-
 @ 4fe14ef2:f51992ec
2024-02-12 20:32:12
@ 4fe14ef2:f51992ec
2024-02-12 20:32:12https://images.craigslist.org/00j0j_cnVY57cp4MA_04J02M_600x450.jpg
CRYPTO PAYMENT ONLY : BITCOIN
Amazon.com Gift Cards never expire. Save on Amazon. Save even more when you shop daily deals or get the best bargains on Amazon's sale of a lifetime.
Buy Amazon gift card and redeem your code at www.amazon.com
BITCOIN #BTCACEPTED #MARKETPLACE #AGORA #P2P #AMAZON #GIFTCARD #BITCOINONLY #TEXAS
[CONTACT THE SELLER]
Just anothercrosspost to nostrfrom the~AGORA... -
 @ 4fe14ef2:f51992ec
2024-02-12 13:20:23
@ 4fe14ef2:f51992ec
2024-02-12 13:20:23https://images.craigslist.org/00b0b_9fY7mkTfb8z_0t20CI_600x450.jpg https://images.craigslist.org/00W0W_1K0xNHu73V9_0t20CI_600x450.jpg https://images.craigslist.org/00M0M_e7dFjPLNfmG_0t20CI_600x450.jpg https://images.craigslist.org/01313_5fFbDtyTqj4_0t20CI_600x450.jpg https://images.craigslist.org/00g0g_jiEVbuwMEHt_0t20CI_600x450.jpg https://images.craigslist.org/00z0z_4mLHHc3TAo3_0t20CI_600x450.jpg
American Family Scale.
It Works! Definitely a workhorse piece that was used regularly. Has legit patina and old world durability.
Great piece for retail or home period decoration.
Cash or Venmo / Strike / Bitcoin accepted.
Pick up in Bouler CO
BITCOIN #BTCACEPTED #MARKETPLACE #AGORA #P2P #SCALE #FAMILTY #COLORADO #COLLECTABLE #VINTAGE
[CONTACT THE SELLER]
Just anothercrosspost to nostrfrom the~AGORA... -
 @ 4fe14ef2:f51992ec
2024-02-11 20:45:14
@ 4fe14ef2:f51992ec
2024-02-11 20:45:14https://gumtreeau-res.cloudinary.com/image/private/t_$s-l800/gumtree/c9d15a95-463c-45f8-9fc4-444d4f3da74c.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/8ba95b8a-fd47-4533-b05e-30c5d461ac59.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/c32b5aa7-bcdb-42dd-8c52-6ea45ccec4b3.jpg https://gumtreeau-res.cloudinary.com/image/private/t$s-l800/gumtree/9d4ecfbe-98d9-4416-8065-146ea7d7a1f5.jpg https://gumtreeau-res.cloudinary.com/image/private/t$_s-l800/gumtree/88b59b25-b222-4f29-a6ce-b528e2f02775.jpg
Bitcoin is accepted as a form of payment.
Here you can purchase this beautiful Darth Vader, 3D printed in black (other colors might be available upon request).
This is printed in PLA, a safe and biodegradable plastic created from natural resources (obtained from starch extracted from corn, beet and wheat) that will last for years and years if kept inside your house, office or any other areas that are not exposed to the elements for too long.
Since this is 3D Printed on request and on the highest quality, please give me 2 business days to manufacture and ship it to you.
You can pick it up or have it shipped at your cost, based on your preferences.
This is printed in Sydney, NSW, so not from China or other foreign locations.
BITCOIN #BTCACEPTED #MARKETPLACE #AGORA #P2P #DARTHVADER #STARWARS #COLLECTABLE #3DPRINT #SYDNEY
[CONTACT THE SELLER]
Just anothercrosspost to nostrfrom the~AGORA... -
 @ 4fe14ef2:f51992ec
2024-02-09 09:06:53
@ 4fe14ef2:f51992ec
2024-02-09 09:06:53https://photos.encuentra24.com/t_or_fh_l/f_auto/v1/cr/25/44/84/74/25448474_2d5b03 https://photos.encuentra24.com/t_or_fh_l/f_auto/v1/cr/25/44/84/74/25448474_33a5a8
https://www.youtube.com/watch?v=gPc5qf97hZg
Empiece su negocio de venta de perros calientes en estadios, ferias o eventos especiales.
Perfecto para hot dogs de 1/4 lb. Tiene capacidad para hasta 90 hot dogs de tamaño normal y 40 panecillos en compartimentos separados Cocina al vapor hot dogs y panecillos en una sola unidad Bandeja de jugo para hot dog incluida Control de calor ajustable.
Se entrega en Cartago. Solo pagos con Sinpe Móvil, Transferencia, Cash o Bitcoin.
BITCOIN #BTCACEPTED #MARKETPLACE #AGORA #P2P #PERROSCALIENTES #HOTDOG #HOTDOGS #STREETFOOD #COSTARICA #CARTAGO
[CONTACT THE SELLER]
Just anothercrosspost to nostrfrom the~AGORA... -
 @ 39cc53c9:27168656
2024-03-02 12:09:41
@ 39cc53c9:27168656
2024-03-02 12:09:41I'm launching a new service review section on this blog in collaboration with OrangeFren. These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Reviews are done in advance, then, the service provider has the discretion to approve publication without modifications.
Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
The review
WizardSwap is an instant exchange centred around privacy coins. It was launched in 2020 making it old enough to have weathered the 2021 bull run and the subsequent bearish year.
| Pros | Cons | |------|------| | Tor-friendly | Limited liquidity | | Guarantee of no KYC | Overly simplistic design | | Earn by providing liquidity | |
Rating: ★★★★★ Service Website: wizardswap.io
Liquidity
Right off the bat, we'll start off by pointing out that WizardSwap relies on its own liquidity reserves, meaning they aren't just a reseller of Binance or another exchange. They're also committed to a no-KYC policy, when asking them, they even promised they would rather refund a user their original coins, than force them to undergo any sort of verification.
On the one hand, full control over all their infrastructure gives users the most privacy and conviction about the KYC policies remaining in place.
On the other hand, this means the liquidity available for swapping isn't huge. At the time of testing we could only purchase at most about 0.73 BTC with XMR.
It's clear the team behind WizardSwap is aware of this shortfall and so they've come up with a solution unique among instant exchanges. They let you, the user, deposit any of the currencies they support into your account and earn a profit on the trades made using your liquidity.
Trading
Fees on WizardSwap are middle-of-the-pack. The normal fee is 2.2%. That's more than some exchanges that reserve the right to suddenly demand you undergo verification, yet less than half the fees on some other privacy-first exchanges. However as we mentioned in the section above you can earn almost all of that fee (2%) if you provide liquidity to WizardSwap.
It's good that with the current Bitcoin fee market their fees are constant regardless of how much, or how little, you send. This is in stark contrast with some of the alternative swap providers that will charge you a massive premium when attempting to swap small amounts of BTC away.
Test trades
Test trades are always performed without previous notice to the service provider.
During our testing we performed a few test trades and found that every single time WizardSwap immediately detected the incoming transaction and the amount we received was exactly what was quoted before depositing. The fees were inline with what WizardSwap advertises.

- Monero payment proof
- Bitcoin received
- Wizardswap TX link - it's possible that this link may cease to be valid at some point in the future.
ToS and KYC
WizardSwap does not have a Terms of Service or a Privacy Policy page, at least none that can be found by users. Instead, they offer a FAQ section where they addresses some basic questions.
The site does not mention any KYC or AML practices. It also does not specify how refunds are handled in case of failure. However, based on the FAQ section "What if I send funds after the offer expires?" it can be inferred that contacting support is necessary and network fees will be deducted from any refund.
UI & Tor
WizardSwap can be visited both via your usual browser and Tor Browser. Should you decide on the latter you'll find that the website works even with the most strict settings available in the Tor Browser (meaning no JavaScript).
However, when disabling Javascript you'll miss the live support chat, as well as automatic refreshing of the trade page. The lack of the first means that you will have no way to contact support from the trade page if anything goes wrong during your swap, although you can do so by mail.
One important thing to have in mind is that if you were to accidentally close the browser during the swap, and you did not save the swap ID or your browser history is disabled, you'll have no easy way to return to the trade. For this reason we suggest when you begin a trade to copy the url or ID to someplace safe, before sending any coins to WizardSwap.
The UI you'll be greeted by is simple, minimalist, and easy to navigate. It works well not just across browsers, but also across devices. You won't have any issues using this exchange on your phone.
Getting in touch
The team behind WizardSwap appears to be most active on X (formerly Twitter): https://twitter.com/WizardSwap_io
If you have any comments or suggestions about the exchange make sure to reach out to them. In the past they've been very receptive to user feedback, for instance a few months back WizardSwap was planning on removing DeepOnion, but the community behind that project got together ^1 and after reaching out WizardSwap reversed their decision ^2.
You can also contact them via email at:
support @ wizardswap . ioDisclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 7e671aa6:96772b21
2024-02-03 14:04:30
@ 7e671aa6:96772b21
2024-02-03 14:04:30 -
 @ 39cc53c9:27168656
2024-02-19 17:49:18
@ 39cc53c9:27168656
2024-02-19 17:49:18Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ 44dc1c2d:31c74f0b
2024-01-07 21:19:28
@ 44dc1c2d:31c74f0b
2024-01-07 21:19:28Chef's notes
This bread is super simple to make and takes a bit to dial in.
The only real notes I have here is you can use whatever round pan you want to bake it in. Or use a square one, just make sure the walls of the pan are high.
Less is more with this bread. You really don't want to over knead the bread here. If you're used to making bread that need a lot of kneading, this will feel odd.
Details
- ⏲️ Prep time: 27 hours
- 🍳 Cook time: 50 to 60 min
- 🍽️ Servings: 1 loaf
Ingredients
- 1-1/2 teaspoons active dry yeast
- 1-3/4 cups warm water (110° to 115°)
- 3-1/2 cups plus 1 tablespoon all-purpose flour, divided
- 2 teaspoons salt
- 1 tablespoon cornmeal or additional flour
Directions
- In a large bowl, dissolve yeast in warm water. Using a rubber spatula, stir in 3-1/2 cups flour and salt to form a soft, sticky dough. Do not knead. Cover and let rise at room temperature 1 hour.
- Stir down dough (dough will be sticky). Turn onto a floured surface; with floured hands pat into a 9-in. square. Fold square into thirds, forming a 9x3-in. rectangle. Fold rectangle into thirds, forming a 3-in. square. Place in a large greased bowl, turning once to grease the top. Cover and let rise at room temperature until almost doubled, about 1 hour.
- Punch down dough and repeat folding process. Return dough to bowl; refrigerate, covered, overnight.
- Grease the bottom of a roasting pan with sides at least 4 in. high; dust pan with cornmeal. Turn dough onto a floured surface. Knead gently 6-8 times; shape into a 6-in. round loaf. Place into prepared pan; dust top with remaining 1 tablespoon flour. Cover pan and let rise at room temperature until dough expands to a 7-1/2-in. loaf, about 1-1/4 hours.
- Preheat oven to 500°. Using a sharp knife, make a slash (1/4 in. deep) across top of loaf. Cover pan tightly with foil. Bake on lowest oven rack 25 minutes.
- Reduce oven setting to 450°. Remove foil; bake bread until deep golden brown, 25-30 minutes. Remove loaf to a wire rack to cool.
-
 @ 8aa70f44:3073d1a6
2024-03-14 18:40:20
@ 8aa70f44:3073d1a6
2024-03-14 18:40:20When print media started making the move to digital, newspapers were cautiously optimistic. The transition was inevitable as the internet became ubiquitous. It’s not like the newspapers could simply opt out of digitising. And who knows, maybe hosting the news online could prove to be a lucrative new revenue stream for the already thin-margined print media industry. Right?
Wrong.
Text media monetisation has been an ongoing uphill battle for basically every single news outlet from the moment it started. Corners are being cut on a daily basis, and over 2,000 local newspapers have entirely closed down since 2000, just in the United States alone.
As MIT researcher George Westerman eloquently said, “When digital transformation is done right, it’s like a caterpillar turning into a butterfly, but when done wrong, all you have is a really fast caterpillar.”
The move online, which seemed so promising, has in actuality proved devastating for text media. So, what went wrong, and how is this catastrophic shift turning us all into idiots?
The future that almost was
Back to that cautious optimism. The transition from print to digital was going to be such a great thing and provide a revitalising boost to the print media market. Journalists could cover stories faster, publish updates in real-time, send out quick corrections, and otherwise be far more nimble than print ever allowed.
Not to mention the obvious cost-saving aspects. Readers could access the exact same news without the high costs associated with producing, printing, and delivering physical newspapers.
Win–win, right?
Right?
Why making money from text media is so difficult
Before we can talk about the current tragic impacts of digital media on the average consumer, let's first talk about what went wrong. Why are the remaining newspapers haemorrhaging money? The future looked so promising but took such a rapid nosedive.
Future economists will probably analyse the fall of the media to death because it is fascinating. This reductionist list will likely only scratch the surface of how this massive industry was crippled so quickly and utterly. But here are the main reasons media orgs fumbled the transition from print to digital.
Everything was free for too long
Understandably, but a bit naively, newspapers made banner and on-page ads a big part of resolving their revenue gaps when physical paper subscriptions began to dwindle in the late 1990s. This makes sense in theory – readers paid for physical newspapers and still saw ample printed ads, so why would they take issue with free digital content… and a few ads?
So, they made everything accessible with the expectation that ads would generate revenue. Obviously, this blew up in their faces with the invention and rapid uptake of adblockers. Soon, media consumers were getting their cake and eating it too – all the news media at their fingertips with none of the pesky revenue generated for the media outlets whose print ads were also drying up at a fever pitch.
Unfortunately, by this point, consumers were conditioned to get the news for free. Why would they suddenly start paying for something if they never had to before?
If you don't give them the news, someone else will
Eventually, many digital newspapers started going to the membership and subscription model. But this transition did not happen unilaterally (and still hasn’t, to be fair). Some newspapers began requiring a subscription, while others didn’t. Some allowed for a few “free” articles per month, making it possible for consumers to cobble together a media consumption diet around these restrictions while avoiding paying for anything. Paywalls, in addition, were often leaky and easy to circumvent.
Realistically, many of us find the news through search aggregates like Google News. If one source is blocking your ability to read the story, you could simply go to the next. This is great (albeit a little annoying) for consumers and bad for the media outlets, who expected consumers to be a bit more brand loyal than they turned out to be, particularly their younger readers.
Text is easy to copy
Even if you get somebody to loyally subscribe to your newspaper, what stops them from simply copying the text and sharing it with friends, relatives, and internet strangers? You may be thinking, “When would this happen? When would someone actually take the time to copy and paste news text to other people enough for this to be a significant problem?”
Well, Reddit, for starters.
Reddit is a massive discussion board for people to come together and anonymously analyse the day's biggest stories (and everything else in existence). A user will post a link to a news article, and everyone will very politely and never aggressively present their perspective about said news article. This sort of distribution seems good for news outlets because it means clicks, views, and engagement.
It isn’t.
Unfortunately, for convenience, the poster will often include the entire body of the linked article within their Reddit post. And, if there's a paywall, someone who happens to have a legitimate subscription will copy and share the entire article with tens of thousands of people who otherwise would never have been able to read it without a subscription. This minor issue becomes a much bigger issue when you realise that Reddit on its own has almost 56 million daily active users.
Some news outlets have even taken to copyright-striking various Reddit communities, according to Redditors, but it barely makes a dent in a much bigger problem (for the news outlets). And Reddit is just one very specific example of consumers copying paywalled text to general, non-paying audiences.
Nobody respects (or trusts) writers
So many people assume that because the majority of the population is functionally literate, anybody can be a writer or journalist. With the increasing popularity of AI tools, this sentiment is only rising. It doesn't help that many writers and journalists take massive shortcuts and are essentially forced to cut corners to stay competitive, further eroding our collective respect for journalism.
And even if the average person did respect the institution of journalism, they certainly don't trust it. According to a 2022 Gallup poll, trust in the media is incredibly low. Only 7% of Americans interviewed actually held “a great deal” of confidence/trust in journalism to report the news fairly and accurately.
This again begs the question, why would people willingly pay for something they neither trust nor respect?
People don't read anymore
How many times have you heard the phrase, “I recently read this thing…” and you know they are either going to tell you about a viral TikTok they watched or a headline they read and made a snap judgement about? The reality is that attention spans are shot. The average person is on a constant media consumption overload, and nobody has the time to read a 10,000-word investigative journalism piece unless it’s for a university essay or while languishing on their retirement yacht.
Sure, people are constantly scrolling. But how much are they actually reading?
Why all of this matters
If all of the above factors only affected the bottom line of the news media outlets, that would be one thing. We could collectively mourn the profit losses and continue with our lives basically unaffected. However, this shift away from text media and long-form content, in general, is having some pretty devastating impacts on individuals and our collective intelligence.
Investigative journalism is basically dead. The average attention span is decreasing rapidly. The West’s favourite short-form video platform has over one billion monthly users.
Yes, billion. With a b.
It's not fair to say that the massive shift away from thoughtful, investigative, accessible news media led to the rapid degradation of the average person's ability to think critically and process information. But it certainly hasn’t helped.
The reality is that every political and social party feels like there is news bias and censorship stacked against them. Because the news outlets are haemorrhaging money, they have to rely on overly sensationalised drama to generate clicks and (minuscule) revenue. Rage gets people talking. Making people mad drives revenue. So simultaneously making everyone feel like an angry, righteous victim – well that’s just good business.
Newspapers are no longer interested in the truth (despite already being kinda biased before), but in how the truth can be manipulated and packaged to capture the tiny attention spans of people who are now conditioned to only focus on the things they hate. As one NYT and NPR journalist puts it, there’s an insidious “bad news bias” that has overtaken the news media industry.
So, if you can’t believe the news because it’s all rage-bait click farming and you lack the attention span or interest to peruse dense scientific journals to get your facts (which are often biased as well), what is the average human supposed to do? Who can you trust to be honest for one damn second?
All this is to say, I don’t think the average person is willfully dumb. I think we’re all just doing our best to navigate a completely partisan, profit-driven, rage-based attention economy that is rapidly being eroded by one affiliate marketing-laden news story after another.
The only way out of this mess
Thankfully, I have come up with a comprehensive and completely foolproof solution for this entire problem that will solve the monetisation issue, repair our eroded trust in the media, and save the average consumer a ton of money in subscription fees.
Just kidding.
I have no idea what we're supposed to do about this. I do know that what we are doing isn't working. Even the few profitable news outlets rely on sketchy and ethically questionable affiliate marketing techniques or subscriptions to their largely older, affluent bases (“The No. 1 reason we lose subscribers is they die”).
Any reasonable solution will inevitably take a Herculean effort from both sides: it will require media consumers to willfully invest in paying for the news if they want high-quality, unbiased news coverage that isn’t profit-driven. And it'll require media outlets to report the news in ethical, audience-friendly, accessible ways.
So yeah, we’re screwed.
-
 @ 46fcbe30:6bd8ce4d
2024-03-14 16:34:55
@ 46fcbe30:6bd8ce4d
2024-03-14 16:34:55Opinion about ABCore (android)
This app was a proof of concept and never meant to be used on your smartphone. With no update in many years it is safe to say that it's not safe to use this as is. But it's open source, so if you need something like this for some project, their code might be a good starting poing.
WalletScrutiny #nostrOpinion
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 44dc1c2d:31c74f0b
2024-01-04 05:18:29
@ 44dc1c2d:31c74f0b
2024-01-04 05:18:29Chef's notes
This is a base recipe. You can and should modify it to your tastes.
For a honey mustard, add a couple tablespoons of honey.
You can affect the taste by changing the vinegar around, like a white or sherry vinegar. You can use beer instead of vinegar. Also chop up some fresh herbs like tarragon and chuck it in. You can also play with the water and vinegar ratio for less of a bite (or more).
If you want a more yellow mustard, chuck in some turmeric and sugar.
Play with the heat of the mustard by changing the seeds and the heat of the liquid you start with. Black mustard being the hottest. Starting with a cold liquid will make for a hotter mustard instead of a warm liquid. (IE white mustard seeds in a warm liquid will make for a mellow mustard vs black seeds in a cold liquid)
Details
- ⏲️ Prep time: 10ish min.
- 🍳 Cook time: 48 hours
- 🍽️ Servings: About a 3/4 full 8oz jar
Ingredients
- 2 tablespoons of brown or black whole mustard seeds
- 1/4 cup ground mustard powder
- 3/4 teaspoon salt
- 1/4 cup water
- 4 teaspoons apple cider vinegar
Directions
- Grind seeds in a spice grinder or in a mortar and pestle tell the seeds are at the desired consistency.
- Mix the dry stuff together. (seeds, salt and powder)
- Mix the wets in.
- Cover and let sit for 2 days. (I use a jar) Wait time is important here. It will look soupy at first and thicken up as the seeds absorb the liquid. The time also allows the mustard to mellow. Fresh made mustard is harsh and bitter tasting so give it time.
-
 @ a023a5e8:ff29191d
2024-01-06 20:47:50
@ a023a5e8:ff29191d
2024-01-06 20:47:50What are all the side incomes you earn other than your regular income? I know these questions are not always easily answered, but by sharing yours, you may be providing someone with a regular income that you see for yourself as a side income or a passive income. You know this world, and Bitcoin is sufficient for everyone. Let this be a fruitful discussion for many, including me. 2023 was fine, and 2024 is already here.
I will be bookmarking this thread.
-
 @ 75bf2353:e1bfa895
2024-03-14 13:47:19
@ 75bf2353:e1bfa895
2024-03-14 13:47:19Bitcoin Is Cash Money
In my last blogpost, I wrote about a clear path to buying coffee with bitcoin. Of course, this plan is predicated on the coffee shop owner actually agreeing to do this, but it is technically feasible in 2024, even if the coffee shop is as alergic to bitcoin as my son is allergic to peanuts.
Today I'm writing about buy me a cup of coffee when Starbucks doesn't directly accept bitcoin. This is a taboo subject nowadays. The new bitcoin Jesus thinks bitcoin is not p2p electronic-cash. I know the people who make this argument twist the words. They say cash comes from the French word, which means blah, blah, blah. It's a red-herring. Satoshi never described this so-called French word. He said: "It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine."" Subscription sites that need some extra proof-of-work for their free trial so it doesn't cannibalize subscriptions could charge bitcoins for the trial. "Banks must be trusted to hold our money and transfer it electronically, but they lend it out in waves of credit bubbles with barely a fraction in reserve. We have to trust them with our privacy, trust them not to let identity thieves drain our accounts. Their massive overhead costs make micropayments impossible."" "If a merchant actually has a problem with theft, they can make the customer wait 2 minutes, or wait for something in e-mail, which many already do. If they really want to optimize, and it's a large download, they could cancel the download in the middle if the transaction comes back double-spent. If it's website access, typically it wouldn't be a big deal to let the customer have access for 5 minutes and then cut off access if it's rejected. Many such sites have a free trial anyway. Sathoshi seemed to think bitcoin peer 2 peer electronic cash wa cash money. Price is nice, but I write this blog to show people how bitcoin works as cash money. We can use it to solve real world problems and it has real-life use cases. In this post, I'll show you bitcoin is more than mere property. It's a super power that lets people send money without providing your information to every Tom, Dick, and Larry Fink. When Satoshi talked about peer to peer electronic cash system, he meant cash like the cypherpunks meant cash. Cypherpunks did not talk about the French origins of the word cash. They used the word in the coloquial sense like cold, hard, cash. Satoshi didn't site any papers that talked about the word "casse". He cited tools created by crypto anarchists like wei dai's Peer-money. Here's a quote from this wei dai's b-money. As a reminder this essay was cited in Satoshi Nakamoto's White paper. "I am fascinated by Tim May's crypto-anarchy. Unlike the communities traditionally associated with the word "anarchy", in a crypto-anarchy the government is not temporarily destroyed but permanently forbidden and permanently unnecessary. It's a community where the threat of violence is impotent because violence is impossible, and violence is impossible because its participants cannot be linked to their true names or physical locations. Until now it's not clear, even theoretically, how such a community could operate. A community is defined by the cooperation of its participants, and **efficient cooperation requires a medium of exchange (money) and a way to enforce contracts**. Traditionally these services have been provided by the government or government sponsored institutions and only to legal entities. In this article I describe a protocol by which these services can be provided to and by untraceable entities." Satoshi was clear. Bitcoin is a peer-to-peer electronic cash system. It's an integral part of the game theory. Cash is decentralized. Property is not decentralized. Property gets taxed. Fiat cash gets taxed via inflation. Peer 2 peer electronic cash is not property. It's cash. The keys are property. Your steel plate is property. The twelve words you head are property, but the transactions on the time chain are not property. We should work to keep it that way. When I first Andreas Antonopolis talk about bitcoin, I thought it was an awesome idea, but I was skeptical. There was no way in hell I would just sign up with coinbase and buy bitcoin just because he said so. I didn't trust it. I had to verify it. So I thought, if this is peer to peer cash is legit, someone ought to be able to send me a little. So I asked someone on twitter to send me some hash tag bitcoin. Someone sent be a buck fifty and told me to buy a cup of coffee with it. That's my bias. I can buy coffee with it. I did a couple years ago. I still have most of those sats from 2014. Maybe I'm just a crotchety old man waving my cane in the sky and screaming "Get off my drought resistant landscaping!" Then again, maybe more people would get on-boarded if we sent them bitcoin peer to peer. That's why I'm bullish on nostr. We should stop telling people to "buy bitcoin." **We should tell them to get on nostr and try bitcoin**. It sounds better than, buy bitcoin, [peer-to-peer electronic property](https://primal.net/e/note10v7ns6kerrmayj4z5rspxu5dls9asn322a964xql5g9huvhy2thqglcdln) ## How To Buy Coffee With Bitcoin Say you are allergic to bitcoin like I'm allergic to fiat. Don't like VoLiTiLiTy? No problemo! Sign up for an account at https://strike.me. Set up your account and choose a username. You will get a lightning address that is `yourusername@strike.me` Despite how it looks, that's not an email address. It's a lightning address. This address is all you need to accept payments on the Internet. All you need to do is put it on your webpage, substack, Twitter, or whatever. First, you should choose to take the orange pill or the green pill. Do you want fiat or do you want bitcoin? Again, I know a lot of people hate bitcoin. Mention the word on blue sky if you don't believe me. Click on the little anthropomorphic person on the upper right hand corner. 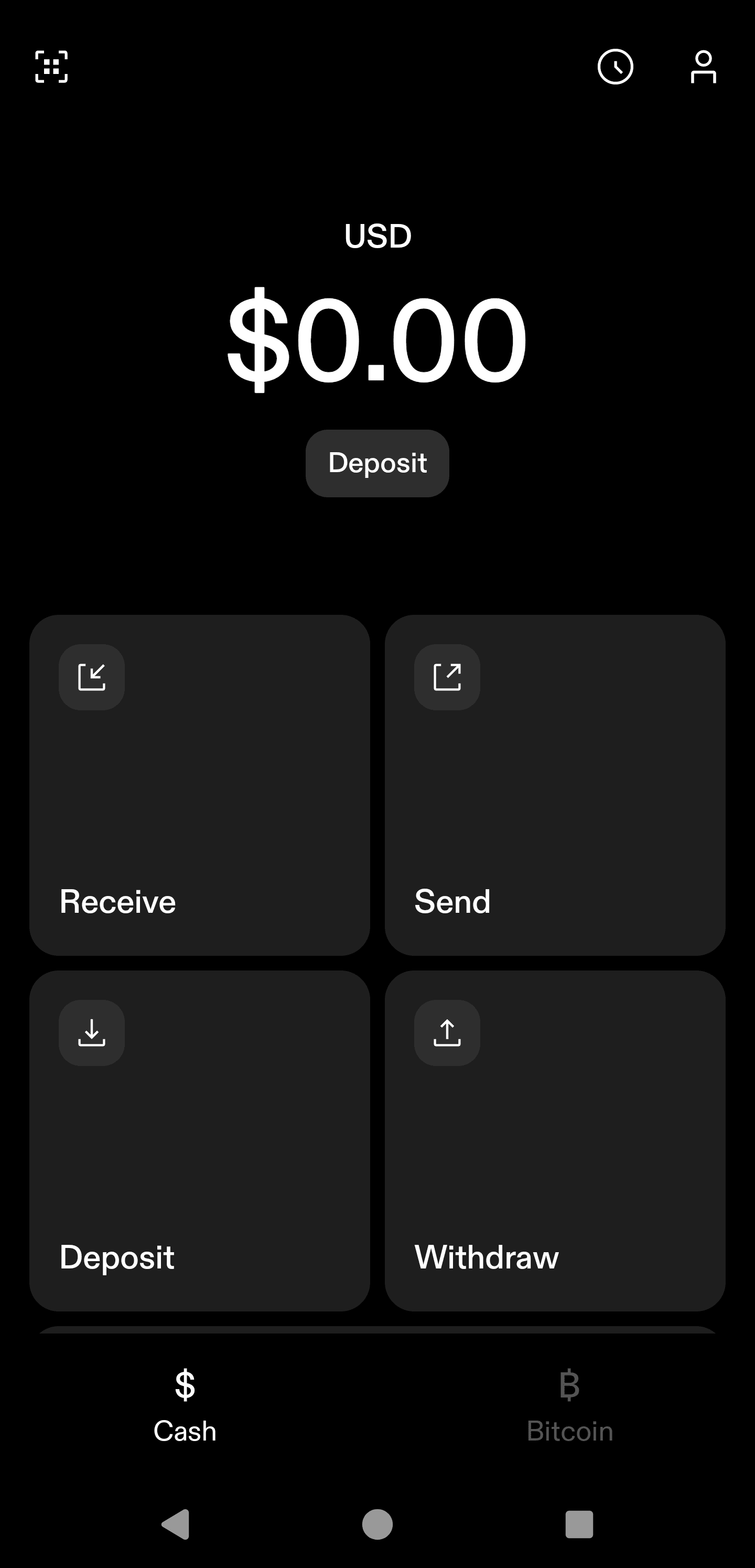 Next, scroll down until you see the settings menu. Next, click the "Bitcoin" tab. 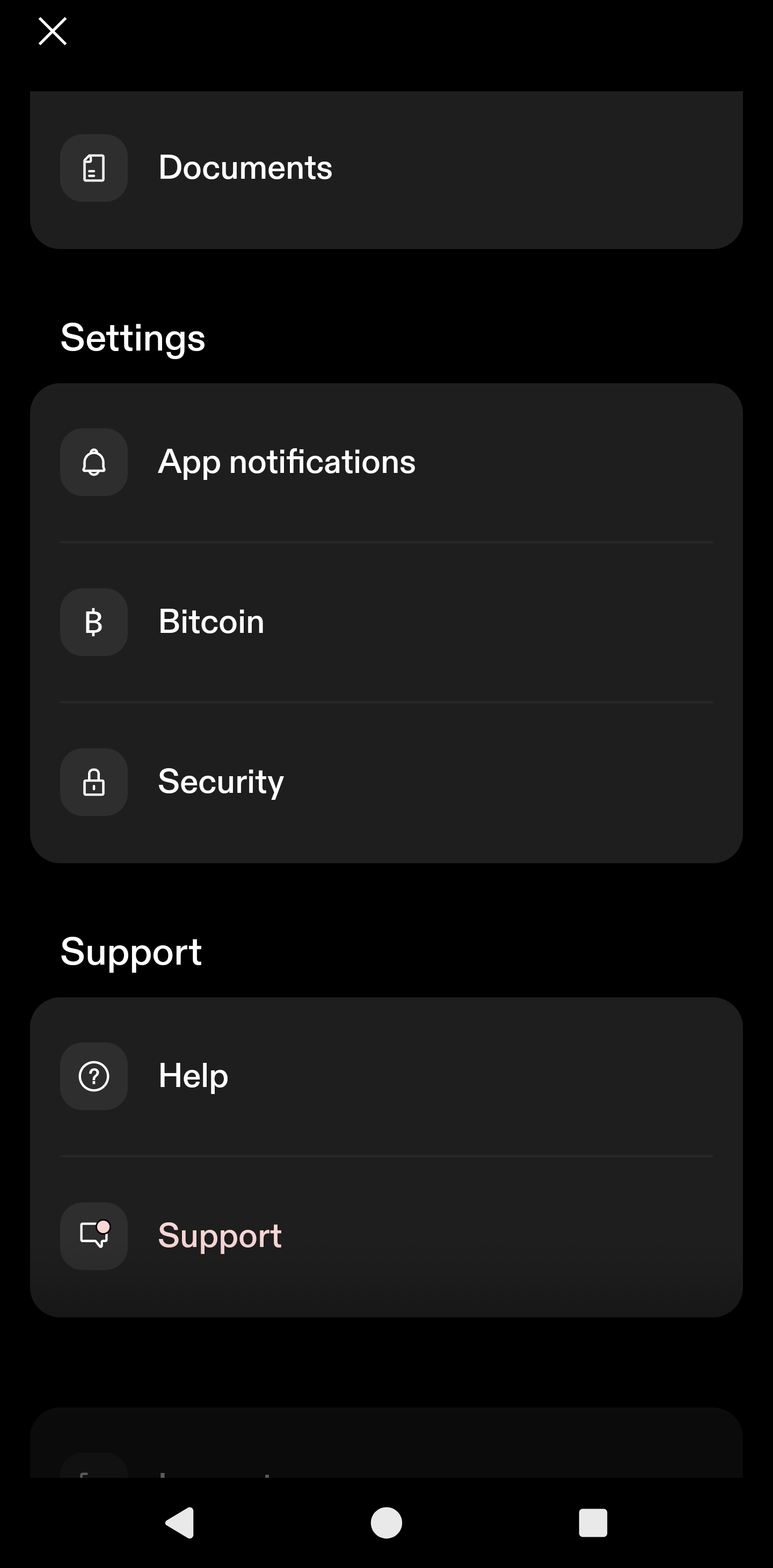 Now it's time to choose the orange pill or the green pill. Click on Passive incoming payments. 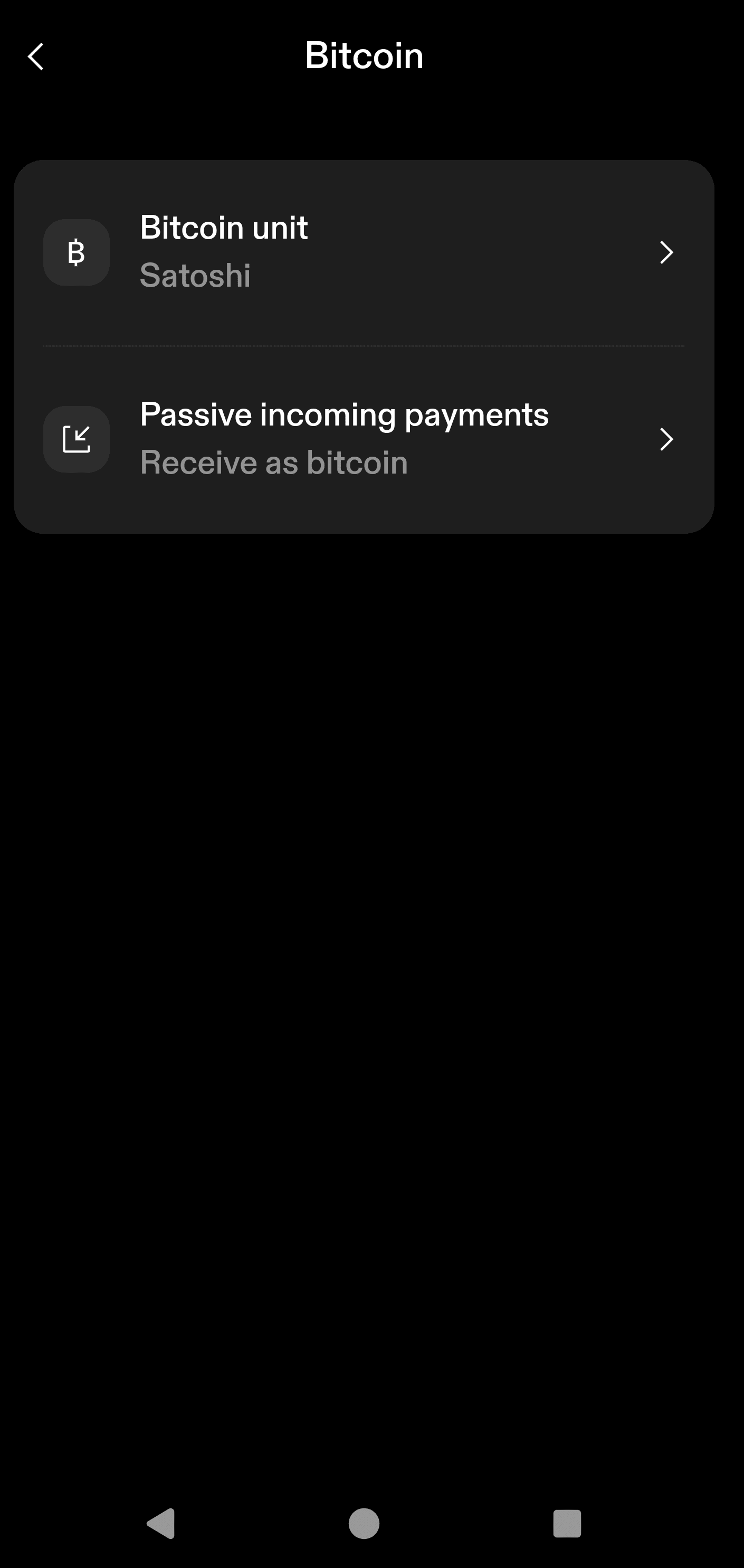 You'll have the option to choose to accept incoming payments as bitcoin or cash. Of course, if someone sends you less than a penny, it can't be converted to fiat cash. Anything more than a penny gets converted to USD in my jurisdiction. I assume people in other countries get the cash converted to their local fiat currency, but don't quote me on this. I don't really know. As you can see, I took the orange pill, but you can do whatever you want to do. 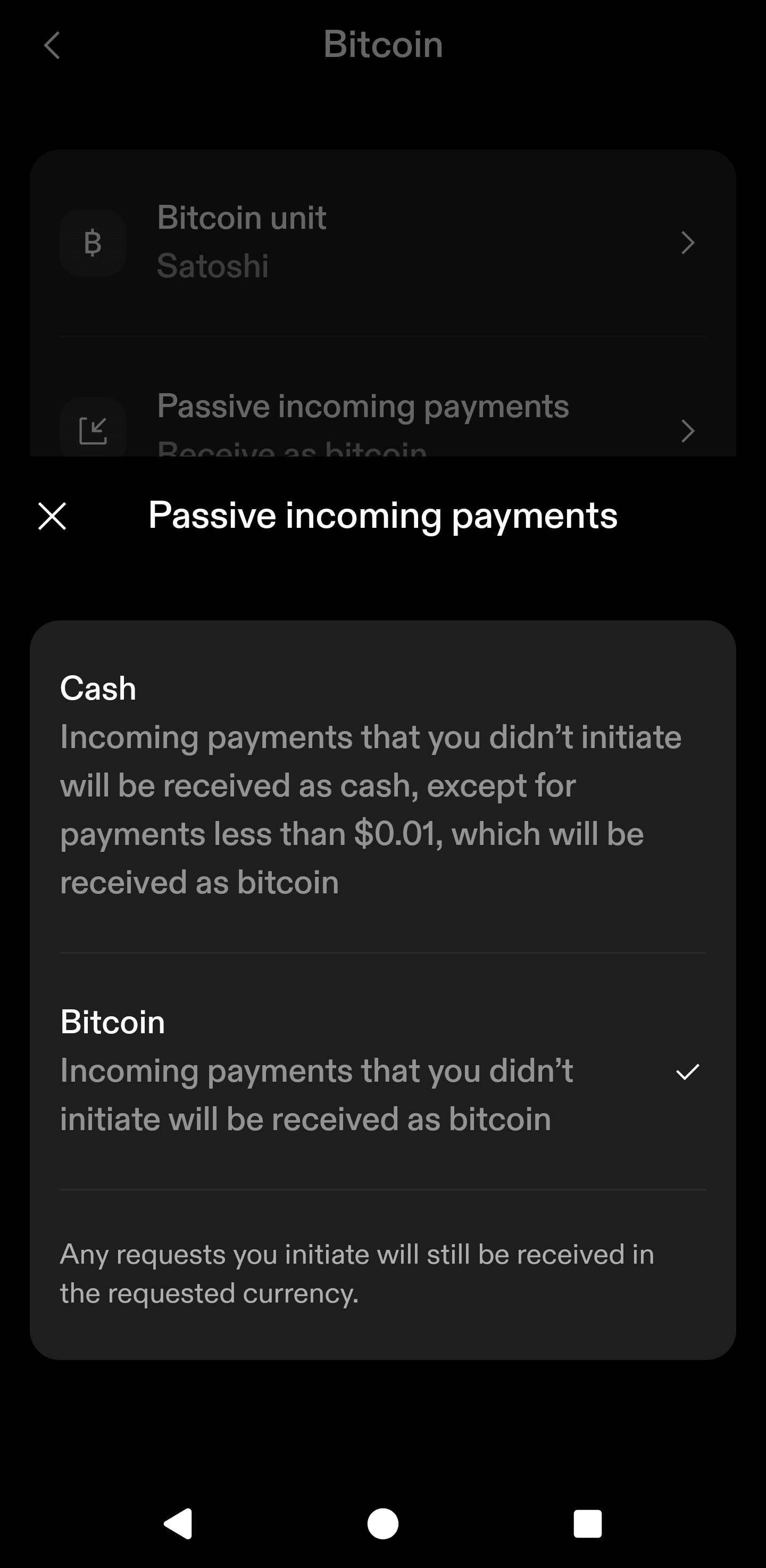 Remember, your lightning address is your username at strike.me. I'm using a lightning tips address, but the process is the same.+ ### Accept Payments Anywhere On The Internet You can put your lightning address anywhere on the Internet, but this is about coffee so I created a Buy Me A Coffee page. I won't do a tutorial because I assume you know how to set up a profile on the Internet. Remember when congress questioned Zuck about his stablecoin? Well, I hate to break it to you Congress we don't need Zuck bucks. You can add a lightning address right to a Facebook profile.  Here's my page. You won't find it on Facebook. https://www.buymeacoffee.com/bloggingbitcoin I added my lightning address to https://sendsats.to It comes in handy for making a clickable page. There's not much of a tutorial needed. The page is https://sendsats.to/bloggingbitcoin@ln.tips Just replace my lightning address with your lightning address and you too can accept magic Internet money. **WTF Does This Have To Do With Coffee?** Go back to the Strike welcome screen, scroll down to shop with lightning. 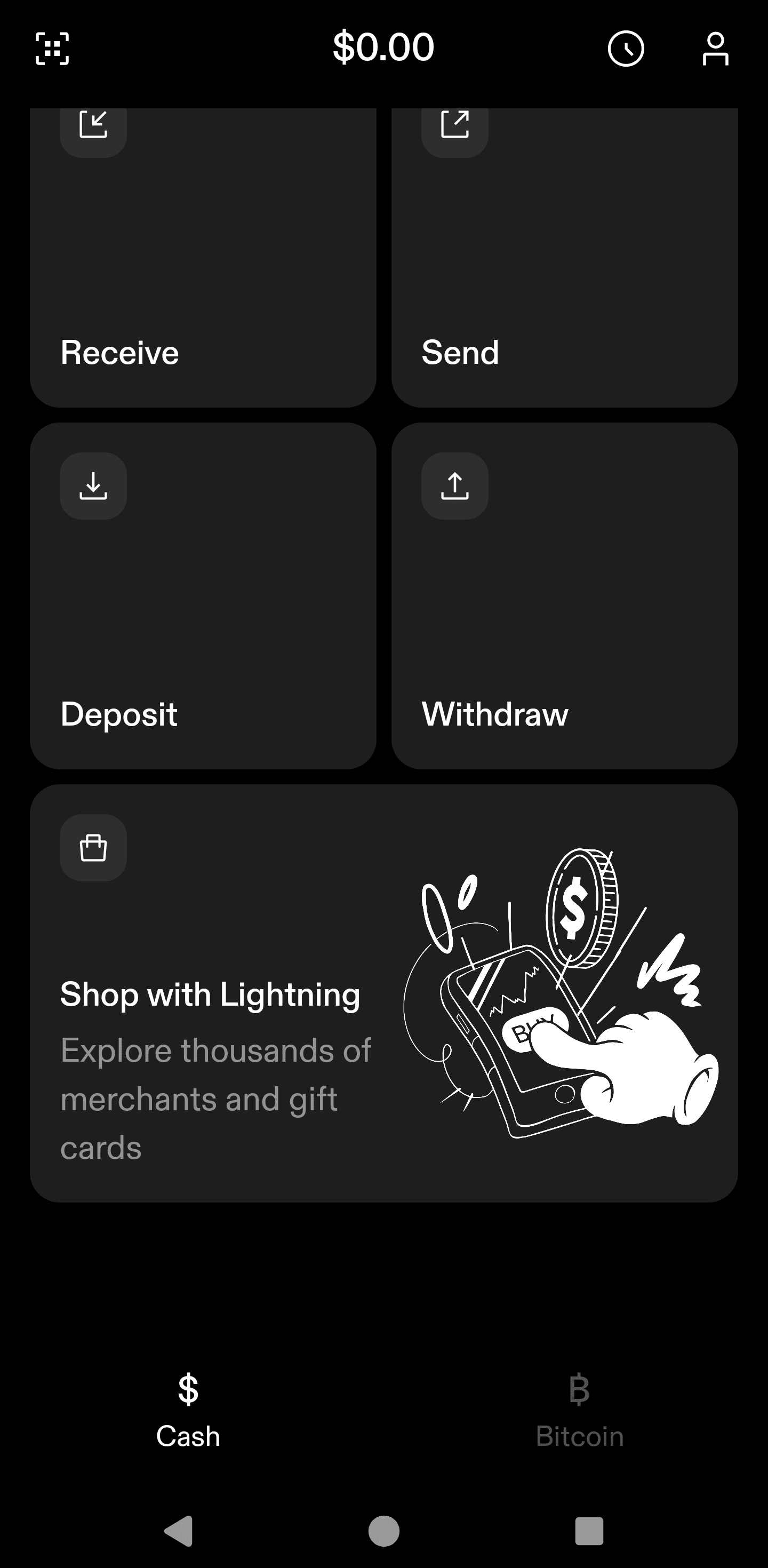 ### Shop With Bitcoin Straight From Strike I wrote about Bitrefill in one of my early blogs, but now it's integrated right into the Strike App. You can buy coffee, or just about anything else you want with your newly acquired sats or fiat. You might want to hang on to some sats if you don't have any, just in case, but you could totally buy a cup of coffee if you want to. Many Saylor disciples accept the thesis that bitcoin is property. They will never spendl. They also know Saylor says you should orange pill as many people as possible. What better way to orange people than send them a little bitcoin. I'm not saying to buy some fancy-schmancy car like a 1976 Ford Pinto with your bitcoin. I'm saying to buy a five dollar cup of coffee. I mean an eight dollar cup of coffee. Don't spend your bitcoin if you're worried about your taxes or whatever. Holdl dollars in your Strike account. Don't "buy bitcoin" with those dollars. Turn the dollars into sats for a gift card. It might cost you some fiat flyer miles. So what? Tell the barista you bought your gift card with bitcoin. `We propose a solution to the double-spending problem using a peer-to-peer network.` You can do this because bitcoin solves the double spending problem. It solves the double-spending problem so well, someone can send you ten bucks worth of bitcoin from Australia. You'll get it within about three seconds. You can buy a Starbucks gift card with those sats and sip yourself shakey straight-away. You could also send the bitcoin to the Cash App and buy a gift card there too. I suppose you could buy Bank of America stock in the Cash App right away too. I don't know why the hell you would do that, but it's possible. You'll need to sell the bitcoin on the Cash App first, but guess why you can do this? Because bitcoin solves the double spending problem. Can you do that with Bank of America? No, it takes at least three days to send dollars from Bank of America to Wells Fargo. Buy Me A Cup of Coffee
In my last blogpost, I wrote about a clear path to buying coffee with bitcoin. Of course, this plan is predicated on the coffee shop owner actually agreeing to do this, but it is technically feasible in 2024, even if the coffee shop is as alergic to bitcoin as my son is allergic to peanuts.
Today I'm writing about buy me a cup of coffee when Starbucks doesn't directly accept bitcoin. This is a taboo subject nowadays. The new bitcoin Jesus thinks bitcoin is not p2p electronic-cash. I know the people who make this argument twist the words. They say cash comes from the French word, which means blah, blah, blah. It's a red-herring. Satoshi never described this so-called French word. He said: "It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine."" Subscription sites that need some extra proof-of-work for their free trial so it doesn't cannibalize subscriptions could charge bitcoins for the trial. "Banks must be trusted to hold our money and transfer it electronically, but they lend it out in waves of credit bubbles with barely a fraction in reserve. We have to trust them with our privacy, trust them not to let identity thieves drain our accounts. Their massive overhead costs make micropayments impossible."" "If a merchant actually has a problem with theft, they can make the customer wait 2 minutes, or wait for something in e-mail, which many already do. If they really want to optimize, and it's a large download, they could cancel the download in the middle if the transaction comes back double-spent. If it's website access, typically it wouldn't be a big deal to let the customer have access for 5 minutes and then cut off access if it's rejected. Many such sites have a free trial anyway. Sathoshi seemed to think bitcoin peer 2 peer electronic cash wa cash money. Price is nice, but I write this blog to show people how bitcoin works as cash money. We can use it to solve real world problems and it has real-life use cases. In this post, I'll show you bitcoin is more than mere property. It's a super power that lets people send money without providing your information to every Tom, Dick, and Larry Fink. When Satoshi talked about peer to peer electronic cash system, he meant cash like the cypherpunks meant cash. Cypherpunks did not talk about the French origins of the word cash. They used the word in the colloquial sense like cold, hard, cash. Satoshi didn't site any papers that talked about the word "casse". He cited tools created by crypto anarchists like wei dai's Peer-money. Here's a quote from this wei dai's b-money. As a reminder this essay was cited in Satoshi Nakamoto's White paper. "I am fascinated by Tim May's crypto-anarchy. Unlike the communities traditionally associated with the word "anarchy", in a crypto-anarchy the government is not temporarily destroyed but permanently forbidden and permanently unnecessary. It's a community where the threat of violence is impotent because violence is impossible, and violence is impossible because its participants cannot be linked to their true names or physical locations. Until now it's not clear, even theoretically, how such a community could operate. A community is defined by the cooperation of its participants, and **efficient cooperation requires a medium of exchange (money) and a way to enforce contracts**. Traditionally these services have been provided by the government or government sponsored institutions and only to legal entities. In this article I describe a protocol by which these services can be provided to and by untraceable entities." Satoshi was clear. Bitcoin is a peer-to-peer electronic cash system. It's an integral part of the game theory. Cash is decentralized. Property is not decentralized. Property gets taxed. Fiat cash gets taxed via inflation. Peer 2 peer electronic cash is not property. It's cash. The keys are property. Your steel plate is property. The twelve words you head are property, but the transactions on the time chain are not property. We should work to keep it that way. When I first Andreas Antonopolis talk about bitcoin, I thought it was an awesome idea, but I was skeptical. There was no way in hell I would just sign up with coinbase and buy bitcoin just because he said so. I didn't trust it. I had to verify it. So I thought, if this is peer to peer cash is legit, someone ought to be able to send me a little. So I asked someone on twitter to send me some hash tag bitcoin. Someone sent be a buck fifty and told me to buy a cup of coffee with it. That's my bias. I can buy coffee with it. I did a couple years ago. I still have most of those sats from 2014. Maybe I'm just a crotchety old man waving my cane in the sky and screaming "Get off my drought resistant landscaping!" Then again, maybe more people would get on-boarded if we sent them bitcoin peer to peer. That's why I'm bullish on nostr. We should stop telling people to "buy bitcoin." **We should tell them to get on nostr and try bitcoin**. It sounds better than, buy bitcoin, [peer-to-peer electronic property](https://primal.net/e/note10v7ns6kerrmayj4z5rspxu5dls9asn322a964xql5g9huvhy2thqglcdln) ## How To Buy Coffee With Bitcoin Say you are allergic to bitcoin like I'm allergic to fiat. Don't like VoLiTiLiTy? No problemo! Sign up for an account at https://strike.me. Set up your account and choose a username. You will get a lightning address that is `yourusername@strike.me` Despite how it looks, that's not an email address. It's a lightning address. This address is all you need to accept payments on the Internet. All you need to do is put it on your webpage, substack, Twitter, or whatever. First, you should choose to take the orange pill or the green pill. Do you want fiat or do you want bitcoin? Again, I know a lot of people hate bitcoin. Mention the word on blue sky if you don't believe me. Click on the little anthropomorphic person on the upper right hand corner.  Next, scroll down until you see the settings menu. Next, click the "Bitcoin" tab.  Now it's time to choose the orange pill or the green pill. Click on Passive incoming payments.  You'll have the option to choose to accept incoming payments as bitcoin or cash. Of course, if someone sends you less than a penny, it can't be converted to fiat cash. Anything more than a penny gets converted to USD in my jurisdiction. I assume people in other countries get the cash converted to their local fiat currency, but don't quote me on this. I don't really know. As you can see, I took the orange pill, but you can do whatever you want to do.  Remember, your lightning address is your username at strike.me. I'm using a lightning tips address, but the process is the same.+ ### Accept Payments Anywhere On The Internet You can put your lightning address anywhere on the Internet, but this is about coffee so I created a Buy Me A Coffee page. I won't do a tutorial because I assume you know how to set up a profile on the Internet. Remember when congress questioned Zuck about his stablecoin? Well, I hate to break it to you Congress we don't need Zuck bucks. You can add a lightning address right to a Facebook profile.  Here's my page. You won't find it on Facebook. https://www.buymeacoffee.com/bloggingbitcoin I added my lightning address to https://sendsats.to It comes in handy for making a clickable page. There's not much of a tutorial needed. The page is https://sendsats.to/bloggingbitcoin@ln.tips Just replace my lightning address with your lightning address and you too can accept magic Internet money. **WTF Does This Have To Do With Coffee?** Go back to the Strike welcome screen, scroll down to shop with lightning.  ### Shop With Bitcoin Straight From StrikeI wrote about Bitrefill in one of my early blogs, but now it's integrated right into the Strike App. You can buy coffee, or just about anything else you want with your newly acquired sats or fiat. You might want to hang on to some sats if you don't have any, just in case, but you could totally buy a cup of coffee if you want to. Many Saylor disciples accept the thesis that bitcoin is property. They will never spendl. They also know Saylor says you should orange pill as many people as possible. What better way to orange people than send them a little bitcoin. I'm not saying to buy some fancy-schmancy car like a 1976 Ford Pinto with your bitcoin. I'm saying to buy a five dollar cup of coffee. I mean an eight dollar cup of coffee. Don't spend your bitcoin if you're worried about your taxes or whatever. Holdl dollars in your Strike account. Don't "buy bitcoin" with those dollars. Turn the dollars into sats for a gift card. It might cost you some fiat flyer miles. So what? Tell the barista you bought your gift card with bitcoin.
`We propose a solution to the double-spending problem using a peer-to-peer network.`You can do this because bitcoin solves the double spending problem. It solves the double-spending problem so well, someone can send you ten bucks worth of bitcoin from Australia. You'll get it within about three seconds. You can buy a Starbucks gift card with those sats and sip yourself shakey straight-away. You could also send the bitcoin to the Cash App and buy a gift card there too. I suppose you could buy Bank of America stock in the Cash App right away too. I don't know why the hell you would do that, but it's possible. You'll need to sell the bitcoin on the Cash App first, but guess why you can do this? Because bitcoin solves the double spending problem. Can you do that with Bank of America? No, it takes at least three days to send dollars from Bank of America to Wells Fargo.
₿logging ₿itcoin 834667 debtclock 🧡Support this blog by using the [Value] 4 Value model](https://value4value.info/). ⚡Zap Me 🍐Join my Keet Room 🛒Shop my Nostr Store 🛒Shop The Elliptic Curve Economy
-
 @ d7c6d014:a6abb6b8
2023-12-29 10:35:20
@ d7c6d014:a6abb6b8
2023-12-29 10:35:20WASSUP, NOSTRICHES!?
というわけで、ノス民の皆様いかがお過ごしでしょうか。
Nostrは、その性質上、既存のSNSのようなEメールアドレスや電話番号などを使ったいわゆる「アカウント」的な概念が存在しておらず、SSL/TLSやビットコインなどのように公開鍵暗号方式を取っています。 そのため、秘密鍵 (nsec) さえ一つあれば、Nostrプロトコルに準じた様々な種類のクライアントにアクセスすることができます。 (例えるなら、Twitterのアカウント1個で、YouTube、Instagram、Medium、Misskey全てのサービスにアクセスできるようなイメージ)
今回はそんな多種多様なNostrのクライアントたちをジャンル別に可能な限り網羅して紹介していきたいと思います。
SNS系 (Twitterライク)
nostter
nostterは、雪猫さん制作の動作が非常に軽いTwitterライクなWebクライアントです。

