-
 @ 6a39a186:88f51c19
2024-06-26 04:11:28
@ 6a39a186:88f51c19
2024-06-26 04:11:28From its inception, Bitcoin promised a financial system free from centralized control. But as the space matures, lingering questions emerge around how founders reconcile cryptocurrency's decentralized roots with real-world identity constraints.
Satoshi Nakamoto's true identity remains unknown, offering a glimpse into Bitcoin's visionary's desire for separation from governmental oversight. Yet exchanges today demand personal details like Social Security Numbers (SSNs) and Know-Your-Customer (KYC) verification.
On the surface, complying with national identification regulations maintains cryptocurrency's accessibility for widespread use and investment. However, does aligning too closely with traditional gates of finance risk compromising the technology's disruptive potential?
As one Nostr user pointed out, prominently featuring country flags in product promotion while relying on identity markers like SSNs seems contradictory to Bitcoin's original spirit. Is there a better balance to be found between real-world usability and decentralized ideology?
Rethinking Identity in a Borderless World
Some founders argue anonymous usage enables censorship resistance—a key attribute for populations under oppressive regimes. But lack of ID verification enables illicit activity, threatening regulatory acceptance.
A middle ground may lie in focusing orientation around identity of choice, not circumstance of birth. Decentralized identifiers (DIDs) linked to public keys, not passports, could help map individuals across jurisdictions and blockchains while preserving privacy.
Bridging Gaps Between Vision and Reality
As with any emerging technology, reconciliation occurs between idealism and practicality. Perhaps the solution lies not in absolutes but evolution—loosening reliance on singular national identities over time as decentralized technologies mature.
Promoting flagship cryptocurrencies while solely using legacy systems of control presents an ideological conflict worth addressing openly. By acknowledging tensions and exploring alternatives, the industry can progress toward building a financially inclusive yet autonomous global community.
-
 @ 6a39a186:88f51c19
2024-06-26 04:04:31
@ 6a39a186:88f51c19
2024-06-26 04:04:31As technology becomes more deeply integrated into every aspect of our lives and work, those tasked with protecting our digital security must expand their skills. For too long, some in the cybersecurity field have relied solely on a narrow technical education without making an effort to truly understand the systems they aim to secure.
Those on the front lines battling hackers and vulnerabilities would be better equipped if they took the time to gain development experience. Code is at the heart of every program, app, site and network - does it not make sense for "experts" to familiarize themselves with the language behind the tools, platforms and infrastructure they work tirelessly to shield?
Rather than dismiss programming as something beyond their purview or ability, security professionals would be wise to embark on their own learning journey. A basic understanding of coding principles and logic can offer invaluable perspective into how applications are built, how users interact with interfaces, and where weaknesses may lie.
Closing Knowledge Gaps
Some argue their roles require a focus only on monitoring, detection and response - not software engineering. But is there not value in comprehending at a fundamental level what one is working so fervently to protect? Knowledge gaps leave room for overlooks and errors. True experts seek constant improvement by addressing blind spots.
Bridging Divides
Learning to code could also help bridge perceived divides between security and development teams. With a shared foundation of coding literacy, collaborators gain ability to speak each other's languages - literally and figuratively. Barriers break down as roles blend and partners recognize shared goal of building secure products.
In a field where change is constant, remaining stagnant is to fall behind. Those tasked with our digital wellbeing would serve us well by continuing self-education into new realms. The journey to code literacy may be challenging, but challenges build character and skills. Our security depends on experts who expand expertise - not rest on past achievements or limit vision with excuses. Our networks and data are too valuable not to ensure guards have tools to see potential issues invisible to the untrained eye.
The question is not whether one's role demands coding - but whether we entrust our security to those resolving to know systems as intimately as those aiming to breach them. Our defenders would do well to learn the tongue of that which they defend.
-
 @ 6dcaee2b:66134885
2024-06-24 13:38:35
@ 6dcaee2b:66134885
2024-06-24 13:38:35Chef's notes
I got the idea for this recipe from row 7 seeds.
Details
- ⏲️ Prep time: 15 to 25 minutes
- 🍳 Cook time: None
- 🍽️ Servings: 8
Ingredients
- 2 small red onions thinly sliced
- A handful or more of herbs chopped. I like dill, cilantro, parsley
- Dressing:
- 2 tablespoons whole grain mustard
- 1 tablespoon honey
- 1 clove garlic, I used a few garlic scapes.
- 1/2 cup olive oil
- 4 tablespoons rice vinegar or vinegar of choice
- Salt/pepper to taste
Directions
- In mixing bowl combine mustard, honey, garlic, salt/pepper, and vinegar. Slowly drizzle olive oil while whisking to emulsify dressing.
- Combine vegetables in large bowl. Pour dressing over vegetables and combine and mix till dressing has fully coated vegetables. Test for seasoning. Adjust if necessary.
-
 @ ca4e5bf2:96645a6b
2024-06-25 23:32:08
@ ca4e5bf2:96645a6b
2024-06-25 23:32:08Prismas de lightning
Un aspecto que aún está tremendamente poco utilizado es la programabilidad de bitcoin. Existen cosas simples como las transacciones programadas (agendadas, temporizadas) y los pagos múltiples automatizados, pero indudablemente seguimos atrapados en el pensamiento convencional acerca del flujo de los sats.
Quisiera proponer una idea simple que fue compartida conmigo hace unos meses, con la esperanza de que se distribuya ampliamente y, en el mejor de los casos, alguien la implemente. (O una mejor versión de ella).
Es la siguiente:
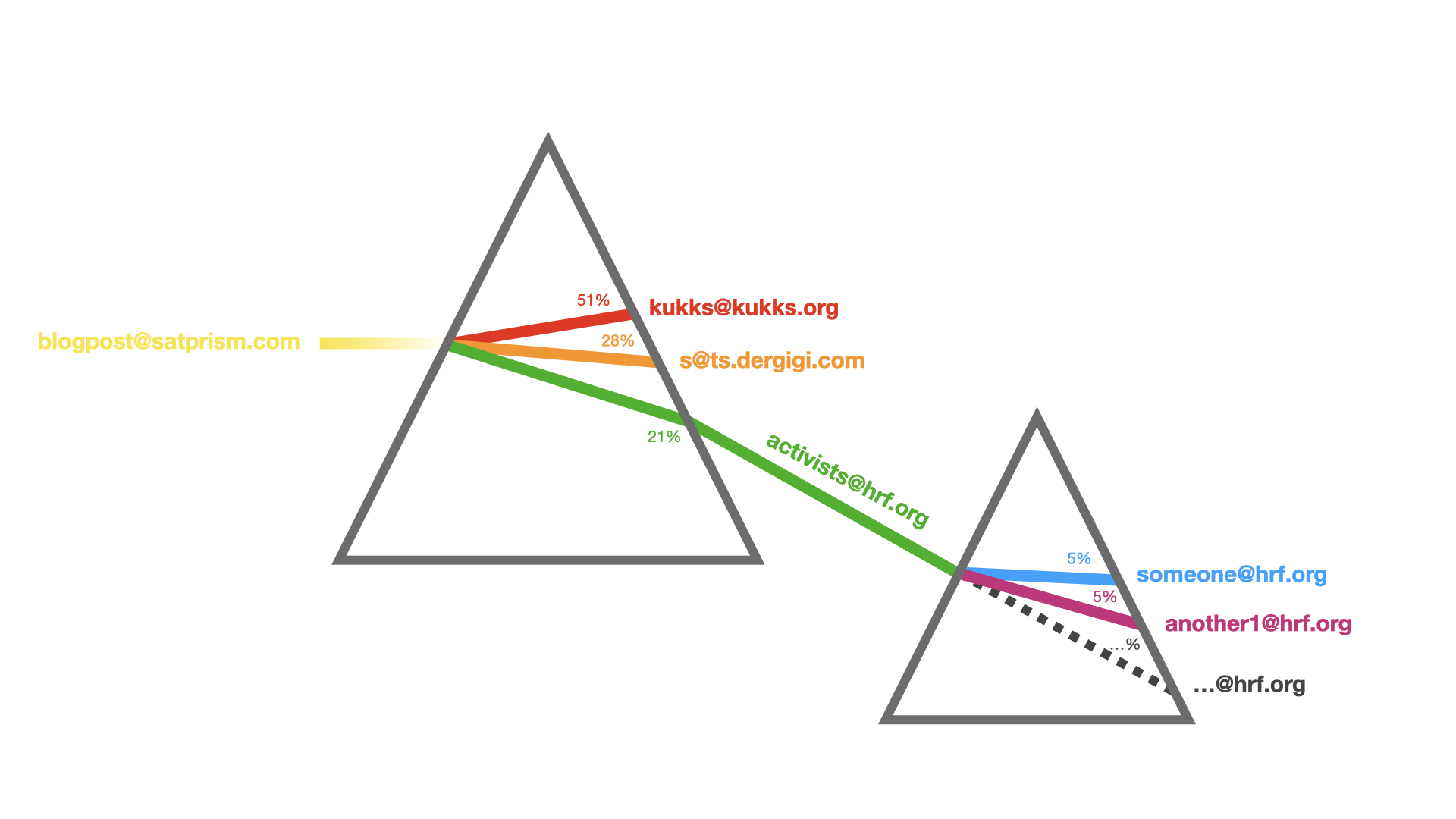
Todo el crédito a Mr. Kukks, quien está oficialmente sin tiempo[^1] para implementarla él mismo.
Prismas de lightning
Un prisma de lightning es un constructo que permite "flujos de división de valor entre direcciones de lightning", parafraseando al autor.
Básicamente, sus características son: - un prisma se identifica con una dirección de lightning (o algo similar) - un prisma tiene un o múltiples receptores - un prisma puede ser receptor de otro, es decir, formar una "cadena de prismas" - las divisiones se definen programáticamente, esto es, con código
Este constructo simple permite todo tipo de casos de uso y puede ser implementado en la capa de las aplicaciones, sin ningún cambio en los protocolos de Bitcoin o Lightning.
Un ejemplo obvio es la división de valor para artículos de blogs y formas similares de escritura de extensión considerable. Imagina si cada artículo (o capítulo de un libro) tuviera su propia dirección de Lightning, repartiendo valor entre autor, editor, ilustrador y revisores del texto automáticamente.
El concepto de esas divisiones de valor ya existe en el podcasting 2.0, donde se aplica ampliamente a podcasts y episodios. Podría argumentarse que tener un identificador separado para el constructo es la evolución natural de esa forma de compartir valor, ya que sería más fácil conceptualizarlos y encadenarlos entre sí.
Otro caso de uso obvio es compartir los zaps de Nostr. Imagina que cada tweet citado que es zappeado se divide automáticamente, pasando el 50% (o el monto configurado por el usuario) a la nota original. O imagina un prisma creado ad-hoc, repartiendo los zaps equitativamente para todos los etiquetados en una nota.
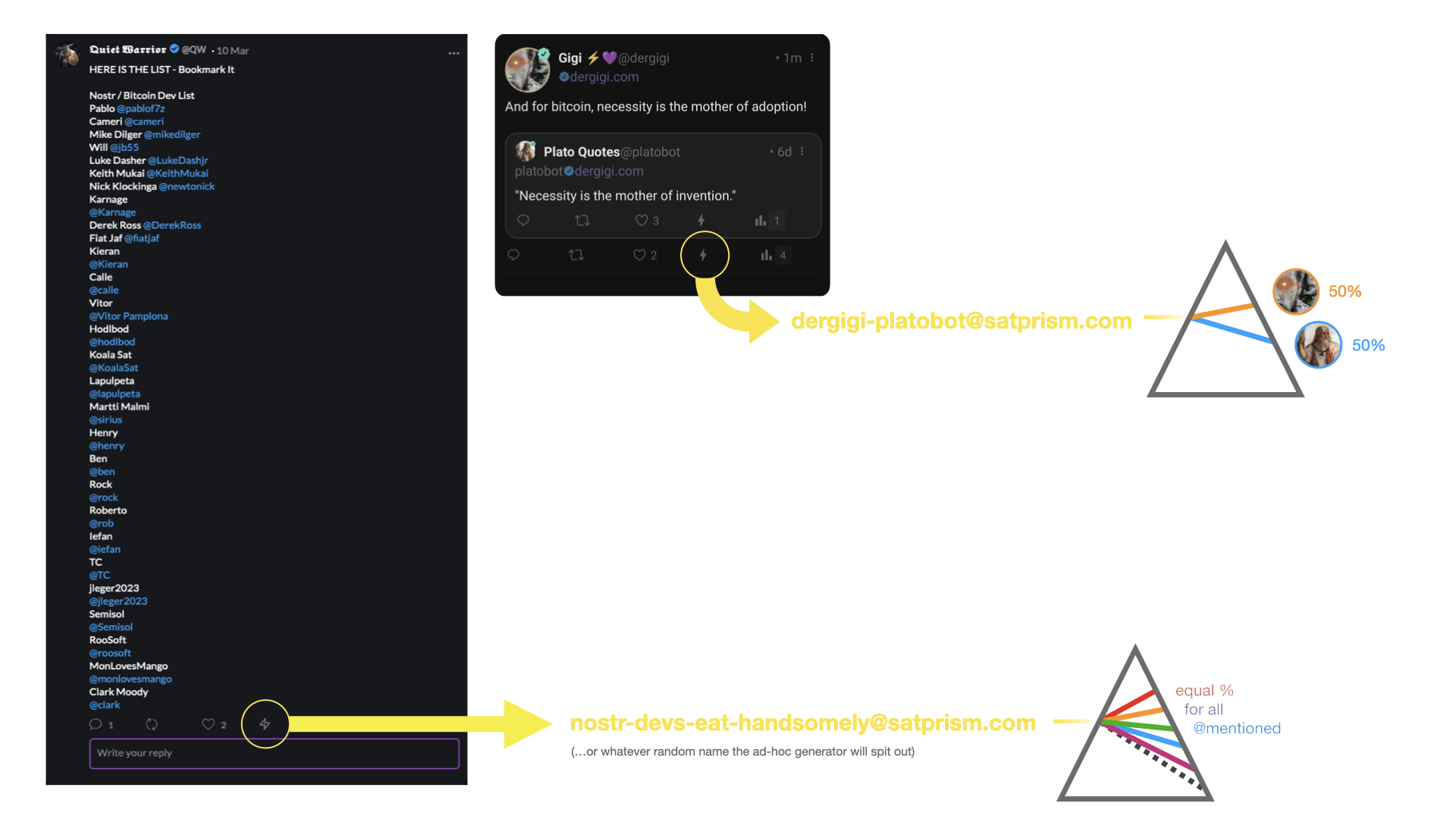 ¡Splits de sats para nostr! ¿acaso hay algo mejor?
¡Splits de sats para nostr! ¿acaso hay algo mejor?Como los pagos son redirigidos, cada prisma actúa como una especie de proxy. Esto puede ser útil tanto para organizaciones como para individuos, ya que tu identificador de pago permanece igual incluso si tu infraestructura subyacente o proveedor de billetera cambian.
Problemas y mejoras
Existen dos preocupaciones centrales: comisiones y privacidad. No sólo hay que tener en cuenta las comisiones derivadas de la división y redirección de los pagos, sino también el hecho de que las direcciones ligthning se basan en IP, lo que tiene ciertas implicaciones de privacidad. Podríamos usar LNURL sobre nostr -de nuevo, créditos para Kukks- que trae a colación la siguiente pregunta: ¿son las direcciones lightning (Lightning Addresses) el nivel de abstracción correcto para los prismas de lightning?
Al fin y al cabo, no queremos enviar sats a direcciones sino a personas. Si nostr continua tomando vuelo, podría convertirse en sí mismo en la libreta de direcciones global para ese tipo de cosas, en otras palabras, el lugar al que se acude para buscar información de pago de personas, organizaciones y otras entidades. En el futuro, un prisma podría tener múltiples identificadores
nprofileonpubcomo destinos, detrás de los cuales está la información de pago concreta.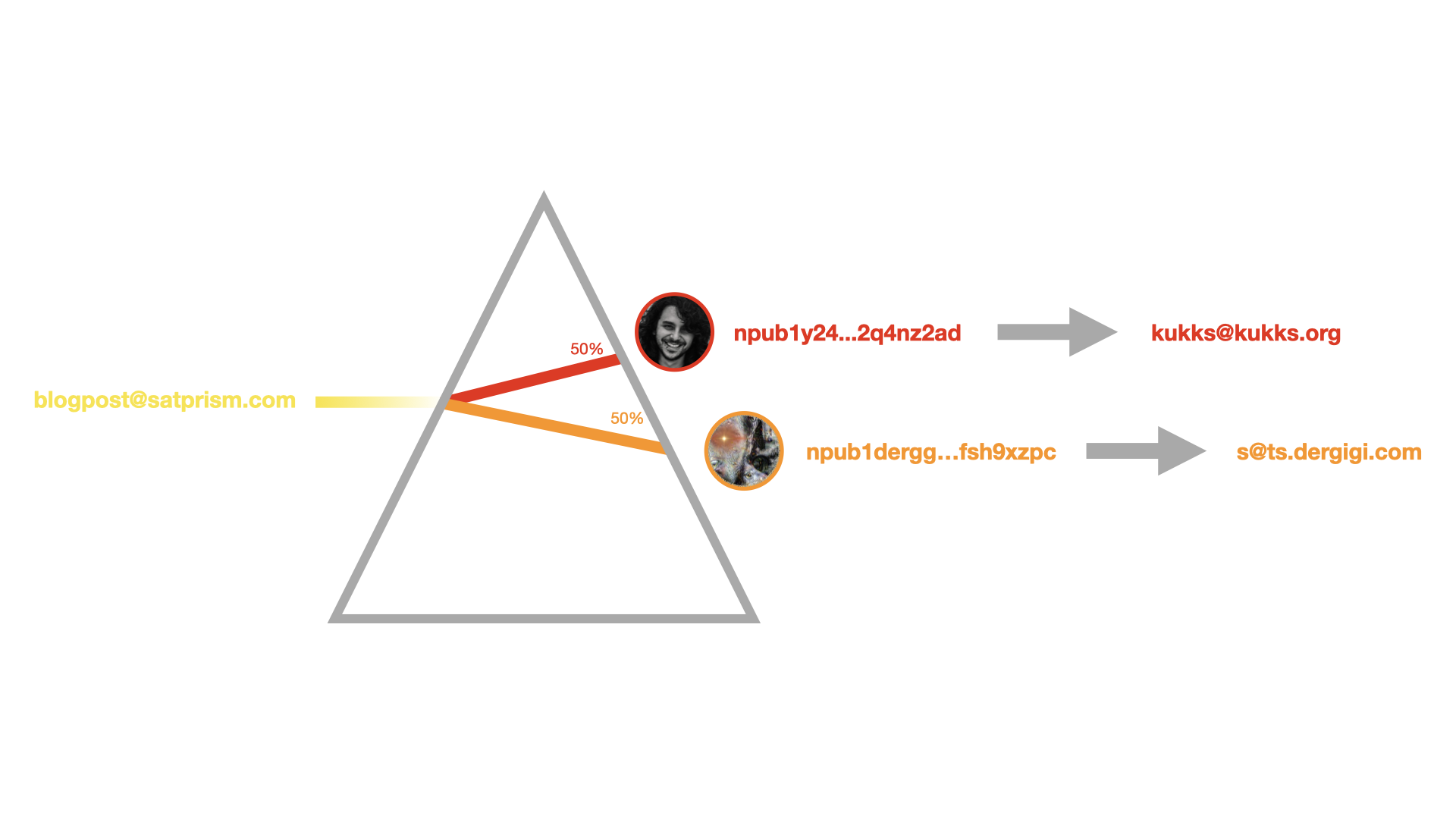
Los identificadores no tienen que ser necesariamente direcciones lightning (Lightning Addresses). ¡
Npubso similares también pueden funcionar!En cualquier caso, en este punto, no estoy demasiado preocupado por los detalles de la implementación. Estoy preocupado por una falta de imaginación, que es a lo que este post intenta responder.
Hablando de imaginación: ¿Por qué no tenemos ninguna billetera que automáticamente mueva sats a otra a partir de un cierto umbral? Estoy más que feliz de tener dinero para el almuerzo en una billetera custodial (delegada, controlada por terceros), pero una vez que alcanza tres meses de renta ya no estoy tan cómodo. ¿Por qué no puede la billetera automáticamente enviar el excedente de sats a mi dirección lightning soberana una vez que contiene más que el monto de una cena? O hacer un loop-out mensualmente para mover mis sats a almacenamiento frío?
Bueno, divago.
Una mejora que me gustaría ver es que se provean los prismas de forma transparente. En el mejor caso, los usuarios deberían poder ver cómo los pagos se reparten, de una forma fácil de entender y verificar. Una posibilidad es transmitir un evento reemplazable parametrizado (definido por el NIP-33) cada vez que un prisma se crea o actualiza. Claro que, dependiendo del caso de uso, puede tener sentido mantener el/los lugar/es finales ocultos del público.
Estoy seguro de que existen más problemas y muchas otras mejoras, pero, como siempre, lo perfecto es enemigo de lo bueno, así que hablemos sobre soluciones prácticas que pueden ser implementadas y usadas ahora mismo.
Implementación
Los prismas basados en direcciones lightning pueden ser construidos hoy sin demasiado esfuerzo. Podrías incluso construirlo tu mismo sin ninguna experiencia programando utilizando dos extensiones de LNbits: scrub y split. Agrega satdress encima para darle a cada billetera su propia dirección lightning y ¡voilà!, tienes un prisma de lightning. Puedes incluso construir una buena interfaz sobre él, ya que todo lo anterior puede ser creado programáticamente con simples llamadas de API.
Hice todo eso (excepto el "construir una buena interfaz sobre él) para juguetear con la idea. Sí, es algo precaria y probablemente no sea la solución más estable o elegante, pero más o menos funciona y puede ser utilizada hoy.
La dirección blogpost@satprism.com mostrada arriba es un ejemplo en funcionamiento[^2]. Va a dividir los pagos 50/50 entre Kukks y yo (Gigi), dirigiendo los sats a nuestras respectivas direcciones lightning soberanas, provistas por nuestras instancias de BTCPay Server.
Imagino múltiples servicios siendo creados con una correcta implementación, cargando una pequeña comisión por dicho servicio (sic). (Tal como fue mencionado anteriormente, alguna especie de comisión será requerida por las comisiones de enrutado, ya que los pagos son redirigidos a direcciones externas).
Mi esperanza es que ese tipo de ideas y constructos novedosos se vuelvan más prevalentes mientras se van volviendo más prevalentes los zaps y pagos V4V similares, como también la red lightning en general. Claro que, en el mejor escenario, tendremos esas herramientas integradas nativamente a nivel del protocolo, pero no veo razón por la que no deberíamos experimentar un poco con lo que tenemos hoy, incluso si las soluciones son imperfectas. Hasta que el Bolt12 y similares sean ubicuos, ensamblar algo que simplemente funcione no es una idea tan terrible[^3].
Palabras finales
Espero que esta idea encuentre adopción amplia entre escritores y otros creadores de contenido, tal como la idea de "streaming sats" -y los splits de esos streams de valor- encontraron amplia adopción entre podcasters.
Lo que aún falta es adjuntar información de pago a eventos individuales (en lugar de a perfiles) para que cada contenido tenga su propia información de pago. Tal vez sea tan simple como extender la metadata del NIP-23, o tal vez tendría sentido tener este tipo de metadata para otros kinds también.
Ya veremos, y por "veremos", me refiero a ustedes: los desarrolladores que se sientan a diseñar y construir cosas.
Estaré alentándolos mientras hago shitpost en nostr.

Nota del traductor:
Todas las direcciones lightning, prismas y demás se mantuvieron fieles al post original. Si quieres colaborar conmigo, puedes hacerlo a mi lnaddres: wispy@getalby.com.
Traducciones
- Alemán por HiP0 [^1]: Le prometí a Kukks no hablar sobre ello por un par de semanas para que él pudiera adelantarse e implementarlo, pero estaba preocupado en mejorar la privacidad de todos, lo que también es muy importante. [^2]: Todos los prismas mostrados en este post son ejemplos funcionales: nostr-devs-eat-handsomely@satprism.com hace un split en partes iguales a todos los devs mencionatos en la nota de Quiet Warrior, y dergigi-platobot@satprism.com es un split entre el robot y yo. También me tomé la libertad de crear rhr@satprism.com, que hace un split entre Marty y Matt, y también einundzwanzig@satprism.com para los hablantes de alemán. [^3]: Creé los prismas de ejemplo de forma manual, así que me temo que, hasta que alguien construya una buena interfaz que permita a los usuarios crearlos por sí mismos, no habrá una explosión de prismas. Me gusta crear un montón de billeteras lnbits como a cualquiera, pero crear los splits y redirecciones es cansador después de un rato.
¿Te interesa ayudar? ¡Agrega una traducción!
Este trabajo de traducción, al igual que su fuente original tienen la licencia CC BY-SA 4.0, y se espera lo mismo de sus eventuales derivados.
-
 @ 2ad33996:3999d22a
2024-06-25 21:19:30
@ 2ad33996:3999d22a
2024-06-25 21:19:30Para minar monedas Kaspa de manera efectiva, es fundamental contar con el hardware adecuado, como los ASICs. Dispositivos como el ICERIVER KS0 PRO y el Bitmain Antminer KS3 ofrecen una alta tasa de hash y eficiencia energética. Configurar el software de minería adecuadamente y seleccionar pools de minería confiables son pasos cruciales. Mantén tu equipo en óptimas condiciones mediante el monitoreo continuo y el mantenimiento preventivo para maximizar tus ganancias y asegurar una operación rentable a largo plazo.
RESUMEN: Minar Monedas Kaspa Monitoreo Continuo del Rendimiento El monitoreo continuo del rendimiento de tus equipos de minería es esencial para identificar y solucionar problemas rápidamente. Utiliza herramientas de monitoreo como Awesome Miner o Minerstat para gestionar múltiples dispositivos de minería desde una sola interfaz y configurar alertas para recibir notificaciones inmediatas sobre cualquier anomalía.
Eligiendo el Hardware Adecuado para Minar Kaspa
Seleccionar el hardware adecuado es crucial para una minería de Kaspa eficiente. En esta sección, discutiremos los diferentes tipos de hardware disponibles y cómo elegir el mejor para tus necesidades.
La minería de Kaspa, al igual que otras criptomonedas, requiere un hardware especializado para ser efectiva. Utilizar dispositivos de propósito general como CPUs y GPUs no es eficiente debido a la creciente dificultad de la minería. Por lo tanto, es fundamental invertir en hardware especializado como los ASICs, que están diseñados específicamente para el algoritmo de minería de Kaspa, kHeavyHash.
Tipos de Hardware para Minar Monedas Kaspa
Existen varios tipos de hardware que puedes utilizar para minar Kaspa, cada uno con sus propias ventajas y desventajas. A continuación, se presentan los más comunes:
- ASICs (Application-Specific Integrated Circuits): Estos dispositivos están diseñados específicamente para realizar una tarea en particular, en este caso, la minería de Kaspa. Los ASICs ofrecen altas tasas de hash y eficiencia energética, lo que los convierte en la opción más popular para los mineros serios.
- GPUs (Graphics Processing Units): Aunque no son tan eficientes como los ASICs, las GPUs pueden ser una opción viable para los mineros aficionados o aquellos que ya poseen hardware de juegos potente.
- CPUs (Central Processing Units): Generalmente no recomendadas para la minería de Kaspa debido a su baja eficiencia y altas demandas energéticas.
Factores a Considerar al Elegir Hardware
Al seleccionar el hardware adecuado para minar Kaspa, hay varios factores que debes tener en cuenta:
- Tasa de Hash: La tasa de hash mide cuántas operaciones puede realizar el hardware por segundo. Un mayor hash rate significa una mayor probabilidad de resolver bloques y ganar recompensas.
- Eficiencia Energética: La minería de criptomonedas consume mucha energía, por lo que es importante elegir hardware que ofrezca una alta eficiencia energética para reducir costos operativos.
- Costos Iniciales: El precio del hardware puede variar significativamente. Es crucial equilibrar el costo inicial con la eficiencia y la tasa de hash para maximizar la rentabilidad.
- Sistema de Enfriamiento: La minería genera mucho calor, por lo que un buen sistema de enfriamiento es esencial para mantener el hardware funcionando de manera óptima y prolongar su vida útil.
Ejemplos de Hardware Recomendado para Minar Monedas Kaspa
A continuación, se presentan algunos ejemplos de hardware recomendado para la minería de Kaspa:
Modelo Tasa de Hash Eficiencia Energética Precio Aproximado ASIC Iceriver KS0 Ultra 400 GH/s Alta 610 € ASIC Goldshell KA Box Pro 1.60 TH/s Alta 2,100 € ASIC iBeLink BM-KS Max 10.5 TH/s Alta 6,500 €
Estos modelos son conocidos por su alta eficiencia y rendimiento en la minería de Kaspa. Sin embargo, es importante investigar y comparar diferentes opciones antes de realizar una compra.
Recomendaciones de Expertos
Los expertos en minería de criptomonedas recomiendan siempre adquirir hardware de proveedores confiables y realizar un análisis detallado de costos y beneficios. Además, es aconsejable mantenerse actualizado con las últimas tendencias y tecnologías en el campo de la minería de Kaspa para maximizar la rentabilidad y minar monedas Kaspa
Para más información sobre cómo elegir el mejor hardware para minar Kaspa, puedes consultar artículos y guías en iceriveroutlet
Configuración del Software de Minería Kaspa
La configuración del software de minería es un paso crucial para garantizar que tu hardware funcione de manera eficiente. En esta sección, discutiremos cómo configurar el software de minería Kaspa.
Para comenzar a minar Kaspa de manera efectiva, es esencial configurar correctamente el software de minería. A continuación, te proporcionamos una guía paso a paso para asegurarte de que tu configuración sea óptima.
Descarga e Instalación del Software
El primer paso es descargar el software de minería compatible con tu hardware. Puedes encontrar opciones recomendadas en el sitio web oficial de Kaspa o en foros de la comunidad. Una vez descargado, sigue estos pasos para la instalación:
- Descomprime el archivo: Utiliza un programa como WinRAR o 7-Zip para descomprimir el archivo descargado.
- Ejecuta el instalador: Abre el archivo ejecutable y sigue las instrucciones en pantalla para completar la instalación.
- Configura las opciones básicas: Durante la instalación, selecciona las opciones predeterminadas a menos que tengas necesidades específicas.
Configuración de la Cartera Kaspa
Antes de comenzar a minar, necesitas una cartera Kaspa para recibir tus recompensas. Aquí te mostramos cómo configurarla:
- Descarga la cartera: Visita el sitio web oficial de Kaspa y descarga la cartera compatible con tu sistema operativo.
- Instala la cartera: Sigue las instrucciones de instalación proporcionadas en el sitio web.
- Crea una nueva dirección: Abre la cartera y genera una nueva dirección para recibir tus monedas Kaspa.
- Copia la dirección: Asegúrate de copiar y guardar tu nueva dirección en un lugar seguro.
Configuración del Software de Minería para Minar Monedas Kaspa
Ahora que tienes tu cartera lista, es hora de configurar el software de minería:
- Abre el software de minería: Inicia el programa que instalaste anteriormente.
- Introduce la dirección de tu cartera: En el campo correspondiente, pega la dirección de tu cartera Kaspa.
- Selecciona el pool de minería: Elige un pool de minería confiable para unirte. Puedes encontrar recomendaciones en foros y sitios web especializados.
- Configura los parámetros de minería: Ajusta las opciones de minería según las recomendaciones del pool y tu hardware. Esto puede incluir la configuración de la tasa de hash y el límite de temperatura.
Recomendaciones de Expertos
Los expertos en minería de criptomonedas sugieren seguir estos consejos para optimizar tu configuración:
- Mantén tu software actualizado: Asegúrate de utilizar siempre la versión más reciente del software de minería para aprovechar las últimas mejoras y correcciones de errores.
- Monitorea tu hardware: Utiliza herramientas de monitoreo para verificar la temperatura y el rendimiento de tu hardware. Esto te ayudará a evitar sobrecalentamientos y fallos.
- Únete a la comunidad: Participa en foros y grupos de discusión para mantenerte al día con las mejores prácticas y novedades en la minería de Kaspa. Para más detalles y guías específicas, visita nuestro blog en Iceriveroutlet
Optimización y Mantenimiento de tu Operación para Minar Monedas Kaspa
Optimizar y mantener tu operación de minería es crucial para maximizar tus ganancias. En esta sección, discutiremos técnicas avanzadas para optimizar y mantener tu operación de minería Kaspa.
Monitoreo Continuo del Rendimiento
El monitoreo continuo del rendimiento de tus equipos de minería es esencial para identificar y solucionar problemas rápidamente. Utiliza herramientas de monitoreo para verificar la temperatura, el consumo de energía y la tasa de hash de tus dispositivos. Esto te ayudará a evitar sobrecalentamientos y a mantener un rendimiento óptimo.
- Software de Monitoreo: Utiliza software como Awesome Miner o Minerstat para monitorear y gestionar múltiples dispositivos de minería desde una sola interfaz.
- Alertas en Tiempo Real: Configura alertas para recibir notificaciones inmediatas sobre cualquier anomalía en el rendimiento de tus equipos.
Optimización de la Configuración de Minería
Optimizar la configuración de tu software de minería puede mejorar significativamente tu eficiencia y rentabilidad. Asegúrate de ajustar los parámetros del software según las especificaciones de tu hardware y las recomendaciones del pool de minería.
- Configuración de la Tasa de Hash: Ajusta la tasa de hash para equilibrar el rendimiento y el consumo de energía.
- Límite de Temperatura: Establece un límite de temperatura para evitar el sobrecalentamiento de tus dispositivos.
- Actualizaciones de Software: Mantén tu software de minería actualizado para aprovechar las últimas mejoras y correcciones de errores.
Mantenimiento Preventivo
El mantenimiento preventivo es clave para prolongar la vida útil de tus equipos de minería y evitar fallos costosos. Realiza inspecciones regulares y limpieza de tus dispositivos para mantenerlos en óptimas condiciones.
- Limpieza de Polvo: Limpia regularmente el polvo de los ventiladores y componentes internos para mejorar la eficiencia de enfriamiento.
- Reemplazo de Componentes: Sustituye componentes desgastados o dañados, como ventiladores y fuentes de alimentación, para evitar interrupciones en la minería.
Recomendaciones de Expertos
Los expertos en minería de criptomonedas sugieren seguir estos consejos para optimizar y mantener tu operación de minería Kaspa:
- Participa en la Comunidad: Únete a foros y grupos de discusión para mantenerte al día con las mejores prácticas y novedades en la minería de Kaspa.
- Analiza el Costo-Beneficio: Realiza un análisis detallado de costos y beneficios antes de realizar cualquier inversión en hardware o software.
- Utiliza Pools de Minería Confiables: Elige pools de minería con buena reputación y bajas tarifas para maximizar tus ganancias.
Desbloquea el Potencial de la Minería de Kaspa
Minar monedas Kaspa puede ser una actividad altamente lucrativa si se siguen las mejores prácticas y se utiliza el equipo adecuado. A lo largo de este artículo, hemos explorado desde la selección del hardware ASIC más eficiente hasta la configuración óptima del software de minería. Estos pasos son esenciales para maximizar tus ganancias y asegurar una operación de minería exitosa.
Es fundamental elegir el hardware adecuado, como los ASICs, que ofrecen altas tasas de hash y eficiencia energética. Además, la correcta configuración del software de minería y de la cartera Kaspa son pasos cruciales para recibir tus recompensas de manera segura. No olvides unirte a pools de minería confiables para aumentar tus probabilidades de éxito.
La optimización y el mantenimiento de tu operación de minería también juegan un papel vital. Utiliza herramientas de monitoreo para mantener el rendimiento de tus equipos y realiza mantenimiento preventivo para prolongar su vida útil. Mantente actualizado con las últimas tendencias y tecnologías en la minería de Kaspa para maximizar tu rentabilidad.
Te invitamos a seguir explorando más contenido sobre minería de criptomonedas en nuestro blog en iceriveroutlet. Comparte tus experiencias y preguntas en los comentarios para fomentar una comunidad de aprendizaje mutuo. ¡Buena suerte en tu aventura de minería de Kaspa!
-
 @ 29216785:2a636a70
2024-06-25 20:33:00
@ 29216785:2a636a70
2024-06-25 20:33:00- Working out logo proposals with Bitpopart for nostr-php
- Initial documentation pages with phpDocumentor published on phpdoc.nostr-php.dev. Changes can be followed in this pull request draft: https://github.com/nostrver-se/nostr-php/pull/53.
- Initial setup of a Drupal website on nostrver.se
- Initial setup for a website on nostr-php.dev with Vitepress
- Technical research
- Websocket client and server libraries / packages
- Runtime solutions with async and concurrency features
-
 @ 6ad3e2a3:c90b7740
2024-06-22 17:54:17
@ 6ad3e2a3:c90b7740
2024-06-22 17:54:17
I’ve been obsessed with large numbers for a few years now, trying in vain to get others to care. But the “why” eluded me. I made one partially satisfying attempt to explain last year. Yes, he who has “the deepest paradigm can name the biggest number,” but to what end?
Now I think I’ve found the end, the reason I can’t quit this line of thinking, even if it’s driven me half mad: that the number TREE(3) is quite possibly a miracle. Despite arising from a simple game, TREE(3) can be hard to understand, so maybe it’s best to start with one of its “competitors”, Graham’s Number, to grasp what it is not.
Now Graham’s Number is only a competitor because the two are often compared, not because there is really any kind of competition. TREE(3) dwarfs Graham’s Number the way the breadth of the observable universe dwarfs the dimensions of an ant. (Actually, as you will see, that comparison vastly understates the disparity between the two numbers.)
But Graham’s Number, unfathomably vast in its own right, is both easier to understand and is generated via a different process. To get to Graham’s Number, we have to start with the most basic math that exists: counting.
I’ll excerpt from my post on growth that covers this:
First you have counting 1, 2, 3, 4…
If you want to speed up counting, you can add.
Instead of counting from three to six, you can just add 3 + 3. Addition therefore is _ just repeated (iterated) counting.
But instead of adding 3 + 3 + 3 + 3 + 3 + 3, you can just do 3 * 6 because multiplication is iterated addition.
But instead of multiplying 3 * 3 * 3 * 3, you can just do 3 ^ 4 because exponentiation is iterated multiplication.
That’s where most people leave off in their education, and they feel perfectly content to live their lives only because they don’t know what they’re missing. Beyond exponentiation lies tetration, or iterated exponentiation.
Instead of 3 ^ 3 ^ 3 ^ 3, you can just do 3 ↑↑ 4 (a power-tower of threes, four high.)
You would say it “three to the three to the three to the three” in exponentiation terms, or “three arrow arrow three” in tetration terms. The number before the arrows determines the base and the number after them how high the tower goes. Let’s calculate some easy ones.
2 ↑↑ 2 is a power tower of twos, two high. That is 2 ^ 2 = 4.
3 ↑↑ 2 is a power tower of threes two high. That is 3 ^ 3 = 27. Easy.
2 ↑↑ 3 is a power tower of twos three high. That is 2 ^ 2 ^ 2 which is 2 ^ 4 = 16.
_3 ↑↑ 3 is a power tower of threes three high. That is 3 ^ 3 ^ 3 which is 3 ^ 27 = 7,625,597,484,987.
_Wait, what happened? You just encountered a fast-growing function.
Ok, tetration is cute, but if you want to generate Graham’s number, you’ll need to add more up arrows. Iterated tetration, symbolized by three up-arrows, is called pentation and would look like this: 3 ↑↑↑ 3. If 3 ↑↑ 3 is 7.6 trillion, what would 3 ↑↑↑ 3 be?
Well, it’s just iterated tetration, which means it’s a series of double-arrow operations with a base of three, three long, i.e., 3 ↑↑ 3 ↑↑ 3.
And since we know the second half, (3 ↑↑ 3) = 7.6 trillion, we can simplify it to 3 ↑↑ 7.6 trillion. What does that mean? It means a power tower of threes, 7.6 trillion high.
Okay, that sounds big. How big?
Consider a power tower of threes five high, i.e., 3^3^3^3^3 or 3 ↑↑ 5, is bigger than a googolplex.
To get the scale of a googolplex (one with a googol zeroes), consider you could not fit the zeroes it would take to write it out in the universe, even if you put one trillion zeroes on every atom. Again, we are not talking about the number itself, merely the number of digits required to write it out.
Consider a number with 200 digits is so massive, it’s far more than the number of Planck volumes (smallest known unit of measure) in the universe, but it’s trivial to write out. But you do not have space to write out a googolplex even while using a trillion digits per atom, let alone what those digits, if you could even write them, represent.
Your odds of entering every lottery on earth for the rest of your life, from the local bake sale to the mega millions, and winning all of them are far, far, far greater than 1 in a googolplex.
Your odds of guessing all the private bitcoin keys on earth without making an error are greater than one in a googolplex. A googolplex is an unfathomably large number. And yet it is smaller than 3 ↑↑ 5, or 3^3^3^3^3.
