on cradled wood panel - Completed January 14, 2024
 MULATTIERA IN AUTUNNO 30x30cm, Oil on cradled wood panel - Completed November 23, 2023
MULATTIERA IN AUTUNNO 30x30cm, Oil on cradled wood panel - Completed November 23, 2023
 TRAMONTO A KOS 40x40cm, oil on board canvas - Completed November 7, 2023
TRAMONTO A KOS 40x40cm, oil on board canvas - Completed November 7, 2023
 HIDDEN SMILE 40x40cm, oil on board - Completed September 28, 2023
HIDDEN SMILE 40x40cm, oil on board - Completed September 28, 2023
 INIZIO D'AUTUNNO 40x40cm, oil on canvas - Completed September 23, 2023
INIZIO D'AUTUNNO 40x40cm, oil on canvas - Completed September 23, 2023
 BOE NEL LAGO 30x30cm, oil on canvas board - Completed August 15, 2023
BOE NEL LAGO 30x30cm, oil on canvas board - Completed August 15, 2023
 BARCHE A RIPOSO 40x40cm, oil on canvas board - Completed July 25, 2023
BARCHE A RIPOSO 40x40cm, oil on canvas board - Completed July 25, 2023

IL RISVEGLIO 30x40cm, oil on canvas board - Completed July 18, 2023

LA QUIETE PRIMA DELLA TEMPESTA 30x40cm, oil on canvas board - Completed March 30, 2023
 LAMPIONE SUL LAGO 30x30cm, oil on canvas board - Completed March 05, 2023
LAMPIONE SUL LAGO 30x30cm, oil on canvas board - Completed March 05, 2023
 DUE NELLA NEVE 60x25cm, oil on board - Completed February 4, 2023
DUE NELLA NEVE 60x25cm, oil on board - Completed February 4, 2023
 UNA CAREZZA 30x30cm, oil on canvas board - Completed January 17, 2023
UNA CAREZZA 30x30cm, oil on canvas board - Completed January 17, 2023
 REBEL WAVES 44x32cm, oil on canvas board
REBEL WAVES 44x32cm, oil on canvas board
 THE SCREAMING WAVE 40x30cm, oil on canvas board
THE SCREAMING WAVE 40x30cm, oil on canvas board

"LA DONZELLETTA VIEN DALLA CAMPAGNA..." 30x40cm, oil on canvas board

LIGHTHOUSE ON WHITE CLIFF 30x40cm, oil on canvas board
-
 @ 2b998b04:86727e47
2025-05-16 06:33:03
@ 2b998b04:86727e47
2025-05-16 06:33:03For years, I wandered through the Web3 space—intrigued by its promises, pulled in by buzzwords like “decentralization,” “DAOs,” and “stakeholder democracy.”
But over time, the signals got drowned out by noise.
I saw venture capital pour into projects that had no product. I watched communities reward performative governance and token hype, rather than real work or impact. Even in faith-based circles, “Web3 for good” often meant shiny apps that served insiders more than outsiders.
Then I found my way back to where I began: Bitcoin.
Not as a speculative asset—but as a philosophy. A discipline. A foundation.
Proof of Work doesn’t need marketing. It doesn’t ask for permission. It either works—or it doesn’t.
Web3 taught me a lot. But Bitcoin gave me a plumb line. And from now on, that’s the line I’m building on.
This is Part 1 of a multi-part series. Follow for future entries.\ \ — Andrew G. Stanton\ Bitcoiner, builder, believer.
This article was co-drafted using ChatGPT to accelerate the writing process. Final content was reviewed and edited by me.
-
 @ b8af284d:f82c91dd
2025-05-16 08:38:57
@ b8af284d:f82c91dd
2025-05-16 08:38:57Liebe Abonnenten,
am Sonntag ging es im Essay „Das AGI-Project” um die geopolitischen Auswirkungen von künstlicher Intelligenz. Die USA und China befinden sich in einem Wettrennen, um die ökonomische und militärische Vorherrschaft. Das folgende Gespräch mit dem Künstler Künstler Snicklink dreht sich die konkreten Auswirkungen von KI auf unser Leben.
Snickling ist bereits zum zweiten Mal bei BlingBling zum Interview. Wer ihn noch nicht kennt, sollte das schnell nachholen. Spätestens seit 2023 ist der KI-Künstler einer breiteren Öffentlichkeit bekannt. Seine Videos sind oft messerscharfe Satire-Kunst, die mittels Collagen und DeepFakes den Irrsinn unserer Zeit auf den Punkt bringen. Hinter Snicklink steckt der Mensch und Berliner Künstler Willy Kramer, der immer wieder auch künstliche Intelligenz und die Zukunft der Menschen zum Thema hat.

