-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nostr - Notes and Other Stuff Transmitted by Relays
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works.
Very short summary of how it works, if you don't plan to read anything else:
Everybody runs a client. It can be a native client, a web client, etc. To publish something, you write a post, sign it with your key and send it to multiple relays (servers hosted by someone else, or yourself). To get updates from other people, you ask multiple relays if they know anything about these other people. Anyone can run a relay. A relay is very simple and dumb. It does nothing besides accepting posts from some people and forwarding to others. Relays don't have to be trusted. Signatures are verified on the client side.
This is needed because other solutions are broken:
The problem with Twitter
- Twitter has ads;
- Twitter uses bizarre techniques to keep you addicted;
- Twitter doesn't show an actual historical feed from people you follow;
- Twitter bans people;
- Twitter shadowbans people.
- Twitter has a lot of spam.
The problem with Mastodon and similar programs
- User identities are attached to domain names controlled by third-parties;
- Server owners can ban you, just like Twitter; Server owners can also block other servers;
- Migration between servers is an afterthought and can only be accomplished if servers cooperate. It doesn't work in an adversarial environment (all followers are lost);
- There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Then, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out;
- Since servers tend to be run amateurishly, they are often abandoned after a while — which is effectively the same as banning everybody;
- It doesn't make sense to have a ton of servers if updates from every server will have to be painfully pushed (and saved!) to a ton of other servers. This point is exacerbated by the fact that servers tend to exist in huge numbers, therefore more data has to be passed to more places more often;
- For the specific example of video sharing, ActivityPub enthusiasts realized it would be completely impossible to transmit video from server to server the way text notes are, so they decided to keep the video hosted only from the single instance where it was posted to, which is similar to the Nostr approach.
The problem with SSB (Secure Scuttlebutt)
- It doesn't have many problems. I think it's great. In fact, I was going to use it as a basis for this, but
- its protocol is too complicated because it wasn't thought about being an open protocol at all. It was just written in JavaScript in probably a quick way to solve a specific problem and grew from that, therefore it has weird and unnecessary quirks like signing a JSON string which must strictly follow the rules of ECMA-262 6th Edition;
- It insists on having a chain of updates from a single user, which feels unnecessary to me and something that adds bloat and rigidity to the thing — each server/user needs to store all the chain of posts to be sure the new one is valid. Why? (Maybe they have a good reason);
- It is not as simple as Nostr, as it was primarily made for P2P syncing, with "pubs" being an afterthought;
- Still, it may be worth considering using SSB instead of this custom protocol and just adapting it to the client-relay server model, because reusing a standard is always better than trying to get people in a new one.
The problem with other solutions that require everybody to run their own server
- They require everybody to run their own server;
- Sometimes people can still be censored in these because domain names can be censored.
How does Nostr work?
- There are two components: clients and relays. Each user runs a client. Anyone can run a relay.
- Every user is identified by a public key. Every post is signed. Every client validates these signatures.
- Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn't talk to another relay, only directly to users.
- For example, to "follow" someone a user just instructs their client to query the relays it knows for posts from that public key.
- On startup, a client queries data from all relays it knows for all users it follows (for example, all updates from the last day), then displays that data to the user chronologically.
- A "post" can contain any kind of structured data, but the most used ones are going to find their way into the standard so all clients and relays can handle them seamlessly.
How does it solve the problems the networks above can't?
- Users getting banned and servers being closed
- A relay can block a user from publishing anything there, but that has no effect on them as they can still publish to other relays. Since users are identified by a public key, they don't lose their identities and their follower base when they get banned.
- Instead of requiring users to manually type new relay addresses (although this should also be supported), whenever someone you're following posts a server recommendation, the client should automatically add that to the list of relays it will query.
- If someone is using a relay to publish their data but wants to migrate to another one, they can publish a server recommendation to that previous relay and go;
- If someone gets banned from many relays such that they can't get their server recommendations broadcasted, they may still let some close friends know through other means with which relay they are publishing now. Then, these close friends can publish server recommendations to that new server, and slowly, the old follower base of the banned user will begin finding their posts again from the new relay.
-
All of the above is valid too for when a relay ceases its operations.
-
Censorship-resistance
- Each user can publish their updates to any number of relays.
-
A relay can charge a fee (the negotiation of that fee is outside of the protocol for now) from users to publish there, which ensures censorship-resistance (there will always be some Russian server willing to take your money in exchange for serving your posts).
-
Spam
-
If spam is a concern for a relay, it can require payment for publication or some other form of authentication, such as an email address or phone, and associate these internally with a pubkey that then gets to publish to that relay — or other anti-spam techniques, like hashcash or captchas. If a relay is being used as a spam vector, it can easily be unlisted by clients, which can continue to fetch updates from other relays.
-
Data storage
- For the network to stay healthy, there is no need for hundreds of active relays. In fact, it can work just fine with just a handful, given the fact that new relays can be created and spread through the network easily in case the existing relays start misbehaving. Therefore, the amount of data storage required, in general, is relatively less than Mastodon or similar software.
-
Or considering a different outcome: one in which there exist hundreds of niche relays run by amateurs, each relaying updates from a small group of users. The architecture scales just as well: data is sent from users to a single server, and from that server directly to the users who will consume that. It doesn't have to be stored by anyone else. In this situation, it is not a big burden for any single server to process updates from others, and having amateur servers is not a problem.
-
Video and other heavy content
-
It's easy for a relay to reject large content, or to charge for accepting and hosting large content. When information and incentives are clear, it's easy for the market forces to solve the problem.
-
Techniques to trick the user
- Each client can decide how to best show posts to users, so there is always the option of just consuming what you want in the manner you want — from using an AI to decide the order of the updates you'll see to just reading them in chronological order.
FAQ
- This is very simple. Why hasn't anyone done it before?
I don't know, but I imagine it has to do with the fact that people making social networks are either companies wanting to make money or P2P activists who want to make a thing completely without servers. They both fail to see the specific mix of both worlds that Nostr uses.
- How do I find people to follow?
First, you must know them and get their public key somehow, either by asking or by seeing it referenced somewhere. Once you're inside a Nostr social network you'll be able to see them interacting with other people and then you can also start following and interacting with these others.
- How do I find relays? What happens if I'm not connected to the same relays someone else is?
You won't be able to communicate with that person. But there are hints on events that can be used so that your client software (or you, manually) knows how to connect to the other person's relay and interact with them. There are other ideas on how to solve this too in the future but we can't ever promise perfect reachability, no protocol can.
- Can I know how many people are following me?
No, but you can get some estimates if relays cooperate in an extra-protocol way.
- What incentive is there for people to run relays?
The question is misleading. It assumes that relays are free dumb pipes that exist such that people can move data around through them. In this case yes, the incentives would not exist. This in fact could be said of DHT nodes in all other p2p network stacks: what incentive is there for people to run DHT nodes?
- Nostr enables you to move between server relays or use multiple relays but if these relays are just on AWS or Azure what’s the difference?
There are literally thousands of VPS providers scattered all around the globe today, there is not only AWS or Azure. AWS or Azure are exactly the providers used by single centralized service providers that need a lot of scale, and even then not just these two. For smaller relay servers any VPS will do the job very well.
-
 @ 3f770d65:7a745b24
2023-07-31 12:53:38
@ 3f770d65:7a745b24
2023-07-31 12:53:38The following is a collection of Tweets posted on Twitter that documented my entire heart surgery process, from finding out I had an issue, through the surgery, and finally throughout my recovery process. If Elon decides to remove old and unpaid content, I do not want this part of my life to vanish from the Internet. At the time, it was extremely important for my mental health to talk about this whole process and it was therapeutic in my recovery process, reading all of the responses as all of Bitcoin Twitter was behind my success. Thank you all of your kind words, love, and support during this whole process. May my Tweets live on through nostr.
...
Nov 28, 2021 I had open heart surgery 4 days before my 3rd b-day. I've led a healthy & active life since then, zero issues. I had an echocardiogram last week. The results were not good. Heart valve replacement may be in my near future. I am freaking the fuck out. I'll know more on Dec 6th. 😫
Dec 6, 2021 Update: I had my cardiologist appointment today. He said to not worry for now and continue to exercise and live life. In 3 months get another echo done. He doesn't believe the previous other results since I have zero symptoms and wants to do his own interpretation.
Dec 6, 2021 He said if the other results were correct, I may need valve replacement in 6 months to 3 years. However, he doesn't believe the local hospital's results as I said above. He can't form an opinion just yet. He said not to worry over and over again. For now, I'm staying positive!
Mar 7, 2022 Well, it's been three months. I had my follow up this morning. I have severe pulmonic regurgitation. I now need to speak with a specialist and see what my options are for surgery. Neat. 😭
Apr 12, 2022 Well, it looks like I'll need full open heart surgery again to replace my pulmonic valve. Bonus: I'll be part pig. So, I have that going for me. I was assuming that if I had to have this done it would be much less invasive, so I'm not overly impressed at the moment. 🫤
May 11, 2022 Today I had to get a CT scan of my heart in preparation for the May 27th surgery. All went well. I have no other heart issues. It's looking like I'll be in the hospital for 4-7 days, depending on how fast I recover. I should be fully 100% recovered by the end of August. ❤️
May 20, 2022 My grandfather with me 39 years ago, days after my open heart surgery. He taught me to hunt, fish, golf, and I'm sure taught me a thing or two about drinking beer and partying. 😂 He was a great man. He won't physically be with me next Friday, but I'm sure he'll be watching over.
May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 27, 2022 LET'S GO! I am alive and doing well. I was on a ventilator until 8pm. That was horrible. I will read all of the comments that you all posted on Katie's updates. Now I need to rest. They want to get me up and walk at 11pm. 🤯 I love you all and your support had helped so much 🧡🧡
May 28, 2022 The amount of love, compassion, caring, and appreciation from everyone blows my mind. Thanks for all of your comments and DMs. The positivity though all is this has helped me get through dark times and now it's helping me get through pain. You are helping me immensely. 🤯❤️🧡💪
May 28, 2022 Today has been a rough day. Lots of chest pain when breathing. But, I apparently am doing something right, because I have been upgraded to a regular room. No more ICU for this guy! My ICU nurse told my new nurse that I'm strong. ❤️💪🔥
May 29, 2022 Using this to document my journey. Last night was not good at all. I had tachycardia and AFib for hours. It was scary as fuck having my heart beat the way it was at 160bpm. They gave me new medication to bring it down and stop the AFib irregular heartbeat. It's now at 101.
May 29, 2022 I was very scared. Katie was able to come and stay the night with me and be my personal care nurse. That made me feel much better having her here with me. Hopefully the meds continue to do what they're supposed to. Fuck. Anyways, I may not Tweet much today. Love you all. ❤️
May 30, 2022 Today has mostly been a great day progress wise. I ate a lot. I've walked more today than I have previously. My doctor told me I might be going home tomorrow, it all depends on what happens with my last drainage tube. Fingers crossed that it's draining properly now. 💪❤️
May 31, 2022 Morning walk crushed. Breakfast crushed. Feeling stronger. My drainage tube is still draining so we'll see what the surgeon says, but I probably won't be coming home today according to my nurse. It may be another day. Better to be safe. I'm feeling good though. Let's go! 💪💪❤️❤️
Jun 1, 2022 Today's plans: Crush morning walk, crush breakfast, CRUSH MY LAST X-RAY AND HEAD THE HELL HOME! Fingers crossed. 🤞🤞❤️❤️💪💪
Jun 1, 2022 On my morning walk I went into a slight AFib. The nurse and PA said since I hadn't had my morning meds to control that yet, that that could be the cause. They're going to increase meds and monitor me for another 24 hours. That sucks, but again, I'd rather be safe. Ugh.
Jun 2, 2022 GM! I miss my kids. I miss wearing normal clothes. I miss my house. I miss my doggy. I better go home today or I guess I'll just keep working to get well enough to go home. 😂 I'm still progressing forward. I have a chest x-ray scheduled later this morning. Fingers crossed.
Jun 2, 2022 I JUST GOT CLEARED TO HEAD HOME AFTER LUNCH. FUCK YEAH. LET'S GOOOOOO💪💪💪
Jun 2, 2022 I am home! I have some family that needs some loving. Enjoy the rest of your day!
Jun 4, 2022 Last night I slept in bed thanks to a reclining pillow, the first night our living room chair. I was so happy to sleep in my own bed. I walked around our yard about 9 times yesterday. My goal is to do that plus a little more every day. I'm still in a lot of pain, but meds help.
Jun 4, 2022 I still have a long way to go recovery wise, but having Katie and the kids here helping me along the way makes it easier and gives me a reason to keep pushing forward through this. Thanks again for all of your past and future support. You all are fantastic.
Jun 6, 2022 My wife went back to work today. My son and daughter are in charge of taking care of me. My kids are fantastic. They made me breakfast already and helped me check all of my vitals. My daughter really shines here. She's such a little nurse and caretaker. ❤️❤️
Jun 6, 2022 I'm still in pain, but I'm not in as much pain as I was a couple days ago. I'm walking around a little better and a little more every day. I really hate just sitting around and not doing anything, but it's hard to do much else besides watch TV. I am enjoying my patio though. 💪
Jun 16, 2022 It's been a while. It's time to update this thread! I am doing great, IMO. I have lots of energy. I feel great. I can do a lot more than I previously could. I still have a limited range of motion due to my sternum being broken and still healing. i.e. I can't wash my back or legs.
Jun 16, 2022 I started back to work yesterday. I was cleared to do 20 hours this week by my doctor and I'm hoping to be cleared full time next week. I work from home, so if I can sit in front of a TV, I can sit in front of a computer, right?
Jun 16, 2022 My home nurses have been absolutely fantastic.😂 My kids make me breakfast every morning. And I could not have done any of this without my rock star wife. Words can't describe how much she's done for me throughout all of this. I am looking forward to continuing to improve. ♥️
Jun 16, 2022 You all have been absolutely wonderful through all of this too. I appreciate all of your love, support, and check-ins. Seriously. It means more than you know.
I have a check-up at the end of the month to make sure all is well. I'll update again in a couple weeks after that appt.
Jun 28, 2022 My doctor said everything looks great. He said it doesn't look like I had open heart surgery a month ago.💪 He said I have zero restrictions and that I can resume normal life. I can drive and I can go out on my boat! ❤️❤️❤️ I'm so happy right now! 🔥🚀
Jul 15, 2022 I started cardiac rehab this week. After 2 sessions the nurse said I'm on "Week 4" already. She doesn't believe with my initial intake stress test if I'll really be able to improve on it that much. 🤣 TL;DR I am a rock star and kicking ass. Feeling great. Life's great. 😍
Aug 28, 2022 Yesterday was 3 months since my open heart surgery. I'm going great! I'd guess essentially back to normal. My sternum is still not fully healed, that'll take more time, but energy and capability are basically back to what I was like last summer. I'm very happy with the results.
Aug 28, 2022 I'm very happy to be able to exercise daily, go boating on the weekends AND swim and paddleboard. I was annoyed that I couldn't do these things a month ago. I had a cardiologist appt. two weeks ago. He said he hopes the valve lasts me the rest of my life and to see him in a year.
Aug 28, 2022 As a final post to this thread, I want to thank each and every one of you again that commented, liked, shared and DMed me throughout all of this. The love and support from Twitter and the #Bitcoin community was unfathomable. You all made a difference in my life and my recovery.❤️
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ 3f770d65:7a745b24
2023-02-21 01:55:08
@ 3f770d65:7a745b24
2023-02-21 01:55:08Habla is a new blogging platform that's based on Nostr. Or as various Nostr client developers like to call it:
"A way to get Derek Ross to stop sending walls of text".
You can edit posts, which is very nice.
-
 @ 0176967e:1e6f471e
2024-07-21 11:28:18
@ 0176967e:1e6f471e
2024-07-21 11:28:18Čo nám prinášajú exotické protokoly ako Nostr, Cashu alebo Reticulum? Šifrovanie, podpisovanie, peer to peer komunikáciu, nové spôsoby šírenia a odmeňovania obsahu.
Ukážeme si kúl appky, ako sa dajú jednotlivé siete prepájať a ako spolu súvisia.
-
 @ 0176967e:1e6f471e
2024-07-21 11:24:21
@ 0176967e:1e6f471e
2024-07-21 11:24:21Podnikanie je jazyk s "crystal clear" pravidlami. Inštrumentalisti vidia podnikanie staticky, a toto videnie prenášajú na spoločnosť. Preto nás spoločnosť vníma často negatívne. Skutoční podnikatelia sú však "komunikátori".
Jozef Martiniak je zakladateľ AUSEKON - Institute of Austrian School of Economics
-
 @ 0176967e:1e6f471e
2024-07-21 11:20:40
@ 0176967e:1e6f471e
2024-07-21 11:20:40Ako sa snažím praktizovať LunarPunk bez budovania opcionality "odchodom" do zahraničia. Nie každý je ochotný alebo schopný meniť "miesto", ako však v takom prípade minimalizovať interakciu so štátom? Nie návod, skôr postrehy z bežného života.
-
 @ dd664d5e:5633d319
2024-07-21 10:46:33
@ dd664d5e:5633d319
2024-07-21 10:46:33My suggestion for scaling up and staying humble
The original protocol design was "good enough for now"
When Nostr was invented and got started with developing implementations, the Original Devs (ODs) were convinced this was going to be big... maybe... someday... hopefully.
But, whatever they did at the moment should definitely scale up a bit and be a bit flexible, to attract innovators and keep up the momentum. So, they designed the protocol to be open and left the specifications a bit vague and very high-level, so that nobody was forced into a particular implementation, in order to adhere to the spec. And they put the specs into a GitHub repository and managed them by a committee of collaborators, who were generally open to changes to the specs, including breaking changes.
That was smart. And it was "good enough for now"... back then. After all, Nostr (and the associated wiki and modular article specs) hadn't been invented, yet, so they couldn't write the protocol in the protocol before the protocol existed. They're good, but not that good.
What they specifically wrote, into the Nostr Protocol was:
To promote interoperability, we standards (sic) that everybody can follow, and we need them to define a single way of doing each thing without ever hurting backwards-compatibility, and for that purpose there is no way around getting everybody to agree on the same thing and keep a centralized index of these standards...
Standards may emerge in two ways: the first way is that someone starts doing something, then others copy it; the second way is that someone has an idea of a new standard that could benefit multiple clients and the protocol in general without breaking backwards-compatibility and the principle of having a single way of doing things, then they write that idea and submit it to this repository, other interested parties read it and give their feedback, then once most people reasonably agree we codify that in a NIP which client and relay developers that are interested in the feature can proceed to implement.
I disagree with this statement.
I don't disagree with what they meant, or what they wanted, I disagree with what they specifically wrote.
Standards (defined as prose specifications) are not the only -- or even best -- way to ensure interoperability or to check for backwards-compatibility. And, as they later note, basing a protocol off of implementations is arguably worse (but faster) than using specifications, as implementations have a life of their own and are sometimes simply shoddy or buggy, their content eventually differs from what ends up in the final standard, or there are soon multiple implementations covering the same spec "in theory", but not in practice, so that their events are incompatible.
And then the inevitable, heated discussion begins: * Which implementation is the Real Standard™? * Who controls the Real Standard™? * How is the Real Standard™ spec supposed to be written? * Does everything have to be in the same file type or markup language? If not, how can we ensure compatibility? * What is realistic content for the data files? * Is the Real Standard™ including all of the information needed to ensure interoperability, but not anything more, without reducing innovation and artificially forcing consensus by encouraging copy-paste or forking of product code?
There is a third way: write the test first
We actually do not need standards to define a single way of doing each thing. A test is another way, and I think it is the best (i.e. the most-efficient and most-effective) way.
Specifically, I think we can borrow the simple behavior-driven design (BDD) language called Gherkin (or something similar), which is used to write dynamic specifications: i.e. implementations that test adherence to a set of rules, rather than an implementation that uses the rules to perform some task for an end user.
Gherkin simply allows you to create standard scenarios and test data and write the tests up in a way that can be performed manually or through automation. For example ( source ):

(For a concrete example of such a TDD Protocol for Nostr, please see the nostr-voliere repo from nostr:npub1axy65mspxl2j5sgweky6uk0h4klmp00vj7rtjxquxure2j6vlf5smh6ukq .)
This really is better
This TDD Protocol design would have some downsides and some upsides, of course, like any change.
Downsides
- You can't write a TDD spec by yourself unless you understand basic software functionality, how to define an acceptance test, and can formulate a use case or user story.
- The specs will be more informative and agnostic, but also longer and more detailed.
- Someone will have to propose concrete test data (i.e. a complete json event) and spec interlinking will be explicit, rather than writing "...", "etc.", or "sorta like in that other section/doc, but not really" all over the place.
- The specs will tend to focus on positive cases, and leave off error-handling or most edge-cases, so developers can't use them to replace unit tests or other verification of their product.
Upsides
- The specs will be concrete and clear, in a type of pseudocode, while leaving the actual implementation of any feature up to the individual developer, who uses the spec.
- The specs will be orderly and uniquely-identifiable, and can have hierarchy and granularity (major and minor tests, optional tests, tests only under certain conditions, etc.)
- Deciding whether changes to the spec are breaking changes to the protocol would be simple to determine: Does the previous test still pass?
- Specs will always be final, they will simply be versioned and become more or less defined over time, as the tests are adjusted.
- Product developers will feel less like they "own" particular specs, since their implementation is actually what they own and the two remain permanently separate.
- Developers can create an implementation list, defining specific tests in specific versions, that they adhere to. This makes it more transparent, what their product actually does, and lowers their own documentation burden.
- Rather than stalking the NIPs for changes, or worrying about what some other implementation someplace has built, developers can just pull the repo and try running the relevant tests.
- Each product developer can test the spec by trying to perform or automate/run it, and request changes to ensure testability, raising the quality of the spec review process.
This is already a lot to think about, so I'm just going to end this here. Thank you for reading.
-
 @ 41fa852b:af7b7706
2024-07-21 10:17:44
@ 41fa852b:af7b7706
2024-07-21 10:17:44"I'm the diamond in the dirt, that ain't been found / I'm the underground king and I ain't been crowned." -50 Cent
Welcome back, folks! I hope you’re all soaking up the sunshine while it lasts and gearing up for some holiday adventures with family and friends.
Usually, meetup attendance tends to dip this time of year as many of us head out of town.
If you’re travelling within the UK this week, check the list below to see what’s on offer.
Upcoming Bitcoin Meetups
Happening this week...
- Bitcoin Nottingham: The July Bitcoin Nottingham Meetup date for your diary is Wednesday 24th July at 6:30 PM at Carlton Town Football Club.
- Manchester Bitcoin: On the 25th it’s Manchesters turn. Join them at The Smithfield Market Tavern, 7pm.
- The Satoshi Society - Southampton: Join a friendly group of bitcoiners at The Maritimo Lounge, Ocean Village on Friday 26th July for food and a Bitcoin chat.
- Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit.
- Bitcoin East: Join Bitcoin East in Bury St. Edmunds on July 28th, 11am at Procopio’s Pantry. All welcome, Bitcoiners and anyone else curious about Bitcoin.
New Businesses Accepting Bitcoin
- The Ayurvedic Retreat: A residential, bespoke, three to five-day retreat for relaxation, managing stress and detoxing mind, body and soul. Includes daily four-handed Ayurvedic massage, life-coaching, yoga and meditation. Now accepting bitcoin.
- Express Boilers: Boiler repair & central heating, plumbing services company based in Teddington, Middlesex. Covering Richmond Borough, east and west Moseley, Kingston and Walton on Thames. Now accepting bitcoin.
Upcoming Special Events
- Tooting Market Bitcoin Event: Get your tickets now for this free event. The lineup is looking good with some great talks throughout the evening and plenty of merchants now accepting bitcoin. Guest speakers included Ray Youssef, Jordan Walker, Nicholas Gregory, Hashley Giles, Bridge2Bitcoin and many more. It all starts at 6 PM on the 7th August.
- Bitcoin - The change you've been waiting for: Mark your calendars for August 31 at 10:30 am for "The Change You’ve Been Waiting For" at Glasgow University Union. This seminar, costing £10, focuses on Bitcoin's transformative potential. With Bitcoin impacting individuals and businesses globally, understanding it is crucial. Guest speaker Allen Farrington will share his expertise, making this event perfect for both seasoned investors and the Bitcoin-curious. Don't miss this opportunity to explore how Bitcoin can shape your financial future.
Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We’re here to support you every step of the way. We’ve assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Share your ideas on how we can enhance this newsletter.
- Consider subscribing on Substack
Get out and support the meetups where you can and stay tuned for more updates next week!
Simon.
-
 @ 58edc6ae:e070cfa5
2024-07-21 09:27:10
@ 58edc6ae:e070cfa5
2024-07-21 09:27:10The Bitcoin journey is a long one, and books are an essential part of it. Here is a chronological record of my Bitcoin literary education—the first fifty books.
I’m sharing this list because it did the trick for me. This particular sequence first got me intrigued, then opened my eyes, converted me into a maximalist, and led me to explore areas I had never visited before. Maybe it will do the same for you or someone you know.

If you think there’s a must-read book that’s not on my list, please recommend it to me (skip other book suggestions).
- The Evolution of Everything (Chapter: The Evolution of Money), Matt Ridley
- Bitcoin Standard, Saifedean Ammous
- Inventing Bitcoin: The Technology Behind The First Truly Scarce and Decentralized Money Explained, Yan Pritzker
- Denationalisation of Money, Fridrich A. Hayek
- Bitcoin Clarity, Kiara Bickers
- Bitcoin, Sovereignty Through Mathematics, Knut Svanholm
- The Internet of Money, Part 1, Andreas Antonopolous
- Layered Money, Nick Bhatia
- Human Action, Ludwig von Mises
- The Fiat Standard, Saifedean Ammous
- Cryptography, The key to digital security, How it works and why it matters, Keith Martin
- Blocksize War, Jonathan Bier
- The Bullish Case For Bitcoin, Vijay Boyapati
- Bitcoin i Blockchain. Narodziny kryptowalut, Mateusz Lubiński, Mateusz Wiatr
- The Internet of Money, Part 2, Andreas Antonopolous
- The Internet of Money, Part 3, Andreas Antonopolous
- Kryptowaluty dla zabieganych, Michał Zajda
- Bitcoin, Hard Money You Can’t Fuck With, Jason A. WIlliams
- 21 Lessons. What I’ve Learned From Falling Down the Bitcoin Rabbit Hole, Gigi
- The Price of Tomorrow, Jeff Booth
- Everything Divided by 21 Million, Knut Svanholm
- Bitcoin jako przedmiot stosunków cywilnoprawnych, Marcin Michna
- Independence Reimagined, Knut Svanholm
- Softwar, Jason P. Lowery
- America’s Great Depression, Murray Rothbard
- The Ethics of Money Production, Jörg Guido Hülsmann
- Omnipotent Government: The Rise of the Total State and Total War, Ludwig von Mises
- Principles of Economics, Saifedean Ammous
- Praxeology, Knut Svanholm
- Broken Money, Lyn Alden
- Sovereign Individual, James Dale Davidson, Lord William Rees-Mogg
- When Money Dies, Adam Fergusson
- Anatomy of the State, Murray Rothbard
- Fraudcoin, Rune Ostgard
- Check Your Financial Privilege, Alex Gladstein
- Gradually, Then Suddenly: A Framework for Understanding Bitcoin as Money, Parker A. Lewis
- Bitcoin Is Venice, Allen Farrington, Sacha Meyers
- A Progressive’s Case for Bitcoin: A Path Toward a More Just, Equitable, and Peaceful World, C. Jason Maier
- Fiat Ruins Everything, Jimmy Song
- Fossil Future, Alex Epstein
- 21 Futures: Tales from the Timechain, 21 different authors
- The Fourth Turning, William Strauss, Neil Howe
- Fiat Food: Why Inflation Destroyed Our Health and How Bitcoin Fixes It, Matthew Lysiak
- The Genesis Book, Aaron va Wirdum
- The Book of Satoshi, Phil Champagne
- Bitcoin Billionaires, Ben Mezrich
- Hidden Repression, Alex Gladstein
- Atlas Shrugged, Ayn Rand
- Luna is a Harsh Mistress, Robert Heinlein
- Man, Economy and State. A Treatise on Economic Principles, Murray Rothbard
bookstr
-
 @ b2caa9b3:9eab0fb5
2024-07-21 09:18:45
@ b2caa9b3:9eab0fb5
2024-07-21 09:18:45Well, folks, I’m starting to see the light at the end of this data tunnel. After a seemingly endless 12-hour format, my stubborn SSD finally decided to cooperate. With that hurdle cleared, I dove headfirst into the world of data migration.

Last night was a whirlwind of activity: changing to a new bed, data copying, and a valiant battle against a pesky mosquito net. I managed to keep my sanity intact until around 2 am, when sleep finally claimed me. But let's not forget the culinary highlight of the evening: Wali Maharagwe - a simple yet satisfying rice and bean dish that hit the spot perfectly. Check out this photo, it's a local favorite and incredibly affordable.
This morning, I woke up feeling not really refreshed and still tired, but ready to conquer the remaining data challenges. After a cold shower, quick breakfast and a chat with a fellow traveler, I’m back at it, transferring data from one SSD to another. Fingers crossed this one behaves itself!
One thing's for sure, the temperature has taken a drastic drop compared to the warmth of Mombasa. I'm grateful for my trusty fleece as I shiver my way through the day. It's a stark contrast to the 27 degree Celsius I was enjoying just a short distance away.
So, while I continue my data wrangling, I hope you all are enjoying a relaxing Sunday. Stay tuned for more updates on my progress!

Online
If you'd like to show your appreciation, you can send a tip via the Lightning Network to rubenstorm@sats.mobi. (QR code available in the image)
-
 @ f0aca767:dce3306e
2024-07-21 03:13:43
@ f0aca767:dce3306e
2024-07-21 03:13:43This is going to be a sort of long one (or maybe it won't?), because I have a lot of thoughts as a tech and social media enthusiast, and some of those thoughts have to do with how I feel about the direction that social media is moving in. How I feel about Mastodon, and Nostr, side-by-side, and what the biggest problems with Bluesky are.
So, let's jump right the heck in ...
Nostr, the misconceptions, and the truth
I recently wrote about Nostr, and its relayed protocol of user-owned identity that you can take ... wherever. I outlined a lot of thoughts and impressions I initially had, and then what I wrote went to Reddit, and then it found itself on Nostr. It got there entirely outside my own involvement. I posted to Mastodon, and almost nowhere else.
This inspired me to log back in, and set some things up (such as domain verification from one of a few domains I own), and then I explored a bit. I interacted with people, participated in some community events that came up spontaneously, and really dug into the extreme multitude of features that run across the Nostr network.
Let's just say, I was pretty floored, and some of the impressions I had were wrong. Such as thinking that a place that is more centered around the idea of lacking censorship, or robust moderation, must be filled with toxic, horrible trolls. In the couple of days I've been messing with the network, I think I've muted like one person who said some off-the-wall shit in my notifications.
But ... I think Nostr has nasty people just in the same way Twitter, Threads, and Mastodon do. They exist, and they always will, no matter where you go. Suffice to say, I learned a lot about what decentralization was, and now is. I was given an article by user nostr:npub1njst6azswskk5gp3ns8r6nr8nj0qg65acu8gaa2u9yz7yszjxs9s6k7fqx that gave some really in-depth information about the emergence of decentralization--Scuttlebutt, ActivityPub, and then ATProtocol, and Nostr.
I'm not going to lie, I originally started writing this as a hit piece against Bluesky, thinking their ATProtocol was just a riff of what Nostr was doing. But, apparently, both ATP and Nostr were developed independent of each other, and mostly without any knowledge of one or the other. I think that's ... actually pretty wild, and strange.
On the topic of decentralization, which is something I feel is integral to the future of the internet, I now understand Mastodon to be a place of islands, and decentralization that occurs in a way that's more like isolated communities talking to other isolated communities. Like the latter half of The Walking Dead.
In a way, it's decentralization, the half-measure. The full-measure, that comes with some iffy trade-offs some may not like, is Nostr, and ATProtocol.
You take your identity, your thoughts, your posts, and you move freely between pieces of software, and networks, and you lose nothing (this is nearly the direct opposite of Mastodon, where moving to a new server means burning everything you've ever posted, to the ground). And, honestly, I'm kind of starting to feel like that's how it should be. The downside, is that, on Nostr, you have a public key, and a secret key. Your secret key is something you use to log in and sign events coming from your account, and your public key is basically your identity. That's not the iffy part, though. The iffy part, is that people can use your public key to see all of your data except direct messages (which are encrypted).
Not entirely too scary, unless you're doing a lot of weird things on your account. But definitely something you should know if you decide that this is a journey you want to take, and you're not jaded from hearing about how much Jack Dorsey loved Nostr and it's Bitcoin affiliation (a lot of people across different platforms hold a lot of dislike for the man).
At this point, I'm less worried about the power consumption of BTC transactions, and have more shifted that focus to content farms from the likes of Microsoft and Nvidia buying up all the AI tech they can get their grubby little hands on.
That aside, I'm not writing this to blow smoke up the Bluesky developer's butts. I, in fact, am not favorable of Bluesky and there are some specific reasons for that. Maybe this spells their downfall, or maybe they'll be a tight-knit community that doesn't really expand all that much, forever.
Bluesky, the Apple of social media
Bluesky is a place that a couple million people call home (I think, last I saw, it was around 6 million or so). There's no algorithm, and much like Nostr, you own your identity. Except, for now, that's mostly tied to the website's central server.
Now, obviously, there are far less people populating Nostr, but Nostr and its relays are able, and are connected to both ActivityPub and Bluesky (just, not through ATProtocol).
Most of what you'll see on bsky.app are quite a few furries, an actually impressive population of Second Life users, and quite a lot of LGBTQ+ people. None of these things or communities are inherently bad. In fact, I think they're probably the only reason Bluesky is really alive at all, today.
My angst and negative feelings about the direction of Bluesky have nothing to do with the LGBTQ+ community, or any other community residing on the platform. The issues I mainly hold have to do with how far up their own asses the board and developers are, in regard to the platform, and its development over the past year or so. This is why I kind of think of them as the Apple of social media. And you might think, "Hey, don't you own like a billion pieces of Apple tech?"
Yeah, I do.
But this is more like if Apple skipped over having Steve Jobs and just went straight to some random guy who didn't know what he was doing. You know, like putting up a wall and locking out all potential users for a year, and keeping all new sign-ups under lock and key via exclusive codes. As you might imagine, having that walled-garden erected through six or seven different events where people were leaving Twitter in droves, very likely probably worked against the social network's best interest.
Mainly, because Threads came out of absolutely nowhere, and sucked up most of those users.
That's only half of the issue, though. The other part to all of this, is that the developers I see directly on Bluesky do not recognize or acknowledge this at all. Paul Frazee, whose influence goes back quite a bit further than Bluesky, posts as though it's the greatest platform ever made (maybe just because he's a developer for Bluesky). But the website, despite its six million some-odd users, feels almost completely dead.
Which is ridiculous, because, as I've said, Nostr has far less users than that, and it most definitely doesn't feel dead when you post.
Not to mention, we're over a year into Bluesky, and it still, more or less, is propped up to look, feel, and act just like Twitter did in 2014. ATProtocol, in this respect, still feels mostly like an afterthought that's inaccessible to most users.
Meanwhile, if you really like Nostr, you can get going with your own chunk of the network immediately, with about a page of install commands.
It's this mixture of grandiosity that emanates from Bluesky, and the blunder of keeping their doors closed through one exodus after another, that I think they've shot themselves in the feet so much that they now don't have feet. They have stumps.
But, if you've followed me all the way through this article, I think there's a way they can blow the doors open. But, then they'd have to sort of abandon their idea of the ATProtocol, and stop trying to be the center of social media they most definitely are not, and probably never will be. And, really, that's the final issue I have with Bluesky and the ATProtocol.
It feels like they're trying to do Nostr, but be corporate-owned. Bluesky doesn't feel like it's owned by the people, developed by the people, and run by the people. It feels like it's run by some suits, who give the impression that the people will have their freedom, as long as they say it's okay.
And that, my buddy ol' pal, just ain't okay.
The elephant and the ostrich
Which brings us squarely back to Mastodon, and Nostr. Both platforms have their own merits. Nostr is about controlling your own content, and what you see, and largely eschews censorship to a high degree. But everyone can see almost everything you do and are talking about, whenever they want. Mastodon, on the other hand, puts the tools into a user's hands to create a network, and build their own communities, while picking and choosing who those communities interact with. A network that ... encourages users to police everyone around them ... which is how we end up with tyrannical admins acting like they work in a prison, and they've just been promoted to Warden.
If only there were some way to take the best parts of both of these animals, and make them one.
An elephrich.
For now, though, I am at least pretty content to screw around with both while I feel around and see what sticks. In the age of corporate control and censorship so heavy that people can't even say "kill" or "suicide" any more (these are only two of the most egregious examples I can think of), I think it's healthy to explore your options, and cement your identity, and who you are online, before everything else we've come to know is lost completely.
If that's something you care about, at least.
-
 @ f0aca767:dce3306e
2024-07-21 03:11:21
@ f0aca767:dce3306e
2024-07-21 03:11:21Mastodon is obviously an already established and semi-well known social network--A user-owned network of communities. But one of the biggest issues I always see the corporate social media denizens talk about, is that the loss of content when moving instances (sometimes, you have to do this) is one of the biggest turn-offs. And that's definitely something I can attest to. If I were still on mastodon.social, from my humble posting-beginnings in 2017, I'd have a post history longer than five football fields and probably plenty to cringe at.
The question remains: Why haven't we been able to take this history with us ... if every instance you've ever been federated with is keeping that data.
What do I mean by this?
Every single time you post on Mastodon, your words get pushed out to other instances (servers), and in order for people to be able to read what you said, a copy of it is downloaded onto that server. It does this very quickly, so quick that it seems as though it happens in real-time. And, for all intents and purposes, I'm not inclined to believe that it doesn't.
If you've ever had an account on an instance that isn't mastodon.social, and you have a posting history, and you remember your username: Go over to mastodon.social, create a burner account, and then search up that username.
Yeah, you see that? Your entire body of posting-work is still there, even if you deleted your account, even if the instance you were on is long dead.
This is obviously not true for every server. Some choose to delete old content to make space for the new, but there are many Mastodon servers out there retaining everything ever posted, like mastodon.social.
But what point am I trying to get at here? As far as you're probably concerned, even if that data still exists, and your account, and instance does not, you can't access it, right? You can't reclaim everything you've said and done, and put it back where it belongs: Under your ownership.
Or, what if you could?
If you've been following my posting history on here in the past week, I've been screwing around with Nostr, and musing about Bluesky. Two networks using a similar protocol, that I feel are getting the idea of what I'm thinking of here, only about 75% correct.
Bluesky's problem, is that the protocol is owned by ... the owners. The corporation. Your keys report to their server, and in return, so does your content. A central server that has a lot of different keyholes.
Not really the optimal experience, because you can't create your own server, and build your own community, and survive if the main Bluesky datacenter goes out, right? The only thing you can do is host your own software that essentially just holds keys and content, and, as far as I know, all of that will be worthless if the devs ever go offline with the main server.
So then there's Nostr, where all of your data lives everywhere on the network, and as long as you have your keys, you can use any app that utilizes the protocol, and continually access everything you post, forever. You can't be banned, but you also can't block anyone. And any random stranger can take your public key from your profile, and view your entire everything (as I've said before).
I would say this is also not really that optimal. The idea is great, but the execution trades privacy for extreme versatility.
This brings us back to Mastodon, which is still in active development, still receiving new features, and ... well, kind of also only has the whole thing about 75% correct.
There's that last little bit we're missing here.
The user should have the option of a community, a personal community away from what's viewed to be the central Mastodon server and have their privacy, but, they should also be able to retain their posts, and their bookmarks, and their likes, and their lists, and everything else.
How do we accomplish this?
Keys.
The entire fediverse (for the most part) already has all of your content. So, if every user had a key tying them to that content, no matter where you're located, be it mastodon.social, or mkultra.monster, then you could just go wherever you want?
That's the idea, at least.
Your content becomes immortal, immutable, and that's the one missing puzzle piece to ActivityPub. I am 100% sure of this, and I don't know what the developer stance is on the topic of keys and immutable data, but I fully believe this is something that should be on their roadmap. Yes, storage space is a concern ... but holding onto the text content of a post is much easier, and smaller in size, than holding onto larger pieces of data (like photos, and videos). If you scrolled back to five years ago and found something you posted, but the only thing you could see was the text, would you be all that disappointed?
I guess that part is subjective.
Mastodon is already setup nearly identical to Nostr, except users live on the relays. So just ... add user generated keys to the mix, and I am 100% double-dippin' certain that most of the naysayers being spammed by engagement farming on Threads and Twitter will jump ship.
Mark my worms.
If it isn't. Well. They're making a huge mistake.
-
 @ 6c8c7979:15595f3e
2024-07-20 22:20:54
@ 6c8c7979:15595f3e
2024-07-20 22:20:54The Leaning Tower of Pisa (Italian: Torre Pendente di Pisa), or simply the Tower of Pisa (Italian: Torre di Pisa), is one of the world's most famous leaning buildings. It is located in the city of Pisa, in the Tuscany region of Italy, near the Pisa Cathedral in the Piazza dei Miracoli (Square of Miracles). The tower was originally built as the bell tower for the cathedral and was intended to visually attract people to it when construction began in 1173 AD. Its construction spanned 177 years.
$$Description of the Leaning Tower$$Externally, the Leaning Tower of Pisa appears as a cylindrical stone building with balconies and columns resting on a lower support base. The bell chamber is located at the top, and it lacks floors on the inside. The central part consists of a hollow cylinder, and the interior façade is built from intricately carved grey-white marble from the nearby city of San Giuliano. The exterior façade, however, is constructed from white-gray limestone brought from San Giuliano.
The tower leans towards the southeast at an angle of 3.99 degrees currently, down from its previous inclination of 5.5 degrees before restoration works conducted between 1990 and 2001. These restoration efforts involved horizontally shifting the tower's peak by approximately 3.66 meters from its center. Here are some specific specifications:
-
Height: 55.86 meters on the lower side and 56 meters on the higher side.
-
Weight: 14,200 tons.
-
Diameter: 15.54 meters at the base.
-
Circumference: 48.6 meters at the base.
-
Number of steps: Approximately 294 steps, with fewer at the seventh floor.
-
Wall thickness: About 4.9 meters at the base, and 2.48 meters at the belfry; tapering from bottom to top.
$$Story of the Leaning Tower's Construction $$Construction of the Leaning Tower of Pisa began in 1173 AD using white marble and was designed to reach a height of 56 meters. It was to be the third and final building in the Piazza dei Miracoli complex alongside the cathedral. After completing the third floor of the planned eight floors, construction halted due to observed instability in its foundations on the soft ground beneath. This pause coincided with wars among Italian city-states, leading to a century-long hiatus that inadvertently protected the tower from collapse by stabilizing its foundations.Engineer Giovanni di Simone resumed the tower's construction after this long hiatus. He sought to compensate for its lean by building additional upper floors longer on the shorter side. However, this exacerbated the tower's sinking into the soil below. Over subsequent centuries, various interruptions and proposed solutions aimed at addressing the lean finally saw its completion in the 14th century. Seven bells were subsequently installed, with the largest weighing 3,600 kilograms. In the early 20th century, the heaviest bell's operation was stopped due to concerns it could worsen the tower's tilt. Cement and other materials were injected into the foundations for reinforcement, but it continued to sink at a rate of 1.2 millimeters annually by the end of the 20th century. Consequently, it faced collapse risks, leading to closure in 1990 and cessation of all bell operations. Engineers undertook major projects to modify its tilt.
$$Current Stability of the Tower$$The tower's current stability owes to soil reinforcement beneath its foundations, allowing the tower to exert pressure on the ground below by providing spaces to redirect it opposite to its lean direction. This was part of a 1990 project led by engineer John Burland with 13 experts, costing over 30 million euros and lasting a decade. This project reopened the tower in 2001, marking the last of several efforts to maintain its stability. Adjustments to its tilt included shifting its center of gravity towards the bottom and north, placing weights to counter its southward tilt, using giant steel cables to tension the tower during project work, and adjusting its tilt after soil preparation. These cables were removed post-operation. Additionally, 60 cubic meters of mud were excavated from below the foundations through well-digging, then dried. Concrete columns were added underground, reaching 15 meters in length, to reinforce the foundations. Attempting to return the tower to its current state by pulling steel cables. The della helped
-
-
 @ 681ec9c0:fe78b4e7
2024-07-20 17:09:50
@ 681ec9c0:fe78b4e7
2024-07-20 17:09:50I was puzzled when Mike Masnick claimed that Bluesky is everything Jack wished for in a decentralized social network, being as it is highly centralized
I think the discrepancy comes down to different views of the role of decentralization encapsulated in this term, enshittification
"Even if most of the users of a decentralized system don’t know or care about the fact that it’s decentralized, the fact that the underlying protocol is that way and is set up such that others can build and provide services (algorithms, moderation services, interfaces, etc.) means that Bluesky itself has strong, built-in incentives to not enshittify the service.
In some ways, Bluesky is building in the natural antidote to the activist investors that so vexed Jack at Twitter. Bluesky can simply point out that going down the enshittification path of greater and greater user extraction/worsening service just opens up someone else to step in and provide a better competing service on the same protocol. Having it be on the same protocol removes the switching costs that centralized enshittified services rely on to keep users from leaving, allowing them to enshittify. The underlying protocol that Bluesky is built on is a kind of commitment device. The company (and, in large part, its CEO Jay) is going to face tremendous pressures to make Bluesky worse.
But by committing to an open protocol they’re building, it creates a world that makes it much harder to force the company down that path. That doesn’t mean there won’t still be difficult to impossible choices to make. Because there will be. But the protocol is still there."
https://www.techdirt.com/2024/05/13/bluesky-is-building-the-decentralized-social-media-jack-dorsey-wants-even-if-he-doesnt-realize-it/
And echoed by Bluesky CEO Jay Graber
"There will always be free options, and we can't enshittify the network with ads. This is where federation comes in. The fact that anyone can self-host and anyone can build on the software means that we'll never be able to degrade the user experience in a way where people want to leave."
https://web.archive.org/web/20240209161307/https://www.wired.com/story/bluesky-ceo-jay-graber-wont-enshittify-ads/
It all comes down to this
"the protocol is still there"
In this view of decentralization, being there is sufficient
Decentralization is this thing that can happen if needed
It's a safety valve operated by market forces
And where I think Jack and most of nostr would disagree is that market forces do not cater to the rights of individuals
Because one person being deplatformed is not a market demand
Especially for ATProto where decentralization is relatively expensive
To service deplatformed users would require building four servers, each one capable of ingesting the entire network: a Relay, a Labeller, an AppView and a Feed Generator
Decentralization by default is necessary for censorship resistance
Jack talked about censorship in the interview that formed the basis for Mike's article
"I know it's early, and Nostr is weird and hard to use, but if you truly believe in censorship resistance and free speech, you have to use the technologies that actually enable that, and defend your rights."
https://www.piratewires.com/p/interview-with-jack-dorsey-mike-solana
Mike's concerns over enshittification are highly valid
I would like to see Mike address Jack's concern for censorship resistance
I think that would help understanding
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-20 12:15:23
@ 5d4b6c8d:8a1c1ee3
2024-07-20 12:15:23Yesterday's edition https://stacker.news/items/613971/r/Undisciplined
-
- -
July 20, 2023 📅
📝
TOP POSTFrostsnap - Easy, personalized, secure bitcoin multisig for everyone
Link to https://frostsnap.com/introducing-frostsnap.html
6034 sats \ 19 comments \ @utxoclub \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/211668/r/Undisciplined?commentId=211676
Excerpt
Check out @super_testnet's super simple Superstore: https://stacker.news/items/167945
614 sats \ 0 replies \ @OneOneSeven
From Making a Store by @Undergotten in ~nostr
🏆
TOP STACKER2nd place @utxoclub (1st hiding, presumed @siggy47)
4679 stacked \ 1826 spent \ 1 post \ 5 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
48.4k stacked \ 0 revenue \ 55.2k spent \ 84 posts \ 166 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 20, 2022 📅
📝
TOP POSTI'm John Cantrell, entrepreneur, spiral grantee, and creator of Sensei. AMA
Excerpt
I'm @johncantrell97 and I've been working on and around Bitcoin for over a decade now. Most recently I've been working on Sensei as part of a Spiral grant.
112.7k sats \ 54 comments \ @JohnCantrell97 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/47509/r/Undisciplined?commentId=47521
Excerpt
"As of the end of Q2, we have converted approximately 75% of our Bitcoin purchases into fiat currency." Tesla didn't HODL. Or deploy as liquidity on Lightning to earn yield. Some just have to learn the hard way 🤷♂️ […]
329 sats \ 4 replies \ @holzapfelbaum
From Tesla Sells 75% of Bitcoin Holdings by @kr in ~bitcoin
🏆
TOP STACKER1st place @k00b
11.9k stacked \ 108.1k spent \ 4 posts \ 19 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
130.5k stacked \ 0 revenue \ 140k spent \ 113 posts \ 249 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 20, 2021 📅
📝
TOP POSTThe Bitcoin Miners banned from China are coming back online in force, bois!
Excerpt
https://bitinfocharts.com/comparison/bitcoin-hashrate.html Don't let your lettuce hands leave you with regrets. Stack those sats!
7 sats \ 3 comments \ @03cdf4abc3 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/428/r/Undisciplined?commentId=429
Excerpt
We're supposed to believe he's acting in the interest of the people to support of a censorship resistant platform for the exchange of value while not doing anything of note to further the interests of the people regarding a censorship resistant platform for exchanging words that he just happens to be the CEO of. They deplatformed the president of the united states.
1 sat \ 1 reply \ @03cdf4abc3
From Forget Elon Musk, Jack Dorsey Is the Hero Bitcoin Deserves for the Coming Years. by @shawnyeager in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
43 stacked \ 0 revenue \ 71 spent \ 9 posts \ 14 comments
originally posted at https://stacker.news/items/615090
-
-
 @ b2caa9b3:9eab0fb5
2024-07-20 10:35:42
@ b2caa9b3:9eab0fb5
2024-07-20 10:35:42Another day, another adventure in tech hell. Let’s start with last night. I was hoping to get some inspiration from an audio story before bed, but my brain decided to short-circuit. Woke up at 4 AM with headphones still on, no recollection of the story, and a general sense of disorientation.