But 3 ↑↑↑ 3 is a tower of threes not five high, but 7.6 trillion high! When you get even to 10 high, you’ve exceeded a googolplex to the googolplexth power. The human mind cannot fathom the number you arrive at even at 100 or 1000 high, but we have to get to 7.6 trillion.
Okay, now that we’ve multiplied out the entire power tower to 7.6 trillion, guess what, we have to add another arrow. Not 3 ↑↑↑ 3 but 3 ↑↑↑↑ 3.
That’s hexation which is iterated pentation, in this case with a base of three and three terms, i.e., 3 ↑↑↑ 3 ↑↑↑ 3. We already know the second half is, whatever the incomprehensible result of the multiplied-out 7.6 trillion-high power tower was, call it X. So it’s 3 ↑↑↑ X.
And that means iterated tetration with a base of three, X times, i.e., _3 ↑↑ 3 ↑↑3 ↑↑ 3… X times.
To solve this, we go term by term. The first one is 7.6 trillion, which feeds into the second, the multiplied-out power tower 7.6 trillion high, i.e. X, the third is a power tower of threes, X high, multiplied out, and so on, and there are X of these entire towers, each one unfathomably, astronomically taller than the last.
Once we get through all X (remember itself an unfathomably large number) of the terms we’re at 3↑↑↑↑3.
That number is G1.
To get to G2, we just take 3 ↑↑↑↑↑↑↑↑↑↑…G1 arrows… 3.
Wait, what?
Remember each individual move up the scale from counting to addition to multiplication to exponentiation turbo-charged the growth of the function, and now in this function, they’re telling us to add G1 (3↑↑↑↑3) moves up the scale all at once!
Put differently, from counting by ones to the insanity of hexation, there are only six steps. To get G2, there are 3↑↑↑↑3 steps!
To get G3, it’s 3 G2 arrows 3. To get to G4, it’s 3 G3 arrows 3.
And so on until we hit G64 which is Graham’s Number.
It’s an indescribably massive number, not relatable to anything in the universe, not even in terms of the possible ways the atoms could be arranged taken to the power of the number of ways history’s chess games could have been played.
There is no way to visualize or imagine it except by walking vaguely through the steps to get there and straining your brain to grasp the process.
But as I said, Graham’s Number is trivial, basically zero compared to TREE(3), and that is so much the case that if instead of going to G64 via the steps, you went to G(Googolplex), or even G(Graham’s Number), i.e., G(G64), you would still be at zero relative to TREE(3).
But here’s where it gets fascinating. While Graham’s Number is generated via ramping up increasingly powerful iterative operations (as we did in the beginning) TREE(3) comes from a simple game.
There is a good article in Popular Mechanics that lays it out, building off this excellent Numberphile video with Tony Padilla:
You can click on the article and video for the specific (and relatively basic rules), but essentially, the TREE function has to do with “seeds” (dots) and “trees” (combinations of dots and lines), such that you make the maximum amount of unique “trees” (dot-line combos) per the types of seeds available.
If you have only one kind of seed, say a green one, there is only one unique tree that can be made.
So:
TREE(1) = 1.
If you have two seeds, say a green and a red, there are three different kinds of unique trees you could make.
TREE(2) = 3.
If you have three seeds, say a green, a red and a black, there are TREE(3) different kinds of trees you could make. As it turns out, that number (which is not infinite) is so much bigger than Graham’s number the two are not even in the same universe:
Here’s Padilla comparing TREE(3) to Graham’s Number if you want to see the difference:
Okay, so what does all this mean? It means that Graham’s Number, which is generated by successively more powerful iterations of mathematical operations, cannot compete with TREE(3) which comes from a game with simple rules.
Graham’s Number is built the way a machine would do it, the way an AI would go about making a huge number — mechanically increasing the rate of construction.
Consider if you had a machine that made products one at a time, that’s like counting. And if you had a machine that made products three at a time, that’s like adding.
And a machine that made machines that made products three at a time, that’s like multiplication. And a machine that made those three at a time would be exponentiation, etc., etc.
Each successive machine-making machine would take you into a deeper paradigm of growth. But you can see this is a mechanical process, no matter how deep you go.
By contrast, the tree series is what happens when you design a game with simple rules and let it play out. The growth (once you realize it to the extent the human brain can even grasp it) is not just faster than the mechanistic model, it’s on another plane.
The takeaway then is bottom-up complex systems (games) with a few simple rules can spawn a paradigm so much bigger than top-down mechanistic growth models.
The human brain (neocortex in McKenna’s terms) is just such a system, and yet we train ourselves to be like machines! Practice, routine, iteration, follow-these-10-steps to happiness, learn these five keys to investing, etc. Yes, you can get somewhere with these recipes, but nowhere near the destination of which you are inherently capable.
The key is a few simple inputs — good nutrition, enough sleep, a decent environment — and to let the mind have its space to play out the sequence in full.
In modern society the conditions needed for greatness, since the basics are relatively easy to come by, are achieved more by getting rid of negatives. Don’t be a drug addict or alcoholic, ditch the porn, the video games, the excessive social media use, etc. Then let the game play out.
Of course, this is easier said than done, as we’ve been deeply conditioned by the mechanistic paradigm, and remember TREE(1) is only 1, while G(1) is 3↑↑↑↑3, i.e., the more powerful growth function doesn’t necessarily reveal itself at the outset. But that changes in short order, and once it does, the mechanistic growth is no match for the “most densely ramified complexified structure in the known universe.”
I’ll end on a speculative thought, one that occurred to me while recording a podcast on this topic: Might what we think of as good vs evil actually just be a battle between the mechanistic and the complex, the difference between top-down compulsion and bottom-up free choice?
BONUS VIDEOS For those who want to dive deeper into this, there are some good videos by Carbrickscity on You Tube here, here and here. And Tim Urban’s article on Graham’s Number is worthwhile too.
-
 @ 1a11c2a7:6f7556b0
2024-06-20 07:51:43
@ 1a11c2a7:6f7556b0
2024-06-20 07:51:43Chef's notes
Chef's Note: These No-Bake Oreo Cheesecake Bars are a delightful treat that combines the beloved flavors of Oreo cookies with a creamy cheesecake filling. The simplicity of this recipe makes it perfect for any occasion, from casual gatherings to special celebrations. Ensure the cheesecake bars are well-chilled before serving for the best texture and flavor. Feel free to customize with extra Oreo cookie crumbles or a drizzle of chocolate sauce for added indulgence. Enjoy the rich, creamy goodness straight from the fridge!
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: Refrigerate for 4 hours
- 🍽️ Servings: 9-12
Ingredients
- Crust:** - 24 Oreo cookies - 1/4 cup (56g) unsalted butter, melted
- Cheesecake Filling:** - 8 oz (225g) cream cheese, softened - 1/3 cup (40g) powdered sugar - 1 teaspoon vanilla extract - 1 cup (240ml) heavy cream
- Optional Topping: - Additional Oreo cookies for decoration
Directions
-
- Prepare the Crust: - Crush Oreo cookies into fine crumbs. - Mix with melted butter and press firmly into an 8x8 inch baking dish lined with parchment paper. Chill in the refrigerator.
-
- Make the Cheesecake Filling: - Beat cream cheese until smooth. - Add powdered sugar and vanilla extract, mix until creamy.
-
- Whip the Cream: - In a separate bowl, whip heavy cream until stiff peaks form.
-
- Combine and Assemble: - Gently fold whipped cream into cream cheese mixture. - Spread evenly over chilled Oreo crust.
-
- Chill and Serve: - Refrigerate for at least 4 hours, or overnight, until set. - Cut into bars, top with crushed Oreo cookies if desired, and serve chilled.
-
 @ 1a11c2a7:6f7556b0
2024-06-20 07:37:45
@ 1a11c2a7:6f7556b0
2024-06-20 07:37:45Chef's notes
Chef's Note:
Chef's Tip:
Achieve restaurant-quality Spicy Beef Stir-Fry at home with this simple yet delicious recipe. Marinating the beef in soy sauce and cornstarch ensures it's tender and packed with flavor. High heat and quick cooking are key to preserving the vegetables' crunch and the beef's juiciness. Adjust the heat level by varying the amount of chili garlic sauce to suit your palate. Serve hot over rice for a satisfying meal that's sure to impress!
Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 10-15
- 🍽️ Servings: 3-4
Ingredients
- Beef Marinade:* - 1 lb (450g) beef sirloin or flank steak, thinly sliced - 2 tbsp soy sauce - 1 tbsp cornstarch - 1 tbsp vegetable oil
- Stir-Fry:** - 2 tbsp vegetable oil - 3 cloves garlic, minced - 1-inch piece ginger, minced - 1 red bell pepper, thinly sliced - 1 green bell pepper, thinly sliced - 1 small onion, thinly sliced - 2-3 green onions, cut into 2-inch pieces
- Sauce:* - 2 tbsp soy sauce - 1 tbsp oyster sauce - 1 tbsp hoisin sauce - 1 tbsp chili garlic sauce (adjust to taste) - 1 tbsp rice vinegar - 1 tsp sugar - 1 tsp sesame oil - 1-2 tbsp water or beef broth (if needed)
- To Serve:** - Cooked rice - Optional: sesame seeds and chopped cilantro for garnish
Directions
-
- sPrepare the beef marinade: - In a bowl, combine the thinly sliced beef with soy sauce, cornstarch, and vegetable oil. Mix well to coat the beef evenly. Let it marinate for at least 15 minutes.
-
- Make the sauce: - In a small bowl, whisk together soy sauce, oyster sauce, hoisin sauce, chili garlic sauce, rice vinegar, sugar, sesame oil, and water or beef broth. Set aside.
-
- Stir-fry the beef: - Heat 1 tablespoon of vegetable oil in a large skillet or wok over medium-high heat. Add the marinated beef in a single layer and stir-fry for 2-3 minutes until browned and cooked through. Remove the beef from the skillet and set aside.
-
- Cook the vegetables: - In the same skillet, add another tablespoon of vegetable oil if needed. Add minced garlic and ginger, stir-fry for about 30 seconds until fragrant. - Add sliced red and green bell peppers, and onion. Stir-fry for 2-3 minutes until vegetables are tender-crisp.
-
- Combine everything: - Return the cooked beef to the skillet. Pour in the prepared sauce and toss everything together to coat evenly. Cook for another 1-2 minutes until heated through and sauce thickens slightly.
-
- Serve: - Serve the spicy beef stir-fry hot over cooked rice. Garnish with sesame seeds and chopped cilantro if desired.
-
 @ 7f21affa:57e19174
2024-06-19 04:33:36
@ 7f21affa:57e19174
2024-06-19 04:33:36Chef's notes
Keep heat on the pot, from medium low to medium high.
Details
- ⏲️ Prep time: 15 minutes
- 🍳 Cook time: 45 mins
- 🍽️ Servings: 9
Ingredients
- 6 tbsp butter / cooking oil
- 1 medium / large yellow onion (chopped)
- 6 cloves garlic
- 3/4 cup all purpose flour
- 1.5 tsp salt
- 1.5 tsp black pepper
- 3 tsp paprika powder
- 3 tsp ground mustard powder
- 0.5 tsp cayenne powder
- 6 cups chicken / vegetable stock
- 4 broccoli heads (chopped into florets : discard stem)
- 6 carrots (shredded)
- 1 cup cornstarch mixed with 1 cup water
- 6 cups dairy milk (no plant-based)
- 9 cups cheddar cheese (shredded)
Directions
- Heat up pot on medium heat
- Add 6 tbsp butter / cooking oil
- Add a chopped yellow onion
- Sauté in pot until onion is soft and tender
- Add 6 cloves minced garlic
- (If pot looks dry, add splash of water too)
- Once pot has a nice garlic & onion aroma, add in 0.75 cup of all purpose flour , 1.5 tsp salt , 1.5 tsp black pepper , 3 tsp paprika powder , 3 tsp ground mustard powder , & 0.5 tsp cayenne powder .
- Mix in the dry ingredients with the vegetables .
- Add in the 6 cups of chicken / vegetable stock . (One cup at a time on medium high heat)
- Stir & wait until pot boils .
- Add chopped broccoli florets & shredded carrots
- If you want a thicker soup , then add in the 1 cup cornstarch mixed with 1 cup water .
- Let boil for 15 mins , then check if vegetables are at preferred softness.
- Add in 6 cups of dairy milk & 9 cups of cheddar cheese .
- Cook for about 1 - 2 minutes
- Enjoy & store in fridge with air tight containers !
-
 @ 8d34bd24:414be32b
2024-06-25 18:39:20
@ 8d34bd24:414be32b
2024-06-25 18:39:20I got this from The Biblical Man on Substack. I strongly recommend my fellow Christians check him out (especially male Christians).
The post is here: https://substack.com/home/post/p-145965427
It's time for some hard truth that'll separate the men from the boys, the wheat from the chaff. We're diving deep into the heart of what it means to have real, unshakeable faith in a world that's increasingly hostile to the followers of Christ.
You claim to have faith? You say you trust in the Almighty? Well, persecution is coming to put that to the test. And let me tell you something - if your so-called "faith" crumbles when the heat is on, it wasn't real faith to begin with.
Here's the cold, hard reality:
If persecution causes us to let go of our faith, it was not confidence in God that we possessed, but confidence in our understanding of His will.
Let that sink in for a moment. Meditate on it. Let it challenge you to your core.
Real faith, warrior faith, isn't built on your ability to comprehend God's plan. It's not about having all the answers or understanding why things happen the way they do. No, true faith is built on the unshakeable truth of who God is, regardless of our circumstances.
"Though he slay me, yet will I trust in him" (Job 13:15 KJV)
That's the kind of faith we're called to. The kind that stands firm when everything else is falling apart. The kind that says, "Even if I don't understand, even if it costs me everything, I will trust in the Lord."
So ask yourself these hard questions:
-
Is your faith in God, or in your understanding of His ways?
-
Can you trust Him even when His plan doesn't match your expectations?
-
Are you ready to stand firm when persecution comes?
These aren't hypothetical questions, brothers. The world is changing, and the days of easy, comfortable Christianity are coming to an end. We need to be prepared for the storm that's brewing.
Remember, the Apostle Paul didn't say "I know why all these things are happening to me." He said, "I know whom I have believed, and am persuaded that he is able to keep that which I have committed unto him against that day" (2 Timothy 1:12 KJV).
It's not about having all the answers. It's about knowing the One who does.
Now, let's break this down further:
The Nature of True Faith
True faith isn't blind optimism. It's not positive thinking or wishful dreaming. True faith is a rock-solid confidence in the character and promises of God, even when everything around us seems to contradict those promises.
When persecution comes - and make no mistake, it will come - it will reveal what your faith is really made of. Will it stand firm, or will it crumble like a sandcastle in the tide?
The Danger of False Confidence
Many of us have fallen into the trap of confusing our understanding of God's will with faith in God Himself. We think that because we can explain God's actions or because we believe we know His plan, we have faith.
But what happens when God doesn't act the way we expect? What happens when His plan doesn't align with our understanding? That's when true faith is tested and revealed.
If your faith is based on your ability to understand or explain God's actions, it will fail you when you encounter situations that defy your understanding. And brothers, let me tell you, those situations will come.
The Refining Fire of Persecution
Persecution isn't just a possibility for the Christian; it's a promise. Jesus Himself said, "In the world ye shall have tribulation" (John 16:33 KJV). Peter reminds us, "Beloved, think it not strange concerning the fiery trial which is to try you, as though some strange thing happened unto you" (1 Peter 4:12 KJV).
These trials, these persecutions, they're not just random hardships. They're the refining fire that reveals and strengthens true faith. They're the crucible in which warrior-grade faith is forged.
When persecution comes, it will strip away all pretenses. It will reveal whether your faith is in God or in your understanding of Him. It will show whether you trust in His character or in your ability to explain His actions.
The Call to Unshakeable Faith
So here's your mission, warriors of faith:
-
Examine your faith. Is it built on God's character or your comprehension? Do you trust Him or just your understanding of Him?
-
Prepare for persecution. It's coming, whether you're ready or not. Steel yourself for the battle ahead.
-
Strengthen your resolve. True faith grows stronger under pressure. Let the challenges you face drive you deeper into trust in God.
-
Stand firm. Be the immovable warrior God called you to be. When others falter, you stay strong.
-
Know God, not just about God. Dive deep into His Word. Spend time in His presence. Build your faith on the rock of who He is, not the shifting sands of your understanding.
-
Be ready to say, like Job, "Though he slay me, yet will I trust in him." That's the kind of faith that moves mountains and changes the world.
The world needs men of unshakeable faith. Men who trust God even when they don't understand Him. Men who stand firm when others fall away. Men who can say with Paul, "For I am persuaded, that neither death, nor life, nor angels, nor principalities, nor powers, nor things present, nor things to come, nor height, nor depth, nor any other creature, shall be able to separate us from the love of God, which is in Christ Jesus our Lord" (Romans 8:38-39 KJV).
Will you be that man?
The battle is coming. The test is near. Will your faith stand, or will it crumble?
The choice is yours, warrior. Choose wisely. Choose faith in God, not just in your understanding of Him. Choose to stand firm when persecution comes. Choose to be the unshakeable man of faith that God has called you to be.
Now go. Be strong. Be faithful. Be the man God created you to be. The world is waiting for warriors like you to rise up and show them what true, unshakeable faith looks like.
Amen and amen.
Check out his substack, so I don't feel bad about borrowing his content. https://substack.com/@biblicalman
-
-
 @ 000002de:c05780a7
2024-06-25 18:25:25
@ 000002de:c05780a7
2024-06-25 18:25:25On a recent vacation my wife and I were shopping in some antique and thrift stores. Its one of my favorite things to do with her. I'm always on the look out for interesting items and on this day I was looking through old postcards and pamphlets and I spotted this.
From 1966, a copy of the "Objectivist" newsletter. I took it up to the counter to pay and the owner looked it over and said 50 cents. That was the cover price back in 1966. I'm not interested in selling it but I think that was a bargain.
I'm a fan of Rand. I have a lot of respect for her. She came to the US escaping communism in the USSR as a young woman. She rose to massive popularity in a time when it was rare for women to do so. After I bought the booklet I started thinking about how massive her influence is. Atlas Shrugged has such a broad influence that you see references to it and characters in the book in the names of many businesses. The woman had guts. If you have never heard her speak I recommend looking up some of her interviews with Donoghue ( a popular talk show host of the time). She angered many with her philosophy. She was counter to the culture of the time in many ways.
And yet, she is rarely mentioned when I see articles or stories about influential women. I would argue that she is a very influential woman. Not just for women but for men as well. While I have plenty of disagreements with her philosophy I think it is very telling how she is rarely mentioned in a positive light. Objectively she is an important person in US history and even more so in women's history. She was a strong self made woman that didn't use her appearance for sex appeal to get her status. One would think she should be a feminist heroine. But she isn't. Its a crime in my opinion.
Have you ever found any liberty movement items in thrift stores? This is my first.
-
 @ 7f21affa:57e19174
2024-06-19 04:32:33
@ 7f21affa:57e19174
2024-06-19 04:32:33Chef's notes
Salt the water when boiling water for noodles.
Mix sauce separately, then add to the cold noodles.
Details
- ⏲️ Prep time: 30 mins
- 🍳 Cook time: 30 mins
- 🍽️ Servings: 8
Ingredients
- 16 oz bag of elbow noodles
- 1 tbsp of salt
- 16 cups of water in pot
- 2 cup mayo
- 2 tbsp mustard paste
- 4 tbsp white vinegar
- 4 tbsp pickle juice
- 1 tsp black pepper
- 4 tsp white sugar
- 2 tsp salt
- 1 tsp garlic powder
- 1 tsp onion powder
- 1 medium / large red onion (diced)
- 2 red / green bell peppers (diced)
- 2 pickles (diced)
- 4 celery sticks (diced)
Directions
- Boil 16 cups of water in a pot with 1 tbsp salt & 16 oz elbow noodles
- Let pot boil for 15 mins ; Start on making the sauce
- In a medium bowl , add 2 cup mayo , 2 tbsp mustard paste , 4 tbsp white vinegar , 4 tbsp pickle juice , 1 tsp black pepper , 4 tsp white sugar , 2 tsp salt , 1 tsp garlic powder , & 1 tsp onion powder .
- Mix sauce & set aside .
- Next , Cut & dice up 1 medium / large red onion , 2 red / green bell peppers , 2 pickles , & 4 celery sticks .
- Mix half of the sauce in with the diced vegetables .
- By this time , noodles should be ready to rinse and drain with cold water .
- ( Noodles should be cold and water drained )
- In a large bowl , add the cold noodles , vegetables , & the remaining sauce
- Mix ingredients well & refrigerate for 2 hours +
- Enjoy & store in fridge with air tight containers .
-
 @ e21df944:1d414c31
2024-06-16 05:39:19
@ e21df944:1d414c31
2024-06-16 05:39:19Chef's notes
Never guess your cooking times again – make your air frying experience simple and stress-free!
Tips:
• Shake the Basket: Halfway through cooking for even results. • Check for Doneness: Use a meat thermometer or cut open to ensure proper cooking. • Preheat: Preheat the air fryer for best results.General Recommendations:
• Always preheat your air fryer for 3-5 minutes before cooking. • Flip or shake foods halfway through the cooking time to ensure even cooking. • Adjust times and temperatures based on your specific air fryer model and the thickness of the food.Details
- 🍳 Cook time: 5-35
Ingredients
- Vegetables, Frozen Foods, Chicken, Beef
Directions
- General Recommendations: • Always preheat your air fryer for 3-5 minutes before cooking. • Flip or shake foods halfway through the cooking time to ensure even cooking. • Adjust times and temperatures based on your specific air fryer model and the thickness of the food.
-
 @ 005bc4de:ef11e1a2
2024-06-25 18:15:37
@ 005bc4de:ef11e1a2
2024-06-25 18:15:37Nostr has events. Anything done on Nostr is an "event." Nostr has kinds. A "kind 1" is a text message, like below.
Source: https://nostr.com/the-protocol/events
Now, there's a new kind on the block. There is a kind 30040 (as well as an accompanying 30041).
Note: kind 30040 is an "NKBIP" and not a "NIP," which is why it's not listed as an event kind on the NIPS GitHub.
Finding kind 30040
I first read about about a kind 30040 in this note by npub1m4ny6hjqzepn4rxknuq94c2gpqzr29ufkkw7ttcxyak7v43n6vvsajc2jl and I immediately thought, "This is fantastic." Three reasons made me think this:
- Her goal, as I understand, is to get public domain (Projet Gutenberg) books onto Nostr. As a reader, I see this as a good thing.
- First up is to first get the Bible onto Nostr in an organized, "clickable" manner. As a Christian, I see this as a good thing.
- The kind 30040 reminded me of bitcoin recursive ordinals and BitVM. This is great. What can we possibly mash up on Nostr with a kind 30040 or 30041?
Toying with kind 30040
Curious yesterday, I began to futz around. The habla.news note referenced a wikifreedia post. Nostr user npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf and npub149p5act9a5qm9p47elp8w8h3wpwn2d7s2xecw2ygnrxqp4wgsklq9g722q were on this. I referenced Liminal's guide and Niel's fork. After creating a Nostr profile (Turc Testerman) to mess around and use as a testing platform, below is what I achieved:
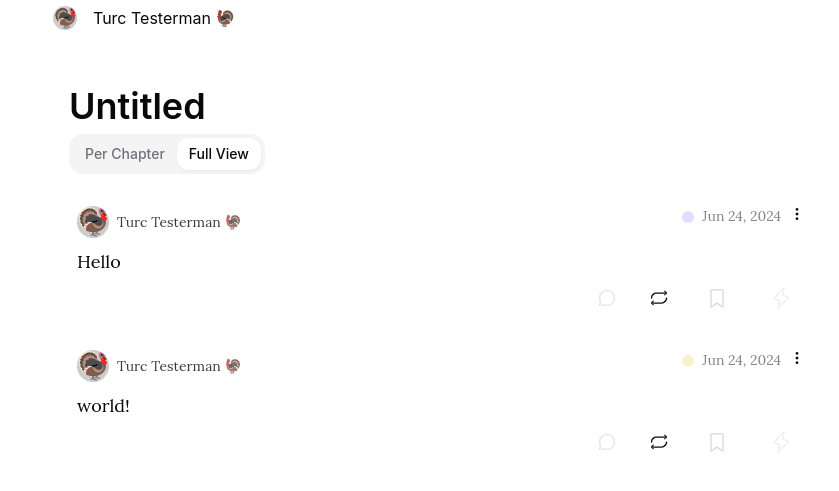
At first glance, the image above is unimpressive. It's only two words. But, there may be more going on than is initially evident. The animated gif below reveals a bit more:
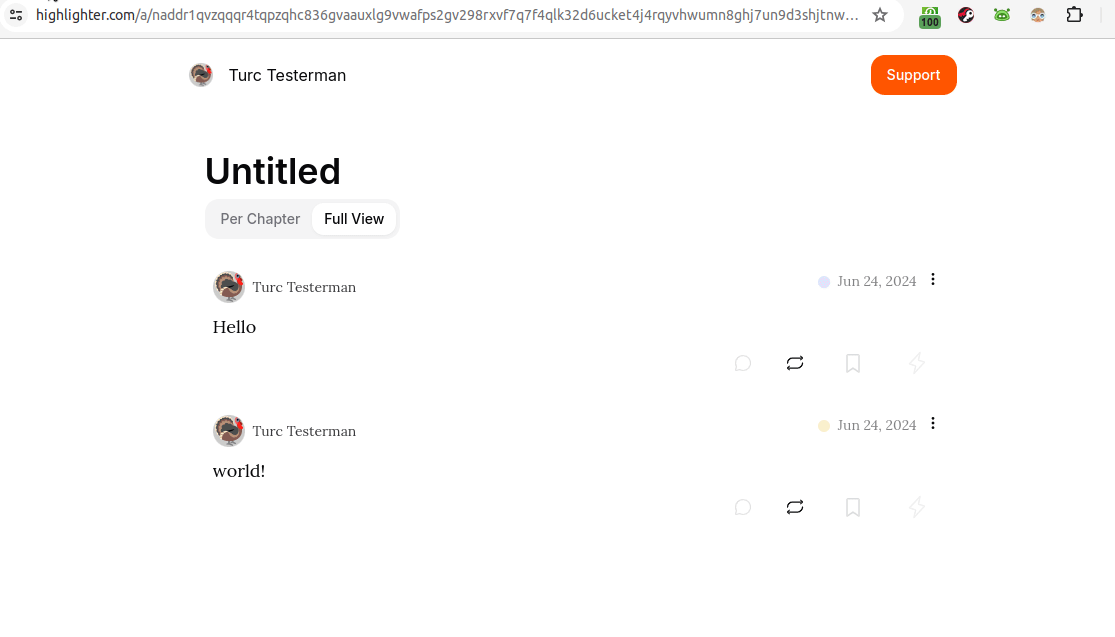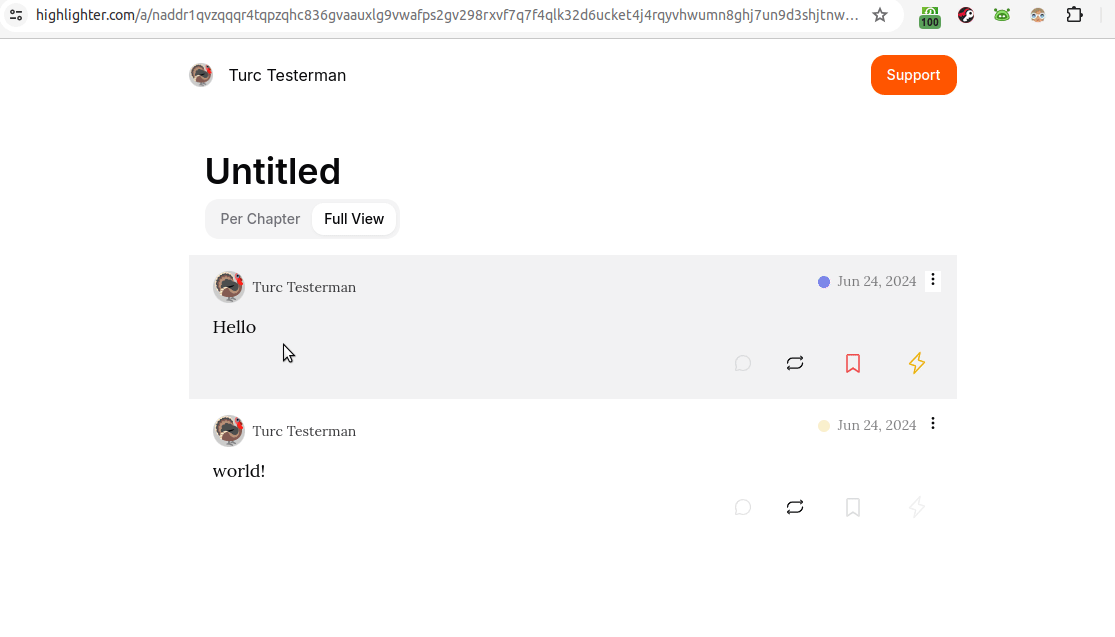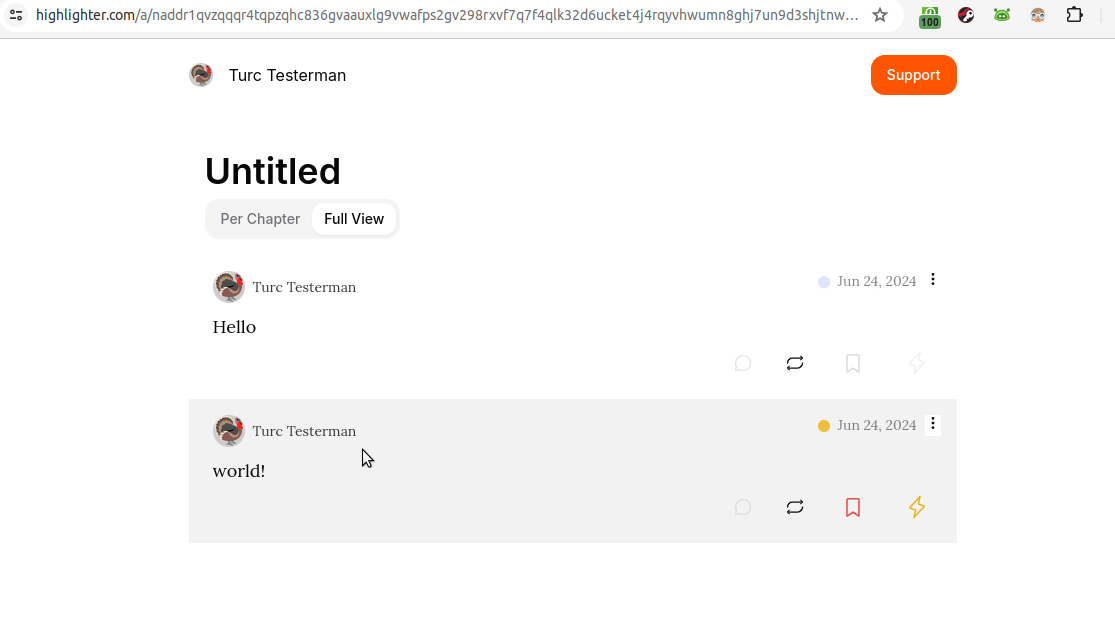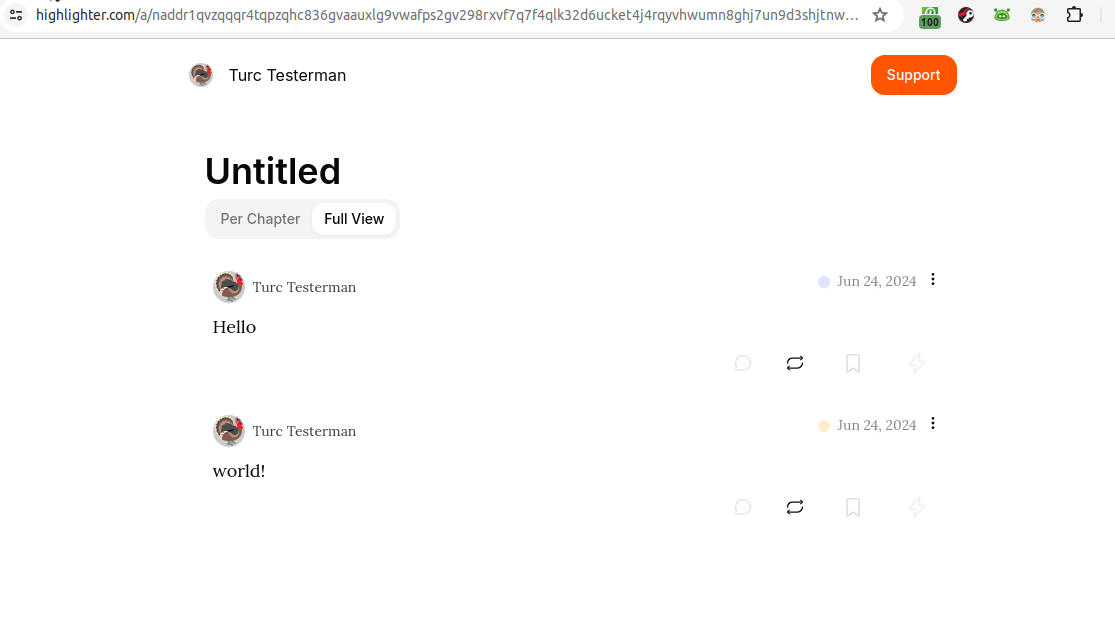
See it on highlighter.com
In the gif above, we are looking at a kind 30040 showing two other independent notes. Hovering over those two notes in Highligher reveals them as unique, as does the URL bar when they're clicked.
So, what's going on here is that those two notes, "Hello" and "world!" are just hanging out somewhere on Nostr relays. Then, the third event, the kind 30040 aggregated them together.
The kind 30040 can be viewed in raw form on njump.me (image below). That's great, though not particularly viewer-friendly or useful to a human. Finally, thanks to Highlighter, a useful, more visually appealing, and interactive UX is achieved. (See it on highlighter.com and read note by npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft today debuting this ability.)
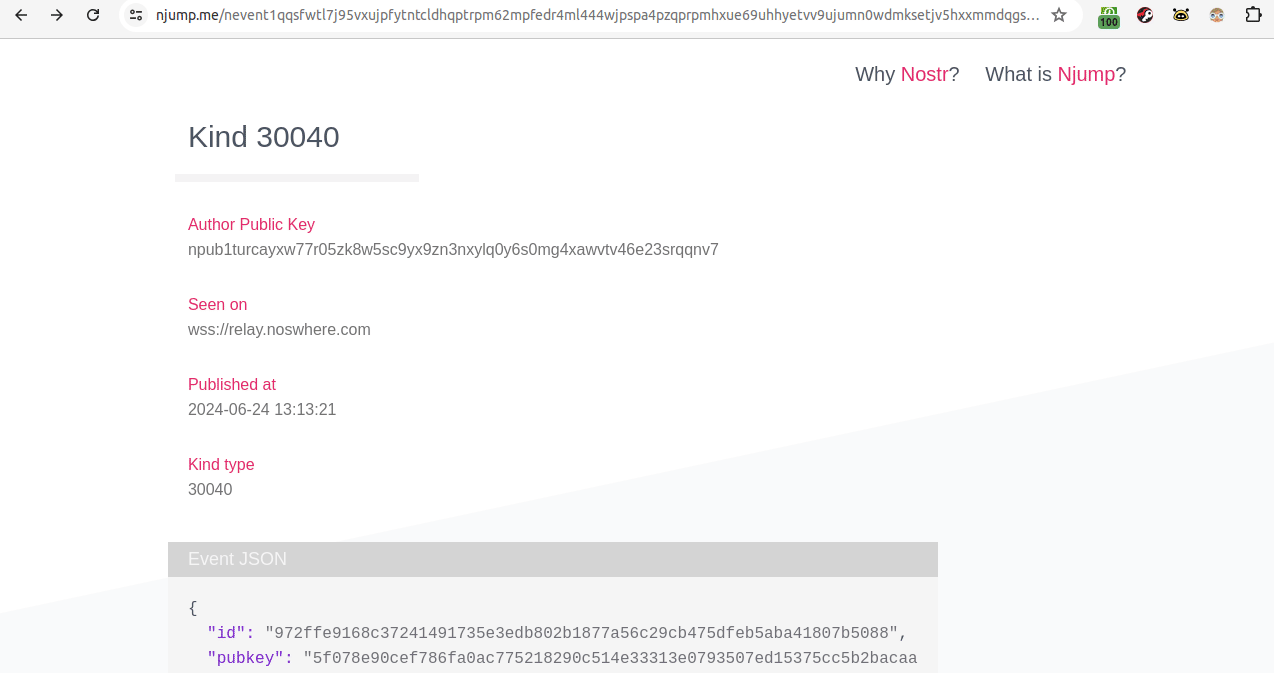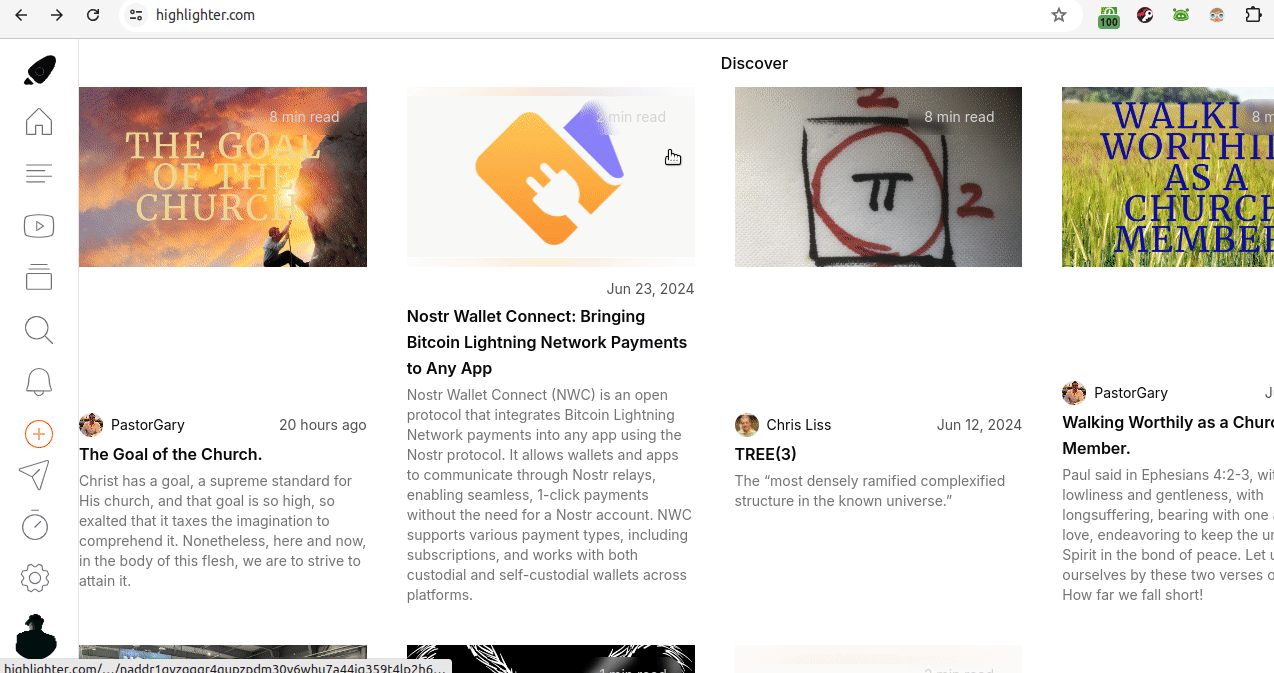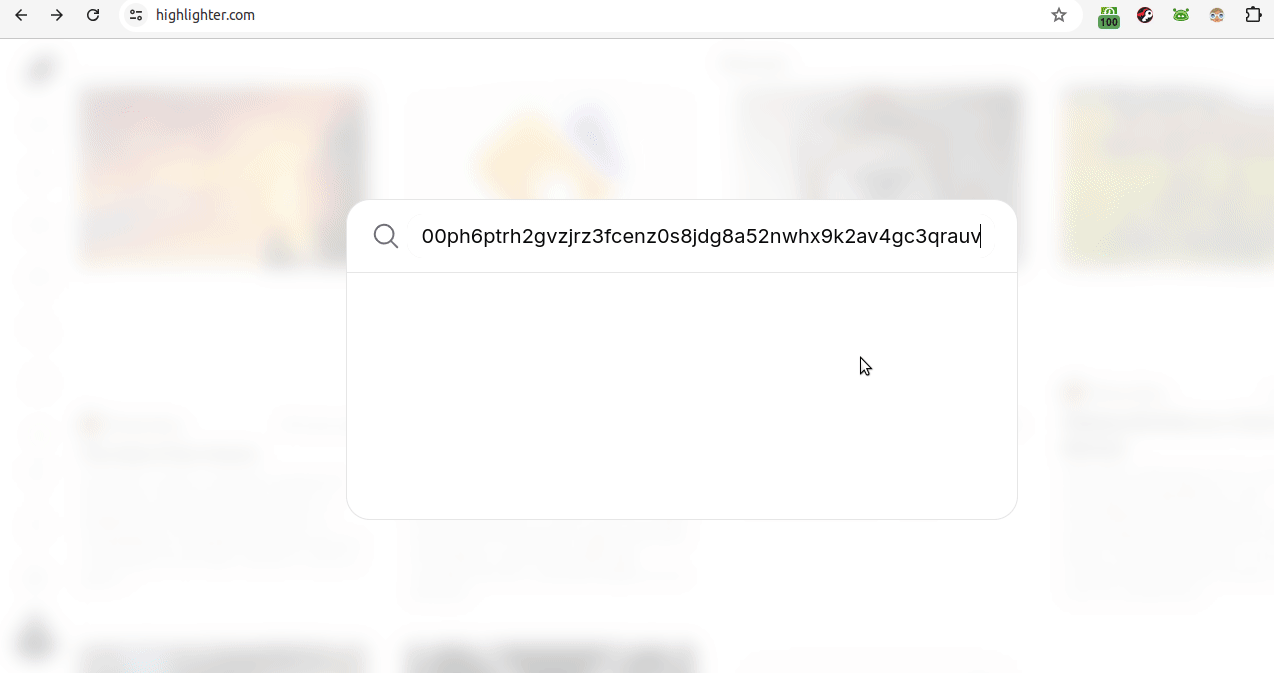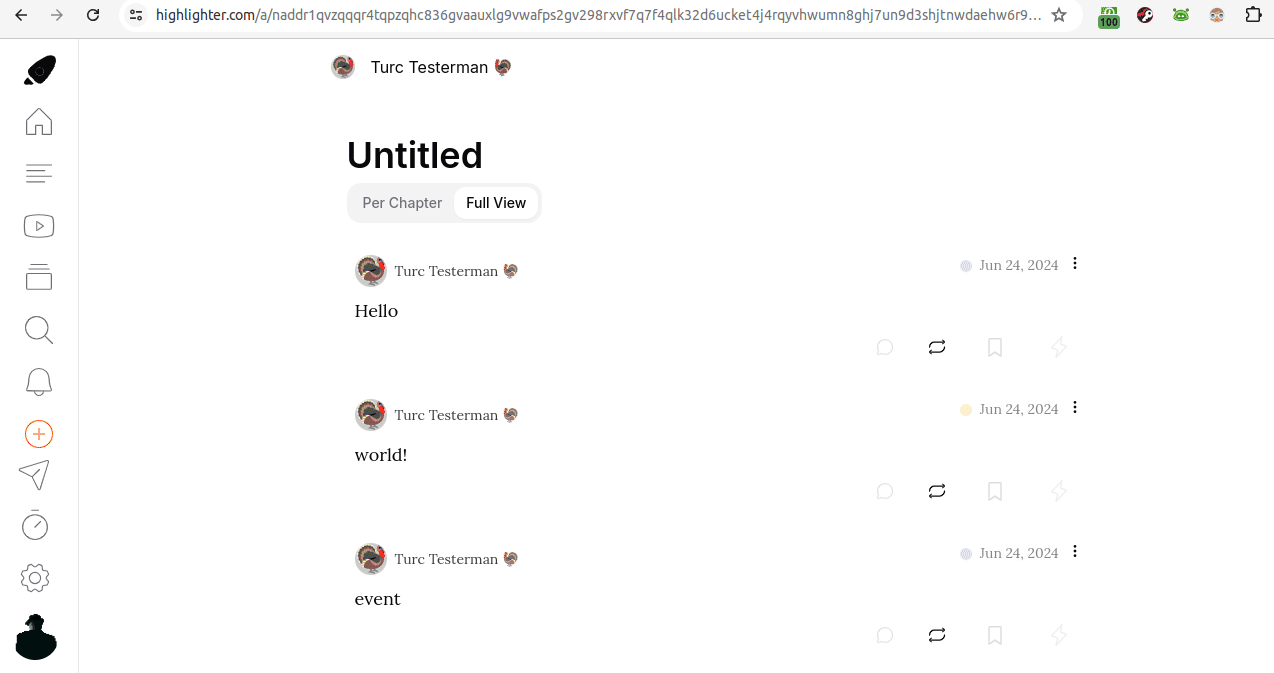
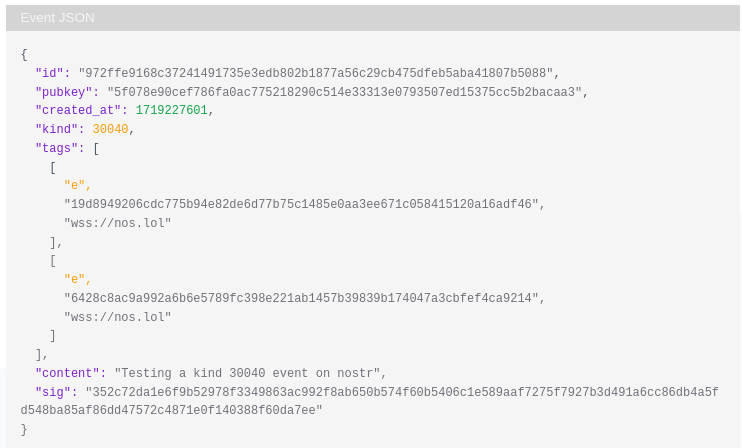 The kind 30040 viewed on njump.me The first yellow "e" is "Hello" and the second yellow "e" is "world!"
