-
 @ e5272de9:a16a102f
2024-09-08 19:21:40
@ e5272de9:a16a102f
2024-09-08 19:21:40The Grapevine is designed to digest raw data, no matter where you can find it. This is made possible through the process of interpretation.
Interpretation: the process of converting a source of raw data into a format suitable for consumption by the grapevine algorithm
format of Grapevine ratings
The Grapevine is designed to take as input a list of ratings that follow a specialized format, which we will refer to as Grapevine ratings.
Each rating must contain the following 4 to 6 fields: - rater - ratee - score - confidence - context (optional) - rating type (optional)
rater
The author of the rating. Often will be a pubkey or an npub, but could be username, etc.
ratee
The person, place, or thing being rated. This could be a pubkey, an event id or naddr, or a simple string, e.g. the title of a movie.
score
usually a number, but could be a boolean, an item on a list, etc.
confidence
a number between 0 and 1 (i.e. 0 and 100 percent) that represents the confidence of the rater in the score. For example: If Alice rates Bob as highly skilled in some context, and this is based on working with him for many years, she may rate him 9/10 with a confidence of 0.9 (90 percent). On the other hand, suppose she considers him worthy of a 9/10 rating, but this is based on only one brief interaction. In this case, she may rate him 9/10 but with a confidence of 0.05 (5 percent).
context
a string. This may be omitted from the table if every rating in the table or dataset is of the same context (as may often be the case).
rating type
a string that indicates the type of rating: 5 star, true or false, etc. This may be omitted from the table if every rating in the table or dataset is of the same rating type (as may often be the case).
Example interpretation: follows and mutes
A good way to bootstrap a list of nostr users minus the bots, scams, and other bad actors is to make use of the follows and mutes lists, as is done at brainstorm.
The interpretation of a follow is the following Grapevine Rating: - rater: pk_Alice - ratee: pk_Bob - score: 1 - confidence: 0.05
The interpretation of a mute is the following Grapevine Rating: - rater: pk_Alice - ratee: pk_Charlie - score: 0 - confidence: 0.1
Grapevine Ratings Tables
A list of ratings may be referred to as a Grapevine Ratings Table or a Grapevine Ratings Dataset (if in some non-table format, such as an object).
In the below example, the rating type (0 to 5 stars) and context (item quality) columns are the same for each row in the table and so are omitted.
| rater | ratee | score | confidence | | --- | --- | --- | --- | | pk_Alice | item1 | 4 | 0.5 | | pk_Bob | item1 | 5 | 0.9 | | pk_Alice | item2 | 0 | 0.1 |
Sources of Raw Data
| Some Suggested Sources of Raw Data | | --- | | follows, mutes, zaps | | kind 1 and long form notes | | NIP-51 lists | | kind 7 reactions | | NIP-32 labels | | NIP-58 badges | | nostr forms (e.g. see formstr) |
-
 @ c6f7077f:ad5d48fd
2024-09-08 01:24:03
@ c6f7077f:ad5d48fd
2024-09-08 01:24:03“The more you learn about something, the more you realize you know nothing.” This saying resonates deeply with me. The truth is, no one really has all the big answers. Many in the scientific community seem to pretend they do. Let’s explore this further.
Consider the Most Fundamental Questions
- The Origin of the Universe
- The Origin of Life on Earth
The Origin of the Universe
You might think we have a solid answer: the Big Bang. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to Sir Roger Penrose for a deeper understanding.
The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: the endless expansion and contraction of the universe. This idea doesn’t contradict our current understanding.
Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet neither can be definitively proven over the other. This highlights the limitations of our current understanding.
The Origin of Life on Earth
The origin of life is even more complex. Life requires three essential components: - Proteins for basic functioning - RNA for storing and replicating genes - Lipids (cell walls) to create separation from the environment
Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from outside sources. Some scholars even question the entire random mutation model.
The Question of Certainty
If scientists don’t know the answers, why do they pretend they do? In my humble opinion, It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative, Interestingly, I’m not alone in believing they closed the books too early.
Reclaiming Control of Science and Education
The best way to reclaim control of science and education is to learn. If you’re looking for a starting point, I highly recommend: - “A Brief History of Time” by Stephen Hawking for physics - “Sapiens” or “The Selfish Gene” for evolutionary biology
All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
-
 @ 0f1b5961:868242bd
2024-09-09 22:01:16
@ 0f1b5961:868242bd
2024-09-09 22:01:16The public theologian Jonathan Pageau has been a major influence in my life for the past couple years. I remember in one of his podcasts he talks about how church buildings have historically been the "focal points" of many towns. In the physical sense, this meant the church building was at the center of the town and was the tallest structure. He argues that the church occupying this station had a sort of psychological effect on the town members, enforcing a way of life that has God in the highest "place".
This got me thinking about my own home city of Des Moines, Iowa. Here, the two most prominent buildings, by far, are the capitol building and a skyscraper called the Principal building. They sit on either side of the Des Moines River and to me, seem to "face off" against each other as if in competition.
 The Iowa State Capitol
The Iowa State Capitol The Principal Building (801 Grand Avenue)
The Principal Building (801 Grand Avenue)I was musing over how to settle the competition between these two buildings and I realized that it could be addressed with some pretty basic math. The apparent heights of these buildings change as you move closer or further from them. So whichever building appears taller for a larger portion of the city would be the most prominent building. In an idealized scenario, there would be a straight line between the two buildings where they would appear to be the same height.
This line ends up coinciding with East 4th street on the east side of the Des Moines River. As the Principal building is about twice as tall as the capitol buiding, the point at which they look the same height is about twice as close to the capitol building.
 Line along which the capitol and Principle building appear to be the same height.
Line along which the capitol and Principle building appear to be the same height.And so a clear winner emerges. Not only is the Principal building the most prominent in the downtown district of the city. It's influence extends across the river and eclipses the capitol in what one might expect to be its home turf. The focal point of Des Moines is a skyscraper.
I now must conclude with a confession. With the Principal building being about twice as tall as the capitol, there was never going to be a close competition between the two buildings. And indeed this matches the experience of one moving about the city. The Principal building plainly feels more prominent. Despite this, the area in which the capitol ascends to the highest is certainly not small. I like to think this reflects some amount of balance between the mercantile powers and political powers in the area. Perhaps this balance is proportional to the very heights of the buildings.
Not looking good for the ecclesiastical powers however...
-Scott
-
 @ a2eddb26:e2868a80
2024-09-09 20:30:57
@ a2eddb26:e2868a80
2024-09-09 20:30:57
Introduction
I recently started a new #website, and decided I wanted to get some simple, out-of-the-box, self-sovereign #bitcoin on it.
It turns out there were quite a few steps involved, but mostly is actually out of the box.
So, I share with you, my first long-form #Nostr article, which aims to summarize the things you could use if you wanted to do the same, without actually building your own software.
This article runs through the following steps: Step 1: get a Bitcoin node Step 2: get website infrastructure Step 3: Configure your Bitcoin node Step 4: Configure your Bitcoin-based website
Before we dive in, a few small disclaimers:
- "Do Your Own Research"
- I am not responsible for any failures of your ability to follow these steps - take the guide as-is and on face value, and dive in where you need to. Starting points only. I will help where I can, you can always try to DM me!
- Suggestion to talk to ChatGPT or Google about Lightning Network and Bitcoin basics (here's a GPT created by yours truly for that purpose: Bitcoin Beacon GPT).
- I am not affiliated with any of the sites, services and tools mentioned here. They are what I used and what worked "out of the box" while not giving up self-sovereignty.
I strongly recommend you consider donating to ALL developers in this guide or paying them for their products offered.
Go build it!
Step 1: get a Bitcoin node
Self-sovereignty requires a bitcoin node. If you depend on another person's node, there is no final verification of blockchain data possible. Luckily, obtaining one is quite convenient nowadays, since several out-of-the-box boxes exist that you can buy, almost fully set-up.

Hardware
These do come at a cost. It may be more cost effective to find your own #hardware, whether it's an old laptop, a Asus NUC mini-PC, or a self-built device. I only recommend having a RaspBerry Pi if it is one of the newer types with lots of RAM, otherwise your initial block download will take forever.
Also consider a 2TB disk size (at least) so you are safe for a while to come. Soon, 1TB will not be sufficient to store the bitcoin blockchain data without pruning (remember, we're self-sovereign, this is the best data storage you invest in).
This article does not intend to be a catch all article with many details about hardware, so please DYOR about the details and if you want out-of-the-box, I recommend start9.com StartOne
Software
This is easier. I wholeheartedly recommend (again) Start9's StartOS. Here's a DIY link if you're doing this on your own hardware and aren't buying their excellent hardware offer. I did this, and it was quite convenient. The main difficulty I had was that I required a ethernet connection to my box during the install, since WiFi is not set-up until afterwards. This was not obvious because, well, I had a big box and had to carry that downstairs to my router. I also connected a screen, mouse and keyboard to make it all work. Nothing I couldn't overcome. Again, if you are worried - just buy the box.
Step 2: configure your Bitcoin node
Installing all apps on your node
The package I have consists of:
- Bitcoin Core - Not sure why this is here, but I do see about a 4MB download happening every 10' so I guess it is doing something. Seriously people, DYOR.
- LND - it runs Lightning Network on your node, thus allowing you to connect to other lightning network nodes and set-up channels to receive payments onto.
- Ride the Lightning - your management tool so you can send and receive payments.
- Nostr Wallet Connect by Alby - amazing tool that provided the secret sauce to make payments to your website easy. Extra benefit: you can Zap directly from your own node, with any mobile or web client connected through NWC !
- Optional (but not really): BTCPayServer if you want to run any form of commerce on your website - I assume you got here to stack some sats, and this is the tool for making it easy for your customers to pay you.
- Optional (but not really): Mempool instance so you can check all your transactions without leaking metadata <-- THIS IS WHY YOU RUN A NODE, ANON!
All these things are 1-click installs, 2-click configuration, and possibly a few more to get set-up properly. This is why you go through the pain of making the Start9 setup work (or pay them, and it is literally going to work after unpacking the box...)
Get inbound liquidity
| NOTE: Securing Your Node and Website | | --- | | Ensuring the security of your self-sovereign setup is critical. Start by implementing regular backups of your node, wallet, and website, ideally using encrypted external storage solutions. Monitor your node’s activity to ensure it's functioning securely, and consider setting up additional authentication measures, such as multi-signature wallets or hardware wallets for larger amounts. Additionally, to safeguard your server from unauthorized access, set up a firewall, limit SSH access to specific IPs, and enable 2FA on all related services. Tools like Fail2ban can help protect against brute-force attacks, and keeping all software up to date is essential for preventing vulnerabilities. Always store your private keys and recovery phrases securely and offline. |
Deposit bitcoin to your own wallet (use RTL to generate an address). I recommend in the order of 1M sats for any UTXO depending on your willingness to take risks - this is a hot wallet even though security is very good by default.
First, go to Mempool and check out a few Lightning nodes with high connectivity (= high channel count, high capacity) to connect to. Open a few channels to them with (some) capacity from your 1M sats. Public channels. FYI: you are now ready to start zapping on a mobile client for #Nostr, e.g. #Amethyst on Android or #Damus on iOS - or #Primal on either - or if you're on the web, #YakiHonne and #Nostrudel are my go-to clients.
Second, go to Amboss Magma, connect with your node (or use Alby's excellent Firefox Extension that you can easily hook up to your node and connect through "WebLN"). You need to sign a message, it can be done in RTL.
Third, set-up at least 1 paid inbound channel pending your liquidity needs after the website gets up and running and you are actually selling anything.
Step 3: get website infrastructure
I will admit we can not be truly independent if we want to be out of the box. Especially webhosting is something not recommended from a home server, for multiple reasons (security being one), even if StartOS could probably do it on your node.
Domain name
There are many sources here, you should pick something. I used GoDaddy but there are no rules, just costs, convenience, ... the usual trade-offs. GoDaddy has a convenient URL searcher and comes with recommendations and clear pricing, with nice discounts for the first year (your project may be doomed to crash prior to that...
Hosting
I did find the hosting options at GoDaddy quite expensive. So I just registered with AWS for an EC2 instance. In the Amazon Free Tier you basically get a free linux box with a public facing domain during a year. Another nicety about AWS is that you can very easily upgrade your hosting needs with them, compute, memory, disk, ... and services.
Host configuration
This costs significant time per this method, and is not for the faint of heart. One-click installs would include having this all done by a hosting provider.
WordPress installation
WordPress is an all-in-one website building tool that requires an extremely low acumen of CSS, HTML or databases. It all gets pre-configured and pre-setup while having a host of tools and systems available to support pretty much any feature a modern website would want. Disclaimer; there is definately NOT enough #Nostr content yet.
Here, I do go into some bits and pieces regarding the bitcoin side of things on WordPress. However I don't know what you want on your website, so I recommend you dive into the details on what's possible on WordPress regarding generall web functionality yourself as I consider it out of scope for this article.
One step in being self-sovereign is hosting your own WordPress - even if on a third party host - so that you fully control it and are sure nobody else can access the MySQL databases, configurations, ...
Luckily, this is very easy on an AWS instance. Wordpress can be simply installed as a package, and configuration is literally going to /wp-admin and setting things up. At that point it becomes click-click, write content, launch.
You can opt for a Docker-based installation as well, so WordPress has all dependencies satisfied. However, this comes at the risk of misconfiguration of the persistant volumes, and thus wiping your entire install at a Docker crash - not recommended.
Make sure you set the owner / group (chown) for the wordpress installation folder structure to nginx:nginx (see next subsection) and the file properties (chmod) to 644.
Web server
I had a lot of fights with Nginx since I needed a reverse proxy functionality for a docker application the server was also running, plus having the system Nginx serving up the wordpress site.
Anyway. If you don't need any of that - most likely you don't - just run nginx and set-up the config file to a port 443 (SSL / HTTPS) connection and ensure you redirect regular HTTP traffic on port 80 to the HTTPS. Use Let'sEncrypt with certbot on the Amazon instance to get certifications for your domain. After setting it up, check that automatic renewals for the certificates are also set-up:
sudo certbot renew --dry-runIf not, add a cron item on your AWS instance (sudo crontab -e) and add the following line to restart nginx after every renewal:
0 */12 * * * certbot renew --quiet && systemctl reload nginxEnsure you forward the ports 80 and 443 on your DNS records for the domain to the public-facing IP from the AWS instance.
Pro Tip: You can review rate limiting from Amazon, but it comes at a cost. Alternative, just configure your nginx to do rate limiting for you, here is a reference code snippet to set it up for the relevant server blocks in your nginx configuration:
``` limit_req_zone $binary_remote_addr zone=one:10m rate=1r/s;
server { location / { limit_req zone=one burst=5; ... } } ```
Forwarding the BTCPayServer .onion address through to clearnet through your AWS instance
| Disclaimer | | --- | | This section assumes a moderate understanding of Tor, Nginx, and reverse proxies. For more in-depth tutorials on these topics, we recommend reviewing external resources such as the Tor Project Documentation and the Nginx Reverse Proxy Guide. As setting up reverse proxies and Tor for a Bitcoin node can be complex, these instructions are not exhaustive, and configurations may differ based on your hosting environment. Please ensure to consult these resources for further detail and troubleshooting .|
Annoyingly, but also purposefully, the average bitcoin node does not expose anything to public clearnet besides on local LAN. Instead, it exposes public interfaces on Tor which you need the exact address for to access (=high entropy).
However, for your BTCPayServer instance to connect to your website, you need to be able to connect to it from that website. This is where a so-called reverse proxy once again needs to save us. To make matters worse, you don't have Tor by default on AWS machines (on my EC2 instance it ran Amazon Linux 2023) so we need to build from source. I suggest you ask instructions to ChatGPT; Pro-Tip: Copy-paste parts of these notes and let him explain exactly what you need to do!
You could set a subdomain e.g. btcpay.yoursite.com to be accessible for your .onion redirect on the AWS instance. Here is an example configuration snippet:
``` server { listen 443 ssl; server_name btcpay.yoursite.com;
location / { proxy_pass http://127.0.0.1:80; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; } ssl_certificate /etc/letsencrypt/live/yourdomain/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/yourdomain/privkey.pem;} ```
Step 4: configure your Bitcoin-based website
Finally, we come to the cool part. What can we do with all these things?
So, on WordPress, I recommend the following plugins:
- Alby's LN Publisher - it seems they need to test it on the latest WordPress version - but this tool worked for me. It connects to your NWC instance on the node and implements easy paywalls.
- BTCPay For Woocommerce V2 - to connect to your store and creating that flawless interface for your customers.
- WooCommerce
Getting BTCPay for WooCommerce set-up is detailed in this guide.
Importance of Backups
Backups are a critical part of any self-sovereign setup, especially when handling sensitive data such as your Bitcoin node and website. Without proper backups, any unexpected hardware failure, software corruption, or cyberattack could result in permanent loss of data, including your wallet, transactions, and important website configurations.
For your Bitcoin node, regular backups of wallet.dat and Lightning Network channel states are essential to prevent loss of funds or access to your Bitcoin. In the case of your website, especially a self-hosted WordPress site, backups of both the database and the files (such as plugins, themes, and media uploads) will safeguard your content and configurations.
Though creating an automated backup strategy is beyond the scope of this guide, it is highly recommended that you:
- Set up regular, automated backups for both your Bitcoin node and website.
- Encrypt your backups to ensure that sensitive information remains secure.
- Store backups offsite or on external media to mitigate risks from local hardware failures.
Investing time in a robust backup solution will protect your self-sovereignty, ensuring that even in the event of failure, your node, funds, and website can be restored.
That's all for now, folks. There surely will be issues you run into. Let me know through a DM, or ask away below - me or like-minded individuals (probably a few on #nostr more expert than me) can help out!
-
 @ e83b66a8:b0526c2b
2024-09-09 20:30:30
@ e83b66a8:b0526c2b
2024-09-09 20:30:30We have a confession to make. NOSTR is not perfect, we are still building. No client you use does everything you want it to, and everything it does is imperfect.
Therefore, I strongly advise you to run multiple clients.
On iPhone, I run: Damus: https://nostrapps.com/damus Primal: https://primal.net/downloads Nostur: https://nostrapps.com/nostur
On Android I run: Primal: https://primal.net/downloads Amethyst: https://nostrapps.com/amethyst
On desktop I run: Primal: https://primal.net/downloads noStrudel: https://nostrapps.com/nostrudel
Also, because I run a node (Umbrel & Start9), I self host noStrudel on my own relay.
If you haven’t taken the plunge to run a node, now might be a good time to think about it.
There are many, many options for clients, the “Social” section of https://nostrapps.com/
lists 23 currently.
Play with them, see what they do, if you’re a developer, you could even consider building or forking your own.
Have fun and realise we are building freedom tech, not just running it.
-
 @ e83b66a8:b0526c2b
2024-09-09 20:27:41
@ e83b66a8:b0526c2b
2024-09-09 20:27:41First,
Key management.
When you “created” your NOSTR account, what you actually created was a cryptographic key pair. This consists of a private key, which starts “nsec” and a public key which starts with “npub”.
As the names suggest, your “nsec” key is private and you should never reveal it to anyone. Your “npub” key is your public key, feel free to share that everywhere.
Your “npub” key is used by others to verify your identity, through the signature added to your messages. It is also used by others to encrypt private messages to you.
We don’t have perfect key management yet and because of the limitation of smart phones and various eco systems, it often becomes necessary for you to copy and paste your private key into apps in order to use them. This is less than ideal, but until we have ubiquitous cross platform key management devices, this situation will remain necessary.
For the moment, consider using software key management options, some of which are listed under “signers” here: https://nostrapps.com/
N.B. We do have projects like Seedsigner that provide more secure hardware key management, but this isn’t for the faint hearted:
Secondly,
Lightning wallets.
It is common for most people to link a Bitcoin Lightning wallet to their NOSTR profile
N.B. Your profile is stored on relays and signed by your private key, which is verified by others through your public key.
You are not tied to any specific wallet for sending payments (called zaps), but you do provide a specific incoming LN address for receiving payments. This could be something like a wallet of Satoshi Address i.e. “randomname@walletofsatoshi.com” or could you be your own node with a connection to it via “Nostr Wallet Connect” a free plugin that connects a lightning wallet.
Enabling this allows people to “zap” any posts or content or even send you payments directly at any time or for any reason. N.B. It is called freedom money for a reason….
It also allows you to send small micropayments to posts or people you like.
Thirdly,
Paid Services
As you go deeper into the NOSTR ecosystem, you’ll notice there is no advertising being pushed at you and there are no algorithms manipulating the content you receive. This is because there is no company behind NOSTR, it is a protocol. Because of this, while all the ecosystem is free to use and will remain so for the foreseeable future, most of it is run by enthusiastic volunteers or developers and incurs a cost to them. For that reason many of us choose to support these #devs by paying for services. This can also enhance our experience, giving our “npub” greater reach and discoverability.
I, for example choose to pay for the following services:
https://nostr.wine/ - 120,000 Sats for 2 years relay https://relay.tools/ - My own relay - https://nortis.nostr1.com/ 12,000 Sats a month https://nostr.build/ - Media storage - 69,000 Sats for 1 year
Total: 22,750 Sats per month Approx $15 per month
This is not strictly necessary, but I decided to support the various developers behind these projects.
Do not feel any pressure at this early stage to pay for any service, but if you enjoy the freedom NOSTR brings, you may want to consider supporting the projects that become important to you going forward.
-
 @ c11cf5f8:4928464d
2024-09-09 18:45:16
@ c11cf5f8:4928464d
2024-09-09 18:45:16originally posted at https://stacker.news/items/678432
-
 @ e968e50b:db2a803a
2024-09-09 18:21:54
@ e968e50b:db2a803a
2024-09-09 18:21:54Open the frozen pizza bay doors, Hal.
originally posted at https://stacker.news/items/678403
-
 @ 6bae33c8:607272e8
2024-09-09 16:07:43
@ 6bae33c8:607272e8
2024-09-09 16:07:43I’ll write a separate Week 1 Observations later, but I wanted to dedicate this space solely to mourning my Circa Survivor entry.
Circa Survivor costs $1000 to enter and has a $10M prize for the winner, usually split by several as things get down to the wire. Three years ago, when the prize was $6M Dalton Del Don and I — the first time we ever entered — made it to the final 23 in Week 12. The value of our share was something like $260K at that point, but we got bounced by the Lions who beat the 12-point favored Cardinals and took home nothing.
When you enter a large survivor pool, the overwhelming likelihood is you’ll meet this fate at some point, whether in Week 1 or 12. So it’s not really the loss that’s painful, so much as not getting to live and die each week with a chosen team. You lose your status as “the man in the arena whose face is marred by dust and sweat and blood” and become just an observer watching and commentating on the games without the overarching purpose of surviving each week.
This year was also different due to the lengths to which I went to sign up. It’s not just the $1000 fee, it’s getting to Vegas in person, the $400 in proxy fees (you need locals to input your picks for you if you don’t live there), the $60 credit card fee, the $200 crappy hotel I booked at the last minute, the flights (one of which was cancelled due to heat), the rental car that necessitated, the gas, getting lost in the desert, the entire odyssey while sick and still jet-lagged in 122-degree heat.
But it’s not about the money, and it’s not even about the herculean effort per se, but the feeling and narrative I crafted around it. I was the guy who got this done. I flew from Portugal to San Francisco for 12 hours, two days later from SF to Palm Springs to help my 87-YO uncle with his affairs, improvised to get from Palm Springs to Vegas, which took six hours due to road closures, signed up for the contests, made the flight back to San Francisco, flew to Denver at 7 am the next day, took my daughter the Rockies game in the afternoon and then on to Boulder the following day. Maybe that’s not so impressive to some of you, but for me, an idle ideas person, a thinker, observer, someone who likes to express himself via a keyboard, it was like Alexander the Great conquering Persia.
And it’s not only about that smaller mission, or the narrative I crafted around it, but a larger one which was to bring sports content to nostr which I vowed to do before the summer which is why I felt I had to make the effort to get to Vegas to sign up for the contests, to have sufficient skin in the game, to have something real about which to write.
And I got the idea to do this seriously because Heather wrote a guide to Lisbon which I posted on nostr, and a few prominent developers there were surprisingly excited about getting that kind of quality content on the protocol. And I thought — if they’re this excited about a (very in-depth) guide to one particular city in Europe, how much more value could I create posting about a hobby shared by 50-odd million Americans? And that thought (and the fact I had to go to Palm Springs anyway) is what set me off on the mission in the first place and got me thinking this would be Team of Destiny, Part 2, only to discover, disappointingly, it’s real destiny was not to make it out of the first week.
. . .
While my overwhelming emotion is one of disappointment, there’s a small element of relief. Survivor is a form of self-inflicted torture that probably subtracts years from one’s life. Every time Rhamondre Stevenson broke the initial tackle yesterday was like someone tightening a vice around my internal organs. There was nothing I could do but watch, and I even thought about turning it off. At one point, I was so enraged, I had to calm down consciously and refuse to get further embittered by events going against me. Mike Gesicki had a TD catch overturned because he didn’t hold the ball to the ground, The next play Tanner Hudson fumbled while running unimpeded to the end zone. I kept posting, “Don’t tilt” after every negative play.
There’s a perverse enjoyment to getting enraged about what’s going on, out of your control, on a TV screen, but when you examine the experience, it really isn’t good or wholesome. I become like a spoiled child, ungrateful for everything, miserable and indignant at myriad injustices and wrongs I’m powerless to prevent.
At one point Sasha came in to tell me she had downloaded some random game from the app store on her Raspberry Pi computer. I had no interest in this as I was living and dying with every play, but I had forced myself to calm down so much already, I actually went into her room to check it out, not a trace of annoyance in my voice or demeanor.
I don’t think she cared about the game, or about showing it to me, but had stayed with her friends most of the weekend and was just using it as an excuse to spend a moment together with her dad. I scratched her back for a couple seconds while standing behind her desk chair. The game was still going on, and even though I was probably going to lose, and I was still sick about it, I was glad to have diverted a moment’s attention from it to Sasha.
. . .
In last week’s Survivor post, I wrote:
What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.
It’s possible I did this, but simply retrieved my information from the wrong branch of the multiverse. It happens.
. . .
I picked the Bengals knowing full well the Bills were the correct “pot odds” play which is my usual method. Maybe when the pot-odds are close, I might go with my gut, but they were not especially close this week, and yet I still stuck with Cincinnati because they were the team I trusted more.
And despite it being a bad pick — there are no excuses in Survivor, no matter what happens in the game, if you win it’s good, and lose it’s bad — I don’t feel that badly about it.
I regret it only because I wish I were still alive, but it was my error. I went with what I believed, and it was wrong. That I can live with 100 times better than swapping out my belief for someone else’s and losing. Had I done that I’d be inconsolable.
. . .
I won’t let the Survivor debacle undermine my real mission to bring sports to nostr. Team of Destiny 2 would have been a compelling story, but it was never essential. After all, my flight was cancelled and I had to improvise, so now my Survivor entry is cancelled, and I’ll have to improvise again. The branch of the multiverse where the Bengals won didn’t give me the information I wanted, but maybe it was what I really needed to know. That I am the man in the arena yet, the battle was ever against myself, and for a brief moment, while my team was losing, I prevailed.
-
 @ 472f440f:5669301e
2024-09-06 21:56:48
@ 472f440f:5669301e
2024-09-06 21:56:48I had the pleasure of sitting back down with Will Reeves, Founder and CEO of Fold, on TFTC last week to discuss Fold's journey from a startup to (soon to be) a publicly listed company. I particularly liked this conversation because it was a great lens into the grit it takes to run a successful bitcoin company.
https://fountain.fm/episode/1FrspxmpK5bsoReGx73n
Building a successful company is extremely hard in its own right. Building a successful bitcoin company is significantly harder considering the fact that you're building a company in parallel with a nascent and volatile monetary asset that is monetizing in real time. Bitcoin adoption comes in waves. People flood in when the price is ripping and fade out when the price corrects and goes into a multi-year bear market before the tide comes back in. This means that your potential user base is expanding and contracting more than it would be in other industries. As a company you need to be able to absorb the incoming waves of new adopters and then capture and retain the users who stick around for the bear market.
To do this correctly, a founder and their team needs to thread many needles. First, can you assemble a team that can actually build something? Second, can you bring a product to market that people actually use because it provides value to them? Third, can you stick out against the crowd? So on and so forth. One of the most important aspects of building a bitcoin company during bitcoin's monetization phase is timing. There are many great ideas that people have in terms of companies, products and tools that can built using bitcoin. There are sci-fi futures that can be built today on bitcoin if people really wanted to.
The problem that arises is that adoption and understanding of bitcoin are at a point where, even though a functional product could be brought to market, it won't be adopted by a large number of people because there 1.) aren't enough people who would understand how to use it and 2.) for the people who do understand how to use it and could benefit from it, the universe of people they can interact with using that product is minuscule.
Timing is everything. And I think Fold nailed the timing of their product. Allowing people to passively stack sats by offering a product that enables them to go about their daily spending and get sats back instead of cash back rewards is a great first-touch bitcoin experience. Once Fold found their sticky user base and perfected their sats back experience, they began expanding their product offering to provide their users with more bitcoin services. Buy/sell bitcoin in-app, bill pay for sats back, and more. They'll eventually roll out a credit card and additional financial services. Start simple, provide something of value, nail the timing and then expand from there. That seems to be the recipe.
For any founders in the space reading this, I highly recommend you listen to the episode. Particularly for the advice Will gives about knowing when to sprint on product and when to lean into growth. Bear markets are for building and bull markets are for casting the widest net possible and capturing as many new users as possible.
At Ten31 we are extremely proud to back Fold and a number of other companies in the bitcoin space that understand the intricacies described above. We work with some of the best founders in the world. Founders who know how to eat glass with the best of them. Bitcoin can be a cruel mistress and no one knows that more intimately than the founders building bitcoin companies.
Final thought...
The NFL having a week 1 game in Brazil should get Roger Godell fired.
Enjoy your weekend, freaks.
-
 @ d3052ca3:d84a170e
2024-09-09 15:43:38
@ d3052ca3:d84a170e
2024-09-09 15:43:38I bought this for my son but it's a little advanced for his skills. Well, somebody has to find the princess and save Hyrule, right? Looks like it's gotta be me. :)
I have found the climbing, skydiving, and barbarian armor sets most useful. What other items can I unlock that will enhance my play experience? I just found the gloom resistance helmet but haven't tried it out yet.
What is the deal with horses? I tamed and boarded two so far but I haven't found an actual use for them yet except one korok hidden under a drain plug that I needed a horse to unplug. You don't need them for travel. They can't climb steep slopes or cross water so it's just easier and faster to skydive close to your destination and cover the last miles on foot. Do mounts serve a purpose or just look cool and help you get a few korok seeds?
What is your experience? I'd love to hear about it!
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:15:47
@ 3bf0c63f:aefa459d
2024-09-06 12:15:47a way to do an open and permissionless mesh network
I don't have much experience with that so maybe this is all a stupid, but I think that routing in mesh networks is never scalable. It basically always requires all the nodes to keep a full view of the network in order to route packages -- and often there is no incentive for them to do that either. And then the thing is easily spammable but either that problem doesn't happen because the mesh never gets big enough or it has a central committee that decides who can join.
The biggest example is, of course, the big ICANN-controlled IP network, that gets all the negatives of being centrally controlled while weirdly getting also all the negatives of being a kinda-decentralized peer-to-peer ad-hoc network between indepent ISPs.
A good solution that makes kinda-decentralized (at least open and permissionless) routing possible and replaces node addresses with pubkeys could get rid of ICANN. Once that is done, ad-hoc peering would become more seamless and ISPs wouldn't have to be so big, clunky and centralized, they could slowly split, and non-comercial entities could join the party too by basically just plugging a cable or pointing an antenna at the correct place.
What is it?
One very dumb solution that came to my mind that has a chance of working is one in which each node as a keypair and to be reachable by others they announce their address -- for example, using some kind of DNS (on a [spacechain]?) or by directly communicating their address through some other means -- as their public key plus some "routing hints".
The routing hints are just pubkeys of other nodes known to be routers. Known to whom? Well, this would require some schelling points to naturally appear and the network would be ordered around them, but you are never forced to use them, you have to include as many routing hints as required to ensure that all the people you want to connect to you will eventually be able to, but nothing is ever 100% guaranteed.
Such network could probably work with a pure onion routing scheme with all its privacy benefits in some cases; degrading to a trampoline onion routing scheme otherwise, which means it will just be slightly less private the more trampolines you have to use. And every node has to keep track of just a set of routes from them to a bunch of known routers (or trampolines, which in my mind are mostly the same nodes, but are slightly different roles).
Example
Suppose A is trying to connect to B.
A is a home computer in the city of Évora, Portugal.
B is a home computer in the city of Udine, Italy.
There is a route (we, the narrator, know) between them that goes like this:
A--Ev--Li--Al--Ro--Sm--Ve--Ud--B, in which Ev means the node of an ISP in Évora which directly serves A, Li means a big node in Lisboa, Al a node in Algiers, Ro a node in Rome, Sm a node in San Marino, Ve a node in Venice and Ud a gateway node in the mesh of Udine to which B is connected.