https://www.youtube.com/watch?v=ThX3b5OSqUg
Willy, ich fand dein letztes Video beeindruckend gerade, weil es mal keine Satire war, sondern einen ernsten Ton hatte. Du sagst darin, dass kreative Arbeit bald vollständig von Künstlicher Intelligenz ersetzt werden könnte. Kannst du das jemandem erklären, der sich wenig mit KI auskennt? Was kommt da auf uns zu und warum?
Das ist eine große Frage. Ich betrachte das aus zwei Perspektiven: einer kreativen und einer gesellschaftlichen. Kreativ gesehen ist KI ein unglaublich mächtiges Werkzeug. Stell dir vor, ich könnte hundert Assistenten engagieren – oder ich nutze KI-Tools, die günstiger, schneller und oft präziser sind. Das ist die praktische Seite. Gesellschaftlich und technologisch geht es um viel mehr als nur Kunst oder einzelne Projekte. KI ist eine Entwicklung, die ich mit der Entdeckung des Feuers oder der Öffnung der Büchse der Pandora vergleiche. Das klingt dramatisch, aber ich übertreibe nicht. Ich beschäftige mich seit zehn Jahren intensiv mit dem Thema. Am Anfang war es spekulativ, und ich hatte kaum Gesprächspartner. Google und ein paar kleinere Firmen fingen gerade an, KI zu erforschen. Ich habe Workshops gegeben, aber viele hielten mich für einen Spinner. Trotzdem war mir klar, wohin das führt.
Vor zehn Jahren habe ich ein Video namens Emphasized Prophecy gemacht: Ein Typ sitzt am Strand, mit einem leeren Schreibtisch und einer kleinen Box, und erstellt per Sprachbefehl eine multimediale Kampagne. Heute, zehn Jahre später, arbeite ich mit einem Setup, das genau das ermöglicht – und noch mehr.
Welche Tools nutzt du konkret? Du bist ja schon tief in der praktischen Anwendung von KI.
Ich bin kein Programmierer, der stundenlang Skripte schreibt, aber ich bin ziemlich involviert. Alles begann so richtig mit dem „ChatGPT-Moment“ vor zweieinhalb Jahren, als plötzlich alle die Möglichkeiten von KI erkannten. Inzwischen nutze ich eine Suite aus etwa 200 verschiedenen Plugins und Services. Früher gab es spezialisierte KI für spezifische Aufgaben, etwa für den Stimmklang oder die „Deutschheit“ einer Stimme. Heute werden die Modelle größer und vielseitiger. Man braucht nur noch ein oder zwei Modelle, die Stimmen, Bilder, Videos und sogar Programmierung abdecken. Bald wird es ein einziges, universelles Modell geben.
Wir befinden uns in einem globalen Wettlauf, vor allem zwischen den USA und China. Jeder will das eine Modell entwickeln, das alle kreativen und administrativen Aufgaben erledigt – ähnlich wie Google damals die Suche revolutionierte.
Welche Benutzeroberfläche oder Tools wie Grok, ChatGPT setzen sich durch?
Jede Plattform hat ihre Stärken. Grok zum Beispiel hat direkten Zugriff auf Social-Media-Daten, was ein Vorteil ist. OpenAI hingegen punktet mit ausgefeilten Denkmodellen. Es ist wie bei einem Basketballteam: Der eine spielt stark in der Verteidigung, der andere wirft präzise Dreier. Für 99 Prozent der Nutzer macht das keinen Unterschied. Ob du mit ChatGPT einen Liebesbrief, einen Finanzamtsbrief oder psychologische Beratung formulierst – die Unterschiede sind marginal. Die Technologie entwickelt sich so rasant, dass wir alle paar Monate völlig neue Möglichkeiten bekommen, die im Alltag direkt nutzbar sind und Dinge ermöglichen, die vorher undenkbar waren.
Du hast erwähnt, dass der nächste Schritt KI-Agenten sein könnten, die untereinander kommunizieren. Kannst du das ausführen?
Stell dir die Digitalisierung wie die Erfindung des Rades vor: Es war ein Fortschritt, aber es waren nur Fahrräder. Jetzt kommt die Dampfmaschine – KI-Agenten sind die nächsten „Fahrzeuge“. Diese Agenten nutzen Sprachbefehle nicht nur, um Antworten zu geben, sondern um komplexe Aufgaben zu lösen: Kampagnen erstellen, Finanzberichte schreiben, Fünfjahrespläne für Patienten basierend auf den besten Forschungspapieren entwickeln. Aktuell braucht man noch Know-how, um die richtigen Anweisungen zu geben. Bald wird das überflüssig, weil KI dein Profil kennt und mit einem einfachen „Go“ alles erledigt – von der Suche nach der nächsten Apotheke bis zur Planung einer Operation.
Heißt das, wir steuern auf eine Überflussgesellschaft zu?
Das ist die Utopie, ja. KI kann eine Welt schaffen, in der es keinen Mangel mehr gibt – alles ist verfügbar, erschwinglich oder sogar kostenlos. Niemand hat mehr materielle oder körperliche Sorgen. Aber das bringt neue Herausforderungen: Wie gehen wir als Menschen damit um? Unsere Gesellschaft definiert Wert über Status, Arbeit, Besitz. Wenn das wegfällt, weil nur noch fünf Prozent der Menschen arbeiten, müssen wir uns neu erfinden. Wir brauchen eine Postleistungsgesellschaft, in der Kreativität, Freundlichkeit oder vielleicht Spiritualität den Ton angeben.
Das klingt nach einem Verteilungsproblem. Muss da nicht massiv umverteilt werden?
Das ganze Interview gibt es hier zu lesen: https://blingbling.substack.com/p/eine-welt-ohne-mangel
-
 @ 7b20d99d:d2a541a9
2025-05-16 04:03:23
@ 7b20d99d:d2a541a9
2025-05-16 04:03:23In a world where we often hear talk of financial bubbles, speculation, and individual enrichment through cryptocurrencies, Hope With Bitcoin resolutely takes the opposite approach. Here, Bitcoin is not an end in itself, but a means to reach out. A tool serving a simple, universal human cause: bringing smiles and hope back to those who need it most.
Far from big, empty promises and empty charitable projects, Hope With Bitcoin is committed to a philosophy of direct impact, total transparency, and lasting transformation of lives.
🔗 Official project link : https://linktr.ee/hopewithbtc
🟢 Why “Hope With Bitcoin”?
It all started with an observation: too many people are living in oblivion. In some regions, particularly in Africa, it doesn't take much to bring back a smile: a meal, a word, a gesture. But often, aid initiatives get lost in an administrative maze, corruption, or a lack of follow-ups. And in the world of Bitcoin, we see many promises of humanitarian aid without ever seeing results.
Hope With Bitcoin was launched to change that. The goal is clear:
Using the power of Bitcoin to provide direct, visible, measurable and lasting help.
We wanted to show that Bitcoin can nourish, heal, raise awareness, connect, and not just speculate.
🔵 What we do concretely
Hope With Bitcoin isn't an abstract concept. It's a set of concrete actions carried out on the ground, with rigor and heart.
Here's what we do:
🍛 Food distribution and health aid
Thanks to donations collected in Bitcoin, we provide concrete help to those who need it most.
We distribute hot meals and basic food items (rice, spaghetti, oil, charcoal, etc.) to struggling families, vulnerable children, and orphanages.
But our work doesn't stop there. A portion of the funds is also used to purchase essential medicines and contribute to the payment of healthcare, particularly for sick or injured people who cannot afford treatment.
Each action is carefully documented and made public to ensure complete transparency and strengthen the trust of our donors.
✅ Missions accomplished: every satoshi counts
Since Hope With Bitcoin's inception, we've carried out several concrete actions thanks to the donations received. Here's a clear, transparent, and verifiable overview of our actions:
🔹 PoW 1 – 10 000 Satoshi Received
📅 Date : 01/09/2025
📍 Purchase food for two children in need

🔹 PoW 2 – 10 000 Satoshi Received
📅 Date : 01/11/2025
📍 Purchase food for two children in need


🔹 PoW 3 — 220,500 Satoshi received
📍 Preparing food for thirty children in need
📅 Date : 01/13/2025

🔹 PoW 4— 31,000 Satoshi received
📍 Purchase food for six children in need
📅 Date : 01/16/2025