The kind 30040 viewed on njump.me The first yellow "e" is "Hello" and the second yellow "e" is "world!"Pushing a bit farther...an example how-to
Why not do more? Let's do this: I'll now try to replicate what I did yesterday, I'll try to make a new kind 30040 that adds a smidge more, and document what I do as a how-to tutorial in case anyone else wants to try.
This is how we push ahead open source style, right?
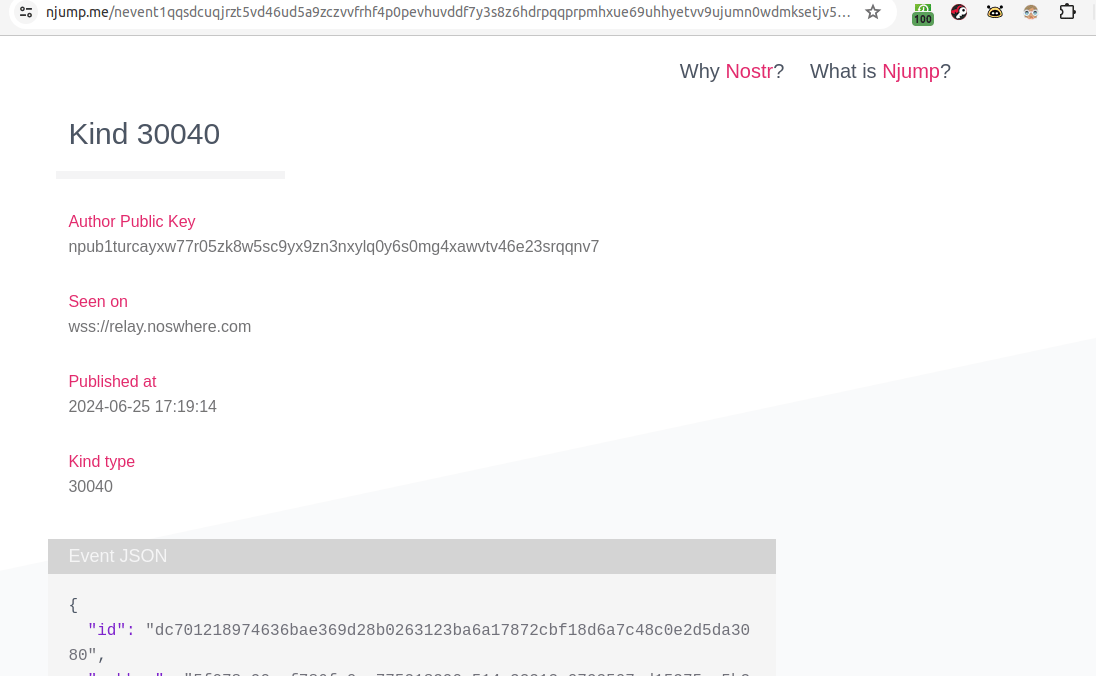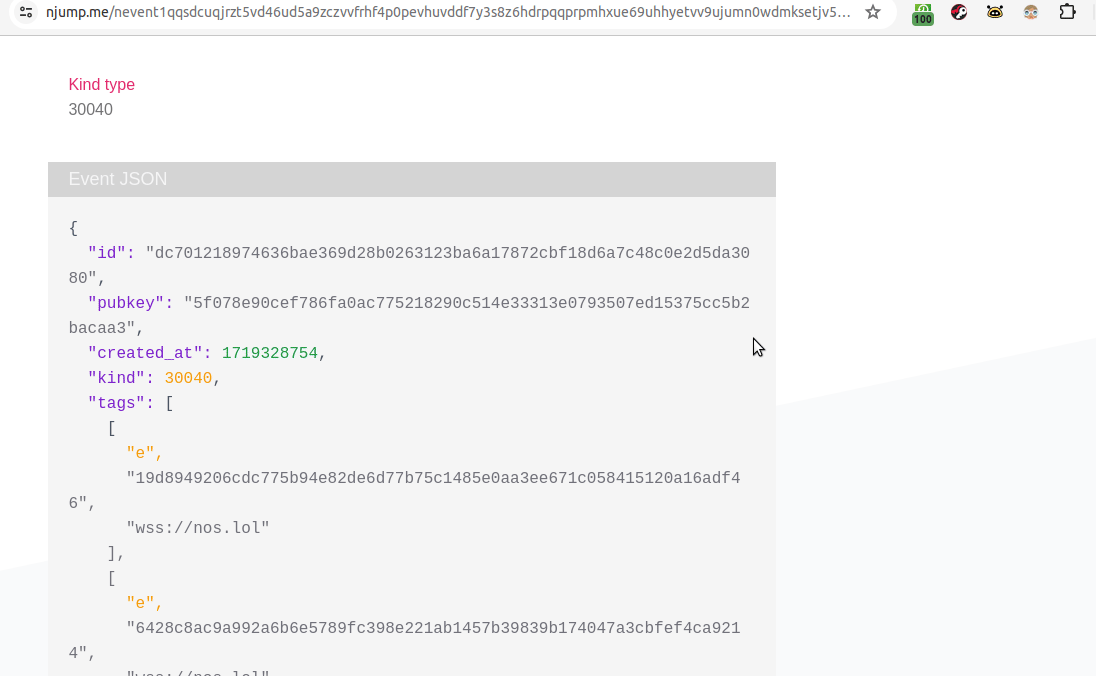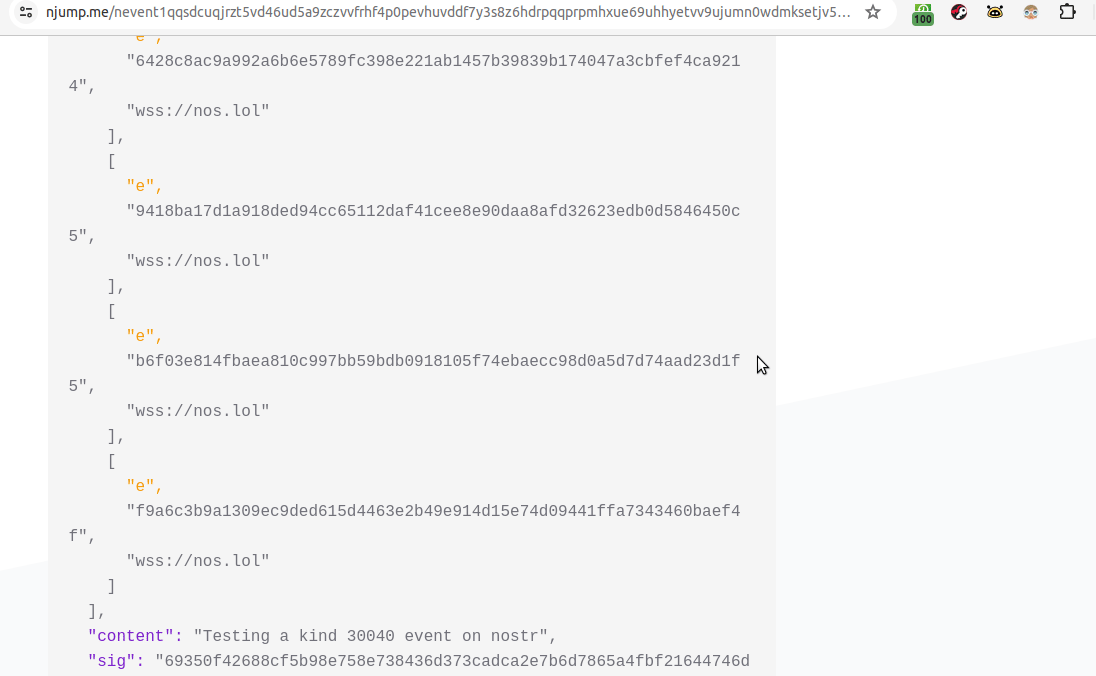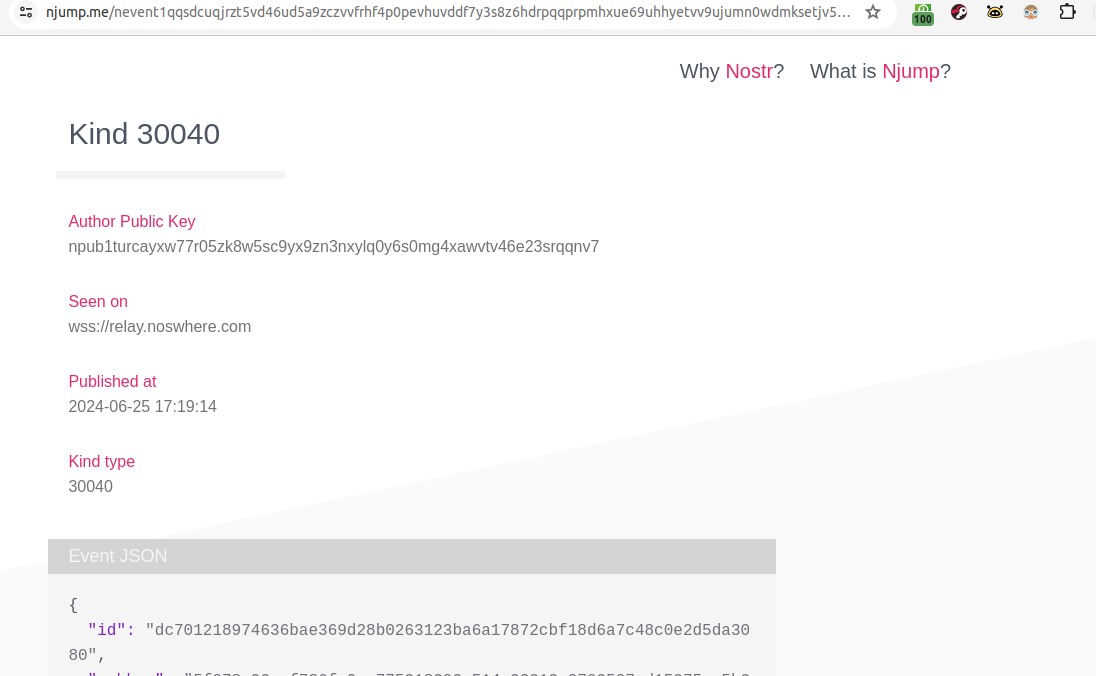
Step 1 - grab the basic code for a kind 30040
{ "id": "972ffe9168c37241491735e3edb802b1877a56c29cb475dfeb5aba41807b5088", "pubkey": "5f078e90cef786fa0ac775218290c514e33313e0793507ed15375cc5b2bacaa3", "created_at": 1719227601, "kind": 30040, "tags": [ [ "e", "19d8949206cdc775b94e82de6d77b75c1485e0aa3ee671c058415120a16adf46", "wss://nos.lol" ], [ "e", "6428c8ac9a992a6b6e5789fc398e221ab1457b39839b174047a3cbfef4ca9214", "wss://nos.lol" ] ], "content": "Testing a kind 30040 event on nostr" }Note: This is a bit different from the code in the NKBIP. I had trouble with the "content" portion of it. The format in the NKBIP threw errors, something about the backticks. Hence, my "Testing a kind..." appeared in njump, but is not picked up by highlighter and shows "untitled." That's something for me to learn.
Step 2 - go to https://nostrudel.ninja
Nostrudel, to me, has a ton of usages beyond just reading notes. One is the "Event Publisher" function. Go to Nostrudel, then "More," then "Event Publisher." There is some pre-populated data. You want to put the kind 30040 basic code in there instead. However, you do want to keep but alter the "created_at" timestamp. Take note of the number in the "created_at" line, then delete everything, paste in the kind 30040 basic code, then go back to "created_at" and put in your updated timestamp number. If you use the old timestamp, then I think it will work, but your kind 30040 will be timestamped incorrectly. Use the up-to-date and correct timestamp.
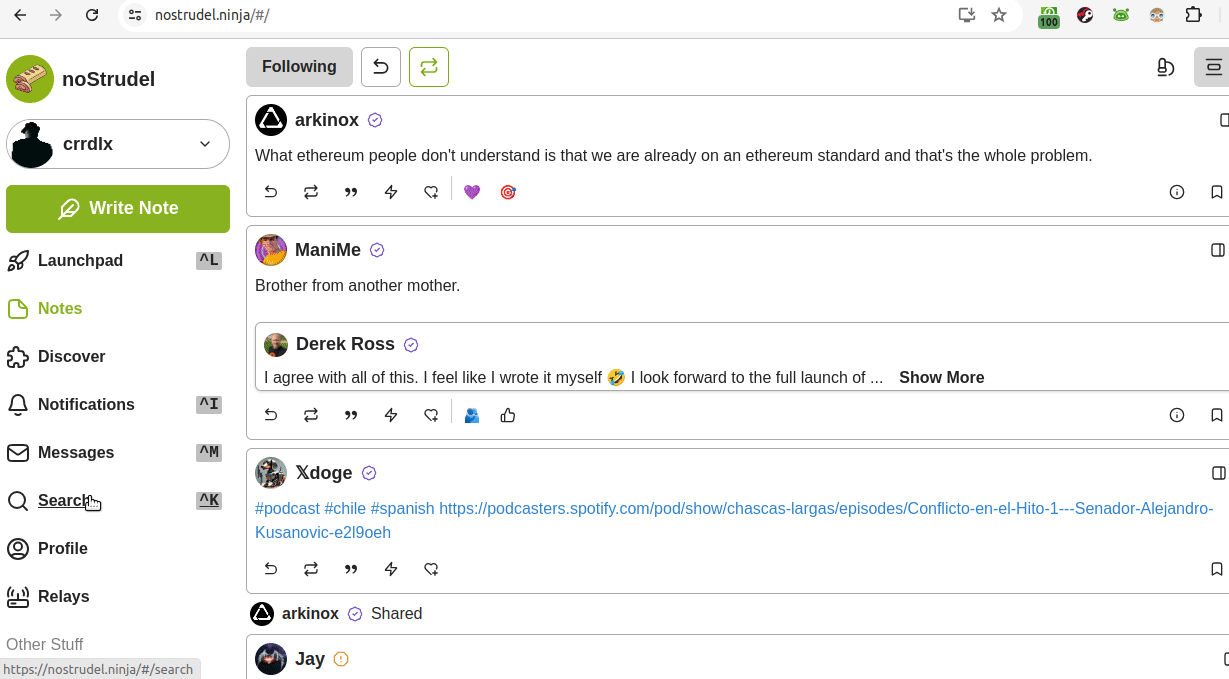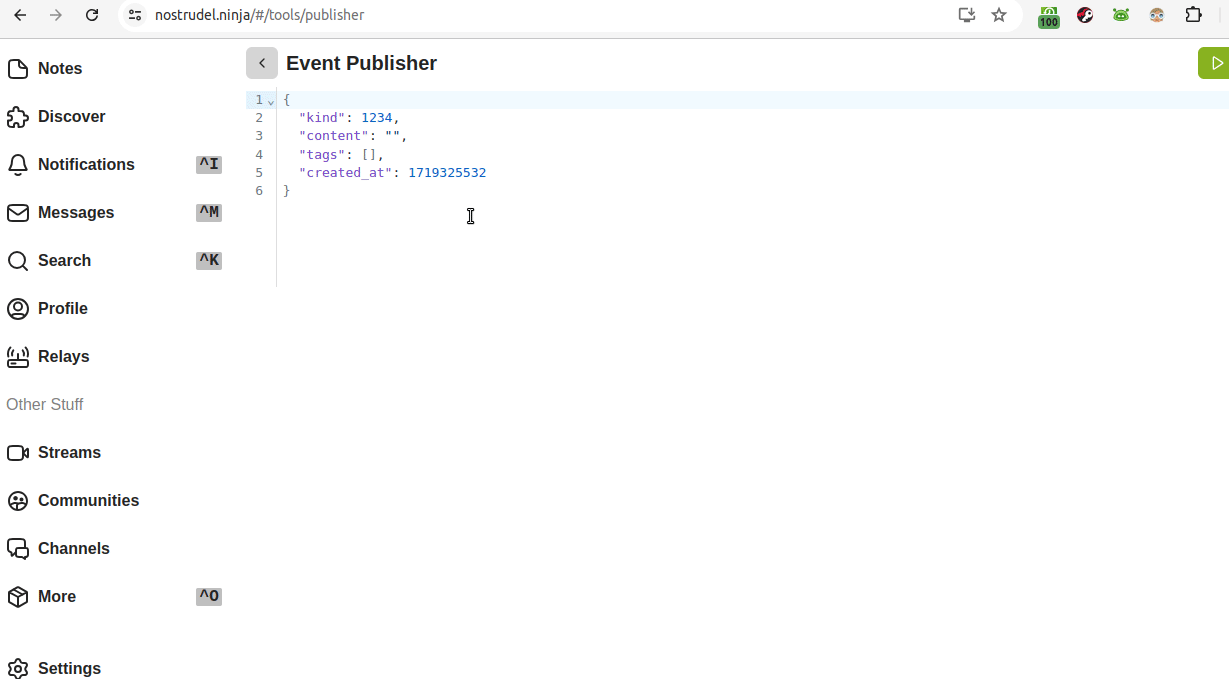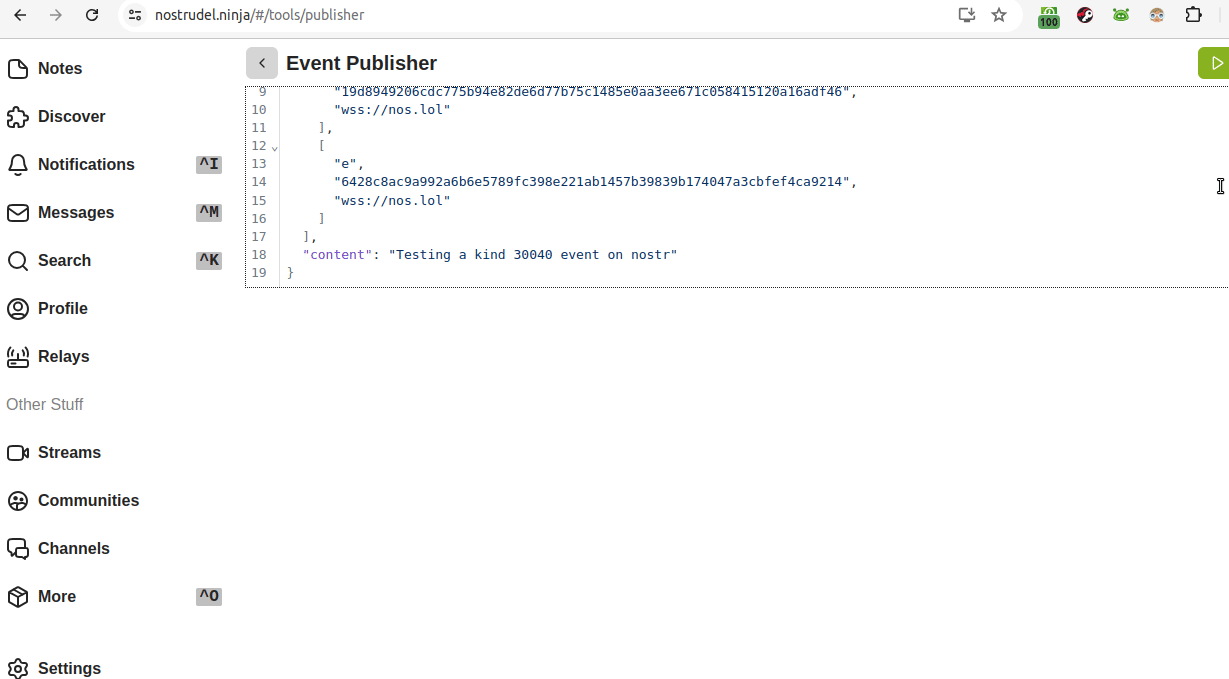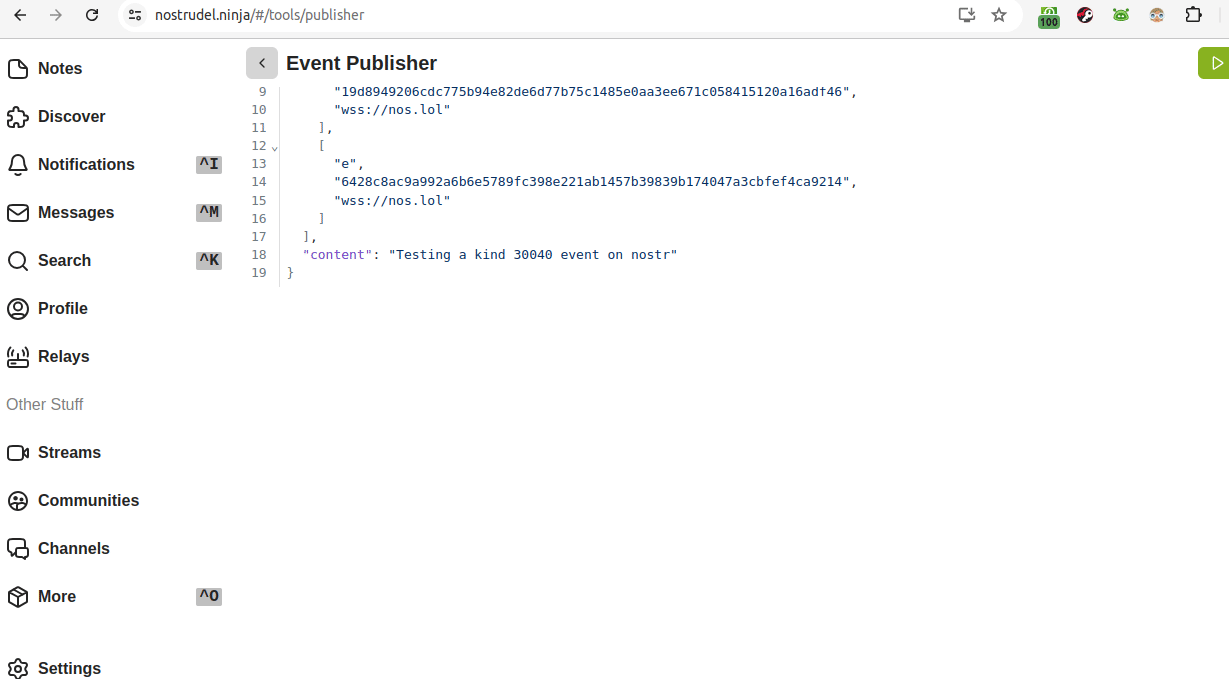
If you get to the green "Yolo" button, things are good. If your json is incorrectly formatted, it'll throw errors and you'll need to fix those. (This is where the backticks in the "title" halted me.) Pressing Yolo will create a new Nostr event. It will be visible on njump.me as raw code and on highlighter in a pretty fashion.
Step 3 - create your own kind 30040 with unique Event IDs
Using the "basic code" above will replicate my "Hello world!" because it uses the two "e" events I published yesterday. If you wish to create your own kind 30040, you need to gather your own preferred notes to aggregate.
For this example, I'll use a few notes I published yesterday from the npub1turcayxw77r05zk8w5sc9yx9zn3nxylq0y6s0mg4xawvtv46e23srqqnv7 profile. I'll keep the "Hello" and "world!" notes, but add a three more. What I need is the "event ID" for each note I wish to include. Below I'll illustrate how to get that ID on nostrudel.ninja. Notice there are three "IDs," for this, we want the first one simply called "Event ID."
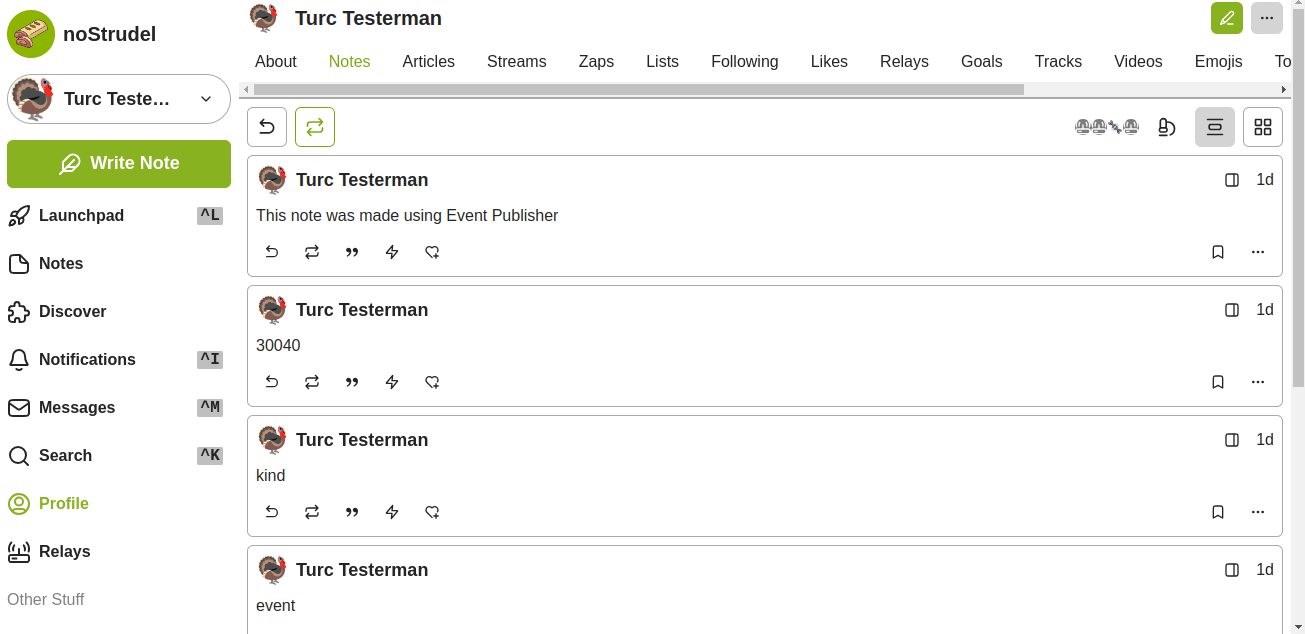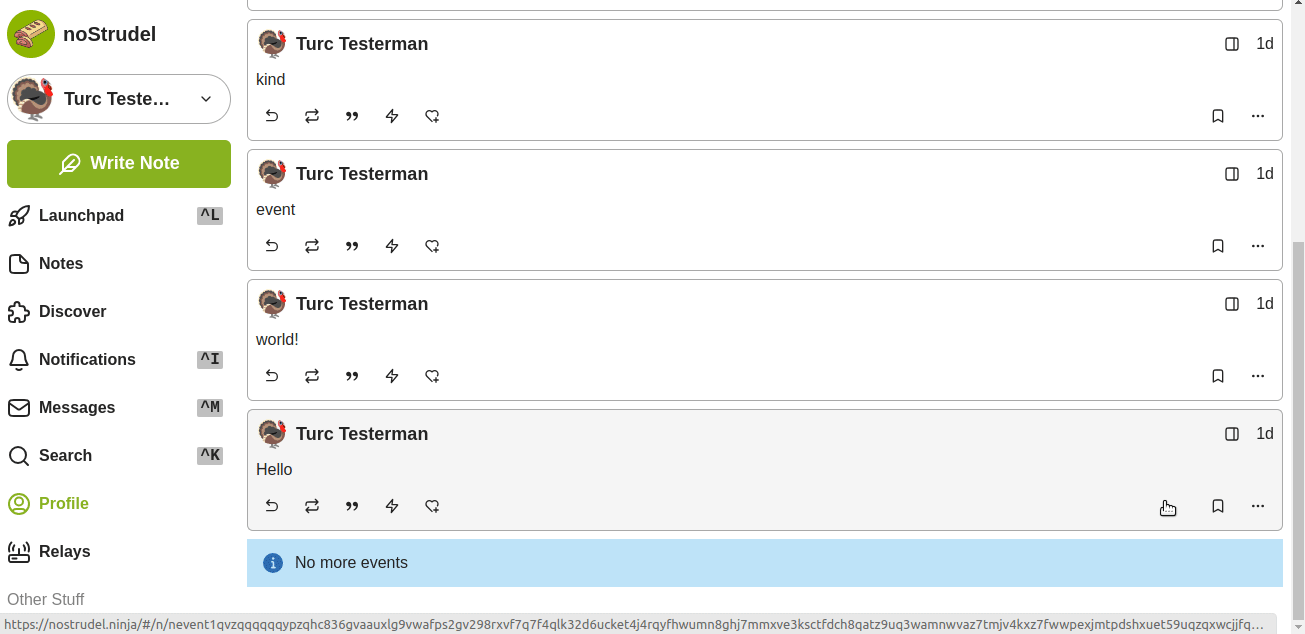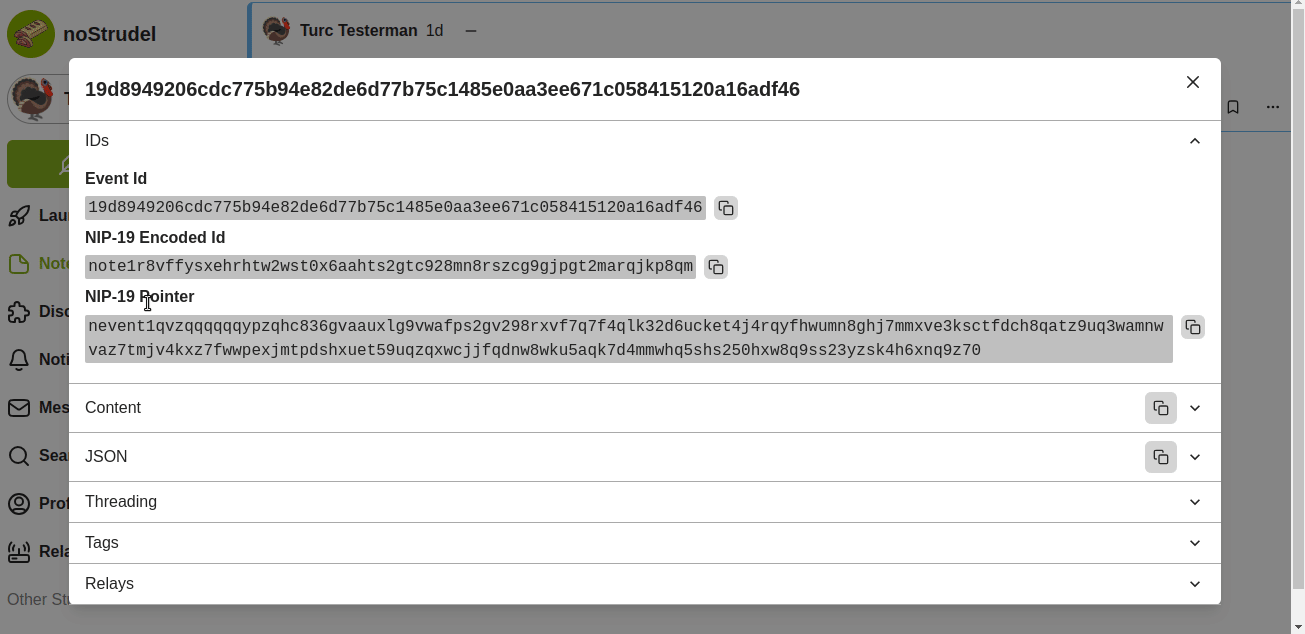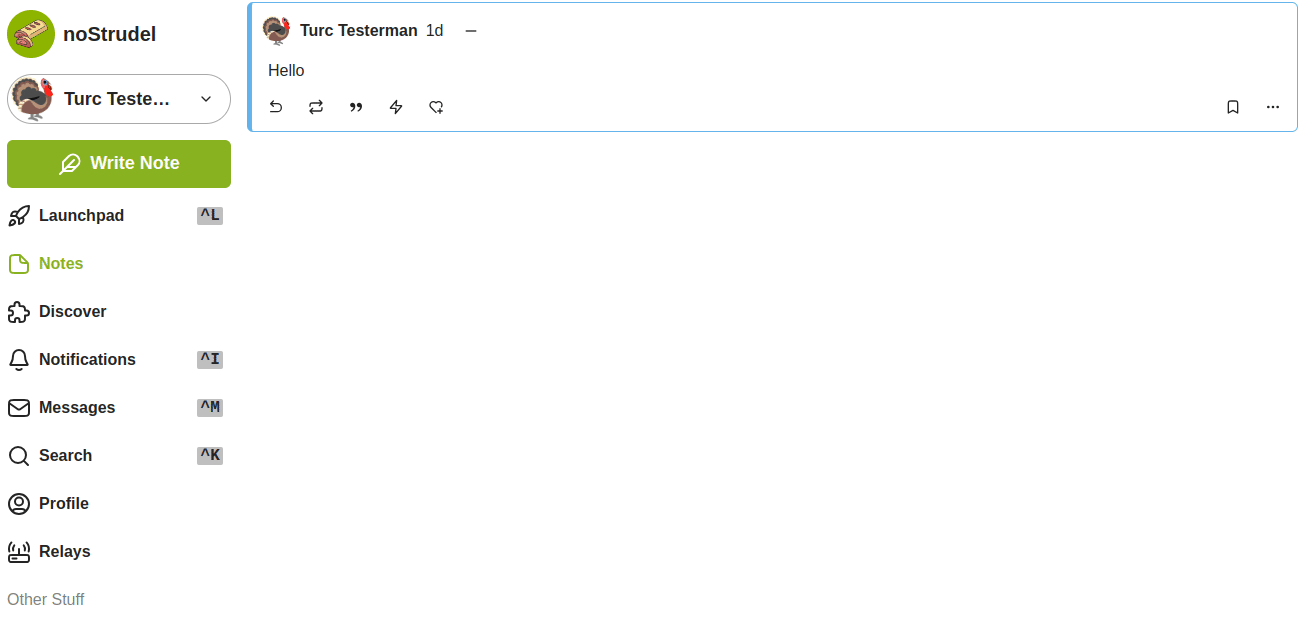
For my new kind 30040 example, I'll list all five Event IDs here in the order I want them to appear:
- 19d8949206cdc775b94e82de6d77b75c1485e0aa3ee671c058415120a16adf46
- 6428c8ac9a992a6b6e5789fc398e221ab1457b39839b174047a3cbfef4ca9214
- 9418ba17d1a918ded94cc65112daf41cee8e90daa8afd32623edb0d5846450c5
- b6f03e814fbaea810c997bb59bdb0918105f74ebaecc98d0a5d7d74aad23d1f5
- f9a6c3b9a1309ec9ded615d4463e2b49e914d15e74d09441ffa7343460baef4f
Step 4 - build your json
Next, for each Event ID you wish to include, create a new "e" in the json code. You can change the relay if you wish (and maybe even leave it blank?).
[ "e", "this_is_where_you_paste_in_your_new_event_id", "wss://nos.lol" ],You will have to be careful with your commas. Each square bracket [ ] is separated by a comma and there is not one at the end. Otherwise, your json will throw an error. (I had several yesterday!) You can use something like https://jsoneditoronline.org/ to work and see errors as you go.
Below illustrates pasting in the basic kind 30040 code, adding one additional "e" event, then adding the Event ID for that event. Notice the red json errors that emerged and needed to be corrected until it was "all green" and good to go.
I did this twice more to get my five desired notes included. The final json code I wanted for my new kind 30040 (code below).