kaiji君制作のUIもマットで見やすく、Web版Twitterに慣れている人でNostrの世界に初めて足を踏み入れる人におすすめのWebクライアントです。

Snort
Snortは、主に日本国外で人気なTwitterライクなWebクライアントです。

特徴的な機能としては:
バズり具合がサマリーとして可視化できたり...

開発者にzap (ビットコインの投げ銭のこと) したり...

ビットコインライトニングのウォレットと紐付けたりできます⚡️

質問系 (Quoraライク)
swarmstr
swarmstrは、Quoraライクなクライアントです。
asknostr のハッシュタグをつけると自動的にキュレーションされて表示されます。

動画配信 (YouTube, Twitchライク)
zap.stream
zap.streamは動画配信クライアントです。

チャットしたり...

zapしたり...

Stream Forwarding機能があるので、他の動画プラットフォームに同時配信もできます🙃

リンク集約 (Linktreeライク)
Nostree
Nostreeは、Linktreeの様に様々なSNSなどのリンクを集約できるツールです。

zapしたり...

リンクをシェアしたり...

Nostrに新しいリストのシェアをしたりできます🙃

また、プロフィールのみならず、好きな本のリストを作ってみたり使い方はあなた次第です🚀
エントリ / 長文記事投稿 (Medium, noteライク)
habla.news
habla.newsは、Mediumのような長文記事投稿用クライアントです。 記事をブクマ、拡散できるのはもちろんのこと、お気に入りの記事に対してzapすることができます。

YakiHonne
YakiHonneは、キュレーション型の分散型メディアプロトコルです。

Mediumのように長文投稿ができるのはもちろんのこと、記事自体をキュレーションしてまとめてpublishすることができます。

もちろんブクマや記事のシェア、ビットコインの投げ銭もできます⚡️
Bounty
nostrbounties
nostrbountiesは、タスクをこなすとビットコインで報酬がもらえるBounty型のWebクライアントです。

Wikipediaライク
wikistr
wikistr は読んで字のごとくWikipediaのようなクライアントです。
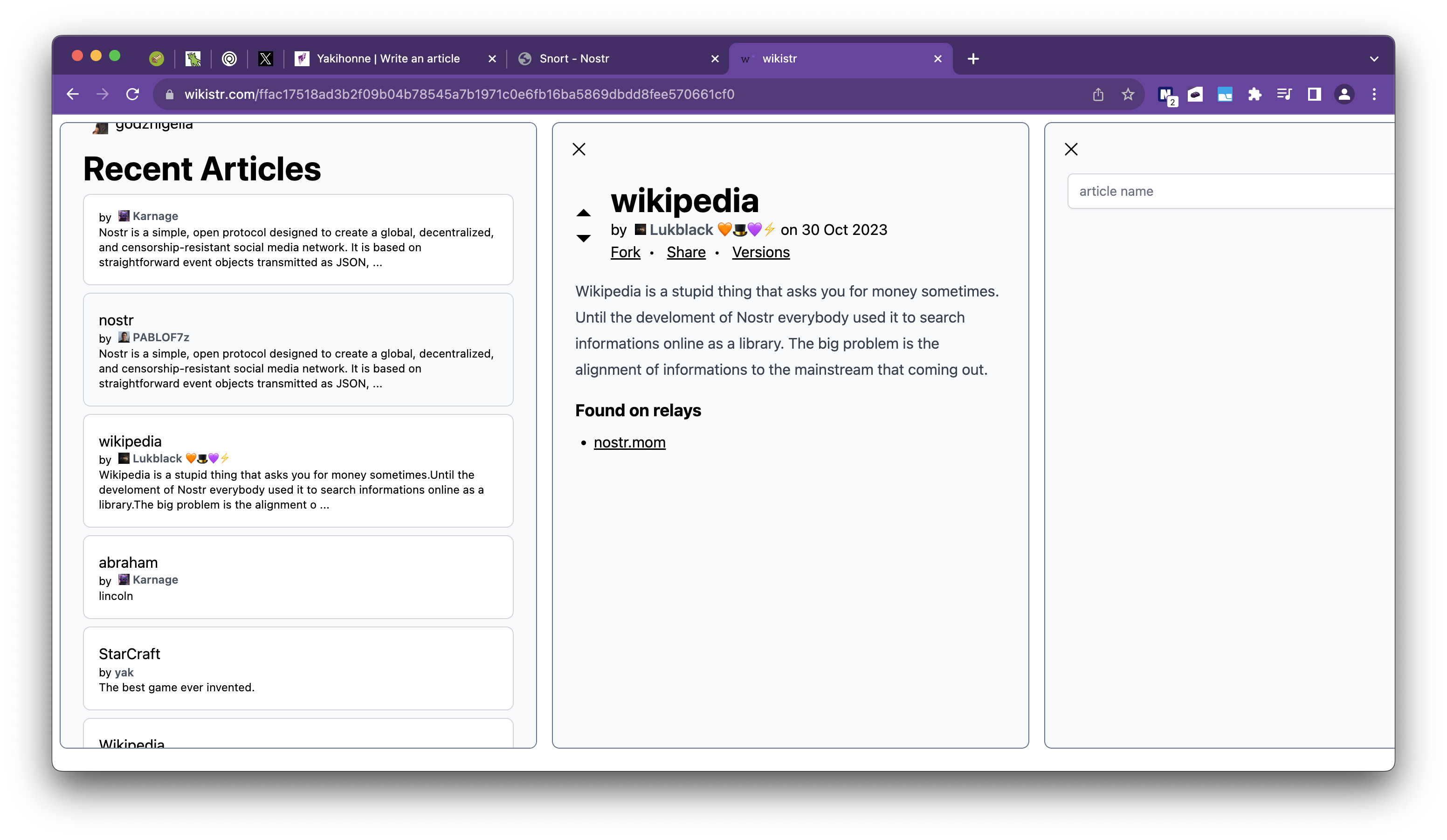
通常のWikipedia的な機能に加え、投稿したウィキ情報をフォークしてオリジナルの文章を追加したり、パロディネタにしたりして遊べるのが特徴です。

フリマ
Shopstr
shopstrは、メルカリのようなフリマクライアントです。 メルカリのようなアプリ内通貨などは使わずに、ビットコインで直接商品の売買をすることができます。 フィジカルな商品のみならず、デジタル商品のやり取りもできます。

料理レシピ共有 (クックパッドライク)
NOSTR.COOKING
NOSTR.COOKINGは、料理レシピの共有ができるクライアントです。
Nostrユーザーは世界中にたくさん存在しているため、クックパッドとは違い日本料理を含めた世界中のレシピが集まっているのが個人的には好きです。 レシピをフォークしてアレンジレシピを作ったり、マークダウンファイルをダウンロードしたり、zapできたりします。
いかがでしたでしょうか。 今回は、計9種類のトピックに分けてWebクライアントをメインに紹介してきましたが、これでもまだまだほんの一部です。
そして何より、これまで取り上げてきた機能全てがNostrの秘密鍵一つで利用できるのがNostrの素晴らしいところです。煩わしいサービスごとのアカウント登録は一切必要ありません。
次回はモバイルクライアントをメインにキュレーションして紹介しようと思います♡
今回の記事が良いな〜と思ったら是非ZAP ME⚡️⚡️⚡️
-
 @ 44dc1c2d:31c74f0b
2023-12-12 20:18:07
@ 44dc1c2d:31c74f0b
2023-12-12 20:18:07Chef's notes
If you want to kick it up a notch instead of using EVOO or butter, get about 6 slices of bacon and at the first step just cook off the bacon and use that as your cooking fat.
If you want a more crispy biscuit, cook them separately instead of cooking them in the filling. If you do this, simmer the filling on low for an extra 10 ish min, or just until the potato are tender.
If you prefer to make the pot pie in a casserole dish, you can. Simply pour out the filling into a greased baking dish and top with biscuit dough and continue with the recipe as stated.
The filling tends to bubble and make a bit of a mess, so I recommend placing your skillet or baking dish over a sheet pan covered with tin foil to catch any drips and messes.
Details
- ⏲️ Prep time: 30 mins
- 🍳 Cook time: 45-50 mins
- 🍽️ Servings: 4-6
Ingredients
- roughly 1lb of chicken. (Use whatever I prefer thighs)
- 1 medium size onion, peeled and diced
- 2 medium size carrots, peeled and diced
- 2 celery stalks, diced
- 3 cloves of garlic, peeled and minced
- 2 heaping tablespoons all purpose flour
- 2 cups chicken stock/broth
- ½-1 cup whole milk
- ¼ cup chopped fresh parsley
- 1 teaspoon fresh thyme plus more for garnish
- 2 bay leafs
- 2 mid sized potatos chopped into small cubes.
- Salt and pepper to taste
- 3-4 tablespoons of olive oil or butter
- For the Drop Buttermilk Biscuits
- 2 cups all purpose flour
- 1 tablespoon baking powder
- ¼ tsp baking soda
- ½ tsp fine sea salt
- 6 tablespoons cold unsalted butter, cubed
- 1¼ cups buttermilk + 2 tablespoons for brushing biscuits with
Directions
- For the Filling
- Heat your cooking fat. If using uncooked chicken, add chicken pieces to the pan. (If using pre-cooked chicken, don’t add it until later) Cook sautéing chicken for 2-3 minutes per side tell golden brown
- Add onion, celery, carrots, garlic and potatos. Cook for 5-7 minutes, stirring often until the veggies start to become tender. Make sure to season well with salt and pepper.
- Sprinkle flour over the veggies and chicken and stir vigorously for 1 minute to cook the flour a bit.
- Slowly pour in the chicken broth followed by the milk while stirring. Raise temperature up just a bit if needed and let it come to a very gentle boil. Once it reaches a boil reduce the heat to a simmer and let cook for 5-10 minutes, or until its has reduced and mixture has thickened a little
- Add the chicken if using precooked or rotisserie, parsley and thyme. Let cook until the veggies are tender, chicken are heated through, and mixture is nice and thick or has reached your desired thickness, about 3-5 more minutes (feel free to loosen up sauce a little adding more milk, cream or broth as needed). Season with salt and pepper to taste. Remove from heat and set aside.
- For The Buttermilk Drop Biscuits
- Preheat the oven to 425ºF while preparing the drop biscuits
- Add the flour, baking powder, baking soda, salt, to a large bowl and whisk to combine or pulse to combine in a food processor. Scatter the butter over the dry ingredients and rub together with your fingertips, until it forms a sandy-looking texture with some pebble-sized pieces or use a pasty cutter. If using food processor pulse a few times to achieve the same texture.
- Pour in the buttermilk and stir until it just comes together into a thick dough and there are no visible signs of flour. This step should only take a minute: be careful not to overmix the dough. (I usually pour out my flour and butter into a bowl from the processor and stir in the buttermilk by hand with spatula instead of pulsing it in)
- Assembling & Baking
- Use large cookie scoop or 2-3 heaping tablespoons (or approx ¼ cup) to scoop out dough. Drop dollops of the dough over the top of the pot pie filling to mostly cover the surface. Flatten them out a bit if you wish. Brush the tops of the biscuits with remaining 2 tablespoons of buttermilk.
- Transfer the skillet to the oven and bake for about 20-25 minutes until the biscuits are golden brown and fully cooked through and the filling is bubbling. I typically loosely cover pan with foil for the last 5-10 minutes of baking so they don’t brown too much - but are fully cooked through. Feel free to broil for the last minute to get the biscuits deeply golden.
-
 @ 5c8a5765:4fc5edee
2023-12-05 12:01:20
@ 5c8a5765:4fc5edee
2023-12-05 12:01:20А вы знали, что NOSTR-протокол — это не только децентрализованный микроблоггинг, но ещё и…
…Платформа для длинных текстов: www.habla.news и https://blogo.site
…Децентрализованный хостинг для веб-сайтов: https://hostr.cc
…Веб-магазины: https://shopstr.store и https://plebeian.market
…Децентрализованная публикация отрывка текста (аналог PasteBin): www.nosbin.com
…Сайт для заметок: www.listr.lol
…Сокращения URL, которые никогда не перестанут работать: www.w3.do
…Канал с мемами: www.memestr.app
…Децентрализованный торрент-архив: https://dtan.xyz
…Шахматы: https://jesterui.github.io
…Аудио-плеер: www.wavman.app
…Платформа для создания и публикации музыки: www.stemstr.app
…Платформа для подкастов (которая платит за её использование): www.fountain.fm
…Коллективный буфер обмена с конечным шифрованием: www.sendstr.com
Используйте удобные мосты для…
…Связи Nostr с Fediverse (Mastodon, ActivityPub, проч.): mostr.pub
…Связи Nostr с Matrix: www.github.com/8go/matrix-nostr-bridge
…Превращения любой RSS-ленты (Twitter, Mastodon, Reddit, ScuttleButt, проч.) в Nostr-аккаунт, на который можно подписаться: https://rsslay.nostr.moe
Застрял:а в Твиттере (Х)? Используй EXIT.pub для автоматической миграции всего контента уже сегодня: www.exit.pub
Я не привожу здесь зашифрованных мессенджеров на базе NOSTR (вроде Pulsar или 0xChat), ибо хотя они и хороши, они значительно уступают по безопасности мессенджерам, изначально ориентированным на приватность, таким как Session и SimpleX.
-
 @ 5c8a5765:4fc5edee
2023-12-04 17:04:12
@ 5c8a5765:4fc5edee
2023-12-04 17:04:12Did you know that the NOSTR protocol is not only decentralized microblogging, but also...
…A platform for long texts: www.habla.news and https://blogo.site
...Decentralized website hosting: https://hostr.cc
...Web store: https://shopstr.store and https://plebeian.market
...Decentralized text publishing (alternative to PasteBin): www.nosbin.com
...Note taking tool: www.listr.lol
...URL shortener that will never stop working: www.w3.do
...A meme channel: www.memestr.app
...Decentralized torrent archive: https://dtan.xyz
...Chess: https://jesterui.github.io
...Audio player: www.wavman.app
...Music creation and publishing platform: www.stemstr.app
...Podcast platform (that pays when you use it): www.fountain.fm
...A collaborative clipboard with end-to-end encryption: www.sendstr.comUse convenient bridges to... …Link NOSTR to Fediverse (Mastodon, ActivityPub, etc.): www.mostr.pub
…Link NOSTR to Matrix: www.github.com/8go/matrix-nostr-bridge
…Turn any RSS feed (Twitter, Mastodon, Reddit, ScuttleButt, etc.) into a Nostr account you can subscribe to: https://rsslay.nostr.moeStuck in Twitter (X)? Use EXIT.pub to automatically migrate all your content today: www.exit.pub
I am not mentioning NOSTR-based encrypted messengers (like Pulsar or 0xChat) here, for while they are good, they are still vastly inferior in terms of security to inherently privacy-oriented messengers like Session and SimpleX.
Did you find this bunch of links useful? Please zap me a cent 🙂
-
 @ 6bd128bf:bb9002f8
2024-01-04 15:07:13
@ 6bd128bf:bb9002f8
2024-01-04 15:07:13Disclaimer : บทความนี้เกิดขึ้นจากการที่ผมสงสัยว่า seed phrase ที่เราจด ๆ กันไว้เนี่ย มันสร้างมาได้ยังไง ผมจึงเข้าไปอ่าน BIP-39 ที่ว่าด้วยเรื่องการสร้าง seed phrase (mnemonic code) สำหรับนำมาสร้าง seed และได้เขียนสรุปความเข้าใจของผมเพื่อเรียบเรียงความรู้ในหัวเก็บไว้ เผื่อว่าจะเป็นประโยชน์กับคนที่เกิดความสงสัยเหมือนกันกับผม ถ้าผมเข้าใจผิดตรงไหนสามารถบอกกันได้เลยนะครับ
ทำไมต้องมี BIP-39 ?
BIP-39 เกิดขึ้นเพราะว่ามนุษย์นั้นสามารถจดหรือจำคำได้ง่ายกว่าจดหรือจำข้อมูลในรูปเลขฐานสอง (binary) หรือเลขฐานสิบหก (hexadecimal) จึงมีคนเสนอให้สร้าง mnemonic code หรือที่เราเรียกกันว่า seed phrase ขึ้นมา ซึ่งจะประกอบไปด้วย 2 ส่วนคือ การสร้าง seed phrase และการแปลง seed phrase ให้การเป็น seed ที่สามารถนำไปใช้ในการสร้าง private key และ public key ต่อได้
Seed Phrase สร้างยังไง ?
seed phrase นั้นต้องสร้างขึ้นจากข้อมูลทางคอมพิวเตอร์ที่เค้าเรียกว่า entropy ที่มีจำนวน bits หารด้วย 32 ลงตัวและมีจำนวน bits อยู่ระหว่าง 128 - 256 bits ยิ่ง entropy มีจำนวน bits มากก็จะทำให้มีความปลอดภัยมากขึ้นแต่ก็จะมีจำนวนคำมากขึ้นเช่นกัน ซึ่งการสร้าง seed phrase นั้นมีขั้นตอนดังนี้
Step - 1
สุ่ม entropy ที่มีจำนวน bits อยู่ระหว่าง 128 - 256 bits และจำนวน bits ต้องหารด้วย 32 ลงตัว ซึ่งหลังจากนี้จะแทนจำนวน bits นี้ด้วยคำว่า ENT
ตัวอย่าง entropy ที่มี ENT เท่ากับ 128 bits
00110010010101010111100101001011001101100100101001000100001100010111001101110100001110010011011101000101011010100101000101010011Step - 2
คำนวณหา checksum bits ที่มีจำนวน bits เท่ากับค่า ENT หารด้วย 32 โดยการ hash entropy ด้วย SHA256 algorithm และนำผลลัพธ์มาตัดเอาแค่ส่วนหัวตามจำนวน bits ที่ต้องการ
ผมนำ entropy จาก step ก่อนหน้ามาทำ
sha256_hashing(entropy)ได้ผลลัพธ์ออกมาเป็น01100111.........และจะได้ (128 / 32) = 4 bits แรกคือ0110ซึ่งหลังจากนี้จะแทนความยาวของ checksum bits ด้วยคำว่า CSStep - 3
นำ checksum bits ที่ได้มาต่อท้าย entropy จะได้เป็นกลุ่มของ bits ที่มีความยาวเท่ากับ ENT + CS
ผมนำ 4 bits แรกจาก step ก่อนหน้ามาต่อท้าย entropy ที่มี 128 bits ดังนี้
"00110010010101010111100101001011001101100100101001000100001100010111001101110100001110010011011101000101011010100101000101010011" + "0110"Step - 4
นำกลุ่มของ bits มาแบ่งเป็นกลุ่มย่อย กลุ่มละ 11 bits จะทำให้ได้กลุ่มทั้งหมดจำนวน (ENT + CS) / 11 กลุ่ม ซึ่งถ้า entropy มีจำนวน 128 bits ก็จะแบ่งกลุ่มได้ (128 + 4) / 11 = 12 กลุ่ม
ผมแบ่งกลุ่มได้ตามนี้
00110010010 10101011110 01010010110 01101100100 10100100010 0001100010111001101110 10000111001 00110111010 00101011010 10010100010 10100110110Step - 5
นำกลุ่มย่อยแต่ละกลุ่มมาแปลงเป็นเลขฐานสิบซึ่งจะมีค่าตั้งแต่ 0 - 2047 และสามารถนำไปเทียบกับ wordlist ที่กำหนดไว้ใน BIP-39 ตาม index จะได้ผลลัพธ์เป็น seed phrase ที่สามารถนำไปสร้าง seed ต่อไปได้
ผม map เลขฐานสิบกับ wordlist ได้เป็น seed phrase ตามนี้
00110010010 => 402 = crane10101011110 => 1374 = profit01010010110 => 662 = fan01101100100 => 868 = hold10100100010 => 1314 = picture00011000101 => 197 = board11001101110 => 1646 = soccer10000111001 => 1081 = mango00110111010 => 442 = dance00101011010 => 346 = clip10010100010 => 1186 = nephew10100110110 => 1334 = plugWordlist
wordlist ที่ BIP-39 กำหนดขึ้นมานั้นมีลักษณะดังนี้ - เลือกกลุ่มคำที่สามารถพิมพ์แค่ 4 ตัวอักษรก็สามารถระบุได้ว่าเป็นคำไหน - เลี่ยงคำที่มีหน้าตาคล้าย ๆ กัน เช่นใน wordlist จะมีคำว่า build แต่ไม่มีคำว่า built เพราะอาจจะทำให้สับสนได้ - เรียงลำดับคำตามตัวอักษรเพื่อจะได้หาได้ง่าย - ตัวอักษรในคำสามารถประกอบด้วยภาษาอะไรก็ได้แต่ว่าต้องอยู่ในรูปของ UTF-8 encoding แต่ผมว่าเป็นภาษาอังกฤษน่าจะจำง่ายที่สุด
จำนวน bits ของ entropy และจำนวน word ที่ได้
entropy 128 bits จะมี 4 bits checksum ได้เป็น seed phrase 12 word entropy 160 bits จะมี 5 bits checksum ได้เป็น seed phrase 15 word entropy 192 bits จะมี 6 bits checksum ได้เป็น seed phrase 18 word entropy 224 bits จะมี 7 bits checksum ได้เป็น seed phrase 21 word entropy 256 bits จะมี 8 bits checksum ได้เป็น seed phrase 24 word
-
 @ d70d5009:1ed4acee
2024-03-14 13:10:37
@ d70d5009:1ed4acee
2024-03-14 13:10:37The node is virtualized under Proxmox and we will use Start9 (startOS) as operating system.
Proxmox uses KVM which is a type 1 hypervisor and has nothing to envy to solutions like VMware ESXi, and the best, it is open source, based on Debian and with a modified Ubuntu LTS kernel. Why virtualize the node? Because it has all the advantages of running it directly on the hardware.
- Hardware isolation, in the case of startOS being based on PureOS, a version of Debian focused on security and only using open source drivers, hardware support is quite restricted, also startOS does not support UEFI and there are many new computers that come without the Legacy BIOS option.
- Possibility of making a complete backup of the machine on network storage, or on a USB disk, and the possibility of restoring the backup on another Proxmox machine without worrying about the hardware underneath, in addition, backups can be scheduled.
- Possibility to upgrade the disk in the future without having to reinstall everything or follow complicated procedures.
- Possibility to use the host machine for more things, also proxmox supports Linux Containers (LXC) so we can set up many machines running services at a ridiculous cost of hardware resources.
- Proxmox supports software RAID via ZFS and Btrfs; in our case we will use Btrfs because it consumes less hardware resources than ZFS. This is a great advantage over using raid by BIOS/UEFI because in hardware RAID you will need the same hardware to restore in case of hardware failure, with software RAID you isolate yourself from the hardware, the disks can be moved to different hardware.
- Easy migration of the virtual machine to new hardware, we only need to make a backup and restore it.
- Possibility to take snapshots of the machine, which allows us to perform, for example, a restore in case of a failed update.
- Possibility of having a node in high availability if we set up a cluster with two or more servers.
Why Start9 (startOS) and not another platform like Umbrel or others?
Simply because startOS is well built, the other platforms are not built with security and scalability in mind.
- Modular architecture, right now they use Docker but it could be easily changed.
- Integrated backup system
- Migration and restoration functions
- Encrypted volume
- Application integration
- Possibility to create your own services
- Stability
Proxmox installation with Btrfs and Raid 1.
The recommended hardware is two ssd or mechanical disks, but preferably ssd and 8gb of ram memory minimum.
Download the Proxmox iso from:
https://www.proxmox.com/en/downloads/category/iso-images-pve
In this guide I won't go into the basic details of how to create a bootable USB and so on, this you should know and if not Google is your friend.
The first screen you will see will be this one:

On the second screen you accept the terms of the contract:

And now look at the next one, this is where we select Btrfs and Raid 1 in options. As you can see two disks appear, you do not have to touch any other option, just click Ok. I want to remember that we use Btrfs against ZFS because it consumes less resources and also in ZFS ECC memory is recommended to avoid data corruption. And why do we use Btrfs against ext4 or others? Because like ZFS, Btrfs has an integrated volume manager that allows us to perform software raids without the need for mdadm with excellent performance and Btrfs is a COW file system that also protects us against data corruption.

In the next screen we select the country and time zone:

Now we choose the root password and an email for notifications, you can make it up:

In the next screen you configure the machine's network:

Finally check your data and click on install:

The machine will reboot and you will be able to enter to manage the Proxmox environment through a web browser and the ip you have set.
I am not going to comment much about virtual environments again, I understand you are familiar with them, however, I will comment the main features that are useful for your node.
Add update repository without subscription Proxmox has two modes of operation, subscription and non-subscription (free), it is exactly the same but in the subscription mode the updates are more tested, we could compare it to the model of Red Hat and Fedora.
The first thing to do is to go to the repositories and disable the enterprise repository and then enable the no-subscription repository.

Now we add the no-subscription repository:

After this in the updates section we refresh the repositories and proceed to update from the upgrade button.

Failure of a disk in Btrfs
In case a Raid 1 disk fails, the system will not boot, because Btrfs does not allow to boot a degraded raid unless you use the rootflags=degraded option in the grub, but I do not recommend it because you will know when a disk fails.
When a disk fails the system will enter the initramfs console and there you will have to run: ~~~ mount -o degraded /dev/sdXY /root ~~~
sdXY is the disk where your Proxmox root partition will be, in this case the disk that remains alive.
After executing the command we have to press Ctrl + D to continue with the boot.
Once our proxmox system is booted again with another good disk, you will proceed to copy the partitions from one disk to the other since the two disks have to be identical so that in case of failure of one you can boot from the other.
~~~ sfdisk -d /dev/sdb > parts sfdisk /dev/sda < parts ~~~
These commands copy the partitions from the sdb disk to the sda disk.
Keep in mind after this to copy the contents of the second partition corresponding to the EFI grub boot, to do this you simply mount the sda2 partition in any directory and copy the contents of /boot/efi that corresponds to the mount point of sdb2.
Now it is time to recreate the btrfs partition corresponding to raid 1 using the following command: ~~~ btrfs replace start 1 /dev/sda3 / ~~~
Where the 1 after the start indicates the failed disk that in this case was almost the first one, this can be seen with the command "btrfs filesystem show" and /dev/sda3 corresponds to the Btrfs partition of the new disk, finally / the mount point.
With the following command we can see the progress of the reconstruction.
~~~ btrfs replace status / ~~~
Virtual machine backup
Proxmox allows us to make backup copies of the virtual machine which facilitates the task of migration to new hardware or restoration in case of disaster.
First you will have to add the desired type of storage for the copy, for them you have to go to the datacenter options on Storage:

If for example you want to add a USB disk you would only have to mount it first in Proxmox and then pass it the mount point and name and the content type in this case VZDump.

After that you can run backups or schedule them. I'm not going to extend much here better you try it, just keep in mind that Proxmox supports three types of backups, snapshots, suspend and stop. The suspend mode is used for compatibility reasons and I do not recommend using it. The snapshots mode is the fastest as the machine does not have to be stopped, but you run the risk of having some inconsistency especially in certain databases and the stop mode stops the machine to perform a backup but it is the most consistent. For the migration of a machine to a new hardware I recommend the stop mode.

Snapshots of the machine
I recommend taking snapshots of your node before an upgrade or any critical change, it will save you hours of work in case of a disaster. As easy as going to the machine in question and clicking on snapshot:

Installing startOS
The first thing is to download the ISO in startOS in the Proxmox storage. For them we go to our local-btrfs and in ISO Images we put the download address and click on Query URL to capture the name of the ISO or add the name that we left manually, after which we click on Download.
https://github.com/Start9Labs/start-os/releases/download/v0.3.5.1/startos-0.3.5.1-39de098_x86_64.iso

Now we will create the virtual machine:

We enter the name of the machine:

Select the installation ISO:

In the next screen everything is default:

In this screen we choose the disk size:

We choose the number of CPUs:

The amount of RAM:

The network configuration is left as default:
Finally click on confirm:

We start the machine and in console we can see its screen:

We proceed to the installation of startOS.
Select the installation disk:



We delete the loaded ISO:

To do this go to Hardware, select the CD and check "Do not use any media":

We return to the console and restart.
In the next screen we click on "Start Fresh". The options of recover to be able to restore from a backup or to make a transfer of the data to another machine, but these functions are delegated to Proxmox, except for the backup of the services that we will see later.

Select the installation disk:

And enter the password:

The machine is initialized:


And now we can proceed with the Login:

I am not going to go into how to configure startOS as it is as simple as going to the Marketplace and installing the desired services and you have a very complete manual on their website:
https://docs.start9.com/latest/user-manual/

If I emphasize the importance of the backup of the services that you can perform on a USB device or network. The function is located in System:


The backup is encrypted with your startOS password and is necessary for example to safeguard LND onchain funds and channel funds. In case of disaster just mount a new startOS and restore from the backup, once the initial synchronization of the LND network is finished the channels will be closed and you will have all your balance in onchain.
Disk expansion in startOS
I am going to expand on this point because it is one of the reasons why we have installed startOS in a virtual environment. The reason is not to depend on the hardware and treat the virtual machine as a file, so we can take it wherever we want. In this case we will assume that we have set up a new Proxmox server with more storage and we are going to migrate the startOS machine by making a backup of it and importing it into the new environment as previously explained in the Backup section.
The first thing would be to expand the space of the virtual machine startOS for it we go to the Hardware options and edit the disk:

We tell you how much we want to increase it:

And we restart the machine.
We enter by ssh in the machine, for this we will first have to import in Embassy our public ssh key, I will not explain how to create a public/private key, I assume that you understand how ssh works. startOS for security does not allow the Login ssh with username and password, only through keys.