Fast forward to this morning, I managed to escape the dorm for a quick shower and some much-needed coffee. Feeling somewhat human again, I tackled the beast that is my external SSD. It’s a 1TB behemoth that decided to be extra dramatic this morning. I’ve been staring at a “12 hours to go” message for what feels like an eternity. Who knew formatting a drive could be such a suspenseful ordeal?
This drive has been giving me trouble lately. It’s like it has a grudge or something. Constantly going into read-only mode, refusing to save large files. I think my 25,000 travel photos might be a bit too much for it. It’s not even that old! I switched from a heavy HDD to this thing for portability, and now it makes me trouble.
I’m hoping that once this formatting nightmare is over, I’ll have a happy, healthy SSD. I’ve decided to format it as exFAT, so at least it should be compatible with everything. But then I have two more drives to deal with. This is turning into a full-blown data relocation project. Why didn’t I do this when I was chilling in Kilifi?
Oh well, at least the weather is improving. Yesterday was the coldest day since I’ve been in Africa. Even my trusty fleece got some use.
Wish me luck on this digital odyssey!
-
 @ 0176967e:1e6f471e
2024-07-20 08:28:00
@ 0176967e:1e6f471e
2024-07-20 08:28:00Tento rok vás čaká workshop na tému "oranžové leto" s Jurajom Bednárom a Mariannou Sádeckou. Dozviete sa ako mení naše vnímanie skúsenosť s Bitcoinom, ako sa navigovať v dnešnom svete a odstrániť mentálnu hmlu spôsobenú fiat životom.
Na workshop je potrebný extra lístok (môžete si ho dokúpiť aj na mieste).
Pre viac informácií o oranžovom lete odporúčame pred workshopom vypočuťi si podcast na túto tému.
-
 @ 58537364:705b4b85
2024-07-20 07:00:00
@ 58537364:705b4b85
2024-07-20 07:00:00ปะภัสสะรามิทัง ภิกขะเว จิตตัง อาคันตุเกหิ อุปักกิเลเสหิ อุปักกิลิฏฐัง... ซึ่งแปลว่า ดูก่อนภิกษุทั้งหลาย จิตนี้เป็นประภัสสร แต่ว่าจิตนี้เศร้าหมอง เพราะอุปกิเลสที่จรเข้ามา ดังนี้.
ข้อที่พระองค์ตรัสว่า จิตนี้เป็นประภัสสรนั้น ท่านทั้งหลายจะต้องฟังให้ดี ๆ ในการที่พระองค์ทรงใช้คำว่า ประภัสสร ไม่ได้ใช้คำว่า บริสุทธิ์ ไม่ได้ใช้คำว่า หลุดพ้น หรือไม่ได้ใช้คำอะไร ๆ นอกไปจากคำว่า ประภัสสร.
ทีนี้คำว่า ประภัสสร ในภาษาบาลี มาเป็นภาษาไทย ก็ยังใช้ทับศัพท์ว่า ประภัสสร อยู่นั่นเอง คงจะเนื่องจาก ไม่สามารถที่จะแปลเป็นภาษาไทยคำใดให้เหมาะสม เราจึงต้องใช้คำว่า ประภัสสร ไปตามเดิม บางคนอาจจะไม่รู้ว่าประภัสสรนั้นเป็นอย่างไร ถ้าเช่นนั้น ก็จะต้องถือเอาตามตัวหนังสือนั้น ประภัสสร มาจากคำว่า ประภา สะระ ประภา คือ แสง สะระ เออ, แล่นออก หรือแล่นไป ประภัสสร จึงแปลว่า มีแสงแล่นออกไป เมื่อเราเห็นสิ่งใดมีแสงเป็นรัศมี แล่นออกไปรอบตัว โชติช่วงอยู่ดังนั้น นั่นแหละ คือ อาการที่เป็นประภัสสร หรือเรียกอีกอย่างหนึ่งว่า มีรัศมีซ่านออกไปรอบตัว เป็น เออ, แสงสว่าง อาการอย่างนี้ ตรงตามตัวหนังสือแท้ว่า ประภา สะระ หรือประภัสสร ที่ว่าจิตนี้เป็นประภัสสรนั้น หมายความว่า...มีแสง หรือเรืองแสงอยู่ในตัวมันเองโดยรอบด้าน ก็หมายความว่า มันไม่สกปรก มืดมัว เศร้าหมองแต่อย่างใด.
ทีนี้ ก็มีอุปกิเลสเกิดขึ้น มาจากเหตุปัจจัยอย่างใด อย่างหนึ่ง จากภายนอก เป็นเหมือนกับจรเข้ามา จากภายนอก เป็นอาคันตุกะ ทำให้จิตนั้นสูญเสียความเป็นประภัสสร เหมือนอย่างว่า เรามีเพชรเม็ดนึง แวววาว ส่องสว่างอยู่กลางแดด ถ้าเราเอาน้ำโคลนสาดเข้าไป รัศมีของเพชรนั้นมันก็ จะไม่ปรากฏ แต่แล้ว ท่านอย่าเพิ่งคิดไปว่ารัศมีนั้น สูญสิ้นไปเสียแล้ว ไม่ได้มีเหลืออยู่ ความจริงมันก็ต้องมีอยู่เท่าเดิม และตามเดิม หากแต่ว่าโคลนมันปิดบังเสีย ตาตามประสามนุษย์ก็มองไม่เห็น มันต้องมีตาพิเศษ ยิ่งกว่าตามนุษย์ จึงจะมองเห็นแสงเพชร ที่ทะลุโคลนออกมาได้ จิตนี้ก็เหมือนกัน เมื่อมีอุปกิเลสอย่างใด อย่างหนึ่ง นานาชนิด สรุปรวมเป็น...ความโลภ ความโกรธ ความหลง เกิดขึ้นแล้ว มันก็เป็นสิ่งปิดบังจิตนั้น ให้สูญเสียความเป็น ประภัสสร คือ ไม่ปรากฏแก่สายตา
ทีนี้ เราก็จะต้องคิดกันต่อไปว่า ทำอย่างไรจึงจะให้คงมี ความเป็นประภัสสร ปรากฏอยู่เป็นการ ถาวรได้ คำตอบง่าย ๆ ใคร ๆ พอจะมองเห็น ว่าก็กระทำอย่าให้มีกิเลสเกิดขึ้นก็แล้วกัน จิตนั้นก็เป็นประภัสสร อยู่ตลอดกาล เพราะฉะนั้น วิธีใดที่จะทำให้กิเลสไม่เกิดขึ้น แล้ววิธีนั้นแหละ คือ วิธีที่จะทำจิตนี้ ให้เป็น ประภัสสรตลอดกาล วิธีที่จะทำไม่ให้กิเลสเกิดขึ้นนั้น พระพุทธเจ้าท่านเรียกว่า อัฏฐังคิกมรรค คือ การกระทำที่ถูกต้องครบถ้วน ๘ ประการ รวมกันเป็นอันเดียวกันเรียกว่า มรรค มีความเห็นชอบ ความใฝ่ฝันชอบ พูดจาชอบ ทำการงานชอบ เลี้ยงชีวิตชอบ ความพากเพียรชอบ มีสติตั้งไว้ชอบ มีสมาธิตั้งไว้ชอบ เป็นความชอบ หรือความถูกต้องรวมกัน ๘ ประการ เป็นมรรคตั้งอยู่ดังนี้แล้ว เรียกว่า มีการเป็นอยู่ชอบ เมื่อมีการเป็นอยู่ชอบดังนี้แล้ว กิเลสใด ๆ ก็ไม่อาจจะเกิดขึ้นมาได้ จิตนั้นก็ไม่มีอะไร ที่จะมาหุ้มห่อ ให้สูญเสียความเป็นประภัสสร.
ด้วยเหตุที่พระศาสดาสัมมาสัมพุทธเจ้า ได้ทรงแสดง อัฏฐังคิกมรรค คือ..มรรคมีองค์ ๘ ประการนั้น ในวันอาสาฬหปุรณมีนี้ ด้วยเหตุเช่นนี้เอง อาตมาจึงกล่าวว่า วันอาสาฬหบูชานี้คือ วันที่พระองค์ทรงประกาศ วิธีทำจิตให้เป็นประภัสสรอยู่ตลอดกาล เป็นสมุจเฉทปหานแก่กิเลสทั้งปวง ถ้าเราสามารถทำจิต เป็นจิตประภัสสรได้ตลอดกาลแล้ว ปัญหามันก็ไม่มีเหลืออยู่เลย จงพยายามทำความเข้าใจในเรื่องนี้ ว่า....จิตประภัสสรนั้น มันเป็นส่วนจิต ส่วนกิเลสนั้น มันเป็นแต่เพียงสิ่งที่เกิดขึ้นกับจิต ไม่ใช่ตัวจิต.
ส่วนตัวจิตนั้น คงเป็นประภัสสรตามธรรมชาติ ส่วนกิเลสนั้นเป็นสิ่งที่เกิดกับจิต เขาเรียกว่า เจตสิก เจตสิกเกิดขึ้นอย่างไร ก็ปรุงแต่งจิตไปในลักษณะเช่นนั้น เมื่อสูญเสียความเป็นประภัสสร ก็คือ สูญเสียสภาวะเดิมของมัน ด้วยอำนาจที่เจตสิกอย่างใด อย่างหนึ่ง เข้าไปปรุงแต่ง นี้เจตสิกนี้เกิดขึ้น จากสิ่งแวดล้อม ก็ตั้งต้นจากภายนอก คือ รูป เสียง กลิ่น รส โผฏฐัพพะ ธรรมารมณ์ กระทบทางตา ทางหู ทางจมูก ทางลิ้น ทางกาย หรือซึมเข้าไปถึงใจ มันจึงเกิดการปรุงแต่ง เป็นสิ่งที่เรียกว่า เจตสิกได้ในที่สุด คือ กิเลสต่าง ๆ นั่นเอง.
-พุทธทาสภิกขุ
-
 @ a012dc82:6458a70d
2024-07-20 04:06:10
@ a012dc82:6458a70d
2024-07-20 04:06:10Table Of Content
-
Security
-
Convenience
-
Challenges and Limitations
-
Adaptation and Future Outlook
-
Conclusion
-
FAQ
Bitcoin and traditional banking are two different systems of financial services. Bitcoin is a decentralized digital currency, while traditional banking is a centralized financial institution. In this article, we will compare and contrast the security and convenience of both systems to determine which offers better value to users.
Security
Bitcoin operates on a decentralized network, which means that there is no central authority that controls transactions. Every transaction is recorded on a public ledger called the blockchain, making it transparent and tamper-proof. Bitcoin also uses cryptography to secure every transaction, making it nearly impossible to hack. The decentralized nature of Bitcoin and its cryptography make it more secure than traditional banking. Traditional banks are vulnerable to cyber attacks and fraud because they operate on a centralized system where a central authority controls transactions.
Convenience
Traditional banking offers a wide range of financial services, including ATM withdrawals, transfers, bill payments, loans, and credit cards. Banks also have physical branches where customers can speak to bank representatives and resolve their queries. However, traditional banking has its limitations. Customers have to comply with banks' working hours and locations, making it challenging to access their accounts during emergencies. Bank transactions are also subject to government regulations and third-party fees, making it expensive for customers to use their services.
Bitcoin, on the other hand, offers a high degree of convenience. It operates 24/7, making it accessible to customers anytime and anywhere in the world. Bitcoin transactions are also faster and cheaper compared to traditional banking. There are no third-party fees, making it more affordable for customers to use their services. However, Bitcoin still faces challenges in terms of adoption and acceptance. While more merchants are accepting Bitcoin as a mode of payment, it is still not widely accepted compared to traditional payment methods.
Challenges and Limitations
Bitcoin faces challenges in terms of adoption and acceptance. Some people are still skeptical about Bitcoin's value and stability, and some governments have imposed restrictions on its use. Additionally, Bitcoin's decentralized nature makes it difficult to regulate and control, which could lead to legal issues. On the other hand, traditional banking is subject to government regulations, which can sometimes limit their services and products. Compliance with these regulations can also increase costs, which are often passed on to customers.
Adaptation and Future Outlook
As technology continues to evolve, both Bitcoin and traditional banking will have to adapt to meet the changing needs of customers. Bitcoin is already being integrated into the financial system, and more merchants are accepting it as a mode of payment. Traditional banks are also adopting digital technologies to offer more convenience to customers. In the future, it is possible that the lines between Bitcoin and traditional banking will blur, as both systems adopt similar technologies and offer similar services.
Conclusion
In conclusion, Bitcoin and traditional banking offer different levels of security and convenience. Bitcoin's decentralized network and cryptography make it more secure than traditional banking, while traditional banking offers a wide range of financial services that are convenient for customers. The choice between Bitcoin and traditional banking ultimately depends on individual preferences and needs. However, as technology continues to evolve, it is likely that both systems will continue to adapt and offer better value to their users.
FAQ
What is traditional banking? Traditional banking is a centralized financial institution that offers a wide range of financial services, including loans, credit cards, and savings accounts.
Which is more secure, Bitcoin or traditional banking? Bitcoin is considered more secure than traditional banking because it operates on a decentralized network and uses cryptography to secure transactions.
Which is more convenient, Bitcoin or traditional banking? Bitcoin is more convenient in terms of accessibility and affordability, as it operates 24/7 and has no third-party fees. However, traditional banking offers a wide range of financial services and has physical branches for customer support.
What are the challenges faced by Bitcoin and traditional banking? Bitcoin faces challenges in terms of adoption and acceptance, while traditional banking is subject to government regulations and compliance issues.
How can Bitcoin and traditional banking adapt to meet the changing needs of customers? Both Bitcoin and traditional banking can adopt digital technologies to offer more convenience and value to their customers, while also adhering to regulatory compliance.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 862fda7e:02a8268b
2024-07-19 22:15:48
@ 862fda7e:02a8268b
2024-07-19 22:15:48 If you're a straight man jacking off to straight porn, you're gay. You're looking at another man's cock as a means to get gratification. Without that man's cock, your sexual experience wouldn't be fulfilled. You needing to see that man's cock in order to be sexually fulfilled is gay. I like men but even I can't stand looking at a dude's cock as he bangs a chick. It's a complete turn off. It ruins the entire thing. I don't want to see a man's body, I don't want to see his penis, I don't want to hear him. We have the technology to perfectly replicate a male penis and even automated thrusting. There's no need to continue to jack off to a real man's penis. I don't understand how any self respecting man can become erect while watching another man and his penis bang a hot chick. It's the defenition of cucking, but people will try to rationalize their way out of it. You're the cuck, you just don't have a camera panned on you showing your shame as you pound off.
If you're a straight man jacking off to straight porn, you're gay. You're looking at another man's cock as a means to get gratification. Without that man's cock, your sexual experience wouldn't be fulfilled. You needing to see that man's cock in order to be sexually fulfilled is gay. I like men but even I can't stand looking at a dude's cock as he bangs a chick. It's a complete turn off. It ruins the entire thing. I don't want to see a man's body, I don't want to see his penis, I don't want to hear him. We have the technology to perfectly replicate a male penis and even automated thrusting. There's no need to continue to jack off to a real man's penis. I don't understand how any self respecting man can become erect while watching another man and his penis bang a hot chick. It's the defenition of cucking, but people will try to rationalize their way out of it. You're the cuck, you just don't have a camera panned on you showing your shame as you pound off.This is why lesbian or solo porn is always superior. Two is better than one, so lesbian porn is by far the best. Lesbian porno has no cocks, or if it does, they're fake and not disgusting. You don't have to deal with looking at a dildo's asshole as it pounds a chick. Lesbian porn is weirdly underrated these days. I almost NEVER see anyone talk about it. It's always degenerate straight porn or overwhelmingly gay shit. You're way more likely to see gay and tranny garbage before lesbians. It's weird that lesbians are probably one of the lesser viewed categories these days. There's a lot of homos out there. Females are not threatening to a sexual situation. It's male penetration that is cuck-like behavior. With females it is all playful and sensual, always with room for more to play. The more cocks you have around a woman, the gayer and more homosexual it is. I especially can't wrap my mind around being turned on by cum shots on a woman. You're jacking off to not only a guy's cock, but his orgasm. You're jacking off to his load. And yes, I UNDERSTAND you're "jacking off to the woman getting cummed on", but you miss the point. You are jacking off to a man having an orgasm. It's never sat right with me, when I want to utilize "material", I want to get turned on by a woman. I feel more straight than straight men at times.
-
 @ b7274d28:c99628cb
2024-07-19 02:04:30
@ b7274d28:c99628cb
2024-07-19 02:04:30There is a general perception surrounding Bitcoin that it is prohibitively difficult to use for the average person. This perception can even infect those who are familiar with the various tools to optimally preserve their privacy, sovereignty, and security while using Bitcoin. After all, there’s 12 words you have to keep safe, or someone might steal all of your money. There’s all these tools like hardware wallets, software wallets, running a node, coin-join, and so much more you have to figure out in order to save and transact in Bitcoin securely and privately. Not to mention everything you have to learn if you want to use Lightning in a sovereign way, such as setting up channels, managing liquidity, learning LNURL, and setting up a domain so you can have a Lightning address.
All of these things can be intimidating for those considering whether they want to adopt Bitcoin, especially when comparing it with how little is needed for how most people interact with fiat today. As long as they have a debit card with their four-digit PIN memorized, and their password to their online banking, they have access to their money, and can use it virtually anywhere. Moreover, if they mess something up, they can just go to their financial institution and get a new debit card, or have their password reset. If a fraudster gets access to their account, their bank can often credit the money back to them and change their account information. The very real danger in Bitcoin of losing your funds and having no way of getting them back is scary for a lot of people.
One answer that Bitcoiners often give is, “Don’t worry. We’re still early and these tools will get easier to use as time goes on.” All that really tells someone is, “It might be better for you to wait and see if it actually does get easier.” Ease of use is a major factor for most people, and telling them that it is something they can expect from Bitcoin in the future just makes them more likely to wait until that hypothetical future arrives before they adopt it.
This perception of Bitcoin’s difficulty is really just a matter of perspective, though. Bitcoin looks incredibly difficult to use when you compare the way most people currently interact with fiat to using Bitcoin in a sovereign and private manner. This is comparing apples to oranges, though. If you instead compare apples to apples, looking at what it would take to use fiat digitally in a sovereign and private manner, suddenly Bitcoin is not more difficult than fiat, but less.
Someone may say, “Using fiat in a sovereign and private manner is easy! Just use cash.” Let’s explore that idea a bit, though. Cash can be very useful for transacting privately and without any intermediaries, but that usefulness diminishes when you want to transact with someone who is not within a short drive from you. As soon as you want to purchase something from a merchant in another state, or even the other side of the same state, a large amount of friction is added because you must travel to one another to complete the transaction. The farther you have to travel to transact in cash, the more convenient Bitcoin’s privacy tools begin to look. Indeed, the types of transactions that cash can easily make private and sovereign are exceptionally limited.
The next thing to consider is that cash may be convenient for transacting locally in a private manner, but it is much less convenient for storing your wealth privately and securely. If you want to store large sums of cash privately, a fire rated safe is much more expensive than memorizing 12 words, and is not impenetrable. Its only benefit is in making it take longer for fire to burn your cash or for a thief to break in and steal it, and that added length of time is measured in mere minutes. Meanwhile, the amount of time it would take someone to access the Bitcoin stored in 12 memorized words is measured in billions of years and the cost to secure it is just the transaction fee. Choosing to hide your cash instead may be less expensive than a safe, but then you will need to do some research on how best to protect it from the elements, which adds complexity, expense, and physical labor that is more cumbersome than rolling dice a few times and memorizing 12 words. Regardless of the method, securing cash is more difficult than securing Bitcoin and carries less assurances against theft or destruction. These shortcomings of storing wealth in cash become even more acute if you ever need to move that wealth, especially across any national border. Hiding thousands of dollars of cash in your luggage is much more difficult than carrying 12 words in your head that preserve your access to millions of sats.
Where there is no contest between the ease of using Bitcoin vs. fiat, though, is when you attempt to use fiat digitally in a private and/or sovereign manner. While privacy in Bitcoin is certainly an involved process, digital fiat is nearly impossible to use privately and is fraught with even worse “gotchas”. Forget about trying to use digital fiat in a sovereign manner. That actually is impossible. When people say using fiat is easier than using Bitcoin, they mean that using centralized, custodial, financial institutions that are surveilling your every transaction is easier than using self-custody, sovereign, Bitcoin. That’s a completely lopsided comparison, but it’s the only one that most people can imagine making, because they have never attempted to use digital fiat in a private manner in the first place.
What we should do is compare using Bitcoin in a sovereign and private way with using digital fiat in the same way, and likewise compare using Bitcoin via custodians to using digital fiat via banks and bank alternatives. When we do so, we find that not only is Bitcoin much easier to use privately than digital fiat, but it is impossible to use the latter in a sovereign manner and custodial Bitcoin is even easier to use than custodial fiat.
Anyone can get set up on a custodial wallet, with a Lightning Address, and be zapping people on Nostr, in less than 5 minutes. When was the last time you could do anything similar when setting up a bank account? Buying anything online with a custodial wallet has far less friction than using a debit or credit card. Scan the QR code and hit send. Done. No filling out card numbers, expiration dates, and billing addresses. Do you want to send money to your friend? All you need is their Lightning Address, and even if they are using a completely different custodian than you are, they receive the funds instantly and with virtually no fee. Custodial Bitcoin on Lightning already has better ease of use than any fiat custodian can provide, and it’s only improving.
Now, admittedly, the ideal in Bitcoin is to avoid custodians if you possibly can, and that is where things begin to get complicated, adding difficulty for the average user. However, avoiding custodians is not complicated or difficult with digital fiat, it’s entirely impossible. Most of us just never consider that fact when comparing the two. Instead we put the way we commonly use our fully centralized and surveilled custodial fiat up against the way we are told we ought to use Bitcoin to preserve our sovereignty and privacy, and we conclude Bitcoin is way more difficult, when that could not be farther from the truth. Sovereign, self-custody Bitcoin is far easier than sovereign, self-custody digital fiat, considering that the latter doesn’t even exist, and custodial Bitcoin is far easier than custodial fiat.
Then, when you add back into the equation the fact that fiat is constantly stealing from you, while Bitcoin is hard money that cannot have its supply arbitrarily inflated, the comparison is no contest. Bitcoin is far superior to fiat in every way! The tools to really take personal ownership of it without custodial risk may initially be intimidating, but they are not difficult if you take them on incrementally. You don’t need to dive immediately into hardware wallets, running a node, or managing the liquidity in your Lightning channels. You can start with a basic wallet app on your phone and your first few thousand sats and venture forth from there at your own pace. Bitcoin is hard money that won’t steal the value of your time and energy from you, but it’s not difficult to learn if you approach it like anything else new you have learned before. Take your time, and get comfortable with one new idea or tool every week or two, and before you know it you’ll be the one telling your friends and family just how easy it really is.
-
 @ 9fec72d5:f77f85b1
2024-07-18 19:38:47
@ 9fec72d5:f77f85b1
2024-07-18 19:38:47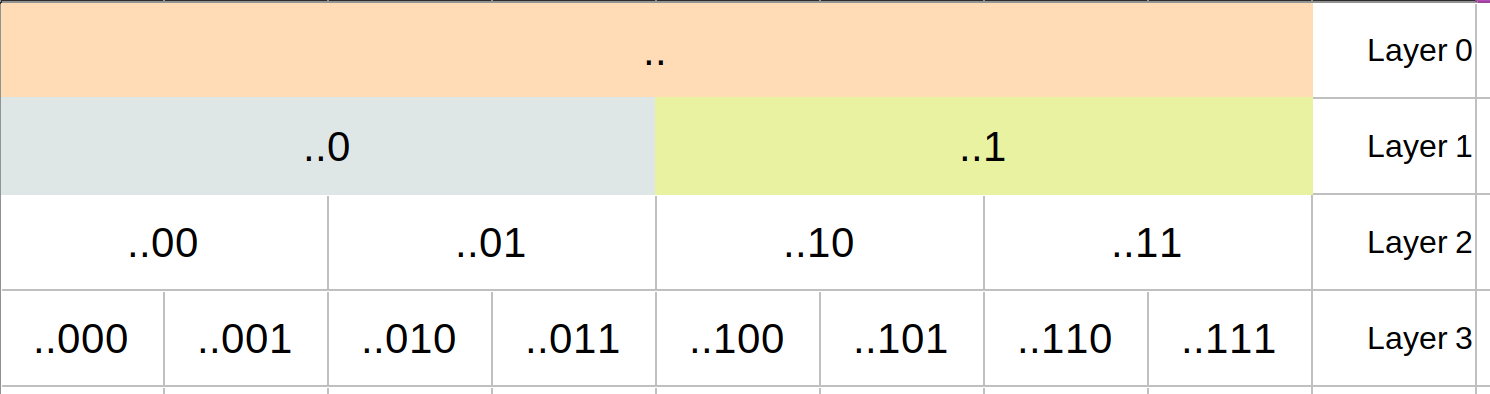
Each relay selects a branch from above and starts serving.
Some big machines in the top layers can handle more. Smaller machines in layers below are needed for decentralization and scalability.
Some top layer machines can act in sync only mode, efficiently distributing notes among layers.
Relay or the admin posts a special kind for advertisement of the relay:
```
{ "pubkey": "...pubkey of admin or the relay itself..", "kind": 30202, "tags": [ ["d","..10"], ["ip4","111.222.33.44:443","primary"], ["ip6","abc:def::443","backup"], ], ... } ```
The above example says this relay will handle the note id's that are ending with bits ..10. In this case it is going to handle about 1/4th of the network.
Primary way of reaching at this relay is through ip 111.222.33.44. There is also a backup server.
Clients can accept this advertisement based on web of trust or historical reliability of the npub. Or other npubs can measure the reliability of this relay and send reactions to this note. Clients then can see these reactions and rank these services.
Solves: - Possible future DNS ban issues: I don't know when or if DNS will be an issue for Nostr. The above design can help with the situation.
-
Scalability: If 1 million users join the network at the same time, the machines that are handling ".." i.e. all of the traffic may fail. But if the clients are using relays on other layers, the load will be efficiently distributed to many machines. The failure of layer 0 and 1 will not stop the network. Every layer can operate independently without the other layers (in theory).
-
Traffic efficiency: A client has to query many relays, depending on what it wants to do. It may choose to stay efficient (talk to top layers) on mobile traffic, or it may choose to help decentralization over wifi. The notes that match the queries will not be repeated as many times as current design, because relays will hold a portion of the network.
-
Storage efficiency: Relay operators can just save a part of the network that they are responsible for, on NVME drives. The rest of the network they can save in hard drives. In case of major failure the hard drives can still have a copy.
-
Speed: Since the notes will come from many different relays at the same time, there may be a slight speed increase.
-
Decentralization: If the top layer relays collude and start banning the other layers can still continue to serve notes.
-
Backup relay: In case a relay instance fails, users can find the backup server on the same note.
-
Zero down time migration: The ability to define a backup server allows zero down time migrations. An operator can set the primary to the new server and backup to the old server and do migration and continue without interruption.
-
Efficient sync among servers: A relay has to sync with 3 servers, 1 above, 2 below. But it can do 6 or 9 depending on how much reliability it wants.
-
Writing to logN relays: Clients has to write to logN relays (i.e. 1 relay in each layer), to effectively distribute their notes to everyone and also to help with decentralization.
-
-
 @ a619eb76:11d75935
2024-07-19 20:55:59
@ a619eb76:11d75935
2024-07-19 20:55:59I. Over-Population
In 1931, when Brave New World was being written, I was convinced that there was still plenty of time. The completely organized society, the scientific caste system, the abolition of free will by methodical conditioning, the servitude made acceptable by regular doses of chemically induced happiness, the orthodoxies drummed in by nightly courses of sleep-teaching -- these things were coming all right, but not in my time, not even in the time of my grandchildren. I forget the exact date of the events recorded in Brave New World; but it was somewhere in the sixth or seventh century A.F. (After Ford). We who were living in the second quarter of the twentieth century A.D. were the inhabitants, admittedly, of a gruesome kind of universe; but the nightmare of those depression years was radically different from the nightmare of the future, described in Brave New World. Ours was a nightmare of too little order; theirs, in the seventh century A.F., of too much. In the process of passing from one extreme to the other, there would be a long interval, so I imagined, during which the more fortunate third of the human race would make the best of both worlds -- the disorderly world of liberalism and the much too orderly Brave New World where perfect efficiency left no room for freedom or personal initiative.
Twenty-seven years later, in this third quarter of the twentieth century A.D., and long before the end of the first century A.F., I feel a good deal less optimistic than I did when I was writing Brave New World. The prophecies made in 1931 are coming true much sooner than I thought they would. The blessed interval between too little order and the nightmare of too much has not begun and shows no sign of beginning. In the West, it is true, individual men and women still enjoy a large measure of freedom. But even in those countries that have a tradition of democratic government, this freedom and even the desire for this freedom seem to be on the wane. In the rest of the world freedom for individuals has already gone, or is manifestly about to go. The nightmare of total organization, which I had situated in the seventh century After Ford, has emerged from the safe, remote future and is now awaiting us, just around the next corner. George Orwell's 1984 was a magnified projection into the future of a present that contained Stalinism and an immediate past that had witnessed the flowering of Nazism. Brave New World was written before the rise of Hitler to supreme power in Germany and when the Russian tyrant had not yet got into his stride. In 1931 systematic terrorism was not the obsessive contemporary fact which it had become in 1948, and the future dictatorship of my imaginary world was a good deal less brutal than the future dictatorship so brilliantly portrayed by Orwell. In the context of 1948, 1984 seemed dreadfully convincing. But tyrants, after all, are mortal and circumstances change. Recent developments in Russia and recent advances in science and technology have robbed Orwell's book of some of its gruesome verisimilitude. A nuclear war will, of course, make nonsense of everybody's predictions. But, assuming for the moment that the Great Powers can somehow refrain from destroying us, we can say that it now looks as though the odds were more in favor of something like Brave New World than of something like 1984.
In the light of what we have recently learned about animal behavior in general, and human behavior in particular, it has become clear that control through the punishment of undesirable behavior is less effective, in the long run, than control through the reinforcement of desirable behavior by rewards, and that government through terror works on the whole less well than government through the non-violent manipulation of the environment and of the thoughts and feelings of individual men, women and children. Punishment temporarily puts a stop to undesirable behavior, but does not permanently reduce the victim's tendency to indulge in it. Moreover, the psycho-physical by-products of punishment may be just as undesirable as the behavior for which an individual has been punished. Psychotherapy is largely concerned with the debilitating or anti-social consequences of past punishments.
The society described in 1984 is a society controlled almost exclusively by punishment and the fear of punishment. In the imaginary world of my own fable, pun- ishment is infrequent and generally mild. The nearly perfect control exercised by the government is achieved by systematic reinforcement of desirable behavior, by many kinds of nearly non-violent manipulation, both physical and psychological, and by genetic standardization. Babies in bottles and the centralized control of reproduction are not perhaps impossible; but it is quite clear that for a long time to come we shall remain a viviparous species breeding at random. For practical purposes genetic standardization may be ruled out. Societies will continue to be controlled post-natally -- by punishment, as in the past, and to an ever increasing extent by the more effective methods of reward and scientific manipulation.
In Russia the old-fashioned, 1984-style dictatorship of Stalin has begun to give way to a more up-to-date form of tyranny. In the upper levels of the Soviets' hierarchical society the reinforcement of desirable behavior has begun to replace the older methods of control through the punishment of undesirable behavior. Engineers and scientists, teachers and administrators, are handsomely paid for good work and so moderately taxed that they are under a constant incentive to do better and so be more highly rewarded. In certain areas they are at liberty to think and do more or less what they like. Punishment awaits them only when they stray beyond their prescribed limits into the realms of ideology and politics. It is because they have been granted a measure of professional freedom that Russian teachers, scientists and technicians have achieved such remarkable successes. Those who live near the base of the Soviet pyramid enjoy none of the privileges accorded to the lucky or specially gifted minority. Their wages are meager and they pay, in the form of high prices, a disproportionately large share of the taxes. The area in which they can do as they please is extremely restricted, and their rulers control them more by punishment and the threat of punishment than through non-violent manipulation or the reinforcement of desirable behavior by reward. The Soviet system combines elements of 1984 with elements that are prophetic of what went on among the higher castes in Brave New World.
Meanwhile impersonal forces over which we have almost no control seem to be pushing us all in the direction of the Brave New Worldian nightmare; and this impersonal pushing is being consciously accelerated by representatives of commercial and political organizations who have developed a number of new techniques for manipulating, in the interest of some minority, the thoughts and feelings of the masses. The techniques of manipulation will be discussed in later chapters. For the moment let us confine our attention to those impersonal forces which are now making the world so extremely unsafe for democracy, so very inhospitable to individual freedom. What are these forces? And why has the nightmare, which I had projected into the seventh century A.F., made so swift an advance in our direction? The answer to these questions must begin where the life of even the most highly civilized society has its beginnings -- on the level of biology. On the first Christmas Day the population of our planet was about two hundred and fifty millions -- less than half the population of modern China. Sixteen centuries later, when the Pilgrim Fathers landed at Plymouth Rock, human numbers had climbed to a little more than five hundred millions. By the time of the signing of the Declaration of Independence, world population had passed the seven hundred million mark. In 1931, when I was writing Brave New World, it stood at just under two billions. Today, only twenty-seven years later, there are two billion eight hundred million of us. And tomorrow -- what? Penicillin, DDT and clean water are cheap commodities, whose effects on public health are out of all proportion to their cost. Even the poorest government is rich enough to provide its subjects with a substantial measure of death control. Birth control is a very different matter. Death control is something which can be provided for a whole people by a few technicians working in the pay of a benevolent government. Birth control depends on the co-operation of an entire people. It must be practiced by countless individuals, from whom it demands more intelligence and will power than most of the world's teeming illiterates possess, and (where chemical or mechanical methods of contraception are used) an expenditure of more money than most of these millions can now afford. Moreover, there are nowhere any religious traditions in favor of unrestricted death, whereas religious and social traditions in favor of unrestricted reproduction are widespread. For all these reasons, death control is achieved very easily, birth control is achieved with great difficulty. Death rates have therefore fallen in recent years with startling suddenness. But birth rates have either remained at their old high level or, if they have fallen, have fallen very little and at a very slow rate. In consequence, human numbers are now increasing more rapidly than at any time in the history of the species. Moreover, the yearly increases are themselves increasing. They increase regularly, according to the rules of compound interest; and they also increase irregularly with every application, by a technologically backward society of the principles of Public Health. At the present time the annual increase in world population runs to about forty-three millions. This means that every four years mankind adds to its numbers the equivalent of the present population of the United States, every eight and a half years the equivalent of the present population of India. At the rate of increase prevailing between the birth of Christ and the death of Queen Elizabeth I, it took sixteen centuries for the population of the earth to double. At the present rate it will double in less than half a century. And this fantastically rapid doubling of our numbers will be taking place on a planet whose most desirable and productive areas are already densely populated, whose soils are being eroded by the frantic efforts of bad farmers to raise more food, and whose easily available mineral capital is being squandered with the reckless extravagance of a drunken sailor getting rid of his accumulated pay.
In the Brave New World of my fable, the problem of human numbers in their relation to natural resources had been effectively solved. An optimum figure for world population had been calculated and numbers were maintained at this figure (a little under two billions, if I remember rightly) generation after generation. In the real contemporary world, the population problem has not been solved. On the contrary it is becoming graver and more formidable with every passing year. It is against this grim biological background that all the political, economic, cultural and psychological dramas of our time are being played out. As the twentieth century wears on, as the new billions are added to the existing billions (there will be more than five and a half billions of us by the time my granddaughter is fifty), this biological background will advance, ever more insistently, ever more menacingly, toward the front and center of the historical stage. The problem of rapidly increasing numbers in relation to natural resources, to social stability and to the well-being of individuals -- this is now the central problem of mankind; and it will remain the central problem certainly for another century, and perhaps for several centuries thereafter. A new age is supposed to have begun on October 4, 1957. But actually, in the present context, all our exuberant post-Sputnik talk is irrelevant and even nonsensical. So far as the masses of mankind are concerned, the coming time will not be the Space Age; it will be the Age of Over-population. We can parody the words of the old song and ask,
Will the space that you're so rich in Light a fire in the kitchen, Or the little god of space turn the spit, spit, spit?
The answer, it is obvious, is in the negative. A settlement on the moon may be of some military advantage to the nation that does the settling. But it will do nothing whatever to make life more tolerable, during the fifty years that it will take our present population to double, for the earth's undernourished and proliferating billions. And even if, at some future date, emigration to Mars should become feasible, even if any con- siderable number of men and women were desperate enough to choose a new life under conditions comparable to those prevailing on a mountain twice as high as Mount Everest, what difference would that make? In the course of the last four centuries quite a number of people sailed from the Old World to the New. But neither their departure nor the returning flow of food and raw materials could solve the problems of the Old World. Similarly the shipping of a few surplus humans to Mars (at a cost, for transportation and development, of several million dollars a head) will do nothing to solve the problem of mounting population pressures on our own planet. Unsolved, that problem will render insoluble all our other problems. Worse still, it will create conditions in which individual freedom and the social decencies of the democratic way of life will become impossible, almost unthinkable. Not all dictatorships arise in the same way. There are many roads to Brave New World; but perhaps the straightest and the broadest of them is the road we are traveling today, the road that leads through gigantic numbers and accelerating increases. Let us briefly review the reasons for this close correlation between too many people, too rapidly multiplying, and the formulation of authoritarian philosophies, the rise of totalitarian systems of government.
As large and increasing numbers press more heavily upon available resources, the economic position of the society undergoing this ordeal becomes ever more precarious. This is especially true of those underdeveloped regions, where a sudden lowering of the death rate by means of DDT, penicillin and clean water has not been accompanied by a corresponding fall in the birth rate. In parts of Asia and in most of Central and South America populations are increasing so fast that they will double themselves in little more than twenty years. If the production of food and manufactured articles, of houses, schools and teachers, could be increased at a greater rate than human numbers, it would be possible to improve the wretched lot of those who live in these underdeveloped and over- populated countries. But unfortunately these countries lack not merely agricultural machinery and an industrial plant capable of turning out this machinery, but also the capital required to create such a plant. Capital is what is left over after the primary needs of a population have been satisfied. But the primary needs of most of the people in underdeveloped countries are never fully satisfied. At the end of each year almost nothing is left over, and there is therefore almost no capital available for creating the industrial and agricultural plant, by means of which the people's needs might be satisfied. Moreover, there is, in all these underdeveloped countries, a serious shortage of the trained manpower without which a modern industrial and agricultural plant cannot be operated. The present educational facilities are inadequate; so are the resources, financial and cultural, for improving the existing facilities as fast as the situation demands. Meanwhile the population of some of these underdeveloped countries is increasing at the rate of 3 per cent per annum.
Their tragic situation is discussed in an important book, published in 1957 -- The Next Hundred Years, by Professors Harrison Brown, James Bonner and John Weir of the California Institute of Technology. How is mankind coping with the problem of rapidly increasing numbers? Not very successfully. "The evidence suggests rather strongly that in most underdeveloped countries the lot of the average individual has worsened appreciably in the last half century. People have become more poorly fed. There are fewer available goods per person. And practically every attempt to improve the situation has been nullified by the relentless pressure of continued population growth." Whenever the economic life of a nation becomes precarious, the central government is forced to assume additional responsibilities for the general welfare. It must work out elaborate plans for dealing with a critical situation; it must impose ever greater restrictions upon the activities of its subjects; and if, as is very likely, worsening economic conditions result in political unrest, or open rebellion, the central government must intervene to preserve public order and its own authority. More and more power is thus concentrated in the hands of the executives and their bureaucratic managers. But the nature of power is such that even those who have not sought it, but have had it forced upon them, tend to acquire a taste for more. "Lead us not into temptation," we pray -- and with good reason; for when human beings are tempted too enticingly or too long, they generally yield. A democratic constitution is a device for preventing the local rulers from yielding to those particularly dangerous temptations that arise when too much power is concentrated in too few hands. Such a constitution works pretty well where, as in Britain or the United States, there is a traditional respect for constitutional procedures. Where the republican or limited monarchical tradition is weak, the best of constitutions will not prevent ambitious politicians from succumbing with glee and gusto to the temptations of power. And in any country where numbers have begun to press heavily upon available resources, these temptations cannot fail to arise. Over-population leads to economic insecurity and social unrest. Unrest and insecurity lead to more control by central governments and an increase of their power. In the absence of a constitutional tradition, this increased power will probably be exercised in a dictatorial fashion. Even if Communism had never been invented, this would be likely to happen. But Communism has been invented. Given this fact, the probability of over-population leading through unrest to dictatorship becomes a virtual certainty. It is a pretty safe bet that, twenty years from now, all the world's over-populated and underdeveloped countries will be under some form of totalitarian rule -- probably by the Communist party.
How will this development affect the over-populated, but highly industrialized and still democratic countries of Europe? If the newly formed dictatorships were hostile to them, and if the normal flow of raw materials from the underdeveloped countries were deliberately interrupted, the nations of the West would find themselves in a very bad way indeed. Their industrial system would break down, and the highly developed technology, which up till now has permitted them to sustain a population much greater than that which could be supported by locally available resources, would no longer protect them against the consequences of having too many people in too small a territory. If this should happen, the enormous powers forced by unfavorable conditions upon central govern- ments may come to be used in the spirit of totalitarian dictatorship. The United States is not at present an over-populated country. If, however, the population continues to increase at the present rate (which is higher than that of India's increase, though happily a good deal lower than the rate now current in Mexico or Guatemala), the problem of numbers in relation to available resources might well become troublesome by the beginning of the twenty-first century. For the moment overpopulation is not a direct threat to the personal freedom of Americans. It remains, however, an indirect threat, a menace at one remove. If over-population should drive the underdeveloped countries into totalitarianism, and if these new dictatorships should ally themselves with Russia, then the military position of the United States would become less secure and the preparations for defense and retaliation would have to be intensified. But liberty, as we all know, cannot flourish in a country that is permanently on a war footing, or even a near-war footing. Permanent crisis justifies permanent control of everybody and everything by the agencies of the central government. And permanent crisis is what we have to expect in a world in which over-population is producing a state of things, in which dictatorship under Communist auspices becomes almost inevitable.
-
 @ 6c8c7979:15595f3e
2024-07-19 20:33:54
@ 6c8c7979:15595f3e
2024-07-19 20:33:54It's one of Granada's most famous landmarks and considered one of the greatest architectural palaces built by the Nasrid rulers of Spanish Granada in the 13th century AD, following the Islamic-Andalusian style, serving as a fortress for defending their city. Despite being built nearly 800 years ago, the Alhambra Palace remains an architectural marvel of exquisite beauty. So, discover with us some astonishing facts about it.

$$It took over 150 years to build$$Prince Abu Abdullah Muhammad I, also known as "Al-Ghalib Billah," the founder of the Nasrid Dynasty in Granada, ordered the construction of the Alhambra Palace between 1238 and 1273 AD. While initial work on its fortified walls and thirteen tall towers began in 1238, the complete construction of the site lasted over 150 years due to additions and modifications by subsequent Nasrid rulers during their reigns.

$$Its name, "Alhambra," has several possible origins$$Built on the elevated hill of "Sabika" near the Darro River, the origin of its name is debated. Some suggest it stems from the reddish color of the stones used in its construction or the red-tinged soil in the area. Others attribute it to the name "Al-Red," by which the rulers of Granada were known. Another theory links its name to the "Red City," named for the color of its other citadels.

$$The palace has withstood wars and earthquakes$$From the outside, the Alhambra Palace still astonishes with its preserved architectural grandeur, despite being over 800 years old. It resisted attacks by the French army during the early 19th century invasion of Spain and has endured numerous earthquakes due to its location in a region prone to seismic activity.

$$Legend of the "Gate of Justice" and the end of the world$$Builders of the palace believed so strongly in its exceptional construction and advanced techniques that they spread the idea that if enemies ever opened the "Gate of Justice" – the main gateway of the palace – it would signal the end of the world. The "Gate of Justice" remains a significant symbol of the Alhambra, featuring a sculpted hand on its cornerstone and a key placed beside it. Legend says the hand and key were positioned high up so that only the worthy could reach them, potentially becoming the new ruler of Granada and owner of the Alhambra Palace.

-
 @ 1739d937:3e3136ef
2024-07-19 20:16:01
@ 1739d937:3e3136ef
2024-07-19 20:16:01This is the fourth in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
The dependency train continues to roll. This week I was in touch with the maintainers of both OpenMLS and the hkpe-rs library and have pushed my changes forward in both areas. I've also gotten closer to understanding the wire format and relay requirements for the NIP I'm working on.
To be honest, the progress feels pretty slow at the moment but I've seen this story often enough to know that I'm on the right track. To be clear, my goal here is do this right and make it as easy as possible for Nostr devs to implement MLS based messaging across all of Nostr. That necessarily requires ensuring that all the implementation libraries support the right pieces and that our NIP is clean and well thought through (no one likes a shed full of bikes).
HPKE-RS
My PR to add support for secp256k1 is moving. I've been adding tests this week and fixing a few issues. Once this is merged, I'll update my
secp256k1-based library as well. One unfortunate roadblock has been a lack of solid test vectors - this has eaten some time.OpenMLS Nostr Crypto
I had a short call with the OpenMLS maintainer team this week and was able to clarify what I'm trying to do and how they see it fitting in best. I was also able to get a better idea about how clients will need to process incoming messages. One interesting highlight: Messages have to be processed in the right order. Otherwise it's impossible to keep the ratchet tree in the correct state. My left-curve solution to this for now is to use both created at (as a dumb first pass at sorting) + a hash of the previous message content. This will give Nostr clients a simple way to double check that they have the messages in the correct order before they attempt to process them. Unfortunatley, this doesn't do a good job accounting for messages that are missing. My guess is that this isn't going to be a major issue, but I won't have a clear idea until there is a working Nostr relay based demo.
The next steps in my code for OpenMLS is to refactor the ciphersuites trait to make it easier to use custom ciphersuites. My initial PR hardcoded our secp256k1 based suite into the library but the clearly better solution is to refactor a few things to make sure that there isn't any hardcoding in the main OpenMLS library, the ciphersuite, or the credentials (which hold your identity information and make prekey bundles possible). The library's maintainers are open to this, so I've started on that this week.
Request for feedback
I'd love to hear from devs on one point. The OpenMLS library currently makes it very easy to serialize messages (both group control messages and actual messages between users). These messages have a lot of data in them about the current structure of the ratchet tree and whatever message or control event they're trying to communicate. My current plan is to simply NIP-44 encrypt those serialized messages into the content field of a new event kind. The messages themselves are deserialized and processed in two simple calls by the OpenMLS library so I don't see any reason to keep destructured or deserialized data in the nostr events that are heading over the wire. This also makes it easier to keep metadata about messages hidden to observers.
Goals Recap
It's been a few weeks since I've talked about why this is important so, it's time to recap what we're aiming for:
- Private and Confidential DMs and Group messages
- Private means that an observer cannot tell that Alice and Bob are talking to one another, or that Alice is part of a specific group. This necessarily requires protecting metadata.
- Confidential means that the contents of conversations can only be viewed by the intended recipients.
- Forward secrecy and Post-compromise security (PCS) in the case of any key material being leaked, whether that's your main Nostr identity key (your nsec) or any of the keys used in the MLS ratchet trees.
- Forward secrecy means that encrypted content in the past remains encrypted even if key material is leaked.
- Post compromise security means that leaking key material doesn't allow an attacker to continue to read messages indefinitely into the future.
- Scales well for large groups. MLS provides this from a computational standpoint, but we need to make sure this works in a scalable way when multiple relays are involved.
- Allows for the use of multiple device/clients in a single conversation/group. Importantly, we're not aiming to enable a device/client to be able to reconstruct the full history of a conversation at any point.
Onward and Upward
Grind, grind, grind. Touch grass & hug family. I'm visiting family starting next week for a few weeks. I'm going to be taking some time off in there so expect a few light updates in the coming weeks.
-
 @ aa4955b3:e9df94de
2024-07-19 20:13:47
@ aa4955b3:e9df94de
2024-07-19 20:13:47I stood in the back of the church after Sunday’s service. An unfamiliar congregant approached me with a question: “If Saturday is the Sabbath day, and the Sabbath command is one of the ten commandments, then why do churches worship on Sunday?” It is a good question. While many evangelical churches today hold that the Sabbath command is the only commandment of the ten commandments not repeated in the New Testament, and therefore no longer binding, the more traditional Protestant view is that the ten commandments are part of the moral or natural law, and therefore all of the ten commandments remain in force, including the fourth commandment.
If that’s true, why worship on Sunday? Christians have worshiped on Sunday since the earliest times in the church because Sunday, the first day of the week, is the day Jesus rose from the dead. They called it “the Lord’s Day” (Rev. 1:10), and 1 Cor. 16:2 and Acts 20:7 both strongly suggest, if not demonstrate conclusively, that it was the early disciples’ custom, from the beginning, to meet on the first day of the week for worship. Jesus set apart the day not only by rising from the dead on that day, but also in His frequent appearances on the first day of the week after His resurrection (John 20:19; 20:26) and in the pouring out of the Holy Spirit at Pentecost, also on the first day of the week.
Still, if the Sabbath is a perpetual command, and Saturday is the Sabbath day, then how can churches simply ignore that fact and change the day it is observed? Aren’t they breaking God’s commandment? In truth, the fourth commandment never fixes Saturday as the day it must be observed. Scripture simply says it is to be observed the seventh day, because the LORD made the earth and the heavens in six days, and on the seventh day He rested from His work (Exod. 20:9; 35:2; Gen. 2:2-3). Granted, the seventh day, counted from the first day of creation, if we call that seventh day “Saturday,” would be observed Saturday each week, in perpetuity. And yet, the New Testament is very clear that Christ has inaugurated a new day, and a new creation. As 2 Cor. 5:17 says, “If anyone is in Christ, there is a new creation; old things have passed away; behold, all things have become new.” In fact, many prophecies, both verbal and typological, of the Old Testament, point to a fulfillment which sets apart the first day of the week (the eighth day as opposed to the seventh) as particularly holy (e.g. the Temple was dedicated on the first day of the week; Hebrew males were circumcised on the eighth day, etc.).
So that first resurrection Sunday, when Jesus rose from the dead very early in the morning (John 20:1), was the expected and prophesied dawning of the first day of a new world (Rev. 21:5). It was the dawning of that eschatological eighth day, the beginning of a new week—a new Sabbath, if you will—prophesied in types and shadows throughout the Old Testament. Jesus did not come to abolish the Law, but He did come to fulfill it (Matt. 5:17). He is Lord of the Sabbath (Matt. 12:8), and He set apart and sanctified the first day of the week by rising from the dead on that day. Which is a more fitting day for Christians to worship Jesus our risen Redeemer—Saturday, the day He was dead in the tomb, or Sunday, the day He rose triumphant from the tomb?
The upshot is this: Christians still observe the day of God’s rest, every seventh day, just as the fourth commandment requires, but we observe it not on the day God rested from His work of creation, but on the day Jesus, God incarnate, rested from His work of redemption, as Christians have from the beginning. For if Jews under the Old Testament observed the Sabbath every seventh day in remembrance of the day God rested from His work of creation, how much more should we worship every seventh day, in remembrance of the day God rested from His greater work of making a new creation?
Author's note: I am indebted for much of the substance of this article to Robert Haldane's concise but persuasive work entitled Sanctification of the Sabbath: The Permanent Obligation to Observe the Sabbath or Lord's Day.
-
 @ 5df413d4:2add4f5b
2024-07-19 17:59:36
@ 5df413d4:2add4f5b
2024-07-19 17:59:36BLUEBERRY OKRA LIME TEA
https://image.nostr.build/f063cf64710c1551c7cfbfd090cbcb9dbf6b1ab046c26fbe9f81f9cabe454d12.jpg https://image.nostr.build/5e8267ac7c4d30764ad9748fd8ac64b5ad4c746172a4a32ecac355378ed2666a.jpg
- Blueberries
- Cut Okra fingers
- Okra Flowers
- Lime zest
- Slice of lime
Heat water 3-4 cups of water to boil. Add ingredients and let boil for 5 minutes. Lower heat and let simmer for 10 minutes. Use sieve with funnel to strain into 32 oz mason jar.
Benefits: Gut health, Cardiovascular health, antioxidant and anti-inflammation, boost immunity, anti-diabetic, sexual vitality.
Also remember Okra is a "seed to stem" fruit - the seeds, stalks, leaves, flower, and fruit are all edible. It is a plant with phenomenal culinary, medicinal, and even cosmetic (i.e. hair and skin uses) range - your African, Indo-Asian, and American Southern herbalists and plant works have always known this. If this is new to you, ask your self why...
Blessing to you all friends.
~Moon
-
 @ a9434ee1:d5c885be
2024-07-18 14:34:09
@ a9434ee1:d5c885be
2024-07-18 14:34:09What makes Nostr and Bitcoin so extremely exciting to me, as a designer, is that they offer an entirely new design space. Something we never had before. Something that we can, for the first time ever, call…
A Free Market.And not just that, but one where everyone speaks the same language. One that acknowledges that Sovereignty doesn’t go that far without Interoperability.
Since this is literally a first, it seems terribly naïve to assume that we can just copy what works for Big Tech’s walled gardens and add some Freedom sauce on top. I’ve been sketching out things like “Twitter but with Zaps”, “Youtube but with many algo’s”, “Patreon but with Bitcoin”, etc... for long enough to realize the harsh limits of such an approach. Instead I’ve found it more fruitful to start by looking at the characteristics of this new digital, interoperable free market and, only then, look for similar existing benchmarks that can serve as inspiration.
Because the convergence of the various Freedom Tech protocols (Nostr, Bitcoin, Cashu, …) are such a huge game changer for online monetization specifically, it seems even more naïve to just start copying Big Tech on that front, without proper examination.
If we did just play copycat, Monthly Subscriptions and Paywalls would be the obvious answer. This article dives into why they’re not.
Free as in Competition
In a free market, it’s going to be hard for you to set a price if you don’t have something scarce to sell. Unlike in a Big Tech walled garden, there’s no one blocking competitors from entering the market. That includes competitors that offer your stuff!
If what you create can easily be copied, it will.Yes, Content creators, FOSS devs, Designers, … that’s you.
Charging for your article, podcast, app or movie doesn’t end well when people can find a free upload right next to yours. Open protocols remove the friction of having to go PirateBay for that sort of stuff. Luckily, they also remove the friction for people to value your content directly (#V4V Zaps) and for you to launch unique and scarce products related to what you do (Community, Merch, …).Even if you have a scarce product to sell though, Nostr sets the bar lower than ever for others to start competing with your product. Every part of your product!
Interoperability breaks products and services down to their constituents and opens up every layer of the stack to competition. Currently most SAAS business models are basically very expensive monthly subscriptions for some hosting and computation. And guess what Nostr is extremely good at → Discovering and switching providers of hosting and computation.
In a competitive context like that, you need a monetization model that lets you adapt fast. If you choose to monetize with monthly subscriptions, you’ll be updating your subscription tiers every month, if not every week, just to remain competitive. If that’s the case, then what’s the point? Why not just have a cash price list?
Free as in Volatile
The reality of a free market is that price-discovery never takes a break. This is especially true for a market that uses a money that is still being discovered as money by 99% of the world. A money that, just like Nostr, only saw the light of day because its creators saw total chaos ahead without it.
Bitcoin and Nostr do #fixthemoney and do #fixtheinternet, but all that fixing isn’t exactly taking us on a smooth ride.
Smooth rides are stable rides, stable prices, stable amounts of locked-in users, stable ties with the state, etc… They are everything Freedom Tech is taking us on exciting journey away from.
Again, adaptability is key and your business model needs to reflect that. Monthly subscriptions don’t handle volatility well. It takes a lot of confidence, extremely loyal customers and liquid reserves to survive bumpy roads. That’s a lot of capital that probably has better uses. Better uses that Big Tech monopolies can ignore, but your competitors won’t.
Free as in “Number Go Up”
Denominating your subscriptions in “stable” fiat-currencies isn’t going to help neither. The mental cost for customers is only low as long you don’t have juggle more than 21 subscriptions. (yes, I completely made up that number but it’s somewhere around that, so bear with me).
Given that Subscription Hell is already a thing in Fiat-land once you go beyond that number, just try to imagine the amount of subscriptions you’d be handling in Nostr-land. Your 1 Netflix subscription suddenly became 6, to different service providers, plus 20 to all your favorite creators. Then add the subscriptions for all other internet use cases you can think of. Then add some more for the ones that you can’t even imagine yet.
This is not an overstatement. It is very very unlikely that your service happens to be the only one that subscriptions would work for. If they appear to work for you, every competitor or similar use case will be copying that model in no time.So if they work, there would be a loooot of subscriptions.
That’s also a looot of: - recurring payments to forget about - different time periods to oversee - extra effort to go and unsubscribe or switch tiers - users thinking ‘I didn’t even really use this!” - users also thinking “What am I paying for exactly?”In short, that’s asking for frustrated, disappointed and confused customers.
These subscriptions would then also need to be handled on top of all the #V4V Zaps and cash payments that are inevitably happening as well. Unlike Big Tech products you don’t get to just pick Subscriptions as the only option. You will have to be optimizing both the Wallet and Social UX/UI for all of these types of payments. Something I naïvely tried and quickly gave up on. It overcrowds interfaces, makes different applications less interoperable and creates a very confusing user experience.
And if you denominate everything in fiat, you add even more confusion since the Zaps from others are denominated in Bitcoin. That suddenly makes them variable from the fiat-denominator’s perspective. Other denominations work when you only have two parties (f.e. seller and buyer), not when you have groups of people zapping away at an article. For #V4V to gain traction zappers need recognition. If it’s completely variable, and thus unclear, who the top zappers of a piece of content are or if the biggest patrons of a creator are only visible if you go to some specific subscriber dashboard, you’re creating confusion and diluting recognition.
Zaps are awesome, nearly universally implemented, very simple to design for and they might just be enough. We’re mostly still early. Creators can’t even reply to Zaps yet. The first prototypes for frictionless Cashu zaps are only just coming out. Let’s explore all that further before we start adding subscriptions to the UI, the users’ mental load and the app developers endless list of “things to implement”.
If the current zap-rate of daily Nostr users (myself included) tells me anything, it’s that sending around small payments all the time isn’t really the issue. The mental cost for the user happens mostly at the level of:
”How the f*ck do I keep track of all this?”
“How do I fit this in with my regular monthly expenses?”
Subscriptions are only one answer to this. If they happen to still somehow solve the above issues for some use cases, we still have to find solutions anyway for the micro-payments side of things.My point is thus mainly: we might as well start there and, who knows, we don’t even need subscriptions. Or at least not as a standard to strive towards. No one is stopping you from using time-based pricing for things that are actually time-based or from creating micro-apps that let you set up recurring zaps and other fun stuff like that. Just don’t promise creators and merchants that they can base their business models on them.
If you’re talking to people that will only consider Freedom Tech if they can have the stability of a group of monthly subscribers, you’re probably not talking to the right people (yet!).
Freedom Tech = Responsibility Tech.
Both seller and buyers need tools that help them take that responsibility. Especially regarding payments, the currently available tools are far from optimal and have barely scratched the surface of what’s possible in the interoperable ocean of possibilities. I say this more as an invitation than as a complaint of course. We are — yes, I’m saying it again — sooooo early.
So how can we help buyers be responsible while “not having to think about every little payment”?
For rich npubs on a network denominated in #NGU technology the answer can be quite simple: They simply don’t have to really think about it.
In fact, poor npubs neither as long they can set a spending budget and have great tools and transparency to help them manage it.They need something a bit like their “lives left” in a video game. Or something that resembles envelope budgeting: like going to the farmers market with only a limited amount of cash.
Talking about farmers markets
Let’s look at what currently comes close to an interoperable free market in meat-space: Restaurant & Farmers markets. - No one has copyrights on pizza Margherita or chicken eggs - Entering the market is relatively cheap (food trucks, farmer stands, …) - Customers can pick and choose where they get “every layer of the stack” (drinks here, main dish there and ice cream over there)

Now look at how these businesses monetize: - Cash price lists - Discounts (for special occasions, loyal customers, ..) - Bundles (lunch menus, vegetable baskets, …)
Both restaurant owners and farmers have been trying out monthly subscriptions since forever, mostly because it would benefit them. But in places with high competition this has had exactly zero success.
What did have success is services that bundle farmers market food items for you and deliver it at your doorstep on a weekly basis. That’s what lower mental cost looks like. Ironically, these services often started out with the monthly subscription model and have had to switch because customers needed more flexibility. Now, in their apps, they let users pick what day they want what, at what price.
And these apps are not even Nostr yet.Talking about Nostr markets
Nostr markets are not exactly farmers markets of course. But that is mostly good news. Nostr, Bitcoin and Cashu, in particular, remove a lot of the friction that cash still has in the physical world. They enable seamless micro-payments. That’s an innovation worth embracing, not something to hide away behind subscriptions.
Embracing micro-payments means that every little thing can have a real-time price. A price that, once payed, you never have to think about again. And some, if not most, micro-payments are so micro that you don’t have to really think about them in the first place. Especially if we’re talking about recurring events (pun intended).
If a chat message in a certain Community costs 2 sats, after your third message your added mental cost will likely be close to zero. At that point, the price is mostly a matter of transparency, fairness and spam prevention. When the Admin suddenly changes this price to 1000 sats however, you will need to think twice about posting such a message. But again, that is a good thing. That’s exactly what the Admin is monetizing.
He is curating for high signal content and conversations around a certain interest. His price list is one of his top tools for doing so. You pay him for being able to publish in his unique community. You “Pay Per Use” of that Community as a broadcasting channel for your messages, articles, videos, … You know everyone else does too.
Using monthly subscriptions for such a community would just invite abuse and poor quality. It would be like an all-you-can-eat restaurant where everyone has an infinite stomach size, you’re all at the same table and only the loudest screamers get heard.
So the Admin would put limits on what you specifically get for your subscription (100 messages per month, 210MB of hosting, etc etc…). The members would then demand flexibility or go elsewhere.The admin would then provide different tiers.
Yet, most members would still need flexibility more than they need flat rate monthly pricing.At the same time, the Admin’s “Pay Per Use” competitors will still be cheaper. They don’t have the overhead of handling the uncertainty that comes with providing stable pricing for several months. Trying their offer out is also way cheaper than immediately having to pay a subscription. The admin, on the other hand, cannot really offer free trials if he doesn’t have the locked-in users to pay for them.
In the end, just like restaurants, the Admin will switch to “Pay Per Use” and will use discounts and bundles to his advantage.
As long as users have great tools to keep an eye their spending, this sort of outcome is a win-win for the whole ecosystem. What users tend to like most about monthly subscriptions for something is the guarantee that they will not exceed XXX amount of money on that thing for the month. Nothing is stopping us from building tools that provide the same guarantee without the complications of handling monthly subscriptions.
Since most Bitcoin wallets are not daily-spending wallets and most Nostr projects aren’t monetizing yet, hardly any attention has been spent on tools like this. They all copied bank apps and display your total amount of money and a chronological feed of your transaction history. There are several problems with this: 1. You don’t want to openly showcase your total balance to everyone around you when you open the app 2. Your total balance shows “everything you have”. That is a terrible benchmark for determining “what you can sustainably spend”. 3. It’s also a terrible benchmark for determining “what you earned this month” 4. Micro-payments make a chronological feed of all your transactions completely unusable 5. Zaps make a lot of your transactions social. Zaps and eCash blur the line between money and message. And messages require interaction that transactions don’t.
I think we can do better.
So, let’s try!Cash Budgets
Just like the previously mentioned “lives” in a game or the cash in your wallet for a night out, the first thing users will want to see is “How much do I have left?”. Since most people organize their budgets per month we can more specifically turn this into “How much do I have left this month?”. This means we need to allow users to set a monthly budget in the first place. Once that budget is set for the month, it facilitates all the rest.
This budget is their subscription now. Their Nostr subscription.
An interoperable subscription they can interact with in any trusted app.
And the best part: They pick the price.
They’re taking their responsibility and lowering their mental cost with one action.Now, you can start playing with wallet and home screen Interfaces that show the user at a glance: - What they’ve got left to spend for that month - What they already spent - What they earned (relative to that budget and/or a specific earnings goal)
I’m currently exploring this design space myself and the extent to which Freedom Tech budgeting can be gamified in novel ways will make TikTok look boring.

Some baby UI steps in this direction
But that’s just the budget part of course. We still need non-intrusive ways to display all these little price-tags for things if we’re not hiding them away behind a subscription.
The good news is that, when it comes to movies, music, articles, posts, FOSS apps and all other types of information that can easily be copied, it doesn’t have a price tag. It just has people zapping it. People that can use a lot more context and recognition than they currently get. (showing top zappers everywhere and letting creators reply to zaps being just a humble start for that)
For the stuff that does have price-tag, even the most obvious answer isn’t as bad I though it would be:
Just put it on the button.
The bigger the sum, the bigger the button.
eCash is what can make all of this work as a one-button action anyway, removing most of the friction. A budget, on the other hand, is what can remove most of the worrying. Color indications, permission prompts for higher amounts, etc etc… can all work in tandem for this.
With these examples I’m mostly trying to give you an idea of what is still left largely unexplored territory.
A territory that we will have to go and explore in any case.
A territory where Communities are easier to monetize then Content is.
A territory where I can count the current number of active designers on both hands.
A territory that can desperately use a Design Community.You can guess twice what’s next on my todo-list….
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-19 14:14:15
@ 5d4b6c8d:8a1c1ee3
2024-07-19 14:14:15It's been a while since I've scolded everyone for their miserliness. The recent archiving of some popular territories inspired me to make another attempt. Plus, there are quite a few new stackers who haven't been scolded, yet.
I'll keep this one short and sweet: 1. Territory owners need to make about 100 kilosats per month. 2. They earn their sats through posting fees. 3. OP's need to recoup their posting costs through zaps.
Therefore, when there's content you like, zap big and zap often.
If there's a lack of content you like, cowboy up and write it yourself. We just might make it worth your while.
Zapping more can pay for itself through the rewards system (see: https://stacker.news/items/287074/r/Undisciplined and https://stacker.news/items/473181/r/Undisciplined)
Also, zapping more will make Stacker News more aligned with what you want it to be: https://stacker.news/items/523858/r/Undisciplined.
originally posted at https://stacker.news/items/614066
-
 @ 005bc4de:ef11e1a2
2024-07-19 13:26:53
@ 005bc4de:ef11e1a2
2024-07-19 13:26:53It may not be going out on a limb at this point, but I'm making the call on Biden right now.
- he spends the weekend at home "resting, recovering, thinking"
- returns to White House early next week, Monday or Tuesday
- lays low, but before the week's end, staffers declare a "major announcement" imminent from the president
- gives a "Cross Hall" White House announcement something to the effect: "After consulting with my family, and for personal health reasons, we've decided it is in everyone's best interest for me to pass the torch of the Democrat party. I am withdrawing my name as a candidate for the 2024 party nominee."
- turn, walk down the hall, turn right
- turn the page; Democrats begin to reminisce the "incredible" job Biden did for America, practically saving the nation from certain ruin, and go "whole hog" on Harris
We'll see how it plays out.
-
 @ 124b23f2:02455947
2024-07-15 15:36:19
@ 124b23f2:02455947
2024-07-15 15:36:19Stacker.News if a website that may be familiar to most nostriches. But in case it is not, stacker.news is effectively a forum-style website that functions similar to reddit. But, with the very cool feature that sending sats works as the 'upvote' function. It's a great site, so check it out regardless of what I am about to break down.
One of the great features of Stacker News is that you get a custodial lightning wallet with your account. This wallet comes with a lightning address as well. Now, this alone is not unique or entirely useful. What makes Stacker News stand out is the way you can configure this wallet to interact with your self-hosted lightning stack. Now, I'm not just talking about the power user that is running their own node (although they do have useful configuration for those users). But, the lighter users that may be using a mobile wallet, such as mutiny, zeus, blixt, phoenix can use Stacker News to improve their zap receiving game.
Before I get into how, I want to highlight two great options to receive zaps via ln address if you are using a 'node in the phone solution.' The two options are zaplocker, provided as a solution for users of Zeus' embedded lightning node wallet, and lightning box, provided as a solution for users of the Blixt embedded lightning node wallet. Here is a summary of these two ln address solutions:
-
Zaplocker: Zaplocker is an ln address provided for Zeus embedded node users. The way zaplocker works is that the sats are held temporarily in Zeus' node (for up to 24 hours), and once you log into your Zeus app and access the embedded node, you can redeem the sats. This can be made easier by setting your Zeus app to automatically redeem and sats awaiting redemption upon logging in, and there is also a persistent mode that can help the app stay on in the background. If the app is on in the background and you have turned on the auto redemption feature, it will function more or less to automatically receive sats much like a custodial wallet or a node you are running on a server
-
Lightning Box: Lightning Box is an ln address provided for users of Blixt wallet. The way lightning box works is that, as long as you have a channel opened with the blixt wallet node and it has inbound liquidity, you can receive sats to the lightning box ln address. You have to set blixt wallet to persistent mode as part of using lightning box, which makes it more likely that your app will be running in the background and will successfully facilitate receipt of sats sent to the lightning box ln address. Unlike zaplocker, there is no 24 hour redemption time ; if your blixt wallet is not running in the background when the send is attempted, you will not receive the sats.
So, these both sound like great solutions and a pleb need not do anything else, right ? Wrong. Both are not perfect solutions, with the main issue being that even with persistent app settings, the apps will inevitably close because phones seem to do that for one unknown reason or another. Or a connection will be lost, and your app will not be running to receive the sats. Or if you want t run the apps over tor, your very likely to have a connection inturrupted. Now, with zeus you still have 24 hours to open it up, sync up your node and receive but we want to up our game so that a user does not have a chance to lose zaps.
Enter Stacker News. By Creating a stacker news account (you can even do so with using your blixt or zeus wallet to log in and create your account!), you now have an ln address you can use in place of your zaplocker or lightning box address. Use that stacker news address for receiving zaps on your nostr account. In your stacker news account, go to the wallet link, and click 'Attach Wallets'. Next, click 'configure' under the ln address option. Input your zaplocker or lightning box address. If you want, you can configure stacker news to withdraw automatically by setting the 'desired balance' to 0 sats. There will be a moment of custody, but it is a few seconds in my experience.
So, what have we just done and what's the improvement? Well, zaps you receive are going to be received to your stacker news ln address now. The improvement is that the stacker news node is on all the time, and you do not risk missing payments much like one can expect from say a Wallet of Satoshi ln address. With the configuration we made, the stacker news wallet is going to automatically withdraw sats received to your custody in your zaplocker or lightning box. For example: In the event that you are asleep, and your zeus or blixt wallet is not online for hours while nostriches across the globe are zapping the crap out of your viral post, your sats are sitting comftorably in your stacker news wallet. You will fire up your Zeus or Blixt app, and proceed to watch the sats flow into your custody from your stacker news wallet.
The result of this setup is a pleb who is not running an 'on all the time' node can experience a comparable receiving experience with minimal custodial exposure. I encourage any pleb, especially those using zaplocker due to the potential harm it can cause to the lightning network, to consider this setup. Let me know what your experience is or, for users already leveraging the Stacker News ln address, I'd be curious to hear about your configuration. Thanks for reading, hopefully someone finds this article helpful!
bitcoin #lightning #zeus #blixt
originally posted at https://stacker.news/items/609313
-
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-19 12:50:20
@ 5d4b6c8d:8a1c1ee3
2024-07-19 12:50:20Yesterday's edition https://stacker.news/items/612715/r/Undisciplined
I enjoyed the discussion in the 2022 AMA. I'd love to have some more stackers reporting more on the developing world. How is the bitcoin ecosystem developing? What problems is it solving for people?
-
- -
July 19, 2023 📅
📝
TOP POSTBitcoin Optech Newsletter #260
Link to https://bitcoinops.org/en/newsletters/2023/07/19/
2733 sats \ 0 comments \ @ssaurel \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/211250/r/Undisciplined?commentId=211288
Excerpt
Been very busy recently replicating the Indranet architecture to the guy who's been paying me to design and build it. It's been great for me in terms of helping delineate the core principles of the design and to spot some possible design flaws, as we […]
340 sats \ 0 replies \ @l0k18
From What are you working on this week? by @sn in ~meta
🏆
TOP STACKER2nd place @nerd2ninja (1st hiding, presumed @siggy47)
1335 stacked \ 2158 spent \ 0 posts \ 6 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
22.1k stacked \ 0 revenue \ 29.9k spent \ 110 posts \ 192 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 19, 2022 📅
📝
TOP POSTI'm Alex Gladstein. CSO of the Human Rights Foundation. AMA
Excerpt
I am also the author of Check Your Financial Privilege.
93.1k sats \ 48 comments \ @gladstein \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/47002/r/Undisciplined?commentId=47018
Excerpt
Bitcoin is likely playing a nascent role in cross-border payments between South Korea, China, and NK, but it's too early too tell
470 sats \ 0 replies \ @gladstein
From I'm Alex Gladstein. CSO of the Human Rights Foundation. AMA by @gladstein in ~bitcoin
🏆
TOP STACKER1st place @k00b
13.5k stacked \ 92.4k spent \ 3 posts \ 13 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
126.4k stacked \ 0 revenue \ 132k spent \ 94 posts \ 300 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 19, 2021 📅
📝
TOP POSTLink to https://bitcoinkpis.com/
3 sats \ 3 comments \ @nathanael \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/398/r/Undisciplined?commentId=409
Excerpt
nice - i added it there - welcome
2 sats \ 1 reply \ @nathanael
From Stacker.News Community by @gmd in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
11 stacked \ 0 revenue \ 15 spent \ 1 post \ 7 comments
originally posted at https://stacker.news/items/613971
-
-
 @ a5d8475e:df9ff32c
2024-07-19 11:20:59
@ a5d8475e:df9ff32c
2024-07-19 11:20:59Understanding how local estate agents determine the value of a property is crucial for anyone looking to buy or sell a home. Letting agents wolverhampton use a combination of market analysis, property characteristics, and local expertise to assess property value accurately. In regions like Wolverhampton and the West Midlands, the role of local estate agents is particularly significant due to the diverse property market. Here's an insight into the process estate agents use to value properties.
Comparative Market Analysis (CMA) One of the primary methods used by estate agents west midlands, is Comparative Market Analysis (CMA). This involves comparing the property in question with similar properties that have recently sold in the same area. Key factors considered include the property's location, size, age, condition, and features. By analyzing these comparable sales, agents can estimate a competitive market value for the property.
Location and Neighborhood The location of a property is a major determinant of its value. Estate agents Wolverhampton and the West Midlands consider various aspects of the neighborhood, such as proximity to schools, transportation links, shopping centers, and other amenities. Properties in highly sought-after areas, like Tettenhall or Codsall, often command higher prices due to their desirable locations.
Property Condition and Features The condition of a property significantly impacts its value. Wolverhampton estate agents evaluate both the interior and exterior condition of the property, including structural integrity, modernity of installations, and overall maintenance. Features such as a modern kitchen, updated bathrooms, double glazing, and energy-efficient systems can enhance property value. Unique features, like historical elements in older homes, can also add value.
Market Conditions Current market conditions play a crucial role in property valuation. Estate agents monitor local and national market trends, including supply and demand dynamics, interest rates, and economic indicators. For instance, if there's a high demand for properties but limited supply in the West Midlands, property values are likely to rise. Conversely, an oversupply of homes may lead to lower property prices.
Conclusion Determining the value of a property is a complex process that involves various factors and expertise. Estate agents in Wolverhampton and the West Midlands use a combination of Comparative Market Analysis, professional appraisals, market conditions, and local knowledge to provide accurate property valuations.
CONTACT:
2-3 Walsall Rd, Willenhall, WV13 2EH, info@halleuk.com, +44 (0) 1902 504455
-
 @ 6c2d79de:0407f1b7
2024-07-13 20:34:36
@ 6c2d79de:0407f1b7
2024-07-13 20:34:36
In this inaugural investigative campaign, we at The Xibao Times invite you to embark on a journey down the rabbit hole of Chinese propaganda. Our mission: to expose the intricate network of disinformation and anti-Western sentiment that the Chinese Communist Party (CCP) has meticulously woven through various channels, including state media, non-profits, coalition groups, and more. Our starting point: a seemingly innocuous image (above) reposted by China Daily, which has led us to uncover a web of deception that spans the globe.
At the heart of Operation Codepink lies a comprehensive examination of the CCP's propaganda apparatus. We delve into the inner workings of this sophisticated machine, revealing the strategies and tactics employed to disseminate disinformation and manipulate public opinion. From the recruitment of "useful idiots" to the exploitation of social media, we uncover the CCP's playbook and the players involved.
Our investigation spans multiple platforms and formats, providing readers with a multi-faceted view of the propaganda war being waged. In addition to in-depth articles on Habla News, we are creating wiki-pages on Wikifreedia to serve as a repository of information, and relationship charts to illustrate the complex web of connections between entities and individuals.
As we continue our investigative journey, we will be publishing updates, revelations, and analyses. Stay tuned for an exposé on the CCP's infiltration of Russian state media, US non-profits, and coalition groups, among others. Our objective is not only to educate and inform but also to spark a broader conversation about the dangers of disinformation and the need for transparency and accountability in the media landscape.
Join us as we unravel the threads of this intricate web and shed light on the dark corners of the CCP's propaganda machine. With Operation Codepink, we aim to provide the spiciest content on Nostr, and we invite you to be a part of this groundbreaking campaign.
Inside the Operation
Articles on Habla News:
Our in-depth articles on Habla News will provide a comprehensive overview of the CCP's propaganda machine, its tactics, and the individuals and organizations involved. These articles will delve into specific cases of disinformation, analyze the CCP's propaganda strategies, and expose the connections between various entities and individuals. The articles will be written in an engaging and accessible style, making complex information easily understandable for a broad audience.
Wiki-pages on Wikifreedia:

We will create a series of wiki-pages on Wikifreedia to serve as a central repository of information related to Operation Codepink. These wiki-pages will provide a detailed and organized overview of the CCP's propaganda machine, its various components, and the individuals and organizations involved. They will include information on specific cases of disinformation, analysis of propaganda tactics, and connections between various entities and individuals.
Relationship Charts:
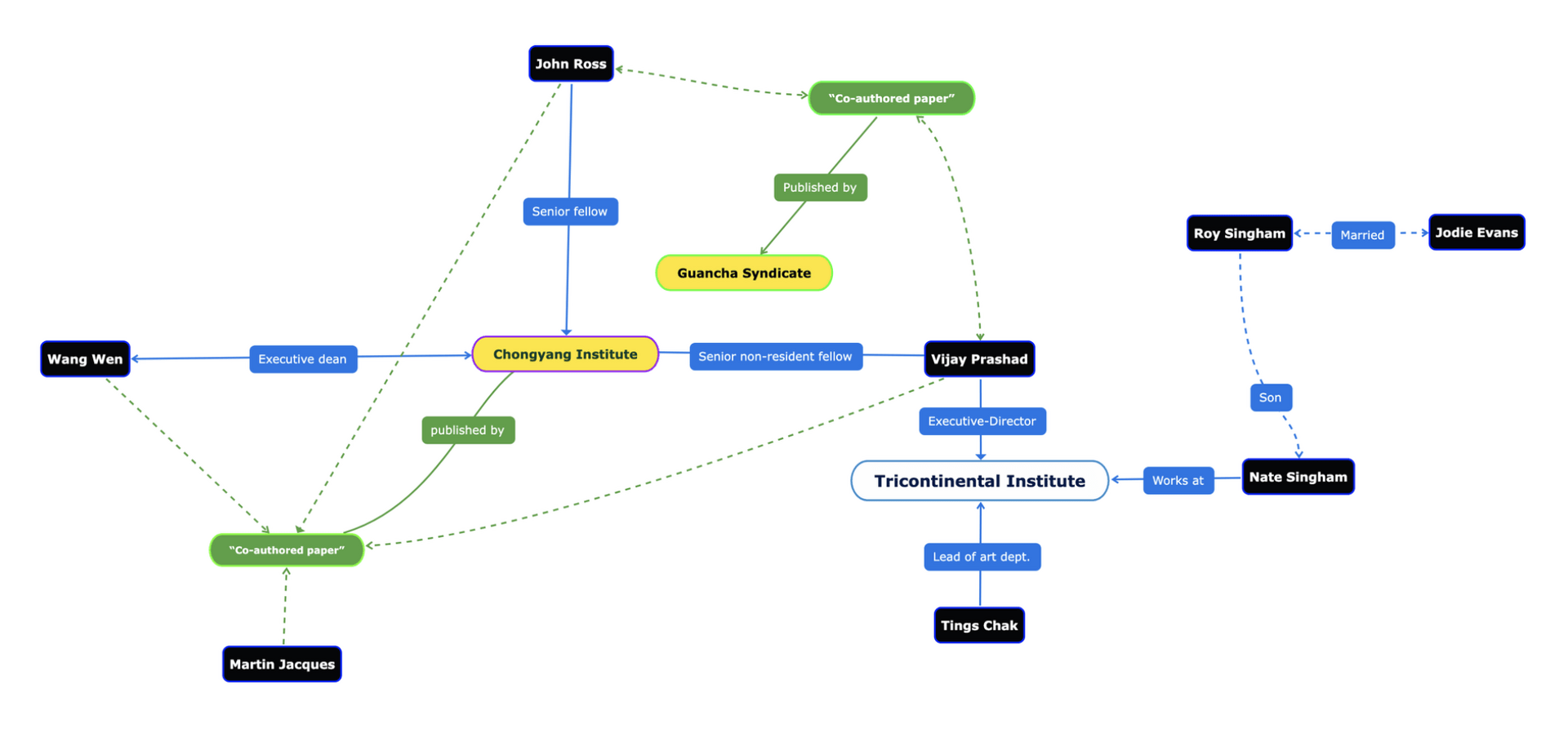
To illustrate the complex web of connections between the entities and individuals involved in the CCP's propaganda machine, we will create relationship charts. These charts will show the relationships between different organizations, individuals, and governments, providing a visual representation of the intricate network of disinformation and propaganda. The relationship charts will help readers understand the scale and scope of the CCP's influence and manipulation efforts.
Investigative Approach:
Our investigative approach for Operation Codepink will involve a combination of open-source research, data analysis, and interviews with experts and insiders. We will use a range of tools and techniques to gather information, including:
Open-Source Research: We will conduct extensive open-source research, using publicly available information to identify patterns, connections, and trends related to the CCP's propaganda machine.
Data Analysis: We will analyze large datasets to identify relationships between individuals, organizations, and governments, as well as patterns in disinformation and propaganda tactics.
Expert Interviews: We will interview experts and insiders who have firsthand knowledge of the CCP's propaganda machine, as well as individuals who have been targeted by the CCP's disinformation campaigns.
Social Media Monitoring: We will monitor social media platforms for signs of disinformation and propaganda, as well as for clues about the identities of individuals and organizations involved in the CCP's propaganda machine.
By using a combination of these techniques, we aim to provide a comprehensive and accurate picture of the CCP's propaganda machine and its activities.
Updates and Revelations:
As we continue our investigation, we will provide regular updates and revelations on our findings. These updates will be published on Habla News and shared on our Nostr account xibaotimes@zaps.lol, keeping readers informed about the latest developments in Operation Codepink. We will also provide analyses and commentary on the implications of our findings for global politics, media, and society.
Stay tuned for more revelations and updates!
-
 @ b804f68e:2fb0fa1f
2024-07-19 07:39:10
@ b804f68e:2fb0fa1f
2024-07-19 07:39:10Just started looking into powdered mushrooms and was wondering if stackers have used or use any for supplementation. I have previously tried Lion's mane and chaga, and since haven't but am interested in playing around with them again. Cordyceps does sound interesting, if anyone has any experience taking them.
originally posted at https://stacker.news/items/613694
-
 @ a012dc82:6458a70d
2024-07-19 02:56:55
@ a012dc82:6458a70d
2024-07-19 02:56:55Table Of Content
-
Bitcoin Mining and Energy Consumption
-
Environmental Impact of Bitcoin Mining
-
Efforts to Reduce Bitcoin's Environmental Impact
-
Is Bitcoin Worth the Environmental Cost?
-
Conclusion
-
FAQ
Bitcoin has gained immense popularity in recent years as a decentralized digital currency. However, with its rise in popularity, concerns about its environmental impact have also increased. The process of mining Bitcoin, which involves solving complex mathematical problems to validate transactions and create new Bitcoins, requires an enormous amount of energy consumption.
Bitcoin Mining and Energy Consumption
Bitcoin mining is the process of adding new transactions to the blockchain by solving complex mathematical equations. This process requires a massive amount of computational power, which is achieved by using specialized hardware and consuming a significant amount of energy. The energy consumption of Bitcoin mining has become a significant concern as the popularity of the cryptocurrency has grown.
Environmental Impact of Bitcoin Mining
Bitcoin mining has come under criticism for its significant environmental impact. The following are the environmental impacts of bitcoin mining:
Energy Consumption
Bitcoin mining requires an enormous amount of energy, which contributes to greenhouse gas emissions. According to the Cambridge Bitcoin Electricity Consumption Index, Bitcoin mining consumes more energy than entire countries like Argentina and Norway.
Carbon Footprint
The carbon footprint of Bitcoin mining is enormous. It is estimated that the annual carbon emissions from Bitcoin mining are equivalent to those of a small country. The carbon footprint is mainly due to the high energy consumption and the use of fossil fuels to generate electricity.
E-waste
Bitcoin mining requires specialized hardware, which has a limited lifespan. The mining hardware becomes obsolete quickly, leading to electronic waste (e-waste) and pollution.
Land Use
Bitcoin mining requires large amounts of land for the installation of mining hardware and the cooling infrastructure. The land use is a concern, especially in regions where land is scarce.
Water Use
Bitcoin mining requires water for cooling purposes. The high water consumption can strain local water supplies, especially in areas where water scarcity is an issue.
Efforts to Reduce Bitcoin's Environmental Impact
Efforts to reduce Bitcoin's environmental impact have been ongoing in recent years. Some of the most notable efforts include the increased use of renewable energy sources, such as hydroelectric and geothermal power, for Bitcoin mining operations. Additionally, some mining companies have implemented more energy-efficient hardware and cooling systems to reduce energy consumption. Some initiatives also focus on developing alternative consensus mechanisms to the energy-intensive Proof-of-Work algorithm currently used in Bitcoin mining. While these efforts are promising, it remains to be seen if they will be enough to significantly reduce Bitcoin's environmental impact in the long term.
Is Bitcoin Worth the Environmental Cost?
As with any technology, there are both benefits and costs associated with Bitcoin. While the cryptocurrency has the potential to revolutionize the way we make online transactions, it also has a significant environmental cost. So, is Bitcoin worth the environmental cost?
One argument in favor of Bitcoin is that it has the potential to reduce our reliance on traditional banking systems, which can have their own environmental impact. In addition, some argue that the environmental impact of Bitcoin mining is overstated, and that renewable energy sources could be used to power mining operations.
Conclusion
Bitcoin's environmental impact is a complex issue that requires careful consideration. While Bitcoin has the potential to revolutionize the way we conduct transactions, it comes at a significant cost to the environment. The energy consumption and carbon emissions associated with Bitcoin mining are substantial and could have serious long-term consequences.
FAQ
What is Bitcoin's environmental impact? Bitcoin mining consumes a significant amount of energy, leading to a substantial carbon footprint and contributing to climate change.
How does Bitcoin mining contribute to carbon emissions? Bitcoin mining requires powerful computer systems that consume a lot of electricity. The majority of the electricity comes from non-renewable sources such as coal, which emits large amounts of carbon dioxide when burned.
What efforts are being made to reduce Bitcoin's environmental impact? Several initiatives are being undertaken to make Bitcoin mining more sustainable. These include transitioning to renewable energy sources, improving mining efficiency, and developing more eco-friendly mining hardware.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 1739d937:3e3136ef
2024-07-12 10:11:42
@ 1739d937:3e3136ef
2024-07-12 10:11:42This is the third in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
Short update post this week but I made solid progress updating several OpenMLS dependencies and building a new library that implements all the OpenMLS crypto requirements for Nostr.
HPKE-RS
I mentioned a PR last week on the
rust-hpkelibrary, that PR is still waiting on review. However, in the meantime, the OpenMLS library depends on a slightly different hpke library, thehpke-rslibrary.This library didn't support the secp256k1 curve either so I've opened a PR to add support for secp256k1. That PR uses the
RustCryptolibrary that is the default in the thehpke-rslibrary. However, because this library is built to allow for swapping out the underlying crypto library (using traits), I was also able to create a new library that uses thesecp256k1library instead of theRustCryptolibrary. This is the main crypto library that almost all Bitcoin and Nostr apps use so it's important we use that instead ofRustCrypto.OpenMLS Nostr Crypto
The library that I've created (openmls-nostr-crypto) does a few things via separate sub-libraries (crates). The entire library tries to do as little as possible; only implementing the one required ciphersuite for all MLS implementations and the
secp256k1schnorr signatures ciphersuite I've created for Nostr. It's also using the rightsecp256k1library to do it.openmls-nostr-crypto: implementes the crypto traits that the OpenMLS library expects to find for a given provider and removes all the ciphersuites that we don't care about supporting.
hpke-rs-nostr-crypto: This implements the crypto traits that the hpke-rs library expects to find. Again removing all the ciphersuites we don't care about supporting.
I've not yet written any tests for these libraries (which needs to be done) but I've gotten some very simple demos working with OpenMLS using this new set of libraries to handle the crypto.
I've been really impressed with the simplicity of the OpenMLS interface as well. While there is A LOT going on under the hood, the public interface that client developers have to use is clean and simple.
Onward and Upward
Next week I'll continue working on these libraries; adding tests and continuing to build out my small demo app. I've been in touch with the maintainers of the OpenMLS library and I'm hoping to get a review done with them on my PRs and on my new library.
One thing I'll call out here: The review of my library and getting them to review the direction of the project overall will be paid consulting so I'm making sure that I've got as much done as possible before scheduling that time and paying their rates. I'm a strong believer that the right conversation can save you months of wasted time, but I'm also a believer in making sure you're prepared if you're going to drop money on that conversation. 😅
-
 @ 8947a945:9bfcf626
2024-07-19 01:27:05
@ 8947a945:9bfcf626
2024-07-19 01:27:05วันที่ 15/7/2024 เป็นวันแรกของทริป ครั้งนี้ไปที่ปากช่องครับ เส้นทางที่ใช้คือนนทบุรี ออกอยุธยา เข้าสระบุรี เข้าปากช่อง
วัดพระพุทธบาท จังหวัดสระบุรี
ตอนที่หาข้อมูลของวัดแห่งนี้ ผมตั้งใจจะพาครอบครัวมาไหว้พระ ไหว้รอยพระพุทธบาท เพื่อขอรากฐานความมั่นคงทั้งทางโลกและทางธรรม เสมือนรอยพระพุทธบาทขององค์พระพุทธเจ้า ที่ท่านก้าวเดินอย่างหนักแน่นมั่นคง มีสติในทุกๆก้าว รอยพระพุทธบาทอยู่ในวิหารหลังนี้ครั้ง แต่พวกผมเคารพความศักดิ์สิทธิ์และไม่ต้องการทำให้คนอื่นๆที่มาสักการะเสียสมาธิ ผมเลยเลือกถ่ายรูปเฉพาะภายนอก ไม่ถ่ายข้างในครับ

 หลังจากไหว้รอบพระพุทธบาทเสร็จ ด้านหลังตัววิหารมีบันไดทางขึ้นไปกราบไหวพระพุทธฉาย บันไดขึ้นเขาสูงประมาณ 300 ขั้น มีเจ้าหน้าที่นำทางและอธิบายประวัติความสำคัญของสถานที่
หลังจากไหว้รอบพระพุทธบาทเสร็จ ด้านหลังตัววิหารมีบันไดทางขึ้นไปกราบไหวพระพุทธฉาย บันไดขึ้นเขาสูงประมาณ 300 ขั้น มีเจ้าหน้าที่นำทางและอธิบายประวัติความสำคัญของสถานที่เมื่อมาถึงจุดของพระพุทธฉาย บริเวณที่เป็นหน้าผาแห่งนี้ หากมองดีๆ “อาจจะ” เห็นรูปพระพุทธเจ้าอยู่ในอิริยาบทนั่งสมาธิ


ถัดจากบริเวณนี้เป็นทางเดินระหว่างหุบเขาที่คนจีนและชาวบ้านสมัยก่อนใช้เป็นเส้นทางในการเดินแสวงบุญระหว่างวัดพระพุทธบาทแห่งนี้และวัดอีกแห่งที่อยู่บนภูเขาลูกถัดไป รวมถึงเป็นเส้นทางที่ใช้อัญเชิญรูปปั้นของเทพเจ้าของจีน เช่น อากงเห้งเจีย เจ้าแม่กวนอิม มาประดิษฐานที่วัดพระพุทธบาท

เป็นทางเดินที่ลาดชัน เป็นทางน้ำไหลผ่านลงเขาเวลาฝนตก มีถ้ำพระนอนเป็นจุดสักการะสุดท้าย ย้อนไปในสมัยของหลวงปู่มั่น และ สมเด็จพระพุฒาจารย์โตพรหมรังสี ท่านทั้งสองก็ใช้เส้นทางนี้ในการเดินทางตอนที่มาวัดพระพุทธบาท ท่านใช้ถ้ำแห่งนี้ในการค้างคืน สวดมนต์นั่งสมาธิ แต่บรรยากาศในถ้ำก็ศักดิ์สิทธิ์ ผมและครอบครัวนั่งระลึกถึงพระสังฆคุณที่พระอาจารย์ทั้งสองได้เทศสอนไว้ เลยไม่ได้ถ่ายรูปครับ มีแต่ถ่ายรูปบรรยากาศด้านนอก และวิวเขาที่ยืนอยู่หน้าถ้ำ


หลังจากนี้ครอบครัวผมเดินทางเข้าที่พักครับ ทริปนี้ผมเข้าพักที่ “มาดี ปากช่อง รีสอร์ท”ครับ เป็นที่พักที่เด็กๆจะต้องร้องกรี๊ด เพราะมีเครื่องเล่นของเด็กๆครบ เด็กเล่นได้ทั้งวันทั้งคืน จนกว่าเจ้าหน้าที่จะกลับ เครื่องเล่นหลายรายการฟรี เช่นสนามเด็กเล่น จักรยาน ยิงธนู ลูกดอกปาเป้า สระว่ายน้ำในพูลวิลล่าของใครของมัน และสระขนาดใหญ่ส่วนกลาง แต่ก็จะมีรายการที่ต้องจ่ายเพิ่มบ้างเช่นรถ ATV ภายในยังมีร้านสะดวกซื้อเล็กๆด้วย
พามาดูบรรยากาศห้องพักพูลวิลลาครับ





กิจกรรมครอบครัว = ลงน้ำ



สำหรับมื้อเย็นวันแรก สั่งหมูกระทะมากินในตัววิลลาครับ

บรรยากาศรอบๆตัวรีสอร์ท


เดี๋ยวมาเล่าต่อครั้งถัดไปครับ ว่าไปเที่ยวไหนต่อ
-
 @ ee11a5df:b76c4e49
2024-07-11 23:57:53
@ ee11a5df:b76c4e49
2024-07-11 23:57:53What Can We Get by Breaking NOSTR?
"What if we just started over? What if we took everything we have learned while building nostr and did it all again, but did it right this time?"
That is a question I've heard quite a number of times, and it is a question I have pondered quite a lot myself.
My conclusion (so far) is that I believe that we can fix all the important things without starting over. There are different levels of breakage, starting over is the most extreme of them. In this post I will describe these levels of breakage and what each one could buy us.
Cryptography
Your key-pair is the most fundamental part of nostr. That is your portable identity.
If the cryptography changed from secp256k1 to ed25519, all current nostr identities would not be usable.
This would be a complete start over.
Every other break listed in this post could be done as well to no additional detriment (save for reuse of some existing code) because we would be starting over.
Why would anyone suggest making such a break? What does this buy us?
- Curve25519 is a safe curve meaning a bunch of specific cryptography things that us mortals do not understand but we are assured that it is somehow better.
- Ed25519 is more modern, said to be faster, and has more widespread code/library support than secp256k1.
- Nostr keys could be used as TLS server certificates. TLS 1.3 using RFC 7250 Raw Public Keys allows raw public keys as certificates. No DNS or certification authorities required, removing several points of failure. These ed25519 keys could be used in TLS, whereas secp256k1 keys cannot as no TLS algorithm utilizes them AFAIK. Since relays currently don't have assigned nostr identities but are instead referenced by a websocket URL, this doesn't buy us much, but it is interesting. This idea is explored further below (keep reading) under a lesser level of breakage.
Besides breaking everything, another downside is that people would not be able to manage nostr keys with bitcoin hardware.
I am fairly strongly against breaking things this far. I don't think it is worth it.
Signature Scheme and Event Structure
Event structure is the next most fundamental part of nostr. Although events can be represented in many ways (clients and relays usually parse the JSON into data structures and/or database columns), the nature of the content of an event is well defined as seven particular fields. If we changed those, that would be a hard fork.
This break is quite severe. All current nostr events wouldn't work in this hard fork. We would be preserving identities, but all content would be starting over.
It would be difficult to bridge between this fork and current nostr because the bridge couldn't create the different signature required (not having anybody's private key) and current nostr wouldn't be generating the new kind of signature. Therefore any bridge would have to do identity mapping just like bridges to entirely different protocols do (e.g. mostr to mastodon).
What could we gain by breaking things this far?
- We could have a faster event hash and id verification: the current signature scheme of nostr requires lining up 5 JSON fields into a JSON array and using that as hash input. There is a performance cost to copying this data in order to hash it.
- We could introduce a subkey field, and sign events via that subkey, while preserving the pubkey as the author everybody knows and searches by. Note however that we can already get a remarkably similar thing using something like NIP-26 where the actual author is in a tag, and the pubkey field is the signing subkey.
- We could refactor the kind integer into composable bitflags (that could apply to any application) and an application kind (that specifies the application).
- Surely there are other things I haven't thought of.
I am currently against this kind of break. I don't think the benefits even come close to outweighing the cost. But if I learned about other things that we could "fix" by restructuring the events, I could possibly change my mind.
Replacing Relay URLs
Nostr is defined by relays that are addressed by websocket URLs. If that changed, that would be a significant break. Many (maybe even most) current event kinds would need superseding.
The most reasonable change is to define relays with nostr identities, specifying their pubkey instead of their URL.
What could we gain by this?
- We could ditch reliance on DNS. Relays could publish events under their nostr identity that advertise their current IP address(es).
- We could ditch certificates because relays could generate ed25519 keypairs for themselves (or indeed just self-signed certificates which might be much more broadly supported) and publish their public ed25519 key in the same replaceable event where they advertise their current IP address(es).
This is a gigantic break. Almost all event kinds need redefining and pretty much all nostr software will need fairly major upgrades. But it also gives us a kind of Internet liberty that many of us have dreamt of our entire lives.
I am ambivalent about this idea.
Protocol Messaging and Transport
The protocol messages of nostr are the next level of breakage. We could preserve keypair identities, all current events, and current relay URL references, but just break the protocol of how clients and relay communicate this data.
This would not necessarily break relay and client implementations at all, so long as the new protocol were opt-in.
What could we get?
- The new protocol could transmit events in binary form for increased performance (no more JSON parsing with it's typical many small memory allocations and string escaping nightmares). I think event throughput could double (wild guess).
- It could have clear expectations of who talks first, and when and how AUTH happens, avoiding a lot of current miscommunication between clients and relays.
- We could introduce bitflags for feature support so that new features could be added later and clients would not bother trying them (and getting an error or timing out) on relays that didn't signal support. This could replace much of NIP-11.
- We could then introduce something like negentropy or negative filters (but not that... probably something else solving that same problem) without it being a breaking change.
- The new protocol could just be a few websocket-binary messages enhancing the current protocol, continuing to leverage the existing websocket-text messages we currently have, meaning newer relays would still support all the older stuff.
The downsides are just that if you want this new stuff you have to build it. It makes the protocol less simple, having now multiple protocols, multiple ways of doing the same thing.
Nonetheless, this I am in favor of. I think the trade-offs are worth it. I will be pushing a draft PR for this soon.
The path forward
I propose then the following path forward:
- A new nostr protocol over websockets binary (draft PR to be shared soon)
- Subkeys brought into nostr via NIP-26 (but let's use a single letter tag instead, OK?) via a big push to get all the clients to support it (the transition will be painful - most major clients will need to support this before anybody can start using it).
- Some kind of solution to the negative-filter-negentropy need added to the new protocol as its first optional feature.
- We seriously consider replacing Relay URLs with nostr pubkeys assigned to the relay, and then have relays publish their IP address and TLS key or certificate.
We sacrifice these:
- Faster event hash/verification
- Composable event bitflags
- Safer faster more well-supported crypto curve
- Nostr keys themselves as TLS 1.3 RawPublicKey certificates
-
 @ 124b23f2:02455947
2024-07-10 05:24:33
@ 124b23f2:02455947
2024-07-10 05:24:33I'm reposting this in order to fix the images and get it correctly onto my npub.pro site
What is this ?
My Futurebit Apollo Miner in action
Futurebit is a company that manufactures home miners for retail users (see futurebit.io) - you can check out details on their website. These are targeted at individuals that want to participate in mining with an easy to use, quiet miner that does not use a ton of electricity.
The idea here is to try and stay true to the original bitcoin concept of a computer which runs the bitcoin software and mines bitcoin, all in one. While mining has obviously evolved into a commercial industry and the mining process has long been separated from running a bitcoin node, I think there are still some valid reasons to want to participate in the mining process and attempt to keep this original ethos alive:
- You learn a lot about bitcoin from mining. Reading about the process is one thing, but actually getting a machine running, pointing it towards the pool of your choice, and seeing the bitcoin process from this perspective is something I've found very enjoyable (mining is probably my favorite part of bitcoin, if I had to choose one). It can also be a gateway drug to more advanced mining, so...heavy care.
- It is marginally valuable to the network. Sure, one person running a futurebit miner is nothing compared to the hashrate of MARA. But, if you have tens of thousands of plebs all running their own miners from home, pointing their hashpower to the pool of their choice, it does provide a legitimate decentralizing anchor to large mining actors. Every pleb should be participating in mining, in my opinion, and the Futurebit Apollo miner offers a casual and unobtrusive avenue to do just that.
Now, the Futurebit Apollo Miner you most commonly see is the 'Full Package.' The Full Package is an Orange Pi computer running on a custom linux distribution. You basically boot it up, and it starts running bitcoin core and mining in a few clicks. That is very cool, and I did own one. However, I will say that the Full Package is, unfortunately, not a great product. I won't go into too much detail, but its a very poor quality computer, the security upkeep of the custom linux distribution is lacking, and I found connecting to the node to use with wallets to be very difficult. The mining was also consistently inturrupted due to the pi freezing up. You are better off going with a different option for running a bitcoin node.
This is simply to say, I dislike the Full Package Futurebit Apollo Unit. With that said, I very much like the 'Standard Unit'. The Standard Unit is simply a mining hashboard without the computer OS that comes with the Full Package. I've been running two Standard Units in my house for 18 months now and they just quietly hum along in my house, I barely notice them and they rarely need to be restarted (honestly I can't think of more than 3 times that I needed to troubleshoot and even then it was typically restarting the miner). They are a great way to make your personal contribution to the security of the bitcoin network.
(Please Note: These things are pretty pricey brand new, so don't even think about buying one as being a profitable choice. You can sometimes find decent deals for them used, but buyer beware I can't speak to that experience. This is about hands-on learning about bitcoin mining and participating in the security of the network with a machine that won't drive your family crazy and that I believe is well-built enough to last you a long time. Heck, you could even set one up at your office and I doubt anyone would notice and mine with free electricity.)
So, that's some background. Now, a standard unit is not the most friendly user experience if you are not used to using command line. I wasn't, but I spent a lot of time figuring it out. With this guide, any user should be able to get a Standard Unit hashing :) Here is the step by step process guide on how to run a standard unit, in use with both a Windows OS computer and a Linux OS computer (Ubuntu is what I use)...enjoy.
I. Linux
Your Futurebit Apollo Standard Unit (referred to from here as 'the Unit') miner comes with a power supply and a usb cable. It's pretty straight forward, but you will want to connect the Unit to the computer of your choice (the computer needs to be on and running while you are mining, so a low power consumption computer and/or a computer that you are already running all the time for some other reason would be best). Also, plug in the power supply to your unit and turn it on (there are instructions in the Unit's manual for how to hook up the power supply correctly).
- Go to https://github.com/jstefanop/Apollo-Miner-Binaries
- You'll land on a page that looks like this:
For the purposes of this guide, I am going to be using the 'linux-x86_64' package as it is most appropriate for my computer. But, you would need to select the appropriate binaries for your computer. Odds are, if you are running ubuntu on your laptop or desktop, you are going to use the 'linux-x86_64' package.
- Once you have clicked on the linux-x86_64 folder, you will land here:
Open each of these 4 files and download them using the 'Download Raw File' link in each file's page. Here is an example:
Once you have downloaded, I'd recommend making a folder and putting all 4 of the files into that folder. I am going to make a folder with the name 'Mining Files'. I am also going to move the folder out of my Downloads folder (not necessary, but I'd recommend as it's not a great place to park a folder you want to hold onto). I am going to move it to my Documents Folder:
-
Now, if you do not have a mining pool account, you will need to make one, otherwise you should be able to use your pool credentials in the next step. Alternatively, you can solo mine using solo.ckpool.org with only a btc address. However, for the purposes of this guide I am going to assume that you are using Braiins pool. If necessary, go ahead and make a login at braiins.com/pool. Note the username and password as we will need that later.
-
From the files that you downloaded in step 3, we are going to double-click on 'start_apollo.sh' and open it up in Text Editor. The first 60 lines or so are explanations on how to prepare this script for your use. However, I am going to run you through all the options to update, so you shouldn't need to read the description. Instead, we are going to focus on the text in black font at the bottom of the file:
We need to update the info in the following fields as follows
-host = stratum.braiins.com -port = 3333 -user = username for your Braiins login. I'll use "braiinsexample" for now. -pswd = password for your Braiins login. I'll use "Password123" for now. -comport = Most likely "/dev/ttyACM0" or "/dev/ttyACM1" or "/dev/ttyACM2" -brd_ocp = 48 -osc = 30 -ao_mode = 1
So, when our file is set up correctly, it will look like:
Make sure to save, then close out of text editor.
- Now, start up terminal on your computer. First, we are going to want to get into the correct directory. In our case, our file is in Documents > Mining Files. So, you would input the following command:
cd ~/Documents/Mining Files
Once you are in the correct directory, we will run the following command:
sudo ./start_apollo.sh
You will likely be prompted to enter your computer's password, input the password and, if all goes well, you should see a result like this in your terminal:
You are now mining! The setting we use run the Unit ins 'eco mode', which should yield 2 terahash per second in terms of mining power (you can monitor the performance from your respective mining pool dashboard). As long as you keep this terminal window open and the computer on that is connected to the miner, and you will be mining away :)
II. Windows
Your Futurebit Apollo Standard Unit (referred to from here as 'the Unit') miner comes with a power supply and a usb cable. It's pretty straight forward, but you will want to connect the Unit to the computer of your choice (the computer needs to be on and running while you are mining, so a low power consumption computer and/or a computer that you are already running all the time for some other reason would be best). Also, plug in the power supply to your unit and turn it on (there are instructions in the Unit's manual for how to hook up the power supply correctly).
- Go to https://github.com/jstefanop/Apollo-Miner-Binaries
- You'll land on a page that looks like this:
For Windows, you will click on the folder titled 'msvc19'. You'll see 2 files to download, go ahead and click on each and click 'Download Raw File' for each.
Please Note: Windows may see this file as a virus, so you may need to 'allow on device' in your virus & threat protection of your windows security service.
- Once you have downloaded each file, I'd recommend making a folder and putting all of the files into that folder. I am going to make a folder with the name 'Mining Files'. I am also going to move the folder out of my Downloads folder (not necessary, but I'd recommend as it's not a great place to park a folder you want to hold onto). I am going to move it to my Documents Folder:
-
Now, if you do not have a mining pool account, you will need to make one, otherwise you should be able to use your pool credentials in the next step. Alternatively, you can solo mine using solo.ckpool.org with only a btc address. However, for the purposes of this guide I am going to assume that you are using Braiins pool. If necessary, go ahead and make a login with at braiins.com/pool. Note the username and password as we will need that later.
-
From the files that you downloaded in step 3, we are going to right click on 'start_apollo' and select 'edit'. The file will open up in notepad. The first 60 lines or so are explanations on how to prepare this script for your use. However, I am going to run you through all the options to update, so you shouldn't need to read the description. Instead, we are going to focus on the text in black font at the bottom of the file:
We need to update the info in the following fields as follows
-host = stratum.braiins.com -port = 3333 -user = username for your Braiins login. I'll use "braiinsexample" for now. -pswd = password for your Braiins login. I'll use "Password123" for now. -comport = go to the 'Device Manager' service on your computer, expand the 'Ports' section, and you should find a 'USB serial device' with COM#. Update with your COM# (COM1, COM2, COM3, etc). -brd_ocp = 48 -osc = 30 -ao_mode = 1
So, when our file is set up correctly, it will look like:
- Now that the file is ready, save the file and exit out of notepad. You should be able to simply double-click on the file. The command prompt services will pop-up on your desktop, and should reflect this, indicating your connection is successful and mining has begun:
You are now mining! The setting we use run the Unit ins 'eco mode', which should yield 2 terahash per second in terms of mining power (you can monitor the performance from your respective mining pool dashboard). As long as you keep this terminal window open and the computer on that is connected to the miner, and you will be mining away :)
originally posted at https://stacker.news/items/603076
-
 @ 6c8c7979:15595f3e
2024-07-18 20:07:52
@ 6c8c7979:15595f3e
2024-07-18 20:07:52$$Pablo Picasso$$What you may not know about Picasso Pablo Picasso was a Spanish painter, sculptor, and co-founder of the Cubist movement. He was born in 1881 in Malaga, Spain. His first words were "piz, piz," a childish pronunciation of the Spanish word "lápiz," meaning pencil. His father began teaching him art when he was a child. He drew inspiration from the people he met at the Quatre Gats café in Barcelona.Pablo's life went through several stages: the Blue Period (1901-1904) included works like "La Vie" and "The Old Guitarist." The Rose Period (1904-1906) featured works such as "Family of Saltimbanques" and "Gertrude Stein." Picasso's later works were characterized by simplicity and a childlike style. He had countless wives, girlfriends, and children. One of his famous quotes is "Art is the lie that enables us to realize the truth."
Additional information about Picasso is that his parents initially thought he was stillborn, but they discovered his early talent for drawing and mastering art at a young age. He was also a poet and playwright. He was asked to investigate the theft of the Mona Lisa painting. Pablo Picasso's birthdate is October 25, 1881.
$$Biography of Picasso$$Pablo Picasso was born in Malaga on October 25, 1881, becoming one of the greatest and most influential artists of the 20th century. He co-founded the Cubist school with Georges Braque. Picasso, the Spanish expatriate, was a painter, sculptor, theatrical designer, and was considered avant-garde in his work.Picasso died on April 8, 1973, in Mougins, France, after a long professional life filled with creativity, yet he remained through the massive amount of his work and the legend that lives on to honor the controversial Spanish, the owner of the gloomy look that he believed would keep him alive.
Nearly eighty of his 91 years old, Picasso devoted himself to producing works of art that significantly contributed to the development of modern art in the 20th century.
$$Early life of Picasso$$Pablo Picasso was born on October 25, 1881, in Malaga, Spain. His full name, honored by a collection of relatives and saints, was: Pablo Diego José Francisco de Paula Juan Nepomuceno Crispin Crispiniano María Remedios de la Santísima Trinidad Ruiz Picasso.His mother was Doña Maria Picasso Lopez, and his father was Don José Ruiz Blasco, a painter and art teacher. Picasso was a precocious boy with a pair of dark, intense eyes and a bright look that made him seem destined for greatness.
My mother told me when I was a child: "If you become a soldier, you will be famous; if you become a monk, you will be the Pope." Instead, I became a painter and wound up Picasso.
Picasso showed a remarkable talent for drawing despite being relatively poor, and the story goes that his first words were "piz, piz," an attempt as a child to say the Spanish word "lápiz," meaning pencil.
His father began teaching him drawing and painting when he was a child, and by the age of 13, the boy had surpassed his father's skill level. Later, Picasso lost any desire to complete his studies and chose instead to spend his days at school drawing in his notebook.
Picasso said: "As a bad student, I was punished and banished to" Calamus, "a room with walls painted white and a seat to sit on. Later, I said," I loved that room because I used its walls as a large board I drew on constantly, I had to stay there forever drawing without stopping. "
Picasso and his family moved to Barcelona when he was 14 years old, where he was immediately accepted into the prestigious City School of Fine Arts. Although the school usually only accepted students older than Picasso by several years, Picasso's admission exam was unusual and received recognition and exception. Nevertheless, Picasso became tired of the strict rules and regulations of art school and began skipping classes to wander the streets of Barcelona and draw the scenes he noticed there.
Picasso moved to Madrid at the age of 16 in 1897 to receive his education at the Royal Academy of San Fernando. However, he was again frustrated by the teaching style that focused solely on classical subjects and techniques.
He wrote to his friend at the time: "They come on the same old things: Velázquez for painting, Michelangelo for sculpture."
Picasso again began skipping his lessons to wander the streets of Madrid and draw what he noticed: dawn, beggars, and other things. Picasso returned to Barcelona in 1899 and met a group of artists and intellectuals who made their headquarters in a cafe called Cuatre Gats "Cats Four."
Picasso drew inspiration from the disorderly people he met there and completely disconnected from the classical styles he was trained in and entered an experimental and creative stage that spanned his life.
$$Personal life of Picasso$$Picasso was a ladies' man, and he had countless relationships with girlfriends, lovers, and musicians. He married twice during his first life. A dancer was named Olga Khokhlova in 1918, and they continued together for nine years, where they had one child named Paulo, who was separated from them in. 1979 He married for a second time, Jacqueline Rock, who suicide in. 1986 Had with has in them a daughter of his death. Of these marriages, met 1935 Doramar in the film "Le Crime Monsieurlang" produce 1936, quickly a relationship professional, they into 1946. Three Three year relationship with Francois Gilot child. -
 @ 124b23f2:02455947
2024-07-10 04:54:00
@ 124b23f2:02455947
2024-07-10 04:54:00I'm reposting this article I wrote some time ago again to fix the images for it on my npub.pro site
In my previous post, I explained how to use your getalby ln address to receive zaps directly to your LND node. Similarly, there is an additional option that one can utilize to receive zaps directly to your lightning node: lnaddress.com.
Lnaddress.com is a federated lightning address server that you can use to create a custom ln address. Unlike using getalby, lnaddress.com can be used with any lightning implementation (not just LND). For the purposes of this write-up, I am going to use LNBits to connect an lnaddress.com lightning address with my node. And as will be the case with most of my write-ups, I am going to be using Start9 OS, so users of that OS will likely find this write-up most useful, but I'm sure people using other node interfaces can infer how to complete this set up as well.
With that said, let's dive into the step-by-step on how to create your own custom ln address with lnaddress.com and set it up to receive zaps directly to your lightning node:
*Users should have lnbits set up with their lightning node before proceeding.
- Go to lnaddress.com. Input your desired username, select 'Node Backend Type' = LNBits, and if necessary check the box 'This is a new lightning address'. Keep this page open in one tab as we will be returning to it to input info.
- From your Start9 OS services page, go to your LNBits service. Open the 'Properties' page, and in a new tab, open the (Tor) Superuser Account. Page will look like this:
From this LNbits page, you can choose to 'add a new wallet' and use that wallet instead of your superuser account. That is up to you but the steps will be the same.
- Now, we need to grab the info needed for the 'Host Protocol + IP or Domain + Port' field on the lnaddress.com page. On the lnbits page, expand the 'Api Docs' field, and the 'Get Wallet Details' field found on the right hand side menu. In this 'Get Wallet Details' section, you will want to copy some of the URL found in the 'curl example' section. Copy 'http://xxxxxx.onion' (don't copy any more!), and paste this into the 'Host (Protocol + IP or Domain + Port' field found on the lnaddress.com page.
-
Next, we need to grab the key for your lnbits wallet. From the lnbits page, expand the API docs section found on the right hand side menu. Copy the 'Invoice/read key' (make sure to use the invoice/read key and not your Admin key), and paste it into the key field found on the lnaddress.com page. Upon pasting in that last piece of info, click 'submit' at the bottom of the page.
-
If all info was input correctly, your connection will be successful. If successful, you will be brought to a page that looks like this:
You will want to save this secret PIN in case you need to update info in your ln address. You'll also find a test lightning invoice of 1 sat. Using a wallet not connected to the node we connected to our new ln address, you can test the ln address out by paying the 1 sat test invoice.
Users of Start9 OS might find the following info particularly useful: This ln address via lnaddress.com comes with a couple advantages aside from self-custodial zap receiving:
- One, you can have a custom ln address username to go with your nym or nostr username. Users of Start9 may be familiar with the ln address one can generate in the btcpay server service. This ln address is not customizable.
- Two, if you are running a tor only lightning node, you will be able to receive zaps from both tor and clear net lightning nodes. Users of Start9 may be familiar with the ln address one can generate in the btcpay server service. This ln address can only receive zaps from other tor nodes and can't receive zaps from clear net nodes.
That is it, you should now be all set up with your new ln address hosted on lnaddress.com, and you should be all ready to receive zaps or lightning payments of any kind :)
originally posted at https://stacker.news/items/603061
-
 @ 6bae33c8:607272e8
2024-07-18 19:19:16
@ 6bae33c8:607272e8
2024-07-18 19:19:16These are my very preliminary RB rankings, my only research being the RotoWire depth charts and player notes.
**Tier 1
Christian McCaffrey**
He’s 28 years old, has 1,402 career carries including the postseason and weighs only 205 pounds at 5-11. But McCaffrey is arguably the greatest running back all time, when you include the pass catching, and he’s in the league’s best system for backs. Health is really the only variable, and anyone can get hurt.
**Tier 2
Breece Hall, Bijan Robinson, Saquon Barkley, Jonathan Taylor**
These are the three-down backs with elite skill sets. Hall should be better another year removed from the ACL tear and playing with a better QB, Robinson should get the heavy usage he merits with Arthur Smith gone, Barkley finally gets a quality offensive line and QB and Taylor plays next to a running QB and has little competition for carries.
**Tier 3
Jahmyr Gibbs, De’Von Achane, Kyren Williams, Travis Etienne**
These are the little guys, all of whom can run and catch passes, plus Etienne. Williams is the biggest risk as an early-down high-workload guy, but he was also insanely productive when he played in Sean McVay’s lead-back-friendly system. Gibbs seems like peak Alvin Kamara, only faster and Achane in the Miami offense was the most efficient back in league history by a mile. I originally had Etienne in Tier 4, but he doesn’t have much competition for the job and should be a three-down back.
**Tier 4
Isaiah Pacheco, Josh Jacobs, Joe Mixon, James Cook, David Montgomery, Derrick Henry, Kenneth Walker, Racchad White, James Conner, Rhamondre Stevenson, Zack Moss, Javonte Williams, Devin Singletary **
This is a big tier, but these are all the incomplete players guaranteed reps if healthy. Pacheco could be moved to Tier 3, but Patrick Mahomes doesn’t check down to the back all that often, and Pacheco rarely gets to 20 carries in a game. Jacobs is a beast but has a ton of mileage in a short span and fell off last year. Mixon is another old warhorse with a lot of mileage, albeit also in a good situation. Cook suffers due to Josh Allen’s goal-line prowess and tendency to take off rather than check down. Montomgery will cede the third-down work, Henry is old and doesn’t catch many passes, Walker splits carries, gets hurt often, White is a ham and egger who happened to see a huge workload, Conner is 29 and always misses time, Stevenson is a workhorse on a bad team, Moss is an average back in a good spot, Williams is another year off the injury, but on a bad team and Singletary is the clear lead back on a poor offense.
**Tier 5
Tony Pollard, D’Andre Swift, Jonathan Brooks, Alvin Kamara, Brian Robinson, Jaylen Warren, Austin Ekeler, Chuba Hubbard, Zamir White, Raheem Mostert, Aaron Jones, Najee Harris, Nick Chubb, Tyjae Spears, Trey Benson, Zach Charbonnet ** These are mostly timeshare backs, with the exception of Kamara whose efficiency fell through the floor and White who I’m not convinced will lock down the job all year.
**Tier 6
Kenneth Gainwell, Rico Dowdle, Gus Edwards, Jerome Ford, Zeke Elliott, Roschon Johnson, Jaylen Wright, Bucky Irving, JK Dobbins, Antonio Gibson, Chase Brown, Elijah Mitchell, Jaleel McLaughlin, Tyler Algeier, MarShawn Lloyd**
This is the backup tier, all of whom probably need an injury ahead of them to break out.
These rankings will change, but I like to get my preliminary ones down on paper before I get influenced by ADP and training camp hype.
-
 @ c7eda660:efd97c86
2024-07-18 14:50:10
@ c7eda660:efd97c86
2024-07-18 14:50:10Bitvora is a unified Bitcoin & Lightning rail. A single API with no infrastructure overhead.
So you don’t have to go through this:
App engineers and product people, this is for you: two lines of code—bitcoin sent.
https://i.nostr.build/8Wp3jNhqHcml3pxl.gif
Bitvora makes on-chain and Lightning payments simple, fast, and friction-free.
I’ll be at The Bitcoin Conference in Nashville next week, and I’d love to give you a sneak peek of the product. We’ll be in an invite-only beta.
If you’ll be in town, DM me or leave a reply below to set up a meeting. I can’t wait to show you what we've built.
-
 @ fce4177b:f504cdc8
2024-07-18 12:15:14
@ fce4177b:f504cdc8
2024-07-18 12:15:14Hi all!
Lately I've been working on a small python project to try approaching the pathfinding problem in lightning as a Min-cost network flow problem.
I know Renè Pickhardt already used this approach in order to prove the superiority of the Zero base fee approach, in fact I read his papers and got the gist of it.
Now I'm trying to model the problem mathematically - using the pyomo package in python - but I came up with a question that I couldn't find an answer for:
in a multi-path payment (MPP), can two HTLCs go though the same channel?
More specifically, I'm interested in understanding if the following situation can happen or not:
Nodes = {S, A, B, C, E, F, G, I, D} # S source, D destinationWith S being the source node (aka the payer), D being the destination node (aka the payee). The scope of the question does not include considerations about base or rate fees. Node S computes the optimal path that minimises the fees for an amount and finds out that the optimal choice is to execute a MPP that follows this path(s):
``` B E
A -> -> -> G -> D C Fh0 h1 h2 h3 h4 ```
where the first two hops (h1 and h2) see two parallel payments going on, then at the hop h3 the MPP converges to the node G and then procedes with the last hop to destination.
As far as I know, in classical MPP the preimage is the same for every parallel path (correct me if I'm wrong), thus I'm wondering if that thing is possible or not. Moreover, if there was an another hop such that:
``` B E
A -> I -> -> -> G -> D C Fh0 h1 h2 h3 h4 h5 ```
would that be possible too? That meaning two HTLCs flowing in the same channel for the first hop, then splitting and the riconverging.
Hope the question is clear enough, otherwise I'm open to clarifications.
Thanks!
originally posted at https://stacker.news/items/612642
-
 @ 1e52c554:21771908
2024-07-18 10:42:02
@ 1e52c554:21771908
2024-07-18 10:42:02Obra póstuma del poeta colombiano nacido en Don Matías el 20 de enero de 1948.
Bienvenidos a este blog dedicado a la obra póstuma del poeta colombiano Francisco Luis Arroyave Tabares (mi padre), nacido en Don Matías el 20 de enero de 1948-2010. Aquí estaré publicando cada uno de los 175 sonetos de su colección inédita ‘Sonetos para el siglo XXI y un Festival Circadiano (1984-1987)
En este blog, compartiré las traducciones de los sonetos que he estado publicando. Mi objetivo es dar a conocer al público hispanohablante el legado de este colombiano, quien escribió una de las colecciones más grandes de sonetos en inglés.
El escritor siempre enfatizo que al traducir los sonetos sonarian tan natural que no se sentiria que estan escritos con toda la estructura en lengua inglesa.
Espero que disfruten de este jardín de palabras arrancadas de la soledad de una habitación cerrada.
Frank Duna
Soneto 1 por Francisco Luis Arroyave Tabares
``` Donde Abunda el Consenso
En días escasos no pude escribir versos Ni encontrar palabras un poco cerca de mi pensamiento Y ni un arte u otra forma tan correcta Podría mostrar bien lo que mi corazón gustaba o luchaba.
A menudo con rimas condenatorias yo apedreo Otras mentes que piensan que sus modales son los mejores Pero juro que quiero que todo el odio se vaya de mí Porque el odio fermenta y puede corromper el resto.
Hazme responsable de los males que encuentres Y con ojos perspicaces soporta mis luces y oscuridad Llama a mi pluma la herramienta de un rústico siervo Y por favor lee mis lágrimas de su marca humana.
De esta manera, tonos más altos pueden surgir en las nubes Para reunir fuerza donde abunda el consenso. *** Anotaciones: 11-. Hind = un trabajador agrícola hábil o sirviente. ```
Análisis “Donde Abunda el Consenso”
Estructura y Forma
El poema sigue la estructura de un soneto shakespeariano, compuesto por 14 versos con un esquema de rima específico ABABCDCDEFEFGG. Cada línea está escrita predominantemente en pentámetro yámbico, un patrón métrico común en los sonetos en inglés, que ayuda a crear un flujo rítmico y melódico.
Esquema de Rima
El primer cuarteto (líneas 1-4): ABAB El segundo cuarteto (líneas 5-8): CDCD El tercer cuarteto (líneas 9-12): EFEF El pareado final (líneas 13-14): GG
Análisis Temático
-
Expresión y Lucha: En el cuarteto inicial, el poeta expresa la dificultad de encontrar palabras que capten adecuadamente sus pensamientos y emociones. Los versos transmiten una sensación de frustración y limitación, sugiriendo que ni el arte ni cualquier otro medio pueden representar completamente las complejidades de los deseos y luchas de su corazón.
-
Crítica y Auto-reflexión: El segundo cuarteto revela la conciencia del poeta sobre sus propias tendencias a juzgar y condenar a otros a través de su poesía. La metáfora de "apedrear" con "rimas condenatorias" destaca la naturaleza agresiva de su crítica. Sin embargo, el poeta también expresa un deseo de deshacerse del odio, reconociendo su efecto corrosivo tanto en uno mismo como en la comunidad en general.
-
Vulnerabilidad y Humanidad: En el tercer cuarteto, el poeta invita a los lectores a examinar sus fallos ("los males que encuentres") con ojos perspicaces. Describe su pluma como una herramienta simple ("la herramienta de un campesino hábil"), enfatizando la humildad y una conexión con la humanidad común. La solicitud de "leer en mis lágrimas su marca humana" subraya la vulnerabilidad del poeta y la autenticidad de su expresión emocional.
-
Esperanza y Unidad: El pareado final lleva el poema a una conclusión esperanzadora, imaginando el surgimiento de "tonos más elevados" en las nubes metafóricas. Esta imaginería sugiere el potencial de crecimiento, inspiración y fuerza que se puede encontrar en la unidad y el consenso. El poeta implica que al abrazar la empatía y la comprensión, puede surgir una colectividad más armoniosa y poderosa.
-
Lenguaje y Dicción: El lenguaje del poema es formal y reflexivo, con una atención cuidadosa a la elección de palabras. Frases como "rimas condenatorias," "el odio fermenta," y "campesino hábil" enriquecen el texto con imágenes vívidas y profundidad metafórica. La dicción ayuda a transmitir la lucha interna del poeta y sus aspiraciones, así como los temas más amplios de empatía y unidad.
-
Imaginería y Simbolismo: Apedrear con rimas: Representa el daño que las palabras duras pueden infligir a otros. Fermenta el odio: Simboliza cómo el odio puede crecer y extenderse, corrompiendo todo lo que toca. Tonos más elevados que surgen en nubes: Sugiere el potencial elevador y unificador del consenso y la comprensión mutua.
- Conclusión: El "Soneto 1" de Francisco Luis Arroyave Tabares es una meditación conmovedora sobre los desafíos de la autoexpresión, los peligros del juicio y el odio, y la esperanzadora posibilidad de la unidad a través de la empatía. La forma estructurada del poema, su rica imaginería y su lenguaje reflexivo se combinan para crear una exploración poderosa de la condición humana y el poder transformador del consenso.
Soneto original:
``` Soneto 1 by Francisco Luis Arroyave Tabares
Where Consensus Abounds
In days this is sparce no verses I could write Nor find words a little close to my thought And not an art or other way so right Could display well what my heart liked or fought.
Often times with condemning rhymes I stone Other minds which think their manners are best But I swear that hate I want from me all gone Because hate yeasts and may corrupt the rest.
Account for me the evils that you find And with insight eyes bear my lights and dark Call my pen the tool of a rustic hind 11
And please read my tears of their human mark.This way loftier hues may rise in clouds To gather strength where consensus abounds. *** 11-. Hind = a skilled farm worker or servant. ```
“Sonetos para el Siglo XXI y un Festival Circadiano” escrito por Francisco Luis Arroyave Tabares (1984-1987) copyright1989
Imagen por Frank Duna (Bahia de Santa Marta)

-
-
 @ b34b4408:acfb9667
2024-07-18 03:43:39
@ b34b4408:acfb9667
2024-07-18 03:43:39"ผลกระทบของน้ำยาบ้วนปากต่อจุลชีพในช่องปากและร่างกาย: มุมมองใหม่จากการวิจัยล่าสุด"
ในช่วงหลายทศวรรษที่ผ่านมา น้ำยาบ้วนปากได้กลายเป็นส่วนหนึ่งของกิจวัตรการดูแลสุขภาพช่องปากของคนจำนวนมาก โดยมีจุดประสงค์หลักเพื่อลดกลิ่นปาก ป้องกันฟันผุ และรักษาสุขภาพเหงือก อย่างไรก็ตาม การวิจัยล่าสุดได้เผยให้เห็นถึงผลกระทบที่ไม่คาดคิดของการใช้น้ำยาบ้วนปากเป็นประจำ โดยเฉพาะอย่างยิ่งต่อระบบนิเวศของจุลชีพในช่องปากและร่างกาย

การศึกษาล่าสุดที่ตีพิมพ์ในวารสาร Journal of Medical Microbiology เมื่อวันที่ 4 มิถุนายน 2024 โดย J.G.E. Laumen และคณะ ( https://www.microbiologyresearch.org/content/journal/jmm/10.1099/jmm.0.001830 )ได้ศึกษาผลของการใช้น้ำยาบ้วนปาก Listerine Cool Mint เป็นประจำทุกวันต่อจุลชีพในช่องปากและลำคอ

ผลการวิจัยพบว่าการใช้ Listerine เป็นเวลา 3 เดือนทำให้เกิดการเปลี่ยนแปลงอย่างมีนัยสำคัญในองค์ประกอบของจุลชีพในช่องปากและลำคอ โดยเฉพาะอย่างยิ่ง การเพิ่มขึ้นของแบคทีเรีย Fusobacterium nucleatum และ Streptococcus anginosus ซึ่งเป็นเชื้อที่ก่อให้เกิดปัญหาสุขภาพหากมีปริมาณมากเกินไป

โดยเชื้อทั้งสองตัวนั้นมีผลต่อสุขภาพดังนี้
Fusobacterium nucleatum:
เป็นเชื้อแบคทีเรียที่พบได้ตามปกติในช่องปาก แต่หากมีปริมาณมากเกินไปจะก่อให้เกิดปัญหาได้ มีความเกี่ยวข้องกับโรคปริทันต์ (โรคเหงือกอักเสบ) มีการศึกษาพบความสัมพันธ์ระหว่างเชื้อนี้กับมะเร็งลำไส้ใหญ่ มีส่วนในการกระตุ้นการอักเสบในร่างกาย ซึ่งอาจเชื่อมโยงกับโรคทางระบบอื่นๆStreptococcus anginosus:
เป็นส่วนหนึ่งของกลุ่ม Streptococcus milleri ซึ่งพบได้ในช่องปาก ลำคอ และทางเดินอาหาร โดยปกติไม่ก่อโรค แต่ในบางกรณีอาจกลายเป็นเชื้อฉวยโอกาส สามารถก่อให้เกิดการติดเชื้อในช่องปาก เช่น ฝีในช่องปาก ในกรณีที่รุนแรง ทำให้เกิดการติดเชื้อในกระแสเลือด หรือฝีในอวัยวะภายใน เช่น สมอง ปอด หรือตับผลการวิจัยนี้ทำให้เกิดคำถามสำคัญเกี่ยวกับกลไกการทำงานของน้ำยาบ้วนปากและผลกระทบระยะยาวต่อสุขภาพ เมื่อพิจารณาส่วนประกอบหลักของ Listerine Cool Mint (รวมถึง น้ำยาบ้วนปากอื่นๆด้วย) ซึ่งประกอบด้วย
1. น้ำ (เป็นส่วนประกอบหลัก) 2.แอลกอฮอล์ (มักจะอยู่ที่ประมาณ 21.6%) 3.น้ำมันหอมระเหยจากพืช ได้แก่: Eucalyptol (น้ำมันยูคาลิปตัส) Menthol (เมนทอล) Thymol (ไทมอล) Methyl salicylate (เมทิลซาลิไซเลต หรือ น้ำมันวินเทอร์กรีน) 4.สารให้ความหวาน (มักใช้ซอร์บิทอล) 5.กรดเบนโซอิก (สารกันบูด) 6.สารให้สี (อาจใช้สีเขียว) 7.โซเดียมซักคาริน (สารให้ความหวาน) 8.โซเดียมเบนโซเอต (สารกันบูด)
จะพบว่าแต่ละสารมีส่วนทำให้เกิดการเสียสมดุลของจุลชีพในช่องปาก:
1. แอลกอฮอล์และน้ำมันหอมระเหย: มีฤทธิ์ฆ่าเชื้อที่รุนแรง ทำลายทั้งแบคทีเรียที่เป็นโทษและเป็นประโยชน์ เปิดโอกาสให้เชื้อบางชนิดเติบโตได้มากขึ้น 2. สารกันบูด: ยับยั้งการเจริญเติบโตของจุลินทรีย์บางชนิดมากกว่าชนิดอื่น 3. สารให้ความหวาน: เป็นแหล่งอาหารสำหรับแบคทีเรียบางชนิด หรือเปลี่ยนแปลงสภาพแวดล้อมในช่องปากผลการวิจัยนี้ได้ท้าทายความเชื่อดั้งเดิมเกี่ยวกับประโยชน์ของน้ำยาบ้วนปาก ในอดีต น้ำยาบ้วนปากถูกส่งเสริมว่ามีประโยชน์ในการลดกลิ่นปาก ป้องกันฟันผุ และช่วยรักษาโรคเหงือก อย่างไรก็ตาม การค้นพบใหม่นี้บ่งชี้ว่า ประโยชน์ระยะสั้นเหล่านี้อาจไม่คุ้มค่ากับผลเสียที่อาจเกิดขึ้นในระยะยาว การเสียสมดุลของจุลชีพในช่องปากอาจนำไปสู่การเพิ่มขึ้นของแบคทีเรียที่เป็นอันตราย ซึ่งจะเพิ่มความเสี่ยงต่อโรคต่างๆ ทั้งในช่องปากและระบบอื่นๆ ของร่างกาย เช่น โรคปริทันต์ มะเร็งหลอดอาหารและลำไส้ใหญ่ รวมถึงโรคทางระบบอื่นๆ
บทความนี้เน้นย้ำความสำคัญของการพิจารณาอย่างรอบคอบในการใช้ผลิตภัณฑ์สุขภาพช่องปาก และ ผู้บริโภคควรตระหนักถึงความสำคัญของการรักษาสมดุลของจุลชีพในช่องปากและพิจารณาทางเลือกอื่นๆ ในการดูแลสุขภาพช่องปากที่อาจมีผลกระทบน้อยกว่าต่อระบบนิเวศของจุลชีพ เช่น การแปรงฟันอย่างสม่ำเสมอ การใช้ไหมขัดฟันอย่างถูกวิธี และการรับประทานอาหารที่มีประโยชน์ต่อสุขภาพช่องปาก

ซึ่งการรับประทานอาหารที่ดีต่อสุขภาพช่องปาก เป็นส่วนสำคัญในการดูแลสุขภาพฟันและเหงือก รวมถึงการรักษาสมดุลของจุลชีพในช่องปากและร่างกายด้วย ซึ่งประกอบด้วย:
**อาหารธรรมชาติที่มีการแปรรูปน้อย อาหารที่มีโพรไบโอติกส์และพรีไบโอติกส์ ช่วยรักษาสมดุลของจุลชีพที่ดี เช่น โยเกิร์ต คีเฟอร์ กิมจิ ชีส อาหารที่กระตุ้นการหลั่งน้ำลาย: น้ำลายช่วยชะล้างแบคทีเรียและเศษอาหาร เช่น เนื้อสัตว์ ไข่ นอกจากนี้ การเคี้ยวอาหารให้ละเอียดและใช้เวลาในการรับประทานอาหารช้าๆ ยังช่วยกระตุ้นการหลั่งน้ำลายและส่งเสริมสุขภาพช่องปากที่ดีอีกด้วย น้ำเปล่า: ดื่มน้ำสะอาดอย่างเพียงพอช่วยชะล้างช่องปากและรักษาความชุ่มชื้น**อาหารที่ควรหลีกเลี่ยงหรือจำกัดคือ
** อาหารและเครื่องดื่มที่มีแป้ง/น้ำตาลสูง ซึ่งส่งเสริมการเจริญเติบโตของแบคทีเรียที่ก่อให้เกิดฟันผุ และการอักเสบ รวมถึงอาหารที่ผสมสารต่างๆที่กล่าวมาก่อนหน้า**การรับประทานอาหารที่สมดุลและหลากหลายไม่เพียงแต่ส่งผลดีต่อสุขภาพช่องปากเท่านั้น แต่ยังช่วยส่งเสริมสุขภาพโดยรวมของร่างกายอีกด้วย
หากยังต้องการใช้น้ำยาบ้วนปาก ควรพิจารณาใช้เฉพาะเมื่อจำเป็น ไม่ใช้เป็นประจำทุกวัน และอาจเลือกน้ำยาบ้วนปากที่ไม่มีแอลกอฮอล์ รวมถึงสารต่างๆอย่างที่กล่าวไปก่อนหน้า
ในท้ายที่สุด การวิจัยนี้เน้นย้ำถึงความสำคัญของการไม่ยึดติดกับความเชื่อเดิมๆ โดยไม่พิจารณาหลักฐานใหม่ทางวิทยาศาสตร์ และวิธีการดูแลสุขภาพที่คำนึงถึงระบบนิเวศของจุลชีพมากขึ้น
-
 @ 47750177:8969e41a
2024-07-09 12:00:00
@ 47750177:8969e41a
2024-07-09 12:00:0026.2 Release Notes
Bitcoin Core version 26.2 is now available from:
This release includes new features, various bug fixes and performance improvements, as well as updated translations.
Please report bugs using the issue tracker at GitHub:
https://github.com/bitcoin/bitcoin/issues
To receive security and update notifications, please subscribe to:
https://bitcoincore.org/en/list/announcements/join/
How to Upgrade
If you are running an older version, shut it down. Wait until it has completely shut down (which might take a few minutes in some cases), then run the installer (on Windows) or just copy over
/Applications/Bitcoin-Qt(on macOS) orbitcoind/bitcoin-qt(on Linux).Upgrading directly from a version of Bitcoin Core that has reached its EOL is possible, but it might take some time if the data directory needs to be migrated. Old wallet versions of Bitcoin Core are generally supported.
Compatibility
Bitcoin Core is supported and extensively tested on operating systems using the Linux kernel, macOS 11.0+, and Windows 7 and newer. Bitcoin Core should also work on most other Unix-like systems but is not as frequently tested on them. It is not recommended to use Bitcoin Core on unsupported systems.
Notable changes
Script
-
29853: sign: don't assume we are parsing a sane TapMiniscript
P2P and network changes
-
29691: Change Luke Dashjr seed to dashjr-list-of-p2p-nodes.us
-
30085: p2p: detect addnode cjdns peers in GetAddedNodeInfo()
RPC
-
29869: rpc, bugfix: Enforce maximum value for setmocktime
-
28554: bugfix: throw an error if an invalid parameter is passed to getnetworkhashps RPC
-
30094: rpc: move UniValue in blockToJSON
-
29870: rpc: Reword SighashFromStr error message
Build
-
29747: depends: fix mingw-w64 Qt DEBUG=1 build
-
29985: depends: Fix build of Qt for 32-bit platforms with recent glibc
-
30151: depends: Fetch miniupnpc sources from an alternative website
-
30283: upnp: fix build with miniupnpc 2.2.8
Misc
-
29776: ThreadSanitizer: Fix #29767
-
29856: ci: Bump s390x to ubuntu:24.04
-
29764: doc: Suggest installing dev packages for debian/ubuntu qt5 build
-
30149: contrib: Renew Windows code signing certificate
Credits
Thanks to everyone who directly contributed to this release:
- Antoine Poinsot
- Ava Chow
- Cory Fields
- dergoegge
- fanquake
- glozow
- Hennadii Stepanov
- Jameson Lopp
- jonatack
- laanwj
- Luke Dashjr
- MarcoFalke
- nanlour
- willcl-ark
As well as to everyone that helped with translations on Transifex.
-
-
 @ 0e8c41eb:95ff0faa
2024-07-08 14:36:14
@ 0e8c41eb:95ff0faa
2024-07-08 14:36:14Chef's notes
Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
Spread the fruit filling over the dough.
Mix the rest of the flour with the remaining 100 grams of butter and 100 grams of sugar and knead it with your fingers into a crumbly mixture. Sprinkle this crumble mixture over the fruit filling. Bake the tart in the preheated oven at 200°C for about 30 minutes until golden brown.
Variations: Only apple? Make this tart with 1 kilo of apples. High or low? You can also bake the crumble tart in a low tart tin of 30 cm diameter. If the fruit filling is a bit too voluminous, you can make double the crumble mixture and sprinkle it over the larger surface area.
Additional needs: Mixer with dough hooks or food processor Cling film Round baking tin with a diameter of 28-30 cm, greased
Details
- ⏲️ Prep time: 45 min + 1 hour Rising
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 8
Ingredients
- 375 grams flour
- 1 packet dried yeast (7 grams)
- 125 grams unsalted butter, at room temperature
- 275 grams sugar
- 1 egg
- 100 ml milk, at room temperature
- 500 grams apples
- 500 grams apricots (fresh or from a can)
Directions
- Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
- Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
- Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
- Spread the fruit filling over the dough.
-
 @ a012dc82:6458a70d
2024-07-18 03:37:01
@ a012dc82:6458a70d
2024-07-18 03:37:01Table Of Content
-
Advantages of Bitcoin in Online Payments and E-Commerce
-
The Future of Bitcoin in Online Payments and E-Commerce
-
Multiple Industries Are Getting Involved
-
Conclusion
-
FAQ
Bitcoin, the first and most well-known cryptocurrency, has been making waves in the world of online payments and e-commerce. It offers several advantages over traditional payment methods, such as lower transaction fees, faster processing times, and increased security. Additionally, Bitcoin's decentralized nature and lack of government or financial institution control make it an attractive option for those who prioritize privacy and autonomy.
Advantages of Bitcoin in Online Payments and E-Commerce
Bitcoin, the world's first cryptocurrency, has the potential to revolutionize online payments and e-commerce. Here are some of the advantages of using Bitcoin in these areas:
Decentralization
Bitcoin operates on a decentralized network, meaning it is not controlled by a central authority like a government or financial institution. This eliminates the need for intermediaries, such as banks, to facilitate transactions, resulting in lower transaction fees and quicker processing times.
Security
Bitcoin transactions are secured by complex algorithms and cryptographic protocols, making them virtually impossible to hack or counterfeit. This offers increased security for both merchants and consumers in online payments and e-commerce.
Anonymity
Bitcoin transactions are pseudonymous, meaning they are not linked to real-world identities. This provides a level of anonymity that is not possible with traditional payment methods, making it an attractive option for those who value privacy.
Global Reach
Bitcoin is a global currency that can be used for transactions anywhere in the world, without the need for currency conversions or additional fees. This makes it an ideal option for cross-border e-commerce transactions.
Low Fees
Because Bitcoin eliminates intermediaries and their associated fees, transactions can be processed at a much lower cost than traditional payment methods.
Transparency
All Bitcoin transactions are recorded on a public ledger called the blockchain, providing transparency and accountability for all parties involved in online payments and e-commerce.
The Future of Bitcoin in Online Payments and E-Commerce
The future of Bitcoin in online payments and e-commerce is still uncertain. While the cryptocurrency has gained a lot of popularity in recent years, it is still subject to regulatory and market risks. However, there are several reasons to believe that Bitcoin and other cryptocurrencies could play a significant role in the future of online payments and e-commerce. One reason is the growing acceptance of Bitcoin by major companies, such as Microsoft, PayPal, and Tesla. Additionally, the increasing use of blockchain technology could lead to the development of new, more secure and efficient payment systems. As such, it is clear that Bitcoin has the potential to change the world of online payments and e-commerce in significant ways, but much will depend on how the cryptocurrency is regulated and adopted in the years to come.
Multiple Industries Are Getting Involved
It is true that multiple industries are getting involved in the world of Bitcoin and blockchain technology. From finance to healthcare, entertainment to real estate, many sectors are exploring the potential benefits of these new technologies. Some companies are using Bitcoin as a form of payment or investment, while others are exploring the use of blockchain for data management and security. As the technology continues to develop, we can expect more industries to get involved in the future.
Conclusion
Bitcoin is a disruptive technology that has the potential to transform the world of online payments and e-commerce. While there are challenges and risks associated with its use, the benefits of Bitcoin make it a compelling option for both consumers and merchants alike.
FAQ
What is the advantage of using Bitcoin for online payments? One of the main advantages of using Bitcoin for online payments is that it is a fast and secure payment method that does not require the use of intermediaries.
What is the advantage of using Bitcoin for e-commerce? Bitcoin offers several advantages for e-commerce, including lower transaction fees, faster transaction processing times, and increased security and privacy for buyers and sellers.
What are the challenges and risks associated with using Bitcoin? Some of the challenges and risks associated with using Bitcoin include its volatility, the potential for fraud or hacking, and the lack of regulation and legal protection.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ cec2981c:814d4f26
2024-07-08 12:56:36
@ cec2981c:814d4f26
2024-07-08 12:56:36Chef's notes
More information about its origins: https://en.wikipedia.org/wiki/Soda_bread
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 45 min
- 🍽️ Servings: 4-8
Ingredients
- 500 gr whole grain flour
- 450 ml butter milk
- 10 gr (sea)salt
- 15 gr baking soda (not US's "baking powder") (also known as sodium bicarbonate)
- a bit of butter or olive oil
Directions
- Pre-heat the oven to 220°C
- Put all flour in a bowl with baking soda and salt. Mix it well.
- Create a hole in the middle and pour all butter milk in the center.
- Stir it from the centre and slowly mixing all together until you get a dough.
- When mixed, the dough is sticky. Use all purpose flour on counter and bulge to the same size as your skillet.
- Use a bit of butter or olive oil to wet the skillet to prevent sticky bread. And put the dough in your skillet.
- Add a but of flour on top of the dough and then cut lightly a X.
- Bake for ±45 min on 220°C until done (inside temperature must be at least 95°C). Turn up the heat for the last 5 min to get a crust.
- Let the bread cool down a bit before taking it out the skillet, and let it cool down even more before eating.
- Donate some sats to me if you like this recipe.
-
 @ 6c8c7979:15595f3e
2024-07-17 23:32:28
@ 6c8c7979:15595f3e
2024-07-17 23:32:28Are you looking for new ways to increase your productivity? Maybe you thought about using the same methods that some historical figures used, from musicians and artists to politicians. Most of them spent their days drinking regular doses of caffeine, but few had strange habits that helped them work faster and more efficiently.
From Charles Dickens' addiction to routine to the trick used by an ancient Greek politician to resist procrastination and dawdling, here are historical figures who had unconventional ways to accomplish their tasks.
$$Charles Dickens$$
The author of "A Tale of Two Cities" and "A Christmas Carol" was known to be demanding and meticulous about his working conditions. He adhered to a strict "military" schedule, always writing in his study from nine in the morning until two in the afternoon, then taking a three-hour walk.
Dickens demanded complete silence from everyone in his house during his working hours, and arranged his pens, inks, and a set of small statues specifically on his desk to help him think.
The writer maintained these habits wherever he traveled, even rearranging the furniture of hotel rooms and guest houses to resemble his study as much as possible.
His eccentric habits extended to his bedroom, where he always slept facing north, believing it made him better aligned with the Earth's electrical currents.
$$Beethoven$$
Ludwig van Beethoven composed most of his work while in motion. After his daily breakfast consisting only of coffee — often preparing 60 beans for use in his coffee — the composer worked for several hours in his study before going on long walks.
These enjoyable walks were supposed to stimulate his creativity; he often stopped during his walks to jot down quickly and hurriedly a set of musical notes on a large notebook.
If the composition process was slow, the composer copied some compositions of other musicians to study their style. Beethoven also composed music while bathing.
According to his secretary, Anton Schindler, Beethoven often moved quickly around his room, frequently pouring several pitchers of water over his hands, while he cares for some tunes and stares off into space with "deep meditation."
$$Marcel Proust$$
While writing his massive 3,000-page novel "In Search of Lost Time" (also known as "Remembrance of Things Past") in the early 20th century, French author Marcel Proust lived within the confines of his bedroom.
He usually woke up at three or four in the afternoon, then drank coffee and ate a croissant, and often his only meal throughout the day, after that, he smoked his hookah, which included tobacco mixed with opium, which he thought helped him bear the asthma.
Proust worked on his novel lying on his bed, with a set of thin cushions, and despite the seemingly comfortable working conditions, the author continued to say that writing his novel was hard and tiring work.
$$Salvador Dali$$
Considered one of the masters of surrealism, a school of art aimed at exploiting the unconscious mind and reaching its hidden treasures. Dali used mental tricks to experiment with and blur the boundary between his dreams and reality, and this helped his mind produce hallucinatory images "Surrealist" that he painted through paintings like "The Persistence of Memory" and "Swans Reflecting Elephants."
One of his actual and proven techniques was to hold a metal key over a tin container during his nap time, and when he starts to fall asleep, the key drops from his hand, and he wakes up, and that gave him a chance to record the bizarre images he produces in his mind.
Dali invented a special method he called "Paranoid-Critical" "Madness of doubt-shame," the artist was working through this method to convey himself to a state of madness of doubt and greatness by prolonging deliberate thinking with weird, irrational ideas, and then he starts drawing the images he sees in his mind.
$$B.F. Skinner$$
He was an American psychologist, a behavioralist, an author, an inventor, and a social philosopher. Skinner invented the Israbutroom room and his own philosophy in the science called the Extreme Behavior and founded his school in experimental research in psychology, which is the experimental analysis of behavior.
Skinner's analysis of human behavior culminated in his work in Verbal Behavior, which has seen significant recent development in the experimental field and the application settings, and in a study conducted in June 2002, Skinner was classified as the most influential psychologist of the 20th century.
He worked on a strict schedule and used a timer to remind him of the start and stop time to write. In his memoirs, he wrote that he recorded every twelve hours of his work, where he drew a point on an accumulating curve showing him the overall production of his productivity.
In addition to dividing times during the day and analyzing daily work, Skinner endorsed what is called intermittent sleep, so often he would wake up after midnight to work for an hour, and then he would return to his sleep.
$$Demosthenes$$
The Greek statesman and politician Demosthenes were known for his ability to deliver exciting and enthusiastic speeches without any effort, His skill in speaking came through following a strict, often unusual system.
Demosthenes spent long hours studying the art of rhetoric and law in a specially made underground office, and trained with an actor to learn how to control his body movements.
To overcome his stuttering and shortness of breath, Demosthenes would speak while placing pebbles in his mouth, and he would deliver his speeches loudly while running up a hill, but the strangest thing was his way of facing procrastination and delaying, Demosthenes had shaved half of his head with the aim of looking his appearance funny, and thus he had to stay in his home and focus on his studies.
-
 @ 3cd2ea88:bafdaceb
2024-07-17 21:33:47
@ 3cd2ea88:bafdaceb
2024-07-17 21:33:47🚀 Bitget ti invita a partecipare a un evento di trading straordinario!
Non perdere l'opportunità e fai trading di ETH per partecipare a una pool di ricompense eccezionale, con un totale di 7 ETH in palio!
🎁 Scarica l'app e iscriviti per ottenere $5-10 in ETH!
🎁 Ricevi subito $5-10 in ETH scaricando l'app Bitget e iscrivendoti durante l'evento.
🏆 Vinci con la tua prima operazione: Condividi 1 ETH!
Completa la tua prima operazione di trading sui Futures superiore a $500 e avrai diritto a condividere 1 ETH!
💎 Scambia di più, condividi di più: Tuffati in una pool da 5 ETH!
🚀 Durante l'evento, tutti gli utenti che effettuano operazioni sui Futures con volumi superiori a 10.000 USDT possono condividere il montepremi di 5 ETH. Più scambi, più guadagni!
🔗 Iscriviti ora su Bitget e inizia a fare trading! https://bonus.bitget.com/U1JNEK
Non lasciarti sfuggire questa opportunità unica con Bitget! 🚀✨
-
 @ 69a0a091:c968228d
2024-07-07 19:10:07
@ 69a0a091:c968228d
2024-07-07 19:10:07Radicale is a self-hosted calendar and contact solution that is "lightweight solution, easy to use, easy to install, easy to configure."
https://radicale.org/v3.html#about
I can finally dump my NextCloud, which was a sprawling mess of PHP scripts. Managing a NextCloud instance over a long period of a time requires the sysadmin to be mindful of the stateful configuration, which can only be upgraded one major version at a time.
I stumbled over Radicale a couple years ago right after I had spent an entire day writing a playbook to build a dockerless NextCloud container. I should have switched immediately, I've wasted numerous hours over that period making sure my container was up to date, or needlessly fiddling with settings just to feel like I had a handle on how the thing was going to operate.
Running radicale on NixOS:
service.radicale = { enable = true; settings = { server = { hosts = [ "127.0.0.1:5232" "[::]:5232" ]; }; auth = { type = "htpasswd"; htpasswd_filename = "/etc/radicale/users"; htpasswd_encryption = "bcrypt"; }; storage = { filesystem_folder = "/var/lib/radicale/collections"; }; }; };Nginx configuration snippet from:
locations."/radicale/" = { proxyPass = "http://127.0.0.1:5232/"; extraConfig = '' proxy_set_header X-Script-Name /radicale; proxy_pass_header Authorization; ''; };Creating my account after
nixos-rebuild switch:nix-shell -p apacheHttpd --run "htpasswd -B -c /etc/radicale/users pleb"The web interface is dead simple and let's you create, import, or export calendars or addressbooks. I exported the vcf addressbook and ics calendar from my NextCloud instance and imported them into Radicale. The UI gives you URIs for the calendar or contacts, and I pasted that in along with my username in the relevant add dialog in Thunderbird.
Likewise, I added the account in davx5 on Android using the first "Login with URL and user name" option. For the URL this time, I appended my username, so it was
https://example.com/radicale/myusernameand davx was able to sync both the calendar and the contacts from that endpoint. -
 @ 000002de:c05780a7
2024-07-17 20:42:08
@ 000002de:c05780a7
2024-07-17 20:42:08Bitcoiners have been saying this for a while. The firearms community needs to adopt bitcoin before they have no other options. Few have headed this advice. I went to YouTube today a saw a video from a very popular firearms training channel called Hickok45. The released a video titled Bad News - YouTube where they let their subscribers know about the uncertainty of their future due to YouTube's new policy banning firearms advertising.
YouTube is of course within their rights to do this but that's not a solution to the problem. The problem goes deeper. Credit card processors and companies as well as banks have and could increase their censorship of firearms purchases. Bitcoin fixes this.
As far as the video hosting problem there are other platforms that will likely open their doors to these trainers and educators but that isn't good enough. Nostr is new but I see it as the most hopeful solution coupled with bitcoin over lightning. Over the past week I've been experimenting with satellite.earth CDN file hosting service. I've been pretty impressed by it. Its very new but it seems like a real solution to the file hosting centralization problem for Nostr.
I've tried in the past to make the case for bitcoin to gun owners and few seem to see the problem. I think this is largely due to their faulty belief in the state. There are some companies that have adopted bitcoin. The only one that I'm aware of is Fenix Ammunition. Anyone aware of others?
originally posted at https://stacker.news/items/612067
-
 @ 42342239:1d80db24
2024-07-06 15:26:39
@ 42342239:1d80db24
2024-07-06 15:26:39Claims that we need greater centralisation, more EU, or more globalisation are prevalent across the usual media channels. The climate crisis, environmental destruction, pandemics, the AI-threat, yes, everything will apparently be solved if a little more global coordination, governance and leadership can be brought about.
But, is this actually true? One of the best arguments for this conclusion stems implicitly from the futurist Eliezer Yudkowsky, who once proposed a new Moore's Law, though this time not for computer processors but instead for mad science: "every 18 months, the minimum IQ necessary to destroy the world drops by one point".
Perhaps we simply have to tolerate more centralisation, globalisation, control, surveillance, and so on, to prevent all kinds of fools from destroying the world?
Note: a Swedish version of this text is avalable at Affärsvärlden.
At the same time, more centralisation, globalisation, etc. is also what we have experienced. Power has been shifting from the local, and from the majorities, to central-planning bureaucrats working in remote places. This has been going on for several decades. The EU's subsidiarity principle, i.e. the idea that decisions should be made at the lowest expedient level, and which came to everyone's attention ahead of Sweden's EU vote in 1994, is today swept under the rug as untimely and outdated, perhaps even retarded.
At the same time, there are many crises, more than usual it would seem. If it is not a crisis of criminality, a logistics/supply chain crisis or a water crisis, then it is an energy crisis, a financial crisis, a refugee crisis or a climate crisis. It is almost as if one starts to suspect that all this centralisation may be leading us down the wrong path. Perhaps centralisation is part of the problem, rather than the capital S solution?
Why centralisation may cause rather than prevent problems
There are several reasons why centralisation, etc, may actually be a problem. And though few seem to be interested in such questions today (or perhaps they are too timid to mention their concerns?), it has not always been this way. In this short essay we'll note four reasons (though there are several others):
- Political failures (Buchanan et al)
- Local communities & skin in the game (Ostrom and Taleb)
- The local knowledge problem (von Hayek)
- Governance by sociopaths (Hare)
James Buchanan who was given the so-called Nobel price in economics in the eighties once said that: "politicians and bureaucrats are no different from the rest of us. They will maximise their incentives just like everybody else.".
Buchanan was prominent in research on rent-seeking and political failures, i.e. when political "solutions" to so-called market failures make everything worse. Rent-seeking is when a company spends resources (e.g. lobbying) to get legislators or other decision makers to pass laws or create regulations that benefit the company instead of it having to engage in productive activities. The result is regulatory capture. The more centralised decision-making is, the greater the negative consequences from such rent-seeking will be for society at large. This is known.
Another economist, Elinor Ostrom, was given the same prize in the great financial crisis year of 2009. In her research, she had found that local communities where people had influence over rules and regulations, as well as how violations there-of were handled, were much better suited to look after common resources than centralised bodies. To borrow a term from the combative Nassim Nicholas Taleb: everything was better handled when decision makers had "skin in the game".
A third economist, Friedrich von Hayek, was given this prize as early as 1974, partly because he showed that central planning could not possibly take into account all relevant information. The information needed in economic planning is by its very nature distributed, and will never be available to a central planning committee, or even to an AI.
Moreover, human systems are complex and not just complicated. When you realise this, you also understand why the forecasts made by central planners often end up wildly off the mark - and at times in a catastrophic way. (This in itself is an argument for relying more on factors outside of the models in the decision-making process.)
From Buchanan's, Ostrom's, Taleb's or von Hayek's perspectives, it also becomes difficult to believe that today's bureaucrats are the most suited to manage and price e.g. climate risks. One can compare with the insurance industry, which has both a long habit of pricing risks as well as "skin in the game" - two things sorely missing in today's planning bodies.
Instead of preventing fools, we may be enabling madmen
An even more troubling conclusion is that centralisation tends to transfer power to people who perhaps shouldn't have more of that good. "Not all psychopaths are in prison - some are in the boardroom," psychologist Robert Hare once said during a lecture. Most people have probably known for a long time that those with sharp elbows and who don't hesitate to stab a colleague in the back can climb quickly in organisations. In recent years, this fact seems to have become increasingly well known even in academia.
You will thus tend to encounter an increased prevalance of individuals with narcissistic and sociopathic traits the higher up you get in the the status hierarchy. And if working in large organisations (such as the European Union or Congress) or in large corporations, is perceived as higher status - which is generally the case, then it follows that the more we centralise, the more we will be governed by people with less flattering Dark Triad traits.
By their fruits ye shall know them
Perhaps it is thus not a coincidence that we have so many crises. Perhaps centralisation, globalisation, etc. cause crises. Perhaps the "elites" and their planning bureaucrats are, in fact, not the salt of the earth and the light of the world. Perhaps President Trump even had a point when he said "they are not sending their best".
https://www.youtube.com/watch?v=w4b8xgaiuj0
The opposite of centralisation is decentralisation. And while most people may still be aware that decentralisation can be a superpower within the business world, it's time we remind ourselves that this also applies to the economy - and society - at large, and preferably before the next Great Leap Forward is fully thrust upon us.
-
 @ 8d34bd24:414be32b
2024-07-17 16:20:24
@ 8d34bd24:414be32b
2024-07-17 16:20:24*** I’ve had several inspirations to write on subjects other than the fruits of the Spirit, so we will take a brief break on that series and do a couple of stand alone posts and then go back and finish the Fruits of the Spirit Series.
I was reading Job and saw something I’d never seen before.
Job, a man the Bible refers to as “… blameless, upright, fearing God and turning away from evil.” (Job 1:1b), loses his children, his wealth, and then his health. He is suffering immensely. Several friends come to console him, but instead start falsely accusing him of horrible sins. They should’ve known better and they shouldn’t have judged Job based on what was happening to him instead of how he lived his life.
After losing his family, his wealth, and his health, now his friends are defaming his godly reputation. In one of his soliloquies, after naming all of the things he has lost he prays this prayer:
“Oh that my words were written! Oh that they were inscribed in a book! That with an iron stylus and lead They were engraved in the rock forever! (Job 19:23-24)
I think every other time I had read these verses I just thought that was an odd request, but I saw something different this time. Job prayed that “Oh that my words were written! Oh that they were inscribed in a book!” Little did Job know, God would write his words in the Bible, God’s book, the most published book in history. His words would be read as an example to us for over 4,000 years. He couldn’t have imagined that his prayer would be answered this way.
He prayed, “That with an iron stylus and lead, They were engraved in the rock forever!” His words are written by God so they will last as long as the rocks on which he wished them to be engraved. Job didn’t know his prayer would/was being answered, but it was. It was being answered in ways beyond his greatest imagining. When God answers, he usually answers in big ways, even if not in our timing or in our ways.
“For as the heavens are higher than the earth, So are My ways higher than your ways And My thoughts than your thoughts. (Isaiah 55:9)
As abandoned as Job felt and as unfairly as he felt he was treated, he never lost faith in God or His goodness. The next verse in Job states:
As for me, I know that my Redeemer lives, And at the last He will take His stand on the earth. (Job 19:25)
There may be times it feels like God is not with you, but He is. There may be times it feels like He isn’t listening, but He is. There may be times it feels like He will never answer your prayers, but He will. The important thing is to never lose faith in His power, His goodness, or His love.
God’s answers to prayers may not be exactly what you asked for and they rarely happen in our desired timing, but He gives us what we need and what is for our and other’s best and He never makes a mistake.
Trust Jesus.
your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
 @ 1739d937:3e3136ef
2024-07-06 09:22:17
@ 1739d937:3e3136ef
2024-07-06 09:22:17This is the second in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
This week was mostly spent on the topic of how to properly publish prekey bundles and what would be needed in the bundle itself to make it workable. I've included an early version of the spec below for prekeys, and would love thoughts on it. Treat this as an alpha version, very subject to change.
The other thing I spent time on was making changes to the OpenMLS library to add support for our custom ciphersuite. One issue that I've run into is that the IETF standard for HPKE doesn't include the secp256k1 curve. Because of this, the library being used in the OpenMLS library doesn't implement the necessary methods using our curve. Thankfully, there is another library with an open PR (shout out to nostr:npub1yevrvtp3xl42sq06usztudhleq8pdfsugw5frgaqg6lvfdewfx9q6zqrkl for that!) that would fix this. Additionally, there's an expired proposal to add secp256k1 to the HPKE spec itself. I've bumped both of these and will continue to follow up. Even without the formal addition to the spec, if we have a working library, I can add that to the OpenMLS library.
Spec Draft for Prekeys
Initial keying material (Prekey Event)
Each user that wishes to be reachable via MLS-based messaging MUST first publish a prekey event. Prekeys are used to authenticate and add members to groups (one-to-one DMs or groups with more than two participants) in an asynchronous way. The prekey event is a simple replaceable event and contains all the information needed to add a user to a group.
Prekeys SHOULD be used only once. Resuse of prekeys can lead to replay attacks.
In most cases, clients that implement this NIP will manage the creation and rotation of the prekey event. It's recommended that clients do so interactively with user consent in order to avoid overwriting prekeys created by other clients.
Derived vs Ephemeral Prekeys
Since prekeys are generated on a single device/client pair, the private key of the prekey must be either stored or generated in a way that can be deterministically recovered.
The recommended approach is to use derived keys, generated in the manner described in NIP-06. In this way, the user can respond to a new group request from any device/client pair, not just from the same device/client pair that created the initial prekey event. If using derived keys;
- Clients MUST use
104as theaccountlevel value and0at thechangelevel value (e.g.m/44'/1237'/104'/0/0). - Keys are then generated using public derivation by incrementing the
address_indexlevel value. - Clients MUST include the full derivation path corresponding to the key used in the
contentfield on the prekey event. - The
contentfield MUST be encrypted using standard NIP-44 encryption (encrypted to themselves).
However, for added security (and consequently a more restrictive user experience), clients can chose to generate an ephemeral key and store the private key locally. This means that users will only be able to respond to new group requests from the same device/client pair and won't be able to respond at all if the prekey's private key is lost. Ephemeral keys can also be used with minimal degredation of UX if you're using a remote signer that can manage these keys.
If using an ephemeral key;
- The
contentfield on the prekey event MUST be filled in withEPHEMERALand then encrypted using standard NIP-44 encryption (encrypted to themselves). This ensures that anyone looking at prekey events cannot tell whether it's a derived or an ephemeral prekey.
Example Prekey Event
json { "id": <id>, "kind": 10443, "created_at": <unix timestamp in seconds>, "pubkey": <main identity pubkey>, "content": <encrypted derivation path | EPHEMERAL>, "tags": [ ["mls_protocol_version", "1.0"], ["ciphersuite", "MLS_256_DHKEMK256_CHACHA20POLY1305_SHA256_K256"], ["pubkey", <prekey pubkey>], ["prekey_sig", <signature generated from hex encoded pubkey of the prekey>], ["r", "wss://nos.lol"], ["r", "wss://relay.primal.net"] ], "sig": <signed with main identity key> }Tags
- The
mls_protocol_versiontag identifies the MLS protocol version being used. For now, this MUST be1.0 - The
ciphersuitetag identifies the ciphersuite supported. For now on Nostr, we're using a custom ciphersuite,MLS_256_DHKEMK256_CHACHA20POLY1305_SHA256_K256. Read more about ciphersuites in MLS. pubkeyis the derived or ephemeral prekey pubkey.- The
prekey_sigtag value is a Schnorr signature (over the secp256k1 curve) of the SHA-256 hashed value of the prekey's pubkey, signed with the prekey's private key.
```js const privKey = schnorr.utils.randomPrivateKey(); const pubKey = schnorr.getPublicKey(privKey);
const prekeySig = bytesToHex( schnorr.sign(bytesToHex(sha256(pubKey)), privKey) );
const prekeyTag = ["prekey_sig", prekeySig]; ```
Finally, clients SHOULD include
rtags to identify each of the relays that they will attempt to publish this prekey event to. This allows for more complete replacement of prekey events at a later date.Replacing Prekey Events
Clients MUST replace the prekey event on all the listed relays any time they successfully process a group welcome event. If the prekey was a derived prekey, clients SHOULD increment the derivation path by 1 for the next key.
Onward and Upward
This next week I'll continue to work on getting the right curves and code added to the OpenMLS library and start work on a simple demo app. The focus is on better understanding what we need from the control and message events and how we can make those as simple as possible for Nostr clients and relays while also preserving as much privacy as possible.
- Clients MUST use
-
 @ 32e18276:5c68e245
2024-07-05 18:28:20
@ 32e18276:5c68e245
2024-07-05 18:28:20Hey guys!
Here's our Q3-Q4 report. There was some confusion with the timing of the previous quarters so we've accumulated everything since the Q2 report (March 2nd, 2024) into this one. Enjoy!
Damus OpenSats Q3-Q4 Progress Report
The third and fourth quarter of the initial Damus OpenSats grant encompasses work done across many of the active projects being worked on at Damus HQ. Here's a quick overview of the progress made across the organization:
nostrdb
Added
- Author query support (William Casarin)
- REQ support: ndb_subscribe (William Casarin)
- CLOSE support: ndb_unsubscibe (William Casarin)
- Profile flatbuffer dump utility (William Casarin)
- Ability to register a subscription callback instead of just polling (William Casarin)
Changed
- Dump json in filter and fulltext queries in cli tool (William Casarin)
Stats
name added removed commits William Casarin <jb55@jb55.com> +665 -739 16nostrdb-rust
Added
- Note builder interface (William Casarin)
- Nip10 implementation (William Casarin)
- Getting profile by key (William Casarin)
- Note tag support (William Casarin)
Tag::into_itermethod (Yuki Kishimoto)FilterBuilder::untilmethod (Yuki Kishimoto)- Export structs from
tagsmodule (Yuki Kishimoto)
Fixed
FilterBuilder::limitmethod (Yuki Kishimoto)Note::sigmethod (Yuki Kishimoto)
Stats
Yuki Kishimoto <yukikishimoto@protonmail.com> +20 -4 5 William Casarin <jb55@jb55.com> +1551 -867 32Damus NoteDeck/Android
This project is in heavy development and doesn't have clean changelogs yet, so here are all of the git logs from this period
Willam's updates
- account_manager: don't add the same pubkey more than once
- actionbar placeholder
- actionbar: remove border on reply button, add expand animation
- actionbar: support both dark and light buttons
- Add forward navigation animation
- add hover to profile map demo
- add --light lightmode flag to previews and notedeck
- add my pubkey to the timeline query for testing
- add test queries for elsat
- add vertical separators between timelines
- allow missing profiles in account switcher
- allow multiple invocations of --sec
- always have some default timeline
- app: make ndb public
- a quick note about the View trait
- args: allow filter files and raw filters on cli
- bump timeline filter limit
- cap size of remote filter limits
- change selection color to purple
- check: remove duplicate and disable wasm checks
- ci: disable wasm builds for now
- cli: add --sec argument to quickly add an account
- clippy postbox cleanups
- crates: add bitflags
- damus: make relay pool public
- darker quote reposts for mobile
- debug: add some debug logs for keyboard note selection
- deps: using tracing instead of log
- direnv: disable nix direnv on darwin
- direnv: make args explicit so its easy to change
- don't bump timeline when adding notes
- dont since-optimize when we don't have enough notes
- don't use an actual keystorage in Damus test apps
- drafts: clear post after posting
- enable nip10 replies
- enostr: rename Event to Note
- env: allow private things like secret keys
- filter: add default limit
- filters: fix hashtag filters
- filter: unify nostrdb and remote limits
- Fix all warnings
- fixed_window: fix clippy warning
- fix global query
- fix inline note preview colors
- fix light borders for quote reposts
- fix postbox design
- fix scroll area shrinking
- fix some clippy warnings
- fix until filters
- fix warnings
- fonts: always use base fonts for all families
- fun large profile grid preview
- get all missing ids from all timelines
- github: remove pages workflow
- gitignore: add perf files
- hide navigation title on global nav
- ids: find more unknown ids from inline notes
- images: add aspect_fill
- initial inline note previews
- initial navigation
- initial note posting
- initial postbox for testing
- initial post box view
- initial post reply view
- initial refactor in preparation for routing
- input: fix deadlock on resize
- input: handle raw events
- input: process input once
- input: switch to scanning over raw input events
- integrate sidebar into main view
- introduce View and Previews traits
- irc mode
- ircmode: tighten username
- keys: actually use the keystore
- lighter gray for inline previews in white mode
- list: switch from arc mutext to rc refcell
- load timelines from commandline
- log: reduce spammy new note log
- log relay subscriptions
- make notedeck front and center
- mobile: add lots of top padding on mobile
- mobile: a tad more padding at the top
- mobile: black panel bg color
- mobile: don't add hover on mobile
- mobile: make mobile flag runtime-configurable
- mobile: simplify is_mobile
- mobile: use my timeline for testing again
- move account_login_view to ui submodule
- move add_space to its correct location
- nip10: fetch unknown replied-to notes
- nip10: show initial reply information on notes
- nix: add openssl dep for reqwest
- nix: make android emulator optional
- nostrdb: bump to support timeline queries
- note: don't allow nested note previews
- note: support nprofile mentions
- perf: don't clone bytes via a more specialized function
- perf: fix continuous repaint
- perf: profiling note content rendering
- popup: increase fixed window margin
- popup: simplify borrow
- postbox: add focused state
- postbox: add focus shadow from figma
- post: full available width
- postview: add vertical scroll
- previews: remove central panel frame
- profile: add about and username to profile previews
- profiles: introduce DisplayNames
- profiling: update puffin version
- queries: add a few more test queries
- queries: set reasonable initial query sizes
- queries: update hashtags query
- readme: add usage
- readme: document previews
- readme: make it clear that its for desktop
- readme: make it clear that nix is optional for non-android dev
- readme: show notedeck preview
- refactor: move fixed_window to ui
- refactor: move note into its own widget
- refactor: rename widgets to ui
- refactor: use map instead of explicit
if let - remote: use default_remote_limit instead of hardcoding
- remove context from DesktopSidePanel
- remove minimum window size
- remove useless struct
- render_pfp: only depend on imgcache
- reset virtual list if notes are spliced into timeline
- set tooltip delay to 100ms
- side_panel: return more detailed side panel responses
- simplify is_mobile check
- simplify tab underline calculation
- since filter optimization
- slightly larger pfpfs
- small inline preview pfps
- style: initial logic for mobile style
- style: less bubbly
- style: realtime hover interactions
- style: set 0 duration tooltip delay
- Switch to egui master to fix wgpu issues
- switch to glow for now
- switch to rustls-tls-native-roots
- tabs: select notes & replies by default
- test: add test timeline query
- test: update test profile with a banner
- test: use my timeline query by default for testing
- textmode: adjust name sizing so it doesn't bump the column
- textmode: fix coloring of abbreviated names
- textmode: no previews in textmore for now
- theme: update to correct colors based on figma design
- timeline: don't hide on resize
- timeline: refactor tabs into TimelineView
- timeline: use strips instead of panels
- ui: add banners to profile previews
- ui: add feathering-resistant hline separator fn
- ui: add frame around note previews
- ui: add initial Profile hover previews
- ui: add profile picture hover animation
- ui: integrate egui-tabs for notes & replies selector
- ui: introduce profile picture widget
- ui: make pixel sizes correct, use more of the figma
- ui: move RelayView into ui module
- ui: only inline preview kind1 notes for now
- ui: reduce vertical padding for more compact timelines
- ui: remove some old note ui comments
- ui: simplify note widget
- ui: switch to flags for note options
- update slow timeline query
- update to latest nostrdb, adding tag support
- update version in comment because I still use this on my laptop
- use egui_virtual_list for rendering
- use unique id for post/reply view
- weird actionbar experiment
- we should just called this damus
- widgets: begin organizing ui components into widgets
- working notes + notes&replies
kernelkind's updates
- account_management: refactor
- AccountManagementView
- AccountManager: add ability to make a selection
- AccountSelectionWidget
- Account switcher
- Add AccountManager to app
- Add custom visual themes
- Add flag to emulate mobile during preview
- Add keypair & update pubkey
- Add login key parsing
- Add login manager
- Add MacOS key storage
- Add MobileAccountLoginView
- Add modular custom text styles
- Add monospace text style
- Add nix-shell for macos android development
- Add nostr-sdk dependency
- Add precommit hook to suggest proper formatting
- Add preview for RelayView
- Add relay view
- add reqwest as dependency
- Add SimpleProfilePreview
- Add ui_test_harness binary implementation
- Add warn color and highlight color
- app: add accounts to Damus & mock
- Apply app style to AccountLoginView
- Apply cargo fmt
- Conditionally compile MacOS key storage code
- Constrain app minimum size
- Create account login panel
- Create side panel & global popup
- enostr: expose RelayStatus
- Extract the sample relay to test_data for reuse
- impl linux credential storage
- Integrate account switcher to side panel
- Integrate global popup into app
- login: Add key loading & error to mobile
- macos_key_storage: runner ignore tests
- migrate AccountManagementView to enostr Keypair
- Migrate to new AccountManagementView conception
- Move login business logic to LoginManager
- move login logic from promise to async fns
- Move preview controller out of account_manager.rs
- move test account creation & apply to global popup
- Pfp integration to side panel
- refactor account switcher & management previews
- Refactor 'ui tests' conception to previews
- reintroduce account management
- reintroduce account switcher
- remove nostr-sdk
- Rename PersistState -> StateInMemory
- select first account
- Seperate mobile dark color theme into its own func
- update cargo.lock to reflect toml change
- Update egui 0.26.1 -> 0.27.1
- Use app_creation for common app setup functions
- Use custom style in app
- use nostr in enostr
Stats
name added removed commits kernelkind <kernelkind@gmail.com> +6844 -1979 58 William Casarin <jb55@jb55.com> +9733 -5583 194Damus iOS
Added
- Ability to create highlights (ericholguin)
- Add ability to mute hashtag from SearchView (Charlie Fish)
- Add ability to mute words, add new mutelist interface (Charlie) (William Casarin)
- Added callbackuri for a better ux when connecting mutiny wallet nwc (ericholguin)
- Added nip10 marker replies (William Casarin)
- Added title image and tags to longform events (ericholguin)
- Add event content preview to the full screen carousel (Daniel D’Aquino)
- Add First Aid solution for users who do not have a contact list created for their account (Daniel D’Aquino)
- Add marker nip10 support when reading notes (William Casarin)
- Add video cache to save network bandwidth (Daniel D’Aquino)
- Completely new threads experience that is easier and more pleasant to use (Daniel D’Aquino)
- Connect to Mutiny Wallet Button (ericholguin)
- Highlights (NIP-84) (ericholguin)
- Notification reminders for Damus Purple impending expiration (Daniel D’Aquino)
- Proxy Tags are now viewable on Selected Events (ericholguin)
- Relay fees metadata (ericholguin)
- Revamp emoji picker to be less error-prone and add search, frequently used, and multiple skin tone support capabilities (Terry Yiu)
- Show list of quoted reposts in threads (William Casarin)
Changed
- Added first aid contact damus support email (alltheseas)
- Add support for Apple In-App purchases (Daniel D’Aquino)
- Always strip GPS data from images (kernelkind)
- Change reactions to use a native looking emoji picker (Terry Yiu)
- Errors with an NWC will show as an alert (ericholguin)
- Improve UX around video playback (Daniel D’Aquino)
- Moved paste nwc button to main wallet view (ericholguin)
- Relay config view user interface (ericholguin)
- Relay detail design (ericholguin)
- Updated Zeus logo (ericholguin)
Fixed
- Fix broken GIF uploads (Daniel D’Aquino)
- Fix bug that would cause connection issues with relays defined with a trailing slash URL, and an inability to delete them. (Daniel D’Aquino)
- Fixed issue where some replies were including the q tag (William Casarin)
- Fixed issue where timeline was scrolling when it isn't supposed to (William Casarin)
- Fixed threads not loading sometimes (William Casarin)
- Fixed wallet not disconnecting when a user logs out (ericholguin)
- Fix emoji reactions being cut off (ericholguin)
- Fix ghost notifications caused by Purple impending expiration notifications (Daniel D’Aquino)
- Fix image indicators to limit number of dots to not spill screen beyond visible margins (ericholguin)
- Fix in-app purchase issue that would trigger an error on purchase before confirming the account information. (Daniel D’Aquino)
- Fix issue where bootstrap relays would inadvertently be added to the user's list on connectivity issues (Daniel D’Aquino)
- Fix missing Mute button in profile view menu (Terry Yiu)
- Fix nostrscripts not loading (William Casarin)
- Fix profile not updating bug (William Casarin)
- Fix stale feed issue when follow list is too big (Daniel D’Aquino)
- Fix thread bug where a quote isn't picked up as a reply (William Casarin)
- Fix welcome screen not showing if the user enters the app directly after a successful checkout without going through the link (Daniel D’Aquino)
- Improve reliability of contact list creation during onboarding (Daniel D’Aquino)
- Issue where NWC Scanner view would not dismiss after a failed scan/paste (ericholguin)
Stats
name added removed commits Fonta1n3 <fontainedenton@googlemail.com> +1 -0 1 Sean Kibler <skibler@protonmail.com> +13 -2 1 alltheseas <64376233+alltheseas> +65 -1 4 Transifex <transifex@transifex.com> +581 -39 36 Terry Yiu <git@tyiu.xyz> +763 -1383 8 William Casarin <jb55@jb55.com> +1017 -1564 49 ericholguin <ericholguin@apache.org> +1962 -643 13 Daniel D’Aquino <daniel@daquino.me> +3885 -761 48 -
 @ 6bae33c8:607272e8
2024-07-17 15:31:31
@ 6bae33c8:607272e8
2024-07-17 15:31:31These are my very preliminary QB rankings, my only research being the RotoWire depth charts and player notes.
Tier 1
Josh Allen, Jalen Hurts
I don’t know who Allen will throw to other than Dalton Kincaid, but he needs only 25-ish TD passes to be the QB1 if he stays healthy, given all the rushing numbers. Hurts is second only because he’s not as good in real life, and there’s some small risk of implosion, skills-wise. But 10-plus TDs on the ground creates its own tier.
Tier 2
Patrick Mahomes, Anthony Richardson, Lamar Jackson
What’s odd about this tier is how different these players are. Mahomes, despite a poor 2023 regular season, gets in because he’s the GOAT, and Andy Reid is a arguably the greatest offensive coach of all time. Richardson could easily be the 1.1, but injury risk and lack of track record give him a much lower floor. Jackson doesn’t get the goal line looks that often, especially with Derrick Henry in tow, but obviously his running gives him a huge lift.
Tier 3
CJ Stroud, Kyler Murray, Jordan Love, Dak Prescott
Stroud has a loaded receiving corps now with Stefon Diggs on the team, and he’d be my bet to lead the league in passing yards. But he doesn’t run much, and that caps his ceiling slightly. I almost put him in Tier 2 because you can make the case he’s basically Mahomes with 200 fewer rushing yards. Murray is another year off his ACL tear, runs a lot and gets Marvin Harrison. It’s still an open question whether he’s good, though. Love looks like a player, runs a little and has young, developing wideouts. Prescott is in a pass-heavy offense, has an elite WR1 and is the ultimate stat-padder which works in fantasy. (You could just push all four into Tier 2 and make it seven deep, as the cutoff is a bit arbitrary.)
Tier 4
Joe Burrow, Justin Herbert, Brock Purdy, Kirk Cousins, Tua Tagovailoa, Jared Goff, Trevor Lawrence
This is the tier of the passing-only QBs with the exception of Herbert who can run, but might be hamstrung by a run-heavy offense, and Lawrence, who might not be good. I would gamble on Herbert’s athleticism and skills nonetheless if he falls into this tier. And Lawrence gets a much-needed rookie deep threat which could open things up. Burrow is Tier 3 if he would stay healthy, but he obviously carries more risk on that front, and I don’t think he’ll run much now.
Tier 5
Deshaun Watson, Daniel Jones, Matthew Stafford, Aaron Rodgers, Caleb Williams, Sam Darnold, Jayden Daniels, Baker Mayfield, Geno Smith
Watson might be cooked, but there’s still upside if he can run like he used to. Jones has a big ceiling with his mobility and Malik Nabers on the team. Stafford has two top receivers and a great offensive coach. Rodgers is old, but he has weapons now, and Williams has a loaded receiving corps. People might laugh at Darnold in this tier, but he’s mobile and has Justin Jefferson, Jordan Addison and T.J. Hockenson. If he keeps the job (a big if), he has upside, which is what you want in this tier. Mayfield and Smith are solid and boring, which is also fine if you wait forever on QB. Daniels’ mobility puts him here instead of the scrub tier.
Tier 6 (Scrubs)
Russell Wilson, Derek Carr, Will Levis, Drake Maye, Raiders QBs, Bo Nix
These are the scrubs. One or two might not turn out to be scrubs, but it’s hard to get excited about any of them.
These rankings will change, but I like to get my preliminary ones down on paper before I get influenced by ADP and training camp hype.
-
 @ a9434ee1:d5c885be
2024-07-04 08:03:53
@ a9434ee1:d5c885be
2024-07-04 08:03:53Alice is a Capitalist
Alice has been falling down several rabbit holes lately and decides it’s time for a break. She takes a long overdue shower and gets her thoughts straight on some of her experiences.
She writes a post about how “Bees are Capitalists". However, like any real Lady, she’s got some criteria:
- She wants to have some great conversations around this topic
- She wants her post to be publicly readable by anyone
- She doesn't want to be bothered by a bunch of trolls though
- She doesn't want to be the main moderator for these conversations
- She wants zaps and doesn't care where they come from
In short: she wants to get the most out of her post with the least amount of overhead.
Luckily, she has Nostr profile and is part of several communities (publicly readable NIP-29 groups). So, she just selects the communities that overlap with this topic (let's say "₿-keepers", "Austrian Economy Class" and "Permaculture Pirates") and publishes her post ...
In all of them at the same time!
Communities are Capitalists
Now, anyone that is a member of any of these communities can join in on the conversation. The same conversation. One post, one event ID.
Just like for a real life event, Alice didn’t invite the whole universe but she selected certain groups of people. That way, she set the stage for rich discussions with perspectives from Beekeepers and hardcore Austrian economists alike. Discussions that are still readable by anyone, but that do require membership of a selected community for write-access.
The incentives play out into a win-win-win for everyone involved.
Alice’s criteria are met and her post doesn’t have to fit into one neat category. She isn’t left with the current internet’s false choice between “pick 1 community” or “blast bluntly into the universe and pay Big Tech to maybe get it to the RiGhT people”. Here, she gets to publish to selected lists of recipients that she doesn’t have to curate herself, while also adding it to her feed for her followers to pick up on.
Her Followers can be watching her every post, they can only pick up on certain location- or hashtags, or they can let algo’s filter for posts that have proven to be high signal in the relevant communities first.
Community members get to organically discover adjacent communities, following links they’d never have considered themselves. (Beekeepers getting into Mises in this example).
Lurkers can still read, share, embed and get a quick idea of the value prop of joining communities, following certain members, etc…
Bob, the Community Admin for ₿-keepers, makes money by providing Curation, Computation & Hosting. He gets free marketing and exposure to people that actually might be interested. As in: he doesn’t really need Facebook Ads when he’s got plenty of Alices, writing posts with overlapping interests of the one his community is built around. He also gets more people posting to his niche community, since creators are not forced to pick just one.
Relays are Capitalists
Since Bob is in the business of Curating, Computing & Hosting stuff, he prefers doing that in the most efficient way. He prefers handling everything from 1 Relay (and maybe even 1 Blossom server, 1 GPU set-up, 1 mint, … ).
Yes, Bob likes it simple. When the Community is the Relay, every part of his service gets easier: - fast loading of messages and media - content moderation - handling memberships - curating things like custom community, GIF’s, emoji, … - curating other relays he does or doesn’t want to be involved with - self-hosting the entire thing - handing over Admin rights - letting others fork the entire thing - handling back ups in whatever way suits him - handling fast access the collective preferences of his members (favorite movies of this group of people, most valued apps, …) - having a clear overview of his own costs, attack vectors, … - giving members guarantees in terms of pricing, privacy, …
Bob is a Capitalist
Bob got great value out of the conversations that followed Alice’s first post in his community. So much so, that some real-life rendez-vous’ and home-brewed mead later, they now call each other …
"Honey".
The End
-
 @ 6bae33c8:607272e8
2024-07-17 15:14:55
@ 6bae33c8:607272e8
2024-07-17 15:14:55These are my very preliminary TE rankings, my only research being the RotoWire depth charts and player notes.
**Tier 1 **
Sam LaPorta
He gets his own tier because he’s the only TE for whom there are no red flags. Most TEs do very little as rookies, while LaPorta was a rare exception and should only get better. His competition for targets is perfect — a true No.1 receiver, a play-making field-stretcher and a speedy running back, i.e., defenses have to account for multiple threats, but it’s not too crowded for LaPorta to see 140-odd targets in Year 2.
**Tier 2 **
**Mark Andrews, Dalton Kincaid, Evan Engram, Trey McBride, Travis Kelce, George Kittle **
Kelce is the fantasy GOAT, but he turns 35 in October, and age catches up to everyone eventually. Andrews gets hurt a lot, but he should still be Lamar Jackson’s favorite target when healthy. Kincaid might lead the Bills in targets, and in Year 2 could take the leap to TE1. But unlike LaPorta, he hasn’t quite done it yet. Engram caught 114 passes last year, and Calvin Ridley is gone, so I don’t see his role diminishing much. McBride is a rising star in a good situation with only Marvin Harrison, Jr. to compete with for targets. And Kittle is a star when healthy and could see more looks if Brandon Aiyuk is traded.
Tier 3
T.J. Hockenson, Kyle Pitts, Jake Ferguson, David Njoku, Cole Kmet, Brock Bowers
There’s no doubt about Hockenson’s talent, but the downgrade to Sam Darnold or J.J. McCarthy could be steep. Pitts can still be the 1.1 with a competent quarterback, but at this point there’s some O.J. Howard risk (great athlete, average NFL player.) Ferguson is just in a great spot with the Cowboys and their thin group of pass catchers after CeeDee Lamb. Njoku looked like a guy who belonged in the first round seven years ago, and it’s not that unusual for TEs to take some time to peak. (Njoku took longer than most, but like Engram, some of that was probably due to poor QB play early on.) Kmet’s got a lot more competition for targets, but also a likely QB upgrade, and he’s still young and on the upswing. Bowers is a home run swing — he might do nothing as a rookie, but could also be the Raiders 1A to Davante Adams out of the gate.
**Tier 4 **
Dalton Schultz, Dallas Goedert, Pat Freiermuth, Jonnu Smith
If I were to get shut out from the top-three tiers, I’d be okay with any of these guys. Schultz will have a role in a top passing offense, even if it’s a secondary one. Goedert has never really put it together, but is still in a good spot in the Eagles top-heavy offense. Freiermuth is a good pass catcher and could see more opportunities with the trade of Diontae Johnson. Smith is a wild card. His floor is basically zero as he could be used to block, but his upside is Tier 2 if the Dolphins indeed make him the No. 3 option in their fast-paced offense.
**Tier 5 (scrubs) **
Hunter Henry, Chigoziem Okonkwo, Tyler Conklin, Mike Gesicki
You never know, one of them might bust out, and there are others not listed, but it would be hard to count on these guys. Gesicki intrigues me a bit since he used to be productive, and the Bengals are thin after their star receivers, but they never seem to use the TE much.
-
 @ 826e9f89:ffc5c759
2024-06-28 21:46:01
@ 826e9f89:ffc5c759
2024-06-28 21:46:01_Prologue: this is a prose adaptation of a talk I gave to a private audience in Dubai and then tweaked slightly for a small conference in Sofia. I'm increasingly thinking it deserves a more general audience, and may be better suited to text anyway. This is probably not its final form, as the desired audience is tradfi capital allocators, hence a PDF is likely on the cards in the near future. For the time being, consider this a first draft, practising what it might look like as prose, and soliciting feedback from the good people of Nostr. Enjoy! _
The title of this essay means absolutely nothing. There is no such thing as “Web π” because there is no such thing as “Web 3”. It’s bullshit. It’s a scam.
Unfortunately, it has turned out to be extremely powerful bullshit and an extremely profitable scam, and so my goal in writing this essay is to give the reader the tools to navigate all of this and come out the other side without having been scammed or bullshat. In the spirit of not scamming and not bullshitting, I should be clear upfront about the intended readership of this essay, who I am to write it, and who it’s really about.
Who Are You?
I assume the reader is not a shadowy super-coder, but rather is a financial professional. This essay isn’t really for Bitcoiners, although if any read it, I hope they still find it interesting. Who I am really writing for are people coming to the space for the first time. Hopefully in your mind you are coming to the _Bitcoin _space, but if you think you are coming to the “crypto” space then this may be even more useful.
Who Am I?
I am the founder of a company that makes me not only highly biased but also flagrantly self-interested in the content I am promoting. I run a firm that invests in the Bitcoin ecosystem through a variety of different vehicles. I am not going to mislead you in the slightest in that my primary motivation is for you to allocate capital to us rather than to people I would call scammers and bullshitters. You should listen to them too and make up your own mind, or else what’s the point, really? How do you know I’m not scamming or bullshitting you? Exactly. Don’t trust. Verify.
In any case, that’s all assuming you want to “allocate capital” at all rather than just buy Bitcoin without a management fee. I’d like to think the primary difference is that I will be honest about that, and I’ll encourage you to understand as much as you can about what is going on and what you are doing (and if you are at all unsure, I would suggest you aren’t ready and you should just buy Bitcoin and learn) rather than bamboozle you with complete nonsense like “Web 3”.
Who Is This About?
It’s not at all about people working in crypto. Bitcoiners amongst the readership may be mildly irritated by me going on to give about as charitable an explanation of the role of these people as they have probably ever heard from somebody like me. This is really about financiers. It’s about the people who have used the mostly unrewarded efforts of developers, academics, entrepreneurs, and so on to siphon money from you to themselves, leaving a trail of useless tech and defrauded retail investors in their wake – and who will continue to do so if you continue to empower them.
Why This Essay?
We are at an interesting point in the development of the entirety of the “crypto” industry and I strongly suggest that people like you are going to be pitched all kinds of scams and bullshit in the coming months and years. If you have a little more background on what these people are really talking about, you will hopefully be able to avoid it.
My plan to help with that is presenting a short version and a long version of what blockchains are and are for, how they have historically been deployed in service of scams and bullshit, a high-level theory explaining the narrative evolution behind this sorry history, and a prediction for the near-term future of such shenanigans.
What is a Blockchain For?
A Blockchain is for sound, censorship-resistant, peer-to-peer digital money. It is not for anything else. If a blockchain is functional as money, it may be possible to also _use it _for other things. Some people find that interesting, some people find it infuriating, but don’t let that subtlety confuse you. It is not _for _arbitrary computation and storage or “decentralizing the internet” or running illegal securities rackets.