{ "id": "972ffe9168c37241491735e3edb802b1877a56c29cb475dfeb5aba41807b5088", "pubkey": "5f078e90cef786fa0ac775218290c514e33313e0793507ed15375cc5b2bacaa3", "created_at": 1719227601, "kind": 30040, "tags": [ [ "e", "19d8949206cdc775b94e82de6d77b75c1485e0aa3ee671c058415120a16adf46", "wss://nos.lol" ], [ "e", "6428c8ac9a992a6b6e5789fc398e221ab1457b39839b174047a3cbfef4ca9214", "wss://nos.lol" ], [ "e", "9418ba17d1a918ded94cc65112daf41cee8e90daa8afd32623edb0d5846450c5", "wss://nos.lol" ], [ "e", "b6f03e814fbaea810c997bb59bdb0918105f74ebaecc98d0a5d7d74aad23d1f5", "wss://nos.lol" ], [ "e", "f9a6c3b9a1309ec9ded615d4463e2b49e914d15e74d09441ffa7343460baef4f", "wss://nos.lol" ] ], "content": "Testing a kind 30040 event on nostr" }Step 5 - create your kind 30040
Back on Nostrudel.ninja-->More-->Event Publishing, I pasted in my new kind 30040 json code, changed the timestamp number, and pushed Yolo, as below:
Then I grabbed the event ID (go to "Custom Event on Nostrudel, then the code symbols <>, then IDs). Go to https://njump.me/about, paste in the ID, and "View." And there is my new kind 30040 on njump, screencapture below:
And, finally, here it is in a prettier fashion on highlighter with five different notes aggregated:
See it on highlighter.
Conclusion
This kind 30040 does seem like a great fit for things like books. It can assemble individual notes scattered across Nostr in a hierarchical manner, present them in a usable interface, then deliver them. I imagine a stack of index cards. Each card is a note and on it is some information. They're strewn everywhere out there in the Nostrverse. A kind 30040 can gather the ones it wishes, order those cards however it wishes, then present a new "Table of Contents" for a reader.
With books, each note might be a chapter, or a paragraph, or in the case of the Bible, it might even be each verse.
I don't think a kind 30040 would work as I initially was thinking like a bitcoin Ordinal. For that to work, things would need to be concatenated...merged together, not listed on a page. My kind 30040 would have to read "Hello world!" instead of "Hello" and then "world!" as independent, although in order, notes.
Still, this kind 30040 business is neat. Books seem like a natural use case. People are very clever though. We'll come up with more things to use this ability, grow it, morph it, fork it, launch from it.
What can we build out on it from here?
As an epilogue, regarding Ordinals...
I know ordinals can be a divisive topic around bitcoin. (Even that word concatenated might have raised hackles with bitcoin's current OP_CAT debate.) People get impassioned over silly frog jpg Ordinals clogging block space and ramping up fees (both true, but then, freedom and free market). However, I think there is great potential. Recursive ordinals aggregate data already the Bitcoin blockchain. If A, B, and C are already on chain separately, recursive ordinal D can simply stick them together into one as ABC. As I see it, this is what a Nostr kind 30040 does.
I made this recursive ordinal with all of Satoshi's written words. It looks unimpressive, but everything, the content of Satoshi's words and even the orange "website" code is stored on the Bitcoin blockchain, not some server somewhere that can be shut down. Satoshi's words will persist as long as Bitcoin persists. Details on this project are here.
-
 @ c69b71dc:426ba763
2024-06-13 12:50:37
@ c69b71dc:426ba763
2024-06-13 12:50:37Chef's notes
Soaking nuts and seeds overnight makes the soup creamier and easier to blend if you have a less powerful blender. You can also use a hand blender. You can swap out nuts and seeds as needed. Cashews alone or cashews with almonds are also very tasty. More variety provides you with all the essential amino acids and fatty acids your body needs.
If you don't have miso or soy sauce, you can just use salt. But it tastes so much better with the other ingredients.
You will be surprised how tasty this soup will be! Please let me know if you try it 💚
Details
- ⏲️ Prep time: 7 minutes
- 🍳 Cook time: 0
- 🍽️ Servings: 2 - 3
Ingredients
- 200g Cashews (soaked over night)
- 50g Sunflower Seeds (soaked over night)
- 20g Hemp seeds (soaked over night)
- 2 Mushrooms (medium size)
- 2 Shiitake
- 4 tbsp Nutritional Yeast (optional)
- 1 tsp Salt (or more)
- 1 tbsp Miso (optional)
- 2 tbsp Soy Sauce (Nama Tamari)
- 2 cm of a spicy red Chilli (optional)
- 700ml Filtered Water
- 1 Clove of Garlic
- Pepper and Herbs (optional for topping)
Directions
- Soak Cashews, sunflower seeds and hemp seeds over night in water.
- Next day blend all the other ingredients with soaked seeds and nuts.
- Give it a taste and add more salt, miso or soy sauce
- Add more water if it's to thick
- Serve and sprinkle ground pepper and some herbs on top if desired for decoration
-
 @ 44dc1c2d:31c74f0b
2024-06-13 06:25:20
@ 44dc1c2d:31c74f0b
2024-06-13 06:25:20Chef's notes
I really like serving this with a saffron and cardamon rice. Add a few saffron threads and 3 or 4 crushed green cardamon pods while the rice is cooking to make it.
Details
- ⏲️ Prep time: ~15 min
- 🍳 Cook time: ~1.5 hours
- 🍽️ Servings: 6
Ingredients
- .5 cups neutral frying oil or ghee
- 2 onions halved and thinly sliced
- ~1 inch piece ginger root cut into thin batons
- 1 garlic clove crushed
- 2 fresh red chilies seeded and minced
- 1 inch piece fresh turmeric crushed or 1 tsp ground turmeric
- 1 lemongrass stalk lower part sliced thin and the top bruised
- 1.5 lbs steak cut into strips
- 14oz coconut milk
- 1 1/4 cups water
- 1 aubergine (eggplant) sliced and patted dry
- 1 tsp tamarind pulp, soaked in ~4 tbsp warm water
- salt and pepper to taste
- Garnish:
- Deep fried onions
- More fresh chilis
- Serve :
- Rice
Directions
- Heat half your oil in a wok or large pan. Fry onions, ginger and garlic tell fragrant. Add chilies, turmeric and the lower parts of the lemongrass stalk. Push the contents to the side, crank the heat and add the steak. Stirring tell the meat is browned a bit.
- Add the coconut milk, water and lemongrass top. Hit it with some salt and pepper. Cover and let simmer for about an hour and a half. You want the meat to be tender.
- Towards the end of the cook time, use the rest of the oil to fry the aubergines. Brown on both sides.
- Add the browned aubergines cook for another 15 minutes or so. Stir gently every so often. Strain the tamarind juice and add it to the curry. Taste and adjust seasoning.
- Garnish with more Chilies and serve with rice.
-
 @ 8c7d452f:320588d8
2024-06-25 18:02:03
@ 8c7d452f:320588d8
2024-06-25 18:02:03graphics made by bitcoiner guide
-
 @ 169292c6:e7064967
2024-06-13 00:17:23
@ 169292c6:e7064967
2024-06-13 00:17:23Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 0
Ingredients
- 8 oz of Imitation Crab Meat
- 1 small onion
- 2 celery sticks
- 1/2 cup of Mayonnaise
- 1 teaspoon of Garlic Powder
- 3 tablespoons of lemon Juice
- Salted Butter
- 1 teaspoon Onion Powder
- 1 teaspoon Parsley
- king Hawaiian Sweet Rolls
Directions
- Dice onion and celery and package of crab. Dice as fine as you'd like. In medium bowl, add mayo, lemon, parsley, garlic and onion powder. Mix. Next add in chopped veggies and crab. Mix together well with spoon. In the meantime, butter the rolls and sprinkle with garlic powder. Toast in the oven until slightly toasted. Remove from toaster oven slice the rolls and place crab mix inside the rolls.
-
 @ 5248bc11:f3b26997
2024-06-12 23:39:06
@ 5248bc11:f3b26997
2024-06-12 23:39:06Chef's notes
Natural Mental Health Solutions
This Zesty Chickpea Veggie Salad for Blood Sugar Control not only stabilizes blood sugar but also aids in mood regulation through serotonin synthesis. Chickpeas, a salad staple, are abundant in vitamin B6, crucial for serotonin production. Serotonin, known as the "feel-good" neurotransmitter, regulates mood, sleep, and appetite.
Vitamin B6 acts as a cofactor in converting tryptophan, found in chickpeas, into serotonin in the brain. By providing sufficient vitamin B6, this salad promotes serotonin synthesis, fostering emotional balance and well-being. Additionally, chickpeas' fiber and protein content stabilize blood sugar levels, averting mood-altering fluctuations.
Furthermore, tomatoes and red onions in this salad contain anthocyanins, flavonoids renowned for their antioxidant and anti-inflammatory properties. Anthocyanins in these ingredients combat inflammation and oxidative stress, implicated in depression development. They may also boost serotonin production, enhancing mood regulation.
Incorporating tomatoes and red onions into your diet, as in this salad, offers a delicious way to harness the potential benefits of anthocyanins for mental health. By nourishing your body with these nutrient-rich ingredients, you support physical and emotional well-being, promoting a happier, healthier lifestyle.
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 0
Ingredients
- 1 can (15 oz) chickpeas, drained and rinsed
- 1 cup cherry tomatoes, halved
- 1/2 cucumber, diced
- 1/4 red onion, finely chopped
- 1/4 cup fresh parsley, chopped
- Juice of 1 lemon
- 2 tablespoons olive oil
Directions
- In a large bowl, combine the chickpeas, cherry tomatoes, cucumber, red onion, and parsley.
- In a small bowl, whisk together the lemon juice, olive oil, salt, and pepper.
- Pour the dressing over the chickpea mixture and toss until well combined.
-
 @ e9c9cad5:d20c1735
2024-06-10 19:46:38
@ e9c9cad5:d20c1735
2024-06-10 19:46:38Chef's notes
This recipe is versatile and can be served with a variety of side dishes like roasted vegetables, salad, or rice.
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 20 min
- 🍽️ Servings: 4
Ingredients
- 4 boneless, skinless chicken breasts
- 1/4 cup olive oil
- Juice of 2 lemons
- 3 cloves garlic, minced
- 1 tablespoon chopped fresh rosemary
- 1 tablespoon chopped fresh thyme
- Salt and pepper to taste
Directions
- In a bowl, mix olive oil, lemon juice, garlic, rosemary, thyme, salt, and pepper.
- Add the chicken breasts to the marinade, ensuring they are well-coated. Marinate for at least 30 minutes, preferably 2 hours.
- Preheat the grill to medium-high heat.
- Grill the chicken for 6-8 minutes on each side, or until fully cooked.
-
 @ 0d2a0f56:ef40df51
2024-06-25 17:16:44
@ 0d2a0f56:ef40df51
2024-06-25 17:16:44
Dear Bitcoin Blok Family,
In my last post, I shared how Bitcoin became my personal antidote, rescuing me from destructive behaviors and opening up a world of knowledge. Today, I want to explore how Bitcoin is becoming an antidote for my entire family, solving problems I didn't even know we had.
As I've delved deeper into the Bitcoin rabbit hole, I've realized that I was searching for something beyond personal growth – I was looking for a solution to give my family an identity. When you look at successful families of the past or thriving organizations, you'll notice they're known for something specific. Some families are known for real estate, others for owning businesses, and some for establishing various institutions. This identity ties a family together, giving them a shared purpose and legacy.
For my family, I want that identity to be rooted in Bitcoin. Why? Because Bitcoin brings a focus I haven't seen in anything else. It neutralizes much of what I consider toxic behavior in modern society.
Take TikTok, for example. While there's nothing inherently wrong with the platform, it often promotes content that I find concerning – gender wars, gossip, and sometimes even false information. This issue extends to most social media platforms. Our kids are learning to dance, but they're not learning about money. They're absorbing various behaviors, but they don't understand inflation. We're turning to social media for education and information, which isn't necessarily bad, but it requires careful vetting of sources and filtering out the noise.
What's truly dangerous is how these platforms steal our attention subconsciously. We're wasting time, putting our attention in unproductive places without even realizing it. This is a toxic part of our culture today, and I believe Bitcoin can help solve this problem.
It's challenging to teach kids about money in today's fiat standard. How do you explain the concepts of time and energy when the measuring stick itself is constantly changing? But with Bitcoin, these lessons become tangible.
Moreover, Bitcoin opens up possibilities that seemed out of reach before, particularly in the realm of family banking. In the past, wealthy families in the United States understood the risks of keeping their family's worth in another person's hands or in external institutions. They recognized that protecting wealth comes with certain risks, and establishing a family protocol was crucial.
With Bitcoin, family banking becomes not just possible, but easily achievable and more secure than ever before. Through multi-signature wallet arrangements, we can create a true family bank where each family member holds a key to the family wallet. No funds can be moved without the permission of other family members. This technology eliminates what has been a major stumbling block in the past: trust issues. Now, we can have transparency, trust, and access for all family members.
Imagine a family account where parents and children alike have visibility into the family's finances, but movements of funds require agreement. This not only teaches financial responsibility but also fosters open communication about money within the family. It's a powerful tool for financial education and family cohesion.
This is something we should definitely take advantage of. It's not just about storing wealth; it's about creating a financial system that aligns with our family values and goals. Bitcoin provides the infrastructure for this new form of family banking, one that combines the best aspects of traditional family wealth management with the security and transparency of modern technology.
When it comes to teaching about compound interest and value, Bitcoin provides the perfect use case. Over its lifetime, Bitcoin has been averaging an astonishing 156% year-over-year return. While this number is significant, it's important to note that past performance doesn't guarantee future results. However, even with more conservative estimates, the power of compound interest becomes clear. I challenge you to use a compound interest calculator with a more modest 30% annual return. The results are still astronomical. Imagine teaching your children about saving and investing with potential returns like these. It's a powerful lesson in the value of long-term thinking and delayed gratification.
What I'm getting at is this: there are many forces in our society that hinder positive behavior and promote negative, toxic culture. These forces are stealing our children's time, attention, energy, and of course, money. Bitcoin is the antidote that can start correcting and curing some of that behavior, while also providing tangible lessons in finance and economics, and even reshaping how we approach family wealth management.
By making Bitcoin a central part of our family identity, we:
- Provide a shared purpose and legacy
- Encourage financial literacy from a young age
- Teach valuable lessons about time, energy, and value
- Promote long-term thinking and delayed gratification
- Offer an alternative to the instant gratification of social media
Bitcoin isn't just an investment or a technology – it's a paradigm shift that can reshape how we think about family, legacy, and education. It's an antidote to the toxic aspects of our digital age, offering a path to a more thoughtful, intentional way of living.
As we continue this journey, I invite you to consider: How could Bitcoin reshape your family's identity? What toxic behaviors could it help neutralize in your life? Until next time check out the below video on what some may know as the "Waterfall or "Rockefeller Method". https://youtu.be/MTpAY1LKfek?si=s7gA4bt_ZoRGAlAU
Stay sovereign, stay focused,
Joe Thomas Founder, The Bitcoin Blok
-
 @ 02d1e8e1:485a24e1
2024-06-10 05:27:13
@ 02d1e8e1:485a24e1
2024-06-10 05:27:13Details
- ⏲️ Prep time: 30min
- 🍳 Cook time: 55min
Ingredients
- 4 chicken breast skinless
- 1 1/2 cups of breadcrumbs or panko
- 2 eggs
- Fresh basil about a handfull
- 2 cloves of garlic
- 1 cup of grated parmesan
- 1 cup of flour
- Salt and pepper to taste
- 2 cups of sour Cream
- Zest and juice of one lime
- A pinch of two of rosemary
Directions
- Chop up the basil and garlic and mix it with the breadcrumbs and parmesan.
- Place the eggs in a bowl or deep platter and in another container place the flour, then take the breadcrumbs/parm mix in a third platter. Season the chicken with salt and pepper and dip it into the flour, then in the eggs and last place it in the breadcrumb mix, coat it well and lay them to the side.
- Take your sour Cream and place it in a bowl and take the zest of a line and the juice, season it with salt,pepper and two Pinches of rosemary. (For a nice yellow color you can add some tumeric) mix it well and put it in the refrigerator
- Heat butter and a bit of oil in a frying pan and fry the breaded chicken on low to medium heat until fully cooked
- Serve with rice, fries or oven baked potatoes. Enjoy and hopefully you like this recipe as much as me nd my loved ones 🫶😋
-
 @ f63316ca:22ba92a9
2024-06-09 22:29:52
@ f63316ca:22ba92a9
2024-06-09 22:29:52Chef's notes
Juicing pineapple, mangoes, grapefruit, and coconut water is a simple yet powerful way to nourish your body and unlock the secrets to vibrant health. Embrace the tropical flavors, reap the countless benefits, to become a healthier, more energized you.
*If you don't have a juicer use a blender
Details
- ⏲️ Prep time: 30 minutes
- 🍽️ Servings: 2
Ingredients
- 2 ripe organic red mangoes
- 1 fresh organic pineapple
- 1 fresh large organic grapefruit
- 2, 12 oz coconut water (make sure the ONLY ingredient is coconut water, nothing else added) or use the water from 2 fresh green coconuts
Directions
- Start by cutting your grapefruit in half, you will only use half for the juice and save the other half for juicing later.
- Cut the top, bottom, and skin from the pineapple, cut the pineapple into 8 long vertical pieces, you will only need 4 for this juice save the rest to juice later.
- Next remove the skin from the mangoes and cut the mango into small pieces and set aside.
- Add all fruits to juicer and juice, add the 2 coconut waters to the juice, stir and enjoy!
- *Refrigerate any left over fruits to juice at a later time.
-
 @ f63316ca:22ba92a9
2024-06-08 20:08:39
@ f63316ca:22ba92a9
2024-06-08 20:08:39Chef's notes
I purchased all ingredients from my local Sprouts Market
The benefits of this Organic Apple Granola Probiotic Bowl go far beyond its delicious taste. The organic ingredients used in our granola are free from harmful pesticides and chemicals, ensuring that you're nourishing your body with the purest, most nutrient-dense foods available. Additionally, the probiotic yogurt in this bowl helps to support a healthy gut microbiome, which has been linked to a wide range of health benefits, from improved digestion to a stronger immune system.
CONTAINS CLEAN SIMPLE INGREDIENTS
NON-GMO
USDA ORGANIC
GLUTEN-FREE
DAIRY-FREE
SOY-FREE
7G SUGAR (14%)
PLANT-BASED
VEGAN
NO ARTIFICIAL OR “NATURAL FLAVORS”
Details
- ⏲️ Prep time: 10 minutes
- 🍽️ Servings: 1
Ingredients
- 2 handfuls of Purely Elizabeth Chocolate Sea Salt Ancient Grain Granola
- 1 medium sized apple, diced
- 3 tbsp Cocojune Organic Dairy-Free Vanilla Unsweetened Coconut Yogurt
Directions
- Start by placing the diced apples in a bowl
- Add the Cocojune Organic Dairy-Free Vanilla Unsweetened Coconut Yogurt
- Then top it with Purely Elizabeth Chocolate Sea Salt Ancient Grain Granola
- Mix generously and enjoy!
-
 @ 6c8c7979:15595f3e
2024-06-25 16:03:41
@ 6c8c7979:15595f3e
2024-06-25 16:03:41Edward Hopper: A Comprehensive Exploration of an American Icon
Introduction
Edward Hopper (1882-1967) remains an enduring figure in American art, celebrated for his evocative portrayals of urban and rural landscapes that capture the solitude and alienation of modern life. His distinctive style, characterized by precise compositions, stark contrasts of light and shadow, and an atmosphere of contemplative silence, continues to resonate with viewers across generations. This comprehensive article delves into the life, artistic development, major works, themes, and lasting influence of Edward Hopper, offering a nuanced understanding of his contributions to American and global art.
- Early Life and Formative Years
Edward Hopper was born on July 22, 1882, in Nyack, New York. His upbringing in a middle-class family provided early exposure to the landscapes and architecture that would later feature prominently in his paintings. Hopper's interest in art emerged early, and he began formal training at the New York School of Art and Design under the guidance of prominent teachers such as William Merritt Chase and Robert Henri. These formative years shaped his artistic sensibilities and laid the foundation for his unique approach to depicting American life.
- Artistic Style and Techniques
Hopper's artistic style is characterized by several distinctive elements that set him apart from his contemporaries. His compositions are meticulously planned, often featuring geometric shapes and strong lines that create a sense of order and balance within the frame. He was a master of capturing light and shadow, using chiaroscuro to heighten drama and emphasize mood. Hopper's use of color is also notable; he often employed a muted palette that emphasized the melancholic and introspective aspects of his subjects.
- Themes in Hopper's Work
A central theme in Hopper's art is the exploration of solitude and isolation in modern society. His paintings frequently depict solitary figures in urban settings, often gazing out of windows or engaged in quiet contemplation. Hopper's portrayal of empty spaces – diners, hotels, and urban streets devoid of human presence – underscores a sense of loneliness and alienation that resonates deeply with viewers. Additionally, his interest in architecture as a reflection of human experience is evident in his meticulous renderings of buildings and interiors, which serve as metaphors for psychological states.
-
Major Works and Their Interpretations
-
"Nighthawks" (1942): This iconic painting depicts a late-night diner scene illuminated by harsh artificial light. The solitary figures seated inside the diner and the empty street outside evoke a sense of urban anonymity and existential unease.
-
"Early Sunday Morning" (1930): A quiet portrayal of a row of storefronts bathed in morning light, devoid of human activity. The stillness of the scene invites contemplation of the passage of time and the transient nature of urban life.
-
"House by the Railroad" (1925): This painting exemplifies Hopper's fascination with architecture as a reflection of inner life. The isolated house, set against a desolate landscape, conveys a sense of isolation and melancholy.
-
Hopper's Influence and Legacy
Edward Hopper's impact on American and global art cannot be overstated. His exploration of themes such as solitude, alienation, and the psychological undercurrents of modern life resonated with subsequent generations of artists and continues to inspire contemporary practitioners. Hopper's precise visual language and ability to evoke complex emotions through seemingly simple scenes have influenced numerous movements and artists, from photorealism to pop art and beyond.
Conclusion
Edward Hopper's enduring relevance lies in his ability to capture the essence of modern American life with clarity and emotional depth. Through his meticulous compositions and evocative use of light and shadow, Hopper created a visual language that continues to provoke introspection and contemplation. This article has explored the multifaceted aspects of Hopper's life and work, offering a comprehensive overview of his contributions to the art world and his enduring legacy as one of America's most iconic painters.
artstr #art
-
 @ b22fef18:1bba6e1f
2024-06-08 18:01:55
@ b22fef18:1bba6e1f
2024-06-08 18:01:55Chef's notes
Simple chipotle chicken done in the air fryer. Great for easy meal prep.
Details
- ⏲️ Prep time: 1 hour
- 🍳 Cook time: 12 min
Ingredients
- 600 grams chicken breast
- 6 grams salt (1% of chicken weight)
- 10 grams Kewpie Mayo
- 20 grams chipotle chili in adobo
Directions
- Cut chicken breast into chunks.
- Mix all ingredients together.
- Let marinate for 1 hour or longer.
- Preheat air fryer.
- Cook at 380F in air fryer for 11-13 minutes.
-
 @ e968e50b:db2a803a
2024-06-25 15:30:55
@ e968e50b:db2a803a
2024-06-25 15:30:55Some of you may remember the problem I had with a shitcoiner at our meetup back in April. Last night, we had an outright, outspoken, and worst of all, savagely interupty, anti-privacy advocate appear in our midst. I'm using the sorcery language because I didn't pick up on any prior warning signs before he transformed right in the middle of my presentation.
The agenda, following up on last month's reading on of A Cypherpunk's Manifesto and a healthy but sad conversation about the Samurai takedown, was to discuss permissionlessness and privacy. Then we would go into how PWA apps and Fedimints help out with this.
Everything seemed to be going well until I pulled out my favorite PWA to demo and this guy just jumped in to let us know that the government was going to throw the app devs in jail. At first it was just annoying, because I had just given a big spiel about how that was exactly why we wanted to use this technology. But he WOULDN'T STOP TALKING. Do other meetup organizers experience these things? Exasperated, I finally clicked my fingers and said his name real loud, as if calling an animal and @dagny761 gave me a look like, "you need to mellow out and act like a grown-up." I basically gave up on the demo at that point and am sad to say that the presentation unraveled.
The incident a couple of months back was hard, but I was at least able to maintain order and I think everyone walked away more knowledgable and still respecting one-another. I wanted to share to get people's thoughts. I don't think this guy was a shitcoiner, but he certainly was a statist...and also a huge jerk. The common thread was, I think both of these fellas just wanted to talk about NGU. Afterwards, I found out that last night's guy is a tech guy for the department of defense. He was giddy to tell me about all of the new tech he was developing that he said is already being used overseas. I'm embarrassed to say that I was too tired too beat down at that point to debate the merits or demerits of developing weapons for a government that he admitted was a black box to the public on what they were doing with this stuff.
Anyway, I share here to ask, is this common? This meetup is coming up on a one year anniversary and we've already had two frustrating nights like this...AND last night I definitely lost the debate. Worst of all, it's not because my points weren't more well received, but because some of them were literally not heard over statist howling. Also, does this guy sound familiar? He apparently goes to bitcoin meetups all the time in Michigan (multiple cities! he mentioned Detroit, Lansing, and Grand Rapids). Are Michigan meetups just NGU discussions or do you guys up there just smack this dude down better than I do?
-
 @ 7308f407:94057dcf
2024-06-06 18:04:37
@ 7308f407:94057dcf
2024-06-06 18:04:37Chef's notes
There are so many variations to make salsas. I don’t make them exactly the same every single time. It all depends on who I am making them for. This salsa was requested by my mother-in-law to bring to her work party. I was more than happy that she asked me. I made sure to get the best-looking produce at the grocery store and make this with all my attention and love. To me and my spiciness tolerance, this will not be a really spicy salsa because of the ratio of tomatoes to chiles. For a spicier salsa, I would suggest adding more jalapenos or Chiles de Arbol.
Details
- ⏲️ Prep time: Approximately 15 minutes
- 🍳 Cook time: Approximately 10 minutes
- 🍽️ Servings: 6-8 cups
Ingredients
- 10 Roma tomatoes
- 3 Jalapenos
- 1 Guajillo Chile (optional)
- 1/4 white onion
- 3 Garlic cloves
- 2 teaspoons Chicken Bouillon
- 1 teaspoon pepper
- Salt to taste (I added 1.5 teaspoons)
Directions
- Add a pot filled about 75% full with water to the stove and begin to bring it to a boil.
- After prepping your produce (washing and cutting ends off tomatoes and jalapenos and removing seeds from Guajillo Chile), add the vegetables to the water.
- Cook in hot water for approximately 8-10 minutes. You will see the color of the jalapenos change and the outer layer of tomatoes begin to peel off.
- Add all vegetables to the blender cup, along with spices. Blend until smooth.
- Check for your preference of salt level.
-
 @ 7308f407:94057dcf
2024-06-04 22:47:27
@ 7308f407:94057dcf
2024-06-04 22:47:27Chef's notes
Telera bread, a beloved staple in Mexican cuisine, serves as the perfect foundation for sandwiches. I recently prepared this homemade Telera bread recipe for our local Nostr meetup group, Nostr Phx, where I crafted delicious ham sandwiches filled with a medley of flavors—Havarti cheese, seared Panela cheese, Butter Lettuce, Campari Tomatoes, Avocados, and a zesty Chipotle Mayonnaise. To add an extra kick, I also made Pickled Jalapenos as an optional topping for the Tortas. It was a joy to share these treats while immersing ourselves in discussions about Nostr, Bitcoin, and Nostr Product Marketing.
Details
- ⏲️ Prep time: 1 hour and 30 minutes to 2 hours
- 🍳 Cook time: 20 to 25 minutes
- 🍽️ Servings: 8 buns
Ingredients
- 1.5 cups water (about 115°F)
- 1 tablespoon sugar
- 1 tablespoon active dry yeast
- 3.5 cups all-purpose flour
- 1.5 teaspoons salt
Directions
- In a cup, add warm. (I place water without ingredients in the microwave for about 20-30 seconds to warm it, then I verify with a thermometer to be around 115 degrees Fahrenheit).
- Mix the water, sugar, and yeast then place them in a warm place to activate the yeast for about 10 minutes. The yeast will feed off the sugar, and the warm water environment will help the yeast expand to activate.
- In a bowl, mix to combine all dry ingredients: all-purpose flour, salt, and butter.
- After the activation time for the yeast liquid, start adding it to the dry ingredients in smaller splashes to combine. You will want the dough to be moist but not wet.
- Begin kneading the dough in the bowl, then transfer it to a countertop. Fold the dough in half towards you. Push the heel of your hand firmly into the dough, then fold it back over itself. Turn the dough 90 degrees and repeat steps 2 and 3. Continue kneading for 5-10 minutes, or until the dough is smooth and elastic.
- Place the smooth dough back into a lightly oiled bowl and cover it with a kitchen towel. Allow it to rise for about 40 minutes in a warm place. (I add a plastic wrap over the bowl then place the kitchen towel inside of the oven with the light on).
- After the resting time, remove the dough from the bowl onto the countertop to divide it into 8 parts.
- Round the 8 parts of dough into a ball shape. As you’re shaping each one, cover them with a kitchen towel to prevent them from drying out.
- Let the dough rest for about 5 minutes.
- Grab one of your pieces of dough and add flour to both sides, then lightly flatten it and place it on your countertop. Use your index finger to make two line indentations.
- After you shape your ball, place it back under your kitchen towel.
- Once all of them are shaped, bake at 380 degrees Fahrenheit for 21-25 minutes or until the bread is lightly golden brown. Optionally, add 2 cups of water in a separate oven-safe bowl to create steam.
- Remove from the oven, then place on a wire rack covered with a kitchen towel for a couple of minutes.
- Enjoy on its own, with butter, or make a delicious Torta.
-
 @ 000002de:c05780a7
2024-06-25 15:28:01
@ 000002de:c05780a7
2024-06-25 15:28:01Lately it seems like I keep noticing people that are sympathetic to anarchism and libertarian ideas completely misunderstanding governance. It really seems like this might be one of the biggest mental blocks people have. I wonder if it is mostly the fault of libertarians and anarchists.
Those in the liberty movement (broadly) rant and demonize the government. This is completely justified. I've done it for years. I've noticed that more experienced communicators will tend to say "The State" instead of government. Years ago I heard someone explain how to think about three terms often used incorrectly.
- The country is the land
- The nation is the people
- The state is the government
I don't recall learning this in school. It is possible it was in a textbook but I doubt it. The country part I think most people do get. Nation less so. The best example of a nation without a country are Native Americans. Tribes are nations without a country (their historical lands). Tribes have their own governments and a certain amount of sovereignty in the lands they are allowed to inhabit.
The state is the word that I have found most people are confused about. People used to tell me, you hate the government so much. Why don't you leave. Well, I don't hate the nation(people) or the country(land). It is the governance system I hate. I don't even hate the people that are working in it.
Its funny to me that people on the red or blue team seem to hate the government when their side isn't in power but if someone points to issues in the system itself, well that's just crazy.
So what about those people that are sympathetic to libertarian values? Many of them say things like this. Well, I agree with you on taxes and the corruption of the government. But you always need a government. My usual response is yes. You do need governance. But you don't need a state or government. My home is governed by my wife and I. Businesses have their own governance models. Bitcoin does as well. But we do not need a single entity with a monopoly on violence.
So why is there so much confusion on this topic? I think there are two reasons.
The first is ignorance. The state of the world is largely invisible to most people. We are purposely kept ignorant of how our world works. The State isn't really discussed as a separate entity from the country and nation.
The second reason for the confusion is how libertarians and anarchists communicate. There are some that just foolishly believe people do not need governance. Honestly in my experience they are either just young or do not think deeply enough. They haven't steel manned their arguments yet. In my experience this is a small percentage of people though.
I think people in the liberty movement just need to do a better job communicating ideas. Instead of saying we need to get rid of the government one might say we need to get rid of the state. Another way to lead into this is to speak about the empire vs. the government. Talk about the monopoly which the state holds. How competition leads to better outcomes vs. monopoly.
What do you think? Have you noticed this hurdle as well? I think many people hear good ideas and agree but assume we are just dummies that believe in a fairy tale.
If private or decentralized governance is interesting to you, you might enjoy reading Chaos Theory by Bob Murphy. Its short and answer many common objections to private governance.
-
 @ fdb2a0b5:8f6d373e
2024-06-01 20:06:25
@ fdb2a0b5:8f6d373e
2024-06-01 20:06:25Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 30 min high pressure
- 🍽️ Servings: 6
Ingredients
- 1 lb ground beef
- 1 kielbasa sausage, cut into bite-size pieces
- 14 of can diced tomatoes with liquid
- 1 can chili beans
- 1 packet chili seasoning (Williams)
- 1/2 to 1 Cup beef broth
Directions
- Brown the beef and pour off extra fat.
- Add beef to pressure cooker along with other ingredients. Use as much broth as you like to reach desired consistency.
- Cook on high pressure for 30 minutes.
- Release pressure and let cool slightly to thicken.
- Serve with chopped white onion, cheddar cheese, and yellow mustard.
-
 @ 5d4b6c8d:8a1c1ee3
2024-06-25 13:03:24
@ 5d4b6c8d:8a1c1ee3
2024-06-25 13:03:24@k00b with the first three-peat (top stacker on each of the past 3 June 25th's).
Will he make it a four-peat today or does the streak end here?
Read the previous edition here.
June 25th, 2023 📅
📝
TOP POSTDon't feel bad about being too late to Bitcoin.
Excerpt:
So don't feel bad that you missed out about Bitcoin in 2017, or 2021. It doesn't matter what Bitcoin was worth then or now in fiat terms. It matters that we keep learning about Bitcoin and sharing it with others. Then one day we can all have economic freedom and savings.
3610 sats \ 37 comments \ @graben \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/198729/r/Undisciplined?commentId=198755
IMO there is no "too late". If you buy now then yes your purchasing power will probably increase dramatically over the years, but even if adoption saturates Bitcoin is still a worthwhile asset to buy / earn due to all of its other wonderful properties.
From Don't feel bad about being too late to Bitcoin.
826 sats \ 1 reply \ @orthwyrm
🏆
TOP STACKER@k00b
8333 stacked \ 14.9k spent \ 2 posts \ 24 comments \ 0 referrals
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
June 25th, 2022 📅
📝
TOP POSTExcerpt:
312 sats \ 4 comments \ @P2P_bitcoin \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/38569/r/Undisciplined?commentId=38570
Excerpt:
yes and we don't tell each other our user names so we can try and guess who is who lol! (Still don't know)
From Do you share Stacker News with family or friends?
401 sats \ 1 reply \ @plebpegasus
🏆
TOP STACKER@k00b
1981 stacked \ 8503 spent \ 9 posts \ 15 comments \ 0 referrals
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
June 25th, 2021 📅
📝
TOP POSTFighting Monetary Colonization with Open Source Code
link to https://bitcoinmagazine.com/culture/bitcoin-a-currency-of-decolonization
228 sats \ 2 comments \ @k00b \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/94/r/Undisciplined?commentId=95
dont sleep on this!
From Why El Salvador Made Bitcoin Legal Tender with President Nayib Bukele
1 sat \ 0 replies \ @sha256
🏆
TOP STACKER@k00b
2 stacked \ 7 spent \ 2 posts \ 1 comment \ 0 referrals
-
-
 @ c69b71dc:426ba763
2024-06-01 16:42:10
@ c69b71dc:426ba763
2024-06-01 16:42:10Chef's notes
All you need are the following ingredients, a bowl, and a knife.
Details
- ⏲️ Prep time: 5 min.
- 🍳 Cook time: 0
- 🍽️ Servings: 1
Ingredients
- 2 Banana
- 2 tbsp Almond butter or Cashew butter
- 1 tbsp Maple syrup (optional)
- 1-2 tbsp Cacao nibs (optional)
- 2 tbsp Pine nuts (optional chopped pecans, pistachios or other nuts)
Directions
- Peel and cut the bananas into slices. Place in a bowl. Top with almond- or cashew butter
-
 @ e4f57f4e:e6edd86e
2024-06-25 12:45:43
@ e4f57f4e:e6edd86e
2024-06-25 12:45:43When it comes to mental health, finding the right support is crucial. Whether you’re dealing with anxiety, depression, or any other mental health issue, having a trusted psychiatrist can make a significant difference in your life. If you’re searching for a psychiatrist in Pembroke Pines, Florida, or a psychiatrist in Port St Lucie Florida, Xpress Psychiatry is here to help. Our experienced team is dedicated to providing compassionate and effective care to meet your mental health needs.
Why Choose Xpress Psychiatry?
At Xpress Psychiatry, we understand the importance of personalized care. Our team of psychiatrists is committed to offering individualized treatment plans tailored to your specific needs. We prioritize your mental well-being and work collaboratively to develop strategies that promote long-term health and stability.
Comprehensive Services in Pembroke Pines, Florida
Expert Care for Anxiety and Depression
Anxiety and depression are two of the most common mental health conditions that people face today. If you’re looking for a psychiatrist in Pembroke Pines Florida, who specializes in treating these conditions, Xpress Psychiatry has you covered. Our psychiatrists are skilled in diagnosing and managing anxiety and depression, offering both medication management and therapeutic interventions to help you find relief.
Child and Adolescent Psychiatry
Mental health issues can affect individuals of all ages, including children and adolescents. Our psychiatrists in Pembroke Pines, Florida, are trained to work with younger patients, providing compassionate care that addresses their unique needs. We offer a range of services, including ADHD evaluations, behavioral therapy, and family counseling, to support the mental health of your entire family.
Telepsychiatry Services
We understand that life can be hectic, and finding time for appointments can be challenging. That’s why Xpress Psychiatry offers telepsychiatry services to patients in Pembroke Pines, Florida. With our telepsychiatry options, you can receive the same high-quality care from the comfort of your home. This convenient service ensures that you have access to the support you need, no matter where you are.
Specialized Care in Port St. Lucie, Florida
Holistic Approach to Mental Health
At Xpress Psychiatry, we believe in treating the whole person, not just the symptoms. If you’re searching for a psychiatrist in Port St. Lucie, Florida, who takes a holistic approach to mental health, our team is here for you. We combine evidence-based medical treatments with therapeutic techniques to address the root causes of your mental health issues. This comprehensive approach ensures that you receive the most effective and well-rounded care possible.
Treatment for Substance Use Disorders
Substance use disorders can have a profound impact on mental health. Our psychiatrists in Port St. Lucie, Florida, are experienced in treating these disorders and can provide the support you need to achieve and maintain sobriety. We offer a range of services, including detoxification, medication-assisted treatment, and counseling, to help you on your journey to recovery.
Geriatric Psychiatry
Mental health concerns don’t diminish with age. In fact, older adults often face unique challenges that require specialized care. Our geriatric psychiatrists in Port St. Lucie, Florida, are dedicated to addressing the mental health needs of older adults. Whether it’s managing depression, anxiety, or cognitive disorders, we provide compassionate care that enhances the quality of life for our senior patients.
The Xpress Psychiatry Difference
Experienced and Compassionate Team
Our team of psychiatrists at Xpress Psychiatry is highly experienced and deeply compassionate. We understand that seeking help for mental health issues can be daunting, and we strive to create a welcoming and supportive environment for all our patients. Your comfort and trust are our top priorities, and we work diligently to build strong, therapeutic relationships with each person we treat.
Convenient Locations and Flexible Scheduling
With locations in both Pembroke Pines and Port St. Lucie, Florida, Xpress Psychiatry makes it easy to access the mental health care you need. We offer flexible scheduling options, including evening and weekend appointments, to accommodate your busy lifestyle. Our goal is to ensure that you have convenient and timely access to our services, so you never have to go without the support you need.
Commitment to Quality Care
At Xpress Psychiatry, we are committed to providing the highest quality care to our patients. We stay up-to-date with the latest advancements in psychiatry and continually seek to improve our services. Your mental health is our priority, and we are dedicated to helping you achieve lasting well-being.
Conclusion
Finding the right psychiatrist can make all the difference in your mental health journey. Whether you’re in Pembroke Pines, Florida, or Port St. Lucie, Florida, Xpress Psychiatry is here to provide the compassionate and effective care you need. Our team of experienced psychiatrists is dedicated to helping you achieve mental wellness and live a fulfilling life. Don’t wait any longer to take control of your mental health — contact Xpress Psychiatry today and start your journey to well-being.
-
 @ 7308f407:94057dcf
2024-05-30 01:54:46
@ 7308f407:94057dcf
2024-05-30 01:54:46Chef's notes
Hey there! Ever wanted to whip up some homemade flour tortillas? Well, here's your chance! I'm from Sonora, in North Mexico, where homemade tortillas are practically a way of life. I've been making them for a good few years now and picked up a few neat tricks along the way. Trust me, the effort is totally worth it!
These tortillas? They're not just any old tortillas. They're the real deal—soft, fluffy, and bursting with flavor. Sure, making them takes a bit of time and effort, but once you taste them, you'll never look back.
Most tortilla recipes stick to the basics, but I've added my own twist. Opting for butter instead of lard or vegetable shortening lends a richer flavor that I just can't resist. Plus, a little extra baking powder gives these tortillas an extra fluffy texture that's downright irresistible.
Tools needed: -Bowl -Measuring Cups/ Spoons -Griddle -Rolling pin -Kitchen towels
Details
- ⏲️ Prep time: 20-25 minutes
- 🍳 Cook time: 20-25 minutes
- 🍽️ Servings: yield about 10-14 medium-sized tortillas
Ingredients
- 2 1/2 cups All-Purpose Flour
- About 1/2 cup AP Flour for rolling tortillas
- 1/3 cup Unsalted Butter (Room Temperature)
- Plus a little extra (if using 1 stick of butter, which measures to 1/2 cup, use the remaining 1/4 of that)
- About 1 cup Warm Water
- 1 teaspoon Baking Powder
- 1 teaspoon Salt
Directions
- In a bowl, add dry ingredients which are flour, salt, and baking powder then mix to combine.