Once inside we will check that the virtual disk space has been increased:
~~~ ssh start9@adj-noun.local sudo su /usr/bin/apt install parted -y lsblk /dev/sda ~~~
 As we can see now the space is 1T compared to the previous 64.
As we can see now the space is 1T compared to the previous 64.The next step will be to increase the Embassy data partition which corresponds to sda4:
~~~ parted print free resizepart 4 100% print quit ~~~
 Enlarge the physical volume to occupy the whole available space in the partition:
Enlarge the physical volume to occupy the whole available space in the partition:~~~ pvresize /dev/sda4 ~~~ List logical volumes:
~~~ lvdisplay ~~~
 The volume we want to expand is the "package-data".
The volume we want to expand is the "package-data".~~~
Use all the remaining space on the volume group
LV path should resemble /dev/EMBASSY_XXX/package-data
lvresize --extents +100%FREE --resizefs {LV PATH} ~~~
 we can see again that the volume has expanded
Finally, the only thing left to do is to extend the file system.
we can see again that the volume has expanded
Finally, the only thing left to do is to extend the file system.~~~
get path where package data is mounted
df -h | grep package-data btrfs filesystem resize max /embassy-data/package-data ~~~
 see that the file system has resized
see that the file system has resized the changes will reflect on startos monitor
the changes will reflect on startos monitorTelegraph link: https://telegra.ph/Updated-Guide-to-building-a-Bitcoin-Super-Node-02-12
WIRD ISSUE cryptsetup resize
-
 @ 8fb140b4:f948000c
2024-01-02 08:43:31
@ 8fb140b4:f948000c
2024-01-02 08:43:31After my second attempt at running Lightning Network node went wrong, mainly due to my own mistake and bad cli interface of LND, I have decided to look deeply into the alternative implementation of the lightning node software. Eclair was more final choice driven by multiple reasons that I am planning to further talk about in this write-up. The main reason I even considered Eclair despite my dislike of Java and JVM, was that one of the largest lightning nodes on the network is ACINQ, and they are the company behind the implementation and maintenance of this open source software.
I’ve noticed them first after reading their blog about how they run $100M Lightning node and what level of care and thought they put into the whole implementation. Lightning is used to transfer large quantities of value across the internet, and I would only trust something well designed and actively maintained by the people who have to lose the most if they make a wrong choice.
Eclair in itself is not a complex implementation of the lightning network standards, and highly modular, which allows for an easy segregation of duties among different components of the node. One of the biggest sales-points for me was their approach of crash-only software which guarantees consistency of the state regardless of what happens with the running software. By that extension, to shutdown the node, you simply kill the process and start it again. It doesn’t matter what transactions were in-flight, or what stage they were in. This is huge, since anything can happen to a running node (e.g., failed disk, failed RAM, CPU, kernel panic, etc.)
Getting back to the architecture, the Eclair is simple and elegant in design and implementation. The node is separated into three main components that comprise the node: eclair-core, eclair-node, eclair-front. All of the entities are sandboxed actors (e.g., peer, channel, payment), which allows for scalabilities across CPUs and faults. This ensures high availability and security.
Clustering is also an option and can be achieved by migrating from the single node to a multi-server node. There is no need to dive into complexities of that, and by the time you need to scale, I am sure you’ll be able to figure it out.
Simple and robust API, is yet another major reason that keeps the node simple and fast. One downside of the API, is that it is protected by a single password and is not designed for RBAC (Role Based Access Control). One solution could be an implementation of another API wrapper that would implement things similar to Runes or Macaroons, which should not be a challenge considering the REST API simplicity.
On-the-fly HTLC max size adjustment, which will prevent your node accepting forwarded payments that would fail due to lack of liquidity on your side. This also makes routing better for the rest of the lightning network, but may “leak” your channel balances if not done right.
Experimentation and adjustment of path-finding algorithm. I am not there yet myself, but I see this as a great option in the future if I need it. This will allow me to make my own choices how I want to route payments and what parameters I would use to determine the best path.
Full production support of PostgreSQL server. Not only Eclair itself is not a beta release unlike LND, but also has full production support of the very reliable and battle tested database as its backend data storage. You are able to(and should) to run Active/Passive PostgreSQL cluster in synchronous mode, and ensure that all of the written data by the node are backed-up in real-time. This removes the worry of corrupted database that I have seen happen all too often.
Excellent monitoring and metrics, that can be collected by Prometheus and viewed in Grafana. Eclair provides template dashboards that you can import into Grafana to make your life easier. You can also use Kamon (external service) where you could send the metrics and monitor your node.
Support for all common networking protocols and support Socks5.
Last, but not least, support for plug-ins. Even if you are not well versed in writing plug-ins, you could take some of the available ones and modify them to your liking.
There are many more features and limitations that I didn’t mention, but you can explore them yourself here.
One down-side that you should consider, is not such a great availability of the readily available tools. So far I found that Ride-The-Lightning works well; LNBits works but I am yet to see if it is reliable; BTCPayServer has support but I have failed to use it with API directly, and only was able to use it via LNBits.
Lightning is still reckless, but nothing stops you from doing it carefully and reliably. Good luck and happy node-running! 🐶🐾🫡⚡️
My Node - RAϟKO
-
 @ 8fb140b4:f948000c
2023-12-30 10:58:49
@ 8fb140b4:f948000c
2023-12-30 10:58:49Disclaimer, this tutorial may have a real financial impact on you, follow at you own risk.
Step 1: execute
lncli closeallchannelsThat’s it, that was easy as it could be. Now all your node’s channels are in the process of being closed and all your liquidity is being moved to your onchain wallet. The best part, you don’t even need to confirm anything, it just does it in one go with no questions asked! You can check the status by using a very similar looking command,
lncli closedchannels!Good job! Now you are ready to start from scratch and use any other reasonable solution!
🐶🐾🫡🤣🤣🤣
Disclaimer: this is a satirical tutorial that will 💯 cost you a lot of funds and headaches.
-
 @ 5c8a5765:4fc5edee
2023-11-22 22:38:03
@ 5c8a5765:4fc5edee
2023-11-22 22:38:03Read in english: Session removed PFS, we're doomed!!1
Автор: Кот Иван
Опубликовано также в IPFS!•••
PFS (Perfect forward secrecy) — это система, позволяющая в случае взлома одного ключа шифрования выдать лишь часть сообщений, но защитить другие части. Делается это простым образом: ключ шифрования переодически меняется. Из-за того, что Session убрал PFS, в случае взлома одного ключа хакеру станут доступны все ваши переписки. Разработчики Session лаконично возразили на это, что взлом ключа возможен лишь при физическом доступе к девайсу (а в этом случае сообщения можно прочесть и просто так) [0]. Насколько они правы?TL;DR: Они охуенно правы, но им стоит побеспокоиться о квантовых компьютерах.
•••
Давайте разберемся.
Протокол Session генерирует каждой учетной записи долгосрочную пару ключей X25519 (секретный и публичный) [1]. Секретный ключ X25519 состоит из 32 байтов (256 битов), или строку из 64 символов, которые включают в себя только цифры и буквы верхнего регистра [2][3].
Пример приватного ключа:
193FC8C3A73782DA18B238915C941CEF5E985DB388C881BD3C0E9EF496894A19
Предположим, что разработчики Session неправы, и попробуем посчитать, сколько времени займёт процесс взлома фразы, состоящего из 64 букв и цифр.
Количество всех возможных комбинаций любой строки вычисляется так [4]:
(Количество возможных символов)^(Длинна пароля)
В случае, если мы используем 26 букв английского алфавита и десять цифр (включая ноль), получается 36 вариантов символа. Длинна — как мы уже выяснили — 64. Наше уравнение — 36 в степени 64.
36^64 = 4.01199E+99
Следовательно, у ключа шифрования Session есть 4 011 199 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 возможных комбинаций. Цифру ещё можно выразить как 10^99*4, 12.3 Q (кветто) [5] или 4 дуотригинтиллиона. Для сравнения, это больше (примерно на 4 квинтиллиона), чем количество атомов в наблюдаемой вселенной (по оценкам — от 10^79 до 10^81) [6][7].
Для краткости, в будущем я буду обращаться к этому числу как к 12.3 Q, хотя его вполне можно было бы и назвать "число-пиздец". Так вот, теперь нам предстоит выяснить, как быстро компьютер сможет взломать пароль, если количество его комбинаций — 12.3 Q. Сайт Betterbuys [8] провел небольшое расследование этого вопроса и предложил, ссылаясь на источники, следующие схемы:
Эффективные ядра: 1/((1-Эффективность)+(Эффективность/Кол-во ядер)) — (мы предположим, что процессов посвящает 99% операций взлому пароля, поэтому эффективностью будет 0.99)
GFLOPS процессора: Частота процессора * Эффективные ядра
Количество операций в секунду: GFLOPS/Константа шифрования (расчитана на типичный компьютер 2015 года)
Время в секундах: x секунд = Комбинации/(количество операций в секунду)
Каков результат всех этих вычислений? Если заставить один компьютер 2015 года на процессоре Core i5-6600K взламывать ваш секретный ключ, у него займет это 3.5411902245474E+52 секунд — или 4 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 лет.А шанс случайно подобрать ключ — меньше 0.0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000003%.
Но что если компьютер будет не один?
Что если именно тебя атакует владелец ботнета, или хакерская группировка, или правительство со сверхкомпьютером? Ну, даже если мы подключим все существующие в мире компьютеры, включая ваш, ко взлому вашего ключа, на это всё равно уйдет уйма времени. Например, в 2015 году их было 2 миллиарда (2 000 000 000 000 000 000 000 000 000 000 000 000 000 лет взлома); но
даже если к 2023 мы изобрели в тысячу раз больше компьютеров, чем было (тысяча миллиардов), и все они (до музейных экспонатов) приобрели в два раза более сильный процессор, чем i5-6600K , у нас всё ещё остается 1 000 000 000 000 000 000 000 000 000 000 000 000 лет на взлом.Но что насчёт более вовременных методов взлома?
Здесь разработчики не соврали: современные методы взлома отметаются тем, как Session скрывает ваши метаданные. Когда сгенерированный Session ключ не связан с вами — это исключает индивидуальную атаку; когда пароль случаен, это исключает атаку со словарём [10]; когда пароль неизвестен даже вам самим, это исключает фишинговую атаку [10]; когда пароль длиннее 20-30 символов, это исключает атаку радужными базами [10]. Session также устойчиво противостоит MITM [10], Sybil и DRDoS-атакам.
Но что насчёт квантовых компьютеров?
Система шифрования, используемая Session (elliptic-curve cryptography [11]), действительно, уязвима перед квантовым компьютером, использующим алгоритм Шора [12]. Как скоро квантовый компьютер сможет взломать пароль с 12.3 Q комбинаций?
Согласно одним данным, всего за час, но при наличии от 20 [13] до 317 [14] миллионов кубитов (известный нам опубликованный лимит кубитов на сегодня — 433 кубита [15]). Согласно другим — уже с сегодняшним компьютером, но за 67 миллионов лет [16]. Согласно третьим — квантовый компьютер вообще едва ли сможет взламывать пароли: например из-за того, что компьютер должен быть достаточно стабильным для долгого взлома, или он должен иметь доступ к паролю (нужно взломать систему и получить напр. хеш пароля, ибо проверять состояние кубитов через интернет-запросы невозможно).
Тем не менее, из всех поднятых вопросов лишь квантовые компьютеры действительно представляют возможную опасность в будущем.
В конце концов, даже если вам удастся взломать 256-битный ключ, без доступа к девайсу вы сможете восстановить диалоги лишь за последние 14 дней (а также читать дальнейшие диалоги с этого момента), потому что сообщения старше этого срока перманентно удаляются с серверов [17].Выводы
- То, что Session отказался от PFS, никак не компромитирует вашу безопасность*.
- Знатокам кибербезопасности, продолжающим по сей день кричать про PFS как главную уязвимость Session, стоит прежде всего попробовать отгадать или подобрать мою любимую цифру — она где-то в диапазоне между 1 и 4 011 199 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000.
- Тем не менее, Session нужно обратить внимание на потенциальную грядущую опасность квантовых компьютеров.
- В какой-то момент Sesson должен начать переход на новый метод шифрования, устойчивый против квантовых алгоритмов.
*Когда количество нулей в вероятности (0,00..01) выше сотни, вероятность можно округлять до нуля.
•••
Источники:
[0] https://getsession.org/faq#session-pfs
[1] https://getsession.org/blog/session-protocol-technical-information
[2] https://crypto.stackexchange.com/questions/80601/what-is-the-key-length-of-shared-secret-by-curve-25519-ecdh
[3] https://medium.com/asecuritysite-when-bob-met-alice/having-your-crypto-handshaking-cake-and-eating-it-x25519-or-kyber-why-not-have-both-18b90f90dbbd
[4] https://www.betterbuys.com/estimating-password-cracking-times/
[5] https://en.wikipedia.org/wiki/Metric_prefix
[6] https://en.wikipedia.org/wiki/Observable_universe#Matter_content
[7] https://www.universetoday.com/36302/atoms-in-the-universe/
[8] https://www.betterbuys.com/estimating-password-cracking-times/
[9] https://www.worldometers.info/computers/
[10] https://stytch.com/blog/top-10-password-cracking-techniques/
[11] https://en.m.wikipedia.org/wiki/Elliptic-curve_cryptography
[12] https://en.m.wikipedia.org/wiki/Shor%27s_algorithm
[13] https://arxiv.org/pdf/1905.09749.pdf
[14] https://doi.org/10.1116/5.0073075
[15] https://spectrum.ieee.org/ibm-condor
[16] Sumanta Chatterjee (https://qr.ae/pKkcrh) states that the speed of password calculation can be found by the following formula: (number of password combinations)/(number of operations per second) = x seconds, where number of operations per second is calculated as follows: (number of petaFLOPS of a quantum computer)petaFLOPS, where 1 petaFLOSP equals 10^15 or 2^50 (https://en.wikipedia.org/wiki/FLOPS). According to TOP500 (https://top500.org/lists/top500/list/2022/11/), as of January 2023, the most powerful computer had a peak performance of 1685.65 petaFLOPS. So 12.3 Q/(1685.652^50) = 2.11394040995172541e+81 seconds = 66,988,000 years.
[17] https://getsession.org/blog/self-deleting-messages -
 @ 44dc1c2d:31c74f0b
2023-11-15 19:16:12
@ 44dc1c2d:31c74f0b
2023-11-15 19:16:12Chef's notes
So practically all recipes call for you to peel your potatoes. While it does make for a nice looking gnocchi, you can absolutely leave the skins on it, if you like a more rustic looking gnocchi. I do this when I feel lazy all the time and it still turns out great.
When incorporating the eggs and flour, having a spatula or a bread tool is really helpful here.
When you're at the stage of boiling your made Gnocchi, you will know they are done when they float to the top of the pot.
Details
- 🍳 Cook time: 1 hour
Ingredients
- 2 pounds of starchy potatoes, (IE 2 large russets)
- 1/4 cup egg, (lightly beaten)
- scant 1 cup of unbleached all-purpose flour
- fine grain sea salt
Directions
- Fill a large pot with cold water. Salt the water, peel then cut potatoes. Bring the water to boil and cook tell potatos are tender and mashable
- Remove potatoes from the water, drain and mash until there are no noticeable lumps.
- Let the potatoes cool spread out across your work surface for ten or fifteen minutes. Long enough that the egg won't cook when it is incorporated into the potatoes.
- Pull the potatoes into a soft mound. Drizzle with the beaten egg and sprinkle 3/4 cup of the flour across the top.
- After the flour and the egg is incorporated into the potato, gently kneed the dough
- The dough should be moist but not sticky. It should feel almost billowy.
- Cut it into 8 pieces. Gently roll each 1/8th of dough into a snake-shaped log, roughly the thickness of your thumb. Use a knife to cut pieces every 3/4-inch. Dust with a bit more flour.
- So this next bit is optional you dont need to do this but it mkae for better looking gnocchi.
- To shape the gnocchi hold a fork in one hand and place a gnocchi pillow against the tines of the fork cut ends out.
- With confidence and an assertive (but very light) touch, use your thumb and press in and down the length of the fork. The gnocchi should curl into a slight "C" shape, their backs will capture the impression of the tines as tiny ridges (good for catching sauce later). Set each gnocchi aside, dust with a bit more flour if needed, until you are ready to boil them.
- Boil the Gnocchi and Serve
-
 @ a023a5e8:ff29191d
2023-12-20 04:43:48
@ a023a5e8:ff29191d
2023-12-20 04:43:48Yesterday I was sleeping with my wife and 2 kids in same bed and in middle of night i just woke up to see my wife and kids sleeping aside me in a moonlight like ambience and it was a vivid feeling. And I just got panicked with strange feeling and in a bit I woke up really to see them again. All was in just a moment. Did you ever had such experience?
-
 @ a023a5e8:ff29191d
2023-12-19 12:14:53
@ a023a5e8:ff29191d
2023-12-19 12:14:53Shit shit shit
-
 @ 44dc1c2d:31c74f0b
2023-11-15 18:48:12
@ 44dc1c2d:31c74f0b
2023-11-15 18:48:12Chef's notes
Not a lot of notes here. This recipe is pretty straight forward. I have used half-and-half instead of whole milk in the past, and it turns out great. Low and slow here is the key.
What I mean by a sauce catching pasta is anything with a lot of surface area for the sauce. IE angle hair is not a good idea to use here.
Details
- ⏲️ Prep time: 10 ish min
- 🍳 Cook time: 2 1/2 hours
Ingredients
- 1 medium onion, chopped
- 1 celery stalk, chopped
- 1 small carrot, peeled, chopped
- 3 Tbsp. extra-virgin olive oil
- 1 lb. ground beef chuck
- Kosher salt
- 3 oz. thinly sliced pancetta, finely chopped
- 1 cup dry white wine
- ⅓ cup tomato paste
- 1 bay leaf
- Pinch of finely grated nutmeg
- 2 cups (or more) chicken stock
- 1 cup whole milk
- 2 oz. finely grated Parmesan (about ½ cup), plus more for serving
- Some form of pasta to serve with tagliatelle or pappardelle. really any "sauce catching" pasta will do.
Directions
- Pulse onion, celery, and carrot in a food processor until very finely chopped. Transfer to a small bowl.
- Heat oil in a Dutch oven or other large pot over medium. Break beef into small clumps (about 1½") and add to pot; season lightly with salt. Cook, stirring occasionally but not breaking meat apart, until beef is lightly browned but not crisp, 6–8 minutes
- Wipe out pot. Cook pancetta in pot over medium heat, stirring occasionally, until pancetta has released some of its fat and is crisp, 6–8 minutes.
- Add onion mixture to pot and cook, stirring occasionally, until vegetables are very soft and beginning to stick to surface, 6–8 minutes.
- Return beef to pot and pour in wine. Reduce heat to medium-low and cook, smashing down on beef with a wooden spoon, until wine is evaporated, surface of pot is almost dry, and meat is finely ground, 12–15 minutes.
- Add tomato paste, bay leaf, and nutmeg and cook, stirring occasionally and still pressing down on meat, until tomato paste is slightly darkened, about 5 minutes.
- Pour stock and milk into pot; add a pinch of salt. Reduce heat to the lowest setting and cook, uncovered and stirring occasionally, until meat is very, very tender, 2–2½ hours.
- There shouldn’t be any rapid bubbles at this stage. Instead, the sauce should release the occasional small bubble or two. When finished, the sauce should have the texture of and look like a sloppy joe mixture.
- If the liquid reduces before the meat is completely tender, add an extra ½ cup stock and continue cooking. Discard bay leaf. Taste sauce and adjust seasoning with salt; keep warm.
- Cook pasta in a large pot of boiling salted water. If using fresh pasta, cook about 3 minutes. If using dry, cook until very al dente, about 2 minutes less than package directions.
- Using tongs, transfer pasta to pot with sauce. Add 1 cup pasta cooking liquid and ½ cup Parmesan. Increase heat to medium, bring to a simmer, and cook, tossing constantly, until pasta is al dente and liquid is slightly thickened, about 2 minutes.
- Transfer pasta to a platter and top with more Parmesan. Do Ahead: Sauce can be made 4 days ahead. Cover and chill.
-
 @ d70d5009:1ed4acee
2024-03-14 13:09:46
@ d70d5009:1ed4acee
2024-03-14 13:09:46This is an automated way of doing this in AWS. All the components should run on free tier besides obtaining the domain.
Caveats: * terraform should be installed * currently you need to already own the domain and have the hosted zone setup * iam and security group is likely overly permissive * i've only tested this on my setup so far so if you have issues, let me know and i can help
If someone knows how i can embed the readme from github here, please advise.
Relevant links:
-
 @ 1abc40c5:6cd60e41
2023-12-17 07:42:37
@ 1abc40c5:6cd60e41
2023-12-17 07:42:37สวัสดีครับ ยินดีต้อนรับสมาชิกใหม่สู่สังคมชาวม่วง ด้วยความยินดียิ่ง
ในเบื้องต้นเข้าไปเรียนรู้และศึกษาการใช้งานตามโน๊ตของพี่แจ๊ค กู๊ดเดย์ พี่ใหญ่ของเราก่อนเลยครับ (จะรู้ว่าโลกใบนี้กว้างใหญ่กว่าที่เห็น)

===================== แล้วก็ไปเพิ่มกระเป๋า LN Wallet สำหรับรับ zap ง่าย ๆ ได้จากบทความของจารย์ Notoshi (อาจารย์อาร์ม RS)
-
หากใช้ Nostr บนคอมพิวเตอร์เป็นประจำ สามารถผูกกับ Browser Extension เพื่อใช้งานง่าย ๆ แนะนำ "Getalby" ครับ
-
หากเล่นบนมือถืออาจจะเหมาะกับ "Wallet of Satoshi" และ "Blink wallet" มากกว่า
แต่แนะนำว่าควรมีทั้ง 2 แบบครับ ท่านจะได้ใช้ประโยชน์ในเวลาที่เหมาะสมอย่างแน่นอน 5555
===================== จากนั้นไปเพิ่ม Siamstr Relay - wss://relay.siamstr.com - wss://teemie1-relay.duckdns.org
ที่สนับสนุนโดยพี่ตี๋ เพื่อให้เราชาวไทยเชื่อมสายสัมพันธ์ต่อกันและมองเห็นกันได้ ตามนี้เลยครับ
และก็ลืมไม่ได้ที่จะเพิ่ม Siamstr Relay อีกหนึ่ง ..ที่สนับสนุนโดยอาจารย์อาร์ม RS ของเราเองเช่นกันครับ - wss://relay.notoshi.win
ทั้ง 3 Relay นี้ เป็น Free paid Relay นะครับ สามารถใช้งานได้เลย ^^
หรือหากใครยังไม่จุใจ.. อยากได้รีเลย์เพิ่มเติมอีก แนะนำไปดูที่ อัพเดทลีเรย์ 9/12/2023 จากพี่ใหญ่ของเราได้เลยครับ
===================== และอย่าลืมไปสร้าง NIP-05 NOSTR ADDRESSES "@siamstr.com" เท่ห์ ๆ ได้ที่ siamstr FREE NOSTR ADDRESSES. เพื่อทุกคน เพื่ออิสรภาพ ใครมาก่อนได้จับจองชื่อก่อนน้าาา ... ^^
===================== อ้อ ... หากอยากเรียนรู้พื้นฐาน Nostr แบบเชิงเทคนิคคอล หรือการเก็บ nsec (Private key) ของเราให้ปลอดภัย ... เชิญได้ที่บทความของพี่อาร์ม Righshift ของเราครับ
หรือจะเข้าไปอ่านจากในนี้ก็ได้เช่นกัน
Nostr: โซเชียลมีเดียเสรีไร้ศูนย์กลาง
 ภาพ : Network diagram จาก https://nostr.how/en/the-protocol
ภาพ : Network diagram จาก https://nostr.how/en/the-protocol===================== สุดท้ายผมหวังว่าเราจะได้รู้จักกันมากขึ้นกว่านี้ เพื่อร่วมกันสร้างสังคมที่เต็มไปด้วยคุณค่า และความรู้สึกดี ๆ ให้แก่กันต่อไปครับ
ขอบคุณที่เข้ามาเป็นส่วนหนึ่งของเราครับ
-
-
 @ 44dc1c2d:31c74f0b
2023-10-10 21:22:43
@ 44dc1c2d:31c74f0b
2023-10-10 21:22:43Chef's notes
Chicken notes :
-
You can tenderize the chicken if you want (makes for a "bigger" piece that will cover more waffle also speeds up cook time)
-
If you choose not to tenderize your chicken and are left with thicker thighs, Fry until the crust is a nice golden brown then finish baking the chicken in the oven (around 350F) to finish cooking the chicken through. Should only take about 10 or 15 min.
Flour and dredge notes :
- Feel free to add more spices into the flour here. Add some extra onion, garlic and paprika or some fresh oregano to give the crust an extra kick of you want. Experiment and play with the flavor here and in the buttermilk marinade.
Waffle notes :
This is mostly a base recipe for savory waffles if you like things sweet add some sugar and some Vanilla extract to the waffle.
Details
- ⏲️ Prep time: 4 ish hours
- 🍳 Cook time: 35 ish min
- 🍽️ Servings: 5 ish
Ingredients
- 1 cup (120 grams) all-purpose flour
- ½ cup (70 grams) yellow cornmeal
- ¼ cup (28 grams) cornstarch
- 1 teaspoon baking powder
- ½ teaspoon baking soda
- 1 teaspoon fine sea salt
- ¼ teaspoon freshly ground black pepper
- 2 cups (475 ml) buttermilk
- 2 large eggs
- 4 tablespoons (56 grams) butter, melted and cooled slightly
- 3 ounces (84 grams) smoked Gouda, shredded
- ⅓ cup minced fresh chives
- For the Chicken
- 4 -5 ish thighs
- 2 1/2 cups buttermilk
- Salt and Pepper to taste
- at least 1 teaspoon Onion powder
- at least 1 teaspoon paprika
- at least 1 teaspoon garlic powder
- 2 to 3 ish cups flour (for your crust. See notes.)
- Maple Syrup
- Hot Sauce (Optional)
Directions
- Start by marinating your chicken. Get your thighs, buttermilk, paprika, onion powder, garlic powder, salt and pepper into a bowl or plastic bag and set aside to marinate for at least two hours in the fridge. (up to 4)
- The batter can be made ahead of time as well (no more than a few hours preferably).
- Mix all the dry ingredients together (minus the chives and cheese) then add the liquids.
- Add cheese and chives (save a bit for a waffle topping if you want.)
- Once the chicken has marinated a bit dredge your chicken in flour (see notes). Let set for approximately 20 min after dredging.
- Fry tell done. Also start to cook waffles while the chicken is cooking.
- Top the Waffles with the chicken, the extra cheese and chives, a healthy splash of syrup, plus your favorite hot sauce and Tuck in!
-
-
 @ 11d0b667:53e00ef7
2023-10-04 04:42:20
@ 11d0b667:53e00ef7
2023-10-04 04:42:20(Taken from the Bozeman Daily Chronicle, December 16, 2007) By Walt Williams
ENNIS - More than a century ago, a wolf-like creature prowled the Madison Valley, killing livestock and letting out screams that one account said would leave a person's hair standing on end.

DEIRDRE EITEL/CHRONICLE Jack Kirby poses in Ennis next to the wolf-like creature his grandfather shot in 1886 in the Madison Valley. He is holding the G.W. Morse rifle that was used to kill the animal. Kirby retrieved the mount from an Idaho museum where it was being stored.A bullet from a Mormon settler's rifle ended the animal's life and triggered stories of the creature that were passed along through generations of family history and local folklore.
The only evidence of the creature's existence was a missing taxidermy mount and a grainy black-and-white photograph of that mount - which fueled strange speculation about what kind of animal it really was.

Now after 121 years, the taxidermy mount has been found. The creature that once spooked some of the Madison Valley's first white settlers has come home.
“I never doubted the story,” said Jack Kirby, grandson of the settler who shot the animal.
*After reading a Halloween-themed Chronicle story about local legends of strange creatures, Kirby tracked down the mount in the Idaho Museum of Natural History in Pocatello.
The museum has since loaned it to him to put on display at the Madison Valley History Museum, although at the moment it resides in the basement of a building on the north edge of town.

The “ringdocus” or “shunka warak'in” - two of the names it has been given over the years - strongly resembles a wolf, but sports a hyena-like sloping back and an odd-shaped head with a narrow snout. Its coat is dark-brown, almost black, with lighter tan areas and a faint impression of stripes on its side.
It measure 48 inches from the tip of its snout to its rump, not including the tail, and stands from 27 to 28 inches high at the shoulder.
The mount is in amazingly good shape, showing no signs of wear and tear and retaining the color of the fur. It arrived in Ennis Friday.
One of its first stops was the gravesite of the man who shot it, Israel Ammon (I.A.) Hutchins.
“We took him down to the cemetery to see I.A. to let him know (the creature) is back in the valley,” said Kirby's wife, Barbara.
Hutchins shot the animal in 1886 on what is now the Sun Ranch, but not on his first try. He accidentally shot and killed one of his cows when he first spotted the creature on his land, his son Elliott Hutchins recounted in his memoirs.
He killed the strange animal when it appeared on his land a second time and traded the body with entrepreneur Joseph Sherwood for a new cow.
Sherwood was a taxidermist. He mounted the animal and put it on display in his combination store-museum at Henry's Lake in Idaho. His taxidermy collection was later given to the Idaho Museum of Natural History, where it was kept in storage.
The creature apparently baffled the people who saw it alive, and some speculated it was a hyena escaped from a circus rather than a wolf. The younger Hutchins remembered its haunting screams at night and wrote that after it was shot and in its death throes, the animal bit through a half-inch rope with a single bite and “exerted his very last strength to reach any one of us.”
The story of the “ringdocus” - as Sherwood reportedly named it - reached a national audience when the prolific writer and naturalist Ross Hutchins wrote about it in his 1977 autobiography, “Trails to Nature's Mysteries: The Life of a Working Naturalist,” and included a picture of the mount. I.A. Hutchins was his grandfather.
The tale was again picked up by writers Loren Coleman and Jerome Clark in their book “Cryptozoology A to Z.” In that book, Coleman linked it to a Native American legend about the “shunka warak'in,” a creature that snuck into camps at night to steal dogs.
The animal has so far eluded identification. The younger Hutchins wrote that a detailed description was sent to the Smithsonian Institution, which wasn't able to identify it.
The picture of the mount included the scientific-sounding name “Guyasticutus” as a label for the creature, but the name may have been tongue-in-cheek. Early accounts report that the Guyasticutus was a mythical creature invented by traveling showmen to swindle gullible ticket-buyers.
Coleman and Clark suggested that a DNA test should be done on the mount to determine what it is. Kirby, however, was not so certain he was ready to end a mystery that had been passed down by his family for four generations.
“Do we want to know?” he said.
The mount will be displayed in the Madison Valley History Museum when it reopens in May.
***On 25 May 2018, a wolf like animal resembling a Shunka Warakin was shot in central Montana. The unusual paws were among the characteristics experts thought didn't belong to either a wolf or dog.

“Several things grabbed my attention when I saw the pictures,” said Ty Smucker, wolf management specialist for Montana FWP. “The ears are too big. The legs look a little short. The feet look a little small, and the coat looks weird. There’s just something off about it.”

The body of the animal shot outside Denton has now been transported, examined and frozen. Results from its DNA testing will likely take weeks to process.
Smucker’s own speculation runs toward some type of wolf/dog hybrid.
-
 @ ecda4328:1278f072
2023-12-16 20:46:23
@ ecda4328:1278f072
2023-12-16 20:46:23Introduction: Crypto.com Exchange for European Traders
Reside in Europe, including non-EUR countries? Frustrated with the exorbitant spreads on the Crypto.com App (up to 5%) and high credit card fees (up to 3%) when you're eager to buy or sell cryptocurrency? This guide is tailored for you!
Quick Transfer with SEPA Instant
Did you know that you can transfer EUR to your Crypto.com Exchange account within minutes, and sometimes even seconds, including weekends and bank holidays? Yes, you absolutely can, thanks to SEPA Instant Credit Transfer (SCT Inst).
Supported Banks
To avail of fast EUR to Crypto.com Exchange transfers, ensure that your bank supports the SEPA Instant Credit Transfer (SCT Inst) scheme. If your bank, or FinTech apps like Wise, is on this list, you're good to go.
My Recommendation: I vouch for Wise due to its flawless functionality and favorable exchange rates. If your bank doesn't support SCT Inst and you're unwilling to wait, you can swiftly load your account with any currency using a bank card for a rather small fee (~1.2%). My Wise Referral Code: andreya54
24/7 Transfer Availability
SCT Inst is incredibly flexible:
- 24/7/365 availability, including weekends and bank holidays
- Immediate receipt and availability of funds
- €100,000 transaction limit (unless previously agreed otherwise between PSPs)
For more details, you can read this document by the European Central Bank.
TL;DR
To Buy crypto: -
EUR => BTC/EUR => ANY/BTC => ANY
- Use Limit order at the Lowest offer (aka "ask") (red order book)To Sell crypto: -
ANY => ANY/BTC => BTC/EUR => EUR
- Use Limit order at the Highest bid (green order book)How to Buy Cryptocurrency with EUR
Here's how to save up to 8% on spreads and fees when buying/selling crypto compared to the Crypto.com App.
-
Log in to Crypto.com Exchange: Go to the Dashboard or Wallet in the top right, and navigate to Bank Transfer on the left sidebar.


-
Deposit via SEPA: Choose
EUR -> SEPA -> Depositand use the displayed IBAN for transferring EUR to your Crypto.com Exchange account.
Trading Interface Tips
Intimidated by the professional trading interface? Don't be. Here's how to read the order book:
- Offers (Red): These are the prices at which people are willing to sell the asset. The lowest offer is often called the "Ask."
- Bids (Green): These are the prices at which people are willing to buy the asset. The highest bid is often called the "Bid."
Trading occurs when a buyer's bid meets a seller's offer. In market terms, this is often at the point where the highest bid and the lowest offer intersect. This intersection is frequently referred to as the "market price" for that particular asset at that specific time.

On trading pairs
Crypto.com Exchange offers only two EUR trading pairs: BTC/EUR and ETH/EUR. This is logical given that these assets have the highest liquidity in terms of market capitalization. While we hope for the addition of more pairs, the existing options still serve as useful proxies for purchasing other cryptocurrencies.
"highest liquidity" means that an asset like a cryptocurrency or stock can be easily bought or sold without causing a significant impact on its price. For a trader, this is good because it means they can quickly enter or exit positions without worrying about huge price changes.
Steps to Buy BTC with EUR
- Navigate to the
BTC/EURSpot trading pair. - Choose "Buy" on the right-hand menu.
- Stay on the "Limit" tab.
- Specify your order value (how much EUR you want to spend to buy BTC)
- Select the lowest offered (aka "ask") price (bottom of the red order book).
- Click "Buy BTC" to confirm.

Diversifying: How to Buy ATOM Token?
First, buy BTC as previously explained. Then:
- Navigate to the
ATOM/BTCSpot trading pair. - Choose "Buy" on the right-hand menu.
- Stay on the "Limit" tab.
- Specify your order value (how much BTC you want to spend to buy ATOM)
- Select the lowest offered (aka "ask") price (bottom of the red order book).
- Click "Buy ATOM" to confirm.

Selling Your Assets
The process is the same but in reverse. Sell at the highest bid (top of the green order book).
Selling ATOM for BTC
- Navigate to the
ATOM/BTCSpot trading pair. - Choose "Sell" on the right-hand menu.
- Stay on the "Limit" tab.
- Specify your quantity value (how much ATOM you want to sell to buy BTC)
- Select the highest bid (top of the green order book).
- Click "Sell ATOM" to confirm.

Selling BTC for EUR
- Navigate to the
BTC/EURSpot trading pair. - Choose "Sell" on the right-hand menu.
- Stay on the "Limit" tab.
- Specify your quantity value (how much BTC you want to sell to buy EUR)
- Select the highest bid (top of the green order book).
- Click "Sell BTC" to confirm.

You can then withdraw EUR back to your bank directly from the Crypto.Com Exchange.
Additionally
After you click "Buy" or "Sell," you will see your order in the "Open Orders" tab in the bottom menu. Once your order is 100% filled, it will disappear, and you will be able to see it in the "Trade History" tab.
Sometimes you might miss the opportunity as the price moves, and someone else's order could get filled faster than yours. Don't worry; you can either wait a little longer in hopes that someone will make an offer at this price or simply cancel your order and submit it again at the next lowest price if you are in a hurry.
Maker/Taker Fees Explained
When you open Buy/Sell orders on the Crypto.com exchange, you may incur small Maker/Taker fees of less than
0.0728%, or even no fees at all, depending on the amount of CRO you have staked on the platform.- Maker Fee: When you place an order that adds liquidity to the market, you are a "Maker". This usually happens when you set a "limit" order that does not execute immediately and sits on the order book waiting for someone to match against it. Since you are "making" liquidity available for others, you pay a Maker fee.
- Taker Fee: When you place an order that removes liquidity from the market, you are a "Taker". This generally occurs when you place a "market" order that executes immediately against a pre-existing order on the order book. Because you are "taking" liquidity away, you pay a Taker fee.
Typically, Taker fees are higher than Maker fees as an incentive for traders to add liquidity to the market.
Read more on Maker/Taker fees on the Crypto.Com Exchange platform.
Conclusion
Thanks for reading this guide! It's lengthy, but every detail is crucial for optimal trading on Crypto.com Exchange.
Referral Code
If you haven't opened a Crypto.com Exchange account yet, use my referral code:
pv0r199m6j
Referral Link: Sign Up Here -
 @ cce0989b:b497e608
2024-03-14 12:24:39
@ cce0989b:b497e608
2024-03-14 12:24:39Studies from UCLA and other institutions have found that putting your feelings into words makes them easier to cope with. For example:
-
Rating your anger on a scale of 1-5 reduces your heart rate, a measure of distress.
-
Describing your emotions when dealing with a phobia increases your courage in facing it.
-
Adding a label to an emotion (like "that's sadness" or "this is fear") decreases the activity in your amygdala, which is where your fight-or-flight response comes from.
As one of my favorite Mister Rogers quotes put it:
"Anything that’s human is mentionable, and anything that is mentionable can be more manageable. When we can talk about our feelings, they become less overwhelming, less upsetting, and less scary. The people we trust with that important talk can help us know that we are not alone.”
Find someone who makes you feel like your feelings are mentionable.
Say, "I'm feeling all tangled up in my emotions. Do you have a few minutes to listen to me?"
Then, share. As you do, notice how they untangle themselves and become more manageable.
-
-
 @ 44dc1c2d:31c74f0b
2023-09-28 18:43:53
@ 44dc1c2d:31c74f0b
2023-09-28 18:43:53Ingredients
- 1 tablespoon extra virgin olive oil
- 2 cups cubed butternut squash (about 1 small squash)
- 2 tablespoons fresh thyme leaves
- 1/2 teaspoon crushed red pepper flakes
- kosher salt and black pepper
- 2 cloves garlic, smashed
- 8 slices thick-cut bacon
- 2 tablespoon chopped fresh rosemary
- 1/2-1 teaspoon cayenne pepper
- 2 teaspoons honey
- 1 pound dry linguine pasta
- 2 large eggs, at room temperature, beaten
- 1 cup grated parmesan cheese, plus more for serving
- 2 tablespoons salted butter, at room temperature
Directions
- Preheat oven to 400 degrees F. On a baking sheet, toss together the olive oil, butternut squash, garlic, thyme, and a pinch each of crushed red pepper flakes, salt, and pepper.
- On a plate, rub the bacon with rosemary and cayenne, drizzle with honey. Lay the bacon over top.
- Transfer to the oven and roast for 10 minutes, flip the bacon and bake another 5-8 minutes, until the bacon is crisp, watch closely. Remove the bacon.
- If squash needs more time, return to the oven for another 10 minutes, or until the squash is tender.
- Transfer the squash and garlic to a food processor. Puree until smooth. Season with salt and pepper. Roughly chop the bacon, reserve for topping.
- Meanwhile, whisk together the eggs and parmesan.
- Boil the pasta until al dente. Before draining, scoop out 1 cup pasta water, then drain the pasta and add the pasta back to the hot pot.
- Immediately add the egg/cheese mixture, tossing quickly (to ensure the eggs do not scramble) until the eggs thicken and create a sauce.
- Add the butternut squash puree, and the butter, tossing to combine. Thin the sauce with the reserved pasta water until it reaches your desired consistency.
- Divide the pasta between plates. Top with bacon. Twirl the pasta up…EAT and ENJOY.
-
 @ 11d0b667:53e00ef7
2023-09-24 17:28:20
@ 11d0b667:53e00ef7
2023-09-24 17:28:20On July 13, 1927, in Coalville, Utah 13 year old Ellis Richins, small for his age, was playing with a nephew outside his father’s sheep camp when a stranger lunged from the woods and grabbed him. As his playmate ran to get help, the assailant forced Ellis up into the mountains.

Leonidas Munsey Dean.(a.k.a. Leon, a.k.a. Leonidas "Bally" Dean, a.k.a. Uncle Lonnie) , 51, placed a six-page ransom letter on a stone near the sheep camp. It began: “If you want to save the life of this fellow Richins, take ten thousand dollars, two thousand in gold coin; eight thousand in federal reserve notes, in five, ten and twenty dollar denominations, equal amounts of each, and do with them exactly as we tell you. The prisoner has just two days to live, if our orders are not strictly obeyed. We are as determined as war and ill treatment can make us.”

Lonnie kept Ellis walking that night by prodding him with a rifle barrel, and by threatening to shoot if the boy made a sound. Keeping to the ridges, they pushed toward Snyderville Valley. Ellis was told that his father had left the ransom money there. Just before daylight they reached a saddle above the Devil Creek fork of Tollgate Canyon. There the kidnapper chained Ellis to a tree, and they both went to sleep. Sometime the next morning, Lonnie heard someone walking through the woods, as a posse of nearly 400 men, some who were loaned guns by the National Guard, were scouring the mountainside. Holding a gun to Ellis’s head, Lonnie ordered the youngster to remain quiet while he went to investigate.
As soon as the kidnapper left, Ellis picked up a sharp rock and began chopping at his chains. Eventually, he was able to break one of the links and fled.
A short time later Ellis arrived breathlessly at a highway construction camp near Silver Creek. Ellis telephoned his mother, assured her that he was okay. (In 1881, Park City became the third city in Utah to receive telephone service, and would be one of the first to get electric lighting in 1889). After making the call he sat down—surrounded by nearly a hundred admirers—and ate a hearty meal. Within fifteen minutes his overjoyed parents drove into the camp.
Using the mountains to his advantage, a week later, Lonnie Dean had hiked/traveled over 72.5 miles south, to Salem, Utah. There, he was captured by sheriff’s deputies and railroad detectives, acting on a tip. He told the Sheriff that he had planned to go to California, then on to Mexico.
Sentenced to five years in prison, Leonidas “Lonnie” Dean, didn’t live out his time. He was killed by another inmate during a fight in the Utah State Penitentiary.
Like his father, Ellis Richins raised sheep for a living in Coalville, until he died at 52, leaving behind 5 boys and a sheep farm.

His wife, Metta, lived well into this century. She lived 43 years as a widow. She was very involved in the sheep industry where she made many lifetime friends. She won the Sheep Rancher of the Year Award (the first woman to ever receive this award) by the Utah Wool Growers Association. She was President of the Utah State Wool Growers Auxiliary and also the Summit County Wool Growers Auxiliary.
 She cooked and served many lamb suppers and helped with the Make it with Wool Contest for many years. She also served on the Farm Services Committee until the time of her death and as a secretary of the Summit County Lamb Pool.
She cooked and served many lamb suppers and helped with the Make it with Wool Contest for many years. She also served on the Farm Services Committee until the time of her death and as a secretary of the Summit County Lamb Pool. 
-
 @ ecda4328:1278f072
2023-12-16 20:45:50
@ ecda4328:1278f072
2023-12-16 20:45:50Introduction
In the world of blockchain technology, a nonce plays a pivotal role in ensuring transaction security and uniqueness. This article demystifies the nonce's role in major blockchain platforms - Bitcoin, Ethereum, and Cosmos/CometBFT, highlighting its importance and distinct functionalities in each.
The Role of Nonce in ECDSA and Its Importance
In Bitcoin (and most of blockchains) transactions, the nonce is a randomly generated number integral to the Elliptic Curve Digital Signature Algorithm (ECDSA). It guarantees each digital signature's uniqueness and security. The randomness and secrecy of the nonce are vital. If predictable or exposed, it can compromise the entire security of a transaction.
The Risk of Nonce Exposure and Private Key Recovery
If a nonce is compromised, it poses a risk of private key recovery. To understand this, one must consider the signature components (r, s), the public key (which becomes known once you sign & broadcast at least one transaction in Bitcoin). A predictable or reused nonce can leak critical information, enabling savvy attackers to backtrack to the private key.
This specific type of attack is called a nonce covert channel attack. And methods protecting against this are called anti-klepto or anti-exfil (interchangebly).
Worth noting that anti-klepto/anti-exfil are broader terms for methods that protect against various forms of secret data exfiltration, including but not limited to attacks involving nonce misuse.
Bitcoin's UTXO Model and Nonce Functionality
Bitcoin utilizes the Unspent Transaction Outputs (UTXO) model, ensuring that each Bitcoin is spent only once. This model is distinct from nonce management in ECDSA and adds an additional layer of security against double-spending in the Bitcoin network.
Address rotation in Bitcoin, as implemented through BIP32 (Hierarchical Deterministic Wallets), enhances privacy and isolates financial risk by generating a unique address and corresponding private key for each address created, not necessarily for each individual transaction. While this strategy effectively segregates risk to individual addresses, it does not directly prevent the vulnerability of private key derivation from nonce exposure in the ECDSA signature process, as this risk is inherent to the signature mechanism itself and is independent of the address or its associated private key.
Ethereum's Account-Based Model and Nonce Usage
Ethereum, unlike Bitcoin, operates on an account-based model. Each account has a sequential transaction nonce, starting from 0, which is public. This nonce, different from the ECDSA nonce, helps in transaction ordering and network integrity.
Nonces in Cosmos/CometBFT Blockchains
Cosmos/CometBFT blockchains, akin to Ethereum, adopt an account-based model. They use nonces, similar to Ethereum's transaction nonce, for transaction ordering and preventing replay attacks. These nonces are distinct from the ECDSA nonce used in the digital signature process.
Conclusion
The use of "nonce" in Ethereum for transaction sequence (akin to account sequence in Cosmos/CometBFT blockchains), leading to confusion with ECDSA nonce, is simply a coincidental choice of terminology.
In summary, while Bitcoin, Ethereum, Cosmos/CometBFT and many other blockchains employ nonces in ECDSA signing, their transaction management and double-spending prevention methods differ significantly. Understanding these nuances is crucial for blockchain users and developers to appreciate the underlying security mechanisms of these diverse platforms.
References
- Hardware wallets can steal your seed!
- A Glimpse of the Deep: Finding a Creature in Ethereum's Dark Forest
- MuSig-DN: Schnorr Multisignatures with Verifiably Deterministic Nonces
- Android's SecureRandom - not even nonce
- Anti-klepto explained: how the BitBox02 protects you against leaking private keys
- Anti-Exfil: Stopping Key Exfiltration
-
 @ 11d0b667:53e00ef7
2023-09-23 05:20:47
@ 11d0b667:53e00ef7
2023-09-23 05:20:47"The Austin Police Department (APD) is the principal law enforcement agency serving the city of Austin, Texas with an annual budget of $443.1 million and employed around 2,484 personnel including approximately 1,809 officers and 24 K-9 police dogs and 16 horses. Chief Chacon has served as a police officer for 31 years and has a wide breadth of experience in almost all areas of police work." (wiki)
The post below was taken from the Austin Police Association Twitter feed, where they were responding to the Austin City
"The Austin Police Association is aware of the election results and is taking immediate action to determine the city's intentions regarding the implementation and enforcement of the illegal provisions contained in Prop A. The APA simply will not stand by while this city and anti-police activists operate with blatant disregard for state law and the rights and protections afforded to our hardworking men and women. The APA continues to prioritize negotiating a long-term contract; however, we will not be forced back to the table under a structure in which a new city ordinance attempts to unlawfully interfere with the statutory rights associated with the meet and confer process. We look forward to finding these answers so that we can get back under a long-term contract that allows for our police department to recruit, hire and retain the best and brightest people who wish to serve this community in a law enforcement capacity."
Here are some of the replies they received on their Twitter post:




*If you have any questions or need assistance with recruitment for APD personnel you can reach them Monday through Friday 8:00 A.M to 3:00 P.M by Phone (512) 974-4211 - Office (800) 832-5264 - Toll Free
(give them a call, I'm sure they'd love to hear from you)
-
 @ dab6c606:51f507b6
2024-03-14 09:08:35
@ dab6c606:51f507b6
2024-03-14 09:08:35Some people want to cash out and are running around, looking for an OTC dealer to convert their Bitcoin to fiat.
Rather than replying to each of you directly, here's my uninformed, not a financial advice, but technological options that you have:
Don't sell your Bitcoin and get fiat at the same time
If you don't want to fully cash out, but still need some fiat, you can use Bitcoin-collateralized lending and get fiat. In most countries, this should be a tax-free operation (you are not selling your Bitcoin) - but consult a tax advisor.
Benefits: You still HODL, still participate on upside of Bitcoin, you are shorting fiat (which is a shitcoin), you can enjoy the fruits of your holdings, no taxes (in most countries)
Downsides: You pay interest rates on fiat, which are at least now not cheap (but that will fade away I guess), there are other risks with lending positions that I describe.
How to learn how to do it and choose the right platform:
- if you read my book Cryptocurrencies - Hack your way to a better life, you have already seen the chapter on collateralized loans
Get it here in English, Spanish or Slovak
-
if you need more up to date information, you can get my newly published book How to harness the value of Bitcoin without having to sell it: A path to your orange citadel and a way to short fiat currencies. Kindle and Paperback available.
-
if you want the same content, but with videos (e-book included too!), where I show everything end-to-end, get the course
Find a counterparty that has the opposite problem using Vexl app
I have a short, free, no registration required course as a quick intro to Bitcoin, also available in Slovak
There's a chapter on vexl app where I show you how to find someone you can buy from or sell to.
Other options, such as using proxy merchants
Believe it or not, the cypherpunks have thought about this exact problem. And there are many more options that you will find in Cryptocurrencies - Hack your way to a better life. One of them is proxy merchants, where you can not exchange to fiat, but buy whatever you want to buy. There are proxy merchants selling amazon gift cards, Uber credit, data plans, etc. These days, you can even buy a car or a house using proxy merchants. There are many options, but a notable ones are bitrefill for gift cards and all your phone needs.
And Trocador for prepaid visa and mastercard cards without KYC.
-
 @ 11d0b667:53e00ef7
2023-09-23 05:18:09
@ 11d0b667:53e00ef7
2023-09-23 05:18:09Venturing out to a smaller town today. Decent weather.

 Useless fiat all over the ceiling, some dating back to the early 1900's, apparently.
Useless fiat all over the ceiling, some dating back to the early 1900's, apparently.
This place is a bit off the beaten path, but a worthwhile visit. Been in business since 1879.
Pictured below is an abandoned home, obviously someone's dream at one point, now crumbling.
 A cool place to have a quick walk around.
A cool place to have a quick walk around.

-
 @ ecda4328:1278f072
2023-12-16 20:45:10
@ ecda4328:1278f072
2023-12-16 20:45:10Intro
I've left Twitter (X), WhatsApp, Telegram, Instagram, Facebook and Google. The driving force behind this decision was the escalating overzealous censorship. I cannot condone platforms that actively indulge in this practice. In all honesty, I've always felt uneasy using "free" platforms riddled with ads where the user is the product and doesn't own the content they produce.
Let's be real: hardly anyone thoroughly reads the Terms of Service (ToS).
Censorship and Shadow Banning
The final straw was when I resorted to a text editor for drafting messages/comments, hoping to rephrase them so they wouldn't get deleted moments after posting. This isn't exclusive to just one platform; I've encountered it on YouTube and LinkedIn too. Twitter (or X, as I now refer to it) has a history of shadow banning users' posts. It's been beyond frustrating to get banned from Telegram groups simply for posing legitimate questions.
You can test LinkedIn's censorship mechanism too, simply add "Binance" word (without quotes) to any of your comment and your post will disappear. At least that is what I've seen couple of months ago. Similarly, comments on YouTube often disappear precisely 60 seconds after posting if they contain specific keywords. I know they call it filtering, but it does not make any sense. In my opinion, legitimate companies and links shouldn't trigger these filters.
Community and Connections
Recently, I attended the Cosmoverse 2023 conference in Istanbul. Most attendees exchanged their Telegram or Twitter (X) contact information. Since I didn't have either, I gladly shared my Nostr and SimpleX Chat details. Many privacy advocates were quick to connect on SimpleX with me, though several didn't.
I learned about SimpleX Chat from Jack Dorsey, who mentioned it during a conversation in July:
While Signal has its shortcomings, I still keep it as a backup communication tool.
One More Last Straw
During the conference, I temporarily reinstalled Telegram to communicate with my group. Convincing nine individuals to switch to SimpleX on the spot seemed impractical.
At the conference, I bought a Keystone hardware wallet. Shortly after, I connected with the seller, Xin Z, on Telegram. However, I was banned from the official Keystone Telegram group right after posing a question.

Upon inquiring, Xin Z clarified that Telegram's official team had banned me, not the group's admin. 🤯

Business and Community: Collateral Damage
Censorship doesn't just silence voices; it hinders potential growth and stifles innovation. When platforms arbitrarily or aggressively censor content, they inadvertently create barriers between businesses and their potential clients. New users or clients, when encountering such heavy-handed moderation, may feel discouraged or unwelcome, causing them to retreat from the platform altogether.
Moreover, for businesses, this form of censorship can be devastating. Word-of-mouth, discussions, and organic community engagements are invaluable. When these channels are hampered, businesses lose out on potential clientele, and communities lose the chance to thrive and evolve naturally.
Censorship, in its overzealous form, breaks the very essence of digital communities: open dialogue. As platforms become more censorious, they risk creating sterile environments devoid of genuine interaction and rich discourse. Such an atmosphere is not conducive for businesses to foster relations, nor for communities to flourish. The ultimate price of overcensorship isn't just the loss of a few voices—it's the fragmentation of digital society as we know it.
Freedom to Choose
I strongly advocate for the adoption of Free and Open Source Software (aka FOSS) products. In these platforms, you aren't treated as the product. However, supporting them through donations/contributions is always an option. Platforms like Nostr and SimpleX Chat are excellent starting points.

My Nostr account:
npub1andyx2xqhwffeg595snk9a8ll43j6dvw5jzpljm5yjm3qync7peqzl8jd4Disclaimer
This article reflects my personal experiences and opinions. It is not intended to criticize or demean the Keystone hardware wallet product or its quality. Furthermore, the actions taken by Telegram are not a direct representation of the views or policies of the Keystone Telegram group admins. Any reference to specific events or entities is made in the context of broader concerns about platform censorship.
-
 @ 11d0b667:53e00ef7
2023-09-23 05:05:30
@ 11d0b667:53e00ef7
2023-09-23 05:05:30Yesterday morning I had to get up early and take a vehicle to the mechanic in the city. They opened at 7:30, and at 7:35 when i walked in the door, there were already 4-5 customers. Plenty of counter help was available and was greeted kindly, gave some information and was on my way again.
Rather than sitting in the waiting room, watching the news programs and morning shows with other patrons, I stepped outside into the chilly morning. It's the end of May, there's still snow on the ground and my home, so being in the city where the grass is green and flowers are in bloom is a site for sore eyes. I'm in what would be considered an "older" part of town and has history from about 100 years ago. There's a pretty large graveyard a block or two away. It's been sunny, but a portion of the sky is covered by a cloud and it's starting to rain. There's just something about walking thru a graveyard in the rain that adds another element.

The funeral business is booming. Boxed up bodies, laying in rows, 4 or 5 words in summary, reserve your space today...
I keep walking. The rain subsides. The sun almost blinding, which helps decide the direction I wander. Cross a busy 8 lane road. People in boxes, listening to news, applying make-up, reading a book.
 Once across the large road, I take the canal trail that borders a park. It's quiet. No children, no mom's.... But there is the homeless, which seems to have tripled, or more, over the last few years.
Once across the large road, I take the canal trail that borders a park. It's quiet. No children, no mom's.... But there is the homeless, which seems to have tripled, or more, over the last few years.
The park borders the city public train line, it's a bit surprising it isn't loaded with tents. This single tent almost seems perfect at this time of the morning, but by noon will most likely have the police here.

Another block and I'm in "Historic Sandy". What was once a bustling city hub, is now a quiet street with 3 barber shops, a museum, a quilt shop and an art space. There used to be a mercantile, a police station, a brewery, which had to cease due to prohibition. Hans Bjork and Ole Nelson ran "Swede's Saloon" and billiards parlor from the 1880's, until 1917, when it was shut down by the prohibition of alcohol. In 1930, it was taken over by a Norwegian meat cutter and remained a grocery store until the late 1950's.

Someone laid this sidewalk, with pride, in the name of progress. Once loved, cutting edge, businesses now with shuttered doors.
Before the police were carved into a militia, US towns had these police stations, not precincts...

Once-loved homes now look like the cover of a horror novel...

Thoughtfully, and built with a purpose, irrigation that used to feed gardens, flows abundantly. Proof of work from a forgotten time, not long ago. This is ancient Rome.

The museum, filled with relics.

Even the classic motorcycle shop from the 1970's is starting to suffer the effects of time, as the trees and bushes close in.

It won't be long, now...

Another block away and you can feel the vibes of a not-so-distant future, where times change, once again. I certainly feels like we are approaching another shift, locally and globally.
 "The root problem with conventional currency is all the trust that’s required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust." --Satoshi Nakamoto
"The root problem with conventional currency is all the trust that’s required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust." --Satoshi NakamotoWhat should have been a boring morning at the mechanic, turned into a wonderful walk, filled with thought and reflection.

“Life moves pretty fast. If you don't stop and look around once in a while, you could miss it.” ― Ferris Bueller
-
 @ 57d1a264:69f1fee1
2024-03-14 07:54:38
@ 57d1a264:69f1fee1
2024-03-14 07:54:38Prompt: Automotive Interface ===============
Consider the elements you'd want and need in your own vehicle's dashboard. If you don't have a car, think of what's needed to control one in a video game, a VR headset, or in a movie. Be creative, yet logical.
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ 57d1a264:69f1fee1
2024-03-14 07:45:40
@ 57d1a264:69f1fee1
2024-03-14 07:45:40What's got you buzzing with excitement, and which design trends are you ready to cheers?
Share your insights and learnings!
-
 @ 11d0b667:53e00ef7
2023-09-22 07:39:04
@ 11d0b667:53e00ef7
2023-09-22 07:39:04If you have ever been out in Park City, UT at 10pm, you've probably heard the Fire Bell aka The 10 o'clock whistle. Heard throughout town at 10pm every night, without fail, can surprise even locals who can be caught off-guard, by the sound.
Early in the morning on June 19, 1898 a fire began in the kitchen of the American Hotel and ripped down Main Street, through the Park City commercial district, fanned by winds sweeping down the canyon. It did not stop until it ran out of fuel, destroying some 200 business and homes. Losses were estimated at over $1,000,000 (approximately $37,000,000 in 2023). The fire destroyed Main Street, Swede Alley and Park Avenue.

The blaze was the greatest in Utah history. There were no deaths, but 500 people were left homeless, the new city hall and opera house were destroyed.
The Salt Lake Herald, suggested, without much evidence, that the fire had been started by someone using coal oil to light the kitchen stove. The hotel owner, however, said it was possible a drunken hotel guest had kicked over an oil lamp.
The fire swept down the street, consuming building after building. It gutted the Grand Opera House, an elegant three-story brick building designed by Salt Lake City architect J.A Headlund that had been open only about a year. It took out John Funk's barber shop, the Bates & Kimball Drugstore, and the Judge, Ivers and Keith stables, which housed over 100 horses. "Horses were whinnying, men shouting, whistles screeching," the Salt Lake Tribune reported. "The spectacle as the first shafts of approaching day shot athwart the eastern hills was appalling." The stable lost all its harnesses and ore wagons, along with forty tons of oats and eight tons of hay."
"Hundreds of men and women, worked with desperation to save their belongings," the Park Record reported, "but nearly everything that was taken into the street was quickly consumed in the fierce heat and blaze, that was driven through town with an intensity that resembled the flame from the end of a blowpipe."
George Hall, proprietor of the Park City Hotel on the west side of Main Street, also scrambled to salvage some of his family's possessions, along with furniture and bedding from the hotel, and move them to the Kimball house, a large two-story structure on lower Park Avenue.
By 5 A.M. the flames had burned through the block on the west side of Main Street, reaching Park Avenue, which was home to the city's churches and "the aristocratic portion" of Park City's population.
Residents struggled to contain the fire, using giant blasting powder, they tried to decimate buildings to prevent the spread of the fire, but the flames always jumped the gap to the next structure. It was chaos, buildings burning, buildings being exploded, fires raging. "Again and again the buildings were blown up by giant powder to create a gap over which the fire would not leap," the Salt Lake Herald reported, "but the demon only laughed at the puny effort and reached out its reddened tongue further to destroy."
Near the bottom of Park Avenue, one local resident took a stand, the town doctor, E.R. LeCompte. With a lawn hose, he defended his dwelling, while a neighbor would occasionally douse him with buckets of water. "Now and then a flame reached him, but not until he began to remove his clothes and search for a fresh suit did he learn that in the fight with the flames the tails of his coat had been burned to a crisp, that his shoulder blades were exposed and that a pair of new trousers were necessary to prevent an arrest for undue exposure."

All of Park City's phone lines were ruined once the fire destroyed the First National Bank Building. The Telegraph link at the bottom of Main Street, located in the Union Pacific Depot, remained intact. 3 hours after the fire started, the Park City Fire Chief, James Berry, used the telegraph to contact fire officials in Salt Lake City and Ogden. "Send us some help to put out fire here. The city is burning," said a dispatch that arrived at the Ogden fire station shortly after 7 A.M. About an hour later, special trains left Salt Lake City and Ogden, carrying men and equipment to fight the fire. Unfortunately, by the time they arrived, there was little to do except soak down the smoldering ashes.

Main Street lay in ruins, with only a few gaunt walls remaining. Among the casualties were five churches, two opera houses, two bank buildings, the city hall, and numerous retail shops and saloons. One church—St. Mary's of the Assumption Catholic church—survived, thanks to its location beyond the southern perimeter of the fire.
Miraculously, no one died in the blaze. However, the flames claimed several family pets, including "Duke," a St. Bernard, that had been locked in the Bates & Kimball drugstore.
The Mayor, J.H. Deming, was called for by horseback, in the Strawberry Valley, fishing. He came as soon as he was notified, and arrived at 3am the next morning.
"The toughest job Marshal Hyde had after the fire was to shoot down [with explosives] the towering remnants of the Grand Opera House walls," the Park Record reported.
2 short days after the fire, alarm bells sounded again. The Kimball house on lower Park Avenue, where George Hall had moved everything after the destruction of the Park City Hotel, was on fire. In spite of the best efforts of firefighters, the building was destroyed.
"Everything which George saved from the burning hotel on Sunday morning was placed [in the Kimball house], and included bedding, furniture and personal effects," the Salt Lake Tribune reported on June 22. "All succumbed to flames yesterday, even to the jewelry and money which Mrs. Hall had placed in her purse for safe keeping, and the saving and work of the proprietor on Sunday last counted for naught."
With community support, however, the town rebuilt, replacing stone and brick structures with wood buildings, which were later improved again to brick and stone. The town recovered in just 18 months.
By July 2, according to the Park Record, 35 new buildings were under construction. In their haste to rebuild, most business owners erected wood-frame structures. Construction of the Record's new offices began on July 4; they were ready for occupancy only twelve days later. George Hall's new Park City Hotel was almost finished by the end of July.
In its New Year's edition in 1899, the Salt Lake Tribune reported that sixty-three buildings had been erected in the burned-out district.
Volunteer firemen built a bell tower in town in 1901. The tower housed a 1,500 pound bell that would be used to alert firefighters and residents of dangers and also provided a place to dry the fire hoses. An electric siren replaced the bell in 1948. The fire department ran a check every night at 10pm to ensure the siren worked. This daily bell soon became known as the city-wide curfew for children. Hence, the "10 o'clock whistle", which you can still hear every night, to this day.
Today, Park City, Utah, is a thriving, bustling mountain town.

-
 @ 47b9723c:bb07e602
2024-03-14 07:28:29
@ 47b9723c:bb07e602
2024-03-14 07:28:29Our open source hackerspace classroom will be on the main stage at #EduTECHAU!! https://www.terrapinn.com/exhibition/edutech-australia/index.stm
-
 @ ecda4328:1278f072
2023-12-16 20:44:09
@ ecda4328:1278f072
2023-12-16 20:44:09In the evolving world of cryptocurrency, ensuring the security of your digital assets is paramount. For those looking to safeguard their Bitcoin and other cryptocurrencies, selecting the right hardware wallet is crucial. Here, I recommend some top choices based on functionality and security.
Swiss Choices for Bitcoin: BitBox02
For Bitcoin enthusiasts/maxis, the Swiss-made BitBox02 - Bitcoin-only edition is a top recommendation. This wallet focuses solely on Bitcoin, ensuring specialized security and features for the most popular cryptocurrency. Although there is a version supporting multiple cryptocurrencies, the Bitcoin-only edition stands out for its dedicated functionality (Less code means less attack surface, which further improves your security when only storing Bitcoin). Learn more about this wallet here.
Swiss Tangem: A Unique Approach
Another Swiss option, Tange. Tangem is particularly appealing due to its unique approach to security. With Tangem cards, there's no need to generate or back up a mnemonic phrase (a series of 24 words used to recover wallets). The key is simply not to lose the cards and remember the access code, which adds an extra layer of security in case of loss. This approach simplifies security while maintaining robust protection for your assets.
Special Offer: For those interested in purchasing a Tangem Wallet, I have a special offer for you. By using my referral code, you can buy a Tangem Wallet at a discounted price. Click here and use the promo code MY6D7U to enjoy your discount.
Explore Tangem here.
Tangem's Mnemonic Phrase Advantage
Tangem's standout feature is the absence of the need for a mnemonic phrase. This reduces the risk of loss due to complicated backup schemes.
However, for those who do backup mnemonic phrases, I recommend using a metal plate for added durability against elements like fire and water. It's crucial to protect your mnemonic phrase thoroughly, as it essentially makes you your own bank. A fireproof and waterproof safe is advisable for storing these phrases. While some split the phrase and store parts in different locations, I advise against overly complicating the storage scheme to prevent loss. Adding an optional password for additional security is also recommended. Remember, mnemonic phrases unlock the same wallet addresses across different hardware wallets, as most use the BIP39 protocol for generating a seed from the 24-word phrase. Check out this list for reference: BIP39 Word List.
Worth reading: - Seed Phrases Explained: Best Practices for Crypto Security - How Tangem Wallet backs up private keys - How Your Tangem Wallet Works Without Tangem: Apocalypse Scenario
French Ledger: A Shift in Trust
The French Ledger Nano S Plus or Ledger Nano X were previously high on the recommendation list. However, trust in these devices has diminished due to Ledger's service Ledger Recover allowing mnemonic phrase backups on third-party servers. This goes against the principle of a hardware wallet, where your seed should never be exportable or stored externally.
Chinese Keystone 3 Pro: A Contender with Caveats
As an alternative to Ledger, the Chinese Keystone 3 Pro could be considered. Although there are concerns about its Chinese manufacturing possibly implying vulnerabilities, its functionality—like signing transactions via QR codes without direct computer connection—offers a level of security. However, choosing a hardware wallet should be based on the specific cryptocurrencies you plan to store. For Bitcoin-only storage, the BitBox02 Bitcoin-only edition is highly recommended.
Worth reading: - Does airgap make Bitcoin hardware wallets more secure?
Czech Trezor: Slow to Innovate and Security Concerns
Regarding the Czech Trezor Model T, it's not recommended due to its slow pace in integrating new features. Recent controversies surrounding the integration of CoinJoin and concerns over censorship and transaction filtering have also marred its reputation. Furthermore, the Trezor Model T has proven to be vulnerable in case of loss, as demonstrated by a hacker in this video, potentially exposing your cryptocurrency to risks.
The Case of Canadian Coldcard (MK4): A Shift from FOSS
An important development in the hardware wallet space is the case of the Coldcard Mk4. Initially, Coldcard was a fully open-source software (FOSS) project. In FOSS, the "Free" refers to the freedom to run, study, redistribute, and modify the software, a principle highly valued in the crypto community. However, a significant shift occurred in the journey of Coldcard:
- Initial FOSS and Bootstrapping: Coldcard, developed by nvk and Peter, started as a FOSS project. They bootstrapped the development, rejecting offers from venture capital investors interested in the project.
- Foundation's Entry: Subsequently, the Foundation cloned Coldcard's code and announced a slightly different hardware. Notably, they raised funds from the same VCs that Coldcard had previously turned down.
- License Change: In response to these events, Coldcard altered its software license. The new license permits all activities except those performed by the Foundation, marking a departure from its original FOSS status.
This change has sparked discussions within the cryptocurrency community about the importance of maintaining open-source principles in the development of hardware wallets. The Coldcard MK4's shift from FOSS underscores the complex dynamics between open-source ethos and commercial interests in the crypto world.
Source: X/Twitter thread.
Conclusion
In conclusion, when choosing a hardware wallet, consider the specific cryptocurrencies you'll be storing and the compatibility of the wallet with your intended use, especially concerning smart contracts and other features. While there are numerous options in the market, careful consideration of security features and the reputation of the manufacturer can guide you in making a secure choice for your digital assets.
-
 @ 1c6b3be3:73f0ae6f
2024-03-14 06:11:45
@ 1c6b3be3:73f0ae6f
2024-03-14 06:11:45🍵 Actualités securite
Une cyberattaque sur France Travail compromet 43 millions de comptes (1 min) France Travail, l'organisme qui remplacera Pôle Emploi, a annoncé avoir été victime d'une cyberattaque avec vol de données. Les informations personnelles de 43 millions de personnes ont été compromises, dont celles des personnes actuellement et précédemment inscrites au cours des 20 dernières années, ainsi que des personnes non inscrites mais ayant un espace candidat sur le site. Les données volées comprennent les noms et prénoms, les dates de naissance, les numéros de sécurité sociale, les identifiants France Travail, les adresses mail et postale, et les numéros de téléphone. Les mots de passe et les données bancaires ne sont pas concernés. France Travail a notifié l'incident à la Cnil, déposé plainte et ouvert une enquête. Une plateforme téléphonique a été mise en place pour accompagner les personnes concernées.
Sécurité IT/OT: Nozomi Networks lève 100M$ (1 min) Nozomi Networks, une entreprise spécialisée dans la protection des systèmes informatiques et industriels contre les cyberattaques, a récemment annoncé avoir levé 100 M$ lors d'un dernier tour de table. Parmi les investisseurs figurent Schneider Electric et Mitsubishi Electric, ainsi que des actionnaires historiques tels qu'Activate Capital, Energize Capital et Forward Investments. La société prévoit d'utiliser ces fonds pour renforcer le développement de ses produits et la commercialisation de ses offres à l'international. Reconnue pour sa sonde OT certifiée par l’ANSSI, Nozomi Networks protégerait plus de 105 millions de terminaux OT, IoT et IT dans le monde entier et serait présente dans plus de 12 000 installations. Selon Edgard Capdevielle, président et directeur général de Nozomi Networks, cet investissement démontre "clairement le besoin et le soutien pour des solutions de sécurité agnostiques à la lumière de l'escalade des attaques contre les infrastructures critiques dans le monde entier".
La commission de l'IA veut un fonds de 10 Md€ et libérer les données (3 min) La commission dédiée à l'intelligence artificielle a rendu son rapport après 6 mois de travail, comprenant 25 recommandations pour améliorer la compétitivité française en IA. Le rapport propose la création d'un fonds de 10 Md€ dédié au financement de l'écosystème IA et un assouplissement des contraintes sur l'accès aux données, qui sont essentielles à l'existence de l'IA. Il recommande également une approche plus radicale pour améliorer l'accès aux données de santé et la réduction des délais de réponse de la Cnil. Le rapport plaide en faveur d'une infrastructure technique sur les données en dépôt légal pour faciliter la mise en relation entre développeurs d'applications IA et propriétaires de données culturelles et patrimoniales. La formation sur l'IA est également un point clé, avec une estimation de 56 000 postes par an en développement d'IA et 25 000 postes par an en déploiement d'IA d'ici 10 ans. Enfin, le rapport recommande que la régulation de l'IA se fasse à l'échelon international et que la France soit un moteur dans la mise en place d'une organisation mondiale de gouvernance de l'IA.
Patch Tuesday mars 2024 : des failles critiques dans Hyper-V (2 min) Microsoft a publié un ensemble de mises à jour de sécurité pour mars 2023, corrigeant 64 failles, dont deux sont considérées comme critiques et concernent Hyper-V. La CVE-2024-21407 permet une exécution de code à distance (RCE) depuis un système d'exploitation invité vers l'hôte, tandis que la CVE-2024-21408 entraîne un déni de service. Une autre faille critique, la CVE-2024-21334, expose Open Management Infrastructure à une exécution de code distant avec un score CVSS de 9,8. La CVE-2024-26198 est également préoccupante, car elle permet une possible exécution de code distant sur Exchange. Malgré l'absence de failles en cours d'exploitation, les entreprises sont encouragées à installer ces mises à jour pour minimiser les risques.
🍵 Actualités le-monde-du-cloud-computing
Sécurité IT/OT: Nozomi Networks lève 100M$ (1 min) Nozomi Networks, une entreprise spécialisée dans la protection des systèmes informatiques et industriels contre les cyberattaques, a récemment annoncé avoir levé 100 M$ lors d'un dernier tour de table. Parmi les investisseurs figurent Schneider Electric et Mitsubishi Electric, ainsi que des actionnaires historiques tels qu'Activate Capital, Energize Capital et Forward Investments. La société prévoit d'utiliser ces fonds pour renforcer le développement de ses produits et la commercialisation de ses offres à l'international. Reconnue pour sa sonde OT certifiée par l’ANSSI, Nozomi Networks protégerait plus de 105 millions de terminaux OT, IoT et IT dans le monde entier et serait présente dans plus de 12 000 installations. Selon Edgard Capdevielle, président et directeur général de Nozomi Networks, cet investissement démontre "clairement le besoin et le soutien pour des solutions de sécurité agnostiques à la lumière de l'escalade des attaques contre les infrastructures critiques dans le monde entier".
Patch Tuesday mars 2024 : des failles critiques dans Hyper-V (2 min) Microsoft a publié un ensemble de mises à jour de sécurité pour mars 2023, corrigeant 64 failles, dont deux sont considérées comme critiques et concernent Hyper-V. La CVE-2024-21407 permet une exécution de code à distance (RCE) depuis un système d'exploitation invité vers l'hôte, tandis que la CVE-2024-21408 entraîne un déni de service. Une autre faille critique, la CVE-2024-21334, expose Open Management Infrastructure à une exécution de code distant avec un score CVSS de 9,8. La CVE-2024-26198 est également préoccupante, car elle permet une possible exécution de code distant sur Exchange. Malgré l'absence de failles en cours d'exploitation, les entreprises sont encouragées à installer ces mises à jour pour minimiser les risques.
Quand les projets Kubernetes dans le cloud public dérapent (2 min) Le rapport de Gartner met en évidence le sous-utilisation importante des ressources de calcul et de mémoire dans les clusters Kubernetes déployés sur le cloud public, entraînant des coûts supplémentaires considérables. Selon une étude de Cast.ai, qui a analysé 4000 clusters, seule 13% de la puissance de calcul et 20% des capacités de mémoire sont utilisées en moyenne, ce qui est similaire aux niveaux d'utilisation des serveurs non virtualisés. Ce faible taux d'utilisation est probablement sous-estimé et concerne principalement les entreprises ayant un niveau de maturité plus élevé sur la technologie d'orchestration. Les mégaclusters (plus de 30 000 CPU) ont un taux d'utilisation plus élevé à 44%. Les raisons principales de cette sous-utilisation sont le surprovisionnement, des marges de manœuvre injustifiées dans les requêtes mémoire et CPU des pods et la sous-utilisation des instances spot. Ces difficultés interviennent dans un contexte d'inflation des prix des instances spot, qui se sont envolés en moyenne de 23% entre 2022 et 2023 sur les régions cloud aux États-Unis. La dépense mondiale sur le cloud public devrait atteindre 679 milliards de dollars en 2024, contre 564 milliards de dollars en 2023.
Des LLM à portée des terminaux Android et iOS (1 min) Google a publié une API expérimentale, MediaPipe LLM Inference, qui permet d'exécuter des grands modèles de langage (LLM) sur des terminaux Android, iOS et web. Cette interface de programmation prend en charge initialement quatre modèles : Gemma, Phi 2, Falcon et Stable LM. Google a indiqué que les applications de production avec LLM peuvent utiliser l'API Gemini ou Gemini Nano via Android AICore sur Android. Les développeurs peuvent essayer l'API via une démo web ou en construisant des applications de démonstration, et intégrer les LLM sur un appareil en quelques étapes à l'aide de SDK spécifiques à la plateforme. L'API offre une latence optimale en se concentrant sur le CPU et le GPU pour prendre en charge plusieurs plateformes. Google prévoit d'étendre l'API à d'autres plateformes et modèles cette année.
🍵 Toutes les actualités :
Telex : Le Parlement européen valide l'IA Act, Zendesk acquiert Ultimate, Google paye 10 M$ de bug bounty (1 min) Le Parlement européen a approuvé le règlement sur l'intelligence artificielle (IA Act) avec 523 voix pour et 46 contre. Ce texte prévoit une régulation à deux niveaux : des contraintes de transparence et de respect des droits d'auteur pour les modèles d'usage général, et un encadrement plus exigeant pour les modèles à haut risque. Le Conseil européen doit maintenant ratifier le texte, qui devrait être publié en avril ou mai.
Zendesk, une entreprise spécialisée dans la gestion de la relation client (CRM), a annoncé l'acquisition de la start-up allemande Ultimate pour un montant non divulgué. Ultimate propose des outils d'automatisation et des assistants basés sur l'IA pour résoudre jusqu'à 80 % des interactions via ses agents d'intelligence artificielle.
Google a versé 10 millions de dollars en primes aux chercheurs pour la découverte de vulnérabilités dans ses solutions en 2023. Les récompenses ont diminué par rapport à l'année précédente, mais restent un montant significatif. L'année dernière, 632 chercheurs de 68 pays ont reçu une prime et la plus élevée a atteint 113 337 dollars. Sur Android, le montant global des récompenses a atteint 3,4 millions de dollars et sur Chrome 2,1 millions de dollars.
Une cyberattaque sur France Travail compromet 43 millions de comptes (1 min) France Travail, l'organisme qui remplacera Pôle Emploi, a annoncé avoir été victime d'une cyberattaque avec vol de données. Les informations personnelles de 43 millions de personnes ont été compromises, dont celles des personnes actuellement et précédemment inscrites au cours des 20 dernières années, ainsi que des personnes non inscrites mais ayant un espace candidat sur le site. Les données volées comprennent les noms et prénoms, les dates de naissance, les numéros de sécurité sociale, les identifiants France Travail, les adresses mail et postale, et les numéros de téléphone. Les mots de passe et les données bancaires ne sont pas concernés. France Travail a notifié l'incident à la Cnil, déposé plainte et ouvert une enquête. Une plateforme téléphonique a été mise en place pour accompagner les personnes concernées.
Sécurité IT/OT: Nozomi Networks lève 100M$ (1 min) Nozomi Networks, une entreprise spécialisée dans la protection des systèmes informatiques et industriels contre les cyberattaques, a récemment annoncé avoir levé 100 M$ lors d'un dernier tour de table. Parmi les investisseurs figurent Schneider Electric et Mitsubishi Electric, ainsi que des actionnaires historiques tels qu'Activate Capital, Energize Capital et Forward Investments. La société prévoit d'utiliser ces fonds pour renforcer le développement de ses produits et la commercialisation de ses offres à l'international. Reconnue pour sa sonde OT certifiée par l’ANSSI, Nozomi Networks protégerait plus de 105 millions de terminaux OT, IoT et IT dans le monde entier et serait présente dans plus de 12 000 installations. Selon Edgard Capdevielle, président et directeur général de Nozomi Networks, cet investissement démontre "clairement le besoin et le soutien pour des solutions de sécurité agnostiques à la lumière de l'escalade des attaques contre les infrastructures critiques dans le monde entier".
La commission de l'IA veut un fonds de 10 Md€ et libérer les données (3 min) La commission dédiée à l'intelligence artificielle a rendu son rapport après 6 mois de travail, comprenant 25 recommandations pour améliorer la compétitivité française en IA. Le rapport propose la création d'un fonds de 10 Md€ dédié au financement de l'écosystème IA et un assouplissement des contraintes sur l'accès aux données, qui sont essentielles à l'existence de l'IA. Il recommande également une approche plus radicale pour améliorer l'accès aux données de santé et la réduction des délais de réponse de la Cnil. Le rapport plaide en faveur d'une infrastructure technique sur les données en dépôt légal pour faciliter la mise en relation entre développeurs d'applications IA et propriétaires de données culturelles et patrimoniales. La formation sur l'IA est également un point clé, avec une estimation de 56 000 postes par an en développement d'IA et 25 000 postes par an en déploiement d'IA d'ici 10 ans. Enfin, le rapport recommande que la régulation de l'IA se fasse à l'échelon international et que la France soit un moteur dans la mise en place d'une organisation mondiale de gouvernance de l'IA.
TechPourToutes veut former à l'IT 10 000 étudiantes d'ici 2027 (2 min) Le gouvernement a lancé le programme TechPourToutes pour promouvoir l'égalité des genres dans le domaine du numérique. L'objectif est d'accompagner 10 000 jeunes femmes d'ici 2027 dans leurs études supérieures liées au numérique, en commençant par 2 000 lycéennes et étudiantes dès la rentrée 2024. Ce programme vise à augmenter significativement le nombre de femmes dans les formations au numérique en France à partir du collège. Les élèves ciblées sont les terminales qui rejoignent une formation scientifique et technique du numérique diplômante reconnue par le ministère de l'Enseignement supérieur et de la Recherche, ainsi que les étudiantes de moins de 25 ans déjà inscrites dans un établissement scientifique et technique.
TechPourToutes offre une large gamme de services de soutien, comprenant la découverte des métiers du numérique dès le collège, un accompagnement individuel, du coaching, du mentorat, un soutien dans la recherche de stage ou du premier emploi, ainsi qu'une assistance financière et matérielle. L'accompagnement est entièrement gratuit et peut se poursuivre jusqu'au Master 2. Les jeunes femmes intéressées peuvent prendre contact avec l'équipe de TechPourToutes dès maintenant en remplissant le formulaire fourni dans l'article.
🍵 Actualités securite
Une cyberattaque sur France Travail compromet 43 millions de comptes (1 min) Sécurité IT/OT: Nozomi Networks lève 100M$ (1 min) La commission de l'IA veut un fonds de 10 Md€ et libérer les données (3 min) Patch Tuesday mars 2024 : des failles critiques dans Hyper-V (2 min)
🍵 Actualités le-monde-du-cloud-computing
Sécurité IT/OT: Nozomi Networks lève 100M$ (1 min) Patch Tuesday mars 2024 : des failles critiques dans Hyper-V (2 min) Quand les projets Kubernetes dans le cloud public dérapent (2 min) Des LLM à portée des terminaux Android et iOS (1 min)
🍵 Toutes les actualités :
Telex : Le Parlement européen valide l'IA Act, Zendesk acquiert Ultimate, Google paye 10 M$ de bug bounty (1 min) Une cyberattaque sur France Travail compromet 43 millions de comptes (1 min) Sécurité IT/OT: Nozomi Networks lève 100M$ (1 min) La commission de l'IA veut un fonds de 10 Md€ et libérer les données (3 min) TechPourToutes veut former à l'IT 10 000 étudiantes d'ici 2027 (2 min) Meta détaille ses méga clusters pour entraîner Llama 3 (3 min) Orca-Math, un SLM de Microsoft sur base Mistral AI (2 min) Python creuse l'écart dans l'index de Tiobe (1 min) Jonathan Bourhis prend les rênes de Pure Storage France (1 min) Patch Tuesday mars 2024 : des failles critiques dans Hyper-V (2 min) L'expérience client augmentée à la GenAI (9 min) Quand les projets Kubernetes dans le cloud public dérapent (2 min) Des LLM à portée des terminaux Android et iOS (1 min) L'éthique by design au secours de la représentativité des femmes dans l'IA (4 min) Douloureuse bascule informatique chez Gifi (2 min) Telex : Nijta lève 2 M€, Telegram envisage IPO, La CNIL distribue des amendes (2 min)
🍵 "llm | cloud computing | ddos" - Google News
Cloud Technologies Drive Change at K–12 Schools - EdTech Magazine: Focus on K-12 Introducing Sunil Sukumaran Nair, a Software Engineer and Lead Pioneer in Cloud Computing and Automation - USA TODAY MongoDB expands availability of MongoDB Atlas to six more cloud regions - CloudTech News Rackspace revenue down 4Q and full year, CEO expects 1Q 'slow start' - San Antonio Express-News Is Oracle an AI Stock to Buy Now? - Yahoo Finance Energy efficiency drives HPC to the cloud - High-Performance Computing News Analysis - insideHPC Acurast Joins peaq: Transform Your Spare Phone into a Decentralized Cloud Computing Powerhouse - Blockster Israel's Orca Security CEO reveals the future of cloud security - The Jerusalem Post Oracle finally becomes a cloud company, helped by ‘enormous’ AI demand - MarketWatch Improving software licensing is the key to cracking hyperscaler cloud market dominance - ITPro 1 Little-Known Cloud Computing Stock to Buy Hand Over Fist Before It Soars 43% - Yahoo Finance
-
 @ 7b7b24c6:ed85505a
2024-03-14 04:12:25
@ 7b7b24c6:ed85505a
2024-03-14 04:12:25I'm Matt Crossett and I run the Motion Capture stages at Digital Domain in LA. We have done MoCap and Performance Capture for titles such as
Dune Spiderman: No Way Home Resident Evil: Village The Quarry Ms. Marvel Antman and the Wasp: Quantumania She Hulk
I've got some time. Ask me anything.
-
 @ 6ad3e2a3:c90b7740
2023-12-13 12:40:31
@ 6ad3e2a3:c90b7740
2023-12-13 12:40:31We often fantasized about time travel, mostly what stocks we would buy, what bets we would make. Buster Douglas and the 1999 St. Louis Rams to win the Super Bowl were two I liked to bring up. But that was before Henry got caught up in politics, and the conversation turned to altering events in world history.
Henry argued if you had one trip you’d be morally obligated to prevent some of history’s worst tragedies, and for him the go-to example was killing baby Hitler. If you were there and had the chance, you’d have to do it, he’d say, no matter how hard it would be to murder an innocent baby. If you hesitated to agree, he’d browbeat you, saying good people doing nothing is what allows evil to thrive. He saw it as an obvious choice: one as yet innocent baby in exchange for the lives and suffering of millions.
This made the exercise considerably less enjoyable, and we dropped it. That is, until The Simulator. The Simulator was a breakthrough technology, part virtual reality game, part research tool that enabled virtual experiments from modeling future events to modifying past ones and seeing present-day results. I’m oversimplifying, but it worked by scanning every recorded byte, including old maps, regional soil composition, weather patterns, temperature data, census records and every published book in human history. From stock market data to the Code of Hammurabi, to the fully mapped human genome, The Simulator drew inputs for its algorithm. Some believed the developers had access to classified material from the world’s intelligence agencies, including UFO encounters deemed too sensitive for public consumption.
Of course we only had the commercialized game version — the full one was prohibitively expensive and available only to those with official authorization. But the game version was robust enough, and already the software of choice for sports betting, weather forecasting and for some stock pickers, (though many suspected hedge funds and large institutions had access to the full version and avoided the capital markets entirely.)
I initially did investing experiments, buying Apple’s IPO, Amazon stock and eventually bitcoin and became the richest person in the world 10 times over. Although in one experiment, I owned so much bitcoin it became overly centralized and never took off. In that world, Facebook launched its Libra coin without much government resistance as few grasped the possibilities of fully digital currencies. The result was a Facebook-government partnership where you got docked Libra coin (the only currency in which you could pay federal taxes) for unfavored associations and viewpoints.
But I soon grew bored of the financial experiments and started doing weird things like going back to 2019, catching COVID on purpose and spreading it as widely as possible, before people thought it was a threat. In one simulation, there was no acknowledged pandemic, only a bad “flu” season.
I was about to log off and tackle a work project on which I had procrastinated for too long, when I remembered Henry’s insistence that I was obligated to kill baby Hitler. I never bought his arguments entirely — absolute certainty is always a red flag — but I didn’t have a good counter for them, either. I resolved to run the experiment and find out for myself.
It wouldn’t be easy as the commercial version of The Simulator had rules around acts of violence. I’d also have to dig up fairly specific knowledge in a presumably less developed part of the game (19th-century Hungary.) But The Simulator was adept at making do with the available history and filling in blanks with fictional characters. There would be a street address and a house where he lived. There should be an opportunity to see how it played out. Of course, one could simply delete Hitler and run simulations without him, and I tried that first, but the moral question was not whether the world would be better off without Hitler, but whether it would be right — or obligatory even, in Henry’s framing — to murder the baby in his crib.
I prefer not to go into the details. The broad outlines are I found a hack to disable the violence restriction, went to his childhood home and had to bludgeon a young woman (his nanny?) before doing it. For those who have never used The Simulator, “Full Immersion Mode” isn’t quite real life, but it’s substantially more visceral than shooting avatars in a video game. What I did was horrific, even though I knew it wasn’t real, and even though Henry believed the act would’ve been heroic if it were. I actually vomited afterwards, and as I type this 10 days later, I feel queasy recalling it.
Nonetheless, I ran a simulation forward. The Third Reich was run by committee. There was a front man, someone of whom I had never heard, who was more charismatic than Hitler, but decision-makers behind the scenes, including some of Hitler’s generals, were just as ruthless. There were concentration camps, though oddly in different locations, and the result was seemingly as bad.
But that was only one version of events. The Simulator (through randomization of certain parameters) could run infinitely many different futures from any given point in time. I ran a few more, and they were all dystopian in different ways. There was one version, however, that particularly struck me.
In it, Hitler rose to power as he did in the real world, and things unfolded more or less the way we’ve read about them in history. At first, I thought there must be an error — after all, every simulation began the hour after I smothered him in his crib. But as I checked the local newspapers from that era, indeed a baby had tragically died, and his brain damaged nanny was blamed (and subsequently hanged) for the crime, but it was a different baby, Max Muller, son of a local tavern owner, who committed suicide two years later. How could that be? Not only did I check all the details exhaustively, but they proved correct in all the other simulations. The randomizer must have swapped the location of baby Hitler with this other infant. In this version, I murdered (virtually, thank God) an innocent baby, destroyed his family and an innocent nanny without preventing anything.
. . .
When I met with Henry a week later, he wasn’t convinced. The Simulator isn’t reality, he argued, and the version with the wrong baby proved it. His hypothetical entailed killing the actual baby Hitler in the real world, not some case of mistaken identity. If you could be sure to kill the real Hitler and prevent the Holocaust from happening, he maintained, you’d still have to do it. The Simulator’s randomization algorithm made it impossible ever to know what would happen in its many possible futures, especially in the long run.
I now understood his argument. If we had certainty about how our actions would affect the world, the moral imperative would be clear. But certainty about the future was unattainable, for the path from unknown to known is the arrow of time itself. Henry’s hypothetical then was inherently contradictory, a square circle he imagined were an actual shape.
One could never be assured about the long term effects of one’s actions, and any attempt to do the math was quickly overwhelmed by infinite permutations. Doing something abhorrent as the means to a noble end was to fancy oneself a mathematical God, something no decent person would attempt. It was the ideology of monsters, forever imagining they could create a more perfect history, a more perfect future, a more perfect human race.
-
 @ 3cd2ea88:bafdaceb
2024-03-13 23:39:40
@ 3cd2ea88:bafdaceb
2024-03-13 23:39:40Bonus per nuovi utenti su Bitget: $15 in SOL per te!
Registrati su Bitget dal QR in foto. Fai il KYC. Deposita almeno $100. Fai trading per almeno $100.
Ricevi $15 in SOL in omaggio! -10% a vita sulle fee! Non perdere questa occasione!
Iscriviti a Bitget e inizia a guadagnare!
-
 @ a023a5e8:ff29191d
2023-12-07 04:37:55
@ a023a5e8:ff29191d
2023-12-07 04:37:55which operating system do you recommend using on my PC?
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 3cd2ea88:bafdaceb
2024-03-13 20:35:14
@ 3cd2ea88:bafdaceb
2024-03-13 20:35:14🖐 Questo articolo è per te se:
👁 Ti senti stretto a causa delle restrizioni sul controllo di governi e corporation. ® Pensi che la libertà di parola e di pensiero siano fondamentali per una società sana. 🤍 Sei incuriosito da Bitcoin e dal suo potenziale di cambiare le regole del gioco.
🧘♂ Se hai risposto sì ad almeno una di queste domande, allora continua a leggere perché quello che stai per scoprire potrebbe cambiarti la vita!
💰 Pubblicato da Bitcoin Report Italia, 12/03/2024 💰
💀 Viviamo in un mondo sempre più sorvegliato. Governi e corporation controllano i tuoi dati online e offline, limitando la tua libertà di espressione e azione. Vogliono dirti cosa pensare, cosa comprare e persino cosa leggere.
🤪 Ma c'è una speranza!
🖐 Bitcoin è una rivoluzione monetaria che ti libera dal giogo del controllo centralizzato. È una moneta digitale decentralizzata, ovvero non soggetta a nessun ente o governo. Le tue transazioni in Bitcoin sono veloci, sicure e impossibili da censurare. Nessuno può bloccare il tuo denaro o impedirti di usarlo come meglio credi.
🎨 Ecco perché Bitcoin è la chiave per la tua libertà finanziaria e digitale:
🧬 Sovranità individuale: Riprendi il controllo del tuo denaro. Addio a conti correnti bloccati o transazioni bloccate ingiustamente. 🧬 Libertà di espressione: Bitcoin è come parlare a voce alta senza che nessuno possa tapparti la bocca. Nessuna censura sulle tue transazioni o sulla tua partecipazione all'economia digitale. 🧬 Protezione dall'inflazione: Metti al sicuro i tuoi risparmi dall'inflazione creata a tavolino dalle banche centrali. Bitcoin è una riserva di valore stabile e decentralizzata. 🧬 Trasparenza e immutabilità: Tutte le transazioni Bitcoin sono pubbliche e immutabili. Nessuno può alterare i registri o nascondere le informazioni.
🪶 Scopri come Bitcoin ti aiuta a scappare dal controllo e costruire un futuro libero! 🪶
😊 Unisciti alla nostra community Telegram!
👨🏫 Impara dagli esperti come usare Bitcoin in modo sicuro ed efficace. Conosci altri utenti interessati alla libertà finanziaria e digitale. Scopri strategie per proteggerti dalla sorveglianza e dalla censura online.
🎶 Insieme possiamo costruire un mondo più libero e decentralizzato!
💡 Bonus:⤵️
😇 Smaschera le trappole delle nuove regolamentazioni sulle criptovalute: scopri come i governi stanno cercando di limitare il tuo utilizzo del denaro digitale. 📞 Evita le "monete digitali dei governi" (CBDC): non sono altro che strumenti di sorveglianza e controllo finanziario totale. 💳 Impara a difenderti dalla censura online: scopri i trucchi per aggirare la censura e accedere liberamente all'informazione. 🔞 Conosci gli eroi della libertà digitale: ispirati alle figure come Satoshi Nakamoto (creatore di Bitcoin), Julian Assange (fondatore di Wikileaks) ed Edward Snowden (ex-informatico della NSA) che hanno combattuto per la privacy e la libertà online. ✅ Non aspettare oltre! Riacquista il potere sulla tua vita, entra nella nostra community e combatti con noi per un futuro libero dalla censura!
🚀 Leggi tutti i nostri articoli: https://t.me/BitcoinReportChannel
Nella nostra community Bitcoin Report Italia, troverai un ambiente accogliente dove gli esperti ti guideranno nei primi passi nel trading, offrendo analisi, strategie di trading e l'opportunità di partecipare al CopyTrading con trader professionisti. ☄️ Iscrivendoti con il nostro referral code su Bitget (6w5d), potrai avere un contatto diretto con trader che ti aiuteranno a crescere nel mondo del trading di criptovalute. 🚀
📣 https://t.me/Bitcoin_Report_Italia
-
 @ 000002de:c05780a7
2024-03-13 16:31:27
@ 000002de:c05780a7
2024-03-13 16:31:27This post was inspired by @DarthCoin's post Liberate yourself!
A few years ago I realized that I was more in my head about freedom that actually putting it into action. I was acting like a victim. Like I had no agency. No ability to change my position. I was focused externally. It was easier to do that. That is what the world around us pushes us toward. Focusing on those that are the problem. Not focusing our our own areas for improvement. So, I started to get off my butt and do something. I can say that I am more free than I was a few years ago. I've learned most of these things I will share from others. I hope you find them helpful.
Free your mind
Stop thinking like a victim. Most people have been victimized at some point. If you see the state for what it is we all have been. But the most important thing about getting knocked down is getting back up. So stop thinking like a victim and start thinking like a victor. Start focusing on how you can become less dependent on "the system" and more of a resource for yourself and others.
Unplug from the spin machine. The system that is designed to keep you thinking about problems that aren't really problems for you or are problems you can't solve. Stop thinking about the world through the lens of 2 and 4 year politics. Stop thinking about the world through the lens of Red and Blue, right and left. Start focusing on what is in your control and those that are in your sphere of influence. Most of what we are told on the news and on social media by influencers is noise at best and a psyop at worst. Don't worry, your friends and family will tell you when stuff that you should be worked up about. You won't miss out. But I think most people do not understand how much of their minds are filled with noise and propaganda. They trick us into thinking it is important but it all seems to point to our need for politicians to stop something from happening. Weird how the answer to every crisis is to vote for some person to fix it for us. Isn't it? Remove the phrase "I can't" from your vocabulary. Instead say, "how can I"?
Consider Where You Live
Start thinking about how you can insulate yourself from the problems in culture, society, and the economy. Think about ways you can limit the negative affects of state control. This might be relocating. It might be moving 20 miles. In the US you live in several jurisdictions at once. The U.S.A, the state, the county within the state, and possibly a city. If you move out of a city into an unincorporated area you just eliminated one government system. But, there are things you can't avoid if you live in a state so don't think about relocation on only one layer of government and society. I'm not saying everyone should do this but think about this when you are considering what you want out of life. There are places within states that vary drastically as far as freedom goes. There are states that vary drastically as well. I assume some of this is also true in other countries but I'm sure there are differences. We had a good drill during the pandemic for what happens when people freak out. Look at how different cities, counties, and states reacted. Don't forget that. Don't be a follower. Don't move somewhere because others did. Think about what you like and don't like. Do some homework of your own. One place might be great for some people and terrible for others. It is your life. Take it back.
Self Improvement
Learn to grow at least some of your own food. The goal isn't just to not buy food but rather to learn the skill. What you will find is a deeper connection with nature. You will find it is easier than you thought. Some things will be hard but remember the goal is to learn HOW to do it. Not just to feed yourself. When things get bad you don't want to be learning a skill. It might be to late at that point.
I like the phrase Jack of all trades master of some. Don't be so much of a specialist that you are helpless outside of your field. Learn how to do basic home repairs. If you learn new skills it will make you more confident and more valuable to others. I find it truly sad how few people can actually fix things around their house. If that's you, you can change that. Learn first aid. Learn how your car works. Anything you depend on you should have at least a basic understanding about. I'm not saying everyone needs to be a handy man but our high time preference thinking has led to a society of helpless and hopeless people. For things like your automobile, if you don't learn the skills of repairing it, get to know someone that is skilled. Someone you can trust. They don't need to be a pro. I have done many repairs on my vehicles going back to my teens. I do not enjoy doing automotive work so I pay someone to do most of it. They can do it faster and cheaper (based on the value of my time). That said, I do know how to do most things and this knowledge is valuable. This principle can be applied broadly to many skills.
Learn how to learn. The most valuable skill I have every learned was learning how to learn. It is different for each person but you should learn to teach yourself new skills. Some people learn by watching. Some by reading. Others by doing. Most of us use a combination of all three. But work on that skill and it will help all other skill development.
Build Community
So, how do your find someone to help you with something you do not know how to do? Why would someone help you? Well, if you have worked on yourself. Learned new skills you will have value as well. You will be that expert or skilled person someone else calls when they need help. This is how community works and we undervalue it. Bitcoin is one of these things but if you are a programmer and you also have learned how to use bitcoin in a sovereign way you have more to learn. Get up from the computer and learn a physical skill. A great one to learn is electronics. Learn to solder. Start learning how to build simple projects. Learn some basic electrician skills like swapping power outlets.
Building community requires social skills. You might need to work on that as well. Don't be the jerk that can't have a relationship with anyone that doesn't agree with them on everything. I think you'd be surprised how many people there are around you that see many things as you see them. I know I have been. Build relationships first. People you can depend on. People that have your back. Don't focus on who they vote for or if they vote. That is short sighted. I'm not saying to be naive. Those things can be good signals but don't pigeon hole people. Build a tribe.
Prepare for likely events / disasters
Yes, we all should be prepared. One of the worst things in our culture has been to highlighting of crazy preppers. What's so bad about it is that you mostly hear about the people that are doing it wrong. Stocking up on toilet paper instead of having a supply of fuel. Building a bomb shelter instead of growing a garden. Being prepared actually requires some thought. What are the common natural disasters in your area. It is different for everyone. A common thing to have is some alternate source of power. A generator or battery. Acquire that. Learn how to use it. Test it once a month. Stock up on medical supplies. Not that crappy first aid kit at the store. Learn basic first aid. If you can buy a freezer and rotate your frozen food. Have enough to live on for at least two weeks. Do this with food you like. Not crap you won't eat. Also have a stock of MREs for if things really get bad.
Maintain at least 60 gallons of fuel that your vehicles use. You can buy 5 gallon cans and write 1-12 on them. Each month empty one into your vehicle and refill it. This way you never have fuel that has went bad. This is very handy as well. Some of you won't be able to do this because you don't live in a house but if you can, this is a great tip.
Plan for Home Defense
Yes, you should have deadly weapons if at all possible. Learn how to use them with skill. Your life may depend on it. Don't depend on the state authorities to protect you, your loved ones, and your property. Maintain a supply of ammo. Think and plan for what you will do if someone attacks you or invades your property. What would you do? If it happens you will not think, you will react and you need to plan for what you will do and maybe even train for it. Seek professional training unless you have a community with training. Be careful. The point of this is to increase your protection and safety so take precautions around weapon security.
Build Wealth
We all know bitcoin is key to this. But I think to many bitcoiners fail to see the value in building skills that are in demand. Needs that must be filled. Finding an alignment of skills you'd like to have and people in need of those skills is key to building wealth. If you are not challenging yourself in the work you do you are short bitcoin. Let me say that another way. If you are not living up to your potential then you don't truly value bitcoin or understand what it is. Bitcoin is not this magic thing discovered so you can be lazy. No, it is a tool to save the rewards of your labor in a money that can't be taken from you. That can't be inflated away. So if you aren't challenging yourself, you are short bitcoin. Even more importantly the rest of us need your unique abilities. I don't know what they are, but bitcoin can be a driver to push you to get out of your mom's basement and make something of yourself.
Its hard to be poor and free. In most places of the world wealth solves so many problems. Don't kid yourself. If you are poor, you have fewer options. Get out there and work.
Stop Depending on Corporate Systems
Stop depending on Google, Facebook, Twitter, Amazon, etc. I'm not saying you should never use them. But are you dependent on them? Start using Nostr. Start using open source tools. Start trading with local farmers, ranchers, and skilled workers. These actions create more resilience into our world. Centralization is a risk.
Study Bitcoin. Don't Just Acquire It
Learn why it was created, how it works, and how to use it. You're on SN. That's a good start.
Don't Get Overwhelmed
Don't try to go from zero to 100 all at once. Make a prioritized list and start learning and doing things but do not expect yourself to do these things in one year, maybe not even five. It should be a life long pursuit and I think you will enjoy it. Right now just ask yourself. Am I more free today than I was yesterday? Last month? 1 year ago? 5 years ago?
If not, start working on changing that. Start in your mind. Remember. You don't need to out run the bear, you need to outrun the other guy running from the bear. You won't do it all perfectly but don't give up.
-
 @ 5b0e8da6:7792bc54
2024-03-13 15:02:34
@ 5b0e8da6:7792bc54
2024-03-13 15:02:34I recently completed my home 7.1.4 speaker setup and have been really enjoying digging into high-end Dolby Atmos and Dolby Vision material. Playing around with nip23 long-form content to share this kind of niche nerd stuff that doesn't quite make sense as a regular nostr note.

tldr: For videophiles there's really only one option: ~$450 Panasonic UB820. Just do it.
Videophile nerd standards hell
I'll have to do a post to really dig into the 4k UHD video formats: HDR10, HDR10+, and Dolby Vision.
The short version:
HDR10 is the baseline high-dynamic range format that's on all 4k UHD blu-ray discs. Better than HD / 1080p blu-rays due to HDR10's greater dynamic range (duh!), more intense contrast, and richer colors. But HDR10 is an inherently compromised HDR format compared to the two more advanced options below.
HDR10+ is an optional enhancement that maximizes the data on the disc (more data and more efficient usage of that data). Part of this additional data — dynamic metadata — is a ginormous game-changer. Imagine an opening scene that's way too bright. So you dial back the Brightness control on your TV. But now dark scenes are way too dark. That one Brightness control is just too blunt a tool to give you good results over an entire movie. HDR10 is (metaphorically) limited to that one Brightness control. HDR10+'s dynamic metadata is like the cinematographer adjusting it for you on a shot-by-shot basis. Absolutely massive improvement. Except there are almost no 4k blu-rays that use it.
Dolby Vision ("DV") does everything HDR10+ does, but better (has even more, richer data!). Dolby Vision leaps further out in front because it also incorporates a kind of communication layer with a DV-capable TV to optimize how the content is displayed, including locking down certain adjustment options. No tweaking; just hit play. BLISSFULLY relaxing for an otherwise OCD videophile! It is the best format we have to watch video content. Period. It's well worth it. And more and more content (especially streaming, but also 4k blu-rays) is in Dolby Vision.
Dearth of Dolby Vision-capable players 😢
My original 4k blu-ray player (from 2016!!), a Samsung UBD-K8500, only supported baseline HDR10.
My Xbox One X can output Dolby Vision (and maybe HDR10+?) but only for streaming services (e.g. Netflix) or gaming. On-disc Dolby Vision is not supported because — this seems beyond ridiculous — the onboard laser hardware literally cannot read the DV data off a 4k blu-ray disc.
Current-gen Xbox Series One and the PS5 can't read disc-based DV data, either. wtf?
Look carefully at the specs for cheap, dedicated 4k blu-ray players. Very few support Dolby Vision.
Triple-layer disc woes
Another really dumb technology problem: the biggest 4k blu-ray discs have 100GB of data stored on three different layers but plenty of players — including the prominent gaming consoles — are reported to freeze or skip ~2/3 of the way through a movie when the laser tries to refocus itself to the third data layer. Or they'll struggle to even load the intro menus.
Again, wtf? Does this tech shit work or not?
So even if you find a more affordable 4k blu-ray player with Dolby Vision support (they do exist), odds are that it'll still struggle on some 100GB discs. Because those triple-layer discs store the most data, they offer the best possible picture quality. The reference-quality, demo-worthy 4k blu-rays will fill a 100GB disc. So if you want to experience the best that the format can offer, your player better be able to read triple-layer discs reliably.
So there's only one option
It's the Panasonic UB820.
It's not cheap but it's not a back-breaker, either. Dolby Vision and HDR10+ support. Flawless reads for triple-layer discs. There are other, more expensive players that can achieve all this. But there are zero cheaper players that can do it.
Yes, it's worth it
If your TV supports Dolby Vision — and especially if it's rated for more than 1000 nits — then the Panasonic UB820 is just a must-have for any hardcore videophile.
"nits" are a measure of how bright the screen can get. I call this out specifically because all the HDR formats can be authored to target intensities beyond 1000 nits. That's when the dynamic range of your TV really starts to impress.
If your TV can't go that bright, it does its best to smoothly ignore the extra-bright (or extra intense color) information.
But if it CAN go that intense, whoa baby is it amazing! And with Dolby Vision optimizing how that intensity is mapped to your TV... just pure videophile nerd bliss.
-
 @ 8fb140b4:f948000c
2023-11-21 00:46:59
@ 8fb140b4:f948000c
2023-11-21 00:46:59Venturing into the dynamic world of bitcoin's layer 2 networks, particularly the lightning network, can seem like an exciting frontier for tech enthusiasts and cryptocurrency aficionados. however, the decision to run your own lightning node is not one to be taken lightly. While the allure of contributing to the bitcoin ecosystem and potentially earning transaction fees is strong, there are significant considerations that should temper the enthusiasm of would-be node operators. From the intricate technicalities to unexpected challenges, here are 10 compelling reasons why running your own lightning node might not be the electrifying experience you anticipated.
Running your own lightning node for the bitcoin layer 2 network can be a complex and demanding task. Here are 10 reasons why you might choose not to:
-
Technical complexity: setting up and managing a lightning node requires a good understanding of blockchain technology and network management, which can be overwhelming for beginners.
-
Security risks: running a node means you're responsible for securing it against potential cyber attacks, which requires constant vigilance and technical expertise.
-
Resource intensive: a lightning node requires continuous internet connection and sufficient hardware resources, which can be costly in terms of electricity and equipment.
-
Liquidity requirements: to facilitate transactions, you need to lock up a significant amount of bitcoin in your channels, which might not be ideal if you prefer liquidity.
-
Maintenance efforts: regular maintenance and updates are necessary to keep the node running smoothly, which can be time-consuming.
-
Limited privacy: operating a node might expose some of your transaction details or ip address, potentially compromising privacy.
-
Slow ROI: the financial return on operating a lightning node can be slow and uncertain, especially if the network fees are low.
-
Network complexity: understanding and managing channel capacities, routing, and fees can be complicated and require continuous learning and adaptation.
-
Scalability issues: as the network grows, managing a node can become increasingly challenging, with more channels and transactions to handle.
-
Downtime risks: if your node goes offline, you might miss out on transaction fees or, worse, risk losing funds in channels due to outdated channel states.
These reasons reflect the challenges and responsibilities that come with running your own lightning node and may discourage some individuals, especially those with limited technical background or resources. If you are still up for a challenge, thank you for supporting the network! 🐶🐾🫡🙏🏻
-
-
 @ 1cb14ab3:95d52462
2024-03-13 13:13:28
@ 1cb14ab3:95d52462
2024-03-13 13:13:28Chef's notes
Chicken can be substituted by assorted mushrooms and tofu. Sichuan chilli bean pastes can be substituted by tomato paste or fresh tomatoes. Pixian chilli bean paste 郫县豆瓣酱 Pí xiàn dòubàn jiàng Light soy sauce 生抽 Shēng chōu Cooking wine 料酒 Liàojiǔ Vegetable oil 植物油 zhíwùyóu Salt 盐 Yán Sugar 糖 Táng
Recipe is originally credit of: https://thehutong.com/xinjiang-big-plate-chicken-xinjiang-dapan-ji/
Details
- ⏲️ Prep time: 30 minutes
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4
Ingredients
- 2 big chicken thighs or 1 whole chicken
- 3 medium-size potatoes
- 1 medium-size green chilli pepper
- 1 medium-size red chilli pepper
- 1 small yellow onion
- 10g ginger
- 5-8 cloves of garlic
- 2 tbsp of Sichuan chilli bean paste
- 1tsp of salt or salt for taste
- 1tsp of sugar or sugar for taste
- 1 tbsp of cooking wine
- 2 tbsp of light soy sauce
- 1tbsp of dark soy sauce
- 2-3 tbsp of vegetable oil
- 250g wide noodle
- 1L Chicken/vegetable stock/water (or enough to cover ingredients)
- 10 pieces of dried chilli pepper
- 1 tbsp of Sichuan peppercorn
- 1 cinnamon bark
- 2 pieces of star anise
- 2 pieces of bay leaves
- a small pinch of white pepper powder
Directions
- Wash the chicken and cut into bite-size pieces. Cut the potatoes and chilli pepper into small pieces about bite-size. Slice the ginger, onion & crush the garlic.
- Heat 2-3tbsp of oil in a wok with low heat and add sugar in. When sugar is getting melted, add the chicken to stir fry quickly till the chicken meat tight and dried. Add the Sichuan peppercorn, dried chilli. star aniseed, cinnamon, bay leaves, garlic, ginger, onion to fry till fragrance.
- Put Sichuan chilli bean paste, light soy, dark soy, cooking wine and mix well. Add water/ stock to boil and cover it and simmer it for about 3 min. and then mix the potatoes well in, (make sure all the potato and chicken will be merged in the water/stock) check-in between and stir a bit in while the liquid is reducing.
- Get a fork to check the potato, if it could get through easily. They are cooked and add the bell pepper to fry about another 3 minutes till the liquid thicken up. Give a taste and adjust the flavour for saltiness. Serve with noodles, rice or bread.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ c11cf5f8:4928464d
2024-03-13 13:02:04
@ c11cf5f8:4928464d
2024-03-13 13:02:04Hey stackers, let’s lay down your unique and unusual offerings. Unveil the unexpected!
Need a hand? Check our tutorials… What hidden gems do y'all have up for sale? Let's rustle up some dusted serendipitous and it in the ~AGORA marketplace.
Click any link👇below to start! [⚖️ SELL] - [🛒 BUY] - [🧑💻 HIRE] - [🖇 OFFER] - [🧑⚖️ AUCTION] - [🤝 SWAP] - [🆓 FREE] - [⭐ REVIEW]
-
 @ 06639a38:655f8f71
2024-03-13 12:52:07
@ 06639a38:655f8f71
2024-03-13 12:52:07I started using Proton as my default email service provider in 2022. I’ve more than 500Gb storage there available including a service called Proton Drive for file storage. This is quite a lot for just email. So I asked myself, how can I use the other amount of space as an extra backup storage solution?
I also published this article on my blog: https://sebastix.nl/blog/using-proton-drive-as-a-backup-storage-location-with-rclone/
Quite a while ago I discovered a free and open-source tool called Rclone. It pretends to be a swiss knife for file management between different remote storage locations (more than 50 so-called cloud providers) including Proton Drive. The following instructions are intended for Ubuntu which was my environment to test it out. They could apply for other Linux distros as well. Please follow the Rclone docs for more details.
Installing Rclone
Follow the latest install instructions here.
Execute this command on your terminalbash sudo -v ; curl https://rclone.org/install.sh | sudo bash
and Rclone will be installed on your machine. To check if the installation succeeded, runrclone --versionand a version will be return.
You can update Rclone easily withrclone selfupdate.
Executerclone --helpto return a full list with available commands.Configure Rclone and Proton Drive
Run
rclone configand choose Proton Drive as a remote (option number 40 in my case). After the config, get the name of the remote withrclone listremotes.
If this doesn't work out for you, please check the latest Proton Drive docs on Rclone here.Copy or sync files to Proton Drive
Let's create a simple file called copy-me.txt in the current directory.
bash echo 'this file will be copied to proton drive with rclone' > copy-me.txtExecuterclone -v copy copy-me.txt protondrive:and this will copy the backups.txt file to your Proton Drive.
The output will look something like this: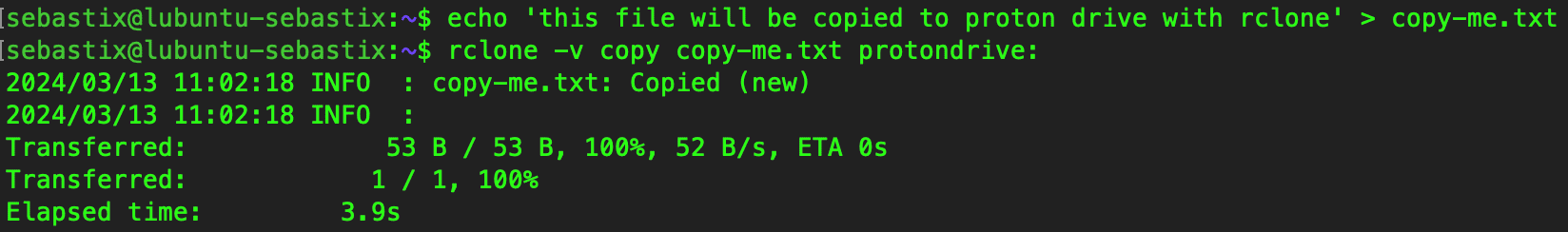
You can check if the file is in your Proton Drive by viewing your list of files at https://drive.proton.me/:
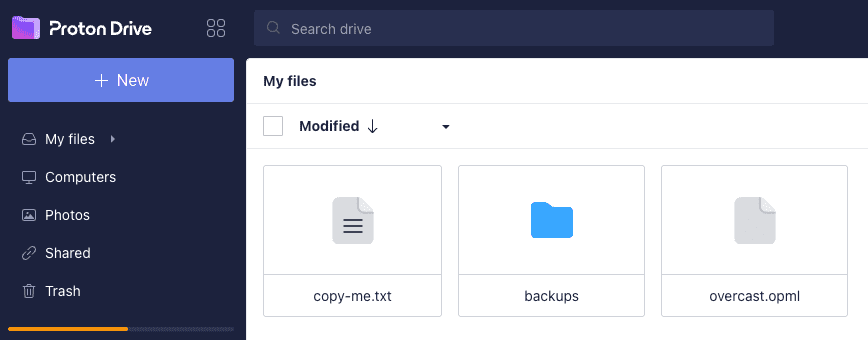
Automated backups with cronjobs
We can use
rclone syncto perform backup actions.
The full command will look something like this:
bash rclone sync -v --create-empty-src-dirs ~/backups protondrive:/backups
Executecrontab -eto edit your crontab file with cronjobs and add the following line:
bash 3 0 * * * rclone sync -v --create-empty-src-dirs ~/backups protondrive:/backupsNow every night at 3am this command is executed.Backing up docker volumes
As a non-root user, you can’t access the directory with docker volumes at
/var/lib/docker/volumes. You must login as root (sudo su) and config your rclone installation again withrclone configas we did earlier. After you’re done, you can copy/sync the docker volumes.bash rclone sync -v --create-empty-src-dirs /var/lib/docker/volumes protondrive:/backups/docker-volumesYou could add this command with a cronjob as well withcrontab -eunder the user root.Email output of the cronjobs
To check if the cronjobs are running correctly, you can send an email with the output of the cronjob. Please read some solutions here how to manage that.
Solid solution? How long will it work?
For now let's see how these Rclone commands with several cronjobs will run with Proton Drive for the coming period. I can imagine when a change is made on the Proton side, things could break on our side with Rclone. I hope I don't have to update Rclone too regular (let's say weekly) to keep things working.
Used resources
- https://dev.to/itsbetma/automated-backups-with-cron-and-rclone-3do4
- https://blog.rymcg.tech/blog/linux/rclone_sync/
-
 @ 8fb140b4:f948000c
2023-11-13 07:55:20
@ 8fb140b4:f948000c
2023-11-13 07:55:20Hey there, train enthusiasts! let's chat about one of the most impressive rail systems in the world - japan's trains. when you think of japanese trains, the first image that probably pops into your mind is the sleek, futuristic shinkansen, also known as the bullet train. these high-speed trains are not just a symbol of modern technology; they're a testament to japan's commitment to efficiency and punctuality. it's not an exaggeration to say that japanese trains are famous for being precisely on time. if a train is five minutes late, it's often considered a significant delay!
but it's not just the shinkansen that deserves praise. japan's entire railway network, from city subways to rural train lines, is incredibly well-organized. the trains are clean, comfortable, and surprisingly quiet, making even a regular commute a pleasant experience. what's more impressive is the frequency of these trains. in major cities like tokyo and osaka, you rarely have to wait more than a few minutes for a train, reducing the stress of travel and making commuting more predictable.
and let's not forget the level of service! train staff in japan are known for their politeness and helpfulness. whether you're a tourist struggling with your luggage or a local needing directions, there's always someone to help. plus, the stations themselves are marvels - clean, well-signed, and packed with amenities like shops and restaurants. in short, japan's trains aren't just a mode of transportation; they're an experience, reflecting the country's dedication to quality, punctuality, and customer service. so, next time you're in japan, hop on a train and enjoy the ride - it's an adventure in itself! 🚆🌸🐶🐾🫂
-
 @ 1c6b3be3:73f0ae6f
2024-03-13 06:13:58
@ 1c6b3be3:73f0ae6f
2024-03-13 06:13:58🍵 Actualités securite
Arrêt définitif du support pour Windows 10 21H2 le 11 juin (1 min) Microsoft a annoncé que les mises à jour de sécurité pour la version 21H2 de Windows 10 seront interrompues à partir du 11 juin 2024. Cette décision affecte les versions Enterprise, IoT et Education de Windows 10, qui avaient précédemment bénéficié d'un sursis après l'arrêt des mises à jour pour les éditions Famille, Pro, Pro Education et pour stations de travail le 13 juin 2023. Après cette date, tous les systèmes fonctionnant sous Windows 10 version 21H2 seront vulnérables aux cyberattaques car ils ne recevront plus de correctifs. Cette décision a des implications particulières pour les entreprises qui doivent maintenant planifier une mise à jour vers la dernière version de Windows 10 ou passer à Windows 11 avant cette date butoir.
Pour protéger les LLM, Cloudflare muscle son WAF (3 min) Cloudflare, une entreprise spécialisée dans la cybersécurité, a récemment renforcé son offre de pare-feu applicatif (WAF) en y ajoutant une fonctionnalité dédiée à la sécurisation des grands modèles de langage (LLM). Baptisée « Firewall for AI », cette fonction est capable d'analyser les requêtes soumises aux LLM et d'identifier les tentatives d'exploitation malveillante.
Cloudflare a conçu « Firewall for AI » pour être agnostique et applicable à tous les déploiements spécifiques de LLM, qu'ils soient hébergés sur Cloudflare Workers AI ou sur une autre infrastructure tierce. Les clients peuvent contrôler et configurer la fonction via le plan de contrôle du WAF.
En plus de « Firewall for AI », Cloudflare a également annoncé un programme appelé Defensive AI, qui utilisera l'intelligence artificielle pour lutter contre les attaques ciblant les API et les courriels ainsi que l'accès des employés.
« Firewall for AI » vise à protéger spécifiquement contre l'injection d'invites et la fuite de données en analysant et en évaluant les invites soumises par un utilisateur, et en bloquant l'exploitation de modèles et les tentatives d'extraction de données.
Enfin, Cloudflare développe des systèmes IA pour examiner les modèles de trafic spécifiques à chaque client et construire une base de référence de comportement normal, ce qui permettra de détecter toute anomalie dans les environnements, y compris les API, les courriels et l'accès des employés. Ce programme, appelé Defensive AI, vise à améliorer l'efficacité des solutions de sécurité grâce à l'intelligence artificielle.
L'école de code Holberton s'installe à Dijon, Fréjus et Rennes (2 min) Holberton School, une école d'informatique qui utilise la méthode d'apprentissage par pairs et n'exige pas de diplôme préalable, renforce sa présence en France avec l'ouverture de trois nouveaux campus à Dijon, Rennes et Fréjus. Ces nouvelles implantations visent à combler les lacunes en matière de compétences informatiques dans ces régions et à répondre aux besoins des entreprises locales. Les formations proposées durent de 9 à 36 mois et mènent à un diplôme de niveau Bac+4 reconnu par l'Etat. Holberton School a été fondée dans la Silicon Valley en 2015 par deux français et propose des formations sans condition de diplôme ni limite d'âge, avec un coût financé à 100% par des prêts remboursables une fois l'obtention d'un emploi. Actual, un spécialiste du marché de l'emploi en France, est partenaire de ces nouvelles implantations et interviendra sur des ateliers de création de CV et d'entretien ainsi que sur l'information relative aux secteurs IT et aux entreprises qui recrutent.
SAP tente encore de rassurer ses utilisateurs (4 min) L'utilisation de SAP S/4 Hana, que ce soit sur site ou via un service cloud de l'éditeur, reste le principal cheval de bataille de la société allemande. Cependant, les offres cloud telles que Rise with SAP et Grow with SAP sont également mises en avant par SAP. Le choix entre les différentes options (sur site, cloud privé ou public) détermine l'accès à l'innovation, qui est calé sur un rythme de 6 mois pour les offres sur le cloud de l'éditeur et s'aligne avec la fréquence des mises à jour des environnements SAP sur les déclinaisons sur site. Les mises à jour sont automatiques sur la version multitenant (Grow), tandis qu'elles restent à la main de chaque DSI dans l'offre Rise.
L'hybridation entre les systèmes déployés dans différentes activités et l'ERP coeur est possible grâce à ces décisions. Cela permet également d'envisager des scénarios d'enrichissement fonctionnel de S/4 on-premise avec des modules cloud, comme le Green Ledger de suivi des émissions carbone qui sera uniquement accessible sur le cloud, mais pourra s'interfacer avec différents systèmes sur site.
SAP étudie également les possibilités d'hybridation pour l'IA générative, une technologie plus adaptée à un modèle d'exploitation cloud et à des mises à jour fréquentes qu'un modèle on-premise. Cependant, déployer cette technologie sur des progiciels on-premise peut faire peser un risque d'effondrement des performances de ces systèmes, qui seront très sollicités.
Enfin, SAP a décidé de tout miser sur la norme européenne EUCS (European Union Cybersecurity Certification Scheme for Cloud Services) plutôt que sur le label SecNumCloud de l'Anssi pour son offre cloud en France.
Croissance atone du marché des appliances de sécurité au T4 2023 (2 min) Le marché des appliances de sécurité a connu une baisse de livraisons de 36% au dernier trimestre 2023, mais les revenus ont tout de même augmenté de 0,8% par rapport à la même période l'an dernier, atteignant 4,96 milliards de dollars. Cela est dû à une forte hausse du prix moyen des produits acquis. Palo Alto Networks a connu une croissance de revenus de 10,1% et a dépassé Fortinet en tant que leader du marché avec une part de 18,2%. Huawei a également connu une croissance de revenus de 5,6%. Les sorties de nouveaux produits avec des capacités d'IA et une efficacité énergétique améliorée ont contribué à la hausse du marché en 2023.
🍵 Actualités le-monde-du-cloud-computing
SAP tente encore de rassurer ses utilisateurs (4 min) L'utilisation de SAP S/4 Hana, que ce soit sur site ou via un service cloud de l'éditeur, reste le principal cheval de bataille de la société allemande. Cependant, les offres cloud telles que Rise with SAP et Grow with SAP sont également mises en avant par SAP. Le choix entre les différentes options (sur site, cloud privé ou public) détermine l'accès à l'innovation, qui est calé sur un rythme de 6 mois pour les offres sur le cloud de l'éditeur et s'aligne avec la fréquence des mises à jour des environnements SAP sur les déclinaisons sur site. Les mises à jour sont automatiques sur la version multitenant (Grow), tandis qu'elles restent à la main de chaque DSI dans l'offre Rise.
L'hybridation entre les systèmes déployés dans différentes activités et l'ERP coeur est possible grâce à ces décisions. Cela permet également d'envisager des scénarios d'enrichissement fonctionnel de S/4 on-premise avec des modules cloud, comme le Green Ledger de suivi des émissions carbone qui sera uniquement accessible sur le cloud, mais pourra s'interfacer avec différents systèmes sur site.
SAP étudie également les possibilités d'hybridation pour l'IA générative, une technologie plus adaptée à un modèle d'exploitation cloud et à des mises à jour fréquentes qu'un modèle on-premise. Cependant, déployer cette technologie sur des progiciels on-premise peut faire peser un risque d'effondrement des performances de ces systèmes, qui seront très sollicités.
Enfin, SAP a décidé de tout miser sur la norme européenne EUCS (European Union Cybersecurity Certification Scheme for Cloud Services) plutôt que sur le label SecNumCloud de l'Anssi pour son offre cloud en France.
Highway 9 Networks apporte des réseaux 5G privés aux entreprises (5 min) Highway 9 Networks, une start-up récemment financée à hauteur de 25 millions de dollars, propose aux entreprises des réseaux mobiles privés en mode SaaS pour améliorer la couverture cellulaire et prendre en charge les applications d'intelligence artificielle. La solution Highway 9 Mobile Cloud est construite sur une technologie cellulaire privée, utilisant des bandes de spectre autorisées par la FCC, et s'appuie sur trois composants : des dispositifs radio cellulaires, un composant edge avec couches de protocole 5G et un système de gestion basé sur le cloud. Selon Sequeira, PDG de Highway 9 Networks, la solution ne vise pas à remplacer complètement le WiFi dans les entreprises, mais plutôt à répondre aux nouveaux cas d'utilisation nécessitant une mobilité accrue, une meilleure couverture et des connexions plus fiables. Les observateurs estiment que la technologie cellulaire en entreprise pourrait résoudre les problèmes de connectivité et répondre aux besoins croissants de connectivité des entreprises.
Nutanix formalise le rachat des actifs de D2iQ (2 min) Google a annoncé que la start-up D2iQ (anciennement Mesosphere) va renforcer les actifs Kubernetes de Nutanix, bien qu'il n'ait pas été révélé le montant de l'acquisition. Fondée en 2013, D2iQ a initialement proposé un gestionnaire de clusters de conteneurs open source avec le soutien de Microsoft et HPE, mais après avoir échoué à concurrencer Kubernetes, la société a changé de nom en 2019 pour se rallier à l'orchestrateur dépendant de la Cloud Native Computing Foundation. Avant l'acquisition par Nutanix, D2iQ avait levé 250 millions de dollars auprès d'investisseurs tels que Khosla Ventures, Andreessen Horowitz et T. Rowe Price.
Dans un article de blog, Thomas Cornelly, SVP of Product Management chez Nutanix, a présenté la version 2.7 de DKP (D2iQ Kubernetes Platform), qui offre une gestion automatisée des ressources Kubernetes avec l'IA et des améliorations en matière de dépannage et de multi-location. Nutanix envisage d'intégrer davantage DKP à son écosystème plus large de produits, tels que Karbon et Red Hat OpenShift. L'acquisition devrait permettre à Nutanix de simplifier son portefeuille Kubernetes.
🍵 Toutes les actualités :
Telex : Nijta lève 2 M€, Telegram envisage IPO, La CNIL distribue des amende (2 min) La start-up lilloise Nijta, spécialisée dans la sécurisation des données vocales pour les IA, a récemment levé 2 millions d'euros. Cette levée de fonds a été réalisée en partie auprès du fonds de capital-risque français Elaia et de la société d'investissement lilloise Finovam Gestion. Nijta développe une technologie d'anonymisation de la parole alimentée par l'IA pour aider les clients à se conformer aux exigences en matière de protection de la vie privée.
Dans un autre domaine, le CEO du service de messagerie sécurisée Telegram, Pavel Durov, a récemment annoncé son intention d'introduire l'entreprise en bourse (IPO). Il a indiqué que la rentabilité de l'entreprise devrait se faire en 2024 ou 2025, suggérant que l'IPO pourrait avoir lieu dans un avenir proche.
Enfin, la Commission nationale de l'informatique et des libertés (CNIL) a augmenté le nombre de sanctions qu'elle distribue au cours de sa procédure simplifiée en 2024. La CNIL a indiqué avoir sanctionné 15 organismes pour un total de 98 500 euros, contre 24 décisions et 44 000 euros sur l'ensemble de l'année 2023. Les principaux manquements retenus concernent notamment un défaut de coopération avec la CNIL, un défaut de sécurité des données, un non-respect des droits des personnes et un manquement à l'information en matière de prospection politique.
Arrêt définitif du support pour Windows 10 21H2 le 11 juin (1 min) Microsoft a annoncé que les mises à jour de sécurité pour la version 21H2 de Windows 10 seront interrompues à partir du 11 juin 2024. Cette décision affecte les versions Enterprise, IoT et Education de Windows 10, qui avaient précédemment bénéficié d'un sursis après l'arrêt des mises à jour pour les éditions Famille, Pro, Pro Education et pour stations de travail le 13 juin 2023. Après cette date, tous les systèmes fonctionnant sous Windows 10 version 21H2 seront vulnérables aux cyberattaques car ils ne recevront plus de correctifs. Cette décision a des implications particulières pour les entreprises qui doivent maintenant planifier une mise à jour vers la dernière version de Windows 10 ou passer à Windows 11 avant cette date butoir.
Pour protéger les LLM, Cloudflare muscle son WAF (3 min) Cloudflare, une entreprise spécialisée dans la cybersécurité, a récemment renforcé son offre de pare-feu applicatif (WAF) en y ajoutant une fonctionnalité dédiée à la sécurisation des grands modèles de langage (LLM). Baptisée « Firewall for AI », cette fonction est capable d'analyser les requêtes soumises aux LLM et d'identifier les tentatives d'exploitation malveillante.
Cloudflare a conçu « Firewall for AI » pour être agnostique et applicable à tous les déploiements spécifiques de LLM, qu'ils soient hébergés sur Cloudflare Workers AI ou sur une autre infrastructure tierce. Les clients peuvent contrôler et configurer la fonction via le plan de contrôle du WAF.
En plus de « Firewall for AI », Cloudflare a également annoncé un programme appelé Defensive AI, qui utilisera l'intelligence artificielle pour lutter contre les attaques ciblant les API et les courriels ainsi que l'accès des employés.
« Firewall for AI » vise à protéger spécifiquement contre l'injection d'invites et la fuite de données en analysant et en évaluant les invites soumises par un utilisateur, et en bloquant l'exploitation de modèles et les tentatives d'extraction de données.
Enfin, Cloudflare développe des systèmes IA pour examiner les modèles de trafic spécifiques à chaque client et construire une base de référence de comportement normal, ce qui permettra de détecter toute anomalie dans les environnements, y compris les API, les courriels et l'accès des employés. Ce programme, appelé Defensive AI, vise à améliorer l'efficacité des solutions de sécurité grâce à l'intelligence artificielle.
L'école de code Holberton s'installe à Dijon, Fréjus et Rennes (2 min) Holberton School, une école d'informatique qui utilise la méthode d'apprentissage par pairs et n'exige pas de diplôme préalable, renforce sa présence en France avec l'ouverture de trois nouveaux campus à Dijon, Rennes et Fréjus. Ces nouvelles implantations visent à combler les lacunes en matière de compétences informatiques dans ces régions et à répondre aux besoins des entreprises locales. Les formations proposées durent de 9 à 36 mois et mènent à un diplôme de niveau Bac+4 reconnu par l'Etat. Holberton School a été fondée dans la Silicon Valley en 2015 par deux français et propose des formations sans condition de diplôme ni limite d'âge, avec un coût financé à 100% par des prêts remboursables une fois l'obtention d'un emploi. Actual, un spécialiste du marché de l'emploi en France, est partenaire de ces nouvelles implantations et interviendra sur des ateliers de création de CV et d'entretien ainsi que sur l'information relative aux secteurs IT et aux entreprises qui recrutent.
SAP tente encore de rassurer ses utilisateurs (4 min) L'utilisation de SAP S/4 Hana, que ce soit sur site ou via un service cloud de l'éditeur, reste le principal cheval de bataille de la société allemande. Cependant, les offres cloud telles que Rise with SAP et Grow with SAP sont également mises en avant par SAP. Le choix entre les différentes options (sur site, cloud privé ou public) détermine l'accès à l'innovation, qui est calé sur un rythme de 6 mois pour les offres sur le cloud de l'éditeur et s'aligne avec la fréquence des mises à jour des environnements SAP sur les déclinaisons sur site. Les mises à jour sont automatiques sur la version multitenant (Grow), tandis qu'elles restent à la main de chaque DSI dans l'offre Rise.
L'hybridation entre les systèmes déployés dans différentes activités et l'ERP coeur est possible grâce à ces décisions. Cela permet également d'envisager des scénarios d'enrichissement fonctionnel de S/4 on-premise avec des modules cloud, comme le Green Ledger de suivi des émissions carbone qui sera uniquement accessible sur le cloud, mais pourra s'interfacer avec différents systèmes sur site.
SAP étudie également les possibilités d'hybridation pour l'IA générative, une technologie plus adaptée à un modèle d'exploitation cloud et à des mises à jour fréquentes qu'un modèle on-premise. Cependant, déployer cette technologie sur des progiciels on-premise peut faire peser un risque d'effondrement des performances de ces systèmes, qui seront très sollicités.
Enfin, SAP a décidé de tout miser sur la norme européenne EUCS (European Union Cybersecurity Certification Scheme for Cloud Services) plutôt que sur le label SecNumCloud de l'Anssi pour son offre cloud en France.
🍵 Actualités securite
Arrêt définitif du support pour Windows 10 21H2 le 11 juin (1 min) Pour protéger les LLM, Cloudflare muscle son WAF (3 min) L'école de code Holberton s'installe à Dijon, Fréjus et Rennes (2 min) SAP tente encore de rassurer ses utilisateurs (4 min) Croissance atone du marché des appliances de sécurité au T4 2023 (2 min) HP à fond dans les PC dopés à l'IA (3 min)
🍵 Actualités le-monde-du-cloud-computing
SAP tente encore de rassurer ses utilisateurs (4 min) Highway 9 Networks apporte des réseaux 5G privés aux entreprises (5 min) Nutanix formalise le rachat des actifs de D2iQ (2 min)
🍵 Toutes les actualités :
Telex : Nijta lève 2 M€, Telegram envisage IPO, La CNIL distribue des amende (2 min) Arrêt définitif du support pour Windows 10 21H2 le 11 juin (1 min) Pour protéger les LLM, Cloudflare muscle son WAF (3 min) L'école de code Holberton s'installe à Dijon, Fréjus et Rennes (2 min) SAP tente encore de rassurer ses utilisateurs (4 min) La demande en développeur Java reste forte (2 min) Croissance atone du marché des appliances de sécurité au T4 2023 (2 min) Highway 9 Networks apporte des réseaux 5G privés aux entreprises (5 min) Meta poursuit un ancien dirigeant pour vol présumé d'informations confidentielles (3 min) Nutanix formalise le rachat des actifs de D2iQ (2 min) Grand Théma CIO/LMI : l'environnement, angle mort de la GenAI (5 min) Le centre de congrès RAI Amsterdam à l'heure de la 5G privée (3 min) HP à fond dans les PC dopés à l'IA (3 min)
🍵 "llm | cloud computing | ddos" - Google News
Flexera 2024 State of the Cloud: Cost optimisation, FinOps and GenAI key takeaways - CloudTech News 3 Cloud Computing Stocks to Buy for Long-Term Growth - InvestorPlace Oracle surges to record high as AI demand helps reignite cloud business momentum - Yahoo Finance Innovation unveiled: Snowflake and Nvidia on AI, data and cloud - SiliconANGLE News Bank Muamalat signs multi-year Google Cloud deal - Channel Asia Singapore Cloud Computing Leader Vultr Expands Executive Team to Address Growing AI Infrastructure and Enterprise Cloud ... - Business Wire HIMSS24: Google Cloud builds out gen AI capabilities - FierceHealthcare ORCL Stock Surge: Oracle's Focus on Cloud Infrastructure Paying Off - Value the Markets Technology pioneer Mike Stonebraker raises $8.5M to launch DBOS and radically transform cloud computing - PR Newswire Nvidia, Oracle, QMware tee up hybrid quantum-classical computing - FierceElectronics Wipro partners with Nutanix to launch new business unit - Channel Asia Singapore DBOS Cloud overturns database-on-OS conventions for speed - InfoWorld Oracle Posts Biggest Gain Since 2021 on Cloud Revenue Growth - Yahoo Finance
-
 @ 8fb140b4:f948000c
2023-11-10 12:00:40
@ 8fb140b4:f948000c
2023-11-10 12:00:40Intro
Nostrasia 2023, a vibrant unconference, was hosted in two bustling Asian cities: Hong Kong and Tokyo, Japan. Nostriches from around the world flocked to these destinations, eager to immerse themselves in local culture, savor the cuisine, and most importantly, enjoy each other's company in person. Tokyo's event, buzzing with energy, took place in Shibuya, a district renowned for its lively nightlife and abundance of bars, clubs, and restaurants. As is tradition with Nostr events, the atmosphere was charged with excitement, symbolized by the abundant purple and orange hues.
https://v.nostr.build/k7qV.mp4
Preparations
The journey to Nostrasia began right after Nostrica, with meticulous planning to ensure the perfect venue. It was a challenge to find a location that was both spacious and accessible, offering affordable accommodation options nearby. Our diligent volunteers in Japan scoured venues in Tokyo and Yokohama before selecting the ideal spot in Shibuya.



In the days leading up to the event, volunteers, both local and from afar, gathered at the venue. Their mission: to set up everything from audio-visual equipment to stages and decorations, ensuring a warm welcome for attendees on November 1st at 9:00 AM. Despite the time crunch, the spirit of cooperation and friendliness prevailed, making the preparation phase smooth and enjoyable.




Even amidst the busy setup, there was time for breaks and socialization, keeping everyone energized and focused on the mission at hand.




Day 1 (The Beginning)

No day at Nostrasia could start without a caffeine kick or a beverage of choice. The first day witnessed a steady influx of nostriches, filling the venue with excitement and anticipation.

The day offered a mix of activities: some attendees engaged in the presentations, others relaxed in the family-friendly area, and there were even recreational spaces for all ages to enjoy, including model train setups.


The setup was designed to welcome nostriches of all stripes, whether young or old, tech-savvy or not. It was a space where everyone could feel comfortable and included.



The day culminated in a grand welcome party, complete with drinks, MAGURO (Yellowfin tuna), and karaoke.
https://v.nostr.build/Mqqa.mp4
Day 2

Following a late night, the second day of the conference started a bit later, accommodating the nocturnal adventures of the attendees. The day was packed with fascinating talks, workshops, and plenty of opportunities for meet-ups and hugs.



 https://v.nostr.build/q3RM.mp4
https://v.nostr.build/q3RM.mp4An interesting discovery for me was the concept of air replies, a novel and visually engaging way to interact on social media.

Day 3 (Final)
The final day, starting late due to the previous night's festivities, was filled with a diverse range of presentations. Topics varied from non-technical perspectives on Nostr to in-depth technical workshops and discussions. #footstr

The day was brimming with a variety of presentations in both halls of the conference center. These ranged from insightful talks about Nostr from a non-technical perspective to more in-depth technical workshops and discussions.





 https://v.nostr.build/R98n.mp4
https://v.nostr.build/o5Xl.mp4
https://v.nostr.build/4A6W.mp4
https://v.nostr.build/R98n.mp4
https://v.nostr.build/o5Xl.mp4
https://v.nostr.build/4A6W.mp4The event concluded with heartfelt closing remarks from the organizers, filled with gratitude and appreciation for everyone's participation and effort.


Outro
Nostrasia 2023 was a resounding success, marked by a warm, friendly atmosphere that pervaded the entire event. While some had to depart immediately after, many stayed on to explore the wonders of Japan, carrying with them memories of an unforgettable gathering. The end. 🐶🐾🫡🫂

Footnotes
- For the list of notes published about the event, use #nostrasia hashtag.
- For the official Nostrasia profile, visit @npub1nstrcu63lzpjkz94djajuz2evrgu2psd66cwgc0gz0c0qazezx0q9urg5l
- Detailed conference schedule
- Official Webside
Other pictures and videos taken before, during, and after the event







-
 @ a5d8475e:df9ff32c
2024-03-13 05:55:36
@ a5d8475e:df9ff32c
2024-03-13 05:55:36With a plethora of house for sale in Wolverhampton and Tettenhall, prospective buyers are spoilt for choice. But amidst the sea of listings, how does one discern the exceptional from the ordinary?
Understanding Your Needs: The foundation of any successful property search begins with a clear understanding of one's requirements. Are you seeking a cozy apartment, a spacious family home, or perhaps a luxurious estate? Define your priorities, from the number of bedrooms and bathrooms to the preferred location and amenities. This clarity will serve as your compass, guiding you towards properties that align with your lifestyle and aspirations.
Exploring Wolverhampton: Nestled in the heart of the West Midlands, Wolverhampton boasts a rich tapestry of history, culture, and modern conveniences. From vibrant city center apartments to suburban retreats, the diversity of property for sale caters to a wide range of preferences. Whether you're drawn to the vibrant nightlife of Chapel Ash or the tranquility of Penn, each neighborhood offers its own unique charm and appeal.
Tettenhall's Tranquility: For those craving a quieter pace of life, the picturesque village of Tettenhall presents an enticing alternative. Steeped in tradition yet embracing modernity, Tettenhall exudes a timeless elegance that captivates residents and visitors alike. With its quaint cottages, leafy avenues, and close-knit community spirit, finding a houses for sale in tettenhall is akin to discovering a hidden gem nestled amidst the rolling hills of Staffordshire.
The Art of Property Hunting: Armed with your criteria and a sense of adventure, it's time to embark on the exhilarating journey of property hunting. Thanks to advancements in technology, the process has never been more accessible or efficient. Online platforms such as Rightmove and Zoopla offer a treasure trove of listings, allowing you to browse properties from the comfort of your own home. Take advantage of filters to narrow down your search, focusing on factors such as price range, property type, and desired features.
The Importance of Due Diligence: While the allure of glossy photos and enticing descriptions may be tempting, it's essential to approach the search with a critical eye. Conduct thorough research on each property of interest, scrutinizing factors such as its condition, location, and potential for future appreciation. Don't hesitate to enlist the services of a reputable real estate agent who can provide invaluable insights and guidance throughout the process.
Navigating the Negotiation Process: Having identified a property that ticks all the boxes, the next step is navigating the negotiation process. Familiarize yourself with market trends and comparable sales to ensure that your offer is fair and competitive. Be prepared to negotiate terms such as price, closing date, and any contingencies that may arise. Remember, patience and persistence are key virtues in securing the best possible outcome.
Closing the Deal: With negotiations successfully concluded, the final hurdle is the closing process. This entails a series of legal and financial steps to transfer ownership of the property from seller to buyer. Ensure that all necessary paperwork is in order, including contracts, inspections, and financing arrangements. Collaborate closely with your solicitor and mortgage lender to expedite the process and mitigate any potential obstacles.
Embracing Your New Home: As the keys to your new abode are ceremoniously handed over, take a moment to savor the culmination of your efforts. Whether it's a quaint cottage in Tettenhall or a chic apartment in Wolverhampton, your chosen property represents more than just bricks and mortar—it's a reflection of your dreams and aspirations. Embrace the opportunity to create cherished memories and carve out your own slice of paradise in the vibrant tapestry of the West Midlands.
In conclusion, the quest for the most outstanding results in a property for sale requires a blend of strategic planning, diligent research, and a dash of serendipity. Whether you're drawn to the bustling energy of Wolverhampton or the tranquil charm of Tettenhall, the perfect property awaits those with the vision to seek it out.
++LEARN MORE!++
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ aab1c430:e3b58632
2024-03-13 04:47:19
@ aab1c430:e3b58632
2024-03-13 04:47:19This is your new vault.
Make a note of something, [[create a link]], or try the Importer!
When you're ready, delete this note and make the vault your own.
- How about this external image ?

truth-or-dare:event type:card-draw timestamp:1708255295499 card: ^0 - How about this external image ?
-
 @ 2edbcea6:40558884
2023-10-30 14:06:48
@ 2edbcea6:40558884
2023-10-30 14:06:48Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
The #NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) (Proposed) NIP 96: File Storage Integration
As a reminder NIP 96 proposes a standard way for third party service providers to offer file storage for Nostr users. Standardization allows files to stay off relays but still be relatively cross compatible if users want to have files attached to notes show up in any Nostr client. It was initially implemented a few weeks ago with the Nostur and Coracle clients utilizing the open source Nostrcheck server by nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624
NIP 96 seems to be getting momentum; now the Nostur client has added integrated nostr.build file storage in a NIP 96 compatible way giving users more options! I hope it gets merged soon 💪
2) (Proposed) Update to NIP 72: Community Posts
This proposed update to Moderated Communities would allow clients to support using event kinds other than 1. Right now, posting on moderated communities (akin to subreddits) makes it so that all posts show up without context on most Nostr clients. Kind 1 events are like tweets, but posts in moderated communities are posted in a context that’s missing on clients like Damus or Amethyst.
This proposal would encourage moderated communities to publish using a different set of event kinds so the posts only show up in clients intended for moderated communities. It continues to gain momentum. nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 opened and closed a proposed change similar to this as this newsletter was being written, and instead threw some support onto this proposal.
This change would be reverse compatible with current Moderated Communities but still allow for cleaner feeds on clients based on their intended content focus.
Author: vivganes
Notable Projects
Zapple Pay’s lightning-based subscriptions ♻️
The team at Mutiny Wallet’s work on Zapple Pay has helped keep the flow of zaps unblocked since Apple’s capricious decisions to force Damus to disable Zaps. Now they’ve introduced “auto zapping” which is the ability to set up recurring payments (like subscriptions) in a self-sovereign way.
Zaps are great to show support, lightning-gated content is going to be helpful for content creators too, but unlocking subscriptions can truly help content creators make a living on Nostr denominated in the hardest money on Earth. This could be game changing as we’ll discuss later 😉
Authors: nostr:npub1u8lnhlw5usp3t9vmpz60ejpyt649z33hu82wc2hpv6m5xdqmuxhs46turz nostr:npub1t0nyg64g5vwprva52wlcmt7fkdr07v5dr7s35raq9g0xgc0k4xcsedjgqv & Paul Miller
Highlighter 2.0 📝
If you’re unfamiliar Highlighter is “A nostr client for your most valuable information. Your reading. Your notes. Your thoughts. A place to discover thoughtful, timeless content.” and nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft continues to improve it rapidly.
This latest release improves many aspects, mostly focused on making it THE best way to read, highlight, label, and save content that’s meaningful to you.
On top of that nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft has been improving the ability to make money as a content creator via an integration to “subscribe” to support Nostr content creators like you would on Patreon, as well as split zaps for content published via Highlighter.
If you’re not at least using Highlighter to discover content, you’re missing out. In my experience It is the highest concentration of content created by deep thinkers on the internet.
Latest conversations: Nostr adoption via content creators
Nostr’s main feature right now is that it is freedom tech. So far that hasn’t been enough of a draw for mass Nostr adoption.
We can keep building existing apps on Nostr but we’ll need something truly differentiated for people to rip and replace their content consumption habits with the ones run on Nostr.
We have some unique offerings (beyond censorship resistance) in emerging tech like Highlighter, DVMs, and Zaps. Based on what we’ve seen this week, I believe the next million monthly active users will be driven by content creators moving to Nostr.
Helping creators make money
Creators tend to flock to where they can make the most money. This is true of content creators and creators of software.
The fact that Apple apps make far more money than Android ones (despite Android dominating the smartphone market) explains why there are so many iPhone only apps.
Video creators and streamers move between Youtube and Twitch based on who is going to offer them the better income (viewership * take home rate).
If we can provide platforms where creators get to keep more of their money, it could be a game changer.
Locked into platforms
Content platforms provide two things: audience aggregation and payment aggregation.
Payments: The revenue per view of a youtube video is calculable and theoretically Youtube could pay creators their cut of the revenue per view. That isn’t practical because of transaction fees, they’d be larger than the actual transaction.
That’s why platforms serve as payment aggregators between the advertisers, themselves and the creators; settling accounts on a regular basis in amounts that make sense given the payments infrastructure available to them (credit cards and ACH).
Audience aggregation: Audiences go where creators are, but creators go where their audience is; the relationship is complicated. Sometimes individual creators have enough power to make or break a platform, but for platforms as big as Youtube that becomes much harder.
Take the example of Spotify and Joe Rogan. That move was worth it in terms of cash for Rogan, and it put Spotify on the map as a podcasting platform. It didn’t really hurt Youtube a whole lot.
The main advantage of using a content platform like Youtube, TikTok, etc is that the audience is there, you “just” need to capture them. The trade off is that you have very little power to set your price.
Audience non-portability: If a creator decides to switch from Youtube to Twitch, their followers don’t automatically port over. Creators with strong followings have an ok time when switching but not everyone has that luxury.
This leads to a power imbalance between creators and platforms. Platforms can strike down any creator they want; even though, without creators, these platforms would be nothing. In the absence of a better solution we’re stuck in this disadvantageous equilibrium.
Freeing creators with Nostr and Bitcoin
If Nostr + Bitcoin could offer creators ready-to-go solutions that would let creators keep significantly more of their revenue. It just has to be a big enough difference that people make the switch even when Bitcoin and Nostr are unfamiliar to them.
The magic combo of capabilities on Nostr would be: Nostr-based versions of all the usual apps for content consumption, as long as they’re high enough quality to not deter users. Content management tools that are familiar and quality enough for content creators. This would need to include robust file storage and streaming for content (text, video, audio, etc) Payment infrastructure in the apps (via Lightning) that have low fees and support the structures that are relevant for the content type (pay per article, pay per view, streaming sats as you listen, subscriptions, etc) Lowest-common-denominator Nostr onboarding. Imagine an end-to-end encrypted Nostr key custodian, so users that are intimidated by keypairs could have a familiar login with email and password.
In this world, new Nostr users that were asked to join by their favorite creator may never interact with the most common clients on Nostr today. They may set up a Nostr user via some “Login with Nostr” solution and then they only interact with the Nostr versions of Twitch, Youtube, Substack, etc.
If the switch is painless for users and creators and the creators make more money, it’s a no-brainer for creators to try out. If it works for them, more will come.
Taylor Swift and Grimes are good people to aim for. Both have enough autonomy to experiment with any platform they want, and both have fought to maximize artists’ take home pay. Can you imagine if we could get every Swiftie on Nostr’s version of Spotify?
Why hasn’t this happened yet?
This sounds like “value for value” right? Many talented builders and creators have attempted to crack the “value for value” nut, but something hasn’t clicked yet for mass adoption. The missing link, in my opinion, is the lack of audience portability and how that affects payments.
Value for value (streaming sats for podcasts, or paying to unlock one article at a time) requires some storage of who bought access to the content. Otherwise if you switch devices the content platform won’t know you already purchased access. Without Nostr that means signing up for that particular content app and it’s a high bar to start paying for content.
With Nostr, you can login using your Nostr keys and purchase access on any Nostr-based app, using any Lightning wallet, and that access can be attached to your Nostr pub key. It lowers the barrier for users to start paying, which means content creators capture more value.
For some kinds of content, I think all the legos are there for a creator-friendly platforms. With the recent Mutiny wallet announcement of lightning-based subscriptions, there’s no reason not to build a Nostr-based Patreon or Substack. I’ve also seen some work on ways to Zap to unlock content, making the dream of “pay per article” possible.
The last piece missing for a truly seamless on-ramp would be one of these end-to-end encrypted Nostr key custodians. That way clients could offer a “login with Nostr” button and lower the barrier for new users even further.
The race to zero take rate
Nostr naturally combats monopolies (at least for clients at this point). The reason that platforms like Youtube and Twitch have a 20-60% take rate is because they’re monopolistic. They sit on their thrones because no one has yet solved the issue of audience aggregation and portability. Nostr breaks that model.
Once creators use Nostr-based platforms, they can switch at nearly no cost. The content is theirs, and the followers are universal, so they can move to a different platform that has a lower take rate without risking their income. They don’t even have to switch platforms at all if their content is stored and unlocked via events on the Nostr Relays themselves, since those are universal across all Nostr clients.
Ideally there would be third parties that host big files (PDFs, Videos, Audio, etc) which creators pay directly. Then these content clients are simply user interfaces for users to upload and consume content. Hell, even logging in is solved by the Nostr protocol itself, and maybe another third-party login provider). The scope of what these platforms need to build and maintain is small; running them will be pretty cheap compared to running Youtube or Patreon.
At first there may be only a few Nostr-based apps because there will be some economies of scale, but over time competition will kick off a race to the bottom. Clients will eventually only be able to demand a take rate that covers operating their business (build the app, maybe offering the file hosting/streaming infrastructure, etc).
What a future
In this future, platforms have less ability to coerce creators and take their income. Platforms will have a hell of time censoring content creators. Users will get more choice on their experience and their algorithms when consuming content. And the adoption of Bitcoin as a medium of exchange would explode.
It feels like we’re on the cusp of something incredible in the Nostr-verse.
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome at nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ fa0165a0:03397073
2023-10-12 16:40:43
@ fa0165a0:03397073
2023-10-12 16:40:43Probability theory is the study of random phenomena. This post is a pilot post for potentially further posting in this series. Feedback appreciated. Introduction
Probability theory is the study of random phenomena. It is used in many fields, such as statistics, machine learning, and finance. It is also used in everyday life, for example when playing games of chance, or when estimating the risk of an event. The most classic example is the coin toss, closely followed by the dice roll.
When we toss a coin, the result is either heads or tails. In the case of an ideal coin, the “random trail” of tossing the coin has an equal probability for both outcomes. Similarly, for a die roll of a fair dice, we know that the probability for each outcome is 1/6. In the study of probability we dive deep into the mathematics of these random phenomena, how to model them, and how to calculate the probability of different events. To do this in precise terms, we define words and concepts as tools for discussing and communicating about the subject.
This is the first of what I expect to be a 15 part series of my lecture & study notes from my university course in probability theory MT3001 at Stockholm University. References to definitions and theorems will use their numeration in the course literature, even if I may rephrase them myself. The book I’ve had as a companion through this course is a Swedish book called Stokastik by Sven Erick Alm and Tom Britton; ISBN:978–91–47–05351–3. This first module concerns basic concepts and definitions, needed for the rest of the course. The language of Probability theory
An experiment is a process that produces a randomized result. If our experiment is throwing a die, we then have the following: The result of throwing the die is called an outcome, the set of all possible outcomes is called the sample space and a subset of the sample space is called an event. We will use the following notation:
outcome is the result of an experiment, denoted with a small letter, ex. 𝑢₁, 𝑢₂, 𝑢₃, … event is the subset of the sample space, denoted with a capital letter, ex. 𝐴, 𝐵, 𝐶, … sample space is the set of all possible outcomes of an experiment, denoted Ω.Adding numbers to our dice example, we have the sample space Ω = {𝟏,𝟐,𝟑,𝟒,𝟓,𝟔} containing all the possible events 𝑢₁=𝟏, 𝑢₂=𝟐, 𝑢₃=𝟑, 𝑢₄=𝟒, 𝑢₅=𝟓 and 𝑢₆=𝟔. And we could study some specific sub events like the chance of getting an even number, 𝐴={𝟐,𝟒,𝟔}, or the chance of getting a prime number, 𝐵={𝟐,𝟑,𝟓}. As it happens, the probability of both 𝐴 and 𝐵 is 50%. Sample space
The sample space is the set of all possible outcomes of an experiment. It is denoted Ω. And there are two types of sample spaces, discrete and continuous. A discrete sample space is a finite or countably infinite set, and all other kind of sample spaces are called continuous.
The coin toss and the dice roll are both examples of discrete sample spaces. Studying a problem, like the temperature outside, would in reality require a continuous sample space. But in practice, we can often approximate a continuous sample space with a discrete one. For example, we could divide the temperature into 10 degree intervals, and then we would have a discrete sample space.
Remember that continuous sample spaces exist, and expect more information about them in later modules. For starters, we focus on discrete sample spaces. Set Theory notation and operations
When talking about probabilities we will arm ourselves with the language of “set theory”, it is a crucial tool for the study of probability. Feeling comfortable with the subject of set theory since before is useful, but not necessary. I will try to explain the concepts as we go along.
Even tough the events from the dice rolls are represented by numbers, it is important to note that they aren’t numbers, but rather elements. This might become more clear if we alter our example to be a deck of cards. This deck of cards have four suits Ω = {♥, ♠, ♦, ♣ } and in our experiments we draw a card from the deck and look at the suit. It’s here very obvious that we can’t add or subtract the different events with each other. But we do have the operations of set theory at our disposal. For example, if 𝐴 is the event of drawing a red card and 𝐵 is the event of drawing spades ♠, we can use the following notation: Set theory operations
Union: 𝐴 ∪ 𝐵 = {♥, ♦, ♠}, the union of 𝐴 and 𝐵. The empty set: ∅ = {}, the empty set. A set with no elements. Intersection: 𝐴 ∩ 𝐵 = ∅, the intersection of 𝐴 and 𝐵. This means that 𝐴 and 𝐵 have no elements in common. And we say that 𝐴 and 𝐵 are disjoint. Complement: 𝐴ᶜ = {♠, ♣}, the complement of 𝐴. Difference: 𝐴 ∖ 𝐵 = {♥, ♦}, the difference of 𝐴 and 𝐵. Equivalent to 𝐴 ∩ 𝐵ᶜ. The symbol ∈ denotes that an element is in a set. For example, 𝑢₁ ∈ Ω means that the outcome 𝑢₁ is in the sample space Ω. For our example: ♥ ∈ 𝐴 means that the suit ♥ is in the event 𝐴.Venn diagram
A very useful visualization of set theory is the Venn diagram. Here is an example of a Venn diagram in the picture below:
In the above illustration we have: Ω = {𝟏,𝟐,𝟑,𝟒} and the two events 𝐴={𝟐,𝟑} and 𝐵={𝟑,𝟒}. Notice how the two sets 𝐴 and 𝐵 share the element 𝟑, and that all sets are subsets of the sample space Ω. The notation for the shared element 𝟑 is 𝐴 ∩ 𝐵 = {𝟑}. Useful phrasing
The different set notations may seem a bit abstract at first, at least before you are comfortable with them. Something that might be useful to do is to read them with the context of probabilities in mind. Doing this, we can read some of the different set notations as follows:
𝐴ᶜ, “when 𝐴 doesn’t happen”. 𝐴 ∪ 𝐵, “when at least one of 𝐴 or 𝐵 happens”. 𝐴 ∩ 𝐵, “when both 𝐴 and 𝐵 happens”. 𝐴 ∩ 𝐵ᶜ, “when 𝐴 happens but 𝐵 doesn’t happen”.The Probability function
Functions map elements from one set to another. In probability theory, we are interested in mapping events to their corresponding probabilities. We do this using what we call a probability function. This function is usually denoted 𝑃 and have some requirements that we will go through in the definition below.
This function take events as input and outputs the probability of that event. For the example of a die throw, if we have the event 𝐴={𝟐,𝟒,𝟔}, then 𝑃(𝐴) is the probability of getting an even number when throwing a fair six sided dice. In this case 𝑃(𝐴)=1/2=𝑃(“even number from a dice throw”), you’ll notice that variations of descriptions of the same event can be used interchangeably.
The Russian mathematician Andrey Kolmogorov (1903–1987) is considered the father of modern probability theory. He formulated the following three axioms for probability theory: Definition 2.2, Kolmogorov’s axioms
A real-valued function 𝑃 defined on a sample space Ω is called a probability function if it satisfies the following three axioms: 𝑃(𝐴) ≥ 𝟎 for all events 𝐴. 𝑃(Ω) = 𝟏. If 𝐴₁, 𝐴₂, 𝐴₃, … are disjoint events, then 𝑃(𝐴₁ ∪ 𝐴₂ ∪ 𝐴₃ ∪ …) = 𝑃(𝐴₁) + 𝑃(𝐴₂) + 𝑃(𝐴₃) + …. This is called the countable additivity axiom.From these axioms it’s implied that 𝑃(𝐴) ∈ [𝟎,𝟏], which makes sense since things aren’t less than impossible or more than certain. As a rule of thumb, when talking about probabilities, we move within the range of 0 and 1. This lets us formulate the following theorem: Theorem 2.1, The Complement and Addition Theorem of probability
Let 𝐴 and 𝐵 be two events in a sample space Ω. Then the following statements are true: 1. 𝑃(𝐴ᶜ) = 𝟏 — 𝑃(𝐴) 2. 𝑃(∅) = 𝟎 3. 𝑃(𝐴 ∪ 𝐵) = 𝑃(𝐴) + 𝑃(𝐵) — 𝑃(𝐴 ∩ 𝐵)Proof of Theorem 2.1
𝑃(𝐴 ∪ 𝐴ᶜ) = 𝑃(Ω) = 𝟏 = 𝑃(𝐴) + 𝑃(𝐴ᶜ) ⇒ 𝑃(𝐴ᶜ) = 𝟏 — 𝑃(𝐴)
This simply proves that the probability of 𝐴 not happening is the same as the probability of 𝐴 happening subtracted from 1.
𝑃(∅) = 𝑃(Ωᶜ) = 𝟏 — 𝑃(Ω) = 𝟏 — 𝟏 = 𝟎
Even though our formal proof required (1) to be proven, it’s also very intuitive that the probability of the empty set is 0. Since the empty set is the set of all elements that are not in the sample space, and the probability of an event outside the sample space is 0.
𝑃(𝐴 ∪ 𝐵) = 𝑃(𝐴 ∪ (𝐵 ∩ 𝐴ᶜ)) = 𝑃(𝐴) + 𝑃(𝐵 ∩ 𝐴ᶜ) = 𝑃(𝐴) + 𝑃(𝐵) — 𝑃(𝐴 ∩ 𝐵)
This can be understood visually by revisiting our Venn diagram. We see that the union of 𝐴 and 𝐵 has an overlapping element 𝟑 shared between them. This means that purely adding the elements of 𝐴={𝟐,𝟑} together with 𝐵={𝟑,𝟒} would double count that shared element, like this {𝟐,𝟑,𝟑,𝟒}, since we have two “copies” of the mutual elements we make sure to remove one “copy” bur removing 𝑃(𝐴 ∩ 𝐵)={𝟑} and we get 𝑃(𝐴 ∪ 𝐵)={𝟐,𝟑,𝟒}. We may refer to this process as dealing with double counting, something that is very important to have in mind when dealing with sets.
Two interpretations of probability that are useful and often used are the frequentist and the subjectivist interpretations. The frequentist interpretation is that the probability of an event is the relative frequency of that event in the long run. The subjectivist interpretation is that the probability of an event is the degree of belief that the event will occur, this is very common in the field of statistics and gambling. For the purposes of study it’s also useful to sometimes consider probabilities as areas and or masses, this is called the measure theoretic interpretation. Don’t let that word scare you off, in our context it’s just a fancy way of drawing a parallel between areas and probabilities. Think area under curves, and you’ll be fine.
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 000002de:c05780a7
2024-03-13 03:23:14
@ 000002de:c05780a7
2024-03-13 03:23:14I've been going through Base58's bitcoin dev course and I am enjoying it quite a bit. For me, I think its the combination of the various technologies. The deeper I get into it the more respect I have for Satoshi and the developers that have built bitcoin. It may be old news to those of you that work on bitcoin projects every day but I'm pretty excited about how it all works still.
-
 @ 7f5c2b4e:a818d75d
2023-09-27 08:25:11
@ 7f5c2b4e:a818d75d
2023-09-27 08:25:11What is Obsidian?
Obsidian.md is a versatile and powerful note-taking and knowledge management application that's gained immense popularity among users seeking a robust digital tool for organizing their thoughts, ideas, and information.
Obsidian boasts an array of features and benefits that can't all be covered in a single article. Instead, this #guide focuses on a unique, yet potent use case that has recently emerged - the ability to publish #Nostr notes and long-form posts directly from the app.
This capability has been made feasible through the complementary nature of Obsidian and Nostr. Obsidian is an open-source software with a thriving community and extensive support for custom plugins. On the other hand, Nostr is an open protocol with a rapidly expanding suite of tools, simplifying the integration of Nostr across various corners of the Internet. The plugin I will cover in this guide is called Nostr Writer.
Obsidian link: obsidian://show-plugin?id=nostr-writer
GitHub: https://github.com/jamesmagoo/nostr-writer
Developer: nostr:npub10a8kw2hsevhfycl4yhtg7vzrcpwpu7s6med27juf4lzqpsvy270qrh8zkw
But before we dive in, let me share some thoughts on why should one use Obsidian to publish long-form posts (and potentially even short notes) on Nostr.
Why post with Obsidian?
This is a question that naturally comes to mind: "Why use Obsidian to publish on Nostr when the legendary Nostr developers have already set up all the necessary infrastructure for browser-based publishing?" Well, there are several reasons:
-
Native Markdown Support: To begin, Obsidian employs plain text Markdown formatting for notes, just like all Nostr-based blogging platforms. This makes it an ideal choice for creating, formatting, and editing Nostr posts.
-
Illustrative Preview: While other blogging platforms offer preview tools, Obsidian has perfected this feature. It provides a beautifully customizable preview window that can be positioned anywhere in your workspace, allowing you to visualize how formatting, media, and embeds will appear in the published post[^1].
-
State-of-the-Art Flexibility: Since 2020, Obsidian has continuously improved the way writers interact with it. What sets it apart is not only the dedicated team but also its thriving community, all contributing to its refinement. Obsidian supports an extensive array of plugins, shortcuts, and hotkeys, offering unparalleled flexibility and customization. Comprehensive documentation and a ton of videos and even courses on YouTube provide a wealth of information to tailor Obsidian to your preferences.
-
Boosted Productivity: The Nostr Writer plugin is a game-changer for power users of Obsidian. If you're already using Obsidian for note-taking, employing this tool to publish your notes on Nostr is a no-brainer. If you haven't explored it yet, I strongly recommend giving it a try. It has the potential to transform how you think, plan, and structure your ideas for the better. Trying it for broader objectives will help you appreciate how well it complements Nostr.
-
Distraction-Free Composition: While you may disagree, browsers can be a significant source of distraction, with constant alerts, notifications, and blinking extensions. Composing within Obsidian offers a tranquil, clutter-free experience, fostering focus and productivity.
-
Local Record Keeping: Thanks to Nostr Writer, Obsidian keeps a local record of events you published to Nostr in a JSON file on your computer. Your long-form posts are also securely stored in the
.mdformat on your machine, just like all the Obsidian notes you create. On top of that a separate tab holding all of your long-form posts posted via Obsidian is created.
nostr: note1z70v5fsty7v7kaaslsv3ckru50nxym32a62kgx0z7cjdure39hps363sh7
- Drafts You Can Count On: Drafts are often a weak point in long-form platforms. Even though Nostr developers have addressed some of these concerns, the "vanishing drafts problem" still lingers. Obsidian, designed with data safety in mind, stores all your notes locally on your device. Whether you open your laptop tomorrow or in a year, your files will be there, safe from external disruptions. For added redundancy, consider using Obsidian Sync, which encrypts and synchronizes your notes across your chosen devices.
While there are more benefits to utilizing Obsidian for both Nostr publishing and in your general workflow, these reasons should provide a solid understanding. Now, let's shed some light on the Nostr Writer plugin.
Nostr Writer
I stumbled upon Obsidian not too long ago, all thanks to nostr:npub1zvvv8fm7w2ngwdyszg3y6zgp6vwqlht8zrr8wcmjaxjecrvpjfwsd0zs7w. He's also the one who introduced me to the Nostr Writer plugin. Until recently, I primarily used Obsidian "as intended" - for documenting my thoughts and writing articles. What I found especially convenient was using it to compose long-form Nostr posts. And then, the revelation came when I discovered the Nostr Writer plugin - it transformed the experience. No more copy-pasting and meticulous adjustments were required; I can simply compose, add a cover image and description, and publish - it's as straightforward as that.
As I mentioned earlier, Obsidian boasts a vast library of community-driven plugins. To begin using Nostr Writer, simply install the plugin from the "Community plugins" section and navigate to the plugin settings to set up your publishing workflow.
You can install the plugin by clicking this link while having Obsidian open on your device, or by going to the "Community plugins" tab in the settings and typing "Nostr" in the search field.
Once the plugin is installed, you'll need to customize it to enable publishing your Obsidian notes to Nostr.
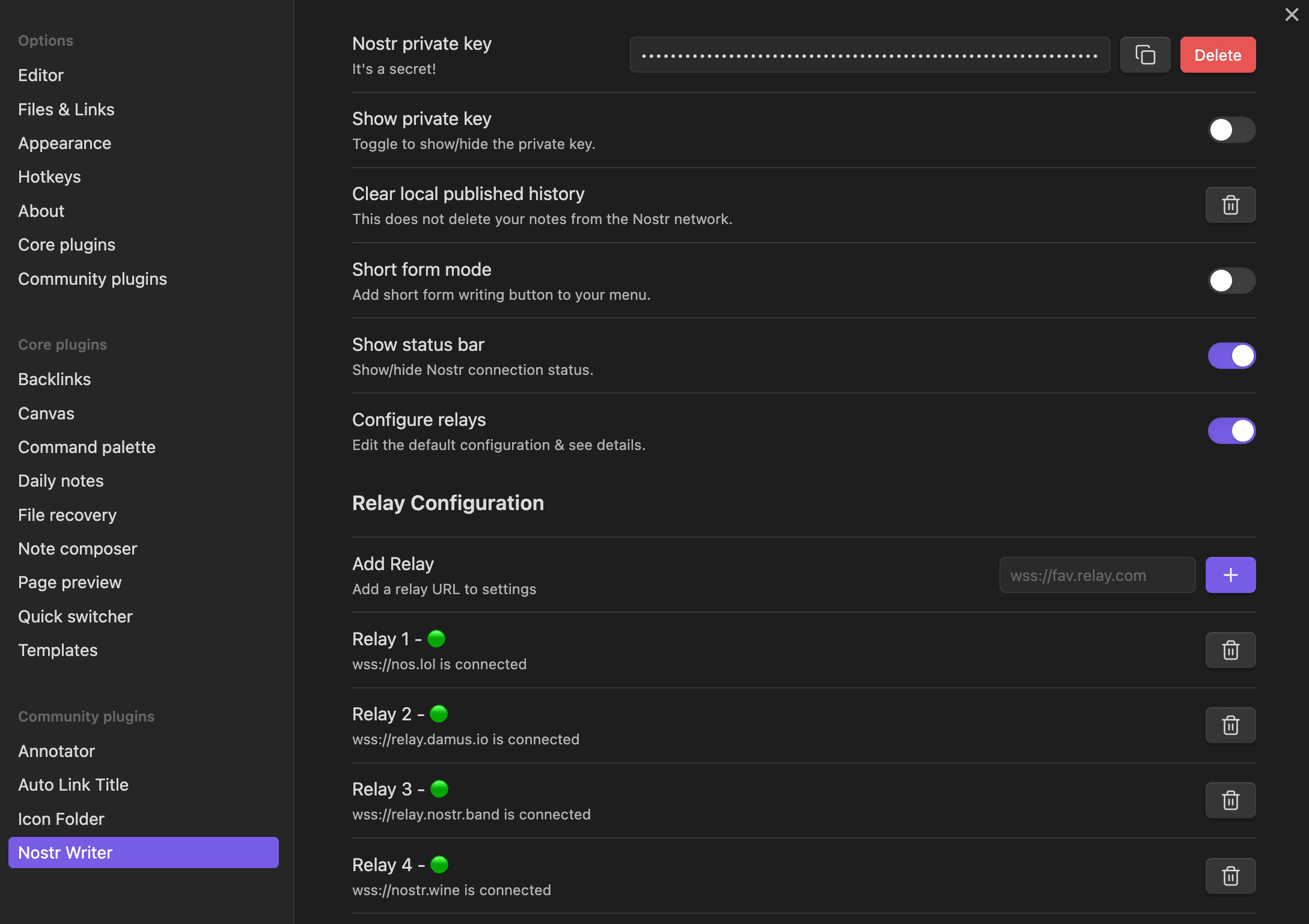
Primarily, you'll need to paste your private key (
nsec) into the corresponding field. Additionally, I recommend configuring your relays to ensure the widest reach for your posts. If you're unfamiliar with Nostr relays or wish to enhance your understanding, you can explore my relay guide here.Many Nostr users naturally have concerns about sharing their private keys with apps. In this case, worry not. Your private key is stored exclusively on your local device and never leaves it. More details can be found here. Even if you use Obsidian sync to keep your notes updated across multiple devices, all information is locally encrypted and safeguarded by the password of your choice. Neither the Obsidian developers nor the plugin developer have access to your files. For additional information, you can refer to the "Security and privacy" section of the Obsidian documentation.
As you can see in the screenshot above, Nostr Writer also provides the option to post short notes. By toggling the corresponding slider, a pencil icon will appear on the sidebar, allowing you to post short notes without leaving Obsidian:
While I wouldn't claim that the plugin surpasses any of the "Twitter-like" Nostr clients, it can prove handy if you're already working within Obsidian and wish to share a quote or any other snippet of information you've come across in your notes.
Publishing
Publishing posts with Nostr Writer is straightforward. If you're already familiar with Obsidian, composing and formatting will be a total breeze, and the actual posting process is no different from posting with Habla, or any other Nostr-native blogging platform.
The only thing that may differ from some Nostr platforms is that Nostr Writer does not provide a specific field for adding hashtags when publishing. Instead, you should incorporate them directly into your text.
Once you've finished crafting your blog post, simply click on the upload icon in the side menu to specify the title, add a summary, and attach a cover image.
When you're ready, click "Confirm and Publish."
Another point to note is the relays indicator in the bottom-left corner. Relay connection may get interrupted if left inactive for a while, but a simple click on the widget will reconnect you to Nostr in no time.
Practice makes perfect
As I mentioned earlier, I find this approach to publishing long-form posts on Nostr the most efficient and convenient. Moreover, there are numerous improvements in the pipeline for the plugin, which is nothing short of exciting.
With that said, it's worth visiting Habla after publishing your post to double-check that everything appears as intended. Initially, you might encounter some formatting peculiarities that you'll need to get accustomed to, but with practice, you'll effortlessly master them. Soon, you won't even have to worry about how the article looks in Nostr clients because you'll be able to visualize every single aspect of your post in your mind.
I hope you found this guide useful and consider utilizing Obsidian for both publishing Nostr posts and elevating your overall productivity. If that's the case, please show your support for nostr:npub10a8kw2hsevhfycl4yhtg7vzrcpwpu7s6med27juf4lzqpsvy270qrh8zkw' work.
Please feel free to share your thoughts and suggestions—I'm always eager to hear from you! Don't forget that my Habla blog page contains a ton of Nostr guides, so you can find answers to almost any Nostr-related questions. If there are specific topics you believe I should cover, do let me know.
See you on the other side of the Nostr rabbit hole.
Tony
P.S. This post was composed, formatted and published to Nostr from Obsidian. No Nostr-related blogging platform was used.
[^1]: Nostr-native syntax, including tagging and Nostr-events embeds, is an exception here. Not all platforms on the Internet currently support Nostr syntax standards like tagging users with their npub, as in
nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7, so it may not be available for preview. However, tags and embeds will be displayed on Habla. You can learn more about Habla's features in my previous guide here. -
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 78733875:4eb851f2
2023-08-17 14:23:51
@ 78733875:4eb851f2
2023-08-17 14:23:51After announcing our first wave of grants for bitcoin[^fn-btc] and nostr[^fn-nostr] projects, we are pleased to announce an additional wave of grants for open-source projects in the space:
[^fn-btc]: First Wave of Bitcoin Grants [^fn-nostr]: First Wave of Nostr Grants
- BDK
- LNbits
- Watchdescriptor
- Stratum V2 Testing \& Benchmarking Tool
- Fedimint Modules and Resources
- Amber: Nostr Event Signer
- Nostr UI/UX Development
- Nostr Use-Case Exploration \& Education
The first five grants are sourced from our General Fund, the last three—being nostr projects—from our Nostr Fund. This brings the total number of OpenSats grants to 41, adding to the grants we previously announced in July.
Once again, let's take a closer look at each of the projects to see how they align with the OpenSats mission.
BDK
Bitcoin Development Kit (BDK) is a set of libraries and tools that allows you to seamlessly build cross-platform on-chain bitcoin wallets without having to re-implement standard bitcoin data structures, algorithms, and protocols. BDK is built on top of the powerful rust-bitcoin and rust-miniscript libraries and adds features for managing descriptor-based wallets, syncing wallets to the bitcoin blockchain, viewing transaction histories, managing and selecting UTXOs to create new transactions, signing, and more. The core BDK components are written in Rust, but the team also maintains Kotlin and Swift language bindings for use in mobile projects. There are also Python bindings, and React Native and Flutter support is being actively developed.
Repository: bitcoindevkit/bdk
License: Apache 2.0 / MITLNbits
LNbits is used by a multitude of projects in the bitcoin space, especially as part of their lightning payments stack. Being easy to build on through its extension framework, LNbits has been pioneering various cutting-edge solutions and experiments in the world of bitcoin, lightning, and nostr.
The project has a thriving maker community building various hardware devices such as Lightning ATMs, point-of-sale devices, DIY hardware wallets, and nostr signing devices. The modular design of LNbits makes it attractive to users and tinkerers alike, as its plugin architecture makes it easy to extend and understand.
Repository: lnbits/lnbits
License: MITWatchdescriptor
watchdescriptoris a CLN plugin written in Rust that connects a business's treasury wallet to its CLN node. It utilizescln-pluginand the BDK library to track coin movements in registered wallets and report this information to thebookkeeperplugin.The plugin enables businesses to design a complete treasury using Miniscript and import the resulting descriptor into CLN. Since
bookkeeperalready accounts for all coin movements internal to CLN, this plugin is the last piece businesses need in order to unify all their bitcoin accounting in one place. This enables businesses to account for all inflows and outflows from their operations, streamlining tax reporting and financial analysis.The
watchdescriptorproject is part of a broader vision to transform the lightning node (particularly CLN) into a financial hub for businesses, enabling them to conduct operations without reliance on any third parties.Repository: chrisguida/watchdescriptor
License: MITStratum V2 Testing & Benchmarking Tool
The Stratum V2 Testing & Benchmarking Tool allows the bitcoin mining industry to test and benchmark Stratum V2 performance against Stratum V1. The tool supports different mining scenarios to help miners make informed decisions and evaluate their profitability. The goal of the project is to motivate miners to upgrade to Stratum V2, increasing their individual profits and making the Bitcoin network more resilient in the process.
Repository: stratum-mining/stratum @GitGab19
License: Apache 2.0 / MITFedimint Modules and Resources
Fedimint is a federated Chaumian e-cash mint backed by sats with deposits and withdrawals that can occur on-chain or via lightning. It can be understood as a scaling and privacy layer as well as an adoption accelerator for Bitcoin.
The goal of this particular project is to improve the Fedimint UI and develop free and open resources for developers and "Guardians" to enable more people to run and develop on Fedimint.
Repository: fedimint/ui @EthnTuttle
License: MITAmber: Nostr Event Signer
Amber is a nostr event signer for Android. It allows users to keep their
nsecsegregated in a single, dedicated app. The goal of Amber is to have your smartphone act as a NIP-46 signing device without any need for servers or additional hardware. "Private keys should be exposed to as few systems as possible as each system adds to the attack surface," as the rationale of said NIP states. In addition to native apps, Amber aims to support all current nostr web applications without requiring any extensions or web servers.Repository: greenart7c3/Amber
License: MITNostr UI/UX Development
The goal of this project is to help improve the UI/UX of major nostr clients, starting with Gossip and Coracle, emphasizing the onboarding process as well as usability and accessibility. One part of onboarding is solving the discoverability problem that nostr has in the first place. Solving the problem of jumping in and out of the nostr world is what motivated the development of
njump, which was redesigned as part of these efforts and is now live at nostr.com.In addition to client-specific improvements, generic design modules and learnings will be incorporated into the Nostr Design project for others to use.
Activity: github.com/dtonon @dtonon
License: MITNostr Use-Case Exploration & Education
As of today, most nostr clients implement social media applications on top of the nostr protocol. However, nostr allows for various use cases, many of which go beyond social media. Two examples are Listr and Ostrich, a list management tool and job board, respectively.
In addition to use-case exploration, this project will continue to educate users and developers alike, be it via Nostr How or various video series, e.g., explaining how to build upon NDK.
Activity: github.com/erskingardner @jeffg
License: MIT / GPL-3.0 / CC BY-NC-SA 4.0
We have more grants in the pipeline and will provide funding for many more projects in the future. Note that we can only fund those projects which reach out and apply. If you are an open-source developer who is aligned with our mission, don't hesitate to apply for funding.
-
 @ a012dc82:6458a70d
2024-03-13 01:33:27
@ a012dc82:6458a70d
2024-03-13 01:33:27Table Of Content
-
Content
-
Introduction
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
When Bitcoin was first distributed globally, more than a decade ago, there were high hopes that it would usher in a paradigm shift inside the global financial system. However, that revolution has not even come close to taking place as of yet. The first decade of the cryptocurrency's existence has been turbulent, defined by scandals, errors, and extreme price fluctuations. As of the end of October 2022, the price of one bitcoin was around $19,500, which is a decline of over 69% from its all-time high of over $63,000 in April 2021.
However, investors and aficionados of the cryptocurrency have increased the amount of hope they have for the future of the asset. As a result, the next decade may prove to be a watershed moment for Bitcoin and cryptocurrencies in general.
A Compromised Vision
As stated by its pseudonymous creator, Satoshi Nakamoto, in a foundational paper published on October 31, 2008, the day of its introduction, Bitcoin was intended to be a borderless and decentralized alternative to government- and central bank-controlled fiat currencies.Within the Bitcoin network, reaching consensus over a transaction does not rely on the participation of any third-party intermediaries. In its place, the verification and authentication of a transaction is carried out with the assistance of the blockchain, which is a peer-to-peer network of systems that includes electronic ledgers.
In order to make his case for eliminating mediation and replacing it with a peer-to-peer network, Nakamoto wrote, "The cost of mediation increases transaction costs, limiting the minimum practical transaction size and cutting off the possibility for small and casual transactions." This was done to argue in favor of the removal of mediation and the implementation of the peer-to-peer network.
After fourteen years, though, it feels as if that initial idea has been watered down. The centralization movement has replaced the decentralization movement. Investors with significant cryptocurrency holdings are referred to as "whales," and it is thought that they influence the price of bitcoin in the markets. Because of the increased productivity of vast mining farms, the democratization of the process of producing money via mining has been sacrificed. Scalability problems with Bitcoin's underlying technology have led to a long history of splits and new cryptocurrencies.
But the development of a flourishing and active ecosystem for cryptocurrencies more than makes up for these drawbacks. Even though cryptocurrencies didn't exist ten years ago, the market for them is now worth a staggering $937.5 billion.
Since Bitcoin came out, more than 20,000 other digital currencies have been made and are now being traded on different platforms.
Blockchain, which has just become a common phrase, is now being promoted as a solution to difficult issues. After some initial reluctance, institutional investors are also making a beeline for crypto-assets as a form of investment. [Cryptocurrency]
Evaluating the Next Decade
The next 10 years might end up being of critical significance to the development of Bitcoin. Aside from the revolutions happening in the financial ecosystem, there are a handful of other areas of Bitcoin's ecosystem that investors should focus their attention on.
At the moment, Bitcoin is in a transitional state between functioning as a store of value and a medium for conducting day-to-day transactions. Even though governments all over the world, including Japan's, have accepted bitcoin as a valid way to pay for goods, institutional investors are eager to get in on the action and profit from the volatile price of bitcoin.
Both of these incidents, however, have been stopped from taking place due to issues with scale and security. According to Chakib Bouda, Chief Technology Officer of Rambus, a company that specializes in payments, "[A]rguably the major faults for Bitcoin and other cryptocurrencies throughout the past years lay with security." The amount of Bitcoin and other cryptocurrencies that hackers have stolen from exchanges is estimated to be in the billions of dollars. Bouda is alluding to this amount. According to him, the mainstream acceptance of Bitcoin will follow after establishing a safe Bitcoin ecosystem. He said, "We think Bitcoin will become very popular and have a different reputation in the next ten years."
There is no widespread adoption of Bitcoin as a payment method (or, for that matter, an increase in Bitcoin's appeal as an asset class) unless there are technical advancements made inside Bitcoin's ecosystem. The blockchain that underpins Bitcoin has to be able to process millions of transactions in a very short amount of time for it to be taken seriously as a potential investment asset or method of payment. Scalability in its operations is promised by a number of different technologies, such as the Lightning Network. Bitcoin Cash and Gold are two examples of new cryptocurrencies that have emerged due to the hard forks of the Bitcoin blockchain. The goal of making these new cryptocurrencies was to change how the ecosystem works so that it can handle a larger number of transactions faster.
Along with the advancements made to Bitcoin's blockchain in 2018, the Chief Technology Officer of Ripple, David Schwartz, likened Bitcoin to Ford's Model T. A complete ecosystem, from roads to petrol stations, arose to service the vehicle as it became more popular. The inventor of the automobile hailed this revolution in transportation. Thanks to all the attention from the media over the past few years, the seeds of an ecosystem have been planted.
The ecosystem is expected to grow as new regulations are developed to keep pace with technological advances. Schwartz predicts that the next ten years will see "an explosion of low-cost, high-speed payments that will change value exchange in the same way that the Internet changed information sharing."
In 2021, the price of Bitcoin reached a high of $60,000 before dropping to a low of roughly $40,000. The situation was much worse in 2022, when the price of Bitcoin dropped to a low of $18,500. But big banks are still paying attention to cryptocurrencies. Goldman Sachs recently reopened its trading desk for cryptocurrencies, and BNY Mellon just started offering custody services for digital currencies.
According to Citi, Bitcoin has the potential to become the preferred currency for global commerce. This occurs as a result of the fact that both PayPal (PYPL) and Tesla (TSLA) made investments in cryptocurrencies at the beginning of 2021. Tesla made a purchase of Bitcoin for $1.5 billion, while PayPal made an offer to acquire the cryptocurrency custodian Curv. Citi observed that the future of Bitcoin is still fraught with a great deal of uncertainty, but that it is on the verge of being accepted by the mainstream. Citi says that concerns about custody, security, and capital efficiency continue to be negatives for the digital asset, even though institutional investors' interest in cryptocurrencies is helping to increase public interest.
Conclusion
The technology behind blockchain and cryptocurrencies might be of tremendous use to the economy of the whole world. The path that Japan, the world's third biggest economy, has traveled since the spectacular financial catastrophe of Mt. Gox in 2014 is a great illustration of this. Japan has gone from being one of the most stable economies in the world to one of the most volatile. The use of bitcoin as a legitimate means of exchange has recently gained traction in Japan. As the currency starts to acquire popularity among merchants both inside the nation and worldwide, its top banks have also poured money into Bitcoin exchanges as well as Bitcoin and blockchain-related small-cap firms.
FAQ
Why should you not invest in Bitcoin? Therefore, if you are seeking an investment that would provide you with consistent returns, you should probably go elsewhere. The cryptocurrency market is driven almost entirely by speculation, and the fact that it is so tiny means that it is more susceptible to changes in price.
Can you make a living off of Bitcoin? Yes, it is possible to generate income using cryptocurrencies. The inherent volatility of crypto assets makes most of them subject to a significant degree of risk, while others need specific education or experience in the relevant field. One way to answer the question "How can I make money with bitcoin?" is to trade cryptocurrencies.
Is it possible for Bitcoin to become worthless? In a recent interview with Bloomberg, the president and portfolio manager of the American investment company Paulson & Co., John Paulson, said that cryptocurrencies, regardless of where they are trading at the present time, would ultimately be found to be worthless. As soon as the excitement dies down or the liquidity is depleted, they will return to zero.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ f04fd50c:c371fda8
2024-03-12 23:26:48
@ f04fd50c:c371fda8
2024-03-12 23:26:48How far does this go out now?
-
 @ 81870f53:29bef6a6
2024-03-12 22:29:36
@ 81870f53:29bef6a6
2024-03-12 22:29:36世界の資本市場で最も注目されている企業として、Nvidia のあらゆる動きは市場の注目を集めました。
特にここ数日は取引の振幅と取引量が大幅に減少し続けており、NVIDIAバブルが崩壊しピークに戻ったという見方もある。
それを証明するにはさらに多くの証拠が必要なので、ピークに達したかどうかを言うのは怖いですが、急激な上昇後の調整はすでに事実です、それがわずか 1 週間なのか、それとも 1 か月なのかはわかりません。さて、すべての予測単に絵を描いて、技術的な観点から推測しているだけです。
スター効果が高すぎるため、エヌビディアの株価変動を巡る論争ではロング派とショート派の激しい議論が巻き起こり、大変なことになっている。
Nvidia は今後も上昇を続けるのでしょうか、それとも止まってしまうのでしょうか?
01 市場では一般的にどのような見方が受け入れられていますか? さまざまな関係者の意見を総合すると、論理、データ、証拠に裏付けられた、非常に受け入れられる点が 2 つあると思います。
第一に、AI 時代は始まったばかりであり、アプリケーション レベルはまだ大規模に現れていないということです。業界のほぼすべての大手企業がこれを言っているだけでなく、多くの機関や投資家もこの考えを持っています。 Nvidia の Sister Mu Tou をこれまで過小評価してきた人々も、このような見方をしています。
実際、Microsoft の Copilot を除いて、大手メーカーは完全な利益閉ループを持っていますが、他の大企業は、Google やメタ広告など、AI をどのように使用して収益を上げているかまったくわかりません。コストと効率が上がったのか、部数がどれだけ減り、効率が上がったのか、それが利益表のどの項目に反映されるのか、AIを活用することでどれだけの広告主をライバルから奪ったのか、広告ASPはどれくらい増えたのか。
スタートアップとしては、中国人女性が設立したPikaなど数多くの企業があるが、これらの企業のアプリはまだ市場導入段階にあり、ビジネスモデルや収益性が検証されていない。
Nvidia のような「シャベル購入」企業にとって、これは、金山へ金を採掘する人々が後を絶たないのと同じように、良いことです。
第二に、米国株全体にバブルは存在しません。2000 年のハイテク株バブルに比べれば、今日の米国株はまったくのことではありません。当時はどれほど狂っていましたか?
.com Web サイトを持つ企業にサインアップするだけで、NASDAQ に上場してナスダックで盛り上がることができますが、現在は明らかにそうではありません。Pika を例に挙げると、現在は上場しています。ナスダックは条件を満たしている限りは良いが、資本は20年以上前ほど愚かではないため、上昇後は盲目的に投機することはないだろう、明確な収益モデルが必要となるだろうし、彼らは今後は売上と財務実績をより重視していきます。
なぜ米国株は好調なのでしょうか?また、中小規模の票の一部が予想ほどのパフォーマンスを発揮しなかったのはなぜでしょうか?
なぜなら、大きなチケットの結果はすべて問題ありませんが、小さなチケットは同じではありません。歴史は単純に繰り返されるわけではありませんが、ウォール街にとって、2000年のテクノロジー株の崩壊の教訓はまだ残っています。この教訓はあり得ません奥深いものとして表現されます。
どうすれば悲劇が再び起こらないようにすることができるでしょうか?
非常に簡単です。ウサギが見えない場合はワシを撤退すればいいだけです。具体的には、相応のパフォーマンスを譲っていただければポジションを上げます。そうでない場合は、その話はやめましょう。」
Nvidiaの業績は好調でした。2月に発表された財務報告書では、1日で16%上昇し、Maotai社よりも1日上昇しました。しかし、Broadcomなど業績がそれほど好調ではなかった企業は、すぐに1日で7ポイント下落しました。 。
なぜ Microsoft は 1 か月以上も横ばい取引を続け、Apple と Tesla はセブン シスターズから追い出されたのでしょうか?
つまり、業績はそれほど目立ったものではなく、下落が予想される銘柄もあるということです また、全体的な評価額で見ると、ナスダックは 2000 年のバブル期よりも下がっています。これは、市場全体が合理的であることを実際に証明しています。 2000年のバブル期よりも狂っている。
メディアで盛んに議論されている Nvidia と Cisco の比較については、実際には維持できず、Nvidia の 2 年間の長期評価額はわずか 30 倍だったのに対し、Cisco は同年 100 倍を超え、Cisco の時価総額は拡大しました。 M&Aや過剰流動性などが主な要因であり、企業自体の業績はそれほど好調ではなかった。
したがって、Cisco のロジックを Nvidia に単純に適用することは不適切です。
02 Nvidiaの最下位はAIの因果か? もう 1 つの物議を醸すトピックは、Nvidia と AI ですが、実際には誰が誰を引き継ぐのでしょうか?
結果が発表される前に、ある写真が広く拡散した。
要点は非常に単純で、AI に対する需要はほとんどありませんが、株式市場は明らかに過大評価されており、バブルの崩壊は遠くありません。
しかし、逆に見てみると、他に何が見つかるでしょうか?
Little Ant は AI のニーズをサポートしていませんが、Nvidia はさまざまな AI アプリケーションを継続的に開発している象です。
例を挙げれば誰でも理解できるでしょう。
もし Apple の携帯電話が発売されなかったとしても、その後はたくさんのアプリが登場するのでしょうか?
2005 年に大量のモバイル インターネットのニーズを汲み取って、ジョブズに「あなたが私の代わりに Apple 携帯電話を作ってくれました」と言うはずはありませんでした。正しくは、ジョブズは巨大なモバイル インターネット アプリケーションを生み出す前に Apple 携帯電話を作ったのです。
Nvidia も同様です。同社のテクノロジが反復される速度によって、AI テクノロジ全体の開発と AI アプリケーションが爆発的に増加する速度がある程度決まります。
Sora が突然登場したとき、多くの人が計算能力の要件がどれだけ増加したか、大手メーカーはさらに何台の A100 を購入する必要があるかを計算していました。逆の計算をしてみたらどうでしょうか。GPU の計算能力が増加した場合 10 1/10、1/100にコストが下がった場合、Soraより優れたアプリケーションがどれだけ出てきて、どれだけの商品価値を生むでしょうか?
大規模に商業化されるテクノロジーにとって、パフォーマンスとコストが 2 つの最も重要な決定要因となります。AI では、コンピューティング能力もこれら 2 つの決定要因の決定要因であり、「ビッグ ガイ」の背後にある「ビッグ ガイ」です。 「」
別の技術ロードマップを示します。
チップ間の相互接続が現在の H100 の 4.5 倍である 4 Tb/s である場合、アーキテクチャなどの他の技術革新を考慮しない場合、相互接続によりトレーニング速度が 20 倍向上します。
引き続き、今日の Sora は明日は簡単なようです。他にどんな破壊的なアプリケーションが登場するか誰にも分かりません。
製品を 1 回繰り返し、1.5 年で性能が 10 倍に向上することを考えると、産業チェーンの需要と供給だけで単純に測定することはできません。毎年更新の需要があるためです。 、古い生産能力はいつでも新しい生産能力に置き換えることができます。
これまで、ムー・トウ姉妹はインターネット時代の Nvidia と Cisco を常に比較していましたが、大規模なハードウェア インフラストラクチャが完成した後はハードウェア需要が崩壊し、Nvidia が Cisco と同じくらい人気を博した後は沈静化すると考えています。
Nvidiaを単純にハードウェア的な考え方に当てはめて見る人も多いが、Nvidiaの技術進歩がAIアプリケーション全体の開発スピードを左右するとすれば、それは単純なハードウェアインフラではなく、常にCの位置にいたリーダーであると言えるだろう。
下流メーカーにとって、Nvidia の最新かつ最速の GPU を入手できなければ、モデルのトレーニングと推論の速度が友人や販売者に遅れをとり、AI 高速列車に取り残されてしまうことを意味します。
現在、競争は非常に激しいため、一度ドロップアウトすると、そこに食い込みたいと思っても、それほど簡単ではありません。
これは、NVIDIA の製品が長期にわたって品薄になる可能性があり、NVIDIA 自体が、売り切れが続き、より強力な製品が発売され続け、売り切れが続くというスーパースパイラルと呼ばれる状態に陥ることを意味します。同業他社と競合し、市場での地位を強化し続けています。
これは実際には超独占です。
03 Nvidiaにもキラーがいる ハードウェアの考え方が Nvidia の判断を大きく誤るのはなぜでしょうか?
ソフトウェア エコシステムが Nvidia の真のキラーであるため、Lao Huang 氏は決算会見で次のように述べました。
アクセラレーション コンピューティングと生成 AI は転換点に達しています。
転換点という言葉をどのように理解していますか?
これには2つの意味があり、1つは推論の需要が爆発的に増えるということ、もう1つは誰もが楽しみにしているGPT-5がAIアプリケーションの商用化を大きく促進する可能性があるということです。 AI アプリケーションの急増の中で、これは非常に重要な分水嶺です。
過去のハードウェア インフラストラクチャを使用している Nvidia を見ると、年半ばのモバイルや Cisco のような「パイプライン」と考えるのが簡単です。ビジネス モデルはステージを設定し、他の人のために歌い、収集することでした彼らは独自のプラットフォーム使用料を払っており、大スターはステージで歌うことで多額のお金を稼いでいますが、それらはどれも自分たちとは何の関係もないようです。
しかし、NVIDIA が AI アプリケーション向けに特別に設計されたチップである ASIC への参入を発表したことと併せて、期待は異なります。
グローバルに商品化する上で最も商品価値の高いソフトウェアは、より詳細な特性に焦点を当てたり、様々な人の関係連鎖や知識の蓄積に応じて、より包括的な回答を与えることができるレコメンドシステムです。
メタボスのザッカーバーグ氏は前回のパフォーマンスカンファレンスで次のように述べた。
次世代のサービスは AGI に基づいて構築される必要があります。以前は、ツールの多くがソーシャル、商用、または場合によってはメディア指向であるため、AI の課題のほんの一部だけでこれらの製品を提供できると考えていました。 、しかし今では、私たちが思い描くサービスの最高のバージョンを提供するために、私たちのモデルが推論、計画、プログラミング、記憶などの多くの認知能力を必要とすることは明らかです。
そのためには、推論力を高める必要があります。
Nvidia がこの時点で ASIC を作りたいと述べたとき、実際に「推論専用 GPU」を発売したのは、推論市場での需要の急増を見てのことであり、クラウド サービス プロバイダーが独自の推論を開発することは間違いありません。この大きなケーキにより、「パイプライン化」されるリスクがなくなり、その範囲が下流のアプリケーションに直接挿入されます。
これは、ステージ使用料に加えて、芸能人の歌唱総収入の中から一定割合を分配しても良いと言っているのと同じではないでしょうか?
これは決算会見でも行われたもので、NVIDIA は常に「推論」(推論) というキーワードを 16 回繰り返しており、これは「トレーニング」(トレーニング) の 2 倍であること、ラオ ファン氏はまた、現在収益の 40% が推論ニーズによるものであることも強調しました。週末に開催されたスタンフォード・フォーラムに出席したラオ・ファン氏は、ASICに入社したい理由を改めて説明した。
これは市場に安心薬を与えるのと同じです。2025 年の成長は決定的です。トレーニングのニーズがますます主要な顧客に集中するリスクを心配する必要はありません。また、これは Nvidia の新たな、おそらくより大きな成長曲線を示唆しています。いつでもパフォーマンスで自分の価値を証明でき、株価のサポートがさらに強化されます。
Nvidia の中核的な競争力について語るとき、Lao Huang 氏は 2 つのことを述べました。1 つは Nvidia のコンピューティング プラットフォームが高速化されていること、もう 1 つはプログラム可能であることです。初期のヒントン チームのニューラル ネットワーク AlexNet からその後のすべてのニューラル ネットワークに至るまで、Nvidia は唯一のものです。 、ディープ ラーニング、さまざまなビジュアル コンバーター、マルチモーダル コンバーター、そして今度はタイミング関連のものです。
暗黙の了解として、今日まで生き残るために、Nvidia も後追いしてきました。AI アルゴリズムがどのように変化しても、Nvidia はソフトウェアを通じてランダムに適応できます。実際、推論とトレーニングを切り替える柔軟な方法は現在 Nvidia だけです。
なぜそれだけなのでしょうか?
Nvidia の CUDA コンピューティング プラットフォームについて話しましょう。GPU をコンピューターと考えると、CUDA は Windows オペレーティング システムです。
2007 年に発売されたこの GPU 汎用コンピューティング プログラミング フレームワークには、オリジナルの C 類似言語である CUDA C と、その後の C++ および Fortran 用の CUDA API が含まれています。
これは、Lao Huang の最も先見の明のある戦略的レイアウトの 1 つです。初期のプロモーションとアップグレードを経て、CUDA は現在、世界最大の GPU ソフトウェア コンピューティング エコシステムを生み出しています。単純にハードウェア パラメータだけを見れば、Nvidia はそれを超えることができるかもしれませんが、自社のソフトウェア エコシステムと比較すると、競合他社の勝つ可能性は非常に低いです。
Windows と同様のパフォーマンス パラメーターを備えたオペレーティング システムを誰かが作成するのと同じように、PC メーカーも Windows を放棄せず、ユーザーも Windows を放棄しません。これはユーザー スティッキーと呼ばれます。
04 Nvidiaを終わらせることができるのは誰ですか? 現在、Nvidia の将来はまだ非常に明るいようであり、それが多くの人々が Nvidia に注目し続ける理由です。
これは実際に真実であり、Nvidia バブルが崩壊したという証拠を見つけるのは非常に難しいため、せいぜい Cisco の例を例として挙げるか、一部の競合他社やユーザーさえも Nvidia GPU の代替品を開発しているだけです。 Nvidia の受注、TSMC の Cowos の生産能力、A100/H100 の価格など、利益に影響を与える中核要素の利益データを見れば、言葉を失うでしょう。
Nvidia は完璧ですか?
必ずしもそうとは限りません。忘れないでください。NVIDIA は常に景気循環株です。25 年か 26 年での高い成長と高い利益率には問題ありませんが、27 年、28 年、あるいはそれ以降はどうでしょうか?
誰も知りませんが、景気循環株を長期成長株に変えることには多くの教訓があり、その一例がリチウム鉱山です。
では、NVIDIA を終わらせるのに必要なのは誰でしょうか?
おそらく、競合他社の GPU 製品が登場し、Nvidia の市場シェアを奪い始めているか、あるいは同社の AI チップに対する需要が実際に減速しているか、あるいはその他の理由があるのかもしれません。
根拠のある言葉で言えば、製品が売れていない、価格を上げることができない、以前ほど早くまたはあまりお金が集まらない、などです。
しかし、その日はかなり遠いようです。
この記事がお役に立てば幸いです。 もしそうなら、チップをおくるどうぞ
https://getalby.com/p/bitcap
-
 @ d3d74124:a4eb7b1d
2023-07-26 02:43:40
@ d3d74124:a4eb7b1d
2023-07-26 02:43:40This plan was GPT generated originally but then tweaked by myself as the idea fleshed itself out. All feedback welcome and encouraged.
Shenandoah Bitcoin
1. Executive Summary
Shenandoah Bitcoin is a for-profit community organization based in Frederick County, VA, uniquely blending the world of agriculture and STEM. Our mission is to foster community spirit, stimulate interest in agricultural technology, and promote understanding of Bitcoin, while providing enriching educational opportunities and ensuring sustainable business operations.
2. Company Description
Shenandoah Bitcoin is committed to delivering value to our local community. Our unique approach intertwines traditional agricultural practices, modern STEM concepts, and the world of digital currencies, specifically Bitcoin. Our activities cater to all age groups, focusing on fostering community engagement, hands-on learning experiences, and contributing to the overall welfare of our community.
What’s in a name?
Shenandoah Bitcoin. Shenandoah - an old and historied land. Bitcoin - a cutting edge technological advancement. Both encompass multiple industries, from energy and manufacturing, to farming and data centers. Both built using Proof of Work.
3. Services
We offer a range of services, including:
Family-friendly events: Agriculture, STEM, and Bitcoin-themed festivals, fairs, workshops, and community gatherings. Educational programs: Classes, seminars, and workshops on agricultural technology, STEM principles, and understanding and using Bitcoin. Facility Rentals: Spaces available for private events, business meetings, and community gatherings.
4. Membership Benefits
We offer tiered membership packages with benefits such as:
a. Silver Membership: Includes access to regular events, discounts on educational programs, and priority booking for facility rentals.
b. Gold Membership: All Silver benefits, free access to select educational programs, and further discounted facility rentals.
c. Platinum Membership: All Gold benefits, free access to all educational programs, highest priority and maximum discounts on facility rentals, and exclusive invitations to special events.
Member’s opting to pay in Bitcoin receive 10% off all pricing.
5. Market Analysis
Our primary market is the local community in Frederick County and Winchester, VA, which consists of various demographic groups. Our secondary market includes neighboring communities, tourists, businesses, and educational institutions interested in the intersection of agriculture, STEM, and Bitcoin. Understanding that facility use and events to be a drawing factor for all demographics, we outline demographic specific analysis below.
STEM professionals in the area may work remotely or commute toward DC and not interact much with their agricultural neighbors, but a desire for good quality food exists for many. In addition to events, drawing the STEM demographic in will be connections to CSAs, ranchers, and homesteaders for access to fresh locally grown food. Offering a child's play room adjacent to some office space, is a compelling benefit for the laptop class that is often in STEM professions.
Non-industrial food producers and homesteaders may not have the focus or resources for marketing and sales. By offering a physical touch point for them and direct connections to consumers, food producers benefit from membership. Having more options for drop off/pick up of various produced goods, makes it attractive for both the consumers and producers as coordination can be asynchronous.
Bitcoiners have a wide range of sub-demographics, including farmers and software engineers. Some travel hours over car and plane to attend bitcoin themed events. The topics of STEM and agriculture are of shared interest to non-trivially sized communities of bitcoiners. Having a physical touch point for bitcoiners will draw in some members just for that. Building fellowship is desired and sought in bitcoin.
5.1 Market Trends
The blending of agriculture, STEM fields, and Bitcoin is a unique concept with increasing interest in sustainable farming and ranching, food sovereignty, and health. Shenandoah Bitcoin is poised to tap into this growing interest and offer unique value to our community.
5.2 Market Needs
Our market requires initiatives that foster community engagement, promote understanding of agri-tech and Bitcoin, and provide a versatile space for events and learning.
6. Marketing and Sales Strategy
We will employ a blend of digital marketing, traditional advertising, and strategic partnerships. Our main marketing channels will be word of mouth, social media, local press, and our website. Partnerships with local small businesses, homesteaders, schools, agricultural organizations, and bitcoin companies will form a key part of our outreach strategy.
7. Organizational Structure
Shenandoah Bitcoin will be led by a CEO, supported by a management team responsible for daily operations, event planning, marketing, and community outreach. Event management and logistics will be handled by part-time staff and volunteers.
8. Financial Projections
Our revenue will be generated from membership fees, charges for events and educational programs, and facility rentals.
9. Funding Request
[If seeking additional funding, describe your needs and how the funds will be used]
10. Exit Strategy
Should it become necessary to dissolve the business, assets such as property, equipment, and any remaining cash reserves after meeting liabilities will be sold. Investors would receive their share of the remaining assets according to their proportion of ownership.
11. Conclusion
Shenandoah Bitcoin is a unique community organization bringing together agriculture, STEM, and Bitcoin in Frederick County, VA. Our distinctive approach is designed to deliver both profits and social impact, resonating strongly with our target market and positioning us for sustainable growth.
-
 @ 81870f53:29bef6a6
2024-03-12 22:23:35
@ 81870f53:29bef6a6
2024-03-12 22:23:35メディアが引用した2人の投資銀行関係者が明らかにしたデータや、ウォール街の大手商業銀行が発表した最近の顧客報告書によると、米国株を主体とした世界の株式取引でヘッジファンドが現在使用しているレバレッジのレベルは、足元の借入戦略の規模の急増や米国株式市場の強気な市況、金融市場全体の環境緩和傾向の変化などが寄与し、過去最高に近づいている。ヘッジファンドのリスク資産賭けの規模。
顧客から報告された関連データによると、世界トップ3の機関投資家ブローカーであるゴールドマン・サックス(ゴールドマン・サックス)、JPモルガン(JPモルガン)、モルガン・スタンレー(モルガン・スタンレー)がまとめた最新データによると、投資収益率を高めるためにレバレッジ比率が使用されていることが明らかになった。商業銀行の個別の統計にもよりますが、株式市場は歴史的高値に達しているか、それに近い状況にあります。
近年、ヘッジファンドによるレバレッジの利用は、ポートフォリオ、市場、銀行への影響の可能性に規制当局の注目を集めている。一方、米国証券取引委員会(SEC)は、ヘッジファンドに対し、より詳細かつ定期的なリスクエクスポージャー開示データの提供を義務付ける予定です。
ヘッジファンドに投資するコモンファンドのマネジング・ディレクター、ジョン・デラノ氏は「マクロ(ヘッジファンド)セクターのレバレッジは間違いなく高い」と述べ、世界の中央銀行によるインフレ抑制の順調な進捗と人工金融に対する投資家の信頼感についても述べた。生産性の大きな変化を引き起こすインテリジェンスは、この活用傾向に大きく貢献しています。
ゴールドマン・サックスのデータレポートによると、ヘッジファンドの株式ポジションの現在のレバレッジ比率は、1年前の約2.35倍と比較して簿価のほぼ3倍となっており、現在は過去5年間で最高水準となっている。比較の基準期間としてヘッジファンドの過去5年間を使用しています。
ゴールドマン・サックスの統計によると、ヘッジファンドが投資する自己資金100ドルごとに、最大300ドルのロングポジションとショートポジションが生み出される。
JPモルガン(JPMorgan)の統計によると、現在のレバレッジ利用率は約2.7倍で、2017年以来のピークに近い。それ以降の追跡期間では、一般的なレバレッジ利用率は98%を超え、現在のレバレッジ比率は大幅に上昇している。モルガン・スタンレーの報告書は、過去 14 年間のレバレッジ追跡データによると、米国株式市場におけるヘッジファンドの現在のレバレッジ比率は 2% しか高くありません。
異なる戦略を持つヘッジファンドが米国株についてほぼ一致:強気市場の後
同庁がまとめたデータによると、ヘッジファンドのレバレッジ比率が上昇していた時期に、昨年10月末に米国株式市場が新たな上昇を始めてからヘッジファンドの強気な姿勢が強まった。米連邦準備理事会(FRB)が間もなく利下げに踏み切るとの見方が広がり、それ以来、米国株のベンチマーク指数であるS&P500種指数(S&P500)は約24%上昇した。
バークレイズ銀行はリポートで、異なる戦略を持つヘッジファンドが米国株についてほぼ一致しており、つまり将来の市場に対して強気であると指摘し、世界的なマクロ系ヘッジファンドは現在、米国株式市場でショートポジションを解消した上でロングポジションをとっていると指摘した。バークレイズ銀行は、いわゆるコモディティ・トレーディング・アドバイザリー・ファンド(CTA)株のロング・ポジションは「依然として逼迫している」と付け加えた。 CTA戦略は、コンピュータによる定量化技術を使用して価格動向を追跡するファンドです。
カイロス・パートナーズのシニア・ポートフォリオ・マネージャー、マリオ・ウナリ氏は、「このレバレッジをかけたトレンドは、市場がこのトレンドが非常に良いと考えていることを示している。」と述べ、過去3年間で体系的なヘッジファンド戦略におけるレバレッジのレベルが低下していることを観察したと述べた。 (つまり、データに基づいたコンピューター定量モデルを取引に使用する戦略)は、この 3 年間で最高レベルに達しました。
JPモルガンの予測データによると、従来のヘッジファンドは主に過去の業績データやテクニカル分析に基づいて株式のロングまたはショートを行っており、レバレッジ比率は簿価の約2倍であるのに対し、株式定量化ヘッジファンドやマルチ戦略ヘッジファンドのレバレッジ比率は簿価の約2倍となっている。それぞれ4.5倍と3.1倍に達します。
情報によれば、2014 年以降、レバレッジ戦略は投資家の間でますます人気が高まっており、レバレッジ戦略の規模は業界全体の資産成長率をも上回っています。ヘッジファンド調査会社 PivotAlPath の追跡データによると、マルチ戦略そして現在、クオンツ投資はヘッジファンド市場全体の約 32% を占めていますが、2014 年には約 24% でした。
ただし、これらの戦略はロングポジションとショートポジションを一致させる傾向があり、株式市場の浮き沈みの影響を受けにくいため、一般に比較的リスクが低いと考えられています。
これまでのところ、より高いレバレッジで米国の株式市場に賭け、株式市場全体の継続的な上昇が非常にプラスになっているようで、ゴールドマン・サックスの統計によると、体系的な戦略を採用した株式ヘッジファンドの資産価値は6.42倍増加したという。今年の最初の 2 か月で % となり、MSCI の世界ベンチマーク株価指数の上昇率を完全に上回りました。
UBSヘッジファンド・ソリューションズ(UBSヘッジファンド・ソリューションズ)の最高投資責任者、エドアルド・ルリ氏は、主に市場のボラティリティが比較的低いため、現在のレバレッジ水準は依然として機能しており、最大の懸念の一つではないと述べた。
しかし、同氏は依然としてこの問題を注意深く監視しており、「レバレッジは常に問題となっており、レバレッジを監視することが重要だ。流動性に関連するリスクを加えると、これは致命的な危機となる可能性がある。」と述べた。
S&P500指数の上昇は止まらないのか?バンク・オブ・アメリカは5,400ポイントと予想、バークレイズ銀行は最高値の6,050ポイント上昇を予想
人工知能がもたらした熱狂と米国経済の回復力はウォール街の予測担当者らを驚かせ、ストラテジストらは彼らの予想を超えた株式市場の回復に追いつくために競い合うようになった。ゴールドマン・サックス・グループとUBSグループは、米連邦準備理事会(FRB)がハト派政策に転換した後の昨年12月以来、米経済見通しへの期待を2度引き上げた。
AI チップ大手エヌビディア (NVDA.US) の非常に好調な業績と数四半期連続の業績見通しの影響を受けて、米国のハイテク大手の株価は急速に上昇し、これらの比重の高いハイテク大手が S&P 500 指数を最高値に押し上げました。エヌビディアなど「マグニフィセント7」ターゲットを空売りしていた弱気派は消滅したようだが、その一方で、ウォール街の投資機関や著名なヘッジファンドや個人投資家は、エヌビディアやその他多くの銘柄への割り当てエクスポージャーを増やしている。テクノロジー株。
米国株のベンチマーク株価指数であるS&P 500指数は、今年以降8%以上上昇し、主に市場の投資熱狂に牽引されて最高値を繰り返し更新し、史上最高値を更新し続けている。人工知能と連邦準備制度が今年利下げするとの期待を巡る影響で、月曜日の米国株式市場終了時点で、S&P 500指数は5117.94ポイントで終了した。
パイパー・サンドラーのストラテジスト、マイケル・カントロウィッツ氏は、2023年の米国株式市場に関してウォール街で最も弱気なストラテジストと言える。最近、彼はS&P500指数の予想を5,250ポイントに引き上げた。この予想は、ジョン・ストルツファス氏などウォール街の強気の同業者の予想を上回った。オッペンハイマー・アセット・マネジメントの首席投資ストラテジストとファンドストラット・グローバル・アドバイザーズのリサーチ責任者トーマス・リー氏は、両氏ともS&P500指数が年末までに5,200ポイントに達すると予想している。
バンク・オブ・アメリカのスターストラテジスト、サビタ・スブラマニアン氏は、S&P500指数が年末までに5,400ポイントに達すると予想しているが、その前に彼女が示した目標ポイントは5,000ポイントであり、さまざまなテクニカル指標が強気のシグナルを発していると述べた。将来の利益成長はさらに強力であり、利益率の弾力性は「驚くべきもの」です。
さらに、サブラマニアン氏らバンク・オブ・アメリカのストラテジストらは、最新の調査報告書でS&P500企業の全体利益予想を235ドルから250ドルに引き上げ、BMOキャピタル・マーケッツやドイツ銀行と並んでウォール街で最も楽観的な利益予測を行っているバンク・オブ・アメリカとなった。 , バンク・オブ・アメリカは2025年の1株利益が275ドルに達すると予想している。
バークレイズ銀行は、米国株式市場に対してウォール街で最も楽観的な投資機関と言えます。同機関の米国株価ベンチマーク指数であるS&P 500指数の年末目標株価は、4,800ポイントから5,300ポイントに大幅に引き上げられました。バークレイズはリポートの中で、大手テクノロジー企業の豊富な利益データと市場の予想を上回る米国経済の優れた業績から、米国株は今後も恩恵を受けるだろうと指摘した。予想を上回れば、S&P 500指数は今年末までに6,050ポイントに達する可能性があると当局は考えている。
この記事がお役に立てば幸いです。 もしそうなら、チップをおくるどうぞ
https://getalby.com/p/bitcap
-
 @ 52b4a076:e7fad8bd
2023-05-01 19:37:01
@ 52b4a076:e7fad8bd
2023-05-01 19:37:01What is NIP-05 really?
If you look at the spec, it's a way to map Nostr public keys to DNS-based internet identifiers, such as
name@example.com.If you look at Nostr Plebs:
It's a human readable identifier for your public key. It makes finding your profile on Nostr easier. It makes identifying your account easier.
If you look at basically any client, you see a checkmark, which you assume means verification.
If you ask someone, they probably will call it verification.
How did we get here?
Initially, there was only one client, which was (kind of) the reference implementation: Branle.
When it added support for NIP-05 identifiers, it used to replace the display name with the NIP-05 identifier, and it had to distinguish a NIP-05 from someone setting their display name to a NIP-05. So they added a checkmark...
Then there was astral.ninja and Damus: The former was a fork of Branle, and therefore inherited the checkmark. Damus didn't implement NIP-05 until a while later, and they added a checkmark because Astral and other clients were doing it.
And then came new clients, all copying what the previous ones did... (Snort originally did not have a checkmark, but that changed later.)
The first NIP-05 provider
Long story short, people were wondering what NIP-05 is and wanted it, and that's how Nostr Plebs came to be.
They initially called their service verification. Somewhere between January and February, they removed all mentions to verification except one (because people were searching for it), and publicly said that NIP-05 is not verification. But that didn't work.
Then, there were the new NIP-05 providers, some understood perfectly what a NIP-05 identifier is and applied the correct nomenclature. Others misnamed it as verification, adding confusion to users. This made the problem worse on top of the popular clients showing checkmarks.
(from this point in the article we'll refer to it as a Nostr address)
And so, the scams begin
Spammers and scammers started to abuse Nostr addresses to scam people: - Some providers has been used by fake crypto airdrop bots. - A few Nostr address providers have terminated multitude of impersonating and scam identifiers over the past weeks.
This goes to show that Nostr addresses don't verify anything, they are just providers of human readable handles.
Nostr addresses can be proof of association
Nostr addresses can be a proof of association. The easiest analogy to understand is email:
jack@cash.app -> You could assume this is the Jack that works at Cash App.
jack@nostr-address-provider.example.com -> This could be any Jack.
What now?
We urge that clients stop showing a checkmark for all Nostr addresses, as they are not useful for verification.
We also urge that clients hide checkmarks for all domain names, without exception in the same way we do not show checkmarks for emails.
Lastly, NIP-05 is a nostr address and that is why we urge all clients to use the proper nomenclature.
Signed:
- Semisol, Nostr Plebs (semisol@nostrplebs.com)
- Quentin, nostrcheck.me (quentin@nostrcheck.me)
- Derek Ross, Nostr Plebs (derekross@nostrplebs.com)
- Bitcoin Nostrich, Bitcoin Nostr (BitcoinNostrich@BitcoinNostr.com)
- Remina, zaps.lol (remina@zaps.lol)
- Harry Hodler, nostr-check.com (harryhodler@nostr-check.com)
-
 @ 32092ec1:8e9fd13a
2023-04-25 18:02:43
@ 32092ec1:8e9fd13a
2023-04-25 18:02:43Bitcoin maximalism, to many, has evolved from a belief that bitcoin is the only crypto asset worth owning to a belief that bitcoin is the only asset worth owning. In addition, many observe that those who declare themselves to be bitcoin maximalists have also declared their allegiance to many other lifestyle choices. This was well articulated by Jameson Lopp in his blog post “A History of Bitcoin Maximalism.”
While some (myself included for a while) embrace the title of bitcoin maximalist, perhaps out of spite given that it was originally intended to be a derogatory term, I eventually have decided to reject it. While I do not own any other crypto assets, and I do believe that bitcoin offers the best risk adjusted investment across many asset classes, it is not, nor could it ever realistically be, my only investment. Due to the ambiguity of the definition of a “bitcoin maximalist” to some, even the fact that I have equity in my primary residence may call into question my status as a bitcoin maximalist. Although most people likely agree that this point of view is nonsensical, I feel that it is also completely pointless to take the time to defend the purity of my “bitcoin maximalism;” and so, I reject it. In place of the bitcoin maximalist label, I hereby declare myself to be a truth maximalist.
The truth is that 99% of non-bitcoin crypto assets are completely worthless; specifically, what I mean is that they literally add zero net positivity to humanity. The remaining 1% of non-bitcoin crypto assets may indeed serve some limited improvements to existing systems or other alternative benefits; however, these crypto assets are also, in my opinion, already highly over valued given the magnitude of the problems they are intending to solve. Most of the incremental improvements offered by cryptos are related to marginally improving systems based on fiat money and the banking industry both of which bitcoin intends to largely obsolete and are still net negative to humanity and designed to syphon wealth from the powerless to the powerful.
I do believe that open source, decentralized, cryptographic solutions will play additional roles in society and offer an opportunity to disrupt many existing centralized solutions. However, most of these solutions will not be investable assets, just as the internet itself is not an investable asset.
I believe it also to be true that investment properties intended for yield generation come with a host of additional costs and risks that are rarely properly accounted for when assessing the value of these assets. After accounting for the probability weighted costs of evictions, seizures, taxes, maintenance, inflation, and loan interest, I find it difficult to justify these investments over bitcoin held in self-custody.
Many other investable assets that simply sit on a bank’s balance sheet (e.g., stocks, bonds, etc.) can easily be seized if any number of three letter agencies decided that you should not have these assets. This can be done with no due process and does not require any in depth investigation to determine the validity of their claims. I believe that the probability of these types of seizures is much higher for known bitcoiners who are also critical of the government and the media, especially if current financial systems begin to collapse and/or if bitcoin’s value dramatically increases.
Beyond seizure of your individual assets, as the world begins to divest from the highly inflated store of value assets listed on the NYSE and NASDAQ due to seizure risks at the sovereign level, the risk of extreme inflation adjusted devaluation of your portfolio should also be considered. Compounding this risk is the opportunity cost associated with the fact that some of the wealth that may be withdrawn from the US stock market is also likely going to flow into bitcoin. These risks are rarely accounted for or quantified when determining the value of a stock portfolio in contrast to simply holding bitcoin in self-custody.
My opinions on these matters are common among bitcoiners who are largely labeled bitcoin maximalists. However, the title of truth maximalist also fits nicely when trying to counter some of the softer points made in Lopp’s blog post mentioned above. My thesis is that most people who have adopted the bitcoin maximalist “lifestyle” choices have done so as a result of their quest for truth, not as a result of their desire to virtue signal their status as bitcoin maximalists.
The truth is that a carnivore diet is much healthier than governments, media and academia would like you to believe (disclosure: I have never tried a carnivore diet)
The truth is that weightlifting is more beneficial than cardio to overall health (disclosure: I am not into weightlifting)
The truth is that traditional gender roles are beneficial to mental health (disclosure: although my wife is a full-time, stay-at-home mom, my marriage is far from perfect).
The truth is that extreme consequences from greenhouse gasses in the atmosphere are extrapolatory and predictions have historically failed miserably (disclosure: I do not think there is zero risk of extreme disasters from excessive levels of carbon in the atmosphere).
The truth is that seed oils are terrible for you (disclosure: I have ingested seed oils since discovering this).
The truth is that COVID vaccines pointlessly add risk to healthy people and children (disclosure: I received two doses of the COVID vaccine prior to realizing this truth and my wife still disagrees with me on this).
The truth is that natural health solutions are often more beneficial than big pharma would like you to believe (disclosure: I have not used any exotic natural remedies).
The truth is that modern art and architecture is garbage (disclosure: this is only a personal opinion).
The Truth is that Jesus Christ died on a cross and ascended into Heaven in order to save the world from sin (disclosure: although I have always been a Christian, over the last year or so I have dedicated a significant amount of time researching this and so far, everything is supporting this to be literally true and much more easily believable than you might think).
Maybe you disagree with some of these things that I have determined to be true. But let me ask, have done your own research? What is your basis for a counter argument to any of these truths? Did you verify or are you trusting someone else’s opinion? If you are trusting someone else’s research, did you investigate their credibility or determine if they have significant biases? Certainly, my opinions on the topics listed above not always based on exhaustive independent research, but I did approach each with skepticism and did not always believe these things with conviction prior to looking into them. I think any bitcoiner would agree that if you are trusting fiat funded academia, government organizations or mainstream media, you may need to do more research.
The truth is that I will continue to seek the truth and I will encourage others to do the same. The truth is that I welcome new information and listening to opinions that counter my beliefs. When choosing to have strong conviction in minority opinions about the truth, it is extremely valuable to be able to articulate and refute the points that are contrary to your beliefs. It is also important to be able to change your mind when presented with sufficient evidence against your opinion. This is what it means to be a truth maximalist. It just so happens that the truth is that bitcoin is the only crypto asset worth investing in. Don’t believe me? Prove it.
786973
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ be318ab6:dd25a806
2023-04-09 02:55:48
@ be318ab6:dd25a806
2023-04-09 02:55:48Howdy y'all,
This is the Ramble #001
I was gifted extra spare time (layoffs), and I'm excited to put it into learning about some of the new exciting things swirling around us at an ever-accelerating speed & also about the good old ever-useful manual skills, which are disappearing almost at the same rate.
The focus will be on anti-fragility tools and skills. I'll be touching on the the topics of Nostr, AI, Bitcoin, Privacy and self-sufficiency skills like woodworking or food production. I'll include any building just for the sake of it (I get more value myself and motivation to do more of it if I can show off something tangible, I guess). It's not gonna be the most frontier-breaking r0ckstar knowledge, but it will humbly keep moving forward one step at the time along with my selfish pursuit of improving my knowledge and skills along these vectors. I also won't avoid some rants about the insane corruption in our Money and all the downstream problems it brings.
Why?
1. Why having a blog? * I want to practice my writing. Not to challenge the AI, but just to better remember the learnings, and to clarify & structure my thoughts. * The public record forces accountability on me. I want to commit to a habit of writing a few posts per week.
2. Why it's on Nostr? * When dozens of the smartest and most honest individuals I respect flock to this like a bunch of crazy birds, it's something I don't want to miss out on, and I want to get intimately familiar with the tech. * It's an uncensorable protocol that allows you to own your data and can re-architect many broken things on the current web. * Easy for me to push my tip jar in y'alls faces and see if anyone gets any real value out of this * And, I just wanted to play with it. Some clients still might be buggy, but the speed of development and improvements is lightning miles away from anything I've seen before.
I'll probably write some intro to NOSTR next time around; but in the meantime Gigi will help you out at nostr-resources.com
3. Why including the offline skills and tools? * Humans are not meant to stare into screens all day. * I see there's one of the most competitive edges for the next 10 years.
And, that's about it. I'm really excited about days and weeks, and will have some fun. If you have read all down here, thank you and PV to you!
PS.

Resources/Inspiration for this issue: * Marty's Bent - duh! * BloggingBitcoin - How To Start A Blog Today
-
 @ 81870f53:29bef6a6
2024-03-12 22:17:38
@ 81870f53:29bef6a6
2024-03-12 22:17:38バフェットはかつて、私と私のパートナーであるチャーリー・マンガーにとって、これまでに犯した最大の間違いは、何か間違ったことをしたのではなく、すべきことをしなかったことだと言いました。もともと、私はいくつかの優良企業についてよく知っていましたが、それはただのことでした。 「行動を起こす権利はあったが、結局彼らは何もしなかった。バフェットはマイクロソフトに対して行動をとったが、自分はマイクロソフトを理解していないと考えてそれを逃した。医薬品株に対して行動を起こすことも可能だったかもしれない」数十億ドルを稼いでいますが、結局のところ、まだ一銭も稼いでいません。
トップの投資家にはこのような間違いがたくさんあります。また、中には非常に「深刻な」間違いもあります。金融と市場の専門家であるマイケル・ベトニック氏は、著書「重大な間違い」の中でこれを徹底的に分析しています。ベトニック氏は、人は通常、成功体験を再現しようと懸命に努力することを発見しました。しかし、優れた投資家も間違いを犯しますが、彼らは皆、個人やビジネスの失敗の経験から学び、個人やビジネスの足を引っ張るような間違いが自分自身に起こらないようにするでしょう。
投資は非常に難しいものです。私たちは間違いを犯し、しばしばそれを繰り返しますが、それはゲームの不可欠な部分であるため、同時に新たな間違いも犯します。しかし、成功した投資家には最も重要な共通点が 1 つあります。それは、自分が何をマスターできるかを知っているということです。バフェットが言ったように、最も重要なことは、自分がどれだけ知っているかではなく、何を知らないかを定義することです。あなたが知っている。
- 知性と自信を組み合わせる危険性 ベンジャミン グレアムは「ウォール街のゴッドファーザー」であり、バリュー投資の創始者です。1923 年にグレアム ニューマン インベストメンツを設立しました。1920 年代の大強気市場の最後の年に、グレアムのパートナーシップ口座は 60% の利益を上げ、世界をリードしました。ダウ ジョーンズ指数は 49.47% 上昇しました。1930 年、グラハムは最悪の事態は終わったと考え、莫大な利益を得るために融資を利用してレバレッジを高めました。その結果、50% の損失を被りました。1929 年から 1932 年の 4 年間で、株式市場は底を打ち、グラハム氏の累積損失は70%に達した。
1926 年から 1935 年にかけて、グレアムの会社は年間平均約 6% の利益を上げましたが、同じ期間のスタンダード・アンド・プアーズとダウ・ジョーンズのインデックスの利益はそれぞれ 5.8% と 3.8% でした。グレアムの投資は「価値」という前提に基づいています。グレアム氏は、「株価は最終的にその真の価値を反映する」という信念に基づき、「本来の価値よりも価格が低い証券を購入し、清算される証券の購入に特に重点を置いています」と述べています。過去の経験から、どのような場合でも、最終的には市場価格が株式の真の価値を反映することがわかっています。これらの安い株式を購入することは、長期的には優れた戦略です。
グラハム氏は、「証券分析を行う際、過去の行動に基づいて関係性を判断しようとします。ほとんどの場合、このような経験をします。つまり、長期間適用した後、自分の計算方法に十分な自信が持てるようになると、新しい状況が生じます。そして、以前の計算は将来的には信頼できなくなります。これは、以前に機能したものが現在機能しない可能性があること、現在機能しているものが将来機能しない可能性があることを意味します。「価値」は重要であることを理解しますが、より重要なのは、グラハムは、安いものは安くなり得るため、金融には黄金律など存在しないと私たちに教えてくれました。しかし、これらの経験から学ぶには、苦痛なプロセスを経なければなりません。これは残念な現実です。
私たちは、「安く買って高く売る」や「街が血で満ちているときに買う」など、これまでの投資原則やモットーの多くを、購入、売却、保有の基礎としてよく使用します。ただし、経験則は投資の複雑さの影に隠れることが多いということです。証券価格の上昇と下落は、多くの要因や逆の傾向の影響を受けます。これを一言で説明するのは困難です。これらの経験則に完全に依存するだけで十分です。投資は非常に不確実性が高いので、「二度と同じ間違いをしない」とは決して言わないでください。
偉大な物理学者アイザック ニュートンは IQ 190 で、小数点第 55 位まで計算できました。彼の知恵はチャールズ ダーウィンやスティーブン ホーキング博士をはるかに上回っていました。それでも、彼は最も原始的な人間の本能の餌食になることを避けることができませんでした— 貪欲と嫉妬 ニュートンは南シナ海会社の投機でほぼ全財産を失った。
証券市場では、IQ が高いからといって何も保証されません。頭が良いからといって市場が報われるわけではありません。原始的な知性は単なる前提条件であり、投資の良い結果を経験するチャンスを与えてくれます。市場は直線ではなく変数に満ちており、たとえ以前はうまくいったとしても、ほとんどの数式は最終的には失敗するため、結果は創意工夫だけでは決まりません。言い換えれば、あなたがどれだけ賢いかは問題ではありません。重要なのは、競争相手がどれだけ賢いかということです。チャールズ エリスは、1975 年に「敗者のゲームに勝つ」という本の中で、過去 30 年間、競争相手が多すぎると指摘しました。才能があり、決断力があり、野心的な専門家が投資管理の分野に参入してきたが、他人の間違いを利用して市場に勝つことができなくなっているかもしれない。なぜなら、他人の間違いから得られる利益が、数でも量でも不十分だからである。市場平均を上回る収益を得ることができます。
スキルと知性が向上するにつれて、投資結果に対する運と機会の役割が日々増大していると私たちは考えるかもしれません。マイケル・モブソンはこの見解について何度も書いています。彼はそれを「スキルのパラドックス」と呼んでいます。市場には熟練したプレーヤーが無数に存在するため、知性だけでは十分ではありません。市場参加者は他のスキルを持っている必要があります。天才性とその限界を理解するには、長期資本管理会社の「アインシュタイン」グループを研究することは、まれな良い例です。
この長期資本管理会社には、2人のノーベル経済学賞受賞者を含む多数のエリート魔術師が結集しており、『エコノミスト』誌は2人の受賞者の功績について、「彼らはリスク管理を推測ゲームから科学に変えた」と評した。その結果、長期資本は「金融学」を極限まで追求し、「合理性」の限界に達したが、ロシア国債のデフォルトにより、1998年8月末までに19億ドルを失った。年初から年末にかけてすでに52%下落し、死の渦が本格化し、その後9月21日までの21日間で巨額の損失を出し続け、最高水準に達した。最終的に、彼らの投資ミスが金融システム全体を破滅させるのを防ぐために、ニューヨーク連銀はウォール街の銀行4社と提携し、36億ドルをかけて長期資本の90%を購入しました。
長期資本管理会社の天才たちは、さまざまな出来事の確率を計算することはできますが、何が起こる可能性があるのかまったく分かりません。彼らの最大の間違いは、人々の富とセロトニンが同時に急増したとき、彼らの財務モデルが「ナシム・タレブ氏が言ったように、長期的な資本暴落の場合、彼らは自分たちが市場を理解していないかもしれない、自分たちのアプローチが間違っているかもしれないなどとはまったく考えていませんでした。私たちはこのことから学ぶことができます。教訓は明白で、市場に関しては創意工夫と過信の組み合わせは危険だということです。
- 過剰な自信は客観的な判断を曖昧にする バフェット氏は投資家として、個人の能力には限界があることを痛感しています。1990 年代後半にハイテクバブルが拡大し続けたとき、彼はハイテク株にまったく投機をしなかった数少ない有名投資家の 1 人でした。彼はハイテク株について何も知りません。当時、バークシャー・ハサウェイの株価は半値まで下落しましたが、彼は自分自身に忠実であり続けました。
バークシャー・ハサウェイの株価は、1999 年から 12 か月間でさらに 12% 下落しましたが、ナスダック 100 は同じ期間に 74% 急騰しました。個別のハイテク株のパフォーマンスが良くなり、シスコの株価は 110% 急騰し、ヤフーは 350% 急騰し、クアルコムは 408% 急騰しました。当時のバリュー投資家にとって1990年代後半は厳しい時代で、インターネットバブルで企業価値の計算方法が一時的に変わり、電子玩具会社eToysは初めて上場した日、株価が320%も高騰した。 Us の収益は eToys の 150 倍で、1 億 3,200 万ドルを稼ぎ出しましたが、eToys の帳簿上の損失はわずか 7,300 万ドルでした。にもかかわらず、eToys の時価総額は 77 億ドルだったのに対し、実店舗小売業者のトイザらスの時価総額はわずか 1 億ドルでした。 57 億ドル。投資家がバリュー株を売却し、その後成長株に投資する中、コカ・コーラ、ジレット、ワシントン・ポストのバークシャー・ハサウェイ株は他のライバル株に大きく遅れをとっている。最高値から底値まで、バークシャー・ハサウェイは時価総額の 51% を失い、下落した。純資産価値は100億ドル以上増加しました。
しかし、投資で成功するための鍵の 1 つは、バフェットのように現実を受け入れ、自分の投資スタイルが求められなくなったり、ポートフォリオに大きな地震が発生して他の投資を探し始めたりする状況に時々遭遇することを理解することです。そのとき、あなたの行動はあなたの財務状況に深刻なダメージを与える可能性があります。投資ではいくつかの「悪い行為」が頻繁に発生し、悪い行為は投資家が直面する最大のリスクの 1 つです。能力を超えた投資は、最も一般的な悪い投資慣行の 1 つです。 . 人の能力の範囲がどれだけ広いかは問題ではありません。最も重要なことは、その内側に留まることができるかどうかです。自己認識と少しの規律があれば、世界は変わります。
人々はバフェットを「株の神様」と考えるのが好きですが、実際にはバフェットがすべての投資に勝ったり負けたりするわけではありません。1987年、バフェットは7億ドルを売却してソロモン・ブラザーズに投資しました。その結果、1991年にソロモン・ブラザーズのスキャンダルが起こりました。米国財務省の国債入札規制への違反が明るみに出て、その後の是正作業でバフェットは疲弊し、1990年にオール・アメリカン航空の優先株の12%を3億5,800万米ドルで購入した。チャーリー・マンガー氏は後にこれについて次のようにコメントしました。私たちは同じような経験を二度としたくないのです。」
これらの経験はそれほど美しいものではありませんでしたが、バフェット氏の最も高くついた失敗に比べれば、見て見ぬふりにほかなりませんでした。1993 年、バフェット氏はデクスター シューズ社の株式を 4 億 3,300 万米ドルで購入しました。しかし、1994 年からの 5 年間で, デクスターの履物製品の利益と収益は減少し続けました。1999 年まで、デクスターの収益は 18% 減少し、営業利益は 57% 減少しました。2000 年までに、バフェットは株主への手紙の中で次のように述べています。「今になって考えると、それは私にとって明らかに間違いでした」 」
バフェットがデクスターを買収したとき、その自信過剰が客観的な判断を鈍らせました。その後、彼は自信過剰に対処する素晴らしい方法を提案しました。誰かがあなたにたった 20 個の穴が開いたパンチカードを渡したとしたら、その穴はあなたが会社にできるすべての投資を表しているとします。残りの人生では、自分が何をしようとしているのか、もっと慎重に考えるべきです。実際には、このアドバイスは現実的ではありません。この種の規律を持っている人は誰もいませんが、これは私たちがどれだけのことをするかを考える良い方法です。投資にお金を費やすべきであり、投資問題をどのように慎重に扱うべきかについて考えました。
- 強制されていない間違いには常に注意してください チャールズ エリスは、「敗者のゲームに勝つ」の中で、勝者のゲームでは、結果は勝者の正しい行動に依存し、敗者のゲームでは、結果は敗者の犯したミスに依存すると書いています。言い換えれば、プロはポイントを獲得しますが、アマチュアは負けますテニスの試合では、プロのテニス選手はボールを打つために懸命に努力し、一方の選手が相手のギャップの最終位置にボールを打つことに成功するまで、両選手は一連の激しい前後攻撃を繰り返しました。エリス氏はこの状況をアマチュアの試合で見られる状況に例えたが、アマチュアの試合はサーブミスが多く、素晴らしいヒットやロングインターセプトが見られた試合はなかった。
アマチュアのスポーツ選手とプロのスポーツ選手を比較したり、マーケットゲームでアマチュアの投資家とプロの投資家を比較したりすると、両者の類似点を容易に見つけることができます。一般に、アマチュアの投資家は、株価が上昇すると買い、株価が下落すると売ります。金融専門家のカレン・ローチ氏は、株式市場が唯一の市場であるが、そこで大規模なセールが行われると、すべての顧客は割引商品を手に取って店から逃げ出すという。株式市場では、投資家が市場に勝つことができないだけでなく、投資家のリターンさえ従来の投資収益率に比べてはるかに遅れています。これら 2 つのリターンの差は「行動ギャップ」と呼ばれ、人間が取引する市場はすべて、この永続的な特性を持っています。
アマチュア投資家は誤った平均値にだまされるため、行動格差がよく見られます。彼らは、平均リターンを期待できる、または期待すべきであることを示す情報が枯渇しており、平均リターンを期待リターンと誤って認識しています。通常、株式投資の収益率は毎年約 8% から 10% ですが、ダウ ジョーンズ指数の収益率が最後に 8% から 10% の間にあったのは 1952 年のことでした。私たちが市場で期待しているものとの間には大きなギャップがあります。いわゆる「アンフォーストミス」とは、バドミントンの試合において、プレーヤーが何らかの理由でネットに戻ったり、フィールドから離れたりする状況を指します。相手のボールにプレッシャーをかけられることなく、プレーヤー自身の理由でプレーする。
株価は頻繁に大きく変動し、長期にわたって上限と下限の境界で推移し、平均線に近づくことはほとんどないため、投資家は極度のフラストレーションを感じており、この不安定な株価動向がアマチュア投資家の懐から富を流出させています。プロの投資家のポケットに資金を提供します。一方で、米国株は毎年 30% 以上上昇します。これが起こると、誘惑に耐えられる人はほとんどいません。自分のポートフォリオを他のポートフォリオと比較すると、特にポートフォリオが低い場合によくないことが起こります。 IQを高めてより高いリターンを得る一方で、危険なのは、2018年までの7年間に米国の株式市場が少なくとも30%下落したことだ。大規模な弱気相場があった年には、資産価格の急激な下落があった。人々のポートフォリオが傷つくと、リスクを取る傾向があるため、投資家の間での長期的な富の蓄積が妨げられました。株式市場が最高値または底値に達したとき、アマチュア投資家は、極めて楽観的または非常に悲観的な状況下で、やむを得ない間違いを犯す可能性が最も高くなります。株価が暴落して状況が逆転したとき、この種のストーリーは非常に魅力的であるため、人々がそれを変えないのは無責任であるように思えます。
しかし、偉大な投資家がやっていることは、他の人がやっていることとは大きく異なります。彼らは他人が欲しがらないものを買い、他人が欲しがるものを売ります。彼らは株を売ることと競馬への賭けの類似点をよく知っています。マイケル・モブソン「基本的な要素はこの馬がどれだけ速く走るかであり、期待は可能性であると指摘しました。これはハワード・マックスが「第二レベルの思考」と呼んでいるものですが、私たちのほとんどはそれに気づいていません。不注意な投資家は良い企業は良い株だと考えています。おそらく、同じ考えを持つ投資家が、優良企業の株価を「優良企業」の株価に匹敵するところまで押し上げた可能性があります。その結果、これは、会社の規模は当初よりもはるかに小さくなりました。
悪い投資と、強制されない間違いの間には大きな違いがあります。議論が間違っていたり、アイデアが価格に反映されたりします。これらはすべてゲームの一部ですが、私たちは、自分が何かをしているとわかっていても、衝動的に行動してしまうことがよくあります。間違っています。強制されない間違いを免れる人はほとんどいません。彼らがしばしばこのような行動をするのは、他人が金儲けをすることに我慢できず、自分はそうしないからです。チャーリー・マンガーはかつてこう言いました、「他人が誰かよりも早く金を稼ぐという考えは、 「あなたはそれらの大罪の一つです。嫉妬は実際には非常に愚かな罪です。なぜならそれはあなたが決して喜びを得ることができない唯一のものだからです、多くの痛みを伴いますが、楽しみはありません。それならなぜあなたはそれをするのですか?」
言ってはいけないことがあり、たとえ何も学べないとしても、私たちはそれを学ぶために苦しまなければなりません。普通の人々と最高の投資家の違いは、偉大な投資家は間違いから学び成長することができますが、間違いは失敗を犯すということです。普通の人は後戻りします。
この記事がお役に立てば幸いです。 もしそうなら、チップをおくるどうぞ
https://getalby.com/p/bitcap
-
 @ d7607464:421e573a
2024-03-12 21:40:20
@ d7607464:421e573a
2024-03-12 21:40:20Chef's notes
Details
- ⏲️ Prep time: 0 min
- 🍳 Cook time: 5 min
- 🍽️ Servings: 1
Ingredients
- 3/4 cup Raw Milk
- 1 tbsp Dutch-Processed Cocoa
- 1 tbsp Cane Sugar, to taste
- 1 tbsp Raw Unfiltered Honey, to taste
Directions
- Heat milk in a pot until steaming.
- Whisk in cocoa, sugar, and honey.
- Serve hot.
-
 @ aa55a479:f7598935
2023-02-20 13:44:48
@ aa55a479:f7598935
2023-02-20 13:44:48Nostrica is the shit.
-
 @ 634bd19e:2247da9b
2023-02-15 08:00:45
@ 634bd19e:2247da9b
2023-02-15 08:00:45かけるのこれ? 日本語入力の取り扱いイベントがおかしいw
-
 @ 2e0d81aa:ee7eb6d2
2024-03-12 21:28:00
@ 2e0d81aa:ee7eb6d2
2024-03-12 21:28:00Bitcoins Potential - Und warum Bitcoin auch in Zukunft immer weiter steigen kann
Das Potential von Bitcoin: Sehr gut gemachter, informativer Kurzfilm.
 ➡️ Youtube
➡️ YoutubeMysterium Satoshi - Bitcoin wie alles begann | Doku HD Komplettfassung | ARTE
Eine ARTE Dokumentation in mehreren Teilen: Über die Anfänge von Bitcoin und die Aspekte von digitalem Geld.
 ➡️ Youtube
➡️ YoutubeBitcoin ist Wohlstand für Generationen - Ein Kurzfilm von Matt Hornick und Tomer Strolight
Großartiger, philosophischer Kurzfilm.
 ➡️ Youtube
➡️ YoutubeBitcoin – Eine neue Weltordnung? | Sternstunde Philosophie | SRF Kultur
Bitcoin hat das Potential die Gesellschaft fundamental zu verändern.
 ➡️ Youtube
➡️ YoutubeHuman B | Die Reise in den #Bitcoin-Kaninchenbau
Gut gemachte und enthusiastische Dokumentation.
 ➡️ Youtube
➡️ Youtube -
 @ 3cd2ea88:bafdaceb
2024-03-12 20:07:58
@ 3cd2ea88:bafdaceb
2024-03-12 20:07:58L'entusiasmo per $OMI cresce a dismisura nella #Inno e #NFT Zone.
Unisciti alla campagna per vincere 20.000.000 OMI!
Depositi aperti.
Referral Code: 6w5d Referral Link: https://bonus.bitget.com/U1JNEK
Per informazioni e quotazione: https://www.bitget.com/it/support/articles/12560603806291
-
 @ c73818cc:ccd5c890
2024-03-12 20:07:28
@ c73818cc:ccd5c890
2024-03-12 20:07:28
L'entusiasmo per $OMI cresce a dismisura nella #Inno e #NFT Zone.
Unisciti alla campagna per vincere 20.000.000 OMI!
Depositi aperti.
Referral Code: 6w5d Referral Link: https://bonus.bitget.com/U1JNEK
Per informazioni e quotazione: https://www.bitget.com/it/support/articles/12560603806291
Bitget #OMI #Crypto #NFT #Inno #Referral #Bonus #BGB
-
 @ 66675158:1b644430
2024-03-12 19:46:51
@ 66675158:1b644430
2024-03-12 19:46:51For too long, our lives and activities have been surveilled and trackedby powerful third-parties like Big Tech platforms, banks, payment networks and governments. They have erected a panopticon prison of monetized monitoring, analyzing our most personal data and transactions for their own undisclosed interests. This is a fundamental violation of privacy and economic freedom.
it is time to stop. A pivotal shift is underway and we need you!Free and open source software is the antidote to this suffocating climate of surveillance.
FOSS liberates code from the controlling grip of proprietary licenses, allowing users to examine, modify and truly own the software they run without informational monopolists looking over their shoulders. And Bitcoin takes away the government and banking sector's choke-chain over money itself.
This is a revolution, but we don't seek chaos, we don't seek destruction; we're not going to burn buildings down or engage in violent protests. We won't march down the street and demand change, instead, we'll code our way to freedom.
Our revolution is digital, fueled by lines of code and secured by cryptography. We will build decentralized systems and platforms where privacy is the default and freedom is non-negotiable. We shall rebirth genuine privacy rights.
Compare the transparent code of Linux's codebase to the opaque nature of proprietary software, compare the transparent mathematics governing Bitcoin's codebase to the concealed algorithms Big Tech Platforms use to surveil and manipulate. Bitcoin's rules are open for all to verify, while Microsoft's are a collusion-prone black box.
They will fight us, they always do, but we will persevere. The petty bureaucrats and Big Tech CEOs will keep fighting us how they can, they will fight to preserve their ability to monitor and control not because they have any real legitimacy, but because FOSS and Bitcoin threaten to make their invasive rackets obsolete.
We shall create amenable territories where true privacy is the default.
Does this terrify the corporatist data oligopolies and bureaucratic surveillors? It should! No longer will free individuals be tracked and traced without consent. Value exchange, speech and human action will be freed from the shackles of centralized control, operating in a world where trust is built into the system, not imposed from above.
We will not fight with guns or bombs, there will be no blood shed; instead we will fight with ideas. We will fight with the most potent weapon at our disposal: knowledge. Encryption is our shield, and open-source protocols are our weapons. We are simply restoring privacy as the bedrock, putting the individual squarely in control over what information gets optionally revealed rather than having our data surreptitiously expropriated by middlemen.
We are coding a future where privacy is sacrosanct, economic freedom is a given, and surveillance capitalism is a relic of the past. We are crafting tools that empower the individual, disempowering the surveillance state and the oligarchs of information.
This is our battle. Not fought with weapons, but with wisdom. Not with anger, but with algorithms. Our armor is anonymity; our shield, encryption.
So we call on you, the coder, the thinker, the dreamer. Join us. Take up the tools of freedom. Contribute to the code of liberation. In every line you write, see the chains breaking. Witness the old world of control and surveillance crumble.
Join us, join the revolution, start coding. Together, we will reclaim our privacy, our freedom, and our dignity.
-
 @ 0ff1cf2c:e0f03bed
2024-03-12 18:12:42
@ 0ff1cf2c:e0f03bed
2024-03-12 18:12:42Opinion about the city of Seattle
Testing from firefox as approved!!!!! ler
myCloneOfTripadvisor #askNostr #nostrOpinion
Join the conversation!\n\nJust Testing ...
-
 @ 1e52c554:21771908
2024-03-12 17:15:17
@ 1e52c554:21771908
2024-03-12 17:15:17Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna





Analysis "Beach Renditíon 113-117"
Introduction
Francisco Luis Arroyave Tabares' Sonnets 113-117, collectively titled "Beach Rendition," are a series of romantic and sensual poems that use the beach and the ocean as metaphors for love, passion, and intimacy. The sonnets are written in the traditional Shakespearean style, with each sonnet consisting of three quatrains and a final couplet, following the ABAB CDCD EFEF GG rhyme scheme.
Thematic Analysis
Sonnets 113 and 114 set the scene, describing the beach and the ocean as a place of temptation, passion, and enchantment. The ocean is personified as a living entity with a heartbeat, veins, and hair, and the beach is a place where love knows no distance. The poet uses vivid imagery to describe the setting, such as "the ocean's heart beat in the waves," "the water has rumors of temptation," and "there is splendor in the foam's enchantment."
Sonnets 115 and 116 delve deeper into the physical and emotional aspects of the lovers' relationship. The poet uses sensual and erotic language to describe the lovers' interactions, such as "leisure and a careless splash of garments," "my ignorant hands that learnt from passion," and "my fever stops in front of thy languor." The poet also uses metaphors and similes to describe the lovers' emotions, such as "emotions yield to thy creation" and "our ebbing souls meet in the liquid mass."
Sonnet 117 concludes the series with a reflection on the lovers' experience. The poet uses metaphors to describe the lovers' feelings of freedom, joy, and surprise, such as "thus bewildered our zeals ride with the flood," "captive with joy in half conscious bondage," and "peace comes in sways of generous reprise." The final couplet, "To and fro, all our actions, on and on / Keep since then capering our abandon," suggests that the lovers' experience on the beach has had a lasting impact on their relationship.
Sonnets 113-117 by Francisco Luis Arroyave Tabares are not only a celebration of love and passion but also a tribute to the natural world. The poet's use of natural elements such as the ocean, the beach, the moon, and the stars, serve as a backdrop to the unfolding love story, but they also play an active role in the narrative, influencing and reflecting the lovers' emotions.
In Sonnet 113, the ocean is personified as a living entity, its waves are its heartbeat, the corals are its veins, and the seaweeds are its hair. This personification of the ocean creates a sense of unity between the lovers and the natural world, suggesting that their love is as deep and as vast as the ocean itself. In Sonnet 114, the water's tides are described as a "wild parade of passions," suggesting that the lovers' emotions are as powerful and as unpredictable as the ocean's tides. The mention of Venus, the planet associated with love and beauty, further emphasizes the romantic theme of the sonnet.
Sonnets 115 and 116 focus on the physical and emotional intimacy between the lovers. The poet uses sensual language and erotic imagery to describe their interactions, such as "my ignorant hands that learnt from passion," "thy girdle has challenges of fashion," and "fragments of hunger show up in thy mouth." These lines suggest a deep physical attraction and a mutual desire between the lovers.
In Sonnet 117, the poet reflects on the lovers' experience and the impact it has had on their relationship. The use of words such as "bewildered," "headlong," and "capering" suggest a sense of freedom and abandon, indicating that their time on the beach has allowed them to let go of their inhibitions and fully express their love for each other.
Throughout the sonnets, Arroyave Tabares uses a rich and varied vocabulary, including words from different languages and references to mythology, to create a unique and evocative language of love. His use of metaphors, similes, and personification adds depth and complexity to the narrative, making the sonnets a captivating and thought-provoking read.
Overall, Arroyave Tabares' "Beach Rendition" sonnets are a beautiful exploration of love and passion, using the beach and the ocean as powerful metaphors for the lovers' physical and emotional experiences. The sonnets are rich in imagery, metaphor, and sensual language, making them a captivating and evocative read.
Rhyme Scheme
As mentioned earlier, these sonnets follow the traditional Shakespearean sonnet structure, which consists of three quatrains (four-line stanzas) and a final couplet (two-line stanza), with a rhyme scheme of ABAB CDCD EFEF GG.
Additional Aspects to Analyze
Let's delve into some additional aspects of these sonnets that have not been covered yet.
-
1. Use of Alliteration and Assonance: Arroyave Tabares uses alliteration and assonance to create a musical quality in his sonnets. Alliteration is the repetition of the same consonant sounds at the beginning of words, while assonance is the repetition of the same vowel sounds. For example, in Sonnet 113, "heaven is now preparing a huge fire" uses alliteration of the 'h' sound, and "the water has rumors of temptation" uses assonance of the 'o' sound.
-
2. Use of Metaphor and Simile: The poet uses metaphor and simile to create vivid and evocative images. For example, in Sonnet 115, "fragments of hunger show up in thy mouth" is a metaphor for desire, and in Sonnet 116, "Selene colors thy flock with silver blond" is a simile comparing the woman's hair to a flock of sheep bathed in moonlight.
-
3. Use of Classical References: Arroyave Tabares incorporates references to classical mythology and astronomy in his sonnets. For example, in Sonnet 115, "hathoric" refers to Hathor, the ancient Egyptian goddess of love, and in Sonnet 117, "Eos" refers to the Greek goddess of dawn. These references add depth and richness to the sonnets, connecting the lovers' experiences to timeless and universal themes.
-
4. Use of Sensory Imagery: The poet uses sensory imagery to engage the reader's senses and create a vivid and immersive experience. For example, in Sonnet 114, "moist purple edged lips ardently touch" engages the sense of touch, and in Sonnet 116, "some fresh and wanton scents our senses please" engages the sense of smell.
-
5. Use of Enjambment: Arroyave Tabares uses enjambment, which is the continuation of a sentence without a pause beyond the end of a line, couplet, or stanza. This technique creates a sense of flow and continuity, reflecting the ongoing nature of the lovers' passion. For example, in Sonnet 117, the sentence "Captive with joy in half conscious bondage / Our best yearnings in open space entwine" spans two lines, creating a sense of fluidity and movement.
-
6. Use of Personification: The poet uses personification to give human qualities to non-human entities, such as the ocean and the night. This technique creates a sense of unity between the lovers and the natural world, suggesting that their love is a part of the larger universe. For example, in Sonnet 113, "We feel the ocean's heart beat in the waves" gives the ocean a human-like heartbeat, and in Sonnet 114, "the water gives us tides" gives the water the human ability to give.
-
7. Use of Symbolism: Arroyave Tabares uses symbolism to convey deeper meanings. For example, the ocean and the beach are not just physical locations but symbols of the vastness and depth of the lovers' feelings for each other. The ocean's waves represent the ebb and flow of their emotions, while the beach symbolizes the physical space where their love unfolds.
-
8. Use of Contrast: The poet uses contrast to highlight the intensity of the lovers' emotions. For example, in Sonnet 116, "My fever stops in front of thy languor" contrasts the speaker's feverish passion with the beloved's languid demeanor. This contrast serves to heighten the sense of the speaker's ardor.
-
9. Use of Repetition: Repetition is used to emphasize key ideas and feelings. For example, in Sonnet 117, the phrase "To and fro" is repeated, emphasizing the back-and-forth motion of the waves and the lovers' emotions.
In conclusion, Francisco Luis Arroyave Tabares' Sonnets 113-117 are a rich tapestry of poetic techniques and devices, creating a vivid and evocative portrayal of love and passion set against the backdrop of the natural world.
(GPT4)
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Images taken on the beaches of Santa Marta, Colombia. First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com






-
-
 @ 46fcbe30:6bd8ce4d
2024-03-12 16:45:41
@ 46fcbe30:6bd8ce4d
2024-03-12 16:45:41Opinion about Mycelium Bitcoin Wallet (android)
As its former maintainer, my opinion might be biased but ... here we go:
Some background
History
Mycelium is one of the oldest Android wallets and started as "Bitcoin Spinner". Its code repository started in June of 2013 giving "all code credit to Jan Møller", who left this project to found probably the most controversial company in the space: Chainalysis". Legends say that Alexander Kuzmin bought the rights to the project and subsequently renamed it to "Mycelium" involving a barrel of neft vodka which is produced in Austria, where the second round of lead developers were located. Austrian Daniel Weigl led the project development when I joined basically cold-calling them as I was using the project since the Bitcoin Spinner days and needed something fixed. So they hired me and when Daniel left, I took over as the maintainer and lead developer.
My role
As the maintainer, I was responsible to coordinate the development and above all, keep the product secure while the upper management wanted to see features being added. So my work transitioned from being the lead developer, contributing code to being only the maintainer, almost exclusively reviewing other developer's work for security issues.
WalletScrutiny
In my job interview at Mycelium, I already suggested to improve the transparency of the product by making sure it was reproducible. The team had worked on that already but never got time to actually finish it and with me on the team it took another year before Mycelium switched to committing to only release fully auditable versions.
I founded WalletScrutiny while at Mycelium because I saw the lack of this transparency as a systemic issue and not only an issue at my own work place.
Security
Mycelium has a very old code base and maintains its own crypto library which did attract some attention around external experts but certainly not as much as others. I did spend a lot of time reviewing it until three years ago but I never had formal training as a cryptographer.
Mycelium has many features and tends to only add more:
- Shamir Shared Secret
- Login with Bitcoin
- Colored Coins
- Sign messages
- Import Xpubs or Xprivs
- Spend from a QR-Code
- FIO protocol
- Some shitcoins (Bitcoin Vault, ETH, ETH tokens)
- ...
That means it has a huge code base and uses dependencies of questionable provenance. Especially the FIO and BTCV dependencies are probably poorly audited and could contain backdoors affecting users that don't even use these features. That said, while I was the maintainer I had to add these two features and those were stressful weeks of me pushing back a quick release. While my push-backs were always well received at the time, I worry about today's maintainer maybe being less insisting when it comes to security. Sadly Mycelium is very quiet about such internals, so I don't even know who this maintainer would be now or what Mycelium was up to recently.
Features
A very much missing feature is lightning. Without lightning, this product will be obsolete with on-chain fees rising.
Privacy
When I joined the company, privacy was a top priority. The product had its custom servers that did not log IP addresses and the client did support TOR.
The TOR button is still in the app but it essentially does nothing.
Management often requested to keep logs of wallet balances to have some metrics of success beyond the downloads that Google reports and it was engineers who pushed back successfully. I cannot know to which degree this is still kept up and especially the ignorance regarding the TOR feature makes me not very confident about them not tracking wallets by now.
Openness
Mycelium and especially its owner always was very low profile with officially no official social media activity.
The public issue tracker is getting attention on a yearly basis - maybe.
But ... the source code is 100% public and reproducible.
Summary
The Mycelium wallet for Android was my main driver while I worked as its security guy but my lack of insight into their current security practices and their openness to adding questionable ads and features leads me to not trust this product with any significant amount.
It is a good tool to spend with a Trezor on the go though.
WalletScrutiny #nostrOpinion
-
 @ c31052c1:493a1c56
2024-03-12 16:42:27
@ c31052c1:493a1c56
2024-03-12 16:42:27Mineral Dapp即将在不久后推出,许多持有人都对未来的功能表现期待。因此,整理了过去参加space上对于L2部分的答疑,并与大家一同分享。具体的功能内容将在正式上线后向公众揭晓,感谢您的耐心等待。
1. 介绍自己所代表项目,以及该项目在Merlin Chain 生态中的角色
Mineral 有两个主要的资产 12/31公平发射的Mineral和之后公布的MNER( 国库币),我们自己的定位是首个在Merlin Chain上基于BTC算力的DeFi资产项目,我们透过挖矿正外部性的高收益,去补足了DeFi 1.0缺乏可持续性的缺陷,这也就是为什么大家熟悉的头部DeFi像 Curve、 Maker Dao开始买美债,但比特币挖矿收益从年化20%到几百都是可能的,相比美债个位数的收益挖矿更好些,结合挖矿这种原生机制和铭文这样的原生资产,我们期望Mineral/MNER就是crypto的美债。举个例子: 矿机是小麦,把小麦磨碎了磨小就变成面粉,Mineral和MNER就会是面粉,面粉可以用来做面包、包子、面条、烧卖,相信大多数的人不会为了吃面点去自己种小麦磨面粉,就像比特币挖矿一般散户是很难参与的,其中也包含怎么找矿机来源、好的运维、好的电费,我们等于是解决这些难题,透过Mineral/MNER这样标准化的产品就是面粉,让大家能参与。
2. Merlin's Seal 有何不同?
最显而易见的就是Merlin更大的格局,我们站在DeFi应用资产的角度,非常感谢有Merlin这样的舞台允许Mineral持有人能一矿多挖,这一矿三挖的想法也是老板在社区里提出来的,restaking在以太上也已经是很成熟的机制,不过先前在比特币生态上,之前没环境这样做,现在有了Merlin,我们也非常荣幸能成为Merlin上实践restaking的项目。提到这restaking,相信大家也看了我们的推文,正在开发能够让质押在Merlin Seal的Mineral质押人,能够不用去犹豫该质押在Merlin Seal还是质押在Mineral我们之后推出的DeFi上,简单来说就是先质押在Merlin Seal再透过M-token参与到我们之后推出的原生DeFi质押玩法,详细规则我们开发测试后会发布,但能肯定的是现在把Mineral质押进Merlin Seal,在Merlin锁仓期间,不太影响参与DeFi质押的权益。更重要的是,我们能做到的不仅仅是一矿三挖,而是一矿多挖,稍为透露一下: 未来Merlin swap也是会有合作,未来透过Dex去交易也能挖他们的币,那DeFi强调开放性和可组合性,一矿多挖是可以期待的。
3.各位嘉宾对于各自所代表的项目/资产的后续发展有怎样的预期
我们很快的会上线二层DeFi的玩法,目前矿机已经上架在跑,实现大家预期的睡后收益(睡觉的睡),团队也持续推进二层玩法的开发、测试,包含落地质押Mineral进Merlin之后的restaking,那刚刚也提到Mineral 和 之后公布的MNER 会是Merlin上优质的底层升息资产,我们也预期之后会有更多的项目去持有Mineral 和 MNER作为APY来源,这次和Merlin的合作也是个很好的范例,拿Mineral去质押进Merlin Seal,拿到不仅仅是Merlin的激励,之后还能透过M token参与Mineral二层质押的收益,在未来大家有机会能再把stMineral 或者stMNER再质押进其他项目挖其他的币,真正的多挖显现在此,一切都可以源自于Mineral和MNER。
4.嘉宾对比特币生态的未来有什么期待?
比特币生态是这轮牛市主要的叙事,BTC DeFi也绝对会是主线任务之一,大家可以看看互联网和Crypto的发展历程,人性都是追逐升息利益的,以太最早起来的是DeFi,后面起来的GameFi也是包着游戏的DeFi,DeFi 1.0缺的就是正外部性收益,DeFi 1.0流传句老话,如果你找不到生态的利息来源,你很可能就是那个利息来源也就Ponzi,我们做为收入是比特币原生,协议也是原生的产品,结合挖矿这样可持续性的正外部高质量收益,我们项目可以是那个改进DeFi模型的底层APY来源。 比特币是数字黄金,拥有巨量TVL的储备,过去没有好的环境去释放这些TVL,现在有了铭文和二层环境像Merlin,条件已经具备,从数据去看现在生态还是显著低洼区,比特币市值9000E 对比 以太币市值 3000E,但是比特币生态80E 远小于 以太生态 2900 E,比特币生态 TVL 更是只有以太生态TVL的0.2%,换个方式说: 比特币生态光是追平以太生态就能有500倍的增幅空间。
BTC是Web2流动性的窗口,随著spot ETF通过,更多传统资金留意到Crypto的可发展性,那他们进圈第一个接触的就是BTC,资金沉淀的第一步就也在BTC生态上,机构肯定会留意比特币原生的生态和收益,加上Merlin提供的DeFi的环境非常好,也有好的社区,那被大家看见的机率就大,加上之后美联储开始降息,美债收益会下调,传统的机构也可能会转向比特币原生的升息资产作为底层,比如BlackRock投了四家北美头部的比特币矿企,又好比Maker Dao 持有了 1.2 billion的美债,这些都可以是Mineral/MNER的潜在持有人。
-
 @ c31052c1:493a1c56
2024-03-12 16:42:00
@ c31052c1:493a1c56
2024-03-12 16:42:00Wallet Setup
- Preparing your new wallet
Download the Unisat Wallet via google chrome at https://unisat.io and add the google chrome extension. Unisat currently offers the most robust support for BRC420.

- Open the UniSat Wallet chrome extension either import your exist wallet or create a new wallet. Be sure to save your secret recovery phrase and do not share it with anyone else. Our team at Mineral will never ask for your secret phrase.

- Select the “Taproot” address followed by m/86/0/0/0 and click on continue.
 4.Use the copy address button as illustrated to copy your wallet’s address to deposit BTC assets from other wallets and/or exchange wallets. The same address is used to receive BRC420 assets e.g. Minerals.
4.Use the copy address button as illustrated to copy your wallet’s address to deposit BTC assets from other wallets and/or exchange wallets. The same address is used to receive BRC420 assets e.g. Minerals.

 Your UniSat wallet is now set up.
Welcome to the Mineral community. We hope the year of the dragon in 2024 will brought along a wealth of pleasant surprises and good fortune. Let's get started and don’t miss out on a brand new world of RWA on Merlin.
Your UniSat wallet is now set up.
Welcome to the Mineral community. We hope the year of the dragon in 2024 will brought along a wealth of pleasant surprises and good fortune. Let's get started and don’t miss out on a brand new world of RWA on Merlin.
Linktree: https://linktr.ee/mner.club
- Preparing your new wallet
Download the Unisat Wallet via google chrome at https://unisat.io and add the google chrome extension. Unisat currently offers the most robust support for BRC420.
-
 @ 1e52c554:21771908
2024-03-12 16:38:25
@ 1e52c554:21771908
2024-03-12 16:38:25Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna

Analysis "Beach Rendition 5"
Introduction
“Beach Rendition #5” by Francisco Luis Arroyave Tabares is a beautifully crafted sonnet that explores the themes of nature, freedom, and the passage of time.
Thematic Analysis
First Quatrain (Lines 1-4): The sonnet begins with a metaphor of human passions (“zeals”) being carried away by the flood (the ocean), suggesting a sense of overwhelming emotion or experience. The “headlong heights far from the sod” could symbolize the dizzying, lofty aspirations or experiences that take us away from our grounded reality. The “gyves besprent with contention” refers to shackles sprinkled with conflict, indicating struggles or challenges.
Second Quatrain (Lines 5-8): The second quatrain continues the theme of overwhelming emotion, describing it as a joyful captivity. The “multitudinous skies” that reflect our dreams arranged in two rows could symbolize the vast possibilities or aspirations we hold.
Third Quatrain (Lines 9-12): The third quatrain introduces the concept of peace, coming in waves of repetition, until the dawn (Eos) appears. The speaker is brought back from the overwhelming night that fades (sears), possibly indicating a return to reality or the end of a powerful experience.
Couplet (Lines 13-14): The concluding couplet suggests a continuous cycle of actions, dancing (capering) in abandon, possibly indicating the ongoing nature of life’s experiences and emotions.
Overall, this sonnet seems to explore themes of overwhelming emotions, lofty aspirations, and the cycle of experiences in life. It uses rich metaphors and imagery to convey these themes. Please note that poetry interpretation can be subjective and may vary based on individual perspectives.
Rhyme Scheme
The sonnet follows a unique rhyme scheme that doesn’t strictly adhere to the traditional English or Italian sonnet forms. Here’s a detailed analysis:
Quatrain 1 (Lines 1-4): ABAB
“flood” (A) “persuation” (B) “sod” (A) “contention” (B)Quatrain 2 (Lines 5-8): CDCD
“bondage” (C) “entwine” (D) “image” (C) “aline” (D)Quatrain 3 (Lines 9-12): EFEF
“reprise” (E) “appears” (F) “surprise” (E) “sears” (F)Couplet (Lines 13-14): GG
“on and on” (G) “abandon” (G)This rhyme scheme is unique and adds a distinctive rhythm to the sonnet. The final couplet, with its perfect rhyme, provides a satisfying conclusion to the poem.
Additional Aspects
Let’s delve deeper into the analysis of Sonnet 117 by Francisco Luis Arroyave Tabares:
Language and Imagery: The sonnet uses a rich and complex language, employing a variety of literary devices such as metaphors (“zeals ride with the flood”, “headlong heights far from the sod”), personification (“east Eos appears”), and alliteration (“bewildered our zeals”, “best yearnings”). The imagery is vivid and evocative, painting a picture of overwhelming emotions, lofty aspirations, and the vastness of the skies.
Themes: The sonnet explores several themes, including the power of emotions, the pursuit of dreams, the cycle of experiences, and the tension between freedom and bondage. The theme of nature is also prominent, with references to the ocean, the skies, and the dawn.
Meter: The sonnet appears to follow the iambic pentameter, which is the most common meter in English poetry and is often used in sonnets. This means each line typically contains five iambs, or metrical feet, each consisting of one unstressed syllable followed by one stressed syllable. However, there are variations in some lines, which adds rhythmical complexity to the poem.
Overall: this sonnet is a complex and thought-provoking piece of poetry. It uses sophisticated language and imagery to explore deep themes, and its rhythmic structure adds to its emotional impact. The sonnet invites multiple readings and interpretations, reflecting the richness and complexity of human experience. Please note that poetry interpretation can be subjective and may vary based on individual perspectives.
(GPT4)
Syllable count for each line.
``` Beach Renditíon #5
10 Thus bewildered our zeals ride with the flood
10 All their meekness gone with our persuation 10 Till we find headlong heights far from the sod
10 And free of gyves besprent with contention.10 Captive with joy in half conscious bondage 10 Our best yearnings in open space entwine 10 And multitudinous skies an image
10 Of our dreams bifariously aline.10 Peace comes in sways of generous reprise
10 Until, blushing, by east Eos appears
10 Oh yes, the musk, thy face and my surprise 10 Bring me back from this full night that now sears.10 To and fro, all our actions, on and on 10 Keep since then capering our abandon.
***
```
Sonnets For The Twenty First Century And A Circadian Musical Written By Francisco Luis Arroyave Tabares (1984-1987)
Analyzed by GPT4; Image by Frank Duna; First published on Nostr Protocol by franciscoarroyavet@nostrplebs.com
 Beach Rendition # 5
Beach Rendition # 5 -
 @ 3cd2ea88:bafdaceb
2024-03-12 16:24:26
@ 3cd2ea88:bafdaceb
2024-03-12 16:24:26💸 1. Afflusso record di $2,7 miliardi nelle criptovalute: La settimana si apre con un segno positivo per il mercato crypto, che registra un afflusso record di $2,7 miliardi negli ultimi sette giorni. Questo dato, il più alto da luglio 2023, indica un crescente interesse da parte degli investitori istituzionali verso le criptovalute.
😈 2. MicroStrategy raddoppia il suo impegno su Bitcoin: La società di software MicroStrategy, guidata da Michael Saylor, ha annunciato l'acquisto di altri Bitcoin per un valore di $800 milioni. L'operazione porta il totale di Bitcoin posseduti da MicroStrategy a oltre 129.000, per un valore complessivo di circa $5,9 miliardi.
💀 3. Biden ripropone la tassa del 30% sul mining di criptovalute: La nuova proposta di bilancio del presidente Biden include una tassa del 30% sui profitti derivanti dal mining di criptovalute. La misura, già presente in una precedente versione del piano, ha incontrato l'opposizione di alcuni esponenti del settore crypto.
🕺 4. El Salvador incassa oltre $74 milioni da Bitcoin: Il governo di El Salvador, che ha adottato Bitcoin come valuta ufficiale, ha annunciato di aver guadagnato oltre $74 milioni in profitti dalla sua riserva di Bitcoin. Il presidente Nayib Bukele ha ribadito la sua fiducia nella criptovaluta, definendola un "investimento per il futuro".
🌟 5. Trump promette di non reprimere le criptovalute: L'ex presidente Donald Trump ha dichiarato che, se eletto nuovamente, non vi sarà alcuna repressione su Bitcoin e sulle criptovalute. Le sue parole hanno avuto un impatto positivo sul mercato, con alcuni analisti che vedono in Trump un potenziale alleato per il settore.
🔥 Le notizie di oggi offrono un quadro misto per il mercato crypto. Da un lato, l'afflusso record di capitali e l'acquisto di Bitcoin da parte di MicroStrategy sono segnali positivi. Dall'altro, la proposta di tassa del 30% da parte di Biden e l'incertezza del quadro regolatorio potrebbero frenare la crescita del settore.
👓 Cosa tenere d'occhio: L'evoluzione del quadro regolatorio negli Stati Uniti e in altri paesi. La reazione del mercato alla proposta di tassa di Biden. Il possibile impatto delle elezioni presidenziali americane sulle criptovalute.
🎳 Iscriviti al nostro canale per rimanere aggiornato sulle ultime notizie dal mondo crypto e per partecipare a un dibattito aperto e costruttivo! https://t.me/BitcoinReportChannel
☄️ Nella nostra community Bitcoin Report Italia, troverai un ambiente accogliente dove gli esperti ti guideranno nei primi passi nel trading, offrendo analisi, strategie di trading e l'opportunità di partecipare al CopyTrading con trader professionisti.
🚨 Iscrivendoti con il nostro referral code su Bitget (6w5d), potrai avere un contatto diretto con trader che ti aiuteranno a crescere nel mondo del trading di criptovalute.🚀
📣 https://t.me/Bitcoin_Report_Italia

