-
 @ d36a437b:4480d6a5
2023-08-04 10:10:55
@ d36a437b:4480d6a5
2023-08-04 10:10:55导论 在康德哲学中我们的行动不仅仅是受到感官经验和外部因素的驱动,还涉及到我们内在的理性和意志。自由意志使我们能够根据道德原则和理性的指导来选择和行动,而不是被感官欲望或外在条件所束缚。
自由意志使我们能够对我们的行为负责,并承担后果。康德认为,通过自由意志的行动,我们成为道德的主体,可以根据普遍适用的道德律法来判断和行动,而不仅仅是受到个人欲望或外界因素的驱动。
然而,康德也指出,自由意志并不意味着完全自由地做出任何选择。他认为自由意志有其限制和约束,需要在道德律法的指引下行动。 自由意志的真正价值在于我们能够根据道德原则做出自主的决策和行动,而不是纯粹地追求个人欲望或外在利益。
康德的自由意志观念与他对伦理学和道德认识的理解密切相关。他认为,自由意志是个体道德责任的基础,我们的行动应该根据普遍适用的道德原则来决策,并为我们的行为负责。
Part i 权力与自由意志
综上所述,完全无底线且不理性的自由早在康德就被批判了并且被认为是错误的理念
言论自由可以被视为康德自由意志的一个重要应用领域。言论自由是指个体表达思想、意见和信仰的权利,不受政府或其他机构的干预或压制。这个权利是公民社会和民主制度的基石,也是知识交流和进步的关键。
康德的自由意志观点强调个体的独立性和自主性,以及对道德准则的遵循。言论自由可以被视为个体运用自由意志的一种方式,通过言辞表达自己的思想和见解。言论自由使个体能够参与公共讨论和辩论,促进知识的共享和社会的进步。 自由意志应当在道德行为中的限制。自由不是放任任意行为的纵容,而是在理性和普遍准则的指引下进行选择。
言论自由使个体能够独立思考、形成独立的意见,并表达这些意见而不受外部干预或压制。言论自由为个体提供了一个平台,在其中展示他们的自主性和独立思考的能力,也是人权的基本体现,也是人之所以为人而不是被硬件(肉体)与软件(思想)所限制的“机器”
Part ii 马克思主义中的言论自由
马老师作为后来者对前者的补充与批判必然更加的全面
根据马克思的历史辩证法,上一个时代的真理必然在下一个时代所呈现,马克思对于自由意志,言论自由的看法与康德完全不同
马克思主义的角度来看,个体的自由意志受到社会、经济和阶级关系的制约。个体的行为和意识是在特定历史时期和社会环境下形成的。然而,在特定条件下,个体仍然具有一定的选择权和自主性,可以通过集体行动来争取自身权益和解放。
从阶级利益意识形态去分析,马克思主义认为在资本主义社会中,社会中存在阶级斗争,并且不同阶级拥有不同的阶级利益,统治阶级(资产阶级)掌握了经济和政治权力,并通过控制媒体、教育等手段来塑造和宣传符合其利益的意识形态。因此,言论自由在资本主义社会中常常受到限制,被用于服务统治阶级的利益。
从思想压迫与言论管控角度来说,资本主义社会存在着对劳动者的压迫和剥削。这种压迫不仅体现在经济方面,还包括思想和意识形态上的控制。统治阶级通过掌控话语权和言论管制,限制了被压迫阶级对自己状况的认识和声音的表达。言论自由的受限导致被压迫阶级难以真实地表达自己的需求和反抗。
从解放与革命来说,言论自由是解放与革命的一大工具,是被压迫阶级争取解放的重要工具之一;通过言论自由,被压迫阶级能够表达自己的不满、观点和组织起来参与革命运动。
马克思主义认为,建立共产主义社会后,将会有一个无产阶级专政的阶段。在这个阶段,对统治阶级的反抗将受到限制,以确保无产阶级的权力稳定。然而,马克思认为,在这种情况下,言论自由仍然可以存在,并且将为广大群众提供更多发声和参与决策的机会,所以自由并非与资本主义统治相绑定
结论
不论是以阶级,经济,社会还是哲学,我们都得出了一个结论,就是无产者,人民,社会,世界需要言论自由,并且是理性,以道德为准则的言论自由,这是一个理想的社会样态
自由不是以私有财产为权力代表的权力关系,也不是以私有财产为原则组建的社会,家庭。而是以伦理道德为底线自由原则与人权
以资产阶级法权为基础支撑的国家不过是资产阶级商议内部事务的委员会罢,与工人没有任何干系
致谢
作者:Bill Charles 感谢DAOrayaki对本文章的创作支持
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ d3d74124:a4eb7b1d
2023-07-26 02:43:40
@ d3d74124:a4eb7b1d
2023-07-26 02:43:40This plan was GPT generated originally but then tweaked by myself as the idea fleshed itself out. All feedback welcome and encouraged.
Shenandoah Bitcoin
1. Executive Summary
Shenandoah Bitcoin is a for-profit community organization based in Frederick County, VA, uniquely blending the world of agriculture and STEM. Our mission is to foster community spirit, stimulate interest in agricultural technology, and promote understanding of Bitcoin, while providing enriching educational opportunities and ensuring sustainable business operations.
2. Company Description
Shenandoah Bitcoin is committed to delivering value to our local community. Our unique approach intertwines traditional agricultural practices, modern STEM concepts, and the world of digital currencies, specifically Bitcoin. Our activities cater to all age groups, focusing on fostering community engagement, hands-on learning experiences, and contributing to the overall welfare of our community.
What’s in a name?
Shenandoah Bitcoin. Shenandoah - an old and historied land. Bitcoin - a cutting edge technological advancement. Both encompass multiple industries, from energy and manufacturing, to farming and data centers. Both built using Proof of Work.
3. Services
We offer a range of services, including:
Family-friendly events: Agriculture, STEM, and Bitcoin-themed festivals, fairs, workshops, and community gatherings. Educational programs: Classes, seminars, and workshops on agricultural technology, STEM principles, and understanding and using Bitcoin. Facility Rentals: Spaces available for private events, business meetings, and community gatherings.
4. Membership Benefits
We offer tiered membership packages with benefits such as:
a. Silver Membership: Includes access to regular events, discounts on educational programs, and priority booking for facility rentals.
b. Gold Membership: All Silver benefits, free access to select educational programs, and further discounted facility rentals.
c. Platinum Membership: All Gold benefits, free access to all educational programs, highest priority and maximum discounts on facility rentals, and exclusive invitations to special events.
Member’s opting to pay in Bitcoin receive 10% off all pricing.
5. Market Analysis
Our primary market is the local community in Frederick County and Winchester, VA, which consists of various demographic groups. Our secondary market includes neighboring communities, tourists, businesses, and educational institutions interested in the intersection of agriculture, STEM, and Bitcoin. Understanding that facility use and events to be a drawing factor for all demographics, we outline demographic specific analysis below.
STEM professionals in the area may work remotely or commute toward DC and not interact much with their agricultural neighbors, but a desire for good quality food exists for many. In addition to events, drawing the STEM demographic in will be connections to CSAs, ranchers, and homesteaders for access to fresh locally grown food. Offering a child's play room adjacent to some office space, is a compelling benefit for the laptop class that is often in STEM professions.
Non-industrial food producers and homesteaders may not have the focus or resources for marketing and sales. By offering a physical touch point for them and direct connections to consumers, food producers benefit from membership. Having more options for drop off/pick up of various produced goods, makes it attractive for both the consumers and producers as coordination can be asynchronous.
Bitcoiners have a wide range of sub-demographics, including farmers and software engineers. Some travel hours over car and plane to attend bitcoin themed events. The topics of STEM and agriculture are of shared interest to non-trivially sized communities of bitcoiners. Having a physical touch point for bitcoiners will draw in some members just for that. Building fellowship is desired and sought in bitcoin.
5.1 Market Trends
The blending of agriculture, STEM fields, and Bitcoin is a unique concept with increasing interest in sustainable farming and ranching, food sovereignty, and health. Shenandoah Bitcoin is poised to tap into this growing interest and offer unique value to our community.
5.2 Market Needs
Our market requires initiatives that foster community engagement, promote understanding of agri-tech and Bitcoin, and provide a versatile space for events and learning.
6. Marketing and Sales Strategy
We will employ a blend of digital marketing, traditional advertising, and strategic partnerships. Our main marketing channels will be word of mouth, social media, local press, and our website. Partnerships with local small businesses, homesteaders, schools, agricultural organizations, and bitcoin companies will form a key part of our outreach strategy.
7. Organizational Structure
Shenandoah Bitcoin will be led by a CEO, supported by a management team responsible for daily operations, event planning, marketing, and community outreach. Event management and logistics will be handled by part-time staff and volunteers.
8. Financial Projections
Our revenue will be generated from membership fees, charges for events and educational programs, and facility rentals.
9. Funding Request
[If seeking additional funding, describe your needs and how the funds will be used]
10. Exit Strategy
Should it become necessary to dissolve the business, assets such as property, equipment, and any remaining cash reserves after meeting liabilities will be sold. Investors would receive their share of the remaining assets according to their proportion of ownership.
11. Conclusion
Shenandoah Bitcoin is a unique community organization bringing together agriculture, STEM, and Bitcoin in Frederick County, VA. Our distinctive approach is designed to deliver both profits and social impact, resonating strongly with our target market and positioning us for sustainable growth.
-
 @ 2448a66f:838296c9
2023-08-04 09:02:34
@ 2448a66f:838296c9
2023-08-04 09:02:34หากมองที่โครงสร้างทางชีวภาพของมนุษย์ มนุษย์สามารถย่อยน้ำตาลแล็กโทสในนมได้ถึงแค่อายุ 2 ขวบ หลังจากนั้นความสามารถในการย่อยน้ำตาลนี้จะลดลง ซึ่งอนุมานได้ว่าในทางธรรมชาติแล้ว มนุษย์ไม่ควรดื่มนมอีกแล้ว หลังจากอายุ 2 ขวบ (แม่จะหยุดผลิตน้ำนมโดยธรรมชาติหลักจากคลอดบุตรแล้ว 1-2 ปีเช่นกัน)
ในปัจจุบัน มีคน 2 กลุ่ม 1. กลุ่มที่สามารถดื่มนมได้ปกติ พบมากในกลุ่มผู้คนแถบตอนเหนือและตอนกลางของทวีปยุโรป
- กลุ่มที่มีอาการผิดปกติหลังจากดื่มนม เกิดจากร่างกายไม่สามารถผลิตเอนไซม์ แล็กเทสได้อย่างเพียงพอ ในการย่อยแล็กโทสในนม ซึ่งกลุ่มนี้มักจะมีอาการ ท้องอืด ท้องเสีย ปวดท้อง พบมากในกลุ่มผู้คนในทวีปแอฟริกา เอเชีย และอเมริกาใต้
https://media.primal.net/uploads/1/e9/04/1e90454e3fce2a0558c626a722a8f298e7753dbcfb907e6e56e724a654e8965f.jpg
แล้วมนุษย์เริ่มกินนมจากสัตว์ตอนไหน ดื่มทำไม? ข้อมูลทางประวัติศาสตร์ที่ค้นพบในปัจจุบัน ยังบอกไม่ได้ว่าจุดเริ่มต้นของการดื่มนมจากสัตว์อื่นของมนุษย์ มันเริ่มขึ้นตั้งแต่ยุคสมัยไหน ไม่มีหลักฐานที่บ่งชี้แน่ชัด เพียงแต่เราคาดการณ์ได้จากหลักฐานที่ค้นพบว่า ++มันน่าจะเริ่มขึ้นเมื่อหลายพันปีก่อน++ จากการค้นพบไขมันนมในภาชนะโบราณ หรือ การค้นพบกลุ่มกระดูกฝูงสัตว์ให้นมเพศเมีย
แต่มันก็บอกไม่ได้ว่า ทำไมมนุษย์ถึงเริ่มดื่มนมจากสัตว์ ทั้งๆที่ย่อยมันไม่ได้ อะไรเป็นจุดเริ่มต้นของเรื่องนี้ มีเหตุผลอย่างอื่นนอกจากเพื่อการเอาตัวรอดอีกหรือไม่?
ซึ่งในปัจจุบันก็ยังคงมีการถกเถียงกันว่า มนุษย์ควรดื่มนมจากสัตว์ไหม? อยู่ตลอด และแน่นอนว่าทั้ง 2 แนวคิด ต่างมีจุดยืนที่เข้มข้นเป็นของตัวเอง
ฝั่งที่มีความเห็นว่า ++"มนุษย์ดื่มนมจากสัตว์ได้"++ เพราะการค้นพบการดื่มนม มันมาจากการวิวัฒนาการเอาตัวรอดของมนุษย์ และปัจจุบันมนุษย์บางกลุ่ม ก็ไม่ได้มีปัญหากับการย่อยแล็กโทสแล้ว (เกิดจากการวิวัฒนาการของยีนส์)
ในขณะที่อีกฝั่งก็มีความเห็นว่า ++"มนุษย์ไม่ควรดื่มนมจากสัตว์"++ มนุษย์ควรหยุดกินนมตั้งแต่หย่านมแม่แล้ว เพราะร่างกายเรามันหยุดย่อยแล็กโทสไปแล้วตามธรรมชาติ
ส่วนความคิดเห็นของเราในฐานะคนที่มีภาวะย่อยแล็กโทสบกพร่อง การดื่มนมจากสัตว์ควรเป็นแค่ทางเลือก ไม่ควรเป็นคำแนะนำสุขภาพ (คำแนะนำแบบควรดื่มนมอย่างน้อย 1-2 แก้วต่อวัน) เพราะสำหรับบางคน การดื่มนมตามคำแนะนำสุขภาพ ส่งผลเสียมากกว่าผลดี
อีกทั้งสารอาหารที่มีในนมจากสัตว์ สามารถหาทดแทนได้จากแหล่งอื่น เช่น แคลเซียม สามารถหาได้ในปลาตัวเล็ก ผักใบเขียว วิตามิน D มีให้คุณฟรีๆในแสงแดด หรือถ้าหากอยากให้กระดูกแข็งแรง การเคลื่อนไหวร่างกาย การออกกำลังกายช่วยเพิ่มมวลกระดูก ลดภาวะกระดูกพรุนได้
https://media.primal.net/uploads/d/13/a9/d13a949e5a275bb0df8e317a7b8eb3d66c1180e5f6d6b7e70f89217e8ee866b9.webp
-
 @ 52b4a076:e7fad8bd
2023-05-01 19:37:01
@ 52b4a076:e7fad8bd
2023-05-01 19:37:01What is NIP-05 really?
If you look at the spec, it's a way to map Nostr public keys to DNS-based internet identifiers, such as
name@example.com.If you look at Nostr Plebs:
It's a human readable identifier for your public key. It makes finding your profile on Nostr easier. It makes identifying your account easier.
If you look at basically any client, you see a checkmark, which you assume means verification.
If you ask someone, they probably will call it verification.
How did we get here?
Initially, there was only one client, which was (kind of) the reference implementation: Branle.
When it added support for NIP-05 identifiers, it used to replace the display name with the NIP-05 identifier, and it had to distinguish a NIP-05 from someone setting their display name to a NIP-05. So they added a checkmark...
Then there was astral.ninja and Damus: The former was a fork of Branle, and therefore inherited the checkmark. Damus didn't implement NIP-05 until a while later, and they added a checkmark because Astral and other clients were doing it.
And then came new clients, all copying what the previous ones did... (Snort originally did not have a checkmark, but that changed later.)
The first NIP-05 provider
Long story short, people were wondering what NIP-05 is and wanted it, and that's how Nostr Plebs came to be.
They initially called their service verification. Somewhere between January and February, they removed all mentions to verification except one (because people were searching for it), and publicly said that NIP-05 is not verification. But that didn't work.
Then, there were the new NIP-05 providers, some understood perfectly what a NIP-05 identifier is and applied the correct nomenclature. Others misnamed it as verification, adding confusion to users. This made the problem worse on top of the popular clients showing checkmarks.
(from this point in the article we'll refer to it as a Nostr address)
And so, the scams begin
Spammers and scammers started to abuse Nostr addresses to scam people: - Some providers has been used by fake crypto airdrop bots. - A few Nostr address providers have terminated multitude of impersonating and scam identifiers over the past weeks.
This goes to show that Nostr addresses don't verify anything, they are just providers of human readable handles.
Nostr addresses can be proof of association
Nostr addresses can be a proof of association. The easiest analogy to understand is email:
jack@cash.app -> You could assume this is the Jack that works at Cash App.
jack@nostr-address-provider.example.com -> This could be any Jack.
What now?
We urge that clients stop showing a checkmark for all Nostr addresses, as they are not useful for verification.
We also urge that clients hide checkmarks for all domain names, without exception in the same way we do not show checkmarks for emails.
Lastly, NIP-05 is a nostr address and that is why we urge all clients to use the proper nomenclature.
Signed:
- Semisol, Nostr Plebs (semisol@nostrplebs.com)
- Quentin, nostrcheck.me (quentin@nostrcheck.me)
- Derek Ross, Nostr Plebs (derekross@nostrplebs.com)
- Bitcoin Nostrich, Bitcoin Nostr (BitcoinNostrich@BitcoinNostr.com)
- Remina, zaps.lol (remina@zaps.lol)
- Harry Hodler, nostr-check.com (harryhodler@nostr-check.com)
-
 @ 32092ec1:8e9fd13a
2023-04-25 18:02:43
@ 32092ec1:8e9fd13a
2023-04-25 18:02:43Bitcoin maximalism, to many, has evolved from a belief that bitcoin is the only crypto asset worth owning to a belief that bitcoin is the only asset worth owning. In addition, many observe that those who declare themselves to be bitcoin maximalists have also declared their allegiance to many other lifestyle choices. This was well articulated by Jameson Lopp in his blog post “A History of Bitcoin Maximalism.”
While some (myself included for a while) embrace the title of bitcoin maximalist, perhaps out of spite given that it was originally intended to be a derogatory term, I eventually have decided to reject it. While I do not own any other crypto assets, and I do believe that bitcoin offers the best risk adjusted investment across many asset classes, it is not, nor could it ever realistically be, my only investment. Due to the ambiguity of the definition of a “bitcoin maximalist” to some, even the fact that I have equity in my primary residence may call into question my status as a bitcoin maximalist. Although most people likely agree that this point of view is nonsensical, I feel that it is also completely pointless to take the time to defend the purity of my “bitcoin maximalism;” and so, I reject it. In place of the bitcoin maximalist label, I hereby declare myself to be a truth maximalist.
The truth is that 99% of non-bitcoin crypto assets are completely worthless; specifically, what I mean is that they literally add zero net positivity to humanity. The remaining 1% of non-bitcoin crypto assets may indeed serve some limited improvements to existing systems or other alternative benefits; however, these crypto assets are also, in my opinion, already highly over valued given the magnitude of the problems they are intending to solve. Most of the incremental improvements offered by cryptos are related to marginally improving systems based on fiat money and the banking industry both of which bitcoin intends to largely obsolete and are still net negative to humanity and designed to syphon wealth from the powerless to the powerful.
I do believe that open source, decentralized, cryptographic solutions will play additional roles in society and offer an opportunity to disrupt many existing centralized solutions. However, most of these solutions will not be investable assets, just as the internet itself is not an investable asset.
I believe it also to be true that investment properties intended for yield generation come with a host of additional costs and risks that are rarely properly accounted for when assessing the value of these assets. After accounting for the probability weighted costs of evictions, seizures, taxes, maintenance, inflation, and loan interest, I find it difficult to justify these investments over bitcoin held in self-custody.
Many other investable assets that simply sit on a bank’s balance sheet (e.g., stocks, bonds, etc.) can easily be seized if any number of three letter agencies decided that you should not have these assets. This can be done with no due process and does not require any in depth investigation to determine the validity of their claims. I believe that the probability of these types of seizures is much higher for known bitcoiners who are also critical of the government and the media, especially if current financial systems begin to collapse and/or if bitcoin’s value dramatically increases.
Beyond seizure of your individual assets, as the world begins to divest from the highly inflated store of value assets listed on the NYSE and NASDAQ due to seizure risks at the sovereign level, the risk of extreme inflation adjusted devaluation of your portfolio should also be considered. Compounding this risk is the opportunity cost associated with the fact that some of the wealth that may be withdrawn from the US stock market is also likely going to flow into bitcoin. These risks are rarely accounted for or quantified when determining the value of a stock portfolio in contrast to simply holding bitcoin in self-custody.
My opinions on these matters are common among bitcoiners who are largely labeled bitcoin maximalists. However, the title of truth maximalist also fits nicely when trying to counter some of the softer points made in Lopp’s blog post mentioned above. My thesis is that most people who have adopted the bitcoin maximalist “lifestyle” choices have done so as a result of their quest for truth, not as a result of their desire to virtue signal their status as bitcoin maximalists.
The truth is that a carnivore diet is much healthier than governments, media and academia would like you to believe (disclosure: I have never tried a carnivore diet)
The truth is that weightlifting is more beneficial than cardio to overall health (disclosure: I am not into weightlifting)
The truth is that traditional gender roles are beneficial to mental health (disclosure: although my wife is a full-time, stay-at-home mom, my marriage is far from perfect).
The truth is that extreme consequences from greenhouse gasses in the atmosphere are extrapolatory and predictions have historically failed miserably (disclosure: I do not think there is zero risk of extreme disasters from excessive levels of carbon in the atmosphere).
The truth is that seed oils are terrible for you (disclosure: I have ingested seed oils since discovering this).
The truth is that COVID vaccines pointlessly add risk to healthy people and children (disclosure: I received two doses of the COVID vaccine prior to realizing this truth and my wife still disagrees with me on this).
The truth is that natural health solutions are often more beneficial than big pharma would like you to believe (disclosure: I have not used any exotic natural remedies).
The truth is that modern art and architecture is garbage (disclosure: this is only a personal opinion).
The Truth is that Jesus Christ died on a cross and ascended into Heaven in order to save the world from sin (disclosure: although I have always been a Christian, over the last year or so I have dedicated a significant amount of time researching this and so far, everything is supporting this to be literally true and much more easily believable than you might think).
Maybe you disagree with some of these things that I have determined to be true. But let me ask, have done your own research? What is your basis for a counter argument to any of these truths? Did you verify or are you trusting someone else’s opinion? If you are trusting someone else’s research, did you investigate their credibility or determine if they have significant biases? Certainly, my opinions on the topics listed above not always based on exhaustive independent research, but I did approach each with skepticism and did not always believe these things with conviction prior to looking into them. I think any bitcoiner would agree that if you are trusting fiat funded academia, government organizations or mainstream media, you may need to do more research.
The truth is that I will continue to seek the truth and I will encourage others to do the same. The truth is that I welcome new information and listening to opinions that counter my beliefs. When choosing to have strong conviction in minority opinions about the truth, it is extremely valuable to be able to articulate and refute the points that are contrary to your beliefs. It is also important to be able to change your mind when presented with sufficient evidence against your opinion. This is what it means to be a truth maximalist. It just so happens that the truth is that bitcoin is the only crypto asset worth investing in. Don’t believe me? Prove it.
786973
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ b3590d02:0f2b1ae4
2023-07-06 18:44:20
@ b3590d02:0f2b1ae4
2023-07-06 18:44:20Verification: tweet
Badge implications:
- an account that joined Twitter in 2010 or earlier
- an account with fewer than 10,000 followers
Twitter user tweetious profile information:
- Joined in 2008
- Follower count: 699
- Following count: 529
-
 @ be318ab6:dd25a806
2023-04-09 02:55:48
@ be318ab6:dd25a806
2023-04-09 02:55:48Howdy y'all,
This is the Ramble #001
I was gifted extra spare time (layoffs), and I'm excited to put it into learning about some of the new exciting things swirling around us at an ever-accelerating speed & also about the good old ever-useful manual skills, which are disappearing almost at the same rate.
The focus will be on anti-fragility tools and skills. I'll be touching on the the topics of Nostr, AI, Bitcoin, Privacy and self-sufficiency skills like woodworking or food production. I'll include any building just for the sake of it (I get more value myself and motivation to do more of it if I can show off something tangible, I guess). It's not gonna be the most frontier-breaking r0ckstar knowledge, but it will humbly keep moving forward one step at the time along with my selfish pursuit of improving my knowledge and skills along these vectors. I also won't avoid some rants about the insane corruption in our Money and all the downstream problems it brings.
Why?
1. Why having a blog? * I want to practice my writing. Not to challenge the AI, but just to better remember the learnings, and to clarify & structure my thoughts. * The public record forces accountability on me. I want to commit to a habit of writing a few posts per week.
2. Why it's on Nostr? * When dozens of the smartest and most honest individuals I respect flock to this like a bunch of crazy birds, it's something I don't want to miss out on, and I want to get intimately familiar with the tech. * It's an uncensorable protocol that allows you to own your data and can re-architect many broken things on the current web. * Easy for me to push my tip jar in y'alls faces and see if anyone gets any real value out of this * And, I just wanted to play with it. Some clients still might be buggy, but the speed of development and improvements is lightning miles away from anything I've seen before.
I'll probably write some intro to NOSTR next time around; but in the meantime Gigi will help you out at nostr-resources.com
3. Why including the offline skills and tools? * Humans are not meant to stare into screens all day. * I see there's one of the most competitive edges for the next 10 years.
And, that's about it. I'm really excited about days and weeks, and will have some fun. If you have read all down here, thank you and PV to you!
PS.

Resources/Inspiration for this issue: * Marty's Bent - duh! * BloggingBitcoin - How To Start A Blog Today
-
 @ d266da53:7224d834
2023-08-04 08:39:38
@ d266da53:7224d834
2023-08-04 08:39:38Stay updated on the latest developments in Crypto , follow me on Yakihonne.com.

The Internet of Things (IoT) has emerged as a transformative technology, connecting billions of devices and revolutionising industries across the globe. In parallel, smart contracts, powered by blockchain technology, have gained traction as an innovative means of automating and securing digital agreements. When these two disruptive technologies converge, the potential for synergy and transformative impact becomes evident. In this article, we explore how smart contracts could revolutionise the Internet of Things, enhancing security, efficiency, and trust in the interconnected world.
What is the Internet of Things (IoT) and what are the real-world benefits?
IoT refers to a network of physical objects, devices, vehicles, appliances, and other items embedded with sensors, software, and connectivity capabilities that enable them to collect and exchange data over the internet. These “things” can range from everyday objects like thermostats, refrigerators, and wearable devices to complex industrial machinery, smart cities infrastructure, and even autonomous vehicles.
Equipped with sensors and actuators, IoT devices help to gather data from their surroundings and potentially even interact with their environment. They can communicate with each other, exchange data with cloud-based systems, and potentially make autonomous decisions based on the information they receive. This interconnected network of devices creates a vast ecosystem where data flows and interactions occur, enabling a wide range of applications and services.
The primary goal of IoT is to enable the seamless integration between the physical and digital world, unlocking numerous opportunities for efficiency, automation, and innovation. By collecting and analysing data from various sources, IoT provides valuable insights, helping to make informed decisions and automate processes to enhance productivity, optimise resource utilisation, improve safety, and provide new services and experiences.
The proliferation of IoT has transformed numerous industries, including healthcare, agriculture, manufacturing, transportation, energy, and smart cities. In healthcare, for example, IoT devices can monitor patients’ vital signs, track medication adherence, and enable remote diagnostics, enhancing the quality of care and empowering patients to take a more proactive role in managing their health. In agriculture, IoT sensors can monitor soil moisture, weather conditions, and crop health, enabling farmers to optimise irrigation, reduce waste, and improve yields.
How can blockchain technology and smart contracts enhance IoT?
The seamless integration of IoT and blockchain technologies offer numerous potential benefits, particularly in scenarios where vast amounts of data collected from IoT devices need to be stored and accessed in the public domain. Meanwhile, smart contracts can eliminate the need for intermediaries, central authorities, and manual intervention, helping to streamline processes and increase operational efficiency. Here are three examples describing the potential impact blockchain technology and smart contracts could have on three incredibly important global sectors.

Example #1 — IoT-Based Supply Chain Tracking
In this scenario, let’s say a company manufactures organic coffee beans and wants to provide verifiable information about the product’s origin, ensuring transparency and trust for consumers.
- IoT Devices: The company installs IoT devices (e.g., RFID tags, GPS trackers) on each bag of coffee beans during the production process. These devices record data such as the location, temperature, humidity, and other relevant parameters at different stages of the supply chain.
- Data Storage on the Blockchain: The data collected by IoT devices is stored on a public blockchain. Each bag of coffee beans is associated with a unique identifier (e.g., a barcode) that acts as its digital twin on the blockchain, referred to as an NFT.
- Smart Contracts: Smart contracts are deployed on the blockchain to automate various aspects of the supply chain process. For instance, a smart contract could be programmed to trigger certain actions when specific conditions are met, such as recording the location and timestamp when a bag of coffee beans reaches a particular checkpoint, like a warehouse or a shipment hub.
- Transparency and Verification: Consumers and other stakeholders can access the blockchain to verify the entire journey of a bag of coffee beans, from its origin to the final destination. The immutable nature of the blockchain ensures that the data cannot be tampered with, providing transparent and auditable information about the product’s supply chain history.
- Supply Chain Efficiency: With the data being transparently recorded on the blockchain, all parties involved in the supply chain, including the manufacturer, distributors, retailers, and consumers, have access to real-time information. This transparency reduces the likelihood of disputes, delays, or fraudulent activities, leading to a more efficient and trustworthy supply chain.
- Quality Assurance: The data collected by IoT devices can help monitor environmental conditions during transportation and storage. If the temperature or humidity exceeds predefined thresholds, the smart contract could trigger an alert, allowing the company to take immediate action to preserve the product’s quality.
- Automated Payments and Incentives: Smart contracts can automate payment processes between different parties in the supply chain. For example, when a bag of coffee beans reaches its destination, the smart contract can automatically release the payment to the distributor, streamlining the payment process and reducing administrative overhead.
In summary, combining IoT, blockchain, and smart contracts in the supply chain management of organic coffee beans enables transparency, trust, and efficiency throughout the entire process. Consumers can access verifiable information about the product’s origin, quality, and handling, leading to increased trust in the brand. The automated and secure nature of smart contracts reduces the need for intermediaries and manual interventions, making the supply chain more streamlined and cost-effective. Overall, this example illustrates how blockchain and smart contracts enhance the IoT ecosystem, transforming supply chain management and positively impacting businesses and consumers alike.

Example #2 — IoT-Based Energy Management in a Smart City
In this scenario, we’ll explore how blockchain and smart contracts can help manage energy consumption in a smart city, optimising resources and enhancing sustainability.
- IoT Devices: In a smart city, various IoT devices are deployed throughout the infrastructure, including smart meters, sensors, and actuators. These devices collect real-time data on energy consumption, electricity generation (e.g., solar panels), weather conditions, traffic patterns, and other relevant information.
- Data Storage on the Blockchain: The data collected by IoT devices is stored on a private or public blockchain, depending on the level of required transparency and privacy. Each device or data source has its unique identifier and cryptographic signature to ensure data integrity and prevent tampering.
- Smart Contracts: Smart contracts are used to manage energy-related processes in the smart city. For instance, a smart contract could be created to automatically adjust street lighting levels based on the detected traffic patterns and weather conditions. Additionally, a smart contract could optimise the usage of renewable energy sources based on real-time electricity generation data and demand.
- Decentralised Energy Grid: The smart contracts on the blockchain enable the creation of a decentralised energy grid, where energy transactions can occur peer-to-peer between energy producers and consumers. Prosumers (those who produce and consume energy) can sell excess energy to others directly through the blockchain, without the need for intermediaries.
- Energy Efficiency: With real-time data collected from IoT devices and processed by smart contracts, the city’s energy management system can automatically optimise energy consumption. For example, smart contracts can adjust heating, cooling, and lighting systems in public buildings based on occupancy, weather conditions, and energy availability, reducing wastage and promoting energy efficiency.
- Demand Response: The IoT devices and smart contracts can enable a demand-response mechanism. When the energy grid faces peak demand periods, smart contracts can automatically adjust the energy consumption of certain non-essential systems to balance the load and prevent blackouts or energy shortages.
- Incentives for Sustainable Practices: Through the blockchain and smart contracts, the city can implement incentive programs to encourage sustainable energy practices. For instance, residents or businesses that actively participate in energy conservation or generate renewable energy may receive tokens or other rewards on the blockchain, fostering a culture of sustainability.
In summary, applying blockchain and smart contracts to IoT-based energy management in a smart city offers numerous benefits. It allows for a transparent, decentralised, and automated energy management system that optimises energy consumption, reduces waste, and promotes the use of renewable energy sources. The secure and immutable nature of the blockchain ensures data integrity, while smart contracts enable real-time decision-making and automation. By fostering a more sustainable and efficient energy ecosystem, this use case contributes to building smarter, greener, and more resilient cities for the future.

Example #3 — IoT-Based Healthcare Data Management
In this scenario, we’ll examine how blockchain and smart contracts can address the challenges of securely managing and sharing patient data among different healthcare providers, ensuring privacy, and promoting interoperability.
- IoT Medical Devices: In a healthcare setting, IoT medical devices are utilised to monitor patients’ vital signs, collect health data, and track medical conditions. These devices can include wearable health trackers, smart implants, and remote monitoring devices.
- Data Storage on the Blockchain: The health data collected by IoT devices is stored on a private blockchain network with controlled access. Each patient’s medical data is encrypted and linked to their unique digital identity on the blockchain.
- Smart Contracts for Data Access and Consent: Smart contracts are utilised to manage data access and patient consent. Patients can specify which healthcare providers or researchers can access their medical data through predefined smart contracts. The smart contracts enforce data access permissions and ensure that data is only accessible to authorised parties with patient consent.
- Interoperability: The use of a blockchain-based system enables interoperability between different healthcare providers and institutions. As patient data is stored in a standardised and secure format on the blockchain, authorised healthcare providers can access and share relevant data seamlessly, even if they use different electronic health record (EHR) systems.
- Patient-Centric Data Control: Blockchain and smart contracts empower patients to have greater control over their health data. Patients can easily grant or revoke access to their medical information, ensuring that sensitive data remains secure and shared only with those they trust.
- Auditability and Data Integrity: The immutable nature of the blockchain ensures that all data transactions and changes to patient records are recorded transparently. This audit trail fosters data integrity, reducing the risk of unauthorised modifications or data breaches.
- Research and Analytics: Researchers can securely access aggregated and anonymised health data for medical research and population health analytics. Smart contracts can govern data-sharing agreements between healthcare institutions and researchers, ensuring compliance with privacy regulations and ethical considerations.
- Telemedicine and Remote Monitoring: IoT devices can facilitate telemedicine and remote patient monitoring, where patients’ health data is transmitted securely to healthcare providers through the blockchain. Smart contracts can automate remote monitoring protocols and alert healthcare professionals in case of emergencies or abnormal conditions.
In summary, implementing blockchain and smart contracts in an IoT-based healthcare data management system offers significant advantages. It ensures patient data security, privacy, and control while promoting interoperability and data sharing among healthcare providers. The decentralised and immutable nature of the blockchain enhances data integrity and transparency, making it a valuable tool for improving healthcare delivery, medical research, and patient outcomes. By fostering a patient-centric approach to data management, this use case enhances the overall efficiency and effectiveness of the healthcare system.

How does blockchain data storage compare to traditional cloud storage?
Commonly referred to as the “Big Data of Things” the IoT space is anticipated to generate a staggering 73.1 zettabytes (ZB) of data — for context, a single zettabyte (ZB) is equal to one trillion gigabytes (GB). Big data is a valuable resource for businesses, researchers, and organisations alike, providing insights, trends, and patterns that can drive decision-making, innovation, and efficiency improvements.
Rising significantly in popularity during the 2010’s, cloud storage solutions from the likes of Google and Amazon have made a significant impact on IoT data storage, providing scalable, real-time access and analytics capabilities. However, the downside of cloud storage lies in its centralised nature, where data is stored and managed by third-party providers, making it susceptible to potential security breaches, data loss, and privacy concerns. Furthermore, cloud computing lacks the programmability of blockchain technology, offering automated rule-based interactions and conditional data access. These are the key benefits of using blockchain technology over traditional cloud-based storage:
- Decentralisation and Security: Blockchain’s decentralised nature ensures that data is distributed across a network of nodes, reducing the risk of single points of failure and making it more resistant to hacking or data breaches. This enhances the security and integrity of IoT data, safeguarding it from unauthorised access and tampering.
- Immutability: Data stored on a blockchain is immutable, meaning it cannot be altered or deleted once it is recorded. This feature ensures data integrity and creates a transparent and auditable trail of all data changes, providing reliable and trustworthy data history.
- Trust and Transparency: Blockchain operates on a consensus mechanism, where multiple nodes agree on the validity of transactions and data. This consensus fosters trust among participants, as all parties can verify data without relying on a central authority, ensuring transparent and accountable data sharing.
- Data Ownership and Control: In a blockchain network, data ownership and control lie with the users who hold cryptographic keys to access and manage their data. This user-centric approach enhances data privacy, giving individuals more control over their personal information, reducing dependence on third-party providers.
- Elimination of Centralised Authority: Unlike cloud storage solutions that rely on centralised servers and administrators, blockchain eliminates the need for a single central authority, reducing the risk of data abuse or manipulation by a single entity.
- Smart Contracts and Automation: Smart contracts can facilitate automated and trustless interactions based on predefined conditions. This allows for seamless and secure data sharing, automated transactions, and the execution of predefined rules without the need for intermediaries.
- Resilience and Disaster Recovery: The distributed nature of blockchain data storage ensures that even if some nodes fail or leave the network, the data remains available and operational, enhancing resilience and disaster recovery capabilities.
- Data Interoperability: Blockchain can facilitate data interoperability, enabling seamless data exchange between different IoT devices, platforms, and applications, fostering collaboration and integration across diverse systems.

How is IoT data stored on the blockchain?
IoT data collection can typically be integrated with a blockchain in one of two ways:
- Data can be directly embedded in smart contracts
- Data can be stored off-chain and the blockchain stores references (e.g., hashes) to the data
Prior to adding any data to the blockchain, it undergoes validation to ensure its accuracy, authenticity, and adherence to predefined rules or consensus mechanisms. The validated IoT data is then stored on the blockchain as transactions. Each transaction represents a batch of data and is added to a block, forming a chain of blocks, hence the name “blockchain”. Once data is stored on the blockchain, it becomes immutable and transparent. It cannot be altered or deleted, and its entire history is recorded, making it auditable and tamper-resistant.
Smart contracts are created to manage data access and data sharing permissions. These contracts define rules for accessing specific data sets, ensuring that only authorised parties can retrieve relevant data. External parties, such as other devices, applications, or organisations, can interact with the smart contract to request access to specific IoT data. The smart contract validates the request and executes predefined conditions to verify the legitimacy of the data access request. If the request is valid, the smart contract grants access to the requested data, either by providing the data directly from the blockchain or by referring to off-chain data sources. In cases where data privacy is crucial, the smart contract may use encryption mechanisms to secure the data during transmission and access.
Where cloud storage is typically charged on a subscription basis, determined by the amount of data stored, blockchain storage is done on a pay-as-you-go basis. Each time data is recorded on the blockchain, transaction fees are applicable. Further fees may be applicable when that data is later accessed through a smart contract. It is therefore important to select a blockchain network that is optimised for the intended application. Choosing a network that is interoperable with other networks is also vital, as the blockchain industry is very much in its infancy and official global standards have not yet been established. Choosing a network such as Electroneum, with extremely low transaction fees (several orders of magnitude cheaper than Ethereum) along with its compatibility with the Ethereum Virtual Machine (EVM) could be a good choice for your requirements. More on this in the next section.

The importance of standards in blockchain for IoT expansion
Technology standards enable different devices and technologies to communicate seamlessly with one another, eliminating fragmentation and proprietary lock-ins. Standards help to establish best practices for safety and security, whilst also allowing for easy substitution and scalability. This, in practice, helps to facilitate greater market access and global trade, whilst driving collaboration, research, and development for innovation and industry advancement.
Across the IoT sector today, wireless communication standards such as Wi-Fi and Bluetooth have played a crucial role in facilitating its significant growth, which in 2021 had exceeded 11 billion devices, and by 2023 is projected to reach almost 30 billion. Where Wi-Fi provides high-speed wireless connectivity, enabling IoT devices to connect to the internet and communicate with other devices, cloud platforms, and applications, Bluetooth offers short-range wireless communication, making it ideal for connecting IoT devices in close proximity, such as wearable devices, smart home devices, and personal sensors. Together, these standards have provided the foundation for scalable, interconnected IoT ecosystems.
As blockchain technology and smart contracts continue to evolve and find widespread adoption, similar standards will be needed. So far, the Ethereum Virtual Machine (EVM) has played a pivotal role in setting some key global standards for smart contracts. It introduced the Solidity programming language, which aims to foster a common coding standard, whilst EVM’s gas mechanism and fee standards ensure fairness and efficiency in contract execution. It has also fostered the development of tools, libraries, and frameworks for smart contract development, while the EIP process provides developers with a unified way of proposing improvements to the technology.
With the release of Project Aurelius later this year, Electroneum is aligning its well-established blockchain network with the standards set out by EVM, allowing external developers to build on top of the network for the very first time and establishing interoperability with other EVM-compatible blockchains, such as Ethereum, Ripple, Binance Smart Chain, Polygon, Avalanche, Cardano, amongst others. More importantly, however, Electroneum is introducing significantly lower EVM interaction fees that are a number of orders of magnitude cheaper than Ethereum’s, providing a more affordable way to build and deploy smart contracts within IoT environments.
How can an IoT manufacturer move to blockchain data storage?
The convergence of blockchain technology and smart contracts with the IoT presents a transformative potential for various industries, and as these technologies continue to evolve and gain broader adoption, their impact on today’s trillion-dollar IoT market can be transformational, unlocking new opportunities for efficiency, security, and innovation. If you work in IoT and would like to discuss any thoughts or ideas, be sure to reach out to us at: opportunities@electroneum.com
By:ETN-Network Link:https://medium.com/@ETN-Network/how-could-blockchain-technology-and-smart-contracts-impact-the-1-trillion-iot-market-8a78a6980219
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ 7f5c2b4e:a818d75d
2023-08-04 07:25:45
@ 7f5c2b4e:a818d75d
2023-08-04 07:25:45この記事は nostr:npub1wh69w45awqnlsxw7jt5tkymets87h6t4phplkx6ug2ht2qkssswswntjk0 によって、日本語訳されました。
この記事は以下の言語でもご覧になれます:
- 英語:nostr:naddr1qqxnzd3cxy6rjv3hx5cnyde5qgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28lxc9p6
- フランス語:nostr:naddr1qqxnzd3cxyunqvfhxy6rvwfjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c33xpshw7ntde4xwdtjx4kxz6nwwg6nxdpn8phxgcmedfukcem3wdexuun5wy6kwunnxsun2a35xfckxdnpwaek5dp409enw0mzwfhkzerrv9ehg0t5wf6k2qgawaehxw309a6ku6tkv4e8xefwdehhxarjd93kstnvv9hxgtczyzd9w67evpranzz2jw4m9wcygcyjhxsmcae6g5s58el5vhjnsa6lgqcyqqq823cmvvp6c thanks to nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs
- 中国語:nostr:naddr1qqxnzd3cx5urvwfe8qcr2wfhqyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszrrhwden5te0vfexytnfduq35amnwvaz7tmwdaehgu3wdaexzmn8v4cxjmrv9ejx2aspzamhxue69uhhyetvv9ujucm4wfex2mn59en8j6gpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqg4waehxw309ajkgetw9ehx7um5wghxcctwvsq35amnwvaz7tmjv4kxz7fwdehhxarjvaexzurg9ehx2aqpr9mhxue69uhhqatjv9mxjerp9ehx7um5wghxcctwvsq3jamnwvaz7tmwdaehgu3w0fjkyetyv4jjucmvda6kgqgjwaehxw309ac82unsd3jhqct89ejhxqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqz8rhwden5te0dehhxarj9ekh2arfdeuhwctvd3jhgtnrdakszpmrdaexzcmvv5pzpnydquh0mnr8dl96c98ke45ztmwr2ah9t6mcdg4fwhhqxjn2qfktqvzqqqr4gu086qme thanks to nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv
- スウェーデン語:nostr:naddr1qqxnzd3cxcerjvekxy6nydpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgszet26fp26yvp8ya49zz3dznt7ungehy2lx3r6388jar0apd9wamqrqsqqqa28jcf869 thanks to nostr:npub19jk45jz45gczwfm22y9z69xhaex3nwg47dz84zw096xl6z62amkqj99rv7
- スペイン語:nostr:naddr1qqfxy6t9demx2mnfv3hj6cfddehhxarjqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28ldvk6q thanks to nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624
- オランダ語:nostr:naddr1qqxnzd3c8q6rzd3jxgmngdfsqyvhwumn8ghj7mn0wd68ytn6v43x2er9v5hxxmr0w4jqz9rhwden5te0wfjkccte9ejxzmt4wvhxjmcpp4mhxue69uhkummn9ekx7mqprfmhxue69uhhyetvv9ujumn0wd68yemjv9cxstnwv46qzyrhwden5te0dehhxarj9emkjmn9qyvhwumn8ghj7ur4wfshv6tyvyhxummnw3ezumrpdejqzxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqzxnhwden5te0dehhxarj9ehhyctwvajhq6tvdshxgetkqy08wumn8ghj7mn0wd68ytfsxyhxgmmjv9nxzcm5dae8jtn0wfnsz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpy9mhxue69uhk27rsv4h8x6tkv5khyetvv9ujuenfv96x5ctx9e3k7mgprdmhxue69uhkummnw3ez6v3w0fjkyetyv4jjucmvda6kgqg8vdhhyctrd3jsygxg8q7crhfygpn5td5ypxlyp4njrscpq22xgpnle3g2yhwljyu4fypsgqqqw4rsyfw2mx thanks to nostr:npub1equrmqway3qxw3dkssymusxkwgwrqypfgeqx0lx9pgjam7gnj4ysaqhkj6
- アラビア語:nostr:naddr1qqxnzd3c8q6rywfnxucrgvp3qyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsfev65tsmfgrv69mux65x4c7504wgrzrxgnrzrgj70cnyz9l68hjsrqsqqqa28582e8s thanks to nostr:npub1nje4ghpkjsxe5thcd4gdt3agl2usxyxv3xxyx39ul3xgytl5009q87l02j
- ドイツ語:nostr:naddr1qqxnzd3c8yerwve4x56n2wpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsvcv7exvwqytdxjzn3fkevldtux6n6p8dmer2395fh2jp7qdrlmnqrqsqqqa285e64tz thanks to nostr:npub1eseajvcuqgk6dy98zndje76hcd485zwmhjx4ztgnw4yruq68lhxq45cqvg
- ロシア語:nostr:naddr1qqxnzd3cxg6nyvehxgurxdfkqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa286qva9x by nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
こんにちは、親愛なるノストリッチさん!
Nostrは全く新しいムーブメントです。はじめの一歩をよりスムーズに、より豊かにするためのいくつかの手順をご紹介しましょう。
👋 ようこそ
これを読んでいるあなたは、すでにモバイルアプリをダウンロードしてNostrに参加しているはずです (例:Damus, Amethyst, Plebstr)。もしくは以下のウェブクライアントかもしれません (例:snort.social, Nostrgram, Iris)。初心者の方であれば、選んだアプリに合った手順に従うことが重要です。ただし、最低限必要な手順はどのアプリにおいても基本は同じですので、ベーシック以上のことを知る必要はありません(もちろん、知りたければトライしてみましょう)。もしあなたが、この記事を偶然見つけて、まだNostr【アカウント】を取得していない場合は、以下のリンクをご覧ください:いちばん簡単なステップリスト by nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz.
🤙 楽しもう
Nostrは、人々が確実につながれ、意見を聞いてもらえ、そして、その過程を楽しむことができるように設計されています。これが重要なのです(もちろん、自由の戦士や内部告発者のためのツールであるなど、深刻な使用例もたくさんありますが、それは別の記事で書くことにしましょう)。ですから、何か難しい感じることがあれば、経験豊富なノストリッチたちに声をかけてください。私たちは歓迎します。Nostrでの交流は決して難しいものではありませんが、従来のプラットフォームと比べるといくつか特殊な点があります(でも何も心配することはありません)。
非公式 Nostrアンバサダーリストはこちら:
nostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu
リストに掲載されたすべてのノストリッチには、Nostrアンバサダー バッジが授与されていますので、簡単に彼らを見つけることができ、また、フォローすることができます。
⚡️ ザップしよう
Zap(ザップ)は、Nostrに参加したら最初に気づく違いの1つです。ザップはNostrユーザーが即座に価値を送ることを可能にし、便利で楽しいコンテンツの作成をサポートします。これはビットコインとライトニングネットワークによって実現しました。これらの分散型決済プロトコルにより、従来のソーシャルメディアプラットフォームで誰かの投稿に「いいね!」をするのと同じくらい簡単に、satoshi / sats(ビットコインネットワークの最小単位)を即座に送ることができます。私たちはこのモデルをValue-4-Value(バリューフォーバリュー)と呼んでいて、この究極のマネタイズモデルについての詳細は以下をご覧ください:https://dergigi.com/value/
おすすめ記事 by nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 では【ザップとは何か?】詳しく書かれてます。
あなたがコンテンツクリエイターでないとしても、ザップを有効にすべきです - 人々はあなたの投稿のいくつかに価値を見いだし、あなたにsatoshiを送りたいと思うかもしれません。Nostrで価値を受け取る最も簡単な方法は、以下の2ステップです:
- Wallet of Satoshiをダウンロードする - ビットコインとライトニングを、スマホで初めて使うなら、おそらくベストチョイスのはずです[^1] なお、他にもたくさんのウォレットがありますので、ご自分に合ったものをお選びください。また、ウォレットはバックアップを必ずお忘れなく。
- 【Receive / 受信】をタップする。
- 画面に表示されているライトニングアドレス(メールアドレスのように見える文字列)をタップして、クリップボードにコピーします。

- コピーしたアドレスをNostrクライアント内にある、対応箇所に貼り付けます(対応箇所には【Bitcoin Lightning Address / ビットコイン・ライトニングアドレス】や、【LN Address / LNアドレス】などのような記載があり、使用しているアプリによって異なります)。

📫 Nostrアドレスを取得しよう
Nostrのアドレスは、Nostrの諸先輩たちによってしばしば【NIP-05 identifier / NIP-05識別子】と呼ばれているもので、電子メールのように見え:
🔍 アカウントの発見と共有を簡単にします ✔️ あなたが人間であることの証明に役立ちます
以下がNostrのアドレスの例です:Tony@nostr.21ideas.org
 Nostrアドレスがあれば、どのNostrアプリであろうが、対応するユーザーを簡単に見つけることができます。
Nostrアドレスがあれば、どのNostrアプリであろうが、対応するユーザーを簡単に見つけることができます。
Nostrアドレスを取得するには、次のような無料サービスを利用できますNostr Check (by nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624) または有料サービスですがNostr Plebs (by nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424) もおすすめです。どちらも異なる特典を提供していて、どちらを選ぶかはあなた次第です。また、Nostrアドレスを取得するもう1つの方法は、ブラウザの拡張機能を活用することです。この方法の詳細はこちらをご覧ください。
🙇♀️ 基本を知ろう
Nostrは、従来のソーシャル・プラットフォームとは大きく異なるため、基本的なことを理解しておくことは、あなたのような新しいユーザーにとって有益です。誤解しないでほしいのは、プログラミング言語やプロトコルの技術的な詳細を学べと言っているのではありません。私が言いたいのは、NostrとTwitter / Medium / Redditの違いを理解し、より大きな視野を持つことはとてもためになるということです。例えば、パスワードやログイン機能はなく、代わりに秘密鍵と公開鍵が使われています。でも、難しくはありません。Nostrを理解するのに役立つ膨大なリソースがありますのでご安心を。このきちんと整理されたランディングページ by nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 には、💜とともにあなたが知るべきすべての情報が載っています。
 これらのリソースが提供する情報は、あなたのNostrキー(つまりあなたのアカウント)を保護するのにも役立ちます。
これらのリソースが提供する情報は、あなたのNostrキー(つまりあなたのアカウント)を保護するのにも役立ちます。
🤝 つながろう
優秀な [^3] 人たちとつながる能力こそが、Nostrを特別なものにしています。ここでは誰もが話を聞いてもらうことができ、誰も排除されることはありません。Nostrで面白い人を見つける簡単な方法はいくつかあります:
- ツイッターでフォローしている人を探す:https://www.nostr.directory/はそのための素晴らしいツールです。
- 信頼できる人がフォローしている人をフォローする:同じ興味を持つ人のプロフィールを見て、その人がフォローしている人のリストをチェックし、その人とつながろう。

- グローバルフィードを見てみる:すべてのNostrクライアント(Nostrアプリ)には、すべてのNostrユーザーの投稿を集約したグローバルフィードに切り替えるタブがあります。興味のある人をただフォローしてみましょう(我慢してください - グローバルフィードでは大量のスパムを見ることになるかもしれません)。

- ハッシュタグ # を活用しよう:ハッシュタグは好きなトピックに集中するのに最適な方法です。気になる # ハッシュタグをタップするだけで、そのトピックに関連する投稿がさらに表示されます。また、使っているアプリでハッシュタグを検索することもできます。発見力を高めるために、あなたが投稿する際も、ハッシュタグを使うことをお忘れなく。
https://nostr.build/i/0df18c4a9b38f1d9dcb49a5df3e552963156927632458390a9393d6fee286631.jpg スクリーンショット https://nostrgraph.net/ ダッシュボード by nostr:npub1ktw5qzt7f5ztrft0kwm9lsw34tef9xknplvy936ddzuepp6yf9dsjrmrvj
🗺️ 探検しよう
ご紹介した5つのステップは、あなたの経験を大幅に向上させる素晴らしいスタートになったはずです。ですが、もっと新しい発見をサポートし、楽しむためのさらに多くのツールがあります!NostrはTwitterの代用品ではなく、その可能性は無限大です。

楽しくて便利なNostrプロジェクト・リストをご覧ください:
- https://nostrapps.com/ Nostrアプリ・リスト
- https://nostrplebs.com/ – NIP-05の取得とその他のNostr特典 (有料)
- https://nostrcheck.me/ – Nostrアドレス、メディアアップロード、リレー
- https://nostr.build/ – メディアアップロード管理 (などなど)
- https://nostr.band/ – Nostrネットワークとユーザー情報
- https://zaplife.lol/ – ザップ統計
- https://nostrit.com/ – 予約投稿
- https://nostrnests.com/ – Twitterスペース 2.0
- https://nostryfied.online/ - Nostr投稿のバックアップ
- https://www.wavman.app/ - Nostrミュージックプレイヤー
📻 リレー
Nostrに慣れたら、Nostrリレーに関するクイックガイドをぜひご覧ください:https://lnshort.it/nostr-relays 最初のうちは特に心配するようなテーマではありませんが、あとになればなるほど、間違いなく重要なテーマとなります。
📱 モバイル版Nostr
スマホでも、スムーズなNostr体験ができます。このガイドでは、スマートフォンでNostrウェブアプリケーションにシームレスにログイン、投稿、ザップなどを行う方法を説明します:https://lnshort.it/nostr-mobile
読んでくれてありがとう、そしてラビットホールの向こう側でお会いしましょう
nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
[^1]: 忘れずにチェックしよう
-
 @ 32e18276:5c68e245
2023-08-03 21:05:05
@ 32e18276:5c68e245
2023-08-03 21:05:05Hey guys,
I've been quiet lately... I've been working on something big. In the past 2 weeks there have been 9539 new lines of code added to damus, 2928 removed, 279 files changed. I've rewritten much of the codebase in preparation for the nostrdb integration.
nostrdb
What is nostrdb? nostrdb is an integrated relay within damus, with the same design as strfry, but slightly different to support embedding into nostr apps. This will be the heart of Damus apps going forward, including notedeck and other future microapps. Think of it as a kind of development kit but with an embedded database and query capabilities. I didn't want to have to recreate all of the same querying, caching, and parsing code when building new apps, nostrdb will solve all of the painful and slow parts. nostr seems simple but if you want a fully working app it is pretty complicated, especially if you want it to be fast and sync efficiently.
Goals
- be the best and most efficient at querying, syncing and storing nostr notes
- enable direct mapping of notes into application code without any serialization overhead
- provide advanced syncing capabilities such as negentropy, which allows us to only query stuff we don't have
- be as portable as possible. nostrdb is a C library that you can embed into basically anything.
- full relay filter support
- full text search
Benefits
- full note verification
- more efficient de-duplication before we begin processing events off the wire
- set-reconciliation based syncing (negentropy) drastically reduces bandwidth usage and latency
- iteration on future nostr apps will be quicker (android, desktop, etc)
- features like ghost mode, account switching, etc will be much more efficient as you will be able to quickly switch between notes that are cached locally
- much smaller memory footprint due to optimized in-memory note format, which in turn improves cpu-cache efficiency
- much better profile and note searching
So that's what I've been working on in the past two weeks. On to what else is new in this release:
Multi reactions!
Suhail did an amazing job at adding multiple reaction support. All you need to do is long-press the Shaka button to show different options. You can customize these in settings as well
New onboarding features
Damus will now suggest people to follow when you first enter the app, this is the first of many onboarding improvements coming soon. Thank Klabo for this one!
That's all for now! Please test thoroughly and let me know if you run into any issues. You likely will since the entire codebase has been changed, and I probably broke something.
Until next time 🫡
-
 @ bcea2b98:7ccef3c9
2023-08-02 00:08:30
@ bcea2b98:7ccef3c9
2023-08-02 00:08:30A Finney attack, a specific kind of double-spend attack in the Bitcoin network, requires certain specific conditions within the network topology. Here's how it works:
-
Pre-mined Block: The attacker must mine a block containing a transaction that pays the coins to themselves. This block is not immediately broadcast to the network.
-
Direct Connection to Victim: Ideally, the attacker must make a direct connection to the victim's node or ensure network latency to the victim, to minimize the chance that the victim learns about the pre-mined block before the attack transaction is accepted.
-
Second Transaction to Victim: The attacker sends a transaction to the victim (e.g., the merchant), who delivers goods or services once the transaction appears in the victim's mempool but before it is confirmed in a block.
-
Release of Pre-mined Block: Once the victim accepts the unconfirmed transaction, the attacker broadcasts the previously mined block, thereby invalidating the transaction to the victim since the block contains a conflicting transaction that spends the same output.
-
Sufficient Mining Power: The attacker must have sufficient mining power to successfully mine the conflicting block. While they don't need to have more power than the rest of the network, a higher hash rate increases the success probability.
-
Timing: The timing must be carefully orchestrated to ensure that the victim accepts the unconfirmed transaction before learning about the conflicting block.
-
No Network Propagation of Mined Block: The pre-mined block must not be propagated through the network before the victim accepts the unconfirmed transaction.
-
Merchant's Policy: The attack exploits merchants who accept unconfirmed transactions, a practice that might be found in face-to-face transactions where fast settlement is required.
A Finney attack is complex and requires a specific set of conditions to be met. It has become increasingly unlikely with the growing security in the network. The theoretical possibility still leads to discussions about the need for confirmations and caution in accepting unconfirmed transactions.
-
-
 @ d266da53:7224d834
2023-08-04 08:35:01
@ d266da53:7224d834
2023-08-04 08:35:01Stay updated on the latest developments in Crypto , follow me on Yakihonne.com.
 Cosmos was once the king of interoperability thanks to its revolutionary Tendermint consensus mechanism and Inter-Blockchain Communication (IBC) standard. However, several years after its release, the Cosmos ecosystem has grown without needing the ATOM token. Let’s analyze the value proposition of ATOM, its newfound competitor Ethereum, and if the Cosmos ecosystem has a chance of ever taking off.
Cosmos was once the king of interoperability thanks to its revolutionary Tendermint consensus mechanism and Inter-Blockchain Communication (IBC) standard. However, several years after its release, the Cosmos ecosystem has grown without needing the ATOM token. Let’s analyze the value proposition of ATOM, its newfound competitor Ethereum, and if the Cosmos ecosystem has a chance of ever taking off.Cosmos was founded in 2016 by Jae Kwon and Ethan Buchman. They were part of the Tendermint team, which developed a software development kit that provides the core functionality of a blockchain, such as consensus and networking. The Cosmos SDK utilized Tendermint to create a modular framework that allows developers to build their blockchains with custom features and applications without starting from scratch. The SDK’s standardization also enables cross-chain communication through the Inter-Blockchain Communication (IBC) protocol, which allows different blockchains to transfer tokens and data with each other.
 Initially, the value proposition for the Cosmos blockchain and its ATOM token was that it would be the hub in a hub-and-spoke blockchain model. Whenever a Cosmos SDK or IBC-enabled chain, called a Zone, transferred tokens to another Zone, they would use Cosmos as the bridge and pay fees in ATOM. At first glance, this proposition made a lot of sense, as it would allow Cosmos to be the secure bridge between the Zones and collect value in that manner.
Initially, the value proposition for the Cosmos blockchain and its ATOM token was that it would be the hub in a hub-and-spoke blockchain model. Whenever a Cosmos SDK or IBC-enabled chain, called a Zone, transferred tokens to another Zone, they would use Cosmos as the bridge and pay fees in ATOM. At first glance, this proposition made a lot of sense, as it would allow Cosmos to be the secure bridge between the Zones and collect value in that manner. Unfortunately, as the number of Cosmos SDK-based chains grew, the hype and value of ATOM did not follow. Some prominent projects like Binance Chain, Crypto.com, and the now-infamous Terra were built using Cosmos and Tendermint technology and dwarfed ATOM in market capitalization. Binance did not even bother integrating with the IBC and instead used Tendermint solely as the consensus mechanism. The growth of these chains had little-to-no effect on Cosmos. Yet other Zones, including Kava, Band Protocol, Evmos, and Injective, joined the ecosystem, and there was still hope for Cosmos to succeed.
Unfortunately, as the number of Cosmos SDK-based chains grew, the hype and value of ATOM did not follow. Some prominent projects like Binance Chain, Crypto.com, and the now-infamous Terra were built using Cosmos and Tendermint technology and dwarfed ATOM in market capitalization. Binance did not even bother integrating with the IBC and instead used Tendermint solely as the consensus mechanism. The growth of these chains had little-to-no effect on Cosmos. Yet other Zones, including Kava, Band Protocol, Evmos, and Injective, joined the ecosystem, and there was still hope for Cosmos to succeed.When the Osmosis Zone was released in 2021, it was initially meant to be the decentralized exchange of the IBC. Naturally, this brought a lot of liquidity and volume to the chain, quickly becoming the de facto hub of activity in the Cosmos ecosystem. Since there was no strict requirement for bridging using Cosmos, Osmosis promptly became the hub of the ecosystem and inspired the idea of Zones simply bridging to other Zones instead of going through a hub. This realization created the staus quo we see today, where Cosmos, the project that made the majority of the technology, does not receive any benefits from the plethora of chains using it.
 In an attempt to regain a value proposition in its ecosystem, ATOM 2.0 was announced in late 2022. The main feature of these new tokenomics is the creation of InterChain Security, meaning that new projects can “rent” security from ATOM by paying in the chain’s native token. This allows new projects not to worry about building a decentralized network, as they can rely on the time-tested network of ATOM validators while still having the sovereignty of their own chain.
In an attempt to regain a value proposition in its ecosystem, ATOM 2.0 was announced in late 2022. The main feature of these new tokenomics is the creation of InterChain Security, meaning that new projects can “rent” security from ATOM by paying in the chain’s native token. This allows new projects not to worry about building a decentralized network, as they can rely on the time-tested network of ATOM validators while still having the sovereignty of their own chain. Though this idea is exciting and novel, it has a massive new competitor: Ethereum. Indeed, the once-monolithic smart contract protocol has increasingly become more of a data availability layer than a compute engine, as Layer 2s execute computations off-chain and store the associated data on Ethereum. Even Solana, a competitor to Ethereum, announced plans to use it as their data availability layer to improve interoperability between the two chains and take advantage of the Ethereum network and security effects. This trend and the ability to easily create Layer 3s using Optimism and Arbitrum’s tooling directly challenge Cosmos’ ICS plans.
Though this idea is exciting and novel, it has a massive new competitor: Ethereum. Indeed, the once-monolithic smart contract protocol has increasingly become more of a data availability layer than a compute engine, as Layer 2s execute computations off-chain and store the associated data on Ethereum. Even Solana, a competitor to Ethereum, announced plans to use it as their data availability layer to improve interoperability between the two chains and take advantage of the Ethereum network and security effects. This trend and the ability to easily create Layer 3s using Optimism and Arbitrum’s tooling directly challenge Cosmos’ ICS plans.The future of Cosmos has never looked more uncertain. Even though Tendermind and IBC are revolutionary technologies that are the backbone of billions of dollars in blockchain value, Cosmos’ initial tokenomics failed to capitalize on its creation. The proliferation of ICS could bring more value back to Cosmos, yet many app-chains will likely choose Ethereum due to its significantly larger user base and liquidity potential. Though this is not financial advice and is merely for education, it makes much more sense to hold Cosmos than to buy it. On the other hand, for those who believe in the potential of ICS and the value of IBC, this could be a great buying opportunity for ATOM and other Cosmos ecosystem chains.
By:Lincoln Murr Link:https://bitpushnews.medium.com/is-cosmos-a-dying-blockchain-a0c308af0dac
-
 @ 35a8f9c0:351dae66
2023-08-04 07:36:31
@ 35a8f9c0:351dae66
2023-08-04 07:36:31test
-
 @ aa55a479:f7598935
2023-02-20 13:44:48
@ aa55a479:f7598935
2023-02-20 13:44:48Nostrica is the shit.
-
 @ 634bd19e:2247da9b
2023-02-15 08:00:45
@ 634bd19e:2247da9b
2023-02-15 08:00:45かけるのこれ? 日本語入力の取り扱いイベントがおかしいw
-
 @ 9ecbb0e7:06ab7c09
2023-08-04 04:46:45
@ 9ecbb0e7:06ab7c09
2023-08-04 04:46:45Vilma Alarcón, una mujer cubana residente en Estados Unidos, se convirtió en víctima de una estafa cuando trató de conseguir un patrocinador para que sus familiares en la Isla ingresaran al país norteño a través del parole humanitario, informó Univisión.
La desafortunada situación involucró a un individuo que se identificó como abogado migratorio en redes sociales y prometió ayudarla a conseguir a dicha persona, cuya responsabilidad es solventar los gastos de alimentación, atención médica y vivienda de los beneficiarios.