🔹 PoW 5— 30,000 Satoshi received
📍 Purchase food for 10 students in need
📅 Date : 01/18/2025

🔹 PoW 6 – 11,093 Satoshi received
📍 Purchase food for two children in need
📅 Date : 01/22/2025
 #### \
🔹 PoW 7 – 52,000 Satoshi Received
#### \
🔹 PoW 7 – 52,000 Satoshi Received📍 Preparing food for eight children in need
📅 Date : 01/27/2025
 #### \
🔹 PoW 8 – 116,866 Satoshi Received
#### \
🔹 PoW 8 – 116,866 Satoshi Received📍Financial support for Maria Jimenez's health
📅 Date : 02/13/2025

🔹 PoW 9 – 8,001 Satoshi Received
📍 Hope With Bitcoin t-shirt print
📅 Date : 02/15/2025


🔹 PoW 10 – 22,602 Satoshi Received
📍 Purchase of food for five children in need (three on site and two takeaway)
📅 Date : 02/17/2025

🔹 PoW 11– 350,000 Satoshi Received
📍 Purchase of food (rice, corn, spaghetti, oil, salt, sugar, coal...) at the Bon Arbre orphanage
Thank you letter received: HERE
📅 Date : 03/06/2025

🔹 PoW 12 – 35,000 Satoshi received
📍 Purchase of medicine for a person in need
📅 Date : 04/02/2025