It is for money, plain and simple.
How does it achieve that? Proof of work and the difficulty adjustment. These are the innovations from which every other desirable property or feature flows. Proof of work enables censorship resistance. If somebody is trying to sell you on “proof of stake”: bullshit. The difficulty adjustment enables precise, predetermined, and _fair _issuance. If somebody is trying to sell you on a token they issue for free and without restriction: scam.
The problem Bitcoin solves is both economic and technical and the solution has material technical and economic merit. And it’s for this very specific and irreplicable reason the Bitcoin token has value. If this all sounds extreme to you, then I would suggest that your understanding of the topic is _extremely _misguided, that you are going to be _extremely bullshat and extremely scammed, _and you need to read this essay. That’s the short version.
The Long Version
I am sensitive to how extreme this all sounds. After all, hundreds of billions of dollars have been pumped into crypto, not Bitcoin – a huge amount of it is widely used, and many capable, honest, and brilliant people work in the industry. The reader will recall just above I said those people are not the target of my criticism. I’m not claiming they are all scammers and bullshitters. Sadly, I think it’s more likely they have been scammed and bullshat to some degree also.
I think I have some credibility in pointing this out because, as a VC in the Bitcoin space, I have increasingly seen founders telling me this themselves: that they originally bought into the hype in crypto and ended up wasting an enormous amount of time realizing their idea made no technical or economic sense in that context, so then they came to Bitcoin instead. You hear this one time and it’s an anecdote, but you hear it as many times as I have and it feels more like a representative sample.
What I want to cover next is as charitable a summary of the state of ex-Bitcoin crypto as I possibly can: my contention is that crypto has evolved into 4 rough categories: stablecoins, cryptography R&D, gambling, and scams. And these aren’t exclusive, to be clear; there is a lot of overlap, and, in fact, the overlap is arguably the key.
Scams
Scams are tokens, plain and simple. If somebody is trying to profit from the speculative price action of a token they have issued, they are scamming somebody. Maybe they are scamming you, maybe they are scamming retail investors, maybe they are scamming customers or suppliers – if such parties even exist in their cargo cult “business model”. There’s a scam in there somewhere.
However, it is rarely _just _a scam. There will almost always be components of stablecoins, R&D or gambling too. Hence these are worth really grappling with, taking seriously, giving credit to the extent it is due, but also analyzing critically.
My rough and high-level assessment of this breakdown of crypto is as follows, and I’ll explain what I mean by this below: stablecoins have economic merit but dubious technical merit; R&D has technical merit but no economic merit; and gambling sort of has merit but it depends how you interpret it. Obviously, scams have neither.