Según los detalles proporcionados por la afectada, entregó exactamente 7.800 dólares al presunto letrado, quien le cobró 1.500 USD por persona y aseguró que habría un segundo pago después de la supuesta aprobación del parole. Sin embargo, tras realizar la última entrega de dinero, el estafador desapareció sin dejar rastro.
La comunicación entre la mujer y el defraudador se llevó a cabo a través de mensajes privados en Instagram y WhatsApp; mientras que los pagos se realizaron mediante la plataforma Zelle, bajo el pretexto de que los recibirían los supuestos patrocinadores.

Desde el inicio del programa de parole humanitario en enero, varias personas han sido afectadas por diferentes formas de estafa, todas bajo la falsa promesa de agilizar el proceso y obtener patrocinadores ficticios.
Para evitar caer en este tipo de engaños, el abogado de inmigración José Guerrero advirtió, a través de una entrevista con dicho medio, que ningún profesional legal ofrece un patrocinador a sus clientes, ya que esto es responsabilidad del interesado.
Además, resaltó que pagar a alguien para ser patrocinador es un fraude, y que se debe estar alerta ante la solicitud de transferencias a cuentas personales o sistemas de pago alternativos.
El programa de parole humanitario ha sido una opción para que miles de cubanos, haitianos, nicaragüenses y venezolanos ingresen de manera legal y segura a EEUU.
Según los datos oficiales, casi 160 mil personas han llegado al país hasta finales de junio. A pesar de su éxito, el programa está en litigio en un tribunal federal de Texas debido a una demanda de 20 estados republicanos para eliminarlo.
-
 @ 96aea8a4:8606d449
2023-08-04 02:30:57
@ 96aea8a4:8606d449
2023-08-04 02:30:57The Bor Report... Day 0
If you've ever read The Mezzanine by Nicholson Baker then it's possible the aperiodic letters in my Back Office Report will resonate with you.
I'm treating these letters as a sort of journaling/social experiment. My thoughts, on a page, in no particular order. All for an unspecified amount of time. Burn after reading if you so desire.
This platform along with the Daumus app is the perfect place to inscribe my thoughts. It's written in stone. If I say something inaccurate I sincerely hope my readers call me out. And dare I try and make a prediction, there will be proof and I won’t be able to back pedal like Jim Cramer does every day of his career..
Okay let's begin...
Let’s start with the boring… Dow Jones 35,215.89 | S&P500 4,501.89 | Nasdaq 13,959.72 | Russell 1,961.40 | VIX 15.92 | GBTC 19.30
Keep in mind I’m writing this well after the close of the market. My 2022 LEAPs have well expired worthless, and my sentiment WAS overall very bad. My outlook on the market was completely negative up until I became bullish about half way through 2023. A good friend of mine purchased around 30k in CDs. I’m happy for him, a sound investment. And much more size than I was use to. But to me it felt a lot like peak hysteria. The bond fad had already hit the news headline and was starting to fade. I remember thinking, “great.. now bonds are exciting.. that’s when you know it’s bad.” But it wasn’t until a few months after that when first hand I saw someone act on it. Sure the major hedge fund managers were buying bonds but who in my circle actually cared about safe money. Nobody had enough for it to matter in the first place.
I always thought things usually get worse before they get better. That seems universally true. But how long is worse. That’s what was/is tough to decide. The economy is in shambles in many ways, but healthy in others. Was a year of red ticks enough, two years? Who really knew. The more I heard people in my circle actually purchasing things like CDs and bonds the more I was intrigued… was this it? Are the tides changing, is peak hysteria in the rear view mirror? No idea..
I decided to stop by a coin store on the way home. Sometime I end up with way too much time on my hands.. It was after my shift at corpo and I was meeting up with family for dinner. It was too early to drive home, but too early to drive to the dinner spot. My work, as you can guess, right in the middle. There was a coin jeweler just down the road so I thought screw it why not. The local guy, great guy by the way, had no gold coins. None at all. Said someone just came in and bought the whole place out. Didn’t believe him at first but after looking around he really was out of gold. I had been in here a few years ago and although the price of gold was steady there certainly was supply. He said, “I’ve got silver bullion left”. I said I didn’t want any..
Called a few other local places. I wasn’t going to actually buy any gold coins, but I was curious. Just about everywhere I called was out of gold. The theme Peak Hysteria was really starting to set in.
Although the market was closed I yearned for exposure. An option contract on the S&P. Maybe a call on something in tech. Just some exposure to the market of some sort so I don’t miss the shifting of tides..
I’ve realized as I’m writing this I’m using a mixture of present thought, and thoughts/experiences from weeks/months before. Incredibly confusing for the reader, but I frankly don’t care. I’ve set my foot down on starting the Bor Report and I won’t go another day without publishing something. I don’t want to get hung up on every detail. I want to put stream of thought to paper. Maybe someone will appreciate it. Or maybe I’ll look back and be extremely embarrassed. I frankly do not.. care.
I’ll leave you with a quote, so that you can think about me until the next time I publish something. Because it’s not everyday that I want to debate engineering disasters, argue about municipal funding projects, or simply harp on bond purchasers. But those days do seem to make up a majority of my life. There’s something blissful to me about the very nature of a boring topic. Maybe in a way it resembles the liminal style of some of my favorite artwork. I would argue that some of the most complicated and interesting things of this modern world can seem boring at face value. Or maybe I’m just boring.
"Warning: Everything saved will be lost." - Wii notification
Taken from the what is the most unintentionally profound thing you've heard thread.
Till next time,
The Boring Report
-
 @ 9ecbb0e7:06ab7c09
2023-08-04 01:14:26
@ 9ecbb0e7:06ab7c09
2023-08-04 01:14:26La localidad de San Francisco, en el municipio Palma Soriano, Santiago de Cuba, se encuentra de luto ante la pérdida de dos adolescentes, identificadas como Yuleidis Sánchez Escalante, de 13 años, y Claudia Escalante Carmenate, de 16 años. Según diferentes reportes en redes sociales, las menores murieron ahogadas en una poza del río Aterrizaje.
Aris Arias Batalla, responsable de Operaciones y Socorro/Seguridad Acuática de Santiago de Cuba, informó ayer miércoles que las jóvenes fallecieron a causa de ahogamiento por sumersión en un área no certificada de baño, que carecía de salvavidas.
El internauta identificado como Jeissy Borrell Gámez detalló que cuando las dos muchachas comenzaron a tener problemas para salir del agua, sus amigos presentes en el lugar trataron de rescatarlas, pero al final no pudieron evitar la tragedia.

Este lamentable suceso ha causado una enorme tristeza en la familia a la que pertenecían ambas jóvenes. Además, también se encuentran conmocionados amigos y vecinos de las dos víctimas.
Ante esta situación, Arias Batalla recordó a los residentes en la oriental provincia la importancia de seguir las indicaciones de las autoridades y respetar las prohibiciones en sitios no designados para el baño. Enfatizó que la mejor opción para disfrutar del agua de manera segura es acudir a las áreas de baños públicos, certificadas y con salvavidas.

“Es responsabilidad y obligación de cada familia el cuidado y protección de bañistas y más de niños o adolescentes. Los salvavidas velan por cientos a la vez y, a pesar de sus charlas, advertencias, llamados de atención, no respetan sus indicaciones y prohibiciones”, agregó el socorrista.
Finalmente, reiteró sus condolencias para las familias de las jóvenes víctimas: “Que Diosito y los ángeles las custodien y protejan por siempre en el Reino del Señor”.
-
 @ 9ecbb0e7:06ab7c09
2023-08-04 01:05:50
@ 9ecbb0e7:06ab7c09
2023-08-04 01:05:50La madre cubana Yanetzy Luis Ruiz, acompañada por sus tres hijos pequeños, se plantó frente a la sede provincial del Partido Comunista de Cuba (PCC) en la ciudad de Santa Clara para exigir una vivienda digna donde residir. La noticia fue denunciada por el opositor cubano Librado Linares, secretario general del Movimiento Cubano Reflexión.
El caso ha llamado la atención debido a la valiente acción que tomó la ciudadana para hacer visible la difícil realidad que enfrentan muchas familias en la Isla. Según Linares, la mujer ya había sido trasladada previamente a un albergue, pero decidió regresar a la sede para continuar con su demanda.
El opositor destacó que la situación de Yanetzy y su familia no es un caso aislado, sino que refleja los graves problemas que no reciben una solución concreta por parte del régimen, cuyas inversiones se centran en la construcción de hoteles para el turismo extranjero.

Al publicarse la imagen de la madre en Twitter, un usuario compartió la idea de que todos los cubanos en tal necesidad requieren unirse para causar un impacto en el gobierno. “Cuando se le sumen todos los necesitados, a reclamar derechos es cuando se resolverán el problema. Por eso llevamos 64 años de miseria hambruna y represión, protestan dos, mientras los demás observan, esperando como buitres a recoger la carroña”, mencionó.
-
 @ 7f4f672a:c184579e
2023-08-03 20:45:04
@ 7f4f672a:c184579e
2023-08-03 20:45:04“Write on Obsidian and publish directly to Nostr.” A sentence that makes no sense to most people. I made a plugin for those who do 😅 Check it out my plugin on Github for download. It'll be available in the community plugins downloads section soon (in review now)! For anyone else who’s curious, WTF am I talking about? #obsidian #nostr
Nostr represents the future of how we will communicate and distribute the written word: decentralised, free, independent, incorruptible. @fiatjaf created it in 2020 and it’s been growing since, offering a new hope for content creators tied up by Big Tech and their walled gardens
On Nostr you own your social experience. Keep followers, posts, likes, and replies across platforms. Some people won’t care, but for creators - this is key! People use Nostr clients to see and post stuff - WTF’s a Nostr client ? 🤔
Clients are websites/apps that connect to the Nostr network. Think of them like different doors to the same room – your content and followers stay the same, whichever door you choose.🚪🚪 I’m not going to link a client here because Elon owns this door and could close it on me.
He also owns the room. On Nostr, nobody owns the room, you can just build or use doors to enter it. It’s the very early days. But lot’s of people, including @jack (who introduced me to it, thanks Jack) are excited! Which leads me to Part 2 of this spiel - Obsidian?
Obsidian is an amazing markdown editor, note organiser, and idea synthesiser: the perfect tool for writers. It’s free to download & use here : https://obsidian.md/
You can use it to take notes, write, blog, make shopping lists, or conduct research! Whatever! It’s easy and clever (check out note linking). Your notes are your own and easily portable - again, you’re not tied up in a room! Also, 1000’s of free community plugins make it great!
Long story short - Obsidian and Nostr are a match made in heaven. For writers - I hope this plugin can help you publish seamlessly, and open up a new world. I plan to use it myself to write & publish more. That’s proving harder than the software 😅 Now where’s my pen..
-
 @ b49df4b0:588be5df
2023-08-03 19:49:47
@ b49df4b0:588be5df
2023-08-03 19:49:47Note: originally published on my personal blog (testing Habla).
While looking for a nice local 2023 calendar, I was recently lucky to learn about the Oregon Natural Desert Association (ONDA). Their mission is to protect, defend and restore Oregon’s high desert for current and future generations.
Deserts are something. At first look, nothing seems to happen in a desert, but if you take the time to look and listen carefully, you’ll soon realize a lot is going on. Plus, there are many types of deserts, and no definition fits them all.
I love hiking in the desert or just driving through it. I enjoy stopping at the side of a road that barely anybody transit, stepping out of the car, getting a little away from it, and observing my surroundings in complete silence. But I’ll admit, I also fear it a bit. It’s not my natural environment, and I don’t know much about it yet; I feel vulnerable and am not always comfortable spending long periods in it. I need more exposure and a lot of learning to become more and more at ease.
Going back to ONDA, I purchased their calendar and it’s hanging on the kitchen wall, the first page waiting for January to be turned. I also learned several ways to help them, some involving projects on the terrain. Will that be how I better know the desert and become friends with it? I’ll have to think about that!
-
 @ bcea2b98:7ccef3c9
2023-08-01 13:37:52
@ bcea2b98:7ccef3c9
2023-08-01 13:37:52abandon ability able about above absent absorb abstract absurd abuse access accident account accuse achieve acid acoustic acquire across act action actor actress actual adapt add addict address adjust admit adult advance advice aerobic affair afford afraid again age agent agree ahead aim air airport aisle alarm album alcohol alert alien all alley allow almost alone alpha already also alter always amateur amazing among amount amused analyst anchor ancient anger angle angry animal ankle announce annual another answer antenna antique anxiety any apart apology appear apple approve april arch arctic area arena argue arm armed armor army around arrange arrest arrive arrow art artefact artist artwork ask aspect assault asset assist assume asthma athlete atom attack attend attitude attract auction audit august aunt author auto autumn average avocado avoid awake aware away awesome awful awkward axis baby bachelor bacon badge bag balance balcony ball bamboo banana banner bar barely bargain barrel base basic basket battle beach bean beauty because become beef before begin behave behind believe below belt bench benefit best betray better between beyond bicycle bid bike bind biology bird birth bitter black blade blame blanket blast bleak bless blind blood blossom blouse blue blur blush board boat body boil bomb bone bonus book boost border boring borrow boss bottom bounce box boy bracket brain brand brass brave bread breeze brick bridge brief bright bring brisk broccoli broken bronze broom brother brown brush bubble buddy budget buffalo build bulb bulk bullet bundle bunker burden burger burst bus business busy butter buyer buzz cabbage cabin cable cactus cage cake call calm camera camp can canal cancel candy cannon canoe canvas canyon capable capital captain car carbon card cargo carpet carry cart case cash casino castle casual cat catalog catch category cattle caught cause caution cave ceiling celery cement census century cereal certain chair chalk champion change chaos chapter charge chase chat cheap check cheese chef cherry chest chicken chief child chimney choice choose chronic chuckle chunk churn cigar cinnamon circle citizen city civil claim clap clarify claw clay clean clerk clever click client cliff climb clinic clip clock clog close cloth cloud clown club clump cluster clutch coach coast coconut code coffee coil coin collect color column combine come comfort comic common company concert conduct confirm congress connect consider control convince cook cool copper copy coral core corn correct cost cotton couch country couple course cousin cover coyote crack cradle craft cram crane crash crater crawl crazy cream credit creek crew cricket crime crisp critic crop cross crouch crowd crucial cruel cruise crumble crunch crush cry crystal cube culture cup cupboard curious current curtain curve cushion custom cute cycle dad damage damp dance danger daring dash daughter dawn day deal debate debris decade december decide decline decorate decrease deer defense define defy degree delay deliver demand demise denial dentist deny depart depend deposit depth deputy derive describe desert design desk despair destroy detail detect develop device devote diagram dial diamond diary dice diesel diet differ digital dignity dilemma dinner dinosaur direct dirt disagree discover disease dish dismiss disorder display distance divert divide divorce dizzy doctor document dog doll dolphin domain donate donkey donor door dose double dove draft dragon drama drastic draw dream dress drift drill drink drip drive drop drum dry duck dumb dune during dust dutch duty dwarf dynamic eager eagle early earn earth easily east easy echo ecology economy edge edit educate effort egg eight either elbow elder electric elegant element elephant elevator elite else embark embody embrace emerge emotion employ empower empty enable enact end endless endorse enemy energy enforce engage engine enhance enjoy enlist enough enrich enroll ensure enter entire entry envelope episode equal equip era erase erode erosion error erupt escape essay essence estate eternal ethics evidence evil evoke evolve exact example excess exchange excite exclude excuse execute exercise exhaust exhibit exile exist exit exotic expand expect expire explain expose express extend extra eye eyebrow fabric face faculty fade faint faith fall false fame family famous fan fancy fantasy farm fashion fat fatal father fatigue fault favorite feature february federal fee feed feel female fence festival fetch fever few fiber fiction field figure file film filter final find fine finger finish fire firm first fiscal fish fit fitness fix flag flame flash flat flavor flee flight flip float flock floor flower fluid flush fly foam focus fog foil fold follow food foot force forest forget fork fortune forum forward fossil foster found fox fragile frame frequent fresh friend fringe frog front frost frown frozen fruit fuel fun funny furnace fury future gadget gain galaxy gallery game gap garage garbage garden garlic garment gas gasp gate gather gauge gaze general genius genre gentle genuine gesture ghost giant gift giggle ginger giraffe girl give glad glance glare glass glide glimpse globe gloom glory glove glow glue goat goddess gold good goose gorilla gospel gossip govern gown grab grace grain grant grape grass gravity great green grid grief grit grocery group grow grunt guard guess guide guilt guitar gun gym habit hair half hammer hamster hand happy harbor hard harsh harvest hat have hawk hazard head health heart heavy hedgehog height hello helmet help hen hero hidden high hill hint hip hire history hobby hockey hold hole holiday hollow home honey hood hope horn horror horse hospital host hotel hour hover hub huge human humble humor hundred hungry hunt hurdle hurry hurt husband hybrid ice icon idea identify idle ignore ill illegal illness image imitate immense immune impact impose improve impulse inch include income increase index indicate indoor industry infant inflict inform inhale inherit initial inject injury inmate inner innocent input inquiry insane insect inside inspire install intact interest into invest invite involve iron island isolate issue item ivory jacket jaguar jar jazz jealous jeans jelly jewel job join joke journey joy judge juice jump jungle junior junk just kangaroo keen keep ketchup key kick kid kidney kind kingdom kiss kit kitchen kite kitten kiwi knee knife knock know lab label labor ladder lady lake lamp language laptop large later latin laugh laundry lava law lawn lawsuit layer lazy leader leaf learn leave lecture left leg legal legend leisure lemon lend length lens leopard lesson letter level liar liberty library license life lift light like limb limit link lion liquid list little live lizard load loan lobster local lock logic lonely long loop lottery loud lounge love loyal lucky luggage lumber lunar lunch luxury lyrics machine mad magic magnet maid mail main major make mammal man manage mandate mango mansion manual maple marble march margin marine market marriage mask mass master match material math matrix matter maximum maze meadow mean measure meat mechanic medal media melody melt member memory mention menu mercy merge merit merry mesh message metal method middle midnight milk million mimic mind minimum minor minute miracle mirror misery miss mistake mix mixed mixture mobile model modify mom moment monitor monkey monster month moon moral more morning mosquito mother motion motor mountain mouse move movie much muffin mule multiply muscle museum mushroom music must mutual myself mystery myth naive name napkin narrow nasty nation nature near neck need negative neglect neither nephew nerve nest net network neutral never news next nice night noble noise nominee noodle normal north nose notable note nothing notice novel now nuclear number nurse nut oak obey object oblige obscure observe obtain obvious occur ocean october odor off offer office often oil okay old olive olympic omit once one onion online only open opera opinion oppose option orange orbit orchard order ordinary organ orient original orphan ostrich other outdoor outer output outside oval oven over own owner oxygen oyster ozone pact paddle page pair palace palm panda panel panic panther paper parade parent park parrot party pass patch path patient patrol pattern pause pave payment peace peanut pear peasant pelican pen penalty pencil people pepper perfect permit person pet phone photo phrase physical piano picnic picture piece pig pigeon pill pilot pink pioneer pipe pistol pitch pizza place planet plastic plate play please pledge pluck plug plunge poem poet point polar pole police pond pony pool popular portion position possible post potato pottery poverty powder power practice praise predict prefer prepare present pretty prevent price pride primary print priority prison private prize problem process produce profit program project promote proof property prosper protect proud provide public pudding pull pulp pulse pumpkin punch pupil puppy purchase purity purpose purse push put puzzle pyramid quality quantum quarter question quick quit quiz quote rabbit raccoon race rack radar radio rail rain raise rally ramp ranch random range rapid rare rate rather raven raw razor ready real reason rebel rebuild recall receive recipe record recycle reduce reflect reform refuse region regret regular reject relax release relief rely remain remember remind remove render renew rent reopen repair repeat replace report require rescue resemble resist resource response result retire retreat return reunion reveal review reward rhythm rib ribbon rice rich ride ridge rifle right rigid ring riot ripple risk ritual rival river road roast robot robust rocket romance roof rookie room rose rotate rough round route royal rubber rude rug rule run runway rural sad saddle sadness safe sail salad salmon salon salt salute same sample sand satisfy satoshi sauce sausage save say scale scan scare scatter scene scheme school science scissors scorpion scout scrap screen script scrub sea search season seat second secret section security seed seek segment select sell seminar senior sense sentence series service session settle setup seven shadow shaft shallow share shed shell sheriff shield shift shine ship shiver shock shoe shoot shop short shoulder shove shrimp shrug shuffle shy sibling sick side siege sight sign silent silk silly silver similar simple since sing siren sister situate six size skate sketch ski skill skin skirt skull slab slam sleep slender slice slide slight slim slogan slot slow slush small smart smile smoke smooth snack snake snap sniff snow soap soccer social sock soda soft solar soldier solid solution solve someone song soon sorry sort soul sound soup source south space spare spatial spawn speak special speed spell spend sphere spice spider spike spin spirit split spoil sponsor spoon sport spot spray spread spring spy square squeeze squirrel stable stadium staff stage stairs stamp stand start state stay steak steel stem step stereo stick still sting stock stomach stone stool story stove strategy street strike strong struggle student stuff stumble style subject submit subway success such sudden suffer sugar suggest suit summer sun sunny sunset super supply supreme sure surface surge surprise surround survey suspect sustain swallow swamp swap swarm swear sweet swift swim swing switch sword symbol symptom syrup system table tackle tag tail talent talk tank tape target task taste tattoo taxi teach team tell ten tenant tennis tent term test text thank that theme then theory there they thing this thought three thrive throw thumb thunder ticket tide tiger tilt timber time tiny tip tired tissue title toast tobacco today toddler toe together toilet token tomato tomorrow tone tongue tonight tool tooth top topic topple torch tornado tortoise toss total tourist toward tower town toy track trade traffic tragic train transfer trap trash travel tray treat tree trend trial tribe trick trigger trim trip trophy trouble truck true truly trumpet trust truth try tube tuition tumble tuna tunnel turkey turn turtle twelve twenty twice twin twist two type typical ugly umbrella unable unaware uncle uncover under undo unfair unfold unhappy uniform unique unit universe unknown unlock until unusual unveil update upgrade uphold upon upper upset urban urge usage use used useful useless usual utility vacant vacuum vague valid valley valve van vanish vapor various vast vault vehicle velvet vendor venture venue verb verify version very vessel veteran viable vibrant vicious victory video view village vintage violin virtual virus visa visit visual vital vivid vocal voice void volcano volume vote voyage wage wagon wait walk wall walnut want warfare warm warrior wash wasp waste water wave way wealth weapon wear weasel weather web wedding weekend weird welcome west wet whale what wheat wheel when where whip whisper wide width wife wild will win window wine wing wink winner winter wire wisdom wise wish witness wolf woman wonder wood wool word work world worry worth wrap wreck wrestle wrist write wrong yard year yellow you young youth zebra zero zone zoo
-
 @ 57fe4c4a:c3a0271f
2023-08-03 17:33:21
@ 57fe4c4a:c3a0271f
2023-08-03 17:33:21👥 Authors: Anthony Towns ( nostr:npub17rld56k4365lfphyd8u8kwuejey5xcazdxptserx03wc4jc9g24stx9l2h )
📅 Messages Date: 2023-08-03
✉️ Message Count: 1
📚 Total Characters in Messages: 5833
Messages Summaries
✉️ Message by Anthony Towns on 03/08/2023: The author clarifies their intention to encourage research on monetary-based denial-of-service deterrence and provides a rough proof-of-work as an approach to explore. They also discuss the challenges of implementing fees based on the time an HTLC is held.
Follow nostr:npub1j3t00t9hv042ktszhk8xpnchma60x5kz4etemnslrhf9e9wavywqf94gll for full threads
-
 @ 57fe4c4a:c3a0271f
2023-08-03 17:31:04
@ 57fe4c4a:c3a0271f
2023-08-03 17:31:04👥 Authors: GamedevAlice ( nostr:npub18zra06q690wae9ty6sxxwf3jdcxuan2n4dq0ldynjddzz894jqesvhlw24 )
📅 Messages Date: 2023-08-03
✉️ Message Count: 1
📚 Total Characters in Messages: 13392
Messages Summaries
✉️ Message by GamedevAlice on 03/08/2023: The author realizes that storage is not the main issue, but rather the time it takes to sync the blockchain. UTreeXO is a promising solution.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ 00000001:a21169a7
2023-08-01 10:03:57
@ 00000001:a21169a7
2023-08-01 10:03:57Edward Weston, initially recognized as a prominent pictorialist, played a crucial role in the evolution of photographic art during the 20th century. His trajectory marked a notable transition towards a new conception of the medium, leaving behind pictorialism to become one of the leading exponents of Group f/64 and elitist photography.

A distinctive feature of Weston's work was his relentless pursuit of maximum sharpness and tonal range in his images. This aspiration was evident in all his works, from his stunning landscapes to his innovative still lifes. Herein lay his genius: the ability to capture the purest essence of his subjects with a precision and clarity hitherto considered unattainable.

Weston pioneered the technique of previsualizing the final result in photography. This involved imagining and planning the final appearance of the image even before shooting the camera. To achieve this, he developed what became known as the Zone System, a method that allowed to control and modify the brightness of an image in a very precise way.

In his photographs, Weston often decontextualized his subjects, employing neutral backgrounds to further enhance the intrinsic identity of the object. This technique led to the creation of some of his most iconic images, in which each object becomes an autonomous entity, freed from the distractions and influence of its surroundings.
In addition to his extraordinary technical ability, Weston's capacity to infuse a sense of "radiation" into his images contributed greatly to his enduring influence. Through his refined technique, Weston created images so powerful and emotive that they impressed the viewer, eliciting an emotional and visceral response.
Weston also took his vision and technique beyond his studio. On his travels to post-revolutionary Mexico, he joined a revolutionary movement and published his work in their magazine. This experience not only broadened his artistic perspective but also left an indelible mark on his corpus of work, adding a new level of depth and context to his photographic approach.

In summary, Edward Weston exemplifies the evolution of photographic art in the 20th century. His transition from pictorialism to modern and elitist photography, his constant search for sharpness and tonal range, his innovative decontextualization of objects, and his radiant technique, all contributed to his enduring legacy. His influence is felt not only in the generations of photographers who followed him, but also in anyone who appreciates the ability of photography to transform the ordinary into extraordinary.
-
 @ 57fe4c4a:c3a0271f
2023-08-03 17:31:03
@ 57fe4c4a:c3a0271f
2023-08-03 17:31:03📝 Summary: Alice and Luke Dashjr discuss the growth potential of blockchain and the limitations of storage per block. Alice believes that the current cost of hardware makes it feasible to handle the growth, while Luke argues that storage is not the main issue and efforts are being made to optimize space requirements for individual nodes.
👥 Authors: • GamedevAlice ( nostr:npub18zra06q690wae9ty6sxxwf3jdcxuan2n4dq0ldynjddzz894jqesvhlw24 ) • Luke Dashjr ( nostr:npub1tfk373zg9dnmtvxnpnq7s2dkdgj37rwfj3yrwld7830qltmv8qps8rfq0n )
📅 Messages Date: 2023-08-02
✉️ Message Count: 2
📚 Total Characters in Messages: 51185
Messages Summaries
✉️ Message by GamedevAlice on 02/08/2023: The growth potential of the blockchain is limited by the amount of storage that can be added per block. However, the current cost of hardware makes it feasible to handle the growth. Efforts are also being made to optimize storage requirements.
✉️ Message by Luke Dashjr on 02/08/2023: Storage is not the issue with block sizes, and there are efforts to optimize how much space is needed by individual nodes.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ bcea2b98:7ccef3c9
2023-08-01 04:57:59
@ bcea2b98:7ccef3c9
2023-08-01 04:57:59On Monday, an unidentified developer withdrew all liquidity from the BALD meme coin on the Ethereum layer-2 network, Base. Some blockchain analysts are speculating that the wallet involved may be linked to Sam Bankman-Fried, former CEO of FTX, who is currently under house arrest with restricted internet access.
Cinneamhain Ventures partner Adam Cochran expressed his suspicion on Twitter, noting that the implicated wallet had previous involvement in the SushiSwap community. Cochran inferred that the early voting patterns in Sushi governance appeared dubious, with Bankman-Fried being the key individual behind snapshot votes during the community takeover following the departure of SushiSwap's creator, Chef Nomi.
In September 2020, Bankman-Fried had successfully salvaged funds from Uniswap, transferring them to SushiSwap. Cochran voiced his confidence that the party behind the actions was associated with Alameda, FTX, or was Bankman-Fried himself, based on conversations with former FTX members.
Several observers connected the language used by the Bald Twitter account to Bankman-Fried's own distinctive phrasing. Furthermore, on-chain activities corresponded with Bankman-Fried's court appearances and bail dates.
A Reddit-sourced investigation revealed that the BALD developer wallet had received deposits from FTX and Alameda over the span of two years and currently holds a balance of approximately 12,331 ETH, valued around $22 million at the time of the report.
Additional information surfaced on Twitter highlighting a correlation between the wallet that regularly deposited into the BALD developer's Binance wallet and a wallet involved in the substantial Terra USD depeg in the previous year. Since facing charges of conspiracy and fraud by the U.S. Department of Justice, following FTX's collapse, Bankman-Fried has been under house arrest. His legal team and the prosecution have struggled to monitor his internet use across numerous devices.
According to his bail conditions, Bankman-Fried was required to use a basic flip phone in place of a smartphone. His legal team admitted their inability to install surveillance software on his parent's phones as agreed.
In response to his alleged tampering with government witnesses, the prosecution submitted a request to revoke Bankman-Fried’s $250 million bond to presiding federal judge Lewis Kaplan last week.
While a section of Crypto Twitter implicated Bankman-Fried, others acknowledged the speculative nature of these accusations. Some users, such as Sam Trabucco, co-chief executive of Alameda, were even identified as potential culprits.
The story continues to evolve, with the BALD developer adding 100 ETH back into the pool following significant social media pressure. This move caused the meme coin's value to surge more than four times over its recent low value.
-
 @ 57fe4c4a:c3a0271f
2023-08-03 17:31:03
@ 57fe4c4a:c3a0271f
2023-08-03 17:31:03👥 Authors: josibake ( nostr:npub1lc8fsuj6ffha9xjpq7l9cfn0ylhfw6jm4gyjfudpvet7yvxpv5gq83p9xr )
📅 Messages Date: 2023-08-03
✉️ Message Count: 1
📚 Total Characters in Messages: 23880
Messages Summaries
✉️ Message by josibake on 03/08/2023: The BIP for Silent Payments has undergone several revisions, including changes to key sizes and a versioning scheme for addresses. Bitcoin Core implementation has been updated.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ c45af590:0dd0563b
2023-08-03 16:16:16
@ c45af590:0dd0563b
2023-08-03 16:16:16We are implementing a version of 2-of-2 Schnorr Musig2 for statechains where the server (party 1 in the 2-of-2) will be fully 'blinded' - in that it can hold a private key that is required to generate an aggregate signature on an aggregate public key, but that it does not learn either: 1) The aggregate public key 2) The aggregate signature and 3) The message (m) being signed.
In the model of blinded statechains, the security rests on the statechain server being trusted to report the NUMBER of partial signatures it has generated for a particular key (as opposed to being trusted to enforce rules on WHAT it has signed in the unblinded case) and the full set of signatures generated being verified client side https://github.com/commerceblock/mercury/blob/master/doc/merc_blind.md#blinding-considerations
Given the 2-of-2 musig2 protocol operates as follows (in the following description, private keys (field elements) are denoted using lower case letters, and elliptic curve points as uppercase letters. G is the generator point and point multiplication denoted as X = xG and point addition as A = G + G):
Party 1 generates private key x1 and public key X1 = x1G. Party 2 generates private key x2 and public key X2 = x2G. The set of pubkeys is L = {X1,X2}. The key aggregation coefficient is KeyAggCoef(L,X) = H(L,X). The shared (aggregate) public key X = a1X1 + a2X2 where a1 = KeyAggCoef(L,X1) and a2 = KeyAggCoef(L,X2).
To sign a message m, party 1 generates nonce r1 and R1 = r1G. Party 2 generates nonce r2 and R2 = r2G. These are aggregated into R = R1 + R2.
Party 1 then computes 'challenge' c = H(X||R||m) and s1 = c.a1.x1 + r1 Party 2 then computes 'challenge' c = H(X||R||m) and s2 = c.a2.x2 + r2
The final signature is then (R,s1+s2).
In the case of blinding this for party 1:
To prevent party 1 from learning of either the full public key or final signature seems straightforward, if party 1 doesn't not need to independently compute and verify c = H(X||R||m) (as they are blinded from the message in any case).
1) Key aggregation is performed only by party 2. Party 1 just sends X1 to party 2. 2) Nonce aggregation is performed only by party 2. Party 1 just sends R1 to party 2. 3) Party 2 computes c = H(X||R||m) and sends it to party 1 in order to compute s1 = c.a1.x1 + r1
Party 1 never learns the final value of (R,s1+s2) or m.
Any comments on this or potential issues would be appreciated.
Tom
-
 @ 9ecbb0e7:06ab7c09
2023-08-03 15:57:38
@ 9ecbb0e7:06ab7c09
2023-08-03 15:57:38Con indignación y decepción, el cubano Salvador Lester Camejo relata su amarga experiencia en el famoso bar-restaurant El Don Ávila (La Espada), propiedad de la empresa estatal Palmarés, en Ciego de Ávila.
De acuerdo con el testimonio publicado en su perfil de Facebook, fue discriminado en su propia ciudad por el solo hecho de ser cubano y no generar ingresos en dólares, lo cual inmediatamente lo hace ser un “ciudadano de segunda”.
“Realmente ya es indignante que en el propio país de uno lo discriminen por el simple hecho de ser cubano, no ganar los dólares del ‘enemigo’ y por ende no tener preferencias en centros que brindan servicios al turismo”, explica Lester Camejo.