🔹 PoW 13 – 60,910 Satoshi received
📍 Purchase food for two children in need
🖼 Coming soon
📅 Date : 05/18/2025
Each of these Proofs of Work (PoW) is publicly published on Nostr or Geyser to ensure complete transparency. You can view them individually to see the real impact of your donations.
📣 Bitcoin Adoption Awareness
We take advantage of each field trip to speak with shopkeepers, local vendors, and young people. The idea is to show that Bitcoin can be used practically in their daily lives: to sell, buy, and exchange.
🟠 Our results to date
Since the creation of Hope With Bitcoin on January 8, 2025, we have succeeded in:
- Collect a total of 957,971 Satoshi thanks to the generosity of contributors around the world.
- Help 87 people directly through our distribution actions. (Proof of work)
- Raise awareness among several merchants about the use of Bitcoin.
- Create a close-knit, caring community focused on human impact.
These numbers aren't statistics. They're lives, faces, stories. Every person helped represents a victory, proof that Bitcoin solidarity is possible.
🟣 Our ambitions for the future
Hope With Bitcoin doesn't want to be just a one-time donation project. We believe in sustainability, independence, and structured growth.
### 🐖 Launch of a pig farm to sustainably finance our actions
To make our humanitarian work self-sufficient and sustainable, we have launched a project to create a pig farm, the proceeds of which will be used to fund food distribution, the purchase of medicines, and other solidarity initiatives led by Hope With Bitcoin.
This project aims to generate regular income while having a tangible local impact:
-
🥣 Continuously support food and health aid
-
👷♂️ Create jobs for young people and unemployed people
-
♻️ Reinvest profits in other humanitarian projects
To kick-start this project, we've established a detailed budget estimate that includes the purchase of piglets, pen construction, feed, veterinary care, and management fees. 👉 Estimated cost: approximately 5,525,200 Satoshi
More details on the budget here: https://primal.net/e/nevent1qqsfmrafup9dma3wvgeqgasydjhy06rhkn8d268txmztp60533mp3xg0vuk5a
🐓 Towards a united and evolving ecosystem
Ultimately, we aim to diversify our business into chicken and goat farming and develop micro-agricultural projects. The goal is to build a resilient, local, and 100% Bitcoin-funded ecosystem that serves the most vulnerable.
💛 You can support this project now on Geyser:
https://geyser.fund/project/hopewithbitcoin/goals/552
🌍 Expansion of the area of action
We want to reach:
- More regions
- More beneficiaries
- More businesses willing to accept Bitcoin
⚫ Why Bitcoin?
The choice of Bitcoin is not ideological. It is practical, thoughtful, and strategic.
Here's why we made this choice:
- ✅ Fast and low-cost transactions
- ✅ No geographical or banking barriers
- ✅ Immutability of donations: funds cannot be diverted
- ✅ Complete traceability thanks to blockchain
- ✅ Financial education for recipients
In short, Bitcoin allows us to rebuild trust in donations and make acts of solidarity visible.
🟢 How to support us?
You can be part of the change. Here's how:
- 🤝 Donate in Bitcoin (https://geyser.fund/project/hopewithbitcoin)
- 📢 Share our posts to help us gain visibility
- 🧠 Recommend us to a partner, company, or influencer
- 💬 Join the community on Twitter, Nostr, or subscribe to Geyser to stay informed and actively participate.
Even a simple retweet can make a difference. Because every Satoshi counts.
Hope With Bitcoin is a declaration of love to humanity. It's a belief that technology can serve the heart. It's a demonstration that Bitcoin can nourish, not just enrich.
We are not an NGO, we are not a company. We are a movement, an initiative, a momentum. And this is just the beginning.
“With a little Bitcoin and a lot of love, we can change lives.”
🔗 Join us now : https://linktr.ee/hopewithbtc
-