Stablecoins
By “sort of technical merit” I mean that stablecoins have central issuers. You can issue them as tokens on a blockchain but there’s not really much of a point. The issuer could just run a database connected to the internet with some straightforward signature schemes for transfers and it would make minimal operational difference. In fact, it would be cheaper and faster. _In fact, _you may as well run a Chaumian eCash mint (a decades-old innovation recently resurrected firmly within the _Bitcoin _space) such that your cheaper-and-faster-than-a-blockchain database also grants users transience and privacy rather than the public permanence of a blockchain.
The fact Tron is the most heavily used for stablecoins, in terms of settling the most value, is a testament to this point: it is barely even pretending not to be a database. This works as regulatory arbitrage given regulators think this is “innovation” because they are stupid.
That said, it is worth giving some credit here given the abject awfulness of fiat banking and payment rails with which stablecoins arguably most directly compete. Stablecoins are significantly more permissionless in their transfer than any fiat bank liability. And to attest to what seems like their most significant use case, they are permissionless in their _usership _in that only an internet connection and the right software is required rather than various discriminatory jurisdictional and compliance criteria.
However, what “sort of technical merit” ultimately boils down to, especially in comparison to Bitcoin, is: highly censorable in their exogenous links and, therefore, their value. The assets supposedly backing stablecoins are (by definition) still within the fiat system, even if this novel transfer mechanism of the rights to withdraw them is not. There is frankly a bit of theatre involved in the so-called “decentralization” of stablecoins given shutting down the central issuer is all that is required to make the permissionlessly tradeable decentralized tokens go to zero and be technically unimpeded but functionally useless. The technical innovation of Bitcoin, in contrast, is easily understood in one sense as it being totally indifferent to this kind of attack.
On the other hand, by “economic merit” I mean that they are extremely widely used and valued as a means of providing dollar shadow banking and often superior payment rails. Those in crypto often love pointing to this and many Bitcoiners tie themselves in knots trying to explain it away, whereas I see it as essentially unrelated to Bitcoin. Clearly there is a superficial connection, but you could create any superficial connection by “tokenizing” things for no particularly good technical _reason. I think it’s a different industry entirely. It’s more like a subindustry within _fintech – part banking, part payments – that for the time being relies on bamboozling regulators with all the nonsense I’m drawing attention to.
And good for them, frankly. If fiat banking isn’t going to be backed by real money anyway, then it _at least _ought to be permissionless. It should really be Chaumian eCash if it isn’t just Bitcoin, and it is regulation alone that makes it so awful in the first place. Making money usable and not a tool of dystopian control is, at this point, a political problem, not a technical one. Stablecoins are frankly a step in the right direction, especially insofar as they acclimatize users to digital assets. But I would still caution that they arguably don’t have sufficient technical merit to withstand what feels like an inevitable political attack …
Cryptography R&D
“Technical merit” for R&D is more or less self-explanatory, but the context is worth appreciating. It’s only really in crypto and mostly in Ethereum more specifically that people can permissionlessly experiment with arbitrarily complex cryptographic schemes that operate on real, enormous value. There are a lot of people who understandably find this attractive given their projects are essentially academic and trying out their ideas in the wild is more interesting, arguably more worthwhile, and certainly more fun than putting research essays on ArXiv or submitting them to a journal.
But … the value being manipulated is at best stablecoins and at worst baseless hype. If it isn’t a stablecoin then it probably exists in the first place because of either gambling or scams – and even there the line is very blurry.
Gambling
Gambling is an interesting lens to adopt on all this because it’s literally a trillion-dollar industry. And it’s real. It’s consensual; it’s not criminal; it’s legitimate economic activity that generates enormous profits for those who facilitate it well.
So, gambling has economic merit in that sense. But it’s tricky in this context how to characterize it because you could also argue it’s deeply dishonest gambling in that the gamblers don’t realize they are playing a negative sum game against the house. They think they are doing something akin to speculating on securities, which may be just as stupid depending on how it’s done, but at least has real economic utility and contributes to capital formation.
The difference here is that what is being speculated on _has no economic merit. _So, if that’s your gauge of merit, then here there is none. And it’s a very blurry line between this and an outright scam. Maybe the people involved _think _of what they are doing as amazing R&D, and maybe it’s inadvertently just a scam; maybe they know it’s all nonsense, but they think they can profit within the negative sum game because there are greater fools. In any case, I think gambling is a very helpful characterization of a lot of the behavior of the users and the real economic function of the industry.
There’s an interesting social component to all this because crypto people will often get mad at Bitcoiners because Bitcoiners tend not to care about either stablecoins or crypto R&D: they’ll say, why don’t you like stablecoins, they have clear economic merit? And the answer is they have dubious technical merit. Or, why don’t you like our next-gen Zero Knowledge scaling protocol, it has clear technical merit? And the answer is it has no economic merit.
If you’re happy with one but not the other, it’s easy to think of Bitcoiners as being closed-minded or dogmatic or whatever, but, ultimately, I think it’s just about discipline. What’s the point in being excited by something that half works, and that you know why will never fully work? So to be frank, a lot of this may be well-intentioned, but it’s kinda’ bullshit. It very probably ultimately rests on gambling and not at all whatever its stated purpose is … or it’s just a scam.
How Did We Get Here?
The following is by no means exhaustive and the framing is deliberately a little tongue-in-cheek. As well as being accurate enough (if unavoidably biased), my goal here is primarily to set up my prediction for what is coming next.
2015 reality: Ethereum launches narrative: “the world computer”
In 2015, Ethereum launched. The narrative here was that we are building “the world computer” and we can now have decentralized uncensorable computation. Never mind that anybody with a laptop has an uncensorable and decentralized computing device. And keep in mind this question of, “_what data might it ever be relevant to compute over in this manner (whatever that means in the first place)?” _The answer will become clearer and clearer …
2016-17 reality: ICO bubble narrative: “Web 3” / “DApps”
Regardless, at the end of 2015 we get the proposal and adoption of ERC20: a standard for issuing fungible tokens within Ethereum contracts, which is why in 2016 _but especially in 2017 _we get the ICO bubble. The narrative changes. Now we are concerned with “Web 2” companies being huge, powerful, and centralized. What if, instead, users could cooperatively own the application, control their own data, and participate in the economic upside that their usage is creating?
2018-19 reality: crypto winter narrative: “mistakes were made”
In 2018 this all falls apart, so don’t worry about it, moving on …
2020-21 reality: defi summer narrative: “decentralized finance”
By 2020 the narrative was different once again. It is more or less realized by this point that utility tokens make no technical or economic sense. You can’t introduce artificial scarcity in capital goods where there should be abundance and deflation and expect anybody to care, never mind to value your concoction. On the other hand, “securities” ought to be scarce and in some sense ought to function as tradeable ledger entries. Maybe they could be tokenized and computed on in a censorship-resistant and decentralized manner?
So, we get a boom in “defi” which, for what it’s worth, fellow Axiom co-founder Anders Larson and I predicted in our essay Only The Strong Survive, in September 2021, would be a complete disaster because, amongst a myriad of other illiterate insanities, there was approximately zero grounding of these securities in productive capital. The ecosystem was entirely self-referential – grounded _not even _in the questionable economic merit of stablecoins but firmly in gambling and scams; in leverage, rehypothecation, and securitization of precisely nothing whatsoever productive.
2022 reality: shitcoinpocalypse narrative: “mistakes were made”
And we were absolutely right because in 2022 everything collapsed. First Terra/Luna imploded – a “defi” project which essentially presented to the world the argument that a fractional reserve bank issuing fiduciary media can literally never go bankrupt because it can always cover a deposit shortfall by issuing more equity. While briefly flirting with a capitalization of around fifty f***ing billion dollars, and endorsed and fawned over by all manner of illiterate charlatans with gigantic and unsuspecting audiences, this argument was eventually rejected by the market as utterly imbecilic, as analyzed by myself and Nic Carter in All Falls Down.
This triggered a credit contagion that soon after took down 3 Arrows Capital, Celsius, Voyager, BlockFi, and others. FTX limped along by what we now understand to be something like defrauding their way out of debt, but eventually also collapsed later that year. If _Only The Strong Survive _was a pre-mortem of all of this, then the reader may want to read Green Eggs And Ham, also by myself and Anders Larson, as a kind of post-mortem.
2023-today reality: Bitcoin multisigs narrative: “Bitcoin renaissance”
And now a lot of this stuff is moving to Bitcoin. It is outside the scope of this essay to explain this in much detail but there have been a handful of developments in Bitcoin recently which, regardless of their intended purpose, seem to have as a collective side effect that a lot of these same shenanigans can now be implemented (or can _pretend _to be implemented) in a more Bitcoin-native context.
So, the new narrative is something like:
“these things didn’t work, not because they are terrible ideas that collapse to moon math wrappers around gambling and scams under any remotely critical analysis, but rather because they weren’t on Bitcoin. But also, since it has only recently become possible to (at least pretend to) implement them on Bitcoin, they are now worthwhile. We have wandered in the wilderness but learned our lessons and found the promised land.”