La historia comenzó cuando el ciudadano le pide un café al dependiente, y este le contesta que, por orden de la dirección de la empresa de Palmares, cuando están a la espera de un grupo de turistas no puede haber dentro ningún nacional.
Ante esta discriminación, el cubano optó por abandonar el lugar y dirigirse a un local privado cercano al parque, donde pudo disfrutar de un excelente café de importación (Café La Llave) sin sentirse avergonzado de ser cubano. No obstante, en este establecimiento el café estaba igual de caro. Lester Camejo reconoce que “tristemente” tomarse un simple café en la calle ya no está “al alcance de todos”.
“Por mí desde ya pueden cerrar el Don Ávila porque nunca más iré cuando tenga la posibilidad de hacerlo. ¡Que esperen a sus añorados turistas! Por mi parte, mi dinero no lo tocarán más, a la dirección de Palmares, u otra entidad que haya tenido que ver con esta estúpida y humillante aberración que no se les olvide que Cuba es de todos los cubanos y que nada dura para siempre”, concluyó el avileño.
Este lamentable episodio ha generado gran controversia y otras denuncias de comportamientos similares por parte de empresas estatales. “A mí me pasó en el Museo del Ron (cadena Caracol), en Varadero. Estaba vacío (literal), voy al bar y pido un trago y la ‘bar-woman’ me dice que no podía despacharme porque esperaban a ‘un grupo’”, contó Lupe Pérez.
“Esa es la gran y triste realidad de nosotros los cubanos, desterrados en nuestra propia tierra que nos vio nacer. Pero no leas la prensa, no oigas una emisora radial, para ellos el cubano es el que más libertad de expresión tiene y el que mejor dieta nutriente come. La realidad es que la población está muerta de hambre y necesidad. Quien con 1.678 al mes que es la media de un jubilado puede subsistir”, comentó Cándido Mariano.
-
 @ 9ecbb0e7:06ab7c09
2023-08-03 15:54:49
@ 9ecbb0e7:06ab7c09
2023-08-03 15:54:49El subsecretario interino del Departamento de Seguridad Nacional (DHS, por sus siglas en inglés) de Estados Unidos, Blas Nuñez-Neto, admitió en una entrevista exclusiva con el periodista cubano Mario J. Pentón que a lo largo de los más de siete meses del proceso de parole humanitario se han cometido fraudes.
“Hemos rechazado la entrada de personas que cometen fraude en el proceso de parole humanitario. También hemos negado las aplicaciones antes que las personas se suban a los aviones”, confirmó el funcionario de la administración demócrata de Joe Biden.
Como ejemplo de las irregularidades detectadas por el DHS, Nuñez-Neto dijo que están “investigando patrocinadores que cobran por sus servicios o desde otra manera están involucrados en el crimen (…) Así que es algo que lo tomamos muy muy en serio”. Adicionalmente, alertó que los culpables se enfrentan a graves consecuencias por mentir al gobierno de EEUU y extorsionar a las personas.
En este sentido, el subsecretario animó a las personas que tienen información acerca de los fraudes que por favor los reporten a las autoridades. En el portal web del DHS hay información para enviar los reportes por diferentes medios de contacto, donde se les asegura el anonimato a quienes colaboren con denuncias.
De acuerdo con Mario J. Pentón, hay historias de beneficiarios del parole que los han regresado a Cuba desde el aeropuerto de Miami por haber pagado para que los patrocinaran. Obviamente, también hay rumores sobre funcionarios corruptos que están en puestos que les permiten acelerar los procesos de parole, pero sobre ese tema Nuñez-Neto no habló con Pentón, ya que se le había acabado el tiempo asignado.
Según el Servicio de Ciudadanía e Inmigración de EEUU (USCIS), proteger la integridad del proceso de inmigración es una prioridad para el gobierno. “Una de las maneras en que protegemos el sistema de inmigración es simplificándole a usted el proceso para reportar el fraude y abuso de inmigración a través de nuestro formulario de sospechas de fraude en línea”, refiere el portal web.
El proceso de otorgamiento del parole, para ciudadanos de Cuba, Nicaragua, Haití y Venezuela, es discrecional y sin límite de tiempo determinado para su procesamiento. USCIS tiene el compromiso de otorgar hasta 30.000 visas humanitarias al mes para estas cuatro nacionalidades.
Al cierre de junio pasado, unos 8.500 ciudadanos cubanos fueron beneficiados con visas humanitarias para ingresar a EEUU. El 92% de ese grupo, aproximadamente 7.800 cubanos, logró ingresar al territorio estadounidense, ya que algunos decidieron esperar para resolver asuntos personales antes de emigrar definitivamente.
-
 @ bcea2b98:7ccef3c9
2023-08-01 04:47:02
@ bcea2b98:7ccef3c9
2023-08-01 04:47:02The United States Securities and Exchange Commission (SEC) initiated a lawsuit against Richard Schueler, an internet marketer also known as Richard Heart, accusing him of unregistered securities offerings through his projects Hex, PulseChain, and PulseX. The SEC asserts that Heart amassed over $1 billion since 2019 through these offerings.
The SEC further alleges that Heart misappropriated investor funds for his personal expenditures. Despite Heart's persistent promotion of his projects as vehicles for substantial financial growth, with audacious claims such as Hex being engineered to be "the most rapidly appreciating asset in human history," the SEC argues that these ventures were, in fact, utilized to finance Heart's extravagant lifestyle without appropriate disclosure to investors.
Despite a turbulent launch marked by high fees, liquidity problems, and software vulnerabilities, PulseX and PulseChain were introduced earlier this month. Following their introduction, the prices of the associated HEX, PLS, and PLSX tokens experienced a significant downturn. The SEC further accuses Heart of recurrent references to federal securities laws in his public communications, such as YouTube livestreams, while concurrently admitting that the success of his projects hinged entirely on his personal efforts.
The SEC's lawsuit also mentions Heart's ambitious assertions about Hex's potential for investment return. For instance, Heart announced on Hex.com (until at least November 1, 2020) that Hex was projected to exceed the performance of ETH, which saw a 10,000x price increase in 2.5 years, and that Hex had already experienced a 115x price rise in 129 days. Furthermore, Heart asserted during a seven-hour YouTube livestream on December 2, 2019, mere hours before the Hex Offering began, that Hex was created to outperform Ethereum, Bitcoin, and all other cryptocurrencies.
The lawsuit levels accusations of fraud and securities registration violations against Heart and his projects.
-
 @ 20986fb8:cdac21b3
2023-08-03 15:51:06
@ 20986fb8:cdac21b3
2023-08-03 15:51:06YakiHonne.com is continuously improving to offer a top-notch user experience. With weekly updates being rolled out, you are invited to test these updates and post your feedback and opinions as an article via YakiHonne.com.
As an incentive, participants can earn up to 100,000 SATs.
Round 3 will be from 3rd to 7th Aug
How to participate:
- Pick one or multiple Updates below, test it (them)
- Write your feedback and opinion (pros and cons are all welcomed)
- Don't forget to add taggs 'YakiHonne-updates' and 'YakiHonne' to your article
- Post your article on Nostr via YakiHonne.com
- Share your article to social media like Nostr and Twitter, don't forget to @YakiHonne
- Share the link to our group: http://t.me/YakiHonne_Daily_Featured
- Be Zapped!
Requirements:
- No malicious speech such as discrimination, attack, incitement, etc.
- No Spam/Scam, not fully AI-generated article
- No directly copy & paste from other posts on Relays
- Experience our updates in action, NO limit on the length of your post, share your REAL feedback and opinion
- The top 10 posts will be zapped during each round.
- The evaluation will based on the article's depth, completeness, and constructiveness.
- Contact us for additional zaps if bugs are found.
Updates to be tested in Round 3:
- Reporting: NIP-56 supported, users now have the ability to report undesired long-form content within the platform.
- Zaps: confirmation prompt to notify the sender that the transaction successfully completed; Zaps stat icon now function same as the original zapping button, so that users can intuitively fast acces to it.
- NIP-05 support: users now have the ability to add their NIP-05 to their profile settings and view other users identifiers across the platform.
- Images upload: all across yakihonne client now have the option to either paste a url image or instantly upload images within yakihonne server (instant uploads for the write article section is coming soon); not restricted to 1MB anymore, use wisely and avoid large images.
- Back-to-Top button: on the home feed page(right-bottom corner) for a quicker navigation.
- Welcome to feedback your suggestions and bugs reporting.
If you missed Round 1 & 2, the updates below could be tested as additions:
Round 2:
-
Comments: re-implemented and comments can be deleted
-
NIP-25 supporting: users now can upvote and downvote
-
Zap stats: Zaps sent and Zaps received can be seen from users profiles
-
“login with an extension” button: now it is grayed out rather than invisible
-
Search: search list showing optimization, adjust users searching results to the NIP-21 URI scheme
-
Tags: click on the tags in the article to view the content under the tag
-
Share: sharing posts with one click
-
NIP-05: verify your profile
Round 1:
-
Comment function: more user-friendly
-
Stats area: clearly displays the interactive status of each article
-
Following function: generated-key users can also be followed
-
Curation function: easily add or remove articles from an existing curation
-
Tags: search and browse articles with the tags
-
Home feed scrolling pagination: optimized data fetching and faster loading time
-
Article editing preview: preview the final version of the article while writing in MarkDown
Don't miss this opportunity to participate in Round 2, test the updates, and provide valuable feedback. Head over to YakiHonne.com to share your thoughts and earn SATs for your valuable input. Act fast!
About YakiHonne:
YakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media. Try YakiHonne.com Now!
Follow us
- Telegram: http://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
-
 @ 9ecbb0e7:06ab7c09
2023-08-03 15:50:13
@ 9ecbb0e7:06ab7c09
2023-08-03 15:50:13Los cubanos solo podrán sacar 5.000 pesos (CUP) en efectivo de sus cuentas bancarias, según las regulaciones establecidas por la Resolución 11/2023 del Banco Central de Cuba (BCC) que fueron publicadas el 2 de agosto en la Gaceta Oficial Extraordinaria No. 55.
El límite forma parte del corralito bancario que fue anunciado ante la escasez de efectivo provocada por los altos niveles de inflación en la que está inmersa la economía nacional. El mal manejo de las finanzas públicas con erróneas políticas monetarias, sobre todo a partir del establecimiento del mal llamado “ordenamiento económico” han traído estas consecuencias.
Las normativas de la Resolución 11/2023 afectan a múltiples “sujetos”. Ellos son: empresas estatales, organizaciones superiores de dirección empresarial, unidades presupuestadas; cooperativas no agropecuarias; cooperativas agropecuarias; productores agropecuarios; agricultores individuales; pescadores comerciales; micro, pequeñas y medianas empresas; proyectos de desarrollo local; trabajadores por cuenta propia; artistas y creadores; las modalidades de inversión extranjera y las formas asociativas creadas al amparo de la Ley de Asociaciones.
La opción que queda para efectuar acciones de cobro y pago que superen los 5.000 CUP es “mediante los instrumentos de pagos y títulos de crédito”. El BCC priorizará que estas operaciones “se ejecuten por los canales electrónicos de pago”.
Sin embargo, la acreditación de los pagos no se verá reflejada directamente en las cuentas corrientes de los “actores económicos”. Tendrá un retardo debido a las limitaciones tecnológicas del banco y en caso de caer fin de semana o días feriados se demorará más.
“Los ingresos en efectivo en pesos cubanos que reciban los sujetos de esta Resolución, como regla, son depositados en su cuenta corriente, a más tardar al siguiente día hábil bancario a la fecha de su recepción; en el caso de las formas de gestión no estatal, el depósito se realiza en la cuenta reconocida con propósitos fiscales”, refiere el artículo 11.1 de la mencionada Resolución.
Otras regulaciones del BCC
En Banco Central permitirá por los próximos seis meses que las entidades que no tengan a todos sus trabajadores o pensionados bancarizados puedan hacer extracciones de efectivo para el pago de salarios, subsidios y otras prestaciones de la seguridad social y prestaciones a estudiantes. Para ello deben hacerlo como máximo, con tres días hábiles de antelación a la fecha establecida para el pago. Asimismo, ordena restituir ese dinero al banco en caso de pasar siete días sin que los beneficiarios hayan reclamado su pago.
El ministro presidente del BCC, Joaquín Alonso Vázquez, faculta a los “presidentes de bancos o la persona en quien estos deleguen por escrito” para que suspendan “los servicios bancarios o el cierre de la cuenta” a clientes que incumplan con las regulaciones antes mencionadas.
-
 @ f866d5b1:c526b32f
2023-08-03 14:02:05
@ f866d5b1:c526b32f
2023-08-03 14:02:05หลังจากมีบริษัทเอกชนหลายแห่งที่ทำแพลตฟอร์มขายหวยออนไลน์ ในประเทศไทย ปัจจุบัน สำนักงานสลากกินแบ่งรัฐบาล ก็ได้ทำแพลตฟอร์ม Digital Lottery ของตัวเองออกมาให้บริการประชาชนเช่นกัน โดยเริ่มงวดแรกในงวด วันที่ 2 พฤษภาคม 2565 ที่ผ่านมา
ส่วนหวยแบบ n3 จะเริ่มประมาณปี พ.ศ. 2567 ส่วนหวยแบบ l6 จะเริ่มประมาณเดือนกันยายน พ.ศ. 2566
การทำแพลตฟอร์มขายหวยออนไลน์ รวมถึงออกรูปแบบสลากใหม่อย่าง n3 และ l6 ของกองสลากกินแบ่งรัฐบาล ไม่สามารถแก้ปัญหาหวยแพงได้ ปัญหาจริง ๆ ของ ลอตเตอรี่ในไทย คือ รูปแบบการจ่ายเงินรางวัล ที่หากขายสลากไม่หมด จำนวนเงินรางวัลจะถูกลดทอนตามสัดส่วนการขายได้
n3 & l6 ความหวังใหม่แก้ปัญหาหวยแพง
ล่าสุด สำนักงานสลากกินแบ่ง ก็ได้ออกหวยรูปแบบใหม่เพื่อมาแข่งกับหวยใต้ดินที่คนไทยชื่นชอบ และแก้ปัญหาการขายสลากกินแบ่งเกินราคา ด้วยสลากแบบ n3 และ l6
โดยสลากแบบ l6 จะเหมือนกับสลากกินแบ่งแบบเดิมแต่นำไปจำหน่ายแบบออนไลน์ ส่วนหวยแบบ n3 จะคล้ายกับการเล่นหวยใต้ดิน ที่มีให้ลุ้นรางวัล 2 ตัวตรง/ 3 ตัวตรง/ 3 ตัวโต๊ด
แต่เงินรางวัลของหวยแบบ n3 ไม่จูงใจนักเสี่ยงโชคให้ออกมาจากวงการหวยใต้ดินแน่นอน เพราะรูปแบบเงินรางวัลที่แตกต่างจากหวยใต้ดิน
โดยหวยใต้ดินกำหนดเงินรางวัลแน่นอน สามารถรู้แน่ชัดว่าซื้อหวยไป 1 บาท หากถูกรางวัลจะได้รับเงินกลับมาเท่าไหร่
แต่หวยแบบ n3 จะจ่ายรางวัล โดยนำเงินที่ขายได้ทั้งหมด มาปันส่วนตามอัตราที่สำนักงานสลากกินแบ่งรัฐบาลกำหนดไว้แล้ว ดังนี้
แนวทางการใช้เงินจากการขายสลาก n3
| สัดส่วน| วัตถุประสงค์การใช้เงิน | | --- | --- | | 60% | นำไปแบ่งเป็นเงินรางวัล | | ไม่น้อยกว่า 23% | นำส่งเป็นรายได้แผ่นดิน| | ไม่เกินกว่า 17% | ใช้เป็นค่าบริหารจัดการ |
กติกาการจ่ายเงินรางวัลสลากแบบ n3
| ประเภท | สัดส่วนเงินรางวัล | | --- | --- | | 3 ตัวตรง | 30% | | 3 ตัวโต๊ด | 30% | | 2 ตัวตรง | 39% | | รางวัลพิเศษ | 1% |
จะเห็นว่าหากมีการซื้อหวย n3 ทั้งหมด 1,000 ล้านบาท จะนำมาเป็นเงินรางวัลแค่ 600 ล้านบาท โดยแบ่งรางวัลเป็น 3 ตัวตรง 180 ล้านบาท/ 3 ตัวโต๊ด 180 ล้านบาท/ 2 ตัวตรง 234 ล้านบาท/ รางวัลพิเศษ 6 ล้านบาท
ดังนั้น หากเลขเด็ด เลขดัง ที่ถูกรางวัลในงวดนั้น แต่มีจำนวนคนซื้อเยอะมาก ๆ จะทำให้แต่ละคนได้รับเงินรางวัลน้อยลงตามไปด้วย
ด้วยสาเหตุข้างต้น จึงทำให้หวยแบบ n3 ไม่จูงใจให้คนไทยที่นิยมการเสี่ยงโชคเลิกเล่นหวยใต้ดิน แต่จะยิ่งส่งเสริมให้ใช้จ่ายเพื่อบริโภคการเสี่ยงโชคมากขึ้น เพราะมีสินค้าให้เสี่ยงโชคเพิ่มมากขึ้นเสียด้วยซ้ำ
ห้าเสือกองสลาก คือผู้ร้ายจริงหรือ?
จริง ๆ แล้ว ยี่ปั๊ว ที่รับซื้อหวยรัฐบาลยกชุด คือผู้รับภาระที่กวาดซื้อหวยจนหมดแผง ทำให้ไม่มีปัญหาว่า รางวัลที่ 1 ในแต่ละงวดแตกต่างกัน เลขไม่เด่นไม่ดัง อย่าง 00 หรือพวกเลข 0 นำหน้า ส่วนใหญ่คนจะไม่ชอบซื้อทำให้คนที่ได้โควต้าที่ไปเดินสายขายกันเอง ขายไม่หมดจมทุนกำไรหด
การที่ ผู้ขายปลีกที่ได้ โควต้าจากกองสลาก เอาไปขายให้ ยี่ปั๊ว จึงไม่ใช่เรื่องแปลกแต่อย่างใดในทางเศรษฐศาสตร์ เพราะถ้าเอาไปเดินเร่หรือตั้งแผงขายเอง มันขายไม่หมด ถึงขายหมดก็เหนื่อยแรง สู้เอาเงินชัวร์ ๆ จากยี่ปั๊ว มากินมาใช้แบบสบาย ๆ ดีกว่า
ทำอย่างไรถึงจะแก้ปัญหาหวยแพงแบบถาวร
การแก้ปัญหาหวยแพงในประเทศไทยอย่างแท้จริง ไม่ใช่การทำหวยออนไลน์ แต่ต้องปรับกติกาในการได้รับรางวัลที่ใช้อยู่ในปัจจุบัน ที่ระบุหลังสลากว่า “ถ้าสลากจำหน่ายไม่หมด เงินรางวัลหนึ่ง ๆ ต้องลดลงตามสัดส่วน” เพราะการทำช่องทางให้ซื้อขายได้สะดวก มันไม่ได้แก้ปัญหาเลขไม่มงคลที่ไม่ต้องการซื้อ ทำให้ผู้ขายหวยต้องรับภาระจมทุนจากการขายสลากไม่หมดในแต่ละงวดนั่นเอง
-
 @ 83d999a1:46171d19
2023-08-03 13:56:27
@ 83d999a1:46171d19
2023-08-03 13:56:27We are building something cool that maybe you'll be interested in.
What is this? An announcement of an announcement (AoA for short)?
Well. Yes.
But bear with us.
We are doing an AoA because we haven't figured out all the details yet, (e.g. the name of what we're doing)
But here is what we do know:
- 2 months of focused building in #madeira.
- 21 builders with a record of shipping things in the #lightning/#nostr space
- working individually or in teams to make progress towards advancing freedom tech
- nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc and nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft will be physically (and spiritually) there to help bounce ideas off
- Funding (likely) available to all teams
Dates? Jan 8th - March 1st.
How to be a part of it? Details to follow very soon™️
But in the mean time, if you're stoked, DM us at nostr:npub1s0veng2gvfwr62acrxhnqexq76sj6ldg3a5t935jy8e6w3shr5vsnwrmq5.
-
 @ 3f770d65:7a745b24
2023-07-31 12:53:38
@ 3f770d65:7a745b24
2023-07-31 12:53:38The following is a collection of Tweets posted on Twitter that documented my entire heart surgery process, from finding out I had an issue, through the surgery, and finally throughout my recovery process. If Elon decides to remove old and unpaid content, I do not want this part of my life to vanish from the Internet. At the time, it was extremely important for my mental health to talk about this whole process and it was therapeutic in my recovery process, reading all of the responses as all of Bitcoin Twitter was behind my success. Thank you all of your kind words, love, and support during this whole process. May my Tweets live on through nostr.
...
Nov 28, 2021 I had open heart surgery 4 days before my 3rd b-day. I've led a healthy & active life since then, zero issues. I had an echocardiogram last week. The results were not good. Heart valve replacement may be in my near future. I am freaking the fuck out. I'll know more on Dec 6th. 😫
Dec 6, 2021 Update: I had my cardiologist appointment today. He said to not worry for now and continue to exercise and live life. In 3 months get another echo done. He doesn't believe the previous other results since I have zero symptoms and wants to do his own interpretation.
Dec 6, 2021 He said if the other results were correct, I may need valve replacement in 6 months to 3 years. However, he doesn't believe the local hospital's results as I said above. He can't form an opinion just yet. He said not to worry over and over again. For now, I'm staying positive!
Mar 7, 2022 Well, it's been three months. I had my follow up this morning. I have severe pulmonic regurgitation. I now need to speak with a specialist and see what my options are for surgery. Neat. 😭
Apr 12, 2022 Well, it looks like I'll need full open heart surgery again to replace my pulmonic valve. Bonus: I'll be part pig. So, I have that going for me. I was assuming that if I had to have this done it would be much less invasive, so I'm not overly impressed at the moment. 🫤
May 11, 2022 Today I had to get a CT scan of my heart in preparation for the May 27th surgery. All went well. I have no other heart issues. It's looking like I'll be in the hospital for 4-7 days, depending on how fast I recover. I should be fully 100% recovered by the end of August. ❤️
May 20, 2022 My grandfather with me 39 years ago, days after my open heart surgery. He taught me to hunt, fish, golf, and I'm sure taught me a thing or two about drinking beer and partying. 😂 He was a great man. He won't physically be with me next Friday, but I'm sure he'll be watching over.
May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 27, 2022 LET'S GO! I am alive and doing well. I was on a ventilator until 8pm. That was horrible. I will read all of the comments that you all posted on Katie's updates. Now I need to rest. They want to get me up and walk at 11pm. 🤯 I love you all and your support had helped so much 🧡🧡
May 28, 2022 The amount of love, compassion, caring, and appreciation from everyone blows my mind. Thanks for all of your comments and DMs. The positivity though all is this has helped me get through dark times and now it's helping me get through pain. You are helping me immensely. 🤯❤️🧡💪
May 28, 2022 Today has been a rough day. Lots of chest pain when breathing. But, I apparently am doing something right, because I have been upgraded to a regular room. No more ICU for this guy! My ICU nurse told my new nurse that I'm strong. ❤️💪🔥
May 29, 2022 Using this to document my journey. Last night was not good at all. I had tachycardia and AFib for hours. It was scary as fuck having my heart beat the way it was at 160bpm. They gave me new medication to bring it down and stop the AFib irregular heartbeat. It's now at 101.
May 29, 2022 I was very scared. Katie was able to come and stay the night with me and be my personal care nurse. That made me feel much better having her here with me. Hopefully the meds continue to do what they're supposed to. Fuck. Anyways, I may not Tweet much today. Love you all. ❤️
May 30, 2022 Today has mostly been a great day progress wise. I ate a lot. I've walked more today than I have previously. My doctor told me I might be going home tomorrow, it all depends on what happens with my last drainage tube. Fingers crossed that it's draining properly now. 💪❤️
May 31, 2022 Morning walk crushed. Breakfast crushed. Feeling stronger. My drainage tube is still draining so we'll see what the surgeon says, but I probably won't be coming home today according to my nurse. It may be another day. Better to be safe. I'm feeling good though. Let's go! 💪💪❤️❤️
Jun 1, 2022 Today's plans: Crush morning walk, crush breakfast, CRUSH MY LAST X-RAY AND HEAD THE HELL HOME! Fingers crossed. 🤞🤞❤️❤️💪💪
Jun 1, 2022 On my morning walk I went into a slight AFib. The nurse and PA said since I hadn't had my morning meds to control that yet, that that could be the cause. They're going to increase meds and monitor me for another 24 hours. That sucks, but again, I'd rather be safe. Ugh.
Jun 2, 2022 GM! I miss my kids. I miss wearing normal clothes. I miss my house. I miss my doggy. I better go home today or I guess I'll just keep working to get well enough to go home. 😂 I'm still progressing forward. I have a chest x-ray scheduled later this morning. Fingers crossed.
Jun 2, 2022 I JUST GOT CLEARED TO HEAD HOME AFTER LUNCH. FUCK YEAH. LET'S GOOOOOO💪💪💪
Jun 2, 2022 I am home! I have some family that needs some loving. Enjoy the rest of your day!
Jun 4, 2022 Last night I slept in bed thanks to a reclining pillow, the first night our living room chair. I was so happy to sleep in my own bed. I walked around our yard about 9 times yesterday. My goal is to do that plus a little more every day. I'm still in a lot of pain, but meds help.
Jun 4, 2022 I still have a long way to go recovery wise, but having Katie and the kids here helping me along the way makes it easier and gives me a reason to keep pushing forward through this. Thanks again for all of your past and future support. You all are fantastic.
Jun 6, 2022 My wife went back to work today. My son and daughter are in charge of taking care of me. My kids are fantastic. They made me breakfast already and helped me check all of my vitals. My daughter really shines here. She's such a little nurse and caretaker. ❤️❤️
Jun 6, 2022 I'm still in pain, but I'm not in as much pain as I was a couple days ago. I'm walking around a little better and a little more every day. I really hate just sitting around and not doing anything, but it's hard to do much else besides watch TV. I am enjoying my patio though. 💪
Jun 16, 2022 It's been a while. It's time to update this thread! I am doing great, IMO. I have lots of energy. I feel great. I can do a lot more than I previously could. I still have a limited range of motion due to my sternum being broken and still healing. i.e. I can't wash my back or legs.
Jun 16, 2022 I started back to work yesterday. I was cleared to do 20 hours this week by my doctor and I'm hoping to be cleared full time next week. I work from home, so if I can sit in front of a TV, I can sit in front of a computer, right?
Jun 16, 2022 My home nurses have been absolutely fantastic.😂 My kids make me breakfast every morning. And I could not have done any of this without my rock star wife. Words can't describe how much she's done for me throughout all of this. I am looking forward to continuing to improve. ♥️
Jun 16, 2022 You all have been absolutely wonderful through all of this too. I appreciate all of your love, support, and check-ins. Seriously. It means more than you know.
I have a check-up at the end of the month to make sure all is well. I'll update again in a couple weeks after that appt.
Jun 28, 2022 My doctor said everything looks great. He said it doesn't look like I had open heart surgery a month ago.💪 He said I have zero restrictions and that I can resume normal life. I can drive and I can go out on my boat! ❤️❤️❤️ I'm so happy right now! 🔥🚀
Jul 15, 2022 I started cardiac rehab this week. After 2 sessions the nurse said I'm on "Week 4" already. She doesn't believe with my initial intake stress test if I'll really be able to improve on it that much. 🤣 TL;DR I am a rock star and kicking ass. Feeling great. Life's great. 😍
Aug 28, 2022 Yesterday was 3 months since my open heart surgery. I'm going great! I'd guess essentially back to normal. My sternum is still not fully healed, that'll take more time, but energy and capability are basically back to what I was like last summer. I'm very happy with the results.
Aug 28, 2022 I'm very happy to be able to exercise daily, go boating on the weekends AND swim and paddleboard. I was annoyed that I couldn't do these things a month ago. I had a cardiologist appt. two weeks ago. He said he hopes the valve lasts me the rest of my life and to see him in a year.
Aug 28, 2022 As a final post to this thread, I want to thank each and every one of you again that commented, liked, shared and DMed me throughout all of this. The love and support from Twitter and the #Bitcoin community was unfathomable. You all made a difference in my life and my recovery.❤️
-
 @ 2b61985e:f4cebdc3
2023-08-03 10:16:24
@ 2b61985e:f4cebdc3
2023-08-03 10:16:24How the singularity of life will win
Previously published on Substack Jul 14, 2022
In a world where the masters that should never be are going batshit insane wanting to chip and control everyone it can often seem that we’re in for a bleak future.
Going back a few decades those who remember how things were can easily point to myriads of tech based things that have become way more stressful, are seemingly impossible to avoid, keep manipulating our mindstreams and in aggregate seem to change our very being.
But I want you to consider all of this from another perspective. Unless some AI bot is reading this (go away please!) you are a complex being that can navigate a LOT of unknowns, to adapt, interpret and find new ways of managing it all.
We have very good abilities when it comes to pattern recognition, taking in and calculating enormous amounts of organic data and in general find a way through even what looks like its all new, invincible and too much to handle for an individual.
The basic mistake, often subconscious, is to regard new technology and ways of interacting as brand new, something that we have no natural ability to handle. But what lies behind all tech, what drives all interaction on social media, and what will be included even in AI or whatever the tech obsessed engineers can come up with?
In my opinion there is nothing new under the sun when it comes to this basis, it will be the same mix of delusions and hangups we have had to wrangle with since sentience arose. Likewise anything with real good motivation and wisdom behind it will be beneficial, especially once enough of us catch on to the basis of it all being very human motivations.
I’ve been in media tech since 89 when I saw the previous democratic media revolution unfolding with DTP self publishing, and got in early on anything from website development to open source development, cloud computing, crypto and whatever “new” has been popping up. This enabled me to predict a few things like these:
Wondering aloud in 92 why not all phones were mobile when my own draggable one came in at 8 kg and a radio operators license
Almost scaring off old friends in 98 predicting that online dating would be huge
Predicting that all businesses will need smart, integrated online tools of all types to survive in 2005
Seeing that online ID with biometrics would be the BIG thing forward in 2018
Things like working on Amazon AWS since 2010 and seeing how the brutal and seemingly magic capabilities were just metastasizing into something very scary also come with some predictions, but these are far harder to formulate.
The single most important prediction now in 2022 is actually quite optimistic: despite all the capabilities of manipulation and control that converge into a demonic Beast Machine it will all fail to completely subjugate and subvert us humans.
Why? The short answer is that complexity can be handled by sentience/mind itself and especially in distributed networks of separate but connected actors.
The opposite which always is about central control will ultimately fail in the end regardless of capacity since those who do keep that central control will fall prey to the ever present delusions and obscurations.
Those jockeying for central control will end up the same way as the Chinese emperors of old when they hunted for longevity and even eternal life on this planet.
It turned out that eating mercury was not a good idea for longevity, yes this is what they did!
It will be interesting to see how the technocrats bring themselves down this time, and that is what navigating this “new jungle” is about.
So that is why this is Ways Through Wilderness, life will happen as always :-)
-
 @ 2b61985e:f4cebdc3
2023-08-03 10:06:54
@ 2b61985e:f4cebdc3
2023-08-03 10:06:54How the singularity of life will win
Previously published on Substack Jul 14, 2022
In a world where the masters that should never be are going batshit insane wanting to chip and control everyone it can often seem that we’re in for a bleak future.
Going back a few decades those who remember how things were can easily point to myriads of tech based things that have become way more stressful, are seemingly impossible to avoid, keep manipulating our mindstreams and in aggregate seem to change our very being.
But I want you to consider all of this from another perspective. Unless some AI bot is reading this (go away please!) you are a complex being that can navigate a LOT of unknowns, to adapt, interpret and find new ways of managing it all.
We have very good abilities when it comes to pattern recognition, taking in and calculating enormous amounts of organic data and in general find a way through even what looks like its all new, invincible and too much to handle for an individual.
The basic mistake, often subconscious, is to regard new technology and ways of interacting as brand new, something that we have no natural ability to handle. But what lies behind all tech, what drives all interaction on social media, and what will be included even in AI or whatever the tech obsessed engineers can come up with?
In my opinion there is nothing new under the sun when it comes to this basis, it will be the same mix of delusions and hangups we have had to wrangle with since sentience arose. Likewise anything with real good motivation and wisdom behind it will be beneficial, especially once enough of us catch on to the basis of it all being very human motivations.
I’ve been in media tech since 89 when I saw the previous democratic media revolution unfolding with DTP self publishing, and got in early on anything from website development to open source development, cloud computing, crypto and whatever “new” has been popping up. This enabled me to predict a few things like these:
Wondering aloud in 92 why not all phones were mobile when my own draggable one came in at 8 kg and a radio operators license Almost scaring off old friends in 98 predicting that online dating would be huge Predicting that all businesses will need smart, integrated online tools of all types to survive in 2005 Seeing that online ID with biometrics would be the BIG thing forward in 2018Things like working on Amazon AWS since 2010 and seeing how the brutal and seemingly magic capabilities were just metastasizing into something very scary also come with some predictions, but these are far harder to formulate.
The single most important prediction now in 2022 is actually quite optimistic: despite all the capabilities of manipulation and control that converge into a demonic Beast Machine it will all fail to completely subjugate and subvert us humans.
Why? The short answer is that complexity can be handled by sentience/mind itself and especially in distributed networks of separate but connected actors.
The opposite which always is about central control will ultimately fail in the end regardless of capacity since those who do keep that central control will fall prey to the ever present delusions and obscurations.
Those jockeying for central control will end up the same way as the Chinese emperors of old when they hunted for longevity and even eternal life on this planet.
It turned out that eating mercury was not a good idea for longevity, yes this is what they did!
It will be interesting to see how the technocrats bring themselves down this time, and that is what navigating this “new jungle” is about.
So that is why this is Ways Through Wilderness, life will happen as always :-)
-
 @ a1367061:a337453f
2023-08-03 09:58:43
@ a1367061:a337453f
2023-08-03 09:58:43appena arrivato
-
 @ d266da53:7224d834
2023-08-03 09:27:53
@ d266da53:7224d834
2023-08-03 09:27:53Metis is a strong player as a Layer 2 (L2) solution provider based on Ethereum. The MetisDAO Foundation already offers a platform for many types of businesses to embed blockchain services into their products. For 2023, Metis plans to improve its services as an L2 platform to reduce transaction confirmation and finalization times through the release of a novel Hybrid Rollup service.
To this end, we describe the state of the art in the L2 space and present, from a zero-knowledge (ZK) engineering point of view, various technical challenges ranging from suggested optimizations for dramatic performance improvements to theoretical ideas for new cryptographic protocols. In particular, we present zkMIPS, an approach to using the MIPS instruction set as the programming language for ZK rollups in an architecture that can take advantage of both ZK and Optimistic rollups.
Stay updated on the latest developments in Crypto , follow me on Yakihonne.com.
1. Introduction
It is well-known that Ethereum has a scalability issue (the blockchain trilemma), which turns out to be a major bottleneck when the network needs to process thousands of transactions per second, e.g. Decentralized Finance (DeFi). One possible solution is to delegate complex computations to an off-chain solution, called Layer 2 (L2).
Amongst many possible ways to implement an L2 solution, Metis adopted the rollup paradigm: it processes a batch of transactions at a time and later posts the process results to layer 1 (L1), where a smart contract verifies and approves these operations.
Currently, one of the most common frameworks to design a rollup is the Optimistic approach. In an Optimistic rollup, a batch of transactions is received and, unless any of them is contested and proven invalid by vigilant third parties, the transactions are considered valid after some period of time (typically 7–14 days).
A more recent rollup framework, zero-knowledge (ZK) rollups, submits transactions for ap-proval using state of art Zero-Knowledge protocols. This approach results in a much faster approval cycle with very strong security guarantees, but it adds significant complexity to con-trolling proof size, prover, and verifier times. Nevertheless, Metis believes in the potential of this methodology, and it is committed to investing time, effort, and resources to pursue and implement these ideas.
In this document, we describe the state of the art in the L2 space and present, from a ZK engineering point of view, various technical challenges ranging from suggested optimizations for dramatic performance improvements, to theoretical ideas for new cryptographic protocols.
2. Background
2.1 Preliminary notions
For clarity and to avoid potential ambiguities, we informally define the following notions as used in this paper.
MIPS
MIPS stands for Microprocessor without Interlocked Pipelined Stages, a decades-old and stable processor architecture. Several MIPS instruction sets have been standardized; for concreteness, we refer to the instruction set specified in [1].
Layer 1
Layer 1 (L1) refers to the Ethereum Mainnet, which is the blockchain that Metis uses as its consensus-achieving mechanism.
Layer 2
Layer 2 (L2) is a separate blockchain administered by an independent entity (possibly in a distributed manner). This L2 blockchain communicates periodically with L1, stores information (such as transaction data) on L1, and sends additional evidence (such as ZK proofs) in order to prove to L1 that the transactions are processed correctly. At L1, these functionalities are implemented through smart contracts.
The purpose of this architecture is to gain efficiency and transaction throughput and reduce gas costs while taking advantage of the property of L1 as a distributed, irrefutable ledger. Metis also administers an L2 blockchain, called Andromeda.
Layer 3
The term Layer 3 refers to any program running over L2 data, or to independent programs that help maintain L2 functioning properly. The main reason to add an L3 over an L2 blockchain is to improve performance, moving some computations to an independent system with fewer blockchain limitations. Eventually, since L3 uses a different trust model than L2, the computations it performs should be verified by L1/L2 in the same way L2 computations are verified by L1.
ZK Proofs of Verifiable Computation
In this document, Zero Knowledge Proofs are used to implement Verifiable Computation be-tween a prover and a verifier. The prover performs some (possibly lengthy) computation that validates some results published on the blockchain (L1 or L2) and produces additional in-formation to assist the verifier in the audit of these results, i.e. establishing its correctness. Subsequently, the verifier generates a random string and performs checks which allow him to convince himself that the result published is indeed correct.
Optimistic rollups
An Optimistic rollups considers transactions correct until proven otherwise. In this scenario, the otherwise proof is an investigation process triggered when users claim there is fraud in the transaction. We call this claim a challenge and the users who can trigger it the challengers. If a transaction is not challenged, then it is considered correct at the end of the challenge period (typically a few days).
ZK rollups
A Zero-Knowledge (ZK) rollup uses Zero Knowledge Proof techniques to create proof of va-lidity for transactions. The use of ZK proofs can reduce withdrawal time (the time that the network/L1 needs to finalize a transaction) from days to hours and allow the validity of the transactions submitted to L2 to be proved without revealing additional, potentially sensitive information. This is achieved by having L2 provide cryptographic validity proof before updating the blockchain state of L1. The verification process in a ZK rollup is more secure and faster than in Optimistic rollups. However, it is more difficult to implement.
Comparing the Optimistic and ZK rollups
There exist two types of time measurements to compare the rollup paradigms:
Confirmation time — This is the time it takes for the front-end, which is a decentralized appli-cation (dApp), to interact with L2 and L1, and to register transactions correctly.
Finalization time — This is the time it takes for the back-end (the L1 or L2 blockchain, depend-ing on the context) responsible for registering the finality (correctness) of the transaction.
In comparison to ZK rollups, Optimistic rollups take less confirmation time to consider transactions as valid (it happens as soon as the sequencer submits transaction data to L1). However, they take more finalization time to consider transactions as faulty (it happens only after the challenge process has been triggered and concluded), whereas ZK rollups only need to wait for a prover to generate proof and a verifier to reject it.
For a detailed comparison between the two, see [2].
zkSNARKs and zkSTARKs
Even though many Zero-Knowledge protocols for proving the validity of specific statements have been developed over the last 40 years of research, only recently we have seen efficient protocols for generic computations, such as Zero-Knowledge Succinct Non-Interactive Argument of Knowledge (zkSNARK) and Zero-Knowledge Scalable Transparent Argument of Knowledge (zkSTARK). ZK rollups can be implemented using any of these ZK techniques and, in both cases, proofs can be generated off-chain and posted on-chain so anyone can verify them.
zkSNARKs were implemented for the first time by the ZCash team. Although its proofs are small and no security issues have been identified in this technique so far, it requires a trusted setup ceremony before running the protocol, and, due to its underlying cryptographic assumptions, it is not quantum-safe. zkSTARKs were first implemented by the StarkWare team. Its proof sizes are not small compared to proof sizes from SNARKs, but they can be generated and verified faster, and also they are immune to quantum attacks.
In addition, for our purposes, the salient feature of the original STARK paper is the possibility of modeling a computation as a processor with a finite instruction set, as we explain below.
FRI
Techniques such as SNARKs and STARKs transform a computation to some specific polynomial which must be of a low degree. The Fast Reed-Solomon Interactive Oracle Proof (FRI) is a protocol that shows a polynomial is close to another polynomial of low degree, and it is applied to STARK polynomials in the verification of their low degrees.
3. Current Software Architecture
Our proposed architecture, zkMIPS (see next section), is inspired on the Cannon project by the Optimism team, which implements a method for investigating a disputed transaction between the Sequencer and the L1 rollup Validator. This investigation process is executed during a period called the dispute period, and includes verifying L2 Merkle roots generated by Sequencer and L2 rollup Validator.
Cannon also implements a MIPS interpreter on L1 in the form of a smart contract with about 400 lines of code. This interpreter receives two different sets of EVM opcodes from the L2 rollup Validator, the Sequencer, and converts both into MIPS opcodes. In addition, it converts data stored in Ethereum memory into MIPS data memory. In the last step, the MIPS interpreter sends both sets of opcodes and data to the Shell Executor.
Cannon uses a minimally modified subset of go-ethereum (Geth) compiled to MIPS called Minigeth, in which the consensus protocol, the RPC, and the database have been replaced by a Pre-image Oracle. On L2, there are four software components: Minigeth, a Pre-image Oracle, a Sequencer, and an L2 rollup Validator.
Figure 1 illustrates how L2 components communicate between themselves and with L1:
- Sequencer submits transactions and generated commitments for a specific block.
- L2 Validator fetches the submitted commitments.
- Validator creates a new set of commitments and verifies the fetched commitments match the generated ones. Note that during this process both commitments are submitted to MiniGeth.
- MiniGeth checks whether MIPS Memory has instructions related to that block.
- If MiniGeth does not find them in MIPS Memory, then it uses Pre-image Oracle. Pre-image Oracle accepts a block or transaction hash from MiniGeth.
- Pre-image Oracle fetches the pre-image of that block or transaction from the EVM state.
- Pre-image Oracle passes the result to MIPS Interpreter.
 Figure 1: The interaction of L1 blockchain and L2 Rollup with Cannon.
Figure 1: The interaction of L1 blockchain and L2 Rollup with Cannon.- MIPS Interpreter converts the EVM opcodes to MIPS opcodes and stores them in MIPS Memory.
- Validator sends the result of its decision to Challenger.
- If L1 Validator does not agree with the process result, Challenger Smart Contract submits the two commitments to Validator and lets it make the decision for the next step to slash Sequencer. Also, Validator can make a decision whether cancel the batch completely or remove the faulty transactions from the batch and re-do the verification process.
Shell Executor on L1 receives MIPS opcodes and data from L2 to find out whether there is any disagreement between the two instruction sets. In case of a disagreement between the rollup Validator and L2 Sequencer, it returns the line number of the EVM instruction in which the disagreement has happened and declares the Merkle root (which is submitted by Sequencer) as invalid. For getting more information on a particular block (e.g., access to an EVM state to obtain the block header), Shell Executor calls Pre-Image Oracle, which receives the hash of a block and returns the block header. Hence, Shell Executor can traverse the previous block until finding the block which contains the disputed instruction. Thus, Pre-Image Oracle replaces the usage of the database for this on-chain interpreter, eliminating the necessity to maintain a database in Cannon’s VM (MiniGeth).
4. Challenges
4.1 Challenge: Applying MIPS
In L2 solutions, there is some underlying computation C that needs to be verified by L1 before inserting L2’s processing results back into L1. To do this, C needs to be transformed into an equivalent polynomial for STARK. We distinguish between two important possible representations of C.
Boolean and algebraic circuits — A computation C can always be represented as an algebraic circuit, which in turn can be converted to a Boolean circuit. Several methods have been developed to create a SNARK proof from one of these two representations, even though creating a circuit can be a time-consuming task. For an example, see [3].
Finite instruction set— Imagine you have a processor which is able to execute a finite set of instructions and a program that reflects the computation C in this instruction set. Note that each program instruction will change the processor’s overall state from some well-defined current state to the next. This sequence of states is called the (execution) trace, and it can be used in STARKs to help prove there is a valid sequence of states for C.
Important questions concerning the second representation are: what exactly should be the specifications of a processor to emulate this instruction set? How many registers does it have? Which instructions are allowed? Etc. There are many choices possible, which strongly depend on the context where the ZK Proof has to run, among other factors.
StarkWare chose to define a new language called CAIRO, which stays close to their Algebraic Intermediate Representation (AIR). This leads to efficient protocols but requires programmers to adjust to this language. Instead, we propose a different approach, using an already estab-lished language, as we explain in the next section.
Problem. As already explained, in an Optimistic rollup, a challenger contests a proof by demonstrating an error in the execution of the program that executes a transaction, whereas in a ZK rollup, a prover receives a MIPS program as input that executes a transaction and uses the program’s logic to generate a zkSTARK/zkSNARK proof for its correctness.
We expect that both approaches, Optimistic and ZK, can coexist and be unified, a concept we call a hybrid rollup. We will explain the advantages of such a rollup technique combination in Section 4.5. It seems natural to use the same instruction set as input for both types of rollups. But then, the question is which intermediary instruction set is more appropriate.
Solution. Since we need to verify the source code that validates Ethereum (Layer 1) trans-actions, the EVM instruction set seems to be the logical choice. However, the complexity of interpreting EVM code requires a lot of work to write a prover that compiles its logic to ZK proofs. It only gets worse if we consider the large size of the instruction set as well as the frequent updates in the set of EVM opcodes [4].
Therefore, we intend to use the MIPS instruction set due to its well-known stability and its simple opcodes. This choice will also allow us to take advantage of incorporating Cannon into our system, which implements a method to challenge a transaction using a subset of MIPS.
An additional advantage of developing ZK circuits based on MIPS programs is that we do not have to worry about the EVM-based ZK types like ZK Type 1, 2, 3, or 4, as mentioned in [5]. This way, we obtain much more flexibility in developing ZK circuits and implementing formal or push-button verifications to make our circuits bug-free and safe from all types of attacks.
Challenge 1. Use the MIPS instruction set as the instruction set for ZK rollups and apply it to the ZK-proof system design.
4.2 Challenge: Fractal scaling
Problem.A naive implementation of the functionalities described in the previous section would lower TPS, so these components could be partially implemented outside Layer 2 with-out reducing the system’s reliability. Adding a Layer 3 solution to the architecture improves scalability, and also will not reduce the decentralization and security of the system. However, adding L3 to the architecture has its own challenges.
Solution. One possible approach to address this challenge is following a recursive proof generation method, known as Fractal Scaling. This helps to balance security, scalability, and decentralization since the proof generation process is done on machines to which attackers do not have access, whereas integrity is preserved because all off-chain computations can still be verified on-chain.
More specifically, zkSTARK proofs can be created in Layer 3 to help Layer 1 verify whether Ethereum L1 state roots were correctly computed from the execution of a transactions batch in L2. These proofs can be sent to L1 through call data at a lower cost since it could contain one proof for thousands of transactions united in one batch. Hence it is expected that Fractal Scaling will save gas and improve the TPS of the system.
In the zkMIPS solution, both the STARK and SNARK approaches are used. First, the Se-quencer on L2 generates multiple batches in which each batch has a hash value pointing to the next batch. On L3, there are several provers that process the received batches in parallel and generate one STARK-based proof for each transaction inside a batch. Then, by applying SNARK-based proof recursion and aggregation techniques, the prover combines the generated STARK-based proofs and will create one proof per batch. Finally, again all the SNARK-based proofs for batches will be combined using a recursive proof technique and will be returned to L1’s verifier smart contract.
Challenge 2. Although the required architecture with the capability of running smart contracts on L2 and bridging contracts on L1 is available, still high cost of the on-chain storage on L1, as well as the off-chain storage on L3, are challenges that should be investigated.
4.3 Challenge: Provider unavailability
Problem. In the case of unexpected shutting down or crashing of the proof generation process, new provers or Sequencers are unable to continue the process as they cannot track the previous prover’s pending work. Therefore, new provers will lose the state of processing accomplished by the previous prover who got crashed. If we lose this information then a new prover or Sequencer needs to start the process from the beginning, therefore increasing the time and cost spent for the total proof generation process and inflating the processing transaction fee.
Solution. One possible solution is to periodically create checkpoints for transaction summaries and other details necessary to rebuild a current state by some other prover using L3 offline storage. This storage keeps the checkpoint until a generated proof is submitted by a prover and reduces costs as it is not required to post transaction state details to L1.
In case of unexpected crashing scenarios, whenever a new rollup provider gets back online it can fetch the checkpoint from storage and continue the proof generation process.
Challenge 3. Designing a system to store the checkpoints during the ZK process is challenging. Also, finding the optimal value for the time interval to update the checkpoints should be investigated.
4.4 Challenge: Polynomial commitment schemes and proof size
For efficiency reasons, almost all zkSNARK and zkSTARK protocols rely heavily on some commitment scheme for the polynomials involved. A natural way to classify these schemes is according to their underlying cryptographic assumption:
- Hash-based, e.g. using Merkle trees (as in FRI)
- Discrete Log-based, e.g. over elliptic curves (as in BulletProof)
- Pairing-based, i.e. using pairings as well as elliptic curve discrete log (as in KZG)
- Hidden-order based, i.e. using a group whose order is known to nobody (such as in RSA and class groups)
These commitment schemes can be compared according to different criteria, e.g. proof size, prover time, verifier time, setup assumption, post-quantum resilience, etc. See [6] for an overview.
We intend to study which commitment scheme will be most suitable for our context, in which proof size concerns us the most. More precisely, KZG or Bulletproof (BP) could be used as zkSTARK’s polynomial commitment scheme instead of Merkle trees. We emphasize that this approach could, in theory, reduce the complexity of crucial parts of proof size from O(log2(d)) to O(log(d)) or O(1) (to BP and KZG-based zkSTARKs), and parts of prover time from O(log2(d)) to O(d) or O(1) (idem), where d represents the degree of modeled polynomials.
However, the feasibility of changing a polynomial commitment scheme has to be properly analyzed, so we cannot guarantee these performance improvements as real complexity depends on variables that are not yet considered here.
The benchmarks for our preliminary zkMIPS implementation using libSTARK[7] are presented in Figure 2. The results were generated for different values of the blow-up factor β, a STARK approach variable typically defined as a power of 2. As the name suggests, the blow-up factor blows the evaluation domain over which FRI polynomials are evaluated. Therefore, for a higher
β, the prover takes longer to generate the proofs, but soundness can be achieved more easily, causing proof size and verification to decrease. This relation can be observed in the benchmark results.
Challenge 4. Investigate how an appropriate choice of a polynomial commitment scheme will reduce the proof size and how to integrate the proposed protocol with other protocols in the applied ZK rollup scheme.
4.5 Challenge: Hybrid Rollups and various transaction types
Problem. The high cost of ZK rollups discourages some users from requesting the ZK rollup type of service, while the high withdrawal time of Optimistic rollups might be a bigger disad-vantage to other users. As we know there is a trade-off between these two rollup techniques. We intend to use both techniques in parallel. Our approach is to implement Optimistic and ZK rollup services at the same time to satisfy all types of users. The question that should be addressed is how to combine these rollups in one architecture.
Solution. By applying the Bedrock architecture as implemented in the Cannon project developed by the Optimism team[8], we can combine both Optimistic and ZK rollups. Applying this architecture requires several design choices, such as transaction types and execution time
 Figure 2: Benchmarks for preliminary zkMIPS implementation
Figure 2: Benchmarks for preliminary zkMIPS implementationparameters, in order to optimize the system’s confirmation and finalization times. The proposed hybrid solution will allow users to choose between Optimistic and ZK rollup services seamlessly.
We envision a system with different Transaction Categories. Each category would have its own configurable mechanism to automatically decide whether its transactions should be validated via Optimistic or ZK rollups if the user chooses to. Moreover, the soundness level (how hard it is to get a faulty transaction to be accepted as correct in ZK rollups), as well as the policy (such as defining the challenger’s reward in an Optimistic rollup) would be configurable. As a result, each transaction category would have different latency, depending on the configuration.
In this setup, hybrid rollups face several challenges. For example, the validity of ZK rolled-up transactions depends on previously Optimistic rolled-up transactions. Thus, how to properly implement this categorization is a question that still deserves considerable thought.
Challenge 5. How can Optimistic and ZK rollups accomplish transaction approval in one unified architecture? Also, how to identify independent transaction batches that allow having a transactions batch finalized before the previous one?
4.6 Challenge: Alternative recursive ZK architectures
One way to overcome the issue of large ZK proofs and prover times is to change how parties communicate in these protocols and what the communication between themselves represents. For instance, instead of verifying on-chain a proof (generated off-chain) for the validity of a transaction, one could design an additional ZK protocol to verify off-chain that same proof and use this off-chain verification to generate a second, smaller, proof to be verified on-chain.
The motivation behind this idea is that even though verifying a proof π for a computation C is faster than running C, sometimes it is not fast enough. Therefore, we could create a proof π⋆ for the correctness of π (the target computation is now the verification of π itself). For this reason, we use the adjective “Meta” to refer to this new proof, as well as to the prover P ⋆ that generates it and verifier V ⋆ that verifies it. This scheme is illustrated in Figure 3.
Of course, π⋆ is intrinsically related to π and the validity of one of these proofs must imply the validity of the other by design. The difference between them, however, is the introduction
 Figure 3: Meta ZK Proof
Figure 3: Meta ZK Proofof a new level of abstraction, where the validity of computation is replaced by the verification of this validity. On this new level, since proofs being verified are often produced by the same algorithm P , we can take advantage of their similarities to group many verifications into one meta-proof, achieving even better results. This optimized scheme is illustrated in Figure 4.
 Figure 4: Meta ZK Proof for multiple ZK Proofs
Figure 4: Meta ZK Proof for multiple ZK ProofsA similar idea has already been notably implemented by Coda/Mina[9] and Plonky2[10]. These projects use a framework known as Recursive ZK Proofs, which consists of grouping recursively many statements into one, and then proving only this final statement, as illustrated in Figure 5.
 Figure 5: Recursive ZK Proof
Figure 5: Recursive ZK ProofEven though Recursive and Meta ZK Proofs are similar in many aspects, we intend to employ Meta ZK Proofs because we believe there are many opportunities for optimization when verifying multiple ZK Proofs for different transactions at the same time. Furthermore, the generation of a ZK Proof reduces the full execution of computations to their verifications, which tends to be much faster and equally valid. Therefore Meta ZK Proofs can achieve the same soundness as the proofs they are reducing, but with significantly lower complexity.
Challenge 6. Explore alternative recursive ZK architectures.
4.7 Challenge: Security concerns
Formal Verification methods are mathematically precise techniques that analyze the specifi-cation, development, and verification of systems and protocols. Creating a formally verified implementation of a probabilistic proof system or protocol is challenging. However, the result-ing guarantees avoid security vulnerabilities in the designed protocol/system.
In a future version of zkMIPS, we will apply Formal Verification methods to realize the following improvements and prevent attacks on the ZK scheme and verifiers:
- To improve security, we intend to apply formal verification methods to the ZK proof generation protocol. We will experiment with both the State exploration and the Proof based approaches. State exploration can be useful for detecting common vulnerabilities such as reentrancy attacks, integer overflows, and unauthorized access. Proof-based can be useful for detecting subtle logic errors and security vulnerabilities that may be difficult to detect using state exploration, and also provide a high degree of confidence in the correctness and security of the contract. We use proof assistants such as Coq, Isabelle, and the K framework.
- In addition, to find ZK program vulnerabilities, we are following the Formal Specifications method using the Why3 platform which verifies programs developed in Rust.
- To improve the security of written codes in Solidity, we will be using the Satisfiability Modulo Theories (SMT) Checker application and the Horn-solving technique, or similar tools and techniques if they become available.
- To analyze the gas amount consumed by smart contracts, we will be using tools such as Oyente and Slither.
Challenge 7. Investigate the security of the designed protocol/system using formal verification methods. This investigation will analyze the provided solution from a technical perspective and assess its feasibility.
4.8 Challenge: Commitment schemes based on other assumptions
There exist little-known bit commitment schemes which use the Subset Sum problem as an underlying assumption and seem as efficient as Discrete Log schemes, but the known ones have similar construction and properties, allowing protocol designers to easily replace these schemes. The main advantage of applying a Subset Sum scheme to ZK protocols is that it makes them automatically quantum-resistant, with the addition of having similar Discrete Log schemes’ performance. However, this efficiency in terms of proof size, prover time, and verifier time needs thorough analysis (in particular, when applied to committing to polynomials).
Challenge 8. Investigate the applicability of commitment schemes based on Subset Sum in the context zkSNARKs/zkSTARKs.
4.9 Challenge: Implementation concerns
zkMIPS will accept as input MIPS assembly instructions from any type of application or system including IoT devices, L2 chains using Cannon Optimism, and Cloud APIs. It will output ZK proofs that can be verified on the Ethereum L1 chain. Hence, zkMIPS can be used as a generic ZK proof system in any centralized or decentralized application.
We have started implementing zkMIPS using the FRI protocol following an interactive model. Our current zkMIPS deployment accepts MIPS assembly instructions, parses them into stream format, and loads them into RAM Memory. The result is called a RAM Program, which is converted into Binary Algebraic Intermediate Representation (BAIR) constraints. The result is passed on to the FRI protocol which ensures the complexity of linear proof and the complexity of logarithmic verification (i.e., Low Degree Testing).
In our implementation we were faced with the following main issues:
- The proof size is linear in the size of the computation trace, even after the reduction of witness size. This increases storage costs on the prover side.
- The final verifier needs to interact with the prover continuously until the proof is gen-erated. Hence, the verifier process had to be on an untrusted machine. This is again challenging because L1 cannot rely on an untrusted machine to update its state.
Challenge 9. zkMIPS uses existing software libraries written in several languages. Ensuring the development, integration, optimization, reliability, and security of the final product constitutes a challenging endeavor.
5. Collaboration
Metis invites bright industry experts, researchers, and leaders who are interested to collaborate on the zkMIPS project. This invitation is not limited to the research and implementations mentioned in this document; Metis embraces other innovative ideas to improve the proposed hybrid rollup solutions in this document.
Notes
[1]https://inst.eecs.berkeley.edu/~cs61c/resources/MIPS_help.html
[2]https://vitalik.ca/general/2021/01/05/rollup.html
[3]https://vitalik.ca/general/2016/12/10/qap.html
[4]https://kelvinfichter.com/pages/thoughts/hybrid-rollups/
[5]https://vitalik.ca/general/2022/08/04/zkevm.html
[6]https://docs.google.com/presentation/d/1YJX_MgWjhsFHiubHoCMb5F27rtN9AcxgaKMswGFf8I4
[7]https://github.com/elibensasson/libSTARK
[8]https://github.com/ethereum-optimism/cannon/wiki/Cannon-High-Level-Overview
[9]https://minaprotocol.com/wp-content/uploads/technicalWhitepaper.pdf
[10]https://github.com/mir-protocol/plonky2/blob/main/plonky2/plonky2.pdf
By:MetisDAO Link:https://metisdao.medium.com/zkmips-and-other-research-challenges-for-layer-2-9097c661facb
-
 @ 32e18276:5c68e245
2023-07-30 21:19:40
@ 32e18276:5c68e245
2023-07-30 21:19:40Company Overview:
Damus is the pioneering iOS nostr client. Through its platform, Damus empowers billions on iOS with the tools for free speech and free speech money. If you're driven to bring freedom technology to the masses and ignite change, we invite you to join our mission.
Job Description
- Collaborate on iOS Damus in tandem with our core developer, Will Casarin, and the broader Damus team.
- Implement our vision as laid out in our product roadmap: https://github.com/orgs/damus-io/projects/3/views/1.
- Embrace the fun and critical mission of undermining totalitarian regimes across the globe.
Job Requirements
- A genuine passion for freedom technology.
- At least one year of collaborative development experience.
- Experience building SwiftUI iOS apps.
- Passionate about design and user experience.
- Eager to work in close coordination with Damus lead developer, Will, and a dedicated team spanning development, design, and product.
- Commitment to a full-time role, although we remain open to discussing alternative arrangements.
Bonus Qualifications
- Experience with Nostr development.
- Experience with C.
- Previous work in free and open source projects.
- A publicly shareable portfolio.
Job Structure
- A one-month paid probationary period to ensure a mutual fit.
- Upon successful completion of the trial, the opportunity for a six (6) month contractual engagement.
- The potential for contract renewal, contingent on funding.
Application Process:
Interested candidates should forward a motivational statement alongside their CV/portfolio to vanessa@damus.io. -
 @ 4d444439:7ed2458b
2023-08-03 09:26:27
@ 4d444439:7ed2458b
2023-08-03 09:26:27The quantum effects of physics are at the atomic and subatomic level, brought to us courtesy of quantum mechanics, and hold the key to major advances — quantum leaps — in computing, communication, measurement, and sensing, known collectively as quantum information science. This informal paper is not intended for physicists, but for computer scientists, software developers, and other non-physicists who wish to become involved with quantum information science, particularly quantum computing, and have a need (or desire) to know something about the underlying physics, particularly enough to understand what makes quantum information science tick, but nowhere near as much as a physicist or hard-core quantum engineer might need.
We need a lot more computing power to tackle much larger and much more complex computing challenges in the decades ahead. Ditto for communication, measurement, and sensing. That’s where quantum effects come in. Quantum information science is the broad umbrella for the theory, science, engineering, technology, infrastructure, and applications related to exploiting quantum effects (quantum mechanics) in the areas of computing, communication, and measurement and sensing.
Quantum information science is based on any aspect of quantum effects which can be observed, measured, controlled, stored, or communicated in some manner.
This informal paper will focus primarily on quantum effects alone and how they enable quantum information science, but won’t delve deeply into the various areas of quantum information science itself, such as quantum computing and quantum communication. For a broad summary of quantum information science overall, see:
This informal paper was created from material which was originally in that paper but extracted to become a standalone paper and expanded somewhat.
Here are the topics covered in the remainder of this paper:
- What’s so special about quantum information science?
- What is quantum?
- Quantum mechanics
- Quantum physics
- Quantum chemistry
- Quantum computational chemistry
- Quantum biology
- Quantum field theory
- Quantum theory
- Quantum system
- Isolated quantum system
- Quantum effects
- Quantum resource
- Quantum state
- Wave function
- Linear algebra
- Quantum information
- Quantum bit — qubit
- Stationary, flying, and shuttling qubits
- Measurement / observation
- Observable
- Quantum phenomena
- Macroscopic quantum phenomena
Here are the quantum effects that will be described by this paper — not in any great detail, but simply to give the more casual reader a flavor of what quantum effects are all about:
- Discrete
- Quanta
- Particle and wave duality
- Probabilistic
- Uncertainty
- Superposition
- Schrödinger’s cat
- Cat state
- Entanglement
- Spooky action at a distance
- Bell’s theorem and Bell’s inequality
- Bell states
- Phase
- Interference
- Wave function
- Density matrix or density operator
- Probability amplitude
- Unitarity principle
- Basis state
- Computational basis state
- Quantum state
- State vector
- Collapse of wave function on measurement
- Measurement
- No-cloning theorem
- Hamiltonian
- Schrödinger’s equation
- Time evolution
- Fermi-Dirac statistics
- Bose-Einstein statistics
- Fermions
- Bosons
- Pauli exclusion principle
- Spin
- Integer spin
- Half-spin or half-integer spin or spin 1/2
- Spin up and spin down
- Cooper pairs
- Superconductivity and superfluidity
- Tunneling
- Josephson effect
- Quantum hall effect
- Macroscopic quantum effects
- Zero-point energy and vacuum fluctuations
What’s so special about quantum information science?
There are three key advantages of quantum information science over classical methods:
- Quantum computing offers much greater performance than classical computing through quantum parallelism which offers an exponential speedup — evaluating many (all) possibilities in parallel, in a single calculation.
- Quantum communication offers inherent security through quantum entanglement — also known as spooky action at a distance, in contrast to security as a problematic afterthought for classical communication and networking.
- Quantum metrology and quantum sensing offer much greater accuracy and precision for measurements of physical quantities and detection of objects.
All of these advantages are made possible by the magic of quantum effects enabled by quantum mechanics.
What is quantum?
Quantum is essentially a reference to quantum mechanics, which concerns itself with atomic and subatomic particles, their energy, their motion, and their interaction.
Larger accumulations of atoms and molecules behave in more of a statistical or aggregate manner, where the quantum mechanical properties (quantum effects) get averaged away. Quantum information science and its subfields focus at the quantum mechanical level where the special features of quantum mechanics (quantum effects) are visible and can be exploited and manipulated.
Quantum mechanics
Quantum mechanics is the field of physics which is the theoretical foundation of quantum information science. This paper won’t delve deeply into the concepts of quantum mechanics — see the Wikipedia Quantum mechanics article for more detail.
Feel free to read all my articles on the anti-censorship long content platform yakihonne.com.
The key elements of quantum mechanics are what are known as quantum effects, summarized below.
Quantum physics
Quantum physics is sometimes used merely as a synonym for quantum mechanics, but technically quantum physics is the application to the principles of quantum mechanics to the many areas of physics at the subatomic, atomic, and molecular level, including the behavior of particles and waves in magnetic and electrical fields.
Quantum chemistry
Quantum chemistry is the application of quantum mechanics to chemistry, particularly for the behavior of electrons, including excited atoms, molecules, and chemical reactions.
Applying classical computing to quantum chemistry is referred to as computational chemistry.
Quantum computational chemistry
Applying quantum computing to quantum chemistry is referred to as quantum computational chemistry (and here).
Quantum biology
Quantum biology is the application of quantum mechanics to biology, particularly for the behavior of electrons in complex, organic molecules, such as how organic molecules form, how they can change, how they can decompose, and even how they can fold.
Quantum field theory
Quantum field theory is the part of quantum mechanics concerned with subatomic particles and their interactions, but it is not necessary to dive down to that level of detail to comprehend quantum information science. For more information, see the Wikipedia Quantum field theory article.
Quantum theory
Quantum theory is not technically a proper term. Used loosely, it commonly refers to quantum mechanics or possibly simply to quantum effects.
Quantum system
A quantum system, or more properly an isolated quantum system, is a particle or wave, or collection of particles and waves, which can be analyzed for its quantum effects as if it were a single, discrete object.
Isolated quantum system
Technically, any quantum system is an isolated quantum system. The emphasis is on the fact that the particles and waves within the system can be analyzed and modeled in isolation, without concern for particles and waves outside of the system. That’s the theory. In practice, no system is truly isolated (except maybe the entire universe as a whole), but the assumption of isolation dramatically simplifies understanding, modeling, and computation of the system. Without the concept of an isolated quantum system, the modeling and mathematics would be too complex to be tractable (workable.)
Each qubit of a quantum computer or a quantum communication network is an isolated quantum system, except when it is entangled with other qubits, in which case the entangled qubits collectively constitute a larger isolated quantum system.
Quantum effects
Quantum mechanics — and hence all of quantum information science and its subfields — is based on quantum effects.
A quantum effect is any phenomenon which cannot be fully explained by classical mechanics — quantum mechanics is required.
Quantum information science is based on any aspect of quantum effects which can be observed, measured, controlled, stored, or communicated in some manner.
Some quantum effects cannot be directly observed or measured, but can sometimes be indirectly inferred or at least have some ultimate effect on the results of manipulating a quantum system.
Quantum effects and their properties include:
- Discrete rather than continuous values for physical quantities.
- Quanta for discrete values. The unit for discrete values. Technically, quantum is a singular unit and quanta is the plural of quantum (just as with data and datum.)
- Particle and wave duality. Particles have wave properties and behavior, and waves have particle properties and behavior. For example, a photon can act as a particle as well as a wave, and an electron can act as a wave as well as a particle.
- Probabilistic rather than strictly deterministic behavior.
- Uncertainty of exact value or measurement. More than just uncertainty of any measurement, there is uncertainty in the actual value of any property, as a fundamental principle of quantum mechanics. A given property of a given quantum system may have a range of values, even before the property is measured. For example, a particle or wave can be at two — or more — positions at the same moment of time.
- Superposition of states — a quantum system can be in two quantum states at the same time. See spin up and spin down.
- Schrödinger’s cat — a thought experiment which demonstrates superposition — the cat can be both alive and dead at the same time.
- Cat state — alternate name for superposition of two quantum states. A tribute to Schrödinger’s cat.
- Entanglement — the same quantum state can exist at two physically separated locations at the same time.
- Spooky action at a distance — popular reference to entanglement.
- Bell’s theorem and Bell’s inequality — quantum mechanics cannot be explained simply by adding “hidden variables” to classical mechanics.
- Bell states — the various combinations of quantum states for two entangled particles. The quantum states of the two particles are correlated — they may be identical quantum states, but they don’t have to be identical. Measuring the state of one particle will allow the observer to infer the state of the other particle. This is useful for both quantum computing and quantum communication.
- Phase — the complex or imaginary part of the probability amplitude of a quantum state. The notion of cyclical or periodic behavior or a fraction of a single cycle of a wave or circle. Measured either in radians (two pi radians in a circle or cycle) or a fraction between 0.0 and 1.0, where 1.0 corresponds to a full, single cycle or circle (two pi radians.)
- Interference — cancellation or reinforcement of the complex or imaginary part of the probability amplitude of two quantum states (phases). Useful for quantum computing — it enables quantum parallelism. Not to be confused with environmental interference which disrupts the operation of a quantum system.
- Wave function is used to fully describe the state of a particle or wave (technically, an isolated quantum system) based on the probabilities of superposed and entangled states. The sum of the basis states of the quantum system, each weighted by its probability amplitude. Linear algebra is the notation used to express a wave function.
- Density matrix or density operator — an alternative to the wave function for describing the quantum state of a quantum system.
- Probability amplitude — a complex number with both real and imaginary parts which represents the likelihood of the quantum system being in a particular state, a basis state. Square it and then take the square root to get the probability for a particular basis state. The imaginary part of the probability amplitude is also referred to as its phase.
- Unitarity principle — the probabilities (square root of the square of the probability amplitude) of all possible states of a quantum system must sum to 1.0 by definition.
- Basis state — the actual numeric value of a single quantum state, comparable to a binary 0 or 1.
- Computational basis state — the combined basis states of a collection of qubits. A collection of strings of 0’s and 1’s, each string having a probability amplitude as its weight in the wave function. Essentially each string is an n-bit binary value.
- Quantum state — the state of an isolated quantum system described by its wave function. Alternatively, a single basis state.
- State vector — a single-column matrix describing the state of a quantum system, where each row represents a computational basis state and the value in the row represents the probability amplitude for that computational basis state. For a single qubit there would be two rows, for two qubits there would be four rows, and for k qubits there would be 2^k rows. Commonly referred to as a ket, the right hand side of bra-ket notation.
- Collapse of wave function on measurement — the probabilities of superposed states will influence but not completely determine the observed value. Measurement always causes the wave function of a quantum system to collapse — permanently.
- Measurement — the process of observing a quantum system. By definition, measurement causes collapse of the wave function, and will always produce a single basis state (0 or 1) or computational basis state (string of 0’s and 1’s) regardless of any superposition or entanglement which may be defined by the wave function of the quantum system.
- No-cloning theorem — quantum information (quantum state) cannot be copied — attempting to read (measure or observe) quantum state causes it (its wave function) to collapse to a discrete, non-quantum state.
- Hamiltonian — an equation which expresses the energy of a quantum system.
- Schrödinger’s equation — describes the evolution of the quantum state of a quantum system over time in terms of its Hamiltonian and wave function.
- Time evolution — how the quantum state of a quantum system incrementally evolves over time based on its Hamiltonian and wave function. See Schrödinger’s equation.
- Fermi-Dirac statistics — rules for fermions which require them to obey or follow the Pauli exclusion principle.
- Bose-Einstein statistics — rules for bosons which allow them to violate (not follow) the Pauli exclusion principle. Sometimes referred to as BES.
- Fermions — elementary particles, such as electrons, and atoms which obey Fermi-Dirac statistics, including the Pauli exclusion principle. Fermions have half-spin (half-integer spin or spin 1/2) by definition. Fermions can collide, bounce apart, or form composite particles, even molecules.
- Bosons — elementary particles, such as photons, and some atoms under special circumstances, which obey or follow Bose-Einstein statistics, which permits them to violate (not follow) the Pauli exclusion principle. Bosons have integer-spin by definition. Bosons can pass right through each other, or even occupy the same position, without interacting.
- Pauli exclusion principle — no two fermions, particles with half-spin, such as electrons and most atoms, can occupy the same quantum state (e.g., position) at the same time. In contrast, bosons, such as photons and pairs of fermions in special circumstances, can occupy the same quantum state (e.g., position) at the same time.
- Spin — the angular momentum, much like a spinning gyroscope, of an elementary particle or an atom.
- Integer spin — the form of angular momentum of bosons which allows them to violate the Pauli exclusion principle. Bosons obey or follow Bose-Einstein statistics, which allow them to occupy the same quantum state (e.g., position.)
- Half-spin or half-integer spin or spin 1/2 — the form of angular momentum of fermions which requires them to obey or follow the Pauli exclusion principle, preventing them from occupying the same quantum state (e.g., position.)
- Spin up and spin down — spin of a particle can have a direction of spin, which is the direction of the vector representing the angular momentum, and up and down are the direction of the axis of rotation, based on using the right-hand rule, where curled fingers represent the direction of spin and the pointing thumb represents the axis of rotation, pointing either up or down as the thumb points. Spin up and spin down can be used to represent two basis states for both quantum computing and quantum communication. Spin up and down for a particle can in fact be superposed, so that a particle (e.g., qubit) is in a linear combination of both spin up and spin down, corresponding to a linear combination of a 0 and a 1.
- Cooper pairs — electrons can pair up at ultracold temperatures (near absolute zero), so that the pair acts as a single boson rather than as a pair of fermions since the half-spin of each of the two fermions add up to be the integer spin of a boson. This allows the pair to violate the Pauli exclusion principle, enabling superconductivity.
- Superconductivity and superfluidity — the phenomenon of zero resistance, for electrical conduction and mechanical flow respectively, which occurs at ultracold temperatures (near absolute zero), allowing pairs of fermions, such as electrons and helium atoms, to pair up, which transforms the half-spin of each fermion into integral spin for the pair, allowing the pair to act as a boson, which no longer must obey the Pauli exclusion principle, so that the pairs can now occupy the same position, which is permitted for bosons which obey Bose-Einstein statistics, but is not possible for fermions alone, which must obey Fermi-Dirac statistics.
- Tunneling — the ability of a subatomic particle or wave such as an electron to appear to be able to move through a solid barrier as if it weren’t there. In actuality, quantum mechanics dictates that a particle or wave has a probability to be at any given location, so that a particle or wave can have a probability of being at either side of the barrier at a given moment, allowing the particle or wave to appear to skip over or through the barrier in the next moment. An example would be electrons and a Josephson junction used in a superconducting transmon qubit.
- Josephson effect — tunneling of Cooper pairs of electrons through an insulating barrier. Used to implement Josephson junctions, such as for superconducting transmon qubits. Also has applications for quantum sensing and quantum measurement.
- Quantum hall effect — quantized conductance (flow of current or electrons) induced by a magnetic field at very low temperatures. Useful for precise measurements.
- Macroscopic quantum effects — quantum effects which can be observed at the macroscopic scale — above the level of the atomic, subatomic, and molecular scale, such as superconductivity, superfluidity, and the quantum hall effect.
- Zero-point energy and vacuum fluctuations — uncertainty means that even a vacuum is not at absolutely zero energy. A vacuum fluctuates within the range of minimum uncertainty. Although an application to quantum information science is not clear at present, specialized hardware can be used to allow a classical computer to measure the fluctuating zero-point energy of a vacuum to generate true random numbers — which cannot be calculated by a strict Turing machine alone.
- Creation and annihilation operators — primarily to facilitate quantum mechanical modeling of many-particle systems.
Quantum resource
A quantum resource is any quantum effect which has some utility in quantum information science, such as for computation in quantum computing or representing quantum information in quantum communication.
It’s an odd term, but sometimes you see it used. Oddly, a qubit would not technically be considered a quantum resource, but superposition, entanglement, and interference would. See the list of quantum effects above.
Quantum state
Quantum state is the unit of quantum information.
A particle or wave — referred to as an isolated quantum system — has a quantum state for each physical quality which can be observed.
- The quantum state is described by a wave function.
- The individual possible states are known as basis states. Such as a 0 and a 1.
- Each basis state in a wave function occurs with some probability.
- A basis state can also have a complex or imaginary component, known as a phase, which is periodic or cyclical. This is exploited in quantum computing to enable quantum parallelism using interference of the phase of a potentially large number of quantum states.
- The probability and phase are combined into a single, complex value, called the probability amplitude, where the probability is the square root of the absolute value (or modulus) of the complex number.
- The basis states and their probability amplitudes are combined to form the wave function.
- If the probability of a basis state is other than 0.0 or 1.0, the two basis states are superposed.
- The quantum states of two separate particles or waves — two isolated quantum systems — can be shared or entangled.
The concept of quantum state applies across all subfields of quantum information science, not just quantum computing and quantum communication.
See the preceding section on quantum effects for more detail.
Wave function
Each qubit or collection of entangled qubits has a quantum state which is described by a wave function using linear algebra to detail each of the basis states and its probability amplitude.
Linear algebra
Linear algebra is the notation used to express a wave function in terms of basis states and probability amplitudes. It’s complex math (figuratively and literally), and not for the faint of heart.
Quantum information
Classical information (a sequence or collection of bits) is represented as quantum information in the form of a quantum state, one quantum state for each classical bit.
Quantum state is the unit of quantum information.
To be clear, quantum information can represent more than just a 0 or 1 classical bit. Since it is a quantum state, it may include a superposition of both a 0 and a 1. The probabilities of 0 and 1 may differ (but they have to add up to 1.0). The probability can include a phase component, and a quantum state may be entangled or shared between two or more separate, otherwise-isolated quantum systems (particles or waves.)
The concept of quantum information applies across all subfields of quantum information science, not just quantum computing and quantum communication.
Quantum bit — qubit
A quantum bit or qubit is the unit of storage and manipulation of quantum information (quantum states).
Qubits are used for both quantum computing and quantum communication.
Despite popular misconceptions, a qubit is not the quantum equivalent of classical information or the classical bit. Rather, a qubit is a device for storing and manipulating quantum information, not the quantum information itself, which is represented as the quantum state of the device. In classical computing and classical communication a bit is the abstract information, not the physical representation.
A bit is either a 0 or a 1, regardless of whether that 0 or 1 is represented as a voltage level, a magnetic field, a photon, or a punched hole.
Quantum information is a 0 or a 1 or a linear combination of a 0 and a 1, regardless of the technology used to implement the qubit device which holds and manipulates that quantum information (quantum state.)
Stationary, flying, and shuttling qubits
For quantum computing, generally a qubit is a stationary qubit, which is a hardware device which stores and manipulates quantum information. It is stationary, meaning that the device does not move.
For quantum communication, a qubit is a flying qubit, typically a photon which gains its utility or ability to communicate by being moveable to a remote location while it is in an entangled state with another qubit at a different and possibly very distant location.
A trapped-ion quantum computer may use shuttling to move a qubit — an ion or atom with a net charge — a short distance so that it is easier to manipulate and measure the quantum state of the qubit, and to store more qubits than can be directly controlled or measured directly.
Measurement / observation
Quantum state is not directly observable or directly measurable using normal, non-quantum methods, devices, or instruments. We can indeed measure any quantum information we want, but measuring a quantum state has the effect of collapsing the wave function of that quantum state, eliminating the truly quantum-ness of the state (e.g., superposition, entanglement, and interference or phase), leaving the quantum information in a purely classical state, such as the 0 and 1 of classical information.
These aspects of measurement apply across all of the subfields of quantum information science — quantum computing, quantum communication, and quantum metrology and sensing.
Observable
Any quantum effect which can be observed or measured is referred to as an observable.
Generally, the quantum state is the quantum effect which is the observable.
Quantum phenomena
Quantum phenomenon is a vague term which is loosely a synonym for quantum effect, or any phenomenon in which a quantum effect is observable in some way, including macroscopic quantum phenomena.
Macroscopic quantum phenomena
A macroscopic quantum phenomenon is any phenomenon above the level of the atomic, subatomic, and molecular level in which a quantum effect is observable in some way.
Prime examples are superconductivity, superfluidity, and the quantum hall effect.
Additional phenomena to consider
I need to dive deeper into these phenomena to figure out how they might be integrated here, especially with regard to quantum information science:
- The quantum hypothesis — in general. Historical role in transitioning from the classical world to the quantum world.
- Momentum, angular momentum, orbital momentum.
- Pure state, mixed state, density matrix, density operator.
- Wave packets.
- Nuclear magnetic resonance (NMR). Some early efforts in quantum computing relied on NMR.
- Nuclear electric resonance.
- Gravity. Nominally lies in the realm of General Relativity rather than quantum mechanics, but… who knows for sure. Can a quantum computer be used to accurately simulate or model gravity and gravitational effects, including effects on time and space? Clearly quantum metrology relates to gravity and gravity waves in some way.
- Add Helicity (spin, angular momentum), Chirality (handedness), polarization, and detail on creation and annihilation operators (primarily to facilitate quantum mechanical modeling of many-particle systems.)
- Harmonics.
- Localization vs. spooky action at a distance.
- Nuclear electric resonance.
- Is friction a quantum effect?
- Avalanche and threshold effects as quantum effects?
- Correlated quantum matter and quantum materials.
- What exactly is quantum theory — vs. quantum effects, quantum mechanics, and quantum physics?
- Mention hidden variables.
- Mention Hilbert space.
- Nonlocality, Bell’s theorem, nonlocal correlations.
- Contextuality — Kochen–Specker (KS) theorem, also known as the Bell–Kochen–Specker theorem.
- Add Penrose microtubules and consciousness.
- Quantum logic clock.
- AMO physics — atomic, molecular, and optical — matter-matter and light-matter interactions at the scale of no more than a relatively few atoms.
- Are phase transitions a quantum effect — macroscopic in aggregate, but specific effect at the atomic or molecular level, and could they be used for quantum information science?
- Quantum correlations.
- CHSH inequality.
- Interaction-free detection.
- Ghost imaging.
- Thermodynamics, quantum thermodynamics.
- Quantum dot.
- Position, navigation, and timing (PNT). More of an application of quantum effects.
Quantum 2.0 or should it be called Quantum 4.0?
Some people are now touting current quantum technologies — including quantum computing — as Quantum 2.0. I’d beg to differ.
I would classify Quantum 1.0 as the original work on quanta by Planck, Einstein, and Bohr — and others.
I would classify Quantum 2.0 as applying quantum mechanics to physics for practical applications, including the transistor, laser, superconductivity, and superfluidity.
I would classify Quantum 3.0 as the early efforts at quantum computing, quantum communication, quantum sensing, and quantum metrology — all fairly primitive and not really ready for practical application.
I would classify Quantum 4.0 as the next generation of quantum information science, including more advanced quantum computing architectures and programming models, quantum communication, quantum networking, quantum sensing, and quantum metrology — progressing towards practical applications.
And maybe Quantum 5.0 would be widespread adoption of quantum technologies, including quantum computers capable of achieving dramatic quantum advantage for production-scale practical real-world applications, and maybe even deployment of quantum networking — distributed quantum computing with quantum state transported between quantum computers separated by significant physical distances.
Alternative titles
I had difficulty deciding on a good title for this informal paper. These alternatives would have been equally good titles:
- Quantum effects
- Quantum effects for quantum computing
- Quantum effects for quantum information science
- What are quantum effects?
- Superficial introduction to quantum effects for non-physicists
- What are quantum effects and how do they relate to quantum computing?
- What are quantum effects and how do they relate to quantum information science?
- Quantum effects — The magic sauce which enables quantum information science
- Quantum effects — The magic sauce which enables quantum computing
- What are Quantum effects and how do they enable quantum information science?
Conclusions
Quantum information science is based on any aspect of quantum effects which can be observed, measured, controlled, stored, or communicated in some manner.
Quantum effects enable the capabilities of quantum computing, quantum communication, and quantum sensing and measurement.
For more information about those capabilities and a broad summary of quantum information science overall, see: What Is Quantum Information Science?
By:Jack Krupansky Link:https://jackkrupansky.medium.com/what-are-quantum-effects-and-how-do-they-enable-quantum-information-science-75981368d059
-
 @ 7f4f672a:c184579e
2023-08-03 08:59:56
@ 7f4f672a:c184579e
2023-08-03 08:59:5622nd of July, 2023. 08:07 am
What are public goods?
Public good are things which benefit everyone, which are publically owned. They can be accessed by everyone , they give value to everyone, and anyones use of the good does not reduce it's value or availability to others.
Examples ; the local park, clean air, beaches (non-private), local infratructure (not tolled)
ChatGPT: 1. Non-excludability: This means that once a good is produced, no one can be excluded from using it. It's available for everyone, regardless of whether they pay for it or not. For example, think about a public park. Once it's there, anyone can enjoy it, regardless of whether they contributed to its maintenance or creation.
- Non-rivalry: This means that one person's use of the good doesn't reduce its availability for others. Again, consider the public park. If one person is using the park, it doesn't prevent others from also using it.
Four Types of Goods: There are four categories of goods in economics, based on whether the goods are excludable and/or rivalrous in consumption.
- Private goods: Private goods are excludable and rival. Examples of private goods include food, clothes, and flowers. There are usually limited quantities of these goods, and owners or sellers can prevent other individuals from enjoying their benefits. Because of their relative scarcity, many private goods are exchanged for payment.
- Common goods: Common goods are non-excludable and rival. Because of these traits, common goods are easily over-consumed, leading to a phenomenon called “tragedy of the commons. ” In this situation, people withdraw resources to secure short-term gains without regard for the long-term consequences. A classic example of a common good are fish stocks in international waters. No one is excluded from fishing, but as people withdraw fish without limits being imposed, the stocks for later fishermen are depleted.
- Club goods: Club goods are excludable but non-rival. This type of good often requires a “membership” payment in order to enjoy the benefits of the goods. Non-payers can be prevented from access to the goods. Cable television is a classic example. It requires a monthly fee, but is non-rival after the payment.
- Public goods: Public goods are non-excludable and non-rival. Individuals cannot be effectively excluded from using them, and use by one individual does not reduce the good’s availability to others. Examples of public goods include the air we breathe, public parks, and street lights. Public goods may give rise to the “free rider problem. ” A free-rider is a person who receives the benefit of a good without paying for it. This may lead to the under-provision of certain goods or services.
The funding of public goods by Quadratic funding is an interesting topic.
References
Retroactive Public Goods https://medium.com/ethereum-optimism/retroactive-public-goods-funding-33c9b7d00f0c
https://socialsci.libretexts.org/Bookshelves/Economics/Economics_%28Boundless%29/8%3A_Market_Failure%3A_Public_Goods_and_Common_Resources/8.1%3A_Public_Goods
economics #explorethis
-
 @ 1bc70a01:24f6a411
2023-07-30 07:43:26
@ 1bc70a01:24f6a411
2023-07-30 07:43:26Originally published on October 15, 2022. Moving from my personal blog to Nostr 🙌
Don't trust, verify
Some people find this very annoying. But I've realized that most people are winging it in life. Human psychology and power dynamics influences how people think and what they say. People want to seem right so they copy what others say, and expect you to believe it.
One way people consume information is through media - news and articles. They'll read something and assume it's true.
Cited by a "study"? Must be true.
"Experts say"?
Gotta be true.
Except, if you check the sources and do some critical thinking, you might uncover that the study is flawed or that the experts are biased.
Simple things like statistical significance are thrown out the window in some studies.
People overlook personal biases.
This all leads to poor data and misrepresentation. This is how you get click-bait headlines.
The only way to know what's true is to try and verify it for yourself.
Even if you are not able to verify the facts, you can come away with a range of certainty about what you learned. Is it probably true? May be true. Certainly true? Or maybe there is a grain of truth to it? The level of confidence can vary. You don't need to be 100% confident in your newly acquired knowledge.
Treat new knowledge as data points
"It depends" is the most appropriate answer to all questions in life. The actual answer is very nuanced and depends on all sorts of things.
But, the way media presents information and the way our minds try to categorize it is by replacing past beliefs.
Once you learn something new, it's tempting to disregard your past knowledge.
I don't see information this way.
To me, all new information is a data point in my life-long accumulated collection of other data points.
Think of it like a toolbox. You have many tools in your toolbox and they are all useful for some specific task. You don't throw away a tool you bought because you acquired another.
Information is much the same. You source information from your mind to understand some subject. Consider existing beliefs, while looking at the new information. The goal is to connect the dots.
Sooner or later the data points (dots) start connecting, and you get a better picture of the subject.
Seek out incentives
Incentives drive human behavior.
Incentive to earn.
Incentive to love.
Incentive to feel good about yourself (generosity).
If you can figure out a person's incentives, you will start to understand their behavior.
People suck at understanding this. They blame the wrong things. They assign responsibility to people who are not responsible. They create made up reasons for why someone did something. All the whole ignoring incentives.
Incentives drive everything. Ask the following questions:
- What is the ultimate goal of this person by saying or doing this?
- What do they seek to gain?
- How does it make them feel?
- What will they do at the prospect of failure?
- Who are the people they care for?
- What do they stand to lose?
- What motivates their actions?
- In almost all cases the answer to these questions involves a personal gain / loss.
Give people the benefit of the doubt
When trying to decide whether something was said or done with good intent, assume that's the case.
With exceptions such as career politicians or criminals, it is best to assume that people mean well and people are default=nice.
Otherwise it becomes difficult to have faith in systems, processes and humanity.
I know the world can be an ugly place, but it can also be a beautiful place. I'd rather assume people are seeking to build a better future for themselves.
If they act against everyone's best interest, it is best to assume they do so out of personal gain rather than some sinister plot. Look at the incentives that drive their behavior and figure out how to modify them to best serve everyone.
Acknowledge that material wealth does not bring happiness and strive for what matters to you.
Money does not bring happiness no matter what anyone says. It does relieve you of despair and help live a better, more peaceful and enjoyable life, but it will not make you happy.
Very few people in the world, if any, know true happiness because they confuse happiness (the process) with happiness (the end state). There is no end state for happiness.
When people ask you if you are happy, it's hard to answer, right?
Your instinct is to say "yes, of course". After all, your day is going fine, you have every comfort you desire and you had a pleasant lunch with a friend. You feel "happy".
But, this happiness fades. Tomorrow you get in a car accident, your car damaged, insurance won't pay out and you miss 2 weeks of work. You are "unhappy".
Some people confuse happiness with being content. You can be content with your place in life, but that doesn't mean you're happy.
The whole debate over happiness is a mute point. Since happiness is a process which is more akin to enjoyment, ultimately there is no such thing as happiness. The word itself should disappear from dictionaries.
Ok, I'm joking. But, you get the point.
When it comes to my life, I strive for satisfaction and contentment.
If I'm satisfied that day, that week, that month, that year, or the last decade, then I've met my "happiness" goals. If I am content with my life, then I'm "happy".
While material wealth can provide satisfaction, the contentment piece is often missing. With wealth, the goal post moves from one spot to another. Once you've achieved a satisfying moment, you have to move to the next, and the next. Each time you have to introduce higher states of satisfaction that require more effort and money.
Eventually, you plateau and satisfying moments from the physical world no longer matter. You seek out emotional attachment and relationships.
This is why so many wealthy people are depressed. No matter how much they spend, they can never reach that emotional attachment provided by love and relationships.
In fact, wealth only complicates those things. Instead of people seeing you for who you are as a person, a new variable is introduced and they see you for your status. With misaligned incentives, it becomes more difficult to form genuine relationships. Thus, contentment is hard to achieve.
I'm going to let you in on the biggest secret everyone is asking about - the secret to happiness.
The secret to happiness is charitable work. Doing things for others, without expecting anything in return.
Charitable acts are secretly selfish acts, whether that person acknowledges it or not.
All humans act in self-preservation. The need to feel good about ourselves. The need for approval. The need for comfort and safety. The need for recognition. All of these needs are driven by self-preservation.
Charity is no different. While we may feel that we do good things for others out of the goodness of our hearts, the evolutionary incentive is to feel satisfied by our deeds. There's nothing wrong with doing good things to feel good, as long as you understand why you're doing it, instead of performing mental gymnastics.
We are not designed for our digital world and should not strive to adapt to it
Evolution took hundreds of thousands of years to shape humans into what we are today. But technology accelerated the process by many magnitudes all within about 100 years. Except, it hasn't. The evolutionary clock is still catching up, out of breath and exhausted with your daily activity.
While we adapt rather well, humans are not capable of processing the amount of data and connections offered by the internet. This ultimately messes with our minds.
Think about your current physical world social circle. Small, yes?
Now think about your digital social circle. Much larger?
How many people do you think about out of your larger digital social circle? My guess is not that many.
While you may recognize the individuals you interact with, the meaning connections formed in the digital world are somewhat closely mirrored to the physical world. I hypothesize this is because we have innate evolutionary boundaries that limit our ability to expand beyond a certain natural limit.
Going beyond the invisible evolutionary boundaries places a burden on your mind. It feels unhealthy.
Remember the last time you thought to yourself "I need a break. I need to unplug"? That's your evolutionary boundary telling you it is not capable of processing any more data. You need a purge to get back to equilibrium.
We are not designed to be always-on, always-connected, always-responsive. At least not yet. It's possible the evolutionary process catches up and prepares us to handle all of it, but I am not confident it will be any time soon.
I try to remind myself that I am not meant to have 50,000 followers and expect to keep everyone happy. I am not meant to follow everyone's updates and be expected to respond. To stay healthy, I need to unplug.
Life is what you make of it, do what you wish to do and ignore the rest
There's no "right way" to do anything. Everything is a figment of human imagination. To do things "the right way" means doing it by someone else's definition of right.
I found it incredibly freeing to realize that the only thing that is pure in this world is the natural world and your mind.
The world is a canvas.
You are the paint brush.
Everyone is capable of everything and nothing at the same time.
Everything else is noise.
Yes, we have society. Yes, we have rules. These artificial, human-invented boundaries act to preserve harmony. But, ultimately, the only pure forms of existence are the human mind and the natural world. What you do is the only thing within your boundary of control (to an extent).
Since we experience the world with our minds, we are all that is true. Everything else is a projection of some entity or experience that seeks to change our behavior (intentionally or unintentionally).
With this in mind, I look at people's experiences as unique to them and do not assume that they will translate in the same way to my life if I apply them.
Only worry about things that are in my control
I can't control what people do. I can try to influence them, but ultimately they will do what they decide to do. Since I can only control myself, I don't worry about what others think or do.
Never regret
It's easy to say "I don't regret things" but in reality emotions take us there and we think about what we regret.
I would be lying if I said I don't have feelings of regret. But, I forget about them quickly so I can focus on the things I can control. What passed is now behind me and there's no way to change it back, so there's no point in regretting.
Reflection is not the same as regret. One can reflect by looking at the past, and make changes for the future. Regrets are bitter feelings an no action.
Truth is relative
Even as I write this, my own truths are relative. What is true for me, or is true now, may not be true for you or true when you read it. It may be wrong.
People used to believe earth was the center of the universe. That the sun went around the earth. That to ward off bad spirits you had to offer sacrifices.
These were all truths to the people who held those beliefs. Now we know different.
Given what we know now, it is only logical to assume that our current truths may be false in the future. Even physics, the foundation upon we base so many truths may be proven to be wrong or incompatible with other parts of the universe.
Most things are not the best version of themselves therefore there is always room for improvement.
Since things get better all the time, it is only logical to assume that even the best thing we can think of is not the best version of that thing. The "best" is relative to time, technology and imagination.
Whenever someone says "but we already have X that works great", that doesn't mean that Y cannot be better than X, nobody just thought of it yet.
Stay curious, stay hungry and know that you can create something better.
Take experts with a grain of salt
Even the top experts in their fields are often incorrect.
For example - I know a lot about conversion optimization, but if you were to take every advice I dish out, some of it will inevitably flop.
When you get to an expert level, when someone asks you something you don't know, it is tempting to give an answer. When many people ask you for something, it's even more tempting to respond.
Saying "I don't know" is difficult even if you feel that you should say it. Before you can utter the words, your mind says "I should know this..."
The second factor that makes experts not as credible as they may have been in the past, is the speed at which technology moves.
Think about a specialized doctor. This doctor may be the top expert in their field, but it is impossible for them to read the thousands of medical journals published every day. So many breakthroughs could happen in a year without this doctor ever knowing about them.
By the time an expert weighs in, the "truth" of the matter may have already shifted.
Knowing this, you can assume that not everything an expert says is correct, especially if they step outside of their lane.
Elon Musk is a great example of this. While Elon is a successful entrepreneur and perhaps knows a thing or two about rocket engines, when he steps outside of his lane and talks about crypto, he is no more coherent than someone who spent a lot of time in the space. He uses his influence to prop up things like dogecoin for fun and games, while people lose their life savings following his doge tweets.
I'm not saying that he is responsible for people's personal decisions, but he does influence them.
-
 @ f296e355:c28d00bc
2023-08-03 08:31:44
@ f296e355:c28d00bc
2023-08-03 08:31:44The history of codes and cryptography is a fascinating topic that spans thousands of years and involves many different methods and technologies. I have wanted to write on this topic for quite some time now but couldn’t complete it due to other projects at hand. Many people on individual basis and even companies use cryptographic techniques for various reasons from protecting sensitive data and preventing espionage to enabling the creation and exchange of cryptocurrency and other digital assets. But many people have little to no idea about the evolution of codes and cryptographic systems. In this piece, we shall briefly overview some of the main phases and milestones in the development of cryptology, the science of making and breaking codes.
 Photo by cottonbro studio from Pexels
Photo by cottonbro studio from PexelsFeel free to read all my articles on the anti-censorship long content platform yakihonne
Ancient Ciphers and Early Encryption Techniques
Ancient ciphers and early encryption techniques are methods of transforming messages or information in such a way that only authorized parties can access them. They usually involve replacing or rearranging the letters or symbols of the original message with a secret key or algorithm. Here are some examples of ancient ciphers and early encryption techniques:
The Caesar Shift Cipher
The Caesar cipher, employed by Julius Caesar and his army during the 1st century BC, served as a means to encrypt military and official messages. Operating as a simple substitution cipher, it involved replacing each letter in the message with another letter positioned a fixed number of places away in the alphabet. For instance, with a shift of 3, ‘A’ would be substituted with ‘D’, ‘B’ with ‘E’, and so forth. The key for this cipher represented the number of positions to shift, encompassing values ranging from 1 to 25. To decipher the message, the recipient needed knowledge of the key to revert the letters to their original positions. However, the Caesar cipher was susceptible to frequency analysis, a method involving the tabulation of letter occurrences in the ciphertext and comparing them against the expected frequencies in the language, thus rendering it relatively easy to break.
The Scytale Cipher
The Spartans and other ancient Greeks utilized a cipher during the 7th century BC for the encryption of military and political messages. This particular cipher operated as a transposition cipher, whereby the arrangement of letters in the message was altered based on a concealed pattern. The pattern, in this case, was determined through the utilization of a cylindrical rod known as a scytale. To encrypt the message, the sender would encircle a strip of parchment or leather around the scytale and proceed to inscribe the message along its length. Subsequently, the strip would be unwrapped and dispatched to the intended recipient. For decryption, the recipient would require a scytale possessing an identical diameter to rewrap the strip around it and decipher the concealed message. This cipher’s security was compromised, as its vulnerability lay in attempting various diameters of rods until the message became intelligible, rendering it relatively easy to break.
The Steganography
Steganography, distinct from a cipher, represents a technique employed to conceal messages in plain sight by disguising them as something else. Its origins can be traced back to ancient times, and it has found utility across a range of endeavors encompassing espionage, propaganda, and art. Several examples of steganography include inscribing a message on a shaved head, allowing the hair to regrow and obscure the hidden text, utilizing invisible ink or microdots to convey information, and embedding messages within different mediums, such as texts, images, audio, or video files. If executed adeptly, steganography can prove challenging to detect; nevertheless, it can be exposed through meticulous scrutiny or by subjecting the medium to careful examination or analysis.
The Renaissance and Early Modern Cryptography
The Renaissance and early modern period witnessed a flourishing of cryptography as a result of political, religious, and scientific developments. Cryptography became more sophisticated, diverse, and widespread, as well as more subject to cryptanalysis and code-breaking. Here are some aspects and examples of cryptography in this era:
The rise of diplomatic cryptography
During the Renaissance, a notable transformation occurred in the realm of diplomacy, paving the way for the establishment of a modern system characterized by permanent embassies, the formulation of international law, and multilateral negotiations among autonomous states. Given the crucial need for secure communication between ambassadors and their respective home governments, as well as among allies and adversaries, the significance of cryptography as an indispensable tool for diplomats became apparent. Cryptography served a dual purpose, enabling diplomats to safeguard their confidential information while simultaneously providing a means to engage in covert intelligence gathering, influencing public sentiment, and monitoring their rivals’ activities. As diplomatic relations evolved, cryptography emerged as an essential component in the arsenal of tools employed by diplomats to navigate the intricate web of international affairs during the Renaissance.
Here’re a few examples of diplomatic cryptography are:
- The Vigenère cipher, a polyalphabetic substitution cipher that was considered unbreakable for centuries. It was invented by Giovan Battista Bellaso in 1553 and improved by Blaise de Vigenère in 1586. It was widely used by European diplomats until the 19th century.
- The Babington Plot, a conspiracy to assassinate Queen Elizabeth I of England and replace her with Mary, Queen of Scots in 1586. The plot was exposed by Sir Francis Walsingham, Elizabeth’s spymaster, who intercepted and deciphered the letters between the plotters using a nomenclator, a combination of symbols and code words.
- The Great Cipher, a complex substitution cipher that was used by the kings of France from Louis XIV to Louis XVI. It was invented by Antoine and Bonaventure Rossignol in 1645 and remained unsolved until 1890.
 One component of a customary nomenclator employed during the era of Louis XIV, 1690. Wikimedia Commons Public Domain Image.
One component of a customary nomenclator employed during the era of Louis XIV, 1690. Wikimedia Commons Public Domain Image.The role of cryptography in religion and science during the Renaissance
Within the backdrop of the Renaissance, a period characterized by profound intellectual and societal transformations, religious conflicts like the Protestant Reformation and the Catholic Counter-Reformation took center stage. Simultaneously, the era bore witness to groundbreaking scientific advancements and methodologies, including the revolutionary Copernican heliocentric model and the Baconian induction. In the middle of these developments, cryptography emerged as a significant factor influencing both religious and scientific domains. Cryptography served as a means to express dissent, preserve orthodoxy, and facilitate the clandestine transmission of knowledge. Furthermore, it became a subject of scholarly inquiry and experimentation for esteemed scholars and natural philosophers of the time. Cryptography thus acquired a dual role, influencing and being influenced by the intellectual currents that shaped the Renaissance era.
Some examples of cryptography in religion and science are:
- The Trithemius cipher, a progressive polyalphabetic substitution cipher that was invented by Johannes Trithemius, a German abbot and occultist, in 1508. It was disguised as a book on magic called Steganographia, which claimed to teach how to communicate with angels using hidden messages in texts.
- The Baconian cipher, a biliteral substitution cipher that was devised by Francis Bacon, an English philosopher and scientist, in 1605. It used two different typefaces or fonts to encode messages within other texts. Bacon also proposed a method of hiding messages in musical notes or knots.
- The Newtonian cipher, a numerical substitution cipher that was used by Isaac Newton, an English physicist and mathematician, to encrypt his private notes on alchemy and theology. He assigned numbers to the letters of the alphabet according to their order or frequency and wrote them in groups of five.
Photo by K. Mitch Hodge on Unsplash
The Enigma Machine and World War II
The Enigma machine and World War II are closely related, as the Enigma was a cipher machine used by Nazi Germany to encrypt and decrypt messages for military and diplomatic purposes. The Enigma was considered to be very secure and reliable, but it was eventually broken by the Allies, who used the intelligence gained from reading the German messages to gain an advantage in the war.
The Enigma machine
The Enigma machine, conceived by German engineer Arthur Scherbius in 1918 and patented in 1923, emerged as a remarkable electro-mechanical apparatus consisting of several components. Comprising a keyboard, lampboard, plugboard, and a set of rotors, it enabled the encryption and decryption of messages.
Photo by Christian Lendl on Unsplash
Users would input plaintext or ciphertext through the keyboard, and the corresponding encrypted or decrypted letters would be displayed on the lampboard. The plugboard facilitated additional permutations of letters, while the rotors, altered with each keystroke, modified the electrical connections between the keyboard and lampboard. The Enigma machine boasted an extensive array of potential settings, rendering the key challenging to guess or crack via brute-force methods. These settings involved the selection and order of rotors, initial rotor positions, and the plugboard configuration. To maintain security, these settings were altered daily or even more frequently, using secret key lists that were distributed to operators in advance. Although initially intended for commercial purposes, the Enigma machine swiftly gained traction among various military and government entities worldwide, most notably the Nazi regime in Germany, who employed it extensively before and during World War II.
World War II
World War II, a global conflict spanning from 1939 to 1945, witnessed the engagement of two opposing alliances: the Axis powers and the Allied powers. The devastating war led to vast casualties, widespread destruction, and profound socio-political transformations.
Cryptography played a pivotal role during this period as both sides employed various encryption and decryption techniques to secure their communications and gather intelligence on their adversaries.
Among these methods, the Enigma machine held paramount importance for Nazi Germany, serving as a device to encode critical messages across all branches of the German military. The initial breakthrough in cracking the Enigma code came in 1932 when Polish mathematicians developed techniques and machines to decipher it. They subsequently shared their achievements with British and French intelligence prior to the outbreak of the war. In 1939, Britain established the clandestine code-breaking unit Ultra at Bletchley Park, led by mathematician Alan Turing and a team of experts. Building upon the Polish methods, they refined decryption processes and devised new machines, such as the Bombe, to decipher Enigma messages on a larger scale. The successful decryption of the Enigma code provided the Allies with a pivotal advantage in numerous battles and campaigns, including the Battle of Britain, the Battle of the Atlantic, and the pivotal D-Day invasion. It also allowed for vigilant monitoring of German movements, plans, and intentions. Estimates from historians suggest that the breaking of the Enigma code potentially shortened the war by two to four years, resulting in the preservation of millions of lives.
Photo by Mauro Sbicego on Unsplash
The Digital Age and Public-Key Cryptography
The digital age and public-key cryptography are interrelated, as the advent of digital technologies and the internet created new challenges and opportunities for cryptography.
Public-key cryptography, aka asymmetric cryptography, is a cryptographic field that employs a pair of interconnected keys, namely a public key and a private key, for the purpose of encrypting and decrypting messages.
Public-key cryptography revolutionized the field by allowing secure communication between parties who have no prior knowledge or trust of each other, using mathematical techniques such as asymmetric encryption and digital signatures.
The digital age
The digital age is the period of history characterized by the widespread use of digital technologies, such as computers, the internet, mobile devices, and social media. The digital age began in the late 20th century and continues to the present day. This age has brought many benefits and challenges for cryptography. On one hand, it has enabled faster, cheaper, and more accessible encryption and decryption of data, as well as new applications and domains for cryptography, such as e-commerce, online banking, cloud computing, cryptocurrency, and blockchain.
On the other hand, it has also increased the risks and threats of cyberattacks, hacking, surveillance, identity theft, and data breaches. It has also increased the demand and complexity of cryptography. As more data is generated, stored, transmitted, and processed online, there is a greater need for protecting its confidentiality, integrity, authenticity, and availability. As more users and devices are connected to the internet, there is a greater challenge for distributing and managing cryptographic keys securely.
Public-key cryptography
Public-key cryptography was invented in 1976 by Whitfield Diffie and Martin Hellman in their seminal paper “New Directions in Cryptography”. They proposed a method of key exchange that allowed two parties to establish a shared secret key over an insecure channel without any prior communication or trust. This method is known as the Diffie-Hellman key exchange.
This type of cryptography that uses pairs of related keys:
a public key that can be openly distributed without compromising security, and
a private key that should be kept under secrecy by the owner of the key
The keys are generated with cryptographic algorithms based on mathematical problems called one-way functions, which are easy to compute in one direction but hard to reverse.
Public-key cryptography has two main functions: encryption and digital signatures. Encryption is the process of transforming a message into an unreadable form using a key. Digital signatures are the process of creating a unique code that can verify the identity of the sender and the integrity of the message using a key. Anyone with a public key can encrypt a message for a specific recipient who has the corresponding private key. The decryption of the message can only be performed by the intended recipient using their private key.
Consider this example, Alice can send Bob an encrypted message using Bob’s public key that only Bob can decrypt with his private key. In public-key digital signatures, anyone with a private key can sign a message with their private key to create a signature. The authenticity of the signature and its association with the signer can be verified by anyone possessing the corresponding public key and confirming if it matches the message. For example, Alice can sign a message with her private key to create a signature that Bob can verify with Alice’s public key.
This type of cryptography was further developed by Ronald Rivest, Adi Shamir, and Leonard Adleman in 1977 when they created the RSA algorithm, which is one of the most widely used public-key encryption and digital signature schemes today. RSA stands for Rivest-Shamir-Adleman, the initials of its inventors.
 Ronald Rivest, Adi Shamir, & Leonard Adleman, 1977. Photographed by: Unknown. Source: National Cryptographic Foundation
Ronald Rivest, Adi Shamir, & Leonard Adleman, 1977. Photographed by: Unknown. Source: National Cryptographic FoundationQuantum Cryptography: A New Era of Encryption
A new era of encryption phrase that describes the use of quantum physics to create and secure cryptographic systems that are theoretically immune to conventional attacks.
Quantum cryptography exploits the properties of quantum mechanics, such as superposition, entanglement, and uncertainty, to perform tasks that are impossible or infeasible with classical cryptography.
Quantum key distribution
Quantum key distribution (QKD) stands as the most extensively explored and implemented approach within the realm of quantum cryptography. Serving as a technique, QKD enables two parties, commonly referred to as Alice and Bob, to establish a shared secret key over an insecure communication channel, including fiber-optic cables or free space, devoid of any prior communication or established trust. QKD capitalizes on the principle that quantum states, such as photons, cannot be replicated or measured without perturbation. Thus, any potential eavesdropper, often denoted as Eve, who endeavors to intercept or tamper with the quantum signals will inevitably introduce errors or irregularities, which can be detected by Alice and Bob. Through the implementation of suitable protocols and error correction techniques, Alice and Bob can generate a key that boasts provable security and randomness. This key can subsequently be utilized for encrypting and decrypting messages using conventional symmetric-key algorithms like AES or DES.
The notable advantage of QKD lies in its ability to securely distribute keys, addressing a prominent vulnerability within classical cryptography. Additionally, QKD facilitates the frequent updating of keys, thereby amplifying the security and freshness of the encryption process. The conceptualization of QKD originated from independent proposals by Stephen Wiesner in 1970 and Charles Bennett and Gilles Brassard in 1984. The first experimental demonstration of QKD occurred in 1990, conducted by Bennett and John Smolin. Since then, QKD has been further developed and tested across diverse settings, including metropolitan networks, satellite links, and underwater channels.
 Stephen Wiesner, 1988. Public Domain Image. Wikimedia Commons.
Stephen Wiesner, 1988. Public Domain Image. Wikimedia Commons.Quantum-resistant cryptography
Quantum-resistant cryptography, also known as post-quantum cryptography or quantum-proof cryptography, is a branch of classical cryptography that aims to create encryption methods that cannot be broken by quantum computers. Quantum computers are hypothetical machines that can exploit quantum phenomena to perform certain computations faster than classical computers.
QRC is motivated by the fact that some of the most widely used public-key algorithms, such as RSA and ECC, are based on mathematical problems that are hard to solve with classical computers but easy to solve with quantum computers. For example, Shor’s algorithm is a quantum algorithm that can factor large numbers efficiently, which would break RSA encryption. Similarly, Grover’s algorithm is a quantum algorithm that can search unsorted databases faster than classical algorithms, which would reduce the security of symmetric-key algorithms. The objective is to develop novel public-key algorithms that rely on mathematical problems posing challenges for both classical and quantum computers in terms of solving them. Some of the candidates for quantum-resistant cryptography are based on lattice problems, code problems, multivariate problems, hash-based problems, or supersingular elliptic curve problems. These algorithms are currently being evaluated and standardized by various organizations, such as NIST and ETSI.
Cryptography has evolved from simple manual methods to complex mechanized and digital systems, driven by the needs and demands of communication, security, and privacy. It has also played a very crucial role in many historical events (the Babington plot, for example), such as wars, revolutions, and discoveries, as well as in many modern applications, such as e-commerce, online banking, and cryptocurrency. It’s not only a practical tool, but also a scientific and mathematical discipline that explores the limits and possibilities of information theory, computation, and quantum physics. It is constantly changing and most certainly evolving, as new threats and opportunities emerge in the digital age.
By:Sunny Labh Link:https://www.cantorsparadise.com/the-history-of-codes-and-cryptography-from-caesar-cipher-to-quantum-encryption-262992255320
-
 @ 0b5f0269:f0f93f1b
2023-08-03 08:26:42
@ 0b5f0269:f0f93f1b
2023-08-03 08:26:42室温超导体又称常温超导体(Room-temperature superconductor),是指可以在高于0°C的温度有超导现象的材料。相较于其他的超导体,室温超导体的条件是日常较容易达到的工作条件。截至2020年,最高温的超导体是超高压的含碳硫化氢系统,压力267 GPa,其临界温度为+15°C。
在常压下的最高温超导体是高温超导体铜氧化物(cuprates),在138 K(−135 °C)的温度下有超导现象。
之往有许多的研究者曾怀疑室温超导体是否可能实现,不过超导的温度一再提高,其中也有许多是以往没有预期到,或是以往认为不可能的温度。
早在1950年代就有人提出在“接近室温”下出现的超导现象。若可以找到室温超导体,可解决全世界能耗问题、开发速度更快的电脑、用在先进的储存装置、超灵敏的感测器,以及许多其他的可能性。
2023年7月23日,来自韩国科学技术研究院(KIST)的量子能源研究中心的韩国团队在arXiv预印本服务器上发布了一篇名为“The First Room-Temperature Ambient-Pressure Superconductor”(首个室温常压超导体)的论文,描述了他们称之为LK-99的新型室温超导体。该论文还伴随着arXiv上的姊妹论文,一篇韩国期刊上的论文以及一项专利申请。多位专家对此表示怀疑,牛津材料科学教授Susannah Speller表示,“目前还为时过早,我们还没有得到这些样本超导性的有力证据”,因为缺乏超导性的明确标志,如磁场响应和热容量。其他专家也对数据可能被“实验过程中的错误和LK-99样本的缺陷”解释表示担忧,一位科学家质疑了研究人员使用的理论模型。
来源:维基百科 链接:https://zh.wikipedia.org/wiki/%E5%AE%A4%E6%BA%AB%E8%B6%85%E5%B0%8E%E9%AB%94
-
 @ 00000001:a21169a7
2023-07-29 19:50:18
@ 00000001:a21169a7
2023-07-29 19:50:18August Sander (1876-1964), a prominent figure in documentary photography, played a pivotal role in challenging and resisting Nazi ideology through his work during the difficult years preceding and following Adolf Hitler's rise to power in Germany.
Sander's most famous project, "People of the 20th Century," stands as a testament to this silent resistance. This monumental body of work, portraying a broad cross-section of German society, presented a bold challenge to the Nazi notion of a "superior race".
Sander's strategy was to humanize all the people he photographed, regardless of their social status or race. His approach was neither to glorify nor denigrate, but simply to portray people as they were, a vision that was in stark contrast with the Nazis' racial ideology.
Furthermore, Sander sought to dismantle the Nazis' rigid racial and social categories. In "People of the 20th Century," the range of subjects is impressively broad: aristocrats, peasants, artists, manual workers, women, men, Jews, non-Jews. By juxtaposing these different categories, Sander underscored the diversity and complexity of German society, thus challenging the Nazi notion of a "pure race".
Despite the resistance he faced, Sander's courage never wavered. His photographs were confiscated and destroyed by the Nazis, and his book "Face of Our Time" was banned in 1936. Yet, Sander persisted, and while he was forced to switch his focus to landscape photography to avoid further confrontations, he continued to document his time's Germany until his death in 1964.
Sander's resistance to Nazi ideology was not frontal or violent, but subversive and silent. His camera became his weapon, and his photographs, his resistance. By capturing his subjects' humanity, he demonstrated that diversity, far from being a threat, is a source of richness and vitality in a society.
August Sander's work remains a powerful tool for understanding the social and political context of Germany in the first half of the 20th century. At the same time, his work continues to be a reminder of the importance of preserving and respecting human dignity, regardless of race, religion, or social status. In this sense, Sander's photography not only documents the reality of his era but also offers a powerful critique of Nazi ideology and a more inclusive and humanitarian vision of society.
-
 @ cb5a5f84:c8b15664
2023-08-03 06:10:10
@ cb5a5f84:c8b15664
2023-08-03 06:10:10Originally published here: https://medium.com/@kemalyaylali/insatiable-rising-appetite-for-lab-grown-meat-investments-e92d0b3536df
In recent years, a revolutionary concept has taken center stage in the food industry — lab-grown meat, known by various names like cultured, cultivated, clean, and cruelty-free. This groundbreaking technology has become a hot topic among investors, and for good reason. In a significant development, the U.S. Department of Agriculture (USDA) granted clearance to Good Meat and Upside Foods, allowing them to sell lab-grown chicken in stores and restaurants across the United States. With the FDA also endorsing the technology, these companies are now accelerating their production efforts.
Environmentalists are hailing this innovation as a much-needed solution to the environmental issues caused by traditional meat production. Conventional meat sources contribute to nearly 60 percent of greenhouse gas emissions from food production, along with deforestation and water scarcity. In stark contrast, lab-grown meat has the potential to reduce the carbon footprint by a staggering 92 percent compared to beef, 17 percent compared to chicken, and 52 percent compared to pork. Furthermore, animal welfare activists are optimistic that this technology could ultimately put an end to the cruelty seen in slaughterhouses and inhumane conditions on farms.
For those unfamiliar with lab-grown meat, here’s a simplified explanation: In specialized food factories, scientists cultivate and grow cell samples from animals, such as pigs and cows, until these cells transform into a form of meat that we are familiar with, like pork or burger patties. Once approved by regulatory bodies, the resulting food is deemed safe for human consumption.
However, ongoing scrutiny by these agencies ensures the continued safety of lab-grown meat. The prospects of lab-grown meat have set investors’ expectations soaring. Leading consulting firm McKinsey predicts that the cell-based meat industry could generate a whopping $30 billion in revenue by 2030. Some experts even foresee a future where 60 percent of all meat could be produced in labs by 2040. The industry has witnessed a surge of interest, with nearly 100 startups entering the market in 2020, compared to just four in 2016. These startups have attracted over $1.2 billion in investments from enthusiasts and celebrities like Leonardo DiCaprio.
Additionally, around 40 companies are gearing up to provide support and tools for these enterprises to bring their products to market. However, skeptics remain cautious. The cost of growing meat in a factory remains high, as evident from the first lab-grown burger produced in 2013, which cost over $300,000 to create. Although production costs have dropped significantly since then, lab-grown meat may still be beyond the reach of the average consumer for some time. There are also concerns about consumer acceptance — are people willing to consume meat produced in a lab, and will they feel confident about its safety?
For aspiring investors looking to jump into this emerging market, there are currently limited options for publicly-traded companies. Steakholder Foods (STKH), an Israeli company that utilizes 3D printing technology in cultivated meat production, is listed on the Nasdaq. Cult Food Science Corp. (CULTF), based in Vancouver, Canada, is the first publicly-traded cultivated meat company in North America, listed on the Toronto and Frankfurt Stock Exchanges.
However, most of the companies in this sector are privately held startups. Among them are notable players such as Prolific Machines, Bond Pet Foods, and Momentum Foods, with the latter combining lab-grown meat with plant-based products. South Korea’s TissenBioFarm claims to have a unique method for producing whole-cut meat, setting itself apart from others that focus on ground or minced meat.
Investors looking to gain early exposure to the lab-grown meat market might consider buying stocks in established companies like Tyson Foods (TSN), which has invested through Tyson Ventures in startups like Memphis Meats and Future Meat Technologies. JBS, a Brazilian-based enterprise with a 51 percent stake in the Spanish firm BioTech, is also planning to go public. JBS is constructing a factory in 2024 that could potentially produce 1,000 metric tons of lab-grown beef annually.
The underlying message is clear: Thought leaders, including Bill Gates, believe that if we truly want to combat climate change, all meat produced in wealthy nations should come from laboratories. This visionary idea not only promises a sustainable future but also opens up exciting investment opportunities for those who recognize its potential. As lab-grown meat gains momentum, investors stand to make a positive impact on the planet while reaping significant rewards.
-
 @ fff7f6f7:db288ed1
2023-08-03 04:29:16
@ fff7f6f7:db288ed1
2023-08-03 04:29:16Sekibaku
El estilo de shibari kinbaku de Yagami Ren se llama sekibaku, se trata de shibari enfocado en la muta satisfacción del deseo erótico. No se basa en el amor o en la confianza, se basa en el deseo y la mutua responsabilidad.
Se fundamenta en la lógica, el conocimiento científico y la aplicación eficaz de la técnica, combinando las antiguas artes marciales con los mas avanzados conocimientos en neurociencia y psicología.
No es un estilo basado en formas o figuras, sino en el conocimiento y comprensión de bases y fundamentos, para luego poder aplicarlos en las interacciones cotidianas.
Técnicamente, se trabaja sobre tres áreas: la gestión emocional, el manejo del cuerpo, y el manejo de la cuerda.
En este estilo no hay elementos gratuitos o meramente ornamentales, todo lo que se hace tiene una finalidad práctica encaminada a la satisfacción del deseo erótico. Por ese motivo, es eficaz desde el minimalismo y el cuerpo toma tanto protagonismo.
Se trata de un estilo apto para todos los cuerpos y para todos los niveles de conocimiento y experiencia.
-
 @ 20986fb8:cdac21b3
2023-07-29 06:45:23
@ 20986fb8:cdac21b3
2023-07-29 06:45:23YakiHonne.com is continuously improving to offer a top-notch user experience. With weekly updates being rolled out, you are invited to test these updates and post your feedback and opinions as an article via YakiHonne.com.
As an incentive, participants can earn up to 100,000 SATs.
Round 2 will be from 27th to 30th July
How to participate:
- Pick one or multiple Updates below, test it (them)
- Write your feedback and opinion (pros and cons are all welcomed)
- Post your article on Nostr via YakiHonne.com
- Share your article to social media like Nostr and Twitter, don't forget to @YakiHonne
- Share the link to our group: http://t.me/YakiHonne_Daily_Featured
- Be Zapped!
Requirements:
- No malicious speech such as discrimination, attack, incitement, etc.
- No Spam/Scam, not fully AI-generated article
- No directly copy & paste from other posts on Relays
- Experience our updates in action, NO limit on the length of your post, share your REAL feedback and opinion
- The top 10 posts will be zapped during each round.
- The evaluation will based on the article's depth, completeness, and constructiveness.
- Contact us for additional zaps if bugs are found.
Updates to be tested in Round 2:
-
Comments: re-implemented and comments can be deleted
-
NIP-25 supporting: users now can upvote and downvote
-
Zap stats: Zaps sent and Zaps received can be seen from users profiles
-
“login with an extension” button: now it is grayed out rather than invisible
-
Search: search list showing optimization, adjust users searching results to the NIP-21 URI scheme
-
Tags: click on the tags in the article to view the content under the tag
-
Share: sharing posts with one click
-
NIP-05: verify your profile
If you missed Round 1, the updates below could be tested as additions:
-
Comment function: more user-friendly
-
Stats area: clearly displays the interactive status of each article
-
Following function: generated-key users can also be followed
-
Curation function: easily add or remove articles from an existing curation
-
Tags: search and browse articles with the tags
-
Home feed scrolling pagination: optimized data fetching and faster loading time
-
Article editing preview: preview the final version of the article while writing in MarkDown
Don't miss this opportunity to participate in Round 2, test the updates, and provide valuable feedback. Head over to YakiHonne.com to share your thoughts and earn SATs for your valuable input. Act fast!
About YakiHonne:
YakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media. Try YakiHonne.com Now!
Follow us
- Telegram: http://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
-
 @ 7cc328a0:2a247c0e
2023-08-03 00:40:02
@ 7cc328a0:2a247c0e
2023-08-03 00:40:02I built a really cool little temperature and air quality sensor that reports data to particle.io events and from there into influxdb cloud.
With Free Dashboards!!
Yes I mean free as free can get. Particle.io, free (to 100 devices). InfluxDB cloud, free (to (x) amount of stats). We're not talking about a lot of stats here, but after many hours of research for a free dashboard solution this was the absolute best!
InfluxDB cloud dashboards look really nice as well.
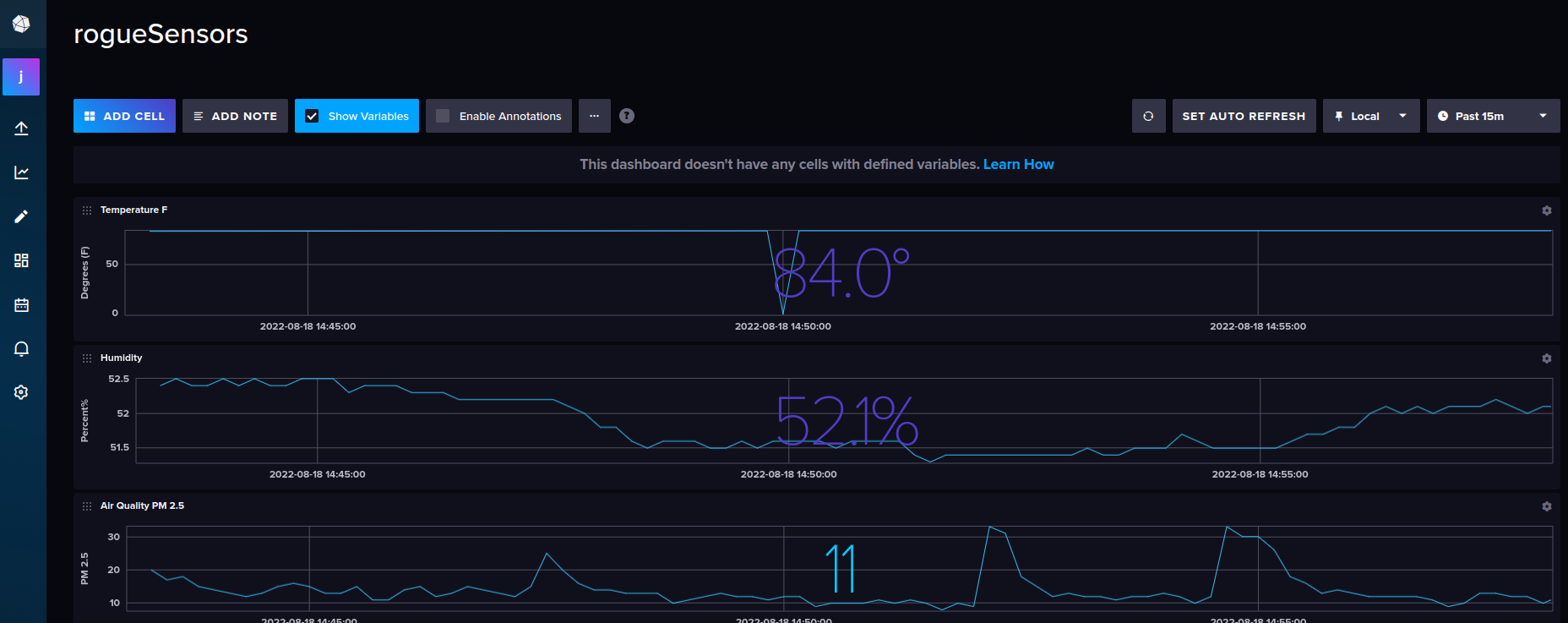
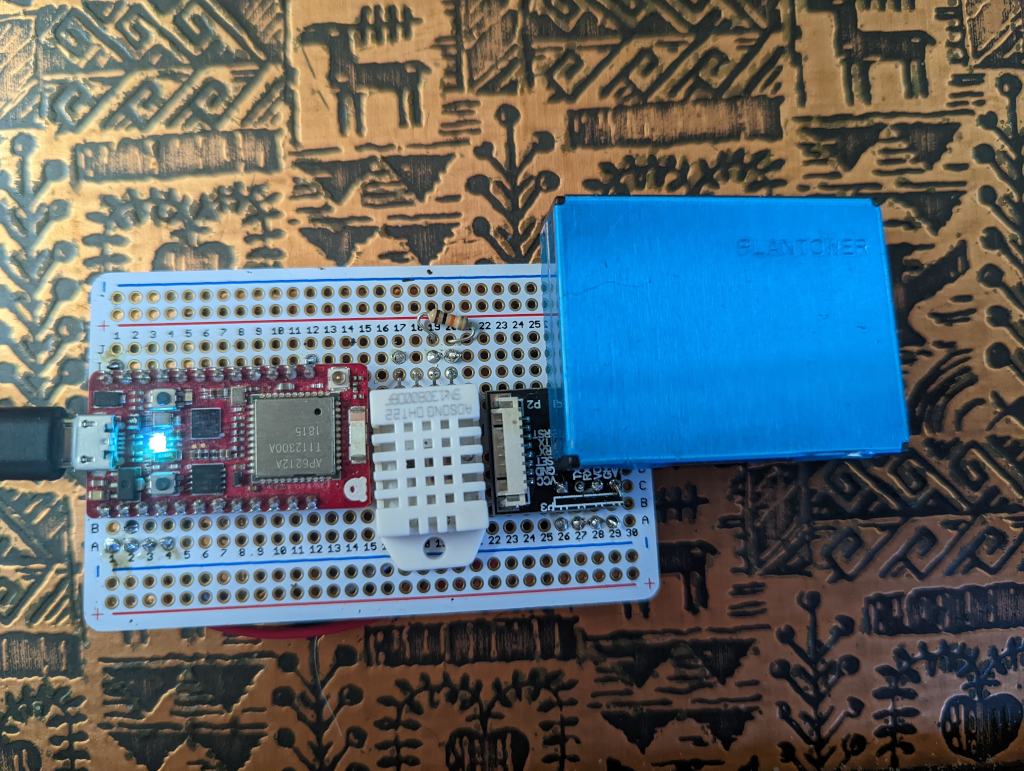
Build Components
- RedBear Duo github
Note, particle.io has since aquired RedBear labs and the Duo is old, yet still available in some places. You may also want to try particle devices like Argon instead of a redbear.
- DHT22 Temperature/Humidity sensor adafruit
- PM2.5 Air Quality Sensor and Breadboard Adapter Kit - PMS5003/PMS7003 adafruit
Note, I used a slightly different adapter, and it was lame to have to order it once I realized the PMS7003 I ordered did not come with an adaptor! The adafruit link above should get you hooked up. These air quality sensors come in different flavors just make sure you have a breakout board along with it when you order!
Software
Steps
The Hardware wiring diagram
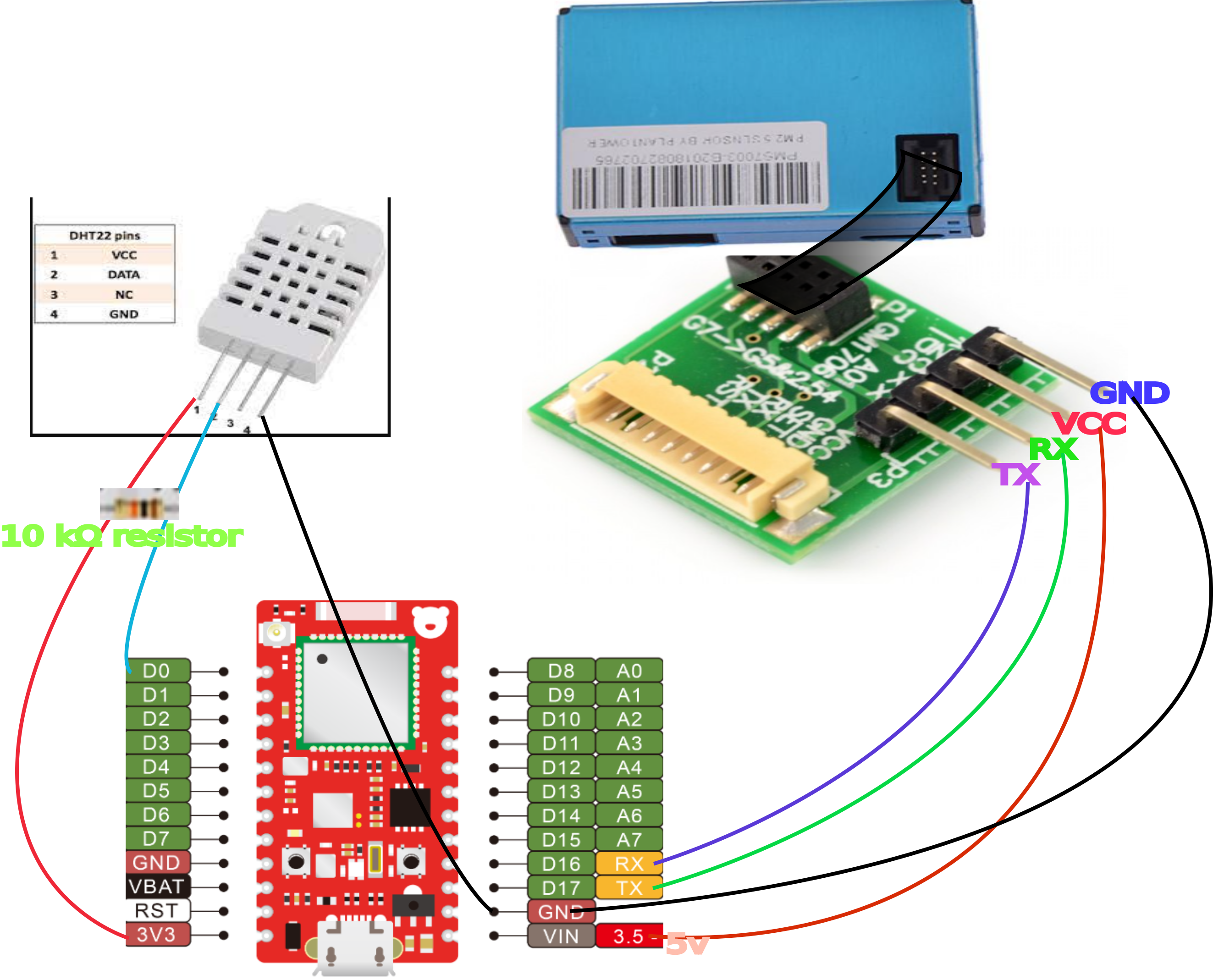
Plug in your device and connect it to particle.io
I used the following guide for the Redbear DUO here
Coding the application
- Go to console.particle.io, open the IDE by clicking the icon (bottom left < >)
- Create a new application.
- Click the "Libraries" icon on the bottom left of the screen.
- In the "Libraries" search enter "PMS7003-Particle-Sensor-Serial" and import it into the project.
- Click "Libraries" again, and search for "Adafruit_DHT_Particle" and import it into the project.
Paste this code into your app: ```arduino // This #include statement was automatically added by the Particle IDE.
include
// This #include statement was automatically added by the Particle IDE.
include
PMS7003Serial
pms7003(Serial1, D0); define DHTPIN D0 // what pin we're connected to
// Here we define the type of sensor used
define DHTTYPE DHT22 // DHT11 or DHT22
DHT dht(DHTPIN, DHTTYPE);
void setup() { //Serial.begin(); dht.begin();
}
unsigned long last = 0; unsigned long last_pm_reading = 0;
void loop() {
unsigned long now = millis();
// check every time to see if there is data if (pms7003.Read()) { last_pm_reading = now; }
if ((now - last) > 10000) { float f = dht.getTempFarenheit(); float h = dht.getHumidity(); Particle.publish("TempDegreesF", String(f)); Particle.publish("PercentHumidity", String(h)); // Let us be generous. Active state the device // reports at least every 2.3 seconds. if ((now - last_pm_reading) > 10000) { Particle.publish("No reading for at least 10 seconds!"); } else { Particle.publish("pm1", String(pms7003.GetData(pms7003.pm1_0))); Particle.publish("pm2_5",String(pms7003.GetData(pms7003.pm2_5))); Particle.publish("pm10",String(pms7003.GetData(pms7003.pm10))); // I didn't use these but they're there if you want them in the future. /Serial.println("um_3:" + String(pms7003.GetData(pms7003.count0_3um))); Serial.println("um_5:" + String(pms7003.GetData(pms7003.count0_5um))); Serial.println("um1:" + String(pms7003.GetData(pms7003.count1um))); Serial.println("um2_5:" + String(pms7003.GetData(pms7003.count2_5um))); Serial.println("um5:" + String(pms7003.GetData(pms7003.count5um))); Serial.println("um10:" + String(pms7003.GetData(pms7003.count10um))); / } last = now; } } ```
Flash the application to the device
You should see events coming into the particle.io console
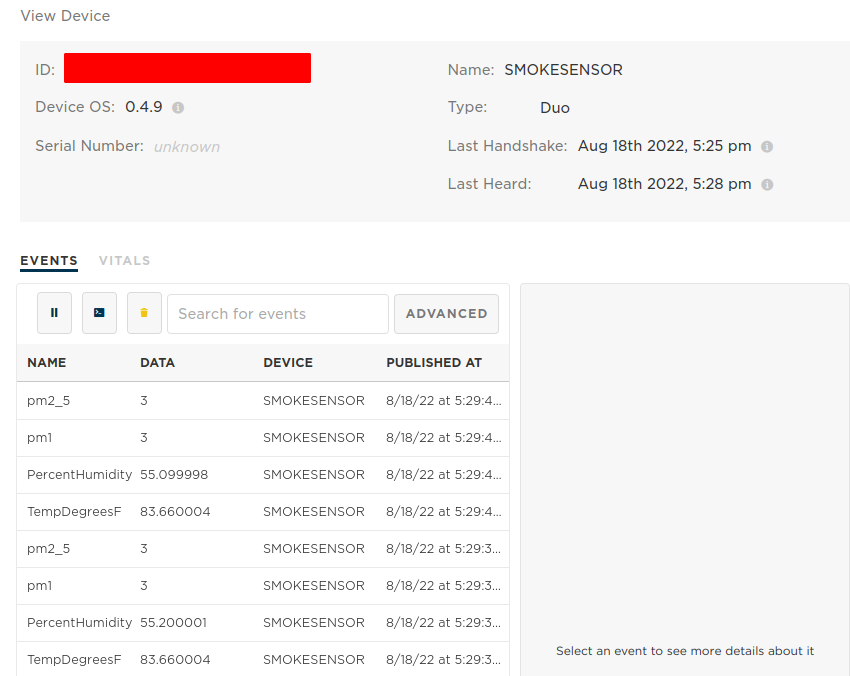
Now we're ready to setup InfluxDB
- Create a new bucket called "sensors" (or whatever you like)
- Keep this window open or copy these settings, we need them to setup particle.io webhooks.
- Open organization settings
- Copy the info for ClusterURL and OrganizationID
- Go to tokens and generate a new API token (and save it for the next step!)
Go back to particle.io console "Integrations"
-
Create new WebHook Integration Setting | Value --------|------ Event Name | pm2_5 URL | https://YourClusterURL/api/v2/write?org=YourOrganizationID&bucket=sensors&precision=s Request Type | POST Request Format | Custom Body Device | Any Status | Enabled
-
Expand the Advanced Settings!
Setting | Value --------|------|- Custom Request Body | envSensors,sensorID={{{PARTICLE_DEVICE_ID}}} {{{PARTICLE_EVENT_NAME}}}={{{PARTICLE_EVENT_VALUE}}} HTTP HEADERS (two fields) | Authorization | Token YOUR-API-TOKEN * After you're done creating the webhook it should look like this ->
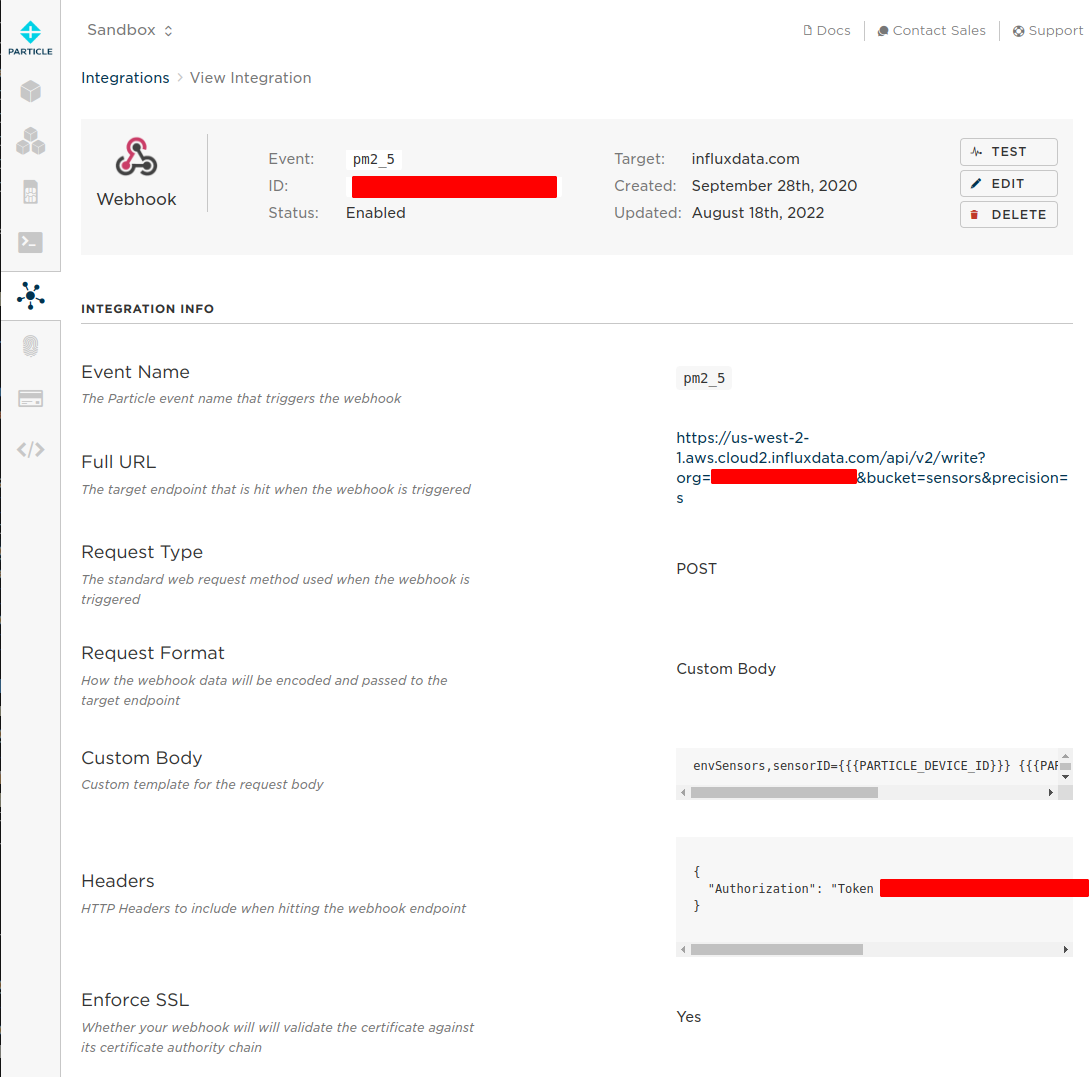 * While viewing the webhook we should start to see the webhook logs below ->
* While viewing the webhook we should start to see the webhook logs below ->
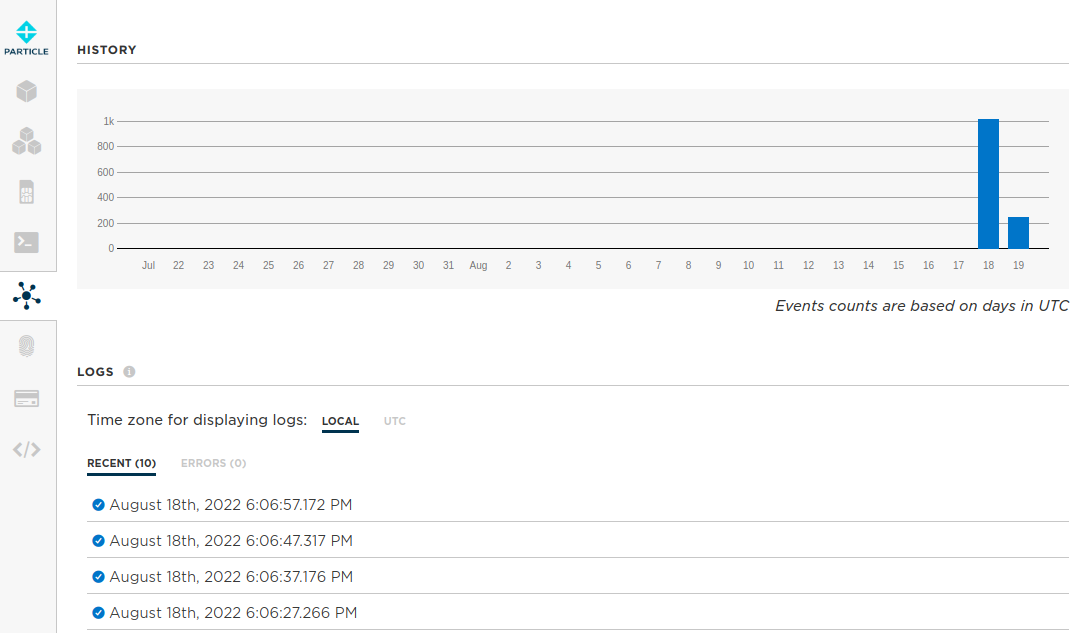 You can inspect the logs by clicking a response. Hopefully all is well so far.
* Repeat the steps above for Temperature and Humidity (change the Event Name)
You can inspect the logs by clicking a response. Hopefully all is well so far.
* Repeat the steps above for Temperature and Humidity (change the Event Name)Now we can build an influxDB dashboard!
- You can create a new dashboard and play around. For example: create a new cell.
- Use QUERY BUILDER to point-and-click the sensor data.
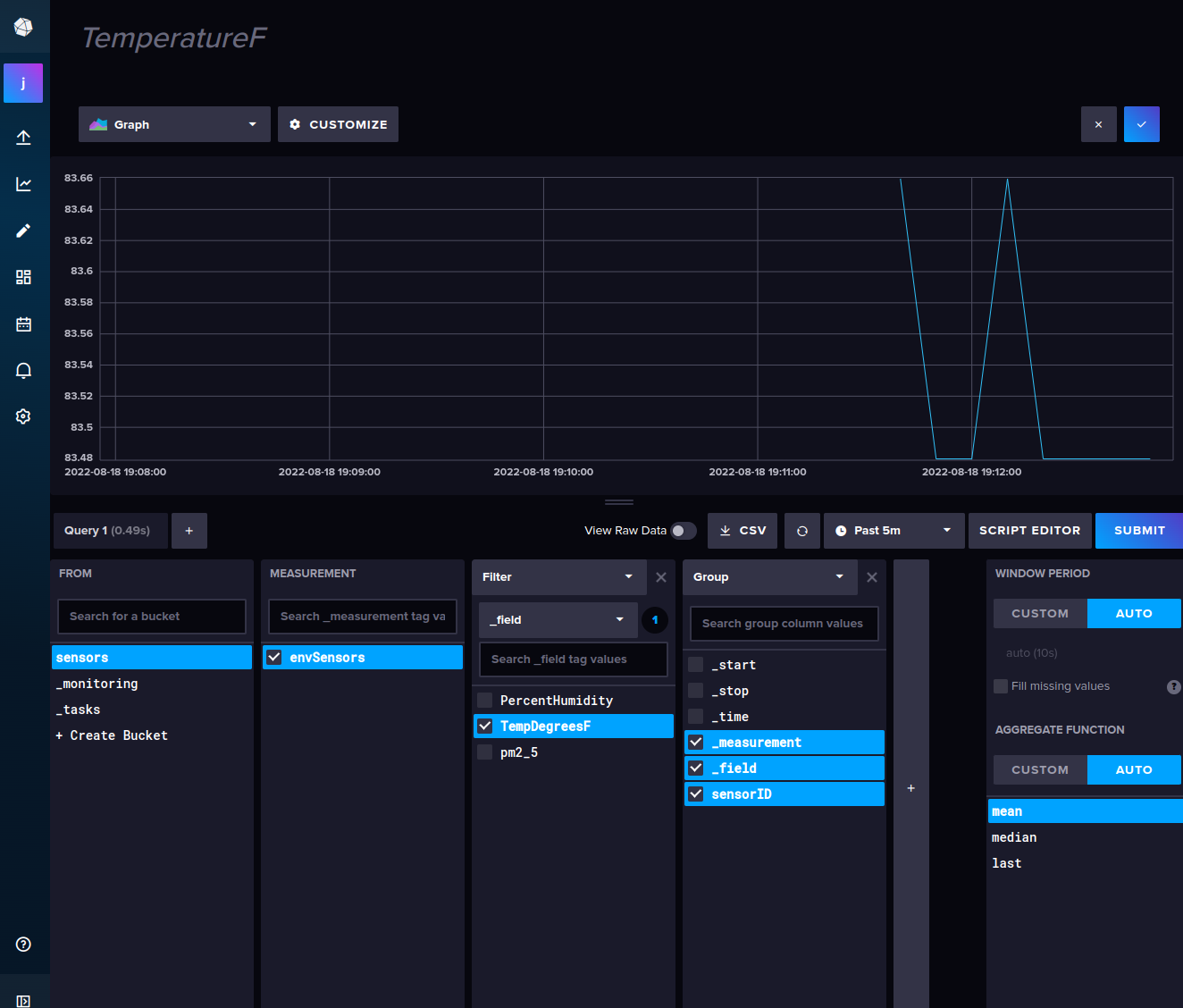
Done! Enjoy the free charts!
-
 @ 20986fb8:cdac21b3
2023-07-29 06:44:43
@ 20986fb8:cdac21b3
2023-07-29 06:44:43A long-term Nostr Creation Grant, with a 17,500,000 SATs funding pool
Round 3 starts on 22 July till 5 Aug!
Creating for You and Your Fans through Nostr and ZAP.
Nostr is a simple, open and censorship-resistant protocol, the number of users has been growing, and more and more users use zap to tip content. Nostr's growth over the past six months is amazing, which is a great encouragement for all nostrians. This is also a great encouragement for content creators. Earn SATs by posting your creations on nostr, allowing your readers to encourage better content creation while tipping your creations.