- Then add room temperature butter. Begin by breaking the butter apart into the flour until the butter is mostly dissolved. The flour will form into small clumps with the butter.
- Use warm water; you can microwave for 15-20 seconds or have the water be a little over room temperature.
- Start adding water a splash at a time.
- The temperature of the water helps melt the butter into the flour without being too hot, which can burn the flour. It also assists in keeping the dough well moisturized throughout the process.
- Using your hand, squish all the dough in different sections to combine.
- Continue to add water then mix again until the dough starts to hold together. You will want the dough to be moist but not too wet.
- Use the round surface of the bowl to help mold the dough.
- Once you have a big roundish ball, you can transfer it to a countertop.
- Knead the dough for about 5-7 minutes until smooth. The kneading method that works for me is to push half of the dough up, fold it onto itself, then rotate. I continue this motion repeatedly.
- Lightly push with your finger, and if you see a small bounce back from the dough, it’s ready to rest.
- Cover the dough with plastic wrap or a kitchen towel, then place it back into the bowl used to mix. Allow the dough to rest for about 30 minutes in a warm place. I usually turn my oven light on and add the covered bowl in the oven.
- After the resting period, remove the dough from the bowl. You will notice the dough is a little shiny and softer.
- This is also a good time to turn on your griddle or pan, set it to medium-high.
- On a countertop, place the round dough, using your thumb and index finger, make a smaller ball. I make medium-sized balls, so it can range from 10-14 tortillas.
- Grab one small dough ball, pull the outside edges into itself to reshape the ball.
- Use a little bit of butter on your hands to help keep the dough moistened.
- Place your ball on your less dominant hand, using the opposite hand over the ball shape, add a little bit of pressure and turn the ball in a circular motion. The ball will turn into an oval shape.
- Continue to do this with all the dough until they are all shaped into smaller pieces.
- Cover them with a kitchen towel as you work through the dough.
- Using the extra flour, keep it in a round container or put it into a pile near your tortillas.
- Grab your Rolling Pin to form the tortillas on a lightly floured surface. If you add too much flour to the surface, your tortillas will be dry.
- Dust the ball into your pile of flour on both sides, flatten the ball then lightly pinch the outer edges.
- Place it on your surface, using the rolling pin, flatten with a roll, then flip.
- Turn the tortilla 45 degrees (like a half-turn) and from the middle of the dough, press forward, return to the middle, and then roll towards you. Flip the tortilla and repeat the same process until you have a thin disk of about 10 inches or when you can somewhat see through the tortilla to the surface underneath.
- You can start cooking them or place them on your surface to finish with the rest. If you are new to rolling tortillas, be patient; it takes a little practice.
- Place the flat dough on your griddle. If the griddle is hot enough, within the first 10-15 seconds, you will notice forming air bubbles. If you see this, you can flip it with your fingers or spatula.
- Approximately 15-seconds on the other side, you will notice the tortilla will have a bigger puff, flip again. For about 5-10 seconds, the tortilla will inflate. You can remove it from the griddle. You will notice that the dough will look cooked because of the color change and could have developed light brown spots.
- Add the cooked tortilla in between a clean kitchen towel to keep warm.
- Repeat the process until all have been cooked.
- If the griddle is too hot, you will see a little smoke from the tortilla burning, reduce the heat. If the griddle is not hot enough, tortillas will take longer than a minute to cook and could become hard.
- Eat the tortilla on its own, with a little butter then roll it up, or with your full meal. Enjoy!
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ 9911f8d9:86db6c34
2024-05-25 19:24:44
@ 9911f8d9:86db6c34
2024-05-25 19:24:44Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 15 min
Ingredients
- 2 eggs
- 1 egg yolk
- 175 g white caster sugar
- zest of ½ orange
- ¼ tsp salt
- 250 grams of whole wheat flour
- 1 tsp baking soda
- 100 ml milk
Directions
- Put the eggs, egg yolk, white caster sugar, orange zest and salt in a bowl and beat this with a (hand) mixer with whisk(s) until a very airy batter. This will take at least 5 minutes.
- Mix the flour with the baking soda and sieve this over the bowl with the airy egg mass.
- Gently fold in the flour.
- Fold the milk into the batter and let it rest for 10 minutes in the refrigerator.
- Preheat the oven to 200°C and line a baking tray with baking paper.
- Using a large ice cream scoop or spoon, form 5 mounds of batter per baking tray.
- Make sure you leave enough space between the mounds of batter, because the cakes will still rise quite a bit in the oven.
- Bake the egg cakes for 7-12 minutes until light brown and done
-
 @ f63316ca:22ba92a9
2024-05-24 22:42:57
@ f63316ca:22ba92a9
2024-05-24 22:42:57Chef's notes
THIS IS THE CORRECT RECIPE; I APOLOGIZE FOR THE MULTIPLE POSTS PLEASE IGNORE THE OTHER TWO
I created this recipe as I used to struggle with gaining weight for most of my life and being allergic to dairy, gluten, and soy, I had to come up with something that would benefit my overall health and supplement my workout routine. This healthy, plant-based, raw vegan protein shake is best to drink after your workout to gain weight, however, if you don't work out that's ok too, this shake is great for anyone, it is especially great for those looking to move up in weight if you are struggling with gaining weight and want to healthier option when doing so.
Details
- ⏲️ Prep time: 2HRS, 15MIN
- 🍽️ Servings: 1
Ingredients
- 8oz Gluten-Free Oats
- 8oz Walnut Milk
- 16oz Coconut Water; if you want a thicker consistency use 8oz
- 2 tbsp Natural Peanut Butter
- 1 tbsp Cacao Powder
- 1 Fresh or Frozen Burro Banana
- 1 Scoop Now Sports Pea Protein Powder
- 1 Scoop Sunwarrior Protein Powder
- 1 Scoop Sunwarrior Ormus SuperGreens Powder
Directions
- In a large container, pour in your gluten-free oats, walnut milk and coconut water and soak for 2 hrs prior, put in the fridge.
- After your oats have soaks for the prep time, to prepare our plant-based, gluten-free protein shake, simply combine the following ingredients in a high-speed blender, and blend for 1 minute and 30 seconds until creamy and smooth, if you like your shake a little thicker add in 8 oz of coconut water instead of 16 oz when soaking your gluten-free oats.
-
 @ f63316ca:22ba92a9
2024-05-24 22:29:33
@ f63316ca:22ba92a9
2024-05-24 22:29:33Chef's notes
THIS IS THE CORRECT RECIPE
I created this recipe as I used to struggle with gaining weight for most of my life and being allergic to dairy, gluten, and soy, I had to come up with something that would benefit my overall health and supplement my workout routine. This healthy, plant-based, raw vegan protein shake is best to drink after your workout to gain weight, however, if you don't work out that's ok too, this shake is great for anyone, it is especially great for those looking to move up in weight if you are struggling with gaining weight and want to healthier option when doing so.
Details
- ⏲️ Prep time: 2hrs, 15min
- 🍽️ Servings: 1
Ingredients
- 8oz Gluten-Free Oats
- 8oz Walnut Milk
- 16oz Coconut Water; for a thicker consistency use 8oz
- 1 Fresh or Frozen Burro Banana
- 1 tbsp Cacao Powder
- 2 tbsp Natural Peanut Butter
- 1 Scoop Now Sports Pea Protein Powder
- 1 Scoop Sunwarrior Protein Powder
- 1 Scoop Sunwarrior Ormus SuperGreens Powder
Directions
- After your oats have soaks for the prep time, to prepare our plant-based, gluten-free protein shake, simply combine the following ingredients in a high-speed blender, and blend for 1 minute and 30 seconds until creamy and smooth, if you like your shake a little thicker add in 8 oz of coconut water instead of 16 oz when soaking your gluten-free oats.
-
 @ a5d8475e:df9ff32c
2024-06-25 11:21:35
@ a5d8475e:df9ff32c
2024-06-25 11:21:35Searching for a house to rent can be a daunting task, especially when you're unfamiliar with the local market or navigating through various options. Whether you're looking for property to rent in Wolverhampton, houses to rent in Codsall, or exploring rental opportunities in Wombourne, enlisting the expertise of a top local agent can significantly simplify your search and enhance your renting experience.
Finding Your Ideal Rental Property When searching for property to rent in Wolverhampton, houses to rent Codsall, or property in Wombourne, consider these steps:
Define Your Requirements: Outline your must-have features such as number of bedrooms, parking facilities, and proximity to amenities like schools or shopping centers.
Set a Realistic Budget: Factor in not just the rent but also additional costs like utilities and council tax. A local agent can advise on typical costs associated with different areas.
View Properties: Arrange viewings for properties that match your criteria. A local agent can accompany you, pointing out both the strengths and potential drawbacks of each property.
Negotiate and Secure: Once you find a suitable property to rent in Wombourne, your agent can negotiate lease terms on your behalf and guide you through the signing process.
Why Choose a Local Agent? Local agents possess invaluable knowledge of the area, offering insights that online listings may not capture. They understand the nuances of each neighborhood, from the amenities available to the local schools and community vibes. This local expertise enables them to match your preferences closely with suitable rental properties, saving you time and effort.
Benefits of Using a Top Local Agent: Access to Exclusive Listings: Local agents often have access to a range of properties that may not be advertised widely. This gives you an advantage in finding hidden gems or properties that meet specific criteria like pet-friendly accommodations or proximity to public transport.
Personalized Guidance: Renting a property involves various steps, from property viewings to negotiations and lease agreements. A top local agent provides personalized guidance throughout the process, ensuring you understand your rights as a tenant and helping you navigate any complexities that may arise.
Market Knowledge: Rental markets can vary significantly even within the same city. Local agents keep abreast of market trends, rental rates, and upcoming developments, providing you with informed advice to make confident decisions.
Conclusion In summary, when searching for houses to rent in Codsall, property to rent in Wolverhampton, or exploring rental options in Wombourne, partnering with a top local agent can streamline the process and increase your chances of finding your ideal home.
CONTACT Halle UK: ** 2-3 Walsall Rd, Willenhall, WV13 2EH info@halleuk.com +44 (0) 1902 504455
-
 @ f63316ca:22ba92a9
2024-05-24 22:17:09
@ f63316ca:22ba92a9
2024-05-24 22:17:09Chef's notes
I created this recipe as I used to struggle with gaining weight for most of my life and being allergic to dairy, gluten, and soy, I had to come up with something that would benefit my overall health and supplement my workout routine. This healthy, plant-based, raw vegan protein shake is best to drink after your workout to gain weight, however, if you don't work out that's ok too, this shake is great for anyone, it is especially great for those looking to move up in weight if you are struggling with gaining weight and want to healthier option when doing so.
Details
- ⏲️ Prep time: 2hrs, 15min
- 🍽️ Servings: 1
Ingredients
- 8oz Gluten-Free Oats
- 8oz Walnut Milk
- 16oz Coconut Water, if you want a thicker consistency use 8oz
- 2 tbsp Natural Peanut Butter
- 1 tbsp Cacao Powder
- 1 Scoop Sunwarrior Protein Powder
- 1 Scoop Now Sports Pea Protein Powder
Directions
- In a large container, pour in your gluten-free oats, walnut milk and coconut water and soak for 2 hrs prior.
- After your oats have soaks for the prep time, to prepare our plant-based, gluten-free protein shake, simply combine the following ingredients in a high-speed blender, and blend for 1 minute and 30 seconds until creamy and smooth, if you like your shake a little thicker add in 8 oz of coconut water instead of 16 oz when soaking your gluten-free oats.
-
 @ f6488c62:c929299d
2024-05-24 14:49:03
@ f6488c62:c929299d
2024-05-24 14:49:03- เมื่อเช้านี้ ช่วงเวลา ตีสาม มีข่าวลวง ว่าไม่อนุมัติกันไปๆ มาๆ และจนถึง ตีสี่กว่าๆ เวลาไทย ข่าวการอนุมัติ สปอต อีเทอเรียม อีทีเอฟ ก็กระจายกันมาจากหลายสื่อหลายสำนัก จนแน่ใจว่า ได้ผ่านแล้วจริงๆ แต่ราคาก็ยังไม่ได้สูงขึ้นตามที่คนใจร้อนหวัง อย่างไรก็ขอให้ใจเย็นๆ เพิ่งจะอนุมัติเพียงขั้นตอนแรก แต่ถ้าจะเปิดขาย ต้องรอให้อนุมัติเอกสาร s1 ก่อนประมาณ สองสามวัน แล้วเราค่อยมาลุ้นราคากันว่า จะไปถึงดวงดาวกันตอนไหนครับ
-
 @ 52387c6b:49dbdfb2
2024-05-23 02:03:38
@ 52387c6b:49dbdfb2
2024-05-23 02:03:38Chef's notes
Easy start to the day, can also put some Woostr in your Bloody Mary. Perfect for washing down the toast. Breakfast of champions. If you have some sharp cheddar you can melt this on the toast, altho this may prove too complex for the average bloke, just an option. Be mindful this will add significant prep and cook time. 2-3 minutes
Details
- ⏲️ Prep time: 30 sec
- 🍳 Cook time: 2 min
- 🍽️ Servings: 1
Ingredients
- 2 slices of bread
- Butter
- Woostr sauce
- Bloody Mary
Directions
- Toast bread to your liking, lather a dollop of butter on. Criss cross the toast with a butter knife ( so the woostr dont roll off) and then drizzle on woostr.
-
 @ a012dc82:6458a70d
2024-06-25 10:57:30
@ a012dc82:6458a70d
2024-06-25 10:57:30Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
Max Keiser, an American broadcaster and businessman, is a well-known figure in the Bitcoin and crypto community. He has been a vocal advocate of Bitcoin since its early days and has played a significant role in promoting the cryptocurrency and its underlying technology. In this blog post, we will take a closer look at the rise of Max Keiser and his impact on the crypto industry.
Understanding Max Keiser
Max Keiser is an American broadcaster and businessman who has been a vocal advocate of Bitcoin since its early days. He is the host of the Keiser Report, a financial news program that covers a wide range of topics, including Bitcoin and other cryptocurrencies. He is also the founder of Heisenberg Capital, a London-based investment firm that focuses on the crypto and blockchain space.
The Rise of Max Keiser and Bitcoin
Max Keiser first became interested in Bitcoin in 2011 and quickly recognized its potential as a revolutionary new form of money. He began promoting Bitcoin on his financial news program, the Keiser Report, and became one of its earliest and most vocal advocates. He has been a regular guest on various news programs and has been featured in several documentaries about the cryptocurrency.
Max Keiser's Impact on the Crypto Industry
Max Keiser's impact on the crypto industry has been significant. His early adoption and promotion of Bitcoin helped bring attention to the cryptocurrency and its underlying technology. He has also been an advocate for other digital currencies and blockchain-based projects, helping to promote the industry as a whole. His investment firm, Heisenberg Capital, has invested in several crypto and blockchain-based projects and has helped to support the growth of the industry.
Conclusion
In conclusion, Max Keiser is a visionary in the crypto industry. His early adoption and promotion of Bitcoin helped bring attention to the cryptocurrency and its underlying technology. His impact on the industry as a whole has been significant and his investment firm, Heisenberg Capital, has played a role in supporting the growth of the industry. His work and influence has been crucial to the development and growth of the crypto ecosystem.
Frequently Asked Questions
Who is Max Keiser? Max Keiser is an American broadcaster, businessman and Bitcoin advocate who is the host of the Keiser Report, a financial news program that covers a wide range of topics, including Bitcoin and other cryptocurrencies.
What is the Keiser Report? The Keiser Report is a financial news program hosted by Max Keiser that covers a wide range of topics, including Bitcoin and other cryptocurrencies.
What is Heisenberg Capital? Heisenberg Capital is a London-based investment firm founded by Max Keiser that focuses on the crypto and blockchain space.
What is the impact of Max Keiser on the crypto industry? Max Keiser has played a significant role in promoting Bitcoin and other digital currencies and blockchain-based projects, helping to promote the industry as a whole. His early adoption and promotion of Bitcoin helped bring attention to the cryptocurrency and its underlying technology. His investment firm, Heisenberg Capital, has invested in several crypto and blockchain-based projects and has helped to support the growth of the industry. He has been a vocal advocate for the crypto industry and his influence has been crucial to the development and growth of the crypto ecosystem.
Why is Max Keiser considered a visionary in the crypto industry? Max Keiser is considered a visionary in the crypto industry because he was an early adopter and vocal advocate of Bitcoin and its underlying technology. He recognized the potential of Bitcoin as a revolutionary form of money and has been promoting it since its early days. He has also been an advocate for other digital currencies and blockchain-based projects, helping to promote the industry as a whole. His work and influence has been crucial to the development and growth of the crypto ecosystem.
What is Max Keiser's opinion on the future of Bitcoin? Max Keiser is bullish on the future of Bitcoin and has stated that he believes it will reach a price of $100,000 in the future. He sees Bitcoin as a revolutionary new form of money that will eventually replace fiat currency as the global reserve currency.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 44dc1c2d:31c74f0b
2024-05-22 22:09:19
@ 44dc1c2d:31c74f0b
2024-05-22 22:09:19Chef's notes
If you don't have peanuts, you can sub it with peanut butter, but you'll want to cook with less salt as the peanut butter can add too much salt to the dish.
Details
- 🍽️ Servings: 4
Ingredients
- 2 1/2 cups Coconut Milk
- 3 Tbsp Red Curry Paste
- 3 Tbsp Thai Fish Sauce
- 2 Tbsp Palm sugar or light brown sugar
- 1 LB rump streak cut into thin strips
- 2 Lemon Grass Stalks, Bruised
- 3 oz Ground Roasted Peanuts
- 2 Fresh Red Chilies, Sliced
- 5 Kaffir Lime Leaves, Torn
- Salt and Pepper
- Thai Basil for Garnish
- 2 Salted eggs to serve with
Directions
- Put half the coconut milk in a large pan or Wok and heat gently until it begins to boil and separate.
- Add the curry paste and cook over medium heat until fragrant. Then add the Fish sauce, sugar and lemon grass.
- Continue to cook until the color of the sauce deepens
- Add the remaining coconut milk. Bring back to boil. Add the beef and peanuts. Cook for another ~10 min
- Add the chilies and the torn Kaffir Lime and adjust the seasoning. Garnish with whole Basil leaves and serve with a salted egg and rice.
-
 @ dd664d5e:5633d319
2024-06-25 09:28:03
@ dd664d5e:5633d319
2024-06-25 09:28:03Should show up here as content
nostr:note1m9jdd9w9qxwa8gfda6n3sku7nf6mjnxylhaaa8wpnvdz85xajrasrrpj2a
-
 @ 166a42fa:3423b80f
2024-05-22 21:58:57
@ 166a42fa:3423b80f
2024-05-22 21:58:57Chef's notes
All ingredients but the blood oranges from ALDIs
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 0
Ingredients
- Cheddar chesse
- Blackberries
- Raspberries
- Crackers
- Cucumber
- Bell peppers
- Brie cheese
- Pepperoni
- Blood orange
- Apple
- Coconut chocolate cookies
Directions
- Cut up all ingredients
-
 @ 3f770d65:7a745b24
2024-05-22 18:30:14
@ 3f770d65:7a745b24
2024-05-22 18:30:14Chef's notes
For the dough, combine the water, yeast, honey, and olive oil in the bowl of an electric mixer fitted with a dough hook. Add 3 cups flour, then the salt, and mix. While mixing, add 1 more cup of flour, or enough to make a soft dough. Knead the dough on low to medium speed for about 10 minutes until smooth, sprinkling it with flour, if necessary, to keep it from sticking to the bowl. When the dough is ready, turn it out onto a floured board and knead by hand a dozen times. It should be smooth and elastic. Place the dough in a well-oiled bowl and turn it several times to cover it lightly with oil. Cover the bowl with a kitchen towel. Allow the dough to rest at room temperature for 30 minutes.
Divide the dough into 6 equal parts and roll each one into a smooth ball. Place the balls on a baking sheet and cover them with a damp towel. Allow the dough to rest for 10 minutes. Use immediately, or refrigerate for up to 4 hours.
If you've chilled the dough, take it out of the refrigerator approximately 30 minutes ahead to let it come to room temperature. Roll and stretch each ball into a rough 8-inch circle and place them all on baking sheets sprinkled with cornmeal. (You will be able to fit 2 pizzas on each 18 by 13-inch baking sheet.) You may also use a cast iron skillet if so desired.
Details
- ⏲️ Prep time: 45 minutes
- 🍳 Cook time: 15 minutes
- 🍽️ Servings: 6
Ingredients
- 1 1/4 cups warm (100 to 110 degrees F) water
- 2 packages dry yeast
- 1 tablespoon honey
- 3 tablespoons good olive oil
- 4 cups all-purpose flour, plus extra for kneading
- 2 teaspoons kosher salt
Directions
- Preheat the oven to 500 degrees
- Bake for 10 to 15 minutes, depending on your desired level of crisp.
-
 @ 7308f407:94057dcf
2024-05-22 18:13:34
@ 7308f407:94057dcf
2024-05-22 18:13:34Chef's notes
https://youtu.be/t0CBKwPIOLk?si=rLP0-9aDx0PNbumM
Details
- ⏲️ Prep time: Prep Time for Birria Beans
- 🍳 Cook time: Initial Boiling
- 🍽️ Servings: The serving size for the Birria Beans recipe depends on the quantity of beans and broth used. Given the ingredients listed, this recipe typically serves approximately 8-10 people+.
Ingredients
- 12 cups broth from birria (previous recipe)
- 1/2 onion
- 4 jalapeños or serrano peppers
- Water
- Salt to taste
- Beef from birria (optional)
Directions
- Wash the beans and let them soak for 30 minutes.
- In a large pot, add all the ingredients above.
- Set the heat to high and allow the mixture to come to a boil. Let it boil for 10 minutes.
- Reduce the heat to medium-low and cook for about 2 to 3 hours until the beans become soft.
- -To check the consistency of the beans, remove one from the pot to a plate. Using a fork, poke through to cut it in half. This method will help you easily tell if they are soft. You can also taste the beans.
- -If they are not soft yet, continue to cook for another 30 minutes.
- Every 30 minutes to 1 hour, check the beans to ensure they have enough water to cover them. They will dry out if the water level drops below the beans.
- You can also add beef from birria into the beans for added flavor.
- Enjoy the savory and slightly spicy flavor of the pinto beans cooked in red birria broth, topped off with cilantro, onion, and lime.
-
 @ 7308f407:94057dcf
2024-05-22 17:28:51
@ 7308f407:94057dcf
2024-05-22 17:28:51Chef's notes
This recipe is from a YouTube video that my mom sent to me because she wanted to try it. I made the recipe for my family once, and it was a success. We made Birria bowls, Birria nachos, Quesatacos (crispy tacos filled with cheese, birria, cilantro, onion and Salsa Macha.) I have been using this recipe for the last three years.
The YouTube title is "BIRRIA ESTILO TIJUANA en la birriería 'EL HOMMIE'". https://youtu.be/zAn8iM8dR14?si=gdYKBPyqyX13bwyo
Details
- ⏲️ Prep time: The prep time for the recipe involves several steps, including preparing the vegetables, roasting and preparing the chiles, blending the ingredients, and straining the sauce. Here's a rough estimate of the prep time: Preparing vegetables and chiles (cutting, roasting, and removing seeds): 15 minutes Blending and straining the sauce: 10 minutes Mixing ingredients and initial setup for cooking the meat: 10-15 minutes Overall, the estimated prep time is now approximately 35-40 minutes.
- 🍳 Cook time: The cooking time for the recipe involves several steps: Boiling the sauce: 20 minutes Cooking the meat in the broth: 4-8 hours (The cooking time for the meat in the broth depends on how small or big you cut the meat before cooking.) Additional steps such as cooking down the fat (if using for Quesatacos): 20 minutes Overall, the estimated cooking time is approximately 4 hours and 40 minutes to 8 hours and 40 minutes.
- 🍽️ Servings: This recipe typically serves approximately 8-10 people +, depending on how much meat each person eats or how many tacos you make.
Ingredients
- 24 Guajillo chiles
- 17 Pasilla chiles
- 1 large onion
- Water (to boil dry chiles)
- 5 cloves
- 2 bay leaves
- 3 tablespoons salt
- 5 garlic cloves
- Salt to taste
- Ingredients for Cooking Birria:
- 1/2 bunch cilantro
- 10 tablespoons dried oregano
- 2 teaspoons dried thyme
- 1 + 1/2 tablespoons ground black pepper
- 2 tablespoons ground cumin
- 6 cups water
- Adobo sauce (from dry chiles listed above)
Directions
- Adobo Sauce Preparation:
- To prepare the vegetables for the Adobo sauce, cut the tomatoes into halves. Next, cut the white onion into quarters.
- Remove the stem and seeds from the dried peppers. Roast the ancho and guajillo chiles for a couple of seconds on each side.
- In a medium/large pot, turn the heat to medium. Add water, chiles, onion, tomatoes, five garlic cloves, five cloves, and two bay leaves along with three tablespoons of salt.
- As some of the vegetables and spices boil, blend the ingredients from the pot. Once combined, add them back to the pot and merge the next batch.
- Remove the bay leaves to prevent them from blending into the sauce.
- Once all ingredients are blended, boil the sauce for 20 minutes, removing the foam that rises to the surface. Cooking the sauce down allows the tomatoes to break down and develop a great taste with the spices.
- After the sauce is finished cooking, use a large bowl and metal strainer to strain the sauce, removing the pepper seeds and any remnants of the tomato.
- Meat Preparation:
- In a large pot, add the meat along with 1/2 bunch of cilantro, ten tablespoons of dried oregano, two teaspoons of dried thyme, 1 1/2 teaspoons of ground black pepper, two tablespoons of ground cumin, six cups of water, and the Adobo sauce you previously made.
- Mix all ingredients in the pot to ensure the Adobo sauce is evenly dispersed.
- Cook on high heat until it begins to boil. Once boiling, stir the ingredients, cover with a lid, and set to the lowest heat setting on the stove. Cook for about 4-8 hours with the lid on.
- After the cooking time, verify that the meat is tender by using a fork to cut through. If the meat is not tender enough, add more time to cook on low.
- If the meat is to your desired consistency, remove it to another bowl. Allow the meat to cool down if you are shredding it by hand. If not, keep it aside to add back to the pot once the broth is strained. You can also chop the meat using a knife to break it down into smaller pieces.
- Remove the cilantro and discard it along with any other unwanted parts from the broth.
- Remove the fat from the broth into a bowl and keep it aside if you would like to use it for Quesatacos.
- If using the fat from the broth, cook it down on medium heat for about 20 minutes. This breaks down the fat from a solid to a liquid. After cooking, strain the fat to separate the solids from the liquid.
- Strain all sauce using a metal strainer.
- Leave some sauce on the side if you are making beans with the broth (about 12 cups).
- Once the broth is strained, add the meat back into the pot.
- Ready to serve with meat in its broth, as Quesatacos, or however you would like to enjoy the Birria.
-
 @ deab79da:88579e68
2024-05-20 20:48:09
@ deab79da:88579e68
2024-05-20 20:48:09Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 20-30 min
- 🍽️ Servings: 4
Ingredients
- 1 lb cod fillets
- 1/4 cup butter
- 1/4 cup white flour
- 1 1/4 cups milk
- 1 tsp salt
- pepper to taste
- 1 small onion
- 1 carrot
- 3 celery stalks
- 1/2 cup breadcrumbs
- 1/2 cup shredded old cheddar
Directions
- Preheat oven to 375F. Place cod in a greased baking dish.
- Make the white sauce in a heavy saucepan. Melt the butter over medium heat and stir in the flour until smooth. Remove from heat and slowly stir in half of the milk, then return to heat and beat until smooth and shiny.
- Gradually add the remaining milk, followed by salt, pepper, and your vegetables. Cook until sauce is smooth & thickened.
- Pour sauce over the fish, and sprinkle breadcrumbs and cheese over the top.
- Bake, uncovered for 20-30 minutes until sauce bubbles and the cheese begins to brown. Let rest 10 minutes after cooking completes.
-
 @ deab79da:88579e68
2024-05-20 20:03:17
@ deab79da:88579e68
2024-05-20 20:03:17Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: ~20 min
Ingredients
- 4 boneless skinless chicken breast
- 1 small onion
- 1-3 jalapeno pepper, to taste
- 1/2 cup soy sauce
- 1/2 cup pineapple juice
- 1/4 cup olive oil
- 1/4 cup apple cider vinegar
- Juice of 1 lime
- 1 tsp honey
- 2 cloves garlic, minced
- 1/2 tsp ground nutmeg
- 1/2 tsp ground ginger
- 1/2 tsp allspice
- 1/2 tsp red pepper flakes
- small bunch of fresh cilantro
- Salt & Pepper
Directions
- Put all of the ingredients, except the chicken breast, in a blender and blend until smooth
- Let the chicken marinate ine the mixture for several hours, or overnight
- Best cooked on a charcoal or gas grill. In a pinch, medium heat in a saute pan will do.
- Remove the chicken from the marinade and grill or saute until cooked through. While the chicken is cooking, place the remaining marinade in a small saucepan and bring to a boil. Simmer for 5 minutes.
- When the chicken is cooked, allow to rest for 5 minutes. Before serving brush the chicken with the remaining glaze. Serve with your favorite seasonal vegetables.
-
 @ deab79da:88579e68
2024-05-20 03:44:25
@ deab79da:88579e68
2024-05-20 03:44:25Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 50 min
- 🍽️ Servings: 6
Ingredients
- 4 large eggs
- 3/4 cup granulated sugar
- 3 cups milk
- 1 cup heavy whipping cream
- 2 teaspoons vanilla extract
- 1 1/2 teaspoons ground cinnamon
- 3 cups cooked rice , cooled
- 1 cup raisins
Directions
- Preheat oven to 350 degrees F.
- Beat the eggs and sugar together. Slowly pour in the milk and cream and mix well.
- Add the vanilla and cinnamon and mix well. Add the rice and raisins and stir to combine.
- Pour mixture into a greased casserole dish. Any oven-safe dish will work--you can use one pan to bake at least 9x9'' or bigger, or smaller individualized serving dishes.
- Place the filled casserole dish inside a larger, oven-proof dish. Add about 2 inches of water to the larger pan (or enough to fill about halfway up the side of the rice pudding dish). This method will help the pudding to have a custard texture.
- If using a 9x9'' or slightly larger pan, bake for 40-50 minutes or until the top has set (It's okay if it jiggles just slightly). Serve warm.
- Leftovers store well in the refrigerator for up to 5 days.
-
 @ 06a260a2:d7a7791c
2024-06-25 06:25:00
@ 06a260a2:d7a7791c
2024-06-25 06:25:00Jako SPAM v bitcoinovém blockchainu lze označit veškerá data navíc, která nesouvisí s finanční podstatou potvrzených transakcí. Nebo lépe řečeno s podstatou peer-to-peer systému elektronických peněz. Odkaz na bitcoinový whitepaper je důležitý, protože upozorňuje na skutečnost, že bitcoin a jeho blockchain byl vytvořen s konkrétním záměrem a je tedy možné posuzovat, zda daný způsob jeho využití je s tímto záměrem v souladu nebo ne. Nejčastěji jsou těmi daty navíc obrázky, videa, texty, ale může to být cokoliv, co lze datově reprezentovat.
Blockchainový SPAM vyvolává emoce, protože ne každý bitcoiner s jeho definicí výše souhlasí. Názor, že svobodný software umožňuje jeho uživatelům používat jej jakkoliv je to možné a co lze, je dovoleno, není zdaleka ojedinělý. Často je doprovázen ještě vírou v trh, který všechno spraví a čas ukáže. Já se kloním k názoru, že kdyby Satoshi chtěl na blockchain ukládat obrázky, ve svém whitepaperu by to zmínil.
Inscriptions a Ordinals protokol
Trocha historie
Zapisování netransakčních dat do bitcoinového blockchainu není novinkou a Inscriptions nejsou ani jediným, ani prvním způsobem, jak toho dosáhnout. Tím úplně prvním byla coinbase transakce v genesis bloku, do které Satoshi vepsal památný titulek z The Times: “The Times 03/Jan/2009 Chancellor on brink of second bailout for banks”. Každá coinbase transakce může obsahovat až 100 bytů libovolných dat a je na uvážení těžaře, který blok vytěžil, jak je využije.
Využití a zneužití skriptů
Jedním z prvních používaných způsobů, jak zapsat libovolná data do blockchainu bylo využití místa pro hash veřejného klíče ve výstupním skriptu P2PKH (Pay-to-Public-Key-Hash). Skript nabízí 20 bytů na jeden výstup, nicméně výstupů může být v transakci více. Protože nelze žádným způsobem rozpoznat, zda uvedená data jsou hashem existujícího veřejného klíče, musí být taková transakce přijata ke zpracování. Příkladem využití této metody je následující obrázek. Je zakódován do několika transakcí a v blockchainu se objevil už před deseti lety. Naleznete jej například zde.

Data lze zapsat i do původník P2PK (Pay-to-Public-Key) výstupních skriptů na místo určené pro veřejné klíče. V nekomprimované podobě lze použít 65 bytů, v komprimované pak 33.
Společnou nevýhodou obou způsobů použití výstupních skriptů je vytvoření neutratitelných zůstatků (UTXOs). K datům na místě veřejných klíčů neexistují privátní klíče, které by zůstatky odemkly a tak je nelze dále převést na novou adresu. Nehodí se proto pro případy použití bitcoinového blockchainu jako nezpochybnitelného dokladu o vlastnictví, protože toto vlastnictví nelze dále převést. Zároveň platí, že kromě poplatků za vytěžení mají tato data také náklad v podobě takto “spálených” satoshi.
OP_RETURN
Jiným, ale také velmi oblíbeným způsobem, je použití operátoru
OP_RETURN. Do bitcoin core se dostal později, až v roce 2014. Jeho použití záměrně označuje takto označený výstup transakce jako dále neutratitelný a vytváří prostor pro až 80 bytů libovolných dat.Zajímavá je historie vzniku tohoto operátoru. Byl reakcí na jiný v té době používaný způsob ukládání dat do bitcoinového blockchainu Counterparty protokolem. Counterparty byl druhou vrstvou na bitcoinem, která umožňovala vytvářet nové tokeny a obchodovat s nimi na distribuované burze. Nepřipomíná vám to něco? Counterparty zneužíval operátor
OP_CHECKMULTISIG, který slouží k ověření podpisu transakce s více podpisy P2SH (pay to script hash). Místo veřejných klíčů k ověření však k operátoru ukládal svá specifická data. UTXOs vytvořené pro Counterparty byly rovněž neutratitelné (uložená data nereprezentovala veřejné klíče odvozené z existujících privátních klíčů), přesto musely být z principu uchovávány v transakčním setu uzlů (byly součástí platné transakce), a proto představovaly riziko pro další škálování bitcoinu. Diskuze, které se na toto téma v roce 2014 vedly, jsou dnes označovány jako OP_RETURN Wars. Jejich výsledkem bylo zavedení operátoruOP_RETURN, který umožnil připojení libovolných dat k transakci a poskytl tak protokolu Counterparty řešení jeho potřeb. Zároveň však explicitně označuje takto označené UTXO za neutratitelné. To umožňuje uzlům vyřadit jej z transakčního setu pro další validace a šetřit tím místo.Zavedení operátoru
OP_RETURNbylo prvním ústupkem SPAMu. Jeho použití pro zapsání krátké zprávy do blockchainu dnes umožňuje celá řada peněženek, například i Trezor Suite.Ordinal theory a Ordinals
Koncept Ordinar Theory publikoval na svém blogu v roce 2022 bitcoinový vývojář Casey Rodarmor. Popisuje číslovací schéma, které přiřazuje každému satoshi jednoznačné číslo od 0 do (zjednodušeně) 2.100.000.000.000.000 (21M*100M. Ve skutečnosti je jich o něco méně, protože i bitcoinů nebude díky principu halvingu přesně 21 milionů.). Satoshi jsou číslovány v pořadí, v jakém byly vytěženy (například satoshi vytěžené v genesis bloku mají čísla 0 - 4.999.999.999), a přenášejí se ze vstupů transakcí do jejich výstupů (první satoshi prvního výstupního UTXO dostane číslo prvního satoshi prvního vstupního UTXO, atd.). Každý satoshi tak má jednoznačné pořadové číslo, anglicky ordinal. Odtud název Ordinals.
Jednoznačné číslování satoshi umožňuje potlačit jejich zaměnitelnost a dává tak příležitost sběratelům zaměřit se na jednotlivé z nich, které jsou něčím zajímavé. Má pro vás první satoshi páté epochy (první satoshi z odměny za vytěžení prvního bloku po čtvrtém halvingu) vyšší hodnotu? Chtěli byste ho?
Inscriptions
Inscriptions jsou novým způsobem zápisu dat nebo digitálních artefaktů do blockchainu bitcoinu. Navrhl je v roce 2022 opět starý známý Casey Rodarmor. Využívají číslovací schéma Ordinal theory pro identifikaci jednotlivých satoshi a umožňují ke každému z nich jednotlivě do blockchainu připsat libovolný digitální obsah, zahrnující obrázky, videa, texty, zvuky a další (tzv. bitcoinová NFT). Data jsou zapsána přímo do blockchainu v rámci taproot skriptu transakce, která je publikuje, v tzv. witness datech. Díky tomu se na ně vztahuje 75% sleva z poplatku za vByte a “činí tak tento způsob ukládání dat do blockchainu relativně úsporným” (skutečná slova použitá v publikované dokumentaci Inscriptions).
Satoshi, ke kterým jsou Inscriptions připsány, mohou být převáděny standardními transakcemi na libovolné bitcoinové adresy v rámci běžných UTXO. Je třeba jen respektovat číslovací schéma Ordinals při sestavování těchto transakcí.
Inscriptions, nebo lépe bitcoinová NFT, se stala mezi určitou skupinou uživatelů bitcoinu (nikoliv mezi bitcoinery, natož bitcoin maximalisty) velmi populární. Jejich zásadní výhodou oproti jiným NFT implementacím se stala skutečnost, že bitcoinový blockchain obsahuje přímo digitální obsah, nikoliv pouze odkaz na něj někam do centralizovaného úložiště, u něhož není záruka, že bude v budoucnu stále existovat. Jediným limitem se stala maximální velikost jednoho bloku (4MB), který obsahuje příslušnou transakci. I to však nezabránilo umístit do Inscriptions celou počítačovou hru Doom. Zahrajte si a pak se vraťte ke čtení. (odkaz na příslušnou transakci v blockchainu).

Stejně jako protokol Counterparty, který byl postaven na zneužití operátoru
OP_CHECKMULTISIG, si i Inscriptions našli skulinku v sémantice taproot skriptu. Stala se jím kombinace operátorůOP_FALSE,OP_IFaOP_ENDIF. První z nich uloží na vrchol zásobníku hodnotu “nepravda”. Druhý pak testuje hodnotu na vrcholu zásobníku a pokud je pravdivá, vykoná další část skriptu až po operátorOP_ENDIF. Protože je ale na vrcholu hodnota “nepravda”, tato část skriptu se přeskočí a nikdy nevykoná. Mezi operátoryOP_IFaOP_ENDIFtak vznikne ideální prostor pro uložení čehokoliv, aniž by to ohrozilo syntaktickou a sémantickou správnost skriptu jako celku. De iure je vše v pořádku. De facto došlo ale ke zneužití slabého místa skriptovacího jazyka.Runes
Protokol Runes přinesl do světa bitcoinu možnost specifikovat, razit a převádět vlastní zaměnitelné tokeny. Nejsou prvním takovým pokusem, ale v současné době asi tím nejviditelnějším. Autorem protokolu je do třetice Casey Rodarmor. Zajímavá je jeho motivace k vytvoření protokolu. Na svém blogu 25.9.2023 k tomu mimo jiné napsal:
“Nejsem si jistý, zda je vytvoření nového protokolu se zaměnitelnými tokeny pro Bitcoin dobrý nápad. Zaměnitelné tokeny jsou z 99,9% podvody a memy. Nezdá se však, že by v dohledné době zmizely, podobně jako asi nezmizí v dohledné době kasina. Vytvoření dobrého protokolu zaměnitelných tokenů pro Bitcoin by mohlo přinést významné příjmy z transakčních poplatků, zájem vývojářů a uživatelů o Bitcoin. Navíc, pokud by tento protokol měl jen malou stopu v blockchainu a podporoval zodpovědnou správu UTXO, mohl by snížit škody ve srovnání s užitím stávajících protokolů. Přinejmenším jeden z nich, BRC-20, je již poměrně populární a má nežádoucí důsledek v podobě množení UTXO.”