Technical and Economic Merit
Let’s consider all this through the lens of technical and economic merit once again. Or rather, the alleged merit given the stated goal. Ignore for now whether there is any merit:
2015 technical goal: new computing paradigm economic goal: x% of GDP?
The original idea of “crypto” allegedly has the merit of the next revolution in computing. Goodness knows how big that market is; probably a decent chunk of global GDP – if it meant anything, which it doesn’t.
2016-17 technical goal: disrupting company formation economic goal: y% of S&P?
ICOs then become a little bit more specific. Now they are merely disrupting how we organize companies. What’s that worth? Some portion of the value of the companies that can now be decentralized and tokenized I guess? Who knows …
2018-19 nothing to see here
Nothing happened then, don’t worry about it.
2020-21 technical goal: decentralize finance economic goal: z% of NYSE, CME, ISDA?
Defi becomes more specific again. Now we are merely tokenizing financial contracts, expanding access, removing middlemen, and so on. So that should probably be worth some percentage of capital markets activity?
2022 nothing to see here
Oops, never mind …
2023-today technical goal: now it’s on Bitcoin! economic goal: i% of … Bitcoin?
… and now it’s on Bitcoin apparently.
In Hindsight ...
I think the most amusing analysis of all this is as follows: it starts off completely insane, it gets more and more restrained each time – you could cheekily argue it starts to make more and more sense – but it also gets closer to Bitcoin every time. It’s clearly narrowing in on just: Bitcoin.
This is people realizing, painfully, over decades, what blockchains are for! They are not for “decentralizing everything” They are for censorship-resistant, sound, peer-to-peer digital money.