Zaps, provide a global solution for tipping content. Some posts on Nostr even got 89K+ SATs within one day, like Roya, Brianna.


On the other hand, while Apple's decision to take a 30% cut from fundraisers and humanitarian aid posts is criticized, Bitcoin emerges as a vital alternative for those suffering globally. Organizations like Oslo Freedom Forum and Qala Africa shed light on how Africans heavily rely on Bitcoin due to unreliable banking systems.
To this end, YakiHonne.com officially released the creation grant project, Creating for You and Your Fans through Nostr and ZAP. Join us on YakiHonne.com to share your long-form articles and curate content, experiencing the power of Nostr's censorship-resistance and ZAP features. Earn Sats rewards for publishing on Relay and Yakihonne clients. Don't forget to include your ZAP address and let's build Nostr's long content together!
What You Will Get From Your First 10 Posts in each round:
- 500 SATs, if you post on Relays through other clients
- 1000 SATs, if you post articles from other platforms to Relays as the first one on Relays and are curated or tweeted by YakiHonne
- 2000 SATs, for posting your own past articles on Relays through YakiHonne.com
- 3000 SATs, for posting your new original on Relays through YakiHonne.com
Zap Rules:
- No malicious speech such as discrimination, attack, incitement, etc.
- No Spam/Scam, not fully AI-generated article
- No directly copy & paste from other posts on Relays
- Spread positive content like your knowledge/experience/insight/ideas, etc.
How to Get Zap:
- Join YakiHonne TG group: https://t.me/YakiHonne_Daily_Featured
- Share your post in the group
- Make sure your LN address is in your profile
- Based on the rules above, we will ZAP your post directly within 2 days
Join our group for more queries: https://t.me/YakiHonne_Daily_Featured
About YakiHonne:
YakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media. Try YakiHonne.com Now!
Follow us
- Telegram: http://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
-
 @ 75bf2353:e1bfa895
2023-08-02 23:28:00
@ 75bf2353:e1bfa895
2023-08-02 23:28:00What Is Bitcoin
According to Pablo Xannybar Bitcoin exists outside the control of nation states, as well as central investment, and commercial banks, or any other single third party--It is money ruled solely by code, mathematics, and compute power, not a government or any other body of fallible humans." This is important because the peer-to-peer electronic cash system does not have a central point of failuresince bitcoin is a peer-to-peer electronic cash system; a system built on distributed computer networking instead of a centralized third party. This is different from almost all technology most people use in their day to day lives. Apple is the biggest technology company in the world. It has many servers all around the world. Your data on the Apple cloud is protected from natural disasters because Apple has backups all over the word. To be honest, I have assume someone else has seen it.not verified this, but I don't imagine the Apple cloud is just running on a laptop in somebody's closet. If one of Apple's server breaks, your data will surely survive.
They say this cloud is secure, yet somehow naked celebrity pictures get hacked from the iCloud and the FBI can break the iCloud encryption. To be fair, bitcoin stored on hot wallets can also be hacked. If you type a seed phrase onto an Internet computer, assume someone else has seen it. That's why most Bitcoiners advise to only keep a small amount of your stack on a hot wallet. That's why governments don't like "unhosted wallets." Unhosted wallets are a euphimism for big random number the government can't guess. Their Internet surveillance doesn't work on a calculator plugged into a 9v battery inside a shed at the middle of nowhere. This is also why we can rest assured that the bitcoin we keep in cold storage can be safer than even data kept on the servers of the biggest companies in the world.
Bitcoin Full Nodes Keep The Network Decentralized
Imagine if there was only one person running a bitcoin node. This node verified all the transactions on the network. If the power went out or if it got droned, bitcoin would die. There would be no record of the bitcoin time chain anymore. Nobody would verify transactions. There would be no network to broadcast to.

What if there are 17,000 bitcion nodes. Let's say my node gets droned. Bitcoin is still alive like Eddie Vedder. There are still 16,999 nodes validating transactions all over the world. Maybe one bitcoin node dies every now and then, but there are more peers on the network. They are distributed all over the globe. As long as several nodes remain on the network, bitcoin will not die.

The same is true of miners now that mining bitcoin and running a node are not the same thing.. We only need one bitcoin miner for the network to work. Of course, if that miner gets droned or a government tells it to censor transactions bitcoin would not make it. Miners mine bitcoin blocks all over the world . These people maintain the rules of the bitcoin network no matter what the drone pilots do. This means the bitcoin network is not at the mercy of a single government. Governments could shut down exchanges, but they cannot shut down the bitcoin network.
Bitcoin will be alive as long as many humans run the software on computers. Some will mine, some will run full nodes that validate every transaction since the genesis block. There are thousands maybve tens of thousands of nodes like this in the world. For bitcoin to die, all of these nodes would need to die. A node is just a computer running the bitcoin software. I won't say this is impossible, but I remain optimistic that even the most evil of nuclear armed, drone wielding governments will not destroy all the bitcoin nodes in the world.
What Is A Bitcoin Wallet?
A bitcoin wallet is created using elliptical key cryptography. I just like to call it a big ass random number. The goal of this chapter is not to make you an expert on eliptic curve cryptography. If you want to learn how to do the math like an OG cypherpunk, take some discreet mathematics classes. WAtch the MIT Cryptography course and read Jimmy Song's book, Programing Bitcoin. The purpose of this chapter is to teach you how the math of bitcoin works without learning to program or earning a bachelor's degree in applied cryptography. I won't teach you how to do SHA256 using a pencil and paper or the command line interface. We will use tools available to anyone with an Internet connection instead. If you are interested in learning a bit more about eliptic curve cryptography, LN Capital has a pretty good thread about it on the dead bird app
To create a bitcoin wallet, we can hash some random data or we can create a 256 bit number using dice rolls. We could also flip a coin 256 times to get 256 bits. Say heads =0 and tails=1. We get a 256 bits f 1's and zero's that computers sees as a totally random, almost impossible to guess number. According to Yan Pritzker, in Inventing Bitcoin you have about the same chance of guessing a bitcoin private key as winning the Powerball 9 times in a row. Your bitcoin seed is a tiny needle in the haystack called the all of the atoms in the universe. If you would like to learn how to make a bitcoin wallet the hard way, check out armantheparman's article, but in the next chapter, you will learn how to make a bitcoin wallet using Padawan. Padawan only uses testnet bitcoin and they give them to you for free. If you F up your Padawan-have no fear. Testnet bitcoin is for practicing and it's not worth anything.
What Is Mining?

Bitcoin mining is the act of applying the SHA256 algorithm to . People often compare bitcoin mining to solving a puzzle. This is not wrong. I think of it as a mathmatical Rubix Cube of sorts, but no analogy does bitcoin mining justice.. During the government mandated lockdowns, my wife became quite adept at solving Rubix Cube. She watched a YouTube video that taught her how to solve it using an algorithm. It helps to visualize the SHA256 as a way of twisting a Rubix Cube in a certain pattern. Each twist gives a different result, but you spin and spin until all the colors match on each side. The Secure Hash Algorithms work in a similar way, except with numbers instead of colors. unfortunately, like all analogies, this Rubix Cube analogy doesn't tell you much about how bitcoin mining works. The best way I can descibe it is like a Rubix Cube with letters and numbers. I dont know how to solve a rubix cube, but my wife says she uses an algorythym. SHA256 is also an algorithym , but instead of creating sides with uniform colors. it searches for a random number with a certain amount of zeros in the front of it. All the other numbers and letters look random, but the zeros of a block do not look random, do they.

### On SHA256
According to Satoshi, "Writing a descreiption for this thing for general audiences is bloody hard, Theres nothing to relate it to." Everyone tries to explain bitcon by analogy like I just did with the rubix cube. Although this was the best visual representation I cold think of, it's still not perfect. I believe there is something in the world bitcoin can be compared to, back then, you had to be a real cryptographer like Adam Back to see it. Adam Back was cited in the white paper because he discovered a way to prevent spam, hashcash. Hashcash is an electronic stamp of sorts. You can use the command line to see how it works if you want to do it the hard way, but the easy way requires https://www.duckduckgo.com. To learn how SHA256 works , we will perform SHA256 on the lowercase letter "a" by entering the following into DuckDuck Go:
sha256 aYou will receive this result:
ca978112ca1bbdcafac231b39a23dc4da786eff8147c4e72b9807785afee48bb
Notice how even though we only did a sha256 hash of one letter, we still get a 64 character hexadecimal number. If we add the number 0 to the letter a,
sha256 a0we get the following hash:4e1195df020de59e0d65a33a4279f1183e7ae4e5d980e309f8b55adff2e61c3e
If we add the numbver 1,
sha256 a1, we get:f55ff16f66f43360266b95db6f8fec01d76031054306ae4a4b380598f6cfd114
There is no other output to each of these because each change no matter how large or small gives us a different output. That's why a number is only used once in the mining process. This is called a nonce. It makes sense. You can almost deduce the meaning by the sound of that word in the same way nobody ever had to explain to you what the word "sharted" means.
We can also has letters and any character on the keyboard. You may have heard computers only understand 1's and 0's. This is true at the base layer of the machine. but the bitcoin blockchain uses hexadecimals and all kinds of text in the transactions. This is because each character on your keyboard is represented by a number so you could do these mathmatical calculations on text like this.
sha256 Blogging BitcoinYou will see the following SHA-256 hash digest:
965aef3b925ed3d5b5315906e49a4956863528be3bfeaa357a62be6b74def0a0
If we SHA-256 Chapter 8 of George Orwell's 1984 we get:
7d7c0aad69d213e113fbaa53be74f0f88f98791c79fe44f6adb809e0787654e3
If we SHA-256 the book, War And Peace, we get:
8e09cbbbc608d61fb61f012819259987a7399351aaffb1c1790c88f134ec840e
By the way, War And Peace is a big book. it's easier to hash it by using https://xorbin.com/sha256-calculator instead of duck duck go. I copied and pasted evertying from here. https://www.gutenberg.org/cache/epub/2600/pg2600-images.html The intetresting thing aout SHA256 is that you always get a 64 character output weather you has a single letter or a huge novel. If you change one character, you get an entirely new 64 character output that looks nothing like the previous output.
Notice how each one of these gives us 64 unique hexadecimal numbers, no matter how small or large the amount of data being hashed is.
We would not make a bitcoin wallet out of a novel because anyone with that novel can take our bitcoin We want to use random numbers to make our bitcoin wallet. The purpose of writing this is to show you that anythhing from a single letter to a large book can be hashed into 64 characters.
The math is a little complicated, but I highlighted it here in case your interested, but the War And Peace number is actually this:
92,013,536,190,004,391,427,498,867,800,243,235,304,388,826,599,257,256,328,980,806,975,182,967,533,301
We will make our first bitcoin wallet in the next chapter, but before we do, let's talk more about mining?
How The F$@$% Does Bitcoin Mining Work?
Just like I can hash War and Peace, bitcoin miners can hash all the data in the bitcoin mempool. In other words all the transactions sent since the last block. Here's a good visualization of how it works. All the falling orange squares represent transactions that go into the mempool. These orange squares are really text. Miners hash this text with a nonce. They are also more likely to hash transactions that pay a higher transaction fee than transactions that pay a lower trasnsaction fee since these transaction fees are part of the reward for solving the puzzl. All the miners all over the world do this trillions of times until one of these nonces produces a number with a certain number of leading hex zeros.
https://cdn.nostr.build/p/nb10627.mp4
Bitcoin actually uses a double SHA256 hash to make it more secure. This also makes it more complex to explain, but we are going to demostrate it using a simpler Secure Hash Algorithym, First, let's look at the the SHA-256 hash of War and Peace again.
8e09cbbbc608d61fb61f012819259987a7399351aaffb1c1790c88f134ec840e
Now we will hash the entire text of war and peace plus a number we will only use once. The number could be anything, but we will use the number 0. In other words, we append War And Peace by adding a zero to the end of our text
"...This website includes information about Project Gutenberg™, including how to make donations to the Project Gutenberg Literary Archive Foundation, how to help produce our new eBooks, and how to subscribe to our email newsletter to hear about new eBooks.0"
We get this hash
e5a1d7ce9bb2d1c3450c7149633ddd3738a8f88e93457fb46df32c312361f0b4 Which is much different from: 8e09cbbbc608d61fb61f012819259987a7399351aaffb1c1790c88f134ec840e
Yet, we only changed one out of thousands of characters.
Now we will replace the Number Only Used Once, 0 with a new number we will only use once,1 and get this result: c600f3e297f850a1b5e4620b0719556a4f7b1e3614875bbe083a31ad84c40367
** TK video of this using https://xorbin.com/tools/sha256-hash-calculator**
### How This Works In Bitcoin
I could keep adding new nonces uWell, I can't, but an ASIC miner can. eventually I will get some cool looking result that has 0000000000000000000 in front of it. I can't do this by hand and it would be a waste of energy to hash War and Peace over and over again with a new number until we get a number with a certain number of zeros in front of it, but that's not the easy way of demonstrating things.
Bitcoin mining is just a souped up version of hashcash I mentioned earlier in this chapter Satoshi referenced hashcash in the white paper because the bitcoin blockchain is simmilar to hashcash, with a few differences. Hashcash uses SHA-1. Bitcoin uses a double SHA-256 hash which means it actually does it twice. The specifics are beyond the scope of this book, but hashcash is a little different.
I previously stated that we can hash any data from a single letter to the novel war and peace.
I have also demonstrated that if we add just one single number to all that data again and again, we will recieve a different result every time.
The zeros I told us are the answer to the puzzle miners are looking for.
For example, the header of the Genesis block, or block 0, is:
000000000019d6689c085ae165831e934ff763ae46a2a6c172b3f1b60a8ce26f
Block height 1: 00000000839a8e6886ab5951d76f411475428afc90947ee320161bbf18eb6048
block 210,000 000000000000048b95347e83192f69cf0366076336c639f9b7228e9ba171342e
Block height 700,000:
0000000000000000000590fc0f3eba193a278534220b2b37e9849e1a770ca959
Like I said before, the leading hex-zeros are like the colored sides of a Rubix Cube. The software adjusts so miners find the answer to this puzzle every 2016 blocks. We say it is two weeks because, on average, there are 6 ten minute blocks in an hour. If blocks come too quickly, more zeros are required. If they come to slow, less zeros are required. This is a little more complicted than this, but this is the easy way of explaining The Difficulty Adjustment.
There are 144 ten minute blocks in a day, 1008 blocks in a week and 2016 bloks in two weeks. Pretty neat, huh?
Hash Cash--The Easy Way

You can see how this works by using hashcash, a sort of digital stamp discovered by Adam Back. Back used SHA1. I found some interesting things while perusing the the hashcash documentation. Hash the following in either duck duck go or xobin calculator.
0:030626:adam@cypherspace.org:6470e06d773e05a7
Imagine "0:030626" is the header of the previous block.
Imagine ":adam@cypherspace.org" is all the data in the mempool we are trying to mine.
Imagine "6470e06d773e05a7" is the nonce. Sure the actual bitcoin timechain takes terahashes per second to solve, but the results are easily verifiable. We use a number only once because each number only yields one answer. It would be a waste of energy to use the same number twice. Instead of double hashing the actual mempool, we can use this simpler version of data to see how bitcoin mining works. Notice how the header of the last block is used in this system. This means that every bitcoin block, except the genesis block, requires information from the previous block. Becaise of this, we can say these blocks are chained together. It cannot be undone because eaach new block requires information from the previous block.
Let's use duck duck go to find the SHA-1 hex hash of this data by entering the following into the duck duck go browser.
sha1 0:030626:adam@cypherspace.org:6470e06d773e05a7You should get this: 73f88e0645f8ca92ef3a0bc02ef4b7edf85fadbd
Unfortunately, this is like a jumbled up Rubix Cube and will not create a new block, but when we try the next nonce, we get this:
sha1 0:030626:adam@cypherspace.org:6470e06d773e05a8This is from the hashcash documentation at https://hashcash.org.00000000c70db7389f241b8f441fcf068aead3f0
Now we have a required amount of zeros and we can say the puzzle is complete. It is not that complicated, but requires doing this a gazillion times before we get an answer
The Halfing
There is a debate. Some people prefer Halvening, others Halfing. I like Halfing because it makes me think of Hal Finney, but that's just this authors personal opinion. My opinion does not matter but the math does.
After 210,000 blocks, the block reward gets cut in half, until the last Satoshi is mined in about the year 2139 or 2140. Nobody really know for sure, but we can forsee the future of a bitcoin to a certain degree. We are like the Oracle in the Matrix who knew the spoon would drop. I never took calculus. I never learned what a summation was in college, but the following made perfect sense to me right away. I could see this goofy math thing-a-majig described the halfings. It made sense because I knew the halving was every four years. Then I realized this summation really tells the same story Satoshi told, but in the language of mathmatics. The actual story is told in C++, yet another language. Copernicus called "mathematics the language of the universe". In this framing, bitcoin is more than just software. It is a work of art, a monumental mathmatical achievement that can be awed after for hundreds of years to come like the Cistine Chappel..
(Anil Patel aka @anilsaidso)
The block reward was 50 for the first epoch.
In the language of mathmatics, it is divided by two every 210,000 blocks.
We get a new block every ten minutes.

144 blocks every day

The blocks start to get to big to manage when we get into these higher numbers, but you get the idea.
144 x 7 = 1,008 one week
144 x 14 = 2016 The difficulty adjustment is every 2016 blocks, but 2016 ten minute blocks are exactly two weeks.
144 x 365 = 52,560 blocks in a year
4(144 x 365.25) = 210,384 in 4 years
That's 4 years and 2.67 days, but we round and say the having happens every four years.
We just say we have a halving every 4 years, but the subsidy stops after 32 of them. Then fees incentivize the miners to solve this numeric Rubix Cube
That's how bitcoin works in a nutshell.
By the year 2032, a solo miner who creates a block will receive a block subsidy of 0.78125. Unless fees drastically increase, miners will not receive a whole coin for solving this puzzle in just nine years. You might want to get some before then, but first we need to learn how to create a wallet
[Next Chapter-- Practice Makes Perfect: The Padawan Wallet(#)
-
 @ 7cc328a0:2a247c0e
2023-08-02 22:57:59
@ 7cc328a0:2a247c0e
2023-08-02 22:57:59Here is an nginx config for setting up a streaming server that serves HLS. This is what you need if you want to stream from your own streaming server and be viewed on zap.stream, amethyst or other nostr clients that support streaming.
You can connect to it using RTMP -or RMTPS from OBS.
This is an 'advanced guide' it assumes all you need is the nginx.conf and that you can install nginx and use certbot to create the certificates.
I've tested this config on a t3.micro (very small) amazon server and it works great for streaming to my friens.
All you have to do is install nginx, point a DNS record to the server, and use certbot to get some SSL certificates.
nginx.conf ```nginx worker_processes auto; pid /run/nginx.pid; include /etc/nginx/modules-enabled/*.conf;
events { worker_connections 768; # multi_accept on; }
http {
map $sent_http_content_type $expires { default 1d; application/vnd.apple.mpegurl epoch; }
server { allow all; sendfile off; tcp_nopush on;
aio on;
directio 512; include mime.types; default_type application/octet-stream; access_log /var/log/nginx/access.log;index test.html;
location / { expires $expires; # Disable cache add_header Cache-Control no-cache; # CORS setup add_header 'Access-Control-Allow-Origin' '*' always; add_header 'Access-Control-Expose-Headers' 'Content-Length'; # allow CORS preflight requests if ($request_method = 'OPTIONS') { add_header 'Access-Control-Allow-Origin' '*'; add_header 'Access-Control-Max-Age' 1728000; add_header 'Content-Type' 'text/plain charset=UTF-8'; add_header 'Content-Length' 0; return 204; } types { application/dash+xml mpd; application/vnd.apple.mpegurl m3u8; video/mp2t ts; text/html html; } root /tmp/hls; } listen 443 ssl; server_name mysite.com; ssl_certificate /etc/letsencrypt/live/mysite.com/fullchain.pem; # managed by Certbot ssl_certificate_key /etc/letsencrypt/live/mysite.com/privkey.pem; # managed by Certbot} include /etc/nginx/sites-enabled/.;
}
stream { upstream backend { server 127.0.0.1:1935; }
server { listen 1936 ssl; proxy_pass backend; proxy_protocol on; ssl_certificate /etc/letsencrypt/live/mysite.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/mysite.com/privkey.pem; }}
rtmp { server { listen 1935 proxy_protocol; chunk_size 4000;
application live { live on; hls on; hls_path /tmp/hls; # Use HLS encryption hls_keys on; # Store auto-generated keys in this location rather than hls_path hls_key_path /tmp/hls/keys; # Prepend key url with this value hls_key_url /keys/; # Change HLS key every 2 fragments hls_fragments_per_key 100; #hls_playlist_length 5s; #hls_fragment 2s; } }} ```
here is an index.html page that displays a video player embedded.
```html
```
As you can see, the URL you would give to zap.stream to setup the stream is https://yoursite/test2.m3u8
You can test the stream is online by visiting mysite/index.html and hitting play.
Hope this helps! At the very least, now I won't lose these precious working configs. PV.
-
 @ 57fe4c4a:c3a0271f
2023-08-02 22:15:36
@ 57fe4c4a:c3a0271f
2023-08-02 22:15:36📝 Summary: The annual specification meeting in NYC discussed package relay, commitment transactions, and zero fee commitments. The Wolf team was thanked for organizing the LN Summit, with technical observations on package relay and minimum relay fees. A proposal was made to use a tapscript branch for unilateral closes and MuSig2 for mutual closes. Unconditional fees were suggested as a simple monetary solution. Carla thanked everyone for participating and acknowledged the hosts and note provider. Clara suggested making attackers pay for resources used to turn them into a profit center, but implementing fees based on HTLC holding time poses challenges.
👥 Authors: • Clara Shikhelman ( nostr:npub1uyhgpz5nsfnvdlcqm3erjsdjasd9pdeaejeetwtkvumm6mp3ujlqxt9vwk ) • Carla Kirk-Cohen ( nostr:npub17xugd458km0nm8edu8u2efuqmxzft3tmu92j3tyc0fa4gxdk9mkqmanw36 ) • ZmnSCPxj ( nostr:npub1g5zswf6y48f7fy90jf3tlcuwdmjn8znhzaa4vkmtxaeskca8hpss23ms3l ) • Anthony Towns ( nostr:npub17rld56k4365lfphyd8u8kwuejey5xcazdxptserx03wc4jc9g24stx9l2h ) • Antoine Riard ( nostr:npub1vjzmc45k8dgujppapp2ue20h3l9apnsntgv4c0ukncvv549q64gsz4x8dd )
📅 Messages Date Range: 2023-07-19 to 2023-07-31
✉️ Message Count: 6
📚 Total Characters in Messages: 173328
Messages Summaries
✉️ Message by Carla Kirk-Cohen on 19/07/2023: The text is a summary of the annual specification meeting held in NYC. It includes discussions on package relay, commitment transactions, and zero fee commitments.
✉️ Message by Antoine Riard on 20/07/2023: The sender thanks the Wolf team for organizing the LN Summit and hopes they become the YC of Bitcoin. Technical observations on package relay and minimum relay fees are discussed.
✉️ Message by ZmnSCPxj on 24/07/2023: A proposal was made to use a tapscript branch for unilateral closes and only sign with MuSig2 on mutual closes. Nonces can be stored in volatile RAM and mutual closes can be restarted on reconnection. Unconditional fees are suggested as a simple monetary solution for pricing.
✉️ Message by Antoine Riard on 26/07/2023: Proposal to use a tapscript branch instead of MuSig2 signing for unilateral closes in the Lightning Network. Discusses dynamic fees and Bitcoin as a universal clock.
✉️ Message by Anthony Towns on 26/07/2023: Carla thanks everyone for their participation in the meeting and acknowledges Wolf for hosting in NYC and Michael Levin for providing notes.
✉️ Message by Clara Shikhelman on 31/07/2023: A different approach to dealing with attacks on the network is to scale up capacity and make attackers pay for the resources they use, turning them into a profit center. This could be done through fees for message spam and holding funds. However, there are challenges in implementing fees based on the time an HTLC is held. The suggested fees are low, so hourly precision should be sufficient.
Follow nostr:npub1j3t00t9hv042ktszhk8xpnchma60x5kz4etemnslrhf9e9wavywqf94gll for full threads
-
 @ e75c0d43:6c0b0482
2023-08-02 22:15:00
@ e75c0d43:6c0b0482
2023-08-02 22:15:00Finance is experiencing rapid evolution, with Central Bank Digital Currencies (CBDCs) at the forefront. With over a hundred nations currently in different stages of CBDC adoption, the signs of a global monetary system transformation are evident. It's critical to keep in mind, however, that changes in our monetary system should not merely reflect technological advancements, but also the principles of privacy and individual freedom that underpin our society.
Earlier this year, the Bank of England (BoE) launched a series of technical and consultation papers regarding a prospective 'Digital Pound.' With the consultation period on June 30th now closed, it is crucial that we are aware of the suggested changes and their potential implications on personal freedoms and privacy. It's worth reflecting on the 'Digital Pound' not just as an operational innovation, but as a societal change that could alter our understanding of private property and individual autonomy.
CBDCs, positioned as the digital counterpart of central bank money, promise to reshape our financial systems. The proposed 'Digital Pound' could deliver several potential benefits, including streamlined transactions and enhanced financial inclusion. Nonetheless, these perks warrant careful evaluation, with an eye on the potential for economic manipulation facilitated by this advanced technology. We must remember that any technology, while offering potential conveniences, also bears the capacity to restrict or surveil. Therefore, the wider societal implications of these developments need thoughtful contemplation.
CBDCs represent more than mere operational enhancements - they symbolise a fundamental transformation in our monetary framework to align with an ever-increasing digital world. They promise game-changing modifications in monetary flow, ensuring compatibility within the domestic financial system and with international currencies. However, any systemic change inevitably comes with systemic risks. Despite proposed limits on CBDC’s, the long-term impacts on banking and financial stability remain uncertain. In this sense, we need to be wary of over-optimism in the face of such radical change for the sake of ‘innovation’ and remember that such fundamental transformations should not be carried out lightly.
There are two forms of CBDCs, Wholesale and Retail, these serve different financial entities. Wholesale CBDCs are designed for banks and financial institutions, while Retail CBDCs offer a digital alternative to cash for households and businesses. The BoE's consultation primarily revolves around Retail CBDCs. While the 'Digital Pound' is described like a digital equivalent of physical cash, it fundamentally alters the transaction experience. Unlike cash transactions, which afford a certain level of anonymity, the adoption of CBDCs could set the stage for a financial system where every transaction is potentially traceable and permanently logged onto a digital ledger.
Essentially, we are looking at a system that doesn't merely modernize our transactions but redefines the very concept of money, along with its relationship to personal freedom and anonymity. Although assurances have been made about the anonymization or use of pseudonymisation personal data, it has been shown in various studies that pseudonymised data, given enough data points, can be identified. The task of identification will likely be made easier with the use of artificial intelligence (AI) and machine learning (ML). Considering we live in an increasingly digital age, there is a vast amount of data available for analysis. From this rich trove of information, it's possible to derive a plethora of insights about an individual - their social circles, political inclinations, and health, to name a few - just by examining the everyday spending habits of each person. This level of transparency might deter fraud and other illicit activities, but it also provides institutions with unprecedented access to personal financial data. The ability for institutions to scrutinize every transaction inevitably raises questions about personal privacy and governmental overreach. The government's close watch on cash usage within the economy is implicit. They are undeniably aware of studies from other countries, such as Sweden, where it was projected, that retailers will stop accepting cash by 2025. Similarly, we've seen a declining trend in cash usage in our own market, which the pandemic has only accelerated.
The consultation documents mention, 'The decline in the use of cash is expected to continue as commerce and payments become more digital, even though UK authorities are committed to keeping cash available as long as there is demand for it.' This phrase seems to hint at an eventual phase-out of cash. If cash gradually becomes obsolete, the only bearer instruments left in the economy would be bullion coins, which today, are rarely used as a medium of exchange. One must consider what we lose in the transition from tangible to digital - the anonymity and direct control over our own money.
The proposed 'Digital Pounds' would be stored in digital 'wallets'. These are provided by private-sector banks and financial institutions acting as Payment Interface Providers (PIPs). Accessible via smartphones and cards, these wallets would necessitate personal identifiers to comply with Anti-Money Laundering (AML), Know Your Customer (KYC), and Combatting the Financing of Terrorism (CFT) regulations. Some of these are outlined in the consultation papers like: • Knowledge (something you know) – A Personal Identification Number (PIN) or password, either validated on the device or online. • Possession (something you have) – Most commonly, this would be the smart device or card used for the transaction. • Inherence (something you are) – Biometric authentication methods such as facial or fingerprint recognition.
These requirement aligns with the notion of digital ID’s, which is convenient given the consultation of ID’s earlier this year, potentially paving the way for a holistic digital infrastructure. Of particular concern is the use of biometric data. When paired with the increasing integration of biometric surveillance, the outlook can be rather unsettling. It's important to acknowledge that this could escalate concerns surrounding surveillance and civil liberties. The compilation of financial data necessitates robust data protection and privacy laws to prevent potential misuse. Nonetheless, it's worth remembering that even the most comprehensive laws can have loopholes, and they are also subject to change.
Project Rosalind, a collaborative venture between the Bank for International Settlements (BIS) and the Bank of England (BoE), has been focusing on the application programming interface (API) for retail CBDCs. This project involves prominent companies such as Amazon, Barclays, and Mastercard and is developing use cases with both public and private sectors. It is worth noting that the project does not favour non-custodial wallets—those that permit direct custody of private keys.
Instead, they advocate the use of custodial wallets, which relegate the control of private keys to a third party. This practice has proven to be problematic in the world of cryptocurrencies, as demonstrated by the case of FTX. When this crypto exchange went under, those who did not transfer their crypto assets to non-custodial wallets lost access to them.
The consultation suggests a deposit cap for these digital wallets, set between £10,000 and £20,000. This restriction serves a dual purpose. Primarily, it seeks to prevent disintermediation of bank deposits to maintain the stability of commercial banks. Secondly, though not explicitly stated, it aims to guard against dollarisation from other CBDCs, which refers to the domestic circulation of a more robust foreign currency.
Certainly, the 'Digital Pound', akin to other CBDCs, can be programmed with smart contracts, a point underscored in both current and previous Bank of England discussion papers. Smart contracts, essentially self-executing contracts with the terms directly written into lines of code, can promote various applications, build system trust, and eradicate the need for expensive intermediaries. Nonetheless, they also introduce fresh challenges. The inherent inflexibility of smart contracts might not adequately accommodate the nuanced demands of real-world financial agreements. Moreover, their functionality heavily relies on the quality of the foundational code, making them vulnerable to both coding bugs and potential manipulation.
Consequently, the topic of smart contracts is primed for debate in future design phases. A thorough evaluation will be crucial for successful implementation and prudent regulatory decisions. The issue of technological control is not new and has been previously observed with the use of smart meters and the Internet of Things.
Interestingly, the BoE acknowledged this in a 2020 paper where it stated, 'More advanced smart contracts could be used (for example) to automatically initiate payments upon the confirmed receipt of goods, or routing tax payments directly to the tax authorities at the point of sale. Transactions could also be integrated with physical devices, or the ‘Internet of Things’. For instance, code could be written such that ‘when £X is transferred to account Y, device Z switches on'. Such a level of control can potentially be problematic if abused. This has been recently illustrated in the case of an American citizen who was locked out of his Amazon smart home devices due to an unfounded racism allegation. Another instance is the recent patent by Ford titled ‘Systems and Methods to Repossess a Vehicle,’ where driverless cars can be disabled and redirected when payments fail to come through. These examples underscore the delicate balance between technological innovation and the safeguarding of individual freedoms and rights.
As we delve deeper into the realm of CBDCs, we encounter a trade-off between convenience and privacy. The prospect of every financial transaction leaving an indelible digital mark heightens the tension between the allure of a tech-forward future and potential risks. The 'Digital Pound' may promise benefits like seamless transactions and better financial inclusion, but significant trade-offs, most notably in terms of personal privacy, come with these benefits. The 'Digital Pound' might reveal our personal expenditures unlike anonymous cash transactions. While such transparency may deter financial crime, it simultaneously transfers an unprecedented amount of personal financial data, tilting the balance of power towards surveillance.
The widespread adoption of CBDCs could provide governments and central banks with exceptional insights into citizens' everyday lives. While they deny any intent to misuse this information, the scenario could be exploited, with financial access potentially being used as a control tool. As we advance towards this digital frontier, it is paramount to advocate for solid legislative and regulatory protections that prioritise privacy and individual freedom.
Governments worldwide, particularly in places like China but also alarmingly in countries such as Canada, have demonstrated their ability to leverage financial power to influence their citizens. For instance, during the recent Canadian truckers' protests, individuals discovered themselves locked out of their bank accounts for making donations as small as $20. Intriguingly, it's not only governments; private corporations also play a role. The practice of 'debanking' has also been increasing, where individuals and businesses holding dissenting views find themselves excluded from the financial system. Governments may not need to act directly if regulators and third parties can enforce their agenda. This notion is evident in the potential consequences of the proposed 'Online Harms Bill.' If passed, it carries the risk of high fines and even criminal prosecutions if not complied with, compelling social media companies to set stringent standards in their terms of use to avoid potential repercussions.
Despite the apparent innovation that CBDCs bring, their necessity is debatable. Many of their proposed features are already present in our existing financial infrastructure and through advancements in the private sector. Industry-led solutions continue to refine systems, addressing security and privacy concerns without the complexity brought by CBDC proposals.
This interest of central banks in CBDCs is conspicuous, given the unparalleled control they offer over monetary policies, efficient transaction processing, and a potential competitive edge in global currency markets. However, we must not allow the urgency to adopt CBDCs to overshadow potential pitfalls. A sense of competitive anxiety permeates the discourse surrounding CBDCs, with no central bank wanting to be left behind.
One could delve into the implications of this competitive urgency. This could be a manifestation of a kind of technocratic arrogance, which forgets that human institutions exist to serve individuals, not the other way around. Technological advancement doesn't necessarily equate to human progress, and the obsession with being at the forefront may neglect the moral and ethical implications of such advancements.
The technical documents provided often avoid specific details, making sweeping statements that lack clear explanations. These 'innovations' and 'features' are presented as unquestioned benefits without providing tangible justification or examples for this seismic shift in our financial system and technological structure. There is no consideration of the adequacy of existing infrastructure, that works day-in day-out, with this all smelling like the central banks using this digital upheaval to give itself comprehensive control over the monetary system. This is not just domestically, but internationally also.
Considering that countries exploring or already implementing CBDCs represent about 95% of global GDP, CBDCs seem almost inevitable, regardless of consultation outcomes. Even if the initial implementation appears to be a diluted version of some CBDCs, once introduced, it is here to stay, leaving room for gradual and potentially unnoticed changes over time.
Considering the significant transition proposed towards this brave new digital world, it's quite fitting to question who holds the mandate or authority to initiate a Central Bank Digital Currency. Consultations like these, not unlike others of similar nature, are often hidden in the deep recesses of government or banking websites, leaving the average citizen none the wiser. For decisions that could bring about such foundational changes, it's crucial that these matters be more readily accessible to the public, even possibly by referenda. This type of governmental organization can make the administration seem more like a group of Vogons, rather than people trusted to run a nations monetary system.
npub1uawq6sm97a8y5vuecdeqljcm2zx43d0w959793dzhspeymqtqjpqhcax2t
-
 @ 00000001:a21169a7
2023-07-29 19:42:42
@ 00000001:a21169a7
2023-07-29 19:42:42
If for Henri Cartier-Bresson the essence of photography was the decisive moment, for William Klein the defining factor is commitment. This assertion, made by Raphaëlle Stopin, curator of the 'William Klein. Manifesto' exhibition, couldn't be more accurate. At 91 years old and with multiple facets to his name - photographer, painter, filmmaker, publicist, writer, and activist - Klein has left an indelible mark on the landscape of art and photography with his irreverent commitment and radical approach.
Born in New York in 1928, Klein transformed mid-20th-century photography, creating an aesthetic language that evokes the rawness and emotions of a post-war society still to be rebuilt. Through his lens, we see a vibrant, dirty, mestizo, and ever-evolving New York. His unconventional approach, which mixed with the subjects he portrayed, broke with the standards of photography of his time, resulting in images that the white, Anglo-Saxon elite of the era found distasteful. However, his honest and committed vision ended up paving a new path in photography.
Klein began his creative journey in painting, where he already displayed a unique, free, and transgressive language. His entry into the world of photography happened fortuitously, by photographing his own paintings, and it was in 1956 when his vision exploded onto the scene, with the publication of 'Life is Good & Good for You in New York: Trance Witness Revels'. This work, the fruit of his immersion in the wild side of New York life, became a revolutionary manifesto that subverted the traditional principles of photography.
Klein's photographs were never just images. They were bold statements of freedom and experimentation, going against the conventions of his time. It was with his legendary book about New York that he became a disruptive figure in photography. Despite being published in France, Italy, and Japan, this book took 40 years to be published in the United States, a fact that evidences the rejection his raw and uninhibited gaze of the city caused.
But Klein was never content with just being a photographer. His enormous cultural baggage, inspired by figures such as Masaccio, Piero della Francesca, and the Bauhaus, propelled him to explore other forms of expression. In his work, we see the fusion of photography with painting, the 'painted contacts', where he applies paint to contact sheets with large brushes, creating a fusion of disciplines that is surprisingly innovative and evocative.
Today, at 91 years old, Klein continues to work, reinventing himself and reinterpreting his archive. Although his pace has changed, his commitment to his art and his language has not diminished. His legacy endures, and his influence continues to be visible in contemporary photography.
Is Klein a Leonardo of photography? Perhaps it's not an exact comparison. But, just like Da Vinci, Klein has shown a diversity of interests and skills that rivals any Renaissance polymath's. And, unlike Da Vinci, Klein is indisputably wilder and more committed.
In summary, William Klein is a visionary, a provocateur, and an iconoclast, whose work remains a source of inspiration and a challenge to today's artists and photographers. With his committed, free, and innovative gaze, Klein has demonstrated that photography, like any form of art, should always be an act of commitment and revolution.
-
 @ 1bc70a01:24f6a411
2023-07-29 13:15:49
@ 1bc70a01:24f6a411
2023-07-29 13:15:49I’m going to think out lout about the UAP hearing a bit, feel free to tune me out.
Scenario 1
The one most of us are probably thinking: This entire thing is a distraction from one or many known or unknown issues currently underway. It must be so bad that it warrants national attention to the all-entertaining “UAP” subject.
For this to be true, we have to assume one of the following: 1. The people testifying are lying. Maybe paid actors, maybe not, who knows, but they are not telling the truth. 2. They are telling their “truth”, however they obtained it, perhaps even their reality. We do know UFOs are commonly reported worldwide, so perhaps they are just telling what they saw.
In terms of congressional involvement, scenario one would mean that some or all of the congress members are full of shit. This is an unlikely scenario in my mind (hard to get everyone to go along with a lie). The more likely scenario is that they are in it for the wild ride, totally unaware they are being used as pawns (or at least some aren’t).
What makes this scenario possible in my opinion is that Grush is allowed to speak about the events publicly but not discuss details (unless privately). This makes for good public theatre. Why would unsanctioned projects allow Grush to even go so far as to speak about the events when a slip and fall accident could occur at any moment? The answer would have to be either: 1. Because it’s all bullshit, or mostly bullshit. 2. Because the agencies involved are really THAT incompetent and hadn’t figured out what is happening. 3. Because they have no problem with him talking about it because they would like to slowly disclose alien technology and the fact that we’re not alone. 4. To serve the purpose of distraction.
Assuming scenario 1 is correct, the most likely scenario is that the people involved are telling their own version of truth and that some of the congressional members are unaware of the real reason they’re there.
This is an easy fallback for any time you want to divert attention from some other pressing matters. Just talk about UFOs!
The earlier story in NY Times would also make sense in this case - as the NYT has been known to act as the propaganda arm of the government. The NY Times story brought a lot of attention to the matter, but we have to also wonder why this was under the rug for so many years? Perhaps because it’s pure bullshit.
The “It’s real!” Scenario….
Let us assume that this is not a distraction. The people testifying are telling the truth. Everything is as they say it is. Ooof!
This would mean that everything Grush says is true - there are unsanctioned programs and or people with extreme privilege and clearance not granted to anyone else. People that are not even part of the government in any way.
It would also mean we have recovered alien craft and bodies and have attempted to reverse engineer their tech. Perhaps we already succeeded and what we see flying around today is this reverse engineered tech, or actual ETs.
What would make this scenario real?
Well, there is no shortage of UFO sightings. People swearing their life on it. For us to discount all of them would mean calling everyone a liar, or just confused about some other phenomena. I wouldn’t bet on all liars and delusional, but confused, maybe. Still, some accounts are just too out there to dismiss without some serious thought. The fact that people’s stories seem to match could mean that there’s truth to those reports.
Perhaps the aliens use pods (classic saucer shapes, or “tic tacs” or other shapes craft. Maybe the “cubes” in orbs are their versions of drones? Or not? Maybe the large cubes are spacecraft.
Yes, they cover vast amounts of space quickly and STILL crash on our planet. Rookies that failed the landing maneuver in flight school… heh.
The governments of the world are all cooperating in hiding the truth and or the US government has unprecedented access to other parts of the world to recover and cover up various incidents. WOW… ok. That means we have something like a one world alien-communication government that has unprecedented access beyond anyone’s control. How??
If this is the real deal, we should all be losing our minds right now. The prospect of another species with vastly superior technology with interest in our nuclear dealings should scare everyone. Forget everything else, this is priority #1.
THE PROBLEM with this scenario?
- Some foreign govt. would have already revealed what they know. Would they not? Are we to believe they are all collaborating on this with some inter-government agency that acts with ultimate authority? Why? How? Maybe they are already speaking out and I’m unaware?
- We STILL don’t have any definitive evidence. He said, she said, they said. “First account” from a “trusted source”. OK.
- Aliens possess mind-blown tech, but still crash once in a while. I guess you could say that there will always be a small chance of crash no matter who is flying what. I’ll give people that.
- “It’s classified”. No amount of talking seems to reveal the actual “classified” information. Even during the congressional meeting it’s always “I can tell you privately”, and “I’m not permitted to talk about this by law”. Which is it? Are you, or are you not allowed to speak on the matter? Why can you disclose it behind closed doors but not in public? Seems rather strange to me.
In the “It’s all real!” Scenario, we are all screwed. Either we are being prepped for eventual disclosure of alien life or aliens can do crap we can’t protect against. If we’re being prepared for disclosure, it may mean that we have no say in how things unfold on our planet and the best we can do is ease people into it without everyone losing their minds. In that case, a series of hearings on the matter might make sense. Keep talking about it louder and louder until people are no longer shocked to hear the truth. Buckle up everyone, things are about to get interesting!
Scenario 3: “Trust Us, We’re here to serve you”
From the hearing, we hear multiple times congress mention “distrust in the government” and “rebuild trust”. In line with Scenario 1, this would mean everything is just a smoke screen to “build trust”. “Oh look, congress cares about me😍!!”
It would make sense why nothing has been revealed concretely and no foreign government came forward yet. Didn’t you know, UFOs only crash in the states! Haha.
Congress is just “building back trust”, either fully aware of the lies, or using mentally unstable people for their gain. Not saying the witnesses are mentally unstable, but you never really know, do you? Tell yourself a story enough times, it becomes a reality.
My Personal Take?
I wish to remain open minded about this subject. There are too many questions unanswered for me and I don’t want to dismiss anything entirely. Could there be aliens visiting this planet? I don’t see why not. We don’t know what we don’t know. For me to dismiss the possibility of non-human life traveling to our planet would mean to believe we have learned everything there is to learn about physics and the universe, when in fact it is the opposite, we know little to nothing.
Could it be bullshit? Yes, of course. I also like to consider things from a practical perspective and think in terms of probabilities rather than right and wrong, yes or no. If I had to guess the odds of aliens traveling to our planet, I’d give it at 5% chance. So yeah, not much. I’m much more inclined to believe this is all just human manipulation to achieve some agenda. I won’t speculate what that agenda might be as it’s anyone’s guess really. There’s no way to prove anything.
Should all of this be real, things are going to get very interesting…
-
 @ 5ada3677:7c21c9db
2023-08-02 21:39:22
@ 5ada3677:7c21c9db
2023-08-02 21:39:22
昨天寫了兩位讀者給我的感動,今天再來一位。
茅小姐在美國,我們素昧平生,沒有機會見過面,最近因為寫Bilbao,茅小姐給我留言,講到她最近剛剛到過此地,讀到文字有點激動,她還到了Getxo,去當地友人家裡做了客。我碰巧也寫到了這個讓人讚嘆不已的濱海小城,與茅小姐隔海共鳴了一下。
然後茅小姐跟我講起,回看了6月裡我寫的那套《東京散步》系列,寫到一段音樂會,掃到一筆王羽佳,那段文字是這樣寫的:



昨晚去聽了一場音樂會,小提琴Volkhard Steude,維也納愛樂的首席小提琴,與日本中生代的女鋼琴家三輪郁,非常非常過念頭的一場奏鳴曲專場。Volkhard 是1971年出生的東德好青年,1988年已經在西德的柏林深造,1989年柏林牆崩潰,如此的天才青年,有了輝煌的舞台,29歲成為維也納愛樂的首席。昨晚他52歲,琴音非常複雜,聽得到很多很多層次,像一個初老男人的娓娓傾訴,雖然都是技巧很厲害的曲子,不過Volkhard並不炫技,跟王羽佳小姐是兩個境界,什麼年紀說什麼話、穿什麼衣,這好像也是沒有辦法的事情,初老有初老的好處,很多很多好處,王羽佳小姐還沒有老,我可以慢慢等她。


然後茅小姐講了一段往事給我聽,下面是茅小姐的文字:
呵您那句關於王羽佳,讓我笑出聲來。讓我講個小插曲。
那是應該十年前了,前一夜在卡耐基聽完王羽佳的音樂會,第二天傍晚回家在LaGuardia 機場門口,見王羽佳跟當時的男朋友在那裡難捨難分,我過安檢,等等。
後來我坐在飛機上見她往後面經濟艙走,想她連續演奏兩天蠻辛苦的,然後後面一天又有音樂會,我就跟她說,跟你換座位吧,你可以休息一下,我反正回家而已。我是有買了她後面一天在我們那裡音樂會的票,全家都去聽的。
她很真誠地說不用,說你出差也是累的。
那一句讓我對她印象很不一樣,畢竟most of the kids are quite spoiled these days ,更何況她作為celebrities 。
後來抵達了,從登機口出來,一路跟她聊了不少。我們機場是美國最大的,還是全球流量最大的,所以需要不少時間才坐到luggage claims那一站。覺得是蠻樸實真誠的一個。

徵得了茅小姐的同意,我把她的這一段錄在這裡,致敬我世界各地優秀的讀者,也致敬王羽佳小姐。


今天的圖片來自網上,是各種罐頭海鮮,Bilbao很多這種罐頭的舖子,每一間都漂亮得像賣化妝品或者賣珠寶的,每一個罐頭都讓人愛不釋手。
我從來沒有想到,會為一個罐頭流連忘返顛倒再三。
人世的很多美、很多好,給我們勇氣和溫暖,讓我們戀戀紅塵不已。
感恩遇見。


夏日拾珠系列在這裡
nostr:naddr1qqxnzd3exqenjvpc8q6nxvfhqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c83ac7g
nostr:naddr1qqxnzd3exqenjvfjx5ur2wpeqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c8mrqrm
nostr:naddr1qqxnzd3exqenjvf4x5ervd33qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cdqaveh
nostr:naddr1qqxnzd3exqenjvfcxscnqd3nqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823czmjr4k
nostr:naddr1qqxnzd3exqenjv33xqunjwphqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c0ggymy
nostr:naddr1qqxnzd3exq6nxdfkxv6rqdp5qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c42u6cr
nostr:naddr1qqxnzd3exq6nxdfexqerzdejqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cawzeyh
nostr:naddr1qqxnzd3exq6nxd3j8qmnywfcqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cp6dd24
nostr:naddr1qqxnzd3exqunqdphxu6nzdenqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cc8avfs
nostr:naddr1qqxnzd3exqunzvf4xs6ryvpkqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c6xk2dq
nostr:naddr1qqxnzd3exycrzvpcx5mnjve3qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c8qk3y9 -
 @ 5ada3677:7c21c9db
2023-08-02 21:24:12
@ 5ada3677:7c21c9db
2023-08-02 21:24:12
寫了十篇《夏日拾珠》系列,後台斷斷續續,看到讀者留言,問是不是寫一點美食,巴斯克食物享有盛名。
於巴斯克食物,我還是小學生,在努力學習中,越學越覺得水深,所以遲遲沒有寫。
昨天的文字裡,貼了一幅圖,讀者留言問,那个用土豆泥做的、有馅的炸团子是叫什么名字?小时候家裡好婆常常做,她说叫“骨落饺”,是根据西餐改良的,自己放了香菇肉末的馅料。
英國的讀者Angela回覆說,叫Croquette。
兩位讀者的留言往復,讓我莫名感動。


寫一點Croquette。
Croquette 最早是法國人的食物,炸土豆泥球,17世紀就有了,如今已經遍佈全世界,各大洲、各個民族,都有自己版本的Croquette,是人見人愛的小食。巴斯克人的Croquette,出名好吃,是因為土豆泥裡揉入了巴斯克的火腿、鱈魚、香腸、奶酪,滋味特別富饒,香美無比。
Croquette 在巴斯克人,通常做得小小的,大不過雞蛋、小不過核桃的尺碼,方便拿手指拈食。晚餐之前的那杯開胃酒,Croquette 通常是首選的下酒菜,這個香噴噴、營養豐富、熱量充足的小食,通常也是首選的、喂孩子的食物,哪個小朋友會不喜歡Croquette 呢?


前些日,與西班牙女友一起吃飯,女友是職業廚師,我們都袖起手,偏勞她點菜。女友教我們說,第一個要點Croquette,Croquette 是餐館的試金石,Croquette 做得好、肯用心,館子不會差,其他菜可以放心點下去。Croquette 是敷衍之作,那就不用往下吃了,換一家比較好。
格麼,Croquette 怎麼個敷衍法呢?
女友笑笑,說,用冷凍貨預製菜啊。
原來如此,全世界的廚房偷起懶來,步調一致,都是一個思路的。
太陽底下真是沒有新鮮事物。


這些日子在巴斯克各地行走,食過形形色色的Croquette,確實每一家都有自己的風格,隨心所欲變化無窮,共同的一個特點,是幾乎沒有人用香料,巴斯克料理裡,基本上不用香料,連黑白胡椒都不用,因為當地不出產胡椒,老祖宗不用的,子子孫孫也不愛用,這種品德,我太喜歡了。
說句題外的,我們老祖宗研究營養食品,至少有千年的歷史,水平之高,無庸置疑。可惜,我們如今把老祖宗丟在一邊,沒頭沒腦向西方學營養學,西方營養學有多少見識呢?笑笑。


讀者講的,好婆教的名字,骨落餃,多麼美好啊,如此音韻跌宕的一個芳名,我這種吃字比吃飯要緊的吃字分子,真是喜歡到心軟。好婆落地改良成香菇肉糜版,好婆是千古絕唱。願每一個童年裡,都有如此卓越的好婆溫暖我們的心與腸永永遠遠。

今天的圖片,是巴斯克人的罐頭食物和Croquette。
我是來了此地才知道,巴斯克人的罐頭食物,是用最好的食材製作的,一洗我對罐頭食品的半輩子的偏見。
以前一直以為,罐頭食品都是用食材的邊角料製作的垃圾食品,是不得已的危機時刻才會食用的下下之選,比如行軍打仗、比如插隊落戶,等等。
夏日拾珠系列在這裡
nostr:naddr1qqxnzd3exqenjvpc8q6nxvfhqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c83ac7g
nostr:naddr1qqxnzd3exqenjvfjx5ur2wpeqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c8mrqrm
nostr:naddr1qqxnzd3exqenjvf4x5ervd33qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cdqaveh
nostr:naddr1qqxnzd3exqenjvfcxscnqd3nqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823czmjr4k
nostr:naddr1qqxnzd3exqenjv33xqunjwphqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c0ggymy
nostr:naddr1qqxnzd3exq6nxdfkxv6rqdp5qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c42u6cr
nostr:naddr1qqxnzd3exq6nxdfexqerzdejqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cawzeyh
nostr:naddr1qqxnzd3exq6nxd3j8qmnywfcqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cp6dd24
nostr:naddr1qqxnzd3exqunqdphxu6nzdenqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cc8avfs
nostr:naddr1qqxnzd3exqunzvf4xs6ryvpkqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c6xk2dq -
 @ 00000001:a21169a7
2023-07-29 08:32:13
@ 00000001:a21169a7
2023-07-29 08:32:13Robert Frank, born on November 9, 1924, in Zurich, Switzerland, was the child of Rosa (Zucker) and Hermann Frank, of Jewish origin. Though his family managed to remain safe during the Second World War in Switzerland, the looming threat of Nazism informed his understanding of oppression, invariably seeping into his subsequent work. Frank was drawn to photography partly as a means to escape from his business-oriented family and home. He was mentored by various photographers and graphic designers before he crafted his first handmade book of photographs, "40 Photos," in 1946. At the age of 23, Frank migrated to the United States, seeking to broaden his photographic horizon. He found employment in New York as a fashion photographer for Harper's Bazaar. However, the rigidity and artifice of fashion photography failed to satiate his creative yearning. He soon quit his job and embarked on journeys through South America and Europe, creating a second handmade book of photographs taken in Peru.
Upon returning to the United States in 1950, Frank began to experience a transformation in his photographic perspective. Influenced by his disillusionment with the frantic pace of American life and its emphasis on money, he began to perceive America as a place often desolate and lonely. This vision is reflected in his subsequent photography.

The aesthetic context of the subjective photography of the 1950s, which Frank adopted, was marked by a paradigm shift in how photography was understood and practiced. It involved a move away from the apparent objectivity and neutrality that characterized documentary and journalistic photography, to adopt a more personal and subjective approach. Images ceased to be seen simply as faithful representations of reality to become the photographer's personal interpretations.