 @ 502ab02a:a2860397
2025-05-16 01:57:09
@ 502ab02a:a2860397
2025-05-16 01:57:09หลังจากที่เราคุยกันไปแล้วเกี่ยวกับ milk 2.0 ว่ามี Perfect Day ที่เป็นหัวหาดด้านเวย์ที่ไม่มีวัว แล้วเราก็มี Formo หัวหาดด้านชีสที่ไม่มีวัว ซึ่ง 2 เจ้านี้ต่างมีสิ่งที่แต่ละคนขาดอยู่ นั่นคือ เจ้านึงขาดเคย์ซีนเด็ดๆ อีกเจ้าไม่ได้มีเวย์ที่เจ๋งพอ และแน่นอนครับ ทุกปัญหาย่อมมีธุรกิจเกิดขึ้นมาเพื่อแก้ปัญหา
วันนี้เราจะมาพบกับอีกผู้เล่นนึง ที่แก้ปัญหาทั้งหมดด้วยการ สร้างสิ่งที่ขาดขึ้นมาใหม่ ตามคาแรคเตอร์ของ "มังกรจีน" ใช่ครับ เราเคยคิดว่าโลกเทคโนโลยีมีแต่ฝรั่งเป็นเจ้าสำนัก แต่ตอนนี้ทุกมุมโลกต่างแย่งชิงอนาคตกันหมด ไม่มีใคร slow life อีกต่อไปแล้ว
เพราะในโลกที่นมไม่ใช่นม ชีสไม่ใช่ชีส และวัวไม่จำเป็นต้องกินหญ้า เรากำลังเข้าสู่ยุคที่ “นม 2.0” กำลังถูกออกแบบใหม่… ด้วยจุลินทรีย์ บริษัทหนึ่งจากจีนชื่อว่า Changing Biotech กำลังจะทำให้มันกลายเป็นความจริง ด้วยเป้าหมายที่ไม่ธรรมดา เปลี่ยนโครงสร้างนมทั้งระบบ โดยไม่ต้องใช้วัวแม้แต่ตัวเดียวเช่นกันครับ
หลายคนอาจคุ้นชื่อ Perfect Day บริษัทอเมริกันที่เป็นรายแรก ๆ ในโลกที่สามารถผลิตเวย์โปรตีนจากเชื้อราแบบไม่ใช้สัตว์ ด้วยเทคโนโลยี precision fermentation ซึ่งตอนนี้มีแบรนด์ไอศกรีม เนย และโยเกิร์ตของตัวเองกระจายขายในห้างทั่วอเมริกา แต่ Changing Biotech กลับเลือกเดินอีกเส้นทาง เส้นทางที่อาจลึกกว่า แยบยลกว่า และอาจ “กลืน” ตลาดในเอเชียโดยที่ผู้บริโภคไม่รู้ตัว
แน่นอนว่าสิทธิบัตรการค้นคว้าต่างๆมีมูลค่าสูง เบื้องหลังเทคโนโลยีของ Changing Biotech ไม่ใช่แค่การเลียนแบบ แต่คือการ สร้างใหม่ตั้งแต่ระดับจุลินทรีย์ พวกเขาไม่ได้แค่ยืมเชื้อราสำเร็จรูปอย่าง Trichoderma มาใส่ยีนโปรตีน แต่ “เพาะสายพันธุ์จุลินทรีย์ขึ้นมาเอง” เพื่อควบคุมการผลิตโปรตีนอย่างมีประสิทธิภาพ ทั้งเวย์และเคซีน ซึ่งเป็นสององค์ประกอบหลักของนมแท้ นี่คือสิ่งที่แม้แต่ Perfect Day เองก็ยังไม่ได้โฟกัสเต็มตัว เพราะยังผลิตแต่เวย์เพียงอย่างเดียว Perfect Day ใช้ Trichoderma reesei เชื้อราชนิดที่วงการอาหารใช้กันมานานในการหมักเวย์โปรตีน เชื้อราชนิดนี้ปลอดภัย และได้รับการอนุมัติให้ใช้ในอาหารในหลายประเทศ แต่ Changing Biotechกลับล้ำไปอีกขั้น พวกเขาไม่ได้ยืมของใครมาใช้ แต่ 'สร้างจุลินทรีย์แพลตฟอร์มของตัวเอง' (customized microbial chassis) และมี ความสามารถด้าน strain engineering แบบ in-house ซึ่งทำให้พวกเขาควบคุมประสิทธิภาพการผลิต และลดต้นทุนได้แบบลึกสุดใจไม่ต้องซื้อให้เปลืองครับ
การผลิตเคซีนได้ในระดับอุตสาหกรรมหมายถึงอะไร? มันหมายถึง ชีสที่ยืดได้จริง หลอมได้จริง และ “เนื้อสัมผัสแบบชีสแท้” ที่แบรนด์ plant-based ยังเลียนแบบไม่ได้ และนั่นคือกุญแจสำคัญที่ทำให้ Changing Biotech ถูกจับตามองในวงการ alt-dairy ว่าอาจเป็น “Formo เวอร์ชันจีน” ที่จะครองตลาดชีสทั้งเอเชีย Changing Biotech ตั้งเป้าผลิต ทั้งเวย์และเคซีน ซึ่งทำให้สามารถพัฒนาผลิตภัณฑ์ที่มี “เนื้อสัมผัสและการหลอมตัวแบบชีสแท้จริง” ได้ครบวงจรกว่า โดยเฉพาะพวก mozzarella และ cheddar ที่ต้องพึ่งเคซีนในการขึ้นรูป จุดนี้คือกุญแจสำคัญในการตีตลาด “ชีสพรีเมียม” ที่วัตถุดิบจากพืชทำไม่ได้
แต่ที่น่าจับตายิ่งกว่านั้นคือ ทุนและเครือข่ายในประเทศ ที่ Perfect Day ไม่มี แม้ฝั่งอเมริกาจะมีเงินลงทุนหลักเกิน 800 ล้านดอลลาร์ แต่ฐานการผลิตอยู่ในสหรัฐฯ ซึ่งทำให้มีต้นทุนสูงกว่า ส่วนในจีน Changing Biotech ได้รับแรงหนุนจากรัฐบาลจีนผ่านนโยบายสนับสนุน “เทคโนโลยีอาหารแห่งอนาคต” และมีแนวโน้มว่าจะได้สิทธิพิเศษด้าน supply chain และการผลิตระดับอุตสาหกรรมภายในประเทศจีน ซึ่งเป็น ตลาดที่ Perfect Day เจาะยาก รวมถึงได้รับแรงหนุนจากกองทุนอาหารแห่งอนาคตอย่าง Bits x Bites ที่ทำงานร่วมกับรัฐบาลจีนโดยตรงในแผน 5 ปีด้านเทคโนโลยีอาหาร เป้าหมายชัดเจน ลดการพึ่งพาโปรตีนจากสัตว์ และสร้างระบบนมแห่งชาติแบบไร้สัตว์
โมเดลของพวกเขาต่างกับ Perfect Day ที่เน้นการสร้างแบรนด์ (เช่น Brave Robot, Modern Kitchen) และขายตรงกับผู้บริโภค แต่ Changing Biotech ไม่ใช่การตั้งแบรนด์ขายแข่งกันในห้าง แต่เป็น “ผู้อยู่เบื้องหลัง” ของแบรนด์ใหญ่อื่น ๆ โดยซัพพลายโปรตีนให้แบบ OEM ให้กับผู้ผลิตอาหารในจีน ซึ่งทำให้สามารถฝังตัวเข้า supply chain ของอุตสาหกรรมนมจีนได้เงียบ ๆ แต่ทรงพลัง โมเดลนี้คล้ายกับ Givaudan หรือ DSM ที่เน้นการเป็นผู้อยู่เบื้องหลังผลิตภัณฑ์แบรนด์อื่น
จะเรียกว่า Perfect Day คือ Apple ของนมไร้สัตว์ก็ได้ แต่ Changing Biotech กำลังเป็น Huawei ของอุตสาหกรรมนม ที่สร้างเทคโนโลยีขึ้นเองทั้งระบบ ควบคุมเบ็ดเสร็จตั้งแต่เชื้อจุลินทรีย์ยันขั้นตอนผลิต แล้วส่งต่อให้แบรนด์อื่นใช้แบบครบวงจร
ในวันที่ผู้บริโภคในจีนตักไอศกรีม “จากครีมจุลินทรีย์” หรือกินชีส “ไม่มีสัตว์เจือปน” อาจไม่มีใครรู้เลยว่าเบื้องหลังของรสสัมผัสนั้น คือจุลินทรีย์จากโรงงานที่พัฒนาโดย Changing Biotech ทั้งสิ้น
คำถามคือ แล้วมันดีต่อสุขภาพแค่ไหน? มันดีกว่าการรีดนมจากวัวจริง ๆ หรือแค่ดีต่อ narrative ของคนเมืองที่อยาก feel good แค่นั้น?
แล้วถ้าทุกประเทศเดินตามเทรนด์นี้ ใครกันแน่จะเป็นเจ้าของ “สูตรโปรตีนแห่งอนาคต” ที่ครองอำนาจอาหารของทั้งโลก?
คำตอบอาจไม่ได้อยู่ในกล่องนม แต่ในห้องแล็บจุลินทรีย์ของบริษัทที่เราไม่เคยได้ยินชื่อ
ยิ่งเราคุยกันนานเท่าไร ยิ่งรู้สึกแล้วใช่ไหมครับว่า อาหารอนาคต ไม่ใช่อาหารที่จะเกิดขึ้นในอนาคต แต่เป็น อาหารที่เราจะถูกครอบงำในอนาคต ซึ่งเริ่มไปแล้ว . . . วันนี้
นึกภาพวันที่ทุกคนล้วนรังเกียจนมจากวัว แล้วยินดีโอบกอดรับนมจากจุลินทรีย์ ด้วยความยินดีปรีดา
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 5490af12:d4710677
2025-05-16 00:28:35
@ 5490af12:d4710677
2025-05-16 00:28:35| | | ------------------------------------------------------------------------- | | bitcoinmetronome.com | | cornjoin.com | | decentralisedvalueexchange.com | | decentralizedvalueexchange.com | | memeswaps.com | | bitcoinculture.org |
-
 @ 472f440f:5669301e
2025-05-16 00:18:45
@ 472f440f:5669301e
2025-05-16 00:18:45Marty's Bent
It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
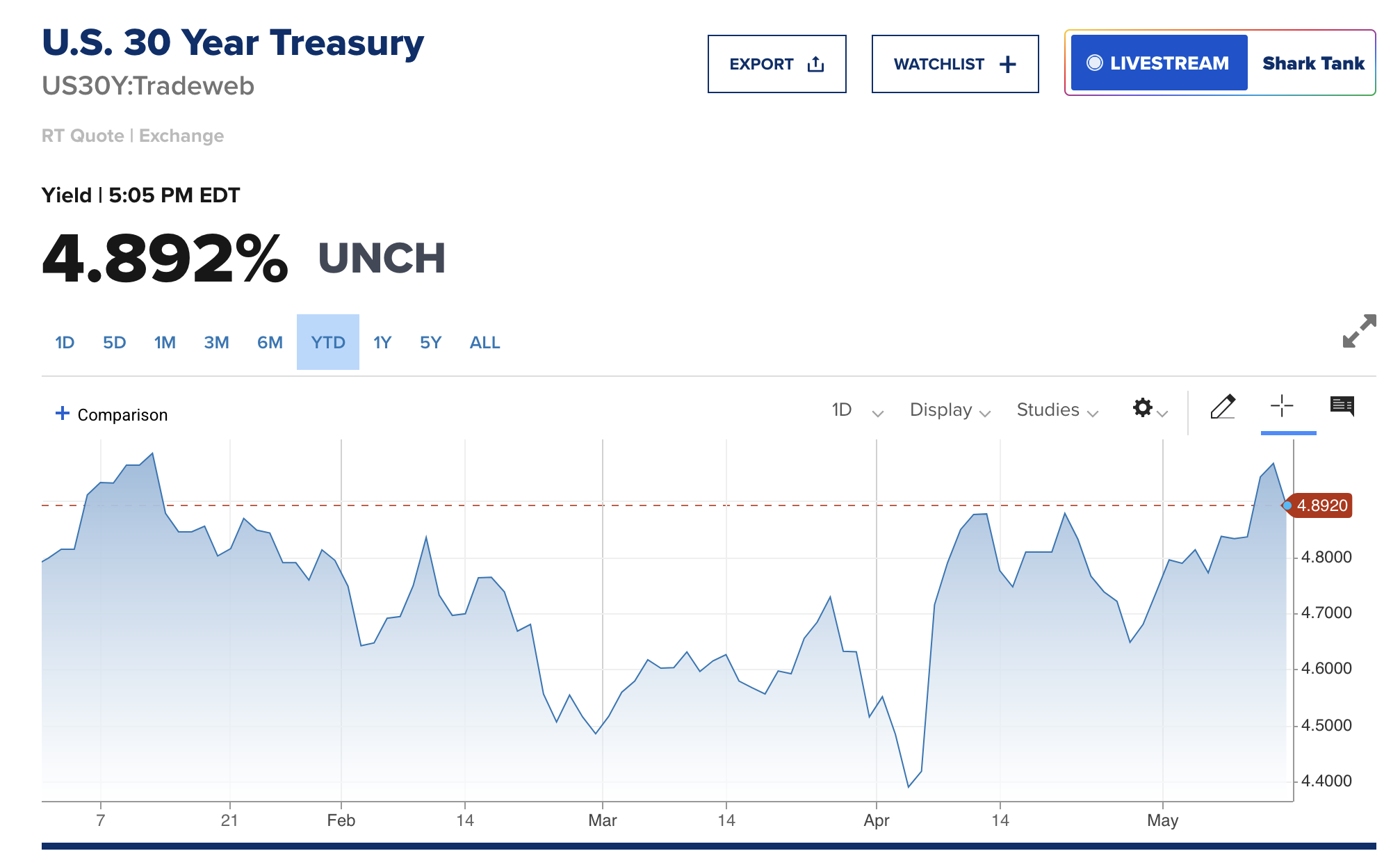
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
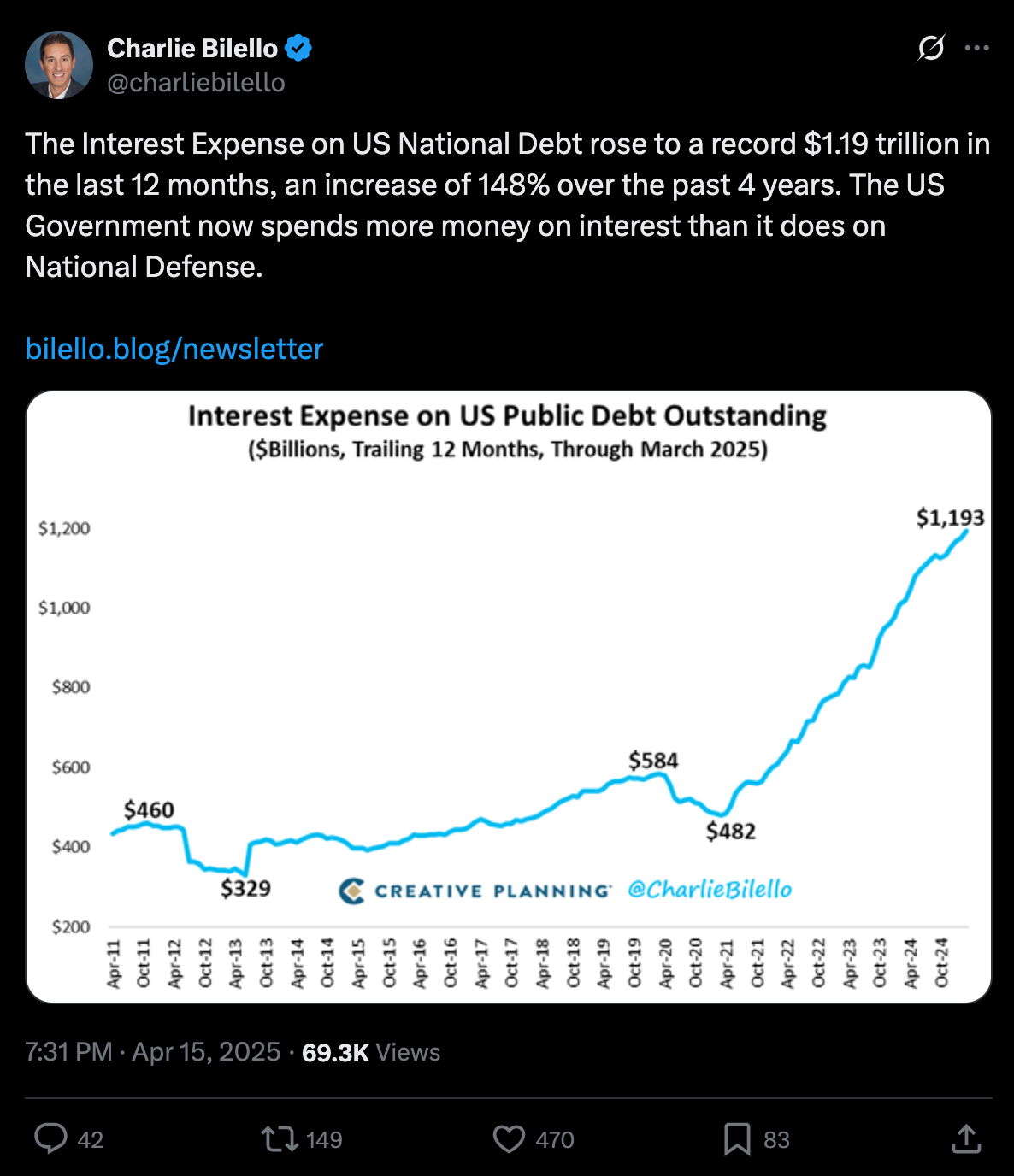
via Charlie Bilello
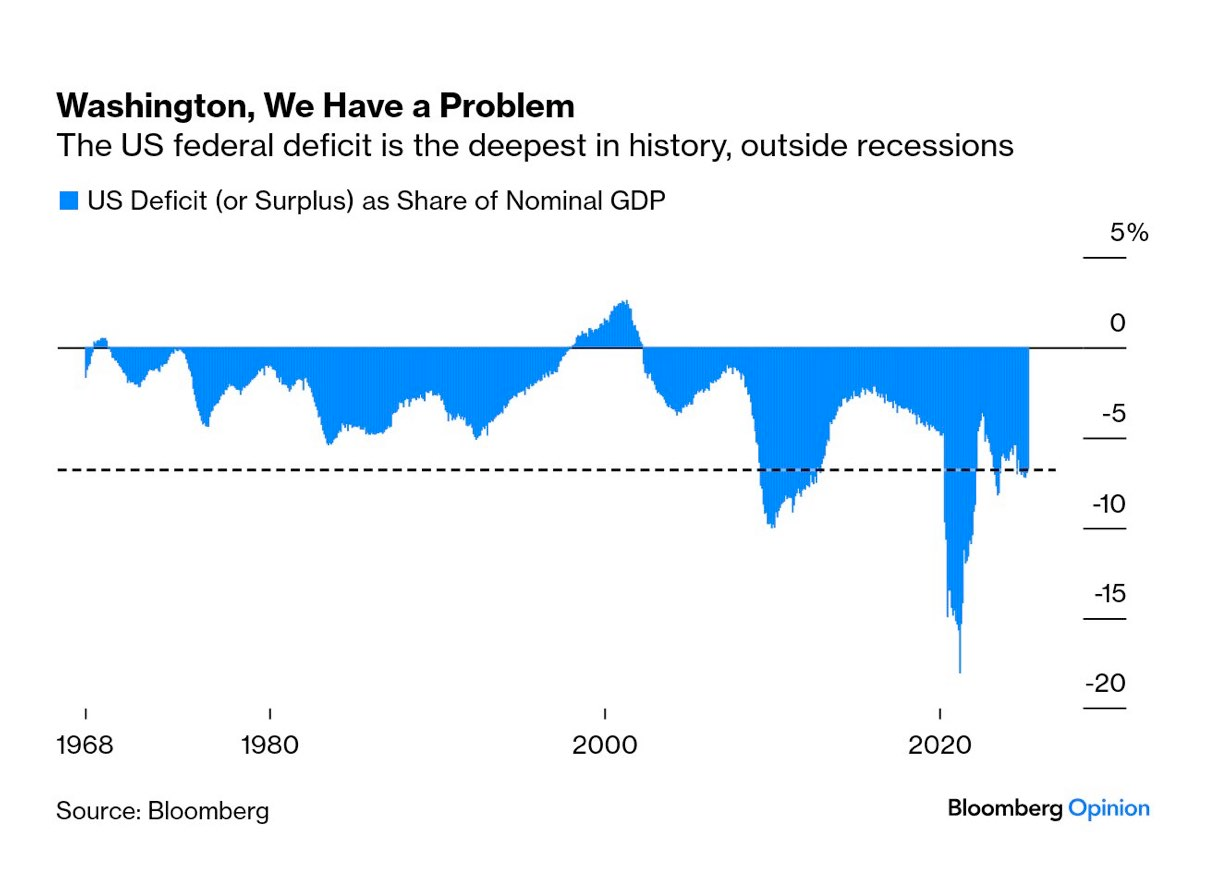
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
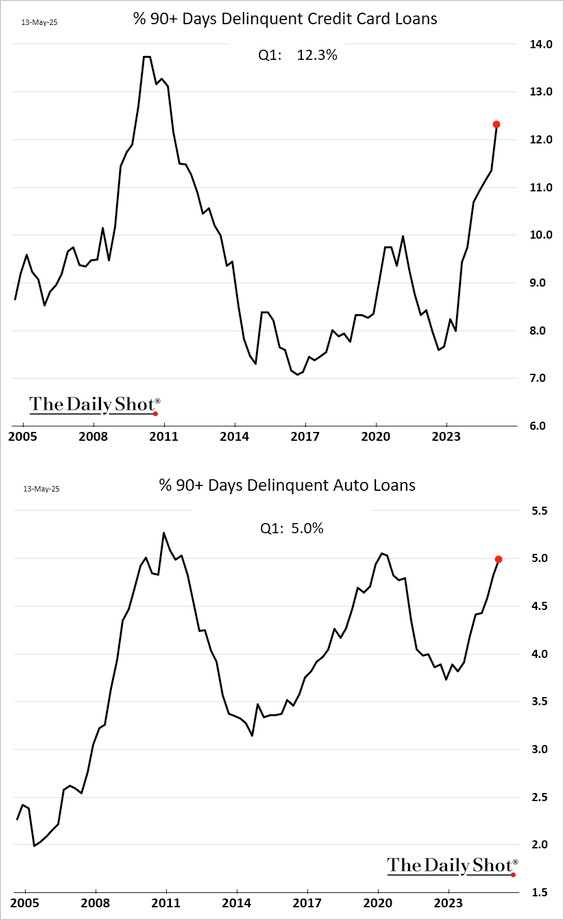
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ cefb08d1:f419beff
2025-05-16 06:37:33
@ cefb08d1:f419beff
2025-05-16 06:37:33https://stacker.news/items/981350
-
 @ c9badfea:610f861a
2025-05-15 23:51:35
@ c9badfea:610f861a
2025-05-15 23:51:35- Install SDAI (it's free and open source)
- Launch the app, and allow notifications when prompted
- Complete the introduction to get started
- Set Local Diffusion Microsoft ONNX as provider
- In the configuration step, Download a model (such as Real Vision) and wait for the process to finish
- Once the model is downloaded, tap on it and then select Setup
- You can now create images offline by entering a Prompt and tapping 🪄 Imagine
ℹ️ Download the tracking-free FOSS variant
ℹ️ Internet connection is only required for the initial model download
ℹ️ To speed up image generation, consider reducing the image size (e.g. 256x256)
-
 @ 28e13303:84bb7266
2025-05-15 23:37:29
@ 28e13303:84bb7266
2025-05-15 23:37:29⚠️ Disclaimer: This article is for educational purposes only. Flash USDT is a blockchain simulation tool used for wallet testing, UI development, or demonstration purposes. It should not be used for fraudulent activity. @crypptrcver is not responsible for misuse.
💡 What Is Flash USDT? Flash USDT is a synthetic transaction method that simulates the transfer of Tether (USDT) into a wallet. These transactions appear instantly in wallet balances — without ever being confirmed on the blockchain — and disappear after a short time or block interval.
Think of it as a temporary, visual representation of USDT that looks real in a wallet but vanishes after expiry.
🧠 Flash USDT: The Basics 👁️ Visible in supported wallets confirmed on-chain ⏱️ Disappears after 20–60 minutes (or X blocks) 💸 Can be withdrawn and traded ⚙️ Used in wallet testing, UI simulation, and balance display demos Also known as:
Flash USDT Wallet Tool Flash USDT Sender Atomic Flash USDT Flash USDT Binance Sim 🛠️ How Flash USDT Works You input a wallet address (TRC20, ERC20, or BEP20) Flash USDT software sends an instant transaction Wallet displays the amount — as if it were real After expiry (e.g., 30 minutes), the tokens vanish It creates the illusion of a deposit without requiring real blockchain confirmation. Most users use Flash USDT for:
Wallet UI testing “Proof of funds” simulations Demo environments Smart contract UX testing 🔧 Supported Networks & Wallets Flash USDT supports all major token standards:
🔸 TRC20 (Tron Network) 🔸 ERC20 (Ethereum) 🔸 BEP20 (Binance Smart Chain) It works with wallets such as:
✅ Trust Wallet ✅ MetaMask ✅ TronLink ✅ Binance Wallet ✅ Atomic Wallet The balance appears instantly, just like a real incoming USDT deposit.
🔥 Features of Flash USDT Sender FeatureDescriptionNetwork supportTRC20 / ERC20 / BEP20Visibility duration20 minutes — 2 hoursWallet compatibilityNon-KYC wallets that show unconfirmed TXsFlash USDT Binance modeSimulates deposits into BSC walletsAdjustable transaction sizeSend any custom USDT amountStealth expiryClean disappearance without trace
This is especially helpful in scenarios where you need to test token flows, design wallet apps, or simulate incoming funding activity
📞 How to Buy Flash USDT To get your Flash USDT transaction or software setup:
💬 Telegram: @crypptrcver 📱 WhatsApp: +1 941 217 1821
Available packages:
🎯 One-time Flash USDT Send 💻 Full Flash USDT Software Tool 📱 Flash Sender for Mobile/Android 🌐 Multi-wallet Simulation Package You can request TRC20, ERC20, or BEP20 flash transactions depending on the wallet or network you’re working with.
⚠️ Legal & Ethical Use Only While Flash USDT is a powerful blockchain simulation tool, using it to deceive, fake trades, or commit fraud is illegal. Flash transactions should only be used for:
✅ Personal testing ✅ Blockchain development ✅ Wallet UI testing ✅ Research and education Any misuse is your full responsibility.
❓ Frequently Asked Questions What is Flash USDT? A temporary USDT transaction that appears in a wallet balance without confirming on the blockchain. It disappears after a set time or block count.
Is Flash USDT real money? No. It is a simulated deposit, not spendable or tradable.
Can I use Flash USDT on Binance? You can send it to BSC (BEP20) wallets, but you cannot use it on the Binance exchange. It’s for display/testing only.
How do I buy Flash USDT? Contact @crypptrcver on Telegram or WhatsApp to purchase a transaction or the full sender software.
What does Atomic Flash USDT mean? It refers to Flash USDT transactions that are time-bound and expire silently, simulating atomic wallet behavior.
🧠 Final Thoughts Flash USDT is one of the most advanced crypto testing tools available in 2025. Whether you’re simulating wallet behavior, demonstrating a smart contract front end, or simply showing a visual “deposit” for testing, Flash USDT provides an incredibly realistic experience — without ever moving real funds.
👉 Ready to simulate your first USDT transaction?
💬 Telegram: @crypptrcver 📱 WhatsApp: +1 941 217 1821
Packages available for:
TRC20 BEP20 ERC20 Custom wallet simulations
⚠️ Disclaimer: This article is for educational purposes only. Flash USDT is a blockchain simulation tool used for wallet testing, UI development, or demonstration purposes. It should not be used for fraudulent activity. @crypptrcver is not responsible for misuse.
💡 What Is Flash USDT?
Flash USDT is a synthetic transaction method that simulates the transfer of Tether (USDT) into a wallet. These transactions appear instantly in wallet balances — without ever being confirmed on the blockchain — and disappear after a short time or block interval.
Think of it as a temporary, visual representation of USDT that looks real in a wallet but vanishes after expiry.
🧠 Flash USDT: The Basics
- 👁️ Visible in supported wallets
- confirmed on-chain
- ⏱️ Disappears after 20–60 minutes (or X blocks)
- 💸 Can be withdrawn and traded
- ⚙️ Used in wallet testing, UI simulation, and balance display demos
Also known as:
- Flash USDT Wallet Tool
- Flash USDT Sender
- Atomic Flash USDT
- Flash USDT Binance Sim
🛠️ How Flash USDT Works
- You input a wallet address (TRC20, ERC20, or BEP20)
- Flash USDT software sends an instant transaction
- Wallet displays the amount — as if it were real