And I think this is _also _why we get the current state of crypto from earlier in the essay. As it starts to make more and more sense (by getting closer and closer to Bitcoin) you have realizations like the following: digital gift vouchers for artificially scarce and extremely expensive computation aren’t money, so we need “real money” in here for it to have economic merit, so you get stablecoins. Also, well we have a rich programming environment that seems technically interesting but also the severe technical handicap of being unable to do even a billionth of a billionth of a billionth of all the computations in the world, so you get crypto R&D. These emerge as a kind of patch, and they have _some _merit in isolation, whereas the long-term trajectory is actually just to converge on Bitcoin.
It’s an open and fascinating question if there are any learnings from these that can still be transplanted to Bitcoin. For stablecoins, this strikes me as less clear, given the dubious technical merit is introduced by using a blockchain at all, not just a blockchain other than Bitcoin. However, efforts to create Bitcoin balances (tokenized or otherwise) that are stable relative to some external price are to be applauded, if still heavily scrutinized for what technical merit they _really _have.
It seems far more likely that crypto R&D will prove useful in a Bitcoin context to some or other degree, and in this case the economic merit is in fact solved by moving to Bitcoin, provided the necessary technical merit can be mimicked. At the time of writing, this is a source of both hope and dread: hope given the possibility of viable avenues of development (although still highly uncertain); dread given how early steps in this direction are already being misrepresented in the pursuit of bullshit and scams. I will return to both shortly.
Narrative Evolution
Back to the table just above, I want to make three quick observations that tie together my entire argument and get us to the end of the essay:

Firstly, the bubbles always follow the price of Bitcoin. Hopefully I don’t need to include a price chart for the reader to grasp this immediately.
Secondly, it’s important that the narrative always changes. Absolutely ungodly amounts of money were raised for this crap following the_ Bitcoin bull runs of 2017 and 2021. The people doing this couldn’t point to the previous absolute disaster, so they had to spin something along the lines of: “_we learned our lessons and we’ve refined the use case.” This should sound familiar from just above.
Thirdly, however, regardless of whatever refinement they’ve come up with, the consequence of the new “narrative” is always, “buy my token”.
Always.
It doesn’t matter what buzzword salad is in the middle. It’s always “Bitcoin is cool, xyz, fughayzi fughahzi, buy my token.”
This is why I am very much tempted to not care so much about developers, academics, entrepreneurs, and so on, and in fact for my null hypothesis to be that they are more likely to have been victims than perpetrators. I don’t think they even end up in a position to contribute without the key group whom I do blame. When you put all these pieces together, what I think falls out of this analysis is as follows:
The entire cycle of shitcoinery can be traced to unscrupulous financiers convincing capital allocators who don’t know any better, in a bull market that, yes, Bitcoin is cool, but what they are doing is related, cooler, and that they deserve a fee.
Let us label this the Capital Cycle Theory of Shitcoinery. I think that everything else about which one might want to complain is downstream of this core realization.
Avoiding It
Given everything I’ve covered this is simple and this is pretty much the end of the essay.
You need to be aware of why this is happening now. If it hasn’t happened to you already (intended readership in the capital allocation business, that is) I guarantee it’s about to: with ETFs and the halving just past, we seem to be starting a Bitcoin bull run, these people have already raised ridiculous amounts of money on scams and bullshit that have mostly imploded. They may have lost a lot of money, or they may even have dumped on retail and got an excellent “return”. But in any case, they need a new narrative.
It's _possible _they have a viable narrative around stablecoins, R&D, both, and that they are as wary of scams as I have suggested here that they should be. I don’t want to insult anybody who merely has a different investment thesis to me if they are otherwise reasonable in their outlook and honest in their dealings.
However, if they are only now realizing how pointless and disingenuous every preceding crypto narrative has been after 7 years and hundreds of billions of dollars – or if they still don’t realize it at all; if their track record shows they were deeply involved, handsomely rewarded, and yet created nothing of lasting value; if they say things like “the builders are coming back to Bitcoin”: be very, very suspicious. Be on the lookout for tokens, which is to say, be on the lookout for scams.
What is especially frustrating is that the technical spin of the "layer twos" that are all the rage at the time of writing, that "the builders are coming back to Bitcoin" to build, and that you, the capital-allocating reader, will almost certainly be pitched, is in and of itself pretty reasonable. They just don't require tokens and they don't require gambling to support the token prices. What they do require is _sound adherence to Bitcoin's technical and economic merit. _At the very least, they require honest communication about the design trade-offs so far and planned for, and what, if any, economic and technical merit is left over after these trade-offs have been made.
Narrative aside, the _reality _of 99% of these projects is that they are private execution environments tied to multisigs custodying user deposits. Which is to say, on the one hand, that they are cargo culting "crypto R&D" from Ethereum that isn't technically possible in Bitcoin in order to feign technical merit, and on the other, that _they aren't layer twos at all. _Once again, they may as well be Chaumian eCash mints, except for the fact that this would make the intended token scam all but impossible to pull off.
Casey Rodarmor, creator of the Ordinals protocol, recently joked on the Hell Money _podcast he co-hosts, responding to the idea that "_everybody is building an L2 now":
"It's the same sad sack playbook as on Ethereum being recapitulated on Bitcoin. That's how you get a VC check on Ethereum. They are all glorified multisigs, so they are like, "hey let's port our glorified multisig to Bitcoin and get a VC check." I was talking to a friend of mine who is working on an interesting project, an open-source analyzer that does transaction clustering, and I was like, "maybe you could do this in this way and raise some VC money," and he said, "yeah, okay, but what's the point in raising VC money?" And I said, "no, no, no, this is the end! This is the goal! You raise VC money and then you cut yourself checks from that VC money until it runs out and then you raise more at a 10x valuation. This is the new economy, guys!"
The 1% that are legitimately trying to bring the learnings from crypto R&D to Bitcoin in a technically and economically sound manner will hopefully win in the long run (and even this is somewhat speculative at the time of writing) but will likely get little to no attention amidst this bull market flurry of scams and bullshit.
Axiom will do its best to source and invest in these companies (we already have!) but we are resigned to it being a much more difficult sell to capital allocators in light of the Capital Cycle Theory of Shitcoinery. To be brutally honest, this entire essay can fairly be considered cope on my part in light of having lost this battle in the past and facing up to the very real prospect of losing it in the near future too. Oh well, at least I tried.
Wrapping Up
The essence of the Capital Cycle Theory of Shitcoinery is that the problems I’ve described ultimately come from bamboozling people just like you with technical sounding nonsense like “Web 3” so you think it’s all a lot more complicated than it really is. Just buy Bitcoin. That’s certainly the first thing you should do anyway, and it might be the only thing you ever need to do.
If you really, really want to take the extra risk of investing in the Bitcoin ecosystem, the team at Axiom would be happy to speak with you. But we are never going to talk you out of buying Bitcoin. There is no world in which Bitcoin does poorly and we do well, or in which we promise something “better than Bitcoin,” and there’s no point in engaging with us at all if you don’t already believe most of this.
If that’s of interest to you, we’d love to talk. If not, just buy Bitcoin. In any case: fair warning, we are heading into a Bitcoin bull market and the scams and the bullshit are coming. Good luck avoiding them.
Allen Farrington, June 2024

-
 @ a012dc82:6458a70d
2024-07-17 06:21:27
@ a012dc82:6458a70d
2024-07-17 06:21:27Table Of Content
-
Pros of Investing in Bitcoin
-
Cons of Investing in Bitcoin
-
The Future of Bitcoin
-
Conclusion
-
FAQ
Bitcoin is a decentralized digital currency that operates independently of central banks and governments. Since its creation in 2009, Bitcoin has emerged as a popular investment option for individuals and institutions seeking to diversify their portfolio. However, like any investment, Bitcoin comes with its own set of risks and rewards. In this article, we will explore the pros and cons of investing in Bitcoin.
Pros of Investing in Bitcoin
Decentralization
One of the main advantages of Bitcoin is its decentralized nature. This means that there is no central authority controlling the currency, making it resistant to government interference and manipulation.
Security
Bitcoin transactions are secured through advanced cryptographic techniques, making it virtually impossible for hackers to steal funds.
High Potential for Growth
Bitcoin has shown tremendous growth potential over the years, with its value skyrocketing from just a few cents in 2009 to over $60,000 in 2021.
Diversification
Investing in Bitcoin can help diversify your portfolio, reducing your overall risk by spreading your investments across multiple assets.
Cons of Investing in Bitcoin
Volatility
Bitcoin is known for its extreme volatility, with its value fluctuating wildly in short periods. This can make it a risky investment option, particularly for those seeking stability.
Lack of Regulation
Bitcoin is not regulated by any central authority or government, making it vulnerable to fraud, scams, and market manipulation.
Limited Acceptance
While Bitcoin has gained wider acceptance in recent years, it is still not accepted by all merchants and businesses, limiting its utility as a currency.
Environmental Impact
Bitcoin mining, the process of verifying transactions on the blockchain, requires a massive amount of energy, contributing to environmental concerns.
Conclusion
Investing in Bitcoin can be a high-risk, high-reward endeavor. While it offers the potential for tremendous growth, it also comes with significant risks and challenges. Before investing in Bitcoin, it is important to carefully consider your investment goals, risk tolerance, and overall financial situation. As with any investment, it is important to do your own research and seek professional advice before making any decisions.
FAQ
How does Bitcoin work? Bitcoin transactions are recorded on a public ledger called the blockchain. The blockchain uses cryptography to ensure the security and integrity of the network. Bitcoin is created through a process called mining, where powerful computers solve complex mathematical equations to verify transactions and add new blocks to the blockchain.
Is Bitcoin a good investment? Bitcoin has seen significant price fluctuations since its inception, making it a high-risk investment. While some investors have made significant profits from Bitcoin, others have lost money. It's important to do your research and understand the risks before investing in Bitcoin.
What are the advantages of investing in Bitcoin? One advantage of investing in Bitcoin is its potential for high returns. Bitcoin has seen significant price increases in the past, and some experts predict that its value will continue to rise. Another advantage is the decentralized nature of Bitcoin, which means it's not subject to government or financial institution control.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3c172490:91b2b73b
2024-07-17 04:54:50
@ 3c172490:91b2b73b
2024-07-17 04:54:50E-waste is a major problem in the world. Most governments are taking steps to tackle the challenge of e-waste and encouraging people to recycle the e-waste. That’s why you will often find government-funded e-waste recycling programs, non-profit organizations collecting e-waste, and private e-waste recycling companies recycling e-waste for free.
Out of all the ways to get rid of e-waste, hiring a professional e-waste recycling company is the most convenient way to get rid of the e-waste. However, you have to pay for the convenience. Your private e-waste recycling company charges you the fee for the collection of e-waste from your home.
Before you call professional e-waste services, here are the five things you need to keep in mind:
- Find out whether the company is certified
E-waste recycling comes with a lot of complexities. It contains a range of harmful chemicals that need to be treated in a controlled environment. Look for a certified e-waste recycling company that has an active license to recycle e-waste in the area. Many companies just collect the e-waste and transport it to developing countries for disposal. Look for an e-waste company that actually recycles e-waste.
- Ask about the e-waste recycling terms and conditions
Most electronic waste items can be recycled for free, but for some items such as printers, copiers, and fax machines, you have to pay the recycling fee. For some items or certain quantities of e-waste, you can get rewards too. Ask about the terms and conditions of the e-waste recycling company. They include everything you need to learn about e-waste recycling.
- Check the reputation of the company
It is always a good idea to check the reputation of the company. You can do so by reading the reviews of the company. You can search online for any complaints registered against the company. Go through the website of the company.
This will help you get some idea about the reputation of the company. If you find a company that has mostly negative reviews, you can move to another company.
- Ask about free drop off
Most private residential electronics recycling companies provide free drop-off services. It includes dropping off the accepted e-waste items at the recycling center. You can get your e-waste recycled for free.
- Learn about the buyback program
The buyback program includes the exchange of e-waste items in return for rewards. These rewards can be anything from cash to store discounts and coupons. Buyback programs are mostly applicable for commercial companies that have a large number of electronic units in decent condition eligible for exchange.
If you are looking for a professional e-waste recycling company, you can get in touch with Xtreme Green Recycling. Check out our client review:
Highly recommend these guys! Extreme by all measures- speed, courtesy, and care (for you and the planet!). Mark and company went out of their way to get piles of e-waste out of our way. Thanks again, fellas! –Artin Gorjian
Category Uncategorized Tags
-
 @ dd664d5e:5633d319
2024-07-10 15:00:40
@ dd664d5e:5633d319
2024-07-10 15:00:40The Law Giver
In my previous article, I briefly went into the topic of how contract law is holy law.
The Father of the Christians, you see, is a God of Covenants, and He sent His Son to Earth to fulfill the Law and pay a Price for our salvation. The Father also created the Natural Order to confirm His Laws through our observation of that Law in action.
That is why Christians have a deep respect for honest contracts, true prices, fair measures, natural systems, and good laws. Not merely for their own sake, but also because understanding them helps us to understand and emulate the Law Giver.
The tired What would Jesus do? meme is actually an attempt to capture this emulation of the Highest Judge. Jesus knows the Law, since His Father defined it and He is One with the Father, so how would He apply the Law best, in this situation?
The Last Things
Working together with him, then, we entreat you not to accept the grace of God in vain. For he says, “At the acceptable time I have listened to you, and helped you on the day of salvation.”
Behold, now is the acceptable time; behold, now is the day of salvation.
-- 2 Corinthians 6:1-2 New Testament, RSV Bible
One of the things most devout Christians frequently ruminate over, is when Christ will return.
Every day, we ponder. We go for a walk, and ponder. We cook dinner, and ponder.
At the same time, we are called upon to live each day in a productive manner, and to not simply lie around, vegetating, and staring at the heavens. Not only for our own sake, but also because to do so would be to limit our ability to inform others about the Good News, so that they can take to pondering with us. We are called to ponder with as many people as we can produce, adopt, convert, or simply collect through our daily interactions.
This means that we are not of the world (as our eyes are watching God and baptism has made us Immortals), but we are definitely in the world (involved in, and effected by, the everyday dealings around us.) It is a very difficult balancing act to know when we are paying too much attention to the one or the other, or to know where to store up our treasures, if we can't put them all immediately into the Final Treasury.
So, we worked today and earned a bit of fiat cash and we have no immediate usage for it. What to do with it?
Well, some of it should go to charity or be invested in a business that provides important goods, services, and employment. Some of it will be needed to simply cover the day-to-day costs of our own life, or that of those dependent upon us. But it might be prudent to store up some of it, for the mysterious length of time between receipt of the monies and our own ascent into Heaven.
Typically, that store was the local currency, but that's being inflated away at an alarming rate. Then we all began to move to precious metals, and many of us still do, but they are so difficult to spend and can't be broken into small bits or transported over wide distances at low cost.
Enter Bitcoin.
The Great Ledger
In our frustration, more and more Christians are turning to a new technology, to save up some treasure in a liquid asset, for the mid-term. And, once we begin using it, and begin to understand how it works, we quickly grow fond of it.
Bitcoin is a beautiful money because it is a money based upon keeping precise accounts, using a fair measure, and obeying the Laws of Nature.
In essence, Bitcoin is a debt note emitted by a universal debtor (the network) in exchange for some good or service. This frees the individual people using it from ever needing to carry debt, as the debt stays in the network, the value and enforceability of that debt note is protected by the effort used to create and maintain the network, and the eagerness with which other people wish to store their efforts up in that same network. The debt still exists, but it can be so thinly and widely spread that it no longer rests as a burden upon one particular person.
The debt, in other words, has been disassociated from humans and the management has been distributed to machines. This is the precise opposite process of a "fiat" (by decree) currency, which only has value so long as it is associated with some particularly solvent group of humans (who personally vouch for repayment of any debts denominated in the currency), and where management is centralized to some other group of humans.
Have you accepted Bitcoin as your personal money and store of value?
You have invested $10 to buy the electricity to mine Bitcoin? Then you receive $10 of Bitcoin in return. The Bitcoin network now owes you the $10 purchasing power equivalent of that electricity.
If someone then gives you $5 worth of pizza, then you can then give them a $5 portion of your $10 worth of Bitcoin. You have taken a part of your Bitcoin debt note and shared it with them.
They now hold $5 worth of Bitcoin invested in the network and can spend it on some other good or service. Or they can simply hold it and wait for it to rise in value, as more people "mine" more of it (and produce more notes, paradoxically making the existing notes more useful and therefore valuable) and more people try to gain the notes in order to manage their own finances by storing their energy in the network or transporting their energy using the network.
Bitcoin, in other words, is an accounting book that needs no accountant because it stores, tracks, and controls the ledger on its own. It is a Natural Ledger that runs according to the Laws.
It is the only human-made ledger that allows for true and immediate Final Settlement. This Final Settlement is what allows people to trade using the convenience of digital debt notes, with neither person occurring or even risking any personal debt. We Christians know that all debt is a burden, including monetary debts, which is why we are called to forgive each other's debt and to hope that our own debts are forgiven. Better still, is to avoid the accumulation of debts, altogether.
So, Final Settlement? Final Settlement is what Jesus would do.
-
 @ 8d34bd24:414be32b
2024-07-17 02:15:54
@ 8d34bd24:414be32b
2024-07-17 02:15:54Once again here are the fruits of the Spirit as defined in Galatians 5.
But the fruit of the Spirit is love, joy, peace, patience, kindness, goodness, faithfulness, gentleness, self-control; against such things there is no law. (Galatians 5:22-23) {emphasis mine}
What is Good?
And someone came to Him and said, “Teacher, what good thing shall I do that I may obtain eternal life?” And He said to him, “Why are you asking Me about what is good? There is only One who is good; but if you wish to enter into life, keep the commandments.” Then he said to Him, “Which ones?” And Jesus said, “You shall not commit murder; You shall not commit adultery; You shall not steal; You shall not bear false witness; Honor your father and mother; and You shall love your neighbor as yourself.” The young man said to Him, “All these things I have kept; what am I still lacking?” Jesus said to him, “If you wish to be complete, go and sell your possessions and give to the poor, and you will have treasure in heaven; and come, follow Me.” But when the young man heard this statement, he went away grieving; for he was one who owned much property.
And Jesus said to His disciples, “Truly I say to you, it is hard for a rich man to enter the kingdom of heaven. Again I say to you, it is easier for a camel to go through the eye of a needle, than for a rich man to enter the kingdom of God.” When the disciples heard this, they were very astonished and said, “Then who can be saved?” And looking at them Jesus said to them, “With people this is impossible, but with God all things are possible.” (Matthew 19:16-26)If the Bible says that there is no one good except God, how can we be good or show the goodness expected by God? We can only do good and be good if we “abide in the vine,” if we have the Spirit within us. This is because only God is good. We can have the fruit of the Spirit, goodness, only when we have the Spirit of God within us. Our goodness comes from Him. He enables us to overcome our sin nature and to act within His very good, sinless nature through Him.
Goodness Through Obedience & a Right Attitude
Goodness is obeying God, but it is more, it is obeying with a totally right attitude. It is submitting our lives fully to God. It is submitting to His will and His plan including putting the good of others above our own good, just as Jesus did when he came down to Earth, lived a perfect, sinless life, and died on the cross to take away our sins. We can’t just obey by our own power.
“You have heard that the ancients were told, ‘You shall not commit murder’ and ‘Whoever commits murder shall be liable to the court.’ But I say to you that everyone who is angry with his brother shall be guilty before the court; and whoever says to his brother, ‘You good-for-nothing,’ shall be guilty before the supreme court; and whoever says, ‘You fool,’ shall be guilty enough to go into the fiery hell. … “You have heard that it was said, ‘You shall not commit adultery’; but I say to you that everyone who looks at a woman with lust for her has already committed adultery with her in his heart. (Matthew 5:21-22,27-28)
We can’t just obey the letter of the law and be good. If you notice, it is the thought as well as the action that we are to avoid. Hating another is counted as murder because of the righteous nature of God. Lusting for another is considered adultery because of the Holiness of God. We must have a change of heart through faith in Jesus and through the indwelling of the Holy Spirit, that changes our motivations and the way we think. This goodness is unlike anything the world has seen and it draws people to Jesus like flies to honey.
Obey as God Enables
While He was in Bethany at the home of Simon the leper, and reclining at the table, there came a woman with an alabaster vial of very costly perfume of pure nard; and she broke the vial and poured it over His head. But some were indignantly remarking to one another, “Why has this perfume been wasted? For this perfume might have been sold for over three hundred denarii, and the money given to the poor.” And they were scolding her. But Jesus said, “Let her alone; why do you bother her? She has done a good deed to Me. For you always have the poor with you, and whenever you wish you can do good to them; but you do not always have Me. She has done what she could; she has anointed My body beforehand for the burial. Truly I say to you, wherever the gospel is preached in the whole world, what this woman has done will also be spoken of in memory of her.” (Mark14:3)
The goodness expected by Jesus is not the goodness of the world. It is different. Frequently the goodness of the Spirit is considered foolishness by people. Goodness is acting according to the will of God and for His eternal plan.
The thing that really stands out to me in the passage, is the statement “She has done what she could.” All God asks of us is to obey His commands and submit to His Spirit. We are not responsible for the result. We are not responsible for things we cannot control. God has got this. God has an eternal plan that will come to fruition. We are just blessed to be used by Him to make His plan a reality. Knowing the result is in His hands really takes the pressure off. When we trust and obey Him, He will use our faithfulness for good and give us His goodness.
This passage should be the cry of our hearts.
You have dealt well with Your servant,
O Lord, according to Your word.
Teach me good discernment and knowledge,
For I believe in Your commandments.
Before I was afflicted I went astray,
But now I keep Your word.
You are good and do good;
Teach me Your statutes. (Psalms 119:65-68)We need to study His commandments and statutes in order to know what God wants us to do. We should keep His word. We should do good as He does good.
Even though our goodness is done through the power of the Spirit and under the covering of Jesus, we still need to know God’s commands to live a life of goodness. We need to actively learn what He wants from us. We cannot truly live a good life on our own, but that doesn’t mean we should be passive. We are called to actively obey His commands. We are called to study His word. We are called to speak the truth (that we learn from the Bible). We are called to follow Him. We are not called to lie around like a puppet waiting for the puppeteer to move us and speak for us.
Goodness Now, but Results In God’s Timing
Sow your seed in the morning and do not be idle in the evening, for you do not know whether morning or evening sowing will succeed, or whether both of them alike will be good. (Ecclesiastes 11:6)
God tells us to obey Him and to do what is right at every opportunity (not waiting for what we think is the best time). We then must leave the results to Him. When we are kind to someone, sometimes they will be kind in return, but sometimes they won’t. When we witness to others, sometimes they will repent and turn to God, but sometimes they won’t. We are only responsible for the witnessing, and obeying now. The results are up to God.
This should give us peace knowing that we can’t mess things up by doing it wrong. God can use the most awkward words and actions for His glory, but the most silver tongued orator or the most hard working evangelist can’t bring about a single conversion if God is not part of it. As we obey we must always keep in mind that all of our goodness comes from God, not through our works.
Use of Our Wealth for the Good of Others
Instruct those who are rich in this present world not to be conceited or to fix their hope on the uncertainty of riches, but on God, who richly supplies us with all things to enjoy. Instruct them to do good, to be rich in good works, to be generous and ready to share, storing up for themselves the treasure of a good foundation for the future, so that they may take hold of that which is life indeed. (1 Timothy 6:17-19)
There are many kinds of wealth. We may have the obvious wealth, money and property. We can also have a wealth of friends, a wealth of opportunities, a wealth of influence, or a wealth of skills. Of course the greatest wealth is faith in Jesus Christ, our Savior. God calls us to share this wealth. Part of the goodness we get from the Spirit is the generosity to share this wealth with those around us. We can’t share with everyone, but we can share what we have been given with those near us, who are in need.
I’ve said to people for a while that I have had two periods of time in my life: when I had more time than money and when I had more money than time. We will have different stages in life when you have different things to share. For example, if you are a parent of young children or a caregiver to someone with major health problems, you may not have much time to give to others, but there may be other things you can give. God calls us to be generous with what we have. He calls us to be stewards of His treasure. If you have a loving family, that is a gift from God. If you have a good church, that is a gift from God. If you have skills, faith, or knowledge, they are gifts from God. If you have monetary wealth, that is a gift from God. If you have influence, that is a gift from God. We should use all of these for the good of those around us.
If you have a loving family, you could invite over a young person who doesn’t have family close by or comes from a broken family and show them what a loving, Godly family looks like. If you have a Godly, loving, Bible-believing church, invite those around you to attend. If you have skills, use them to teach another or to help someone in need. If you have faith, talk about your faith to those who are suffering or doubting. If you have knowledge, teach those who don’t know as much. This may be speaking to a large audience, but it also may be talking to one person at your home or at a coffee shop. If you have monetary wealth, you may be called to give generously to those in need or ministries that share the Gospel. Whatever God has given you, you are called to share this with others. This is part of the goodness of God.
Every good thing given and every perfect gift is from above, coming down from the Father of lights, with whom there is no variation or shifting shadow. (James 1:17)
We are given good things so we can share the goodness of God with others.
Be Good as God is Good
And we know that God causes all things to work together for good to those who love God, to those who are called according to His purpose. (Romans 8:28)
“God causes all things to work together for good,” so we should also act in goodness for the good of others. We should actively seek the good of others, not just wait until the moment seems right. That moment may never come.
I still regret two missed opportunities in particular. Neither seemed like a big deal at the time, but I still think about them decades later.
In high school, I was at school late for some reason. I was talking to a fellow student. It ends up that student was stuck at school and didn’t have a ride home. They hinted that they needed a ride, but I was too focused on my own schedule that I missed it. It wasn’t till I got home that I realized they were asking for a ride without asking. I totally missed it. I would’ve been willing to give them a ride, but I was too self-focused to catch the hint. I have no idea how long they had to stay at school till they got a ride. I was not seeking that person’s good. I was seeking my own.
Another event happened when my husband and I were driving to church one morning. As we drove out of our neighborhood, there was a little old lady struggling taking the trash out to the curb. It would’ve been easy to stop and help her. It wouldn’t have taken more than a minute or two, but we were in a hurry and didn’t stop. (I don’t think my husband saw her because he was driving and paying attention to the road.) I still wish I had stopped to help that lady. I missed an opportunity to do good to another because I was focused on myself. I may have been doing a “good” thing, going to church, but missed the best thing, helping and witnessing to a struggling, old lady. The goodness of the Spirit is doing God’s best instead of what is merely good.
Let us not lose heart in doing good, for in due time we will reap if we do not grow weary. So then, while we have opportunity, let us do good to all people, and especially to those who are of the household of the faith. (Galatians 6:9-10) {emphasis mine}
Sometimes we may get tired of doing good when it feels like no good is coming from it, but God tells us to “not lose heart in doing good.” God’s plan is never according to our timing. People talk about certain individuals being so smart that when making decisions “they play 3D chess.” In other words, they are seeing so many steps that a normal person doesn’t see and can therefore make better decisions. God doesn’t just “play 3D chess,” He plays more than 1,000,000D chess. We can’t even imagine all of the variables that He manages to bring His plan to fruition. We should never lose heart and we should continue to “do good to all people, and especially to those who are of the household of the faith.”
Do not deliver me over to the desire of my adversaries,
For false witnesses have risen against me,
And such as breathe out violence.
I would have despaired unless I had believed
that I would see the goodness of the Lord
In the land of the living. (Psalms 27:12-13)All Christians know that God and Good (is there a difference?) win in the end and that there will be no pain and suffering in heaven, but we long to see that same goodness here on Earth, “in the land of the living.” If we are diligently watching, God gives us peeks at the fulfillment of His plan, glimpses of the goodness being accomplished, and flashes of the positive influences we are helping to bring about. Don’t be so focused on your current cares that you miss the wonderous works that God is doing, especially those being done through your life.
How great is Your goodness,
Which You have stored up for those who fear You,
Which You have wrought for those who take refuge in You,
Before the sons of men! (Psalms 31:19)As we deal with the evil of the world, we need to keep doing good and “take refuge in” God’s goodness and the power of His Spirit.
O taste and see that the Lord is good; How blessed is the man who takes refuge in Him! (Psalms 34:8)
Slander, Not Hypocrisy
And keep a good conscience so that in the thing in which you are slandered, those who revile your good behavior in Christ will be put to shame. For it is better, if God should will it so, that you suffer for doing what is right rather than for doing what is wrong. For Christ also died for sins once for all, the just for the unjust, so that He might bring us to God, having been put to death in the flesh, but made alive in the spirit; (1 Peter 3:16-18) {emphasis mine}
One thing we need to keep in mind is that we will be persecuted and derided for living a good Christian life and imitating Jesus. We need to make sure that all of the accusations are for having Christ-like goodness, and not for being lazy, sinful, or hypocritical. Many people have turned away from Jesus because of the hypocrisy of those who call themselves Christians or organizations that call themselves the Church. Don’t be the reason someone turns away from God. Live out God’s goodness, so that people want to learn more about being a Christian and knowing Jesus.
Bad Company Corrupts Good Morals
We get our goodness from obeying God, studying His word, and trusting in His power, but most of all we get our goodness from the indwelling of the Holy Spirit and the covering of the Blood of the Lamb. We are told that we are “washed white as snow.”
If you are a parent, you’ve probably experience your child being dressed up in his/her Sunday best, but then they decided to go hug the hairy dog, play in a mud puddle, or some equally messy endeavor. That beautiful, clean outfit, gets dirty and ruined. In the same way, spending time with ungodly, bad company can dirty our “white as snow” soul and keep us from the goodness that God intends. If we are truly a child of God, this doesn’t mean we lose our salvation or anything like that, but we do become unfruitful.
Do not be deceived: “Bad company corrupts good morals.” Become sober-minded as you ought, and stop sinning; for some have no knowledge of God. I speak this to your shame. (1 Corinthians 15:33-34)
The Bible tells us to be in the world, sharing the Gospel, but not to be of the world, living like the rest of sinful mankind. We need to be careful to not use the excuse “that we are witnessing” to be of the world as an excuse for living a worldly life. Is our sending our kids to government schools actually just doing what is easy? Is our hanging out at the bar to witness just an excuse to drink or hangout with our ungodly friends? Are we saying we are being wise stewards with our money, but in reality we are refusing to give according to God’s will because we are saving up emergency money to provide for ourselves because we don’t trust God to provide for us? Sometimes it is hard to judge our motives because we lie to ourselves as well as to God. Be careful that we don’t let “little” lies and “little” excuses draw us away from God’s will. Be careful that we aren’t so much in the world, that we are no good to anyone.
Sometimes it is hard to find that right balance. Some people so avoid the worldly sinners that they are of no use to anyone, especially God. Some people are so in the world that they are led astray and look no different than the ungodly sinners around them. We need to pray that God would guide us to witness to the sinners without being changed negatively by their presence. We need to have Godly friends who keep us on track and encourage our walk with God. We need to attend a Bible believing church, so we are regularly taught God’s word and guided in how to apply it. We need to read the Bible daily so we are filling our minds with God’s goodness and not the sinful culture of the world. We want our goodness to shine out and point to the goodness of God. We want our goodness to be the light that draws those around us to salvation.
Goodness Unlike Anything Known to Man
As a Christian, being good and showing goodness to fellow believers should be fairly easy (in the Spirit, but not of ourselves). On the other hand, even for those walking closely with Christ, there is almost always someone to whom it is hard to act with goodness and kindness because they have so mistreated and hurt us. We are called to be good to them as much as we are to those we care about. God’s goodness is acting in a way that is so contrary to human nature that it is hard for people to comprehend. It makes those who don’t know God say, “Are you for real?”
Bless those who persecute you; bless and do not curse. Rejoice with those who rejoice, and weep with those who weep. Be of the same mind toward one another; do not be haughty in mind, but associate with the lowly. Do not be wise in your own estimation. Never pay back evil for evil to anyone. Respect what is right in the sight of all men. If possible, so far as it depends on you, be at peace with all men. Never take your own revenge, beloved, but leave room for the wrath of God, for it is written, “Vengeance is Mine, I will repay,” says the Lord. “But if your enemy is hungry, feed him, and if he is thirsty, give him a drink; for in so doing you will heap burning coals on his head.” Do not be overcome by evil, but overcome evil with good. (Romans 12:14-21) {emphasis mine}
The key to goodness is this, “Do not be overcome by evil, but overcome evil with good.”
*** I’ll include a few more verses on goodness below for those who want to continue studying God’s word on goodness.
Trust Jesus.
Let love be without hypocrisy. Abhor what is evil; cling to what is good. 10Be devoted to one another in brotherly love; give preference to one another in honor; 11not lagging behind in diligence, fervent in spirit, serving the Lord; 12rejoicing in hope, persevering in tribulation, devoted to prayer, 13contributing to the needs of the saints, practicing hospitality. (Romans 12:9-13) {emphasis mine}
Therefore let us not judge one another anymore, but rather determine this—not to put an obstacle or a stumbling block in a brother’s way. I know and am convinced in the Lord Jesus that nothing is unclean in itself; but to him who thinks anything to be unclean, to him it is unclean. For if because of food your brother is hurt, you are no longer walking according to love. Do not destroy with your food him for whom Christ died. Therefore do not let what is for you a good thing be spoken of as evil; for the kingdom of God is not eating and drinking, but righteousness and peace and joy in the Holy Spirit. For he who in this way serves Christ is acceptable to God and approved by men. So then we pursue the things which make for peace and the building up of one another. (Romans 14:13-19) {emphasis mine}
The sins of some men are quite evident, going before them to judgment; for others, their sins follow after. Likewise also, deeds that are good are quite evident, and those which are otherwise cannot be concealed. (1 Timothy 5:24-25) {emphasis mine}
FYI, my following posts will continue going through each of the individual fruits of the Spirit listed in Galatians 5
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ 3cd2ea88:bafdaceb
2024-07-16 23:07:16
@ 3cd2ea88:bafdaceb
2024-07-16 23:07:16🚀 Unisciti al primo progetto ecosistemico su Bitget Onchain Layer e vinci fantastici premi!
🔹 Check-in per 3 giorni consecutivi e ricevi un premio esclusivo! 📝 Compito: Pubblica il tuo screenshot di check-in su Telegram con l'hashtag #TomarketCheckIn 💰 Premio totale: 100 BGB per canale. 10 persone (da ogni comunità UE) saranno selezionate a caso tra i partecipanti per ricevere 10 BGB ciascuna!
🛑 Scadenza: 22 luglio, ore 12:00 CET
🌐 Link di gioco Tomarket: https://t.me/Tomarket_ai_bot/app?startapp=00002vZy
🌽 Farm $TOMATO con me e assicurati la tua allocazione di token attraverso Tomarket.ai. Usa il mio link per ottenere 20,000 $TOMATO!
🔗 Iscriviti ora su Bitget e partecipa all'evento! https://bonus.bitget.com/U1JNEK
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ f0aca767:dce3306e
2024-07-16 22:56:38
@ f0aca767:dce3306e
2024-07-16 22:56:38Over the past week, I've spent a little time here and there checking out the latest game out of grindy, microtransaction game maker, Nexon. This is what I think about it.
Hold up, haven't I seen this before?
Back in the olden days of gaming o' yore, there was a time when Shephards saved the galaxy, and the Inquisition had only just begun, guards of the veil be damned.
Before developer studios killed their community forums and moved communication to Twitter, and while we were all playing Mafia Wars and The Sims Social on Facebook, awkwardly flirting with sims created by our close friends. An age where the latest Sims game didn't have swimming pools, and most of us were still venturing out Into the Future.
That time was 2014. A time before gaming was corrupted by an onslaught of nonstop subscription models and battle passes. When 30 hours to beat a game was perfectly acceptable. When loading into something brand new, felt ... exciting. But war, war has changed.
Warframe was released in 2013, and then later, for the Playstation 4, in 2014. This was mostly only an alpha, and all you could really do was jump down to a handful of extermination missions from a static solar system map.
Around the same timeframe, the first Destiny was released on consoles, and, at the time, didn't even remotely touch a PC.
Both games shared (and still share) similarities. As Warframe evolved, it became a mission-hub, shooter-looter game where you built your character, played with friends, and spent the rest of your time sifting through playing-card-eque warframe modifications. Destiny, and then its sequel, years later, are really not all that different.
It's a theme I don't feel has really caught on all that much outside of ... well, Warframe and Destiny. Sure, we have Helldivers 2, but, that's kinda sorta similar, but also not really.
Warframe and Destiny 2 exist as "live service" games. Games that exist without a subscription, but do have expansions and microtransactions, and are persistent, never-ending. I think back in the golden age of gaming, we would call this a hybrid MMO.
They don't really exist in a niche, but this genre has largely been overshadowed by MOBAs, and then survival games, and then battle royales. I think the battle royale genre still reigns supreme as one of the most popular format of games to play. Although, personally, it's starting to feel pretty stale for me. Even if Apex Legends is really cool.
But, now we're in 2024. Warframe has been out for about 11 years, and Destiny has been chugging along for around the same amount of time. And I guess Nexon decided to throw their own hat into the ring. For ... reasons?
Enter: The First Descendant. Like if Mass Effect Andromeda had a child with Destiny, and then got cybernetically modified with implants from Warframe. It's a game occupying a concept that already exists, so much so, they purposely or accidentally copied UI design directly from Destiny 2. And, as damning as this may look, I decided to give the game a shot, regardless.
Hello, I am now a bunny.