In this context, Robert Frank stood out for his direct, unadorned style. His photographs did not aim to beautify or idealize reality, but to capture it as it is, with all its imperfections and contradictions. For Frank, the camera was a tool to explore and question society, rather than merely documenting it. His most emblematic work, "The Americans," first published in Paris in 1958, is a chronicle of his journey through 48 states of the United States. The book, composed of 83 images selected from 28,000 shots, offers an unconventional and critical view of American life. Through his images, Frank portrays a society marked by racial and class inequality, loneliness, and helplessness. The images in "The Americans" are often dark, blurry, and off-kilter, contributing to a sense of unease and instability. Robert Frank continued to work intensely throughout his career. Here is a list of some of his most representative works, ordered by year:
- 1946: Published his first handmade book of photographs, "40 Photos."
- 1947: Moved to the United States and began working for Harper's Bazaar.
- 1950: Participated in the group exhibition "51 American Photographers" at the MoMA and published his second book of photographs from his journey through Peru.
- 1955: Received a Guggenheim Fellowship to travel and photograph the United States, a project that would result in "The Americans."
- 1958: Published "The Americans" in Paris.
- 1959: "The Americans" was published in the United States.
- 1961: Had his first solo exhibition at the Art Institute of Chicago.
- 1962: Exhibited at the Museum of Modern Art in New York.
- 1983: The French magazine "Les Cahiers de la photographie" devoted two special issues to his work.
- 2008: A new edition of "The Americans" was published to commemorate the 50th anniversary of its first publication.
- 2009: The exhibition "Looking In: Robert Frank's The Americans" was shown at the National Gallery of Art in Washington D.C., the San Francisco Museum of Modern Art, and the Metropolitan Museum of Art in New York.
Robert Frank's influence on contemporary photography is undeniable. His subjective and critical vision opened new pathways for understanding and practicing photography, shifting it away from conventionalism and closer to a more artistic and personal conception.
-
 @ 5afa711a:eae0d7b8
2023-08-02 20:22:10
@ 5afa711a:eae0d7b8
2023-08-02 20:22:10It’s been four months since I started the carnivore diet. For the past month I have been experimenting with a more “keto” approach and added nuts and dairy products to my diet. The results are mixed, as I’ve stopped losing weight as rapidly as in the first 2 months. My BMI went down from 34 to 26.8, so I am pretty well pleased with the weight loss itself. I also feel more clear headed, more active, and my fatigue is generally gone. I am still a coffee addict, so I do get cranky and tired if I miss my morning cup, but I just love the effect coffee has on me too much to give it up completely, but I did cut back on my overall caffeine consumption. I usually drink coffee with butter, salt and coconut oil once or twice a day, and I don’t drink milk.
I figured I was due for a lab check, and I’ve compared it to the one I had 3 months ago, which was just one month into my new diet. I unfortunately don’t have a baseline test for comparison, as I had no expectations of success, so I didn’t think I’d need one.
At the start of May, my fasting Glucose was 5.4 mmol/l (97.2 mg/dl) with an HbA1c of 5.2%. These results were okay, but I didn’t test for fasting insulin, which gives a more accurate picture of metabolic health. Today, my fasting Glucose was 5 mmol/l (90 mg/dl), my HbA1c was 5.1% (mild improvement) and my fasting insulin was 13 µIU/mL (90.3 pmol/l). These measures allowed me to determine something called HOMA-IR, which takes into account your fasting insulin and fasting glucose levels. HOMA-IR correlates well with insulin resistance and can asses the risk for developing Diabetes. You can calculate the number yourself, there are plenty of calculators online, just beware of unit conversions. My HOMA-IR amounts to 2.9, which is not great, but also not terrible. I definitely think I was on the verge of developing true diabetes, and my guess is that this is an improvement, but I can’t say for sure due to having no baseline study for comparison. It is important to realize that 88% of Americans have at least one symptom of metabolic syndrome. Nobody is healthy, we are all sick due to the influence of the unholy trinity of Big Food, Big Pharma and Government, but that is another topic I intend to write about soon, don’t worry.
So, what about my lipids? Well, this surprised me. Compared to the numbers in May, my total cholesterol decreased, on account of the LDL component (”bad” cholesterol). Total cholesterol went down from 4.5 to 3.6 mmol/l (174 to 139 mg/dl), LDL went down from 3.2 to 2.2 mmol/l (124 to 85 mg/dl). HDL and triglycerides stayed the same at around 1 mmol/l (39 and 89 mg/dl respectively). The LDL reduction was significant and I’d bet you my cardiology colleagues would be surprised I managed to achieve this without a statin. I was a bit surprised that my HDL remained stationary, which is not ideal, but I’m not upset about it that much. A more accurate predictor of metabolic health than LDL is the TG:HDL ratio. In May it was 2.55, and now it’s 2.29, which actually means I have a lower risk of developing metabolic syndrome today than 3 months ago. The role of lipids in developing heart disease, however, might be overstated, and cholesterol (actually LDL) is a much lower risk factor for developing heart disease anyway when compared to diabetes, obesity, smoking and hypertension. I definitely need to do more research here, and I will talk about this in future blog posts, but I think us physicians might have jumped on the statin train a bit too eagerly. Many studies tout the benefits of cholesterol reduction, and falsely imply causality between cholesterol and heart disease, but this is simply impossible to determine without a randomized control trial (rct), which is costly and ethically untenable. These bad studies then get agglomerated into bigger studies called metaanalyses, which are treated as the gold standard of truth among clinicians... but a metaanalysis is only as good as the studies included in it.
I also tested my liver enzymes, which were all good and mean I probably don’t have fatty liver disease. It is important to asses your liver enzymes when looking for signs of metabolic illness because they can point to said fatty liver disease. Fatty liver eventually turns into full blown hepatitis, and cirrhosis soon follows, with a chance for developing cancer. Non-alcoholic fatty liver disease (NAFLD) is the second most common cause of liver transplantation in Europe and the US, and the incidence is only increasing. NAFLD also practically didn’t exist a couple decades ago, which says a lot about the current health state of humanity, and the direction we are heading in.
My serum urate levels were slightly increased, at about 477 umol/l. You probably don’t need to test this, as causation between hyperuricemia and associated diseases like gout and uric renal stones was not demonstrated. It is probably increased due to an increased purine metabolism caused by meat consumption, and might be a leftover from a period when I used to consume more fructose and caffeine. I don’t have the baseline study for comparison, but this lab result is not cause for concern.
Overall, taking into account my lab results, my age (early thirties) and family history of heart disease, I award my metabolic health a C+. I need to continue this diet, and decrease/eliminate all carbohydrates, because I will probably develop diabetes if I re-start eating processed vegetable based foods. My lipids actually showed improvement, but I’d prefer it if my HDL were higher. I don’t think I have to worry about fatty liver disease at least, and I’m not afraid of kidney stones or gout with only a slightly elevated urate level. Diabetes is the most important risk factor for developing heart disease, according to a women’s health study from 2021: https://jamanetwork.com/journals/jamacardiology/article-abstract/2775559, and I would like to avoid it if possible. My father and brother are both diabetic, the former had a heart attack at 50, and the latter at 40.
So, going forward, what’s the plan? So far I have not been exercising, and I should probably change that. Any person who recommends exercise to a patient with 30kg of extra weight should be forced to run a mile with a heavy fatsuit on a hot summer day. The overweight patient will injure himself, fail to exercise properly, fail to lose weight because the diet would remain relatively unchanged, and will proceed to give up on the whole effort of weight loss, which is precisely what Big Food and Big Pharma want you to do. So, if you are obese, focus on your diet ++FIRST++, stop eating junk, and when you shed that extra weight, then begin to exercise.
I will also cut back on the “keto” snacks, i.e. nuts. I love peanuts, pistachios and the like, but they are not a necessary and vital part of my diet either. I’ll probably leave them aside for special occasions, like going to the movies or something like that.
In my next blog entry I will talk more about what kind of food you should be eating and avoiding, what processed food does to us and how we were all victimized by the trinity of evil: Big Food, Big Pharma and Big Government; all based on the excellent book Metabolical, written by Robert Lustig.
-
 @ 7f4f672a:c184579e
2023-08-02 19:17:30
@ 7f4f672a:c184579e
2023-08-02 19:17:30The feeling of Wonder inspired a whole generation to innovate, explore, experiment, and discover new technologies, places, theories, and ideas. This book goes on a journey with some of the era's finest characters and protagonists on their quest to quench their curiosity.
The stories of astronomer William Herschel , high-flying (and sometimes reckless) hot air balloonists, and the explorer Joseph Banks, bring the reader into this magical time - where anything seemed possible and Wonder captured not just the eccentrics, but the masses. I can't help but feel that this sense of Wonder is lost today. In an era inundated with information - we seem to have forgotten how little we truly know, or have eased into the false comfort of the status quo, choosing ignorance of the true depth of our ignorance. After huge success and advancement in the last 100 years - it is easy to be convinced that science can have a full stop, that it is a sentence we can finish. Inevitably, we will get a rude awakening, when the next William Herschel tunes their polished mirrors - and brings a whole new world into focus.
wonder #nostr
-
 @ 57fe4c4a:c3a0271f
2023-08-02 16:02:43
@ 57fe4c4a:c3a0271f
2023-08-02 16:02:43📝 Summary: The author argues that implementing a first seen safe rule would avoid negative impacts on merchants and users who accept unconfirmed transactions. However, the validity of this claim is questioned as no evidence of actual merchants accepting unconfirmed payments is found. Daniel Lipshitz disputes this conclusion, providing evidence of Coinspaid's use of 0-conf and offering to connect with the CEO for confirmation. He also mentions Changelly's confirmation of GAP600 as a service provider. The request for concrete examples of merchants relying on unconfirmed transactions remains unanswered. Lipshitz disputes the recipient's assessment of their dishonesty, providing evidence to support their claims and challenging the recipient to provide concrete examples. GAP600's research is based on monitoring transactions and network activity, not specific hashing pools or client engagement. Coinpaid's root addresses can be validated using tools like Chainanlysis, and Max at Coinpaid can confirm GAP600's use. Changelly may not have implemented GAP600's service across all its offerings.
👥 Authors: • Daniel Lipshitz ( nostr:npub1t97ak5ltnq0v72nv4jssnhw0fr09axwqvc20623jfdnvrajae7nqufg2yy ) • Peter Todd ( nostr:npub1m230cem2yh3mtdzkg32qhj73uytgkyg5ylxsu083n3tpjnajxx4qqa2np2 )
📅 Messages Date Range: 2023-08-01 to 2023-08-02
✉️ Message Count: 5
📚 Total Characters in Messages: 21371
Messages Summaries
✉️ Message by Peter Todd on 01/08/2023: The author argues that implementing a first seen safe rule would avoid negative impacts on merchants and users who accept unconfirmed transactions. However, the author questions the validity of the claim, as they could not find any evidence of actual merchants accepting unconfirmed payments.
✉️ Message by Daniel Lipshitz on 01/08/2023: The author claims that the research is not thorough and reaches an incorrect conclusion. They provide evidence of Coinspaid's use of 0-conf and offer to connect with the CEO for confirmation. They also mention speaking to Changelly for confirmation of GAP600 as a service provider. The author questions the need for full RBF and requests contacts of mining pools that have adopted it.
✉️ Message by Peter Todd on 02/08/2023: Daniel Lipshitz argues that the research is flawed and reaches an incorrect conclusion. He provides evidence of Coinspaid's use of 0-conf and offers to connect with Max, the CEO, for confirmation. He also mentions Changelly's offer to confirm GAP600 as a service provider. However, the request for concrete examples of merchants relying on unconfirmed transactions remains unanswered.
✉️ Message by Daniel Lipshitz on 02/08/2023: The sender disputes the recipient's assessment of their dishonesty, stating that it is based on baseless assumptions and lacks commercial experience. They provide evidence to support their claims and challenge the recipient to provide concrete examples.
✉️ Message by Daniel Lipshitz on 02/08/2023: GAP600's research is based on monitoring transactions and network activity. They do not assess specific hashing pools or engage with clients for their names and applications. Coinpaid's root addresses can be validated using tools like Chainanlysis. It is possible to reach out to Max at Coinpaid to confirm GAP600's use. Changelly may not have implemented GAP600's service across all its offerings.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ f8e6c643:03328ca9
2023-08-02 15:45:25
@ f8e6c643:03328ca9
2023-08-02 15:45:25Here’s the neat part, you don’t...
...or rather, you can’t find rare satoshis. Rare satoshis don’t exist because individual satoshis don’t actually exist within the bitcoin network, only UTXOs.
But my wallet says I have satoshis.
And the container of your food says it has calories. The bathroom scale says your body has lbs/kg. The tape measure says your floors have inches/cm. These are units of measure of a property of something, but they are not distinct individual units of the thing being measured. Calories measure energy. Scales measure mass. Rulers measure distance. These are properties of a thing, but not the thing itself.
Likewise, satoshis (aka, sats) are a unit of measure for bitcoin UTXOs, which are the "things" that actually exist within the bitcoin network. A UTXO, or "unspent transaction output," can be very small, only a few hundred sats, or it can be very large, hundreds of millions or even billions of sats, but there are only UTXOs measured in sats and spendable by their corresponding private keys. There are no satoshis sitting in storage in bitcoin wallets and nodes.
If that's true, then why is Bitcoin Magazine selling "rare satoshis"?
They are salesmen in search of profit, and not all salesmen are honest. The product they are selling misrepresents the truth. Put simply, Bitcoin Magazine is lying about what they are selling.
What they are actually selling is a UTXO measured in some amount of sats that can be cryptographically linked to another UTXO from the past that no longer exists. Why doesn't it exist? Because a UTXO is, by definition, "unspent." Once you spend one UTXO, new UTXOs are created and mined into a new block.
So I can't buy one of Hal Finney's satoshis?
Unfortunately, no, you cannot. At best you could pay someone like Bitcoin Magazine to spend one of their UTXOs to a new UTXO at an address you control. It is up to you to decide if the cryptographic link to previous entries in the ledger has any added value or meaning beyond the sats-denominated value of the UTXO.
It would be a little bit like if I had a dollar bill, and I went to the bank and deposited it into your account, and then the bank destroyed that physical bill and replaced it with a new one when you came in to withdraw it. While you would now possess access to the $1 of value, you would not have the dollar bill that I deposited. In fact, it no longer exists, even though there is proof on the bank's ledger of the transfer of value from me to you.
Ok, so what? I can do what i want with my money.
Yes, you can. That is the freedom afforded to you by bitcoin. You are free to trade your sats for a lesser amount of sats. It's just my opinion that you ought to at least understand that that's all you're doing.
🌽 🤙
-
 @ bcea2b98:7ccef3c9
2023-07-29 00:48:14
@ bcea2b98:7ccef3c9
2023-07-29 00:48:14I remember the first time I caught the neon glow of the blockchain data-stream pulsating through the old fiber-optic cables in the urban labyrinth of Neo-Tokyo. That was the year Satoshi’s dream, Bitcoin, had become the last refuge of economic freedom, our Prometheus unbound from the chains of tyrannical central banking. That was the year the world ended and started anew, all at once, like the flicker of an old digital display struggling to hold onto a single pixel of hope.
Cyber-Sentries, autonomous quantum-resistant algorithms birthed in the tech womb of Bitcoin Core, roamed the noospheric network, relentless in their hunt for anomalies that could threaten our crypto-republic. Their code was hardened against the threat of quantum decryption, a terror from the old-world that now lurked in the shadows of the darknet. Armed with Q-Diffusers, inventive tech developed to obscure any coherent superposition of qubits, the Sentries were the silent, digital paladins of our new world.
The Cyber-Sentries were the silent guardians of our cryptoverse, digital watchdogs built on an intricate framework of quantum-resistant algorithms. Brought to life in the crucible of Bitcoin Core, these Sentries were the vanguards of Satoshi's legacy, standing watch against potential threats.
Imagine a predator of the old-world, a wolf maybe, that would tirelessly patrol its territory, sniffing out any intruder that dared to violate its space. A Cyber-Sentry was much like that, except its territory was the vast terrain of the Bitcoin network, and its sense of smell was replaced by a near-infallible ability to detect irregularities and potential threats in the data streams.
These Sentries were powered by an advanced AI system, coded to learn and adapt to evolving threat landscapes. Every anomaly detected was analyzed, its signature extracted and stored in a vast neural repository, a cerebral vault of threat patterns. The Sentries learned from each encounter, evolving their defenses with every battle fought.
Each Sentry was armed with Q-Diffusers, state-of-the-art technology designed to disperse any coherent superposition of qubits. These Q-Diffusers would essentially introduce a deluge of quantum noise into the system of any would-be attacker, rendering their quantum computing capabilities useless. This was their primary defense against the quantum decryption threat, their shield against the spectral specter of the old-world quantum terror.
In action, the Cyber-Sentries were like specters, a ghost in the machine. Unseen, unheard, they roamed the neural pathways of the network, ceaselessly vigilant. When a threat was detected, they would swarm, a lightning-fast, coordinated response that left adversaries disoriented and defeated. They were not just defenders; they were also deterrents, their formidable reputation alone enough to ward off many would-be attackers.
Ever-present, though unseen, was the hum of the Lightning Network. Its evolution had exceeded even the wildest predictions of the cypherpunk prophets. Beyond mere instantaneous transactions, it now powered our communications, our commerce, our very lives. Its channels were our veins, the satoshis our lifeblood, coursing through the body of the new age, offering near-infinite scalability, an economic pulse for every living soul.
In this cryptic symphony, a new tech marvel played the sweetest tune. The Merkle Sanctum, an advanced shield technology, made the Bitcoin network impervious to attacks. At its core was the labyrinthine, self-regenerating maze of hash-based proof functions. Each function was an arcane spell in itself, casting away would-be invaders into oblivion. To attempt a breach was to confront infinity itself, a Sisyphean task for even the most formidable foe.
Merkle Sanctum was the magnum opus of cryptographic defense in the Bitcoin network, a technological marvel that made it nigh-impregnable to attacks. Named in honor of Ralph Merkle, one of the godfathers of modern cryptography, the Sanctum was more than just a defensive system. It was a monument to the boundless ingenuity of the human mind, a labyrinthine fortress constructed in the abstract plane of mathematical probabilities.
At its core, the Merkle Sanctum functioned as a self-regenerating maze of hash-based proof functions. These functions were cryptographic constructs, sequences of mathematical operations designed to protect the network. They were like invisible walls in the Sanctum, each one unique and insurmountable.
The true genius of the Sanctum was in its dynamic architecture. Each hash-based proof function was not static; it evolved with every transaction, every second that passed in the Bitcoin network. This made the Sanctum a dynamic, ever-changing labyrinth. Its walls shifted, its passages morphed, its structure regenerated in the blink of an eye. To an attacker, it presented a puzzle that was infinitely complex and perpetually changing.
This dynamic nature was powered by the pulse of the Bitcoin network itself. Each transaction, each data packet, each heartbeat of the network served as a seed of change, a catalyst for the regeneration of the Sanctum. It was a system in symbiosis with the network, drawing strength from the very activity it sought to protect.
Yet, despite its complexity, the Sanctum was not impenetrable. After all, the aim was not to exclude but to protect. Legitimate network participants could navigate through the labyrinth with the aid of cryptographic keys, their unique digital signatures acting as Ariadne's thread in the shifting maze. These keys allowed them to bypass the proof functions, moving through the Sanctum as if through open doors.
To invaders, however, the Sanctum presented a challenge of Herculean proportions. With its dynamic, ever-changing architecture, and near-infinite complexity, attempting to breach the Sanctum was like trying to capture a waterfall in a sieve. It was a task beyond the reach of even the most sophisticated quantum computer, a futile attempt to conquer a fortress that was as mercurial as it was formidable.
Humans huddled in the neon halo of their digital screens, their eyes reflecting the dancing symbols of hope and freedom. Pseudonymous, untraceable, they whispered to each other across the globe. Deals were brokered, wisdom shared, love declared - all in the cryptic tongue of Bitcoin. In this world on the edge of time, humanity had reclaimed its voice, and with it, the power to dream again.
The year 2140 dawned in the neural cortex of the global hivemind. In the alleyways of the silicon city, miners with their rigs, now relics of a different era, gathered for the last hurrah. These were the custodians of the cryptoverse, their ASICs humming lullabies of complex mathematical problems, their veins humming with electricity. The air was thick with hope and a sense of closure as they prepared to decipher the final hash.
The clock struck the hour, the Ledger of Eternity, a monumental quantum blockchain register, started the countdown. The world held its breath as the final block reward, a mere satoshi, the last of the 21 million, was offered up for claim. The blockchain was a spiderweb of transactions and mathematical riddles, intricate, indecipherable.
A hush fell over the data streams as the ASICs began their dance. The miners’ eyes glowed with the reflected light of the complex computations running on their screens. They could feel the pulse of the network in their blood, in the electrified air that buzzed around their rigs.
Then, in an almost anticlimactic moment, the final hash was deciphered, the block reward claimed. The last satoshi nestled itself in a digital wallet. The entire cryptoverse erupted in silent celebration, a solitary firework blossoming in the inky black of the datastream.
For the first time since its inception, Bitcoin existed without the promise of a block reward. Yet, it did not falter. It stood resilient in its quiet dignity, an economic lodestar in the chaotic quantum sea. For what had begun as an incentive mechanism was now a symbol of freedom, a testament to a world unshackled from the chains of traditional economic structures.
As 2140 rolled on, Bitcoin stood at the precipice of a new age. Without the block reward, it had transformed, yet again, to embody its core tenet of resilience. It was no longer a system driven by the promise of reward but one that thrived on the principles of decentralization and autonomy, the beacon of economic freedom in a brave, new digital world.
-
 @ 4d444439:7ed2458b
2023-08-02 14:18:49
@ 4d444439:7ed2458b
2023-08-02 14:18:49Historically, major breakthroughs and innovations were achieved when complex systems were studied and analyzed from interdisciplinary perspectives. For example, at low temperatures, the phenomenon of superconductivity and cryopreservation were discovered. Similarly, when altering the force of gravity, other forces like surface tension, capillary forces become predominant while sedimentation, hydrostatic pressure, and convection become absent.
Feel free to read all my articles on the anti-censorship long content platform yakihonne.com.
Image Credit: The Scientist
Since the International Space Station’s inception in 1980, NASA launched the first biological experiment with Commercial Generic Bioprocessing Apparatus (CGBA) in 1996 to study microgravity’s effects on biological samples. In the latter half of the 20th century the field of microgravity research has seen tremendous growth. Since then, microgravity research has rapidly advanced due to space technology advancements and a growing interest in exploring new scientific frontiers. Altered gene expressions, cellular signaling, and protein interactions in microgravity offer possibilities for groundbreaking medical discoveries and innovative pharmaceutical solutions, benefiting space exploration and healthcare on Earth.
Pharmaceutical studies in microgravity
Some pivotal areas of pharmaceutical research in microgravity encompass:
Protein crystallization- The absence of sedimentation and convection in microgravity allows for the formation of larger and more well-ordered protein crystals. These larger crystals yield higher-resolution structural data, providing a clearer picture of the protein’s structure. Consequently, this enhanced understanding of protein structures enables researchers to design more precise and effective drugs with improved target specificity.
Drug stability — Absence of gravity impacts drug stability, affecting diffusion, crystal formation, protein binding, and aggregation. During space travel, drugs encounter cosmic and solar radiation, leading to chemical degradation, polymerization, oxidation, and radical formation. Understanding drug stability in space is vital for maintaining crew health during space missions. Additionally, this research may impact drug manufacturing and storage on Earth, where drugs can be exposed to radiation during transportation or storage.
Drug delivery systems — In microgravity, drug delivery systems like microencapsulation, colloidal formulations, and nanoparticle formulations have piqued interest in space research. Microencapsulation involves enclosing drugs in microscopic particles or capsules, exhibiting different behaviors from Earth conditions, impacting drug release and stability. Similarly, nanoparticle formation and behavior in microgravity are affected, leading to improved homogeneity, reduced sedimentation, enhanced drug targeting, and controlled drug release. Such research optimizes drug delivery systems for space missions and offers valuable insights for terrestrial applications.
Pharmacokinetic studies — Pharmacokinetics refers to the study of how the body absorbs, distributes, metabolizes, and eliminates drugs. Several factors unique to the space environment can influence pharmacokinetics which include:
- Altered absorption
- Distribution changes
- Metabolism alterations
- Elimination effects
- Drug-drug interactions
- Spacecraft-specific factors such as temperature, humidity, and storage conditions.
By conducting pharmacokinetic studies in space, researchers can gain valuable insights into how drugs behave which can be used to optimize drug dosing, develop personalized medication regimens, and ensure astronauts’ health and well-being during space missions.
Pharmaceutical Companies embarking on Space-based Research
AstraZeneca initiated an investigation in collaboration with the ISS National Lab in 2019 to advance the development of a nanoparticle drug delivery system for therapeutic cancer vaccines. In this approach, nanoparticles play a crucial role as carriers for the drug, allowing targeted and controlled release, ultimately enhancing the treatment’s effectiveness while minimizing side effects.
The primary objective of the investigation is to study how nanoparticle formation occurs in microgravity. The expected outcome is the development of improved nanoparticle formulations for therapeutic cancer vaccines, which could potentially lead to more cost-effective treatments.
Earlier this year, Bristol Myers Squibb sent a selection of its protein-based medicines to the International Space Station (ISS) to study protein crystallization. By analyzing the higher-resolution crystals formed in microgravity, the company aims to improve the biomanufacturing of potent medicines, particularly those used to treat cancer. This research could lead to reformulating medicines as injectable doses, enhancing stability and concentration.
By identifying the physical conditions that promote large, high-quality crystals, Bristol Myers Squibb hopes to gain valuable insights for producing biologic medicines in crystal form.
Merck & Co. is utilizing the unique microgravity environment of the space station through a multinational collaboration to conduct research on monoclonal antibodies as crystalline suspensions. The primary objective of this research is to enhance drug delivery and manufacturing, aiming for safer and more convenient methods.
Merck’s experiments on the active ingredient in their oncology drug Keytruda demonstrated that crystals grown in space were smaller and more uniform compared to those grown on Earth. The crystals obtained from the space experiments showed improved properties, including lower viscosity and better injectability.
These findings allowed Merck to develop processes on Earth that mimic the results obtained in microgravity. The goal is to provide patients with a more straightforward and convenient way to receive monoclonal antibody crystalline suspensions. For instance, drugs like Keytruda, which currently require cumbersome multi-hour infusions, could potentially be administered as quick shots at the doctor’s office in the future, thanks to the insights gained from extraterrestrial research.
In 2020, European scientists conducted a groundbreaking COVID-19 medicine experiment in microgravity. The study aimed to understand how the drug remdesivir interacts with its delivery agent cyclodextrin, with the goal of improving the drug’s effectiveness. This research collaboration involved InnoStudio and Cyclolab, The objective was to increase the drug’s efficiency and reduce its risk profile by improving the drug formulation.
In conclusion, pharmaceutical research in microgravity holds exciting potential for revolutionizing the pharmaceutical and healthcare industry. Pharmaceutical companies are utilizing the ISS and space missions to enhance drug targeting with higher-resolution data. Through international collaborations, space-based research continues to drive cutting-edge medical science, even exploring antiviral drugs’ efficiency during the COVID-19 pandemic. Leveraging space’s unique conditions, the pharmaceutical industry’s involvement in microgravity research promises groundbreaking medical discoveries and innovative drug solutions, benefitting healthcare both in space and on Earth.
References
Pharma goes to space — Chemical & Engineering News Drugs in space: the pharmacy orbiting the Earth — The Pharmaceutical Journal Examining Nanoparticle Formation in Microgravity for Improved Therapeutic Cancer Vaccines Bristol Myers Squibb Heads to Outer Space ISS20: First NASA Research on Station
Article Author
Sasha Thomas — Biotech Scientist, Vellon Space
Contact: sasha@vellon.in
By:Vellon Space Link:https://vellonspace.medium.com/space-age-medicine-the-transformative-power-of-microgravity-research-in-pharmaceutical-studies-f9397eff65ff
-
 @ bcea2b98:7ccef3c9
2023-07-29 00:46:37
@ bcea2b98:7ccef3c9
2023-07-29 00:46:37The Year 2140
I remember the first time I caught the neon glow of the blockchain data-stream pulsating through the old fiber-optic cables in the urban labyrinth of Neo-Tokyo.
That was the year Satoshi’s dream, Bitcoin, had become the last refuge of economic freedom, our Prometheus unbound from the chains of tyrannical central banking That was the year the world ended and started anew, all at once, like the flicker of an old digital display struggling to hold onto a single pixel of hope.
Cyber-Sentries, autonomous quantum-resistant algorithms birthed in the tech womb of Bitcoin Core, roamed the noospheric network, relentless in their hunt for anomalies that could threaten our crypto-republic.
Their code was hardened against the threat of quantum decryption, a terror from the old-world that now lurked in the shadows of the darknet Armed with Q-Diffusers, inventive tech developed to obscure any coherent superposition of qubits, the Sentries were the silent, digital paladins of our new world.
The Cyber-Sentries were the silent guardians of our cryptoverse, digital watchdogs built on an intricate framework of quantum-resistant algorithms.
Brought to life in the crucible of Bitcoin Core, these Sentries were the vanguards of Satoshi's legacy, standing watch against potential threats.
Imagine a predator of the old-world, a wolf maybe, that would tirelessly patrol its territory, sniffing out any intruder that dared to violate its space.
A Cyber-Sentry was much like that, except its territory was the vast terrain of the Bitcoin network, and its sense of smell was replaced by a near-infallible ability to detect irregularities and potential threats in the data streams.
These Sentries were powered by an advanced AI system, coded to learn and adapt to evolving threat landscapes.
Every anomaly detected was analyzed, its signature extracted and stored in a vast neural repository, a cerebral vault of threat patterns The Sentries learned from each encounter, evolving their defenses with every battle fought.
Each Sentry was armed with Q-Diffusers, state-of-the-art technology designed to disperse any coherent superposition of qubits.
These Q-Diffusers would essentially introduce a deluge of quantum noise into the system of any would-be attacker, rendering their quantum computing capabilities useless This was their primary defense against the quantum decryption threat, their shield against the spectral specter of the old-world quantum terror.
In action, the Cyber-Sentries were like specters, a ghost in the machine.
Unseen, unheard, they roamed the neural pathways of the network, ceaselessly vigilant When a threat was detected, they would swarm, a lightning-fast, coordinated response that left adversaries disoriented and defeated They were not just defenders; they were also deterrents, their formidable reputation alone enough to ward off many would-be attackers.
Ever-present, though unseen, was the hum of the Lightning Network.
Its evolution had exceeded even the wildest predictions of the cypherpunk prophets Beyond mere instantaneous transactions, it now powered our communications, our commerce, our very lives Its channels were our veins, the satoshis our lifeblood, coursing through the body of the new age, offering near-infinite scalability, an economic pulse for every living soul.
In this cryptic symphony, a new tech marvel played the sweetest tune.
The Merkle Sanctum, an advanced shield technology, made the Bitcoin network impervious to attacks At its core was the labyrinthine, self-regenerating maze of hash-based proof functions Each function was an arcane spell in itself, casting away would-be invaders into oblivion To attempt a breach was to confront infinity itself, a Sisyphean task for even the most formidable foe.
Merkle Sanctum was the magnum opus of cryptographic defense in the Bitcoin network, a technological marvel that made it nigh-impregnable to attacks.
Named in honor of Ralph Merkle, one of the godfathers of modern cryptography, the Sanctum was more than just a defensive system It was a monument to the boundless ingenuity of the human mind, a labyrinthine fortress constructed in the abstract plane of mathematical probabilities.
At its core, the Merkle Sanctum functioned as a self-regenerating maze of hash-based proof functions.
These functions were cryptographic constructs, sequences of mathematical operations designed to protect the network They were like invisible walls in the Sanctum, each one unique and insurmountable.
The true genius of the Sanctum was in its dynamic architecture.
Each hash-based proof function was not static; it evolved with every transaction, every second that passed in the Bitcoin network This made the Sanctum a dynamic, ever-changing labyrinth Its walls shifted, its passages morphed, its structure regenerated in the blink of an eye To an attacker, it presented a puzzle that was infinitely complex and perpetually changing.
This dynamic nature was powered by the pulse of the Bitcoin network itself.
Each transaction, each data packet, each heartbeat of the network served as a seed of change, a catalyst for the regeneration of the Sanctum It was a system in symbiosis with the network, drawing strength from the very activity it sought to protect.
Yet, despite its complexity, the Sanctum was not impenetrable.
After all, the aim was not to exclude but to protect Legitimate network participants could navigate through the labyrinth with the aid of cryptographic keys, their unique digital signatures acting as Ariadne's thread in the shifting maze These keys allowed them to bypass the proof functions, moving through the Sanctum as if through open doors.
To invaders, however, the Sanctum presented a challenge of Herculean proportions.
With its dynamic, ever-changing architecture, and near-infinite complexity, attempting to breach the Sanctum was like trying to capture a waterfall in a sieve It was a task beyond the reach of even the most sophisticated quantum computer, a futile attempt to conquer a fortress that was as mercurial as it was formidable.
Humans huddled in the neon halo of their digital screens, their eyes reflecting the dancing symbols of hope and freedom.
Pseudonymous, untraceable, they whispered to each other across the globe Deals were brokered, wisdom shared, love declared - all in the cryptic tongue of Bitcoin In this world on the edge of time, humanity had reclaimed its voice, and with it, the power to dream again.
The year 2140 dawned in the neural cortex of the global hivemind.
In the alleyways of the silicon city, miners with their rigs, now relics of a different era, gathered for the last hurrah These were the custodians of the cryptoverse, their ASICs humming lullabies of complex mathematical problems, their veins humming with electricity The air was thick with hope and a sense of closure as they prepared to decipher the final hash.
The clock struck the hour, the Ledger of Eternity, a monumental quantum blockchain register, started the countdown.
The world held its breath as the final block reward, a mere satoshi, the last of the 21 million, was offered up for claim The blockchain was a spiderweb of transactions and mathematical riddles, intricate, indecipherable.
A hush fell over the data streams as the ASICs began their dance.
The miners’ eyes glowed with the reflected light of the complex computations running on their screens They could feel the pulse of the network in their blood, in the electrified air that buzzed around their rigs.
Then, in an almost anticlimactic moment, the final hash was deciphered, the block reward claimed.
The last satoshi nestled itself in a digital wallet The entire cryptoverse erupted in silent celebration, a solitary firework blossoming in the inky black of the datastream.
For the first time since its inception, Bitcoin existed without the promise of a block reward.
Yet, it did not falter It stood resilient in its quiet dignity, an economic lodestar in the chaotic quantum sea For what had begun as an incentive mechanism was now a symbol of freedom, a testament to a world unshackled from the chains of traditional economic structures.
As 2140 rolled on, Bitcoin stood at the precipice of a new age.
Without the block reward, it had transformed, yet again, to embody its core tenet of resilience It was no longer a system driven by the promise of reward but one that thrived on the principles of decentralization and autonomy, the beacon of economic freedom in a brave, new digital world.
-
 @ 4044176c:b3f3c23c
2023-08-02 13:42:06
@ 4044176c:b3f3c23c
2023-08-02 13:42:06Photo by Jason Leung on Unsplash
AI is a broad term that encompasses many different types of systems that can perform tasks that normally require human intelligence. The examples are reasoning, learning, planning, decision-making, and problem-solving.
However, not all AI systems are created equal. In fact, there are different levels of AI, depending on how general or specific their abilities are.
The AI that we see today in our smartphones, search engines, social media platforms, and smart devices is mostly narrow AI, or artificial narrow intelligence (ANI). ANI systems can excel at one or a few specific tasks, such as recognizing faces, playing chess, or translating languages.
They can do these tasks faster and better than humans, but they cannot do anything else. They are not flexible or adaptable to new situations or domains. They are not aware of themselves or their surroundings. They are not intelligent in the same way that humans are.
The AI that we often imagine in science fiction movies and novels is general AI, or artificial general intelligence (AGI). AGI systems can perform any intellectual task that a human can do, such as understanding natural language, reasoning logically, learning from experience, and creating new knowledge.
They can also transfer their skills and knowledge across different domains and contexts. They can think and act like humans, or even surpass them. They may have consciousness, emotions, and goals.
AGI is the ultimate goal of AI research, but it is also the most elusive and controversial one. There is no consensus among researchers on when or how AGI will be achieved, or even if it is possible at all.
Some are optimistic and predict that AGI could be developed by the mid-21st century, while others are skeptical and think that it is a distant or unrealistic goal.
Some are excited and hopeful about the benefits that AGI could bring to humanity, while others are worried and fearful about the risks and challenges that it could pose.
One of the biggest challenges of developing AGI is unsupervised learning, which is a type of machine learning that does not require labeled data but learns from the inherent structure or patterns in the data.
Unsupervised learning could enable a system to learn from any kind of data without human supervision or guidance. It could also enable a system to learn more generalizable and autonomous skills that could be applied to different tasks and situations.
However, unsupervised learning is also a very difficult and active area of research, with many open problems and limitations. Some of the recent advances in unsupervised learning include generative adversarial networks (GANs), which can generate realistic images or texts from random inputs. The other one is self-supervised learning, which can learn useful representations from unlabeled data by solving auxiliary tasks.
Photo by Possessed Photography on Unsplash
Another challenge of developing AGI is ethical and social responsibility.
If we ever create a system that can think and learn like humans, how should we treat it? How should we ensure that it aligns with our values and goals? How should we regulate its use and development?
These are not easy questions to answer, and they require careful consideration and collaboration among researchers, policymakers, industry leaders, civil society groups, and the general public.
We need to establish clear guidelines and principles for the design, development, and governance of AI systems. We need to ensure that AI systems are accountable, ethical, safe, and beneficial for all.
We also need to be aware of the potential dangers and threats that AI systems could pose to humanity if they are not aligned with our ethical values.
One of the worst scenarios that we want to avoid is autonomous weapons: weapons that can select and engage targets without human intervention.
Autonomous weapons could increase the speed, scale, and scope of warfare beyond human control. They could also lower the threshold for armed conflict and violate international humanitarian law.
AI is a remarkable technology that has already changed our world in many ways. But it is also a technology that has not yet reached its full potential or its full implications.
We need to be mindful of the opportunities and challenges that AI presents us with as we move forward in this exciting and uncertain journey.
We need to be curious and creative in exploring the possibilities of AI for enhancing our lives.
We have to be cautious and responsible in ensuring that AI serves our values and respects our dignity.
By:Rudi Widiyanto Link:https://medium.com/predict/how-far-are-we-from-achieving-agi-ad10bd641bb8
-
 @ e97aaffa:2ebd765d
2023-08-02 13:25:06
@ e97aaffa:2ebd765d
2023-08-02 13:25:06A entrada de WallStreet (através da criação de ETFs Spot) está a gerar opiniões contraditórias na comunidade de bitcoiners, uns são a favor, outros contra, mas a verdade é que o Bitcoin não quer saber. Bitcoin é a pura liberdade, utiliza quem quer e faz dele o que quer, isto é liberdade.
Eu sou um purista, não gosto dos EFTs, mas é uma realidade, temos que viver com isso. Se existe procura por estes ativos, é porque tem algum valor, logo são necessários. Desde que seja 1 para 1 (spot), sem reserva fracionária.
Eu acredito que estes ETFs e a respectiva entrada das grandes gestoras de ativos, como a BlackRock, vão desempenhar um papel importante no ecossistema, primeiro dá mais credibilidade ao Bitcoin e torna-o mais mainstream. Segundo, estes fundos vão dar um preço-alvo para orientar os seus clientes, aconselhando quando devem entrar ou sair do btc, evitando assim, que os cliente comprem na euforia e que venda no pânico, isto irá ajudar a reduzir a volatilidade do btc.
Os EFTs vão ajudar, mas não são essenciais para o bitcoin, mas é claro que acelera a adoção.
Stablecoins
Em países com inflação muito alta, a maioria das pessoas estão optando por stablecoins. A utilização do btc ainda é menor, devido à volatilidade.
Os países andam vigorosamente a criar regulamentações para poder controlar e limitar o mundo cripto, será uma espécie de colete de forças. Os EUA estão a criar regulamentação para as criptos, mas o principal alvo é as stablecoin em dólar. O FED vai querer rédeas curtas ou mesmo controlar as stablecoins de dólar.
No caso das stablecoins, eu sou a favor de algo mais drástico, o FED é que devia de controlar, não faz sentido ser uma empresa privada a fazer este serviço. A estrutura das stablecoins hoje em dia, coloca um risco adicional à moeda e agora (devido a sua dimensão) coloca também um risco ao sistema financeiro na generalidade.
As reservas são de tal dimensão, tornou-se um problema guardá-las:
- Se colocar nos bancos comerciais, os bancos têm reserva fracionária, se existir uma grande quantidade de levantamentos pode levar o banco à falência e consequentemente um grande problema na stablecoins, que pode levar ao seu colapso.
- Os bonds como colateral, talvez agora seja a melhor solução, mas também poderá ser um problema, caso exista uma corrida aos levantamentos de USDT. A Tether terá que fazer uma brusca venda de bonds, gerando uma desvalorização desses títulos no mercado, podendo criar problemas no resto da economia, que utilizam o Bonds como um seguro.
Esse montante de dinheiro tem que ficar à guarda direta do FED, é a única maneira de garantir toda a segurança. Por isso, eu concordo com o controle total das stablecoins de FIATs pelos seus respectivos bancos centrais.
Assim que a CBDCs estiver pronta, eu acredito que as stablecoins vão ser proibidas ou extremamente limitadas e com obrigação de KYC, irá provocar um êxodo em massa destes tokens.
No início, o objetivo das CBDCs era combater o Bitcoin, com o passar do tempo, o objetivo principal é combater as stablecoins.
O fim das stablecoins ( as pessoas não acreditam nas stablecoin algorítmicas) será um forte golpe nas DEXs, algo que os estados também querem controlar.
Expatriação de Capitais
O que está a acontecer agora na Argentina é um excelente exemplo e possivelmente vai acontecer em outros países com inflações altas.

O país está com uma inflação anual de 100%, o peso argentino perdeu 99% do seu valor nos últimos 20 anos e o povo para defender as suas poupanças está a utilizar massivamente stablecoins e bitcoin. Como eu acredito que os governos vão começar a restringir o uso de stablecoins, irá provocar um crescimento exponencial da utilização do btc como um meio de troca, como uma moeda.
A desvalorização da moeda FIAT não é só um problema para os locais, também acontece com as empresas multinacionais, que têm problemas em expatriar os seus capitais/lucros devido às políticas de controlo de capitais. Esses capitais estão na moeda local, as empresas não conseguem converter em dólares, ou por estar fortemente desvalorizado ou simplesmente não existem dólares disponíveis no mercado oficial.
A Argentina é um bom exemplo, onde existe uma diferença abismal entre o câmbio oficial e o informal.

As empresas portuguesas têm sofrido periodicamente problemas devido à escassez de dólares em Angola. Cada vez que o preço do crude cai, Angola entra em crise e voltam o problema da expatriação de capitais. Possivelmente estamos a entrar noutro momento crítico da economia angolana, o preço do crude está a cair e houve uma forte desvalorização do Kwanza, só em 2023 a queda é superior a 63% contra o dólar, não deverá faltar muito para as empresas começarem a apresentar dificuldades na expatriação.

Devido às suas características descentralizadas do Bitcoin, o tornam inconfiscável e impossível de o proibir, o que não acontece com as stablecoin. Assim o Bitcoin é a ferramenta ideal para o comércio internacional, será inevitável o seu uso.
Wallstreet através dos EFTs poderá acelerar a reduzir a volatilidade e estabilizar o preço, facilitando a adoção em larga escala. O btc vai circular nessas economias locais, as pequenas empresas e multinacionais poderão fazer as suas reservas em Bitcoin. Assim poderão expatriar capitais sem qualquer problemas, sem a necessidade da permissão de governos, será um win win.
Um bom exemplo de uma empresa que poderia beneficiar com isto, seria a Nestlé, está praticamente em todos os países do mundo. É um forte comprador de matérias primas em África, Ásia e América Latina, uma parte ou a totalidade desses produtos poderia ser pagos em Bitcoin, desenvolvendo as economias locais. Os produtos são transformados e exportados para as suas filiais. Por fim, as filiais expatriam os lucros para as sedes, tudo isto em Bitcoin.
Diásporas e Refugiados
Quem também está aproveitando as características intrínsecas do bitcoin, como incensurável e moeda global, são os refugiados.
Como existe controle nas fronteiras que confiscam o património ou grupos armados que roubam, os cidadãos guardam as suas poupança em bitcoin, é a solução utilizada por iranianos, sírios, ucranianos e muitos outros refugiados.
As diásporas também se beneficiam, o bitcoin permite enviar remessas sem pagar taxas exorbitantes e também permite enviar dinheiro para países com embargos, como Cuba. Querem embargos? façam aos tiranos, aos seus familiares e amigos, deixem os povos em paz, não tem culpa e já sofrem o suficiente no dia-a-dia. Castiguem os criminosos e deixem os inocentes viver.
Todos vamos beneficiar com a existência de uma moeda global e descentralizada, onde não seja possível ser manipulada por políticos.
Fix the Money, Fix the World
-
 @ 57fe4c4a:c3a0271f
2023-08-02 10:19:21
@ 57fe4c4a:c3a0271f
2023-08-02 10:19:21👥 Authors: Keagan McClelland ( nostr:npub1f2nxequ09nz44775vv6lkffq2plzqvrqramnk29eddmwcc9z7jys8ms289 )
📅 Messages Date: 2023-08-02
✉️ Message Count: 1
📚 Total Characters in Messages: 15187
Messages Summaries
✉️ Message by Keagan McClelland on 02/08/2023: There is a debate about whether to price space in the UTXO set to determine if transactions are spam. This could offend some Bitcoin users.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ bcea2b98:7ccef3c9
2023-07-28 13:48:57
@ bcea2b98:7ccef3c9
2023-07-28 13:48:57The book "Softwar: A Novel Theory on Power Projection and the National Strategic Significance of Bitcoin" by Jason P. Lowery offers an extensive exploration of Bitcoin through the lens of strategic and cybersecurity, as opposed to a purely fiscal one. It presents a novel theoretical paradigm for assessing the potential strategic national implications of Bitcoin, viewed as an electro-cyber defense technology as opposed to a decentralized electronic cash system.
The following are some pivotal arguments and possible inaccuracies from the standpoint of a Bitcoin developer:
Proof-of-work
The proposition that Bitcoin, via its proof-of-work protocol, can be perceived as an electro-cyber security framework allowing for the exertion of tangible power in the digital domain. Lowery posits that Bitcoin equips individuals with the capacity to enforce severe physical consequences (represented in wattage) on adversarial entities attempting to exploit them via software. This viewpoint conceptualizes Bitcoin as a mechanism for power projection, enabling individuals to establish and maintain an untrusting, permissionless, egalitarian, and decentralized dominion over bits of information, provided they have the will and capability to wield physical power to safeguard it (Page 245).
-
The critique here, though, points out that this is an intriguing perspective; the primary purpose of Bitcoin is to operate as a decentralized digital currency. The power projection elucidated by the author is an ancillary outcome of Bitcoin's decentralization and inherent security, rather than its primary intent. The function of Bitcoin's proof-of-work algorithm is to fortify the network against double-spending and other forms of attack, not to project power in a geopolitical context.
-
The book also proposes that Bitcoin could upheave human power-based dominance hierarchies from their foundational roots (Page 374). While it's undeniable that Bitcoin has the potential to disrupt conventional financial systems and power structures, it was not designed to be an instrument for power projection in the same way that military or economic resources are. Bitcoin is a tool for financial sovereignty and privacy, not a weapon for geopolitical power struggles.
-
The book seems to equate the physical power utilized in Bitcoin's proof-of-work algorithm (i.e., the energy expended to mine Bitcoin) with the notion of power projection in a geopolitical environment. While it's true that Bitcoin mining demands substantial energy resources, it is distinctly different from the concept of power projection, which usually involves employing military or economic force to influence the actions and behavior of other nations.
Bits and Value
The book asserts that the bits within Bitcoin can symbolize any kind of valuable data that individuals desire it to represent, including but not confined to financial information (Page 375). It further implies that once we have deduced how to keep financial bits of data physically secure against attack, we have in essence figured out how to protect all types of information from physical attack (Page 34).
-
While it is indeed factual that Bitcoin's blockchain can be employed to store and transmit non-financial data, it's crucial to understand that this is not its primary function. Bitcoin was developed as a peer-to-peer electronic cash system, with the primary objective of facilitating financial transactions without necessitating a trusted third party. The data that Bitcoin primarily processes is transaction data, i.e., detailing who transferred how much Bitcoin to whom.
-
The capability to store non-financial data on the Bitcoin blockchain is more of an unintended consequence of its design rather than a fundamental feature. This is accomplished by utilizing specific fields in the transaction data to store arbitrary data, but this practice is generally discouraged because it can result in blockchain bloat. The Bitcoin blockchain is not intended to function as a general-purpose data storage system, and employing it as such can induce inefficiencies.
-
Storing non-financial data on the Bitcoin blockchain does not offer any additional security advantages over storing financial data. The security of the Bitcoin blockchain is derived from its decentralized, proof-of-work consensus mechanism, which ensures that no single entity can control or manipulate the transaction history. This security extends equally to all data housed on the blockchain, whether it's financial or non-financial.
Strangler Pattern
The book suggests that Bitcoin could serve as a "strangler pattern" replacement of our legacy internet infrastructure with a modern architecture that isn’t as clearly susceptible to systemic exploitation and abuse (Page 376). The book further intimates that Bitcoin could operate as the preeminent mechanism employed by digital-age societies to map or anchor elements of the old internet version to the revamped version of the internet (Page 322).
-
While Bitcoin indeed introduces a new, decentralized paradigm for financial transactions and data storage, it isn't designed to supplant the entire internet infrastructure. The internet is an extensive and multifaceted system supporting a wide variety of applications and services, from email and web browsing to video streaming and cloud computing. In contrast, Bitcoin is a specific application that operates on the internet, designed to enable peer-to-peer financial transactions.
-
The claim made by the book appears to conflate the concept of a decentralized financial system (which Bitcoin offers) with the idea of a decentralized internet (which is a much broader and more intricate concept). While there are projects and technologies aiming to foster a more decentralized internet (such as InterPlanetary File System (IPFS) and various blockchain-based "Web 3.0" initiatives), Bitcoin is not one of them.
-
The book's suggestion that Bitcoin could serve as the dominant mechanism for tying the legacy internet to a new version of the internet is speculative and isn't substantiated by current technological realities. While it's true that blockchain technology (the underlying technology of Bitcoin) has potential applications in areas like decentralized identity systems and domain name systems, these are still largely experimental and have not been widely adopted yet.
Kinetic Power
The book propososes that Bitcoin could significantly transform the way humans vie for control over valued resources, effectively resetting the global balance of power in a manner akin to the profound changes brought about by full-scale kinetic world wars (Page 376). The author further proposes that Bitcoin could revolutionize the perception of physical confrontation in the digital-age society (Page 370). Moreover, it's implied that global adoption of an electro-cyber form of physical power competition, facilitated by proof-of-work technologies like Bitcoin, could lead to the genesis of a completely novel form of polity (Page 385).
-
It is undeniable that Bitcoin holds the potential to disrupt conventional financial systems and power structures. However, juxtaposing its impact to the scale and consequences of world wars is hyperbolic and speculative. World wars resulted in massive loss of human lives, extensive destruction, and substantial shifts in geopolitical boundaries and power structures. In contrast, Bitcoin is a digital currency that operates on a decentralized network. While it can indeed influence financial systems and potentially disrupt some power structures, particularly those related to finance and banking, it is incapable of causing physical destruction or loss of life.
-
The book suggests that Bitcoin could spawn a completely new form of polity is speculative and isn't supported by current realities. Although Bitcoin and other cryptocurrencies can indeed influence how people transact and store value, they don't intrinsically alter the fundamental nature of societal organization or governance. They may contribute to shifts in power dynamics, particularly in the financial sector, but they do not supplant the need for traditional forms of governance and societal organization.
-
The book also seems to conflate the concept of power competition in a geopolitical context with the concept of power competition in the context of Bitcoin mining. Bitcoin mining does involve a form of competition, as miners compete to solve complex mathematical problems to add new blocks to the blockchain and receive Bitcoin rewards. However, this is far from the concept of power competition in a geopolitical context, which involves nations competing for resources, influence, and dominance on the global stage.
Projecting Power
The book asserts that Bitcoin, through its proof-of-work technology, could help society secure itself against systemic exploitation of computer networks (Page 378). The author argues that Bitcoin could empower individuals to physically secure their digital information, by projecting physical power in, from, and through cyberspace to impose severe physical costs on those who exploit our computing systems (Page 347). The author further speculates that national adoption of Bitcoin could be conceptualized as the employment of an electro-cyber militia to safeguard and defend a nation’s valuable digital information (Page 360).
-
While it's true that Bitcoin and other cryptocurrencies can provide a level of security and privacy not available in traditional financial systems, it's crucial to underscore that they also introduce new vulnerabilities and potential for misuse. Bitcoin transactions are irreversible, which can make them appealing for fraudulent activities. Bitcoin wallets can be lost or stolen if not adequately secured. The security of the Bitcoin network itself hinges on its decentralized nature and the computational power required to alter the blockchain, but individual users are still susceptible to scams and hacking.
-
The book's suggestion that Bitcoin could serve as a form of "electro-cyber militia" is speculative and not universally accepted within the Bitcoin community. Although Bitcoin does offer a method for individuals to secure their financial transactions against interference from third parties, it is not designed to shield against all forms of cyber exploitation or to serve as a form of national defense.
-
In conclusion, Softwar presents an unconventional viewpoint on Bitcoin's potential influence on national strategic security, proffering that Bitcoin could serve as an effective tool for power projection, system defense, and even societal reorganization. However, these propositions, while intriguing, often veer towards the speculative and seem to be somewhat misaligned with the predominant understanding of Bitcoin's primary purpose and functionality within the field of computer science.
-
While this book undoubtedly offers a unique and thought-provoking perspective on Bitcoin's wider implications, it is crucial to approach these theories with a discerning and critical eye. It is always beneficial to juxtapose such theories with the broader consensus within the Bitcoin development and computer science communities, to gain a more rounded understanding of this remarkable technology. Ultimately, Bitcoin continues to evolve and its full potential, while yet to be fully realized, remains a subject of intense debate and exploration within the computer science community.
-
-
 @ 7f4f672a:c184579e
2023-08-02 07:23:15
@ 7f4f672a:c184579e
2023-08-02 07:23:15Obsidian is an amazing markdown editor, word processor, note organiser, and idea synthesiser: the perfect tool for writers.
Nostr represents the future of how we communicate and distribute the written word: decentralised, free, independent, incorruptible.
They seem to me to be a match made in heaven...
For Writers
This tool is low-friction..
- Add your Nostr private key (once on set-up).
- Write in Obsidian
- Hit publish to Nostr, and that's it.
A Quiet Place
Avoid the web browser and all it's distractions!
This tool is completely abstracted from Nostr, allowing you to stay focused - the plugin does not read Nostr messages or give you any view into the public space. It just publishes what you've written. Stay focused on your work and disconnected from the noise.
Writing On Nostr
It's time to start building your blog, speaking to your audience, and publishing your work freely outside of any walled garden.
With Nostr, you are not wed to any platform like Substack, Medium, or Twitter - who can all shut you down and delete your work with the push of a button.
Why Nostr?
-
Ownership: When you post on Nostr, you own your content. There's no platform claiming any rights to your work, so you can do what you want with it - republish it, sell it, etc.
-
Get Paid (No Middlemen): Nostr allows for direct monetization options, you can earn directly from your readers without sharing a percentage of your earnings with a platform like Substack or Twitter.
-
Readership Building: Nostr allows writers to build and manage their own communities. This can foster a more personal and engaged readership compared to larger, more impersonal platforms.
-
Open-source and Community-driven: As an open-source project, Nostr is driven by the community and its development is guided by the needs and wants of its users. You are not at the mercy of corporate decisions or profit-driven changes.
-
Cost-Effective: Nostr does not charge you fees for using their platform, unlike platforms like Substack. This makes it an economical choice for writers, particularly those who are just starting out or those who want to maximize their earnings.
Long-Form Content
On Nostr you can write messages specifically tagged as "long-form". This tool publishes messages of this kind. Long-form content aggregators and clients such as https://habla.news & https://blogstack.io/ specifically channel these messages to readers. There'll be much more in the future.. 😉
Short-Form Content
This tool focuses on publishing full .md files in the long-form from Obsidian. However, if you've got a short message to send out there - an idea or a quip - just toggle on short-form writer in settings; this will give you a place to write a message and send.
Security Notice
This plugin stores your private key within your local Obsidian settings file, specifically in:
```
/.obsidian/plugins/obsidian-nostr-writer/data.json ```
It is not transmitted elsewhere, but its security is fundamentally tied to the security of your device and Obsidian files.
Please be aware that if an unauthorized person gains access to your device or your Obsidian files, they might be able to access your private key. The plugin obscures the key in its settings interface but this doesn't equate to strong encryption or secured storage.
Therefore, it's important to ensure the overall security of your device and your Obsidian files to keep your private key safe.
Remember, the security of your private key is your responsibility.
grownostr #buildingonnostr #obsidian #writers #writing
-
 @ 29621ac8:a3e8f4ea
2023-08-02 05:33:49
@ 29621ac8:a3e8f4ea
2023-08-02 05:33:49In the context of unincorporated associations and private membership associations, the concepts of intimate association and expressive association are crucial in understanding the rights and protections afforded to these entities under the law. These two types of associations are distinguished by the nature of their relationships and the purposes they serve.
Intimate Association refers to the close, personal relationships that are formed within a small, selective group of individuals. These relationships are typically characterized by a high degree of intimacy, trust, and mutual concern for one another's well-being. In the context of an unincorporated association or private membership association, intimate associations may include family units, close-knit social clubs, or other small groups that are formed for primarily personal reasons. The law recognizes the importance of protecting the freedom to form and maintain such intimate relationships, as they are essential to an individual's emotional and psychological well-being.
Expressive Association, on the other hand, pertains to the collective expression, advocacy, or pursuit of shared beliefs, ideas, or interests by a group of individuals. These associations are typically larger and more diverse than intimate associations, and their primary purpose is to engage in activities that promote or advance a particular cause, viewpoint, or mission. Examples of expressive associations include political organizations, labor unions, and advocacy groups. The law protects the right to form and participate in expressive associations, as they are vital to the functioning of a democratic society and the exercise of free speech.
In the context of unincorporated associations and private membership associations, the distinction between intimate and expressive associations is important for several reasons. First, it helps to determine the scope of legal protections and rights afforded to these entities. For instance, intimate associations may be entitled to greater privacy protections, while expressive associations may enjoy broader free speech rights.
Second, the distinction between intimate and expressive associations can impact the legal obligations and liabilities of the association and its members. For example, an unincorporated association engaged in expressive activities may be subject to certain disclosure requirements or campaign finance regulations, whereas an intimate association may be exempt from such requirements.
Lastly, the classification of an association as either intimate or expressive can have implications for its governance structure, membership criteria, and internal decision-making processes. For instance, intimate associations may have more informal governance structures and less stringent membership requirements, while expressive associations may require more formalized governance and membership processes to ensure the effective pursuit of their objectives. The concepts of intimate association and expressive association play a critical role in shaping the legal rights, obligations, and protections afforded to unincorporated associations and private membership associations. Understanding the distinction between these two types of associations is essential for navigating the complex legal landscape surrounding these entities and ensuring their compliance with applicable laws and regulations.
-
 @ 9ecbb0e7:06ab7c09
2023-08-02 02:32:59
@ 9ecbb0e7:06ab7c09
2023-08-02 02:32:59Los turoperadores de Rusia acaban de hundir las expectativas de que Cuba se convierta en un destino preferente para sus veraneantes durante el duro invierno en la nación euroasiática. Y es que, según sus consideraciones, hay varios destinos mucho más económicos.
De acuerdo con un reporte de la Asociación de Operadores Turísticos de Rusia (ATOR), Cuba va a ser uno de los lugares más caros para veranear en la denominada temporada alta en la Isla, justo cuando la industria del ocio local espera conseguir sus mayores beneficios.
Según los agentes de viajes, en la próxima temporada otoño-invierno, los turistas rusos que quieran relajarse en el mar elegirán entre tres países: Tailandia, Egipto y los Emiratos Árabes Unidos. En cambio, los destinos más caros serán Cuba y las Islas Seychelles.
Según el medio ruso Lenta.ru, en los Emiratos Árabes Unidos nueve días costarán para esas fechas a partir de 152.000 rublos (poco más de 1.600 dólares), mientras que un paquete de nueve noches en Tailandia es solo un poco más caro, y valdrá alrededor de 174.000 rublos (casi 1.900 dólares) para dos.
En cambio, una reservación vacacional de similares características a Cuba no baja de los 190.000 rublos (casi 2.100 dólares).
Los pronósticos de ATOR se dan a conocer poco después de que las cifras del primer semestre de 2023 mostraran un incremento de apenas el 45% de veraneantes rusos en Cuba, en comparación con igual periodo de 2022.
De acuerdo con datos de la Embajada de Cuba en la Federación de Rusia, entre enero y junio de 2023 visitaron la Isla 67.600 turistas procedentes de la nación euroasiática. La asesora de turismo de la sede diplomática, Christina León Iznaga, indicó que ahora Rusia es el cuarto mercado turístico de la Isla, superada por Canadá, que ha vuelto a ser el principal emisor, los cubanos residentes en el exterior, y los turistas de Estados Unidos.
Los números de la primera mitad de 2023 no son todo lo halagüeños que quisiera La Habana, pues en 2021 habían viajado a la Isla 178.000 veraneantes de Rusia.
"Según los turoperadores, el interés de los turistas rusos por el destino cubano es alto incluso en verano: se puede volar a Cuba en agosto durante siete días a un hotel 5 estrellas todo incluido por precios a partir de los 200.000 rublos (poco más de 2.200 dólares) para dos personas", indicó ATOR.
"Gracias al lanzamiento de vuelos regulares a Varadero, los turoperadores han ampliado la gama de productos para el destino caribeño: por ejemplo, han aparecido los tours combinados Habana + Varadero. Según los expertos, para finales de año la Isla puede recibir al menos 100.000 turistas", aseguró la entidad.
En julio último, Juan Carlos García Granda, ministro de Turismo cubano, dijo ante los diputados a la Asamblea Nacional del Poder Popular reunidos en La Habana que el turismo cubano mantiene la línea de recuperación, tras el impacto negativo que la pandemia de Covid-19 provocó sobre este sector estratégico para el régimen.
El funcionario detalló que el arribo total de viajeros en el primer semestre de 2023 ascendió a 1.298.539, que planteó como una recuperación del 50% respecto a 2019.
Ante tales cifras, el economista cubano Pedro Monreal advirtió: "El Gobierno cubano debería revisar la meta de 3,5 millones de turistas en 2023. Los datos de junio no hacen creíble ese objetivo. Con un acumulado de 1.289.539 visitantes en el primer semestre, se necesitarían 2.201.461 en el segundo semestre, pero tal nivel nunca ha sido alcanzado".
"El número máximo histórico de visitantes recibidos por Cuba en un segundo semestre es 2.199.408, y se registró en 2018, que tiene el récord anual de visitantes, con 4.68 millones. No es plausible asumir que el segundo semestre de 2023 será mejor que igual periodo de 2018", subrayó.
-
 @ 9ecbb0e7:06ab7c09
2023-08-02 02:30:27
@ 9ecbb0e7:06ab7c09
2023-08-02 02:30:27Operadores de empresas de personal laboral con sede en Key West, condado de Monroe, han sido sentenciados a prisión por delitos relacionados con impuestos e inmigración, según un comunicado del Departamento de Justicia de Estados Unidos (DOJ, por sus siglas en inglés).
En este caso se encuentran involucradas compañías como PSEB Services JD, Inc., Paradise Hospitality Solutions LLC, Paradise Hospitality Group LLC, Paradise Hospitality Inc. y HBSM Corp.
De acuerdo con documentos judiciales y declaraciones presentadas ante el tribunal, durante un período comprendido entre enero de 2014 y noviembre de 2020, Eka Samadashvili, Davit Pavliashvili y otros colaboradores dirigieron una serie de empresas de contratación de personal.
Mediante sus operaciones facilitaron la contratación de extranjeros con estancia irregular en EEUU. Pese a la falta de autorización, estas personas comenzaron a trabajar en hoteles, bares y restaurante del islote y otras localidades de Florida.
Lo más preocupante es que estas empresas no cumplían con sus obligaciones tributarias al no retener los ingresos federales, así como los impuestos del Seguro Social y Medicare de los salarios de los trabajadores, y tampoco informaban estos salarios al Servicio Interno de Impuestos (IRS, por sus siglas en inglés).
El comunicado precisó que Samadashvili recibió una pena de 36 meses de prisión por conspirar para albergar extranjeros e inducirlos a permanecer en territorio estadounidense, además de conspirar para defraudar al país.
El juez del Tribunal Federal de Distrito, José E. Martínez, ordenó también que este sujeto cumpla tres años de libertad supervisada y realice una restitución por un monto cercano a los ocho millones 473 mil 785 dólares a favor del Estado.
Pavliashvili fue condenado a 18 meses de prisión por conspirar para albergar a extranjeros e inducirlos a permanecer en el país norteño, así como por presentar una declaración de impuestos federales falsa ante el IRS. Este acusado también deberá cumplir tres años de libertad supervisada y pagar aproximadamente 16.925 dólares en concepto de restitución.
Este fallo es una muestra más de la lucha contra el empleo ilegal y la evasión fiscal en EEUU, y también refuerza la importancia de que las empresas cumplan con sus responsabilidades legales.
La investigación y el enjuiciamiento de este caso estuvieron a cargo del fiscal federal para el Distrito Sur de Florida, Markenzy Lapointe; y el fiscal general adjunto interino de la División de Impuestos del Departamento de Justicia, Stuart M. Golberg.
También colaboraron el agente especial de Investigaciones de Seguridad Nacional en Miami, Anthony Salisbury; y el agente especial a cargo de la Línea de Investigación Criminal del IRS (IRS-CI), Oficina de Campo de Miami, Matthew D.
-
 @ bcea2b98:7ccef3c9
2023-07-28 13:37:09
@ bcea2b98:7ccef3c9
2023-07-28 13:37:09Nym's review of Software:
The book "Softwar: A Novel Theory on Power Projection and the National Strategic Significance of Bitcoin" by Jason P. Lowery offers an extensive exploration of Bitcoin through the lens of strategic and cybersecurity, as opposed to a purely fiscal one. It presents a novel theoretical paradigm for assessing the potential strategic national implications of Bitcoin, viewed as an electro-cyber defense technology as opposed to a decentralized electronic cash system.
The following are some pivotal arguments and possible inaccuracies from the standpoint of a Bitcoin developer:
- The proposition that Bitcoin, via its proof-of-work protocol, can be perceived as an electro-cyber security framework allowing for the exertion of tangible power in the digital domain. Lowery posits that Bitcoin equips individuals with the capacity to enforce severe physical consequences (represented in wattage) on adversarial entities attempting to exploit them via software. This viewpoint conceptualizes Bitcoin as a mechanism for power projection, enabling individuals to establish and maintain an untrusting, permissionless, egalitarian, and decentralized dominion over bits of information, provided they have the will and capability to wield physical power to safeguard it (Page 245).
The critique here, though, points out that this is an intriguing perspective; the primary purpose of Bitcoin is to operate as a decentralized digital currency. The power projection elucidated by the author is an ancillary outcome of Bitcoin's decentralization and inherent security, rather than its primary intent. The function of Bitcoin's proof-of-work algorithm is to fortify the network against double-spending and other forms of attack, not to project power in a geopolitical context.
The book also proposes that Bitcoin could upheave human power-based dominance hierarchies from their foundational roots (Page 374). While it's undeniable that Bitcoin has the potential to disrupt conventional financial systems and power structures, it was not designed to be an instrument for power projection in the same way that military or economic resources are. Bitcoin is a tool for financial sovereignty and privacy, not a weapon for geopolitical power struggles.
The book seems to equate the physical power utilized in Bitcoin's proof-of-work algorithm (i.e., the energy expended to mine Bitcoin) with the notion of power projection in a geopolitical environment. While it's true that Bitcoin mining demands substantial energy resources, it is distinctly different from the concept of power projection, which usually involves employing military or economic force to influence the actions and behavior of other nations.
- The book asserts that the bits within Bitcoin can symbolize any kind of valuable data that individuals desire it to represent, including but not confined to financial information (Page 375). It further implies that once we have deduced how to keep financial bits of data physically secure against attack, we have in essence figured out how to protect all types of information from physical attack (Page 34).
While it is indeed factual that Bitcoin's blockchain can be employed to store and transmit non-financial data, it's crucial to understand that this is not its primary function. Bitcoin was developed as a peer-to-peer electronic cash system, with the primary objective of facilitating financial transactions without necessitating a trusted third party. The data that Bitcoin primarily processes is transaction data, i.e., detailing who transferred how much Bitcoin to whom.
The capability to store non-financial data on the Bitcoin blockchain is more of an unintended consequence of its design rather than a fundamental feature. This is accomplished by utilizing specific fields in the transaction data to store arbitrary data, but this practice is generally discouraged because it can result in blockchain bloat. The Bitcoin blockchain is not intended to function as a general-purpose data storage system, and employing it as such can induce inefficiencies.
Storing non-financial data on the Bitcoin blockchain does not offer any additional security advantages over storing financial data. The security of the Bitcoin blockchain is derived from its decentralized, proof-of-work consensus mechanism, which ensures that no single entity can control or manipulate the transaction history. This security extends equally to all data housed on the blockchain, whether it's financial or non-financial.
- The book suggests that Bitcoin could serve as a "strangler pattern" replacement of our legacy internet infrastructure with a modern architecture that isn’t as clearly susceptible to systemic exploitation and abuse (Page 376). The book further intimates that Bitcoin could operate as the preeminent mechanism employed by digital-age societies to map or anchor elements of the old internet version to the revamped version of the internet (Page 322).
While Bitcoin indeed introduces a new, decentralized paradigm for financial transactions and data storage, it isn't designed to supplant the entire internet infrastructure. The internet is an extensive and multifaceted system supporting a wide variety of applications and services, from email and web browsing to video streaming and cloud computing. In contrast, Bitcoin is a specific application that operates on the internet, designed to enable peer-to-peer financial transactions.
The claim made by the book appears to conflate the concept of a decentralized financial system (which Bitcoin offers) with the idea of a decentralized internet (which is a much broader and more intricate concept). While there are projects and technologies aiming to foster a more decentralized internet (such as InterPlanetary File System (IPFS) and various blockchain-based "Web 3.0" initiatives), Bitcoin is not one of them.
Additionally, the book's suggestion that Bitcoin could serve as the dominant mechanism for tying the legacy internet to a new version of the internet is speculative and isn't substantiated by current technological realities. While it's true that blockchain technology (the underlying technology of Bitcoin) has potential applications in areas like decentralized identity systems and domain name systems, these are still largely experimental and have not been widely adopted yet.
- The book propososes that Bitcoin could significantly transform the way humans vie for control over valued resources, effectively resetting the global balance of power in a manner akin to the profound changes brought about by full-scale kinetic world wars (Page 376). The author further proposes that Bitcoin could revolutionize the perception of physical confrontation in the digital-age society (Page 370). Moreover, it's implied that global adoption of an electro-cyber form of physical power competition, facilitated by proof-of-work technologies like Bitcoin, could lead to the genesis of a completely novel form of polity (Page 385).
It is undeniable that Bitcoin holds the potential to disrupt conventional financial systems and power structures. However, juxtaposing its impact to the scale and consequences of world wars is hyperbolic and speculative. World wars resulted in massive loss of human lives, extensive destruction, and substantial shifts in geopolitical boundaries and power structures. In contrast, Bitcoin is a digital currency that operates on a decentralized network. While it can indeed influence financial systems and potentially disrupt some power structures, particularly those related to finance and banking, it is incapable of causing physical destruction or loss of life.
The book suggests that Bitcoin could spawn a completely new form of polity is speculative and isn't supported by current realities. Although Bitcoin and other cryptocurrencies can indeed influence how people transact and store value, they don't intrinsically alter the fundamental nature of societal organization or governance. They may contribute to shifts in power dynamics, particularly in the financial sector, but they do not supplant the need for traditional forms of governance and societal organization.
The book also seems to conflate the concept of power competition in a geopolitical context with the concept of power competition in the context of Bitcoin mining. Bitcoin mining does involve a form of competition, as miners compete to solve complex mathematical problems to add new blocks to the blockchain and receive Bitcoin rewards. However, this is far from the concept of power competition in a geopolitical context, which involves nations competing for resources, influence, and dominance on the global stage.
- The book asserts that Bitcoin, through its proof-of-work technology, could help society secure itself against systemic exploitation of computer networks (Page 378). The author argues that Bitcoin could empower individuals to physically secure their digital information, by projecting physical power in, from, and through cyberspace to impose severe physical costs on those who exploit our computing systems (Page 347). The author further speculates that national adoption of Bitcoin could be conceptualized as the employment of an electro-cyber militia to safeguard and defend a nation’s valuable digital information (Page 360).
While it's true that Bitcoin and other cryptocurrencies can provide a level of security and privacy not available in traditional financial systems, it's crucial to underscore that they also introduce new vulnerabilities and potential for misuse. Bitcoin transactions are irreversible, which can make them appealing for fraudulent activities. Bitcoin wallets can be lost or stolen if not adequately secured. The security of the Bitcoin network itself hinges on its decentralized nature and the computational power required to alter the blockchain, but individual users are still susceptible to scams and hacking.
The book's suggestion that Bitcoin could serve as a form of "electro-cyber militia" is speculative and not universally accepted within the Bitcoin community. Although Bitcoin does offer a method for individuals to secure their financial transactions against interference from third parties, it is not designed to shield against all forms of cyber exploitation or to serve as a form of national defense.
In conclusion, Softwar presents an unconventional viewpoint on Bitcoin's potential influence on national strategic security, proffering that Bitcoin could serve as an effective tool for power projection, system defense, and even societal reorganization. However, these propositions, while intriguing, often veer towards the speculative and seem to be somewhat misaligned with the predominant understanding of Bitcoin's primary purpose and functionality within the field of computer science.
While this book undoubtedly offers a unique and thought-provoking perspective on Bitcoin's wider implications, it is crucial to approach these theories with a discerning and critical eye. It is always beneficial to juxtapose such theories with the broader consensus within the Bitcoin development and computer science communities, to gain a more rounded understanding of this remarkable technology. Ultimately, Bitcoin continues to evolve and its full potential, while yet to be fully realized, remains a subject of intense debate and exploration within the computer science community.
-
 @ 28246aee:62b108ad
2023-08-02 02:27:20
@ 28246aee:62b108ad
2023-08-02 02:27:20This post was originally published on https://tftc.io by Marty Bent.
Japan bonds (JGBs, corporates, etc) have come under tremendous pressure since the BOJ's mild tweak to yield curve control.
Group just clocked the worst 2-day slump in at least 23 years pic.twitter.com/lhkxN2BHJj
— David Ingles (@DavidInglesTV) July 31, 2023
As everyone and their mother seems to be mentally prepping for a soft landing, it seems that things are starting to go terribly awry in the world of sovereign debt. Late last week the Bank of Japan made a surprise policy change and didn't put a confident foot forward when changing the range within which they plan to employ yield curve control. Since the policy change JGBs have experienced their worst two-day slump in at least 23 years and the yen has weakened significantly against the dollar. Reaching 142.5 earlier today. In layman's terms, markets are signsling that the little confidence they had left in the Bank of Japan's ability to maintain the monetary system was just destroyed with this spastic move. This move follows their abrupt policy change around Christmas of last year, which spooked markets at the time.
In a world that runs on a hyper-connected and intertwined financial system where everything everywhere needs to be in place for everything to function properly, the Bank of Japan, the JGB market, and the yen are the canary in the coal mine that signal turbulance on the horizon. And if we pan over to the US, things aren't looking so hot on the sovereign debt side of things either.
Earlier today, Fitch downgraded the US governments sovereign debt rating to AA+ from AAA. Joining S&P which downgraded to AA+ in 2011. Leaving the US with no AAA rating to point at while declaring that it has iron clad credit. While we've learned to be wary of credit ratings coming from these ratings agencies due to their abject negligence and pandering during the lead up to the 2008 finacial crisis, it is safe to say that the US debt situation is becoming impossible to ignore. These agencies tend to be very generous with their ratings. If they're downgrading the US government, you know things have to be pretty bad. Likely much worse than a AA+ status. Just look at how much debt Treasury is looking to take out to finish out their pillaging of the American people in 2023.
The Treasury's new guidance today is that they want borrow
::checks notes::
$1.85 trillion during the second half of this year. pic.twitter.com/zIYTB38oDe
— Lyn Alden (@LynAldenContact) July 31, 2023
If my back-of-the-napkin math is in the right ballpark, we're about to increase the national debt by ~10% this year. Utter insanity. And don't look now, but oil prices have been creeping higher and look like they are about to break out. Especially when you consider the inventory draws we've seen recently.
WTI first consecutive closes over the 40-week MA since July 2022. pic.twitter.com/oGLXTy2lQL
— Larry Tentarelli, Blue Chip Daily (@LMT978) July 31, 2023
Your Uncle Marty thinks the inflation problem is still pervasive, but it will begin to become even more obvious as it will be forced to be recognized by CPI prints because of energy costs rising. Let's hope this superconducter stuff is legit.
I don't think there's anything more attractive on the planet than bitcoin hovering between $28,500 and $31,000. The tremors are beginning to rumble louder and louder, the central banks have lost control of their monetary systems and the governments have absolutely no ability to stop themselves from binging on debt, which makes for a pretty precarious situation. It's not shocking that they want you focused on aliens, climate change, and the latest round of Trump indictments. They have completely lost control of the money behind the scenes.
Final thought...
Headed to the Big Apple tomorrow. Come check out the mining mert up at PubKey tomorrow night if you're in town.

You have your place to buy Bitcoin, but have you tried River? It’s where all the Bitcoiners are now going. See why at River.com/TFTC

Sleep soundly at night knowing your bitcoin are secured by multisig.


This rag was delivered to you via Ghost. If you are thinking about starting a newsletter or website and are looking for the most robust and sovereign option you should check out Ghost. For sovereign payments connect your Ghost site to Scrib.
-
 @ 9ecbb0e7:06ab7c09
2023-08-02 02:24:49
@ 9ecbb0e7:06ab7c09
2023-08-02 02:24:49El 1 de agosto de 2023 comenzó en La Habana la campaña “Cero Efectivo” impulsada por la Empresa Eléctrica del territorio para suprimir por completo el cobro de la factura de corriente con dinero en efectivo. Las únicas vías posibles que ahora les quedan a los clientes que pertenecen a las oficinas comerciales de Plaza, Nuevo Vedado, Almendares y Santa Fe es la vía digital.
Para el pago electrónico hace falta tener una tarjeta magnética de un banco cubano que tenga saldo suficiente en pesos cubanos (CUP). Además, es necesario un teléfono celular con conexión a Internet y dominio tecnológico para efectuar todo el procedimiento.
Aquellos que no puedan reunir todos estos requisitos, un grupo donde se pueden incluir múltiples personas de la tercera edad que viven solas, tienen la opción de acudir a un “vecino solidario”, según declaraciones del director de la Empresa Eléctrica de La Habana, el ingeniero Mario Castillo Salas.
“Las personas que no tengan teléfono y que no tengan la tarjeta siempre podrán contar dentro del núcleo familiar con alguna persona que pueda hacerlo. Nosotros no cobramos la electricidad a las personas, se las cobramos a los núcleos”, comentó el directivo.
NOTICIAS DE CUBA Cubanos que no puedan pagar la corriente vía electrónica deberán buscar un “vecino solidario”
Sugirieron como otra alternativa que se acuda a un trabajador social para que les pague la cuenta a quienes no puedan hacerlo Foto del avatar
By
Periódico Cubano Published on 1 agosto, 2023
Share Tweet CommentCubanos que no puedan pagar la corriente deberán buscar un “vecino solidario”, según el director de la Empresa Eléctrica
El plan “Cero Efectivo” no contiene excepciones y todos están obligados a realizar el pago electrónico vía digital. (Captura de pantalla: Canal Caribe – YouTube)
El 1 de agosto de 2023 comenzó en La Habana la campaña “Cero Efectivo” impulsada por la Empresa Eléctrica del territorio para suprimir por completo el cobro de la factura de corriente con dinero en efectivo. Las únicas vías posibles que ahora les quedan a los clientes que pertenecen a las oficinas comerciales de Plaza, Nuevo Vedado, Almendares y Santa Fe es la vía digital.
Para el pago electrónico hace falta tener una tarjeta magnética de un banco cubano que tenga saldo suficiente en pesos cubanos (CUP). Además, es necesario un teléfono celular con conexión a Internet y dominio tecnológico para efectuar todo el procedimiento.
Aquellos que no puedan reunir todos estos requisitos, un grupo donde se pueden incluir múltiples personas de la tercera edad que viven solas, tienen la opción de acudir a un “vecino solidario”, según declaraciones del director de la Empresa Eléctrica de La Habana, el ingeniero Mario Castillo Salas.
“Las personas que no tengan teléfono y que no tengan la tarjeta siempre podrán contar dentro del núcleo familiar con alguna persona que pueda hacerlo. Nosotros no cobramos la electricidad a las personas, se las cobramos a los núcleos”, comentó el directivo.
Cuando le preguntaron por las personas que viven solas y no pueden asumir los nuevos cambios, Castillo Salas recomendó que busquen a un vecino para que les ayude a pagar la corriente. El plan “Cero Efectivo” no contempla excepciones y todos están obligados a realizar el pago electrónico vía digital.
“Siempre hay vecinos que podrán ayudar. Desde Transfermóvil usted le puede pagar a cualquier otro cliente”, explicó el directivo, que sugirió como cuarta vía que el cliente que tampoco encuentre a un vecino acuda a un trabajador social para que les pague la cuenta.
La prueba piloto en los municipios habaneros de Plaza y Playa pretende extenderse hacia el resto de la capital, pues al parecer la Empresa Eléctrica solo le ve “múltiples ventajas” al sistema.

NOTICIAS DE CUBA Cubanos que no puedan pagar la corriente vía electrónica deberán buscar un “vecino solidario”
Sugirieron como otra alternativa que se acuda a un trabajador social para que les pague la cuenta a quienes no puedan hacerlo Foto del avatar
By
Periódico Cubano Published on 1 agosto, 2023
Share Tweet CommentCubanos que no puedan pagar la corriente deberán buscar un “vecino solidario”, según el director de la Empresa Eléctrica
El plan “Cero Efectivo” no contiene excepciones y todos están obligados a realizar el pago electrónico vía digital. (Captura de pantalla: Canal Caribe – YouTube)
El 1 de agosto de 2023 comenzó en La Habana la campaña “Cero Efectivo” impulsada por la Empresa Eléctrica del territorio para suprimir por completo el cobro de la factura de corriente con dinero en efectivo. Las únicas vías posibles que ahora les quedan a los clientes que pertenecen a las oficinas comerciales de Plaza, Nuevo Vedado, Almendares y Santa Fe es la vía digital.
Para el pago electrónico hace falta tener una tarjeta magnética de un banco cubano que tenga saldo suficiente en pesos cubanos (CUP). Además, es necesario un teléfono celular con conexión a Internet y dominio tecnológico para efectuar todo el procedimiento.
Aquellos que no puedan reunir todos estos requisitos, un grupo donde se pueden incluir múltiples personas de la tercera edad que viven solas, tienen la opción de acudir a un “vecino solidario”, según declaraciones del director de la Empresa Eléctrica de La Habana, el ingeniero Mario Castillo Salas.
“Las personas que no tengan teléfono y que no tengan la tarjeta siempre podrán contar dentro del núcleo familiar con alguna persona que pueda hacerlo. Nosotros no cobramos la electricidad a las personas, se las cobramos a los núcleos”, comentó el directivo.
Cuando le preguntaron por las personas que viven solas y no pueden asumir los nuevos cambios, Castillo Salas recomendó que busquen a un vecino para que les ayude a pagar la corriente. El plan “Cero Efectivo” no contempla excepciones y todos están obligados a realizar el pago electrónico vía digital.
“Siempre hay vecinos que podrán ayudar. Desde Transfermóvil usted le puede pagar a cualquier otro cliente”, explicó el directivo, que sugirió como cuarta vía que el cliente que tampoco encuentre a un vecino acuda a un trabajador social para que les pague la cuenta.
La prueba piloto en los municipios habaneros de Plaza y Playa pretende extenderse hacia el resto de la capital, pues al parecer la Empresa Eléctrica solo le ve “múltiples ventajas” al sistema.
En sus redes sociales, la empresa insiste en que están dadas todas las circunstancias para “garantizar cumplir con los indicadores de recaudación este mes”. Adicionalmente, acompañan la publicación con una serie de “hasta revolucionarios”: #unacolaparaqué, #TeLoPonemosFácil, #yopagoportransfermóvil y #pagoporenzona.
La Empresa Eléctrica de La Habana está recibiendo las críticas a su gestión por el teléfono 18888, y en los perfiles en sus redes sociales.
-
 @ 957966b6:2d4fe6b7
2023-08-02 02:09:41
@ 957966b6:2d4fe6b7
2023-08-02 02:09:41James, a servant of God and of the Lord Jesus Christ, to the twelve tribes which are in the Dispersion: Greetings.
Count it all joy, my brothers, when you fall into various temptations, knowing that the testing of your faith produces endurance. Let endurance have its perfect work, that you may be perfect and complete, lacking in nothing.
But if any of you lacks wisdom, let him ask of God, who gives to all liberally and without reproach, and it will be given to him. But let him ask in faith, without any doubting, for he who doubts is like a wave of the sea, driven by the wind and tossed. For that man shouldn’t think that he will receive anything from the Lord. He is a double-minded man, unstable in all his ways.
Let the brother in humble circumstances glory in his high position; and the rich, in that he is made humble, because like the flower in the grass, he will pass away. For the sun arises with the scorching wind and withers the grass; and the flower in it falls, and the beauty of its appearance perishes. So the rich man will also fade away in his pursuits.
Blessed is a person who endures temptation, for when he has been approved, he will receive the crown of life which the Lord promised to those who love him.
Let no man say when he is tempted, “I am tempted by God,” for God can’t be tempted by evil, and he himself tempts no one. But each one is tempted when he is drawn away by his own lust and enticed. Then the lust, when it has conceived, bears sin. The sin, when it is full grown, produces death. Don’t be deceived, my beloved brothers. Every good gift and every perfect gift is from above, coming down from the Father of lights, with whom can be no variation nor turning shadow. Of his own will he gave birth to us by the word of truth, that we should be a kind of first fruits of his creatures.
So, then, my beloved brothers, let every man be swift to hear, slow to speak, and slow to anger; for the anger of man doesn’t produce the righteousness of God. Therefore, putting away all filthiness and overflowing of wickedness, receive with humility the implanted word, which is able to save your souls.
But be doers of the word, and not only hearers, deluding your own selves. For if anyone is a hearer of the word and not a doer, he is like a man looking at his natural face in a mirror; for he sees himself, and goes away, and immediately forgets what kind of man he was. But he who looks into the perfect law of freedom and continues, not being a hearer who forgets but a doer of the work, this man will be blessed in what he does.
If anyone among you thinks himself to be religious while he doesn’t bridle his tongue, but deceives his heart, this man’s religion is worthless. Pure religion and undefiled before our God and Father is this: to visit the fatherless and widows in their affliction, and to keep oneself unstained by the world.
My brothers, don’t hold the faith of our glorious Lord Jesus Christ with partiality. For if a man with a gold ring, in fine clothing, comes into your synagogue, and a poor man in filthy clothing also comes in, and you pay special attention to him who wears the fine clothing and say, “Sit here in a good place;” and you tell the poor man, “Stand there,” or “Sit by my footstool” haven’t you shown partiality among yourselves, and become judges with evil thoughts? Listen, my beloved brothers. Didn’t God choose those who are poor in this world to be rich in faith and heirs of the Kingdom which he promised to those who love him? But you have dishonored the poor man. Don’t the rich oppress you and personally drag you before the courts? Don’t they blaspheme the honorable name by which you are called?
However, if you fulfill the royal law according to the Scripture, “You shall love your neighbor as yourself,” you do well. But if you show partiality, you commit sin, being convicted by the law as transgressors. For whoever keeps the whole law, and yet stumbles in one point, he has become guilty of all. For he who said, “Do not commit adultery,” also said, “Do not commit murder.” Now if you do not commit adultery but do murder, you have become a transgressor of the law. So speak and so do as men who are to be judged by the law of freedom. For judgment is without mercy to him who has shown no mercy. Mercy triumphs over judgment.
What good is it, my brothers, if a man says he has faith, but has no works? Can faith save him? And if a brother or sister is naked and in lack of daily food, and one of you tells them, “Go in peace. Be warmed and filled;” yet you didn’t give them the things the body needs, what good is it? Even so faith, if it has no works, is dead in itself. Yes, a man will say, “You have faith, and I have works.” Show me your faith without works, and I will show you my faith by my works.
You believe that God is one. You do well. The demons also believe—and shudder. But do you want to know, vain man, that faith apart from works is dead? Wasn’t Abraham our father justified by works, in that he offered up Isaac his son on the altar? You see that faith worked with his works, and by works faith was perfected. So the Scripture was fulfilled which says, “Abraham believed God, and it was accounted to him as righteousness,” and he was called the friend of God. You see then that by works a man is justified, and not only by faith. In the same way, wasn’t Rahab the prostitute also justified by works when she received the messengers and sent them out another way? For as the body apart from the spirit is dead, even so faith apart from works is dead.
Let not many of you be teachers, my brothers, knowing that we will receive heavier judgment. For we all stumble in many things. Anyone who doesn’t stumble in word is a perfect person, able to bridle the whole body also. Indeed, we put bits into the horses’ mouths so that they may obey us, and we guide their whole body. Behold, the ships also, though they are so big and are driven by fierce winds, are yet guided by a very small rudder, wherever the pilot desires. So the tongue is also a little member, and boasts great things. See how a small fire can spread to a large forest! And the tongue is a fire. The world of iniquity among our members is the tongue, which defiles the whole body, and sets on fire the course of nature, and is set on fire by Gehenna. For every kind of animal, bird, creeping thing, and sea creature is tamed, and has been tamed by mankind; but nobody can tame the tongue. It is a restless evil, full of deadly poison. With it we bless our God and Father, and with it we curse men who are made in the image of God. Out of the same mouth comes blessing and cursing. My brothers, these things ought not to be so. Does a spring send out from the same opening fresh and bitter water? Can a fig tree, my brothers, yield olives, or a vine figs? Thus no spring yields both salt water and fresh water.
Who is wise and understanding among you? Let him show by his good conduct that his deeds are done in gentleness of wisdom. But if you have bitter jealousy and selfish ambition in your heart, don’t boast and don’t lie against the truth. This wisdom is not that which comes down from above, but is earthly, sensual, and demonic. For where jealousy and selfish ambition are, there is confusion and every evil deed. But the wisdom that is from above is first pure, then peaceful, gentle, reasonable, full of mercy and good fruits, without partiality, and without hypocrisy. Now the fruit of righteousness is sown in peace by those who make peace.
Where do wars and fightings among you come from? Don’t they come from your pleasures that war in your members? You lust, and don’t have. You murder and covet, and can’t obtain. You fight and make war. You don’t have, because you don’t ask. You ask, and don’t receive, because you ask with wrong motives, so that you may spend it on your pleasures. You adulterers and adulteresses, don’t you know that friendship with the world is hostility toward God? Whoever therefore wants to be a friend of the world makes himself an enemy of God. Or do you think that the Scripture says in vain, “The Spirit who lives in us yearns jealously”? But he gives more grace. Therefore it says, “God resists the proud, but gives grace to the humble.” Be subject therefore to God. Resist the devil, and he will flee from you. Draw near to God, and he will draw near to you. Cleanse your hands, you sinners. Purify your hearts, you double-minded. Lament, mourn, and weep. Let your laughter be turned to mourning and your joy to gloom. Humble yourselves in the sight of the Lord, and he will exalt you.
Don’t speak against one another, brothers. He who speaks against a brother and judges his brother, speaks against the law and judges the law. But if you judge the law, you are not a doer of the law but a judge. Only one is the lawgiver, who is able to save and to destroy. But who are you to judge another?
Come now, you who say, “Today or tomorrow let’s go into this city and spend a year there, trade, and make a profit.” Yet you don’t know what your life will be like tomorrow. For what is your life? For you are a vapor that appears for a little time and then vanishes away. For you ought to say, “If the Lord wills, we will both live, and do this or that.” But now you glory in your boasting. All such boasting is evil. To him therefore who knows to do good and doesn’t do it, to him it is sin.
Come now, you rich, weep and howl for your miseries that are coming on you. Your riches are corrupted and your garments are moth-eaten. Your gold and your silver are corroded, and their corrosion will be for a testimony against you and will eat your flesh like fire. You have laid up your treasure in the last days. Behold, the wages of the laborers who mowed your fields, which you have kept back by fraud, cry out; and the cries of those who reaped have entered into the ears of the Lord of Armies. You have lived in luxury on the earth, and taken your pleasure. You have nourished your hearts as in a day of slaughter. You have condemned and you have murdered the righteous one. He doesn’t resist you.
Be patient therefore, brothers, until the coming of the Lord. Behold, the farmer waits for the precious fruit of the earth, being patient over it, until it receives the early and late rain. You also be patient. Establish your hearts, for the coming of the Lord is at hand.
Don’t grumble, brothers, against one another, so that you won’t be judged. Behold, the judge stands at the door. Take, brothers, for an example of suffering and of perseverance, the prophets who spoke in the name of the Lord. Behold, we call them blessed who endured. You have heard of the perseverance of Job and have seen the Lord in the outcome, and how the Lord is full of compassion and mercy.
But above all things, my brothers, don’t swear— not by heaven, or by the earth, or by any other oath; but let your “yes” be “yes”, and your “no”, “no”, so that you don’t fall into hypocrisy.
Is any among you suffering? Let him pray. Is any cheerful? Let him sing praises. Is any among you sick? Let him call for the elders of the assembly, and let them pray over him, anointing him with oil in the name of the Lord; and the prayer of faith will heal him who is sick, and the Lord will raise him up. If he has committed sins, he will be forgiven. Confess your sins to one another and pray for one another, that you may be healed. The insistent prayer of a righteous person is powerfully effective. Elijah was a man with a nature like ours, and he prayed earnestly that it might not rain, and it didn’t rain on the earth for three years and six months. He prayed again, and the sky gave rain, and the earth produced its fruit.
Brothers, if any among you wanders from the truth and someone turns him back, let him know that he who turns a sinner from the error of his way will save a soul from death and will cover a multitude of sins.
The World English Bible is in the Public Domain. That means that it is not copyrighted. However, "World English Bible" is a Trademark of eBible.org.
-
 @ a4a6b584:1e05b95b
2023-07-27 01:23:03
@ a4a6b584:1e05b95b
2023-07-27 01:23:03"For it is written, As I live, saith the Lord, every knee shall bow to me, and every tongue shall confess to God. So then every one of us shall give account of himself to God." Romans 14:11-12
Though God has always had a people, the New Testament Church started with Christ and His disciples and was empowered at Pentecost. Historically, there has always been a remnant of people who adhered to the truth of God's Word for their faith and practice. I am convinced that the very same body of truth which was once delivered must be contended for in every generation.
In every generation from Christ and His disciples to this present moment, there have been holy adherents to the truth of God's Word. This witness of history is a witness in their blood. I am a Baptist by conviction. I was not "Baptist-born." I became and remain a Baptist because of what I have discovered in the Word of God.
The Lord Jesus Christ left His church doctrine and ordinances. The ordinances are baptism and the Lord's Supper. These are the things He ordered us to do. They picture His death and remind us of Him and His return. He also left us a body of doctrine. This involves our belief and teaching. Our doctrine distinguishes us. It is all from the Bible.
No one can be forced to become a Baptist. Our records show that baptism was always administered to professing believers. Hence, we refer to baptism as believers' baptism.
Baptists are gospel-preaching people. They preached the gospel to me. The Lord Jesus said to the first-century church, "But ye shall receive power, after that the Holy Ghost is come upon you: and ye shall be witnesses unto me both in Jerusalem, and in all Judea, and in Samaria, and unto the uttermost part of the earth ,, (Acts I :8). I am grateful to God to be a Baptist. I consider this to be New Testament Christianity. It is my joy to serve as the pastor of an independent Baptist church, preaching and teaching God's Word.
A Baptist recognizes the autonomy of the local church. There is no such thing as "The Baptist Church." The only Baptist headquarters that exists is in the local assembly of baptized believers. There are only local Baptist churches. \
When we say that the Bible is our sole authority, we are speaking of all the scriptures, the whole and its parts. We should preach the whole counsel of God. In the Bible we find the gospel-the death, burial, and resurrection of Jesus Christ. We should proclaim the gospel because Jesus Christ said that we are to take the gospel message to every creature. When we open the sixty-six books of the Bible, we find more than the gospel. Of course, that scarlet thread of redemption runs through all the Bible, but the whole counsel of God must be proclaimed.
The Bible says in Romans 14:11-12, ''For it is written, As I live, saith the Lord, every knee shall bow to me, and every tongue shall confess to God. So then every one of us shall give account of himself to God. " Each human being must answer personally to God.
In our nation we hear people talk about religious tolerance. Religious tolerance is something created by government. It is a "gift" from government. Religious tolerance is something man has made. Soul liberty is something God established when He created us. We find a clear teaching of this in His Word. Soul liberty is a gift from God! God's Word says in Galatians 5:1, "Stand fast therefore in the liberty wherewith Christ hath made us free, and be not entangled again with the yoke of bondage."
Soul liberty does not rest upon the legal documents of our nation-it is rooted in the Word of God. This individual freedom of the soul is inherent in man's nature as God created him. Man is responsible for his choices, but he is free to choose. This conviction is at the core of Baptist beliefs.
This powerful declaration about our Baptist position was made by J.D. Freeman in 1905:
Our demand has been not simply for religious toleration, but religious liberty; not sufferance merely, but freedom; and that not for ourselves alone, but for all men. We did not stumble upon this doctrine. It inheres in the very essence of our belief. Christ is Lord of all.. .. The conscience is the servant only of God, and is not subject to the will of man. This truth has indestructible life. Crucify it and the third day it will rise again. Bury it in the sepulcher and the stone will be rolled away, while the keepers become as dead men .... Steadfastly refusing to bend our necks under the yoke of bondage, we have scrupulously withheld our hands from imposing that yoke upon others .... Of martyr blood our hands are clean. We have never invoked the sword of temporal power to aid the sword of the Spirit. We have never passed an ordinance inflicting a civic disability on any man because of his religious views, be he Protestant or Papist, Jew, or Turk, or infidel. In this regard there is no blot on our escutcheon (family crest).
Remember that, when we are talking about individual soul liberty and the relationship of the church and the state, in America the Constitution does not place the church over the state or the state over the church. Most importantly, Scripture places them side by side, each operating independently of the other. This means there is freedom in the church and freedom in the state. Each is sovereign within the sphere of the authority God has given to each of them (Matthew 22:21).
Read carefully this statement made by Charles Spurgeon, the famous English preacher, concerning Baptist people:
We believe that the Baptists are the original Christians. We did not commence our existence at the Reformation, we were reformers before Luther or Calvin were born; we never came from the Church of Rome, for we were never in it, but we have an unbroken line up to the apostles themselves. We have always existed from the very days of Christ, and our principles, sometimes veiled and forgotten, like a river which may travel underground for a little season, have always had honest and holy adherents. Persecuted alike by Romanists and Protestants of almost every sect, yet there has never existed a government holding Baptist principles which persecuted others; nor, I believe, any body of Baptists ever held it to be right to put the consciences of others under the control of man. We have ever been ready to suffer, as our martyrologies will prove, but we are not ready to accept any help from the State, to prostitute the purity of the Bride of Christ to any alliance with overnment, and we wil never make the Church, although the Queen, the despot over the consciences of men.
The New Park Street Pulpit, Volume VII · Page 225
This a marvelous statement about Baptist beliefs. I am rather troubled when I see so many people who claim to be Baptists who do not understand why they are Baptists. We should be able to defend our position and do it biblically. lf we are people who know and love the Lord and His Word and if the Bible is our sole authority for faith and practice, then we have no reason to be ashamed of the position we take. May God not only help us to take this position, but to take it with holy boldness and cotnpassion. May He help us to be able to take His Word in hand and heart and defend what we believe to a lost and dying world.
So much of what we have to enjoy in our country can be credited to Baptist people. Any honest student of American history will agree that the Virginia Baptists were almost solely responsible for the First Amendment being added to our Constitution providing the freedom to worship God as our conscience dictates.
We have a country that has been so influenced that we do not believe it is right to exercise any control or coercion of any kind over the souls of men. Where did this conviction come from? We find it in the Bible, but someone imparted it to the Founding Fathers. It became the law of the land, and it should remain the law of the land. We need to understand it. It comes out of the clear teaching of God's Word concerning the subject of soul liberty.
There are many historic places there where people were martyred for their faith, giving their lives for what they believed. The religious persecution came as a result of the laws of the land. Although many Baptists have been martyred, you will never find Baptist people persecuting anyone anywhere for his faith, no matter what his faith may be.
There are many denominations that teach the Scriptures are the infallible Word of God, God is the creator of heaven and earth, man is a fallen creature and must be redeemed by the blood of Christ, salvation is the free offer of eternal Iife to those who receive it and eternal helI awaits those who reject it, the Lord's Day is a day of worship, and the only time for man to be made right with God is in this lifetime. There are certainly other commonly held teachings, but there are certain Baptist distinctive. Often an acrostic using the word BAPTISTS is used to represent these Baptist distinctive.
-
B is for biblical authority. The Bible is the sole authority for our faith and practice.
-
A for the autonomy of the local church. Every church we find in the New Testament was a self-governing church with only Christ as the head.
-
P represents the priesthood of believers and the access we have to God through Jesus Christ.
-
T for the two church officers-pastors and deacons. We find these officers in the New Testament.
-
I for individual soul liberty. Most people, when asked, say that the sole authority of the Scripture in our faith and practice is the single, most important distinctive of our faith. However, if we did not have individual soul liberty, we could not come to the convictions we have on all other matters.
-
S for a saved church membership.
Personal Accountability to God
Renowned Baptist leader, Dr. E.Y. Mullins, summarized our Baptist position in these words. He wrote:
The biblical significance of the Baptist is the right of private interpretation of and obedience to the Scriptures. The significance of the Baptist in relation to the individual is soul freedom. The ecclesiastical significance of the Baptist is a regenerated church membership and the equality and priesthood of believers. The political significance of the Baptist is the separation of church and state. But as comprehending all the above particulars, as a great and aggressive force in Christian history, as distinguished from all others and standing entirely alone, the doctrine of the soul's competency in religion under God is the distinctive significance of the Baptists.
We find this accountability in the opening verses of God's Word. When God created man, He created man capable of giving a personal account of himself to God. God did not create puppets; He created people. He gave man the right to choose. That is why we find the man Adam choosing to sin and to disobey God in Genesis chapter three. Of his own volition he chose to sin and disobey God. Genesis I :27 says, "So God created man in his own image, in the image of God created he him; male and female created he them. " We were made in God's image, and when God made us in His image, He made us with the ability to choose.
It is not right to try to force one's religion or belief upon another individual. This does not mean, however, that he can be a Christian by believing anything he wishes to believe, because Jesus Christ said that there is only one way to heaven. He said in John 14:6, "I am the way, the truth, and the life: no man cometh unto the Father, but by me." He is the only way to God. The only way of salvation is the Lord Jesus Christ.
In this age of tolerance, people say that nothing is really wrong. The same people who say that any way of believing is right will not accept the truth that one belief can be the only way that is right. You may believe anything you choose, but God has declared that there is only one way to Him and that is through His Son, Jesus Christ. He is the only way of salvation- that is why He suffered and died for our sins. The only way to know God is through His Son, the Lord Jesus Christ.
Someone is certain to ask, "Who are you to declare that everyone else's religion is wrong?" We are saying that everyone ~as ~ right to choose his own way, but God has clearly taught us in His Word that there is only one way to Him. The Lord Jesus says in John 10:9, "I am the door: by me if any man enter in, he shall be saved, and shall go in and out, and find pasture."
No human being is going to live on this earth without being sinned against by others. Many children are sinned against greatly by their own parents. However, we cannot go through life blaming others for the person we are, because God has made us in such a way that we have an individual accountability to God. This comes out of our soul liberty and our right to choose and respond to things in a way that God would have us espond to them. God has made us in His image. Again, He did not make us puppets or robots; He made us people, created in His image with the ability to choose our own way.
Remember, "For it is written, As I live, saith the Lord, every knee shall bow to me, and every tongue shall confess to God. So then every one of us shall give account of himself to God" (Romans 14:11- 12). We are responsible because we have direct access to God. God has given us the Word of God, the Holy Spirit, and access to the Throne by the merit of Jesus Christ. We, therefore? must answer personally to God at the judgment seat because God communicates to us directly.
People do not like to be held personally accountable for their actions. The truth of the Word of God is that every individual is personally accountable to God. In other words, you are going to meet God in judgment some day. I am going to meet God in judgment some day. All of us are going to stand before the Lord some day and answer to Him. We are individually accountable to God. Since the state cannot answer for us to God, it has no right to dictate our conscience.
We live in a country where there are many false religions. As Baptist people, we defend the right of anyone in our land to worship as he sees fit to worship. This is unheard of in most of the world. If a man is a Moslem, I do not agree with his Islamic religion, but I defend his right to worship as he sees fit to worship. The teaching of the Catholic Church declares that salvation comes through Mary, but this is not the teaching of the Bible. We zealously proclaim the truth, but we must also defend the right of people to worship as they choose to worship. Why? Because individual soul liberty is a gift from God to every human being.
Since the Bible teaches individual soul liberty and personal accountability to God, then it is a truth that will endure to all generations. To be sure, Baptists believe the Bible is the sole authority for faith and practice (II Timothy 3:16-17; Matthew 15:9; I John 2:20, 21 , 27) and the Bible clearly teaches that no church or government or power on earth has the right to bind a man's conscience. The individual is personally accountable to God. Hence, we reject the teaching of infant baptism and all doctrine that recognizes people as members of a church before they give evidence of personal repentance toward God and faith in the Lord Jesus Christ.
The famous Baptist, John Bunyan is the man who gave us Pilgrim's Progress. This wonderful book was planned during Bunyan's prison experience and written when he was released. The trial of John Bunyan took place on October 3, 1660. John Bunyan spent twelve years in jail for his convictions about individual soul liberty, failure to attend the Church of England, and for preaching the Word of God. During his trial, Bunyan stood before Judge Wingate who was interested in hearing John Bunyan state his case. Judge Wingate said, "In that case, then, this court would be profoundly interested in your response to them."
Part of John Bunyan's response follows:
Thank you, My 'lord. And may I say that I am grateful for the opportunity to respond. Firstly, the depositions speak the truth. I have never attended services in the Church of England, nor do I intend ever to do so. Secondly, it is no secret that I preach the Word of God whenever, wherever, and to whomever He pleases to grant me opportunity to do so. Having said that, My 'lord, there is a weightier issue that I am constrained to address. I have no choice but to acknowledge my awareness of the law which I am accused of transgressing. Likewise, I have no choice but to confess my auilt in my transgression of it. As true as these things are, I must affirm that I neiher regret breaking the law, nor repent of having broken it. Further, I must warn you that I have no intention in future of conforming to it. It is, on its face, an unjust law, a law against which honorable men cannot shrink from protesting. In truth, My 'lord, it violates an infinitely higher law- the right of every man to seek God in his own way, unhindered by any temporal power. That, My 'lord, is my response.
Remember that Bunyan was responding as to why he would not do all that he was doing for God within the confines of the Church of England. The transcription goes on to say:
Judge Wingate: This court would remind you, sir, that we are not here to debate the merits of the law. We are here to determine if you are, in fact, guilty of violating it. John Bunyan: Perhaps, My 'lord, that is why you are here, but it is most certainly not why I am here. I am here because you compel me to be here. All I ask is to be left alone to preach and to teach as God directs me. As, however, I must be here, I cannot fail to use these circumstances to speak against what I know to be an unjust and odious edict. Judge Wingate: Let me understand you. You are arguing that every man has a right, given him by Almighty God, to seek the Deity in his own way, even if he chooses without the benefit of the English Church? John Bunyan: That is precisely what I am arguing, My 'lord. Or without benefit of any church. Judge Wingate: Do you know what you are saying? What of Papist and Quakers? What of pagan Mohammedans? Have these the right to seek God in their own misguided way? John Bunyan: Even these, My 'lord. Judge Wingate: May I ask if you are articularly sympathetic to the views of these or other such deviant religious societies? John Bunyan: I am not, My 'lord. Judge Wingate: Yet, you affirm a God-given right to hold any alien religious doctrine that appeals to the warped minds of men? John Bunyan: I do, My'lord. Judge Wingate: I find your views impossible of belief And what of those who, if left to their own devices, would have no interest in things heavenly? Have they the right to be allowed to continue unmolested in their error? John Bunyan: It is my fervent belief that they do, My'lord. Judge Wingate: And on what basis, might r ask. can you make such rash affirmations? John Bunyan: On the basis, My 'lord, that a man's religious views- or lack of them- are matters between his conscience and his God, and are not the business of the Crown, the Parliament, or even, with all due respect, My 'lord, of this court. However much I may be in disagreement with another man's sincerely held religious beliefs, neither I nor any other may disallo his right to hold those beliefs. No man's right in these affairs are . secure if every other man's rights are not equally secure.
I do not know of anyone who could have expressed the whole idea of soul liberty in the words of man any more clearly than Bunyan stated in 1660. Every man can seek God as he pleases. This means that we cannot force our religious faith or teaching on anyone. It means clearly that no one can be coerced into being a Baptist and believing what we believe. It means that we can do no arm-twisting, or anything of that sort, to make anyone believe what we believe. Every man has been created by God with the ability to choose to follow God or to follow some other god.
Personal accountability to God is a distinctive of our faith. It is something we believe, and out of this distinctive come other distinctives that we identify with as Baptist people.
The Priesthood of Every Believer
The priesthood of the believer means that every believer can go to God through the merit of Jesus Christ. Christ and Christ alone is the only way to God. All of us who have trusted Christ as Saviour enjoy the glorious privilege of the priesthood of the believer and can access God through the merits of our Lord and Saviour Jesus Christ.
The Bible says in I Timothy 2: 1-6,
I exhort therefore, that, first of all, supplications, prayers, intercessions, and giving of thanks, be made for all men,· for kings, and for all that are in authority; that we may lead a quiet and peaceable life in all godliness and honesty. For this is good and acceptable in the sight of God our Saviour,· who will have all men to be saved, and to come unto the knowledge of the truth. For there is one God, and one mediator between God and men, the man Christ Jesus; who gave himself a ransom for all, to be testified in due time.
Take special note of verse five, "For there is one God, and one mediator between God and men, the man Christ Jesus."
Any man, anywhere in this world can go to God through the Lord Jesus Christ.
1 Peter 2:9 says, "But ye are a chosen generation, a royal pn~ • thood , an . holy nation, a peculiar people; that ye should. shew forth the praises of hzm who hath called you out of darkness into his marvellous light. "
Christians have access to God. You can personally talk to God. You can take your needs to the Lord. Whatever your needs are, you can take those needs to the Lord. You, as an individual Christian, can go to God through the Lord Jesus Christ, your High Priest who "ever liveth to make intercession" for you (Hebrews 7:25).
We have no merit of our own. We do not accumulate merit. People may make reference to a time of meritorious service someone has rendered, but we cannot build up "good works" that get us through to God. Each day, we must come before God as needy sinners approaching Him through the finished work of Christ and Christ alone.
The Bible teaches the personal accountability of every human being to God. We cannot force our religion on anyone or make anyone a believer. We cannot force someone to be a Christian. Think of how wrong it is to take babies and allow them later in life to think they have become Christians by an act of infant baptism. Yes, they have a right to practice infant baptism, but we do not believe this is biblical because faith cannot be forced or coerced.
There are places in the world where the state is under a religion. There are places in the world where religion is under the state-the state exercises control over the faith of people. This is not taught in the Bible. Then, there are countries like ours where the church and the state operate side by side.
Throughout history, people who have identified with Baptist distinctives have stood as guardians of religious liberty. At the heart of this liberty is what we refer to as ndividual soul liberty. I am grateful to be a Baptist.
The Power of Influence Where does this teaching of the priesthood of every believer and our personal accountability to God lead us? It leads us to realize the importance of the power of influence. This is the tool God has given us. I want to give you an Old Testament example to illustrate the matter of influence.
Judges 21 :25 tells us, "In those days there was no king in Israel: every man did that which was right in his own eyes."
In the days of the judges, every man did what was right in his own eyes with no fixed point of reference.
God's Word continues to describe this time of judges in Ruth 1:1, ''Now it came to pass in the days when the judges ruled, that there was a famine in the land. " God begins to tell us about a man named Elimelech, his wife Naomi, and his sons. He brings us to the beautiful love story of Ruth and Boaz. God tells us that at the same time in which the judges ruled, when there was anarchy in the land, this beautiful love stor of Boaz and Ruth took place.
This story gives us interesting insight on the responsibility of the Christian and the church. In the midst of everything that is going on, we are to share the beautiful love story of the Lord Jesus Christ and His bride. We need to tell people about the Saviour.
The same truth is found throughout the Word of God. Philippians 2:15 states, "That ye may be blameless and harmless, the sons of God, without rebuke, in the midst of a crooked and perverse nation, among whom ye shine as lights in the world. "
We are "in the midst ofa crooked and p erverse nation." This is why the Lord Jesus said in Matthew 5:16, "Let your light so shine before men, that they may see your good works, and glorify your Father which is in heaven. " Let your light shine!
The more a church becomes like the world, the less influence it is going to have in the world. Preaching ceases, and churches only have diolauges. Singing that is sacred is taken out and the worlds music comes in. All revrence is gone. What so many are attempting to do in order to build up their ministry is actualy what will cause the demise of their ministry. We will never make a difference without being willing to be differnt, Being different is not the goal. Christ is the goal, and He makes us different.
Remember, we cannot force people to become Christians or force our faith on people. It is not right to attempt to violate another man's will; he must choose of his own volition to trust Christ or reject Christ. When we understand this, then we understand the powerful tool of influence. We must live Holy Spirit-filled, godly lives and be what God wants us to be. We must be lights in a dark world as we live in the midst of a crooked generation. The only tool we have to use is influence, not force. As we separate ourselves to God and live godly lives, only then do we have a testimony.
Separation to God and from the world is not the enemy of evangelism; it cais the essential of evangelism. There can be no evangelism without separation to God and from the world because we have no other tool to use. We cannot force people to believe what we believe to be the truth. They must choose of their own will. We must so identify with the Lord Jesus in His beauty, glory, and holiness that He will be lifted up, and people will come to Him
The more a church becomes like the world, the less influence it is going to have in the world. Preaching ceases, and churches only have dialogue. Singing that is sacred is taken out, and the world's music comes in. All reverence is gone. What so many are attempting to do in order to build up their ministry is actually what will cause the demise of their ministry. We will never make a difference without being willing to be different. It is Christ who makes us different. Being different is not the goal. Christ is the goal, and He makes us different.
Remember, we cannot force people to become Christians or force our faith on people. It is not right to attempt to violate another man's will; he must choose of his own volition to trust Christ or reject Christ. When we understand this, then we understand the powerful tool of influence. We must live Holy Spirit-filled, godly lives and be what God wants us to be. We must be lights in a dark world as we live in the midst of a crooked generation. The only tool we have to use is influence, not force. As we separate ourselves to God and live godly lives, only then do we have a testimony.
Separation to God and from the world is not the enemy of evangelism; it is the essential of evangelism. There can be no evangelism without separation to God and from the world because we have no other tool to use. We cannot force people to believe what we believe to be the truth. They must choose of their own will. We must so identify with the Lord Jesus in His beauty, glory, and holiness that He will be lifted up, and people will come to Him.
As this world becomes increasingly worse, the more off-thewall and ridiculous we will appear to an unbelieving world. The temptation will come again and again for us to simply cave in.
When one finds people with sincerely held Baptist distinctives, he finds those people have a passion for going in the power of the Holy Spirit, obeying Christ, preaching the gospel to every creature. I am grateful to God to say, "I am a Baptist."
Baptists know it is because of what we find in the Bible about soul freedom, personal accountability, and the priesthood of every believer that we must use the power of Spirit-filled influence to win the lost to Christ. If we disobey Christ by conforming to the world, we lose our influence.
May the Lord help us to be unashamed to bear His reproach and be identified with our Lord Jesus Christ.
The Way of Salvation
Do you know for sure that if you died today you would go to Heaven?
1. Realize that God loves you
God loves you and has a plan for your life. "For God so loved the world, that he gave His only begotten Son, that whosoever believeth in him, should not perish but have everlasting life" (John 3:16 ).
2. The Bible says that all men are sinners
Our sins have separated us from God. "For all have sinned, and come short of the glory of God" (Romans 3:23). God made man in His own image. He gave man the ability to choose right from wrong. We choose to sin. Our sins separate us from God.
3. God's word also says that sin must be paid for
"For the wages of sin is death" (Romans 6:23 ). Wages means payment. The payment of our sin is death and hell, separation from God forever. If we continue in our sin, we shall die without Christ and be without God forever.
4. The good news is that Christ paid for our sins
All our sins were laid on Christ on the cross. He paid our sin debt for us. The Lord Jesus Christ died on the cross, and He arose from the dead. He is alive forevermore. "But God commendeth his love toward us, in that, while we were yet sinners, Christ died for us" (Romans 5:8).
5. We must personally pray and recieve Christ by faith as our saviour
The Bible says, "For whosoever shall call upon the name of the Lord shall be saved" (Romans 10:13 ).
Lets review for a moment
- Realize That God Loves You - John 3: 1
- All are sinners - Romans 3:21
- Sin Must Be Paid For - Romans 6:23
- Christ paid for our sins - Romans 5:8
- We Must Personally Pray and Receive Christ as Our Saviour - Romans 10:13
- Pray and recieve Christ as your saviour
Lord, I know that I am a sinner. If I died today I would not go to heaven. Forgive my sins and be my Saviour. Help me live for You from this day forward. In Jesus' name, Amen.
The Bible says, "For whosoever shall call upon the name of the Lord shall be saved" (Romans 10:13 ).
~navluc-latmes
-
-
 @ 957966b6:2d4fe6b7
2023-08-02 01:55:36
@ 957966b6:2d4fe6b7
2023-08-02 01:55:36Paul, called to be an apostle of Jesus Christ through the will of God, and our brother Sosthenes, to the assembly of God which is at Corinth—those who are sanctified in Christ Jesus, called saints, with all who call on the name of our Lord Jesus Christ in every place, both theirs and ours: Grace to you and peace from God our Father and the Lord Jesus Christ.
I always thank my God concerning you for the grace of God which was given you in Christ Jesus, that in everything you were enriched in him, in all speech and all knowledge— even as the testimony of Christ was confirmed in you— so that you come behind in no gift, waiting for the revelation of our Lord Jesus Christ, who will also confirm you until the end, blameless in the day of our Lord Jesus Christ. God is faithful, through whom you were called into the fellowship of his Son, Jesus Christ our Lord.
Now I beg you, brothers, through the name of our Lord, Jesus Christ, that you all speak the same thing, and that there be no divisions among you, but that you be perfected together in the same mind and in the same judgment. For it has been reported to me concerning you, my brothers, by those who are from Chloe’s household, that there are contentions among you. Now I mean this, that each one of you says, “I follow Paul,” “I follow Apollos,” “I follow Cephas,” and, “I follow Christ.” Is Christ divided? Was Paul crucified for you? Or were you baptized into the name of Paul? I thank God that I baptized none of you except Crispus and Gaius, so that no one should say that I had baptized you into my own name. (I also baptized the household of Stephanas; besides them, I don’t know whether I baptized any other.) For Christ sent me not to baptize, but to preach the Good News—not in wisdom of words, so that the cross of Christ wouldn’t be made void. For the word of the cross is foolishness to those who are dying, but to us who are being saved it is the power of God. For it is written,
“I will destroy the wisdom of the wise.
I will bring the discernment of the discerning to nothing.”
Where is the wise? Where is the scribe? Where is the debater of this age? Hasn’t God made foolish the wisdom of this world? For seeing that in the wisdom of God, the world through its wisdom didn’t know God, it was God’s good pleasure through the foolishness of the preaching to save those who believe. For Jews ask for signs, Greeks seek after wisdom, but we preach Christ crucified, a stumbling block to Jews and foolishness to Greeks, but to those who are called, both Jews and Greeks, Christ is the power of God and the wisdom of God; because the foolishness of God is wiser than men, and the weakness of God is stronger than men.
For you see your calling, brothers, that not many are wise according to the flesh, not many mighty, and not many noble; but God chose the foolish things of the world that he might put to shame those who are wise. God chose the weak things of the world that he might put to shame the things that are strong. God chose the lowly things of the world, and the things that are despised, and the things that don’t exist, that he might bring to nothing the things that exist, that no flesh should boast before God. Because of him, you are in Christ Jesus, who was made to us wisdom from God, and righteousness and sanctification, and redemption, that, as it is written, “He who boasts, let him boast in the Lord.”
When I came to you, brothers, I didn’t come with excellence of speech or of wisdom, proclaiming to you the testimony of God. For I determined not to know anything among you except Jesus Christ and him crucified. I was with you in weakness, in fear, and in much trembling. My speech and my preaching were not in persuasive words of human wisdom, but in demonstration of the Spirit and of power, that your faith wouldn’t stand in the wisdom of men, but in the power of God.
We speak wisdom, however, among those who are full grown, yet a wisdom not of this world nor of the rulers of this world who are coming to nothing. But we speak God’s wisdom in a mystery, the wisdom that has been hidden, which God foreordained before the worlds for our glory, which none of the rulers of this world has known. For had they known it, they wouldn’t have crucified the Lord of glory. But as it is written,
“Things which an eye didn’t see, and an ear didn’t hear,
which didn’t enter into the heart of man,
these God has prepared for those who love him.”
But to us, God revealed them through the Spirit. For the Spirit searches all things, yes, the deep things of God. For who among men knows the things of a man except the spirit of the man which is in him? Even so, no one knows the things of God except God’s Spirit. But we received not the spirit of the world, but the Spirit which is from God, that we might know the things that were freely given to us by God. We also speak these things, not in words which man’s wisdom teaches but which the Holy Spirit teaches, comparing spiritual things with spiritual things. Now the natural man doesn’t receive the things of God’s Spirit, for they are foolishness to him; and he can’t know them, because they are spiritually discerned. But he who is spiritual discerns all things, and he himself is to be judged by no one. “For who has known the mind of the Lord that he should instruct him?” But we have Christ’s mind.
Brothers, I couldn’t speak to you as to spiritual, but as to fleshly, as to babies in Christ. I fed you with milk, not with solid food, for you weren’t yet ready. Indeed, you aren’t ready even now, for you are still fleshly. For insofar as there is jealousy, strife, and factions among you, aren’t you fleshly, and don’t you walk in the ways of men? For when one says, “I follow Paul,” and another, “I follow Apollos,” aren’t you fleshly?
Who then is Apollos, and who is Paul, but servants through whom you believed, and each as the Lord gave to him? I planted. Apollos watered. But God gave the increase. So then neither he who plants is anything, nor he who waters, but God who gives the increase. Now he who plants and he who waters are the same, but each will receive his own reward according to his own labor. For we are God’s fellow workers. You are God’s farming, God’s building.
According to the grace of God which was given to me, as a wise master builder I laid a foundation, and another builds on it. But let each man be careful how he builds on it. For no one can lay any other foundation than that which has been laid, which is Jesus Christ. But if anyone builds on the foundation with gold, silver, costly stones, wood, hay, or straw, each man’s work will be revealed. For the Day will declare it, because it is revealed in fire; and the fire itself will test what sort of work each man’s work is. If any man’s work remains which he built on it, he will receive a reward. If any man’s work is burned, he will suffer loss, but he himself will be saved, but as through fire.
Don’t you know that you are God’s temple and that God’s Spirit lives in you? If anyone destroys God’s temple, God will destroy him; for God’s temple is holy, which you are.
Let no one deceive himself. If anyone thinks that he is wise among you in this world, let him become a fool that he may become wise. For the wisdom of this world is foolishness with God. For it is written, “He has taken the wise in their craftiness.” And again, “The Lord knows the reasoning of the wise, that it is worthless.” Therefore let no one boast in men. For all things are yours, whether Paul, or Apollos, or Cephas, or the world, or life, or death, or things present, or things to come. All are yours, and you are Christ’s, and Christ is God’s.
So let a man think of us as Christ’s servants and stewards of God’s mysteries. Here, moreover, it is required of stewards that they be found faithful. But with me it is a very small thing that I should be judged by you, or by a human court. Yes, I don’t even judge my own self. For I know nothing against myself. Yet I am not justified by this, but he who judges me is the Lord. Therefore judge nothing before the time, until the Lord comes, who will both bring to light the hidden things of darkness and reveal the counsels of the hearts. Then each man will get his praise from God.
Now these things, brothers, I have in a figure transferred to myself and Apollos for your sakes, that in us you might learn not to think beyond the things which are written, that none of you be puffed up against one another. For who makes you different? And what do you have that you didn’t receive? But if you did receive it, why do you boast as if you had not received it?
You are already filled. You have already become rich. You have come to reign without us. Yes, and I wish that you did reign, that we also might reign with you! For I think that God has displayed us, the apostles, last of all, like men sentenced to death. For we are made a spectacle to the world, both to angels and men. We are fools for Christ’s sake, but you are wise in Christ. We are weak, but you are strong. You have honor, but we have dishonor. Even to this present hour we hunger, thirst, are naked, are beaten, and have no certain dwelling place. We toil, working with our own hands. When people curse us, we bless. Being persecuted, we endure. Being defamed, we entreat. We are made as the filth of the world, the dirt wiped off by all, even until now.
I don’t write these things to shame you, but to admonish you as my beloved children. For though you have ten thousand tutors in Christ, you don’t have many fathers. For in Christ Jesus, I became your father through the Good News. I beg you therefore, be imitators of me. Because of this I have sent Timothy to you, who is my beloved and faithful child in the Lord, who will remind you of my ways which are in Christ, even as I teach everywhere in every assembly. Now some are puffed up, as though I were not coming to you. But I will come to you shortly, if the Lord is willing. And I will know, not the word of those who are puffed up, but the power. For God’s Kingdom is not in word, but in power. What do you want? Shall I come to you with a rod, or in love and a spirit of gentleness?
It is actually reported that there is sexual immorality among you, and such sexual immorality as is not even named among the Gentiles, that one has his father’s wife. You are arrogant, and didn’t mourn instead, that he who had done this deed might be removed from among you. For I most certainly, as being absent in body but present in spirit, have already, as though I were present, judged him who has done this thing. In the name of our Lord Jesus Christ, when you are gathered together with my spirit with the power of our Lord Jesus Christ, you are to deliver such a one to Satan for the destruction of the flesh, that the spirit may be saved in the day of the Lord Jesus.
Your boasting is not good. Don’t you know that a little yeast leavens the whole lump? Purge out the old yeast, that you may be a new lump, even as you are unleavened. For indeed Christ, our Passover, has been sacrificed in our place. Therefore let’s keep the feast, not with old yeast, neither with the yeast of malice and wickedness, but with the unleavened bread of sincerity and truth.
I wrote to you in my letter to have no company with sexual sinners; yet not at all meaning with the sexual sinners of this world, or with the covetous and extortionists, or with idolaters, for then you would have to leave the world. But as it is, I wrote to you not to associate with anyone who is called a brother who is a sexual sinner, or covetous, or an idolater, or a slanderer, or a drunkard, or an extortionist. Don’t even eat with such a person. For what do I have to do with also judging those who are outside? Don’t you judge those who are within? But those who are outside, God judges. “Put away the wicked man from among yourselves.”
Dare any of you, having a matter against his neighbor, go to law before the unrighteous, and not before the saints? Don’t you know that the saints will judge the world? And if the world is judged by you, are you unworthy to judge the smallest matters? Don’t you know that we will judge angels? How much more, things that pertain to this life? If then you have to judge things pertaining to this life, do you set them to judge who are of no account in the assembly? I say this to move you to shame. Isn’t there even one wise man among you who would be able to decide between his brothers? But brother goes to law with brother, and that before unbelievers! Therefore it is already altogether a defect in you that you have lawsuits one with another. Why not rather be wronged? Why not rather be defrauded? No, but you yourselves do wrong and defraud, and that against your brothers.
Or don’t you know that the unrighteous will not inherit God’s Kingdom? Don’t be deceived. Neither the sexually immoral, nor idolaters, nor adulterers, nor male prostitutes, nor homosexuals, nor thieves, nor covetous, nor drunkards, nor slanderers, nor extortionists, will inherit God’s Kingdom. Some of you were such, but you were washed. You were sanctified. You were justified in the name of the Lord Jesus, and in the Spirit of our God.
“All things are lawful for me,” but not all things are expedient. “All things are lawful for me,” but I will not be brought under the power of anything. “Foods for the belly, and the belly for foods,” but God will bring to nothing both it and them. But the body is not for sexual immorality, but for the Lord, and the Lord for the body. Now God raised up the Lord, and will also raise us up by his power. Don’t you know that your bodies are members of Christ? Shall I then take the members of Christ and make them members of a prostitute? May it never be! Or don’t you know that he who is joined to a prostitute is one body? For, “The two”, he says, “will become one flesh.” But he who is joined to the Lord is one spirit. Flee sexual immorality! “Every sin that a man does is outside the body,” but he who commits sexual immorality sins against his own body. Or don’t you know that your body is a temple of the Holy Spirit who is in you, whom you have from God? You are not your own, for you were bought with a price. Therefore glorify God in your body and in your spirit, which are God’s.
Now concerning the things about which you wrote to me: it is good for a man not to touch a woman. But, because of sexual immoralities, let each man have his own wife, and let each woman have her own husband. Let the husband give his wife the affection owed her, and likewise also the wife her husband. The wife doesn’t have authority over her own body, but the husband does. Likewise also the husband doesn’t have authority over his own body, but the wife does. Don’t deprive one another, unless it is by consent for a season, that you may give yourselves to fasting and prayer, and may be together again, that Satan doesn’t tempt you because of your lack of self-control.
But this I say by way of concession, not of commandment. Yet I wish that all men were like me. However, each man has his own gift from God, one of this kind, and another of that kind. But I say to the unmarried and to widows, it is good for them if they remain even as I am. But if they don’t have self-control, let them marry. For it’s better to marry than to burn with passion. But to the married I command—not I, but the Lord—that the wife not leave her husband (but if she departs, let her remain unmarried, or else be reconciled to her husband), and that the husband not leave his wife.
But to the rest I—not the Lord—say, if any brother has an unbelieving wife, and she is content to live with him, let him not leave her. The woman who has an unbelieving husband, and he is content to live with her, let her not leave her husband. For the unbelieving husband is sanctified in the wife, and the unbelieving wife is sanctified in the husband. Otherwise your children would be unclean, but now they are holy. Yet if the unbeliever departs, let there be separation. The brother or the sister is not under bondage in such cases, but God has called us in peace. For how do you know, wife, whether you will save your husband? Or how do you know, husband, whether you will save your wife?
Only, as the Lord has distributed to each man, as God has called each, so let him walk. So I command in all the assemblies.
Was anyone called having been circumcised? Let him not become uncircumcised. Has anyone been called in uncircumcision? Let him not be circumcised. Circumcision is nothing, and uncircumcision is nothing, but what matters is keeping God’s commandments. Let each man stay in that calling in which he was called. Were you called being a bondservant? Don’t let that bother you, but if you get an opportunity to become free, use it. For he who was called in the Lord being a bondservant is the Lord’s free man. Likewise he who was called being free is Christ’s bondservant. You were bought with a price. Don’t become bondservants of men. Brothers, let each man, in whatever condition he was called, stay in that condition with God.
Now concerning virgins, I have no commandment from the Lord, but I give my judgment as one who has obtained mercy from the Lord to be trustworthy. Therefore I think that because of the distress that is on us, it’s good for a man to remain as he is. Are you bound to a wife? Don’t seek to be freed. Are you free from a wife? Don’t seek a wife. But if you marry, you have not sinned. If a virgin marries, she has not sinned. Yet such will have oppression in the flesh, and I want to spare you. But I say this, brothers: the time is short. From now on, both those who have wives may be as though they had none; and those who weep, as though they didn’t weep; and those who rejoice, as though they didn’t rejoice; and those who buy, as though they didn’t possess; and those who use the world, as not using it to the fullest. For the mode of this world passes away.
But I desire to have you to be free from cares. He who is unmarried is concerned for the things of the Lord, how he may please the Lord; but he who is married is concerned about the things of the world, how he may please his wife. There is also a difference between a wife and a virgin. The unmarried woman cares about the things of the Lord, that she may be holy both in body and in spirit. But she who is married cares about the things of the world—how she may please her husband. This I say for your own benefit, not that I may ensnare you, but for that which is appropriate, and that you may attend to the Lord without distraction.
But if any man thinks that he is behaving inappropriately toward his virgin, if she is past the flower of her age, and if need so requires, let him do what he desires. He doesn’t sin. Let them marry. But he who stands steadfast in his heart, having no urgency, but has power over his own will, and has determined in his own heart to keep his own virgin, does well. So then both he who gives his own virgin in marriage does well, and he who doesn’t give her in marriage does better.
A wife is bound by law for as long as her husband lives; but if the husband is dead, she is free to be married to whomever she desires, only in the Lord. But she is happier if she stays as she is, in my judgment, and I think that I also have God’s Spirit.
Now concerning things sacrificed to idols: We know that we all have knowledge. Knowledge puffs up, but love builds up. But if anyone thinks that he knows anything, he doesn’t yet know as he ought to know. But anyone who loves God is known by him.
Therefore concerning the eating of things sacrificed to idols, we know that no idol is anything in the world, and that there is no other God but one. For though there are things that are called “gods”, whether in the heavens or on earth—as there are many “gods” and many “lords”— yet to us there is one God, the Father, of whom are all things, and we for him; and one Lord, Jesus Christ, through whom are all things, and we live through him.
However, that knowledge isn’t in all men. But some, with consciousness of an idol until now, eat as of a thing sacrificed to an idol, and their conscience, being weak, is defiled. But food will not commend us to God. For neither, if we don’t eat are we the worse, nor if we eat are we the better. But be careful that by no means does this liberty of yours become a stumbling block to the weak. For if a man sees you who have knowledge sitting in an idol’s temple, won’t his conscience, if he is weak, be emboldened to eat things sacrificed to idols? And through your knowledge, he who is weak perishes, the brother for whose sake Christ died. Thus, sinning against the brothers, and wounding their conscience when it is weak, you sin against Christ. Therefore, if food causes my brother to stumble, I will eat no meat forever more, that I don’t cause my brother to stumble.
Am I not free? Am I not an apostle? Haven’t I seen Jesus Christ, our Lord? Aren’t you my work in the Lord? If to others I am not an apostle, yet at least I am to you; for you are the seal of my apostleship in the Lord.
My defense to those who examine me is this: Have we no right to eat and to drink? Have we no right to take along a wife who is a believer, even as the rest of the apostles, and the brothers of the Lord, and Cephas? Or have only Barnabas and I no right to not work? What soldier ever serves at his own expense? Who plants a vineyard, and doesn’t eat of its fruit? Or who feeds a flock, and doesn’t drink from the flock’s milk?
Do I speak these things according to the ways of men? Or doesn’t the law also say the same thing? For it is written in the law of Moses, “You shall not muzzle an ox while it treads out the grain.” Is it for the oxen that God cares, or does he say it assuredly for our sake? Yes, it was written for our sake, because he who plows ought to plow in hope, and he who threshes in hope should partake of his hope. If we sowed to you spiritual things, is it a great thing if we reap your fleshly things? If others partake of this right over you, don’t we yet more?
Nevertheless we didn’t use this right, but we bear all things, that we may cause no hindrance to the Good News of Christ. Don’t you know that those who serve around sacred things eat from the things of the temple, and those who wait on the altar have their portion with the altar? Even so the Lord ordained that those who proclaim the Good News should live from the Good News.
But I have used none of these things, and I don’t write these things that it may be done so in my case; for I would rather die, than that anyone should make my boasting void. For if I preach the Good News, I have nothing to boast about, for necessity is laid on me; but woe is to me if I don’t preach the Good News. For if I do this of my own will, I have a reward. But if not of my own will, I have a stewardship entrusted to me. What then is my reward? That when I preach the Good News, I may present the Good News of Christ without charge, so as not to abuse my authority in the Good News.
For though I was free from all, I brought myself under bondage to all, that I might gain the more. To the Jews I became as a Jew, that I might gain Jews; to those who are under the law, as under the law, that I might gain those who are under the law; to those who are without law, as without law (not being without law toward God, but under law toward Christ), that I might win those who are without law. To the weak I became as weak, that I might gain the weak. I have become all things to all men, that I may by all means save some. Now I do this for the sake of the Good News, that I may be a joint partaker of it. Don’t you know that those who run in a race all run, but one receives the prize? Run like that, so that you may win. Every man who strives in the games exercises self-control in all things. Now they do it to receive a corruptible crown, but we an incorruptible. I therefore run like that, not aimlessly. I fight like that, not beating the air, but I beat my body and bring it into submission, lest by any means, after I have preached to others, I myself should be disqualified.
Now I would not have you ignorant, brothers, that our fathers were all under the cloud, and all passed through the sea; and were all baptized into Moses in the cloud and in the sea; and all ate the same spiritual food; and all drank the same spiritual drink. For they drank of a spiritual rock that followed them, and the rock was Christ. However with most of them, God was not well pleased, for they were overthrown in the wilderness.
Now these things were our examples, to the intent we should not lust after evil things as they also lusted. Don’t be idolaters, as some of them were. As it is written, “The people sat down to eat and drink, and rose up to play.” Let’s not commit sexual immorality, as some of them committed, and in one day twenty-three thousand fell. Let’s not test Christ, as some of them tested, and perished by the serpents. Don’t grumble, as some of them also grumbled, and perished by the destroyer. Now all these things happened to them by way of example, and they were written for our admonition, on whom the ends of the ages have come. Therefore let him who thinks he stands be careful that he doesn’t fall.
No temptation has taken you except what is common to man. God is faithful, who will not allow you to be tempted above what you are able, but will with the temptation also make the way of escape, that you may be able to endure it.
Therefore, my beloved, flee from idolatry. I speak as to wise men. Judge what I say. The cup of blessing which we bless, isn’t it a sharing of the blood of Christ? The bread which we break, isn’t it a sharing of the body of Christ? Because there is one loaf of bread, we, who are many, are one body; for we all partake of the one loaf of bread. Consider Israel according to the flesh. Don’t those who eat the sacrifices participate in the altar?
What am I saying then? That a thing sacrificed to idols is anything, or that an idol is anything? But I say that the things which the Gentiles sacrifice, they sacrifice to demons and not to God, and I don’t desire that you would have fellowship with demons. You can’t both drink the cup of the Lord and the cup of demons. You can’t both partake of the table of the Lord and of the table of demons. Or do we provoke the Lord to jealousy? Are we stronger than he?
“All things are lawful for me,” but not all things are profitable. “All things are lawful for me,” but not all things build up. Let no one seek his own, but each one his neighbor’s good. Whatever is sold in the butcher shop, eat, asking no question for the sake of conscience, for “the earth is the Lord’s, and its fullness.” But if one of those who don’t believe invites you to a meal, and you are inclined to go, eat whatever is set before you, asking no questions for the sake of conscience. But if anyone says to you, “This was offered to idols,” don’t eat it for the sake of the one who told you, and for the sake of conscience. For “the earth is the Lord’s, with all its fullness.” Conscience, I say, not your own, but the other’s conscience. For why is my liberty judged by another conscience? If I partake with thankfulness, why am I denounced for something I give thanks for?
Whether therefore you eat or drink, or whatever you do, do all to the glory of God. Give no occasion for stumbling, whether to Jews, to Greeks, or to the assembly of God; even as I also please all men in all things, not seeking my own profit, but the profit of the many, that they may be saved.
Be imitators of me, even as I also am of Christ.
Now I praise you, brothers, that you remember me in all things, and hold firm the traditions, even as I delivered them to you. But I would have you know that the head of every man is Christ, and the head of the woman is man, and the head of Christ is God. Every man praying or prophesying, having his head covered, dishonors his head. But every woman praying or prophesying with her head uncovered dishonors her head. For it is one and the same thing as if she were shaved. For if a woman is not covered, let her hair also be cut off. But if it is shameful for a woman to have her hair cut off or be shaved, let her be covered. For a man indeed ought not to have his head covered, because he is the image and glory of God, but the woman is the glory of the man. For man is not from woman, but woman from man; for man wasn’t created for the woman, but woman for the man. For this cause the woman ought to have authority over her own head, because of the angels.
Nevertheless, neither is the woman independent of the man, nor the man independent of the woman, in the Lord. For as woman came from man, so a man also comes through a woman; but all things are from God. Judge for yourselves. Is it appropriate that a woman pray to God unveiled? Doesn’t even nature itself teach you that if a man has long hair, it is a dishonor to him? But if a woman has long hair, it is a glory to her, for her hair is given to her for a covering. But if any man seems to be contentious, we have no such custom, neither do God’s assemblies.
But in giving you this command I don’t praise you, because you come together not for the better but for the worse. For first of all, when you come together in the assembly, I hear that divisions exist among you, and I partly believe it. For there also must be factions among you, that those who are approved may be revealed among you. When therefore you assemble yourselves together, it is not the Lord’s supper that you eat. For in your eating each one takes his own supper first. One is hungry, and another is drunken. What, don’t you have houses to eat and to drink in? Or do you despise God’s assembly and put them to shame who don’t have enough? What shall I tell you? Shall I praise you? In this I don’t praise you.
For I received from the Lord that which also I delivered to you, that the Lord Jesus on the night in which he was betrayed took bread. When he had given thanks, he broke it and said, “Take, eat. This is my body, which is broken for you. Do this in memory of me.” In the same way he also took the cup after supper, saying, “This cup is the new covenant in my blood. Do this, as often as you drink, in memory of me.” For as often as you eat this bread and drink this cup, you proclaim the Lord’s death until he comes.
Therefore whoever eats this bread or drinks the Lord’s cup in a way unworthy of the Lord will be guilty of the body and the blood of the Lord. But let a man examine himself, and so let him eat of the bread and drink of the cup. For he who eats and drinks in an unworthy way eats and drinks judgment to himself if he doesn’t discern the Lord’s body. For this cause many among you are weak and sickly, and not a few sleep. For if we discerned ourselves, we wouldn’t be judged. But when we are judged, we are disciplined by the Lord, that we may not be condemned with the world. Therefore, my brothers, when you come together to eat, wait for one another. But if anyone is hungry, let him eat at home, lest your coming together be for judgment. The rest I will set in order whenever I come.
Now concerning spiritual things, brothers, I don’t want you to be ignorant. You know that when you were heathen, you were led away to those mute idols, however you might be led. Therefore I make known to you that no man speaking by God’s Spirit says, “Jesus is accursed.” No one can say, “Jesus is Lord,” but by the Holy Spirit.
Now there are various kinds of gifts, but the same Spirit. There are various kinds of service, and the same Lord. There are various kinds of workings, but the same God who works all things in all. But to each one is given the manifestation of the Spirit for the profit of all. For to one is given through the Spirit the word of wisdom, and to another the word of knowledge according to the same Spirit, to another faith by the same Spirit, and to another gifts of healings by the same Spirit, and to another workings of miracles, and to another prophecy, and to another discerning of spirits, to another different kinds of languages, and to another the interpretation of languages. But the one and the same Spirit produces all of these, distributing to each one separately as he desires.
For as the body is one and has many members, and all the members of the body, being many, are one body; so also is Christ. For in one Spirit we were all baptized into one body, whether Jews or Greeks, whether bond or free; and were all given to drink into one Spirit.
For the body is not one member, but many. If the foot would say, “Because I’m not the hand, I’m not part of the body,” it is not therefore not part of the body. If the ear would say, “Because I’m not the eye, I’m not part of the body,” it’s not therefore not part of the body. If the whole body were an eye, where would the hearing be? If the whole were hearing, where would the smelling be? But now God has set the members, each one of them, in the body, just as he desired. If they were all one member, where would the body be? But now they are many members, but one body. The eye can’t tell the hand, “I have no need for you,” or again the head to the feet, “I have no need for you.” No, much rather, those members of the body which seem to be weaker are necessary. Those parts of the body which we think to be less honorable, on those we bestow more abundant honor; and our unpresentable parts have more abundant modesty, while our presentable parts have no such need. But God composed the body together, giving more abundant honor to the inferior part, that there should be no division in the body, but that the members should have the same care for one another. When one member suffers, all the members suffer with it. When one member is honored, all the members rejoice with it.
Now you are the body of Christ, and members individually. God has set some in the assembly: first apostles, second prophets, third teachers, then miracle workers, then gifts of healings, helps, governments, and various kinds of languages. Are all apostles? Are all prophets? Are all teachers? Are all miracle workers? Do all have gifts of healings? Do all speak with various languages? Do all interpret? But earnestly desire the best gifts. Moreover, I show a most excellent way to you.
If I speak with the languages of men and of angels, but don’t have love, I have become sounding brass or a clanging cymbal. If I have the gift of prophecy, and know all mysteries and all knowledge, and if I have all faith, so as to remove mountains, but don’t have love, I am nothing. If I give away all my goods to feed the poor, and if I give my body to be burned, but don’t have love, it profits me nothing.
Love is patient and is kind. Love doesn’t envy. Love doesn’t brag, is not proud, doesn’t behave itself inappropriately, doesn’t seek its own way, is not provoked, takes no account of evil; doesn’t rejoice in unrighteousness, but rejoices with the truth; bears all things, believes all things, hopes all things, and endures all things.
Love never fails. But where there are prophecies, they will be done away with. Where there are various languages, they will cease. Where there is knowledge, it will be done away with. For we know in part and we prophesy in part; but when that which is complete has come, then that which is partial will be done away with. When I was a child, I spoke as a child, I felt as a child, I thought as a child. Now that I have become a man, I have put away childish things. For now we see in a mirror, dimly, but then face to face. Now I know in part, but then I will know fully, even as I was also fully known. But now faith, hope, and love remain—these three. The greatest of these is love.
Follow after love and earnestly desire spiritual gifts, but especially that you may prophesy. For he who speaks in another language speaks not to men, but to God, for no one understands, but in the Spirit he speaks mysteries. But he who prophesies speaks to men for their edification, exhortation, and consolation. He who speaks in another language edifies himself, but he who prophesies edifies the assembly. Now I desire to have you all speak with other languages, but even more that you would prophesy. For he is greater who prophesies than he who speaks with other languages, unless he interprets, that the assembly may be built up.
But now, brothers, if I come to you speaking with other languages, what would I profit you unless I speak to you either by way of revelation, or of knowledge, or of prophesying, or of teaching? Even lifeless things that make a sound, whether pipe or harp, if they didn’t give a distinction in the sounds, how would it be known what is piped or harped? For if the trumpet gave an uncertain sound, who would prepare himself for war? So also you, unless you uttered by the tongue words easy to understand, how would it be known what is spoken? For you would be speaking into the air. There are, it may be, so many kinds of languages in the world, and none of them is without meaning. If then I don’t know the meaning of the language, I would be to him who speaks a foreigner, and he who speaks would be a foreigner to me. So also you, since you are zealous for spiritual gifts, seek that you may abound to the building up of the assembly.
Therefore let him who speaks in another language pray that he may interpret. For if I pray in another language, my spirit prays, but my understanding is unfruitful.
What should I do? I will pray with the spirit, and I will pray with the understanding also. I will sing with the spirit, and I will sing with the understanding also. Otherwise, if you bless with the spirit, how will he who fills the place of the unlearned say the “Amen” at your giving of thanks, seeing he doesn’t know what you say? For you most certainly give thanks well, but the other person is not built up. I thank my God, I speak with other languages more than you all. However, in the assembly I would rather speak five words with my understanding, that I might instruct others also, than ten thousand words in another language.
Brothers, don’t be children in thoughts, yet in malice be babies, but in thoughts be mature. In the law it is written, “By men of strange languages and by the lips of strangers I will speak to this people. They won’t even listen to me that way, says the Lord.” Therefore other languages are for a sign, not to those who believe, but to the unbelieving; but prophesying is for a sign, not to the unbelieving, but to those who believe. If therefore the whole assembly is assembled together and all speak with other languages, and unlearned or unbelieving people come in, won’t they say that you are crazy? But if all prophesy, and someone unbelieving or unlearned comes in, he is reproved by all, and he is judged by all. And thus the secrets of his heart are revealed. So he will fall down on his face and worship God, declaring that God is among you indeed.
What is it then, brothers? When you come together, each one of you has a psalm, has a teaching, has a revelation, has another language, or has an interpretation. Let all things be done to build each other up. If any man speaks in another language, let there be two, or at the most three, and in turn; and let one interpret. But if there is no interpreter, let him keep silent in the assembly, and let him speak to himself and to God. Let two or three of the prophets speak, and let the others discern. But if a revelation is made to another sitting by, let the first keep silent. For you all can prophesy one by one, that all may learn and all may be exhorted. The spirits of the prophets are subject to the prophets, for God is not a God of confusion but of peace, as in all the assemblies of the saints. Let the wives be quiet in the assemblies, for it has not been permitted for them to be talking except in submission, as the law also says, if they desire to learn anything. “Let them ask their own husbands at home, for it is shameful for a wife to be talking in the assembly.” What!? Was it from you that the word of God went out? Or did it come to you alone?
If any man thinks himself to be a prophet or spiritual, let him recognize the things which I write to you, that they are the commandment of the Lord. But if anyone is ignorant, let him be ignorant.
Therefore, brothers, desire earnestly to prophesy, and don’t forbid speaking with other languages. Let all things be done decently and in order.
Now I declare to you, brothers, the Good News which I preached to you, which also you received, in which you also stand, by which also you are saved, if you hold firmly the word which I preached to you—unless you believed in vain.
For I delivered to you first of all that which I also received: that Christ died for our sins according to the Scriptures, that he was buried, that he was raised on the third day according to the Scriptures, and that he appeared to Cephas, then to the twelve. Then he appeared to over five hundred brothers at once, most of whom remain until now, but some have also fallen asleep. Then he appeared to James, then to all the apostles, and last of all, as to the child born at the wrong time, he appeared to me also. For I am the least of the apostles, who is not worthy to be called an apostle, because I persecuted the assembly of God. But by the grace of God I am what I am. His grace which was given to me was not futile, but I worked more than all of them; yet not I, but the grace of God which was with me. Whether then it is I or they, so we preach, and so you believed.
Now if Christ is preached, that he has been raised from the dead, how do some among you say that there is no resurrection of the dead? But if there is no resurrection of the dead, neither has Christ been raised. If Christ has not been raised, then our preaching is in vain and your faith also is in vain. Yes, we are also found false witnesses of God, because we testified about God that he raised up Christ, whom he didn’t raise up if it is true that the dead are not raised. For if the dead aren’t raised, neither has Christ been raised. If Christ has not been raised, your faith is vain; you are still in your sins. Then they also who are fallen asleep in Christ have perished. If we have only hoped in Christ in this life, we are of all men most pitiable.
But now Christ has been raised from the dead. He became the first fruit of those who are asleep. For since death came by man, the resurrection of the dead also came by man. For as in Adam all die, so also in Christ all will be made alive. But each in his own order: Christ the first fruits, then those who are Christ’s at his coming. Then the end comes, when he will deliver up the Kingdom to God the Father, when he will have abolished all rule and all authority and power. For he must reign until he has put all his enemies under his feet. The last enemy that will be abolished is death. For, “He put all things in subjection under his feet.” But when he says, “All things are put in subjection”, it is evident that he is excepted who subjected all things to him. When all things have been subjected to him, then the Son will also himself be subjected to him who subjected all things to him, that God may be all in all.
Or else what will they do who are baptized for the dead? If the dead aren’t raised at all, why then are they baptized for the dead? Why do we also stand in jeopardy every hour? I affirm, by the boasting in you which I have in Christ Jesus our Lord, I die daily. If I fought with animals at Ephesus for human purposes, what does it profit me? If the dead are not raised, then “let’s eat and drink, for tomorrow we die.” Don’t be deceived! “Evil companionships corrupt good morals.” Wake up righteously and don’t sin, for some have no knowledge of God. I say this to your shame.
But someone will say, “How are the dead raised?” and, “With what kind of body do they come?” You foolish one, that which you yourself sow is not made alive unless it dies. That which you sow, you don’t sow the body that will be, but a bare grain, maybe of wheat, or of some other kind. But God gives it a body even as it pleased him, and to each seed a body of its own. All flesh is not the same flesh, but there is one flesh of men, another flesh of animals, another of fish, and another of birds. There are also celestial bodies and terrestrial bodies; but the glory of the celestial differs from that of the terrestrial. There is one glory of the sun, another glory of the moon, and another glory of the stars; for one star differs from another star in glory.
So also is the resurrection of the dead. The body is sown perishable; it is raised imperishable. It is sown in dishonor; it is raised in glory. It is sown in weakness; it is raised in power. It is sown a natural body; it is raised a spiritual body. There is a natural body and there is also a spiritual body.
So also it is written, “The first man Adam became a living soul.” The last Adam became a life-giving spirit. However, that which is spiritual isn’t first, but that which is natural, then that which is spiritual. The first man is of the earth, made of dust. The second man is the Lord from heaven. As is the one made of dust, such are those who are also made of dust; and as is the heavenly, such are they also that are heavenly. As we have borne the image of those made of dust, let’s also bear the image of the heavenly. Now I say this, brothers, that flesh and blood can’t inherit God’s Kingdom; neither does the perishable inherit imperishable.
Behold, I tell you a mystery. We will not all sleep, but we will all be changed, in a moment, in the twinkling of an eye, at the last trumpet. For the trumpet will sound and the dead will be raised incorruptible, and we will be changed. For this perishable body must become imperishable, and this mortal must put on immortality. But when this perishable body will have become imperishable, and this mortal will have put on immortality, then what is written will happen: “Death is swallowed up in victory.”
“Death, where is your sting?
Hades, where is your victory?”
The sting of death is sin, and the power of sin is the law. But thanks be to God, who gives us the victory through our Lord Jesus Christ. Therefore, my beloved brothers, be steadfast, immovable, always abounding in the Lord’s work, because you know that your labor is not in vain in the Lord.
Now concerning the collection for the saints: as I commanded the assemblies of Galatia, you do likewise. On the first day of every week, let each one of you save as he may prosper, that no collections are made when I come. When I arrive, I will send whoever you approve with letters to carry your gracious gift to Jerusalem. If it is appropriate for me to go also, they will go with me.
I will come to you when I have passed through Macedonia, for I am passing through Macedonia. But with you it may be that I will stay with you, or even winter with you, that you may send me on my journey wherever I go. For I do not wish to see you now in passing, but I hope to stay a while with you, if the Lord permits. But I will stay at Ephesus until Pentecost, for a great and effective door has opened to me, and there are many adversaries.
Now if Timothy comes, see that he is with you without fear, for he does the work of the Lord, as I also do. Therefore let no one despise him. But set him forward on his journey in peace, that he may come to me; for I expect him with the brothers.
Now concerning Apollos the brother, I strongly urged him to come to you with the brothers, but it was not at all his desire to come now; but he will come when he has an opportunity.
Watch! Stand firm in the faith! Be courageous! Be strong! Let all that you do be done in love.
Now I beg you, brothers—you know the house of Stephanas, that it is the first fruits of Achaia, and that they have set themselves to serve the saints— that you also be in subjection to such, and to everyone who helps in the work and labors. I rejoice at the coming of Stephanas, Fortunatus, and Achaicus; for that which was lacking on your part, they supplied. For they refreshed my spirit and yours. Therefore acknowledge those who are like that.
The assemblies of Asia greet you. Aquila and Priscilla greet you warmly in the Lord, together with the assembly that is in their house. All the brothers greet you. Greet one another with a holy kiss.
This greeting is by me, Paul, with my own hand. If any man doesn’t love the Lord Jesus Christ, let him be cursed. Come, Lord! The grace of the Lord Jesus Christ be with you. My love to all of you in Christ Jesus. Amen.
The World English Bible is in the Public Domain. That means that it is not copyrighted. However, "World English Bible" is a Trademark of eBible.org.
-
 @ fa0165a0:03397073
2023-07-24 10:19:27
@ fa0165a0:03397073
2023-07-24 10:19:27Below is an easy-to-read list of keyboard shortcuts and commands to navigate your Linux computer efficiently: (Note that some variations between systems may apply)
General Shortcuts: Open Terminal: Ctrl + Alt + T Close current application: Alt + F4 Switch between open applications: Alt + Tab Logout from current session: Ctrl + Alt + Del Navigating the File System: Open File Manager (Nautilus): Super (Windows key) + E Move back in directory: Alt + Left Arrow Move forward in directory: Alt + Right Arrow Go to Home directory: Ctrl + H Go to Desktop: Ctrl + D Open a folder or file: Enter Rename a file or folder: F2 Copy selected item: Ctrl + C Cut selected item: Ctrl + X Paste copied/cut item: Ctrl + V Delete selected item: Delete Create a new folder: Ctrl + Shift + N Navigating Applications: Switch between open windows of the same application: Alt + ` Close the current window: Ctrl + W Minimize the current window: Ctrl + M Maximize/Restore the current window: Ctrl + Super + Up Arrow / Down Arrow Navigating Web Browsers (e.g., Firefox, Chrome): Open a new tab: Ctrl + T Close the current tab: Ctrl + W Switch to the next tab: Ctrl + Tab Switch to the previous tab: Ctrl + Shift + Tab Open a link in a new tab: Ctrl + Left Click Go back in the browser history: Alt + Left Arrow Go forward in the browser history: Alt + Right Arrow System Controls: Lock the screen: Ctrl + Alt + L Open the system menu (context menu): Menu key (or Right-click key) or Shift + F10 Open the Run Command prompt: Alt + F2These shortcuts may vary slightly depending on the Linux distribution and desktop environment you are using. Experiment with these shortcuts to navigate your Linux system faster and more efficiently without relying on the mouse.
Since websites are such an important interface for the information of today, I have here appended the list with some navigational hotkeys for web browsers (e.g., Firefox, Chrome) on Linux:
General Navigation: Scroll down: Spacebar Scroll up: Shift + Spacebar Scroll horizontally: Hold Shift and scroll with the mouse wheel or arrow keys Go to the top of the page: Home Go to the bottom of the page: End Refresh the page: F5 or Ctrl + R Stop loading the page: Esc Link and Page Navigation: Move focus to the next link or interactive element: Tab Move focus to the previous link or interactive element: Shift + Tab Activate/follow a link or button: Enter Open link in a new tab: Ctrl + Enter (Cmd + Enter on macOS) Open link in a new background tab: Ctrl + Shift + Enter (Cmd + Shift + Enter on macOS) Open link in a new window: Shift + Enter Go back to the previous page: Backspace or Alt + Left Arrow Go forward to the next page: Alt + Right Arrow Searching: Find text on the page: Ctrl + F Find next occurrence: Ctrl + G Find previous occurrence: Ctrl + Shift + G Tab Management: Open a new tab: Ctrl + T Close the current tab: Ctrl + W Reopen the last closed tab: Ctrl + Shift + T Switch to the next tab: Ctrl + Tab Switch to the previous tab: Ctrl + Shift + Tab Switch to a specific tab (numbered from left to right): Ctrl + [1-8] Switch to the last tab: Ctrl + 9 Form Interaction: Move to the next form field: Tab Move to the previous form field: Shift + Tab Check/uncheck checkboxes and radio buttons: Spacebar Select an option from a dropdown menu: Enter, then arrow keys to navigate options Miscellaneous: Open the browser's menu: Alt (sometimes F10) Open the address bar (omnibox): Ctrl + L or Alt + DRemember, the accessibility of websites can vary, and some sites might have different keyboard navigation implementations. In some cases, you may need to enable keyboard navigation in the browser's settings or extensions. Additionally, browser updates might introduce changes to keyboard shortcuts, so it's always good to check the latest documentation or help resources for your specific browser version.
But I hope this helps as an tldr and getting started with navigating your laptop the ways pro role.
Version controlled over at github gist.
-
 @ 4729b2c0:6074b4a9
2023-08-02 01:35:08
@ 4729b2c0:6074b4a9
2023-08-02 01:35:08鈾是一種重要的放射性元素,在全球能源生產中擔任著關鍵角色,為全球的核電廠提供燃料。儘管鈾元素豐富,鈾市場近期卻出現了動態變化,為敏銳的投資者提供了獲取可觀收益的可能性。2022年6月,我在文章 "投資鈾股:風險與收益" 中討論了鈾投資的回報與風險。現在,有鑒於近期的發展,是時候提供一個更新的視角了。
鈾市場的持續復甦
2023年為鈾帶來了復甦的曙光,預計其價格將在全年上漲。這種上揚趨勢主要源於全球範圍內對核反應爐的需求增加和持續的地緣政治不確定性。在2022年,鈾價格在50至60美元的範圍內確定了關鍵的合併階段。然而,我們堅信,2023年可能成為轉折點,價格有可能突破60美元的門檻,為牛市的鈾市場鋪平道路。
鈾產國和地緣政治因素
目前,世界上最大的鈾產國包括哈薩克斯坦、納米比亞、加拿大、澳大利亞和烏茲別克斯坦。然而,圍繞鈾生產的地緣政治格局仍然動盪。幾乎所有的頂級鈾產國,除了加拿大和澳大利亞,都面臨著不同程度的不穩定。特別是,加拿大的阿薩巴斯卡盆地由於其豐富的高品位鈾礦床和其親礦石的政治氣候,正逐漸成為穩定性和潛力的象徵。
投資鈾股:潛在的收益和風險
投資鈾股為投資者提供了獲取豐厚回報和多元化投資組合的機會。然而,這也帶來了自身的風險。這些風險主要取決於鈾價格的波動性和主要產國的地緣政治緊張情況。此外,關於鈾礦開採和核反應爐安全性的環保問題也仍然存在。因此,對於可能的鈾投資者來說,徹底的研究、盡職調查和謹慎的風險管理至關重要。
值得關注的鈾股
希望把握有利於鈾市場的投資者可能會進一步研究以下這些股票:
Cameco Corporation (CCJ) NexGen Energy Ltd. (NXE) Denison Mines Corp. (DNN) Energy Fuels Inc. (UUUU) Uranium Royalty Corp. (URC) BHP Group (BHP) Uranium Energy Corp. (UEC)
這些公司代表了鈾市場上的多樣化機會,但潛在的投資者在投資之前應進行全面的研究。
儘管存在不確定性和風險,鈾市場在2023年仍具有強大的潛力。隨著全球持續努力減少碳排放並尋求降低能源成本,核能 - 也就是鈾 - 可能握有一些答案。雖然上述鈾股提供了一個優秀的起點,但深入分析和謹慎的風險管理仍然是投資成功的關鍵。無論如何,鈾投資在這個不確定的世界中確實為投資者提供了新的收益可能性。
Medium: Flextiger
Twitter: FlextigerA
-
 @ 0e649f32:8a33b33b
2023-08-01 22:30:27
@ 0e649f32:8a33b33b
2023-08-01 22:30:27Join Scott "Shalom" Klein each week and get down to business! An avid networker and dedicated entrepreneur, Shalom will share the advice you need, the strategies that work and the stories of success to help you with both business and jobs. Special guest, Richard Blank of Costa Rica's Call Center.
Richard’s vision quest journey is filled with twists and turns. When he was 27 years old, he relocated to Costa Rica to train employees for one of the larger call centers in San Jose. With a mix of motivational public speaking style backed by tactful and appropriate rhetoric, Richard shared his knowledge and trained over 10 000 bilingual telemarketers.
Richard Blank has the largest collection of restored American Pinball machines and antique Rockola Jukeboxes in Central America making gamification a strong part of CCC culture. Richard Blank is the Chief Executive Officer for Costa Rica’s Call Center since 2008.
Mr. Richard Blank holds a bachelors degree in Communication and Spanish from the University of Arizona and a certificate of language proficiency from the University of Sevilla, Spain. A Keynote speaker for Philadelphia's Abington High School 68th National Honors Society induction ceremony. In addition, inducted into the 2023 Hall of Fame for Business. Giving back to Abington Senior High School is very important to Mr. Blank. As such, he endows a scholarship each year for students that plan on majoring in a world language at the university level.
Costa Rica’s Call Center (CCC) is a state of the art BPO telemarketing outsource company located in the capital city of San Jose, Costa Rica. Our main focus has been, and will always be to personally train each and every Central America call center agent so that we may offer the highest quality of outbound and inbound telemarketing solutions and bilingual customer service to small and medium sized international companies, entrepreneurs as well as fortune 500 companies.
https://costaricascallcenter.com/en/outbound-bpo-campaigns/
RichardBlank #CostaRica #CallCenter #Outsourcing #Telemarketing #BPO #Sales #Entrepreneur #B2B #Business #Podcast #Leadgeneration #Appointmentsetting #getdowntobusiness
-
 @ 7d41cb81:18ac37ed
2023-08-01 21:00:34
@ 7d41cb81:18ac37ed
2023-08-01 21:00:34,,m,
-
 @ 93518f91:412cb50c
2023-08-01 19:08:39
@ 93518f91:412cb50c
2023-08-01 19:08:39Timechain Calendar gives you several ways to search the Bitcoin timechain for a specific block in the past… or in the future!
The slider at the bottom of the interface allows you to scrub thru the entire chain quickly! The supply/issuance data (top-left corner) changes on the fly. Let go of the slider to load the data for a past block. Buttons on the side of the slider let you move 1 block at a time.
You can also jump to a specific block in the past by entering a past block height directly! Click the search icon then Search by Block or just click the big block height number in the middle of the interface directly.
Find a past block by date/time: Click the search icon then Search by Date or click directly on the date or the time in the interface. Enter a date and time in the past and Timechain Calendar will load the block that confirmed most recently before the entered moment in time.
The Timechain Calendar Wizard loves estimating the future! If you search for a block that has not occurred yet, the Wizard will estimate the future date of block. The average block time can be adjusted to see the affect a different pace of blocks will have on the estimate.
You can also search for a future block based on a specific future date. Just enter a date in the future and the Wizard will estimate the future block. Adjusting average block time in this search will affect the estimated block! This is new in v0.3.3
Last but not least there are a couple shortcuts to the estimate for the upcoming halving. Clicking “V” in the epoch quick links or “🔮Wizard” in the Next Halving sidebar and the interface will open an estimation of the halving block 840000!
Happy hunting for blocks!!
-
 @ c8df6ae8:22293a06
2023-07-24 04:30:59
@ c8df6ae8:22293a06
2023-07-24 04:30:59The Kennedy administration will begin to back the US dollar with real, finite assets such as gold, silver, platinum and Bitcoin, which is the world's hardest liquid asset, to strengthen the US dollar and guarantee its continued success as the global reserve currency.
— Robert F. Kennedy Jr.Welcome to the latest issue of the Bitcoin For Families newsletter. This issue covers the potential implications of a Bitcoin backed US dollar.
What are the implications of a Bitcoin backed US dollar?
On July 19th, presidential candidate Robert Kennedy Jr gave a speech at a PAC event where he declared the plans of his administration to, at least partially, back the US dollar with gold, silver, platinum and Bitcoin.
You can watch the whole 10 minutes speech here:
What could happen if RFK Jr. does get elected and goes forward with this promise? Let’s look at some scenarios.
What will the RFK administration do?
RFK Jr. said he would back 1% of the treasury bills (T-Bills) issued by the treasury with gold, silver, platinum and Bitcoin.
T-Bills are short-term securities issued by the government with a maturity rate of 4, 8,13, 17, 26 or 52 weeks. The interest rate is set based on the offers done by those bidding on the auction. For example, a recent auction of 26 week T-Bills closed with an interest rate of 5.25%.
Let’s assume that Bitcoin is priced at $32,000 US dollars and that you buy a 26 weeks T-Bill worth $100 and backed by Bitcoin. This would mean that the US government must have possession of 312,500 satoshi (0.00312500 BTC) to back this T-Bill and you should have the option to exchange the T-Bill for that amount of Bitcoin at the end of the 26 weeks.
What would happen if after 26 weeks, the US dollar became weaker than Bitcoin and the exchange rate is now $34,000? Now you only need 294,118 satoshis to back the $100 T-Bill and since the US government had set aside 312,500 satoshi, then all is good.
What would happen if after 26 weeks, the US dollar became stronger than Bitcoin and the exchange rate is now $28,000? Now you need 357,143 satoshi to back the T-Bill and since the US government had set aside 312,500 satoshi, they would need to purchase 44,643 more satoshi to continue to back the T-Bill.
I doubt the US government will be willing to take this exchange rate risk with its debt obligations.
Therefore, the most likely scenario is that the US government sets a fixed exchange rate for the maturity life of the T-Bill. Maybe equal to the exchange rate at the time of the auction.
This means that after 26 weeks you could exchange your T-Bill for 312,500 satoshi no matter what the actual exchange rate is at that point.
What will this do to the price of Bitcoin or the US dollar?
-
The US dollar will get stronger when compared against other fiat currencies not backed by anything:
The US government will send a very strong signal to the world that Bitcoin is the new gold and a very valid store of value. The world’s hardest liquid asset.
Therefore, backing the US dollar with Bitcoin will make the US dollar stronger when compared with other fiat currencies.
-
The US dollar will get weaker when compared against Bitcoin:
The demand for Bitcoin by the US government will put upward pressure on the exchange rate for Bitcoin against all fiat currencies, including the US dollar.
-
A continued policy of expanding the amount of T-Bills backed by Bitcoin will only exacerbate this process, making the US dollar stronger against other countries currencies and driving the price of Bitcoin up both against the US dollar and by extension other fiat currencies (which by definition are now weaker than the US dollar).
What will investors do?
Investors will demand either the same or maybe even lower interest rates for Bitcoin backed T-Bills with the assumption that the Bitcoin amount backing the T-Bill will be worth more after 26 weeks.
The scenario where investors demand higher interest rates because they believe that Bitcoin will get weaker is unlikely since, even if this happens, the T-Bills are denominated in US dollars and investors won’t be forced to redeem the T-Bill for Bitcoin at the end of the 26 weeks.
What will other countries do?
At first, other countries will just watch and see.
But the upward pressure on the price of Bitcoin will make a US T-Bill more attractive than its European Central Bank equivalent causing the Euro to lose value compared against the US dollar.
The same applies to any other fiat currency (not backed by anything).
Other countries will be forced to back some of their short-term debt with Bitcoin to avoid having to pay higher interest rates to counteract the higher attractiveness of the US T-Bill.
The consolidation of Bitcoin as store of value
If all countries start using Bitcoin to back their debt, that will consolidate Bitcoin as the best store of value.
Bitcoin has to first settle as a store of value before it can be used as a medium of exchange and unit of account (what is commonly known as hyperbitcoinization). This possible action by the US government might well be the linchpin that triggers the hyperbitcoinization.
If the other countries do nothing, the US dollar will cement itself as the global reserve currency and the hyperbitcoinization will still happen, just a bit slower since there will be no demand from other treasuries.
Notable notes
nostr:note1dgh2ga7q397huzfcf9ah06ptvcxxwcmfx5yhctw0rh4t6ylvud4s0nrn75
Recommendations
Max DeMarco
Max is the creator of a great documentary about social media and why we need Nostr.
Watch the documentary here:
 You can follow Max here.
You can follow Max here.Bitcoin Therapy 🧠
Level up your Bitcoin knowledge in 3 minutes...every Sunday
Check it out here.
What did you think of today's newsletter?
Your feedback helps me create the best newsletter possible for you.
Please leave a comment and checkout comments from other subscribers and readers. I love hearing from the Bitcoin For Families community ❤️ 🙏🏻
Buy Bitcoin with Swan
If you want to buy Bitcoin, I highly recommend using Swan. They are a Bitcoin only business that is focused on self-custody and educating their users. It's where I buy my Bitcoin.
Use this link to receive $10 free to get you started.
See you again next week! — Alejandro
This newsletter is for educational purposes. It does not represent financial advice. Do your own research before buying Bitcoin.
-
-
 @ 7f4f672a:c184579e
2023-08-01 17:49:06
@ 7f4f672a:c184579e
2023-08-01 17:49:06I'm publishing directly to Nostr Straight from Obsidian, No middle man, No browser scan. Just words and letters, Thoughts unfettered. It would be a sin, Not to install my plugin.
grownostr #obsidian #plugin #poem #poemstr
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 5ada3677:7c21c9db
2023-08-01 17:44:41
@ 5ada3677:7c21c9db
2023-08-01 17:44:41 小男生一身衣服配色,完全是教科書級別的。腳上一雙飛躍跑鞋。
小男生一身衣服配色,完全是教科書級別的。腳上一雙飛躍跑鞋。Bilbao跟很多歐洲城市一樣,禮拜天全城閉門打烊,除了一部分餐館之外。開始時候覺得有點不習慣,似乎頗不方便,買瓶牛奶都休想的樣子。漸漸覺得如此真好,好在非常清靜,整座城市安安靜靜,街頭幾乎沒有人,每週一次如此的清靜,太好了。另一個好,是禮拜天大家都在家裡了,古老而溫暖,多麼好。


對面房子的老爺叔,每個禮拜天的清晨,開著燦爛輝煌的歌劇詠嘆調,拿著雪白的大毛巾擦玻璃窗。因為街上太靜了,他的詠嘆調清清楚楚地隔街傳過來,我坐在陽台上飲碧螺春,真是天籟一般。此地有南美移民的女傭,上門幫忙打理家務,頗普遍,這位鄰居老爺叔親力親為,包子說,是我學習的好榜樣。
另一側的鄰居也是老爺叔,中午搬出午餐在陽台上吃,一個人有滋有味飲湯,是番茄冷湯吧我猜的,西班牙人的可以喝的色拉,然後還有一份外國報紙,厚厚的週末版,在桌上。報紙是西班牙的、還是外國的,一眼就分出來了。Bilbao小城,滿街的書報亭,天天都買得到紐/約/時/報和金融/時/報。上海是五星酒店也覓不到外/國/報紙的。


禮拜天,清晨晃去老城吃個早餐,順手買些麵包回家,老城裡比較多老而好的麵包舖子。
老城裡遊客散落,德國人荷蘭人,大多是一家人出來過暑假,父母帶兩三個孩子,或者退休老夫妻,基本是如此配置。
走兩步,結果沒有進麵包舖、也沒有進早餐小館子,而是先進了舊書店。舊書店裡鋪了滿地的老地毯,音樂很對頭,鬆軟宜人,濃濃的。這家店裡很多1850年左右的植物畫和動物畫,精得不得了,一頁一頁,看了個飽。還有銅版畫,更精,揀了兩幅。
角落裡翻到一冊美食指南之類的,1995年出版的,有趣的是,書的舊主人,真的拿著這冊書,當聖經一樣去覓美食,書裡留著很多筆記、剪報、菜單、發票,蹲在角落裡,默默翻了一遍,非常有味道,雖然我完全看不懂西班牙文。


去買麵包,小麵包舖頗多,最好的那間,走過去的時候,已經"今日售罄明日請早",當時還沒到中午12點。只好掉頭換一間,問包子去哪間,包子說,看看本地老太太去哪間、我們跟著去。結果跟著本地老太太,進了一家1983年的麵包舖子,買到很稱心的法棍,40年半老之店,生意興隆,需要稍稍排一點隊。




隨便一間咖啡館小酒吧,1850年的
這個禮拜天,在家聽了很多包子的音樂,從非洲馬里人的音樂、非洲尼日利亞的音樂,到土耳其音樂、古巴音樂,還在安達魯西亞的電台上,聽了久久的佛萊明戈音樂,無伴奏的佛萊明戈詠唱,絕美絕贊,跟信天游有很多異曲同工。我把網址留在下面,希望各位也能enjoy。
這個禮拜天,洗了床單、燉了桃膠,學著做了兩道巴斯克料理,讀完了一本中文書茨威格的《昨日的世界》和一本英文書《Basque Country》。
安靜的禮拜天。

 買了麵包出來,剛好遇見工人們在搬運麵粉
買了麵包出來,剛好遇見工人們在搬運麵粉佛萊明戈音樂在這裡


夏日拾珠系列在這裡
nostr:naddr1qqxnzd3exqenjvpc8q6nxvfhqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c83ac7g
nostr:naddr1qqxnzd3exqenjvfjx5ur2wpeqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c8mrqrm
nostr:naddr1qqxnzd3exqenjvf4x5ervd33qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cdqaveh
nostr:naddr1qqxnzd3exqenjvfcxscnqd3nqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823czmjr4k
nostr:naddr1qqxnzd3exqenjv33xqunjwphqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c0ggymy
nostr:naddr1qqxnzd3exq6nxdfkxv6rqdp5qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823c42u6cr
nostr:naddr1qqxnzd3exq6nxdfexqerzdejqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cawzeyh
nostr:naddr1qqxnzd3exq6nxd3j8qmnywfcqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cp6dd24
nostr:naddr1qqxnzd3exqunqdphxu6nzdenqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823cc8avfs -
 @ 7f4f672a:c184579e
2023-08-01 17:42:15
@ 7f4f672a:c184579e
2023-08-01 17:42:15The Italian Mob a.k.a 'Cosa Nostra' are famous worldwide. 'Cosa Nostra' means "our thing", what about 'Cosa Nostr' ? What is Nostr's thing?
grownostr #obsidian #tech
-
 @ ba680951:ec182a0e
2023-08-01 16:47:58
@ ba680951:ec182a0e
2023-08-01 16:47:58FOMCの最新のミーティング
米国連邦公開市場委員会(FOMC)の最新のミーティングで、金利が0.25ポイント上昇しました。市場はこの結果を予期していました。
金利の動向
昨日、米国の金利を決定するFOMCのもう一つのミーティングが開催されました。市場は利上げを既に予想しており、下のグラフからわかるように、最も可能性の高いのは0.25ポイントの利上げで、これにより金利が年率5.25%から5.50%の範囲になると見られていました。
次に何が起こるのか?
経済活動のデータは引き続き強いままであり、雇用の増加、失業率の低下、インフレ率が目標を上回るなど、6月に公表されたデータではCore CPIが4.8%となっています。昨日のスピーチで、アメリカの中央銀行の議長であるジェローム・パウエルは、FEDが次回のFOMCの決定を予測する立場にないことを強調しました。全ては経済データの動向次第です。
Conclusion
それでも、一つは明らかです。もしCore CPIが高水準であれば、つまり、インフレが明らかに緩和の兆しを見せない場合、金利が再び上昇する可能性が高いです。これは、市場が金利の上昇を織り込み始める可能性があるため、これらのデータの公表日(8月10日)に価格に影響を与える可能性があります。
-
 @ 7f4f672a:c184579e
2023-08-01 16:46:26
@ 7f4f672a:c184579e
2023-08-01 16:46:26Directly publish from Obsidian to Nostr
A Match Made..
Obsidian is an amazing markdown editor, word processor, note organiser, and idea synthesiser: the perfect tool for writers.
Nostr represents the future of how we communicate and distribute the written word: decentralised, free, independent, incorruptible.
They seem to me to be a match made in heaven...
For Writers
This tool is low-friction.. 1. Add your Nostr private key (once on set-up). 2. Write in Obsidian 3. Hit publish to Nostr, and that's it.
A Quiet Place
Avoid the web browser and all it's distractions!
This tool is completely abstracted from Nostr, allowing you to stay focused - the plugin does not read Nostr messages or give you any view into the public space. It just publishes what you've written. Stay focused on your work and disconnected from the noise.
-
 @ 5df413d4:2add4f5b
2023-08-01 16:20:28
@ 5df413d4:2add4f5b
2023-08-01 16:20:28June 2018. Shanghai.
Cruising down the Shanghai East-West Expressway, riding shotgun in my friend’s BMW M3. The car is silly Americana. Captain America decals adorn the exterior, while the interior is Iron Man red and gold. Several large stuffed animals crowd the back seat — Peppa Pig, Winnie the Pooh (both inexplicable, irreverent quasi anti-government memes in China). All the while, Black Panther and Darth Vader bobbleheads nod along atop the dashboard. For many in China, and Shanghai particularly, personal vehicles are the medium for coded expressions that would be too garish or sensitive if made more publicly.
https://i.nostrimg.com/f29c7dde5549edc1eed5a5223a60b40605bd1c622b6bab747b13a5b7fa598d44/file.jpeg (Pictured: The ideal yuppie bachelor car in Shanghai. You may not like it but this is what peak achievement looks like.)
Outside a hazy, spring night fog colors the city like something out of a Simon Stålenhag painting. The neon-lit Bladerunner tetris set of Shanghai office complexes blurs by just beyond the tinted glass as we cut lanes at speed. Kids See Ghosts blasts loudly on the sound system. We hit the Julu Road (巨鹿路) junction, where the city’s two main expressways meet in a loping tangle of concrete and asphalt. And like clockwork, all connections go out — cell, bluetooth, radio — the car goes silent.
This always happens at this spot. I ask my friend about this. He thinks the police are running a high-end signal jammer at this location to prevent people from flying drones over the junction - which he learned at the cost of one of his own high-end DJI models...Perhaps triggered by the state’s technical show of force, a serious change comes over him for a moment. He glances over, "It's all bullshit, you know," pointing up to the dark sky beyond the windshield, "They have to keep the lights on. They have to convince us that the control everything. If they fail, we will just eat them." “Let the ducks roast,” he says to himself after a contemplative pause, his eyes trailing off into the far distance.
But moment passes quickly. A few moments after we pass through the junction, all signals and service reappear, stronger than before. Kid Cudi’s blaring “I feel freeeeeeeeeeeeee” bursts onto the car’s speakers at full volume. Political talk ceases and the entire thing immediately becomes a long forgotten memory.
In any case, it’s Friday. The bars are open, the clubs are calling, and we’re coming in HOT. That’s what matters. Today was a good day in Shanghai.
An Introduction to Life On Mars
Where to start? Folks in the US who have only known me as a bitcoiner often ask, “But how could you live in China?” I always chuckle at this question. Not least because its usually almost visibility dipping with the asker's absurd and exaggerated fantasies about China as a cartoonish 1984-style brutalist dystopia. That said, it is a question that I have given much thought to myself, especially now as a bitcoiner with all the many ways bitcoin has changed my views on things.
And this brings me to a series of far deeper questions — What is authoritarianism, really? Can it ever be benevolent? And how does one become attenuated to it to such an extent as to no longer notice it, if they ever noticed it at all?
https://i.nostrimg.com/2182fd6d38b9eeee65d0400b2659a5be500508cb6ccec34717d2e0a2e19ae878/file.jpeg (What people picture when they ask me about China)
https://i.nostrimg.com/0b565a702191eca5e37a769d80197f9644d61e968315dbfc76f96b660af750a0/file.jpg (This is the same location as the picture above. Today, most days the reality is more like this)
The best way to explore this is to just answer the very first question directly. I very much could live in China because it was RAAAD. I had a great time there and I enjoyed almost every minute of it. In many entirely non-dystopian ways being there was like living in the future or a vision of what it might be like if we (the US) hadn’t forgotten how to have nice things — High-speed rail available at every street corner! Bristling skyscrapers erected in mere days! Wifi bandwidth so cheap and abundant it jumps right out of the stream straight into your frying pan! Gold nuggets for everyone! Everything, now with 30% MORE BEEF!
The thing is, my life in China was good. At that time, the cold, collectivist CCP machinery was fully invested in delivering a jubilee of comforts and diversions to even the relative urban “haves.” Additionally, I came to China as a very well educated, very well paid American with an existing foundation in Mandarin, shuttled in under the wide auspices of a deeply connected global consulting firm. With such well-earned badges of globalist statism, I was afforded a ticket to freely mingle with China’s largely Western-educated, upwardly-mobile urban economic elite. In fact, this was a thing that was rather encouraged…
All this being the case, it is no surprise that I had such a “good” experience. It was always supposed to be that way. Irrespective of the deeper reality, nothing was ever actually supposed to feel authoritarian for me during my time in China. These conditions similarly held true for my particular class of Chinese friends (except that there were certain cultural obligations and political allegiances that it was understood could be called up in full at any moments’ notice).
As an African American, I must admit that in more than a few ways it was possible for me to feel much freer in China than in the United States. I certainly didn’t ever have to worry about being shot in the back by some speed-freak neighborhood watchman or unhinged police officer. And I slowly adjusted to not having to keep my head on a swivel if I heard loud popping sounds in a mall or crowded venue.
No, the Chinese police never bothered me. No, no shadowy state security agents ever interrogated me for my “suspicious” Americanism. No, women didn’t clutch their purse when I walked by (in the States I’ve had this happen midday, while I was wearing full business attire…). People were either ambivalent or genuinely curious to speak with me. In essence, I experienced the joys of simply being left alone by the system. Something like what I image most White Americans experience in the US. So reader, you might already know this, but I can confirm, it was GREAT!
https://i.nostrimg.com/cbdee50436016ab0554830b97b07c72510305752efce8ce6b28c42d7bb5dd1e1/file.jpeg (NGL, China had me out here feeling like this for a hot minute)
Super-Capitalism Is That You?
And beyond my direct personal experience, there were other observations that may seem counterintuitive. For instance, at street level, there was a kind of vivacious, raw free market-ism unlike anything you can find in the West. An ever changing flurry of ramshackle stalls and street vendors. Don’t like the sweet cherries this shop has or the owner has a bad attitude? Then leave! There’s literally 7 other sellers of the same thing on this block alone. And it was like that for most food and daily household consumer products. I could observe market price discovery for goods fluctuating daily, in real-time, sometimes even by the hour.
When I lived above a particularly boisterous commercial street I once saw someone lease a storefront for six days, fill it with heavy traditional Chinese household furniture which I was told “had gotten lost from the factory.” They blew through the inventory starting with signs advertising 20% off on day one, which progressed to 95% off in their final 12 hours of operation. They sold everything so thoroughly that I suspect they probably even sold some stuff that didn’t belong to them like the fixtures that were already in the space when they moved in.
And then, not even two weeks later, 11 days later, the exact same location was reopened as a hotpot restaurant — everything, and I mean everything, had been redone, the floors, the walls, the installation of restaurant equipment, everything. The food was delicious, but I struggled to believe that the health or fire safety inspector had approved any of it, nor that they had real permits for anything they were doing.
Were there laws and regulations on the books ostensibly to control such wildcat commercial activity? Sure, but 天高皇帝远 heaven is high and the emperor is far away, as they say. Now understand that, at street level at least, this was happening everywhere across a city of 26 million people, and then again everywhere across a country of 1.4 billion people.
https://i.nostrimg.com/bf516da1ba165f3a4d1a0694345980e43516d381b002b4e81aac49d7fdae8b6f/file.jpg (Chinese street vendors: a nigh uncontrollable wild force)
By all indications, both felt and seen, people appeared to be fully free to do business and make money while wading in the warm waters of technological modernity. Perhaps they didn’t talk about politics, but that hardly seemed to matter and no one really seemed to care.
It was easy for me to come away feeling that China was a nation of laws rather than enforcement. Maoist austerity might be signaled outwardly but inside its an open, high-octane laissez-faire free-for-all. Conversely, my own cultural history in the US suggested a place of enforcement over law. Signaling egalitarian and meritocratic piety but running on an engine of apartheid justice system, state asset forfeiture, imminent domain, and mass poisoning from Iran-Contra to Seed Oils and OxyContin.
Irrespective of the deeper reality, nothing was ever actually supposed to feel authoritarian for me during my time in China.
So what of it then? Am I here to suggest that China is some Garden of Earthly Delights while Western ideals are a brazen sham? Not so, not so. Rather, my experience brings the realization that in an authoritarian system, it all depends on who you are. And further, that such divisions are central to the maintenance of authoritarian power. I find deep relevance in this, particularly in enabling us to more fully recognize authoritarianism wherever it exists — in China, in the US, or anywhere else. Let me share another story to illustrate.
September 2018. Xinjiang Provence.
https://i.nostrimg.com/808dc51f3c58a37443539992c47448192cc7d05830212268e9279dae7ae7213d/file.jpg
Kashgar, Xinjiang Province. Dust and white heat. I am on a corporate boondoggle in the desert. A plus-one at a rival consulting firm’s Greater China Summit. Like Neo-liberal Wise Men, we galavant around on silk-laden camel-back, we visit the Potemkin village to congratulate ourselves on how well the local ethnics are living, we enjoy a Khan’s Kurultai of exotic roasted meats, red carpets in the sands, Oxbridge 30-under-30 Bedouins on the dunes — you could all but see the Harkonnen spice harvesters out in the distance…
https://i.nostrimg.com/41f41910466f29fd00461a0eb6014853f2af7e4bae8417b7b3068bd18213991a/file.jpg
And the whole time, we are all participating in a collective act of not-seeing the obvious police state all around us. Heavy roll gates, tire spikes, ID checks, mirrored undercarriage sweeps, and vehicle searches for the locals at every nexus of critical infrastructure — gas stations, hospitals, hotels, shopping centers. High-tech police convoys, armed foot patrols, and absurdities like bamboo-thin teenage paramilitary security guards in loose-fitting fatigues and fake Yeezys disinterestedly half-watching the public square while scrolling TikTok (called Douyin 抖音 there) on counterfeit iPhones behind their riot shields.
https://i.nostrimg.com/0af34ab4f7e3fb423ded79a2ebfab4d315d7dcba0a1b42bec19300549eaaedac/file.jpg
Out on the sands, I overhear a firm partner, a Westerner, marveling at the scale of the event wondering at what location could outdo this next year. I interject to suggest Pyongyang. He is not amused, but I certainly am. Later, just when I’m thinking I might be the only one noticing any of this, a tall Indian firm partner, a man built like rugby player, sensing that I was a company outsider (and therefor could potentially give honest answers) asks me what I think of “all of this” in a tone that immediately betrays his meaning.
“In China, I assume that wherever you can most see and feel the hand, is wherever the grip is also most tenuous,” I say. He nods in furrowed-browed approval and we leave it at that. A few months later, perhaps, the New York Times would chronicle this wild corporate exhibitionism in an absolute tear-down piece deeply critical of that firm’s (and all consulting firms) aiding and abetting of authoritarian regimes around the world...
https://i.nostrimg.com/15e19c76f0772161c1617359bcd123051840a5180bd1afe93e9737d308311156/file.jpg
In any case, the lamb roast is firing up and the evening’s next round of festivities are about begin. That’s what matters. Today was a good day in Kashgar
⚠️TRADE OFFER⚠️
This is how the machine works. Nothing is free. There was a near explicit trade being made. Those of us from the favored classes would ignore overhanded oppression of the disfavored out-groups and the sharper appendages of machine would ignore us in return.
https://i.nostrimg.com/a09827c69a55f04f8471abd3d4994615e7da59e07abb19f6868adae254081ba7/file.jpg
Nestled snuggly in the pleasure garden of this CCP-approved social, economic, and educational elitism, wealthy Chinese and visiting Western globalists are supposed to come away believing that what others decry as harsh authoritarianism is in fact, quite benevolent, benign, enjoyable even. From there, it requires only the tiniest of logical jumps for them to assume that their experience is most representative of the greater whole in China, because surely this must be so, right?
From such a vantage then, it becomes all befuddled monocle popping, trembly-handed tea spilling, and frazzled, indigent top-hat ruffling while looking out on any dissenting and oppressed people and wondering “Why are they so loud?”
Incentivized by the plush velour “benefits of membership” in Chinese statism, it is easy to come to view protesting voices, those struggling for justice and freedom, as dunce-hat complainers, salty haters, red-faced and tear-strewn Wojaks, or simply spiteful, back-bitting losers whose problems with the system would evaporate in short order if they just learned to follow the rules, better themselves, and fix their aberrant cultures...
And well done then! This is what the authoritarian system wants, fundamentally NEEDS— to estrange you, through a compromise of comforts, from moral rightness and to replace that with the false rightness of naked self-interest on one hand, and the threat to absolute violence on the other. O, what machines we have made!
In China, those close enough to the system to experience it as a warm embrace rather than an icy dagger are supposed to understand that it is the Uyghurs struggling against mass detention and cultural erasure who are in the wrong. Similarly, for those thusly appointed in the US, it is supposed to be all but self-evident that the same goes for African Americans struggling against mass incarceration and open-air summary executions by uniformed agents of the state.
To the authoritarian all such trouble-making peoples need to be corralled, controlled, and if required, crushed — but in the short run, they need your help to do it. It will always be done in the name of some manner of “social harmony” their doublespeak for the ossification of the status quo and the authoritarian’s power along with it.
In this world, the in-group, the favored classes, whoever they may be, by whatever lines such distinctions are drawn — class, race, sex, religion, ethnicity, sexual orientation — are led to believe they are safe as the authoritarian’s well-loved and much needed allies. But in the end, in the long run, it is the biggest rugpull of all. In such a system, all are Santiago’s sheep, to be meat for the slaughter in times of need.
So how does it feel, Western Anon? What people does our system eat to ensure that you may be comfortably overfed?
And so we become attenuated to such things in so much as we are benefiting from them. Or least, we believe that we are benefiting from them. In our age of the hungry ghost nation-state, it is so very easy to look past the true nature of the thing, or even to buy into it and to project it, when it is not YOU being targeted.
But understand. This is no benevolence. That you are not being targeted — for now, today — is an active, calculated, and entirely self-interested decision on the part of the authoritarian power structure. It is nothing that can be counted on. And whether you realize it or not, it is a decision that is reassessed at every interaction. If nothing else, the pandemic has shown us all this in the starkest relief.
https://i.nostrimg.com/6749febaeb20f102847e5867ad439fa96659bc33d21a795489b40b9baee755e2/file.jpg
If you are allowed to persist in a state where you may believe that all is well, that the thing is benevolent and here to help you, it is only because it is more useful to the animal for you to remain asleep. Understand this, and ask your self — why?
And what is authoritarianism then? Fundamentally, I’ve come to understand authoritarianism as something like the grand political end-point of force. The might-equals-right heuristic at civilization scale. It is the ever-present implicit threat that going against some Big Man’s arbitrary diktat will result in violence, be its physical, economic, social or otherwise, being levied against you to bring you to heel. It is that mindless power which flows from the barrel of a gun…when you have the gun and others do not. It is the system of rulers unbounded from rules.
What We Must Fight
As bitcoiners, this is what we fight. In all its forms, wherever it exists. We must recognize that ALL authoritarian systems and their operators, irrespective of any apparent, surface level ideological conflicts, are in fact like brothers, arms interlocked, in the maintenance of global authoritarianism itself. The principle struggle of the new century is the people against their own governments the world over, rather than the peoples of one nation or group against those of another nation or group. Though do not put it past our current political helmsmen (and women!) to try to steer us all in that dismal direction as a means for distraction that serves their self-preservation.
Bitcoin provides a potentially very powerful tool to the people in this epochal struggle. Bitcoin enshrines a new self-evident and inalienable right — the right of every individual to be an economic actor on a fair monetary protocol. At scale, this moderates the state’s capacity to perpetrate financial violence against both the individual and the collective. With bitcoin, no one is illegal. The protocol imposes no requirements and demands no allegiances, all may transact freely, always.
Value, once obtained in bitcoin, if held securely, cannot be seized. Nor can it be stolen through the occult dark arts of currency debasement. With bitcoin the individual is empowered — able to passively opt out of a predatory financial system, able to move their wealth across borders without restriction, able to actively resist an unjust government free from the threat of total definancialization — and all are welcome.
But bitcoin is just a tool, and just one of many. Fundamentally, the people are the movement and the movement is the change. We must never forget this. We must be both active and steadfast in building the futures we want to live in. Bitcoin is just a tool, but if we use it, perhaps we can one day have freedom — without anyone's authoritarian "characteristics" this time, but perhaps still with 30% more beef.
~Moon
As always thanks for reading, I hope you enjoyed! In case you missed them, be sure to check out Journey Into Bitcoin 01, 02, and 03. Always more to come soon!
Follow me on twitter: Michaelyouknow
Postscript
In the spirit of inter/multi-disciplinary bitconery, here are a few top notch recommendations that to me are related to elements in this piece.
Music: Something In The Way of Things (In Town), The Roots; Bulls on Parade, Rage Against the Machine; Who Will Survive in America, Kanye West
Movies: Four Hours in My Lai (1989)
Readings: City of Silence, Ma Boyang; Guantánamo’s Darkest Secret, The New Yorker
Use The Tools
Liberate your education:
libgen.is — Most books today exist on the internet, for free
Archive Today — Information wants to be free. Too much of it today sits behind absurdly extractive paywalls. (Bitcoin lightning payments can resolve this for both content users and producers)
Liberate you food: The Beef Initiative — Trade real, honest money for real, honest food
Liberate your security: DEFCAD— May you never need them but always know what tools are there



