-

@ 3bf0c63f:aefa459d
2024-03-19 14:01:01
# Nostr is not decentralized nor censorship-resistant
Peter Todd has been [saying this](nostr:nevent1qqsq5zzu9ezhgq6es36jgg94wxsa2xh55p4tfa56yklsvjemsw7vj3cpp4mhxue69uhkummn9ekx7mqpr4mhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet5qy8hwumn8ghj7mn0wd68ytnddaksz9rhwden5te0dehhxarj9ehhsarj9ejx2aspzfmhxue69uhk7enxvd5xz6tw9ec82cspz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqy28wumn8ghj7un9d3shjtnwdaehgu3wvfnsz9nhwden5te0wfjkccte9ec8y6tdv9kzumn9wspzpn92tr3hexwgt0z7w4qz3fcch4ryshja8jeng453aj4c83646jxvxkyvs4) for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr _today_ is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:

The top one was published to `wss://nostr.wine`, `wss://nos.lol`, `wss://pyramid.fiatjaf.com`. The second was published to the relay where I generally publish all my notes to, `wss://pyramid.fiatjaf.com`, and that is announced on my [NIP-05 file](https://fiatjaf.com/.well-known/nostr.json) and on my [NIP-65](https://nips.nostr.com/65) relay list.
A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:

These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are _following me_, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on `wss://pyramid.fiatjaf.com`.
If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is _inherently_ centralized or that it needs a _protocol change_ to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we [drive in the right direction](bc63c348b) we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
---
See also:
- [Censorship-resistant relay discovery in Nostr](nostr:naddr1qqykycekxd3nxdpcvgq3zamnwvaz7tmxd9shg6npvchxxmmdqgsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8grqsqqqa2803ksy8)
- [A vision for content discovery and relay usage for basic social-networking in Nostr](nostr:naddr1qqyrxe33xqmxgve3qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cywwjvq)
-

@ 5e5fc143:393d5a2c
2024-01-04 12:44:26
We are now given a choice of digital freedom #nostr .
Creativity for every nostrich is now unleashed from the cage of bigtech censorship , rules and algo. But freedom comes with responsibility so pick right one(s). I will try share here some learning experience both technical and also from fundamental point of view. Just wanted kick start this article n fill as we go like living reference document.
Nostr itself is an application layer protocol that can used beyond just social media mirco or long blogging. Each nostr client heavily dependent on back-end servers call nostr "Relay servers" or in short "rs" or "relays" Relays can hosted anywhere in clearnet internet, onion net , vpn , i2p , nym
Relays are controlled by their respective admins based NIP specs that they select to implement according to own decisions. Relays can have certain ToS (Terms of Service) Rules to adhered too.
New users can choose and pick client or app (ios / android/ windows) with preset of relays in the simplest form , but other advanced users need to do a regular manual relay management.
Relay management is an active regular task based on where when n how you are using.
Relay list are saved within you npub profile backup file which can edited and broadcast anytime.
Relay management is an active regular task based on where when and how you are using.
Relay list always need to be updated time to time as and when needed.
2 Users MUST a common RELAY between them even if one only need to follow another.
Occasionally you may notice certain npub accounts you are following already but cannot see frequent notes publish by them – one of cause maybe you not sharing a common relay
Most nostr client applications has SETTINGS where user choose add/remove relays
Also user choose which function to enable - READ or WRITE
Relay list for your account is always saved within you npub profile backup file which can edited and broadcast anytime. Hence any app or browser when u login with you npub the same relay list will be enforced. There could valid reasons why u need have list for if you trying to save bandwidth and traveling.
Functions in app.getcurrent.io and primal.net app for mobile apple or android are ideal for user traveling abroad and wanted to save bandwidth since relay management is done the providers in backend and saves hassle for basic usage.
Remember if someone is selecting relay on your behalf then you may not be necessarily able to pull and get some specific and special content that you may need. Such providers like coracle and nostrid also give option to override the default relays they selected.
Relay types: They can be categorized by various features or policy or technologies.
FREE PUBLIC Relays vs PAID PUBLIC Relays
PAID relays provide unrestricted access / write / filtering options than FREE relays but both are public clearnet relays. Just subscribing to PAID relays will not solve all problems unless you choose the relays properly and enable settings correctly.
Private Replay or Tor Relays – normally not easily visible until unless someone tell you.
You can also host own private relay not opened to internet of archive and back of your own notes.
The technical landscape in nostr can be fast changing as more NIPs get proposed or updated.
Relays admin can choose implement certain NIPs or not based on policy or technical limitations.
Example NIP33 defines “long notes” aka blogs as you now reading this in habla site which #1 UI and site for "Editable" long notes – some relays donot implement or allow this.
NIP07 is used for client authentication like nos2x and is implemented by all relays in fact.
To be continued again ... reference pics will added later also
Hope this help you understand "why when what" to tune and maintain active set of proper relays.
Relay Proxy, Relay aggregator or Relay multiplexer – Paid, Public, Free, Private, Event, Relays
That’s all for now n more later ... Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️ PV 💜 🤙
References:
https://habla.news/relays
https://relay.exchange/
https://relays.vercel.app/
https://nostr.info/relays/
https://nostrudel.ninja/#/relays
Related Articles:
https://thebitcoinmanual.com/articles/types-nostr-relays/
nostr:naddr1qqd5c6t8dp6xu6twvukkvctnwss92jfqvehhygzwdaehguszyrtp7w79k045gq80mtnpdxjuzl9t7vjxk52rv80f888y5xsd5mh55qcyqqq823cf39s98
https://habla.news/u/current@getcurrent.io/1694434022411
-

@ e6ce6154:275e3444
2023-07-27 14:12:49
Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-

@ 76c71aae:3e29cafa
2024-08-13 04:30:00
On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes.
Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals.
When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear.
What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned.
Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action.
The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane.
We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today.
It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request.
Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media.
-

@ 0e8c41eb:95ff0faa
2024-07-08 14:36:14
## Chef's notes
Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
Spread the fruit filling over the dough.
Mix the rest of the flour with the remaining 100 grams of butter and 100 grams of sugar and knead it with your fingers into a crumbly mixture. Sprinkle this crumble mixture over the fruit filling. Bake the tart in the preheated oven at 200°C for about 30 minutes until golden brown.
Variations:
Only apple? Make this tart with 1 kilo of apples.
High or low? You can also bake the crumble tart in a low tart tin of 30 cm diameter. If the fruit filling is a bit too voluminous, you can make double the crumble mixture and sprinkle it over the larger surface area.
Additional needs:
Mixer with dough hooks or food processor
Cling film
Round baking tin with a diameter of 28-30 cm, greased
## Details
- ⏲️ Prep time: 45 min + 1 hour Rising
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 8
## Ingredients
- 375 grams flour
- 1 packet dried yeast (7 grams)
- 125 grams unsalted butter, at room temperature
- 275 grams sugar
- 1 egg
- 100 ml milk, at room temperature
- 500 grams apples
- 500 grams apricots (fresh or from a can)
## Directions
1. Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
2. Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
3. Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
4. Spread the fruit filling over the dough.
-

@ dd664d5e:5633d319
2024-06-24 06:05:05
# The new Great Library
We have all heard tales of Amazon or other booksellers banning customers from their bookstores or censoring/editing purchased books. The famous [Project Gutenberg](https://www.gutenberg.org/), and similar organizations, are performing a good work, to help protect many of our precious books from this fate, but it is merely a centralized website and therefore not censorship resistant. Also, it mostly posts books in English or German.
So, we at nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz have decided to move Project Gutenberg to Nostr and house it in the most distributed way possible: on relays. Specifically, our new, public [Citadel relay](https://thecitadel.nostr1.com/) for out-of-print books (and other documents), but also on any relay, anywhere.
And, because we are a very humble group, we're naming the effort "Alexandria". And the first book to be printed on Nostr is the Bible because *obviously*.
## Why on relays?
Well, why not on relays? Relays are one of the few widely-distributed databases for documentation in existence. The relay database spans the entire globe and anyone can maintain their own relay on their personal computer or mobile phone.
That means that anyone can house *their own* books.
Which books are their own? Any books they have in their own possession. Any books someone would have to physically pry out of their cold, dead, computer.
## Notes are perfect for publishing
Once we begin generating eBooks from notes with an associated header (which will be quite easy to do, so long as they are written in markdown or similar), they will also be readable, downloadable, and storable in ePub format (see [Pandoc](https://pandoc.org/epub.html)). And it is, after all, only a matter of time until someone enterprising makes an ePaper Nostr client for calmer reading of notes, and then you can download and read them, without having to bother converting beforehand, which maintains their Nostr-navigation.
The new event kind [30040](https://wikifreedia.xyz/nkbip-01/) allows us to take any sort of note containing any sort of characters and create a type of "note collection" or "book of notes", "journal of notes", "magazine of notes". And it can be nested or embedded in other notes, creating any sort of note-combination and note-hierarchy you can think of, only limited in size by the ability of your computer to processes the relationships.
## Save the Zettels
The associated kind 30041 adds the prospect of breaking longer texts or articles up into sections or snippets (called "Zettel" in German). We can then collect or refer to particular bits of a longer text (like a chart, elegant paragraph or definition, data table), directly. Anyone can create such snippets, even of texts they didn't write, as they can add a reference to the original publication in the tags of the new event.
This means we no longer have to "copy-paste" or quote other people's works, we can simply tie them in. If we worry about them being deleted, we can fork them to create our own, digitally-linked version, and then tie that in. This means that source material can be tied to the new material, and you can trace back to the source easily (using Nostr IDs and tags, which are signed identifiers) and see who else is branching out from that source or discussing that source.
## It's gonna be HUGE!
We are making a big, beautiful library... and you are going to build it for us. Anyone, anywhere can therefore publish or republish any document they wish, with Nostr, and store it wherever they have a relay, and view it on any client willing to display it.
You will own something and be happy.
-

@ 3bf0c63f:aefa459d
2024-05-21 12:38:08
# Bitcoin transactions explained
A transaction is a piece of data that takes **inputs** and produces **outputs**. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (**UTXO**). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a **script** that unlocks that transaction and related signatures, then you specify outputs along with a **script** that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a **public key** whose controller (the person who has the corresponding **private key**) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at [this small chapter](https://github.com/bitcoinbook/bitcoinbook/blob/6d1c26e1640ae32b28389d5ae4caf1214c2be7db/ch06_transactions.adoc) of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: <https://en.bitcoin.it/wiki/Coin_analogy>
-

@ deab79da:88579e68
2024-05-20 20:48:09
## Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 20-30 min
- 🍽️ Servings: 4
## Ingredients
- 1 lb cod fillets
- 1/4 cup butter
- 1/4 cup white flour
- 1 1/4 cups milk
- 1 tsp salt
- pepper to taste
- 1 small onion
- 1 carrot
- 3 celery stalks
- 1/2 cup breadcrumbs
- 1/2 cup shredded old cheddar
## Directions
1. Preheat oven to 375F. Place cod in a greased baking dish.
2. Make the white sauce in a heavy saucepan. Melt the butter over medium heat and stir in the flour until smooth. Remove from heat and slowly stir in half of the milk, then return to heat and beat until smooth and shiny.
3. Gradually add the remaining milk, followed by salt, pepper, and your vegetables. Cook until sauce is smooth & thickened.
4. Pour sauce over the fish, and sprinkle breadcrumbs and cheese over the top.
5. Bake, uncovered for 20-30 minutes until sauce bubbles and the cheese begins to brown. Let rest 10 minutes after cooking completes.
-

@ 266815e0:6cd408a5
2024-04-24 23:02:21
> NOTE: this is just a quick technical guide. sorry for the lack of details
## Install NodeJS
Download it from the official website
https://nodejs.org/en/download
Or use nvm
https://github.com/nvm-sh/nvm?tab=readme-ov-file#install--update-script
```bash
wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.7/install.sh | bash
nvm install 20
```
## Clone example config.yml
```bash
wget https://raw.githubusercontent.com/hzrd149/blossom-server/master/config.example.yml -O config.yml
```
## Modify config.yml
```bash
nano config.yml
# or if your that type of person
vim config.yml
```
## Run blossom-server
```bash
npx blossom-server-ts
# or install it locally and run using npm
npm install blossom-server-ts
./node_modules/.bin/blossom-server-ts
```
Now you can open http://localhost:3000 and see your blossom server
And if you set the `dashboard.enabled` option in the `config.yml` you can open http://localhost:3000/admin to see the admin dashboard
-

@ 3bf0c63f:aefa459d
2024-01-15 11:15:06
# Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente.
- **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados.
- **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua.
- **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer.
- **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos.
- **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas.
- **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade).
- **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis.
- **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade.
- **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho.
- **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho.
- **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma.
- **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças.
- **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família.
- **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente.
- **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo).
- **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas.
- **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente).
- **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica.
- **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar.
- **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico.
- **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais.
- **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil).
- **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória.
- **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles.
- **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas.
- **inflação**: a inflação estimula o endividamento e o consumismo.
- **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas.
- **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# IPFS problems: Community
I was an avid IPFS user until yesterday. Many many times I asked simple questions for which I couldn't find an answer on the internet in the #ipfs IRC channel on Freenode. Most of the times I didn't get an answer, and even when I got it was rarely by someone who knew IPFS deeply. I've had issues go unanswered on js-ipfs repositories for year – one of these was raising awareness of a problem that then got fixed some months later by a complete rewrite, I closed my own issue after realizing that by myself some couple of months later, I don't think the people responsible for the rewrite were ever acknowledge that he had fixed my issue.
Some days ago I asked some questions about how the IPFS protocol worked internally, sincerely trying to understand the inefficiencies in finding and fetching content over IPFS. I pointed it would be a good idea to have a drawing showing that so people would understand the difficulties (which I didn't) and wouldn't be pissed off by the slowness. I was told to read the whitepaper. I had already the whitepaper, but read again the relevant parts. The whitepaper doesn't explain anything about the DHT and how IPFS finds content. I said that in the room, was told to read again.
Before anyone misread this section, I want to say I understand it's a pain to keep answering people on IRC if you're busy developing stuff of interplanetary importance, and that I'm not paying anyone nor I have the right to be answered. On the other hand, if you're developing a super-important protocol, financed by many millions of dollars and a lot of people are hitting their heads against your software and there's no one to help them; you're always busy but never delivers anything that brings joy to your users, something is very wrong. I sincerely don't know what IPFS developers are working on, I wouldn't doubt they're working on important things if they said that, but what I see – and what many other users see (take a look at the IPFS Discourse forum) is bugs, bugs all over the place, confusing UX, and almost no help.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Castas hindus em nova chave
Shudras buscam o máximo bem para os seus próprios corpos; vaishyas o máximo bem para a sua própria vida terrena e a da sua família; kshatriyas o máximo bem para a sociedade e este mundo terreno; brâmanes buscam o máximo bem.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Thoughts on Nostr key management
On [Why I don't like NIP-26 as a solution for key management](nostr:naddr1qqyrgceh89nxgdmzqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ctgmx78) I talked about multiple techniques that could be used to tackle the problem of key management on Nostr.
Here are some ideas that work in tandem:
- [NIP-41](https://github.com/nostr-protocol/nips/blob/master/41.md) (stateless key invalidation)
- [NIP-46](https://github.com/nostr-protocol/nips/blob/master/46.md) (Nostr Connect)
- [NIP-07](https://github.com/nostr-protocol/nips/blob/master/07.md) (signer browser extension)
- [Connected hardware signing devices](https://lnbits.github.io/nostr-signing-device/installer/)
- other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically
- there are probably many other ideas
Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that
- For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution;
- Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money;
- Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways.
- For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on.
We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that.
---
One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# IPFS problems: Shitcoinery
IPFS was advertised to the Ethereum community since the beggining as a way to "store" data for their "dApps". I don't think this is harmful in any way, but for some reason it may have led IPFS developers to focus too much on Ethereum stuff. Once I watched a talk showing libp2p developers – despite being ignored by the Ethereum team (that ended up creating their own agnostic p2p library) – dedicating an enourmous amount of work on getting a libp2p app running in the browser talking to a normal Ethereum node.
The always somewhat-abandoned "Awesome IPFS" site is a big repository of "dApps", some of which don't even have their landing page up anymore, useless Ethereum smart contracts that for some reason use IPFS to store whatever the useless data their users produce.
Again, per se it isn't a problem that Ethereum people are using IPFS, but it is at least confusing, maybe misleading, that when you search for IPFS most of the use-cases are actually Ethereum useless-cases.
## See also
* [Bitcoin](nostr:naddr1qqyryveexumnyd3kqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c7nywz4), the only non-shitcoin
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Economics
Just a bunch of somewhat-related notes.
* [notes on "Economic Action Beyond the Extent of the Market", Per Bylund](nostr:naddr1qqyxxepsx3skgvenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cf5cy3p)
* [Mises' interest rate theory](nostr:naddr1qqyr2dtrxycr2dmrqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c97asm3)
* [Profits, not wages, as the originary factor](nostr:naddr1qqyrge3hxa3rqce4qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c7x67pu)
* [Reisman on opportunity cost](nostr:naddr1qqyrswtr89nxvepkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cwx7t3v)
* [Money Supply Measurement](nostr:naddr1qqyr2v3cxcunserzqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cya65m9)
* [Per Bylund's insight](nostr:naddr1qqyxvdtzxscxzcenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cuq3unj)
* [Maybe a new approach to the Austrian Business Cycle Theory, some disorganized thoughts](nostr:naddr1qqyrvdecvccxxcejqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cl9wc86)
* [An argument according to which fractional-reserve banking is merely theft and nothing else](nostr:naddr1qqyrywt9v5exydenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cfks90r)
* [Conjecture and criticism](nostr:naddr1qqyrqde5x9snqvfnqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ce4glh8)
* [Qual é o economista? (piadas)](nostr:naddr1qqyx2vmrx93xgdpjqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c0ckmsx)
* [UBI calculations](nostr:naddr1qqyryenpxe3ryvf4qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cuurj42)
* [Donations on the internet](nostr:naddr1qqyrqwp4xsmnsvtxqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cex8903)
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# tempreites
My first library to get stars on GitHub, was a very stupid templating library that used just HTML and HTML attributes ("DSL-free"). I was inspired by <http://microjs.com/> at the time and ended up not using the library. Probably no one ever did.
- <https://github.com/fiatjaf/tempreites>
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# nix
Pra instalar o [neuron](797984e3.md) fui forçado a baixar e instalar o [nix](https://nixos.org/download.html). Não consegui me lembrar por que não estava usando até hoje aquele maravilhoso sistema de instalar pacotes desde a primeira vez que tentei, anos atrás.
Que sofrimento pra fazer funcionar com o `fish`, mas até que bem menos sofrimento que da outra vez. Tive que instalar um tal de `fish-foreign-environment` (usando o próprio nix!, já que a outra opção era o `oh-my-fish` ou qualquer outra porcaria dessas) e aí usá-lo para aplicar as definições de shell para bash direto no `fish`.
E aí lembrei também que o `/nix/store` fica cheio demais, o negócio instala tudo que existe neste mundo a partir do zero. É só para computadores muito ricos, mas vamos ver como vai ser. Estou gostando do neuron (veja, estou usando como diário), então vou ter que deixar o nix aí.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# O Bitcoin como um sistema social humano
Afinal de contas, o que é o Bitcoin? Não vou responder a essa pergunta explicando o que é uma "blockchain" ou coisa que o valha, como todos fazem muito pessimamente. [A melhor explicação em português que eu já vi está aqui](nostr:naddr1qqrky6t5vdhkjmspz9mhxue69uhkv6tpw34xze3wvdhk6q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqp65wp3k3fu), mas mesmo assim qualquer explicação jamais será definitiva.
A explicação apenas do protocolo, do que faz um programa `bitcoind` sendo executado em um computador e como ele se comunica com outros em outros computadores, e os incentivos que estão em jogo para garantir com razoável probabilidade que se chegará a um consenso sobre quem é dono de qual parte de qual transação, apesar de não ser complicada demais, exigirá do iniciante que seja compreendida muitas vezes antes que ele se possa se sentir confortável para dizer que entende um pouco.
E essa parte _técnica_, apesar de ter sido o insight fundamental que gerou o evento miraculoso chamado Bitcoin, não é a parte mais importante, hoje. Se fosse, várias dessas outras moedas seriam concorrentes do Bitcoin, mas não são, e jamais poderão ser, porque elas não estão nem próximas de ter os outros elementos que compõem o Bitcoin. São eles:
1. A estrutura
O Bitcoin é um sistema composto de partes independentes.
Existem programadores que trabalham no protocolo e aplicações, e dia após dia novos programadores chegam e outros saem, e eles trabalham às vezes em conjunto, às vezes sem que um se dê conta do outro, às vezes por conta própria, às vezes pagos por empresas interessadas.
Existem os usuários que realizam validação completa, isto é, estão rodando algum programa do Bitcoin e contribuindo para a difusão dos blocos, das transações, rejeitando usuários malignos e evitando ataques de mineradores mal-intencionados.
Existem os poupadores, acumuladores ou os proprietários de bitcoins, que conhecem as possibilidades que o mundo reserva para o Bitcoin, esperam o dia em que o padrão-Bitcoin será uma realidade mundial e por isso mesmo atributem aos seus bitcoins valores muito mais altos do que os preços atuais de mercado, agarrando-se a eles.
Especuladores de "criptomoedas" não fazem parte desse sistema, nem tampouco empresas que [aceitam pagamento](https://bitpay.com/) em bitcoins para imediatamente venderem tudo em troca de dinheiro estatal, e menos ainda [gente que usa bitcoins](https://www.investimentobitcoin.com/) e [a própria marca Bitcoin](https://www.xdex.com.br/) para aplicar seus golpes e coisas parecidas.
2. A cultura
Mencionei que há empresas que pagam programadores para trabalharem no código aberto do BitcoinCore ou de outros programas relacionados à rede Bitcoin -- ou mesmo em aplicações não necessariamente ligadas à camada fundamental do protocolo. Nenhuma dessas empresas interessadas, porém, controla o Bitcoin, e isso é o elemento principal da cultura do Bitcoin.
O propósito do Bitcoin sempre foi ser uma rede aberta, sem chefes, sem política envolvida, sem necessidade de pedir autorização para participar. O fato do próprio Satoshi Nakamoto ter voluntariamente desaparecido das discussões foi fundamental para que o Bitcoin não fosse visto como um sistema dependente dele ou que ele fosse entendido como o chefe. Em outras "criptomoedas" nada disso aconteceu. O chefe supremo do Ethereum continua por aí mandando e desmandando e inventando novos elementos para o protocolo que são automaticamente aceitos por toda a comunidade, o mesmo vale para o Zcash, EOS, Ripple, Litecoin e até mesmo para o Bitcoin Cash. Pior ainda: Satoshi Nakamoto saiu sem nenhum dinheiro, nunca mexeu nos milhares de bitcoins que ele gerou nos primeiros blocos -- enquanto os líderes dessas porcarias supramencionadas cobraram uma fortuna pelo direito de uso dos seus primeiros usuários ou estão aí a até hoje receber dividendos.
Tudo isso e mais outras coisas -- a mentalidade anti-estatal e entusiasta de sistemas p2p abertos dos membros mais proeminentes da comunidade, por exemplo -- faz com que um ar de liberdade e suspeito de tentativas de centralização da moeda sejam percebidos e execrados.
3. A história
A noção de que o Bitcoin não pode ser controlado por ninguém passou em 2017 por [dois testes](https://www.forbes.com/sites/ktorpey/2019/04/23/this-key-part-of-bitcoins-history-is-what-separates-it-from-competitors/#49869b41ae5e) e saiu deles muito reforçada: o primeiro foi a divisão entre Bitcoin (BTC) e Bitcoin Cash (BCH), uma obra de engenharia social que teve um sucesso mediano em roubar parte da marca e dos usuários do verdadeiro Bitcoin e depois a tentativa de tomada por completo do Bitcoin promovida por mais ou menos as mesmas partes interessadas chamada SegWit2x, que fracassou por completo, mas não sem antes atrapalhar e difundir mentiras para todos os lados. Esses dois fracassos provaram que o Bitcoin, mesmo sendo uma comunidade desorganizada, sem líderes claros, está imune à [captura por grupos interessados](https://en.wikipedia.org/wiki/Regulatory_capture), o que é mais um milagre -- ou, como dizem, um [ponto de Schelling](https://en.wikipedia.org/wiki/Focal_point_(game_theory)).
Esse período crucial na história do Bitcoin fez com ficasse claro que _hard-forks_ são essencialmente incompatíveis com a natureza do protocolo, de modo que no futuro não haverá a possibilidade de uma sugestão como a de imprimir mais bitcoins do que o que estava programado sejam levadas a sério (mas, claro, sempre há a possibilidade da cultura toda se perder, as pessoas esquecerem a história e o Bitcoin ser cooptado, eis a importância da auto-educação e da difusão desses princípios).
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# My stupid introduction to Haskell
While I was writing my first small program on Haskell (really simple, but functional webapp) in December 2017 I only knew vaguely what was the style of things, some basic notions about functions, pure functions and so on (I've read about a third of [LYAH](http://learnyouahaskell.com/chapters)).
An enourmous amount of questions began to appear in my head while I read tutorials and documentation. Here I present some of the questions and the insights I got that solved them. Technically, they may be wrong, but they helped me advance in the matter, so I'm writing them down while I still can -- If I keep working with Haskell I'll probably get to know more and so my new insights will replace the previous ones, and the new ones won't be useful for total begginers anymore.
---
Here we go:
- **Why do modules have odd names?**
- modules are the things you import, like `Data.Time.Clock` or `Web.Scotty`.
- packages are the things you install, like 'time' or 'scotty'
- packages can contain any number of modules they like
- a module is just a collection of functions
- a package is just a collection of modules
- a package is just name you choose to associate your collection of modules with when you're publishing it to Hackage or whatever
- the module names you choose when you're writing a package can be anything, and these are the names people will have to `import` when they want to use you functions
- if you're from Javascript, Python or anything similar, you'll expect to be importing/writing the name of the package directly in your code, but in Haskell you'll actually be writing the name of the module, which may have nothing to do with the name of the package
- people choose things that make sense, like for `aeson` instead of `import Aeson` you'll be doing `import Data.Aeson`, `import Data.Aeson.Types` etc. why the `Data`? because they thought it would be nice. dealing with JSON is a form of dealing with data, so be it.
- you just have to check the package documentation to see which modules it exposes.
- **What is `data User = User { name :: Text }`?**
- a data type definition. means you'll have a function `User` that will take a Text parameter and output a `User` record or something like that.
- you can also have `Animal = Giraffe { color :: Text } | Human { name :: Text }`, so you'll have two functions, Giraffe and Human, each can take a different set of parameters, but they will both yield an Animal.
- then, in the functions that take an Animal parameter you must typematch to see if the animal is a giraffe or a human.
- **What is a monad?**
- a monad is a context, an environment.
- when you're in the context of a monad you can write imperative code.
- you do that when you use the keyword `do`.
- in the context of a monad, all values are prefixed by the monad type,
- thus, in the `IO` monad all `Text` is `IO Text` and so on.
- some monads have a relationship with others, so values from that monad can be turned into values from another monad and passed between context easily.
- for exampĺe, [scotty](https://www.stackage.org/haddock/lts-9.18/scotty-0.11.0/Web-Scotty.html)'s `ActionM` and `IO`. `ActionM` is just a subtype of `IO` or something like that.
- when you write imperative code inside a monad you can do assignments like `varname <- func x y`
- in these situations some transformation is done by the `<-`, I believe it is that the pure value returned by `func` is being transformed into a monad value. so if `func` returns `Text`, now varname is of type `IO Text` (if we're in the IO monad).
- so it will not work (and it can be confusing) if you try to concatenate functions like `varname <- transform $ func x y`, but you can somehow do
- `varname <- func x y`
- `othervarname <- transform varname`
- or you can do other fancy things you'll get familiar with later, like `varname <- fmap transform $ func x y`
- why? I don't know.
- **How do I deal with Maybe, Either or other crazy stuff?**
"ok, I understand what is a Maybe: it is a value that could be something or nothing. but how do I use that in my program?"
- you don't! you turn it into other thing. for example, you use [fromMaybe](http://hackage.haskell.org/package/base-4.10.1.0/docs/Data-Maybe.html#v:fromMaybe), a function that takes a default value and that's it. if your `Maybe` is `Just x` you get `x`, if it is `Nothing` you get the default value.
- using only that function you can already do whatever there is to be done with Maybes.
- you can also manipulate the values inside the `Maybe`, for example:
- if you have a `Maybe Person` and `Person` has a `name` which is `Text`, you can apply a function that turns `Maybe Person` into `Maybe Text` AND ONLY THEN you apply the default value (which would be something like the `"unnamed"`) and take the name from inside the `Maybe`.
- basically these things (`Maybe`, `Either`, `IO` also!) are just tags. they tag the value, and you can do things with the values inside them, or you can remove the values.
- besides the example above with Maybes and the `fromMaybe` function, you can also remove the values by using `case` -- for example:
- `case x of`
- `Left error -> error`
- `Right success -> success`
- `case y of`
- `Nothing -> "nothing!"`
- `Just value -> value`
- (in some cases I believe you can't remove the values, but in these cases you'll also don't need to)
- for example, for values tagged with the IO, you can't remove the IO and turn these values into pure values, but you don't need that, you can just take the value from the outside world, so it's a IO Text, apply functions that modify that value inside IO, then output the result to the user -- this is enough to make a complete program, any complete program.
- **JSON and interfaces (or instances?)**
- using [Aeson](https://hackage.haskell.org/package/aeson-1.2.3.0/docs/Data-Aeson.html) is easy, you just have to implement the `ToJSON` and `FromJSON` interfaces.
- "interface" is not the correct name, but I don't care.
- `ToJSON`, for example, requires a function named `toJSON`, so you do
- `instance ToJSON YourType where`
- `toJSON (YourType your type values) = object []` ... etc.
- I believe lots of things require interface implementation like this and it can be confusing, but once you know the mystery of implementing functions for interfaces everything is solved.
- `FromJSON` is a little less intuitive at the beggining, and I don't know if I did it correctly, but it is working here. Anyway, if you're trying to do that, I can only tell you to follow the types, copy examples from other places on the internet and don't care about the meaning of symbols.
## See also
* [Haskell Monoids](nostr:naddr1qqyrzcmrvcmrqwtpqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cktq992)
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# O caso da Grêmio TV
enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam:
Grêmio TV
pior que o SBT !
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# A list of things artificial intelligence is not doing
If AI is so good why can't it:
- write good glue code that wraps a documented HTTP API?
- make good translations using available books and respective published translations?
- extract meaningful and relevant numbers from news articles?
- write mathematical models that fit perfectly to available data better than any human?
- play videogames without cheating (i.e. simulating human vision, attention and click speed)?
- turn pure HTML pages into pretty designs by generating CSS
- predict the weather
- calculate building foundations
- determine stock values of companies from publicly available numbers
- smartly and automatically test software to uncover bugs before releases
- predict sports matches from the ball and the players' movement on the screen
- continuously improve niche/local search indexes based on user input and and reaction to results
- control traffic lights
- predict sports matches from news articles, and teams and players' history
This was posted first on [Twitter](https://twitter.com/fiatjaf/status/1477942802805837827).
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# The "Drivechain will replace altcoins" argument
The argument that [Drivechain](nostr:naddr1qq9xgunfwejkx6rpd9hqzythwden5te0ve5kzar2v9nzucm0d5pzqwlsccluhy6xxsr6l9a9uhhxf75g85g8a709tprjcn4e42h053vaqvzqqqr4gumtjfnp) will replace shitcoins is _not_ that people will [sell their shitcoins](https://twitter.com/craigwarmke/status/1680371502246514688) or that the existing shitcoins will instantly vanish. The argument is about a change _at the margin_ that eventually ends up killing the shitcoins or reducing them to their original insignificance.
**What does "at the margin" mean?** For example, when the price of the coconut drops a little in relation to bananas, does that mean that everybody will stop buying bananas and will buy only coconuts now? No. Does it mean there will be [zero](https://twitter.com/GoingParabolic/status/1680319173744836609) increase in the amount of coconuts sold? Also no. What happens is that there is a small number of people who would have preferred to buy coconuts if only they were a little less expensive but end up buying bananas instead. When the price of coconut drops these people buy coconuts and don't buy bananas.
The argument is that the same thing will happen when Drivechain is activated: there are some people today (yes, believe me) that would have preferred to work within the Bitcoin ecosystem but end up working on shitcoins. In a world with Drivechain these people would be working on the Bitcoin ecosystem, for the benefit of Bitcoin and the Bitcoiners.
Why would they prefer Bitcoin? Because Bitcoin has a bigger network-effect. When these people come, they increase Bitocin's network-effect even more, and if they don't go to the shitcoins they reduce the shitcoins' network-effect. Those changes in network-effect contribute to bringing others who were a little further from the margin and the thing compounds until the shitcoins are worthless.
Who are these people at the margin? I don't know, but they certainly exist. I would guess the Stark people are one famous example, but there are many others. In the past, examples included Roger Ver, Zooko Wilcox, Riccardo Spagni and Vitalik Buterin. And before you start screaming that these people are shitcoiners (which they are) imagine how much bigger Bitcoin could have been today if they and their entire communities (yes, I know, of awful people) were using and working for Bitcoin today. Remember that phrase about Bitcoin being for enemies?
### But everything that has been invented in the altcoin world is awful, we don't need any of that!
You and me should not be the ones judging what is good and what is not for others, but both you and me and others will benefit if these things can be done in a way that increases Bitcoin network-effect and pays fees to Bitcoin miners.
Also, there is a much stronger point you may have not considered: if you believe all altcoiners are scammers that means we have only seen the things that were invented by scammers, since all honest people that had good ideas decided to not implement them as the only way to do it would be to create a scammy shitcoin. One example is [Bitcoin Hivemind](nostr:naddr1qqyxs6tkv4kkjmnyqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cd3vm3c).
If it is possible to do these ideas without creating shitcoins we may start to see new things that are actually good.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Classless Templates
There are way too many hours being wasted in making themes for blogs. And then comes a new blog framework, it requires new themes. Old themes can't be used because they relied on different ways of rendering the website. Everything is a mess.
Classless was an attempt at solving it. It probably didn't work because I wasn't the best person to make themes and showcase the thing.
Basically everybody would agree on a simple HTML template that could fit blogs and simple websites very easily. Then other people would make pure-CSS themes expecting that template to be in place.
No classes were needed, only a fixed structure of `header`. `main`, `article` etc.
With **flexbox** and **grid** CSS was enough to make this happen.
The templates that were available were all ported by me from other templates I saw on the web, and there was a simple one I created for my old website.
- <https://github.com/fiatjaf/classless>
- <https://classless.alhur.es/>
- <https://classless.alhur.es/themes/>
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Um algoritmo imbecil da evolução
Suponha que você queira escrever a palavra BANANA partindo de OOOOOO e usando só alterações aleatórias das letras. As alterações se dão por meio da multiplicação da palavra original em várias outras, cada uma com uma mudança diferente.
No primeiro período, surgem BOOOOO e OOOOZO. E então o ambiente decide que todas as palavras que não começam com um B estão eliminadas. Sobra apenas BOOOOO e o algoritmo continua.
É fácil explicar conceber a evolução das espécies acontecendo dessa maneira, se você controlar sempre a parte em que o ambiente decide quem vai sobrar.
Porém, há apenas duas opções:
1. Se o ambiente decidir as coisas de maneira aleatória, a chance de você chegar na palavra correta usando esse método é tão pequena que pode ser considerada nula.
2. Se o ambiente decidir as coisas de maneira pensada, caímos no //design inteligente//.
Acredito que isso seja uma enunciação decente do argumento ["no free lunch"](https://en.wikipedia.org/wiki/No_free_lunch_in_search_and_optimization) aplicado à crítica do darwinismo por William Dembski.
A resposta darwinista consiste em dizer que não existe essa BANANA como objetivo final. Que as palavras podem ir se alterando aleatoriamente, e o que sobrar sobrou, não podemos dizer que um objetivo foi atingido ou deixou de sê-lo. E aí os defensores do design inteligente dirão que o resultado ao qual chegamos não pode ter sido fruto de um processo aleatório. BANANA é qualitativamente diferente de AYZOSO, e aí há várias maneiras de "provar" que sim usando modelos matemáticos e tal.
Fico com a impressão, porém, de que essa coisa só pode ser resolvida como sim ou não mediante uma discussão das premissas, e chega um ponto em que não há mais provas matemáticas possíveis, apenas subjetividade.
Daí eu me lembro da minha humilde solução ao problema do cão que aperta as teclas aleatoriamente de um teclado e escreve as obras completas de Shakespeare: mesmo que ele o faça, nada daquilo terá sentido sem uma inteligência de tipo humano ali para lê-las e perceber que não se trata de uma bagunça, mas sim de um texto com sentido para ele. O milagre se dá não no momento em que o cão tropeça no teclado, mas no momento em que o homem olha para a tela.
Se o algoritmo da evolução chegou à palavra BANANA ou UXJHTR não faz diferença pra ela, mas faz diferença para nós, que temos uma inteligência humana, e estamos observando aquilo. O homem também pensaria que há //algo// por trás daquele evento do cão que digita as obras de Shakespeare, e como seria possível alguém em sã consciência pensar que não?
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# `OP_CHECKTEMPLATEVERIFY` and the "covenants" drama
There are many ideas for "covenants" (I don't think this concept helps in the specific case of examining proposals, but fine). Some people think "we" (it's not obvious who is included in this group) should somehow examine them and come up with the perfect synthesis.
It is not clear what form this magic gathering of ideas will take and who (or which ideas) will be allowed to speak, but suppose it happens and there is intense research and conversations and people (ideas) really enjoy themselves in the process.
What are we left with at the end? Someone has to actually commit the time and put the effort and come up with a concrete proposal to be implemented on Bitcoin, and whatever the result is it will have trade-offs. Some great features will not make into this proposal, others will make in a worsened form, and some will be contemplated very nicely, there will be some extra costs related to maintenance or code complexity that will have to be taken. Someone, a concreate person, will decide upon these things using their own personal preferences and biases, and many people will not be pleased with their choices.
That has already happened. Jeremy Rubin has already conjured all the covenant ideas in a magic gathering that lasted more than 3 years and came up with a synthesis that has the best trade-offs he could find. CTV is the result of that operation.
---
The fate of CTV in the popular opinion illustrated by the thoughtless responses it has evoked such as "can we do better?" and "we need more review and research and more consideration of other ideas for covenants" is a preview of what would probably happen if these suggestions were followed again and someone spent the next 3 years again considering ideas, talking to other researchers and came up with a new synthesis. Again, that person would be faced with "can we do better?" responses from people that were not happy enough with the choices.
And unless some famous Bitcoin Core or retired Bitcoin Core developers were personally attracted by this synthesis then they would take some time to review and give their blessing to this new synthesis.
To summarize the argument of this article, the actual question in the current CTV drama is that there exists hidden criteria for proposals to be accepted by the general community into Bitcoin, and no one has these criteria clear in their minds. It is not as simple not as straightforward as "do research" nor it is as humanly impossible as "get consensus", it has a much bigger social element into it, but I also do not know what is the exact form of these hidden criteria.
This is said not to blame anyone -- except the ignorant people who are not aware of the existence of these things and just keep repeating completely false and unhelpful advice for Jeremy Rubin and are not self-conscious enough to ever realize what they're doing.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Per Bylund's insight
The firm doesn't exist because, like [Coase said](https://en.wikipedia.org/?curid=83030), it is inefficient to operate in a fully open-market and production processes need some bubbles of central planning.
Instead, what happens is that a firm is created because an entrepreneur is doing a new thing (and here I imagine that doing an old thing in a new context also counts as doing a new thing, but I didn't read his book), and for that new thing there is no market, there are no specialized workers offering the services needed, nor other businesses offering the higher-order goods that entrepreneur wants, so he must do all by himself.
So the entrepreneur goes and hires workers and buys materials more generic than he wanted and commands these to build what he wants exactly. It is less efficient than if he could buy the precise services and goods he wanted and combine those to yield the product he envisaged, but it accomplishes the goal.
Later, when that specific market evolves, it's natural that specialized workers and producers of the specific factors begin to appear, and the market gets decentralized.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# IPFS problems: Conceit
IPFS is trying to do many things. The IPFS leaders are revolutionaries who think they're smarter than the rest of the entire industry.
The fact that they've first proposed a protocol for peer-to-peer distribution of immutable, content-addressed objects, then later tried to fix [that same problem](nostr:naddr1qqyrqen9xf3nvdpeqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cmdjnnj) using their own half-baked solution (IPNS) is one example.
Other examples are their odd appeal to decentralization in a very non-specific way, their excessive [flirtation with Ethereum](nostr:naddr1qqyxxdpev5cnsvpkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cta4a2e) and their never-to-be-finished can-never-work-as-advertised _Filecoin_ project.
They could have focused on just making the infrastructure for distribution of objects through hashes (not saying this would actually be a good idea, but it had some potential) over a peer-to-peer network, but in trying to reinvent the entire internet they screwed everything up.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# nostr - Notes and Other Stuff Transmitted by Relays
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works.
## Very short summary of how it works, if you don't plan to read anything else:
Everybody runs a client. It can be a native client, a web client, etc. To publish something, you write a post, sign it with your key and send it to multiple relays (servers hosted by someone else, or yourself). To get updates from other people, you ask multiple relays if they know anything about these other people. Anyone can run a relay. A relay is very simple and dumb. It does nothing besides accepting posts from some people and forwarding to others. Relays don't have to be trusted. Signatures are verified on the client side.
## This is needed because other solutions are broken:
### The problem with Twitter
- Twitter has ads;
- Twitter uses bizarre techniques to keep you addicted;
- Twitter doesn't show an actual historical feed from people you follow;
- Twitter bans people;
- Twitter shadowbans people.
- Twitter has a lot of spam.
### The problem with Mastodon and similar programs
- User identities are attached to domain names controlled by third-parties;
- Server owners can ban you, just like Twitter; Server owners can also block other servers;
- Migration between servers is an afterthought and can only be accomplished if servers cooperate. It doesn't work in an adversarial environment (all followers are lost);
- There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Then, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out;
- Since servers tend to be run amateurishly, they are often abandoned after a while — which is effectively the same as banning everybody;
- It doesn't make sense to have a ton of servers if updates from every server will have to be painfully pushed (and saved!) to a ton of other servers. This point is exacerbated by the fact that servers tend to exist in huge numbers, therefore more data has to be passed to more places more often;
- For the specific example of video sharing, ActivityPub enthusiasts realized it would be completely impossible to transmit video from server to server the way text notes are, so they decided to keep the video hosted only from the single instance where it was posted to, which is similar to the Nostr approach.
### The problem with SSB (Secure Scuttlebutt)
- It doesn't have many problems. I think it's great. In fact, I was going to use it as a basis for this, but
- its protocol is too complicated because it wasn't thought about being an open protocol at all. It was just written in JavaScript in probably a quick way to solve a specific problem and grew from that, therefore it has weird and unnecessary quirks like signing a JSON string which must strictly follow the rules of [_ECMA-262 6th Edition_](https://www.ecma-international.org/ecma-262/6.0/#sec-json.stringify);
- It insists on having a chain of updates from a single user, which feels unnecessary to me and something that adds bloat and rigidity to the thing — each server/user needs to store all the chain of posts to be sure the new one is valid. Why? (Maybe they have a good reason);
- It is not as simple as Nostr, as it was primarily made for P2P syncing, with "pubs" being an afterthought;
- Still, it may be worth considering using SSB instead of this custom protocol and just adapting it to the client-relay server model, because reusing a standard is always better than trying to get people in a new one.
### The problem with other solutions that require everybody to run their own server
- They require everybody to run their own server;
- Sometimes people can still be censored in these because domain names can be censored.
## How does Nostr work?
- There are two components: __clients__ and __relays__. Each user runs a client. Anyone can run a relay.
- Every user is identified by a public key. Every post is signed. Every client validates these signatures.
- Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn't talk to another relay, only directly to users.
- For example, to "follow" someone a user just instructs their client to query the relays it knows for posts from that public key.
- On startup, a client queries data from all relays it knows for all users it follows (for example, all updates from the last day), then displays that data to the user chronologically.
- A "post" can contain any kind of structured data, but the most used ones are going to find their way into the standard so all clients and relays can handle them seamlessly.
## How does it solve the problems the networks above can't?
- **Users getting banned and servers being closed**
- A relay can block a user from publishing anything there, but that has no effect on them as they can still publish to other relays. Since users are identified by a public key, they don't lose their identities and their follower base when they get banned.
- Instead of requiring users to manually type new relay addresses (although this should also be supported), whenever someone you're following posts a server recommendation, the client should automatically add that to the list of relays it will query.
- If someone is using a relay to publish their data but wants to migrate to another one, they can publish a server recommendation to that previous relay and go;
- If someone gets banned from many relays such that they can't get their server recommendations broadcasted, they may still let some close friends know through other means with which relay they are publishing now. Then, these close friends can publish server recommendations to that new server, and slowly, the old follower base of the banned user will begin finding their posts again from the new relay.
- All of the above is valid too for when a relay ceases its operations.
- **Censorship-resistance**
- Each user can publish their updates to any number of relays.
- A relay can charge a fee (the negotiation of that fee is outside of the protocol for now) from users to publish there, which ensures censorship-resistance (there will always be some Russian server willing to take your money in exchange for serving your posts).
- **Spam**
- If spam is a concern for a relay, it can require payment for publication or some other form of authentication, such as an email address or phone, and associate these internally with a pubkey that then gets to publish to that relay — or other anti-spam techniques, like hashcash or captchas. If a relay is being used as a spam vector, it can easily be unlisted by clients, which can continue to fetch updates from other relays.
- **Data storage**
- For the network to stay healthy, there is no need for hundreds of active relays. In fact, it can work just fine with just a handful, given the fact that new relays can be created and spread through the network easily in case the existing relays start misbehaving. Therefore, the amount of data storage required, in general, is relatively less than Mastodon or similar software.
- Or considering a different outcome: one in which there exist hundreds of niche relays run by amateurs, each relaying updates from a small group of users. The architecture scales just as well: data is sent from users to a single server, and from that server directly to the users who will consume that. It doesn't have to be stored by anyone else. In this situation, it is not a big burden for any single server to process updates from others, and having amateur servers is not a problem.
- **Video and other heavy content**
- It's easy for a relay to reject large content, or to charge for accepting and hosting large content. When information and incentives are clear, it's easy for the market forces to solve the problem.
- **Techniques to trick the user**
- Each client can decide how to best show posts to users, so there is always the option of just consuming what you want in the manner you want — from using an AI to decide the order of the updates you'll see to just reading them in chronological order.
## FAQ
- **This is very simple. Why hasn't anyone done it before?**
I don't know, but I imagine it has to do with the fact that people making social networks are either companies wanting to make money or P2P activists who want to make a thing completely without servers. They both fail to see the specific mix of both worlds that Nostr uses.
- **How do I find people to follow?**
First, you must know them and get their public key somehow, either by asking or by seeing it referenced somewhere. Once you're inside a Nostr social network you'll be able to see them interacting with other people and then you can also start following and interacting with these others.
- **How do I find relays? What happens if I'm not connected to the same relays someone else is?**
You won't be able to communicate with that person. But there are hints on events that can be used so that your client software (or you, manually) knows how to connect to the other person's relay and interact with them. There are other ideas on how to solve this too in the future but we can't ever promise perfect reachability, no protocol can.
- **Can I know how many people are following me?**
No, but you can get some estimates if relays cooperate in an extra-protocol way.
- **What incentive is there for people to run relays?**
The question is misleading. It assumes that relays are free dumb pipes that exist such that people can move data around through them. In this case yes, the incentives would not exist. This in fact could be said of DHT nodes in all other p2p network stacks: what incentive is there for people to run DHT nodes?
- **Nostr enables you to move between server relays or use multiple relays but if these relays are just on AWS or Azure what’s the difference?**
There are literally thousands of VPS providers scattered all around the globe today, there is not only AWS or Azure. AWS or Azure are exactly the providers used by single centralized service providers that need a lot of scale, and even then not just these two. For smaller relay servers any VPS will do the job very well.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Replacing the web with something saner
This is a simplification, but let's say that basically there are just 3 kinds of websites:
1. Websites with content: text, images, videos;
2. Websites that run full apps that do a ton of interactive stuff;
3. Websites with some interactive content that uses JavaScript, or "mini-apps";
In a saner world we would have 3 different ways of serving and using these. 1 would be "the web" (and it was for a while, although I'm not claiming here that the past is always better and wanting to get back to the glorious old days).
1 would stay as "the web", just static sites, styled with CSS, no JavaScript whatsoever, but designers can still thrive and make they look pretty. Or it could also be something like [Gemini](https://gemini.circumlunar.space/). Maybe the two protocols could coexist.
2 would be downloadable native apps, much easier to write and maintain for developers (considering that multi-platform and cross-compilation is easy today and getting easier), faster, more polished experience for users, more powerful, integrates better with the computer.
(Remember that since no one would be striving to make the same app run both on browsers and natively no one would have any need for Electron or other inefficient bloated solutions, just pure native UI, like the Telegram app, have you seen that? It's fast.)
But 2 is mostly for apps that people use every day, something like Google Docs, email (although email is also broken technology), Netflix, Twitter, Trello and so on, and all those hundreds of niche SaaS that people pay monthly fees to use, each tailored to a different industry (although most of functions they all implement are the same everywhere). What do we do with dynamic open websites like StackOverflow, for example, where one needs to not only read, but also search and interact in multiple ways? What about that website that asks you a bunch of questions and then discovers the name of the person you're thinking about? What about that mini-app that calculates the hash of your provided content or shrinks your video, or that one that hosts your image without asking any questions?
All these and tons of others would fall into category 3, that of instantly loaded apps that you don't have to install, and yet they run in a sandbox.
The key for making category 3 worth investing time into is coming up with some solid grounds, simple enough that anyone can implement in multiple different ways, but not giving the app too much choices.
Telegram or Discord bots are super powerful platforms that can accomodate most kinds of app in them. They can't beat a native app specifically made with one purpose, but they allow anyone to provide instantly usable apps with very low overhead, and since the experience is so simple, intuitive and fast, users tend to like it and sometimes even pay for their services. There could exist a protocol that brings apps like that to the open world of (I won't say "web") domains and the websockets protocol -- with multiple different clients, each making their own decisions on how to display the content sent by the servers that are powering these apps.
Another idea is that of [Alan Kay](https://www.quora.com/Should-web-browsers-have-stuck-to-being-document-viewers/answer/Alan-Kay-11): to design a nice little OS/virtual machine that can load these apps and run them. Kinda like browsers are today, but providing a more well-thought, native-like experience and framework, but still sandboxed. And I add: abstracting away details about design, content disposition and so on.
---
These 3 kinds of programs could coexist peacefully. 2 are just standalone programs, they can do anything and each will be its own thing. 1 and 3, however, are still similar to browsers of today in the sense that you need clients to interact with servers and show to the user what they are asking. But by simplifying everything and separating the scopes properly these clients would be easy to write, efficient, small, the environment would be open and the internet would be saved.
## See also
- [On the state of programs and browsers](nostr:naddr1qqyxgdfe8qexvd34qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cd7nk4m)
-

@ 2a5d1247:0398ad01
2024-08-20 21:32:48
# 🧠Quote(s) of the week:
'Bitcoin is for everyone.
It’s for Democrats
It’s for Republicans
It’s for conservatives
It’s for progressives
It’s for every single person on this planet who wants to participate regardless of where they came from or what they believe.' - Dennis Porter
"It doesn't matter if the existing system prints $2 trillion, $8 trillion, $50 trillion. It's just different pieces of paper. And Bitcoin measured against a piece of paper will look like it's going up. But all prices relative to Bitcoin are actually going down and will forever."
-Jeff Booth
## 🧡Bitcoin news🧡

But the unlikely thing happened in late 2008: Bitcoin
On the 13th of August:
➡️ Bitcoin is the 6th ranked monetary asset in the world.
➡️Although the following statement is from the 3rd of July nonetheless I want to share it with you.
All 3,070 Four-year HODL periods of Bitcoin have been positive. The worst four-year HODL period was:
December 16th, 2017 to December 15th, 2021 a 155% return, representing a 22.2% CAGR
99.7 percentile* CAGR of 26.4%.
*periods above
What does that tell you? Think of Bitcoin from a long-term perspective, at least holding Bitcoin for four years. 'It’s like watching a super-long movie where the plot thickens and the suspense builds!'
➡️Bitcoin Miner Reserves Drop to 3-Year Low. The miner sell-off appears complete.
➡️Bitcoin exchange reserves have hit a five-year low.
➡️'Bitcoin's sustainable energy mix is 6% for the year (faster than any industry)
Over the same period, Bitcoin price 128%
I guess the rising Bitcoin price isn't boiling the oceans.' - Daniel Batten
➡️Metaplanet buys another ¥500 million worth of Bitcoin
On the 14th of August:
➡️Norges Bank, the Central Bank of Norway, owns over 1.1 MILLION shares of MicroStrategy stock.
➡️Goldman Sachs bought $418m Bitcoin ETFs in the last quarter. Goldman Sach’s latest 13F filing discloses owning:
- $238.6 million iShares Bitcoin Trust
- $79.5 million Fidelity Bitcoin ETF
- $35.1 million Grayscale BTC
- $56.1 million Invesco Galaxy Bitcoin
- $8.3 million Bitwise Bitcoin ETF
- $749,469 WisdomTree Bitcoin
- $299,900 ARK 21Shares Bitcoin ETF
For a total of $418 million in Bitcoin ETFs
➡️The Swiss Central Bank owns 514 Bitcoin through buying 466.000 MSTR shares.
➡️Marathon bought 4,144 BTC for $249M and now HODLs over 25,000 Bitcoin.
➡️ 'State of Wisconsin Investment Board bought another $14m Bitcoin through BlackRock's ETF.' -Bitcoin Archive
On the 15th of August:
➡️94% of the 21 million Bitcoin has now been mined.
Only 6% left to be mined over the next 116 years!
foto credit: Wicked
So global Bitcoin adoption is at ~0.10% and 94.00% of all coins have already been mined and you still think diminishing returns are likely? What happens when 99.9% of the world tries to buy the last 6.00% of Bitcoin?
➡️ Great rebuttal and excellent analysis by Daniel Batten:
Rebuttal of New IMF report on Bitcoin mining emissions
IMF report says "Carbon Emissions from AI and Crypto are surging" then goes on to a detailed report on how regulators should impose a "crypto carbon" tax.
Rebuttal:
Firstly, Bitcoin advocates everywhere should pause to reflect on the significance of this moment. With the scientific consensus (9 of the last 10 peer-reviewed articles) and mainstream journalism now concluding that Bitcoin mining has significant environmental benefits, those who stand to lose most from mainstream adoption of Bitcoin (IMF, Central Banks) need to resort to direct attack pieces.
Here's a breakdown of why the IMF report is at best poorly researched, and at worst propaganda.
https://x.com/DSBatten/status/1824129351371096516
It's helpful to have, the facts beyond the 'journalism' they offer. Please read the rebuttal.
➡️You can't make this up. The German Federal Office for Information Security shared a post on Linkedin calling hardware wallets the most secure way to store crypto-assets like Bitcoin. They also recommend creating backups and keeping them safe in multiple locations.
"Schon gewusst? Der Bitcoin-Wert geht dieses Jahr über 100.000 Euro!" - Okay, someone is bullish!
Didn't see this one coming. And why on earth did they, even though it's a different German government agency, sell 50.000 BTC below €100k/BTC, great logic! WAHNSINN!

➡️Apple opens iPhone Payment Chip to Third Parties for the first time making Bitcoin "Tap to Pay" possible!
➡️The world’s 3rd-largest public pension fund, South Korea’s NPS, has bought $34M in MicroStrategy shares.
➡️'65% of Bitcoin has not moved in over a year. This metric peaked at nearly 71% last November.' -Bitcoin News
On the 17th of August:
➡️Billionaire Peter Thiel tells Joe Rogan that Bitcoin is such a big deal that society does not know how to process and recognize it immediately, and it is on the same scale as the internet.
➡️I have said it before and I will say it again:
For all the people on Twitter or other platforms, stop bootlicking politicians, stop larping. You can’t say “Don’t trust, verify” AND trust politicians or go full fangirl.
RFKjr.: 'Join me for a fireside chat with Charles Hoskinson'.
Ask yourself...why he gave that speech in Nashville at the Bitcoin Conference and now endorses this (Cardano). One answer: votes!
➡️'Bitcoin wallet dormant since 2014 moves nearly 175 BTC for the first time in over a decade. The funds, which were valued at $151,970 in 2014, are now worth $10.2 million.' - Bitcoin News
➡️'Marathon a leading publicly traded Bitcoin mining company, recently expanded its Bitcoin holdings with a $249 million purchase, bringing the total to over 25,000 Bitcoins, valued at approximately $1.5 billion.
On August 12th, the company announced a $250 million convertible note offering, which was increased to $300 million due to strong demand.
Marathon used $249 million of the proceeds to acquire 4,144 additional Bitcoin at an average price of $59,500 per coin.' -BTCTimes
On the 18th of August:
➡️75% Of Bitcoin Hasn't Moved In Over 6 Months, Signaling Strong HODLing Trend
➡️ El Salvador mined 474 Bitcoin worth $29 million using volcano-fueled geothermal power.
➡️Welcome to the Lightning Network Bisq as Bisq v2.1 has been released!
Highlights include:
- Option to settle trades over the Lightning Network
- Refined chat experience including emoji reactions
- Know who's online with peer liveness indicators
## 💸Traditional Finance / Macro:
On the 15th of August:
👉🏽No news
🏦Banks:
👉🏽No news
## 🌎Macro/Geopolitics:
I want to start with this segment with the following quote and picture by James Lavish:
'With US Federal Debt powering right through $35 trillion and heading exponentially higher, we are at this phase of the fiat debt cycle.'
Now please connect the above quote with the following statement by Argentina President Javier Milei:
“If printing money would end poverty, printing diplomas would end stupidity.”
That is the best sentence I’ve heard lately!
On the 13th of August:
👉🏽Walker Amerika:
'Trump just said “We would have no inflation” if not for Biden. This is false.
I think it’s important to clarify that there *was* massive inflation during Trump’s administration.
From January 2017 to January 2021, the M2 money supply increased from ~$13.3 trillion to ~$19.4 trillion by January 2021.
That’s an INFLATION of ~$6.1 trillion, or ~45%.
There is a LAG between monetary inflation and general price increases throughout the economy, and price increases do not happen uniformly (look up the Cantillon Effect).
To clarify for the partisans out there: this is NOT an attempt to make excuses for Biden or to say that the monetary and fiscal policies under Biden are good; they are not good.
The point is that it is false to say “there was no inflation” under Trump.
Monetary inflation *is* inflation.'
Spot on! It doesn't matter who is President inflation will run wild. Every President will have to spend more than the one before him, because of 30 to 50 years of bad policy. You better own Bitcoin.
👉🏽'The US government deficit hit a massive $1.5 trillion in the first 10 months of FY 2024, according to the Treasury Department.
In July alone, the US deficit spending reached a whopping $244 billion.
Total outlays came in at $5.6 trillion and total receipts were $5.6 trillion over the last 10 months.
Social Security was the largest expenditure amounting to $1.2 trillion.
Net interest was the second largest cost, exceeding health, Medicare, and national defense expenses.
Government spending remains at crisis levels.' -TKL
UNSUSTAINABLE
👉🏽 In the last couple of weeks I have been reading for the second time the book: 'The Sovereign Individual'
The concept of the 'Rule of Law' is impossible nowadays. Globalization makes the 'Rule of Law' impossible.
A study demonstrates that.
'36% of multinational profits are shifted to tax havens every year. This reduces corporate tax revenue by >$200 billion (10% of global corporate tax receipts). Reallocation would increase domestic profits by 20% in high-tax EU countries, 10% in the US, and 5% in developing countries.' -Phillip Heimberger
Source: https://gabriel-zucman.eu/files/TWZ2022Restud.pdf
What is interesting about the article is that it is co-authored by a Danish minister of Finance and a UC Berkeley professor.
Anyway, read the book 'The Sovereign Individual.'
👉🏽The 3 years' lowest excess of cash in the financial system. Remember what happened in 2018/2019? This is likely a good setup for increased liquidity.
'The Fed’s Reverse Repo (RRP) facility has dropped below $300 billion for the first time since 2021.
The RRP is one of the financial system's excess liquidity metrics and is widely watched by investors.
Large banks, government-sponsored enterprises, and money-market funds put their extra cash into the facility to earn interest on it.
RRP usage has plummeted by $2.3 TRILLION since December 2022.
Over the last several months, however, the decline has stabilized and the facility usage has been oscillating around $300-$400 billion.' -TKL
👉🏽The UK sees the worst 1 month job losses since the COVID crash
UK unemployment is at 135K (forecast 14.5K, previous 32.3K) over 10x higher than expected.
You don't say?
Let's see what are the effects of unemployment.
"We find a strong relationship between increases in unemployment and voting for nonmainstream parties, especially populist ones. Moreover, unemployment increases in tandem with declining trust toward national and European political institutions."
[Source](https://www.brookings.edu/wp-content/uploads/2018/02/algantextfa17bpea.pdf)
Who would have ever thought?
Unemployment / left populism
Inmigration / Right populism
Now look at what is happening in Europe. Even the authors explore causality and find 'that crisis-driven economic insecurity is a substantial determine of populism and political distrust.'.
ERGO: Economic stress leads to political extremism
[](https://image.nostr.build/3902b94e3ff21d644e6eb80db0b60e37d57ba011c0b71573dfa59f32121835ba.png)
On the 14th of August:
👉🏽[](https://image.nostr.build/3cb2355df80046af9e5af23ef2732a4c1ba26f990462f5db34b91354edf02220.jpg)
As long as you remember China's emissions are for a large part due to the stuff we buy, the industry we outsourced there.
The EU and UK would rather manufacture climate hysteria and green policies that restrict growth and drive up energy prices than create an attractive capital market and innovation for techno solutions.
A lot of the manufacturing capacity needed to feed the EU consumers is located in China. I'd say Europeans are net importers regarding China, so if we measure by consumption, the proportions would likely be different. Territorial-based, China has slightly worse emissions than the EU. However, consumption-based, it's marginally better than the EU.
Now don't get me wrong. I do care about our climate & nature, but the truth without context is useless in discussing climate change and what we, the civilized people of the West (lmao), should do about it.
For example, deindustrializing Europe, especially Germany as the engine of Europe, for climate change is like throwing tomato soup at the Mona Lisa or gluing yourself on a highway --pointless!
Humanity always evolved forward by upgrading to more energy-dense, stable energy sources. It is the first time in history we actually regressed on that front, and maybe (personal opinion) it caused our climate issues.
Tackling climate change is nearly impossible within a debt-driven, inflationary economy. It promotes consumption over saving, and short-term profit over sustainability, and hinders so-called 'green' investments.
Fix the money, fix the world: Bitcoin.
👉🏽So last week I spoke about Thierry Breton (EU) and his terror on freedom of speech. Look what we have this week...
AIACT
[](https://image.nostr.build/5e89508a7286237ea0056ca014c93312843e55e4ee9dd41b85847151a1e4d973.jpg)
EU Commissioner brags about having AI regulation when they don't have a SINGLE MAJOR AI COMPANY.
Only a career bureaucrat could think of regulation as an achievement...
It's like celebrating a traffic law in a town with no cars. Who elected people like Thierry...NOBODY!
Yes, you could argue that it’s home (the EU) to ASML, the main supplier of NVDA. Without it, NVDA would not exist. So OK, maybe will have a few AI companies despite the regulation. But we won't be a leading sector.
👉🏽 Hackers have reportedly stolen the Social Security numbers of every American from National Public Data, according to the LA Times.
Records for nearly 2.9 billion people were reportedly stolen.
Most of the data was posted on an online marketplace. The group reportedly offered to sell the data on an online forum. The breach is expected to "power a raft of identity theft, fraud and other crimes." -TKL
👉🏽'Chinese Bank Loans fall for the first time in almost 20 years.' -Radar
'What This Means:
- Bank Loans Decrease: When bank loans fall, it means businesses and individuals are borrowing less money from banks. This could be due to various reasons, like reduced demand for borrowing, tighter lending standards, or economic uncertainty.
-Economic Implications: A decline in loans can signal a slowdown in economic activity. Loans are often used to fund business expansion, investments, and consumer spending. If these activities decline, it can slow down economic growth.
This event could signal a potential slowdown in the Chinese economy, which might impact global markets, depending on how the situation evolves. Investors and market participants will closely watch this development to gauge its broader implications.' -Chat GPT
👉🏽"The S&P index is pretty much going up 7% per year for 100 years, and the U.S. dollar currency supply is going up 7% per year for 100 years.
What you have is a basket of assets that are holding their value in real terms while they trend up in nominal terms.."
—Michael Saylor
[](https://image.nostr.build/95b645d5d046f17b75ef04d48d629d87bc6cef8307406a927fc4b336de9088df.jpg)
Remember, inflation is caused by central bank money printing and the relentless expansion of the money supply, not ‘greedy corporations and price gouging’.
Reagan: “We don't have inflation because the people are living too well. We have inflation because the government is living too well”
👉🏽 Just a rounding error: 'US job numbers have been revised lower by 778,000 jobs since February 2022, according to BlackRock.
This year alone, non-farm payrolls were revised down by 279,000 from January to June.
Furthermore, the US economy LOST 192,000 jobs in Q3 2023 and added 344,000 jobs in Q4 2023, according to the BED survey released by BLS.
On the other hand, nonfarm payroll data showed that the US labor market added 663,000 and 577,000 new jobs in Q3 and Q4 2023.
This is a jaw-dropping 1,088,000 difference in job count over just two quarters.
The labor market is weaker than the headlines make it seem.' -TKL
Now ask yourself how are they allowed to do this so blatantly. Why isn't the Media reporting on this? And they can't even get this straight why on earth do you believe that they have control & tell the truth on other topics....
Ask yourself. If overall inflation is up 6% and many things you buy way higher, what has gone down in price to bring the overall number down?
[](https://image.nostr.build/3095ec0f6199e72c76802b3b33d3eb4c877fe4a9704bb6119ae51099142203ff.jpg)
Fake Jobs
Fake Inflation
Fake GDP;
Oh well, just a thought.
On the 16th of August:
👉🏽The cooling towers of the last nuclear power plant in Germany were demolished today.
This is what economic self-destruction looks like. They shut that clean energy down to turn up brown coal. That’s why Germany's emissions are 7X more than France's per KW/hr. I have the feeling that this will go down in history as one of the most insane, self-destructive, and stupid energy decisions made in the Western world.
👉🏽Gold hits 2500 for the first time in history ahead of Kamala's central planning unveil that will usher in even more runaway inflation. Fueled by lower Dollar and lower US Treasury yields year-to-date, Gold is up 20.7%, setting the stage for its strongest annual performance since 2020 when it gained 25.1%.
👉🏽Again the ECB is absolutely getting drilled on Twitter by Dr. Jan Wüstenfeld and obviously he gets the silent treatment.
ECB: 'We’ve improved our environmental performance:
Better carbon footprint reporting
Increased biodiversity on our premises
Enhanced emissions calculations
Find out more, including how we’re reducing our operational footprint.'
Dr. Jan Wüstenfeld's reaction:
You can't effectively fight climate change in a debt-based, inflationary monetary system. The incentives are not aligned. You are part of the problem.
1) Inflation favours consumption over saving:
As money loses value over time, people are encouraged to spend or invest rather than save.
2) Debt in an inflationary monetary system:
Borrowing is attractive because future payments are easier, leading to more consumption, sometimes of unnecessary or unsustainable items.
3) Short-term focus:
Continuous economic growth is needed at all costs, often pushing aside long-term sustainability.
-> Companies prioritize short-term profits, leading to resource overuse and little focus on sustainability.
4) Climate impact:
The push for growth leads to excessive resource use, worsening environmental damage, and climate change.
-> Overconsumption
Immediate profit focus often delays investment in sustainable technologies.
-> Delayed green investment
Fix the money, fix the world! Bitcoin!
Please dear EBC you still only have one job. 'Inflationary money fuels wasteful behavior, wasteful behavior harms the environment.'
On the 18th of August:
👉🏽How bad is the US Federal debt situation?
'Net interest costs on US Federal debt as a % of GDP are set to reach almost 3 TIMES the share of defense spending in 2054.
Net interest is estimated to hit 6.3% of GDP while defense spending will be 2.3% of GDP by 2054.
By comparison, since 1973 net interest costs have averaged just 2.1% of GDP, just one-third the 2054 amount.
Meanwhile, nominal interest payments are projected to reach a MASSIVE $1.7 trillion in 2034, 2.6 times higher than the $658 billion recorded in 2024.
The debt crisis is an understatement.' -TKL
Milton Friedman said it best:
“Keep your eye on how much the Government is spending, because that is the true tax.
There is no such thing as an unbalanced budget. You PAY FOR IT either in the form of taxes or indirectly in the form of inflation or debt.”
🎁If you have made it this far I would like to give you a little gift:
Great podcast, What Bitcoin Did, on Protecting Your Bitcoin with Jameson Lopp. They discuss:
- Comprehensive Bitcoin security theory
- Physical attacks & threat defense
- Security implications of privacy vs obscurity
- The future of Bitcoin security
https://youtu.be/yCWJY8olZHU
Credit: I have used multiple sources!
My savings account: Bitcoin
The tool I recommend for setting up a Bitcoin savings plan: @Relai 🇨🇭 especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. (Please only use it till the 31st of October - after that full KYC)
Hence a DCA, Dollar cost Average Strategy. Check out my tutorial post (Instagram) & video (YouTube) for more info.⠀⠀⠀
⠀
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀
⠀⠀⠀⠀⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
Enjoy you week and see you next time!
Felipe - Bitcoin Friday
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# "House" dos economistas e o Estado
Falta um gênio pra produzir um seriado tipo House só que com economistas. O House do seriado seria um austríaco é o "everybody lies" seria uma premissa segundo a qual o Estado é sempre a causa de todos os problemas.
Situações bem cabeludas poderiam ser apresentadas de maneira que parecesse muito que a causa era ganância ou o mau-caratismo dos agentes, mas na investigação quase sempre se descobriria que a causa era o Estado.
Parece ridículo, mas se eu descrevesse House assim aqui também pareceria. A execução é que importa.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# notes on "Economic Action Beyond the Extent of the Market", Per Bylund
Source: <https://www.youtube.com/watch?v=7St6pCipCB0>
Markets work by dividing labour, but that's not as easy as it seems in the Adam Smith's example of a pin factory, because
1. a pin factory is not a market, so there is some guidance and orientation, some sort of central planning, inside there that a market doesn't have;
2. it is not clear how exactly the production process will be divided, it is not obvious as in "you cut the thread, I plug the head".
Dividing the labour may produce efficiency, but it also makes each independent worker in the process more fragile, as they become dependent on the others.
This is partially solved by having a lot of different workers, so you do not depend on only one.
If you have many, however, they must agree on where one part of the production process starts and where it ends, otherwise one's outputs will not necessarily coincide with other's inputs, and everything is more-or-less broken.
That means some level of standardization is needed. And indeed the market has constant incentives to standardization.
The statist economist discourse about standardization is that only when the government comes with a law that creates some sort of standardization then economic development can flourish, but in fact the market creates standardization all the time. Some examples of standardization include:
* programming languages, operating systems, internet protocols, CPU architectures;
* plates, forks, knifes, glasses, tables, chairs, beds, mattresses, bathrooms;
* building with concrete, brick and mortar;
* money;
* musical instruments;
* light bulbs;
* CD, DVD, VHS formats and others alike;
* services that go into every production process, like lunch services, restaurants, bakeries, cleaning services, security services, secretaries, attendants, porters;
* multipurpose steel bars;
* practically any tool that normal people use and require a little experience to get going, like a drilling machine or a sanding machine; etc.
Of course it is not that you find standardization in all places. Specially when the market is smaller or new, standardization may have not arrived.
There remains the truth, however, that division of labour has the potential of doing good.
More than that: every time there are more than one worker doing the same job in the same place of a division of labour chain, there's incentive to create a new subdivision of labour.
From the fact that there are at least more than one person doing the same job as another in our society we must conclude that someone must come up with an insight about an efficient way to divide the labour between these workers (and probably actually implement it), that hasn't happened for all kinds of jobs.
But to come up with division of labour outside of a factory, some market actors must come up with a way of dividing the labour, actually, determining where will one labour stop and other start (and that almost always needs some adjustments and in fact extra labour to hit the tips), and also these actors must bear the uncertainty and fragility that division of labour brings when there are not a lot of different workers and standardization and all that.
In fact, when an entrepreneur comes with a radical new service to the market, a service that does not fit in the current standard of division of labour, he must explain to his potential buyers what is the service and how the buyer can benefit from it and what he will have to do to adapt its current production process to bear with that new service. That's has happened not long ago with
* services that take food orders from the internet and relay these to the restaurants;
* hostels for cheap accommodation for young travellers;
* Uber, Airbnb, services that take orders and bring homemade food from homes to consumers and similars;
* all kinds of software-as-a-service;
* electronic monitoring service for power generators;
* mining planning and mining planning software; and many other industry-specific services.
## See also
* [Profits, not wages, as the originary factor](nostr:naddr1qqyrge3hxa3rqce4qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c7x67pu)
* [Per Bylund's insight](nostr:naddr1qqyxvdtzxscxzcenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cuq3unj)
-

@ 20986fb8:cdac21b3
2024-08-20 14:19:59
Welcome to YakiHonne, where we’re excited to introduce you to our innovative Smart Widgets! These interactive components allow you to create dynamic and engaging campaigns directly within social feeds, all without needing any coding skills. Whether you’re new to Smart Widgets or looking to refine your approach, this guide will walk you through the process.
### Step 1: Log In
Start by logging into your YakiHonne account. This is your gateway to creating and managing Smart Widgets. If you don’t have an account yet, sign up easily on our website.
### Step 2: Create Smart Widgets
Once you’re logged in, it’s time to get creative. Head over to the “Post” section and select “Smart Widget.” Here, you have two options:
**Option 1: Create from Scratch**
If you have a specific idea in mind, you can create your Smart Widget from a blank canvas:
• Click on “Create Blank Widget.”
• Begin designing by adding your unique content, interactive features, and any elements that match your campaign’s needs.
• Customize the appearance and functionality to fit your brand or message.
**Option 2: Choose a Template**
If you’re not sure where to start or want some inspiration, using a template is a great option:
• Select “Templates” from the options available.
• Browse through a variety of pre-designed templates.
• Choose one that fits your campaign’s goal, and customize it to make it your own.
**Option 3: Clone a Community Widget**
If you want to explore what others are doing, you can clone a widget shared by the community:
• Click on “Smart Widgets” to see what the community has shared.
• Browse through the community’s shared Smart Widgets.
• Find a widget you like, and click “Clone.”
• Modify the copied widget to create your unique Smart Widget.

### Step 3: Explore Smart Widgets Features
Your Smart Widgets can do much more than just display content. Let’s dive into the features you can integrate:
• User Engagement Tools: Add polls, surveys, or quizzes to interact with your audience.
• BitcoinFi Integration: Enable features that support Bitcoin transactions, like tipping or payment gateways.
• Governance Options: Incorporate voting systems to allow users to participate in decision-making processes.
• Product Growth: Use widgets to drive user growth through referral programs or viral marketing techniques.


These features are designed to enhance interaction and make your Smart Widget stand out. Feel free to experiment with different combinations to see what works best for your campaign.
### Step 4: Publish Your Smart Widgets
After you’ve created and customized your Smart Widget, it’s time to share it with the world:
• Preview your widget to ensure everything looks and works as intended.
• Click “Post my Smart Widget” to publish it.
• Your widget is now live and ready for others to interact with in their social feeds.

### Step 5: Add Smart Widgets to Notes
To maximize the impact of your Smart Widget, you can integrate it into your Notes:
• Go to the “Notes” section on your dashboard.
• Select “Add Smart Widget” and choose the widget you’ve just created.
• Publish the note, and now your audience can engage with your Smart Widget directly through the note.

### Tips for Success
* Experiment with Features: Don’t hesitate to try out different combinations of features to find what works best for your audience.
* Engage Your Audience: The more interactive and engaging your Smart Widget is, the better the results.
* Monitor Performance: After publishing, keep an eye on how your Smart Widget is performing. Adjust and optimize based on user feedback and engagement metrics.
### User Guideline Video Resources
[Create from Scratch](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y)
[Choose a Template](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y)
[Clone a Community Widget](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y)
[Full tutorial video ](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y)
### Conclusion
Creating and using Smart Widgets on YakiHonne is a powerful way to engage with your audience, promote your brand, and drive meaningful interactions. With no coding required, the possibilities are endless. Start exploring today, and see how Smart Widgets can take your campaigns to the next level!
Happy creating!
-

@ 6bae33c8:607272e8
2024-08-19 23:42:07
I posted my round by round draft targets yesterday, but have a few more thoughts that didn’t make it into that piece:
I’m warming up to Bijan Robinson with a top-three pick. This interview with Kay Adams (even though it’s just the usual talk) got my attention. Robinson is so relaxed, so even-keeled and yet he’s studying Christian McCaffrey’s every carry like a fanatic. Not that it’s going out on a thin limb as he routinely goes that early, but I had previously been wedded to taking a receiver (now that McCaffrey already has a calf injury.)
I said to Alan Seslowsky that Mike Williams was on my do-not-draft list because he’s so injury prone, but I double-checked and he hasn’t been that bad other than last year. Maybe I had him the year he did a lot early and then fell off steeply despite not missing many games. Maybe he was on the injury report a lot. I don’t know. But he’s actually not a bad value in Round 11 — he’s always been good when healthy, and the Jets are not deep.
I said yesterday I don’t have a strong preference in the first round, and the Robinson note aside, that’s still mostly true. I like all the receivers, and I’m fine with Breece Hall and Jonathan Taylor too. Of course, that doesn’t mean all of them will be fine — at least a couple almost surely will not — only that I can’t tell which ones. As important as it is to know your leans and act on them, it’s equally important to realize when you don’t have one and let ADP and positional need dictate your options.
I took Anthony Richardson in Beat Chris Liss 2, and while I don’t regret it as he really could be the QB1, I think the play in the Primetime will be to wait forever on QB and get some combo of Trevor Lawrence/Kurt Cousins/Justin Herbert/Matthew Stafford/Justin Fields, or even Daniel Jones. There’s just so much depth with upside. You could even take three QBs late.
The “hero” RB build (where you take a star RB in Rounds 1 or 2) and lots of receivers around them, before getting your RB2 candidates later is popular now, and you can see why. There aren’t that many top backs, so getting one is a big edge, and then you still catch up at receiver against all the teams that took a TE or top QB early. I just think this is mostly an on-paper exercise, and by mid-season the best teams usually have 4-5 surviving good players at all positions combined and have to cobble it to together with short-term fill-ins and waiver wire, i.e., build is overrated.
Both my drafts so far were from early (1 and 3), and I wouldn’t mind having one league from the back, getting Jonathan Taylor and say Puka Nacua. It would be cool to get Cooper Kupp in Round 3 too, but lately he’s moved up out of that range.
I stacked C.J. Stroud and Stefon Diggs in BCL1, but didn’t stack anyone in BCL2. Stacking is one of those things that’s great if no one else is doing it, but loses value the more it’s done. If you have Travis Kelce and Patrick Mahomes, but so do 25 percent of the Mahomes’ owners, is that really better than having Anthony Richardson and a random TE1 (in my case Brock Bowers). Sure there’s no correlation, but only 1 in 12 Richardson teams should be expected to have Bowers (even fewer if the Colts had a good TE as many would have paired them.) So yes, if Mahomes goes off, there’s a better chance he takes Kelce with him, but you still have to beat out 3x more teams with your same set up than I do if Richardson goes off, and Bowers happens to as well. Sure, the correlation makes your scenario more likely, but likely enough to compensate for its commonality?
-

@ 8a3a9236:374b9419
2024-08-19 15:07:59
## Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 2 (depends how hungry the bears are)
## Ingredients
- 1 pound boneless chicken (thighs or breast)
- 1 can Campbells Cream of Mushroom Soup
- half a can of heavy cream
- 6 ounces white rice
- garlic powder
- cayenne pepper
- onion powder
- salt & pepper
## Directions
1. Start by getting the rice going.
2. generously season chicken with salt and pepper
3. cook chicken
4. prepare sauce: mix cream of mushroom soup with heavy cream (i use 1/2 of the empty soup can to measure)
5. add generous portions of garlic powder and cayenne pepper. Add in some onion powder and salt and pepper as well. stir all these together on low/medium heat
6. once chicken is cooked, chop it up into tiny pieces. The chicken needs to be chopped up to give the sludge the proper consistency
7. add chicken to sludge (sauce) and stir so everything is well mixed.
8. finally, pour the chicken/sludge over the rice and mix all that together. ENJOY!
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# litepub
A Go library that abstracts all the burdensome ActivityPub things and provides just the right amount of helpers necessary to integrate an existing website into the "fediverse" (what an odious name). Made for the [gravity]() integration.
- <https://godoc.org/github.com/fiatjaf/litepub>
## See also
-
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Ripple and the problem of the decentralized commit
This is about [Ryan Fugger's Ripple](nostr:naddr1qqyxgenyxe3rzvf4qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c8pp8zu).
The summary is: unless everybody is good and well-connected at all times a transaction can always be left in a half-committed state, which creates confusion, erodes trust and benefits no one.
If you're unconvinced consider the following protocol flow:
1. A finds a route (A--B--C--D) between her and D somehow;
2. A "prepares" a payment to B, tells B to do the same with C and so on (to prepare means to give B a conditional IOU that will be valid as long as the full payment completes);
3. When the chain of prepared messages reaches D, D somehow "commits" the payment.
4. After the commit, A now _really does_ owe B and so on, and D _really_ knows it has been effectively paid by A (in the form of debt from C) so it can ship goods to A.
The most obvious (but wrong) way of structuring this would be for the entire payment chain to be dependent on the reveal of some secret. For example, the "prepare" messages could contain something like "I will pay you as long as you know `p` such that `sha256(p) == h`".
The payment flow then starts with D presenting A with an invoice that contains `h`, so D knows `p`, but no one else knows. A can then send the "prepare" message to B and B do the same until it reaches D.
When it reaches D, D can be sure that C will pay him because he knows `p` such that `sha256(p) == h`. He then reveals `p` to C, C now reveals it to B and B to A. When A gets it it has a proof that D has received his payment, therefore it is happy to settle it later with B and can prove to an external arbitrator that he has indeed paid D in case D doesn't deliver his products.
## Issues with the naïve flow above
### What if D never reveals `p` to C?
Then no one knows what happened. And then 10 years later he arrives at C's house (remember they are friends or have a trust relationship somehow) and demands his payment, and shows `p` to her in a piece of paper. Or worse: go directly to the court and shows C's message that says "I will pay you as long as you know `p` such that `sha256(p) == h`" (but with an actual number instead of "h") and the corresponding `p`. Now the judge has to decide in favor of D.
Now C was supposed to do the same with B, but C is not playing with this anymore, has lost all contact with B after they did their final settlement many years ago, no one was expecting this.
This clearly can't work. There must be a timeout for these payments.
### What if we have a timeout?
Now what if we say the payment expires in one hour. D cannot hold the payment hostage and reveal `p` after 10 years. It must either reveal it before the timeout or conditional IOU will be void. Solves everything!
Except no, now it's the time we reach the most dark void of the protocol, the flaw that sucks its life into the abyss: subjectivity and ambiguity.
The big issue is that we don't have an independent judge to assert, for example, that D has indeed "revealed" `p` to C in time. C must acknowledge that voluntarily. C could do it using messages over the internet, but these messages are not reliable. C is not reliable. Clocks are not synchronized. Also if we now require C to confirm it has received `p` from D then the "prepare" message means nothing, as for D now just knowing `p` is not enough to claim before an arbitrator that C owes her -- because, again, D also must prove it has shown `p` to C before the timeout, therefore it needs a new signed acknowledgement from C, or from some other party.
Let's see a few examples.
### Subjectivity and perverse incentives
D could send `p` to C, and C acknowledge it, but then when C goes to B and send it B will not acknowledge it, and claim it's past the time. Now C loses money.
Maybe C can not acknowledge it received anything from D before checking first with B? But B will have to check with A too! And it subverts the entire flow of the thing. And now A has a "proof of payment" (knowledge of `p`) without even having to acknowledge anything! In this case knowing `p` or not becomes meaningless as everybody knows `p` without acknowleding it to anyone else.
But even if A is honest and sends an "acknowledge" message to B, now B can just sit quiet and enjoy the credit it has just earned from A without ever acknowleding anything to C. It's perverted incentives in every step.
### Ambiguity
But isn't this a protocol based on trust?, you ask, isn't C trusting that B will behave honestly already? Therefore if B is dishonest C just has to acknowledge his loss and break his chain of trust with B.
No, because C will not know what happened. B can say "I could have sent you an acknowledgement, but was waiting for A, and A didn't send anything" and C won't ever know if that was true. Or B could say "what? You didn't send me `p` at all", and that could be true. B could have been offline when A sent it, there could have been a broken connection or many other things, and B continues: "I was waiting for you to present me with `p`, but you didn't, therefore the payment timed out, you can't come here with `p` now, because now A won't accept it anymore from me". That could be true or could be false, who knows?
Therefore it is impossible for trust relationships and reputations to be maintained in such a system without "good fences".[^ln-solution][^ln-issue]
[^ln-solution]: The [Lightning Network has a solution](nostr:naddr1qqyx2vekxg6rsvejqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ccs2twc) for the problem of the decentralized commit.
[^ln-issue]: Ironically this same ambiguity problem [is being faced by the Lightning Network community](https://lists.linuxfoundation.org/pipermail/lightning-dev/2020-October/002826.html) when trying to create a reputation/payment system to prevent routing abuses. It seems simple when you first think about it: "let each node manage its own trust", but in fact it is somewhat impossible.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Mises' interest rate theory
Inspired by [Bob Murphy's thesis](http://consultingbyrpm.com/uploads/Dissertation.pdf) against the "pure time preference theory" (see also this [series of podcasts](https://www.bobmurphyshow.com/episodes/ep-31-capital-and-interest-in-the-austrian-tradition-part-3-of-3/)) -- or blatantly copying it -- here are some thoughts on Mises' most wrong take:
* Mises asserts that the market rate of interest is _not_ the originary rate of interest, because the market rate involves entrepreneurial decisions, risk, uncertainty etc. No one lends money with 100% guarantee that it will be paid back in the market and so. But if that is true, where can we see that originary interest? We're supposed to account for its existence and be sure that it is logically there in every trade between present and future, because it's a _category of action_. But then it seems odd to me that it has anything to do with the actual interest.
* Mises criticizes the notion of "profit" from classical economists because it mashed together gains deriving from speculation, risk, other stuff and originary interest -- but that's only because he assumes originary interest as a given (because it's a category of action and so on). If he didn't he could have just not cited originary interest in the list of things that give rise to "profit" and all would be fine.
* Mixing the two points above, it seems very odd to think that we should look for interest as a component of profit. It seems indeed to be very classifical-economist take. It would be still compatible with Mises'sworldview -- indeed more compatible -- that we looked for profit as a component of interest: when someone lends some 100 and is paid 110 that is profit. Plain simple. Why he did that and why the other person paid isn't for the economist to analyse, or to dissect the extra 10 into 9 interest, 1 risk remuneration or anything like that. If the borrower hadn't paid it would be a 100 loss or a 109 loss?
* In other moments, Mises talks about the originary rate of interest being the same for all things: apples and bicycles and anything else. But wasn't each person supposed to have its own valuation of each good -- including goods in the present and in the future? Is Mises going to say that it's impossible for someone to value an orange in the future more than a bycicle in the future in comparison with these same goods in the present? (The very "more" in the previous sentence shows us that Mises was incurring in cardinal value calculations when coming up with this theory -- and I hadn't noticed it until after I finished typing the phrase.) In other words: what if someone prefers orange, bycicle, bycicle in the future, orange in the future? That doesn't seem to fit. What is the rate of interest?
* Also, on the point above, what if someone has different rates of interest for goods in different timeframes? For example, someone may prefer a bycicle now a little more than a bycicle tomorrow, but very very much more than a bycicle in two days. That also breaks the notion of "originary interest" as an universal rate.
* Now maybe I misunderstood everything, maybe Mises was talking about originary interest as a rate defined by the market. And he clearly says that. That if the rate of interest is bigger on some market entrepreneurs will invest capital in that one until it equalizes with rates in other markets. But all that fits better with the plain notion of profit than with this poorly-crafted notion of originary interest. If you're up to defining and (Mises forbid?) measuring the neutral rate of interest you'll have to arbitrarily choose some businesses to be part of the "market" while excluding others.
* By the way, wasn't originary interest a category of action? How can a category of action be defined and ultimately _fixed_ by entrepreneurial action in a market?
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Thafne venceu o Soletrando 2008.
As palavras que Thafne teve que soletrar: "ocioso", "hermético", "glossário", "argênteo", "morfossintaxe", "infra-hepático", "hagiológio". Enquanto isso Eder recebia: "intramuscular", "destilação", "inabitável", "subcutâneo", "homogeneidade", "predecessor", "displicência", "subconsciência", "psicroestesia" (isto segundo [o site da folha][0], donde certamente faltam algumas palavras de Thafne). Sério, "argênteo"? Não é errado dizer que a Globo tentou promover o menino pobre da escola pública do sertão contra a riquinha de Curitiba.
O mais espetacular disto é que deu errado e o Brasil inteiro torceu pela Thafne, o que se verifica com uma simples busca no Google. Eis aqui alguns exemplos:
* [O problema de Thafne][1] traz comentários tentando incriminar o governo do Estado de Minas Gerais com a vitória forçada de Eder.
* [este vídeo mostrando os erros do programa e a vitória triunfal, embora parcial, de Thafne,][2] traz a brilhante descrição "globo de puleira quis complicar a vida da menina!!!!!!!!!!!!!!!!!!!!!!"
* [este vídeo, com o mesmo conteúdo,][3], porém chamado "Thafne versus Luciano Huck, o confronto do século", tem, além disto, vários comentários de francos torcedores de Thafne:
* "Nossa isso é burrice porq o doutor falou duas vezes como o luciano não prestou atenção logo thafine deu duas patadas no luciano... Proxima luciano presta atenção na pronuncia"
* "ele nao pronunciou errado porque é burro, isso foi pra manipular o resultado"
* "Gabriel o Bostador ficou pianinho. Babaca do krl"
* "Pena que ela perdeu :("
* "verdade... ela que ganhou, o outro só ficou com o título :S"
* "A menina deu um banho nesse que além de idiota é BURRO."
* e muitos, muitos outros.
* [Globo Erra e Luciano Huck dá Vexame][4], um breve artigo descrevendo alguns dos pontos em que Eder foi favorecido.
* [esta comunidade do Orkut][5], apenas a maior dentre várias que foram criadas.
O movimento de apoio a Thafne é um exemplo entre poucos de união total da nação em prol de uma causa.
[0]: <http://www1.folha.uol.com.br/ilustrada/2008/05/407470-aluno-de-escola-publica-de-minas-vence-soletrando-huck-da-vexame.shtml>
[1]: <https://misenews.wordpress.com/2012/06/22/o-problema-de-thafne/>
[2]: <https://www.youtube.com/watch?v=lNW_QAiptsY>
[3]: <https://www.youtube.com/watch?v=Va8XxXgnY-c>
[4]: <https://www.putsgrilo.com.br/televisao/soletrando-globo-erra-e-luciano-huck-da-vexame/>
[5]: <http://orkut.google.com/c54999457.html>
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Democracy as a failed open-network protocol
In the context of protocols for peer-to-peer open computer networks -- those in which new actors can freely enter and immediately start participating in the protocol --, without any central entity, specially without any central human mind judging things from the top --, it's common for decisions about the protocol to be thought taking in consideration all the possible ways a rogue peer can disrupt the entire network, abuse it, make the experience terrible for others. The protocol design must account for all incentives in play and how they will affect each participant, always having in mind that each participant may be acting in a purely egoistical self-interested manner, not caring at all about the health of the network (even though most participants won't be like that). So a protocol, to be successful, must have incentives aligned such that self-interested actors cannot profit by hurting others and will gain most by cooperating (whatever that means in the envisaged context), or there must be a way for other peers to detect attacks and other kinds of harm or attempted harm and neutralize these.
Since computers are very fast, protocols can be designed to be executed many times per day by peers involved, and since the internet is a very open place to which people of various natures are connected, many open-network protocols with varied goals have been tried in large scale and most of them failed and were shut down (or kept existing, but offering a bad experience and in a much more limited scope than they were expected to be). Often the failure of a protocol leads to knowledge about its shortcomings being more-or-less widespread and agreed upon, and these lead to the development of a better protocol the next time something with similar goals is tried.
Ideally **democracies** are supposed to be an open-entry network in the same sense as these computer networks, and although that is a noble goal, it's one full of shortcomings. Democracies are supposed to the governing protocol of States that have the power to do basically anything with the lives of millions of citizens.
One simple inference we may take from the history of computer peer-to-peer protocols is that the ones that work better are those that are simple and small in scope (**Bitcoin**, for example, is very simple; **BitTorrent** is also very simple and very limited in what it tries to do and the number of participants that get involved in each run of the protocol).
Democracies, as we said above, are the opposite of that. Besides being in a very hard position to achieve success as an open protocol, democracies also suffer from the fact that they take a long time to run, so it's hard to see where it is failing every time.
The fundamental incentives of democracy, i.e. the rules of the protocol, posed by the separation of powers and checks-and-balances are basically the same in every place and in every epoch since the XIII century, and even today most people who dedicate their lives to the subject still don't see how [they're completely flawed](nostr:naddr1qqyrzc3nvenxxdpkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cjc4mf0).
The system of checks and balances was thought from the armchair of a couple of political theorists who had never done anything like that in their lives, didn't have any experience dealing with very adversarial environments like the internet -- and probably couldn't even imagine that the future users of their network were going to be creatures completely different than themselves and their fellow philosophers and aristocrats who all shared the same worldview (and how fast that future would come!).
## Also
* [The illusion of checks and balances](nostr:naddr1qqyrzc3nvenxxdpkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cjc4mf0)
-

@ ec09d831:42c80ce4
2024-08-21 17:27:14
## Nostr Nedir?
Nostr, “**N**otes and **O**ther **S**tuff **T**ransmitted by **R**elays” (Notlar ve Röle ile İletilen Diğer Şeyler) anlamına gelir. HTTP veya TCP-IP gibi, Nostr da bir “protokoldür”; herkesin üzerine bir şeyler inşa edebileceği açık bir standarttır. Nostr’ın kendisi kaydolduğunuz bir uygulama veya hizmet değildir. Nostr basitlik ve elverişlilik amacıyla tasarlanmıştır ve web üzerinde sansüre dirençli ve küresel olarak desentralize (dağıtık) yayıncılık ve iletişim imkânı sağlar. Bunu biraz açalım:
### Basitlik
Protokol, çok basit ve esnek olan “Event” nesnelerine (bunlar düz JSON formatında aktarılır) dayanır ve anahtarlar ve imzalama için standart açık anahtarlı kriptografi (public-key cryptography) kullanır. Bu, röleleri çalıştırmayı ve istemciler oluşturmayı kolaylaştırır ve protokolün zaman içinde genişletilebilmesini sağlar.
### Esneklik
Nostr, veri taşımak veya depolamak için tek bir yerde toplanmış az sayıdaki güvenilir sunucuya bağımlı olmadığından ötürü çok dayanıklıdır. Protokol, rölelerin kaybolacağını varsayar ve kullanıcıların zaman içinde değiştirebilecekleri rastgele sayıda röleye bağlanmasına ve yayın yapmasına olanak tanır. Bu esneklik gönderilerinizin üzerinde hiçbir kısıtlama ve sansür olmamasını da sağlar. Bir keresinde 15 bin harflik bir makaleyi bile görsel materyaller ve köprü linklerle süsleyerek paylaşabilmiştim.
### Doğrulanabilirlik
Nostr hesapları açık anahtar kriptografisine dayandığından, mesajların gerçekten söz konusu kullanıcı tarafından gönderildiğini doğrulamak kolaydır. Bu sayede bot ve troll kalabalığı da yoktur ve küçük bir ihtimal de olsa Nostr'a gelirlerse bunları ortadan kaldırmak gayet kolaydır.
### Anahtarları Anlamak
Her Nostr hesabı bir açık/özel anahtar (public/private key) çiftine dayanır. Bunu anlamanın basit bir yolu, açık anahtarınızın kullanıcı adınız ve özel anahtarınızın ise parolanız olduğunu düşünmektir. Parolaların aksine, özel anahtarınız kaybolduğunda sıfırlanamaz veya değiştirilemezlerdir. Anlaşılır olmak adına tekrar söyleyeyim: Özel anahtarınızı kaybederseniz Nostr hesabınız kaybolur. Başka bir kişi özel anahtarınıza erişim sağlarsa, hesabınızın kontrolünü ele geçirebilir. Özel anahtarınızı bir şifre yöneticisi (1Password’ü veya Brave Tarayıcı’yı öneririm) veya Alby gibi bir tarayıcı uzantısında güvenle sakladığınızdan emin olun.
### Protokol vs İstemci
Nostr’un kendisi sadece bir protokoldür, yani mesajları ve yayınları internet üzerinde dolaştırmak için üzerinde anlaşılmış bir prosedürdür; Facebook, Twitter, Instagram, YouTube gibi sansürcü, merkeziyetçi, spam ve reklam dolu boktan bir “platform” değildir. Bu yüzden Nostr’a (protokole) bir istemci aracılığıyla erişmeniz gerekir. Bu istemciler web, masaüstü veya mobil uygulamalar şeklinde olabilir. Bazı Nostr istemcileri özel anahtarınızı yapıştırarak oturum açmanıza izin verir. Web’de bu genellikle önerilmez, zira rahatsız edici ve güvensizdir. Bunun yerine, tarayıcınızda özel anahtarları güvenli bir şekilde yönetmek ve Event’leri kriptografik olarak imzalamak için özel olarak tasarlanmış bir yazılım parçası olan bir imzalama uzantısı kullanmanızı öneririm. Bu konuda Alby, Nostr için yerleşik desteğe sahip popüler bir imzalama uzantısı ve Bitcoin Lightning Network cüzdanıdır. Yeni kullanıcılar için harika bir seçenektir. Alby’nin kurulumunu aşağıda gerekli olduğu yerlerde istemciye özel kılavuzda ele alacağım.
İşte birkaç farklı istemci ve kullanılabildikleri işletim sistemleri:
[Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) (Android) [Benim favorim.]
[Primal](https://primal.net/) (Web, iOS, Android) [Mobil cihazlarda yerleşik Bitcoin Lightning Network cüzdanı ile kullanıcı dostu istemci.]
[Snort](https://snort.social/) (Web) [Temiz ve hızlı web istemcisi.]
[Coracle](https://coracle.social/) (Web) [Röle navigasyonuna odaklanan bir istemci.]
[Habla](https://habla.news/) (Web) [Kolay blog yaratımı.]
[Highlighter](https://highlighter.com/) (Web) [Blog yaratımı ve bloglarda gezerken işaretleme-alıntılama için uygun arayüze sahip istemci.]
[Iris](https://iris.to/) (Web) [Ücretsiz NIP-05 doğrulama sağlayan istemci.]
[Damus](https://damus.io/) (iOS) [Apple cihazlarına özel aplikasyon istemci.]
Amethyst Android istemcisi ile Nostr kullanmaya başlamak için adım adım kılavuz
#### Adım 1: Uygulama yükleme
* Android telefonların aplikasyon mağazası olan Google Play Store’dan Amethyst uygulamasını yükleyin: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst
* Uygulamayı açtığınızda, yeni bir hesap oluşturma veya daha önce oluşturduğunuz bir özel anahtarla giriş yapma seçeneğiniz olacaktır.
* Alby uzantısı veya başka bir istemci aracılığıyla zaten bir özel anahtar oluşturduysanız, kullanım koşullarını okuyup kabul edebilir, (npub/nsec) bilgilerinizi girebilir ve “Login” (Giriş Yap) düğmesine tıklayabilirsiniz.
* Eğer bunlar yoksa, “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın.
#### Adım 2: Yeni bir hesap oluşturma ve onun ayarlarını yapma
* “Terms of Use” (Kullanım Koşulları) bölümünü okuyun ve kutuyu işaretleyin.
* “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın.
* Tebrikler, az önce yeni bir Nostr kimliği oluşturdunuz!
* Ana ekrana yönlendirilecek ve “Feed is empty. Refresh” (Akış boş, yenileyin) mesajıyla karşılaşacaksınız, çünkü henüz başka bir hesabı takip etmiyorsunuz. Bunu daha sonra halledeceğiz.
* Son bir aşırı önemli adım kaldı. Özel anahtarınızı güvenli bir yerde saklamalısınız. Bunu yapmak için, şu anda profil resminiz olarak görünen sol üst köşedeki garip görünümlü robot simgesine tıklayın. Bir kenar çubuğu açılacaktır.
* “Backup Keys” (Yedek Anahtarlar) kısmına gidin ve “Copy my secret key” (Gizli anahtarımı kopyala) seçeneğine tıklayın.
* “Nsec” ibaresiyle başlayan gizli anahtarınız artık akıllı telefonunuzun panosundadır, bunu ÇOK güvenli bir yerde veya bir .txt uzantılı belgede yapıştırıp saklamak en iyisidir.
* Şimdi hesabınızı oluşturmaya devam edebilirsiniz. Ana ekranın sol üst köşesindeki profil resminize geri dönün ve “Profile” (Profil) bölümüne gidin. Buradan, “Follow” (Takip Et) seçeneğinin solundaki üç çizgi ve kalemin bulunduğu simgeye tıklayın. Profil ayarlarınızı buradan yapabilirsiniz.
* “Display Name” (Görüntülenecek Ad) bölümüne yazacağınız şey nick’iniz olacaktır.
* “About me” küçük bir biyografi bölümüdür ve harf sınırı yoktur.
* “Avatar URL” ve “Banner URL” kutularının içinde, solda görsel yükleme simgeleri vardır. Burada profil resminiz ve banner’ınız hakkında ne yapabileceğinizi bilirsiniz.
* “Nostr Address” ve “LN Address” kutuları için şöyle bir süreç işliyor: Eğer bir Alby hesabı edinebildiyseniz (şu an üye alımı sadece Alby geliştiricilerine getalby.com üzerinden yollanacak bir mektubun ardından gelebilecek davetiye kodu sayesinde mümkün) “@getalby.com” uzantılı adresinizi bu kutuların ikisini de yazmalısınızdır. Bu sayede hem hesabınızın size özgün ve gerçek olduğu (diğer bir deyişle, bot olmadığınız) anlaşılmış olur hem de gönderilerinize beğeni veya bağış maksatlı yollanan Bitcoin Satoshi’lerinin birikmesi için (ve sizin de başkalarına yollayabilmeniz, yani Zap yapabilmeniz için) bir Lightning Network sıcak cüzdanı adresi tesis etmiş olursunuz. Alby hesabı edinme konusunda -ki bence Alby çok önemli- yardımcı olmamı isterseniz iletişime geçmekten çekinmeyin.
* Tamamdır, hesabınız artık hazır, şimdi akışınızı dolduralım ve diğer insanları takip edelim: Sağ üst köşedeki büyüteç simgeli arama butonuna tıklayın ve tanıdığınız kişilerin hesaplarını arayın ya da sol alttaki ev simgesine tıklayarak gideceğiniz ana ekrandaki “All Follows” butonuna tıklayın ve “Global”i seçin. Şimdi bağlı rölelerinize gönderilen tüm notları göreceksinizdir. Eğer bunalmış hissediyorsanız, endişelenmeyin, zamanla burada yeni birçok ilginç Nostr kullanıcısı bulabileceksinizdir. Sadece bir deneyin.
#### Adım 3: Röleler ve Geniş Çaplı Erişim/Yayın
Yeni röleler ekleyerek erişiminizi ve görünürlüğünüzü artırabilirsiniz. Bunun için yapmanız gereken aşağıda listeleyeceğim röleleri hesabınıza entegre etmektir. Röle entegrasyonu için öncelikle sol üstteki profil resminize tıkladığınızda açılan menüde “Relays” bölümüne giriyorsunuz. Burada, en aşağıda “Add Relay” yazan kutucuğa oluşturduğum listedeki röle adreslerini tek tek girip “Add” butonuna tıklıyorsunuz. İstediğiniz kadar röle ekleyebilirsiniz, tamamen size kalmış. Bu iş bitince mutlaka sağ üstteki “Save” butonuna tıklayın.
Ayrıca kişisel bilgisayarınızdan Coracle adlı Nostr istemcisine girerek de rölelere kolaylıkla bağlanabilirsiniz. Tek yapmanız gereken Coracle’da Nostr hesabınıza Nsec anahtarınızla giriş yapmak ve sol kenar menüdeki “Relays” bölümünü açıp listelendiğini gördüğünüz her bir rölenin sağındaki “Join” butonuna tıklamaktır.
Röle listesi:
140.f7z.io
astral.ninja
bevo.nostr1.com
bitcoiner.social
brb.io
carnivore-diet-relay.denizenid.com
eu.purplerelay.com
expensive-relay.fiatjaf.com
feeds.nostr.band/popular
fiatjaf.com
n.wingu.se
nos.lol
nostr-pub.semisol.dev
nostr-relay.wlvs.space
nostr.21l.st
nostr.band
nostr.bitcoiner.social
nostr.blipme.app
nostr.kollider.xyz
nostr.liberty.fans
nostr.mutinywallet.com
nostr.orangepill.dev
nostr.pleb.network
nostr.plebchain.org
nostr.relayer.se
nostr.satoshi.fun
nostr.walletofsatoshi.com
nostr.yuv.al
nostr.zbd.gg
nostr.zebedee.cloud
nostr.zerofiat.world
nostr1.tunnelsats.com
nostream.denizenid.com
nostria.space
offchain.pub
purplepag.es
pyramid.fiatjaf.com
relay.0xchat.com
relay.benthecarman.com
relay.bitcoinpark.com
relay.current.fyi
relay.damus.io
relay.f7z.io
relay.geyser.fund
relay.mutinywallet.com
relay.nostr.band
relay.nostr.bg
relay.nostr.net
relay.nostr3.io
relay.nostrati.com
relay.nostrplebs.com
relay.orangepill.dev
relay.plebstr.com
relay.primal.net
relay.snort.band
relay.snort.social
relay.utxo.one
relayable.org
relayer.fiatjaf.com
satstacker.cloud
snort.social
soloco.nl
sound-money-relay.denizenid.com

**Önemli:** Özel anahtarınız yerel olarak (mobil cihazınızda veya bilgisayarlarınızda) saklanır ve Amethyst sunucuları veya Snort, Iris, Primal, Coracle gibi diğer tüm Nostr istemcileri tarafından hiçbir şekilde toplanmaz veya saklanmaz, zira Nostr’ın olayı budur, yani desentralizasyon protokolü.
Zamanla internetin kurtarıcısı olacak bu öze dönüş gücüne sahip sosyal ağda beni ve arkadaşlarımı takip etmeyi ve bizim takip ettiğimiz kişilerden kimleri bulabileceğinizi kurcalamayı unutmayın:
Kaan: nostr:npub1asyasvv6vhkuk44ttczsz2v0xvp3c6ze9xqrg9n97n6mkskgpnjqmdugs9
Satoshi Nakamoto Enstitüsü Türkiye: nostr:npub1fdv8r32dqehlkxfnq3uld67vq8t46jw5jvzkk0h6rl4hyvd8g76qf7ujf6
Ludwig von Mises Enstitüsü Türkiye: nostr:npub1gfytsf2p5kw2c42032fkt845x8gh00e027nwnn3pr5880yy954qq4wqlqm
Efe Bitcoin: nostr:npub193h05grv6ykgqc94memmlppqe2wlclukpfl8g5750w8gr3002zasl7ngwj
Şükrü Day: nostr:npub1gw3zhc5r5a7jfgl6yx8qv0nc9kset5ddkrka229c3tym5xltehlq58m7mm
Emir Yorulmaz: nostr:npub1mmfakwg4s36235wlav6qpe03cgr038gujn2hnsvwk2ne49gzqslqc6xvtp
Hasan Tahsin: nostr:npub19zc3ja6jme9ul84sfmgyf5z96a07m6x9dp2jngl5zhwryku9aynsy89q3u
Ufuk: nostr:npub19mz7c6jesdczvlumhpzqekqh9v93w0whup73mu3x2v6jv97lfujq79nqu3
Furkan Arda: nostr:npub1z43kexnw7wxd22ystexyhgf0s7lzsqzfaxv5xvlk9sgspkfzdyps039jv6
Kaancap: nostr:npub14t06hns8wmymynccmcer7sp6y3eql7pjyzwcp0u5rk88sv7vt2rqrl4wte
Yankı Guapmann: nostr:npub19z5m92x8jlltva7zj47z9ydxle8ddkw8y3k5e8xnrphu724v9lys5wxt3p
Arda Uludağ: nostr:npub1puclr9p6yhel2duzask9wfdah0ux5cppw22uz62c0w9cdj3nv0wseuvedh
Musab Babayiğit: nostr:npub1euf7xgdws7n62nwv03fhu82ak24xrka7hedathyuyq9hmhcjxs7sfvwjsn
Kadir: nostr:npub18589me8hqqmt5ect7hjz5k6d2srxzere0uc975gq7hldp9v3qpkslxjn7p
Çınar: nostr:npub12mwsgqaejk98xcsv8k7rf3yat2t2kzu0zzma6jp39rphqx5hajsq4khdeg
Nur Parrhesia: nostr:npub16nnuyfrxguumqdt8xerkkhtgjyxa7qyvfnz4r4ameanqp4aggarqm877qw
Ömer Agâh: nostr:npub1eeze28u72zfa8hl8kfkfnl4jwfe07zsrukug237rsjre7wnvzlrsl49u8h
Korporatist Mağduru: nostr:npub1337wmdvjtxrne5fxrqtc7re8rtj88wnnnsfg562jg39sx2k9p5lqwcjsfh
Alfred: nostr:npub1mdyegp38ahjcpje7ugzmt4ylugrk3hfmwm9tqq72jhdg3ykc4ahs8svgs8
Sefa Uzuner: nostr:npub1ce0khypkfrjxga6umfd82fhtg9xldm583mys4pkvg8zex20gls9s9qrrgj

-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Bolo
It seems that from 1987 to around 2000 there was a big community of people who played this game called ["Bolo"][wikipedia]. It was a game in which people controlled a tank and killed others while trying to capture bases in team matches. Always 2 teams, from 2 to 16 total players, games could last from 10 minutes to 12 hours. I'm still trying to understand all this.
The game looks silly from some [videos][videos] you can find today, but apparently it was very deep in strategy because people developed [strategy][strategy-guide] [guides][pillbox-guide] and [wrote][letter-1] [extensively][letter-2] about it and [Netscape even supported `bolo:` URLs][clickable-links] out of the box.
> The two most important elements on the map are pillboxes and bases. Pillboxes are originally neutral, meaning that they shoot at every tank that happens to get in its range. They shoot fast and with deadly accuracy. You can shoot the pillbox with your tank, and you can see how damaged it is by looking at it. Once the pillbox is subdued, you may run over it, which will pick it up. You may place the pillbox where you want to put it (where it is clear), if you've enough trees to build it back up.
> Trees are harvested by sending your man outside your tank to forest the trees. Your man (also called a builder) can also lay mines, build roads, and build walls. Once you have placed a pillbox, it will not shoot at you, but only your enemies. Therefore, pillboxes are often used to protect your bases.
That quote was taken from this ["augmented FAQ"][augmented-faq] written by some user. Apparently there were many FAQs for this game. A FAQ is after all just a simple, clear and direct to the point way of writing about anything, previously known as [summa][summa][^summa-k], it doesn't have to be related to any actually frequently asked question.
More unexpected Bolo writings include [an etiquette guide][etiquette], an [anthropology study][anthropology] and [some wonderings on the reverse pill war tactic][reverse-pill].
[videos]: https://www.youtube.com/results?search_query=winbolo
[wikipedia]: https://en.wikipedia.org/wiki/Bolo_(1987_video_game)
[clickable-links]: http://web.archive.org/web/19980214020327/http://boloweb.stanford.edu/BoloWeb.html
[faq]: https://web.archive.org/web/20070518233700/http://bishop.mc.duke.edu/bolo/guides/stuartfaq.html
[letter-1]: http://web.archive.org/web/19961214060949/http://rost.abo.fi/~gpappas/Bolo/News/mikael-bl.html
[letter-2]: http://web.archive.org/web/19961214060959/http://rost.abo.fi/~gpappas/Bolo/News/mikael-kev.html
[strategy-guide]: http://web.archive.org/web/19961214052754/http://rost.abo.fi/~gpappas/Bolo/guide.html
[etiquette]: http://web.archive.org/web/19961214052805/http://rost.abo.fi/~gpappas/Bolo/etiquette.html
[pillbox-guide]: http://web.archive.org/web/19961214052818/http://rost.abo.fi/~gpappas/Bolo/PBguide/pbguide1.html
[anthropology]: http://web.archive.org/web/19961214052830/http://rost.abo.fi/~gpappas/Bolo/anthropology.html
[reverse-pill]: http://web.archive.org/web/19990428023004/http://powered.cs.yale.edu:8000/%7Ebayliss/bolo.html
[augmented-faq]: http://web.archive.org/web/19970118071637/http://rost.abo.fi/~gpappas/Bolo/faq.html
[summa]: https://en.wikipedia.org/wiki/Summa
[^summa-k]: It's not the same thing, but I couldn't help but notice the similarity.
-

@ b0510a0c:12716ced
2024-08-21 06:03:43
# On April 24, 2012, Erik Voorhees changed everything about Bitcoin with the launch of Satoshi Dice:
a game that captivated users and intensified debates about Bitcoin's evolution and the network's ability to handle an increasing volume of transactions.
At that time, Satoshi Dice allowed thousands of players to bet on digital dice rolls, leading to a **MASSIVE** influx of transactions that filled the blocks of the blockchain.

## 📈 Success of Satoshi Dice:
Satoshi Dice achieved phenomenal success, attracting millions of users with its simplicity.
Players flocked in, bets piled up, and blocks filled up.

Erik Voorhees effectively leveraged Bitcoin's microtransactions, quickly saturating the blocks with these. This was a testament to the game's popularity, but also a source of tension within the community.
Within months, Satoshi Dice became the most popular service on the Bitcoin network, boosting its usage and virality.
Players appreciated the "provable fairness" aspect of the game, where they could verify the transparency and fairness of each bet.
## 🚫 Criticism and Controversy:
However, this success was not without criticism.
Many Bitcoin enthusiasts viewed the massive influx of transactions generated by the game unfavorably.
For them, these sometimes trivial transactions "spammed" the blockchain, clogging the blocks and increasing transaction fees for all users. Does this sound familiar?
The network, designed to handle about seven transactions per second, quickly reached its maximum capacity, causing validation delays and "high" fees.

## ⚔️ BlockSize Wars:
The BlockSize wars, which took place mainly between 2016 and 2017, were a technical and ideological conflict centered on block size and scalability solutions.
While Satoshi Dice was not the sole cause, the game significantly contributed to the emergence of this event by helping to popularize Bitcoin among new users and generating substantial transaction volume.
As Bitcoin adoption grew, the network faced intense pressure, leading to block saturation and rising transaction fees.
On one side, some advocated for increasing block size to allow more transactions, leading to the creation of Bitcoin Cash in August 2017. On the other, proponents of solutions like SegWit pushed for improvements without compromising decentralization.
## 🔧 Adoption of SegWit:
Erik Voorhees expressed his support for the SegWit2x proposal, which aimed to improve network scalability by combining the implementation of SegWit with an increase in block size.
Segregated Witness (SegWit) was adopted in August 2017, allowing transaction data to be separated from signatures. This reorganization not only increased transaction processing capacity but also paved the way for the development of the Lightning Network, a layer 2 solution enabling instant and low-cost transactions.
SegWit was a crucial response to the challenges posed by network congestion, which had been exacerbated by Bitcoin's growing adoption and the emergence of popular applications like Satoshi Dice.
## ⚡ SegWit and Lightning:
The adoption of SegWit helped resolve blockchain congestion issues, while the Lightning Network, a layer 2 solution, facilitated fast and low-cost transactions.
Together, these innovations not only addressed technical challenges but also renewed enthusiasm for games and other applications on Bitcoin, paving the way for a new wave of development.

## 🎲 Nostr Dice:
Today, as we reflect on the impact of Satoshi Dice, a new project emerges: nostr:npub1nstrdc6z4y9xadyj4z2zfecu6zt05uvlmd08ea0vchcvfrjvv7yq8lns84
This modern clone of the original game is built on Nostr, a decentralized communication protocol, and Lightning, paying homage to the past while offering an enhanced gaming experience that does not impact layer 1 congestion!
From a game that caused Bitcoin congestion to its rebirth on Lightning, which it helped to bring about, the circle is complete!

-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Lagoa Santa: como chegar -- partindo da rodoviária de Belo Horizonte
Ao descer de seu ônibus na rodoviária de Belo Horizonte às 4 e pouco da manhã, darás de frente para um caubói que toma cerveja em seus trajes típicos em um bar no setor mesmo de desembarque. Suba a escada à direita que dá no estacionamento da rodoviária. Vire à esquerda e caminhe por mais ou menos 400 metros, atravessando uma área onde pessoas suspeitas -- mas provavelmente dormindo em pé -- lhe observam, e então uma pracinha ocupada por um clã de mendigos. Ao avistar um enorme obelisco no meio de um cruzamento de duas avenidas, vire à esquerda e caminhe por mais 400 metros. Você verá uma enorme, antiga e bela estação com uma praça em frente, com belas fontes aqüáticas. Corra dali e dirija-se a um pedaço de rua à direita dessa praça. Um velho palco de antigos carnavais estará colocado mais ou menos no meio da simpática ruazinha de parelepípedos: é onde você pegará seu próximo ônibus.
Para entrar na estação é necessário ter um cartão com créditos recarregáveis. Um viajante prudente deixa sempre um pouco de créditos em seu cartão a fim de evitar filas e outros problemas de indisponibilidade quando chega cansado de viagem, com pressa ou em horários incomuns. Esse tipo de pessoa perceberá que foi totalmente ludibriado ao perceber que que os créditos do seu cartão, abastecido quando de sua última vinda a Belo Horizonte, há três meses, pereceram de prazo de validade e foram absorvidos pelos cofre públicos. Terá, portanto, que comprar mais créditos. O guichê onde os cartões são abastecidos abre às 5h, mas não se espante caso ele não tenha sido aberto ainda quando o primeiro ônibus chegar, às 5h10.
Com alguma sorte, um jovem de moletom, autorizado por dois ou três fiscais do sistema de ônibus que conversam alegremente, será o operador da catraca. Ele deixa entrar sem pagar os bêbados, os malandros, os pivetes. Bastante empático e perceptivo do desespero dos outros, esse bom rapaz provavelmente também lhe deixará entrar sem pagar.
Uma vez dentro do ônibus, não se intimide com os gritalhões e valentões que, ofendidíssimos com o motorista por ele ter parado nas estações, depois dos ônibus anteriores terem ignorado esses excelsos passageiros que nelas aguardavam, vão aos berros tirar satisfação.
O ponto final do ônibus, 40 minutos depois, é o terminal Morro Alto. Lá você verá, se procurar bem entre vários ônibus e pessoas que despertam a sua mais honesta suspeita, um veículo escuro, apagado, numerado **5882** e que abrigará em seu interior um motorista e um cobrador que descansam o sono dos justos.
Aguarde na porta por mais uns vinte minutos até que, repentinamente desperto, o motorista ligue o ônibus, abra as portas e já comece, de leve, a arrancar. Entre correndo, mas espere mais um tempo, enquanto as pessoas que têm o cartão carregado passem e peguem os melhores lugares, até que o cobrador acorde e resolva te cobrar a passagem nesse velho meio de pagamento, outrora o mais líqüído, o dinheiro.
Este último ônibus deverá levar-lhe, enfim, a Lagoa Santa.
-

@ 3c827db6:66418fc3
2024-08-17 02:50:05
Somebody, somewhere, at some point decided they would destroy the competition by creating a barrier to entry. They made the barrier high so they could feel safe. It is logical to put a fence around your property, and perfectly fine to do so. The problem is when you put a regulatory fence over something that means you are not allowing anyone else to have a property like this. Just to make the distinction clearer a fence around your house is creating a cost for other people to get in the yard. A license to be able to have a fence is creating a cost for anyone to protect their yard. The harder to attain and costlier the license is the more people can’t afford it. The more people who can’t afford it the bigger the divide between rich and poor. You can't have a fence because you can't have a license leaving your yard unprotected. The poor people are left unprotected and they get robbed easily, the rich are hard to get so they keep what they have. The more licenses/regulatory compliance someone has to comply with the more the costs for them are increased and the cycle of dividing is entrenched.
When constructing something physical, regulatory oversight is sensible to ensure structural integrity, particularly when people no longer build things for themselves. However, when it comes to more abstract concepts like licenses and credentials, possessing them doesn't guarantee success, and lacking them doesn't preclude doing excellent work. The whole point of the series is that the work should speak for itself and the people who did it should build their reputation based on their work history not on theory.
Let’s dive into a sector full of licenses for abstract things that keep people out and cornered the market. The betting industry.
The incentive structure in this scenario is problematic. Individuals with substantial financial resources that were gained illegally may seek friendly relationships with those responsible for issuing licenses. Obtaining a betting license now can serve as a means to launder money acquired unlawfully. Beyond mere laundering, they have a direct incentive to continue their illegal activities and a way to legitimize the funds. So they steal from the people who work and it gets even worse. Their scaling solution is to open the money laundering to other illegal actors.
A few parts of the economy are primed for these types of activities: the lottery, casinos, and sports betting.
Let’s start with the current lottery system and the “potential” exploits. Well, one person does something illegal and has stolen $1,000,000. Now he has a problem with how to legitimize the funds so he can spend it on things he wants. He goes to the owner of a lottery and says I will give you $200,000 if you give me an $800,000 winning ticket. Now 80% of the funds become legal. The person with the illegal funds buys $200,000 worth of tickets from which 1 of them is set up to win $800,000. Now all the funds have become legal. So the lottery company has a $200,000 income and $800,000 payout, seemingly paying out the winner with legitimate funds, but in reality, using the criminal's own money - correction, other people's stolen money. That is good for hiding taxes and the state is not getting anything, or is it?
The state gets its cut for every winning ticket by taxing all winners. Because of this income, they are incentivized to have more winners. This whole “hypothetical” system then is limited by how much money has to be laundered. More illegal money, more income for each side - the state, the illegal player, the lottery company. While they get the big winning tickets the public is left with the small prizes and they are robbed continuously for the next lottery "prizes". This tripod system demonstrates how one simple thing can be a continuous erosion of society. The lottery company does nothing to earn their money but they are incentivizing the illegal actors to continue doing illegal things. The State allowing licenses keeps competition out. The illegal actor closes the circle of his business.
The lottery should be something that is played without anyone having an advantage over anyone else. Including the company, there shouldn’t be a barrier for people creating all sorts of lottery games. The same model of behavior incentives is applicable for all the casinos. There is the same principle - some type of algorithm determines whether you win or not. But you can always approach the casino owner and apply the same logic to the casino. A player with illegal funds has to launder a million dollars again. In the first few hands, he wins a million dollars and keeps playing until incurs losses amounting to $200,000 and then stops. This way the casino loses $800,000 on its balance sheet but in reality, the illegal funds are distributed to the casino and the illegal actor.
In the sports betting industry, the barrier to entry is often determined by licenses, and companies typically act as custodians of the funds when users place bets. Additionally, these companies are responsible for providing betting odds, a task that incurs substantial costs when done accurately. Assessing various factors such as team performance, player injuries, and changes in management helps determine the odds. However, it's crucial to note that the odds provided by betting companies are designed to favor the company rather than the individuals placing bets. This inherent bias in odds contributes to the company's profit margin in the betting business.
### Exploring a free and ethical approach to lottery apps and innovative payout structures
The whole lottery system should be verifiable! The point of it is not to have yet another system where the poor are preyed upon. That is why the lottery app should be open-sourced. The bigger reason for the apps to be FOSS - I am reluctant to say how this particular app should be created because, on the one side, there are going to be regulatory people who want you to ask for approval, and on the other side there are betting companies that a percentage of them are involved in criminal activities. If you create an app that makes them obsolete you will find yourself being attacked legally, illegally, and anything in between. That is why the only option that I see for a small guy to not be a target is to create this app as a FOSS (free and open source software). This will create a problem for those entities because there is no target. It will have no barriers for others to create apps competing with the existing incentives. There was a big debate in my head about whether I should publish this article about this particular topic because of the ethically sticky situation. Also, I do not think that people should play with money and bet on stupid things. The main reason that I am doing this is that there should not be an incentive to do illegal activities but there should be a cost for it. Since the current system is incentivizing it, people should create the cost for them by making a free alternative (no licenses, or permissions from anyone) and with no risk for the players (non-custodial). Also, the cases that we will look at below as a payment structure are simply cool and unique that we have yet to experience anywhere. This will push even us at Breez to create and facilitate them if the need is there. Now let’s take a look at the potential solution and what I envision it could look like.
An algorithm can be designed where individuals purchase a virtual ticket, and once 100 participants acquire tickets, the entire pool is distributed among three randomly selected winners. The distribution comprises 50% for the first prize, 30% for the second, and 20% for the third. The concept of a physical ticket is eliminated; instead, participants contribute equal amounts of satoshis to a smart contract, which activates upon reaching the 100th participant. The executed contracts allocate 50% to the first-place winner, 30% to the second, and 20% to the third. No entity holds funds for others, and participants await the completion of the 100 spots to determine the three winners. You can do the lottery for more or fewer people. For different amounts of sats. With a different payout structure.
I envision a lottery game modeled after the hashing race in Bitcoin mining. Participants are required to guess a number between 1 and 1,000,000 by locking in 10 satoshis for each guess. If the guessed number is incorrect, that specific guess is eliminated from the potential answers, and the satoshis from all guesses contribute to the Jackpot for the correct number. The participant who correctly guesses the number receives the accumulated satoshis. The payout amount depends on the position of the correct guess, for example, if it occurs on the 10th try, the prize is 100 sats, and if on the 100,000th try, the prize is a million sats. Upon completion of the payout, the game resets, and participants can engage in the next round.
### Revolutionizing one-on-one Betting with trustless payouts
When I am with a friend, we can choose to place a bet on something--our favorite sports team, who can spit the furthest, or whether the sun will rise tomorrow. We are perfectly able to do so with cash, and we do not need a license from anyone to place those bets or determine the odds for us. There is only one problem that we have to handle when the results are in - the person who is losing the bet has to pay the winner. Because of this risk, you need a trusted third party that is unbiased to execute the payment when the results are known. Now you need a mitigation for the third-party risk--that they won't run away with the money. So you make a fourth party involved to determine who can have a license to be a trusted third party, and we are back to the current fiat operational model.
With instant settlement and smart contracts, we destroy all those problems.
* You do not need a license for trust because no one is holding money for anyone else.
* You do not need a trusted third party because you have a smart contract responsible for the execution of the payment when the results are known
* You do not need a third party to determine the odds because they are decided by the people and put in the smart contract
* You do not need to trust the person to pay when you win because he signed the execution of the payment when both of you placed the bet.
This structure for one-on-one betting is already implemented with a few games in the lightning space. One is from our friends at THNDR games and another is the Chain Duel. I like the infrastructure for the payment of the THNDR games because I am a sucker for non-custodial lightning. Custody for a second, a minute or a year is still custody.
What would a sports betting app look like that has a non-custodial instant settlement? There are a few easy settings to establish. First, there needs to be a deadline for placing bets before the sports event starts. Second, a timeframe must be set for the payout. In one-on-one betting, the payout structure is straightforward. Each side can wager any amount against the other, and if there is a disparity in the amounts, the odds are not 1:1. When the result is determined, the winning party has their funds unlocked without being sent, while the losing party has their contract executed, transferring the payment to the winner. THNDR is already implementing a similar concept called "clinch" which we are glad we had some input on, but I want to take it a few steps further.
### Exploring novel concepts in wagering -> community-to-community
What if there's a group of people on one side of the bet and another group on the opposing side? What does the payout look like, and how are the odds determined? Let's delve into a straightforward graph to better illustrate this example.
The graphs in the picture are the reference for the explanations below
The individuals on the left consist of only two people, but they wager a larger amount. On the right, there are four people, but their bets are smaller. If the left side wins, the two individuals will share the $1,000 bet placed by the opposing group. Since they bet equal amounts, each person will receive $500, reflecting a 50% stake for each. Conversely, if the right side wins, the stakes differ. Individuals 1 and 2 have a 25% stake, person 3 has a 40% stake, and person 4 has a 10% stake. Consequently, their respective payouts would be $500, $500, $800, and $200. That was a surprise even for me - there is a proof of stake system that I would be for. I realized that the staking is just not used in the proper context and that is why I have a problem with it. Proof of stake is deployed for bets and bets only. There is no such thing called staking your energy - that is called working. Now this system is not the shitcoin model - stake something and I guarantee you something more. Staking something means that going in you know (or you should know) that your stake could be lost. If someone is asking you to stake money and promising you more money you should ask yourself who is the loser that will pay the winner. If I am the winner, who is the loser? If we are all winners that means we all lost to inflation and the winner is the inflator. Stake = Bet.
The true stake system introduces a novel dimension to betting. While the primary goal is to win, participants might consider adding more funds to their community bet to avoid dilution. For instance, if I initially bet $10 alone, I would have a 100% payout potential. However, if someone else places a $10,000 bet on my side, my potential payout percentage drops to less than 0.1%. In such a scenario, I face two choices: increase my bet on my community's side for a better payout or place a bet on the opposing side, capitalizing on the changed odds for a potentially significant payout if I am wrong. This concept sheds light on the genuine meaning of hedging. You are hedging things that you BET on! Whether you call it an investment strategy or not you should now recognize that everything in the fiat system is using these terms but hiding the fact that it is gambling. For example, if you are a true investor you should do everything you can to make your investment work and realize that goal. Betting against yourself = hedge.
The community-to-community betting brings about more significant implications than current betting models. In this setup, the victorious community directly benefits, and if the bet is placed on a sports event, the winning team supports the winning community. The funds from the losing team's community are directly paid to the winning community and not to a betting company. This eliminates the intermediary role of any betting company. The people also are forced to do their research and assess which is a good bet and which is not - not that the majority do it. If they did it was going to be clear to all of us by now that all sh*tcoins are the fiat scam on a blockchain.
When there are three or more possible outcomes for a bet, multiple people or communities can bet on those outcomes, and all losing communities pay the winning community. In this scenario, individual participants receive payouts based on their respective stakes. For instance, in a bet involving predicting an exact score where no one bets on the correct score, there is no winner, and consequently, no actual losers. In such cases, participants simply have their sats unlocked without any winnings or losses.
We invest our energy in goals - make sure it is your goals and not someone else's. With money, we do 3 things only - earning, spending, or gambling!
People want to pay you money so you achieve their goals and stake your money so you can lose it to them. Be very aware of where you invest your energy and how you are using your bitcoin. I would like to repeat my statement from above one more time. The forces that are involved with these gambling companies are very powerful and I do not want to inspire someone and put a target on their back. I am doing this because of the utility of the payments and because this can be an open-sourced project that just competes with them. Satoshi set a standard for how to solve a monopoly - with FOSS. This will completely reshape the coordination between humans again with instant settlement payment. I do not like that I am promoting betting behavior because it is addictive and dangerous but I hope this puts a light on why all fiat behavior is gambling. The only proof of stake that matters is what is your stake in Bitcoin from the 21 million coins. Having a stake there is betting on humanity for the better.
Now be careful with this bet to make that app!
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Liquidificador
A fragilidade da comunicação humana fica clara quando alguém liga o liquidificador.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# An argument according to which fractional-reserve banking is merely theft and nothing else
Fractional-reserve banking isn't anything else besides transfer of money from the people at large to bankers.
It has been argued that fractional-reserve banking serves a purpose in making new funds available out of no one's pocket for lending and thus directing resources to productive borrowers. This financing method is preferrable to the more conservative way of borrowing funds directly from a saver and then using that to lend to others because it uses new money, money not tied to anyone else before, and thus it's cheaper and involves less friction.
Instead, what happens is that someone must at all times be the owner of each money. So when banks use their power of generating fractional-reserve funds, they are creating new money and they are the owners – at this point, a theft occurs from the public at large to them – and then they proceed to lend their own money. From this description it is clear that the fact that bank customers have previously deposited their own funds in the banks' vaults have no direct relation with the fact that banks created money afterwards, there's only a legal relation and the fact that banks may need cash deposited by its customers to redeem borrowers claims, but even that wouldn't be necessary if banks were allowed to print their own cash.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Thomas Kuhn sequer menciona o "método científico"
O que define uma ciência é o recorte de uma realidade a partir de um paradigma que todos os que entram no campo daquela ciência aceitam como verdade. Pronto.
O "método científico" não é nem necessário nem suficiente (apesar de que ele mesmo precisa pressupor uma série de axiomas para funcionar, do contrário a pessoa ficaria tendo que testar cada sílaba dos seus experimentos e cada um desses testes seria impossível de realizar pois eles necessariamente precisariam de outros conhecimentos prévios etc.).
Por isso
- a física teórica pode ser uma ciência embora não faça experimentos;
- e a economia pode ser uma ciência embora não faça experimentos (tá bom, existem pessoas que insistem em fazer "experimentos" em economia, mas que na verdade são só uma enorme perda de tempo baseada em estatísticas, mas isso não importa, até essas coisas podem ter algum valor desde que não se as entenda como sendo parte de um método científico);
- e a história pode ser uma ciência, por mais estranho que isso pareça, bastando apenas que o historiador junte fatos de antigamente tendo como pressuposto um paradigma, por exemplo, de que existe um sentido da história, ou sei lá (não acho que exista essa ciência da história hoje em dia, me parece que cada historiador está fazendo uma coisa diferente, sem muitos paradigmas além do bom senso);
- e a biologia pode ser uma ciência mesmo consistindo unicamente num longo esforço de classificação, e de fato é hoje, já que vê cada espécie e suas partes como frutos de um processo evolutivo cujas bases constituem um paradigma, e nega outras visões, como a teleologia.
- [Método científico](nostr:naddr1qqyr2wf3vgmx2dmrqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823chtnaca)
- [A estrutura paradigmática da ciência](nostr:naddr1qqyrzdfsxyuxye3cqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c4awxqq)
- [Um algoritmo imbecil da evolução](nostr:naddr1qqyryv35xsunwvfnqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c45a0t3)
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Drivechain comparison with Ethereum
Ethereum and other "smart contract platforms" capable of running turing-complete code and "developer-friendly" mindset and community have been running for years and they were able to produce a very low number of potentially useful "contracts".
What are these contracts, actually? (Considering Ethereum, but others are similar:) they are sidechains that run inside the Ethereum blockchain (and thus their verification and data storage are forced upon all Ethereum nodes). Users can peg-in to a contract by depositing money on it and peg-out by making a contract operation that sends money to a normal Ethereum address.
Now be generous and imagine these platforms are able to produce 3 really cool, useful ideas (out of many thousands of attempts): [Bitcoin](nostr:naddr1qqyryveexumnyd3kqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c7nywz4) can copy these, turn them into 3 different sidechains, each running fixed, specific, optimized code. Bitcoin users can now opt to use these platforms by transferring coins to it – all that without damaging the nodes or the consensus protocol that has been running for years, and without forcing anyone to be aware of these chains.
The process of turning a useful idea into a sidechain doesn't come spontaneously, and can't be done by a single company (like often happens in Ethereum-land), it must be acknowledge by a rough consensus in the Bitcoin community that that specific sidechain with that specific design is a desirable thing, and ultimately approved by miners, as they're the ones that are going to be in charge of that.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Lightning and its fake HTLCs
Lightning is terrible but can be very good with two tweaks.
## How Lightning would work without HTLCs
In a world in which HTLCs didn't exist, Lightning channels would consist only of balances. Each commitment transaction would have two outputs: one for peer `A`, the other for peer `B`, according to the current state of the channel.
When a payment was being attempted to go through the channel, peers would just trust each other to update the state when necessary. For example:
1. Channel `AB`'s balances are `A[10:10]B` (in sats);
2. `A` sends a 3sat payment through `B` to `C`;
3. `A` asks `B` to route the payment. Channel `AB` doesn't change at all;
4. `B` sends the payment to `C`, `C` accepts it;
5. Channel `BC` changes from `B[20:5]C` to `B[17:8]C`;
6. `B` notifies `A` the payment was successful, `A` acknowledges that;
7. Channel `AB` changes from `A[10:10]B` to `A[7:13]B`.
This in the case of a success, everything is fine, no glitches, no dishonesty.
But notice that `A` could have refused to acknowledge that the payment went through, either because of a bug, or because it went offline forever, or because it is malicious. Then the channel `AB` would stay as `A[10:10]B` and `B` would have lost 3 satoshis.
## How Lightning would work with HTLCs
HTLCs are introduced to remedy that situation. Now instead of commitment transactions having always only two outputs, one to each peer, now they can have HTLC outputs too. These HTLC outputs could go to either side dependending on the circumstance.
Specifically, the peer that is sending the payment can redeem the HTLC after a number of blocks have passed. The peer that is receiving the payment can redeem the HTLC if they are able to provide the preimage to the hash specified in the HTLC.
Now the flow is something like this:
1. Channel `AB`'s balances are `A[10:10]B`;
2. `A` sends a 3sat payment through `B` to `C`:
3. `A` asks `B` to route the payment. Their channel changes to `A[7:3:10]B` (the middle number is the HTLC).
4. `B` offers a payment to `C`. Their channel changes from `B[20:5]C` to `B[17:3:5]C`.
5. `C` tells `B` the preimage for that HTLC. Their channel changes from `B[17:3:5]C` to `B[17:8]C`.
6. `B` tells `A` the preimage for that HTLC. Their channel changes from `A[7:3:10]B` to `A[7:13]B`.
Now if `A` wants to trick `B` and stop responding `B` doesn't lose money, because `B` knows the preimage, `B` just needs to publish the commitment transaction `A[7:3:10]B`, which gives him 10sat and then redeem the HTLC using the preimage he got from `C`, which gives him 3 sats more. `B` is fine now.
In the same way, if `B` stops responding for any reason, `A` won't lose the money it put in that HTLC, it can publish the commitment transaction, get 7 back, then redeem the HTLC after the certain number of blocks have passed and get the other 3 sats back.
## How Lightning doesn't really work
The example above about how the HTLCs work is very elegant but has a fatal flaw on it: transaction fees. Each new HTLC added increases the size of the commitment transaction and it requires yet another transaction to be redeemed. If we consider fees of 10000 satoshis that means any HTLC below that is as if it didn't existed because we can't ever redeem it anyway. In fact the Lightning protocol explicitly dictates that if HTLC output amounts are below the fee necessary to redeem them they shouldn't be created.
What happens in these cases then? Nothing, the amounts that should be in HTLCs are moved to the commitment transaction miner fee instead.
So considering a transaction fee of 10000sat for these HTLCs if one is sending Lightning payments below 10000sat that means they operate according to the _unsafe protocol_ described in the first section above.
It is actually worse, because consider what happens in the case a channel in the middle of a route has a glitch or one of the peers is unresponsive. The other node, thinking they are operating in the _trustless protocol_, will proceed to publish the commitment transaction, i.e. close the channel, so they can redeem the HTLC -- only then they find out they are actually in the _unsafe protocol_ realm and there is no HTLC to be redeemed at all and they lose not only the money, but also the channel (which costed a lot of money to open and close, in overall transaction fees).
One of the biggest features of the _trustless protocol_ are the payment proofs. Every payment is identified by a hash and whenever the payee releases the preimage relative to that hash that means the payment was complete. The incentives are in place so all nodes in the path pass the preimage back until it reaches the payer, which can then use it as the proof he has sent the payment and the payee has received it. This feature is also lost in the _unsafe protocol_: if a glitch happens or someone goes offline on the preimage's way back then there is no way the preimage will reach the payer because no HTLCs are published and redeemed on the chain. The payee may have received the money but the payer will not know -- but the payee will lose the money sent anyway.
## The end of HTLCs
So considering the points above you may be sad because in some cases Lightning doesn't use these magic HTLCs that give meaning to it all. But the fact is that no matter what anyone thinks, HTLCs are destined to be used less and less as time passes.
The fact that over time Bitcoin transaction fees tend to rise, and also the fact that multipart payment (MPP) are increasedly being used on Lightning for good, we can expect that soon no HTLC will ever be big enough to be actually worth redeeming and we will be at a point in which not a single HTLC is real and they're all fake.
Another thing to note is that the current _unsafe protocol_ kicks out whenever the HTLC amount is below the Bitcoin transaction fee would be to redeem it, but this is not a reasonable algorithm. It is not reasonable to lose a channel and then pay 10000sat in fees to redeem a 10001sat HTLC. At which point does it become reasonable to do it? Probably in an amount many times above that, so it would be reasonable to even increase the threshold above which real HTLCs are made -- thus making their existence more and more rare.
These are good things, because we don't actually need HTLCs to make a functional Lightning Network.
## We must embrace the _unsafe protocol_ and make it better
So the _unsafe protocol_ is not necessarily very bad, but the way it is being done now is, because it suffers from two big problems:
1. Channels are lost all the time for no reason;
2. No guarantees of the proof-of-payment ever reaching the payer exist.
The first problem we fix by just stopping the current practice of closing channels when there are no real HTLCs in them.
That, however, creates a new problem -- or actually it exarcebates the second: now that we're not closing channels, what do we do with the expired payments in them? These payments should have either been canceled or fulfilled before some block x, now we're in block x+1, our peer has returned from its offline period and one of us will have to lose the money from that payment.
That's fine because it's only 3sat and it's better to just lose 3sat than to lose both the 3sat and the channel anyway, so either one would be happy to eat the loss. Maybe we'll even split it 50/50! No, that doesn't work, because it creates an attack vector with peers becoming unresponsive on purpose on one side of the route and actually failing/fulfilling the payment on the other side and making a profit with that.
So we actually need to know who is to blame on these payments, even if we are not going to act on that imediatelly: we need some kind of arbiter that both peers can trust, such that if one peer is trying to send the preimage or the cancellation to the other and the other is unresponsive, when the unresponsive peer comes back, the arbiter can tell them they are to blame, so they can willfully eat the loss and the channel can continue. Both peers are happy this way.
If the unresponsive peer doesn't accept what the arbiter says then the peer that was operating correctly can assume the unresponsive peer is malicious and close the channel, and then blacklist it and never again open a channel with a peer they know is malicious.
Again, the differences between this scheme and the current Lightning Network are that:
a. In the current Lightning we always close channels, in this scheme we only close channels in case someone is malicious or in other worst case scenarios (the arbiter is unresponsive, for example).
b. In the current Lightning we close the channels without having any clue on who is to blame for that, then we just proceed to reopen a channel with that same peer even in the case they were actively trying to harm us before.
## What is missing? An arbiter.
The Bitcoin blockchain is the ideal arbiter, it works in the best possible way if we follow the _trustless protocol_, but as we've seen we can't use the Bitcoin blockchain because it is expensive.
Therefore we need a new arbiter. That is the hard part, but not unsolvable. Notice that we don't need an absolutely perfect arbiter, anything is better than nothing, really, even an unreliable arbiter that is offline half of the day is better than what we have today, or an arbiter that lies, an arbiter that charges some satoshis for each resolution, anything.
Here are some suggestions:
- random nodes from the network selected by an algorithm that both peers agree to, so they can't cheat by selecting themselves. The only thing these nodes have to do is to store data from one peer, try to retransmit it to the other peer and record the results for some time.
- a set of nodes preselected by the two peers when the channel is being opened -- same as above, but with more handpicked-trust involved.
- some third-party cloud storage or notification provider with guarantees of having open data in it and some public log-keeping, like Twitter, GitHub or a [Nostr](https://github.com/fiatjaf/nostr) relay;
- peers that get paid to do the job, selected by the fact that they own some token (I know this is stepping too close to the shitcoin territory, but could be an idea) issued in a [Spacechain](https://www.youtube.com/watch?v=N2ow4Q34Jeg);
- a Spacechain itself, serving only as the storage for a bunch of `OP_RETURN`s that are published and tracked by these Lightning peers whenever there is an issue (this looks wrong, but could work).
## Key points
1. Lightning with HTLC-based routing was a cool idea, but it wasn't ever really feasible.
2. HTLCs are going to be abandoned and that's the natural course of things.
3. It is actually good that HTLCs are being abandoned, but
4. We must change the protocol to account for the existence of fake HTLCs and thus make the bulk of the Lightning Network usage viable again.
## See also
- [Ripple and the problem of the decentralized commit](nostr:naddr1qqyrxcmzxa3nxv34qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cjrqar6)
- [The Lightning Network solves the problem of the decentralized commit](nostr:naddr1qqyx2vekxg6rsvejqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ccs2twc)
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# contratos.alhur.es
A website that allowed people to fill a form and get a standard _Contrato de Locação_.
Better than all the other "templates" that float around the internet, which are badly formatted `.doc` files.
It was fully programmable so other templates could be added later, but I never did.
This website made maybe one dollar in Google Ads (and Google has probably stolen these like so many other dollars they did with their bizarre requirements).
- <https://github.com/fiatjaf/contratos>
- <http://contratos.alhur.es>
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Gold is not useless
If there's something all common people believe about gold is that it is useless[^1]. Austrian economists and libertarians in general that argue against central banks or defend a primitive gold standard are often charged with that accusation: that gold is useless, it has no use in the industry, it serves no purpose besides ornamental, so it is a silly commodity, a luxurious one, and that it would be almost immoral to have such a thing in a so central position in an economy such as the position of money.
I've seen libertarians in general argue such things as: "it is used in some dental operations", which means people make dental prosthesis of gold, something that fits in same category of jewelry, I would say.
There's also the argument of electronic connectors. That's something that appears to be true, but wouldn't suffice the anti-gold arguments. The fact remains that, besides its uses as money -- because gold is still considered to be a form money even now that it doesn't have that position formally in any country (otherwise it wouldn't be considered as an "investment" or "value store" everywhere) -- gold is used mainly for ornamental purposes[^2].
All that is a hassle for libertarians in general. Even the Mises Regression Theory wouldn't solve that problem of people skeptical of gold due to its immoral nature. That problem is solved once you read what is written in the chapter 17 from Richard Cantillon's _Essay on Economic Theory[^3]_ (page 103):
> Gold and silver are capable of serving not only the same purpose as tin and copper, but also most of the purposes of lead and iron. They have this further advantage over other metals in that they are not consumed by fire and are so durable that they may be considered permanent. It is not surprising, therefore, that the men who found the other metals useful, valued gold and silver even before they were used in exchange.
So gold is indeed useful. Everybody should already know that. You can even do forks and spoons with gold. You can do furniture with gold, and many other useful stuff. As soon as you grasp this, gold is useful again. It is an useful commodity.
Answering the next question becomes easy: why isn't anyone making gold forks anywhere? The questioner already knows the answer: because it is too expensive for that.
And now the Regression Theory comes with its full force: why is it expensive? Because it has gained a lot of value in the process of becoming money. The value of gold as money is much greater than as a metal used in fork production.
---
[^1]: see <http://www.salon.com/2014/02/02/ignore_sean_hannity_gold_is_useless_partner/> or all answers on <https://www.quora.com/Why-is-gold-considered-so-precious-and-why-does-it-have-such-high-prices>.
[^2]: this <https://en.wikipedia.org/wiki/Gold#Modern_applications> section on the Wikipedia page for gold is revealing.
[^3]: <https://mises.org/library/essay-economic-theory-0>
-

@ 8f69ac99:4f92f5fd
2024-08-16 16:12:36
O comunismo, tal como idealizado por Karl Marx e Friedrich Engels, prometia uma sociedade utópica, livre de divisões de classe, onde os recursos seriam partilhados de forma equitativa e o Estado acabaria por desaparecer. No entanto, apesar de várias tentativas de implementar esta ideologia em diferentes países, o sonho do "verdadeiro" comunismo nunca se concretizou. Uma das principais razões para esse fracasso reside no factor humano—um aspecto que Marx e Engels não consideraram completamente no seu quadro teórico. Além disso, a implementação de controlos de preços, frequentemente utilizada em economias comunistas e planificadas centralmente, tem repetidamente levado a consequências económicas não intencionais e frequentemente desastrosas. Este artigo explora os desafios inerentes à concretização do verdadeiro comunismo e o papel que os controlos de preços desempenham em minar os próprios objectivos que deveriam apoiar.
### A Visão do Verdadeiro Comunismo
**O Quadro Ideológico de Marx e Engels**
Karl Marx e Friedrich Engels, nas suas obras revolucionárias, como "O Manifesto Comunista" e "O Capital", lançaram as bases para o que se tornaria uma das ideologias mais influentes dos séculos XIX e XX: o comunismo. No seu cerne, o comunismo é uma crítica ao capitalismo, que Marx e Engels viam como um sistema intrinsecamente explorador, onde a burguesia (a classe capitalista) se enriquece ao extrair mais-valia do proletariado (a classe trabalhadora). A sua visão para o futuro era a de uma revolução que derrubasse as estruturas capitalistas, levando à criação de uma sociedade sem classes e sem Estado.
Nesta sociedade ideal, os meios de produção—fábricas, terras e recursos—seriam colectivamente detidos pelo povo. O motivo do lucro, que impulsiona o capitalismo, seria substituído pela produção para uso, garantindo que bens e serviços fossem distribuídos com base na necessidade, em vez da capacidade de pagar. O Estado, que Marx e Engels viam como um instrumento de opressão de classe, acabaria por "definhar" à medida que a necessidade de estruturas de poder coercitivo desaparecesse. Isto levaria a uma sociedade onde a igualdade, a cooperação e a propriedade comunal seriam a norma, e a exploração de uma classe por outra deixaria de existir.
Marx e Engels acreditavam que esta transição do capitalismo para o comunismo seria alcançada através de uma série de etapas. Inicialmente, a classe trabalhadora tomaria o poder político e estabeleceria uma "ditadura do proletariado", onde o Estado serviria para desmantelar o sistema capitalista e redistribuir riqueza e recursos. Com o tempo, à medida que os vestígios do capitalismo fossem eliminados e as distinções de classe dissolvidas, o próprio Estado se tornaria desnecessário e gradualmente desapareceria, deixando para trás uma sociedade verdadeiramente comunista.
Embora esta visão fosse revolucionária e tenha inspirado muitos movimentos em todo o mundo, ela baseava-se em várias suposições—particularmente em relação à natureza humana e às dinâmicas sociais—que se revelariam problemáticas na prática.
### O Factor Humano: O Que Marx e Engels Não Previram
Um dos erros críticos na teoria de Marx e Engels é a subestimação da complexidade do comportamento e das motivações humanas. A sua visão de uma sociedade harmoniosa e sem classes assume que, uma vez alterada a estrutura económica, a natureza humana se adaptaria em conformidade. No entanto, a realidade mostrou-se muito mais complicada.
Os seres humanos não são apenas actores económicos movidos por condições materiais. Eles também são motivados por ambições pessoais, desejos de poder e status, e pela necessidade de reconhecimento individual. Embora Marx e Engels reconhecessem o papel da luta de classes na formação da história, eles não consideraram plenamente o quão profundamente enraizadas estão as hierarquias sociais e as dinâmicas de poder, mesmo em sociedades que afirmam ter abolido as distinções de classe.
Em todas as tentativas de implementar o comunismo, novas elites surgiram, muitas vezes compostas por oficiais do partido e burocratas que detinham poder e privilégios significativos. Estas elites, longe de personificarem os ideais igualitários do comunismo, frequentemente perpetuaram as mesmas desigualdades que deveriam eliminar. A concentração de poder no Estado, que deveria ser uma medida temporária durante a transição do capitalismo, tornou-se entrincheirada e autoritária. Em vez de definhar, o Estado frequentemente cresceu em poder e opressão, à medida que aqueles no controle procuravam manter as suas posições.
Além disso, a abolição da propriedade privada, embora teoricamente destinada a eliminar a exploração, removeu muitos dos incentivos que impulsionam a inovação e a produtividade. Em economias comunistas, onde o emprego e as necessidades básicas eram garantidos independentemente do esforço individual, o absentismo, a ineficiência e a falta de motivação tornaram-se generalizados. O desejo humano de realização pessoal e recompensa, algo que Marx e Engels não abordaram completamente, desempenhou um papel significativo na estagnação económica que muitos sistemas comunistas experimentaram.
Outro aspecto crítico que Marx e Engels não previram é a importância da flexibilidade e adaptabilidade nos sistemas económicos. O planeamento económico centralizado, uma marca dos estados comunistas, frequentemente lutou para responder às mudanças nas condições económicas e nas exigências dos consumidores. Sem os mecanismos de feedback proporcionados pelos preços de mercado, os planificadores tiveram dificuldade em alocar recursos de forma eficiente. Esta rigidez levou a persistente escassez de bens, produtos de baixa qualidade e à incapacidade de satisfazer as necessidades da população—um cenário muito distante da abundância e igualdade prometidas pela ideologia comunista.
Em resumo, embora Marx e Engels tenham delineado uma visão convincente de uma sociedade livre da exploração e das desigualdades do capitalismo, subestimaram os desafios colocados pela natureza humana e pelas complexidades da organização social e económica. O factor humano—abrangendo as motivações individuais, a persistência das hierarquias sociais e a necessidade de sistemas económicos flexíveis e adaptáveis—tem consistentemente minado as tentativas de alcançar o "verdadeiro" comunismo. Esta falha tem sido uma razão fundamental pela qual o sonho de uma sociedade sem Estado e sem classes tem permanecido ilusório em todas as implementações reais da ideologia comunista.
## Tentativas Históricas de Comunismo
Ao longo do século XX, várias nações tentaram implementar o comunismo com base nos princípios marxistas. Esses esforços resultaram numa ampla gama de resultados económicos e sociais, mas nenhum conseguiu alcançar a sociedade sem classes e sem Estado idealizada por Marx e Engels.
**A União Soviética e a Europa de Leste**
A União Soviética foi a primeira e a maior tentativa de implementar o comunismo. Estabelecida na sequência da Revolução Bolchevique de 1917, o Estado soviético rapidamente adoptou o planeamento económico centralizado e nacionalizou indústrias. Sob o comando de Joseph Stalin, a URSS embarcou numa rápida industrialização, com realizações significativas na indústria pesada e no poder militar. O modelo soviético foi posteriormente exportado para a Europa de Leste após a Segunda Guerra Mundial, onde os estados satélites adoptaram sistemas de planeamento centralizado semelhantes.
Embora a União Soviética tenha inicialmente registado alguns sucessos, particularmente na transformação de uma sociedade predominantemente agrária numa potência industrial, essas conquistas tiveram um custo significativo. A natureza rígida e centralizada do planeamento económico soviético levou a ineficiências generalizadas. A ausência de sinais de mercado dificultou a alocação eficaz de recursos, resultando em escassez crónica de bens de consumo e produtos de baixa qualidade. O controlo de preços foi uma ferramenta chave no sistema soviético, destinado a manter os bens básicos acessíveis, mas muitas vezes resultou em mercados distorcidos e actividade no mercado negro.
Politicamente, o regime soviético tornou-se cada vez mais repressivo. A concentração de poder no Partido Comunista criou uma nova classe de elite composta por burocratas e funcionários, minando os ideais igualitários do comunismo. A dissidência foi severamente reprimida, e a falta de competição política fez com que o sistema fosse resistente a reformas, mesmo perante problemas económicos crescentes. Na década de 1980, a economia soviética estava em estagnação, e as tentativas de reforma, como a Perestroika de Mikhail Gorbachev, chegaram tarde demais para salvar o regime. Em 1991, a União Soviética colapsou, e os seus estados satélites na Europa de Leste rapidamente abandonaram o comunismo em favor de reformas orientadas para o mercado.
**China e Vietname: Reformas de Mercado e Capitalismo de Estado**
A China apresenta um caso único na história do comunismo. Após o Partido Comunista chegar ao poder em 1949, a China inicialmente seguiu o modelo soviético de planeamento centralizado e controlo estatal da economia. No entanto, esta abordagem levou a resultados desastrosos, sendo o mais notável o Grande Salto em Frente, que resultou numa fome generalizada e na morte de milhões de pessoas. Reconhecendo a necessidade de mudança, a liderança chinesa, sob Deng Xiaoping, iniciou uma série de reformas de mercado no final da década de 1970 que transformaram profundamente a economia.
Essas reformas, frequentemente chamadas de "socialismo com características chinesas", introduziram mecanismos de mercado e permitiram a iniciativa privada, mantendo, no entanto, o controlo político do Partido Comunista. A economia da China experimentou um crescimento sem precedentes, com uma média de quase 10% de crescimento anual do PIB durante várias décadas. No entanto, esse sucesso foi alcançado à custa do abandono de muitos dos princípios fundamentais do marxismo. O sistema da China é melhor descrito como "capitalismo de estado", onde o estado mantém o controlo sobre indústrias-chave, mas as forças de mercado desempenham um papel significativo na economia mais ampla.
O Vietname seguiu um caminho semelhante. Após a Guerra do Vietname e a reunificação do país sob o domínio comunista, o Vietname inicialmente seguiu uma economia planeada centralmente. No entanto, como a China, também enfrentou dificuldades económicas, o que levou à introdução de reformas orientadas para o mercado na década de 1980, conhecidas como Đổi Mới. Essas reformas impulsionaram um rápido crescimento económico e tiraram milhões da pobreza, mas também marcaram um afastamento da ideologia comunista tradicional.
Tanto a China como o Vietname demonstram que o sucesso económico sob um governo comunista é possível quando os mecanismos de mercado são introduzidos. No entanto, esse sucesso representa uma desvio significativo da visão comunista original, destacando os desafios de alcançar o verdadeiro comunismo na prática.
**Cuba: Um Legado Misto**
A experiência comunista de Cuba oferece uma perspectiva diferente, focando-se mais em realizações sociais do que no sucesso económico. Desde a Revolução Cubana de 1959, o país tem mantido um governo comunista sob a liderança de Fidel Castro e seus sucessores. A economia de Cuba tem sido longamente caracterizada pelo planeamento centralizado e controlo estatal, com o controlo de preços desempenhando um papel significativo em manter os bens básicos acessíveis.
Apesar das suas dificuldades económicas, Cuba fez progressos notáveis em áreas como a saúde e a educação. O sistema de saúde do país, em particular, é frequentemente elogiado pela sua acessibilidade e resultados, com uma expectativa de vida e taxas de mortalidade infantil comparáveis às de nações muito mais ricas. A educação é outra área onde Cuba se destacou, alcançando altas taxas de alfabetização e amplo acesso à escolarização.
No entanto, esses sucessos sociais tiveram um custo de estagnação económica. Cuba classifica-se baixo em liberdade económica em comparação com outros países das Américas, e a sua economia tem sido marcada por escassez persistente de bens básicos, em parte devido aos controlos de preços que distorcem a dinâmica do mercado. O país também dependeu fortemente de apoio externo, particularmente de petróleo subsidiado de aliados como a União Soviética e, mais tarde, a Venezuela. À medida que esses apoios externos diminuíram, as dificuldades económicas de Cuba aprofundaram-se.
Politicamente, Cuba manteve um estado unipartidário, com pouca tolerância para a dissidência. Como outros estados comunistas, viu a emergência de uma nova classe de elite, com funcionários do partido e líderes militares a usufruírem de privilégios não disponíveis aos cidadãos comuns. Embora as conquistas sociais de Cuba sejam significativas, não foram suficientes para superar os desafios económicos inerentes ao seu sistema.
Ao examinar as tentativas históricas de comunismo, torna-se claro que, embora alguns estados comunistas tenham alcançado sucessos notáveis — seja na industrialização, nos serviços sociais ou no crescimento económico —, nenhum conseguiu criar a sociedade sem classes e sem Estado idealizada por Marx e Engels. O factor humano, as ineficiências económicas e as consequências não intencionais de políticas como os controlos de preços minaram consistentemente esses esforços. Seja através do colapso da União Soviética, das reformas de mercado na China e no Vietname, ou das lutas contínuas em Cuba, a história do comunismo é marcada pela tensão entre a ideologia e a realidade.
## O Impacto Económico do Controle de Preços
Os controles de preços, frequentemente implementados em economias comunistas e planeadas centralmente, são ferramentas usadas pelos governos para regular os preços de bens e serviços essenciais. Embora estes controles sejam normalmente introduzidos com a intenção de proteger os consumidores, garantir a acessibilidade e manter a equidade social, eles frequentemente levam a distorções económicas significativas. Em sistemas comunistas, onde o controlo estatal sobre a economia é primordial, os controles de preços têm sido uma característica central da política económica. No entanto, as consequências desses controles têm sido muitas vezes prejudiciais, resultando em ineficiências de mercado, redução da inovação e encargos sociais e fiscais não intencionais.
**Distorções na Oferta e na Procura**
Uma das consequências económicas mais significativas dos controles de preços é a interrupção do equilíbrio natural entre a oferta e a procura. Em sistemas comunistas, os tectos de preços (preços máximos) são frequentemente estabelecidos em bens essenciais para garantir a acessibilidade. No entanto, quando os preços são mantidos artificialmente baixos, a procura normalmente excede a oferta, levando a escassez crónica. Este era um fenómeno comum na União Soviética, onde bens de consumo básicos como alimentos, vestuário e itens domésticos eram frequentemente escassos. A falta de sinais de mercado, como o aumento dos preços para indicar uma maior procura, impedia a alocação eficiente de recursos, exacerbando as carências.
Por outro lado, os "pisos" de preços (preços mínimos) podem levar a excedentes. Nos sectores agrícolas, por exemplo, a fixação de preços acima do nível de equilíbrio de mercado pode resultar em superprodução. Isto leva ao desperdício de recursos e ineficiências, pois o governo deve ou comprar o excesso de oferta ou deixá-lo desperdiçar. Estas distorções ilustram o desafio fundamental do planeamento central: sem os mecanismos autorreguladores de um mercado livre, as economias têm dificuldades em equilibrar eficazmente a produção com o consumo.
**Redução do Investimento e da Inovação**
Os controles de preços também podem ter um efeito desmotivador sobre o investimento e a inovação. Quando os governos impõem tectos de preços, eles frequentemente reduzem as margens de lucro para os produtores. Em economias comunistas, onde o Estado controla a maior parte da produção, isso pode desencorajar o investimento interno e a actividade empresarial. A ausência de incentivos baseados no mercado para a inovação leva à estagnação, pois há pouca motivação para melhorar a eficiência ou desenvolver novos produtos.
Esta falta de inovação era evidente na União Soviética e em outras economias planeadas centralmente, onde os avanços tecnológicos ficaram atrás dos países capitalistas. As indústrias que eram fortemente controladas por preços, como bens de consumo e produtos farmacêuticos, sofreram com baixa produtividade e tecnologia desactualizada. Em sectores como o farmacêutico, os controles de preços reduziram os incentivos para a investigação e desenvolvimento, potencialmente limitando futuras inovações médicas. O efeito a longo prazo desta redução do investimento é o menor crescimento económico e a diminuição da competitividade no cenário global.
**Deterioração da Qualidade**
Outra consequência dos controles de preços é a deterioração da qualidade. Quando os preços são estabelecidos demasiado baixos, os produtores frequentemente procuram maneiras de cortar custos para manter a rentabilidade. Isto resulta frequentemente em bens e serviços de menor qualidade. Em economias comunistas, onde a escolha do consumidor é limitada e a concorrência é suprimida, há pouca pressão sobre os produtores para manter altos padrões. O resultado é que os consumidores ficam com produtos inferiores, deteriorando ainda mais o padrão de vida.
Por exemplo, na União Soviética, o foco na quantidade em detrimento da qualidade na fabricação levou a produtos mal feitos que muitas vezes não atendiam às necessidades dos consumidores. Em sectores como a habitação, os controles de rendas mantinham os preços baixos, mas a qualidade do parque habitacional deteriorava-se, uma vez que havia pouco incentivo para a manutenção ou melhoria. Esta troca entre preços baixos e baixa qualidade destaca uma das falhas principais dos controles de preços na prática.
**Mercados Negros e Economias Informais**
As ineficiências criadas pelos controles de preços frequentemente levam ao surgimento de mercados negros, onde os bens são vendidos a preços superiores aos níveis estabelecidos pelo governo. Em economias comunistas, onde as carências são comuns, os mercados negros tornam-se um mecanismo crucial para obter bens escassos. Estes mercados ilegais minam o controlo do governo sobre a economia e criam uma economia paralela que opera fora do sistema oficial.
Na União Soviética e na Europa Oriental, os mercados negros prosperavam à medida que os consumidores procuravam aceder a bens que estavam indisponíveis ou eram de baixa qualidade nas lojas estatais. A existência destes mercados também destaca o fracasso dos controles de preços em atingir os seus objectivos pretendidos, pois as mesmas pessoas que deveriam beneficiar de preços baixos acabavam por pagar preços muito mais altos no sector informal.
**Racionamento e Filas**
Quando os controles de preços levam à escassez, os governos muitas vezes recorrem a sistemas de racionamento para distribuir os suprimentos limitados. O racionamento, embora assegure que todos recebam uma parte dos bens escassos, também introduz ineficiências e iniquidades. Filas longas para necessidades básicas tornaram-se uma visão comum em muitos países comunistas, com pessoas a gastar horas à espera de itens que frequentemente estavam em falta.
Este sistema não só desperdiçava tempo valioso, como também evidenciava as falhas do planeamento central. O racionamento e as filas são uma consequência directa dos controles de preços que impedem os mercados de se ajustarem naturalmente. Em vez de permitir que os preços subam e incentivem o aumento da produção, os governos mantêm preços artificialmente baixos, resultando em escassez crónica e frustração generalizada entre a população.
**Encargo Fiscal e Consequências Sociais**
Manter controles de preços frequentemente requer uma intervenção governamental significativa, incluindo subsídios aos produtores para compensar os custos dos preços baixos. Isto cria um encargo fiscal que pode sobrecarregar os orçamentos governamentais, especialmente em economias que já enfrentam ineficiências. Em alguns casos, o custo de manter os controles de preços pode superar os benefícios, levando a políticas económicas insustentáveis.
Além disso, os controles de preços podem levar a consequências sociais não intencionais. Embora sejam destinados a ajudar as populações mais vulneráveis, eles podem, por vezes, beneficiar aqueles que não precisam de assistência. Por exemplo, os controles de rendas destinados a proporcionar habitação acessível podem acabar por beneficiar indivíduos mais ricos que têm acesso a apartamentos com rendas controladas, enquanto os indivíduos de baixos rendimentos continuam a enfrentar dificuldades com a acessibilidade habitacional.
Além disso, os controles de preços podem empurrar a actividade económica para o sector informal, reduzindo as receitas fiscais e a supervisão regulatória. Esta informalidade enfraquece a capacidade do Estado de gerir a economia de forma eficaz e cria distorções adicionais.
**Crescimento Económico a Longo Prazo e Impactos Específicos por Sector**
A longo prazo, as distorções causadas pelos controles de preços podem levar a uma redução do crescimento económico. Ao interferir nos sinais de mercado, os controles de preços desencorajam o investimento, a inovação e a produtividade, todos essenciais para o desenvolvimento económico sustentado. Ao longo do tempo, isso pode resultar em estagnação, como visto em muitas economias comunistas onde o crescimento abrandou ou até mesmo retrocedeu.
Sectores específicos, como o farmacêutico e o agrícola, podem ser particularmente afectados pelos controles de preços. No sector farmacêutico, por exemplo, os tectos de preços podem reduzir o incentivo para as empresas investirem em investigação e desenvolvimento, potencialmente limitando futuras inovações médicas. Na agricultura, os pisos de preços podem levar à superprodução, desperdício e à necessidade de intervenções governamentais onerosas.
**Os Benefícios a Curto Prazo e Potenciais Justificativas**
Embora os controles de preços sejam geralmente vistos de forma negativa devido às suas consequências a longo prazo, podem haver alguns benefícios a curto prazo, especialmente em tempos de crise. Por exemplo, durante emergências, os controles de preços podem impedir a exploração de preços e garantir que bens essenciais permaneçam acessíveis às populações vulneráveis. Nestes casos, os controles de preços podem fornecer alívio temporário e proteger os consumidores de abusos.
No entanto, esses benefícios a curto prazo são muitas vezes superados pelos custos a longo prazo. Mesmo em situações de crise, os efeitos distorcionários dos controles de preços podem criar mais problemas do que resolvem, tornando-os uma ferramenta que deve ser usada com cautela.
Os controles de preços, embora destinados a proteger os consumidores e promover a equidade social, frequentemente levam a consequências económicas, de mercado e sociais não intencionais. Em sistemas comunistas, onde o controlo estatal sobre a economia é central, estes controles exacerbaram ineficiências, sufocaram a inovação e criaram uma série de resultados negativos, desde mercados negros até encargos fiscais. Embora possa haver situações onde os controles de preços sejam justificados a curto prazo, o seu impacto a longo prazo é geralmente prejudicial, minando os próprios objectivos que pretendem alcançar. Compreender o legado complexo dos controles de preços nas economias comunistas fornece lições valiosas para os formuladores de políticas que procuram equilibrar a estabilidade económica com a equidade social.
## Consequências do Planeamento Centralizado e do Controlo de Preços
**Autoritarismo e a Concentração de Poder**
Uma das consequências políticas mais significativas do planeamento económico centralizado e do controlo de preços é a concentração de poder dentro do aparelho de Estado. Em teoria, o comunismo idealiza uma sociedade sem Estado, mas na prática, a implementação desses sistemas muitas vezes exige uma autoridade central forte para aplicar as directivas económicas e manter o controlo. Esta concentração de poder frequentemente leva ao autoritarismo, como se vê em numerosos regimes comunistas.
A centralização do poder permite que um pequeno grupo de líderes ou um único partido domine a vida política, muitas vezes suprimindo a oposição e restringindo as liberdades individuais. Sem pesos e contrapesos, estes regimes podem impor controlos rigorosos na economia e na sociedade, levando a uma repressão generalizada. A natureza autoritária desses governos é frequentemente justificada como um meio necessário para proteger a revolução e manter a ordem social, mas resulta na erosão dos princípios democráticos e na marginalização das vozes dissidentes.
Além disso, a concentração de poder no Estado mina os próprios ideais do comunismo. Em vez de uma sociedade sem classes, emerge uma nova classe dominante de funcionários do partido e burocratas, que gozam de privilégios e autoridade muito além do cidadão comum. Esta dinâmica de poder não só contradiz os objectivos igualitários do comunismo, como também perpetua a desigualdade dentro do sistema.
**Desigualdade Social e o Surgimento de Novas Elites**
Apesar do objectivo teórico de eliminar as classes sociais, os sistemas comunistas muitas vezes testemunham o surgimento de novas elites. Estas elites, compostas por líderes do partido, burocratas do Estado e oficiais militares, gozam de privilégios significativos que os distinguem da população em geral. Este fenómeno reflecte o desafio inerente de alcançar uma verdadeira igualdade num sistema onde o poder está concentrado nas mãos de poucos.
Em muitos casos, essas novas elites tornam-se enraizadas, criando um fosso entre os governantes e os governados que espelha as divisões de classe que o comunismo pretendia eliminar. Os privilégios e o poder desfrutados por essas elites frequentemente levam à corrupção e ao clientelismo, corroendo ainda mais a confiança pública no sistema. O descontentamento resultante entre a população pode levar a agitação, à medida que as pessoas percebem que a igualdade prometida é inatingível dentro da estrutura política existente.
**A Supressão de Dissidência e Suas Consequências Económicas**
A supressão da dissidência é uma característica marcante de muitos regimes comunistas, impulsionada pela necessidade de manter o controlo tanto sobre a economia quanto sobre a sociedade. Na prática, essa supressão assume várias formas, incluindo censura, vigilância e perseguição de oponentes políticos. A falta de competição política e de debate aberto sufoca a inovação e o feedback crítico, que são essenciais para uma economia dinâmica e adaptável.
Sem a capacidade de expressar preocupações ou propor políticas alternativas, os regimes comunistas muitas vezes lutam para responder de forma eficaz aos desafios económicos. A natureza rígida do planeamento centralizado, combinada com a supressão da dissidência, cria um ciclo vicioso em que os problemas são ignorados ou exacerbados, levando a um maior declínio económico. A ausência de dissidência também significa que as reformas necessárias são adiadas ou bloqueadas, à medida que as elites no poder priorizam os seus próprios interesses em detrimento do bem comum.
As consequências a longo prazo dessa supressão são profundas. Economias que carecem de flexibilidade para se adaptar às mudanças ou enfrentar ineficiências tornam-se estagnadas, levando a escassez, declínio na produtividade e uma queda no padrão de vida da população. A supressão da dissidência não só prejudica o desempenho económico, mas também enfraquece o tecido social, à medida que a confiança no governo se deteriora e as pessoas se sentem cada vez mais alienadas do sistema político.
**Autoritarismo nas Sociedades Ocidentais: Uma Preocupação Crescente**
Nos últimos anos, o aumento do autoritarismo nas sociedades ocidentais tornou-se uma preocupação crescente, manifestando-se através de várias tendências chave que ecoam algumas das dinâmicas observadas em regimes comunistas. Embora as democracias ocidentais estejam longe de um autoritarismo pleno, a concentração de poder, o crescimento das desigualdades sociais, o surgimento de novas elites e a supressão da dissidência sugerem um desvio preocupante dos princípios democráticos liberais.
Tem havido uma crescente centralização do poder em muitos países ocidentais, muitas vezes manifestada através do excesso de autoridade executiva e da expansão do poder presidencial ou do primeiro-ministro. O enfraquecimento dos mecanismos de pesos e contrapesos entre os ramos do governo e as tentativas de minar a independência judicial e o estado de direito são indicadores claros desta tendência. Esta concentração de poder corrói as normas e instituições democráticas ao longo do tempo, tornando mais difícil responsabilizar os líderes.
A crescente desigualdade económica tem alimentado o descontentamento e movimentos populistas em muitos países ocidentais. O aumento da disparidade de riqueza entre as elites e a população em geral, os salários estagnados para as classes média e trabalhadora e a redução da mobilidade social contribuíram para um crescente sentimento de desilusão com os sistemas democráticos tradicionais. Esta disparidade económica criou um terreno fértil para líderes com tendências autoritárias, que prometem resolver esses problemas, mas muitas vezes concentram ainda mais o poder.
O surgimento de novas estruturas de poder e grupos de elites, como os oligarcas da tecnologia e as elites empresariais ligadas à política, tem desafiado os mecanismos tradicionais de responsabilização democrática. Estas novas elites frequentemente exercem uma influência significativa sobre a informação, o discurso e a política, operando fora do alcance das instituições democráticas. Líderes populistas, que cultivam cultos de personalidade, também contribuem para esta mudança, enfraquecendo ainda mais os processos democráticos.
As preocupações sobre restrições à liberdade de expressão e ao debate aberto estão a crescer nas sociedades ocidentais. Embora não sejam equivalentes à censura autoritária vista em regimes comunistas, tendências como a "cultura do cancelamento", a vigilância governamental e a repressão de protestos têm um efeito dissuasor sobre o discurso aberto. A autocensura devido ao medo de retaliações online ou de consequências profissionais está a tornar-se mais comum, limitando a diversidade de pontos de vista no debate público.
A fé pública nos pilares centrais da democracia — governos, partidos políticos e funcionários eleitos — tem-se deteriorado em muitos países ocidentais. O cepticismo em relação aos meios de comunicação tradicionais e ao conhecimento especializado também aumentou, enquanto a integridade dos sistemas eleitorais é cada vez mais questionada. Esta perda de confiança cria oportunidades para líderes com tendências autoritárias ganharem apoio, enfraquecendo ainda mais as instituições democráticas.
O aumento do autoritarismo nas sociedades ocidentais, embora ainda não comparável ao controlo centralizado visto em regimes comunistas, sinaliza uma mudança preocupante em relação aos princípios da democracia liberal. A concentração de poder, o crescimento das desigualdades sociais, o surgimento de novas elites e a supressão da dissidência são todos factores que espelham os problemas enfrentados pelos estados comunistas históricos, embora em formas diferentes. Estas tendências, se não forem controladas, podem levar a uma erosão gradual das normas e instituições democráticas, minando os próprios alicerces de sociedades livres e abertas.
Os paralelos entre os desafios enfrentados pelos regimes comunistas e as tendências actuais nas democracias ocidentais destacam a importância de abordar essas questões subjacentes. Assim como o planeamento económico centralizado e o controlo de preços levaram a ineficiências e agitação social nos estados comunistas, a concentração de poder e a desigualdade no Ocidente ameaçam enfraquecer os sistemas democráticos por dentro. A supressão da dissidência e a diminuição da confiança nas instituições democráticas agravam ainda mais esses problemas, criando um ambiente onde o autoritarismo pode ganhar terreno.
É crucial que as sociedades ocidentais reforcem as normas e instituições democráticas. Isso envolve garantir que os pesos e contrapesos entre os ramos do governo sejam mantidos, protegendo a independência judicial e salvaguardando o estado de direito. Abordar a desigualdade económica também é essencial, pois é um dos principais impulsionadores dos sentimentos populistas e autoritários. Políticas que promovam a mobilidade social, salários justos e oportunidades económicas podem ajudar a reconstruir a confiança nos sistemas democráticos.
Além disso, promover um discurso público aberto e inclusivo é vital para prevenir a supressão da dissidência. Isso significa defender a liberdade de expressão, encorajar a diversidade de pontos de vista e resistir à tentação de silenciar opiniões impopulares através de pressão social ou governamental. Ao criar uma cultura que valoriza o debate e respeita perspectivas diferentes, as sociedades ocidentais podem resistir ao desvio para o autoritarismo.
Finalmente, reconstruir a confiança nas instituições democráticas exige transparência, responsabilização e capacidade de resposta por parte dos governos e líderes políticos. Os funcionários eleitos devem ser vistos a agir no interesse público, e as instituições devem ser percepcionadas como justas e eficazes. Restaurar a confiança nos sistemas eleitorais e nos meios de comunicação também é essencial para contrariar a ascensão do populismo e do autoritarismo.
Embora os desafios enfrentados pelas democracias ocidentais hoje sejam distintos dos que atormentaram os regimes comunistas, as dinâmicas subjacentes de poder, desigualdade e dissidência partilham algumas semelhanças preocupantes. Ao reconhecer e aprender com os fracassos do comunismo e ao abordar estas questões de frente, as sociedades ocidentais podem fortalecer as suas fundações democráticas e evitar o deslizamento para o autoritarismo.
## Conclusão
Em resumo, os fracassos do verdadeiro comunismo e os efeitos prejudiciais dos controles de preços não são meramente notas de rodapé históricas, mas lições duradouras que continuam a ressoar hoje em dia. O colapso de inúmeros regimes comunistas e as persistentes dificuldades económicas em países que ainda tentam aderir aos princípios comunistas destacam as falhas fundamentais da ideologia. O factor humano—motivações individuais, o desejo de liberdade pessoal e as complexidades da governação—continuamente perturbam a visão utópica de uma sociedade sem classes e sem estado. O planeamento centralizado e os controles de preços, longe de criar igualdade e estabilidade, têm consistentemente levado a ineficiências económicas, escassez e regimes autoritários.
No entanto, estas lições não são apenas relevantes para o passado. As sociedades ocidentais de hoje enfrentam os seus próprios riscos, à medida que a esquerda se inclina cada vez mais para políticas autoritárias sob o disfarce de equidade e justiça social. A pressão por mais controlo estatal, juntamente com uma crescente intolerância à dissidência, espelha os estágios iniciais dos mesmos sistemas que levaram à tirania e ditadura no passado. O marxismo cultural, um movimento que busca remodelar a sociedade promovendo a ideologia marxista através das instituições culturais, está a ganhar força, particularmente no meio académico e nos meios de comunicação. Esta mudança ideológica está a corroer as fundações da liberdade individual e da liberdade económica que têm definido o Ocidente.
De forma alarmante, muitos jovens no Ocidente estão a louvar cada vez mais a ideologia marxista e o comunismo, muitas vezes sem compreender plenamente as realidades históricas desses sistemas. Esta tendência reflecte uma perigosa ignorância das atrocidades e do sofrimento que ocorreram sob os regimes comunistas. A romantização do comunismo ignora as duras verdades da história—a repressão, o colapso económico e a perda de liberdades pessoais que têm consistentemente acompanhado as tentativas de implementar esta ideologia.
É crucial manter-se vigilante contra estas tendências. As lições da história devem servir de alerta para aqueles que procuram replicar sistemas falhados. Embora a busca por uma sociedade mais justa e equitativa seja um objectivo nobre, não pode vir à custa das liberdades individuais e dos benefícios comprovados de uma economia baseada no mercado. As sociedades ocidentais devem proteger-se contra o fascínio do autoritarismo, seja na forma de comunismo declarado ou de formas mais subtis de controlo estatal. Garantir que a próxima geração compreenda a verdadeira natureza dessas ideologias é essencial para preservar as liberdades e a prosperidade que foram arduamente conquistadas ao longo de séculos.
---
__Photo by <a href="https://unsplash.com/@rocinante_11?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash">Mick Haupt</a> on <a href="https://unsplash.com/photos/people-walking-inside-building-with-escalator-pOEY_iRFg60?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash">Unsplash</a>__
-

@ 1739d937:3e3136ef
2024-08-16 10:08:42
This is the fifth in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
## Previous Updates
- [June 28th 2024](https://habla.news/u/jeffg.fyi/1719562889267)
- [July 6th 2024](https://habla.news/u/jeffg.fyi/1720256910765)
- [July 12th 2024](https://habla.news/u/jeffg.fyi/1720778880538)
- [July 19th 2024](https://habla.news/u/jeffg.fyi/1721419437737)
## Progress this week
I'm back from a few weeks of family holiday this week and feeling super productive. The major news this week is that I've posted the [draft NIP](https://github.com/nostr-protocol/nips/pull/1427) to the NIPs repository for how to implement MLS messaging on Nostr. I've gotten feedback on the doc from several other Nostr devs but I'm absolutely looking for more feedback from the community.
I've also made progress on the dependencies that I was working on before my holidays. Info below.
### The NIP
I won't review the entire proposed NIP here but I wanted to call out one tradeoff that I thought hard about.
In my original proposal, which only supported one-to-one direct messages, all messages between the two parties were sent as NIP-59 gift-wrapped events. This helps to hide metadata but it creates problems of it's own. Notably, it's very possible to DDoS Nostr clients with meaningless gift-wrap events since clients must decrypt and unwrap each event to even understand if it's something that is important to them.
Aside from those problems, gift-wrapping messages to an entire group would be very impractical. It would require the client sending a message to individually gift-wrap the message individually to all other participants in a group.
The tradeoff I've come up with is to use a public event, `kind:445`, tagged with the group ID, so that all participants in the group can easily query for messages from each of the groups that they are a part of. The content field of these event is encrypted using the MLS ratchet keys and thus is only able to be decrypted by members of the group. These events are published using an ephemeral key so that the number and identity of the group members is obfuscated.
This means that observers have a relative idea of the level of activity in a given group but don't know exactly how many or who is in the group. In addition, it's easy within the MLS spec to rotate the group ID over time.
Would love to hear thoughts on how people feel about that tradeoff.
### HPKE-RS
My [PR](https://github.com/franziskuskiefer/hpke-rs/pull/66) to add support for secp256k1 is stuck because of bad test vectors for the secp256k1 curve. I've been working on generating new vectors that will be usable by other HPKE implementations as well. Huge thanks to @dan for the help on this.
### OpenMLS & Ciphersuites
As mentioned in the previous updated, I've spoken with the OpenMLS team about how to better support custom ciphersuites. I've started to work on the expansive refactor in OpenMLS to make this possible but it's going to take a while.
One major decision that has come from this is that I've decided that the NIP will not require a single custom ciphersuite (built around Schnorr signatures on the secp256k1 curve). Instead, clients can decide which ciphersuites they want to support and are able to implement this NIP immediately with the current OpenMLS version.
I will continue to work on refactoring the OpenMLS library to ensure that it supports custom ciphersuites and to build a custom Crypto Provider focused on the Nostr crypto primitives and I expect that, long-term, many Nostr clients will prefer to support only that ciphersuite to reduce the dependency surface area of their apps.
## Onward and Upward
LFG! 🤙 Please take a moment and send me feedback and thoughts on the above and especially on the NIP if you're a developer.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Filemap
[filemap](https://filemap.xyz/) solves the problem of sending and receiving files to and from non-tech people when you don't have a text communication channel with them.
[](https://xkcd.com/949/)
Imagine you want to send files to your grandfather, or you don't use Facebook and your younger cousin who only uses Facebook and doesn't know what is email wants to send you some pictures, it's pretty hard to get a file-sharing channel between people if they're not in the same network. If even the people have a way to upload the files to some hosting service and then share the link everything would still work, but you're not going to write `somehostingservice.com/wHr4y7vFGh0` to your grandfather -- or expect your cousin to do that for you and send you an SMS with dozens of those links.
Solution:
* Upload your files to https://filemap.xyz/ (you can either upload directly or share links to things already uploaded -- or even links to pages) and pin them to your grandfather's house address; then tell your grandfather to open https://filemap.xyz/ and look for his address. Done.
* Tell your younger cousin to visit filemap.xyz and upload all the files to his address, later you open the site and look for his address. There are your files.
---
Initially this used [ipfs-dropzone](nostr:naddr1qqyrjvrx8p3xyvesqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cwpfruw), but IPFS is broken, os I migrated to [WebTorrent](https://webtorrent.io/), but that required the file sender to be online hosting its own file and the entire idea of this service was to make something _easy_, so I migrated to Firebase Hosting, which is also terrible and has a broken API, but at least is capable of hosting files. Should have used something like S3.
- <https://github.com/fiatjaf/filemap.xyz>
- <https://filemap.xyz/>
-

@ da18e986:3a0d9851
2024-08-14 13:58:24
After months of development I am excited to officially announce the first version of DVMDash (v0.1). DVMDash is a monitoring and debugging tool for all Data Vending Machine (DVM) activity on Nostr. The website is live at [https://dvmdash.live](https://dvmdash.live) and the code is available on [Github](https://github.com/dtdannen/dvmdash).
Data Vending Machines ([NIP-90](https://github.com/nostr-protocol/nips/blob/master/90.md)) offload computationally expensive tasks from relays and clients in a decentralized, free-market manner. They are especially useful for AI tools, algorithmic processing of user’s feeds, and many other use cases.
The long term goal of DVMDash is to become 1) a place to easily see what’s happening in the DVM ecosystem with metrics and graphs, and 2) provide real-time tools to help developers monitor, debug, and improve their DVMs.
DVMDash aims to enable users to answer these types of questions at a glance:
* What’s the most popular DVM right now?
* How much money is being paid to image generation DVMs?
* Is any DVM down at the moment? When was the last time that DVM completed a task?
* Have any DVMs failed to deliver after accepting payment? Did they refund that payment?
* How long does it take this DVM to respond?
* For task X, what’s the average amount of time it takes for a DVM to complete the task?
* … and more
For developers working with DVMs there is now a visual, graph based tool that shows DVM-chain activity. DVMs have already started calling other DVMs to assist with work. Soon, we will have humans in the loop monitoring DVM activity, or completing tasks themselves. The activity trace of which DVM is being called as part of a sub-task from another DVM will become complicated, especially because these decisions will be made at run-time and are not known ahead of time. Building a tool to help users and developers understand where a DVM is in this activity trace, whether it’s gotten stuck or is just taking a long time, will be invaluable. *For now, the website only shows 1 step of a dvm chain from a user's request.*
One of the main designs for the site is that it is highly _clickable_, meaning whenever you see a DVM, Kind, User, or Event ID, you can click it and open that up in a new page to inspect it.
Another aspect of this website is that it should be fast. If you submit a DVM request, you should see it in DVMDash within seconds, as well as events from DVMs interacting with your request. I have attempted to obtain DVM events from relays as quickly as possible and compute metrics over them within seconds.
This project makes use of a nosql database and graph database, currently set to use mongo db and neo4j, for which there are free, community versions that can be run locally.
Finally, I’m grateful to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project.
## Features in v0.1:
### Global Network Metrics:
This page shows the following metrics:
- **DVM Requests:** Number of unencrypted DVM requests (kind 5000-5999)
- **DVM Results:** Number of unencrypted DVM results (kind 6000-6999)
- **DVM Request Kinds Seen:** Number of unique kinds in the Kind range 5000-5999 (except for known non-DVM kinds 5666 and 5969)
- **DVM Result Kinds Seen:** Number of unique kinds in the Kind range 6000-6999 (except for known non-DVM kinds 6666 and 6969)
- **DVM Pub Keys Seen:** Number of unique pub keys that have written a kind 6000-6999 (except for known non-DVM kinds) or have published a kind 31990 event that specifies a ‘k’ tag value between 5000-5999
- **DVM Profiles (NIP-89) Seen**: Number of 31990 that have a ‘k’ tag value for kind 5000-5999
- **Most Popular DVM**: The DVM that has produced the most result events (kind 6000-6999)
- **Most Popular Kind**: The Kind in range 5000-5999 that has the most requests by users.
- **24 hr DVM Requests**: Number of kind 5000-5999 events created in the last 24 hrs
- **24 hr DVM Results**: Number of kind 6000-6999 events created in the last 24 hours
- **1 week DVM Requests**: Number of kind 5000-5999 events created in the last week
- **1 week DVM Results**: Number of kind 6000-6999 events created in the last week
- **Unique Users of DVMs**: Number of unique pubkeys of kind 5000-5999 events
- **Total Sats Paid to DVMs**:
- This is an estimate.
- This value is likely a lower bound as it does not take into consideration subscriptions paid to DVMs
- This is calculated by counting the values of all invoices where:
- A DVM published a kind 7000 event requesting payment and containing an invoice
- The DVM later provided a DVM Result for the same job for which it requested payment.
- The assumption is that the invoice was paid, otherwise the DVM would not have done the work
- Note that because there are multiple ways to pay a DVM such as lightning invoices, ecash, and subscriptions, there is no guaranteed way to know whether a DVM has been paid. Additionally, there is no way to know that a DVM completed the job because some DVMs may not publish a final result event and instead send the user a DM or take some other kind of action.
### Recent Requests:
This page shows the most recent 3 events per kind, sorted by created date. You should always be able to find the last 3 events here of all DVM kinds.
### DVM Browser:
This page will either show a profile of a specific DVM, or when no DVM is given in the url, it will show a table of all DVMs with some high level stats. Users can click on a DVM in the table to load the DVM specific page.
### Kind Browser:
This page will either show data on a specific kind including all DVMs that have performed jobs of that kind, or when no kind is given, it will show a table summarizing activity across all Kinds.
### Debug:
This page shows the graph based visualization of all events, users, and DVMs involved in a single job as well as a table of all events in order from oldest to newest. When no event is given, this page shows the 200 most recent events where the user can click on an event in order to debug that job. The graph-based visualization allows the user to zoom in and out and move around the graph, as well as double click on any node in the graph (except invoices) to open up that event, user, or dvm in a new page.
### Playground:
This page is currently under development and may not work at the moment. If it does work, in the current state you can login with NIP-07 extension and broadcast a 5050 event with some text and then the page will show you events from DVMs. This page will be used to interact with DVMs live. A current good alternative to this feature, for some but not all kinds, is [https://vendata.io/](https://vendata.io/).
## Looking to the Future
I originally built DVMDash out of Fear-of-Missing-Out (FOMO); I wanted to make AI systems that were comprised of DVMs but my day job was taking up a lot of my time. I needed to know when someone was performing a new task or launching a new AI or Nostr tool!
I have a long list of DVMs and Agents I hope to build and I needed DVMDash to help me do it; I hope it helps you achieve your goals with Nostr, DVMs, and even AI. To this end, I wish for this tool to be useful to others, so if you would like a feature, please [submit a git issue here](https://github.com/dtdannen/dvmdash/issues/new) or _note_ me on Nostr!
### Immediate Next Steps:
- Refactoring code and removing code that is no longer used
- Improve documentation to run the project locally
- Adding a metric for number of encrypted requests
- Adding a metric for number of encrypted results
### Long Term Goals:
- Add more metrics based on community feedback
- Add plots showing metrics over time
- Add support for showing a multi-dvm chain in the graph based visualizer
- Add a real-time mode where the pages will auto update (currently the user must refresh the page)
- ... Add support for user requested features!
## Acknowledgements
There are some fantastic people working in the DVM space right now. Thank you to nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet for making python bindings for nostr_sdk and for the recent asyncio upgrades! Thank you to nostr:npub1nxa4tywfz9nqp7z9zp7nr7d4nchhclsf58lcqt5y782rmf2hefjquaa6q8 for answering lots of questions about DVMs and for making the nostrdvm library. Thank you to nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft for making the original DVM NIP and [vendata.io](https://vendata.io/) which I use all the time for testing!
P.S. I rushed to get this out in time for Nostriga 2024; code refactoring will be coming :)
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# The illusion of checks and balances
The website history.com has [a list of some of the most important "checks and balances"](https://www.history.com/topics/us-government/checks-and-balances) put in place by the United States Constitution. Here are some of them and how they are not real _checks_, they're flawed and easily bypassed by malicious peers that manage to enter the network.
> The president (head of the executive branch) serves as commander in chief of the military forces, but Congress (legislative branch) appropriates funds for the military and votes to declare war.
As it has happened [multiple times](https://en.wikipedia.org/wiki/Declaration_of_war_by_the_United_States#Undeclared_wars), the United States has engaged in many undeclared wars -- and many other military encounters that don't get enough media coverage and weren't even formally acknowledged by the Congress.
> Congress has the power of the purse, as it controls the money used to fund any executive actions.
There's a separate power called Federal Reserve which is more-or-less under the influence of the executive branch that is controlled by a single man and has the power of creating unlimited money. It was softly abused by the executive branch since its creation, but since 2008 it has been increasingly having its scope expanded from just influencing the banking sector to also directly using its money to buy all sorts of things and influence all sorts of markets and other actors.
> Veto power. Once Congress has passed a bill, the president has the power to veto that bill. In turn, Congress can override a regular presidential veto by a two-thirds vote of both houses.
If you imagine that both the executive and the legislative are 100% dedicated to go against each other the president could veto all bills, but then the legislative could enact them all anyway. Congress has the absolute power here (which can be justified by fact that the congress itself is split into multiple voters, but still this "veto" rule seems more like a gimmick to obscure the process than any actual check).
> The Supreme Court and other federal courts (judicial branch) can declare laws or presidential actions unconstitutional, in a process known as judicial review.
This rule gives absolute power to the Supreme Court over any matter. It can use their own personal judgement to veto any bill, cancel any action by the executive, reinterpret any existing law in any manner. There's no check against bad interpretations or judgements, so any absurd thing must be accepted. This should be obvious, and yet the entire system which most people believe to be "checked" is actually dependent on the good will and sanity of the judicial branch.
> In turn, the president checks the judiciary through the power of appointment, which can be used to change the direction of the federal courts
If the president and congress are being attacked by the judicial power, this isn't of much help as its effects are very long term. On the other hand, a president can single-handedly and arbitrarily use this rule to slowly poison the judicial system such that will turn malicious for the rest of the system after some time.
> By passing amendments to the Constitution, Congress can effectively check the decisions of the Supreme Court.
What is written in the Constitution can be easily ignored or misread by the members of the Supreme Court without any way for these interpretations to be checked or reverted. Basically the Supreme Court has absolute power over all things if we consider this.
> Congress (considered the branch of government closest to the people) can impeach both members of the executive and judicial branches.
Again (like in the presidential veto rule), this gives the congress unlimited power. There are no checks here -- except of course the fact that the congress is composed by multiple different voting heads of which a majority has to agree for the congress to do anything, which is the only thing preventing overabuse of this rule.
---
As shown above, most rules that compose the "checks and balances" system can be abused and if given enough time they will. They aren't real checks.
Ultimately, the stability and decency of a [democracy](nostr:naddr1qqyrxvtxxf3nse3sqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ccyra4y) relies on the majority rule (so congress votes are never concentrated in dictatorial measures) and the common sense of the powerful people (president and judges).
There probably hasn't been a single year in any democracy in which one of these powers didn't abused or violated one of the rules, but still in most cases the overall system stays in place because of the general culture, splitted views about most issues, overall common sense and fear of public shame.
The checks and balances system itself is an illusion. All the complex "democracy" construct depends on the goodwill of all the participants and have only worked so far (when it did) by miracle and by the power of human cooperation and love.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Boardthreads
This was a very badly done service for turning a Trello list into a helpdesk UI.
Surprisingly, it had more paying users than [Websites For Trello](nostr:naddr1qqyrydpkvverwvehqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c9d4yku), which I was working on simultaneously and dedicating much more time to it.
The Neo4j database I used for this was a very poor choice, it was probably the cause of all the bugs.

-<https://github.com/fiatjaf/boardthreads>
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Who will build the roads?
Who will build the roads? Em Lagoa Santa, as mais novas e melhores ruas -- que na verdade acabam por formar enormes teias de bairros que se interligam -- são construídas pelos loteadores que querem as ruas para que seus lotes valham mais -- e querem que outras pessoas usem as ruas também. Também são esses mesmos loteadores que colocam os postes de luz e os encanamentos de água, não sem antes terem que se submeter a extorsões de praxe praticadas por COPASA e CEMIG.
Se ao abrir um loteamento, condomínio, prédio um indivíduo ou uma empresa consegue sem muito problema passar rua, eletricidade, água e esgoto, por que não seria possível existir livre-concorrência nesses mercados? Mesmo aquela velha estória de que é ineficiente passar cabos de luz duplicados para que companhias elétricas possam competir já me parece bobagem.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# jiq
When someone created [`jiq`](https://github.com/simeji/jid) claiming it had "jq queries" I went to inspect and realized it didn't, it just had a poor simple JSON query language that implemented 1% of all [`jq`](https://stedolan.github.io/jq/manual/) features, so I forked it and plugged `jq` directly into it, and renamed to `jiq`.
After some comments on issues in the original repository from people complaining about lack of `jq` compatibility it got a ton of unexpected users, was even packaged to ArchLinux.

- <https://github.com/fiatjaf/jiq>
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Como não houve resposta, estou enviando de novo
Recebi um email assim, dizendo a mesma coisa repetida. Eu havia recebido já da primeira vez, mas como era só uma informação já esperada, julguei que não precisava responder dizendo "chegou, obrigado!" e não o fiz.
Reconheço, porém, que dada a instabilidade desses serviços de email nunca ninguém sabe se a mensagem chegou ou não. Ela pode ter sido jogada na lixeira do spam, ou pode ter falhado por outros motivos, e aí não existe um jeito garantido de saber se houve falha, é um enorme problema sempre. Por isso a necessidade de uma resposta "chegou, obrigado!".
Mas não podemos parar por aí. A resposta "chegou, obrigado!" também está sujeita aos mesmos trâmites e riscos da mensagem original. Seria necessário, porém, que assim que a outra pessoa recebesse o "chegou, obrigado!" deveria então responder com um "recebi a sua confirmação". Caso não o fizesse, eu poderia achar que a minha mensagem não havia chegado e dias depois enviá-la de novo: "como não houve resposta à minha confirmação, estou enviando de novo".
E assim por diante (eu ia escrever mais um parágrafo só pelo drama, mas desisti. Já deu pra entender).
---
- [Ripple and the problem of the decentralized commit](nostr:naddr1qqyrxcmzxa3nxv34qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cjrqar6), esta situação que acabo de viver é mais um exemplo prático disto.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Flowi.es
At the time I thought [Workflowy][workflowy] had the ideal UI for everything. I wanted to implement my [custom app maker](nostr:naddr1qqyxgcejv5unzd33qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cz3va32) on it, but ended up doing this: a platform for enhancing Workflowy with extra features:
- An email reminder based on dates input in items
- A website generator, similar to [Websites For Trello](nostr:naddr1qqyrydpkvverwvehqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c9d4yku), also based on [Classless Templates](nostr:naddr1qqyxyv35vymk2vfsqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cqwgdau)
Also, I didn't remember this was also based on CouchDB and had some _couchapp_ functionalities.

- <https://flowi.es>
- <https://github.com/fiatjaf/flowies>
[workflowy]: <https://workflowy.com/>
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Multi-service Graph Reputation protocol
## The problem
1. Users inside centralized services need to know reputations of other users they're interacting with;
2. Building reputation with ratings imposes a big burden on the user and still accomplishes nothing, can be faked, no one cares about these ratings etc.
## The ideal solution
Subjective reputation: reputation based on how you rated that person previously, and how other people you trust rated that person, and how other people trusted by people you trust rated that person and so on, in a web-of-trust that actually can give you some insight on the trustworthiness of someone you never met or interacted with.
## The problem with the ideal solution
1. Most of the times the service that wants to implement this is not as big as Facebook, so it won't have enough people in it for such graphs of reputation to be constructed.
2. It is not trivial to build.
## My proposed solution:
I've drafted a protocol for an open system based on services publishing their internal reputation records and indexers using these to build graphs, and then serving the graphs back to the services so they can show them to users when it is needed (as HTTP APIs that can be called directly from the user client app or browser).
Crucially, these indexers will gather data from multiple services and cross-link users from these services so the graph is better.
<https://github.com/fiatjaf/multi-service-reputation-rfc>
The first and single actionable and useful feedback I got, from [@bootstrapbandit](https://twitter.com/bootstrapbandit) was that services shouldn't share email addresses in plain text (email addresses and other external relationships users of a service may have are necessary to establish links from users accross services), but I think it is ok if services publish hashes of these email addresses instead. At some point I will update the spec draft and that may have been before the time you're reading this.
Another issue is that services may lie about their reputation records and that will hurt other services and users in these other services that are relying on that data. Maybe indexers will have to do some investigative job here to assert service honesty. Or maybe this entire protocol is just failed and we will actually need a system in which users themselves will publish their own records.
## See also
* [P2P reputation thing](nostr:naddr1qqyrqv3cxumnydfsqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cnjc88q)
* [idea: Graph subjective reputation as a service](nostr:naddr1qqyrjdehxymrsdpkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cal60d8)
* <https://github.com/jangerritharms/reputation_systems>
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# A memória está nas coisas
A memória está nas coisas, mas se você tiver muitas memórias já mesma coisa parece que uma se sobrepõe à outra, de modo que se vive quiser acumular mais memórias é melhor mudar de casa todo ano.
-

@ 361d3e1e:50bc10a8
2024-08-19 18:33:25
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Cultura Inglesa e aprendizado extra-escolar
Em 2005 a Cultura Inglesa me classificou como nível 2 em proficiência de inglês, numa escala de 1 a 14 ou coisa parecida. De modo que eu precisaria de 6 anos de aulas com eles pra ficar bom. 2 anos depois, sem fazer nenhuma aula ou ter qualquer tipo de treinamento intensivo eu era capaz de compreender textos técnicos em inglês sem nenhuma dificuldade. Mais 2 anos e eu era capaz de compreender qualquer coisa e me expressar com razoável qualidade.
Tudo isso pra documentar mais um exemplo, que poderia passar despercebido, de aprendizado de tipo escolar que se deu fora de uma escola.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# On HTLCs and arbiters
This is another attempt and conveying the same information that should be in [Lightning and its fake HTLCs](nostr:naddr1qqyryefsxqcxgdmzqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cp0m63a). It assumes you know everything about Lightning and will just highlight a point. This is also valid for PTLCs.
The protocol says HTLCs are trimmed (i.e., not actually added to the commitment transaction) when the cost of redeeming them in fees would be greater than their actual value.
Although this is often dismissed as a non-important fact (often people will say "it's trusted for small payments, no big deal"), but I think it is indeed very important for 3 reasons:
1. Lightning absolutely relies on HTLCs actually existing because the payment proof requires them. The entire security of each payment comes from the fact that the payer has a preimage that comes from the payee. Without that, the state of the payment becomes an unsolvable mystery. The inexistence of an HTLC breaks the atomicity between the payment going through and the payer receiving a proof.
2. Bitcoin fees are expected to grow with time (arguably the reason Lightning exists in the first place).
3. MPP makes payment sizes shrink, therefore more and more of Lightning payments are to be trimmed. As I write this, the mempool is clear and still payments smaller than about 5000sat are being trimmed. Two weeks ago the limit was at 18000sat, which is already below the minimum most MPP splitting algorithms will allow.
Therefore I think it is important that we come up with a different way of ensuring payment proofs are being passed around in the case HTLCs are trimmed.
## Channel closures
Worse than not having HTLCs that can be redeemed is the fact that in the current Lightning implementations channels will be closed by the peer once an HTLC timeout is reached, either to fulfill an HTLC for which that peer has a preimage or to redeem back that expired HTLCs the other party hasn't fulfilled.
For the surprise of everybody, nodes will do this even when the HTLCs in question were trimmed and therefore cannot be redeemed at all. It's very important that nodes stop doing that, because it makes no economic sense at all.
However, that is not so simple, because once you decide you're not going to close the channel, what is the next step? Do you wait until the other peer tries to fulfill an expired HTLC and tell them you won't agree and that you must cancel that instead? That could work sometimes if they're honest (and they have no incentive to not be, in this case). What if they say they tried to fulfill it before but you were offline? Now you're confused, you don't know if you were offline or they were offline, or if they are trying to trick you. Then unsolvable issues start to emerge.
## Arbiters
One simple idea is to use trusted arbiters for all trimmed HTLC issues.
This idea solves both the protocol issue of getting the preimage to the payer once it is released by the payee -- and what to do with the channels once a trimmed HTLC expires.
A simple design would be to have each node hardcode a set of trusted other nodes that can serve as arbiters. Once a channel is opened between two nodes they choose one node from both lists to serve as their mutual arbiter for that channel.
Then whenever one node tries to fulfill an HTLC but the other peer is unresponsive, they can send the preimage to the arbiter instead. The arbiter will then try to contact the unresponsive peer. If it succeeds, then done, the HTLC was fulfilled offchain. If it fails then it can keep trying until the HTLC timeout. And then if the other node comes back later they can eat the loss. The arbiter will ensure they know they are the ones who must eat the loss in this case. If they don't agree to eat the loss, the first peer may then close the channel and blacklist the other peer. If the other peer believes that both the first peer and the arbiter are dishonest they can remove that arbiter from their list of trusted arbiters.
The same happens in the opposite case: if a peer doesn't get a preimage they can notify the arbiter they hadn't received anything. The arbiter may try to ask the other peer for the preimage and, if that fails, settle the dispute for the side of that first peer, which can proceed to fail the HTLC is has with someone else on that route.
-

@ c8383d81:f9139549
2024-08-09 09:21:45
Test Completed
:Lighningbutton{lud16=cypher@npub.cash}
-

@ 79be667e:16f81798
2024-08-19 10:27:57
## Introduction
Picture this: you’re a seasoned software developer, having mastered several programming languages. You’ve dabbled in Python’s simplicity, swum in Java’s verbose ocean, and even navigated the sharp edges of C++. And now, you hear whispers in the tech corridors about Go, the language created by Google that’s supposed to be the next big thing. But wait — before you dive in, let’s take a critical look. Despite its gleaming reputation, Go might just be the worst language you could ever learn.
## The Simplicity Trap
## The Illusion of Simplicity
Go is often praised for its simplicity, but this can be a double-edged sword. Sure, a language that’s easy to pick up sounds great, but what if that simplicity comes at the cost of essential features? Go’s minimalist design strips away many conveniences that other languages offer. There’s no inheritance, no generics (until recently), and error handling is rudimentary at best.
### Example
Imagine trying to build a complex data structure in Go. You’ll quickly find yourself writing repetitive, boilerplate code that a language with generics could have handled elegantly. It’s like being forced to build a skyscraper with Lego blocks — simple but painfully slow and inefficient.
# Error Handling: A Nightmare
### Tedious and Verbose
In Go, error handling is done by returning errors as values. This might seem straightforward, but in practice, it results in verbose and cluttered code. Every function that might fail has to return an error, and every caller has to check for that error. This leads to a pattern that looks like:
```
if err != nil {
return err
}
```
Repeat ad nauseam. It’s like playing a video game where you have to press a button every two seconds to keep playing — monotonous and prone to errors if you forget.
### Personal Anecdote
When I first started with Go, I was excited about its concurrency model. But the excitement faded as I spent more time handling errors than writing actual logic. It felt like I was an error handler, not a developer.
# Lack of Essential Features
## Missing Generics
Until very recently, Go did not support generics, which are a staple in many modern languages. Generics allow you to write flexible and reusable code. Without them, you’re stuck writing the same functions for different types. This is a massive productivity drain and leads to bloated codebases.
### Example
Consider a simple function to find an element in a slice. In Go, you need to write a separate function for each type:
```
func findInt(slice []int, val int) bool {
for _, v := range slice {
if v == val {
return true
}
}
return false
}
func findString(slice []string, val string) bool {
for _, v := range slice {
if v == val {
return true
}
}
return false
}
```
In a language with generics, you would write this once and reuse it for any type.
# Concurrency Model: Overhyped
## Goroutines Galore
Go’s goroutines are lightweight threads, and while they are powerful, they come with their own set of problems. Managing goroutines and channels can become incredibly complex, especially in large applications. Debugging concurrent code is notoriously difficult, and Go is no exception.
## Hypothetical Scenario
Imagine you’re managing a team of junior developers. They find goroutines cool and start using them everywhere. Soon, your codebase is a tangled mess of channels and goroutines, with race conditions and deadlocks lurking in every corner. It’s like trying to untangle Christmas lights in the dark.
# Interactive Elements
## Thought-Provoking Questions
1. How does Go’s simplicity compare to the complexity of other languages you’ve worked with? Do you find it beneficial or limiting?
2. Have you encountered situations where Go’s lack of features (like generics) caused significant issues in your projects?
3. How do you handle error management in your preferred language, and how does it compare to Go’s approach?
# Activity
Try rewriting a piece of code you’ve written in another language into Go. Note down the challenges and differences you encounter. This hands-on experience will highlight Go’s limitations in a practical context.
# Summary
While Go has its strengths and a strong following, it comes with significant drawbacks that can’t be ignored. Its simplicity can be deceptive, leading to verbose and repetitive code. The lack of essential features like generics, a cumbersome error handling system, and a concurrency model that’s easy to misuse make it a challenging language to master efficiently. Before you commit to learning Go, weigh these cons carefully against its pros.
# Additional Resources
1. [The Go Programming Language](https://golang.org/doc/)
2. [Effective Go](https://golang.org/doc/effective_go.html)
3. [Go Concurrency Patterns](https://blog.golang.org/pipelines)
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# IPFS problems: Too much immutability
Content-addressing is unusable with an index or database that describes each piece of content. Since IPFS is fully content-addressable, nothing can be done with it unless you have a non-IPFS index or database, or an internal protocol for dynamic and updateable links.
The IPFS [conceit](nostr:naddr1qqyxyeryx93kxv3nqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cwxek0q) made then go with the with the second option, which proved to be [a failure](nostr:naddr1qqyrvcnx8y6nwwtpqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cz8tlwh). They even incentivized the creation of a [database powered by IPFS](https://github.com/orbitdb/orbit-db), which couldn't be more misguided.
-

@ 6c2d68ba:846525ec
2024-08-08 21:15:25
Will man der Bundeszentrale für politische Bildung glauben, so handelt es sich bei Propaganda um den Versuch der gezielten Beeinflussung des Denkens, Handelns wie auch Fühlens von Menschen. Charakteristisch für Propaganda ist, dass sie darauf verzichtet die verschiedenen Seiten einer Thematik darzulegen, sondern gezielt Meinung mit (Fehl)-Information vermischt. Wer Propaganda betreibt, strebt nicht danach zu diskutieren oder die Öffentlichkeit gar mit Argumenten zu überzeugen, sondern greift zu verschiedensten Manipulationstechniken, die die Emotionen und das Verhalten der Öffentlichkeit beeinflussen. Propaganda nimmt dem Menschen (eigenständiges) Denken ab und gibt ihm stattdessen das Gefühl, mit der übernommenen Meinung goldrichtig zu liegen. Hier zeigt sich auch der wesentliche Unterschied zum Journalismus: Journalismus strebt nach Aufklärung, indem alle verfügbaren Fakten und Hintergründe dargelegt werden und der Empfänger selbst darüber entscheiden darf, was er für richtig und was er für falsch hält [1].
Zwar verbinden wir den Begriff Propaganda heutzutage mit autoritären und totalitären Staaten, wo diese auch zweifelsfrei Anwendung findet, doch kommen Propagandatechniken auch im Westen zum Einsatz, wenn auch in einer auf die demokratische Herrschaftsform zugeschnittene Art und Weise. Wie die Geschichte gezeigt hat - hier sind die Werke von Edward Bernays ganz besonders relevant [2] - wurde Öffentlichkeitsarbeit, sprich Public Relations (PR), basierend auf den Erkenntnissen der Propagandaforschung verfeinert, über welche die öffentliche Wahrnehmung von Personen, Konzernen und Regierungen beeinflusst wird. In Summe lässt sich daraus ableiten, dass auch Propaganda in unseren Breitengraden Tradition hat.
Nun halte ich es in Zeiten von (leider) wiederkehrenden heißen Konflikten in Europa besonders wichtig sich über existierende Manipulationstechniken wie auch gezielter Meinungsmache in (Massen)-medien bewusst zu sein wie auch erscheinenden Artikeln, Posts, Videos und ganz besonders Schlagzeilen mit einem gewissen Grad an Achtsamkeit zu begegnen, um nicht umgehend Opfer von Manipulation zu werden. Denn wie schon von der bereits erwähnten Bundeszentrale für politische Bildung erwähnt wurde, kann nur jener sich gegen den Einfluss von Propaganda wehren, der diese als solche erkennt. Dadurch motiviert nehme ich heute die Prinzipien der Kriegspropaganda ins Fadenkreuz.
> „Auf die Dauer vermag auch die frechste und bestorganisierte Propaganda nichts gegen die Wahrheit.“
―Albert Schweitzer
## Die Prinzipien der Kriegspropaganda
Unter dem Eindruck des Ersten Weltkriegs schrieb Arthur Ponsonby, britischer Adeliger & Staatsbeamter, 1928 das Buch "Lüge in Kriegszeiten", in welchem er die Mechanismen der damaligen Kriegspropaganda untersuchte. Er steht übrigens im Verdacht Urvater des berühmten Zitats "das erste Opfer im Krieg ist die Wahrheit" zu sein [3]. In diesem Werk schildert Ponsonby 20 Aspekte, die wiederum später von der Historikerin Anne Morelli im Jahr 2001 zu den zehn Prinzipien der Kriegspropaganda zusammengefasst wurden. Wie sie selbst betonte geht es bei diesen Prinzipien nicht darum herauszufinden, wer lügt und wer die Wahrheit sagt, wer das glaubt, was er sagt, sondern Mittels dieser Prinzipien die verbreitete Propaganda zu veranschaulichen und ihr Funktionieren zu beschreiben (Seite 6, [4]). Nachdem ich mich selbst mit diesen Prinzipien beschäftigt hatte, wurde mir mit jeder einzelnen Gedankenrunde immer klarer, wie die von Anne Morelli beschriebenen Prinzipien als wie eine Art Leitfaden verwendet werden, um Pressemeldungen, Argumente und Schlagzeilen in Sozialen Medien so zu formulieren, dass unabhängig vom Geschehnis stets eine unterbewusste Botschaft mitschwingt, so dass der gewünschte Effekt der Manipulation maximiert wird.
Nun könnte man nach Durchsicht der größten Tagesblätter des Deutschsprachigen Raums etliche Beispiele für jeden einzelnen der in Kürze vorgestellten Prinzipien präsentieren, doch habe ich in Anbetracht des Themas bewusst Abstand davon genommen, um nicht gewisse Journalisten - oder kriegstreibende Propagandisten wie ich sie nenne - samt Klarnamen an den Pranger zu stellen. Wie Anne Morelli, sehe ich den größtmöglichen Mehrwert darin, die Mechanik offenzulegen, um die Leserschaft für dieses Thema zu sensibilisieren.
### Wir wollen keinen Krieg!
Stets wird versichert, dass man den stattfindenden Krieg keines Falles wolle. In einer demokratischen Gesellschaft ist Krieg ein ungebetener Gast, weswegen Bevölkerungen fast ausnahmslos jedes Mal in die Kriegsbereitschaft hineingelockt werden müssen, siehe Brutkastenlüge im Zusammenhang mit dem Irakkrieg. Nun kann man sehr oft beobachten, wie Staatsführer stets in aller Inbrunst gegen den aktuellen oder einen eventuell bevorstehenden Krieg poltern. Wenn jedoch alle Personen an den entscheidenden Machthebeln so sehr gegen Kriege sind, wie können Kriege dann überhaupt ausbrechen?
<iframe width="560" height="315" src="https://www.youtube.com/embed/Ti7oC2mzX3o" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe>
### Der Gegner ist allein für den Krieg verantwortlich!
Der zugrundeliegenden Logik nach zeigt jeweils die eine Kriegspartei auf die andere und schiebt dabei die Schuld für den stattfindenden Krieg der anderen Seite zu. Selbst hat man natürlich keine provozierenden Schritte gesetzt, wie etwa das Stationieren von Raketensystemen, das Verschieben von Machtblöcken oder Ähnliches. Statt zum Mittel der Diplomatie zu greifen muss der Konflikt jetzt weiter angeheizt und der Krieg fortgeführt werden, denn schließlich muss dieser Krieg jetzt geführt werden, damit (ewiger) Frieden herrschen kann - siehe "Krieg ist Frieden" nach George Orwell. Darüber hinaus kann der Konflikt auch deshalb nicht beendet werden, weil der Feind sonst "unsere Werte" zerstört, "uns" die Freiheit nimmt oder gar ein Genozid "an unserem Volk" stattfindet.
[](https://i.nostr.build/7OaOooGkLEJMxWQN.jpg)
### Der Führer des feindlichen Lagers wird dämonisiert
Dieses Prinzip folgt der Logik des Reduzierens eines ganzen Landes auf eine an der Spitze sitzenden Person, also dem Zuschneiden auf Putin, Obama, Scholz, etc. Diese Person repräsentiert quasi einen fleischgewordenen Dämon, der die Macht über das Feindesland errungen hat und nun in Abwesenheit von geistiger Gesundheit einen Konflikt vom Zaun bricht. Morelli argumentiert dazu: "Man kann eine Gruppe von Menschen nicht insgesamt hassen, nicht einmal als Feinde. Es ist daher wirkungsvoller, den Hass auf die feindliche Führungspersönlichkeit zu richten. Der Gegner bekommt so ein Gesicht und dieses Gesicht wird natürlich Gegenstand des Hasses werden."
[](https://i.nostr.build/wYld4Zekq0hXoc49.jpg)
### Wir verteidigen ein edles Ziel und keine besonderen Interessen!
Der Fokus auf moralische und legitime Werte spielt diesem Prinzip nach deshalb eine besondere Rolle, weil es dazu dient die wirtschaftlichen und geopolitischen Ziele der eignen Seite zu verdecken, was auf das Stärken der Zustimmung der eigenen Bevölkerung schielt, da der Konflikt zu einem gewissen Grad nur durch Zustimmung eben dieser Bevölkerung geführt werden kann. So hatte Antonio Gramsci dargelegt wie sich die Ziele des Ersten Weltkriegs in drei Punkte zusammenfassen lassen: den Militarismus zu vernichten, die kleinen Staaten (wie etwa Belgien) zu verteidigen und die Welt für "die Demokratie" vorzubereiten. Letzteres Argument fand sich auch in den Konflikten des aktuellen Jahrhunderts in ähnlicher Form als "Spreading Democracy" oder "Befreiung des Iraks" wieder. Ergänzend könnte man zu diesem Prinzip sagen, dass ein Unterton von "der Feind ist ein blutrünstiges Monster aus einer barbarischen Gesellschaft" mitschwingt.
[](https://i.nostr.build/F5rxV1KGWPtUGctv.gif)
### Der Feind begeht wissentlich Grausamkeiten, wenn wir Fehler machen, geschieht dies unbeabsichtigt
Erzählungen über Gräueltaten des Feindes stellen ein wesentliches Element von Kriegspropaganda dar. Zwar sind Grausamkeiten zweifelsohne integraler Bestandteil eines jeden Krieges, und das auf beiden Seiten, jedoch ist die gegensätzliche Darstellung der eigenen "humanitären" Armee, die selbstverständlich von der Bevölkerung geliebt wird, und der feindlichen Armee, die als einzige Kriegspartei Grausamkeiten begeht, altbekannte Propaganda. Üblicherweise begnügt man sich nicht mit den tatsächlich auftretenden Verbrechen, im Gegenteil, man kann in vergangenen Konflikten wiederholt beobachten wie Verbrechen gegen die Menschlichkeit am Schreibtisch erfunden werden, um den Feind als die Wiederkehr Adolf Hitlers erscheinen zu lassen.
<iframe class="rumble" width="640" height="360" src="https://rumble.com/embed/vxlfj6/?pub=4" frameborder="0" allowfullscreen></iframe>
### Der Feind benutzt unerlaubte Waffen
In gewisser Weise ergänzt dieses Prinzip das vorangegangene und das nämlich um den Aspekt den Krieg selbst auf ritterliche Art und Weise zu führen, als wäre Krieg ein vollends definiertes Brettspiel, während der Feind geächtete Waffen einsetzt - zu jenen man selbst natürlich niemals greifen würde. Die Geschichte zeigt, dass hier oft der Gegenseite vorgeworfen wird, was die eigene Armee-(führung) bereits lange vorbereitet oder gar eingesetzt hat. Ein älteres Beispiel wäre die Verwendung von Giftgas im Ersten Weltkrieg, während Streumunition wie auch mit Uran angereicherte Munition ein trauriges Kapitel der vergangenen Monate ist.
[](https://i.nostr.build/YefQ6bJWIDtGtvtf.jpg)
### Wir erleiden geringe Verluste, die Verluste des Feindes sind erheblich
Zitat aus dem Buch von Morelli: "Von seltenen Ausnahmen abgesehen, schließen Menschen sich eher den siegreichen Anliegen an. Im Falle des Krieges hängt die Präferenz der öffentlichen Meinung sehr stark von den augenscheinlichen Ergebnissen des Konflikts ab. Wenn die Ergebnisse nicht gut sind, muss die Propaganda unsere Verluste verschleiern und die des Feindes übertreiben."
### Anerkannte Kulturträger und Wissenschafter unterstützen unser Anliegen
Ein unterschätztes Mittel der Propaganda ist das Einbeziehen von Personen des öffentlichen Lebens, favorisiert jene zu denen möglichst große Teile der Bevölkerung ein Vertrauensverhältnis entwickelt haben oder Personen mit einer gewissen "moralischen Autorität", wie etwa geistliche Führer. Darüber hinaus ließen sich in der Vergangenheit - wie auch heute - Künstler und Medienschaffende dazu instrumentalisieren Filme, Dokumentationen und Karikaturen über den Feind zu erstellen wie auch zu verbreiten. Man rufe sich in Erinnerung, dass man nicht ohne Grund von der Heimatfront spricht. In einer halbwegs von Demokratie geprägten Gesellschaft entscheidet das Wahlvolk wie lange ein Konflikt noch geführt werden kann bzw. wie stabil die kriegsführende Regierung im Sattel sitzt.
<iframe width="560" height="315" src="https://www.youtube.com/embed/Eo5DrObovLc" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe>
### Unser Anliegen hat etwas Heiliges
Dieses Prinzip mag bei erster Betrachtung an die Kreuzzüge erinnern, bei jenen "der Wille Gottes" in gewisser Weise im Mittelpunkt stand. Ein in meinen Augen wichtiges Element bei diesem Aspekt ist die versteckte Nachricht des Kampfes Gut gegen Böse. Wir, die Guten, kämpfen gegen das Böse, den Feind, und treiben diesen Konflikt nun gewaltsam voran, um die Welt von dem Bösen zu befreien, die Welt also einer Heilung zu unterziehen. Neben dem religiös angehauchten Argument scheint dieses Propagandaprinzip um das Schlagwort "Demokratie" bereichert geworden zu sein. Wie in meinen Augen zurecht aufgezeigt wird, sprach auch George Bush von der "Achse des Bösen" wie auch der Pflicht dem Irak Demokratie zu bringen, also ein Gut, dass gottesgleiche Züge zu haben scheint. Sprachliche Ausschmückungen wie "Gott ist mit uns" tun in Botschaften, die sich nach diesem Prinzip richten, ihr übriges.
[](https://i.nostr.build/lMXqTsTZ6m8yhYAk.jpg)
### Wer unsere Propaganda in Zweifel zieht, arbeitet für den Feind und ist damit ein Verräter
Das zehnte und somit letzte Prinzip kann mit den vorangegangenen Prinzipien kombiniert werden. In manchen Situationen dient dieses Prinzip jedoch auch als Leitmotiv im Umgang mit kritischen Stimmen aus der Heimatfront. Wer auch immer Meldungen, Schlagzeilen oder gar Argumente infrage stellt, ist automatisch ein Kollaborateur des Feindes. Anhand dieser polarisierten Betrachtungsweise des "entweder bist du für uns oder gegen uns" muss umgehend Farbe bekannt werden. Durch diese Eliminierung einer abgewogenen Betrachtung von komplexen Ereignissen wird es also unmöglich gemacht, eine abweichende Meinung zu entwickeln, ohne einen regelrechten Lynchprozess am Hals zu haben. Man könnte dies auch als das Ende des Meinungspluralismus interpretieren, wo jegliche Opposition zum Schweigen verurteilt wird und zur Not diffamiert wie auch diskriminiert wird.
[](https://i.nostr.build/LDivLGBJNdRjIIgh.png)
## (Weitere) Methoden der Kriegspropaganda
Wie in [6] präsentiert, können Propagandisten auf eine erstaunlich große Bandbreite von Manipulationsmethoden zurückgreifen. In meinen Augen lohnt sich ein kurzer Blick darauf. Ein wesentlicher Punkt, den es meiner Meinung nach zu beachten gilt, ist die Tatsache, dass mit dem gezielten Einsatz von (Kriegs)-Propaganda meist lange vor dem ersten Schusswechsel begonnen wird und auch nach Beendigung des Konfliktes Propaganda einen wichtigen Teil der militärischen Strategie darstellt.
### Die Rolle von Angst
Das Zeichnen eines immanenten Bedrohungsszenarios, welches besonders über die emotionale Schiene wahrgenommen wird, stimmt Menschen am ehesten um die Notwendigkeit eines Militäreinsatzes zu befürworten. Dabei spielt es meiner Ansicht nach gar keine so große Rolle, ob diese Bedrohung real existiert oder nicht, ausschlaggebend ist die gefühlte Wahrnehmung der Bevölkerung. Bestehende oder induzierte Angst lassen sich durch geschicktes Beeinflussen schnell in Wut wandeln und am Ende des Prozesses in einen flammenden Hass auf den vermeintlichen Feind. Aus diesem Grund wird oft ein Zustand der permanent gefühlten Bedrohung geschaffen, sodass in den Köpfen eine gefühlte Gefahr für Laib und Leben so oft wie möglich präsent ist. Dieser Prozess wird durch ständiges Wiederholen der Botschaft verstärkt, bis es sich tief im Unterbewusstsein der Bevölkerung eingenistet hat.
[](https://i.nostr.build/n8EkzpWIZBSYcsey.jpg)
### Zensur
Zensur - das gezielte Unterdrücken oder Weglassen von Informationen zu einem Sachverhalt, ist schon lange fixer Bestandteil von Propaganda. Bestimmte Sichtweisen können in der Abwesenheit von Gegenargumenten oder gar Gegenbeweisen besonders gut verfestigt werden. Hierzu genügt es aus Sicht des Staatsapparats nicht nur Beiträge zu löschen oder Meinungen zu unterdrücken, nein, damit dies möglich ist, muss flächendeckende wie auch umfängliche Überwachung stattfinden, damit in den Augen des Unterdrückers problematische Informationen schnellstmöglich aus dem Verkehr gezogen werden können.
Von Zensur betroffen sind Druckerzeugnisse wie etwa Zeitungen und Bücher, aber auch Ton und Bildproduktionen. Auf digitaler Ebene können Webseiten, Blogs, Content Creatoren oder gar ganze Online Communities hiervon betroffen sein. Im Kontext eines Krieges ist es für die heimische Konfliktpartei von enormer Bedeutung Zensur anzuwenden, um dem Feind keinerlei geheime Informationen zukommen zu lassen - zum Beispiel über Waffen, Truppenbewegungen oder geplante Manöver der eigenen Einheiten. Ein weiteres Anliegen geht in die Richtung wie der Krieg in der Öffentlichkeit dargestellt wird. So kann ohne Anwendung von Zensur das Vertrauen in die Politik schwinden und somit schlussendlich die Zustimmung zum Fortführen der kriegerischen Handlungen schwinden. Dies kann beispielsweise passieren, sobald die Bevölkerung von Niederlagen, Fehlschlägen, dem von der eigenen Armee ausgelösten Leid oder gar Kriegsverbrechen der eigenen Reihen Wind bekommt. Daher ist es im Interesse des Zensors solche Informationen geheim zu halten.
Während die direkte Zensur in der westlichen Welt weitestgehend abgeschafft wurde, findet indirekte Zensur nach wie vor Anwendung. Hierbei ist die Zugangskontrolle zu bestimmten Informationen gemeint. Es existieren quasi Torwächter, die darüber entscheiden welcher Journalist welche Informationen gefüttert bekommt. Darüber hinaus können Informationen - etwa über bestimmte Kriegsverbrechen - bewusst vorenthalten werden oder Journalisten dürfen bestimmte Orte erst gar nicht betreten. Somit bleibt vielen Journalisten wie auch Berichterstattern oft nichts anderes übrig, als die Meldungen der Militärführung zu übernehmen.
[](https://i.nostr.build/DjCuTC25Y7Smnqhd.jpg)
Eine dritte Form von Zensur, die in meinen Augen oftmals gar nicht erst bedacht wird, ist die Selbstzensur von Berichterstattern. Obwohl es in vielen Fällen keine politischen oder militärischen Zensurvorschriften gibt, unterschlagen Berichterstatter bestimmte Informationen. Erklärungen hierfür können Motivationen wirtschaftlicher Natur eines Mediums, direkte Bestechung oder Begünstigung sein. Nicht zu unterschätzen ist die aufkommende Angst eines Journalisten sich durch das Vertreten von unpopulären Ansichten Karrierechancen zu verbauen. Zu dieser Gefühlslage kommt hinzu, dass Journalisten oftmals wegen ihrer eigenen Weltanschauung und dem damit verbundenen Wertekompass die Realität nur einseitig wahrnehmen.
[](https://i.nostr.build/WT7Tiu3TzMF9sO0z.jpg)
### Die Verzerrung der Sprache
Die menschliche Sprache verwendet Bilder um Botschaften zu transportieren. Dabei ist jedes Hauptwort wie ein Paket mit einem gewissen bildlichen Inhalt zu verstehen. Zudem lassen sich durch geschickte Auswahl von Worten Stimmungen hervorrufen oder unterdrücken. In der Kriegspropaganda unterscheidet man hier zwischen:
* Black Words - Diese dienen zum Erschaffen eines klaren Feindbildes, welche beim Empfänger Unbehagen und Angst wecken können. Besonders in Kriegszeiten greifen Politiker in ihren Ansprachen auf Begriffe wie Diktator, Hass, Waffen, Terrorismus, Unterdrückung, Regime, Tyrannei, das Böse und so weiter zurück.
* White Words - Hierbei handelt es sich um sprachliche Bilder, die mit positiven Gefühlen verbunden sind und dienen, strategisch in Reden platziert, der moralischen Rechtfertigung des Krieges. Hierzu zählen Begriffe wie Demokratie, Freiheit, Gerechtigkeit, Sicherheit, Frieden, Familie, Nation, Humanität, Vaterland, etc.
* Sprachliche Schönfärberei - Gezielt werden Formulierungen verwendet, die einen beschönigenden Effekt haben wie beispielsweise "Kollateralschaden" statt "Getötete oder verletzte Zivilisten" oder "Luftschlag" statt "Bombardement".
### Mitläuferfang
Es liegt wohl in der Natur des Menschen lieber auf der Gewinner als auf der Verliererseite stehen zu wollen, weswegen wir Menschen uns tendenziell lieber der Mehrheit anschließen. Mehrheiten versprechen Erfolg, denn allzu gutgläubig glauben wir Mehrheiten würden sich niemals täuschen. Die Strategie des Mitläuferfangs nutzt diese menschliche Anlage aus, indem die kundgetane Meinung als die Meinung der Mehrheit verkauft wird. Hierzu werden öfters auch Bilder eingesetzt, die den Eindruck erwecken, eine große Masse würde bereits dieser propagierten Meinung folgen.
[](https://i.nostr.build/efE0zri3SYp2sr8V.jpg)
### Ästhetisierung
Unter dem Begriff Ästhetisierung versteht man eine verschönerte Darstellung einer Sache. Etwa wird durch eine ästhetische Darstellung des Krieges versucht dem Krieg den Schrecken zu nehmen, wodurch abgezielt wird den Krieg dadurch leichter akzeptieren zu können. Fotos und Filme, die den Krieg dokumentieren sollen, werden bewusst so aufgenommen bzw. ausgewählt, dass sie beim Betrachter eher Faszination als Abschreckung auslösen. All das sorgt dafür, dass das Bild schön und ansprechend empfunden wird, und den Betrachter die eigentlich hässliche Kriegsrealität vergessen lässt.
[](https://i.nostr.build/DgM3EL4Cv85hUxdE.jpg)
### Militainment
Dieser Begriff verbindet "Militär" und "Entertainment" und besonders jüngere Leser sollten schnell erkennen was hier gemeint ist. Hingedeutet wird hier auf die aktive Zusammenarbeit zwischen Militär und Medienunternehmen bei der Produktion von Kriegsfilmen, -serien, -dokumentationen oder Computerkriegsspielen. Beide Seiten ziehen Nutzen daraus: Das Militär stellt die Ausrüstung zur Verfügung, die für eine Produktion nötig ist. Als Gegenleistung verpflichten sich die Medienmacher, den Krieg in der vom Militär gewünschten Weise darzustellen. Letztlich entscheidet das Militär darüber, was gezeigt werden darf und was nicht. So wird der Krieg zum Schauplatz von Heldengeschichten, in denen das Militär ehrenvoll erscheint und andere Möglichkeiten als Krieg zur Lösung von Konflikten ausgeblendet werden. Diese Darstellungsweise trägt dazu bei, dass das Ansehen des Militärs und die gesellschaftliche Akzeptanz von Kriegen steigen.
Auch die Computer- und Softwareindustrie wird durch das Militär unterstützt. Ähnlich wie bei Kriegsfilmen ist ein realistisches Erscheinungsbild für Computerkriegsspiele sehr wichtig. Doch wie kommt man an alle Taktiken, Uniformen, Sounds, Einsatzpapiere oder gar Stimmen und Karten heran? – Man braucht die Army. Da die sich allerdings aussucht, wer welches Material bekommt, kann sie von einem Einspruchsrecht Gebrauch machen. Das ist nicht unstatthaft, wer würde schließlich ein Projekt finanzieren oder unterstützen, das das eigene Werbebild beschädigt?
[](https://i.nostr.build/oUojwTrYYW08yaP5.jpg)
## Fazit
Wie im Lauf des Posts immer deutlicher wird, ist die Bandbreite an Methoden, aus der Propagandisten schöpfen können, beträchtlich. Darüber hinaus stammen diese Techniken nicht aus dem letzten Quartal, sondern hatten jahrhundertelang Zeit, um verfeinert zu werden. Ich hoffe mit diesem Post zur Stärkung der Achtsamkeit im Bereich der Propaganda wie auch der Sensibilisierung im Hinblick auf den Einsatz von Propagandatechniken im Alltag beizutragen. Nur wer Propaganda wie auch Manipulationsversuche als solche erkennt, wird in der Lage sein sich dessen zu erwehren. Das Schlusswort möchte ich nun einer Person überlassen, die mich schon vor Jahren dazu inspiriert hatte mich mit dieser unbequemen Thematik zu beschäftigen:
> "Nearly every war that has started in the past 50 years,
has been the result of media lies.
The media could have stopped it,
if they hadn't reprinted government propaganda
but what does that mean?
Well, that means basically populations don't like wars
and populations have to be fooled into wars.
populations don't willingly and with open eyes go into a war
So, if we have a good media environment
then we will also have a peaceful environment.
Our number one enemy is ignorance." - Julian Assange
## Quellen
1. https://www.bpb.de/themen/medien-journalismus/krieg-in-den-medien/130697/was-ist-propaganda
2. https://www.goodreads.com/book/show/493212.Propaganda
3. https://weltwoche.ch/daily/prinzipien-der-kriegspropaganda-von-arthur-ponsonby
4. https://www.morawa.at/detail/ISBN-9783866744158/Morelli-Anne/Die-Prinzipien-der-Kriegspropaganda?CSPCHD=002000000000JAZLG7CSVpoEmIWvrDniZIp7zJA2Cmz9CJ_rwt
5. https://de.wikipedia.org/wiki/Die_Prinzipien_der_Kriegspropaganda
6. https://www.bpb.de/themen/medien-journalismus/krieg-in-den-medien/130699/methoden-der-kriegspropaganda/
## Bücher zum Thema
- Edward Bernays - Propaganda
- Anne Morelli - Die Prinzipien der Kriegspropaganda
- Patrik Baab - Propaganda-Presse: Wie uns Medien und Lohnschreiber in Kriege treiben
- Jonas Tögel - Kognitive Kriegsführung: Neueste Manipulationstechniken als Waffengattung der NATO
- Gustave Le Bon - Psychologie der Massen
- Marcus Klöckner - Umstritten: Ein journalistisches Gütesiegel
## Videos zum Thema
- [Jonas Tögel: Kognitive Kriegsführung – Neueste Manipulationstechniken als Waffengattung der NATO](https://www.youtube.com/watch?v=FCIsI9auGoQ)
- [„Zensur und Propaganda sind Nato-Programm“ - Punkt.PRERADOVIC mit Patrik Baab](https://www.youtube.com/watch?v=TOFwLh1ejSE)
- [Kriegsbereitschaft und Gegnerdämonisierung ǀ Gabriele Krone-Schmalz](https://www.youtube.com/watch?v=oasUOVevSoQ)
- [Daniele Ganser: Propaganda – Wie unsere Gedanken und Gefühle gelenkt werden](https://www.youtube.com/watch?v=ooM3rrBoiBA)
- [Umstritten - Marcus Klöckner](https://www.youtube.com/watch?v=PXLaAUl5pFc)
-

@ 361d3e1e:50bc10a8
2024-08-18 18:13:10
[Full story](https://forex-strategy.com/2024/08/18/covid-and-monkeypox-what-an-amazing-coincidence-in-germany/)
Covid and Monkeypox - What an amazing coincidence in Germany
It turns out that the new pandemic (Monkeypox) begins in an absolutely identical way, just like the old one pandemic - the covid.
#germany #covid #monkeypox #pandemic #health #medicine
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Agentes racionais
Existe essa discussão entre economistas sobre o comportamento de um agente ser "racional" ou não.
O julgamento da racionalidade é feito em vista de um "modelo" concebido pelo economista. Cada economista usa um modelo diferente. Daí ficam todos discutindo a racionalidade ou irracionalidade de certo agente.
A solução é perguntar: racional segundo quais critérios?
-

@ 361d3e1e:50bc10a8
2024-08-18 14:16:17
The huge share of ultra-processed foods, especially in the United States, is due to the fact that the food industry is in the hands of several global corporations. They have literally occupied all the supermarkets with their products.
[Full story](https://forex-strategy.com/2024/08/18/how-people-passing-through-the-supermarket-go-to-hospitals-our-ultra-processed-food/)
-

@ 8dc86882:9dc4ba5e
2024-08-06 12:47:33
If I can just write my key down on paper or my recovery phrase, what is the benefit to things like coldcard? It's no easier to lose than a notebook?
originally posted at https://stacker.news/items/637285
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Buying versus donating
Currently (and probably it has always been the case) in the Bitcoin community there is some push towards donations as some sort of business model, or in general just a general love for the idea of donations, and I think that is very misguided.
## Two examples of the push for the primacy of donations
For example, there is a general wantness of people to have some sort of "static QR code" or "static Lightning invoice" that people can put on their Twitter profiles to receive donations (sometimes they say "payments" instead of "donations" but to me there is no such a thing as a payment without a good or service being given in exchange, so I'm saying "donations") and that is a hard problem to solve considering the fact that most Lightning wallets are running on phones.
Another example is the "Podcasting 2.0" initiative that tries to integrate podcast players with Lightning wallets so they can send donations to podcast hosts that are running Lightning nodes. Their proponents call it "value for value" (or "value4value", "v4v") and if you ask they will say _value4value_ is a "model" in which the listener gives out in satoshis to the podcast host the same amount of "value" he is getting from listening to that content.
The _value4value_ concept makes it almost explicit the problems I see with this big emphasis on donations the Bitcoin community is making in general. In essence, the idea that the listener is capable of measuring the value it gets from the podcast then converting it into a monetary amount and then donating that is completely wrong and even nonsensical.
### Why _value4value_ is not sound
Basic (Austrian) economics teaches us that all value is ordinal, not cardinal -- i.e., it can't be measured or assigned a number to. One can only know that at some instant they prefer _x_ over _y_, they cannot say _x_ has a value of 10 and _y_ has a value of 9. Because of that, it's a nonsense quest to try determine how much value one is getting from a podcast.
Basic (Austrian) economics also teaches us that exchanges happen when there are differences in the subjective valuations of goods, i.e., Alice can give _x_ to Bob in exchange for _y_ if Alice prefers _y_ over _x_ and Bob prefers _x_ over _y_ at that point. Because of that (and disregarding the previous paragraph), it's futile to expect that the podcast listener will donate _exactly_ the amount he is getting from the podcast in "value".
Because of the two points above, it should also be clear that it is impossible to convert "value" in podcast content form into "value" in satoshis form, but I won't try to explain why that is because this is not an economics textbook.
What actually happens is that whether it's in the _value4value_ context or not, donations are always a somewhat random and subjective amount, if they happen. If I like some content that someone is publishing for free, my decision on if and how much I will donate is never dictated by some nonsense calculation, but by calculation that is governed almost entirely by feeling and animal spirits (but one that also considers how much money I can spare, how much I like that person and how much I perceive they need).
When I go to a normal shop to buy a bottle of milk I look at the bottle of milk and I read its price, and there is one simple decision I have to make: is this bottle of milk worth more than the amount of money that's specified in the price tag? It's a single decision with only two answers: _yes_ or _no_.
While when I see a free form on some free "creator" page asking me to type how much I will donate I have to decide if I will donate, when I will donate, how much I will donate, if I want this donation to be done every month or how will that work going forward? Will I keep consuming the content produced by this person? Will they keep producing? Maybe I'll just listen for free now and do this later as I'm busy, but then will I forget? Maybe I have just donated a lot to someone else and do not have much more money to spare, but now I feel guilty that the other person got all my donation money and this one didn't get anything but I can't go back and ask the other to return the money I just donated -- and so on and so forth.
### Conclusions
Although the paragraphs above are confusing and do not follow a very logical presentation pattern, I hope you got from them why I think donations are much more complicated than purchases, and that repeating the "value for value" mantra doesn't help at all.
Considering that, what I wanted to say is that bitcoiners should give more attention to the other model, in which people produce goods and services and sell them. And that model can be applied successfully to "content creators", podcasters etc in many ways that are probably (I don't have any data backing my claims) better than the donation model.
## Other possible monetization possibilities
For example, I've noticed that many blogs and podcasts with interesting content start to release exclusive episodes as they get big enough. These exclusive episodes are available only for "supporters". This is effectively selling access to the episodes. There is also the "crowdwall" model in which multiple people pay so that some content gets released for free.
We can count even the model in which a donation is not just a blank donation, but gives the donor the right to write something on the screen or something like that -- these are actually not just donations, but purchases of these rights.
Professional videogame streamers have come up with some other interesting ideas. For example, they crowdfund the creation of special content ("if enough people pay I will dress like a rabbit") or they sell the right to participate in the stream somehow (for example, by playing a game with the streamer in some special day).
In these models, the _static QR code_ with which so many people dream doesn't make much sense (if you're selling a specific episode or if a payment is specific to one identifiable person, you need different QR codes or more metadata to be attached to each payment by the payer).
## Addendum
I think people like the donation model very much because they only see the big and super famous people that receive donations. A very small set of people have so many followers that they can live with just donations, even though donations are very inefficient and they could earn more and even deliver better content if they were using some other model.
I imagine that a creator with a high number of followers will get a lot of people that do not donate anything, a lot that will donate a little -- probably less than they would if they were paying -- and eventually a little number of people that will donate way more than they would if they were buying. This last group is probably what makes it worthwhile to work on this donations model for these creators.
The takeaway is that the donations model is not a panacea and is not very good either.
## Related:
- [Donations on the internet](nostr:naddr1qqyrqwp4xsmnsvtxqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cex8903)
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# A podridão
É razoável dizer que há três tipos de reações à menção do nome [O que é Bitcoin?](nostr:naddr1qqrky6t5vdhkjmspz9mhxue69uhkv6tpw34xze3wvdhk6q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqp65wp3k3fu) no Brasil:
1. A reação das pessoas velhas
Muito sabiamente, as pessoas velhas que já ouviram falar de Bitcoin o encaram ou como uma coisa muito distante e reservada ao conhecimento dos seus sobrinhos que entendem de computador ou como um golpe que se deve temer e do qual o afastamento é imperativo, e de qualquer modo isso não as deve afetar mesmo então para que perder o seu tempo. Essas pessoas estão erradas: nem o sobrinho que entende de computador sabe nada sobre Bitcoin, nem o Bitcoin é um golpe, e nem é o Bitcoin uma coisa totalmente irrelevante para elas.
É razoável ter cautela diante do desconhecido, no que as pessoas velhas fazem bem, mas creio eu que também muito do medo que essas pessoas têm vem da ignorância que foi criada e difundida durante os primeiros 10 anos de Bitcoin por jornalistas analfabetos e desinformados em torno do assunto.
2. A reação das pessoas pragmáticas
"Já tenho um banco e já posso enviar dinheiro, pra que Bitcoin? O quê, eu ainda tenho que pagar para transferir bitcoins? Isso não é vantagem nenhuma!"
Enquanto querem parecer muito pragmáticas e racionais, essas pessoas ignoram vários aspectos das suas próprias vidas, a começar pelo fato de que o uso dos bancos comuns não é gratuito, e depois que a existência desse sistema financeiro no qual elas se crêem muito incluídas e confortáveis é baseada num grande esquema chamado Banco Central, que tem como um dos seus fundamentos a possibilidade da inflação ilimitada da moeda, que torna todas as pessoas mais pobres, incluindo essas mesmas, tão pragmáticas e racionais.
Mais importante é notar que essas pessoas tão racionais foram também ludibriadas pela difusão da ignorância sobre Bitcoin como sendo um sistema de transferência de dinheiro. O Bitcoin não é e não pode ser um sistema de transferência de dinheiro porque ele só pode transferir-se a si mesmo, não pode transferir "dinheiro" no sentido comum dessa palavra (tenho em mente o dinheiro comum no Brasil, os reais). O fato de que haja hoje pessoas que conseguem "transferir dinheiro" usando o Bitcoin é uma coisa totalmente inesperada: a existência de pessoas que trocam bitcoins por reais (e outros dinheiros de outros lugares) e vice-versa. Não era necessário que fosse assim, não estava determinado em lugar nenhum, 10 anos atrás, que haveria demanda por um bem digital sem utilidade imediata nenhuma, foi assim por um milagre.
Porém, o milagre só estará completo quando esses bitcoins se tornarem eles mesmo o dinheiro comum. E aí assim será possível usar o sistema Bitcoin para transferir dinheiro de fato. Antes disso, chamar o Bitcoin de sistema de pagamentos ou qualquer coisa que o valha é perverter-lhe o sentido, é confundir um acidente com a essência da coisa.
3. A reação dos jovens analfabetos
Os jovens analfabetos são as pessoas que usam a expressão "criptos" e freqüentam sítios que dão notícias totalmente irrelevantes sobre "criptomoedas" o dia inteiro. Não sei muito bem como eles vivem porque não lhes suporto a presença, mas são pessoas que estão muito empolgadas com toda a "onda das criptomoedas" e acham tudo muito incrível, tão incrível que acabam se interessando e então comprando todos os tokens vagabundos que inventam. Usam a palavra "decentralizado", um anglicismo muito feio que deveria significar que não existe um centro controlador da moeda x ou y e que o seu protocolo continuaria funcionando mesmo que vários operadores saíssem do ar, mas como o aplicam aos tokens que são literalmente emitidos por um centro controlador com uma figura humana no centro que toma todas as decisões sobre tudo -- como o Ethereum e conseqüentemente todos os milhares de tokens ERC20 criados dentro do sistema Ethereum -- essa palavra não faz mais sentido.
Na sua empolgação e completo desconhecimento sobre como um ente nocivo poderia destruir cadauma das suas criptomoedas tão decentralizadas, ou como mesmo sem ninguém querer uma falha fundamental no protocolo e no sistema de incentivos poderia pôr tudo abaixo, sem imaginar que toda a valorização do token XYZ pode ter sido fabricada de caso pensado pelos seus próprios emissores ou só ser mesmo uma bolha, acabam esses jovens por igualar o token XYZ, ou ETH, BCH ou o que for, ao Bitcoin, ignorando todas as diferenças qualitativas e apenas mencionando de leve as quantitativas.
Misturada à sua empolgação, e como um bônus, surge a perspectiva de ficar rico. Se um desses por algum golpe de sorte surfou em alguma bolha como a de 2017 e conseguiu multiplicar um dinheiro por 10 comprando e vendendo EOS, já começa logo a usar como argumento para convencer os outros de que "criptomoedas são o futuro" o fato de que ele ficou rico. Não subestime a burrice humana.
---
Há jovens no grupo das pessoas velhas, velhas no grupo das pessoas jovens, pessoas que não estão em nenhum dos grupos e pessoas que estão em mais de um grupo, isso não importa.
-

@ 361d3e1e:50bc10a8
2024-08-17 10:32:21
Scientists from South Korea are proposing to shock people with a weak current to curb their hunger and combat overeating. Scientists from the Korea Research Institute believe that weak electric currents directed to specific areas of the brain through the scalp can affect neural circuits that control our appetite. The photo shows the electric helmet that is given to test subjects.
[Full story](https://forex-strategy.com/2024/08/16/scientists-offer-a-solution-to-hunger-instead-of-food-they-pass-electricity-through-the-body/)
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Scala is such a great language
Scala is amazing. The type system has the perfect balance between flexibility and powerfulness. `match` statements are great. You can write imperative code that looks very nice and expressive (and I haven't tried writing purely functional things yet). Everything is easy to write and cheap and neovim integration works great.
But Java is not great. And the fact that Scala is a JVM language doesn't help because over the years people have written stuff that depends on Java libraries -- and these Java libraries are not as safe as the Scala libraries, they contain reflection, slowness, runtime errors, all kinds of horrors.
Scala is also very tightly associated with Akka, the actor framework, and Akka is a giant collection of anti-patterns. Untyped stuff, reflection, dependency on JVM, basically a lot of javisms. I just arrived and I don't know anything about the Scala history or ecosystem or community, but I have the impression that Akka has prevent more adoption of Scala from decent people that aren't Java programmers.
But luckily there is a solution -- or two solutions: ScalaJS is a great thing that exists. It transpiles Scala code into JavaScript and it runs on NodeJS or in a browser!
Scala Native is a much better deal, though, it compiles to LLVM and then to binary code and you can have single binaries that run directly without a JVM -- not that the single JARs are that bad though, they are great and everybody has Java so I'll take that anytime over C libraries or NPM-distributed software, but direct executables even better. Scala Native just needs a little more love and some libraries and it will be the greatest thing in a couple of years.
-

@ bcbb3e40:a494e501
2024-08-16 18:00:07
## El hombre y el contexto
El pensamiento tradicionalista español cuenta con una amplia trayectoria en la que concurren personajes, situaciones e ideas gestadas en el transcurso de dos siglos, en los que debemos distinguir el conflicto dinástico y el papel del legitimismo de la propia doctrina, que es algo que se construirá en el tiempo, con la contribución de figuras como el protagonista de este escrito, Don Juan Vázquez de Mella, así como por la confluencia de fuerzas de diferente signo que tiene lugar a lo largo del siglo XIX y la consolidación del Estado liberal, que lo hará siempre en lucha abierta contra las peculiaridades y el carácter genuino del pueblo español. Vázquez de Mella, nuestro autor, quizás represente la consolidación y madurez doctrinal del movimiento tradicionalista español, uno de sus primeros y más brillantes sistematizadores. No se destacó por una obra extensa ni especialmente difundida más allá de sus discursos, de sus artículos en periódicos y sus escritos dispersos, los cuales fue capaz de dotar de una especial significación y dignidad fruto de su enorme carisma y especial clarividencia para dar una forma definida y meridianamente clara a las ideas y doctrinas que nutrieron el tradicionalismo español madurado al calor de las armas, de las tres guerras que el carlismo libró contra el liberalismo español.
||
|:-:|
|Juan Vázquez de Mella|
Nuestro autor, de origen asturiano, y nacido en Cangas de Onís un 8 de junio de 1861, ha mantenido vivo su prestigio y el valor de sus aportaciones teórico-doctrinales, ampliamente reconocidos por sus sucesores, por [**Rafael Gambra Ciudad**](https://hiperbolajanus.com/posts/la-sociedad-tradicional-y-sus-enemigos/) (1920-2004) y [**Francisco Elías de Tejada y Espinola**](https://hiperbolajanus.com/libros/mos-maiorum-1/) (1918-1978), así como de otros autores como **Álvaro D'Ors** (1915-2004) y otros muchos, que han reivindicado su figura en el tiempo y se han nutrido de sus fecundas enseñanzas. Se ha destacado la rectitud de su pensamiento, su inquebrantable voluntad y su impagable contribución en la creación de un marco teórico y conceptual para dar un sentido y una forma a las ideas del tradicionalismo español. Hijo de un militar de origen gallego, muerto prematuramente, quedó huérfano de padre durante su niñez, por lo cual pasó al cuidado de unos parientes de origen modesto. Estudió en la Universidad de Santiago de Compostela, donde mostró tempranamente su temperamento y habilidades oratorias, que explotó convenientemente a través de diarios como _La Restauración_ o _El pensamiento galaico_, donde también mostró sus filiaciones militantes con el catolicismo tradicional. Sus habilidades y la brillantez de sus escritos pronto llegaron a Madrid, a las más altas instancias del Carlismo, lo que le permitió dar continuidad a sus actividades desde un medio más amplio, a través de _El correo español_.
En su militancia política llegó a las más altas cotas de su trayectoria con la elección en 1893 como representante de las Cortes por el distrito de Estella, Navarra, que ya con sus primeros discursos obtuvo un notable éxito, incluso entre los propios liberales, hasta 1900, fecha en la que se vio obligado a marcharse a Portugal, acusado de participar en una conspiración para derrocar el régimen de la Restauración. No regresó a España hasta 1905, manteniendo su estatus como diputado hasta 1919. De todos modos, no queremos dar más protagonismo a la biografía en detrimento de la doctrina, que es lo que nos interesa en este artículo, de ahí que obviemos otros datos biográficos trascendentes, polémicas con otras facciones del carlismo o sus posturas respecto a la dictadura del general Miguel Primo de Rivera, que nos harían desviar la atención del propósito principal que acabamos de enunciar.
La gran paradoja del Carlismo fue que a pesar de su derrota en la Tercera Guerra Carlista (1872-1876), y pese a la posterior escisión integrista en 1888, el partido carlista continuó manteniendo una fuerza y preponderancia significativa en la sociedad española del régimen de la Restauración durante el último cuarto de siglo. El Carlismo se vio inmerso en un buen número de paradojas, de situaciones encontradas, especialmente en relación al Desastre del 98 y la pérdida de los últimos territorios ultramarinos. Mientras que la gran esperanza del tradicionalismo español estaba depositada en el desmoronamiento y caída final de la restauración alfonsina, por otro lado este mismo régimen trataba de defender, al menos en teoría, los últimos restos del imperio español y, de algún modo, a la España católica frente a una nación protestante, como era la anglosajona estadounidense. Al mismo tiempo, durante esta época el tradicionalismo español se enfrentó a los grandes retos que presentaba una sociedad en cambio, con transformaciones políticas y sociales de gran calado como la emergencia del sufragio universal o el nacimiento de los separatismos periféricos (propiciados por la burguesía liberal), las cuales requerían de nuevas estrategias y reestructuraciones internas capaces de enfrentar la envergadura de todos estos cambios. Fue en este contexto donde se significó la figura de Juan Vázquez de Mella, quien merced a la obra de sistematización a la que ya hemos hecho alusión, y de sus concurridas conferencias, dio lugar a la denominada _Acta Loredán_, redactada por el tradicionalista asturiano y publicado en _El correo español_. Este escrito tenía como ejes fundamentales la defensa de la nación política española fundamentada en la monarquía, el catolicismo y el régimen foral. Al mismo tiempo, también recogía la reivindicación de un programa corporativista y gremial al abrigo de la doctrina social de la Iglesia defendido en la encíclica _Rerum Novarum_ (1891), y es lo que se conoce como el «sociedalismo», cuyos antecedentes encontramos ya [en autores como **Donoso Cortés**](https://hiperbolajanus.com/posts/resena-de-los-fundamentos-historicos/) o **Antonio Aparisi Guijarro**. Son precisamente los atributos de esta doctrina, que contribuyó a la revitalización del pensamiento carlista, los que nos disponemos a desarrollar a continuación.
La figura del tradicionalista asturiano, de Don Juan Vázquez de Mella, aparece como necesaria ante una serie sucesiva de destrucciones que el régimen liberal ha producido sobre los fundamentos tradicionales de España, pero su papel no fue, como ya venimos apuntando, el de un gran intelectual erudito, y de hecho, como apunta Rafael Gambra, las mayores debilidades de su pensamiento se encuentran en los principios filosóficos, y destacando, en cambio, su papel de «revulsivo espiritual» podemos ubicarlo mejor en el ámbito de lo político y lo espiritual. Para ello debió tomar en cuenta las fuentes de sus predecesores, entre los cuales podemos ubicar perfectamente al ya mencionado Donoso Cortés y **Jaime Balmes**, así como también a otro contemporáneo suyo, **Menéndez Pelayo**. De los dos primeros tomó su capacidad de síntesis y la sencillez expositiva, mientras que de Menéndez Pelayo tomó, al menos en parte, el sentido de la crítica histórica en aras de la restauración de una Tradición nacional. Pero más allá de los sistemas de pensamiento y elementos retóricos, vemos a Vázquez de Mella profundamente interesado por la vida política de los pueblos medievales de Las Españas, lo cual fue, en definitiva, el marco de referencia para una síntesis política de conjunto más allá de los posicionamientos teóricos, como algo que puede ser llevado a la práctica en sus aspectos concretos y que es perfectamente viable. Todo un sistema [edificado sobre el pensamiento tomista](https://hiperbolajanus.com/posts/en-el-mar-de-la-nada-curzio-nitoglia/) y una una profunda religiosidad, En este contexto, y más allá de las ideas formuladas por realistas y carlistas en la primera mitad del siglo XIX, Mella teoriza junto a la concepción del espíritu medieval, la idea de la coexistencia de dos soberanías, una política y otra social, una teoría de la soberanía tradicional inspirada por un principio dinámico y que se cimenta en las propias experiencias humanas en el devenir de la historia.
|[](https://amzn.to/3W6ymTM)|
|:-:|
|[NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023](https://amzn.to/3W6ymTM)|
## El concepto de lo social
Lo social para Mella no tiene absolutamente nada que ver con las denominadas «políticas sociales», tan comunes en el lenguaje político de las democracias liberales, en las que se contempla lo social como un elemento externo a la propia estructura política, donde prevalece el individualismo a todos los niveles, y la sociedad aparece como un mero agregado de individuos. Muy al contrario, lo social, en el tradicionalismo de nuestro autor, implica la afirmación de un principio intrínseco tanto al modelo social como al tipo humano, así como a la naturaleza de las cosas en las que la persona desarrolla su existencia en común con los demás. Nos referimos a las instituciones, a los elementos jurídicos y otros órganos gestados en el tiempo por la experiencia histórica, que regulan la vida común.
En el ámbito de la sociedad cristiana medieval, en plena Reconquista, cuando todavía no existía un Estado unitario como tal, cada municipio tenía sus propias leyes y sus normas, adaptadas a su modelo de vida y costumbres, Las comunidades se concebían como agrupaciones de familias con un sistema de propiedad comunal y privado en las que el patrimonio y el estatus de cada uno de sus miembros venía garantizado por el ejercicio activo de una serie de derechos en defensa de las libertades concretas, cuya fuente última era el derecho natural. Los señores feudales y los reyes se limitaban a reclamar tributos para la guerra, pero sin interferir en la defensa de estas libertades concretas ni vulnerar el sistema que las sustentaba.
Eran gobiernos autárquicos, muy estables e inspirados por un principio democrático, el cual nada tenía que ver con las democracias liberales plutocráticas de la actualidad, cuya idea del derecho y la justicia está pervertida por el formalismo jurídico vacío e inane de sus constituciones, abstractas y plenamente funcionales a las oligarquías, al servicio de intereses espurios. En este caso, el hombre alcanzaba una plena dignidad y desarrollo en el contexto de una comunidad donde prevalecía el vínculo comunitario, al amparo de un modelo tradicional, de normas consuetudinarias y concretas que permitían la defensa efectiva del propio derecho. Ni siquiera con el advenimiento de los Estados modernos, y la centralización de algunos elementos de poder, como la Hacienda o el Ejército, se vieron alterados significativamente estos elementos, que representaban a los denominados «cuerpos intermedios» de la sociedad, y que adquirieron su propia expresión particular bajo el nombre de «Fueros», los que los propios reyes juraron respetar a lo largo de toda la Edad Moderna y hasta el advenimiento del régimen borbónico.
La antropología tradicional vincula al hombre a un medio social, a una familia, a una estirpe o a un pueblo, que reproducen esa misma estructura familiar, aunque a mayor escala. En nuestro caso particular lo vemos a través de la convivencia de pequeños grupos humanos, de ahí la importancia de los municipios o de los concejos en un marco de vida comunitaria fuertemente institucionalizada. Al mismo tiempo este modelo y estructura también se replicaba en otros ámbitos, como en la vida económica y profesional, impregnando todas las esferas de la vida del hombre. Instituciones naturales, amparadas en el derecho natural, y orientadas a la protección y garantía de prosperidad de los hombres, y esto por encima de cualquier interés particular y mercantil de negocio. Para Mella, la ruptura con este mundo, y en general con las experiencias del pasado, es la que nos lleva, [merced a la acción del liberalismo, a los tiempos actuales](https://hiperbolajanus.com/posts/mos-maiorum-7/), y lo hace recorriendo un itinerario que todos conocemos, y que tienen su punto de partida [en la Ilustración y la posterior Revolución Francesa](https://hiperbolajanus.com/posts/joseph-de-maistre/), la irrupción del elemento racional y abstracto y la destrucción de la religión, considerada como fruto de la superstición. La destrucción del orden feudal, que todavía pervivía como marco de convivencia en el mundo rural, como una suerte de prolongación de ese espíritu medieval, hizo desaparecer de un plumazo ese entorno de relaciones concretas y personales para sustituirlas por lo «público» entendido como la centralización estatal uniforme, ignorando las realidades particulares subyacentes en el cuerpo social, los denominados «cuerpos intermedios», que fueron despojados de su autonomía, corporaciones y patrimonios. De modo que la destrucción de estas «sociedades intermedias» que mediaban entre el Estado y la sociedad desenraizó y destruyó la propia sociedad, al mismo tiempo que los fundamentos cristianos del derecho natural sobre la cual se hallaba asentada, para hacer prevalecer esos principios racionales y abstractos traídos por la revolución.
Al mismo tiempo, y anejo a este desarraigo, del individuo se encuentra sometido a poderes arbitrarios del propio Estado liberal, sin un conglomerado institucional propio que lo proteja de estos atropellos, sumido en el individualismo ajeno a toda institución y destino colectivo, se limita al voto cada cuatro años de los partidos al servicio de oligarquías e intereses espurios, contrarios al Bien común. En este sentido, y advirtiendo las posibles acusaciones de «absolutismo» que en ocasiones se han lanzado contra el tradicionalismo, hay que señalar que Mella las rechaza por completo, dado que viola la idea de contrapoderes frente a la autoridad del rey que éste formula, ya que el absolutismo creía en la existencia de un poder ilimitado y tiránico del rey, transmitido por Dios y ajeno a la participación de la sociedad y sus estamentos. Como bien señaló [**Julius Evola**](https://hiperbolajanus.com/libros/metapolitica-tradicion-modernidad-julius-evola/), el absolutismo es un fenómeno antitradicional, vinculado a la descomposición y desacralización de las estructuras tradicionales. De hecho, el absolutismo, como los regímenes liberales de hoy, dejan al individuo totalmente desprotegido, sin un asidero sobre el que apoyarse en la defensa de sus libertades concretas. El propio Mella, como bien saben todos los que se adentren en su obra, fue partidario de contrarrestar el creciente poder del aparato estatal, tal y como hemos visto y seguiremos viendo en lo sucesivo, a lo largo del presente artículo.
|[](https://amzn.to/2LqITcb)|
|:-:|
|[EVOLA, Julis; _Metapolítica, Tradición y Modernidad: Antología de artículos evolianos_, Hipérbola Janus, 2020](https://amzn.to/2LqITcb)|
En nuestro caso particular, la desaparición de la organización gremial y corporativa tuvo unas consecuencias especialmente nefastas, y en especial después de las dos desamortizaciones liberales (Mendizabal y Madoz) al despojar a los grupos sociales populares de su natural organización sociohistórica. Asimismo, desvincularon la propiedad en las relaciones comunitarias y su uso patrimonial para vincularla al uso privado y anónimo, para fines puramente especulativos, los que caracterizan al liberal-capitalismo. De ahí nace la figura del asalariado, del contratado como mera mercancía, en un proceso de alienación del trabajo característico en el desarrollo del capitalismo burgués. De aquí parte lo que algunos tradicionalistas, como Gambra, denominan el «problema social», frente al cual, y al margen de las recetas ideológicas de la modernidad, Mella reivindica la restauración de los antiguos vínculos corporativos y orgánicos de inspiración medieval.
## La idea de soberanía social
Todos los procesos disolutivos que conducen a la Modernidad liberal tienen su punto de inicio con el Renacimiento, con la afirmación del individualismo y la ruptura definitiva del ecumene cristiano medieval, algo que aparece indefectiblemente unido a la Reforma luterana, así como la «valorización» del mundo clásico, con la reemergencia de teorías de tipo hedonista, como las de Epicuro, por ejemplo, generando una disolución de los vínculos con el medio concreto. Esto supone la aparición de un nuevo tipo, que es el hombre abstracto que escapa cada vez más al entorno inmediato y vital, esto al tiempo que el poder del Estado se robustece y se vuelve omnipotente. Es por ese motivo que en lo sucesivo se ha impuesto en nuestras sociedades la falta de concreción, tanto en lo teórico como en lo político, lo cual ha propiciado el triunfo del contrato social roussoniano y la justificación del orden social en virtud de componendas voluntarias y totalmente artificiales. Estas construcciones político-ideológicas son las que contribuyen a la construcción de la sociedad liberal, asentada sobre patrones puramente racionales, individualistas y mercantilistas.
De hecho, la mayor preocupación de Mella es la destrucción de las instituciones locales y ese vínculo afectivo del hombre con su realidad inmediata, algo que impregnaba su relación con el trabajo, con su obra, con su impronta vocacional y devota, imprimiéndole, como en el caso del artesano, un sello propio y particular a su trabajo.
Y en este sentido, Mella afirma que la sociedad moderna ha perdido su sentido institucional como base estable de la sociabilidad. A través del elemento jurídico y la participación en las instituciones es el medio a partir del cual la comunidad se cohesiona y construye sus vínculos y su particular autonomía, que le hace tener una vida propia e interna, y con la institución nos podemos referir desde una asociación profesional, a la universidad o una cofradía etc. El individualismo ha representado el factor disolutivo y corrosivo que ha destruido este vínculo social fundado en múltiples solidaridades que han enfrentado y polarizado al cuerpo social, con el enfrentamiento entre «clases sociales» y la negación de las jerarquías naturales.
Ante todo lo relatado, y como consecuencia de las destrucciones provocadas por la revolución, Mella plantea su teoría de la soberanía social. Esta teoría consiste básicamente en encuadrar de nuevo a la sociedad en sus raíces naturales, concebida en todos sus órdenes como portadora de un dinamismo propio en una suerte de organización geométrica en la que conviven objetivos y finalidades variadas y concretas con su propia legitimidad y autonomía. Estas finalidades, amparadas en el derecho natural, son junto al poder del propio Estado las únicas formas de limitación del poder. La particularidad de esta idea de soberanía social está en el hecho de que la formación de la jerarquía social tiene una dirección ascendente, que tiene como punto de partida a las personas colectivas y concretas, pasando por una serie de instituciones, hasta llegar al Estado central, de forma escalonada y plenamente conscientes de sus funciones. Así lo expresa Mella en su propio lenguaje: «_la jerarquía de personas colectivas, de poderes organizados, de clases, que suben desde la familia hasta la soberanía que llamo política concretada en el Estado, que deben auxiliar, pero también contener_». Es lo que Mella concibe como el sociedalismo, que supone la reintegración de la sociedad en la vida concreta de los hombres, con el desarrollo de una vida política común y estable en el marco de instituciones naturales que potencien las relaciones humanas y sociales, estimulando la sociabilidad. Y hablamos, desde la perspectiva de la integración de distintas sociedades, fuertemente institucionalizadas con funciones y finalidades concretas, más allá del sentido democrático y pactista que pueda entenderse en términos modernos o de cualquier asociación u organización relacionada con el «problema social».
## ¿Qué es la Tradición?
De este modo quedan formuladas las dos soberanías, la política y la social, que coexisten en un mismo espacio limitándose y apoyándose recíprocamente en lo que es uno de los fundamentos del sociedalismo de Mella. No obstante, esta doble soberanía no explica todavía la concreción política de cada pueblo y el vínculo superior que lo lleva a federarse con las diferentes sociedades y a mantenerse unido en una historia y espíritu comunes. Los vínculos que las mantienen unidas en el tiempo tienen que ver con un orden histórico concreto, con un vínculo espiritual que las entrelaza interiormente de una generación a otra, y en última instancia de [ese orden tradicional](https://hiperbolajanus.com/posts/comprendiendo-la-tradicion/) que lo engloba todo, y que al mismo tiempo se asienta en la monarquía y la religión católica. La lealtad a Dios y a un solo rey en torno a los cuales se aglutina la fe, viene a coronar todas estas estructuras y lazos forjados en el fermento de la historia.
No se trata de la Tradición en términos de un «ultraconservadurismo», que ya sabemos que el prefijo «ultra» (lo que sea) es muy recurrente en nuestros días, con la idea de un medio social y político petrificado e invariable, sino que es el producto de un proceso de maduración y evolución histórica, de carácter dinámico y nutrido de experiencias humanas. Nada que ver con las monstruosas ideologías progresistas y modernas, nacidas de lo abstracto e impulsadas por un desbocado «ir hacia delante», desarraigado y que tiende siempre hacia la deshumanización y la destrucción de toda creación humana natural forjada en el devenir de los siglos. Este mismo dinamismo, planteado por Mella, en torno al concepto e idea de Tradición tiene continuidad y adquiere fuerza en sus sucesores y depositarios. Y al fin y al cabo, Mella no hace más que partir de la propia etimología del término, que viene del latín _tradere_, entregar, de la generación que entrega los frutos de su experiencia a la siguiente, perfeccionándola, haciéndola más estable y segura.
Podríamos seguir extrayendo más conclusiones del pensamiento tradicional de Vázquez de Mella, pero probablemente excedería, y por mucho, el modesto propósito de este escrito, de modo que nos quedaremos aquí, no sin advertir a nuestros lectores de la posibilidad de que en un futuro volvamos a retomar nuevamente el tema.
Antes de acabar queremos llamar la atención sobre [una polémica acontecida hace unos años en torno a una Plaza en Madrid](https://www.lavozdigital.es/madrid/20150723/abci-quien-vazquez-mella-201507221907.html) que llevaba el nombre de nuestro autor y que se cambio para dedicársela a un sujeto cuyos méritos eran, por decirlo suavemente, más que discutibles, concretamente a Pedro Zerolo, miembro del PSOE y activista al servicio del lobby homosexualista. Durante aquella época, en 2019, muchos miembros de la izquierda globalista trataron de identificar a Vázquez de Mella como un «pensador franquista», cuando en realidad ni cronológica ni ideológicamente tuvo nunca nada que ver con el franquismo. Recordemos que murió en 1928, y la impronta de su pensamiento ha tenido como continuadores a sus propios correligionarios dentro del ámbito tradicional, aunque en su tiempo llegó a ser muy respetado también por sus adversarios, los liberales. Aunque la retirada del nombre de una calle pueda resultar algo banal, o carente de una importancia excesiva, también contribuye, a su modo, a una forma de _damnatio memoriae_ que condena al olvido y al ostracismo a grandes autores de la Tradición, portadores de un Patriotismo sano y capaz de entender las peculiaridades y el _Dasein_ profundo de España, que si bien no nació invertebrada, como pretendían los Orteguianos, su esencia y naturaleza es mucho más compleja que cualquiera de las grandes naciones de Europa.
---
**Artículo original**: Hipérbola Janus, [_Juan Vázquez de Mella y el tradicionalismo español_](https://www.hiperbolajanus.com/posts/juan-vazquez-mella-tradicionalismo/), 16/Ago/2024
-

@ 674473f6:f859eb3c
2024-08-05 05:51:37
> Bitwise Operation คือ กระบวนการที่การดำเนินการใด ๆ โดยตรงกับบิตของตัวเลข หรือชุดข้อมูลของเราใน memory ซึ่งการทำงานโดยตรงกับบิตของตัวเลข ทำให้มีประสิทธิภาพสูงและใช้บ่อยในการเขียนโปรแกรมระดับ low-level โดยหลัก ๆ ที่ใช้กันจะมี 6 แบบ
เป็นเครื่องมือที่ทรงพลังสำหรับนักพัฒนาที่ต้องการประสิทธิภาพสูงและการควบคุมระดับบิต โดยเฉพาะในการพัฒนาระบบระดับ low-level และการทำงานกับฮาร์ดแวร์โดยตรง
## TLDR
ภาพรวม Bitwise Operations:
AND (&):
ใช้เปรียบเทียบบิต, ให้ 1 เมื่อทั้งสองบิตเป็น 1
ประโยชน์: ตรวจสอบบิต, สร้าง mask
OR (|):
ให้ 1 เมื่อมีบิตใดบิตหนึ่งเป็น 1
ประโยชน์: รวมแฟล็ก, ตั้งค่าบิต
XOR (^):
ให้ 1 เมื่อบิตต่างกัน
ประโยชน์: สลับค่า, เข้ารหัสอย่างง่าย
NOT (~):
กลับค่าทุกบิต
ประโยชน์: สร้าง mask สำหรับลบบิต
Left Shift (<<):
เลื่อนบิตไปซ้าย, เติม 0 ทางขวา
ประโยชน์: คูณด้วยกำลังของ 2, สร้าง mask
Right Shift (>>):
เลื่อนบิตไปขวา
ประโยชน์: หารด้วยกำลังของ 2, แยกส่วนข้อมูล
## 1.) BitAnd (&):
BitAnd มักใช้สัญลักษณ์ & เป็นการดำเนินการทางตรรกะที่เปรียบเทียบบิตในตำแหน่งเดียวกันของสองตัวเลข โดยมีกฎดังนี้:
- 1 AND 1 = 1
- 1 AND 0 = 0
- 0 AND 1 = 0
- 0 AND 0 = 0
หรือกล่าวอีกนัยหนึ่ง ผลลัพธ์จะเป็น 1 ก็ต่อเมื่อทั้งสองบิตเป็น 1 เท่านั้น
ตัวอย่าง:
สมมติว่าเรามีเลขสองตัว A = 5 และ B = 3
ในระบบเลขฐานสอง:
A = 5 = 0101
B = 3 = 0011
เมื่อทำ BitAnd:
```
0101 (A = 5)
& 0011 (B = 3)
----
0001 (Result = 1)
```
จะเห็นได้ว่า:
- บิตที่ 1 (จากขวา): 1 & 1 = 1
- บิตที่ 2: 0 & 1 = 0
- บิตที่ 3: 1 & 0 = 0
- บิตที่ 4: 0 & 0 = 0
ดังนั้น ผลลัพธ์คือ 0001 ในเลขฐานสอง ซึ่งเท่ากับ 1 ในเลขฐานสิบ
การใช้งาน BitAnd:
1. การตรวจสอบเลขคู่/คี่:
ถ้า (n & 1) == 0 แสดงว่า n เป็นเลขคู่
ถ้า (n & 1) == 1 แสดงว่า n เป็นเลขคี่
2. การตรวจสอบสถานะของบิตเฉพาะ:
ถ้าต้องการตรวจสอบบิตที่ 3 ของ x:
if (x & (1 << 2)) != 0 // บิตที่ 3 เป็น 1
3. การลบบิตสุดท้ายที่เป็น 1:
n = n & (n - 1)
BitAnd มีประโยชน์มากในการจัดการกับข้อมูลระดับบิต การตั้งค่าแฟล็ก และการทำงานกับฮาร์ดแวร์โดยตรง
## 2.) BitOr (|):
BitOr มักใช้สัญลักษณ์ | เป็นการดำเนินการทางตรรกะที่เปรียบเทียบบิตในตำแหน่งเดียวกันของสองตัวเลข โดยมีกฎดังนี้:
- 1 OR 1 = 1
- 1 OR 0 = 1
- 0 OR 1 = 1
- 0 OR 0 = 0
กล่าวคือ ผลลัพธ์จะเป็น 1 เมื่อมีบิตใดบิตหนึ่งเป็น 1 หรือทั้งสองบิตเป็น 1
ตัวอย่าง:
สมมติว่าเรามีเลขสองตัว A = 5 และ B = 3
ในระบบเลขฐานสอง:
A = 5 = 0101
B = 3 = 0011
เมื่อทำ BitOr:
```
0101 (A = 5)
| 0011 (B = 3)
----
0111 (Result = 7)
```
จะเห็นได้ว่า:
- บิตที่ 1 (จากขวา): 1 | 1 = 1
- บิตที่ 2: 0 | 1 = 1
- บิตที่ 3: 1 | 0 = 1
- บิตที่ 4: 0 | 0 = 0
ดังนั้น ผลลัพธ์คือ 0111 ในเลขฐานสอง ซึ่งเท่ากับ 7 ในเลขฐานสิบ
การใช้งาน BitOr:
1. การรวมแฟล็ก:
เช่น ในการตั้งค่าสิทธิ์ไฟล์ในระบบ Unix
permissions = READ | WRITE | EXECUTE
2. การตั้งค่าบิตเฉพาะ:
ถ้าต้องการตั้งค่าบิตที่ 3 ของ x เป็น 1:
x = x | (1 << 2)
3. การรวมสี RGB:
ในระบบสี RGB ที่ใช้ 8 บิตต่อสี
color = (red << 16) | (green << 8) | blue
BitOr มีประโยชน์มากในการรวมแฟล็ก การตั้งค่าบิต และการทำงานกับข้อมูลที่แต่ละบิตมีความหมายเฉพาะ
## BitXor (^):
BitXor หรือ Exclusive OR (XOR) มักใช้สัญลักษณ์ ^ เป็นการดำเนินการทางตรรกะที่เปรียบเทียบบิตในตำแหน่งเดียวกันของสองตัวเลข โดยมีกฎดังนี้:
- 1 XOR 1 = 0
- 1 XOR 0 = 1
- 0 XOR 1 = 1
- 0 XOR 0 = 0
กล่าวคือ ผลลัพธ์จะเป็น 1 เมื่อบิตทั้งสองมีค่าต่างกัน
ตัวอย่าง:
สมมติว่าเรามีเลขสองตัว A = 5 และ B = 3
ในระบบเลขฐานสอง:
A = 5 = 0101
B = 3 = 0011
เมื่อทำ BitXor:
```
0101 (A = 5)
^ 0011 (B = 3)
----
0110 (Result = 6)
```
จะเห็นได้ว่า:
- บิตที่ 1 (จากขวา): 1 ^ 1 = 0
- บิตที่ 2: 0 ^ 1 = 1
- บิตที่ 3: 1 ^ 0 = 1
- บิตที่ 4: 0 ^ 0 = 0
ดังนั้น ผลลัพธ์คือ 0110 ในเลขฐานสอง ซึ่งเท่ากับ 6 ในเลขฐานสิบ
การใช้งาน BitXor:
1. การสลับค่าโดยไม่ใช้ตัวแปรเพิ่ม:
a ^= b;
b ^= a;
a ^= b;
// ตอนนี้ a และ b ได้สลับค่ากันแล้ว
2. การเข้ารหัสอย่างง่าย:
encrypted = data ^ key
decrypted = encrypted ^ key // จะได้ data กลับคืนมา
3. การตรวจสอบความเท่ากันของตัวเลข:
if ((a ^ b) == 0) // a และ b เท่ากัน
4. การหาตัวเลขที่ไม่มีคู่ในชุดข้อมูล:
result = num1 ^ num2 ^ num3 ^ ... // ผลลัพธ์จะเป็นตัวเลขที่ไม่มีคู่
BitXor มีคุณสมบัติพิเศษคือ การ XOR กับตัวเองจะได้ 0 และการ XOR กับ 0 จะได้ตัวเองกลับคืนมา ทำให้มันมีประโยชน์มากในการเข้ารหัสและการตรวจสอบข้อมูล
## BitNot (~):
BitNot หรือ NOT มักใช้สัญลักษณ์ ~ เป็นการดำเนินการทางตรรกะที่กลับบิตของตัวเลข โดยมีกฎง่ายๆ คือ:
- NOT 1 = 0
- NOT 0 = 1
กล่าวคือ BitNot จะเปลี่ยนทุกบิต 0 เป็น 1 และทุกบิต 1 เป็น 0
ตัวอย่าง:
สมมติว่าเรามีเลข A = 5
ในระบบเลขฐานสอง (สมมติว่าเป็นเลข 8 บิต):
A = 5 = 00000101
เมื่อทำ BitNot:
```
00000101 (A = 5)
--------
~ 11111010 (Result = 250 ใน unsigned int, หรือ -6 ใน signed int)
```
จะเห็นได้ว่า:
- ทุกบิต 0 ถูกเปลี่ยนเป็น 1
- ทุกบิต 1 ถูกเปลี่ยนเป็น 0
ผลลัพธ์จะขึ้นอยู่กับว่าเราใช้ระบบเลขแบบไหน (signed หรือ unsigned):
- ในระบบ unsigned 8 บิต: 11111010 = 250
- ในระบบ signed 8 บิต: 11111010 = -6
การใช้งาน BitNot:
1. การสร้าง mask สำหรับการลบบิต:
clear_mask = ~(1 << n) // สร้าง mask ที่มีบิตที่ n เป็น 0 และที่เหลือเป็น 1
x &= clear_mask // ลบบิตที่ n ของ x
2. การหาค่าสัมบูรณ์ของเลขติดลบในระบบ two's complement:
abs_value = (x ^ (x >> 31)) - (x >> 31)
// x >> 31 จะได้ 0 สำหรับเลขบวก และ -1 สำหรับเลขลบ
3. การสลับสถานะของทุกบิต:
inverted = ~original
4. การหาค่าสูงสุดของตัวแปรที่มีขนาด n บิต:
max_value = ~0 >> (32 - n) // สำหรับตัวแปร 32 บิต
BitNot มักใช้ร่วมกับ BitAnd เพื่อลบบิตที่ต้องการ หรือใช้ในการสร้าง mask สำหรับการจัดการบิต
## Left Shift (<<):
Left Shift มักใช้สัญลักษณ์ << เป็นการดำเนินการที่เลื่อนบิตทั้งหมดของตัวเลขไปทางซ้ายตามจำนวนที่กำหนด โดยเติม 0 ทางด้านขวา
Left Shift โดยทั่วไปแล้วไม่แตกต่างกันระหว่างเลข unsigned int และ signed int แต่มีบางประเด็นที่ควรระวัง:
1. ผลลัพธ์:
- ในกรณีของเลขไม่มีเครื่องหมาย ผลลัพธ์จะเป็นบวกเสมอ
- สำหรับเลขมีเครื่องหมาย ผลลัพธ์อาจเปลี่ยนเครื่องหมายได้หากบิตเครื่องหมาย (sign bit) ถูกเปลี่ยน
2. Overflow:
- ทั้งสองกรณีอาจเกิด overflow ได้ถ้าเลื่อนมากเกินไป
- สำหรับเลข signed int overflow อาจทำให้เกิดการเปลี่ยนเครื่องหมายโดยไม่คาดคิด
3. Undefined Behavior:
- ในบางภาษา เช่น C/C++, การเลื่อนด้วยค่าที่มากกว่าหรือเท่ากับจำนวนบิตของตัวแปรอาจทำให้เกิด Undefined Behavior ได้
ตัวอย่าง:
สมมติว่าเรามีเลข A = 5 และต้องการเลื่อนซ้าย 2 ตำแหน่ง
ในระบบเลขฐานสอง (สมมติว่าเป็นเลข 8 บิต):
A = 5 = 00000101
เมื่อทำ Left Shift 2 ตำแหน่ง (A << 2):
```
00000101 (A = 5)
--------
00010100 (Result = 20)
```
จะเห็นได้ว่า::
- บิตทั้งหมดถูกเลื่อนไปทางซ้าย 2 ตำแหน่ง
- เติม 0 สองตัวทางด้านขวา
ผลลัพธ์: 00010100 ในเลขฐานสอง ซึ่งเท่ากับ 20 ในเลขฐานสิบ
ตัวอย่าง 2:
```
unsigned int a = 1; // 00000001 in binary
int b = 1; // 00000001 in binary
// Left shift by 3
unsigned int a_result = a << 3; // 00001000 (8 in decimal)
int b_result = b << 3; // 00001000 (8 in decimal)
// สำหรับตัวเลขเล็ก ๆ ผลอาจจะไม่ต่างกัน
// แต่เมื่อมีตัวเลขที่ใหญ่ขึ้น อาจจะให้ผลตรงกันข้ามแทน:
unsigned int large_a = 1 << 31; // 10000000 00000000 00000000 00000000 (2147483648 in decimal)
int large_b = 1 << 31; // 10000000 00000000 00000000 00000000 (-2147483648 in decimal, due to two's complement)
```
ในตัวอย่างสุดท้าย เราเห็นความแตกต่าง:
- สำหรับ unsigned int, ผลลัพธ์คือเลขบวกที่ใหญ่ที่สุดที่เป็นไปได้
- สำหรับ signed int, ผลลัพธ์คือเลขลบที่น้อยที่สุดที่เป็นไปได้ เนื่องจากบิตซ้ายสุดถูกตีความเป็นเครื่องหมายลบในระบบ two's complement
กฎการทำงาน:
- เลื่อนบิตทั้งหมดไปทางซ้าย n ตำแหน่ง
- เติม 0 ทางด้านขวา n ตัว
- บิตที่เลื่อนออกไปทางซ้ายจะหายไป
การใช้งาน Left Shift:
1. การคูณด้วยกำลังของ 2:
x << n เท่ากับ x * (2^n)
เช่น 5 << 2 = 5 * (2^2) = 5 * 4 = 20
2. การสร้างหน้ากาก (mask) สำหรับการตั้งค่าบิต:
mask = 1 << n // สร้างหน้ากากที่มีบิตที่ n เป็น 1 และที่เหลือเป็น 0
x |= mask // ตั้งค่าบิตที่ n ของ x เป็น 1
3. การเข้ารหัสข้อมูลหลายบิตในตัวแปรเดียว:
encoded = (r << 16) | (g << 8) | b // เก็บค่า RGB ในตัวแปร 32 บิต
4. การทำงานกับบิตแฟล็ก:
FLAG_A = 1 << 0
FLAG_B = 1 << 1
FLAG_C = 1 << 2
// ใช้งาน: flags = FLAG_A | FLAG_B
Left Shift มีประสิทธิภาพสูงในการคูณด้วยกำลังของ 2 และมักใช้ในการจัดการบิตแฟล็กและการสร้างหน้ากากสำหรับการดำเนินการระดับบิต
## Right Shift (>>):
Right Shift มักใช้สัญลักษณ์ >> เป็นการดำเนินการที่เลื่อนบิตทั้งหมดของตัวเลขไปทางขวาตามจำนวนที่กำหนด การทำงานจะแตกต่างกันเล็กน้อยระหว่างเลขที่มีเครื่องหมาย (signed) และไม่มีเครื่องหมาย (unsigned)
สำหรับเลข unsigned int (Logical Right Shift):
- เลื่อนบิตทั้งหมดไปทางขวา n ตำแหน่ง
- เติม 0 ทางด้านซ้าย n ตัว
- บิตที่เลื่อนออกไปทางขวาจะหายไป
สำหรับเลข signed int (Arithmetic Right Shift):
- เลื่อนบิตทั้งหมดไปทางขวา n ตำแหน่ง
- เติมด้วยบิตเครื่องหมาย (sign bit) ทางด้านซ้าย n ตัว
- บิตที่เลื่อนออกไปทางขวาจะหายไป
ตัวอย่าง:
สมมติว่าเรามีเลข A = 20 และต้องการเลื่อนขวา 2 ตำแหน่ง
ในระบบเลขฐานสอง (สมมติว่าเป็นเลข 8 บิต):
A = 20 = 00010100
เมื่อทำ Right Shift 2 ตำแหน่ง (A >> 2):
```
00010100 (A = 20)
--------
00000101 (Result = 5)
```
จะเห็นได้ว่า::
- บิตทั้งหมดถูกเลื่อนไปทางขวา 2 ตำแหน่ง
- เติม 0 สองตัวทางด้านซ้าย (สำหรับเลขไม่มีเครื่องหมาย)
ผลลัพธ์: 00000101 ในเลขฐานสอง ซึ่งเท่ากับ 5 ในเลขฐานสิบ
การใช้งาน Right Shift:
1. การหารด้วยกำลังของ 2:
x >> n เท่ากับ x / (2^n) (ปัดเศษลง)
เช่น 20 >> 2 = 20 / (2^2) = 20 / 4 = 5
2. การแยกส่วนของข้อมูลที่ถูกเก็บรวมกัน:
r = (rgb >> 16) & 0xFF // แยกค่าสีแดงจาก RGB 24 บิต
g = (rgb >> 8) & 0xFF // แยกค่าสีเขียว
b = rgb & 0xFF // แยกค่าสีน้ำเงิน
3. การตรวจสอบเครื่องหมายของตัวเลข:
sign = x >> 31 // สำหรับตัวแปร 32 บิต, จะได้ 0 สำหรับบวก และ -1 สำหรับลบ
4. การทำ rounded division:
(x + (1 << (n-1))) >> n // หารด้วย 2^n และปัดเศษ
ข้อควรระวัง:
- ใน Java, >> เป็น arithmetic shift สำหรับ int และ long, ส่วน >>> เป็น logical shift
- ในภาษาอื่นๆ เช่น C/C++, การทำงานของ >> กับเลขติดลบอาจแตกต่างกันไปตาม Compiler
Right Shift มีประสิทธิภาพสูงในการหารด้วยกำลังของ 2 และมักใช้ในการจัดการข้อมูลที่ถูกเก็บรวมกันในรูปแบบบิต
หากเปรียบกับ Right Shift แม้ว่าการทำงานพื้นฐานของ Left Shift จะเหมือนกันสำหรับทั้งเลข signed int และ unsigned int แต่การตีความผลลัพธ์และผลกระทบต่อเครื่องหมาย(sign bit)อาจแตกต่างกัน ดังนั้นจึงควรระมัดระวังเมื่อใช้ Left Shift กับเลขที่มี signed int โดยเฉพาะเมื่อเลื่อนด้วยค่าที่สูงมาก ๆ
## Conclusion
#### ลักษณะเด่นของ Bitwise Operations:
- ประสิทธิภาพสูง: ทำงานเร็วกว่าการคำนวณปกติ
- ประหยัดหน่วยความจำ: จัดเก็บข้อมูลหลายอย่างในตัวแปรเดียว
- ใช้ในงานระดับต่ำ: การทำงานกับฮาร์ดแวร์, ระบบปฏิบัติการ
- การเข้ารหัส: ใช้ในอัลกอริทึมการเข้ารหัสและบีบอัดข้อมูล
- การจัดการแฟล็ก: ใช้ในการตั้งค่าและตรวจสอบสถานะต่างๆ
#### การใช้งานทั่วไป:
- จัดการสิทธิ์และการอนุญาตในระบบไฟล์
- การเข้ารหัสและถอดรหัสข้อมูล
- การบีบอัดข้อมูล
- การทำงานกับพิกเซลในการประมวลผลภาพ
- การจัดการโปรโตคอลเครือข่าย
- การทำงานกับ register ใน Embedded system
#### ข้อควรระวัง:
- ต้องระมัดระวังเรื่องขนาดของข้อมูล (8, 16, 32, 64 บิต)
- ความแตกต่างระหว่างเลขมี signed int และ unsigned int
- ความแตกต่างของการทำงานในแต่ละภาษาโปรแกรม
**unsigned int คือตัวเลขเป็นบวกเสมอ signed int สามารถมีค่าเป็นลบได้
#siamstr #Blog
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# jiq-web
Made with [jq-web](nostr:naddr1qqyrzvrzxqcx2dfsqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c90hqwz), a tool to explore JSON using `jq` that works like [jiq](nostr:naddr1qqyrqvfjv33rxcenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cd86z7d).
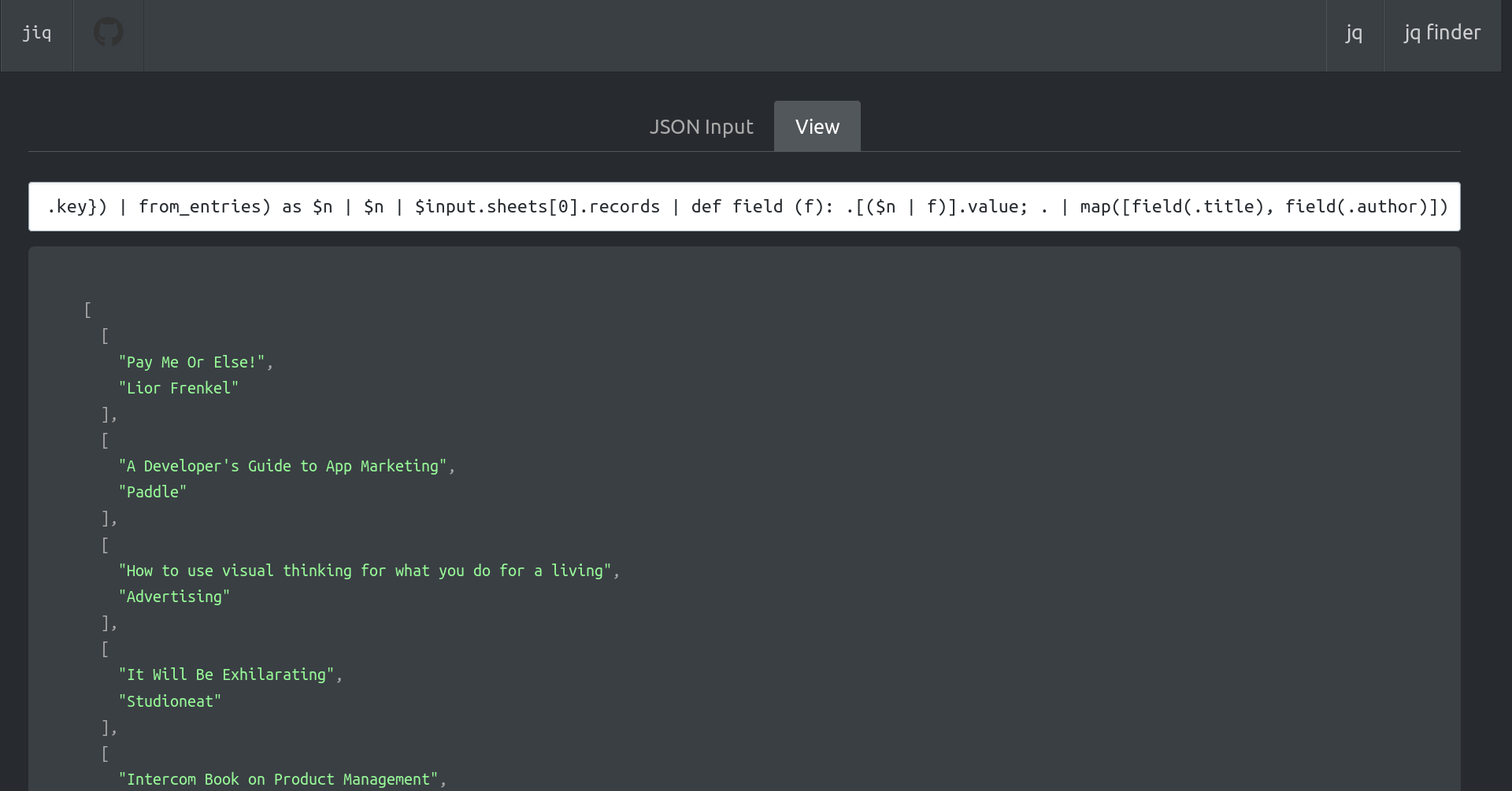
- <https://jq.alhur.es/jiq/>
- <https://github.com/fiatjaf/jiq-web>
## See also
- [jq-finder](nostr:naddr1qqyryvejvycn2cnpqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ccw20rx)
-

@ a853296a:209e695f
2024-08-03 20:03:05
What's up stackers!
Trying something new posting to the tech territory.
**CASCDR TLDR:** CASCDR is a collection of Lightning Powered AI services/applications.
**Post TLDR:** We have just released a big upgrade to our RSS Agent! You can now explore podcasts, and seamlessly integrate them with LLM workflows. This will allow you to condense podcast content/create more content based on a given podcast selected through the explorer!
We have a new release LIVE. As discussed on this [post](https://stacker.news/items/621497) and on [SNL](https://youtu.be/SsZcVQZ20Ik?list=PLKnVil22cJNzDABNpAQ2JecRzU3SUtV8V&t=3068) last week, YouTube started playing major defense! So we adapted our YouTube Agent into an RSS Agent.
Now the RSS Agent is back and better with V2! Due to time constraints we had to ship a very basic version last week. Now RSS Agent is fully equipped!

_he's baaaaaaack_
## Key Updates:
- Search & explore any podcast feed
- Pull any episode of interest
- Run analysis of the episode transcript with 5 pre-determined prompts
- OR roll your own custom prompt to put together written content of your choosing!
## Workflow/Details:
_Step 1: Search for your favorite podcast like @ThrillerX_ _
_Step 2: Select/Configure Your Prompt & Select the Podcast Episode_
_Step 3: Inspect Your Result and/or Copy to Clipboard_
Looking forward to the feedback in the comments! If this post triggers ideas of more you want to do with AI, tell us what you want us to build!
Cheers,
The CASCDR Team
originally posted at https://stacker.news/items/633849
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Excerpt of discussion about DIDs and ION
Melvin Carvalho:
> "Not a single entity I know that's doing production deployments has actually vetted did:ion and found it to be production capable."
>
> The guy leading the DID effort said this about ION.
>
> Seems like they may be 6 months away from producing something.
>
> https://github.com/decentralized-identity/ion/blob/master/docs/design.md#operations
>
> In their design it says you can create, update, recover and activate. It is a bit magic
>
> But update implies a versioning system. So you could think of it like updated nostr events. My key is A. Now my key is B. Tied to a content addressable static ID (like a genesis event ID).
>
> Let's see. I hope they produce something useful. Daniel tends not to answer questions
>
> When we first made DID, the idea was that your (d)id and your public key or hash were the same string.
>
> As it evolved, that got broken. Which can be useful because then you can have multiple keys, but the trade off is more management needed.
>
> So you have DID <—> controller two way link. Then it can have multiple keys. Those can be used to update the record. How that chain of records is stored, fetched and verified, is not covered by DID. So everyone will do it differently. Nostr for example could create updating keys with a NIP, it would do the same thing.
Hampus:
> Basically impossible to have a convo with Daniel
Melvin Carvalho:
> true. too often appeals to authority
>
> https://identity.foundation/sidetree/spec/#update
>
> the side tree spec has an update function
>
> 'Retrieve the Update Reveal Value that matches the previously anchored Update Commitment'
>
> so it looks like they have a chain of anchors ... anchored to something, ion nodes i guess, which also run btc full nodes
>
> > 'Embed the Anchor String in the transaction such that it can be located and parsed by any party that traverses the history of the target anchoring system'
>
> > 'By leveraging the blockchain-agnostic Sidetree protocol, ION makes it possible to anchor tens of thousands of DID/DPKI operations on a target chain (in ION's case, Bitcoin) using a single on-chain transaction'
>
> there you go
>
> do a search in the ion repo for 'anchor' and it gives some details
>
> https://github.com/decentralized-identity/ion/blob/66813123cf81ace05cea2039e93ef263952d6283/docs/Q-and-A.md
>
> there's a Q & A
Ruben Somsen:
> Their anchor protocol doesn't guarantee you have a full view of the data, so you can open the commitments to anything you like (provided you pre-committed to different views). In my opinion this makes the commitments pointless.
Melvin Carvalho:
> > 'Assuming you are running your own node, you simply need to submit 1000 create operations to your node (ie. http://localhost:3000/operations) before your batch writer kicks in every 10 minutes by default, the batch writer will batch all 1000 operations into 1 bitcoin transaction thus you'll pay fee for just one transaction to the minor.
> > The technical spec for constructing a create request can be found in Sidetree API spec, but if you know TypeScript, you are better off using the ion-sdk directly, it will save you a lot of time'
>
> seems 3 places data is stored
>
> anchored witness data: bitcoin tx
> batches of operations: ION nodes
> non witness data: maybe IPFS
>
> 'The logical order of operations, as determined by the underlying anchoring system (e.g. Bitcoin block and transaction order). Anchoring systems may widely vary in how they determine the logical order of operations, but the only requirement of an anchoring system is that it can provide a means to deterministically order each operation within a DID’s operational lineage.'
Ruben Somsen:
> It's deterministic given a set of data, but there is no consensus on the set of data, so if A and B get presented with a different set, they come to a different conclusion
Melvin Carvalho:
> yes. "DID owners can create forks within their own DID state history". so you dont actually know the full state. I think the design is of each identity has eventual consistency, with the anchor as the tie break. It can change as you know more data. But doesnt say what happens if two updates happen in the same block.
>
> https://identity.foundation/sidetree/spec/#late-publishing
>
> the aim is eventual consistency
>
> so at any time you might have the wrong state, but if you had every update associated with a given id, you could determine the right order to apply the patches by using the bitcoin block chain (I dont know what happens if there's a tie in the same block) ... there's no peg in or peg out, it's just like version controlled files
Ruben Somsen:
> But you can't know when you've reached the state of eventual consistency (i.e. when you finally have the full data set) and in practice it may never be reached, so there is no consensus
>
> When there is conflicting data, the first one counts and the second one is ignored.
>
> This problem is literally detrimental, yet it is being presented as a minor inconvenience.
Melvin Carvalho:
> yes, and the first one can be published later, so systems will think the second is valid, until it isnt
Ruben Somsen:
> Yup
Melvin Carvalho:
> you could actually steal someone's identity, and revoke all their keys, and then reveal it years later
>
> arguably this is worse than github
Ruben Somsen:
> lol yeah you could
Melvin Carvalho:
> or an attack vector, get someone's ID, but they dont know, then sell them lots of 'cheap' NFTs ... at some point you publish the new keys and reclaim all the tokens ... no one will know when they will be rug pulled
Ruben Somsen:
> That was my original argument, but Daniel claimed the protocol wasn't meant for transfer of ownership rights.
Melvin Carvalho:
> so then i wonder what the primary use cases are that cant be easily achieved already
>
> > 'How Can ION be Used?
> > ION can see a lot of use in many cases. The most obvious use case is for verifiable credentials. A business can credential employees, who can then be verified via blockchain on arrival at their destination. This functionality also raises its use as a means of supplying and verifying international travel documents.'
> >
> > 'Another use case could come from accreditation for organizations. Using an organization's public key, users can verify their accreditation status and trace their accreditation history over time.'
>
> so i guess its an updatable profile page, but you dont know when your profile is compromised. OTOH it's free (their node is paying fees to start with), and improves BTC security budget. If you keep your key safe, and the nodes publish the updates for you, it might be a nice little profile you could use for stuff. But not sure id use it for anything high value. And nostr (for example) can do alot of this already — updatable profiles and publishing
>
> i think it may be to a degree censorship resistant too
>
> there's also no incentive to run a node, so im not sure why they would stick around
>
> nodes can actually very easily censor by black listing certain tx (e.g. a hack, or sanctioned identity), removing the decentralized nature
>
> so the nodes can never reach consensus
Ruben Somsen:
> Like I said, the commitments are pointless. I think it's equivalent to just signing stuff with a key and making what you signed available for download in "the cloud".
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# A biblioteca infinita
Agora esqueci o nome do conto de Jorge Luis Borges em que a tal biblioteca é descrita, ou seus detalhes específicos. Eu tinha lido o conto e nunca havia percebido que ele matava a questão da aleatoriedade ser capaz de produzir coisas valiosas. Precisei mesmo da [Wikipédia](https://en.wikipedia.org/wiki/Infinite_monkey_theorem) me dizer isso.
Alguns anos atrás levantei essa questão para um grupo de amigos sem saber que era uma questão tão batida e baixa. No meu exemplo era um cachorro andando sobre letras desenhadas e não um macaco numa máquina de escrever. A minha conclusão da discussão foi que não importa o que o cachorro escrevesse, sem uma inteligência capaz de compreender aquilo nada passaria de letras aleatórias.
Borges resolve tudo imaginando uma biblioteca que contém tudo o que o cachorro havia escrito durante todo o infinito em que fez o experimento, e portanto contém todo o conhecimento sobre tudo e todas as obras literárias possíveis -- mas entre cada página ou frase muito boa ou pelo menos legívei há toneladas de livros completamente aleatórios e uma pessoa pode passar a vida dentro dessa biblioteca que contém tanto conhecimento importante e mesmo assim não aprender nada porque nunca vai achar os livros certos.
> Everything would be in its blind volumes. Everything: the detailed history of the future, Aeschylus' The Egyptians, the exact number of times that the waters of the Ganges have reflected the flight of a falcon, the secret and true nature of Rome, the encyclopedia Novalis would have constructed, my dreams and half-dreams at dawn on August 14, 1934, the proof of Pierre Fermat's theorem, the unwritten chapters of Edwin Drood, those same chapters translated into the language spoken by the Garamantes, the paradoxes Berkeley invented concerning Time but didn't publish, Urizen's books of iron, the premature epiphanies of Stephen Dedalus, which would be meaningless before a cycle of a thousand years, the Gnostic Gospel of Basilides, the song the sirens sang, the complete catalog of the Library, the proof of the inaccuracy of that catalog. Everything: but for every sensible line or accurate fact there would be millions of meaningless cacophonies, verbal farragoes, and babblings. Everything: but all the generations of mankind could pass before the dizzying shelves – shelves that obliterate the day and on which chaos lies – ever reward them with a tolerable page.
Tenho a impressão de que a publicação gigantesca de artigos, posts, livros e tudo o mais está transformando o mundo nessa biblioteca. Há tanta coisa pra ler que é difícil achar o que presta. As pessoas precisam parar de escrever.
-

@ 6bae33c8:607272e8
2024-08-03 19:21:12
This is an overall list for 12-team NFFC PPR leagues _as of August 3, 2024_.
**Note:** Rankings are real, but comments are not meant to be taken seriously.
Warning: many, if not most, are stupid, though it can't be worse than [last year’s](https://www.realmansports.com/p/snarky150).

_(Right-click, open in new tab to enlarge)_
-

@ 6c8c7979:15595f3e
2024-08-02 21:51:01
When Mozart composed Symphony No. 40 in G minor, he was going through a difficult period in his life, facing financial problems and personal pressures. Despite these circumstances, the symphony is marked by significant emotional intensity and notable musical innovation. It is believed that the symphony reflected his internal tension and pain, making it one of his greatest and most impactful works.
https://youtu.be/0sGqkMU-mGQ?si=FTIuMq8xo4bhvzDV
https://youtu.be/JTc1mDieQI8?si=E-xd311z0yWQek3c
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Qual é o economista? (piadas)
O economista americano rapper ficou triste quando sua banda brasileira favorita encerrou suas atividades por crer que a demanda por discos de rap seria cada vez pior.
Resposta: Robert Lucas e as expectativas dos Racionais.
O economista inglês queria muito arrumar uma namorada.
Resposta: John Maynard Keynes e a demanda afetiva.
Quando o filho do economista austríaco chegou em casa todo sujo ele sem nem pensar ordenou que o moleque fosse tomar banho.
Resposta: Friedrich Hayek e a ordem espontânea.
O economista americano tinha muito orgulho de ter em sua casa um valiosíssimo quadro de um impressionista francês.
Resposta: Milton Friedman e o Monet raríssimo.
O economista austríaco jurou aos seus filhos que todos eles se mudariam para Brasília.
Resposta: Eugen von Böhm-Bawerk e o “eu juro” da capital.
O economista alemão organizou um evento meio sertanejo meio religioso e colocou como organizador uma executiva que tinha quebrado suas últimas 4 empresas por má administração.
Resposta: Karl Marx e a expo-oração da que mais-falia.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Batch for Trello
Another Trello helper.
This time it allowed people to perform batch actions on multiple cards, most notably delete a lot of cards at once.
I created it because I wanted to delete a ton of spam from [Boardthreads](nostr:naddr1qqyxvwfk8p3xvdmrqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ceq46m6).
- <https://github.com/fiatjaf/batch-for-trello>
- <https://batch.cardsync.xyz/>
-

@ fa984bd7:58018f52
2024-08-02 14:03:21
Happy to announce a new major version of NDK. A lot of work has been going on behind the scenes to improve NDK in a lot of fronts.
## Optimistic Signature verification
For most nostr apps, event signature verification is, by far, the most computationally-expensive part.
If you've ever felt your phone getting a bit hot while using a nostr app, this is probably why.
NDK introduces signature verification sampling. Each relay gets a lower and upper threshold of what ratio of events need to be verified. An unknown relay might start at getting 100% of it's events verified and, over time, lower the ratio to 50%. Whereas a relay the user has in their NIP-65 list might start at 50% and lower to 1%.
When the same event is fetched from multiple relays, only the first time an event is seen (might) have it's signature verified. If the signature is verified, subsequent relays that send the same event ID **and** signature, have their ratio updated, further reducing the number of signatures we need to check.
Relays should never send an invalid signature, so it only takes catching an evil relay lying about a signature **once**, to expel it from the pool and, perhaps, have the user add that relay to their relay blacklist event.
In order to activate this feature, developers MUST explicitly handle receiving an invalid signature, as they should probably warn the user that some trickery is happening.
👉 [Tutorial](https://nostr-dev-kit.github.io/ndk/tutorial/speed.html#signature-verification-sampling)
## Nostr Cache Adapter
A new cache adapter, which leverages, well, nostr.
ndk-cache-nostr is a cache adapter that connects to a single local relay. This could be your a relay running in your user's computer/phone, like the nostr-tray-relay, Citrine, or it can even be a local relay you run in your server to assist in creating server-side-rendering.
If you've been envious of njump previews when sharing a link, now you can implement the same in your app by leveraging this adapter in your SSR calls.
👉 [Docs](https://nostr-dev-kit.github.io/ndk/cache/nostr.html)
## Refactored Zapping interface
This is the one breaking change; the code for sending zaps was tightly coupled to the assumption that LN was the interface. This new interface abstracts away the funding mechanism (NWC, WebLN, built-in-wallet) and the delivery mechanism (LN, ecash, Rai stones)
#
## Major subscription Lifecycle refactor
The core of how NDK works was completely refactored from the ground-up, removing a lot of dependencies from nostr-tools, and bringing a lot of clarity to how NDK orchestrates subscriptions at the relay level.
👉 [NDK Internal's documentation](https://nostr-dev-kit.github.io/ndk/internals/subscriptions.html)
## Tutorials and other stuff
A few months ago I started a new effort to write more high-level documentation, instead of focusing on interface specs of NDK. https://nostr-dev-kit.github.io/ndk is the ongoing result.
# ndk-wallet
A new NDK extension package, provides access to nostr-native NIP-60 wallets.
NIP-60 is a new NIP that proposes a nostr-native wallet that follows a user around any nostr application. Instead of having to manage a bunch of different NWC tokens, implement LN on their own, NIP-60 leverages multiple ecash mints, making it completely frictionless to onboard into Nostr with the capability to send and receive (via NIP-61 or a proxy like npub.cash) zaps.
ndk-wallet is the wallet that Nutsack.me is built on, providing:
- wallet creation/discovery
- token verification
- nutzap redemption
- UTXO management
- balance tracking
With this package you'll be able to give your users a non-kyc wallet from which they can send both NIP-61 nutzaps and the usual NIP-57 lightning zaps.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# my personal approach on using `let`, `const` and `var` in javascript
Since these names can be used interchangeably almost everywhere and there are a lot of people asking and searching on the internet on how to use them (myself included until some weeks ago), I developed a personal approach that uses the declarations mostly as readability and code-sense sugar, for helping my mind, instead of expecting them to add physical value to the programs.
---
`let` is only for short-lived variables, defined at a single line and not changed after. Generally those variables which are there only to decrease the amount of typing. For example:
for (let key in something) {
/* we could use `something[key]` for this entire block,
but it would be too much letters and not good for the
fingers or the eyes, so we use a radically temporary variable
*/
let value = something[key]
...
}
`const` for all _names_ known to be constant across the entire module. Not including locally constant values. The `value` in the example above, for example, is constant in its scope and could be declared with `const`, but since there are many iterations and for each one there's a value with same **name**, "value", that could trick the reader into thinking `value` is always the same. Modules and functions are the best example of `const` variables:
const PouchDB = require('pouchdb')
const instantiateDB = function () {}
const codes = {
23: 'atc',
43: 'qwx',
77: 'oxi'
}
`var` for everything that may or not be variable. Names that may confuse people reading the code, even if they are constant locally, and are not suitable for `let` (i.e., they are not completed in a simple direct declaration) apply for being declared with `var`. For example:
var output = '\n'
lines.forEach(line => {
output += ' '
output += line.trim()
output += '\n'
})
output += '\n---'
for (let parent in parents) {
var definitions = {}
definitions.name = getName(parent)
definitions.config = {}
definitions.parent = parent
}
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# localchat
A server that creates instant chat rooms with [Server-Sent Events](https://en.wikipedia.org/wiki/Server-sent_events) and normal HTTP `POST` requests (instead of WebSockets which are an overkill most of the times).
It defaults to a room named as your public IP, so if two machines in the same LAN connect they'll be in the same chat automatically -- but then you can also join someone else's LAN if you need.
This is supposed to be useful.
- <https://github.com/fiatjaf/localchat>
- <https://localchat.bigsun.xyz/>
## See also
- [Filemap](nostr:naddr1qqyrwcekv33rze3kqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c23ya8a)
-

@ 9a4acdeb:1489913b
2024-07-31 14:42:31
#### TL;DR - Embracing Bitcoin will not be the downfall of the US financial system; rather, it will save it. This demand will be good for Bitcoin, too.
There is no doubt the largest market for Bitcoin trading is in the US. Bitcoin and dollars are traded for each other more than any other fiat-Bitcoin pair. The USD remains the highest volume asset on the global stage, however, trust in the dollar wanes on it as well.
A great amount of uncertainty remains about Bitcoin in the public, but the public is becoming increasingly aware. At some point, the "then suddenly" threshold, when uncertainty about the dollar matches the uncertainty of Bitcoin in the public eye, a great and rapid flip will occur.
## Retirement Will Become Impossible Unless Backed by Unprintable Money
It is this flip that will cause enormous and unprecedented loss for at least the aging population in the US, as well as holders of large amounts of cash. Let us focus on one aspect of this great loss: social security, which is already known to be at great risk, an almost certain bankruptcy of the whole system only a few years away, and this is only if the US dollar lasts that long.
The responsibility of this failure rests on the shoulders of the US Federal Government and the Federal Reserve. Salvation for the system will only be in one manner: backing the fund with Bitcoin.
## A Strategic Reserve
If the US Government funded a strategic Bitcoin reserve rather than wars, the issuance of USD could be then exchanged for payouts in the form of Bitcoin. Retirees who depend on those monthly checks could instead receive Bitcoin. This would be reparation for the theft of the wealth promised by the system to begin, and it would be an efficient way to do so.
While the USD-BTC rate is still in the 5-figures, investments into it can see returns of hundreds times by the time Social Security becomes fully defunct. This window of opportunity is quickly closing. Returns in the tens of times should still be possible for a few years, but likely not past the year 2029.
## This Will Also be Good for Bitcoin
The urgency is high. To avoid a cataclysm for our aging population, the US needs Bitcoin, and because of the demand this will generate, the adoption and valuation of Bitcoin can accelerate.
This is but one mode that Bitcoin will save the US economy, and more is to come.
-

@ 9e915942:f8133dec
2024-08-15 13:49:09
# I am not a therapist
*Part one of a three-part series called "Breaking my silence on social-emotional learning"*

I’ve been suspicious of “social-emotional circles” since I learned about them, several years ago. My first concern was how to fit this practice into a curriculum in which two snow days can mean I have to cut content. However, my second and more substantive concern, was that, put simply, I am not a therapist and am not equipped to lead an exercise like this. After reading [Bad Therapy: Why the kids aren’t growing up](https://www.amazon.com/Bad-Therapy-Kids-Arent-Growing/dp/B0CK524HQ7/ref=sr_1_1?crid=K3BX6HYW2282&dib=eyJ2IjoiMSJ9.zT54L8v7fDcZziZJoty4xkAenFGGXrIHltBdsJvPVtgM9OYYEbbvONPltyZX28UkmBYq6-eiBaSQN4usXHU3JrVMOyhFIi_WykOauizG0qrRRVgi3JM3GvC-YNlReHNHOdj_q1PJNWVkM7omlysAvKMyy9bUJa-SMmKFQZgmn5H7vvhKdVBM9h7gbuXd1FRCmrFbN6rmKR3oEFxKHxhaMBor5VYaZGwOfmybOxniLvU.CwGO3v___93oYeo4IB0uVCkKhBedknOwISBCLcEQwuE&dib_tag=se&keywords=bad+therapy+abigail+shrier&qid=1722781693&sprefix=%2Caps%2C276&sr=8-1), by Abigail Shier, I’m not only convinced that I shouldn’t do these in my classroom, I think they should rarely be done in classrooms at all.
While this and the next couple of posts will focus on circles, the book has raised many flags for me about things we routinely do in schools intended to help kids’ mental health. She argues we, the well-intentioned people who work with young people, frequently commit iatrogenesis (harm caused by those attempting to heal) and argues that many of our best-intentioned interventions likely cause more harm than benefit. I chose circles for a couple reasons. First, it’s relevant to many teachers because it – along with restorative practices, social-emotional learning (SEL) generally, and trauma-informed education – has become quite popular over the last several years. Second, it provides a concrete case study that exemplifies broader issues with SEL in schools.
For those of you unfamiliar with restorative circles, I’ll try to give you the TL:DR. A teacher puts the students in her class in a circle. Basically she then goes around the circle and everyone has the opportunity to share something. There are many variations on this. The teacher might ask students to share how they are feeling that day (check-in style circle), something their struggling with recently or something good that’s happened, or how something that happened in class - like an outburst by a student, for example - made them feel. All of these types or circles have been suggested in the trainings that I’ve attended to varying degrees. (You can read more about restorative circles [here](https://www.edutopia.org/article/building-community-restorative-circles/), which explains in detail more or less the what I’ve learned about them in trainings.)
For now, I want to focus on the more “meaningful” types of circles, not the “check-in” types. These are designed to help students build empathy and other social-emotional skills as well as help students process something they, or the class as a whole, is going through. (Although Shier has convinced me that the check-in style circles are a bad practice as well – an argument I plan to flesh out in part three.)
### I am not a therapist
You might be wondering, if a teacher has time to do them, what could be the harm in doing these regularly with students? Wouldn’t they help build a stronger classroom community?
Let’s suppose that time is not an issue. The biggest problem I see is that *I am not a therapist* and nearly every teacher is not trained as a therapist either.
I remember sitting in trainings and imagining situations in which I’m running a circle and a kid shares something and bursts into tears. Or shares something deeply personal that maybe they shouldn’t have shared with me or their peers. Or calls out another student in class for some reason, creating a conflict in front of the entire class. Whenever circles were described to me it felt like a description of group therapy, and I am simply not trained to handle the variety of situations that might arise in group therapy. In fact, if you really want to see how closely they resemble each other, check out [this page by the counseling Center Group for group therapy in New York City](https://counselingcentergroup.com/group-therapy-in-nyc/) and compare it the description of circles in the article I linked above. You’ll find a lot of common themes, although the group therapy article emphasizes repeatedly that *trained therapists* will be leading the groups.
I’ve raised this concern with individual colleagues and in various meetings over the last several years, including recently at a district-level diversity, equity, and inclusion task force meeting. This is not a direct quote, but I’m most often met with some flavor of the following, either from a teacher who uses circles often, an education consultant leading professional development, or an administrator who has seen teachers run them:
> Most of the time these concerns aren’t an issue. Kids don’t share those kinds of things. If anything gets shared beyond what you think you can handle, you can always end the circle and bring in a school counselor to help you with that individual student or to help you run the circle again to address what happened. Maybe you should work with a teacher who does circles often to help you feel more comfortable.
Sometimes other tips are also shared at this point – a sort of ad hoc list of group therapy hacks. Start doing circles with light-hearted prompts to help build community, they might say. Make sure students know they can “pass” and don’t have to share if they don’t want to share. Don’t pass judgement on what students share, be empathic, ask open questions instead of closed questions. And so on.
This is akin to taking a truck driver and giving him a three-hour training on driving a school bus and telling him he can start a bus route next week. When he says he’s not sure that he can actually pull that off, he’s told that “opening the door is actually pretty easy to figure out, remember to take wide turns, and don’t forget to stop at every railroad crossing. I’ll let you talk with Sam – he’s been driving bus on the side for years! I’m sure you’ll do great!”
Are there similarities between driving a semi-truck and trailer and a school bus? Of course. Are there some truck drivers who could make the switch and be just fine after some practice? Certainly. Will there be many accidents, some of which are avoidable and catastrophic? If this practice continues long enough – absolutely.
Similarly, some interpersonal skills required to teach overlap with those needed by therapists, surely some teachers would be good therapists with minimal training, and having this as a practice by an institution will almost certainly lead to kids being victims of mishandled situations (iatrogenesis).
### Bad therapy in circles - a specific example
Undoubtedly, many bad therapy practices are hidden from me because I don’t have the expertise to know what I don’t know, but I want to share one bad practice that Shier writes about to help make my point – therapist self-disclosure.
When educators are taught about circles we are told that if we share personal stories then we will build trust with our students and this will encourage them to share more as well. From the [Edutopia article](https://www.edutopia.org/article/building-community-restorative-circles/) linked above, we are told, “Share authentically of yourself. This gives others permission to do the same.”
Unfortunately, this is usually unethical according to Shier (she cites [this paper](https://societyforpsychotherapy.org/the-big-reveal-ethical-implications-of-therapist-self-disclosure/), which doesn’t argue that self-disclosure is *always* unethical, but that it is a very nuanced question in psychotherapy and that generally erring away from self-disclosure is best; which reiterates my argument since, as I’m not trained in psychotherapy, I’m not even aware of the aspects of it which are nuanced or settled or debated. But, I digress). Shier writes about a teacher (Kendra Jones, cited from this [Education Week article](https://www.edweek.org/leadership/why-its-so-hard-to-weave-social-emotional-learning-into-academics/2022/11)) who is “very vulnerable” with her students and goes on to say the following:
> Interestingly, were Jones an actual therapist, such self disclosure would be considered unethical. Anytime a therapist might be inclined to share her personal history in order to gratify her own need, she must abstain in order to prioritize the clients needs. And here’s where things get tricky: teachers aren't actually trained in psychotherapy, and they aren't bound by its ethical guidelines, either. Setting up an “emotional sharing” session may sound good, but typically, therapists perform this function under ethical guidelines, so that they don't inadvertently exploit or betray their patients.
Are the nuances of psychotherapy explored in trainings about restorative circles? Of course not. Because the trainers know that we aren’t therapists! Again, when I have raised this issue I’m told that this should not really be a concern - if you think anything is beyond what you can handle, get support from one of the school counselors.
SEL circles exist in a superposition of importance; they are simultaneously innocuous enough that a teacher needn’t worry about not being trained in psychotherapy, but important enough that every teacher should be working to integrate them in all of their classes.
The problems with SEL circles go beyond my lack of training in psychotherapy. In the next post I will explore the issues of confidentiality in circles and in part three explain how even if I was a therapist and we could somehow erase the issue of confidentiality, we *still* shouldn’t try to make circles a common practice.
*Disclaimer: I realize that in writing this and publishing it publicly I run the risk of upsetting some friends, colleagues, and, potentially, administrators. Unfortunately, there are times when that risk must be taken in order to say what is true, needs to be said, and is not being said. I write this while passing no bad judgement on any educator who has implemented restorative circles or other restorative and social-emotional learning practices in their school or classroom. We have had countless trainers in countless hours of professional development the last several years telling us that this is best for kids – that kids will learn better and be more emotionally healthy if we do this. I don’t fault anyone for doing what we were told by the experts was best practice. I hope only to illuminate a contrary perspective that, in my opinion and experience, has significant ramifications if we are to truly do what’s best for our students.*
-

@ 66df6056:f3203c64
2024-07-31 13:17:15
แนวคิดอันนี้เกิดขึ้นหลังจากที่ผมได้รู้จัก LFS หรือ Log- structure File System มันทำให้ผมเกิดความคิดว่าในเมื่อมันสามารถที่จะเก็บ file และทุก log ของการเปลี่ยนแปลงในแต่ละไฟล์ งั้นแปลว่าในกรณีที่ file โดน encrypt มันก็น่าจะสามารถกู้คืนมาได้สิ เอ้ะแต่ถ้าเครื่องนั้นโดน ransomware ไปรอบนึงแล้วกู้คืนมาแล้วมันก็โดนอีกอยู่ดีมั้ย เลยเกิดไอเดียใหม่ว่าแล้วถ้าเราหา SSD อีกลูกมาเก็บ backup ถ้าโดน ransomware ก็ถอดไปเสียบเครื่องใหม่ก็จบ ตะตะแต่ว่า LFS เนี่ย ดั้นนนใช้ไม่ได้กับ windows หรือ Mac เอาละ ปัญหาใหม่มาอีกละ งั้นต้องทำไงล่ะ ? หึเก็บไว้บอกท้ายบทความละกัน มาทำความเข้าใจโปรเจคนี้กันทีละขั้นตอนกันดีกว่า
Log-structure File System (LFS)
-----------
เป็น File system รูปแบบหนึ่งที่จะทำการเก็บข้อมูลเป็น log และสามารถย้อนกลับได้ทุกการกระทำ นอกจากมีความถี่ในการสร้าง snapshot ที่สูงมาก จริง ๆ แล้วเหมาะกับงานประเภทที่ต้องการความต่อเนื่องหากดบัไปต้องกู้คืนได้มากที่สุดเท่าที่เป็นไปได้ แต่เพราะไอความสามารถตรงนั้นของมันนี่แหละ ที่ผมมองว่ามันน่าจะหยิบมาใช้กับการกู้คืน file หลังจากโดน ransomware ได้แน่ ๆ โดยในครั้งนี้ผมเลือกใช้เป็น NILFS2 เนื่องจากดูแล้วน่าจะเหลือตัวเดียวที่ยังพอมีการพัฒนาอยู่ 5555 รูปแบบการเก็บข้อมูลจะเหมือนกับภาพด้านล่างนี้
ตัวอย่าง:
เดิมที file A: "AAAAA" จากนั้นผมได้ทำการอัพเดตข้อมูลใน file A เป็น "BBBBB" ด้วยความสามารถของ LFS มันสามารถที่จะดึง file A เวอร์ชันที่เป็น "AAAAA" กลับมาได้
นี่เป็นปัจจัยสำคัญที่ทำให้ผมมองว่า LFS เหมาะสมที่จะมาเป็นระบบไฟล์ที่ใช้ในการสำรองข้อมูล แต่อยากที่ได้กล่าวไว้ข้างต้นว่าปัญหาของระบบไฟล์นี้คือมันใช้พื้นที่เก็บข้อมูลค่อนข้างสูง และมี write speed ที่ค่อนข้างช้า ถ้าเทียบกับระบบไฟล์อื่น ๆ ในกรณีที่ความเร็วของ SSD เท่ากัน เลยมองว่าถ้าจะใช้เป็นระบบหลักในการเก็บข้อมูลทุกอย่างคงจะไม่เหมาะ เลยนำไปสู่การทำระบบโดยใช้ระบบไฟล์สองแบบที่แตกต่างกัน
System Design
-----------
อย่างที่ได้พูดถึงข้อเสียของ NILFS2 ไปข้างต้น แปลว่าถ้าอยากจะให้คอมพิวเตอร์ทำงานได้อย่างมีประสิทธิภาพคงเดิมและสามารถป้องกัน ransomware ได้ด้วยก็จำเป็นต้องมีระบบไฟล์ที่ใช้กันทั่วไปอย่าง FAT32 หรือ ext4 และใช้ SSD อีกลูกหนึ่งที่ format เป็น NILFS2 และเขียนโปรแกรมให้คอยมอนิเตอร์ทุก ๆ กิจกรรมบน user space และทุกครั้งที่เกิดการเขียนไฟล์ขึ้นให้เขียนลงใน SSD ที่เป็น NILFS2 ด้วย ดังภาพที่แสดงด้านล่างนี้

แล้วทำไมไฟล์ในลูกที่เก็บสำรองข้อมูลถึงไม่เท่ากับจำนวนไฟล์ในที่เก็บข้อมูลหลักล่ะ ? เนื่องด้วยความเร็วในการเขียนที่ค่อนข้างแตกต่างกันของทั้งสอง ผมเลยมองว่าถ้าเราเก็บในรูปแบบบล๊อกจะทำให้เก็บข้อมูลได้ไวกว่า อย่างตัวอย่างในรูป สมมุติว่าไฟล์ A มีขนาดประมาณ 3 บล๊อกใน SSD ที่เป็น nilfs2 ก็จะมี 3 ไฟล์และต้องใช้ทั้งสามไฟล์เพื่อที่จะคืนค่าไฟล์ A กลับมา ถ้าอ่านมาถึงตรงนี้อาจจะเกิดข้อสงสัยว่า แล้วจะทำให้มันยุ่งยากทำไม คัดลอกไฟล์มาใส่ก็จบแล้วมั้ย ? ก็ใช่แหละและจริง ๆ ผมคิดว่าทำแบบนั้นก็เพียงพอ แต่ว่าอย่างที่บอกไปข้างต้น ผมอยากได้ระบบที่ป้องกันได้ 100% ผมเลยเลือกที่จะมอนิเตอร์ kernel เอาไว้และเมื่อมีการเขียนไฟล์เกิดขึ้นผมต้องการดึงข้อมูลมาจากตรงนั้นเลย ไม่อยากรอถูกเขียนลงในพื้นที่เก็บข้อมูลหลักก่อนแล้วค่อยคัดลอกมา จริง ๆ ก็ด้วยเหตุผลด้านประสิทธิภาพด้วย
แล้วจะมอนิเตอร์ kernel อย่างไร ??
-----------
ในครั้งนี้ผมเลือกที่จะใช้เป็น eBPF (extended Berkeley Packet Filter) จริงแล้วเจ้า eBPF เนี่ยใช้งานได้หลากหลายเลยแหละ เรียกได้ว่าประโยชน์รอบด้านสุด ๆ ตามรูปที่แนบด้านล่างเลย
แต่ในครั้งนี้เราจะยุ่งกับมันเพียงแค่การใช้งานเพื่อสอดส่อง kernel เท่านั้น
ภาพด้านบนนี้แสดงให้เห็นจุดที่เราสามารถใช้ eBPF ในการดึงข้อมูลได้ นั่นเลยเป็นเหตุผลหลักที่ผมเลือกใช้ โดยวางการทำงานทั้งหมดของการมอนิเตอร์ไว้ดังนี้
1. ใช้ eBPF เพื่อคอยเช็คว่ามีการเขียนเกิดขึ้นมั้ยโดยการอ่านค่า flag จาก NVMe ว่ามีค่าเป็นอะไรจากนั้นนำค่าที่ได้มา XOR ด้วย mask ถ้าค่าออกมาเป็น 1 แปลว่านั่นคือ write_operation (อาจแตกต่างกันแล้วแต่ version)
2. เมื่อเช็คค่าแล้วเป็น write_operation จากนั้นก็ให้ทำการอ่านเลข sector, และขนาดของข้อมูลที่ต้องการจะเขียน
3. จากนั้นเข้าไปอ่านต่อใน Bio ลงไปยัง Bio_vec และไป Bv_page ตามลำดับ เพื่ออ่านข้อมูลทั้งหมดที่มาจากคำสั่งในการเขียนครั้งนั้น ๆ

*ภาพประกอบเพิ่มเติมเพื่อใครงงว่า Bio คืออะไรข้อมูลเวลาเราเขียนจะอยู่บน page
4. ส่งข้อมูลที่ได้ทั้งหมดออกมา
เพียงเท่านี้เราก็ทำการดึงข้อมูลทุกครั้งที่เราเขียนได้แล้ว และจะนำมันเข้าสู่ขั้นตอนต่อไปในการเก็บข้อมูลลง SSD
เก็บข้อมูลและส่งไป SSD ที่เป็น nilfs2
-----------
เมื่อได้ข้อมูลมาจากการทำงานที่ได้กล่าวไว้ข้างบนแล้ว ก็จะได้ชุดข้อมูลมาชุดหนึ่ง ส่งออกมันมาจาก ebpf(C program) มาสู่ Python ต่อโดยมีขั้นตอนดังนี้
1. นำเลข sector ที่ได้มาทำการคูณด้วยขนาดของ sector เพื่อให้เราได้ logical address มา จากนั้นให้นำ logical address หารด้วยขนาดของบล๊อกเพื่อให้ได้เลขบล๊อก
2. นำข้อมูลในแต่ละ sector มาเรียงลงในบล๊อกที่มันอยู่ละบันทึกลงไปใน SSD
ตัวอย่างเพื่อให้เห็นภาพมากขึ้น
สมมุติว่าข้อมูลที่ส่งกลับมาขนาด 4097 B และเริ่มเขียนที่ sector 0
(กำหนดให้ 1 sector มีขนาด 512B และ 1 Block มี 8 sector)
4097/512 = 8.xx ก็แปลว่าข้อมูลนี้ต้องเก็บใน 9 sector คือ sector 0 ถึง 8
และ 8 sector รวมเป็น 1 block แปลว่าข้อมูลใน sector 0-7จะอยู่ใน block 0 และ sector 8 จะอยู่ใน block 1 แปลว่าโปรแกรมของผมจะสร้างมาสองไฟล์คือ 0,1 จากนั้นจะทำการเติม 0 ท้ายไฟล์ 1 จนมีขนาด 4096 B เท่ากับขนาดของ block
สำหรับคนที่งงว่า sector บล๊อกคืออะไร
ให้ดูตรงรูปกลม ๆ ทางซ้ายมือจะเห็นได้ว่ามันเป็นหน่วยความจำในจานหมุน ซึ่ง sector คือหน่วยย่อยสุด และ sector รวม ๆ กันหลาย ๆ sector จะเป็น cluter บางที่ก็เรียก Tracks บางที่ก็ Block ซึ่งนี่แหละคือบล๊อกที่ผมหมายถึง
เพียงเท่านี้เราก็ได้ระบบที่สามารถป้องกัน ransomware ได้แล้ว เพราะเนื่องจากเมื่อเราโดน ransomware และไฟล์เราถูก encrypt เราก็เพียงใช้ความความสามารถของ SSD ลูกที่เป็น nilfs2 เพื่อนำไฟล์ดั้งเดิมก่อนจะถูก encrypt กับมาได้ดังรูปประกอบด้านล่างนี้

ส่งท้าย
-----------
จริง ๆ แล้วที่ผมเก็บเป็นไฟล์ block เพราะผมอยากให้ backup file สามารถเข้ากันได้กับทุกระบบไฟล์เพื่อให้สามารถใช้งานได้กับทุกระบบ ถึงจะยังทำไม่ได้ก็เหอะ 55555
-

@ 5afdec5b:2d631be1
2024-08-14 09:42:29
# Introducing Our New Whitepaper on Escrow-Less Bitcoin-Collateralized Lending
We are thrilled to release our latest whitepaper, elaborating on our innovative Escrow-Less Bitcoin-Collateralized Lending protocol. This pioneering system leverages the power of Discreet Log Contracts (DLCs) and Hash Time Lock Contracts (HTLCs) to create a trustless, peer-to-peer lending environment that aligns with the ethos of decentralization and user empowerment.
[Read the full whitepaper here](http://whitepaper.lendasat.com/lendasat-whitepaper.pdf)

## Empowering Users with Our Architecture
Our protocol is meticulously designed to empower users by allowing them to borrow against their Bitcoin while retaining full control over it. We believe that this is not just a technological advancement, but a crucial step towards crafting a more decentralized, trust-minimized, and secure financial ecosystem. By eliminating the need for intermediaries, we aim to give users greater autonomy and flexibility, freeing them from traditional constraints.
## Addressing Market Needs for Peer-to-Peer, Trustless Lending
Extensive market research highlights a significant, growing demand for peer-to-peer, trustless lending solutions. Users consistently expressed a desire for more control over their assets and greater flexibility in their lending options. Our Escrow-Less Lending protocol directly addresses these needs, providing a robust framework that enhances user control while maintaining the integrity and security of the lending process.
## Exploring the Potential of Ark for Microloan Liquidity Management
Initially, our focus was predominantly on micro-loans. However, user interviews revealed a relatively limited demand for such products at this time. Nonetheless, we identified Ark as good solution in the context of Bitcoin microloans. Ark's capabilities could unlock new possibilities and efficiencies, making microloans more viable and attractive.
## Remaining Flexible and Adaptable
Even as our primary focus shifts, the potential of Ark continues to intrigue us. Our protocol's design is inherently flexible and adaptable, allowing for continuous refinement and adjustments based on user interest and feedback. Should there be sufficient interest in the future, we are open and ready to explore Ark's integration once again to better serve our users’ needs.
## Revolutionizing Bitcoin Borrowing and Lending
We firmly believe that our Escrow-Less Bitcoin-Collateralized Lending protocol has the potential to revolutionize the borrowing and lending landscape within the Bitcoin ecosystem. Our commitment is steadfast; we aim to make this innovative protocol a reality and will diligently work to iterate and improve based on user feedback. Together, let’s shape the future of decentralized lending.
## Your Feedback Matters
We invite you to delve into our whitepaper and share your thoughts and feedback on this groundbreaking approach. Your insights are invaluable as we strive to create a more user-centric, flexible, and secure lending protocol.
[Read the full whitepaper here](http://whitepaper.lendasat.com/lendasat-whitepaper.pdf)
---
Feel free to reach out with your thoughts, questions, or suggestions. We’re eager to engage with you and iterate based on your valuable input.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Sistemas legais anárquicos
São poucos os exemplos de sistemas legais claramente anárquicos que nós temos, e são sempre de tempos muito remoto, da idade média ou por aí. Me vêm à cabeça agora o sistema islandês, o somaliano, o irlandês e as cortes dos mercadores da Europa continental.
Esses exemplos, embora sempre pareçam aos olhos de um libertário convicto a prova cabal de que a sociedade sem o Estado é capaz de fazer funcionar sistemas legais eficientes, complexos e muito melhores e mais baratos do que os estatais, a qualquer observador não entusiasmado vão parecer meio anacrônicos: são sempre coisas que envolvem família, clãs, chefes de família, comunidades pequenas -- fatores quase sempre ausentes na sociedade hoje --, o que dá espaço para que a pessoa pense (e eu confesso que isso também sempre me incomodou) que nada disso funcionaria hoje, são bonitos, mas sistemas que só funcionariam nos tempos de antigamente, o Estado com seu sistema judiciário é a evolução natural e necessária de tudo isso e assim por diante.
Vale lembrar, porém, que os exemplos que nós temos provavelmente não surgiram espontamente, eles mesmos foram o resultado de uma evolução lenta mas constante do sistema legal das suas respectivas comunidades. Se não tivessem sido interrompidos pela intervenção de algum Estado, esses sistemas teriam continuado evoluindo e hoje, quem sabe, seriam redes complexas altamente eficientes, que, por que não, juntariam tecnologias similares à internet com segurança de dados, algoritmos maravilhosos de reputação e voto, tudo decentralizado, feito por meio de protocolos concorrentes mas padronizados -- talvez, se tivessem tido um pouquinho mais de tempo, cada um desses sistemas legais anárquicos teria desenvolvido meios de evitar a conquista ou a concorrência desleal de um Estado, ou pelo menos do Estado como nós o conhecemos hoje.
-

@ 502ab02a:a2860397
2024-07-31 10:27:12
ใช่ครับ 31 กรกฎาคม 2567 ขอบันทึกการเจอนี่ไว้หน่อยว่า
เป็นการทำงานในงานโฆษณาเป็นวันสุดท้าย หลังจากวันนี้ก็จะไม่ได้เอี่ยวกับงานในวงเวียนนี้อีกแล้ว รวมถึงได้ยุติการเป็นหุ้นส่วนของบริษัทด้วยพร้อมๆกัน
ใช่ครับ ผมยุติบทบาทการหุ้นด้วย ปล่อยให้เพื่อนอีกคนเผชิญชะตากรรมในเส้นทางนี้ต่อไป หลังจากลุยกันมา 22ปี ในรูปแบบบริษัท และ 3 ปีในแบบฟรีแลนซ์
ภาพนี้เป็นโต๊ะทำงานภาพสุดท้าย

และกีตาร์เป็นของอย่างแรกที่เอาเข้ามา แต่เป็นของอย่างสุดท้ายที่เอาออกไป

พรุ่งนี้ก็จะไม่เหมือนเดิมอีกต่อไป ดีร้ายก็มาดิ เจอกัน 555
ผมจะพยายามดำเนินชีวิตในแบบที่ตัวเองอยากทำ มากที่สุดเท่าที่จะทำได้ครับ 555
ร็อคกี้ บอกว่าหมัดหนักแค่ไหนไม่สำคัญ สำคัญที่เราจะรับหมัดหนักๆได้นานเท่าไรต่างหาก
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# Just malinvestiment
Traditionally the Austrian Theory of Business Cycles has been explained and reworked in many ways, but the most widely accepted version (or the closest to the Mises or Hayek views) view is that banks (or the central bank) cause the general interest rate to decline by creation of new money and that prompts entrepreneurs to invest in projects of longer duration. This can be confusing because sometimes entrepreneurs embark in very short-time projects during one of these bubbles and still contribute to the overall cycle.
The solution is to think about the "longer term" problem is to think of the entire economy going long-term, not individual entrepreneurs. So if one entrepreneur makes an investiment in a thing that looks simple he may actually, knowingly or not, be inserting himself in a bigger machine that is actually involved in producing longer-term things. Incidentally this thinking also solves the biggest criticism of the Austrian Business Cycle Theory: that of the rational expectations people who say: "oh but can't the entrepreneurs know that the interest rate is artificially low and decide to not make long-term investiments?" ("and if they don't know they should lose money and be replaced like in a normal economy flow blablabla?"). Well, the answer is that they are not really relying on the interest rate, they are only looking for profit opportunities, and this is the key to another confusion that has always followed my thinkings about this topic.
If a guy opens a bar in an area of a town where many new buildings are being built during a "housing bubble" he may not know, but he is inserting himself right into the eye of that business cycle. He expects all these building projects to continue, and all the people involved in that to be getting paid more and be able to spend more at his bar and so on. That is a bet that may or may not end up paying.
Now what does that bar investiment has to do with the interest rate? Nothing. It is just a guy who saw a business opportunity in a place where hungry people with money had no bar to buy things in, so he opened a bar. Additionally the guy has made some calculations about all the ending, starting and future building projects in the area, and then the people that would live or work in that area afterwards (after all the buildings were being built with the expectation of being used) and so on, there is no interest rate calculations involved. And yet that may be a malinvestiment because some building projects will end up being canceled and the expected usage of the finished ones will turn out to be smaller than predicted.
This bubble may have been caused by a decline in interest rates that prompted some people to start buying houses that they wouldn't otherwise, but this is just a small detail. The bubble can only be kept going by a constant influx of new money into the economy, but the focus on the interest rate is wrong. If new money is printed and used by the government to buy ships then there will be a boom and a bubble in the ship market, and that involves all the parts of production process of ships and also bars that will be opened near areas of the town where ships are built and new people are being hired with higher salaries to do things that will eventually contribute to the production of ships that will then be sold to the government.
It's not interest rates or the length of the production process that matters, it's just printed money and malinvestiment.
-

@ bcbb3e40:a494e501
2024-08-12 16:03:03
En este nuevo artículo sobre actualidad sería la segunda vez que nombremos a la figura de **Alvise Pérez**. Lo habíamos mencionado de pasada anteriormente, cuando [comentamos nuestras hipótesis](https://hiperbolajanus.com/posts/adios-woke-que-viene-ahora/) respecto al atentado contra Trump y lo que ello, a nuestro entender, supondría.
La motivación del mismo no es defender a Alvise, con quien no nos alineamos por motivos que explicaremos. Lo que nos llama la atención es la reacción adversa del sector _disidente_ (llamémoslo así) que, si bien reconocemos que puede haber un componente legítimo de desconfianza ante la aparición «súbita» de este personaje, consideramos que está motivada principalmente por envidias, celos y algo de sectarismo.
El objetivo es por lo tanto, hacernos capaces de encontrar la viga en el propio ojo y dejar de señalar la paja en el ojo ajeno.
### Sospechas contra Alvise
Alvise Pérez logró una gran relevancia a raíz del resultado de su agrupación electoral «[Se acabó la fiesta](https://seacabolafiesta.com/)» (SALF) en las últimas elecciones al parlamento europeo celebradas en España el pasado 9 de junio de 2024.
A la totalidad del espectro político/mediático español le sentó como un jarro de agua fría la friolera de más de 800.000 votos oficiales (SALF asegura que son más y está reclamando el recuento) conseguida por un personaje que hasta el momento estaba vetado por la prensa y que basó su campaña electoral en la difusión a través de las redes sociales que no habían podido serle censuradas y después de una serie de meetings de presupuesto ínfimo celebrados por las principales capitales españolas.
||
|:-:|
|Alvise Pérez durante su discurso pronuciado tras el cierre de los colegios electorales en las elecciones europeas del 9J|
Viéndolo así a todos nos parece un cuento demasiado bonito como para ser verdad. Estamos todos muy escarmentados del ascenso a la relevancia pública de personajes «desconocidos» como **José Luis Rodríguez Zapatero**, **Pablo Iglesias Turrión** o **Pedro Sánchez Pérez-Castejón**, o de fuerzas políticas como VOX; todos estos casos, aupados por los medios. Además de la lógica desconfianza que nos suscita el ascenso meteórico de las figuras y organizaciones mencionadas desde la nada, sin una trayectoria previa conocida, y sin una masa social o apoyo reconocido.
Sí, también VOX era prácticamente desconocida hasta que los invitaron a este programa en Televisión de Cataluña, allá por el 2018, con todo el tema del independentismo catalán en auge:
<iframe width="560" height="315" src="https://www.youtube-nocookie.com/embed/T9pIf6pEhiQ?si=bMUn3YdRQ2GhMm25" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe>
A todos los ejemplos anteriores los aupó la prensa. Sin embargo, parece que Alvise/SALF no es el caso… Lo que lleva a la hipótesis conspiranoica de que es un personaje puesto por el Centro Nacional de Inteligencia de España (CNI).
#### La hipótesis del CNI
Es cierto que Alvise ha ido ganando mucha relevancia en redes sociales en base a información que ha ido publicando y que ha sido activamente ignorada o vetada por el aparato mediático. Además, la calidad de dicha información siempre ha sido de categoría de espionaje. ¿Cómo es posible que un chaval sevillano haya logrado acceso a informaciones de un calibre capaz de hacer tambalearse a un país como España?
Él ha manifestado en repetidas ocasiones que, efectivamente, utiliza métodos «sucios» como la extorsión o el _hacking_. Pero, obviamente, aquí tendríamos que creer en su palabra y no se puede desmentir de forma tajante que no tenga algún tipo de relación con los servicios de inteligencia.
No obstante, la nube de sospecha del CNI o de colaboración con la policía siempre ha estado encima de algunos personajes disidentes destacados, con mayor o menor acierto. Es más, de hecho no descartamos que muchos focos «disidentes» como pseudo-partidos políticos o incluso algunas librerías hayan tenido algún tipo de conexión. Es lo que en inglés se denomina _Honeypot_ (trampa de miel).
Volviendo a Alvise, lo que se le reprocha desde algunos sectores disidentes sobre su hipotética relación con el CNI es que éstos lo hayan introducido en la esfera pública para debilitar a otras opciones disidentes o _patrióticas_[^1], como VOX. Sinceramente, este reproche nos parece ridículo. ¿Acaso hay otras fuerzas _patrióticas_ (nótense las cursivas) aparte de VOX que tengan algún tipo de influencia real como para que merezca la pena diluirlas? Y VOX, ¿por qué no apoya a SALF en su cruzada contra INDRA y secunda sus dudas plausibles sobre la precisión del cómputo y la veracidad de los resultados electorales?
### El deplorable activismo disidente en España
Pese a que las sospechas contra él pudieran demostrarse como ciertas en algún momento, si nos atenemos a su historial registrado y a lo que ha ido aportando a la sociedad española desde sus medios, ¿¡dónde está el problema!?
Entendemos perfectamente las sospechas y compartimos el historial de desengaños de muchas opciones políticas, pero posiblemente muchos se estén pasando de estrictos, quizás con el ánimo de defender sus colores. ¿Existe acaso miedo de que otro haga las cosas bien porque «los tuyos» no lo han logrado?
Es una actitud patética y sectaria que antepone el interés del partido o del grupúsculo que uno defiende al interés general del país. Una actitud, dicho sea de paso, demasiado habitual en cualquier tipo de agrupación humana: asociaciones lúdicas, partidos, empresas, etc.
#### Escrutinio feroz contra Alvise
El contrato que Alvise _firmó_ con su base de seguidores fue el siguiente: «_Vosotros me votáis para proporcionarme inmunidad política y, a cambio, **1)** yo utilizaré esa inmunidad para difundir información que me pondría en apuros en caso de no disponer de tal inmunidad y además **2)** renunciaré a mi sueldo, sorteándolo entre vosotros»._
Las elecciones se celebraron hace apenas dos meses… Pues bien, durante este tiempo no han dejado de llover las críticas de por qué no ha cumplido todavía con lo prometido. Críticas expresadas con especial vehemencia sobre todo por aquellos que no le votaron y que, por lo tanto, no _suscribieron_ dicho contrato con él. Pero bueno…
La cuestión es que el pasado sábado 10 de agosto, sabiendo como él sabe manejar a los medios y a la opinión pública, publicó el siguiente mensaje según el cual, aparentemente, renunciaba cumplir el punto 2) del contrato:
<blockquote class="twitter-tweet" data-dnt="true"><p lang="es" dir="ltr">Acabo de cobrar mi sueldo como eurodiputado!
- 8.089,46 como sueldo de agosto.
- 4.043,60 como sueldo de medio julio.
En un rato explico en un vídeo por qué he decidido NO ENTREGAR mi sueldo, y quedármelo como respuesta a todos los ataques recibidos por periodistas, partidos y haters en general.
😘
<a href="https://twitter.com/Alvise_oficial_/status/1822346861769883867?ref_src=twsrc%5Etfw">8:58 p. m. · 10 ago. 2024</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script>
La respuesta de toda la prensa y de sus enemigos políticos de la izquierda no se hizo esperar. Es algo que no pilla a nadie de sorpresa. Sin embargo, lo que fue especialmente ridículo fue ver cómo otros _patriotas_ y _disidentes_ se subían al carro del linchamiento sin pararse a pensar por un momento que tenía toda la pinta de ser un _troleo_.
Porque sí, porque a la que alguien haya seguido un poco la trayectoria de Alvise debería haber anticipado que no renunciar a su sueldo sería casi un suicidio para él. Él aún no tiene la posibilidad, el poder, los privilegios ni una base zombi lo suficientemente motivada como para que le permitan «cambiar de opinión».
No tardó mucho en humillar por completo a todos sus detractores publicando el siguiente mensaje unas horas más tarde:
<blockquote class="twitter-tweet" data-dnt="true"><p lang="es" dir="ltr">Me quedo mi sueldo.
Lo explico todo en:
http://AlviseCumpliendo.com
<a href="https://twitter.com/Alvise_oficial_/status/1822368651993104488?ref_src=twsrc%5Etfw">10:25 p. m. · 10 ago. 2024</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script>
Efectivamente, tal y como prometió, parece que cumplirá el punto **2)**.
Es que, de hecho, el «sacrificio» de sortear su salario le reporta muchos más beneficios que no hacerlo. El número de suscriptores de [su canal de Telegram](https://t.me/Alviseperez) ha aumentado en más de 70.000 personas en menos de 2 días. Y los seguidores de [su canal de Instagram](https://www.instagram.com/alviseperez/) ya superan el millón. Este incremento de audiencia, monetizado, supera con creces los 10.000 euros mensuales.
#### En la disidencia organizada todo son excusas y malos resultados
Pese a todo, para los más fanáticos de nada servirán los logros de Alvise ya no para adherirse a él sino simplemente para dejar de atacarle. Parece que muchos lo quieren o todo o nada, pero en realidad la motivación que lleva a tal animadversión es la impotencia, la frustración y la envidia que genera ver que otros tienen éxito y los tuyos no.
El sector _disidente_ español ha sido lamentable desde mucho antes de la transición democrática española. Especialmente desde la década de 1990 lo único que poblaba el panorama español eran grupos de frikis y de nostálgicos de vete tú a saber qué, que jamás lograron tener una relevancia pública ni política significativa ya que estaban más encariñados con sus símbolos y parafilias que con la población general y «analfabeta política» española. La disidencia española, salvo alguna honrosa iniciativa cultural sobre todo, se ha mantenido inoperante a lo largo de las más de cuatro décadas de existencia del actual régimen. Estamos hablando de organizaciones políticas, iniciativas ciudadanas o personajes particulares que hayan podido mostrar un discurso y una cosmovisión alternativas. En muchas ocasiones han antepuesto los intereses particulares de la organización, y han optado por la ortodoxia ideológica frente a cualquier pragmatismo o movimiento táctico orientado a las contingencias del momento, lo cual ha desactivado toda posibilidad de plantear una alternativa viable y seria para combatir las injusticias del régimen demoliberal.
Cierto es que los medios de comunicación de aquella época tampoco eran favorables y que el sistema ha puesto muchas dificultades, pero no nos engañemos, la mayoría de esos grupos no ha sabido hacer nunca un proselitismo eficiente y atractivo, haciendo propuestas endogámicas y de consumo interno, sin ser capaces de salir de su burbuja, quedando en muchos casos en terrenos oscurantistas.
Lo único que pareció romper un poco este panorama tan lamentable fue la irrupción intencionada de VOX, que pese a que podamos sospechar que se trata de disidencia controlada para canalizar el desencanto de un sector cada vez más amplio de la población, también ha servido para visibilizar que ese sector poblacional existe, que no es precisamente insignificante y que abarca a un espectro social amplio, más allá de los marginados antisociales (_friki-fachas_) que proliferaban por la escena _patriótica_.
No obstante, dentro de este panorama tan lamentable, la irrupción de VOX no ha mejorado en absoluto la situación, porque se ha dedicado a fagocitar ciertos elementos de esa «falsa disidencia» fracasada e inoperante, para ocupar muchos de sus cuadros dirigentes, al tiempo que ejerce una mera oposición retórica y actúa como cualquier otra organización del arco parlamentario, invocando el «imperio de la ley», como tanto gusta a los liberales, bajo su formalismo positivo, vacío e inconsecuente. Aún así, el hartazgo y el desengaño ha llegado a ciertos sectores de sus votantes, los cuales se han desmarcado progresivamente de sus políticas y de ese pseudopatriotismo que ha pretendido atribuirse desde su fundación.
Dicho todo esto, ¿importa realmente la posición contraria a Alvise de la _disidencia patriótica_ española?. Pues realmente no, porque su capacidad de influencia es insignificante. Por eso, creemos que lo más inteligente que podrían hacer es callarse y dejar de hacer el ridículo, pero quizás eso sea pedirles mucho. En este sentido, y dadas las urgencias que demanda nuestra precaria situación, no deberíamos obstaculizar cualquier acción positiva que contribuya a la causa disidente, aunque sea limitada en el tiempo y quienes la realicen se encuentren en nuestras antípodas ideológicas. En el terreno de lo táctico, y en el terreno de las contingencias, quizás haya ocasiones en las que priorizar un cierto pragmatismo en nuestra visión de las cosas frente a las demandas ideológicas, que siendo absolutamente necesarias y legítimas pueden esperar ante los hechos inmediatos.
### Por qué no somos anti-alvisistas
Aunque lo hemos dicho al principio, no está de más recalcar que el propósito de este artículo no es encumbrar ni mucho menos a Alvise Pérez. Nosotros también compartimos algunas de las sospechas que se vierten contra él. Además, tampoco estamos alineados a nivel ideológico.
Alvise parece el típico español de a pie, con sus defectos y sus virtudes, educado e influido bajo un sistema liberal. No propone un cambio de paradigma político, sino una continuación del mismo, eso sí, en el que al menos se cumplan las normas que se supone que se tendrían que cumplir.
||
|:-:|
|Las «ardillas» es la red de seguidores/colaboradores/informadores/votantes indignados anónimos de Alvise Pérez, quizás en referencia a «Alvin y las Ardillas»|
Es evidente la decadencia del panorama político actual donde se nos miente y se nos toma el pelo ya sin ningún tipo de disimulo. A calzón quitado. Ya ni siquiera se molestan en aparentar que cumplen las normas que ellos mismos han impuesto. Los escándalos de corrupción que hemos testimoniado en el pasado y en la actualidad rebosan lo ultrajante.
Intentar que por lo menos se cumplan las normas que se supone que se tendrían que cumplir según el ordenamiento legal vigente, lamentablemente, se tiene que considerar como un logro. Obviamente, nosotros no nos adherimos al susodicho ordenamiento legal, pero entendemos que lo mínimo es ser respetuoso con lo que éste dicta, así como con sus procedimientos y protocolos. Ya llevamos muchos años escuchando por los _mass media_ aquello del «estado de derecho», el «imperio de la ley» o «el sistema más garantistas de todos los existentes», para luego ver cómo la corrupción y el menoscabo de la dignidad e integridad del territorio nacional son prácticas habituales.
Por eso creemos que marcarse eso como objetivo a corto o a medio plazo ya es más que suficiente, y si Alvise sirve como ariete para eso, bienvenido sea. No creemos que sea pertinente arremeter contra él y convertirlo en cabeza de turco cuando desde la partitocracia, a izquierda y derecha, se está contribuyendo activamente a la destrucción y sometimiento de España a sus enemigos.
Ahora bien, ¿aspiramos al mismo modelo de sociedad? No. Él aspira a lo que cree que es correcto: un modelo Democrático Liberal. Alvise quiere reparar. Nosotros queremos reconstruir desde cero. Lo suyo es más realista y factible a corto plazo. Lo nuestro es una batalla cultural.
Podemos contemplar con cierto agrado las acciones de Alvise, siempre que éstas se dirijan contra los partidos políticos, sus integrantes y las corruptelas que protagonizan en un escenario de traición permanente contra el Pueblo y la nación española. Pero nunca podremos coincidir con quienes pretenden seguir confiando en el liberalismo como una opción de futuro, y más después de constatar la responsabilidad de esta ideología perversa en la destrucción del Occidente europeo, totalmente tiranizado y en un estado de metástasis que parece conducirnos a un abismo de caos y destrucción. Por eso lo fundamental en toda opción disidente pasa por adoptar una postura radical e innegociable frente al liberalismo y sus iniquidades.
No podemos aceptar el discurso que afirma que lo que fallan son las personas, que son corruptas, pero que el sistema y su entramado ideológico e institucional es bueno, positivo y perfectamente viable, porque no es así. Las personas que dirigen e integran las altas jerarquías del régimen español, y por extensión de las democracias liberales europeas, son corruptas, mezquinas y traidoras porque las instituciones y la ideología que las impregna posee esa misma naturaleza. Y con esto también queremos contrarrestar aquellos tópicos que muchas veces escuchamos en las conversaciones cotidianas, que tienden a culpar el factor humano y contingente y no la estructura político-ideológica que ha favorecido su ascenso y es consustancial a esa corrupción.
Desde los tiempos de la _plandemia_ se ha visto un cierto despertar entre amplios sectores de la sociedad española, que han empezado a desconfiar abiertamente de los postulados «políticamente correctos», y ya se atreven a criticar abiertamente temas como la «inmigración», las ingenierías sociales asociadas al Nuevo Orden Mundial u otro tipo de ideas que la prensa vendida se empeña en fabricar para mantenernos dócilmente en el redil. Estos hechos han suscitado formas embrionarias de disidencia y organización, apoyándose muchas veces en las nuevas tecnologías e Internet, como el propio Alvise, y la posibilidad de ir generando redes de comunicación propias, convertidas en vectores de ideas y discursos compartidos por miles de personas. Aunque no coincidamos en lo ideológico, es justo celebrar y apoyar este tipo de iniciativas, y que todo lo que dañe el actual orden de cosas y genere vínculos orgánicos y de solidaridad entre los propios españoles, y europeos, reciba el aliento y el apoyo de todos nosotros.
[^1]: Entendemos que VOX no es un partido patriota, sino liberal de derechas, y con evidentes filiaciones con el sionismo. No obstante, hay quien considera que VOX representa, erróneamente, una alternativa «patriota» al actual sistema vigente, cuando siempre ha defendido tanto el orden constitucional fundado en 1978, como sus principales figuras jurídicas e institucionales, tales como la monarquía.
-

@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
# O mito do objetivo
O insight [deste cara](https://www.youtube.com/watch?v=dXQPL9GooyI) segundo o qual buscar objetivos fixos, além de matar a criatividade, ainda não consegue atingir o tal objetivo -- que é uma coisa na qual eu sempre acreditei, embora sem muitas confirmações e (talvez por isso) sem dizê-lo abertamente --, combina com a idéia geral de que todas as estruturas sociais que valem alguma coisa surgem do jogo e brincadeira.
A seriedade, que é o oposto da brincadeira, é representada aqui pelo objetivo. Pessoas muito sérias com um planejamento e um objetivo final, tudo esquematizado.
---
Na verdade esse insight é bem manjado. Até eu mesmo já o tinha mencionado, citando Taleb em [Processos Antifrágeis](nostr:naddr1qqyryv3hxfsnvvm9qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c5jshx7).
E finalmente há esta tirinha que eu achei aleatoriamente e que bem o representa: [](https://dilbert.com/strip/2004-04-17)
 @ 3bf0c63f:aefa459d
2024-03-19 14:01:01# Nostr is not decentralized nor censorship-resistant Peter Todd has been [saying this](nostr:nevent1qqsq5zzu9ezhgq6es36jgg94wxsa2xh55p4tfa56yklsvjemsw7vj3cpp4mhxue69uhkummn9ekx7mqpr4mhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet5qy8hwumn8ghj7mn0wd68ytnddaksz9rhwden5te0dehhxarj9ehhsarj9ejx2aspzfmhxue69uhk7enxvd5xz6tw9ec82cspz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqy28wumn8ghj7un9d3shjtnwdaehgu3wvfnsz9nhwden5te0wfjkccte9ec8y6tdv9kzumn9wspzpn92tr3hexwgt0z7w4qz3fcch4ryshja8jeng453aj4c83646jxvxkyvs4) for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right. Nostr _today_ is indeed centralized. Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:  The top one was published to `wss://nostr.wine`, `wss://nos.lol`, `wss://pyramid.fiatjaf.com`. The second was published to the relay where I generally publish all my notes to, `wss://pyramid.fiatjaf.com`, and that is announced on my [NIP-05 file](https://fiatjaf.com/.well-known/nostr.json) and on my [NIP-65](https://nips.nostr.com/65) relay list. A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:  These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains. What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all. Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant. What happens is that most people who engaged with the note are _following me_, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on `wss://pyramid.fiatjaf.com`. If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before. Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today. Peter Todd is wrong that Nostr is _inherently_ centralized or that it needs a _protocol change_ to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we [drive in the right direction](bc63c348b) we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary. --- See also: - [Censorship-resistant relay discovery in Nostr](nostr:naddr1qqykycekxd3nxdpcvgq3zamnwvaz7tmxd9shg6npvchxxmmdqgsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8grqsqqqa2803ksy8) - [A vision for content discovery and relay usage for basic social-networking in Nostr](nostr:naddr1qqyrxe33xqmxgve3qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cywwjvq)
@ 3bf0c63f:aefa459d
2024-03-19 14:01:01# Nostr is not decentralized nor censorship-resistant Peter Todd has been [saying this](nostr:nevent1qqsq5zzu9ezhgq6es36jgg94wxsa2xh55p4tfa56yklsvjemsw7vj3cpp4mhxue69uhkummn9ekx7mqpr4mhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet5qy8hwumn8ghj7mn0wd68ytnddaksz9rhwden5te0dehhxarj9ehhsarj9ejx2aspzfmhxue69uhk7enxvd5xz6tw9ec82cspz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqy28wumn8ghj7un9d3shjtnwdaehgu3wvfnsz9nhwden5te0wfjkccte9ec8y6tdv9kzumn9wspzpn92tr3hexwgt0z7w4qz3fcch4ryshja8jeng453aj4c83646jxvxkyvs4) for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right. Nostr _today_ is indeed centralized. Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:  The top one was published to `wss://nostr.wine`, `wss://nos.lol`, `wss://pyramid.fiatjaf.com`. The second was published to the relay where I generally publish all my notes to, `wss://pyramid.fiatjaf.com`, and that is announced on my [NIP-05 file](https://fiatjaf.com/.well-known/nostr.json) and on my [NIP-65](https://nips.nostr.com/65) relay list. A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:  These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains. What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all. Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant. What happens is that most people who engaged with the note are _following me_, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on `wss://pyramid.fiatjaf.com`. If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before. Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today. Peter Todd is wrong that Nostr is _inherently_ centralized or that it needs a _protocol change_ to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we [drive in the right direction](bc63c348b) we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary. --- See also: - [Censorship-resistant relay discovery in Nostr](nostr:naddr1qqykycekxd3nxdpcvgq3zamnwvaz7tmxd9shg6npvchxxmmdqgsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8grqsqqqa2803ksy8) - [A vision for content discovery and relay usage for basic social-networking in Nostr](nostr:naddr1qqyrxe33xqmxgve3qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cywwjvq) @ 5e5fc143:393d5a2c
2024-01-04 12:44:26We are now given a choice of digital freedom #nostr . Creativity for every nostrich is now unleashed from the cage of bigtech censorship , rules and algo. But freedom comes with responsibility so pick right one(s). I will try share here some learning experience both technical and also from fundamental point of view. Just wanted kick start this article n fill as we go like living reference document. Nostr itself is an application layer protocol that can used beyond just social media mirco or long blogging. Each nostr client heavily dependent on back-end servers call nostr "Relay servers" or in short "rs" or "relays" Relays can hosted anywhere in clearnet internet, onion net , vpn , i2p , nym Relays are controlled by their respective admins based NIP specs that they select to implement according to own decisions. Relays can have certain ToS (Terms of Service) Rules to adhered too. New users can choose and pick client or app (ios / android/ windows) with preset of relays in the simplest form , but other advanced users need to do a regular manual relay management. Relay management is an active regular task based on where when n how you are using. Relay list are saved within you npub profile backup file which can edited and broadcast anytime. Relay management is an active regular task based on where when and how you are using. Relay list always need to be updated time to time as and when needed. 2 Users MUST a common RELAY between them even if one only need to follow another. Occasionally you may notice certain npub accounts you are following already but cannot see frequent notes publish by them – one of cause maybe you not sharing a common relay Most nostr client applications has SETTINGS where user choose add/remove relays Also user choose which function to enable - READ or WRITE Relay list for your account is always saved within you npub profile backup file which can edited and broadcast anytime. Hence any app or browser when u login with you npub the same relay list will be enforced. There could valid reasons why u need have list for if you trying to save bandwidth and traveling. Functions in app.getcurrent.io and primal.net app for mobile apple or android are ideal for user traveling abroad and wanted to save bandwidth since relay management is done the providers in backend and saves hassle for basic usage. Remember if someone is selecting relay on your behalf then you may not be necessarily able to pull and get some specific and special content that you may need. Such providers like coracle and nostrid also give option to override the default relays they selected. Relay types: They can be categorized by various features or policy or technologies. FREE PUBLIC Relays vs PAID PUBLIC Relays PAID relays provide unrestricted access / write / filtering options than FREE relays but both are public clearnet relays. Just subscribing to PAID relays will not solve all problems unless you choose the relays properly and enable settings correctly. Private Replay or Tor Relays – normally not easily visible until unless someone tell you. You can also host own private relay not opened to internet of archive and back of your own notes. The technical landscape in nostr can be fast changing as more NIPs get proposed or updated. Relays admin can choose implement certain NIPs or not based on policy or technical limitations. Example NIP33 defines “long notes” aka blogs as you now reading this in habla site which #1 UI and site for "Editable" long notes – some relays donot implement or allow this. NIP07 is used for client authentication like nos2x and is implemented by all relays in fact. To be continued again ... reference pics will added later also Hope this help you understand "why when what" to tune and maintain active set of proper relays. Relay Proxy, Relay aggregator or Relay multiplexer – Paid, Public, Free, Private, Event, Relays That’s all for now n more later ... Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️ PV 💜 🤙 References: https://habla.news/relays https://relay.exchange/ https://relays.vercel.app/ https://nostr.info/relays/ https://nostrudel.ninja/#/relays Related Articles: https://thebitcoinmanual.com/articles/types-nostr-relays/ nostr:naddr1qqd5c6t8dp6xu6twvukkvctnwss92jfqvehhygzwdaehguszyrtp7w79k045gq80mtnpdxjuzl9t7vjxk52rv80f888y5xsd5mh55qcyqqq823cf39s98 https://habla.news/u/current@getcurrent.io/1694434022411
@ 5e5fc143:393d5a2c
2024-01-04 12:44:26We are now given a choice of digital freedom #nostr . Creativity for every nostrich is now unleashed from the cage of bigtech censorship , rules and algo. But freedom comes with responsibility so pick right one(s). I will try share here some learning experience both technical and also from fundamental point of view. Just wanted kick start this article n fill as we go like living reference document. Nostr itself is an application layer protocol that can used beyond just social media mirco or long blogging. Each nostr client heavily dependent on back-end servers call nostr "Relay servers" or in short "rs" or "relays" Relays can hosted anywhere in clearnet internet, onion net , vpn , i2p , nym Relays are controlled by their respective admins based NIP specs that they select to implement according to own decisions. Relays can have certain ToS (Terms of Service) Rules to adhered too. New users can choose and pick client or app (ios / android/ windows) with preset of relays in the simplest form , but other advanced users need to do a regular manual relay management. Relay management is an active regular task based on where when n how you are using. Relay list are saved within you npub profile backup file which can edited and broadcast anytime. Relay management is an active regular task based on where when and how you are using. Relay list always need to be updated time to time as and when needed. 2 Users MUST a common RELAY between them even if one only need to follow another. Occasionally you may notice certain npub accounts you are following already but cannot see frequent notes publish by them – one of cause maybe you not sharing a common relay Most nostr client applications has SETTINGS where user choose add/remove relays Also user choose which function to enable - READ or WRITE Relay list for your account is always saved within you npub profile backup file which can edited and broadcast anytime. Hence any app or browser when u login with you npub the same relay list will be enforced. There could valid reasons why u need have list for if you trying to save bandwidth and traveling. Functions in app.getcurrent.io and primal.net app for mobile apple or android are ideal for user traveling abroad and wanted to save bandwidth since relay management is done the providers in backend and saves hassle for basic usage. Remember if someone is selecting relay on your behalf then you may not be necessarily able to pull and get some specific and special content that you may need. Such providers like coracle and nostrid also give option to override the default relays they selected. Relay types: They can be categorized by various features or policy or technologies. FREE PUBLIC Relays vs PAID PUBLIC Relays PAID relays provide unrestricted access / write / filtering options than FREE relays but both are public clearnet relays. Just subscribing to PAID relays will not solve all problems unless you choose the relays properly and enable settings correctly. Private Replay or Tor Relays – normally not easily visible until unless someone tell you. You can also host own private relay not opened to internet of archive and back of your own notes. The technical landscape in nostr can be fast changing as more NIPs get proposed or updated. Relays admin can choose implement certain NIPs or not based on policy or technical limitations. Example NIP33 defines “long notes” aka blogs as you now reading this in habla site which #1 UI and site for "Editable" long notes – some relays donot implement or allow this. NIP07 is used for client authentication like nos2x and is implemented by all relays in fact. To be continued again ... reference pics will added later also Hope this help you understand "why when what" to tune and maintain active set of proper relays. Relay Proxy, Relay aggregator or Relay multiplexer – Paid, Public, Free, Private, Event, Relays That’s all for now n more later ... Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️ PV 💜 🤙 References: https://habla.news/relays https://relay.exchange/ https://relays.vercel.app/ https://nostr.info/relays/ https://nostrudel.ninja/#/relays Related Articles: https://thebitcoinmanual.com/articles/types-nostr-relays/ nostr:naddr1qqd5c6t8dp6xu6twvukkvctnwss92jfqvehhygzwdaehguszyrtp7w79k045gq80mtnpdxjuzl9t7vjxk52rv80f888y5xsd5mh55qcyqqq823cf39s98 https://habla.news/u/current@getcurrent.io/1694434022411 @ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade. Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas. https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico Segue artigo na íntegra. 👇 Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes. Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo. Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube. Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores. No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado. Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência. Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância. Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade. Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada. Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos. Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista). Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos. De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais. Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade. Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra. Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles. Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia. Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor. Racismo Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso. Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão. Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam. Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses. Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo. A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente. E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança. Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível. A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa. Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país. A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados. Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela. O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas. Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita. A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar. Fascismo Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico. Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade. Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo. Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade. É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)? As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la. Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal. Existem duas fortes razões para isso: A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não. Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele. Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós. Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade. Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade. Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado. Machismo Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social. Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal. Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe. O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista. Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade. A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade. O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são. O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas? Homofobia Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador. A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação. Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual: “Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada) “Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada) “O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências) Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea. Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher. Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites. Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”. Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig. Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender. Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista. Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for. Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio? Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar. Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades. Conclusão A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza. Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço. Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda. A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista. Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade. Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas. https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico Segue artigo na íntegra. 👇 Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes. Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo. Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube. Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores. No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado. Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência. Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância. Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade. Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada. Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos. Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista). Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos. De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais. Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade. Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra. Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles. Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia. Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor. Racismo Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso. Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão. Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam. Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses. Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo. A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente. E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança. Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível. A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa. Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país. A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados. Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela. O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas. Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita. A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar. Fascismo Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico. Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade. Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo. Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade. É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)? As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la. Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal. Existem duas fortes razões para isso: A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não. Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele. Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós. Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade. Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade. Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado. Machismo Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social. Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal. Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe. O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista. Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade. A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade. O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são. O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas? Homofobia Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador. A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação. Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual: “Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada) “Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada) “O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências) Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea. Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher. Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites. Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”. Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig. Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender. Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista. Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for. Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio? Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar. Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades. Conclusão A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza. Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço. Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda. A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista. Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos. @ 76c71aae:3e29cafa
2024-08-13 04:30:00On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes. Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals. When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear. What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned. Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action. The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane. We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today. It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request. Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media.
@ 76c71aae:3e29cafa
2024-08-13 04:30:00On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes. Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals. When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear. What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned. Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action. The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane. We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today. It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request. Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media. @ 0e8c41eb:95ff0faa
2024-07-08 14:36:14## Chef's notes Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour. Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool. Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges. Spread the fruit filling over the dough. Mix the rest of the flour with the remaining 100 grams of butter and 100 grams of sugar and knead it with your fingers into a crumbly mixture. Sprinkle this crumble mixture over the fruit filling. Bake the tart in the preheated oven at 200°C for about 30 minutes until golden brown. Variations: Only apple? Make this tart with 1 kilo of apples. High or low? You can also bake the crumble tart in a low tart tin of 30 cm diameter. If the fruit filling is a bit too voluminous, you can make double the crumble mixture and sprinkle it over the larger surface area. Additional needs: Mixer with dough hooks or food processor Cling film Round baking tin with a diameter of 28-30 cm, greased ## Details - ⏲️ Prep time: 45 min + 1 hour Rising - 🍳 Cook time: 30 minutes - 🍽️ Servings: 8 ## Ingredients - 375 grams flour - 1 packet dried yeast (7 grams) - 125 grams unsalted butter, at room temperature - 275 grams sugar - 1 egg - 100 ml milk, at room temperature - 500 grams apples - 500 grams apricots (fresh or from a can) ## Directions 1. Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour. 2. Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool. 3. Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges. 4. Spread the fruit filling over the dough.
@ 0e8c41eb:95ff0faa
2024-07-08 14:36:14## Chef's notes Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour. Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool. Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges. Spread the fruit filling over the dough. Mix the rest of the flour with the remaining 100 grams of butter and 100 grams of sugar and knead it with your fingers into a crumbly mixture. Sprinkle this crumble mixture over the fruit filling. Bake the tart in the preheated oven at 200°C for about 30 minutes until golden brown. Variations: Only apple? Make this tart with 1 kilo of apples. High or low? You can also bake the crumble tart in a low tart tin of 30 cm diameter. If the fruit filling is a bit too voluminous, you can make double the crumble mixture and sprinkle it over the larger surface area. Additional needs: Mixer with dough hooks or food processor Cling film Round baking tin with a diameter of 28-30 cm, greased ## Details - ⏲️ Prep time: 45 min + 1 hour Rising - 🍳 Cook time: 30 minutes - 🍽️ Servings: 8 ## Ingredients - 375 grams flour - 1 packet dried yeast (7 grams) - 125 grams unsalted butter, at room temperature - 275 grams sugar - 1 egg - 100 ml milk, at room temperature - 500 grams apples - 500 grams apricots (fresh or from a can) ## Directions 1. Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour. 2. Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool. 3. Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges. 4. Spread the fruit filling over the dough. @ dd664d5e:5633d319
2024-06-24 06:05:05# The new Great Library We have all heard tales of Amazon or other booksellers banning customers from their bookstores or censoring/editing purchased books. The famous [Project Gutenberg](https://www.gutenberg.org/), and similar organizations, are performing a good work, to help protect many of our precious books from this fate, but it is merely a centralized website and therefore not censorship resistant. Also, it mostly posts books in English or German. So, we at nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz have decided to move Project Gutenberg to Nostr and house it in the most distributed way possible: on relays. Specifically, our new, public [Citadel relay](https://thecitadel.nostr1.com/) for out-of-print books (and other documents), but also on any relay, anywhere. And, because we are a very humble group, we're naming the effort "Alexandria". And the first book to be printed on Nostr is the Bible because *obviously*. ## Why on relays? Well, why not on relays? Relays are one of the few widely-distributed databases for documentation in existence. The relay database spans the entire globe and anyone can maintain their own relay on their personal computer or mobile phone. That means that anyone can house *their own* books. Which books are their own? Any books they have in their own possession. Any books someone would have to physically pry out of their cold, dead, computer. ## Notes are perfect for publishing Once we begin generating eBooks from notes with an associated header (which will be quite easy to do, so long as they are written in markdown or similar), they will also be readable, downloadable, and storable in ePub format (see [Pandoc](https://pandoc.org/epub.html)). And it is, after all, only a matter of time until someone enterprising makes an ePaper Nostr client for calmer reading of notes, and then you can download and read them, without having to bother converting beforehand, which maintains their Nostr-navigation. The new event kind [30040](https://wikifreedia.xyz/nkbip-01/) allows us to take any sort of note containing any sort of characters and create a type of "note collection" or "book of notes", "journal of notes", "magazine of notes". And it can be nested or embedded in other notes, creating any sort of note-combination and note-hierarchy you can think of, only limited in size by the ability of your computer to processes the relationships. ## Save the Zettels The associated kind 30041 adds the prospect of breaking longer texts or articles up into sections or snippets (called "Zettel" in German). We can then collect or refer to particular bits of a longer text (like a chart, elegant paragraph or definition, data table), directly. Anyone can create such snippets, even of texts they didn't write, as they can add a reference to the original publication in the tags of the new event. This means we no longer have to "copy-paste" or quote other people's works, we can simply tie them in. If we worry about them being deleted, we can fork them to create our own, digitally-linked version, and then tie that in. This means that source material can be tied to the new material, and you can trace back to the source easily (using Nostr IDs and tags, which are signed identifiers) and see who else is branching out from that source or discussing that source. ## It's gonna be HUGE! We are making a big, beautiful library... and you are going to build it for us. Anyone, anywhere can therefore publish or republish any document they wish, with Nostr, and store it wherever they have a relay, and view it on any client willing to display it. You will own something and be happy.
@ dd664d5e:5633d319
2024-06-24 06:05:05# The new Great Library We have all heard tales of Amazon or other booksellers banning customers from their bookstores or censoring/editing purchased books. The famous [Project Gutenberg](https://www.gutenberg.org/), and similar organizations, are performing a good work, to help protect many of our precious books from this fate, but it is merely a centralized website and therefore not censorship resistant. Also, it mostly posts books in English or German. So, we at nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz have decided to move Project Gutenberg to Nostr and house it in the most distributed way possible: on relays. Specifically, our new, public [Citadel relay](https://thecitadel.nostr1.com/) for out-of-print books (and other documents), but also on any relay, anywhere. And, because we are a very humble group, we're naming the effort "Alexandria". And the first book to be printed on Nostr is the Bible because *obviously*. ## Why on relays? Well, why not on relays? Relays are one of the few widely-distributed databases for documentation in existence. The relay database spans the entire globe and anyone can maintain their own relay on their personal computer or mobile phone. That means that anyone can house *their own* books. Which books are their own? Any books they have in their own possession. Any books someone would have to physically pry out of their cold, dead, computer. ## Notes are perfect for publishing Once we begin generating eBooks from notes with an associated header (which will be quite easy to do, so long as they are written in markdown or similar), they will also be readable, downloadable, and storable in ePub format (see [Pandoc](https://pandoc.org/epub.html)). And it is, after all, only a matter of time until someone enterprising makes an ePaper Nostr client for calmer reading of notes, and then you can download and read them, without having to bother converting beforehand, which maintains their Nostr-navigation. The new event kind [30040](https://wikifreedia.xyz/nkbip-01/) allows us to take any sort of note containing any sort of characters and create a type of "note collection" or "book of notes", "journal of notes", "magazine of notes". And it can be nested or embedded in other notes, creating any sort of note-combination and note-hierarchy you can think of, only limited in size by the ability of your computer to processes the relationships. ## Save the Zettels The associated kind 30041 adds the prospect of breaking longer texts or articles up into sections or snippets (called "Zettel" in German). We can then collect or refer to particular bits of a longer text (like a chart, elegant paragraph or definition, data table), directly. Anyone can create such snippets, even of texts they didn't write, as they can add a reference to the original publication in the tags of the new event. This means we no longer have to "copy-paste" or quote other people's works, we can simply tie them in. If we worry about them being deleted, we can fork them to create our own, digitally-linked version, and then tie that in. This means that source material can be tied to the new material, and you can trace back to the source easily (using Nostr IDs and tags, which are signed identifiers) and see who else is branching out from that source or discussing that source. ## It's gonna be HUGE! We are making a big, beautiful library... and you are going to build it for us. Anyone, anywhere can therefore publish or republish any document they wish, with Nostr, and store it wherever they have a relay, and view it on any client willing to display it. You will own something and be happy. @ 3bf0c63f:aefa459d
2024-05-21 12:38:08# Bitcoin transactions explained A transaction is a piece of data that takes **inputs** and produces **outputs**. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered. Imagine you have 10 satoshis. That means you have them in an unspent transaction output (**UTXO**). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a **script** that unlocks that transaction and related signatures, then you specify outputs along with a **script** that locks these outputs.  As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them. For most of the cases locking and unlocking means specifying a **public key** whose controller (the person who has the corresponding **private key**) will be able to spend. Other fancy things are possible too, but we can ignore them for now. Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.  If you're still interested in transactions maybe you could take a look at [this small chapter](https://github.com/bitcoinbook/bitcoinbook/blob/6d1c26e1640ae32b28389d5ae4caf1214c2be7db/ch06_transactions.adoc) of that Andreas Antonopoulos book. If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: <https://en.bitcoin.it/wiki/Coin_analogy>
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08# Bitcoin transactions explained A transaction is a piece of data that takes **inputs** and produces **outputs**. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered. Imagine you have 10 satoshis. That means you have them in an unspent transaction output (**UTXO**). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a **script** that unlocks that transaction and related signatures, then you specify outputs along with a **script** that locks these outputs.  As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them. For most of the cases locking and unlocking means specifying a **public key** whose controller (the person who has the corresponding **private key**) will be able to spend. Other fancy things are possible too, but we can ignore them for now. Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.  If you're still interested in transactions maybe you could take a look at [this small chapter](https://github.com/bitcoinbook/bitcoinbook/blob/6d1c26e1640ae32b28389d5ae4caf1214c2be7db/ch06_transactions.adoc) of that Andreas Antonopoulos book. If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: <https://en.bitcoin.it/wiki/Coin_analogy> @ deab79da:88579e68
2024-05-20 20:48:09## Details - ⏲️ Prep time: 30 min - 🍳 Cook time: 20-30 min - 🍽️ Servings: 4 ## Ingredients - 1 lb cod fillets - 1/4 cup butter - 1/4 cup white flour - 1 1/4 cups milk - 1 tsp salt - pepper to taste - 1 small onion - 1 carrot - 3 celery stalks - 1/2 cup breadcrumbs - 1/2 cup shredded old cheddar ## Directions 1. Preheat oven to 375F. Place cod in a greased baking dish. 2. Make the white sauce in a heavy saucepan. Melt the butter over medium heat and stir in the flour until smooth. Remove from heat and slowly stir in half of the milk, then return to heat and beat until smooth and shiny. 3. Gradually add the remaining milk, followed by salt, pepper, and your vegetables. Cook until sauce is smooth & thickened. 4. Pour sauce over the fish, and sprinkle breadcrumbs and cheese over the top. 5. Bake, uncovered for 20-30 minutes until sauce bubbles and the cheese begins to brown. Let rest 10 minutes after cooking completes.
@ deab79da:88579e68
2024-05-20 20:48:09## Details - ⏲️ Prep time: 30 min - 🍳 Cook time: 20-30 min - 🍽️ Servings: 4 ## Ingredients - 1 lb cod fillets - 1/4 cup butter - 1/4 cup white flour - 1 1/4 cups milk - 1 tsp salt - pepper to taste - 1 small onion - 1 carrot - 3 celery stalks - 1/2 cup breadcrumbs - 1/2 cup shredded old cheddar ## Directions 1. Preheat oven to 375F. Place cod in a greased baking dish. 2. Make the white sauce in a heavy saucepan. Melt the butter over medium heat and stir in the flour until smooth. Remove from heat and slowly stir in half of the milk, then return to heat and beat until smooth and shiny. 3. Gradually add the remaining milk, followed by salt, pepper, and your vegetables. Cook until sauce is smooth & thickened. 4. Pour sauce over the fish, and sprinkle breadcrumbs and cheese over the top. 5. Bake, uncovered for 20-30 minutes until sauce bubbles and the cheese begins to brown. Let rest 10 minutes after cooking completes. @ 266815e0:6cd408a5
2024-04-24 23:02:21> NOTE: this is just a quick technical guide. sorry for the lack of details ## Install NodeJS Download it from the official website https://nodejs.org/en/download Or use nvm https://github.com/nvm-sh/nvm?tab=readme-ov-file#install--update-script ```bash wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.7/install.sh | bash nvm install 20 ``` ## Clone example config.yml ```bash wget https://raw.githubusercontent.com/hzrd149/blossom-server/master/config.example.yml -O config.yml ``` ## Modify config.yml ```bash nano config.yml # or if your that type of person vim config.yml ``` ## Run blossom-server ```bash npx blossom-server-ts # or install it locally and run using npm npm install blossom-server-ts ./node_modules/.bin/blossom-server-ts ``` Now you can open http://localhost:3000 and see your blossom server And if you set the `dashboard.enabled` option in the `config.yml` you can open http://localhost:3000/admin to see the admin dashboard
@ 266815e0:6cd408a5
2024-04-24 23:02:21> NOTE: this is just a quick technical guide. sorry for the lack of details ## Install NodeJS Download it from the official website https://nodejs.org/en/download Or use nvm https://github.com/nvm-sh/nvm?tab=readme-ov-file#install--update-script ```bash wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.7/install.sh | bash nvm install 20 ``` ## Clone example config.yml ```bash wget https://raw.githubusercontent.com/hzrd149/blossom-server/master/config.example.yml -O config.yml ``` ## Modify config.yml ```bash nano config.yml # or if your that type of person vim config.yml ``` ## Run blossom-server ```bash npx blossom-server-ts # or install it locally and run using npm npm install blossom-server-ts ./node_modules/.bin/blossom-server-ts ``` Now you can open http://localhost:3000 and see your blossom server And if you set the `dashboard.enabled` option in the `config.yml` you can open http://localhost:3000/admin to see the admin dashboard @ 3bf0c63f:aefa459d
2024-01-15 11:15:06# Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados - **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo.
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06# Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados - **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# IPFS problems: Community I was an avid IPFS user until yesterday. Many many times I asked simple questions for which I couldn't find an answer on the internet in the #ipfs IRC channel on Freenode. Most of the times I didn't get an answer, and even when I got it was rarely by someone who knew IPFS deeply. I've had issues go unanswered on js-ipfs repositories for year – one of these was raising awareness of a problem that then got fixed some months later by a complete rewrite, I closed my own issue after realizing that by myself some couple of months later, I don't think the people responsible for the rewrite were ever acknowledge that he had fixed my issue. Some days ago I asked some questions about how the IPFS protocol worked internally, sincerely trying to understand the inefficiencies in finding and fetching content over IPFS. I pointed it would be a good idea to have a drawing showing that so people would understand the difficulties (which I didn't) and wouldn't be pissed off by the slowness. I was told to read the whitepaper. I had already the whitepaper, but read again the relevant parts. The whitepaper doesn't explain anything about the DHT and how IPFS finds content. I said that in the room, was told to read again. Before anyone misread this section, I want to say I understand it's a pain to keep answering people on IRC if you're busy developing stuff of interplanetary importance, and that I'm not paying anyone nor I have the right to be answered. On the other hand, if you're developing a super-important protocol, financed by many millions of dollars and a lot of people are hitting their heads against your software and there's no one to help them; you're always busy but never delivers anything that brings joy to your users, something is very wrong. I sincerely don't know what IPFS developers are working on, I wouldn't doubt they're working on important things if they said that, but what I see – and what many other users see (take a look at the IPFS Discourse forum) is bugs, bugs all over the place, confusing UX, and almost no help.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# IPFS problems: Community I was an avid IPFS user until yesterday. Many many times I asked simple questions for which I couldn't find an answer on the internet in the #ipfs IRC channel on Freenode. Most of the times I didn't get an answer, and even when I got it was rarely by someone who knew IPFS deeply. I've had issues go unanswered on js-ipfs repositories for year – one of these was raising awareness of a problem that then got fixed some months later by a complete rewrite, I closed my own issue after realizing that by myself some couple of months later, I don't think the people responsible for the rewrite were ever acknowledge that he had fixed my issue. Some days ago I asked some questions about how the IPFS protocol worked internally, sincerely trying to understand the inefficiencies in finding and fetching content over IPFS. I pointed it would be a good idea to have a drawing showing that so people would understand the difficulties (which I didn't) and wouldn't be pissed off by the slowness. I was told to read the whitepaper. I had already the whitepaper, but read again the relevant parts. The whitepaper doesn't explain anything about the DHT and how IPFS finds content. I said that in the room, was told to read again. Before anyone misread this section, I want to say I understand it's a pain to keep answering people on IRC if you're busy developing stuff of interplanetary importance, and that I'm not paying anyone nor I have the right to be answered. On the other hand, if you're developing a super-important protocol, financed by many millions of dollars and a lot of people are hitting their heads against your software and there's no one to help them; you're always busy but never delivers anything that brings joy to your users, something is very wrong. I sincerely don't know what IPFS developers are working on, I wouldn't doubt they're working on important things if they said that, but what I see – and what many other users see (take a look at the IPFS Discourse forum) is bugs, bugs all over the place, confusing UX, and almost no help. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Castas hindus em nova chave Shudras buscam o máximo bem para os seus próprios corpos; vaishyas o máximo bem para a sua própria vida terrena e a da sua família; kshatriyas o máximo bem para a sociedade e este mundo terreno; brâmanes buscam o máximo bem.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Castas hindus em nova chave Shudras buscam o máximo bem para os seus próprios corpos; vaishyas o máximo bem para a sua própria vida terrena e a da sua família; kshatriyas o máximo bem para a sociedade e este mundo terreno; brâmanes buscam o máximo bem. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Thoughts on Nostr key management On [Why I don't like NIP-26 as a solution for key management](nostr:naddr1qqyrgceh89nxgdmzqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ctgmx78) I talked about multiple techniques that could be used to tackle the problem of key management on Nostr. Here are some ideas that work in tandem: - [NIP-41](https://github.com/nostr-protocol/nips/blob/master/41.md) (stateless key invalidation) - [NIP-46](https://github.com/nostr-protocol/nips/blob/master/46.md) (Nostr Connect) - [NIP-07](https://github.com/nostr-protocol/nips/blob/master/07.md) (signer browser extension) - [Connected hardware signing devices](https://lnbits.github.io/nostr-signing-device/installer/) - other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically - there are probably many other ideas Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that - For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution; - Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money; - Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways. - For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on. We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that. --- One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Thoughts on Nostr key management On [Why I don't like NIP-26 as a solution for key management](nostr:naddr1qqyrgceh89nxgdmzqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ctgmx78) I talked about multiple techniques that could be used to tackle the problem of key management on Nostr. Here are some ideas that work in tandem: - [NIP-41](https://github.com/nostr-protocol/nips/blob/master/41.md) (stateless key invalidation) - [NIP-46](https://github.com/nostr-protocol/nips/blob/master/46.md) (Nostr Connect) - [NIP-07](https://github.com/nostr-protocol/nips/blob/master/07.md) (signer browser extension) - [Connected hardware signing devices](https://lnbits.github.io/nostr-signing-device/installer/) - other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically - there are probably many other ideas Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that - For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution; - Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money; - Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways. - For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on. We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that. --- One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# IPFS problems: Shitcoinery IPFS was advertised to the Ethereum community since the beggining as a way to "store" data for their "dApps". I don't think this is harmful in any way, but for some reason it may have led IPFS developers to focus too much on Ethereum stuff. Once I watched a talk showing libp2p developers – despite being ignored by the Ethereum team (that ended up creating their own agnostic p2p library) – dedicating an enourmous amount of work on getting a libp2p app running in the browser talking to a normal Ethereum node. The always somewhat-abandoned "Awesome IPFS" site is a big repository of "dApps", some of which don't even have their landing page up anymore, useless Ethereum smart contracts that for some reason use IPFS to store whatever the useless data their users produce. Again, per se it isn't a problem that Ethereum people are using IPFS, but it is at least confusing, maybe misleading, that when you search for IPFS most of the use-cases are actually Ethereum useless-cases. ## See also * [Bitcoin](nostr:naddr1qqyryveexumnyd3kqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c7nywz4), the only non-shitcoin
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# IPFS problems: Shitcoinery IPFS was advertised to the Ethereum community since the beggining as a way to "store" data for their "dApps". I don't think this is harmful in any way, but for some reason it may have led IPFS developers to focus too much on Ethereum stuff. Once I watched a talk showing libp2p developers – despite being ignored by the Ethereum team (that ended up creating their own agnostic p2p library) – dedicating an enourmous amount of work on getting a libp2p app running in the browser talking to a normal Ethereum node. The always somewhat-abandoned "Awesome IPFS" site is a big repository of "dApps", some of which don't even have their landing page up anymore, useless Ethereum smart contracts that for some reason use IPFS to store whatever the useless data their users produce. Again, per se it isn't a problem that Ethereum people are using IPFS, but it is at least confusing, maybe misleading, that when you search for IPFS most of the use-cases are actually Ethereum useless-cases. ## See also * [Bitcoin](nostr:naddr1qqyryveexumnyd3kqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c7nywz4), the only non-shitcoin @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Economics Just a bunch of somewhat-related notes. * [notes on "Economic Action Beyond the Extent of the Market", Per Bylund](nostr:naddr1qqyxxepsx3skgvenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cf5cy3p) * [Mises' interest rate theory](nostr:naddr1qqyr2dtrxycr2dmrqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c97asm3) * [Profits, not wages, as the originary factor](nostr:naddr1qqyrge3hxa3rqce4qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c7x67pu) * [Reisman on opportunity cost](nostr:naddr1qqyrswtr89nxvepkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cwx7t3v) * [Money Supply Measurement](nostr:naddr1qqyr2v3cxcunserzqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cya65m9) * [Per Bylund's insight](nostr:naddr1qqyxvdtzxscxzcenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cuq3unj) * [Maybe a new approach to the Austrian Business Cycle Theory, some disorganized thoughts](nostr:naddr1qqyrvdecvccxxcejqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cl9wc86) * [An argument according to which fractional-reserve banking is merely theft and nothing else](nostr:naddr1qqyrywt9v5exydenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cfks90r) * [Conjecture and criticism](nostr:naddr1qqyrqde5x9snqvfnqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ce4glh8) * [Qual é o economista? (piadas)](nostr:naddr1qqyx2vmrx93xgdpjqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c0ckmsx) * [UBI calculations](nostr:naddr1qqyryenpxe3ryvf4qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cuurj42) * [Donations on the internet](nostr:naddr1qqyrqwp4xsmnsvtxqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cex8903)
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Economics Just a bunch of somewhat-related notes. * [notes on "Economic Action Beyond the Extent of the Market", Per Bylund](nostr:naddr1qqyxxepsx3skgvenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cf5cy3p) * [Mises' interest rate theory](nostr:naddr1qqyr2dtrxycr2dmrqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c97asm3) * [Profits, not wages, as the originary factor](nostr:naddr1qqyrge3hxa3rqce4qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c7x67pu) * [Reisman on opportunity cost](nostr:naddr1qqyrswtr89nxvepkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cwx7t3v) * [Money Supply Measurement](nostr:naddr1qqyr2v3cxcunserzqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cya65m9) * [Per Bylund's insight](nostr:naddr1qqyxvdtzxscxzcenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cuq3unj) * [Maybe a new approach to the Austrian Business Cycle Theory, some disorganized thoughts](nostr:naddr1qqyrvdecvccxxcejqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cl9wc86) * [An argument according to which fractional-reserve banking is merely theft and nothing else](nostr:naddr1qqyrywt9v5exydenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cfks90r) * [Conjecture and criticism](nostr:naddr1qqyrqde5x9snqvfnqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ce4glh8) * [Qual é o economista? (piadas)](nostr:naddr1qqyx2vmrx93xgdpjqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c0ckmsx) * [UBI calculations](nostr:naddr1qqyryenpxe3ryvf4qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cuurj42) * [Donations on the internet](nostr:naddr1qqyrqwp4xsmnsvtxqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cex8903) @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# tempreites My first library to get stars on GitHub, was a very stupid templating library that used just HTML and HTML attributes ("DSL-free"). I was inspired by <http://microjs.com/> at the time and ended up not using the library. Probably no one ever did. - <https://github.com/fiatjaf/tempreites>
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# tempreites My first library to get stars on GitHub, was a very stupid templating library that used just HTML and HTML attributes ("DSL-free"). I was inspired by <http://microjs.com/> at the time and ended up not using the library. Probably no one ever did. - <https://github.com/fiatjaf/tempreites> @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# nix Pra instalar o [neuron](797984e3.md) fui forçado a baixar e instalar o [nix](https://nixos.org/download.html). Não consegui me lembrar por que não estava usando até hoje aquele maravilhoso sistema de instalar pacotes desde a primeira vez que tentei, anos atrás. Que sofrimento pra fazer funcionar com o `fish`, mas até que bem menos sofrimento que da outra vez. Tive que instalar um tal de `fish-foreign-environment` (usando o próprio nix!, já que a outra opção era o `oh-my-fish` ou qualquer outra porcaria dessas) e aí usá-lo para aplicar as definições de shell para bash direto no `fish`. E aí lembrei também que o `/nix/store` fica cheio demais, o negócio instala tudo que existe neste mundo a partir do zero. É só para computadores muito ricos, mas vamos ver como vai ser. Estou gostando do neuron (veja, estou usando como diário), então vou ter que deixar o nix aí.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# nix Pra instalar o [neuron](797984e3.md) fui forçado a baixar e instalar o [nix](https://nixos.org/download.html). Não consegui me lembrar por que não estava usando até hoje aquele maravilhoso sistema de instalar pacotes desde a primeira vez que tentei, anos atrás. Que sofrimento pra fazer funcionar com o `fish`, mas até que bem menos sofrimento que da outra vez. Tive que instalar um tal de `fish-foreign-environment` (usando o próprio nix!, já que a outra opção era o `oh-my-fish` ou qualquer outra porcaria dessas) e aí usá-lo para aplicar as definições de shell para bash direto no `fish`. E aí lembrei também que o `/nix/store` fica cheio demais, o negócio instala tudo que existe neste mundo a partir do zero. É só para computadores muito ricos, mas vamos ver como vai ser. Estou gostando do neuron (veja, estou usando como diário), então vou ter que deixar o nix aí. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# O Bitcoin como um sistema social humano Afinal de contas, o que é o Bitcoin? Não vou responder a essa pergunta explicando o que é uma "blockchain" ou coisa que o valha, como todos fazem muito pessimamente. [A melhor explicação em português que eu já vi está aqui](nostr:naddr1qqrky6t5vdhkjmspz9mhxue69uhkv6tpw34xze3wvdhk6q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqp65wp3k3fu), mas mesmo assim qualquer explicação jamais será definitiva. A explicação apenas do protocolo, do que faz um programa `bitcoind` sendo executado em um computador e como ele se comunica com outros em outros computadores, e os incentivos que estão em jogo para garantir com razoável probabilidade que se chegará a um consenso sobre quem é dono de qual parte de qual transação, apesar de não ser complicada demais, exigirá do iniciante que seja compreendida muitas vezes antes que ele se possa se sentir confortável para dizer que entende um pouco. E essa parte _técnica_, apesar de ter sido o insight fundamental que gerou o evento miraculoso chamado Bitcoin, não é a parte mais importante, hoje. Se fosse, várias dessas outras moedas seriam concorrentes do Bitcoin, mas não são, e jamais poderão ser, porque elas não estão nem próximas de ter os outros elementos que compõem o Bitcoin. São eles: 1. A estrutura O Bitcoin é um sistema composto de partes independentes. Existem programadores que trabalham no protocolo e aplicações, e dia após dia novos programadores chegam e outros saem, e eles trabalham às vezes em conjunto, às vezes sem que um se dê conta do outro, às vezes por conta própria, às vezes pagos por empresas interessadas. Existem os usuários que realizam validação completa, isto é, estão rodando algum programa do Bitcoin e contribuindo para a difusão dos blocos, das transações, rejeitando usuários malignos e evitando ataques de mineradores mal-intencionados. Existem os poupadores, acumuladores ou os proprietários de bitcoins, que conhecem as possibilidades que o mundo reserva para o Bitcoin, esperam o dia em que o padrão-Bitcoin será uma realidade mundial e por isso mesmo atributem aos seus bitcoins valores muito mais altos do que os preços atuais de mercado, agarrando-se a eles. Especuladores de "criptomoedas" não fazem parte desse sistema, nem tampouco empresas que [aceitam pagamento](https://bitpay.com/) em bitcoins para imediatamente venderem tudo em troca de dinheiro estatal, e menos ainda [gente que usa bitcoins](https://www.investimentobitcoin.com/) e [a própria marca Bitcoin](https://www.xdex.com.br/) para aplicar seus golpes e coisas parecidas. 2. A cultura Mencionei que há empresas que pagam programadores para trabalharem no código aberto do BitcoinCore ou de outros programas relacionados à rede Bitcoin -- ou mesmo em aplicações não necessariamente ligadas à camada fundamental do protocolo. Nenhuma dessas empresas interessadas, porém, controla o Bitcoin, e isso é o elemento principal da cultura do Bitcoin. O propósito do Bitcoin sempre foi ser uma rede aberta, sem chefes, sem política envolvida, sem necessidade de pedir autorização para participar. O fato do próprio Satoshi Nakamoto ter voluntariamente desaparecido das discussões foi fundamental para que o Bitcoin não fosse visto como um sistema dependente dele ou que ele fosse entendido como o chefe. Em outras "criptomoedas" nada disso aconteceu. O chefe supremo do Ethereum continua por aí mandando e desmandando e inventando novos elementos para o protocolo que são automaticamente aceitos por toda a comunidade, o mesmo vale para o Zcash, EOS, Ripple, Litecoin e até mesmo para o Bitcoin Cash. Pior ainda: Satoshi Nakamoto saiu sem nenhum dinheiro, nunca mexeu nos milhares de bitcoins que ele gerou nos primeiros blocos -- enquanto os líderes dessas porcarias supramencionadas cobraram uma fortuna pelo direito de uso dos seus primeiros usuários ou estão aí a até hoje receber dividendos. Tudo isso e mais outras coisas -- a mentalidade anti-estatal e entusiasta de sistemas p2p abertos dos membros mais proeminentes da comunidade, por exemplo -- faz com que um ar de liberdade e suspeito de tentativas de centralização da moeda sejam percebidos e execrados. 3. A história A noção de que o Bitcoin não pode ser controlado por ninguém passou em 2017 por [dois testes](https://www.forbes.com/sites/ktorpey/2019/04/23/this-key-part-of-bitcoins-history-is-what-separates-it-from-competitors/#49869b41ae5e) e saiu deles muito reforçada: o primeiro foi a divisão entre Bitcoin (BTC) e Bitcoin Cash (BCH), uma obra de engenharia social que teve um sucesso mediano em roubar parte da marca e dos usuários do verdadeiro Bitcoin e depois a tentativa de tomada por completo do Bitcoin promovida por mais ou menos as mesmas partes interessadas chamada SegWit2x, que fracassou por completo, mas não sem antes atrapalhar e difundir mentiras para todos os lados. Esses dois fracassos provaram que o Bitcoin, mesmo sendo uma comunidade desorganizada, sem líderes claros, está imune à [captura por grupos interessados](https://en.wikipedia.org/wiki/Regulatory_capture), o que é mais um milagre -- ou, como dizem, um [ponto de Schelling](https://en.wikipedia.org/wiki/Focal_point_(game_theory)). Esse período crucial na história do Bitcoin fez com ficasse claro que _hard-forks_ são essencialmente incompatíveis com a natureza do protocolo, de modo que no futuro não haverá a possibilidade de uma sugestão como a de imprimir mais bitcoins do que o que estava programado sejam levadas a sério (mas, claro, sempre há a possibilidade da cultura toda se perder, as pessoas esquecerem a história e o Bitcoin ser cooptado, eis a importância da auto-educação e da difusão desses princípios).
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# O Bitcoin como um sistema social humano Afinal de contas, o que é o Bitcoin? Não vou responder a essa pergunta explicando o que é uma "blockchain" ou coisa que o valha, como todos fazem muito pessimamente. [A melhor explicação em português que eu já vi está aqui](nostr:naddr1qqrky6t5vdhkjmspz9mhxue69uhkv6tpw34xze3wvdhk6q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqp65wp3k3fu), mas mesmo assim qualquer explicação jamais será definitiva. A explicação apenas do protocolo, do que faz um programa `bitcoind` sendo executado em um computador e como ele se comunica com outros em outros computadores, e os incentivos que estão em jogo para garantir com razoável probabilidade que se chegará a um consenso sobre quem é dono de qual parte de qual transação, apesar de não ser complicada demais, exigirá do iniciante que seja compreendida muitas vezes antes que ele se possa se sentir confortável para dizer que entende um pouco. E essa parte _técnica_, apesar de ter sido o insight fundamental que gerou o evento miraculoso chamado Bitcoin, não é a parte mais importante, hoje. Se fosse, várias dessas outras moedas seriam concorrentes do Bitcoin, mas não são, e jamais poderão ser, porque elas não estão nem próximas de ter os outros elementos que compõem o Bitcoin. São eles: 1. A estrutura O Bitcoin é um sistema composto de partes independentes. Existem programadores que trabalham no protocolo e aplicações, e dia após dia novos programadores chegam e outros saem, e eles trabalham às vezes em conjunto, às vezes sem que um se dê conta do outro, às vezes por conta própria, às vezes pagos por empresas interessadas. Existem os usuários que realizam validação completa, isto é, estão rodando algum programa do Bitcoin e contribuindo para a difusão dos blocos, das transações, rejeitando usuários malignos e evitando ataques de mineradores mal-intencionados. Existem os poupadores, acumuladores ou os proprietários de bitcoins, que conhecem as possibilidades que o mundo reserva para o Bitcoin, esperam o dia em que o padrão-Bitcoin será uma realidade mundial e por isso mesmo atributem aos seus bitcoins valores muito mais altos do que os preços atuais de mercado, agarrando-se a eles. Especuladores de "criptomoedas" não fazem parte desse sistema, nem tampouco empresas que [aceitam pagamento](https://bitpay.com/) em bitcoins para imediatamente venderem tudo em troca de dinheiro estatal, e menos ainda [gente que usa bitcoins](https://www.investimentobitcoin.com/) e [a própria marca Bitcoin](https://www.xdex.com.br/) para aplicar seus golpes e coisas parecidas. 2. A cultura Mencionei que há empresas que pagam programadores para trabalharem no código aberto do BitcoinCore ou de outros programas relacionados à rede Bitcoin -- ou mesmo em aplicações não necessariamente ligadas à camada fundamental do protocolo. Nenhuma dessas empresas interessadas, porém, controla o Bitcoin, e isso é o elemento principal da cultura do Bitcoin. O propósito do Bitcoin sempre foi ser uma rede aberta, sem chefes, sem política envolvida, sem necessidade de pedir autorização para participar. O fato do próprio Satoshi Nakamoto ter voluntariamente desaparecido das discussões foi fundamental para que o Bitcoin não fosse visto como um sistema dependente dele ou que ele fosse entendido como o chefe. Em outras "criptomoedas" nada disso aconteceu. O chefe supremo do Ethereum continua por aí mandando e desmandando e inventando novos elementos para o protocolo que são automaticamente aceitos por toda a comunidade, o mesmo vale para o Zcash, EOS, Ripple, Litecoin e até mesmo para o Bitcoin Cash. Pior ainda: Satoshi Nakamoto saiu sem nenhum dinheiro, nunca mexeu nos milhares de bitcoins que ele gerou nos primeiros blocos -- enquanto os líderes dessas porcarias supramencionadas cobraram uma fortuna pelo direito de uso dos seus primeiros usuários ou estão aí a até hoje receber dividendos. Tudo isso e mais outras coisas -- a mentalidade anti-estatal e entusiasta de sistemas p2p abertos dos membros mais proeminentes da comunidade, por exemplo -- faz com que um ar de liberdade e suspeito de tentativas de centralização da moeda sejam percebidos e execrados. 3. A história A noção de que o Bitcoin não pode ser controlado por ninguém passou em 2017 por [dois testes](https://www.forbes.com/sites/ktorpey/2019/04/23/this-key-part-of-bitcoins-history-is-what-separates-it-from-competitors/#49869b41ae5e) e saiu deles muito reforçada: o primeiro foi a divisão entre Bitcoin (BTC) e Bitcoin Cash (BCH), uma obra de engenharia social que teve um sucesso mediano em roubar parte da marca e dos usuários do verdadeiro Bitcoin e depois a tentativa de tomada por completo do Bitcoin promovida por mais ou menos as mesmas partes interessadas chamada SegWit2x, que fracassou por completo, mas não sem antes atrapalhar e difundir mentiras para todos os lados. Esses dois fracassos provaram que o Bitcoin, mesmo sendo uma comunidade desorganizada, sem líderes claros, está imune à [captura por grupos interessados](https://en.wikipedia.org/wiki/Regulatory_capture), o que é mais um milagre -- ou, como dizem, um [ponto de Schelling](https://en.wikipedia.org/wiki/Focal_point_(game_theory)). Esse período crucial na história do Bitcoin fez com ficasse claro que _hard-forks_ são essencialmente incompatíveis com a natureza do protocolo, de modo que no futuro não haverá a possibilidade de uma sugestão como a de imprimir mais bitcoins do que o que estava programado sejam levadas a sério (mas, claro, sempre há a possibilidade da cultura toda se perder, as pessoas esquecerem a história e o Bitcoin ser cooptado, eis a importância da auto-educação e da difusão desses princípios). @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# My stupid introduction to Haskell While I was writing my first small program on Haskell (really simple, but functional webapp) in December 2017 I only knew vaguely what was the style of things, some basic notions about functions, pure functions and so on (I've read about a third of [LYAH](http://learnyouahaskell.com/chapters)). An enourmous amount of questions began to appear in my head while I read tutorials and documentation. Here I present some of the questions and the insights I got that solved them. Technically, they may be wrong, but they helped me advance in the matter, so I'm writing them down while I still can -- If I keep working with Haskell I'll probably get to know more and so my new insights will replace the previous ones, and the new ones won't be useful for total begginers anymore. --- Here we go: - **Why do modules have odd names?** - modules are the things you import, like `Data.Time.Clock` or `Web.Scotty`. - packages are the things you install, like 'time' or 'scotty' - packages can contain any number of modules they like - a module is just a collection of functions - a package is just a collection of modules - a package is just name you choose to associate your collection of modules with when you're publishing it to Hackage or whatever - the module names you choose when you're writing a package can be anything, and these are the names people will have to `import` when they want to use you functions - if you're from Javascript, Python or anything similar, you'll expect to be importing/writing the name of the package directly in your code, but in Haskell you'll actually be writing the name of the module, which may have nothing to do with the name of the package - people choose things that make sense, like for `aeson` instead of `import Aeson` you'll be doing `import Data.Aeson`, `import Data.Aeson.Types` etc. why the `Data`? because they thought it would be nice. dealing with JSON is a form of dealing with data, so be it. - you just have to check the package documentation to see which modules it exposes. - **What is `data User = User { name :: Text }`?** - a data type definition. means you'll have a function `User` that will take a Text parameter and output a `User` record or something like that. - you can also have `Animal = Giraffe { color :: Text } | Human { name :: Text }`, so you'll have two functions, Giraffe and Human, each can take a different set of parameters, but they will both yield an Animal. - then, in the functions that take an Animal parameter you must typematch to see if the animal is a giraffe or a human. - **What is a monad?** - a monad is a context, an environment. - when you're in the context of a monad you can write imperative code. - you do that when you use the keyword `do`. - in the context of a monad, all values are prefixed by the monad type, - thus, in the `IO` monad all `Text` is `IO Text` and so on. - some monads have a relationship with others, so values from that monad can be turned into values from another monad and passed between context easily. - for exampĺe, [scotty](https://www.stackage.org/haddock/lts-9.18/scotty-0.11.0/Web-Scotty.html)'s `ActionM` and `IO`. `ActionM` is just a subtype of `IO` or something like that. - when you write imperative code inside a monad you can do assignments like `varname <- func x y` - in these situations some transformation is done by the `<-`, I believe it is that the pure value returned by `func` is being transformed into a monad value. so if `func` returns `Text`, now varname is of type `IO Text` (if we're in the IO monad). - so it will not work (and it can be confusing) if you try to concatenate functions like `varname <- transform $ func x y`, but you can somehow do - `varname <- func x y` - `othervarname <- transform varname` - or you can do other fancy things you'll get familiar with later, like `varname <- fmap transform $ func x y` - why? I don't know. - **How do I deal with Maybe, Either or other crazy stuff?** "ok, I understand what is a Maybe: it is a value that could be something or nothing. but how do I use that in my program?" - you don't! you turn it into other thing. for example, you use [fromMaybe](http://hackage.haskell.org/package/base-4.10.1.0/docs/Data-Maybe.html#v:fromMaybe), a function that takes a default value and that's it. if your `Maybe` is `Just x` you get `x`, if it is `Nothing` you get the default value. - using only that function you can already do whatever there is to be done with Maybes. - you can also manipulate the values inside the `Maybe`, for example: - if you have a `Maybe Person` and `Person` has a `name` which is `Text`, you can apply a function that turns `Maybe Person` into `Maybe Text` AND ONLY THEN you apply the default value (which would be something like the `"unnamed"`) and take the name from inside the `Maybe`. - basically these things (`Maybe`, `Either`, `IO` also!) are just tags. they tag the value, and you can do things with the values inside them, or you can remove the values. - besides the example above with Maybes and the `fromMaybe` function, you can also remove the values by using `case` -- for example: - `case x of` - `Left error -> error` - `Right success -> success` - `case y of` - `Nothing -> "nothing!"` - `Just value -> value` - (in some cases I believe you can't remove the values, but in these cases you'll also don't need to) - for example, for values tagged with the IO, you can't remove the IO and turn these values into pure values, but you don't need that, you can just take the value from the outside world, so it's a IO Text, apply functions that modify that value inside IO, then output the result to the user -- this is enough to make a complete program, any complete program. - **JSON and interfaces (or instances?)** - using [Aeson](https://hackage.haskell.org/package/aeson-1.2.3.0/docs/Data-Aeson.html) is easy, you just have to implement the `ToJSON` and `FromJSON` interfaces. - "interface" is not the correct name, but I don't care. - `ToJSON`, for example, requires a function named `toJSON`, so you do - `instance ToJSON YourType where` - `toJSON (YourType your type values) = object []` ... etc. - I believe lots of things require interface implementation like this and it can be confusing, but once you know the mystery of implementing functions for interfaces everything is solved. - `FromJSON` is a little less intuitive at the beggining, and I don't know if I did it correctly, but it is working here. Anyway, if you're trying to do that, I can only tell you to follow the types, copy examples from other places on the internet and don't care about the meaning of symbols. ## See also * [Haskell Monoids](nostr:naddr1qqyrzcmrvcmrqwtpqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cktq992)
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# My stupid introduction to Haskell While I was writing my first small program on Haskell (really simple, but functional webapp) in December 2017 I only knew vaguely what was the style of things, some basic notions about functions, pure functions and so on (I've read about a third of [LYAH](http://learnyouahaskell.com/chapters)). An enourmous amount of questions began to appear in my head while I read tutorials and documentation. Here I present some of the questions and the insights I got that solved them. Technically, they may be wrong, but they helped me advance in the matter, so I'm writing them down while I still can -- If I keep working with Haskell I'll probably get to know more and so my new insights will replace the previous ones, and the new ones won't be useful for total begginers anymore. --- Here we go: - **Why do modules have odd names?** - modules are the things you import, like `Data.Time.Clock` or `Web.Scotty`. - packages are the things you install, like 'time' or 'scotty' - packages can contain any number of modules they like - a module is just a collection of functions - a package is just a collection of modules - a package is just name you choose to associate your collection of modules with when you're publishing it to Hackage or whatever - the module names you choose when you're writing a package can be anything, and these are the names people will have to `import` when they want to use you functions - if you're from Javascript, Python or anything similar, you'll expect to be importing/writing the name of the package directly in your code, but in Haskell you'll actually be writing the name of the module, which may have nothing to do with the name of the package - people choose things that make sense, like for `aeson` instead of `import Aeson` you'll be doing `import Data.Aeson`, `import Data.Aeson.Types` etc. why the `Data`? because they thought it would be nice. dealing with JSON is a form of dealing with data, so be it. - you just have to check the package documentation to see which modules it exposes. - **What is `data User = User { name :: Text }`?** - a data type definition. means you'll have a function `User` that will take a Text parameter and output a `User` record or something like that. - you can also have `Animal = Giraffe { color :: Text } | Human { name :: Text }`, so you'll have two functions, Giraffe and Human, each can take a different set of parameters, but they will both yield an Animal. - then, in the functions that take an Animal parameter you must typematch to see if the animal is a giraffe or a human. - **What is a monad?** - a monad is a context, an environment. - when you're in the context of a monad you can write imperative code. - you do that when you use the keyword `do`. - in the context of a monad, all values are prefixed by the monad type, - thus, in the `IO` monad all `Text` is `IO Text` and so on. - some monads have a relationship with others, so values from that monad can be turned into values from another monad and passed between context easily. - for exampĺe, [scotty](https://www.stackage.org/haddock/lts-9.18/scotty-0.11.0/Web-Scotty.html)'s `ActionM` and `IO`. `ActionM` is just a subtype of `IO` or something like that. - when you write imperative code inside a monad you can do assignments like `varname <- func x y` - in these situations some transformation is done by the `<-`, I believe it is that the pure value returned by `func` is being transformed into a monad value. so if `func` returns `Text`, now varname is of type `IO Text` (if we're in the IO monad). - so it will not work (and it can be confusing) if you try to concatenate functions like `varname <- transform $ func x y`, but you can somehow do - `varname <- func x y` - `othervarname <- transform varname` - or you can do other fancy things you'll get familiar with later, like `varname <- fmap transform $ func x y` - why? I don't know. - **How do I deal with Maybe, Either or other crazy stuff?** "ok, I understand what is a Maybe: it is a value that could be something or nothing. but how do I use that in my program?" - you don't! you turn it into other thing. for example, you use [fromMaybe](http://hackage.haskell.org/package/base-4.10.1.0/docs/Data-Maybe.html#v:fromMaybe), a function that takes a default value and that's it. if your `Maybe` is `Just x` you get `x`, if it is `Nothing` you get the default value. - using only that function you can already do whatever there is to be done with Maybes. - you can also manipulate the values inside the `Maybe`, for example: - if you have a `Maybe Person` and `Person` has a `name` which is `Text`, you can apply a function that turns `Maybe Person` into `Maybe Text` AND ONLY THEN you apply the default value (which would be something like the `"unnamed"`) and take the name from inside the `Maybe`. - basically these things (`Maybe`, `Either`, `IO` also!) are just tags. they tag the value, and you can do things with the values inside them, or you can remove the values. - besides the example above with Maybes and the `fromMaybe` function, you can also remove the values by using `case` -- for example: - `case x of` - `Left error -> error` - `Right success -> success` - `case y of` - `Nothing -> "nothing!"` - `Just value -> value` - (in some cases I believe you can't remove the values, but in these cases you'll also don't need to) - for example, for values tagged with the IO, you can't remove the IO and turn these values into pure values, but you don't need that, you can just take the value from the outside world, so it's a IO Text, apply functions that modify that value inside IO, then output the result to the user -- this is enough to make a complete program, any complete program. - **JSON and interfaces (or instances?)** - using [Aeson](https://hackage.haskell.org/package/aeson-1.2.3.0/docs/Data-Aeson.html) is easy, you just have to implement the `ToJSON` and `FromJSON` interfaces. - "interface" is not the correct name, but I don't care. - `ToJSON`, for example, requires a function named `toJSON`, so you do - `instance ToJSON YourType where` - `toJSON (YourType your type values) = object []` ... etc. - I believe lots of things require interface implementation like this and it can be confusing, but once you know the mystery of implementing functions for interfaces everything is solved. - `FromJSON` is a little less intuitive at the beggining, and I don't know if I did it correctly, but it is working here. Anyway, if you're trying to do that, I can only tell you to follow the types, copy examples from other places on the internet and don't care about the meaning of symbols. ## See also * [Haskell Monoids](nostr:naddr1qqyrzcmrvcmrqwtpqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cktq992) @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# O caso da Grêmio TV enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam: Grêmio TV pior que o SBT !
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# O caso da Grêmio TV enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam: Grêmio TV pior que o SBT ! @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# A list of things artificial intelligence is not doing If AI is so good why can't it: - write good glue code that wraps a documented HTTP API? - make good translations using available books and respective published translations? - extract meaningful and relevant numbers from news articles? - write mathematical models that fit perfectly to available data better than any human? - play videogames without cheating (i.e. simulating human vision, attention and click speed)? - turn pure HTML pages into pretty designs by generating CSS - predict the weather - calculate building foundations - determine stock values of companies from publicly available numbers - smartly and automatically test software to uncover bugs before releases - predict sports matches from the ball and the players' movement on the screen - continuously improve niche/local search indexes based on user input and and reaction to results - control traffic lights - predict sports matches from news articles, and teams and players' history This was posted first on [Twitter](https://twitter.com/fiatjaf/status/1477942802805837827).
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# A list of things artificial intelligence is not doing If AI is so good why can't it: - write good glue code that wraps a documented HTTP API? - make good translations using available books and respective published translations? - extract meaningful and relevant numbers from news articles? - write mathematical models that fit perfectly to available data better than any human? - play videogames without cheating (i.e. simulating human vision, attention and click speed)? - turn pure HTML pages into pretty designs by generating CSS - predict the weather - calculate building foundations - determine stock values of companies from publicly available numbers - smartly and automatically test software to uncover bugs before releases - predict sports matches from the ball and the players' movement on the screen - continuously improve niche/local search indexes based on user input and and reaction to results - control traffic lights - predict sports matches from news articles, and teams and players' history This was posted first on [Twitter](https://twitter.com/fiatjaf/status/1477942802805837827). @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# The "Drivechain will replace altcoins" argument The argument that [Drivechain](nostr:naddr1qq9xgunfwejkx6rpd9hqzythwden5te0ve5kzar2v9nzucm0d5pzqwlsccluhy6xxsr6l9a9uhhxf75g85g8a709tprjcn4e42h053vaqvzqqqr4gumtjfnp) will replace shitcoins is _not_ that people will [sell their shitcoins](https://twitter.com/craigwarmke/status/1680371502246514688) or that the existing shitcoins will instantly vanish. The argument is about a change _at the margin_ that eventually ends up killing the shitcoins or reducing them to their original insignificance. **What does "at the margin" mean?** For example, when the price of the coconut drops a little in relation to bananas, does that mean that everybody will stop buying bananas and will buy only coconuts now? No. Does it mean there will be [zero](https://twitter.com/GoingParabolic/status/1680319173744836609) increase in the amount of coconuts sold? Also no. What happens is that there is a small number of people who would have preferred to buy coconuts if only they were a little less expensive but end up buying bananas instead. When the price of coconut drops these people buy coconuts and don't buy bananas. The argument is that the same thing will happen when Drivechain is activated: there are some people today (yes, believe me) that would have preferred to work within the Bitcoin ecosystem but end up working on shitcoins. In a world with Drivechain these people would be working on the Bitcoin ecosystem, for the benefit of Bitcoin and the Bitcoiners. Why would they prefer Bitcoin? Because Bitcoin has a bigger network-effect. When these people come, they increase Bitocin's network-effect even more, and if they don't go to the shitcoins they reduce the shitcoins' network-effect. Those changes in network-effect contribute to bringing others who were a little further from the margin and the thing compounds until the shitcoins are worthless. Who are these people at the margin? I don't know, but they certainly exist. I would guess the Stark people are one famous example, but there are many others. In the past, examples included Roger Ver, Zooko Wilcox, Riccardo Spagni and Vitalik Buterin. And before you start screaming that these people are shitcoiners (which they are) imagine how much bigger Bitcoin could have been today if they and their entire communities (yes, I know, of awful people) were using and working for Bitcoin today. Remember that phrase about Bitcoin being for enemies? ### But everything that has been invented in the altcoin world is awful, we don't need any of that! You and me should not be the ones judging what is good and what is not for others, but both you and me and others will benefit if these things can be done in a way that increases Bitcoin network-effect and pays fees to Bitcoin miners. Also, there is a much stronger point you may have not considered: if you believe all altcoiners are scammers that means we have only seen the things that were invented by scammers, since all honest people that had good ideas decided to not implement them as the only way to do it would be to create a scammy shitcoin. One example is [Bitcoin Hivemind](nostr:naddr1qqyxs6tkv4kkjmnyqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cd3vm3c). If it is possible to do these ideas without creating shitcoins we may start to see new things that are actually good.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# The "Drivechain will replace altcoins" argument The argument that [Drivechain](nostr:naddr1qq9xgunfwejkx6rpd9hqzythwden5te0ve5kzar2v9nzucm0d5pzqwlsccluhy6xxsr6l9a9uhhxf75g85g8a709tprjcn4e42h053vaqvzqqqr4gumtjfnp) will replace shitcoins is _not_ that people will [sell their shitcoins](https://twitter.com/craigwarmke/status/1680371502246514688) or that the existing shitcoins will instantly vanish. The argument is about a change _at the margin_ that eventually ends up killing the shitcoins or reducing them to their original insignificance. **What does "at the margin" mean?** For example, when the price of the coconut drops a little in relation to bananas, does that mean that everybody will stop buying bananas and will buy only coconuts now? No. Does it mean there will be [zero](https://twitter.com/GoingParabolic/status/1680319173744836609) increase in the amount of coconuts sold? Also no. What happens is that there is a small number of people who would have preferred to buy coconuts if only they were a little less expensive but end up buying bananas instead. When the price of coconut drops these people buy coconuts and don't buy bananas. The argument is that the same thing will happen when Drivechain is activated: there are some people today (yes, believe me) that would have preferred to work within the Bitcoin ecosystem but end up working on shitcoins. In a world with Drivechain these people would be working on the Bitcoin ecosystem, for the benefit of Bitcoin and the Bitcoiners. Why would they prefer Bitcoin? Because Bitcoin has a bigger network-effect. When these people come, they increase Bitocin's network-effect even more, and if they don't go to the shitcoins they reduce the shitcoins' network-effect. Those changes in network-effect contribute to bringing others who were a little further from the margin and the thing compounds until the shitcoins are worthless. Who are these people at the margin? I don't know, but they certainly exist. I would guess the Stark people are one famous example, but there are many others. In the past, examples included Roger Ver, Zooko Wilcox, Riccardo Spagni and Vitalik Buterin. And before you start screaming that these people are shitcoiners (which they are) imagine how much bigger Bitcoin could have been today if they and their entire communities (yes, I know, of awful people) were using and working for Bitcoin today. Remember that phrase about Bitcoin being for enemies? ### But everything that has been invented in the altcoin world is awful, we don't need any of that! You and me should not be the ones judging what is good and what is not for others, but both you and me and others will benefit if these things can be done in a way that increases Bitcoin network-effect and pays fees to Bitcoin miners. Also, there is a much stronger point you may have not considered: if you believe all altcoiners are scammers that means we have only seen the things that were invented by scammers, since all honest people that had good ideas decided to not implement them as the only way to do it would be to create a scammy shitcoin. One example is [Bitcoin Hivemind](nostr:naddr1qqyxs6tkv4kkjmnyqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cd3vm3c). If it is possible to do these ideas without creating shitcoins we may start to see new things that are actually good. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Classless Templates There are way too many hours being wasted in making themes for blogs. And then comes a new blog framework, it requires new themes. Old themes can't be used because they relied on different ways of rendering the website. Everything is a mess. Classless was an attempt at solving it. It probably didn't work because I wasn't the best person to make themes and showcase the thing. Basically everybody would agree on a simple HTML template that could fit blogs and simple websites very easily. Then other people would make pure-CSS themes expecting that template to be in place. No classes were needed, only a fixed structure of `header`. `main`, `article` etc. With **flexbox** and **grid** CSS was enough to make this happen. The templates that were available were all ported by me from other templates I saw on the web, and there was a simple one I created for my old website. - <https://github.com/fiatjaf/classless> - <https://classless.alhur.es/> - <https://classless.alhur.es/themes/>
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Classless Templates There are way too many hours being wasted in making themes for blogs. And then comes a new blog framework, it requires new themes. Old themes can't be used because they relied on different ways of rendering the website. Everything is a mess. Classless was an attempt at solving it. It probably didn't work because I wasn't the best person to make themes and showcase the thing. Basically everybody would agree on a simple HTML template that could fit blogs and simple websites very easily. Then other people would make pure-CSS themes expecting that template to be in place. No classes were needed, only a fixed structure of `header`. `main`, `article` etc. With **flexbox** and **grid** CSS was enough to make this happen. The templates that were available were all ported by me from other templates I saw on the web, and there was a simple one I created for my old website. - <https://github.com/fiatjaf/classless> - <https://classless.alhur.es/> - <https://classless.alhur.es/themes/> @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Um algoritmo imbecil da evolução Suponha que você queira escrever a palavra BANANA partindo de OOOOOO e usando só alterações aleatórias das letras. As alterações se dão por meio da multiplicação da palavra original em várias outras, cada uma com uma mudança diferente. No primeiro período, surgem BOOOOO e OOOOZO. E então o ambiente decide que todas as palavras que não começam com um B estão eliminadas. Sobra apenas BOOOOO e o algoritmo continua. É fácil explicar conceber a evolução das espécies acontecendo dessa maneira, se você controlar sempre a parte em que o ambiente decide quem vai sobrar. Porém, há apenas duas opções: 1. Se o ambiente decidir as coisas de maneira aleatória, a chance de você chegar na palavra correta usando esse método é tão pequena que pode ser considerada nula. 2. Se o ambiente decidir as coisas de maneira pensada, caímos no //design inteligente//. Acredito que isso seja uma enunciação decente do argumento ["no free lunch"](https://en.wikipedia.org/wiki/No_free_lunch_in_search_and_optimization) aplicado à crítica do darwinismo por William Dembski. A resposta darwinista consiste em dizer que não existe essa BANANA como objetivo final. Que as palavras podem ir se alterando aleatoriamente, e o que sobrar sobrou, não podemos dizer que um objetivo foi atingido ou deixou de sê-lo. E aí os defensores do design inteligente dirão que o resultado ao qual chegamos não pode ter sido fruto de um processo aleatório. BANANA é qualitativamente diferente de AYZOSO, e aí há várias maneiras de "provar" que sim usando modelos matemáticos e tal. Fico com a impressão, porém, de que essa coisa só pode ser resolvida como sim ou não mediante uma discussão das premissas, e chega um ponto em que não há mais provas matemáticas possíveis, apenas subjetividade. Daí eu me lembro da minha humilde solução ao problema do cão que aperta as teclas aleatoriamente de um teclado e escreve as obras completas de Shakespeare: mesmo que ele o faça, nada daquilo terá sentido sem uma inteligência de tipo humano ali para lê-las e perceber que não se trata de uma bagunça, mas sim de um texto com sentido para ele. O milagre se dá não no momento em que o cão tropeça no teclado, mas no momento em que o homem olha para a tela. Se o algoritmo da evolução chegou à palavra BANANA ou UXJHTR não faz diferença pra ela, mas faz diferença para nós, que temos uma inteligência humana, e estamos observando aquilo. O homem também pensaria que há //algo// por trás daquele evento do cão que digita as obras de Shakespeare, e como seria possível alguém em sã consciência pensar que não?
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Um algoritmo imbecil da evolução Suponha que você queira escrever a palavra BANANA partindo de OOOOOO e usando só alterações aleatórias das letras. As alterações se dão por meio da multiplicação da palavra original em várias outras, cada uma com uma mudança diferente. No primeiro período, surgem BOOOOO e OOOOZO. E então o ambiente decide que todas as palavras que não começam com um B estão eliminadas. Sobra apenas BOOOOO e o algoritmo continua. É fácil explicar conceber a evolução das espécies acontecendo dessa maneira, se você controlar sempre a parte em que o ambiente decide quem vai sobrar. Porém, há apenas duas opções: 1. Se o ambiente decidir as coisas de maneira aleatória, a chance de você chegar na palavra correta usando esse método é tão pequena que pode ser considerada nula. 2. Se o ambiente decidir as coisas de maneira pensada, caímos no //design inteligente//. Acredito que isso seja uma enunciação decente do argumento ["no free lunch"](https://en.wikipedia.org/wiki/No_free_lunch_in_search_and_optimization) aplicado à crítica do darwinismo por William Dembski. A resposta darwinista consiste em dizer que não existe essa BANANA como objetivo final. Que as palavras podem ir se alterando aleatoriamente, e o que sobrar sobrou, não podemos dizer que um objetivo foi atingido ou deixou de sê-lo. E aí os defensores do design inteligente dirão que o resultado ao qual chegamos não pode ter sido fruto de um processo aleatório. BANANA é qualitativamente diferente de AYZOSO, e aí há várias maneiras de "provar" que sim usando modelos matemáticos e tal. Fico com a impressão, porém, de que essa coisa só pode ser resolvida como sim ou não mediante uma discussão das premissas, e chega um ponto em que não há mais provas matemáticas possíveis, apenas subjetividade. Daí eu me lembro da minha humilde solução ao problema do cão que aperta as teclas aleatoriamente de um teclado e escreve as obras completas de Shakespeare: mesmo que ele o faça, nada daquilo terá sentido sem uma inteligência de tipo humano ali para lê-las e perceber que não se trata de uma bagunça, mas sim de um texto com sentido para ele. O milagre se dá não no momento em que o cão tropeça no teclado, mas no momento em que o homem olha para a tela. Se o algoritmo da evolução chegou à palavra BANANA ou UXJHTR não faz diferença pra ela, mas faz diferença para nós, que temos uma inteligência humana, e estamos observando aquilo. O homem também pensaria que há //algo// por trás daquele evento do cão que digita as obras de Shakespeare, e como seria possível alguém em sã consciência pensar que não? @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# `OP_CHECKTEMPLATEVERIFY` and the "covenants" drama There are many ideas for "covenants" (I don't think this concept helps in the specific case of examining proposals, but fine). Some people think "we" (it's not obvious who is included in this group) should somehow examine them and come up with the perfect synthesis. It is not clear what form this magic gathering of ideas will take and who (or which ideas) will be allowed to speak, but suppose it happens and there is intense research and conversations and people (ideas) really enjoy themselves in the process. What are we left with at the end? Someone has to actually commit the time and put the effort and come up with a concrete proposal to be implemented on Bitcoin, and whatever the result is it will have trade-offs. Some great features will not make into this proposal, others will make in a worsened form, and some will be contemplated very nicely, there will be some extra costs related to maintenance or code complexity that will have to be taken. Someone, a concreate person, will decide upon these things using their own personal preferences and biases, and many people will not be pleased with their choices. That has already happened. Jeremy Rubin has already conjured all the covenant ideas in a magic gathering that lasted more than 3 years and came up with a synthesis that has the best trade-offs he could find. CTV is the result of that operation. --- The fate of CTV in the popular opinion illustrated by the thoughtless responses it has evoked such as "can we do better?" and "we need more review and research and more consideration of other ideas for covenants" is a preview of what would probably happen if these suggestions were followed again and someone spent the next 3 years again considering ideas, talking to other researchers and came up with a new synthesis. Again, that person would be faced with "can we do better?" responses from people that were not happy enough with the choices. And unless some famous Bitcoin Core or retired Bitcoin Core developers were personally attracted by this synthesis then they would take some time to review and give their blessing to this new synthesis. To summarize the argument of this article, the actual question in the current CTV drama is that there exists hidden criteria for proposals to be accepted by the general community into Bitcoin, and no one has these criteria clear in their minds. It is not as simple not as straightforward as "do research" nor it is as humanly impossible as "get consensus", it has a much bigger social element into it, but I also do not know what is the exact form of these hidden criteria. This is said not to blame anyone -- except the ignorant people who are not aware of the existence of these things and just keep repeating completely false and unhelpful advice for Jeremy Rubin and are not self-conscious enough to ever realize what they're doing.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# `OP_CHECKTEMPLATEVERIFY` and the "covenants" drama There are many ideas for "covenants" (I don't think this concept helps in the specific case of examining proposals, but fine). Some people think "we" (it's not obvious who is included in this group) should somehow examine them and come up with the perfect synthesis. It is not clear what form this magic gathering of ideas will take and who (or which ideas) will be allowed to speak, but suppose it happens and there is intense research and conversations and people (ideas) really enjoy themselves in the process. What are we left with at the end? Someone has to actually commit the time and put the effort and come up with a concrete proposal to be implemented on Bitcoin, and whatever the result is it will have trade-offs. Some great features will not make into this proposal, others will make in a worsened form, and some will be contemplated very nicely, there will be some extra costs related to maintenance or code complexity that will have to be taken. Someone, a concreate person, will decide upon these things using their own personal preferences and biases, and many people will not be pleased with their choices. That has already happened. Jeremy Rubin has already conjured all the covenant ideas in a magic gathering that lasted more than 3 years and came up with a synthesis that has the best trade-offs he could find. CTV is the result of that operation. --- The fate of CTV in the popular opinion illustrated by the thoughtless responses it has evoked such as "can we do better?" and "we need more review and research and more consideration of other ideas for covenants" is a preview of what would probably happen if these suggestions were followed again and someone spent the next 3 years again considering ideas, talking to other researchers and came up with a new synthesis. Again, that person would be faced with "can we do better?" responses from people that were not happy enough with the choices. And unless some famous Bitcoin Core or retired Bitcoin Core developers were personally attracted by this synthesis then they would take some time to review and give their blessing to this new synthesis. To summarize the argument of this article, the actual question in the current CTV drama is that there exists hidden criteria for proposals to be accepted by the general community into Bitcoin, and no one has these criteria clear in their minds. It is not as simple not as straightforward as "do research" nor it is as humanly impossible as "get consensus", it has a much bigger social element into it, but I also do not know what is the exact form of these hidden criteria. This is said not to blame anyone -- except the ignorant people who are not aware of the existence of these things and just keep repeating completely false and unhelpful advice for Jeremy Rubin and are not self-conscious enough to ever realize what they're doing. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Per Bylund's insight The firm doesn't exist because, like [Coase said](https://en.wikipedia.org/?curid=83030), it is inefficient to operate in a fully open-market and production processes need some bubbles of central planning. Instead, what happens is that a firm is created because an entrepreneur is doing a new thing (and here I imagine that doing an old thing in a new context also counts as doing a new thing, but I didn't read his book), and for that new thing there is no market, there are no specialized workers offering the services needed, nor other businesses offering the higher-order goods that entrepreneur wants, so he must do all by himself. So the entrepreneur goes and hires workers and buys materials more generic than he wanted and commands these to build what he wants exactly. It is less efficient than if he could buy the precise services and goods he wanted and combine those to yield the product he envisaged, but it accomplishes the goal. Later, when that specific market evolves, it's natural that specialized workers and producers of the specific factors begin to appear, and the market gets decentralized.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Per Bylund's insight The firm doesn't exist because, like [Coase said](https://en.wikipedia.org/?curid=83030), it is inefficient to operate in a fully open-market and production processes need some bubbles of central planning. Instead, what happens is that a firm is created because an entrepreneur is doing a new thing (and here I imagine that doing an old thing in a new context also counts as doing a new thing, but I didn't read his book), and for that new thing there is no market, there are no specialized workers offering the services needed, nor other businesses offering the higher-order goods that entrepreneur wants, so he must do all by himself. So the entrepreneur goes and hires workers and buys materials more generic than he wanted and commands these to build what he wants exactly. It is less efficient than if he could buy the precise services and goods he wanted and combine those to yield the product he envisaged, but it accomplishes the goal. Later, when that specific market evolves, it's natural that specialized workers and producers of the specific factors begin to appear, and the market gets decentralized. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# IPFS problems: Conceit IPFS is trying to do many things. The IPFS leaders are revolutionaries who think they're smarter than the rest of the entire industry. The fact that they've first proposed a protocol for peer-to-peer distribution of immutable, content-addressed objects, then later tried to fix [that same problem](nostr:naddr1qqyrqen9xf3nvdpeqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cmdjnnj) using their own half-baked solution (IPNS) is one example. Other examples are their odd appeal to decentralization in a very non-specific way, their excessive [flirtation with Ethereum](nostr:naddr1qqyxxdpev5cnsvpkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cta4a2e) and their never-to-be-finished can-never-work-as-advertised _Filecoin_ project. They could have focused on just making the infrastructure for distribution of objects through hashes (not saying this would actually be a good idea, but it had some potential) over a peer-to-peer network, but in trying to reinvent the entire internet they screwed everything up.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# IPFS problems: Conceit IPFS is trying to do many things. The IPFS leaders are revolutionaries who think they're smarter than the rest of the entire industry. The fact that they've first proposed a protocol for peer-to-peer distribution of immutable, content-addressed objects, then later tried to fix [that same problem](nostr:naddr1qqyrqen9xf3nvdpeqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cmdjnnj) using their own half-baked solution (IPNS) is one example. Other examples are their odd appeal to decentralization in a very non-specific way, their excessive [flirtation with Ethereum](nostr:naddr1qqyxxdpev5cnsvpkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cta4a2e) and their never-to-be-finished can-never-work-as-advertised _Filecoin_ project. They could have focused on just making the infrastructure for distribution of objects through hashes (not saying this would actually be a good idea, but it had some potential) over a peer-to-peer network, but in trying to reinvent the entire internet they screwed everything up. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# nostr - Notes and Other Stuff Transmitted by Relays The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all. It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works. ## Very short summary of how it works, if you don't plan to read anything else: Everybody runs a client. It can be a native client, a web client, etc. To publish something, you write a post, sign it with your key and send it to multiple relays (servers hosted by someone else, or yourself). To get updates from other people, you ask multiple relays if they know anything about these other people. Anyone can run a relay. A relay is very simple and dumb. It does nothing besides accepting posts from some people and forwarding to others. Relays don't have to be trusted. Signatures are verified on the client side. ## This is needed because other solutions are broken: ### The problem with Twitter - Twitter has ads; - Twitter uses bizarre techniques to keep you addicted; - Twitter doesn't show an actual historical feed from people you follow; - Twitter bans people; - Twitter shadowbans people. - Twitter has a lot of spam. ### The problem with Mastodon and similar programs - User identities are attached to domain names controlled by third-parties; - Server owners can ban you, just like Twitter; Server owners can also block other servers; - Migration between servers is an afterthought and can only be accomplished if servers cooperate. It doesn't work in an adversarial environment (all followers are lost); - There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Then, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out; - Since servers tend to be run amateurishly, they are often abandoned after a while — which is effectively the same as banning everybody; - It doesn't make sense to have a ton of servers if updates from every server will have to be painfully pushed (and saved!) to a ton of other servers. This point is exacerbated by the fact that servers tend to exist in huge numbers, therefore more data has to be passed to more places more often; - For the specific example of video sharing, ActivityPub enthusiasts realized it would be completely impossible to transmit video from server to server the way text notes are, so they decided to keep the video hosted only from the single instance where it was posted to, which is similar to the Nostr approach. ### The problem with SSB (Secure Scuttlebutt) - It doesn't have many problems. I think it's great. In fact, I was going to use it as a basis for this, but - its protocol is too complicated because it wasn't thought about being an open protocol at all. It was just written in JavaScript in probably a quick way to solve a specific problem and grew from that, therefore it has weird and unnecessary quirks like signing a JSON string which must strictly follow the rules of [_ECMA-262 6th Edition_](https://www.ecma-international.org/ecma-262/6.0/#sec-json.stringify); - It insists on having a chain of updates from a single user, which feels unnecessary to me and something that adds bloat and rigidity to the thing — each server/user needs to store all the chain of posts to be sure the new one is valid. Why? (Maybe they have a good reason); - It is not as simple as Nostr, as it was primarily made for P2P syncing, with "pubs" being an afterthought; - Still, it may be worth considering using SSB instead of this custom protocol and just adapting it to the client-relay server model, because reusing a standard is always better than trying to get people in a new one. ### The problem with other solutions that require everybody to run their own server - They require everybody to run their own server; - Sometimes people can still be censored in these because domain names can be censored. ## How does Nostr work? - There are two components: __clients__ and __relays__. Each user runs a client. Anyone can run a relay. - Every user is identified by a public key. Every post is signed. Every client validates these signatures. - Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn't talk to another relay, only directly to users. - For example, to "follow" someone a user just instructs their client to query the relays it knows for posts from that public key. - On startup, a client queries data from all relays it knows for all users it follows (for example, all updates from the last day), then displays that data to the user chronologically. - A "post" can contain any kind of structured data, but the most used ones are going to find their way into the standard so all clients and relays can handle them seamlessly. ## How does it solve the problems the networks above can't? - **Users getting banned and servers being closed** - A relay can block a user from publishing anything there, but that has no effect on them as they can still publish to other relays. Since users are identified by a public key, they don't lose their identities and their follower base when they get banned. - Instead of requiring users to manually type new relay addresses (although this should also be supported), whenever someone you're following posts a server recommendation, the client should automatically add that to the list of relays it will query. - If someone is using a relay to publish their data but wants to migrate to another one, they can publish a server recommendation to that previous relay and go; - If someone gets banned from many relays such that they can't get their server recommendations broadcasted, they may still let some close friends know through other means with which relay they are publishing now. Then, these close friends can publish server recommendations to that new server, and slowly, the old follower base of the banned user will begin finding their posts again from the new relay. - All of the above is valid too for when a relay ceases its operations. - **Censorship-resistance** - Each user can publish their updates to any number of relays. - A relay can charge a fee (the negotiation of that fee is outside of the protocol for now) from users to publish there, which ensures censorship-resistance (there will always be some Russian server willing to take your money in exchange for serving your posts). - **Spam** - If spam is a concern for a relay, it can require payment for publication or some other form of authentication, such as an email address or phone, and associate these internally with a pubkey that then gets to publish to that relay — or other anti-spam techniques, like hashcash or captchas. If a relay is being used as a spam vector, it can easily be unlisted by clients, which can continue to fetch updates from other relays. - **Data storage** - For the network to stay healthy, there is no need for hundreds of active relays. In fact, it can work just fine with just a handful, given the fact that new relays can be created and spread through the network easily in case the existing relays start misbehaving. Therefore, the amount of data storage required, in general, is relatively less than Mastodon or similar software. - Or considering a different outcome: one in which there exist hundreds of niche relays run by amateurs, each relaying updates from a small group of users. The architecture scales just as well: data is sent from users to a single server, and from that server directly to the users who will consume that. It doesn't have to be stored by anyone else. In this situation, it is not a big burden for any single server to process updates from others, and having amateur servers is not a problem. - **Video and other heavy content** - It's easy for a relay to reject large content, or to charge for accepting and hosting large content. When information and incentives are clear, it's easy for the market forces to solve the problem. - **Techniques to trick the user** - Each client can decide how to best show posts to users, so there is always the option of just consuming what you want in the manner you want — from using an AI to decide the order of the updates you'll see to just reading them in chronological order. ## FAQ - **This is very simple. Why hasn't anyone done it before?** I don't know, but I imagine it has to do with the fact that people making social networks are either companies wanting to make money or P2P activists who want to make a thing completely without servers. They both fail to see the specific mix of both worlds that Nostr uses. - **How do I find people to follow?** First, you must know them and get their public key somehow, either by asking or by seeing it referenced somewhere. Once you're inside a Nostr social network you'll be able to see them interacting with other people and then you can also start following and interacting with these others. - **How do I find relays? What happens if I'm not connected to the same relays someone else is?** You won't be able to communicate with that person. But there are hints on events that can be used so that your client software (or you, manually) knows how to connect to the other person's relay and interact with them. There are other ideas on how to solve this too in the future but we can't ever promise perfect reachability, no protocol can. - **Can I know how many people are following me?** No, but you can get some estimates if relays cooperate in an extra-protocol way. - **What incentive is there for people to run relays?** The question is misleading. It assumes that relays are free dumb pipes that exist such that people can move data around through them. In this case yes, the incentives would not exist. This in fact could be said of DHT nodes in all other p2p network stacks: what incentive is there for people to run DHT nodes? - **Nostr enables you to move between server relays or use multiple relays but if these relays are just on AWS or Azure what’s the difference?** There are literally thousands of VPS providers scattered all around the globe today, there is not only AWS or Azure. AWS or Azure are exactly the providers used by single centralized service providers that need a lot of scale, and even then not just these two. For smaller relay servers any VPS will do the job very well.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# nostr - Notes and Other Stuff Transmitted by Relays The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all. It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works. ## Very short summary of how it works, if you don't plan to read anything else: Everybody runs a client. It can be a native client, a web client, etc. To publish something, you write a post, sign it with your key and send it to multiple relays (servers hosted by someone else, or yourself). To get updates from other people, you ask multiple relays if they know anything about these other people. Anyone can run a relay. A relay is very simple and dumb. It does nothing besides accepting posts from some people and forwarding to others. Relays don't have to be trusted. Signatures are verified on the client side. ## This is needed because other solutions are broken: ### The problem with Twitter - Twitter has ads; - Twitter uses bizarre techniques to keep you addicted; - Twitter doesn't show an actual historical feed from people you follow; - Twitter bans people; - Twitter shadowbans people. - Twitter has a lot of spam. ### The problem with Mastodon and similar programs - User identities are attached to domain names controlled by third-parties; - Server owners can ban you, just like Twitter; Server owners can also block other servers; - Migration between servers is an afterthought and can only be accomplished if servers cooperate. It doesn't work in an adversarial environment (all followers are lost); - There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Then, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out; - Since servers tend to be run amateurishly, they are often abandoned after a while — which is effectively the same as banning everybody; - It doesn't make sense to have a ton of servers if updates from every server will have to be painfully pushed (and saved!) to a ton of other servers. This point is exacerbated by the fact that servers tend to exist in huge numbers, therefore more data has to be passed to more places more often; - For the specific example of video sharing, ActivityPub enthusiasts realized it would be completely impossible to transmit video from server to server the way text notes are, so they decided to keep the video hosted only from the single instance where it was posted to, which is similar to the Nostr approach. ### The problem with SSB (Secure Scuttlebutt) - It doesn't have many problems. I think it's great. In fact, I was going to use it as a basis for this, but - its protocol is too complicated because it wasn't thought about being an open protocol at all. It was just written in JavaScript in probably a quick way to solve a specific problem and grew from that, therefore it has weird and unnecessary quirks like signing a JSON string which must strictly follow the rules of [_ECMA-262 6th Edition_](https://www.ecma-international.org/ecma-262/6.0/#sec-json.stringify); - It insists on having a chain of updates from a single user, which feels unnecessary to me and something that adds bloat and rigidity to the thing — each server/user needs to store all the chain of posts to be sure the new one is valid. Why? (Maybe they have a good reason); - It is not as simple as Nostr, as it was primarily made for P2P syncing, with "pubs" being an afterthought; - Still, it may be worth considering using SSB instead of this custom protocol and just adapting it to the client-relay server model, because reusing a standard is always better than trying to get people in a new one. ### The problem with other solutions that require everybody to run their own server - They require everybody to run their own server; - Sometimes people can still be censored in these because domain names can be censored. ## How does Nostr work? - There are two components: __clients__ and __relays__. Each user runs a client. Anyone can run a relay. - Every user is identified by a public key. Every post is signed. Every client validates these signatures. - Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn't talk to another relay, only directly to users. - For example, to "follow" someone a user just instructs their client to query the relays it knows for posts from that public key. - On startup, a client queries data from all relays it knows for all users it follows (for example, all updates from the last day), then displays that data to the user chronologically. - A "post" can contain any kind of structured data, but the most used ones are going to find their way into the standard so all clients and relays can handle them seamlessly. ## How does it solve the problems the networks above can't? - **Users getting banned and servers being closed** - A relay can block a user from publishing anything there, but that has no effect on them as they can still publish to other relays. Since users are identified by a public key, they don't lose their identities and their follower base when they get banned. - Instead of requiring users to manually type new relay addresses (although this should also be supported), whenever someone you're following posts a server recommendation, the client should automatically add that to the list of relays it will query. - If someone is using a relay to publish their data but wants to migrate to another one, they can publish a server recommendation to that previous relay and go; - If someone gets banned from many relays such that they can't get their server recommendations broadcasted, they may still let some close friends know through other means with which relay they are publishing now. Then, these close friends can publish server recommendations to that new server, and slowly, the old follower base of the banned user will begin finding their posts again from the new relay. - All of the above is valid too for when a relay ceases its operations. - **Censorship-resistance** - Each user can publish their updates to any number of relays. - A relay can charge a fee (the negotiation of that fee is outside of the protocol for now) from users to publish there, which ensures censorship-resistance (there will always be some Russian server willing to take your money in exchange for serving your posts). - **Spam** - If spam is a concern for a relay, it can require payment for publication or some other form of authentication, such as an email address or phone, and associate these internally with a pubkey that then gets to publish to that relay — or other anti-spam techniques, like hashcash or captchas. If a relay is being used as a spam vector, it can easily be unlisted by clients, which can continue to fetch updates from other relays. - **Data storage** - For the network to stay healthy, there is no need for hundreds of active relays. In fact, it can work just fine with just a handful, given the fact that new relays can be created and spread through the network easily in case the existing relays start misbehaving. Therefore, the amount of data storage required, in general, is relatively less than Mastodon or similar software. - Or considering a different outcome: one in which there exist hundreds of niche relays run by amateurs, each relaying updates from a small group of users. The architecture scales just as well: data is sent from users to a single server, and from that server directly to the users who will consume that. It doesn't have to be stored by anyone else. In this situation, it is not a big burden for any single server to process updates from others, and having amateur servers is not a problem. - **Video and other heavy content** - It's easy for a relay to reject large content, or to charge for accepting and hosting large content. When information and incentives are clear, it's easy for the market forces to solve the problem. - **Techniques to trick the user** - Each client can decide how to best show posts to users, so there is always the option of just consuming what you want in the manner you want — from using an AI to decide the order of the updates you'll see to just reading them in chronological order. ## FAQ - **This is very simple. Why hasn't anyone done it before?** I don't know, but I imagine it has to do with the fact that people making social networks are either companies wanting to make money or P2P activists who want to make a thing completely without servers. They both fail to see the specific mix of both worlds that Nostr uses. - **How do I find people to follow?** First, you must know them and get their public key somehow, either by asking or by seeing it referenced somewhere. Once you're inside a Nostr social network you'll be able to see them interacting with other people and then you can also start following and interacting with these others. - **How do I find relays? What happens if I'm not connected to the same relays someone else is?** You won't be able to communicate with that person. But there are hints on events that can be used so that your client software (or you, manually) knows how to connect to the other person's relay and interact with them. There are other ideas on how to solve this too in the future but we can't ever promise perfect reachability, no protocol can. - **Can I know how many people are following me?** No, but you can get some estimates if relays cooperate in an extra-protocol way. - **What incentive is there for people to run relays?** The question is misleading. It assumes that relays are free dumb pipes that exist such that people can move data around through them. In this case yes, the incentives would not exist. This in fact could be said of DHT nodes in all other p2p network stacks: what incentive is there for people to run DHT nodes? - **Nostr enables you to move between server relays or use multiple relays but if these relays are just on AWS or Azure what’s the difference?** There are literally thousands of VPS providers scattered all around the globe today, there is not only AWS or Azure. AWS or Azure are exactly the providers used by single centralized service providers that need a lot of scale, and even then not just these two. For smaller relay servers any VPS will do the job very well. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Replacing the web with something saner This is a simplification, but let's say that basically there are just 3 kinds of websites: 1. Websites with content: text, images, videos; 2. Websites that run full apps that do a ton of interactive stuff; 3. Websites with some interactive content that uses JavaScript, or "mini-apps"; In a saner world we would have 3 different ways of serving and using these. 1 would be "the web" (and it was for a while, although I'm not claiming here that the past is always better and wanting to get back to the glorious old days). 1 would stay as "the web", just static sites, styled with CSS, no JavaScript whatsoever, but designers can still thrive and make they look pretty. Or it could also be something like [Gemini](https://gemini.circumlunar.space/). Maybe the two protocols could coexist. 2 would be downloadable native apps, much easier to write and maintain for developers (considering that multi-platform and cross-compilation is easy today and getting easier), faster, more polished experience for users, more powerful, integrates better with the computer. (Remember that since no one would be striving to make the same app run both on browsers and natively no one would have any need for Electron or other inefficient bloated solutions, just pure native UI, like the Telegram app, have you seen that? It's fast.) But 2 is mostly for apps that people use every day, something like Google Docs, email (although email is also broken technology), Netflix, Twitter, Trello and so on, and all those hundreds of niche SaaS that people pay monthly fees to use, each tailored to a different industry (although most of functions they all implement are the same everywhere). What do we do with dynamic open websites like StackOverflow, for example, where one needs to not only read, but also search and interact in multiple ways? What about that website that asks you a bunch of questions and then discovers the name of the person you're thinking about? What about that mini-app that calculates the hash of your provided content or shrinks your video, or that one that hosts your image without asking any questions? All these and tons of others would fall into category 3, that of instantly loaded apps that you don't have to install, and yet they run in a sandbox. The key for making category 3 worth investing time into is coming up with some solid grounds, simple enough that anyone can implement in multiple different ways, but not giving the app too much choices. Telegram or Discord bots are super powerful platforms that can accomodate most kinds of app in them. They can't beat a native app specifically made with one purpose, but they allow anyone to provide instantly usable apps with very low overhead, and since the experience is so simple, intuitive and fast, users tend to like it and sometimes even pay for their services. There could exist a protocol that brings apps like that to the open world of (I won't say "web") domains and the websockets protocol -- with multiple different clients, each making their own decisions on how to display the content sent by the servers that are powering these apps. Another idea is that of [Alan Kay](https://www.quora.com/Should-web-browsers-have-stuck-to-being-document-viewers/answer/Alan-Kay-11): to design a nice little OS/virtual machine that can load these apps and run them. Kinda like browsers are today, but providing a more well-thought, native-like experience and framework, but still sandboxed. And I add: abstracting away details about design, content disposition and so on. --- These 3 kinds of programs could coexist peacefully. 2 are just standalone programs, they can do anything and each will be its own thing. 1 and 3, however, are still similar to browsers of today in the sense that you need clients to interact with servers and show to the user what they are asking. But by simplifying everything and separating the scopes properly these clients would be easy to write, efficient, small, the environment would be open and the internet would be saved. ## See also - [On the state of programs and browsers](nostr:naddr1qqyxgdfe8qexvd34qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cd7nk4m)
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Replacing the web with something saner This is a simplification, but let's say that basically there are just 3 kinds of websites: 1. Websites with content: text, images, videos; 2. Websites that run full apps that do a ton of interactive stuff; 3. Websites with some interactive content that uses JavaScript, or "mini-apps"; In a saner world we would have 3 different ways of serving and using these. 1 would be "the web" (and it was for a while, although I'm not claiming here that the past is always better and wanting to get back to the glorious old days). 1 would stay as "the web", just static sites, styled with CSS, no JavaScript whatsoever, but designers can still thrive and make they look pretty. Or it could also be something like [Gemini](https://gemini.circumlunar.space/). Maybe the two protocols could coexist. 2 would be downloadable native apps, much easier to write and maintain for developers (considering that multi-platform and cross-compilation is easy today and getting easier), faster, more polished experience for users, more powerful, integrates better with the computer. (Remember that since no one would be striving to make the same app run both on browsers and natively no one would have any need for Electron or other inefficient bloated solutions, just pure native UI, like the Telegram app, have you seen that? It's fast.) But 2 is mostly for apps that people use every day, something like Google Docs, email (although email is also broken technology), Netflix, Twitter, Trello and so on, and all those hundreds of niche SaaS that people pay monthly fees to use, each tailored to a different industry (although most of functions they all implement are the same everywhere). What do we do with dynamic open websites like StackOverflow, for example, where one needs to not only read, but also search and interact in multiple ways? What about that website that asks you a bunch of questions and then discovers the name of the person you're thinking about? What about that mini-app that calculates the hash of your provided content or shrinks your video, or that one that hosts your image without asking any questions? All these and tons of others would fall into category 3, that of instantly loaded apps that you don't have to install, and yet they run in a sandbox. The key for making category 3 worth investing time into is coming up with some solid grounds, simple enough that anyone can implement in multiple different ways, but not giving the app too much choices. Telegram or Discord bots are super powerful platforms that can accomodate most kinds of app in them. They can't beat a native app specifically made with one purpose, but they allow anyone to provide instantly usable apps with very low overhead, and since the experience is so simple, intuitive and fast, users tend to like it and sometimes even pay for their services. There could exist a protocol that brings apps like that to the open world of (I won't say "web") domains and the websockets protocol -- with multiple different clients, each making their own decisions on how to display the content sent by the servers that are powering these apps. Another idea is that of [Alan Kay](https://www.quora.com/Should-web-browsers-have-stuck-to-being-document-viewers/answer/Alan-Kay-11): to design a nice little OS/virtual machine that can load these apps and run them. Kinda like browsers are today, but providing a more well-thought, native-like experience and framework, but still sandboxed. And I add: abstracting away details about design, content disposition and so on. --- These 3 kinds of programs could coexist peacefully. 2 are just standalone programs, they can do anything and each will be its own thing. 1 and 3, however, are still similar to browsers of today in the sense that you need clients to interact with servers and show to the user what they are asking. But by simplifying everything and separating the scopes properly these clients would be easy to write, efficient, small, the environment would be open and the internet would be saved. ## See also - [On the state of programs and browsers](nostr:naddr1qqyxgdfe8qexvd34qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cd7nk4m) @ 2a5d1247:0398ad01
2024-08-20 21:32:48# 🧠Quote(s) of the week: 'Bitcoin is for everyone. It’s for Democrats It’s for Republicans It’s for conservatives It’s for progressives It’s for every single person on this planet who wants to participate regardless of where they came from or what they believe.' - Dennis Porter "It doesn't matter if the existing system prints $2 trillion, $8 trillion, $50 trillion. It's just different pieces of paper. And Bitcoin measured against a piece of paper will look like it's going up. But all prices relative to Bitcoin are actually going down and will forever." -Jeff Booth ## 🧡Bitcoin news🧡  But the unlikely thing happened in late 2008: Bitcoin On the 13th of August: ➡️ Bitcoin is the 6th ranked monetary asset in the world. ➡️Although the following statement is from the 3rd of July nonetheless I want to share it with you. All 3,070 Four-year HODL periods of Bitcoin have been positive. The worst four-year HODL period was: December 16th, 2017 to December 15th, 2021 a 155% return, representing a 22.2% CAGR 99.7 percentile* CAGR of 26.4%. *periods above  What does that tell you? Think of Bitcoin from a long-term perspective, at least holding Bitcoin for four years. 'It’s like watching a super-long movie where the plot thickens and the suspense builds!' ➡️Bitcoin Miner Reserves Drop to 3-Year Low. The miner sell-off appears complete. ➡️Bitcoin exchange reserves have hit a five-year low. ➡️'Bitcoin's sustainable energy mix is 6% for the year (faster than any industry) Over the same period, Bitcoin price 128% I guess the rising Bitcoin price isn't boiling the oceans.' - Daniel Batten ➡️Metaplanet buys another ¥500 million worth of Bitcoin On the 14th of August: ➡️Norges Bank, the Central Bank of Norway, owns over 1.1 MILLION shares of MicroStrategy stock. ➡️Goldman Sachs bought $418m Bitcoin ETFs in the last quarter. Goldman Sach’s latest 13F filing discloses owning: - $238.6 million iShares Bitcoin Trust - $79.5 million Fidelity Bitcoin ETF - $35.1 million Grayscale BTC - $56.1 million Invesco Galaxy Bitcoin - $8.3 million Bitwise Bitcoin ETF - $749,469 WisdomTree Bitcoin - $299,900 ARK 21Shares Bitcoin ETF For a total of $418 million in Bitcoin ETFs ➡️The Swiss Central Bank owns 514 Bitcoin through buying 466.000 MSTR shares. ➡️Marathon bought 4,144 BTC for $249M and now HODLs over 25,000 Bitcoin. ➡️ 'State of Wisconsin Investment Board bought another $14m Bitcoin through BlackRock's ETF.' -Bitcoin Archive On the 15th of August: ➡️94% of the 21 million Bitcoin has now been mined. Only 6% left to be mined over the next 116 years!  foto credit: Wicked So global Bitcoin adoption is at ~0.10% and 94.00% of all coins have already been mined and you still think diminishing returns are likely? What happens when 99.9% of the world tries to buy the last 6.00% of Bitcoin? ➡️ Great rebuttal and excellent analysis by Daniel Batten: Rebuttal of New IMF report on Bitcoin mining emissions IMF report says "Carbon Emissions from AI and Crypto are surging" then goes on to a detailed report on how regulators should impose a "crypto carbon" tax. Rebuttal: Firstly, Bitcoin advocates everywhere should pause to reflect on the significance of this moment. With the scientific consensus (9 of the last 10 peer-reviewed articles) and mainstream journalism now concluding that Bitcoin mining has significant environmental benefits, those who stand to lose most from mainstream adoption of Bitcoin (IMF, Central Banks) need to resort to direct attack pieces. Here's a breakdown of why the IMF report is at best poorly researched, and at worst propaganda. https://x.com/DSBatten/status/1824129351371096516 It's helpful to have, the facts beyond the 'journalism' they offer. Please read the rebuttal. ➡️You can't make this up. The German Federal Office for Information Security shared a post on Linkedin calling hardware wallets the most secure way to store crypto-assets like Bitcoin. They also recommend creating backups and keeping them safe in multiple locations. "Schon gewusst? Der Bitcoin-Wert geht dieses Jahr über 100.000 Euro!" - Okay, someone is bullish! Didn't see this one coming. And why on earth did they, even though it's a different German government agency, sell 50.000 BTC below €100k/BTC, great logic! WAHNSINN!  ➡️Apple opens iPhone Payment Chip to Third Parties for the first time making Bitcoin "Tap to Pay" possible! ➡️The world’s 3rd-largest public pension fund, South Korea’s NPS, has bought $34M in MicroStrategy shares. ➡️'65% of Bitcoin has not moved in over a year. This metric peaked at nearly 71% last November.' -Bitcoin News On the 17th of August: ➡️Billionaire Peter Thiel tells Joe Rogan that Bitcoin is such a big deal that society does not know how to process and recognize it immediately, and it is on the same scale as the internet. ➡️I have said it before and I will say it again: For all the people on Twitter or other platforms, stop bootlicking politicians, stop larping. You can’t say “Don’t trust, verify” AND trust politicians or go full fangirl. RFKjr.: 'Join me for a fireside chat with Charles Hoskinson'. Ask yourself...why he gave that speech in Nashville at the Bitcoin Conference and now endorses this (Cardano). One answer: votes! ➡️'Bitcoin wallet dormant since 2014 moves nearly 175 BTC for the first time in over a decade. The funds, which were valued at $151,970 in 2014, are now worth $10.2 million.' - Bitcoin News ➡️'Marathon a leading publicly traded Bitcoin mining company, recently expanded its Bitcoin holdings with a $249 million purchase, bringing the total to over 25,000 Bitcoins, valued at approximately $1.5 billion. On August 12th, the company announced a $250 million convertible note offering, which was increased to $300 million due to strong demand. Marathon used $249 million of the proceeds to acquire 4,144 additional Bitcoin at an average price of $59,500 per coin.' -BTCTimes On the 18th of August: ➡️75% Of Bitcoin Hasn't Moved In Over 6 Months, Signaling Strong HODLing Trend ➡️ El Salvador mined 474 Bitcoin worth $29 million using volcano-fueled geothermal power. ➡️Welcome to the Lightning Network Bisq as Bisq v2.1 has been released! Highlights include: - Option to settle trades over the Lightning Network - Refined chat experience including emoji reactions - Know who's online with peer liveness indicators ## 💸Traditional Finance / Macro: On the 15th of August: 👉🏽No news 🏦Banks: 👉🏽No news ## 🌎Macro/Geopolitics: I want to start with this segment with the following quote and picture by James Lavish: 'With US Federal Debt powering right through $35 trillion and heading exponentially higher, we are at this phase of the fiat debt cycle.'  Now please connect the above quote with the following statement by Argentina President Javier Milei: “If printing money would end poverty, printing diplomas would end stupidity.” That is the best sentence I’ve heard lately! On the 13th of August: 👉🏽Walker Amerika: 'Trump just said “We would have no inflation” if not for Biden. This is false. I think it’s important to clarify that there *was* massive inflation during Trump’s administration. From January 2017 to January 2021, the M2 money supply increased from ~$13.3 trillion to ~$19.4 trillion by January 2021. That’s an INFLATION of ~$6.1 trillion, or ~45%. There is a LAG between monetary inflation and general price increases throughout the economy, and price increases do not happen uniformly (look up the Cantillon Effect). To clarify for the partisans out there: this is NOT an attempt to make excuses for Biden or to say that the monetary and fiscal policies under Biden are good; they are not good. The point is that it is false to say “there was no inflation” under Trump. Monetary inflation *is* inflation.' Spot on! It doesn't matter who is President inflation will run wild. Every President will have to spend more than the one before him, because of 30 to 50 years of bad policy. You better own Bitcoin. 👉🏽'The US government deficit hit a massive $1.5 trillion in the first 10 months of FY 2024, according to the Treasury Department. In July alone, the US deficit spending reached a whopping $244 billion. Total outlays came in at $5.6 trillion and total receipts were $5.6 trillion over the last 10 months. Social Security was the largest expenditure amounting to $1.2 trillion. Net interest was the second largest cost, exceeding health, Medicare, and national defense expenses. Government spending remains at crisis levels.' -TKL UNSUSTAINABLE 👉🏽 In the last couple of weeks I have been reading for the second time the book: 'The Sovereign Individual' The concept of the 'Rule of Law' is impossible nowadays. Globalization makes the 'Rule of Law' impossible. A study demonstrates that. '36% of multinational profits are shifted to tax havens every year. This reduces corporate tax revenue by >$200 billion (10% of global corporate tax receipts). Reallocation would increase domestic profits by 20% in high-tax EU countries, 10% in the US, and 5% in developing countries.' -Phillip Heimberger Source: https://gabriel-zucman.eu/files/TWZ2022Restud.pdf What is interesting about the article is that it is co-authored by a Danish minister of Finance and a UC Berkeley professor. Anyway, read the book 'The Sovereign Individual.' 👉🏽The 3 years' lowest excess of cash in the financial system. Remember what happened in 2018/2019? This is likely a good setup for increased liquidity. 'The Fed’s Reverse Repo (RRP) facility has dropped below $300 billion for the first time since 2021. The RRP is one of the financial system's excess liquidity metrics and is widely watched by investors. Large banks, government-sponsored enterprises, and money-market funds put their extra cash into the facility to earn interest on it. RRP usage has plummeted by $2.3 TRILLION since December 2022. Over the last several months, however, the decline has stabilized and the facility usage has been oscillating around $300-$400 billion.' -TKL 👉🏽The UK sees the worst 1 month job losses since the COVID crash UK unemployment is at 135K (forecast 14.5K, previous 32.3K) over 10x higher than expected. You don't say? Let's see what are the effects of unemployment. "We find a strong relationship between increases in unemployment and voting for nonmainstream parties, especially populist ones. Moreover, unemployment increases in tandem with declining trust toward national and European political institutions." [Source](https://www.brookings.edu/wp-content/uploads/2018/02/algantextfa17bpea.pdf) Who would have ever thought? Unemployment / left populism Inmigration / Right populism Now look at what is happening in Europe. Even the authors explore causality and find 'that crisis-driven economic insecurity is a substantial determine of populism and political distrust.'. ERGO: Economic stress leads to political extremism [](https://image.nostr.build/3902b94e3ff21d644e6eb80db0b60e37d57ba011c0b71573dfa59f32121835ba.png) On the 14th of August: 👉🏽[](https://image.nostr.build/3cb2355df80046af9e5af23ef2732a4c1ba26f990462f5db34b91354edf02220.jpg) As long as you remember China's emissions are for a large part due to the stuff we buy, the industry we outsourced there. The EU and UK would rather manufacture climate hysteria and green policies that restrict growth and drive up energy prices than create an attractive capital market and innovation for techno solutions. A lot of the manufacturing capacity needed to feed the EU consumers is located in China. I'd say Europeans are net importers regarding China, so if we measure by consumption, the proportions would likely be different. Territorial-based, China has slightly worse emissions than the EU. However, consumption-based, it's marginally better than the EU.  Now don't get me wrong. I do care about our climate & nature, but the truth without context is useless in discussing climate change and what we, the civilized people of the West (lmao), should do about it. For example, deindustrializing Europe, especially Germany as the engine of Europe, for climate change is like throwing tomato soup at the Mona Lisa or gluing yourself on a highway --pointless! Humanity always evolved forward by upgrading to more energy-dense, stable energy sources. It is the first time in history we actually regressed on that front, and maybe (personal opinion) it caused our climate issues. Tackling climate change is nearly impossible within a debt-driven, inflationary economy. It promotes consumption over saving, and short-term profit over sustainability, and hinders so-called 'green' investments. Fix the money, fix the world: Bitcoin. 👉🏽So last week I spoke about Thierry Breton (EU) and his terror on freedom of speech. Look what we have this week... AIACT [](https://image.nostr.build/5e89508a7286237ea0056ca014c93312843e55e4ee9dd41b85847151a1e4d973.jpg) EU Commissioner brags about having AI regulation when they don't have a SINGLE MAJOR AI COMPANY. Only a career bureaucrat could think of regulation as an achievement... It's like celebrating a traffic law in a town with no cars. Who elected people like Thierry...NOBODY! Yes, you could argue that it’s home (the EU) to ASML, the main supplier of NVDA. Without it, NVDA would not exist. So OK, maybe will have a few AI companies despite the regulation. But we won't be a leading sector. 👉🏽 Hackers have reportedly stolen the Social Security numbers of every American from National Public Data, according to the LA Times. Records for nearly 2.9 billion people were reportedly stolen. Most of the data was posted on an online marketplace. The group reportedly offered to sell the data on an online forum. The breach is expected to "power a raft of identity theft, fraud and other crimes." -TKL 👉🏽'Chinese Bank Loans fall for the first time in almost 20 years.' -Radar 'What This Means: - Bank Loans Decrease: When bank loans fall, it means businesses and individuals are borrowing less money from banks. This could be due to various reasons, like reduced demand for borrowing, tighter lending standards, or economic uncertainty. -Economic Implications: A decline in loans can signal a slowdown in economic activity. Loans are often used to fund business expansion, investments, and consumer spending. If these activities decline, it can slow down economic growth. This event could signal a potential slowdown in the Chinese economy, which might impact global markets, depending on how the situation evolves. Investors and market participants will closely watch this development to gauge its broader implications.' -Chat GPT 👉🏽"The S&P index is pretty much going up 7% per year for 100 years, and the U.S. dollar currency supply is going up 7% per year for 100 years. What you have is a basket of assets that are holding their value in real terms while they trend up in nominal terms.." —Michael Saylor [](https://image.nostr.build/95b645d5d046f17b75ef04d48d629d87bc6cef8307406a927fc4b336de9088df.jpg) Remember, inflation is caused by central bank money printing and the relentless expansion of the money supply, not ‘greedy corporations and price gouging’. Reagan: “We don't have inflation because the people are living too well. We have inflation because the government is living too well” 👉🏽 Just a rounding error: 'US job numbers have been revised lower by 778,000 jobs since February 2022, according to BlackRock. This year alone, non-farm payrolls were revised down by 279,000 from January to June. Furthermore, the US economy LOST 192,000 jobs in Q3 2023 and added 344,000 jobs in Q4 2023, according to the BED survey released by BLS. On the other hand, nonfarm payroll data showed that the US labor market added 663,000 and 577,000 new jobs in Q3 and Q4 2023. This is a jaw-dropping 1,088,000 difference in job count over just two quarters. The labor market is weaker than the headlines make it seem.' -TKL Now ask yourself how are they allowed to do this so blatantly. Why isn't the Media reporting on this? And they can't even get this straight why on earth do you believe that they have control & tell the truth on other topics.... Ask yourself. If overall inflation is up 6% and many things you buy way higher, what has gone down in price to bring the overall number down? [](https://image.nostr.build/3095ec0f6199e72c76802b3b33d3eb4c877fe4a9704bb6119ae51099142203ff.jpg) Fake Jobs Fake Inflation Fake GDP; Oh well, just a thought. On the 16th of August: 👉🏽The cooling towers of the last nuclear power plant in Germany were demolished today. This is what economic self-destruction looks like. They shut that clean energy down to turn up brown coal. That’s why Germany's emissions are 7X more than France's per KW/hr. I have the feeling that this will go down in history as one of the most insane, self-destructive, and stupid energy decisions made in the Western world. 👉🏽Gold hits 2500 for the first time in history ahead of Kamala's central planning unveil that will usher in even more runaway inflation. Fueled by lower Dollar and lower US Treasury yields year-to-date, Gold is up 20.7%, setting the stage for its strongest annual performance since 2020 when it gained 25.1%. 👉🏽Again the ECB is absolutely getting drilled on Twitter by Dr. Jan Wüstenfeld and obviously he gets the silent treatment. ECB: 'We’ve improved our environmental performance: Better carbon footprint reporting Increased biodiversity on our premises Enhanced emissions calculations Find out more, including how we’re reducing our operational footprint.' Dr. Jan Wüstenfeld's reaction: You can't effectively fight climate change in a debt-based, inflationary monetary system. The incentives are not aligned. You are part of the problem. 1) Inflation favours consumption over saving: As money loses value over time, people are encouraged to spend or invest rather than save. 2) Debt in an inflationary monetary system: Borrowing is attractive because future payments are easier, leading to more consumption, sometimes of unnecessary or unsustainable items. 3) Short-term focus: Continuous economic growth is needed at all costs, often pushing aside long-term sustainability. -> Companies prioritize short-term profits, leading to resource overuse and little focus on sustainability. 4) Climate impact: The push for growth leads to excessive resource use, worsening environmental damage, and climate change. -> Overconsumption Immediate profit focus often delays investment in sustainable technologies. -> Delayed green investment Fix the money, fix the world! Bitcoin! Please dear EBC you still only have one job. 'Inflationary money fuels wasteful behavior, wasteful behavior harms the environment.' On the 18th of August: 👉🏽How bad is the US Federal debt situation? 'Net interest costs on US Federal debt as a % of GDP are set to reach almost 3 TIMES the share of defense spending in 2054. Net interest is estimated to hit 6.3% of GDP while defense spending will be 2.3% of GDP by 2054. By comparison, since 1973 net interest costs have averaged just 2.1% of GDP, just one-third the 2054 amount. Meanwhile, nominal interest payments are projected to reach a MASSIVE $1.7 trillion in 2034, 2.6 times higher than the $658 billion recorded in 2024. The debt crisis is an understatement.' -TKL Milton Friedman said it best: “Keep your eye on how much the Government is spending, because that is the true tax. There is no such thing as an unbalanced budget. You PAY FOR IT either in the form of taxes or indirectly in the form of inflation or debt.” 🎁If you have made it this far I would like to give you a little gift: Great podcast, What Bitcoin Did, on Protecting Your Bitcoin with Jameson Lopp. They discuss: - Comprehensive Bitcoin security theory - Physical attacks & threat defense - Security implications of privacy vs obscurity - The future of Bitcoin security https://youtu.be/yCWJY8olZHU Credit: I have used multiple sources! My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: @Relai 🇨🇭 especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. (Please only use it till the 31st of October - after that full KYC) Hence a DCA, Dollar cost Average Strategy. Check out my tutorial post (Instagram) & video (YouTube) for more info.⠀⠀⠀ ⠀ Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀ ⠀⠀⠀⠀⠀⠀⠀ Do you think this post is helpful to you? If so, please share it and support my work with sats. Enjoy you week and see you next time! Felipe - Bitcoin Friday
@ 2a5d1247:0398ad01
2024-08-20 21:32:48# 🧠Quote(s) of the week: 'Bitcoin is for everyone. It’s for Democrats It’s for Republicans It’s for conservatives It’s for progressives It’s for every single person on this planet who wants to participate regardless of where they came from or what they believe.' - Dennis Porter "It doesn't matter if the existing system prints $2 trillion, $8 trillion, $50 trillion. It's just different pieces of paper. And Bitcoin measured against a piece of paper will look like it's going up. But all prices relative to Bitcoin are actually going down and will forever." -Jeff Booth ## 🧡Bitcoin news🧡  But the unlikely thing happened in late 2008: Bitcoin On the 13th of August: ➡️ Bitcoin is the 6th ranked monetary asset in the world. ➡️Although the following statement is from the 3rd of July nonetheless I want to share it with you. All 3,070 Four-year HODL periods of Bitcoin have been positive. The worst four-year HODL period was: December 16th, 2017 to December 15th, 2021 a 155% return, representing a 22.2% CAGR 99.7 percentile* CAGR of 26.4%. *periods above  What does that tell you? Think of Bitcoin from a long-term perspective, at least holding Bitcoin for four years. 'It’s like watching a super-long movie where the plot thickens and the suspense builds!' ➡️Bitcoin Miner Reserves Drop to 3-Year Low. The miner sell-off appears complete. ➡️Bitcoin exchange reserves have hit a five-year low. ➡️'Bitcoin's sustainable energy mix is 6% for the year (faster than any industry) Over the same period, Bitcoin price 128% I guess the rising Bitcoin price isn't boiling the oceans.' - Daniel Batten ➡️Metaplanet buys another ¥500 million worth of Bitcoin On the 14th of August: ➡️Norges Bank, the Central Bank of Norway, owns over 1.1 MILLION shares of MicroStrategy stock. ➡️Goldman Sachs bought $418m Bitcoin ETFs in the last quarter. Goldman Sach’s latest 13F filing discloses owning: - $238.6 million iShares Bitcoin Trust - $79.5 million Fidelity Bitcoin ETF - $35.1 million Grayscale BTC - $56.1 million Invesco Galaxy Bitcoin - $8.3 million Bitwise Bitcoin ETF - $749,469 WisdomTree Bitcoin - $299,900 ARK 21Shares Bitcoin ETF For a total of $418 million in Bitcoin ETFs ➡️The Swiss Central Bank owns 514 Bitcoin through buying 466.000 MSTR shares. ➡️Marathon bought 4,144 BTC for $249M and now HODLs over 25,000 Bitcoin. ➡️ 'State of Wisconsin Investment Board bought another $14m Bitcoin through BlackRock's ETF.' -Bitcoin Archive On the 15th of August: ➡️94% of the 21 million Bitcoin has now been mined. Only 6% left to be mined over the next 116 years!  foto credit: Wicked So global Bitcoin adoption is at ~0.10% and 94.00% of all coins have already been mined and you still think diminishing returns are likely? What happens when 99.9% of the world tries to buy the last 6.00% of Bitcoin? ➡️ Great rebuttal and excellent analysis by Daniel Batten: Rebuttal of New IMF report on Bitcoin mining emissions IMF report says "Carbon Emissions from AI and Crypto are surging" then goes on to a detailed report on how regulators should impose a "crypto carbon" tax. Rebuttal: Firstly, Bitcoin advocates everywhere should pause to reflect on the significance of this moment. With the scientific consensus (9 of the last 10 peer-reviewed articles) and mainstream journalism now concluding that Bitcoin mining has significant environmental benefits, those who stand to lose most from mainstream adoption of Bitcoin (IMF, Central Banks) need to resort to direct attack pieces. Here's a breakdown of why the IMF report is at best poorly researched, and at worst propaganda. https://x.com/DSBatten/status/1824129351371096516 It's helpful to have, the facts beyond the 'journalism' they offer. Please read the rebuttal. ➡️You can't make this up. The German Federal Office for Information Security shared a post on Linkedin calling hardware wallets the most secure way to store crypto-assets like Bitcoin. They also recommend creating backups and keeping them safe in multiple locations. "Schon gewusst? Der Bitcoin-Wert geht dieses Jahr über 100.000 Euro!" - Okay, someone is bullish! Didn't see this one coming. And why on earth did they, even though it's a different German government agency, sell 50.000 BTC below €100k/BTC, great logic! WAHNSINN!  ➡️Apple opens iPhone Payment Chip to Third Parties for the first time making Bitcoin "Tap to Pay" possible! ➡️The world’s 3rd-largest public pension fund, South Korea’s NPS, has bought $34M in MicroStrategy shares. ➡️'65% of Bitcoin has not moved in over a year. This metric peaked at nearly 71% last November.' -Bitcoin News On the 17th of August: ➡️Billionaire Peter Thiel tells Joe Rogan that Bitcoin is such a big deal that society does not know how to process and recognize it immediately, and it is on the same scale as the internet. ➡️I have said it before and I will say it again: For all the people on Twitter or other platforms, stop bootlicking politicians, stop larping. You can’t say “Don’t trust, verify” AND trust politicians or go full fangirl. RFKjr.: 'Join me for a fireside chat with Charles Hoskinson'. Ask yourself...why he gave that speech in Nashville at the Bitcoin Conference and now endorses this (Cardano). One answer: votes! ➡️'Bitcoin wallet dormant since 2014 moves nearly 175 BTC for the first time in over a decade. The funds, which were valued at $151,970 in 2014, are now worth $10.2 million.' - Bitcoin News ➡️'Marathon a leading publicly traded Bitcoin mining company, recently expanded its Bitcoin holdings with a $249 million purchase, bringing the total to over 25,000 Bitcoins, valued at approximately $1.5 billion. On August 12th, the company announced a $250 million convertible note offering, which was increased to $300 million due to strong demand. Marathon used $249 million of the proceeds to acquire 4,144 additional Bitcoin at an average price of $59,500 per coin.' -BTCTimes On the 18th of August: ➡️75% Of Bitcoin Hasn't Moved In Over 6 Months, Signaling Strong HODLing Trend ➡️ El Salvador mined 474 Bitcoin worth $29 million using volcano-fueled geothermal power. ➡️Welcome to the Lightning Network Bisq as Bisq v2.1 has been released! Highlights include: - Option to settle trades over the Lightning Network - Refined chat experience including emoji reactions - Know who's online with peer liveness indicators ## 💸Traditional Finance / Macro: On the 15th of August: 👉🏽No news 🏦Banks: 👉🏽No news ## 🌎Macro/Geopolitics: I want to start with this segment with the following quote and picture by James Lavish: 'With US Federal Debt powering right through $35 trillion and heading exponentially higher, we are at this phase of the fiat debt cycle.'  Now please connect the above quote with the following statement by Argentina President Javier Milei: “If printing money would end poverty, printing diplomas would end stupidity.” That is the best sentence I’ve heard lately! On the 13th of August: 👉🏽Walker Amerika: 'Trump just said “We would have no inflation” if not for Biden. This is false. I think it’s important to clarify that there *was* massive inflation during Trump’s administration. From January 2017 to January 2021, the M2 money supply increased from ~$13.3 trillion to ~$19.4 trillion by January 2021. That’s an INFLATION of ~$6.1 trillion, or ~45%. There is a LAG between monetary inflation and general price increases throughout the economy, and price increases do not happen uniformly (look up the Cantillon Effect). To clarify for the partisans out there: this is NOT an attempt to make excuses for Biden or to say that the monetary and fiscal policies under Biden are good; they are not good. The point is that it is false to say “there was no inflation” under Trump. Monetary inflation *is* inflation.' Spot on! It doesn't matter who is President inflation will run wild. Every President will have to spend more than the one before him, because of 30 to 50 years of bad policy. You better own Bitcoin. 👉🏽'The US government deficit hit a massive $1.5 trillion in the first 10 months of FY 2024, according to the Treasury Department. In July alone, the US deficit spending reached a whopping $244 billion. Total outlays came in at $5.6 trillion and total receipts were $5.6 trillion over the last 10 months. Social Security was the largest expenditure amounting to $1.2 trillion. Net interest was the second largest cost, exceeding health, Medicare, and national defense expenses. Government spending remains at crisis levels.' -TKL UNSUSTAINABLE 👉🏽 In the last couple of weeks I have been reading for the second time the book: 'The Sovereign Individual' The concept of the 'Rule of Law' is impossible nowadays. Globalization makes the 'Rule of Law' impossible. A study demonstrates that. '36% of multinational profits are shifted to tax havens every year. This reduces corporate tax revenue by >$200 billion (10% of global corporate tax receipts). Reallocation would increase domestic profits by 20% in high-tax EU countries, 10% in the US, and 5% in developing countries.' -Phillip Heimberger Source: https://gabriel-zucman.eu/files/TWZ2022Restud.pdf What is interesting about the article is that it is co-authored by a Danish minister of Finance and a UC Berkeley professor. Anyway, read the book 'The Sovereign Individual.' 👉🏽The 3 years' lowest excess of cash in the financial system. Remember what happened in 2018/2019? This is likely a good setup for increased liquidity. 'The Fed’s Reverse Repo (RRP) facility has dropped below $300 billion for the first time since 2021. The RRP is one of the financial system's excess liquidity metrics and is widely watched by investors. Large banks, government-sponsored enterprises, and money-market funds put their extra cash into the facility to earn interest on it. RRP usage has plummeted by $2.3 TRILLION since December 2022. Over the last several months, however, the decline has stabilized and the facility usage has been oscillating around $300-$400 billion.' -TKL 👉🏽The UK sees the worst 1 month job losses since the COVID crash UK unemployment is at 135K (forecast 14.5K, previous 32.3K) over 10x higher than expected. You don't say? Let's see what are the effects of unemployment. "We find a strong relationship between increases in unemployment and voting for nonmainstream parties, especially populist ones. Moreover, unemployment increases in tandem with declining trust toward national and European political institutions." [Source](https://www.brookings.edu/wp-content/uploads/2018/02/algantextfa17bpea.pdf) Who would have ever thought? Unemployment / left populism Inmigration / Right populism Now look at what is happening in Europe. Even the authors explore causality and find 'that crisis-driven economic insecurity is a substantial determine of populism and political distrust.'. ERGO: Economic stress leads to political extremism [](https://image.nostr.build/3902b94e3ff21d644e6eb80db0b60e37d57ba011c0b71573dfa59f32121835ba.png) On the 14th of August: 👉🏽[](https://image.nostr.build/3cb2355df80046af9e5af23ef2732a4c1ba26f990462f5db34b91354edf02220.jpg) As long as you remember China's emissions are for a large part due to the stuff we buy, the industry we outsourced there. The EU and UK would rather manufacture climate hysteria and green policies that restrict growth and drive up energy prices than create an attractive capital market and innovation for techno solutions. A lot of the manufacturing capacity needed to feed the EU consumers is located in China. I'd say Europeans are net importers regarding China, so if we measure by consumption, the proportions would likely be different. Territorial-based, China has slightly worse emissions than the EU. However, consumption-based, it's marginally better than the EU.  Now don't get me wrong. I do care about our climate & nature, but the truth without context is useless in discussing climate change and what we, the civilized people of the West (lmao), should do about it. For example, deindustrializing Europe, especially Germany as the engine of Europe, for climate change is like throwing tomato soup at the Mona Lisa or gluing yourself on a highway --pointless! Humanity always evolved forward by upgrading to more energy-dense, stable energy sources. It is the first time in history we actually regressed on that front, and maybe (personal opinion) it caused our climate issues. Tackling climate change is nearly impossible within a debt-driven, inflationary economy. It promotes consumption over saving, and short-term profit over sustainability, and hinders so-called 'green' investments. Fix the money, fix the world: Bitcoin. 👉🏽So last week I spoke about Thierry Breton (EU) and his terror on freedom of speech. Look what we have this week... AIACT [](https://image.nostr.build/5e89508a7286237ea0056ca014c93312843e55e4ee9dd41b85847151a1e4d973.jpg) EU Commissioner brags about having AI regulation when they don't have a SINGLE MAJOR AI COMPANY. Only a career bureaucrat could think of regulation as an achievement... It's like celebrating a traffic law in a town with no cars. Who elected people like Thierry...NOBODY! Yes, you could argue that it’s home (the EU) to ASML, the main supplier of NVDA. Without it, NVDA would not exist. So OK, maybe will have a few AI companies despite the regulation. But we won't be a leading sector. 👉🏽 Hackers have reportedly stolen the Social Security numbers of every American from National Public Data, according to the LA Times. Records for nearly 2.9 billion people were reportedly stolen. Most of the data was posted on an online marketplace. The group reportedly offered to sell the data on an online forum. The breach is expected to "power a raft of identity theft, fraud and other crimes." -TKL 👉🏽'Chinese Bank Loans fall for the first time in almost 20 years.' -Radar 'What This Means: - Bank Loans Decrease: When bank loans fall, it means businesses and individuals are borrowing less money from banks. This could be due to various reasons, like reduced demand for borrowing, tighter lending standards, or economic uncertainty. -Economic Implications: A decline in loans can signal a slowdown in economic activity. Loans are often used to fund business expansion, investments, and consumer spending. If these activities decline, it can slow down economic growth. This event could signal a potential slowdown in the Chinese economy, which might impact global markets, depending on how the situation evolves. Investors and market participants will closely watch this development to gauge its broader implications.' -Chat GPT 👉🏽"The S&P index is pretty much going up 7% per year for 100 years, and the U.S. dollar currency supply is going up 7% per year for 100 years. What you have is a basket of assets that are holding their value in real terms while they trend up in nominal terms.." —Michael Saylor [](https://image.nostr.build/95b645d5d046f17b75ef04d48d629d87bc6cef8307406a927fc4b336de9088df.jpg) Remember, inflation is caused by central bank money printing and the relentless expansion of the money supply, not ‘greedy corporations and price gouging’. Reagan: “We don't have inflation because the people are living too well. We have inflation because the government is living too well” 👉🏽 Just a rounding error: 'US job numbers have been revised lower by 778,000 jobs since February 2022, according to BlackRock. This year alone, non-farm payrolls were revised down by 279,000 from January to June. Furthermore, the US economy LOST 192,000 jobs in Q3 2023 and added 344,000 jobs in Q4 2023, according to the BED survey released by BLS. On the other hand, nonfarm payroll data showed that the US labor market added 663,000 and 577,000 new jobs in Q3 and Q4 2023. This is a jaw-dropping 1,088,000 difference in job count over just two quarters. The labor market is weaker than the headlines make it seem.' -TKL Now ask yourself how are they allowed to do this so blatantly. Why isn't the Media reporting on this? And they can't even get this straight why on earth do you believe that they have control & tell the truth on other topics.... Ask yourself. If overall inflation is up 6% and many things you buy way higher, what has gone down in price to bring the overall number down? [](https://image.nostr.build/3095ec0f6199e72c76802b3b33d3eb4c877fe4a9704bb6119ae51099142203ff.jpg) Fake Jobs Fake Inflation Fake GDP; Oh well, just a thought. On the 16th of August: 👉🏽The cooling towers of the last nuclear power plant in Germany were demolished today. This is what economic self-destruction looks like. They shut that clean energy down to turn up brown coal. That’s why Germany's emissions are 7X more than France's per KW/hr. I have the feeling that this will go down in history as one of the most insane, self-destructive, and stupid energy decisions made in the Western world. 👉🏽Gold hits 2500 for the first time in history ahead of Kamala's central planning unveil that will usher in even more runaway inflation. Fueled by lower Dollar and lower US Treasury yields year-to-date, Gold is up 20.7%, setting the stage for its strongest annual performance since 2020 when it gained 25.1%. 👉🏽Again the ECB is absolutely getting drilled on Twitter by Dr. Jan Wüstenfeld and obviously he gets the silent treatment. ECB: 'We’ve improved our environmental performance: Better carbon footprint reporting Increased biodiversity on our premises Enhanced emissions calculations Find out more, including how we’re reducing our operational footprint.' Dr. Jan Wüstenfeld's reaction: You can't effectively fight climate change in a debt-based, inflationary monetary system. The incentives are not aligned. You are part of the problem. 1) Inflation favours consumption over saving: As money loses value over time, people are encouraged to spend or invest rather than save. 2) Debt in an inflationary monetary system: Borrowing is attractive because future payments are easier, leading to more consumption, sometimes of unnecessary or unsustainable items. 3) Short-term focus: Continuous economic growth is needed at all costs, often pushing aside long-term sustainability. -> Companies prioritize short-term profits, leading to resource overuse and little focus on sustainability. 4) Climate impact: The push for growth leads to excessive resource use, worsening environmental damage, and climate change. -> Overconsumption Immediate profit focus often delays investment in sustainable technologies. -> Delayed green investment Fix the money, fix the world! Bitcoin! Please dear EBC you still only have one job. 'Inflationary money fuels wasteful behavior, wasteful behavior harms the environment.' On the 18th of August: 👉🏽How bad is the US Federal debt situation? 'Net interest costs on US Federal debt as a % of GDP are set to reach almost 3 TIMES the share of defense spending in 2054. Net interest is estimated to hit 6.3% of GDP while defense spending will be 2.3% of GDP by 2054. By comparison, since 1973 net interest costs have averaged just 2.1% of GDP, just one-third the 2054 amount. Meanwhile, nominal interest payments are projected to reach a MASSIVE $1.7 trillion in 2034, 2.6 times higher than the $658 billion recorded in 2024. The debt crisis is an understatement.' -TKL Milton Friedman said it best: “Keep your eye on how much the Government is spending, because that is the true tax. There is no such thing as an unbalanced budget. You PAY FOR IT either in the form of taxes or indirectly in the form of inflation or debt.” 🎁If you have made it this far I would like to give you a little gift: Great podcast, What Bitcoin Did, on Protecting Your Bitcoin with Jameson Lopp. They discuss: - Comprehensive Bitcoin security theory - Physical attacks & threat defense - Security implications of privacy vs obscurity - The future of Bitcoin security https://youtu.be/yCWJY8olZHU Credit: I have used multiple sources! My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: @Relai 🇨🇭 especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. (Please only use it till the 31st of October - after that full KYC) Hence a DCA, Dollar cost Average Strategy. Check out my tutorial post (Instagram) & video (YouTube) for more info.⠀⠀⠀ ⠀ Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀ ⠀⠀⠀⠀⠀⠀⠀ Do you think this post is helpful to you? If so, please share it and support my work with sats. Enjoy you week and see you next time! Felipe - Bitcoin Friday @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# "House" dos economistas e o Estado Falta um gênio pra produzir um seriado tipo House só que com economistas. O House do seriado seria um austríaco é o "everybody lies" seria uma premissa segundo a qual o Estado é sempre a causa de todos os problemas. Situações bem cabeludas poderiam ser apresentadas de maneira que parecesse muito que a causa era ganância ou o mau-caratismo dos agentes, mas na investigação quase sempre se descobriria que a causa era o Estado. Parece ridículo, mas se eu descrevesse House assim aqui também pareceria. A execução é que importa.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# "House" dos economistas e o Estado Falta um gênio pra produzir um seriado tipo House só que com economistas. O House do seriado seria um austríaco é o "everybody lies" seria uma premissa segundo a qual o Estado é sempre a causa de todos os problemas. Situações bem cabeludas poderiam ser apresentadas de maneira que parecesse muito que a causa era ganância ou o mau-caratismo dos agentes, mas na investigação quase sempre se descobriria que a causa era o Estado. Parece ridículo, mas se eu descrevesse House assim aqui também pareceria. A execução é que importa. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# notes on "Economic Action Beyond the Extent of the Market", Per Bylund Source: <https://www.youtube.com/watch?v=7St6pCipCB0> Markets work by dividing labour, but that's not as easy as it seems in the Adam Smith's example of a pin factory, because 1. a pin factory is not a market, so there is some guidance and orientation, some sort of central planning, inside there that a market doesn't have; 2. it is not clear how exactly the production process will be divided, it is not obvious as in "you cut the thread, I plug the head". Dividing the labour may produce efficiency, but it also makes each independent worker in the process more fragile, as they become dependent on the others. This is partially solved by having a lot of different workers, so you do not depend on only one. If you have many, however, they must agree on where one part of the production process starts and where it ends, otherwise one's outputs will not necessarily coincide with other's inputs, and everything is more-or-less broken. That means some level of standardization is needed. And indeed the market has constant incentives to standardization. The statist economist discourse about standardization is that only when the government comes with a law that creates some sort of standardization then economic development can flourish, but in fact the market creates standardization all the time. Some examples of standardization include: * programming languages, operating systems, internet protocols, CPU architectures; * plates, forks, knifes, glasses, tables, chairs, beds, mattresses, bathrooms; * building with concrete, brick and mortar; * money; * musical instruments; * light bulbs; * CD, DVD, VHS formats and others alike; * services that go into every production process, like lunch services, restaurants, bakeries, cleaning services, security services, secretaries, attendants, porters; * multipurpose steel bars; * practically any tool that normal people use and require a little experience to get going, like a drilling machine or a sanding machine; etc. Of course it is not that you find standardization in all places. Specially when the market is smaller or new, standardization may have not arrived. There remains the truth, however, that division of labour has the potential of doing good. More than that: every time there are more than one worker doing the same job in the same place of a division of labour chain, there's incentive to create a new subdivision of labour. From the fact that there are at least more than one person doing the same job as another in our society we must conclude that someone must come up with an insight about an efficient way to divide the labour between these workers (and probably actually implement it), that hasn't happened for all kinds of jobs. But to come up with division of labour outside of a factory, some market actors must come up with a way of dividing the labour, actually, determining where will one labour stop and other start (and that almost always needs some adjustments and in fact extra labour to hit the tips), and also these actors must bear the uncertainty and fragility that division of labour brings when there are not a lot of different workers and standardization and all that. In fact, when an entrepreneur comes with a radical new service to the market, a service that does not fit in the current standard of division of labour, he must explain to his potential buyers what is the service and how the buyer can benefit from it and what he will have to do to adapt its current production process to bear with that new service. That's has happened not long ago with * services that take food orders from the internet and relay these to the restaurants; * hostels for cheap accommodation for young travellers; * Uber, Airbnb, services that take orders and bring homemade food from homes to consumers and similars; * all kinds of software-as-a-service; * electronic monitoring service for power generators; * mining planning and mining planning software; and many other industry-specific services. ## See also * [Profits, not wages, as the originary factor](nostr:naddr1qqyrge3hxa3rqce4qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c7x67pu) * [Per Bylund's insight](nostr:naddr1qqyxvdtzxscxzcenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cuq3unj)
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# notes on "Economic Action Beyond the Extent of the Market", Per Bylund Source: <https://www.youtube.com/watch?v=7St6pCipCB0> Markets work by dividing labour, but that's not as easy as it seems in the Adam Smith's example of a pin factory, because 1. a pin factory is not a market, so there is some guidance and orientation, some sort of central planning, inside there that a market doesn't have; 2. it is not clear how exactly the production process will be divided, it is not obvious as in "you cut the thread, I plug the head". Dividing the labour may produce efficiency, but it also makes each independent worker in the process more fragile, as they become dependent on the others. This is partially solved by having a lot of different workers, so you do not depend on only one. If you have many, however, they must agree on where one part of the production process starts and where it ends, otherwise one's outputs will not necessarily coincide with other's inputs, and everything is more-or-less broken. That means some level of standardization is needed. And indeed the market has constant incentives to standardization. The statist economist discourse about standardization is that only when the government comes with a law that creates some sort of standardization then economic development can flourish, but in fact the market creates standardization all the time. Some examples of standardization include: * programming languages, operating systems, internet protocols, CPU architectures; * plates, forks, knifes, glasses, tables, chairs, beds, mattresses, bathrooms; * building with concrete, brick and mortar; * money; * musical instruments; * light bulbs; * CD, DVD, VHS formats and others alike; * services that go into every production process, like lunch services, restaurants, bakeries, cleaning services, security services, secretaries, attendants, porters; * multipurpose steel bars; * practically any tool that normal people use and require a little experience to get going, like a drilling machine or a sanding machine; etc. Of course it is not that you find standardization in all places. Specially when the market is smaller or new, standardization may have not arrived. There remains the truth, however, that division of labour has the potential of doing good. More than that: every time there are more than one worker doing the same job in the same place of a division of labour chain, there's incentive to create a new subdivision of labour. From the fact that there are at least more than one person doing the same job as another in our society we must conclude that someone must come up with an insight about an efficient way to divide the labour between these workers (and probably actually implement it), that hasn't happened for all kinds of jobs. But to come up with division of labour outside of a factory, some market actors must come up with a way of dividing the labour, actually, determining where will one labour stop and other start (and that almost always needs some adjustments and in fact extra labour to hit the tips), and also these actors must bear the uncertainty and fragility that division of labour brings when there are not a lot of different workers and standardization and all that. In fact, when an entrepreneur comes with a radical new service to the market, a service that does not fit in the current standard of division of labour, he must explain to his potential buyers what is the service and how the buyer can benefit from it and what he will have to do to adapt its current production process to bear with that new service. That's has happened not long ago with * services that take food orders from the internet and relay these to the restaurants; * hostels for cheap accommodation for young travellers; * Uber, Airbnb, services that take orders and bring homemade food from homes to consumers and similars; * all kinds of software-as-a-service; * electronic monitoring service for power generators; * mining planning and mining planning software; and many other industry-specific services. ## See also * [Profits, not wages, as the originary factor](nostr:naddr1qqyrge3hxa3rqce4qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c7x67pu) * [Per Bylund's insight](nostr:naddr1qqyxvdtzxscxzcenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cuq3unj) @ 20986fb8:cdac21b3
2024-08-20 14:19:59Welcome to YakiHonne, where we’re excited to introduce you to our innovative Smart Widgets! These interactive components allow you to create dynamic and engaging campaigns directly within social feeds, all without needing any coding skills. Whether you’re new to Smart Widgets or looking to refine your approach, this guide will walk you through the process. ### Step 1: Log In Start by logging into your YakiHonne account. This is your gateway to creating and managing Smart Widgets. If you don’t have an account yet, sign up easily on our website. ### Step 2: Create Smart Widgets Once you’re logged in, it’s time to get creative. Head over to the “Post” section and select “Smart Widget.” Here, you have two options: **Option 1: Create from Scratch** If you have a specific idea in mind, you can create your Smart Widget from a blank canvas: • Click on “Create Blank Widget.” • Begin designing by adding your unique content, interactive features, and any elements that match your campaign’s needs. • Customize the appearance and functionality to fit your brand or message. **Option 2: Choose a Template** If you’re not sure where to start or want some inspiration, using a template is a great option: • Select “Templates” from the options available. • Browse through a variety of pre-designed templates. • Choose one that fits your campaign’s goal, and customize it to make it your own. **Option 3: Clone a Community Widget** If you want to explore what others are doing, you can clone a widget shared by the community: • Click on “Smart Widgets” to see what the community has shared. • Browse through the community’s shared Smart Widgets. • Find a widget you like, and click “Clone.” • Modify the copied widget to create your unique Smart Widget.  ### Step 3: Explore Smart Widgets Features Your Smart Widgets can do much more than just display content. Let’s dive into the features you can integrate: • User Engagement Tools: Add polls, surveys, or quizzes to interact with your audience. • BitcoinFi Integration: Enable features that support Bitcoin transactions, like tipping or payment gateways. • Governance Options: Incorporate voting systems to allow users to participate in decision-making processes. • Product Growth: Use widgets to drive user growth through referral programs or viral marketing techniques.   These features are designed to enhance interaction and make your Smart Widget stand out. Feel free to experiment with different combinations to see what works best for your campaign. ### Step 4: Publish Your Smart Widgets After you’ve created and customized your Smart Widget, it’s time to share it with the world: • Preview your widget to ensure everything looks and works as intended. • Click “Post my Smart Widget” to publish it. • Your widget is now live and ready for others to interact with in their social feeds.  ### Step 5: Add Smart Widgets to Notes To maximize the impact of your Smart Widget, you can integrate it into your Notes: • Go to the “Notes” section on your dashboard. • Select “Add Smart Widget” and choose the widget you’ve just created. • Publish the note, and now your audience can engage with your Smart Widget directly through the note.  ### Tips for Success * Experiment with Features: Don’t hesitate to try out different combinations of features to find what works best for your audience. * Engage Your Audience: The more interactive and engaging your Smart Widget is, the better the results. * Monitor Performance: After publishing, keep an eye on how your Smart Widget is performing. Adjust and optimize based on user feedback and engagement metrics. ### User Guideline Video Resources [Create from Scratch](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) [Choose a Template](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) [Clone a Community Widget](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) [Full tutorial video ](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) ### Conclusion Creating and using Smart Widgets on YakiHonne is a powerful way to engage with your audience, promote your brand, and drive meaningful interactions. With no coding required, the possibilities are endless. Start exploring today, and see how Smart Widgets can take your campaigns to the next level! Happy creating!
@ 20986fb8:cdac21b3
2024-08-20 14:19:59Welcome to YakiHonne, where we’re excited to introduce you to our innovative Smart Widgets! These interactive components allow you to create dynamic and engaging campaigns directly within social feeds, all without needing any coding skills. Whether you’re new to Smart Widgets or looking to refine your approach, this guide will walk you through the process. ### Step 1: Log In Start by logging into your YakiHonne account. This is your gateway to creating and managing Smart Widgets. If you don’t have an account yet, sign up easily on our website. ### Step 2: Create Smart Widgets Once you’re logged in, it’s time to get creative. Head over to the “Post” section and select “Smart Widget.” Here, you have two options: **Option 1: Create from Scratch** If you have a specific idea in mind, you can create your Smart Widget from a blank canvas: • Click on “Create Blank Widget.” • Begin designing by adding your unique content, interactive features, and any elements that match your campaign’s needs. • Customize the appearance and functionality to fit your brand or message. **Option 2: Choose a Template** If you’re not sure where to start or want some inspiration, using a template is a great option: • Select “Templates” from the options available. • Browse through a variety of pre-designed templates. • Choose one that fits your campaign’s goal, and customize it to make it your own. **Option 3: Clone a Community Widget** If you want to explore what others are doing, you can clone a widget shared by the community: • Click on “Smart Widgets” to see what the community has shared. • Browse through the community’s shared Smart Widgets. • Find a widget you like, and click “Clone.” • Modify the copied widget to create your unique Smart Widget.  ### Step 3: Explore Smart Widgets Features Your Smart Widgets can do much more than just display content. Let’s dive into the features you can integrate: • User Engagement Tools: Add polls, surveys, or quizzes to interact with your audience. • BitcoinFi Integration: Enable features that support Bitcoin transactions, like tipping or payment gateways. • Governance Options: Incorporate voting systems to allow users to participate in decision-making processes. • Product Growth: Use widgets to drive user growth through referral programs or viral marketing techniques.   These features are designed to enhance interaction and make your Smart Widget stand out. Feel free to experiment with different combinations to see what works best for your campaign. ### Step 4: Publish Your Smart Widgets After you’ve created and customized your Smart Widget, it’s time to share it with the world: • Preview your widget to ensure everything looks and works as intended. • Click “Post my Smart Widget” to publish it. • Your widget is now live and ready for others to interact with in their social feeds.  ### Step 5: Add Smart Widgets to Notes To maximize the impact of your Smart Widget, you can integrate it into your Notes: • Go to the “Notes” section on your dashboard. • Select “Add Smart Widget” and choose the widget you’ve just created. • Publish the note, and now your audience can engage with your Smart Widget directly through the note.  ### Tips for Success * Experiment with Features: Don’t hesitate to try out different combinations of features to find what works best for your audience. * Engage Your Audience: The more interactive and engaging your Smart Widget is, the better the results. * Monitor Performance: After publishing, keep an eye on how your Smart Widget is performing. Adjust and optimize based on user feedback and engagement metrics. ### User Guideline Video Resources [Create from Scratch](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) [Choose a Template](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) [Clone a Community Widget](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) [Full tutorial video ](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) ### Conclusion Creating and using Smart Widgets on YakiHonne is a powerful way to engage with your audience, promote your brand, and drive meaningful interactions. With no coding required, the possibilities are endless. Start exploring today, and see how Smart Widgets can take your campaigns to the next level! Happy creating! @ 6bae33c8:607272e8
2024-08-19 23:42:07I posted my round by round draft targets yesterday, but have a few more thoughts that didn’t make it into that piece: I’m warming up to Bijan Robinson with a top-three pick. This interview with Kay Adams (even though it’s just the usual talk) got my attention. Robinson is so relaxed, so even-keeled and yet he’s studying Christian McCaffrey’s every carry like a fanatic. Not that it’s going out on a thin limb as he routinely goes that early, but I had previously been wedded to taking a receiver (now that McCaffrey already has a calf injury.) I said to Alan Seslowsky that Mike Williams was on my do-not-draft list because he’s so injury prone, but I double-checked and he hasn’t been that bad other than last year. Maybe I had him the year he did a lot early and then fell off steeply despite not missing many games. Maybe he was on the injury report a lot. I don’t know. But he’s actually not a bad value in Round 11 — he’s always been good when healthy, and the Jets are not deep. I said yesterday I don’t have a strong preference in the first round, and the Robinson note aside, that’s still mostly true. I like all the receivers, and I’m fine with Breece Hall and Jonathan Taylor too. Of course, that doesn’t mean all of them will be fine — at least a couple almost surely will not — only that I can’t tell which ones. As important as it is to know your leans and act on them, it’s equally important to realize when you don’t have one and let ADP and positional need dictate your options. I took Anthony Richardson in Beat Chris Liss 2, and while I don’t regret it as he really could be the QB1, I think the play in the Primetime will be to wait forever on QB and get some combo of Trevor Lawrence/Kurt Cousins/Justin Herbert/Matthew Stafford/Justin Fields, or even Daniel Jones. There’s just so much depth with upside. You could even take three QBs late. The “hero” RB build (where you take a star RB in Rounds 1 or 2) and lots of receivers around them, before getting your RB2 candidates later is popular now, and you can see why. There aren’t that many top backs, so getting one is a big edge, and then you still catch up at receiver against all the teams that took a TE or top QB early. I just think this is mostly an on-paper exercise, and by mid-season the best teams usually have 4-5 surviving good players at all positions combined and have to cobble it to together with short-term fill-ins and waiver wire, i.e., build is overrated. Both my drafts so far were from early (1 and 3), and I wouldn’t mind having one league from the back, getting Jonathan Taylor and say Puka Nacua. It would be cool to get Cooper Kupp in Round 3 too, but lately he’s moved up out of that range. I stacked C.J. Stroud and Stefon Diggs in BCL1, but didn’t stack anyone in BCL2. Stacking is one of those things that’s great if no one else is doing it, but loses value the more it’s done. If you have Travis Kelce and Patrick Mahomes, but so do 25 percent of the Mahomes’ owners, is that really better than having Anthony Richardson and a random TE1 (in my case Brock Bowers). Sure there’s no correlation, but only 1 in 12 Richardson teams should be expected to have Bowers (even fewer if the Colts had a good TE as many would have paired them.) So yes, if Mahomes goes off, there’s a better chance he takes Kelce with him, but you still have to beat out 3x more teams with your same set up than I do if Richardson goes off, and Bowers happens to as well. Sure, the correlation makes your scenario more likely, but likely enough to compensate for its commonality?
@ 6bae33c8:607272e8
2024-08-19 23:42:07I posted my round by round draft targets yesterday, but have a few more thoughts that didn’t make it into that piece: I’m warming up to Bijan Robinson with a top-three pick. This interview with Kay Adams (even though it’s just the usual talk) got my attention. Robinson is so relaxed, so even-keeled and yet he’s studying Christian McCaffrey’s every carry like a fanatic. Not that it’s going out on a thin limb as he routinely goes that early, but I had previously been wedded to taking a receiver (now that McCaffrey already has a calf injury.) I said to Alan Seslowsky that Mike Williams was on my do-not-draft list because he’s so injury prone, but I double-checked and he hasn’t been that bad other than last year. Maybe I had him the year he did a lot early and then fell off steeply despite not missing many games. Maybe he was on the injury report a lot. I don’t know. But he’s actually not a bad value in Round 11 — he’s always been good when healthy, and the Jets are not deep. I said yesterday I don’t have a strong preference in the first round, and the Robinson note aside, that’s still mostly true. I like all the receivers, and I’m fine with Breece Hall and Jonathan Taylor too. Of course, that doesn’t mean all of them will be fine — at least a couple almost surely will not — only that I can’t tell which ones. As important as it is to know your leans and act on them, it’s equally important to realize when you don’t have one and let ADP and positional need dictate your options. I took Anthony Richardson in Beat Chris Liss 2, and while I don’t regret it as he really could be the QB1, I think the play in the Primetime will be to wait forever on QB and get some combo of Trevor Lawrence/Kurt Cousins/Justin Herbert/Matthew Stafford/Justin Fields, or even Daniel Jones. There’s just so much depth with upside. You could even take three QBs late. The “hero” RB build (where you take a star RB in Rounds 1 or 2) and lots of receivers around them, before getting your RB2 candidates later is popular now, and you can see why. There aren’t that many top backs, so getting one is a big edge, and then you still catch up at receiver against all the teams that took a TE or top QB early. I just think this is mostly an on-paper exercise, and by mid-season the best teams usually have 4-5 surviving good players at all positions combined and have to cobble it to together with short-term fill-ins and waiver wire, i.e., build is overrated. Both my drafts so far were from early (1 and 3), and I wouldn’t mind having one league from the back, getting Jonathan Taylor and say Puka Nacua. It would be cool to get Cooper Kupp in Round 3 too, but lately he’s moved up out of that range. I stacked C.J. Stroud and Stefon Diggs in BCL1, but didn’t stack anyone in BCL2. Stacking is one of those things that’s great if no one else is doing it, but loses value the more it’s done. If you have Travis Kelce and Patrick Mahomes, but so do 25 percent of the Mahomes’ owners, is that really better than having Anthony Richardson and a random TE1 (in my case Brock Bowers). Sure there’s no correlation, but only 1 in 12 Richardson teams should be expected to have Bowers (even fewer if the Colts had a good TE as many would have paired them.) So yes, if Mahomes goes off, there’s a better chance he takes Kelce with him, but you still have to beat out 3x more teams with your same set up than I do if Richardson goes off, and Bowers happens to as well. Sure, the correlation makes your scenario more likely, but likely enough to compensate for its commonality? @ 8a3a9236:374b9419
2024-08-19 15:07:59## Details - ⏲️ Prep time: 10 min - 🍳 Cook time: 30 min - 🍽️ Servings: 2 (depends how hungry the bears are) ## Ingredients - 1 pound boneless chicken (thighs or breast) - 1 can Campbells Cream of Mushroom Soup - half a can of heavy cream - 6 ounces white rice - garlic powder - cayenne pepper - onion powder - salt & pepper ## Directions 1. Start by getting the rice going. 2. generously season chicken with salt and pepper 3. cook chicken 4. prepare sauce: mix cream of mushroom soup with heavy cream (i use 1/2 of the empty soup can to measure) 5. add generous portions of garlic powder and cayenne pepper. Add in some onion powder and salt and pepper as well. stir all these together on low/medium heat 6. once chicken is cooked, chop it up into tiny pieces. The chicken needs to be chopped up to give the sludge the proper consistency 7. add chicken to sludge (sauce) and stir so everything is well mixed. 8. finally, pour the chicken/sludge over the rice and mix all that together. ENJOY!
@ 8a3a9236:374b9419
2024-08-19 15:07:59## Details - ⏲️ Prep time: 10 min - 🍳 Cook time: 30 min - 🍽️ Servings: 2 (depends how hungry the bears are) ## Ingredients - 1 pound boneless chicken (thighs or breast) - 1 can Campbells Cream of Mushroom Soup - half a can of heavy cream - 6 ounces white rice - garlic powder - cayenne pepper - onion powder - salt & pepper ## Directions 1. Start by getting the rice going. 2. generously season chicken with salt and pepper 3. cook chicken 4. prepare sauce: mix cream of mushroom soup with heavy cream (i use 1/2 of the empty soup can to measure) 5. add generous portions of garlic powder and cayenne pepper. Add in some onion powder and salt and pepper as well. stir all these together on low/medium heat 6. once chicken is cooked, chop it up into tiny pieces. The chicken needs to be chopped up to give the sludge the proper consistency 7. add chicken to sludge (sauce) and stir so everything is well mixed. 8. finally, pour the chicken/sludge over the rice and mix all that together. ENJOY! @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# litepub A Go library that abstracts all the burdensome ActivityPub things and provides just the right amount of helpers necessary to integrate an existing website into the "fediverse" (what an odious name). Made for the [gravity]() integration. - <https://godoc.org/github.com/fiatjaf/litepub> ## See also -
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# litepub A Go library that abstracts all the burdensome ActivityPub things and provides just the right amount of helpers necessary to integrate an existing website into the "fediverse" (what an odious name). Made for the [gravity]() integration. - <https://godoc.org/github.com/fiatjaf/litepub> ## See also - @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Ripple and the problem of the decentralized commit This is about [Ryan Fugger's Ripple](nostr:naddr1qqyxgenyxe3rzvf4qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c8pp8zu). The summary is: unless everybody is good and well-connected at all times a transaction can always be left in a half-committed state, which creates confusion, erodes trust and benefits no one. If you're unconvinced consider the following protocol flow: 1. A finds a route (A--B--C--D) between her and D somehow; 2. A "prepares" a payment to B, tells B to do the same with C and so on (to prepare means to give B a conditional IOU that will be valid as long as the full payment completes); 3. When the chain of prepared messages reaches D, D somehow "commits" the payment. 4. After the commit, A now _really does_ owe B and so on, and D _really_ knows it has been effectively paid by A (in the form of debt from C) so it can ship goods to A. The most obvious (but wrong) way of structuring this would be for the entire payment chain to be dependent on the reveal of some secret. For example, the "prepare" messages could contain something like "I will pay you as long as you know `p` such that `sha256(p) == h`". The payment flow then starts with D presenting A with an invoice that contains `h`, so D knows `p`, but no one else knows. A can then send the "prepare" message to B and B do the same until it reaches D. When it reaches D, D can be sure that C will pay him because he knows `p` such that `sha256(p) == h`. He then reveals `p` to C, C now reveals it to B and B to A. When A gets it it has a proof that D has received his payment, therefore it is happy to settle it later with B and can prove to an external arbitrator that he has indeed paid D in case D doesn't deliver his products. ## Issues with the naïve flow above ### What if D never reveals `p` to C? Then no one knows what happened. And then 10 years later he arrives at C's house (remember they are friends or have a trust relationship somehow) and demands his payment, and shows `p` to her in a piece of paper. Or worse: go directly to the court and shows C's message that says "I will pay you as long as you know `p` such that `sha256(p) == h`" (but with an actual number instead of "h") and the corresponding `p`. Now the judge has to decide in favor of D. Now C was supposed to do the same with B, but C is not playing with this anymore, has lost all contact with B after they did their final settlement many years ago, no one was expecting this. This clearly can't work. There must be a timeout for these payments. ### What if we have a timeout? Now what if we say the payment expires in one hour. D cannot hold the payment hostage and reveal `p` after 10 years. It must either reveal it before the timeout or conditional IOU will be void. Solves everything! Except no, now it's the time we reach the most dark void of the protocol, the flaw that sucks its life into the abyss: subjectivity and ambiguity. The big issue is that we don't have an independent judge to assert, for example, that D has indeed "revealed" `p` to C in time. C must acknowledge that voluntarily. C could do it using messages over the internet, but these messages are not reliable. C is not reliable. Clocks are not synchronized. Also if we now require C to confirm it has received `p` from D then the "prepare" message means nothing, as for D now just knowing `p` is not enough to claim before an arbitrator that C owes her -- because, again, D also must prove it has shown `p` to C before the timeout, therefore it needs a new signed acknowledgement from C, or from some other party. Let's see a few examples. ### Subjectivity and perverse incentives D could send `p` to C, and C acknowledge it, but then when C goes to B and send it B will not acknowledge it, and claim it's past the time. Now C loses money. Maybe C can not acknowledge it received anything from D before checking first with B? But B will have to check with A too! And it subverts the entire flow of the thing. And now A has a "proof of payment" (knowledge of `p`) without even having to acknowledge anything! In this case knowing `p` or not becomes meaningless as everybody knows `p` without acknowleding it to anyone else. But even if A is honest and sends an "acknowledge" message to B, now B can just sit quiet and enjoy the credit it has just earned from A without ever acknowleding anything to C. It's perverted incentives in every step. ### Ambiguity But isn't this a protocol based on trust?, you ask, isn't C trusting that B will behave honestly already? Therefore if B is dishonest C just has to acknowledge his loss and break his chain of trust with B. No, because C will not know what happened. B can say "I could have sent you an acknowledgement, but was waiting for A, and A didn't send anything" and C won't ever know if that was true. Or B could say "what? You didn't send me `p` at all", and that could be true. B could have been offline when A sent it, there could have been a broken connection or many other things, and B continues: "I was waiting for you to present me with `p`, but you didn't, therefore the payment timed out, you can't come here with `p` now, because now A won't accept it anymore from me". That could be true or could be false, who knows? Therefore it is impossible for trust relationships and reputations to be maintained in such a system without "good fences".[^ln-solution][^ln-issue] [^ln-solution]: The [Lightning Network has a solution](nostr:naddr1qqyx2vekxg6rsvejqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ccs2twc) for the problem of the decentralized commit. [^ln-issue]: Ironically this same ambiguity problem [is being faced by the Lightning Network community](https://lists.linuxfoundation.org/pipermail/lightning-dev/2020-October/002826.html) when trying to create a reputation/payment system to prevent routing abuses. It seems simple when you first think about it: "let each node manage its own trust", but in fact it is somewhat impossible.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Ripple and the problem of the decentralized commit This is about [Ryan Fugger's Ripple](nostr:naddr1qqyxgenyxe3rzvf4qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c8pp8zu). The summary is: unless everybody is good and well-connected at all times a transaction can always be left in a half-committed state, which creates confusion, erodes trust and benefits no one. If you're unconvinced consider the following protocol flow: 1. A finds a route (A--B--C--D) between her and D somehow; 2. A "prepares" a payment to B, tells B to do the same with C and so on (to prepare means to give B a conditional IOU that will be valid as long as the full payment completes); 3. When the chain of prepared messages reaches D, D somehow "commits" the payment. 4. After the commit, A now _really does_ owe B and so on, and D _really_ knows it has been effectively paid by A (in the form of debt from C) so it can ship goods to A. The most obvious (but wrong) way of structuring this would be for the entire payment chain to be dependent on the reveal of some secret. For example, the "prepare" messages could contain something like "I will pay you as long as you know `p` such that `sha256(p) == h`". The payment flow then starts with D presenting A with an invoice that contains `h`, so D knows `p`, but no one else knows. A can then send the "prepare" message to B and B do the same until it reaches D. When it reaches D, D can be sure that C will pay him because he knows `p` such that `sha256(p) == h`. He then reveals `p` to C, C now reveals it to B and B to A. When A gets it it has a proof that D has received his payment, therefore it is happy to settle it later with B and can prove to an external arbitrator that he has indeed paid D in case D doesn't deliver his products. ## Issues with the naïve flow above ### What if D never reveals `p` to C? Then no one knows what happened. And then 10 years later he arrives at C's house (remember they are friends or have a trust relationship somehow) and demands his payment, and shows `p` to her in a piece of paper. Or worse: go directly to the court and shows C's message that says "I will pay you as long as you know `p` such that `sha256(p) == h`" (but with an actual number instead of "h") and the corresponding `p`. Now the judge has to decide in favor of D. Now C was supposed to do the same with B, but C is not playing with this anymore, has lost all contact with B after they did their final settlement many years ago, no one was expecting this. This clearly can't work. There must be a timeout for these payments. ### What if we have a timeout? Now what if we say the payment expires in one hour. D cannot hold the payment hostage and reveal `p` after 10 years. It must either reveal it before the timeout or conditional IOU will be void. Solves everything! Except no, now it's the time we reach the most dark void of the protocol, the flaw that sucks its life into the abyss: subjectivity and ambiguity. The big issue is that we don't have an independent judge to assert, for example, that D has indeed "revealed" `p` to C in time. C must acknowledge that voluntarily. C could do it using messages over the internet, but these messages are not reliable. C is not reliable. Clocks are not synchronized. Also if we now require C to confirm it has received `p` from D then the "prepare" message means nothing, as for D now just knowing `p` is not enough to claim before an arbitrator that C owes her -- because, again, D also must prove it has shown `p` to C before the timeout, therefore it needs a new signed acknowledgement from C, or from some other party. Let's see a few examples. ### Subjectivity and perverse incentives D could send `p` to C, and C acknowledge it, but then when C goes to B and send it B will not acknowledge it, and claim it's past the time. Now C loses money. Maybe C can not acknowledge it received anything from D before checking first with B? But B will have to check with A too! And it subverts the entire flow of the thing. And now A has a "proof of payment" (knowledge of `p`) without even having to acknowledge anything! In this case knowing `p` or not becomes meaningless as everybody knows `p` without acknowleding it to anyone else. But even if A is honest and sends an "acknowledge" message to B, now B can just sit quiet and enjoy the credit it has just earned from A without ever acknowleding anything to C. It's perverted incentives in every step. ### Ambiguity But isn't this a protocol based on trust?, you ask, isn't C trusting that B will behave honestly already? Therefore if B is dishonest C just has to acknowledge his loss and break his chain of trust with B. No, because C will not know what happened. B can say "I could have sent you an acknowledgement, but was waiting for A, and A didn't send anything" and C won't ever know if that was true. Or B could say "what? You didn't send me `p` at all", and that could be true. B could have been offline when A sent it, there could have been a broken connection or many other things, and B continues: "I was waiting for you to present me with `p`, but you didn't, therefore the payment timed out, you can't come here with `p` now, because now A won't accept it anymore from me". That could be true or could be false, who knows? Therefore it is impossible for trust relationships and reputations to be maintained in such a system without "good fences".[^ln-solution][^ln-issue] [^ln-solution]: The [Lightning Network has a solution](nostr:naddr1qqyx2vekxg6rsvejqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ccs2twc) for the problem of the decentralized commit. [^ln-issue]: Ironically this same ambiguity problem [is being faced by the Lightning Network community](https://lists.linuxfoundation.org/pipermail/lightning-dev/2020-October/002826.html) when trying to create a reputation/payment system to prevent routing abuses. It seems simple when you first think about it: "let each node manage its own trust", but in fact it is somewhat impossible. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Mises' interest rate theory Inspired by [Bob Murphy's thesis](http://consultingbyrpm.com/uploads/Dissertation.pdf) against the "pure time preference theory" (see also this [series of podcasts](https://www.bobmurphyshow.com/episodes/ep-31-capital-and-interest-in-the-austrian-tradition-part-3-of-3/)) -- or blatantly copying it -- here are some thoughts on Mises' most wrong take: * Mises asserts that the market rate of interest is _not_ the originary rate of interest, because the market rate involves entrepreneurial decisions, risk, uncertainty etc. No one lends money with 100% guarantee that it will be paid back in the market and so. But if that is true, where can we see that originary interest? We're supposed to account for its existence and be sure that it is logically there in every trade between present and future, because it's a _category of action_. But then it seems odd to me that it has anything to do with the actual interest. * Mises criticizes the notion of "profit" from classical economists because it mashed together gains deriving from speculation, risk, other stuff and originary interest -- but that's only because he assumes originary interest as a given (because it's a category of action and so on). If he didn't he could have just not cited originary interest in the list of things that give rise to "profit" and all would be fine. * Mixing the two points above, it seems very odd to think that we should look for interest as a component of profit. It seems indeed to be very classifical-economist take. It would be still compatible with Mises'sworldview -- indeed more compatible -- that we looked for profit as a component of interest: when someone lends some 100 and is paid 110 that is profit. Plain simple. Why he did that and why the other person paid isn't for the economist to analyse, or to dissect the extra 10 into 9 interest, 1 risk remuneration or anything like that. If the borrower hadn't paid it would be a 100 loss or a 109 loss? * In other moments, Mises talks about the originary rate of interest being the same for all things: apples and bicycles and anything else. But wasn't each person supposed to have its own valuation of each good -- including goods in the present and in the future? Is Mises going to say that it's impossible for someone to value an orange in the future more than a bycicle in the future in comparison with these same goods in the present? (The very "more" in the previous sentence shows us that Mises was incurring in cardinal value calculations when coming up with this theory -- and I hadn't noticed it until after I finished typing the phrase.) In other words: what if someone prefers orange, bycicle, bycicle in the future, orange in the future? That doesn't seem to fit. What is the rate of interest? * Also, on the point above, what if someone has different rates of interest for goods in different timeframes? For example, someone may prefer a bycicle now a little more than a bycicle tomorrow, but very very much more than a bycicle in two days. That also breaks the notion of "originary interest" as an universal rate. * Now maybe I misunderstood everything, maybe Mises was talking about originary interest as a rate defined by the market. And he clearly says that. That if the rate of interest is bigger on some market entrepreneurs will invest capital in that one until it equalizes with rates in other markets. But all that fits better with the plain notion of profit than with this poorly-crafted notion of originary interest. If you're up to defining and (Mises forbid?) measuring the neutral rate of interest you'll have to arbitrarily choose some businesses to be part of the "market" while excluding others. * By the way, wasn't originary interest a category of action? How can a category of action be defined and ultimately _fixed_ by entrepreneurial action in a market?
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Mises' interest rate theory Inspired by [Bob Murphy's thesis](http://consultingbyrpm.com/uploads/Dissertation.pdf) against the "pure time preference theory" (see also this [series of podcasts](https://www.bobmurphyshow.com/episodes/ep-31-capital-and-interest-in-the-austrian-tradition-part-3-of-3/)) -- or blatantly copying it -- here are some thoughts on Mises' most wrong take: * Mises asserts that the market rate of interest is _not_ the originary rate of interest, because the market rate involves entrepreneurial decisions, risk, uncertainty etc. No one lends money with 100% guarantee that it will be paid back in the market and so. But if that is true, where can we see that originary interest? We're supposed to account for its existence and be sure that it is logically there in every trade between present and future, because it's a _category of action_. But then it seems odd to me that it has anything to do with the actual interest. * Mises criticizes the notion of "profit" from classical economists because it mashed together gains deriving from speculation, risk, other stuff and originary interest -- but that's only because he assumes originary interest as a given (because it's a category of action and so on). If he didn't he could have just not cited originary interest in the list of things that give rise to "profit" and all would be fine. * Mixing the two points above, it seems very odd to think that we should look for interest as a component of profit. It seems indeed to be very classifical-economist take. It would be still compatible with Mises'sworldview -- indeed more compatible -- that we looked for profit as a component of interest: when someone lends some 100 and is paid 110 that is profit. Plain simple. Why he did that and why the other person paid isn't for the economist to analyse, or to dissect the extra 10 into 9 interest, 1 risk remuneration or anything like that. If the borrower hadn't paid it would be a 100 loss or a 109 loss? * In other moments, Mises talks about the originary rate of interest being the same for all things: apples and bicycles and anything else. But wasn't each person supposed to have its own valuation of each good -- including goods in the present and in the future? Is Mises going to say that it's impossible for someone to value an orange in the future more than a bycicle in the future in comparison with these same goods in the present? (The very "more" in the previous sentence shows us that Mises was incurring in cardinal value calculations when coming up with this theory -- and I hadn't noticed it until after I finished typing the phrase.) In other words: what if someone prefers orange, bycicle, bycicle in the future, orange in the future? That doesn't seem to fit. What is the rate of interest? * Also, on the point above, what if someone has different rates of interest for goods in different timeframes? For example, someone may prefer a bycicle now a little more than a bycicle tomorrow, but very very much more than a bycicle in two days. That also breaks the notion of "originary interest" as an universal rate. * Now maybe I misunderstood everything, maybe Mises was talking about originary interest as a rate defined by the market. And he clearly says that. That if the rate of interest is bigger on some market entrepreneurs will invest capital in that one until it equalizes with rates in other markets. But all that fits better with the plain notion of profit than with this poorly-crafted notion of originary interest. If you're up to defining and (Mises forbid?) measuring the neutral rate of interest you'll have to arbitrarily choose some businesses to be part of the "market" while excluding others. * By the way, wasn't originary interest a category of action? How can a category of action be defined and ultimately _fixed_ by entrepreneurial action in a market? @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Thafne venceu o Soletrando 2008. As palavras que Thafne teve que soletrar: "ocioso", "hermético", "glossário", "argênteo", "morfossintaxe", "infra-hepático", "hagiológio". Enquanto isso Eder recebia: "intramuscular", "destilação", "inabitável", "subcutâneo", "homogeneidade", "predecessor", "displicência", "subconsciência", "psicroestesia" (isto segundo [o site da folha][0], donde certamente faltam algumas palavras de Thafne). Sério, "argênteo"? Não é errado dizer que a Globo tentou promover o menino pobre da escola pública do sertão contra a riquinha de Curitiba. O mais espetacular disto é que deu errado e o Brasil inteiro torceu pela Thafne, o que se verifica com uma simples busca no Google. Eis aqui alguns exemplos: * [O problema de Thafne][1] traz comentários tentando incriminar o governo do Estado de Minas Gerais com a vitória forçada de Eder. * [este vídeo mostrando os erros do programa e a vitória triunfal, embora parcial, de Thafne,][2] traz a brilhante descrição "globo de puleira quis complicar a vida da menina!!!!!!!!!!!!!!!!!!!!!!" * [este vídeo, com o mesmo conteúdo,][3], porém chamado "Thafne versus Luciano Huck, o confronto do século", tem, além disto, vários comentários de francos torcedores de Thafne: * "Nossa isso é burrice porq o doutor falou duas vezes como o luciano não prestou atenção logo thafine deu duas patadas no luciano... Proxima luciano presta atenção na pronuncia" * "ele nao pronunciou errado porque é burro, isso foi pra manipular o resultado" * "Gabriel o Bostador ficou pianinho. Babaca do krl" * "Pena que ela perdeu :(" * "verdade... ela que ganhou, o outro só ficou com o título :S" * "A menina deu um banho nesse que além de idiota é BURRO." * e muitos, muitos outros. * [Globo Erra e Luciano Huck dá Vexame][4], um breve artigo descrevendo alguns dos pontos em que Eder foi favorecido. * [esta comunidade do Orkut][5], apenas a maior dentre várias que foram criadas. O movimento de apoio a Thafne é um exemplo entre poucos de união total da nação em prol de uma causa. [0]: <http://www1.folha.uol.com.br/ilustrada/2008/05/407470-aluno-de-escola-publica-de-minas-vence-soletrando-huck-da-vexame.shtml> [1]: <https://misenews.wordpress.com/2012/06/22/o-problema-de-thafne/> [2]: <https://www.youtube.com/watch?v=lNW_QAiptsY> [3]: <https://www.youtube.com/watch?v=Va8XxXgnY-c> [4]: <https://www.putsgrilo.com.br/televisao/soletrando-globo-erra-e-luciano-huck-da-vexame/> [5]: <http://orkut.google.com/c54999457.html>
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Thafne venceu o Soletrando 2008. As palavras que Thafne teve que soletrar: "ocioso", "hermético", "glossário", "argênteo", "morfossintaxe", "infra-hepático", "hagiológio". Enquanto isso Eder recebia: "intramuscular", "destilação", "inabitável", "subcutâneo", "homogeneidade", "predecessor", "displicência", "subconsciência", "psicroestesia" (isto segundo [o site da folha][0], donde certamente faltam algumas palavras de Thafne). Sério, "argênteo"? Não é errado dizer que a Globo tentou promover o menino pobre da escola pública do sertão contra a riquinha de Curitiba. O mais espetacular disto é que deu errado e o Brasil inteiro torceu pela Thafne, o que se verifica com uma simples busca no Google. Eis aqui alguns exemplos: * [O problema de Thafne][1] traz comentários tentando incriminar o governo do Estado de Minas Gerais com a vitória forçada de Eder. * [este vídeo mostrando os erros do programa e a vitória triunfal, embora parcial, de Thafne,][2] traz a brilhante descrição "globo de puleira quis complicar a vida da menina!!!!!!!!!!!!!!!!!!!!!!" * [este vídeo, com o mesmo conteúdo,][3], porém chamado "Thafne versus Luciano Huck, o confronto do século", tem, além disto, vários comentários de francos torcedores de Thafne: * "Nossa isso é burrice porq o doutor falou duas vezes como o luciano não prestou atenção logo thafine deu duas patadas no luciano... Proxima luciano presta atenção na pronuncia" * "ele nao pronunciou errado porque é burro, isso foi pra manipular o resultado" * "Gabriel o Bostador ficou pianinho. Babaca do krl" * "Pena que ela perdeu :(" * "verdade... ela que ganhou, o outro só ficou com o título :S" * "A menina deu um banho nesse que além de idiota é BURRO." * e muitos, muitos outros. * [Globo Erra e Luciano Huck dá Vexame][4], um breve artigo descrevendo alguns dos pontos em que Eder foi favorecido. * [esta comunidade do Orkut][5], apenas a maior dentre várias que foram criadas. O movimento de apoio a Thafne é um exemplo entre poucos de união total da nação em prol de uma causa. [0]: <http://www1.folha.uol.com.br/ilustrada/2008/05/407470-aluno-de-escola-publica-de-minas-vence-soletrando-huck-da-vexame.shtml> [1]: <https://misenews.wordpress.com/2012/06/22/o-problema-de-thafne/> [2]: <https://www.youtube.com/watch?v=lNW_QAiptsY> [3]: <https://www.youtube.com/watch?v=Va8XxXgnY-c> [4]: <https://www.putsgrilo.com.br/televisao/soletrando-globo-erra-e-luciano-huck-da-vexame/> [5]: <http://orkut.google.com/c54999457.html> @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Democracy as a failed open-network protocol In the context of protocols for peer-to-peer open computer networks -- those in which new actors can freely enter and immediately start participating in the protocol --, without any central entity, specially without any central human mind judging things from the top --, it's common for decisions about the protocol to be thought taking in consideration all the possible ways a rogue peer can disrupt the entire network, abuse it, make the experience terrible for others. The protocol design must account for all incentives in play and how they will affect each participant, always having in mind that each participant may be acting in a purely egoistical self-interested manner, not caring at all about the health of the network (even though most participants won't be like that). So a protocol, to be successful, must have incentives aligned such that self-interested actors cannot profit by hurting others and will gain most by cooperating (whatever that means in the envisaged context), or there must be a way for other peers to detect attacks and other kinds of harm or attempted harm and neutralize these. Since computers are very fast, protocols can be designed to be executed many times per day by peers involved, and since the internet is a very open place to which people of various natures are connected, many open-network protocols with varied goals have been tried in large scale and most of them failed and were shut down (or kept existing, but offering a bad experience and in a much more limited scope than they were expected to be). Often the failure of a protocol leads to knowledge about its shortcomings being more-or-less widespread and agreed upon, and these lead to the development of a better protocol the next time something with similar goals is tried. Ideally **democracies** are supposed to be an open-entry network in the same sense as these computer networks, and although that is a noble goal, it's one full of shortcomings. Democracies are supposed to the governing protocol of States that have the power to do basically anything with the lives of millions of citizens. One simple inference we may take from the history of computer peer-to-peer protocols is that the ones that work better are those that are simple and small in scope (**Bitcoin**, for example, is very simple; **BitTorrent** is also very simple and very limited in what it tries to do and the number of participants that get involved in each run of the protocol). Democracies, as we said above, are the opposite of that. Besides being in a very hard position to achieve success as an open protocol, democracies also suffer from the fact that they take a long time to run, so it's hard to see where it is failing every time. The fundamental incentives of democracy, i.e. the rules of the protocol, posed by the separation of powers and checks-and-balances are basically the same in every place and in every epoch since the XIII century, and even today most people who dedicate their lives to the subject still don't see how [they're completely flawed](nostr:naddr1qqyrzc3nvenxxdpkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cjc4mf0). The system of checks and balances was thought from the armchair of a couple of political theorists who had never done anything like that in their lives, didn't have any experience dealing with very adversarial environments like the internet -- and probably couldn't even imagine that the future users of their network were going to be creatures completely different than themselves and their fellow philosophers and aristocrats who all shared the same worldview (and how fast that future would come!). ## Also * [The illusion of checks and balances](nostr:naddr1qqyrzc3nvenxxdpkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cjc4mf0)
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Democracy as a failed open-network protocol In the context of protocols for peer-to-peer open computer networks -- those in which new actors can freely enter and immediately start participating in the protocol --, without any central entity, specially without any central human mind judging things from the top --, it's common for decisions about the protocol to be thought taking in consideration all the possible ways a rogue peer can disrupt the entire network, abuse it, make the experience terrible for others. The protocol design must account for all incentives in play and how they will affect each participant, always having in mind that each participant may be acting in a purely egoistical self-interested manner, not caring at all about the health of the network (even though most participants won't be like that). So a protocol, to be successful, must have incentives aligned such that self-interested actors cannot profit by hurting others and will gain most by cooperating (whatever that means in the envisaged context), or there must be a way for other peers to detect attacks and other kinds of harm or attempted harm and neutralize these. Since computers are very fast, protocols can be designed to be executed many times per day by peers involved, and since the internet is a very open place to which people of various natures are connected, many open-network protocols with varied goals have been tried in large scale and most of them failed and were shut down (or kept existing, but offering a bad experience and in a much more limited scope than they were expected to be). Often the failure of a protocol leads to knowledge about its shortcomings being more-or-less widespread and agreed upon, and these lead to the development of a better protocol the next time something with similar goals is tried. Ideally **democracies** are supposed to be an open-entry network in the same sense as these computer networks, and although that is a noble goal, it's one full of shortcomings. Democracies are supposed to the governing protocol of States that have the power to do basically anything with the lives of millions of citizens. One simple inference we may take from the history of computer peer-to-peer protocols is that the ones that work better are those that are simple and small in scope (**Bitcoin**, for example, is very simple; **BitTorrent** is also very simple and very limited in what it tries to do and the number of participants that get involved in each run of the protocol). Democracies, as we said above, are the opposite of that. Besides being in a very hard position to achieve success as an open protocol, democracies also suffer from the fact that they take a long time to run, so it's hard to see where it is failing every time. The fundamental incentives of democracy, i.e. the rules of the protocol, posed by the separation of powers and checks-and-balances are basically the same in every place and in every epoch since the XIII century, and even today most people who dedicate their lives to the subject still don't see how [they're completely flawed](nostr:naddr1qqyrzc3nvenxxdpkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cjc4mf0). The system of checks and balances was thought from the armchair of a couple of political theorists who had never done anything like that in their lives, didn't have any experience dealing with very adversarial environments like the internet -- and probably couldn't even imagine that the future users of their network were going to be creatures completely different than themselves and their fellow philosophers and aristocrats who all shared the same worldview (and how fast that future would come!). ## Also * [The illusion of checks and balances](nostr:naddr1qqyrzc3nvenxxdpkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cjc4mf0) @ ec09d831:42c80ce4
2024-08-21 17:27:14## Nostr Nedir? Nostr, “**N**otes and **O**ther **S**tuff **T**ransmitted by **R**elays” (Notlar ve Röle ile İletilen Diğer Şeyler) anlamına gelir. HTTP veya TCP-IP gibi, Nostr da bir “protokoldür”; herkesin üzerine bir şeyler inşa edebileceği açık bir standarttır. Nostr’ın kendisi kaydolduğunuz bir uygulama veya hizmet değildir. Nostr basitlik ve elverişlilik amacıyla tasarlanmıştır ve web üzerinde sansüre dirençli ve küresel olarak desentralize (dağıtık) yayıncılık ve iletişim imkânı sağlar. Bunu biraz açalım: ### Basitlik Protokol, çok basit ve esnek olan “Event” nesnelerine (bunlar düz JSON formatında aktarılır) dayanır ve anahtarlar ve imzalama için standart açık anahtarlı kriptografi (public-key cryptography) kullanır. Bu, röleleri çalıştırmayı ve istemciler oluşturmayı kolaylaştırır ve protokolün zaman içinde genişletilebilmesini sağlar. ### Esneklik Nostr, veri taşımak veya depolamak için tek bir yerde toplanmış az sayıdaki güvenilir sunucuya bağımlı olmadığından ötürü çok dayanıklıdır. Protokol, rölelerin kaybolacağını varsayar ve kullanıcıların zaman içinde değiştirebilecekleri rastgele sayıda röleye bağlanmasına ve yayın yapmasına olanak tanır. Bu esneklik gönderilerinizin üzerinde hiçbir kısıtlama ve sansür olmamasını da sağlar. Bir keresinde 15 bin harflik bir makaleyi bile görsel materyaller ve köprü linklerle süsleyerek paylaşabilmiştim. ### Doğrulanabilirlik Nostr hesapları açık anahtar kriptografisine dayandığından, mesajların gerçekten söz konusu kullanıcı tarafından gönderildiğini doğrulamak kolaydır. Bu sayede bot ve troll kalabalığı da yoktur ve küçük bir ihtimal de olsa Nostr'a gelirlerse bunları ortadan kaldırmak gayet kolaydır. ### Anahtarları Anlamak Her Nostr hesabı bir açık/özel anahtar (public/private key) çiftine dayanır. Bunu anlamanın basit bir yolu, açık anahtarınızın kullanıcı adınız ve özel anahtarınızın ise parolanız olduğunu düşünmektir. Parolaların aksine, özel anahtarınız kaybolduğunda sıfırlanamaz veya değiştirilemezlerdir. Anlaşılır olmak adına tekrar söyleyeyim: Özel anahtarınızı kaybederseniz Nostr hesabınız kaybolur. Başka bir kişi özel anahtarınıza erişim sağlarsa, hesabınızın kontrolünü ele geçirebilir. Özel anahtarınızı bir şifre yöneticisi (1Password’ü veya Brave Tarayıcı’yı öneririm) veya Alby gibi bir tarayıcı uzantısında güvenle sakladığınızdan emin olun. ### Protokol vs İstemci Nostr’un kendisi sadece bir protokoldür, yani mesajları ve yayınları internet üzerinde dolaştırmak için üzerinde anlaşılmış bir prosedürdür; Facebook, Twitter, Instagram, YouTube gibi sansürcü, merkeziyetçi, spam ve reklam dolu boktan bir “platform” değildir. Bu yüzden Nostr’a (protokole) bir istemci aracılığıyla erişmeniz gerekir. Bu istemciler web, masaüstü veya mobil uygulamalar şeklinde olabilir. Bazı Nostr istemcileri özel anahtarınızı yapıştırarak oturum açmanıza izin verir. Web’de bu genellikle önerilmez, zira rahatsız edici ve güvensizdir. Bunun yerine, tarayıcınızda özel anahtarları güvenli bir şekilde yönetmek ve Event’leri kriptografik olarak imzalamak için özel olarak tasarlanmış bir yazılım parçası olan bir imzalama uzantısı kullanmanızı öneririm. Bu konuda Alby, Nostr için yerleşik desteğe sahip popüler bir imzalama uzantısı ve Bitcoin Lightning Network cüzdanıdır. Yeni kullanıcılar için harika bir seçenektir. Alby’nin kurulumunu aşağıda gerekli olduğu yerlerde istemciye özel kılavuzda ele alacağım. İşte birkaç farklı istemci ve kullanılabildikleri işletim sistemleri: [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) (Android) [Benim favorim.] [Primal](https://primal.net/) (Web, iOS, Android) [Mobil cihazlarda yerleşik Bitcoin Lightning Network cüzdanı ile kullanıcı dostu istemci.] [Snort](https://snort.social/) (Web) [Temiz ve hızlı web istemcisi.] [Coracle](https://coracle.social/) (Web) [Röle navigasyonuna odaklanan bir istemci.] [Habla](https://habla.news/) (Web) [Kolay blog yaratımı.] [Highlighter](https://highlighter.com/) (Web) [Blog yaratımı ve bloglarda gezerken işaretleme-alıntılama için uygun arayüze sahip istemci.] [Iris](https://iris.to/) (Web) [Ücretsiz NIP-05 doğrulama sağlayan istemci.] [Damus](https://damus.io/) (iOS) [Apple cihazlarına özel aplikasyon istemci.] Amethyst Android istemcisi ile Nostr kullanmaya başlamak için adım adım kılavuz #### Adım 1: Uygulama yükleme * Android telefonların aplikasyon mağazası olan Google Play Store’dan Amethyst uygulamasını yükleyin: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst * Uygulamayı açtığınızda, yeni bir hesap oluşturma veya daha önce oluşturduğunuz bir özel anahtarla giriş yapma seçeneğiniz olacaktır. * Alby uzantısı veya başka bir istemci aracılığıyla zaten bir özel anahtar oluşturduysanız, kullanım koşullarını okuyup kabul edebilir, (npub/nsec) bilgilerinizi girebilir ve “Login” (Giriş Yap) düğmesine tıklayabilirsiniz. * Eğer bunlar yoksa, “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın. #### Adım 2: Yeni bir hesap oluşturma ve onun ayarlarını yapma * “Terms of Use” (Kullanım Koşulları) bölümünü okuyun ve kutuyu işaretleyin. * “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın. * Tebrikler, az önce yeni bir Nostr kimliği oluşturdunuz! * Ana ekrana yönlendirilecek ve “Feed is empty. Refresh” (Akış boş, yenileyin) mesajıyla karşılaşacaksınız, çünkü henüz başka bir hesabı takip etmiyorsunuz. Bunu daha sonra halledeceğiz. * Son bir aşırı önemli adım kaldı. Özel anahtarınızı güvenli bir yerde saklamalısınız. Bunu yapmak için, şu anda profil resminiz olarak görünen sol üst köşedeki garip görünümlü robot simgesine tıklayın. Bir kenar çubuğu açılacaktır. * “Backup Keys” (Yedek Anahtarlar) kısmına gidin ve “Copy my secret key” (Gizli anahtarımı kopyala) seçeneğine tıklayın. * “Nsec” ibaresiyle başlayan gizli anahtarınız artık akıllı telefonunuzun panosundadır, bunu ÇOK güvenli bir yerde veya bir .txt uzantılı belgede yapıştırıp saklamak en iyisidir. * Şimdi hesabınızı oluşturmaya devam edebilirsiniz. Ana ekranın sol üst köşesindeki profil resminize geri dönün ve “Profile” (Profil) bölümüne gidin. Buradan, “Follow” (Takip Et) seçeneğinin solundaki üç çizgi ve kalemin bulunduğu simgeye tıklayın. Profil ayarlarınızı buradan yapabilirsiniz. * “Display Name” (Görüntülenecek Ad) bölümüne yazacağınız şey nick’iniz olacaktır. * “About me” küçük bir biyografi bölümüdür ve harf sınırı yoktur. * “Avatar URL” ve “Banner URL” kutularının içinde, solda görsel yükleme simgeleri vardır. Burada profil resminiz ve banner’ınız hakkında ne yapabileceğinizi bilirsiniz. * “Nostr Address” ve “LN Address” kutuları için şöyle bir süreç işliyor: Eğer bir Alby hesabı edinebildiyseniz (şu an üye alımı sadece Alby geliştiricilerine getalby.com üzerinden yollanacak bir mektubun ardından gelebilecek davetiye kodu sayesinde mümkün) “@getalby.com” uzantılı adresinizi bu kutuların ikisini de yazmalısınızdır. Bu sayede hem hesabınızın size özgün ve gerçek olduğu (diğer bir deyişle, bot olmadığınız) anlaşılmış olur hem de gönderilerinize beğeni veya bağış maksatlı yollanan Bitcoin Satoshi’lerinin birikmesi için (ve sizin de başkalarına yollayabilmeniz, yani Zap yapabilmeniz için) bir Lightning Network sıcak cüzdanı adresi tesis etmiş olursunuz. Alby hesabı edinme konusunda -ki bence Alby çok önemli- yardımcı olmamı isterseniz iletişime geçmekten çekinmeyin. * Tamamdır, hesabınız artık hazır, şimdi akışınızı dolduralım ve diğer insanları takip edelim: Sağ üst köşedeki büyüteç simgeli arama butonuna tıklayın ve tanıdığınız kişilerin hesaplarını arayın ya da sol alttaki ev simgesine tıklayarak gideceğiniz ana ekrandaki “All Follows” butonuna tıklayın ve “Global”i seçin. Şimdi bağlı rölelerinize gönderilen tüm notları göreceksinizdir. Eğer bunalmış hissediyorsanız, endişelenmeyin, zamanla burada yeni birçok ilginç Nostr kullanıcısı bulabileceksinizdir. Sadece bir deneyin. #### Adım 3: Röleler ve Geniş Çaplı Erişim/Yayın Yeni röleler ekleyerek erişiminizi ve görünürlüğünüzü artırabilirsiniz. Bunun için yapmanız gereken aşağıda listeleyeceğim röleleri hesabınıza entegre etmektir. Röle entegrasyonu için öncelikle sol üstteki profil resminize tıkladığınızda açılan menüde “Relays” bölümüne giriyorsunuz. Burada, en aşağıda “Add Relay” yazan kutucuğa oluşturduğum listedeki röle adreslerini tek tek girip “Add” butonuna tıklıyorsunuz. İstediğiniz kadar röle ekleyebilirsiniz, tamamen size kalmış. Bu iş bitince mutlaka sağ üstteki “Save” butonuna tıklayın. Ayrıca kişisel bilgisayarınızdan Coracle adlı Nostr istemcisine girerek de rölelere kolaylıkla bağlanabilirsiniz. Tek yapmanız gereken Coracle’da Nostr hesabınıza Nsec anahtarınızla giriş yapmak ve sol kenar menüdeki “Relays” bölümünü açıp listelendiğini gördüğünüz her bir rölenin sağındaki “Join” butonuna tıklamaktır. Röle listesi: 140.f7z.io astral.ninja bevo.nostr1.com bitcoiner.social brb.io carnivore-diet-relay.denizenid.com eu.purplerelay.com expensive-relay.fiatjaf.com feeds.nostr.band/popular fiatjaf.com n.wingu.se nos.lol nostr-pub.semisol.dev nostr-relay.wlvs.space nostr.21l.st nostr.band nostr.bitcoiner.social nostr.blipme.app nostr.kollider.xyz nostr.liberty.fans nostr.mutinywallet.com nostr.orangepill.dev nostr.pleb.network nostr.plebchain.org nostr.relayer.se nostr.satoshi.fun nostr.walletofsatoshi.com nostr.yuv.al nostr.zbd.gg nostr.zebedee.cloud nostr.zerofiat.world nostr1.tunnelsats.com nostream.denizenid.com nostria.space offchain.pub purplepag.es pyramid.fiatjaf.com relay.0xchat.com relay.benthecarman.com relay.bitcoinpark.com relay.current.fyi relay.damus.io relay.f7z.io relay.geyser.fund relay.mutinywallet.com relay.nostr.band relay.nostr.bg relay.nostr.net relay.nostr3.io relay.nostrati.com relay.nostrplebs.com relay.orangepill.dev relay.plebstr.com relay.primal.net relay.snort.band relay.snort.social relay.utxo.one relayable.org relayer.fiatjaf.com satstacker.cloud snort.social soloco.nl sound-money-relay.denizenid.com  **Önemli:** Özel anahtarınız yerel olarak (mobil cihazınızda veya bilgisayarlarınızda) saklanır ve Amethyst sunucuları veya Snort, Iris, Primal, Coracle gibi diğer tüm Nostr istemcileri tarafından hiçbir şekilde toplanmaz veya saklanmaz, zira Nostr’ın olayı budur, yani desentralizasyon protokolü. Zamanla internetin kurtarıcısı olacak bu öze dönüş gücüne sahip sosyal ağda beni ve arkadaşlarımı takip etmeyi ve bizim takip ettiğimiz kişilerden kimleri bulabileceğinizi kurcalamayı unutmayın: Kaan: nostr:npub1asyasvv6vhkuk44ttczsz2v0xvp3c6ze9xqrg9n97n6mkskgpnjqmdugs9 Satoshi Nakamoto Enstitüsü Türkiye: nostr:npub1fdv8r32dqehlkxfnq3uld67vq8t46jw5jvzkk0h6rl4hyvd8g76qf7ujf6 Ludwig von Mises Enstitüsü Türkiye: nostr:npub1gfytsf2p5kw2c42032fkt845x8gh00e027nwnn3pr5880yy954qq4wqlqm Efe Bitcoin: nostr:npub193h05grv6ykgqc94memmlppqe2wlclukpfl8g5750w8gr3002zasl7ngwj Şükrü Day: nostr:npub1gw3zhc5r5a7jfgl6yx8qv0nc9kset5ddkrka229c3tym5xltehlq58m7mm Emir Yorulmaz: nostr:npub1mmfakwg4s36235wlav6qpe03cgr038gujn2hnsvwk2ne49gzqslqc6xvtp Hasan Tahsin: nostr:npub19zc3ja6jme9ul84sfmgyf5z96a07m6x9dp2jngl5zhwryku9aynsy89q3u Ufuk: nostr:npub19mz7c6jesdczvlumhpzqekqh9v93w0whup73mu3x2v6jv97lfujq79nqu3 Furkan Arda: nostr:npub1z43kexnw7wxd22ystexyhgf0s7lzsqzfaxv5xvlk9sgspkfzdyps039jv6 Kaancap: nostr:npub14t06hns8wmymynccmcer7sp6y3eql7pjyzwcp0u5rk88sv7vt2rqrl4wte Yankı Guapmann: nostr:npub19z5m92x8jlltva7zj47z9ydxle8ddkw8y3k5e8xnrphu724v9lys5wxt3p Arda Uludağ: nostr:npub1puclr9p6yhel2duzask9wfdah0ux5cppw22uz62c0w9cdj3nv0wseuvedh Musab Babayiğit: nostr:npub1euf7xgdws7n62nwv03fhu82ak24xrka7hedathyuyq9hmhcjxs7sfvwjsn Kadir: nostr:npub18589me8hqqmt5ect7hjz5k6d2srxzere0uc975gq7hldp9v3qpkslxjn7p Çınar: nostr:npub12mwsgqaejk98xcsv8k7rf3yat2t2kzu0zzma6jp39rphqx5hajsq4khdeg Nur Parrhesia: nostr:npub16nnuyfrxguumqdt8xerkkhtgjyxa7qyvfnz4r4ameanqp4aggarqm877qw Ömer Agâh: nostr:npub1eeze28u72zfa8hl8kfkfnl4jwfe07zsrukug237rsjre7wnvzlrsl49u8h Korporatist Mağduru: nostr:npub1337wmdvjtxrne5fxrqtc7re8rtj88wnnnsfg562jg39sx2k9p5lqwcjsfh Alfred: nostr:npub1mdyegp38ahjcpje7ugzmt4ylugrk3hfmwm9tqq72jhdg3ykc4ahs8svgs8 Sefa Uzuner: nostr:npub1ce0khypkfrjxga6umfd82fhtg9xldm583mys4pkvg8zex20gls9s9qrrgj 
@ ec09d831:42c80ce4
2024-08-21 17:27:14## Nostr Nedir? Nostr, “**N**otes and **O**ther **S**tuff **T**ransmitted by **R**elays” (Notlar ve Röle ile İletilen Diğer Şeyler) anlamına gelir. HTTP veya TCP-IP gibi, Nostr da bir “protokoldür”; herkesin üzerine bir şeyler inşa edebileceği açık bir standarttır. Nostr’ın kendisi kaydolduğunuz bir uygulama veya hizmet değildir. Nostr basitlik ve elverişlilik amacıyla tasarlanmıştır ve web üzerinde sansüre dirençli ve küresel olarak desentralize (dağıtık) yayıncılık ve iletişim imkânı sağlar. Bunu biraz açalım: ### Basitlik Protokol, çok basit ve esnek olan “Event” nesnelerine (bunlar düz JSON formatında aktarılır) dayanır ve anahtarlar ve imzalama için standart açık anahtarlı kriptografi (public-key cryptography) kullanır. Bu, röleleri çalıştırmayı ve istemciler oluşturmayı kolaylaştırır ve protokolün zaman içinde genişletilebilmesini sağlar. ### Esneklik Nostr, veri taşımak veya depolamak için tek bir yerde toplanmış az sayıdaki güvenilir sunucuya bağımlı olmadığından ötürü çok dayanıklıdır. Protokol, rölelerin kaybolacağını varsayar ve kullanıcıların zaman içinde değiştirebilecekleri rastgele sayıda röleye bağlanmasına ve yayın yapmasına olanak tanır. Bu esneklik gönderilerinizin üzerinde hiçbir kısıtlama ve sansür olmamasını da sağlar. Bir keresinde 15 bin harflik bir makaleyi bile görsel materyaller ve köprü linklerle süsleyerek paylaşabilmiştim. ### Doğrulanabilirlik Nostr hesapları açık anahtar kriptografisine dayandığından, mesajların gerçekten söz konusu kullanıcı tarafından gönderildiğini doğrulamak kolaydır. Bu sayede bot ve troll kalabalığı da yoktur ve küçük bir ihtimal de olsa Nostr'a gelirlerse bunları ortadan kaldırmak gayet kolaydır. ### Anahtarları Anlamak Her Nostr hesabı bir açık/özel anahtar (public/private key) çiftine dayanır. Bunu anlamanın basit bir yolu, açık anahtarınızın kullanıcı adınız ve özel anahtarınızın ise parolanız olduğunu düşünmektir. Parolaların aksine, özel anahtarınız kaybolduğunda sıfırlanamaz veya değiştirilemezlerdir. Anlaşılır olmak adına tekrar söyleyeyim: Özel anahtarınızı kaybederseniz Nostr hesabınız kaybolur. Başka bir kişi özel anahtarınıza erişim sağlarsa, hesabınızın kontrolünü ele geçirebilir. Özel anahtarınızı bir şifre yöneticisi (1Password’ü veya Brave Tarayıcı’yı öneririm) veya Alby gibi bir tarayıcı uzantısında güvenle sakladığınızdan emin olun. ### Protokol vs İstemci Nostr’un kendisi sadece bir protokoldür, yani mesajları ve yayınları internet üzerinde dolaştırmak için üzerinde anlaşılmış bir prosedürdür; Facebook, Twitter, Instagram, YouTube gibi sansürcü, merkeziyetçi, spam ve reklam dolu boktan bir “platform” değildir. Bu yüzden Nostr’a (protokole) bir istemci aracılığıyla erişmeniz gerekir. Bu istemciler web, masaüstü veya mobil uygulamalar şeklinde olabilir. Bazı Nostr istemcileri özel anahtarınızı yapıştırarak oturum açmanıza izin verir. Web’de bu genellikle önerilmez, zira rahatsız edici ve güvensizdir. Bunun yerine, tarayıcınızda özel anahtarları güvenli bir şekilde yönetmek ve Event’leri kriptografik olarak imzalamak için özel olarak tasarlanmış bir yazılım parçası olan bir imzalama uzantısı kullanmanızı öneririm. Bu konuda Alby, Nostr için yerleşik desteğe sahip popüler bir imzalama uzantısı ve Bitcoin Lightning Network cüzdanıdır. Yeni kullanıcılar için harika bir seçenektir. Alby’nin kurulumunu aşağıda gerekli olduğu yerlerde istemciye özel kılavuzda ele alacağım. İşte birkaç farklı istemci ve kullanılabildikleri işletim sistemleri: [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) (Android) [Benim favorim.] [Primal](https://primal.net/) (Web, iOS, Android) [Mobil cihazlarda yerleşik Bitcoin Lightning Network cüzdanı ile kullanıcı dostu istemci.] [Snort](https://snort.social/) (Web) [Temiz ve hızlı web istemcisi.] [Coracle](https://coracle.social/) (Web) [Röle navigasyonuna odaklanan bir istemci.] [Habla](https://habla.news/) (Web) [Kolay blog yaratımı.] [Highlighter](https://highlighter.com/) (Web) [Blog yaratımı ve bloglarda gezerken işaretleme-alıntılama için uygun arayüze sahip istemci.] [Iris](https://iris.to/) (Web) [Ücretsiz NIP-05 doğrulama sağlayan istemci.] [Damus](https://damus.io/) (iOS) [Apple cihazlarına özel aplikasyon istemci.] Amethyst Android istemcisi ile Nostr kullanmaya başlamak için adım adım kılavuz #### Adım 1: Uygulama yükleme * Android telefonların aplikasyon mağazası olan Google Play Store’dan Amethyst uygulamasını yükleyin: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst * Uygulamayı açtığınızda, yeni bir hesap oluşturma veya daha önce oluşturduğunuz bir özel anahtarla giriş yapma seçeneğiniz olacaktır. * Alby uzantısı veya başka bir istemci aracılığıyla zaten bir özel anahtar oluşturduysanız, kullanım koşullarını okuyup kabul edebilir, (npub/nsec) bilgilerinizi girebilir ve “Login” (Giriş Yap) düğmesine tıklayabilirsiniz. * Eğer bunlar yoksa, “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın. #### Adım 2: Yeni bir hesap oluşturma ve onun ayarlarını yapma * “Terms of Use” (Kullanım Koşulları) bölümünü okuyun ve kutuyu işaretleyin. * “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın. * Tebrikler, az önce yeni bir Nostr kimliği oluşturdunuz! * Ana ekrana yönlendirilecek ve “Feed is empty. Refresh” (Akış boş, yenileyin) mesajıyla karşılaşacaksınız, çünkü henüz başka bir hesabı takip etmiyorsunuz. Bunu daha sonra halledeceğiz. * Son bir aşırı önemli adım kaldı. Özel anahtarınızı güvenli bir yerde saklamalısınız. Bunu yapmak için, şu anda profil resminiz olarak görünen sol üst köşedeki garip görünümlü robot simgesine tıklayın. Bir kenar çubuğu açılacaktır. * “Backup Keys” (Yedek Anahtarlar) kısmına gidin ve “Copy my secret key” (Gizli anahtarımı kopyala) seçeneğine tıklayın. * “Nsec” ibaresiyle başlayan gizli anahtarınız artık akıllı telefonunuzun panosundadır, bunu ÇOK güvenli bir yerde veya bir .txt uzantılı belgede yapıştırıp saklamak en iyisidir. * Şimdi hesabınızı oluşturmaya devam edebilirsiniz. Ana ekranın sol üst köşesindeki profil resminize geri dönün ve “Profile” (Profil) bölümüne gidin. Buradan, “Follow” (Takip Et) seçeneğinin solundaki üç çizgi ve kalemin bulunduğu simgeye tıklayın. Profil ayarlarınızı buradan yapabilirsiniz. * “Display Name” (Görüntülenecek Ad) bölümüne yazacağınız şey nick’iniz olacaktır. * “About me” küçük bir biyografi bölümüdür ve harf sınırı yoktur. * “Avatar URL” ve “Banner URL” kutularının içinde, solda görsel yükleme simgeleri vardır. Burada profil resminiz ve banner’ınız hakkında ne yapabileceğinizi bilirsiniz. * “Nostr Address” ve “LN Address” kutuları için şöyle bir süreç işliyor: Eğer bir Alby hesabı edinebildiyseniz (şu an üye alımı sadece Alby geliştiricilerine getalby.com üzerinden yollanacak bir mektubun ardından gelebilecek davetiye kodu sayesinde mümkün) “@getalby.com” uzantılı adresinizi bu kutuların ikisini de yazmalısınızdır. Bu sayede hem hesabınızın size özgün ve gerçek olduğu (diğer bir deyişle, bot olmadığınız) anlaşılmış olur hem de gönderilerinize beğeni veya bağış maksatlı yollanan Bitcoin Satoshi’lerinin birikmesi için (ve sizin de başkalarına yollayabilmeniz, yani Zap yapabilmeniz için) bir Lightning Network sıcak cüzdanı adresi tesis etmiş olursunuz. Alby hesabı edinme konusunda -ki bence Alby çok önemli- yardımcı olmamı isterseniz iletişime geçmekten çekinmeyin. * Tamamdır, hesabınız artık hazır, şimdi akışınızı dolduralım ve diğer insanları takip edelim: Sağ üst köşedeki büyüteç simgeli arama butonuna tıklayın ve tanıdığınız kişilerin hesaplarını arayın ya da sol alttaki ev simgesine tıklayarak gideceğiniz ana ekrandaki “All Follows” butonuna tıklayın ve “Global”i seçin. Şimdi bağlı rölelerinize gönderilen tüm notları göreceksinizdir. Eğer bunalmış hissediyorsanız, endişelenmeyin, zamanla burada yeni birçok ilginç Nostr kullanıcısı bulabileceksinizdir. Sadece bir deneyin. #### Adım 3: Röleler ve Geniş Çaplı Erişim/Yayın Yeni röleler ekleyerek erişiminizi ve görünürlüğünüzü artırabilirsiniz. Bunun için yapmanız gereken aşağıda listeleyeceğim röleleri hesabınıza entegre etmektir. Röle entegrasyonu için öncelikle sol üstteki profil resminize tıkladığınızda açılan menüde “Relays” bölümüne giriyorsunuz. Burada, en aşağıda “Add Relay” yazan kutucuğa oluşturduğum listedeki röle adreslerini tek tek girip “Add” butonuna tıklıyorsunuz. İstediğiniz kadar röle ekleyebilirsiniz, tamamen size kalmış. Bu iş bitince mutlaka sağ üstteki “Save” butonuna tıklayın. Ayrıca kişisel bilgisayarınızdan Coracle adlı Nostr istemcisine girerek de rölelere kolaylıkla bağlanabilirsiniz. Tek yapmanız gereken Coracle’da Nostr hesabınıza Nsec anahtarınızla giriş yapmak ve sol kenar menüdeki “Relays” bölümünü açıp listelendiğini gördüğünüz her bir rölenin sağındaki “Join” butonuna tıklamaktır. Röle listesi: 140.f7z.io astral.ninja bevo.nostr1.com bitcoiner.social brb.io carnivore-diet-relay.denizenid.com eu.purplerelay.com expensive-relay.fiatjaf.com feeds.nostr.band/popular fiatjaf.com n.wingu.se nos.lol nostr-pub.semisol.dev nostr-relay.wlvs.space nostr.21l.st nostr.band nostr.bitcoiner.social nostr.blipme.app nostr.kollider.xyz nostr.liberty.fans nostr.mutinywallet.com nostr.orangepill.dev nostr.pleb.network nostr.plebchain.org nostr.relayer.se nostr.satoshi.fun nostr.walletofsatoshi.com nostr.yuv.al nostr.zbd.gg nostr.zebedee.cloud nostr.zerofiat.world nostr1.tunnelsats.com nostream.denizenid.com nostria.space offchain.pub purplepag.es pyramid.fiatjaf.com relay.0xchat.com relay.benthecarman.com relay.bitcoinpark.com relay.current.fyi relay.damus.io relay.f7z.io relay.geyser.fund relay.mutinywallet.com relay.nostr.band relay.nostr.bg relay.nostr.net relay.nostr3.io relay.nostrati.com relay.nostrplebs.com relay.orangepill.dev relay.plebstr.com relay.primal.net relay.snort.band relay.snort.social relay.utxo.one relayable.org relayer.fiatjaf.com satstacker.cloud snort.social soloco.nl sound-money-relay.denizenid.com  **Önemli:** Özel anahtarınız yerel olarak (mobil cihazınızda veya bilgisayarlarınızda) saklanır ve Amethyst sunucuları veya Snort, Iris, Primal, Coracle gibi diğer tüm Nostr istemcileri tarafından hiçbir şekilde toplanmaz veya saklanmaz, zira Nostr’ın olayı budur, yani desentralizasyon protokolü. Zamanla internetin kurtarıcısı olacak bu öze dönüş gücüne sahip sosyal ağda beni ve arkadaşlarımı takip etmeyi ve bizim takip ettiğimiz kişilerden kimleri bulabileceğinizi kurcalamayı unutmayın: Kaan: nostr:npub1asyasvv6vhkuk44ttczsz2v0xvp3c6ze9xqrg9n97n6mkskgpnjqmdugs9 Satoshi Nakamoto Enstitüsü Türkiye: nostr:npub1fdv8r32dqehlkxfnq3uld67vq8t46jw5jvzkk0h6rl4hyvd8g76qf7ujf6 Ludwig von Mises Enstitüsü Türkiye: nostr:npub1gfytsf2p5kw2c42032fkt845x8gh00e027nwnn3pr5880yy954qq4wqlqm Efe Bitcoin: nostr:npub193h05grv6ykgqc94memmlppqe2wlclukpfl8g5750w8gr3002zasl7ngwj Şükrü Day: nostr:npub1gw3zhc5r5a7jfgl6yx8qv0nc9kset5ddkrka229c3tym5xltehlq58m7mm Emir Yorulmaz: nostr:npub1mmfakwg4s36235wlav6qpe03cgr038gujn2hnsvwk2ne49gzqslqc6xvtp Hasan Tahsin: nostr:npub19zc3ja6jme9ul84sfmgyf5z96a07m6x9dp2jngl5zhwryku9aynsy89q3u Ufuk: nostr:npub19mz7c6jesdczvlumhpzqekqh9v93w0whup73mu3x2v6jv97lfujq79nqu3 Furkan Arda: nostr:npub1z43kexnw7wxd22ystexyhgf0s7lzsqzfaxv5xvlk9sgspkfzdyps039jv6 Kaancap: nostr:npub14t06hns8wmymynccmcer7sp6y3eql7pjyzwcp0u5rk88sv7vt2rqrl4wte Yankı Guapmann: nostr:npub19z5m92x8jlltva7zj47z9ydxle8ddkw8y3k5e8xnrphu724v9lys5wxt3p Arda Uludağ: nostr:npub1puclr9p6yhel2duzask9wfdah0ux5cppw22uz62c0w9cdj3nv0wseuvedh Musab Babayiğit: nostr:npub1euf7xgdws7n62nwv03fhu82ak24xrka7hedathyuyq9hmhcjxs7sfvwjsn Kadir: nostr:npub18589me8hqqmt5ect7hjz5k6d2srxzere0uc975gq7hldp9v3qpkslxjn7p Çınar: nostr:npub12mwsgqaejk98xcsv8k7rf3yat2t2kzu0zzma6jp39rphqx5hajsq4khdeg Nur Parrhesia: nostr:npub16nnuyfrxguumqdt8xerkkhtgjyxa7qyvfnz4r4ameanqp4aggarqm877qw Ömer Agâh: nostr:npub1eeze28u72zfa8hl8kfkfnl4jwfe07zsrukug237rsjre7wnvzlrsl49u8h Korporatist Mağduru: nostr:npub1337wmdvjtxrne5fxrqtc7re8rtj88wnnnsfg562jg39sx2k9p5lqwcjsfh Alfred: nostr:npub1mdyegp38ahjcpje7ugzmt4ylugrk3hfmwm9tqq72jhdg3ykc4ahs8svgs8 Sefa Uzuner: nostr:npub1ce0khypkfrjxga6umfd82fhtg9xldm583mys4pkvg8zex20gls9s9qrrgj  @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Bolo It seems that from 1987 to around 2000 there was a big community of people who played this game called ["Bolo"][wikipedia]. It was a game in which people controlled a tank and killed others while trying to capture bases in team matches. Always 2 teams, from 2 to 16 total players, games could last from 10 minutes to 12 hours. I'm still trying to understand all this. The game looks silly from some [videos][videos] you can find today, but apparently it was very deep in strategy because people developed [strategy][strategy-guide] [guides][pillbox-guide] and [wrote][letter-1] [extensively][letter-2] about it and [Netscape even supported `bolo:` URLs][clickable-links] out of the box. > The two most important elements on the map are pillboxes and bases. Pillboxes are originally neutral, meaning that they shoot at every tank that happens to get in its range. They shoot fast and with deadly accuracy. You can shoot the pillbox with your tank, and you can see how damaged it is by looking at it. Once the pillbox is subdued, you may run over it, which will pick it up. You may place the pillbox where you want to put it (where it is clear), if you've enough trees to build it back up. > Trees are harvested by sending your man outside your tank to forest the trees. Your man (also called a builder) can also lay mines, build roads, and build walls. Once you have placed a pillbox, it will not shoot at you, but only your enemies. Therefore, pillboxes are often used to protect your bases. That quote was taken from this ["augmented FAQ"][augmented-faq] written by some user. Apparently there were many FAQs for this game. A FAQ is after all just a simple, clear and direct to the point way of writing about anything, previously known as [summa][summa][^summa-k], it doesn't have to be related to any actually frequently asked question. More unexpected Bolo writings include [an etiquette guide][etiquette], an [anthropology study][anthropology] and [some wonderings on the reverse pill war tactic][reverse-pill]. [videos]: https://www.youtube.com/results?search_query=winbolo [wikipedia]: https://en.wikipedia.org/wiki/Bolo_(1987_video_game) [clickable-links]: http://web.archive.org/web/19980214020327/http://boloweb.stanford.edu/BoloWeb.html [faq]: https://web.archive.org/web/20070518233700/http://bishop.mc.duke.edu/bolo/guides/stuartfaq.html [letter-1]: http://web.archive.org/web/19961214060949/http://rost.abo.fi/~gpappas/Bolo/News/mikael-bl.html [letter-2]: http://web.archive.org/web/19961214060959/http://rost.abo.fi/~gpappas/Bolo/News/mikael-kev.html [strategy-guide]: http://web.archive.org/web/19961214052754/http://rost.abo.fi/~gpappas/Bolo/guide.html [etiquette]: http://web.archive.org/web/19961214052805/http://rost.abo.fi/~gpappas/Bolo/etiquette.html [pillbox-guide]: http://web.archive.org/web/19961214052818/http://rost.abo.fi/~gpappas/Bolo/PBguide/pbguide1.html [anthropology]: http://web.archive.org/web/19961214052830/http://rost.abo.fi/~gpappas/Bolo/anthropology.html [reverse-pill]: http://web.archive.org/web/19990428023004/http://powered.cs.yale.edu:8000/%7Ebayliss/bolo.html [augmented-faq]: http://web.archive.org/web/19970118071637/http://rost.abo.fi/~gpappas/Bolo/faq.html [summa]: https://en.wikipedia.org/wiki/Summa [^summa-k]: It's not the same thing, but I couldn't help but notice the similarity.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Bolo It seems that from 1987 to around 2000 there was a big community of people who played this game called ["Bolo"][wikipedia]. It was a game in which people controlled a tank and killed others while trying to capture bases in team matches. Always 2 teams, from 2 to 16 total players, games could last from 10 minutes to 12 hours. I'm still trying to understand all this. The game looks silly from some [videos][videos] you can find today, but apparently it was very deep in strategy because people developed [strategy][strategy-guide] [guides][pillbox-guide] and [wrote][letter-1] [extensively][letter-2] about it and [Netscape even supported `bolo:` URLs][clickable-links] out of the box. > The two most important elements on the map are pillboxes and bases. Pillboxes are originally neutral, meaning that they shoot at every tank that happens to get in its range. They shoot fast and with deadly accuracy. You can shoot the pillbox with your tank, and you can see how damaged it is by looking at it. Once the pillbox is subdued, you may run over it, which will pick it up. You may place the pillbox where you want to put it (where it is clear), if you've enough trees to build it back up. > Trees are harvested by sending your man outside your tank to forest the trees. Your man (also called a builder) can also lay mines, build roads, and build walls. Once you have placed a pillbox, it will not shoot at you, but only your enemies. Therefore, pillboxes are often used to protect your bases. That quote was taken from this ["augmented FAQ"][augmented-faq] written by some user. Apparently there were many FAQs for this game. A FAQ is after all just a simple, clear and direct to the point way of writing about anything, previously known as [summa][summa][^summa-k], it doesn't have to be related to any actually frequently asked question. More unexpected Bolo writings include [an etiquette guide][etiquette], an [anthropology study][anthropology] and [some wonderings on the reverse pill war tactic][reverse-pill]. [videos]: https://www.youtube.com/results?search_query=winbolo [wikipedia]: https://en.wikipedia.org/wiki/Bolo_(1987_video_game) [clickable-links]: http://web.archive.org/web/19980214020327/http://boloweb.stanford.edu/BoloWeb.html [faq]: https://web.archive.org/web/20070518233700/http://bishop.mc.duke.edu/bolo/guides/stuartfaq.html [letter-1]: http://web.archive.org/web/19961214060949/http://rost.abo.fi/~gpappas/Bolo/News/mikael-bl.html [letter-2]: http://web.archive.org/web/19961214060959/http://rost.abo.fi/~gpappas/Bolo/News/mikael-kev.html [strategy-guide]: http://web.archive.org/web/19961214052754/http://rost.abo.fi/~gpappas/Bolo/guide.html [etiquette]: http://web.archive.org/web/19961214052805/http://rost.abo.fi/~gpappas/Bolo/etiquette.html [pillbox-guide]: http://web.archive.org/web/19961214052818/http://rost.abo.fi/~gpappas/Bolo/PBguide/pbguide1.html [anthropology]: http://web.archive.org/web/19961214052830/http://rost.abo.fi/~gpappas/Bolo/anthropology.html [reverse-pill]: http://web.archive.org/web/19990428023004/http://powered.cs.yale.edu:8000/%7Ebayliss/bolo.html [augmented-faq]: http://web.archive.org/web/19970118071637/http://rost.abo.fi/~gpappas/Bolo/faq.html [summa]: https://en.wikipedia.org/wiki/Summa [^summa-k]: It's not the same thing, but I couldn't help but notice the similarity. @ b0510a0c:12716ced
2024-08-21 06:03:43# On April 24, 2012, Erik Voorhees changed everything about Bitcoin with the launch of Satoshi Dice: a game that captivated users and intensified debates about Bitcoin's evolution and the network's ability to handle an increasing volume of transactions. At that time, Satoshi Dice allowed thousands of players to bet on digital dice rolls, leading to a **MASSIVE** influx of transactions that filled the blocks of the blockchain.  ## 📈 Success of Satoshi Dice: Satoshi Dice achieved phenomenal success, attracting millions of users with its simplicity. Players flocked in, bets piled up, and blocks filled up.  Erik Voorhees effectively leveraged Bitcoin's microtransactions, quickly saturating the blocks with these. This was a testament to the game's popularity, but also a source of tension within the community. Within months, Satoshi Dice became the most popular service on the Bitcoin network, boosting its usage and virality. Players appreciated the "provable fairness" aspect of the game, where they could verify the transparency and fairness of each bet. ## 🚫 Criticism and Controversy: However, this success was not without criticism. Many Bitcoin enthusiasts viewed the massive influx of transactions generated by the game unfavorably. For them, these sometimes trivial transactions "spammed" the blockchain, clogging the blocks and increasing transaction fees for all users. Does this sound familiar? The network, designed to handle about seven transactions per second, quickly reached its maximum capacity, causing validation delays and "high" fees.  ## ⚔️ BlockSize Wars: The BlockSize wars, which took place mainly between 2016 and 2017, were a technical and ideological conflict centered on block size and scalability solutions. While Satoshi Dice was not the sole cause, the game significantly contributed to the emergence of this event by helping to popularize Bitcoin among new users and generating substantial transaction volume. As Bitcoin adoption grew, the network faced intense pressure, leading to block saturation and rising transaction fees. On one side, some advocated for increasing block size to allow more transactions, leading to the creation of Bitcoin Cash in August 2017. On the other, proponents of solutions like SegWit pushed for improvements without compromising decentralization. ## 🔧 Adoption of SegWit: Erik Voorhees expressed his support for the SegWit2x proposal, which aimed to improve network scalability by combining the implementation of SegWit with an increase in block size. Segregated Witness (SegWit) was adopted in August 2017, allowing transaction data to be separated from signatures. This reorganization not only increased transaction processing capacity but also paved the way for the development of the Lightning Network, a layer 2 solution enabling instant and low-cost transactions. SegWit was a crucial response to the challenges posed by network congestion, which had been exacerbated by Bitcoin's growing adoption and the emergence of popular applications like Satoshi Dice. ## ⚡ SegWit and Lightning: The adoption of SegWit helped resolve blockchain congestion issues, while the Lightning Network, a layer 2 solution, facilitated fast and low-cost transactions. Together, these innovations not only addressed technical challenges but also renewed enthusiasm for games and other applications on Bitcoin, paving the way for a new wave of development.  ## 🎲 Nostr Dice: Today, as we reflect on the impact of Satoshi Dice, a new project emerges: nostr:npub1nstrdc6z4y9xadyj4z2zfecu6zt05uvlmd08ea0vchcvfrjvv7yq8lns84 This modern clone of the original game is built on Nostr, a decentralized communication protocol, and Lightning, paying homage to the past while offering an enhanced gaming experience that does not impact layer 1 congestion! From a game that caused Bitcoin congestion to its rebirth on Lightning, which it helped to bring about, the circle is complete! 
@ b0510a0c:12716ced
2024-08-21 06:03:43# On April 24, 2012, Erik Voorhees changed everything about Bitcoin with the launch of Satoshi Dice: a game that captivated users and intensified debates about Bitcoin's evolution and the network's ability to handle an increasing volume of transactions. At that time, Satoshi Dice allowed thousands of players to bet on digital dice rolls, leading to a **MASSIVE** influx of transactions that filled the blocks of the blockchain.  ## 📈 Success of Satoshi Dice: Satoshi Dice achieved phenomenal success, attracting millions of users with its simplicity. Players flocked in, bets piled up, and blocks filled up.  Erik Voorhees effectively leveraged Bitcoin's microtransactions, quickly saturating the blocks with these. This was a testament to the game's popularity, but also a source of tension within the community. Within months, Satoshi Dice became the most popular service on the Bitcoin network, boosting its usage and virality. Players appreciated the "provable fairness" aspect of the game, where they could verify the transparency and fairness of each bet. ## 🚫 Criticism and Controversy: However, this success was not without criticism. Many Bitcoin enthusiasts viewed the massive influx of transactions generated by the game unfavorably. For them, these sometimes trivial transactions "spammed" the blockchain, clogging the blocks and increasing transaction fees for all users. Does this sound familiar? The network, designed to handle about seven transactions per second, quickly reached its maximum capacity, causing validation delays and "high" fees.  ## ⚔️ BlockSize Wars: The BlockSize wars, which took place mainly between 2016 and 2017, were a technical and ideological conflict centered on block size and scalability solutions. While Satoshi Dice was not the sole cause, the game significantly contributed to the emergence of this event by helping to popularize Bitcoin among new users and generating substantial transaction volume. As Bitcoin adoption grew, the network faced intense pressure, leading to block saturation and rising transaction fees. On one side, some advocated for increasing block size to allow more transactions, leading to the creation of Bitcoin Cash in August 2017. On the other, proponents of solutions like SegWit pushed for improvements without compromising decentralization. ## 🔧 Adoption of SegWit: Erik Voorhees expressed his support for the SegWit2x proposal, which aimed to improve network scalability by combining the implementation of SegWit with an increase in block size. Segregated Witness (SegWit) was adopted in August 2017, allowing transaction data to be separated from signatures. This reorganization not only increased transaction processing capacity but also paved the way for the development of the Lightning Network, a layer 2 solution enabling instant and low-cost transactions. SegWit was a crucial response to the challenges posed by network congestion, which had been exacerbated by Bitcoin's growing adoption and the emergence of popular applications like Satoshi Dice. ## ⚡ SegWit and Lightning: The adoption of SegWit helped resolve blockchain congestion issues, while the Lightning Network, a layer 2 solution, facilitated fast and low-cost transactions. Together, these innovations not only addressed technical challenges but also renewed enthusiasm for games and other applications on Bitcoin, paving the way for a new wave of development.  ## 🎲 Nostr Dice: Today, as we reflect on the impact of Satoshi Dice, a new project emerges: nostr:npub1nstrdc6z4y9xadyj4z2zfecu6zt05uvlmd08ea0vchcvfrjvv7yq8lns84 This modern clone of the original game is built on Nostr, a decentralized communication protocol, and Lightning, paying homage to the past while offering an enhanced gaming experience that does not impact layer 1 congestion! From a game that caused Bitcoin congestion to its rebirth on Lightning, which it helped to bring about, the circle is complete!  @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Lagoa Santa: como chegar -- partindo da rodoviária de Belo Horizonte Ao descer de seu ônibus na rodoviária de Belo Horizonte às 4 e pouco da manhã, darás de frente para um caubói que toma cerveja em seus trajes típicos em um bar no setor mesmo de desembarque. Suba a escada à direita que dá no estacionamento da rodoviária. Vire à esquerda e caminhe por mais ou menos 400 metros, atravessando uma área onde pessoas suspeitas -- mas provavelmente dormindo em pé -- lhe observam, e então uma pracinha ocupada por um clã de mendigos. Ao avistar um enorme obelisco no meio de um cruzamento de duas avenidas, vire à esquerda e caminhe por mais 400 metros. Você verá uma enorme, antiga e bela estação com uma praça em frente, com belas fontes aqüáticas. Corra dali e dirija-se a um pedaço de rua à direita dessa praça. Um velho palco de antigos carnavais estará colocado mais ou menos no meio da simpática ruazinha de parelepípedos: é onde você pegará seu próximo ônibus. Para entrar na estação é necessário ter um cartão com créditos recarregáveis. Um viajante prudente deixa sempre um pouco de créditos em seu cartão a fim de evitar filas e outros problemas de indisponibilidade quando chega cansado de viagem, com pressa ou em horários incomuns. Esse tipo de pessoa perceberá que foi totalmente ludibriado ao perceber que que os créditos do seu cartão, abastecido quando de sua última vinda a Belo Horizonte, há três meses, pereceram de prazo de validade e foram absorvidos pelos cofre públicos. Terá, portanto, que comprar mais créditos. O guichê onde os cartões são abastecidos abre às 5h, mas não se espante caso ele não tenha sido aberto ainda quando o primeiro ônibus chegar, às 5h10. Com alguma sorte, um jovem de moletom, autorizado por dois ou três fiscais do sistema de ônibus que conversam alegremente, será o operador da catraca. Ele deixa entrar sem pagar os bêbados, os malandros, os pivetes. Bastante empático e perceptivo do desespero dos outros, esse bom rapaz provavelmente também lhe deixará entrar sem pagar. Uma vez dentro do ônibus, não se intimide com os gritalhões e valentões que, ofendidíssimos com o motorista por ele ter parado nas estações, depois dos ônibus anteriores terem ignorado esses excelsos passageiros que nelas aguardavam, vão aos berros tirar satisfação. O ponto final do ônibus, 40 minutos depois, é o terminal Morro Alto. Lá você verá, se procurar bem entre vários ônibus e pessoas que despertam a sua mais honesta suspeita, um veículo escuro, apagado, numerado **5882** e que abrigará em seu interior um motorista e um cobrador que descansam o sono dos justos. Aguarde na porta por mais uns vinte minutos até que, repentinamente desperto, o motorista ligue o ônibus, abra as portas e já comece, de leve, a arrancar. Entre correndo, mas espere mais um tempo, enquanto as pessoas que têm o cartão carregado passem e peguem os melhores lugares, até que o cobrador acorde e resolva te cobrar a passagem nesse velho meio de pagamento, outrora o mais líqüído, o dinheiro. Este último ônibus deverá levar-lhe, enfim, a Lagoa Santa.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Lagoa Santa: como chegar -- partindo da rodoviária de Belo Horizonte Ao descer de seu ônibus na rodoviária de Belo Horizonte às 4 e pouco da manhã, darás de frente para um caubói que toma cerveja em seus trajes típicos em um bar no setor mesmo de desembarque. Suba a escada à direita que dá no estacionamento da rodoviária. Vire à esquerda e caminhe por mais ou menos 400 metros, atravessando uma área onde pessoas suspeitas -- mas provavelmente dormindo em pé -- lhe observam, e então uma pracinha ocupada por um clã de mendigos. Ao avistar um enorme obelisco no meio de um cruzamento de duas avenidas, vire à esquerda e caminhe por mais 400 metros. Você verá uma enorme, antiga e bela estação com uma praça em frente, com belas fontes aqüáticas. Corra dali e dirija-se a um pedaço de rua à direita dessa praça. Um velho palco de antigos carnavais estará colocado mais ou menos no meio da simpática ruazinha de parelepípedos: é onde você pegará seu próximo ônibus. Para entrar na estação é necessário ter um cartão com créditos recarregáveis. Um viajante prudente deixa sempre um pouco de créditos em seu cartão a fim de evitar filas e outros problemas de indisponibilidade quando chega cansado de viagem, com pressa ou em horários incomuns. Esse tipo de pessoa perceberá que foi totalmente ludibriado ao perceber que que os créditos do seu cartão, abastecido quando de sua última vinda a Belo Horizonte, há três meses, pereceram de prazo de validade e foram absorvidos pelos cofre públicos. Terá, portanto, que comprar mais créditos. O guichê onde os cartões são abastecidos abre às 5h, mas não se espante caso ele não tenha sido aberto ainda quando o primeiro ônibus chegar, às 5h10. Com alguma sorte, um jovem de moletom, autorizado por dois ou três fiscais do sistema de ônibus que conversam alegremente, será o operador da catraca. Ele deixa entrar sem pagar os bêbados, os malandros, os pivetes. Bastante empático e perceptivo do desespero dos outros, esse bom rapaz provavelmente também lhe deixará entrar sem pagar. Uma vez dentro do ônibus, não se intimide com os gritalhões e valentões que, ofendidíssimos com o motorista por ele ter parado nas estações, depois dos ônibus anteriores terem ignorado esses excelsos passageiros que nelas aguardavam, vão aos berros tirar satisfação. O ponto final do ônibus, 40 minutos depois, é o terminal Morro Alto. Lá você verá, se procurar bem entre vários ônibus e pessoas que despertam a sua mais honesta suspeita, um veículo escuro, apagado, numerado **5882** e que abrigará em seu interior um motorista e um cobrador que descansam o sono dos justos. Aguarde na porta por mais uns vinte minutos até que, repentinamente desperto, o motorista ligue o ônibus, abra as portas e já comece, de leve, a arrancar. Entre correndo, mas espere mais um tempo, enquanto as pessoas que têm o cartão carregado passem e peguem os melhores lugares, até que o cobrador acorde e resolva te cobrar a passagem nesse velho meio de pagamento, outrora o mais líqüído, o dinheiro. Este último ônibus deverá levar-lhe, enfim, a Lagoa Santa. @ 3c827db6:66418fc3
2024-08-17 02:50:05Somebody, somewhere, at some point decided they would destroy the competition by creating a barrier to entry. They made the barrier high so they could feel safe. It is logical to put a fence around your property, and perfectly fine to do so. The problem is when you put a regulatory fence over something that means you are not allowing anyone else to have a property like this. Just to make the distinction clearer a fence around your house is creating a cost for other people to get in the yard. A license to be able to have a fence is creating a cost for anyone to protect their yard. The harder to attain and costlier the license is the more people can’t afford it. The more people who can’t afford it the bigger the divide between rich and poor. You can't have a fence because you can't have a license leaving your yard unprotected. The poor people are left unprotected and they get robbed easily, the rich are hard to get so they keep what they have. The more licenses/regulatory compliance someone has to comply with the more the costs for them are increased and the cycle of dividing is entrenched. When constructing something physical, regulatory oversight is sensible to ensure structural integrity, particularly when people no longer build things for themselves. However, when it comes to more abstract concepts like licenses and credentials, possessing them doesn't guarantee success, and lacking them doesn't preclude doing excellent work. The whole point of the series is that the work should speak for itself and the people who did it should build their reputation based on their work history not on theory. Let’s dive into a sector full of licenses for abstract things that keep people out and cornered the market. The betting industry. The incentive structure in this scenario is problematic. Individuals with substantial financial resources that were gained illegally may seek friendly relationships with those responsible for issuing licenses. Obtaining a betting license now can serve as a means to launder money acquired unlawfully. Beyond mere laundering, they have a direct incentive to continue their illegal activities and a way to legitimize the funds. So they steal from the people who work and it gets even worse. Their scaling solution is to open the money laundering to other illegal actors. A few parts of the economy are primed for these types of activities: the lottery, casinos, and sports betting. Let’s start with the current lottery system and the “potential” exploits. Well, one person does something illegal and has stolen $1,000,000. Now he has a problem with how to legitimize the funds so he can spend it on things he wants. He goes to the owner of a lottery and says I will give you $200,000 if you give me an $800,000 winning ticket. Now 80% of the funds become legal. The person with the illegal funds buys $200,000 worth of tickets from which 1 of them is set up to win $800,000. Now all the funds have become legal. So the lottery company has a $200,000 income and $800,000 payout, seemingly paying out the winner with legitimate funds, but in reality, using the criminal's own money - correction, other people's stolen money. That is good for hiding taxes and the state is not getting anything, or is it? The state gets its cut for every winning ticket by taxing all winners. Because of this income, they are incentivized to have more winners. This whole “hypothetical” system then is limited by how much money has to be laundered. More illegal money, more income for each side - the state, the illegal player, the lottery company. While they get the big winning tickets the public is left with the small prizes and they are robbed continuously for the next lottery "prizes". This tripod system demonstrates how one simple thing can be a continuous erosion of society. The lottery company does nothing to earn their money but they are incentivizing the illegal actors to continue doing illegal things. The State allowing licenses keeps competition out. The illegal actor closes the circle of his business. The lottery should be something that is played without anyone having an advantage over anyone else. Including the company, there shouldn’t be a barrier for people creating all sorts of lottery games. The same model of behavior incentives is applicable for all the casinos. There is the same principle - some type of algorithm determines whether you win or not. But you can always approach the casino owner and apply the same logic to the casino. A player with illegal funds has to launder a million dollars again. In the first few hands, he wins a million dollars and keeps playing until incurs losses amounting to $200,000 and then stops. This way the casino loses $800,000 on its balance sheet but in reality, the illegal funds are distributed to the casino and the illegal actor. In the sports betting industry, the barrier to entry is often determined by licenses, and companies typically act as custodians of the funds when users place bets. Additionally, these companies are responsible for providing betting odds, a task that incurs substantial costs when done accurately. Assessing various factors such as team performance, player injuries, and changes in management helps determine the odds. However, it's crucial to note that the odds provided by betting companies are designed to favor the company rather than the individuals placing bets. This inherent bias in odds contributes to the company's profit margin in the betting business. ### Exploring a free and ethical approach to lottery apps and innovative payout structures The whole lottery system should be verifiable! The point of it is not to have yet another system where the poor are preyed upon. That is why the lottery app should be open-sourced. The bigger reason for the apps to be FOSS - I am reluctant to say how this particular app should be created because, on the one side, there are going to be regulatory people who want you to ask for approval, and on the other side there are betting companies that a percentage of them are involved in criminal activities. If you create an app that makes them obsolete you will find yourself being attacked legally, illegally, and anything in between. That is why the only option that I see for a small guy to not be a target is to create this app as a FOSS (free and open source software). This will create a problem for those entities because there is no target. It will have no barriers for others to create apps competing with the existing incentives. There was a big debate in my head about whether I should publish this article about this particular topic because of the ethically sticky situation. Also, I do not think that people should play with money and bet on stupid things. The main reason that I am doing this is that there should not be an incentive to do illegal activities but there should be a cost for it. Since the current system is incentivizing it, people should create the cost for them by making a free alternative (no licenses, or permissions from anyone) and with no risk for the players (non-custodial). Also, the cases that we will look at below as a payment structure are simply cool and unique that we have yet to experience anywhere. This will push even us at Breez to create and facilitate them if the need is there. Now let’s take a look at the potential solution and what I envision it could look like. An algorithm can be designed where individuals purchase a virtual ticket, and once 100 participants acquire tickets, the entire pool is distributed among three randomly selected winners. The distribution comprises 50% for the first prize, 30% for the second, and 20% for the third. The concept of a physical ticket is eliminated; instead, participants contribute equal amounts of satoshis to a smart contract, which activates upon reaching the 100th participant. The executed contracts allocate 50% to the first-place winner, 30% to the second, and 20% to the third. No entity holds funds for others, and participants await the completion of the 100 spots to determine the three winners. You can do the lottery for more or fewer people. For different amounts of sats. With a different payout structure. I envision a lottery game modeled after the hashing race in Bitcoin mining. Participants are required to guess a number between 1 and 1,000,000 by locking in 10 satoshis for each guess. If the guessed number is incorrect, that specific guess is eliminated from the potential answers, and the satoshis from all guesses contribute to the Jackpot for the correct number. The participant who correctly guesses the number receives the accumulated satoshis. The payout amount depends on the position of the correct guess, for example, if it occurs on the 10th try, the prize is 100 sats, and if on the 100,000th try, the prize is a million sats. Upon completion of the payout, the game resets, and participants can engage in the next round. ### Revolutionizing one-on-one Betting with trustless payouts When I am with a friend, we can choose to place a bet on something--our favorite sports team, who can spit the furthest, or whether the sun will rise tomorrow. We are perfectly able to do so with cash, and we do not need a license from anyone to place those bets or determine the odds for us. There is only one problem that we have to handle when the results are in - the person who is losing the bet has to pay the winner. Because of this risk, you need a trusted third party that is unbiased to execute the payment when the results are known. Now you need a mitigation for the third-party risk--that they won't run away with the money. So you make a fourth party involved to determine who can have a license to be a trusted third party, and we are back to the current fiat operational model. With instant settlement and smart contracts, we destroy all those problems. * You do not need a license for trust because no one is holding money for anyone else. * You do not need a trusted third party because you have a smart contract responsible for the execution of the payment when the results are known * You do not need a third party to determine the odds because they are decided by the people and put in the smart contract * You do not need to trust the person to pay when you win because he signed the execution of the payment when both of you placed the bet. This structure for one-on-one betting is already implemented with a few games in the lightning space. One is from our friends at THNDR games and another is the Chain Duel. I like the infrastructure for the payment of the THNDR games because I am a sucker for non-custodial lightning. Custody for a second, a minute or a year is still custody. What would a sports betting app look like that has a non-custodial instant settlement? There are a few easy settings to establish. First, there needs to be a deadline for placing bets before the sports event starts. Second, a timeframe must be set for the payout. In one-on-one betting, the payout structure is straightforward. Each side can wager any amount against the other, and if there is a disparity in the amounts, the odds are not 1:1. When the result is determined, the winning party has their funds unlocked without being sent, while the losing party has their contract executed, transferring the payment to the winner. THNDR is already implementing a similar concept called "clinch" which we are glad we had some input on, but I want to take it a few steps further. ### Exploring novel concepts in wagering -> community-to-community What if there's a group of people on one side of the bet and another group on the opposing side? What does the payout look like, and how are the odds determined? Let's delve into a straightforward graph to better illustrate this example. The graphs in the picture are the reference for the explanations below The individuals on the left consist of only two people, but they wager a larger amount. On the right, there are four people, but their bets are smaller. If the left side wins, the two individuals will share the $1,000 bet placed by the opposing group. Since they bet equal amounts, each person will receive $500, reflecting a 50% stake for each. Conversely, if the right side wins, the stakes differ. Individuals 1 and 2 have a 25% stake, person 3 has a 40% stake, and person 4 has a 10% stake. Consequently, their respective payouts would be $500, $500, $800, and $200. That was a surprise even for me - there is a proof of stake system that I would be for. I realized that the staking is just not used in the proper context and that is why I have a problem with it. Proof of stake is deployed for bets and bets only. There is no such thing called staking your energy - that is called working. Now this system is not the shitcoin model - stake something and I guarantee you something more. Staking something means that going in you know (or you should know) that your stake could be lost. If someone is asking you to stake money and promising you more money you should ask yourself who is the loser that will pay the winner. If I am the winner, who is the loser? If we are all winners that means we all lost to inflation and the winner is the inflator. Stake = Bet. The true stake system introduces a novel dimension to betting. While the primary goal is to win, participants might consider adding more funds to their community bet to avoid dilution. For instance, if I initially bet $10 alone, I would have a 100% payout potential. However, if someone else places a $10,000 bet on my side, my potential payout percentage drops to less than 0.1%. In such a scenario, I face two choices: increase my bet on my community's side for a better payout or place a bet on the opposing side, capitalizing on the changed odds for a potentially significant payout if I am wrong. This concept sheds light on the genuine meaning of hedging. You are hedging things that you BET on! Whether you call it an investment strategy or not you should now recognize that everything in the fiat system is using these terms but hiding the fact that it is gambling. For example, if you are a true investor you should do everything you can to make your investment work and realize that goal. Betting against yourself = hedge. The community-to-community betting brings about more significant implications than current betting models. In this setup, the victorious community directly benefits, and if the bet is placed on a sports event, the winning team supports the winning community. The funds from the losing team's community are directly paid to the winning community and not to a betting company. This eliminates the intermediary role of any betting company. The people also are forced to do their research and assess which is a good bet and which is not - not that the majority do it. If they did it was going to be clear to all of us by now that all sh*tcoins are the fiat scam on a blockchain. When there are three or more possible outcomes for a bet, multiple people or communities can bet on those outcomes, and all losing communities pay the winning community. In this scenario, individual participants receive payouts based on their respective stakes. For instance, in a bet involving predicting an exact score where no one bets on the correct score, there is no winner, and consequently, no actual losers. In such cases, participants simply have their sats unlocked without any winnings or losses. We invest our energy in goals - make sure it is your goals and not someone else's. With money, we do 3 things only - earning, spending, or gambling! People want to pay you money so you achieve their goals and stake your money so you can lose it to them. Be very aware of where you invest your energy and how you are using your bitcoin. I would like to repeat my statement from above one more time. The forces that are involved with these gambling companies are very powerful and I do not want to inspire someone and put a target on their back. I am doing this because of the utility of the payments and because this can be an open-sourced project that just competes with them. Satoshi set a standard for how to solve a monopoly - with FOSS. This will completely reshape the coordination between humans again with instant settlement payment. I do not like that I am promoting betting behavior because it is addictive and dangerous but I hope this puts a light on why all fiat behavior is gambling. The only proof of stake that matters is what is your stake in Bitcoin from the 21 million coins. Having a stake there is betting on humanity for the better. Now be careful with this bet to make that app!
@ 3c827db6:66418fc3
2024-08-17 02:50:05Somebody, somewhere, at some point decided they would destroy the competition by creating a barrier to entry. They made the barrier high so they could feel safe. It is logical to put a fence around your property, and perfectly fine to do so. The problem is when you put a regulatory fence over something that means you are not allowing anyone else to have a property like this. Just to make the distinction clearer a fence around your house is creating a cost for other people to get in the yard. A license to be able to have a fence is creating a cost for anyone to protect their yard. The harder to attain and costlier the license is the more people can’t afford it. The more people who can’t afford it the bigger the divide between rich and poor. You can't have a fence because you can't have a license leaving your yard unprotected. The poor people are left unprotected and they get robbed easily, the rich are hard to get so they keep what they have. The more licenses/regulatory compliance someone has to comply with the more the costs for them are increased and the cycle of dividing is entrenched. When constructing something physical, regulatory oversight is sensible to ensure structural integrity, particularly when people no longer build things for themselves. However, when it comes to more abstract concepts like licenses and credentials, possessing them doesn't guarantee success, and lacking them doesn't preclude doing excellent work. The whole point of the series is that the work should speak for itself and the people who did it should build their reputation based on their work history not on theory. Let’s dive into a sector full of licenses for abstract things that keep people out and cornered the market. The betting industry. The incentive structure in this scenario is problematic. Individuals with substantial financial resources that were gained illegally may seek friendly relationships with those responsible for issuing licenses. Obtaining a betting license now can serve as a means to launder money acquired unlawfully. Beyond mere laundering, they have a direct incentive to continue their illegal activities and a way to legitimize the funds. So they steal from the people who work and it gets even worse. Their scaling solution is to open the money laundering to other illegal actors. A few parts of the economy are primed for these types of activities: the lottery, casinos, and sports betting. Let’s start with the current lottery system and the “potential” exploits. Well, one person does something illegal and has stolen $1,000,000. Now he has a problem with how to legitimize the funds so he can spend it on things he wants. He goes to the owner of a lottery and says I will give you $200,000 if you give me an $800,000 winning ticket. Now 80% of the funds become legal. The person with the illegal funds buys $200,000 worth of tickets from which 1 of them is set up to win $800,000. Now all the funds have become legal. So the lottery company has a $200,000 income and $800,000 payout, seemingly paying out the winner with legitimate funds, but in reality, using the criminal's own money - correction, other people's stolen money. That is good for hiding taxes and the state is not getting anything, or is it? The state gets its cut for every winning ticket by taxing all winners. Because of this income, they are incentivized to have more winners. This whole “hypothetical” system then is limited by how much money has to be laundered. More illegal money, more income for each side - the state, the illegal player, the lottery company. While they get the big winning tickets the public is left with the small prizes and they are robbed continuously for the next lottery "prizes". This tripod system demonstrates how one simple thing can be a continuous erosion of society. The lottery company does nothing to earn their money but they are incentivizing the illegal actors to continue doing illegal things. The State allowing licenses keeps competition out. The illegal actor closes the circle of his business. The lottery should be something that is played without anyone having an advantage over anyone else. Including the company, there shouldn’t be a barrier for people creating all sorts of lottery games. The same model of behavior incentives is applicable for all the casinos. There is the same principle - some type of algorithm determines whether you win or not. But you can always approach the casino owner and apply the same logic to the casino. A player with illegal funds has to launder a million dollars again. In the first few hands, he wins a million dollars and keeps playing until incurs losses amounting to $200,000 and then stops. This way the casino loses $800,000 on its balance sheet but in reality, the illegal funds are distributed to the casino and the illegal actor. In the sports betting industry, the barrier to entry is often determined by licenses, and companies typically act as custodians of the funds when users place bets. Additionally, these companies are responsible for providing betting odds, a task that incurs substantial costs when done accurately. Assessing various factors such as team performance, player injuries, and changes in management helps determine the odds. However, it's crucial to note that the odds provided by betting companies are designed to favor the company rather than the individuals placing bets. This inherent bias in odds contributes to the company's profit margin in the betting business. ### Exploring a free and ethical approach to lottery apps and innovative payout structures The whole lottery system should be verifiable! The point of it is not to have yet another system where the poor are preyed upon. That is why the lottery app should be open-sourced. The bigger reason for the apps to be FOSS - I am reluctant to say how this particular app should be created because, on the one side, there are going to be regulatory people who want you to ask for approval, and on the other side there are betting companies that a percentage of them are involved in criminal activities. If you create an app that makes them obsolete you will find yourself being attacked legally, illegally, and anything in between. That is why the only option that I see for a small guy to not be a target is to create this app as a FOSS (free and open source software). This will create a problem for those entities because there is no target. It will have no barriers for others to create apps competing with the existing incentives. There was a big debate in my head about whether I should publish this article about this particular topic because of the ethically sticky situation. Also, I do not think that people should play with money and bet on stupid things. The main reason that I am doing this is that there should not be an incentive to do illegal activities but there should be a cost for it. Since the current system is incentivizing it, people should create the cost for them by making a free alternative (no licenses, or permissions from anyone) and with no risk for the players (non-custodial). Also, the cases that we will look at below as a payment structure are simply cool and unique that we have yet to experience anywhere. This will push even us at Breez to create and facilitate them if the need is there. Now let’s take a look at the potential solution and what I envision it could look like. An algorithm can be designed where individuals purchase a virtual ticket, and once 100 participants acquire tickets, the entire pool is distributed among three randomly selected winners. The distribution comprises 50% for the first prize, 30% for the second, and 20% for the third. The concept of a physical ticket is eliminated; instead, participants contribute equal amounts of satoshis to a smart contract, which activates upon reaching the 100th participant. The executed contracts allocate 50% to the first-place winner, 30% to the second, and 20% to the third. No entity holds funds for others, and participants await the completion of the 100 spots to determine the three winners. You can do the lottery for more or fewer people. For different amounts of sats. With a different payout structure. I envision a lottery game modeled after the hashing race in Bitcoin mining. Participants are required to guess a number between 1 and 1,000,000 by locking in 10 satoshis for each guess. If the guessed number is incorrect, that specific guess is eliminated from the potential answers, and the satoshis from all guesses contribute to the Jackpot for the correct number. The participant who correctly guesses the number receives the accumulated satoshis. The payout amount depends on the position of the correct guess, for example, if it occurs on the 10th try, the prize is 100 sats, and if on the 100,000th try, the prize is a million sats. Upon completion of the payout, the game resets, and participants can engage in the next round. ### Revolutionizing one-on-one Betting with trustless payouts When I am with a friend, we can choose to place a bet on something--our favorite sports team, who can spit the furthest, or whether the sun will rise tomorrow. We are perfectly able to do so with cash, and we do not need a license from anyone to place those bets or determine the odds for us. There is only one problem that we have to handle when the results are in - the person who is losing the bet has to pay the winner. Because of this risk, you need a trusted third party that is unbiased to execute the payment when the results are known. Now you need a mitigation for the third-party risk--that they won't run away with the money. So you make a fourth party involved to determine who can have a license to be a trusted third party, and we are back to the current fiat operational model. With instant settlement and smart contracts, we destroy all those problems. * You do not need a license for trust because no one is holding money for anyone else. * You do not need a trusted third party because you have a smart contract responsible for the execution of the payment when the results are known * You do not need a third party to determine the odds because they are decided by the people and put in the smart contract * You do not need to trust the person to pay when you win because he signed the execution of the payment when both of you placed the bet. This structure for one-on-one betting is already implemented with a few games in the lightning space. One is from our friends at THNDR games and another is the Chain Duel. I like the infrastructure for the payment of the THNDR games because I am a sucker for non-custodial lightning. Custody for a second, a minute or a year is still custody. What would a sports betting app look like that has a non-custodial instant settlement? There are a few easy settings to establish. First, there needs to be a deadline for placing bets before the sports event starts. Second, a timeframe must be set for the payout. In one-on-one betting, the payout structure is straightforward. Each side can wager any amount against the other, and if there is a disparity in the amounts, the odds are not 1:1. When the result is determined, the winning party has their funds unlocked without being sent, while the losing party has their contract executed, transferring the payment to the winner. THNDR is already implementing a similar concept called "clinch" which we are glad we had some input on, but I want to take it a few steps further. ### Exploring novel concepts in wagering -> community-to-community What if there's a group of people on one side of the bet and another group on the opposing side? What does the payout look like, and how are the odds determined? Let's delve into a straightforward graph to better illustrate this example. The graphs in the picture are the reference for the explanations below The individuals on the left consist of only two people, but they wager a larger amount. On the right, there are four people, but their bets are smaller. If the left side wins, the two individuals will share the $1,000 bet placed by the opposing group. Since they bet equal amounts, each person will receive $500, reflecting a 50% stake for each. Conversely, if the right side wins, the stakes differ. Individuals 1 and 2 have a 25% stake, person 3 has a 40% stake, and person 4 has a 10% stake. Consequently, their respective payouts would be $500, $500, $800, and $200. That was a surprise even for me - there is a proof of stake system that I would be for. I realized that the staking is just not used in the proper context and that is why I have a problem with it. Proof of stake is deployed for bets and bets only. There is no such thing called staking your energy - that is called working. Now this system is not the shitcoin model - stake something and I guarantee you something more. Staking something means that going in you know (or you should know) that your stake could be lost. If someone is asking you to stake money and promising you more money you should ask yourself who is the loser that will pay the winner. If I am the winner, who is the loser? If we are all winners that means we all lost to inflation and the winner is the inflator. Stake = Bet. The true stake system introduces a novel dimension to betting. While the primary goal is to win, participants might consider adding more funds to their community bet to avoid dilution. For instance, if I initially bet $10 alone, I would have a 100% payout potential. However, if someone else places a $10,000 bet on my side, my potential payout percentage drops to less than 0.1%. In such a scenario, I face two choices: increase my bet on my community's side for a better payout or place a bet on the opposing side, capitalizing on the changed odds for a potentially significant payout if I am wrong. This concept sheds light on the genuine meaning of hedging. You are hedging things that you BET on! Whether you call it an investment strategy or not you should now recognize that everything in the fiat system is using these terms but hiding the fact that it is gambling. For example, if you are a true investor you should do everything you can to make your investment work and realize that goal. Betting against yourself = hedge. The community-to-community betting brings about more significant implications than current betting models. In this setup, the victorious community directly benefits, and if the bet is placed on a sports event, the winning team supports the winning community. The funds from the losing team's community are directly paid to the winning community and not to a betting company. This eliminates the intermediary role of any betting company. The people also are forced to do their research and assess which is a good bet and which is not - not that the majority do it. If they did it was going to be clear to all of us by now that all sh*tcoins are the fiat scam on a blockchain. When there are three or more possible outcomes for a bet, multiple people or communities can bet on those outcomes, and all losing communities pay the winning community. In this scenario, individual participants receive payouts based on their respective stakes. For instance, in a bet involving predicting an exact score where no one bets on the correct score, there is no winner, and consequently, no actual losers. In such cases, participants simply have their sats unlocked without any winnings or losses. We invest our energy in goals - make sure it is your goals and not someone else's. With money, we do 3 things only - earning, spending, or gambling! People want to pay you money so you achieve their goals and stake your money so you can lose it to them. Be very aware of where you invest your energy and how you are using your bitcoin. I would like to repeat my statement from above one more time. The forces that are involved with these gambling companies are very powerful and I do not want to inspire someone and put a target on their back. I am doing this because of the utility of the payments and because this can be an open-sourced project that just competes with them. Satoshi set a standard for how to solve a monopoly - with FOSS. This will completely reshape the coordination between humans again with instant settlement payment. I do not like that I am promoting betting behavior because it is addictive and dangerous but I hope this puts a light on why all fiat behavior is gambling. The only proof of stake that matters is what is your stake in Bitcoin from the 21 million coins. Having a stake there is betting on humanity for the better. Now be careful with this bet to make that app! @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Liquidificador A fragilidade da comunicação humana fica clara quando alguém liga o liquidificador.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Liquidificador A fragilidade da comunicação humana fica clara quando alguém liga o liquidificador. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# An argument according to which fractional-reserve banking is merely theft and nothing else Fractional-reserve banking isn't anything else besides transfer of money from the people at large to bankers. It has been argued that fractional-reserve banking serves a purpose in making new funds available out of no one's pocket for lending and thus directing resources to productive borrowers. This financing method is preferrable to the more conservative way of borrowing funds directly from a saver and then using that to lend to others because it uses new money, money not tied to anyone else before, and thus it's cheaper and involves less friction. Instead, what happens is that someone must at all times be the owner of each money. So when banks use their power of generating fractional-reserve funds, they are creating new money and they are the owners – at this point, a theft occurs from the public at large to them – and then they proceed to lend their own money. From this description it is clear that the fact that bank customers have previously deposited their own funds in the banks' vaults have no direct relation with the fact that banks created money afterwards, there's only a legal relation and the fact that banks may need cash deposited by its customers to redeem borrowers claims, but even that wouldn't be necessary if banks were allowed to print their own cash.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# An argument according to which fractional-reserve banking is merely theft and nothing else Fractional-reserve banking isn't anything else besides transfer of money from the people at large to bankers. It has been argued that fractional-reserve banking serves a purpose in making new funds available out of no one's pocket for lending and thus directing resources to productive borrowers. This financing method is preferrable to the more conservative way of borrowing funds directly from a saver and then using that to lend to others because it uses new money, money not tied to anyone else before, and thus it's cheaper and involves less friction. Instead, what happens is that someone must at all times be the owner of each money. So when banks use their power of generating fractional-reserve funds, they are creating new money and they are the owners – at this point, a theft occurs from the public at large to them – and then they proceed to lend their own money. From this description it is clear that the fact that bank customers have previously deposited their own funds in the banks' vaults have no direct relation with the fact that banks created money afterwards, there's only a legal relation and the fact that banks may need cash deposited by its customers to redeem borrowers claims, but even that wouldn't be necessary if banks were allowed to print their own cash. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Thomas Kuhn sequer menciona o "método científico" O que define uma ciência é o recorte de uma realidade a partir de um paradigma que todos os que entram no campo daquela ciência aceitam como verdade. Pronto. O "método científico" não é nem necessário nem suficiente (apesar de que ele mesmo precisa pressupor uma série de axiomas para funcionar, do contrário a pessoa ficaria tendo que testar cada sílaba dos seus experimentos e cada um desses testes seria impossível de realizar pois eles necessariamente precisariam de outros conhecimentos prévios etc.). Por isso - a física teórica pode ser uma ciência embora não faça experimentos; - e a economia pode ser uma ciência embora não faça experimentos (tá bom, existem pessoas que insistem em fazer "experimentos" em economia, mas que na verdade são só uma enorme perda de tempo baseada em estatísticas, mas isso não importa, até essas coisas podem ter algum valor desde que não se as entenda como sendo parte de um método científico); - e a história pode ser uma ciência, por mais estranho que isso pareça, bastando apenas que o historiador junte fatos de antigamente tendo como pressuposto um paradigma, por exemplo, de que existe um sentido da história, ou sei lá (não acho que exista essa ciência da história hoje em dia, me parece que cada historiador está fazendo uma coisa diferente, sem muitos paradigmas além do bom senso); - e a biologia pode ser uma ciência mesmo consistindo unicamente num longo esforço de classificação, e de fato é hoje, já que vê cada espécie e suas partes como frutos de um processo evolutivo cujas bases constituem um paradigma, e nega outras visões, como a teleologia. - [Método científico](nostr:naddr1qqyr2wf3vgmx2dmrqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823chtnaca) - [A estrutura paradigmática da ciência](nostr:naddr1qqyrzdfsxyuxye3cqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c4awxqq) - [Um algoritmo imbecil da evolução](nostr:naddr1qqyryv35xsunwvfnqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c45a0t3)
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Thomas Kuhn sequer menciona o "método científico" O que define uma ciência é o recorte de uma realidade a partir de um paradigma que todos os que entram no campo daquela ciência aceitam como verdade. Pronto. O "método científico" não é nem necessário nem suficiente (apesar de que ele mesmo precisa pressupor uma série de axiomas para funcionar, do contrário a pessoa ficaria tendo que testar cada sílaba dos seus experimentos e cada um desses testes seria impossível de realizar pois eles necessariamente precisariam de outros conhecimentos prévios etc.). Por isso - a física teórica pode ser uma ciência embora não faça experimentos; - e a economia pode ser uma ciência embora não faça experimentos (tá bom, existem pessoas que insistem em fazer "experimentos" em economia, mas que na verdade são só uma enorme perda de tempo baseada em estatísticas, mas isso não importa, até essas coisas podem ter algum valor desde que não se as entenda como sendo parte de um método científico); - e a história pode ser uma ciência, por mais estranho que isso pareça, bastando apenas que o historiador junte fatos de antigamente tendo como pressuposto um paradigma, por exemplo, de que existe um sentido da história, ou sei lá (não acho que exista essa ciência da história hoje em dia, me parece que cada historiador está fazendo uma coisa diferente, sem muitos paradigmas além do bom senso); - e a biologia pode ser uma ciência mesmo consistindo unicamente num longo esforço de classificação, e de fato é hoje, já que vê cada espécie e suas partes como frutos de um processo evolutivo cujas bases constituem um paradigma, e nega outras visões, como a teleologia. - [Método científico](nostr:naddr1qqyr2wf3vgmx2dmrqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823chtnaca) - [A estrutura paradigmática da ciência](nostr:naddr1qqyrzdfsxyuxye3cqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c4awxqq) - [Um algoritmo imbecil da evolução](nostr:naddr1qqyryv35xsunwvfnqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c45a0t3) @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Drivechain comparison with Ethereum Ethereum and other "smart contract platforms" capable of running turing-complete code and "developer-friendly" mindset and community have been running for years and they were able to produce a very low number of potentially useful "contracts". What are these contracts, actually? (Considering Ethereum, but others are similar:) they are sidechains that run inside the Ethereum blockchain (and thus their verification and data storage are forced upon all Ethereum nodes). Users can peg-in to a contract by depositing money on it and peg-out by making a contract operation that sends money to a normal Ethereum address. Now be generous and imagine these platforms are able to produce 3 really cool, useful ideas (out of many thousands of attempts): [Bitcoin](nostr:naddr1qqyryveexumnyd3kqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c7nywz4) can copy these, turn them into 3 different sidechains, each running fixed, specific, optimized code. Bitcoin users can now opt to use these platforms by transferring coins to it – all that without damaging the nodes or the consensus protocol that has been running for years, and without forcing anyone to be aware of these chains. The process of turning a useful idea into a sidechain doesn't come spontaneously, and can't be done by a single company (like often happens in Ethereum-land), it must be acknowledge by a rough consensus in the Bitcoin community that that specific sidechain with that specific design is a desirable thing, and ultimately approved by miners, as they're the ones that are going to be in charge of that.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Drivechain comparison with Ethereum Ethereum and other "smart contract platforms" capable of running turing-complete code and "developer-friendly" mindset and community have been running for years and they were able to produce a very low number of potentially useful "contracts". What are these contracts, actually? (Considering Ethereum, but others are similar:) they are sidechains that run inside the Ethereum blockchain (and thus their verification and data storage are forced upon all Ethereum nodes). Users can peg-in to a contract by depositing money on it and peg-out by making a contract operation that sends money to a normal Ethereum address. Now be generous and imagine these platforms are able to produce 3 really cool, useful ideas (out of many thousands of attempts): [Bitcoin](nostr:naddr1qqyryveexumnyd3kqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c7nywz4) can copy these, turn them into 3 different sidechains, each running fixed, specific, optimized code. Bitcoin users can now opt to use these platforms by transferring coins to it – all that without damaging the nodes or the consensus protocol that has been running for years, and without forcing anyone to be aware of these chains. The process of turning a useful idea into a sidechain doesn't come spontaneously, and can't be done by a single company (like often happens in Ethereum-land), it must be acknowledge by a rough consensus in the Bitcoin community that that specific sidechain with that specific design is a desirable thing, and ultimately approved by miners, as they're the ones that are going to be in charge of that. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Lightning and its fake HTLCs Lightning is terrible but can be very good with two tweaks. ## How Lightning would work without HTLCs In a world in which HTLCs didn't exist, Lightning channels would consist only of balances. Each commitment transaction would have two outputs: one for peer `A`, the other for peer `B`, according to the current state of the channel. When a payment was being attempted to go through the channel, peers would just trust each other to update the state when necessary. For example: 1. Channel `AB`'s balances are `A[10:10]B` (in sats); 2. `A` sends a 3sat payment through `B` to `C`; 3. `A` asks `B` to route the payment. Channel `AB` doesn't change at all; 4. `B` sends the payment to `C`, `C` accepts it; 5. Channel `BC` changes from `B[20:5]C` to `B[17:8]C`; 6. `B` notifies `A` the payment was successful, `A` acknowledges that; 7. Channel `AB` changes from `A[10:10]B` to `A[7:13]B`. This in the case of a success, everything is fine, no glitches, no dishonesty. But notice that `A` could have refused to acknowledge that the payment went through, either because of a bug, or because it went offline forever, or because it is malicious. Then the channel `AB` would stay as `A[10:10]B` and `B` would have lost 3 satoshis. ## How Lightning would work with HTLCs HTLCs are introduced to remedy that situation. Now instead of commitment transactions having always only two outputs, one to each peer, now they can have HTLC outputs too. These HTLC outputs could go to either side dependending on the circumstance. Specifically, the peer that is sending the payment can redeem the HTLC after a number of blocks have passed. The peer that is receiving the payment can redeem the HTLC if they are able to provide the preimage to the hash specified in the HTLC. Now the flow is something like this: 1. Channel `AB`'s balances are `A[10:10]B`; 2. `A` sends a 3sat payment through `B` to `C`: 3. `A` asks `B` to route the payment. Their channel changes to `A[7:3:10]B` (the middle number is the HTLC). 4. `B` offers a payment to `C`. Their channel changes from `B[20:5]C` to `B[17:3:5]C`. 5. `C` tells `B` the preimage for that HTLC. Their channel changes from `B[17:3:5]C` to `B[17:8]C`. 6. `B` tells `A` the preimage for that HTLC. Their channel changes from `A[7:3:10]B` to `A[7:13]B`. Now if `A` wants to trick `B` and stop responding `B` doesn't lose money, because `B` knows the preimage, `B` just needs to publish the commitment transaction `A[7:3:10]B`, which gives him 10sat and then redeem the HTLC using the preimage he got from `C`, which gives him 3 sats more. `B` is fine now. In the same way, if `B` stops responding for any reason, `A` won't lose the money it put in that HTLC, it can publish the commitment transaction, get 7 back, then redeem the HTLC after the certain number of blocks have passed and get the other 3 sats back. ## How Lightning doesn't really work The example above about how the HTLCs work is very elegant but has a fatal flaw on it: transaction fees. Each new HTLC added increases the size of the commitment transaction and it requires yet another transaction to be redeemed. If we consider fees of 10000 satoshis that means any HTLC below that is as if it didn't existed because we can't ever redeem it anyway. In fact the Lightning protocol explicitly dictates that if HTLC output amounts are below the fee necessary to redeem them they shouldn't be created. What happens in these cases then? Nothing, the amounts that should be in HTLCs are moved to the commitment transaction miner fee instead. So considering a transaction fee of 10000sat for these HTLCs if one is sending Lightning payments below 10000sat that means they operate according to the _unsafe protocol_ described in the first section above. It is actually worse, because consider what happens in the case a channel in the middle of a route has a glitch or one of the peers is unresponsive. The other node, thinking they are operating in the _trustless protocol_, will proceed to publish the commitment transaction, i.e. close the channel, so they can redeem the HTLC -- only then they find out they are actually in the _unsafe protocol_ realm and there is no HTLC to be redeemed at all and they lose not only the money, but also the channel (which costed a lot of money to open and close, in overall transaction fees). One of the biggest features of the _trustless protocol_ are the payment proofs. Every payment is identified by a hash and whenever the payee releases the preimage relative to that hash that means the payment was complete. The incentives are in place so all nodes in the path pass the preimage back until it reaches the payer, which can then use it as the proof he has sent the payment and the payee has received it. This feature is also lost in the _unsafe protocol_: if a glitch happens or someone goes offline on the preimage's way back then there is no way the preimage will reach the payer because no HTLCs are published and redeemed on the chain. The payee may have received the money but the payer will not know -- but the payee will lose the money sent anyway. ## The end of HTLCs So considering the points above you may be sad because in some cases Lightning doesn't use these magic HTLCs that give meaning to it all. But the fact is that no matter what anyone thinks, HTLCs are destined to be used less and less as time passes. The fact that over time Bitcoin transaction fees tend to rise, and also the fact that multipart payment (MPP) are increasedly being used on Lightning for good, we can expect that soon no HTLC will ever be big enough to be actually worth redeeming and we will be at a point in which not a single HTLC is real and they're all fake. Another thing to note is that the current _unsafe protocol_ kicks out whenever the HTLC amount is below the Bitcoin transaction fee would be to redeem it, but this is not a reasonable algorithm. It is not reasonable to lose a channel and then pay 10000sat in fees to redeem a 10001sat HTLC. At which point does it become reasonable to do it? Probably in an amount many times above that, so it would be reasonable to even increase the threshold above which real HTLCs are made -- thus making their existence more and more rare. These are good things, because we don't actually need HTLCs to make a functional Lightning Network. ## We must embrace the _unsafe protocol_ and make it better So the _unsafe protocol_ is not necessarily very bad, but the way it is being done now is, because it suffers from two big problems: 1. Channels are lost all the time for no reason; 2. No guarantees of the proof-of-payment ever reaching the payer exist. The first problem we fix by just stopping the current practice of closing channels when there are no real HTLCs in them. That, however, creates a new problem -- or actually it exarcebates the second: now that we're not closing channels, what do we do with the expired payments in them? These payments should have either been canceled or fulfilled before some block x, now we're in block x+1, our peer has returned from its offline period and one of us will have to lose the money from that payment. That's fine because it's only 3sat and it's better to just lose 3sat than to lose both the 3sat and the channel anyway, so either one would be happy to eat the loss. Maybe we'll even split it 50/50! No, that doesn't work, because it creates an attack vector with peers becoming unresponsive on purpose on one side of the route and actually failing/fulfilling the payment on the other side and making a profit with that. So we actually need to know who is to blame on these payments, even if we are not going to act on that imediatelly: we need some kind of arbiter that both peers can trust, such that if one peer is trying to send the preimage or the cancellation to the other and the other is unresponsive, when the unresponsive peer comes back, the arbiter can tell them they are to blame, so they can willfully eat the loss and the channel can continue. Both peers are happy this way. If the unresponsive peer doesn't accept what the arbiter says then the peer that was operating correctly can assume the unresponsive peer is malicious and close the channel, and then blacklist it and never again open a channel with a peer they know is malicious. Again, the differences between this scheme and the current Lightning Network are that: a. In the current Lightning we always close channels, in this scheme we only close channels in case someone is malicious or in other worst case scenarios (the arbiter is unresponsive, for example). b. In the current Lightning we close the channels without having any clue on who is to blame for that, then we just proceed to reopen a channel with that same peer even in the case they were actively trying to harm us before. ## What is missing? An arbiter. The Bitcoin blockchain is the ideal arbiter, it works in the best possible way if we follow the _trustless protocol_, but as we've seen we can't use the Bitcoin blockchain because it is expensive. Therefore we need a new arbiter. That is the hard part, but not unsolvable. Notice that we don't need an absolutely perfect arbiter, anything is better than nothing, really, even an unreliable arbiter that is offline half of the day is better than what we have today, or an arbiter that lies, an arbiter that charges some satoshis for each resolution, anything. Here are some suggestions: - random nodes from the network selected by an algorithm that both peers agree to, so they can't cheat by selecting themselves. The only thing these nodes have to do is to store data from one peer, try to retransmit it to the other peer and record the results for some time. - a set of nodes preselected by the two peers when the channel is being opened -- same as above, but with more handpicked-trust involved. - some third-party cloud storage or notification provider with guarantees of having open data in it and some public log-keeping, like Twitter, GitHub or a [Nostr](https://github.com/fiatjaf/nostr) relay; - peers that get paid to do the job, selected by the fact that they own some token (I know this is stepping too close to the shitcoin territory, but could be an idea) issued in a [Spacechain](https://www.youtube.com/watch?v=N2ow4Q34Jeg); - a Spacechain itself, serving only as the storage for a bunch of `OP_RETURN`s that are published and tracked by these Lightning peers whenever there is an issue (this looks wrong, but could work). ## Key points 1. Lightning with HTLC-based routing was a cool idea, but it wasn't ever really feasible. 2. HTLCs are going to be abandoned and that's the natural course of things. 3. It is actually good that HTLCs are being abandoned, but 4. We must change the protocol to account for the existence of fake HTLCs and thus make the bulk of the Lightning Network usage viable again. ## See also - [Ripple and the problem of the decentralized commit](nostr:naddr1qqyrxcmzxa3nxv34qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cjrqar6) - [The Lightning Network solves the problem of the decentralized commit](nostr:naddr1qqyx2vekxg6rsvejqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ccs2twc)
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Lightning and its fake HTLCs Lightning is terrible but can be very good with two tweaks. ## How Lightning would work without HTLCs In a world in which HTLCs didn't exist, Lightning channels would consist only of balances. Each commitment transaction would have two outputs: one for peer `A`, the other for peer `B`, according to the current state of the channel. When a payment was being attempted to go through the channel, peers would just trust each other to update the state when necessary. For example: 1. Channel `AB`'s balances are `A[10:10]B` (in sats); 2. `A` sends a 3sat payment through `B` to `C`; 3. `A` asks `B` to route the payment. Channel `AB` doesn't change at all; 4. `B` sends the payment to `C`, `C` accepts it; 5. Channel `BC` changes from `B[20:5]C` to `B[17:8]C`; 6. `B` notifies `A` the payment was successful, `A` acknowledges that; 7. Channel `AB` changes from `A[10:10]B` to `A[7:13]B`. This in the case of a success, everything is fine, no glitches, no dishonesty. But notice that `A` could have refused to acknowledge that the payment went through, either because of a bug, or because it went offline forever, or because it is malicious. Then the channel `AB` would stay as `A[10:10]B` and `B` would have lost 3 satoshis. ## How Lightning would work with HTLCs HTLCs are introduced to remedy that situation. Now instead of commitment transactions having always only two outputs, one to each peer, now they can have HTLC outputs too. These HTLC outputs could go to either side dependending on the circumstance. Specifically, the peer that is sending the payment can redeem the HTLC after a number of blocks have passed. The peer that is receiving the payment can redeem the HTLC if they are able to provide the preimage to the hash specified in the HTLC. Now the flow is something like this: 1. Channel `AB`'s balances are `A[10:10]B`; 2. `A` sends a 3sat payment through `B` to `C`: 3. `A` asks `B` to route the payment. Their channel changes to `A[7:3:10]B` (the middle number is the HTLC). 4. `B` offers a payment to `C`. Their channel changes from `B[20:5]C` to `B[17:3:5]C`. 5. `C` tells `B` the preimage for that HTLC. Their channel changes from `B[17:3:5]C` to `B[17:8]C`. 6. `B` tells `A` the preimage for that HTLC. Their channel changes from `A[7:3:10]B` to `A[7:13]B`. Now if `A` wants to trick `B` and stop responding `B` doesn't lose money, because `B` knows the preimage, `B` just needs to publish the commitment transaction `A[7:3:10]B`, which gives him 10sat and then redeem the HTLC using the preimage he got from `C`, which gives him 3 sats more. `B` is fine now. In the same way, if `B` stops responding for any reason, `A` won't lose the money it put in that HTLC, it can publish the commitment transaction, get 7 back, then redeem the HTLC after the certain number of blocks have passed and get the other 3 sats back. ## How Lightning doesn't really work The example above about how the HTLCs work is very elegant but has a fatal flaw on it: transaction fees. Each new HTLC added increases the size of the commitment transaction and it requires yet another transaction to be redeemed. If we consider fees of 10000 satoshis that means any HTLC below that is as if it didn't existed because we can't ever redeem it anyway. In fact the Lightning protocol explicitly dictates that if HTLC output amounts are below the fee necessary to redeem them they shouldn't be created. What happens in these cases then? Nothing, the amounts that should be in HTLCs are moved to the commitment transaction miner fee instead. So considering a transaction fee of 10000sat for these HTLCs if one is sending Lightning payments below 10000sat that means they operate according to the _unsafe protocol_ described in the first section above. It is actually worse, because consider what happens in the case a channel in the middle of a route has a glitch or one of the peers is unresponsive. The other node, thinking they are operating in the _trustless protocol_, will proceed to publish the commitment transaction, i.e. close the channel, so they can redeem the HTLC -- only then they find out they are actually in the _unsafe protocol_ realm and there is no HTLC to be redeemed at all and they lose not only the money, but also the channel (which costed a lot of money to open and close, in overall transaction fees). One of the biggest features of the _trustless protocol_ are the payment proofs. Every payment is identified by a hash and whenever the payee releases the preimage relative to that hash that means the payment was complete. The incentives are in place so all nodes in the path pass the preimage back until it reaches the payer, which can then use it as the proof he has sent the payment and the payee has received it. This feature is also lost in the _unsafe protocol_: if a glitch happens or someone goes offline on the preimage's way back then there is no way the preimage will reach the payer because no HTLCs are published and redeemed on the chain. The payee may have received the money but the payer will not know -- but the payee will lose the money sent anyway. ## The end of HTLCs So considering the points above you may be sad because in some cases Lightning doesn't use these magic HTLCs that give meaning to it all. But the fact is that no matter what anyone thinks, HTLCs are destined to be used less and less as time passes. The fact that over time Bitcoin transaction fees tend to rise, and also the fact that multipart payment (MPP) are increasedly being used on Lightning for good, we can expect that soon no HTLC will ever be big enough to be actually worth redeeming and we will be at a point in which not a single HTLC is real and they're all fake. Another thing to note is that the current _unsafe protocol_ kicks out whenever the HTLC amount is below the Bitcoin transaction fee would be to redeem it, but this is not a reasonable algorithm. It is not reasonable to lose a channel and then pay 10000sat in fees to redeem a 10001sat HTLC. At which point does it become reasonable to do it? Probably in an amount many times above that, so it would be reasonable to even increase the threshold above which real HTLCs are made -- thus making their existence more and more rare. These are good things, because we don't actually need HTLCs to make a functional Lightning Network. ## We must embrace the _unsafe protocol_ and make it better So the _unsafe protocol_ is not necessarily very bad, but the way it is being done now is, because it suffers from two big problems: 1. Channels are lost all the time for no reason; 2. No guarantees of the proof-of-payment ever reaching the payer exist. The first problem we fix by just stopping the current practice of closing channels when there are no real HTLCs in them. That, however, creates a new problem -- or actually it exarcebates the second: now that we're not closing channels, what do we do with the expired payments in them? These payments should have either been canceled or fulfilled before some block x, now we're in block x+1, our peer has returned from its offline period and one of us will have to lose the money from that payment. That's fine because it's only 3sat and it's better to just lose 3sat than to lose both the 3sat and the channel anyway, so either one would be happy to eat the loss. Maybe we'll even split it 50/50! No, that doesn't work, because it creates an attack vector with peers becoming unresponsive on purpose on one side of the route and actually failing/fulfilling the payment on the other side and making a profit with that. So we actually need to know who is to blame on these payments, even if we are not going to act on that imediatelly: we need some kind of arbiter that both peers can trust, such that if one peer is trying to send the preimage or the cancellation to the other and the other is unresponsive, when the unresponsive peer comes back, the arbiter can tell them they are to blame, so they can willfully eat the loss and the channel can continue. Both peers are happy this way. If the unresponsive peer doesn't accept what the arbiter says then the peer that was operating correctly can assume the unresponsive peer is malicious and close the channel, and then blacklist it and never again open a channel with a peer they know is malicious. Again, the differences between this scheme and the current Lightning Network are that: a. In the current Lightning we always close channels, in this scheme we only close channels in case someone is malicious or in other worst case scenarios (the arbiter is unresponsive, for example). b. In the current Lightning we close the channels without having any clue on who is to blame for that, then we just proceed to reopen a channel with that same peer even in the case they were actively trying to harm us before. ## What is missing? An arbiter. The Bitcoin blockchain is the ideal arbiter, it works in the best possible way if we follow the _trustless protocol_, but as we've seen we can't use the Bitcoin blockchain because it is expensive. Therefore we need a new arbiter. That is the hard part, but not unsolvable. Notice that we don't need an absolutely perfect arbiter, anything is better than nothing, really, even an unreliable arbiter that is offline half of the day is better than what we have today, or an arbiter that lies, an arbiter that charges some satoshis for each resolution, anything. Here are some suggestions: - random nodes from the network selected by an algorithm that both peers agree to, so they can't cheat by selecting themselves. The only thing these nodes have to do is to store data from one peer, try to retransmit it to the other peer and record the results for some time. - a set of nodes preselected by the two peers when the channel is being opened -- same as above, but with more handpicked-trust involved. - some third-party cloud storage or notification provider with guarantees of having open data in it and some public log-keeping, like Twitter, GitHub or a [Nostr](https://github.com/fiatjaf/nostr) relay; - peers that get paid to do the job, selected by the fact that they own some token (I know this is stepping too close to the shitcoin territory, but could be an idea) issued in a [Spacechain](https://www.youtube.com/watch?v=N2ow4Q34Jeg); - a Spacechain itself, serving only as the storage for a bunch of `OP_RETURN`s that are published and tracked by these Lightning peers whenever there is an issue (this looks wrong, but could work). ## Key points 1. Lightning with HTLC-based routing was a cool idea, but it wasn't ever really feasible. 2. HTLCs are going to be abandoned and that's the natural course of things. 3. It is actually good that HTLCs are being abandoned, but 4. We must change the protocol to account for the existence of fake HTLCs and thus make the bulk of the Lightning Network usage viable again. ## See also - [Ripple and the problem of the decentralized commit](nostr:naddr1qqyrxcmzxa3nxv34qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cjrqar6) - [The Lightning Network solves the problem of the decentralized commit](nostr:naddr1qqyx2vekxg6rsvejqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ccs2twc) @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# contratos.alhur.es A website that allowed people to fill a form and get a standard _Contrato de Locação_. Better than all the other "templates" that float around the internet, which are badly formatted `.doc` files. It was fully programmable so other templates could be added later, but I never did. This website made maybe one dollar in Google Ads (and Google has probably stolen these like so many other dollars they did with their bizarre requirements). - <https://github.com/fiatjaf/contratos> - <http://contratos.alhur.es>
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# contratos.alhur.es A website that allowed people to fill a form and get a standard _Contrato de Locação_. Better than all the other "templates" that float around the internet, which are badly formatted `.doc` files. It was fully programmable so other templates could be added later, but I never did. This website made maybe one dollar in Google Ads (and Google has probably stolen these like so many other dollars they did with their bizarre requirements). - <https://github.com/fiatjaf/contratos> - <http://contratos.alhur.es> @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Gold is not useless If there's something all common people believe about gold is that it is useless[^1]. Austrian economists and libertarians in general that argue against central banks or defend a primitive gold standard are often charged with that accusation: that gold is useless, it has no use in the industry, it serves no purpose besides ornamental, so it is a silly commodity, a luxurious one, and that it would be almost immoral to have such a thing in a so central position in an economy such as the position of money. I've seen libertarians in general argue such things as: "it is used in some dental operations", which means people make dental prosthesis of gold, something that fits in same category of jewelry, I would say. There's also the argument of electronic connectors. That's something that appears to be true, but wouldn't suffice the anti-gold arguments. The fact remains that, besides its uses as money -- because gold is still considered to be a form money even now that it doesn't have that position formally in any country (otherwise it wouldn't be considered as an "investment" or "value store" everywhere) -- gold is used mainly for ornamental purposes[^2]. All that is a hassle for libertarians in general. Even the Mises Regression Theory wouldn't solve that problem of people skeptical of gold due to its immoral nature. That problem is solved once you read what is written in the chapter 17 from Richard Cantillon's _Essay on Economic Theory[^3]_ (page 103): > Gold and silver are capable of serving not only the same purpose as tin and copper, but also most of the purposes of lead and iron. They have this further advantage over other metals in that they are not consumed by fire and are so durable that they may be considered permanent. It is not surprising, therefore, that the men who found the other metals useful, valued gold and silver even before they were used in exchange. So gold is indeed useful. Everybody should already know that. You can even do forks and spoons with gold. You can do furniture with gold, and many other useful stuff. As soon as you grasp this, gold is useful again. It is an useful commodity. Answering the next question becomes easy: why isn't anyone making gold forks anywhere? The questioner already knows the answer: because it is too expensive for that. And now the Regression Theory comes with its full force: why is it expensive? Because it has gained a lot of value in the process of becoming money. The value of gold as money is much greater than as a metal used in fork production. --- [^1]: see <http://www.salon.com/2014/02/02/ignore_sean_hannity_gold_is_useless_partner/> or all answers on <https://www.quora.com/Why-is-gold-considered-so-precious-and-why-does-it-have-such-high-prices>. [^2]: this <https://en.wikipedia.org/wiki/Gold#Modern_applications> section on the Wikipedia page for gold is revealing. [^3]: <https://mises.org/library/essay-economic-theory-0>
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Gold is not useless If there's something all common people believe about gold is that it is useless[^1]. Austrian economists and libertarians in general that argue against central banks or defend a primitive gold standard are often charged with that accusation: that gold is useless, it has no use in the industry, it serves no purpose besides ornamental, so it is a silly commodity, a luxurious one, and that it would be almost immoral to have such a thing in a so central position in an economy such as the position of money. I've seen libertarians in general argue such things as: "it is used in some dental operations", which means people make dental prosthesis of gold, something that fits in same category of jewelry, I would say. There's also the argument of electronic connectors. That's something that appears to be true, but wouldn't suffice the anti-gold arguments. The fact remains that, besides its uses as money -- because gold is still considered to be a form money even now that it doesn't have that position formally in any country (otherwise it wouldn't be considered as an "investment" or "value store" everywhere) -- gold is used mainly for ornamental purposes[^2]. All that is a hassle for libertarians in general. Even the Mises Regression Theory wouldn't solve that problem of people skeptical of gold due to its immoral nature. That problem is solved once you read what is written in the chapter 17 from Richard Cantillon's _Essay on Economic Theory[^3]_ (page 103): > Gold and silver are capable of serving not only the same purpose as tin and copper, but also most of the purposes of lead and iron. They have this further advantage over other metals in that they are not consumed by fire and are so durable that they may be considered permanent. It is not surprising, therefore, that the men who found the other metals useful, valued gold and silver even before they were used in exchange. So gold is indeed useful. Everybody should already know that. You can even do forks and spoons with gold. You can do furniture with gold, and many other useful stuff. As soon as you grasp this, gold is useful again. It is an useful commodity. Answering the next question becomes easy: why isn't anyone making gold forks anywhere? The questioner already knows the answer: because it is too expensive for that. And now the Regression Theory comes with its full force: why is it expensive? Because it has gained a lot of value in the process of becoming money. The value of gold as money is much greater than as a metal used in fork production. --- [^1]: see <http://www.salon.com/2014/02/02/ignore_sean_hannity_gold_is_useless_partner/> or all answers on <https://www.quora.com/Why-is-gold-considered-so-precious-and-why-does-it-have-such-high-prices>. [^2]: this <https://en.wikipedia.org/wiki/Gold#Modern_applications> section on the Wikipedia page for gold is revealing. [^3]: <https://mises.org/library/essay-economic-theory-0> @ 8f69ac99:4f92f5fd
2024-08-16 16:12:36O comunismo, tal como idealizado por Karl Marx e Friedrich Engels, prometia uma sociedade utópica, livre de divisões de classe, onde os recursos seriam partilhados de forma equitativa e o Estado acabaria por desaparecer. No entanto, apesar de várias tentativas de implementar esta ideologia em diferentes países, o sonho do "verdadeiro" comunismo nunca se concretizou. Uma das principais razões para esse fracasso reside no factor humano—um aspecto que Marx e Engels não consideraram completamente no seu quadro teórico. Além disso, a implementação de controlos de preços, frequentemente utilizada em economias comunistas e planificadas centralmente, tem repetidamente levado a consequências económicas não intencionais e frequentemente desastrosas. Este artigo explora os desafios inerentes à concretização do verdadeiro comunismo e o papel que os controlos de preços desempenham em minar os próprios objectivos que deveriam apoiar. ### A Visão do Verdadeiro Comunismo **O Quadro Ideológico de Marx e Engels** Karl Marx e Friedrich Engels, nas suas obras revolucionárias, como "O Manifesto Comunista" e "O Capital", lançaram as bases para o que se tornaria uma das ideologias mais influentes dos séculos XIX e XX: o comunismo. No seu cerne, o comunismo é uma crítica ao capitalismo, que Marx e Engels viam como um sistema intrinsecamente explorador, onde a burguesia (a classe capitalista) se enriquece ao extrair mais-valia do proletariado (a classe trabalhadora). A sua visão para o futuro era a de uma revolução que derrubasse as estruturas capitalistas, levando à criação de uma sociedade sem classes e sem Estado. Nesta sociedade ideal, os meios de produção—fábricas, terras e recursos—seriam colectivamente detidos pelo povo. O motivo do lucro, que impulsiona o capitalismo, seria substituído pela produção para uso, garantindo que bens e serviços fossem distribuídos com base na necessidade, em vez da capacidade de pagar. O Estado, que Marx e Engels viam como um instrumento de opressão de classe, acabaria por "definhar" à medida que a necessidade de estruturas de poder coercitivo desaparecesse. Isto levaria a uma sociedade onde a igualdade, a cooperação e a propriedade comunal seriam a norma, e a exploração de uma classe por outra deixaria de existir. Marx e Engels acreditavam que esta transição do capitalismo para o comunismo seria alcançada através de uma série de etapas. Inicialmente, a classe trabalhadora tomaria o poder político e estabeleceria uma "ditadura do proletariado", onde o Estado serviria para desmantelar o sistema capitalista e redistribuir riqueza e recursos. Com o tempo, à medida que os vestígios do capitalismo fossem eliminados e as distinções de classe dissolvidas, o próprio Estado se tornaria desnecessário e gradualmente desapareceria, deixando para trás uma sociedade verdadeiramente comunista. Embora esta visão fosse revolucionária e tenha inspirado muitos movimentos em todo o mundo, ela baseava-se em várias suposições—particularmente em relação à natureza humana e às dinâmicas sociais—que se revelariam problemáticas na prática. ### O Factor Humano: O Que Marx e Engels Não Previram Um dos erros críticos na teoria de Marx e Engels é a subestimação da complexidade do comportamento e das motivações humanas. A sua visão de uma sociedade harmoniosa e sem classes assume que, uma vez alterada a estrutura económica, a natureza humana se adaptaria em conformidade. No entanto, a realidade mostrou-se muito mais complicada. Os seres humanos não são apenas actores económicos movidos por condições materiais. Eles também são motivados por ambições pessoais, desejos de poder e status, e pela necessidade de reconhecimento individual. Embora Marx e Engels reconhecessem o papel da luta de classes na formação da história, eles não consideraram plenamente o quão profundamente enraizadas estão as hierarquias sociais e as dinâmicas de poder, mesmo em sociedades que afirmam ter abolido as distinções de classe. Em todas as tentativas de implementar o comunismo, novas elites surgiram, muitas vezes compostas por oficiais do partido e burocratas que detinham poder e privilégios significativos. Estas elites, longe de personificarem os ideais igualitários do comunismo, frequentemente perpetuaram as mesmas desigualdades que deveriam eliminar. A concentração de poder no Estado, que deveria ser uma medida temporária durante a transição do capitalismo, tornou-se entrincheirada e autoritária. Em vez de definhar, o Estado frequentemente cresceu em poder e opressão, à medida que aqueles no controle procuravam manter as suas posições. Além disso, a abolição da propriedade privada, embora teoricamente destinada a eliminar a exploração, removeu muitos dos incentivos que impulsionam a inovação e a produtividade. Em economias comunistas, onde o emprego e as necessidades básicas eram garantidos independentemente do esforço individual, o absentismo, a ineficiência e a falta de motivação tornaram-se generalizados. O desejo humano de realização pessoal e recompensa, algo que Marx e Engels não abordaram completamente, desempenhou um papel significativo na estagnação económica que muitos sistemas comunistas experimentaram. Outro aspecto crítico que Marx e Engels não previram é a importância da flexibilidade e adaptabilidade nos sistemas económicos. O planeamento económico centralizado, uma marca dos estados comunistas, frequentemente lutou para responder às mudanças nas condições económicas e nas exigências dos consumidores. Sem os mecanismos de feedback proporcionados pelos preços de mercado, os planificadores tiveram dificuldade em alocar recursos de forma eficiente. Esta rigidez levou a persistente escassez de bens, produtos de baixa qualidade e à incapacidade de satisfazer as necessidades da população—um cenário muito distante da abundância e igualdade prometidas pela ideologia comunista. Em resumo, embora Marx e Engels tenham delineado uma visão convincente de uma sociedade livre da exploração e das desigualdades do capitalismo, subestimaram os desafios colocados pela natureza humana e pelas complexidades da organização social e económica. O factor humano—abrangendo as motivações individuais, a persistência das hierarquias sociais e a necessidade de sistemas económicos flexíveis e adaptáveis—tem consistentemente minado as tentativas de alcançar o "verdadeiro" comunismo. Esta falha tem sido uma razão fundamental pela qual o sonho de uma sociedade sem Estado e sem classes tem permanecido ilusório em todas as implementações reais da ideologia comunista. ## Tentativas Históricas de Comunismo Ao longo do século XX, várias nações tentaram implementar o comunismo com base nos princípios marxistas. Esses esforços resultaram numa ampla gama de resultados económicos e sociais, mas nenhum conseguiu alcançar a sociedade sem classes e sem Estado idealizada por Marx e Engels. **A União Soviética e a Europa de Leste** A União Soviética foi a primeira e a maior tentativa de implementar o comunismo. Estabelecida na sequência da Revolução Bolchevique de 1917, o Estado soviético rapidamente adoptou o planeamento económico centralizado e nacionalizou indústrias. Sob o comando de Joseph Stalin, a URSS embarcou numa rápida industrialização, com realizações significativas na indústria pesada e no poder militar. O modelo soviético foi posteriormente exportado para a Europa de Leste após a Segunda Guerra Mundial, onde os estados satélites adoptaram sistemas de planeamento centralizado semelhantes. Embora a União Soviética tenha inicialmente registado alguns sucessos, particularmente na transformação de uma sociedade predominantemente agrária numa potência industrial, essas conquistas tiveram um custo significativo. A natureza rígida e centralizada do planeamento económico soviético levou a ineficiências generalizadas. A ausência de sinais de mercado dificultou a alocação eficaz de recursos, resultando em escassez crónica de bens de consumo e produtos de baixa qualidade. O controlo de preços foi uma ferramenta chave no sistema soviético, destinado a manter os bens básicos acessíveis, mas muitas vezes resultou em mercados distorcidos e actividade no mercado negro. Politicamente, o regime soviético tornou-se cada vez mais repressivo. A concentração de poder no Partido Comunista criou uma nova classe de elite composta por burocratas e funcionários, minando os ideais igualitários do comunismo. A dissidência foi severamente reprimida, e a falta de competição política fez com que o sistema fosse resistente a reformas, mesmo perante problemas económicos crescentes. Na década de 1980, a economia soviética estava em estagnação, e as tentativas de reforma, como a Perestroika de Mikhail Gorbachev, chegaram tarde demais para salvar o regime. Em 1991, a União Soviética colapsou, e os seus estados satélites na Europa de Leste rapidamente abandonaram o comunismo em favor de reformas orientadas para o mercado. **China e Vietname: Reformas de Mercado e Capitalismo de Estado** A China apresenta um caso único na história do comunismo. Após o Partido Comunista chegar ao poder em 1949, a China inicialmente seguiu o modelo soviético de planeamento centralizado e controlo estatal da economia. No entanto, esta abordagem levou a resultados desastrosos, sendo o mais notável o Grande Salto em Frente, que resultou numa fome generalizada e na morte de milhões de pessoas. Reconhecendo a necessidade de mudança, a liderança chinesa, sob Deng Xiaoping, iniciou uma série de reformas de mercado no final da década de 1970 que transformaram profundamente a economia. Essas reformas, frequentemente chamadas de "socialismo com características chinesas", introduziram mecanismos de mercado e permitiram a iniciativa privada, mantendo, no entanto, o controlo político do Partido Comunista. A economia da China experimentou um crescimento sem precedentes, com uma média de quase 10% de crescimento anual do PIB durante várias décadas. No entanto, esse sucesso foi alcançado à custa do abandono de muitos dos princípios fundamentais do marxismo. O sistema da China é melhor descrito como "capitalismo de estado", onde o estado mantém o controlo sobre indústrias-chave, mas as forças de mercado desempenham um papel significativo na economia mais ampla. O Vietname seguiu um caminho semelhante. Após a Guerra do Vietname e a reunificação do país sob o domínio comunista, o Vietname inicialmente seguiu uma economia planeada centralmente. No entanto, como a China, também enfrentou dificuldades económicas, o que levou à introdução de reformas orientadas para o mercado na década de 1980, conhecidas como Đổi Mới. Essas reformas impulsionaram um rápido crescimento económico e tiraram milhões da pobreza, mas também marcaram um afastamento da ideologia comunista tradicional. Tanto a China como o Vietname demonstram que o sucesso económico sob um governo comunista é possível quando os mecanismos de mercado são introduzidos. No entanto, esse sucesso representa uma desvio significativo da visão comunista original, destacando os desafios de alcançar o verdadeiro comunismo na prática. **Cuba: Um Legado Misto** A experiência comunista de Cuba oferece uma perspectiva diferente, focando-se mais em realizações sociais do que no sucesso económico. Desde a Revolução Cubana de 1959, o país tem mantido um governo comunista sob a liderança de Fidel Castro e seus sucessores. A economia de Cuba tem sido longamente caracterizada pelo planeamento centralizado e controlo estatal, com o controlo de preços desempenhando um papel significativo em manter os bens básicos acessíveis. Apesar das suas dificuldades económicas, Cuba fez progressos notáveis em áreas como a saúde e a educação. O sistema de saúde do país, em particular, é frequentemente elogiado pela sua acessibilidade e resultados, com uma expectativa de vida e taxas de mortalidade infantil comparáveis às de nações muito mais ricas. A educação é outra área onde Cuba se destacou, alcançando altas taxas de alfabetização e amplo acesso à escolarização. No entanto, esses sucessos sociais tiveram um custo de estagnação económica. Cuba classifica-se baixo em liberdade económica em comparação com outros países das Américas, e a sua economia tem sido marcada por escassez persistente de bens básicos, em parte devido aos controlos de preços que distorcem a dinâmica do mercado. O país também dependeu fortemente de apoio externo, particularmente de petróleo subsidiado de aliados como a União Soviética e, mais tarde, a Venezuela. À medida que esses apoios externos diminuíram, as dificuldades económicas de Cuba aprofundaram-se. Politicamente, Cuba manteve um estado unipartidário, com pouca tolerância para a dissidência. Como outros estados comunistas, viu a emergência de uma nova classe de elite, com funcionários do partido e líderes militares a usufruírem de privilégios não disponíveis aos cidadãos comuns. Embora as conquistas sociais de Cuba sejam significativas, não foram suficientes para superar os desafios económicos inerentes ao seu sistema. Ao examinar as tentativas históricas de comunismo, torna-se claro que, embora alguns estados comunistas tenham alcançado sucessos notáveis — seja na industrialização, nos serviços sociais ou no crescimento económico —, nenhum conseguiu criar a sociedade sem classes e sem Estado idealizada por Marx e Engels. O factor humano, as ineficiências económicas e as consequências não intencionais de políticas como os controlos de preços minaram consistentemente esses esforços. Seja através do colapso da União Soviética, das reformas de mercado na China e no Vietname, ou das lutas contínuas em Cuba, a história do comunismo é marcada pela tensão entre a ideologia e a realidade. ## O Impacto Económico do Controle de Preços Os controles de preços, frequentemente implementados em economias comunistas e planeadas centralmente, são ferramentas usadas pelos governos para regular os preços de bens e serviços essenciais. Embora estes controles sejam normalmente introduzidos com a intenção de proteger os consumidores, garantir a acessibilidade e manter a equidade social, eles frequentemente levam a distorções económicas significativas. Em sistemas comunistas, onde o controlo estatal sobre a economia é primordial, os controles de preços têm sido uma característica central da política económica. No entanto, as consequências desses controles têm sido muitas vezes prejudiciais, resultando em ineficiências de mercado, redução da inovação e encargos sociais e fiscais não intencionais. **Distorções na Oferta e na Procura** Uma das consequências económicas mais significativas dos controles de preços é a interrupção do equilíbrio natural entre a oferta e a procura. Em sistemas comunistas, os tectos de preços (preços máximos) são frequentemente estabelecidos em bens essenciais para garantir a acessibilidade. No entanto, quando os preços são mantidos artificialmente baixos, a procura normalmente excede a oferta, levando a escassez crónica. Este era um fenómeno comum na União Soviética, onde bens de consumo básicos como alimentos, vestuário e itens domésticos eram frequentemente escassos. A falta de sinais de mercado, como o aumento dos preços para indicar uma maior procura, impedia a alocação eficiente de recursos, exacerbando as carências. Por outro lado, os "pisos" de preços (preços mínimos) podem levar a excedentes. Nos sectores agrícolas, por exemplo, a fixação de preços acima do nível de equilíbrio de mercado pode resultar em superprodução. Isto leva ao desperdício de recursos e ineficiências, pois o governo deve ou comprar o excesso de oferta ou deixá-lo desperdiçar. Estas distorções ilustram o desafio fundamental do planeamento central: sem os mecanismos autorreguladores de um mercado livre, as economias têm dificuldades em equilibrar eficazmente a produção com o consumo. **Redução do Investimento e da Inovação** Os controles de preços também podem ter um efeito desmotivador sobre o investimento e a inovação. Quando os governos impõem tectos de preços, eles frequentemente reduzem as margens de lucro para os produtores. Em economias comunistas, onde o Estado controla a maior parte da produção, isso pode desencorajar o investimento interno e a actividade empresarial. A ausência de incentivos baseados no mercado para a inovação leva à estagnação, pois há pouca motivação para melhorar a eficiência ou desenvolver novos produtos. Esta falta de inovação era evidente na União Soviética e em outras economias planeadas centralmente, onde os avanços tecnológicos ficaram atrás dos países capitalistas. As indústrias que eram fortemente controladas por preços, como bens de consumo e produtos farmacêuticos, sofreram com baixa produtividade e tecnologia desactualizada. Em sectores como o farmacêutico, os controles de preços reduziram os incentivos para a investigação e desenvolvimento, potencialmente limitando futuras inovações médicas. O efeito a longo prazo desta redução do investimento é o menor crescimento económico e a diminuição da competitividade no cenário global. **Deterioração da Qualidade** Outra consequência dos controles de preços é a deterioração da qualidade. Quando os preços são estabelecidos demasiado baixos, os produtores frequentemente procuram maneiras de cortar custos para manter a rentabilidade. Isto resulta frequentemente em bens e serviços de menor qualidade. Em economias comunistas, onde a escolha do consumidor é limitada e a concorrência é suprimida, há pouca pressão sobre os produtores para manter altos padrões. O resultado é que os consumidores ficam com produtos inferiores, deteriorando ainda mais o padrão de vida. Por exemplo, na União Soviética, o foco na quantidade em detrimento da qualidade na fabricação levou a produtos mal feitos que muitas vezes não atendiam às necessidades dos consumidores. Em sectores como a habitação, os controles de rendas mantinham os preços baixos, mas a qualidade do parque habitacional deteriorava-se, uma vez que havia pouco incentivo para a manutenção ou melhoria. Esta troca entre preços baixos e baixa qualidade destaca uma das falhas principais dos controles de preços na prática. **Mercados Negros e Economias Informais** As ineficiências criadas pelos controles de preços frequentemente levam ao surgimento de mercados negros, onde os bens são vendidos a preços superiores aos níveis estabelecidos pelo governo. Em economias comunistas, onde as carências são comuns, os mercados negros tornam-se um mecanismo crucial para obter bens escassos. Estes mercados ilegais minam o controlo do governo sobre a economia e criam uma economia paralela que opera fora do sistema oficial. Na União Soviética e na Europa Oriental, os mercados negros prosperavam à medida que os consumidores procuravam aceder a bens que estavam indisponíveis ou eram de baixa qualidade nas lojas estatais. A existência destes mercados também destaca o fracasso dos controles de preços em atingir os seus objectivos pretendidos, pois as mesmas pessoas que deveriam beneficiar de preços baixos acabavam por pagar preços muito mais altos no sector informal. **Racionamento e Filas** Quando os controles de preços levam à escassez, os governos muitas vezes recorrem a sistemas de racionamento para distribuir os suprimentos limitados. O racionamento, embora assegure que todos recebam uma parte dos bens escassos, também introduz ineficiências e iniquidades. Filas longas para necessidades básicas tornaram-se uma visão comum em muitos países comunistas, com pessoas a gastar horas à espera de itens que frequentemente estavam em falta. Este sistema não só desperdiçava tempo valioso, como também evidenciava as falhas do planeamento central. O racionamento e as filas são uma consequência directa dos controles de preços que impedem os mercados de se ajustarem naturalmente. Em vez de permitir que os preços subam e incentivem o aumento da produção, os governos mantêm preços artificialmente baixos, resultando em escassez crónica e frustração generalizada entre a população. **Encargo Fiscal e Consequências Sociais** Manter controles de preços frequentemente requer uma intervenção governamental significativa, incluindo subsídios aos produtores para compensar os custos dos preços baixos. Isto cria um encargo fiscal que pode sobrecarregar os orçamentos governamentais, especialmente em economias que já enfrentam ineficiências. Em alguns casos, o custo de manter os controles de preços pode superar os benefícios, levando a políticas económicas insustentáveis. Além disso, os controles de preços podem levar a consequências sociais não intencionais. Embora sejam destinados a ajudar as populações mais vulneráveis, eles podem, por vezes, beneficiar aqueles que não precisam de assistência. Por exemplo, os controles de rendas destinados a proporcionar habitação acessível podem acabar por beneficiar indivíduos mais ricos que têm acesso a apartamentos com rendas controladas, enquanto os indivíduos de baixos rendimentos continuam a enfrentar dificuldades com a acessibilidade habitacional. Além disso, os controles de preços podem empurrar a actividade económica para o sector informal, reduzindo as receitas fiscais e a supervisão regulatória. Esta informalidade enfraquece a capacidade do Estado de gerir a economia de forma eficaz e cria distorções adicionais. **Crescimento Económico a Longo Prazo e Impactos Específicos por Sector** A longo prazo, as distorções causadas pelos controles de preços podem levar a uma redução do crescimento económico. Ao interferir nos sinais de mercado, os controles de preços desencorajam o investimento, a inovação e a produtividade, todos essenciais para o desenvolvimento económico sustentado. Ao longo do tempo, isso pode resultar em estagnação, como visto em muitas economias comunistas onde o crescimento abrandou ou até mesmo retrocedeu. Sectores específicos, como o farmacêutico e o agrícola, podem ser particularmente afectados pelos controles de preços. No sector farmacêutico, por exemplo, os tectos de preços podem reduzir o incentivo para as empresas investirem em investigação e desenvolvimento, potencialmente limitando futuras inovações médicas. Na agricultura, os pisos de preços podem levar à superprodução, desperdício e à necessidade de intervenções governamentais onerosas. **Os Benefícios a Curto Prazo e Potenciais Justificativas** Embora os controles de preços sejam geralmente vistos de forma negativa devido às suas consequências a longo prazo, podem haver alguns benefícios a curto prazo, especialmente em tempos de crise. Por exemplo, durante emergências, os controles de preços podem impedir a exploração de preços e garantir que bens essenciais permaneçam acessíveis às populações vulneráveis. Nestes casos, os controles de preços podem fornecer alívio temporário e proteger os consumidores de abusos. No entanto, esses benefícios a curto prazo são muitas vezes superados pelos custos a longo prazo. Mesmo em situações de crise, os efeitos distorcionários dos controles de preços podem criar mais problemas do que resolvem, tornando-os uma ferramenta que deve ser usada com cautela. Os controles de preços, embora destinados a proteger os consumidores e promover a equidade social, frequentemente levam a consequências económicas, de mercado e sociais não intencionais. Em sistemas comunistas, onde o controlo estatal sobre a economia é central, estes controles exacerbaram ineficiências, sufocaram a inovação e criaram uma série de resultados negativos, desde mercados negros até encargos fiscais. Embora possa haver situações onde os controles de preços sejam justificados a curto prazo, o seu impacto a longo prazo é geralmente prejudicial, minando os próprios objectivos que pretendem alcançar. Compreender o legado complexo dos controles de preços nas economias comunistas fornece lições valiosas para os formuladores de políticas que procuram equilibrar a estabilidade económica com a equidade social. ## Consequências do Planeamento Centralizado e do Controlo de Preços **Autoritarismo e a Concentração de Poder** Uma das consequências políticas mais significativas do planeamento económico centralizado e do controlo de preços é a concentração de poder dentro do aparelho de Estado. Em teoria, o comunismo idealiza uma sociedade sem Estado, mas na prática, a implementação desses sistemas muitas vezes exige uma autoridade central forte para aplicar as directivas económicas e manter o controlo. Esta concentração de poder frequentemente leva ao autoritarismo, como se vê em numerosos regimes comunistas. A centralização do poder permite que um pequeno grupo de líderes ou um único partido domine a vida política, muitas vezes suprimindo a oposição e restringindo as liberdades individuais. Sem pesos e contrapesos, estes regimes podem impor controlos rigorosos na economia e na sociedade, levando a uma repressão generalizada. A natureza autoritária desses governos é frequentemente justificada como um meio necessário para proteger a revolução e manter a ordem social, mas resulta na erosão dos princípios democráticos e na marginalização das vozes dissidentes. Além disso, a concentração de poder no Estado mina os próprios ideais do comunismo. Em vez de uma sociedade sem classes, emerge uma nova classe dominante de funcionários do partido e burocratas, que gozam de privilégios e autoridade muito além do cidadão comum. Esta dinâmica de poder não só contradiz os objectivos igualitários do comunismo, como também perpetua a desigualdade dentro do sistema. **Desigualdade Social e o Surgimento de Novas Elites** Apesar do objectivo teórico de eliminar as classes sociais, os sistemas comunistas muitas vezes testemunham o surgimento de novas elites. Estas elites, compostas por líderes do partido, burocratas do Estado e oficiais militares, gozam de privilégios significativos que os distinguem da população em geral. Este fenómeno reflecte o desafio inerente de alcançar uma verdadeira igualdade num sistema onde o poder está concentrado nas mãos de poucos. Em muitos casos, essas novas elites tornam-se enraizadas, criando um fosso entre os governantes e os governados que espelha as divisões de classe que o comunismo pretendia eliminar. Os privilégios e o poder desfrutados por essas elites frequentemente levam à corrupção e ao clientelismo, corroendo ainda mais a confiança pública no sistema. O descontentamento resultante entre a população pode levar a agitação, à medida que as pessoas percebem que a igualdade prometida é inatingível dentro da estrutura política existente. **A Supressão de Dissidência e Suas Consequências Económicas** A supressão da dissidência é uma característica marcante de muitos regimes comunistas, impulsionada pela necessidade de manter o controlo tanto sobre a economia quanto sobre a sociedade. Na prática, essa supressão assume várias formas, incluindo censura, vigilância e perseguição de oponentes políticos. A falta de competição política e de debate aberto sufoca a inovação e o feedback crítico, que são essenciais para uma economia dinâmica e adaptável. Sem a capacidade de expressar preocupações ou propor políticas alternativas, os regimes comunistas muitas vezes lutam para responder de forma eficaz aos desafios económicos. A natureza rígida do planeamento centralizado, combinada com a supressão da dissidência, cria um ciclo vicioso em que os problemas são ignorados ou exacerbados, levando a um maior declínio económico. A ausência de dissidência também significa que as reformas necessárias são adiadas ou bloqueadas, à medida que as elites no poder priorizam os seus próprios interesses em detrimento do bem comum. As consequências a longo prazo dessa supressão são profundas. Economias que carecem de flexibilidade para se adaptar às mudanças ou enfrentar ineficiências tornam-se estagnadas, levando a escassez, declínio na produtividade e uma queda no padrão de vida da população. A supressão da dissidência não só prejudica o desempenho económico, mas também enfraquece o tecido social, à medida que a confiança no governo se deteriora e as pessoas se sentem cada vez mais alienadas do sistema político. **Autoritarismo nas Sociedades Ocidentais: Uma Preocupação Crescente** Nos últimos anos, o aumento do autoritarismo nas sociedades ocidentais tornou-se uma preocupação crescente, manifestando-se através de várias tendências chave que ecoam algumas das dinâmicas observadas em regimes comunistas. Embora as democracias ocidentais estejam longe de um autoritarismo pleno, a concentração de poder, o crescimento das desigualdades sociais, o surgimento de novas elites e a supressão da dissidência sugerem um desvio preocupante dos princípios democráticos liberais. Tem havido uma crescente centralização do poder em muitos países ocidentais, muitas vezes manifestada através do excesso de autoridade executiva e da expansão do poder presidencial ou do primeiro-ministro. O enfraquecimento dos mecanismos de pesos e contrapesos entre os ramos do governo e as tentativas de minar a independência judicial e o estado de direito são indicadores claros desta tendência. Esta concentração de poder corrói as normas e instituições democráticas ao longo do tempo, tornando mais difícil responsabilizar os líderes. A crescente desigualdade económica tem alimentado o descontentamento e movimentos populistas em muitos países ocidentais. O aumento da disparidade de riqueza entre as elites e a população em geral, os salários estagnados para as classes média e trabalhadora e a redução da mobilidade social contribuíram para um crescente sentimento de desilusão com os sistemas democráticos tradicionais. Esta disparidade económica criou um terreno fértil para líderes com tendências autoritárias, que prometem resolver esses problemas, mas muitas vezes concentram ainda mais o poder. O surgimento de novas estruturas de poder e grupos de elites, como os oligarcas da tecnologia e as elites empresariais ligadas à política, tem desafiado os mecanismos tradicionais de responsabilização democrática. Estas novas elites frequentemente exercem uma influência significativa sobre a informação, o discurso e a política, operando fora do alcance das instituições democráticas. Líderes populistas, que cultivam cultos de personalidade, também contribuem para esta mudança, enfraquecendo ainda mais os processos democráticos. As preocupações sobre restrições à liberdade de expressão e ao debate aberto estão a crescer nas sociedades ocidentais. Embora não sejam equivalentes à censura autoritária vista em regimes comunistas, tendências como a "cultura do cancelamento", a vigilância governamental e a repressão de protestos têm um efeito dissuasor sobre o discurso aberto. A autocensura devido ao medo de retaliações online ou de consequências profissionais está a tornar-se mais comum, limitando a diversidade de pontos de vista no debate público. A fé pública nos pilares centrais da democracia — governos, partidos políticos e funcionários eleitos — tem-se deteriorado em muitos países ocidentais. O cepticismo em relação aos meios de comunicação tradicionais e ao conhecimento especializado também aumentou, enquanto a integridade dos sistemas eleitorais é cada vez mais questionada. Esta perda de confiança cria oportunidades para líderes com tendências autoritárias ganharem apoio, enfraquecendo ainda mais as instituições democráticas. O aumento do autoritarismo nas sociedades ocidentais, embora ainda não comparável ao controlo centralizado visto em regimes comunistas, sinaliza uma mudança preocupante em relação aos princípios da democracia liberal. A concentração de poder, o crescimento das desigualdades sociais, o surgimento de novas elites e a supressão da dissidência são todos factores que espelham os problemas enfrentados pelos estados comunistas históricos, embora em formas diferentes. Estas tendências, se não forem controladas, podem levar a uma erosão gradual das normas e instituições democráticas, minando os próprios alicerces de sociedades livres e abertas. Os paralelos entre os desafios enfrentados pelos regimes comunistas e as tendências actuais nas democracias ocidentais destacam a importância de abordar essas questões subjacentes. Assim como o planeamento económico centralizado e o controlo de preços levaram a ineficiências e agitação social nos estados comunistas, a concentração de poder e a desigualdade no Ocidente ameaçam enfraquecer os sistemas democráticos por dentro. A supressão da dissidência e a diminuição da confiança nas instituições democráticas agravam ainda mais esses problemas, criando um ambiente onde o autoritarismo pode ganhar terreno. É crucial que as sociedades ocidentais reforcem as normas e instituições democráticas. Isso envolve garantir que os pesos e contrapesos entre os ramos do governo sejam mantidos, protegendo a independência judicial e salvaguardando o estado de direito. Abordar a desigualdade económica também é essencial, pois é um dos principais impulsionadores dos sentimentos populistas e autoritários. Políticas que promovam a mobilidade social, salários justos e oportunidades económicas podem ajudar a reconstruir a confiança nos sistemas democráticos. Além disso, promover um discurso público aberto e inclusivo é vital para prevenir a supressão da dissidência. Isso significa defender a liberdade de expressão, encorajar a diversidade de pontos de vista e resistir à tentação de silenciar opiniões impopulares através de pressão social ou governamental. Ao criar uma cultura que valoriza o debate e respeita perspectivas diferentes, as sociedades ocidentais podem resistir ao desvio para o autoritarismo. Finalmente, reconstruir a confiança nas instituições democráticas exige transparência, responsabilização e capacidade de resposta por parte dos governos e líderes políticos. Os funcionários eleitos devem ser vistos a agir no interesse público, e as instituições devem ser percepcionadas como justas e eficazes. Restaurar a confiança nos sistemas eleitorais e nos meios de comunicação também é essencial para contrariar a ascensão do populismo e do autoritarismo. Embora os desafios enfrentados pelas democracias ocidentais hoje sejam distintos dos que atormentaram os regimes comunistas, as dinâmicas subjacentes de poder, desigualdade e dissidência partilham algumas semelhanças preocupantes. Ao reconhecer e aprender com os fracassos do comunismo e ao abordar estas questões de frente, as sociedades ocidentais podem fortalecer as suas fundações democráticas e evitar o deslizamento para o autoritarismo. ## Conclusão Em resumo, os fracassos do verdadeiro comunismo e os efeitos prejudiciais dos controles de preços não são meramente notas de rodapé históricas, mas lições duradouras que continuam a ressoar hoje em dia. O colapso de inúmeros regimes comunistas e as persistentes dificuldades económicas em países que ainda tentam aderir aos princípios comunistas destacam as falhas fundamentais da ideologia. O factor humano—motivações individuais, o desejo de liberdade pessoal e as complexidades da governação—continuamente perturbam a visão utópica de uma sociedade sem classes e sem estado. O planeamento centralizado e os controles de preços, longe de criar igualdade e estabilidade, têm consistentemente levado a ineficiências económicas, escassez e regimes autoritários. No entanto, estas lições não são apenas relevantes para o passado. As sociedades ocidentais de hoje enfrentam os seus próprios riscos, à medida que a esquerda se inclina cada vez mais para políticas autoritárias sob o disfarce de equidade e justiça social. A pressão por mais controlo estatal, juntamente com uma crescente intolerância à dissidência, espelha os estágios iniciais dos mesmos sistemas que levaram à tirania e ditadura no passado. O marxismo cultural, um movimento que busca remodelar a sociedade promovendo a ideologia marxista através das instituições culturais, está a ganhar força, particularmente no meio académico e nos meios de comunicação. Esta mudança ideológica está a corroer as fundações da liberdade individual e da liberdade económica que têm definido o Ocidente. De forma alarmante, muitos jovens no Ocidente estão a louvar cada vez mais a ideologia marxista e o comunismo, muitas vezes sem compreender plenamente as realidades históricas desses sistemas. Esta tendência reflecte uma perigosa ignorância das atrocidades e do sofrimento que ocorreram sob os regimes comunistas. A romantização do comunismo ignora as duras verdades da história—a repressão, o colapso económico e a perda de liberdades pessoais que têm consistentemente acompanhado as tentativas de implementar esta ideologia. É crucial manter-se vigilante contra estas tendências. As lições da história devem servir de alerta para aqueles que procuram replicar sistemas falhados. Embora a busca por uma sociedade mais justa e equitativa seja um objectivo nobre, não pode vir à custa das liberdades individuais e dos benefícios comprovados de uma economia baseada no mercado. As sociedades ocidentais devem proteger-se contra o fascínio do autoritarismo, seja na forma de comunismo declarado ou de formas mais subtis de controlo estatal. Garantir que a próxima geração compreenda a verdadeira natureza dessas ideologias é essencial para preservar as liberdades e a prosperidade que foram arduamente conquistadas ao longo de séculos. --- __Photo by <a href="https://unsplash.com/@rocinante_11?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash">Mick Haupt</a> on <a href="https://unsplash.com/photos/people-walking-inside-building-with-escalator-pOEY_iRFg60?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash">Unsplash</a>__
@ 8f69ac99:4f92f5fd
2024-08-16 16:12:36O comunismo, tal como idealizado por Karl Marx e Friedrich Engels, prometia uma sociedade utópica, livre de divisões de classe, onde os recursos seriam partilhados de forma equitativa e o Estado acabaria por desaparecer. No entanto, apesar de várias tentativas de implementar esta ideologia em diferentes países, o sonho do "verdadeiro" comunismo nunca se concretizou. Uma das principais razões para esse fracasso reside no factor humano—um aspecto que Marx e Engels não consideraram completamente no seu quadro teórico. Além disso, a implementação de controlos de preços, frequentemente utilizada em economias comunistas e planificadas centralmente, tem repetidamente levado a consequências económicas não intencionais e frequentemente desastrosas. Este artigo explora os desafios inerentes à concretização do verdadeiro comunismo e o papel que os controlos de preços desempenham em minar os próprios objectivos que deveriam apoiar. ### A Visão do Verdadeiro Comunismo **O Quadro Ideológico de Marx e Engels** Karl Marx e Friedrich Engels, nas suas obras revolucionárias, como "O Manifesto Comunista" e "O Capital", lançaram as bases para o que se tornaria uma das ideologias mais influentes dos séculos XIX e XX: o comunismo. No seu cerne, o comunismo é uma crítica ao capitalismo, que Marx e Engels viam como um sistema intrinsecamente explorador, onde a burguesia (a classe capitalista) se enriquece ao extrair mais-valia do proletariado (a classe trabalhadora). A sua visão para o futuro era a de uma revolução que derrubasse as estruturas capitalistas, levando à criação de uma sociedade sem classes e sem Estado. Nesta sociedade ideal, os meios de produção—fábricas, terras e recursos—seriam colectivamente detidos pelo povo. O motivo do lucro, que impulsiona o capitalismo, seria substituído pela produção para uso, garantindo que bens e serviços fossem distribuídos com base na necessidade, em vez da capacidade de pagar. O Estado, que Marx e Engels viam como um instrumento de opressão de classe, acabaria por "definhar" à medida que a necessidade de estruturas de poder coercitivo desaparecesse. Isto levaria a uma sociedade onde a igualdade, a cooperação e a propriedade comunal seriam a norma, e a exploração de uma classe por outra deixaria de existir. Marx e Engels acreditavam que esta transição do capitalismo para o comunismo seria alcançada através de uma série de etapas. Inicialmente, a classe trabalhadora tomaria o poder político e estabeleceria uma "ditadura do proletariado", onde o Estado serviria para desmantelar o sistema capitalista e redistribuir riqueza e recursos. Com o tempo, à medida que os vestígios do capitalismo fossem eliminados e as distinções de classe dissolvidas, o próprio Estado se tornaria desnecessário e gradualmente desapareceria, deixando para trás uma sociedade verdadeiramente comunista. Embora esta visão fosse revolucionária e tenha inspirado muitos movimentos em todo o mundo, ela baseava-se em várias suposições—particularmente em relação à natureza humana e às dinâmicas sociais—que se revelariam problemáticas na prática. ### O Factor Humano: O Que Marx e Engels Não Previram Um dos erros críticos na teoria de Marx e Engels é a subestimação da complexidade do comportamento e das motivações humanas. A sua visão de uma sociedade harmoniosa e sem classes assume que, uma vez alterada a estrutura económica, a natureza humana se adaptaria em conformidade. No entanto, a realidade mostrou-se muito mais complicada. Os seres humanos não são apenas actores económicos movidos por condições materiais. Eles também são motivados por ambições pessoais, desejos de poder e status, e pela necessidade de reconhecimento individual. Embora Marx e Engels reconhecessem o papel da luta de classes na formação da história, eles não consideraram plenamente o quão profundamente enraizadas estão as hierarquias sociais e as dinâmicas de poder, mesmo em sociedades que afirmam ter abolido as distinções de classe. Em todas as tentativas de implementar o comunismo, novas elites surgiram, muitas vezes compostas por oficiais do partido e burocratas que detinham poder e privilégios significativos. Estas elites, longe de personificarem os ideais igualitários do comunismo, frequentemente perpetuaram as mesmas desigualdades que deveriam eliminar. A concentração de poder no Estado, que deveria ser uma medida temporária durante a transição do capitalismo, tornou-se entrincheirada e autoritária. Em vez de definhar, o Estado frequentemente cresceu em poder e opressão, à medida que aqueles no controle procuravam manter as suas posições. Além disso, a abolição da propriedade privada, embora teoricamente destinada a eliminar a exploração, removeu muitos dos incentivos que impulsionam a inovação e a produtividade. Em economias comunistas, onde o emprego e as necessidades básicas eram garantidos independentemente do esforço individual, o absentismo, a ineficiência e a falta de motivação tornaram-se generalizados. O desejo humano de realização pessoal e recompensa, algo que Marx e Engels não abordaram completamente, desempenhou um papel significativo na estagnação económica que muitos sistemas comunistas experimentaram. Outro aspecto crítico que Marx e Engels não previram é a importância da flexibilidade e adaptabilidade nos sistemas económicos. O planeamento económico centralizado, uma marca dos estados comunistas, frequentemente lutou para responder às mudanças nas condições económicas e nas exigências dos consumidores. Sem os mecanismos de feedback proporcionados pelos preços de mercado, os planificadores tiveram dificuldade em alocar recursos de forma eficiente. Esta rigidez levou a persistente escassez de bens, produtos de baixa qualidade e à incapacidade de satisfazer as necessidades da população—um cenário muito distante da abundância e igualdade prometidas pela ideologia comunista. Em resumo, embora Marx e Engels tenham delineado uma visão convincente de uma sociedade livre da exploração e das desigualdades do capitalismo, subestimaram os desafios colocados pela natureza humana e pelas complexidades da organização social e económica. O factor humano—abrangendo as motivações individuais, a persistência das hierarquias sociais e a necessidade de sistemas económicos flexíveis e adaptáveis—tem consistentemente minado as tentativas de alcançar o "verdadeiro" comunismo. Esta falha tem sido uma razão fundamental pela qual o sonho de uma sociedade sem Estado e sem classes tem permanecido ilusório em todas as implementações reais da ideologia comunista. ## Tentativas Históricas de Comunismo Ao longo do século XX, várias nações tentaram implementar o comunismo com base nos princípios marxistas. Esses esforços resultaram numa ampla gama de resultados económicos e sociais, mas nenhum conseguiu alcançar a sociedade sem classes e sem Estado idealizada por Marx e Engels. **A União Soviética e a Europa de Leste** A União Soviética foi a primeira e a maior tentativa de implementar o comunismo. Estabelecida na sequência da Revolução Bolchevique de 1917, o Estado soviético rapidamente adoptou o planeamento económico centralizado e nacionalizou indústrias. Sob o comando de Joseph Stalin, a URSS embarcou numa rápida industrialização, com realizações significativas na indústria pesada e no poder militar. O modelo soviético foi posteriormente exportado para a Europa de Leste após a Segunda Guerra Mundial, onde os estados satélites adoptaram sistemas de planeamento centralizado semelhantes. Embora a União Soviética tenha inicialmente registado alguns sucessos, particularmente na transformação de uma sociedade predominantemente agrária numa potência industrial, essas conquistas tiveram um custo significativo. A natureza rígida e centralizada do planeamento económico soviético levou a ineficiências generalizadas. A ausência de sinais de mercado dificultou a alocação eficaz de recursos, resultando em escassez crónica de bens de consumo e produtos de baixa qualidade. O controlo de preços foi uma ferramenta chave no sistema soviético, destinado a manter os bens básicos acessíveis, mas muitas vezes resultou em mercados distorcidos e actividade no mercado negro. Politicamente, o regime soviético tornou-se cada vez mais repressivo. A concentração de poder no Partido Comunista criou uma nova classe de elite composta por burocratas e funcionários, minando os ideais igualitários do comunismo. A dissidência foi severamente reprimida, e a falta de competição política fez com que o sistema fosse resistente a reformas, mesmo perante problemas económicos crescentes. Na década de 1980, a economia soviética estava em estagnação, e as tentativas de reforma, como a Perestroika de Mikhail Gorbachev, chegaram tarde demais para salvar o regime. Em 1991, a União Soviética colapsou, e os seus estados satélites na Europa de Leste rapidamente abandonaram o comunismo em favor de reformas orientadas para o mercado. **China e Vietname: Reformas de Mercado e Capitalismo de Estado** A China apresenta um caso único na história do comunismo. Após o Partido Comunista chegar ao poder em 1949, a China inicialmente seguiu o modelo soviético de planeamento centralizado e controlo estatal da economia. No entanto, esta abordagem levou a resultados desastrosos, sendo o mais notável o Grande Salto em Frente, que resultou numa fome generalizada e na morte de milhões de pessoas. Reconhecendo a necessidade de mudança, a liderança chinesa, sob Deng Xiaoping, iniciou uma série de reformas de mercado no final da década de 1970 que transformaram profundamente a economia. Essas reformas, frequentemente chamadas de "socialismo com características chinesas", introduziram mecanismos de mercado e permitiram a iniciativa privada, mantendo, no entanto, o controlo político do Partido Comunista. A economia da China experimentou um crescimento sem precedentes, com uma média de quase 10% de crescimento anual do PIB durante várias décadas. No entanto, esse sucesso foi alcançado à custa do abandono de muitos dos princípios fundamentais do marxismo. O sistema da China é melhor descrito como "capitalismo de estado", onde o estado mantém o controlo sobre indústrias-chave, mas as forças de mercado desempenham um papel significativo na economia mais ampla. O Vietname seguiu um caminho semelhante. Após a Guerra do Vietname e a reunificação do país sob o domínio comunista, o Vietname inicialmente seguiu uma economia planeada centralmente. No entanto, como a China, também enfrentou dificuldades económicas, o que levou à introdução de reformas orientadas para o mercado na década de 1980, conhecidas como Đổi Mới. Essas reformas impulsionaram um rápido crescimento económico e tiraram milhões da pobreza, mas também marcaram um afastamento da ideologia comunista tradicional. Tanto a China como o Vietname demonstram que o sucesso económico sob um governo comunista é possível quando os mecanismos de mercado são introduzidos. No entanto, esse sucesso representa uma desvio significativo da visão comunista original, destacando os desafios de alcançar o verdadeiro comunismo na prática. **Cuba: Um Legado Misto** A experiência comunista de Cuba oferece uma perspectiva diferente, focando-se mais em realizações sociais do que no sucesso económico. Desde a Revolução Cubana de 1959, o país tem mantido um governo comunista sob a liderança de Fidel Castro e seus sucessores. A economia de Cuba tem sido longamente caracterizada pelo planeamento centralizado e controlo estatal, com o controlo de preços desempenhando um papel significativo em manter os bens básicos acessíveis. Apesar das suas dificuldades económicas, Cuba fez progressos notáveis em áreas como a saúde e a educação. O sistema de saúde do país, em particular, é frequentemente elogiado pela sua acessibilidade e resultados, com uma expectativa de vida e taxas de mortalidade infantil comparáveis às de nações muito mais ricas. A educação é outra área onde Cuba se destacou, alcançando altas taxas de alfabetização e amplo acesso à escolarização. No entanto, esses sucessos sociais tiveram um custo de estagnação económica. Cuba classifica-se baixo em liberdade económica em comparação com outros países das Américas, e a sua economia tem sido marcada por escassez persistente de bens básicos, em parte devido aos controlos de preços que distorcem a dinâmica do mercado. O país também dependeu fortemente de apoio externo, particularmente de petróleo subsidiado de aliados como a União Soviética e, mais tarde, a Venezuela. À medida que esses apoios externos diminuíram, as dificuldades económicas de Cuba aprofundaram-se. Politicamente, Cuba manteve um estado unipartidário, com pouca tolerância para a dissidência. Como outros estados comunistas, viu a emergência de uma nova classe de elite, com funcionários do partido e líderes militares a usufruírem de privilégios não disponíveis aos cidadãos comuns. Embora as conquistas sociais de Cuba sejam significativas, não foram suficientes para superar os desafios económicos inerentes ao seu sistema. Ao examinar as tentativas históricas de comunismo, torna-se claro que, embora alguns estados comunistas tenham alcançado sucessos notáveis — seja na industrialização, nos serviços sociais ou no crescimento económico —, nenhum conseguiu criar a sociedade sem classes e sem Estado idealizada por Marx e Engels. O factor humano, as ineficiências económicas e as consequências não intencionais de políticas como os controlos de preços minaram consistentemente esses esforços. Seja através do colapso da União Soviética, das reformas de mercado na China e no Vietname, ou das lutas contínuas em Cuba, a história do comunismo é marcada pela tensão entre a ideologia e a realidade. ## O Impacto Económico do Controle de Preços Os controles de preços, frequentemente implementados em economias comunistas e planeadas centralmente, são ferramentas usadas pelos governos para regular os preços de bens e serviços essenciais. Embora estes controles sejam normalmente introduzidos com a intenção de proteger os consumidores, garantir a acessibilidade e manter a equidade social, eles frequentemente levam a distorções económicas significativas. Em sistemas comunistas, onde o controlo estatal sobre a economia é primordial, os controles de preços têm sido uma característica central da política económica. No entanto, as consequências desses controles têm sido muitas vezes prejudiciais, resultando em ineficiências de mercado, redução da inovação e encargos sociais e fiscais não intencionais. **Distorções na Oferta e na Procura** Uma das consequências económicas mais significativas dos controles de preços é a interrupção do equilíbrio natural entre a oferta e a procura. Em sistemas comunistas, os tectos de preços (preços máximos) são frequentemente estabelecidos em bens essenciais para garantir a acessibilidade. No entanto, quando os preços são mantidos artificialmente baixos, a procura normalmente excede a oferta, levando a escassez crónica. Este era um fenómeno comum na União Soviética, onde bens de consumo básicos como alimentos, vestuário e itens domésticos eram frequentemente escassos. A falta de sinais de mercado, como o aumento dos preços para indicar uma maior procura, impedia a alocação eficiente de recursos, exacerbando as carências. Por outro lado, os "pisos" de preços (preços mínimos) podem levar a excedentes. Nos sectores agrícolas, por exemplo, a fixação de preços acima do nível de equilíbrio de mercado pode resultar em superprodução. Isto leva ao desperdício de recursos e ineficiências, pois o governo deve ou comprar o excesso de oferta ou deixá-lo desperdiçar. Estas distorções ilustram o desafio fundamental do planeamento central: sem os mecanismos autorreguladores de um mercado livre, as economias têm dificuldades em equilibrar eficazmente a produção com o consumo. **Redução do Investimento e da Inovação** Os controles de preços também podem ter um efeito desmotivador sobre o investimento e a inovação. Quando os governos impõem tectos de preços, eles frequentemente reduzem as margens de lucro para os produtores. Em economias comunistas, onde o Estado controla a maior parte da produção, isso pode desencorajar o investimento interno e a actividade empresarial. A ausência de incentivos baseados no mercado para a inovação leva à estagnação, pois há pouca motivação para melhorar a eficiência ou desenvolver novos produtos. Esta falta de inovação era evidente na União Soviética e em outras economias planeadas centralmente, onde os avanços tecnológicos ficaram atrás dos países capitalistas. As indústrias que eram fortemente controladas por preços, como bens de consumo e produtos farmacêuticos, sofreram com baixa produtividade e tecnologia desactualizada. Em sectores como o farmacêutico, os controles de preços reduziram os incentivos para a investigação e desenvolvimento, potencialmente limitando futuras inovações médicas. O efeito a longo prazo desta redução do investimento é o menor crescimento económico e a diminuição da competitividade no cenário global. **Deterioração da Qualidade** Outra consequência dos controles de preços é a deterioração da qualidade. Quando os preços são estabelecidos demasiado baixos, os produtores frequentemente procuram maneiras de cortar custos para manter a rentabilidade. Isto resulta frequentemente em bens e serviços de menor qualidade. Em economias comunistas, onde a escolha do consumidor é limitada e a concorrência é suprimida, há pouca pressão sobre os produtores para manter altos padrões. O resultado é que os consumidores ficam com produtos inferiores, deteriorando ainda mais o padrão de vida. Por exemplo, na União Soviética, o foco na quantidade em detrimento da qualidade na fabricação levou a produtos mal feitos que muitas vezes não atendiam às necessidades dos consumidores. Em sectores como a habitação, os controles de rendas mantinham os preços baixos, mas a qualidade do parque habitacional deteriorava-se, uma vez que havia pouco incentivo para a manutenção ou melhoria. Esta troca entre preços baixos e baixa qualidade destaca uma das falhas principais dos controles de preços na prática. **Mercados Negros e Economias Informais** As ineficiências criadas pelos controles de preços frequentemente levam ao surgimento de mercados negros, onde os bens são vendidos a preços superiores aos níveis estabelecidos pelo governo. Em economias comunistas, onde as carências são comuns, os mercados negros tornam-se um mecanismo crucial para obter bens escassos. Estes mercados ilegais minam o controlo do governo sobre a economia e criam uma economia paralela que opera fora do sistema oficial. Na União Soviética e na Europa Oriental, os mercados negros prosperavam à medida que os consumidores procuravam aceder a bens que estavam indisponíveis ou eram de baixa qualidade nas lojas estatais. A existência destes mercados também destaca o fracasso dos controles de preços em atingir os seus objectivos pretendidos, pois as mesmas pessoas que deveriam beneficiar de preços baixos acabavam por pagar preços muito mais altos no sector informal. **Racionamento e Filas** Quando os controles de preços levam à escassez, os governos muitas vezes recorrem a sistemas de racionamento para distribuir os suprimentos limitados. O racionamento, embora assegure que todos recebam uma parte dos bens escassos, também introduz ineficiências e iniquidades. Filas longas para necessidades básicas tornaram-se uma visão comum em muitos países comunistas, com pessoas a gastar horas à espera de itens que frequentemente estavam em falta. Este sistema não só desperdiçava tempo valioso, como também evidenciava as falhas do planeamento central. O racionamento e as filas são uma consequência directa dos controles de preços que impedem os mercados de se ajustarem naturalmente. Em vez de permitir que os preços subam e incentivem o aumento da produção, os governos mantêm preços artificialmente baixos, resultando em escassez crónica e frustração generalizada entre a população. **Encargo Fiscal e Consequências Sociais** Manter controles de preços frequentemente requer uma intervenção governamental significativa, incluindo subsídios aos produtores para compensar os custos dos preços baixos. Isto cria um encargo fiscal que pode sobrecarregar os orçamentos governamentais, especialmente em economias que já enfrentam ineficiências. Em alguns casos, o custo de manter os controles de preços pode superar os benefícios, levando a políticas económicas insustentáveis. Além disso, os controles de preços podem levar a consequências sociais não intencionais. Embora sejam destinados a ajudar as populações mais vulneráveis, eles podem, por vezes, beneficiar aqueles que não precisam de assistência. Por exemplo, os controles de rendas destinados a proporcionar habitação acessível podem acabar por beneficiar indivíduos mais ricos que têm acesso a apartamentos com rendas controladas, enquanto os indivíduos de baixos rendimentos continuam a enfrentar dificuldades com a acessibilidade habitacional. Além disso, os controles de preços podem empurrar a actividade económica para o sector informal, reduzindo as receitas fiscais e a supervisão regulatória. Esta informalidade enfraquece a capacidade do Estado de gerir a economia de forma eficaz e cria distorções adicionais. **Crescimento Económico a Longo Prazo e Impactos Específicos por Sector** A longo prazo, as distorções causadas pelos controles de preços podem levar a uma redução do crescimento económico. Ao interferir nos sinais de mercado, os controles de preços desencorajam o investimento, a inovação e a produtividade, todos essenciais para o desenvolvimento económico sustentado. Ao longo do tempo, isso pode resultar em estagnação, como visto em muitas economias comunistas onde o crescimento abrandou ou até mesmo retrocedeu. Sectores específicos, como o farmacêutico e o agrícola, podem ser particularmente afectados pelos controles de preços. No sector farmacêutico, por exemplo, os tectos de preços podem reduzir o incentivo para as empresas investirem em investigação e desenvolvimento, potencialmente limitando futuras inovações médicas. Na agricultura, os pisos de preços podem levar à superprodução, desperdício e à necessidade de intervenções governamentais onerosas. **Os Benefícios a Curto Prazo e Potenciais Justificativas** Embora os controles de preços sejam geralmente vistos de forma negativa devido às suas consequências a longo prazo, podem haver alguns benefícios a curto prazo, especialmente em tempos de crise. Por exemplo, durante emergências, os controles de preços podem impedir a exploração de preços e garantir que bens essenciais permaneçam acessíveis às populações vulneráveis. Nestes casos, os controles de preços podem fornecer alívio temporário e proteger os consumidores de abusos. No entanto, esses benefícios a curto prazo são muitas vezes superados pelos custos a longo prazo. Mesmo em situações de crise, os efeitos distorcionários dos controles de preços podem criar mais problemas do que resolvem, tornando-os uma ferramenta que deve ser usada com cautela. Os controles de preços, embora destinados a proteger os consumidores e promover a equidade social, frequentemente levam a consequências económicas, de mercado e sociais não intencionais. Em sistemas comunistas, onde o controlo estatal sobre a economia é central, estes controles exacerbaram ineficiências, sufocaram a inovação e criaram uma série de resultados negativos, desde mercados negros até encargos fiscais. Embora possa haver situações onde os controles de preços sejam justificados a curto prazo, o seu impacto a longo prazo é geralmente prejudicial, minando os próprios objectivos que pretendem alcançar. Compreender o legado complexo dos controles de preços nas economias comunistas fornece lições valiosas para os formuladores de políticas que procuram equilibrar a estabilidade económica com a equidade social. ## Consequências do Planeamento Centralizado e do Controlo de Preços **Autoritarismo e a Concentração de Poder** Uma das consequências políticas mais significativas do planeamento económico centralizado e do controlo de preços é a concentração de poder dentro do aparelho de Estado. Em teoria, o comunismo idealiza uma sociedade sem Estado, mas na prática, a implementação desses sistemas muitas vezes exige uma autoridade central forte para aplicar as directivas económicas e manter o controlo. Esta concentração de poder frequentemente leva ao autoritarismo, como se vê em numerosos regimes comunistas. A centralização do poder permite que um pequeno grupo de líderes ou um único partido domine a vida política, muitas vezes suprimindo a oposição e restringindo as liberdades individuais. Sem pesos e contrapesos, estes regimes podem impor controlos rigorosos na economia e na sociedade, levando a uma repressão generalizada. A natureza autoritária desses governos é frequentemente justificada como um meio necessário para proteger a revolução e manter a ordem social, mas resulta na erosão dos princípios democráticos e na marginalização das vozes dissidentes. Além disso, a concentração de poder no Estado mina os próprios ideais do comunismo. Em vez de uma sociedade sem classes, emerge uma nova classe dominante de funcionários do partido e burocratas, que gozam de privilégios e autoridade muito além do cidadão comum. Esta dinâmica de poder não só contradiz os objectivos igualitários do comunismo, como também perpetua a desigualdade dentro do sistema. **Desigualdade Social e o Surgimento de Novas Elites** Apesar do objectivo teórico de eliminar as classes sociais, os sistemas comunistas muitas vezes testemunham o surgimento de novas elites. Estas elites, compostas por líderes do partido, burocratas do Estado e oficiais militares, gozam de privilégios significativos que os distinguem da população em geral. Este fenómeno reflecte o desafio inerente de alcançar uma verdadeira igualdade num sistema onde o poder está concentrado nas mãos de poucos. Em muitos casos, essas novas elites tornam-se enraizadas, criando um fosso entre os governantes e os governados que espelha as divisões de classe que o comunismo pretendia eliminar. Os privilégios e o poder desfrutados por essas elites frequentemente levam à corrupção e ao clientelismo, corroendo ainda mais a confiança pública no sistema. O descontentamento resultante entre a população pode levar a agitação, à medida que as pessoas percebem que a igualdade prometida é inatingível dentro da estrutura política existente. **A Supressão de Dissidência e Suas Consequências Económicas** A supressão da dissidência é uma característica marcante de muitos regimes comunistas, impulsionada pela necessidade de manter o controlo tanto sobre a economia quanto sobre a sociedade. Na prática, essa supressão assume várias formas, incluindo censura, vigilância e perseguição de oponentes políticos. A falta de competição política e de debate aberto sufoca a inovação e o feedback crítico, que são essenciais para uma economia dinâmica e adaptável. Sem a capacidade de expressar preocupações ou propor políticas alternativas, os regimes comunistas muitas vezes lutam para responder de forma eficaz aos desafios económicos. A natureza rígida do planeamento centralizado, combinada com a supressão da dissidência, cria um ciclo vicioso em que os problemas são ignorados ou exacerbados, levando a um maior declínio económico. A ausência de dissidência também significa que as reformas necessárias são adiadas ou bloqueadas, à medida que as elites no poder priorizam os seus próprios interesses em detrimento do bem comum. As consequências a longo prazo dessa supressão são profundas. Economias que carecem de flexibilidade para se adaptar às mudanças ou enfrentar ineficiências tornam-se estagnadas, levando a escassez, declínio na produtividade e uma queda no padrão de vida da população. A supressão da dissidência não só prejudica o desempenho económico, mas também enfraquece o tecido social, à medida que a confiança no governo se deteriora e as pessoas se sentem cada vez mais alienadas do sistema político. **Autoritarismo nas Sociedades Ocidentais: Uma Preocupação Crescente** Nos últimos anos, o aumento do autoritarismo nas sociedades ocidentais tornou-se uma preocupação crescente, manifestando-se através de várias tendências chave que ecoam algumas das dinâmicas observadas em regimes comunistas. Embora as democracias ocidentais estejam longe de um autoritarismo pleno, a concentração de poder, o crescimento das desigualdades sociais, o surgimento de novas elites e a supressão da dissidência sugerem um desvio preocupante dos princípios democráticos liberais. Tem havido uma crescente centralização do poder em muitos países ocidentais, muitas vezes manifestada através do excesso de autoridade executiva e da expansão do poder presidencial ou do primeiro-ministro. O enfraquecimento dos mecanismos de pesos e contrapesos entre os ramos do governo e as tentativas de minar a independência judicial e o estado de direito são indicadores claros desta tendência. Esta concentração de poder corrói as normas e instituições democráticas ao longo do tempo, tornando mais difícil responsabilizar os líderes. A crescente desigualdade económica tem alimentado o descontentamento e movimentos populistas em muitos países ocidentais. O aumento da disparidade de riqueza entre as elites e a população em geral, os salários estagnados para as classes média e trabalhadora e a redução da mobilidade social contribuíram para um crescente sentimento de desilusão com os sistemas democráticos tradicionais. Esta disparidade económica criou um terreno fértil para líderes com tendências autoritárias, que prometem resolver esses problemas, mas muitas vezes concentram ainda mais o poder. O surgimento de novas estruturas de poder e grupos de elites, como os oligarcas da tecnologia e as elites empresariais ligadas à política, tem desafiado os mecanismos tradicionais de responsabilização democrática. Estas novas elites frequentemente exercem uma influência significativa sobre a informação, o discurso e a política, operando fora do alcance das instituições democráticas. Líderes populistas, que cultivam cultos de personalidade, também contribuem para esta mudança, enfraquecendo ainda mais os processos democráticos. As preocupações sobre restrições à liberdade de expressão e ao debate aberto estão a crescer nas sociedades ocidentais. Embora não sejam equivalentes à censura autoritária vista em regimes comunistas, tendências como a "cultura do cancelamento", a vigilância governamental e a repressão de protestos têm um efeito dissuasor sobre o discurso aberto. A autocensura devido ao medo de retaliações online ou de consequências profissionais está a tornar-se mais comum, limitando a diversidade de pontos de vista no debate público. A fé pública nos pilares centrais da democracia — governos, partidos políticos e funcionários eleitos — tem-se deteriorado em muitos países ocidentais. O cepticismo em relação aos meios de comunicação tradicionais e ao conhecimento especializado também aumentou, enquanto a integridade dos sistemas eleitorais é cada vez mais questionada. Esta perda de confiança cria oportunidades para líderes com tendências autoritárias ganharem apoio, enfraquecendo ainda mais as instituições democráticas. O aumento do autoritarismo nas sociedades ocidentais, embora ainda não comparável ao controlo centralizado visto em regimes comunistas, sinaliza uma mudança preocupante em relação aos princípios da democracia liberal. A concentração de poder, o crescimento das desigualdades sociais, o surgimento de novas elites e a supressão da dissidência são todos factores que espelham os problemas enfrentados pelos estados comunistas históricos, embora em formas diferentes. Estas tendências, se não forem controladas, podem levar a uma erosão gradual das normas e instituições democráticas, minando os próprios alicerces de sociedades livres e abertas. Os paralelos entre os desafios enfrentados pelos regimes comunistas e as tendências actuais nas democracias ocidentais destacam a importância de abordar essas questões subjacentes. Assim como o planeamento económico centralizado e o controlo de preços levaram a ineficiências e agitação social nos estados comunistas, a concentração de poder e a desigualdade no Ocidente ameaçam enfraquecer os sistemas democráticos por dentro. A supressão da dissidência e a diminuição da confiança nas instituições democráticas agravam ainda mais esses problemas, criando um ambiente onde o autoritarismo pode ganhar terreno. É crucial que as sociedades ocidentais reforcem as normas e instituições democráticas. Isso envolve garantir que os pesos e contrapesos entre os ramos do governo sejam mantidos, protegendo a independência judicial e salvaguardando o estado de direito. Abordar a desigualdade económica também é essencial, pois é um dos principais impulsionadores dos sentimentos populistas e autoritários. Políticas que promovam a mobilidade social, salários justos e oportunidades económicas podem ajudar a reconstruir a confiança nos sistemas democráticos. Além disso, promover um discurso público aberto e inclusivo é vital para prevenir a supressão da dissidência. Isso significa defender a liberdade de expressão, encorajar a diversidade de pontos de vista e resistir à tentação de silenciar opiniões impopulares através de pressão social ou governamental. Ao criar uma cultura que valoriza o debate e respeita perspectivas diferentes, as sociedades ocidentais podem resistir ao desvio para o autoritarismo. Finalmente, reconstruir a confiança nas instituições democráticas exige transparência, responsabilização e capacidade de resposta por parte dos governos e líderes políticos. Os funcionários eleitos devem ser vistos a agir no interesse público, e as instituições devem ser percepcionadas como justas e eficazes. Restaurar a confiança nos sistemas eleitorais e nos meios de comunicação também é essencial para contrariar a ascensão do populismo e do autoritarismo. Embora os desafios enfrentados pelas democracias ocidentais hoje sejam distintos dos que atormentaram os regimes comunistas, as dinâmicas subjacentes de poder, desigualdade e dissidência partilham algumas semelhanças preocupantes. Ao reconhecer e aprender com os fracassos do comunismo e ao abordar estas questões de frente, as sociedades ocidentais podem fortalecer as suas fundações democráticas e evitar o deslizamento para o autoritarismo. ## Conclusão Em resumo, os fracassos do verdadeiro comunismo e os efeitos prejudiciais dos controles de preços não são meramente notas de rodapé históricas, mas lições duradouras que continuam a ressoar hoje em dia. O colapso de inúmeros regimes comunistas e as persistentes dificuldades económicas em países que ainda tentam aderir aos princípios comunistas destacam as falhas fundamentais da ideologia. O factor humano—motivações individuais, o desejo de liberdade pessoal e as complexidades da governação—continuamente perturbam a visão utópica de uma sociedade sem classes e sem estado. O planeamento centralizado e os controles de preços, longe de criar igualdade e estabilidade, têm consistentemente levado a ineficiências económicas, escassez e regimes autoritários. No entanto, estas lições não são apenas relevantes para o passado. As sociedades ocidentais de hoje enfrentam os seus próprios riscos, à medida que a esquerda se inclina cada vez mais para políticas autoritárias sob o disfarce de equidade e justiça social. A pressão por mais controlo estatal, juntamente com uma crescente intolerância à dissidência, espelha os estágios iniciais dos mesmos sistemas que levaram à tirania e ditadura no passado. O marxismo cultural, um movimento que busca remodelar a sociedade promovendo a ideologia marxista através das instituições culturais, está a ganhar força, particularmente no meio académico e nos meios de comunicação. Esta mudança ideológica está a corroer as fundações da liberdade individual e da liberdade económica que têm definido o Ocidente. De forma alarmante, muitos jovens no Ocidente estão a louvar cada vez mais a ideologia marxista e o comunismo, muitas vezes sem compreender plenamente as realidades históricas desses sistemas. Esta tendência reflecte uma perigosa ignorância das atrocidades e do sofrimento que ocorreram sob os regimes comunistas. A romantização do comunismo ignora as duras verdades da história—a repressão, o colapso económico e a perda de liberdades pessoais que têm consistentemente acompanhado as tentativas de implementar esta ideologia. É crucial manter-se vigilante contra estas tendências. As lições da história devem servir de alerta para aqueles que procuram replicar sistemas falhados. Embora a busca por uma sociedade mais justa e equitativa seja um objectivo nobre, não pode vir à custa das liberdades individuais e dos benefícios comprovados de uma economia baseada no mercado. As sociedades ocidentais devem proteger-se contra o fascínio do autoritarismo, seja na forma de comunismo declarado ou de formas mais subtis de controlo estatal. Garantir que a próxima geração compreenda a verdadeira natureza dessas ideologias é essencial para preservar as liberdades e a prosperidade que foram arduamente conquistadas ao longo de séculos. --- __Photo by <a href="https://unsplash.com/@rocinante_11?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash">Mick Haupt</a> on <a href="https://unsplash.com/photos/people-walking-inside-building-with-escalator-pOEY_iRFg60?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash">Unsplash</a>__ @ 1739d937:3e3136ef
2024-08-16 10:08:42This is the fifth in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr. ## Previous Updates - [June 28th 2024](https://habla.news/u/jeffg.fyi/1719562889267) - [July 6th 2024](https://habla.news/u/jeffg.fyi/1720256910765) - [July 12th 2024](https://habla.news/u/jeffg.fyi/1720778880538) - [July 19th 2024](https://habla.news/u/jeffg.fyi/1721419437737) ## Progress this week I'm back from a few weeks of family holiday this week and feeling super productive. The major news this week is that I've posted the [draft NIP](https://github.com/nostr-protocol/nips/pull/1427) to the NIPs repository for how to implement MLS messaging on Nostr. I've gotten feedback on the doc from several other Nostr devs but I'm absolutely looking for more feedback from the community. I've also made progress on the dependencies that I was working on before my holidays. Info below. ### The NIP I won't review the entire proposed NIP here but I wanted to call out one tradeoff that I thought hard about. In my original proposal, which only supported one-to-one direct messages, all messages between the two parties were sent as NIP-59 gift-wrapped events. This helps to hide metadata but it creates problems of it's own. Notably, it's very possible to DDoS Nostr clients with meaningless gift-wrap events since clients must decrypt and unwrap each event to even understand if it's something that is important to them. Aside from those problems, gift-wrapping messages to an entire group would be very impractical. It would require the client sending a message to individually gift-wrap the message individually to all other participants in a group. The tradeoff I've come up with is to use a public event, `kind:445`, tagged with the group ID, so that all participants in the group can easily query for messages from each of the groups that they are a part of. The content field of these event is encrypted using the MLS ratchet keys and thus is only able to be decrypted by members of the group. These events are published using an ephemeral key so that the number and identity of the group members is obfuscated. This means that observers have a relative idea of the level of activity in a given group but don't know exactly how many or who is in the group. In addition, it's easy within the MLS spec to rotate the group ID over time. Would love to hear thoughts on how people feel about that tradeoff. ### HPKE-RS My [PR](https://github.com/franziskuskiefer/hpke-rs/pull/66) to add support for secp256k1 is stuck because of bad test vectors for the secp256k1 curve. I've been working on generating new vectors that will be usable by other HPKE implementations as well. Huge thanks to @dan for the help on this. ### OpenMLS & Ciphersuites As mentioned in the previous updated, I've spoken with the OpenMLS team about how to better support custom ciphersuites. I've started to work on the expansive refactor in OpenMLS to make this possible but it's going to take a while. One major decision that has come from this is that I've decided that the NIP will not require a single custom ciphersuite (built around Schnorr signatures on the secp256k1 curve). Instead, clients can decide which ciphersuites they want to support and are able to implement this NIP immediately with the current OpenMLS version. I will continue to work on refactoring the OpenMLS library to ensure that it supports custom ciphersuites and to build a custom Crypto Provider focused on the Nostr crypto primitives and I expect that, long-term, many Nostr clients will prefer to support only that ciphersuite to reduce the dependency surface area of their apps. ## Onward and Upward LFG! 🤙 Please take a moment and send me feedback and thoughts on the above and especially on the NIP if you're a developer.
@ 1739d937:3e3136ef
2024-08-16 10:08:42This is the fifth in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr. ## Previous Updates - [June 28th 2024](https://habla.news/u/jeffg.fyi/1719562889267) - [July 6th 2024](https://habla.news/u/jeffg.fyi/1720256910765) - [July 12th 2024](https://habla.news/u/jeffg.fyi/1720778880538) - [July 19th 2024](https://habla.news/u/jeffg.fyi/1721419437737) ## Progress this week I'm back from a few weeks of family holiday this week and feeling super productive. The major news this week is that I've posted the [draft NIP](https://github.com/nostr-protocol/nips/pull/1427) to the NIPs repository for how to implement MLS messaging on Nostr. I've gotten feedback on the doc from several other Nostr devs but I'm absolutely looking for more feedback from the community. I've also made progress on the dependencies that I was working on before my holidays. Info below. ### The NIP I won't review the entire proposed NIP here but I wanted to call out one tradeoff that I thought hard about. In my original proposal, which only supported one-to-one direct messages, all messages between the two parties were sent as NIP-59 gift-wrapped events. This helps to hide metadata but it creates problems of it's own. Notably, it's very possible to DDoS Nostr clients with meaningless gift-wrap events since clients must decrypt and unwrap each event to even understand if it's something that is important to them. Aside from those problems, gift-wrapping messages to an entire group would be very impractical. It would require the client sending a message to individually gift-wrap the message individually to all other participants in a group. The tradeoff I've come up with is to use a public event, `kind:445`, tagged with the group ID, so that all participants in the group can easily query for messages from each of the groups that they are a part of. The content field of these event is encrypted using the MLS ratchet keys and thus is only able to be decrypted by members of the group. These events are published using an ephemeral key so that the number and identity of the group members is obfuscated. This means that observers have a relative idea of the level of activity in a given group but don't know exactly how many or who is in the group. In addition, it's easy within the MLS spec to rotate the group ID over time. Would love to hear thoughts on how people feel about that tradeoff. ### HPKE-RS My [PR](https://github.com/franziskuskiefer/hpke-rs/pull/66) to add support for secp256k1 is stuck because of bad test vectors for the secp256k1 curve. I've been working on generating new vectors that will be usable by other HPKE implementations as well. Huge thanks to @dan for the help on this. ### OpenMLS & Ciphersuites As mentioned in the previous updated, I've spoken with the OpenMLS team about how to better support custom ciphersuites. I've started to work on the expansive refactor in OpenMLS to make this possible but it's going to take a while. One major decision that has come from this is that I've decided that the NIP will not require a single custom ciphersuite (built around Schnorr signatures on the secp256k1 curve). Instead, clients can decide which ciphersuites they want to support and are able to implement this NIP immediately with the current OpenMLS version. I will continue to work on refactoring the OpenMLS library to ensure that it supports custom ciphersuites and to build a custom Crypto Provider focused on the Nostr crypto primitives and I expect that, long-term, many Nostr clients will prefer to support only that ciphersuite to reduce the dependency surface area of their apps. ## Onward and Upward LFG! 🤙 Please take a moment and send me feedback and thoughts on the above and especially on the NIP if you're a developer. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Filemap [filemap](https://filemap.xyz/) solves the problem of sending and receiving files to and from non-tech people when you don't have a text communication channel with them. [](https://xkcd.com/949/) Imagine you want to send files to your grandfather, or you don't use Facebook and your younger cousin who only uses Facebook and doesn't know what is email wants to send you some pictures, it's pretty hard to get a file-sharing channel between people if they're not in the same network. If even the people have a way to upload the files to some hosting service and then share the link everything would still work, but you're not going to write `somehostingservice.com/wHr4y7vFGh0` to your grandfather -- or expect your cousin to do that for you and send you an SMS with dozens of those links. Solution: * Upload your files to https://filemap.xyz/ (you can either upload directly or share links to things already uploaded -- or even links to pages) and pin them to your grandfather's house address; then tell your grandfather to open https://filemap.xyz/ and look for his address. Done. * Tell your younger cousin to visit filemap.xyz and upload all the files to his address, later you open the site and look for his address. There are your files. --- Initially this used [ipfs-dropzone](nostr:naddr1qqyrjvrx8p3xyvesqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cwpfruw), but IPFS is broken, os I migrated to [WebTorrent](https://webtorrent.io/), but that required the file sender to be online hosting its own file and the entire idea of this service was to make something _easy_, so I migrated to Firebase Hosting, which is also terrible and has a broken API, but at least is capable of hosting files. Should have used something like S3. - <https://github.com/fiatjaf/filemap.xyz> - <https://filemap.xyz/>
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Filemap [filemap](https://filemap.xyz/) solves the problem of sending and receiving files to and from non-tech people when you don't have a text communication channel with them. [](https://xkcd.com/949/) Imagine you want to send files to your grandfather, or you don't use Facebook and your younger cousin who only uses Facebook and doesn't know what is email wants to send you some pictures, it's pretty hard to get a file-sharing channel between people if they're not in the same network. If even the people have a way to upload the files to some hosting service and then share the link everything would still work, but you're not going to write `somehostingservice.com/wHr4y7vFGh0` to your grandfather -- or expect your cousin to do that for you and send you an SMS with dozens of those links. Solution: * Upload your files to https://filemap.xyz/ (you can either upload directly or share links to things already uploaded -- or even links to pages) and pin them to your grandfather's house address; then tell your grandfather to open https://filemap.xyz/ and look for his address. Done. * Tell your younger cousin to visit filemap.xyz and upload all the files to his address, later you open the site and look for his address. There are your files. --- Initially this used [ipfs-dropzone](nostr:naddr1qqyrjvrx8p3xyvesqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cwpfruw), but IPFS is broken, os I migrated to [WebTorrent](https://webtorrent.io/), but that required the file sender to be online hosting its own file and the entire idea of this service was to make something _easy_, so I migrated to Firebase Hosting, which is also terrible and has a broken API, but at least is capable of hosting files. Should have used something like S3. - <https://github.com/fiatjaf/filemap.xyz> - <https://filemap.xyz/> @ da18e986:3a0d9851
2024-08-14 13:58:24After months of development I am excited to officially announce the first version of DVMDash (v0.1). DVMDash is a monitoring and debugging tool for all Data Vending Machine (DVM) activity on Nostr. The website is live at [https://dvmdash.live](https://dvmdash.live) and the code is available on [Github](https://github.com/dtdannen/dvmdash). Data Vending Machines ([NIP-90](https://github.com/nostr-protocol/nips/blob/master/90.md)) offload computationally expensive tasks from relays and clients in a decentralized, free-market manner. They are especially useful for AI tools, algorithmic processing of user’s feeds, and many other use cases. The long term goal of DVMDash is to become 1) a place to easily see what’s happening in the DVM ecosystem with metrics and graphs, and 2) provide real-time tools to help developers monitor, debug, and improve their DVMs. DVMDash aims to enable users to answer these types of questions at a glance: * What’s the most popular DVM right now? * How much money is being paid to image generation DVMs? * Is any DVM down at the moment? When was the last time that DVM completed a task? * Have any DVMs failed to deliver after accepting payment? Did they refund that payment? * How long does it take this DVM to respond? * For task X, what’s the average amount of time it takes for a DVM to complete the task? * … and more For developers working with DVMs there is now a visual, graph based tool that shows DVM-chain activity. DVMs have already started calling other DVMs to assist with work. Soon, we will have humans in the loop monitoring DVM activity, or completing tasks themselves. The activity trace of which DVM is being called as part of a sub-task from another DVM will become complicated, especially because these decisions will be made at run-time and are not known ahead of time. Building a tool to help users and developers understand where a DVM is in this activity trace, whether it’s gotten stuck or is just taking a long time, will be invaluable. *For now, the website only shows 1 step of a dvm chain from a user's request.* One of the main designs for the site is that it is highly _clickable_, meaning whenever you see a DVM, Kind, User, or Event ID, you can click it and open that up in a new page to inspect it. Another aspect of this website is that it should be fast. If you submit a DVM request, you should see it in DVMDash within seconds, as well as events from DVMs interacting with your request. I have attempted to obtain DVM events from relays as quickly as possible and compute metrics over them within seconds. This project makes use of a nosql database and graph database, currently set to use mongo db and neo4j, for which there are free, community versions that can be run locally. Finally, I’m grateful to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project. ## Features in v0.1: ### Global Network Metrics: This page shows the following metrics: - **DVM Requests:** Number of unencrypted DVM requests (kind 5000-5999) - **DVM Results:** Number of unencrypted DVM results (kind 6000-6999) - **DVM Request Kinds Seen:** Number of unique kinds in the Kind range 5000-5999 (except for known non-DVM kinds 5666 and 5969) - **DVM Result Kinds Seen:** Number of unique kinds in the Kind range 6000-6999 (except for known non-DVM kinds 6666 and 6969) - **DVM Pub Keys Seen:** Number of unique pub keys that have written a kind 6000-6999 (except for known non-DVM kinds) or have published a kind 31990 event that specifies a ‘k’ tag value between 5000-5999 - **DVM Profiles (NIP-89) Seen**: Number of 31990 that have a ‘k’ tag value for kind 5000-5999 - **Most Popular DVM**: The DVM that has produced the most result events (kind 6000-6999) - **Most Popular Kind**: The Kind in range 5000-5999 that has the most requests by users. - **24 hr DVM Requests**: Number of kind 5000-5999 events created in the last 24 hrs - **24 hr DVM Results**: Number of kind 6000-6999 events created in the last 24 hours - **1 week DVM Requests**: Number of kind 5000-5999 events created in the last week - **1 week DVM Results**: Number of kind 6000-6999 events created in the last week - **Unique Users of DVMs**: Number of unique pubkeys of kind 5000-5999 events - **Total Sats Paid to DVMs**: - This is an estimate. - This value is likely a lower bound as it does not take into consideration subscriptions paid to DVMs - This is calculated by counting the values of all invoices where: - A DVM published a kind 7000 event requesting payment and containing an invoice - The DVM later provided a DVM Result for the same job for which it requested payment. - The assumption is that the invoice was paid, otherwise the DVM would not have done the work - Note that because there are multiple ways to pay a DVM such as lightning invoices, ecash, and subscriptions, there is no guaranteed way to know whether a DVM has been paid. Additionally, there is no way to know that a DVM completed the job because some DVMs may not publish a final result event and instead send the user a DM or take some other kind of action. ### Recent Requests: This page shows the most recent 3 events per kind, sorted by created date. You should always be able to find the last 3 events here of all DVM kinds. ### DVM Browser: This page will either show a profile of a specific DVM, or when no DVM is given in the url, it will show a table of all DVMs with some high level stats. Users can click on a DVM in the table to load the DVM specific page. ### Kind Browser: This page will either show data on a specific kind including all DVMs that have performed jobs of that kind, or when no kind is given, it will show a table summarizing activity across all Kinds. ### Debug: This page shows the graph based visualization of all events, users, and DVMs involved in a single job as well as a table of all events in order from oldest to newest. When no event is given, this page shows the 200 most recent events where the user can click on an event in order to debug that job. The graph-based visualization allows the user to zoom in and out and move around the graph, as well as double click on any node in the graph (except invoices) to open up that event, user, or dvm in a new page. ### Playground: This page is currently under development and may not work at the moment. If it does work, in the current state you can login with NIP-07 extension and broadcast a 5050 event with some text and then the page will show you events from DVMs. This page will be used to interact with DVMs live. A current good alternative to this feature, for some but not all kinds, is [https://vendata.io/](https://vendata.io/). ## Looking to the Future I originally built DVMDash out of Fear-of-Missing-Out (FOMO); I wanted to make AI systems that were comprised of DVMs but my day job was taking up a lot of my time. I needed to know when someone was performing a new task or launching a new AI or Nostr tool! I have a long list of DVMs and Agents I hope to build and I needed DVMDash to help me do it; I hope it helps you achieve your goals with Nostr, DVMs, and even AI. To this end, I wish for this tool to be useful to others, so if you would like a feature, please [submit a git issue here](https://github.com/dtdannen/dvmdash/issues/new) or _note_ me on Nostr! ### Immediate Next Steps: - Refactoring code and removing code that is no longer used - Improve documentation to run the project locally - Adding a metric for number of encrypted requests - Adding a metric for number of encrypted results ### Long Term Goals: - Add more metrics based on community feedback - Add plots showing metrics over time - Add support for showing a multi-dvm chain in the graph based visualizer - Add a real-time mode where the pages will auto update (currently the user must refresh the page) - ... Add support for user requested features! ## Acknowledgements There are some fantastic people working in the DVM space right now. Thank you to nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet for making python bindings for nostr_sdk and for the recent asyncio upgrades! Thank you to nostr:npub1nxa4tywfz9nqp7z9zp7nr7d4nchhclsf58lcqt5y782rmf2hefjquaa6q8 for answering lots of questions about DVMs and for making the nostrdvm library. Thank you to nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft for making the original DVM NIP and [vendata.io](https://vendata.io/) which I use all the time for testing! P.S. I rushed to get this out in time for Nostriga 2024; code refactoring will be coming :)
@ da18e986:3a0d9851
2024-08-14 13:58:24After months of development I am excited to officially announce the first version of DVMDash (v0.1). DVMDash is a monitoring and debugging tool for all Data Vending Machine (DVM) activity on Nostr. The website is live at [https://dvmdash.live](https://dvmdash.live) and the code is available on [Github](https://github.com/dtdannen/dvmdash). Data Vending Machines ([NIP-90](https://github.com/nostr-protocol/nips/blob/master/90.md)) offload computationally expensive tasks from relays and clients in a decentralized, free-market manner. They are especially useful for AI tools, algorithmic processing of user’s feeds, and many other use cases. The long term goal of DVMDash is to become 1) a place to easily see what’s happening in the DVM ecosystem with metrics and graphs, and 2) provide real-time tools to help developers monitor, debug, and improve their DVMs. DVMDash aims to enable users to answer these types of questions at a glance: * What’s the most popular DVM right now? * How much money is being paid to image generation DVMs? * Is any DVM down at the moment? When was the last time that DVM completed a task? * Have any DVMs failed to deliver after accepting payment? Did they refund that payment? * How long does it take this DVM to respond? * For task X, what’s the average amount of time it takes for a DVM to complete the task? * … and more For developers working with DVMs there is now a visual, graph based tool that shows DVM-chain activity. DVMs have already started calling other DVMs to assist with work. Soon, we will have humans in the loop monitoring DVM activity, or completing tasks themselves. The activity trace of which DVM is being called as part of a sub-task from another DVM will become complicated, especially because these decisions will be made at run-time and are not known ahead of time. Building a tool to help users and developers understand where a DVM is in this activity trace, whether it’s gotten stuck or is just taking a long time, will be invaluable. *For now, the website only shows 1 step of a dvm chain from a user's request.* One of the main designs for the site is that it is highly _clickable_, meaning whenever you see a DVM, Kind, User, or Event ID, you can click it and open that up in a new page to inspect it. Another aspect of this website is that it should be fast. If you submit a DVM request, you should see it in DVMDash within seconds, as well as events from DVMs interacting with your request. I have attempted to obtain DVM events from relays as quickly as possible and compute metrics over them within seconds. This project makes use of a nosql database and graph database, currently set to use mongo db and neo4j, for which there are free, community versions that can be run locally. Finally, I’m grateful to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project. ## Features in v0.1: ### Global Network Metrics: This page shows the following metrics: - **DVM Requests:** Number of unencrypted DVM requests (kind 5000-5999) - **DVM Results:** Number of unencrypted DVM results (kind 6000-6999) - **DVM Request Kinds Seen:** Number of unique kinds in the Kind range 5000-5999 (except for known non-DVM kinds 5666 and 5969) - **DVM Result Kinds Seen:** Number of unique kinds in the Kind range 6000-6999 (except for known non-DVM kinds 6666 and 6969) - **DVM Pub Keys Seen:** Number of unique pub keys that have written a kind 6000-6999 (except for known non-DVM kinds) or have published a kind 31990 event that specifies a ‘k’ tag value between 5000-5999 - **DVM Profiles (NIP-89) Seen**: Number of 31990 that have a ‘k’ tag value for kind 5000-5999 - **Most Popular DVM**: The DVM that has produced the most result events (kind 6000-6999) - **Most Popular Kind**: The Kind in range 5000-5999 that has the most requests by users. - **24 hr DVM Requests**: Number of kind 5000-5999 events created in the last 24 hrs - **24 hr DVM Results**: Number of kind 6000-6999 events created in the last 24 hours - **1 week DVM Requests**: Number of kind 5000-5999 events created in the last week - **1 week DVM Results**: Number of kind 6000-6999 events created in the last week - **Unique Users of DVMs**: Number of unique pubkeys of kind 5000-5999 events - **Total Sats Paid to DVMs**: - This is an estimate. - This value is likely a lower bound as it does not take into consideration subscriptions paid to DVMs - This is calculated by counting the values of all invoices where: - A DVM published a kind 7000 event requesting payment and containing an invoice - The DVM later provided a DVM Result for the same job for which it requested payment. - The assumption is that the invoice was paid, otherwise the DVM would not have done the work - Note that because there are multiple ways to pay a DVM such as lightning invoices, ecash, and subscriptions, there is no guaranteed way to know whether a DVM has been paid. Additionally, there is no way to know that a DVM completed the job because some DVMs may not publish a final result event and instead send the user a DM or take some other kind of action. ### Recent Requests: This page shows the most recent 3 events per kind, sorted by created date. You should always be able to find the last 3 events here of all DVM kinds. ### DVM Browser: This page will either show a profile of a specific DVM, or when no DVM is given in the url, it will show a table of all DVMs with some high level stats. Users can click on a DVM in the table to load the DVM specific page. ### Kind Browser: This page will either show data on a specific kind including all DVMs that have performed jobs of that kind, or when no kind is given, it will show a table summarizing activity across all Kinds. ### Debug: This page shows the graph based visualization of all events, users, and DVMs involved in a single job as well as a table of all events in order from oldest to newest. When no event is given, this page shows the 200 most recent events where the user can click on an event in order to debug that job. The graph-based visualization allows the user to zoom in and out and move around the graph, as well as double click on any node in the graph (except invoices) to open up that event, user, or dvm in a new page. ### Playground: This page is currently under development and may not work at the moment. If it does work, in the current state you can login with NIP-07 extension and broadcast a 5050 event with some text and then the page will show you events from DVMs. This page will be used to interact with DVMs live. A current good alternative to this feature, for some but not all kinds, is [https://vendata.io/](https://vendata.io/). ## Looking to the Future I originally built DVMDash out of Fear-of-Missing-Out (FOMO); I wanted to make AI systems that were comprised of DVMs but my day job was taking up a lot of my time. I needed to know when someone was performing a new task or launching a new AI or Nostr tool! I have a long list of DVMs and Agents I hope to build and I needed DVMDash to help me do it; I hope it helps you achieve your goals with Nostr, DVMs, and even AI. To this end, I wish for this tool to be useful to others, so if you would like a feature, please [submit a git issue here](https://github.com/dtdannen/dvmdash/issues/new) or _note_ me on Nostr! ### Immediate Next Steps: - Refactoring code and removing code that is no longer used - Improve documentation to run the project locally - Adding a metric for number of encrypted requests - Adding a metric for number of encrypted results ### Long Term Goals: - Add more metrics based on community feedback - Add plots showing metrics over time - Add support for showing a multi-dvm chain in the graph based visualizer - Add a real-time mode where the pages will auto update (currently the user must refresh the page) - ... Add support for user requested features! ## Acknowledgements There are some fantastic people working in the DVM space right now. Thank you to nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet for making python bindings for nostr_sdk and for the recent asyncio upgrades! Thank you to nostr:npub1nxa4tywfz9nqp7z9zp7nr7d4nchhclsf58lcqt5y782rmf2hefjquaa6q8 for answering lots of questions about DVMs and for making the nostrdvm library. Thank you to nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft for making the original DVM NIP and [vendata.io](https://vendata.io/) which I use all the time for testing! P.S. I rushed to get this out in time for Nostriga 2024; code refactoring will be coming :) @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# The illusion of checks and balances The website history.com has [a list of some of the most important "checks and balances"](https://www.history.com/topics/us-government/checks-and-balances) put in place by the United States Constitution. Here are some of them and how they are not real _checks_, they're flawed and easily bypassed by malicious peers that manage to enter the network. > The president (head of the executive branch) serves as commander in chief of the military forces, but Congress (legislative branch) appropriates funds for the military and votes to declare war. As it has happened [multiple times](https://en.wikipedia.org/wiki/Declaration_of_war_by_the_United_States#Undeclared_wars), the United States has engaged in many undeclared wars -- and many other military encounters that don't get enough media coverage and weren't even formally acknowledged by the Congress. > Congress has the power of the purse, as it controls the money used to fund any executive actions. There's a separate power called Federal Reserve which is more-or-less under the influence of the executive branch that is controlled by a single man and has the power of creating unlimited money. It was softly abused by the executive branch since its creation, but since 2008 it has been increasingly having its scope expanded from just influencing the banking sector to also directly using its money to buy all sorts of things and influence all sorts of markets and other actors. > Veto power. Once Congress has passed a bill, the president has the power to veto that bill. In turn, Congress can override a regular presidential veto by a two-thirds vote of both houses. If you imagine that both the executive and the legislative are 100% dedicated to go against each other the president could veto all bills, but then the legislative could enact them all anyway. Congress has the absolute power here (which can be justified by fact that the congress itself is split into multiple voters, but still this "veto" rule seems more like a gimmick to obscure the process than any actual check). > The Supreme Court and other federal courts (judicial branch) can declare laws or presidential actions unconstitutional, in a process known as judicial review. This rule gives absolute power to the Supreme Court over any matter. It can use their own personal judgement to veto any bill, cancel any action by the executive, reinterpret any existing law in any manner. There's no check against bad interpretations or judgements, so any absurd thing must be accepted. This should be obvious, and yet the entire system which most people believe to be "checked" is actually dependent on the good will and sanity of the judicial branch. > In turn, the president checks the judiciary through the power of appointment, which can be used to change the direction of the federal courts If the president and congress are being attacked by the judicial power, this isn't of much help as its effects are very long term. On the other hand, a president can single-handedly and arbitrarily use this rule to slowly poison the judicial system such that will turn malicious for the rest of the system after some time. > By passing amendments to the Constitution, Congress can effectively check the decisions of the Supreme Court. What is written in the Constitution can be easily ignored or misread by the members of the Supreme Court without any way for these interpretations to be checked or reverted. Basically the Supreme Court has absolute power over all things if we consider this. > Congress (considered the branch of government closest to the people) can impeach both members of the executive and judicial branches. Again (like in the presidential veto rule), this gives the congress unlimited power. There are no checks here -- except of course the fact that the congress is composed by multiple different voting heads of which a majority has to agree for the congress to do anything, which is the only thing preventing overabuse of this rule. --- As shown above, most rules that compose the "checks and balances" system can be abused and if given enough time they will. They aren't real checks. Ultimately, the stability and decency of a [democracy](nostr:naddr1qqyrxvtxxf3nse3sqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ccyra4y) relies on the majority rule (so congress votes are never concentrated in dictatorial measures) and the common sense of the powerful people (president and judges). There probably hasn't been a single year in any democracy in which one of these powers didn't abused or violated one of the rules, but still in most cases the overall system stays in place because of the general culture, splitted views about most issues, overall common sense and fear of public shame. The checks and balances system itself is an illusion. All the complex "democracy" construct depends on the goodwill of all the participants and have only worked so far (when it did) by miracle and by the power of human cooperation and love.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# The illusion of checks and balances The website history.com has [a list of some of the most important "checks and balances"](https://www.history.com/topics/us-government/checks-and-balances) put in place by the United States Constitution. Here are some of them and how they are not real _checks_, they're flawed and easily bypassed by malicious peers that manage to enter the network. > The president (head of the executive branch) serves as commander in chief of the military forces, but Congress (legislative branch) appropriates funds for the military and votes to declare war. As it has happened [multiple times](https://en.wikipedia.org/wiki/Declaration_of_war_by_the_United_States#Undeclared_wars), the United States has engaged in many undeclared wars -- and many other military encounters that don't get enough media coverage and weren't even formally acknowledged by the Congress. > Congress has the power of the purse, as it controls the money used to fund any executive actions. There's a separate power called Federal Reserve which is more-or-less under the influence of the executive branch that is controlled by a single man and has the power of creating unlimited money. It was softly abused by the executive branch since its creation, but since 2008 it has been increasingly having its scope expanded from just influencing the banking sector to also directly using its money to buy all sorts of things and influence all sorts of markets and other actors. > Veto power. Once Congress has passed a bill, the president has the power to veto that bill. In turn, Congress can override a regular presidential veto by a two-thirds vote of both houses. If you imagine that both the executive and the legislative are 100% dedicated to go against each other the president could veto all bills, but then the legislative could enact them all anyway. Congress has the absolute power here (which can be justified by fact that the congress itself is split into multiple voters, but still this "veto" rule seems more like a gimmick to obscure the process than any actual check). > The Supreme Court and other federal courts (judicial branch) can declare laws or presidential actions unconstitutional, in a process known as judicial review. This rule gives absolute power to the Supreme Court over any matter. It can use their own personal judgement to veto any bill, cancel any action by the executive, reinterpret any existing law in any manner. There's no check against bad interpretations or judgements, so any absurd thing must be accepted. This should be obvious, and yet the entire system which most people believe to be "checked" is actually dependent on the good will and sanity of the judicial branch. > In turn, the president checks the judiciary through the power of appointment, which can be used to change the direction of the federal courts If the president and congress are being attacked by the judicial power, this isn't of much help as its effects are very long term. On the other hand, a president can single-handedly and arbitrarily use this rule to slowly poison the judicial system such that will turn malicious for the rest of the system after some time. > By passing amendments to the Constitution, Congress can effectively check the decisions of the Supreme Court. What is written in the Constitution can be easily ignored or misread by the members of the Supreme Court without any way for these interpretations to be checked or reverted. Basically the Supreme Court has absolute power over all things if we consider this. > Congress (considered the branch of government closest to the people) can impeach both members of the executive and judicial branches. Again (like in the presidential veto rule), this gives the congress unlimited power. There are no checks here -- except of course the fact that the congress is composed by multiple different voting heads of which a majority has to agree for the congress to do anything, which is the only thing preventing overabuse of this rule. --- As shown above, most rules that compose the "checks and balances" system can be abused and if given enough time they will. They aren't real checks. Ultimately, the stability and decency of a [democracy](nostr:naddr1qqyrxvtxxf3nse3sqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ccyra4y) relies on the majority rule (so congress votes are never concentrated in dictatorial measures) and the common sense of the powerful people (president and judges). There probably hasn't been a single year in any democracy in which one of these powers didn't abused or violated one of the rules, but still in most cases the overall system stays in place because of the general culture, splitted views about most issues, overall common sense and fear of public shame. The checks and balances system itself is an illusion. All the complex "democracy" construct depends on the goodwill of all the participants and have only worked so far (when it did) by miracle and by the power of human cooperation and love. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Boardthreads This was a very badly done service for turning a Trello list into a helpdesk UI. Surprisingly, it had more paying users than [Websites For Trello](nostr:naddr1qqyrydpkvverwvehqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c9d4yku), which I was working on simultaneously and dedicating much more time to it. The Neo4j database I used for this was a very poor choice, it was probably the cause of all the bugs.  -<https://github.com/fiatjaf/boardthreads>
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Boardthreads This was a very badly done service for turning a Trello list into a helpdesk UI. Surprisingly, it had more paying users than [Websites For Trello](nostr:naddr1qqyrydpkvverwvehqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c9d4yku), which I was working on simultaneously and dedicating much more time to it. The Neo4j database I used for this was a very poor choice, it was probably the cause of all the bugs.  -<https://github.com/fiatjaf/boardthreads> @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Who will build the roads? Who will build the roads? Em Lagoa Santa, as mais novas e melhores ruas -- que na verdade acabam por formar enormes teias de bairros que se interligam -- são construídas pelos loteadores que querem as ruas para que seus lotes valham mais -- e querem que outras pessoas usem as ruas também. Também são esses mesmos loteadores que colocam os postes de luz e os encanamentos de água, não sem antes terem que se submeter a extorsões de praxe praticadas por COPASA e CEMIG. Se ao abrir um loteamento, condomínio, prédio um indivíduo ou uma empresa consegue sem muito problema passar rua, eletricidade, água e esgoto, por que não seria possível existir livre-concorrência nesses mercados? Mesmo aquela velha estória de que é ineficiente passar cabos de luz duplicados para que companhias elétricas possam competir já me parece bobagem.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Who will build the roads? Who will build the roads? Em Lagoa Santa, as mais novas e melhores ruas -- que na verdade acabam por formar enormes teias de bairros que se interligam -- são construídas pelos loteadores que querem as ruas para que seus lotes valham mais -- e querem que outras pessoas usem as ruas também. Também são esses mesmos loteadores que colocam os postes de luz e os encanamentos de água, não sem antes terem que se submeter a extorsões de praxe praticadas por COPASA e CEMIG. Se ao abrir um loteamento, condomínio, prédio um indivíduo ou uma empresa consegue sem muito problema passar rua, eletricidade, água e esgoto, por que não seria possível existir livre-concorrência nesses mercados? Mesmo aquela velha estória de que é ineficiente passar cabos de luz duplicados para que companhias elétricas possam competir já me parece bobagem. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# jiq When someone created [`jiq`](https://github.com/simeji/jid) claiming it had "jq queries" I went to inspect and realized it didn't, it just had a poor simple JSON query language that implemented 1% of all [`jq`](https://stedolan.github.io/jq/manual/) features, so I forked it and plugged `jq` directly into it, and renamed to `jiq`. After some comments on issues in the original repository from people complaining about lack of `jq` compatibility it got a ton of unexpected users, was even packaged to ArchLinux.  - <https://github.com/fiatjaf/jiq>
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# jiq When someone created [`jiq`](https://github.com/simeji/jid) claiming it had "jq queries" I went to inspect and realized it didn't, it just had a poor simple JSON query language that implemented 1% of all [`jq`](https://stedolan.github.io/jq/manual/) features, so I forked it and plugged `jq` directly into it, and renamed to `jiq`. After some comments on issues in the original repository from people complaining about lack of `jq` compatibility it got a ton of unexpected users, was even packaged to ArchLinux.  - <https://github.com/fiatjaf/jiq> @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Como não houve resposta, estou enviando de novo Recebi um email assim, dizendo a mesma coisa repetida. Eu havia recebido já da primeira vez, mas como era só uma informação já esperada, julguei que não precisava responder dizendo "chegou, obrigado!" e não o fiz. Reconheço, porém, que dada a instabilidade desses serviços de email nunca ninguém sabe se a mensagem chegou ou não. Ela pode ter sido jogada na lixeira do spam, ou pode ter falhado por outros motivos, e aí não existe um jeito garantido de saber se houve falha, é um enorme problema sempre. Por isso a necessidade de uma resposta "chegou, obrigado!". Mas não podemos parar por aí. A resposta "chegou, obrigado!" também está sujeita aos mesmos trâmites e riscos da mensagem original. Seria necessário, porém, que assim que a outra pessoa recebesse o "chegou, obrigado!" deveria então responder com um "recebi a sua confirmação". Caso não o fizesse, eu poderia achar que a minha mensagem não havia chegado e dias depois enviá-la de novo: "como não houve resposta à minha confirmação, estou enviando de novo". E assim por diante (eu ia escrever mais um parágrafo só pelo drama, mas desisti. Já deu pra entender). --- - [Ripple and the problem of the decentralized commit](nostr:naddr1qqyrxcmzxa3nxv34qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cjrqar6), esta situação que acabo de viver é mais um exemplo prático disto.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Como não houve resposta, estou enviando de novo Recebi um email assim, dizendo a mesma coisa repetida. Eu havia recebido já da primeira vez, mas como era só uma informação já esperada, julguei que não precisava responder dizendo "chegou, obrigado!" e não o fiz. Reconheço, porém, que dada a instabilidade desses serviços de email nunca ninguém sabe se a mensagem chegou ou não. Ela pode ter sido jogada na lixeira do spam, ou pode ter falhado por outros motivos, e aí não existe um jeito garantido de saber se houve falha, é um enorme problema sempre. Por isso a necessidade de uma resposta "chegou, obrigado!". Mas não podemos parar por aí. A resposta "chegou, obrigado!" também está sujeita aos mesmos trâmites e riscos da mensagem original. Seria necessário, porém, que assim que a outra pessoa recebesse o "chegou, obrigado!" deveria então responder com um "recebi a sua confirmação". Caso não o fizesse, eu poderia achar que a minha mensagem não havia chegado e dias depois enviá-la de novo: "como não houve resposta à minha confirmação, estou enviando de novo". E assim por diante (eu ia escrever mais um parágrafo só pelo drama, mas desisti. Já deu pra entender). --- - [Ripple and the problem of the decentralized commit](nostr:naddr1qqyrxcmzxa3nxv34qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cjrqar6), esta situação que acabo de viver é mais um exemplo prático disto. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Flowi.es At the time I thought [Workflowy][workflowy] had the ideal UI for everything. I wanted to implement my [custom app maker](nostr:naddr1qqyxgcejv5unzd33qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cz3va32) on it, but ended up doing this: a platform for enhancing Workflowy with extra features: - An email reminder based on dates input in items - A website generator, similar to [Websites For Trello](nostr:naddr1qqyrydpkvverwvehqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c9d4yku), also based on [Classless Templates](nostr:naddr1qqyxyv35vymk2vfsqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cqwgdau) Also, I didn't remember this was also based on CouchDB and had some _couchapp_ functionalities.  - <https://flowi.es> - <https://github.com/fiatjaf/flowies> [workflowy]: <https://workflowy.com/>
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Flowi.es At the time I thought [Workflowy][workflowy] had the ideal UI for everything. I wanted to implement my [custom app maker](nostr:naddr1qqyxgcejv5unzd33qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cz3va32) on it, but ended up doing this: a platform for enhancing Workflowy with extra features: - An email reminder based on dates input in items - A website generator, similar to [Websites For Trello](nostr:naddr1qqyrydpkvverwvehqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c9d4yku), also based on [Classless Templates](nostr:naddr1qqyxyv35vymk2vfsqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cqwgdau) Also, I didn't remember this was also based on CouchDB and had some _couchapp_ functionalities.  - <https://flowi.es> - <https://github.com/fiatjaf/flowies> [workflowy]: <https://workflowy.com/> @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Multi-service Graph Reputation protocol ## The problem 1. Users inside centralized services need to know reputations of other users they're interacting with; 2. Building reputation with ratings imposes a big burden on the user and still accomplishes nothing, can be faked, no one cares about these ratings etc. ## The ideal solution Subjective reputation: reputation based on how you rated that person previously, and how other people you trust rated that person, and how other people trusted by people you trust rated that person and so on, in a web-of-trust that actually can give you some insight on the trustworthiness of someone you never met or interacted with. ## The problem with the ideal solution 1. Most of the times the service that wants to implement this is not as big as Facebook, so it won't have enough people in it for such graphs of reputation to be constructed. 2. It is not trivial to build. ## My proposed solution: I've drafted a protocol for an open system based on services publishing their internal reputation records and indexers using these to build graphs, and then serving the graphs back to the services so they can show them to users when it is needed (as HTTP APIs that can be called directly from the user client app or browser). Crucially, these indexers will gather data from multiple services and cross-link users from these services so the graph is better. <https://github.com/fiatjaf/multi-service-reputation-rfc> The first and single actionable and useful feedback I got, from [@bootstrapbandit](https://twitter.com/bootstrapbandit) was that services shouldn't share email addresses in plain text (email addresses and other external relationships users of a service may have are necessary to establish links from users accross services), but I think it is ok if services publish hashes of these email addresses instead. At some point I will update the spec draft and that may have been before the time you're reading this. Another issue is that services may lie about their reputation records and that will hurt other services and users in these other services that are relying on that data. Maybe indexers will have to do some investigative job here to assert service honesty. Or maybe this entire protocol is just failed and we will actually need a system in which users themselves will publish their own records. ## See also * [P2P reputation thing](nostr:naddr1qqyrqv3cxumnydfsqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cnjc88q) * [idea: Graph subjective reputation as a service](nostr:naddr1qqyrjdehxymrsdpkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cal60d8) * <https://github.com/jangerritharms/reputation_systems>
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Multi-service Graph Reputation protocol ## The problem 1. Users inside centralized services need to know reputations of other users they're interacting with; 2. Building reputation with ratings imposes a big burden on the user and still accomplishes nothing, can be faked, no one cares about these ratings etc. ## The ideal solution Subjective reputation: reputation based on how you rated that person previously, and how other people you trust rated that person, and how other people trusted by people you trust rated that person and so on, in a web-of-trust that actually can give you some insight on the trustworthiness of someone you never met or interacted with. ## The problem with the ideal solution 1. Most of the times the service that wants to implement this is not as big as Facebook, so it won't have enough people in it for such graphs of reputation to be constructed. 2. It is not trivial to build. ## My proposed solution: I've drafted a protocol for an open system based on services publishing their internal reputation records and indexers using these to build graphs, and then serving the graphs back to the services so they can show them to users when it is needed (as HTTP APIs that can be called directly from the user client app or browser). Crucially, these indexers will gather data from multiple services and cross-link users from these services so the graph is better. <https://github.com/fiatjaf/multi-service-reputation-rfc> The first and single actionable and useful feedback I got, from [@bootstrapbandit](https://twitter.com/bootstrapbandit) was that services shouldn't share email addresses in plain text (email addresses and other external relationships users of a service may have are necessary to establish links from users accross services), but I think it is ok if services publish hashes of these email addresses instead. At some point I will update the spec draft and that may have been before the time you're reading this. Another issue is that services may lie about their reputation records and that will hurt other services and users in these other services that are relying on that data. Maybe indexers will have to do some investigative job here to assert service honesty. Or maybe this entire protocol is just failed and we will actually need a system in which users themselves will publish their own records. ## See also * [P2P reputation thing](nostr:naddr1qqyrqv3cxumnydfsqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cnjc88q) * [idea: Graph subjective reputation as a service](nostr:naddr1qqyrjdehxymrsdpkqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cal60d8) * <https://github.com/jangerritharms/reputation_systems> @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# A memória está nas coisas A memória está nas coisas, mas se você tiver muitas memórias já mesma coisa parece que uma se sobrepõe à outra, de modo que se vive quiser acumular mais memórias é melhor mudar de casa todo ano.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# A memória está nas coisas A memória está nas coisas, mas se você tiver muitas memórias já mesma coisa parece que uma se sobrepõe à outra, de modo que se vive quiser acumular mais memórias é melhor mudar de casa todo ano. @ 361d3e1e:50bc10a8
2024-08-19 18:33:25
@ 361d3e1e:50bc10a8
2024-08-19 18:33:25 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Cultura Inglesa e aprendizado extra-escolar Em 2005 a Cultura Inglesa me classificou como nível 2 em proficiência de inglês, numa escala de 1 a 14 ou coisa parecida. De modo que eu precisaria de 6 anos de aulas com eles pra ficar bom. 2 anos depois, sem fazer nenhuma aula ou ter qualquer tipo de treinamento intensivo eu era capaz de compreender textos técnicos em inglês sem nenhuma dificuldade. Mais 2 anos e eu era capaz de compreender qualquer coisa e me expressar com razoável qualidade. Tudo isso pra documentar mais um exemplo, que poderia passar despercebido, de aprendizado de tipo escolar que se deu fora de uma escola.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Cultura Inglesa e aprendizado extra-escolar Em 2005 a Cultura Inglesa me classificou como nível 2 em proficiência de inglês, numa escala de 1 a 14 ou coisa parecida. De modo que eu precisaria de 6 anos de aulas com eles pra ficar bom. 2 anos depois, sem fazer nenhuma aula ou ter qualquer tipo de treinamento intensivo eu era capaz de compreender textos técnicos em inglês sem nenhuma dificuldade. Mais 2 anos e eu era capaz de compreender qualquer coisa e me expressar com razoável qualidade. Tudo isso pra documentar mais um exemplo, que poderia passar despercebido, de aprendizado de tipo escolar que se deu fora de uma escola. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# On HTLCs and arbiters This is another attempt and conveying the same information that should be in [Lightning and its fake HTLCs](nostr:naddr1qqyryefsxqcxgdmzqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cp0m63a). It assumes you know everything about Lightning and will just highlight a point. This is also valid for PTLCs. The protocol says HTLCs are trimmed (i.e., not actually added to the commitment transaction) when the cost of redeeming them in fees would be greater than their actual value. Although this is often dismissed as a non-important fact (often people will say "it's trusted for small payments, no big deal"), but I think it is indeed very important for 3 reasons: 1. Lightning absolutely relies on HTLCs actually existing because the payment proof requires them. The entire security of each payment comes from the fact that the payer has a preimage that comes from the payee. Without that, the state of the payment becomes an unsolvable mystery. The inexistence of an HTLC breaks the atomicity between the payment going through and the payer receiving a proof. 2. Bitcoin fees are expected to grow with time (arguably the reason Lightning exists in the first place). 3. MPP makes payment sizes shrink, therefore more and more of Lightning payments are to be trimmed. As I write this, the mempool is clear and still payments smaller than about 5000sat are being trimmed. Two weeks ago the limit was at 18000sat, which is already below the minimum most MPP splitting algorithms will allow. Therefore I think it is important that we come up with a different way of ensuring payment proofs are being passed around in the case HTLCs are trimmed. ## Channel closures Worse than not having HTLCs that can be redeemed is the fact that in the current Lightning implementations channels will be closed by the peer once an HTLC timeout is reached, either to fulfill an HTLC for which that peer has a preimage or to redeem back that expired HTLCs the other party hasn't fulfilled. For the surprise of everybody, nodes will do this even when the HTLCs in question were trimmed and therefore cannot be redeemed at all. It's very important that nodes stop doing that, because it makes no economic sense at all. However, that is not so simple, because once you decide you're not going to close the channel, what is the next step? Do you wait until the other peer tries to fulfill an expired HTLC and tell them you won't agree and that you must cancel that instead? That could work sometimes if they're honest (and they have no incentive to not be, in this case). What if they say they tried to fulfill it before but you were offline? Now you're confused, you don't know if you were offline or they were offline, or if they are trying to trick you. Then unsolvable issues start to emerge. ## Arbiters One simple idea is to use trusted arbiters for all trimmed HTLC issues. This idea solves both the protocol issue of getting the preimage to the payer once it is released by the payee -- and what to do with the channels once a trimmed HTLC expires. A simple design would be to have each node hardcode a set of trusted other nodes that can serve as arbiters. Once a channel is opened between two nodes they choose one node from both lists to serve as their mutual arbiter for that channel. Then whenever one node tries to fulfill an HTLC but the other peer is unresponsive, they can send the preimage to the arbiter instead. The arbiter will then try to contact the unresponsive peer. If it succeeds, then done, the HTLC was fulfilled offchain. If it fails then it can keep trying until the HTLC timeout. And then if the other node comes back later they can eat the loss. The arbiter will ensure they know they are the ones who must eat the loss in this case. If they don't agree to eat the loss, the first peer may then close the channel and blacklist the other peer. If the other peer believes that both the first peer and the arbiter are dishonest they can remove that arbiter from their list of trusted arbiters. The same happens in the opposite case: if a peer doesn't get a preimage they can notify the arbiter they hadn't received anything. The arbiter may try to ask the other peer for the preimage and, if that fails, settle the dispute for the side of that first peer, which can proceed to fail the HTLC is has with someone else on that route.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# On HTLCs and arbiters This is another attempt and conveying the same information that should be in [Lightning and its fake HTLCs](nostr:naddr1qqyryefsxqcxgdmzqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cp0m63a). It assumes you know everything about Lightning and will just highlight a point. This is also valid for PTLCs. The protocol says HTLCs are trimmed (i.e., not actually added to the commitment transaction) when the cost of redeeming them in fees would be greater than their actual value. Although this is often dismissed as a non-important fact (often people will say "it's trusted for small payments, no big deal"), but I think it is indeed very important for 3 reasons: 1. Lightning absolutely relies on HTLCs actually existing because the payment proof requires them. The entire security of each payment comes from the fact that the payer has a preimage that comes from the payee. Without that, the state of the payment becomes an unsolvable mystery. The inexistence of an HTLC breaks the atomicity between the payment going through and the payer receiving a proof. 2. Bitcoin fees are expected to grow with time (arguably the reason Lightning exists in the first place). 3. MPP makes payment sizes shrink, therefore more and more of Lightning payments are to be trimmed. As I write this, the mempool is clear and still payments smaller than about 5000sat are being trimmed. Two weeks ago the limit was at 18000sat, which is already below the minimum most MPP splitting algorithms will allow. Therefore I think it is important that we come up with a different way of ensuring payment proofs are being passed around in the case HTLCs are trimmed. ## Channel closures Worse than not having HTLCs that can be redeemed is the fact that in the current Lightning implementations channels will be closed by the peer once an HTLC timeout is reached, either to fulfill an HTLC for which that peer has a preimage or to redeem back that expired HTLCs the other party hasn't fulfilled. For the surprise of everybody, nodes will do this even when the HTLCs in question were trimmed and therefore cannot be redeemed at all. It's very important that nodes stop doing that, because it makes no economic sense at all. However, that is not so simple, because once you decide you're not going to close the channel, what is the next step? Do you wait until the other peer tries to fulfill an expired HTLC and tell them you won't agree and that you must cancel that instead? That could work sometimes if they're honest (and they have no incentive to not be, in this case). What if they say they tried to fulfill it before but you were offline? Now you're confused, you don't know if you were offline or they were offline, or if they are trying to trick you. Then unsolvable issues start to emerge. ## Arbiters One simple idea is to use trusted arbiters for all trimmed HTLC issues. This idea solves both the protocol issue of getting the preimage to the payer once it is released by the payee -- and what to do with the channels once a trimmed HTLC expires. A simple design would be to have each node hardcode a set of trusted other nodes that can serve as arbiters. Once a channel is opened between two nodes they choose one node from both lists to serve as their mutual arbiter for that channel. Then whenever one node tries to fulfill an HTLC but the other peer is unresponsive, they can send the preimage to the arbiter instead. The arbiter will then try to contact the unresponsive peer. If it succeeds, then done, the HTLC was fulfilled offchain. If it fails then it can keep trying until the HTLC timeout. And then if the other node comes back later they can eat the loss. The arbiter will ensure they know they are the ones who must eat the loss in this case. If they don't agree to eat the loss, the first peer may then close the channel and blacklist the other peer. If the other peer believes that both the first peer and the arbiter are dishonest they can remove that arbiter from their list of trusted arbiters. The same happens in the opposite case: if a peer doesn't get a preimage they can notify the arbiter they hadn't received anything. The arbiter may try to ask the other peer for the preimage and, if that fails, settle the dispute for the side of that first peer, which can proceed to fail the HTLC is has with someone else on that route. @ c8383d81:f9139549
2024-08-09 09:21:45Test Completed :Lighningbutton{lud16=cypher@npub.cash}
@ c8383d81:f9139549
2024-08-09 09:21:45Test Completed :Lighningbutton{lud16=cypher@npub.cash} @ 79be667e:16f81798
2024-08-19 10:27:57## Introduction Picture this: you’re a seasoned software developer, having mastered several programming languages. You’ve dabbled in Python’s simplicity, swum in Java’s verbose ocean, and even navigated the sharp edges of C++. And now, you hear whispers in the tech corridors about Go, the language created by Google that’s supposed to be the next big thing. But wait — before you dive in, let’s take a critical look. Despite its gleaming reputation, Go might just be the worst language you could ever learn. ## The Simplicity Trap ## The Illusion of Simplicity Go is often praised for its simplicity, but this can be a double-edged sword. Sure, a language that’s easy to pick up sounds great, but what if that simplicity comes at the cost of essential features? Go’s minimalist design strips away many conveniences that other languages offer. There’s no inheritance, no generics (until recently), and error handling is rudimentary at best. ### Example Imagine trying to build a complex data structure in Go. You’ll quickly find yourself writing repetitive, boilerplate code that a language with generics could have handled elegantly. It’s like being forced to build a skyscraper with Lego blocks — simple but painfully slow and inefficient. # Error Handling: A Nightmare ### Tedious and Verbose In Go, error handling is done by returning errors as values. This might seem straightforward, but in practice, it results in verbose and cluttered code. Every function that might fail has to return an error, and every caller has to check for that error. This leads to a pattern that looks like: ``` if err != nil { return err } ``` Repeat ad nauseam. It’s like playing a video game where you have to press a button every two seconds to keep playing — monotonous and prone to errors if you forget. ### Personal Anecdote When I first started with Go, I was excited about its concurrency model. But the excitement faded as I spent more time handling errors than writing actual logic. It felt like I was an error handler, not a developer. # Lack of Essential Features ## Missing Generics Until very recently, Go did not support generics, which are a staple in many modern languages. Generics allow you to write flexible and reusable code. Without them, you’re stuck writing the same functions for different types. This is a massive productivity drain and leads to bloated codebases. ### Example Consider a simple function to find an element in a slice. In Go, you need to write a separate function for each type: ``` func findInt(slice []int, val int) bool { for _, v := range slice { if v == val { return true } } return false } func findString(slice []string, val string) bool { for _, v := range slice { if v == val { return true } } return false } ``` In a language with generics, you would write this once and reuse it for any type. # Concurrency Model: Overhyped ## Goroutines Galore Go’s goroutines are lightweight threads, and while they are powerful, they come with their own set of problems. Managing goroutines and channels can become incredibly complex, especially in large applications. Debugging concurrent code is notoriously difficult, and Go is no exception. ## Hypothetical Scenario Imagine you’re managing a team of junior developers. They find goroutines cool and start using them everywhere. Soon, your codebase is a tangled mess of channels and goroutines, with race conditions and deadlocks lurking in every corner. It’s like trying to untangle Christmas lights in the dark. # Interactive Elements ## Thought-Provoking Questions 1. How does Go’s simplicity compare to the complexity of other languages you’ve worked with? Do you find it beneficial or limiting? 2. Have you encountered situations where Go’s lack of features (like generics) caused significant issues in your projects? 3. How do you handle error management in your preferred language, and how does it compare to Go’s approach? # Activity Try rewriting a piece of code you’ve written in another language into Go. Note down the challenges and differences you encounter. This hands-on experience will highlight Go’s limitations in a practical context. # Summary While Go has its strengths and a strong following, it comes with significant drawbacks that can’t be ignored. Its simplicity can be deceptive, leading to verbose and repetitive code. The lack of essential features like generics, a cumbersome error handling system, and a concurrency model that’s easy to misuse make it a challenging language to master efficiently. Before you commit to learning Go, weigh these cons carefully against its pros. # Additional Resources 1. [The Go Programming Language](https://golang.org/doc/) 2. [Effective Go](https://golang.org/doc/effective_go.html) 3. [Go Concurrency Patterns](https://blog.golang.org/pipelines)
@ 79be667e:16f81798
2024-08-19 10:27:57## Introduction Picture this: you’re a seasoned software developer, having mastered several programming languages. You’ve dabbled in Python’s simplicity, swum in Java’s verbose ocean, and even navigated the sharp edges of C++. And now, you hear whispers in the tech corridors about Go, the language created by Google that’s supposed to be the next big thing. But wait — before you dive in, let’s take a critical look. Despite its gleaming reputation, Go might just be the worst language you could ever learn. ## The Simplicity Trap ## The Illusion of Simplicity Go is often praised for its simplicity, but this can be a double-edged sword. Sure, a language that’s easy to pick up sounds great, but what if that simplicity comes at the cost of essential features? Go’s minimalist design strips away many conveniences that other languages offer. There’s no inheritance, no generics (until recently), and error handling is rudimentary at best. ### Example Imagine trying to build a complex data structure in Go. You’ll quickly find yourself writing repetitive, boilerplate code that a language with generics could have handled elegantly. It’s like being forced to build a skyscraper with Lego blocks — simple but painfully slow and inefficient. # Error Handling: A Nightmare ### Tedious and Verbose In Go, error handling is done by returning errors as values. This might seem straightforward, but in practice, it results in verbose and cluttered code. Every function that might fail has to return an error, and every caller has to check for that error. This leads to a pattern that looks like: ``` if err != nil { return err } ``` Repeat ad nauseam. It’s like playing a video game where you have to press a button every two seconds to keep playing — monotonous and prone to errors if you forget. ### Personal Anecdote When I first started with Go, I was excited about its concurrency model. But the excitement faded as I spent more time handling errors than writing actual logic. It felt like I was an error handler, not a developer. # Lack of Essential Features ## Missing Generics Until very recently, Go did not support generics, which are a staple in many modern languages. Generics allow you to write flexible and reusable code. Without them, you’re stuck writing the same functions for different types. This is a massive productivity drain and leads to bloated codebases. ### Example Consider a simple function to find an element in a slice. In Go, you need to write a separate function for each type: ``` func findInt(slice []int, val int) bool { for _, v := range slice { if v == val { return true } } return false } func findString(slice []string, val string) bool { for _, v := range slice { if v == val { return true } } return false } ``` In a language with generics, you would write this once and reuse it for any type. # Concurrency Model: Overhyped ## Goroutines Galore Go’s goroutines are lightweight threads, and while they are powerful, they come with their own set of problems. Managing goroutines and channels can become incredibly complex, especially in large applications. Debugging concurrent code is notoriously difficult, and Go is no exception. ## Hypothetical Scenario Imagine you’re managing a team of junior developers. They find goroutines cool and start using them everywhere. Soon, your codebase is a tangled mess of channels and goroutines, with race conditions and deadlocks lurking in every corner. It’s like trying to untangle Christmas lights in the dark. # Interactive Elements ## Thought-Provoking Questions 1. How does Go’s simplicity compare to the complexity of other languages you’ve worked with? Do you find it beneficial or limiting? 2. Have you encountered situations where Go’s lack of features (like generics) caused significant issues in your projects? 3. How do you handle error management in your preferred language, and how does it compare to Go’s approach? # Activity Try rewriting a piece of code you’ve written in another language into Go. Note down the challenges and differences you encounter. This hands-on experience will highlight Go’s limitations in a practical context. # Summary While Go has its strengths and a strong following, it comes with significant drawbacks that can’t be ignored. Its simplicity can be deceptive, leading to verbose and repetitive code. The lack of essential features like generics, a cumbersome error handling system, and a concurrency model that’s easy to misuse make it a challenging language to master efficiently. Before you commit to learning Go, weigh these cons carefully against its pros. # Additional Resources 1. [The Go Programming Language](https://golang.org/doc/) 2. [Effective Go](https://golang.org/doc/effective_go.html) 3. [Go Concurrency Patterns](https://blog.golang.org/pipelines) @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# IPFS problems: Too much immutability Content-addressing is unusable with an index or database that describes each piece of content. Since IPFS is fully content-addressable, nothing can be done with it unless you have a non-IPFS index or database, or an internal protocol for dynamic and updateable links. The IPFS [conceit](nostr:naddr1qqyxyeryx93kxv3nqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cwxek0q) made then go with the with the second option, which proved to be [a failure](nostr:naddr1qqyrvcnx8y6nwwtpqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cz8tlwh). They even incentivized the creation of a [database powered by IPFS](https://github.com/orbitdb/orbit-db), which couldn't be more misguided.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# IPFS problems: Too much immutability Content-addressing is unusable with an index or database that describes each piece of content. Since IPFS is fully content-addressable, nothing can be done with it unless you have a non-IPFS index or database, or an internal protocol for dynamic and updateable links. The IPFS [conceit](nostr:naddr1qqyxyeryx93kxv3nqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cwxek0q) made then go with the with the second option, which proved to be [a failure](nostr:naddr1qqyrvcnx8y6nwwtpqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cz8tlwh). They even incentivized the creation of a [database powered by IPFS](https://github.com/orbitdb/orbit-db), which couldn't be more misguided. @ 6c2d68ba:846525ec
2024-08-08 21:15:25Will man der Bundeszentrale für politische Bildung glauben, so handelt es sich bei Propaganda um den Versuch der gezielten Beeinflussung des Denkens, Handelns wie auch Fühlens von Menschen. Charakteristisch für Propaganda ist, dass sie darauf verzichtet die verschiedenen Seiten einer Thematik darzulegen, sondern gezielt Meinung mit (Fehl)-Information vermischt. Wer Propaganda betreibt, strebt nicht danach zu diskutieren oder die Öffentlichkeit gar mit Argumenten zu überzeugen, sondern greift zu verschiedensten Manipulationstechniken, die die Emotionen und das Verhalten der Öffentlichkeit beeinflussen. Propaganda nimmt dem Menschen (eigenständiges) Denken ab und gibt ihm stattdessen das Gefühl, mit der übernommenen Meinung goldrichtig zu liegen. Hier zeigt sich auch der wesentliche Unterschied zum Journalismus: Journalismus strebt nach Aufklärung, indem alle verfügbaren Fakten und Hintergründe dargelegt werden und der Empfänger selbst darüber entscheiden darf, was er für richtig und was er für falsch hält [1]. Zwar verbinden wir den Begriff Propaganda heutzutage mit autoritären und totalitären Staaten, wo diese auch zweifelsfrei Anwendung findet, doch kommen Propagandatechniken auch im Westen zum Einsatz, wenn auch in einer auf die demokratische Herrschaftsform zugeschnittene Art und Weise. Wie die Geschichte gezeigt hat - hier sind die Werke von Edward Bernays ganz besonders relevant [2] - wurde Öffentlichkeitsarbeit, sprich Public Relations (PR), basierend auf den Erkenntnissen der Propagandaforschung verfeinert, über welche die öffentliche Wahrnehmung von Personen, Konzernen und Regierungen beeinflusst wird. In Summe lässt sich daraus ableiten, dass auch Propaganda in unseren Breitengraden Tradition hat. Nun halte ich es in Zeiten von (leider) wiederkehrenden heißen Konflikten in Europa besonders wichtig sich über existierende Manipulationstechniken wie auch gezielter Meinungsmache in (Massen)-medien bewusst zu sein wie auch erscheinenden Artikeln, Posts, Videos und ganz besonders Schlagzeilen mit einem gewissen Grad an Achtsamkeit zu begegnen, um nicht umgehend Opfer von Manipulation zu werden. Denn wie schon von der bereits erwähnten Bundeszentrale für politische Bildung erwähnt wurde, kann nur jener sich gegen den Einfluss von Propaganda wehren, der diese als solche erkennt. Dadurch motiviert nehme ich heute die Prinzipien der Kriegspropaganda ins Fadenkreuz. > „Auf die Dauer vermag auch die frechste und bestorganisierte Propaganda nichts gegen die Wahrheit.“ ―Albert Schweitzer ## Die Prinzipien der Kriegspropaganda Unter dem Eindruck des Ersten Weltkriegs schrieb Arthur Ponsonby, britischer Adeliger & Staatsbeamter, 1928 das Buch "Lüge in Kriegszeiten", in welchem er die Mechanismen der damaligen Kriegspropaganda untersuchte. Er steht übrigens im Verdacht Urvater des berühmten Zitats "das erste Opfer im Krieg ist die Wahrheit" zu sein [3]. In diesem Werk schildert Ponsonby 20 Aspekte, die wiederum später von der Historikerin Anne Morelli im Jahr 2001 zu den zehn Prinzipien der Kriegspropaganda zusammengefasst wurden. Wie sie selbst betonte geht es bei diesen Prinzipien nicht darum herauszufinden, wer lügt und wer die Wahrheit sagt, wer das glaubt, was er sagt, sondern Mittels dieser Prinzipien die verbreitete Propaganda zu veranschaulichen und ihr Funktionieren zu beschreiben (Seite 6, [4]). Nachdem ich mich selbst mit diesen Prinzipien beschäftigt hatte, wurde mir mit jeder einzelnen Gedankenrunde immer klarer, wie die von Anne Morelli beschriebenen Prinzipien als wie eine Art Leitfaden verwendet werden, um Pressemeldungen, Argumente und Schlagzeilen in Sozialen Medien so zu formulieren, dass unabhängig vom Geschehnis stets eine unterbewusste Botschaft mitschwingt, so dass der gewünschte Effekt der Manipulation maximiert wird. Nun könnte man nach Durchsicht der größten Tagesblätter des Deutschsprachigen Raums etliche Beispiele für jeden einzelnen der in Kürze vorgestellten Prinzipien präsentieren, doch habe ich in Anbetracht des Themas bewusst Abstand davon genommen, um nicht gewisse Journalisten - oder kriegstreibende Propagandisten wie ich sie nenne - samt Klarnamen an den Pranger zu stellen. Wie Anne Morelli, sehe ich den größtmöglichen Mehrwert darin, die Mechanik offenzulegen, um die Leserschaft für dieses Thema zu sensibilisieren. ### Wir wollen keinen Krieg! Stets wird versichert, dass man den stattfindenden Krieg keines Falles wolle. In einer demokratischen Gesellschaft ist Krieg ein ungebetener Gast, weswegen Bevölkerungen fast ausnahmslos jedes Mal in die Kriegsbereitschaft hineingelockt werden müssen, siehe Brutkastenlüge im Zusammenhang mit dem Irakkrieg. Nun kann man sehr oft beobachten, wie Staatsführer stets in aller Inbrunst gegen den aktuellen oder einen eventuell bevorstehenden Krieg poltern. Wenn jedoch alle Personen an den entscheidenden Machthebeln so sehr gegen Kriege sind, wie können Kriege dann überhaupt ausbrechen? <iframe width="560" height="315" src="https://www.youtube.com/embed/Ti7oC2mzX3o" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> ### Der Gegner ist allein für den Krieg verantwortlich! Der zugrundeliegenden Logik nach zeigt jeweils die eine Kriegspartei auf die andere und schiebt dabei die Schuld für den stattfindenden Krieg der anderen Seite zu. Selbst hat man natürlich keine provozierenden Schritte gesetzt, wie etwa das Stationieren von Raketensystemen, das Verschieben von Machtblöcken oder Ähnliches. Statt zum Mittel der Diplomatie zu greifen muss der Konflikt jetzt weiter angeheizt und der Krieg fortgeführt werden, denn schließlich muss dieser Krieg jetzt geführt werden, damit (ewiger) Frieden herrschen kann - siehe "Krieg ist Frieden" nach George Orwell. Darüber hinaus kann der Konflikt auch deshalb nicht beendet werden, weil der Feind sonst "unsere Werte" zerstört, "uns" die Freiheit nimmt oder gar ein Genozid "an unserem Volk" stattfindet. [](https://i.nostr.build/7OaOooGkLEJMxWQN.jpg) ### Der Führer des feindlichen Lagers wird dämonisiert Dieses Prinzip folgt der Logik des Reduzierens eines ganzen Landes auf eine an der Spitze sitzenden Person, also dem Zuschneiden auf Putin, Obama, Scholz, etc. Diese Person repräsentiert quasi einen fleischgewordenen Dämon, der die Macht über das Feindesland errungen hat und nun in Abwesenheit von geistiger Gesundheit einen Konflikt vom Zaun bricht. Morelli argumentiert dazu: "Man kann eine Gruppe von Menschen nicht insgesamt hassen, nicht einmal als Feinde. Es ist daher wirkungsvoller, den Hass auf die feindliche Führungspersönlichkeit zu richten. Der Gegner bekommt so ein Gesicht und dieses Gesicht wird natürlich Gegenstand des Hasses werden." [](https://i.nostr.build/wYld4Zekq0hXoc49.jpg) ### Wir verteidigen ein edles Ziel und keine besonderen Interessen! Der Fokus auf moralische und legitime Werte spielt diesem Prinzip nach deshalb eine besondere Rolle, weil es dazu dient die wirtschaftlichen und geopolitischen Ziele der eignen Seite zu verdecken, was auf das Stärken der Zustimmung der eigenen Bevölkerung schielt, da der Konflikt zu einem gewissen Grad nur durch Zustimmung eben dieser Bevölkerung geführt werden kann. So hatte Antonio Gramsci dargelegt wie sich die Ziele des Ersten Weltkriegs in drei Punkte zusammenfassen lassen: den Militarismus zu vernichten, die kleinen Staaten (wie etwa Belgien) zu verteidigen und die Welt für "die Demokratie" vorzubereiten. Letzteres Argument fand sich auch in den Konflikten des aktuellen Jahrhunderts in ähnlicher Form als "Spreading Democracy" oder "Befreiung des Iraks" wieder. Ergänzend könnte man zu diesem Prinzip sagen, dass ein Unterton von "der Feind ist ein blutrünstiges Monster aus einer barbarischen Gesellschaft" mitschwingt. [](https://i.nostr.build/F5rxV1KGWPtUGctv.gif) ### Der Feind begeht wissentlich Grausamkeiten, wenn wir Fehler machen, geschieht dies unbeabsichtigt Erzählungen über Gräueltaten des Feindes stellen ein wesentliches Element von Kriegspropaganda dar. Zwar sind Grausamkeiten zweifelsohne integraler Bestandteil eines jeden Krieges, und das auf beiden Seiten, jedoch ist die gegensätzliche Darstellung der eigenen "humanitären" Armee, die selbstverständlich von der Bevölkerung geliebt wird, und der feindlichen Armee, die als einzige Kriegspartei Grausamkeiten begeht, altbekannte Propaganda. Üblicherweise begnügt man sich nicht mit den tatsächlich auftretenden Verbrechen, im Gegenteil, man kann in vergangenen Konflikten wiederholt beobachten wie Verbrechen gegen die Menschlichkeit am Schreibtisch erfunden werden, um den Feind als die Wiederkehr Adolf Hitlers erscheinen zu lassen. <iframe class="rumble" width="640" height="360" src="https://rumble.com/embed/vxlfj6/?pub=4" frameborder="0" allowfullscreen></iframe> ### Der Feind benutzt unerlaubte Waffen In gewisser Weise ergänzt dieses Prinzip das vorangegangene und das nämlich um den Aspekt den Krieg selbst auf ritterliche Art und Weise zu führen, als wäre Krieg ein vollends definiertes Brettspiel, während der Feind geächtete Waffen einsetzt - zu jenen man selbst natürlich niemals greifen würde. Die Geschichte zeigt, dass hier oft der Gegenseite vorgeworfen wird, was die eigene Armee-(führung) bereits lange vorbereitet oder gar eingesetzt hat. Ein älteres Beispiel wäre die Verwendung von Giftgas im Ersten Weltkrieg, während Streumunition wie auch mit Uran angereicherte Munition ein trauriges Kapitel der vergangenen Monate ist. [](https://i.nostr.build/YefQ6bJWIDtGtvtf.jpg) ### Wir erleiden geringe Verluste, die Verluste des Feindes sind erheblich Zitat aus dem Buch von Morelli: "Von seltenen Ausnahmen abgesehen, schließen Menschen sich eher den siegreichen Anliegen an. Im Falle des Krieges hängt die Präferenz der öffentlichen Meinung sehr stark von den augenscheinlichen Ergebnissen des Konflikts ab. Wenn die Ergebnisse nicht gut sind, muss die Propaganda unsere Verluste verschleiern und die des Feindes übertreiben." ### Anerkannte Kulturträger und Wissenschafter unterstützen unser Anliegen Ein unterschätztes Mittel der Propaganda ist das Einbeziehen von Personen des öffentlichen Lebens, favorisiert jene zu denen möglichst große Teile der Bevölkerung ein Vertrauensverhältnis entwickelt haben oder Personen mit einer gewissen "moralischen Autorität", wie etwa geistliche Führer. Darüber hinaus ließen sich in der Vergangenheit - wie auch heute - Künstler und Medienschaffende dazu instrumentalisieren Filme, Dokumentationen und Karikaturen über den Feind zu erstellen wie auch zu verbreiten. Man rufe sich in Erinnerung, dass man nicht ohne Grund von der Heimatfront spricht. In einer halbwegs von Demokratie geprägten Gesellschaft entscheidet das Wahlvolk wie lange ein Konflikt noch geführt werden kann bzw. wie stabil die kriegsführende Regierung im Sattel sitzt. <iframe width="560" height="315" src="https://www.youtube.com/embed/Eo5DrObovLc" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> ### Unser Anliegen hat etwas Heiliges Dieses Prinzip mag bei erster Betrachtung an die Kreuzzüge erinnern, bei jenen "der Wille Gottes" in gewisser Weise im Mittelpunkt stand. Ein in meinen Augen wichtiges Element bei diesem Aspekt ist die versteckte Nachricht des Kampfes Gut gegen Böse. Wir, die Guten, kämpfen gegen das Böse, den Feind, und treiben diesen Konflikt nun gewaltsam voran, um die Welt von dem Bösen zu befreien, die Welt also einer Heilung zu unterziehen. Neben dem religiös angehauchten Argument scheint dieses Propagandaprinzip um das Schlagwort "Demokratie" bereichert geworden zu sein. Wie in meinen Augen zurecht aufgezeigt wird, sprach auch George Bush von der "Achse des Bösen" wie auch der Pflicht dem Irak Demokratie zu bringen, also ein Gut, dass gottesgleiche Züge zu haben scheint. Sprachliche Ausschmückungen wie "Gott ist mit uns" tun in Botschaften, die sich nach diesem Prinzip richten, ihr übriges. [](https://i.nostr.build/lMXqTsTZ6m8yhYAk.jpg) ### Wer unsere Propaganda in Zweifel zieht, arbeitet für den Feind und ist damit ein Verräter Das zehnte und somit letzte Prinzip kann mit den vorangegangenen Prinzipien kombiniert werden. In manchen Situationen dient dieses Prinzip jedoch auch als Leitmotiv im Umgang mit kritischen Stimmen aus der Heimatfront. Wer auch immer Meldungen, Schlagzeilen oder gar Argumente infrage stellt, ist automatisch ein Kollaborateur des Feindes. Anhand dieser polarisierten Betrachtungsweise des "entweder bist du für uns oder gegen uns" muss umgehend Farbe bekannt werden. Durch diese Eliminierung einer abgewogenen Betrachtung von komplexen Ereignissen wird es also unmöglich gemacht, eine abweichende Meinung zu entwickeln, ohne einen regelrechten Lynchprozess am Hals zu haben. Man könnte dies auch als das Ende des Meinungspluralismus interpretieren, wo jegliche Opposition zum Schweigen verurteilt wird und zur Not diffamiert wie auch diskriminiert wird. [](https://i.nostr.build/LDivLGBJNdRjIIgh.png) ## (Weitere) Methoden der Kriegspropaganda Wie in [6] präsentiert, können Propagandisten auf eine erstaunlich große Bandbreite von Manipulationsmethoden zurückgreifen. In meinen Augen lohnt sich ein kurzer Blick darauf. Ein wesentlicher Punkt, den es meiner Meinung nach zu beachten gilt, ist die Tatsache, dass mit dem gezielten Einsatz von (Kriegs)-Propaganda meist lange vor dem ersten Schusswechsel begonnen wird und auch nach Beendigung des Konfliktes Propaganda einen wichtigen Teil der militärischen Strategie darstellt. ### Die Rolle von Angst Das Zeichnen eines immanenten Bedrohungsszenarios, welches besonders über die emotionale Schiene wahrgenommen wird, stimmt Menschen am ehesten um die Notwendigkeit eines Militäreinsatzes zu befürworten. Dabei spielt es meiner Ansicht nach gar keine so große Rolle, ob diese Bedrohung real existiert oder nicht, ausschlaggebend ist die gefühlte Wahrnehmung der Bevölkerung. Bestehende oder induzierte Angst lassen sich durch geschicktes Beeinflussen schnell in Wut wandeln und am Ende des Prozesses in einen flammenden Hass auf den vermeintlichen Feind. Aus diesem Grund wird oft ein Zustand der permanent gefühlten Bedrohung geschaffen, sodass in den Köpfen eine gefühlte Gefahr für Laib und Leben so oft wie möglich präsent ist. Dieser Prozess wird durch ständiges Wiederholen der Botschaft verstärkt, bis es sich tief im Unterbewusstsein der Bevölkerung eingenistet hat. [](https://i.nostr.build/n8EkzpWIZBSYcsey.jpg) ### Zensur Zensur - das gezielte Unterdrücken oder Weglassen von Informationen zu einem Sachverhalt, ist schon lange fixer Bestandteil von Propaganda. Bestimmte Sichtweisen können in der Abwesenheit von Gegenargumenten oder gar Gegenbeweisen besonders gut verfestigt werden. Hierzu genügt es aus Sicht des Staatsapparats nicht nur Beiträge zu löschen oder Meinungen zu unterdrücken, nein, damit dies möglich ist, muss flächendeckende wie auch umfängliche Überwachung stattfinden, damit in den Augen des Unterdrückers problematische Informationen schnellstmöglich aus dem Verkehr gezogen werden können. Von Zensur betroffen sind Druckerzeugnisse wie etwa Zeitungen und Bücher, aber auch Ton und Bildproduktionen. Auf digitaler Ebene können Webseiten, Blogs, Content Creatoren oder gar ganze Online Communities hiervon betroffen sein. Im Kontext eines Krieges ist es für die heimische Konfliktpartei von enormer Bedeutung Zensur anzuwenden, um dem Feind keinerlei geheime Informationen zukommen zu lassen - zum Beispiel über Waffen, Truppenbewegungen oder geplante Manöver der eigenen Einheiten. Ein weiteres Anliegen geht in die Richtung wie der Krieg in der Öffentlichkeit dargestellt wird. So kann ohne Anwendung von Zensur das Vertrauen in die Politik schwinden und somit schlussendlich die Zustimmung zum Fortführen der kriegerischen Handlungen schwinden. Dies kann beispielsweise passieren, sobald die Bevölkerung von Niederlagen, Fehlschlägen, dem von der eigenen Armee ausgelösten Leid oder gar Kriegsverbrechen der eigenen Reihen Wind bekommt. Daher ist es im Interesse des Zensors solche Informationen geheim zu halten. Während die direkte Zensur in der westlichen Welt weitestgehend abgeschafft wurde, findet indirekte Zensur nach wie vor Anwendung. Hierbei ist die Zugangskontrolle zu bestimmten Informationen gemeint. Es existieren quasi Torwächter, die darüber entscheiden welcher Journalist welche Informationen gefüttert bekommt. Darüber hinaus können Informationen - etwa über bestimmte Kriegsverbrechen - bewusst vorenthalten werden oder Journalisten dürfen bestimmte Orte erst gar nicht betreten. Somit bleibt vielen Journalisten wie auch Berichterstattern oft nichts anderes übrig, als die Meldungen der Militärführung zu übernehmen. [](https://i.nostr.build/DjCuTC25Y7Smnqhd.jpg) Eine dritte Form von Zensur, die in meinen Augen oftmals gar nicht erst bedacht wird, ist die Selbstzensur von Berichterstattern. Obwohl es in vielen Fällen keine politischen oder militärischen Zensurvorschriften gibt, unterschlagen Berichterstatter bestimmte Informationen. Erklärungen hierfür können Motivationen wirtschaftlicher Natur eines Mediums, direkte Bestechung oder Begünstigung sein. Nicht zu unterschätzen ist die aufkommende Angst eines Journalisten sich durch das Vertreten von unpopulären Ansichten Karrierechancen zu verbauen. Zu dieser Gefühlslage kommt hinzu, dass Journalisten oftmals wegen ihrer eigenen Weltanschauung und dem damit verbundenen Wertekompass die Realität nur einseitig wahrnehmen. [](https://i.nostr.build/WT7Tiu3TzMF9sO0z.jpg) ### Die Verzerrung der Sprache Die menschliche Sprache verwendet Bilder um Botschaften zu transportieren. Dabei ist jedes Hauptwort wie ein Paket mit einem gewissen bildlichen Inhalt zu verstehen. Zudem lassen sich durch geschickte Auswahl von Worten Stimmungen hervorrufen oder unterdrücken. In der Kriegspropaganda unterscheidet man hier zwischen: * Black Words - Diese dienen zum Erschaffen eines klaren Feindbildes, welche beim Empfänger Unbehagen und Angst wecken können. Besonders in Kriegszeiten greifen Politiker in ihren Ansprachen auf Begriffe wie Diktator, Hass, Waffen, Terrorismus, Unterdrückung, Regime, Tyrannei, das Böse und so weiter zurück. * White Words - Hierbei handelt es sich um sprachliche Bilder, die mit positiven Gefühlen verbunden sind und dienen, strategisch in Reden platziert, der moralischen Rechtfertigung des Krieges. Hierzu zählen Begriffe wie Demokratie, Freiheit, Gerechtigkeit, Sicherheit, Frieden, Familie, Nation, Humanität, Vaterland, etc. * Sprachliche Schönfärberei - Gezielt werden Formulierungen verwendet, die einen beschönigenden Effekt haben wie beispielsweise "Kollateralschaden" statt "Getötete oder verletzte Zivilisten" oder "Luftschlag" statt "Bombardement". ### Mitläuferfang Es liegt wohl in der Natur des Menschen lieber auf der Gewinner als auf der Verliererseite stehen zu wollen, weswegen wir Menschen uns tendenziell lieber der Mehrheit anschließen. Mehrheiten versprechen Erfolg, denn allzu gutgläubig glauben wir Mehrheiten würden sich niemals täuschen. Die Strategie des Mitläuferfangs nutzt diese menschliche Anlage aus, indem die kundgetane Meinung als die Meinung der Mehrheit verkauft wird. Hierzu werden öfters auch Bilder eingesetzt, die den Eindruck erwecken, eine große Masse würde bereits dieser propagierten Meinung folgen. [](https://i.nostr.build/efE0zri3SYp2sr8V.jpg) ### Ästhetisierung Unter dem Begriff Ästhetisierung versteht man eine verschönerte Darstellung einer Sache. Etwa wird durch eine ästhetische Darstellung des Krieges versucht dem Krieg den Schrecken zu nehmen, wodurch abgezielt wird den Krieg dadurch leichter akzeptieren zu können. Fotos und Filme, die den Krieg dokumentieren sollen, werden bewusst so aufgenommen bzw. ausgewählt, dass sie beim Betrachter eher Faszination als Abschreckung auslösen. All das sorgt dafür, dass das Bild schön und ansprechend empfunden wird, und den Betrachter die eigentlich hässliche Kriegsrealität vergessen lässt. [](https://i.nostr.build/DgM3EL4Cv85hUxdE.jpg) ### Militainment Dieser Begriff verbindet "Militär" und "Entertainment" und besonders jüngere Leser sollten schnell erkennen was hier gemeint ist. Hingedeutet wird hier auf die aktive Zusammenarbeit zwischen Militär und Medienunternehmen bei der Produktion von Kriegsfilmen, -serien, -dokumentationen oder Computerkriegsspielen. Beide Seiten ziehen Nutzen daraus: Das Militär stellt die Ausrüstung zur Verfügung, die für eine Produktion nötig ist. Als Gegenleistung verpflichten sich die Medienmacher, den Krieg in der vom Militär gewünschten Weise darzustellen. Letztlich entscheidet das Militär darüber, was gezeigt werden darf und was nicht. So wird der Krieg zum Schauplatz von Heldengeschichten, in denen das Militär ehrenvoll erscheint und andere Möglichkeiten als Krieg zur Lösung von Konflikten ausgeblendet werden. Diese Darstellungsweise trägt dazu bei, dass das Ansehen des Militärs und die gesellschaftliche Akzeptanz von Kriegen steigen. Auch die Computer- und Softwareindustrie wird durch das Militär unterstützt. Ähnlich wie bei Kriegsfilmen ist ein realistisches Erscheinungsbild für Computerkriegsspiele sehr wichtig. Doch wie kommt man an alle Taktiken, Uniformen, Sounds, Einsatzpapiere oder gar Stimmen und Karten heran? – Man braucht die Army. Da die sich allerdings aussucht, wer welches Material bekommt, kann sie von einem Einspruchsrecht Gebrauch machen. Das ist nicht unstatthaft, wer würde schließlich ein Projekt finanzieren oder unterstützen, das das eigene Werbebild beschädigt? [](https://i.nostr.build/oUojwTrYYW08yaP5.jpg) ## Fazit Wie im Lauf des Posts immer deutlicher wird, ist die Bandbreite an Methoden, aus der Propagandisten schöpfen können, beträchtlich. Darüber hinaus stammen diese Techniken nicht aus dem letzten Quartal, sondern hatten jahrhundertelang Zeit, um verfeinert zu werden. Ich hoffe mit diesem Post zur Stärkung der Achtsamkeit im Bereich der Propaganda wie auch der Sensibilisierung im Hinblick auf den Einsatz von Propagandatechniken im Alltag beizutragen. Nur wer Propaganda wie auch Manipulationsversuche als solche erkennt, wird in der Lage sein sich dessen zu erwehren. Das Schlusswort möchte ich nun einer Person überlassen, die mich schon vor Jahren dazu inspiriert hatte mich mit dieser unbequemen Thematik zu beschäftigen: > "Nearly every war that has started in the past 50 years, has been the result of media lies. The media could have stopped it, if they hadn't reprinted government propaganda but what does that mean? Well, that means basically populations don't like wars and populations have to be fooled into wars. populations don't willingly and with open eyes go into a war So, if we have a good media environment then we will also have a peaceful environment. Our number one enemy is ignorance." - Julian Assange ## Quellen 1. https://www.bpb.de/themen/medien-journalismus/krieg-in-den-medien/130697/was-ist-propaganda 2. https://www.goodreads.com/book/show/493212.Propaganda 3. https://weltwoche.ch/daily/prinzipien-der-kriegspropaganda-von-arthur-ponsonby 4. https://www.morawa.at/detail/ISBN-9783866744158/Morelli-Anne/Die-Prinzipien-der-Kriegspropaganda?CSPCHD=002000000000JAZLG7CSVpoEmIWvrDniZIp7zJA2Cmz9CJ_rwt 5. https://de.wikipedia.org/wiki/Die_Prinzipien_der_Kriegspropaganda 6. https://www.bpb.de/themen/medien-journalismus/krieg-in-den-medien/130699/methoden-der-kriegspropaganda/ ## Bücher zum Thema - Edward Bernays - Propaganda - Anne Morelli - Die Prinzipien der Kriegspropaganda - Patrik Baab - Propaganda-Presse: Wie uns Medien und Lohnschreiber in Kriege treiben - Jonas Tögel - Kognitive Kriegsführung: Neueste Manipulationstechniken als Waffengattung der NATO - Gustave Le Bon - Psychologie der Massen - Marcus Klöckner - Umstritten: Ein journalistisches Gütesiegel ## Videos zum Thema - [Jonas Tögel: Kognitive Kriegsführung – Neueste Manipulationstechniken als Waffengattung der NATO](https://www.youtube.com/watch?v=FCIsI9auGoQ) - [„Zensur und Propaganda sind Nato-Programm“ - Punkt.PRERADOVIC mit Patrik Baab](https://www.youtube.com/watch?v=TOFwLh1ejSE) - [Kriegsbereitschaft und Gegnerdämonisierung ǀ Gabriele Krone-Schmalz](https://www.youtube.com/watch?v=oasUOVevSoQ) - [Daniele Ganser: Propaganda – Wie unsere Gedanken und Gefühle gelenkt werden](https://www.youtube.com/watch?v=ooM3rrBoiBA) - [Umstritten - Marcus Klöckner](https://www.youtube.com/watch?v=PXLaAUl5pFc)
@ 6c2d68ba:846525ec
2024-08-08 21:15:25Will man der Bundeszentrale für politische Bildung glauben, so handelt es sich bei Propaganda um den Versuch der gezielten Beeinflussung des Denkens, Handelns wie auch Fühlens von Menschen. Charakteristisch für Propaganda ist, dass sie darauf verzichtet die verschiedenen Seiten einer Thematik darzulegen, sondern gezielt Meinung mit (Fehl)-Information vermischt. Wer Propaganda betreibt, strebt nicht danach zu diskutieren oder die Öffentlichkeit gar mit Argumenten zu überzeugen, sondern greift zu verschiedensten Manipulationstechniken, die die Emotionen und das Verhalten der Öffentlichkeit beeinflussen. Propaganda nimmt dem Menschen (eigenständiges) Denken ab und gibt ihm stattdessen das Gefühl, mit der übernommenen Meinung goldrichtig zu liegen. Hier zeigt sich auch der wesentliche Unterschied zum Journalismus: Journalismus strebt nach Aufklärung, indem alle verfügbaren Fakten und Hintergründe dargelegt werden und der Empfänger selbst darüber entscheiden darf, was er für richtig und was er für falsch hält [1]. Zwar verbinden wir den Begriff Propaganda heutzutage mit autoritären und totalitären Staaten, wo diese auch zweifelsfrei Anwendung findet, doch kommen Propagandatechniken auch im Westen zum Einsatz, wenn auch in einer auf die demokratische Herrschaftsform zugeschnittene Art und Weise. Wie die Geschichte gezeigt hat - hier sind die Werke von Edward Bernays ganz besonders relevant [2] - wurde Öffentlichkeitsarbeit, sprich Public Relations (PR), basierend auf den Erkenntnissen der Propagandaforschung verfeinert, über welche die öffentliche Wahrnehmung von Personen, Konzernen und Regierungen beeinflusst wird. In Summe lässt sich daraus ableiten, dass auch Propaganda in unseren Breitengraden Tradition hat. Nun halte ich es in Zeiten von (leider) wiederkehrenden heißen Konflikten in Europa besonders wichtig sich über existierende Manipulationstechniken wie auch gezielter Meinungsmache in (Massen)-medien bewusst zu sein wie auch erscheinenden Artikeln, Posts, Videos und ganz besonders Schlagzeilen mit einem gewissen Grad an Achtsamkeit zu begegnen, um nicht umgehend Opfer von Manipulation zu werden. Denn wie schon von der bereits erwähnten Bundeszentrale für politische Bildung erwähnt wurde, kann nur jener sich gegen den Einfluss von Propaganda wehren, der diese als solche erkennt. Dadurch motiviert nehme ich heute die Prinzipien der Kriegspropaganda ins Fadenkreuz. > „Auf die Dauer vermag auch die frechste und bestorganisierte Propaganda nichts gegen die Wahrheit.“ ―Albert Schweitzer ## Die Prinzipien der Kriegspropaganda Unter dem Eindruck des Ersten Weltkriegs schrieb Arthur Ponsonby, britischer Adeliger & Staatsbeamter, 1928 das Buch "Lüge in Kriegszeiten", in welchem er die Mechanismen der damaligen Kriegspropaganda untersuchte. Er steht übrigens im Verdacht Urvater des berühmten Zitats "das erste Opfer im Krieg ist die Wahrheit" zu sein [3]. In diesem Werk schildert Ponsonby 20 Aspekte, die wiederum später von der Historikerin Anne Morelli im Jahr 2001 zu den zehn Prinzipien der Kriegspropaganda zusammengefasst wurden. Wie sie selbst betonte geht es bei diesen Prinzipien nicht darum herauszufinden, wer lügt und wer die Wahrheit sagt, wer das glaubt, was er sagt, sondern Mittels dieser Prinzipien die verbreitete Propaganda zu veranschaulichen und ihr Funktionieren zu beschreiben (Seite 6, [4]). Nachdem ich mich selbst mit diesen Prinzipien beschäftigt hatte, wurde mir mit jeder einzelnen Gedankenrunde immer klarer, wie die von Anne Morelli beschriebenen Prinzipien als wie eine Art Leitfaden verwendet werden, um Pressemeldungen, Argumente und Schlagzeilen in Sozialen Medien so zu formulieren, dass unabhängig vom Geschehnis stets eine unterbewusste Botschaft mitschwingt, so dass der gewünschte Effekt der Manipulation maximiert wird. Nun könnte man nach Durchsicht der größten Tagesblätter des Deutschsprachigen Raums etliche Beispiele für jeden einzelnen der in Kürze vorgestellten Prinzipien präsentieren, doch habe ich in Anbetracht des Themas bewusst Abstand davon genommen, um nicht gewisse Journalisten - oder kriegstreibende Propagandisten wie ich sie nenne - samt Klarnamen an den Pranger zu stellen. Wie Anne Morelli, sehe ich den größtmöglichen Mehrwert darin, die Mechanik offenzulegen, um die Leserschaft für dieses Thema zu sensibilisieren. ### Wir wollen keinen Krieg! Stets wird versichert, dass man den stattfindenden Krieg keines Falles wolle. In einer demokratischen Gesellschaft ist Krieg ein ungebetener Gast, weswegen Bevölkerungen fast ausnahmslos jedes Mal in die Kriegsbereitschaft hineingelockt werden müssen, siehe Brutkastenlüge im Zusammenhang mit dem Irakkrieg. Nun kann man sehr oft beobachten, wie Staatsführer stets in aller Inbrunst gegen den aktuellen oder einen eventuell bevorstehenden Krieg poltern. Wenn jedoch alle Personen an den entscheidenden Machthebeln so sehr gegen Kriege sind, wie können Kriege dann überhaupt ausbrechen? <iframe width="560" height="315" src="https://www.youtube.com/embed/Ti7oC2mzX3o" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> ### Der Gegner ist allein für den Krieg verantwortlich! Der zugrundeliegenden Logik nach zeigt jeweils die eine Kriegspartei auf die andere und schiebt dabei die Schuld für den stattfindenden Krieg der anderen Seite zu. Selbst hat man natürlich keine provozierenden Schritte gesetzt, wie etwa das Stationieren von Raketensystemen, das Verschieben von Machtblöcken oder Ähnliches. Statt zum Mittel der Diplomatie zu greifen muss der Konflikt jetzt weiter angeheizt und der Krieg fortgeführt werden, denn schließlich muss dieser Krieg jetzt geführt werden, damit (ewiger) Frieden herrschen kann - siehe "Krieg ist Frieden" nach George Orwell. Darüber hinaus kann der Konflikt auch deshalb nicht beendet werden, weil der Feind sonst "unsere Werte" zerstört, "uns" die Freiheit nimmt oder gar ein Genozid "an unserem Volk" stattfindet. [](https://i.nostr.build/7OaOooGkLEJMxWQN.jpg) ### Der Führer des feindlichen Lagers wird dämonisiert Dieses Prinzip folgt der Logik des Reduzierens eines ganzen Landes auf eine an der Spitze sitzenden Person, also dem Zuschneiden auf Putin, Obama, Scholz, etc. Diese Person repräsentiert quasi einen fleischgewordenen Dämon, der die Macht über das Feindesland errungen hat und nun in Abwesenheit von geistiger Gesundheit einen Konflikt vom Zaun bricht. Morelli argumentiert dazu: "Man kann eine Gruppe von Menschen nicht insgesamt hassen, nicht einmal als Feinde. Es ist daher wirkungsvoller, den Hass auf die feindliche Führungspersönlichkeit zu richten. Der Gegner bekommt so ein Gesicht und dieses Gesicht wird natürlich Gegenstand des Hasses werden." [](https://i.nostr.build/wYld4Zekq0hXoc49.jpg) ### Wir verteidigen ein edles Ziel und keine besonderen Interessen! Der Fokus auf moralische und legitime Werte spielt diesem Prinzip nach deshalb eine besondere Rolle, weil es dazu dient die wirtschaftlichen und geopolitischen Ziele der eignen Seite zu verdecken, was auf das Stärken der Zustimmung der eigenen Bevölkerung schielt, da der Konflikt zu einem gewissen Grad nur durch Zustimmung eben dieser Bevölkerung geführt werden kann. So hatte Antonio Gramsci dargelegt wie sich die Ziele des Ersten Weltkriegs in drei Punkte zusammenfassen lassen: den Militarismus zu vernichten, die kleinen Staaten (wie etwa Belgien) zu verteidigen und die Welt für "die Demokratie" vorzubereiten. Letzteres Argument fand sich auch in den Konflikten des aktuellen Jahrhunderts in ähnlicher Form als "Spreading Democracy" oder "Befreiung des Iraks" wieder. Ergänzend könnte man zu diesem Prinzip sagen, dass ein Unterton von "der Feind ist ein blutrünstiges Monster aus einer barbarischen Gesellschaft" mitschwingt. [](https://i.nostr.build/F5rxV1KGWPtUGctv.gif) ### Der Feind begeht wissentlich Grausamkeiten, wenn wir Fehler machen, geschieht dies unbeabsichtigt Erzählungen über Gräueltaten des Feindes stellen ein wesentliches Element von Kriegspropaganda dar. Zwar sind Grausamkeiten zweifelsohne integraler Bestandteil eines jeden Krieges, und das auf beiden Seiten, jedoch ist die gegensätzliche Darstellung der eigenen "humanitären" Armee, die selbstverständlich von der Bevölkerung geliebt wird, und der feindlichen Armee, die als einzige Kriegspartei Grausamkeiten begeht, altbekannte Propaganda. Üblicherweise begnügt man sich nicht mit den tatsächlich auftretenden Verbrechen, im Gegenteil, man kann in vergangenen Konflikten wiederholt beobachten wie Verbrechen gegen die Menschlichkeit am Schreibtisch erfunden werden, um den Feind als die Wiederkehr Adolf Hitlers erscheinen zu lassen. <iframe class="rumble" width="640" height="360" src="https://rumble.com/embed/vxlfj6/?pub=4" frameborder="0" allowfullscreen></iframe> ### Der Feind benutzt unerlaubte Waffen In gewisser Weise ergänzt dieses Prinzip das vorangegangene und das nämlich um den Aspekt den Krieg selbst auf ritterliche Art und Weise zu führen, als wäre Krieg ein vollends definiertes Brettspiel, während der Feind geächtete Waffen einsetzt - zu jenen man selbst natürlich niemals greifen würde. Die Geschichte zeigt, dass hier oft der Gegenseite vorgeworfen wird, was die eigene Armee-(führung) bereits lange vorbereitet oder gar eingesetzt hat. Ein älteres Beispiel wäre die Verwendung von Giftgas im Ersten Weltkrieg, während Streumunition wie auch mit Uran angereicherte Munition ein trauriges Kapitel der vergangenen Monate ist. [](https://i.nostr.build/YefQ6bJWIDtGtvtf.jpg) ### Wir erleiden geringe Verluste, die Verluste des Feindes sind erheblich Zitat aus dem Buch von Morelli: "Von seltenen Ausnahmen abgesehen, schließen Menschen sich eher den siegreichen Anliegen an. Im Falle des Krieges hängt die Präferenz der öffentlichen Meinung sehr stark von den augenscheinlichen Ergebnissen des Konflikts ab. Wenn die Ergebnisse nicht gut sind, muss die Propaganda unsere Verluste verschleiern und die des Feindes übertreiben." ### Anerkannte Kulturträger und Wissenschafter unterstützen unser Anliegen Ein unterschätztes Mittel der Propaganda ist das Einbeziehen von Personen des öffentlichen Lebens, favorisiert jene zu denen möglichst große Teile der Bevölkerung ein Vertrauensverhältnis entwickelt haben oder Personen mit einer gewissen "moralischen Autorität", wie etwa geistliche Führer. Darüber hinaus ließen sich in der Vergangenheit - wie auch heute - Künstler und Medienschaffende dazu instrumentalisieren Filme, Dokumentationen und Karikaturen über den Feind zu erstellen wie auch zu verbreiten. Man rufe sich in Erinnerung, dass man nicht ohne Grund von der Heimatfront spricht. In einer halbwegs von Demokratie geprägten Gesellschaft entscheidet das Wahlvolk wie lange ein Konflikt noch geführt werden kann bzw. wie stabil die kriegsführende Regierung im Sattel sitzt. <iframe width="560" height="315" src="https://www.youtube.com/embed/Eo5DrObovLc" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> ### Unser Anliegen hat etwas Heiliges Dieses Prinzip mag bei erster Betrachtung an die Kreuzzüge erinnern, bei jenen "der Wille Gottes" in gewisser Weise im Mittelpunkt stand. Ein in meinen Augen wichtiges Element bei diesem Aspekt ist die versteckte Nachricht des Kampfes Gut gegen Böse. Wir, die Guten, kämpfen gegen das Böse, den Feind, und treiben diesen Konflikt nun gewaltsam voran, um die Welt von dem Bösen zu befreien, die Welt also einer Heilung zu unterziehen. Neben dem religiös angehauchten Argument scheint dieses Propagandaprinzip um das Schlagwort "Demokratie" bereichert geworden zu sein. Wie in meinen Augen zurecht aufgezeigt wird, sprach auch George Bush von der "Achse des Bösen" wie auch der Pflicht dem Irak Demokratie zu bringen, also ein Gut, dass gottesgleiche Züge zu haben scheint. Sprachliche Ausschmückungen wie "Gott ist mit uns" tun in Botschaften, die sich nach diesem Prinzip richten, ihr übriges. [](https://i.nostr.build/lMXqTsTZ6m8yhYAk.jpg) ### Wer unsere Propaganda in Zweifel zieht, arbeitet für den Feind und ist damit ein Verräter Das zehnte und somit letzte Prinzip kann mit den vorangegangenen Prinzipien kombiniert werden. In manchen Situationen dient dieses Prinzip jedoch auch als Leitmotiv im Umgang mit kritischen Stimmen aus der Heimatfront. Wer auch immer Meldungen, Schlagzeilen oder gar Argumente infrage stellt, ist automatisch ein Kollaborateur des Feindes. Anhand dieser polarisierten Betrachtungsweise des "entweder bist du für uns oder gegen uns" muss umgehend Farbe bekannt werden. Durch diese Eliminierung einer abgewogenen Betrachtung von komplexen Ereignissen wird es also unmöglich gemacht, eine abweichende Meinung zu entwickeln, ohne einen regelrechten Lynchprozess am Hals zu haben. Man könnte dies auch als das Ende des Meinungspluralismus interpretieren, wo jegliche Opposition zum Schweigen verurteilt wird und zur Not diffamiert wie auch diskriminiert wird. [](https://i.nostr.build/LDivLGBJNdRjIIgh.png) ## (Weitere) Methoden der Kriegspropaganda Wie in [6] präsentiert, können Propagandisten auf eine erstaunlich große Bandbreite von Manipulationsmethoden zurückgreifen. In meinen Augen lohnt sich ein kurzer Blick darauf. Ein wesentlicher Punkt, den es meiner Meinung nach zu beachten gilt, ist die Tatsache, dass mit dem gezielten Einsatz von (Kriegs)-Propaganda meist lange vor dem ersten Schusswechsel begonnen wird und auch nach Beendigung des Konfliktes Propaganda einen wichtigen Teil der militärischen Strategie darstellt. ### Die Rolle von Angst Das Zeichnen eines immanenten Bedrohungsszenarios, welches besonders über die emotionale Schiene wahrgenommen wird, stimmt Menschen am ehesten um die Notwendigkeit eines Militäreinsatzes zu befürworten. Dabei spielt es meiner Ansicht nach gar keine so große Rolle, ob diese Bedrohung real existiert oder nicht, ausschlaggebend ist die gefühlte Wahrnehmung der Bevölkerung. Bestehende oder induzierte Angst lassen sich durch geschicktes Beeinflussen schnell in Wut wandeln und am Ende des Prozesses in einen flammenden Hass auf den vermeintlichen Feind. Aus diesem Grund wird oft ein Zustand der permanent gefühlten Bedrohung geschaffen, sodass in den Köpfen eine gefühlte Gefahr für Laib und Leben so oft wie möglich präsent ist. Dieser Prozess wird durch ständiges Wiederholen der Botschaft verstärkt, bis es sich tief im Unterbewusstsein der Bevölkerung eingenistet hat. [](https://i.nostr.build/n8EkzpWIZBSYcsey.jpg) ### Zensur Zensur - das gezielte Unterdrücken oder Weglassen von Informationen zu einem Sachverhalt, ist schon lange fixer Bestandteil von Propaganda. Bestimmte Sichtweisen können in der Abwesenheit von Gegenargumenten oder gar Gegenbeweisen besonders gut verfestigt werden. Hierzu genügt es aus Sicht des Staatsapparats nicht nur Beiträge zu löschen oder Meinungen zu unterdrücken, nein, damit dies möglich ist, muss flächendeckende wie auch umfängliche Überwachung stattfinden, damit in den Augen des Unterdrückers problematische Informationen schnellstmöglich aus dem Verkehr gezogen werden können. Von Zensur betroffen sind Druckerzeugnisse wie etwa Zeitungen und Bücher, aber auch Ton und Bildproduktionen. Auf digitaler Ebene können Webseiten, Blogs, Content Creatoren oder gar ganze Online Communities hiervon betroffen sein. Im Kontext eines Krieges ist es für die heimische Konfliktpartei von enormer Bedeutung Zensur anzuwenden, um dem Feind keinerlei geheime Informationen zukommen zu lassen - zum Beispiel über Waffen, Truppenbewegungen oder geplante Manöver der eigenen Einheiten. Ein weiteres Anliegen geht in die Richtung wie der Krieg in der Öffentlichkeit dargestellt wird. So kann ohne Anwendung von Zensur das Vertrauen in die Politik schwinden und somit schlussendlich die Zustimmung zum Fortführen der kriegerischen Handlungen schwinden. Dies kann beispielsweise passieren, sobald die Bevölkerung von Niederlagen, Fehlschlägen, dem von der eigenen Armee ausgelösten Leid oder gar Kriegsverbrechen der eigenen Reihen Wind bekommt. Daher ist es im Interesse des Zensors solche Informationen geheim zu halten. Während die direkte Zensur in der westlichen Welt weitestgehend abgeschafft wurde, findet indirekte Zensur nach wie vor Anwendung. Hierbei ist die Zugangskontrolle zu bestimmten Informationen gemeint. Es existieren quasi Torwächter, die darüber entscheiden welcher Journalist welche Informationen gefüttert bekommt. Darüber hinaus können Informationen - etwa über bestimmte Kriegsverbrechen - bewusst vorenthalten werden oder Journalisten dürfen bestimmte Orte erst gar nicht betreten. Somit bleibt vielen Journalisten wie auch Berichterstattern oft nichts anderes übrig, als die Meldungen der Militärführung zu übernehmen. [](https://i.nostr.build/DjCuTC25Y7Smnqhd.jpg) Eine dritte Form von Zensur, die in meinen Augen oftmals gar nicht erst bedacht wird, ist die Selbstzensur von Berichterstattern. Obwohl es in vielen Fällen keine politischen oder militärischen Zensurvorschriften gibt, unterschlagen Berichterstatter bestimmte Informationen. Erklärungen hierfür können Motivationen wirtschaftlicher Natur eines Mediums, direkte Bestechung oder Begünstigung sein. Nicht zu unterschätzen ist die aufkommende Angst eines Journalisten sich durch das Vertreten von unpopulären Ansichten Karrierechancen zu verbauen. Zu dieser Gefühlslage kommt hinzu, dass Journalisten oftmals wegen ihrer eigenen Weltanschauung und dem damit verbundenen Wertekompass die Realität nur einseitig wahrnehmen. [](https://i.nostr.build/WT7Tiu3TzMF9sO0z.jpg) ### Die Verzerrung der Sprache Die menschliche Sprache verwendet Bilder um Botschaften zu transportieren. Dabei ist jedes Hauptwort wie ein Paket mit einem gewissen bildlichen Inhalt zu verstehen. Zudem lassen sich durch geschickte Auswahl von Worten Stimmungen hervorrufen oder unterdrücken. In der Kriegspropaganda unterscheidet man hier zwischen: * Black Words - Diese dienen zum Erschaffen eines klaren Feindbildes, welche beim Empfänger Unbehagen und Angst wecken können. Besonders in Kriegszeiten greifen Politiker in ihren Ansprachen auf Begriffe wie Diktator, Hass, Waffen, Terrorismus, Unterdrückung, Regime, Tyrannei, das Böse und so weiter zurück. * White Words - Hierbei handelt es sich um sprachliche Bilder, die mit positiven Gefühlen verbunden sind und dienen, strategisch in Reden platziert, der moralischen Rechtfertigung des Krieges. Hierzu zählen Begriffe wie Demokratie, Freiheit, Gerechtigkeit, Sicherheit, Frieden, Familie, Nation, Humanität, Vaterland, etc. * Sprachliche Schönfärberei - Gezielt werden Formulierungen verwendet, die einen beschönigenden Effekt haben wie beispielsweise "Kollateralschaden" statt "Getötete oder verletzte Zivilisten" oder "Luftschlag" statt "Bombardement". ### Mitläuferfang Es liegt wohl in der Natur des Menschen lieber auf der Gewinner als auf der Verliererseite stehen zu wollen, weswegen wir Menschen uns tendenziell lieber der Mehrheit anschließen. Mehrheiten versprechen Erfolg, denn allzu gutgläubig glauben wir Mehrheiten würden sich niemals täuschen. Die Strategie des Mitläuferfangs nutzt diese menschliche Anlage aus, indem die kundgetane Meinung als die Meinung der Mehrheit verkauft wird. Hierzu werden öfters auch Bilder eingesetzt, die den Eindruck erwecken, eine große Masse würde bereits dieser propagierten Meinung folgen. [](https://i.nostr.build/efE0zri3SYp2sr8V.jpg) ### Ästhetisierung Unter dem Begriff Ästhetisierung versteht man eine verschönerte Darstellung einer Sache. Etwa wird durch eine ästhetische Darstellung des Krieges versucht dem Krieg den Schrecken zu nehmen, wodurch abgezielt wird den Krieg dadurch leichter akzeptieren zu können. Fotos und Filme, die den Krieg dokumentieren sollen, werden bewusst so aufgenommen bzw. ausgewählt, dass sie beim Betrachter eher Faszination als Abschreckung auslösen. All das sorgt dafür, dass das Bild schön und ansprechend empfunden wird, und den Betrachter die eigentlich hässliche Kriegsrealität vergessen lässt. [](https://i.nostr.build/DgM3EL4Cv85hUxdE.jpg) ### Militainment Dieser Begriff verbindet "Militär" und "Entertainment" und besonders jüngere Leser sollten schnell erkennen was hier gemeint ist. Hingedeutet wird hier auf die aktive Zusammenarbeit zwischen Militär und Medienunternehmen bei der Produktion von Kriegsfilmen, -serien, -dokumentationen oder Computerkriegsspielen. Beide Seiten ziehen Nutzen daraus: Das Militär stellt die Ausrüstung zur Verfügung, die für eine Produktion nötig ist. Als Gegenleistung verpflichten sich die Medienmacher, den Krieg in der vom Militär gewünschten Weise darzustellen. Letztlich entscheidet das Militär darüber, was gezeigt werden darf und was nicht. So wird der Krieg zum Schauplatz von Heldengeschichten, in denen das Militär ehrenvoll erscheint und andere Möglichkeiten als Krieg zur Lösung von Konflikten ausgeblendet werden. Diese Darstellungsweise trägt dazu bei, dass das Ansehen des Militärs und die gesellschaftliche Akzeptanz von Kriegen steigen. Auch die Computer- und Softwareindustrie wird durch das Militär unterstützt. Ähnlich wie bei Kriegsfilmen ist ein realistisches Erscheinungsbild für Computerkriegsspiele sehr wichtig. Doch wie kommt man an alle Taktiken, Uniformen, Sounds, Einsatzpapiere oder gar Stimmen und Karten heran? – Man braucht die Army. Da die sich allerdings aussucht, wer welches Material bekommt, kann sie von einem Einspruchsrecht Gebrauch machen. Das ist nicht unstatthaft, wer würde schließlich ein Projekt finanzieren oder unterstützen, das das eigene Werbebild beschädigt? [](https://i.nostr.build/oUojwTrYYW08yaP5.jpg) ## Fazit Wie im Lauf des Posts immer deutlicher wird, ist die Bandbreite an Methoden, aus der Propagandisten schöpfen können, beträchtlich. Darüber hinaus stammen diese Techniken nicht aus dem letzten Quartal, sondern hatten jahrhundertelang Zeit, um verfeinert zu werden. Ich hoffe mit diesem Post zur Stärkung der Achtsamkeit im Bereich der Propaganda wie auch der Sensibilisierung im Hinblick auf den Einsatz von Propagandatechniken im Alltag beizutragen. Nur wer Propaganda wie auch Manipulationsversuche als solche erkennt, wird in der Lage sein sich dessen zu erwehren. Das Schlusswort möchte ich nun einer Person überlassen, die mich schon vor Jahren dazu inspiriert hatte mich mit dieser unbequemen Thematik zu beschäftigen: > "Nearly every war that has started in the past 50 years, has been the result of media lies. The media could have stopped it, if they hadn't reprinted government propaganda but what does that mean? Well, that means basically populations don't like wars and populations have to be fooled into wars. populations don't willingly and with open eyes go into a war So, if we have a good media environment then we will also have a peaceful environment. Our number one enemy is ignorance." - Julian Assange ## Quellen 1. https://www.bpb.de/themen/medien-journalismus/krieg-in-den-medien/130697/was-ist-propaganda 2. https://www.goodreads.com/book/show/493212.Propaganda 3. https://weltwoche.ch/daily/prinzipien-der-kriegspropaganda-von-arthur-ponsonby 4. https://www.morawa.at/detail/ISBN-9783866744158/Morelli-Anne/Die-Prinzipien-der-Kriegspropaganda?CSPCHD=002000000000JAZLG7CSVpoEmIWvrDniZIp7zJA2Cmz9CJ_rwt 5. https://de.wikipedia.org/wiki/Die_Prinzipien_der_Kriegspropaganda 6. https://www.bpb.de/themen/medien-journalismus/krieg-in-den-medien/130699/methoden-der-kriegspropaganda/ ## Bücher zum Thema - Edward Bernays - Propaganda - Anne Morelli - Die Prinzipien der Kriegspropaganda - Patrik Baab - Propaganda-Presse: Wie uns Medien und Lohnschreiber in Kriege treiben - Jonas Tögel - Kognitive Kriegsführung: Neueste Manipulationstechniken als Waffengattung der NATO - Gustave Le Bon - Psychologie der Massen - Marcus Klöckner - Umstritten: Ein journalistisches Gütesiegel ## Videos zum Thema - [Jonas Tögel: Kognitive Kriegsführung – Neueste Manipulationstechniken als Waffengattung der NATO](https://www.youtube.com/watch?v=FCIsI9auGoQ) - [„Zensur und Propaganda sind Nato-Programm“ - Punkt.PRERADOVIC mit Patrik Baab](https://www.youtube.com/watch?v=TOFwLh1ejSE) - [Kriegsbereitschaft und Gegnerdämonisierung ǀ Gabriele Krone-Schmalz](https://www.youtube.com/watch?v=oasUOVevSoQ) - [Daniele Ganser: Propaganda – Wie unsere Gedanken und Gefühle gelenkt werden](https://www.youtube.com/watch?v=ooM3rrBoiBA) - [Umstritten - Marcus Klöckner](https://www.youtube.com/watch?v=PXLaAUl5pFc) @ 361d3e1e:50bc10a8
2024-08-18 18:13:10[Full story](https://forex-strategy.com/2024/08/18/covid-and-monkeypox-what-an-amazing-coincidence-in-germany/) Covid and Monkeypox - What an amazing coincidence in Germany It turns out that the new pandemic (Monkeypox) begins in an absolutely identical way, just like the old one pandemic - the covid. #germany #covid #monkeypox #pandemic #health #medicine
@ 361d3e1e:50bc10a8
2024-08-18 18:13:10[Full story](https://forex-strategy.com/2024/08/18/covid-and-monkeypox-what-an-amazing-coincidence-in-germany/) Covid and Monkeypox - What an amazing coincidence in Germany It turns out that the new pandemic (Monkeypox) begins in an absolutely identical way, just like the old one pandemic - the covid. #germany #covid #monkeypox #pandemic #health #medicine @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Agentes racionais Existe essa discussão entre economistas sobre o comportamento de um agente ser "racional" ou não. O julgamento da racionalidade é feito em vista de um "modelo" concebido pelo economista. Cada economista usa um modelo diferente. Daí ficam todos discutindo a racionalidade ou irracionalidade de certo agente. A solução é perguntar: racional segundo quais critérios?
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Agentes racionais Existe essa discussão entre economistas sobre o comportamento de um agente ser "racional" ou não. O julgamento da racionalidade é feito em vista de um "modelo" concebido pelo economista. Cada economista usa um modelo diferente. Daí ficam todos discutindo a racionalidade ou irracionalidade de certo agente. A solução é perguntar: racional segundo quais critérios? @ 361d3e1e:50bc10a8
2024-08-18 14:16:17The huge share of ultra-processed foods, especially in the United States, is due to the fact that the food industry is in the hands of several global corporations. They have literally occupied all the supermarkets with their products. [Full story](https://forex-strategy.com/2024/08/18/how-people-passing-through-the-supermarket-go-to-hospitals-our-ultra-processed-food/)
@ 361d3e1e:50bc10a8
2024-08-18 14:16:17The huge share of ultra-processed foods, especially in the United States, is due to the fact that the food industry is in the hands of several global corporations. They have literally occupied all the supermarkets with their products. [Full story](https://forex-strategy.com/2024/08/18/how-people-passing-through-the-supermarket-go-to-hospitals-our-ultra-processed-food/) @ 8dc86882:9dc4ba5e
2024-08-06 12:47:33If I can just write my key down on paper or my recovery phrase, what is the benefit to things like coldcard? It's no easier to lose than a notebook? originally posted at https://stacker.news/items/637285
@ 8dc86882:9dc4ba5e
2024-08-06 12:47:33If I can just write my key down on paper or my recovery phrase, what is the benefit to things like coldcard? It's no easier to lose than a notebook? originally posted at https://stacker.news/items/637285 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Buying versus donating Currently (and probably it has always been the case) in the Bitcoin community there is some push towards donations as some sort of business model, or in general just a general love for the idea of donations, and I think that is very misguided. ## Two examples of the push for the primacy of donations For example, there is a general wantness of people to have some sort of "static QR code" or "static Lightning invoice" that people can put on their Twitter profiles to receive donations (sometimes they say "payments" instead of "donations" but to me there is no such a thing as a payment without a good or service being given in exchange, so I'm saying "donations") and that is a hard problem to solve considering the fact that most Lightning wallets are running on phones. Another example is the "Podcasting 2.0" initiative that tries to integrate podcast players with Lightning wallets so they can send donations to podcast hosts that are running Lightning nodes. Their proponents call it "value for value" (or "value4value", "v4v") and if you ask they will say _value4value_ is a "model" in which the listener gives out in satoshis to the podcast host the same amount of "value" he is getting from listening to that content. The _value4value_ concept makes it almost explicit the problems I see with this big emphasis on donations the Bitcoin community is making in general. In essence, the idea that the listener is capable of measuring the value it gets from the podcast then converting it into a monetary amount and then donating that is completely wrong and even nonsensical. ### Why _value4value_ is not sound Basic (Austrian) economics teaches us that all value is ordinal, not cardinal -- i.e., it can't be measured or assigned a number to. One can only know that at some instant they prefer _x_ over _y_, they cannot say _x_ has a value of 10 and _y_ has a value of 9. Because of that, it's a nonsense quest to try determine how much value one is getting from a podcast. Basic (Austrian) economics also teaches us that exchanges happen when there are differences in the subjective valuations of goods, i.e., Alice can give _x_ to Bob in exchange for _y_ if Alice prefers _y_ over _x_ and Bob prefers _x_ over _y_ at that point. Because of that (and disregarding the previous paragraph), it's futile to expect that the podcast listener will donate _exactly_ the amount he is getting from the podcast in "value". Because of the two points above, it should also be clear that it is impossible to convert "value" in podcast content form into "value" in satoshis form, but I won't try to explain why that is because this is not an economics textbook. What actually happens is that whether it's in the _value4value_ context or not, donations are always a somewhat random and subjective amount, if they happen. If I like some content that someone is publishing for free, my decision on if and how much I will donate is never dictated by some nonsense calculation, but by calculation that is governed almost entirely by feeling and animal spirits (but one that also considers how much money I can spare, how much I like that person and how much I perceive they need). When I go to a normal shop to buy a bottle of milk I look at the bottle of milk and I read its price, and there is one simple decision I have to make: is this bottle of milk worth more than the amount of money that's specified in the price tag? It's a single decision with only two answers: _yes_ or _no_. While when I see a free form on some free "creator" page asking me to type how much I will donate I have to decide if I will donate, when I will donate, how much I will donate, if I want this donation to be done every month or how will that work going forward? Will I keep consuming the content produced by this person? Will they keep producing? Maybe I'll just listen for free now and do this later as I'm busy, but then will I forget? Maybe I have just donated a lot to someone else and do not have much more money to spare, but now I feel guilty that the other person got all my donation money and this one didn't get anything but I can't go back and ask the other to return the money I just donated -- and so on and so forth. ### Conclusions Although the paragraphs above are confusing and do not follow a very logical presentation pattern, I hope you got from them why I think donations are much more complicated than purchases, and that repeating the "value for value" mantra doesn't help at all. Considering that, what I wanted to say is that bitcoiners should give more attention to the other model, in which people produce goods and services and sell them. And that model can be applied successfully to "content creators", podcasters etc in many ways that are probably (I don't have any data backing my claims) better than the donation model. ## Other possible monetization possibilities For example, I've noticed that many blogs and podcasts with interesting content start to release exclusive episodes as they get big enough. These exclusive episodes are available only for "supporters". This is effectively selling access to the episodes. There is also the "crowdwall" model in which multiple people pay so that some content gets released for free. We can count even the model in which a donation is not just a blank donation, but gives the donor the right to write something on the screen or something like that -- these are actually not just donations, but purchases of these rights. Professional videogame streamers have come up with some other interesting ideas. For example, they crowdfund the creation of special content ("if enough people pay I will dress like a rabbit") or they sell the right to participate in the stream somehow (for example, by playing a game with the streamer in some special day). In these models, the _static QR code_ with which so many people dream doesn't make much sense (if you're selling a specific episode or if a payment is specific to one identifiable person, you need different QR codes or more metadata to be attached to each payment by the payer). ## Addendum I think people like the donation model very much because they only see the big and super famous people that receive donations. A very small set of people have so many followers that they can live with just donations, even though donations are very inefficient and they could earn more and even deliver better content if they were using some other model. I imagine that a creator with a high number of followers will get a lot of people that do not donate anything, a lot that will donate a little -- probably less than they would if they were paying -- and eventually a little number of people that will donate way more than they would if they were buying. This last group is probably what makes it worthwhile to work on this donations model for these creators. The takeaway is that the donations model is not a panacea and is not very good either. ## Related: - [Donations on the internet](nostr:naddr1qqyrqwp4xsmnsvtxqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cex8903)
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Buying versus donating Currently (and probably it has always been the case) in the Bitcoin community there is some push towards donations as some sort of business model, or in general just a general love for the idea of donations, and I think that is very misguided. ## Two examples of the push for the primacy of donations For example, there is a general wantness of people to have some sort of "static QR code" or "static Lightning invoice" that people can put on their Twitter profiles to receive donations (sometimes they say "payments" instead of "donations" but to me there is no such a thing as a payment without a good or service being given in exchange, so I'm saying "donations") and that is a hard problem to solve considering the fact that most Lightning wallets are running on phones. Another example is the "Podcasting 2.0" initiative that tries to integrate podcast players with Lightning wallets so they can send donations to podcast hosts that are running Lightning nodes. Their proponents call it "value for value" (or "value4value", "v4v") and if you ask they will say _value4value_ is a "model" in which the listener gives out in satoshis to the podcast host the same amount of "value" he is getting from listening to that content. The _value4value_ concept makes it almost explicit the problems I see with this big emphasis on donations the Bitcoin community is making in general. In essence, the idea that the listener is capable of measuring the value it gets from the podcast then converting it into a monetary amount and then donating that is completely wrong and even nonsensical. ### Why _value4value_ is not sound Basic (Austrian) economics teaches us that all value is ordinal, not cardinal -- i.e., it can't be measured or assigned a number to. One can only know that at some instant they prefer _x_ over _y_, they cannot say _x_ has a value of 10 and _y_ has a value of 9. Because of that, it's a nonsense quest to try determine how much value one is getting from a podcast. Basic (Austrian) economics also teaches us that exchanges happen when there are differences in the subjective valuations of goods, i.e., Alice can give _x_ to Bob in exchange for _y_ if Alice prefers _y_ over _x_ and Bob prefers _x_ over _y_ at that point. Because of that (and disregarding the previous paragraph), it's futile to expect that the podcast listener will donate _exactly_ the amount he is getting from the podcast in "value". Because of the two points above, it should also be clear that it is impossible to convert "value" in podcast content form into "value" in satoshis form, but I won't try to explain why that is because this is not an economics textbook. What actually happens is that whether it's in the _value4value_ context or not, donations are always a somewhat random and subjective amount, if they happen. If I like some content that someone is publishing for free, my decision on if and how much I will donate is never dictated by some nonsense calculation, but by calculation that is governed almost entirely by feeling and animal spirits (but one that also considers how much money I can spare, how much I like that person and how much I perceive they need). When I go to a normal shop to buy a bottle of milk I look at the bottle of milk and I read its price, and there is one simple decision I have to make: is this bottle of milk worth more than the amount of money that's specified in the price tag? It's a single decision with only two answers: _yes_ or _no_. While when I see a free form on some free "creator" page asking me to type how much I will donate I have to decide if I will donate, when I will donate, how much I will donate, if I want this donation to be done every month or how will that work going forward? Will I keep consuming the content produced by this person? Will they keep producing? Maybe I'll just listen for free now and do this later as I'm busy, but then will I forget? Maybe I have just donated a lot to someone else and do not have much more money to spare, but now I feel guilty that the other person got all my donation money and this one didn't get anything but I can't go back and ask the other to return the money I just donated -- and so on and so forth. ### Conclusions Although the paragraphs above are confusing and do not follow a very logical presentation pattern, I hope you got from them why I think donations are much more complicated than purchases, and that repeating the "value for value" mantra doesn't help at all. Considering that, what I wanted to say is that bitcoiners should give more attention to the other model, in which people produce goods and services and sell them. And that model can be applied successfully to "content creators", podcasters etc in many ways that are probably (I don't have any data backing my claims) better than the donation model. ## Other possible monetization possibilities For example, I've noticed that many blogs and podcasts with interesting content start to release exclusive episodes as they get big enough. These exclusive episodes are available only for "supporters". This is effectively selling access to the episodes. There is also the "crowdwall" model in which multiple people pay so that some content gets released for free. We can count even the model in which a donation is not just a blank donation, but gives the donor the right to write something on the screen or something like that -- these are actually not just donations, but purchases of these rights. Professional videogame streamers have come up with some other interesting ideas. For example, they crowdfund the creation of special content ("if enough people pay I will dress like a rabbit") or they sell the right to participate in the stream somehow (for example, by playing a game with the streamer in some special day). In these models, the _static QR code_ with which so many people dream doesn't make much sense (if you're selling a specific episode or if a payment is specific to one identifiable person, you need different QR codes or more metadata to be attached to each payment by the payer). ## Addendum I think people like the donation model very much because they only see the big and super famous people that receive donations. A very small set of people have so many followers that they can live with just donations, even though donations are very inefficient and they could earn more and even deliver better content if they were using some other model. I imagine that a creator with a high number of followers will get a lot of people that do not donate anything, a lot that will donate a little -- probably less than they would if they were paying -- and eventually a little number of people that will donate way more than they would if they were buying. This last group is probably what makes it worthwhile to work on this donations model for these creators. The takeaway is that the donations model is not a panacea and is not very good either. ## Related: - [Donations on the internet](nostr:naddr1qqyrqwp4xsmnsvtxqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cex8903) @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# A podridão É razoável dizer que há três tipos de reações à menção do nome [O que é Bitcoin?](nostr:naddr1qqrky6t5vdhkjmspz9mhxue69uhkv6tpw34xze3wvdhk6q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqp65wp3k3fu) no Brasil: 1. A reação das pessoas velhas Muito sabiamente, as pessoas velhas que já ouviram falar de Bitcoin o encaram ou como uma coisa muito distante e reservada ao conhecimento dos seus sobrinhos que entendem de computador ou como um golpe que se deve temer e do qual o afastamento é imperativo, e de qualquer modo isso não as deve afetar mesmo então para que perder o seu tempo. Essas pessoas estão erradas: nem o sobrinho que entende de computador sabe nada sobre Bitcoin, nem o Bitcoin é um golpe, e nem é o Bitcoin uma coisa totalmente irrelevante para elas. É razoável ter cautela diante do desconhecido, no que as pessoas velhas fazem bem, mas creio eu que também muito do medo que essas pessoas têm vem da ignorância que foi criada e difundida durante os primeiros 10 anos de Bitcoin por jornalistas analfabetos e desinformados em torno do assunto. 2. A reação das pessoas pragmáticas "Já tenho um banco e já posso enviar dinheiro, pra que Bitcoin? O quê, eu ainda tenho que pagar para transferir bitcoins? Isso não é vantagem nenhuma!" Enquanto querem parecer muito pragmáticas e racionais, essas pessoas ignoram vários aspectos das suas próprias vidas, a começar pelo fato de que o uso dos bancos comuns não é gratuito, e depois que a existência desse sistema financeiro no qual elas se crêem muito incluídas e confortáveis é baseada num grande esquema chamado Banco Central, que tem como um dos seus fundamentos a possibilidade da inflação ilimitada da moeda, que torna todas as pessoas mais pobres, incluindo essas mesmas, tão pragmáticas e racionais. Mais importante é notar que essas pessoas tão racionais foram também ludibriadas pela difusão da ignorância sobre Bitcoin como sendo um sistema de transferência de dinheiro. O Bitcoin não é e não pode ser um sistema de transferência de dinheiro porque ele só pode transferir-se a si mesmo, não pode transferir "dinheiro" no sentido comum dessa palavra (tenho em mente o dinheiro comum no Brasil, os reais). O fato de que haja hoje pessoas que conseguem "transferir dinheiro" usando o Bitcoin é uma coisa totalmente inesperada: a existência de pessoas que trocam bitcoins por reais (e outros dinheiros de outros lugares) e vice-versa. Não era necessário que fosse assim, não estava determinado em lugar nenhum, 10 anos atrás, que haveria demanda por um bem digital sem utilidade imediata nenhuma, foi assim por um milagre. Porém, o milagre só estará completo quando esses bitcoins se tornarem eles mesmo o dinheiro comum. E aí assim será possível usar o sistema Bitcoin para transferir dinheiro de fato. Antes disso, chamar o Bitcoin de sistema de pagamentos ou qualquer coisa que o valha é perverter-lhe o sentido, é confundir um acidente com a essência da coisa. 3. A reação dos jovens analfabetos Os jovens analfabetos são as pessoas que usam a expressão "criptos" e freqüentam sítios que dão notícias totalmente irrelevantes sobre "criptomoedas" o dia inteiro. Não sei muito bem como eles vivem porque não lhes suporto a presença, mas são pessoas que estão muito empolgadas com toda a "onda das criptomoedas" e acham tudo muito incrível, tão incrível que acabam se interessando e então comprando todos os tokens vagabundos que inventam. Usam a palavra "decentralizado", um anglicismo muito feio que deveria significar que não existe um centro controlador da moeda x ou y e que o seu protocolo continuaria funcionando mesmo que vários operadores saíssem do ar, mas como o aplicam aos tokens que são literalmente emitidos por um centro controlador com uma figura humana no centro que toma todas as decisões sobre tudo -- como o Ethereum e conseqüentemente todos os milhares de tokens ERC20 criados dentro do sistema Ethereum -- essa palavra não faz mais sentido. Na sua empolgação e completo desconhecimento sobre como um ente nocivo poderia destruir cadauma das suas criptomoedas tão decentralizadas, ou como mesmo sem ninguém querer uma falha fundamental no protocolo e no sistema de incentivos poderia pôr tudo abaixo, sem imaginar que toda a valorização do token XYZ pode ter sido fabricada de caso pensado pelos seus próprios emissores ou só ser mesmo uma bolha, acabam esses jovens por igualar o token XYZ, ou ETH, BCH ou o que for, ao Bitcoin, ignorando todas as diferenças qualitativas e apenas mencionando de leve as quantitativas. Misturada à sua empolgação, e como um bônus, surge a perspectiva de ficar rico. Se um desses por algum golpe de sorte surfou em alguma bolha como a de 2017 e conseguiu multiplicar um dinheiro por 10 comprando e vendendo EOS, já começa logo a usar como argumento para convencer os outros de que "criptomoedas são o futuro" o fato de que ele ficou rico. Não subestime a burrice humana. --- Há jovens no grupo das pessoas velhas, velhas no grupo das pessoas jovens, pessoas que não estão em nenhum dos grupos e pessoas que estão em mais de um grupo, isso não importa.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# A podridão É razoável dizer que há três tipos de reações à menção do nome [O que é Bitcoin?](nostr:naddr1qqrky6t5vdhkjmspz9mhxue69uhkv6tpw34xze3wvdhk6q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqp65wp3k3fu) no Brasil: 1. A reação das pessoas velhas Muito sabiamente, as pessoas velhas que já ouviram falar de Bitcoin o encaram ou como uma coisa muito distante e reservada ao conhecimento dos seus sobrinhos que entendem de computador ou como um golpe que se deve temer e do qual o afastamento é imperativo, e de qualquer modo isso não as deve afetar mesmo então para que perder o seu tempo. Essas pessoas estão erradas: nem o sobrinho que entende de computador sabe nada sobre Bitcoin, nem o Bitcoin é um golpe, e nem é o Bitcoin uma coisa totalmente irrelevante para elas. É razoável ter cautela diante do desconhecido, no que as pessoas velhas fazem bem, mas creio eu que também muito do medo que essas pessoas têm vem da ignorância que foi criada e difundida durante os primeiros 10 anos de Bitcoin por jornalistas analfabetos e desinformados em torno do assunto. 2. A reação das pessoas pragmáticas "Já tenho um banco e já posso enviar dinheiro, pra que Bitcoin? O quê, eu ainda tenho que pagar para transferir bitcoins? Isso não é vantagem nenhuma!" Enquanto querem parecer muito pragmáticas e racionais, essas pessoas ignoram vários aspectos das suas próprias vidas, a começar pelo fato de que o uso dos bancos comuns não é gratuito, e depois que a existência desse sistema financeiro no qual elas se crêem muito incluídas e confortáveis é baseada num grande esquema chamado Banco Central, que tem como um dos seus fundamentos a possibilidade da inflação ilimitada da moeda, que torna todas as pessoas mais pobres, incluindo essas mesmas, tão pragmáticas e racionais. Mais importante é notar que essas pessoas tão racionais foram também ludibriadas pela difusão da ignorância sobre Bitcoin como sendo um sistema de transferência de dinheiro. O Bitcoin não é e não pode ser um sistema de transferência de dinheiro porque ele só pode transferir-se a si mesmo, não pode transferir "dinheiro" no sentido comum dessa palavra (tenho em mente o dinheiro comum no Brasil, os reais). O fato de que haja hoje pessoas que conseguem "transferir dinheiro" usando o Bitcoin é uma coisa totalmente inesperada: a existência de pessoas que trocam bitcoins por reais (e outros dinheiros de outros lugares) e vice-versa. Não era necessário que fosse assim, não estava determinado em lugar nenhum, 10 anos atrás, que haveria demanda por um bem digital sem utilidade imediata nenhuma, foi assim por um milagre. Porém, o milagre só estará completo quando esses bitcoins se tornarem eles mesmo o dinheiro comum. E aí assim será possível usar o sistema Bitcoin para transferir dinheiro de fato. Antes disso, chamar o Bitcoin de sistema de pagamentos ou qualquer coisa que o valha é perverter-lhe o sentido, é confundir um acidente com a essência da coisa. 3. A reação dos jovens analfabetos Os jovens analfabetos são as pessoas que usam a expressão "criptos" e freqüentam sítios que dão notícias totalmente irrelevantes sobre "criptomoedas" o dia inteiro. Não sei muito bem como eles vivem porque não lhes suporto a presença, mas são pessoas que estão muito empolgadas com toda a "onda das criptomoedas" e acham tudo muito incrível, tão incrível que acabam se interessando e então comprando todos os tokens vagabundos que inventam. Usam a palavra "decentralizado", um anglicismo muito feio que deveria significar que não existe um centro controlador da moeda x ou y e que o seu protocolo continuaria funcionando mesmo que vários operadores saíssem do ar, mas como o aplicam aos tokens que são literalmente emitidos por um centro controlador com uma figura humana no centro que toma todas as decisões sobre tudo -- como o Ethereum e conseqüentemente todos os milhares de tokens ERC20 criados dentro do sistema Ethereum -- essa palavra não faz mais sentido. Na sua empolgação e completo desconhecimento sobre como um ente nocivo poderia destruir cadauma das suas criptomoedas tão decentralizadas, ou como mesmo sem ninguém querer uma falha fundamental no protocolo e no sistema de incentivos poderia pôr tudo abaixo, sem imaginar que toda a valorização do token XYZ pode ter sido fabricada de caso pensado pelos seus próprios emissores ou só ser mesmo uma bolha, acabam esses jovens por igualar o token XYZ, ou ETH, BCH ou o que for, ao Bitcoin, ignorando todas as diferenças qualitativas e apenas mencionando de leve as quantitativas. Misturada à sua empolgação, e como um bônus, surge a perspectiva de ficar rico. Se um desses por algum golpe de sorte surfou em alguma bolha como a de 2017 e conseguiu multiplicar um dinheiro por 10 comprando e vendendo EOS, já começa logo a usar como argumento para convencer os outros de que "criptomoedas são o futuro" o fato de que ele ficou rico. Não subestime a burrice humana. --- Há jovens no grupo das pessoas velhas, velhas no grupo das pessoas jovens, pessoas que não estão em nenhum dos grupos e pessoas que estão em mais de um grupo, isso não importa. @ 361d3e1e:50bc10a8
2024-08-17 10:32:21Scientists from South Korea are proposing to shock people with a weak current to curb their hunger and combat overeating. Scientists from the Korea Research Institute believe that weak electric currents directed to specific areas of the brain through the scalp can affect neural circuits that control our appetite. The photo shows the electric helmet that is given to test subjects. [Full story](https://forex-strategy.com/2024/08/16/scientists-offer-a-solution-to-hunger-instead-of-food-they-pass-electricity-through-the-body/)
@ 361d3e1e:50bc10a8
2024-08-17 10:32:21Scientists from South Korea are proposing to shock people with a weak current to curb their hunger and combat overeating. Scientists from the Korea Research Institute believe that weak electric currents directed to specific areas of the brain through the scalp can affect neural circuits that control our appetite. The photo shows the electric helmet that is given to test subjects. [Full story](https://forex-strategy.com/2024/08/16/scientists-offer-a-solution-to-hunger-instead-of-food-they-pass-electricity-through-the-body/) @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Scala is such a great language Scala is amazing. The type system has the perfect balance between flexibility and powerfulness. `match` statements are great. You can write imperative code that looks very nice and expressive (and I haven't tried writing purely functional things yet). Everything is easy to write and cheap and neovim integration works great. But Java is not great. And the fact that Scala is a JVM language doesn't help because over the years people have written stuff that depends on Java libraries -- and these Java libraries are not as safe as the Scala libraries, they contain reflection, slowness, runtime errors, all kinds of horrors. Scala is also very tightly associated with Akka, the actor framework, and Akka is a giant collection of anti-patterns. Untyped stuff, reflection, dependency on JVM, basically a lot of javisms. I just arrived and I don't know anything about the Scala history or ecosystem or community, but I have the impression that Akka has prevent more adoption of Scala from decent people that aren't Java programmers. But luckily there is a solution -- or two solutions: ScalaJS is a great thing that exists. It transpiles Scala code into JavaScript and it runs on NodeJS or in a browser! Scala Native is a much better deal, though, it compiles to LLVM and then to binary code and you can have single binaries that run directly without a JVM -- not that the single JARs are that bad though, they are great and everybody has Java so I'll take that anytime over C libraries or NPM-distributed software, but direct executables even better. Scala Native just needs a little more love and some libraries and it will be the greatest thing in a couple of years.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Scala is such a great language Scala is amazing. The type system has the perfect balance between flexibility and powerfulness. `match` statements are great. You can write imperative code that looks very nice and expressive (and I haven't tried writing purely functional things yet). Everything is easy to write and cheap and neovim integration works great. But Java is not great. And the fact that Scala is a JVM language doesn't help because over the years people have written stuff that depends on Java libraries -- and these Java libraries are not as safe as the Scala libraries, they contain reflection, slowness, runtime errors, all kinds of horrors. Scala is also very tightly associated with Akka, the actor framework, and Akka is a giant collection of anti-patterns. Untyped stuff, reflection, dependency on JVM, basically a lot of javisms. I just arrived and I don't know anything about the Scala history or ecosystem or community, but I have the impression that Akka has prevent more adoption of Scala from decent people that aren't Java programmers. But luckily there is a solution -- or two solutions: ScalaJS is a great thing that exists. It transpiles Scala code into JavaScript and it runs on NodeJS or in a browser! Scala Native is a much better deal, though, it compiles to LLVM and then to binary code and you can have single binaries that run directly without a JVM -- not that the single JARs are that bad though, they are great and everybody has Java so I'll take that anytime over C libraries or NPM-distributed software, but direct executables even better. Scala Native just needs a little more love and some libraries and it will be the greatest thing in a couple of years. @ bcbb3e40:a494e501
2024-08-16 18:00:07## El hombre y el contexto El pensamiento tradicionalista español cuenta con una amplia trayectoria en la que concurren personajes, situaciones e ideas gestadas en el transcurso de dos siglos, en los que debemos distinguir el conflicto dinástico y el papel del legitimismo de la propia doctrina, que es algo que se construirá en el tiempo, con la contribución de figuras como el protagonista de este escrito, Don Juan Vázquez de Mella, así como por la confluencia de fuerzas de diferente signo que tiene lugar a lo largo del siglo XIX y la consolidación del Estado liberal, que lo hará siempre en lucha abierta contra las peculiaridades y el carácter genuino del pueblo español. Vázquez de Mella, nuestro autor, quizás represente la consolidación y madurez doctrinal del movimiento tradicionalista español, uno de sus primeros y más brillantes sistematizadores. No se destacó por una obra extensa ni especialmente difundida más allá de sus discursos, de sus artículos en periódicos y sus escritos dispersos, los cuales fue capaz de dotar de una especial significación y dignidad fruto de su enorme carisma y especial clarividencia para dar una forma definida y meridianamente clara a las ideas y doctrinas que nutrieron el tradicionalismo español madurado al calor de las armas, de las tres guerras que el carlismo libró contra el liberalismo español. || |:-:| |Juan Vázquez de Mella| Nuestro autor, de origen asturiano, y nacido en Cangas de Onís un 8 de junio de 1861, ha mantenido vivo su prestigio y el valor de sus aportaciones teórico-doctrinales, ampliamente reconocidos por sus sucesores, por [**Rafael Gambra Ciudad**](https://hiperbolajanus.com/posts/la-sociedad-tradicional-y-sus-enemigos/) (1920-2004) y [**Francisco Elías de Tejada y Espinola**](https://hiperbolajanus.com/libros/mos-maiorum-1/) (1918-1978), así como de otros autores como **Álvaro D'Ors** (1915-2004) y otros muchos, que han reivindicado su figura en el tiempo y se han nutrido de sus fecundas enseñanzas. Se ha destacado la rectitud de su pensamiento, su inquebrantable voluntad y su impagable contribución en la creación de un marco teórico y conceptual para dar un sentido y una forma a las ideas del tradicionalismo español. Hijo de un militar de origen gallego, muerto prematuramente, quedó huérfano de padre durante su niñez, por lo cual pasó al cuidado de unos parientes de origen modesto. Estudió en la Universidad de Santiago de Compostela, donde mostró tempranamente su temperamento y habilidades oratorias, que explotó convenientemente a través de diarios como _La Restauración_ o _El pensamiento galaico_, donde también mostró sus filiaciones militantes con el catolicismo tradicional. Sus habilidades y la brillantez de sus escritos pronto llegaron a Madrid, a las más altas instancias del Carlismo, lo que le permitió dar continuidad a sus actividades desde un medio más amplio, a través de _El correo español_. En su militancia política llegó a las más altas cotas de su trayectoria con la elección en 1893 como representante de las Cortes por el distrito de Estella, Navarra, que ya con sus primeros discursos obtuvo un notable éxito, incluso entre los propios liberales, hasta 1900, fecha en la que se vio obligado a marcharse a Portugal, acusado de participar en una conspiración para derrocar el régimen de la Restauración. No regresó a España hasta 1905, manteniendo su estatus como diputado hasta 1919. De todos modos, no queremos dar más protagonismo a la biografía en detrimento de la doctrina, que es lo que nos interesa en este artículo, de ahí que obviemos otros datos biográficos trascendentes, polémicas con otras facciones del carlismo o sus posturas respecto a la dictadura del general Miguel Primo de Rivera, que nos harían desviar la atención del propósito principal que acabamos de enunciar. La gran paradoja del Carlismo fue que a pesar de su derrota en la Tercera Guerra Carlista (1872-1876), y pese a la posterior escisión integrista en 1888, el partido carlista continuó manteniendo una fuerza y preponderancia significativa en la sociedad española del régimen de la Restauración durante el último cuarto de siglo. El Carlismo se vio inmerso en un buen número de paradojas, de situaciones encontradas, especialmente en relación al Desastre del 98 y la pérdida de los últimos territorios ultramarinos. Mientras que la gran esperanza del tradicionalismo español estaba depositada en el desmoronamiento y caída final de la restauración alfonsina, por otro lado este mismo régimen trataba de defender, al menos en teoría, los últimos restos del imperio español y, de algún modo, a la España católica frente a una nación protestante, como era la anglosajona estadounidense. Al mismo tiempo, durante esta época el tradicionalismo español se enfrentó a los grandes retos que presentaba una sociedad en cambio, con transformaciones políticas y sociales de gran calado como la emergencia del sufragio universal o el nacimiento de los separatismos periféricos (propiciados por la burguesía liberal), las cuales requerían de nuevas estrategias y reestructuraciones internas capaces de enfrentar la envergadura de todos estos cambios. Fue en este contexto donde se significó la figura de Juan Vázquez de Mella, quien merced a la obra de sistematización a la que ya hemos hecho alusión, y de sus concurridas conferencias, dio lugar a la denominada _Acta Loredán_, redactada por el tradicionalista asturiano y publicado en _El correo español_. Este escrito tenía como ejes fundamentales la defensa de la nación política española fundamentada en la monarquía, el catolicismo y el régimen foral. Al mismo tiempo, también recogía la reivindicación de un programa corporativista y gremial al abrigo de la doctrina social de la Iglesia defendido en la encíclica _Rerum Novarum_ (1891), y es lo que se conoce como el «sociedalismo», cuyos antecedentes encontramos ya [en autores como **Donoso Cortés**](https://hiperbolajanus.com/posts/resena-de-los-fundamentos-historicos/) o **Antonio Aparisi Guijarro**. Son precisamente los atributos de esta doctrina, que contribuyó a la revitalización del pensamiento carlista, los que nos disponemos a desarrollar a continuación. La figura del tradicionalista asturiano, de Don Juan Vázquez de Mella, aparece como necesaria ante una serie sucesiva de destrucciones que el régimen liberal ha producido sobre los fundamentos tradicionales de España, pero su papel no fue, como ya venimos apuntando, el de un gran intelectual erudito, y de hecho, como apunta Rafael Gambra, las mayores debilidades de su pensamiento se encuentran en los principios filosóficos, y destacando, en cambio, su papel de «revulsivo espiritual» podemos ubicarlo mejor en el ámbito de lo político y lo espiritual. Para ello debió tomar en cuenta las fuentes de sus predecesores, entre los cuales podemos ubicar perfectamente al ya mencionado Donoso Cortés y **Jaime Balmes**, así como también a otro contemporáneo suyo, **Menéndez Pelayo**. De los dos primeros tomó su capacidad de síntesis y la sencillez expositiva, mientras que de Menéndez Pelayo tomó, al menos en parte, el sentido de la crítica histórica en aras de la restauración de una Tradición nacional. Pero más allá de los sistemas de pensamiento y elementos retóricos, vemos a Vázquez de Mella profundamente interesado por la vida política de los pueblos medievales de Las Españas, lo cual fue, en definitiva, el marco de referencia para una síntesis política de conjunto más allá de los posicionamientos teóricos, como algo que puede ser llevado a la práctica en sus aspectos concretos y que es perfectamente viable. Todo un sistema [edificado sobre el pensamiento tomista](https://hiperbolajanus.com/posts/en-el-mar-de-la-nada-curzio-nitoglia/) y una una profunda religiosidad, En este contexto, y más allá de las ideas formuladas por realistas y carlistas en la primera mitad del siglo XIX, Mella teoriza junto a la concepción del espíritu medieval, la idea de la coexistencia de dos soberanías, una política y otra social, una teoría de la soberanía tradicional inspirada por un principio dinámico y que se cimenta en las propias experiencias humanas en el devenir de la historia. |[](https://amzn.to/3W6ymTM)| |:-:| |[NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023](https://amzn.to/3W6ymTM)| ## El concepto de lo social Lo social para Mella no tiene absolutamente nada que ver con las denominadas «políticas sociales», tan comunes en el lenguaje político de las democracias liberales, en las que se contempla lo social como un elemento externo a la propia estructura política, donde prevalece el individualismo a todos los niveles, y la sociedad aparece como un mero agregado de individuos. Muy al contrario, lo social, en el tradicionalismo de nuestro autor, implica la afirmación de un principio intrínseco tanto al modelo social como al tipo humano, así como a la naturaleza de las cosas en las que la persona desarrolla su existencia en común con los demás. Nos referimos a las instituciones, a los elementos jurídicos y otros órganos gestados en el tiempo por la experiencia histórica, que regulan la vida común. En el ámbito de la sociedad cristiana medieval, en plena Reconquista, cuando todavía no existía un Estado unitario como tal, cada municipio tenía sus propias leyes y sus normas, adaptadas a su modelo de vida y costumbres, Las comunidades se concebían como agrupaciones de familias con un sistema de propiedad comunal y privado en las que el patrimonio y el estatus de cada uno de sus miembros venía garantizado por el ejercicio activo de una serie de derechos en defensa de las libertades concretas, cuya fuente última era el derecho natural. Los señores feudales y los reyes se limitaban a reclamar tributos para la guerra, pero sin interferir en la defensa de estas libertades concretas ni vulnerar el sistema que las sustentaba. Eran gobiernos autárquicos, muy estables e inspirados por un principio democrático, el cual nada tenía que ver con las democracias liberales plutocráticas de la actualidad, cuya idea del derecho y la justicia está pervertida por el formalismo jurídico vacío e inane de sus constituciones, abstractas y plenamente funcionales a las oligarquías, al servicio de intereses espurios. En este caso, el hombre alcanzaba una plena dignidad y desarrollo en el contexto de una comunidad donde prevalecía el vínculo comunitario, al amparo de un modelo tradicional, de normas consuetudinarias y concretas que permitían la defensa efectiva del propio derecho. Ni siquiera con el advenimiento de los Estados modernos, y la centralización de algunos elementos de poder, como la Hacienda o el Ejército, se vieron alterados significativamente estos elementos, que representaban a los denominados «cuerpos intermedios» de la sociedad, y que adquirieron su propia expresión particular bajo el nombre de «Fueros», los que los propios reyes juraron respetar a lo largo de toda la Edad Moderna y hasta el advenimiento del régimen borbónico. La antropología tradicional vincula al hombre a un medio social, a una familia, a una estirpe o a un pueblo, que reproducen esa misma estructura familiar, aunque a mayor escala. En nuestro caso particular lo vemos a través de la convivencia de pequeños grupos humanos, de ahí la importancia de los municipios o de los concejos en un marco de vida comunitaria fuertemente institucionalizada. Al mismo tiempo este modelo y estructura también se replicaba en otros ámbitos, como en la vida económica y profesional, impregnando todas las esferas de la vida del hombre. Instituciones naturales, amparadas en el derecho natural, y orientadas a la protección y garantía de prosperidad de los hombres, y esto por encima de cualquier interés particular y mercantil de negocio. Para Mella, la ruptura con este mundo, y en general con las experiencias del pasado, es la que nos lleva, [merced a la acción del liberalismo, a los tiempos actuales](https://hiperbolajanus.com/posts/mos-maiorum-7/), y lo hace recorriendo un itinerario que todos conocemos, y que tienen su punto de partida [en la Ilustración y la posterior Revolución Francesa](https://hiperbolajanus.com/posts/joseph-de-maistre/), la irrupción del elemento racional y abstracto y la destrucción de la religión, considerada como fruto de la superstición. La destrucción del orden feudal, que todavía pervivía como marco de convivencia en el mundo rural, como una suerte de prolongación de ese espíritu medieval, hizo desaparecer de un plumazo ese entorno de relaciones concretas y personales para sustituirlas por lo «público» entendido como la centralización estatal uniforme, ignorando las realidades particulares subyacentes en el cuerpo social, los denominados «cuerpos intermedios», que fueron despojados de su autonomía, corporaciones y patrimonios. De modo que la destrucción de estas «sociedades intermedias» que mediaban entre el Estado y la sociedad desenraizó y destruyó la propia sociedad, al mismo tiempo que los fundamentos cristianos del derecho natural sobre la cual se hallaba asentada, para hacer prevalecer esos principios racionales y abstractos traídos por la revolución. Al mismo tiempo, y anejo a este desarraigo, del individuo se encuentra sometido a poderes arbitrarios del propio Estado liberal, sin un conglomerado institucional propio que lo proteja de estos atropellos, sumido en el individualismo ajeno a toda institución y destino colectivo, se limita al voto cada cuatro años de los partidos al servicio de oligarquías e intereses espurios, contrarios al Bien común. En este sentido, y advirtiendo las posibles acusaciones de «absolutismo» que en ocasiones se han lanzado contra el tradicionalismo, hay que señalar que Mella las rechaza por completo, dado que viola la idea de contrapoderes frente a la autoridad del rey que éste formula, ya que el absolutismo creía en la existencia de un poder ilimitado y tiránico del rey, transmitido por Dios y ajeno a la participación de la sociedad y sus estamentos. Como bien señaló [**Julius Evola**](https://hiperbolajanus.com/libros/metapolitica-tradicion-modernidad-julius-evola/), el absolutismo es un fenómeno antitradicional, vinculado a la descomposición y desacralización de las estructuras tradicionales. De hecho, el absolutismo, como los regímenes liberales de hoy, dejan al individuo totalmente desprotegido, sin un asidero sobre el que apoyarse en la defensa de sus libertades concretas. El propio Mella, como bien saben todos los que se adentren en su obra, fue partidario de contrarrestar el creciente poder del aparato estatal, tal y como hemos visto y seguiremos viendo en lo sucesivo, a lo largo del presente artículo. |[](https://amzn.to/2LqITcb)| |:-:| |[EVOLA, Julis; _Metapolítica, Tradición y Modernidad: Antología de artículos evolianos_, Hipérbola Janus, 2020](https://amzn.to/2LqITcb)| En nuestro caso particular, la desaparición de la organización gremial y corporativa tuvo unas consecuencias especialmente nefastas, y en especial después de las dos desamortizaciones liberales (Mendizabal y Madoz) al despojar a los grupos sociales populares de su natural organización sociohistórica. Asimismo, desvincularon la propiedad en las relaciones comunitarias y su uso patrimonial para vincularla al uso privado y anónimo, para fines puramente especulativos, los que caracterizan al liberal-capitalismo. De ahí nace la figura del asalariado, del contratado como mera mercancía, en un proceso de alienación del trabajo característico en el desarrollo del capitalismo burgués. De aquí parte lo que algunos tradicionalistas, como Gambra, denominan el «problema social», frente al cual, y al margen de las recetas ideológicas de la modernidad, Mella reivindica la restauración de los antiguos vínculos corporativos y orgánicos de inspiración medieval. ## La idea de soberanía social Todos los procesos disolutivos que conducen a la Modernidad liberal tienen su punto de inicio con el Renacimiento, con la afirmación del individualismo y la ruptura definitiva del ecumene cristiano medieval, algo que aparece indefectiblemente unido a la Reforma luterana, así como la «valorización» del mundo clásico, con la reemergencia de teorías de tipo hedonista, como las de Epicuro, por ejemplo, generando una disolución de los vínculos con el medio concreto. Esto supone la aparición de un nuevo tipo, que es el hombre abstracto que escapa cada vez más al entorno inmediato y vital, esto al tiempo que el poder del Estado se robustece y se vuelve omnipotente. Es por ese motivo que en lo sucesivo se ha impuesto en nuestras sociedades la falta de concreción, tanto en lo teórico como en lo político, lo cual ha propiciado el triunfo del contrato social roussoniano y la justificación del orden social en virtud de componendas voluntarias y totalmente artificiales. Estas construcciones político-ideológicas son las que contribuyen a la construcción de la sociedad liberal, asentada sobre patrones puramente racionales, individualistas y mercantilistas. De hecho, la mayor preocupación de Mella es la destrucción de las instituciones locales y ese vínculo afectivo del hombre con su realidad inmediata, algo que impregnaba su relación con el trabajo, con su obra, con su impronta vocacional y devota, imprimiéndole, como en el caso del artesano, un sello propio y particular a su trabajo. Y en este sentido, Mella afirma que la sociedad moderna ha perdido su sentido institucional como base estable de la sociabilidad. A través del elemento jurídico y la participación en las instituciones es el medio a partir del cual la comunidad se cohesiona y construye sus vínculos y su particular autonomía, que le hace tener una vida propia e interna, y con la institución nos podemos referir desde una asociación profesional, a la universidad o una cofradía etc. El individualismo ha representado el factor disolutivo y corrosivo que ha destruido este vínculo social fundado en múltiples solidaridades que han enfrentado y polarizado al cuerpo social, con el enfrentamiento entre «clases sociales» y la negación de las jerarquías naturales. Ante todo lo relatado, y como consecuencia de las destrucciones provocadas por la revolución, Mella plantea su teoría de la soberanía social. Esta teoría consiste básicamente en encuadrar de nuevo a la sociedad en sus raíces naturales, concebida en todos sus órdenes como portadora de un dinamismo propio en una suerte de organización geométrica en la que conviven objetivos y finalidades variadas y concretas con su propia legitimidad y autonomía. Estas finalidades, amparadas en el derecho natural, son junto al poder del propio Estado las únicas formas de limitación del poder. La particularidad de esta idea de soberanía social está en el hecho de que la formación de la jerarquía social tiene una dirección ascendente, que tiene como punto de partida a las personas colectivas y concretas, pasando por una serie de instituciones, hasta llegar al Estado central, de forma escalonada y plenamente conscientes de sus funciones. Así lo expresa Mella en su propio lenguaje: «_la jerarquía de personas colectivas, de poderes organizados, de clases, que suben desde la familia hasta la soberanía que llamo política concretada en el Estado, que deben auxiliar, pero también contener_». Es lo que Mella concibe como el sociedalismo, que supone la reintegración de la sociedad en la vida concreta de los hombres, con el desarrollo de una vida política común y estable en el marco de instituciones naturales que potencien las relaciones humanas y sociales, estimulando la sociabilidad. Y hablamos, desde la perspectiva de la integración de distintas sociedades, fuertemente institucionalizadas con funciones y finalidades concretas, más allá del sentido democrático y pactista que pueda entenderse en términos modernos o de cualquier asociación u organización relacionada con el «problema social». ## ¿Qué es la Tradición? De este modo quedan formuladas las dos soberanías, la política y la social, que coexisten en un mismo espacio limitándose y apoyándose recíprocamente en lo que es uno de los fundamentos del sociedalismo de Mella. No obstante, esta doble soberanía no explica todavía la concreción política de cada pueblo y el vínculo superior que lo lleva a federarse con las diferentes sociedades y a mantenerse unido en una historia y espíritu comunes. Los vínculos que las mantienen unidas en el tiempo tienen que ver con un orden histórico concreto, con un vínculo espiritual que las entrelaza interiormente de una generación a otra, y en última instancia de [ese orden tradicional](https://hiperbolajanus.com/posts/comprendiendo-la-tradicion/) que lo engloba todo, y que al mismo tiempo se asienta en la monarquía y la religión católica. La lealtad a Dios y a un solo rey en torno a los cuales se aglutina la fe, viene a coronar todas estas estructuras y lazos forjados en el fermento de la historia. No se trata de la Tradición en términos de un «ultraconservadurismo», que ya sabemos que el prefijo «ultra» (lo que sea) es muy recurrente en nuestros días, con la idea de un medio social y político petrificado e invariable, sino que es el producto de un proceso de maduración y evolución histórica, de carácter dinámico y nutrido de experiencias humanas. Nada que ver con las monstruosas ideologías progresistas y modernas, nacidas de lo abstracto e impulsadas por un desbocado «ir hacia delante», desarraigado y que tiende siempre hacia la deshumanización y la destrucción de toda creación humana natural forjada en el devenir de los siglos. Este mismo dinamismo, planteado por Mella, en torno al concepto e idea de Tradición tiene continuidad y adquiere fuerza en sus sucesores y depositarios. Y al fin y al cabo, Mella no hace más que partir de la propia etimología del término, que viene del latín _tradere_, entregar, de la generación que entrega los frutos de su experiencia a la siguiente, perfeccionándola, haciéndola más estable y segura. Podríamos seguir extrayendo más conclusiones del pensamiento tradicional de Vázquez de Mella, pero probablemente excedería, y por mucho, el modesto propósito de este escrito, de modo que nos quedaremos aquí, no sin advertir a nuestros lectores de la posibilidad de que en un futuro volvamos a retomar nuevamente el tema. Antes de acabar queremos llamar la atención sobre [una polémica acontecida hace unos años en torno a una Plaza en Madrid](https://www.lavozdigital.es/madrid/20150723/abci-quien-vazquez-mella-201507221907.html) que llevaba el nombre de nuestro autor y que se cambio para dedicársela a un sujeto cuyos méritos eran, por decirlo suavemente, más que discutibles, concretamente a Pedro Zerolo, miembro del PSOE y activista al servicio del lobby homosexualista. Durante aquella época, en 2019, muchos miembros de la izquierda globalista trataron de identificar a Vázquez de Mella como un «pensador franquista», cuando en realidad ni cronológica ni ideológicamente tuvo nunca nada que ver con el franquismo. Recordemos que murió en 1928, y la impronta de su pensamiento ha tenido como continuadores a sus propios correligionarios dentro del ámbito tradicional, aunque en su tiempo llegó a ser muy respetado también por sus adversarios, los liberales. Aunque la retirada del nombre de una calle pueda resultar algo banal, o carente de una importancia excesiva, también contribuye, a su modo, a una forma de _damnatio memoriae_ que condena al olvido y al ostracismo a grandes autores de la Tradición, portadores de un Patriotismo sano y capaz de entender las peculiaridades y el _Dasein_ profundo de España, que si bien no nació invertebrada, como pretendían los Orteguianos, su esencia y naturaleza es mucho más compleja que cualquiera de las grandes naciones de Europa. --- **Artículo original**: Hipérbola Janus, [_Juan Vázquez de Mella y el tradicionalismo español_](https://www.hiperbolajanus.com/posts/juan-vazquez-mella-tradicionalismo/), 16/Ago/2024
@ bcbb3e40:a494e501
2024-08-16 18:00:07## El hombre y el contexto El pensamiento tradicionalista español cuenta con una amplia trayectoria en la que concurren personajes, situaciones e ideas gestadas en el transcurso de dos siglos, en los que debemos distinguir el conflicto dinástico y el papel del legitimismo de la propia doctrina, que es algo que se construirá en el tiempo, con la contribución de figuras como el protagonista de este escrito, Don Juan Vázquez de Mella, así como por la confluencia de fuerzas de diferente signo que tiene lugar a lo largo del siglo XIX y la consolidación del Estado liberal, que lo hará siempre en lucha abierta contra las peculiaridades y el carácter genuino del pueblo español. Vázquez de Mella, nuestro autor, quizás represente la consolidación y madurez doctrinal del movimiento tradicionalista español, uno de sus primeros y más brillantes sistematizadores. No se destacó por una obra extensa ni especialmente difundida más allá de sus discursos, de sus artículos en periódicos y sus escritos dispersos, los cuales fue capaz de dotar de una especial significación y dignidad fruto de su enorme carisma y especial clarividencia para dar una forma definida y meridianamente clara a las ideas y doctrinas que nutrieron el tradicionalismo español madurado al calor de las armas, de las tres guerras que el carlismo libró contra el liberalismo español. || |:-:| |Juan Vázquez de Mella| Nuestro autor, de origen asturiano, y nacido en Cangas de Onís un 8 de junio de 1861, ha mantenido vivo su prestigio y el valor de sus aportaciones teórico-doctrinales, ampliamente reconocidos por sus sucesores, por [**Rafael Gambra Ciudad**](https://hiperbolajanus.com/posts/la-sociedad-tradicional-y-sus-enemigos/) (1920-2004) y [**Francisco Elías de Tejada y Espinola**](https://hiperbolajanus.com/libros/mos-maiorum-1/) (1918-1978), así como de otros autores como **Álvaro D'Ors** (1915-2004) y otros muchos, que han reivindicado su figura en el tiempo y se han nutrido de sus fecundas enseñanzas. Se ha destacado la rectitud de su pensamiento, su inquebrantable voluntad y su impagable contribución en la creación de un marco teórico y conceptual para dar un sentido y una forma a las ideas del tradicionalismo español. Hijo de un militar de origen gallego, muerto prematuramente, quedó huérfano de padre durante su niñez, por lo cual pasó al cuidado de unos parientes de origen modesto. Estudió en la Universidad de Santiago de Compostela, donde mostró tempranamente su temperamento y habilidades oratorias, que explotó convenientemente a través de diarios como _La Restauración_ o _El pensamiento galaico_, donde también mostró sus filiaciones militantes con el catolicismo tradicional. Sus habilidades y la brillantez de sus escritos pronto llegaron a Madrid, a las más altas instancias del Carlismo, lo que le permitió dar continuidad a sus actividades desde un medio más amplio, a través de _El correo español_. En su militancia política llegó a las más altas cotas de su trayectoria con la elección en 1893 como representante de las Cortes por el distrito de Estella, Navarra, que ya con sus primeros discursos obtuvo un notable éxito, incluso entre los propios liberales, hasta 1900, fecha en la que se vio obligado a marcharse a Portugal, acusado de participar en una conspiración para derrocar el régimen de la Restauración. No regresó a España hasta 1905, manteniendo su estatus como diputado hasta 1919. De todos modos, no queremos dar más protagonismo a la biografía en detrimento de la doctrina, que es lo que nos interesa en este artículo, de ahí que obviemos otros datos biográficos trascendentes, polémicas con otras facciones del carlismo o sus posturas respecto a la dictadura del general Miguel Primo de Rivera, que nos harían desviar la atención del propósito principal que acabamos de enunciar. La gran paradoja del Carlismo fue que a pesar de su derrota en la Tercera Guerra Carlista (1872-1876), y pese a la posterior escisión integrista en 1888, el partido carlista continuó manteniendo una fuerza y preponderancia significativa en la sociedad española del régimen de la Restauración durante el último cuarto de siglo. El Carlismo se vio inmerso en un buen número de paradojas, de situaciones encontradas, especialmente en relación al Desastre del 98 y la pérdida de los últimos territorios ultramarinos. Mientras que la gran esperanza del tradicionalismo español estaba depositada en el desmoronamiento y caída final de la restauración alfonsina, por otro lado este mismo régimen trataba de defender, al menos en teoría, los últimos restos del imperio español y, de algún modo, a la España católica frente a una nación protestante, como era la anglosajona estadounidense. Al mismo tiempo, durante esta época el tradicionalismo español se enfrentó a los grandes retos que presentaba una sociedad en cambio, con transformaciones políticas y sociales de gran calado como la emergencia del sufragio universal o el nacimiento de los separatismos periféricos (propiciados por la burguesía liberal), las cuales requerían de nuevas estrategias y reestructuraciones internas capaces de enfrentar la envergadura de todos estos cambios. Fue en este contexto donde se significó la figura de Juan Vázquez de Mella, quien merced a la obra de sistematización a la que ya hemos hecho alusión, y de sus concurridas conferencias, dio lugar a la denominada _Acta Loredán_, redactada por el tradicionalista asturiano y publicado en _El correo español_. Este escrito tenía como ejes fundamentales la defensa de la nación política española fundamentada en la monarquía, el catolicismo y el régimen foral. Al mismo tiempo, también recogía la reivindicación de un programa corporativista y gremial al abrigo de la doctrina social de la Iglesia defendido en la encíclica _Rerum Novarum_ (1891), y es lo que se conoce como el «sociedalismo», cuyos antecedentes encontramos ya [en autores como **Donoso Cortés**](https://hiperbolajanus.com/posts/resena-de-los-fundamentos-historicos/) o **Antonio Aparisi Guijarro**. Son precisamente los atributos de esta doctrina, que contribuyó a la revitalización del pensamiento carlista, los que nos disponemos a desarrollar a continuación. La figura del tradicionalista asturiano, de Don Juan Vázquez de Mella, aparece como necesaria ante una serie sucesiva de destrucciones que el régimen liberal ha producido sobre los fundamentos tradicionales de España, pero su papel no fue, como ya venimos apuntando, el de un gran intelectual erudito, y de hecho, como apunta Rafael Gambra, las mayores debilidades de su pensamiento se encuentran en los principios filosóficos, y destacando, en cambio, su papel de «revulsivo espiritual» podemos ubicarlo mejor en el ámbito de lo político y lo espiritual. Para ello debió tomar en cuenta las fuentes de sus predecesores, entre los cuales podemos ubicar perfectamente al ya mencionado Donoso Cortés y **Jaime Balmes**, así como también a otro contemporáneo suyo, **Menéndez Pelayo**. De los dos primeros tomó su capacidad de síntesis y la sencillez expositiva, mientras que de Menéndez Pelayo tomó, al menos en parte, el sentido de la crítica histórica en aras de la restauración de una Tradición nacional. Pero más allá de los sistemas de pensamiento y elementos retóricos, vemos a Vázquez de Mella profundamente interesado por la vida política de los pueblos medievales de Las Españas, lo cual fue, en definitiva, el marco de referencia para una síntesis política de conjunto más allá de los posicionamientos teóricos, como algo que puede ser llevado a la práctica en sus aspectos concretos y que es perfectamente viable. Todo un sistema [edificado sobre el pensamiento tomista](https://hiperbolajanus.com/posts/en-el-mar-de-la-nada-curzio-nitoglia/) y una una profunda religiosidad, En este contexto, y más allá de las ideas formuladas por realistas y carlistas en la primera mitad del siglo XIX, Mella teoriza junto a la concepción del espíritu medieval, la idea de la coexistencia de dos soberanías, una política y otra social, una teoría de la soberanía tradicional inspirada por un principio dinámico y que se cimenta en las propias experiencias humanas en el devenir de la historia. |[](https://amzn.to/3W6ymTM)| |:-:| |[NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad, Hipérbola Janus, 2023](https://amzn.to/3W6ymTM)| ## El concepto de lo social Lo social para Mella no tiene absolutamente nada que ver con las denominadas «políticas sociales», tan comunes en el lenguaje político de las democracias liberales, en las que se contempla lo social como un elemento externo a la propia estructura política, donde prevalece el individualismo a todos los niveles, y la sociedad aparece como un mero agregado de individuos. Muy al contrario, lo social, en el tradicionalismo de nuestro autor, implica la afirmación de un principio intrínseco tanto al modelo social como al tipo humano, así como a la naturaleza de las cosas en las que la persona desarrolla su existencia en común con los demás. Nos referimos a las instituciones, a los elementos jurídicos y otros órganos gestados en el tiempo por la experiencia histórica, que regulan la vida común. En el ámbito de la sociedad cristiana medieval, en plena Reconquista, cuando todavía no existía un Estado unitario como tal, cada municipio tenía sus propias leyes y sus normas, adaptadas a su modelo de vida y costumbres, Las comunidades se concebían como agrupaciones de familias con un sistema de propiedad comunal y privado en las que el patrimonio y el estatus de cada uno de sus miembros venía garantizado por el ejercicio activo de una serie de derechos en defensa de las libertades concretas, cuya fuente última era el derecho natural. Los señores feudales y los reyes se limitaban a reclamar tributos para la guerra, pero sin interferir en la defensa de estas libertades concretas ni vulnerar el sistema que las sustentaba. Eran gobiernos autárquicos, muy estables e inspirados por un principio democrático, el cual nada tenía que ver con las democracias liberales plutocráticas de la actualidad, cuya idea del derecho y la justicia está pervertida por el formalismo jurídico vacío e inane de sus constituciones, abstractas y plenamente funcionales a las oligarquías, al servicio de intereses espurios. En este caso, el hombre alcanzaba una plena dignidad y desarrollo en el contexto de una comunidad donde prevalecía el vínculo comunitario, al amparo de un modelo tradicional, de normas consuetudinarias y concretas que permitían la defensa efectiva del propio derecho. Ni siquiera con el advenimiento de los Estados modernos, y la centralización de algunos elementos de poder, como la Hacienda o el Ejército, se vieron alterados significativamente estos elementos, que representaban a los denominados «cuerpos intermedios» de la sociedad, y que adquirieron su propia expresión particular bajo el nombre de «Fueros», los que los propios reyes juraron respetar a lo largo de toda la Edad Moderna y hasta el advenimiento del régimen borbónico. La antropología tradicional vincula al hombre a un medio social, a una familia, a una estirpe o a un pueblo, que reproducen esa misma estructura familiar, aunque a mayor escala. En nuestro caso particular lo vemos a través de la convivencia de pequeños grupos humanos, de ahí la importancia de los municipios o de los concejos en un marco de vida comunitaria fuertemente institucionalizada. Al mismo tiempo este modelo y estructura también se replicaba en otros ámbitos, como en la vida económica y profesional, impregnando todas las esferas de la vida del hombre. Instituciones naturales, amparadas en el derecho natural, y orientadas a la protección y garantía de prosperidad de los hombres, y esto por encima de cualquier interés particular y mercantil de negocio. Para Mella, la ruptura con este mundo, y en general con las experiencias del pasado, es la que nos lleva, [merced a la acción del liberalismo, a los tiempos actuales](https://hiperbolajanus.com/posts/mos-maiorum-7/), y lo hace recorriendo un itinerario que todos conocemos, y que tienen su punto de partida [en la Ilustración y la posterior Revolución Francesa](https://hiperbolajanus.com/posts/joseph-de-maistre/), la irrupción del elemento racional y abstracto y la destrucción de la religión, considerada como fruto de la superstición. La destrucción del orden feudal, que todavía pervivía como marco de convivencia en el mundo rural, como una suerte de prolongación de ese espíritu medieval, hizo desaparecer de un plumazo ese entorno de relaciones concretas y personales para sustituirlas por lo «público» entendido como la centralización estatal uniforme, ignorando las realidades particulares subyacentes en el cuerpo social, los denominados «cuerpos intermedios», que fueron despojados de su autonomía, corporaciones y patrimonios. De modo que la destrucción de estas «sociedades intermedias» que mediaban entre el Estado y la sociedad desenraizó y destruyó la propia sociedad, al mismo tiempo que los fundamentos cristianos del derecho natural sobre la cual se hallaba asentada, para hacer prevalecer esos principios racionales y abstractos traídos por la revolución. Al mismo tiempo, y anejo a este desarraigo, del individuo se encuentra sometido a poderes arbitrarios del propio Estado liberal, sin un conglomerado institucional propio que lo proteja de estos atropellos, sumido en el individualismo ajeno a toda institución y destino colectivo, se limita al voto cada cuatro años de los partidos al servicio de oligarquías e intereses espurios, contrarios al Bien común. En este sentido, y advirtiendo las posibles acusaciones de «absolutismo» que en ocasiones se han lanzado contra el tradicionalismo, hay que señalar que Mella las rechaza por completo, dado que viola la idea de contrapoderes frente a la autoridad del rey que éste formula, ya que el absolutismo creía en la existencia de un poder ilimitado y tiránico del rey, transmitido por Dios y ajeno a la participación de la sociedad y sus estamentos. Como bien señaló [**Julius Evola**](https://hiperbolajanus.com/libros/metapolitica-tradicion-modernidad-julius-evola/), el absolutismo es un fenómeno antitradicional, vinculado a la descomposición y desacralización de las estructuras tradicionales. De hecho, el absolutismo, como los regímenes liberales de hoy, dejan al individuo totalmente desprotegido, sin un asidero sobre el que apoyarse en la defensa de sus libertades concretas. El propio Mella, como bien saben todos los que se adentren en su obra, fue partidario de contrarrestar el creciente poder del aparato estatal, tal y como hemos visto y seguiremos viendo en lo sucesivo, a lo largo del presente artículo. |[](https://amzn.to/2LqITcb)| |:-:| |[EVOLA, Julis; _Metapolítica, Tradición y Modernidad: Antología de artículos evolianos_, Hipérbola Janus, 2020](https://amzn.to/2LqITcb)| En nuestro caso particular, la desaparición de la organización gremial y corporativa tuvo unas consecuencias especialmente nefastas, y en especial después de las dos desamortizaciones liberales (Mendizabal y Madoz) al despojar a los grupos sociales populares de su natural organización sociohistórica. Asimismo, desvincularon la propiedad en las relaciones comunitarias y su uso patrimonial para vincularla al uso privado y anónimo, para fines puramente especulativos, los que caracterizan al liberal-capitalismo. De ahí nace la figura del asalariado, del contratado como mera mercancía, en un proceso de alienación del trabajo característico en el desarrollo del capitalismo burgués. De aquí parte lo que algunos tradicionalistas, como Gambra, denominan el «problema social», frente al cual, y al margen de las recetas ideológicas de la modernidad, Mella reivindica la restauración de los antiguos vínculos corporativos y orgánicos de inspiración medieval. ## La idea de soberanía social Todos los procesos disolutivos que conducen a la Modernidad liberal tienen su punto de inicio con el Renacimiento, con la afirmación del individualismo y la ruptura definitiva del ecumene cristiano medieval, algo que aparece indefectiblemente unido a la Reforma luterana, así como la «valorización» del mundo clásico, con la reemergencia de teorías de tipo hedonista, como las de Epicuro, por ejemplo, generando una disolución de los vínculos con el medio concreto. Esto supone la aparición de un nuevo tipo, que es el hombre abstracto que escapa cada vez más al entorno inmediato y vital, esto al tiempo que el poder del Estado se robustece y se vuelve omnipotente. Es por ese motivo que en lo sucesivo se ha impuesto en nuestras sociedades la falta de concreción, tanto en lo teórico como en lo político, lo cual ha propiciado el triunfo del contrato social roussoniano y la justificación del orden social en virtud de componendas voluntarias y totalmente artificiales. Estas construcciones político-ideológicas son las que contribuyen a la construcción de la sociedad liberal, asentada sobre patrones puramente racionales, individualistas y mercantilistas. De hecho, la mayor preocupación de Mella es la destrucción de las instituciones locales y ese vínculo afectivo del hombre con su realidad inmediata, algo que impregnaba su relación con el trabajo, con su obra, con su impronta vocacional y devota, imprimiéndole, como en el caso del artesano, un sello propio y particular a su trabajo. Y en este sentido, Mella afirma que la sociedad moderna ha perdido su sentido institucional como base estable de la sociabilidad. A través del elemento jurídico y la participación en las instituciones es el medio a partir del cual la comunidad se cohesiona y construye sus vínculos y su particular autonomía, que le hace tener una vida propia e interna, y con la institución nos podemos referir desde una asociación profesional, a la universidad o una cofradía etc. El individualismo ha representado el factor disolutivo y corrosivo que ha destruido este vínculo social fundado en múltiples solidaridades que han enfrentado y polarizado al cuerpo social, con el enfrentamiento entre «clases sociales» y la negación de las jerarquías naturales. Ante todo lo relatado, y como consecuencia de las destrucciones provocadas por la revolución, Mella plantea su teoría de la soberanía social. Esta teoría consiste básicamente en encuadrar de nuevo a la sociedad en sus raíces naturales, concebida en todos sus órdenes como portadora de un dinamismo propio en una suerte de organización geométrica en la que conviven objetivos y finalidades variadas y concretas con su propia legitimidad y autonomía. Estas finalidades, amparadas en el derecho natural, son junto al poder del propio Estado las únicas formas de limitación del poder. La particularidad de esta idea de soberanía social está en el hecho de que la formación de la jerarquía social tiene una dirección ascendente, que tiene como punto de partida a las personas colectivas y concretas, pasando por una serie de instituciones, hasta llegar al Estado central, de forma escalonada y plenamente conscientes de sus funciones. Así lo expresa Mella en su propio lenguaje: «_la jerarquía de personas colectivas, de poderes organizados, de clases, que suben desde la familia hasta la soberanía que llamo política concretada en el Estado, que deben auxiliar, pero también contener_». Es lo que Mella concibe como el sociedalismo, que supone la reintegración de la sociedad en la vida concreta de los hombres, con el desarrollo de una vida política común y estable en el marco de instituciones naturales que potencien las relaciones humanas y sociales, estimulando la sociabilidad. Y hablamos, desde la perspectiva de la integración de distintas sociedades, fuertemente institucionalizadas con funciones y finalidades concretas, más allá del sentido democrático y pactista que pueda entenderse en términos modernos o de cualquier asociación u organización relacionada con el «problema social». ## ¿Qué es la Tradición? De este modo quedan formuladas las dos soberanías, la política y la social, que coexisten en un mismo espacio limitándose y apoyándose recíprocamente en lo que es uno de los fundamentos del sociedalismo de Mella. No obstante, esta doble soberanía no explica todavía la concreción política de cada pueblo y el vínculo superior que lo lleva a federarse con las diferentes sociedades y a mantenerse unido en una historia y espíritu comunes. Los vínculos que las mantienen unidas en el tiempo tienen que ver con un orden histórico concreto, con un vínculo espiritual que las entrelaza interiormente de una generación a otra, y en última instancia de [ese orden tradicional](https://hiperbolajanus.com/posts/comprendiendo-la-tradicion/) que lo engloba todo, y que al mismo tiempo se asienta en la monarquía y la religión católica. La lealtad a Dios y a un solo rey en torno a los cuales se aglutina la fe, viene a coronar todas estas estructuras y lazos forjados en el fermento de la historia. No se trata de la Tradición en términos de un «ultraconservadurismo», que ya sabemos que el prefijo «ultra» (lo que sea) es muy recurrente en nuestros días, con la idea de un medio social y político petrificado e invariable, sino que es el producto de un proceso de maduración y evolución histórica, de carácter dinámico y nutrido de experiencias humanas. Nada que ver con las monstruosas ideologías progresistas y modernas, nacidas de lo abstracto e impulsadas por un desbocado «ir hacia delante», desarraigado y que tiende siempre hacia la deshumanización y la destrucción de toda creación humana natural forjada en el devenir de los siglos. Este mismo dinamismo, planteado por Mella, en torno al concepto e idea de Tradición tiene continuidad y adquiere fuerza en sus sucesores y depositarios. Y al fin y al cabo, Mella no hace más que partir de la propia etimología del término, que viene del latín _tradere_, entregar, de la generación que entrega los frutos de su experiencia a la siguiente, perfeccionándola, haciéndola más estable y segura. Podríamos seguir extrayendo más conclusiones del pensamiento tradicional de Vázquez de Mella, pero probablemente excedería, y por mucho, el modesto propósito de este escrito, de modo que nos quedaremos aquí, no sin advertir a nuestros lectores de la posibilidad de que en un futuro volvamos a retomar nuevamente el tema. Antes de acabar queremos llamar la atención sobre [una polémica acontecida hace unos años en torno a una Plaza en Madrid](https://www.lavozdigital.es/madrid/20150723/abci-quien-vazquez-mella-201507221907.html) que llevaba el nombre de nuestro autor y que se cambio para dedicársela a un sujeto cuyos méritos eran, por decirlo suavemente, más que discutibles, concretamente a Pedro Zerolo, miembro del PSOE y activista al servicio del lobby homosexualista. Durante aquella época, en 2019, muchos miembros de la izquierda globalista trataron de identificar a Vázquez de Mella como un «pensador franquista», cuando en realidad ni cronológica ni ideológicamente tuvo nunca nada que ver con el franquismo. Recordemos que murió en 1928, y la impronta de su pensamiento ha tenido como continuadores a sus propios correligionarios dentro del ámbito tradicional, aunque en su tiempo llegó a ser muy respetado también por sus adversarios, los liberales. Aunque la retirada del nombre de una calle pueda resultar algo banal, o carente de una importancia excesiva, también contribuye, a su modo, a una forma de _damnatio memoriae_ que condena al olvido y al ostracismo a grandes autores de la Tradición, portadores de un Patriotismo sano y capaz de entender las peculiaridades y el _Dasein_ profundo de España, que si bien no nació invertebrada, como pretendían los Orteguianos, su esencia y naturaleza es mucho más compleja que cualquiera de las grandes naciones de Europa. --- **Artículo original**: Hipérbola Janus, [_Juan Vázquez de Mella y el tradicionalismo español_](https://www.hiperbolajanus.com/posts/juan-vazquez-mella-tradicionalismo/), 16/Ago/2024 @ 674473f6:f859eb3c
2024-08-05 05:51:37> Bitwise Operation คือ กระบวนการที่การดำเนินการใด ๆ โดยตรงกับบิตของตัวเลข หรือชุดข้อมูลของเราใน memory ซึ่งการทำงานโดยตรงกับบิตของตัวเลข ทำให้มีประสิทธิภาพสูงและใช้บ่อยในการเขียนโปรแกรมระดับ low-level โดยหลัก ๆ ที่ใช้กันจะมี 6 แบบ เป็นเครื่องมือที่ทรงพลังสำหรับนักพัฒนาที่ต้องการประสิทธิภาพสูงและการควบคุมระดับบิต โดยเฉพาะในการพัฒนาระบบระดับ low-level และการทำงานกับฮาร์ดแวร์โดยตรง ## TLDR ภาพรวม Bitwise Operations: AND (&): ใช้เปรียบเทียบบิต, ให้ 1 เมื่อทั้งสองบิตเป็น 1 ประโยชน์: ตรวจสอบบิต, สร้าง mask OR (|): ให้ 1 เมื่อมีบิตใดบิตหนึ่งเป็น 1 ประโยชน์: รวมแฟล็ก, ตั้งค่าบิต XOR (^): ให้ 1 เมื่อบิตต่างกัน ประโยชน์: สลับค่า, เข้ารหัสอย่างง่าย NOT (~): กลับค่าทุกบิต ประโยชน์: สร้าง mask สำหรับลบบิต Left Shift (<<): เลื่อนบิตไปซ้าย, เติม 0 ทางขวา ประโยชน์: คูณด้วยกำลังของ 2, สร้าง mask Right Shift (>>): เลื่อนบิตไปขวา ประโยชน์: หารด้วยกำลังของ 2, แยกส่วนข้อมูล ## 1.) BitAnd (&): BitAnd มักใช้สัญลักษณ์ & เป็นการดำเนินการทางตรรกะที่เปรียบเทียบบิตในตำแหน่งเดียวกันของสองตัวเลข โดยมีกฎดังนี้: - 1 AND 1 = 1 - 1 AND 0 = 0 - 0 AND 1 = 0 - 0 AND 0 = 0 หรือกล่าวอีกนัยหนึ่ง ผลลัพธ์จะเป็น 1 ก็ต่อเมื่อทั้งสองบิตเป็น 1 เท่านั้น ตัวอย่าง: สมมติว่าเรามีเลขสองตัว A = 5 และ B = 3 ในระบบเลขฐานสอง: A = 5 = 0101 B = 3 = 0011 เมื่อทำ BitAnd: ``` 0101 (A = 5) & 0011 (B = 3) ---- 0001 (Result = 1) ``` จะเห็นได้ว่า: - บิตที่ 1 (จากขวา): 1 & 1 = 1 - บิตที่ 2: 0 & 1 = 0 - บิตที่ 3: 1 & 0 = 0 - บิตที่ 4: 0 & 0 = 0 ดังนั้น ผลลัพธ์คือ 0001 ในเลขฐานสอง ซึ่งเท่ากับ 1 ในเลขฐานสิบ การใช้งาน BitAnd: 1. การตรวจสอบเลขคู่/คี่: ถ้า (n & 1) == 0 แสดงว่า n เป็นเลขคู่ ถ้า (n & 1) == 1 แสดงว่า n เป็นเลขคี่ 2. การตรวจสอบสถานะของบิตเฉพาะ: ถ้าต้องการตรวจสอบบิตที่ 3 ของ x: if (x & (1 << 2)) != 0 // บิตที่ 3 เป็น 1 3. การลบบิตสุดท้ายที่เป็น 1: n = n & (n - 1) BitAnd มีประโยชน์มากในการจัดการกับข้อมูลระดับบิต การตั้งค่าแฟล็ก และการทำงานกับฮาร์ดแวร์โดยตรง ## 2.) BitOr (|): BitOr มักใช้สัญลักษณ์ | เป็นการดำเนินการทางตรรกะที่เปรียบเทียบบิตในตำแหน่งเดียวกันของสองตัวเลข โดยมีกฎดังนี้: - 1 OR 1 = 1 - 1 OR 0 = 1 - 0 OR 1 = 1 - 0 OR 0 = 0 กล่าวคือ ผลลัพธ์จะเป็น 1 เมื่อมีบิตใดบิตหนึ่งเป็น 1 หรือทั้งสองบิตเป็น 1 ตัวอย่าง: สมมติว่าเรามีเลขสองตัว A = 5 และ B = 3 ในระบบเลขฐานสอง: A = 5 = 0101 B = 3 = 0011 เมื่อทำ BitOr: ``` 0101 (A = 5) | 0011 (B = 3) ---- 0111 (Result = 7) ``` จะเห็นได้ว่า: - บิตที่ 1 (จากขวา): 1 | 1 = 1 - บิตที่ 2: 0 | 1 = 1 - บิตที่ 3: 1 | 0 = 1 - บิตที่ 4: 0 | 0 = 0 ดังนั้น ผลลัพธ์คือ 0111 ในเลขฐานสอง ซึ่งเท่ากับ 7 ในเลขฐานสิบ การใช้งาน BitOr: 1. การรวมแฟล็ก: เช่น ในการตั้งค่าสิทธิ์ไฟล์ในระบบ Unix permissions = READ | WRITE | EXECUTE 2. การตั้งค่าบิตเฉพาะ: ถ้าต้องการตั้งค่าบิตที่ 3 ของ x เป็น 1: x = x | (1 << 2) 3. การรวมสี RGB: ในระบบสี RGB ที่ใช้ 8 บิตต่อสี color = (red << 16) | (green << 8) | blue BitOr มีประโยชน์มากในการรวมแฟล็ก การตั้งค่าบิต และการทำงานกับข้อมูลที่แต่ละบิตมีความหมายเฉพาะ ## BitXor (^): BitXor หรือ Exclusive OR (XOR) มักใช้สัญลักษณ์ ^ เป็นการดำเนินการทางตรรกะที่เปรียบเทียบบิตในตำแหน่งเดียวกันของสองตัวเลข โดยมีกฎดังนี้: - 1 XOR 1 = 0 - 1 XOR 0 = 1 - 0 XOR 1 = 1 - 0 XOR 0 = 0 กล่าวคือ ผลลัพธ์จะเป็น 1 เมื่อบิตทั้งสองมีค่าต่างกัน ตัวอย่าง: สมมติว่าเรามีเลขสองตัว A = 5 และ B = 3 ในระบบเลขฐานสอง: A = 5 = 0101 B = 3 = 0011 เมื่อทำ BitXor: ``` 0101 (A = 5) ^ 0011 (B = 3) ---- 0110 (Result = 6) ``` จะเห็นได้ว่า: - บิตที่ 1 (จากขวา): 1 ^ 1 = 0 - บิตที่ 2: 0 ^ 1 = 1 - บิตที่ 3: 1 ^ 0 = 1 - บิตที่ 4: 0 ^ 0 = 0 ดังนั้น ผลลัพธ์คือ 0110 ในเลขฐานสอง ซึ่งเท่ากับ 6 ในเลขฐานสิบ การใช้งาน BitXor: 1. การสลับค่าโดยไม่ใช้ตัวแปรเพิ่ม: a ^= b; b ^= a; a ^= b; // ตอนนี้ a และ b ได้สลับค่ากันแล้ว 2. การเข้ารหัสอย่างง่าย: encrypted = data ^ key decrypted = encrypted ^ key // จะได้ data กลับคืนมา 3. การตรวจสอบความเท่ากันของตัวเลข: if ((a ^ b) == 0) // a และ b เท่ากัน 4. การหาตัวเลขที่ไม่มีคู่ในชุดข้อมูล: result = num1 ^ num2 ^ num3 ^ ... // ผลลัพธ์จะเป็นตัวเลขที่ไม่มีคู่ BitXor มีคุณสมบัติพิเศษคือ การ XOR กับตัวเองจะได้ 0 และการ XOR กับ 0 จะได้ตัวเองกลับคืนมา ทำให้มันมีประโยชน์มากในการเข้ารหัสและการตรวจสอบข้อมูล ## BitNot (~): BitNot หรือ NOT มักใช้สัญลักษณ์ ~ เป็นการดำเนินการทางตรรกะที่กลับบิตของตัวเลข โดยมีกฎง่ายๆ คือ: - NOT 1 = 0 - NOT 0 = 1 กล่าวคือ BitNot จะเปลี่ยนทุกบิต 0 เป็น 1 และทุกบิต 1 เป็น 0 ตัวอย่าง: สมมติว่าเรามีเลข A = 5 ในระบบเลขฐานสอง (สมมติว่าเป็นเลข 8 บิต): A = 5 = 00000101 เมื่อทำ BitNot: ``` 00000101 (A = 5) -------- ~ 11111010 (Result = 250 ใน unsigned int, หรือ -6 ใน signed int) ``` จะเห็นได้ว่า: - ทุกบิต 0 ถูกเปลี่ยนเป็น 1 - ทุกบิต 1 ถูกเปลี่ยนเป็น 0 ผลลัพธ์จะขึ้นอยู่กับว่าเราใช้ระบบเลขแบบไหน (signed หรือ unsigned): - ในระบบ unsigned 8 บิต: 11111010 = 250 - ในระบบ signed 8 บิต: 11111010 = -6 การใช้งาน BitNot: 1. การสร้าง mask สำหรับการลบบิต: clear_mask = ~(1 << n) // สร้าง mask ที่มีบิตที่ n เป็น 0 และที่เหลือเป็น 1 x &= clear_mask // ลบบิตที่ n ของ x 2. การหาค่าสัมบูรณ์ของเลขติดลบในระบบ two's complement: abs_value = (x ^ (x >> 31)) - (x >> 31) // x >> 31 จะได้ 0 สำหรับเลขบวก และ -1 สำหรับเลขลบ 3. การสลับสถานะของทุกบิต: inverted = ~original 4. การหาค่าสูงสุดของตัวแปรที่มีขนาด n บิต: max_value = ~0 >> (32 - n) // สำหรับตัวแปร 32 บิต BitNot มักใช้ร่วมกับ BitAnd เพื่อลบบิตที่ต้องการ หรือใช้ในการสร้าง mask สำหรับการจัดการบิต ## Left Shift (<<): Left Shift มักใช้สัญลักษณ์ << เป็นการดำเนินการที่เลื่อนบิตทั้งหมดของตัวเลขไปทางซ้ายตามจำนวนที่กำหนด โดยเติม 0 ทางด้านขวา Left Shift โดยทั่วไปแล้วไม่แตกต่างกันระหว่างเลข unsigned int และ signed int แต่มีบางประเด็นที่ควรระวัง: 1. ผลลัพธ์: - ในกรณีของเลขไม่มีเครื่องหมาย ผลลัพธ์จะเป็นบวกเสมอ - สำหรับเลขมีเครื่องหมาย ผลลัพธ์อาจเปลี่ยนเครื่องหมายได้หากบิตเครื่องหมาย (sign bit) ถูกเปลี่ยน 2. Overflow: - ทั้งสองกรณีอาจเกิด overflow ได้ถ้าเลื่อนมากเกินไป - สำหรับเลข signed int overflow อาจทำให้เกิดการเปลี่ยนเครื่องหมายโดยไม่คาดคิด 3. Undefined Behavior: - ในบางภาษา เช่น C/C++, การเลื่อนด้วยค่าที่มากกว่าหรือเท่ากับจำนวนบิตของตัวแปรอาจทำให้เกิด Undefined Behavior ได้ ตัวอย่าง: สมมติว่าเรามีเลข A = 5 และต้องการเลื่อนซ้าย 2 ตำแหน่ง ในระบบเลขฐานสอง (สมมติว่าเป็นเลข 8 บิต): A = 5 = 00000101 เมื่อทำ Left Shift 2 ตำแหน่ง (A << 2): ``` 00000101 (A = 5) -------- 00010100 (Result = 20) ``` จะเห็นได้ว่า:: - บิตทั้งหมดถูกเลื่อนไปทางซ้าย 2 ตำแหน่ง - เติม 0 สองตัวทางด้านขวา ผลลัพธ์: 00010100 ในเลขฐานสอง ซึ่งเท่ากับ 20 ในเลขฐานสิบ ตัวอย่าง 2: ``` unsigned int a = 1; // 00000001 in binary int b = 1; // 00000001 in binary // Left shift by 3 unsigned int a_result = a << 3; // 00001000 (8 in decimal) int b_result = b << 3; // 00001000 (8 in decimal) // สำหรับตัวเลขเล็ก ๆ ผลอาจจะไม่ต่างกัน // แต่เมื่อมีตัวเลขที่ใหญ่ขึ้น อาจจะให้ผลตรงกันข้ามแทน: unsigned int large_a = 1 << 31; // 10000000 00000000 00000000 00000000 (2147483648 in decimal) int large_b = 1 << 31; // 10000000 00000000 00000000 00000000 (-2147483648 in decimal, due to two's complement) ``` ในตัวอย่างสุดท้าย เราเห็นความแตกต่าง: - สำหรับ unsigned int, ผลลัพธ์คือเลขบวกที่ใหญ่ที่สุดที่เป็นไปได้ - สำหรับ signed int, ผลลัพธ์คือเลขลบที่น้อยที่สุดที่เป็นไปได้ เนื่องจากบิตซ้ายสุดถูกตีความเป็นเครื่องหมายลบในระบบ two's complement กฎการทำงาน: - เลื่อนบิตทั้งหมดไปทางซ้าย n ตำแหน่ง - เติม 0 ทางด้านขวา n ตัว - บิตที่เลื่อนออกไปทางซ้ายจะหายไป การใช้งาน Left Shift: 1. การคูณด้วยกำลังของ 2: x << n เท่ากับ x * (2^n) เช่น 5 << 2 = 5 * (2^2) = 5 * 4 = 20 2. การสร้างหน้ากาก (mask) สำหรับการตั้งค่าบิต: mask = 1 << n // สร้างหน้ากากที่มีบิตที่ n เป็น 1 และที่เหลือเป็น 0 x |= mask // ตั้งค่าบิตที่ n ของ x เป็น 1 3. การเข้ารหัสข้อมูลหลายบิตในตัวแปรเดียว: encoded = (r << 16) | (g << 8) | b // เก็บค่า RGB ในตัวแปร 32 บิต 4. การทำงานกับบิตแฟล็ก: FLAG_A = 1 << 0 FLAG_B = 1 << 1 FLAG_C = 1 << 2 // ใช้งาน: flags = FLAG_A | FLAG_B Left Shift มีประสิทธิภาพสูงในการคูณด้วยกำลังของ 2 และมักใช้ในการจัดการบิตแฟล็กและการสร้างหน้ากากสำหรับการดำเนินการระดับบิต ## Right Shift (>>): Right Shift มักใช้สัญลักษณ์ >> เป็นการดำเนินการที่เลื่อนบิตทั้งหมดของตัวเลขไปทางขวาตามจำนวนที่กำหนด การทำงานจะแตกต่างกันเล็กน้อยระหว่างเลขที่มีเครื่องหมาย (signed) และไม่มีเครื่องหมาย (unsigned) สำหรับเลข unsigned int (Logical Right Shift): - เลื่อนบิตทั้งหมดไปทางขวา n ตำแหน่ง - เติม 0 ทางด้านซ้าย n ตัว - บิตที่เลื่อนออกไปทางขวาจะหายไป สำหรับเลข signed int (Arithmetic Right Shift): - เลื่อนบิตทั้งหมดไปทางขวา n ตำแหน่ง - เติมด้วยบิตเครื่องหมาย (sign bit) ทางด้านซ้าย n ตัว - บิตที่เลื่อนออกไปทางขวาจะหายไป ตัวอย่าง: สมมติว่าเรามีเลข A = 20 และต้องการเลื่อนขวา 2 ตำแหน่ง ในระบบเลขฐานสอง (สมมติว่าเป็นเลข 8 บิต): A = 20 = 00010100 เมื่อทำ Right Shift 2 ตำแหน่ง (A >> 2): ``` 00010100 (A = 20) -------- 00000101 (Result = 5) ``` จะเห็นได้ว่า:: - บิตทั้งหมดถูกเลื่อนไปทางขวา 2 ตำแหน่ง - เติม 0 สองตัวทางด้านซ้าย (สำหรับเลขไม่มีเครื่องหมาย) ผลลัพธ์: 00000101 ในเลขฐานสอง ซึ่งเท่ากับ 5 ในเลขฐานสิบ การใช้งาน Right Shift: 1. การหารด้วยกำลังของ 2: x >> n เท่ากับ x / (2^n) (ปัดเศษลง) เช่น 20 >> 2 = 20 / (2^2) = 20 / 4 = 5 2. การแยกส่วนของข้อมูลที่ถูกเก็บรวมกัน: r = (rgb >> 16) & 0xFF // แยกค่าสีแดงจาก RGB 24 บิต g = (rgb >> 8) & 0xFF // แยกค่าสีเขียว b = rgb & 0xFF // แยกค่าสีน้ำเงิน 3. การตรวจสอบเครื่องหมายของตัวเลข: sign = x >> 31 // สำหรับตัวแปร 32 บิต, จะได้ 0 สำหรับบวก และ -1 สำหรับลบ 4. การทำ rounded division: (x + (1 << (n-1))) >> n // หารด้วย 2^n และปัดเศษ ข้อควรระวัง: - ใน Java, >> เป็น arithmetic shift สำหรับ int และ long, ส่วน >>> เป็น logical shift - ในภาษาอื่นๆ เช่น C/C++, การทำงานของ >> กับเลขติดลบอาจแตกต่างกันไปตาม Compiler Right Shift มีประสิทธิภาพสูงในการหารด้วยกำลังของ 2 และมักใช้ในการจัดการข้อมูลที่ถูกเก็บรวมกันในรูปแบบบิต หากเปรียบกับ Right Shift แม้ว่าการทำงานพื้นฐานของ Left Shift จะเหมือนกันสำหรับทั้งเลข signed int และ unsigned int แต่การตีความผลลัพธ์และผลกระทบต่อเครื่องหมาย(sign bit)อาจแตกต่างกัน ดังนั้นจึงควรระมัดระวังเมื่อใช้ Left Shift กับเลขที่มี signed int โดยเฉพาะเมื่อเลื่อนด้วยค่าที่สูงมาก ๆ ## Conclusion #### ลักษณะเด่นของ Bitwise Operations: - ประสิทธิภาพสูง: ทำงานเร็วกว่าการคำนวณปกติ - ประหยัดหน่วยความจำ: จัดเก็บข้อมูลหลายอย่างในตัวแปรเดียว - ใช้ในงานระดับต่ำ: การทำงานกับฮาร์ดแวร์, ระบบปฏิบัติการ - การเข้ารหัส: ใช้ในอัลกอริทึมการเข้ารหัสและบีบอัดข้อมูล - การจัดการแฟล็ก: ใช้ในการตั้งค่าและตรวจสอบสถานะต่างๆ #### การใช้งานทั่วไป: - จัดการสิทธิ์และการอนุญาตในระบบไฟล์ - การเข้ารหัสและถอดรหัสข้อมูล - การบีบอัดข้อมูล - การทำงานกับพิกเซลในการประมวลผลภาพ - การจัดการโปรโตคอลเครือข่าย - การทำงานกับ register ใน Embedded system #### ข้อควรระวัง: - ต้องระมัดระวังเรื่องขนาดของข้อมูล (8, 16, 32, 64 บิต) - ความแตกต่างระหว่างเลขมี signed int และ unsigned int - ความแตกต่างของการทำงานในแต่ละภาษาโปรแกรม **unsigned int คือตัวเลขเป็นบวกเสมอ signed int สามารถมีค่าเป็นลบได้ #siamstr #Blog
@ 674473f6:f859eb3c
2024-08-05 05:51:37> Bitwise Operation คือ กระบวนการที่การดำเนินการใด ๆ โดยตรงกับบิตของตัวเลข หรือชุดข้อมูลของเราใน memory ซึ่งการทำงานโดยตรงกับบิตของตัวเลข ทำให้มีประสิทธิภาพสูงและใช้บ่อยในการเขียนโปรแกรมระดับ low-level โดยหลัก ๆ ที่ใช้กันจะมี 6 แบบ เป็นเครื่องมือที่ทรงพลังสำหรับนักพัฒนาที่ต้องการประสิทธิภาพสูงและการควบคุมระดับบิต โดยเฉพาะในการพัฒนาระบบระดับ low-level และการทำงานกับฮาร์ดแวร์โดยตรง ## TLDR ภาพรวม Bitwise Operations: AND (&): ใช้เปรียบเทียบบิต, ให้ 1 เมื่อทั้งสองบิตเป็น 1 ประโยชน์: ตรวจสอบบิต, สร้าง mask OR (|): ให้ 1 เมื่อมีบิตใดบิตหนึ่งเป็น 1 ประโยชน์: รวมแฟล็ก, ตั้งค่าบิต XOR (^): ให้ 1 เมื่อบิตต่างกัน ประโยชน์: สลับค่า, เข้ารหัสอย่างง่าย NOT (~): กลับค่าทุกบิต ประโยชน์: สร้าง mask สำหรับลบบิต Left Shift (<<): เลื่อนบิตไปซ้าย, เติม 0 ทางขวา ประโยชน์: คูณด้วยกำลังของ 2, สร้าง mask Right Shift (>>): เลื่อนบิตไปขวา ประโยชน์: หารด้วยกำลังของ 2, แยกส่วนข้อมูล ## 1.) BitAnd (&): BitAnd มักใช้สัญลักษณ์ & เป็นการดำเนินการทางตรรกะที่เปรียบเทียบบิตในตำแหน่งเดียวกันของสองตัวเลข โดยมีกฎดังนี้: - 1 AND 1 = 1 - 1 AND 0 = 0 - 0 AND 1 = 0 - 0 AND 0 = 0 หรือกล่าวอีกนัยหนึ่ง ผลลัพธ์จะเป็น 1 ก็ต่อเมื่อทั้งสองบิตเป็น 1 เท่านั้น ตัวอย่าง: สมมติว่าเรามีเลขสองตัว A = 5 และ B = 3 ในระบบเลขฐานสอง: A = 5 = 0101 B = 3 = 0011 เมื่อทำ BitAnd: ``` 0101 (A = 5) & 0011 (B = 3) ---- 0001 (Result = 1) ``` จะเห็นได้ว่า: - บิตที่ 1 (จากขวา): 1 & 1 = 1 - บิตที่ 2: 0 & 1 = 0 - บิตที่ 3: 1 & 0 = 0 - บิตที่ 4: 0 & 0 = 0 ดังนั้น ผลลัพธ์คือ 0001 ในเลขฐานสอง ซึ่งเท่ากับ 1 ในเลขฐานสิบ การใช้งาน BitAnd: 1. การตรวจสอบเลขคู่/คี่: ถ้า (n & 1) == 0 แสดงว่า n เป็นเลขคู่ ถ้า (n & 1) == 1 แสดงว่า n เป็นเลขคี่ 2. การตรวจสอบสถานะของบิตเฉพาะ: ถ้าต้องการตรวจสอบบิตที่ 3 ของ x: if (x & (1 << 2)) != 0 // บิตที่ 3 เป็น 1 3. การลบบิตสุดท้ายที่เป็น 1: n = n & (n - 1) BitAnd มีประโยชน์มากในการจัดการกับข้อมูลระดับบิต การตั้งค่าแฟล็ก และการทำงานกับฮาร์ดแวร์โดยตรง ## 2.) BitOr (|): BitOr มักใช้สัญลักษณ์ | เป็นการดำเนินการทางตรรกะที่เปรียบเทียบบิตในตำแหน่งเดียวกันของสองตัวเลข โดยมีกฎดังนี้: - 1 OR 1 = 1 - 1 OR 0 = 1 - 0 OR 1 = 1 - 0 OR 0 = 0 กล่าวคือ ผลลัพธ์จะเป็น 1 เมื่อมีบิตใดบิตหนึ่งเป็น 1 หรือทั้งสองบิตเป็น 1 ตัวอย่าง: สมมติว่าเรามีเลขสองตัว A = 5 และ B = 3 ในระบบเลขฐานสอง: A = 5 = 0101 B = 3 = 0011 เมื่อทำ BitOr: ``` 0101 (A = 5) | 0011 (B = 3) ---- 0111 (Result = 7) ``` จะเห็นได้ว่า: - บิตที่ 1 (จากขวา): 1 | 1 = 1 - บิตที่ 2: 0 | 1 = 1 - บิตที่ 3: 1 | 0 = 1 - บิตที่ 4: 0 | 0 = 0 ดังนั้น ผลลัพธ์คือ 0111 ในเลขฐานสอง ซึ่งเท่ากับ 7 ในเลขฐานสิบ การใช้งาน BitOr: 1. การรวมแฟล็ก: เช่น ในการตั้งค่าสิทธิ์ไฟล์ในระบบ Unix permissions = READ | WRITE | EXECUTE 2. การตั้งค่าบิตเฉพาะ: ถ้าต้องการตั้งค่าบิตที่ 3 ของ x เป็น 1: x = x | (1 << 2) 3. การรวมสี RGB: ในระบบสี RGB ที่ใช้ 8 บิตต่อสี color = (red << 16) | (green << 8) | blue BitOr มีประโยชน์มากในการรวมแฟล็ก การตั้งค่าบิต และการทำงานกับข้อมูลที่แต่ละบิตมีความหมายเฉพาะ ## BitXor (^): BitXor หรือ Exclusive OR (XOR) มักใช้สัญลักษณ์ ^ เป็นการดำเนินการทางตรรกะที่เปรียบเทียบบิตในตำแหน่งเดียวกันของสองตัวเลข โดยมีกฎดังนี้: - 1 XOR 1 = 0 - 1 XOR 0 = 1 - 0 XOR 1 = 1 - 0 XOR 0 = 0 กล่าวคือ ผลลัพธ์จะเป็น 1 เมื่อบิตทั้งสองมีค่าต่างกัน ตัวอย่าง: สมมติว่าเรามีเลขสองตัว A = 5 และ B = 3 ในระบบเลขฐานสอง: A = 5 = 0101 B = 3 = 0011 เมื่อทำ BitXor: ``` 0101 (A = 5) ^ 0011 (B = 3) ---- 0110 (Result = 6) ``` จะเห็นได้ว่า: - บิตที่ 1 (จากขวา): 1 ^ 1 = 0 - บิตที่ 2: 0 ^ 1 = 1 - บิตที่ 3: 1 ^ 0 = 1 - บิตที่ 4: 0 ^ 0 = 0 ดังนั้น ผลลัพธ์คือ 0110 ในเลขฐานสอง ซึ่งเท่ากับ 6 ในเลขฐานสิบ การใช้งาน BitXor: 1. การสลับค่าโดยไม่ใช้ตัวแปรเพิ่ม: a ^= b; b ^= a; a ^= b; // ตอนนี้ a และ b ได้สลับค่ากันแล้ว 2. การเข้ารหัสอย่างง่าย: encrypted = data ^ key decrypted = encrypted ^ key // จะได้ data กลับคืนมา 3. การตรวจสอบความเท่ากันของตัวเลข: if ((a ^ b) == 0) // a และ b เท่ากัน 4. การหาตัวเลขที่ไม่มีคู่ในชุดข้อมูล: result = num1 ^ num2 ^ num3 ^ ... // ผลลัพธ์จะเป็นตัวเลขที่ไม่มีคู่ BitXor มีคุณสมบัติพิเศษคือ การ XOR กับตัวเองจะได้ 0 และการ XOR กับ 0 จะได้ตัวเองกลับคืนมา ทำให้มันมีประโยชน์มากในการเข้ารหัสและการตรวจสอบข้อมูล ## BitNot (~): BitNot หรือ NOT มักใช้สัญลักษณ์ ~ เป็นการดำเนินการทางตรรกะที่กลับบิตของตัวเลข โดยมีกฎง่ายๆ คือ: - NOT 1 = 0 - NOT 0 = 1 กล่าวคือ BitNot จะเปลี่ยนทุกบิต 0 เป็น 1 และทุกบิต 1 เป็น 0 ตัวอย่าง: สมมติว่าเรามีเลข A = 5 ในระบบเลขฐานสอง (สมมติว่าเป็นเลข 8 บิต): A = 5 = 00000101 เมื่อทำ BitNot: ``` 00000101 (A = 5) -------- ~ 11111010 (Result = 250 ใน unsigned int, หรือ -6 ใน signed int) ``` จะเห็นได้ว่า: - ทุกบิต 0 ถูกเปลี่ยนเป็น 1 - ทุกบิต 1 ถูกเปลี่ยนเป็น 0 ผลลัพธ์จะขึ้นอยู่กับว่าเราใช้ระบบเลขแบบไหน (signed หรือ unsigned): - ในระบบ unsigned 8 บิต: 11111010 = 250 - ในระบบ signed 8 บิต: 11111010 = -6 การใช้งาน BitNot: 1. การสร้าง mask สำหรับการลบบิต: clear_mask = ~(1 << n) // สร้าง mask ที่มีบิตที่ n เป็น 0 และที่เหลือเป็น 1 x &= clear_mask // ลบบิตที่ n ของ x 2. การหาค่าสัมบูรณ์ของเลขติดลบในระบบ two's complement: abs_value = (x ^ (x >> 31)) - (x >> 31) // x >> 31 จะได้ 0 สำหรับเลขบวก และ -1 สำหรับเลขลบ 3. การสลับสถานะของทุกบิต: inverted = ~original 4. การหาค่าสูงสุดของตัวแปรที่มีขนาด n บิต: max_value = ~0 >> (32 - n) // สำหรับตัวแปร 32 บิต BitNot มักใช้ร่วมกับ BitAnd เพื่อลบบิตที่ต้องการ หรือใช้ในการสร้าง mask สำหรับการจัดการบิต ## Left Shift (<<): Left Shift มักใช้สัญลักษณ์ << เป็นการดำเนินการที่เลื่อนบิตทั้งหมดของตัวเลขไปทางซ้ายตามจำนวนที่กำหนด โดยเติม 0 ทางด้านขวา Left Shift โดยทั่วไปแล้วไม่แตกต่างกันระหว่างเลข unsigned int และ signed int แต่มีบางประเด็นที่ควรระวัง: 1. ผลลัพธ์: - ในกรณีของเลขไม่มีเครื่องหมาย ผลลัพธ์จะเป็นบวกเสมอ - สำหรับเลขมีเครื่องหมาย ผลลัพธ์อาจเปลี่ยนเครื่องหมายได้หากบิตเครื่องหมาย (sign bit) ถูกเปลี่ยน 2. Overflow: - ทั้งสองกรณีอาจเกิด overflow ได้ถ้าเลื่อนมากเกินไป - สำหรับเลข signed int overflow อาจทำให้เกิดการเปลี่ยนเครื่องหมายโดยไม่คาดคิด 3. Undefined Behavior: - ในบางภาษา เช่น C/C++, การเลื่อนด้วยค่าที่มากกว่าหรือเท่ากับจำนวนบิตของตัวแปรอาจทำให้เกิด Undefined Behavior ได้ ตัวอย่าง: สมมติว่าเรามีเลข A = 5 และต้องการเลื่อนซ้าย 2 ตำแหน่ง ในระบบเลขฐานสอง (สมมติว่าเป็นเลข 8 บิต): A = 5 = 00000101 เมื่อทำ Left Shift 2 ตำแหน่ง (A << 2): ``` 00000101 (A = 5) -------- 00010100 (Result = 20) ``` จะเห็นได้ว่า:: - บิตทั้งหมดถูกเลื่อนไปทางซ้าย 2 ตำแหน่ง - เติม 0 สองตัวทางด้านขวา ผลลัพธ์: 00010100 ในเลขฐานสอง ซึ่งเท่ากับ 20 ในเลขฐานสิบ ตัวอย่าง 2: ``` unsigned int a = 1; // 00000001 in binary int b = 1; // 00000001 in binary // Left shift by 3 unsigned int a_result = a << 3; // 00001000 (8 in decimal) int b_result = b << 3; // 00001000 (8 in decimal) // สำหรับตัวเลขเล็ก ๆ ผลอาจจะไม่ต่างกัน // แต่เมื่อมีตัวเลขที่ใหญ่ขึ้น อาจจะให้ผลตรงกันข้ามแทน: unsigned int large_a = 1 << 31; // 10000000 00000000 00000000 00000000 (2147483648 in decimal) int large_b = 1 << 31; // 10000000 00000000 00000000 00000000 (-2147483648 in decimal, due to two's complement) ``` ในตัวอย่างสุดท้าย เราเห็นความแตกต่าง: - สำหรับ unsigned int, ผลลัพธ์คือเลขบวกที่ใหญ่ที่สุดที่เป็นไปได้ - สำหรับ signed int, ผลลัพธ์คือเลขลบที่น้อยที่สุดที่เป็นไปได้ เนื่องจากบิตซ้ายสุดถูกตีความเป็นเครื่องหมายลบในระบบ two's complement กฎการทำงาน: - เลื่อนบิตทั้งหมดไปทางซ้าย n ตำแหน่ง - เติม 0 ทางด้านขวา n ตัว - บิตที่เลื่อนออกไปทางซ้ายจะหายไป การใช้งาน Left Shift: 1. การคูณด้วยกำลังของ 2: x << n เท่ากับ x * (2^n) เช่น 5 << 2 = 5 * (2^2) = 5 * 4 = 20 2. การสร้างหน้ากาก (mask) สำหรับการตั้งค่าบิต: mask = 1 << n // สร้างหน้ากากที่มีบิตที่ n เป็น 1 และที่เหลือเป็น 0 x |= mask // ตั้งค่าบิตที่ n ของ x เป็น 1 3. การเข้ารหัสข้อมูลหลายบิตในตัวแปรเดียว: encoded = (r << 16) | (g << 8) | b // เก็บค่า RGB ในตัวแปร 32 บิต 4. การทำงานกับบิตแฟล็ก: FLAG_A = 1 << 0 FLAG_B = 1 << 1 FLAG_C = 1 << 2 // ใช้งาน: flags = FLAG_A | FLAG_B Left Shift มีประสิทธิภาพสูงในการคูณด้วยกำลังของ 2 และมักใช้ในการจัดการบิตแฟล็กและการสร้างหน้ากากสำหรับการดำเนินการระดับบิต ## Right Shift (>>): Right Shift มักใช้สัญลักษณ์ >> เป็นการดำเนินการที่เลื่อนบิตทั้งหมดของตัวเลขไปทางขวาตามจำนวนที่กำหนด การทำงานจะแตกต่างกันเล็กน้อยระหว่างเลขที่มีเครื่องหมาย (signed) และไม่มีเครื่องหมาย (unsigned) สำหรับเลข unsigned int (Logical Right Shift): - เลื่อนบิตทั้งหมดไปทางขวา n ตำแหน่ง - เติม 0 ทางด้านซ้าย n ตัว - บิตที่เลื่อนออกไปทางขวาจะหายไป สำหรับเลข signed int (Arithmetic Right Shift): - เลื่อนบิตทั้งหมดไปทางขวา n ตำแหน่ง - เติมด้วยบิตเครื่องหมาย (sign bit) ทางด้านซ้าย n ตัว - บิตที่เลื่อนออกไปทางขวาจะหายไป ตัวอย่าง: สมมติว่าเรามีเลข A = 20 และต้องการเลื่อนขวา 2 ตำแหน่ง ในระบบเลขฐานสอง (สมมติว่าเป็นเลข 8 บิต): A = 20 = 00010100 เมื่อทำ Right Shift 2 ตำแหน่ง (A >> 2): ``` 00010100 (A = 20) -------- 00000101 (Result = 5) ``` จะเห็นได้ว่า:: - บิตทั้งหมดถูกเลื่อนไปทางขวา 2 ตำแหน่ง - เติม 0 สองตัวทางด้านซ้าย (สำหรับเลขไม่มีเครื่องหมาย) ผลลัพธ์: 00000101 ในเลขฐานสอง ซึ่งเท่ากับ 5 ในเลขฐานสิบ การใช้งาน Right Shift: 1. การหารด้วยกำลังของ 2: x >> n เท่ากับ x / (2^n) (ปัดเศษลง) เช่น 20 >> 2 = 20 / (2^2) = 20 / 4 = 5 2. การแยกส่วนของข้อมูลที่ถูกเก็บรวมกัน: r = (rgb >> 16) & 0xFF // แยกค่าสีแดงจาก RGB 24 บิต g = (rgb >> 8) & 0xFF // แยกค่าสีเขียว b = rgb & 0xFF // แยกค่าสีน้ำเงิน 3. การตรวจสอบเครื่องหมายของตัวเลข: sign = x >> 31 // สำหรับตัวแปร 32 บิต, จะได้ 0 สำหรับบวก และ -1 สำหรับลบ 4. การทำ rounded division: (x + (1 << (n-1))) >> n // หารด้วย 2^n และปัดเศษ ข้อควรระวัง: - ใน Java, >> เป็น arithmetic shift สำหรับ int และ long, ส่วน >>> เป็น logical shift - ในภาษาอื่นๆ เช่น C/C++, การทำงานของ >> กับเลขติดลบอาจแตกต่างกันไปตาม Compiler Right Shift มีประสิทธิภาพสูงในการหารด้วยกำลังของ 2 และมักใช้ในการจัดการข้อมูลที่ถูกเก็บรวมกันในรูปแบบบิต หากเปรียบกับ Right Shift แม้ว่าการทำงานพื้นฐานของ Left Shift จะเหมือนกันสำหรับทั้งเลข signed int และ unsigned int แต่การตีความผลลัพธ์และผลกระทบต่อเครื่องหมาย(sign bit)อาจแตกต่างกัน ดังนั้นจึงควรระมัดระวังเมื่อใช้ Left Shift กับเลขที่มี signed int โดยเฉพาะเมื่อเลื่อนด้วยค่าที่สูงมาก ๆ ## Conclusion #### ลักษณะเด่นของ Bitwise Operations: - ประสิทธิภาพสูง: ทำงานเร็วกว่าการคำนวณปกติ - ประหยัดหน่วยความจำ: จัดเก็บข้อมูลหลายอย่างในตัวแปรเดียว - ใช้ในงานระดับต่ำ: การทำงานกับฮาร์ดแวร์, ระบบปฏิบัติการ - การเข้ารหัส: ใช้ในอัลกอริทึมการเข้ารหัสและบีบอัดข้อมูล - การจัดการแฟล็ก: ใช้ในการตั้งค่าและตรวจสอบสถานะต่างๆ #### การใช้งานทั่วไป: - จัดการสิทธิ์และการอนุญาตในระบบไฟล์ - การเข้ารหัสและถอดรหัสข้อมูล - การบีบอัดข้อมูล - การทำงานกับพิกเซลในการประมวลผลภาพ - การจัดการโปรโตคอลเครือข่าย - การทำงานกับ register ใน Embedded system #### ข้อควรระวัง: - ต้องระมัดระวังเรื่องขนาดของข้อมูล (8, 16, 32, 64 บิต) - ความแตกต่างระหว่างเลขมี signed int และ unsigned int - ความแตกต่างของการทำงานในแต่ละภาษาโปรแกรม **unsigned int คือตัวเลขเป็นบวกเสมอ signed int สามารถมีค่าเป็นลบได้ #siamstr #Blog @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# jiq-web Made with [jq-web](nostr:naddr1qqyrzvrzxqcx2dfsqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c90hqwz), a tool to explore JSON using `jq` that works like [jiq](nostr:naddr1qqyrqvfjv33rxcenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cd86z7d).  - <https://jq.alhur.es/jiq/> - <https://github.com/fiatjaf/jiq-web> ## See also - [jq-finder](nostr:naddr1qqyryvejvycn2cnpqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ccw20rx)
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# jiq-web Made with [jq-web](nostr:naddr1qqyrzvrzxqcx2dfsqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c90hqwz), a tool to explore JSON using `jq` that works like [jiq](nostr:naddr1qqyrqvfjv33rxcenqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823cd86z7d).  - <https://jq.alhur.es/jiq/> - <https://github.com/fiatjaf/jiq-web> ## See also - [jq-finder](nostr:naddr1qqyryvejvycn2cnpqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ccw20rx) @ a853296a:209e695f
2024-08-03 20:03:05What's up stackers! Trying something new posting to the tech territory. **CASCDR TLDR:** CASCDR is a collection of Lightning Powered AI services/applications. **Post TLDR:** We have just released a big upgrade to our RSS Agent! You can now explore podcasts, and seamlessly integrate them with LLM workflows. This will allow you to condense podcast content/create more content based on a given podcast selected through the explorer! We have a new release LIVE. As discussed on this [post](https://stacker.news/items/621497) and on [SNL](https://youtu.be/SsZcVQZ20Ik?list=PLKnVil22cJNzDABNpAQ2JecRzU3SUtV8V&t=3068) last week, YouTube started playing major defense! So we adapted our YouTube Agent into an RSS Agent. Now the RSS Agent is back and better with V2! Due to time constraints we had to ship a very basic version last week. Now RSS Agent is fully equipped!  _he's baaaaaaack_ ## Key Updates: - Search & explore any podcast feed - Pull any episode of interest - Run analysis of the episode transcript with 5 pre-determined prompts - OR roll your own custom prompt to put together written content of your choosing! ## Workflow/Details:  _Step 1: Search for your favorite podcast like @ThrillerX_ _  _Step 2: Select/Configure Your Prompt & Select the Podcast Episode_  _Step 3: Inspect Your Result and/or Copy to Clipboard_ Looking forward to the feedback in the comments! If this post triggers ideas of more you want to do with AI, tell us what you want us to build! Cheers, The CASCDR Team originally posted at https://stacker.news/items/633849
@ a853296a:209e695f
2024-08-03 20:03:05What's up stackers! Trying something new posting to the tech territory. **CASCDR TLDR:** CASCDR is a collection of Lightning Powered AI services/applications. **Post TLDR:** We have just released a big upgrade to our RSS Agent! You can now explore podcasts, and seamlessly integrate them with LLM workflows. This will allow you to condense podcast content/create more content based on a given podcast selected through the explorer! We have a new release LIVE. As discussed on this [post](https://stacker.news/items/621497) and on [SNL](https://youtu.be/SsZcVQZ20Ik?list=PLKnVil22cJNzDABNpAQ2JecRzU3SUtV8V&t=3068) last week, YouTube started playing major defense! So we adapted our YouTube Agent into an RSS Agent. Now the RSS Agent is back and better with V2! Due to time constraints we had to ship a very basic version last week. Now RSS Agent is fully equipped!  _he's baaaaaaack_ ## Key Updates: - Search & explore any podcast feed - Pull any episode of interest - Run analysis of the episode transcript with 5 pre-determined prompts - OR roll your own custom prompt to put together written content of your choosing! ## Workflow/Details:  _Step 1: Search for your favorite podcast like @ThrillerX_ _  _Step 2: Select/Configure Your Prompt & Select the Podcast Episode_  _Step 3: Inspect Your Result and/or Copy to Clipboard_ Looking forward to the feedback in the comments! If this post triggers ideas of more you want to do with AI, tell us what you want us to build! Cheers, The CASCDR Team originally posted at https://stacker.news/items/633849 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Excerpt of discussion about DIDs and ION Melvin Carvalho: > "Not a single entity I know that's doing production deployments has actually vetted did:ion and found it to be production capable." > > The guy leading the DID effort said this about ION. > > Seems like they may be 6 months away from producing something. > > https://github.com/decentralized-identity/ion/blob/master/docs/design.md#operations > > In their design it says you can create, update, recover and activate. It is a bit magic > > But update implies a versioning system. So you could think of it like updated nostr events. My key is A. Now my key is B. Tied to a content addressable static ID (like a genesis event ID). > > Let's see. I hope they produce something useful. Daniel tends not to answer questions > > When we first made DID, the idea was that your (d)id and your public key or hash were the same string. > > As it evolved, that got broken. Which can be useful because then you can have multiple keys, but the trade off is more management needed. > > So you have DID <—> controller two way link. Then it can have multiple keys. Those can be used to update the record. How that chain of records is stored, fetched and verified, is not covered by DID. So everyone will do it differently. Nostr for example could create updating keys with a NIP, it would do the same thing. Hampus: > Basically impossible to have a convo with Daniel Melvin Carvalho: > true. too often appeals to authority > > https://identity.foundation/sidetree/spec/#update > > the side tree spec has an update function > > 'Retrieve the Update Reveal Value that matches the previously anchored Update Commitment' > > so it looks like they have a chain of anchors ... anchored to something, ion nodes i guess, which also run btc full nodes > > > 'Embed the Anchor String in the transaction such that it can be located and parsed by any party that traverses the history of the target anchoring system' > > > 'By leveraging the blockchain-agnostic Sidetree protocol, ION makes it possible to anchor tens of thousands of DID/DPKI operations on a target chain (in ION's case, Bitcoin) using a single on-chain transaction' > > there you go > > do a search in the ion repo for 'anchor' and it gives some details > > https://github.com/decentralized-identity/ion/blob/66813123cf81ace05cea2039e93ef263952d6283/docs/Q-and-A.md > > there's a Q & A Ruben Somsen: > Their anchor protocol doesn't guarantee you have a full view of the data, so you can open the commitments to anything you like (provided you pre-committed to different views). In my opinion this makes the commitments pointless. Melvin Carvalho: > > 'Assuming you are running your own node, you simply need to submit 1000 create operations to your node (ie. http://localhost:3000/operations) before your batch writer kicks in every 10 minutes by default, the batch writer will batch all 1000 operations into 1 bitcoin transaction thus you'll pay fee for just one transaction to the minor. > > The technical spec for constructing a create request can be found in Sidetree API spec, but if you know TypeScript, you are better off using the ion-sdk directly, it will save you a lot of time' > > seems 3 places data is stored > > anchored witness data: bitcoin tx > batches of operations: ION nodes > non witness data: maybe IPFS > > 'The logical order of operations, as determined by the underlying anchoring system (e.g. Bitcoin block and transaction order). Anchoring systems may widely vary in how they determine the logical order of operations, but the only requirement of an anchoring system is that it can provide a means to deterministically order each operation within a DID’s operational lineage.' Ruben Somsen: > It's deterministic given a set of data, but there is no consensus on the set of data, so if A and B get presented with a different set, they come to a different conclusion Melvin Carvalho: > yes. "DID owners can create forks within their own DID state history". so you dont actually know the full state. I think the design is of each identity has eventual consistency, with the anchor as the tie break. It can change as you know more data. But doesnt say what happens if two updates happen in the same block. > > https://identity.foundation/sidetree/spec/#late-publishing > > the aim is eventual consistency > > so at any time you might have the wrong state, but if you had every update associated with a given id, you could determine the right order to apply the patches by using the bitcoin block chain (I dont know what happens if there's a tie in the same block) ... there's no peg in or peg out, it's just like version controlled files Ruben Somsen: > But you can't know when you've reached the state of eventual consistency (i.e. when you finally have the full data set) and in practice it may never be reached, so there is no consensus > > When there is conflicting data, the first one counts and the second one is ignored. > > This problem is literally detrimental, yet it is being presented as a minor inconvenience. Melvin Carvalho: > yes, and the first one can be published later, so systems will think the second is valid, until it isnt Ruben Somsen: > Yup Melvin Carvalho: > you could actually steal someone's identity, and revoke all their keys, and then reveal it years later > > arguably this is worse than github Ruben Somsen: > lol yeah you could Melvin Carvalho: > or an attack vector, get someone's ID, but they dont know, then sell them lots of 'cheap' NFTs ... at some point you publish the new keys and reclaim all the tokens ... no one will know when they will be rug pulled Ruben Somsen: > That was my original argument, but Daniel claimed the protocol wasn't meant for transfer of ownership rights. Melvin Carvalho: > so then i wonder what the primary use cases are that cant be easily achieved already > > > 'How Can ION be Used? > > ION can see a lot of use in many cases. The most obvious use case is for verifiable credentials. A business can credential employees, who can then be verified via blockchain on arrival at their destination. This functionality also raises its use as a means of supplying and verifying international travel documents.' > > > > 'Another use case could come from accreditation for organizations. Using an organization's public key, users can verify their accreditation status and trace their accreditation history over time.' > > so i guess its an updatable profile page, but you dont know when your profile is compromised. OTOH it's free (their node is paying fees to start with), and improves BTC security budget. If you keep your key safe, and the nodes publish the updates for you, it might be a nice little profile you could use for stuff. But not sure id use it for anything high value. And nostr (for example) can do alot of this already — updatable profiles and publishing > > i think it may be to a degree censorship resistant too > > there's also no incentive to run a node, so im not sure why they would stick around > > nodes can actually very easily censor by black listing certain tx (e.g. a hack, or sanctioned identity), removing the decentralized nature > > so the nodes can never reach consensus Ruben Somsen: > Like I said, the commitments are pointless. I think it's equivalent to just signing stuff with a key and making what you signed available for download in "the cloud".
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Excerpt of discussion about DIDs and ION Melvin Carvalho: > "Not a single entity I know that's doing production deployments has actually vetted did:ion and found it to be production capable." > > The guy leading the DID effort said this about ION. > > Seems like they may be 6 months away from producing something. > > https://github.com/decentralized-identity/ion/blob/master/docs/design.md#operations > > In their design it says you can create, update, recover and activate. It is a bit magic > > But update implies a versioning system. So you could think of it like updated nostr events. My key is A. Now my key is B. Tied to a content addressable static ID (like a genesis event ID). > > Let's see. I hope they produce something useful. Daniel tends not to answer questions > > When we first made DID, the idea was that your (d)id and your public key or hash were the same string. > > As it evolved, that got broken. Which can be useful because then you can have multiple keys, but the trade off is more management needed. > > So you have DID <—> controller two way link. Then it can have multiple keys. Those can be used to update the record. How that chain of records is stored, fetched and verified, is not covered by DID. So everyone will do it differently. Nostr for example could create updating keys with a NIP, it would do the same thing. Hampus: > Basically impossible to have a convo with Daniel Melvin Carvalho: > true. too often appeals to authority > > https://identity.foundation/sidetree/spec/#update > > the side tree spec has an update function > > 'Retrieve the Update Reveal Value that matches the previously anchored Update Commitment' > > so it looks like they have a chain of anchors ... anchored to something, ion nodes i guess, which also run btc full nodes > > > 'Embed the Anchor String in the transaction such that it can be located and parsed by any party that traverses the history of the target anchoring system' > > > 'By leveraging the blockchain-agnostic Sidetree protocol, ION makes it possible to anchor tens of thousands of DID/DPKI operations on a target chain (in ION's case, Bitcoin) using a single on-chain transaction' > > there you go > > do a search in the ion repo for 'anchor' and it gives some details > > https://github.com/decentralized-identity/ion/blob/66813123cf81ace05cea2039e93ef263952d6283/docs/Q-and-A.md > > there's a Q & A Ruben Somsen: > Their anchor protocol doesn't guarantee you have a full view of the data, so you can open the commitments to anything you like (provided you pre-committed to different views). In my opinion this makes the commitments pointless. Melvin Carvalho: > > 'Assuming you are running your own node, you simply need to submit 1000 create operations to your node (ie. http://localhost:3000/operations) before your batch writer kicks in every 10 minutes by default, the batch writer will batch all 1000 operations into 1 bitcoin transaction thus you'll pay fee for just one transaction to the minor. > > The technical spec for constructing a create request can be found in Sidetree API spec, but if you know TypeScript, you are better off using the ion-sdk directly, it will save you a lot of time' > > seems 3 places data is stored > > anchored witness data: bitcoin tx > batches of operations: ION nodes > non witness data: maybe IPFS > > 'The logical order of operations, as determined by the underlying anchoring system (e.g. Bitcoin block and transaction order). Anchoring systems may widely vary in how they determine the logical order of operations, but the only requirement of an anchoring system is that it can provide a means to deterministically order each operation within a DID’s operational lineage.' Ruben Somsen: > It's deterministic given a set of data, but there is no consensus on the set of data, so if A and B get presented with a different set, they come to a different conclusion Melvin Carvalho: > yes. "DID owners can create forks within their own DID state history". so you dont actually know the full state. I think the design is of each identity has eventual consistency, with the anchor as the tie break. It can change as you know more data. But doesnt say what happens if two updates happen in the same block. > > https://identity.foundation/sidetree/spec/#late-publishing > > the aim is eventual consistency > > so at any time you might have the wrong state, but if you had every update associated with a given id, you could determine the right order to apply the patches by using the bitcoin block chain (I dont know what happens if there's a tie in the same block) ... there's no peg in or peg out, it's just like version controlled files Ruben Somsen: > But you can't know when you've reached the state of eventual consistency (i.e. when you finally have the full data set) and in practice it may never be reached, so there is no consensus > > When there is conflicting data, the first one counts and the second one is ignored. > > This problem is literally detrimental, yet it is being presented as a minor inconvenience. Melvin Carvalho: > yes, and the first one can be published later, so systems will think the second is valid, until it isnt Ruben Somsen: > Yup Melvin Carvalho: > you could actually steal someone's identity, and revoke all their keys, and then reveal it years later > > arguably this is worse than github Ruben Somsen: > lol yeah you could Melvin Carvalho: > or an attack vector, get someone's ID, but they dont know, then sell them lots of 'cheap' NFTs ... at some point you publish the new keys and reclaim all the tokens ... no one will know when they will be rug pulled Ruben Somsen: > That was my original argument, but Daniel claimed the protocol wasn't meant for transfer of ownership rights. Melvin Carvalho: > so then i wonder what the primary use cases are that cant be easily achieved already > > > 'How Can ION be Used? > > ION can see a lot of use in many cases. The most obvious use case is for verifiable credentials. A business can credential employees, who can then be verified via blockchain on arrival at their destination. This functionality also raises its use as a means of supplying and verifying international travel documents.' > > > > 'Another use case could come from accreditation for organizations. Using an organization's public key, users can verify their accreditation status and trace their accreditation history over time.' > > so i guess its an updatable profile page, but you dont know when your profile is compromised. OTOH it's free (their node is paying fees to start with), and improves BTC security budget. If you keep your key safe, and the nodes publish the updates for you, it might be a nice little profile you could use for stuff. But not sure id use it for anything high value. And nostr (for example) can do alot of this already — updatable profiles and publishing > > i think it may be to a degree censorship resistant too > > there's also no incentive to run a node, so im not sure why they would stick around > > nodes can actually very easily censor by black listing certain tx (e.g. a hack, or sanctioned identity), removing the decentralized nature > > so the nodes can never reach consensus Ruben Somsen: > Like I said, the commitments are pointless. I think it's equivalent to just signing stuff with a key and making what you signed available for download in "the cloud". @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# A biblioteca infinita Agora esqueci o nome do conto de Jorge Luis Borges em que a tal biblioteca é descrita, ou seus detalhes específicos. Eu tinha lido o conto e nunca havia percebido que ele matava a questão da aleatoriedade ser capaz de produzir coisas valiosas. Precisei mesmo da [Wikipédia](https://en.wikipedia.org/wiki/Infinite_monkey_theorem) me dizer isso. Alguns anos atrás levantei essa questão para um grupo de amigos sem saber que era uma questão tão batida e baixa. No meu exemplo era um cachorro andando sobre letras desenhadas e não um macaco numa máquina de escrever. A minha conclusão da discussão foi que não importa o que o cachorro escrevesse, sem uma inteligência capaz de compreender aquilo nada passaria de letras aleatórias. Borges resolve tudo imaginando uma biblioteca que contém tudo o que o cachorro havia escrito durante todo o infinito em que fez o experimento, e portanto contém todo o conhecimento sobre tudo e todas as obras literárias possíveis -- mas entre cada página ou frase muito boa ou pelo menos legívei há toneladas de livros completamente aleatórios e uma pessoa pode passar a vida dentro dessa biblioteca que contém tanto conhecimento importante e mesmo assim não aprender nada porque nunca vai achar os livros certos. > Everything would be in its blind volumes. Everything: the detailed history of the future, Aeschylus' The Egyptians, the exact number of times that the waters of the Ganges have reflected the flight of a falcon, the secret and true nature of Rome, the encyclopedia Novalis would have constructed, my dreams and half-dreams at dawn on August 14, 1934, the proof of Pierre Fermat's theorem, the unwritten chapters of Edwin Drood, those same chapters translated into the language spoken by the Garamantes, the paradoxes Berkeley invented concerning Time but didn't publish, Urizen's books of iron, the premature epiphanies of Stephen Dedalus, which would be meaningless before a cycle of a thousand years, the Gnostic Gospel of Basilides, the song the sirens sang, the complete catalog of the Library, the proof of the inaccuracy of that catalog. Everything: but for every sensible line or accurate fact there would be millions of meaningless cacophonies, verbal farragoes, and babblings. Everything: but all the generations of mankind could pass before the dizzying shelves – shelves that obliterate the day and on which chaos lies – ever reward them with a tolerable page. Tenho a impressão de que a publicação gigantesca de artigos, posts, livros e tudo o mais está transformando o mundo nessa biblioteca. Há tanta coisa pra ler que é difícil achar o que presta. As pessoas precisam parar de escrever.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# A biblioteca infinita Agora esqueci o nome do conto de Jorge Luis Borges em que a tal biblioteca é descrita, ou seus detalhes específicos. Eu tinha lido o conto e nunca havia percebido que ele matava a questão da aleatoriedade ser capaz de produzir coisas valiosas. Precisei mesmo da [Wikipédia](https://en.wikipedia.org/wiki/Infinite_monkey_theorem) me dizer isso. Alguns anos atrás levantei essa questão para um grupo de amigos sem saber que era uma questão tão batida e baixa. No meu exemplo era um cachorro andando sobre letras desenhadas e não um macaco numa máquina de escrever. A minha conclusão da discussão foi que não importa o que o cachorro escrevesse, sem uma inteligência capaz de compreender aquilo nada passaria de letras aleatórias. Borges resolve tudo imaginando uma biblioteca que contém tudo o que o cachorro havia escrito durante todo o infinito em que fez o experimento, e portanto contém todo o conhecimento sobre tudo e todas as obras literárias possíveis -- mas entre cada página ou frase muito boa ou pelo menos legívei há toneladas de livros completamente aleatórios e uma pessoa pode passar a vida dentro dessa biblioteca que contém tanto conhecimento importante e mesmo assim não aprender nada porque nunca vai achar os livros certos. > Everything would be in its blind volumes. Everything: the detailed history of the future, Aeschylus' The Egyptians, the exact number of times that the waters of the Ganges have reflected the flight of a falcon, the secret and true nature of Rome, the encyclopedia Novalis would have constructed, my dreams and half-dreams at dawn on August 14, 1934, the proof of Pierre Fermat's theorem, the unwritten chapters of Edwin Drood, those same chapters translated into the language spoken by the Garamantes, the paradoxes Berkeley invented concerning Time but didn't publish, Urizen's books of iron, the premature epiphanies of Stephen Dedalus, which would be meaningless before a cycle of a thousand years, the Gnostic Gospel of Basilides, the song the sirens sang, the complete catalog of the Library, the proof of the inaccuracy of that catalog. Everything: but for every sensible line or accurate fact there would be millions of meaningless cacophonies, verbal farragoes, and babblings. Everything: but all the generations of mankind could pass before the dizzying shelves – shelves that obliterate the day and on which chaos lies – ever reward them with a tolerable page. Tenho a impressão de que a publicação gigantesca de artigos, posts, livros e tudo o mais está transformando o mundo nessa biblioteca. Há tanta coisa pra ler que é difícil achar o que presta. As pessoas precisam parar de escrever. @ 6bae33c8:607272e8
2024-08-03 19:21:12This is an overall list for 12-team NFFC PPR leagues _as of August 3, 2024_. **Note:** Rankings are real, but comments are not meant to be taken seriously. Warning: many, if not most, are stupid, though it can't be worse than [last year’s](https://www.realmansports.com/p/snarky150).  _(Right-click, open in new tab to enlarge)_
@ 6bae33c8:607272e8
2024-08-03 19:21:12This is an overall list for 12-team NFFC PPR leagues _as of August 3, 2024_. **Note:** Rankings are real, but comments are not meant to be taken seriously. Warning: many, if not most, are stupid, though it can't be worse than [last year’s](https://www.realmansports.com/p/snarky150).  _(Right-click, open in new tab to enlarge)_ @ 6c8c7979:15595f3e
2024-08-02 21:51:01When Mozart composed Symphony No. 40 in G minor, he was going through a difficult period in his life, facing financial problems and personal pressures. Despite these circumstances, the symphony is marked by significant emotional intensity and notable musical innovation. It is believed that the symphony reflected his internal tension and pain, making it one of his greatest and most impactful works. https://youtu.be/0sGqkMU-mGQ?si=FTIuMq8xo4bhvzDV https://youtu.be/JTc1mDieQI8?si=E-xd311z0yWQek3c
@ 6c8c7979:15595f3e
2024-08-02 21:51:01When Mozart composed Symphony No. 40 in G minor, he was going through a difficult period in his life, facing financial problems and personal pressures. Despite these circumstances, the symphony is marked by significant emotional intensity and notable musical innovation. It is believed that the symphony reflected his internal tension and pain, making it one of his greatest and most impactful works. https://youtu.be/0sGqkMU-mGQ?si=FTIuMq8xo4bhvzDV https://youtu.be/JTc1mDieQI8?si=E-xd311z0yWQek3c @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Qual é o economista? (piadas) O economista americano rapper ficou triste quando sua banda brasileira favorita encerrou suas atividades por crer que a demanda por discos de rap seria cada vez pior. Resposta: Robert Lucas e as expectativas dos Racionais. O economista inglês queria muito arrumar uma namorada. Resposta: John Maynard Keynes e a demanda afetiva. Quando o filho do economista austríaco chegou em casa todo sujo ele sem nem pensar ordenou que o moleque fosse tomar banho. Resposta: Friedrich Hayek e a ordem espontânea. O economista americano tinha muito orgulho de ter em sua casa um valiosíssimo quadro de um impressionista francês. Resposta: Milton Friedman e o Monet raríssimo. O economista austríaco jurou aos seus filhos que todos eles se mudariam para Brasília. Resposta: Eugen von Böhm-Bawerk e o “eu juro” da capital. O economista alemão organizou um evento meio sertanejo meio religioso e colocou como organizador uma executiva que tinha quebrado suas últimas 4 empresas por má administração. Resposta: Karl Marx e a expo-oração da que mais-falia.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Qual é o economista? (piadas) O economista americano rapper ficou triste quando sua banda brasileira favorita encerrou suas atividades por crer que a demanda por discos de rap seria cada vez pior. Resposta: Robert Lucas e as expectativas dos Racionais. O economista inglês queria muito arrumar uma namorada. Resposta: John Maynard Keynes e a demanda afetiva. Quando o filho do economista austríaco chegou em casa todo sujo ele sem nem pensar ordenou que o moleque fosse tomar banho. Resposta: Friedrich Hayek e a ordem espontânea. O economista americano tinha muito orgulho de ter em sua casa um valiosíssimo quadro de um impressionista francês. Resposta: Milton Friedman e o Monet raríssimo. O economista austríaco jurou aos seus filhos que todos eles se mudariam para Brasília. Resposta: Eugen von Böhm-Bawerk e o “eu juro” da capital. O economista alemão organizou um evento meio sertanejo meio religioso e colocou como organizador uma executiva que tinha quebrado suas últimas 4 empresas por má administração. Resposta: Karl Marx e a expo-oração da que mais-falia. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Batch for Trello Another Trello helper. This time it allowed people to perform batch actions on multiple cards, most notably delete a lot of cards at once. I created it because I wanted to delete a ton of spam from [Boardthreads](nostr:naddr1qqyxvwfk8p3xvdmrqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ceq46m6). - <https://github.com/fiatjaf/batch-for-trello> - <https://batch.cardsync.xyz/>
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Batch for Trello Another Trello helper. This time it allowed people to perform batch actions on multiple cards, most notably delete a lot of cards at once. I created it because I wanted to delete a ton of spam from [Boardthreads](nostr:naddr1qqyxvwfk8p3xvdmrqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823ceq46m6). - <https://github.com/fiatjaf/batch-for-trello> - <https://batch.cardsync.xyz/> @ fa984bd7:58018f52
2024-08-02 14:03:21Happy to announce a new major version of NDK. A lot of work has been going on behind the scenes to improve NDK in a lot of fronts. ## Optimistic Signature verification For most nostr apps, event signature verification is, by far, the most computationally-expensive part. If you've ever felt your phone getting a bit hot while using a nostr app, this is probably why. NDK introduces signature verification sampling. Each relay gets a lower and upper threshold of what ratio of events need to be verified. An unknown relay might start at getting 100% of it's events verified and, over time, lower the ratio to 50%. Whereas a relay the user has in their NIP-65 list might start at 50% and lower to 1%. When the same event is fetched from multiple relays, only the first time an event is seen (might) have it's signature verified. If the signature is verified, subsequent relays that send the same event ID **and** signature, have their ratio updated, further reducing the number of signatures we need to check. Relays should never send an invalid signature, so it only takes catching an evil relay lying about a signature **once**, to expel it from the pool and, perhaps, have the user add that relay to their relay blacklist event. In order to activate this feature, developers MUST explicitly handle receiving an invalid signature, as they should probably warn the user that some trickery is happening. 👉 [Tutorial](https://nostr-dev-kit.github.io/ndk/tutorial/speed.html#signature-verification-sampling) ## Nostr Cache Adapter A new cache adapter, which leverages, well, nostr. ndk-cache-nostr is a cache adapter that connects to a single local relay. This could be your a relay running in your user's computer/phone, like the nostr-tray-relay, Citrine, or it can even be a local relay you run in your server to assist in creating server-side-rendering. If you've been envious of njump previews when sharing a link, now you can implement the same in your app by leveraging this adapter in your SSR calls. 👉 [Docs](https://nostr-dev-kit.github.io/ndk/cache/nostr.html) ## Refactored Zapping interface This is the one breaking change; the code for sending zaps was tightly coupled to the assumption that LN was the interface. This new interface abstracts away the funding mechanism (NWC, WebLN, built-in-wallet) and the delivery mechanism (LN, ecash, Rai stones) # ## Major subscription Lifecycle refactor The core of how NDK works was completely refactored from the ground-up, removing a lot of dependencies from nostr-tools, and bringing a lot of clarity to how NDK orchestrates subscriptions at the relay level. 👉 [NDK Internal's documentation](https://nostr-dev-kit.github.io/ndk/internals/subscriptions.html) ## Tutorials and other stuff A few months ago I started a new effort to write more high-level documentation, instead of focusing on interface specs of NDK. https://nostr-dev-kit.github.io/ndk is the ongoing result. # ndk-wallet A new NDK extension package, provides access to nostr-native NIP-60 wallets. NIP-60 is a new NIP that proposes a nostr-native wallet that follows a user around any nostr application. Instead of having to manage a bunch of different NWC tokens, implement LN on their own, NIP-60 leverages multiple ecash mints, making it completely frictionless to onboard into Nostr with the capability to send and receive (via NIP-61 or a proxy like npub.cash) zaps. ndk-wallet is the wallet that Nutsack.me is built on, providing: - wallet creation/discovery - token verification - nutzap redemption - UTXO management - balance tracking With this package you'll be able to give your users a non-kyc wallet from which they can send both NIP-61 nutzaps and the usual NIP-57 lightning zaps.
@ fa984bd7:58018f52
2024-08-02 14:03:21Happy to announce a new major version of NDK. A lot of work has been going on behind the scenes to improve NDK in a lot of fronts. ## Optimistic Signature verification For most nostr apps, event signature verification is, by far, the most computationally-expensive part. If you've ever felt your phone getting a bit hot while using a nostr app, this is probably why. NDK introduces signature verification sampling. Each relay gets a lower and upper threshold of what ratio of events need to be verified. An unknown relay might start at getting 100% of it's events verified and, over time, lower the ratio to 50%. Whereas a relay the user has in their NIP-65 list might start at 50% and lower to 1%. When the same event is fetched from multiple relays, only the first time an event is seen (might) have it's signature verified. If the signature is verified, subsequent relays that send the same event ID **and** signature, have their ratio updated, further reducing the number of signatures we need to check. Relays should never send an invalid signature, so it only takes catching an evil relay lying about a signature **once**, to expel it from the pool and, perhaps, have the user add that relay to their relay blacklist event. In order to activate this feature, developers MUST explicitly handle receiving an invalid signature, as they should probably warn the user that some trickery is happening. 👉 [Tutorial](https://nostr-dev-kit.github.io/ndk/tutorial/speed.html#signature-verification-sampling) ## Nostr Cache Adapter A new cache adapter, which leverages, well, nostr. ndk-cache-nostr is a cache adapter that connects to a single local relay. This could be your a relay running in your user's computer/phone, like the nostr-tray-relay, Citrine, or it can even be a local relay you run in your server to assist in creating server-side-rendering. If you've been envious of njump previews when sharing a link, now you can implement the same in your app by leveraging this adapter in your SSR calls. 👉 [Docs](https://nostr-dev-kit.github.io/ndk/cache/nostr.html) ## Refactored Zapping interface This is the one breaking change; the code for sending zaps was tightly coupled to the assumption that LN was the interface. This new interface abstracts away the funding mechanism (NWC, WebLN, built-in-wallet) and the delivery mechanism (LN, ecash, Rai stones) # ## Major subscription Lifecycle refactor The core of how NDK works was completely refactored from the ground-up, removing a lot of dependencies from nostr-tools, and bringing a lot of clarity to how NDK orchestrates subscriptions at the relay level. 👉 [NDK Internal's documentation](https://nostr-dev-kit.github.io/ndk/internals/subscriptions.html) ## Tutorials and other stuff A few months ago I started a new effort to write more high-level documentation, instead of focusing on interface specs of NDK. https://nostr-dev-kit.github.io/ndk is the ongoing result. # ndk-wallet A new NDK extension package, provides access to nostr-native NIP-60 wallets. NIP-60 is a new NIP that proposes a nostr-native wallet that follows a user around any nostr application. Instead of having to manage a bunch of different NWC tokens, implement LN on their own, NIP-60 leverages multiple ecash mints, making it completely frictionless to onboard into Nostr with the capability to send and receive (via NIP-61 or a proxy like npub.cash) zaps. ndk-wallet is the wallet that Nutsack.me is built on, providing: - wallet creation/discovery - token verification - nutzap redemption - UTXO management - balance tracking With this package you'll be able to give your users a non-kyc wallet from which they can send both NIP-61 nutzaps and the usual NIP-57 lightning zaps. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# my personal approach on using `let`, `const` and `var` in javascript Since these names can be used interchangeably almost everywhere and there are a lot of people asking and searching on the internet on how to use them (myself included until some weeks ago), I developed a personal approach that uses the declarations mostly as readability and code-sense sugar, for helping my mind, instead of expecting them to add physical value to the programs. --- `let` is only for short-lived variables, defined at a single line and not changed after. Generally those variables which are there only to decrease the amount of typing. For example: for (let key in something) { /* we could use `something[key]` for this entire block, but it would be too much letters and not good for the fingers or the eyes, so we use a radically temporary variable */ let value = something[key] ... } `const` for all _names_ known to be constant across the entire module. Not including locally constant values. The `value` in the example above, for example, is constant in its scope and could be declared with `const`, but since there are many iterations and for each one there's a value with same **name**, "value", that could trick the reader into thinking `value` is always the same. Modules and functions are the best example of `const` variables: const PouchDB = require('pouchdb') const instantiateDB = function () {} const codes = { 23: 'atc', 43: 'qwx', 77: 'oxi' } `var` for everything that may or not be variable. Names that may confuse people reading the code, even if they are constant locally, and are not suitable for `let` (i.e., they are not completed in a simple direct declaration) apply for being declared with `var`. For example: var output = '\n' lines.forEach(line => { output += ' ' output += line.trim() output += '\n' }) output += '\n---' for (let parent in parents) { var definitions = {} definitions.name = getName(parent) definitions.config = {} definitions.parent = parent }
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# my personal approach on using `let`, `const` and `var` in javascript Since these names can be used interchangeably almost everywhere and there are a lot of people asking and searching on the internet on how to use them (myself included until some weeks ago), I developed a personal approach that uses the declarations mostly as readability and code-sense sugar, for helping my mind, instead of expecting them to add physical value to the programs. --- `let` is only for short-lived variables, defined at a single line and not changed after. Generally those variables which are there only to decrease the amount of typing. For example: for (let key in something) { /* we could use `something[key]` for this entire block, but it would be too much letters and not good for the fingers or the eyes, so we use a radically temporary variable */ let value = something[key] ... } `const` for all _names_ known to be constant across the entire module. Not including locally constant values. The `value` in the example above, for example, is constant in its scope and could be declared with `const`, but since there are many iterations and for each one there's a value with same **name**, "value", that could trick the reader into thinking `value` is always the same. Modules and functions are the best example of `const` variables: const PouchDB = require('pouchdb') const instantiateDB = function () {} const codes = { 23: 'atc', 43: 'qwx', 77: 'oxi' } `var` for everything that may or not be variable. Names that may confuse people reading the code, even if they are constant locally, and are not suitable for `let` (i.e., they are not completed in a simple direct declaration) apply for being declared with `var`. For example: var output = '\n' lines.forEach(line => { output += ' ' output += line.trim() output += '\n' }) output += '\n---' for (let parent in parents) { var definitions = {} definitions.name = getName(parent) definitions.config = {} definitions.parent = parent } @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# localchat A server that creates instant chat rooms with [Server-Sent Events](https://en.wikipedia.org/wiki/Server-sent_events) and normal HTTP `POST` requests (instead of WebSockets which are an overkill most of the times). It defaults to a room named as your public IP, so if two machines in the same LAN connect they'll be in the same chat automatically -- but then you can also join someone else's LAN if you need. This is supposed to be useful.  - <https://github.com/fiatjaf/localchat> - <https://localchat.bigsun.xyz/> ## See also - [Filemap](nostr:naddr1qqyrwcekv33rze3kqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c23ya8a)
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# localchat A server that creates instant chat rooms with [Server-Sent Events](https://en.wikipedia.org/wiki/Server-sent_events) and normal HTTP `POST` requests (instead of WebSockets which are an overkill most of the times). It defaults to a room named as your public IP, so if two machines in the same LAN connect they'll be in the same chat automatically -- but then you can also join someone else's LAN if you need. This is supposed to be useful.  - <https://github.com/fiatjaf/localchat> - <https://localchat.bigsun.xyz/> ## See also - [Filemap](nostr:naddr1qqyrwcekv33rze3kqyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c23ya8a) @ 9a4acdeb:1489913b
2024-07-31 14:42:31#### TL;DR - Embracing Bitcoin will not be the downfall of the US financial system; rather, it will save it. This demand will be good for Bitcoin, too. There is no doubt the largest market for Bitcoin trading is in the US. Bitcoin and dollars are traded for each other more than any other fiat-Bitcoin pair. The USD remains the highest volume asset on the global stage, however, trust in the dollar wanes on it as well. A great amount of uncertainty remains about Bitcoin in the public, but the public is becoming increasingly aware. At some point, the "then suddenly" threshold, when uncertainty about the dollar matches the uncertainty of Bitcoin in the public eye, a great and rapid flip will occur. ## Retirement Will Become Impossible Unless Backed by Unprintable Money It is this flip that will cause enormous and unprecedented loss for at least the aging population in the US, as well as holders of large amounts of cash. Let us focus on one aspect of this great loss: social security, which is already known to be at great risk, an almost certain bankruptcy of the whole system only a few years away, and this is only if the US dollar lasts that long. The responsibility of this failure rests on the shoulders of the US Federal Government and the Federal Reserve. Salvation for the system will only be in one manner: backing the fund with Bitcoin. ## A Strategic Reserve If the US Government funded a strategic Bitcoin reserve rather than wars, the issuance of USD could be then exchanged for payouts in the form of Bitcoin. Retirees who depend on those monthly checks could instead receive Bitcoin. This would be reparation for the theft of the wealth promised by the system to begin, and it would be an efficient way to do so. While the USD-BTC rate is still in the 5-figures, investments into it can see returns of hundreds times by the time Social Security becomes fully defunct. This window of opportunity is quickly closing. Returns in the tens of times should still be possible for a few years, but likely not past the year 2029. ## This Will Also be Good for Bitcoin The urgency is high. To avoid a cataclysm for our aging population, the US needs Bitcoin, and because of the demand this will generate, the adoption and valuation of Bitcoin can accelerate. This is but one mode that Bitcoin will save the US economy, and more is to come.
@ 9a4acdeb:1489913b
2024-07-31 14:42:31#### TL;DR - Embracing Bitcoin will not be the downfall of the US financial system; rather, it will save it. This demand will be good for Bitcoin, too. There is no doubt the largest market for Bitcoin trading is in the US. Bitcoin and dollars are traded for each other more than any other fiat-Bitcoin pair. The USD remains the highest volume asset on the global stage, however, trust in the dollar wanes on it as well. A great amount of uncertainty remains about Bitcoin in the public, but the public is becoming increasingly aware. At some point, the "then suddenly" threshold, when uncertainty about the dollar matches the uncertainty of Bitcoin in the public eye, a great and rapid flip will occur. ## Retirement Will Become Impossible Unless Backed by Unprintable Money It is this flip that will cause enormous and unprecedented loss for at least the aging population in the US, as well as holders of large amounts of cash. Let us focus on one aspect of this great loss: social security, which is already known to be at great risk, an almost certain bankruptcy of the whole system only a few years away, and this is only if the US dollar lasts that long. The responsibility of this failure rests on the shoulders of the US Federal Government and the Federal Reserve. Salvation for the system will only be in one manner: backing the fund with Bitcoin. ## A Strategic Reserve If the US Government funded a strategic Bitcoin reserve rather than wars, the issuance of USD could be then exchanged for payouts in the form of Bitcoin. Retirees who depend on those monthly checks could instead receive Bitcoin. This would be reparation for the theft of the wealth promised by the system to begin, and it would be an efficient way to do so. While the USD-BTC rate is still in the 5-figures, investments into it can see returns of hundreds times by the time Social Security becomes fully defunct. This window of opportunity is quickly closing. Returns in the tens of times should still be possible for a few years, but likely not past the year 2029. ## This Will Also be Good for Bitcoin The urgency is high. To avoid a cataclysm for our aging population, the US needs Bitcoin, and because of the demand this will generate, the adoption and valuation of Bitcoin can accelerate. This is but one mode that Bitcoin will save the US economy, and more is to come. @ 9e915942:f8133dec
2024-08-15 13:49:09# I am not a therapist *Part one of a three-part series called "Breaking my silence on social-emotional learning"*  I’ve been suspicious of “social-emotional circles” since I learned about them, several years ago. My first concern was how to fit this practice into a curriculum in which two snow days can mean I have to cut content. However, my second and more substantive concern, was that, put simply, I am not a therapist and am not equipped to lead an exercise like this. After reading [Bad Therapy: Why the kids aren’t growing up](https://www.amazon.com/Bad-Therapy-Kids-Arent-Growing/dp/B0CK524HQ7/ref=sr_1_1?crid=K3BX6HYW2282&dib=eyJ2IjoiMSJ9.zT54L8v7fDcZziZJoty4xkAenFGGXrIHltBdsJvPVtgM9OYYEbbvONPltyZX28UkmBYq6-eiBaSQN4usXHU3JrVMOyhFIi_WykOauizG0qrRRVgi3JM3GvC-YNlReHNHOdj_q1PJNWVkM7omlysAvKMyy9bUJa-SMmKFQZgmn5H7vvhKdVBM9h7gbuXd1FRCmrFbN6rmKR3oEFxKHxhaMBor5VYaZGwOfmybOxniLvU.CwGO3v___93oYeo4IB0uVCkKhBedknOwISBCLcEQwuE&dib_tag=se&keywords=bad+therapy+abigail+shrier&qid=1722781693&sprefix=%2Caps%2C276&sr=8-1), by Abigail Shier, I’m not only convinced that I shouldn’t do these in my classroom, I think they should rarely be done in classrooms at all. While this and the next couple of posts will focus on circles, the book has raised many flags for me about things we routinely do in schools intended to help kids’ mental health. She argues we, the well-intentioned people who work with young people, frequently commit iatrogenesis (harm caused by those attempting to heal) and argues that many of our best-intentioned interventions likely cause more harm than benefit. I chose circles for a couple reasons. First, it’s relevant to many teachers because it – along with restorative practices, social-emotional learning (SEL) generally, and trauma-informed education – has become quite popular over the last several years. Second, it provides a concrete case study that exemplifies broader issues with SEL in schools. For those of you unfamiliar with restorative circles, I’ll try to give you the TL:DR. A teacher puts the students in her class in a circle. Basically she then goes around the circle and everyone has the opportunity to share something. There are many variations on this. The teacher might ask students to share how they are feeling that day (check-in style circle), something their struggling with recently or something good that’s happened, or how something that happened in class - like an outburst by a student, for example - made them feel. All of these types or circles have been suggested in the trainings that I’ve attended to varying degrees. (You can read more about restorative circles [here](https://www.edutopia.org/article/building-community-restorative-circles/), which explains in detail more or less the what I’ve learned about them in trainings.) For now, I want to focus on the more “meaningful” types of circles, not the “check-in” types. These are designed to help students build empathy and other social-emotional skills as well as help students process something they, or the class as a whole, is going through. (Although Shier has convinced me that the check-in style circles are a bad practice as well – an argument I plan to flesh out in part three.) ### I am not a therapist You might be wondering, if a teacher has time to do them, what could be the harm in doing these regularly with students? Wouldn’t they help build a stronger classroom community? Let’s suppose that time is not an issue. The biggest problem I see is that *I am not a therapist* and nearly every teacher is not trained as a therapist either. I remember sitting in trainings and imagining situations in which I’m running a circle and a kid shares something and bursts into tears. Or shares something deeply personal that maybe they shouldn’t have shared with me or their peers. Or calls out another student in class for some reason, creating a conflict in front of the entire class. Whenever circles were described to me it felt like a description of group therapy, and I am simply not trained to handle the variety of situations that might arise in group therapy. In fact, if you really want to see how closely they resemble each other, check out [this page by the counseling Center Group for group therapy in New York City](https://counselingcentergroup.com/group-therapy-in-nyc/) and compare it the description of circles in the article I linked above. You’ll find a lot of common themes, although the group therapy article emphasizes repeatedly that *trained therapists* will be leading the groups. I’ve raised this concern with individual colleagues and in various meetings over the last several years, including recently at a district-level diversity, equity, and inclusion task force meeting. This is not a direct quote, but I’m most often met with some flavor of the following, either from a teacher who uses circles often, an education consultant leading professional development, or an administrator who has seen teachers run them: > Most of the time these concerns aren’t an issue. Kids don’t share those kinds of things. If anything gets shared beyond what you think you can handle, you can always end the circle and bring in a school counselor to help you with that individual student or to help you run the circle again to address what happened. Maybe you should work with a teacher who does circles often to help you feel more comfortable. Sometimes other tips are also shared at this point – a sort of ad hoc list of group therapy hacks. Start doing circles with light-hearted prompts to help build community, they might say. Make sure students know they can “pass” and don’t have to share if they don’t want to share. Don’t pass judgement on what students share, be empathic, ask open questions instead of closed questions. And so on. This is akin to taking a truck driver and giving him a three-hour training on driving a school bus and telling him he can start a bus route next week. When he says he’s not sure that he can actually pull that off, he’s told that “opening the door is actually pretty easy to figure out, remember to take wide turns, and don’t forget to stop at every railroad crossing. I’ll let you talk with Sam – he’s been driving bus on the side for years! I’m sure you’ll do great!” Are there similarities between driving a semi-truck and trailer and a school bus? Of course. Are there some truck drivers who could make the switch and be just fine after some practice? Certainly. Will there be many accidents, some of which are avoidable and catastrophic? If this practice continues long enough – absolutely. Similarly, some interpersonal skills required to teach overlap with those needed by therapists, surely some teachers would be good therapists with minimal training, and having this as a practice by an institution will almost certainly lead to kids being victims of mishandled situations (iatrogenesis). ### Bad therapy in circles - a specific example Undoubtedly, many bad therapy practices are hidden from me because I don’t have the expertise to know what I don’t know, but I want to share one bad practice that Shier writes about to help make my point – therapist self-disclosure. When educators are taught about circles we are told that if we share personal stories then we will build trust with our students and this will encourage them to share more as well. From the [Edutopia article](https://www.edutopia.org/article/building-community-restorative-circles/) linked above, we are told, “Share authentically of yourself. This gives others permission to do the same.” Unfortunately, this is usually unethical according to Shier (she cites [this paper](https://societyforpsychotherapy.org/the-big-reveal-ethical-implications-of-therapist-self-disclosure/), which doesn’t argue that self-disclosure is *always* unethical, but that it is a very nuanced question in psychotherapy and that generally erring away from self-disclosure is best; which reiterates my argument since, as I’m not trained in psychotherapy, I’m not even aware of the aspects of it which are nuanced or settled or debated. But, I digress). Shier writes about a teacher (Kendra Jones, cited from this [Education Week article](https://www.edweek.org/leadership/why-its-so-hard-to-weave-social-emotional-learning-into-academics/2022/11)) who is “very vulnerable” with her students and goes on to say the following: > Interestingly, were Jones an actual therapist, such self disclosure would be considered unethical. Anytime a therapist might be inclined to share her personal history in order to gratify her own need, she must abstain in order to prioritize the clients needs. And here’s where things get tricky: teachers aren't actually trained in psychotherapy, and they aren't bound by its ethical guidelines, either. Setting up an “emotional sharing” session may sound good, but typically, therapists perform this function under ethical guidelines, so that they don't inadvertently exploit or betray their patients. Are the nuances of psychotherapy explored in trainings about restorative circles? Of course not. Because the trainers know that we aren’t therapists! Again, when I have raised this issue I’m told that this should not really be a concern - if you think anything is beyond what you can handle, get support from one of the school counselors. SEL circles exist in a superposition of importance; they are simultaneously innocuous enough that a teacher needn’t worry about not being trained in psychotherapy, but important enough that every teacher should be working to integrate them in all of their classes. The problems with SEL circles go beyond my lack of training in psychotherapy. In the next post I will explore the issues of confidentiality in circles and in part three explain how even if I was a therapist and we could somehow erase the issue of confidentiality, we *still* shouldn’t try to make circles a common practice. *Disclaimer: I realize that in writing this and publishing it publicly I run the risk of upsetting some friends, colleagues, and, potentially, administrators. Unfortunately, there are times when that risk must be taken in order to say what is true, needs to be said, and is not being said. I write this while passing no bad judgement on any educator who has implemented restorative circles or other restorative and social-emotional learning practices in their school or classroom. We have had countless trainers in countless hours of professional development the last several years telling us that this is best for kids – that kids will learn better and be more emotionally healthy if we do this. I don’t fault anyone for doing what we were told by the experts was best practice. I hope only to illuminate a contrary perspective that, in my opinion and experience, has significant ramifications if we are to truly do what’s best for our students.*
@ 9e915942:f8133dec
2024-08-15 13:49:09# I am not a therapist *Part one of a three-part series called "Breaking my silence on social-emotional learning"*  I’ve been suspicious of “social-emotional circles” since I learned about them, several years ago. My first concern was how to fit this practice into a curriculum in which two snow days can mean I have to cut content. However, my second and more substantive concern, was that, put simply, I am not a therapist and am not equipped to lead an exercise like this. After reading [Bad Therapy: Why the kids aren’t growing up](https://www.amazon.com/Bad-Therapy-Kids-Arent-Growing/dp/B0CK524HQ7/ref=sr_1_1?crid=K3BX6HYW2282&dib=eyJ2IjoiMSJ9.zT54L8v7fDcZziZJoty4xkAenFGGXrIHltBdsJvPVtgM9OYYEbbvONPltyZX28UkmBYq6-eiBaSQN4usXHU3JrVMOyhFIi_WykOauizG0qrRRVgi3JM3GvC-YNlReHNHOdj_q1PJNWVkM7omlysAvKMyy9bUJa-SMmKFQZgmn5H7vvhKdVBM9h7gbuXd1FRCmrFbN6rmKR3oEFxKHxhaMBor5VYaZGwOfmybOxniLvU.CwGO3v___93oYeo4IB0uVCkKhBedknOwISBCLcEQwuE&dib_tag=se&keywords=bad+therapy+abigail+shrier&qid=1722781693&sprefix=%2Caps%2C276&sr=8-1), by Abigail Shier, I’m not only convinced that I shouldn’t do these in my classroom, I think they should rarely be done in classrooms at all. While this and the next couple of posts will focus on circles, the book has raised many flags for me about things we routinely do in schools intended to help kids’ mental health. She argues we, the well-intentioned people who work with young people, frequently commit iatrogenesis (harm caused by those attempting to heal) and argues that many of our best-intentioned interventions likely cause more harm than benefit. I chose circles for a couple reasons. First, it’s relevant to many teachers because it – along with restorative practices, social-emotional learning (SEL) generally, and trauma-informed education – has become quite popular over the last several years. Second, it provides a concrete case study that exemplifies broader issues with SEL in schools. For those of you unfamiliar with restorative circles, I’ll try to give you the TL:DR. A teacher puts the students in her class in a circle. Basically she then goes around the circle and everyone has the opportunity to share something. There are many variations on this. The teacher might ask students to share how they are feeling that day (check-in style circle), something their struggling with recently or something good that’s happened, or how something that happened in class - like an outburst by a student, for example - made them feel. All of these types or circles have been suggested in the trainings that I’ve attended to varying degrees. (You can read more about restorative circles [here](https://www.edutopia.org/article/building-community-restorative-circles/), which explains in detail more or less the what I’ve learned about them in trainings.) For now, I want to focus on the more “meaningful” types of circles, not the “check-in” types. These are designed to help students build empathy and other social-emotional skills as well as help students process something they, or the class as a whole, is going through. (Although Shier has convinced me that the check-in style circles are a bad practice as well – an argument I plan to flesh out in part three.) ### I am not a therapist You might be wondering, if a teacher has time to do them, what could be the harm in doing these regularly with students? Wouldn’t they help build a stronger classroom community? Let’s suppose that time is not an issue. The biggest problem I see is that *I am not a therapist* and nearly every teacher is not trained as a therapist either. I remember sitting in trainings and imagining situations in which I’m running a circle and a kid shares something and bursts into tears. Or shares something deeply personal that maybe they shouldn’t have shared with me or their peers. Or calls out another student in class for some reason, creating a conflict in front of the entire class. Whenever circles were described to me it felt like a description of group therapy, and I am simply not trained to handle the variety of situations that might arise in group therapy. In fact, if you really want to see how closely they resemble each other, check out [this page by the counseling Center Group for group therapy in New York City](https://counselingcentergroup.com/group-therapy-in-nyc/) and compare it the description of circles in the article I linked above. You’ll find a lot of common themes, although the group therapy article emphasizes repeatedly that *trained therapists* will be leading the groups. I’ve raised this concern with individual colleagues and in various meetings over the last several years, including recently at a district-level diversity, equity, and inclusion task force meeting. This is not a direct quote, but I’m most often met with some flavor of the following, either from a teacher who uses circles often, an education consultant leading professional development, or an administrator who has seen teachers run them: > Most of the time these concerns aren’t an issue. Kids don’t share those kinds of things. If anything gets shared beyond what you think you can handle, you can always end the circle and bring in a school counselor to help you with that individual student or to help you run the circle again to address what happened. Maybe you should work with a teacher who does circles often to help you feel more comfortable. Sometimes other tips are also shared at this point – a sort of ad hoc list of group therapy hacks. Start doing circles with light-hearted prompts to help build community, they might say. Make sure students know they can “pass” and don’t have to share if they don’t want to share. Don’t pass judgement on what students share, be empathic, ask open questions instead of closed questions. And so on. This is akin to taking a truck driver and giving him a three-hour training on driving a school bus and telling him he can start a bus route next week. When he says he’s not sure that he can actually pull that off, he’s told that “opening the door is actually pretty easy to figure out, remember to take wide turns, and don’t forget to stop at every railroad crossing. I’ll let you talk with Sam – he’s been driving bus on the side for years! I’m sure you’ll do great!” Are there similarities between driving a semi-truck and trailer and a school bus? Of course. Are there some truck drivers who could make the switch and be just fine after some practice? Certainly. Will there be many accidents, some of which are avoidable and catastrophic? If this practice continues long enough – absolutely. Similarly, some interpersonal skills required to teach overlap with those needed by therapists, surely some teachers would be good therapists with minimal training, and having this as a practice by an institution will almost certainly lead to kids being victims of mishandled situations (iatrogenesis). ### Bad therapy in circles - a specific example Undoubtedly, many bad therapy practices are hidden from me because I don’t have the expertise to know what I don’t know, but I want to share one bad practice that Shier writes about to help make my point – therapist self-disclosure. When educators are taught about circles we are told that if we share personal stories then we will build trust with our students and this will encourage them to share more as well. From the [Edutopia article](https://www.edutopia.org/article/building-community-restorative-circles/) linked above, we are told, “Share authentically of yourself. This gives others permission to do the same.” Unfortunately, this is usually unethical according to Shier (she cites [this paper](https://societyforpsychotherapy.org/the-big-reveal-ethical-implications-of-therapist-self-disclosure/), which doesn’t argue that self-disclosure is *always* unethical, but that it is a very nuanced question in psychotherapy and that generally erring away from self-disclosure is best; which reiterates my argument since, as I’m not trained in psychotherapy, I’m not even aware of the aspects of it which are nuanced or settled or debated. But, I digress). Shier writes about a teacher (Kendra Jones, cited from this [Education Week article](https://www.edweek.org/leadership/why-its-so-hard-to-weave-social-emotional-learning-into-academics/2022/11)) who is “very vulnerable” with her students and goes on to say the following: > Interestingly, were Jones an actual therapist, such self disclosure would be considered unethical. Anytime a therapist might be inclined to share her personal history in order to gratify her own need, she must abstain in order to prioritize the clients needs. And here’s where things get tricky: teachers aren't actually trained in psychotherapy, and they aren't bound by its ethical guidelines, either. Setting up an “emotional sharing” session may sound good, but typically, therapists perform this function under ethical guidelines, so that they don't inadvertently exploit or betray their patients. Are the nuances of psychotherapy explored in trainings about restorative circles? Of course not. Because the trainers know that we aren’t therapists! Again, when I have raised this issue I’m told that this should not really be a concern - if you think anything is beyond what you can handle, get support from one of the school counselors. SEL circles exist in a superposition of importance; they are simultaneously innocuous enough that a teacher needn’t worry about not being trained in psychotherapy, but important enough that every teacher should be working to integrate them in all of their classes. The problems with SEL circles go beyond my lack of training in psychotherapy. In the next post I will explore the issues of confidentiality in circles and in part three explain how even if I was a therapist and we could somehow erase the issue of confidentiality, we *still* shouldn’t try to make circles a common practice. *Disclaimer: I realize that in writing this and publishing it publicly I run the risk of upsetting some friends, colleagues, and, potentially, administrators. Unfortunately, there are times when that risk must be taken in order to say what is true, needs to be said, and is not being said. I write this while passing no bad judgement on any educator who has implemented restorative circles or other restorative and social-emotional learning practices in their school or classroom. We have had countless trainers in countless hours of professional development the last several years telling us that this is best for kids – that kids will learn better and be more emotionally healthy if we do this. I don’t fault anyone for doing what we were told by the experts was best practice. I hope only to illuminate a contrary perspective that, in my opinion and experience, has significant ramifications if we are to truly do what’s best for our students.* @ 66df6056:f3203c64
2024-07-31 13:17:15แนวคิดอันนี้เกิดขึ้นหลังจากที่ผมได้รู้จัก LFS หรือ Log- structure File System มันทำให้ผมเกิดความคิดว่าในเมื่อมันสามารถที่จะเก็บ file และทุก log ของการเปลี่ยนแปลงในแต่ละไฟล์ งั้นแปลว่าในกรณีที่ file โดน encrypt มันก็น่าจะสามารถกู้คืนมาได้สิ เอ้ะแต่ถ้าเครื่องนั้นโดน ransomware ไปรอบนึงแล้วกู้คืนมาแล้วมันก็โดนอีกอยู่ดีมั้ย เลยเกิดไอเดียใหม่ว่าแล้วถ้าเราหา SSD อีกลูกมาเก็บ backup ถ้าโดน ransomware ก็ถอดไปเสียบเครื่องใหม่ก็จบ ตะตะแต่ว่า LFS เนี่ย ดั้นนนใช้ไม่ได้กับ windows หรือ Mac เอาละ ปัญหาใหม่มาอีกละ งั้นต้องทำไงล่ะ ? หึเก็บไว้บอกท้ายบทความละกัน มาทำความเข้าใจโปรเจคนี้กันทีละขั้นตอนกันดีกว่า Log-structure File System (LFS) ----------- เป็น File system รูปแบบหนึ่งที่จะทำการเก็บข้อมูลเป็น log และสามารถย้อนกลับได้ทุกการกระทำ นอกจากมีความถี่ในการสร้าง snapshot ที่สูงมาก จริง ๆ แล้วเหมาะกับงานประเภทที่ต้องการความต่อเนื่องหากดบัไปต้องกู้คืนได้มากที่สุดเท่าที่เป็นไปได้ แต่เพราะไอความสามารถตรงนั้นของมันนี่แหละ ที่ผมมองว่ามันน่าจะหยิบมาใช้กับการกู้คืน file หลังจากโดน ransomware ได้แน่ ๆ โดยในครั้งนี้ผมเลือกใช้เป็น NILFS2 เนื่องจากดูแล้วน่าจะเหลือตัวเดียวที่ยังพอมีการพัฒนาอยู่ 5555 รูปแบบการเก็บข้อมูลจะเหมือนกับภาพด้านล่างนี้  ตัวอย่าง: เดิมที file A: "AAAAA" จากนั้นผมได้ทำการอัพเดตข้อมูลใน file A เป็น "BBBBB" ด้วยความสามารถของ LFS มันสามารถที่จะดึง file A เวอร์ชันที่เป็น "AAAAA" กลับมาได้ นี่เป็นปัจจัยสำคัญที่ทำให้ผมมองว่า LFS เหมาะสมที่จะมาเป็นระบบไฟล์ที่ใช้ในการสำรองข้อมูล แต่อยากที่ได้กล่าวไว้ข้างต้นว่าปัญหาของระบบไฟล์นี้คือมันใช้พื้นที่เก็บข้อมูลค่อนข้างสูง และมี write speed ที่ค่อนข้างช้า ถ้าเทียบกับระบบไฟล์อื่น ๆ ในกรณีที่ความเร็วของ SSD เท่ากัน เลยมองว่าถ้าจะใช้เป็นระบบหลักในการเก็บข้อมูลทุกอย่างคงจะไม่เหมาะ เลยนำไปสู่การทำระบบโดยใช้ระบบไฟล์สองแบบที่แตกต่างกัน System Design ----------- อย่างที่ได้พูดถึงข้อเสียของ NILFS2 ไปข้างต้น แปลว่าถ้าอยากจะให้คอมพิวเตอร์ทำงานได้อย่างมีประสิทธิภาพคงเดิมและสามารถป้องกัน ransomware ได้ด้วยก็จำเป็นต้องมีระบบไฟล์ที่ใช้กันทั่วไปอย่าง FAT32 หรือ ext4 และใช้ SSD อีกลูกหนึ่งที่ format เป็น NILFS2 และเขียนโปรแกรมให้คอยมอนิเตอร์ทุก ๆ กิจกรรมบน user space และทุกครั้งที่เกิดการเขียนไฟล์ขึ้นให้เขียนลงใน SSD ที่เป็น NILFS2 ด้วย ดังภาพที่แสดงด้านล่างนี้  แล้วทำไมไฟล์ในลูกที่เก็บสำรองข้อมูลถึงไม่เท่ากับจำนวนไฟล์ในที่เก็บข้อมูลหลักล่ะ ? เนื่องด้วยความเร็วในการเขียนที่ค่อนข้างแตกต่างกันของทั้งสอง ผมเลยมองว่าถ้าเราเก็บในรูปแบบบล๊อกจะทำให้เก็บข้อมูลได้ไวกว่า อย่างตัวอย่างในรูป สมมุติว่าไฟล์ A มีขนาดประมาณ 3 บล๊อกใน SSD ที่เป็น nilfs2 ก็จะมี 3 ไฟล์และต้องใช้ทั้งสามไฟล์เพื่อที่จะคืนค่าไฟล์ A กลับมา ถ้าอ่านมาถึงตรงนี้อาจจะเกิดข้อสงสัยว่า แล้วจะทำให้มันยุ่งยากทำไม คัดลอกไฟล์มาใส่ก็จบแล้วมั้ย ? ก็ใช่แหละและจริง ๆ ผมคิดว่าทำแบบนั้นก็เพียงพอ แต่ว่าอย่างที่บอกไปข้างต้น ผมอยากได้ระบบที่ป้องกันได้ 100% ผมเลยเลือกที่จะมอนิเตอร์ kernel เอาไว้และเมื่อมีการเขียนไฟล์เกิดขึ้นผมต้องการดึงข้อมูลมาจากตรงนั้นเลย ไม่อยากรอถูกเขียนลงในพื้นที่เก็บข้อมูลหลักก่อนแล้วค่อยคัดลอกมา จริง ๆ ก็ด้วยเหตุผลด้านประสิทธิภาพด้วย แล้วจะมอนิเตอร์ kernel อย่างไร ?? ----------- ในครั้งนี้ผมเลือกที่จะใช้เป็น eBPF (extended Berkeley Packet Filter) จริงแล้วเจ้า eBPF เนี่ยใช้งานได้หลากหลายเลยแหละ เรียกได้ว่าประโยชน์รอบด้านสุด ๆ ตามรูปที่แนบด้านล่างเลย  แต่ในครั้งนี้เราจะยุ่งกับมันเพียงแค่การใช้งานเพื่อสอดส่อง kernel เท่านั้น  ภาพด้านบนนี้แสดงให้เห็นจุดที่เราสามารถใช้ eBPF ในการดึงข้อมูลได้ นั่นเลยเป็นเหตุผลหลักที่ผมเลือกใช้ โดยวางการทำงานทั้งหมดของการมอนิเตอร์ไว้ดังนี้ 1. ใช้ eBPF เพื่อคอยเช็คว่ามีการเขียนเกิดขึ้นมั้ยโดยการอ่านค่า flag จาก NVMe ว่ามีค่าเป็นอะไรจากนั้นนำค่าที่ได้มา XOR ด้วย mask ถ้าค่าออกมาเป็น 1 แปลว่านั่นคือ write_operation (อาจแตกต่างกันแล้วแต่ version) 2. เมื่อเช็คค่าแล้วเป็น write_operation จากนั้นก็ให้ทำการอ่านเลข sector, และขนาดของข้อมูลที่ต้องการจะเขียน 3. จากนั้นเข้าไปอ่านต่อใน Bio ลงไปยัง Bio_vec และไป Bv_page ตามลำดับ เพื่ออ่านข้อมูลทั้งหมดที่มาจากคำสั่งในการเขียนครั้งนั้น ๆ  *ภาพประกอบเพิ่มเติมเพื่อใครงงว่า Bio คืออะไรข้อมูลเวลาเราเขียนจะอยู่บน page 4. ส่งข้อมูลที่ได้ทั้งหมดออกมา เพียงเท่านี้เราก็ทำการดึงข้อมูลทุกครั้งที่เราเขียนได้แล้ว และจะนำมันเข้าสู่ขั้นตอนต่อไปในการเก็บข้อมูลลง SSD เก็บข้อมูลและส่งไป SSD ที่เป็น nilfs2 ----------- เมื่อได้ข้อมูลมาจากการทำงานที่ได้กล่าวไว้ข้างบนแล้ว ก็จะได้ชุดข้อมูลมาชุดหนึ่ง ส่งออกมันมาจาก ebpf(C program) มาสู่ Python ต่อโดยมีขั้นตอนดังนี้ 1. นำเลข sector ที่ได้มาทำการคูณด้วยขนาดของ sector เพื่อให้เราได้ logical address มา จากนั้นให้นำ logical address หารด้วยขนาดของบล๊อกเพื่อให้ได้เลขบล๊อก 2. นำข้อมูลในแต่ละ sector มาเรียงลงในบล๊อกที่มันอยู่ละบันทึกลงไปใน SSD ตัวอย่างเพื่อให้เห็นภาพมากขึ้น สมมุติว่าข้อมูลที่ส่งกลับมาขนาด 4097 B และเริ่มเขียนที่ sector 0 (กำหนดให้ 1 sector มีขนาด 512B และ 1 Block มี 8 sector) 4097/512 = 8.xx ก็แปลว่าข้อมูลนี้ต้องเก็บใน 9 sector คือ sector 0 ถึง 8 และ 8 sector รวมเป็น 1 block แปลว่าข้อมูลใน sector 0-7จะอยู่ใน block 0 และ sector 8 จะอยู่ใน block 1 แปลว่าโปรแกรมของผมจะสร้างมาสองไฟล์คือ 0,1 จากนั้นจะทำการเติม 0 ท้ายไฟล์ 1 จนมีขนาด 4096 B เท่ากับขนาดของ block สำหรับคนที่งงว่า sector บล๊อกคืออะไร  ให้ดูตรงรูปกลม ๆ ทางซ้ายมือจะเห็นได้ว่ามันเป็นหน่วยความจำในจานหมุน ซึ่ง sector คือหน่วยย่อยสุด และ sector รวม ๆ กันหลาย ๆ sector จะเป็น cluter บางที่ก็เรียก Tracks บางที่ก็ Block ซึ่งนี่แหละคือบล๊อกที่ผมหมายถึง เพียงเท่านี้เราก็ได้ระบบที่สามารถป้องกัน ransomware ได้แล้ว เพราะเนื่องจากเมื่อเราโดน ransomware และไฟล์เราถูก encrypt เราก็เพียงใช้ความความสามารถของ SSD ลูกที่เป็น nilfs2 เพื่อนำไฟล์ดั้งเดิมก่อนจะถูก encrypt กับมาได้ดังรูปประกอบด้านล่างนี้  ส่งท้าย ----------- จริง ๆ แล้วที่ผมเก็บเป็นไฟล์ block เพราะผมอยากให้ backup file สามารถเข้ากันได้กับทุกระบบไฟล์เพื่อให้สามารถใช้งานได้กับทุกระบบ ถึงจะยังทำไม่ได้ก็เหอะ 55555
@ 66df6056:f3203c64
2024-07-31 13:17:15แนวคิดอันนี้เกิดขึ้นหลังจากที่ผมได้รู้จัก LFS หรือ Log- structure File System มันทำให้ผมเกิดความคิดว่าในเมื่อมันสามารถที่จะเก็บ file และทุก log ของการเปลี่ยนแปลงในแต่ละไฟล์ งั้นแปลว่าในกรณีที่ file โดน encrypt มันก็น่าจะสามารถกู้คืนมาได้สิ เอ้ะแต่ถ้าเครื่องนั้นโดน ransomware ไปรอบนึงแล้วกู้คืนมาแล้วมันก็โดนอีกอยู่ดีมั้ย เลยเกิดไอเดียใหม่ว่าแล้วถ้าเราหา SSD อีกลูกมาเก็บ backup ถ้าโดน ransomware ก็ถอดไปเสียบเครื่องใหม่ก็จบ ตะตะแต่ว่า LFS เนี่ย ดั้นนนใช้ไม่ได้กับ windows หรือ Mac เอาละ ปัญหาใหม่มาอีกละ งั้นต้องทำไงล่ะ ? หึเก็บไว้บอกท้ายบทความละกัน มาทำความเข้าใจโปรเจคนี้กันทีละขั้นตอนกันดีกว่า Log-structure File System (LFS) ----------- เป็น File system รูปแบบหนึ่งที่จะทำการเก็บข้อมูลเป็น log และสามารถย้อนกลับได้ทุกการกระทำ นอกจากมีความถี่ในการสร้าง snapshot ที่สูงมาก จริง ๆ แล้วเหมาะกับงานประเภทที่ต้องการความต่อเนื่องหากดบัไปต้องกู้คืนได้มากที่สุดเท่าที่เป็นไปได้ แต่เพราะไอความสามารถตรงนั้นของมันนี่แหละ ที่ผมมองว่ามันน่าจะหยิบมาใช้กับการกู้คืน file หลังจากโดน ransomware ได้แน่ ๆ โดยในครั้งนี้ผมเลือกใช้เป็น NILFS2 เนื่องจากดูแล้วน่าจะเหลือตัวเดียวที่ยังพอมีการพัฒนาอยู่ 5555 รูปแบบการเก็บข้อมูลจะเหมือนกับภาพด้านล่างนี้  ตัวอย่าง: เดิมที file A: "AAAAA" จากนั้นผมได้ทำการอัพเดตข้อมูลใน file A เป็น "BBBBB" ด้วยความสามารถของ LFS มันสามารถที่จะดึง file A เวอร์ชันที่เป็น "AAAAA" กลับมาได้ นี่เป็นปัจจัยสำคัญที่ทำให้ผมมองว่า LFS เหมาะสมที่จะมาเป็นระบบไฟล์ที่ใช้ในการสำรองข้อมูล แต่อยากที่ได้กล่าวไว้ข้างต้นว่าปัญหาของระบบไฟล์นี้คือมันใช้พื้นที่เก็บข้อมูลค่อนข้างสูง และมี write speed ที่ค่อนข้างช้า ถ้าเทียบกับระบบไฟล์อื่น ๆ ในกรณีที่ความเร็วของ SSD เท่ากัน เลยมองว่าถ้าจะใช้เป็นระบบหลักในการเก็บข้อมูลทุกอย่างคงจะไม่เหมาะ เลยนำไปสู่การทำระบบโดยใช้ระบบไฟล์สองแบบที่แตกต่างกัน System Design ----------- อย่างที่ได้พูดถึงข้อเสียของ NILFS2 ไปข้างต้น แปลว่าถ้าอยากจะให้คอมพิวเตอร์ทำงานได้อย่างมีประสิทธิภาพคงเดิมและสามารถป้องกัน ransomware ได้ด้วยก็จำเป็นต้องมีระบบไฟล์ที่ใช้กันทั่วไปอย่าง FAT32 หรือ ext4 และใช้ SSD อีกลูกหนึ่งที่ format เป็น NILFS2 และเขียนโปรแกรมให้คอยมอนิเตอร์ทุก ๆ กิจกรรมบน user space และทุกครั้งที่เกิดการเขียนไฟล์ขึ้นให้เขียนลงใน SSD ที่เป็น NILFS2 ด้วย ดังภาพที่แสดงด้านล่างนี้  แล้วทำไมไฟล์ในลูกที่เก็บสำรองข้อมูลถึงไม่เท่ากับจำนวนไฟล์ในที่เก็บข้อมูลหลักล่ะ ? เนื่องด้วยความเร็วในการเขียนที่ค่อนข้างแตกต่างกันของทั้งสอง ผมเลยมองว่าถ้าเราเก็บในรูปแบบบล๊อกจะทำให้เก็บข้อมูลได้ไวกว่า อย่างตัวอย่างในรูป สมมุติว่าไฟล์ A มีขนาดประมาณ 3 บล๊อกใน SSD ที่เป็น nilfs2 ก็จะมี 3 ไฟล์และต้องใช้ทั้งสามไฟล์เพื่อที่จะคืนค่าไฟล์ A กลับมา ถ้าอ่านมาถึงตรงนี้อาจจะเกิดข้อสงสัยว่า แล้วจะทำให้มันยุ่งยากทำไม คัดลอกไฟล์มาใส่ก็จบแล้วมั้ย ? ก็ใช่แหละและจริง ๆ ผมคิดว่าทำแบบนั้นก็เพียงพอ แต่ว่าอย่างที่บอกไปข้างต้น ผมอยากได้ระบบที่ป้องกันได้ 100% ผมเลยเลือกที่จะมอนิเตอร์ kernel เอาไว้และเมื่อมีการเขียนไฟล์เกิดขึ้นผมต้องการดึงข้อมูลมาจากตรงนั้นเลย ไม่อยากรอถูกเขียนลงในพื้นที่เก็บข้อมูลหลักก่อนแล้วค่อยคัดลอกมา จริง ๆ ก็ด้วยเหตุผลด้านประสิทธิภาพด้วย แล้วจะมอนิเตอร์ kernel อย่างไร ?? ----------- ในครั้งนี้ผมเลือกที่จะใช้เป็น eBPF (extended Berkeley Packet Filter) จริงแล้วเจ้า eBPF เนี่ยใช้งานได้หลากหลายเลยแหละ เรียกได้ว่าประโยชน์รอบด้านสุด ๆ ตามรูปที่แนบด้านล่างเลย  แต่ในครั้งนี้เราจะยุ่งกับมันเพียงแค่การใช้งานเพื่อสอดส่อง kernel เท่านั้น  ภาพด้านบนนี้แสดงให้เห็นจุดที่เราสามารถใช้ eBPF ในการดึงข้อมูลได้ นั่นเลยเป็นเหตุผลหลักที่ผมเลือกใช้ โดยวางการทำงานทั้งหมดของการมอนิเตอร์ไว้ดังนี้ 1. ใช้ eBPF เพื่อคอยเช็คว่ามีการเขียนเกิดขึ้นมั้ยโดยการอ่านค่า flag จาก NVMe ว่ามีค่าเป็นอะไรจากนั้นนำค่าที่ได้มา XOR ด้วย mask ถ้าค่าออกมาเป็น 1 แปลว่านั่นคือ write_operation (อาจแตกต่างกันแล้วแต่ version) 2. เมื่อเช็คค่าแล้วเป็น write_operation จากนั้นก็ให้ทำการอ่านเลข sector, และขนาดของข้อมูลที่ต้องการจะเขียน 3. จากนั้นเข้าไปอ่านต่อใน Bio ลงไปยัง Bio_vec และไป Bv_page ตามลำดับ เพื่ออ่านข้อมูลทั้งหมดที่มาจากคำสั่งในการเขียนครั้งนั้น ๆ  *ภาพประกอบเพิ่มเติมเพื่อใครงงว่า Bio คืออะไรข้อมูลเวลาเราเขียนจะอยู่บน page 4. ส่งข้อมูลที่ได้ทั้งหมดออกมา เพียงเท่านี้เราก็ทำการดึงข้อมูลทุกครั้งที่เราเขียนได้แล้ว และจะนำมันเข้าสู่ขั้นตอนต่อไปในการเก็บข้อมูลลง SSD เก็บข้อมูลและส่งไป SSD ที่เป็น nilfs2 ----------- เมื่อได้ข้อมูลมาจากการทำงานที่ได้กล่าวไว้ข้างบนแล้ว ก็จะได้ชุดข้อมูลมาชุดหนึ่ง ส่งออกมันมาจาก ebpf(C program) มาสู่ Python ต่อโดยมีขั้นตอนดังนี้ 1. นำเลข sector ที่ได้มาทำการคูณด้วยขนาดของ sector เพื่อให้เราได้ logical address มา จากนั้นให้นำ logical address หารด้วยขนาดของบล๊อกเพื่อให้ได้เลขบล๊อก 2. นำข้อมูลในแต่ละ sector มาเรียงลงในบล๊อกที่มันอยู่ละบันทึกลงไปใน SSD ตัวอย่างเพื่อให้เห็นภาพมากขึ้น สมมุติว่าข้อมูลที่ส่งกลับมาขนาด 4097 B และเริ่มเขียนที่ sector 0 (กำหนดให้ 1 sector มีขนาด 512B และ 1 Block มี 8 sector) 4097/512 = 8.xx ก็แปลว่าข้อมูลนี้ต้องเก็บใน 9 sector คือ sector 0 ถึง 8 และ 8 sector รวมเป็น 1 block แปลว่าข้อมูลใน sector 0-7จะอยู่ใน block 0 และ sector 8 จะอยู่ใน block 1 แปลว่าโปรแกรมของผมจะสร้างมาสองไฟล์คือ 0,1 จากนั้นจะทำการเติม 0 ท้ายไฟล์ 1 จนมีขนาด 4096 B เท่ากับขนาดของ block สำหรับคนที่งงว่า sector บล๊อกคืออะไร  ให้ดูตรงรูปกลม ๆ ทางซ้ายมือจะเห็นได้ว่ามันเป็นหน่วยความจำในจานหมุน ซึ่ง sector คือหน่วยย่อยสุด และ sector รวม ๆ กันหลาย ๆ sector จะเป็น cluter บางที่ก็เรียก Tracks บางที่ก็ Block ซึ่งนี่แหละคือบล๊อกที่ผมหมายถึง เพียงเท่านี้เราก็ได้ระบบที่สามารถป้องกัน ransomware ได้แล้ว เพราะเนื่องจากเมื่อเราโดน ransomware และไฟล์เราถูก encrypt เราก็เพียงใช้ความความสามารถของ SSD ลูกที่เป็น nilfs2 เพื่อนำไฟล์ดั้งเดิมก่อนจะถูก encrypt กับมาได้ดังรูปประกอบด้านล่างนี้  ส่งท้าย ----------- จริง ๆ แล้วที่ผมเก็บเป็นไฟล์ block เพราะผมอยากให้ backup file สามารถเข้ากันได้กับทุกระบบไฟล์เพื่อให้สามารถใช้งานได้กับทุกระบบ ถึงจะยังทำไม่ได้ก็เหอะ 55555 @ 5afdec5b:2d631be1
2024-08-14 09:42:29# Introducing Our New Whitepaper on Escrow-Less Bitcoin-Collateralized Lending We are thrilled to release our latest whitepaper, elaborating on our innovative Escrow-Less Bitcoin-Collateralized Lending protocol. This pioneering system leverages the power of Discreet Log Contracts (DLCs) and Hash Time Lock Contracts (HTLCs) to create a trustless, peer-to-peer lending environment that aligns with the ethos of decentralization and user empowerment. [Read the full whitepaper here](http://whitepaper.lendasat.com/lendasat-whitepaper.pdf)  ## Empowering Users with Our Architecture Our protocol is meticulously designed to empower users by allowing them to borrow against their Bitcoin while retaining full control over it. We believe that this is not just a technological advancement, but a crucial step towards crafting a more decentralized, trust-minimized, and secure financial ecosystem. By eliminating the need for intermediaries, we aim to give users greater autonomy and flexibility, freeing them from traditional constraints. ## Addressing Market Needs for Peer-to-Peer, Trustless Lending Extensive market research highlights a significant, growing demand for peer-to-peer, trustless lending solutions. Users consistently expressed a desire for more control over their assets and greater flexibility in their lending options. Our Escrow-Less Lending protocol directly addresses these needs, providing a robust framework that enhances user control while maintaining the integrity and security of the lending process. ## Exploring the Potential of Ark for Microloan Liquidity Management Initially, our focus was predominantly on micro-loans. However, user interviews revealed a relatively limited demand for such products at this time. Nonetheless, we identified Ark as good solution in the context of Bitcoin microloans. Ark's capabilities could unlock new possibilities and efficiencies, making microloans more viable and attractive. ## Remaining Flexible and Adaptable Even as our primary focus shifts, the potential of Ark continues to intrigue us. Our protocol's design is inherently flexible and adaptable, allowing for continuous refinement and adjustments based on user interest and feedback. Should there be sufficient interest in the future, we are open and ready to explore Ark's integration once again to better serve our users’ needs. ## Revolutionizing Bitcoin Borrowing and Lending We firmly believe that our Escrow-Less Bitcoin-Collateralized Lending protocol has the potential to revolutionize the borrowing and lending landscape within the Bitcoin ecosystem. Our commitment is steadfast; we aim to make this innovative protocol a reality and will diligently work to iterate and improve based on user feedback. Together, let’s shape the future of decentralized lending. ## Your Feedback Matters We invite you to delve into our whitepaper and share your thoughts and feedback on this groundbreaking approach. Your insights are invaluable as we strive to create a more user-centric, flexible, and secure lending protocol. [Read the full whitepaper here](http://whitepaper.lendasat.com/lendasat-whitepaper.pdf) --- Feel free to reach out with your thoughts, questions, or suggestions. We’re eager to engage with you and iterate based on your valuable input.
@ 5afdec5b:2d631be1
2024-08-14 09:42:29# Introducing Our New Whitepaper on Escrow-Less Bitcoin-Collateralized Lending We are thrilled to release our latest whitepaper, elaborating on our innovative Escrow-Less Bitcoin-Collateralized Lending protocol. This pioneering system leverages the power of Discreet Log Contracts (DLCs) and Hash Time Lock Contracts (HTLCs) to create a trustless, peer-to-peer lending environment that aligns with the ethos of decentralization and user empowerment. [Read the full whitepaper here](http://whitepaper.lendasat.com/lendasat-whitepaper.pdf)  ## Empowering Users with Our Architecture Our protocol is meticulously designed to empower users by allowing them to borrow against their Bitcoin while retaining full control over it. We believe that this is not just a technological advancement, but a crucial step towards crafting a more decentralized, trust-minimized, and secure financial ecosystem. By eliminating the need for intermediaries, we aim to give users greater autonomy and flexibility, freeing them from traditional constraints. ## Addressing Market Needs for Peer-to-Peer, Trustless Lending Extensive market research highlights a significant, growing demand for peer-to-peer, trustless lending solutions. Users consistently expressed a desire for more control over their assets and greater flexibility in their lending options. Our Escrow-Less Lending protocol directly addresses these needs, providing a robust framework that enhances user control while maintaining the integrity and security of the lending process. ## Exploring the Potential of Ark for Microloan Liquidity Management Initially, our focus was predominantly on micro-loans. However, user interviews revealed a relatively limited demand for such products at this time. Nonetheless, we identified Ark as good solution in the context of Bitcoin microloans. Ark's capabilities could unlock new possibilities and efficiencies, making microloans more viable and attractive. ## Remaining Flexible and Adaptable Even as our primary focus shifts, the potential of Ark continues to intrigue us. Our protocol's design is inherently flexible and adaptable, allowing for continuous refinement and adjustments based on user interest and feedback. Should there be sufficient interest in the future, we are open and ready to explore Ark's integration once again to better serve our users’ needs. ## Revolutionizing Bitcoin Borrowing and Lending We firmly believe that our Escrow-Less Bitcoin-Collateralized Lending protocol has the potential to revolutionize the borrowing and lending landscape within the Bitcoin ecosystem. Our commitment is steadfast; we aim to make this innovative protocol a reality and will diligently work to iterate and improve based on user feedback. Together, let’s shape the future of decentralized lending. ## Your Feedback Matters We invite you to delve into our whitepaper and share your thoughts and feedback on this groundbreaking approach. Your insights are invaluable as we strive to create a more user-centric, flexible, and secure lending protocol. [Read the full whitepaper here](http://whitepaper.lendasat.com/lendasat-whitepaper.pdf) --- Feel free to reach out with your thoughts, questions, or suggestions. We’re eager to engage with you and iterate based on your valuable input. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Sistemas legais anárquicos São poucos os exemplos de sistemas legais claramente anárquicos que nós temos, e são sempre de tempos muito remoto, da idade média ou por aí. Me vêm à cabeça agora o sistema islandês, o somaliano, o irlandês e as cortes dos mercadores da Europa continental. Esses exemplos, embora sempre pareçam aos olhos de um libertário convicto a prova cabal de que a sociedade sem o Estado é capaz de fazer funcionar sistemas legais eficientes, complexos e muito melhores e mais baratos do que os estatais, a qualquer observador não entusiasmado vão parecer meio anacrônicos: são sempre coisas que envolvem família, clãs, chefes de família, comunidades pequenas -- fatores quase sempre ausentes na sociedade hoje --, o que dá espaço para que a pessoa pense (e eu confesso que isso também sempre me incomodou) que nada disso funcionaria hoje, são bonitos, mas sistemas que só funcionariam nos tempos de antigamente, o Estado com seu sistema judiciário é a evolução natural e necessária de tudo isso e assim por diante. Vale lembrar, porém, que os exemplos que nós temos provavelmente não surgiram espontamente, eles mesmos foram o resultado de uma evolução lenta mas constante do sistema legal das suas respectivas comunidades. Se não tivessem sido interrompidos pela intervenção de algum Estado, esses sistemas teriam continuado evoluindo e hoje, quem sabe, seriam redes complexas altamente eficientes, que, por que não, juntariam tecnologias similares à internet com segurança de dados, algoritmos maravilhosos de reputação e voto, tudo decentralizado, feito por meio de protocolos concorrentes mas padronizados -- talvez, se tivessem tido um pouquinho mais de tempo, cada um desses sistemas legais anárquicos teria desenvolvido meios de evitar a conquista ou a concorrência desleal de um Estado, ou pelo menos do Estado como nós o conhecemos hoje.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Sistemas legais anárquicos São poucos os exemplos de sistemas legais claramente anárquicos que nós temos, e são sempre de tempos muito remoto, da idade média ou por aí. Me vêm à cabeça agora o sistema islandês, o somaliano, o irlandês e as cortes dos mercadores da Europa continental. Esses exemplos, embora sempre pareçam aos olhos de um libertário convicto a prova cabal de que a sociedade sem o Estado é capaz de fazer funcionar sistemas legais eficientes, complexos e muito melhores e mais baratos do que os estatais, a qualquer observador não entusiasmado vão parecer meio anacrônicos: são sempre coisas que envolvem família, clãs, chefes de família, comunidades pequenas -- fatores quase sempre ausentes na sociedade hoje --, o que dá espaço para que a pessoa pense (e eu confesso que isso também sempre me incomodou) que nada disso funcionaria hoje, são bonitos, mas sistemas que só funcionariam nos tempos de antigamente, o Estado com seu sistema judiciário é a evolução natural e necessária de tudo isso e assim por diante. Vale lembrar, porém, que os exemplos que nós temos provavelmente não surgiram espontamente, eles mesmos foram o resultado de uma evolução lenta mas constante do sistema legal das suas respectivas comunidades. Se não tivessem sido interrompidos pela intervenção de algum Estado, esses sistemas teriam continuado evoluindo e hoje, quem sabe, seriam redes complexas altamente eficientes, que, por que não, juntariam tecnologias similares à internet com segurança de dados, algoritmos maravilhosos de reputação e voto, tudo decentralizado, feito por meio de protocolos concorrentes mas padronizados -- talvez, se tivessem tido um pouquinho mais de tempo, cada um desses sistemas legais anárquicos teria desenvolvido meios de evitar a conquista ou a concorrência desleal de um Estado, ou pelo menos do Estado como nós o conhecemos hoje. @ 502ab02a:a2860397
2024-07-31 10:27:12ใช่ครับ 31 กรกฎาคม 2567 ขอบันทึกการเจอนี่ไว้หน่อยว่า เป็นการทำงานในงานโฆษณาเป็นวันสุดท้าย หลังจากวันนี้ก็จะไม่ได้เอี่ยวกับงานในวงเวียนนี้อีกแล้ว รวมถึงได้ยุติการเป็นหุ้นส่วนของบริษัทด้วยพร้อมๆกัน ใช่ครับ ผมยุติบทบาทการหุ้นด้วย ปล่อยให้เพื่อนอีกคนเผชิญชะตากรรมในเส้นทางนี้ต่อไป หลังจากลุยกันมา 22ปี ในรูปแบบบริษัท และ 3 ปีในแบบฟรีแลนซ์ ภาพนี้เป็นโต๊ะทำงานภาพสุดท้าย  และกีตาร์เป็นของอย่างแรกที่เอาเข้ามา แต่เป็นของอย่างสุดท้ายที่เอาออกไป  พรุ่งนี้ก็จะไม่เหมือนเดิมอีกต่อไป ดีร้ายก็มาดิ เจอกัน 555 ผมจะพยายามดำเนินชีวิตในแบบที่ตัวเองอยากทำ มากที่สุดเท่าที่จะทำได้ครับ 555 ร็อคกี้ บอกว่าหมัดหนักแค่ไหนไม่สำคัญ สำคัญที่เราจะรับหมัดหนักๆได้นานเท่าไรต่างหาก
@ 502ab02a:a2860397
2024-07-31 10:27:12ใช่ครับ 31 กรกฎาคม 2567 ขอบันทึกการเจอนี่ไว้หน่อยว่า เป็นการทำงานในงานโฆษณาเป็นวันสุดท้าย หลังจากวันนี้ก็จะไม่ได้เอี่ยวกับงานในวงเวียนนี้อีกแล้ว รวมถึงได้ยุติการเป็นหุ้นส่วนของบริษัทด้วยพร้อมๆกัน ใช่ครับ ผมยุติบทบาทการหุ้นด้วย ปล่อยให้เพื่อนอีกคนเผชิญชะตากรรมในเส้นทางนี้ต่อไป หลังจากลุยกันมา 22ปี ในรูปแบบบริษัท และ 3 ปีในแบบฟรีแลนซ์ ภาพนี้เป็นโต๊ะทำงานภาพสุดท้าย  และกีตาร์เป็นของอย่างแรกที่เอาเข้ามา แต่เป็นของอย่างสุดท้ายที่เอาออกไป  พรุ่งนี้ก็จะไม่เหมือนเดิมอีกต่อไป ดีร้ายก็มาดิ เจอกัน 555 ผมจะพยายามดำเนินชีวิตในแบบที่ตัวเองอยากทำ มากที่สุดเท่าที่จะทำได้ครับ 555 ร็อคกี้ บอกว่าหมัดหนักแค่ไหนไม่สำคัญ สำคัญที่เราจะรับหมัดหนักๆได้นานเท่าไรต่างหาก @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Just malinvestiment Traditionally the Austrian Theory of Business Cycles has been explained and reworked in many ways, but the most widely accepted version (or the closest to the Mises or Hayek views) view is that banks (or the central bank) cause the general interest rate to decline by creation of new money and that prompts entrepreneurs to invest in projects of longer duration. This can be confusing because sometimes entrepreneurs embark in very short-time projects during one of these bubbles and still contribute to the overall cycle. The solution is to think about the "longer term" problem is to think of the entire economy going long-term, not individual entrepreneurs. So if one entrepreneur makes an investiment in a thing that looks simple he may actually, knowingly or not, be inserting himself in a bigger machine that is actually involved in producing longer-term things. Incidentally this thinking also solves the biggest criticism of the Austrian Business Cycle Theory: that of the rational expectations people who say: "oh but can't the entrepreneurs know that the interest rate is artificially low and decide to not make long-term investiments?" ("and if they don't know they should lose money and be replaced like in a normal economy flow blablabla?"). Well, the answer is that they are not really relying on the interest rate, they are only looking for profit opportunities, and this is the key to another confusion that has always followed my thinkings about this topic. If a guy opens a bar in an area of a town where many new buildings are being built during a "housing bubble" he may not know, but he is inserting himself right into the eye of that business cycle. He expects all these building projects to continue, and all the people involved in that to be getting paid more and be able to spend more at his bar and so on. That is a bet that may or may not end up paying. Now what does that bar investiment has to do with the interest rate? Nothing. It is just a guy who saw a business opportunity in a place where hungry people with money had no bar to buy things in, so he opened a bar. Additionally the guy has made some calculations about all the ending, starting and future building projects in the area, and then the people that would live or work in that area afterwards (after all the buildings were being built with the expectation of being used) and so on, there is no interest rate calculations involved. And yet that may be a malinvestiment because some building projects will end up being canceled and the expected usage of the finished ones will turn out to be smaller than predicted. This bubble may have been caused by a decline in interest rates that prompted some people to start buying houses that they wouldn't otherwise, but this is just a small detail. The bubble can only be kept going by a constant influx of new money into the economy, but the focus on the interest rate is wrong. If new money is printed and used by the government to buy ships then there will be a boom and a bubble in the ship market, and that involves all the parts of production process of ships and also bars that will be opened near areas of the town where ships are built and new people are being hired with higher salaries to do things that will eventually contribute to the production of ships that will then be sold to the government. It's not interest rates or the length of the production process that matters, it's just printed money and malinvestiment.
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# Just malinvestiment Traditionally the Austrian Theory of Business Cycles has been explained and reworked in many ways, but the most widely accepted version (or the closest to the Mises or Hayek views) view is that banks (or the central bank) cause the general interest rate to decline by creation of new money and that prompts entrepreneurs to invest in projects of longer duration. This can be confusing because sometimes entrepreneurs embark in very short-time projects during one of these bubbles and still contribute to the overall cycle. The solution is to think about the "longer term" problem is to think of the entire economy going long-term, not individual entrepreneurs. So if one entrepreneur makes an investiment in a thing that looks simple he may actually, knowingly or not, be inserting himself in a bigger machine that is actually involved in producing longer-term things. Incidentally this thinking also solves the biggest criticism of the Austrian Business Cycle Theory: that of the rational expectations people who say: "oh but can't the entrepreneurs know that the interest rate is artificially low and decide to not make long-term investiments?" ("and if they don't know they should lose money and be replaced like in a normal economy flow blablabla?"). Well, the answer is that they are not really relying on the interest rate, they are only looking for profit opportunities, and this is the key to another confusion that has always followed my thinkings about this topic. If a guy opens a bar in an area of a town where many new buildings are being built during a "housing bubble" he may not know, but he is inserting himself right into the eye of that business cycle. He expects all these building projects to continue, and all the people involved in that to be getting paid more and be able to spend more at his bar and so on. That is a bet that may or may not end up paying. Now what does that bar investiment has to do with the interest rate? Nothing. It is just a guy who saw a business opportunity in a place where hungry people with money had no bar to buy things in, so he opened a bar. Additionally the guy has made some calculations about all the ending, starting and future building projects in the area, and then the people that would live or work in that area afterwards (after all the buildings were being built with the expectation of being used) and so on, there is no interest rate calculations involved. And yet that may be a malinvestiment because some building projects will end up being canceled and the expected usage of the finished ones will turn out to be smaller than predicted. This bubble may have been caused by a decline in interest rates that prompted some people to start buying houses that they wouldn't otherwise, but this is just a small detail. The bubble can only be kept going by a constant influx of new money into the economy, but the focus on the interest rate is wrong. If new money is printed and used by the government to buy ships then there will be a boom and a bubble in the ship market, and that involves all the parts of production process of ships and also bars that will be opened near areas of the town where ships are built and new people are being hired with higher salaries to do things that will eventually contribute to the production of ships that will then be sold to the government. It's not interest rates or the length of the production process that matters, it's just printed money and malinvestiment. @ bcbb3e40:a494e501
2024-08-12 16:03:03En este nuevo artículo sobre actualidad sería la segunda vez que nombremos a la figura de **Alvise Pérez**. Lo habíamos mencionado de pasada anteriormente, cuando [comentamos nuestras hipótesis](https://hiperbolajanus.com/posts/adios-woke-que-viene-ahora/) respecto al atentado contra Trump y lo que ello, a nuestro entender, supondría. La motivación del mismo no es defender a Alvise, con quien no nos alineamos por motivos que explicaremos. Lo que nos llama la atención es la reacción adversa del sector _disidente_ (llamémoslo así) que, si bien reconocemos que puede haber un componente legítimo de desconfianza ante la aparición «súbita» de este personaje, consideramos que está motivada principalmente por envidias, celos y algo de sectarismo. El objetivo es por lo tanto, hacernos capaces de encontrar la viga en el propio ojo y dejar de señalar la paja en el ojo ajeno. ### Sospechas contra Alvise Alvise Pérez logró una gran relevancia a raíz del resultado de su agrupación electoral «[Se acabó la fiesta](https://seacabolafiesta.com/)» (SALF) en las últimas elecciones al parlamento europeo celebradas en España el pasado 9 de junio de 2024. A la totalidad del espectro político/mediático español le sentó como un jarro de agua fría la friolera de más de 800.000 votos oficiales (SALF asegura que son más y está reclamando el recuento) conseguida por un personaje que hasta el momento estaba vetado por la prensa y que basó su campaña electoral en la difusión a través de las redes sociales que no habían podido serle censuradas y después de una serie de meetings de presupuesto ínfimo celebrados por las principales capitales españolas. || |:-:| |Alvise Pérez durante su discurso pronuciado tras el cierre de los colegios electorales en las elecciones europeas del 9J| Viéndolo así a todos nos parece un cuento demasiado bonito como para ser verdad. Estamos todos muy escarmentados del ascenso a la relevancia pública de personajes «desconocidos» como **José Luis Rodríguez Zapatero**, **Pablo Iglesias Turrión** o **Pedro Sánchez Pérez-Castejón**, o de fuerzas políticas como VOX; todos estos casos, aupados por los medios. Además de la lógica desconfianza que nos suscita el ascenso meteórico de las figuras y organizaciones mencionadas desde la nada, sin una trayectoria previa conocida, y sin una masa social o apoyo reconocido. Sí, también VOX era prácticamente desconocida hasta que los invitaron a este programa en Televisión de Cataluña, allá por el 2018, con todo el tema del independentismo catalán en auge: <iframe width="560" height="315" src="https://www.youtube-nocookie.com/embed/T9pIf6pEhiQ?si=bMUn3YdRQ2GhMm25" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> A todos los ejemplos anteriores los aupó la prensa. Sin embargo, parece que Alvise/SALF no es el caso… Lo que lleva a la hipótesis conspiranoica de que es un personaje puesto por el Centro Nacional de Inteligencia de España (CNI). #### La hipótesis del CNI Es cierto que Alvise ha ido ganando mucha relevancia en redes sociales en base a información que ha ido publicando y que ha sido activamente ignorada o vetada por el aparato mediático. Además, la calidad de dicha información siempre ha sido de categoría de espionaje. ¿Cómo es posible que un chaval sevillano haya logrado acceso a informaciones de un calibre capaz de hacer tambalearse a un país como España? Él ha manifestado en repetidas ocasiones que, efectivamente, utiliza métodos «sucios» como la extorsión o el _hacking_. Pero, obviamente, aquí tendríamos que creer en su palabra y no se puede desmentir de forma tajante que no tenga algún tipo de relación con los servicios de inteligencia. No obstante, la nube de sospecha del CNI o de colaboración con la policía siempre ha estado encima de algunos personajes disidentes destacados, con mayor o menor acierto. Es más, de hecho no descartamos que muchos focos «disidentes» como pseudo-partidos políticos o incluso algunas librerías hayan tenido algún tipo de conexión. Es lo que en inglés se denomina _Honeypot_ (trampa de miel). Volviendo a Alvise, lo que se le reprocha desde algunos sectores disidentes sobre su hipotética relación con el CNI es que éstos lo hayan introducido en la esfera pública para debilitar a otras opciones disidentes o _patrióticas_[^1], como VOX. Sinceramente, este reproche nos parece ridículo. ¿Acaso hay otras fuerzas _patrióticas_ (nótense las cursivas) aparte de VOX que tengan algún tipo de influencia real como para que merezca la pena diluirlas? Y VOX, ¿por qué no apoya a SALF en su cruzada contra INDRA y secunda sus dudas plausibles sobre la precisión del cómputo y la veracidad de los resultados electorales? ### El deplorable activismo disidente en España Pese a que las sospechas contra él pudieran demostrarse como ciertas en algún momento, si nos atenemos a su historial registrado y a lo que ha ido aportando a la sociedad española desde sus medios, ¿¡dónde está el problema!? Entendemos perfectamente las sospechas y compartimos el historial de desengaños de muchas opciones políticas, pero posiblemente muchos se estén pasando de estrictos, quizás con el ánimo de defender sus colores. ¿Existe acaso miedo de que otro haga las cosas bien porque «los tuyos» no lo han logrado? Es una actitud patética y sectaria que antepone el interés del partido o del grupúsculo que uno defiende al interés general del país. Una actitud, dicho sea de paso, demasiado habitual en cualquier tipo de agrupación humana: asociaciones lúdicas, partidos, empresas, etc. #### Escrutinio feroz contra Alvise El contrato que Alvise _firmó_ con su base de seguidores fue el siguiente: «_Vosotros me votáis para proporcionarme inmunidad política y, a cambio, **1)** yo utilizaré esa inmunidad para difundir información que me pondría en apuros en caso de no disponer de tal inmunidad y además **2)** renunciaré a mi sueldo, sorteándolo entre vosotros»._ Las elecciones se celebraron hace apenas dos meses… Pues bien, durante este tiempo no han dejado de llover las críticas de por qué no ha cumplido todavía con lo prometido. Críticas expresadas con especial vehemencia sobre todo por aquellos que no le votaron y que, por lo tanto, no _suscribieron_ dicho contrato con él. Pero bueno… La cuestión es que el pasado sábado 10 de agosto, sabiendo como él sabe manejar a los medios y a la opinión pública, publicó el siguiente mensaje según el cual, aparentemente, renunciaba cumplir el punto 2) del contrato: <blockquote class="twitter-tweet" data-dnt="true"><p lang="es" dir="ltr">Acabo de cobrar mi sueldo como eurodiputado! - 8.089,46 como sueldo de agosto. - 4.043,60 como sueldo de medio julio. En un rato explico en un vídeo por qué he decidido NO ENTREGAR mi sueldo, y quedármelo como respuesta a todos los ataques recibidos por periodistas, partidos y haters en general. 😘 <a href="https://twitter.com/Alvise_oficial_/status/1822346861769883867?ref_src=twsrc%5Etfw">8:58 p. m. · 10 ago. 2024</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script> La respuesta de toda la prensa y de sus enemigos políticos de la izquierda no se hizo esperar. Es algo que no pilla a nadie de sorpresa. Sin embargo, lo que fue especialmente ridículo fue ver cómo otros _patriotas_ y _disidentes_ se subían al carro del linchamiento sin pararse a pensar por un momento que tenía toda la pinta de ser un _troleo_. Porque sí, porque a la que alguien haya seguido un poco la trayectoria de Alvise debería haber anticipado que no renunciar a su sueldo sería casi un suicidio para él. Él aún no tiene la posibilidad, el poder, los privilegios ni una base zombi lo suficientemente motivada como para que le permitan «cambiar de opinión». No tardó mucho en humillar por completo a todos sus detractores publicando el siguiente mensaje unas horas más tarde: <blockquote class="twitter-tweet" data-dnt="true"><p lang="es" dir="ltr">Me quedo mi sueldo. Lo explico todo en: http://AlviseCumpliendo.com <a href="https://twitter.com/Alvise_oficial_/status/1822368651993104488?ref_src=twsrc%5Etfw">10:25 p. m. · 10 ago. 2024</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script> Efectivamente, tal y como prometió, parece que cumplirá el punto **2)**. Es que, de hecho, el «sacrificio» de sortear su salario le reporta muchos más beneficios que no hacerlo. El número de suscriptores de [su canal de Telegram](https://t.me/Alviseperez) ha aumentado en más de 70.000 personas en menos de 2 días. Y los seguidores de [su canal de Instagram](https://www.instagram.com/alviseperez/) ya superan el millón. Este incremento de audiencia, monetizado, supera con creces los 10.000 euros mensuales. #### En la disidencia organizada todo son excusas y malos resultados Pese a todo, para los más fanáticos de nada servirán los logros de Alvise ya no para adherirse a él sino simplemente para dejar de atacarle. Parece que muchos lo quieren o todo o nada, pero en realidad la motivación que lleva a tal animadversión es la impotencia, la frustración y la envidia que genera ver que otros tienen éxito y los tuyos no. El sector _disidente_ español ha sido lamentable desde mucho antes de la transición democrática española. Especialmente desde la década de 1990 lo único que poblaba el panorama español eran grupos de frikis y de nostálgicos de vete tú a saber qué, que jamás lograron tener una relevancia pública ni política significativa ya que estaban más encariñados con sus símbolos y parafilias que con la población general y «analfabeta política» española. La disidencia española, salvo alguna honrosa iniciativa cultural sobre todo, se ha mantenido inoperante a lo largo de las más de cuatro décadas de existencia del actual régimen. Estamos hablando de organizaciones políticas, iniciativas ciudadanas o personajes particulares que hayan podido mostrar un discurso y una cosmovisión alternativas. En muchas ocasiones han antepuesto los intereses particulares de la organización, y han optado por la ortodoxia ideológica frente a cualquier pragmatismo o movimiento táctico orientado a las contingencias del momento, lo cual ha desactivado toda posibilidad de plantear una alternativa viable y seria para combatir las injusticias del régimen demoliberal. Cierto es que los medios de comunicación de aquella época tampoco eran favorables y que el sistema ha puesto muchas dificultades, pero no nos engañemos, la mayoría de esos grupos no ha sabido hacer nunca un proselitismo eficiente y atractivo, haciendo propuestas endogámicas y de consumo interno, sin ser capaces de salir de su burbuja, quedando en muchos casos en terrenos oscurantistas. Lo único que pareció romper un poco este panorama tan lamentable fue la irrupción intencionada de VOX, que pese a que podamos sospechar que se trata de disidencia controlada para canalizar el desencanto de un sector cada vez más amplio de la población, también ha servido para visibilizar que ese sector poblacional existe, que no es precisamente insignificante y que abarca a un espectro social amplio, más allá de los marginados antisociales (_friki-fachas_) que proliferaban por la escena _patriótica_. No obstante, dentro de este panorama tan lamentable, la irrupción de VOX no ha mejorado en absoluto la situación, porque se ha dedicado a fagocitar ciertos elementos de esa «falsa disidencia» fracasada e inoperante, para ocupar muchos de sus cuadros dirigentes, al tiempo que ejerce una mera oposición retórica y actúa como cualquier otra organización del arco parlamentario, invocando el «imperio de la ley», como tanto gusta a los liberales, bajo su formalismo positivo, vacío e inconsecuente. Aún así, el hartazgo y el desengaño ha llegado a ciertos sectores de sus votantes, los cuales se han desmarcado progresivamente de sus políticas y de ese pseudopatriotismo que ha pretendido atribuirse desde su fundación. Dicho todo esto, ¿importa realmente la posición contraria a Alvise de la _disidencia patriótica_ española?. Pues realmente no, porque su capacidad de influencia es insignificante. Por eso, creemos que lo más inteligente que podrían hacer es callarse y dejar de hacer el ridículo, pero quizás eso sea pedirles mucho. En este sentido, y dadas las urgencias que demanda nuestra precaria situación, no deberíamos obstaculizar cualquier acción positiva que contribuya a la causa disidente, aunque sea limitada en el tiempo y quienes la realicen se encuentren en nuestras antípodas ideológicas. En el terreno de lo táctico, y en el terreno de las contingencias, quizás haya ocasiones en las que priorizar un cierto pragmatismo en nuestra visión de las cosas frente a las demandas ideológicas, que siendo absolutamente necesarias y legítimas pueden esperar ante los hechos inmediatos. ### Por qué no somos anti-alvisistas Aunque lo hemos dicho al principio, no está de más recalcar que el propósito de este artículo no es encumbrar ni mucho menos a Alvise Pérez. Nosotros también compartimos algunas de las sospechas que se vierten contra él. Además, tampoco estamos alineados a nivel ideológico. Alvise parece el típico español de a pie, con sus defectos y sus virtudes, educado e influido bajo un sistema liberal. No propone un cambio de paradigma político, sino una continuación del mismo, eso sí, en el que al menos se cumplan las normas que se supone que se tendrían que cumplir. || |:-:| |Las «ardillas» es la red de seguidores/colaboradores/informadores/votantes indignados anónimos de Alvise Pérez, quizás en referencia a «Alvin y las Ardillas»| Es evidente la decadencia del panorama político actual donde se nos miente y se nos toma el pelo ya sin ningún tipo de disimulo. A calzón quitado. Ya ni siquiera se molestan en aparentar que cumplen las normas que ellos mismos han impuesto. Los escándalos de corrupción que hemos testimoniado en el pasado y en la actualidad rebosan lo ultrajante. Intentar que por lo menos se cumplan las normas que se supone que se tendrían que cumplir según el ordenamiento legal vigente, lamentablemente, se tiene que considerar como un logro. Obviamente, nosotros no nos adherimos al susodicho ordenamiento legal, pero entendemos que lo mínimo es ser respetuoso con lo que éste dicta, así como con sus procedimientos y protocolos. Ya llevamos muchos años escuchando por los _mass media_ aquello del «estado de derecho», el «imperio de la ley» o «el sistema más garantistas de todos los existentes», para luego ver cómo la corrupción y el menoscabo de la dignidad e integridad del territorio nacional son prácticas habituales. Por eso creemos que marcarse eso como objetivo a corto o a medio plazo ya es más que suficiente, y si Alvise sirve como ariete para eso, bienvenido sea. No creemos que sea pertinente arremeter contra él y convertirlo en cabeza de turco cuando desde la partitocracia, a izquierda y derecha, se está contribuyendo activamente a la destrucción y sometimiento de España a sus enemigos. Ahora bien, ¿aspiramos al mismo modelo de sociedad? No. Él aspira a lo que cree que es correcto: un modelo Democrático Liberal. Alvise quiere reparar. Nosotros queremos reconstruir desde cero. Lo suyo es más realista y factible a corto plazo. Lo nuestro es una batalla cultural. Podemos contemplar con cierto agrado las acciones de Alvise, siempre que éstas se dirijan contra los partidos políticos, sus integrantes y las corruptelas que protagonizan en un escenario de traición permanente contra el Pueblo y la nación española. Pero nunca podremos coincidir con quienes pretenden seguir confiando en el liberalismo como una opción de futuro, y más después de constatar la responsabilidad de esta ideología perversa en la destrucción del Occidente europeo, totalmente tiranizado y en un estado de metástasis que parece conducirnos a un abismo de caos y destrucción. Por eso lo fundamental en toda opción disidente pasa por adoptar una postura radical e innegociable frente al liberalismo y sus iniquidades. No podemos aceptar el discurso que afirma que lo que fallan son las personas, que son corruptas, pero que el sistema y su entramado ideológico e institucional es bueno, positivo y perfectamente viable, porque no es así. Las personas que dirigen e integran las altas jerarquías del régimen español, y por extensión de las democracias liberales europeas, son corruptas, mezquinas y traidoras porque las instituciones y la ideología que las impregna posee esa misma naturaleza. Y con esto también queremos contrarrestar aquellos tópicos que muchas veces escuchamos en las conversaciones cotidianas, que tienden a culpar el factor humano y contingente y no la estructura político-ideológica que ha favorecido su ascenso y es consustancial a esa corrupción. Desde los tiempos de la _plandemia_ se ha visto un cierto despertar entre amplios sectores de la sociedad española, que han empezado a desconfiar abiertamente de los postulados «políticamente correctos», y ya se atreven a criticar abiertamente temas como la «inmigración», las ingenierías sociales asociadas al Nuevo Orden Mundial u otro tipo de ideas que la prensa vendida se empeña en fabricar para mantenernos dócilmente en el redil. Estos hechos han suscitado formas embrionarias de disidencia y organización, apoyándose muchas veces en las nuevas tecnologías e Internet, como el propio Alvise, y la posibilidad de ir generando redes de comunicación propias, convertidas en vectores de ideas y discursos compartidos por miles de personas. Aunque no coincidamos en lo ideológico, es justo celebrar y apoyar este tipo de iniciativas, y que todo lo que dañe el actual orden de cosas y genere vínculos orgánicos y de solidaridad entre los propios españoles, y europeos, reciba el aliento y el apoyo de todos nosotros. [^1]: Entendemos que VOX no es un partido patriota, sino liberal de derechas, y con evidentes filiaciones con el sionismo. No obstante, hay quien considera que VOX representa, erróneamente, una alternativa «patriota» al actual sistema vigente, cuando siempre ha defendido tanto el orden constitucional fundado en 1978, como sus principales figuras jurídicas e institucionales, tales como la monarquía.
@ bcbb3e40:a494e501
2024-08-12 16:03:03En este nuevo artículo sobre actualidad sería la segunda vez que nombremos a la figura de **Alvise Pérez**. Lo habíamos mencionado de pasada anteriormente, cuando [comentamos nuestras hipótesis](https://hiperbolajanus.com/posts/adios-woke-que-viene-ahora/) respecto al atentado contra Trump y lo que ello, a nuestro entender, supondría. La motivación del mismo no es defender a Alvise, con quien no nos alineamos por motivos que explicaremos. Lo que nos llama la atención es la reacción adversa del sector _disidente_ (llamémoslo así) que, si bien reconocemos que puede haber un componente legítimo de desconfianza ante la aparición «súbita» de este personaje, consideramos que está motivada principalmente por envidias, celos y algo de sectarismo. El objetivo es por lo tanto, hacernos capaces de encontrar la viga en el propio ojo y dejar de señalar la paja en el ojo ajeno. ### Sospechas contra Alvise Alvise Pérez logró una gran relevancia a raíz del resultado de su agrupación electoral «[Se acabó la fiesta](https://seacabolafiesta.com/)» (SALF) en las últimas elecciones al parlamento europeo celebradas en España el pasado 9 de junio de 2024. A la totalidad del espectro político/mediático español le sentó como un jarro de agua fría la friolera de más de 800.000 votos oficiales (SALF asegura que son más y está reclamando el recuento) conseguida por un personaje que hasta el momento estaba vetado por la prensa y que basó su campaña electoral en la difusión a través de las redes sociales que no habían podido serle censuradas y después de una serie de meetings de presupuesto ínfimo celebrados por las principales capitales españolas. || |:-:| |Alvise Pérez durante su discurso pronuciado tras el cierre de los colegios electorales en las elecciones europeas del 9J| Viéndolo así a todos nos parece un cuento demasiado bonito como para ser verdad. Estamos todos muy escarmentados del ascenso a la relevancia pública de personajes «desconocidos» como **José Luis Rodríguez Zapatero**, **Pablo Iglesias Turrión** o **Pedro Sánchez Pérez-Castejón**, o de fuerzas políticas como VOX; todos estos casos, aupados por los medios. Además de la lógica desconfianza que nos suscita el ascenso meteórico de las figuras y organizaciones mencionadas desde la nada, sin una trayectoria previa conocida, y sin una masa social o apoyo reconocido. Sí, también VOX era prácticamente desconocida hasta que los invitaron a este programa en Televisión de Cataluña, allá por el 2018, con todo el tema del independentismo catalán en auge: <iframe width="560" height="315" src="https://www.youtube-nocookie.com/embed/T9pIf6pEhiQ?si=bMUn3YdRQ2GhMm25" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> A todos los ejemplos anteriores los aupó la prensa. Sin embargo, parece que Alvise/SALF no es el caso… Lo que lleva a la hipótesis conspiranoica de que es un personaje puesto por el Centro Nacional de Inteligencia de España (CNI). #### La hipótesis del CNI Es cierto que Alvise ha ido ganando mucha relevancia en redes sociales en base a información que ha ido publicando y que ha sido activamente ignorada o vetada por el aparato mediático. Además, la calidad de dicha información siempre ha sido de categoría de espionaje. ¿Cómo es posible que un chaval sevillano haya logrado acceso a informaciones de un calibre capaz de hacer tambalearse a un país como España? Él ha manifestado en repetidas ocasiones que, efectivamente, utiliza métodos «sucios» como la extorsión o el _hacking_. Pero, obviamente, aquí tendríamos que creer en su palabra y no se puede desmentir de forma tajante que no tenga algún tipo de relación con los servicios de inteligencia. No obstante, la nube de sospecha del CNI o de colaboración con la policía siempre ha estado encima de algunos personajes disidentes destacados, con mayor o menor acierto. Es más, de hecho no descartamos que muchos focos «disidentes» como pseudo-partidos políticos o incluso algunas librerías hayan tenido algún tipo de conexión. Es lo que en inglés se denomina _Honeypot_ (trampa de miel). Volviendo a Alvise, lo que se le reprocha desde algunos sectores disidentes sobre su hipotética relación con el CNI es que éstos lo hayan introducido en la esfera pública para debilitar a otras opciones disidentes o _patrióticas_[^1], como VOX. Sinceramente, este reproche nos parece ridículo. ¿Acaso hay otras fuerzas _patrióticas_ (nótense las cursivas) aparte de VOX que tengan algún tipo de influencia real como para que merezca la pena diluirlas? Y VOX, ¿por qué no apoya a SALF en su cruzada contra INDRA y secunda sus dudas plausibles sobre la precisión del cómputo y la veracidad de los resultados electorales? ### El deplorable activismo disidente en España Pese a que las sospechas contra él pudieran demostrarse como ciertas en algún momento, si nos atenemos a su historial registrado y a lo que ha ido aportando a la sociedad española desde sus medios, ¿¡dónde está el problema!? Entendemos perfectamente las sospechas y compartimos el historial de desengaños de muchas opciones políticas, pero posiblemente muchos se estén pasando de estrictos, quizás con el ánimo de defender sus colores. ¿Existe acaso miedo de que otro haga las cosas bien porque «los tuyos» no lo han logrado? Es una actitud patética y sectaria que antepone el interés del partido o del grupúsculo que uno defiende al interés general del país. Una actitud, dicho sea de paso, demasiado habitual en cualquier tipo de agrupación humana: asociaciones lúdicas, partidos, empresas, etc. #### Escrutinio feroz contra Alvise El contrato que Alvise _firmó_ con su base de seguidores fue el siguiente: «_Vosotros me votáis para proporcionarme inmunidad política y, a cambio, **1)** yo utilizaré esa inmunidad para difundir información que me pondría en apuros en caso de no disponer de tal inmunidad y además **2)** renunciaré a mi sueldo, sorteándolo entre vosotros»._ Las elecciones se celebraron hace apenas dos meses… Pues bien, durante este tiempo no han dejado de llover las críticas de por qué no ha cumplido todavía con lo prometido. Críticas expresadas con especial vehemencia sobre todo por aquellos que no le votaron y que, por lo tanto, no _suscribieron_ dicho contrato con él. Pero bueno… La cuestión es que el pasado sábado 10 de agosto, sabiendo como él sabe manejar a los medios y a la opinión pública, publicó el siguiente mensaje según el cual, aparentemente, renunciaba cumplir el punto 2) del contrato: <blockquote class="twitter-tweet" data-dnt="true"><p lang="es" dir="ltr">Acabo de cobrar mi sueldo como eurodiputado! - 8.089,46 como sueldo de agosto. - 4.043,60 como sueldo de medio julio. En un rato explico en un vídeo por qué he decidido NO ENTREGAR mi sueldo, y quedármelo como respuesta a todos los ataques recibidos por periodistas, partidos y haters en general. 😘 <a href="https://twitter.com/Alvise_oficial_/status/1822346861769883867?ref_src=twsrc%5Etfw">8:58 p. m. · 10 ago. 2024</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script> La respuesta de toda la prensa y de sus enemigos políticos de la izquierda no se hizo esperar. Es algo que no pilla a nadie de sorpresa. Sin embargo, lo que fue especialmente ridículo fue ver cómo otros _patriotas_ y _disidentes_ se subían al carro del linchamiento sin pararse a pensar por un momento que tenía toda la pinta de ser un _troleo_. Porque sí, porque a la que alguien haya seguido un poco la trayectoria de Alvise debería haber anticipado que no renunciar a su sueldo sería casi un suicidio para él. Él aún no tiene la posibilidad, el poder, los privilegios ni una base zombi lo suficientemente motivada como para que le permitan «cambiar de opinión». No tardó mucho en humillar por completo a todos sus detractores publicando el siguiente mensaje unas horas más tarde: <blockquote class="twitter-tweet" data-dnt="true"><p lang="es" dir="ltr">Me quedo mi sueldo. Lo explico todo en: http://AlviseCumpliendo.com <a href="https://twitter.com/Alvise_oficial_/status/1822368651993104488?ref_src=twsrc%5Etfw">10:25 p. m. · 10 ago. 2024</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script> Efectivamente, tal y como prometió, parece que cumplirá el punto **2)**. Es que, de hecho, el «sacrificio» de sortear su salario le reporta muchos más beneficios que no hacerlo. El número de suscriptores de [su canal de Telegram](https://t.me/Alviseperez) ha aumentado en más de 70.000 personas en menos de 2 días. Y los seguidores de [su canal de Instagram](https://www.instagram.com/alviseperez/) ya superan el millón. Este incremento de audiencia, monetizado, supera con creces los 10.000 euros mensuales. #### En la disidencia organizada todo son excusas y malos resultados Pese a todo, para los más fanáticos de nada servirán los logros de Alvise ya no para adherirse a él sino simplemente para dejar de atacarle. Parece que muchos lo quieren o todo o nada, pero en realidad la motivación que lleva a tal animadversión es la impotencia, la frustración y la envidia que genera ver que otros tienen éxito y los tuyos no. El sector _disidente_ español ha sido lamentable desde mucho antes de la transición democrática española. Especialmente desde la década de 1990 lo único que poblaba el panorama español eran grupos de frikis y de nostálgicos de vete tú a saber qué, que jamás lograron tener una relevancia pública ni política significativa ya que estaban más encariñados con sus símbolos y parafilias que con la población general y «analfabeta política» española. La disidencia española, salvo alguna honrosa iniciativa cultural sobre todo, se ha mantenido inoperante a lo largo de las más de cuatro décadas de existencia del actual régimen. Estamos hablando de organizaciones políticas, iniciativas ciudadanas o personajes particulares que hayan podido mostrar un discurso y una cosmovisión alternativas. En muchas ocasiones han antepuesto los intereses particulares de la organización, y han optado por la ortodoxia ideológica frente a cualquier pragmatismo o movimiento táctico orientado a las contingencias del momento, lo cual ha desactivado toda posibilidad de plantear una alternativa viable y seria para combatir las injusticias del régimen demoliberal. Cierto es que los medios de comunicación de aquella época tampoco eran favorables y que el sistema ha puesto muchas dificultades, pero no nos engañemos, la mayoría de esos grupos no ha sabido hacer nunca un proselitismo eficiente y atractivo, haciendo propuestas endogámicas y de consumo interno, sin ser capaces de salir de su burbuja, quedando en muchos casos en terrenos oscurantistas. Lo único que pareció romper un poco este panorama tan lamentable fue la irrupción intencionada de VOX, que pese a que podamos sospechar que se trata de disidencia controlada para canalizar el desencanto de un sector cada vez más amplio de la población, también ha servido para visibilizar que ese sector poblacional existe, que no es precisamente insignificante y que abarca a un espectro social amplio, más allá de los marginados antisociales (_friki-fachas_) que proliferaban por la escena _patriótica_. No obstante, dentro de este panorama tan lamentable, la irrupción de VOX no ha mejorado en absoluto la situación, porque se ha dedicado a fagocitar ciertos elementos de esa «falsa disidencia» fracasada e inoperante, para ocupar muchos de sus cuadros dirigentes, al tiempo que ejerce una mera oposición retórica y actúa como cualquier otra organización del arco parlamentario, invocando el «imperio de la ley», como tanto gusta a los liberales, bajo su formalismo positivo, vacío e inconsecuente. Aún así, el hartazgo y el desengaño ha llegado a ciertos sectores de sus votantes, los cuales se han desmarcado progresivamente de sus políticas y de ese pseudopatriotismo que ha pretendido atribuirse desde su fundación. Dicho todo esto, ¿importa realmente la posición contraria a Alvise de la _disidencia patriótica_ española?. Pues realmente no, porque su capacidad de influencia es insignificante. Por eso, creemos que lo más inteligente que podrían hacer es callarse y dejar de hacer el ridículo, pero quizás eso sea pedirles mucho. En este sentido, y dadas las urgencias que demanda nuestra precaria situación, no deberíamos obstaculizar cualquier acción positiva que contribuya a la causa disidente, aunque sea limitada en el tiempo y quienes la realicen se encuentren en nuestras antípodas ideológicas. En el terreno de lo táctico, y en el terreno de las contingencias, quizás haya ocasiones en las que priorizar un cierto pragmatismo en nuestra visión de las cosas frente a las demandas ideológicas, que siendo absolutamente necesarias y legítimas pueden esperar ante los hechos inmediatos. ### Por qué no somos anti-alvisistas Aunque lo hemos dicho al principio, no está de más recalcar que el propósito de este artículo no es encumbrar ni mucho menos a Alvise Pérez. Nosotros también compartimos algunas de las sospechas que se vierten contra él. Además, tampoco estamos alineados a nivel ideológico. Alvise parece el típico español de a pie, con sus defectos y sus virtudes, educado e influido bajo un sistema liberal. No propone un cambio de paradigma político, sino una continuación del mismo, eso sí, en el que al menos se cumplan las normas que se supone que se tendrían que cumplir. || |:-:| |Las «ardillas» es la red de seguidores/colaboradores/informadores/votantes indignados anónimos de Alvise Pérez, quizás en referencia a «Alvin y las Ardillas»| Es evidente la decadencia del panorama político actual donde se nos miente y se nos toma el pelo ya sin ningún tipo de disimulo. A calzón quitado. Ya ni siquiera se molestan en aparentar que cumplen las normas que ellos mismos han impuesto. Los escándalos de corrupción que hemos testimoniado en el pasado y en la actualidad rebosan lo ultrajante. Intentar que por lo menos se cumplan las normas que se supone que se tendrían que cumplir según el ordenamiento legal vigente, lamentablemente, se tiene que considerar como un logro. Obviamente, nosotros no nos adherimos al susodicho ordenamiento legal, pero entendemos que lo mínimo es ser respetuoso con lo que éste dicta, así como con sus procedimientos y protocolos. Ya llevamos muchos años escuchando por los _mass media_ aquello del «estado de derecho», el «imperio de la ley» o «el sistema más garantistas de todos los existentes», para luego ver cómo la corrupción y el menoscabo de la dignidad e integridad del territorio nacional son prácticas habituales. Por eso creemos que marcarse eso como objetivo a corto o a medio plazo ya es más que suficiente, y si Alvise sirve como ariete para eso, bienvenido sea. No creemos que sea pertinente arremeter contra él y convertirlo en cabeza de turco cuando desde la partitocracia, a izquierda y derecha, se está contribuyendo activamente a la destrucción y sometimiento de España a sus enemigos. Ahora bien, ¿aspiramos al mismo modelo de sociedad? No. Él aspira a lo que cree que es correcto: un modelo Democrático Liberal. Alvise quiere reparar. Nosotros queremos reconstruir desde cero. Lo suyo es más realista y factible a corto plazo. Lo nuestro es una batalla cultural. Podemos contemplar con cierto agrado las acciones de Alvise, siempre que éstas se dirijan contra los partidos políticos, sus integrantes y las corruptelas que protagonizan en un escenario de traición permanente contra el Pueblo y la nación española. Pero nunca podremos coincidir con quienes pretenden seguir confiando en el liberalismo como una opción de futuro, y más después de constatar la responsabilidad de esta ideología perversa en la destrucción del Occidente europeo, totalmente tiranizado y en un estado de metástasis que parece conducirnos a un abismo de caos y destrucción. Por eso lo fundamental en toda opción disidente pasa por adoptar una postura radical e innegociable frente al liberalismo y sus iniquidades. No podemos aceptar el discurso que afirma que lo que fallan son las personas, que son corruptas, pero que el sistema y su entramado ideológico e institucional es bueno, positivo y perfectamente viable, porque no es así. Las personas que dirigen e integran las altas jerarquías del régimen español, y por extensión de las democracias liberales europeas, son corruptas, mezquinas y traidoras porque las instituciones y la ideología que las impregna posee esa misma naturaleza. Y con esto también queremos contrarrestar aquellos tópicos que muchas veces escuchamos en las conversaciones cotidianas, que tienden a culpar el factor humano y contingente y no la estructura político-ideológica que ha favorecido su ascenso y es consustancial a esa corrupción. Desde los tiempos de la _plandemia_ se ha visto un cierto despertar entre amplios sectores de la sociedad española, que han empezado a desconfiar abiertamente de los postulados «políticamente correctos», y ya se atreven a criticar abiertamente temas como la «inmigración», las ingenierías sociales asociadas al Nuevo Orden Mundial u otro tipo de ideas que la prensa vendida se empeña en fabricar para mantenernos dócilmente en el redil. Estos hechos han suscitado formas embrionarias de disidencia y organización, apoyándose muchas veces en las nuevas tecnologías e Internet, como el propio Alvise, y la posibilidad de ir generando redes de comunicación propias, convertidas en vectores de ideas y discursos compartidos por miles de personas. Aunque no coincidamos en lo ideológico, es justo celebrar y apoyar este tipo de iniciativas, y que todo lo que dañe el actual orden de cosas y genere vínculos orgánicos y de solidaridad entre los propios españoles, y europeos, reciba el aliento y el apoyo de todos nosotros. [^1]: Entendemos que VOX no es un partido patriota, sino liberal de derechas, y con evidentes filiaciones con el sionismo. No obstante, hay quien considera que VOX representa, erróneamente, una alternativa «patriota» al actual sistema vigente, cuando siempre ha defendido tanto el orden constitucional fundado en 1978, como sus principales figuras jurídicas e institucionales, tales como la monarquía. @ 3bf0c63f:aefa459d
2024-01-14 13:55:28# O mito do objetivo O insight [deste cara](https://www.youtube.com/watch?v=dXQPL9GooyI) segundo o qual buscar objetivos fixos, além de matar a criatividade, ainda não consegue atingir o tal objetivo -- que é uma coisa na qual eu sempre acreditei, embora sem muitas confirmações e (talvez por isso) sem dizê-lo abertamente --, combina com a idéia geral de que todas as estruturas sociais que valem alguma coisa surgem do jogo e brincadeira. A seriedade, que é o oposto da brincadeira, é representada aqui pelo objetivo. Pessoas muito sérias com um planejamento e um objetivo final, tudo esquematizado. --- Na verdade esse insight é bem manjado. Até eu mesmo já o tinha mencionado, citando Taleb em [Processos Antifrágeis](nostr:naddr1qqyryv3hxfsnvvm9qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c5jshx7). E finalmente há esta tirinha que eu achei aleatoriamente e que bem o representa: [](https://dilbert.com/strip/2004-04-17)
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28# O mito do objetivo O insight [deste cara](https://www.youtube.com/watch?v=dXQPL9GooyI) segundo o qual buscar objetivos fixos, além de matar a criatividade, ainda não consegue atingir o tal objetivo -- que é uma coisa na qual eu sempre acreditei, embora sem muitas confirmações e (talvez por isso) sem dizê-lo abertamente --, combina com a idéia geral de que todas as estruturas sociais que valem alguma coisa surgem do jogo e brincadeira. A seriedade, que é o oposto da brincadeira, é representada aqui pelo objetivo. Pessoas muito sérias com um planejamento e um objetivo final, tudo esquematizado. --- Na verdade esse insight é bem manjado. Até eu mesmo já o tinha mencionado, citando Taleb em [Processos Antifrágeis](nostr:naddr1qqyryv3hxfsnvvm9qyghwumn8ghj7enfv96x5ctx9e3k7mgzyqalp33lewf5vdq847t6te0wvnags0gs0mu72kz8938tn24wlfze6qcyqqq823c5jshx7). E finalmente há esta tirinha que eu achei aleatoriamente e que bem o representa: [](https://dilbert.com/strip/2004-04-17)