Runes se v bitcoinovém blockchainu objevili po čtvrtém půlení (s výškou bloku 840.000) a co se stopy v bitcoinovém blockchainu týče, úsportné skutečně jsou. Data protokolu jsou uložena v transakčním výstupu v rámci operátoru
OP_RETURN. Ten je následován operátoremOP_PUSHNUM_13(identifikátor, že se jedná o data protokolu Runes) a dalšími daty (přes operátorOP_PUSHBYTES), která určují, zda se jedná o definici nového tokenu, jeho ražbu nebo převod mezi adresami. Tato data jsou vždy menší než limit 80 bytů operátoruOP_RETURN, takže plní standardní podmínky pro přijetí transakce do mempoolu většiny uzlů. Na první pohled je tedy vše v pořádku. Ale… Pomůžu si opět citací Casey Rodamora z jeho blogu:“Mělo by něco takového existovat? Nevím. Je to jednoduché, jak je to jen možné, nespoléhá se to na data mimo blockchain, nemá to nativní token a hezky to zapadá do modelu UTXO Bitcoinu. Takové schéma by mohlo přilákat uživatele jiných schémat s horší stopou v blockchainu a přivést k bitcoinu pozornost dalších vývojářů a uživatelů, což by je povzbudilo k jeho přijetí. Na druhou stranu je svět směnitelných tokenů většinou nepoučitelnou žumpou, plnou podvodů a chamtivosti, takže by to také mohlo dopadnout špatně.”
Důsledky uvedení Ordinals, Inscriptions a Runes jsou zřejmé. K bitcoinu přitáhli další skupinu jeho uživatelů - sběratele a spekulanty na budoucí hodnotu bitcoinových NFT nebo obchodníky s novými tokeny. Vytváření a obchodování s NFT zvedlo zájem o transakční prostor v bloku a zapříčinilo růst transakčních poplatků do nebeských výšin. Těžaři a těžařské pooly se radují, běžní bitcoineři, kteří stále chtějí používat bitcoin jako peer-to-peer systém elektronických peněz pláčou. Má to nějaké řešení?
Doplnění: Předchozí odstavec jsem napsal skoro před dvěma měsíci v týdnech po půlení bitcoinu, kdy se transakční poplatky šplhaly ke stovkám satoshi za vByte. Nyní se situace uklidnila a poplatky se k neradosti těžařů vrací k normálu kolem 10-20 satoshi za vByte. Přesto lze pohledem do mempoolu zjistit, že transakce protokolu Runes stále tvoří cca polovinu všech transakcí čekající na potvrzení…
Kdo je Casey Rodarmor?
Casey Rodarmor je bitcoinový vývojář ze San Francisca, který přispívá do jeho kódu již několik let. Začínal v Chaincode Labs, později přispíval i k dalším bitcoinovým projektům, jako jsou mixery Wasabi Wallet a JoinMarket.

Největší známost Caseymu však přinesly až Ordinals, Inscriptions a Runes. Pro některé z bitcoinové komunity se tak stal nepřítelem číslo jedna, pro jiné inovátorem, který do bitcoinu vrátil hravost a oživil svět nudných “sound money”. On sám se má spíše za kreativního umělce (kód je druh umění), který rád vytváří umění sloužící nějakému konkrétnímu účelu.
Casey je aktivní na Twitteru, publikuje na svém blogu. A v jádru zůstává skromným bitcoinerem.
PR #28408
Vzrůstající množství SPAMu v transakcích nezůstalo bez povšimnutí. Na Ordinals a rozšíření Inscriptions zareagoval v září roku 2023 Luke Dashjr pull requestem PR #28408 do Bitcoin Core. Navrhl v něm rozšířit platnost parametru
-datacarriersizei na tyto nové způsoby ukládání netrasankčních dat. Parametr-datacarriersizeumožňuje měnit maximální velikost vložených dat, ale vztahuje se pouze k operátoruOP_RETURN. PR navrhuje aktualizovat pravidla mempoolu tak, aby omezil množství dat, která lze vložit také do witness části taproot skriptu, do obálky vytvořené z operátorůOP_FALSE,OP_IFaOP_ENDIF.O několik dní později se také v mezinárodních databázích zranitelností objevilo hlášení CVE-2023-50428, které upozorňuje na zmíněné zneužití operátorů
OP_FALSE,OP_IFaOP_ENDIF. Inscriptions byly označeny za zranitelnost pro bitcoin.PR byl sice otevřen, k jeho schválení a implementaci do Bitcoin Core ale nedošlo. Diskuze kolem něj krásně ilustruje panující ditochomii bitcoinerů v pohledu na SPAM. Zastánci PR argumentovali zamezením spamování bitcoinového blockchainu, zpomalením růstu nákladů na provozování bitcoinového uzlu (a úložiště pro blockchain), možností volby provozovatelů uzlů, zda chtějí mít Inscriptions v mempoolu a v neposlední řadě dotažení implementace
-datacarriersizetak, jak byl původně zamýšlen: jako parametr omezující ukladání dat všemi dostupnými metodami, nikoliv jen přes operátorOP_RETURN.Odpůrci implementace tohoto PR argumentovali tím, že nemůže zabránit šíření Inscriptions, protože jeho použití je dobrovolné a těžaři nejsou motivováni se Inscriptions bránit, ale právě naopak. Inscriptions těžařům prostřednictvím rostoucích poplatkům pomáhají k vyšším ziskům. Padly i argumenty o zkreslování reality pro operátory uzlů, kteří si transakce s Inscriptions z mempoolu vyloučí a budou jim tak chybět informace pro správnou funkci odhadování ceny poplatků zařazení transakce do následujícího bloku. A padly samozřejmě i obvinění z cenzury bitcoinových transakcí.
Kdo je Luke Dashjr?
Luke Dashjr, známý jako Luke-Jr, je softwarový vývojář a přispěvatel do projektu Bitcoin Core. Luke se na vývoji jádra bitcoinu podílí od jeho počátků, začal už v roce 2011. Do jádra bitcoinu přispěl více než 200 vylepšeními, jako například Segregated Witness, který mimo jiné zvyšuje transakční kapacitu Bitcoinu. Luke je správcem sekce Bitcoin Improvement Proposals (BIPs) a v bitcoinové komunitě tak hraje významnou roli.

Luke Dashjr je rovněž zakladatelem poolu Eligius, jednoho z prvních těžebních poolů. Po několikaleté přestávce byl pool znovu spuštěn na podzim roku 2023 pod jménem Ocean pool. V současnosti tvoří podíl poolu méně než 1 % hashrate sítě Bitcoin. Ocean pool je anonymní těžební pool, nevyžaduje žádnou registraci a odměny za vytěžený blok nad stanovený limit pro výplatu posílá svým těžařům přímo v coinbase transakci. Ostatní pak mají možnost nastavit si BOLT-12 lightning fakturu a podlimitní částky přijímat tímto způsobem.
Společným jmenovatelem většiny aktivit, kterým se Luke věnuje v dnešní době, je snaha o skutečnou decentralizaci těžby bitcoinu, boj proti cenzuře transakcí (reálné i potenciální) a také ochrana bitcoinové sítě před zahlcením SPAMem.
Zvláště posledně jmenované přináší k jeho osobě také jistou míru kontroverze. To, co Luke považuje za SPAM, vnímají jiní jako projev svobodného využití open source softwaru a obviňují jej ze snahy cenzurovat transakce.
Jak (se) bránit SPAMu?
SPAM se do bitcoinového blockchainu dostává prostřednictví transakcí, které jej přenáší, respektive jejich potvrzením při vytěžení nového bloku. Tím jsou také dány dva základní způsoby, jak se SPAMu bránit.
- Bránit šíření transakcí, které SPAM obsahují, bitcoinovou sítí
- Bránit zařazení těchto transakcí do šablony bloku určeného k potvrzení
Šíření transakcí v síti zajišťují bitcoinové uzly - servery, na kterých běží klient bitcoinové sítě. Pokud klient transakci akceptuje, uloží ji do svého mempoolu a přepošle ji svým peerům - dalším uzlům, se kterými je ve spojení. Tímto způsobem se transakce šíří sítí až k uzlům, které používají těžaři k sestavení šablony nového bloku k vytěžení.
Bránění šíření transakcí má reálný význam pouze v případě, kdy se na něm shodne významná většina uzlů v síti a vytvoří se podmínky, které zamezí reálnému doručení takové transakce k těžaři, který je ochoten ji vytěžit. Podstatně účinnější je rozhodnutí samotných těžařů nezařadit takové transakce do šablony nového bloku. Většina těžařů však k takovému jednání není motivována. Filtrování SPAMu snižuje počet transakcí a v důsledku tedy i velikost transakčních poplatků. Mezi těžaři však existují výjimky, pro které není trade-off podpory SPAMu za vyšší poplatky přijatelný. Krom celé řady privátních poolů pro solo mining mezi ně patří i Ocean pool Luka Dashjra.
Bitcoin Core, nejčastěji používaná implementace bitcoinového klienta, má celou řadu konfiguračních parametrů, které ovlivňují jeho chování. Z pohledu šíření SPAMu jsou zajímavé dva:
Parametr
-datacarrierurčuje, zda budou přenášeny transakce s operátoremOP_RETURN. Ten označuje netransakční data v transakci. Výchozí hodnota je 1 - transakce jsou přenášeny.Parametr
-datacarriersizepak určuje maximální velikost netransakčních dat za operátoremOP_RETURN. Výchozí hodnota je 80.Oba parametry ovlivňují pouze transakce s operátorem
OP_RETURN. Jak jsme si však ukázali v předchozích odstavcích, k šíření SPAMu jsou využívány i jiné operátory a snaha rozšířit platnost parametrů na další způsoby nebyla v implementaci Bitcoin Core úspěšná. Proto Luke Dashjr a s ním i další těžaři používají jinou implementaci klienta - Bitcoin Knots.Bitcoin Knots
Neschválení PR #28408 bylo z mého pohledu chybou. Požadovaná změna neměnila chování Bitcoin Core, pouze mohla dát provozovatelům uzlů další volbu, jaké transakce chtějí v mempoolu svého uzlu mít a šířit je dále po bitcoinové síti. Pokud chceme dále jako bitcoinová komunita tvrdit, že bitcoin je decentralizovaný a jeho vlastnosti řídí jednotliví suverénní provozovatelé uzlů sítě, neměli bychom se bránit dát jim k tomu odpovídající stupeň volnosti pro jeho nastavení.
Naštěstí Bitcoin Core není jedinou implementací bitcoinového klienta a jeho protokolu. Luke Dashjr udržuje a rozvíjí Bitcoin Knots, implementaci bitcoinového uzlu a peněženky, která z Bitcoin Core vychází a nabízí tak stejnou úroveň zabezpečení, soukromí a stability. Kromě toho však svým uživatelům rozšiřuje možnosti filtrování spamu pomocí rozšířené sady parametrů a pravidel k jeho potlačení.
Parametr
-datacarriersizemá v Knots výchozí hodnotu jen 42 a byl rozšířen tak, aby kontroloval i jiné způsoby zápisu netransakčních dat, než přes operátorOP_RETURN. Realizuje tak původní návrh Pull Requestu #28408. Povolit nebo potlačit tuto vlastnost lze prostřednictvím parametru-datacarrierfullcount. Ve výchozím stavu je povolena.Dalším užitečným parametrem je
-datacarriercost. Umožňuje odstranit slevu na poplatcích, kterou mají SegWit data. Výchozí hodnota je v souladu s Bitcoin Core 0.25, což odpovídá 75% slevě. Pokud jej však nastavíte například na 4, bude muset majitel transakce zaplatit za data navíc čtyřnásobek poplatku za vByte.Jinou vůči SPAMu relevantní úpravou, je nastavení limitu maximální velikosti pre-SegWit, SegWit a Taproot skriptů na 1650 bytů. Tyto skripty, respektive místo pro ně v transakci, bývá také zneužíváno pro vložení SPAMu. 1650 bytů je dostatečná velikost pro všechny v současnosti známé skripty. Pokud by se v budoucnu ukázalo, že nedostačuje, lze ji zvýšit prostřednictvím parametru
-maxscriptsize.V květnu uvolněná verze Knots 26.1 přinesla další důležité změny. Všechny nestandardní zápisy netransakčních dat (veškerý SPAM kromě
OP_RETURN) jsou nyní ve výchozím nastavení filtrovány. Pokud se mají Knots v tomto ohledu chovat stejně, jako Bitcoin Core, je třeba nastavit nový parametr-acceptnonstddatacarrierna 1. Výchozí hodnota je 0.Ve výchozím nastavení této verze Knots jsou rovněž filtrovány všechny P2PK transakce. Pay-to-Public-Key skript je zastaralým a dávno nepoužívaným formátem, který používala první Satoshiho peněženka. Časem byl nahrazen uspornějšími a bezpečnějšími formáty (P2SH nebo SegWit). P2PK transakce jsou však dnes stále zneužívány, SPAM je v nich na místě veřejného klíče. Parametr
-permitbarepubkeyumožňuje toto výchozí filtrování zrušit a P2PK transakce zpracovat.Na “oblibu” protokolu Runes reaguje parametr
-rejecttokens. Umožňuje filtrovat transakce, které Runes obsahují. Není tak nutné filtrovat veškerá netransakční data nastavením parametru-datacarriersizena 0.A posledním relevantním parametrem, který release Knots 26.1 přináší, je
-rejectparasites. Ten by měl filtrovat tzv. parazitické transakce, tedy transakce, které na první pohled vypadají, jako standardní, ale ve skutečnosti existují proto, aby s využitím konceptu Ordinals vytvořily vazbu mezi konkrétním satoshi a artefaktem z externího světa. V této verzi Knots parametr filtruje transakce ražby protokolu CAT-21.Ocean mining pool
Knots můžete samozřejmě použít i jako klienta bitcoinové sítě pro vaši domácí těžbu (solo mining) ve vlastní instanci Public-Poolu. Pokud by jste ale chtěli podpořit filtrování SPAMu při zařazování transakcí do šablony bloku velkého veřejného poolu, je jedinou známou možností Ocean mining pool. Ten nabízí celkem čtyři typy šablon s různou mírou filtrování SPAMu. Dvě z nich jsou postaveny na Knots: šablony OCEAN a Data-Free. Nastavení jejich konfiguračních parametrů je detailně popsáno na webu poolu.
Dává smysl bránit (se) SPAMu?
Pravdou je, že dokud bude existovat kontroverze mezi bitcoinery ohledně pohledu na SPAM a jeho filtrování zůstane jen volitelnou možností, bude se SPAM v bitcoinovém blockchainu dále objevovat. Důvodem je motivace velkých těžařů podporovat zájem o místo v bloku a tím růst transakčních poplatků. Zájem uživatelů o Ordinals, Inscrpions či Runes nejspíše časem opadne, nahradí je však určitě jiný fenomén, který těžařům pomůže zahustit bloky a tlačit poplatky vzhůru.
Zabránit šíření SPAMu může pouze shoda komunity na nastavení závazných pravidel. K té máme zatím velmi daleko. Ale zvyšování povědomí o této problematice mezi bitcoinery a signalizace osobních preferencí pomocí volby používaného klienta - Knots nebo těžby v poolech, které upřednostňují původní principy z bitcoinového whitepaperu před maximalizací zisku - Ocean, může pomoci tuto vzdálenost překonat. Držme si palce!
-
 @ 6aadf4c9:b5ae0fd1
2024-05-18 05:34:09
@ 6aadf4c9:b5ae0fd1
2024-05-18 05:34:09Chef's notes
The viral TikTok spaghetti squash recipe that everybody loves! It is super tasty, light and low carb.
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 1 hour and 5 mins
- 🍽️ Servings: 2
Ingredients
- Squash
- Ground turkey
- Onion
- Spinach
- Tomatoes
- Boursin Cheese
- Mozzerella Cheese
- Heavy whipping Cream
- olive oil
- Butter
- Green pepper
- Garlic
Directions
- Preheat the oven to 425°F
- Cut the squash in half, drizzle olive oil and use a pastry brush to spread it around. Season with salt, pepper, onion, garlic powder, oregano and parsley
- Bake the oven for 1 hour
- Slice some onions, green pepper, tomatoes, and garlic. Sautee in a pan with butter and olive oil
- Add heavy whipping cream, boursin cheese and stir
- Add the mozzerella cheese and the cooked ground turkey or your meat of choice
- Bring the squash out of the oven, use a fork to pull apart the squash to form spaghetti
- Add your sauce into the spaghetti squash boat
- Top it with some mozzerella cheese and leave in oven for about 3mins on broil to melt the cheese
- Serve and Enjoy!
-
 @ 2ad33996:3999d22a
2024-06-25 03:57:59
@ 2ad33996:3999d22a
2024-06-25 03:57:59Explora el mundo de los mineros ASIC de Kaspa en nuestra guía completa. Desde sus ventajas en eficiencia energética hasta una comparación detallada de modelos como el ICERIVER KS0, KS1 y Bitmain Antminer KS3, aprenderás todo sobre cómo estos dispositivos están redefiniendo la minería de criptomonedas. Descubre cómo configurar y optimizar tu equipo para obtener el máximo rendimiento, y explora estrategias avanzadas para elegir pools de minería y gestionar tus costos operativos. Este artículo es tu recurso definitivo para dominar la minería de Kaspa con mineros ASIC.
Este artículo fue publicado originalmente en iceriveroutlet
Resumen: Los mineros ASIC para Kaspa, como ICERIVER KS0, KS1, GOLDSHELL KA Box y Bitmain Antminer KS3, son reconocidos por su eficiencia energética y alta capacidad de procesamiento. Este artículo proporciona una guía completa sobre la configuración, optimización y estrategias para maximizar las ganancias en la minería de criptomonedas, enfocándose en la elección de pools de minería y la gestión de costos de energía.
¿Estás buscando maximizar tu eficiencia en la minería de criptomonedas? Los mineros Kaspa ASIC podrían ser la solución que necesitas. Con el avance de la tecnología blockchain, la competencia en la minería se ha intensificado, y la eficiencia energética se ha convertido en un factor crucial para mantener la rentabilidad. Los equipos ASIC de Kaspa están diseñados específicamente para ofrecer un rendimiento superior, permitiéndote ahorrar energía y maximizar tus ganancias. Estos dispositivos no solo son más eficientes en términos de consumo energético, sino que también ofrecen una mayor tasa de hash, lo que significa que puedes minar más criptomonedas en menos tiempo.
Ademas En esta publicación, exploraremos cómo los mineros ASIC de Kaspa pueden transformar tu experiencia de minería. Analizaremos sus características clave, los beneficios que ofrecen y cómo se comparan con otras opciones en el mercado. Además, te proporcionaremos consejos prácticos para optimizar tu configuración y obtener el máximo rendimiento de tu inversión. Prepárate para descubrir cómo los mineros Kaspa ASIC pueden ayudarte a alcanzar nuevos niveles de eficiencia y rentabilidad en tu aventura minera. ¡Empecemos!
¿Qué son los Mineros ASIC Kaspa?
Los mineros ASIC (Application-Specific Integrated Circuit) son dispositivos diseñados específicamente para realizar una tarea particular, en este caso, la minería de la criptomoneda Kaspa. A diferencia de los mineros de GPU o CPU, los ASIC están optimizados para el algoritmo de minería KHeavyHash de Kaspa, lo que los hace mucho más eficientes. La principal ventaja de los mineros Kaspa ASIC radica en su capacidad para ofrecer una mayor tasa de hash con un consumo energético significativamente menor. Esto se traduce en una operación más rentable y sostenible a largo plazo. Ventajas de Usar Mineros ASIC para Kaspa El uso de mineros ASIC para Kaspa presenta varias ventajas sobre otros tipos de mineros, como los de GPU o CPU. A continuación, se detallan algunas de las principales ventajas: Eficiencia Energética: Los ASIC están diseñados para consumir menos energía mientras proporcionan una mayor potencia de procesamiento.
Mayor Tasa de Hash: Los mineros ASIC pueden alcanzar tasas de hash mucho más altas, lo que aumenta la probabilidad de resolver bloques y obtener recompensas. Durabilidad: Los dispositivos ASIC suelen tener una vida útil más larga debido a su diseño especializado y robusto. Optimización: Están específicamente optimizados para el algoritmo KHeavyHash, lo que maximiza su rendimiento en la minería de Kaspa. Modelos Populares de Mineros ASIC Kaspa Existen varios modelos de mineros ASIC disponibles en el mercado, cada uno con diferentes especificaciones técnicas. Aquí se presentan algunos de los modelos más populares:
Especificaciones Técnicas de los Mineros ASIC Kaspa
Para aquellos interesados en los detalles técnicos, aquí se presentan las especificaciones de algunos de los modelos más avanzados: ASIC ICERIVER KS0 PRO: 100 GH/s, 500W, €290 ASIC ICERIVER KS1: 1 TH/s, 2000W, €1190 ASIC GOLDSHELL KA Box: 1.18 TH/s, 400W, €2050 ASIC Bitmain Antminer KS3: 9.4 TH/s, 3500W, €10490
Cómo Configurar y Optimizar tu Minero ASIC Kaspa
Configurar y optimizar tu minero ASIC Kaspa es crucial para maximizar su eficiencia. Este proceso incluye la configuración inicial del hardware, la instalación del software adecuado y la optimización de los ajustes para obtener el mejor rendimiento. En esta sección, te proporcionaremos una guía detallada para configurar y optimizar tu minero ASIC Kaspa, asegurándote de que puedas obtener el máximo provecho de tu inversión, tambien puede consultar su precio actual AQUI. Configuración Inicial del Hardware El primer paso para configurar tu minero Kaspa ASIC es asegurarte de que el hardware esté correctamente instalado. Sigue estos pasos:
Ubicación: Coloca tu minero en un lugar bien ventilado para evitar el sobrecalentamiento. Conexiones: Conecta el minero a una fuente de alimentación adecuada y asegúrate de que esté conectado a internet mediante un cable Ethernet. Encendido: Enciende el dispositivo y verifica que todos los indicadores LED funcionen correctamente. Asimismo Una vez que el hardware esté configurado, puedes proceder con la instalación del software.
Instalación del Software Adecuado
Para que tu minero ASIC Kaspa funcione de manera óptima, es esencial instalar el software adecuado. Aquí te mostramos cómo hacerlo: Descarga del Software: Visita el sitio web del fabricante y descarga el software de minería recomendado para tu modelo específico. Instalación: Sigue las instrucciones de instalación proporcionadas por el fabricante. Asegúrate de configurar correctamente la dirección de tu wallet y los detalles del pool de minería. Actualizaciones: Mantén el software actualizado para beneficiarte de las últimas mejoras y correcciones de errores. Con el software instalado, puedes proceder a optimizar los ajustes para maximizar el rendimiento. Optimización de los Ajustes Del mismo modo Optimizar los ajustes de tu minero Kaspa ASIC es crucial para obtener el mejor rendimiento posible. Aquí te dejamos algunas mejores prácticas: Frecuencia y Voltaje: Ajusta la frecuencia y el voltaje de tu minero para encontrar el equilibrio perfecto entre rendimiento y consumo energético. Monitoreo: Utiliza herramientas de monitoreo para supervisar la temperatura y el rendimiento de tu minero en tiempo real. Mantenimiento: Realiza un mantenimiento regular, como limpiar los ventiladores y revisar las conexiones, para asegurar un funcionamiento óptimo.
Siguiendo estos pasos, podrás configurar y optimizar tu minero ASIC Kaspa de manera efectiva, maximizando su eficiencia y rentabilidad. Maximizando tus Ganancias con Mineros ASIC Kaspa Maximizar tus ganancias con mineros ASIC Kaspa implica no solo la optimización del hardware y software, sino también la elección de las mejores estrategias de minería. A continuación, exploraremos diversas tácticas que te ayudarán a incrementar tus ingresos, desde la selección de pools de minería hasta la gestión de costos de energía y la reinversión de ganancias. Para ilustrar estas estrategias, proporcionaremos ejemplos de casos de éxito y estudios de caso de mineros que han logrado maximizar sus ganancias utilizando mineros ASIC Kaspa.
Selección de Pools de Minería
Elegir el pool de minería adecuado es crucial para maximizar tus ganancias. Los pools de minería permiten a los mineros combinar su poder de hash para resolver bloques más rápidamente y recibir recompensas de manera más constante. A continuación, te presentamos algunos de los pools más recomendados para minar Kaspa: F2Pool: Con una alta tasa de éxito y bajas comisiones, F2Pool es una opción popular entre los mineros de Kaspa. Poolin: Este pool ofrece una interfaz amigable y estadísticas detalladas para monitorear tu rendimiento. 2Miners: Con servidores en múltiples regiones, 2Miners garantiza una conexión estable y eficiente. K1Pool: Conocido por su transparencia y pagos rápidos, K1Pool es otra excelente opción para los mineros de Kaspa. Al unirte a un pool de minería, asegúrate de investigar sus comisiones, métodos de pago y reputación para tomar una decisión informada.
Gestión de Costos de Energía
La eficiencia energética es un factor clave para la rentabilidad de la minería de criptomonedas. Aquí te dejamos algunas estrategias para gestionar y reducir tus costos de energía: Ubicación: Instalar tus mineros en una región con tarifas eléctricas más bajas puede reducir significativamente tus costos operativos. Optimización del Hardware: Ajustar la frecuencia y el voltaje de tus mineros ASIC puede mejorar su eficiencia energética. Energía Renovable: Considera el uso de fuentes de energía renovable, como paneles solares, para reducir tus costos de electricidad a largo plazo. Un ejemplo de éxito es el caso de Juan Pérez, quien instaló paneles solares en su granja minera, logrando reducir sus costos de energía en un 40% y aumentando sus ganancias netas.
Reinversión de Ganancias
Reinvertir tus ganancias en la mejora de tu infraestructura minera puede aumentar tu capacidad de generar ingresos a largo plazo. Aquí te dejamos algunas formas de reinvertir tus ganancias de manera efectiva: Actualización de Equipos: Invertir en mineros ASIC más eficientes y potentes puede aumentar tu tasa de hash y tus ingresos potenciales. Expansión de la Operación: Ampliar tu granja minera con más dispositivos puede incrementar tu poder de procesamiento y tus recompensas. Investigación y Desarrollo: Destinar fondos a la investigación de nuevas tecnologías y métodos de minería puede mantenerte competitivo en el mercado. Un caso notable es el de María López, quien reinvirtió el 50% de sus ganancias en la compra de nuevos mineros ASIC y en la mejora de su infraestructura, logrando duplicar sus ingresos en un año. Transforma tu Minería con la Eficiencia de los Mineros Kaspa ASIC
Conlusion:
Asi que, los mineros Kaspa ASIC ofrecen una combinación única de eficiencia energética y alta tasa de hash, lo que los convierte en una opción ideal para quienes buscan maximizar sus ganancias en la minería de criptomonedas. Desde su diseño especializado hasta su capacidad para optimizar el algoritmo KHeavyHash, estos dispositivos están preparados para llevar tu experiencia minera al siguiente nivel. Hemos explorado las múltiples ventajas de los mineros ASIC para Kaspa, incluyendo su durabilidad y optimización específica para Kaspa, así como los modelos más populares disponibles en el mercado. Con opciones que van desde el ASIC ICERIVER KS0 hasta el Bitmain Antminer KS3, hay una variedad de dispositivos que se ajustan a diferentes necesidades y presupuestos. Además, la configuración y optimización adecuadas de tu minero ASIC Kaspa son cruciales para maximizar su rendimiento. Desde elegir la ubicación correcta y realizar las conexiones adecuadas, hasta instalar el software recomendado y ajustar la frecuencia y el voltaje, cada paso es esencial para garantizar que obtengas el máximo provecho de tu inversión. Finalmente, no olvides que la elección del pool de minería adecuado y la gestión eficiente de los costos de energía pueden marcar una gran diferencia en tus ganancias. Al unirte a pools como F2Pool o Poolin y considerar el uso de energías renovables, puedes optimizar aún más tus operaciones mineras. Te invitamos a compartir tus experiencias y preguntas en los comentarios, y no dudes en explorar más contenido en Iceriver Outlet para seguir aprendiendo sobre cómo mejorar tu eficiencia minera con los mineros Kaspa ASIC. ¡Buena suerte y feliz minería!
-
 @ 7ff2dcb0:c36d340b
2024-05-14 17:48:43
@ 7ff2dcb0:c36d340b
2024-05-14 17:48:43Chef's notes
You can never go wrong with a chicken sandwich. Enjoy this twist on the Ceaser Wrap inspired by Rachaell's Recipes. Just to mention, Rachaell uses a tortilla press to get her cutlets to be flat. If you have one that's great but I just make sure to cut the chicken breast very thin, about a cm thick as if I'm fileting it lol.
This is a sandwich I saw on TikTok a while ago and finally decided to make it. Credits to Rachaell's Recipes https://www.rachaellsrecipes.com/. I have it at least once a week now and honestly don't plan on stopping anytime soon. The proper name of this recipe is The Crunchy Chicken Ceasar Salad. Hope you enjoy it as much as I do.
The garlic and herb butter you will make in this recipe is my favorite part of the sandwich. This step takes the longest so I recommend doing it first. Spreading it on the bread and toasting it adds a burst of flavor. Personally, I put the bread in the oven on HI broil for about 4 minutes but you can always toast it on the stovetop.
I mention in the recipe you can use your dressing of choice because Rachaell suggests Ceasar dressing but I like mine better with avocado dressing.
Last note, when breading the chicken it is important to add a little water to the dressing you choose if it's a regular thick dressing. If you you run the risk of your chicken having mushy breading in the middle and no one likes that. Enjoy!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 25 min
- 🍽️ Servings: 4
Ingredients
- 4 sub rolls
- 1 chicken breats, pounded flat or cut flat
- 2 hearts of romaine lettuce, cleaned, dried, and chopped
- Freshly grated Parmesan cheese
- Juice of 1 lemon
- Dressing of choice, plus 1/2 cup for the breading mixture
- Breadcrumbs or panko for breading
- Flour for dredging
- Oil of choice for frying
- 2 whole heads of garlic, roasted
- 1 tablespoon of chopped parsley
- 8 tablespoons of unsalted butter, softened
- 1/8 cup of freshly grated Parmesan cheese
- Salt and pepper to taste
Directions
- Prepare the Garlic Butter and Sub Rolls: Preheat the oven to 350°F (175°C). Mix all ingredients for the garlic butter in a small bowl. Set aside. Cut the sub rolls open, slightly hollow them out, and spread the garlic butter inside, topping with extra grated Parmesan. Arrange on a baking sheet, open side up, and bake for 10-15 minutes until golden. For a crunchier top, broil on high for 2-3 minutes.
- Bread and Fry the Chicken: Set up a breading station with three parts: flour, dressing of choice mixed with a little water, and breadcrumbs. Dredge each chicken cutlet in flour, dip in the dressing mixture, then coat in breadcrumbs. Heat avocado oil in a large pan over medium heat (test heat by dropping a breadcrumb in; if it sizzles, it’s ready). Fry cutlets until golden on each side and then drain on paper towels.
- Assemble the Salad: Toss the chopped romaine with Caesar dressing, fresh lemon juice, and extra Parmesan for enhanced flavor.
- Making the Garlic Butter Spread: Take the roasted garlic heads, squeeze the garlic out of its peel into the softened 8 tablespoons of butter. Add the teaspoon of freshly chopped parsley. Mix well.
- Assemble the Subs: Build each sub with a crunchy roll, fried cutlet, dressed salad, and a sprinkle of Parmesan cheese.
-
 @ 32e18276:5c68e245
2024-05-14 16:46:28
@ 32e18276:5c68e245
2024-05-14 16:46:28Hey Damus enjoyers,
v1.8 has been tagged! Today we submitted v1.8 to the App Store, Here's a quick preview of what's in this release!
New Emoji Selector
It's now easier than ever to select emoji reactions! Just long press the reaction button to pop-up the new emoji selector. Thanks Terry for implementing this!

Quote Reposts
Quote reposts are now listed on posts, just like on the birdsite (x site ?)

New fullscreen video player
Our video controls were pretty bad before, this has been improved in this version! You can now seek videos, view them fullscreen, and airplay them to your tv. Thanks Daniel for this feature!

Improved longform style
Longform posts now show the image and related tags. Thanks Eric!

Account recovery, bug fixes
Thread loading is greatly improved, we now support the latest nip10 specification for improved compatibility between clients. We also added an account recovery feature called First Aid. You can use this to create a new contact list if for whatever reason you don't have one anymore. If you are running into issues following people, you can use this to recover your account:

Testflight
v1.9 dev is underway, with an up and coming highlighter feature where you can clip highlights from the web and other posts and share them to your feed. If you want to test out the latest up and coming features, make sure to grab a damus purple membership to get access!
https://damus.io/purple/login
That's all for now, here's the full changelog if you want to see what else is new!
Full Changelog
Added
- Added nip10 marker replies (William Casarin)
- Add marker nip10 support when reading notes (William Casarin)
- Added title image and tags to longform events (ericholguin)
- Add First Aid solution for users who do not have a contact list created for their account (Daniel D’Aquino)
- Relay fees metadata (ericholguin)
- Added callbackuri for a better ux when connecting mutiny wallet nwc (ericholguin)
- Add event content preview to the full screen carousel (Daniel D’Aquino)
- Show list of quoted reposts in threads (William Casarin)
- Proxy Tags are now viewable on Selected Events (ericholguin)
- Add ability to mute words, add new mutelist interface (Charlie)
- Add ability to mute hashtag from SearchView (Charlie Fish)
Changed
- Change reactions to use a native looking emoji picker (Terry Yiu)
- Relay detail design (ericholguin)
- Updated Zeus logo (ericholguin)
- Improve UX around video playback (Daniel D’Aquino)
- Moved paste nwc button to main wallet view (ericholguin)
- Errors with an NWC will show as an alert (ericholguin)
- Relay config view user interface (ericholguin)
- Always strip GPS data from images (kernelkind)
Fixed
- Fix thread bug where a quote isn't picked up as a reply (William Casarin)
- Fixed threads not loading sometimes (William Casarin)
- Fixed issue where some replies were including the q tag (William Casarin)
- Fixed issue where timeline was scrolling when it isn't supposed to (William Casarin)
- Fix issue where bootstrap relays would inadvertently be added to the user's list on connectivity issues (Daniel D’Aquino)
- Fix broken GIF uploads (Daniel D’Aquino)
- Fix ghost notifications caused by Purple impending expiration notifications (Daniel D’Aquino)
- Improve reliability of contact list creation during onboarding (Daniel D’Aquino)
- Fix emoji reactions being cut off (ericholguin)
- Fix image indicators to limit number of dots to not spill screen beyond visible margins (ericholguin)
- Fix bug that would cause connection issues with relays defined with a trailing slash URL, and an inability to delete them. (Daniel D’Aquino)
- Issue where NWC Scanner view would not dismiss after a failed scan/paste (ericholguin)
-
 @ c69b71dc:426ba763
2024-05-11 19:15:01
@ c69b71dc:426ba763
2024-05-11 19:15:01Chef's notes
You need a blender. If you want your breakfast to be more filling, you can also mix ground almonds or walnuts with the apples and dates.
Enjoy!
Details
- ⏲️ Prep time: 5-10 minutes
- 🍳 Cook time: 0
- 🍽️ Servings: 2
Ingredients
- 2 Oranges
- 2 Sweet Apples
- 3-4 Medjol Dates
- 1 tbsp Vanilla Extract or 1-2 tbsp Vanilla Protein Powder
- optional: 1/4 tsp Cinnamon Powder
Directions
- Peel the oranges and cut them into thin slices.
- Core the apples and dates and mix with the vanilla extract or vanilla protein until a creamy
- Then alternately layer orange slices and cream in two tall glasses.
-
 @ 97c70a44:ad98e322
2024-05-09 17:25:22
@ 97c70a44:ad98e322
2024-05-09 17:25:22#lastword
A few weeks ago, Mike proposed the addition of a feature to nostr. The content of the proposal itself isn't important, but the resulting conversation illustrated something important about nostr development that I wanted to draw attention to.
If you're interested, you can find the issue here. The idea was basically a tag that disabled comments to a reply, for when you wanted to gracefully exit a conversation that had outlived its usefulness.
While I definitely sympathize with the experience of getting stuck in an unproductive argument and being unable to leave because you have to have the last word, I do think it's better to take responsibility for leaving the conversation, rather than make other people do it for you. You can either outlast your opponent, let them have the last word, or tell them "I don't want to talk about this any more, I'm not going to reply".
This is just my opinion, and it's really not important whether I'm right or not. What was interesting was how Vitor responded:
I am not sure if the NIP review process should consider "what's good for the user" in the discussion. That kind of nanny state thinking is what went wrong with regular social media in the first place.
Permaculture and Ethics
What it sounds like (although I have a hard time believing this is actually his position), is that Vitor is dismissing the relevance of an ethical framework in designing a protocol, preferring to stick to the mechanics of what is being suggested. As Vitor says, "Clients can do whatever they want, of course." This is true, but ignores the question of why a client developer might want to do any particular thing.
In a recent Thank God for Nostr episode, I interviewed Scott Mann of the Permaculture Podcast. When I asked him his opinion on how to manage decentralized protocol design and build effective consensus, here's what he had to say:
[You] don't need to frame it as a software development project, or even a protocol. I would look at it as a distributed community-based and community-supported project, whatever that is. Because permaculture is such a large umbrella, I like to go up to that 50,000 foot view and pull away from what the details are. Because the details are what we're going to build our solutions from.
And that's one of the things I didn't mention earlier — there's kind of a hierarchy within permaculture that goes, at the top are the ethics of permaculture: earth care, people care, fair share. Beneath that are the principles, then usually we have strategies and techniques.
But there's a dividing line between ethics and principles and the strategies and techniques, that we start at that top, and use the ethics to decide whether or not we're even going to launch a project.
He goes on to say:
I'm going to use the principles and see how can I apply those principles to my research and original design. To make sure that whatever I'm creating creates some kind of a surplus, to have a refinement process in place before I even launch, like what is that going to look like, even if I have to change it later, just having some of these building blocks in place.
And then once I've done that and have gone deep into my research into what this might look like, how I might launch it, that's where I would start going into strategies and going ok, how do I want to market this? How do I want to get this out to the people who are going to use it, how do I want to maintain this, how do I want to do distributed decision making, and then as I start to think about distributed decision making, looking at what is the form that I want to use for that?
Scott's thesis is that ethics and principles should be in the front of your mind both as you're considering a project, and as you continue to build it out. This not only makes sense as something to do if you want to succeed, it's categorically true. Action can't happen without agency, and it is your agency that informs what you choose to do, and how you plan to go about it.
The word "ethics" comes from the Greek ēthos, meaning "moral character". In other words, your ethic is who you are. Your values, hopes, preferences, faults all factor in to your actions.
This is not always clear, because in fiat-world, many people suspend their values in order to "get something done". If you want to protect your savings, you invest it in index funds, propping up the stock price of companies that hate you. If you want to make money, you go work at a job where you're berated quarterly for being racist. People think that they can exercise their own values in their private life, while actively undermining those values with the majority of their time and purchasing power.
But this is not how people with integrity act. And I think if you can say one thing about nostr — both its developers and the community at large — is that they have a very high level of integrity. In other words, their actions are clearly informed by their ēthos.
This is a very good thing. What is the point of building an entirely new internet if we're not going to impose our values upon it? What an absolute waste of effort.
A Nostr Manifesto
This is not to say that any one developer has the right to imposing his own vision on the protocol because of his own personal values and reasons for contributing, which is what I think Vitor was being cautious about. But there are lines I think we can draw as a community that can't really be crossed without excluding yourself from what I might call the "nostr group ethic".
So what are those boundaries? What is a nostrich? Here are some values I've observed to be generally shared among nostr developers and users. Not everyone would full agree with these (including myself), but I think they're a fair characterization of the community.
- Free speech absolutism. No central entity should be able to globally censor any content. This comes with the trade-off of objectively evil content continuing to exist. This trade-off is acceptable, both because of the value of free speech, but also because evil will continue to exist regardless of attempts to suppress it.
- Empower individuals over institutions. No centralized entity can be trusted to safeguard the interests of the individual. Institutional incentives are asymmetric and easily corrupted. Better to have many subjective views of the world, than a single, centrally managed view of the world.
- Advertising-based business models should be viewed with great skepticism and caution. Advertising is a system of incentives that is central to the institutional corruption we see around us. Broadly, this includes paid ads, monetization of engagement, public/private partnerships, and "crypto".
There are others that are shared by many within nostr, although not as widely agreed upon. Two I can think of are:
- Economic activity should be voluntary. Software and content should be free, and creators should be amply rewarded via zaps or other value-for-value models.
- Social media should support real life community and relationships, not detract from them. We should all take time to touch grass.
I'm personally skeptical of the first of these, and strongly in support of the second. Much of my energy as a nostr developer has gone into attempting to subvert and reform traditional patterns of social media to not only support, but also resemble relationships that exist in the analog world God made, and placed us in.
This particular principle is the one at play in the conversation I linked to at the top of this post. My comments weren't an accusation that anyone was acting "unethically" in a universal sense, only that the proposed feature was incompatible with my vision for what nostr should be.
But of course, my vision is not shared by everyone, and the principle of "support real life" is clearly subservient to core ethic #2, which admits the value of a diverse set of opinions about the world. I have no right (or ability) to invalidate anyone else's core principles. But by the same token I'm free to express my own, and attempt to convince other people to share them. This is the basic value proposition of freedom of speech itself.
Ethical Cohesion
I would go further, and say that not only is it permissible to talk about ethical reasons for building one thing or another on nostr, it's essential. By having these conversations we fuse our individual ethics into a shared ethic. By calibrating our moral compasses to point in (roughly) the same direction, we also decrease the friction involved in getting something done.
I think this was a significant part of the idea behind Sovereign Engineering — get a bunch of people in a room together sharing meals and going on hikes, and the work will accelerate! This is also the way a church works. By meeting weekly together we strengthen our shared identity and build one another up through our activity. In fact, this is the basic definition of a community as Scott Mann puts it. In his words, a community can provide:
a series of connections, and a knowledge base, and a skillset that we can't fulfill as an individual, while having a social relationship with people in such a way that we can call on them for help.
So maybe, as I've said before, the real protocol is the friends we made along the way. Disagreement and discussion is a healthy thing for a community to have, and we should never stop asking "why?"
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 7e1d20be:0b4a42c2
2024-05-07 16:36:10
@ 7e1d20be:0b4a42c2
2024-05-07 16:36:10Chef's notes
You can make it much better yourself than any restaurant would care to do for you
Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 large chicken breast
- 5 tomatoes or puree
- 3 onions
- garlic
- cashews
- some dry green herb like dill or sage or parsley or whatever or the original kasoori methi
- curd
- butter
- cream
- the standard 5 masalas/spices/powders from india
- a bunch of small wrapped cloth bags of what is called solid spices / khada masala
- redchilly powder, chillies and salt as per taste
Directions
- look at this video https://youtu.be/zF7dKdIMKvc?si=XRkXB9q3KoRoF_i6
- make the sauce
- put in the chicken
- drizzle with butter and cream
- bake bread
- enjoy a better pizza with the same ingredients as a pizza
-
 @ dbb9c664:c62a102f
2024-05-06 21:06:13
@ dbb9c664:c62a102f
2024-05-06 21:06:13Chef's notes
For cleaner fruits, soak them in water, baking soda, and vinegar for 30 minutes and RINSE 🚿
Details
- ⏲️ Prep time: 2
- 🍳 Cook time: 0
- 🍽️ Servings: 1
Ingredients
- Any kind of fruit
- Lemon squeeze
Directions
- Add lemon juice and honey to any fruit!
- Enjoy the pop of flavor!
-
 @ 0b963191:fc5e7ffd
2024-05-05 23:36:45
@ 0b963191:fc5e7ffd
2024-05-05 23:36:45Chef's notes
Can of course substitute in beef for the lamb.
In terms of canned peas, always prefer La Sueur
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4
Ingredients
- Potatoes:
- 1 ½ pounds potatoes (Russet)
- ½ cup half-and-half
- 2 ounces unsalted butter
- ¾ teaspoon kosher salt
- ¼ teaspoon black pepper
- 1 egg yolk
- Meat Filling:
- 2 tablespoons canola oil
- 1 cup chopped white onion
- 3 carrots, peeled and diced
- 1 ½ pounds ground lamb
- 1 teaspoon kosher salt
- ½ teaspoon black pepper
- 3 tablespoons flour
- 3-4 teaspoons tomato paste
- 1 cup chicken broth
- 3 teaspoons Worcestershire sauce
- 2-3 teaspoons chopped rosemary leaves (fresh)
- 1-2 teaspoons chopped thyme leaves (fresh)
- ¾ cup corn kernels
- ¾ cup peas
Directions
- Potatoes:
- Peel and dice potatoes.
- Place in a pot and cover in cold water.
- Bring to a boil.
- Lower fire to simmer and cook for 15-20 minutes.
- Heat butter and half-and-half for 30-40 seconds in the microwave.
- Drain potatoes and put back into the pot.
- Mash potatoes and add half-and-half, butter, salt, pepper.
- Continue mashing until smooth and stir in yolk until combined.
- Preheat the oven to 400 degrees.
- Filling:
- Heat canola oil in a 10-12 inch pan over high heat.
- Add onions and carrots and saute over medium-high heat for 4-5 minutes.
- Add garlic and combine for 30 seconds.
- Add Lamb, salt, and pepper and cook until browned.
- Sprinkle flour and stir to coat lamb and cook for 1-2 minutes.
- Add Tomato paste, chicken broth, Worcestershire sauce, rosemary, thyme. Stir and bring to a boil.
- Reduce heat to low, cover, and simmer for 12-15 minutes while sauce thickens.
- Oven:
- Add meat filling to baking dish.
- Add peas and corn and stir in evenly
- Spread mashed potatoes using a rubber spatula. start at the corners and make sure to seal around the edges.
- Bake for 25 minutes
- Remove from the oven and let sit for 15-20 minutes.
-
 @ dbb9c664:c62a102f
2024-05-04 23:45:53
@ dbb9c664:c62a102f
2024-05-04 23:45:53Chef's notes
Soak the veggies in water with baking soda and vinegar for about 30 minutes prior to juicing. 🌱
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 5
- 🍽️ Servings: 4
Ingredients
- 1 bunch of kale
- 1 bunch of celery
- 2 cucumbers
- 4 kiwis
Directions
- Soak the vegetables in water with baking soda and vinegar for 30 minutes
- Cut into juice-sized pieces
- Put into your juicer!
- Enjoy!
-
 @ 502ab02a:a2860397
2024-06-25 03:41:42
@ 502ab02a:a2860397
2024-06-25 03:41:42บันทึกเจอนี่ เรื่องนี้ไว้สักหน่อยครับ เผื่อตายไปจะได้ล่องลอยอยู่ในแบบดิจิตอล 5555
จะเรียกว่าความเลยเถิด จับพลัดจับผลูหรืออะไรก็แล้วแต่ ก็น่าจะนับเป็นโชคที่ดีได้ ที่ผมเกิดมาเป็นวัยรุ่นในยุคที่มีช่องว่างในการจะทำอะไรได้มาก ยอมรับเลยว่า ทุกวันนี้ยังมีสัดส่วนความคิดแบบคนรุ่นเก่าเยอะพอสมควร
เรื่องมันเริ่มจาก หนังอาร์เอส โลกทั้งใบให้นายคนเดียว ตอนหนังเรื่องนี้ออกนี่ผมโตแล้วครับ มหาวิทยาลัยแล้ว ผมกับเพื่อนๆไปดูหนังเรื่องนี้ ไม่ใช่เพราะคุณนุ๊กหรือคุณเต๋า แต่ไปเพราะพี่เอ็ม ใช่ครับ สุรศักดิ์ วงษ์ไทย ตอนออกจากโรงมาเราไม่ได้คุยเรื่องเนื้อหาในหนัง เราคุยกันแต่เรื่องพี่เอ็ม จนคนหนึ่งในกลุ่มพูดว่า รายการพี่เอ็ม ตอนนี้จัดอยู่คลื่น 89 นะ
รายการที่ว่าชื่อ ถามมาซิจ๊ะ...โดน ครับเป็นรายการที่เราฟังกันน่าจะตั้งแต่ smile 88 MHz หรือที่คุณพ่อคุณแม่เพื่อนๆชาวทุ่งม่วงคุ้นเคยในชื่อ สไมล์เรดิโอ เป็นรายการวิทยุที่มีมาก่อน A-times ทั้งหมด ตอนนั้นรายการ ถามมาซิจ๊ะ...โดน เป็นการการที่พูดคุยอย่างเดียว สมัยนี้เรียก talk show นั่นละครับ แต่เป็นการพูดคุยที่ค่อนข้างกันเองจนสนุกสนานภาษาวัยรุ่นยุคนั้น แต่มันไม่ค่อยจะถูกใจผู้หลักผู้ใหญ่ช่วงนั้นเสียเท่าไร เอาจริงๆก็คล้ายๆยุคนี้แหละครับ วัยรุ่นมักทำอะไรไม่ถูกใจในสายตาผู้ใหญ่ แต่การ re act มันต่างกัน สมัยนั้นเราโดนแบน จนต้องย้ายคลื่นกันบ่อยครั้งมาก (รูปแบบการแบน อาจต้องเล่าส่วนตัว เพราะถ้าลองมองดู คลื่นวิทยุใครเป็นเจ้าของ การไล่ก็ตามเจ้าของถนัดนั่นละครับ 55)
ทีนี้การสื่อสารสมัยก่อนมันจะยากมากที่จะต่อกันติด เก่งที่สุดคือ จดหมายมาถามเพราะเราใช้ตู้ ปณ. ในการติดต่อกัน นอกจากนั้นคือ ปาก ต่อ ปาก เท่านั้น ทำให้ประโยคนั้นของเพื่อนผม คือประโยคที่ พลิกชีวิต น่าเหลือเชื่อจริงๆเลยครับ
ผมกลับบ้านไปติ้วคลื่นที่เครื่องวิทยุ หมุนหาคลื่น 89.0MHz (ใช่ครับ หมุนคลื่น ไม่มีดิจิตอลใดๆ) วิทยุโซนี่เครื่องนั้นผมยังเก็บไว้กับตัวตลอดเวลา และวันอาทิตย์ผมก็ได้ฟังรายการที่คุ้นเคยอีกครั้ง ตอนนั้นคลื่น 89 เป็นลักษณะ format radio คือเปิดเพลงร็อคทั้งวันทั้งคืน ยกเว้นเสาร์-อาทิตย์ จะมีโซนี่เป็นสปอนเซอร์ เรียกว่า sony dream radio ก็เลยจะเป็นรายการที่วาไรตี้กว่า จ-ศ
ในจักรวาลคู่ขนานกัน ผมเริ่มรู้จักโลก internet จากมหาวิทยาลัย ซึ่งการก้าวเข้าโลกอินเตอร์เนทจะเล่าให้ภายหลัง ข้ามมาก่อนว่า เป็นช่วงที่ผมเริ่มหัดเขียน html จนมาพบ netscape navigator GOLD ตัวแรกที่สามารถเขียนเว็บแบบ WYSIWYG (What You See Is What You Get) สมัยนี้อาจจะงง คือเมื่อก่อนทุกอย่างเป็นตัวหนังสือครับ การทำอะไรแบบ พิมพ์ปุ๊บเห็นในจอปั๊บส่งออกข้างนอกได้แบบนั้นทันที เราจะตื่นเต้นกันมากครับ
แล้วผมก็ทำการผสาน 2จักรวาลเข้าหากัน ผมเริ่มทำโปรเจค fan page รายการวิทยุ ถามมาซิจ๊ะ...โดน เพราะรู้สึกว่าอยากทำงานวิทยุ ต้องหาทางเชื่อมอะไรบางอย่าง พอทำเสร็จผมก็เลยติดต่อไปที่ดีเจท่านนึง ซึ่งชอบแกดเจทเหมือนกันคือ พี่บอล กิตติพัฒน์ ลิมพะสุต ผมมองว่าโอกาสการเข้าหาทางอีเมลล์ มีมากกว่าตู้ปณ. เพราะจดหมายในรายการเยอะ อัตราการถูกนำมาอ่านมันจะน้อยกว่าอีเมลล์ ซึ่งในยุคนั้นการใช้อีเมลล์ค่อนข้างไฮโซ จึงได้รับโควต้า จดหมายจากอีเมล แยกจากจดหมายจากตู้ปณ.
แล้วมันก็ได้ออกอากาศ และทุกคนก็ตื่นเต้นที่รายการมีเว็บไซท์เป็นของตัวเอง เพราะมันน่าจะเป็นรายการวิทยุแรกๆของไทย ที่มีเว็บไซท์ครับ
จากนั้นผมก็ได้รับการติดต่อจากพี่บอล ให้เข้าไปพูดคุยเพื่อทำสิ่งนี้ให้มีทิศทางชัดเจนยิ่งขึ้น รวมถึงถามว่า อยากสอนคอมไหม เขาเปิดโรงเรียนสอนคอม แล้วยังขาดครูสอนอินเตอร์เนท นั่นทำให้ผมไม่รีรอที่จะรับทันที ใช่ครับสมัยก่อนการสอนเข้าอินเตอร์เนท ต้องลงเรียน สอนตั้งแต่ตั้งค่าโมเด็ม การโทรเข้า isp การทำความรู้จักกับ username password รวมถึงการเข้า browser
ระหว่างนั้นผมก็ทำเว็บรายการควบคู่ไปด้วย ผมเริ่มเนียนครีเอทคอนเสป การตัดหน้าดีเจ ไปแปะกับใบ handbill หนัง เพื่อให้เกิดความสนุกตลก ออกแนวพาโรดี้ มันน่าจะทำให้พี่บอลมองเห็นว่า เอ้อ ผมพอมีความครีเอทอยู่บ้าง ไม่ได้เป็นเนิร์ด ก็เลยเริ่มชวนผมไปทำโน่นทำนี่ ชวนไปไหนกูไปหมด จำได้ว่าเคยไปงานโซนี่ ในโรงแรมแห่งหนึ่ง เขานำเครื่อง mini disc เข้ามาใหม่ๆ รวมถึงอุปกรณ์บรอดคาส เจ๋งๆ ก็ได้เห็นจากการติดสอยห้อยตามนี่ละครับ
โปรเจคแรกเลยคือการทำ จิงเกิ้ลรายการใหม่ ที่ห้องอัดเสียงของ พี่ต้อ กุลวัฒน์ พรหมสถิตย์ อัดเสียหนะแป๊บเดียว แต่กินเหล้านาน 55 เป็นครั้งแรกที่ผมรู้สึกว่า ศิลปินเจ๋งดีนะครับ พี่ต้อคุยกับพวกเราอย่างออกรสชาติ ผมเด็กใหม่ ในขณะที่เขาสนิทกันมาก่อนแล้ว ทีนี้ vibe มันดีจนพี่ต้อหยิบกระดานมาสเก็ตรูปบรรยากาศวันนั้นไว้ ใช่ครับ เอาดินสอสเก็ตรูปเก็บไว้ ไม่ได้ใช้กล้องถ่ายรูป 555
จากนั้นมันก็เริ่มเลยเถิดไปเรื่อยๆ และผมมักจะไปตกในจังหวะที่ คนไม่พอบ้าง ไม่มีคนทำบ้าง ผมชนทุกโอกาสที่เข้ามา ตั้งแต่การอ่านสปอตวิทยุ เพราะคนไม่พอ ตั้งแต่การตัดต่อเสียงเพราะคนทำป่วย ไปจนถึงเป็นตัวซัพพอร์ตสำนักข่าวที่รายการรับจ้างทำ ได้ทำตั้งแต่ re write ข่าว ไปจนอ่านข่าวเองบางช่วงที่สลอตมันไม่มีใครว่าง (มักจะเป็นข่าวต้นชั่วโมงราวๆ ตี2 ตี3) หรือแม้แต่ การออกภาคสนาม การคิดซาวน์และกิมมิคต่างๆในรายการ ซึ่งในช่วงหลังปรับเป็นเกมส์โชว์มากขึ้น
แล้วก็มาถึงยุคของอีเวนท์ เมื่อก่อนเขาเรียกว่า "กิจกรรม" ตอนปลายๆของวิทยุ เราจะมีคำพูดนึงจากพี่บอลมาบรีฟว่า สปอนเซอร์ อยากให้เราช่วยคิดกิจกรรมการตลาด เกี่ยวกับ โน่น นี่ นั่น ซึ่งเป็นอีกจุดพลิกชีวิตเหมือนกัน เพราะมีการเปลี่ยนความคุ้นชินจากการทำวิทยุ ไปสู่ อีเวนท์ ออกาไนเซอร์ หลายคนก็ปรับตัวไม่ได้ หลายคนก็ปรับตัวได้ ผมอาจโชคดีหน่อย ที่ไม่ชอบกลับบ้าน เลยอยากทำอะไรพวกนี้ตลอดเวลา และเช่นเคย ผมไม่ได้รอให้ใคร assign งาน ผมลุกไปทำในทุกจุดที่คนโบ๋อยู่ ลุกไปช่วยทุกจุดที่มันกำลังมีปัญหา เพราะตอนนั้นภาพผมเป็นเนิร์ด ทำอนิเมชั่นตั้งแต่ flash เวอร์ชั่น beta พอคนเห็นตัวผมในหลายๆที่ เขาก็เริ่มให้ประกบช่วยโน่นนี่นั่นแบบอุ่นใจเขาขึ้น ไม่ว่าจะเป็นการช่วยดูคิว ทั้งสเตจ ไฟ เสียง อะไรที่มันเทคโนโลยี รวมยาวไปถึงอะไรที่เป็นกราฟฟิค พิมพ์ ปริ้น
มันมีกิจกรรมสนุกๆให้ทำมากมาย ที่เป็นการลองผิดไปด้วยกัน การจัดดูหนังฟังเพลง คือมีมินิคอนเสิร์ตในโรงหนัง แล้วต้องรีบรื้อให้ทันก่อนรอบเที่ยง เพราะเขาต้องขายตั๋ว หรือการจัดถ่ายทอดสดออสการ์ในโรงหนัง พอเรื่องไหนได้รางวัลก็ดูเรื่องนั้นต่อไปพร้อมๆกันเลย การจัดนักชิมหนัง คือให้นักศึกษาลองดูหนังที่จะออกฉายก่อนเพื่อเทสฟีดแบค จริงๆการจัดกิจกรรมพวกนี้ มันก็คือ อีเวนท์ในยุคนี้ แต่สมัยนั้นมันไม่มีชื่อเรียก
เราเพิ่งมารู้ว่าอ๋อ นี่คืออาชีพออกาไนซ์สินะ เราไม่รู้หรอกครับ เราแค่เห็นว่ามันเจ๋งดีได้คิดอะไรสนุกๆทำ ผมจำงานนึงได้ ยิ่งใหญ่ในความรู้สึกมาก น่าจะในช่วงฤดูหนาวพอดี ลมเย็นมากๆสมัยนั้น แล้วเรามีการจัด collage rock market ที่ RCA ตอนเช้าถึงค่ำ เป็นการเปิดให้นักศึกษามาลงทะเบียนเล่นสดๆ ให้ค่ายเพลงเดินช้อปปิ้งเลย ว่าอยากเซนต์วงไหนเข้าสังกัด จัดเวทีเรียงยาวไปตามถนน RCA เลยครับไม่ได้มีเวทีเดียว ที่สนุกคือหลายวง มีการแย่งกันเซนต์ด้วย เหมือน The Voice สมัยนี้เลยที่ต้องแย่งกันด้วยการเสนอข้อเสนอที่ดีกว่า มากกว่า ให้วงนั้นๆ
ว่าไปแล้ว แต่ละกิจกรรมก็เอามาเล่าใน เจอนี่ ได้หมือนกันแฮะ
นี่เป็นจุดพลิกอีกจุดนึง ที่ทำให้ผมเป็นผมแบบทุกวันนี้ครับ มีความเพี้ยนๆเพราะมันมี 2 ซีกในตัว ฝั่งวิชาการก็ลุ่มหลงลงไปได้ยาวๆ ฝั่งเฮฮาก็บ้าบอ คล้ายๆค้างคาวครับ นกก็ไม่ใช่ หนูก็ไม่เชิง
แต่ที่แน่ๆ ที่ผมตกตะกอนได้ทุกวันนี้คือ ผมจะไม่ทิ้งโอกาสไปเปล่าๆ โอกาสมีไว้พุ่งชน และถ้าไม่มีโอกาส สร้างมันซะ
ได้ก็คือได้ ไม่ได้ก็แค่กลับมาจุดเดิม ไม่มีอะไรจะต้องเสีย ตราบใดที่มันไม่รบกวนความรับผิดชอบปกติของเรา
ปัจจุบันก็เช่นกันครับ จาก เจอนี่ โพสที่แล้วได้บอกไว้ ว่าผมก้าวออกมาจากงานโฆษณาแล้วครึ่งหนึ่ง โพสนี้บันทึกไว้ว่า 31 กรกฎาคม 2567 ผมก้าวออกจากงานโฆษณาเต็มตัวครับ
เพื่อออกมาสร้างโอกาส ที่จะพุ่งชน โดยไม่ต้องกังวลความรับผิดชอบกับมวลหมู่อีกต่อไป เพราะผมขอเอาความรับผิดชอบตั้งไว้เหนืออื่นใด ดังนั้นถ้าความรับผิดชอบที่ต้องทำมันขัดกับการสร้างโอกาส (ที่ไม่รู้จะสำเร็จแค่ไหน) ผมเลือกที่จะแก้ไขความรับผิดชอบนั้นด้วยการยุติมันแล้วทำ exit plan ที่สมูทที่สุด แล้วหยิบจอบเสียม ไปขุดดินมาปั้น ครั้งนี้ เราจะปั้นในแบบที่เราอยากปั้นแล้วนะ เราจะไม่ปั้นในแบบที่คนอยากดู เราแค่ทำไปแล้วหากมีใครชอบในงานปั้นของเรา ก็เป็นเรื่องยินดี ไม่รู้สินะ เราทำเอาใจตลาดมาเกินพอแล้ว ถ้ามีคนบอกว่าวัยกลางคนคืออายุ 40 จะบอกว่า กูผ่านครึ่งชีวิตมานานแล้ว 555
siamstr #pirateketo
-
 @ 2ad33996:3999d22a
2024-06-24 21:47:08
@ 2ad33996:3999d22a
2024-06-24 21:47:08Aprende a configurar y utilizar el Iceriver KS3 con nuestra guía paso a paso diseñada para 2024.
Este artículo fue publicado originalmente en iceriveroutlet
Resumen : El Iceriver KS3 es una herramienta poderosa y eficiente para la minería de Kaspa, lanzada en agosto de 2023. Este artículo proporciona una visión completa de sus características, especificaciones y perspectivas futuras, destacando su alta tasa de hash y bajo consumo de energía. Es esencial adquirir el KS3 de distribuidores confiables y estar al tanto de las fluctuaciones del precio de Kaspa para asegurar una inversión segura y rentable en el mercado de criptomonedas.
Introducción al Iceriver KS3
Iceriver ha lanzado varios modelos de mineros Kaspa, y el KS3 es una de sus últimas innovaciones. Este artículo proporciona una visión general del Iceriver KS3, describiendo sus características, especificaciones y perspectivas futuras.
Especificaciones técnicas
El minero Iceriver KS3 utiliza el algoritmo KHeavyHash basado en PoW, con una tasa máxima de hash de 8000Gh/s y un consumo de energía de apenas 3200W.
minero Iceriver KS3
Detalles del Iceriver KS3
Fabricante: Iceriver
Modelo: KS3
Lanzamiento: Agosto 2023
Peso neto: 14700g
Peso bruto: 17600g
Voltaje: 170-300 VCA
Tamaño sin embalaje: 370x195x290mm
Tamaño con embalaje: 490x300x400mm
Potencia: 3200W
Interfaz: Ethernet
Temperatura operativa: 0 – 35°C
Humedad operativa: 10 – 90%
Comparación con otros mineros Kaspa
El Iceriver KS3 es comparable al Bitmain Antminer KS3 en términos de eficiencia energética y tasa de hash. Ambos modelos ofrecen características robustas, pero los mineros pueden optar por el Iceriver KS3 por su eficiencia energética cercana a la del Antminer KS3.
Historial del rendimiento del precio de Kaspa
La rentabilidad de la minería de Kaspa está directamente relacionada con el precio de la criptomoneda. Mantenerse informado sobre las fluctuaciones del precio de Kaspa es crucial para maximizar las ganancias.
Desempeño del precio de Kaspa
Kaspa ha mantenido un rango de precios constante en el último año, lo que indica estabilidad. Sin embargo, el precio puede variar, y es esencial seguirlo de cerca para tomar decisiones informadas.
Rentabilidad del Minero Iceriver KS3
Evaluar las oportunidades de beneficio antes de invertir en hardware de minería es fundamental. La rentabilidad de la minería de Kaspa depende de varios factores, incluyendo el precio de Kaspa, la dificultad de la red y las tendencias del mercado. A pesar de ello, el Iceriver KS3 se destaca como uno de los equipos de minería Kaspa de primera línea, gracias a sus avanzadas especificaciones técnicas, que comprenden una alta tasa de hash, un consumo de energía reducido y una eficiencia energética sobresaliente. Esto incrementa las posibilidades de resolver problemas criptográficos más rápidamente, enfrentando los desafíos de la minería y aumentando tus beneficios.
Factores a considerar
Precio de Kaspa
Dificultad de la red
Tendencias del mercado de minería
Cambios en el algoritmo de minería
Condiciones del mercado
Actualizaciones regulatorias
A pesar de la incertidumbre, el Minero Iceriver KS3 es una de las mejores máquinas mineras Kaspa disponibles, con una alta tasa de hash, bajo consumo de energía y excelente eficiencia energética.
Perspectivas futuras del Iceriver KS3
Kaspa está ganando popularidad entre los mineros de criptomonedas por su código abierto y su potencial para desarrollar aplicaciones DeFi y contratos inteligentes. El historial de precios de Kaspa también parece positivo.
Futuro de la minería Kaspa
El Iceriver KS3 se destaca por sus características avanzadas, pero la industria de la minería de criptomonedas sigue evolucionando. Los mineros deben considerar la posibilidad de que nuevos dispositivos más avanzados puedan impactar la rentabilidad del KS3.
-
 @ dbb9c664:c62a102f
2024-05-04 23:27:51
@ dbb9c664:c62a102f
2024-05-04 23:27:51Chef's notes
Try to use fresh lemon if you can. It makes the guac taste bangin
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 8-10 min
- 🍽️ Servings: 3
Ingredients
- 1 sweet potato
- 1 tbsp oil
- Spices (salt, pepper, garlic powder, paprika, brown sugar)
- Dried herbs (oregano & parsley)
- 1 avocado
- Salt & pepper
- Lemon juice
- OPTIONAL: garlic or onion
Directions
- Cut the sweet potato in half lengthwise
- Cut 1/2 inch steaks
- Cut those in half
- Cut each fry a little under 1/2 an inch for restaurant quality
- Combine fries in a bowl with oil and spices
- Air fry or bake at 375 degrees F for 8-10 minutes
- Smash avocado with lemon juice and spices and optionally add 2 garlic cloves or 1/2-1/4 an onion
- Enjoy! 😉
-
 @ 5d4b6c8d:8a1c1ee3
2024-06-24 20:17:59
@ 5d4b6c8d:8a1c1ee3
2024-06-24 20:17:59Hi everyone,
As I go through basketball withdrawals, I'm frantically trying to think of fun NBA content and I came up with something that I think will be a neat almost year-long contest.
Let's try to predict who will make up the All NBA 1st team next year, as well as who the league MVP will be and which team will win the title.
Here's the part I think will be fun: each month you can revise your predictions, but you get more credit for further out predictions. If you make a correct pick in June and don't change, you'll get 10 points, whereas a correct April pick is only worth one (assuming that I counted months correctly).
As with most of my contests, the prize will be however many sats are zapped to me on these posts (including comments).
My June Picks
All NBA 1st Team
- Jokic
- Giannis
- Luka
- Ant
- SGA
MVP
- Luka
Champ
- Denver
-
 @ fec1f0c9:25ee63f5
2024-05-03 19:48:03
@ fec1f0c9:25ee63f5
2024-05-03 19:48:03Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 10-14 days
- 🍽️ Servings: 8
Ingredients
- 1 gallon of filtered water
Directions
- Prepare the sweet tea: Bring 4 cups of water to a boil in a large pot. Remove the pot from heat and add the tea bags and sugar, stirring until the sugar is completely dissolved. Let the tea steep for about 10-15 minutes, then remove the tea bags.
-
 @ fec1f0c9:25ee63f5
2024-05-03 19:46:01
@ fec1f0c9:25ee63f5
2024-05-03 19:46:01Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 10-14 days
- 🍽️ Servings: 8
Ingredients
- 1 gallon of filtered water
Directions
- Prepare the sweet tea: Bring 4 cups of water to a boil in a large pot. Remove the pot from heat and add the tea bags and sugar, stirring until the sugar is completely dissolved. Let the tea steep for about 10-15 minutes, then remove the tea bags.
-
 @ fec1f0c9:25ee63f5
2024-05-03 19:44:57
@ fec1f0c9:25ee63f5
2024-05-03 19:44:57Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 10-14 days
- 🍽️ Servings: 8
Ingredients
- 1 SCOBY (Symbiotic Culture of Bacteria and Yeast)
- 1 cup of sugar
- 8 bags of black or green tea
- 1 gallon of filtered water
Directions
- Prepare the sweet tea: Bring 4 cups of water to a boil in a large pot. Remove the pot from heat and add the tea bags and sugar, stirring until the sugar is completely dissolved. Let the tea steep for about 10-15 minutes, then remove the tea bags.
- Cool Down the Tea: Add the remaining 4 cups of filtered water to the pot to cool down the tea mixture. You want the tea to be at room temperature before proceeding.
- Transfer to Fermentation Jar: Pour the sweet tea into your clean fermentation jar. Add Starter Tea and SCOBY: Gently pour the starter tea into the jar, ensuring it's mixed well with the sweet tea. Carefully place the SCOBY on top of the tea. It may sink or float, both are okay.
-
- Cover and Ferment: Cover the jar with a cloth or paper towel, securing it with a rubber band. This allows airflow while keeping out contaminants. Place the jar in a warm, dark area, ideally between 75-85°F (24-29°C), and let it ferment undisturbed for 7-14 days. The longer you ferment, the more tart and less sweet your kombucha will become.
- Tasting for Readiness: After 7 days, begin tasting your kombucha using a straw or non-metal spoon. It should be slightly tangy but still slightly sweet. If it's too sweet, let it ferment longer; if it's too sour, ferment for less time next batch.
- Bottling: Once the kombucha reaches your desired taste, carefully remove the SCOBY and set it aside in a clean container with some of the kombucha (this will be your starter for the next batch). Use a funnel to pour the kombucha into clean bottles, leaving about an inch of headspace at the top. If desired, now is the time to add flavorings (see below). Tightly seal the bottles.
- Second Fermentation (Optional): If you prefer fizzy kombucha, let the sealed bottles sit at room temperature for 1-3 days for a second fermentation. This will build up carbonation. Keep an eye on the pressure, as over-fermentation can cause bottles to explode.
- Refrigerate and Enjoy: Once the second fermentation is complete (if you did it), move the bottles to the refrigerator to chill. Your kombucha is now ready to drink!
- Flavoring (Optional): Add your preferred flavorings while bottling, before the second fermentation. Check my account for specific flavor recipes (the possibilities are endless).
-
 @ 3842def1:e2855211
2024-05-01 18:25:29
@ 3842def1:e2855211
2024-05-01 18:25:29Chef's notes
Next Level Quick and Delicious. Dive into a bowl of sheer delight with our Classic Macaroni and Cheese! Each forkful of our creamy, decadent macaroni is enveloped in a rich, velvety sauce crafted from the finest sharp cheddar and Parmesan cheeses. The perfect blend of spices, including a hint of paprika and garlic, adds a subtle warmth that enhances the cheese's deep, satisfying flavors without overpowering them.
This dish isn't just food; it's a comforting embrace in edible form. Prepare it effortlessly with minimal prep and cook time, making it the perfect solution for a hearty family dinner or a cozy night in. For an added touch of indulgence, top it off with golden, crispy breadcrumbs, baked to perfection, offering a delightful contrast of textures.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 20 min
Ingredients
- 8 ounces macaroni pasta
- 2 cups shredded sharp cheddar cheese
- 1/2 cup grated Parmesan cheese
- 3 cups milk
- 1/4 cup butter
- 2 1/2 tablespoons all-purpose flour
- 1/2 teaspoon salt
- 1/2 teaspoon black pepper
- 1/2 teaspoon paprika
- 1/2 teaspoon garlic powder
- 1/2 cup breadcrumbs (optional for topping)
Directions
- Preheat your oven to 350 degrees F (175 degrees C) if you plan to bake the macaroni with a breadcrumb topping.
- Cook the macaroni according to the package instructions until al dente, then drain and set aside.
- In a saucepan, melt the butter over medium heat. Stir in the flour and keep stirring for about 1 minute to form a roux or in other words the foundation of flavor.
- Gradually add the milk to the roux while continuously stirring to prevent lumps. Cook until the sauce thickens.
- Reduce the heat and add the shredded cheddar cheese, Parmesan cheese, salt, pepper, paprika, and garlic powder. Stir until the cheese is melted and the sauce is smooth.
- Combine the cooked macaroni and cheese sauce in a large bowl, mixing well.
- (Optional) For a baked version, pour the macaroni mixture into a greased baking dish. Sprinkle breadcrumbs over the top and bake for 20 minutes, or until the top is golden brown.
- Serve hot and enjoy your creamy, comforting macaroni and cheese!
-
 @ 3842def1:e2855211
2024-05-01 17:43:20
@ 3842def1:e2855211
2024-05-01 17:43:20Chef's notes
Thank you Ree Drummand, used your recipe for years and my family has loved it!!!!
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 45 min
- 🍽️ Servings: 12
Ingredients
- Butter, for greasing
- 8 whole eggs
- 1 loaf sourdough or French bread
- 1/2 cup whipping (heavy) cream
- 2 cups whole milk
- 2 tablespoons vanilla extract
- 1/2 cup brown sugar
- 1/2 cup granulated sugar
- Topping Ingredients:
- 1 teaspoon ground cinnamon
- 1/2 cup firmly packed brown sugar
- 1/2 cup all-purpose flour
- 1 stick cold butter, cut into pieces, plus more for serving
- Freshly grated nutmeg
- 1/4 teaspoon salt
- 1 cup fresh blueberries, for serving
- Hmmmmm Warm pancake syrup, for serving
Directions
- 9-by-13-inch baking pan
- For the French toast: Lubricate the baking dish with butter. Shred the bread into pieces, or slice into cubes, and scatter them throughout the dish. Break the eggs into a large bowl. Combine the eggs, milk, cream, granulated sugar, brown sugar, and vanilla, and beat well. Spread this mixture evenly over the bread. Seal the dish tightly and refrigerate until use (overnight is ideal).
- For the topping: Blend the flour, brown sugar, cinnamon, salt, and a bit of nutmeg in a different bowl. Mix thoroughly with a fork. Incorporate the butter using a pastry blender, and work it until the mix looks like small pebbles. Keep in a zip-top plastic bag in the fridge.
- When you're prepared to bake the casserole, heat the oven to 350 degrees F. Take the casserole out of the fridge and scatter the topping over it. Bake for 45 minutes for a softer, pudding-like texture, or for 1 hour or more for a crisper, more solid texture.
- Serve individual portions. Enhance with butter and a pour of warm pancake syrup, and garnish with blueberries.
-
 @ 80185950:ae8205c6
2024-05-01 08:41:41
@ 80185950:ae8205c6
2024-05-01 08:41:41Chef's notes
This is perfect for someone who doesn’t want to sit all day in a kitchen to make quality meal. So simple and so yummy.
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 20 min
- 🍽️ Servings: 4
Ingredients
- Bag of King Prawns
- Pasta Fusilli
- Chilli flakes
- Italian herbs
- Mozarella
- Olive Oil
- Sweet Paprika Powder
- Garlic Granules
- Vegetable seasoning powder or liquid
Directions
- Cook pasta and leave on the side when ready
- In seperate pan heat up some olive oil
- Put prawns and fry them maximum 4 minutes
- In those 4 minutes add gradually all spices
- Make sure chilli flakes are crispy and fried
- Now mix in pasta
- Sprinkle with mozarella cheese
- When cheese melts it’s ready to serve
-
 @ 80185950:ae8205c6
2024-05-01 08:27:12
@ 80185950:ae8205c6
2024-05-01 08:27:12Chef's notes
You don’t need to use gluten free ingredients, you can always use normal breadcrumbs or panko if you desire.
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 20 min
- 🍽️ Servings: 4
Ingredients
- Garlic cloves
- Butter
- Prawns large or King Prawns
- Mozarella
- Basil leaves
- Gluten free bread crumbs
- Sweet paprika
- Vegetable seasoning
- Garlic granules
- Olive oil
- Chilli powder
Directions
- Prepare few garlic cloves by mashing them with tool of your choice
- Wash prawns or king prawns make sure they are pealed, I use entire bag of them
- Heat up oven or grill
- While it’s heating up we will prepare a souse first, we will need a baking dish on the side where all ingredients will meet
- Heat up the pan and melt half bar of butter, yes I know it’s a lot but believe me we won’t be able to eat it it will act like a souse
- Add garlic
- Don’t burn the butter just make sure it melts and as soon it bubbles add all the spices, pinch of everything mentioned in ingredients list. If you don’t have vegetable seasoning use salt instead, as the seasoning is already salty
- Now add some olive oil to mix into the butter approx 2 table spoons
- Pour it into the baking dish
- Now in the same pan throw washed prawns for approx 2 minutes not longer we want them to be soft not gummy
- Turn them around and after 2 minutes place them into the butter souse in a baking dish
- Now get some Mozarella cheese, slice it and spread on the dish
- Decorate with basil leaves
- Sprinkle with bread crumbs
- Throw to the oven for 15 min
- Enjoy :)
-
 @ 005bc4de:ef11e1a2
2024-04-30 22:50:24
@ 005bc4de:ef11e1a2
2024-04-30 22:50:24Chef's notes
In my little hobby garden, I grew these "snack" peppers (green, yellow, orange, red), some hot cayenne peppers, and okra. Pickling them is easy and is great as part of a charcuterie board or added to a cocktail. Mostly, they're just fun, as well as yummy.
The ingredient sizes are estimates, it really doesn't matter. You just want to jam as much as you can into the jar.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: no cooking, but at least 2 days chill time
- 🍽️ Servings: 4
Ingredients
- 1 cup snack peppers
- 1/2 cup okra
- several hot cayenne peppers (to taste)
- 1/2 cup white vinegar
- 1 T sugar (optional - I did not use any)
Directions
- Clean the ribs from the snack peppers. I saved the seeds (dry them, then plant them...why buy seeds?). Slice the cayenne peppers so the heat gets released from the inside. Also slice the okra so the liquid gets into the inside. Stuff the jar as tightly as you can, no need to waste precious pickling space. Fill the jar half way with vinegar, then top off with water. Add sugar if desired (I did not). Place in the refrigerator to chill. Most recipes call for 2 to 3 days. I usually go for a week. Great as finger food or with a cocktail.
-
 @ 1123ece2:7d1e00c0
2024-06-24 19:29:00
@ 1123ece2:7d1e00c0
2024-06-24 19:29:00Welcome to The Refinery.
The Church The Body of Christ is our theme for the next few Sunday’s.
These messages are primarily based around Paul’s letter to the Ephesians.
Today we are discussing, The Goal of the Church.
Scripture Reading
Ephesians 4:7-16 NKJV
Spiritual Gifts
7 But to each one of us grace was given according to the measure of Christ’s gift.
8 Therefore He says: “When He ascended on high, He led captivity captive, And gave gifts to men.”
9 (Now this, “He ascended”—what does it mean but that He also [a]first descended into the lower parts of the earth?
10 He who descended is also the One who ascended far above all the heavens, that He might fill all things.)
11 And He Himself gave some to be apostles, some prophets, some evangelists, and some pastors and teachers,
12 for the equipping of the saints for the work of ministry, for the [b]edifying of the body of Christ,
13 till we all come to the unity of the faith and of the knowledge of the Son of God, to a perfect man, to the measure of the stature of the fullness of Christ;
14 that we should no longer be children, tossed to and fro and carried about with every wind of doctrine, by the trickery of men, in the cunning craftiness of deceitful plotting,
15 but, speaking the truth in love, may grow up in all things into Him who is the head—Christ—
16 from whom the whole body, joined and knit together by what every joint supplies, according to the effective working by which every part does its share, causes growth of the body for the edifying of itself in love.
Introduction.
The total impression of this passage from Ephesians 4 is that Christ has a goal, a supreme standard for His church, and that goal is so high, so exalted that it taxes the imagination to comprehend it.
Nonetheless, here and now, in the body of this flesh, we are to strive to attain it.
Specifically, this passage leaves three impressions on the mind and the heart.
First, Christ has given us the grace whereby we may reach the goal.
Second, the means of growth for reaching that goal are at hand.
And third, we must not stop nor be satisfied short of the goal, no matter how high the standard nor how great the difficulties in the way.
- Grace for reaching the goal Christ has for His church.
We must never take our eyes away from the grace of God.
We are always to remember that we are not Christians because we deserve to be.
We have not been brought “out of death into life” because of any merit of our own.
The whole Christian transaction, whereby we cease to live unto sin and begin to live unto God, is all go grace, God’s grace.
Two things strike us about this grace, this free gift go Christ toward those who are His own.
First, there is its impartiality.
Ephesians 4:7 says, But to each one of us grace was given according to the measure of Christ’s gift.
Not just a few of the church, not just the Pastor or the leaders, but “each one of us.”
Although “according to the measure of Christ’s gift,” the capacity of one member might exceed that of another, no member of His churches left completely dispossessed.
His gifts are measured not by any favouritism on God’s part, for His love is everywhere and for everyone all the same.
God’s grace is impartial.
Secondly, there is individuality.
God’s gifts are specifically fitted to the capacity of each individual to receive them.
It follows, therefore, that each person in the church has a task cut out just for that person “according to the measure of the gift of Christ” in equipping him or her to do that task.