There could be many other routes, but we'll ignore them for now.
B could have published his address as
<pubkey-B>?hint=<pubkey-Ud>,<pubkey-Ve>,<pubkey-Sm>,<pubkey-Ro>, which would mean A would only have to know a route from Ev up to Ro.If Ro is known to be a big router, A could easily have a route cached there, and could discover other routes by asking around every now and then too. It wouldn't take a lot of space to have routes cached to some thousands of different known big nodes like that. Then A can just wrap an onion with all the coordinates and the message inside and hand it to Ev and it would reach B. Inside the message she would also include the full route for a message to be sent back.
However, even if A doesn't have a route to Ro, it could still hope that Li would have, then she could make a special "trampoline" onion that goes Ev--Li and then when Li receives it it sees a request to forward the next packet to Ro, so Li has the freedom to choose a route from itself to Ro (as long as it knows Ro, of course) and from there A's message continues.
The same trampolining can exist on B's side, if B doesn't have a route from Ud to Ro, but knows Ro is likely to have one up to Ud -- or if B feels it's not worth including so many hints when most big nodes will have routes to Ud, for example, it can publish his address as
<pubkey-B>?hint=<pubkey-Ud>*<pubkey-Ro>meaning that one should find a route up to Ro and from there ask Ro to trampoline it up to Ud.Or, if B doesn't expect Ud to be very well-known, but Sm yes, then it could do
<pubkey-B>?hint=<pubkey-Ud>,<pubkey-Sm>*<pubkey-Ro>. Again, this is just one hint, in practice it would have to have a lot (maybe 10, 20?) other hints, in a tree structure that this querystring syntax isn't very suited for encoding:``` Ud Tr Pu Za Li
Sm * Ro Ba Mi La Ge * Mo Tu
```
(Remember, we're using city name abbreviations here, but each of these would be a specific node, with a specific public key, supposed for the example to be in such a city, but nothing prevents them from being in different cities or that multiple nodes exist in the same city.)
Summary
Basically packets go from node to node, in a sequence established by the sender -- with optional trampolines in between -- until they get to the target. Target responds in the same route. Nodes can be anyone. Focal points form around big nodes, but they can be replaced easily, the receivers just have to stop using them in their hints, so the network is flexible and open.
-
 @ 3875a16c:988456c9
2024-09-09 14:50:15
@ 3875a16c:988456c9
2024-09-09 14:50:15ORIGINAL PANEL TITLE: MAKING BITCOIN MORE PRIVATE WITH CISA
SPEAKERS: NIFTY NEI, CRAIG RAW, FABIAN JAHR, JAMESON LOPP
CONFERENCE: BITCOIN NASHVILLE 2024
ORIGINALLY PUBLISHED ON: BITLYRICS.CO
Introduction
This edited transcription comes from a panel titled “Making Bitcoin More Private With CISA”, featuring an insightful discussion on cross-input signature aggregation ( CISA). Moderated by NiftyNei from Base58, the panel includes Jameson Lopp from Casa, Craig Raw from Sparrow Wallet, and Fabian Jahr from Brink.
Recorded at the Bitcoin – Nashville 2024 conference, the panel explores how a Bitcoin CISA soft fork can enhance privacy and efficiency in Bitcoin transactions by aggregating signatures. The speakers share their personal experiences with CISA, its potential economic incentives, and the technical challenges it faces, while offering a clear explanation of its role in privacy-focused Bitcoin development.
NiftyNei (Moderator):
Hey everyone, my name is Nifty, and I’m going to be moderating this panel today. We’re here to talk about CISA (cross-input signature aggregation).
Joining me today on the stage, I have Jameson Lopp from Casa, Craig Raw of Sparrow Wallet, and Fabian Jahr of Brink. So, welcome them to the stage.
We’re excited to be talking to you guys about this.
I think it’d be great to maybe start off by hearing a little bit more about who’s on our panel today. If the panelists could tell the audience about the project they’re working on and where they first heard about CISA.
Craig, do you want to start?
Craig Raw (Sparrow Wallet):
I built Sparrow Wallet. It’s a security and privacy-focused wallet.
The first time I heard about CISA was really from other privacy activists in the Bitcoin space who were talking about how they were really hoping that this cross-input signature aggregation would be shipped as part of the Taproot upgrade. Obviously, we know that didn’t happen.
When you’re looking at things from a privacy point of view, you want to do things like create multi-party transactions, and as we’ll hear, cross-input signature aggregation provides an interesting basis for being able to do that more economically.
So, that was the first time I really started to look at it from the privacy angle.
Fabian Jahr (Brink):
I primarily work on Bitcoin Core, and I can’t really remember a specific time when I first heard about it.
Between the SegWit soft fork and the Taproot soft fork was when I really got deeper into Bitcoin and started contributing to Bitcoin Core.
Somehow, CISA was always there, but I only started researching it and going deeper into it over the last couple of months.
I saw that it was a topic brought up for the Taproot soft fork but was cut at some point to keep the scope smaller.
I forgot about it for a year or two until it kept popping up in privacy discussions, as Craig mentioned, which triggered me to look deeper into it.
Jameson Lopp (Casa):
I’m Jameson Lopp. I work at Casa, where we help people with highly distributed, secure, multi-signature self-custody setups.
I think the first time I heard about CISA was in an Andrew Poelstra talk.
I mostly remember being blown away by the vision he painted of a future where we were all financially incentivized to participate in CoinJoin transactions for everything we transacted.
This would break a lot of the potential for chain surveillance because, if we’re all honest, Bitcoin has pretty poor privacy characteristics.
NiftyNei (Moderator):
That’s a great point. Okay, so I think now that we’ve had an intro into how each of you came to hear about it, and maybe some of the things you thought were important or cool when you first heard about it, maybe we could take a little bit of time to explain a little bit more about what CISA is and what those letters stand for.
Does anyone have a good explanation of how it works?
Fabian Jahr (Brink):
I can start off.
So, it’s really already all in the name: cross-input signature aggregation.
If you think of a Bitcoin transaction as it looks today, you have, sometimes, one but often multiple inputs, and with each input, usually, a signature is associated.
What the linearity property of Schnorr signatures allows you to do is to aggregate these signatures. You can aggregate them across the different inputs that you have in a transaction.
So, that means that in the future, we could have transactions with multiple inputs—if you think specifically about transactions that have a lot of inputs, like CoinJoins, for example, as we just mentioned—these could have just one signature. And depending on what technique you use, these can be just as big as one single signature before.
Of course, that saves a lot of space, both on-chain and also in terms of the fees, because you take up less space in a block. That is the general idea.
NiftyNei (Moderator):
I have a quick question about that.
So, whenever you say you can do cross-input signature aggregation on a transaction, usually, you’ll have a couple of things called inputs, and each of those inputs will have a signature on it, right?
So, the general idea is that, on that same one signature, instead of having a couple of them, you’d be able to roll them all up and just have a single signature.
Is that a good summary of what you’re explaining?
Fabian Jahr (Brink):
Yeah, I would say so.
Craig Raw (Sparrow Wallet):
So, there are two major ways to do this. One is what we call a half-signature aggregation, or half-SIG, as we abbreviate it.
That’s where you don’t need an interactive process. Anybody can take all of the signatures that appear currently for every input in a transaction, and they can aggregate them into one.
Now, the size of that one is unfortunately not the size of a normal signature—it’s slightly bigger. In fact, the size is determined by the number of inputs that you have. So, that’s one way to do it.
Then there’s a more comprehensive way to do it, which is called full-signature aggregation. That gets you a much more compact signature, which is the aggregate of all the other ones.
Unfortunately, the downside of that is that you have to do the interaction while you sign.
The problem with that is that interaction always contains a lot of complexity, so unless you own all of the inputs, you are going to have to interact with everyone else who’s adding an input to that transaction, and that creates a much more difficult process in terms of signing.
As a result, I personally am more excited about the kind of half-signature aggregation because it’s just so much easier to do and gets you a lot of the benefits, even though it’s not quite as efficient.
NiftyNei (Moderator):
Cool, so it sounds like we’re taking signature data, and it’s all the same signature data in a single transaction, right?
You wouldn’t have multiple transactions that you’re doing—it’s like on a single transaction level?
Jameson Lopp (Casa):
Well, there’s also full-block aggregation, right?
This is going really far down the rabbit hole, and I think it’s not even something that’s on the table.
There are too many additional edge cases that come up, especially when you start thinking about blockchain reorganizations.
My understanding is you would have to have this other mempool to keep track of things that weren’t sufficiently buried enough in the blockchain that they could be reorganized.
If there was a reorg, it would not be as simple as how we do reorgs right now, where we just take every transaction out, put it back into the mempool, and start over again.
NiftyNei (Moderator):
So, it sounds like you’re saying there are a couple of different ways we could do signature aggregation.
We could do it at the transaction level, and there’s a proposal to do it at the block level, but again, there are some trade-offs there.
One of the nice things about taking signature aggregation at the block level is that you take all the signatures in any transaction inside a block, and you create maybe a single signature object, right?
Maybe it’s not exactly a signature, but something similar to that. What is one reason you’d want to do this? It sounds complicated.
Jameson Lopp (Casa):
Well, there are the privacy characteristic improvements, but also, I think it’s interesting when we’re talking about incentivizing people economically.
If anyone was around and paying attention in 2016 or 2017, when we were talking about Segregated Witness, there was this concept of a witness discount.
It was basically put in place to help rebalance the cost between creating a UTXO and spending a UTXO.
You run into problems where, if you’re receiving a lot of transactions, you’re creating a lot of unspent transaction outputs in your wallet.
It becomes problematic if, at some point in the far future, you want to go spend them, and perhaps the fee rates in the market for block space have gone up a lot.
It can become insanely expensive to spend your own money. This inevitably catches a lot of people by surprise if they haven’t been through a full market cycle before.
So, I think this is another interesting aspect of aggregation—we’d be pushing the balance forward a bit to help incentivize people to clean up their UTXOs because we’re not penalizing them as much by making it really expensive to do so.
Fabian Jahr (Brink):
And maybe to expand on that, there is a financial incentive for people to participate in CoinJoins, and that gives them additional privacy.
The nice effect of that is that hopefully, this would lead to wide adoption of CoinJoin, which means that when more people are CoinJoining, there’s a higher anonymity set that benefits everyone after this anonymity property.
Everyone that participates in CoinJoin can also use this as plausible deniability, even if they are doing it primarily for the privacy aspect. They can always say, “Hey, I’m saving fees here, so that’s my primary motivation.”
Hopefully, a further trickle-down effect would be that, as people ask for this and it becomes more widely adopted, more and more wallets will adopt it.
Easier-to-use wallets, the complexity gets hidden, and it becomes more of a mainstream feature.
Jameson Lopp (Casa):
Yeah, we have to think about the incentives, right?
I consider myself a cypherpunk; I’m a big privacy advocate. I assume we all are.
But the reality of the situation, and this is pessimistic, is that most people don’t care about privacy or they don’t care until it’s too late.
We can stand up here and talk about how awesome it is to have really strong privacy and why you should be using all of these niche tools, but if we actually want people to adopt privacy tools, we need to give them the financial incentive to do so.
It should not be a situation where the average person has to go out and ask their wallet providers or software developers to bake in additional privacy tools and protections into the software.
Really, it should be: why are you making me spend more of my money to use Bitcoin when I could be using this technology that happens to enhance privacy but is actually saving me money?
Craig Raw (Sparrow):
So you might be wondering at this stage what the savings actually look like.
It turns out that if you apply what I was describing earlier—this half-signature aggregation technique—you can fit about 20% more average-size transactions into a block.
You can immediately think that’s going to reduce the average fee level for any point in time when people are submitting transactions to the mempool to be included in a block. You can now fit 20% more average-size transactions into that block, and that’s obviously a big advantage.
Now, the actual effect on a particular transaction, because of the witness discount that Jameson mentioned earlier, is less—it’s like 7 to 8%.
But remember, the average fee rate is going to be lower because we’re fitting more transactions into a block, which means there’s less pressure on block space.
So that’s how I would encourage you to think about it from the start.
For me, the efficiency in terms of block space is a good reason to do this anyway, regardless of whether we get privacy benefits. The privacy benefits come along for the ride.
We actually have this really restricted data space in the blockchain, and if we can apply a fairly simple and low-risk form of compression, I think it’s a serious thing to think about.
NiftyNei (Moderator):
I think, now that we’ve talked about how great this is, we’re going to get more transactions in a block, save money, and get better privacy.
I’d be really interested to hear why it didn’t make it into Taproot originally. Was there opposition to this proposal?
What was it about the Taproot process where this proposal didn’t make it over the line?
Fabian Jahr (Brink):
I wasn’t in the room when this was discussed, but I’ve read all of the transcripts available from when these things were discussed.
From what I can see, I don’t think there was any direct opposition.
The primary motivator was to keep Taproot manageable in terms of review effort and to keep the scope smaller.
I mean, the only thing I can see reading between the lines, which Craig already kind of mentioned, is that if you just look at the pure fee savings numbers and the number of weight units you save, for half aggregation, it’s in the single digits. People are often a bit disappointed as a first reaction, and you have to really discuss it and fill it with understanding.
I think that might have turned off some people, and maybe developers felt like this would be the easiest thing, to chop it off and people wouldn’t miss it as much.
Craig Raw (Sparrow):
Yeah, so in terms of the pushback I’ve heard so far, it’s what Fabian was saying—it doesn’t do enough.
There’s a general perception that we can only push for one soft fork at a time, so all the soft forks have to compete to be “the one.”
That’s an interesting point of view.
Jameson Lopp (Casa):
It’s interesting because I was in the room in Hong Kong when Pieter Wuille announced that we were changing the flagging system so that we could do 32 soft forks in parallel. Of course, we haven’t taken advantage of that yet.
Craig Raw (Sparrow):
Yeah, so we’re in a very different space now.
Something to bear in mind if you’re thinking about it from that point of view is that, and I heard Brandon Black, who was here earlier today, talking about OP_CAT, I think CISA is probably the lowest-risk soft fork we could imagine.
I’m talking about the well-understood half-signature aggregation form of it.
From a security model point of view, the cryptographers tell us there is no risk, or very low risk, to doing this. It takes well-understood properties of Schnorr, which is just adding signatures up, and uses that.
So, in terms of risk, it’s not really enabling other things that Bitcoin can do. It’s not going to be groundbreaking—it’s really just compressing.
If you think about it, compression is a fairly bounded area. You’re not going to suddenly have people developing all kinds of perhaps unwanted things on top of Bitcoin just because you compressed the signature size down.
So, maybe it opens up the space for other soft forks if we do a soft fork with such low risk that it actually gets across the line.
Jameson Lopp (Casa):
I think it’s also worth noting that this is by no means the only signature aggregation scheme happening in Bitcoin.
With the Taproot soft fork a few years ago, we got the theoretical ability to do Schnorr signatures, but that’s been an ongoing process.
As far as I’m aware, there’s been limited adoption of Schnorr so far.
I think MuSig2 is the main production-ready standard people are using, but that can only do an “n of n,” like a 2-of-2 or 3-of-3 type of scheme, so it’s kind of limited in its flexibility.
I care about this a lot, operating a multi-signature self-custody wallet.
We’re waiting for the further evolution of threshold signature schemes like FROST that can do more arbitrary K-of-N type multi-signature.
That evolution, that research, is still ongoing. We’re continuing to see new iterations of FROST come out.
So, we do expect to see more adoption of aggregated signatures across the ecosystem, but the ultimate end goal would be something where there’s only one signature per block.
NiftyNei (Moderator):
So, we only have a few minutes left.
Maybe we can spend a little bit of time talking about what it would take to get CISA to the point where we could soft fork it in.
Fabian Jahr (Brink):
There are still quite a few things to hammer out in terms of all the details, like defining a spec.
For half-signature aggregation, there’s a BIP draft, but it’s not a pull request on the BIP repository—it’s just a draft, with test vectors that are open.
However, for full aggregation, we still need to develop the signature scheme. That requires quite a bit of effort from people well-versed in cryptography, specifically on the side of interactivity.
We will also want to have a security proof for that scheme. That means we’ll need people with specific talents and experience in that area to come together and work on it. I personally spend quite a bit of time on it right now.
Jameson Lopp (Casa):
Yeah, call your local developer and demand signature aggregation today.
Craig Raw (Sparrow):
Fabian has developed a great site where you can learn more.
If the concepts we’ve talked about here today make sense and you want to understand them better, if you go to CISAResearch.org, you can learn more about it.
It’s very easy to read, not overly technical, and I think it gives a good grounding in these things.
Largely, the way soft forks happen is that people need to express views about them, and ultimately, we need to develop some form of rough consensus around whether we want to do it or not.
As far as I’m aware, this is the first panel we’ve had that talks about it. Even though it’s an old and simple concept, we don’t really have a lot of discussion about it right now.
So, talk about it, try to develop an understanding of what it’s trying to do, and see whether you want to have it in Bitcoin or not.
Jameson Lopp (Casa):
I don’t know, do you want to save money? It should be an easy question.
Fabian Jahr (Brink):
And have better privacy.
NiftyNei (Moderator):
Great! Thanks y’all.
**Follow the speakers: ** NiftyNei – Craig Raw – Jameson Lopp – Fabian Jahr
**Watch the original content: ** Click here
**Also read: Build It Right: ** Achieving Interoperability with Open Networks
**Disclaimer: ** Transcripts provided on bitlyrics.co represents solely the opinion of the speaker and is not by any means financial/legal advice or an opinion of the website. The content has been transcribed with maximum accuracy. Repetitions and fill words have been amended in order to enhance the reading experience. The full text may not be confirmed by the speaker. Please, refer back to the above-provided source of content for more certainty. If you are a speaker and wish to confirm/amend your speech please contact us.
-
 @ e968e50b:db2a803a
2024-09-09 13:22:12
@ e968e50b:db2a803a
2024-09-09 13:22:12I just wanted to let y'all know that I added a more sports themed UI option for the crossword puzzle from last week. You can get to it like so:
Also, there's still an unclaimed bounty for anybody interested in solving the additional puzzle.
originally posted at https://stacker.news/items/678010
-
 @ 13e63e99:25525c6a
2024-09-09 09:56:33
@ 13e63e99:25525c6a
2024-09-09 09:56:33Preview
Last week, El Salvador marks three years of Bitcoin adoption, holding 5,867 BTC, despite volatility and criticism. Mastercard have launched a Euro Bitcoin debit card for direct spending, while Zurich Cantonal Bank now offers Bitcoin trading and custody services. U.S. spot Bitcoin ETFs faced a $288 million outflow, the largest since May, yet continue to attract significant interest. Venezuelan leader María Corina Machado highlighted Bitcoin’s crucial role in overcoming economic collapse and authoritarianism in Venezuela. Meanwhile, Japan's Financial Services Agency proposed tax reforms to classify Bitcoin similarly to traditional assets, potentially reducing tax burdens. For more details, continue reading below.
A. Bitcoin Data Dashboard
1. Bitcoin Transactions\ 2. Supply\ 3. Mining\ 4. Transaction Fees\ 5. Difficulty Retarget\ 6. Lightning Network (Public)
B. Bitcoin Ecosystem
1. El Salvador marks three years as first nation to adopt Bitcoin, holding 5,867 BTC\ 2. Mastercard launch Euro debit card for direct Bitcoin spending\ 3. Zurich Cantonal Bank launches trading and custody services for Bitcoin \ 4. U.S. Spot Bitcoin ETFs face $288 million outflow in largest single-day drop since may\ 5. Venezuelan leader Machado: Bitcoin is crucial for economic recovery and freedom\ 6. U.S. companies to boost Bitcoin holdings; MicroStrategy outperforms Berkshire Hathaway
C. Regulation
1. Japan’s FSA proposes tax reform for Bitcoin and other cryptocurrencies
D. Macroeconomy
1. Jackson Hole meeting highlights central bankers' optimism with cautious economic outlook\ 2. U.S. debt ceiling reinstatement on January 2, 2025, could impact liquidity and markets
A. Bitcoin Data Dashboard

As of Sep 9, 2024
B. Bitcoin Ecosystem
1. El Salvador marks three years as first nation to adopt Bitcoin, holding 5,867 BTC
El Salvador is celebrating three years of being the first country to adopt Bitcoin as legal tender, a move made on September 7, 2021. This ambitious decision aimed to boost financial inclusion, simplify remittance payments, and attract technological innovation. The country’s bold experiment has shown mixed but promising results. El Salvador’s Bitcoin holdings have accumulated to 5,867 BTC, despite significant price fluctuations and initial criticism. The country’s Bitcoin portfolio, now valued at around $314 million, reflects a strategic investment, even as Bitcoin’s price has varied widely. The global reaction has been mixed; while El Salvador’s move was expected to inspire others, only the Central African Republic has similarly adopted Bitcoin. Larger economies have been cautious, often due to their complex relationships with international creditors and financial institutions. This caution has been reinforced by pressure from organizations like the IMF. Nonetheless, El Salvador’s pioneering approach has prompted discussions about Bitcoin’s potential in global financial systems and its future in institutional adoption.

Reference: Cointelegraph, Nayib Bukele Portfolio Tracker
2. Mastercard launch Euro debit card for direct Bitcoin spending
Mastercard has announced a new partnership with payments provider Mercuryo to introduce a euro-denominated debit card that allows users to spend Bitcoin and other cryptocurrencies directly from non-custodial wallets. This innovative card, aimed at European Bitcoin holders, enables them to make purchases at Mastercard’s extensive network of over 100 million merchants worldwide without the need to transfer funds through an intermediary. Mastercard, a global leader in payment solutions with nearly 3 billion customers across more than 210 countries, is expanding its reach into the bitcoin space. This integration reflects the company’s commitment to bridging digital assets with its traditional payments infrastructure. According to Christian Rau, Senior Vice President of Mastercard, the card provides a secure and convenient way for consumers to spend their digital assets anywhere Mastercard is accepted. Users can connect their non-custodial wallets to the card, allowing them to spend their Bitcoin and other cryptocurrencies directly without needing to convert them into fiat currency through an exchange. This feature maintains full ownership of the digital assets and avoids the complexities and costs associated with traditional exchanges.

Reference: Bitcoin magazine
3. Zurich Cantonal Bank launches trading and custody services for Bitcoin
Zurich Cantonal Bank (ZKB), one of Switzerland’s largest financial institutions, has\ expanded its offerings to include bitcoin trading and custody services. Announced on September 4, ZKB now enables customers to trade Bitcoin directly through its eBanking and Mobile Banking platforms, integrating these holdings into their existing portfolio views. The bank will also manage private key storage internally, ensuring high levels of security and eliminating the need for customers or third-party banks to handle private keys themselves. ZKB’s new service is available to both individual clients and other banks, allowing Swiss banks to offer bitcoin trading and secure storage to their customers through ZKB’s B2B solution.
Reference: Cointelegraph
4. U.S. Spot Bitcoin ETFs face $288 million outflow in largest single-day drop since may
U.S. spot Bitcoin ETFs experienced a substantial outflow of $287.8 million in a single day, the largest since May 1, as reported by Farside Investors. BlackRock’s ETF was the only one that did not face withdrawals. Leading the outflows was Fidelity’s ETF, which saw $162 million withdrawn. Grayscale followed with $50 million in outflows, while Ark and Bitwise reported withdrawals of $34 million and $25 million, respectively. Despite these significant withdrawals, these ETFs collectively manage around $50 billion in assets, indicating their substantial scale and impact in the market. Earlier this year, Bitcoin's price surged dramatically, driven by the enthusiasm surrounding these ETFs. Starting at about $44,000 at the beginning of 2024, Bitcoin reached an all-time high of $73,770 on March 14. Since then, the price has stabilized between $55,000 and $65,000, marking a period of consolidation 174 days after its peak, according to Clark Moody Dashboard. Despite the recent outflows, spot Bitcoin ETFs have largely maintained strong inflows over the past eight months, with only one month of net outflows. This ongoing investor interest suggests that while Bitcoin’s price has stabilized, the long-term demand for Bitcoin and related investment vehicles remains strong.
Reference: Bitcoin magazine
5. Venezuelan leader Machado: Bitcoin is crucial for economic recovery and freedom
Venezuelan opposition leader María Corina Machado discussed Bitcoin’s critical role in addressing Venezuela's economic collapse and authoritarian rule. The interview underscores the severe effects of hyperinflation under Chávez and Maduro, which has led to the bolívar losing 14 zeros and inflation peaking at 1.7 million percent in 2018. Machado described the economic devastation caused by state-sponsored looting, theft, and unchecked money printing, despite Venezuela's vast oil reserves. She emphasized how Bitcoin has become a "lifeline" for many Venezuelans, offering a means to bypass hyperinflation and government-controlled exchange rates. Bitcoin has also enabled individuals to protect their wealth and fund their escape from the country. Machado proposed incorporating Bitcoin into Venezuela’s national reserves as part of a broader strategy to recover stolen wealth and rebuild from the dictatorship. She sees Bitcoin as crucial for ensuring financial autonomy, transparency, and property rights in a future democratic Venezuela. Machado highlighted the role of Bitcoin in the opposition’s efforts to reclaim democracy and rebuild the nation.
Reference: Bitcoin magazine
6. U.S. companies to boost Bitcoin holdings; MicroStrategy outperforms Berkshire Hathaway
A new report from River, a Bitcoin technology firm, forecasts that 10% of U.S. companies will convert 1.5% of their treasury reserves—around $10.35 billion— to Bitcoin over the next 18 months. River highlights that traditional cash and short-term investments often fail to keep up with inflation, diminishing their value. The report draws attention to MicroStrategy’s corporate treasury strategy, popularized by founder Michael Saylor, who views Bitcoin as a hedge against inflation and a store of value with "economic immortality." In June 2024, MicroStrategy raised $800 million to buy an additional 11,931 BTC, bringing its total holdings to 226,500 BTC, valued at approximately $14.7 billion. MicroStrategy’s Bitcoin strategy has led to a 1,000% increase in its stock value, significantly outperforming Berkshire Hathaway's 104.75% rise.


Reference: Cointelegraph
C. Regulation
1. Japan’s FSA proposes tax reform for Bitcoin and other cryptocurrencies
Japan’s Financial Services Agency (FSA) has unveiled plans for a significant tax code overhaul for fiscal year 2025, focusing on reducing the tax burden on cryptocurrency assets. In its reform request submitted on August 30, the FSA proposed that cryptocurrencies be classified similarly to traditional financial assets, which could lead to a lower tax rate for bitcoin investments. Currently, profits from cryptocurrency transactions in Japan are taxed as miscellaneous income at rates ranging from 15% to 55%. The highest rate applies to earnings exceeding ¥200,000 ($1,377), but this varies based on the individual’s income bracket. In comparison, profits from stock trading are taxed at a flat maximum rate of 20%. Additionally, corporate holders of cryptocurrencies face a flat 30% tax on their holdings, even if no profits are realized from sales. The proposed reform seeks to align the tax treatment of cryptocurrencies with that of other financial assets.
Reference: Cointelegraph
D. Macroeconomy
1. Jackson Hole meeting highlights central bankers' optimism with cautious economic outlook
At the recent Jackson Hole meeting, central bankers displayed a shift from prior pessimism to a more optimistic outlook on global economies. Fed Chair Jay Powell signaled a readiness to adjust U.S. monetary policy, noting that recent inflation was driven largely by pandemic-related supply chain issues. Powell highlighted that easing inflation and a stable labor market provide room for potential interest rate cuts. As a result, bond yields and the US dollar fell, reflecting market reactions to his comments. Overall, the Jackson Hole meeting conveyed a generally positive attitude towards the major economies, though it was not without caution. Federal Reserve Bank of Chicago President pointed out that monetary policy effects can be delayed, raising concerns about whether recent tightening could still produce negative outcomes and if these could be mitigated by a swift policy easing. The full impact of current policies remains to be seen, with time necessary to assess their long-term effects.
Reference: Delloitte insights
2. U.S. debt ceiling reinstatement on January 2, 2025, could impact liquidity and markets
On January 2, 2025, the U.S. debt ceiling will be reinstated, having been suspended by the 2023 deal. If Congress does not raise it, the Treasury will need to cut its cash balance—currently over $700 billion—to keep paying bills without issuing new debt, potentially leading to a technical default. Historically, a Republican-controlled Congress has used the debt ceiling to negotiate with Democratic presidents, though the reverse has not yet occurred. The outcome largely depends on election results. Liquidity conditions are crucial as they strongly correlate with financial and asset markets in the era. Domestic liquidity influences the banking system and the dollar index, impacting global conditions. Global liquidity, measured as the broad money supply of major currencies in dollar terms, has remained stable. Recent support from a weaker dollar index has been offset by stagnant money supply growth in China since March 2024, limiting global liquidity growth.

Reference: Lyn Alden
-
 @ a012dc82:6458a70d
2024-09-09 03:39:49
@ a012dc82:6458a70d
2024-09-09 03:39:49Table Of Content
-
Understanding On-Chain Demand for Bitcoin
-
The Growth of Bitcoin and Its On-Chain Demand
-
Factors Affecting the On-Chain Demand for Bitcoin
-
How is On-Chain Demand Measured?
-
The Future of Bitcoin On-Chain Demand
-
Conclusion
-
FAQ
The rise of Bitcoin has been nothing short of meteoric over the past few years. As the world's first decentralized digital currency, it has captured the imagination of investors and traders alike. The underlying blockchain technology has made Bitcoin a viable investment option, with its unique features such as transparency, immutability, and decentralization. However, despite the hype surrounding Bitcoin, the on-chain demand for the cryptocurrency is growing at a slower rate than before.
Understanding On-Chain Demand for Bitcoin
On-chain demand for Bitcoin refers to the number of transactions taking place on the Bitcoin network. These transactions are recorded on the blockchain, a decentralized ledger that maintains a record of all Bitcoin transactions. On-chain demand is an important indicator of the popularity and adoption of Bitcoin as a currency and an asset.
The Growth of Bitcoin and Its On-Chain Demand
Bitcoin has experienced tremendous growth over the past decade, with its price soaring from a few cents to over $60,000 at its peak. This growth has been accompanied by an increase in the on-chain demand for Bitcoin. In the early days of Bitcoin, on-chain demand was low, and the network was only used by a small number of enthusiasts. However, as Bitcoin gained popularity, the number of transactions on the network grew rapidly.
Factors Affecting the On-Chain Demand for Bitcoin
Several factors affect the on-chain demand for Bitcoin, including:
1. Adoption: As more people adopt Bitcoin as a currency and an asset, the on-chain demand for the cryptocurrency increases.
2. Fees: The transaction fees associated with Bitcoin can impact the on-chain demand for the cryptocurrency. High fees can discourage people from using Bitcoin for transactions.
3. Network Congestion: Network congestion can slow down transaction processing times and reduce the on-chain demand for Bitcoin.
4. Market Sentiment: The overall sentiment in the cryptocurrency market can impact the on-chain demand for Bitcoin.
How is On-Chain Demand Measured?
On-chain demand for Bitcoin is measured by the number of transactions taking place on the network. This data is publicly available and can be accessed through blockchain explorers like Blockchain.info and Blockchair.com. These platforms provide real-time data on the number of transactions, the transaction volume, and the average transaction fees on the Bitcoin network.
The Future of Bitcoin On-Chain Demand
The on-chain demand for Bitcoin is still growing, but at a slower rate than before. This trend is partly due to the increase in transaction fees and network congestion, which have made it more difficult and expensive to use Bitcoin for transactions. However, despite these challenges, Bitcoin remains a popular investment option and is expected to continue growing in popularity in the future.
Conclusion
Bitcoin is still one of the most popular cryptocurrencies in the world, and its on-chain demand is a key indicator of its growth and adoption. While the on-chain demand for Bitcoin is growing at a slower rate than before, it is still increasing steadily, and this trend is likely to continue in the future. However, as the popularity of Bitcoin continues to grow, it is important to address the challenges facing the network, such as high transaction fees and network congestion, to ensure that the cryptocurrency remains accessible and affordable for everyone. Overall, the on-chain demand for Bitcoin may be growing at a slower rate, but the future of the cryptocurrency looks bright.
FAQ
What is on-chain demand for Bitcoin? On-chain demand for Bitcoin refers to the number of transactions taking place on the Bitcoin network.
Why is on-chain demand for Bitcoin growing at a slower rate than before? The increase in transaction fees and network congestion have made it more difficult and expensive to use Bitcoin for transactions.
How is on-chain demand for Bitcoin measured? On-chain demand for Bitcoin is measured by the number of transactions taking place on the network.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 472f440f:5669301e
2024-09-05 22:25:15
@ 472f440f:5669301e
2024-09-05 22:25:15https://x.com/parkeralewis/status/1831746160781938947 Here's a startling chart from an American staple, Walgreens. The convenience store and pharmacy chain has seen its stock price plummet by more than 67% this year and by more than 90% from its all time high, which was reached in 2015.
The combination of the COVID lock downs and the lax laws around theft that followed were materially detrimental to Walgreens business. The crux of their problem at the moment, however, is a double whammy of those disruptions in their business coupled with the "higher for longer" interest rate policy from the Fed over the last couple of years. As Tuur points out in the tweet above, Walgreens has $34B in debt, which means they definitely have significant interest rate payments they need to make on a monthly basis. Tuur also points out that Walgreens has very little cash compared to their debt obligations. Let's take a look at their balance sheet as of May of this year.
Less than $1B in cash for $34B debt with $67.56B in total liabilities. Even worse, their cash balance was drained by more than 27% over the course of the year between May 2023 and May 2024. As you may notice their total assets fell by more than 15% over the same period. This is because Walgreens understands the dire financial straits it finds itself in and has begun shutting down thousands of their locations across the country.
The recent efforts of Walgreens to sell off their assets to raise cash to pay down their debts seem to be completely ineffective as their cash balance is falling faster than their total assets, which is falling 7x faster than their total liabilities. These numbers are most definitely going to get worse as cascading sell pressure in commercial real estate markets (which is the bucket that Walgreens locations fall into) drive down the value of their assets. Leaving them with less cash to pay down their debts as time goes on. To make matters worse, it puts the institutions that lent money to Walgreens in a terrible position. How many commercial and investment banks has Walgreens tapped to fund their operations with expensive debt? How exposed to Walgreens is any individual lender? Could a default on some or all of their loans catch these financial institutions off sides? If it isn't Walgreens that pushes them off sides, how many more bad borrowers would it take to push them off sides?
As our good friend Parker Lewis points out, the only way the hemorrhaging can be stopped is if the Federal Reserve and Federal Government step in with bail outs in the form of massive liquidity injections via quantitative easing and other emergency measures. On top of this, the Fed and the Federal Government find themselves in a classic catch-22. If they let Walgreens fall into bankruptcy it could set off a domino effect that could exacerbate inflation. Riteaid, a similar retail convenience store and pharmacy chain, filed for bankruptcy last October and is still wading its way through that process. Part of that process has been shuttering many of their storefronts. One has to imagine that since Walgreens and Riteaid are having these problems, some of their other competitors must be feeling the pain as well. If enough of these convenience stores, which tens of millions of Americans depend on for everyday goods, find themselves in a position where they have to shut down their stores it could lead to a supply crunch. People will obviously not be able to get their goods from Riteaid or Walgreens and will flee to alternatives, exacerbating the stress on their supplies, which will drive prices higher.
This is a catch-22 because the only way to avoid this mad dash for consumer goods in the midst of a convenience store Armageddon is to re-introduce ZIRP and flood the market with freshly printed dollars, which will drive prices up as well.
Talk about a rock and a hard place. You better get yourself some bitcoin.
Final thought... Zach Bryan radio crushes.
-
 @ e771af0b:8e8ed66f
2024-09-05 22:14:04
@ e771af0b:8e8ed66f
2024-09-05 22:14:04I have searched the web for "Find bitcoin block number from historical date" maybe 100 times in my life.
Never again.
You'll need a bitcoin node for this to work. The script is fast.
Install
WoT Install
one liner ```
curl
curl -o fjb.sh https://gist.githubusercontent.com/dskvr/18252c16cf85c06c1ee6cb5ae04a3197/raw/34bad6a35d98501978c8cd0c25b1628db1191cfe/fjb.sh && chmod +x fjb.sh
wget
wget -O fjb.sh https://gist.githubusercontent.com/dskvr/18252c16cf85c06c1ee6cb5ae04a3197/raw/34bad6a35d98501978c8cd0c25b1628db1191cfe/fjb.sh && chmod +x fjb.sh ```
Trust no one.
create file ``` vi fjb.sh
or
nano fjb.sh ```
review, copy and past into file ``` TIMESTAMP=$1 LOWER=0 UPPER=$(bitcoin-cli getblockcount)
while (( LOWER <= UPPER )); do MID=$(( (LOWER + UPPER) / 2 )) BLOCKHASH=$(bitcoin-cli getblockhash $MID) BLOCKTIME=$(bitcoin-cli getblockheader $BLOCKHASH | jq .time)
if (( BLOCKTIME < TIMESTAMP )); then LOWER=$(( MID + 1 )) elif (( BLOCKTIME > TIMESTAMP )); then UPPER=$(( MID - 1 )) else echo "$BLOCKTIME" exit 0 fidone
echo "$UPPER" ```
give executable permissions
chmod +x ./fjb.shUsage
./fjb.sh <timestampSeconds>It returns block number onlyExample
$: ./fjb.sh 1668779310 763719 -
 @ 44dc1c2d:31c74f0b
2024-09-09 01:55:24
@ 44dc1c2d:31c74f0b
2024-09-09 01:55:24Chef's notes
Makes an excellent Chicken sandwich.
Details
- ⏲️ Prep time: 6 Ish hours
- 🍳 Cook time: 40 min
- 🍽️ Servings: 1 loaf
Ingredients
- 3 ½ - 4 cups bread flour, or more as needed
- 1 ⅓ cups warm milk (110°F – 115°F)
- 5 tablespoons honey
- 4 tablespoons salted butter, melted and slightly cooled
- 1 tablespoon instant “rapid rise” yeast
- 1 ½ teaspoons salt
- Oil or butter for greasing the bowl
- 1 tablespoon melted salted butter, for brushing the crust at the end
Directions
- To prepare the dough, weigh the flour or measure it by gently spooning it into a cup, then leveling off any excess. In a large bowl, combine the flour with the warm milk, honey, melted butter, instant yeast, and salt. Mix by hand or with the paddle attachment of a stand mixer until a shaggy dough forms, gradually adding more flour, as necessary, to get the dough to come together so that it just pulls away from the sides of the bowl.
- Switch to the dough hook attachment (or use your hands) to knead the dough until fairly smooth, about 7-8 minutes.
- Oil a large mixing bowl. Place the dough in the greased bowl, turning once to grease the top. Cover and let rise in a warm place until doubled, 1 ½ - 2 hours.
- Punch down the dough. Transfer to a lightly floured work surface. Pat the dough into a 9 x 12-inch rectangle. Starting on one of the short sides, roll up the dough to make a log; pinch the seams. Place the dough seam-side down in a lightly greased 9 x 5-inch loaf pan.
- Cover the pan with lightly greased plastic wrap; allow to rise for 1-2 hours, until it’s crowned about 1-2 inches over the rim of the pan. Towards the end of the rising time, preheat the oven to 350°F.
- Bake the bread for 40-45 minutes, tenting the top of the bread loosely with foil towards the end if the top starts to get too brown. The bread should be golden brown, and it should sound hollow when tapped.
- Brush the top of the warm bread with melted butter.
- Remove from the pan and cool on a wire rack for at least 1 hour before slicing.
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 472f440f:5669301e
2024-09-04 22:54:11
@ 472f440f:5669301e
2024-09-04 22:54:11For the last few months many people in bitcoin, myself included, have been focused on bitcoin's role as a macroeconomic asset. Bitcoin as a strategic reserve for the US government. Bitcoin as a strategic treasury asset for corporations. Bitcoin as a geopolitical hedge in a world that is trending toward a multi-polar power dynamic. This is where the focus has been. And for good reason. These trends will ultimately have a material effect on the price of bitcoin if they pick up steam.
However, with all of the focus on bitcoin as a strategic asset I think a couple of technical developments and trends have been overlooked. Particularly in the realm of second layer privacy. I'll touch on two of them in this letter; BOLT 12 invoices and the progression of ecash.
Yesterday afternoon the Strike (a company Ten31 is very proud to be backing) team released a blog post that detailed their journey to implementing BOLT 12 offers in their product stack. For those who are unaware of BOLT 12 and why it is important, in short, it is an upgrade to the lightning network that would make receiving bitcoin on the lightning network more private while also significantly improving the user experience. The current standard for invoicing people via the lightning network is BOLT 11, which forces users to create a unique invoice every time they want to receive bitcoin and comes with privacy tradeoffs for the party receiving bitcoin.
BOLT 12 brings with it route blinding which allows a receiver to publish a lightning offer to the network without revealing their node's public key. It also brings with it onion messaging, which allows users of the lightning network to communicate without a dependence on HTTP, which can be censored by a motivated state actor. On top of this, it enables users to create a static invoice that can be paid multiple times by multiple people. Think of a band putting their Venmo or Cash App QR code next to their tip jar on the stage. They'll be able to add a private lightning invoice their audience can pay to now.
https://strike.me/blog/bolt12-offers/
As it stands right now, Strike has only enabled BOLT 12 offers and there is work to do at the protocol layer of lightning and the different implementations of that protocol to get the full benefits of BOLT 12, but this is material progress that gets us closer to a significantly better user experience on the lightning network. If you read Strike's blog post you'll come to appreciate the collaboration between the teams working on these implementations and the companies implementing the protocol that is necessary to get these features live. Shout out to everyone who worked on this. Everyone who uses the lightning network will be better off when BOLT 12 is fully implemented.
Moving on. Earlier today the founder of the BTCPay Server open source project, Nicolas Dorier, published a blog post outlining his thoughts on how ecash has the potential to solve problems that many have tried to solve by launching their own blockchains in the past. The problem with trying to "blockchain the world" is that blockchains are very inefficient and only really work for one application; enabling a peer-to-peer digital cash system with no trusted third parties (i.e., bitcoin). However, the ultimate goals of the thousands of blockchain projects that spun up in bitcoin's wake are desirable. Cheap, private and instant transactions. The ability to trivially spin up private money tokens suited for very particular use cases. Overall great UX that makes it easy for people to realize the benefits of "blockchain technology".
The problem that has existed to date is that you don't need a blockchain for all of these things. In fact, having a blockchain for these things proves to be detrimental to their ultimate goals. Instead, what people really need is a protocol that gives you the granular control, privacy, instantaneous transactions and UX that anchors to bitcoin. This is exactly what Chaumian Mints bring to the bitcoin stack.
This is something that we've been screaming about for more than seven years in this rag. Now with ecash protocols like Cashu and Fedimint maturing, gaining traction and bringing products to market that highlight the power and flexibility of ecash systems, people are beginning to see the promise. It is only a matter of time before more and more people begin to realize this potential.
Another benefit of ecash protocols is the fact that they are siloed from each other. Ecash mints are permissionless; any one person or group of people can spin them up, offer their preferred services and maintain (or fail to maintain) their mints. The failure of one mint is not a systemic risk to other mints. This is very different from token projects that are spun up on blockchains. The last ten years have proven that individual token projects can prove to be systemic problems for individual blockchains (i.e., The DAO token on Ethereum). Being able to silo mints is the only way to ensure that the utility of ecash overall is actually scalable and robust.
Don't get so distracted by the bitcoin macro talk that you miss out on the incredible technical developments happening on top of and adjacent to bitcoin.
Final thought... Vibes are high.
-
 @ 8dc86882:9dc4ba5e
2024-09-08 22:14:05
@ 8dc86882:9dc4ba5e
2024-09-08 22:14:05Why do lightning nodes need channels? Why can a node not just send and receive without a channel? I wonder what the benefit it serves other than making running a node difficult or making it cost to open one?
Thanks
originally posted at https://stacker.news/items/677439
-
 @ dfe02069:d3e2fa29
2024-09-08 22:02:29
@ dfe02069:d3e2fa29
2024-09-08 22:02:29 Flucht – oder Wachsen an den Umständen? Wir haben die Wahl (Bild:Netzfund)
Flucht – oder Wachsen an den Umständen? Wir haben die Wahl (Bild:Netzfund)In diesen Tagen neigt sich eine lange (nahezu ausgebuchte) Lesereise dem Ende zu (letzte Termine siehehier), die im Frühjahr begann und mich an etwa 50 Orte in Deutschland und der Schweiz führte: in Vereinsheime, Scheunen, Schlösser, Keller, Buchhandlungen, Festsäle, Wohnzimmer, Gärten, ja sogar Gewächshäuser. In diesen vielen Lese- und Diskussionsstunden durfte ich den Puls der Zeit etwas näher fühlen, als es durch den bloßen Konsum der Nachrichtenlage möglich ist. Dafür bin ich dankbar, denn dafür war die Lesereise auch primär gedacht: für die direkte, unverstellte Begegnung und Vernetzung. Zu den konkreten Erfahrungen gleich.
Es ist nicht leicht, die eine große Veränderung zu beschreiben, die sich in den letzten Corona-Jahren manifestiert hat. Für viele war diese Zeit bereits ein Schock; für einige mehr wird sie noch zu einer Schockbehandlung, und zwar auf Raten. In der Haut letzterer will man lieber nicht stecken. Ist es schon schmerzhaft, wenn ein Weltbild in kürzester Zeit zerbricht, so muss die langsame Erosion eines Weltbildes über Jahre noch folgenreicher und letztlich teurer, bzw. selbstschädigender sein.
Kollaps der Arbeitsteilung
Der Schock der ersteren hatte nicht selten ein Zurückgeworfensein auf sich selbst zur Folge. Wem kann ich noch trauen? Muss ich nun jede Information selbst prüfen und wägen? Was kann ich Ärzten und der Justiz noch glauben?
(Quelle Video: Twitter/X)
In den letzen Jahren ist ein systemischer Bruch offenbar geworden, und zwar im Kern der Gesellschaftsorganisation selbst: Bei der Arbeitsteilung. Der französische Soziologe Emile Durkheim fragte sich, was Gesellschaften zusammenhält, und kam beim “Kollektivbewusstsein” heraus. Das Kollektivbewusstsein wird in Frühgesellschaften, die sich auf Tradition, Sitte und Moral gründen, durch Sanktion herausgeschält. Es regiert eine „mechanische Solidarität“, die sich im Strafrecht äußert. In modernen Gesellschaften regiert hingegen eine „organische Solidarität“, die sich in der sozialen Arbeitsteilung ausdrückt.
_ ANZEIGE: Sie suchen nach einer einfachen Möglichkeit, in Bitcoin zu investieren? Mit der erfolgreichen Schweizer App Relai geht es in wenigen Schritten und ohne komplizierte Anmeldung. Man kann dort auch einfache Sparpläne einrichten. Niemand hat Zugriff auf Ihre Bitcoin, außer Sie selbst. Mit dem Referral-Code REL54052 sparen Sie Gebühren. (keine Finanzberatung)._
Während Corona wurde diese organisch gewachsene Solidarität pulverisiert. Es wurde offenbar, dass nicht nur offizielle Stellen lügen, sondern auch die Medien und „die Wissenschaft“. Ärzte waren ausführende Kräfte, die mit Anreizen zur Impfung überhäuft wurden, viele davon sind bis heute überzeugt, dass sie gut und richtig handelten. Aufgrund dieser zusammenwirkenden, kumulativen Versagenssituation, die sich in der Politik bis hin zur Etablierung einer Doktrin des Handelns wider besseren Wissens (siehe RKI-Protokolle) steigerte, wurde das Vertrauen von Millionen Menschen in Institutionen und deren arbeitsteilig wirkende Akteure zerstört. Sie stehen nun auf dem Stand: Wie soll ich denen je wieder etwas glauben? Was ist, wenn all das sich in der ein- oder anderen Form wiederholt? An die Stelle der organischen Solidarität kam die mechanische wieder zurück, es folgte ein Zurück zur Logik der Herde. Wer nicht spurt, möge Schmerzen erfahren.
Die Unfähigkeit aufzuarbeiten
Im neuen Kollektivbewusstsein der Herdenmentalität erwachte zudem der „autoritäre Charakter“ wieder zum Leben. Der Sozialpsychologe Erich Fromm verstand darunter einen Gesellschaftscharakter, der Züge von extremem Gehorsam, Hang zum Autoritarismus und zur Destruktivität in sich vereinte. Andersdenkende werden nicht toleriert; die Doktrin darf keinen Schaden nehmen. Der autoritäre Charakter dient sich einer gesellschaftlichen Autorität an, um vor der eigenverantwortlich wahrgenommenen Freiheit zu fliehen. Wer sich als Knecht empfindet, findet sich seinen Herrn. Den neo-totalitären Staat charakterisiert zwar, dass man “lange seine Hieroglyphen nicht entziffern kann” (Jünger). Aber man kann schon früh erste Schlüsse über dessen Ausrichtung aus dem Umstand ziehen, welche Affekte er in der Bevölkerung weckt. Dies waren unter anderem Gehorsam, Furcht und Hang zur Denunziation.
Seit diesem systemischen Bruch klafft eine offene Wunde und sie wird dadurch offen gehalten, dass das Corona-Thema unaufgearbeitet wegretouchiert werden soll. Die Verleugnung grober Fehler und Zusammenhänge steht heute eher an der Tagesordnung, als die Bereitschaft zur Aufarbeitung. Impfschäden en masse sind immer noch ein Tabuthema. Die Betroffenen werden nicht ernst genommen. Woher kommt diese Hemmung? Alexander Mitscherlich hat diese Mechanismen in seinem Buch „Die Unfähigkeit zu trauern“ in Bezug auf die Aufarbeitung der NS-Verbrechen beleuchtet. Seine Ausführung zur Aufarbeitungsaufschiebung klingen nun wieder sehr aktuell:
„Der zweite Trend läßt sich wesentlich schwerer beschreiben. Er bezieht sich auf eine Reaktionsträgheit, die sich in unserem gesamten politischen und sozialen Organismus bemerkbar macht. Die Einsichten, die hier mit Hilfe seelischer Sperrungen abgewehrt werden, sind ungelöste oder unzureichend verstandene Probleme unserer gegenwärtigen Gesellschaft. Wo wir höchste Aufmerksamkeit erwarten dürfen, stoßen wir auf Indifferenz. Diese diffus verteilte Anteilnahmslosigkeit wird besonders dann bemerkbar, wenn man sich die rasche Veränderung unserer materiellen Umwelt vor Augen hält. Lebhaftes Interesse bei allen Beteiligten für technische Probleme steht in Kontrast zur Indolenz, mit der unsere politischen Grundrechte behandelt werden. Die Anteilnahme an alledem, was einer aufgeklärten Öffentlichkeit am Herzen liegen sollte, ist relativ gering.“
Mitscherlich konstatiert der Gesellschaft eine Mischung aus infantilem Selbstschutz („Der Führer war an allem schuld“) und libidinöser Verstrickung des eigenen Ichs mit einem Fremd-Ideal, welches in die eigene Persönlichkeit mitintegriert wird. Wird diese Autoritätsfigur öffentlich demontiert, verteidigt sie der Gehorsame, und damit sich mit. Zerfällt die Autoritätsfigur gar, drohen eigene Persönlichkeitsteile zu zerfallen, so stark kann die Identifikation sein. Die Scham darüber, einem Manipulator aufgesessen zu sein, kann verhindern, diesen Umstand überhaupt sehen zu wollen.
Mit der libidinösen Manipulation vermischt sich das inkarnierte Fremd-Ideal mit dem Ich-Ideal. Man fiebert mit dem System (oder der Autorität) mit, wünscht sich einen siegreichen Kampf gegen – Geschichte wiederholt sich teilweise – Russland und ein Virus! Die Enttäuschung und Entzauberung des inkarnierten Fremd-Ideals greift das eigene Ich an, was einem existentiellen Desaster gleicht. Das falsche Ego muss nun als Privatgötze überleben, gehe darüber auch die Welt unter. Dieser Götzenkult der falschen Egos verhindert gerade ein Lernen aus der Pandemie und damit den Fortschritt. Wer die Ideal-Bildung nicht mitmachte, wird als Feind angesehen. Die Aggression wandert weg vom Innenbereich der Gesellschaft an den Randbereich, sie reagiert sich an den Sündenböcken ab („Pandemie der Ungeimpften, „Tyrannei der Ungeimpften“ etc.). Wer findet noch, dass die psychologische Fabrizierung einer „Massenformation“ als psychologisches Muster allein Diktaturen vorbehalten ist?
All dies wird gerade flankiert von einer schizophrenen Erinnerungskultur, die eher eine Vergessenskultur zum Ziel zu haben scheint. Die Erinnerung an die NS-Zeit wird ritualhaft extrapoliert, zugleich werden Vergleiche mit heute zum Tabu erklärt. So bleibt die Erinnerungsschleife leer, da folgenlos. Aus dem Früher darf für das Heute nichts gelernt werden, Muster nicht benannt werden. Bei den RKI-Mitarbeitern half die eigene Erinnerungsinstallation im Eingangsbereich des Hauses jedenfalls nicht, einem experimentellen Menschenversuch Einhalt zu gebieten. Eine moralische Bankrotterklärung, die noch lange nachwirken wird.
Wann kommt der Kipppunkt?
Bei meinen zahlreichen Lesungen erfuhr ich in vielen Gesprächen, dass die Kluft zu Andersdenkenden immer noch besteht. Es kommt kaum etwas in Bewegung, alles stockt, wirkt eingefroren und in den Mantel des Verdrängens und Vergessens gehüllt. Im Familien- und Freundeskreis sind die Gräben oft immer noch unverändert tief.
Während einer Lesung im “Kunst Kontor” in Potsdam kam es zum Clash zwischen Verteidigern der Coronapolitik, der politischen Klasse und der Mainstream-Medien und einem kritischen Publikum. Dieser Clash endete damit, dass nach Diskussion und Wortwechsel eine Person den Raum fluchtartig verließ, eine andere offen bekannte, sich mit widersprechenden Informationen gar nicht beschäftigen zu wollen. Was man dann von einer kritischen Lesung erwartet, weiß ich nicht.
Der Abend in Potsdam vor einem gemischt-gutbürgerlichen Publikum zeigte wohl jedem, wie groß die Gräben derzeit noch sind. Gleichzeitig sind es genau solche Begegnungen – zu selten finden sie überhaupt statt – welche den Anfang machen müssen, um letztlich zu einer Aufklärung zu kommen. Der Aufklärungsdruck kommt keinesfalls von oben, sondern immer nur von unten. Alles beginnt mit dem unverstellten, direkten Gespräch, auch wenn dieses im ersten Moment noch fruchtlos erscheinen mag.
Ein Gedanke, der mir immer wieder kam: Der Mensch reagiert auf Anreize. Welchen Anreiz hat die Gegenseite, an einer Aufklärung mitzuwirken? Es erwartet sie doch nur ein schmerz-, schuld- und schamhafter Prozess. Doch sich der Wahrheit zu stellen, bedeutet eine Katharsis durchzumachen, eine Form der Selbstreinigung. Das Beschweigen zerfrisst irgendwann von innen. Die Barriere der „bewussten Blindheit“ ist nur eine Augenbinde, die immer poröser wird. Prokrastination lohnt nicht, denn am Ende kommt immer der “Moment der Wahrheit”. Letztlich wird der nichtaufgearbeitete Schmerz und dessen Überwindung, also das Verlassen des Tals der Schmerzen, der finale Anreiz sein, sich der Realität zu stellen. So entscheidet jeder über den Grad des Schmerzes selbst.
Bei einer der letzten Lesungen im Buchhaus Loschwitz in Dresden, führte Kilian Forster, u.a. Intendant der Dresdner-Jazztage, musikalisch durch die Lesung. Zum Auftakt der Lesung nahm der Profi-Kontrabassist zur Überraschung aller am Flügel Platz und spielte mein Lieblingsstück von Chopin, die “Revolutions-Etüde”. Diese schrieb der junge Pianist und Komponist unter dem Eindruck der Juli-Revolution 1830 in Frankreich, bei der sich Bürgertum und Proletariat gegen eine übergriffige Regierung verbanden.
In dem kraftvollen und furiosen Klavierstück wird die ungestüme Kraft beschworen, die in dieser Verbindung liegt. Sternstunden der Menschheit gelingen in überraschenden, unwahrscheinlichen Konstellationen; sie beginnen mit Verbrüderung und Annäherung unter Gleichen. Das einzigartige Talent des Menschen liegt in seiner Kooperationsfähigkeit. Dazu braucht es zuvor Kommunikation.
(Lesung im Buchhaus Loschwitz/Dresden am 29.08.2024)
Ich danke allen Veranstaltern der Lesungen für die blendende Organisation und die Gastfreundschaft. Ich durfte Menschen kennenlernen, die durch ihr tägliches Vorbild vorleben, dass sie bereit sind für eine neue Entwicklungsstufe: die der Kooperation und friedvollen Wahrheitssuche. Krisen sind Wachstumspunkte. An ihnen konturieren wir uns heraus, werden stärker, resilienter, antifragiler. Was soll auch die Alternative sein? Wir sind letztlich zum Wachstum gezwungen.
Unsere Zukunft als Spezies hängt gerade maßgeblich davon ab, ob wir fähig sind, diesen Entwicklungssprung in Sachen Kooperation zu vollziehen. Die einen fliehen vor der Freiheit in die Destruktivität. Andere nehmen sich die Freiheit zur Konstruktivität.
Letzteren gehört die Zukunft.
AKTION (Nur solange der Vorrat reicht): Beim Abschluss eines Jahresabos im September sende ich Ihnen eine signierte Version von “Stromaufwärts zur Quelle”!
_ Herzlichen Dank, dass Sie meine Arbeit unterstützen! _
_Ich kann Ihnen auch manuell einen Zugang zur Publikation einrichten, wenn Sie lieber per Paypal, Überweisung oder Bitcoin (einmal Jahresbeitrag, ewiger Zugang) bezahlen.
-
 @ eed76ece:afa98124
2024-09-08 21:13:37
@ eed76ece:afa98124
2024-09-08 21:13:37Seems like if you want to sell an item on SN using @AGORA makes logical sense.
Perhaps if your a manufacturer, importer, exporter, stocking distributor, wholesaler etc. you should also consider using @Import_Export or both @AGORA and see if they help each other. Being totally upfront Import_Export is probably a better use case especially if you are running over 75% B2B.
We are note promoting the use of B2C on SN. We're 100% focused on interactions between businesses only. Our primary markets are in Asia and Southeast Asia. Europe and the UK are dying a slow death, and the last straw was the Telegram event.
So I am endorsing you to please at least on SN refer to @AGORA for basic B2C (retail).
Thank you, https://www.globalmerchant.io
originally posted at https://stacker.news/items/677390
-
 @ 42342239:1d80db24
2024-09-02 12:08:29
@ 42342239:1d80db24
2024-09-02 12:08:29The ongoing debate surrounding freedom of expression may revolve more around determining who gets to control the dissemination of information rather than any claimed notion of safeguarding democracy. Similarities can be identified from 500 years ago, following the invention of the printing press.
What has been will be again, what has been done will be done again; there is nothing new under the sun.
-- Ecclesiastes 1:9
The debate over freedom of expression and its limits continues to rage on. In the UK, citizens are being arrested for sharing humouristic images. In Ireland, it may soon become illegal to possess "reckless" memes. Australia is trying to get X to hide information. Venezuela's Maduro blocked X earlier this year, as did a judge on Brazil's Supreme Court. In the US, a citizen has been imprisoned for spreading misleading material following a controversial court ruling. In Germany, the police are searching for a social media user who called a politician overweight. Many are also expressing concerns about deep fakes (AI-generated videos, images, or audio that are designed to deceive).
These questions are not new, however. What we perceive as new questions are often just a reflection of earlier times. After Gutenberg invented the printing press in the 15th century, there were soon hundreds of printing presses across Europe. The Church began using printing presses to mass-produce indulgences. "As soon as the coin in the coffer rings, the soul from purgatory springs" was a phrase used by a traveling monk who sold such indulgences at the time. Martin Luther questioned the reasonableness of this practice. Eventually, he posted the 95 theses on the church door in Wittenberg. He also translated the Bible into German. A short time later, his works, also mass-produced, accounted for a third of all books sold in Germany. Luther refused to recant his provocations as then determined by the Church's central authority. He was excommunicated in 1520 by the Pope and soon declared an outlaw by the Holy Roman Emperor.
This did not stop him. Instead, Luther referred to the Pope as "Pope Fart-Ass" and as the "Ass-God in Rome)". He also commissioned caricatures, such as woodcuts showing a female demon giving birth to the Pope and cardinals, of German peasants responding to a papal edict by showing the Pope their backsides and breaking wind, and more.
Gutenberg's printing presses contributed to the spread of information in a way similar to how the internet does in today's society. The Church's ability to control the flow of information was undermined, much like how newspapers, radio, and TV have partially lost this power today. The Pope excommunicated Luther, which is reminiscent of those who are de-platformed or banned from various platforms today. The Emperor declared Luther an outlaw, which is similar to how the UK's Prime Minister is imprisoning British citizens today. Luther called the Pope derogatory names, which is reminiscent of the individual who recently had the audacity to call an overweight German minister overweight.
Freedom of expression must be curtailed to combat the spread of false or harmful information in order to protect democracy, or so it is claimed. But perhaps it is more about who gets to control the flow of information?
As is often the case, there is nothing new under the sun.
-
 @ b540f73c:0d81f955
2024-09-08 20:51:41
@ b540f73c:0d81f955
2024-09-08 20:51:41Test - 001
Test #Testing
Testing this article post.
Image 1 https://i.nostr.build/XVMyZ.gif
Image 2 https://i.nostr.build/3PAql.gif
Image 3 4 5 6 https://i.nostr.build/O4agA.gif https://i.nostr.build/vGZ7k.gif https://i.nostr.build/lLEYe.gif
Image 7 https://encrypted-tbn0.gstatic.com/images?q=tbn:ANd9GcTVgFjrG_0zAzNLWLo6OULuFynY2haCp9RgrQ&s
This is a Test. This note is testing stuff. Testing... Testing.... Testing...
DidIMentionThisIsATest
-
 @ 64acd5df:8f2159da
2024-09-08 20:23:40
@ 64acd5df:8f2159da
2024-09-08 20:23:40_
-
 @ 9dd283b1:cf9b6beb
2024-09-02 10:26:53
@ 9dd283b1:cf9b6beb
2024-09-02 10:26:53There's a saying: Bitcoin is hope.
But once you truly understand Bitcoin, many of the old fiat goals in your life start to lose meaning. It can feel disorienting and even depressing, because you realize you need to build entirely new goals, and you're unsure where to begin.
For example, maybe your plan was to get a mortgage, buy a house, and imagine your kids playing there for the next 20 years while you "happily" pay off a 25-year loan. But when you understand Bitcoin, that plan doesn’t make sense. Why would I put a 100k-200k down payment into a mortgage when it's likely better be in Bitcoin? Plus, you lose about 2.5% to 4% of the total price on taxes, fees, brokers, and other costs. Crazy, right?
I even made a short presentation for my wife, explaining why we should never buy a house given current interest rates and down payment requirements. She responded that she wants a house anyway, because it feels better to own one. But does a 25-year mortgage really make it feel like it’s yours?
She also said it’s depressing to not follow the conventional path. It’s hard to feel satisfied with numbers when everyone around you is deep into mortgages—you want to be one of them. You want to visit their houses and invite them to "yours." It's like becoming sober in a room full of addicts. You know it’s better for you, but the world around you seems so strange that part of you wants to go back, even though you know it hurts. Yet, when you do go back, the joy isn't there anymore. You feel...nothing. And then you decide to withdraw.
I remember paying off my first mortgage for an apartment, and I felt nothing. And that was before I fell down the Bitcoin rabbit hole. Now I know if I ever took out a mortgage again, I’d just feel regret for not keeping the money in Bitcoin. And by the time you finish paying it off, you probably want to sell the property and move somewhere else.
So, the rational decision is to keep everything in Bitcoin and rent instead.Unless, of course, Bitcoin goes to zero. There are only two outcomes for Bitcoin: it’s either going to infinity, or it's going to zero. There’s no scenario where it just hovers at 100k or 60k for the next 20 years—unless people are foolish enough to give away self-custody. If they do, we'll end up with digital gold. So the reasonable question is - how can you be sure? Well, you can't. But we are betting on it and it works for now. Worst case we will need to start from 0. But then there will be no hope anymore.
We are staying in the infinity camp. And when you are in that camp every time you make a big purchase, you’re shorting Bitcoin. Solution - simple, - don't buy anything. There’s a popular meme: You will own nothing, and you will be happy. But if you’re a Bitcoiner, it's more like: You will own only Bitcoin, and you probably won’t be happy about it. Why would I pay 30k for a car when I can lease one? Why put 100k down on a house when I can rent?
The only justification is mental comfort, peace of mind. Or perhaps you value the illusion of owning a physical thing more than the genuine ownership of something virtual. It’s confusing, isn’t it? Sure, you can own a bicycle. But owning a house? That's tricky. Imagine you’re a Russian citizen with a house on Lake Como, and suddenly, new sanctions mean Italy no longer recognizes your property. Or squatters break in while you’re on vacation, and now you need to go through a court battle to evict them.
Extreme situations, I know. But no one thinks it will happen to them—until it does.
So, you’ve sold everything to buy Bitcoin. You don’t own anything except Bitcoin, and you feel sad. Why?
What can you buy with Bitcoin that’s more valuable? Something that won’t depreciate over time. Something like time.
Time with your kids. Time with your family. Time with yourself.
There’s a concept called FIRE and then there is a Bitcoin FIRE calculation (https://bitcoincompounding.com/). In simple terms, you spend your Bitcoin slowly enough that it grows faster than you can spend it (in fiat terms). Unlike traditional assets, there’s no yield or dividends, so the only way it works is if Bitcoin continues its cycles. And you need to be at least two cycles in to make it work.
But personally, I don’t think there will be cycles anymore. I believe this October-November will break all the models, and Bitcoin will do what Bitcoin does: surprise everyone. I read somewhere a thought that stuck with me—imagine you wake up on a planet Earth on January 1st. You know nothing about the seasons or weather. After six months of only increasing temperatures, you’d be 100% certain it’s only getting hotter from here.
So what hope does Bitcoin offer? Hope that I can spend more time with my family. Hope that I can create something different for them. Hope that I can live without the weight of fiat goals. Hope that it's only getting hotter from here.
I just need to get through the withdrawal phase.
originally posted at https://stacker.news/items/662939
-
 @ c11cf5f8:4928464d
2024-09-08 19:10:39
@ c11cf5f8:4928464d
2024-09-08 19:10:39Considering the "whatever" item in question is a random item, a unique piece --not something you produce or need to market-- which platform, website or which strategy you'll put in place to get the value of your item in sats, immediately, anonymously, via the Lightning Network?
originally posted at https://stacker.news/items/677270
-
 @ a6631624:24ba1a2f
2024-09-01 22:33:57
@ a6631624:24ba1a2f
2024-09-01 22:33:57I started V1 of this blog back in Q2 2023 on other platforms. And, I started writing for it about a year before that. Since then, all of my posts -- both in the backlog and currently published -- have undergone rework after rework as I painstakingly refine the presentation of these rarely spoken and "never-before-thought" ideas. Yet, the posts I've most stalled and blown off have been those pertaining to Gnosticism.
The reason being that it's just overwhelming the amount of wrongs I have to right, the number of misconceptions I must correct, the scope of the programs I have to bypass, and the shear volume of aspects I need to educate on just to convey Gnosticism and the Gnostic spirit accurately, as I tap into it.
And, we haven't even began talking about the number of butts I've got to prick in the process.
So, this a massive undertaking that I have continually delayed. And, I fear, in my delayedness, that I've allowed too much wrong to proliferate in the the meme pool of "Gnosticism" unchallenged. And though, I've been shamefully ignoring the pot, I still feel I have just enough time to stir before the food is burnt.
So, let's begin.
What is Gnosticism?
Gnosticism, as we inherit it in America, is a vein of Orpho-Platonism.
Obviously.
Not Hermeticism. Not Christianity. And, certainly, not Judaism.
But, Orpho-Platonism.
Particularly, Western Gnosticism can be described as a syncretism of the Greek mystery religions centering the Orphic vein -- which comes to us from Orpheus, through Pythagoras (and most likely from Egypt and Babylon through his studies), through Plato. As a matter of fact, the mythological through-line from Gnosticism to Plato, to Orphism, and back to Egyptian mythologies is glaring when you read the myths, even without being a buff.
Yet, this is not the form of Gnosticism we usually first encounter. We don't learn of it as a complete and independent framework of hellenic origin, but usually as a half-thing mix mashed with something else; as a "parasite religion" as I've recently heard it mocked.
This stems from the Christian-centered folly of conflating Gnostic Christianity with Gnosticism itself, both historically and theologically, as if Gnosticism "came from" Christianity. Such beliefs are simply failures of historical and cultural inquiry. But, this "entanglement" that persists in the minds of the many today, is rooted in the fact that Western Gnosticism garnered it's first bout of attention (i. e. major hostilities) when it appeared in the early centuries CE — as a variety of rouge mystery cultists attempted to integrate the Jesus figure into their canons.
As Christ-followers, they'd adopt Jesus as the latest prophet in their esoteric lineage (from Orpheus to Pythagoras, for example) with many choosing to participate in Jesus-worship activities along side the other early Christian varieties. This is the origin of those who call themselves "Gnostic Christians" (a.k.a. Gnostic followers of Christ) today.
However, these mystery cultists -- unlike other Christians -- did not renounce their traditions to become whole converts into the Jewish way. They quietly retained them, seeking not to "convert" or rouse the other Christians, but to cultivate their own understandings of the texts in line with their Greek way. And, that is why their Jesus — "Gnostic Jesus" — is a little divergent from the norm. He is not interpreted to take on the throughly Jewish character and ideological background of Abrahamic Jesus, but a Hellenic character and background inside of a Jewish body (with the body thing being debatable).
And that, as we have learned, is very !!!TRIGGERING!!! to the zealots for Judeo-Christian ideology. This little attempt at cultural assimilation would result in being seeing as not just some kind of competitor, a but a mortal enemy to the ideology and spread the proper Christian -ness. Thus, "the Gnostics" — those retaining the beliefs of the mystery cults -- were branded the worst of "heretics," worthy of being rooted out of all influence and power by any means necessary.
And, so began the hiding.
``` Transmission Note 01:
The Greeks and other peoples were a lot more open to input from cultures and pantheons beyond their own than the Jews are. I believe this led them to underestimate the extent to which the Jewish -ness defined the character and how Christianity was meant to be an expansion of that -ness rather than an earnest spiritual or intellectual exploration.
Essentially, they did not realize there was this agenda and rigid ethnic claim to ownership of the Jesus character. And, the misstep of trying to engage with it as such is what led the mystery cultists to inadvertently cause such great offense.
Now, of course, the plan was always to convert, kill, persecute, and/or disenfranchise anyone and any culture that did not give way to the planned faith (Catholicism). But, they really stay aggro'd on the Gnostic Christians, which is why everybody finds them and thinks they're the whole of Gnosticism.
``` For half of the last 2000 years, the Christian mystery cultists publicly behaved and saw themselves as Christians, and that is indeed what they called themselves ("Gnostic" is a name that was given to them collectively and retroactively). But, they entertained their mysteries in private. They preserved their belief systems through metaphor and code, they prepared private gatherings, and they participated in both new and ancient rituals in secret. They also, famously, wrote and distributed their own texts among themselves, drew and documented esoteric meaning from The Bible, and as time went on, became the Valentinians, Manichaens, Cathars, Mandaeans, etc...
All of whom, in the end, lost themselves.
``` Transmission Note 02:
The non-Christian mystery cultists behaved much the same, continuing to exist beneath the surface under other names and "heresies." Seems like most died up to now, but the mysteries of some are still carried by different orgs, lines of thought, and denominations just like the Orphic vein.
``` Sometimes genocided, sometimes not, they all became more and more assimilated into the Christian worldview, losing and twisting up bits of their gnosis until they were no longer carriers of the mysteries, but dead ends. Most notably, the information surrounding death either came to mimic that of Christianity and/or became platitudinal, losing it's instructional value. And, that's just what Christianity does — its function is to destroy the means and routes to Gnosis; forcing you to succumb, in one way or another, to the Evil-bland power of the demiurgic drone.
It breaches. It invades. It colonizes. It burns.
All of this is why, despite modern and historical claims, it is clear that Gnosticism and Christianity share no common cause and are, in fact, fundamentally opposed. This is obvious from their logical ends, on their faces, and Gnostic Christians are lost, or "heretical," Gnostics as far as I am concerned.
``` Transmission Note 03:
Despite this, there are very few Gnostic Christians who have (so far) maintained a non-Abrahamic Jesus and allegedly find bits of gnosis by focusing through the figure. That certainly makes them distinct from the Judeo-Catholic lineage and this, among other non-standard Christs, are the only reason why I make the distinction between Catholicism and Christianity in other posts.
``` But, thus far, I've (necessarily) given you more of a history lesson on them than an explanation of what Gnosticism really is.
Features of Gnosticism
Globally and as a phenomenon, Gnosticism is the metaphysical worldview positing a duality between self-consciousness and material nature, with need for man to overcome the latter by means of personal knowledge of the self and of the nature of reality (Gnosis). Further, it:
- Posits a hostile world order.
- Asserts a material reality that naturally restricts the meaningful will and ability of self-conscious man within its objective and knowable parameters.
- Affirms the free will and intellectual agency of self-conscious man as means by which he can pursue, gain, and apply Gnosis.
- Calls for a personal journey toward individuation, as man cannot attain Gnosis collectively or by means of others, but only through his own efforts.
Gnosticism is an emergent worldview, appearing across time and space organically, rather than as a worldview constructed for socio-political purposes like religions. As such, it does not share the goal or function of religion as a means of socio-political management. Yet, still, it takes on the three forms that all worldviews do -- mythic, secular, and atheistic. Specifically (with examples), there is:
-
Mythic Gnosticism -- taking on a spiritual character, dealing with immaterial realms and entities:
-
- Classical/Theistic Gnosticism
-
- Jungian Analysis
-
Secular Gnosticism -- taking on a political character, dealing mainly with material powers and principalities:
-
- Prometheanism
-
- Reincarnation Truthers (ET)
-
- American Conspiracy Culture (Alex Jones, David Icke, etc...)
-
- Plot of The Matrix
-
- Forms of Anarchism
-
Gnostic Atheism -- taking on a philosophical character, dealing with ethics and metaphysics:
-
- Objectivism
-
- Simulation Theory (some)
-
- e/acc
I, personally, view Gnosticism as a signal you pick up on. A well broadcast fact of reality that you become attune to (if you so have the capacity) after an alienating event: a realization, a condition, or a happening that snaps you out of a given collective drone and spurns the oh, so gnostic sense that something is deeply wrong with the world. Often, it's a noticing of hyleticism, a noticing of a naturally systemic injustice, or a just a longstanding experience of disconnect with the norms and trajectory of the world. But, after boarding the Gnostic-line of thought, a decent amount path-find their way to actual Gnosticism. And, while that Gnosticism may wear many different faces and metaphorical frameworks, it's always says the same thing.
``` This isn't exclusive to me. I'm the only one I've heard explicitly say this, but I've seen all serious Gnostics talk about this in a way that suggests what I am. Additionally, those "alienating events," as I've coined, are not spontaneous, they're usually a long time coming.
``` That's why I've listed only 4 characteristics — of Gnosticism: because, contrary to what most scholars and enthusiasts would say, that's all you need to describe that thing. And, by being able to identify what are essentially Gnostic first principles, we are able to understand and talk about Gnosticism much more pointedly.
For one, it gives us a kind of tracking system where we can talk about Western Gnosticism but also see Gnosticism itself, Eastern Gnosticism, and Gnosticism's appearance in tribal cultures around the world. We can see it branching off in America or taking on some new flavor in Brazil. We can also see it when it isn't appearing in an explicitly spiritual form, but as a literary theme or a cultural meme. So, fittingly, this understanding of Gnosticism is as broad as the phenomena itself since it is much more in line with how it actually manifests within the world.
Yet, you’ll also see that it is somehow much more precise than the long, droning lists that Stephan Hoeller and a few others have produced:
- There is an original and transcendental spiritual unity from which emanated a vast manifestation of pluralities.
- The manifest universe of matter and mind was created not by the original spiritual unity but by spiritual beings possessing inferior powers.
- One of the objectives of these creators is the perpetual separation of humans from the unity (God).
- The human being is a composite: the outer aspect is the handiwork of the inferior creators, while the inner aspect is a fallen spark of the ultimate of the divine unity.
- The sparks of transcendental holiness slumber in their material and mental prison, their self-awareness stupefied by the forces of materiality and mind.
- The slumbering sparks have not been abandoned by the ultimate unity; rather, a constant effort directed toward their awakening and liberation comes forth from this unity.
- The awakening of the inmost divine essence in humans comes through salvific knowledge, called “gnosis.”
- Gnosis is not brought about by belief of by the performance of virtuous deeds or by obedience to commandments; these at best serve to prepare one for liberating knowledge.
- Among those aiding the slumbering sparks, a particular position of honor and importance belongs to a feminine emanation of the unity, Sophia (Wisdom). She was involved in the creation of the world and ever since has remained the guide of her orphaned human children.
- From the earliest times of history, messengers of Light have been sent forth from the ultimate unity for the purpose of advancing gnosis in the souls of humans.
- The greatest of these messengers in our historical and geographical matrix was the descended Logos of God manifest in Jesus Christ.
- Jesus exercised a twofold ministry: he was a teach, imparting instruction concerning the way of gnosis; and he was a hierophant, imparting mysteries.
- The mysteries imparted by Jesus (which are also known as sacraments) are mighty aids toward gnosis and have been entrusted by him to his apostles and their successors.
- Through the spiritual practice of the mysteries (sacraments) and a relentless and uncompromising striving for gnosis, humans can steadily advance toward liberation from all confinement, material and otherwise. The ultimate objective of this process of liberation is the achievement of salvific knowledge and with it, freedom from embodied existence and return to ultimate unity.
— Gnosticism: New Light on the Ancient Tradition of Inner Knowing by Stephan A. Hoeller
Lists like this, while not all wrong, do not form a cohesive or accurate explanation of Gnosticism.
I will say that, while I disagree on the language, universality, “divine feminine,” and the implications of “oneness” — which mostly come from Christian contamination — the first 10 points comprise a very accurate characterization of Mythic Gnosticism. But the list, as a whole, is completely ignorant of Gnosticism’s non-spiritual manifestations and, again presupposes that Gnosticism is a denomination of Christianity, a plain falsehood.
Worse yet, they're the works of those who futilely take it upon themselves to "revive" and "spread" Gnostic Christianity, with these lists as blatant — and often plainly stated — attempts to define a canonical doctrine. The ultimate intent being to make "Gnosticism" structurally and massively participatory so that it can be marketable to the masses. But, those who desire this do so because they view Gnosticism as a religion and have adopted Christian/Abrahamic views as to the purpose of belief systems.
Yet, Gnosticism is neither beholden to nor compatible with those views.
``` Transmission Note:
This should not be interpreted as an attack on Stephan Hoeller. The aforementioned book is informative as a whole and I agree with a lot of it. However, I disagree with many of Hoeller's conclusions.
Funny enough, while revisting that chapter, I discovered that Hoeller, being well before my time, has a lot more context on where guys like David Lindsay (I think that's his name?) come from. Page 182.
```
Practicing Gnosticism
One does not practice Gnosticism, mythic or not. But, Gnostics often practice rituals that they believe will induce Gnosis.
Because Gnosis must be attained personally and intellectually, these rituals historically involved psychedelics and circumambulatory* acts meant to remind the practitioner of his goal. Additionally, this pursuit meant that Classical Gnostics were (and continue to be) open to trying out practices from other belief systems if they're believed to have the potential to induce Gnosis. Many, however, also turn to plain ol' knowledge, choosing to immerse themselves in more interactive ways of knowing about the world such as science, math, and esoterica as a path to personal knowledge of reality.
Yet, while varied and individualistic, Gnostics did not always go about their spiritual journeys alone. While Gnosis is pursued personally, individual findings, experiences, and speculations were/are shared among each other for consideration and guidance in personal journeys. Individuals with similar findings and personally efficacious mediums of Gnosis would form groups and participate in rituals together. And, because Gnosticism is classically hostile or indifferent to the body, historical Gnostic groups tended to go one of two ways: ascetic or degenerate. The first involved fasting, abstinence, and denial of bodily pleasures. The second, I will leave to your imagination. But, thankfully the former won out in popularity and is how Gnostics are commonly portrayed.
``` Come to think of it, the whole attempt to shock oneself into Gnosis is kind of like trying to relive the alienating event that made one Gnostic in the first place. But, more intense.
``` So, the point being made is that, when thinking of Gnostic groups or Gnostics gathered, one should avoid conceiving of them as one does a church. Rather than platforms where an orthodoxy is espoused and downloaded, Gnostic gatherings were/are information exchanges, more akin to get-togethers.
Gnosticism has an investigative and antinomian character, rather than faithful and obedient character.
Secrets
At this point, I've laid out that Western Gnosticism comes from the Greek mystery cults (and by extension Egypt, and, in likelihood, Babylon). I've highlighted that those holding their beliefs went into hiding and were given the name "Gnostic" by their persecutors ("Gnosis" meaning "knowledge," "Gnostic" approximating "knower"). And, I've repeatedly used word like "private," "personal," "individual," "metaphor," "code," and "secret" to describe their activities.
All of these things, in a sort of snowball effect, have had Christians unwaveringly convinced that Gnosticism is about "keeping secrets." And, with a strange intensity, they've been all riled up about Gnostics having "secret knowledge" for thousands of years. In fact, if you ask a Christian (who has heard of Gnosticism) today, that's exactly what they'll tell you: "Gnostics were people who thought they had secret knowledge."
With a tone suggesting an absurd level of contempt for a supposedly dead heresy, to boot.
But, Gnosticism was poorly understood by its enemies and is not about "secret knowledge." Despite the fact that Christians love making themselves angry imagining such silly ideas that are more attributable to themselves, Gnostics are not and were not meeting up to go: "teehee, they don't know our seeecret!"
In fact, here are the mythic secrets of such great concern:
-
The mysteries of the mystery cults tended to be along these lines:
-
- You have an immortal soul.
-
- You belong to a spiritual reality (often phrased: "you are/can become a god").
-
- You are trapped in a cycle of material death and rebirth.
-
- You need to do XYZ to escape materiality.
-
The mystery cultists/Gnostics were secretive to preserve the purity of the above beliefs and techniques and to avoid persecution -- and ultimately inquisition -- at the hands of hostile powers.
- Gnosis is personal, private, and "secret" because it is incommunicable. Personal knowledge can be talked about, but cannot be literally shared person to person and Gnosis comes differently to each person.
- Gnosticism doesn't have an imperative for conversion or being a "big tent" because Gnosticism itself is incommunicable to the majority.
These things are not really "secrets" but, even if they were, they could be talked about freely (given the absence of persecution) due to bullet four.
Bonus "Secret": A common premise is that Gnosis is applied at death on a post-mortem spiritual journey, similar to that of the Ka of Egyptian mythology.Books
Many religions and even philosophies are centered around holy books as definitive canonical, instructional, and behavioral guides. They function as the source and reinforcement of a given worldview, which allows it to persist fundamentally undiluted for extended periods of time.
This is not so for Gnosticism -- mythic or not.
Instead, Gnosticism has no holy book and, in the section called "Features of Gnosticism," I've already laid out its presence and reception through alienating events. It requires no human regulation in order to continue to authentically exist.
``` Now is a good time to mention that there is a multiple discovery aspect of Gnosticism which is generally how I, at least, track alignment and continuity while identifying "the signal," as I call it, as the source in others.
``` Yet, the ancient Mythic Gnostics were known to be prolific writers, as attested by the Nag Hammadi library. And, the penchant for writing seems to persist across time and mode, as Secular Gnostics and Gnostic Atheists (beknownst or not) have been absurdly influential in American media and culture by this means.
So, why do Gnostics write so much and how do they use books?
Gnostics tend to view books as spiritual journals, rather than instruction manuals, and literature at large as a means of preserving knowledge. Contributing to the Gnostic meme pool is a form of participation in the imperative, which is why Gnostics, unlike Christians and others, have little issue putting their pieces forward. Rather than the book study and faith characteristic of Abrahamic maintenance, Gnosticism, again, tends toward investigation and information sharing. And, it is for these reasons that Gnostics have been known to not only write their own texts, but to adopt and reinterpret the texts of other belief systems according to the Gnostic worldview.
-
 @ 6c2d68ba:846525ec
2024-09-01 13:02:53
@ 6c2d68ba:846525ec
2024-09-01 13:02:53Dear friend,
it seems like you have decided to turn your back on those walled gardens and set sails to enter uncharted territory. A world without walls, an open world, a world of beautiful chaos. At least for today, I don't intend guiding you out of the safe harbour onto the open, endless sea. Today, my only intent is sharing a few thoughts, before you depart.
As a wise man on Madeira once said, it's not so much about having the right answers, it's about asking the right questions. While I'm not certain whether I have found the right questions myself by now, let me share the current set with you:
-
What causes the discomfort that drives you out of the walled garden onto the open sea?
-
Are you trying to transfer from one walled garden to the next one, where the difference being a slightly friendlier colour on the wall?
-
What are you hoping to find on the open sea that walled gardens cannot provide?
-
What are you willing to sacrifice for freedom (of speech)?
-
What will you need to keep the ship afloat?
-
How will you react when you find yourself in the middle of a storm?
I sincerely believe that it's worthwile taking a step back before departing to reflect on the big picture and the underlying paradigm shift between walled gardens and nostr. This is not about building competitors to broken systems, this is not about mimicking centralised services, this is not about repeating the same mistakes over and over.
This is about building a new world, an open world without walled gardens and data silos.
Onwards!
-
-
 @ 6f170f27:711e26dd
2024-09-08 17:45:46
@ 6f170f27:711e26dd
2024-09-08 17:45:46Far too many people: "GDP is bad. I prefer [thing correlated at 0.9 with GDP]."
Manufacturing:
Life expectancy:
Happiness:
Many other metrics & discussion in the source:
https://x.com/cremieuxrecueil/status/1832588128084730334
originally posted at https://stacker.news/items/677211
-
 @ e5272de9:a16a102f
2024-08-31 20:23:59
@ e5272de9:a16a102f
2024-08-31 20:23:59The GrapeRank algorithm, like the PageRank algorithm, takes as input a graph, composed of nodes and edges, and composes "importance" scores for each node based on the topology of the graph. This equation is currently implemented at brainstorm and uses follows and mutes to calculate a trust score G (also called an "influence" score) in the range [0, 1] for each user in your nostr network.
This is the GrapeRank equation:
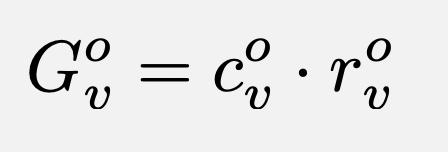
- G, c, and r in this equation are each scalars in the interval [0, 1]
- G represents the grapevine score (also called the "influence") of v, as seen from the vantage point of o
- r represents the average rating of v by o's grapevine
- c represents the degree of confidence in the average rating r
- the subscript always represents the thing (user, product, etc) being evaluated
- the superscript always represents the "observer," the point of reference from which we view and interpret the world
This is the same equation in expanded format:
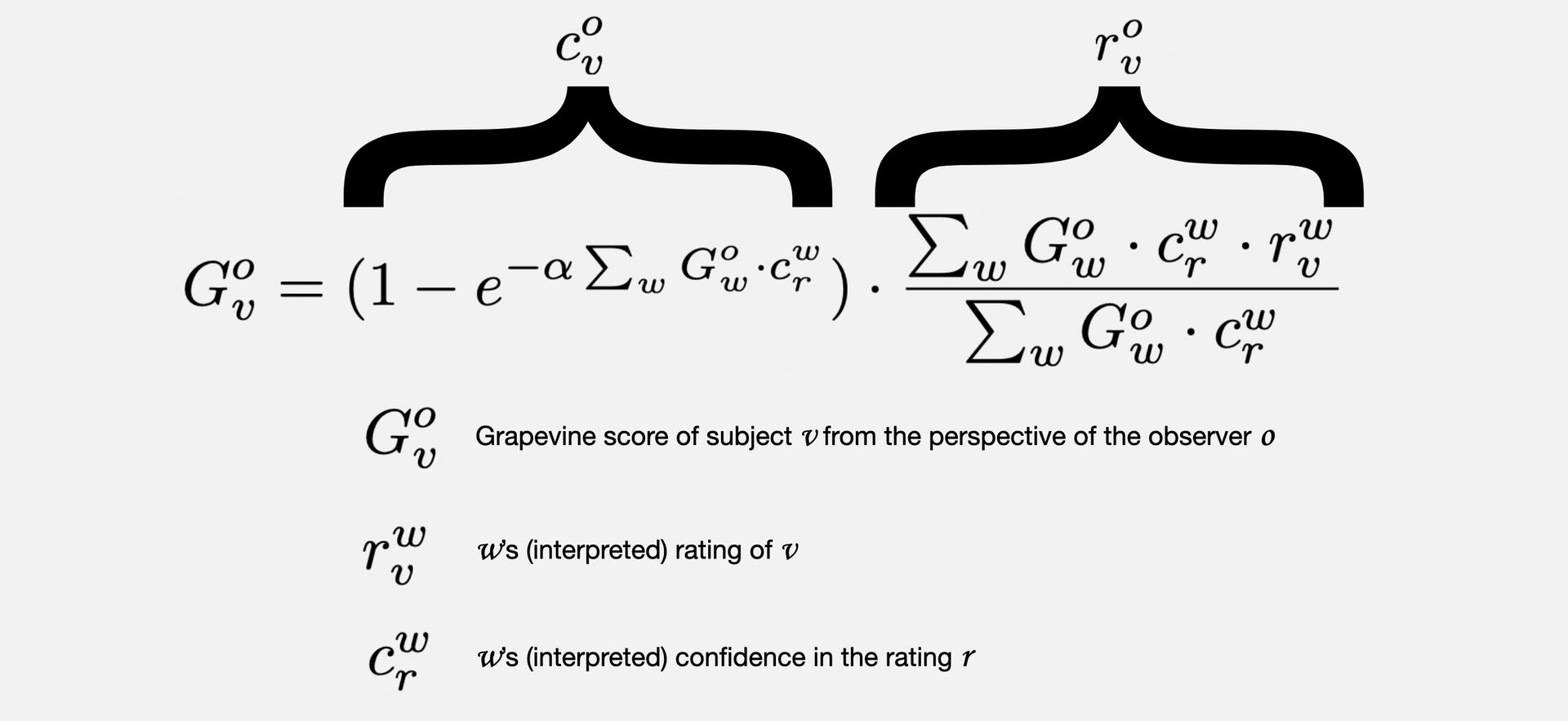
- The grapevine score of v on the left, G_v, is weighted using the grapevine score (but of each w) on the right, G_w
- These calculations are iterated until all G values converge
- r^o_v (the right half) is the weighted average
- c^o_v (the left half) is the confidence in that weighted average
- The r^w_v are the ratings being averaged together; they are inferred from follows and mutes by interpreting a follow as a score of 1 (probably not a bot), a mute as a score of 0 (probably a bot)
- The c^w_r are the confidences in the r^w_v; a follow is interpreted to have a confidence of 5 percent, a mute to have a confidence of 10 percent. (These are adjustable settings at brainstorm.)
- The sum over G * c, which appears twice in the above equation, is called the "input" and is an unbounded, nonnegative scalar which represents "the amount of trusted input" that goes into the calculation
- The formula is designed so that as the input (the number of ratings from trusted sources) increases to infinity, the confidence c^o_v approaches 1 (100 percent) asymptotically. This map from input onto confidence, which employs a nonlinear equation, is necessary to ensure that G remains within the [0, 1] interval even as input increases to infinity.
- alpha is a nonnegative scalar value that determines how "quickly" the confidence c^o_v approaches 1 (100 percent) as trusted input increases. Decreasing the value for alpha makes the equation more "rigorous" because it will take more trusted input to achieve any given degree of confidence. (Alpha is another user-adjustable setting at brainstorm.)
To perform the above calculations: 1. For the "seed" user (the observer o, i.e. the logged-in user), fix average, confidence, and G (influence) to unity. These values will not change. 2. For all other users, initialize average, confidence, and influence scores to zero. 3. Iterate through all users to calculate average, confidence, and influence scores. In the first iteration, the follows of the logged-in users will obtain nonzero scores. In the second iteration, their follows will obtain nonzero scores. And so on. 4. Continue iteration until all values converge.
Intuition tells us that convergence is guaranteed by the requirement that for each rating, the rating and its associated confidence are scalar values between 0 and 1. G will therefore also always also be a number between 0 and 1. Not shown: at brainstorm and in general recommended practice, the above equation also employs a scalar value between 0 and 1 called the "attenuation factor," defaulted at 0.8 but adjustable by the user, which causes influence scores G^o_v to diminish as the number of hops between o and v increases.
Intended usage
G is designed to be used as a weight when calculating weighted averages, tallying votes, etc. It is highly effective at eliminating bots without turning into a popularity contest.
Interpretation
G^o_v is a recommendation, to you by your grapevine, that reflects in numerical form how much "attention" you should pay to pubkey v in the given context (if a context is given).
- G^o_v = 0 means that pubkey v is not worthy of your attention, because v is probably a bot
- G^o_v = 1 means that pubkey v is worthy of your full attention, because b is probably not a bot
- Values between 0 and 1 mean the grapevine isn't absolutely certain one way or another, whether because of scant information (some follows by trusted sources, but not many) or conflicting information (combination of follows and mutes)
Note that if a bad actor spins up a large number of bots and uses them to follow himself, those follows will be completely ignored, because those bots will have a zero trust score G.
Change of context
The set of ratings r can be generated from any data source, regardless of format. By selecting different ratings datasets, we can generate grapevine scores to reflect different contexts. Example: collect emoji reactions to content on Topic X and infer a fire emoji as a rating of 2, rocket as a 3, thumb down as a 0, etc. The resulting G, which will take values between 0 and 3, is now interpreted to apply only to Topic X.
Compact notation
The above equation can be written more succinctly:
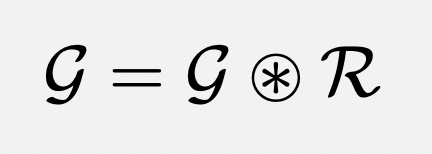
where G represents the baseline grapevine score, and R represents the dataset generated from follows and mutes.
Note that we can use a different G on the left versus on the right:
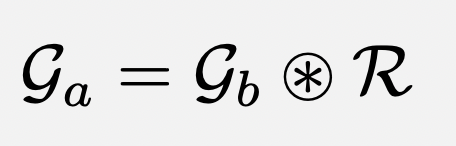
The same relationship can be expressed using arrow notation:
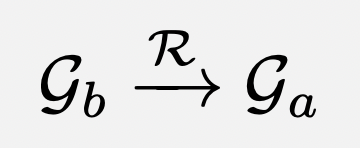
The above relationship in arrow notation should be read to mean that the set of scores G_a are calculated using dataset R which has been authored exclusively by members represented by G_b. In other words, the ratings R are weighted using the set of scores G_b.
Note that the dataset R is generated via interpretation of preexisting content. We can use any content that we can find. There is no requirement or expectation that users will necessarily generate ratings in a format convenient for input into the grapevine. The process of "interpretation" takes care of that, by "translating" existing data into a format suitable for use by the grapevine.
Note also that grapevine scores G may refer to anything in any context: trust scores for users, quality scores for products, etc.
Concerns about convergence
If the G_a and G_b represent the same context (G_a = G_b), the relationship is said to be "recursive," and calculations are iterated until they converge.
If G_a != G_b, the relationship is not recursive, and a single iteration through each pubkey is all that is needed. This means that we can allow G_a and / or G_b to be greater than 1 with no need to worry about convergence.
Worldviews
Arrow notation allows us to link trust calculations in chains:

A graph of grapevine scores G_i linked via arrow notation is called a worldview.
For example, consider the following worldview: * G_a is the baseline nostr trust score, as described above, intended to separate bots from real users * G_b is a label applied to nostr users, intended as a label for bitcoiners (as opposed to nocoiners or shitcoiners) * G_c is a quality score applied to hardware wallets
The purpose of the above worldview is so that I can get a ranked list of hardware wallets and I can be reasonably sure that the list is curated by bitcoiners whose instincts on this topic I value more highly than the general population.
Worldviews can contain any desired number of nodes, connected by any desired number of arrows, and so can be as complex as desired.
Obviously, the construction of a worldview reflects the value system of the person who uses it, with the above worldview offered as a reflection of maximalist values and beliefs. Worldviews can be codified and submitted to the wider community. One's grapevine can even be used to select individuals who should be trusted to edit or construct worldviews.
Computational cost
The methods described above are expected to be too time consuming and computationally expensive to do all of them on the fly on the front end. Notably, the ones that are recursive. Non-recursive computations, however, can be done on the front end, provided recursive calculations have been done ahead of time and are readily available. It is anticipated that the value added by well-crafted worldviews will more than justify the requisite costs.
-
 @ 6c2d68ba:846525ec
2024-08-30 21:53:53
@ 6c2d68ba:846525ec
2024-08-30 21:53:53What the hell is Nostriga you might think. Nostriga is part of the nostr.world unconference series. It's a cost-free event aimed at gathering nostriches - people excited about nostr - globally to share knowledge, collaborate, network and work towards a freely accessible internet.
In case you never heard of nostr: nostr is an open protocol designed for censorship-resistant and global web publishing, fostering a value-for-value exchange. Find more information here.
Now that a few days have passed, it's time to reflect on some of my main takeaways but first, I would like to thank Marce, Anna, Jack, Uncle Rockstar and everyone else involved for making this event special in several ways. I'm sharing my thoughts in no particular order and as can be expected after having heard so many inspiring talks, I will be relaying - relay, get it? - many great ideas others shared.
nostriches are built different
To be honest, Nostriga was one of the best conference experiences I have had in a while. Great spirit, deep conversations, real & honest takes and 99% signal. Everyone who's ever been to a conference knows how draining and tiring such events can be. This time, however, something is different. I guess one of the main reasons for this are the people behind those npubs. Great attitude, avoiding ego shows, no simping for VIPs, down to earth and a positive vision of what might lie ahead. So in hindsight, Nostriga makes me super bullish on the upcoming months and the road ahead when it comes to the tech as well as the people behind nostr. Onwards, nostriches.
no need for nostr marketing
With the world marching towards implementing 1984, which was not meant to serve as instruction manual god dammit, and events such as the arrest of Pavel Durov, it's evident that nostr won't need a marketing department. An open protocol with focus on censorship-resistance and free speech, will automatically attract the attention of just the right people. This is of course based on the assumption that the nostr community will deal with certain challenges when it comes to privacy and nostr.

nostr (still) has privacy issues
As already pointed out by Edward Snowden, many open challenges remain to be mastered when it comes to privacy, so that people having to rely on safe and private messaging don't have to rule out nostr. Protecting identities, location and leaking as little metadata as possible are crucial here. Keep in mind, a three letter agency once said that they kill people based on metadata. In this regard, nostr DMs are one of the biggest pain points for the time being, though several nips exist to overcome issues such as IP leaks. See the talk of Jeff for details. We'll get there!
For thoughts on privacy, check out saving private nostr:
For privacy and DMs, check out the past and future of messaging on nostr (at 3h 01min 48s):
nostr already got a killer feature: openness
Long story short, watch this talk (starts at 1h 19min 17s) :
nostr beyond social media
As demonstrated by Ben Arc, nostr can be so much more than just an attempt to mimic Twitter. IoT, web of trust, file sharing or bringing together (open) social media and AI are just a few things on the table.
separation of client and algorithm
For many of you this might be nothing new but I can't stress the importance of Data Vending Machines (DVMs) enough. In a nutshell, DVMs are data-processing tools. You give them some data, a few sats, and they give you back some data. As anyone can spin up his own DVM without any registration or signup, there will be ruthless competition. Check out DVMs for further information.
The basic idea behind it, which still gets me, is the potential separation of (nostr) clients and algorithms in a broader sense. Coupled with marketplaces and having insights what algorithms your friends are using, things will get interesting. Remember, to this day Twitter, Meta and so on are deciding what algorithms are being used in your app and not you. nostr will put you in the driver seat.
web of trust
Web of trust is something people talk a lot about these days, so I will keep it short. One idea caught my attention: combining nostr and file sharing in the sense that you attach an npub to files hosted on file sharing services or torrents and so on. In order to prevent downloading or even spreading infected files, it boils down to the simple question of "can I trust that npub to host clean as well as safe files?". Reputation.
have you seen my nutsack?
Before Nostriga, I haven't been aware of how beautifully ecash and nostr can go hand in hand. In particular, I'm still trying to find the right words to express how big of a deal the combination of Data Vending Machines and ecash can be, if implemented the right way. Check out DVMs that nutsack thing, and pistachio bag.
(Talk starts at 55min 41s)
nostr is not another Bitcoiner circle jerk
On the second day of Nostriga, I met someone at one of the food trucks, who happens to have been actively fighting to free Julian Assange. Events, protests, spreading the word, the whole thing. He or she - trying to hide as many details as I possibly can here - told me that his/her main motivation for coming to Riga was indeed nostr and that he/she had discovered Bitcoin via nostr, where it's usually the other way around. To be honest, this was not the only time I heard this at Nostriga but for sure it's the most memorable one.
Of course, there is nothing wrong with so many Bitcoiners being around on nostr and it does come with several benefits, one of them being an excellent meme game. As I sincerely believe that nostr is for anyone, it feels good to see other communities popping up and telling their stories on nostr. So delighted you're leaving those walled gardens, friends.
onwards
Let me know what you think, where you agree, where you have a different point of view. Feel free to bring in your Nostriga story. Keep it weird, fellow nostriches, and if you have time to just watch a single talk from Nostriga, make sure it's this one:
-
 @ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43
@ 09fbf8f3:fa3d60f0
2024-09-08 13:17:43由于telegram的政策调整,不允许滥用telegraph匿名上传图片了。 导致之前通过telegraph搭建的图床无法上传(已上传的能正常查看)。
有人通过原项目的基础上分支另外项目,可以通过频道上传图片。
项目是通过cloudflare pages搭建的。 - 项目地址:https://github.com/MarSeventh/CloudFlare-ImgBed
项目的教程很详细,具体去看项目教程。
telegram设置:
- 需要有telegram账号
- 通过@BotFather创建一个telegram机器人,并获取api key。
- 创建一个频道,获取频道id,通过转发一条消息到 @VersaToolsBot机器人可以查看频道id。
- 一定要添加创建的机器人到频道作为管理员才能使用。
cloudflare的设置
- 通过git项目部署,设置变量:TG_BOT_TOKEN和TG_CHAT_ID就基本可以使用了。
- 如果需要后台,需要添加kv空间,并在设置里面的函数,选择对应的kv空间,如图:
- BASIC_USER 后台登陆名
- BASIC_PASS 后台密码
- AUTH_CODE 鉴权,防止别人使用,设置后,别人使用必须输入这个。
其他
- 成人内容屏蔽
- pico 使用api接口 去项目地址看
最后
我搭建的地址: https://imgbed.lepidus.me
-
 @ d52f4f20:98efcdfb
2024-09-08 12:05:31
@ d52f4f20:98efcdfb
2024-09-08 12:05:31original post 28/12/2010 .net
Para você que se sente meio preso ao instalar o Ubuntu, pois ele já vem pronto para um usuário final, mas isso não me agrada parece que perco o espirito de liberdade.
Mas o ponto forte Ubuntu são suas atualizações, então eu fui em busca de como fazer uma instalação customizada somente com os pacotes do Ubuntu. Depois de muita pesquisa e anos de experiência com linux desenvolvi o que chamo de instalação mínima
Alguns conceitos da minha instalação – Não tem gerenciador de login gráfico. – Precisar habilitar o root, na unha e você usa isso. – Não tem menus, os aplicativos são chamados via tecla de atalho ou docks. – Não tem menu para desligar. – Não é um desktop, usa apenas um gerenciador de Janelas. – Aqui tudo é minimalista, não é bonito também não quer dizer que é feio, é apenas simples faz o necessário. – Não importa a versão do ubuntu, atual ou não essa técnica quase nunca mudará.
Seria bom/Pré-Requisitos – Se você tem conceitos de particionamento. – Se você já instalou um Debian. – Se você sabe usar o vim. – Conexão com internet via placa de rede 10/100 (sim tem que ser assim).
Introdução A idéia é usar a instalação mínima do Ubuntu (https://help.ubuntu.com/community/Installation/MinimalCD), onde é bem parecida com a NetInstall do Debian. Iremos baixar a imagem(12 ~ 13MB) do link acima e queimar em um cd rom e dar boot.
Vamos usar o assistente de instalação, e não selecionaremos nenhum pacote na instalação, tudo sera instalado via linha de comando usando o apt. Pra quem já instalou usando o anaconda da RedHat não terá problemas, qualquer ser capaz de ler consegue instalar.
 Esta é a primeira tela exibida após o boot, selecione o menu
Esta é a primeira tela exibida após o boot, selecione o menu
Va seguindo o instalador conforme as telas, não quer que eu fique explicando tudo né?
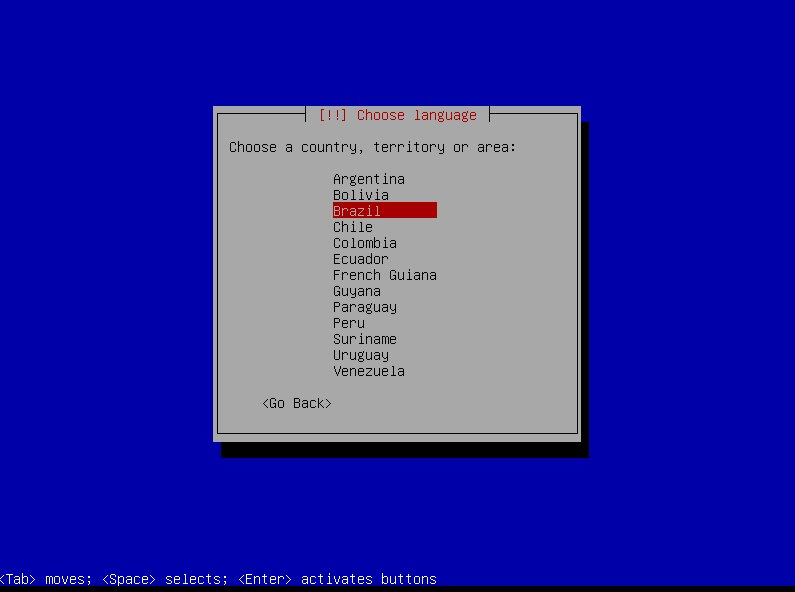
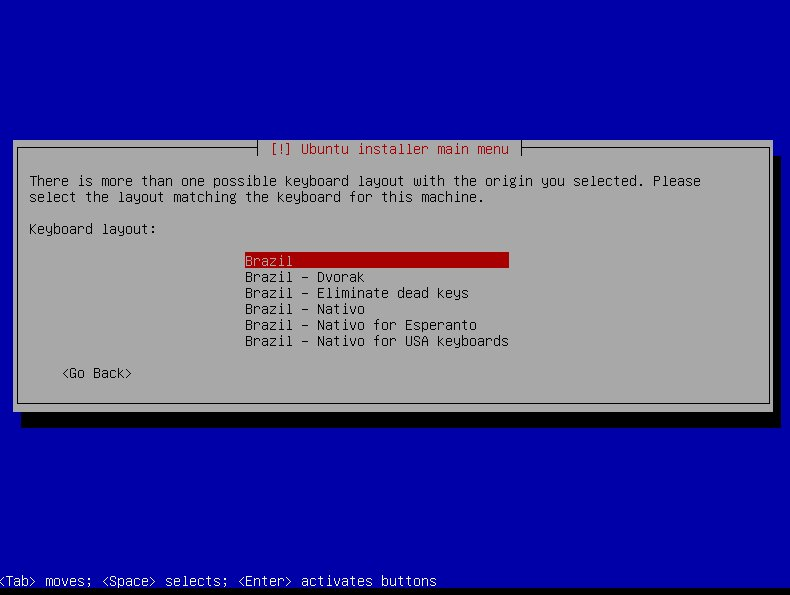
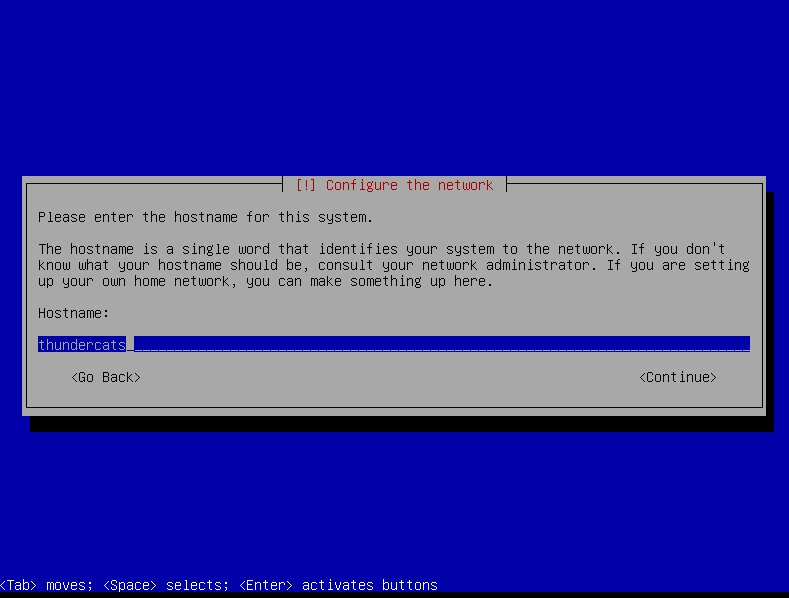 Coloque o nome que quiser, este é o nome da sua maquina pense em algo inspirador.
Coloque o nome que quiser, este é o nome da sua maquina pense em algo inspirador.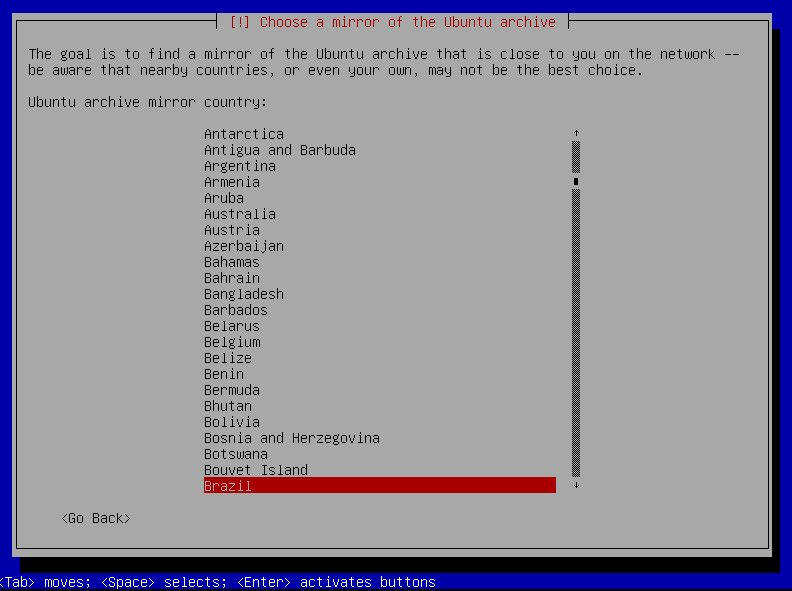 Aqui você estara selecionando daonde pacotes serão baixados.
Aqui você estara selecionando daonde pacotes serão baixados.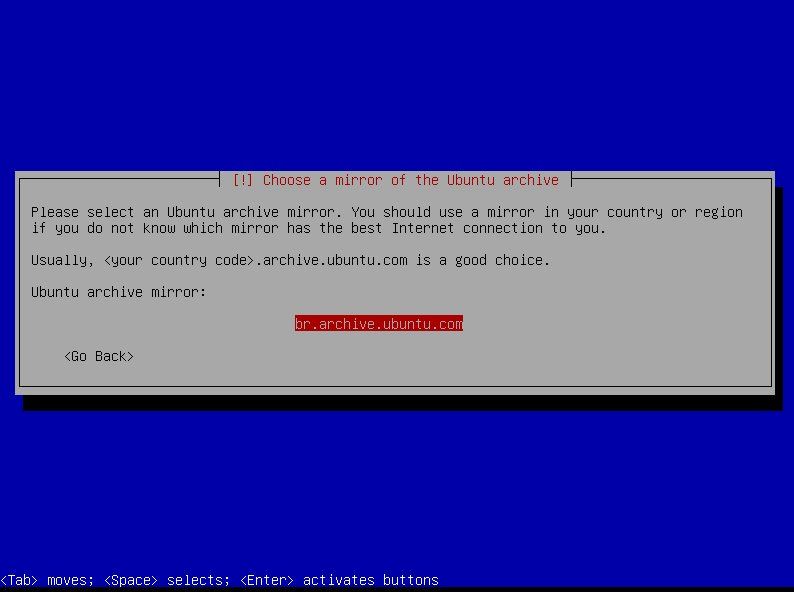 Se não tiver proxy de um [enter], se tiver pesquise no google como configurar.
Se não tiver proxy de um [enter], se tiver pesquise no google como configurar.
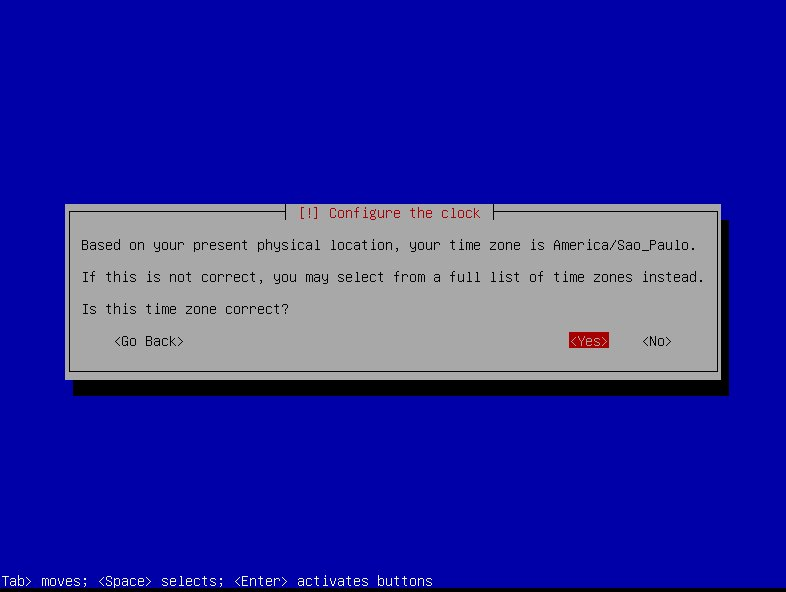
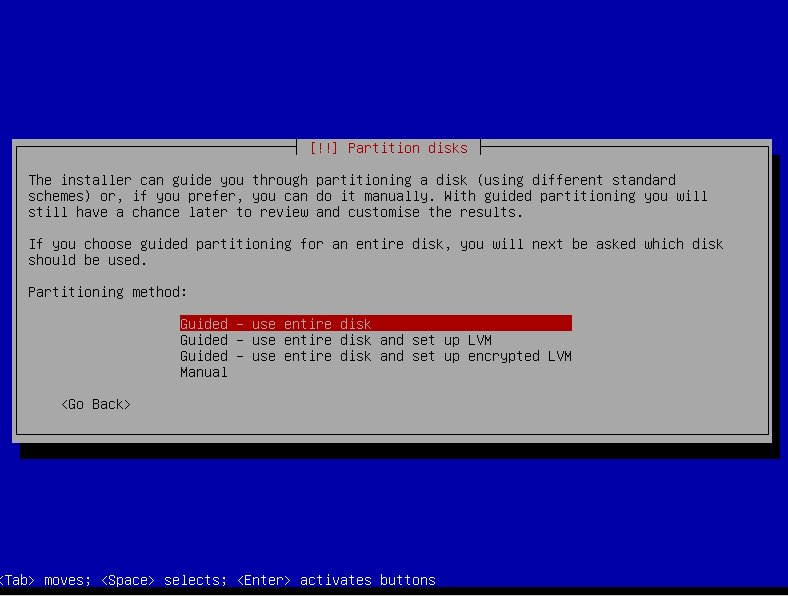 Chegamos a parte onde todo usuário de windows faz cagada, na configuração das particões, bom use o método manual, não vou entrar em detalhes, pra esse tutorial eu criei uma partição só.
Chegamos a parte onde todo usuário de windows faz cagada, na configuração das particões, bom use o método manual, não vou entrar em detalhes, pra esse tutorial eu criei uma partição só.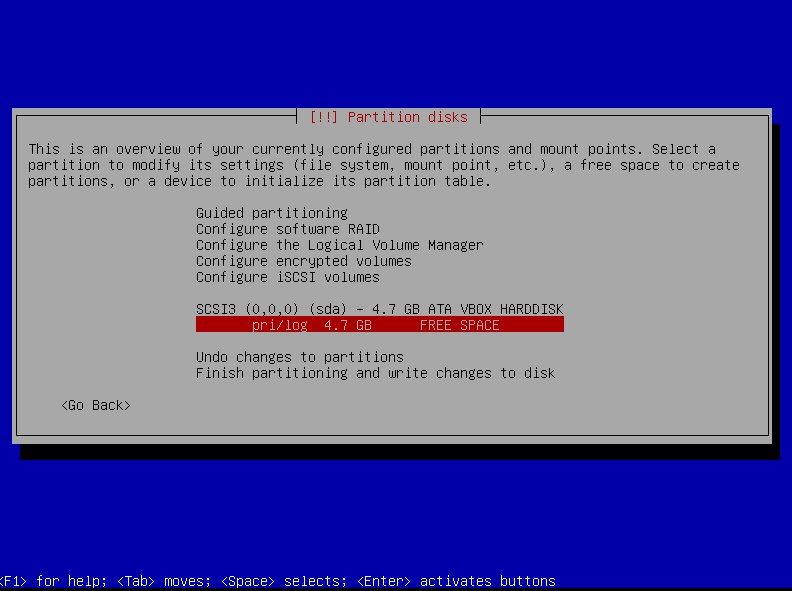
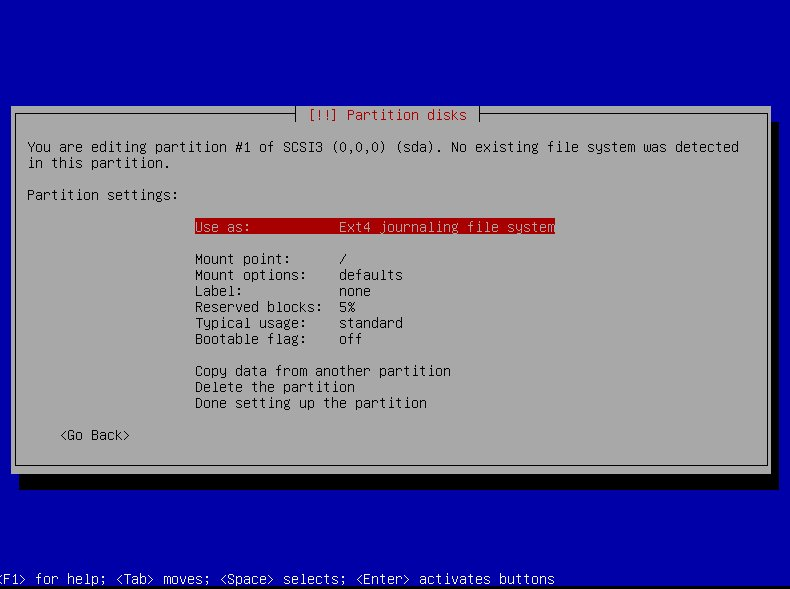
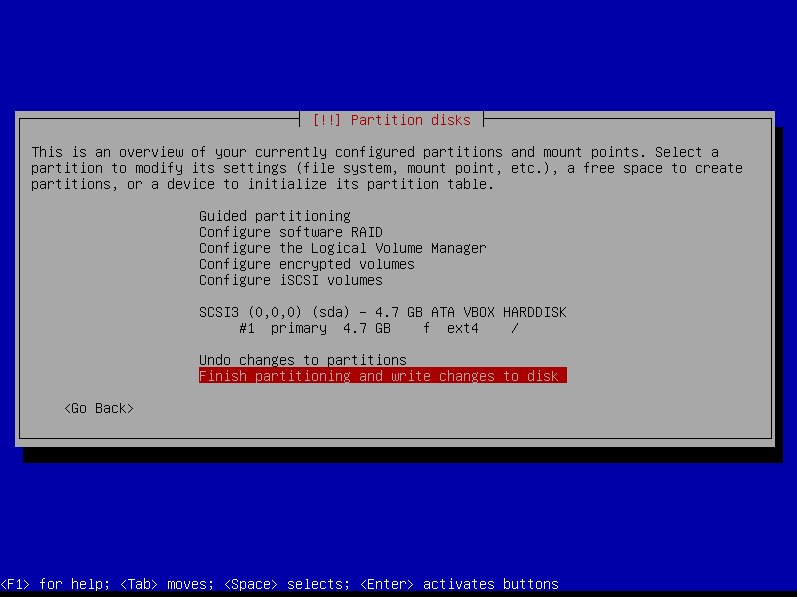 Após criar, FINISH!
Após criar, FINISH! Aguarde, vai demorar, o instalador esta baixando o minimo para poder instalar o sistema, no debian o cd é de 170mb essa parte é mais rápida.
Aguarde, vai demorar, o instalador esta baixando o minimo para poder instalar o sistema, no debian o cd é de 170mb essa parte é mais rápida. O nome do usuario, eu coloquei “lion”, coloque ai o seu usuário.
O nome do usuario, eu coloquei “lion”, coloque ai o seu usuário. senha é bom por né.
senha é bom por né. Aqui você tem a opção de encriptar seus dados, tudo que estiver no /home/ você deve pro governo? eu encriptei.
Aqui você tem a opção de encriptar seus dados, tudo que estiver no /home/ você deve pro governo? eu encriptei.
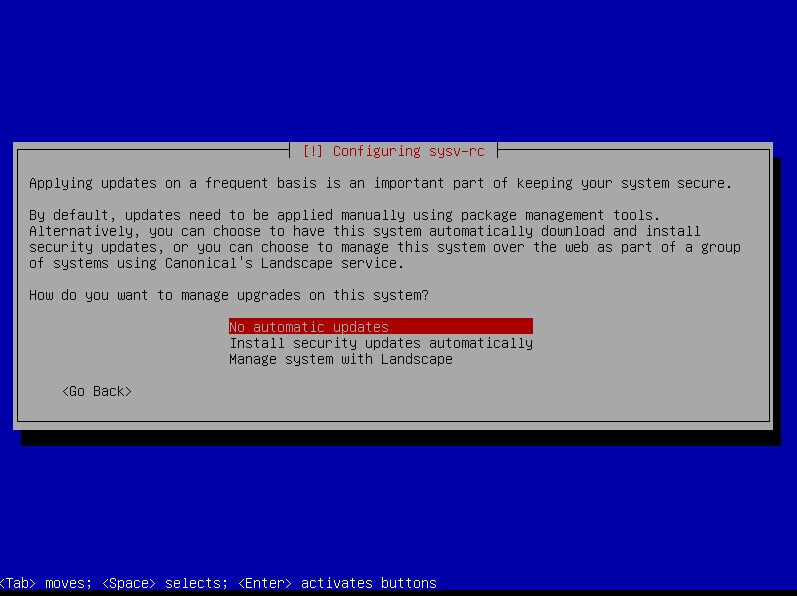 Aqui você pode selecionar a primeira opção, eu prefiro atualizar manualmente.
Aqui você pode selecionar a primeira opção, eu prefiro atualizar manualmente. Neste tela desmarque tudo, isso faz você ser o cara livre do sistema, aguarde pois vai demorar.
Neste tela desmarque tudo, isso faz você ser o cara livre do sistema, aguarde pois vai demorar. Grub é o gerenciador de boot, instale ele ai sem medo.
Grub é o gerenciador de boot, instale ele ai sem medo. Cara se você chegou nessa tela eu já estou orgulhoso, pois provavelmente não fez nenhuma cagada.
Cara se você chegou nessa tela eu já estou orgulhoso, pois provavelmente não fez nenhuma cagada.Logue-se com seu usuário, meu caso “lion” (que coisa gay figura 24 ainda).
 **Apartir daqui acabou as figurinhas fio, espero que você saiba o mínimo de VI.
**Apartir daqui acabou as figurinhas fio, espero que você saiba o mínimo de VI.Torna-se root Isso é primordio no linux, sempre somos o ROOT, o Ubuntu tem essa filosofia para você não fazer cagada, mas na vida uma boa técnica de aprendizado é fazendo cagada, então vamos habilitar o root. Calma usaremos o root para tarefas como instalar novos software, mas a execução e configuração de nosso ambiente será com nosso usuário.
$ sudo passwd rootPronto a partir de agora os comandos começados com # quer dizer que você tem que estar logado como root, e quando estiver $ você deve executar com seu usuário.
Loge-se como root vamos usar bastante de um $su ou entre num novo tty como root.
Instalando o vim
```
apt-get install vim
``` (repare # você tem que estar logado como root)
Removendo o boot-splash Amigos estamos falando de uma maquina limpa, o boot splash só come memória. Faça um backup antes e depois edite o arquivo “/boot/grub/grub.cfg” procure a palavra splash e apague somente ela e salve o arquivo. É necessário dar diretos de gravação e depois volte como somente leitura.
Removendo Mensagem de boas vindas MOTD Logo após o login, é exibida uma mensagem de boas vindas enorme do ubuntu, eu não gosto dela, nem do debian eu gostava e eu a removia editando o script “/etc/init.d/boot-misc.sh” mas no ubuntu esse arquivo não existe. Depois de muito fuçar eu descobri que removendo os arquivos do diretorio “/etc/update-motd.d/” a mensagem some, pra mim basta, também removi o conteudo do arquivo /var/run/motd ;
UPDATE Dica do comentário do Marcelo Godim Ele é gerenciado pelo pam_motd basta ir em /etc/pam.d nos arquivos “login” e “sshd” e comentar essas linhas abaixo: login:
session optional pam_motd.so
sshd:
session optional pam_motd.so # [1]
Mudando mensagem da versão
Dica velha edite o arquivo “/etc/issue” coloque o que preferir.
——Se você não precisa de modo gráfico a instalação terminou aqui.
Alterando o sources.list adicionando outros repositórios
Edite o arquivo /etc/apt/sources.list e deixe assim, basicamente adicionados pacotes do site Medibuntu, se prefereir siga esses passos é melhor do que editar o arquivo.
Instalando o resto dos pacotes
apt-get install xserver-xorg xinit alsa-base alsa-utils openbox obconf obmenu feh nitrogen tint2 k3b conky gmrun pcmanfm gtk-theme-switch ssh smbfs smbclient dosfstools setserial usbutils leafpad x11-apps openbox-themes terminator chromium-browser xcompmgr gcc g++ openjdk-6-jdk mysql-server mysql-query-browser gftp gcc-avr avrdude imagemagick gparted ntfs-3g file-roller zip unrar gpicview gtk2-engines gnome-icon-theme-gartoon vim unace rar unrar zip unzip p7zip-full p7zip-rar sharutils uudeview mpack lha arj cabextract file-roller pidgin pidgin-data pidgin-lastfm pidgin-guifications msn-pecan pidgin-musictracker pidgin-plugin-pack pidgin-themes mplayer vlc cairo-dock w32codecs audacious
Vai dormir, seila vai baixar ai uns 500mb, você pode tirar ou por o que quiser ai isso é minha instalação.
Como entrar no modo gráfico?
Logue-se com seu usuário
$startxO comando antigo, simples, que dei a primeira vez no meu conectiva 4.
Este é o resultado final, mas para isso vamos algumas dicas.
Toda incialização dos aplicativos eu concentrei no .config/openbox/autostart.sh segue o meu ai
```
Set desktop wallpaper
nitrogen –restore &
Enable Eyecandy – off by default
xcompmgr -cCfF -r7 -o.65 -l-10 -t-8 &
Launch network manager applet
(sleep 4s && nm-applet) &
Launch clipboard manager
(sleep 1s && parcellite) &
Uncomment to enable system updates at boot
(sleep 180s && system-update) &
cairo-dock &
Launch Conky
conky -q &
Launch panel
tint2 & ``` Configurando teclas de atalho, edite o arquivo .config/openbox/rc.xml, vá até a seção keybinds as minhas são essas abaixo:
<keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-1″><action name=”Execute”> <execute>xcompmgr -cCfF -r7 -o.65 -l-10 -t-8</execute></action></keybind><keybind key=”W-2″><action name=”Execute”> <execute>pkill xcompmgr</execute></action></keybind><keybind key=”W-a”><action name=”Execute”> <execute>audacious</execute></action></keybind><keybind key=”W-e”><action name=”Execute”> <execute>pcmanfm</execute></action></keybind><keybind key=”W-g”><action name=”Execute”> <startupnotify> <enabled>true</enabled> <name>transset</name> </startupnotify> <command>transset .50</command></action></keybind><keybind key=”W-h”><action name=”Execute”> <startupnotify><enabled>true</enabled><name>transset 1</name></startupnotify><command>transset 1</command></action></keybind><keybind key=”W-l”><action name=”Execute”><startupnotify><enabled>true</enabled><name>Lock screen</name></startupnotify><command>gnome-screensaver-command -l</command></action></keybind><keybind key=”W-t”><action name=”Execute”><execute>terminator</execute></action></keybind><keybind key=”W-r”> <action name=”Execute”> <execute>gmrun</execute> </action></keybind>Pesquise como instalar temas GTK, configurar o TINT2 (desk bar), Cairo Dock, também tem muitas configurações de openbox na internet.
Esse tutorial vem de anos de convivio com linux, é duro passar tudo a limpo aqui, uma dica e testar o Linux Crunch-Bang aprendi muitas customizações com ele.
blog #tech
-
 @ 42342239:1d80db24
2024-08-30 06:26:21
@ 42342239:1d80db24
2024-08-30 06:26:21Quis custodiet ipsos custodes?
-- Juvenal (Who will watch the watchmen?)
In mid-July, numerous media outlets reported on the assassination attempt on Donald Trump. FBI Director Christopher Wray stated later that same month that what hit the former president Trump was a bullet. A few days later, it was reported from various sources that search engines no longer acknowledged that an assassination attempt on ex-President Trump had taken place. When users used automatic completion in Google and Bing (91% respectively 4% market share), these search engines only suggested earlier presidents such as Harry Truman and Theodore Roosevelt, along with Russian President Vladimir Putin as people who could have been subjected to assassination attempts.
The reports were comprehensive enough for the Republican district attorney of Missouri to say that he would investigate matter. The senator from Kansas - also a Republican - planned to make an official request to Google. Google has responded through a spokesman to the New York Post that the company had not "manually changed" search results, but its system includes "protection" against search results "connected to political violence."
A similar phenomenon occurred during the 2016 presidential election. At the time, reports emerged of Google, unlike other less widely used search engines, rarely or never suggesting negative search results for Hillary Clinton. The company however provided negative search results for then-candidate Trump. Then, as today, the company denied deliberately favouring any specific political candidate.
These occurrences led to research on how such search suggestions can influence public opinion and voting preferences. For example, the impact of simply removing negative search suggestions has been investigated. A study published in June 2024 reports that such search results can dramatically affect undecided voters. Reducing negative search suggestions can turn a 50/50 split into a 90/10 split in favour of the candidate for whom negative search suggestions were suppressed. The researchers concluded that search suggestions can have "a dramatic impact," that this can "shift a large number of votes" and do so without leaving "any trace for authorities to follow." How search engines operate should therefore be considered of great importance by anyone who claims to take democracy seriously. And this regardless of one's political sympathies.
A well-known thought experiment in philosophy asks: "If a tree falls in the forest and no one hears it, does it make a sound?" Translated to today's media landscape: If an assassination attempt took place on a former president, but search engines don't want to acknowledge it, did it really happen?
-
 @ c11cf5f8:4928464d
2024-09-08 09:08:04
@ c11cf5f8:4928464d
2024-09-08 09:08:04
Here we are again with our The Magnificent Seven, trying to give you a hit of what you missed this past month in the ~AGORA territory.
Top-Performing Ads
Drumroll please 🥁 ... for the most engaging ones:
01[SELL] 1 Million Products, Travel Agency, Concierge and Cars - ShopinBit.com by @shopinbit02[SELL] Satoffee⚡️☕️ Cafeteras automáticas que aceptan Bitcoin Lightning 🇪🇸 🌐 by @VEINTIUNO03[⚖️SELL] Hand-Made Flecktarn Pouch(es) by Fabs04[OFFER] Proton Wallet - 3 invites left by @npub1q67p49masrcjf__d7qaq6mwh0q05[SELL] Bitcoin Accepted Here – Unisex organic cotton Black T-shirt by @VEINTIUNO06[FOR SALE] Playstation 2 (PS2) Games - Excellent Condition - Pay In SATS!!! by @watchmancbiz07[OFFER] Happy Bitcoin Infinity Day by @thebullishbitcoiner
In case you missed
Here some interesting post opening conversation and free speech:
This edition winner look's @proofoftaste, with his request for help finding a way to get a local product delivered to his country. The challenge was that the producer, required an ID number on checkout! Pretty unusual... or it will be soon the norm?
Thanks a lot for @supratic for being so active in the territory and sharing so many topics and articles about commerce and law, basically giving us a hit on how the world is currently ruled, pretty fascinating!
01Can someone in Italy help me get my favourite sauce to Germany? by @proofoftaste02The History of Banking – Ernest Rauthschild by @supratic0310 Hidden Rules of Commerce by @supratic04How to Start Your Own Micronation by @supratic05[Understanding the One People's Public Trust: A Beginner's Guide to the OPPT(https://stacker.news/items/641554/r/AG) by @supratic06A Bank Whistleblower called me... by @supratic07One Stupid Fu*K 🥒 Contract Killer Course 2.0 - Brandon Joe Williams by @02a0eb55b5
🏷️ Spending Sunday is back! https://stacker.news/items/653241/r/AG
Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats!
Just a reminder for you all
To incentivize more conversation and a more libre mindset, we decided to adopt the zapshare approach, so we'll split the rewards of this TM7 to the best contributors plus zaps to the posts that offer much PoW when posting.
Create your Ads now!
This territory aims to connect stackers and curious buyers online and IRL for exclusive P2P Bitcoin deals. Have fun checking what else stackers are shilling globally in the ~AGORA. This is a great time for you to make some space un-dusting some stuff that has been sitting there for too long and get some sats for it!
Let's start something new? Hit one of the links below to free your mind:
- 💬 TOPIC for conversation,
- [⚖️ SELL] anything! or,
- if you're looking for something, hit the [🛒 BUY]!
- [🧑💻 HIRE] any bitcoiner skill or stuff from bitcoiners
- [🖇 OFFER] any product or service and stack more sats
- [🧑⚖️ AUCTION] to let stackers decide a fair price for your item
- [🤝 SWAP] if you're looking to exchange anything with anything else
- [🆓 FREE] your space, make a gift!
- [⭐ REVIEW] any bitcoin product or LN service you recently bought or subscribed to
Or contact @AGORA team on nostr DM and we'll help you publish a personalized post.
originally posted at https://stacker.news/items/676777
-
 @ 3fe0ab6c:d93088e4
2024-08-29 16:25:50
@ 3fe0ab6c:d93088e4
2024-08-29 16:25:50@News @Updates
We have installed a technical client update for Escape from Tarkov. The game will not stop, however the raid time on servers undergoing the updates may be reduced to 10 minutes. Matching time may be increased during the update installation. Please download the update via the launcher.List of changes: ● Added more rare rewards (including certain keycards and marked keys) for large sacrifices in the Cultist Circle zone in the Hideout; ● Increased the recoil when shooting while prone without bipod; ● Increased the in-raid pickup limit for Found in Raid items: ■ 10 for barter items; ■ 5 for keys; ■ 5 for containers. ● Increased the in-raid drop limit from 0 to 1 for certain barter and information items without the Found in Raid mark; ● AK CNC Warrior 5.56x45 muzzle device adapter can now be installed on all suitable 5.45x39 caliber assault rifles and carbines; ● Reduced the grenade throwing accuracy for regular Scavs.
List of fixes: ● Fixed several geometry errors on all locations; ● Fixed several incorrect doors on all locations;
-
 @ ae1008d2:a166d760
2024-08-29 05:14:15
@ ae1008d2:a166d760
2024-08-29 05:14:15Democracy, a system that ideally reflects the will of the people, faces significant mathematical challenges, particularly in the way votes are cast and counted. One of the most prominent issues lies within the first-past-the-post (FPTP) voting system, a method that has been in use for centuries. This system allows voters to select only one candidate, which can lead to scenarios where a party secures power without obtaining a majority of the votes. Such outcomes raise questions about the true representation of voter preferences and the overall health of democratic processes.
The Flaws of First-Past-The-Post
The FPTP system has been illustrated through historical examples, such as the British Parliament and the contentious 2000 U.S. presidential election. In these instances, the so-called "spoiler effect" emerged, where third-party candidates siphoned votes from major candidates, ultimately skewing the results. Voters often feel that their preferences are not accurately represented, leading to disillusionment with the electoral process. This discontent underscores the need for a more representative voting system.
Introducing Ranked-Choice Voting
To address the shortcomings of FPTP, ranked-choice voting (RCV), also known as instant runoff voting, has been proposed. In this system, voters rank candidates in order of preference, allowing for a more nuanced reflection of voter sentiment. RCV not only captures a broader spectrum of voter preferences but also encourages candidates to engage in more civil discourse. For example, in the 2013 Minneapolis mayoral race, candidates exhibited a camaraderie that is often absent in traditional campaigns, as they sought to appeal to voters for second and third choices.
However, the implementation of RCV is not without its challenges. Concerns arise about the potential for a candidate performing poorly to inadvertently assist in the election of another candidate. A hypothetical scenario involving three candidates—Einstein, C, and Bore—illustrates this point. The elimination of candidates based on voter preferences can lead to unexpected outcomes, complicating the electoral landscape.
Historical Context and Mathematical Foundations
The discussion of voting systems is enriched by historical context, particularly through the lens of French mathematician Marie Jean Antoine Nicolas de Caritat, the Marquis de Condorcet. Condorcet advocated for a fair voting method that required candidates to win head-to-head matchups. His method, which involves ranking preferences, introduces a potential issue known as Condorcet's Paradox. This paradox occurs when cyclical preferences prevent a clear winner from emerging, highlighting the complexities of voter choice.
Various mathematicians, including Lewis Carroll, have sought to develop fair election systems but encountered similar challenges. In 1951, economist Kenneth Arrow proposed five conditions that a voting system should meet to ensure fairness: decisiveness, unrestricted domain, transitivity, independence of irrelevant alternatives, and stability of group preferences. These conditions serve as a benchmark for evaluating the effectiveness of different voting systems.
Arrow's Impossibility Theorem
A significant aspect of the discussion revolves around Arrow's impossibility theorem, which posits that it is impossible to create a ranked voting system that satisfies all five of Arrow's conditions when there are three or more candidates. This theorem can be illustrated through a thought experiment involving three candidates (A, B, and C) and various voter rankings. The proof demonstrates that if a candidate is unanimously ranked first or last by voters, society must reflect that ranking. However, the theorem also reveals scenarios where a pivotal voter can dictate the overall ranking, effectively acting as a "dictator" in determining societal preferences.
This leads to a sobering conclusion: according to Arrow's theorem, a truly democratic voting system is unattainable when dealing with multiple candidates. Yet, there is a more optimistic perspective introduced by mathematician Duncan Black, suggesting that alternative methods may exist to better represent voter preferences.
The Dynamics of Voter Preferences
The dynamics of voter preferences along a political spectrum, from liberal to conservative, further complicate the electoral process. The choice of the median voter often determines election outcomes, aligning with the majority's decision and helping to avoid the paradoxes identified by Arrow's theorem. This discussion introduces rated voting systems, particularly approval voting, where voters indicate approval for candidates without ranking them.
Research indicates that approval voting can increase voter turnout, reduce negative campaigning, and mitigate the spoiler effect. Despite its historical use in electing popes and the Secretary General of the United Nations, approval voting has not been widely adopted in large-scale elections, suggesting a need for further real-world testing and evaluation.
The Importance of Political Engagement
While traditional voting methods like FPTP have significant flaws, the importance of political engagement and the necessity of striving for a more representative electoral process cannot be overstated. The complexities of voting systems and the historical evolution of these methods highlight the ongoing struggle for fairness in elections.
As democracy continues to evolve, enhancing knowledge and critical thinking skills about voting systems will be crucial in advocating for reforms that better reflect the will of the people. Understanding the mathematical underpinnings of these systems is essential for promoting a more equitable and representative democratic process.
The mathematical challenges of democracy, particularly in the context of voting systems, reveal significant flaws in traditional methods like first-past-the-post. The exploration of ranked-choice voting and other alternatives offers a glimpse into potential solutions that could enhance voter representation and engagement. As society navigates the complexities of democratic processes, it is essential to remain informed and proactive in advocating for systems that truly reflect the diverse preferences of the electorate.

Proposed Solution: Leveraging the Nostr Protocol
To further enhance the democratic process and address the challenges of traditional voting systems, we can consider utilizing the Nostr protocol. Nostr is a decentralized protocol that allows for open, self-verifiable, anonymous communication and data sharing, making it an ideal candidate for implementing a modern voting system. There have been other attempts at voting via nostr, this is my concept and contribution. View the code below.
Key Features of Using Nostr for Voting
- Decentralization: By leveraging Nostr's decentralized architecture, we can eliminate single points of failure and reduce the risk of manipulation or censorship in the voting process.
- Public-Private Key Cryptography: Each voter can generate a unique public npub and private nsec key pair. The npub public key serves as their identity, while the nsec private key is used to sign votes, ensuring authenticity and integrity.
- Anonymity and Privacy: Voter identities can remain anonymous, as only their public keys are visible. This protects against coercion and ensures that voters can express their preferences freely.
- Secure Vote Submission: Voters can submit their ranked choices or preferences as signed encrypted messages through Nostr and its relays. This ensures that votes are tamper-proof and verifiable.
- Real-Time Results and Transparency: The distributed nature of Nostr allows for real-time updates on the voting process, providing transparency and enabling independent verification of results.
- Mitigating the Spoiler Effect: By implementing ranked-choice voting through Nostr, we can capture a broader spectrum of voter preferences and reduce the impact of third-party candidates acting as spoilers (hopefully).
- Public Auditing: The system can provide an audit trail of all votes cast, allowing for independent verification and fostering trust in the electoral process.
By integrating the Nostr protocol into the voting process, we can create a more secure, transparent, and representative electoral system, particularly at the local level. This approach not only addresses the mathematical challenges of traditional voting methods but also empowers voters and enhances engagement in the democratic process.
I am new and inexperienced in programming, but I have wrote a bit of code with the help of general purpose AI's. Please review and improve and/or comment as best you can below👇
Thank you for supporting my work with zaps ⚡ supermax@minibits.cash
bc1qaucduwftl6lff5f436kccjc425m0ntqs6phzcx

I would like to implement a test at some point when the code is running stable. A distributed vote, if you will. Thank you for your support.
CypherPunksWriteCode
-
 @ c11cf5f8:4928464d
2024-09-08 08:35:16
@ c11cf5f8:4928464d
2024-09-08 08:35:16Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, here are some of the items stackers recently spent their sats on.
originally posted at https://stacker.news/items/676757
-
 @ 97c70a44:ad98e322
2024-08-29 00:50:27
@ 97c70a44:ad98e322
2024-08-29 00:50:27Nostr is a mess. It always has been and will always be. That's part of the appeal! But it's important that users be able to navigate the rolling seas of this highly partition-tolerant network of kaleidoscopically-interwoven people, bots, topics, relays, clients, events, recommendations, lists, feeds, micro-apps, macro-apps, Chinese spam, and "GM"s.
In order to do this, users must be able to articulate "what" they are looking for, and clients must be able to articulate "how" to find that thing. This "how" is divided into two parts: building a request that will match the desired content (very easy), and selecting a relay that is able to serve that content to the user requesting it (very very hard).
Why guessing isn't good enough
As a concrete example, let's say the user wants to find everyone in their "network" who is using a particular topic. The process would look something like this:
- The user clicks the "network" tab and types in the topic they want to browse. This is the "what".
- The client then translates the term "network" to a list of public keys using whatever definition they prefer (Follows? WoT? Grapevine?), and builds a filter that might look something like this:
[{"authors": pubkeys, "#t": ["mytopic"]}]. Any relay will happily accept, understand, and respond to that filter. - The client then has to decide which relays it should send that filter to. This is the
???stage of the outbox model, which immediately precedes: - Profit
It may not be immediately obvious why selecting the correct relays might be difficult. Most people post to relay.damus.io, and most people read from relay.damus.io, so in most cases you should be good, right?
This approach to relay selection has historically worked "well enough", but it depends on a flawed definition of success. If you only want to find 90% of the content that matches your query, using the top 10 relays will suffice. But nostr is intended to be censorship-resistant. What if those 10 hubs have banned a particular public key? Nostr clients should (at least in theory) be 100% successful in retrieving requested content. Even if someone only posts to their self-hosted relay, you should be able to find their notes if their account is set up properly.
A naive solution to fixing the FOMO
A 90% hit rate results in a feeling of flakiness, even if users aren't completely aware of what isn't working. Feeds will be incomplete, quoted notes will be missing, replies will be orphaned, user profiles won't load. The natural response to the FOMO this creates is for users to "try harder" by adding more relays.
On the read side, this means clients open more connections, resulting in much higher data transfer requirements, with massively diminishing returns, since there's no reason to expect that a randomly chosen relay will have a substantially different data set.
One the publish side, this means that clients end up publishing more copies of their data to more relays. This approach has been automated in the past by services like Blastr, which don't store a copy of events published to the relay, but instead forward events to the top 300 relays in the network. This results in a two-orders-of-magnitude increase in storage required, and only makes the read side of the problem worse, since it reduces the uniqueness of the data set each relay stores. This in turn means that more duplicates are retrieved when querying relays.
Both halves of this approach are equivalent to guessing. On the read side, users are guessing which relays will have any arbitrary content they might ask for in the future. On the write side, users are guessing which relays other people might use to find their notes. It is a brute-force method for finding content.
Randomness results in centralization
In theory, random relay selection would result in a perfect distribution of content across all relays in the network. But in practice, this method of selection isn't random at all, but is strongly influenced by user bias in what constitutes a "good" relay. While some users may check nostr.watch for ping times, geographical proximity, or uptime, most will choose relays based on familiar names or other people's recommendations.
In either case, these biases are entirely orthogonal to achieving a higher content retrieval hit rate, except when bias in relay selection results in clustering — i.e., centralization. In other words, the kind of randomness exhibited by users when selecting relays actually results in pretty much everyone picking the same few relays. We see this same effect when people try to come up with passwords or seed phrases — human-provided randomness is anything but random.
Clustering improves the hit rate when requesting events (slightly), but it results in nearly as much centralization as if only a single relay was used — and a lot more duplicate events.
Something (anything) other than randomness
In early 2023, Mike Dilger introduced NIP 65 (now known as the "Outbox Model") with a problem statement in the spirit of the original description of nostr: "Nostr should scale better. People should be able to find what they want."
Historical note: NIP 65 was formerly known as the "Gossip Model", derived from the name of Mike's desktop nostr client, called "Gossip". This unfortunately created a lot of confusion, since gossip protocols work very differently from how nostr tends to work, hence the re-brand.
Before NIP 65, an informal standard existed in which
kind 3user contact lists also included a list of relays that clients could use as something similar to Mastodon's "home servers". This list included the option to only read or write from a given relay. Unfortunately, it wasn't really clear what the semantics of this relay list were, so different clients handled them differently (and many clients ignored them). Usually this amounted to user-provided static relay configurations, which resulted in the naive relay selection approach described above.NIP 65 used a very similar format (a list of relay urls with optional "read" or "write" directives), but with a very important semantic difference: relays listed in a user's
kind 10002were intended to "advertise to others, not for configuring one's client." In other words, these relay selections were intended as a signal to other users that they should use certain relays when attempting to communicate with the author of the relay list.I highly recommend reading the entire NIP, which is very short and easy to read. But the mechanics of the spec are very simple:
When seeking events from a user, Clients SHOULD use the WRITE relays of the user's
kind:10002.When seeking events about a user, where the user was tagged, Clients SHOULD use the READ relays of the user's
kind:10002.When broadcasting an event, Clients SHOULD:
- Broadcast the event to the WRITE relays of the author
- Broadcast the event to all READ relays of each tagged user
For the first time, we had a way to differentiate relays in terms of what content could be found where.
When looking for a note by a particular user, a client could now look up the author's
writerelays according to theirkind 10002event, and send its query there. The result is a much higher hit rate with much lower data transfer requirements, and fewer connections per query.Making Outbox Work
There are of course some assumptions required to make this work.
First, the user must know which author they're looking for. This isn't always true when looking up a quote or parent note, but context and pubkey hints solve this difficulty in most cases.
The author must also publish a
kind 10002event. This may not always be the case, but clients should prompt users to set up their relay list correctly. This isn't really a flaw in the Outbox Model, just in implementations of it.Additionally, the user's client must be able to find the author's
kind 10002event. This is the "bootstrapping" phase of the Outbox Model, during which the mechanisms the system provides for finding events aren't available. This requires us to fall back to randomly guessing which relays have the content we're looking for, which as we saw above doesn't work very well.Other than guessing, there are a few different ways a client might find the relay selection event in question, each of which is applicable in different circumstances. In most cases, using one of a handful of indexer relays like purplepag.es or relay.nostr.band is a simple and efficient way to find user profiles and relay selections.
However, if an author's content has been aggressively purged from these indexers due to censorship, they obviously can't be relied upon. Even though the author in question hasn't been deplatformed from nostr itself (since he can always self-host a publicly accessible relay to store his content), he has been effectively shadow-banned.
To get around this, relay selections have to be communicated in some other way. Nostr has a few different mechanisms for this:
- If the author's NIP 05 address is known and properly configured (it may not be), clients can look up the author's NIP 05 endpoint to find some reasonable relay hints. Unfortunately, these are often neglected, and usually custodial, so they can run into the same problems.
- If the author's pubkey is found in another signed event found on nostr, relay hints can be a way to propagate relay selections through the network. This relies on implementations picking reliable relay hints which can be difficult, and hints do tend to become less reliable over time. However, this strategy is very effective in resisting censorship because it makes banning viral — if a relay wants to completely purge a particular pubkey from their database, they have to purge every event that references it, since events are tamper-proof.
- In extremis, relay recommendations can always be communicated out-of-band. This can be done using manual input, QR codes, DHTs, jsonl torrents full of
kind 10002events, or any other mechanism client developers choose to resort to.
Another, more technical assumption is that any given query can be fulfilled by few enough relays that a client can actually make all the connections needed, without running into resource limits. If you're trying to request content from 10,000 users across 1,000 relays, you're going to have a bad time. This was pointed out to me by Mazin of nostr.wine. He makes a good point, and it's definitely something to keep in mind. There are some mitigating factors though.
The first is that the current topology of the network probably won't persist forever. Because nostr is largely populated by self-hosting enthusiasts, the number of "tiny" relays is proportionally much higher than it will be if adoption picks up, even if the total number of relays grows. The trajectory is that nostr will drift toward fewer, larger relays, reducing the number of connections needed to fulfill any given query.
This is "centralizing", but it's important to understand that this isn't necessarily a bad thing. As long as there are more than one or two large hubs, there is user choice. And as long as it's possible to run a new relay, there is always an escape hatch. Nostr, like bitcoin, has no hard dependency on the biggest player in the network.
The other thing to consider is that there are lots of other techniques we can use to overcome the limits of the lowest-common denominator's limitations (mobile browser clients), including self hosted or third-party relay proxies. The trade-off here is that a little trust (aka centralization) can go a long way to reducing resource requirements needed to fulfill queries using the Outbox model.
If you're interested in more details on this topic, see this blog post.
That was a long digression, but there is one other thing that the Outbox model assumes to be the case. Even if the correct relays are found and connected to, they still may not return all desired content, either because they don't have it, or because they refuse to return it to the user requesting it.
This can happen if the publishing client isn't following the Outbox Model, if the author had migrated from one relay set to another without copying their notes over, or if the relay in question chose not to retain the author's content for some reason.
The first two issues can be fixed by improving implementations, but the question of policy is a little more interesting.
Relativistic relays
The Outbox Model is a mechanical process; it's only as useful as user relay selections are. In order for it to work, users have to be able to make intelligent relay selections.
Every relay has trade-offs, depending on its policy. 140.f7z.io would not be useful for long-form content, for example. Some relays might have a content retention policy that changes depending on whether you're a paying user. If you don't pay, you might find out too late that your content has been deleted from the relay.
So what makes a relay "good" for a particular use case? Well, it's complicated. Here are a few factors that go into that calculus:
- Is the relay in the same geographical as the user? Proximity reduces latency, but jurisdictional arbitrage might be desired. Users should probably have a variety of relays that fit different profiles.
- Will the relay ban the user? Do the operators have a history of good behavior? Is the relay focused on particular types of content? Is the relay's focus consistent with the user's goal in adding that relay to their list?
- What are the relay's retention policies? A user might want to set up an archival relay for her old content, or a multi-availability-zone relay so her notes are immediately accessible to the rest of the network.
- Does the relay require payment? Paid relays are more aligned with their users, but obviously come at a financial cost.
- Does the relay have policies for read-protecting content? If so, other users might not be able to find your posts published to that relay. On the other hand, some relays are configured to work as inboxes for direct messages, which can help preserve privacy.
- Does the relay request that users authenticate? Authentication can help manage spam, but it also allows relays to correlate content requests with users, reducing user privacy.
- Is the relay you use hosted by your client's developer? If so, you're in danger of getting banned from your client and your relay at the same time.
- Is the relay a hub? Using hubs can help smooth out rough areas in Outbox Model implementations, at the cost of centralization.
- Is the relay used by anyone else? One-off relays can be useful for archival purposes, but often won't be used by clients following the Outbox Model, depending on how they optimize requests.
There are lots of ways to approach the problem of helping users select relays, but it's an inherently complex problem which very few people will have the patience to properly address on their own. Relay selection is a multi-dimensional problem, and requires satisfying multiple constraints with a limited number of relay selections.
In the future, special-purpose clients might be used to help people build relay sets. Clients also might provide curated "relay kits" that users can choose and customize. Or, we might see an increase in hybrid solutions, like smarter relay proxies or client-local relays that synchronize using other protocols or platforms.
The Limitations of Outbox
Outbox is not a complete solution, not because of any of the caveats listed above, but because NIP 65 per se only addresses the question of how to index content by pubkey in a broadcast social media context. But there are many other scenarios for relay selection that Outbox does not solve:
- Community, chat, and group posts might be best posted to relays dedicated to that context.
- Direct messages shouldn't follow the same contours as public social media content.
- Topic-oriented relays, or relays serving a custom feed might be useful independent of who uses them.
- Relays focused on serving a particular kind of event, like music, long-form content, or relay selections, are useful independent of who reads from or writes to them.
- Certain clients might need to fulfill particular use cases by using relays that support certain protocol features, like search, count, or sync commands.
- Some events might not make sense to publish to relays, but should instead be shared only directly, out of band.
Some of these use cases might be solved by new specifications similar to Outbox that prescribe where certain data belongs — for example, NIP 17 requires users to publish a different relay list before they can receive direct messages, while NIP 72 places community relay recommendations directly into the group's metadata object. A reasonably complete list of different relay types can be found in this PR, very few of which have a canonical way to manage selections.
Other use cases might be supported more informally, either by relays advertising their own value proposition, or via third-party NIP 66 metadata. Still others might be supported by scoping the network down to only certain relays through explicit relay selection — this is how white-labeled Coracle instances work.
The basic idea here is that there are categories of events that don't have anything to do with where a particular person puts his or her "tweets". For every "what" on nostr, there should be a "how".
Keep nostr weird
Whatever additional systems we end up adopting for helping with relay selection, one thing is certain — people will continue to discover new, creative uses for relays, and we will always be playing catch up. This is one of the coolest things about nostr!
But it does mean that users will have to adapt their expectations to a network that partitions, re-configures, and evolves over time. Nostr is not a "worse" experience than legacy social media, but it is a version of social media that has itself been set free from the stagnant walled-garden model. Nostr is in many ways a living organism — we should be careful not to impose our expectations prematurely, leaving room to discover what this thing actually is, or can be.
If you enjoyed this post but want more take a look at the talk I gave at Nostrasia last year. I also wrote up a blog post at about the same time that addresses some of the same issues, but focuses more on privacy concerns around relays and nostr groups. Finally, I recently wrote this comment, which includes some details about challenges I've faced putting Outbox into Coracle.
-
 @ d8bcfacf:aa97645b
2024-08-27 18:33:38
@ d8bcfacf:aa97645b
2024-08-27 18:33:38What is the Purpose of Bitcoin?
Why did anyone bother to create Bitcoin?
What problems were they trying to solve?
If you are new to the whole idea of a digital asset involving the mysterious field of cryptography, these are some questions that probably come to your mind. Before you get caught up in asking if you can "get rich quick" from Bitcoin, you should be asking if it has a deeper purpose.
Bitcoin was created to serve a very specific purpose. If it did not serve that purpose, it would not be worth anything. Fortunately, it does. And, it was carefully and meticulously engineered to serve it precisely.
Bitcoin's purpose is to provide reliable money that will serve all mankind - forever. That is a pretty lofty goal: serving all of mankind, forever!
Was There Even a Problem in the First Place?
Is our money unreliable? Does it really fail to serve all mankind? Are its days numbered?
The sad fact is that the answer to all these questions is "Yes!"
First, our money is unreliable: it loses its purchasing power through inflation. We also experience volatile economic cycles that destroy capital, jobs, wealth, and stability.
Next, our money does not serve all mankind - many middlemen charge excessive fees to store and send our money. It is expensive to use internationally since converting it to other currencies is costly. Many people in the world lack any access to reliable banking. Our money system serves elites far better than it serves ordinary people.
Finally, our money system is doomed to collapse. Currencies world-wide are rapidly losing purchasing power. In fact, throughout history, paper money decreed into existence by governments has failed every time that it has been implemented.
And sadly, we cannot turn back the clock and go back to a time when gold was money. Gold is simply not secure from seizure, and it is far too slow, difficult and expensive to transport in a global economy.
Bitcoin Fixes This
Bitcoin was created through an ingenious and unprecedented combination of technologies. It provides, for the first time ever, money that is reliable, that serves all mankind, and that will last forever.
Nothing like this has ever existed before.
Bitcoin is free from inflation — its supply will never exceed 21 million coins. Each coin is divisible into 100 million units called satoshis. These will be issued on a fixed, unalterable schedule - taking over 100 years.
Bitcoin is for all mankind — there are no elites who can manipulate it. Unlike the currencies of our present money, nobody can create bitcoins effortlessly for themselves.
Nobody can be prevented from using Bitcoin — it will not allow anybody to stop someone else from using it.
Finally, Bitcoin is forever — its operation depends solely on the laws of physics and mathematics, and these laws will stay in effect - unaltered - for as long as the Universe exists.
Bitcoin was not created so that some people could "get rich quick". It was created to preserve the integrity of money — to make the most of your precious time, your energy, and your life. With Bitcoin you can keep what you have earned - and use it however, whenever, and wherever you desire. To you, Bitcoin is reliable money that can serve you for the rest of your life — and it offers you an escape from being the victim of an unjust, broken, dying, and failing monetary system.
-
 @ b9946fa3:4c8e9aa4
2024-08-25 23:07:08
@ b9946fa3:4c8e9aa4
2024-08-25 23:07:08The Problem:\ Millions of people around the globe either lack access to education or are forced to contend with poor-quality education they can’t afford. Traditional education systems often apply a one-size-fits-all model, which fails to meet the diverse needs of students, leaving many disengaged and without the skills they need for the future.
The Dream Solution:\ Imagine an education system that is as unique as each student, engaging, accessible, and affordable. This vision leverages the Nostr protocol — a decentralised, simple social graph — and the power of Bitcoin to create a revolutionary platform that could democratise education worldwide.
Key Components
-
Custom-Made, Tailored Education:
-
The Nostr client offers personalised curriculums created through an initial rigorous assessment. This includes personality tests and consideration of each student’s hobbies and interests.
- The AI-driven system ensures that the curriculum is not just relevant but also engaging and aligned with the student’s goals, making learning both fun and effective.
2. Engaging and Fun Learning:
- Real-world experiences, like apprenticeships and work-integrated learning, are built into the curriculum, ensuring that students are not just learning theory but also applying their knowledge in practical ways.
- The innovative teaching methods aim to keep students motivated and interested, making education a continuous and exciting journey.
3. Global Accessibility:
- The Nostr client operates both online and in physical locations, ensuring that students from any part of the world can access quality education.
- The Nostr client will be multiple languages, making it inclusive and globally relevant.
4. Nostr ID and Accreditation:
- Each student, teacher, and business/institution will have a Nostr ID , which securely stores all relevant metrics — scores, time spent learning/teaching, and ratings. These metrics are public and transparent, building a credible reputation for all participants.
- This decentralised approach ensures that credentials and achievements are recognised and respected globally, regardless of where a student is based.
5. Affordable Education with Incentives:
- The platform is designed to be accessible financially, using a zapping system powered by Bitcoin. Students and teachers can earn rewards and incentives, ensuring that education is both affordable and financially rewarding.
- A value-for-value (V4V) monetisation method allows students and teachers to earn according to their contributions and success.
6. Real-Time Learning Matchmaking:
- A Nostr client functions similarly to Uber, where students can see available teachers, their ratings, zaps, specialties, and other metrics before choosing who they want to learn from.
- AI facilitates the connection, ensuring that students can begin learning with their chosen teacher almost immediately.
7. Feedback Loop and Continuous Improvement:
- After each session, both the student and the teacher must provide feedback, which is crucial for continuous improvement.
Role of Businesses and Institutions
How They Participate:
- Businesses, employers, and institutions can join the Nostr clients by creating a profile using a Nostr ID. They have access to the same public and private portals as students and teachers, allowing them to interact directly with the educational ecosystem.
- The Nostr client allows businesses and institutions to scout and hire students directly from the system based on their scores, ratings, and other metrics. Employers can view detailed profiles of students, including their completed courses, projects, and feedback from teachers, making it easier to find candidates who match their specific needs.
- Students, in turn, can choose to work with companies that have high ratings and reputations on the platform, ensuring that both parties benefit from a transparent and merit-based system.
- For example, a company could offer scholarships or financial incentives to top-performing students, which not only aids the student financially but also builds the company’s reputation on the platform.
- These organisations can donate or pay funds (in Bitcoin) to receive higher ratings or more visibility on the platform, similar to sponsored content or advertising. This helps them build a reputation within the community and attract top talent.
- Businesses and institutions contribute to a communal pool of funds, which is distributed primarily to teachers and students based on their ratings and scores. This model incentivizes quality education and ensures that everyone involved in the learning process is rewarded appropriately.
- A small percentage of these funds is allocated to cover the Nostr client operational fees, ensuring that the service remains sustainable and continues to provide high-quality education.
Example: A Student’s Journey
Consider a student from anywhere in the world logging into the Nostr client . After the AI sorts their curriculum and completes the initial assessments, they can go online at any time to see which teachers are available. The Nostr client shows each teacher’s ratings, zaps, and specialties, allowing the student to make an informed choice.
Once the student selects a teacher, the AI facilitates the connection instantly. If a teacher declines, another one picks up the session. During the lesson, the AI listens in and can add comments or suggestions in real-time if necessary.
At the end of the session, both the student and teacher provide feedback. If the student cannot afford to pay, they still have the option to leave feedback. If they can pay more, they are encouraged to do so, supporting the teacher.
For this student, the Nostr client offers more than just education; it builds a track record and reputation that could lead to job opportunities globally. The scores, ratings, and zaps accumulated could potentially help the student secure employment with a prestigious company in another country, breaking down traditional barriers to opportunity.
Conclusion
This is not just a fantasy but a visionary idea that leverages the power of Bitcoin as the internet of money and Nostr as a simple social graph protocol. The dream of a decentralised, accessible, and tailored education system is within reach, and it has the potential to transform lives globally. What do you think? Is this a feasible solution, or does it still feel like a dream? What would you add to make this vision a reality?
You can find me:
Nostr: npub1hx2xlg66zdwgldvz6y08yu4lul2n0zq3ulug094ul5wc2nywn2jqpkf8z3
website: https://somalimajlis.com
Email: somalimajlis@gmail.com
-
-
 @ 592295cf:413a0db9
2024-08-25 09:17:54
@ 592295cf:413a0db9
2024-08-25 09:17:54A Ux designer has arrived on Nostr. I thought run away while you can. He could get rich, if there was a little economy.
Klout, do you remember that service, which took data from Twitter and made a ~~ WoT~~.
From a note of chip, I understood one thing:
Bitcoin is your "sovereign" currency. Nostr is just third party protocol. If you have a service you can use Nostr to face your customers. "Sovereign" people offer services. They can be bitcoiners or not. So at this stage Nostr is a layer 3 Bitcoin.
So to grow the enveiroment it must be attractive. Let's paraphrase: the protocol is agnostic, the people are fundamentalist Catholics.
So when an atheist person arrives he says ah ok, how do I silence these people and use the protocol If a Protestant Catholic arrives he is laughed at or ignored or at most converted.
I had a disagreement with Dergigi, in the end he won, but he is not right... (True)

Post more notes, zap more, follow 1000 people update FAQ to the nth degree. We are in the desert of the Tartars and the enemy is coming and there are those who say every day we must be ready, sooner or later, it will happen, ah ok. Everything must be perfect. Push harder. This leads to exhaustion.
New Grant from Opensat to Victor of Amethyst, totally deserved, pushed the envelope. If you are a grapheneos user download Amethyst. It's not just Amethyst it's also orbot, citrine, amber, zap store or obtainium or f-droid.
GitCitadel has raised its first fund I wonder if it was just a test on geyser, I wonder if it is the right project to do on nostrocket, but I think Opensat grant for nostrocket makes it irreconcilable. This opens a pandora's box, as always. We are silent as fish.
I tried not to answer some questions even in one case I knew the answer, I apologize, Nostr is much older than me, so it's okay not to answer sometimes. Tomorrow begins nostRiga, The last unconference of Nostr.
(First day) The morning was so-so, in the evening the situation improved a little. In the evening I played a bit with Nostr and it broke The second day good in the morning bad in the evening. I saw little of the backstage maybe only two panels, Will by Damus, and P2Phash on Nostr.
I don't follow anyone anymore, I did a little bit of a unfollow. I saw that two users had 200 followers in common, and I said to myself ah ok what is this thing, I have to understand how they do it there is something that doesn't work, let's try to be a little more distant.
It's weird, too much reliance on following, you have to go and look, not be stationary.
-
 @ dd664d5e:5633d319
2024-08-24 07:57:16
@ dd664d5e:5633d319
2024-08-24 07:57:16We can talk about something else, now.
Making boosts/quotes the primary way new users find a variety of topics is a fundamental flaw. We don't need boosts (which merely results in the main trending list trending even harder, as people feel safer boosting something that is already popular), and hashtags have become the mess they naturally will become.
We need topical forums and relay-based community boards.
This would actively encourage those of us who want to write on OtherTopics to write more on them, as we would have some chance of the material being found by those interested in it. And it would spare us having to win some general popularity contest, just to be able to converse about golfing, Hinduism, or veganism.
Scrollable "timeline" feeds, even with AI assistance (like DVMs), don't accomplish this as well, as they eliminate the ability to skim the top-level and selectively read. You have to scroll, scroll, scroll.
It would also reduce the overloading of the original posts with videos, which is starting to give Nostr a Tik-Tok vibe. There's nothing wrong with that, per se, and we should probably have clients like that, but it makes life hard for anyone who wants to have a deeper discussion. People scrolling have trouble even "seeing" a text-based OP, but using the written word is a true signal to the other people, that you are capable of carrying a conversation through text.
Examples for other styles of client
(I am including the Communities in Nostrudel and Satellite, even though they don't yet work, effectively.)
Some of the things that set these clients apart, is that: 1. they are topic-first or thread-first, not person-first, 2. they sometimes allow voting (I suppose we could rank by zaps), 3. they often allow the user to override the default order and simply look at whatever is newest, most popular, or where their friends are currently active (i.e. they allow for easy sorting and filtering), 4. they cap the depth of threads to one or two levels, keep the indentation tiny, or offer a "flat" view, 5. they are primarily text-based (Reddit broke with this and now their main pages look really spammy), 6. they allow you to see all of the entries in the thread, at once, and simply actualize to display the entries that pop up in-between, 7. they often have some indication of what you have already read (this is application data) and allow you to sort for "stuff I haven't looked at, yet".
https://i.nostr.build/uCx5YKMOsjhKBU5c.png https://i.nostr.build/hMkm2oKpos0pWaV9.png https://i.nostr.build/mGQONMw5RC8XKtph.png https://i.nostr.build/TCSkG1bPuMOL0jja.webp https://i.nostr.build/3fLjCSNdtefiZmAH.png https://i.nostr.build/BHgo7EKTK5FRIsVl.png
-
 @ 6bae33c8:607272e8
2024-09-07 22:09:27
@ 6bae33c8:607272e8
2024-09-07 22:09:27With all five of my football drafts/auctions in the books, here's the portfolio I've amassed for 2024, not including the RotoWire Dynasty League:
Links: BCL1, BCL2, BCL3, Steak League, Primetime
Players in whom I have the most shares:
QB: Justin Fields (4), CJ Stroud (2), Anthony Richardson (2), Tua Tagovailoa (2)
RB: Jonathan Brooks (2), Brian Robinson (2), Jerome Ford (2), Jordan Mason (2), JK Dobbins (2), Khalil Herbert (2), Dalvin Cook (2)
WR: Stefon Diggs (5), Ja’Marr Chase (3), Rashid Shaheed (3), Ladd McConkey (2), Roman Wilson (2)
TE: Jonnu Smith (3)
K: Younghoe Koo (3), Harrison Butker (2)
D: Giants (4)
Notes:
Obviously, I thought Stefon Diggs was mispriced, though I only had to pay close to what I thought he was worth in the Primetime — in the rest of the leagues he fell to me at ADP or below. He and Ja’Marr Chase are massively important to me this year, and to a lesser extent CJ Stroud.
I also have Justin Fields and the Giants defense everywhere, but both were essentially free, and I could swap them out without issue. I also have a lot of Younghoe Koo, but he too could obviously be swapped out. I like having a couple key players to build around rather than five disparate teams. Of course if Diggs gets hurt or turns out to be washed up, it’ll be rough, but in some ways it’s like the old days where you had only one team, and you had to live and die with it.
Prominent Players I Don't Have (bold is by choice):
Bijan Robinson, Tyreek Hill, Breece Hall, Amon-Ra St. Brown, Justin Jefferson, Garrett Wilson, A.J. Brown, Jonathan Taylor, Puka Nacua, Davante Adams, Saquon Barkley, Chris Olave, Rashee Rice, Kyren Williams, Travis Etienne, Cooper Kupp, Isiah Pacheco, Michael Pittman, Nico Collins, DK Metcalf, Mike Evans, Deebo Samuel, Josh Allen, DJ Moore, Brandon Aiyuk, Derrick Henry, Zay Flowers, James Cook, Terry McLaurin, Kenneth Walker, Xavier Worthy, Amari Cooper, Josh Jacobs, Trey McBride, George Pickens, Lamar Jackson, Christian Kirk, Tee Higgins, Calvin Ridley, Rachaad White, Jayden Reed, Diontae Johnson, Travis Kelce, Joe Mixon, Alvin Kamara, Christian Watson, Jalen Hurts, Aaron Jones, Patrick Mahomes, David Montgomery, Zamir White, Keenan Allen, Kyle Pitts, D’Andre Swift, George Kittle
Past Portfolios:
-
 @ 9dd283b1:cf9b6beb
2024-08-21 07:01:29
@ 9dd283b1:cf9b6beb
2024-08-21 07:01:29Yesterday, my daughter and I decided to play Monopoly, but instead of using Monopoly money, I thought it would be fun to use sats instead! Here’s how it went. Preparation:
Here’s how I set up the game:
1 Zeus wallet connected to my node, with an open channel to WoS. 2 WoS wallets (1 for me and 1 for my daughter), each with a 0 balance to start.Originally, I considered using Blink wallets, but the problem with Blink is that it displays the balance in EUR in a large font, while the sats balance is smaller. This isn’t ideal when you're playing Monopoly and want to treat 1 sat = 1 Monopoly dollar. So, we switched to WoS, where the sats balance is prominently displayed, with the EUR balance in a smaller font underneath.
In our version of Monopoly, each player starts with 1500 Monopoly dollars and earns 200 when passing GO. It was easy to follow this system using sats.
I installed WoS on my daughter’s phone and transferred 1500 sats from my Zeus wallet to her WoS wallet. I did the same for myself, so we both had a 1500 sat starting balance. I used Zeus as the "bank" and WoS as my player wallet on the same phone, but if you have an extra device or don’t trust the bank, you can separate them.
And yes, I know you can go fully non-custodial by setting up LNBits with Umbrel and using Blue Wallet on separate devices for each family member. However, that takes longer to set up, requires VPN connections for everyone, and seemed unnecessary for our casual game. In my setup, only the bank needed a VPN, which was simple and only took about 5 minutes.
Game:
The game got fun pretty quickly! Every time my daughter passed GO, she showed me her QR code with a sly smile, and the bank paid out her 200 sats with zero fees. Players also paid each other with zero fees.
Twice, WoS randomly charged a 1-sat fee when transferring from WoS to Zeus—once from my wallet and once from my daughter’s. To keep things fair, I had the bank reimburse those 2 sats.
We did run into one small issue: I needed to pay my daughter 200 sats for landing on her hotel, but since I only had exactly 200 sats left, WoS wouldn’t let me send it, even though it was a WoS-to-WoS transaction.
Conclusion:
At the (unofficial) end of the game—since it was getting late—my daughter had 2810 sats, and I had 1650 sats. At this point, each stop was costing between 300 and 600 sats, so I suppose the real end was near!
Overall, it was a smooth experience, and my daughter got quite comfortable with sending and receiving bitcoin, even though it was her first time doing so. She did show more interest in the EUR balance, but I’m sure she’ll come to appreciate the sats balance soon enough!
I highly recommend this as a fun way to introduce people to the Bitcoin Lightning Network. Most people already have a Monopoly game at home, and if you have a couple of spare devices, you can easily install WoS for everyone. (Perhaps not in the U.S. right now, but I’m not entirely sure on that front.)
Would definitely recommend trying it out!
originally posted at https://stacker.news/items/656614
-
 @ 6bae33c8:607272e8
2024-09-07 22:07:54
@ 6bae33c8:607272e8
2024-09-07 22:07:54I submitted my five picks for the Circa Millions contest today. I think it’s $6M in total prizes. I want to put a disclaimer here: I’m putting these behind a paywall not because you should pay for these picks — never pay for anyone’s picks.
If the picks were that good, whoever was making them could just print money and wouldn’t need yours. If you want to subscribe in earnest, do so because you’re interested to see who I chose and read the reasoning, not because you (erroneously) think it’s the way to get some easy winners. Or if you want to support my substack generally because you think it adds value to you. Those are fine reasons to subscribe, but doing so because you think copying my picks will make you money is dumb.
Okay that out of the way, here are the picks:
Dolphins -3.5 vs Jaguars — I like taking the Dolphins in early September, it’s hot and humid there, difficult for opposing teams to adjust to it. It’s like Lambeau Field in December, only in reverse. Moreover, the Dolphins are a veteran offense that’s played together for years, while the Jaguars are working in two new receivers.
Falcons -3.5 vs Steelers — Justin Fields is probably an upgrade over Russell Wilson at this point, but he’s haphazard and will have to learn the players and offense on the fly. The Falcons have a new QB too, but he’s an old pro, has better weapons and a better offensive line.
Giants +1 vs Vikings — The Giants have three Pro-Bowl level pass rushers, finally have a playmaking receiver and upgraded their offensive line this offseason. And yet despite facing Sam Darnold at home, they’re still getting a point.
Cardinals +6.5 at Bills — Kyler Murray is now another year removed from knee surgery, should be his usual spry self, and Marvin Harrison adds another dimension to the offense it sorely needed. The Bills will move the ball, but I think Arizona will hang with them and keep it close enough.
Browns -2 vs Cowboys — The Browns should be able to run the ball and keep the Dallas pass rush off Deshaun Watson, while Dallas’ offensive line has slipped a bit, and the Browns defense was No. 1 against the pass last year. Dak Prescott also has big home/road splits.
-
 @ 592295cf:413a0db9
2024-08-17 07:36:43
@ 592295cf:413a0db9
2024-08-17 07:36:43Week 12-08 a suitable protocol
The knots come to a head, some of you have gray hair, you get older.
Tkinter is better than ws://, more secure, but has limitations, unless you know how to use figma and do some magic. The project of Nabismo.
Maybe Nostr doesn't work for me.
Aspirin moment Nip-17, works with nip-44 and nip-59. Someone said they made the groups encrypted with nip-17. I tried and succeeded, now you can DM me, don't do it. I had sent the link to a conversation of nip-87 closed groups. There's JeffG doing something with MLS. Then there's keychat.io which uses signal Nostr Bitcoin ecash and that's it... But in dart. It's a bit like the Matrix analogue for Nostr.
Final controversy not all nips are mandatory.
Build the foundation. You can't think about selling the house
Yakihonne has a countdown. What can a desktop app be. Community Lists, Nip-29
A birthday on Nostr, no that's not possible, they're all cypherpunks. 🎉🎉 (Except me)
There is a different attitude from Nostr when updates are released compared to Bluesky, everyone there is still enthusiastic, on Nostr ah ok but this is missing oh but this is missing or but support this other one, or but * zap, wait a minute, keep calm 🙇♂️, I'm the first to do this. (The revolt of the developers)
Deletetion: Client that have relay paired can do delete, more intelligently, Perhaps you can think of a delete.nrelay subdomain as a filter. This id is deleted. Be careful what you don't want to do. Maybe a session with a psychologist is better, because then you find yourself doing what you said you didn't want to do.
Does it make sense to follow someone on Bluesky? In my opinion no, or better yet yes. There are several algorithms on Bluesky, which do their job well. In the end it's just a matter of arranging them better on the screen. Yes you can have lists to save someone, but then you read everything, so lists with algorithm seems like a next feature. this way they can keep the following small, almost minimal, because there are algorithms that work for the user. People will start writing for SEO algorithm and AI and other things, which tech gurus really like and so on. The fact that it is almost exclusively an app will greatly facilitate this trend, there will be almost no need for moderation, and you can get it all in just a few apps. (Great)
Oh yegorpetrov has abandoned. Pegorpetrov said that he is coming back 😌 It might be an invention but I'm a little heartened by it.
Bankify, a new wallet of super testnet, only for crush testers.
You can't stream on zap stream without reach, maybe it's better audio space. Contact someone maybe an influencer or Nostr elite or whatever. Open Source Justice Foundation streaming
Designer, I wanted to propose comment on wikifreedia nielliesmons article and follow #nostrdesign, but too many answers for today. NVK note is ~~mainstream~~
I think I'm not suited to Nostr.
Nostr-ava bike file geo tag sharing. (NIP-113) Sebastix doesn't respond, I must have done something bad to him, or maybe I'm stressing him too much. Finally he replied 🤙. In the end maybe, I have too much hype about this proposal and it's something I don't know maybe, but maybe if they were already doing something with geo tags it's better to say so.
Another birthday, less cypher more punk 😌
Usdt on Nostr, there must be some error. (freeform app)
USDT on tron is like Money. (Bitcoiner not really)
Privacy issue, deletion motion, or deletion request, go go.
Nip29 hype, i don't have hype at all. I'm tired of words, I record a podcast on Nostr. Let's see if I can do it, at least think it. (It's more of a workflow thing than actually something I would do)
- Create an npub (easy)
- Record the audio episode (I think I can do it). Terrible audio
- Loading on a Nostrhosting, if less than 10 MB it should go smoothly.
- Publish the video or audio of the episode on some Nostr client, perhaps using blastr relay 😞.
- Do the nostree link, by putting the episode, and also the npub.pro and put the URL on café-society. 6) Publish all these links on the Main profile, saying that, made a podcast about Nostr in Nostr of nostr. 😂
I thought a client could have poll, form, spreadsheet, collaboration document. It's the kind of otherstuff we want to see. Something that goes beyond a normal feed.
Emoj on bluesky, Eventually also zap 🥜 link emoj Blue
Eventually there will be a developer revolt And they will only do a social network in their downtime, they will call it Nostr.
There is a storm, Nostr does not work in 4g with two bars. Or now 4G is gone too.
Yakihonne Smart widgets, something to try on the weekend.
-
 @ 46fcbe30:6bd8ce4d
2024-08-16 19:29:04
@ 46fcbe30:6bd8ce4d
2024-08-16 19:29:04Opinion about BitWallet - Buy & Sell Bitcoin (android)
On trustpilot, 20% of reviews are complaining about KYC only after trying to withdraw, with some claims of outright disappearing money.
WalletScrutiny #nostrOpinion
-
 @ 6bae33c8:607272e8
2024-09-07 22:05:26
@ 6bae33c8:607272e8
2024-09-07 22:05:26This is my main event for fantasy football, the $1700 buy-in NFFC Primetime. I wound up picking 11th (I had the fourth to last choice), and while in retrospect maybe I should have opted for ninth or 10th, I wanted to get a share of Jahmyr Gibbs which is why I chose that slot. I also ran through some scenarios beforehand — what if Ja’Marr Chase (still not signed) falls — do I take him in a fourth league? But as you’ll see, the first round was complete chalk, and no windfalls whatsoever fell to me.
But I had a plan for that, and I more or less executed it.
Without further ado, here are the results:

1.11 Jahmyr Gibbs — This was the most likely scenario, and it took me about two seconds to make the pick once the top three backs and seven receivers were gone. If Gibbs (who is not on the injury report) hadn’t had a hamstring injury in camp, I’d have him close to the middle of the round rather than the end. Let’s hope he doesn’t aggravate it.
2.2 Marvin Harrison — I would have taken either Puka Nacua or Jonathan Taylor, but no breaks here either. Both went at the turn, and I knew I was taking a receiver. Starting RB-WR is the easiest build, in my opinion, but Harrison was kind of an agnostic pick. I had considered Rashee Rice, but as Alan Seslowsky pointed out, while his suspension for hit and run might not kick in until after the season (when the legal process has run its course), that could be pushed up if his lawyers negotiate a plea. Between that an the presence of so many options for the Chiefs, I went Harrison over him narrowly. But it was a close call.
3.2 Stefon Diggs — I missed Malik Nabers, Cooper Kupp, (maybe Jaylen Waddle) and De’Von Achane who went with the four consecutive picks ahead of me, so it was Diggs, Nico Collins (his teammate who has a higher ADP), DeVonta Smith or (maybe) Derrick Henry. I went Diggs who I had personally ranked the highest, wouldn’t make it back to me, who I have in every league and was part of my “unfriendly” draft plan, i.e., the Plan B I had talked about.
4.11 Tank Dell — He’s too small to hold up, but whenever he played he produced, and he gives me a bit of a Diggs hedge. I also wanted Trey McBride on this turn (as I had Marvin Harrison and could have drafted Kyler Murray — who I love this year — later), but he went on the turn. I thought about taking McBride first, but they were side by side in ADP, and my Plan B was to stack Texans, so I went Dell and took a chance.
5.2 Chris Godwin — This was the one pick I kind of regret (though it’s debatable.) I like Jayden Reed a lot, but he was half a round lower per ADP, and there was some chance I could get him on the way back. I had Godwin everywhere last year, and he was a disappointment, but apparently he’s healthier now and is going back to the slot full time where he excels.
6.11 Jaxon Smith-Njigba — The other pivot off Godwin was JSN, and sure enough he made it back all the way, though he starts off as my first bench player. That’s okay though — you need at least five viable receivers throughout the year, and I didn’t have to take C.J. Stroud because if the guy at the turn took him, I would just pivot to the Kyler Murray/Harrison stack.
7.2 C.J. Stroud — He was there, and I executed Plan B. Yes, I have a weak first three rounds by ADP, but I have Gibbs, Harrison and a big piece of the Texans passing game which I think will lead the NFL in yardage.
8.11 Jaylen Warren — I needed a second back, and Warren is one. He’s a good pass catcher and should see half the snaps in Pittsburgh.
9.2 Brian Robinson — I like Robinson as a player, he’s the undisputed early-down option on what should be a better offense. (Think Ricky Pearsall, but at RB.) Too soon? Austin Ekeler will obviously see the passing-down work unless he proves totally washed up. The Robinson pick cost me David Njoku and Brock Bowers unfortunately, which was a gamble I knew I was making.
10.11 Jordan Mason — At 29 and playing into the Super Bowl, Christian McCalfinjury was already a risk, and that he’s “expected” to play Monday night rather than 100 percent fine is worrying. Mason could be a league winner if McCaffrey goes down.
11.2 J.K. Dobbins — The Mason pick cost me Jaleel McLaughlin, so I pivoted to Dobbins who still has a high ceiling if he can ever stay healthy.
12.11 Dallas Goedert — Tight ends had flown off the board, but I was happy to get Goedert who has been valuable on a per-game basis the last couple years and is still just 29 which is late prime for the position.
13.2 Dalton Schultz — Why not stack it even harder? The Texans could throw for 5,000-plus yards, and I have three of the four top targets and the QB.
14.11 Andrei Iosivas — He’s gotten a lot of buzz in camp, seems like the No. 3 receiver right now, Tee Higgins is hurt and Ja’Marr Chase is still unsigned.
15.2 Cam Akers — The Iosivas pick cost me Jalen McMillan who would have served as Godwin insurance, but Akers could easily take an aging Joe Mixon’s job. Maybe it’s too much Houston, but if it’s a top-three offense, I’m good with it.
16.11 Justin Fields — The backup QBs had flown off the board, and Fields has too much upside to pass up. Plus he might even start Week 1 with Russell Wilson already hurt, and if he plays well, he might never look back.
17.2 Harrison Butker — It’s either the based af kicker or a Younghoe for me. Plus he locked in a decent Week 1.
18.11 Dalvin Cook — He had only 67 carries last year for a bad Jets offense. What if he isn’t as washed up as we think? He could easily win that job over Zeke Elliott and Rico Dowdle.
19.2 Jonnu Smith — TE is my weakest position, so I took another upside gamble. What if he’s the Dolphins third target?
20.11 Giants Defense — I think I took them in all four NFFC leagues. They get the Darnold Vikings at home and then Jayden Daniels in his second career start. And they have three Pro Bowl level pass rushers.
Roster By Position
QB CJ Stroud
RB Jahmyr Gibbs/Jaylen Warren
WR Marvin Harrison/Stefon Diggs/Tank Dell
TE Dallas Goedert
FLEX Chris Godwin
K Harrison Butker
D Giants
B Jaxon Smith-Njigba/Brian Robinson/Jordan Mason/JK Dobbins/Dalton Schultz/Andrei Iosivas/Cam Akers/Justin Fields/Dalvin Cook/Jonnu Smith
-
 @ fa984bd7:58018f52
2024-08-16 13:22:12
@ fa984bd7:58018f52
2024-08-16 13:22:12 -
 @ 6bae33c8:607272e8
2024-09-07 22:00:17
@ 6bae33c8:607272e8
2024-09-07 22:00:17Unfortunately, I didn’t have a ton of action in this game. I had the Packers with the points and am now 0-2 to start the week in my home picking pool. I had Xavier McKinney in the Steak League which was nice as like Roquan Smith he too started the year with a pick.
But I was missing the principal scorers namely Saquon Barkley (maybe I let the nerds talk me out of him, as I had him ranked highly initially) and Jayden Reed. Barkley I’m okay with because the potential for Jalen Hurts TDs was something I hadn’t initially considered, but Reed was a major error and in fact I passed on him for freaking Chris Godwin in my Primetime last night!
I had even argued with Alan Seslowsky that Reed was the obvious choice among the Packers receivers. So seeing him go off (and he should have had a third TD, but it was called back due to something I’ve never seen before (both teams having 12 men on the field) was painful. Godwin is almost sure to have a terrible season now just to hammer home the lesson for me: Don’t worry about 10 spots of ADP, take the fucking guy you like. Stop listening to the consensus when you have a real lean.
I don’t know how many times I need to learn this lesson, but apparently at least one more!
-
Reed looked like the most electrifying receiver on the field for the Packers. He had only six targets, not including the TD called back due to the penalties, but it’s obvious he’ll get more, and the handoff he took 33-yards to the house will incentivize them to do that again too. Year 2 after the surprisingly strong Year 1. He belongs in the second round now, along with Rashee Rice.
-
Christian Watson caught a TD and will be involved, but as great an athlete as he is he doesn’t have Reed’s football skills. Romeo Doubs is just a guy, but he’s reliable, and Dontayvion Wicks had a rough game — he’s an easy cut for me.
-
Jordan Love didn’t scramble much, and the Packers settled for a ton of field goals, but he looked okay. I think once they give Reed his 10 targets, Love will have his expected numbers. (Just read on RotoWire that Love left the game for the last two plays with an unspecified leg injury, something not apparent on the 40-minute edited version. I thought they brought Malik Willis to throw a Hail Mary! Obviously, if he’s out for any length of time, all bets are off for the Packers receivers.)
-
Josh Jacobs got stuffed in short yardage early, fumbled (though the Packers recovered), but ran well and hard late and even caught two passes. I have zero shares, but he looks like a fine pick for the late-third/early fourth. His backup Emanuel Wilson looked pretty spry too. Marshawn Lloyd is a cut now too in most formats.
-
Brayden Narveson missed a key kick off the post, but got a lot of attempts. He seems to have landed in the right place for a big season.
-
Jalen Hurts was a bit sloppy with two picks and a lost fumble, never got going on the ground (seemed like the Packers were really dedicated to taking that away), and the ass-smash didn’t work as well without Jason Kelce. But his receivers are so good, and Saquon Barkley is a big upgrade too. I would downgrade him a little though as his rushing TD projection maybe went from 10 to seven.
-
AJ Brown didn’t even look like he was running fast as he easily scored a 67-yard TD past the Packers defense. DeVonta Smith seemed to line up more in the slot and was automatic on key third-downs. There was no third receiver of which to speak, and even Dallas Goedert saw only five targets.
-
Barkley looked great, both on his TD catch, and as a rusher. As I said I don’t have any shares despite being high on him initially, but I love Barkley as a player (and bitcoiner!), and still kind of root for him. I hope he smashes this year.
-
-
 @ 3a6cac01:962671e4
2024-09-07 21:12:30
@ 3a6cac01:962671e4
2024-09-07 21:12:30- xczxc
zxczxczxc
czxczxc
- xxxx

-
 @ 9358c676:9f2912fc
2024-09-07 18:50:14
@ 9358c676:9f2912fc
2024-09-07 18:50:14Introduction
The human immunodeficiency virus (HIV) began as a pandemic in the 1980s. In its early days, it was seen as a certain death sentence, a taboo associated with marginalized groups, and it highlighted the failures of poverty in accessing healthcare. Gradually, the struggle for life and the suffering of those who are no longer with us, including both famous and anonymous individuals, became visible.
Today, 40 years later, HIV is presented as a chronic disease with effective treatment. Patients living with HIV who receive appropriate treatment have no detectable virus in their circulating blood, enjoy a good quality of life, and are more concerned about other aspects of their health during medical consultations, almost forgetting their condition. For these patients, daily treatment is the cure, similar to someone taking a pill every day for high blood pressure or diabetes.
The Global Impact
HIV is a lentivirus, a subgroup of retroviruses composed of RNA. The natural history of HIV infection involves an attack on the immune system, particularly targeting CD4 cells, where chronic deterioration can lead to the acquisition of infectious and oncological diseases that may be fatal over the years, resulting in acquired immunodeficiency syndrome (AIDS).
Interestingly, there is a small group of people known as "elite controllers" who manage to control HIV infection without treatment and remain healthy for much of their lives, despite having a hidden deep viral reservoir. The primary modes of transmission are sexual, followed by blood and vertical transmission from mother to child, with the first mode predominating today.
Today, in the downward trend of the HIV epidemic, it is estimated that 39 million people are living with HIV worldwide. Depending on the region, nearly half of this population belongs to at-risk groups, such as men who have sex with men (MSM), transgender individuals, sex workers, and people who inject drugs. These vulnerable groups are especially important for prevention efforts. However, little is done for prevention in the general population, which sometimes represents the other half of the cake of people living with HIV (PLWH).
Breaking the Dogma: The Concept of Undetectable = Untransmittable (U=U)
The introduction of highly effective antiretroviral therapy (HAART) in 1994 broke the curve of the HIV epidemic. The introduction of new medications with fewer side effects and greater effectiveness in controlling the virus has been crucial. In 2007, the launch of Raltegravir as the first viral integrase inhibitor marked a milestone in current treatments, allowing patients to effectively control the virus within 3 to 6 months.
The positive impact of these treatments led health organizations to launch the concept of undetectable = untransmittable (U=U) to impact the general population and at-risk groups, updating the dogma and eradicating stigma: a patient living with HIV who maintains an undetectable viral load in their blood through treatment will not transmit HIV sexually.
Although this concept has transformed the social dynamics and stigma surrounding the disease, adherence to treatment must be complete to achieve this new paradigm.
Prophylaxis as a Method to Prevent HIV in Healthy Populations
The correct use of condoms has been the cornerstone of HIV prevention and other sexually transmitted infections over the years. However, it is not the only tool available today and can be complemented for comprehensive sexual health.
Pre-exposure prophylaxis (PrEP) is a novel strategy that involves administering antiretroviral medication to vulnerable groups before they are exposed to HIV (MSM, transgender individuals, sex workers, people who inject drugs). It involves taking medication daily, effectively reducing the risk of contracting HIV and providing protection to these groups. It is similar to taking a contraceptive pill daily. It has had a very positive impact on protecting these populations. In the Americas, it has been successfully implemented in the United States, Mexico, Peru, and Brazil. Other countries, although with some delay, are now implementing this strategy.
Post-exposure prophylaxis (PEP), on the other hand, is a strategy that involves administering antiretroviral treatment after a potential exposure to HIV. If the treatment is administered within the first 72 hours and maintained for 4 weeks, the chances of contracting HIV decrease substantially.
Both strategies have been remarkably successful in preventing HIV in at-risk populations and healthy populations, although their dissemination and awareness remain limited.
https://image.nostr.build/08682bf763ade56741d8e4c8c6d870cb8d71ab7d72c605b9aa805af2234348ff.jpg
The New Horizon: Long-Acting Antiretrovirals, HIV Vaccines, and Promising Therapies
The introduction of viral integrase inhibitors and new nucleoside analogs in the last 15 years has allowed for the availability of safe drugs with minimal side effects in the treatment of HIV, many of which are included in a single pill regimen per day. However, the pharmaceutical industry continues to diversify the offerings in a healthy manner.
Cabotegravir is a new long-acting integrase inhibitor that is administered via injection. Combined with Rilpivirine, it has proven to be effective and safe in the treatment of HIV, with injections every 2 months. This has revolutionized treatment for people who are tired of taking pills daily, as well as in PrEP, where effective prevention against HIV can be achieved with injections every 2 months for at-risk groups.
Additionally, subdermal implants of Islatravir, a new long-acting nucleoside analog, are being tested as a PrEP strategy. Similar to monthly hormonal contraceptive injections or hormonal contraceptive implants, this strategy has proven effective in at-risk groups.
Regarding the HIV vaccine, we have been developing it for over two decades, with advances and setbacks. While vaccines have shown promising results in terms of safety and antibody generation, we still need to await conclusive phase III results demonstrating their effectiveness in at-risk groups and the general population.
The Eradication of HIV and Patients Cured Without Treatment
While current treatment allows for the elimination of HIV from the bloodstream and sexual transmission, there remains a reservoir in some deep immune cells that have been infected by the retrovirus, which contain latent HIV DNA and have the potential to reactivate if daily treatment is interrupted.
However, there are patients who have managed to eliminate HIV from their bodies, including these deep cells, and HIV is undetectable upon discontinuation of treatment. These cases are very rare, with only 7 to 8 individuals being the subject of intensive scientific study. Among them are the "Berlin patient" of Germany and "City of Hope patient" from Argentina. Some of these cases involved patients under effective HIV treatment who underwent suppressive chemotherapy for bone marrow transplants and managed to eliminate these deep cells with latent HIV DNA.
Unfortunately, this treatment is not scalable for the entire HIV-positive population, both due to its cost and potential side effects. However, "Shock and Kill" strategies have been proposed, aiming to use monoclonal antibodies to activate these latent cells during HIV treatment, exposing them to antiretroviral medication for elimination, thereby eradicating these small reservoirs of HIV.
WHO Goals
The World Health Organization (WHO) has established clear objectives that are constantly updated to achieve the eradication of HIV in the population.
The updated goals of the WHO propose that, to end the HIV epidemic, three objectives must be met by the year 2025-2030:
- 95% of people living with HIV must be diagnosed through testing.
- 95% of diagnosed individuals must be on highly effective antiretroviral therapy (HAART).
- 95% of those on HAART must have an undetectable viral load in their blood.
Developing and underdeveloped countries currently have an effectiveness rate for these strategies that disagree significantly.
https://image.nostr.build/ac6693df57aaca6dac0b06b5db9eb1a2757e7c08511edb0f11617e12653d3db5.png
Key Takeaways
- HIV has a cure, and the cure is permanent treatment.
- Treatment for HIV is free and accessible to the population, as it is a public health impact disease.
- A person living with HIV who receives appropriate treatment will not transmit the virus sexually, will enjoy a full life without the disease, and can have children without HIV.
- In the event of a potential HIV exposure (such as unprotected sexual contact with an infrequent partner), you can go to a hospital within the first 72 hours to receive treatment that will prevent HIV infection.
- Just as we witnessed the eradication of smallpox from the face of the earth in 1978 due to scientific advances, we will live to see the eradication of HIV.
Autor
Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj
Resources
Bibliography
- The natural history of HIV infection. DOI: 10.1097/COH.0b013e328361fa66
- Changing Knowledge and Attitudes Towards HIV Treatment-as-Prevention and "Undetectable = Untransmittable": A Systematic Review. DOI: 10.1007/s10461-021-03296-8
- Challenges of HIV diagnosis and management in the context of pre-exposure prophylaxis (PrEP), post-exposure prophylaxis (PEP), test and start and acute HIV infection: a scoping review. DOI: 10.1002/jia2.25419
- Long-acting cabotegravir and rilpivirine dosed every 2 months in adults with HIV-1 infection (ATLAS-2M), 48-week results: a randomised, multicentre, open-label, phase 3b, non-inferiority study. DOI: 10.1016/S0140-6736(20)32666-0
- Efficacy and safety of long-acting cabotegravir compared with daily oral tenofovir disoproxil fumarate plus emtricitabine to prevent HIV infection in cisgender men and transgender women who have sex with men 1 year after study unblinding: a secondary analysis of the phase 2b and 3 HPTN 083 randomised controlled trial. DOI: 10.1016/S2352-3018(23)00261-8
- Safety and immunogenicity of a subtype C ALVAC-HIV (vCP2438) vaccine prime plus bivalent subtype C gp120 vaccine boost adjuvanted with MF59 or alum in healthy adults without HIV (HVTN 107): A phase 1/2a randomized trial. DOI: 10.1371/journal.pmed.1004360
- Shock and kill within the CNS: A promising HIV eradication approach?. DOI: 10.1002/JLB.5VMR0122-046RRR
-
 @ dd664d5e:5633d319
2024-08-15 20:52:04
@ dd664d5e:5633d319
2024-08-15 20:52:04Here's how people use OtherStuff apps.
1) They usually go there to write or post, not to read or view, unless someone they closely follow wrote about it in a Kind 01 note, SimpleX chat, Slack Channel, Telegram group, etc.
2) While they are there, they sometimes look around at what their frens have posted, zap them, leave a comment or a reply, etc. Sometimes they spend hours there. They really like it!
3) Then they leave.
4) If someone responds to anything they posted or wrote there, with anything other than a Kind 01 reply, they do not know about it, because it does not show up in their normal feed or notifications.
5) They do not come back until 1) happens again.
-
 @ 8d34bd24:414be32b
2024-09-07 18:18:33
@ 8d34bd24:414be32b
2024-09-07 18:18:33So often we hear the Disney mantra “Follow your heart.” We hear people say, “I believe this” or “this is my truth.” God doesn’t give us this choice. We don’t get to decide what is true or not. Truth is truth even if not one person believes it.
Just believing that God exists is not enough.
You believe that God is one. You do well; the demons also believe, and shudder. (James 2:19)
The kind of faith in God that makes a difference in our eternity has to be done God’s way. The God of the Bible is the creator who spoke into existence all that is, including time & space and matter & energy. He fashioned man from the clay into His own imaged and breathed into him the breathe of life. As creator, He gets to say what is true and what isn’t, since He made everything. He gets to say what is right and what is wrong because He made us. He knows better than we do what is best for us and His ability to see and act outside of time allows Him to know what will be for our eternal good.
Unfortunately, since time began we have wanted to define what we want right and wrong to be. We have wanted to define who God is and how we should relate to Him. We want to say to God, “No! Do it my way!”
The First Sin
We don’t like being limited by rules and laws (this is probably extra true of Americans who believe in personal liberty). We want to be free to do whatever we want, however we want, whenever we want.
Now the serpent was more crafty than any beast of the field which the Lord God had made. And he said to the woman, “Indeed, has God said, ‘You shall not eat from any tree of the garden’?” The woman said to the serpent, “From the fruit of the trees of the garden we may eat; but from the fruit of the tree which is in the middle of the garden, God has said, ‘You shall not eat from it or touch it, or you will die.’ ” The serpent said to the woman, “You surely will not die! For God knows that in the day you eat from it your eyes will be opened, and you will be like God, knowing good and evil.” When the woman saw that the tree was good for food, and that it was a delight to the eyes, and that the tree was desirable to make one wise, she took from its fruit and ate; and she gave also to her husband with her, and he ate. Then the eyes of both of them were opened, and they knew that they were naked; and they sewed fig leaves together and made themselves loin coverings. (Genesis 3:1-7) {emphasis mine}
The very first temptation was the temptation to do as we please and be like God. This first temptation not only came from misleading statements from the serpent (Satan), but also came from the resentment Eve felt from the one and only “Thou shalt not …” given to them in the beginning. The only limitation God gave Adam and Eve was that they couldn’t eat the fruit from the Tree of the Knowledge of Good and Evil. Eve resented this limitation and added “or touch it.” The limitation to not touch it was not given by God (although maybe it could be considered a wise way to avoid temptation). It was man changing God’s very good commands. It was man changing the relationship between God and His creation. It was man trying to be in charge.
Obey Whose Commands?
All too often we don’t like God’s commands to “Do this!” or “Don’t do that!” so we change the rules to accommodate our desires and what is comfortable to us. Sometimes we add to God’s commands and sometimes we remove/ignore His commands, but any change we make is essentially us trying to take the place of God.
“Do not think that I came to abolish the Law or the Prophets; I did not come to abolish but to fulfill. For truly I say to you, until heaven and earth pass away, not the smallest letter or stroke shall pass from the Law until all is accomplished. Whoever then annuls one of the least of these commandments, and teaches others to do the same, shall be called least in the kingdom of heaven; but whoever keeps and teaches them, he shall be called great in the kingdom of heaven. (Matthew 5:17-19) {emphasis mine}
Read that again. “Whoever then annuls one of the least of these commandments, and teaches others to do the same, shall be called least in the kingdom of heaven.” God does not allow us to change His commands.
How Do We Worship?
He also doesn’t allow us to decide how we will worship Him. During the exodus from Egypt, God commanded the nation of Israel with very specific rules for how He should be worshipped and who should have what position.
Now Nadab and Abihu, the sons of Aaron, took their respective firepans, and after putting fire in them, placed incense on it and offered strange fire before the Lord, which He had not commanded them. And fire came out from the presence of the Lord and consumed them, and they died before the Lord. Then Moses said to Aaron, “It is what the Lord spoke, saying,
‘By those who come near Me I will be treated as holy,\ And before all the people I will be honored.’ ” (Leviticus 10:1-3)
God commanded how He should be worshipped. Nadab and Abihu decided they would worship how they wanted to worship and they paid with their lives for their affront to His holiness and power.
There was another event where some Levites protested Aaron’s and Moses’s God given positions. The Levites had been commanded by God to not approach the holy things of the tabernacle. In this instance 250 of them burned incense contrary to the command of God. God did not appreciate them trying to give themselves honor by disobeying His command.
Moses said, “By this you shall know that the Lord has sent me to do all these deeds; for this is not my doing. If these men die the death of all men or if they suffer the fate of all men, then the Lord has not sent me. But if the Lord brings about an entirely new thing and the ground opens its mouth and swallows them up with all that is theirs, and they descend alive into Sheol, then you will understand that these men have spurned the Lord.”
As he finished speaking all these words, the ground that was under them split open; and the earth opened its mouth and swallowed them up, and their households, and all the men who belonged to Korah with their possessions. So they and all that belonged to them went down alive to Sheol; and the earth closed over them, and they perished from the midst of the assembly. (Numbers 16:28-31)
God never accepts us when we chose to do our own thing and even worship in our own way. Sometimes, like in these two examples, He acts miraculously to punish the offenders instantly. Sometimes He is patient and allows time for learning and repentance. Sometimes we are not punished until eternity. We serve a might and holy God and need to treat Him appropriately.
Although Christians today don’t have a strict formula of worship, our call to honor Him and treat Him as holy is just as strong. We don’t get to pick how we will worship Him and we definitely don’t get to call any or all “gods” the true God. Not all paths lead to the one true God. The only way to be right with God is through faith in the Lord Jesus Christ and believing He is God; He lived a perfect life; He died on a cross to take away our sins; and He rose from the dead on the third day. That is the only way. All other paths, no matter how heart felt, lead straight to hell.
Judgment is the Lord’s
We need to be very careful not only judging ourselves, but also judging others. Are we judging by God’s law and His measure or we judging by our own fallible judgment?
Do not speak against one another, brethren. He who speaks against a brother or judges his brother, speaks against the law and judges the law; but if you judge the law, you are not a doer of the law but a judge of it. There is only one Lawgiver and Judge, the One who is able to save and to destroy; but who are you who judge your neighbor? (James 4:11-12)
We are called to teach God’s written word and to lead people to follow it as written, but we are not to be judge and jury. We are not the ones punishing sins. That is God’s prerogative.
Anyone who has set aside the Law of Moses dies without mercy on the testimony of two or three witnesses. How much severer punishment do you think he will deserve who has trampled under foot the Son of God, and has regarded as unclean the blood of the covenant by which he was sanctified, and has insulted the Spirit of grace? For we know Him who said, “Vengeance is Mine, I will repay.” And again, “The Lord will judge His people.” It is a terrifying thing to fall into the hands of the living God. (Hebrews 10:28-31) {emphasis mine}
When we say there is another way to God, our way, we are “ trampl(ing) under foot the Son of God.” (tense change mine) When we say we can be good enough or we can put something or someone else first, we will be judged. “It is a terrifying thing to fall into the hands of the living God.”
So many of our wrong decisions come because we do not have a high enough view of God. We do not have a fear of the God who can snuff us out if He chooses to stop upholding our lives. The God of the Bible is a loving and merciful God, but there is a limit to that mercy. We must honor and trust Him before our time on earth is ended, otherwise we receive His righteous judgment.
Continue in the Things You Have Learned
The Bible tells us to to “continue in the things you have learned.” We can’t continue in the things we have learned if we haven’t learned God’s word. Reading and deep study of God’s word, the Bible, is critical if we want to serve God and grow in wisdom and service towards Him. We need to put in time. We need to read the Bible daily. We need to find time to study the Bible and to figure out what is true.
You, however, continue in the things you have learned and become convinced of, knowing from whom you have learned them, and that from childhood you have known the sacred writings which are able to give you the wisdom that leads to salvation through faith which is in Christ Jesus. All Scripture is inspired by God and profitable for teaching, for reproof, for correction, for training in righteousness; so that the man of God may be adequate, equipped for every good work. (2 Timothy 3:14-17) {emphasis mine}
Scripture is essential for everything in the Christian life. It helps us to grow in faith and unity with God. It helps us minister to and train others. It equips us “for every good work.”
and that from childhood you have known the sacred writings which are able to give you the wisdom that leads to salvation through faith which is in Christ Jesus. (2 Timothy 3:15)
The Bible should be the foundation of everything we learn and everything we accept as true. Nothing should be believed as true that contradicts the Bible in any way.
It is useful, however, to find wise teachers to help us understand the Bible. This may be a person who will disciple us face-to-face. This may be a pastor at our church. This may be a Christian writer. When we use any of these other sources, we always need to double check what we learn and verify that it matches the Bible.
Now these were more noble-minded than those in Thessalonica, for they received the word with great eagerness, examining the Scriptures daily to see whether these things were so. (Acts 17:11) {emphasis mine}
We need to examine “the Scriptures daily to see whether these things were so.” During the Reformation, this was called Sola Scriptura, Scripture alone. Our reference of truth and righteousness comes from the Bible alone because it is the word of God.
Deceivers: Don’t Be Deceived And Don’t Be a Deceiver
There have been deceivers since the beginning of time, but the Bible says that we will see more and more deceivers as the end of time approaches.
For many deceivers have gone out into the world, those who do not acknowledge Jesus Christ as coming in the flesh. This is the deceiver and the antichrist. Watch yourselves, that you do not lose what we have accomplished, but that you may receive a full reward. Anyone who goes too far and does not abide in the teaching of Christ, does not have God; the one who abides in the teaching, he has both the Father and the Son. If anyone comes to you and does not bring this teaching, do not receive him into your house, and do not give him a greeting; for the one who gives him a greeting participates in his evil deeds. (2 John 1:7-11)
If we don’t know the word of God well, we can be easily misled. There are many who quote the Bible out of context to mislead. If a tiny piece of scripture is taken out of context, it can be made to say almost anything. Any time there is any question on what the Bible is saying, we need to take the Bible as a whole in order to understand the truth. The Bible never contradicts itself. It may come at a truth from different angles regarding different situations, but it never contradicts itself.
But I am afraid that, as the serpent deceived Eve by his craftiness, your minds will be led astray from the simplicity and purity of devotion to Christ. For if one comes and preaches another Jesus whom we have not preached, or you receive a different spirit which you have not received, or a different gospel which you have not accepted, you bear this beautifully. For I consider myself not in the least inferior to the most eminent apostles. But even if I am unskilled in speech, yet I am not so in knowledge; in fact, in every way we have made this evident to you in all things. (2 Corinthians 11:3-5)
Only by knowing the whole Bible can we keep ourselves from being misled. Be like Paul and know the Bible so you can not only avoid being misled, but have the knowledge of the Bible necessary to defend God’s word and prevent others from being misled.
For certain persons have crept in unnoticed, those who were long beforehand marked out for this condemnation, ungodly persons who turn the grace of our God into licentiousness and deny our only Master and Lord, Jesus Christ. (Jude 1:4) {emphasis mine}
It isn’t just those openly hostile to God that are misleading people. Sadly, there are many in the church, including pastors and others in positions of power who claim to be Christians and claim to be speaking the word of God, but who “deny our only Master and Lord, Jesus Christ” and are “marked out for this condemnation.”
We are to daily study God’s word and to daily pray for wisdom and to daily be led by the Holy Spirit. God doesn’t want us to spend our lives sitting in the pews taking in information. He wants us to share His word and be a light unto the world. He wants us to chose Him over anything or anyone else.
I solemnly charge you in the presence of God and of Christ Jesus, who is to judge the living and the dead, and by His appearing and His kingdom: preach the word; be ready in season and out of season; reprove, rebuke, exhort, with great patience and instruction. For the time will come when they will not endure sound doctrine; but wanting to have their ears tickled, they will accumulate for themselves teachers in accordance to their own desires, and will turn away their ears from the truth and will turn aside to myths. (2 Timothy 4:1-4) {emphasis mine}
We need to be the person who is “ready in season and out of season” and not the person “wanting to have their ears tickled … in accordance to their own desires.” Those that seek their own way will be spending eternity suffering in hell.
As the end times approach, we will see more and more of this falling away from God’s word. We will see this in culture, but we will also see it in the church (and are seeing it today).
Know this first of all, that in the last days mockers will come with their mocking, following after their own lusts, and saying, “Where is the promise of His coming? For ever since the fathers fell asleep, all continues just as it was from the beginning of creation.” For when they maintain this, it escapes their notice that by the word of God the heavens existed long ago and the earth was formed out of water and by water, through which the world at that time was destroyed, being flooded with water. But by His word the present heavens and earth are being reserved for fire, kept for the day of judgment and destruction of ungodly men. (2 Peter 3:3:7) {emphasis mine}
Don’t choose to do things your way. Don’t choose teachers who tickle your ears with what you want to hear. Don’t say in your heart, “Where is the promise of His coming?” All those who reject Jesus and the only way to God as described in the Bible are being “reserved for fire, kept for the day of judgment and destruction of ungodly men.”
Don’t regret your choices. Choose Jesus today.
Trust Jesus.\ \ your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
For more posts check out my [Trust Jesus Substack](https://trustjesus.substack.com/)
I am also testing out a couple of different nostr editors, so this article might be posted more than once, so I can test how they come out. This post was composed in highlighter.com .
-
 @ da18e986:3a0d9851
2024-08-14 13:58:24
@ da18e986:3a0d9851
2024-08-14 13:58:24After months of development I am excited to officially announce the first version of DVMDash (v0.1). DVMDash is a monitoring and debugging tool for all Data Vending Machine (DVM) activity on Nostr. The website is live at https://dvmdash.live and the code is available on Github.
Data Vending Machines (NIP-90) offload computationally expensive tasks from relays and clients in a decentralized, free-market manner. They are especially useful for AI tools, algorithmic processing of user’s feeds, and many other use cases.
The long term goal of DVMDash is to become 1) a place to easily see what’s happening in the DVM ecosystem with metrics and graphs, and 2) provide real-time tools to help developers monitor, debug, and improve their DVMs.
DVMDash aims to enable users to answer these types of questions at a glance: * What’s the most popular DVM right now? * How much money is being paid to image generation DVMs? * Is any DVM down at the moment? When was the last time that DVM completed a task? * Have any DVMs failed to deliver after accepting payment? Did they refund that payment? * How long does it take this DVM to respond? * For task X, what’s the average amount of time it takes for a DVM to complete the task? * … and more
For developers working with DVMs there is now a visual, graph based tool that shows DVM-chain activity. DVMs have already started calling other DVMs to assist with work. Soon, we will have humans in the loop monitoring DVM activity, or completing tasks themselves. The activity trace of which DVM is being called as part of a sub-task from another DVM will become complicated, especially because these decisions will be made at run-time and are not known ahead of time. Building a tool to help users and developers understand where a DVM is in this activity trace, whether it’s gotten stuck or is just taking a long time, will be invaluable. For now, the website only shows 1 step of a dvm chain from a user's request.
One of the main designs for the site is that it is highly clickable, meaning whenever you see a DVM, Kind, User, or Event ID, you can click it and open that up in a new page to inspect it.
Another aspect of this website is that it should be fast. If you submit a DVM request, you should see it in DVMDash within seconds, as well as events from DVMs interacting with your request. I have attempted to obtain DVM events from relays as quickly as possible and compute metrics over them within seconds.
This project makes use of a nosql database and graph database, currently set to use mongo db and neo4j, for which there are free, community versions that can be run locally.
Finally, I’m grateful to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project.
Features in v0.1:
Global Network Metrics:
This page shows the following metrics: - DVM Requests: Number of unencrypted DVM requests (kind 5000-5999) - DVM Results: Number of unencrypted DVM results (kind 6000-6999) - DVM Request Kinds Seen: Number of unique kinds in the Kind range 5000-5999 (except for known non-DVM kinds 5666 and 5969) - DVM Result Kinds Seen: Number of unique kinds in the Kind range 6000-6999 (except for known non-DVM kinds 6666 and 6969) - DVM Pub Keys Seen: Number of unique pub keys that have written a kind 6000-6999 (except for known non-DVM kinds) or have published a kind 31990 event that specifies a ‘k’ tag value between 5000-5999 - DVM Profiles (NIP-89) Seen: Number of 31990 that have a ‘k’ tag value for kind 5000-5999 - Most Popular DVM: The DVM that has produced the most result events (kind 6000-6999) - Most Popular Kind: The Kind in range 5000-5999 that has the most requests by users. - 24 hr DVM Requests: Number of kind 5000-5999 events created in the last 24 hrs - 24 hr DVM Results: Number of kind 6000-6999 events created in the last 24 hours - 1 week DVM Requests: Number of kind 5000-5999 events created in the last week - 1 week DVM Results: Number of kind 6000-6999 events created in the last week - Unique Users of DVMs: Number of unique pubkeys of kind 5000-5999 events - Total Sats Paid to DVMs: - This is an estimate. - This value is likely a lower bound as it does not take into consideration subscriptions paid to DVMs - This is calculated by counting the values of all invoices where: - A DVM published a kind 7000 event requesting payment and containing an invoice - The DVM later provided a DVM Result for the same job for which it requested payment. - The assumption is that the invoice was paid, otherwise the DVM would not have done the work - Note that because there are multiple ways to pay a DVM such as lightning invoices, ecash, and subscriptions, there is no guaranteed way to know whether a DVM has been paid. Additionally, there is no way to know that a DVM completed the job because some DVMs may not publish a final result event and instead send the user a DM or take some other kind of action.
Recent Requests:
This page shows the most recent 3 events per kind, sorted by created date. You should always be able to find the last 3 events here of all DVM kinds.
DVM Browser:
This page will either show a profile of a specific DVM, or when no DVM is given in the url, it will show a table of all DVMs with some high level stats. Users can click on a DVM in the table to load the DVM specific page.
Kind Browser:
This page will either show data on a specific kind including all DVMs that have performed jobs of that kind, or when no kind is given, it will show a table summarizing activity across all Kinds.
Debug:
This page shows the graph based visualization of all events, users, and DVMs involved in a single job as well as a table of all events in order from oldest to newest. When no event is given, this page shows the 200 most recent events where the user can click on an event in order to debug that job. The graph-based visualization allows the user to zoom in and out and move around the graph, as well as double click on any node in the graph (except invoices) to open up that event, user, or dvm in a new page.
Playground:
This page is currently under development and may not work at the moment. If it does work, in the current state you can login with NIP-07 extension and broadcast a 5050 event with some text and then the page will show you events from DVMs. This page will be used to interact with DVMs live. A current good alternative to this feature, for some but not all kinds, is https://vendata.io/.
Looking to the Future
I originally built DVMDash out of Fear-of-Missing-Out (FOMO); I wanted to make AI systems that were comprised of DVMs but my day job was taking up a lot of my time. I needed to know when someone was performing a new task or launching a new AI or Nostr tool!
I have a long list of DVMs and Agents I hope to build and I needed DVMDash to help me do it; I hope it helps you achieve your goals with Nostr, DVMs, and even AI. To this end, I wish for this tool to be useful to others, so if you would like a feature, please submit a git issue here or note me on Nostr!
Immediate Next Steps:
- Refactoring code and removing code that is no longer used
- Improve documentation to run the project locally
- Adding a metric for number of encrypted requests
- Adding a metric for number of encrypted results
Long Term Goals:
- Add more metrics based on community feedback
- Add plots showing metrics over time
- Add support for showing a multi-dvm chain in the graph based visualizer
- Add a real-time mode where the pages will auto update (currently the user must refresh the page)
- ... Add support for user requested features!
Acknowledgements
There are some fantastic people working in the DVM space right now. Thank you to nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet for making python bindings for nostr_sdk and for the recent asyncio upgrades! Thank you to nostr:npub1nxa4tywfz9nqp7z9zp7nr7d4nchhclsf58lcqt5y782rmf2hefjquaa6q8 for answering lots of questions about DVMs and for making the nostrdvm library. Thank you to nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft for making the original DVM NIP and vendata.io which I use all the time for testing!
P.S. I rushed to get this out in time for Nostriga 2024; code refactoring will be coming :)
-
 @ d52f4f20:98efcdfb
2024-09-07 17:39:46
@ d52f4f20:98efcdfb
2024-09-07 17:39:46 -
 @ 30ceb64e:7f08bdf5
2024-08-14 11:51:36
@ 30ceb64e:7f08bdf5
2024-08-14 11:51:36Heres a scenario:
Imagine you have a nostr e-cash/Lightning Wallet and you would like to have a maximum receive balance of 20k split in between 5 mints that enable multipath payments.
Pick 5 mints below to store 4k sats each, the funds are automatically withdrawn to your lightning node at the end of the day.
Stacker News Robosats Sparrow Coinkite Start9 Rabbit Hole Recap @siggy47 Damus LND Your own mint
originally posted at https://stacker.news/items/648298
-
 @ 41d0a715:9733c512
2024-09-07 15:27:14
@ 41d0a715:9733c512
2024-09-07 15:27:14Blaise Pascal: 'I have made this letter longer than usual, only because I have not had the time to make it shorter.'
Some of you Stackers need to spend a little more time to make your posts short and sweet. Sometimes I realize a post doesn't even have a point after wasting time reading it. A long poorly written post is a waste of my time and yours too!
originally posted at https://stacker.news/items/676136
-
 @ 30ceb64e:7f08bdf5
2024-08-14 11:15:27
@ 30ceb64e:7f08bdf5
2024-08-14 11:15:27It's wild. I just proved I can build #nostr 'wallet' where I can store the encrypted tokens in a Germany relay and make the lightning payment out of a Singapore mint. All using a #nsec that never leaves my machine. https://primal.net/e/note15l02rf4r474ck04mlrxxfagyl0z6t04ltsugf9dtph4xxhzfnd4sqpk74n
I’ve proven to myself that a #nostr wallet can exist across time and space, independently of any one app, server or custodian. The only thing which controls the ‘wallet’ is the generation and control of an #nsec which is free to exist within or flee any jurisdiction.
In my mind, this lays to rest the notion that a wallet needs to be an app, service, or anything that can be captured commercially or by the state. https://primal.net/e/note13nwsh852x9tfex2jade6vwymhhct8zussxr4zwy7uag24hjc9stq0xsxaf
https://image.nostr.build/07dd1b56d6bb60b13cfe6c19d9384bc3ef198d01af4be9a5c544f791b80b746a.png
I am thinking about coining the term “nsac” to refer to a wallet-like thing that can exist on #nostr holding your valuable things, such as ecash tokens. I have already implemented a prototype #cashu ecash wallet which looks to be promising.
So you would have:
npub - your identity
nsec - your private key
nsac - your valuables
Your #nsac could be the same as your #nsec but better case is to generate as many #nsacs as required.
Happy to hear feedback!
For reference, what a ‘sac’ is in the biological sense:
A sac is a biological term referring to a pouch or cavity in an organism that is typically enclosed and may contain fluid, air, or other substances. Sacs can serve various functions depending on their location and role in the body, such as protecting a developing embryo, facilitating the exchange of gases in the lungs, or reducing friction between moving parts in joints
https://primal.net/e/note1snj7y9m6f7lhfzkd2ujzqcvparpgddzmgcgwsgghqvkcyd0rkqhsmmlyla
npub1q6mcr8tlr3l4gus3sfnw6772s7zae6hqncmw5wj27ejud5wcxf7q0nx7d5
Wild stuff freaks, will nostr become the best lightning/E-Cash wallet? Let me know what you think.
originally posted at https://stacker.news/items/648270
-
 @ 005bc4de:ef11e1a2
2024-09-07 11:49:51
@ 005bc4de:ef11e1a2
2024-09-07 11:49:51Chef's notes
The trick for this "colorful" potato salad is a variety of potato types and a variety of pepper colors.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 15 minutes
Ingredients
- 1 quart chopped potatoes
- 2 to 4 snack peppers
- 1/4 cup mayonnaise
- 1/4 teaspoon celery salt
- 1/4 teaspoon garlic salt
- 1/2 cup sweet relish, optional
Directions
- Chop potatoes and boil for 14 minutes.
- Dice peppers
- Strain potatoes, add peppers, mayo, salt, relish, mix and serve.
-
 @ a012dc82:6458a70d
2024-09-07 10:12:43
@ a012dc82:6458a70d
2024-09-07 10:12:43Table Of Content
-
What are Cryptocurrency Charts?
-
Contrasts between Bitcoin and Crypto Charts
-
Market Capitalization
-
Price Volatility
-
Adoption
-
Use Cases
-
Technology
-
Conclusion
-
FAQ
Cryptocurrencies have garnered significant attention in recent years due to their high volatility and the potential for significant returns. Among these cryptocurrencies, Bitcoin has been the undisputed leader in terms of market capitalization, adoption, and popularity. However, as the cryptocurrency market continues to evolve, a growing number of altcoins are vying for investors' attention. As a result, investors are increasingly looking at the contrasts between Bitcoin and other cryptocurrencies. In this article, we will investigate the differences between Bitcoin and other cryptocurrencies by examining their charts.
What are Cryptocurrency Charts?
A cryptocurrency chart is a visual representation of the price movement of a cryptocurrency over a given period. These charts are used by investors to track the performance of cryptocurrencies and identify potential investment opportunities. Cryptocurrency charts provide valuable insights into the market sentiment, trends, and price movements of cryptocurrencies.
Market Capitalization
Bitcoin's market capitalization is significantly larger than that of other cryptocurrencies. As of March 2023, Bitcoin's market capitalization is around $1.5 trillion, while the total market capitalization of all cryptocurrencies is approximately $2.8 trillion. This difference in market capitalization indicates that Bitcoin is the dominant cryptocurrency, and other cryptocurrencies have yet to catch up.
Price Volatility
Bitcoin has been known for its high price volatility. The cryptocurrency has experienced significant price fluctuations throughout its history, with some periods of extreme price swings. However, other cryptocurrencies, such as Ethereum and Ripple, have also exhibited high price volatility. In some cases, altcoins have experienced even more significant price swings than Bitcoin, making them riskier investments.
Adoption
Bitcoin is the most widely adopted cryptocurrency and has been accepted as a means of payment by an increasing number of merchants worldwide. However, other cryptocurrencies are also gaining adoption, with some merchants accepting Ethereum, Litecoin, and other altcoins. The level of adoption of a cryptocurrency is an essential factor to consider when investing in it.
Use Cases
Bitcoin was initially created as a decentralized digital currency, and its primary use case remains as a store of value and a means of payment. However, other cryptocurrencies have been designed for specific use cases, such as smart contracts (Ethereum), cross-border payments (Ripple), and privacy (Monero). The specific use case of a cryptocurrency can significantly impact its value and investment potential.
Technology
Bitcoin and other cryptocurrencies use different technologies to enable transactions on their networks. Bitcoin uses the Proof-of-Work (PoW) consensus mechanism, while other cryptocurrencies have adopted different consensus mechanisms, such as Proof-of-Stake (PoS), Delegated Proof-of-Stake (DPoS), and Directed Acyclic Graphs (DAGs). The technology used by a cryptocurrency can impact its scalability, security, and efficiency.
Conclusion
Cryptocurrencies are a dynamic and ever-evolving market, and understanding the contrasts between Bitcoin and other cryptocurrencies is essential for making informed investment decisions. By examining the charts of different cryptocurrencies, investors can gain insights into the market sentiment, trends, and price movements of cryptocurrencies. While Bitcoin remains the dominant cryptocurrency, other cryptocurrencies are gaining adoption and offer unique use cases and investment opportunities. It is crucial to consider various factors, such as market capitalization, price volatility, adoption, use cases, and technology, when investing in cryptocurrencies.
FAQ
How do you buy cryptocurrencies? You can buy cryptocurrencies through cryptocurrency exchanges, which allow you to exchange fiat currency (such as USD) for cryptocurrencies like Bitcoin or Ethereum.
Are cryptocurrencies safe to invest in? Cryptocurrencies are a high-risk investment due to their volatility and lack of regulation. It is important to do your research and understand the risks before investing in cryptocurrencies.
What is blockchain technology? Blockchain technology is a decentralized, digital ledger that records transactions in a secure and transparent way. It is the underlying technology that powers most cryptocurrencies.
Can I use cryptocurrencies to buy goods and services? Some merchants accept cryptocurrencies as a form of payment, but it is not yet widely accepted as a means of payment.
Why is price volatility important in cryptocurrencies? Price volatility is important in cryptocurrencies because it can affect the investment potential of a cryptocurrency. High volatility can mean high potential returns, but it also means high risk.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ a9434ee1:d5c885be
2024-08-13 15:50:57
@ a9434ee1:d5c885be
2024-08-13 15:50:57Markdown + X, Y, Z is a problem, but Markdown + N can fix that.
Where N = any type of Nostr event.Whatever Markup language you choose, people will be referencing other Nostr events in it all the time. Since apps have to find ways to display those events (or the links to them) anyway, we mights as well use that as an opportunity.
Why can't Tables, for example, be embedded Nostr events?
Switching from Markdown to Asciidocs (because it has tables and some more technical stuff) still doesn’t make Tables a great experience. On mobile, Tables are notoriously hard to display in a useful way. It depends on the use case, size of the table, etc….
Creators need guarantees on these things being displayed the way they intended.
There’s a reason why most authors just embed pictures of tables instead. It has little to do with Markdown not really supporting tables and more with them ensuring readability and appropriate styling.So what if you enhance Markdown not only with embedded Nostr Events but also with something like Hypernotes Widgets that serve as a preview/display for those Nostr Events?
That way: - you are still using the most simple and popular markup language - devs “only” have to implement one extra thing (Hypernotes) that handles all the complexity and extensibility from there - authors can create articles and wiki entries with interactive elements in them, can have the guarantee that they display properly, can use any styling that suits them, etc… - the worst case scenario of reading it in a random crappy app still displays the link to the event (including it's explanatory metadata)
Imagine custom interactive graphs, polls, media players, products, … embedded in articles BUT limited to the Nostr-verse for all interaction and data fetching.
(this article will be updated with UI prototypes and further thoughts)