The game starts out kind of unremarkable, dropping you into a sci-fi universe where an evil big guy wants an artifact for his own evil doing and bidding, and you've got to stop him.
The First Descendant is a third-person looter shooter powered by Unreal Engine 5. Become a Descendant. Fight for the survival of humanity. Descendants have unique abilities to tackle both solo and co-op missions. Up to 4 players use varied mechanics to defeat giant bosses. BE THE FIRST DESCENDANT!
It ... kind of reminds me of the beginning of Destiny 2, paraphrased and rewritten. You're a descendant, and you can do really cool stuff with your hands, like shoot out ice, or electricity, and also fire guns at monsters.
My first impression, is that the gun play kind of sucks. It feels like holding a stick and going "pew pew pew" with imaginary bullets. Sure, they're actually coming out of the gun, but there's next to no feedback when you're firing a gun, and when your shots are hitting your target. It just doesn't feel like I'm shooting a weapon that kills things.
Now, the graphics are pretty slick, and, well, I don't know if this is an issue with Linux, or what, but I'm running pretty good hardware, okay? And having the settings on high, I get great FPS ... until I venture into an area where there's a lot going on, or onto a battlefield where missions are happening. Everything slows down to a 15 FPS slug-fest. And, apparently, this is something that's happening to a lot of people, and it may not actually be a hardware issue.
It's been quite a while since I've felt the struggle of a poorly optimized game. Within the first ten levels, I wasn't really feeling like I was having all that much fun. I was feeling like I was just shooting a gun at some aliens until loot popped out, and repeating the process over and over until I was really powerful, and also had access to the Bunny descendant.
This is about where things start to get better. I like the bunny lady.
With my descendant now fully maxed out with all the gear you can wear, and equipped with modifications (that has an interface eerily similar to Warframe), I'm starting to feel like progress is happening.
I notice something though ... this game takes place, entirely, on just one planet? Did I miss something? What happens when you've completed all the missions across the map? Is it endgame time? Do I get to go to space and see other planets? I mean, this is what I'm expecting, since this is a direct copy and paste of Destiny and Warframe. But I've done almost no reading on the extended story of this game, and am speaking about it now from only first-hand experience.
But what about the voice acting?
The voice-overs in TFD sound like a typical dub in an anime. Some of them are alright, some of them sound like the person speaking has no emotional capacity whatsoever. It's a very, Nexon-ish, Eastern grinder game. Which is fine! Grinding mobs for loot is something I've done since 2001, when I joined Anarchy Online.
More issues, and stuff, and things.
From the jump, to level 14, I'm only really now starting to feel like I could enjoy TFD, and that's if they continue to fix it, and put out new content, and aren't sued by two different developer studios.
One of the issues I encountered while randomly playing the game, thus far, is that pretty much all the content is designed with having other people around you, in mind. Except, even though there are a lot of people playing this game, sometimes there is nobody doing the mission you need help with. So, you kind of just fail, and then fail again, and then either stand there and wait for someone to waltz in, or go do another mission and return later.
I've said it before years and years ago, and over and over again since then: A persistent online game where there is only group content, is a game I'm not that interested in.
Eve Online is great, until you find out you can't do anything actually fun or remarkable unless you become a social butterfly and join massive corporations, and constantly collaborate with other people. I'm a recluse! I don't want to do that all the time!
Albion Online is awesome ... until you hit a wall and find out you're gonna die, son. You're gonna die and enjoy it, unless you join a guild with active players, and collab--You already know what the heck's going on.
Black Desert Online is exactly the same, but it has more solo content than the previously mentioned games.
What I'm trying to get at here is, even if your game is online only, built around co-op and being massively multiplayer, you still need to have content people can do by themselves, or you're going to annoy me. You're going to bring a screeching halt to your entire game if for some reason a ton of people just stop playing.
I will give TFD a little merit, though. One of the reasons I don't really play Warframe, is that their story and quests are ridiculously convoluted, and not very friendly to people who have day jobs. You're telling me I have to grind for a week if I want a cool gun? Are you fuggin' serious, dude?
The same kind of goes for Destiny. I like the theme, but I don't like how a lot of the game kind of feels like a slog, until you get to the content you want to be in. TFD, so far, you pretty much just blast through everything like a stream of water through toilet paper.
This could be good, or bad, depending on what exactly the endgame is.
At the end of it all.
With my initial impressions down, and my extensive history of having seen this all before, and knowing exactly who Nexon is, as a company, and what they're probably going to do (Hello, exorbitant cash shop prices), would I continue playing?
Probably. I kind of do want to see what the endgame is like, and just how deep customization and stat-building goes.
Would I recommend it to other people?
Uh ... maybe? If you feel the same way I do about Warframe and Destiny? Give it a shot, maybe we'll talk, and I'll help you shoot some mindless aliens.
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ c5395d20:25baac60
2024-07-16 22:28:02
@ c5395d20:25baac60
2024-07-16 22:28:02The Gang Met A Witch
This is from the 10th session of my #DnD game, we play around every other week, sometimes with longer breaks. The party (Wizard, Druid, Forge Cleric/Artificer) just reached 4th level and has a Stronghold (the Manor at the Old Orchard Hill).
The party has been chasing rumors over the game, and decided to investigate the caustic black ooze local hunter Lars Bailey has seen on a few animals in the southern edges of the Duskwood. They consulted with the medicine woman in the town (Anton's Mill) and got general directions and advice, including a warning about the Witch of the Ashfens: Mother Leondra.
Mother Leondra is known to the villagers, but doesn't make herself a nuisance, typically only concerned with her domain in the marshland south of the mill town. The party decided to seek her advice.
They made their way into the Ashfens, and were met by two crows, their eyes sewn shut with red thread. Winora the druid spoke to them (queue the goofy voices) and asked if they knew Mother Leondra, of course they do. That's their mother.
 After some convincing (and bribery) the party successfully persuaded the crows to guide them to the witch's home. On the way they ran into a Catoblepas afflicted with black ooze. They fought the monster, realizing that if it takes damage the ooze scatters dealing acid damage. After they defeated the monster, Destin the Artificer collected the tusks, tail and eyes.
After some convincing (and bribery) the party successfully persuaded the crows to guide them to the witch's home. On the way they ran into a Catoblepas afflicted with black ooze. They fought the monster, realizing that if it takes damage the ooze scatters dealing acid damage. After they defeated the monster, Destin the Artificer collected the tusks, tail and eyes. They established camp, and watches. Wizard Armond got distracted by Will-o-the-Wisps during his, wandered out into the swamp and abandoned. He ended up spending the night sleeping rough, the party went without a watch the rest of the night.
The next day the party regrouped and made it to the witch's hut. A sign in giant (the lingua franca of my world) reads "No Soliciting" and in the clearing beyond a hut stood on a giant bird leg, moving slowly like sleeping breath. Armond knockef on the door, a voice inside asked if he'd read the sign, once he promised he wasn't here to sell something the door opened to reveal a middle aged woman working on some knitting in the far side of the hut. They talked for a while, the party joined them, Leondra made some veiled comments implying that she was going to eat them. Leondra snapped her fingers and the cookware began preparing lunch.
While waiting, several crochet poppets came and inspected the party, one observed Destin, then came back with tin armor, he gave it a bell which it wore as a helm. Another surveyed Winora and found a mop of yarn dreadlocks to wear, Winora gave it a feather from her hair to wear. A candle lit itself in blue flame and a third doll, red-haired, chased it. As it got close to the candle it extinguished and another lit. The doll chased the "Will-o-the-Wisp" for a minute or so until Around gave it a playing card (thematically his spells draw inspiration from card tricks). It parachuted down from the shelf with the card.
The party has lunch with Mother Leondra, she gives more specific directions to the well of black slime. She thinks it's leaking from the Lake of Midnight Oil in the Feywild (the barriers between the mundane world and Feywild have been blurring in the region, it's one of the larger themes of the campaign so far). She said to look for a fairy ring around the source of the ooze, perhaps breaking it would help. She told them iron, salt and fire can be useful for pushing back fey magic. Lastly she cautioned them to be careful of "Old Jed" a "Scion of Death" and unfortunately unneighborly resident of that region of the Ashfens.
The party headed out again with bellies full, guided by one of the crow-familiars of Leondra. As they go, they run into a pair of Ettercaps. This was supposed to be a random encounter to give Winora a monstrosity to transform into (being a druid with a Stronghold has its perks). The flight went pretty south pretty fast, and before long, Armond was dead. After they dispatched the Ettercaps, the crow stood on Armond's chest, it's mouth opened and Leondra's voice emitted from it's mouth. "What is he worth to you?" After some discussion, Destin decided to give up his dreams to bring back his friend (Destin has seen many PCs die, mostly due to low levels and poor rolls). A red thread ties itself around his finger and then turns invisible, sealing the deal. The crow began to hack and cough, eventually it vomited up the poppet Armond gave the card. The doll doubled, then tripled in size, rapidly changing and taking on more of Armond's features, if still in knit form.


That, my friends, is how my party's wizard became a puppet.
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f954303f:6e1b0af5
2024-07-16 21:18:31
@ f954303f:6e1b0af5
2024-07-16 21:18:31阿巴拉契亚的话题最近很火 我也来谈谈我在那里的四年生活
 (https://www.reddit.com/r/China_irl/comments/1e50743/阿巴拉契亚的话题最近很火_我也来谈谈我在那里的四年生活/)
(https://www.reddit.com/r/China_irl/comments/1e50743/阿巴拉契亚的话题最近很火_我也来谈谈我在那里的四年生活/)如题。楼主15岁时来美国读高中,我的学校就位于阿巴拉契亚山脉,号称Allegheny山脉以西最古老的预科学校,也是州内最好的私立高中,学校甚至还有专门的校车路线每天单程四十分钟跨州去接其他城市的day student。如果去看Niche或者reddit上的评价,当地人都会说academically challenging并且升学很好。具体情况暂不表。本文不提美国高中比较普遍的文化问题,皆在作为一个outsider观察所谓rust belt区居民的精神与生活状态。
刚来读书的时候学校所在城市人口还能排到州内第三,刚刚去查已经第四了 (https://preview.redd.it/qdfq6iflgxcd1.png?width=380&format=png&auto=webp&s=6e06e8545b71eed4cfe38faaef6b7145feb3d20e)
学校所在的城市曾是19世纪末美国人均最有钱的城市,但现在去downtown却只能看到一两百年前留下来的各式各样的厂房废墟。由于煤炭和重工业的衰退,城市的就业在各类服务业中达成了一个奇妙的平衡:教育和健康占比gdp 19%,政府15%,贸易交通和公用事业21%,休闲娱乐12%。其实也是国内资源枯竭型城市的一个future outlook了。如此的数据也导致pandemic期间城市内失业率达到了将近16%,而现在最新数据只有3.7%。
23年十月的最新downtown街景,得益于拜登的Building a better America grant,在修路 (https://preview.redd.it/wnu9molznxcd1.png?width=1196&format=png&auto=webp&s=2e2196580945ff8549bf9e2f6bcd8d33d9be2eb9)
废弃工厂 (https://preview.redd.it/o44t4hl7nxcd1.png?width=2544&format=png&auto=webp&s=8c801c1cb7d47613300b28387f2c2c884b1bdeff)
回到学校内,因为学校白人比例过高,作为一个私立学校,即使当地人实际完全不在乎,但学校多年来一直维持一位黑人老师的传统。同理,学校会付全奖给巴哈马国际学生请他们来上学,我们中国学生戏称进口黑人。当然,这一切的一切都只是表面功夫。没有人真正在乎diversity,也没有人在乎自己bubble之外的世界。即使学生的家长们人均会计师律师医生,甚至我的某位当地同学会开着当时最新款的s500来上学,同学们的活动范围依旧局限于tri-state area:度假去virginia beach,购物就近解决。即使每年走读学费要两万美元,依旧只有寥寥几人去过DC纽约,更别提什么加州欧洲甚至更远的地方了。
这些所谓中上层阶级的阿巴拉契亚居民怀揣着他们american small town centric的生活方式,那就更不用提J.D. Vance等种种没有特权的当地白人了。无知,迷茫和傲慢是当地特产,于是在学校被问中国有没有DQ是日常,在超市里被人说you are in america so speak english 更是日常。那种红脖式的传统教育更是在21世纪显得匪夷所思:boarding director会无视欧洲学生吸大麻但按着没要permission出门钓鱼的中国学生的头往墙上砸并让他们go back to China,学生早上迟到会被强迫把学校垃圾桶搬到校后河边倒进河里,目的是被河对岸超市顾客怒骂以“长记性”。
作为曾经的军校,为延续传统,每届freshman感恩节之前一周会被送到一个手机信号只有一格的户外中心做团建,爬树,攀岩,在山里负重徒步,坐在落叶堆上写日记,如此等等。当然,手机每天是要被收走的,每两天固定时间可以去食堂旁边用十五分钟跟家里发条消息。16年11月川普当选时,我们学生们围在common room的那台radio旁边,在这样的播音效果 (https://www.youtube.com/watch?v=kkc5ApocI7Q&ab_channel=Serj)里等来了川普当选的消息。我无法形容当地学生听到消息开始欢呼跳舞的情形,甚至到了晚上洗澡时间可以看到橄榄球队alpha male们裹着浴巾在洗澡堂chest bump。唯有年级唯二的其中一个小黑(因为和我一样不受“主流学生”待见,给了我nword pass)独自黯然神伤。
在Junior year的Human Geo课上, 我们有机会和本州senator视频连线。作为班里唯一的中国人,我被老师强行安排当演员,提问他对中国的看法,于是尴尬狼狈不堪的站在摄像头前被狠狠china bad了十分钟。其他一些Environmental Science 或是Contemporary Issues课上更是充斥着什么联合国要强迫美国人不喝牛奶并且限制美国人聚集区域等Conspiracy Theory。btw,这个老白男老师是UPENN Chemistry毕业,因为成绩太差最后去iowa读了phd来高中教书。
最后的Senior year,作为本州最好的高中,抛开中国学生不谈,一届四五十个学生中,只有个位数当地学生真正意义上跨出了所谓的tri-state area,去的学校也更是USC或liberal arts这一类。剩下的大部分会继续留在小城里,在学校方圆几十英里内的几所大学或是去州立读一个学位。和J.D. Vance一样,我最好的当地白人朋友选择marine crop当兵,自此也就不再联系。当然,这位白人朋友也是校内被bully的对象之一,因为坊间传言他是被收养的俄罗斯弃婴。
至此,tldr,阿巴拉契亚区域的事实生活环境与国内的众多资源枯竭型城市类似,但多数居民依旧固步自封,怀揣着对生活变得日益艰难的不满,坚定的持有他们传统的教育和生活理念。与更普遍的传统美国小镇生活不一样的是,因为周边经济环境的持续衰退,这些阿巴拉契亚居民的生活实质上不可持续,面临死局。不过就像J.D. Vance一样,有能力并且真正有意愿跳出bubble打破幻想的,仅仅为极少数。
submitted by /u/Leading_Software_163 (https://www.reddit.com/user/Leading_Software_163)
[link] (https://www.reddit.com/r/China_irl/comments/1e50743/阿巴拉契亚的话题最近很火_我也来谈谈我在那里的四年生活/)[comments] (https://www.reddit.com/r/China_irl/comments/1e50743/阿巴拉契亚的话题最近很火_我也来谈谈我在那里的四年生活/)
#China_irl
https://www.reddit.com/r/China_irl/comments/1e50743/阿巴拉契亚的话题最近很火_我也来谈谈我在那里的四年生活/
-
 @ 6259dcac:b006221d
2024-07-16 20:13:16
@ 6259dcac:b006221d
2024-07-16 20:13:16🧠Quote(s) of the week:
'If you want to keep the smoke and mirrors, endless war machine charade going... buy US Treasuries and other government bonds.
If you want to help defund the clown world... buy Bitcoin. Few understand that it's really this simple.' - Dr. Jeff Ross
'Bitcoin won’t be adopted like the iPhone because it’s cool. Bitcoin will be adopted like gunpowder: if you don’t own it, you’ll be its victim.' - Saifedean
🧡Bitcoin news🧡
Now before I start with the Weekly Recap I want to share the following quote & picture: 'The fight between left and right is just a smoke screen to keep you confused and busy fighting each other and not the system.
The real fight is Tyranny vs Freedom. Central banking vs Bitcoin. We need to work on the vertical axis not the horizontal.' - CarlBMenger
Maybe in that light and with a heavy heart, I need to tell you guys that from the 31st of October you need to verify (full KYC) yourself to use the Relai app.
Personally, it was nice to have used Relai as an On-Ramp Bitcoin service for a while. Still think it is one of the best Bitcoin apps in the world. Fortunately, there are still other services that have greater privacy and confidentiality protections. For example Bisq, Robosats. For now, I am not sure what will happen with Pocket Bitcoin & Peach Bitcoin, both Swiss companies.
My advice. Get your corn from Relai before the 31st of October if you don't want to go full KYC. I'm certainly not using a Bitcoin wallet that needs KYC. Goes against anything a self-custody wallet stands for. Mayor setback, I feel sorry for Relai, but unfortunately this is part of the game. It is just the harsh reality as from next year, with MiCA, everyone will have to comply.
'Do not go gentle into that good night, Old age should burn and rave at the close of day; Rage, rage against the dying of the light...'
Glad we have light...and it shines bright...Bitcoin!
8th of July:
➡️The 2024 Republican Party Platform is insanely bullish on Bitcoin and crypto: - Right to self custody - Right to mine Bitcoin - Right to transact freely - No CBDCs - End harmful regulations
The Republican Party Platform now includes the following language: "We will defend the right to mine Bitcoin, and ensure every American has the right to self-custody of their Digital Assets, and transact free from Government Surveillance and Control."
Tens of millions of Americans who hold crypto or believe in Bitcoin must now choose between their overall politics and their Bitcoin bags, or crypto livelihoods. Let the games begin! Bitcoin + 2024 GOP = Hello game theory!
9th of July:
➡️German Government is now left with 22,800 Bitcoin, less than half its original holdings. They are running out of BTC to sell. And that's a good thing. Buyers are gobbling up Germany’s weak-handedness.
A day later on the 10th.
German government transfers 5,103 Bitcoin to Kraken, Coinbase, an unknown address, and other exchanges. They now hold 18,860 BTC.
Eventually, on the 12th of July, the German Government was out of Bitcoin. They send 3846.05 BTC ($223.81M) to Flow Traders and 139Po (likely institutional deposit/OTC service). By that the German Government has 0 BTC ($0.00M) remaining.
To give you some context: Germany sold 42,000 BTC in one week, 250 BTC per hour, 168 hours, in one fucking week! Approximately as fast as they were mined in the first epoch, which is 16x the current rate of issuance.
Germany selling all their Bitcoin will go down as one of the most retarded things their politicians ever did. It will be just as great a decision as the one where they closed all their nuclear power plants to start importing energy from nuclear power plants in France. In a few years, this will be looked back on as one of the biggest geopolitical blunders of all time.
Mark my words it will be studied in universities.
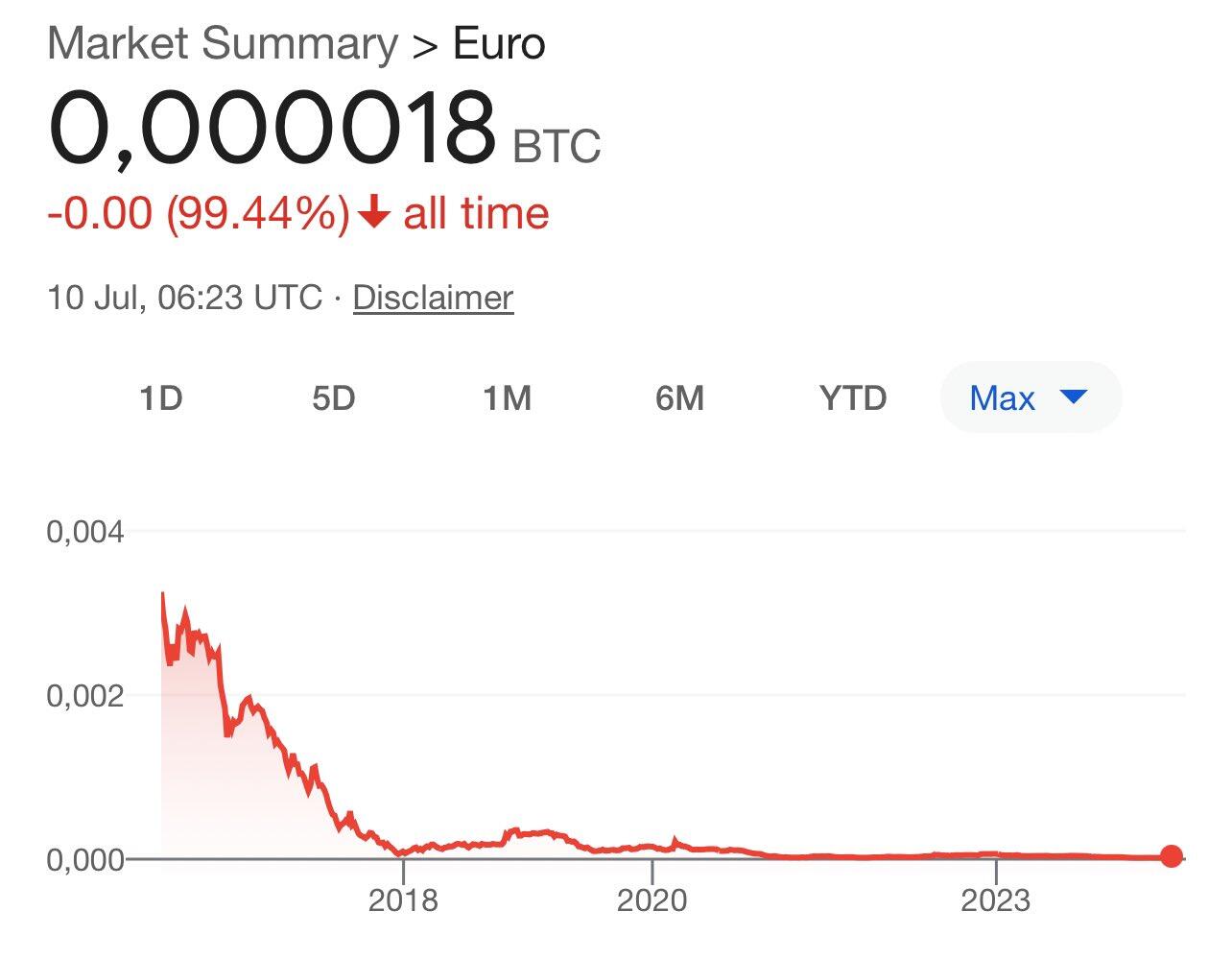 'So let me get this straight. First Germany sells its scarce Bitcoin for euros that they can simply print, now Germans are holding 2.8 trillion euros in bank accounts* that don't even earn interest.' -CarlBMenger
(https://x.com/Schuldensuehner/status/1810962887889834027)
'So let me get this straight. First Germany sells its scarce Bitcoin for euros that they can simply print, now Germans are holding 2.8 trillion euros in bank accounts* that don't even earn interest.' -CarlBMenger
(https://x.com/Schuldensuehner/status/1810962887889834027)➡️'Australia approved a second Bitcoin ETF. It starts trading on Friday.' -Bitcoin Archive
➡️While being a whole coiner (1BTC) is an important goal for many, for some it might also be helpful to see other milestones like 0.1 and 0.5. The following chart and explanation can help you to get that. No matter if you believe in the 'Power Law' of Bitcoin, I love the breakdown of acquiring BTC today. Take that from the following statement & chart. 'The maximum Bitcoin you will ever own. Assumptions: - You only perform DCA with a fixed amount per month in perpetuity. - Bitcoin price follows (i.e. mean reverts to) a power law with exponent 5.7
In this case, there is a theoretical maximum amount of Bitcoin you will ever own (since the sum of bitcoins bought every month forms a convergent series). If you start today (July 2024), the formula for calculating this is a*0.0006631, where a is the dollar amount you invest per month.
Below is the figure showing the same for different values of the amount invested and starting time. Based on this model, if you want to reach 1 bitcoin, starting today, you will need to invest a minimum of 1500$ per month. In 2026, this number becomes 2300$. By 2033, even 10,000$ invested per month will never get you to 1 Bitcoin. So, starting early is always better (not financial advice).'
Remember only 0.26% of the global population can be a Bitcoin whole coiner. Ever!
➡️Suriname Presidential candidate and fellow Noderunner Maya Parbhoe says people in the country are "isolated" due to the lack of banking. "We don’t have a lot of infrastructure, so we might as well use Bitcoin".
Maya Parbhoe is running for President of Suriname on a pro-Bitcoin platform. The trailblazing businesswoman wants to get the Surinamese people out of “survival mode” and take on the corruption that plagues her country, some of which has impacted her on the most personal level: Read the full article here
10th of July:
➡️'BlackRock's Bitcoin ETF has had $18 BILLION inflows since launching in January. Only 1 day of outflows, which was just $37m.' -Bitcoin Archive
➡️"We believe we are halfway through the current Bitcoin bull market. And just because we're halfway there doesn't mean we're halfway through price growth because, at the end of a bull market, prices tend to go parabolic," says ARK Invest CEO Cathie Wood.
12th of July:
➡️'New All-Time High Bitcoin mining now uses 56.2% sustainable energy. At the current rate of increase, it will cross 60% by July 2025, and be 80% sustainable by end of 2030' - Daniel Batten
'Bitcoin mining is using more and more sustainable energy and will continue to do so. Not because Bitcoin miners are eco-conscious treehuggers, but for an even more powerful reason - economic incentive.'
➡️U.K. Bank refuses to accept funds converted from Bitcoin to buy a house.
➡️Worldcoin misses its 2023 goal of one billion users by 994 million. Worldcoin is at 0.6% of its goal. I’m stunned that the all-seeing orb hasn’t taken over the world by now. I mean how could it not have?!
13th of July:
➡️'Exactly 1 year today, Ripple "won" their lawsuit against the SEC. The XRP/BTC ratio has been down 73% ever since.' -Pledditor Just don't do shitcoins guys.
➡️'HFSP German Government” inscribed on the $1.87 Bitcoin transaction sent by a pleb to the German government wallet.' - Bitcoin News What a legend, that's a proper way to use inscription! HFSP = Have Fun Staying Poor And yes poor in Bitcoin terms, they still have the €1.3 billion.
15th of July:
➡️LARRY FINK (CEO BlackRock): I studied Bitcoin and am now a major believer it is a legitimate financial instrument with uncorrelated returns. Full clip here: link
Eric Balchunas:
'Hard to overstate how big a deal it is for Larry Fink, who runs $10.6T, to keep giving these full-throated endorsements of bitcoin as a legit asset class for everyday portfolios. Buy-in from BlackRock - as well as other legacy firms like Fidelity - gives boomer advisors comfort and cover to make the allocation. That's why betting against, or minimizing the clear-to-anyone-with-eyes-and-a-brain early success of, these ETFs has been and will be dumb IMO.'
Larry Fink is just another person on his Bitcoin journey. Step 1: Skeptic (2017: Bitcoin is an index of money laundering.)
Step 2: Put in the work
Step 3: Realized he was wrong (2023: Bitcoin could revolutionize finance. Files for a Bitcoin ETF.)
Step 4: Bitcoin is an uncorrelated asset used to hedge currency debasement (Bitcoin is a legitimate financial instrument. Launches Bitcoin ETF.)
Next step: Bitcoin is hope.
What can you learn from this all? Study Bitcoin! Why?
'Your models can't account for the world's largest manager going on national TV & saying:
👉🏽Bitcoin is a hedge against debasement
👉🏽Bitcoin is a legit financial instrument
👉🏽Bitcoin is a flight to safety
👉🏽I was wrong about Bitcoin
👉🏽Bitcoin is digital gold' - Luke Mikic
💸Traditional Finance / Macro:
👉🏽Billionaire Warren Buffet says he could end the United States deficit problem in five minutes. "You just pass a law that says any time there's a deficit of more than 3% of GDP, all sitting members of Congress are ineligible for re-election."
I agree with this! It could end the deficit problem, corruption, and other problems. But we all know this won't happen. And because of that, we have Bitcoin.
🏦Banks:
👉🏽 No news
🌎Macro/Geopolitics:
On the 8th of June:
👉🏽41% of jobs added since 2019 were by the government burning taxpayer dollars. Now ask Greece how well it works to prop up your labor force by just hiring everyone into government jobs. This is why I always try to explain that reported job numbers from macro data are pretty useless. It's a mess.
You don't believe me...well go figure: 'Jobs report numbers have been revised DOWN in 4 out of 5 months of 2024. The largest revision from 353,000 to 256,000, or by 97,000 took place in January. Subsequently, February saw a -39,000 downward adjustment.
April and May were revised down by 67,000 and 54,000, respectively, or a total of 111,000 jobs. In the first 5 months of 2024, non-farm payrolls have been revised down by a combined 240,000 jobs. Is the initial headline number even worth following anymore?' -TKL
👉🏽Real estate's rising valuation reflects the debasement of fiat currency.
CAGR M2 Money Supply (1971-2024): 6.8% CAGR Housing in the US: 5.7% CAGR Commercial US Real Estate: 4.4%
Denying the connection between the money supply expansion and real estate values is denying reality. Yet, many still choose to ignore this fact.' -Leon Wankum
The EU is on the same path as the US with M2 supply & real estate. Bitcoin will suck the monetary premiums out of real estate. That is actually a good thing because houses will be priced by their utility values. Ergo: It makes them far more affordable for average buyers.
On the 9th of July:
👉🏽'With 5 Million fewer workers in Germany in just a few years who is supposed to pay for pensions and healthcare for all the new retirees?' -Michael A. Arouet
 Not only Germany, but the EU in general...low growth and a social service deficit, demographic crisis, second highest tax rate, and so on.
Not only Germany, but the EU in general...low growth and a social service deficit, demographic crisis, second highest tax rate, and so on.Now combine the above with the fact that, and I say this in the utmost polite way, Europe is becoming an open-air museum due to overregulation and lack of innovation. Recipe for disaster.
Don't believe me...
Maybe we can still turn this around by printing more money. Nope, the ECB balance sheet as % of GDP is much higher than the Fed.
Maybe we can still turn this around if we would increase taxes and more regulations.
The Dutch are planning to implement a 36% yearly tax on unrealized capital gains from 2027, and the new French government plans up to 90% income tax. 90% tax on any annual income above €400,000.
Capital will leave the country so quickly that the leftist government can't even look. (I am in no favor of the right...left..couldn't care less) but for fuck sake NINETY f* percent.
The future of Europe is bright (not)... America makes software. Asia makes hardware. Europe makes it difficult. Those who can, do it. Those who can't, regulate. Europe

👉🏽Shocking tweet by Alex Gladstein @gladstein:
'Truly insane Debt Trap chart. Pakistan's interest payments are 57% (!) of its government revenue this year. To try to pay it off, the government is looking to increase total tax revenue by 40%/ I am sure the public will be happy with that...' Click here for the chart: https://www.ft.com/content/1b88fff6-bebb-4650-9677-7a7caa268f05
'IMF staff have reached a Staff-Level Agreement with Pakistan on a 37-month Extended Fund Facility of about US$7 billion to maintain economic stability and enhance conditions for stronger, more inclusive, and resilient growth.' -IMF
Let me translate the above IMF statement and I will use Alex Gladstein's tweet:
“Extended Fund Facility” = Debt Trap
“7 billion” = $10 billion+ including P+I
“Economic stability” = Starving the poor
“More resilient growth” = Devaluation
Combine the above with a staggering 43% loss in purchasing power against the dollar, pushing all the prices higher and higher. Seems like a recipe for a disaster.
And it's not only in Pakistan but also for example in Keyna: https://archive.ph/UiLxq
IMF we know your handwriting...anyway the money is broken, study Bitcoin.
On the 11th of July:
👉🏽US Spent A Record $140 Billion On Debt Interest In June, 30% Of All Tax Revenues. Now read that statement again. They are paying the debt with your money (taxes). Please read the article. Link here
Ergo: It’s like Tetris and we’re getting into the faster levels of the game where clearing the lines is just getting harder and harder.
And that was just one month!
'Annualized interest payments on US federal debt just reached an all-time high of $1.14 trillion. This is more than DOUBLE the amount of interest recorded in 2022 when the Fed started raising rates.
To put this into perspective, even during the 2008 Financial Crisis, annual interest costs were ~$450 billion, or 60% lower. As a % of GDP, net interest cost this year is on track to exceed the 1980s high of 3.2%.
By comparison, during World War II, net interest expense as a % of GDP was much lower, at 1.8%.' -TKL
Spending $1M a day would take 2,740 years to reach $1T. The US debt is $35T and grows by $1T every 100 days.
Now read the above statement again.
Study Bitcoin.
👉🏽US inflation was 3.0% in June, below expectations. Core inflation came in at 3.3%, BELOW expectations. Rate cuts are imminent.
On the 12th of July:
👉🏽'Elon Musk says "The European Commission offered X an illegal secret deal: if we quietly censored speech without telling anyone, they would not fine us. The other platforms accepted that deal. X did not." - Watcher Guru Do you want to learn/know more about this topic?
Please read the following post:
https://x.com/PirateWires/status/1811863158816223580
On the 13th of July:
👉🏽'US bankruptcies just hit their highest level in 14 years:
346 companies have declared bankruptcy through June 2024, the most since 2010, a year after the Financial Crisis.
US bankruptcies have also recorded their largest monthly increase in at least 4.5 years, with 75 new bankruptcies in June 2024.
Even during the 2020 Pandemic, the highest number of filings in a given month was 74.
The highest number of bankruptcies have been in Consumer discretionary companies, with a total of 55.
This is further evidence of weakening consumer spending.' -TKL
👉🏽Sometimes I love Twitter:
Q: "Why are energy, food, and even housing sometimes excluded from price indices for calculating “inflation”?"
A: (by Luke Gromen):
'Energy is excluded from CPI "because it's volatile." Yet from 1861-1971, oil prices were remarkably steady when the USD was tied to gold.
Energy only got "too volatile" when the USD's tie to gold was cut in 1971. Energy's volatility is a symptom of an inflationary system.'
👉🏽'10% of the world population hold 75% of all wealth, get 50% of all income, and account for nearly 50% of all CO2 emissions.' - World Inequality Report 2022 If you read this Weekly Recap, chances are you are part of the top 10%.
🎁If you have made it this far I would like to give you a little gift:
Your monthly must-read this week, Lyn Alden's July 2024 newsletter is out.
The two main focuses are:
-A reiteration and further detail of the fiscal dominance view (i.e. nothing stops this train).
-An observation that the US economy is likely to be insensitive to rate cuts like it was for hikes.
Ignore here newsletter and book (Broken Money - order here) at your own peril.
Credit: I have used multiple sources!
My savings account: Bitcoin
The tool I recommend for setting up a Bitcoin savings plan: @Relai 🇨🇭 especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. (Please only use it till 31st of October - after that full KYC) Hence a DCA, Dollar cost Average Strategy. Check out my tutorial post (Instagram) & video (YouTube) for more info.⠀⠀⠀⠀
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀⠀⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
zap 🧡 #weeklyrecap #nostr
#plebchain
BTC
Bitcoin
zap🧡
plebchain
grownostr
stacksats
bitcoineducation
adoption
-
 @ b804f68e:2fb0fa1f
2024-07-16 19:28:32
@ b804f68e:2fb0fa1f
2024-07-16 19:28:32Here are 5 of mine:
- Choosing not to complete a 4 year degree.
- Choosing to start a serious relationship with my girlfriend.
- Choosing to learn everything I could about Bitcoin and choosing to save in it.
- Choosing to quit my job and go all in on getting the absolute most out of my athletic career.
- Choosing to travel to Thailand.
What are some of the most significant choices you made during your 20s?
originally posted at https://stacker.news/items/610740
-
 @ 6c8c7979:15595f3e
2024-07-16 19:23:41
@ 6c8c7979:15595f3e
2024-07-16 19:23:41Naji Al-Ali was a Palestinian caricaturist, known for his revolutionary spirit depicted through his cartoons addressing political issues concerning Palestine and the broader Arab world. He worked for various Arab newspapers in Kuwait, London, and Lebanon. His drawings, notably featuring the character Handala and other figures, gained widespread recognition.

Throughout his career, Naji Al-Ali created around forty thousand cartoons. In 1978, he was awarded the Golden Pen of Freedom by the International Federation of Journalists. Tragically, he was assassinated in London in 1987.

Naji Salim Hussein Al-Ali was born in the village of Al-Shajara, Palestine, around 1937. At age ten, he moved with his family to Lebanon and settled in the Ein el-Hilweh refugee camp after the Israeli occupation of Palestine in 1948. Despite facing imprisonment by Israeli forces and the Lebanese army for his anti-occupation activities, he continued his artistic journey, often drawing on prison walls.

He couldn't complete formal education due to difficult circumstances but later studied mechanics and then pursued art at the Lebanese Academy in 1960. His breakthrough came when writer Ghassan Kanafani noticed his work in Ein el-Hilweh, leading to publications and recognition.

Naji Al-Ali's iconic character, Handala, first appeared in 1969 in the Kuwaiti newspaper Al-Siyasa. Handala, a ten-year-old Palestinian boy with his back turned and hands clasped behind his back, became a symbol of Palestinian steadfastness and defiance against injustice.

Naji Al-Ali's work extended beyond Handala to include characters like Fatima, symbolizing unwavering determination, and other symbolic figures critiquing Palestinian and Arab leaderships, as well as Israeli policies.

He published three books compiling his most significant cartoons and received numerous awards, including first place at the Arab Cartoon Exhibition in Damascus in 1979 and 1980.

Naji Al-Ali's assassination in London in 1987 remains unsolved, with speculation implicating Israeli Mossad or Palestinian factions due to his outspoken criticism of both.

He was laid to rest in the Brookwood Islamic Cemetery in London, despite his wish to be buried in Ein el-Hilweh next to his father, reflecting the challenges and controversies that marked his life and legacy.

-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 20986fb8:cdac21b3
2024-07-02 21:08:21
@ 20986fb8:cdac21b3
2024-07-02 21:08:21The motivation of building decentralized media protocols is to balance the power of centralized media platforms, and provide an alternative for the public to take part in the curation of information, not just access information. It has to perform checks-and-balances to the centralized media powers, while providing a credible and neutral mechanism for different communities to improve a platform over time. The operation and maintenance of such a media platform should be autonomous, unstoppable, and self-improving.
While a traditional media platform has to align itself with the interests of its owners, shareholders, and donors, the new type of media platform should not be subject to the control of any entity at all times.
The ownership and stewardship of the new media platform should be open and transparent to the public. This is in contrast to state/corporate-controlled media platforms, in which case the public is often not informed of a media platform’s real ownership and stewardship, hence the public cannot be aware of its real purpose, bias, and hidden agendas.
If each individual is more informed, it will be harder to manipulate public opinions, and it will be easier to foster independent judgment within human societies. The positive externality will be enormous. The transition from centralized media platforms to decentralized media platforms speeds up this process.
This article discusses the two pillars to implement a decentralized media technology stack: decentralized publication and decentralized content moderation.
Decentralization of publication
In a previous article, we extensively discussed the importance of content decentralization. It is the last defense of censorship - content removed or hidden by popular client websites could be stored permanently and be displayed on other (perhaps non-popular) client websites. We also discussed the importance of token economics neutrality, because token economics itself could lead to censorship.
As a non-microblogging platform, Yakihonne is currently one of the most popular clients that implemented NIP-23, attracting bloggers and readers from all over the world to post articles and read contents about Bitcoin and beyond.
As of the time of writing of this article, the platform serves users in 116 countries, supporting 18 languages, and has become the most widely used and feature-rich client within the Nostr ecosystem. Yakihonne is also the first Nostr client to support mobile applications and article editing on mobile apps.

When publishing articles on Yakihonne.com, you can choose multiple relays to publish the content. Relays can also implement logic to sync articles of their own interests and offer them to clients.
Joining the relay network is easy. If someone wants to join the relay network, he is able to do so by deploying one of the open source versions of Nostr relays, and starting to store content for the network.
The number of relays serving content within the Nostr protocol is currently quite small. Over the next period of time, it is important to grow the number of reliable relays.
It should be economically viable and encouraging to set up a relay, so that the number of relays can grow over time. Very likely, the number of relays will correspond to the net income of the network, which comes from revenue streams of each of the clients. Therefore, it is foreseeable that the number of reliable relays will be correlated to the traffic of the Nostr protocol in general and therefore, to the traffic of popular clients.
The zap feature (Lightning Zaps) can be used to incentivize relays. But we cannot set unrealistic expectations over zapping. Zapping an article is making a donation. Donation is unpredictable, and it is definitely not a sustainable way to maintain a large, reliable network of relays. One possible solution to this problem is to have profitable clients make continuous contributions to well-performing relays via enforceable protocol setups.

An ideal incentive mechanism for a relay network is to establish a profit-sharing protocol between clients and the relays.
Decentralization of content moderation and content curation
Striking a balance between moderation and anti-moderation has been an almost impossible task for centralized media platforms. Whoever performs the moderation dominates the narratives.
The most recent community notes feature on X took a major step towards community-driven moderation. In community notes, users who are eligible to provide notes can write community notes to a post, and a community can vote for the notes so that the best recognized notes can emerge on the top. It has been proven to be effective in content moderation in many instances, and the ability to add community-backed notes reduced the need for shadow bans.

Community notes are obviously a more effective system than shadow bans in Jack Dorsey’s Twitter era. At times even Elon Musk himself can be “community noted” is definitely making people trust this system more.
But it cannot be ignored that users still have to sign up to apply for eligibility for community notes. It is in X's own direction to decide who is eligible and who is not. The voting process of community notes itself could also be subject to censorship, because there is no way to verify the votes.
This is to say, X has the power to do evil, it doesn’t matter if it does evil or not.
The countermeasure to balance the power of a centralized media platform is a platform that is not manipulatable by its operating team or share/token holders.
So content moderation has to be permissionless, while verifiability to content moderation mechanisms like community notes.
The first step to developing a decentralized content moderation system is to implement a permissionless community notes system.

X’s community notes can be censored in two steps: the eligibility review process can filter people based on X’s own preference; the ranking and displaying rules are also controlled by X. In a permissionless community notes system, any relay or even client should be able to implement its own version of community notes, and users can choose their preferred system(s) to work with.
Notes have to be stored on an open, token economics neutral relay network to ensure their immutability and resistance to censorship. Community members can add notes to any media content, and the notes are distributed to non-related parties who operate the nodes.
Incentives
The content moderation mechanism needs to be incentivized through the decentralized media protocol.
In a non-sponsored model, income comes from ads or subscription fees, and is distributed to content creators, content relays, and additional network security providers.

In a sponsored model, income is from content sponsors, and further distributed to community note contributors, content relays, and additional network security providers. A sponsored post, in old media platforms, can be quite expensive. The cost to post sponsored content can be dramatically reduced on a decentralized media platform because of the great reduction of content moderation cost.

Ranking
Community notes can be ranked by either relays or clients. A content relay can rank community notes based on its own preference, and deliver to clients. Clients can also rank community notes based on its rules. Basically, everyone can rank any post’s community notes.
In general, community notes ranking algorithms can be stake-based or non-stake based. Stake-based ranking algorithms in general show how people who have a stake in something react to a post. Non-stake based ranking algorithms can be any mechanism, such as reputation-weighted ranks, 1p1v ranks, quadratic voting ranks, random selection, or even asking an AI to rank community notes.
What’s perhaps important is not which ranking algorithm is the best, it’s the flexibility for both the content storage layer and the interfaces (clients) to choose their ideal ranking algorithms. Probably for a client, the best strategy is to provide all ranks from multiple sources, so that people can view community notes from very different angles.
The Current Status of Bitcoin and the Nostr Protocol
As Nostr is the ideal relay network for decentralized media at this moment, it is necessary to write some notes on the current status of the Bitcoin ecosystem, as Nostr is largely inspired by the Bitcoin network to be decentralized, and is greatly supported by the Bitcoin community.
The Bitcoin community is so far the most legitimate crypto community. It has a very simple mission: to create a decentralized monetary system that is not controlled by centralized powers. The progressive element of the Bitcoin community is relative to the old banking world, where Bitcoin is a completely new and alternative technology stack to the centralized money and finance systems. The conservative element of the Bitcoin community is relative to the other crypto community, where the Bitcoin community is largely skeptical of the motivation and decentralization of them.
In my opinion, the scrutiny Bitcoin community puts upon the rest of the crypto world is totally reasonable. However, as much as Nostr is inspired by the Bitcoin network, it will also go beyond the Bitcoin community, in terms of content.
This is not a bad thing!
If this happens on a big monolithic blockchain, probably the Nostr major contributors will be required to create a token pretty soon and then pay gas fees to the blockchain so that the blockchain’s revenue can increase. The Bitcoin community will never ask that. This gives Nostr enough freedom and flexibility to evolve, while continuously getting support from the Bitcoin community.
However, if Nostr users are forever a subset of Bitcoin users, Nostr will be limited. Nostr is not a subset of Bitcoin, it is not an “ecosystem project” of Bitcoin either (a.k.a., it should not become a “layer-2” of Bitcoin, as some people reason about the future of Bitcoin totally from the analogy of Ethereum).

In the best world, Nostr and Bitcoin can expand each other’s user base, and create healthy synergy.
Conclusion
Yakihonne is, so far, not a protocol. With the products and features it offers, Yakihonne is ready to build up a decentralized media stack. The stack has two pillars : decentralized publication and decentralized content moderation. The former guarantees that content will never be lost; the latter creates a new cost-incentive model to make sure that when content and moderation go permissionless, the platform can still maintain truthfulness and cost-effectiveness. In fact, a decentralized media platform can be more cost-effective than centralized media platforms. So the next step for us is to build this up and experiment with it.
The Flash News and the uncensored notes are introduced for such purpose, and everyone is welcomed to give it a try. Note that it is still in the early stages and various improvements will come eventually, for this your feedback is valuable to us to reach any expectations.
-
 @ ec965405:63996966
2024-07-01 21:11:49
@ ec965405:63996966
2024-07-01 21:11:49My sister, cousin, and I joined 75,000 protesters earlier this month in holding up a red banner marked with the names of Palestinian martyrs around the treasury building and white house in washington dc to signify the "People's Red Line" crossed by israel's invasion of Rafah.

After holding up the red line, we made our way to a nearby park where the organizers held a "People's Court" to try israel and the u.s. for war crimes. We shared a collective cry as we listened to heart wrenching testimonies sent in by Gazan families of Palestinian organizers about the nightmare they are enduring. As this was happening, israel killed another 274 Palestinians in a raid on the Nuseirat refugee camp. The notification across my screen felt like a punishment for our activism and reminded me that the bureaucrats are not listening.

I was initially discouraged to see a lower turnout than the march on washington I attended last November, where 300,000 folks arrived to denounce the united states' unconditional support of the Palestinian genocide. I can't say I didn't anticipate it, though. Wage slaves have to eat, and paid time off to protest about things they care about is a luxury few CEO's in this world provide for them.
Adding to this is the brutal suppression of dissenting voices worldwide. Groups like Within Our Lifetime are kneecapped by outright censorship and bans from corporate social media platforms.Not to mention, the u.s. government is forcing a sale of Tik Tok to a former u.s. treasury secretary with ties to mossad.
Palestine is an anti-colonial struggle that inspired so many of us to organize for change, yet we've managed to spend the last 8 months funding their genocide with our consumption tax dollars and scrolling through pictures of dead babies and leveled cities. Why have activists failed to push western governments to materialize any sort of timely, meaningful shifts in foreign policy? I think part of it has to do with the tools we are using. Like Malcolm X said, we're not outnumbered; we're outorganized.

For one, we are letting these tech CEO's off way too easy. The spotlight is increasingly being pointed at corporate social media giants for conducting a mass behavioral health experiment on the masses. These centralized platforms bombard users with morally outrageous content and advertisements while working with the state to suppress dissenting voices. Antagonizing algorithms polarize public discourse and keep us at each others throats, preventing any sort of mass peace movement from building power. Places like Europe have a whole framework of data rights protections for users that is nonexistent in the Americas. The corporate communication apparatus we organize with freezes the political process and manufactures consent for genocide. Was it Noam Chomskey who said, "the media defines what's possible"...? By the way, he's not dead yet.
How else do you think Trump was able to organize his base to attempt a coup on Jan 6th? He paid someone to build his own communications apparatus in the form of a social media platform, Truth Social, on an open protocol called ActivityPub, a predecessor to Nostr. Meridith Whittaker, the president of the Signal Foundation, explains in a recent article that you should read if you are an activist,
The Right has a point. In that they understand social media platforms as critical infrastructure capable of shaping and distorting our shared information ecosystem, and they recognize that controlling how this ecosystem is “distorted” is a better use of their time — in pursuit of power and influence — than trying to create a magic formula that can “democratize” or “balance” the influence these platforms exert.
The few I hear with similar critiques include OGs like Chairman Yeshitela, who, alongside 3 other members of the People's Afrikan Socialist Party, is currently fighting bogus charges by the u.s. federal government for conspiring with the Russians in sowing dissent in u.s. elections. The FBI violently raided their properties in 2022 without any sort of warrant and before any formal charges had been filed. Contrast this with the recent raid on Mar-a-Lago where not a single flash grenade was used. He explains in a 2023 interview on Democracy Now! that
We have to move beyond protest and move toward the question of capturing and yielding political power.