- After expiry (e.g., 30 minutes), the tokens vanish
It creates the illusion of a deposit without requiring real blockchain confirmation. Most users use Flash USDT for:
- Wallet UI testing
- “Proof of funds” simulations
- Demo environments
- Smart contract UX testing
🔧 Supported Networks & Wallets
Flash USDT supports all major token standards:
- 🔸 TRC20 (Tron Network)
- 🔸 ERC20 (Ethereum)
- 🔸 BEP20 (Binance Smart Chain)
It works with wallets such as:
- ✅ Trust Wallet
- ✅ MetaMask
- ✅ TronLink
- ✅ Binance Wallet
- ✅ Atomic Wallet
The balance appears instantly, just like a real incoming USDT deposit.
🔥 Features of Flash USDT Sender
FeatureDescriptionNetwork supportTRC20 / ERC20 / BEP20Visibility duration20 minutes — 2 hoursWallet compatibilityNon-KYC wallets that show unconfirmed TXsFlash USDT Binance modeSimulates deposits into BSC walletsAdjustable transaction sizeSend any custom USDT amountStealth expiryClean disappearance without trace
This is especially helpful in scenarios where you need to test token flows, design wallet apps, or simulate incoming funding activity
📞 How to Buy Flash USDT
To get your Flash USDT transaction or software setup:
💬 Telegram: @crypptrcver\ 📱 WhatsApp: +1 941 217 1821
Available packages:
- 🎯 One-time Flash USDT Send
- 💻 Full Flash USDT Software Tool
- 📱 Flash Sender for Mobile/Android
- 🌐 Multi-wallet Simulation Package
You can request TRC20, ERC20, or BEP20 flash transactions depending on the wallet or network you’re working with.
⚠️ Legal & Ethical Use Only
While Flash USDT is a powerful blockchain simulation tool, using it to deceive, fake trades, or commit fraud is illegal. Flash transactions should only be used for:
- ✅ Personal testing
- ✅ Blockchain development
- ✅ Wallet UI testing
- ✅ Research and education
Any misuse is your full responsibility.
❓ Frequently Asked Questions
What is Flash USDT?
A temporary USDT transaction that appears in a wallet balance without confirming on the blockchain. It disappears after a set time or block count.
Is Flash USDT real money?
No. It is a simulated deposit, not spendable or tradable.
Can I use Flash USDT on Binance?
You can send it to BSC (BEP20) wallets, but you cannot use it on the Binance exchange. It’s for display/testing only.
How do I buy Flash USDT?
Contact @crypptrcver on Telegram or WhatsApp to purchase a transaction or the full sender software.
What does Atomic Flash USDT mean?
It refers to Flash USDT transactions that are time-bound and expire silently, simulating atomic wallet behavior.
🧠 Final Thoughts
Flash USDT is one of the most advanced crypto testing tools available in 2025. Whether you’re simulating wallet behavior, demonstrating a smart contract front end, or simply showing a visual “deposit” for testing, Flash USDT provides an incredibly realistic experience — without ever moving real funds.
👉 Ready to simulate your first USDT transaction?
💬 Telegram: @crypptrcver\ 📱 WhatsApp: +1 941 217 1821
Packages available for:
- TRC20
- BEP20
- ERC20
- Custom wallet simulations
-
 @ 005bc4de:ef11e1a2
2025-05-15 23:15:04
@ 005bc4de:ef11e1a2
2025-05-15 23:15:04Today I rode my bicycle to work and then I had to ride halfway back home to go to a picnic event, kind of a thing. And then I had a bike back to work to help unload stuff and then I had to bike home. So, I got some extra exercise in today and a bit unexpected, but that's good. This image was while I was taking a little walk, it looked like a tiny forest. https://usermedia.actifit.io/125670ce-4e00-493c-a0b4-4c42d542391f This report was published via Actifit app (https://bit.ly/actifit-app | https://bit.ly/actifit-ios). Check out the original version https://actifit.io/@crrdlx/actifit-crrdlx-20250515t231342287z 15/05/2025 24933 Cycling, Jogging, Walking
Originally posted on Hive at https://hive.blog/@crrdlx/actifit-crrdlx-20250515t231342287z
Auto cross-post via Hostr v0.1.16 at https://hostr-home.vercel.app