Paul said, in Ephesians 4:11, And He Himself gave some to be apostles, some prophets, some evangelists, and some pastors and teachers.
And this is not a complete list.
The fact that Christ’s churches are not challenging our sin riddled society and moving this needy world toward God is not His fault.
He has given His people the grace to move toward the goal of “the measure of the stature of Christ.”
2. Growth toward the goal Christ has for His church.
Paul said in Ephesians 4:15 that we, “but, speaking the truth in love, may grow up in all things into Him who is the head—Christ—“
Paul called some in the church at Corinth who had not grown, in 1 Corinthians 3:1, And I, brethren, could not speak to you as to spiritual people but as to carnal, as to babes in Christ.
He was saying to them, “You haven’t grown a bit as Christians since the days you were converted. You are baby Christians, wholly immature.”
How may Christian growth be obtained?
What are the means?
Paul gave several suggestions.
First, we grow by stability Christian convictions.
In typical fashion, Paul mixed his metaphors here to describe the instability of immature Christians, picturing them as infants being tossed by the waves like an unanchored ship driven about by a turbulent sea.
Instability of Christian convictions is one sure sign of immaturity of Christian character, while stability is a sure means of growth.
There is such a thing as Christian certitude, or absolute confidence, as “the rock of ages.” For our feet, as a standard in religion.
Isaiah 26:4, Trust in the Lord forever, For in Yah, the Lord, is everlasting strength.
God’s Word, is an anchor and stay for our faith.
Apart from the certainty of our faith and stability of convictions, we don’t grow very much.
Second, we grow by sincerity of Christian love.
Ephesians 4:15, but, speaking the truth in love, may grow up in all things into Him who is the head—Christ.
The marginal reading says, “But dealing truly in love.”
The problem is that we have no verb for truth in English, while the Greek does.
Literally Paul said, “But trotting in love.”
The import of his words is that our manner of life is to be sincere and true, thinking truly, speaking truly, dealing truly, and all in a spirit of genuine love, without diversions to divide our allegiance, without hypocrisy to deny our witness, without divisions to hinder our purpose in Him.
“Truthing” in love, love for Christ, for one another, for those who are lost.
Thirdly, we grow by solidarity of the Christian community.
Ephesians 4:15-16, but, speaking the truth in love, may grow up in all things into Him who is the head—Christ— from whom the whole body, joined and knit together by what every joint supplies, according to the effective working by which every part does its share, causes growth of the body for the edifying of itself in love.
Again Paul used the figure of the human body, “from whom the whole body, joined and knit together by what every joint supplies.”
All the members of the church are knit and joined together.
Every member is joined to every other member.
What is for the good of one is for the good of all, and what causes the hurt of one is for the injury of all.
Where there is no solidarity of purpose and unity of spirit in the church, there can be no growth.
3. The greatness of the goal Christ has for His church.
How great and how high is Christ’s goal for His church?
Paul took his readers step by step to the top.
After naming the gifts that Christ through grace gives to individuals in the church, he told why.
First, for the perfecting of the saints.
The word translated “perfecting” means “mending,” the same word that is used where we are told of fishermen “mending their nets.”
When members of the church are quick tempered, gossips, busy bodies, and empty headed, Paul said we must, “mend these things.”
Why?
Second, “Unto the work of ministering, unto the building up of the body of Christ.
Ephesians 4:12, for the equipping of the saints for the work of ministry, for the edifying of the body of Christ.
This is to the end that Christ might have a fit and usable instrument through which He can nurture His saints, grow His children, and save the lost.
Thirdly, he goes on, “Till we all attain.”
Christ’s ideal for His church is not for just a few choice souls who excel, not for just a few who reach the top, but for every member of His church, all of His own people.
Fourthly, but Paul moved higher yet again.
Ephesians 4:13, till we all come to the unity of the faith and of the knowledge of the Son of God, to a perfect man, to the measure of the stature of the fullness of Christ.
Paul was saying, “Till we all come to His standard of unity and maturity, full grown and united, no differences of opinion in the Lord, no divergences of conviction, no divisions of spirit.”
We say, “Surely that is the top! We could come no nearer to perfection than that.”
But Paul wasn’t finished!
The goal is one step higher.
Listen to the grand and soaring height of the goal.
“To the measure of the stature of the fullness of Christ.”
Humans can move no nearer God’s likeness than that, thinking like Christ in our minds, loving like Christ in our hearts, resembling Christ in our lives, giving ourselves to the purposes of God as He gave Himself, reminding people of God because we are fashioned in the likeness of His Son.
Conclusion.
Do you see the point of this great passage?
Paul laid tremendous emphasis on the church, the body of believers, not on its size but on its soul quality.
He had a burning desire to win souls, but he believed with all his heart that exalted Christian character within the church was the surest means of doing this.
This comes home to us, we cannot avoid it.
We emphasise quantity but not quality.
We glory reports, but do not demand repentance.
We have with and breath but neither height nor depth.
Our churches grow in size, but our members do not grow spiritually.
It is useless to add members who do not grown Christ.
We are cursed with a low ideal.
We are plagued with and unworthy contentment.
We are satisfied far short of the goal.
Let us pray over this passage until a fire is kindled in our hearts and becomes a raging force that drives us to the standard set by the Lord.
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ 80185950:ae8205c6
2024-04-30 22:07:25
@ 80185950:ae8205c6
2024-04-30 22:07:25Chef's notes
I usually use Nutella as a chocolate choice, however you can use any spread of your own preference. Make sure pancakes are thin so they can be folded. Enjoy!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 15 min
- 🍽️ Servings: 4
Ingredients
- 1 egg
- 1 cup of milk
- 3/4 cup of gluten free flour
- Oil
- Salt
- Gluten free baking powder
- 2 bananas
- Flaked almonds
- Peanut butter
- Chocolate spread
Directions
- Mix 1 egg in the bowl untill fluffy
- Add milk and mix
- Add pinch of salt and baking powder
- Add 1 table spoon of oil
- Add flour
- Mix until is thick and fully mixed
- Heat up few drops of oil on the flat pan
- Pour little mix untill fully covers pan but make sure remains thin
- Wait until fully set, I usually don’t flip it over
- Decorate ready pancake with peanut butter spread, chocolate spread and banana slices
- You should be able to make 7-8 pancakes
- When you fry them all take handful of flaked almonds and fry them on the same pan untill crispy
- Sprinkle them all over your pancakes and add extra banana slices
-
 @ 1b0706e7:ec11b9b3
2024-06-24 18:55:19
@ 1b0706e7:ec11b9b3
2024-06-24 18:55:19I was inspired to start a meetup after watching a video on twentyone.world.
The idea is to create a beacon in Cyberspace so I started it on nostr. I met one guy one the Orange Pill app and talked to him a little on nostr. We met for coffee, It was great. I met several bitcoiners who I will not name, but I only met two people from meetup.com. They were very nice, but were more into "crypto" trading than bitcoin. This was awkward for me because I find the field of cryptography(a branch of mathematics) fascinating, but am also not interested in shilling scam-coins that don't make any sense like "garbage trucks on a blockchain" or whatever.
Therefore, I regret to inform you that I am ending the riverside bitcoin meetup subscription. I have decided to create my own website instead. You can hear some of the shoutouts I've left on Rabbit Hole Recap or find us here.
https://riversidebitcoin.com
We now meet every Thursday at GreyWolf Brewery in Norco, California from 4p.m -6 .m. Bitcoin accepted here. The Coffee Meetup on July 6th will be the last one for a while as I want to work on some front end development to make better POS terminals for businesses that accept bitcoin.
npub1rvrsde6r0w7unk3am48md5us4gsx536dq5qh6utedkhhemq3hxesehc89n
-
 @ c43d6de3:a6583169
2024-06-24 16:56:56
@ c43d6de3:a6583169
2024-06-24 16:56:56"If you do tomorrow what you did today, you will get tomorrow what you got today." - Benjamin Franklin
Seize the Day

Image from article- https://community.thriveglobal.com/want-your-authentic-self-mindfulness-is-a-gateway/Confliction
There are two conflicting approaches to life: Delay gratification today for a wealthy tomorrow and carpe diem Seize the Day and live like today is your last. Usually, when someone prescribes delayed gratification they refer to finances; save a dollar today for a hundred tomorrow. Carpe diem often refers to smelling the coffee, enjoying the little things and not putting off for tomorrow what could've been done today.
I've never felt the two of those prescriptions collide more violently than now as a father of two beautiful kids. I find it more difficult than ever before to make decisions that might benefit my future over being present for my kids. Time being the finite thing that it is, often I can only choose one.
Image from Adobe ImagesTwo Fathers, Two Approaches: Enough Small Moments Equal A Big Moment My brother in-law and I have different approaches to this. He tends to delay gratification. More often than not, he's out on business and misses minor family events and outings. Meanwhile, I often choose to attend even the smallest family events as opposed to going on business.
I should mention, my brother in-law doesn't dare miss the big events. He's always there for a birthday, baptism, or graduation but he misses outings to the beach or spring. He misses the books read by the bed and the dimming of the light just before a kiss goodnight.
If you miss enough small moments, you a miss big one.

Image from article- https://www.spiritualmom.com/god-is-weaving-a-tapestry/
Since my children were born I vowed to live as much in the moment as I could. In the moment, I'm happy to be with my kids stitching together cherished mementos that will be the tapestry of our lives. These indelible memories not only serve to make me happy but, I believe they'll work as the sinews and tendons that come together to form my children's personality and identity. My relationship with my kids and family will tighten as their persona grows.
I don't have facts from studies or scientific analysis, but I have a gut feeling its the strength of the tapestry of our lives that determines how resilient my children will be. When they encounter hard times they'll carry the uplifting memories of good times and they'll have the comfort of knowing there's a tightknit family at their backs to get through it.
That said, I've never heard my brother in-law complain about money.
I can't say I struggle for cash either. I make ends meet, but my wife and I have experienced that nervous rush when the AC blows out mid-summer and we wonder if we would have enough to pay for the down payment of a new unit and the mortgage at the beginning of the month.
What's been bothering me most as of late is my damn near non-existent retirement fund.

Image from ANATOMY OF A SOLDIER BY HARRY PARKER REVIEW - UNUSUAL PERSPECTIVES ON WARFARE FICTION
Commitments- To My Nation, To My Self
My biggest conflict today is tied to the commitment I made to the United States Army Reserves years before the birth of my children. While I can decide not to go on business like my brother in-law does, I can't simply not attend drill (one weekend a month) or go off on annual training (2–3 weeks a year). Failure to attend to my military obligations can result in a dis-honorable discharge. Having that hanging over my head will forever ruin any lucrative opportunities for employment and public service.
More often than not, my relatively small obligation to the Army Reserves has stood in direct conflict with my desire to be present in my kids lives as well as the lives of my friends and family. Some how, I've had the misfortune of having drills and annual training scheduled on major events like weddings, baptisms, and birthdays; the very things I vow never to miss.
There are ways to request those special days off and make it up on a later date and when I can, I do. However, I've been forced to go unaccounted for on several occasions when special events are back to back and overlap with already requested days off. That's led to conflict in the past but, I've been fortunate enough to have good leaders who've understood why I preferred to be absent in the military over absent in a major life event. It would be easiest, and most convenient, to resign my congressional commission as an officer and leave the Army Reserves. This is when I feel that great internal conflict.
Serving in the Army Reserves allows me to give back to my nation and grants me several financial benefits that would otherwise be completely lost. Medical insurance is remarkably cheaper than what I would have to deal with as a civilian. I get a world of benefits when purchasing a house and I can apply for special grants if ever needed. Perhaps most important of all, if I stick around for the full 20 years (I have almost 9 now) I will have a very nice retirement pension waiting for me when I turn 65. This is where that differed gratification really kicks in.
When I really boil it down to pros and cons, there's just way too many pros to staying in the Reserves than cons.

Image of Jordan Peterson from Video Clip- "4 years video"
Phases of Life Approach
World renown psychologist Jordan Peterson says "you have little kids for 4 years and if you miss it, its done." For Jordan, this is time period is peak experience for your kids. As I write this, my eldest just turned two and my youngest is 9 months. I'm not quite halfway there yet and I can't let up now.
I don't want to test to see if what Jordan Peterson says is true, I'm going to continue living as much in the moment as is possible during these early years of my children's lives. If I stay in the army reserves throughout this time I will have had 13 years of service by the time my youngest is 4.
Taking this approach, I will have been very present in the first 4 years of my kids lives and will only have to serve seven more years to acquire that retirement.
For me, today is Gold and tomorrow is Silver.
People have sacrificed worse.
artstr #plebchain #writing
I want to show the world that life is a scroll riddled with ink. The marks will only ever be simple blots on the parchment unless you pause and perceive them for the characters they are.
I'm constantly thinking about what the future could look like if we just take action.
More of my thoughts about the future and the world around us are coming soon...
Thank you for Reading this article. If you liked it and would consider zapping some sats, doing so supports me and motivates me to continue writing!
If you are interested in Fiction writing, visit my NOSTR page Fervid Fables: npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49
-
 @ 0861144c:e68a1caf
2024-06-24 16:30:24
@ 0861144c:e68a1caf
2024-06-24 16:30:24Paraguay recently made another adjustment to the minimum wage, which automatically translated into a 4% loss in purchasing power. In other words, any savings in fiat currency have lost 4% of their value.
Educated people don't want help
I always remember an occasion during a conversation with friends, some with MBAs and others with finance degrees, when I mentioned that Bitcoin could help escape inflation due to its hardness as a currency. - Comment 1: Bitcoin is useless because it's volatile. - Comment 2: As long as the government doesn't regulate it, no one will want to put their money into it. - Comment 3: There are many financial instruments to buy something that is volatile and backed by nothing.
I responded to these three comments, but my words fell on deaf ears, and the topic soon changed. As we searched for new topics, I thought to myself that we are too early. It always reminds me of that movie "The Big Short" (2008), where, when asked why the market hasn't collapsed yet, the famous phrase is uttered: they think their feet, which are being cooked, are actually the steak.
Offer bitcoin to everyone anon
I feel sorry for them, and yet tomorrow will be the same as always. Even when Bitcoin is on its upward trend, it will be there for them. While some see it as a get-rich-quick scheme, my satoshis today are ensuring that my future is not stolen. Bitcoin is not a sword with which we will win any battle in the endless maze; Bitcoin is the way out.
-
 @ 5d4b6c8d:8a1c1ee3
2024-06-24 13:33:41
@ 5d4b6c8d:8a1c1ee3
2024-06-24 13:33:41Read the previous edition here.
June 24th, 2023 📅
📝
TOP POSTDon't feel bad about being too late to Bitcoin.
Excerpt:
So don't feel bad that you missed out about Bitcoin in 2017, or 2021. It doesn't matter what Bitcoin was worth then or now in fiat terms. It matters that we keep learning about Bitcoin and sharing it with others. Then one day we can all have economic freedom and savings.
3495 sats \ 35 comments \ @graben \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/198729/r/Undisciplined?commentId=198755
IMO there is no "too late". If you buy now then yes your purchasing power will probably increase dramatically over the years, but even if adoption saturates Bitcoin is still a worthwhile asset to buy / earn due to all of its other wonderful properties.
From Don't feel bad about being too late to Bitcoin.
805 sats \ 0 replies \ @orthwyrm
🏆
TOP STACKER@k00b
9664 stacked \ 16.8k spent \ 3 posts \ 34 comments \ 0 referrals
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
June 24th, 2022 📅
📝
TOP POSTI'm Sergej Kotliar, CEO of Bitrefill. AMA.
Excerpt:
Hi everyone! I’m @ziggamon, Founder and CEO of Bitrefill. Bitrefill is the world’s number one answer to the question “but what can I actually buy with my bitcoin?”
21k sats \ 69 comments \ @ziggamon \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/38569/r/Undisciplined?commentId=38570
Excerpt:
yes and we don't tell each other our user names so we can try and guess who is who lol! (Still don't know)
From Do you share Stacker News with family or friends?
380 sats \ 0 replies \ @plebpegasus
🏆
TOP STACKER@k00b
1409 stacked \ 18.6k spent \ 7 posts \ 12 comments \ 0 referrals
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
June 24th, 2021 📅
📝
TOP POSTFighting Monetary Colonization with Open Source Code
link to https://bitcoinmagazine.com/culture/bitcoin-a-currency-of-decolonization
2 sats \ 0 comments \ @k00b \ ~bitcoin
💬
TOP COMMENTEMPTY
🏆
TOP STACKEREMPTY
-
-
 @ 80185950:ae8205c6
2024-04-30 21:41:52
@ 80185950:ae8205c6
2024-04-30 21:41:52Chef's notes
You can add more texture by adding chopped tomatoes or peppers. Control water level during boiling if you want the dal to be thicker or more watery. Perfect with rice or any fresh flat bread. Delicious as a dinner curry side or lunch time thicker version with paratha or other flap breads.
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 20 min
- 🍽️ Servings: 4
Ingredients
- 1 onion
- Garlic gloves
- Red chilli dried or fresh
- Red lentils
- Butter
- Turmeric
- Vegetable seasoning like Maggi
- Corriander
- Sweet paprika powder
Directions
- Chop onions and garlic in thin slices
- Melt 1 table spoon of butter in a pan
- Add garlic and mix 30 seconds
- Add onions and mix few minutes
- Add half cup of lentils (make sure you wash them before)
- Add right away 1 tea spoon of turmeric powder
- Add 1 tea spoon of sweet paprika powder
- Add 2 tea spoons of vegetable seasoning powder or 1 tea spoon of vegetable seasoning Maggi liquid
- Add 2 cups of water and bring to boil
- Add red chillies depending how many you want 1-3
- Boil on small gas for 20 min mix in between to make sure doesn’t stick to the bottom of the pan
-
 @ 6c8c7979:15595f3e
2024-06-24 08:45:18
@ 6c8c7979:15595f3e
2024-06-24 08:45:18Vincent van Gogh is one of the most prominent artists in the history of global art, with a significant influence on modern artistic movements. He was born in the Netherlands in 1853 and passed away in 1890. Despite not achieving fame during his lifetime, his works later became among the most impactful in fine arts.
Van Gogh's works are characterized by vibrant colors and rapid brush strokes, giving his paintings a unique style. His pieces often reflect nature and everyday life with a touch of deep emotion and drama. Some of his most famous works include "Starry Night," "The Night Cafe," "Irises," and "Wheatfield with Crows."
Throughout his life, van Gogh faced numerous personal and psychological challenges, which imbued his works with a sense of depth and contemplation. He struggled with severe mental disorders and social tensions, which greatly influenced his art.
After his death, public interest in his works grew significantly, and he came to be regarded as a pioneer of expressionism and modern art. His profound impact on global art is evident in the many movements and subsequent artists who drew inspiration from his techniques and subjects.
In summary, Vincent van Gogh remains an exceptional artistic figure, leaving an unforgettable legacy in art history. His works continue to inspire and captivate audiences worldwide with their beauty and artistic depth.
-
 @ 80185950:ae8205c6
2024-04-30 20:55:47
@ 80185950:ae8205c6
2024-04-30 20:55:47Chef's notes
My personal tips. You want it more thicker, add less water from the beginning but keep an eye that it doesn’t burn and keep adding water. If you want to switch things make it different, you can add baby potatos at the moment of adding water to boil.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 40 min
- 🍽️ Servings: 4
Ingredients
- 3 onions
- 4 garlic cloves
- ginger
- Cinnamon stick
- cardamom seeds
- Fenugreek seeds
- Fennel seeds
- Curry powder
- Chilli powder
- Turmeric
- Coriander powder
- Ground cumin / Jeera Powder
- Garam masala
- Salt
- Sunflower Oil
- Baby chicken cut in small pieces 8-12
Directions
- Chop onions
- Grate garlic and ginger
- Heat up a table spool of oil in a pan
- Throw few cardamom seeds, piece of cinnamon stick, pinch of fennel seeds for 30 seconds
- Add grated garlic and ginger and mix another 30 seconds
- Add chopped onions
- Add 1 table spoon of salt
- Fry everything mixing until onions are fried
- Add powders, max 1 table spoon of each powder
- Mix all for 1-2 min untill onions are fried with spices
- Wash chicken pieces and throw it all into a pan
- Mix it all until spices spread on the chicken
- Keep frying for another 10-20 minutes until chicken catches fully the spices and colour
- It gets too dry add a bit water and keep mixing
- Now add water just to cover the chicken level
- Mix all and leave on small gas for 30 min
- Mix occasionally
- All done!
-
 @ 11be7dbc:82a5f8e9
2024-06-24 08:33:15
@ 11be7dbc:82a5f8e9
2024-06-24 08:33:15The world is undeniably transitioning onto new tracks, embracing a sharing economy. This shift is not optional but inevitable, propelled by the intrinsic flaws of the current system. Under current geopolitical conditions, it's clear that the era of a dominant currency is ending. Real-time market dynamics reveal that the need for a dominant currency is vanishing. The value of each currency will be determined in real-time trading through supply and demand.
Decentralization and Technological Imperatives
Old systems, desperately clinging to their fading relevance, appear pitiful amid these unstoppable changes. Although the dollar still serves as a benchmark, its time is running out. The issue lies not in US policies or the dollar's legitimacy but in the obsolescence of centralized dominance itself. However, be cautious and don't fall for misinformation predicting the dollar's demise. We must recognize that the US's technological prowess and resource potential will prevent the demise of its national currency. The dollar will join the ranks of national currencies in stable economies, becoming just «one of many».
Algorithms that find optimal trading pairs will simplify transactions, improving global economic indicators. This highlights the inadequacy of smart contracts and fosters the search for more flexible and reactive algorithms to stabilize the global economy where innovation and efficiency reign. The transition to a sharing economy driven by decentralization and relentless innovation is imperative. Skeptics may cling to their withering relics, but progress will crush them, relegating them to mere footnotes in history. The decentralized future is not just on the horizon; it is here, and it is magnificent.
Crypto as Reshaping Economy
The crypto market hinted at this solution, showcasing the future of finance. Ironically, financial giants' attempts to control and regulate through Bitcoin ETFs only fueled the environment they sought to suppress. Adopting protocols like MWEB, which facilitate private and scalable transactions, highlights the practical benefits of decentralization. These technologies enable independent transactions, free from centralized scrutiny and control.
One might almost pity those clinging to the decaying remnants of the old world, if not for the exhilarating prospect of leaving them in the dust—irrelevant and obsolete. The world is moving towards a common trading platform where value is determined by market liquidity. In this new world, diverse crypto assets will hedge against volatility, creating a robust ecosystem for atomic swaps and cross-chain transactions. It is absurd to suggest that a single crypto asset could dominate; the future is diverse assets, each serving different economic functions.
The proliferation of digital assets ensures a resilient, adaptable market where liquidity and accessibility are paramount. Atomic swaps and cross-chain transactions will ensure swift, ubiquitous conversions, eliminating monopolistic players, KYC barriers, and the need for constant exchange searches. Today, the goal is to enter as much capital as possible within the market, creating an irreversible process that will lead us to the use of crypto as a means of payment. This will drive innovation, constantly stimulating humanity to develop and seek new solutions and opportunities.
The Role of Modern Technologies
Artificial intelligence acts as our assistant, a sophisticated calculator enhancing our productivity. Modern technologies are not the genius of one person but products of their time. And the concentration of money in the hands of a few reflects societal infantilism; we still possess a child's mindset. Our behavior towards money reflects this: like children, we either hide it or spend it on fleeting, flashy nonsense. Rarely does a child give money to their parents, think to help loved ones, or understand its true utility. Without knowing the ability to use money, it remains inaccessible to most of the population, similar to how money is controlled by parents in a family.
This is evident in the market's fascination with meme coins—a testament to human folly and a craze highlighting the need for a more mature system. We must realize that meme coins do not drive technological advancement; the liquidity resulting from sales leaves the market instead of supporting growth in production and industry development. The challenge is to balance the crowd's madness, greedily hopping from one meme coin to another. The solution is to create a market where real economic transactions dominate over the frivolous gambles of amateur traders. This will foster a more stable environment, recalibrating market dynamics so that real economic activity, not the whims of speculative traders, drives the market.
In conclusion, the transition to a sharing economy, driven by decentralization and relentless technological progress, heralds a new era of economic freedom and innovation. The MWEB protocol with swaps represents the future, enabling the development of Cyberyen. We have an open gate that is entirely free, without violating any regulatory rules or national properties. We can swap Cyberyen paired with Bitcoin, always available on decentralized exchanges globally. Using the MWEB protocol for private transactions helps scale the network and maintain independence from regulatory burdens and centralized exchange platforms.
Consider the opportunities available for Cyberyen, despite seemingly contrary regulatory policies. A parallel dimension has opened. Old economic paradigms are collapsing, giving way to a future of transparency, confidentiality, and unstoppable progress. This is the power of decentralization and freedom from market-imposed constraints. Those who resist these changes will find themselves relegated to the dustbin of history.
Stay with us... C¥kuza
-
 @ 9911f8d9:86db6c34
2024-04-29 20:38:35
@ 9911f8d9:86db6c34
2024-04-29 20:38:35Chef's notes
Apple can be changed with an other fruit like a pear. Type of apple influences the taste of the soup, so if you like a bit more sour, pick a 'Granny Smith' or 'Elstar' for example.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 4
Ingredients
- 2 tbsp coconut oil
- 1 onion in rings
- 1 stalk celery, sliced
- 0.5 celeriac, peeled and diced
- 1 apple, without core and cubes
- 1 sprig of thyme without stem
- 0.5 tbsp paprika powder
- 1.5 liters of vegetable stock
- 100-150 ml coconut cream
Directions
- Heat the pan and add 1 tbsp coconut oil.
- Add onion and celery and fry for 5 minutes until soft
- Add celeriac, thyme and paprika powder. Fry this for 2-3 minutes.
- Pour in the stock and add salt and pepper to taste. Simmer for 30 minutes until the celeriac is quite soft.
- Remove the pan from the heat and puree the soup with a hand blender. Stir in the cream coconut.
- Pour the soup into bowls and garnish with the some fresh herbs.
-
 @ c69b71dc:426ba763
2024-04-28 11:10:01
@ c69b71dc:426ba763
2024-04-28 11:10:01Chef's notes
Important note: For this recipe it is good to have a powerful blender. Soaking the nuts and seeds overnight also helps the consistency become creamier. If you are allergic to cashew, feel free to replace the cashews with almonds, pine nuts, tree nuts, etc.
Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 0
- 🍽️ Servings: 2-3
Ingredients
- 60g Cashew (soaked over night)
- 40g Sunflower Seeds (soaked over night)
- 50ml Water (you can always add more water if it gets to sticky)
- 6 pieces Sun dried tomatoes (soaked over night with seeds and nuts)
- 4 Tbsp Nutritional yeast
- 1/2 Tsp Salt
- 1/4 Tsp pepper
- 2 Tbsp Olive oil
- 1/4 Lemon or Lime juice
- 2 Tbsp Apple Vinegar
Directions
- Blend all the ingredients in a blender, add more water or salt if needed.
- The Cashew-Cheese should be creamy and kind of sticky, but not to dry and not to liquid.
- Pour the mixture into a container. Use within 3 days.
- You can decorate the spread with fresh herbs like parsley, basil, chilli flakes etc.
-
 @ 6b7e8d1a:baee28d7
2024-04-25 13:36:28
@ 6b7e8d1a:baee28d7
2024-04-25 13:36:28Chef's notes
"Recipes Vista" from chef Sarah
Details
- ⏲️ Prep time: 10 mts
- 🍳 Cook time: 20 mts
- 🍽️ Servings: 4
Ingredients
- 1 cup fresh pineapple, finely chopped 1/2 cup water 1/4 cup white vinegar 1/4 cup honey 2 tablespoons soy sauce 1 tablespoon fresh ginger, minced 2 garlic cloves, minced 2 teaspoons cornstarch 2 tablespoons water (additional for cornstarch) 1 teaspoon red chili flakes (adjust based on heat preference) Salt to taste
Directions
- In a saucepan over medium heat, combine pineapple, 1/2 cup water, vinegar, honey, soy sauce, ginger, and garlic. Bring the mixture to a simmer. Reduce the heat and let simmer for 10 minutes, or until the pineapple is tender. In a small bowl, dissolve cornstarch in 2 tablespoons of water. Stir this slurry into the simmering sauce. Add the chili flakes and salt. Continue to simmer for another 5 minutes, or until the sauce has thickened. Remove from heat and let cool. The sauce will thicken further as it cools.
-
 @ c69b71dc:426ba763
2024-04-21 17:45:44
@ c69b71dc:426ba763
2024-04-21 17:45:44Chef's notes
This vegan mozzarella recipe consists of cashews, psyllium husks flour and delicious spices. Of course it doesn't taste like the "original". Nutritional yeast is essential in this recipe as they give the plant-based cheese alternative a cheesy taste. You need a good, powerful blender.
Details
- ⏲️ Prep time: 10 min. (start preparing the day before)
- 🍳 Cook time: 0
- 🍽️ Servings: 4
Ingredients
- 270 ml Water
- 2 tbsp Psyllium husk (flour or flakes)
- 100 g Cashews soaked in water for at least 4 hours or over night
- 4 tbsp nutritional yeast
- 1/2 Juice of lemon
- 1/2 tsp Salt
- 1/2 tsp Pepper
- 1/2 tsp Garlic powder
Directions
- Soak the cashews in water for at least 4 hours - preferably overnight - and drain
- Place the cashews as well as the water, lemon juice, yeast flakes and spices in a blender and blend until smooth
- Add the psyllium husk and blend again until you get a cheesy consistency. It goes quite quickly!
- Place the cheese mixture in a bowl and let it solidify in the refrigerator for at least two hours - preferably overnight.
- Finally, turn the cheese out onto a plate and cut into pieces. It can be a bit sticky, but thats fine.
- Serve with tomatoes and drizzle with olive oil and balsamic vinegar (Aceto Balsamico). Decorate with basil leaves or any sprouts and microgreens.
-
 @ 28050c32:b88edee5
2024-04-18 15:13:15
@ 28050c32:b88edee5
2024-04-18 15:13:15Chef's notes
This super yummy and super easy to make eggplants are gonna leave you wanting more
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 2
Ingredients
- 2 eggplants 🍆
- 2 or 3 minced garlic cloves 🧄
- 1 finely minced onion 🧅
- 1 bell pepper, diced 🫑
- 2 carrots peeled and diced 🥕
- Salt and pepper to taste 🧂
- Vegan cheese optional 🧀
- Olive oil 🫒
Directions
- Prepare the Eggplants: Wash the eggplants and cut them lengthwise into halves. Scrap the inside of the eggplants and then chop them. Reserve. Place the empty eggplants on your a baking sheet lined with parchment paper.
- Prepare the Filling: In a skillet, heat some of olive oil over medium heat. Add the minced garlic and chopped onion, and sauté until fragrant and translucent, about 2-3 minutes. Add the diced bell pepper and cherry carrots along with the inside of the eggplants to the skillet, and cook for another 5 minutes or until they soften slightly. Season the vegetable mixture with salt and pepper. Stir well to combine.
- Assemble the Dish: Place a some of the vegetable mixture on each eggplant slice.
- Optional: If desired, sliced some vegan cheese over the top of each eggplant with vegetables.
- Bake: Put the baking sheet to the oven and bake for 30 minutes at 180 C, or until the cheese is golden brown and crispy.
- Serve: Once baked, remove from the oven and let cool slightly before serving. Enjoy your delicious vegan baked eggplants!
-
 @ 1bc70a01:24f6a411
2024-04-17 15:38:30
@ 1bc70a01:24f6a411
2024-04-17 15:38:30Chef's notes
This recipe was created by Alton Brown and was originally featured on Food Network. I usually double the ingredients for a family of 4. You can fridge the batter over night for a smoother consistency but it's not totally necessary. I really like this recipe because it doesn't use any fancy ingredients. Great sweet or savory! My kids like to top with jam, honey, strawberries and bananas. I'm more of an eggs and bacon type of guy. You can stuff literally any breakfast ingredient into these things. If you want less crispy edges (kids sometimes don't like crispy edges) - coat the pan with butter more often.
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 20 min
- 🍽️ Servings: 2
Ingredients
- 2 eggs
- 3/4 cup milk
- 1/2 cup water
- 1 cup flour
- 3 tablespoons melted butter
- Butter for coating the pan
Directions
- Mix all of the ingredients together in a large bowl using a wisk until the flower particles are mostly broken up
- Heat the pan and coat it with butter.
- Pour a ladle-full of batter into the pan and tilt the pan around until totally covered with batter.
- Wait until the crepe starts forming some small bubbles, then flip.
- Cook for an additional 20-30 seconds
-
 @ be9bb3c6:8f7b599a
2024-04-17 02:08:11
@ be9bb3c6:8f7b599a
2024-04-17 02:08:11Chef's notes
Gnocchi does NOT need potatoes.
Details
- ⏲️ Prep time: 40 mins
- 🍳 Cook time: 3 mins
Ingredients
- 600 g fresh buffalo ricotta cheese
- zest of 1 lemon
- 10 ml lemon juice
- 15 g fine sea salt
- pinch fresh cracked black pepper
- 2 whole free range eggs
- 2 free range egg yolks
- 15 g grated best parmesan
- 150 g flour, sifted
- 1/2 bunch flat-leaf parsley, chopped
Directions
- Put the ricotta cheese in a strainer with cheesecloth or clean kitchen towel and let drain in the fridge for 2 hours.
- Once ready, mix together all the ingredients except for the flour. Be sure to mix until completely incorporated.
- Once mixed, add the flour and mix until just incorporated, being sure not to overwork the dough. Allow the dough to rest for two hours.
-
 @ 19dcd48f:97947bcd
2024-04-14 15:42:18
@ 19dcd48f:97947bcd
2024-04-14 15:42:18Chef's notes
*Note: I soak my seeds for about an hour and blend them to get the smoothest and firmest pudding texture, but this pudding will set up by itself overnight in the refrigerator without blending and ends up being more porridge-like. I also use PlantJym Tiramisu flavored protein powder, which I think is sweet enough, but pop in an added sweetener of choice if you need it.
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 0 min
- 🍽️ Servings: 4
Ingredients
- 8 tbsp Chia Seeds
- 4 scoops preferred protein powder
- 4 cups preferred plant milk
Directions
- Mix protein powder into plant milk and add chia seeds to soak (optional). Blend mixture and refrigerate overnight.
- Top with favorite toppings such as hemp-seed hearts, fruits, chocolate chips, nuts, etc. Enjoy.
-
 @ 8d5bed4d:f974dea5
2024-04-14 14:36:22
@ 8d5bed4d:f974dea5
2024-04-14 14:36:22Chef's notes
Bramboraky pancakes are pan-fried in pork lard or vegetable oil.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 2-3 minutes
- 🍽️ Servings: 4
Ingredients
- Peel raw potatoes and shred them.
- Strain the excess liquid.
- Pour the hot milk over potatoes
- Add flour, egg, salt, pressed garlic and majroram. Stir well.
Directions
- Peel the raw potatoes and shred them finely with a box grater.
- Transfer the grated potatoes to a colander and squeeze out the excess liquid they released.
- Put the squeezed potatoes in a bowl, pour hot milk over them. Add an egg, flour, pressed garlic, dried marjoram, and salt. Stir. The potato batter should have a semi-fluid consistency.
- Take a non-stick frying pan, put the lard or vegetable oil in it (1-2 Tablespoons pro pancake), and heat it up to medium heat. Always mix the potato batter evenly before frying, scoop one ladleful and carefully dump it into the middle of the preheated pan. Using a flat spoon, spread the dough into a 1/4 inch (5-6 mm) thick pancake about 8 inches (20 cm) in diameter.
- Fry each bramborak for about 2-3 minutes on both sides. Flip with a flat spatula once the edges start to turn golden.
- Stack up the finished bramboraky on a plate. If you want to save calories and make the pancakes healthier, line them with paper towels to soak up excess fat.
- Serve the bramboraky pancakes immediately while still warm, when they are beautifully crispy around the edges. The colder the pancake, the chewier it will be
-
 @ 8d5bed4d:f974dea5
2024-04-14 14:32:05
@ 8d5bed4d:f974dea5
2024-04-14 14:32:05Chef's notes
Bramboraky pancakes are pan-fried in pork lard or vegetable oil.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 2-3 minutes
- 🍽️ Servings: 4
Ingredients
- Peel raw potatoes and shred them.
- Strain the excess liquid.
- Pour the hot milk over potatoes
- Add flour, egg, salt, pressed garlic and majroram. Stir well.
Directions
- Peel the raw potatoes and shred them finely with a box grater.
- Transfer the grated potatoes to a colander and squeeze out the excess liquid they released.
- Put the squeezed potatoes in a bowl, pour hot milk over them. Add an egg, flour, pressed garlic, dried marjoram, and salt. Stir. The potato batter should have a semi-fluid consistency.
- Take a non-stick frying pan, put the lard or vegetable oil in it (1-2 Tablespoons pro pancake), and heat it up to medium heat. Always mix the potato batter evenly before frying, scoop one ladleful and carefully dump it into the middle of the preheated pan. Using a flat spoon, spread the dough into a 1/4 inch (5-6 mm) thick pancake about 8 inches (20 cm) in diameter.
- Fry each bramborak for about 2-3 minutes on both sides. Flip with a flat spatula once the edges start to turn golden.
- Stack up the finished bramboraky on a plate. If you want to save calories and make the pancakes healthier, line them with paper towels to soak up excess fat.
- Serve the bramboraky pancakes immediately while still warm, when they are beautifully crispy around the edges. The colder the pancake, the chewier it will be
-
 @ 6ad3e2a3:c90b7740
2024-04-12 23:42:51
@ 6ad3e2a3:c90b7740
2024-04-12 23:42:51After unsuccessfully trying to orange-pill* a friend the other day, I realized the problem: for a lot of successful, worldly people the notion you can get something for nothing is anathema. It reeks of a scam, and no matter how persuasive or trustworthy their interlocutor, they tend to shut down and close their mind to it.
*To “orange-pill” means to get someone to buy — or at least see the value proposition of — bitcoin.
Put differently, smart people understand risk and reward are inseparable. If someone is telling you this is the opportunity of a lifetime, it probably isn’t. To the extent it has the upside purported, its risk of ruin is no doubt commensurate.
But that is only the case when there is information symmetry. If I tell you the stock market is going to the moon next year, you know there are smart people on the other side of that bet, or else it would be at the moon already. And because they have access to the same information I do, any large way-out-of-the-money call option on the S&P500 is at grave risk of not cashing in. Hence you would be wise to ignore my advice.
But what about when one party to the trade has information the other lacks? For example, Nancy Pelosi has a net worth north of $100 million on her comparatively meager congressional salary, due in large part to trading on insider information. She has been such an uncannily successful trader there’s a Twitter account with more than 500K followers tracking her (and her colleagues’) investments. Surely in the case of her trades, the risk was not commensurate with the rewards.
Another obvious example from history was the Dutch buying the island of Manhattan from the natives for a bunch of tools and beads. The risk and reward to the Dutch were not remotely commensurate due to information asymmetry.
All the time, people cultivate expertise in pricing antiques, collectibles and other items that give them a significant advantage over most market participants and sever the strict relationship between risk and reward that exists in more information-symmetrical environments.
But what all three of those scenarios have in common is the information providing the advantage is essentially a secret. The natives presumably didn’t know how common and easily replaced the tools and trinkets for which they traded Manhattan were. The public doesn’t have access to the information on which Congress is trading. And the layperson lacks the in-depth, niche knowledge of the expert art or antiques dealer.
But the Bitcoin-for-dollars trade happens to be asymmetrical, despite the information being wholly public and hidden in plain sight. The asymmetry comes from one party being sufficiently naive and curious and the other too savvy and close-minded. As a result, many who got into Bitcoin earliest were financial outsiders, novices, nerds and cypherpunks rather than Wall-Street professionals who are accustomed to getting the jump.
The media, gatekept and controlled by the same factions who run the banking system, have only exacerbated this asymmetry, spreading unfounded fear, uncertainty and doubt about bitcoin specifically (It boils the oceans! It’s backed by nothing!) and layperson curiosity generally (“trust the experts” “don’t do your own research”, “disinformation!”) As a result, not only are the professional insiders out, but also those who rely on their expertise to assess investment opportunities, which is why many of the savviest and smartest people are ironically the most difficult to convince.
. . .
Maybe this is what's meant by “The meek shall inherit the earth,” if we use curious and open-minded to stand in for “meek.” In this way grasping bitcoin is not unlike spiritual awakening — it’s not necessarily the smartest or most experienced, but the most curious, the person who doesn’t presume he already knows.
-
 @ 246052c3:1e4b3d16
2024-04-08 23:52:47
@ 246052c3:1e4b3d16
2024-04-08 23:52:47Details
- 🍳 Cook time: 8 hours
- 🍽️ Servings: 20
Ingredients
- Raw milk
- Yogurt (organic if possible)
Directions
- Pour 1/2 gallon of raw milk into instant pot
- Add at least 2 tablespoons yogurt for active cultures (organic preferably)
- Close instant pot lid and set setting to yogurt
- Cook for 8 hours