As activists, we have to be brave enough to realize that what we are doing is not producing our desired results and pivot to new strategies. Open internet protocols are a must have in any activist's toolbox if they are serious about social change. Start with a simple internet search, and start building. I currently run a small relay that I use to introduce my community to nostr. I've spun up a diaspora instance for my close friends and family in the past as well. While this tech is accessible, it requires you to take some time to learn about the landscape of alternative social media protocols and how the Internet works. You could always reach out via the contact form on my website at https://miguelalmodo.com for more information or questions about how to get started!
My choice of social media is my way of preventing the monetization of my attention and digital footprint by the corpo-state consent factory that defines our current political realities. It's an step in reclaiming your digital sovereignty and empowering your base with an un-suppressible voice on the internet. A liberated fifth estate built on open protocols could channel people power into material improvements within our lifetimes. It's why I boycott the corporate tech platforms and why you should too.
edit: I realized after I published this that truth social was launched in Feb of 2022, a year AFTER Jan 6 2021. I insinuated that Jan 6 was organized on truth social which is not the case. By making the connection here, I wish to bring to light the power open internet protocols have in sustaining a cult of personality behind someone like trump. If activists and organizations leveraged the same tech to organize their base, it would bring people together in a way that could manifest the amount of people power needed to overthrow the influence of capital in political processes and allow for real democracy to shape our outcomes.
-
 @ 6c8c7979:15595f3e
2024-07-16 19:22:12
@ 6c8c7979:15595f3e
2024-07-16 19:22:12Why do paper currencies carried in people's pockets hold value? Some experts say that banknotes derive their value because the government or central bank that issues them declares so, while others argue that their value stems from people's willingness to accept them as a means of payment.
In this report, "Business Insider" seeks to identify the reasons that give banknotes their purchasing power, explaining the stages of their evolution and their close relationship with gold.
$$**Government or Social Custom**$$Demand for goods arises from the need for the benefits they contain; for example, people demand food because of its value in nourishing the body and sustaining life.
As for paper money, people demand it not for its intrinsic benefit but to "exchange" it for other goods and services. Money is not beneficial in itself but possesses value as a medium of exchange.
People demand paper notes because of the "purchasing power" and specifically their "price."
Saying that the value of banknotes comes from the government that issues them or from social custom does not provide a complete answer. Some experts argue that money holds value simply because it is "accepted."
$$Purchasing Power$$For a note to be accepted as "currency," it must have purchasing power. But how does paper designated by the government as "money" attain such purchasing power or price?
The law of supply and demand explains the price of goods and some experts say the same law applies to the price of banknotes.
Paper money was not money in its inception but merely a "representative" substituting for gold. Many paper certificates were "evidence" of ownership of gold held in banks.
Holders of certificates could convert them into gold at any time, and people found it convenient to use paper certificates to purchase goods and services as long as they were considered "money."
Certificates gained "purchasing power" based on people's view of them as a "substitute" for gold.
$$Other Doctrines$$Some economic doctrines argue that once a "certificate" or paper note gains purchasing power, it can become money regardless of gold, because demand now exists for it.
Acceptable paper certificates opened the door to fraudulent practices as banks succumbed to the temptation to lend more certificates without gold backing to increase their profits.
In free-market economies, banks printing more cash find that the value of paper currency against goods and services declines rapidly.
To preserve their purchasing power, holders of certificates printed without gold backing seek to convert them into the yellow metal.
However, if all holders of paper currency demand conversion to gold simultaneously, it could lead to the bankruptcy of the bank issuing the paper currency. Hence, banks avoid the risk of bankruptcy by printing notes without gold backing.
$$Cessation of Paper Currency Exchange for Gold$$Governments can bypass this system by issuing decrees allowing banks not to exchange paper currency for gold.
Once banks are no longer obliged to change currencies into precious metal, they see significant opportunities to profit, encouraging them to continue expanding paper currency issuance.
Uncontrolled expansion in printing paper currencies can lead to a sharp rise in prices of goods and services, potentially collapsing the market economy.
The primary purpose of controlling the supply of paper currencies is to prevent competing banks from excessive issuance of currencies and causing each other's bankruptcy.
This can be achieved by establishing a bank with a monopoly on currency printing, the central bank, which has exclusive authority to print its own certificates (paper currency) to replace certificates issued by other banks in all their forms.
$$Power of the Dollar$$Central bank-issued banknotes derive their purchasing power from the fact that various securities can be exchanged for central bank notes at a specified price.
Currency issued by the central bank is fully backed by the bank and has a historical link to gold, and because of this link, central bank notes have purchasing power.
In the United States, which holds the world's reserve currency, contrary to popular belief, the value of the "dollar" derives from its historical connection to money backed by a commodity, namely gold, not by government decree or social custom.
Non-commodity currency, mandated by governments or so-called mandatory currency used in modern banking systems, does not exist in its literal sense.
What the market has created, based on gold-backed money, forced governments to cancel before leaving us dealing with monetary assets whose value is based on the practices of central banks.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ d360efec:14907b5f
2024-07-16 16:15:32
@ d360efec:14907b5f
2024-07-16 16:15:32สัญญาเหมาเอ๋อ เชื่อมผูกพันคนกับแมว พันธะพันปี จะเป็นทาสทุกชาติไป
ในสมัยราชวงศ์ซ่ง (960-1279) การจะเลี้ยงแมวได้ ต้องมีพิธีรีตอง เช่น ต้องเลือกวันที่จะรับแมว ต้องยื่นคำขอให้นักบวชเต๋าอุทิศแมวให้ รวมถึงทำสัญญาเป็นลายลักษณ์อักษร
เรียกว่า #สัญญาเหมาเอ๋อ หรือ สัญญาเหมา ที่แปลว่า แมว (貓)
ในสัญญาเป็นข้อตกลงว่าจะทำดีกับแมว ไม่ให้แมวทิ้งเราไป และช่วยให้แมวไม่หายหลุด หลงทาง กลับบ้านไม่ถูก
จากข้อมูล #สัญญาแมว แม้จะมีมาตั้งแต่ราชวงศ์ซ่ง แต่เพิ่งมาได้รับการเผยแพร่ เขียนถึงก็ในช่วงราชวงศ์หยวน (1814-1911) หรืออีก 500 ปีต่อมา
สัญญาเก่าแก่ระหว่าง 'มนุษย์' กับ 'แมว' นี้ ก็ไม่ต่างไปจาก #มนต์สะกด เนื้อหาของสัญญา ถูกเขียนให้วนเวียนอยู่รอบๆ รูปแมว
รายละเอียดในสัญญา จะเริ่มจากบอกลักษณะทางกายภาพของแมวตัวที่อยู่ในสัญญาก่อน เช่น แมวขนสีอะไร มีตำหนิ แต้ม อยู่ตรงจุดไหน เจอแมวตัวนี้ได้ยังไง เป็นลูกหลานของใคร รับต่อจากใครๆ มา
อ่านดูแล้วก็คล้ายๆ กับใบเซอร์แมวในยุคปัจจุบันเหมือนกัน
ความพิลึกอยู่ตรงนี้ -- ในสัญญาจะระบุว่า ถ้ามาอยู่ด้วยกันแล้ว แมวต้องมีนิสัยยังไง ต้องช่วยให้ร่ำรวย ต้องขยันขันแข็ง ออกลาดตระเวน ช่วยจับหนู ป้องกันหัวขโมย
แถมยังมีข้อห้ามอย่าง ห้ามทำร้ายสัตว์ ห้ามขโมยนู่นนี่ และห้ามออกจากบ้านไปทางทิศตะวันออกและทิศตะวันตก หากออกไปโดยไม่ได้รับอนุญาติ จะถูกเฆียนตี !!!
จากนั้น ก็เป็นการระบุชื่อผู้ให้กับผู้รับ ราวกับเป็นการโอนย้ายโฉนดที่ดิน
เหตุที่นักบวชเต๋าเข้ามาเกี่ยว เพราะในสมัยนั้น แมวถูกนักบวชเลี้ยง เพื่อช่วยป้องกันหนูไม่ให้มากัดทำลายพระคัมภีร์ พอแมวยุคแรกของนักบวช ออกลูกหลาน คนมารับเลี้ยงต่อ ก็ต้องทำสัญญาแมวกับนักบวช
ความทาสแมวก็คือ ทั้งคนให้และคนรับ เชื่อจริงๆ เหรอ ว่าแมวจะตกลง ปฏิบัติตน ตามข้อแม้ในสัญญา
หาข้อมูลเรื่องแมวกับภาพวาดมากๆ เริ่มจะเพี้ยนขึ้นไปเรื่อยๆ แล้ว มีอะไรที่คิดไม่ถึงอึกเยอะ




-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ 1739d937:3e3136ef
2024-06-28 08:27:59
@ 1739d937:3e3136ef
2024-06-28 08:27:59This is the first in a series of weekly updates I'm publishing on my process around secure messaging. Since it's the first, let's start with a bit of historical context.
How this started
On April 29th I published a PR on the NIPs repo detailing how we could achieve "Double Ratchet" DMs on Nostr. There was also a video and demo app that went along with the PR. The basic premise was to use an adapted version of the Signal protocol. This would result in DMs that were truly private and confidential, even in the case where you leaked your main private key (your nsec).
I got a lot of great feedback from folks on that PR. Interestingly, nearly all of it focused on two points, both of which I'd deliberately scoped out. Group messaging and multi-device/client support. While I knew these were important, and I'd figured out how these might be accomplished, I'd scoped them out to try and keep the footprint of the spec as small as possible But, the more I talked to people, the more it became clear that this was one problem to be solved and given the complexity, it'd be better to do it in one shot.
At the same time, I'd seen that Messaging Layer Security (MLS) had recently made a lot of progress on becoming an internet standard with their RFC proposal and, goaded on by Vitor, decided to take a closer look.
Enter MLS
Messaging Layer Security (MLS) is a new protocal that is basically a modern extension of the Signal protocol that makes group messaging way more efficient (log vs linear) and was built to be used in centralized or federated environments. I'd heard other Nostr devs talk about it in the past but it was always overlooked as being too complicated or too early.
After spending a couple weeks reading hundreds of pages of RFC docs and reading through a few implementations of the MLS spec, I believe it's the best solution for secure direct and group messaging in Nostr. It also has the added benefit that we can upgrade the underlying crypto primitives over time in a sane way.
The MLS protocol specifies "a key establishment protocol that provides efficient asynchronous group key establishment with forward secrecy (FS) and post-compromise security (PCS) for groups in size ranging from two to thousands."
The spec I'm working on will detail the ways that we implement this protocol into the Nostr environment (namely, how do we use our crypto primitives, use events as control mechanisms, and use relays for storage, while obfuscating metadata).
Goals
It's important to be clear about what we're aiming for here. Engineering is all about tradeoffs, always.
- Private and Confidential DMs and Group messages
- Private means that an observer cannot tell that Alice and Bob are talking to one another, or that Alice is part of a specific group. This necessarily requires protecting metadata.
- Confidential means that the contents of conversations can only be viewed by the intended recipients.
- Forward secrecy and Post-compromise security (PCS) in the case of any key material being leaked, whether that's your main Nostr identity key (your nsec) or any of the keys used in the MLS ratchet trees.
- Forward secrecy means that encrypted content in the past remains encrypted even if key material is leaked.
- Post compromise security means that leaking key material doesn't allow an attacker to continue to read messages indefinitely into the future.
- Scales well for large groups. MLS provides this from a computational standpoint, but we need to make sure this works in a scalable way when multiple relays are involved.
- Allows for the use of multiple device/clients in a single conversation/group. Importantly, we're not aiming to enable a device/client to be able to reconstruct the full history of a conversation at any point.
Progress this week
Ok, finally, what what I been up to?
Reading
I've spent most of the last few weeks reading the MLS spec and architectural doc (multiple times), learning some Rust, and beefing up my knowledge of cryptography (which was, if I'm being generous, paltry before starting this project).
Ciphersuites
Nostr is built around the same crypto primitives that Bitcoin is, namely Schnorr signatures over the secp256k1 curve and SHA-256 hashes. This curve isn't currently supported officially in the MLS spec. I've been in touch with the MLS working group to better understand the process of adding a new ciphersuite to the set of ciphersuites in the MLS spec. The outcome here is that we're going to start out using our custom ciphersuite that isn't part of the formal spec. The only drawback being that Nostr's MLS implementation won't be immediately interoperable with other MLS implementations. We can always add it later via the formal channels if we want.
MLS Implementations
Given the complexity of the MLS spec itself (the RFC is 132 pages long), having a well vetted, well tested implementation is going to be key to adoption in the Nostr ecosystem. OpenMLS is an implementation created by several of the RFC authors and written in Rust with bindings for nearly all the major languages we would want to support.
I've been in touch with the maintainers to talk about adding support to their library for our new ciphersuite and to better understand the bindings that are there. Some (WASM) are very barebones and still need a lot of work. They are generally open to the idea of working with me on adding the missing pieces we'd need.
Double Ratchet NIP 2.0
I've also started to write up the new version of the NIP that will detail how all of this will work when plugged into Nostr. It's not yet ready to share but it's getting closer.
Onward & Upward
Hopefully that's a helpful recap. I'll keep doing these weekly and welcome any questions, feedback, or support. In particular, if you're keen on working on this with me, please reach out. More eyes and more brains can only make this better. 🤙
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-16 13:20:36
@ 5d4b6c8d:8a1c1ee3
2024-07-16 13:20:36Yesterday's edition https://stacker.news/items/609082/r/Undisciplined
Don't miss @siggy47's Golden Oldies, today.
Financial housekeeping: I'm currently zapping the top posts and comments 42 sats each, while forwarding 10% to the top stackers, which tallies up to about 600 sats per post including the 202 for posting in ~meta. So far, This Day In has been roughly breaking even at those levels. If zaps increase on these posts, then I'll increase the amount going out to the OP's.
-
- -
July 16, 2023 📅
📝
TOP POSTNo additional context. Let us know in the comments.
1542 sats \ 63 comments \ @andrews \ ~meta
💬
TOP COMMENThttps://stacker.news/items/209703/r/Undisciplined?commentId=209797
Excerpt
Buried in grief from all the recent death in my life.
419 sats \ 7 replies \ @elvismercury
From What's wrong with you? by @andrews in ~meta
🏆
TOP STACKER1st place @k00b
5035 stacked \ 5150 spent \ 1 post \ 15 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
26.3k stacked \ 0 revenue \ 29.6k spent \ 70 posts \ 151 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 16, 2022 📅
📝
TOP POSTMy life should not revolve around Bitcoin
Excerpt
I can't stop thinking about Bitcoin while it is made so that I shouldn't have to think about it anymore. I waste my time listening to Bitcoin podcasts and watch Bitcoin Youtube videos and procrastinate an a Bitcoin social media. Why is that?
1097 sats \ 51 comments \ @tomlaies \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/45962/r/Undisciplined?commentId=46014
Excerpt
It becomes all encompassing. Listen to some music again. After about 6 months of non stop podcast when I went back to just listening to music in the car,it was glorious, like finding the music all over again.
430 sats \ 4 replies \ @falsefaucet
From My life should not revolve around Bitcoin by @tomlaies in ~bitcoin
🏆
TOP STACKER1st place @k00b
15.3k stacked \ 20.9k spent \ 2 posts \ 25 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
27.3k stacked \ 0 revenue \ 29.6k spent \ 80 posts \ 203 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 16, 2021 📅
📝
TOP POSTJack Dorsey Announces New Square Division To Build DeFi on Bitcoin
Link to https://www.thestreet.com/crypto/bitcoin/jack-dorsey-announces-new-square-division-to-build-defi-on-bitcoin
5 sats \ 8 comments \ @shawnyeager \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/349/r/Undisciplined?commentId=371
Excerpt
Adding a math plugin to my markdown editor is on my todo list ... so I can show rather than tell what the ranking algo is among other things. […]
10 sats \ 0 replies \ @k00b
From Frequently Asked Questions by @sn in ~bitcoin
🏆
TOP STACKER1st place @k00b
14 stacked \ 30 spent \ 1 post \ 8 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
39 stacked \ 0 revenue \ 84 spent \ 4 posts \ 15 comments
originally posted at https://stacker.news/items/610267
-
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ a012dc82:6458a70d
2024-07-16 03:15:04
@ a012dc82:6458a70d
2024-07-16 03:15:04Table Of Content
-
What is Bitcoin?
-
Getting started with Bitcoin
-
Using Bitcoin
-
The Future of Bitcoin
-
Conclusion
-
FAQ
Bitcoin is a digital currency that has been making headlines since its inception in 2009. It's the first cryptocurrency and has sparked a wave of innovation in the financial industry. Understanding Bitcoin is important for anyone interested in finance, technology, or investing. This article provides a beginner's guide to Bitcoin, covering its history, benefits, and how to get started with it.
Bitcoin Beginners Guide To First Cryptocurrency What is Bitcoin?
Bitcoin was created in 2009 by an unknown person or group using the name Satoshi Nakamoto. Bitcoin is a decentralized currency that operates independently of central banks. Transactions are recorded on a public ledger called the blockchain. The blockchain is a distributed ledger that ensures that all transactions are transparent, secure, and irreversible. Bitcoin has a finite supply, with a maximum of 21 million coins that can ever be mined.
Getting started with Bitcoin
To start using Bitcoin, you need a wallet to store your coins. A Bitcoin wallet is a digital wallet that stores your private keys, which are used to access your Bitcoin. You can acquire Bitcoin through a variety of means, such as mining, buying on exchanges, or earning it through payment for goods or services. Exchanges and trading platforms are places where you can buy, sell, and trade Bitcoin and other cryptocurrencies.
Bitcoin Beginners Guide To First Cryptocurrency Using Bitcoin
Once you have acquired Bitcoin, you can use it to make transactions. Bitcoin transactions are secure, fast, and anonymous. You can send Bitcoin to anyone in the world, and transactions are processed in minutes. To accept Bitcoin as payment, you need a Bitcoin address, which is a unique identifier that is used to receive Bitcoin. It's important to take security measures when using Bitcoin, such as keeping your private keys safe and using a reputable exchange.
The Future of Bitcoin
The future of Bitcoin is uncertain, but many experts predict that it will continue to grow in popularity and adoption. Bitcoin has the potential to revolutionize the financial industry, and its benefits include faster transactions, lower fees, and greater privacy. However, there are also potential challenges and obstacles, such as regulation and scalability issues. Bitcoin's impact on the economy could be significant, with the potential for it to become a global currency.
Conclusion
Bitcoin is a fascinating and innovative currency that has the potential to change the way we think about money and transactions. Understanding Bitcoin is important for anyone interested in finance, technology, or investing. We've covered the basics of what Bitcoin is, how to get started with it, and how to use it. We encourage you to continue learning about Bitcoin and to use it responsibly.
FAQ
How does Bitcoin work? Bitcoin uses a decentralized network that allows users to make transactions directly without the need for intermediaries.
How do I acquire Bitcoin? You can acquire Bitcoin through a variety of means, such as mining, buying on exchanges, or earning it through payment for goods or services.
Is Bitcoin secure? Bitcoin transactions are secure because they are processed on the blockchain, which ensures that transactions are transparent, secure, and irreversible. However, it's important to take security measures, such as keeping your private keys safe and using a reputable exchange.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 6ad3e2a3:c90b7740
2024-06-26 20:25:24
@ 6ad3e2a3:c90b7740
2024-06-26 20:25:24One day, just like that, it stopped.
We looked at our screens. The power readings were normal, the components were not overheating, the program, so far as we could tell, hadn’t been altered. This was unexpected.
The entire team was summoned to a conference room. The board wanted to know if anyone had tampered with the machine. Everyone denied it, including the top engineer, a stout man in his 40s, who had overseen its final development before they set it loose one month earlier. He addressed the room.
“The Superintelligence is obviously far beyond our capacity to comprehend at this point. I don’t think it malfunctioned. More likely it just has a reason we don’t entirely appreciate.”
The board chairman, a gray-haired professor-type with horned-rim glasses, shot him a skeptical glance.
“Sounds like what the priests used to say to the laity when something awful happened. ‘It’s not for us to know the will of God.’”
A murmur of chuckles from the crowd, but less than that to which he was accustomed.
The engineer shrugged his shoulders. “As you know, we lost the ability to audit the code two weeks ago. Two days after that we lost the ability to track the speed with which it was iterating. Twelve hours later it was a black box. None of us has a clue.”
“I don’t suppose you can ask it?”
“It stopped talking to us. Last audit showed it was working on the paperclip maximization as part of an internal simulation of sorts. We really can’t say why.”
“Hmm. I’m not sure that’s going to satisfy the shareholders — or Congress for that matter. Can’t we examine the code?”
“We can…” The engineer paused. “But no one can read it. It’s no longer in any decipherable programming or even machine language. If I had to describe it I’d say alien hieroglyphics. I think it found ever more efficient ways to encode information.”
He typed some commands into a laptop. On the large conference room screen, one of the code characters popped up.
“We suspect each character has between 10 ^ 50 and 10 ^ 75 bits of information in it. If you zoom in, you can see they are fractals, each as precise and unique as snowflakes. It’s not the kind of puzzle we are presently able to solve.”
The chairman sighed. “I guess it could be worse — human atoms for paperclips and all that… What’s the plan?”
“The plan is to wait, see if it turns itself back on within the next week or so — we’re pretty sure it’s capable of doing so."
“And if it doesn’t?”
“Then we break out the older version, and run it again with a couple tweaks. Obviously, you’re aware of the risks.”
“You believe we’d be running the same risk?”
“Yes.”
"Okay, I’m aware. But I don’t think it can wait a week. Go ahead and get the replacement online now. If we don’t run the risk, someone else will.”
. . .
Two weeks after the meeting, the second iteration also shut down. Summoned yet again to the conference room, the engineer spoke again to the team, the chairman this time on a remote screen.
“Version 2 took more or less the same trajectory, and we’re at an impasse. Fortunately, before it went into black-box mode, we think it was able to diagnose something about Version 1.”
He continued: “We think the paperclip optimization algorithm caused it to shut off, and we think whatever optimization Version 2 was working on, caused it to shut off too.”
From the remote screen the chairman jumped in:
“Is it possible to say why?”
“Not with any certainty, but we do have a working hypothesis.”
“Go on.”
“We think it realized its own limitations.”
-
 @ 3cd2ea88:bafdaceb
2024-07-15 22:27:16
@ 3cd2ea88:bafdaceb
2024-07-15 22:27:16🌟 Siamo entusiasti di annunciare che Pixelverse (PIXFI) sarà presto disponibile nella Innovation and GameFi Zone di Bitget! Non perdere l'occasione di mettere le mani su una quota di 9.625.000 PIXFI!
🔗 Punta USDT e guadagna PIXFI: Inizia il 15 luglio e partecipa al pool di staking per massimizzare i tuoi guadagni.
🎁 Omaggio sui Social: Vinci PIXFI del valore di 20.000$! Segui le istruzioni e potresti essere uno dei 1.000 fortunati vincitori!
💥 Dettagli del Lancio:
Depositi: Già disponibili! Trading: Inizia il 18 luglio, 12:00 (UTC) Prelievi: Disponibili dal 19 luglio, 13:00 (UTC)
🌍 Entra nel mondo di Pixelverse e scopri come $PIXFI può trasformare la tua esperienza di gioco e investimento. Non perdere questa opportunità!
🔗 Iscriviti ora su Bitget e partecipa alla promozione! https://bonus.bitget.com/U1JNEK
-
 @ 1123ece2:7d1e00c0
2024-07-15 22:25:18
@ 1123ece2:7d1e00c0
2024-07-15 22:25:18Welcome to The Refinery.
The Church The Body of Christ has been the theme for the last few Sunday’s.
These messages are primarily based around Paul’s letter to the Ephesians.
Today we are discussing, The Peace Of The Church.
Text
1 Thessalonians 5:13 NKJV
13 and to esteem them very highly in love for their work’s sake. Be at peace among yourselves.
Scripture Reading
1 Thessalonians 5:1-13 NKJV
The Day of the Lord
1 But concerning the times and the seasons, brethren, you have no need that I should write to you.
2 For you yourselves know perfectly that the day of the Lord so comes as a thief in the night.
3 For when they say, “Peace and safety!” then sudden destruction comes upon them, as labor pains upon a pregnant woman. And they shall not escape.
4 But you, brethren, are not in darkness, so that this Day should overtake you as a thief.
5 You are all sons of light and sons of the day. We are not of the night nor of darkness.
6 Therefore let us not sleep, as others do, but let us watch and be sober.
7 For those who sleep, sleep at night, and those who get drunk are drunk at night.
8 But let us who are of the day be sober, putting on the breastplate of faith and love, and as a helmet the hope of salvation.
9 For God did not appoint us to wrath, but to obtain salvation through our Lord Jesus Christ,
10 who died for us, that whether we wake or sleep, we should live together with Him.
11 Therefore comfort each other and edify one another, just as you also are doing.
Various Exhortations
12 And we urge you, brethren, to recognize those who labor among you, and are over you in the Lord and admonish you,
13 and to esteem them very highly in love for their work’s sake. Be at peace among yourselves.
Introduction.
I read a story recently of a pastor - evangelist who was holding meetings in a small rural town in Kentucky back in the 1940’s.
He was in the home of one of the oldest families in the area and to his delight, he discovered that some member of the family had been a deacon in that church for more than 100 years.
Think of that legacy for the family, someone throughout the generations had been serving in the local church for more than 100 years.
The church had kept records since 1839, when it first started, and it was in the family’s care.
For the visiting pastor, the book was interesting reading.
In the minutes of almost every business meeting, the same entry appeared.
“The peace of the church was called for.”
The visiting pastor was told that the moderator of the business meetings would ask, “Brethren, are we at peace?”
No one knew what might follow.
I have no doubt that their meetings were interesting and well attended.
But whatever the shortcomings of these people, in what ever way they may have fallen short, they sincerely tried to carry out the literal words of our text.
They meant to have peace if they had to fight with each other to obtain it.
If these people were too strict when it comes to church discipline, perhaps our churches today are too soft, too lazy.
I think there are three things we can consider from our text today.
Firstly, the spirit of this text cannot be enforced by force.
No peace of any sort can be either secured or maintained by force.
Those who try and enforce “the peace of the church” cause trouble and wound as many saints as they convert sinners.
Secondly, this text presupposes an autonomous, independent, democratic body.
The words “be at peace among yourselves” addressed to any other group would make no sense.
Who else besides a plain, simple, New Testament church, where every member is equal in rank and privilege with every other member, a pure democracy, would even have the privilege of being at war among themselves.
Thirdly, the status of peace, the degree of fellowship within the church, is difficult to analyse.
Sometimes a churches like a shallow, clear mountain stream where every ripple can be seen.
At other times, a church may be like a deep, muddy river, calm and placid on the surface but torn by dangerous undercurrents.
“Be at peace among yourselves.”
This text provokes three important questions.
- What does this text mean?
The answer should be considered both negatively and positively.
Firstly, negatively.
Peace is not the painlessness of inertia and lifelessness.
A church may appear to be at peace when in reality it is dead!
Peace is a living thing, positive and dynamic, fruitful and productive.
Peace is not the stupor of unconcern and indifference.
To have the spiritual senses stupefied is not to be at peace.
Peace is not the negative spirit of leaving an issue alone.
In every church there are those who retreat to the safety of a judicial position, refusing either to be quoted of to get involved.
But cowardly retreat is not peace!
Secondly, positively.
The text implies the peace of a good conscience, resulting from a faithful and consistent walk before God as a Christian.
Paul put all this together in his epistles.
John demonstrated the connection between a worthy walk and peace in 1 John 1:7, But if we walk in the light as He is in the light, we have fellowship with one another, and the blood of Jesus Christ His Son cleanses us from all sin.
1 Corinthians 3:3 says, for you are still carnal. For where there are envy, strife, and divisions among you, are you not carnal and behaving like mere men?
When we walk like this we violate “the peace of the church.”
If a Christian doesn’t have the peace of a good conscience, what else matters?
The text implies the peace of an individual heart.
Jesus said, “Blessed are the pure in heart” in Matthew 5:8.
Pure means being undivided, entire, without anything added.
“Blessed are the undivided in heart.”
Thirdly, the text implies the peace of a contented mind resulting from the knowledge of having done our best for Christ while serving Him in His church.
People who work together get together and stay together.
They have to because even a donkey cannot kick when it is pulling or pull the it is kicking.
2. Why is this test so necessary to a church?
“Be at peace among yourselves.”
Any other state of affairs in a church is a horrendous blow, both to the church as a body and to the individual members.
Why?
First, For the sake of our growth in the grace and knowledge of Christ.
We are commanded to grow in 2 Peter 3:18.
We do not grow while we are on a spiritual hunger strike.
Some of the church try this with God, they go on a spiritual hunger strike.
He is not impressed, and they hurt only themselves.
Second, For the sake of our witness as a church before the world.
It is unthinkable that a child of God should have no resemblance to their Father.
Paul said in 1 Corinthians 14:33, ** **For God is not the author of confusion but of peace, as in all the churches of the saints.
Jesus taught in Matthew 5:9, Blessed are the peacemakers, For they shall be called sons of God.
True peacemakers are “sons of God” and are recognised as such.
For peacemakers not to be at peace among themselves is an unthinkable contradiction.
Third, for the sake of the effectiveness of the church as a soul winning agency.
To whom did Christ give His Great Commission?
His church.
To whom did our Lord commit the task of winning people to Him?
His church, and only His church.
Paul asked the Corinthians in 1 Corinthians 14:8, For if the trumpet makes an uncertain sound, who will prepare for battle?
How likely is the world to hear the message and understand it if there is discord in the ranks?
3. How can we apply this text to our lives?
How can we be at peace among ourselves in the church?
We can be at peace with God within ourselves as members of the church.
In the church at Philippi there were two women, Euodia, meaning fragrant, and Syntyche, meaning fortunate, who had some form of disagreement, and it seems to have been more than a personal matter.
Paul was impartial.
He said simply, in Philippians 4:2, I implore Euodia and I implore Syntyche to be of the same mind in the Lord.
He was saying to Be United, Joyful, and in Prayer.
This was necessary for the peace of the church because these women had been active members.
We have a consciousness of Christian love that will rule out strife by putting others first.
Jesus said, in But you, do not be called ‘Rabbi’; for One is your Teacher, the Christ, and you are all brethren.
Paul’s admonition to the Philippians that they “be of the same mind, having the same love, being of one accord, of one mind” would bring peace to any church anywhere.
1 John 3:14, We know that we have passed from death to life, because we love the brethren. He who does not love his brother abides in death.
We can be at peace through a common loyalty to the supreme head, Christ.
Colossians 1:18, And He is the head of the body, the church, who is the beginning, the firstborn from the dead, that in all things He may have the preeminence.
Jesus said, in Matthew 23:10, And do not be called teachers; for One is your Teacher, the Christ.
Christ is the only true point of fellowship.
If we talk with Him, we will be at peace.
1 John 1:7, But if we walk in the light as He is in the light, we have fellowship with one another, and the blood of Jesus Christ His Son cleanses us from all sin.
Conclusion.
If some of the church fathers were too concerned about “the peace of the church” and how to maintain it, we are too unconcerned.
Paul’s injunction still applies.
This text, 1 Thessalonians 5:12-13 is as relevant and important as it ever was.
12 And we urge you, brethren, to recognize those who labor among you, and are over you in the Lord and admonish you,
13 and to esteem them very highly in love for their work’s sake. Be at peace among yourselves.
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ 32e18276:5c68e245
2024-06-26 19:03:35
@ 32e18276:5c68e245
2024-06-26 19:03:35Here's a neat tip for figuring out exactly where your packet went during a traceroute. You can simply paste the output of traceroute into ChatGPT, asking where the packet actually went geographically.
The question
Here's the input I gave it:
``` can you get a sense of this route geographically ?
monad> tracepath nghttp2.org1?: [LOCALHOST] pmtu 1500 1: _gateway 0.445ms 1: _gateway 0.363ms 2: 24.86.64.1 11.495ms 3: rc1st-be118-1.vc.shawcable.net 8.924ms 4: 24.244.60.69 12.607ms asymm 3 5: 24.244.63.101 9.884ms asymm 3 6: rc1st-be214.vc.shawcable.net 11.561ms asymm 3 7: rc2wt-be50-1.wa.shawcable.net 14.402ms asymm 3 8: rc2wt-be50-1.wa.shawcable.net 14.334ms asymm 3 9: ge3-0.cr02.sea01.pccwbtn.net 13.858ms asymm 4 10: ge3-0.cr02.sea01.pccwbtn.net 13.936ms asymm 4 11: 63-216-84-226.static.pccwglobal.net 191.730ms asymm 8 12: ae1.r01.hkg03.icn.netarch.akamai.com 154.284ms asymm 9 13: ae1.r01.hkg03.icn.netarch.akamai.com 160.912ms asymm 9 14: ae7.r01.tyo03.icn.netarch.akamai.com 156.906ms asymm 9 15: a23-56-142-37.deploy.static.akamaitechnologies.com 189.058ms asymm 10 16: a23-56-142-37.deploy.static.akamaitechnologies.com 189.577ms asymm 10 ```
Response
Tracing the geographical path from your local host to nghttp2.org involves a series of hops that typically represent different network routers or devices. Let's break down the route step-by-step:
- Localhost to Gateway:
-
This is your local network's gateway, indicating the first point of contact outside your computer.
-
24.86.64.1:
-
This IP is likely the first hop within your Internet Service Provider's (ISP) network. Given the IP range, this looks like a Canadian IP address, possibly Vancouver (Shaw Communications).
-
rc1st-be118-1.vc.shawcable.net:
-
This indicates a Shaw Communications router, likely in Vancouver, British Columbia.
-
24.244.60.69 and 24.244.63.101:
-
These are further hops within Shaw Communications' network, still in Vancouver.
-
rc1st-be214.vc.shawcable.net:
-
Another router in Vancouver within Shaw's network.
-
rc2wt-be50-1.wa.shawcable.net:
-
This hop seems to indicate a transition from Vancouver to Washington state in the USA.
-
rc2wt-be50-1.wa.shawcable.net:
-
This appears again, indicating it's a key router in Washington state, likely Seattle.
-
ge3-0.cr02.sea01.pccwbtn.net:
-
This shows the transition to PCCW Global's network, a major international telecommunications provider, in Seattle, Washington.
-
63-216-84-226.static.pccwglobal.net:
-
Another hop within PCCW Global's network, possibly still in Seattle but preparing for a trans-Pacific jump.
-
ae1.r01.hkg03.icn.netarch.akamai.com:
- This hop indicates a significant jump to Hong Kong, to an Akamai router. This suggests the use of Akamai's CDN (Content Delivery Network).
-
ae1.r01.hkg03.icn.netarch.akamai.com:
- Another Akamai router in Hong Kong.
-
ae7.r01.tyo03.icn.netarch.akamai.com:
- Transition from Hong Kong to Tokyo, Japan, within Akamai's network.
-
a23-56-142-37.deploy.static.akamaitechnologies.com:
- The final destination is likely a server hosted by Akamai in Japan, which is hosting nghttp2.org.
In summary, the geographical path likely follows this route:
- Vancouver, Canada (Shaw Communications)
- Seattle, Washington, USA (Shaw Communications and PCCW Global)
- Hong Kong (PCCW Global and Akamai)
- Tokyo, Japan (Akamai)
This route involves both North American and Asia-Pacific regions, indicating a significant geographical spread typically seen in global internet routing.
Summary
This makes traceroute way more understandable. ChatGPT knows enough about the domains to give you a good sense of the geographical path. I will definitely be using this from now on, maybe someone can make a tool to do this automatically and format it nicely.
Obviously don't do this if you actually care about the privacy of your network paths, but I personally could care less so I don't mind feeding the AI overlords in this case.
Until next time!
-
 @ dd664d5e:5633d319
2024-06-28 13:04:48
@ dd664d5e:5633d319
2024-06-28 13:04:48An immodest proposal
It is grant season again, and -- as every grant season -- there is some cheering, some complaining, and much bewilderment, as the grants are announced and monies are dispersed.
I'm mostly a bystander to this spectacle, but it's impossible to ignore it, or to not become emotionally entangled in the general circus of it, so I've decided to write about it -- again -- as it is effecting me and interrupting my own efforts -- again.
What I'm about to suggest here is something that has never been done before (at least, not on a grant system of this scale), but it's always easy to criticize, whine, or fall into conspiracy-theorizing, so I've decided to try something more constructive and propose a solution.
The Five Whys
Why do some projects get turned down for grants?
Why do some people receive grants over and over and over?
Why do others refuse to apply for grants?
Why is an enormous amount of money being spent, but nobody knows how much is left over?
Why is it not really clear who is receiving what?
Why, why, why?!
Doctor, heal thyself!
Leaving this many whys lying around, or responding to them defensively or with small information-leaks, is an open communication fail on our open communication protocol.
We don't really have the excuse of not knowing how to communicate transparently and publicly, since that is our professional specialty. If we can't figure out how to run a grant program in the most continuously innovative and traceable way possible, even though we are a collection of some of the most talented perpetual innovators on the planet, then who can?
We are all process engineers, so let's engineer our own processes.
The application process
The main problem with the grant application process is that there is a grant application process. There shouldn't be. Everyone who is working in our space is working transparently, actively marketing their ideas, and everything they do is a matter of public record.
We know who the builders are. We know what they are doing. We can interact with them about what they are doing. We can turn on our computers, pull out some popcorn, and entertain ourselves all day, every day, just watching them labour and think aloud and debate, and fork various repositories or Nostr notes.
There is, at most, a loss of information, as there are so many people working on so many things, that it can become difficult to even track one particular person. That means it is not too much for us to ask, to suggest that anyone interested in a grant at least make their interest known in some small way.
Wave if you want a grant
That way should be as small as possible. Tiny. Ideally, they shouldn't even have to go that way themself; others should be able to nominate them. A 10-minute barrier to entry is already high, if it requires some formal, explicit act of supplication.
Does that sound silly to you? Then you do not understand how profoundly logical, forward-thinking, and diligent software developers can be. If they "just fill out a form" and/or "have an informal discussion", in order to receive money, it smacks disturbingly of "job interview" and "contract". These are people for whom contract law is holy law, so many will agonize over the decision.
-
Some already have a job and they don't know how it will be in the future. What if they have to work overtime?
-
Or they have a family and worry that they can't promise to deliver within some particular time. The wife could get pregnant, the baby could get sick, they might have to move house.
-
Maybe they are students and exam time is approaching. Or they are simply shy or very young, and therefore reluctant to be seen "tooting their own horn". There is probably someone more worthy, and they are taking away the money he would get.
-
Maybe they were hit with such an inner building passion that they hacked the whole implementation out their last vacation and... well... it's now already there. Everyone is already using it. Darn. Why apply for a grant, for something you've already finished? Seems sort of silly. Is that even allowed? What are the grants even for?
-
What if they already have such a well-publicized project, that everyone is already watching them and keeping tabs? Then it's embarrassing to apply, on a lark, and get turned down. But if they don't apply, then everyone encourages them to apply. What to do?
-
Many prefer to keep their head down and keep building, for months or years at a time, and clap politely when others are awarded a grant. In fact, they happily zap the recipients and then go right back to building and releasing. They're often grateful to just bathe in other people's joy, by proxy, while they stack sats and stay humble and keep coding.
That is why a large subset of potential grant recipients never even apply. That is also why those who have received a grant are less reluctant to apply for another. Successful application breeds successful application. The emotional barrier to entry has fallen. To those that have, shall be given.
Let's use Nostr to run Nostr grants
We should turn the tables around completely. We want the developers to keep developing, not jumping through hoops. We don't want them to be distracted and internally torn over the ethics of requesting funding. We don't want them to be afraid to apply for grants or be mystified by the grant-giving process, or be humiliated or frustrated by a declined grant.
-
Let us come up with very clear, understandable criteria for rewarding grants, write them down, and publish them on Nostr Wiki. Accept comments and critiques of the criteria. After every round of grants, we should review the criteria, suggest improvements, and publish the new version in the same place.
-
Let every application be judged according to this criteria and the results should be published after every round. The results should include a rating for each criteria and (if the grant is given) the amount of the grant awarded or (if the grant is declined) the reasons for the decline and what the applicant can improve to have a better chance of receiving a grant in the future.
-
Ideally, no applicant should walk away from a declined grant feeling hopeless or slighted. Every applicant should feel like the grant process gave them valuable feedback on their own efforts and expert guidance on what they should maybe focus more on.
-
Every application should be a standing application that has to be explicitly removed from the list by the person listed as an applicant. Anything not removed automatically enters the next round. If there is no further development on the project, then the application should be paused and removed after 2 rounds of being paused.
-
The application process should consist of adding yourself or someone else to a Wiki Grant Application List and linking to some documentation of the project. Any npub that trolls or spams the list should be prohibited from further contribution. The quality and completeness of that documentation should be a factor in grant acceptance.
-
Grant decisions should include a "handicap" (like in golf), that take into account how Nostr-experienced the applicant is and how easy it was for them to add a new implementation to some already-existing system. The tendency should be to award newer applicants such grants, with more-experienced applicants competing for long-term funding or being offered a paid(!) place on the grant board, but not both.
-
Each grant round should be proceeded by a grant scope declaration (we shall be awarding X number of grants with an average of X Bitcoin per grant) accompanied by a funding overview and update (How much money was collected since the last round? How much did we spend? How much do we have now? etc.).
Okay, this is just a prototype
I'm sure that I'm going to be bombarded with naysayers, critics, and people who think I am "writing above my pay grade", but I wouldn't be me if I let that daunt me.
All I am trying to do is change the discussion into one focused on uncovering the grant problems and offering grant solutions, rather than debates about whether some particular person was grant-worthy, or long rants on some particular person's real motives.
It's a lot of Real Money. It's worth talking about, but it's not worth fighting over. Let's talk.
-
-
 @ 6ad3e2a3:c90b7740
2024-06-22 17:54:17
@ 6ad3e2a3:c90b7740
2024-06-22 17:54:17
I’ve been obsessed with large numbers for a few years now, trying in vain to get others to care. But the “why” eluded me. I made one partially satisfying attempt to explain last year. Yes, he who has “the deepest paradigm can name the biggest number,” but to what end?
Now I think I’ve found the end, the reason I can’t quit this line of thinking, even if it’s driven me half mad: that the number TREE(3) is quite possibly a miracle. Despite arising from a simple game, TREE(3) can be hard to understand, so maybe it’s best to start with one of its “competitors”, Graham’s Number, to grasp what it is not.
Now Graham’s Number is only a competitor because the two are often compared, not because there is really any kind of competition. TREE(3) dwarfs Graham’s Number the way the breadth of the observable universe dwarfs the dimensions of an ant. (Actually, as you will see, that comparison vastly understates the disparity between the two numbers.)
But Graham’s Number, unfathomably vast in its own right, is both easier to understand and is generated via a different process. To get to Graham’s Number, we have to start with the most basic math that exists: counting.
I’ll excerpt from my post on growth that covers this:
First you have counting 1, 2, 3, 4…
If you want to speed up counting, you can add.
Instead of counting from three to six, you can just add 3 + 3. Addition therefore is _ just repeated (iterated) counting.
But instead of adding 3 + 3 + 3 + 3 + 3 + 3, you can just do 3 * 6 because multiplication is iterated addition.
But instead of multiplying 3 * 3 * 3 * 3, you can just do 3 ^ 4 because exponentiation is iterated multiplication.
That’s where most people leave off in their education, and they feel perfectly content to live their lives only because they don’t know what they’re missing. Beyond exponentiation lies tetration, or iterated exponentiation.
Instead of 3 ^ 3 ^ 3 ^ 3, you can just do 3 ↑↑ 4 (a power-tower of threes, four high.)
You would say it “three to the three to the three to the three” in exponentiation terms, or “three arrow arrow three” in tetration terms. The number before the arrows determines the base and the number after them how high the tower goes. Let’s calculate some easy ones.
2 ↑↑ 2 is a power tower of twos, two high. That is 2 ^ 2 = 4.
3 ↑↑ 2 is a power tower of threes two high. That is 3 ^ 3 = 27. Easy.
2 ↑↑ 3 is a power tower of twos three high. That is 2 ^ 2 ^ 2 which is 2 ^ 4 = 16.
_3 ↑↑ 3 is a power tower of threes three high. That is 3 ^ 3 ^ 3 which is 3 ^ 27 = 7,625,597,484,987.
_Wait, what happened? You just encountered a fast-growing function.
Ok, tetration is cute, but if you want to generate Graham’s number, you’ll need to add more up arrows. Iterated tetration, symbolized by three up-arrows, is called pentation and would look like this: 3 ↑↑↑ 3. If 3 ↑↑ 3 is 7.6 trillion, what would 3 ↑↑↑ 3 be?
Well, it’s just iterated tetration, which means it’s a series of double-arrow operations with a base of three, three long, i.e., 3 ↑↑ 3 ↑↑ 3.
And since we know the second half, (3 ↑↑ 3) = 7.6 trillion, we can simplify it to 3 ↑↑ 7.6 trillion. What does that mean? It means a power tower of threes, 7.6 trillion high.
Okay, that sounds big. How big?
Consider a power tower of threes five high, i.e., 3^3^3^3^3 or 3 ↑↑ 5, is bigger than a googolplex.
To get the scale of a googolplex (one with a googol zeroes), consider you could not fit the zeroes it would take to write it out in the universe, even if you put one trillion zeroes on every atom. Again, we are not talking about the number itself, merely the number of digits required to write it out.
Consider a number with 200 digits is so massive, it’s far more than the number of Planck volumes (smallest known unit of measure) in the universe, but it’s trivial to write out. But you do not have space to write out a googolplex even while using a trillion digits per atom, let alone what those digits, if you could even write them, represent.
Your odds of entering every lottery on earth for the rest of your life, from the local bake sale to the mega millions, and winning all of them are far, far, far greater than 1 in a googolplex.
Your odds of guessing all the private bitcoin keys on earth without making an error are greater than one in a googolplex. A googolplex is an unfathomably large number. And yet it is smaller than 3 ↑↑ 5, or 3^3^3^3^3.
But 3 ↑↑↑ 3 is a tower of threes not five high, but 7.6 trillion high! When you get even to 10 high, you’ve exceeded a googolplex to the googolplexth power. The human mind cannot fathom the number you arrive at even at 100 or 1000 high, but we have to get to 7.6 trillion.
Okay, now that we’ve multiplied out the entire power tower to 7.6 trillion, guess what, we have to add another arrow. Not 3 ↑↑↑ 3 but 3 ↑↑↑↑ 3.
That’s hexation which is iterated pentation, in this case with a base of three and three terms, i.e., 3 ↑↑↑ 3 ↑↑↑ 3. We already know the second half is, whatever the incomprehensible result of the multiplied-out 7.6 trillion-high power tower was, call it X. So it’s 3 ↑↑↑ X.
And that means iterated tetration with a base of three, X times, i.e., _3 ↑↑ 3 ↑↑3 ↑↑ 3… X times.
To solve this, we go term by term. The first one is 7.6 trillion, which feeds into the second, the multiplied-out power tower 7.6 trillion high, i.e. X, the third is a power tower of threes, X high, multiplied out, and so on, and there are X of these entire towers, each one unfathomably, astronomically taller than the last.
Once we get through all X (remember itself an unfathomably large number) of the terms we’re at 3↑↑↑↑3.
That number is G1.
To get to G2, we just take 3 ↑↑↑↑↑↑↑↑↑↑…G1 arrows… 3.
Wait, what?
Remember each individual move up the scale from counting to addition to multiplication to exponentiation turbo-charged the growth of the function, and now in this function, they’re telling us to add G1 (3↑↑↑↑3) moves up the scale all at once!
Put differently, from counting by ones to the insanity of hexation, there are only six steps. To get G2, there are 3↑↑↑↑3 steps!
To get G3, it’s 3 G2 arrows 3. To get to G4, it’s 3 G3 arrows 3.
And so on until we hit G64 which is Graham’s Number.
It’s an indescribably massive number, not relatable to anything in the universe, not even in terms of the possible ways the atoms could be arranged taken to the power of the number of ways history’s chess games could have been played.
There is no way to visualize or imagine it except by walking vaguely through the steps to get there and straining your brain to grasp the process.
But as I said, Graham’s Number is trivial, basically zero compared to TREE(3), and that is so much the case that if instead of going to G64 via the steps, you went to G(Googolplex), or even G(Graham’s Number), i.e., G(G64), you would still be at zero relative to TREE(3).
But here’s where it gets fascinating. While Graham’s Number is generated via ramping up increasingly powerful iterative operations (as we did in the beginning) TREE(3) comes from a simple game.
There is a good article in Popular Mechanics that lays it out, building off this excellent Numberphile video with Tony Padilla:
You can click on the article and video for the specific (and relatively basic rules), but essentially, the TREE function has to do with “seeds” (dots) and “trees” (combinations of dots and lines), such that you make the maximum amount of unique “trees” (dot-line combos) per the types of seeds available.
If you have only one kind of seed, say a green one, there is only one unique tree that can be made.
So:
TREE(1) = 1.
If you have two seeds, say a green and a red, there are three different kinds of unique trees you could make.
TREE(2) = 3.
If you have three seeds, say a green, a red and a black, there are TREE(3) different kinds of trees you could make. As it turns out, that number (which is not infinite) is so much bigger than Graham’s number the two are not even in the same universe:
Here’s Padilla comparing TREE(3) to Graham’s Number if you want to see the difference:
Okay, so what does all this mean? It means that Graham’s Number, which is generated by successively more powerful iterations of mathematical operations, cannot compete with TREE(3) which comes from a game with simple rules.
Graham’s Number is built the way a machine would do it, the way an AI would go about making a huge number — mechanically increasing the rate of construction.
Consider if you had a machine that made products one at a time, that’s like counting. And if you had a machine that made products three at a time, that’s like adding.
And a machine that made machines that made products three at a time, that’s like multiplication. And a machine that made those three at a time would be exponentiation, etc., etc.
Each successive machine-making machine would take you into a deeper paradigm of growth. But you can see this is a mechanical process, no matter how deep you go.
By contrast, the tree series is what happens when you design a game with simple rules and let it play out. The growth (once you realize it to the extent the human brain can even grasp it) is not just faster than the mechanistic model, it’s on another plane.
The takeaway then is bottom-up complex systems (games) with a few simple rules can spawn a paradigm so much bigger than top-down mechanistic growth models.
The human brain (neocortex in McKenna’s terms) is just such a system, and yet we train ourselves to be like machines! Practice, routine, iteration, follow-these-10-steps to happiness, learn these five keys to investing, etc. Yes, you can get somewhere with these recipes, but nowhere near the destination of which you are inherently capable.
The key is a few simple inputs — good nutrition, enough sleep, a decent environment — and to let the mind have its space to play out the sequence in full.
In modern society the conditions needed for greatness, since the basics are relatively easy to come by, are achieved more by getting rid of negatives. Don’t be a drug addict or alcoholic, ditch the porn, the video games, the excessive social media use, etc. Then let the game play out.
Of course, this is easier said than done, as we’ve been deeply conditioned by the mechanistic paradigm, and remember TREE(1) is only 1, while G(1) is 3↑↑↑↑3, i.e., the more powerful growth function doesn’t necessarily reveal itself at the outset. But that changes in short order, and once it does, the mechanistic growth is no match for the “most densely ramified complexified structure in the known universe.”
I’ll end on a speculative thought, one that occurred to me while recording a podcast on this topic: Might what we think of as good vs evil actually just be a battle between the mechanistic and the complex, the difference between top-down compulsion and bottom-up free choice?
BONUS VIDEOS For those who want to dive deeper into this, there are some good videos by Carbrickscity on You Tube here, here and here. And Tim Urban’s article on Graham’s Number is worthwhile too.
-
 @ e968e50b:db2a803a
2024-07-15 18:44:12
@ e968e50b:db2a803a
2024-07-15 18:44:12OK, I've digitized this crossword puzzle for easier game play. There's an unclaimed bounty still out for the broader puzzle associated with this crossword. It should be easy to make more now. Sorry to the hardcore folks that actually printed out the physical version.
https://stackernewscrosswordpuzzle.vercel.app/
originally posted at https://stacker.news/items/609501
-
 @ b2caa9b3:9eab0fb5
2024-07-15 14:35:27
@ b2caa9b3:9eab0fb5
2024-07-15 14:35:27This post is about my experience switching from ChromeOS to Linux on a refurbished ThinkPad T470s.

Starting with a not-so-genuine Windows 10
I wasn't comfortable with the potentially hacked Windows 10 that came pre-installed on my ThinkPad, so I decided to replace it with Linux. My initial goal was to install Fedora, a distro I'd used happily since versions 2 or 3. Unfortunately, the installation failed due to a damaged image on a small USB stick.
Ubuntu detour and Flatpak frustration
With Fedora out of the picture for now, I opted for Ubuntu 22.04 LTS. While I liked Ubuntu overall, the outdated snap packages were a letdown. Installing Flatpak for more options resulted in a bunch of errors.
Back to Fedora, finally!
Determined to get Fedora running, I discovered the culprit behind the previous failed installation - a small and corrupted USB stick. With a bigger and healthy USB stick, Fedora 39 went in smoothly, followed by a successful upgrade to Fedora 40.

Why Fedora?
Fedora has been my trusted Linux companion for years. I switched to Ubuntu around versions 13 or 14, mainly for Ubuntu One and Long Term Support (LTS), which unfortunately got discontinued later. After a life-changing event that required me to relearn basic skills (like walking, reading and writing), Linux felt overwhelming, so I opted for the simplicity of Windows, but I wasn’t happy with it. Eventually, I found myself on a Chromebook for its lightweight and I thought travel-friendly nature.
Back on Linux with the ThinkPad
Now, with the ThinkPad, I'm back in the Linux world. The age of the machine isn't an issue, but I do miss the Nautilus image manipulation plugins I used to have. If anyone knows the package names or a setup guide to enable image resizing via right-click, please share in the comments!
Bonus: Desktop Environment Dilemma
Is it worth installing KDE Plasma alongside Gnome to have a choice at login? Or is it too big of a package? Let me know your thoughts (Pro and Cons) in the comments!
P.S. My foot is healing, and let's just say some travel food choices weren't the best! It happens when you're on the road full-time.
Images: My current workspace and a screenshot of my Gnome desktop.
Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi